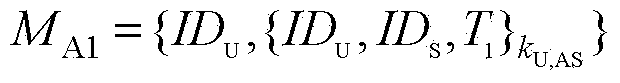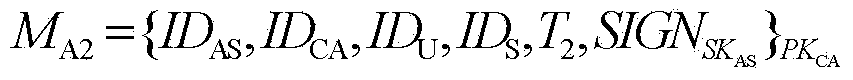Patents
Literature
64 results about "Public key authentication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
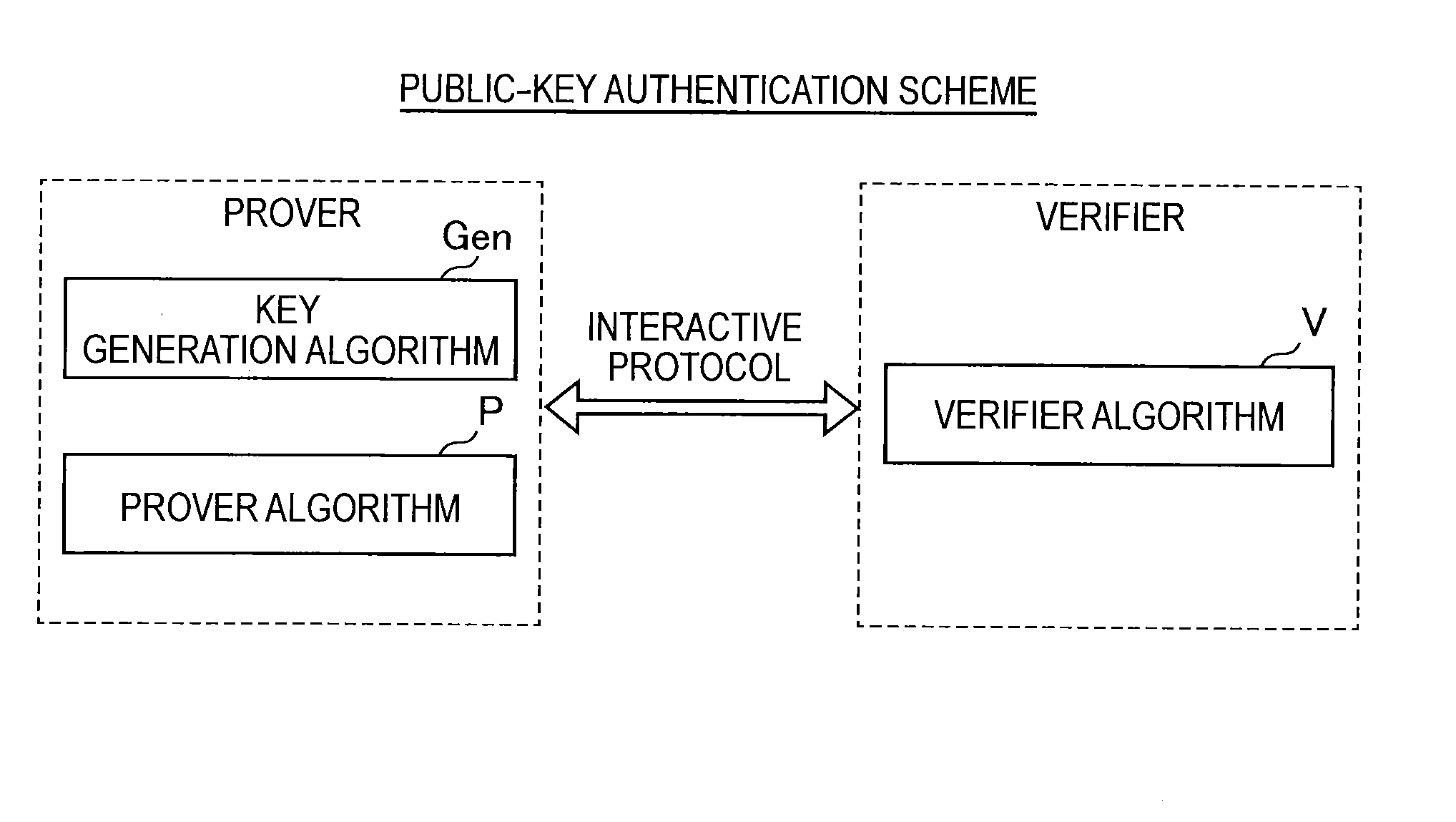
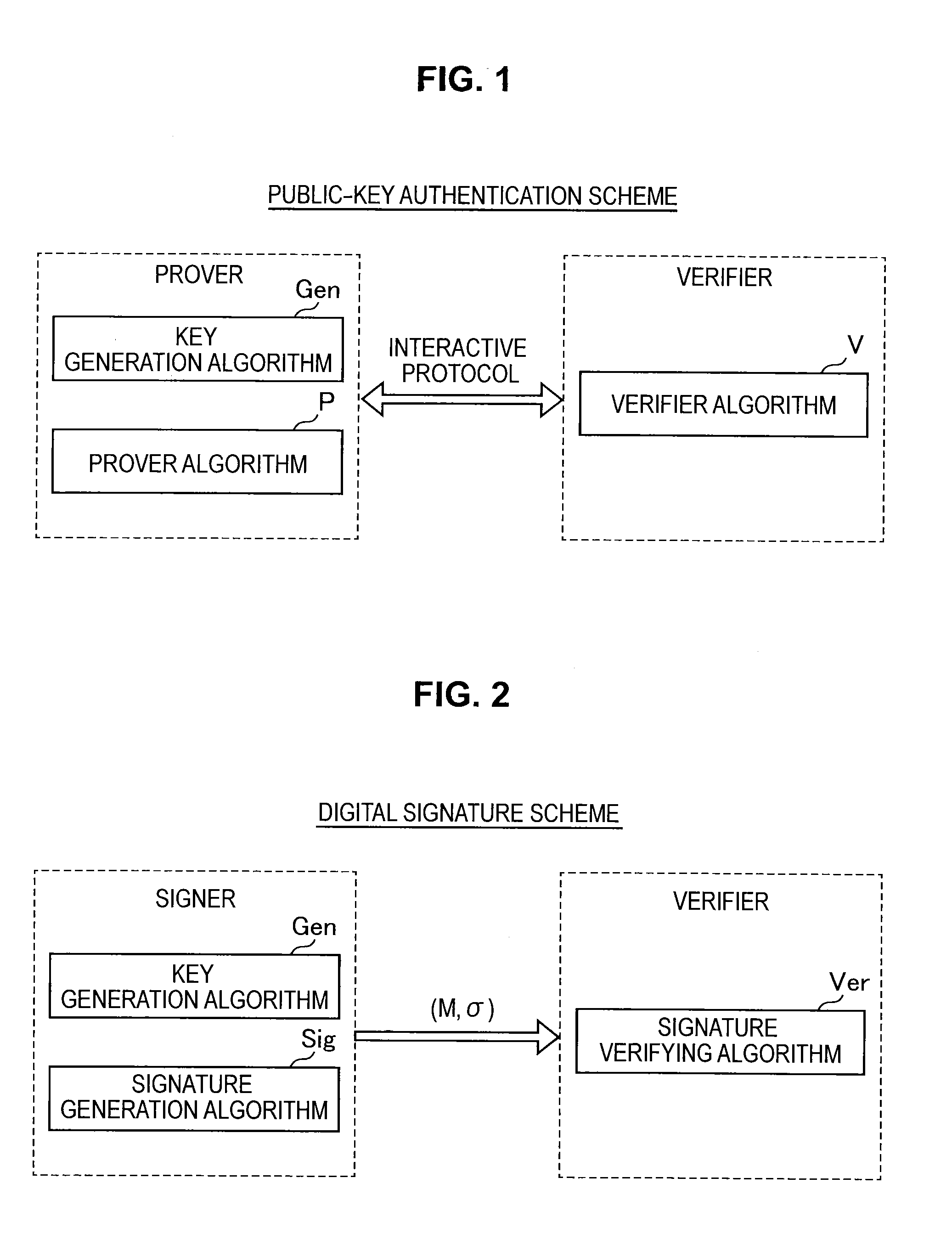
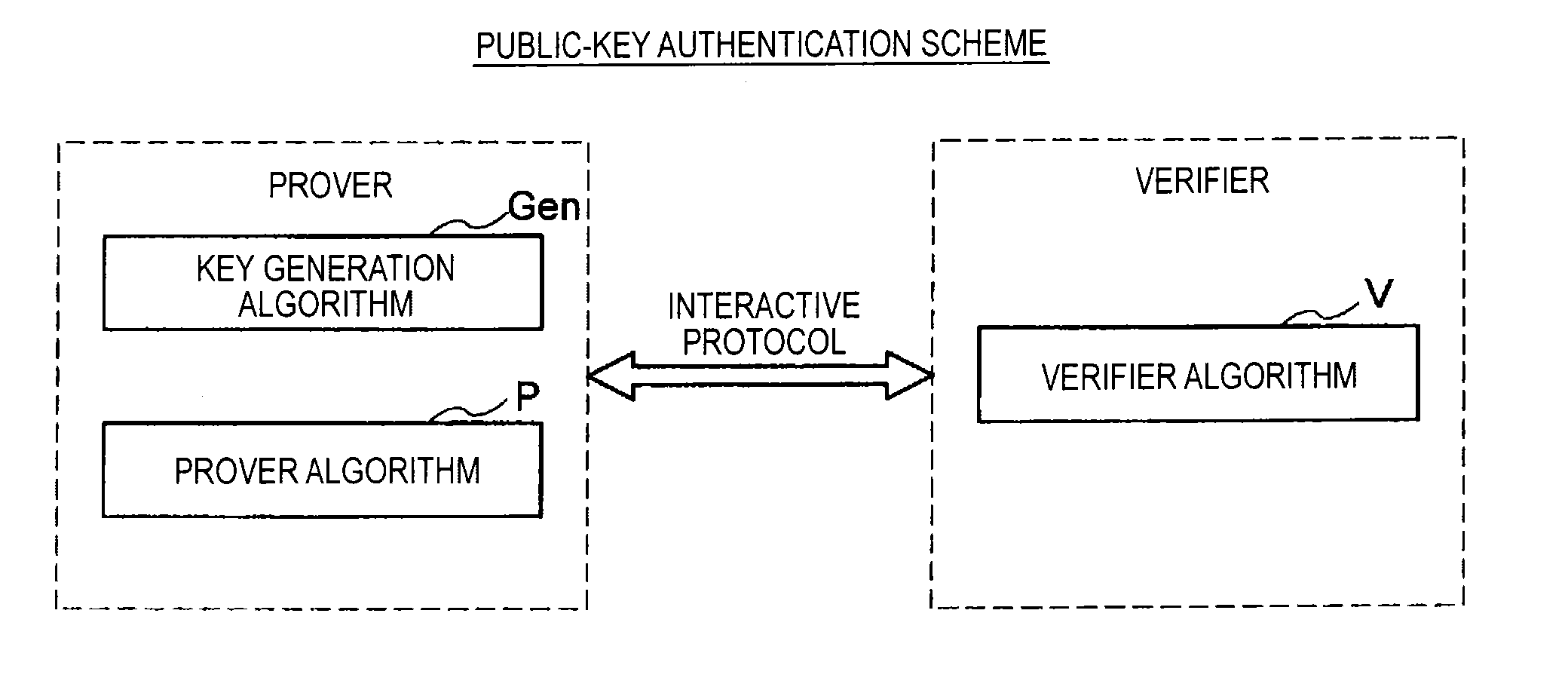
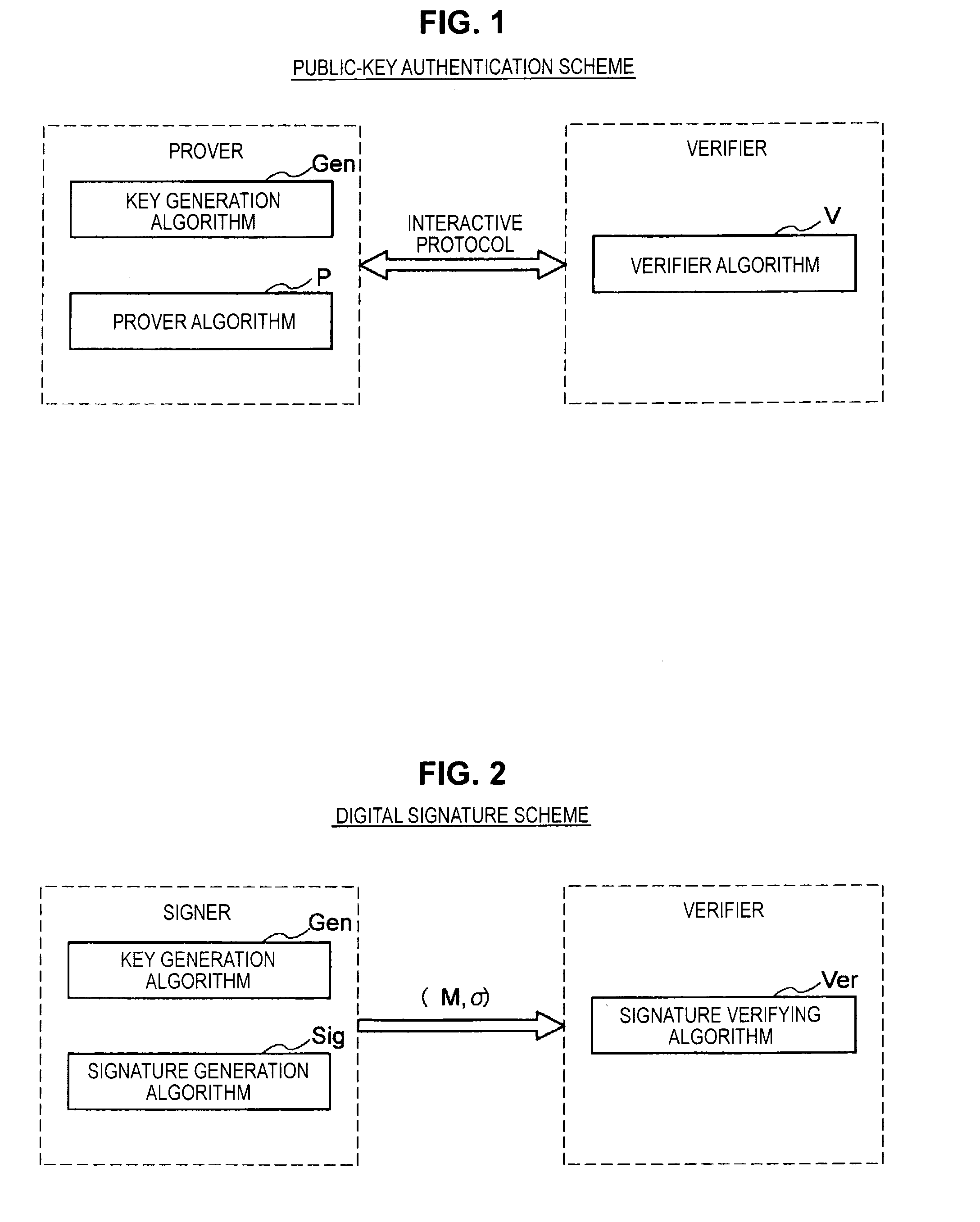
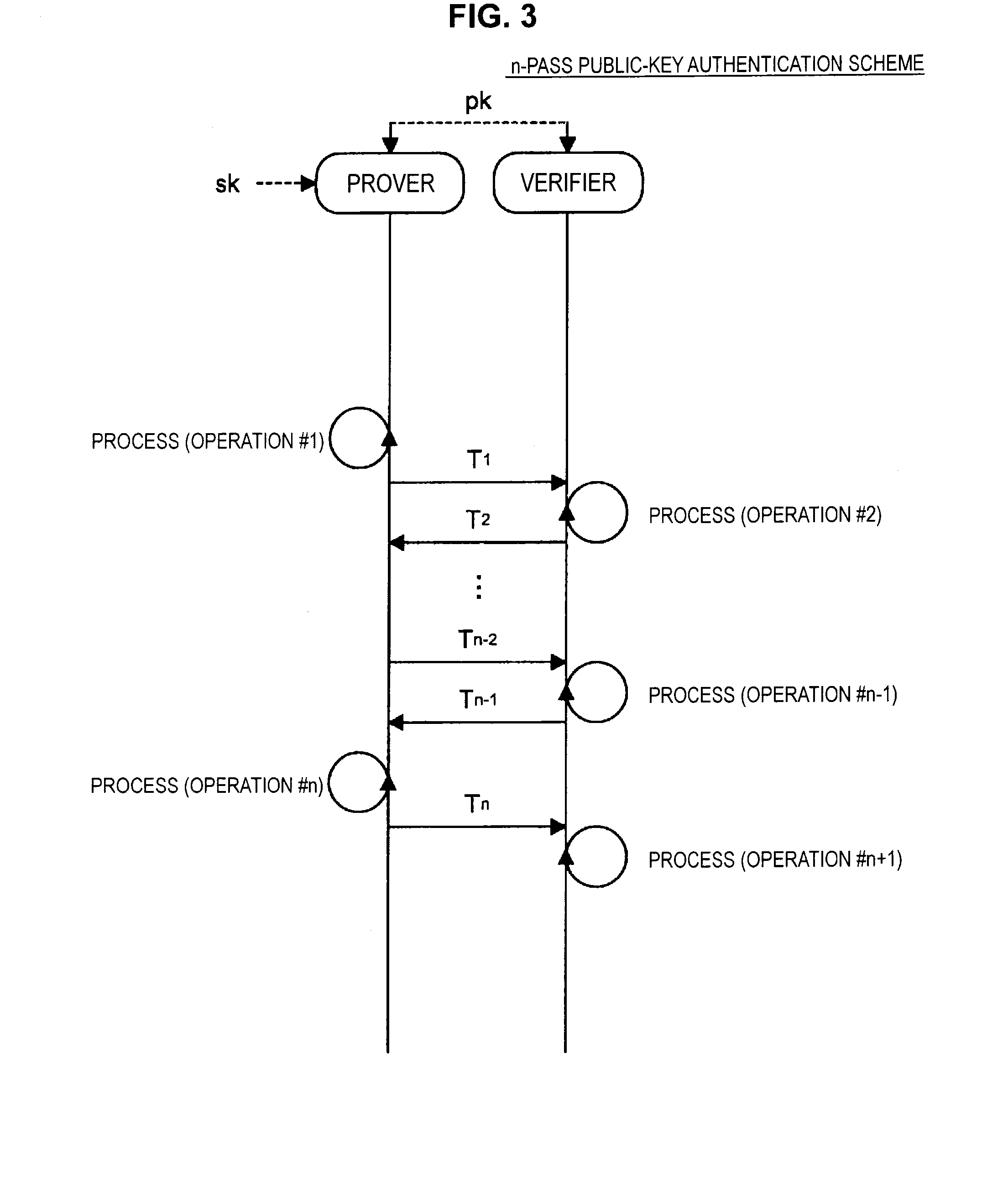
Public key authentication is an alternative means of identifying yourself to a login server, instead of typing a password. It is more secure and more flexible, but more difficult to set up. In conventional password authentication, you prove you are who you claim to be by proving that you know the correct password.
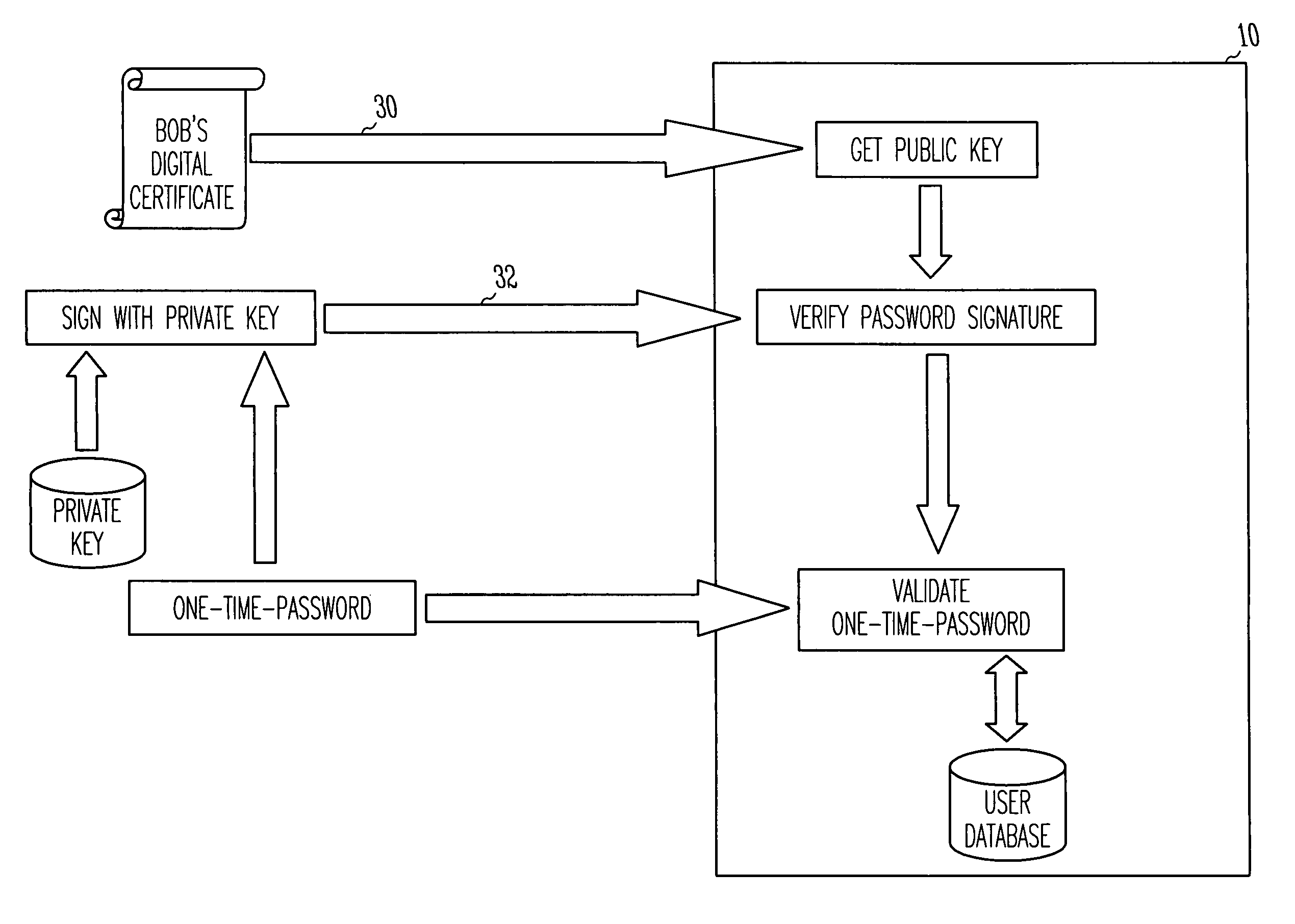
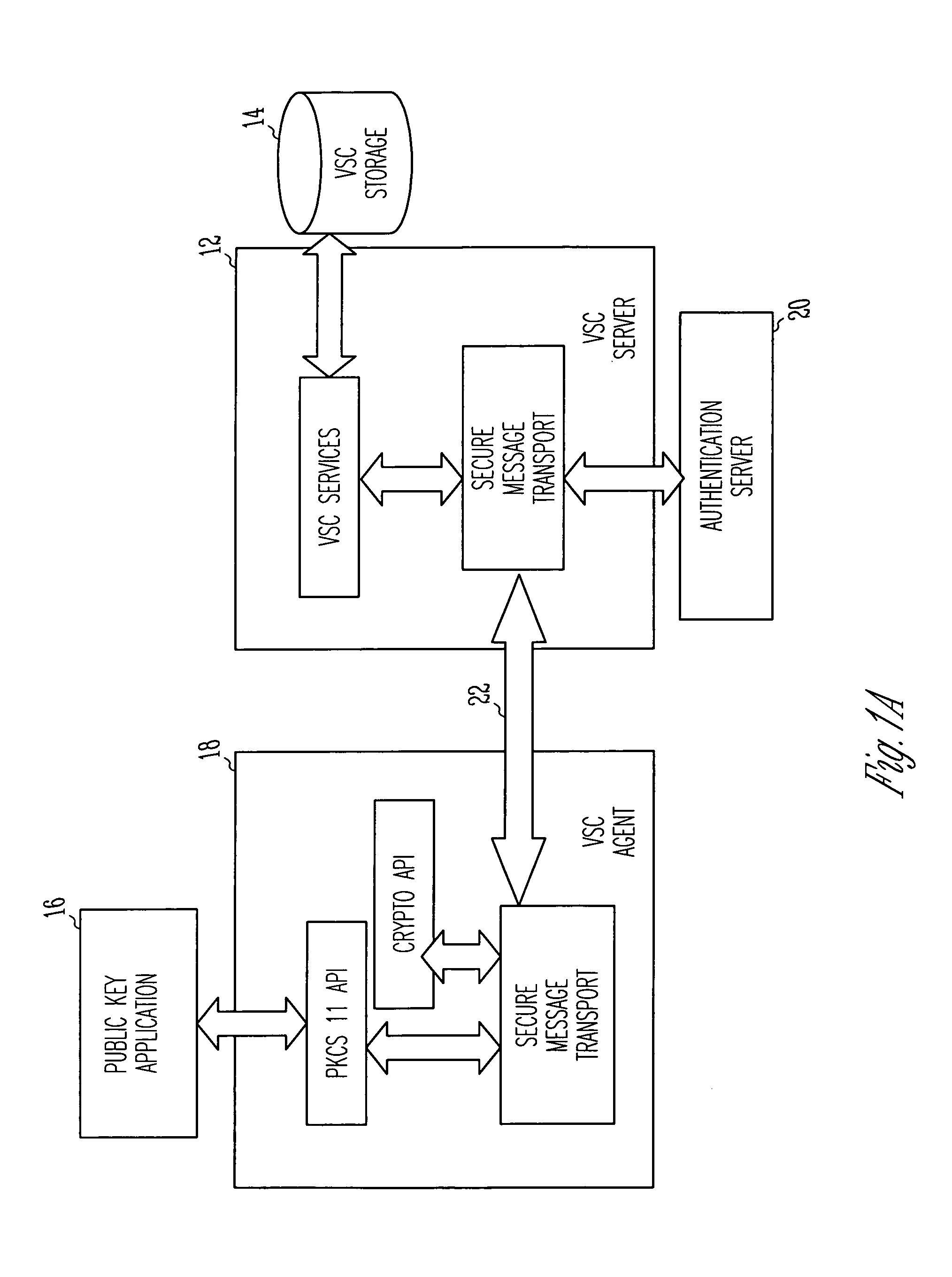
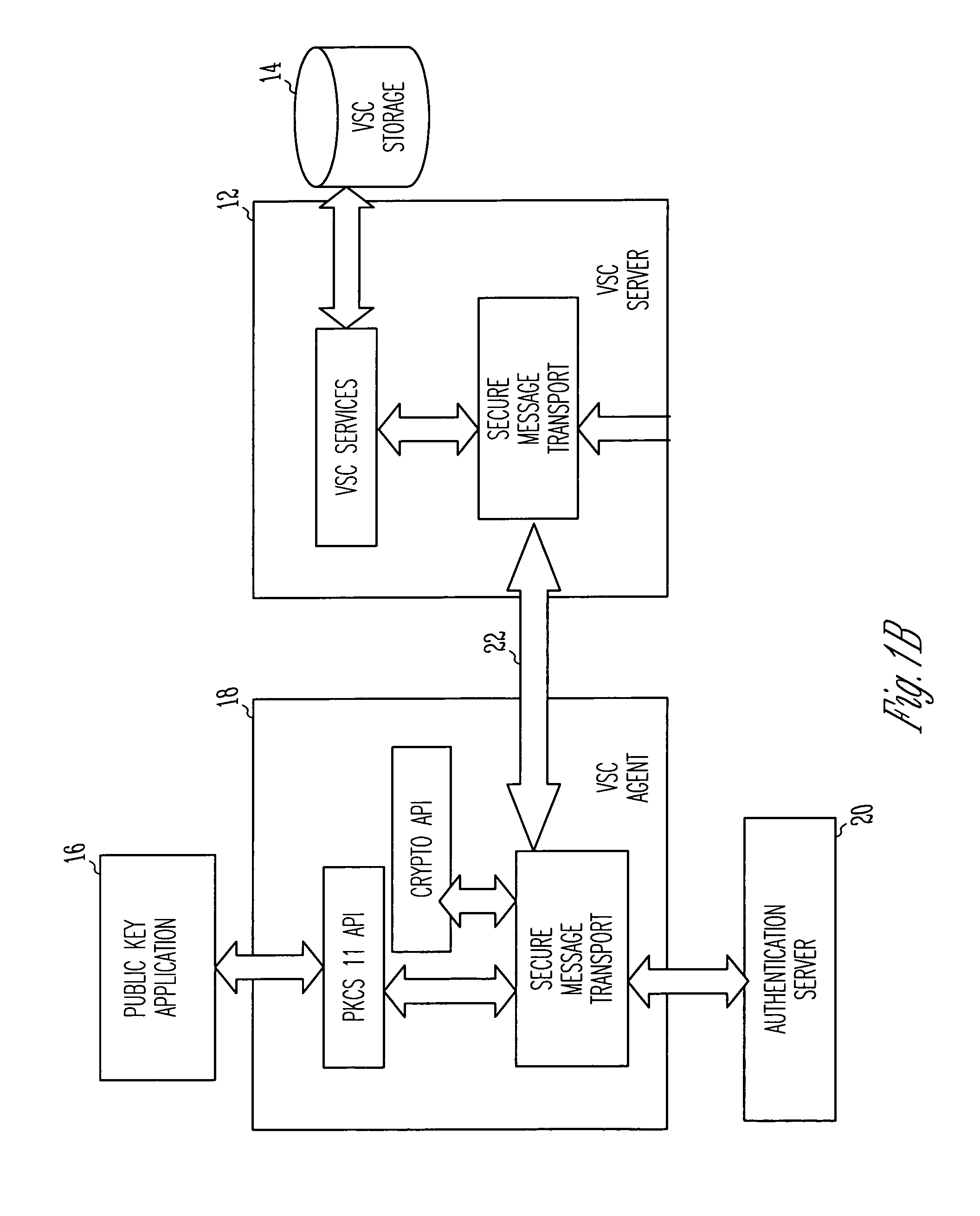
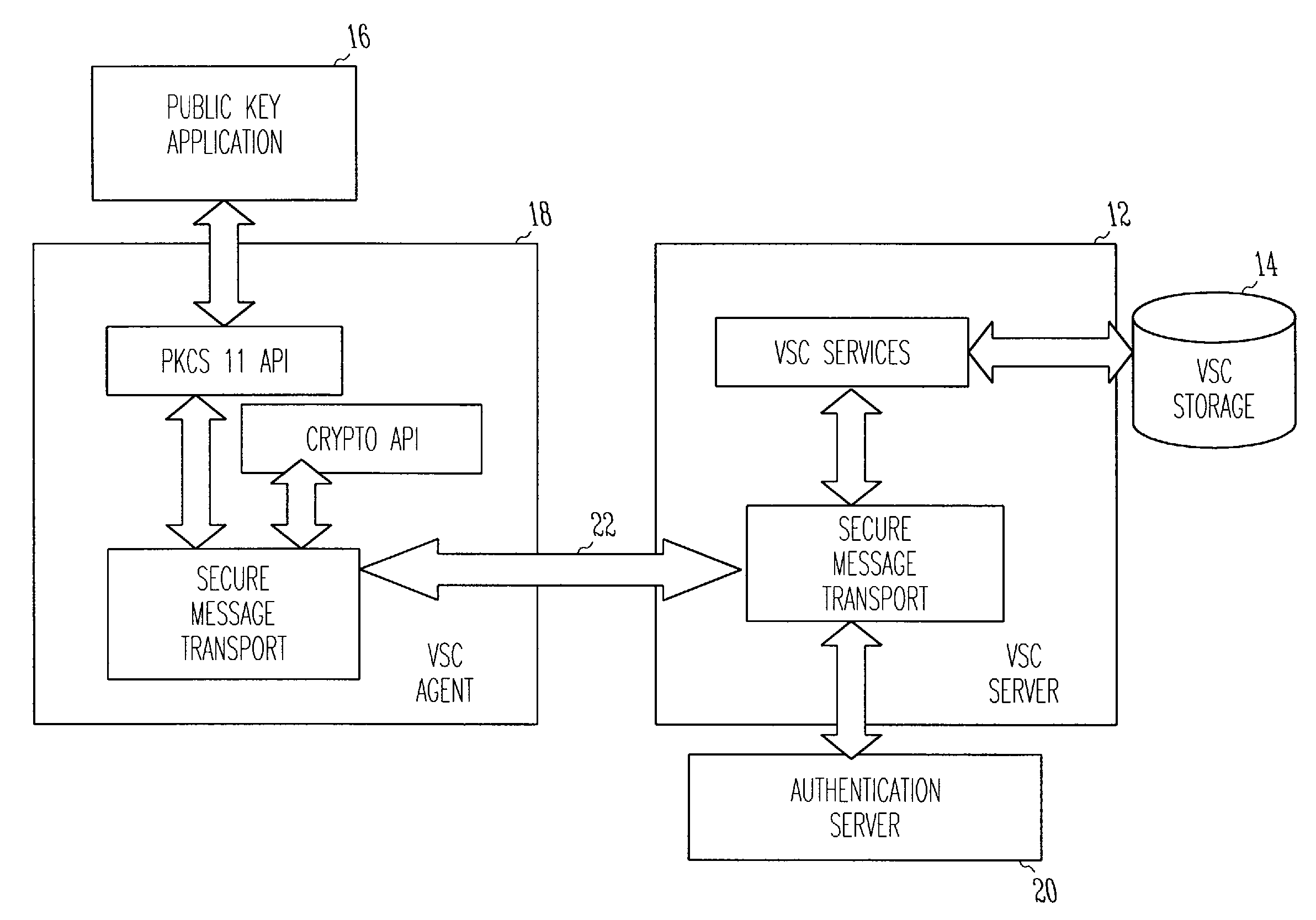
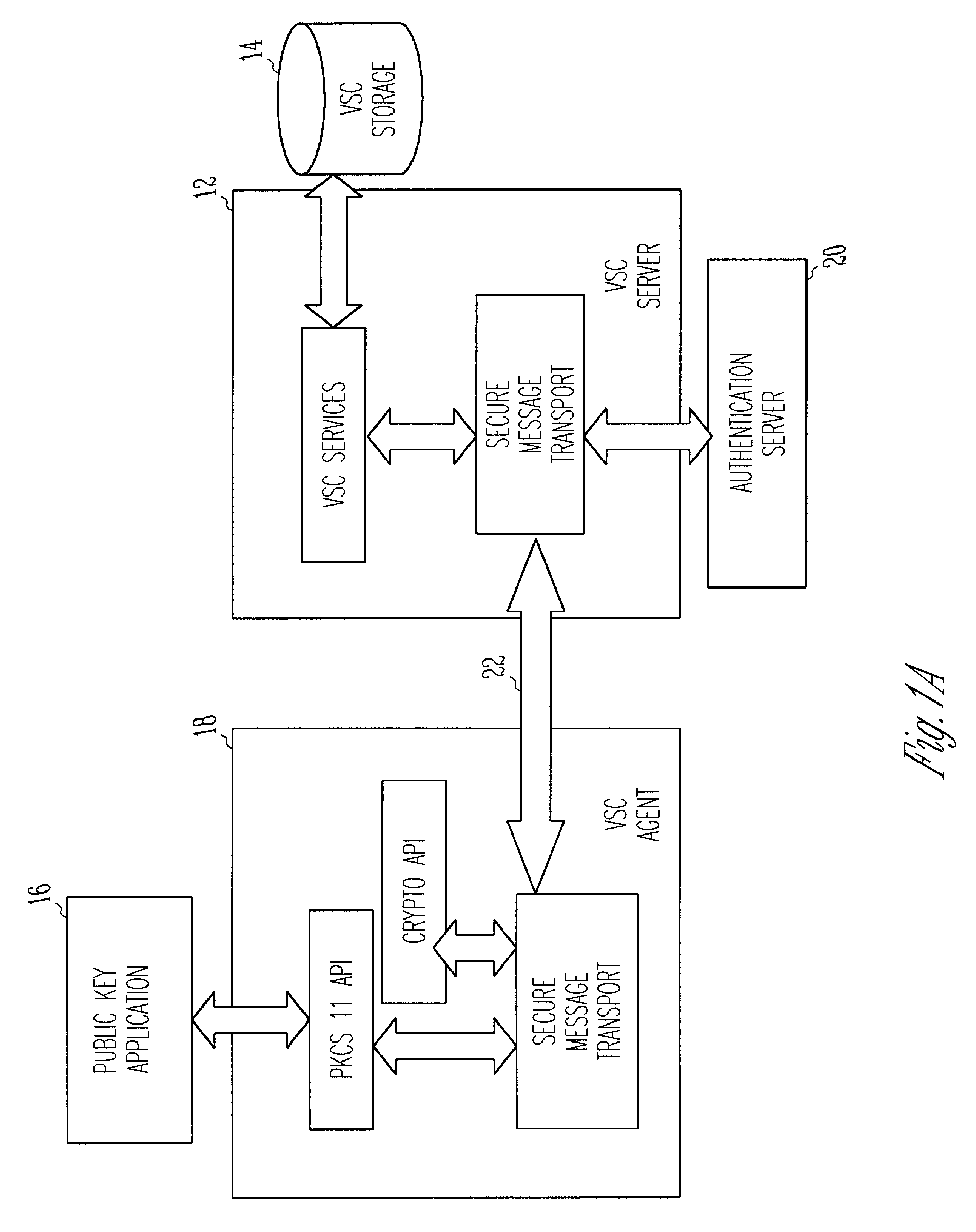
Virtual smart card system and method
InactiveUS7085931B1Digital data processing detailsUser identity/authority verificationPublic key authenticationComputerized system
A public key authentication system and method for use in a computer system having a plurality of users. The system includes a virtual smart card server, storage connected to the virtual smart card server, and a virtual smart card agent connected to the virtual smart card server. The storage includes a plurality of virtual smart cards, wherein each virtual smart card is associated with a user and wherein each smart card includes a private key. The virtual smart card agent authenticates the user and accesses the authenticated user's virtual smart card to obtain the user's private key.
Owner:SAFENET DATA SECURITY ISRAEL
Authentication method to enable servers using public key authentication to obtain user-delegated tickets
InactiveUS6643774B1Key distribution for secure communicationData taking preventionPublic key authenticationDelegation model
