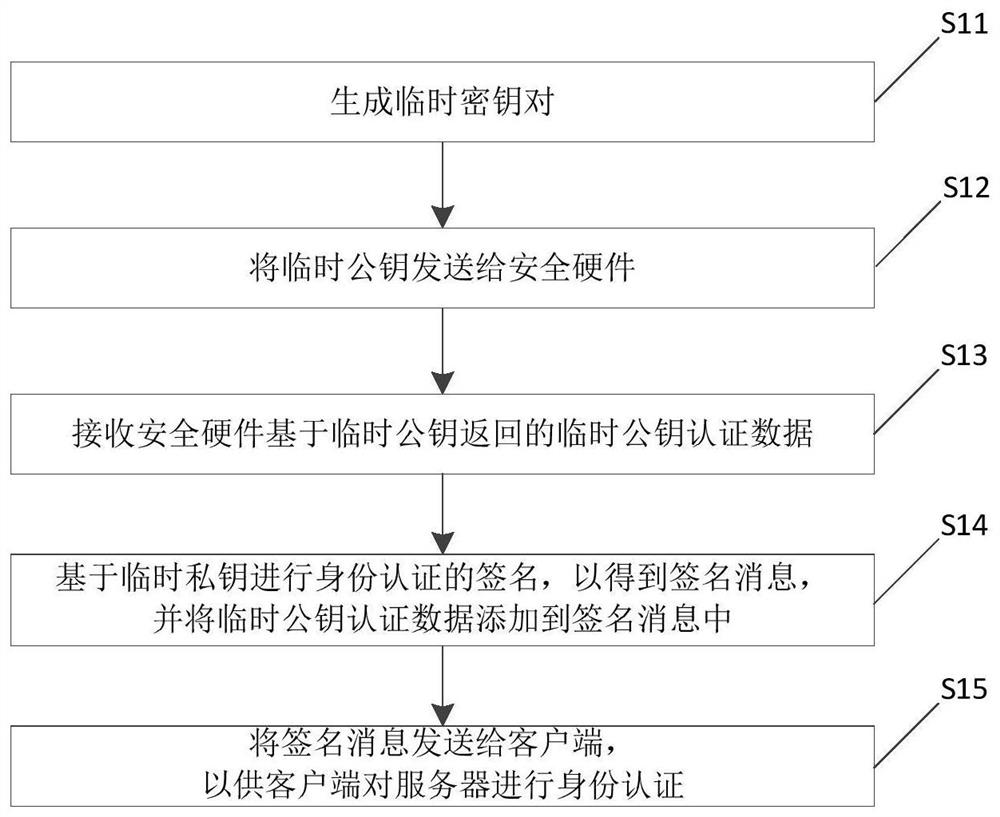
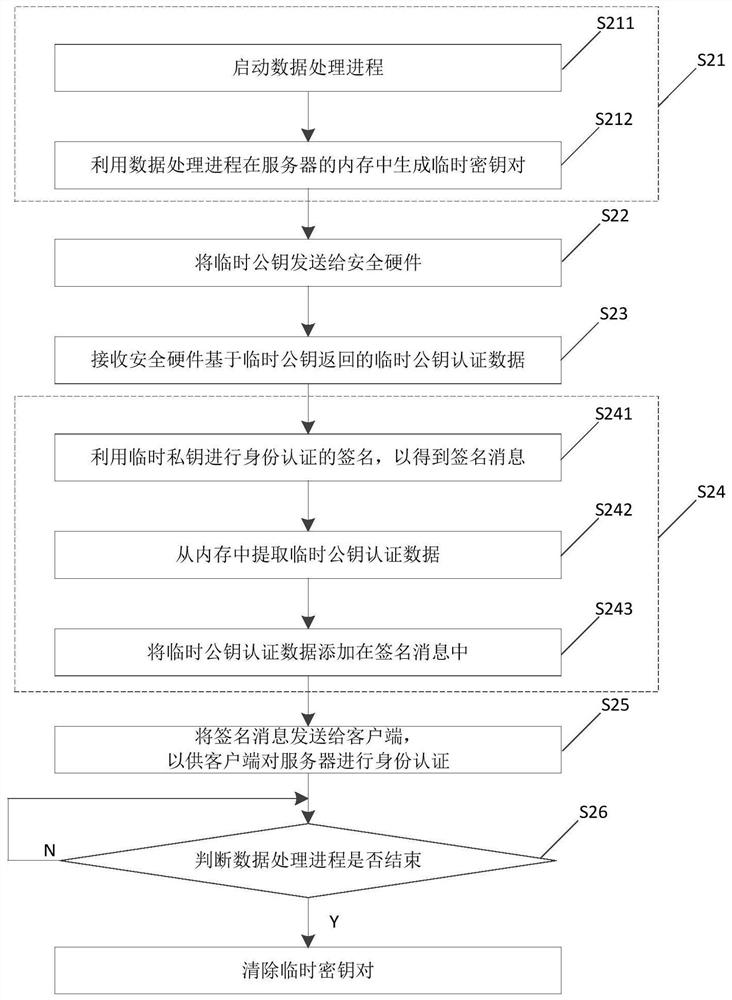
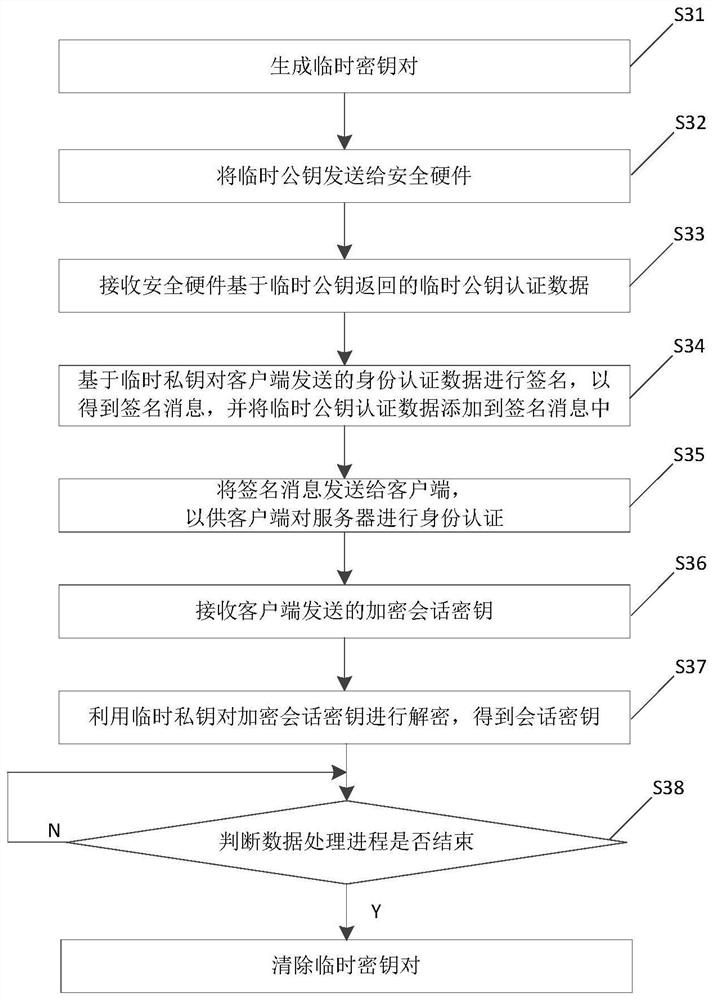
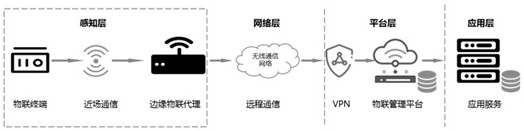
Patents
Literature
47results about How to "Improve identity authentication efficiency" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
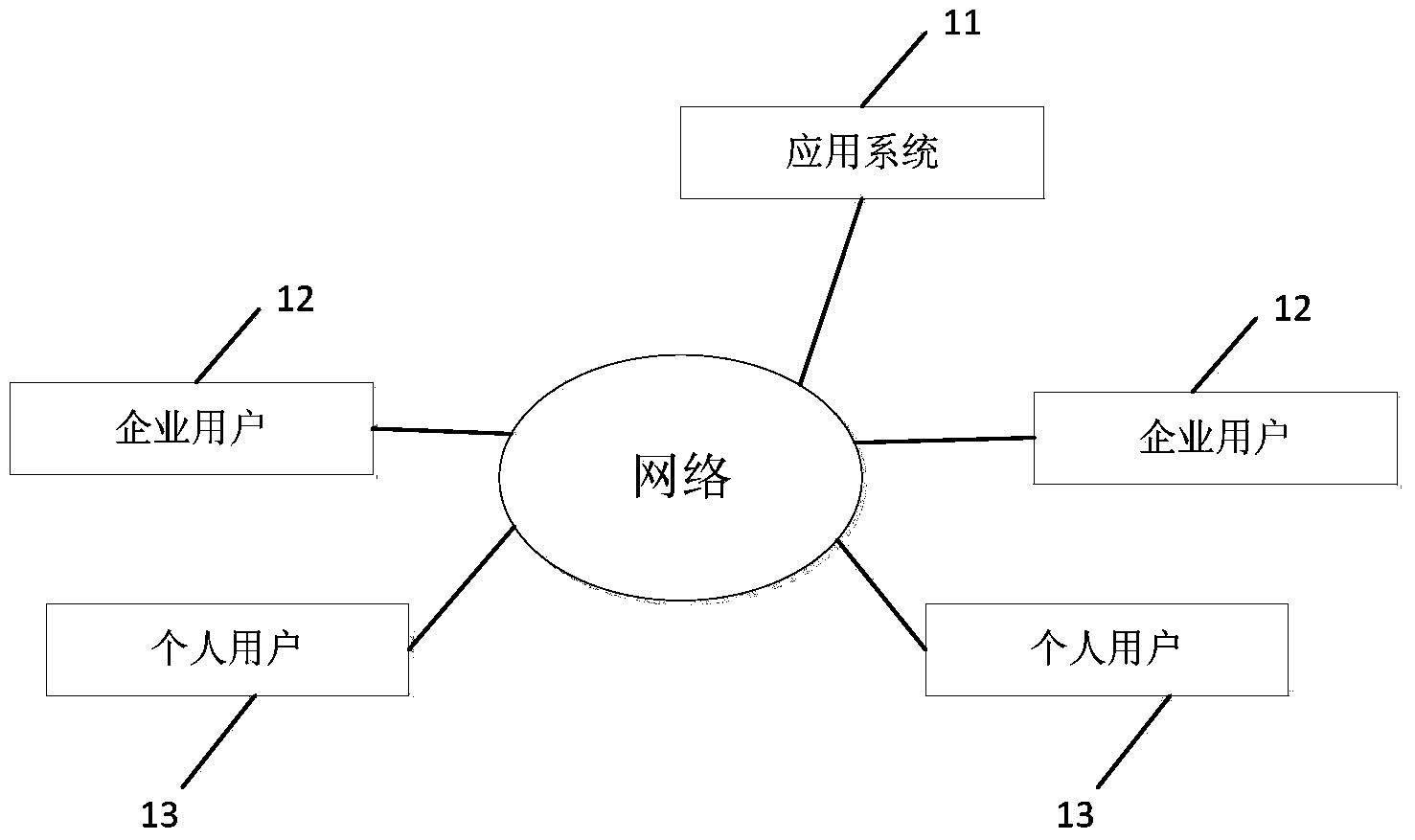
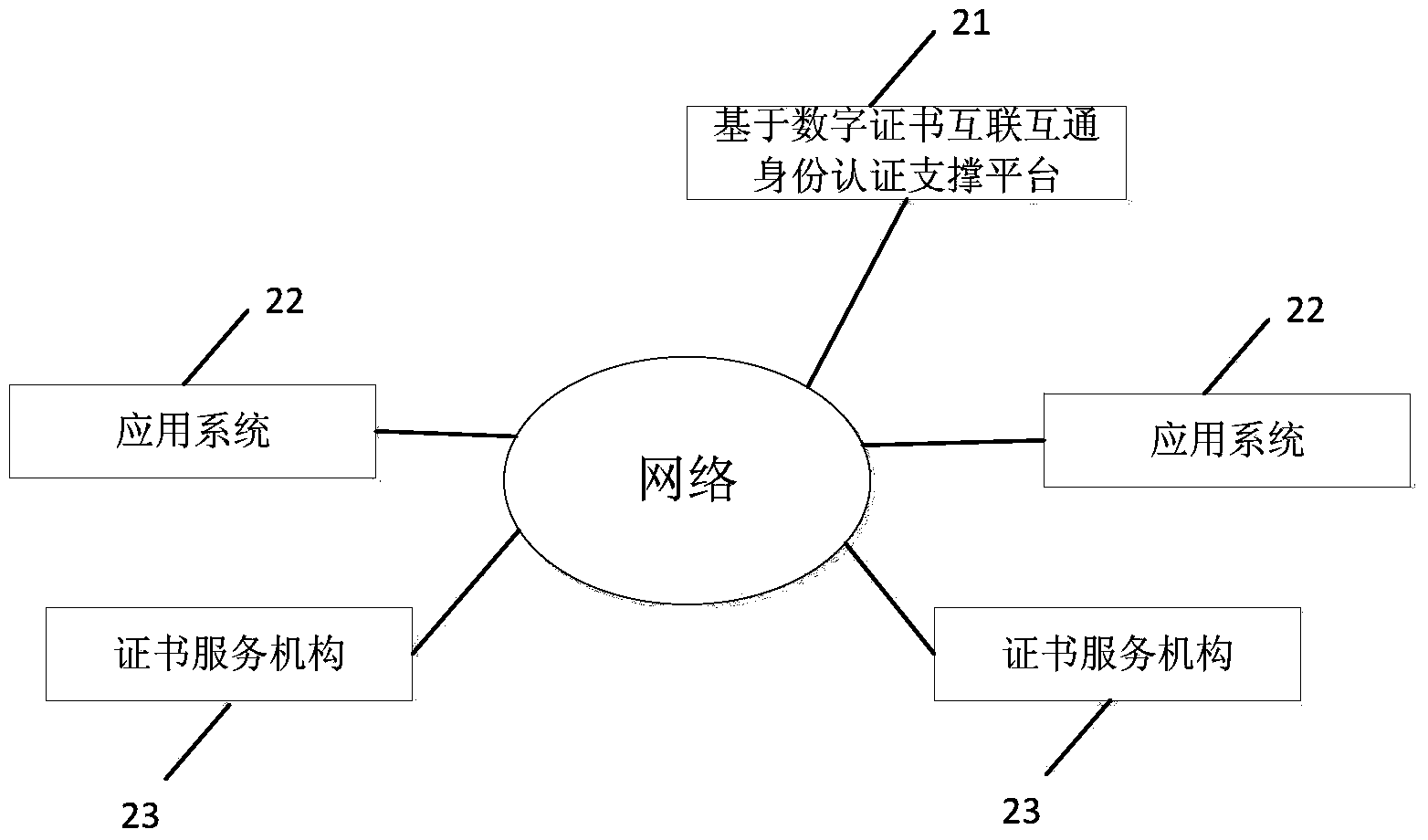
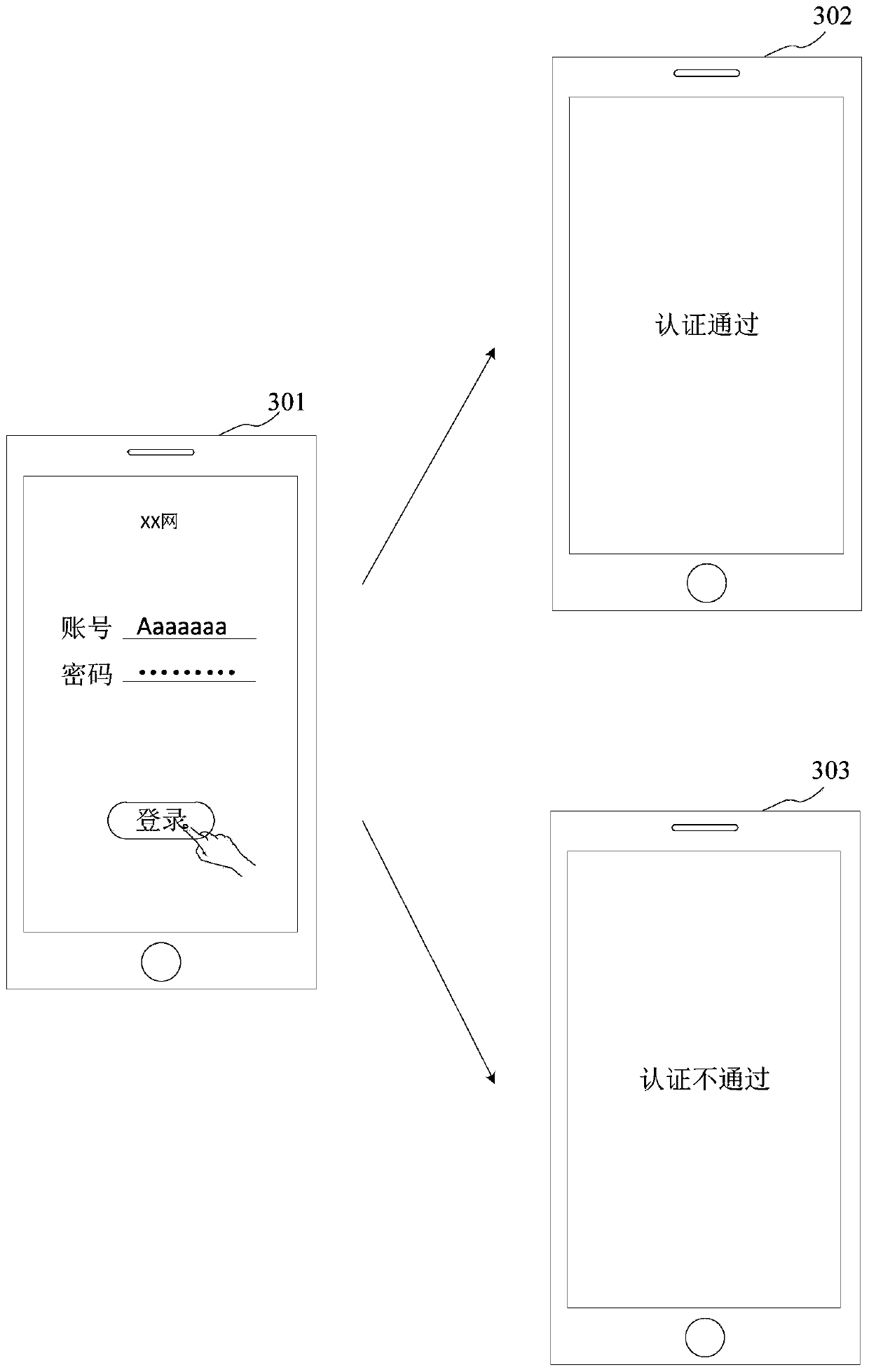
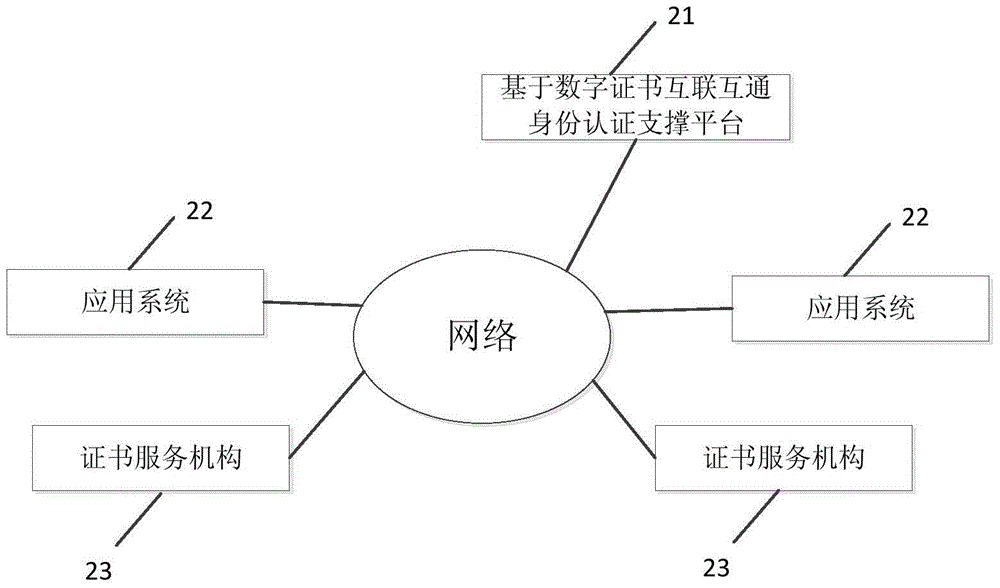
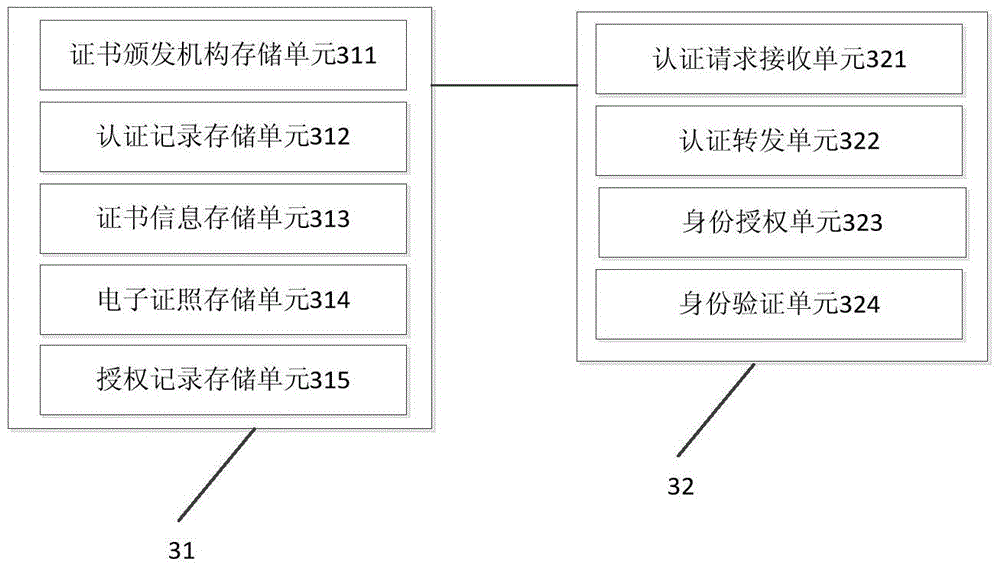
Identity authentication supporting platform and authentication method based on digital certificate interconnection and interworking
ActiveCN103475485AImprove docking efficiencySimplify the identity verification processUser identity/authority verificationDigital data authenticationInternet privacyEngineering
The invention discloses an identity authentication supporting platform and an authentication method based on digital certificate interconnection and interworking to solve the problems that an existing digital certificate is repeatedly issued and approved, and the using cost of a user is high and the using process is complex and to enable the identity of the virtual network to be relevant to the identity of the real world. The requests that digital certificate authentication needs to be carried out on application systems are centralized to the identity authentication supporting platform based on the digital certificate interconnection and interworking to be processed in a unified mode, the application systems are high in communicating efficiency, and the identity authentication procedures are simple and reliable. The identity authentication information based on the digital certificate interconnection and interworking can be shared, the digital certificate authentication does not need to be carried out on all application systems, and the identity authentication efficiency is improved.
