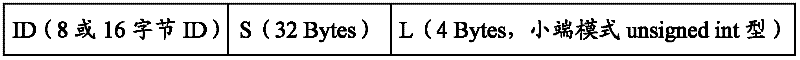Method and device for signing user program and method and device for verifying signature of user program
A user program and program technology, applied in the field of information security, can solve the problems of inability to prevent theft, high cost and inconvenience of program upgrade and function addition, and achieve the effect of preventing malicious tampering or theft and reducing the risk of violent cracking
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] In order to describe the technical content, structural features, achieved goals and effects of the present invention in detail, the following will be described in detail in conjunction with the embodiments and accompanying drawings.
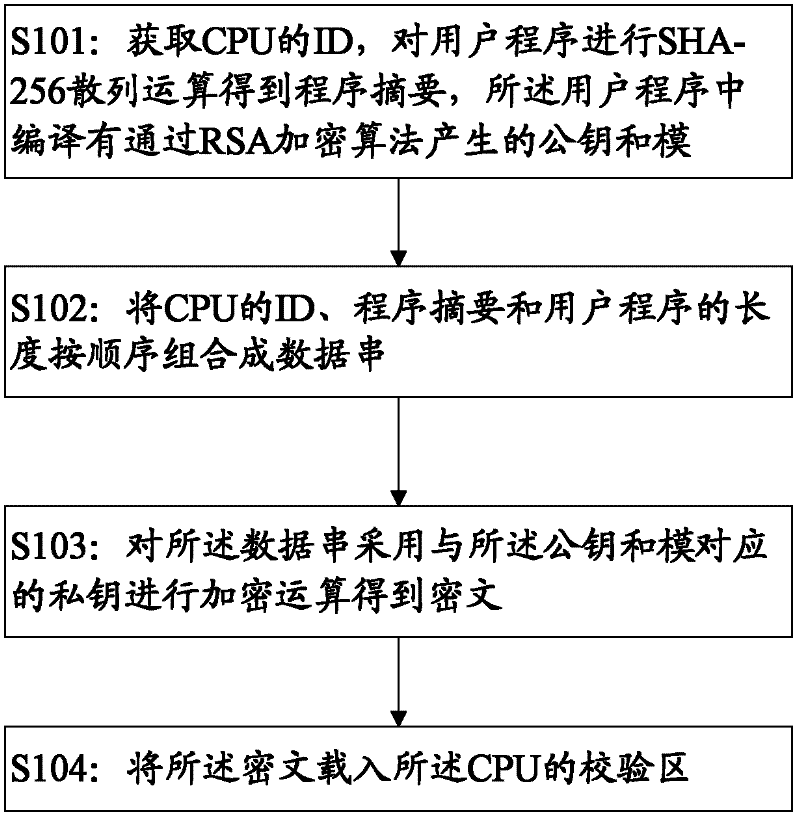
[0038] The present invention mainly solves the security problem of the user program. First, the authorizer must generate a signature key group, specifically: the authorizer generates a key group with a length of 2048 bits through the RSA2048 key generation tool, and the key group specifically includes a public key E, private key D, module N, the authorizer releases the public key E and module N to the developer of the dedicated CPU program, and the developer compiles the public key E and module N into the program.
[0039] see figure 1 , the present invention first proposes a method for signing a user program, comprising steps:
[0040] S101: Obtain the ID of the CPU, and perform a SHA-256 hash operation on the user program to obtain a pr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com