A method, system, and computer-readable code for delegating authority in a public key authentication environment from a client to a server machine or process, in order that the server machine or process can then securely access resources and securely perform tasks on behalf of the client. The authority is delegated by obtaining tickets (or other equivalent representation of user credentials) from a private key system, such as the Kerberos system, where the tickets identify a user's access rights or privileges. The present invention provides several alternative techniques with which this delegation model can be implemented. In these techniques, the client does not directly access the private key system.
Owner:IBM CORP
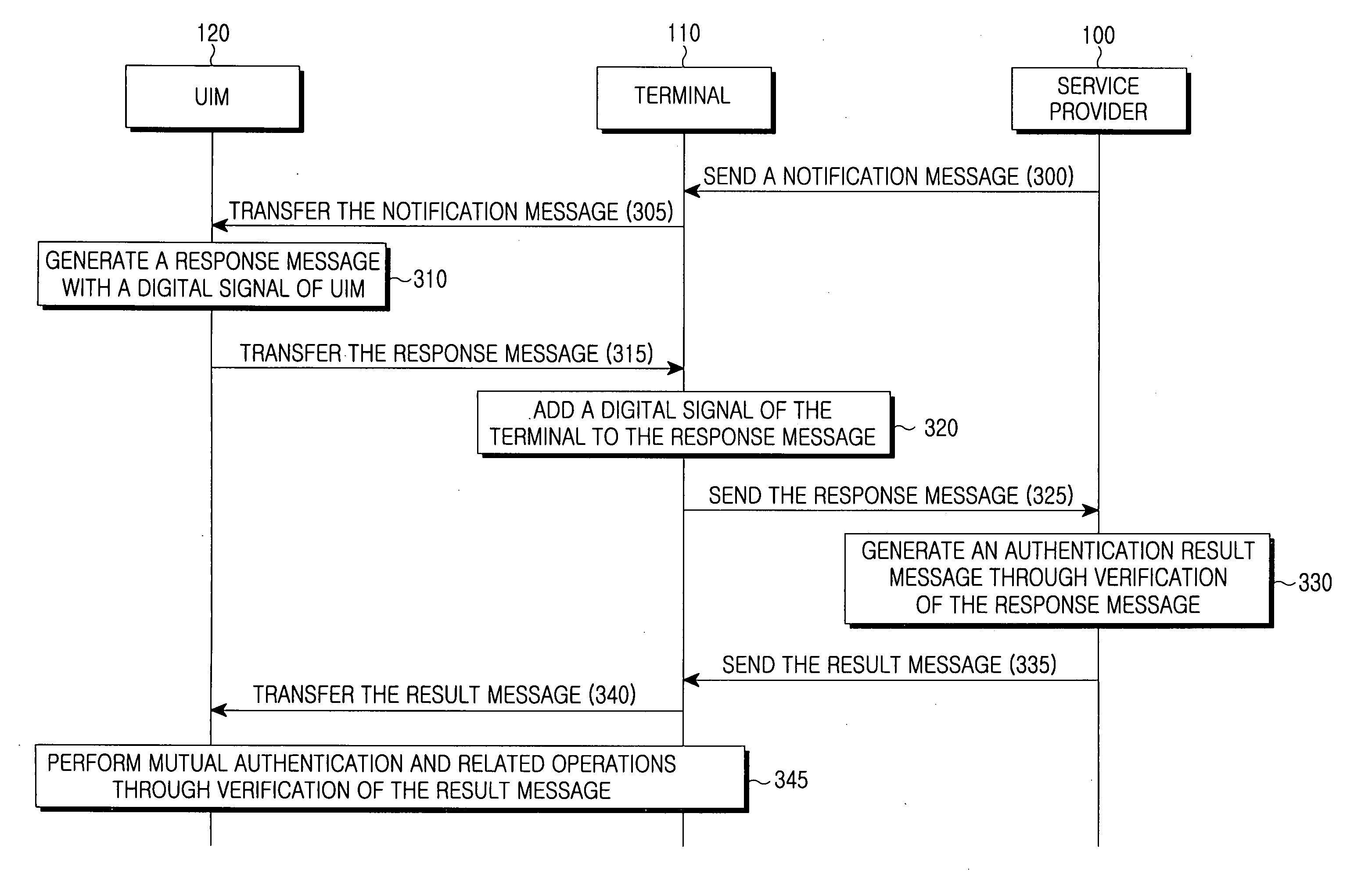
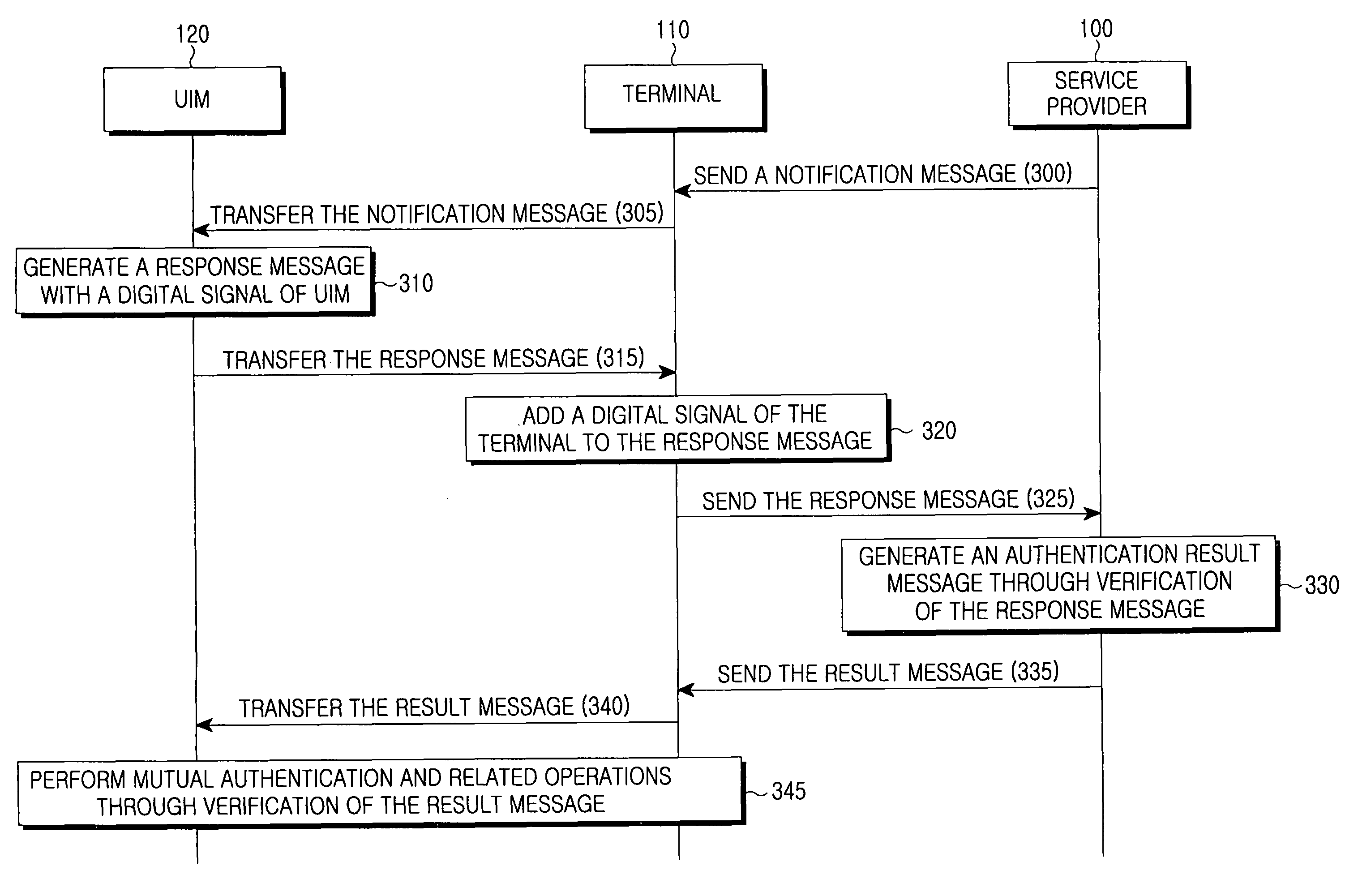
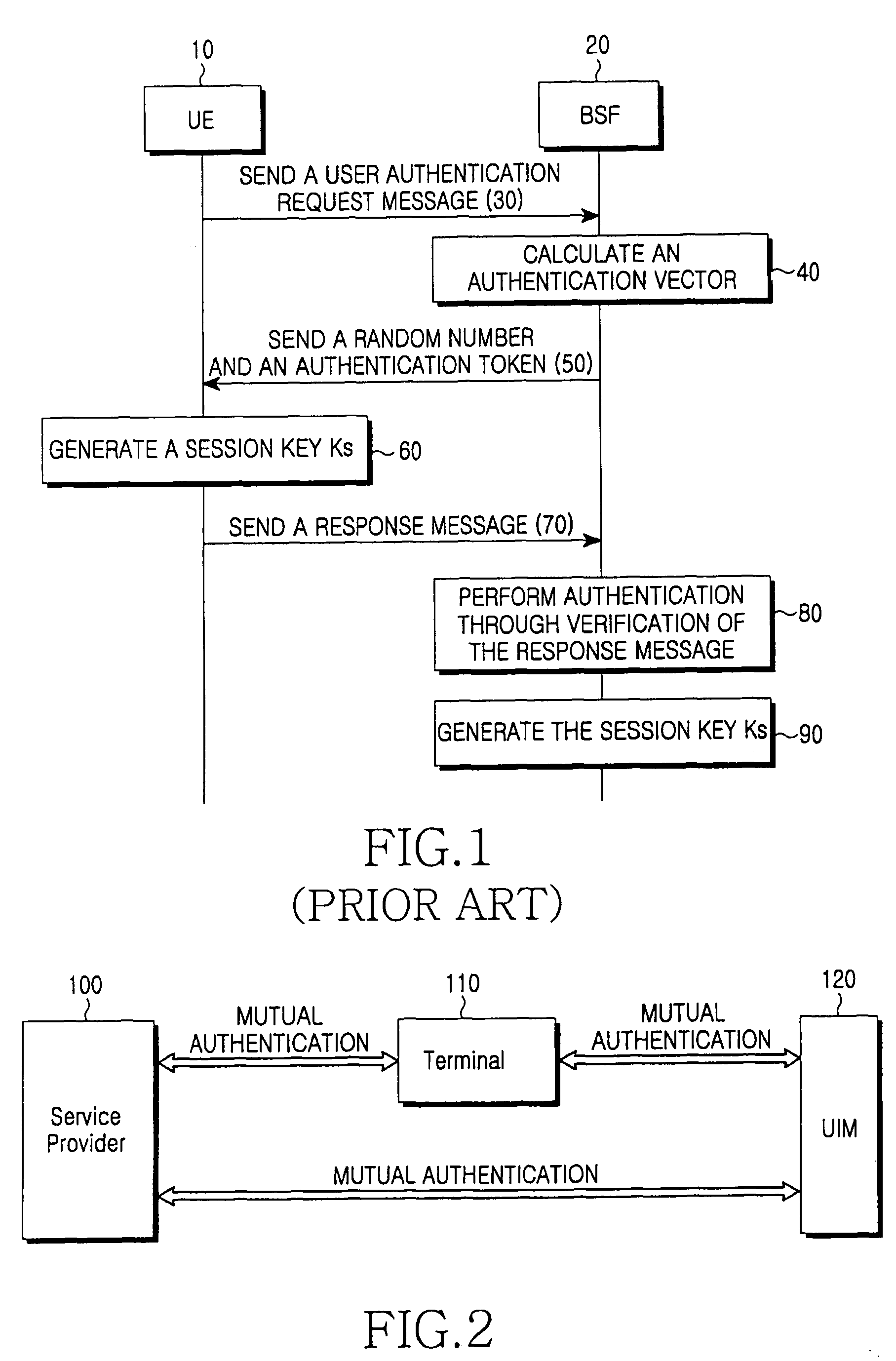
Method for inclusive authentication and management of service provider, terminal and user identity module, and system and terminal device using the method
ActiveUS20060281442A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsPublic key authenticationNetworked system
Disclosed are a method and a system for mutual inclusive authentication between a service provider, a terminal and a user identity module. The authentication system is configured in a structure that can interact with a public key infrastructure of the current network security environment and can be independently used in a specific network system. The inclusive authentication method is divided into public key authentication and symmetric key authentication. Mutual authentication can be made between a service provider, a terminal and a user identity module using any of the two authentication schemes. Then a user can access content on any terminal device using the content license based on the user's identity.