Owner:ZHEJIANG ICINFO TECH
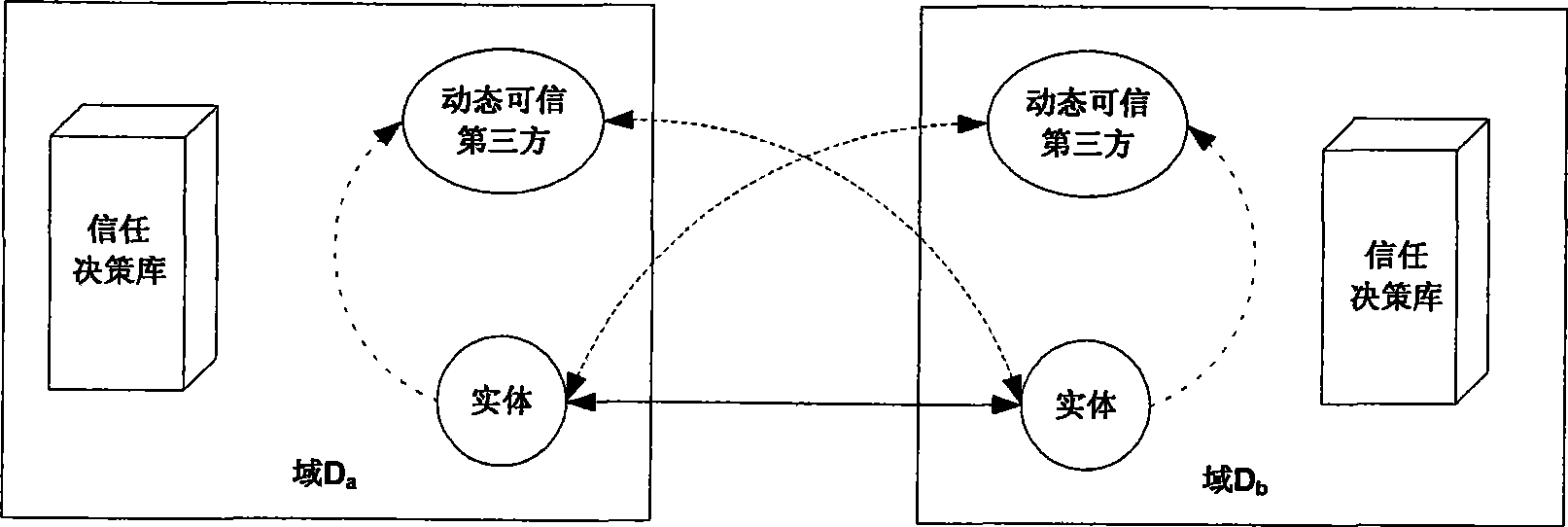
Identification authentication method of open network base on dynamic credible third-party
ActiveCN101378318AImprove reliabilityImprove controllabilityPublic key for secure communicationUser identity/authority verificationThird partyTrusted third party
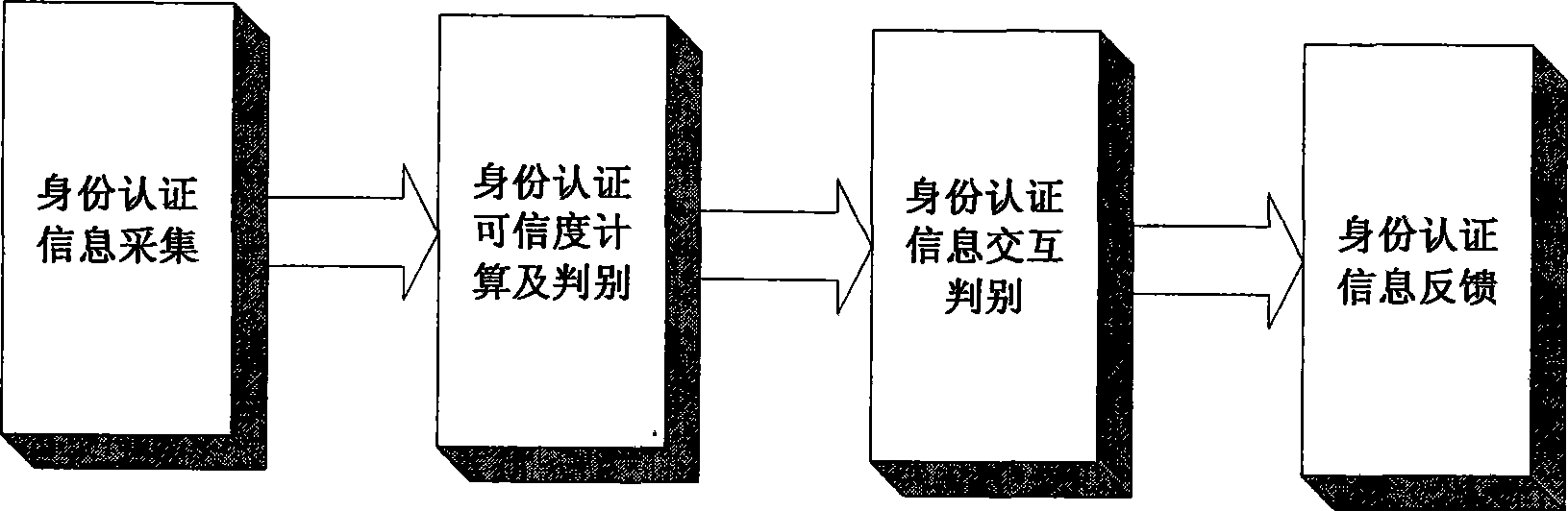
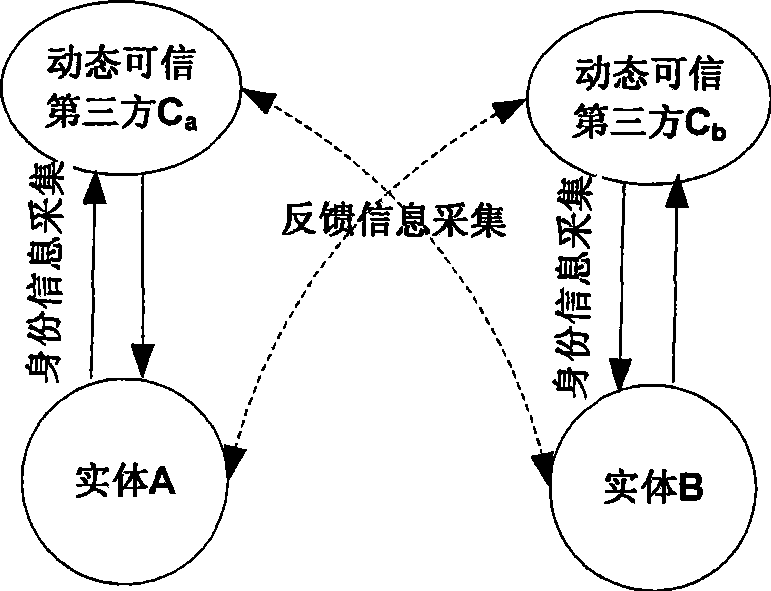
The invention discloses an identity authentication method based on a dynamic trusted third party in an open network. By constructing an authentication system structure containing a trust decision-making database, the dynamic trusted third party and an entity joining the network service, the proposal leads an interactive entity not only to obtain necessary information related to identity authentication but also to obtain a trust feedback set of the trusted third party depended by the interactive entity when the interactive entity is carried out identity authentication; and according to the trust feedback set, the entity independently selects a trust decision-making function and calculates the reliability thereof. The proposal consists of four phases of identity authentication information collecting, identity authentication reliability calculating and judging, identity authentication information mutual judging and identity authentication information feed backing. The invention not only realizes dynamic control to the behavior of the trusted third party by the identity authentication entity in the open network, but also improves the reliability of identity authentication by carrying out reliability calculating and judging.
Owner:NANJING UNIV OF POSTS & TELECOMM
Multi-layer blockchain cross-domain authentication method in Internet of Things application scene
ActiveCN112637189AAvoid Privacy LeakageImprove space utilizationTransmissionInternet privacyThe Internet
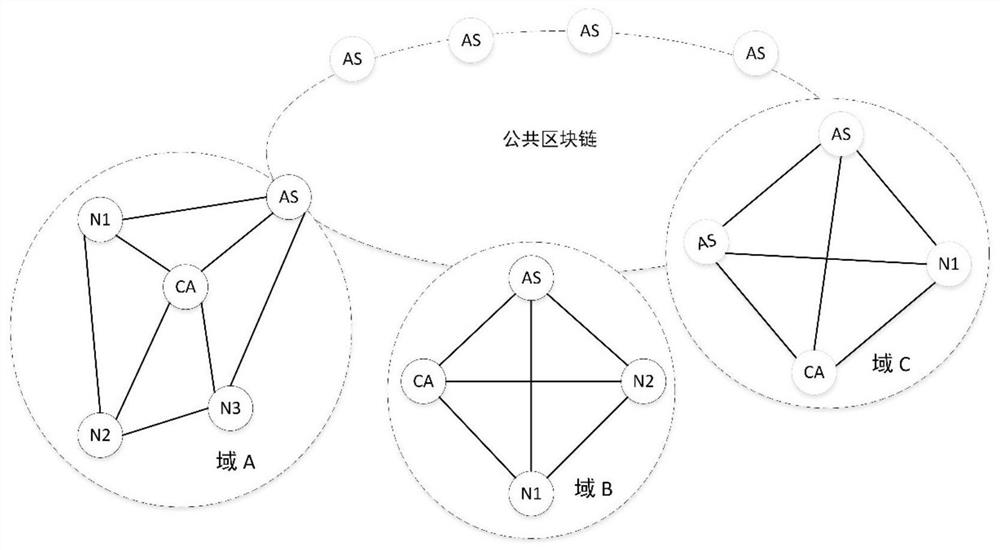
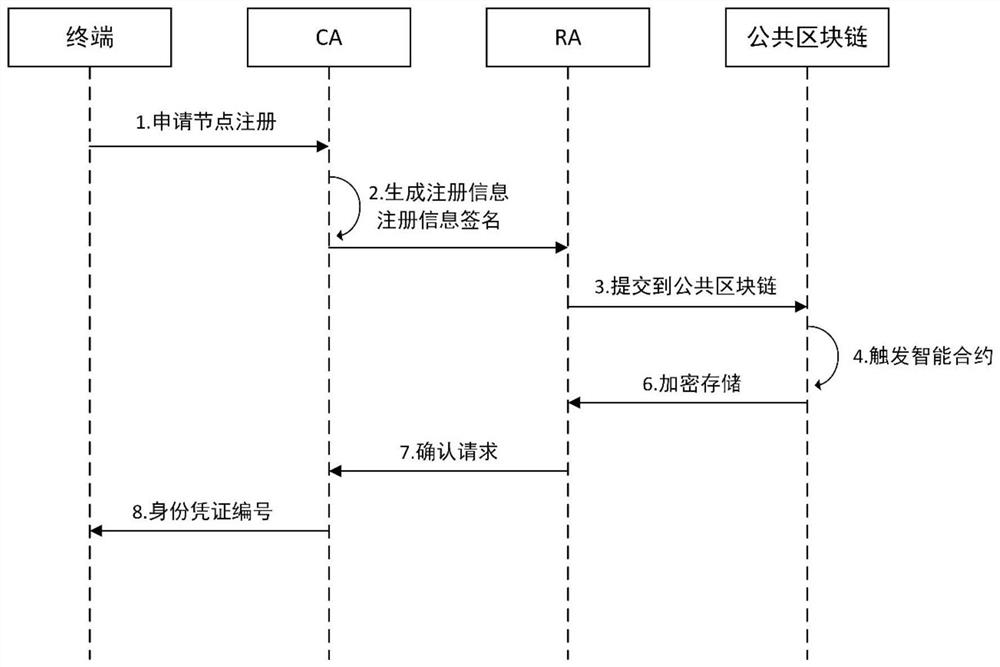
The invention relates to a multi-layer blockchain cross-domain authentication method in an Internet of Things application scene, and belongs to the technical field of Internet of Things and blockchains. According to the method, a blockchain identity registration protocol, a cross-domain identity authentication protocol and a node trust degree evaluation method based on delegation proving of rights and interests are used for carrying out distributed node management and security protection on the blockchain in an application scene of the Internet of Things; and when nodes of different blockchains need to carry out cross-chain identity authentication and data exchange, the across-chain trusted identity authentication is carried out by using a public block chain, so that the user privacy and the data security are ensured. The technical scheme includes the contents in the specification. Compared with an original centralized identity authentication mode, the identity authentication efficiency under the distributed application scene of the Internet of Things is improved, the management problem of certificates under a heterogeneous network is solved, and good safety and usability are achieved.
Owner:CHONGQING UNIV +1
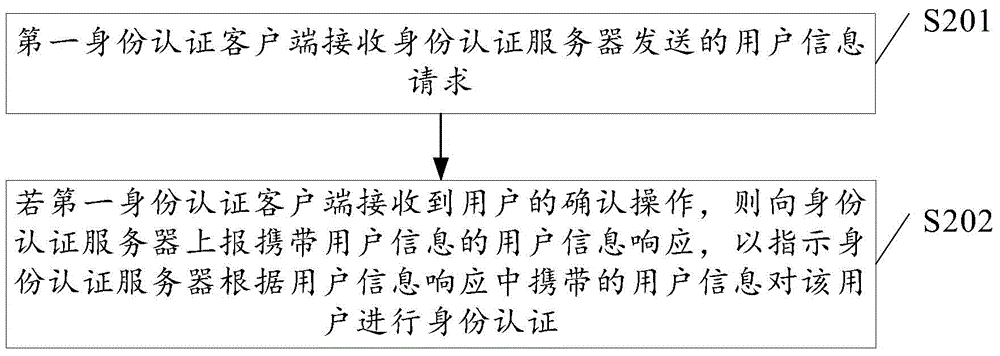
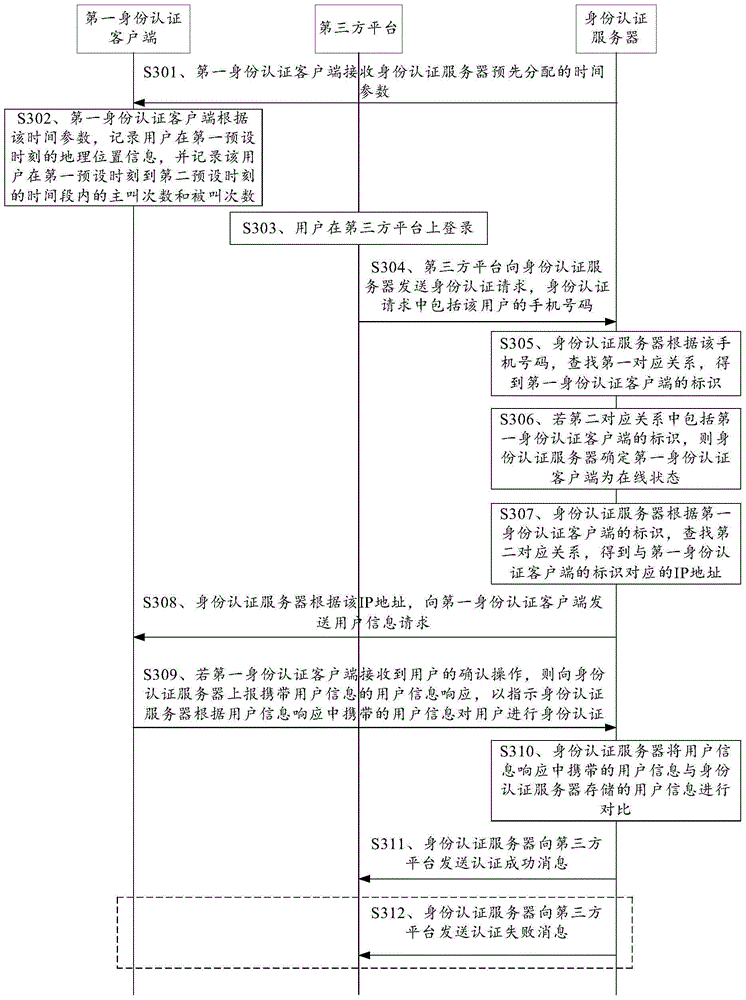
Identity authentication method and identity authentication device
InactiveCN105072112AImprove experienceEasy accessTransmissionSecurity arrangementThird partyPassword
The embodiment of the invention discloses an identity authentication method and an identity authentication device, and relates to the technical field of communication. According to the identity authentication method and the identity authentication device, the problem of relatively poor user experience as a large number of complex user names and passwords need to be remembered is avoided, and the identity authentication efficiency can be improved without downloading a SIM card application. The specific scheme is that an identity authentication server receives an identity authentication request sent by a third-party platform, determines an identifier of a first identity authentication client by searching for a pre-stored corresponding relationship based on a phone number, sends a user information request if the first identity authentication client is in an online state, sends an authentication success message to the third-party platform if a user information response carrying user information is received and the user information is in accordance with user information stored in the identity authentication server, and sends an authentication failure message to the third-party platform if the user information is inconsistent with the user information stored in the identity authentication server or the user information response carrying the user information is not received.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
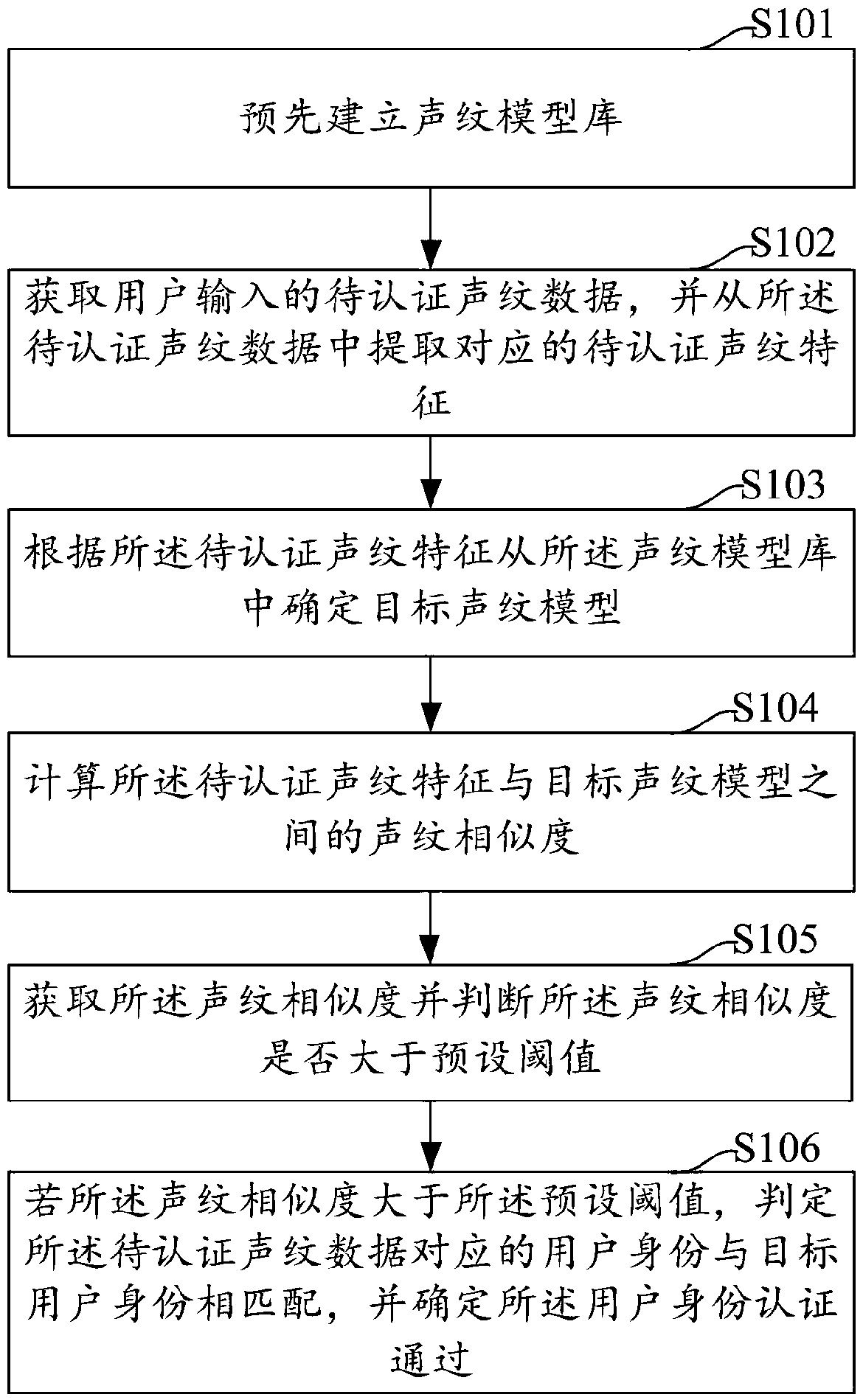
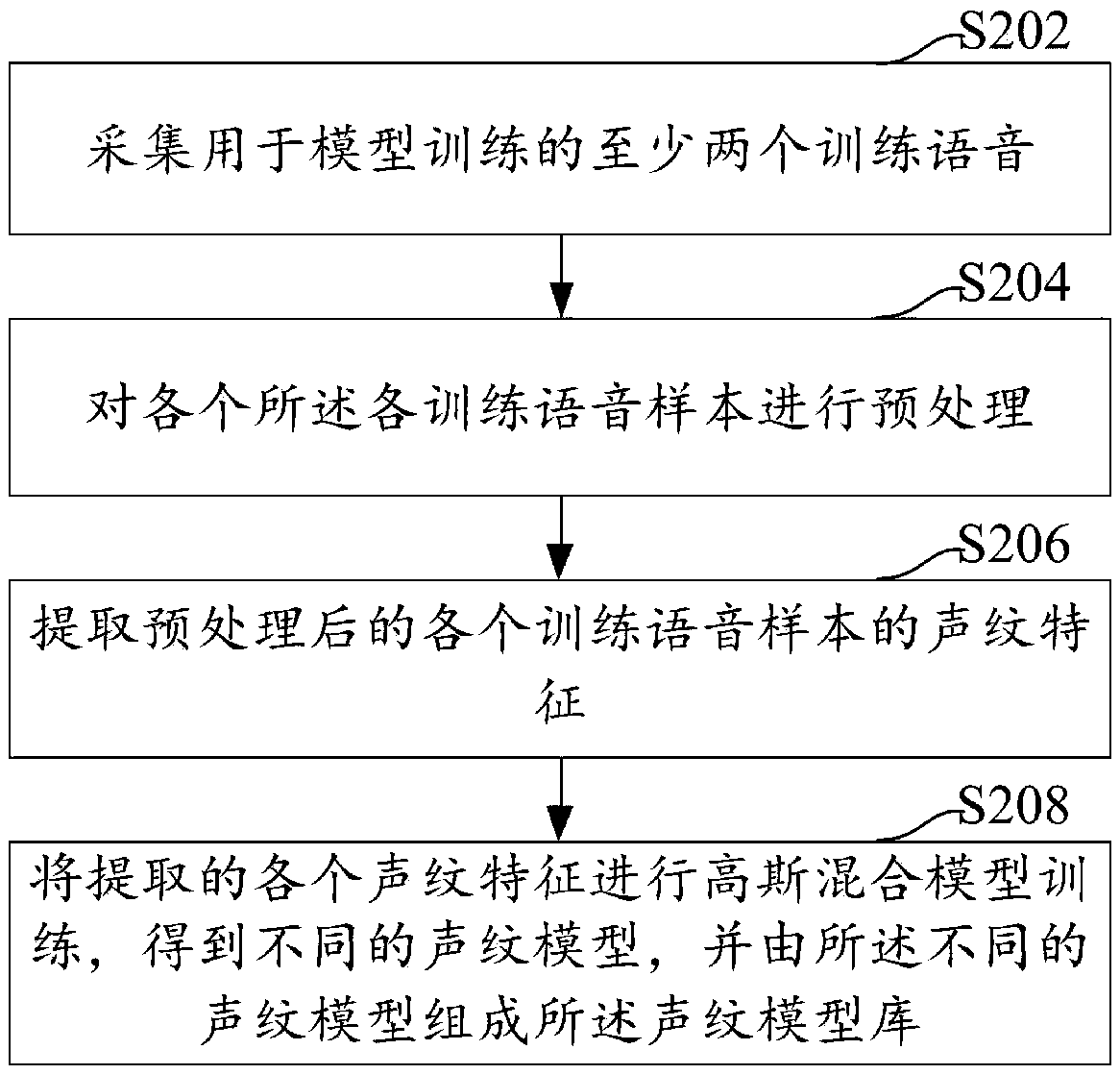
Voiceprint authentication method and apparatus, computer device, and storage medium
PendingCN109243465AImprove identity authentication efficiencyReduced response timeSpeech analysisPattern recognitionUser input
The embodiment of the invention discloses a voiceprint authentication method and apparatus, a computer device and a storage medium. The method includes: acquiring voice print data to be authenticatedinput by a user, and extracting corresponding voice print features to be authenticated from the voice print data to be authenticated; determining a target voiceprint model from the voiceprint model library according to the voiceprint features to be authenticated; calculating a voiceprint similarity between the voiceprint feature to be authenticated and a target voiceprint model; acquiring the voiceprint similarity and judging whether the voiceprint similarity is greater than a preset threshold; if the voiceprint similarity is greater than the preset threshold value, judging the user identity corresponding to the voiceprint data to be authenticated to be matched with the target user identity, and determining the user identity authentication to be passed. The invention provides the voiceprint identification technology, which can improve the identity authentication efficiency and shorten the response time of the authentication.
Owner:PING AN TECH (SHENZHEN) CO LTD
Video data processing method and device and related equipment
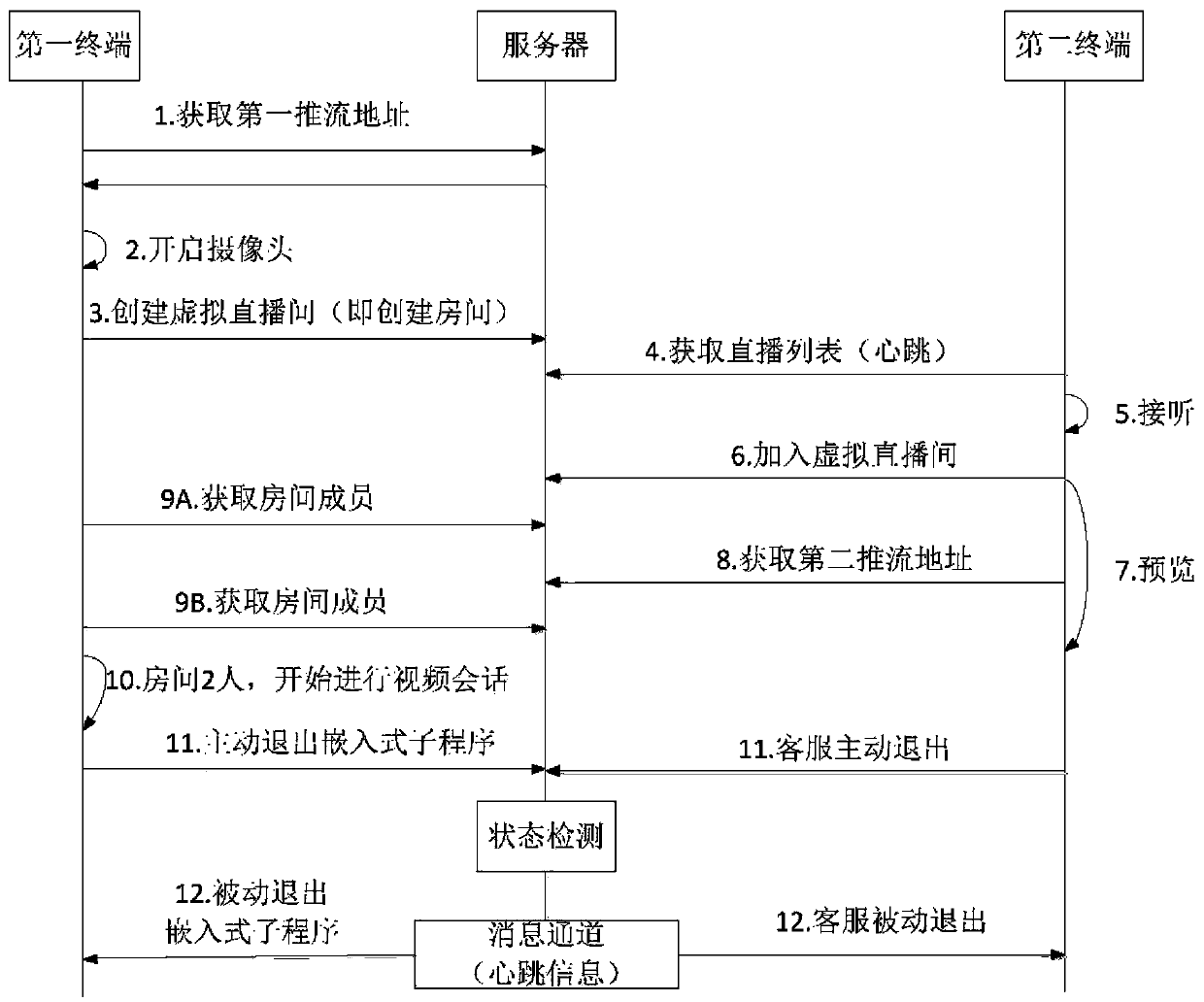
ActiveCN110213522AAvoid identity verificationImprove identity authentication efficiencyTwo-way working systemsSelective content distributionPush pullSession state
The embodiment of the invention discloses a video data processing method and device and related equipment. The method comprises: a server obtaining a push-pull flow request sent by a first terminal; when the server detects that the second terminal responds to the push-pull stream request, monitoring the state of a video session between the first terminal and the second terminal; if it is monitoredthat the state is a session state, the server obtaining a key video frame uploaded by the second terminal; wherein the key video frame is a video frame which is intercepted by the second terminal inthe first video data and contains the first object; wherein the first video data are video data uploaded by a first terminal in the video session; and the server matching the first object in the key video frame with the object in the reference video frame in the service database, and determining the legality of the first object according to a matching result. By adopting the video data processingmethod, the video data processing device and the related equipment disclosed by the embodiment of the invention, the object identification efficiency can be improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Authentication method, device and electronic device
InactiveCN109284593AReduce sending to serverReduce consumptionDigital data authenticationInternet privacyUser input
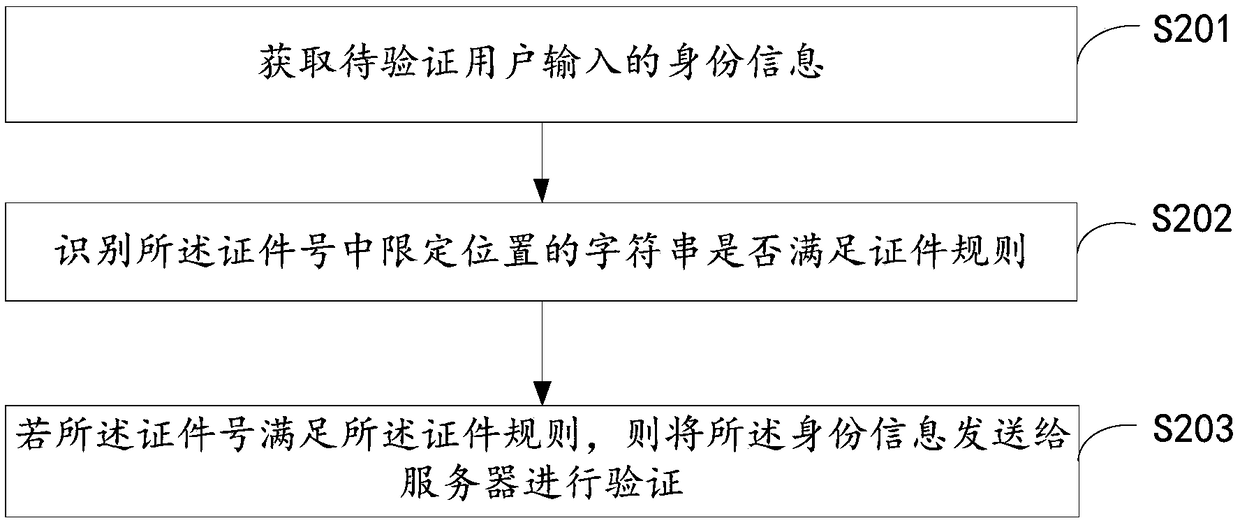
Embodiments of the present invention provide an authentication method, device, and an electronic device. The authentication method comprises the following steps: obtaining the identity information input by the user to be verified, wherein the identity information comprises a certificate number; identifying whether a character string at a defined position in the certificate number satisfies a certificate rule; if the certificate number satisfies the certificate rule, the identity information is sent to the server for verification.
Owner:BEIJING KUANGSHI TECH
Identity authentication, unlocking and payment methods and apparatuses, storage medium, product and device
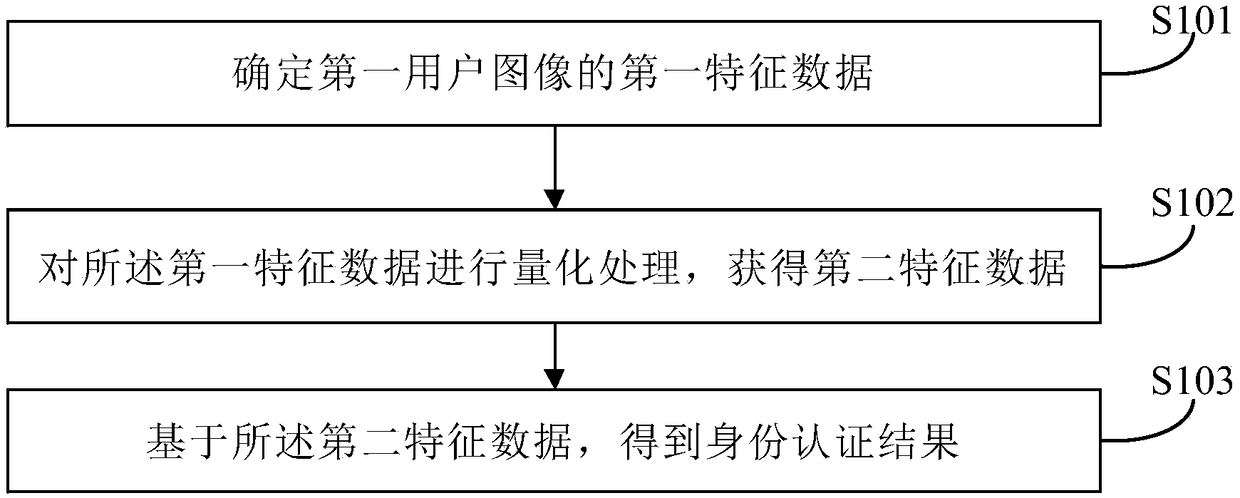
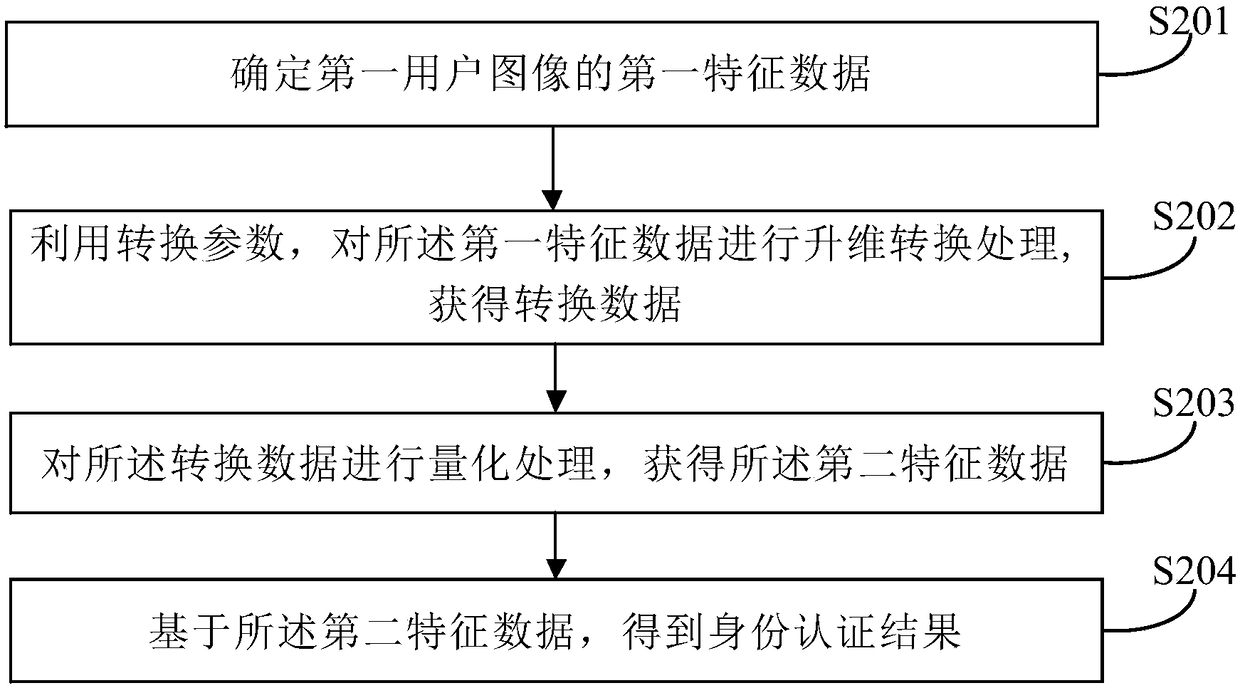
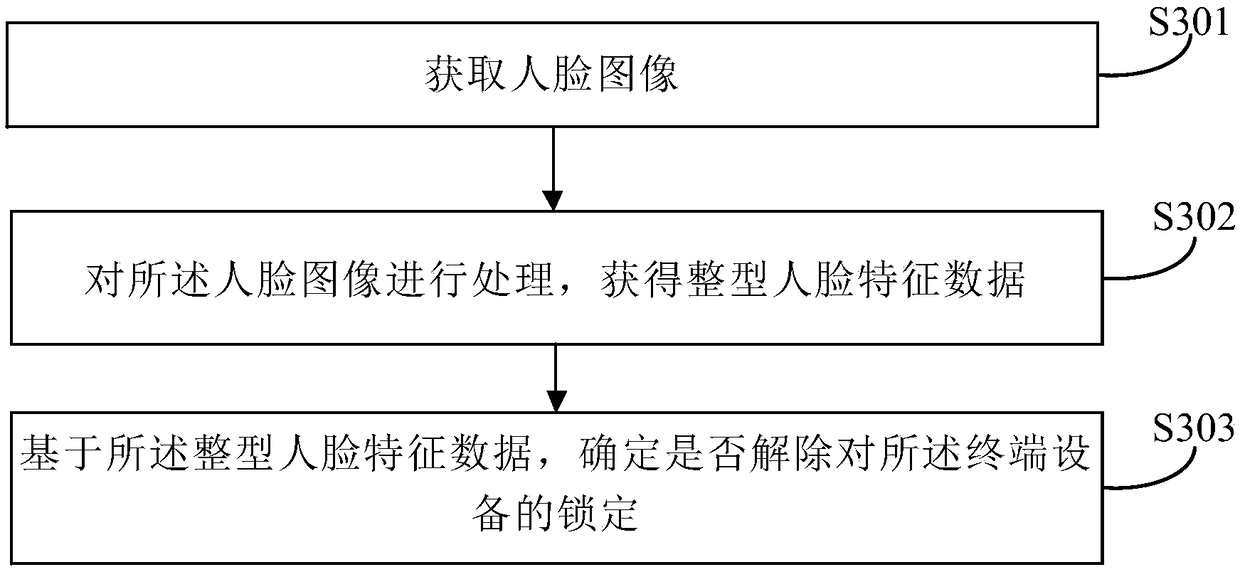
PendingCN108595927AEnsure safetyImprove experienceCharacter and pattern recognitionDigital data authenticationPaymentFeature data
Embodiments of the invention provide identity authentication, unlocking and payment methods and apparatuses, a storage medium, a product and a device, and relate to the field of data processing. The identity authentication method comprises the steps of determining first feature data of a first user image; performing quantization processing on the first feature data to obtain second feature data; and based on the second feature data, obtaining an identity authentication result. Through the identity authentication method and apparatus, the feature data does not need to be encrypted and decryptedin the identity authentication process, so that while the user information security is ensured, the computing resources of the device are saved and the identity authentication efficiency is improved;and therefore, the user experience is optimized.