Owner:SAMSUNG ELECTRONICS CO LTD
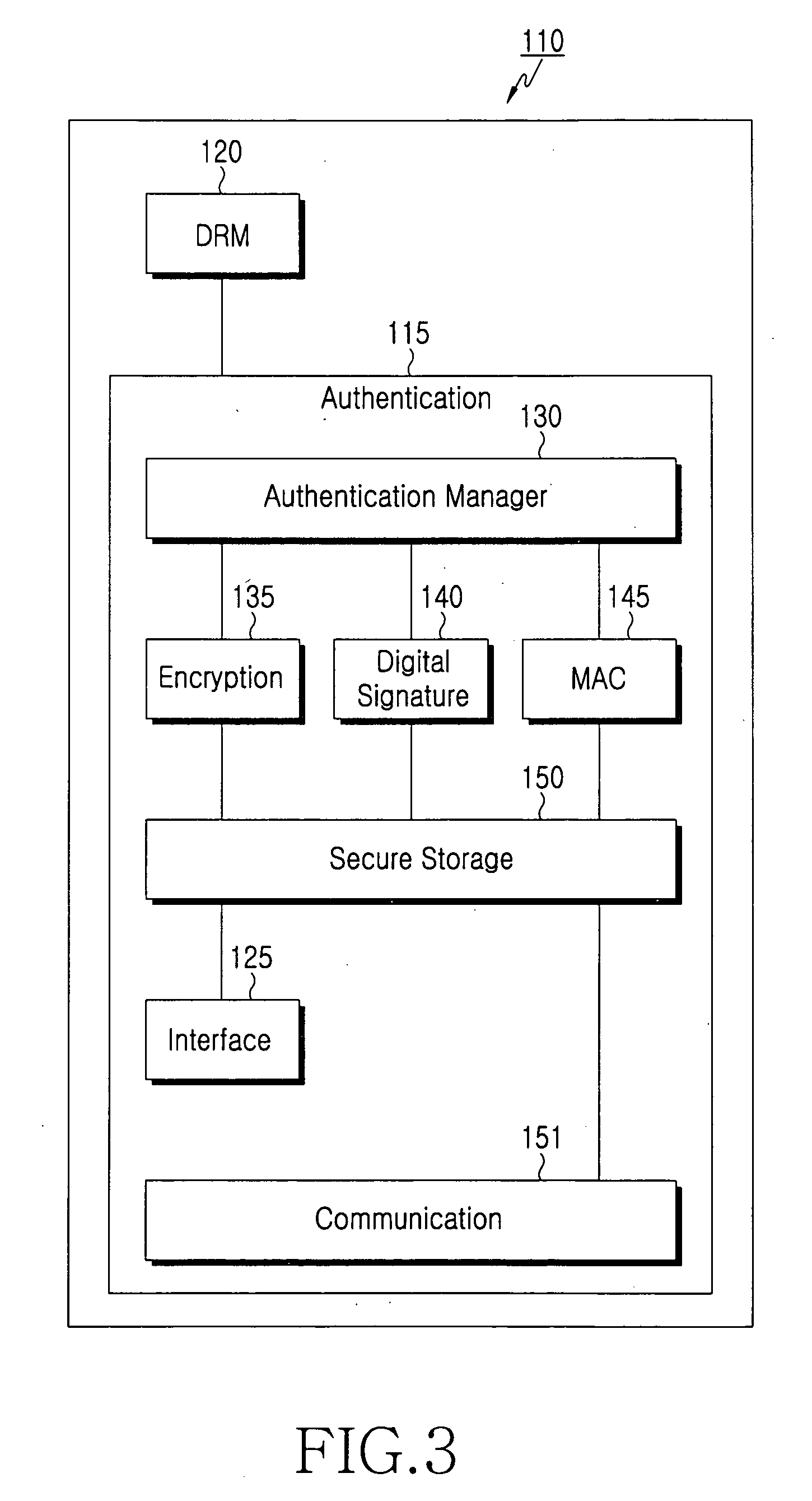
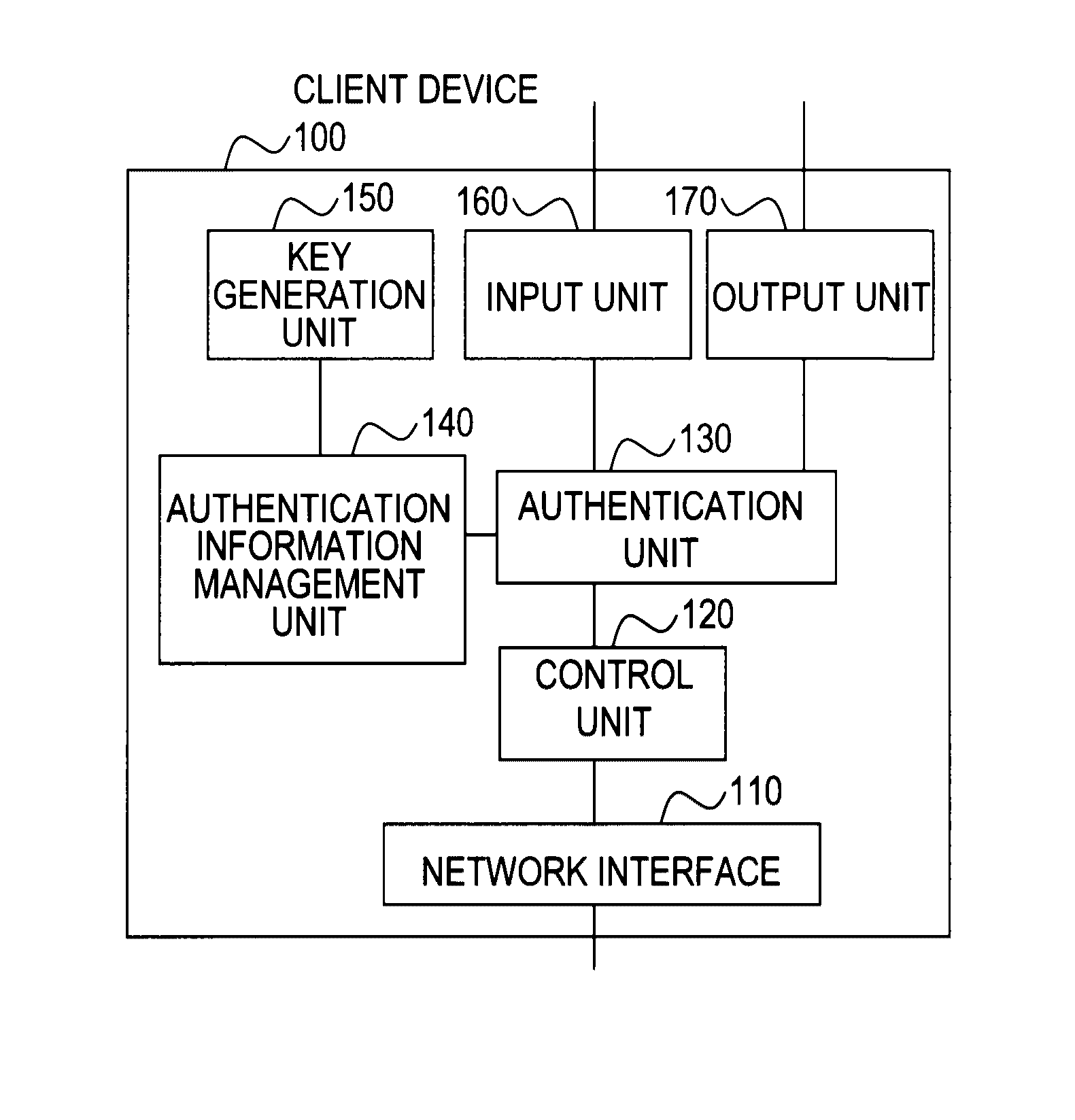
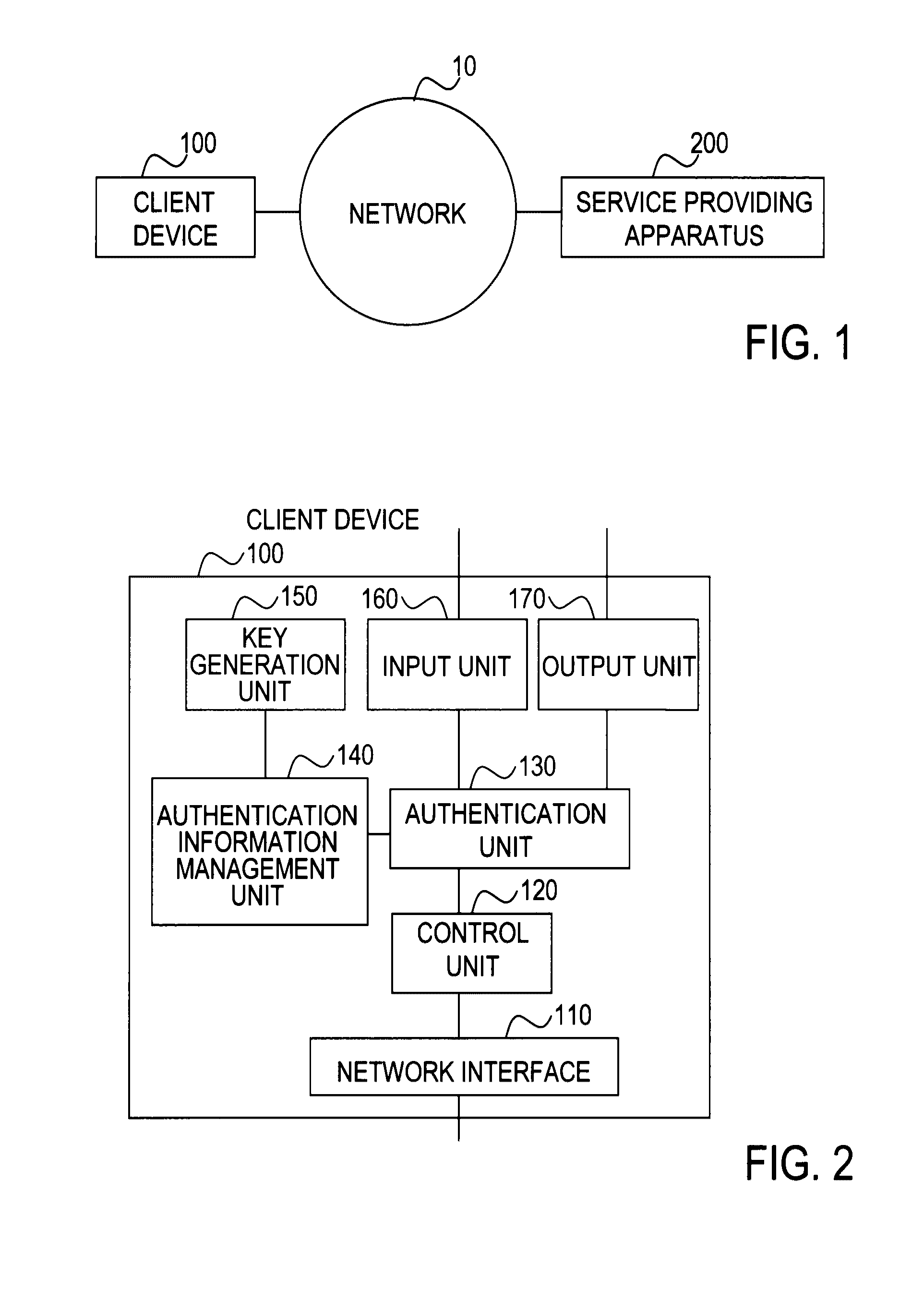
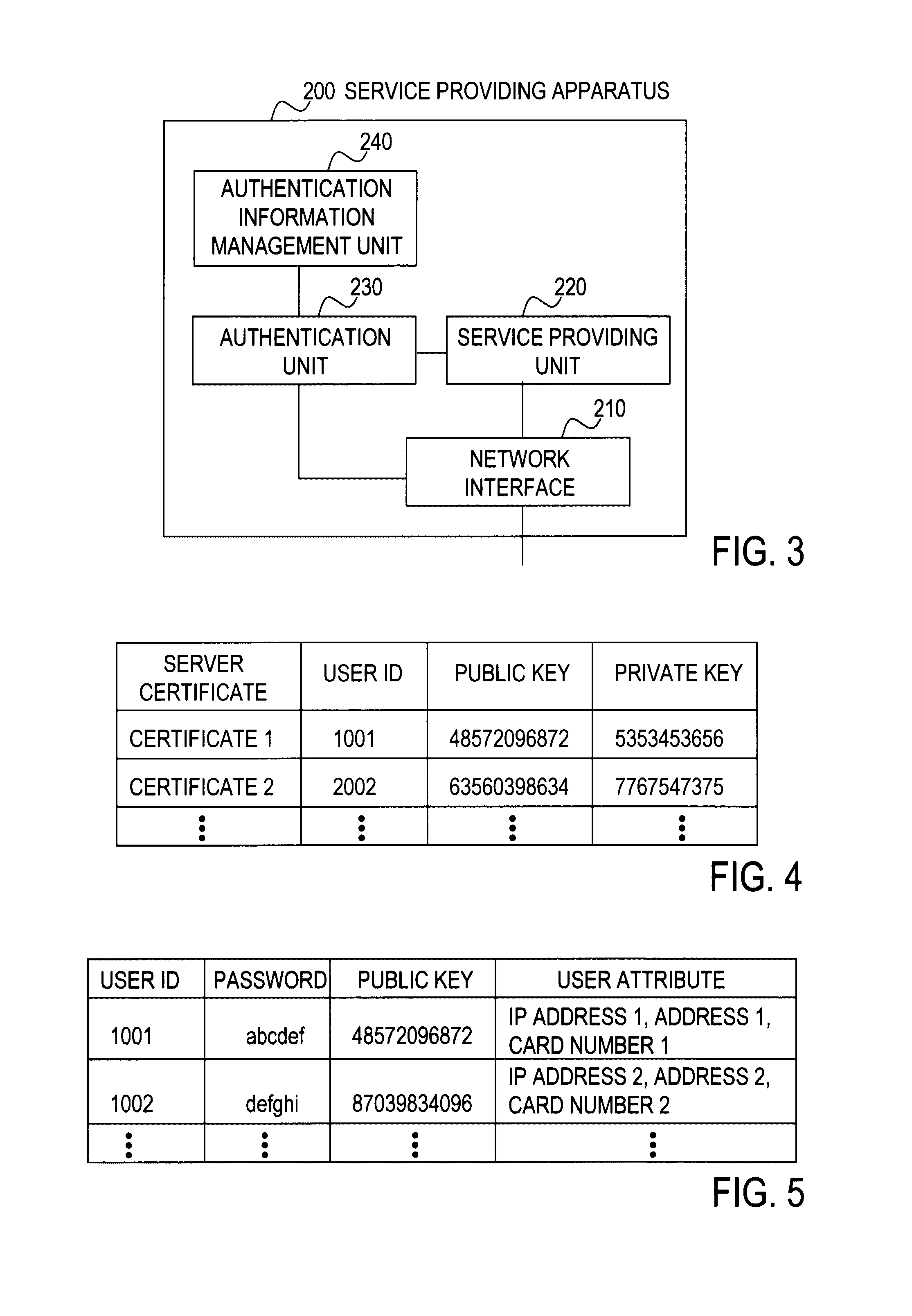
Client device, key device, service providing apparatus, user authentication system, user authentication method, program, and recording medium
ActiveUS20100088519A1Easy to switchEasy to replaceEncryption apparatus with shift registers/memoriesUser identity/authority verificationPublic key authenticationValidation methods
In a user authentication system according to the present invention, at user registration, a client device obtains a signature for a user ID, a password, and a public key by using a private key corresponding to the public key, and sends user information that includes the signature and the above-described information items to a service providing apparatus. The service providing apparatus verifies the signature by using the public key and stores the user information by which the password and the public key are associated with each other. When a request for a service is made, the client device allows authentication processing by sending to the service providing apparatus an authentication response that includes the user ID together with password authentication information, a signature for a challenge sent from the service providing apparatus, or a signature for the password and the challenge, irrespective of whether the authentication method for the service is password authentication, public key authentication, or public-key-and-password combination authentication.
Owner:NIPPON TELEGRAPH & TELEPHONE CORP
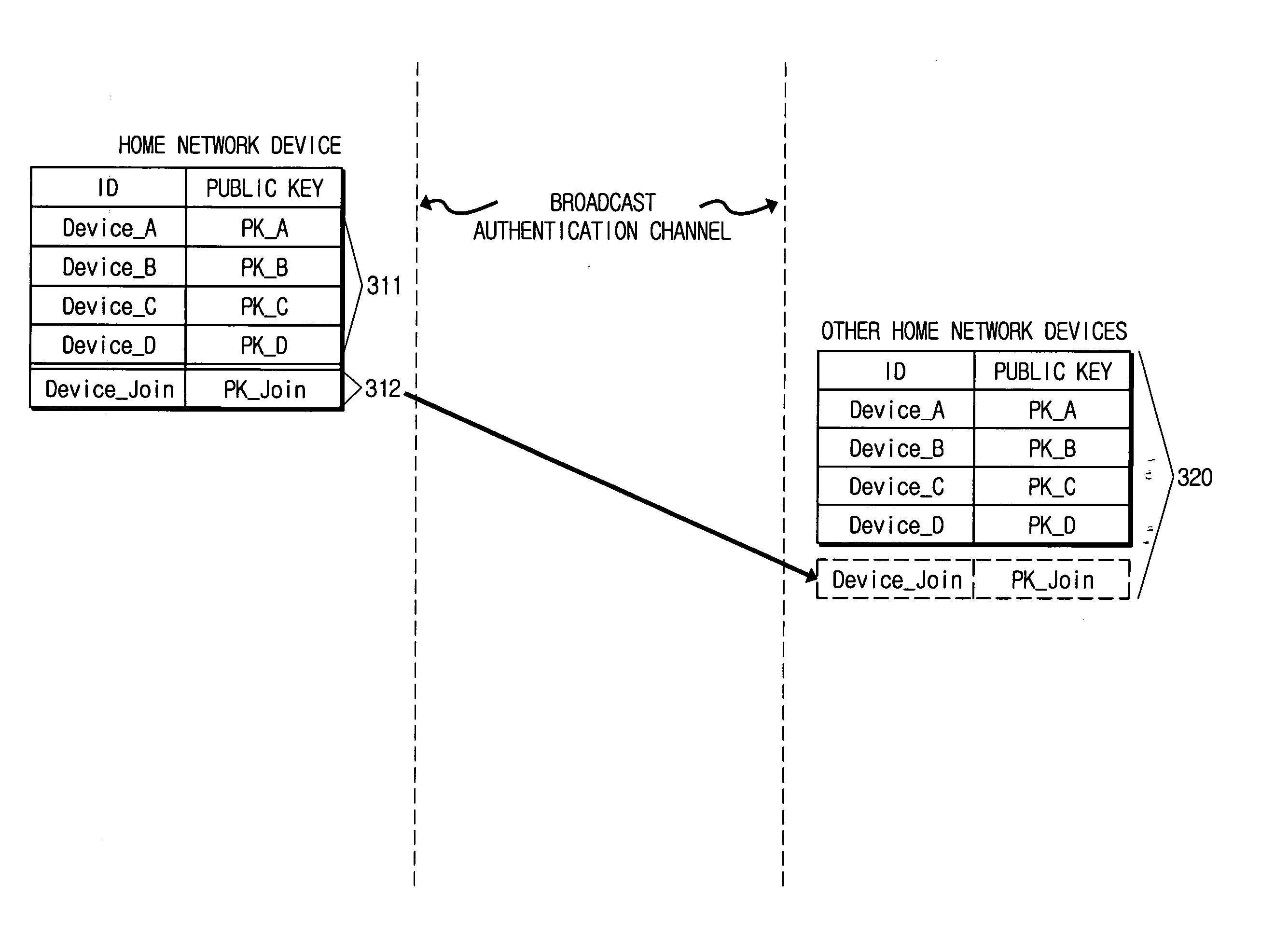
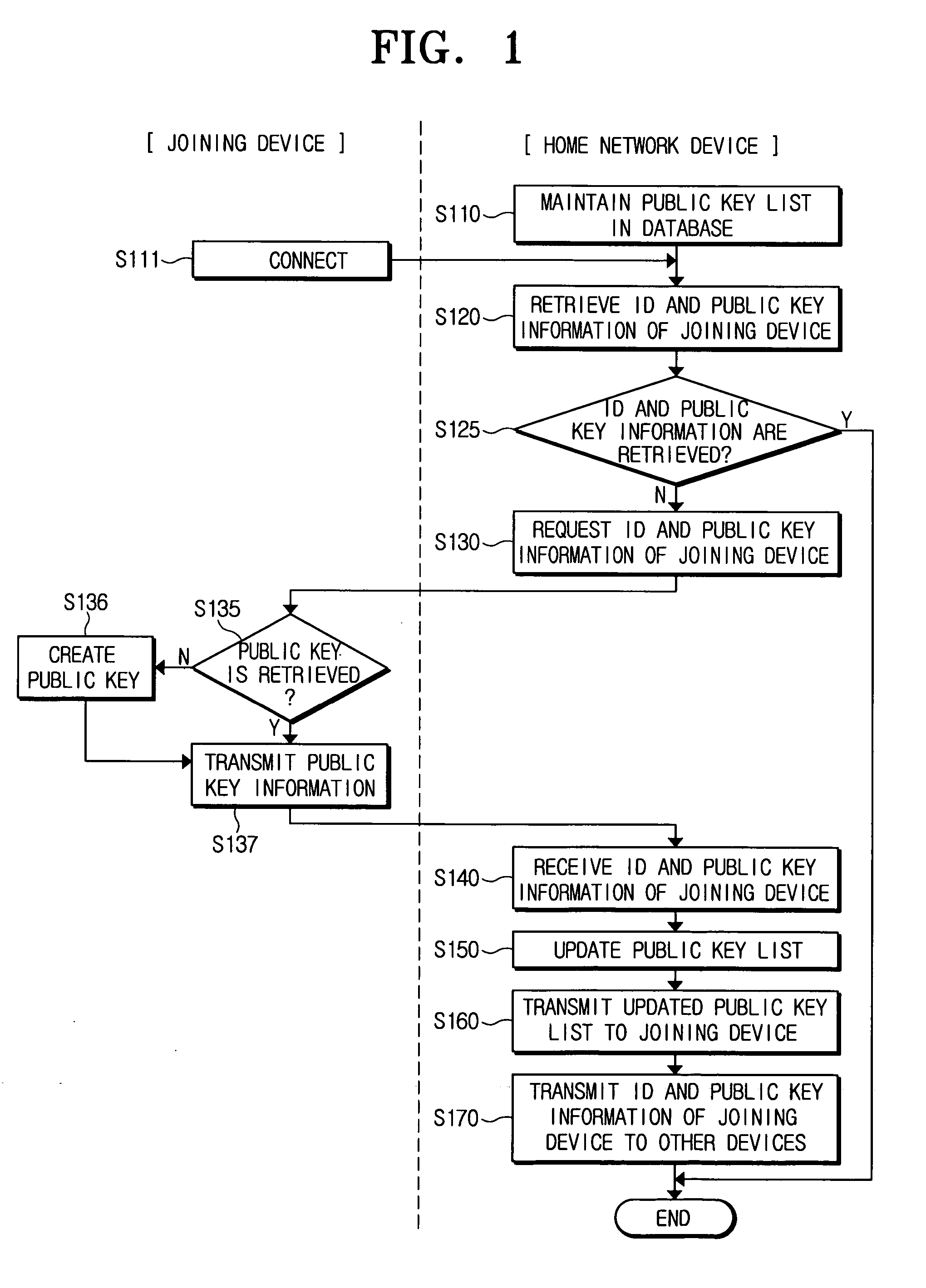
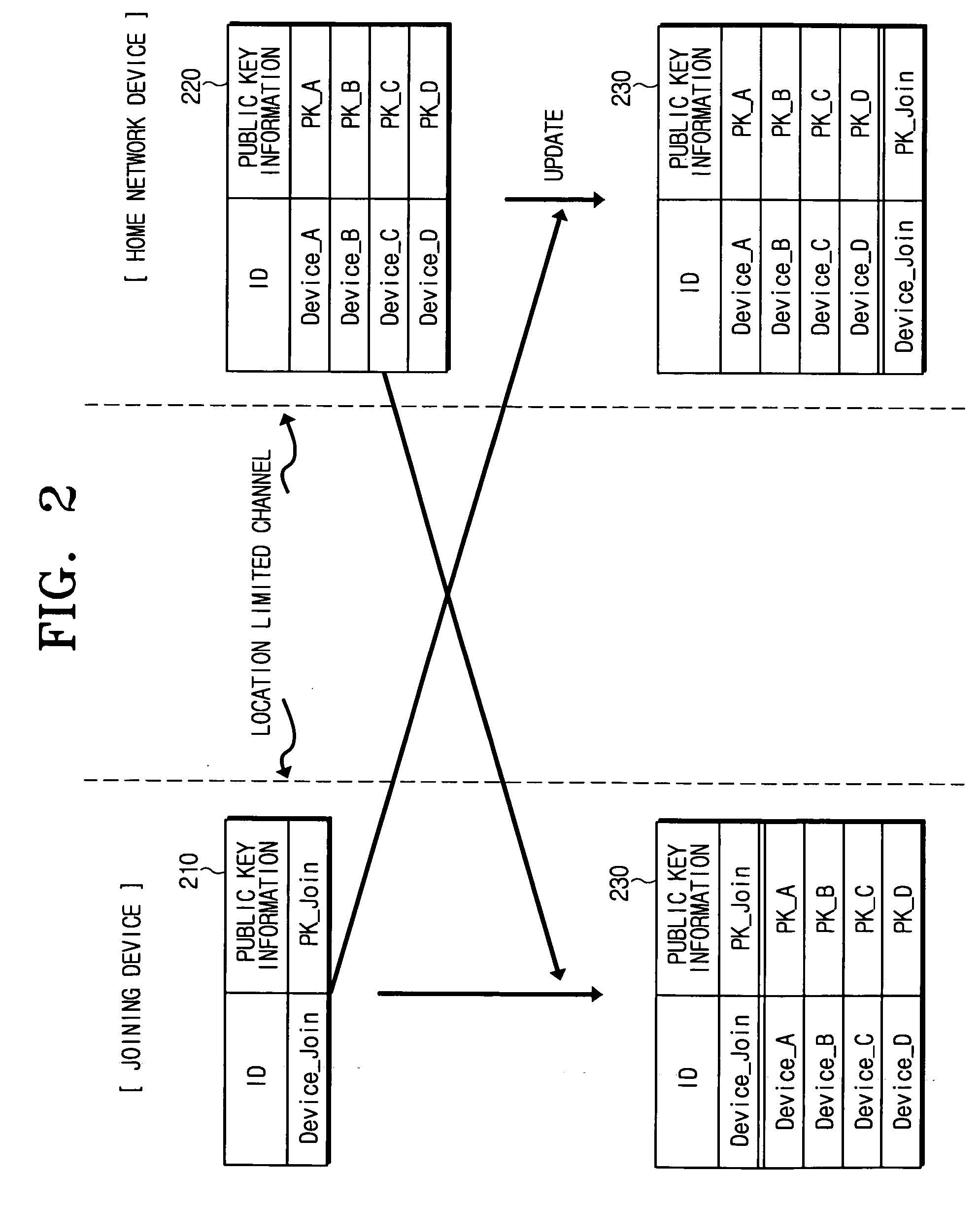
Method and system for public key authentication of a device in home network
InactiveUS20060150241A1Key distribution for secure communicationRandom number generatorsPublic key authenticationNew device
A method and system for authenticating a home network device in a home network. According to the device authentication method, a public key list that includes an ID and public key information corresponding to the ID of home network devices is maintained. When an access of a joining device is received, it is requested to the joining device an ID and information relating to a public key of the joining device. The ID and the public key information are received from the joining device, and the public key list is updated by adding the received ID and public key information. The public key list before updating is transmitted to the joining device. The ID and the public key information of the joining device are transmitted to the home network devices. The joining device is a new device that joins a home network.
Owner:SAMSUNG ELECTRONICS CO LTD
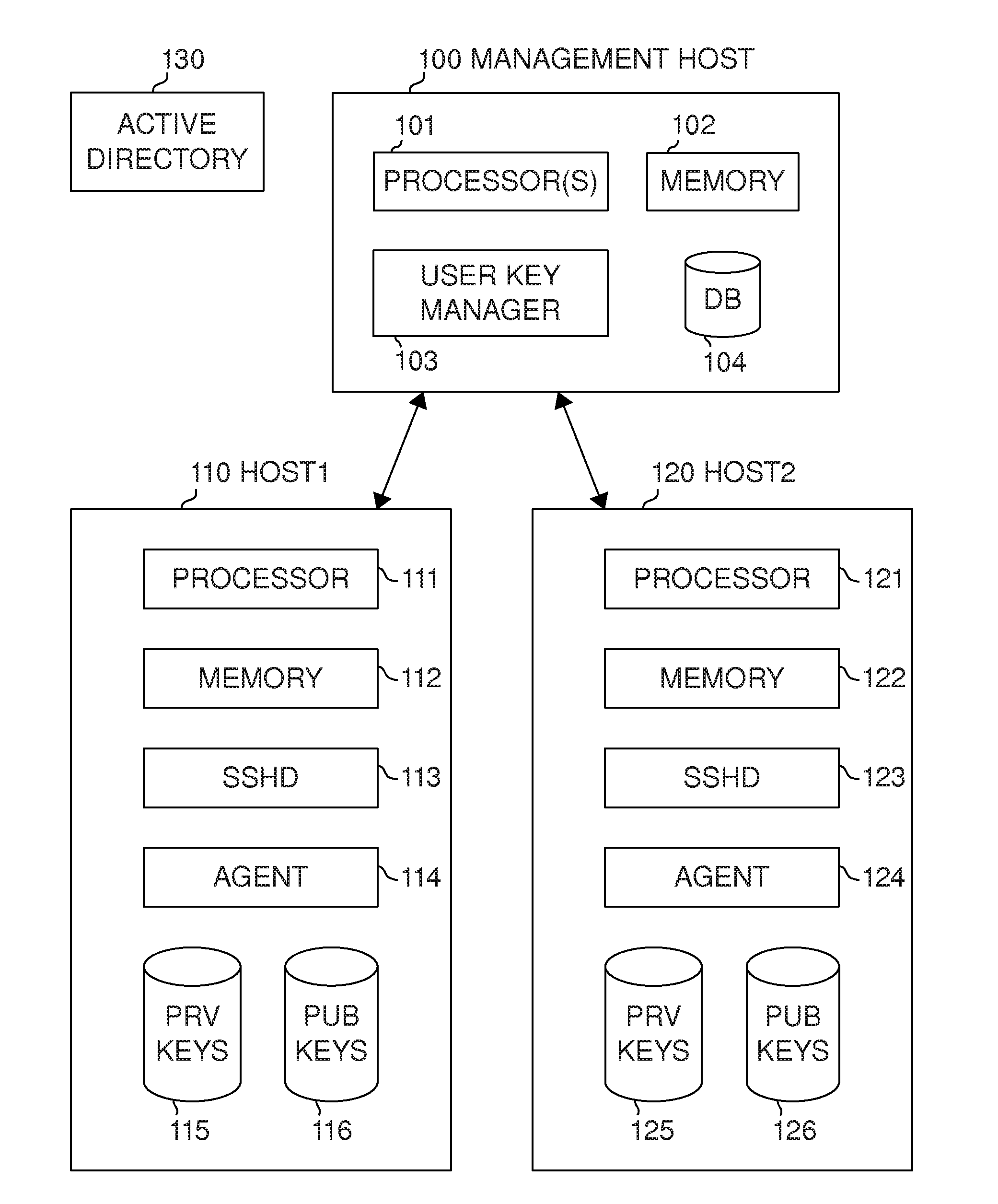
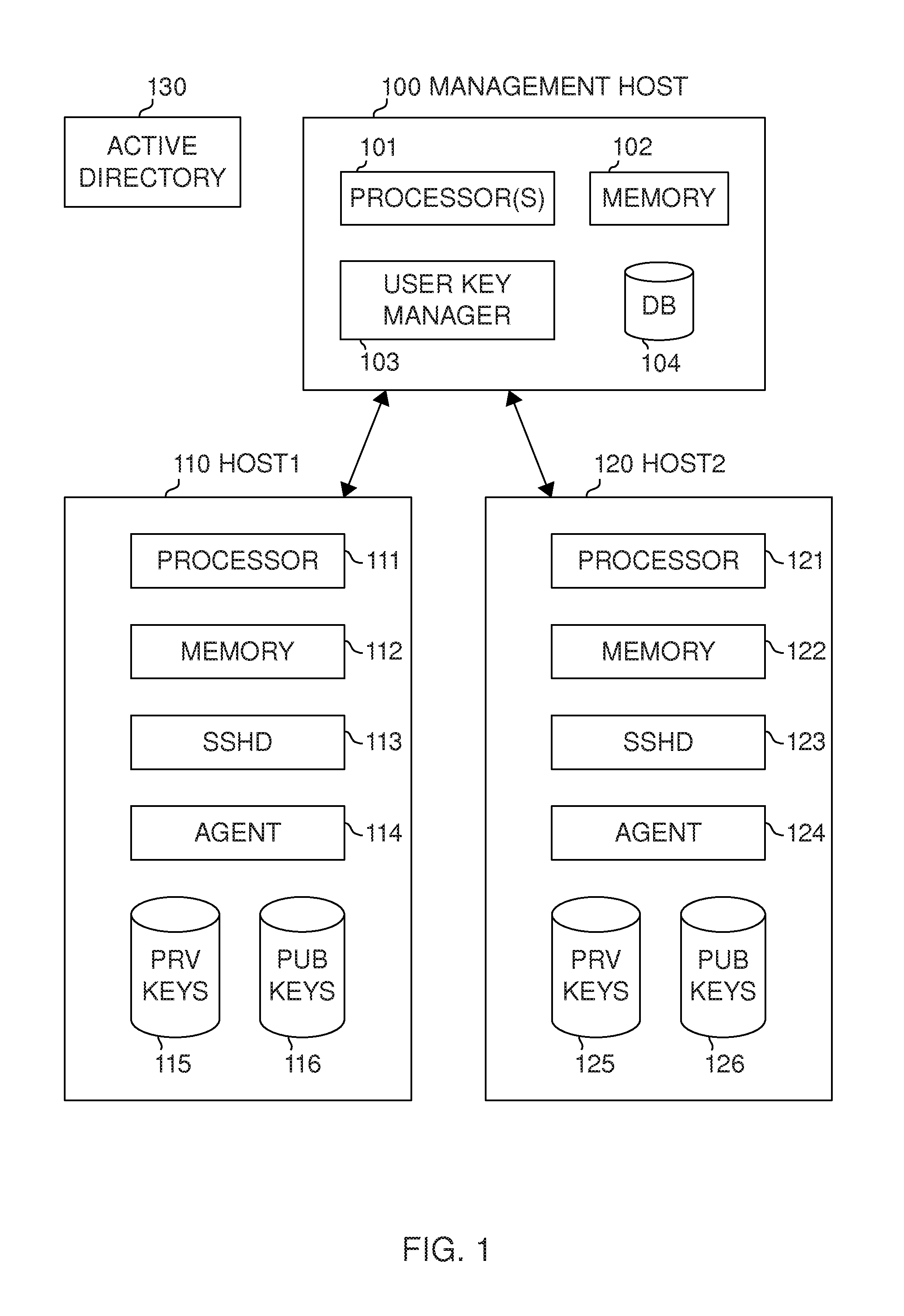
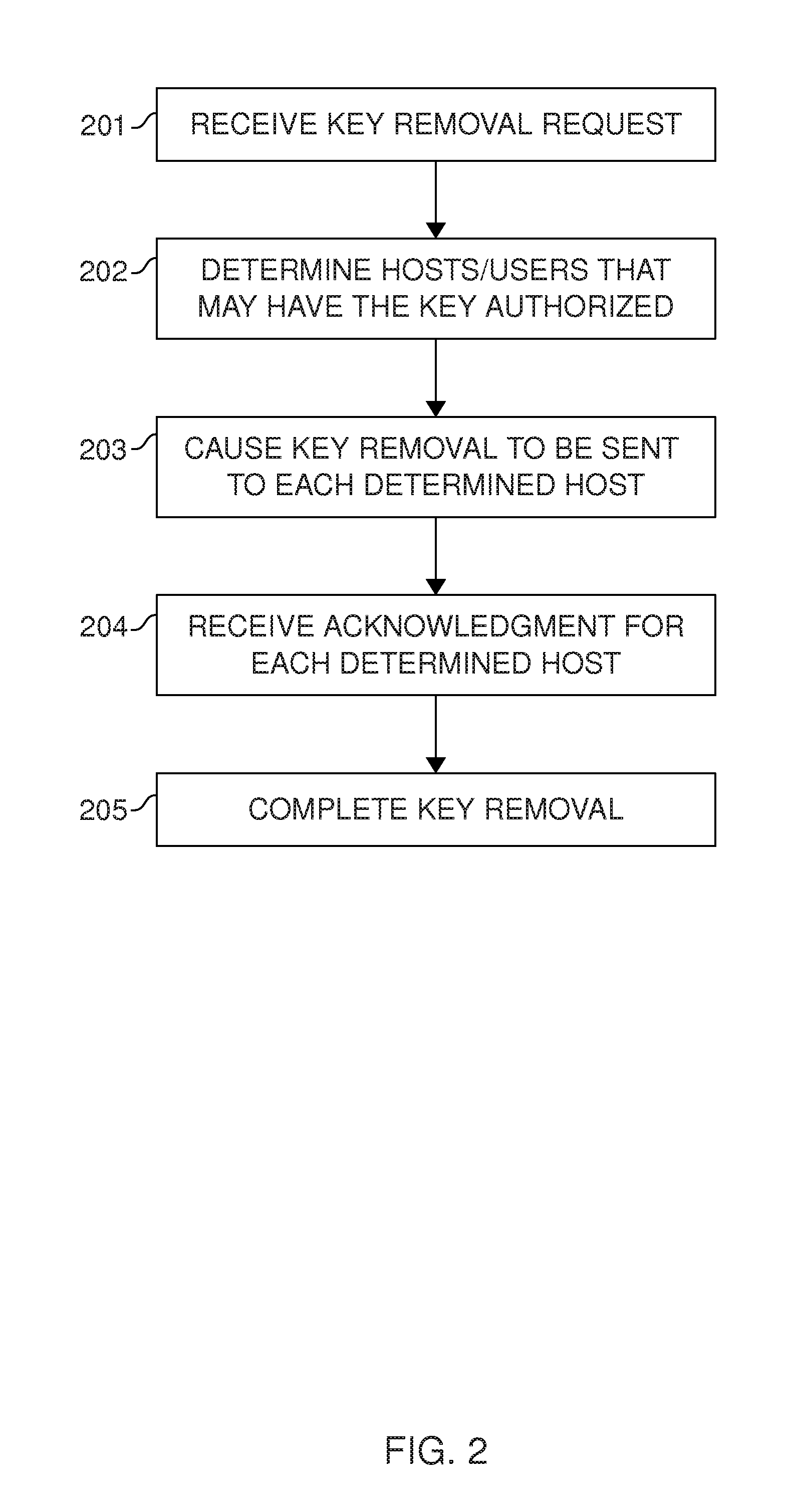
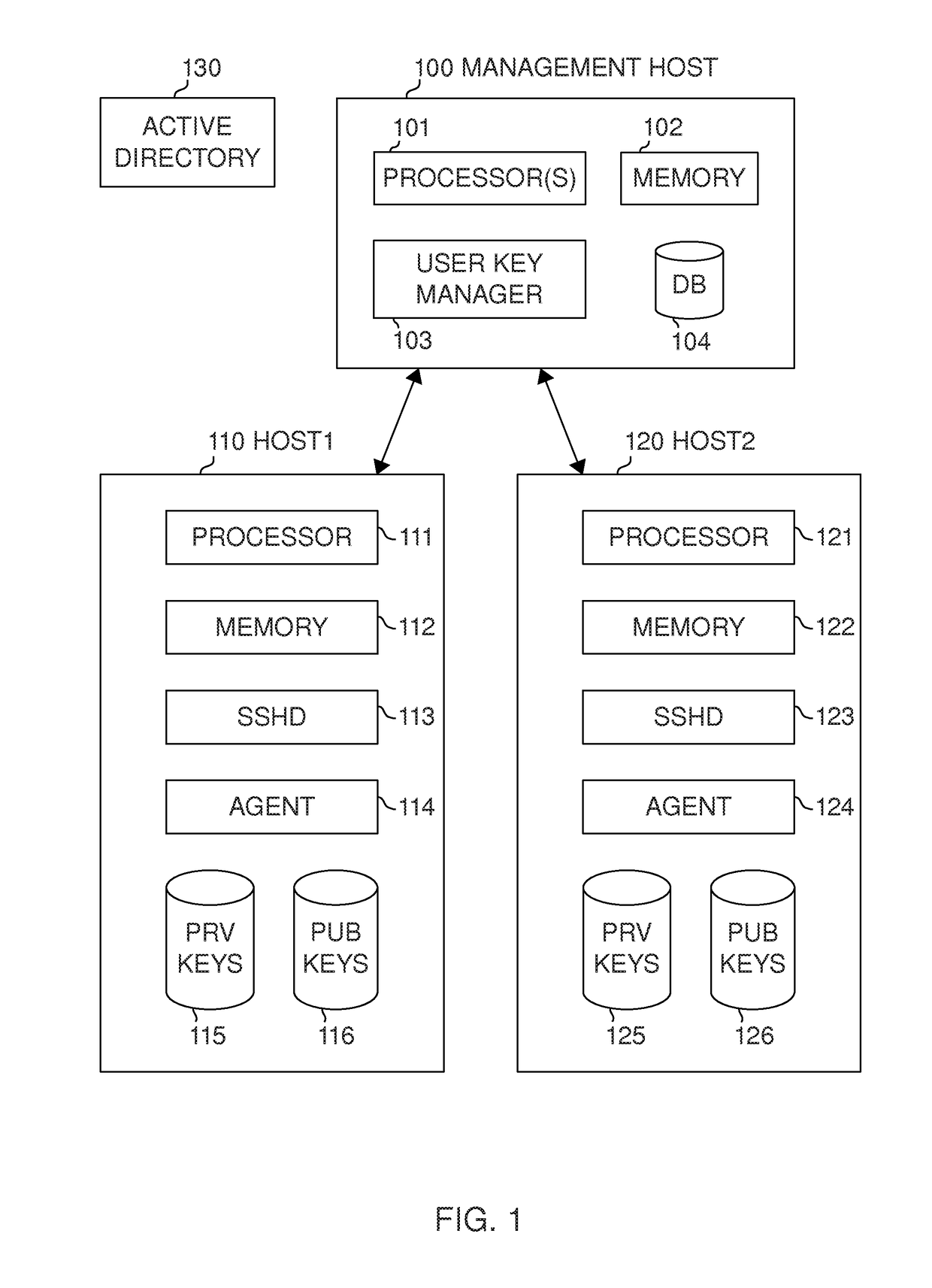
User key management for the Secure Shell (SSH)
ActiveUS20130117554A1Low costImprove securityKey distribution for secure communicationPublic key authenticationSecure Shell
Management of user keys for public key authentication using the SSH in large SSH deployments is automated by deploying a management system in the environment, discovering SSH identity keys and authorized keys, analyzing authorized connections between user accounts, and automatically managing the authorized connections and the key pairs used for authentication.
Owner:SSH COMMUNICATIONS SECURITY
Method for cross-isomerism domain identity authentication and session key negotiation based on access authorization ticket
ActiveCN103780618AHigh security requirementsStrong computing powerUser identity/authority verificationPublic key authenticationKey-agreement protocol
The invention provides a method for cross-isomerism domain identity authentication and session key negotiation based on an access authorization ticket. The method mainly comprises the steps that firstly, a first-level trust relationship is established between a CA of a PKI domain and an AS of a Kerberos domain through a distributed trust model based on a public key authentication mechanism; on the basis, the authorization ticket allowing an outer-domain user to have access to resources of the domain is generated and distributed by the CA or the AS united with a TGS, and through design of a two-way cross-domain authentication and key negotiation protocol based on a symmetric key cryptosystem, a second-level trust relationship allowing the outer-domain user to have access to the resources of the domain is established. On the premise that the requirements for safety of the levels are satisfied, the calculated amount and the communication traffic of a terminal are effectively reduced, public key encryption and decryption operations of a Kerberos domain terminal can be completely avoided, and the implementation is good in the cross-isomerism domain identity authentication process of a dynamic distributed type system, session key negotiation is completed when identity authentication is conducted, and the protocol efficiency is high.
Owner:四川华创智能科技有限公司
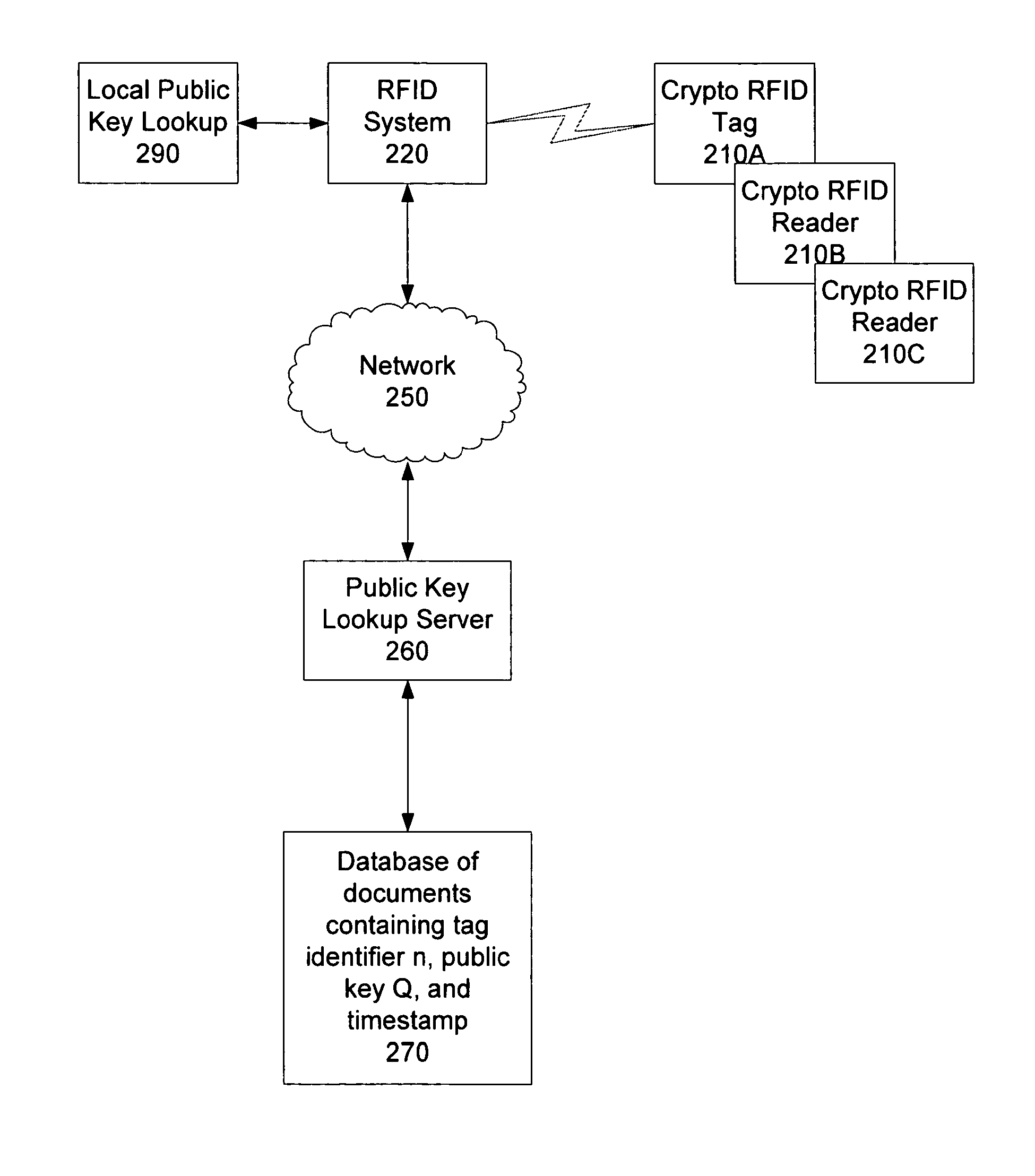
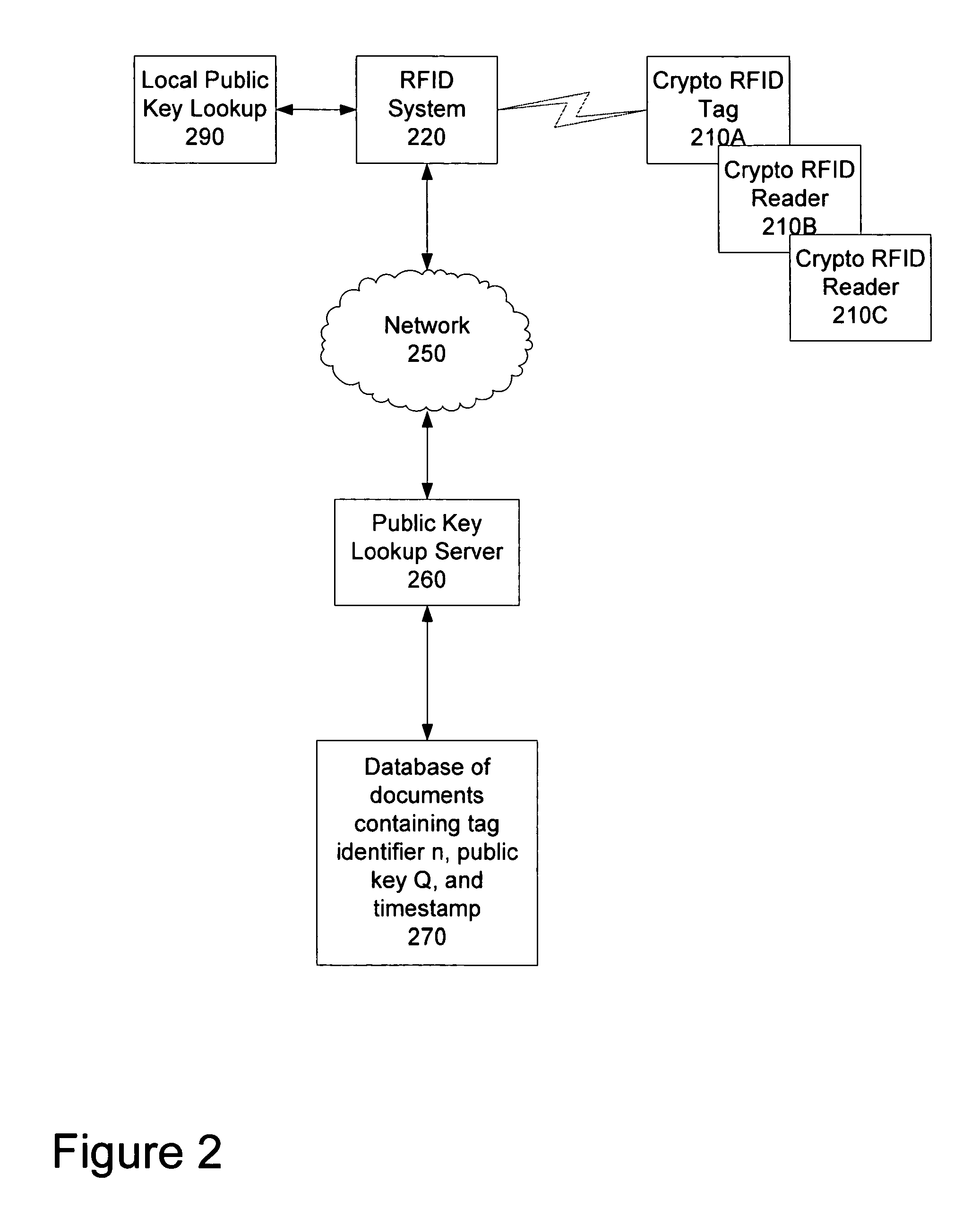
Method and apparatus to provide public key authentication with low complexity devices
A method and apparatus to authenticate limited processing-power systems (LPPS) using elliptic cryptography within a well known elliptic curve E, over a well known finite field F((E(F)). The apparatus comprises a random number generator to choose a random value b, of a similar order of magnitude to the order of E(F). The apparatus further comprises a challenge calculator to calculate a value C=bP and send the challenge to the LPPS, where P is a point on the elliptic curve E(F) which was used as a basis for generating a private key, a, for the LPPS. The apparatus further comprising an RFID reader to receive a challenge response, R=aC=abP from the LPPS, and a crypto calculator to calculate bQ, based on a public key, Q, of the LPPS. The apparatus further comprising a comparison logic to authenticate the LPPS if bQ=aC=abP.
Owner:GEN DIGITAL INC
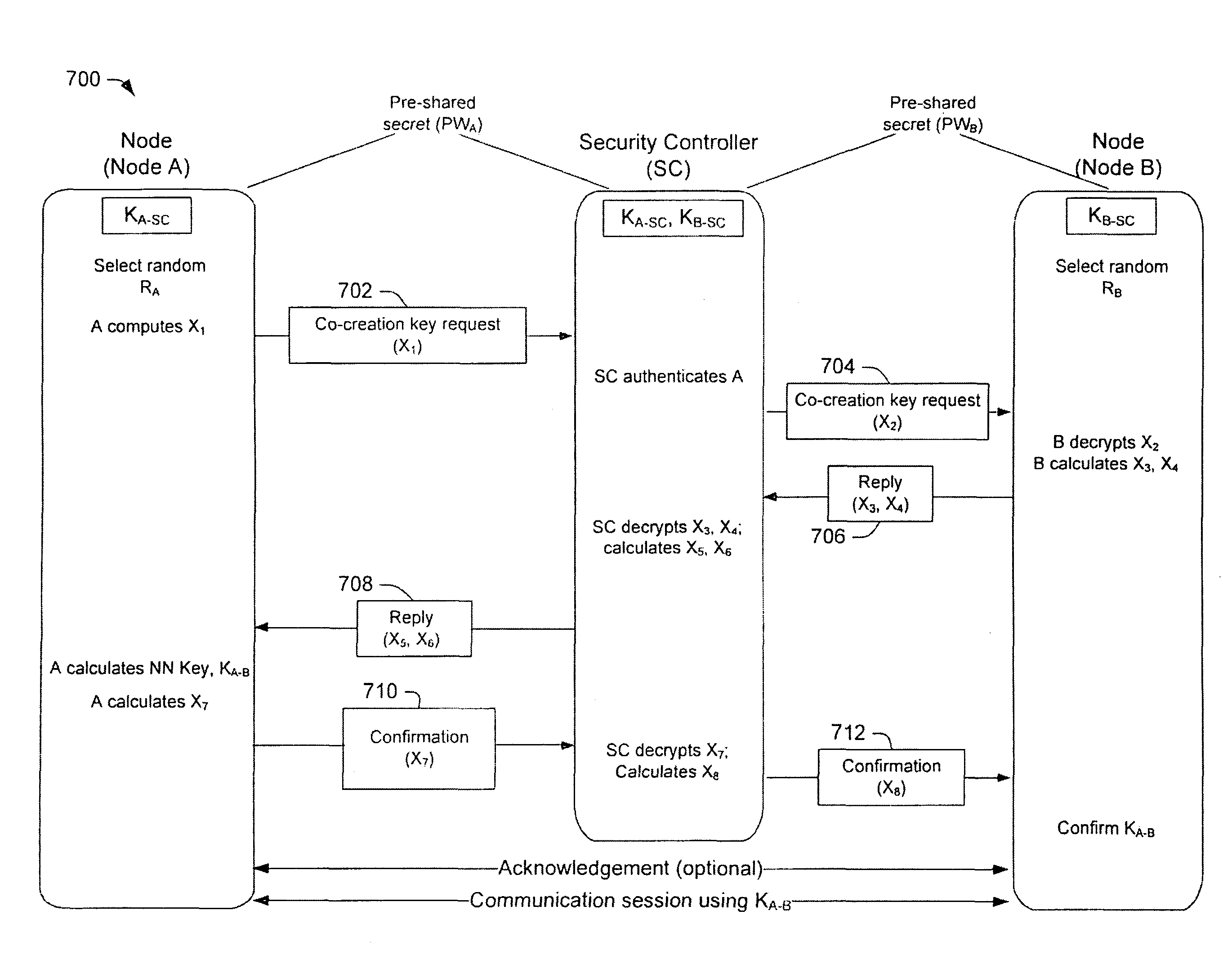
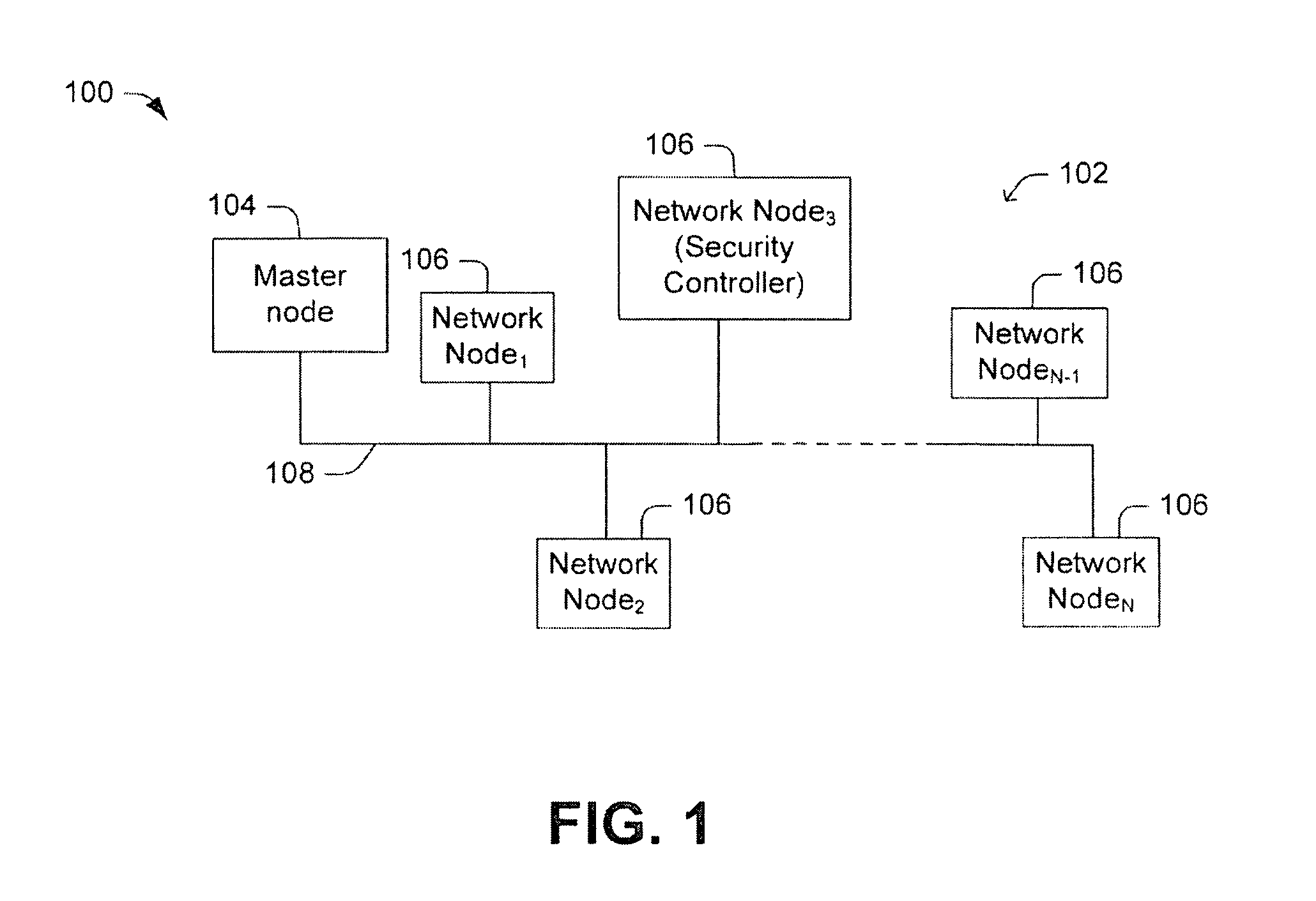
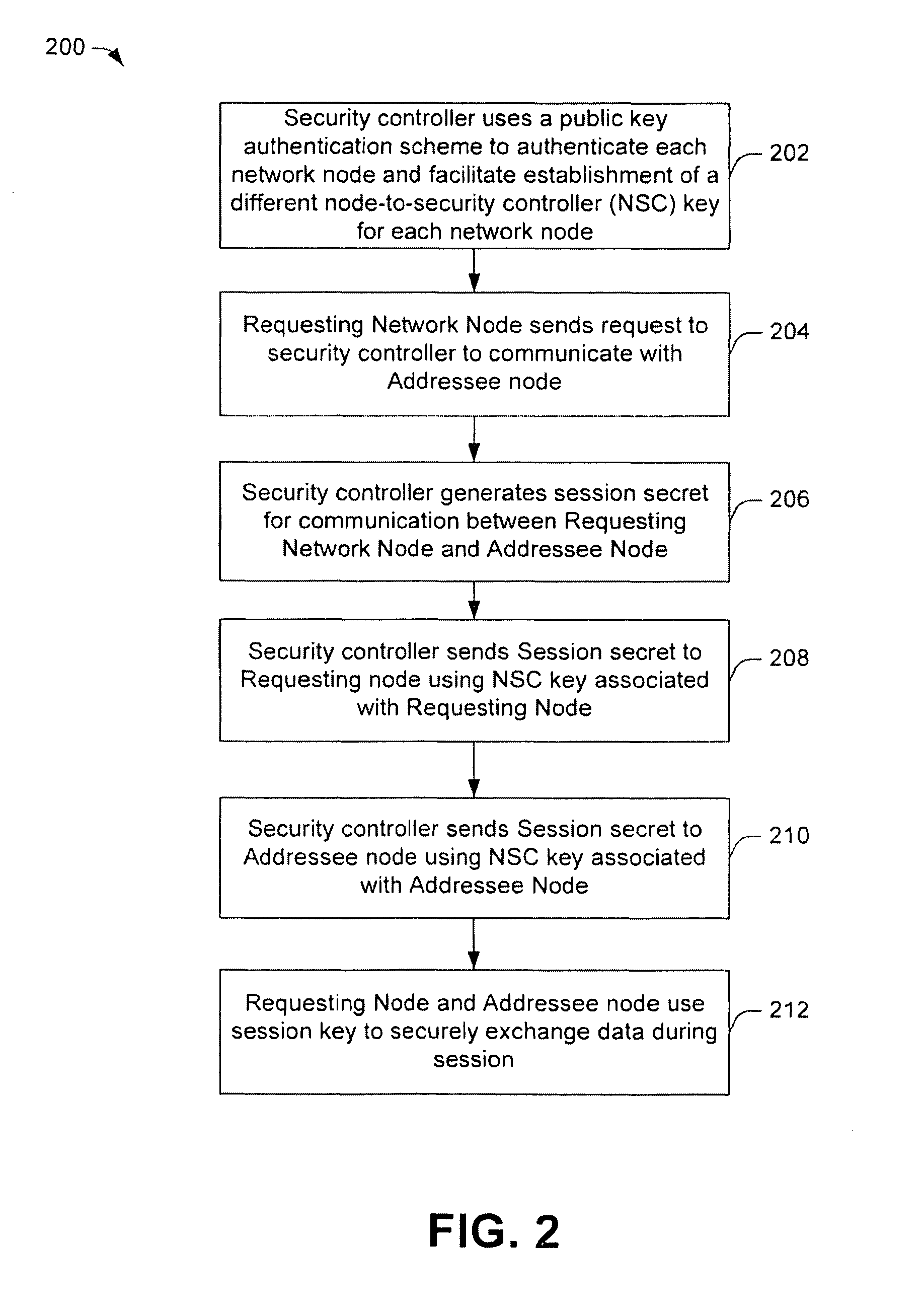
Key management for communication networks
ActiveUS20090296924A1Public key for secure communicationUser identity/authority verificationSecure communicationPublic key authentication
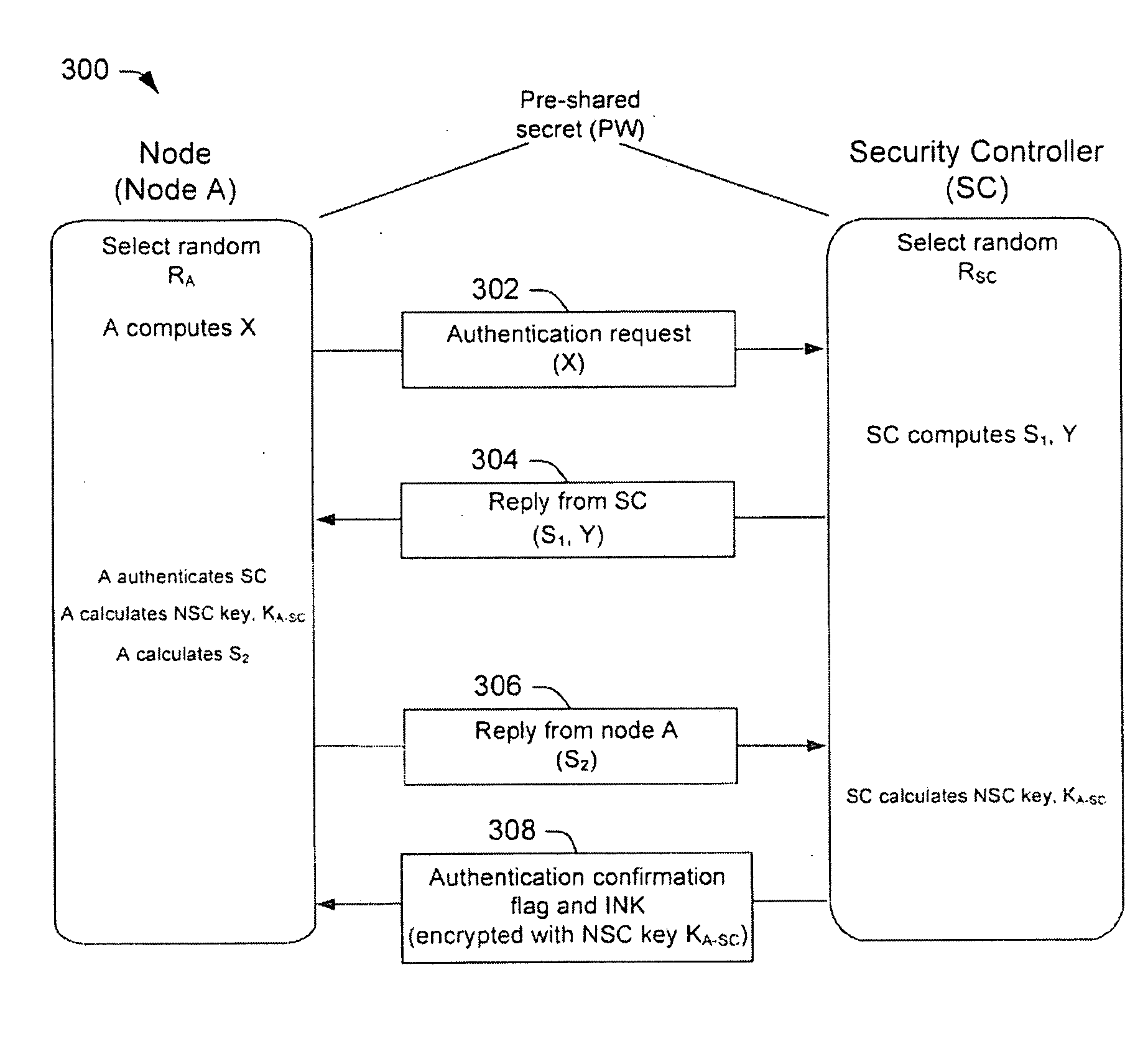
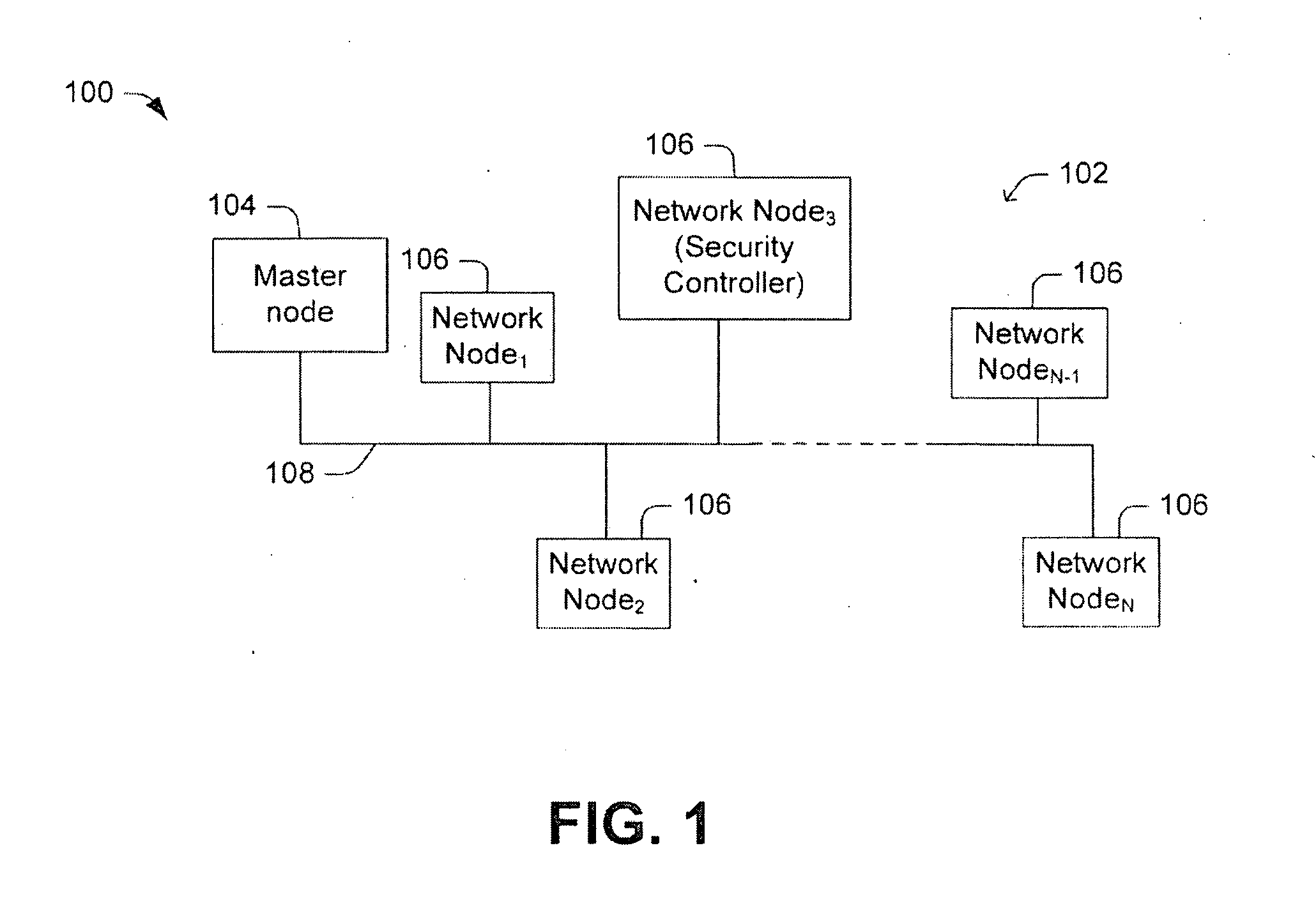
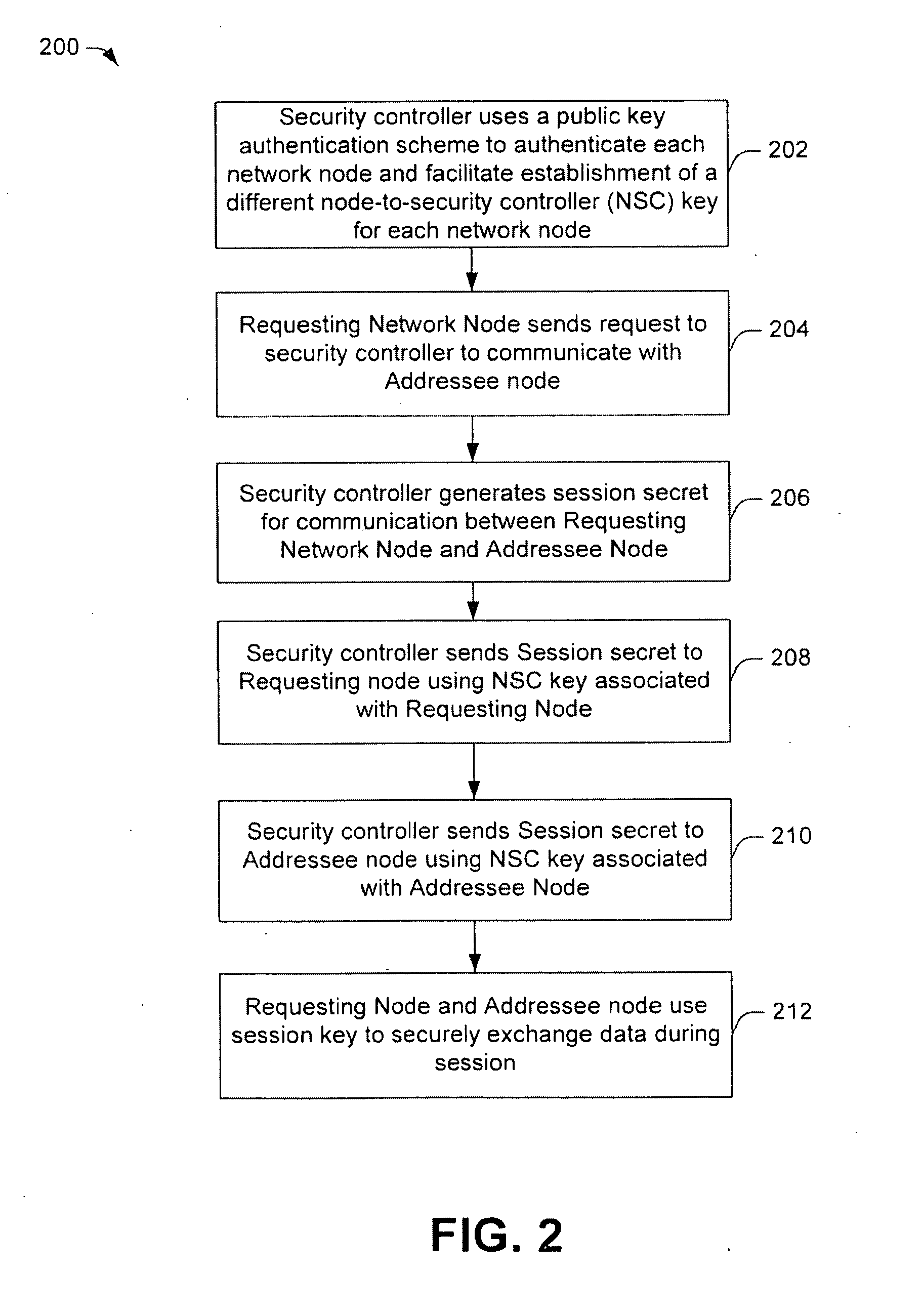
One embodiment of the present invention relates to a method for key management in a communications network. In this method, a public key authentication scheme is carried out between a security controller and a plurality of nodes to establish a plurality of node-to-security-controller (NSC) keys. The NSC keys are respectively associated with the plurality of nodes and are used for secure communication between the security controller and the respective nodes. Other methods and devices are also disclosed.
Owner:MAXLINEAR INC
Parent-Child Card Authentication System
InactiveUS20070226793A1Easily grant authorityEasy to useKey distribution for secure communicationDigital data processing detailsComputer hardwarePublic key authentication
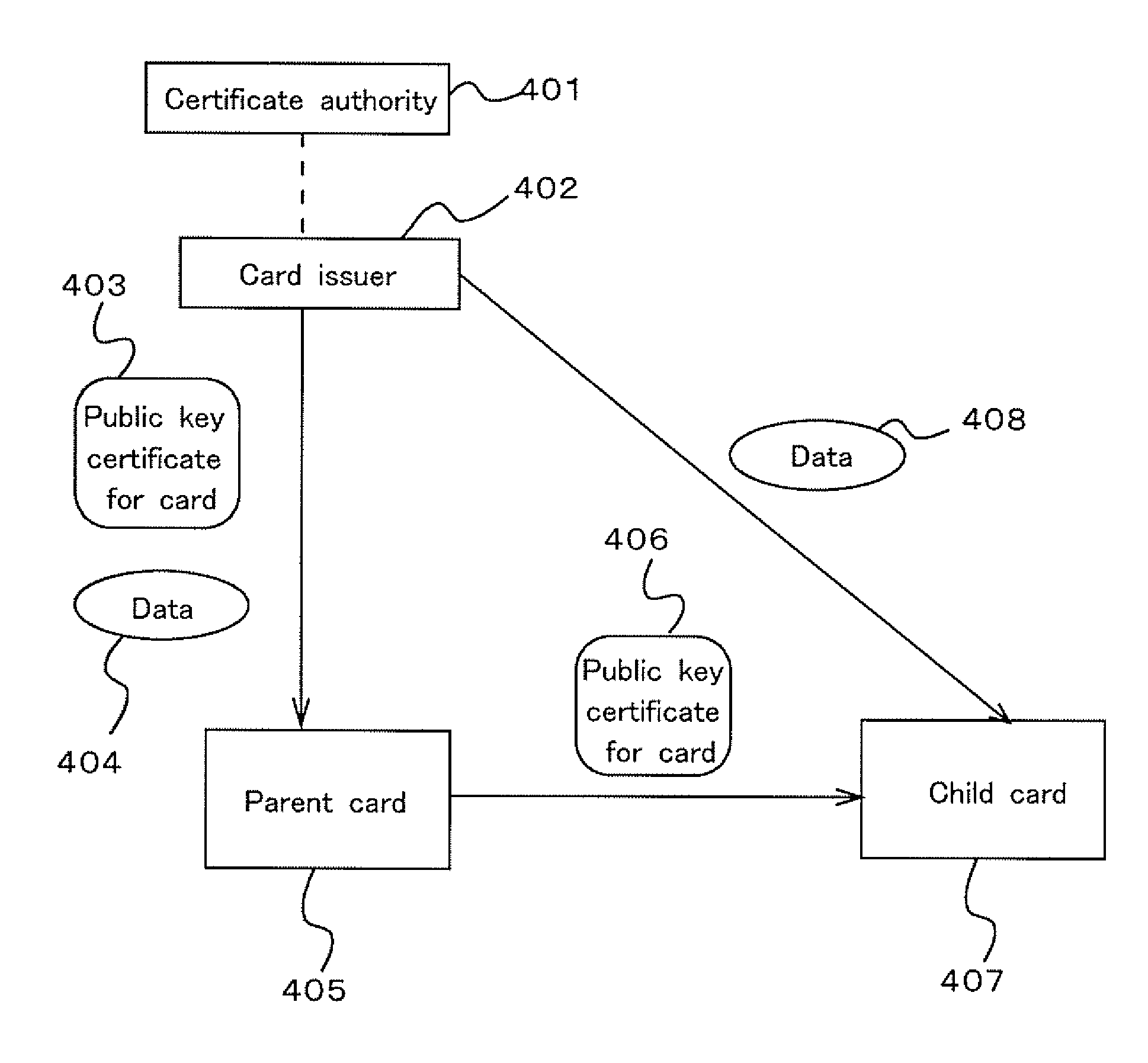