Owner:BEIJING SENSETIME TECH DEV CO LTD
Identity recognition preprocessing method and system and identity recognition method and system
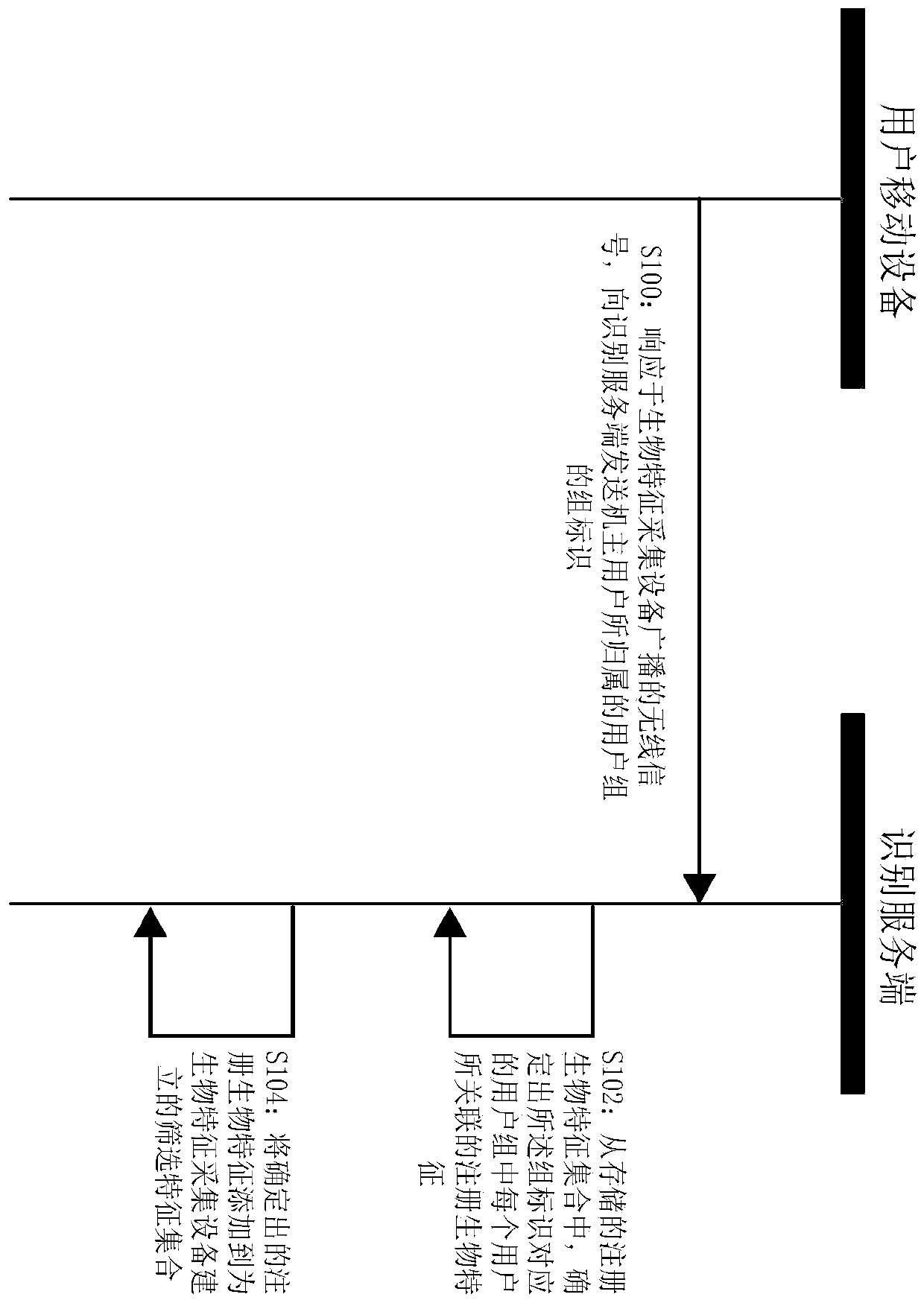
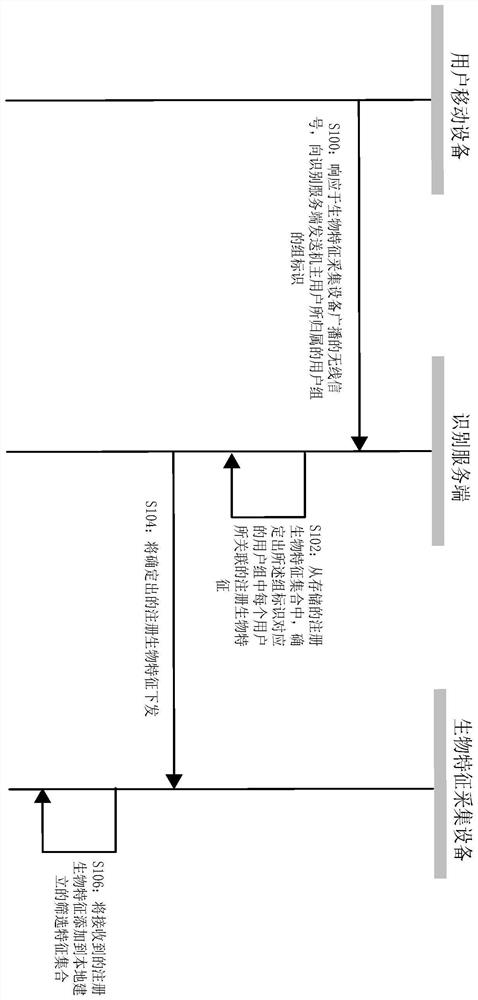
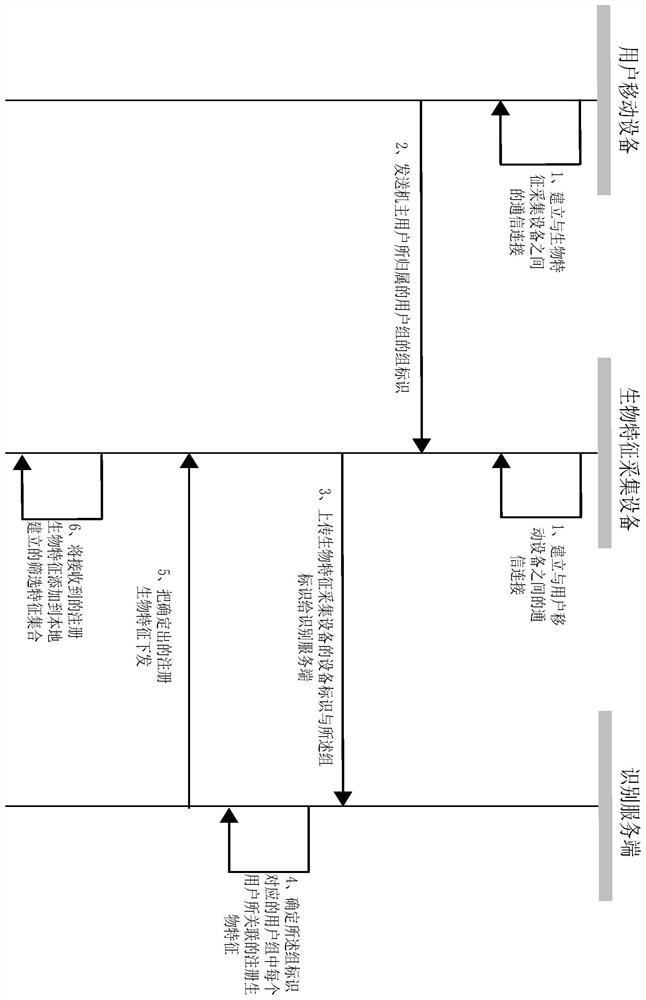
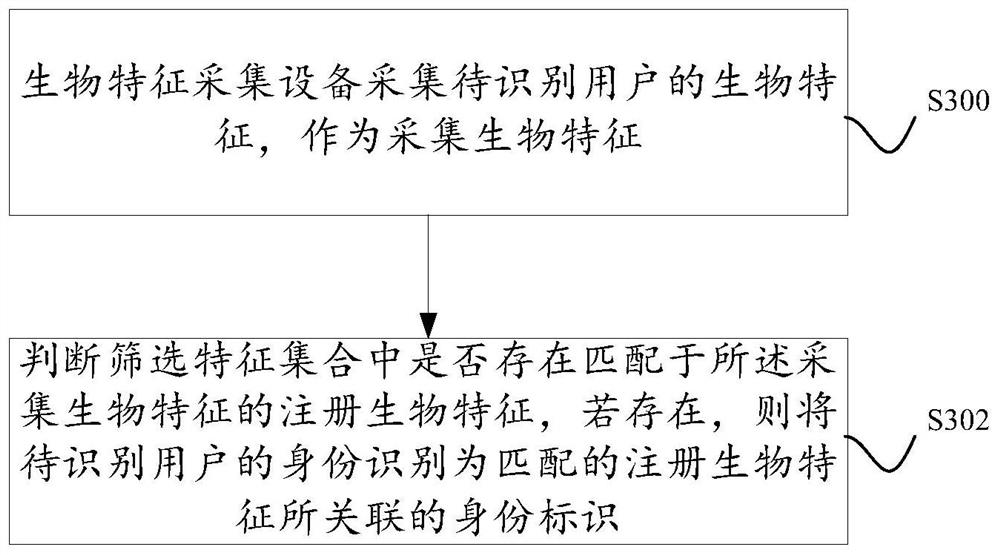
ActiveCN110457882AReduce in quantityImprove identity authentication efficiencyDigital data authenticationPattern recognitionFeature set
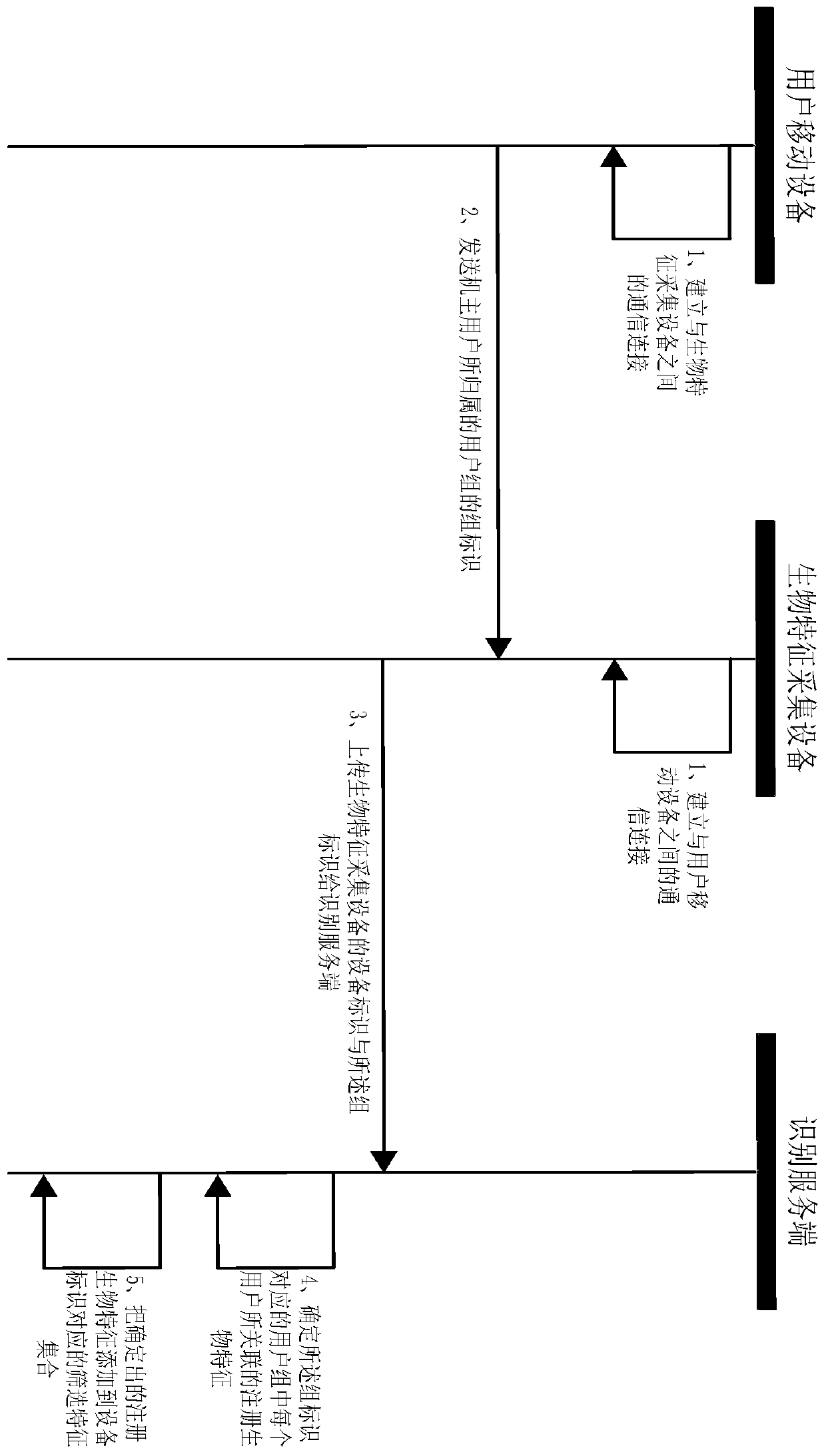
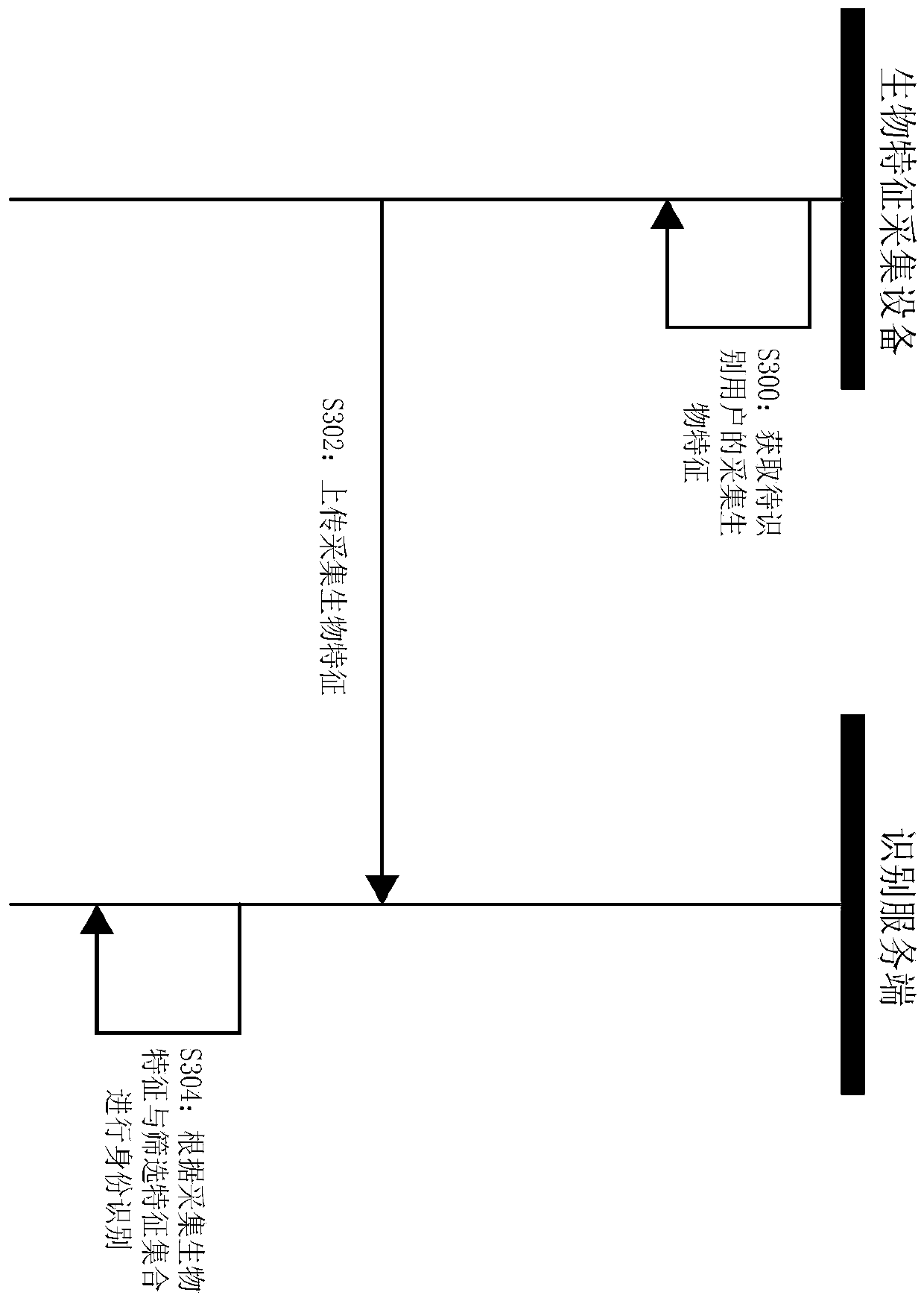
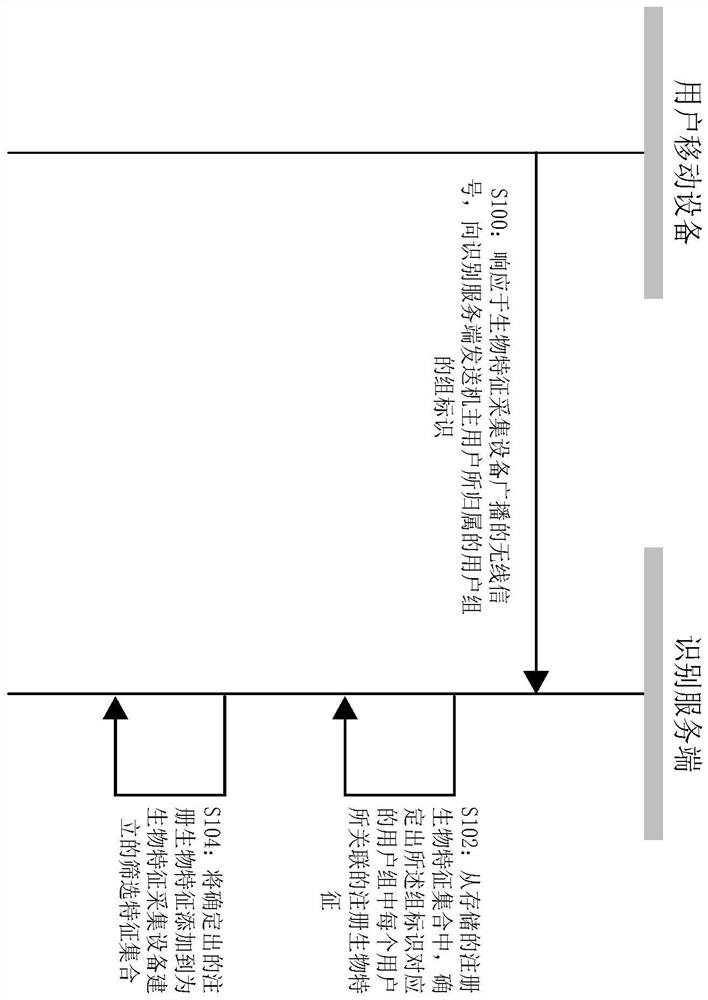
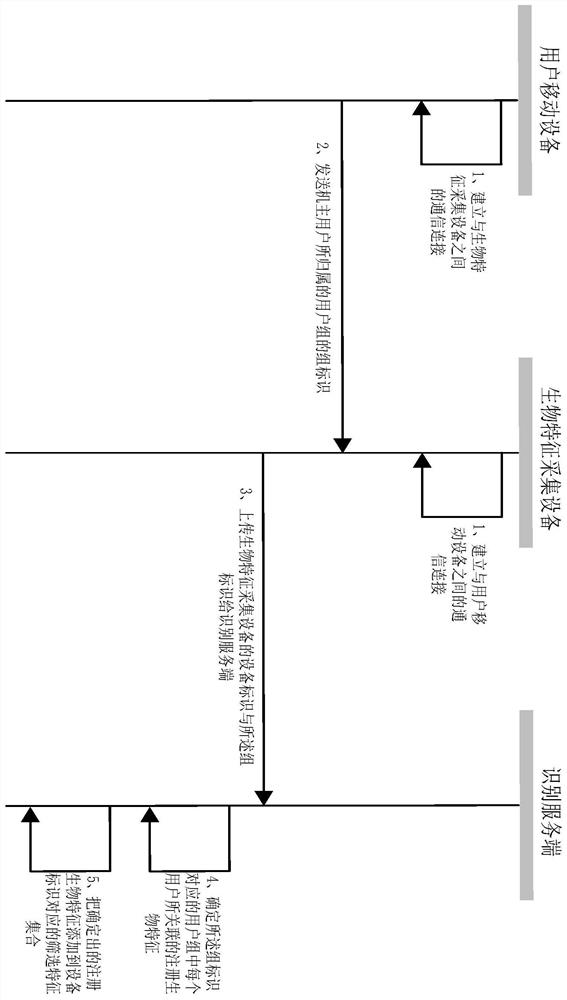
The invention discloses an identity recognition preprocessing method and system and an identity recognition method and system. After any user carrying a mobile device enters a preset nearby area of abiological feature collection device, a mobile device for a user receives a wireless signal broadcasted by the biological feature collection device, and a wireless signal triggers the mobile device toprovide a group identifier of a user group to which the owner user belongs to the identification server. An identification server determines registration biological features associated with each userin the user group corresponding to a group identifier from a registration biological feature set, and adds determined registration biological features to a screening feature set. The identification server subsequently uses each registered biological characteristic in the screening characteristic set to compare with the acquired biological characteristics uploaded by the biological feature collection device so as to carry out user identity identification.