When a special relationship is present between IC card owners, authority of one of the IC card owners cannot be easily given to the other owner of the IC card. However, an IC card of a second owner can issue a public key certificate of the IC card of a first owner so that the IC card of the first owner can be recognized as a child card of the IC card of the second owner. Thus, the first generation card authenticated by a route authentication station is set as an ancestor which can generate a descendent card which receives the authentication. By checking which parent card has issued the public key authentication owned by the child card, it is possible to given the authority of the parent card to the child card.
Owner:PANASONIC CORP
Method for inclusive authentication and management of service provider, terminal and user identity module, and system and terminal device using the method
ActiveUS7953391B2Unauthorised/fraudulent call preventionEavesdropping prevention circuitsTerminal serverPublic key authentication
Disclosed are a method and a system for mutual inclusive authentication between a service provider, a terminal and a user identity module. The authentication system is configured in a structure that can interact with a public key infrastructure of the current network security environment and can be independently used in a specific network system. The inclusive authentication method is divided into public key authentication and symmetric key authentication. Mutual authentication can be made between a service provider, a terminal and a user identity module using any of the two authentication schemes. Then a user can access content on any terminal device using the content license based on the user's identity.
Owner:SAMSUNG ELECTRONICS CO LTD
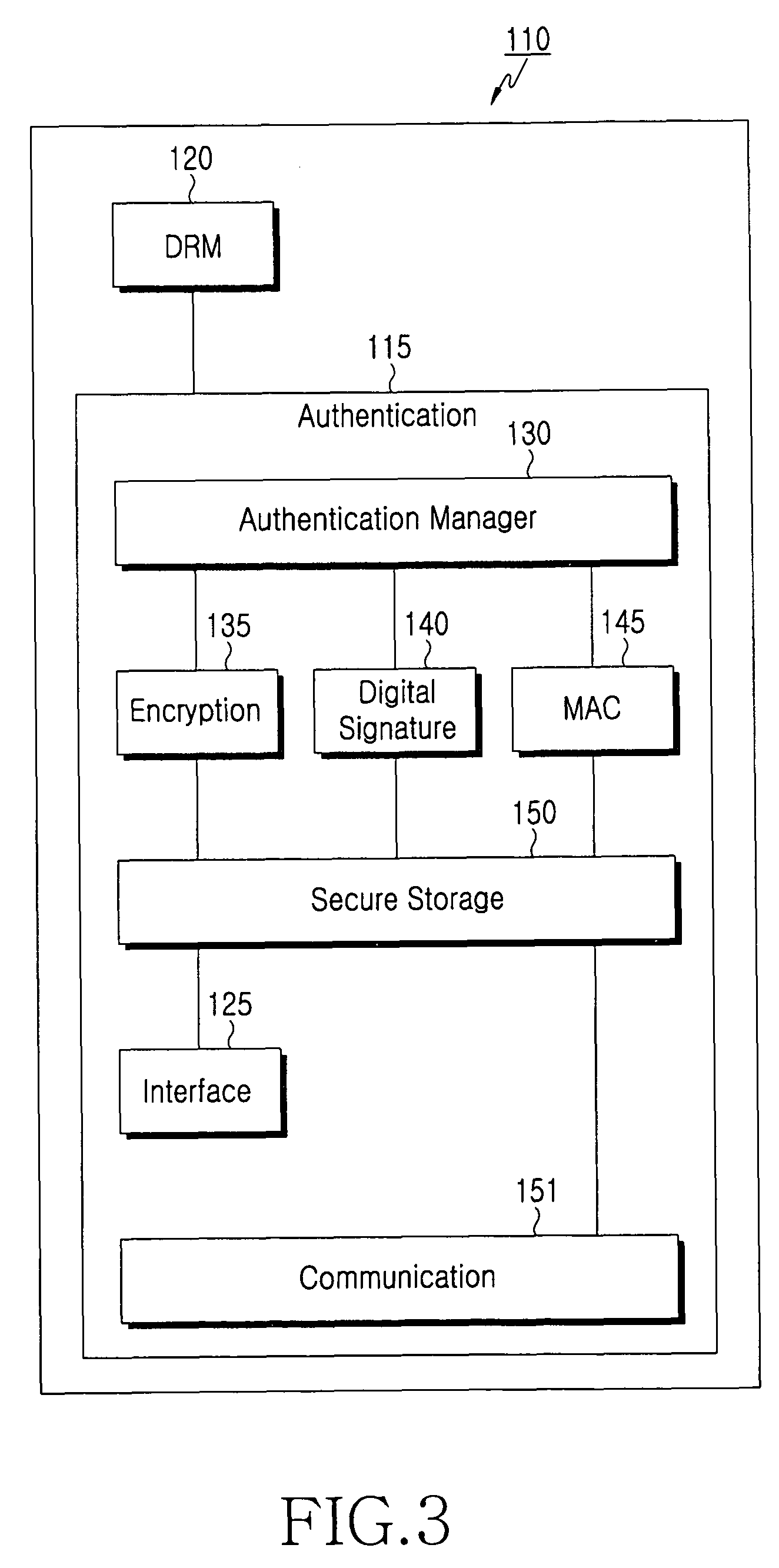
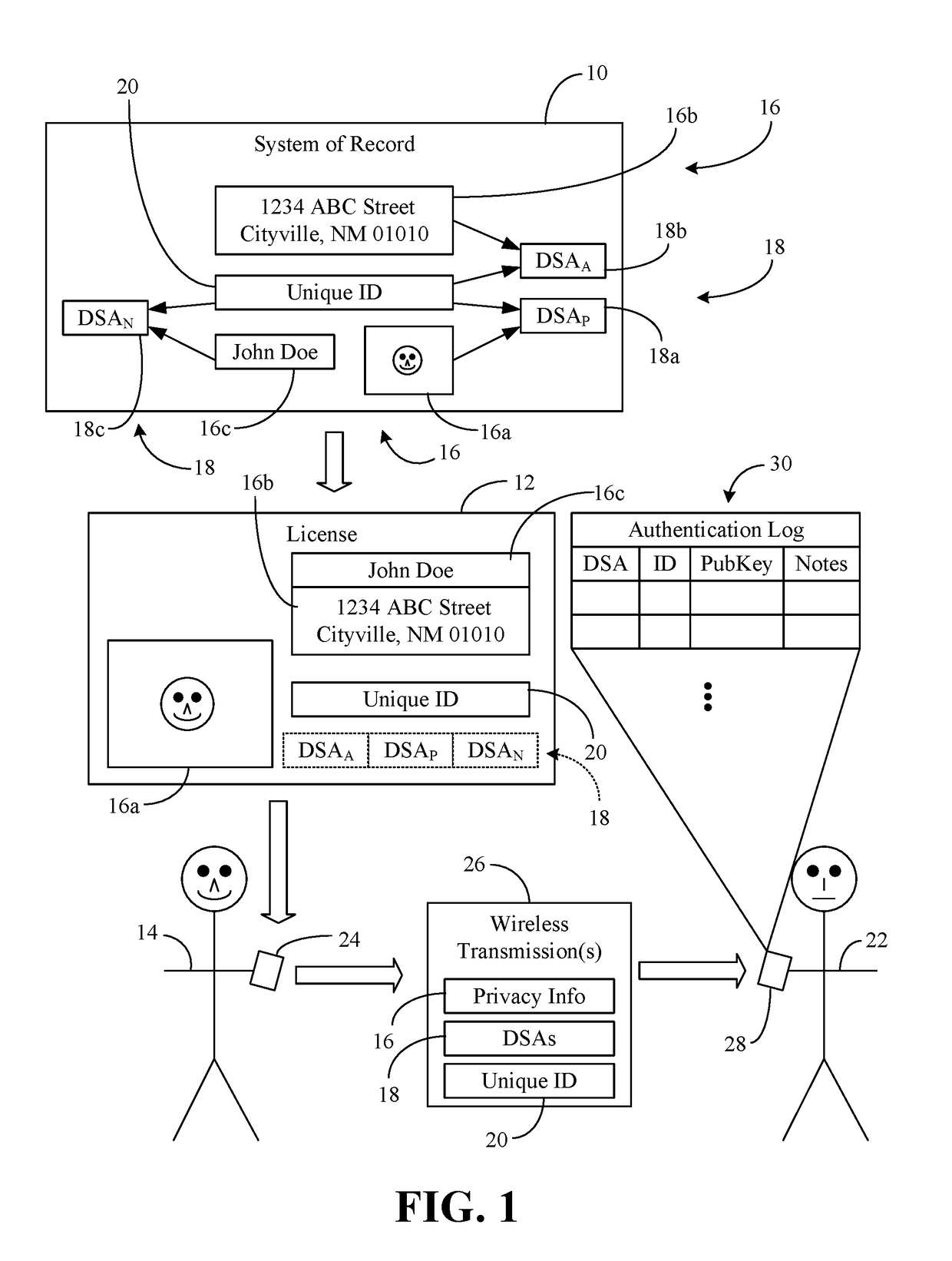
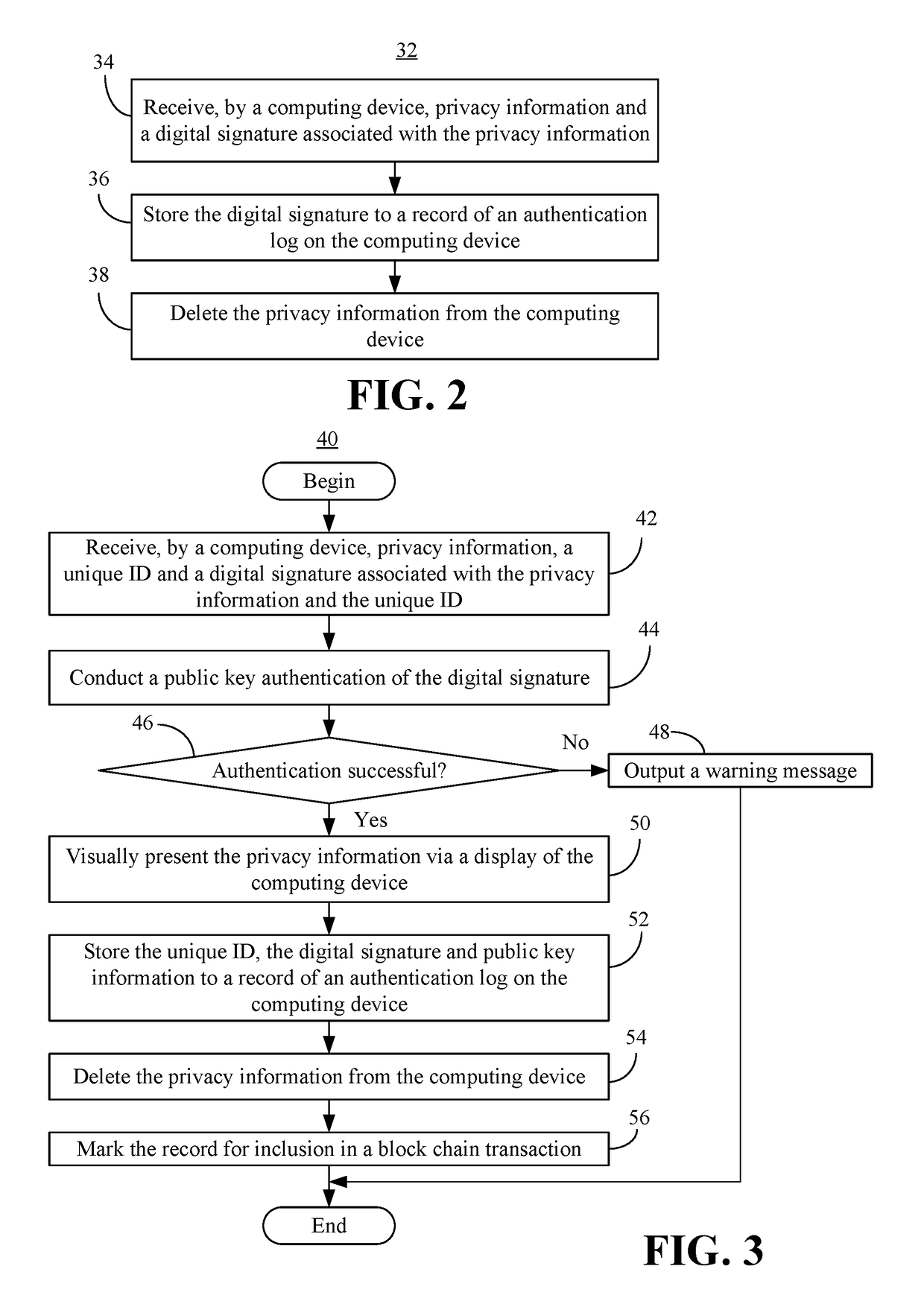
Digital license authentication with secure privacy logging
InactiveUS20180341775A1Public key for secure communicationUser identity/authority verificationPublic key authenticationDigital signature
Methods and systems may provide for technology to receive, by a computing device, privacy information, a unique identifier (ID) and one or more digital signatures associated with the privacy information and the unique ID. Additionally, the technology may store the unique ID and the digital signature(s) to a record of an authentication log on the computing device and delete the privacy information from the computing device. In one example, the technology conducts a public key authentication of the digital signature(s).
Owner:IBM CORP
Method and apparatus to provide public key authentication with low complexity devices
A method and apparatus to authenticate limited processing-power systems (LPPS) using elliptic cryptography within a well known elliptic curve E, over a well known finite field F ((E(F)). The apparatus comprises a random number generator to choose a random value b, of a similar order of magnitude to the order of E(F). The apparatus further comprises a challenge calculator to calculate a value C=bP and send the challenge to the LPPS, where P is a point on the elliptic curve E(F) which was used as a basis for generating a private key, a, for the LPPS. The apparatus further comprising an RFID reader to receive a challenge response, R=aC=abP from the LPPS, and a crypto calculator to calculate bQ, based on a public key, Q, of the LPPS. The apparatus further comprising a comparison logic to authenticate the LPPS if bQ=aC=abP.
Owner:GEN DIGITAL INC
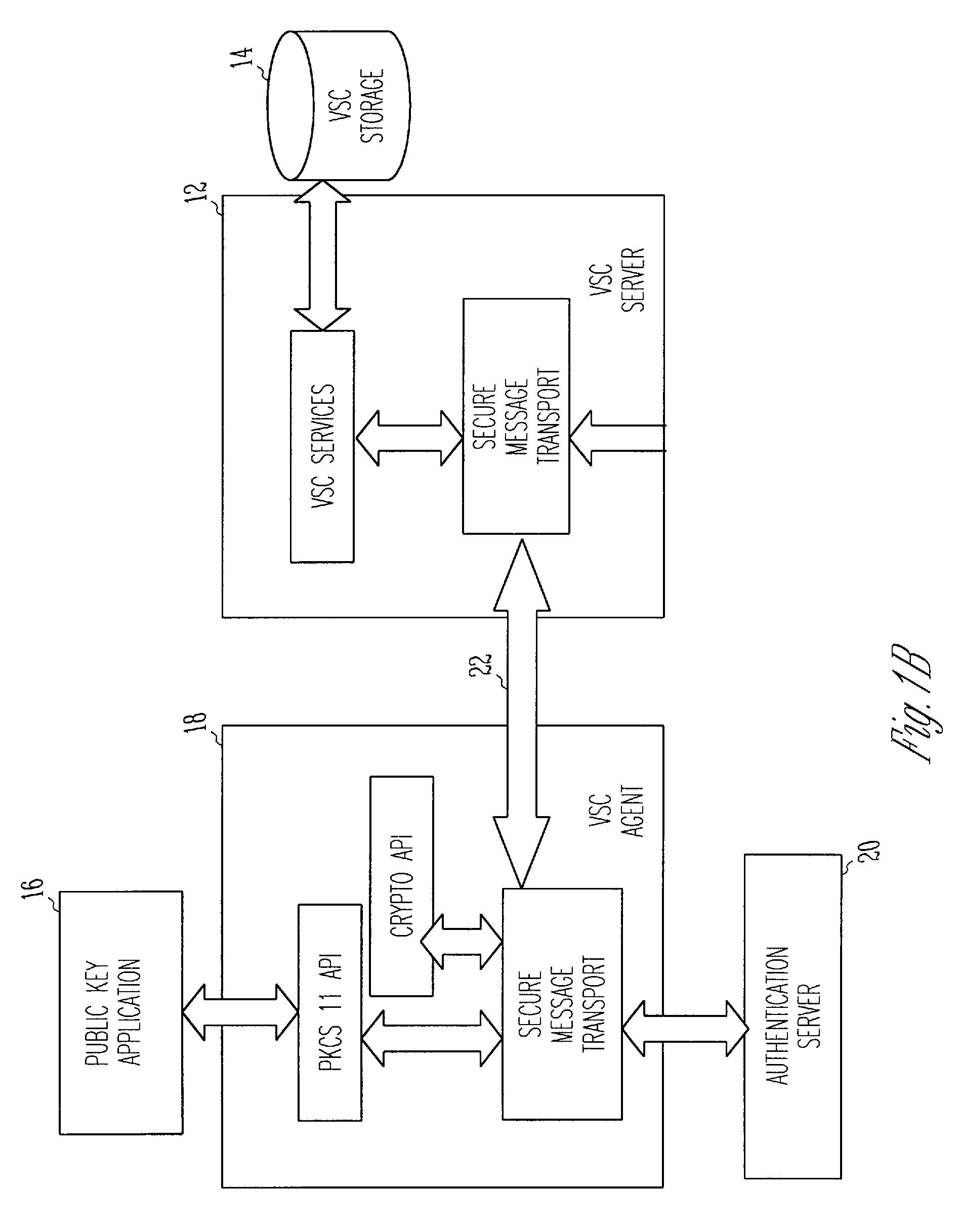
Virtual smart card system and method
InactiveUS20060248347A1Random number generatorsUser identity/authority verificationPublic key authenticationSmart card
A public key authentication system and method for use in a computer system having a plurality of users. The system includes a virtual smart card server, storage connected to the virtual smart card server, and a virtual smart card agent connected to the virtual smart card server. The storage includes a plurality of virtual smart cards, wherein each virtual smart card is associated with a user and wherein each smart card includes a private key. The virtual smart card agent authenticates the user and accesses the authenticated user's virtual smart card to obtain the user's private key.