Owner:ADVANCED NEW TECH CO LTD
Internet online medical identity authentication system and method
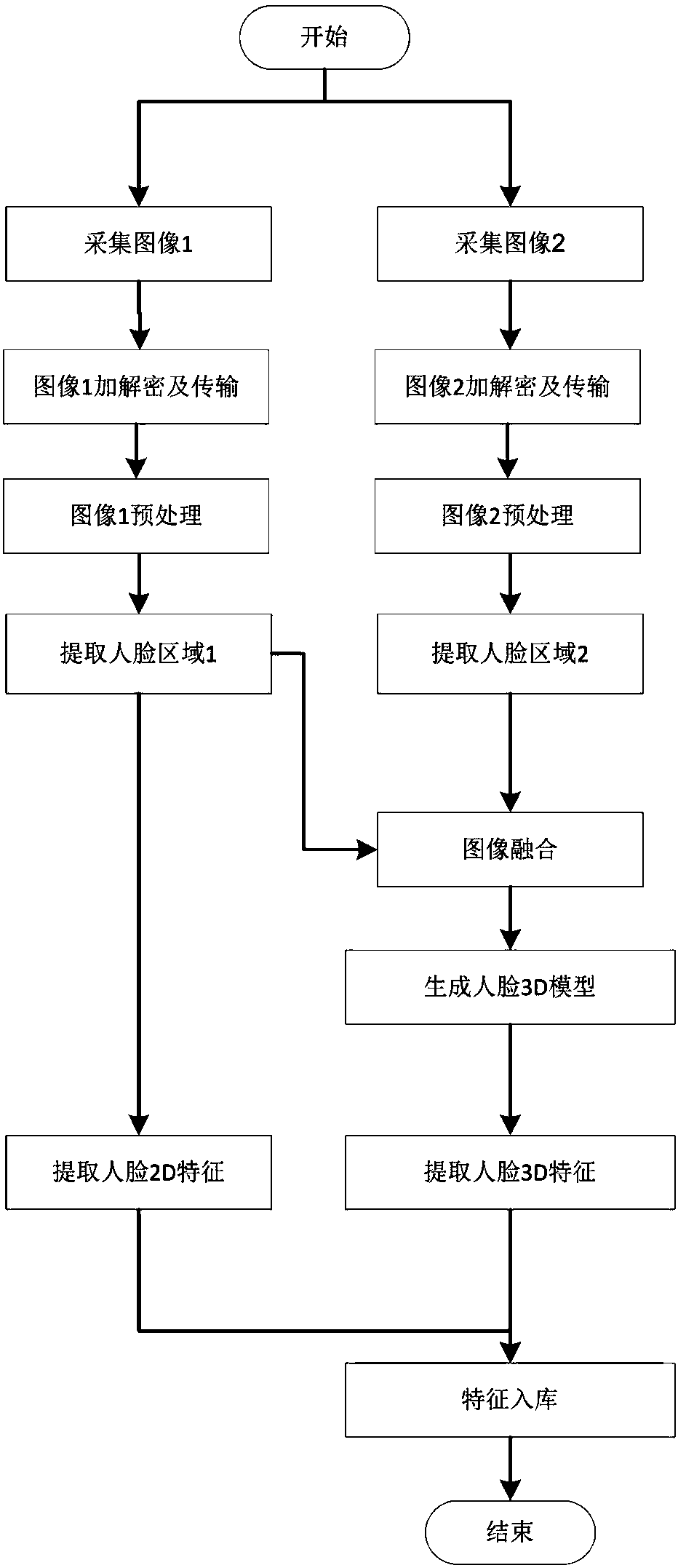
InactiveCN107610764AGuaranteed reliabilityAchieving real-time confirmationHealthcare resources and facilitiesTransmissionApplication serverFeature extraction
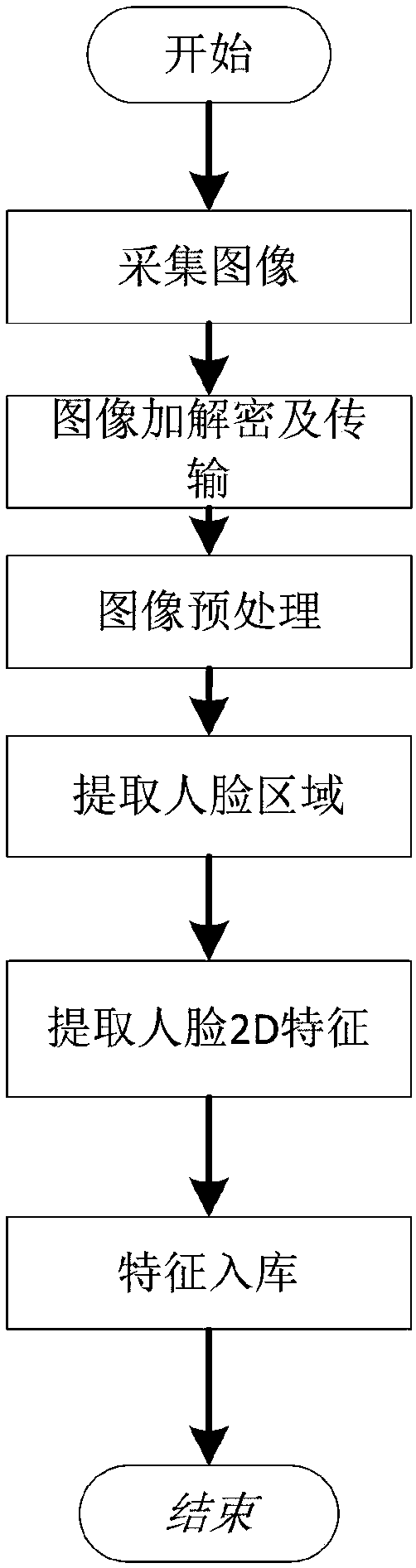
The invention relates to an Internet online medical identity authentication system and method, and the system comprises a client, an application server, and a database server. The client comprises anaudio data collection module, a video and image collection module, an authentication condition detection module, an encryption module and a client communication module. The application server comprises a data processing module, a decryption module, an identity authentication management module, and an application server communication module. Through the 2D+3D feature extraction and verification ofa collected image of a user, the system guarantees the reliability of identity authentication. Through employing a real-time authentication mechanism, the system achieves the real-time confirmation ofthe user's identity in a process of medical services, and improves the identity authentication efficiency. Through employing a mode of collecting a key frame and carrying out the low-resolution videorecording, the system guarantees the traceability of identity authentication. The system guarantees the authenticity of the medical process through audio recording. The system employs the encryptionmodule and the decryption module for encrypting or decrypting communication data, thereby improving the safety and integrity of data transmission.
Owner:FOSHAN UNIVERSITY
Internet behavior auditing system and method based on quantum key encryption technology
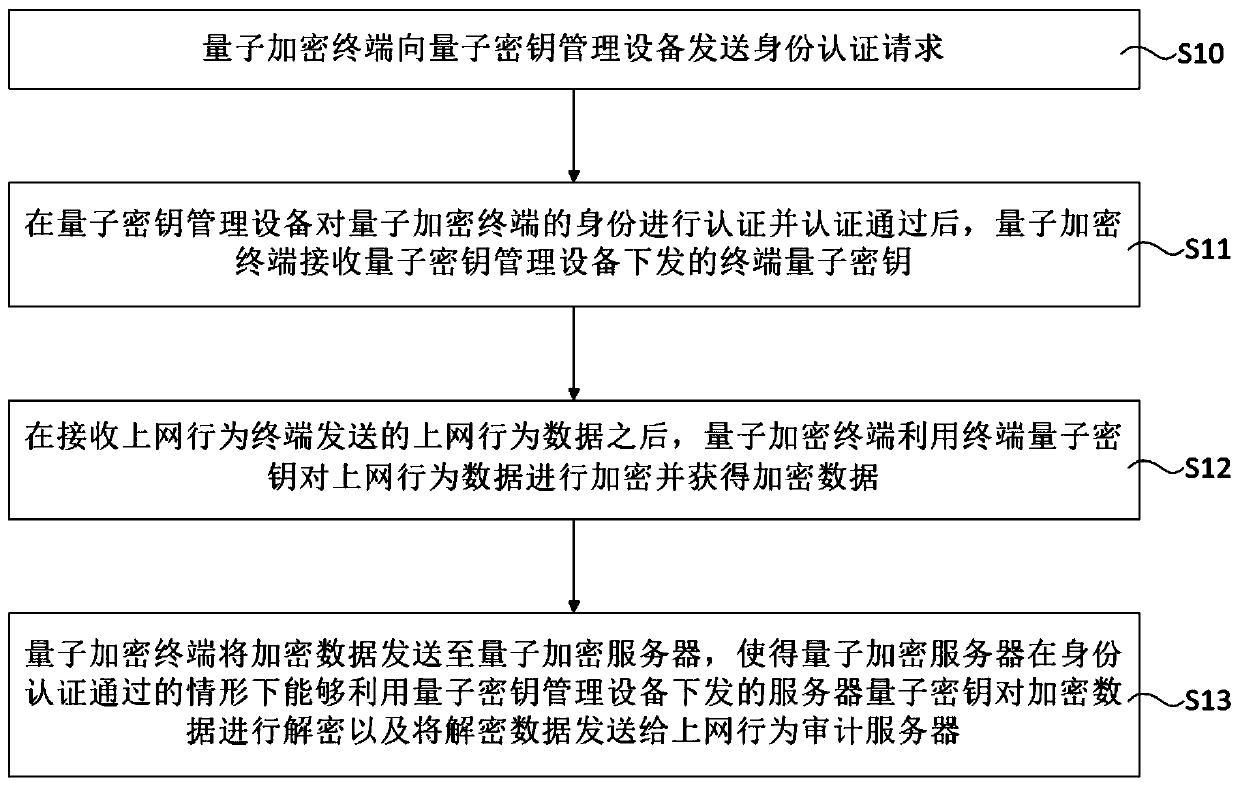
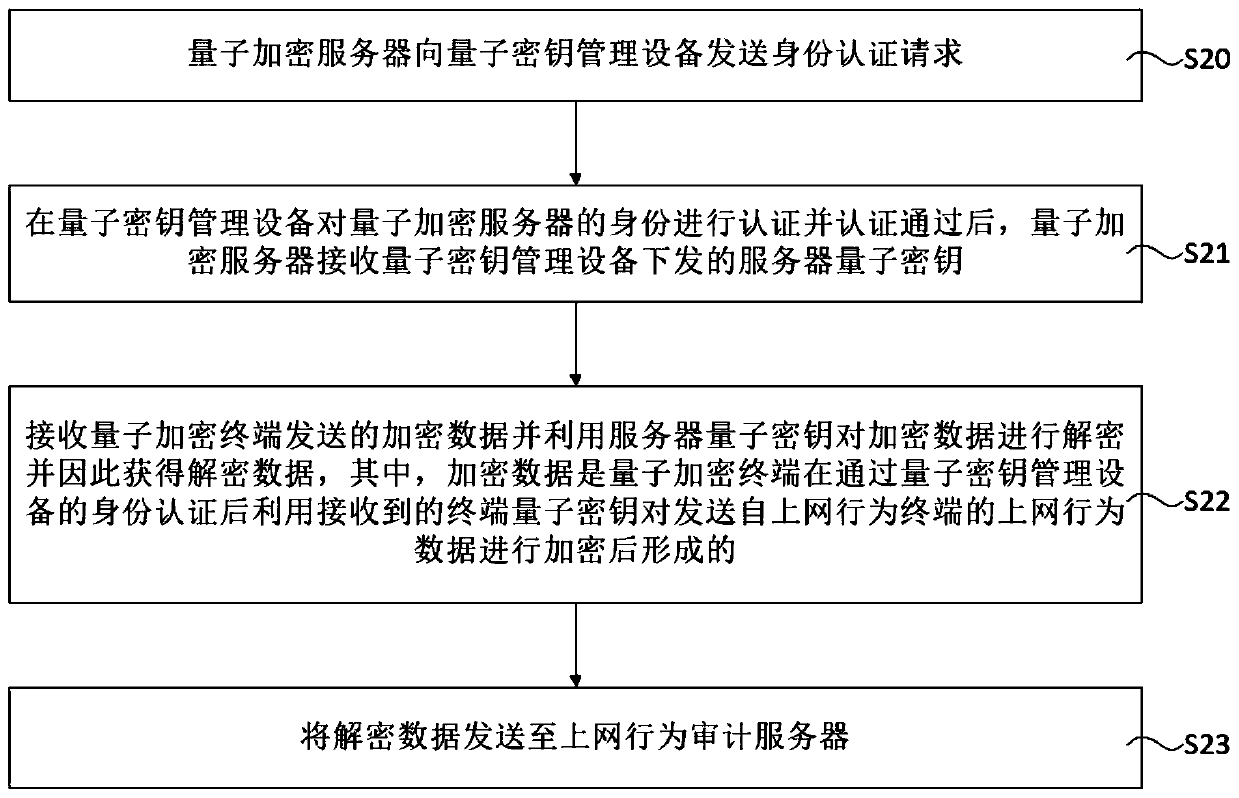
PendingCN110391905AEasy to manage centrallyAvoid installationKey distribution for secure communicationThe InternetData transmission
The invention relates to the technical field of quantum encryption, aims to solve the problem that data of an existing internet behavior terminal cannot be safely transmitted to a public security auditing system, and provides an internet behavior auditing system and method based on a quantum key encryption technology. The internet behavior auditing system comprises quantum key management equipmentwhich is used for generating and issuing a quantum key; a quantum encryption terminal which is in communication connection with the quantum key management equipment so as to encrypt the internet behavior data; a quantum encryption server which is in communication connection with the quantum key management equipment and the quantum encryption terminal and is used for decrypting the encrypted data;an internet behavior terminal which is in communication connection with the quantum encryption terminal so as to send internet behavior data to the quantum encryption terminal; and an internet behavior auditing server which is in communication connection with the quantum encryption server so as to receive decryption data sent by the quantum encryption server. According to the system provided by the invention, the security of data transmission can be greatly improved, the monitoring management of an internet behavior auditing end is facilitated, the laying of channels is reduced, and the datamonitoring range is expanded.
Owner:BEIJING SAFESOFT GREATMAKER CO LTD
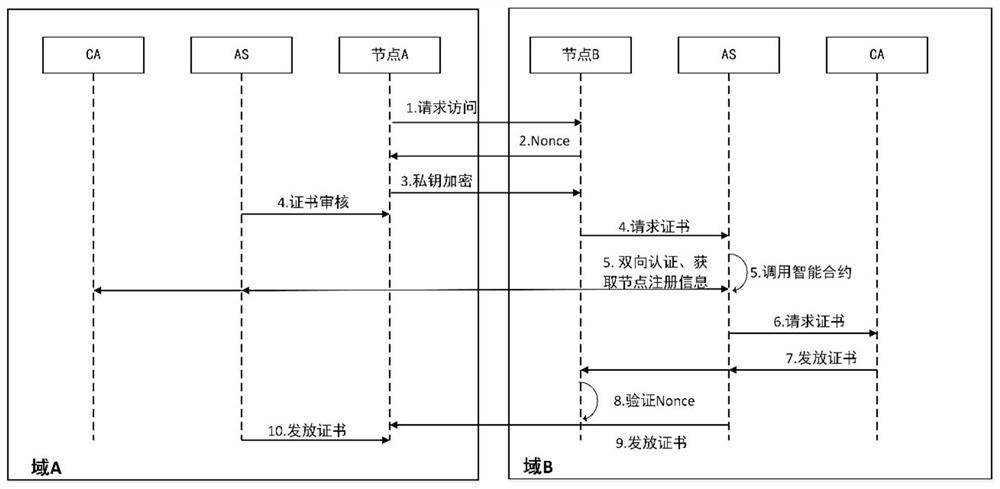
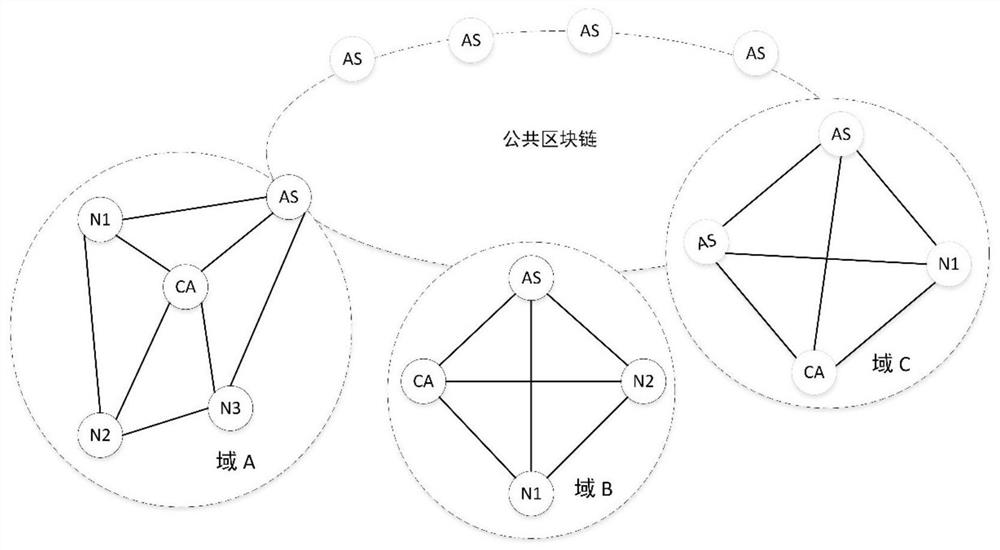
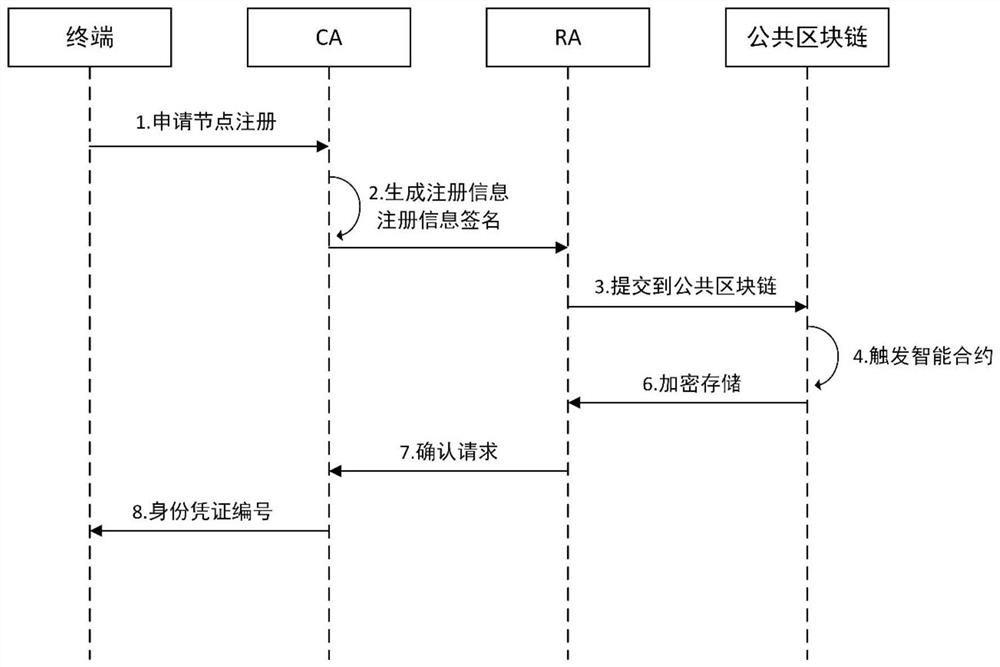
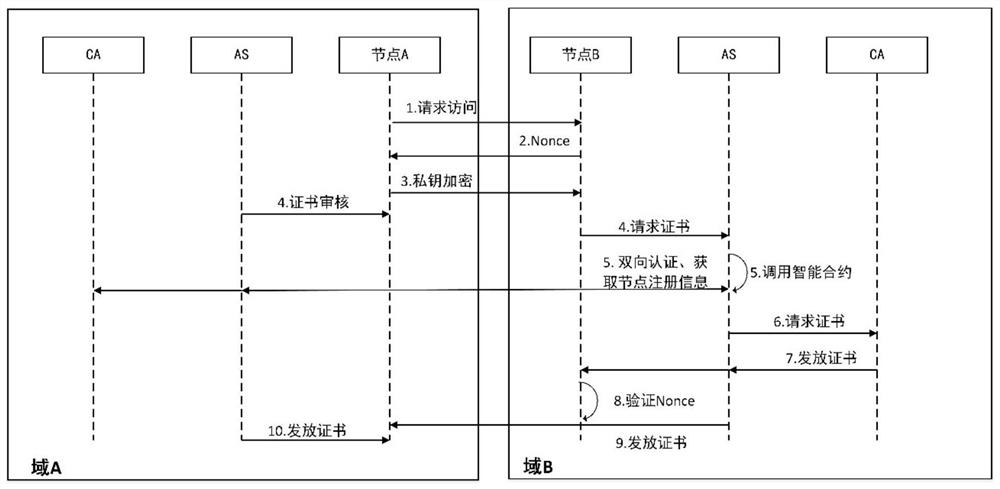
Cross-domain identity authentication method based on block chain certificate
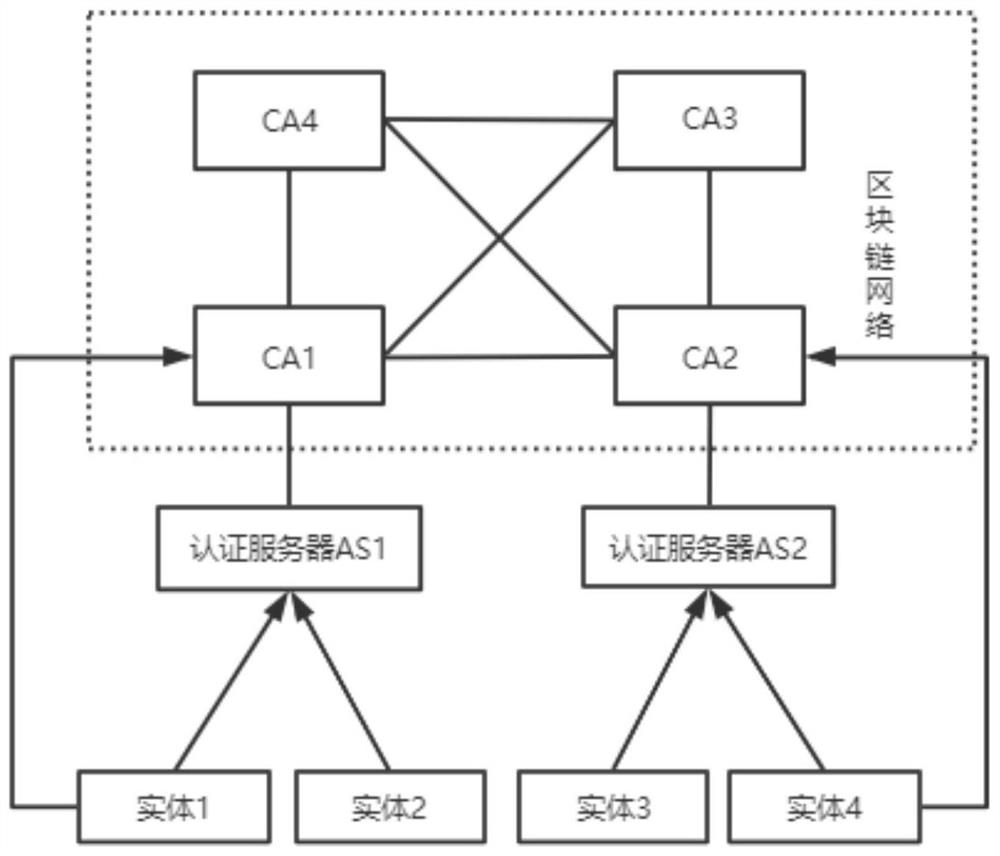
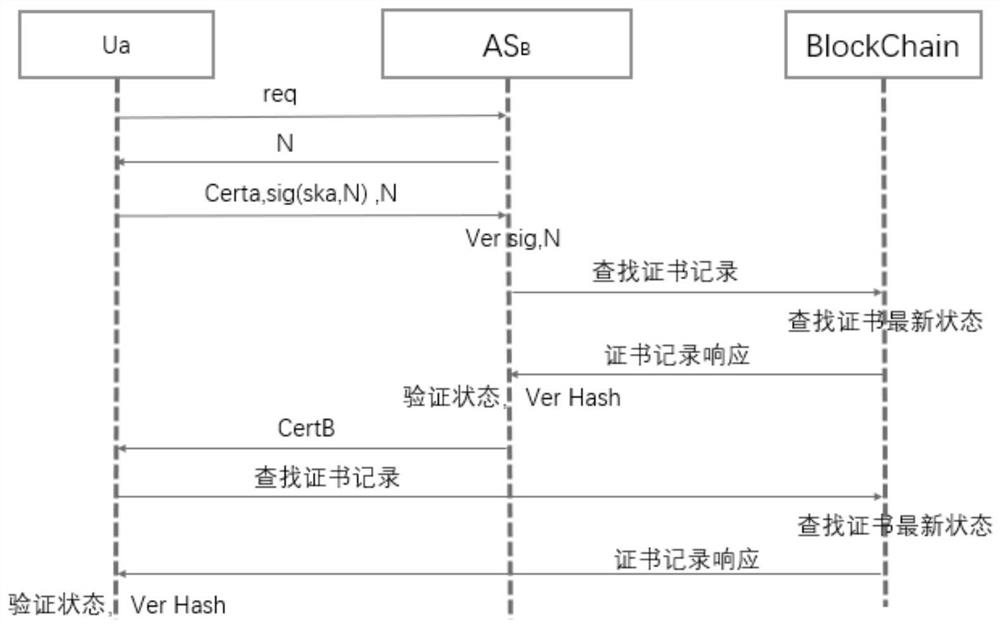
ActiveCN113824563AImprove identity authentication efficiencySolving inefficienciesUser identity/authority verificationEngineeringProxy server