Owner:SAFENET DATA SECURITY ISRAEL
Information processing apparatus, information processing method, and program
ActiveUS20140215222A1Efficient replacementPublic key for secure communicationUser identity/authority verificationInformation processingPublic key authentication
Provided an information processing apparatus including a number generation unit configured to generate numbers used in coefficients of terms included in a pair of multi-order multivariate polynomials F=(f1, . . . , fm), using a predetermined function, from information shared between entities executing an algorithm of a public-key authentication scheme or a digital signature scheme that uses a public key including the pair of multi-order multivariate polynomials F, and an allocation unit configured to allocate the numbers generated by the number generation unit to the coefficients of the multi-order multivariate polynomials for which the pair of multi-order multivariate polynomials F are included in constituent elements.
Owner:SONY CORP
Communication apparatus and communication method thereof
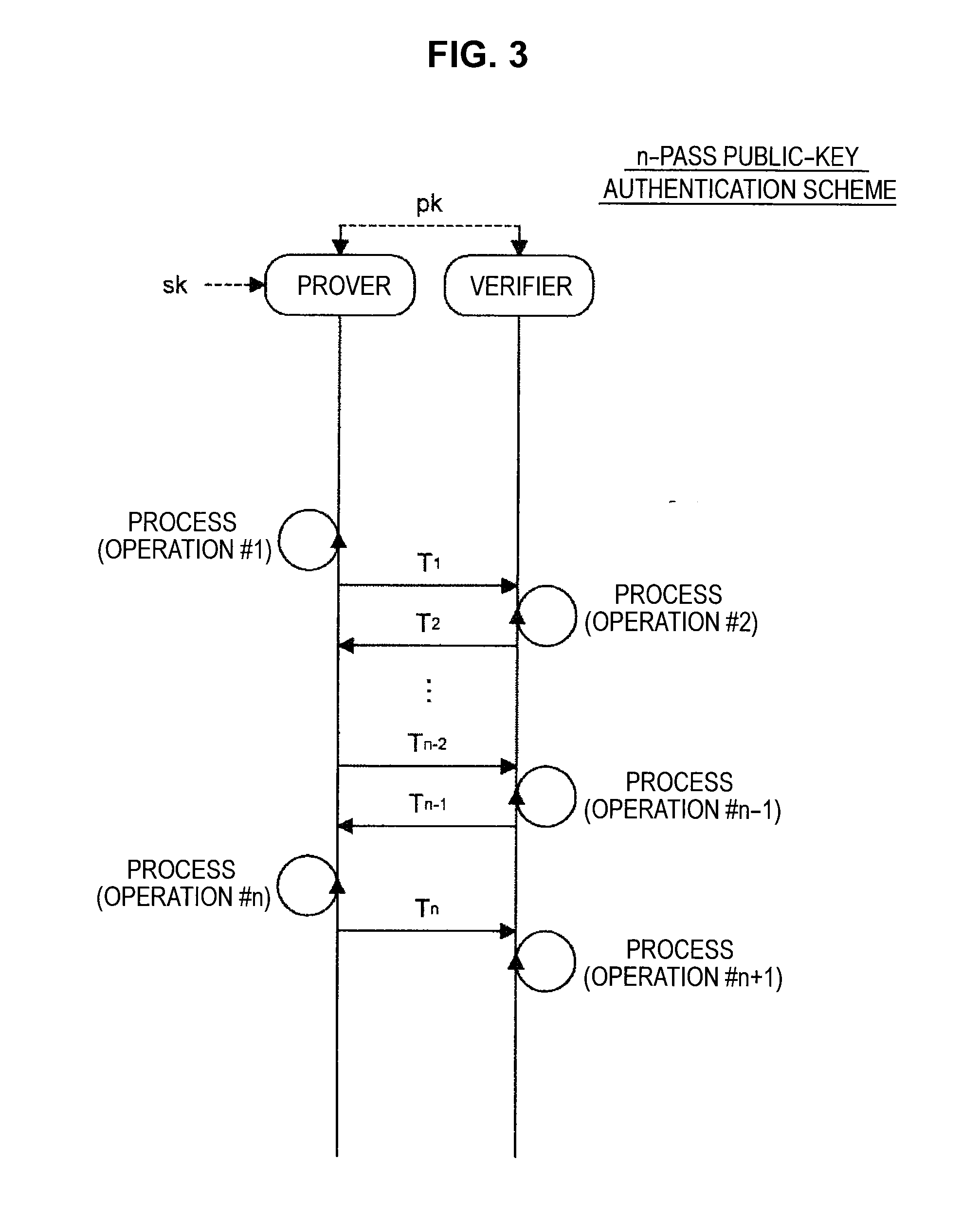
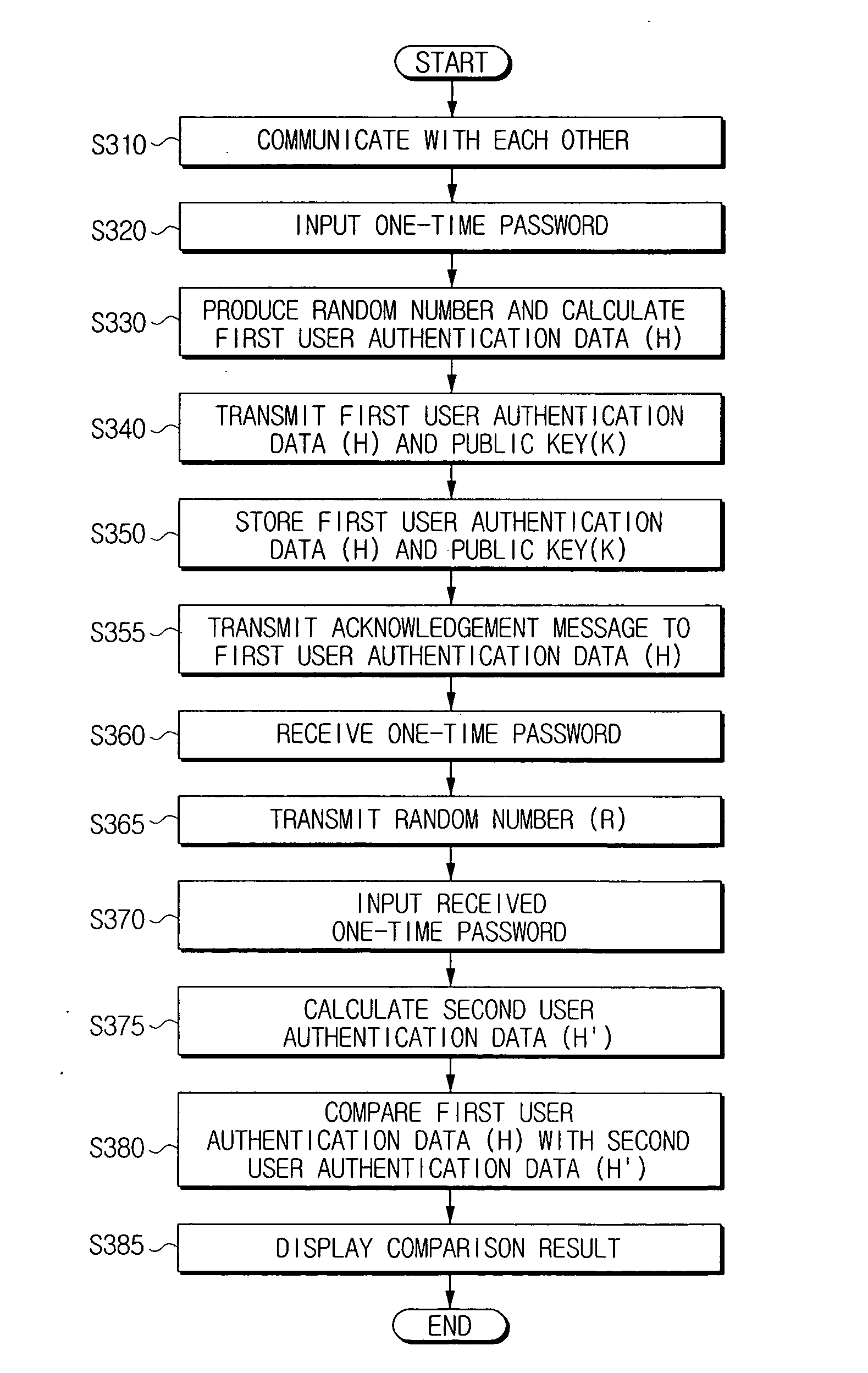
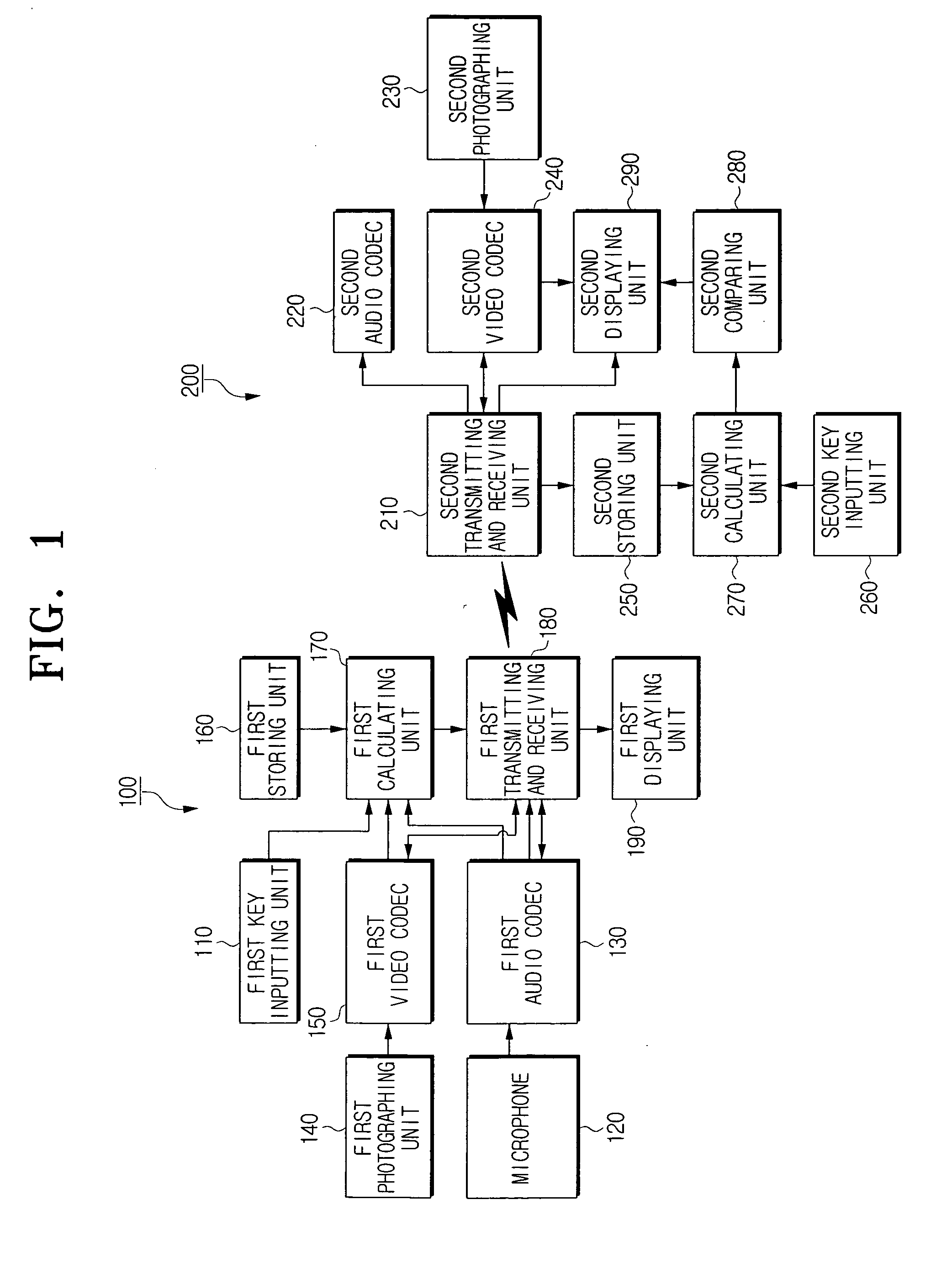
InactiveUS20070255959A1Authentication securityRandom number generatorsPublic key for secure communicationPublic key authenticationPassword
A communication apparatus having a public key authentication function and a communication method thereof are disclosed. The communication apparatus includes a calculating unit to calculate a first user authentication data for authenticating public information, and a transmitting and receiving unit to transmit the calculated first user authentication data and the public information to be authenticated, and to transmit a password in a form in which a user characteristic input for authenticating the public information is reflected. Accordingly, if the parties to a communication unexpectedly request mutual authentication under an IP-based communication environment, the apparatus can safely authenticate the public information with a use of a user characteristic sensing channel.
Owner:SAMSUNG ELECTRONICS CO LTD
Lightweight certificateless authentication method, client and system
PendingCN111245847AReduce operational complexityNo key escrow issuesKey distribution for secure communicationPublic key authenticationThe Internet
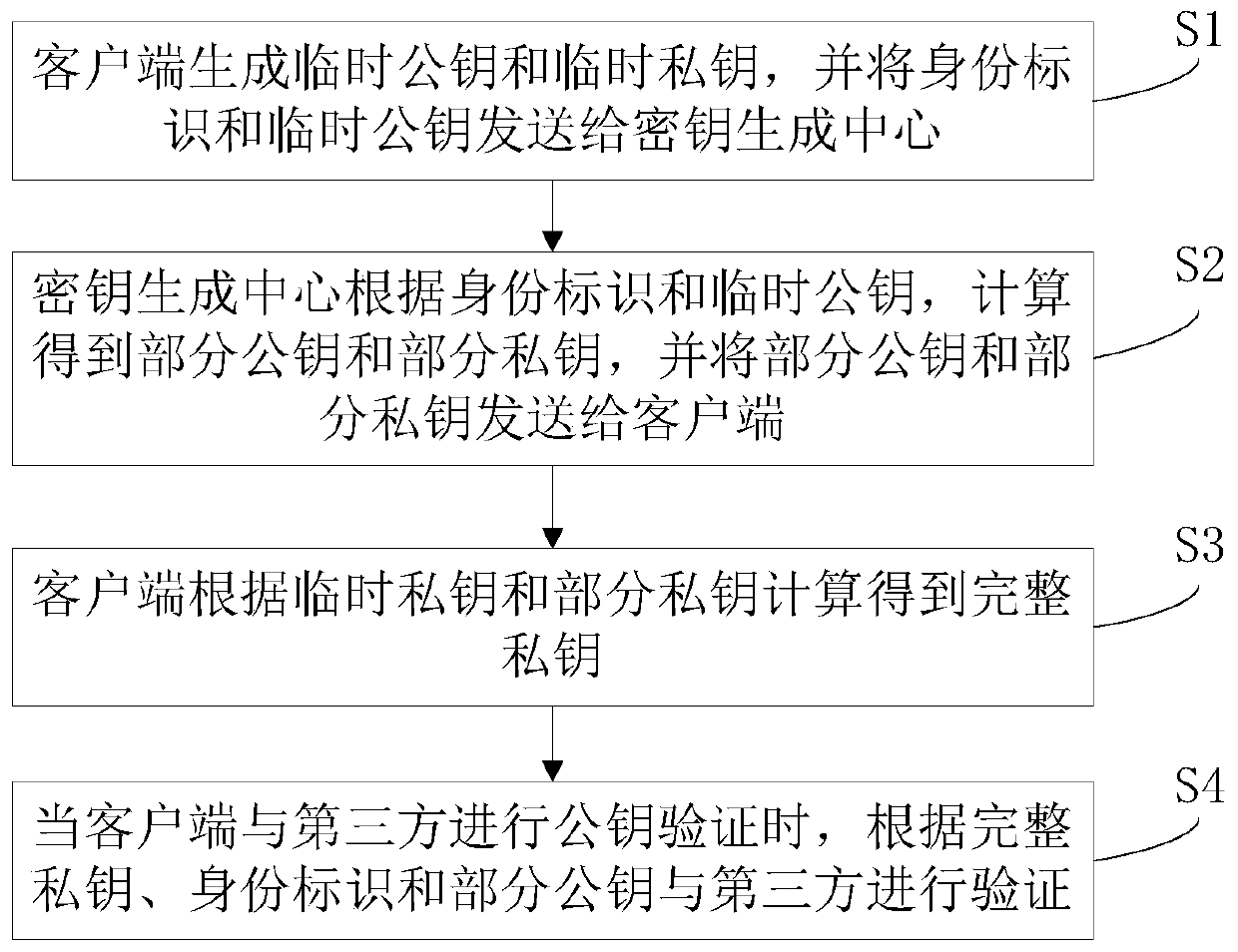
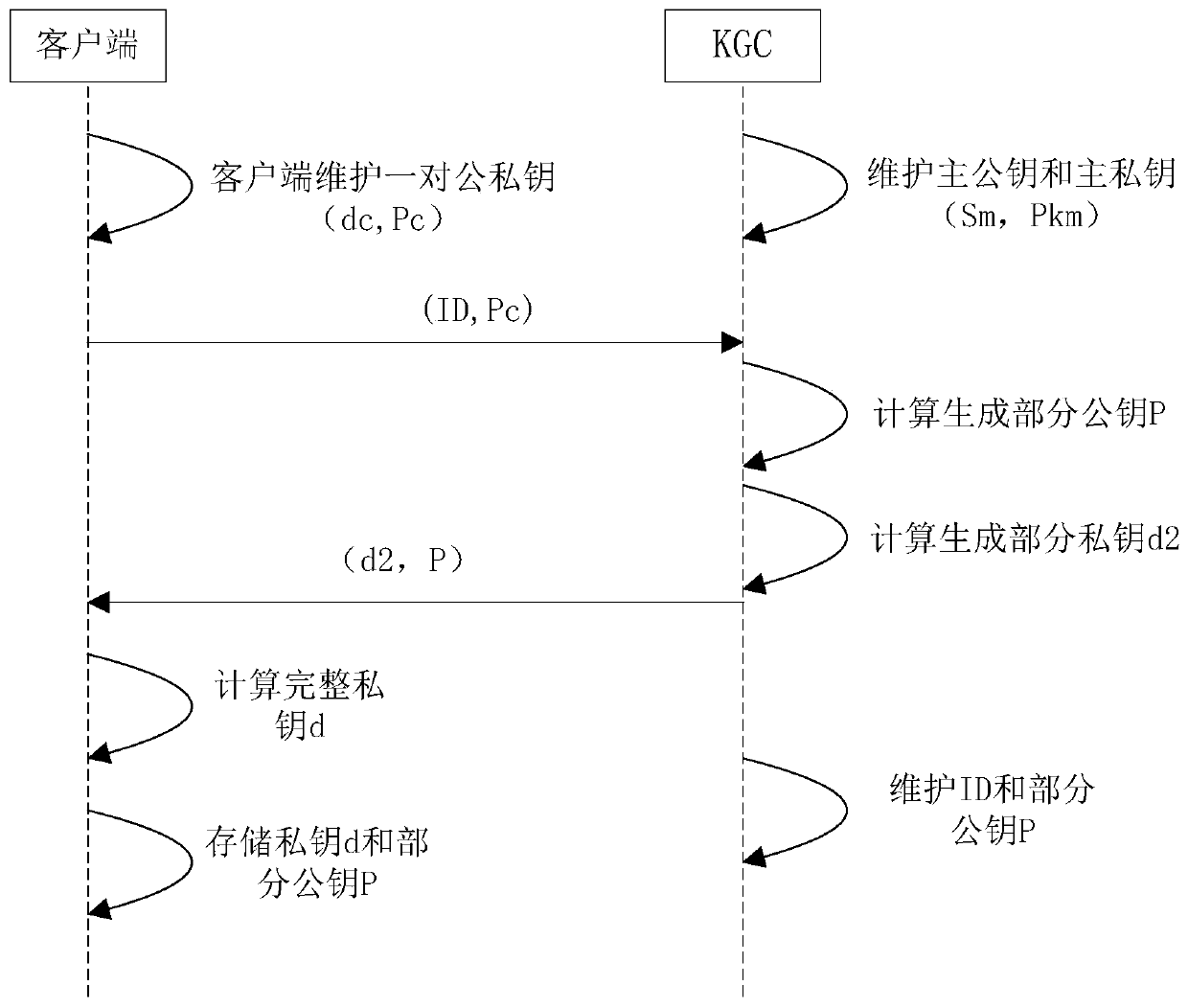
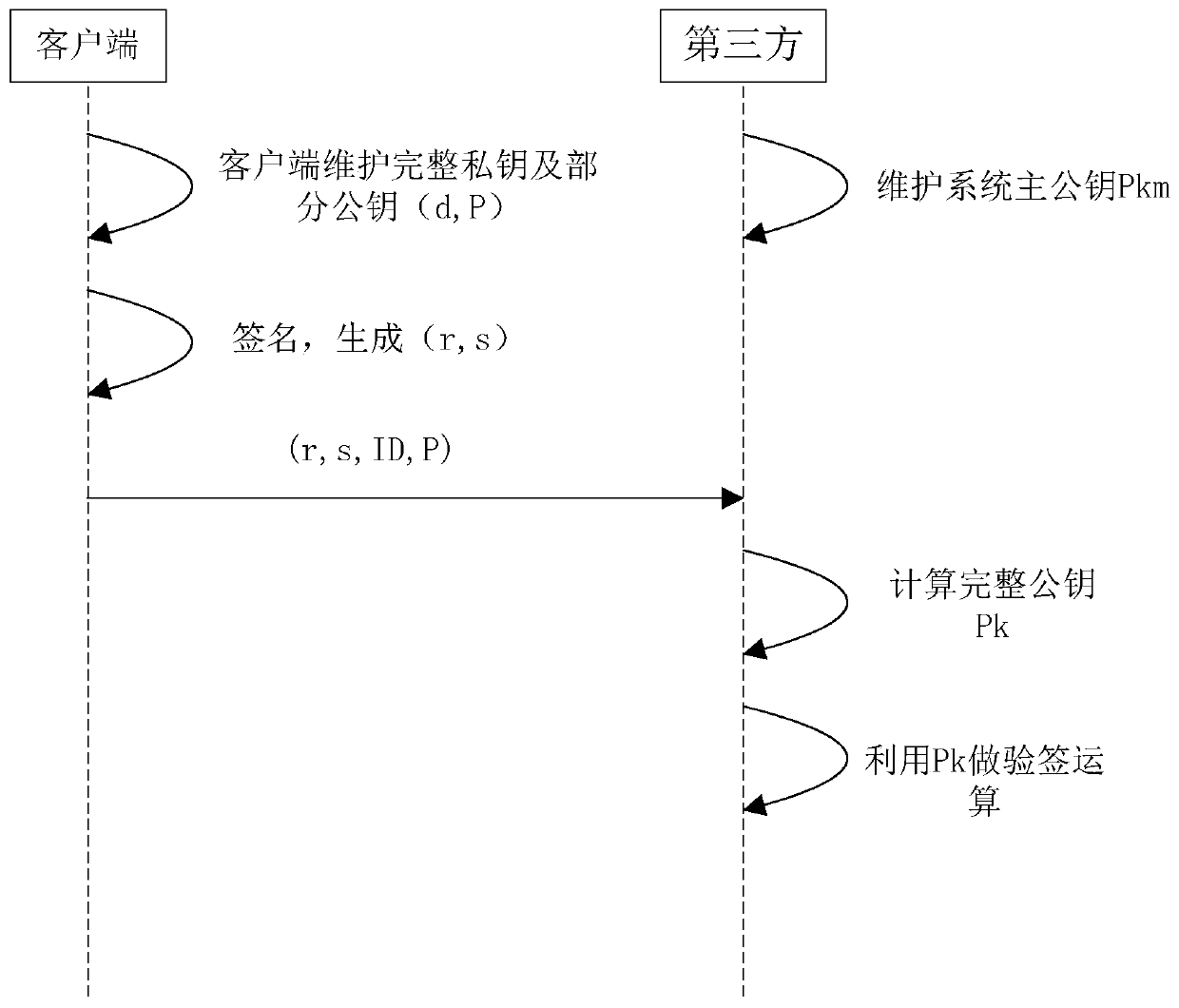
The invention discloses a lightweight certificateless authentication method, client and system, and relates to the technical field of information security. The method comprises the following steps: the client generates a temporary public key and a temporary private key, and sends an identity label and the temporary public key to a key generation center; the key generation center calculates according to the identity identifier and the temporary public key to obtain a part of public key and a part of private key, and sends the part of public key and the part of private key to the client; the client calculates according to the temporary private key and the part of private key to obtain a complete private key; and when the client performs public key verification with a third party, verification is performed with the third party according to the complete private key, the identity identifier and the part of the public key. The method is suitable for the environment of the Internet of Things,is low in operation complexity, can be compatible with an existing public key infrastructure, and does not need complex certificate management, the client has complete autonomy for the private key, does not have a secret key escrow problem, and needs less data to be transmitted during public key authentication.
Owner:BEIJING SANSEC TECH DEV
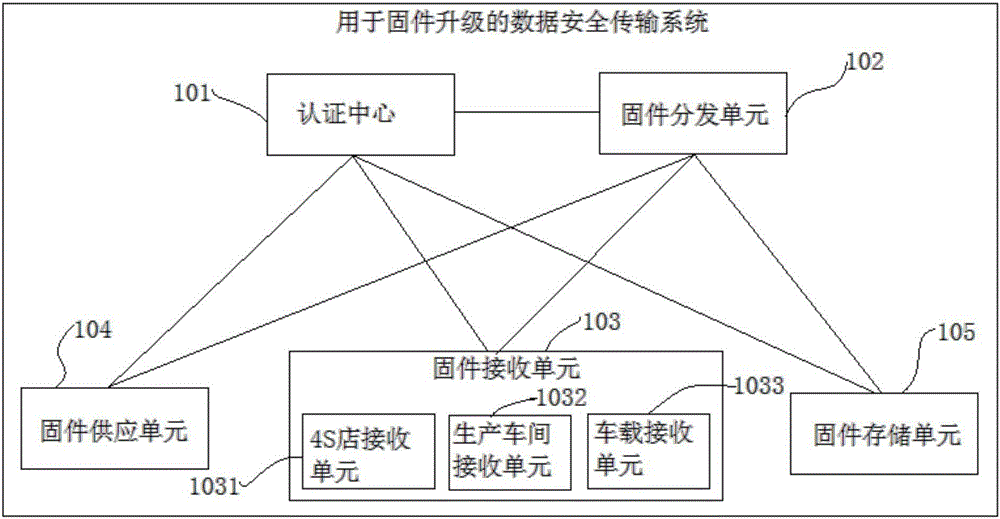
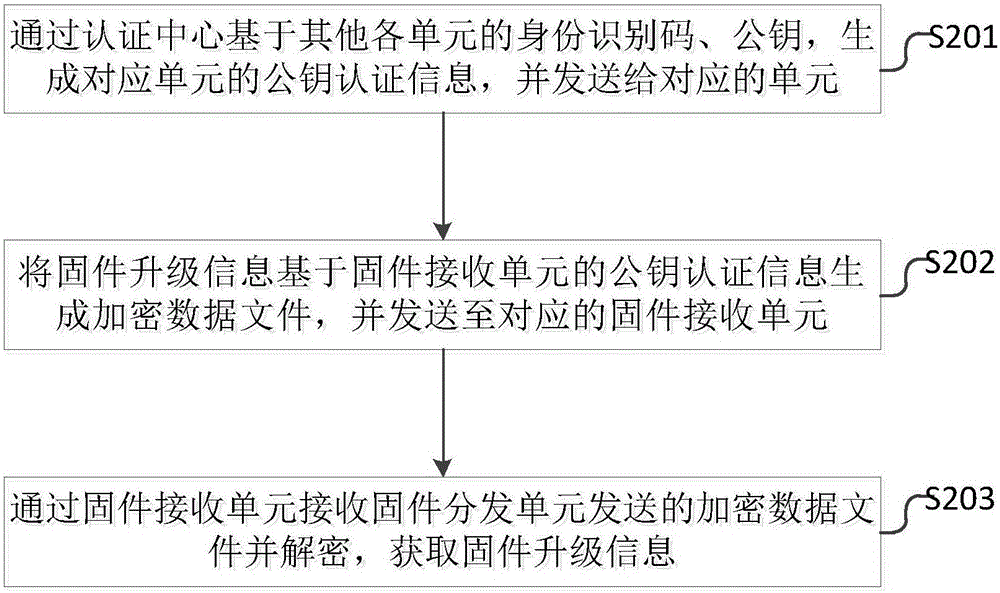
Data secure transmission system and method for firmware upgrade
The invention provides a data secure transmission system and method for firmware upgrade. The system comprises an authentication center, a firmware distribution unit and a firmware receiving unit. The authentication center is configured to generate public key authentication information of corresponding units on the basis of identity identification codes and public keys of the units and send the public key authentication information to the corresponding units. The firmware distribution unit is configured to take the selected firmware upgrade information as a transmission data file, generates an encryption data file on the basis of the public key authentication information of the firmware receiving unit and send the encryption data file to the corresponding firmware receiving unit. The firmware receiving unit is configured to receive and decrypt encryption data file sent by the firmware distribution unit, thereby obtaining the firmware upgrade information. The secure transmission of the data in the firmware upgrade process is fully ensured.
Owner:NIO CO LTD
Wireless security access authentication method
InactiveCN101702807AMaintain Authentication SecurityReduce authentication overheadUser identity/authority verificationWireless network protocolsPublic key authenticationNetwork communication
The invention discloses a wireless security access authentication method, belonging to field of network communication security authentication. The content of the method comprises an EBAF (Elliptic curve based authentication scheme) initialization protocol, an EBAF authentication protocol and a selectable EBAF cancel protocol, wherein the EBAF initialization protocol generates an elliptic curve, generates secret keys of resource owners, and distributes secret keys of terminals; in the EBAF authentication protocol, authentication both parties authenticate a message of a counter party with respective Diffie-Hellman secret keys; and in the EBAF cancel protocol, a group administer generates a new key pair, wherein the terminal which can not be authenticated by the key pair can be cancelled. The invention not only keeps the security of the public key authentication, but also effectively reduces the authentication cost.
Owner:SOUTHEAST UNIV
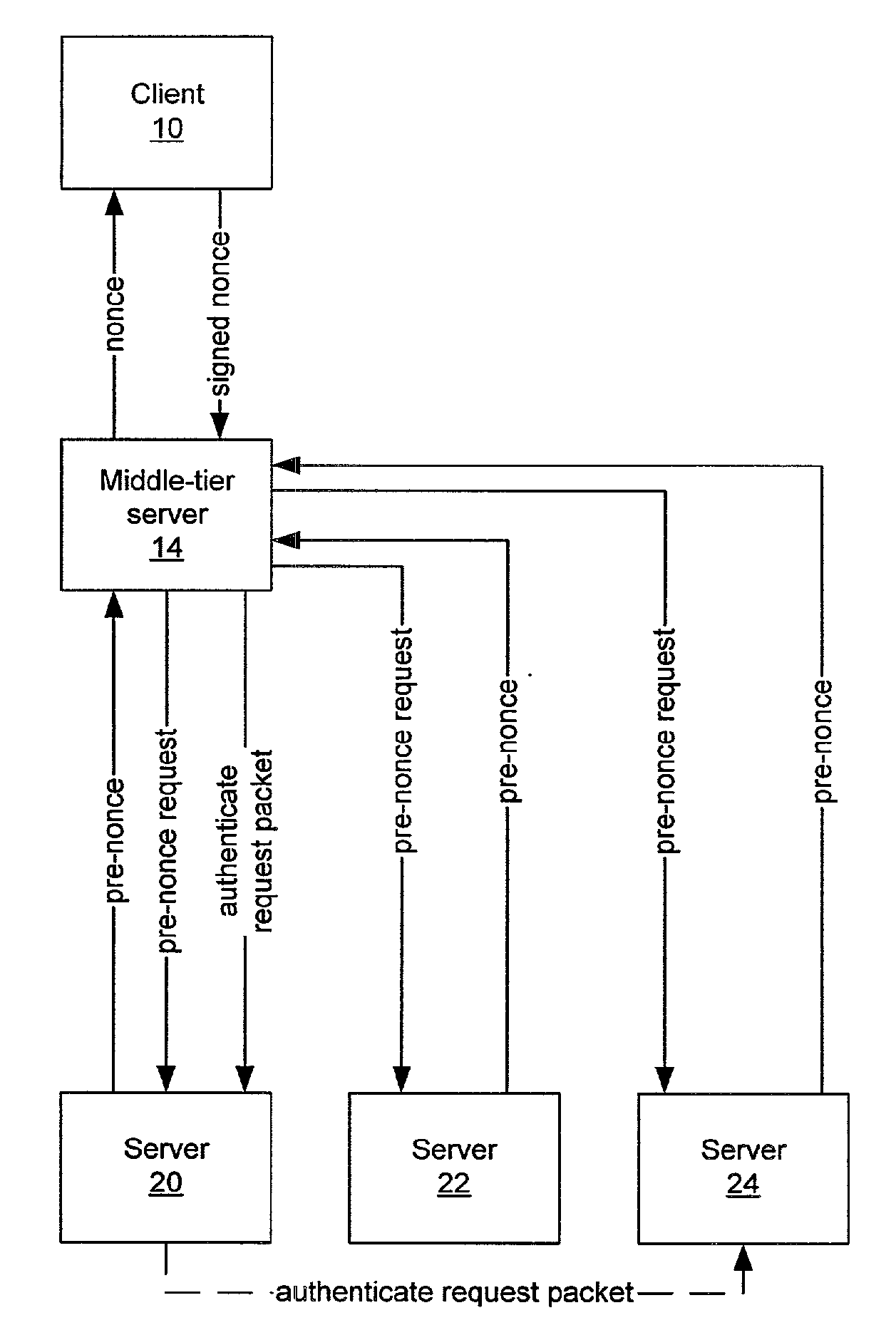
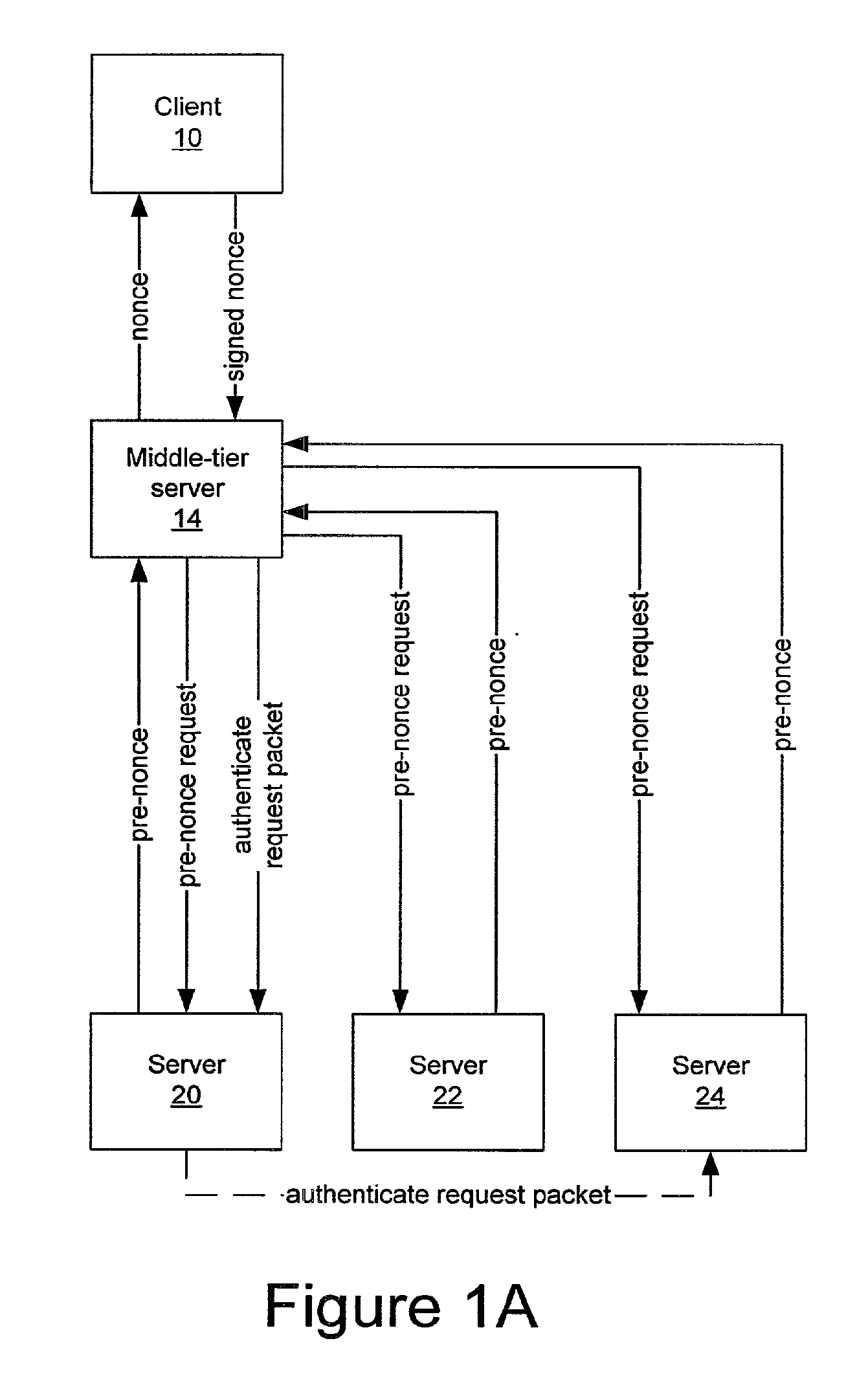
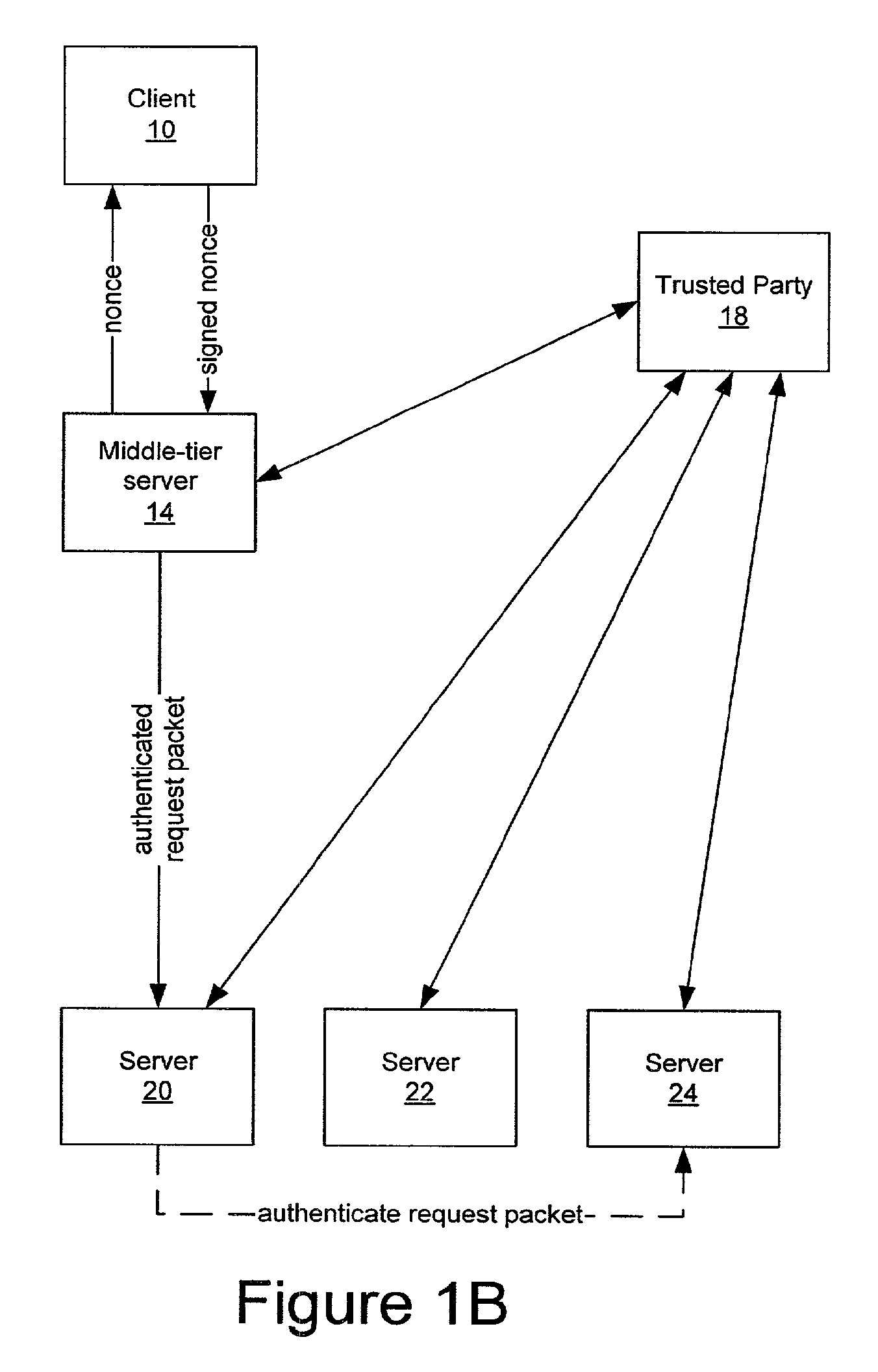
Secure delegation using public key authentication
InactiveUS20090055916A1Synchronising transmission/receiving encryption devicesDigital data processing detailsPublic key authenticationClient-side
A client is impersonalized to a plurality of servers using a middle-tier server. A common nonce associated with each of the plurality of servers is obtained and the common nonce is provided to the client. The common nonce signed by the client is received at the middle-tier server and provided as a signature for transactions from the client to the plurality of servers so as to authenticate the client to the plurality of servers.
Owner:IBM CORP
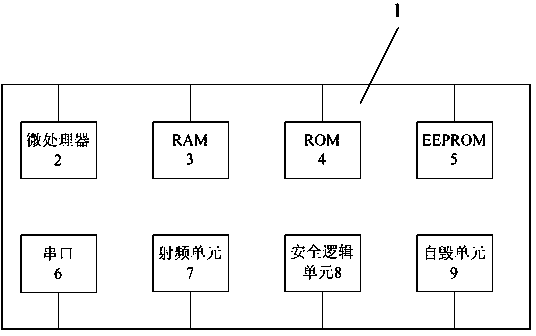
Non-contact processor card based on combined public key authentication and use method
ActiveCN104077511AReduced security requirementsSafe and reliableUser identity/authority verificationDigital data authenticationPublic key authenticationPrevention project
The invention belongs to the technical field of CPU cards and provides a non-contact processor card based on combined public key authentication and a use method. The non-contact processor card comprises a chip, a safe serial port, a radio frequency unit, a micro processor, an RAM, an ROM, an EEPROM, a safe logic unit and a self-destruction unit, wherein the safe serial port, the radio frequency unit, the micro processor, the RAM, the ROM, the EEPROM, the safe logic unit and the self-destruction unit are installed on the chip and are connected with the chip through circuits. The use method of the combined public key authentication is achieved, collusion attack prevention capacity is improved by means of a chaotic random sequence generated by means of chaotic mapping, a puzzling secret key of a reversion prevention project is additionally arranged in a secrete key unit, meanwhile, a self-destruction logic unit for preventing temptation attacks is additionally arranged, transmission secrete keys are not needed, requirements for safety in the communication process are not high, use safety is high, large-scale popularization and use are facilitated, and the CPU card and the use method are suitable for meeting service requirements on the basis of mobile communication.
Owner:上海象形通讯科技股份有限公司
User key management for the secure shell (SSH)
ActiveUS10003458B2Key distribution for secure communicationUser identity/authority verificationPublic key authenticationSecure Shell
Management of user keys for public key authentication using the SSH in large SSH deployments is automated by deploying a management system in the environment, discovering SSH identity keys and authorized keys, analyzing authorized connections between user accounts, and automatically managing the authorized connections and the key pairs used for authentication.
Owner:SSH COMMUNICATIONS SECURITY
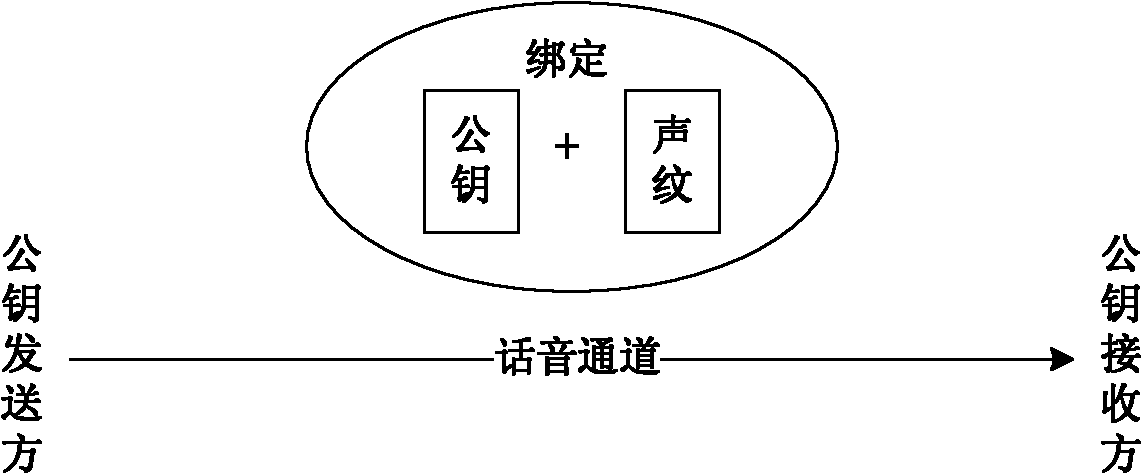
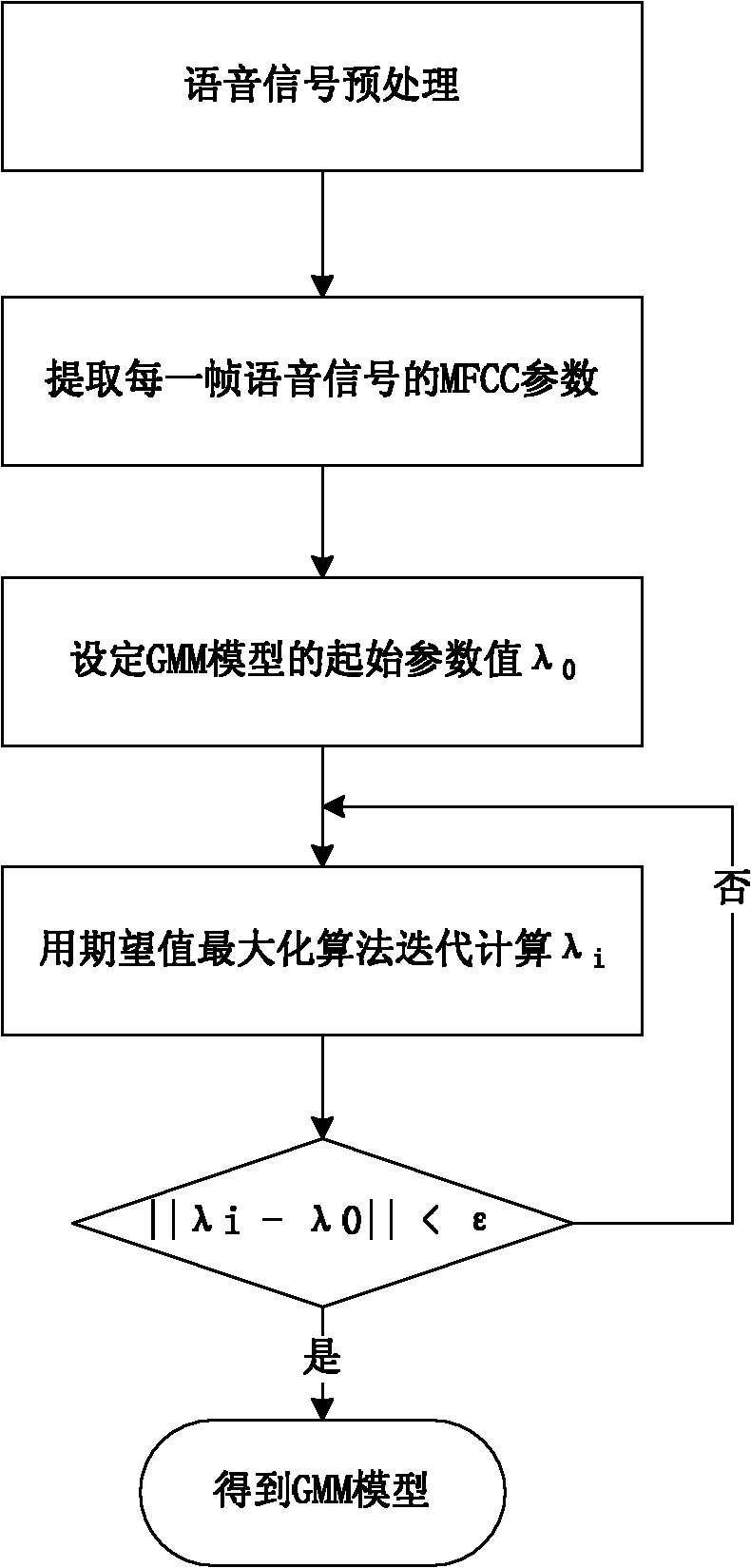
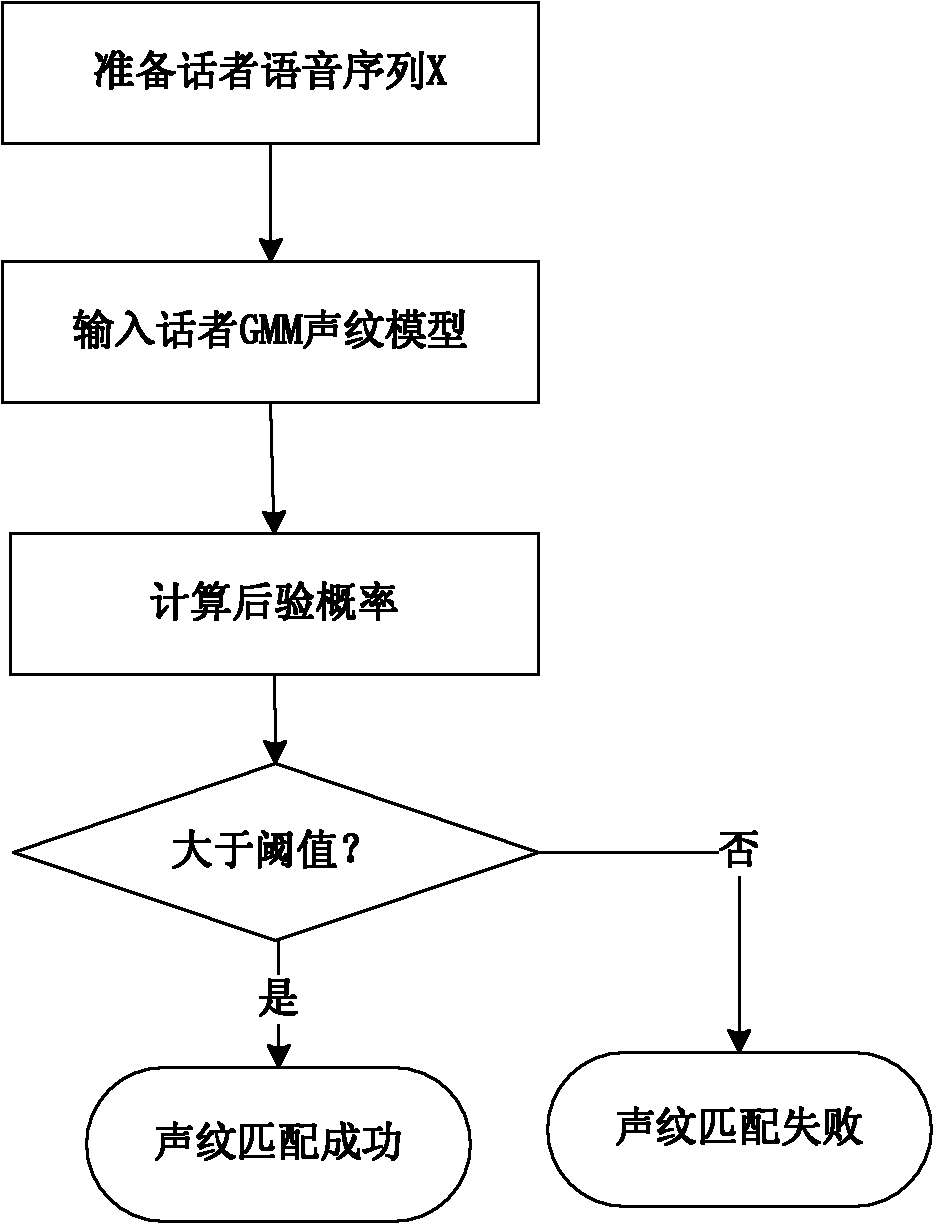
Without-trust third party public key authentication method based on speaker voice print
InactiveCN101938489APublic key for secure communicationSpeech analysisThird partyPublic key authentication
The invention discloses a without-trust third party public key authentication method based on a speaker voice print, comprising the following steps that 1. the two parties determine a voice channel; 2. the two parties enable the voice channel and respectively establish a GMM (Gaussian mixture model) of the speaker voice print of the opposite side; 3. the two parties respectively generate a public and private key pair; the two parties are symmetrical below; 4. a public key sender states a public key for a receiver through the voice; 5. a public key receiver carries out voice print identification on a voice stream for stating the public key by using the speaker GMM to judge whether to be the sender or not, if yes, carrying out a step 6, and if not, denying; 6. the public receiver extracts the public key of the call voice, and the encrypted public key for a random number is generated and sent to a public key sending end; and 7. after the public key sender receives the random number, the random number is encrypted by the public key and sent to the receiver; after the receiver receives the random number, the random number is decrypted and verified by the public key in the step 6, if pass, the public key authentication is successful, and if fail, the public key authentication fails. The invention does not need the third party to participate and is convenient and flexible to use; and the two communication parties directly transfer and authenticate the public key through a voice call, thereby effectively preventing the attack of other people.
Owner:HANGZHOU DIANZI UNIV
Key management for communication networks
ActiveUS8422687B2Key distribution for secure communicationPublic key for secure communicationSecure communicationPublic key authentication
One embodiment of the present invention relates to a method for key management in a communications network. In this method, a public key authentication scheme is carried out between a security controller and a plurality of nodes to establish a plurality of node-to-security-controller (NSC) keys. The NSC keys are respectively associated with the plurality of nodes and are used for secure communication between the security controller and the respective nodes. Other methods and devices are also disclosed.
Owner:MAXLINEAR INC
Information processing apparatus, image processing method, and program
InactiveUS20150010144A1Effective calculationKey distribution for secure communicationPublic key for secure communicationInformation processingPublic key authentication
Provided is an information processing apparatus including a number acquisition unit configured to acquire a number used for a coefficient of each term constituting a set of a multi-order multivariate polynomial F=(f1, . . . , fm), the number generated using a predetermined function from information shared between entities that execute an algorithm of a public-key authentication scheme or a digital signature scheme that uses a public key including the set of the multi-order multivariate polynomial F, and a polynomial calculation unit configured to calculate a multi-order multivariate polynomial for an input value of a variable by allocating the number acquired by the number acquisition unit to coefficients of the multi-order multivariate that includes the set of the multi-order multivariate polynomial F as a structural element. The polynomial calculation unit skips a calculation process for a term in which an input value of at least one variable is 0
Owner:SONY CORP
Combination public key authentication password method based on conic curves
InactiveCN103490890AEasy to manageEasy to set upPublic key for secure communicationUser identity/authority verificationPublic key authenticationPassword
A combination public key authentication password method based on conic curves includes the following steps that 1, a public password parameter based on a residual class ring conic curve is generated; 2, public and private secret keys based on residual class ring conic curves are generated; 3, a primary algorithm based on a combination public key password method based on the conic curves is used.