The invention provides a cross-domain authentication method based on a block chain certificate, and the method comprises the steps that: in a first stage, an entity in a trust domain transmits the own block chain certificate in a cross-domain manner; in a second stage, a block chain proxy server where the entity is located verifies the block chain certificate of a cross-domain block chain proxy server through a block chain; and, in a third stage, after the cross-domain identity authentication is successful, the cross-domain block chain proxy server generates a new cross-domain block chain certificate. The cross-domain block chain certificate is generated, so that the identity authentication efficiency can be improved when the same cross-domain identity authentication operation is performed next time. Each trust domain is provided with a private key generation center to perform unified management on all signature private keys in the domain. The block chain certificate adopts a lightweight structure. On the premise of ensuring the security, the problem of low efficiency in traditional cross-domain identity authentication is solved. In addition, the traditional digital certificate is subjected to lightweight improvement to meet the current requirement, and the communication overhead is further reduced.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
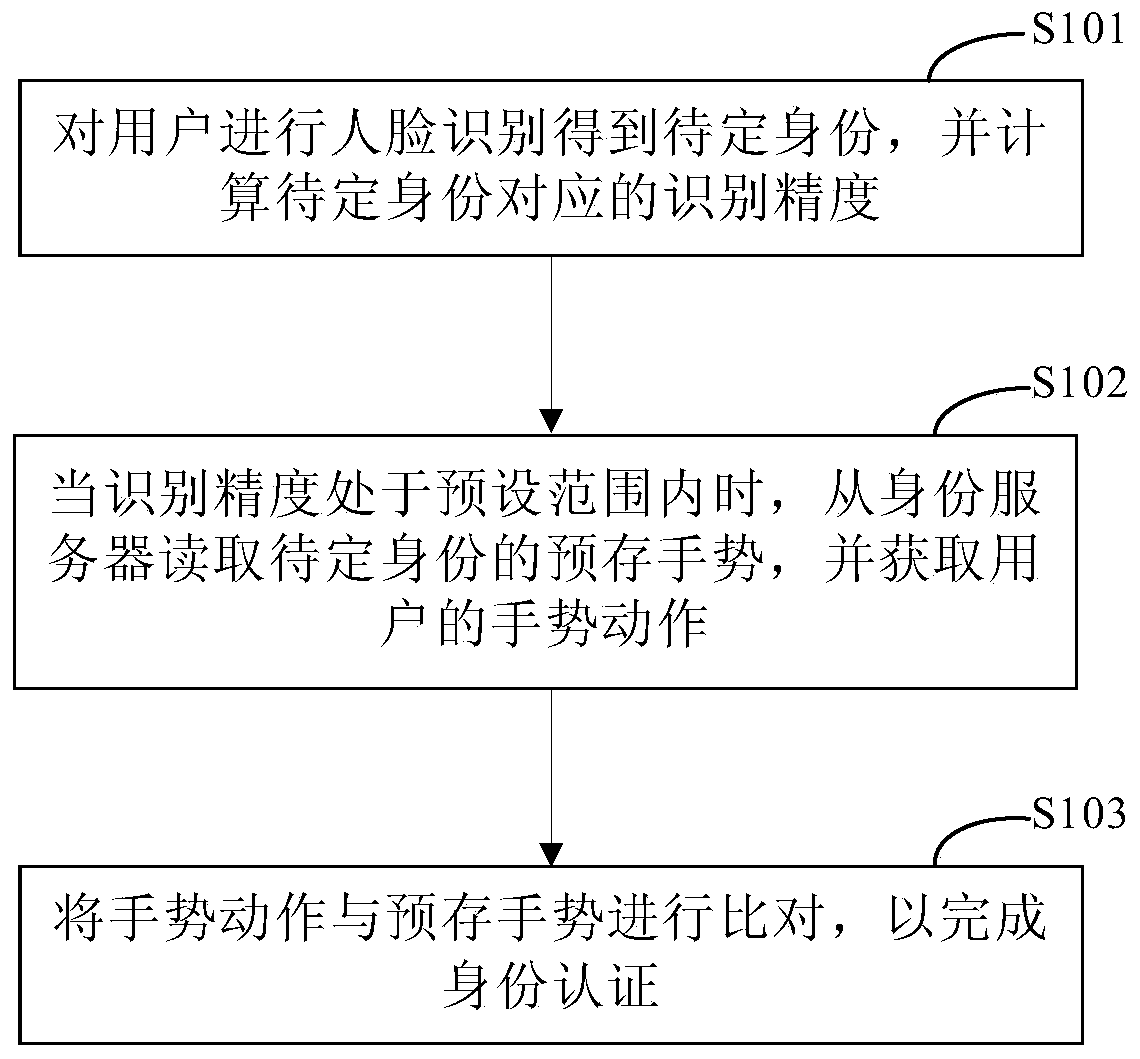
Identity authentication method, payment method and payment equipment
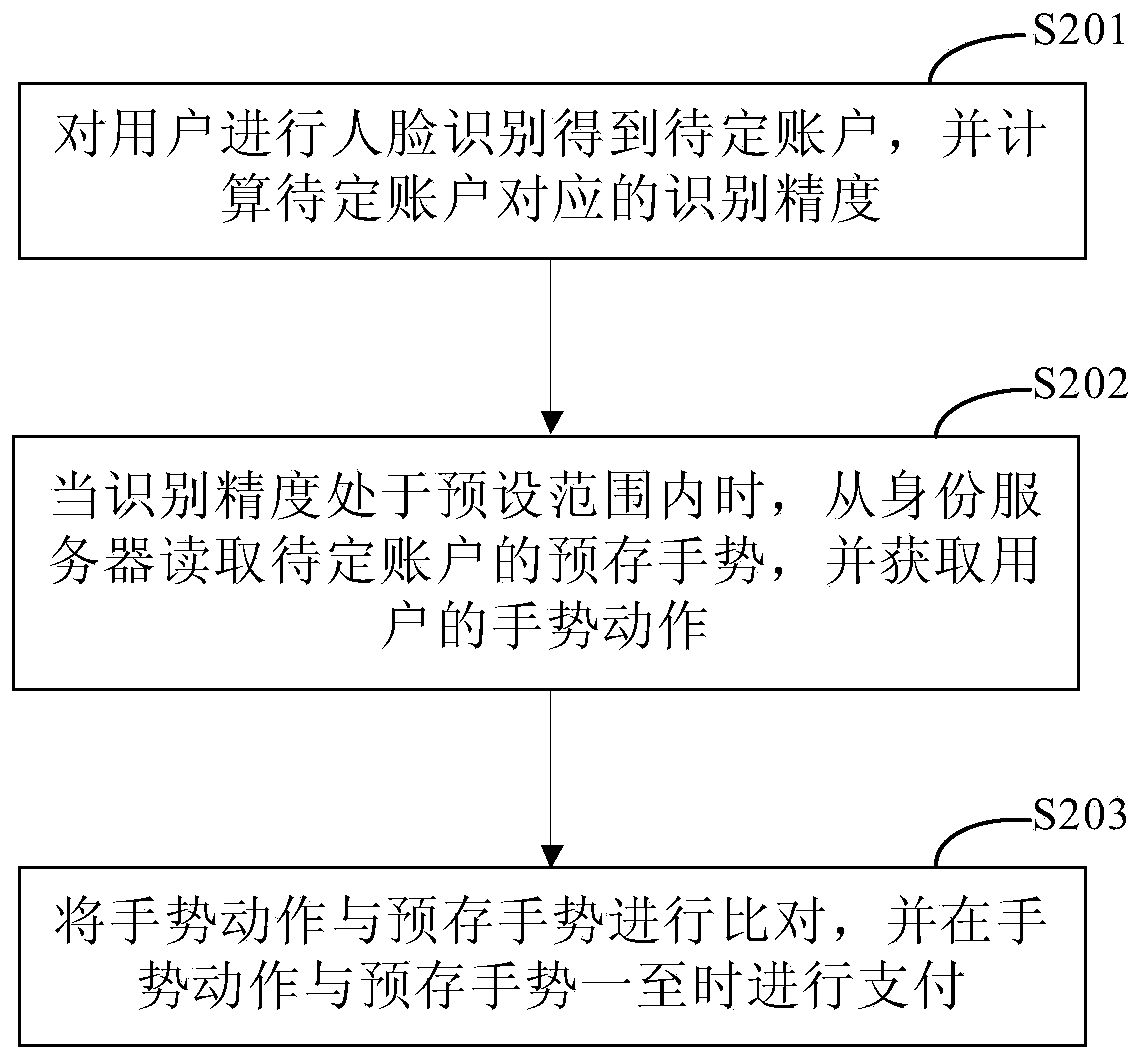
PendingCN111178139AOvercome technical issues with manual operations for verificationImprove identity authentication efficiencyMultiple biometrics useProtocol authorisationPaymentEngineering
The invention discloses an identity authentication method, a payment method and payment equipment, and relates to the technical field of computers. A specific embodiment of the method comprises the steps of performing face recognition on a user to obtain an undetermined identity, and calculating recognition precision corresponding to the undetermined identity; when the recognition precision is within a preset range, reading a pre-stored gesture of the to-be-determined identity from an identity server, and obtaining a gesture action of the user; and comparing the gesture action with a pre-stored gesture to complete identity authentication. According to the embodiment, verification is completed through the gesture of the user, manual operation of the user is not needed any more, and the identity authentication efficiency is improved.
Owner:BEIJING WODONG TIANJUN INFORMATION TECH CO LTD +1
Identity recognition method and device, equipment and storage medium
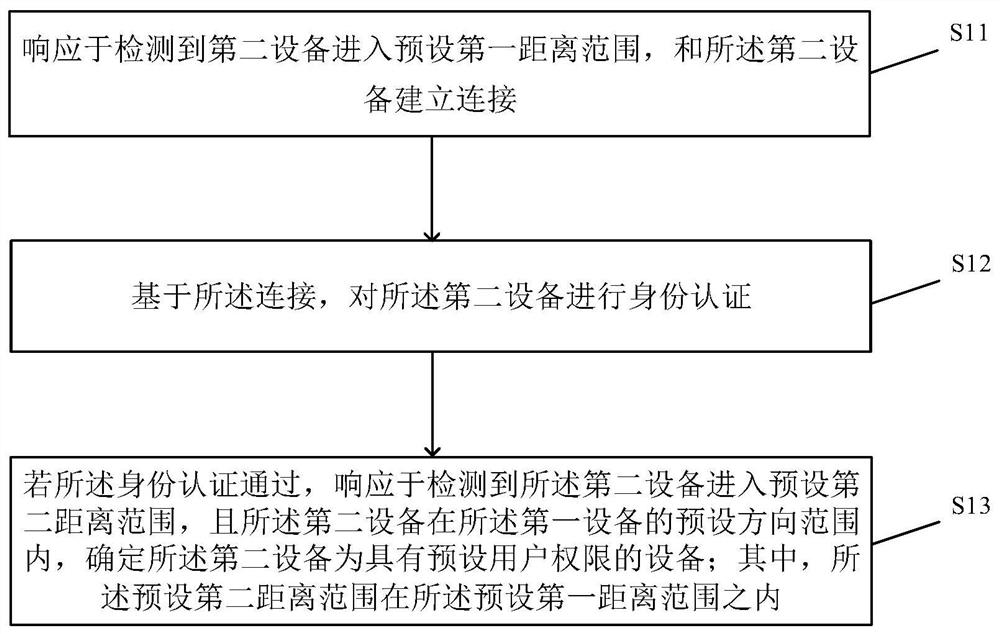
PendingCN113221094AImprove securityImprove identity authentication efficiencyPosition fixationDigital data authenticationTelecommunicationsIdentity recognition
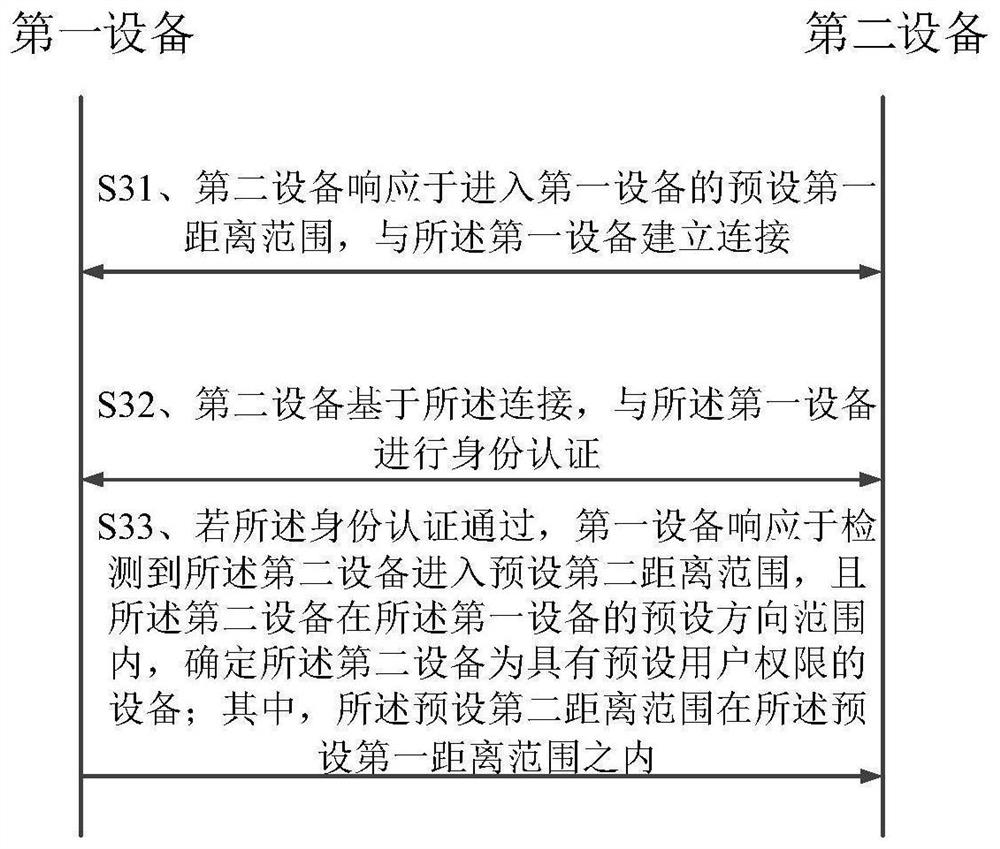
The invention relates to an identity recognition method and device, equipment and a storage medium. The method is applied to a first device, and comprises the following steps: in response to detection that a second device enters a preset first distance range, establishing a connection with the second device; performing identity authentication on the second equipment based on the connection; if the identity authentication is passed, in response to detection that the second equipment enters a preset second distance range and the second equipment is in a preset direction range of the first equipment, determining that the second equipment is equipment with a preset user permission, wherein the preset second distance range is within the preset first distance range. Through the method, non-inductive user experience can be provided, and the use experience of the user is improved.
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
Security protocol authentication method supporting various digital identity information and system thereof
PendingCN112769854AOvercome limitationsReduce complexityUser identity/authority verificationSecure communicationDigital identity
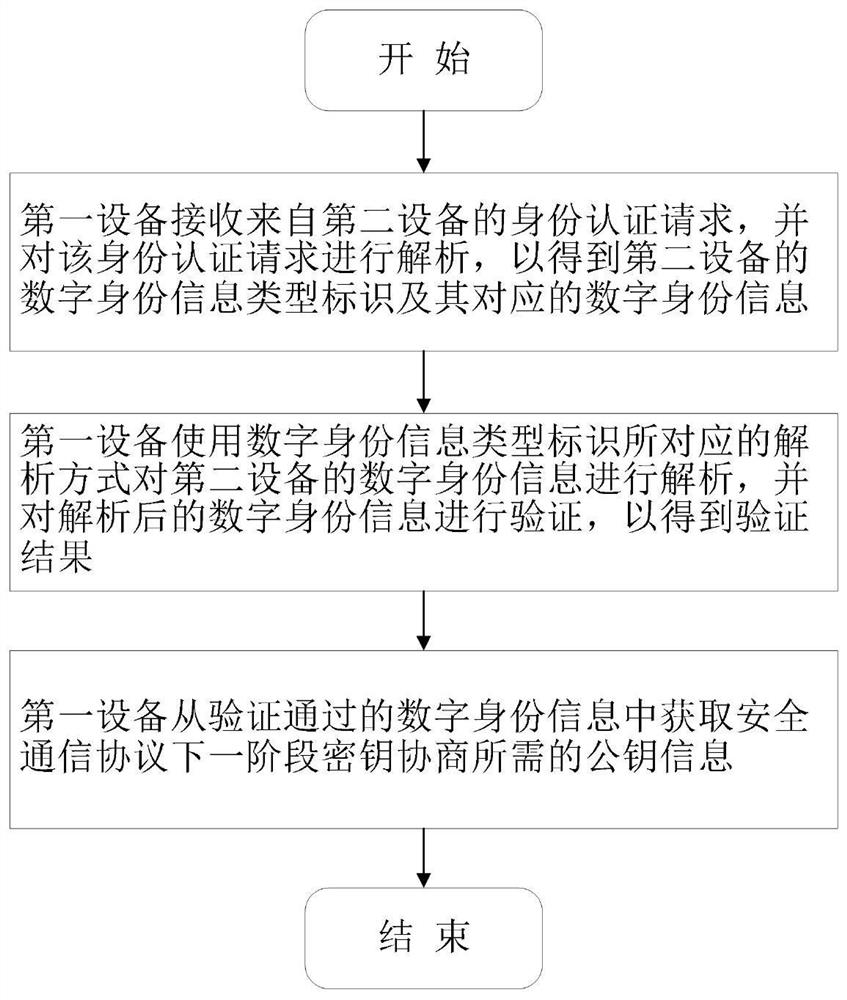
The invention discloses a security protocol authentication method supporting various digital identity information and a system thereof, and the method comprises the steps: (1) first equipment receives an identity authentication request from second equipment, and carries out the analysis of the identity authentication request, so as to obtain a digital identity information type identifier of the second equipment and the digital identity information corresponding to the digital identity information type identifier; (2) the first device analyzes the digital identity information of the second device by using an analysis mode corresponding to the digital identity information type identifier of the second device, and verifies the analyzed digital identity information to obtain a verification result; and (3) the first device obtains public key information required by key negotiation in the next stage of the secure communication protocol from the digital identity information passing verification, and the process is ended. The technical problems that an existing security protocol cannot support a new standard format certificate and the compatibility of the new standard format certificate with an original standard certificate when the new standard format certificate is deployed can be solved.
Owner:北京信安世纪科技股份有限公司 +1
Authentication method and device, electronic equipment and storage medium
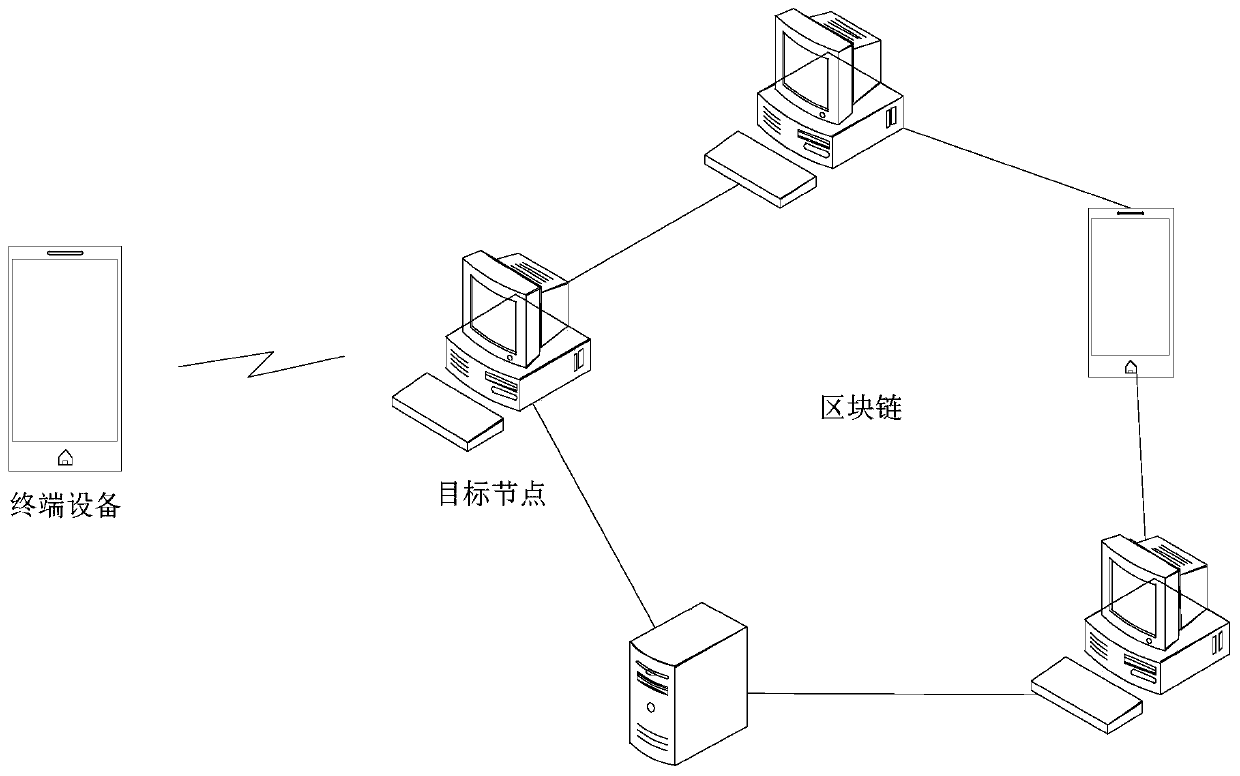
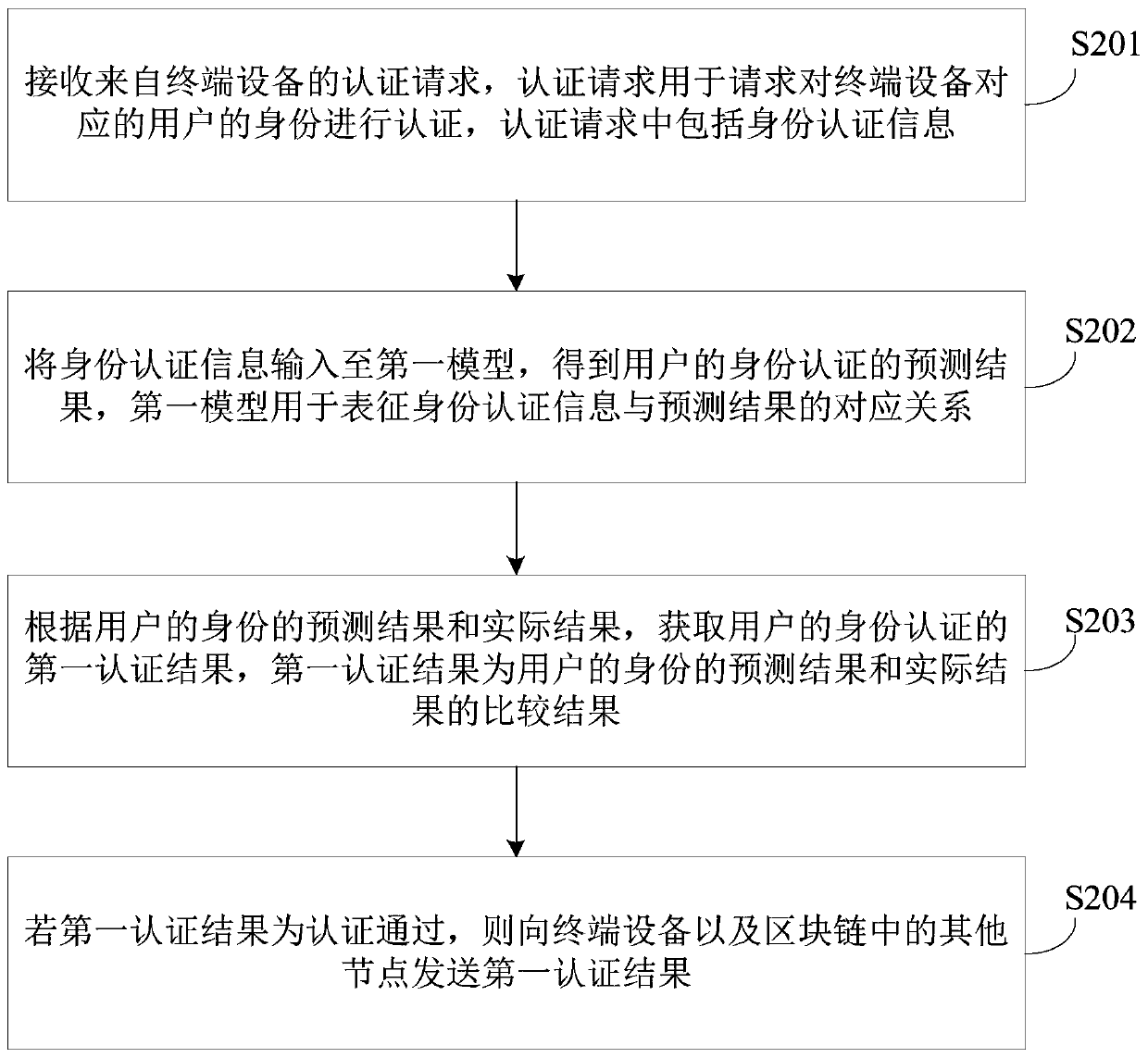
ActiveCN111083156AImprove identity authentication efficiencyData switching networksBlockchainEngineering
The invention provides an authentication method and device, electronic equipment and a storage medium, and the method comprises the steps: receiving an authentication request from terminal equipment,wherein the authentication request is used for requesting the authentication of the identity of a user corresponding to the terminal equipment, and the authentication request comprises identity authentication information; inputting the identity authentication information into a first model to obtain a first authentication result, wherein the first model is used for representing a corresponding relation between the identity authentication information and a prediction result, and the first authentication result is a prediction result of identity authentication of the user; if the first authentication result is that the authentication is passed, sending the first authentication result to the terminal equipment and other nodes in the blockchain. According to the authentication method providedby the invention, the identity authentication efficiency of the user can be improved.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD +1
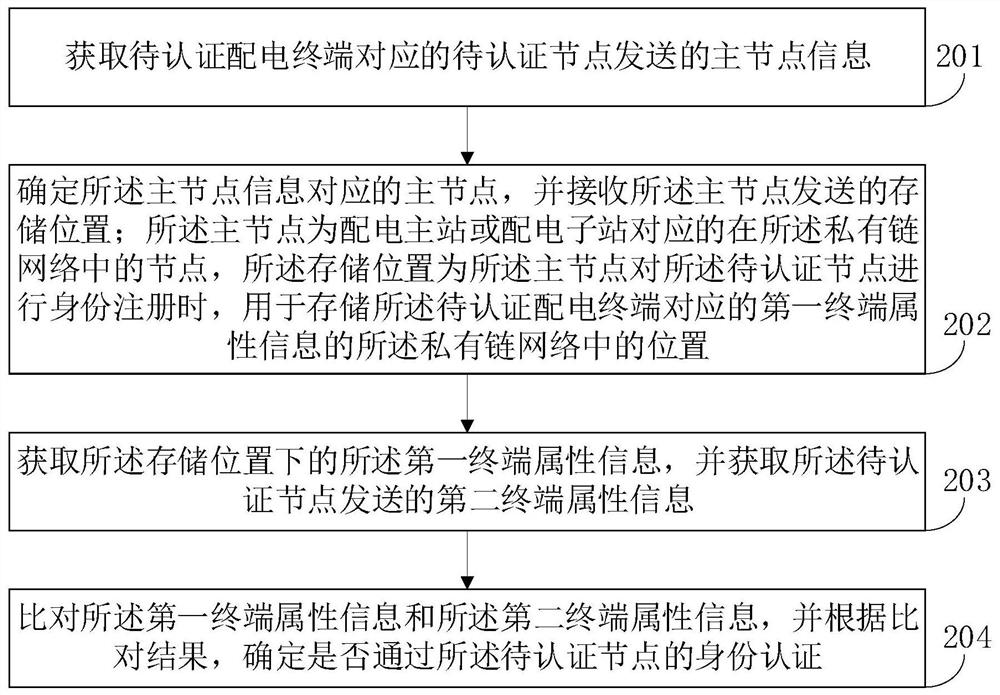
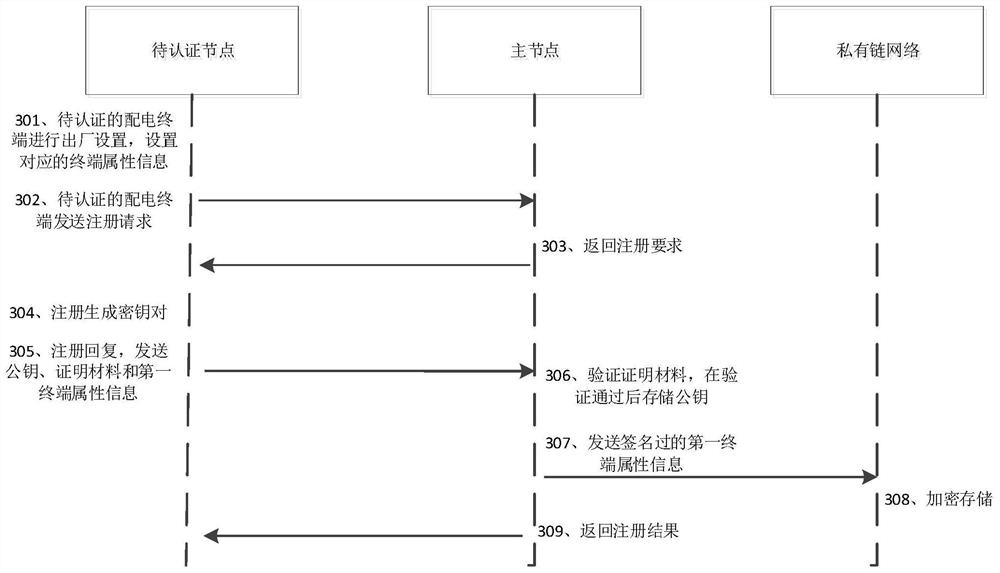
Power distribution terminal authentication method, system and device, computer equipment and storage medium
PendingCN113872986AImprove identity authentication efficiencyCause statute of limitationsTransmissionInformation technology support systemChain networkAuthentication system
The invention relates to a power distribution terminal authentication method, system and device, computer equipment and a storage medium. The method comprises the following steps: acquiring main node information sent by a to-be-authenticated node corresponding to the to-be-authenticated power distribution terminal; determining a main node corresponding to the main node information, and receiving a storage position sent by the main node; obtaining first terminal attribute information in the storage position, and obtaining second terminal attribute information sent by the to-be-authenticated node; and comparing the first terminal attribute information with the second terminal attribute information, and determining whether the identity authentication of the to-be-authenticated node is passed or not according to a comparison result. In the embodiment of the invention, any authenticated node in the private chain network can perform identity authentication on the node to be authenticated, so that identity authentication on a large number of power distribution terminals by depending on limited central trusted equipment can be avoided, the authentication speed is improved, and meanwhile, the timeliness of an authentication system caused by failure of single central trusted equipment can be prevented, therefore, the identity authentication efficiency of the power distribution terminal is effectively improved.
Owner:GUANGZHOU KETENG INFORMATION TECH
Identity recognition preprocessing method and system and identity recognition method and system
PendingCN112464198AReduce in quantityImprove identity authentication efficiencyDigital data authenticationIdentity recognitionEngineering
The invention discloses an identity recognition preprocessing method and system and an identity recognition method and system. After any user carrying the mobile device enters a preset nearby area ofthe biometric feature collection device, the mobile device of the user receives a wireless signal broadcasted by the biometric feature collection device, and the wireless signal triggers the mobile device to provide the group identifier of the user group to which the owner user belongs to the identification server. And the identification server determines a registration biological feature associated with each user in the user group corresponding to the group identifier from the registration biological feature set, and adds the determined registration biological feature to the screening featureset. And the identification server subsequently uses each registered biological characteristic in the screening characteristic set to compare with the acquired biological characteristics uploaded bythe biological characteristic acquisition equipment so as to carry out user identity identification.
Owner:ADVANCED NEW TECH CO LTD
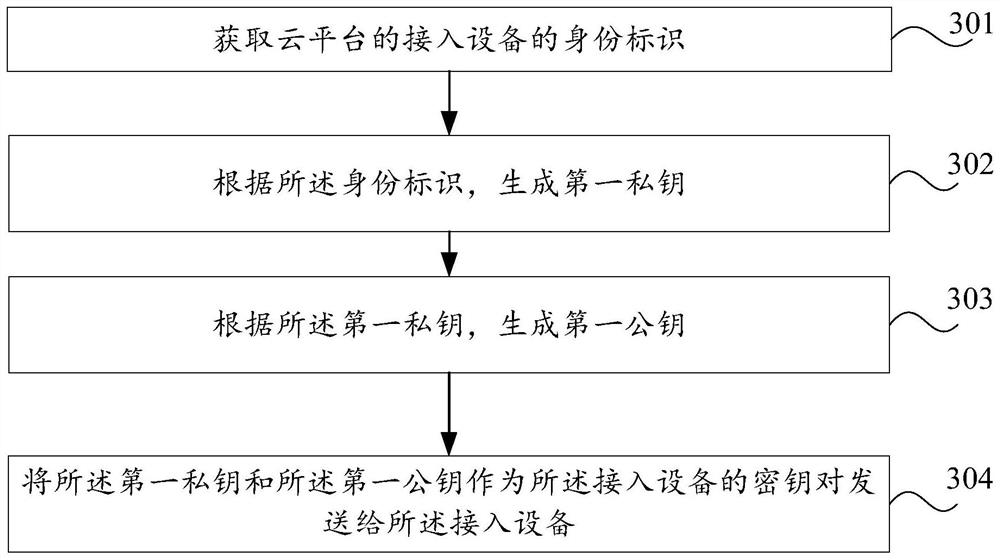
Information interaction method, device and system
PendingCN113204757AImprove identity authentication efficiencyImprove authentication speedDigital data protectionDigital data authenticationEngineeringCommon key
The embodiment of the invention provides an information interaction method, device and system. The method applied to a cloud platform comprises the following steps: acquiring an identity label of access equipment of the cloud platform; generating a first private key according to the identity label; generating a first public key according to the first private key; and sending the first private key and the first public key to the access equipment as a key pair of the access equipment. Therefore, the embodiment of the invention can improve the authentication efficiency.