Owner:ZHEJIANG UNIV OF TECH
Identity authentication method and electronic equipment
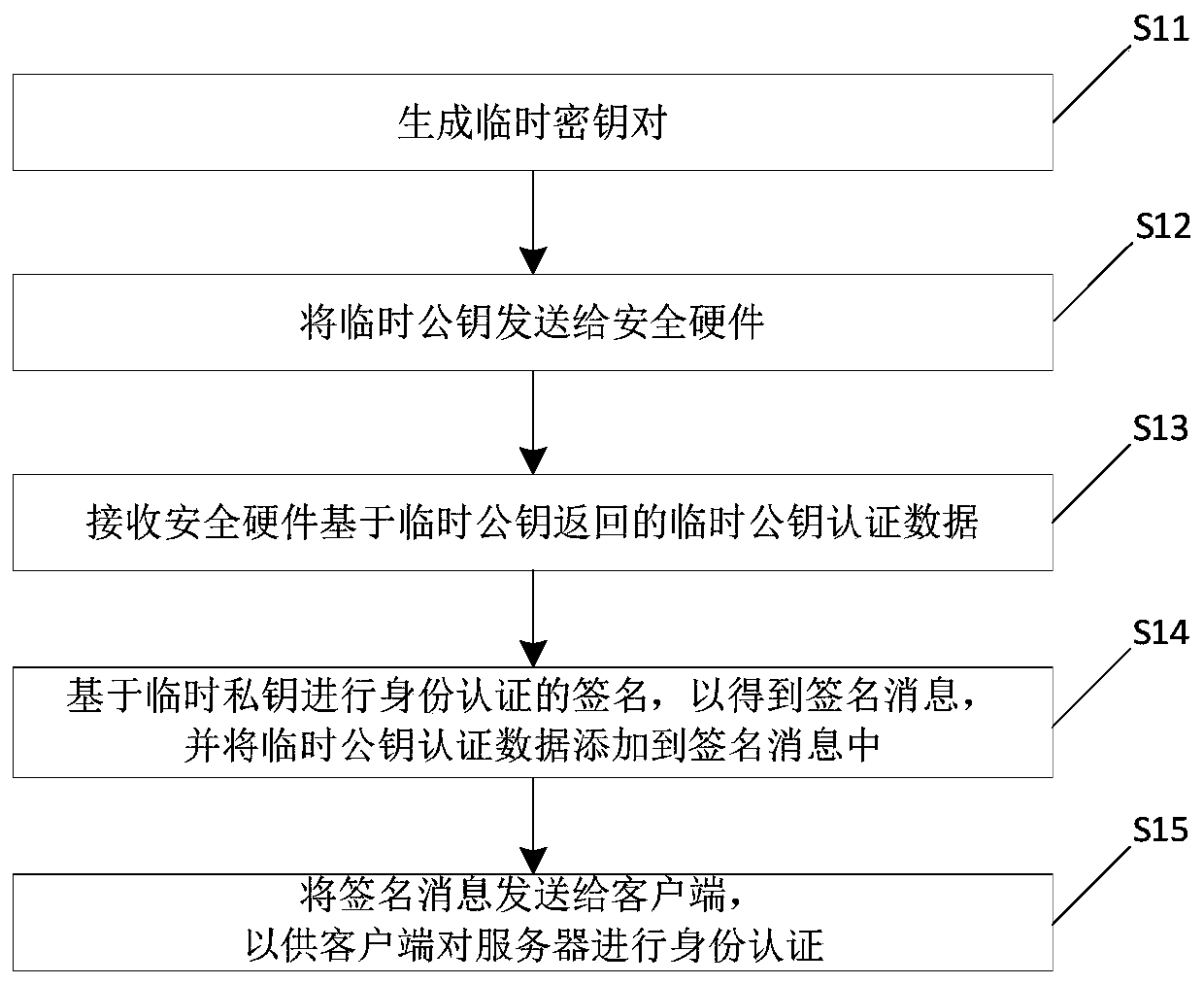
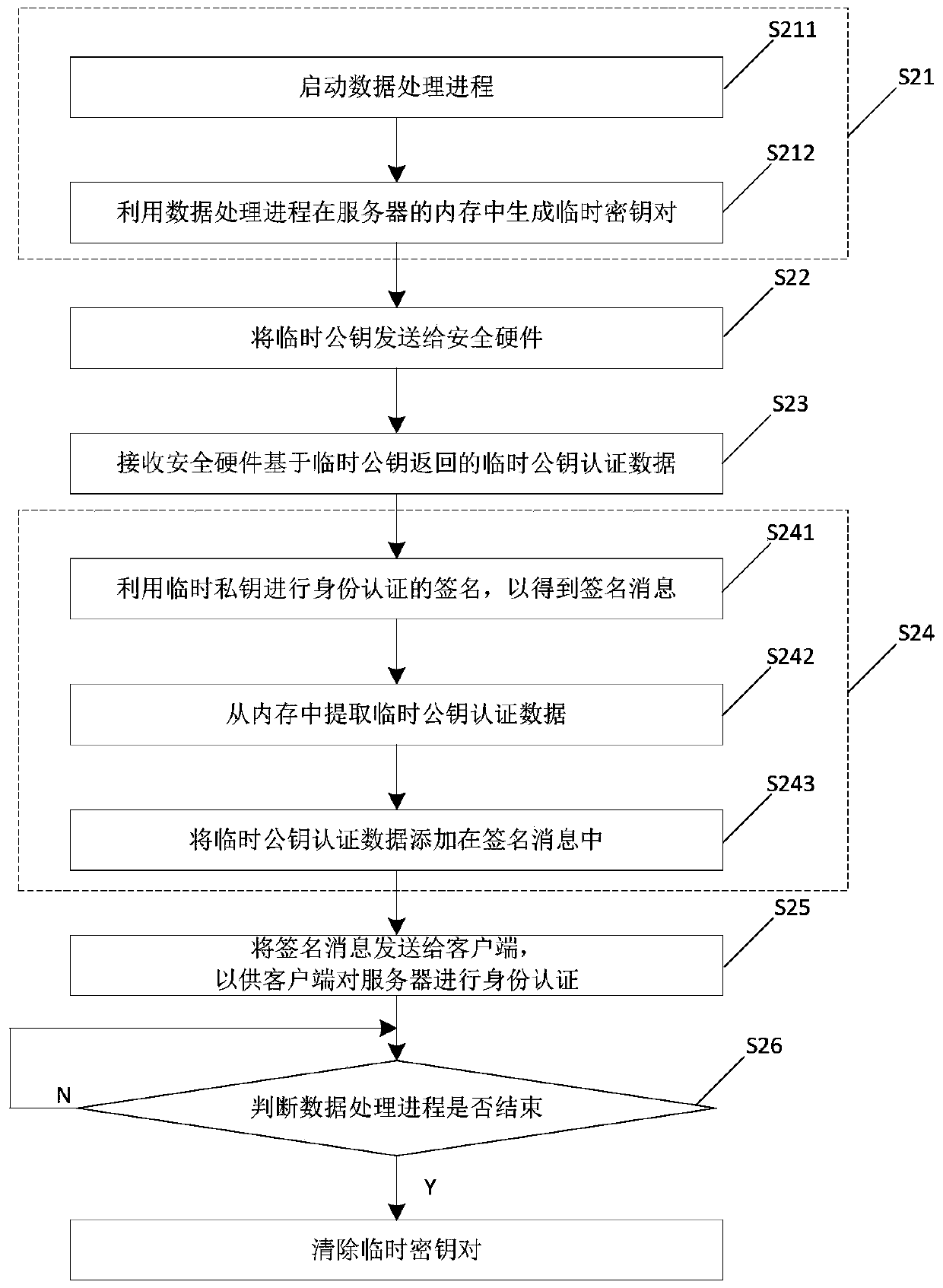
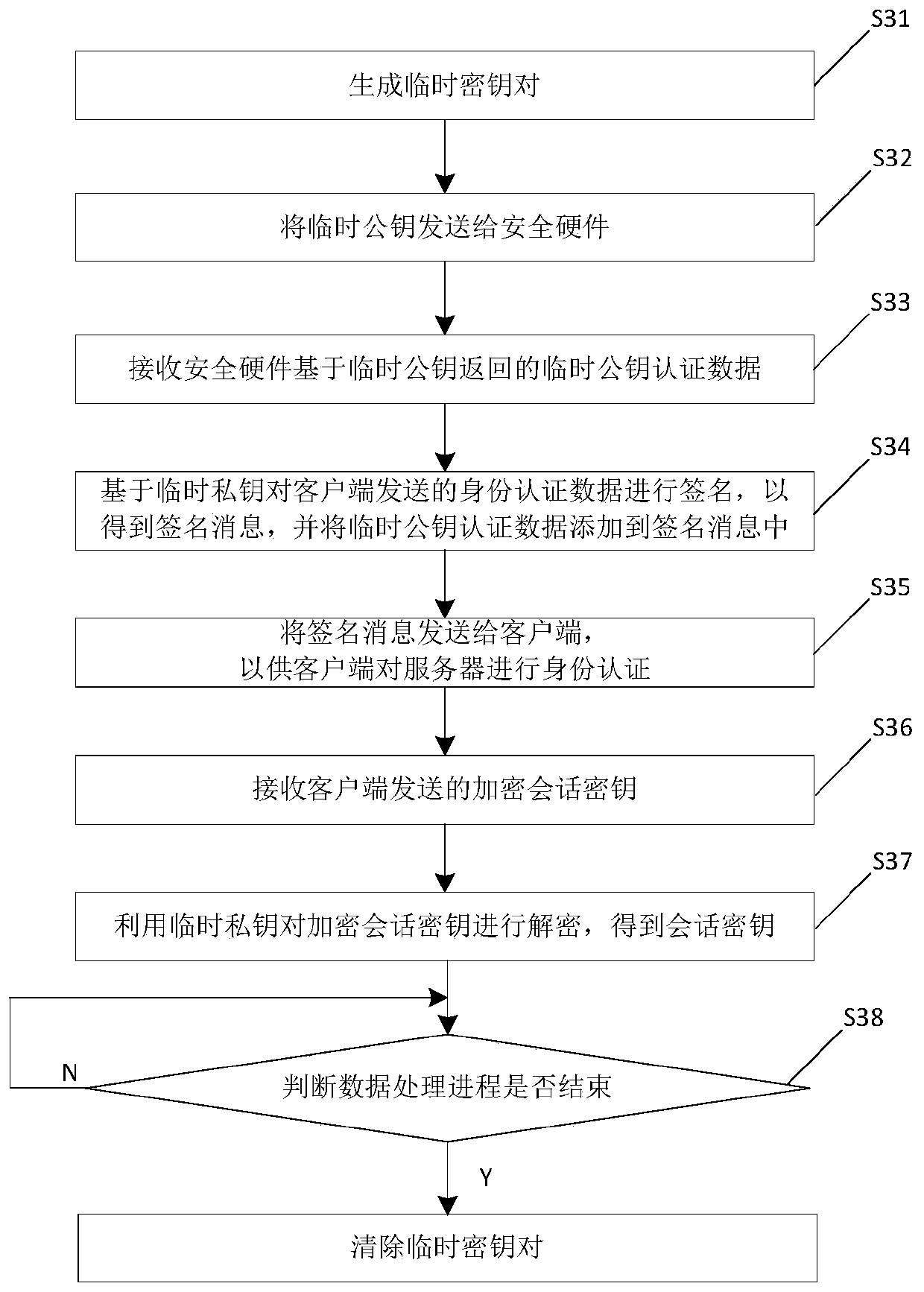
ActiveCN110190964AImprove identity authentication efficiencyDoes not compromise securityKey distribution for secure communicationUser identity/authority verificationPublic key authenticationClient-side
The invention relates to the technical field of video conferences, and particularly discloses an identity authentication method and electronic equipment, and the method comprises the steps: generatinga temporary key pair, wherein the temporary key pair comprises a temporary public key and a temporary private key; sending the temporary public key to the security hardware; receiving temporary public key authentication data returned by the security hardware based on the temporary public key, wherein the temporary public key authentication data is obtained by signing a temporary public key by using a hardware private key by the security hardware; signing the identity authentication data sent by the client based on the temporary private key to obtain a signature message, and adding the temporary public key authentication data into the signature message; and sending the signature message to the client, so that the client performs identity authentication on the server. In the security hardware, only the hardware private key needs to be adopted to sign the temporary public key for one time, and the other signatures of the identity authentication data sent by all the clients can be completed in the server; and the processing performance of the server is used for signing, so that the identity authentication efficiency is greatly improved.
Owner:SUZHOU KEDA TECH
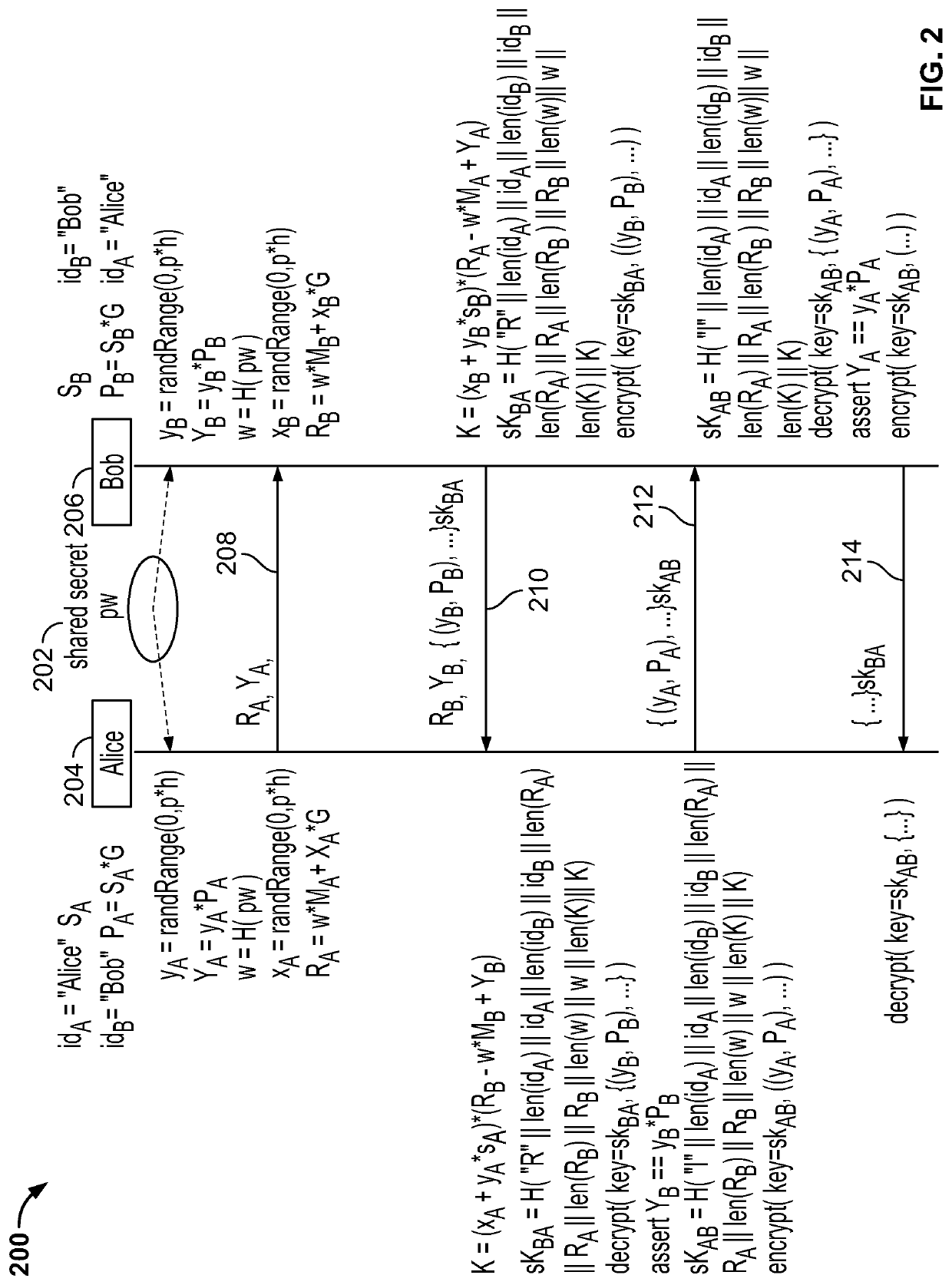
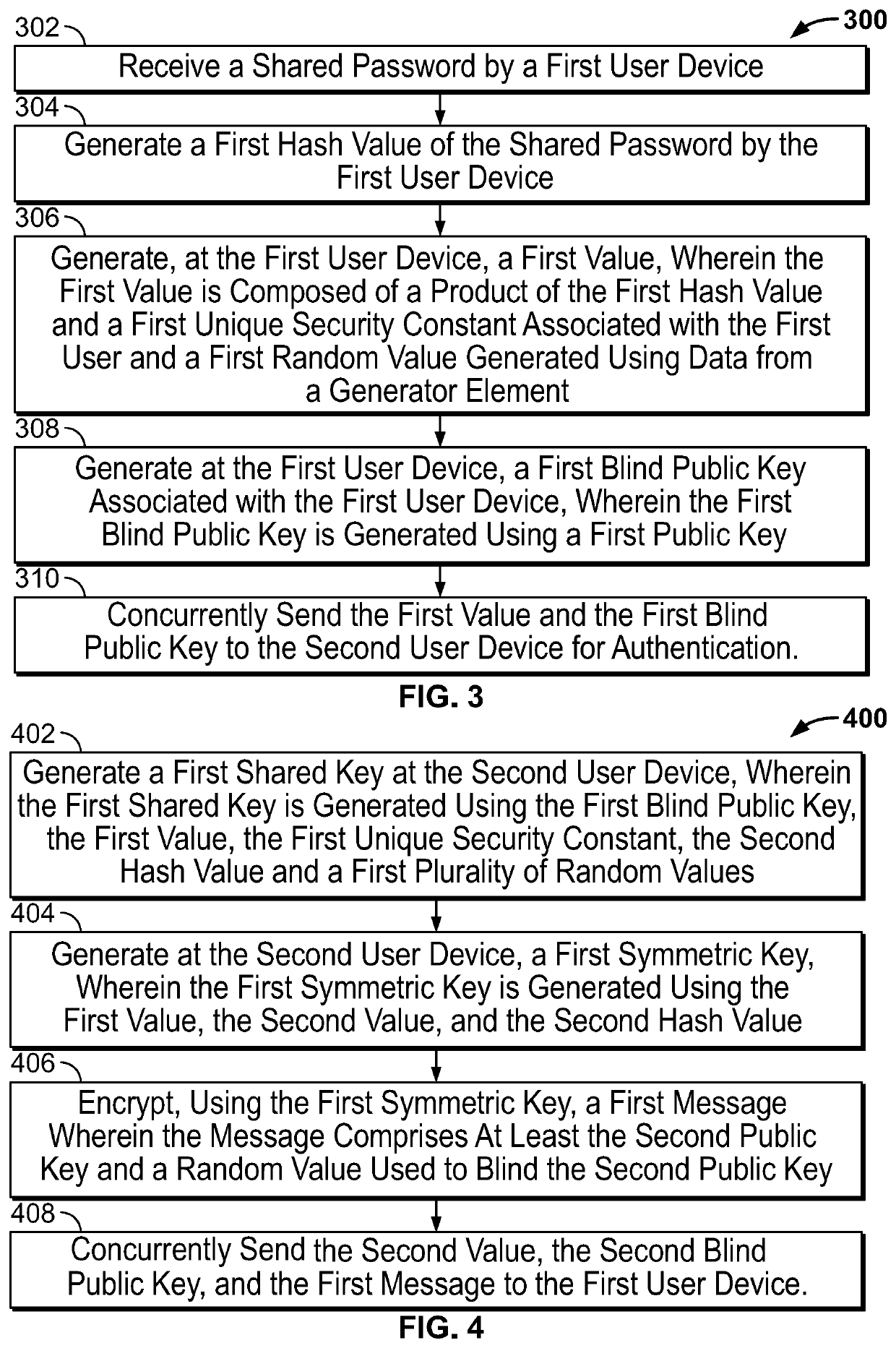
Systems and methods for efficient password based public key authentication
ActiveUS10681038B1Key distribution for secure communicationMultiple keys/algorithms usagePublic key authenticationUser device
In a method for efficient password based public key authentication between a first user device and a second user device, a shared password is received by a first user device which generates a first hash value of the shared password and a first value, wherein the first value is composed of at least a product of the first hash value and a first unique security constant associated with the first user. The first user device then generates a first random value generated using data from a generator element, and a first blind public key associated with the first user device, wherein the first blind public key is generated using a first public key. The first user device concurrently sends the first value and the first blind public key to the second user device for authentication.
Owner:MARVELL ASIA PTE LTD
Character deformation-based graphical password authentication method
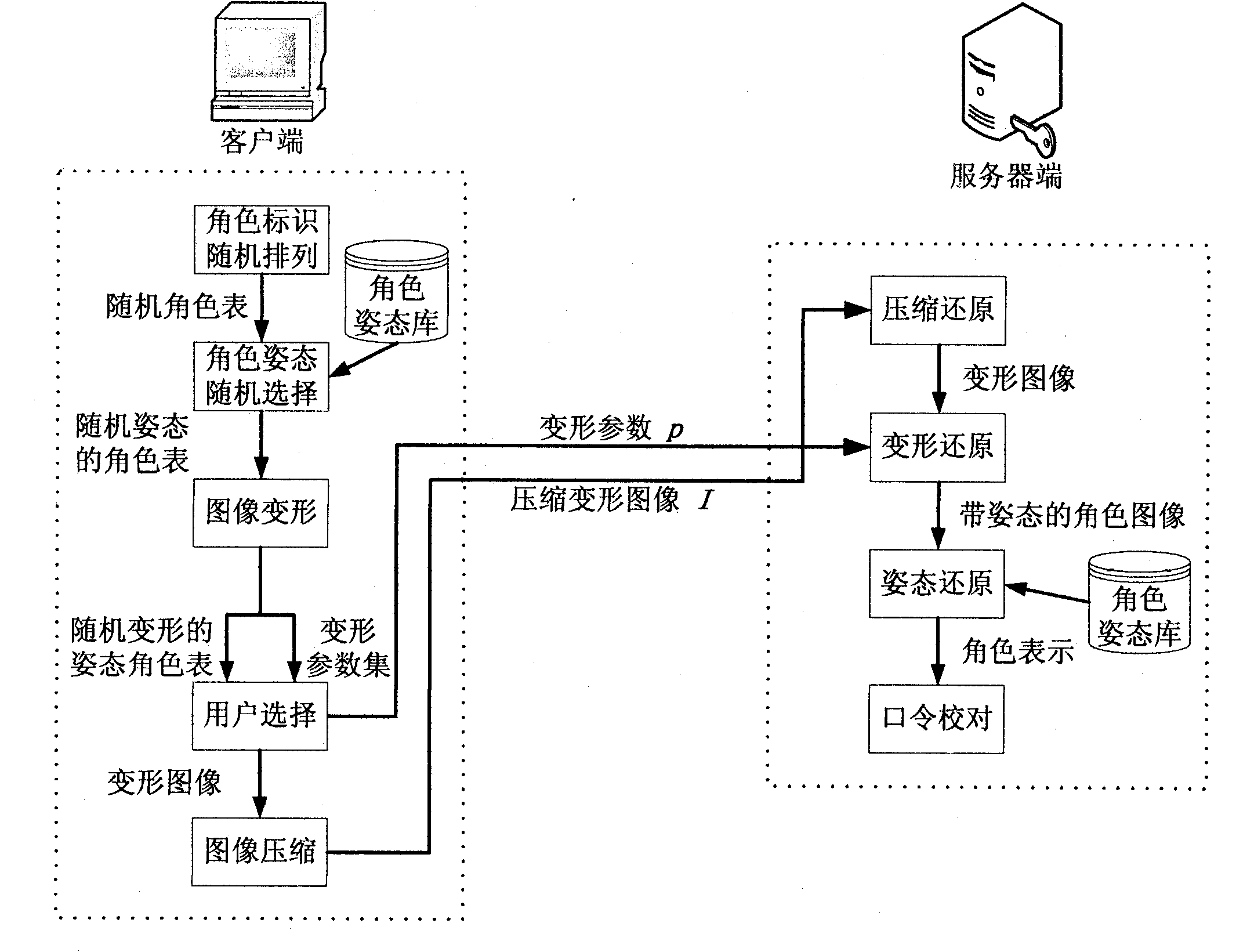
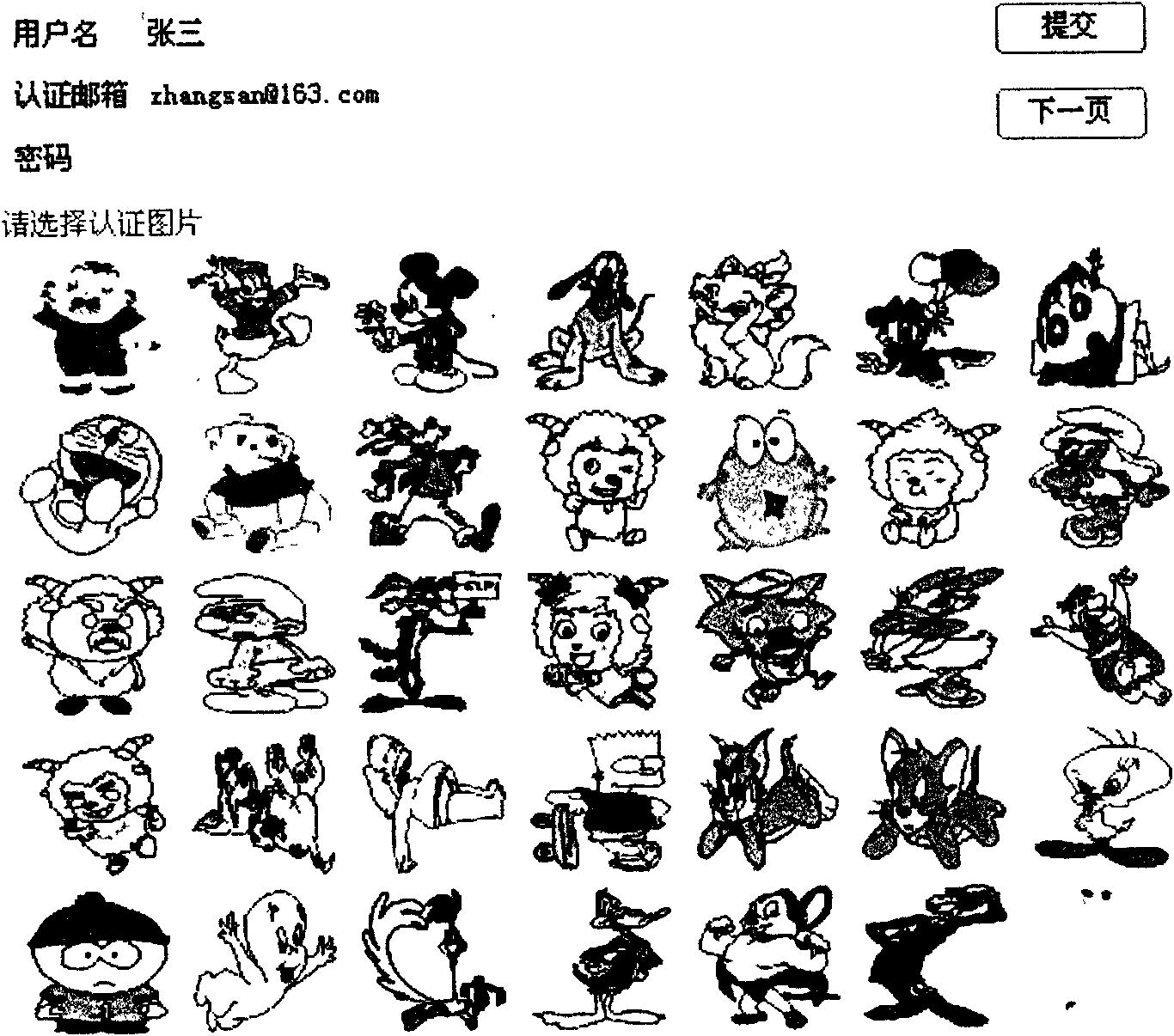
InactiveCN102148686AIncrease code ambiguitySmall amount of memoryPublic key for secure communicationGeometric image transformationPersonalizationGraphics
The invention relates to a character deformation-based graphical password authentication method. The scheme comprises the following steps of: adopting a personalized character deformation graphical password instead of a text password, and presetting a plurality of cartoon character graphics corresponding to a plurality of postures and deformation effects by using a system; constructing an image deformation technology-based public key authentication system in an image password transmission process, transmitting a public key which is an image deformation parameter, and performing authentication by taking an image backward deformation parameter as a private key, wherein a deformation and backward deformation key pair is generated by deformation restrictions, and the private key is insoluble from the public key; enhancing the machine authentication resistance of an image password system by adopting a multi-posture and identical-semanteme cartoon character model generation technology; and fusing a character image deformation technology into the graphical password to increase the coding fuzziness of the password as well as brute force cracking complexity. The method is easy to operate by a user, convenient to memorize and high in system security. The operability and security can be improved by adopting a character picture selection operating way in combination with the cartoon character model generation technology and the image deformation technology.
Owner:SUN YAT SEN UNIV
Parent-child card authentication system
InactiveCN1961526ASafe and easy to grantNo wasted storage areaKey distribution for secure communicationUser identity/authority verificationComputer hardwarePublic key authentication
The invention settle the problems that even when a special relationship is present between IC card owners, authority of one of the IC card owners cannot be easily given to the other owner of the IC card. An IC card of a second owner can issue a public key certificate of the IC card of a first owner so that the IC card of the first owner can be recognized as a child card of the IC card of the second owner. Thus, the first generation card authenticated by a route authentication station is set as an ancestor which can generate a descendent card which receives the authentication. By checking which parent card has issued the public key authentication owned by the child card, it is possible to given the authority of the parent card to the child card.
Owner:PANASONIC CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com