Owner:北京明朝万达科技股份有限公司
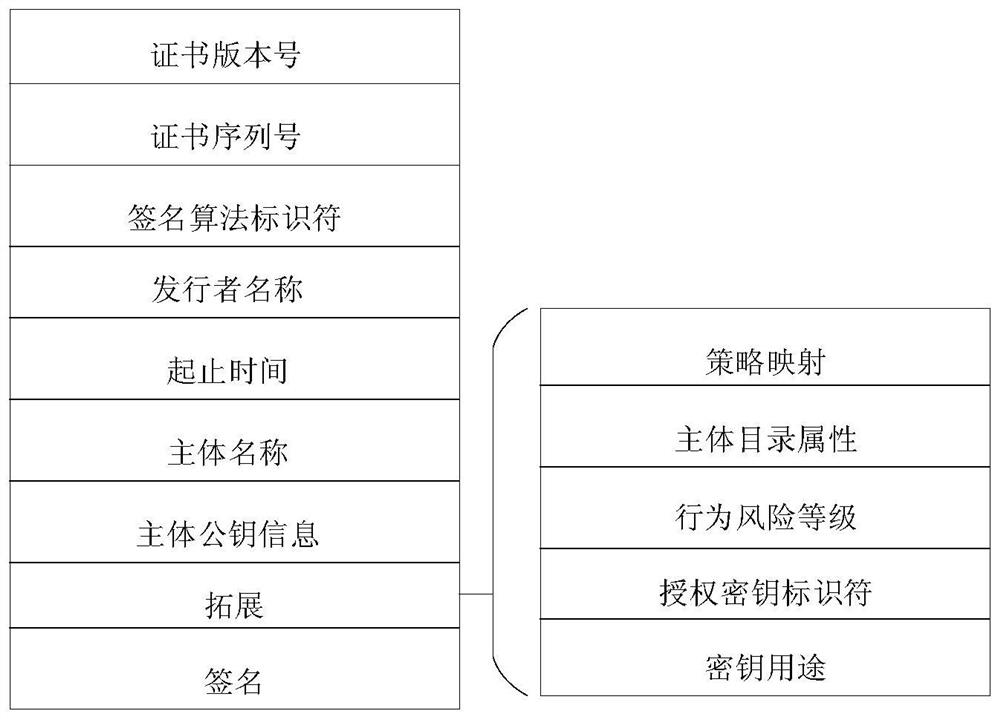
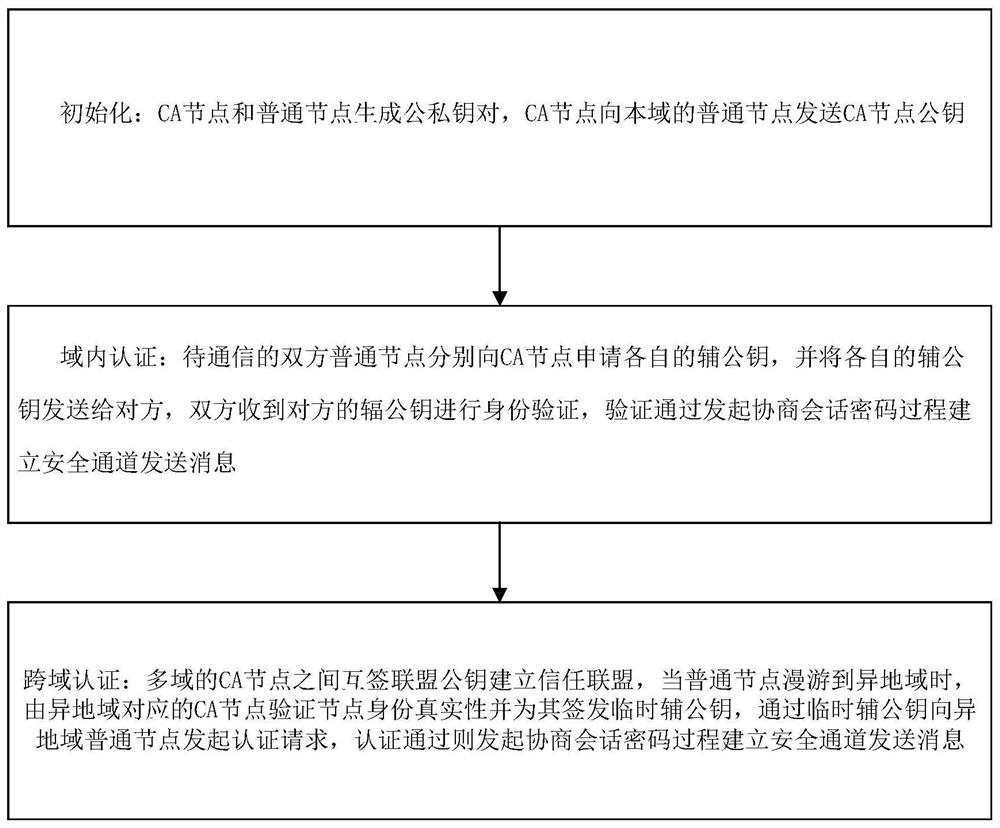
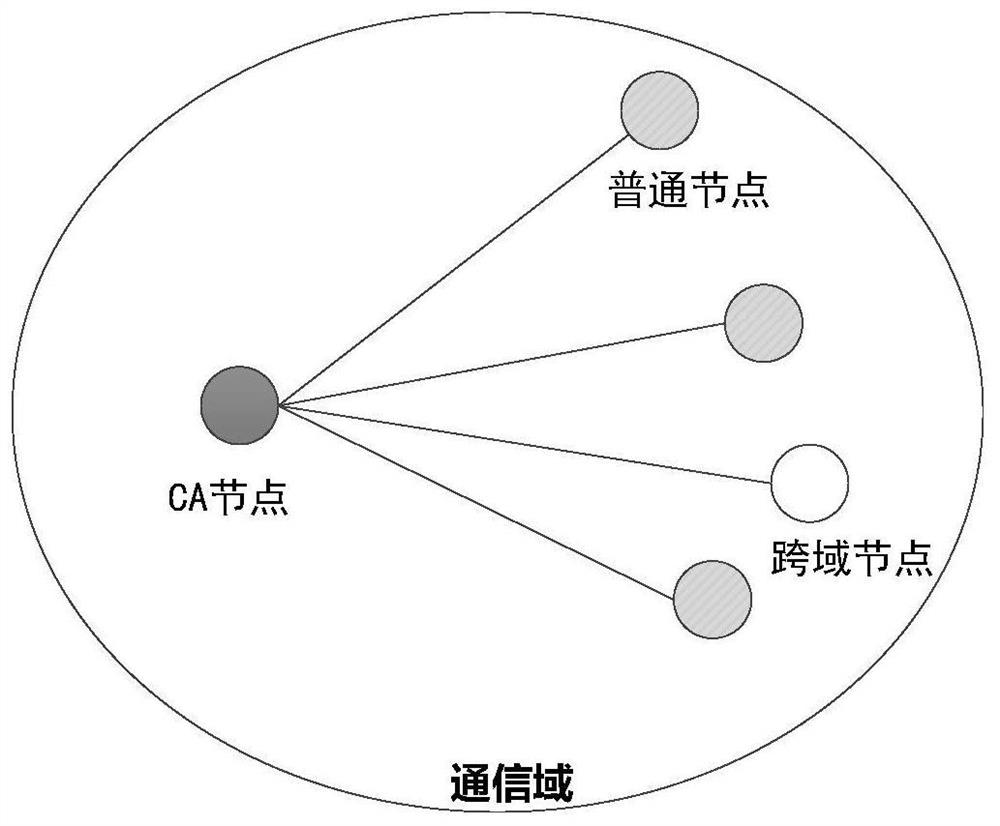
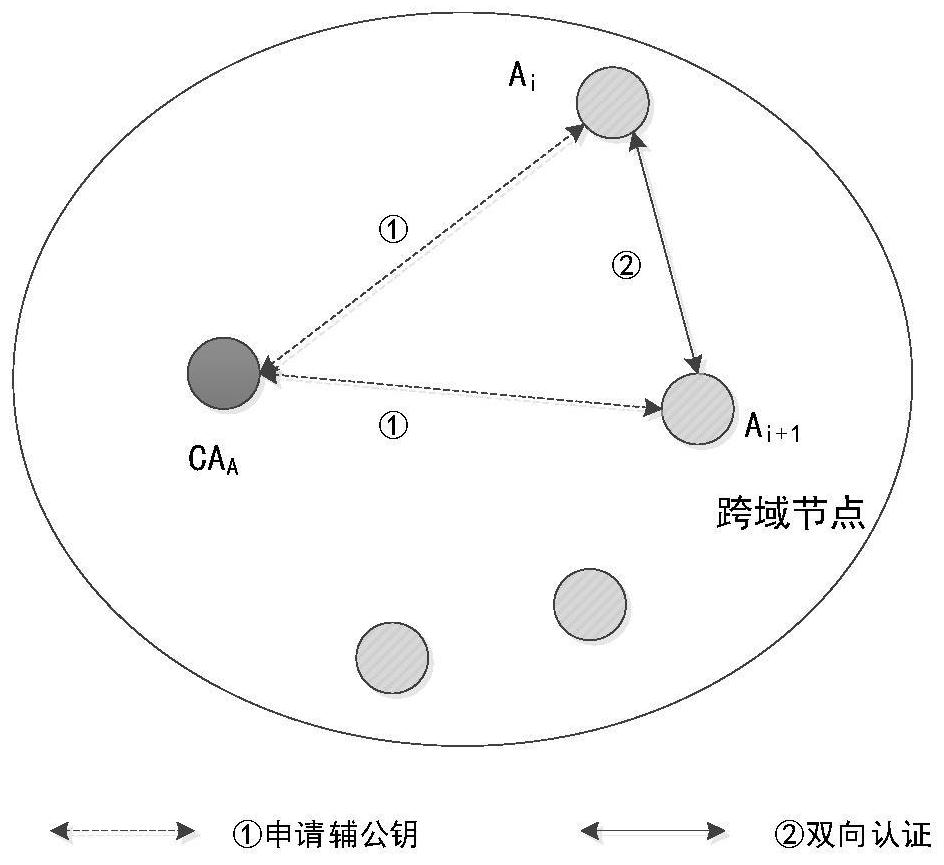
Bidirectional identity authentication method based on lightweight CA, computer program and storage medium
InactiveCN112654042AEnsure safetyPrivacy protectionUser identity/authority verificationSecurity arrangementInternet privacyPassword
The invention relates to a bidirectional identity authentication method based on lightweight CA, which comprises the following steps: initialization: a CA node and a common node generating a public and private key pair, and the CA node sending a CA node public key to the common node in the domain; intra-domain authentication: the common nodes of the two parties to be communicated respectively applying for respective auxiliary public keys from the CA node and sending the respective auxiliary public keys to the opposite parties, and the two parties receiving the auxiliary public keys of the opposite parties to perform identity authentication and establishing a secure channel to send messages by initiating a negotiation session password process; cross-domain authentication: establishing a trust alliance by mutual signing of alliance public keys among CA nodes of multiple domains, verifying the authenticity of node identities by the CA nodes corresponding to different regions and signing and issuing temporary auxiliary public keys for the CA nodes when the common nodes roam to the different regions, and initiating an authentication request to the common nodes in the different regions through the temporary auxiliary public keys, and if the authentication is passed, initiating a negotiation session password process to establish a secure channel to send a message.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
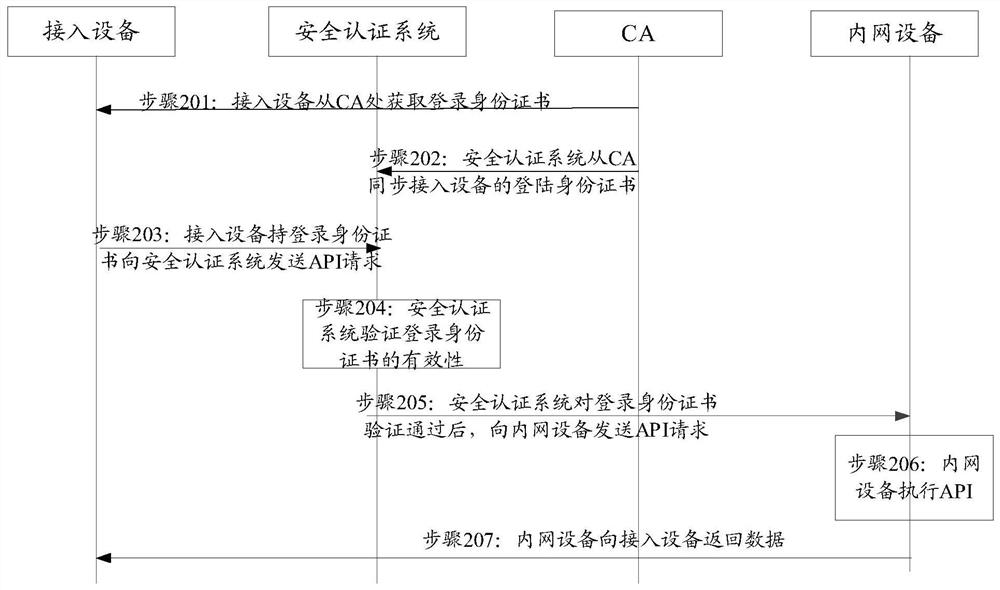
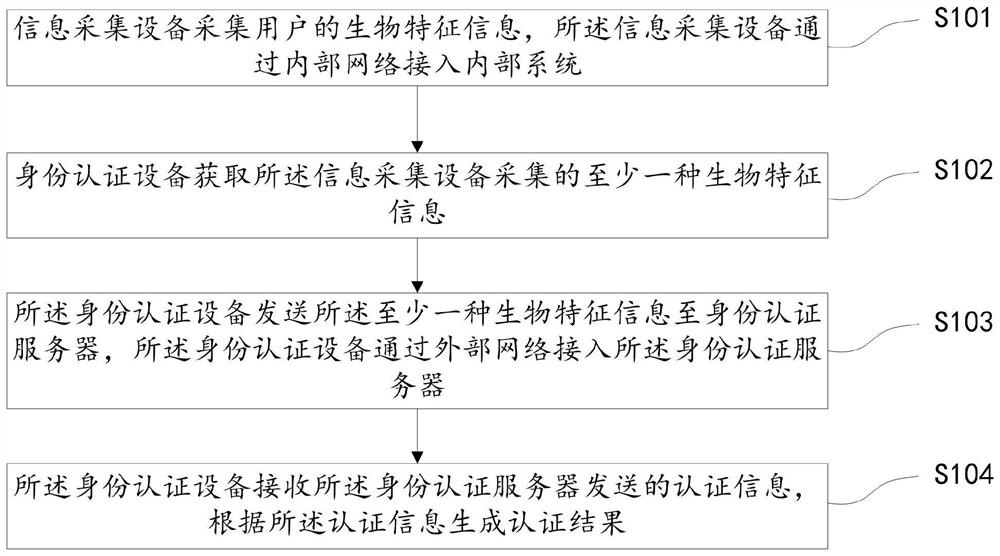
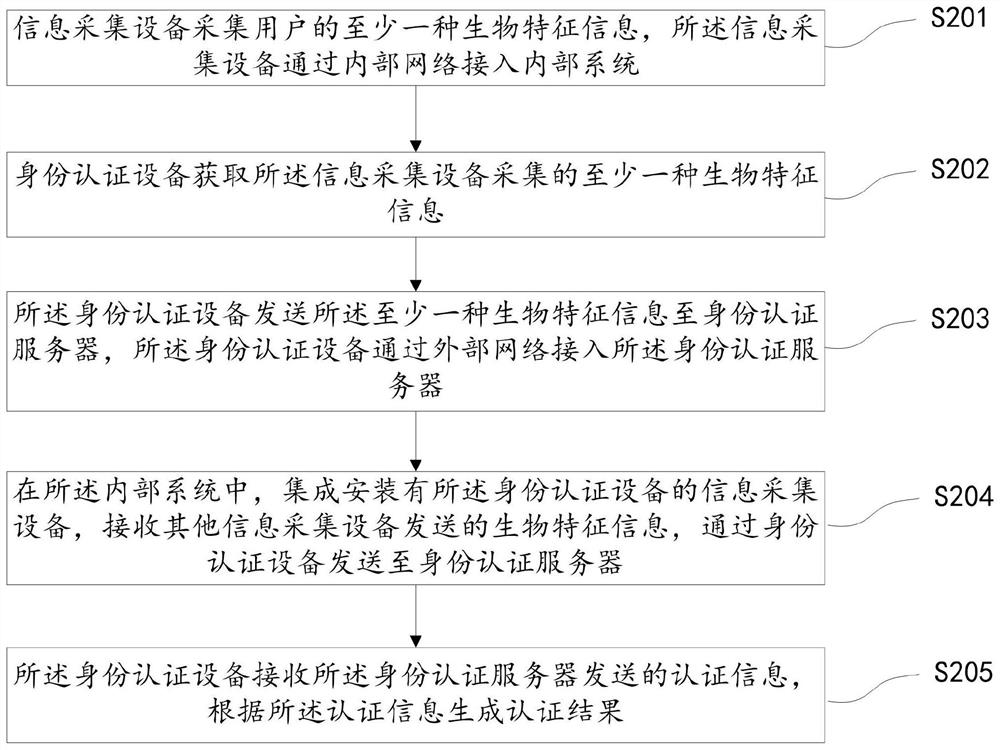
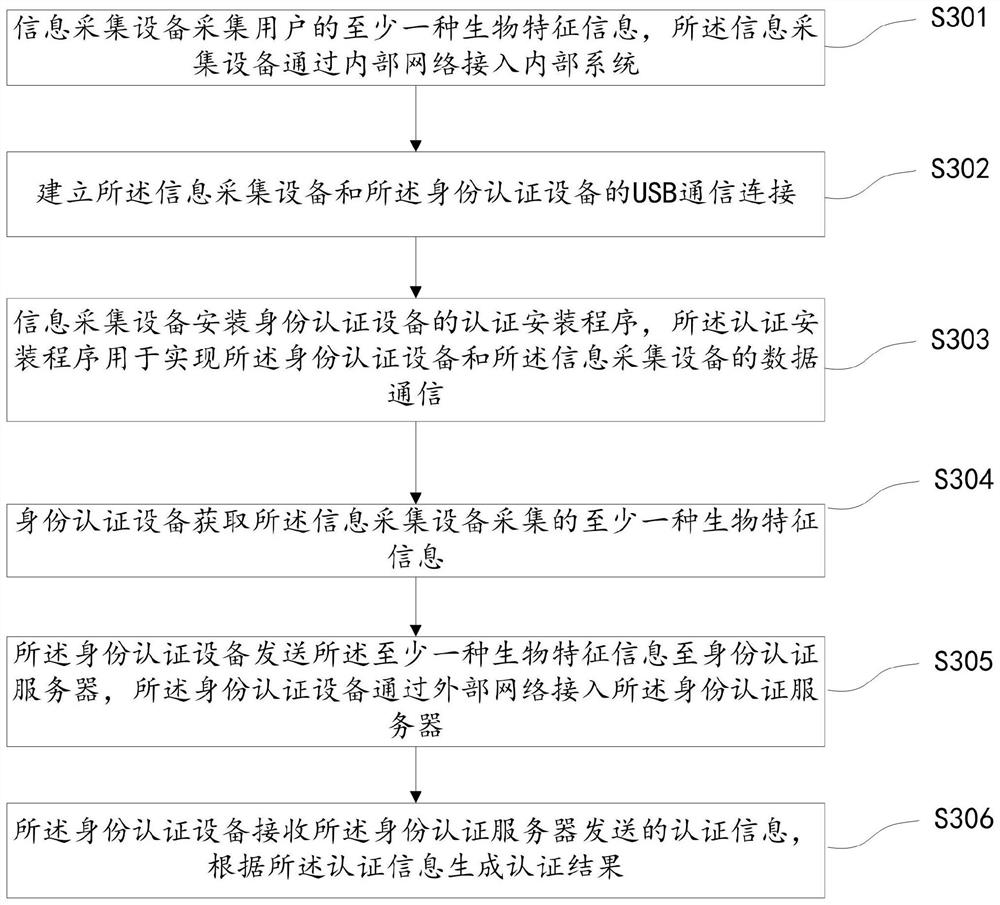
Extranet identity authentication method, system and device based on intranet connection and storage medium
ActiveCN111683085AImprove identity authentication efficiencyAuthentication is reliableCharacter and pattern recognitionTransmissionInternet privacyEngineering
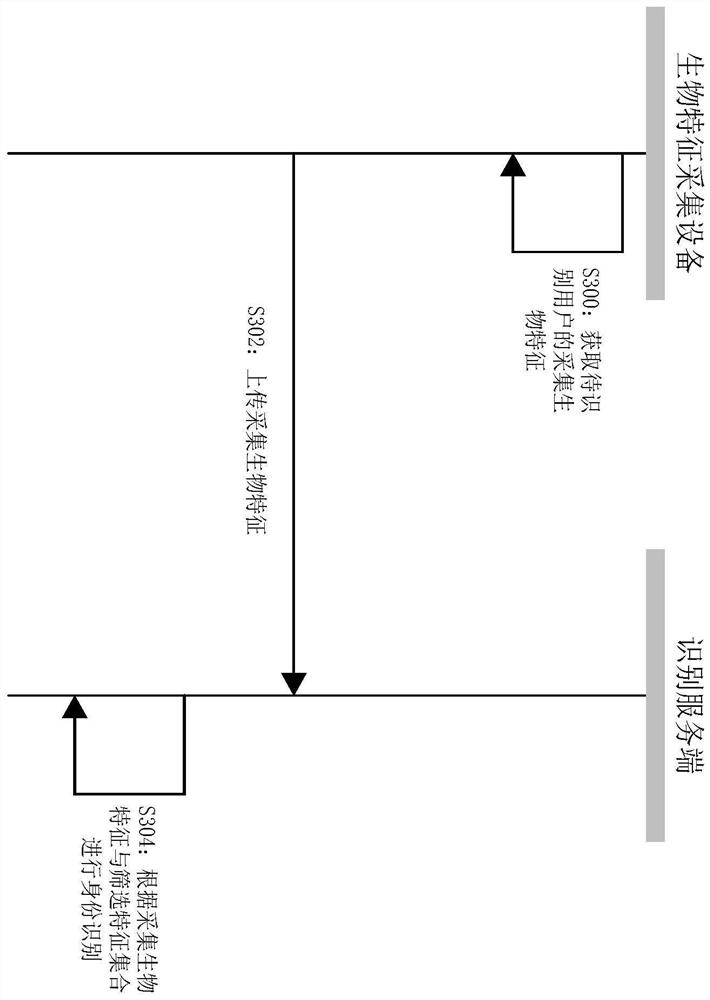
The embodiment of the invention discloses an extranet identity authentication method, system and device based on intranet connection and a storage medium, and the method comprises the steps that an information collection device collects the biological feature information of a user, wherein the information collection device is connected to an internal system through an internal network; an identityauthentication device acquires at least one kind of biological characteristic information acquired by the information collection device; the identity authentication device sends the at least one kindof biological characteristic information to an identity authentication server; and the identity authentication device accesses the identity authentication server through an external network; and theidentity authentication device receives the authentication information sent by the identity authentication server, and generates an authentication result according to the authentication information. According to the scheme, the user identity authentication efficiency is improved, and the authentication process is simplified on the premise of ensuring the safety and reliability of identity authentication.
Owner:XUNTENG (GUANGDONG) TECH CO LTD
Identity authentication method and electronic device
ActiveCN110190964BImprove identity authentication efficiencyKey distribution for secure communicationUser identity/authority verificationPublic key authenticationInternet privacy
Owner:SUZHOU KEDA TECH
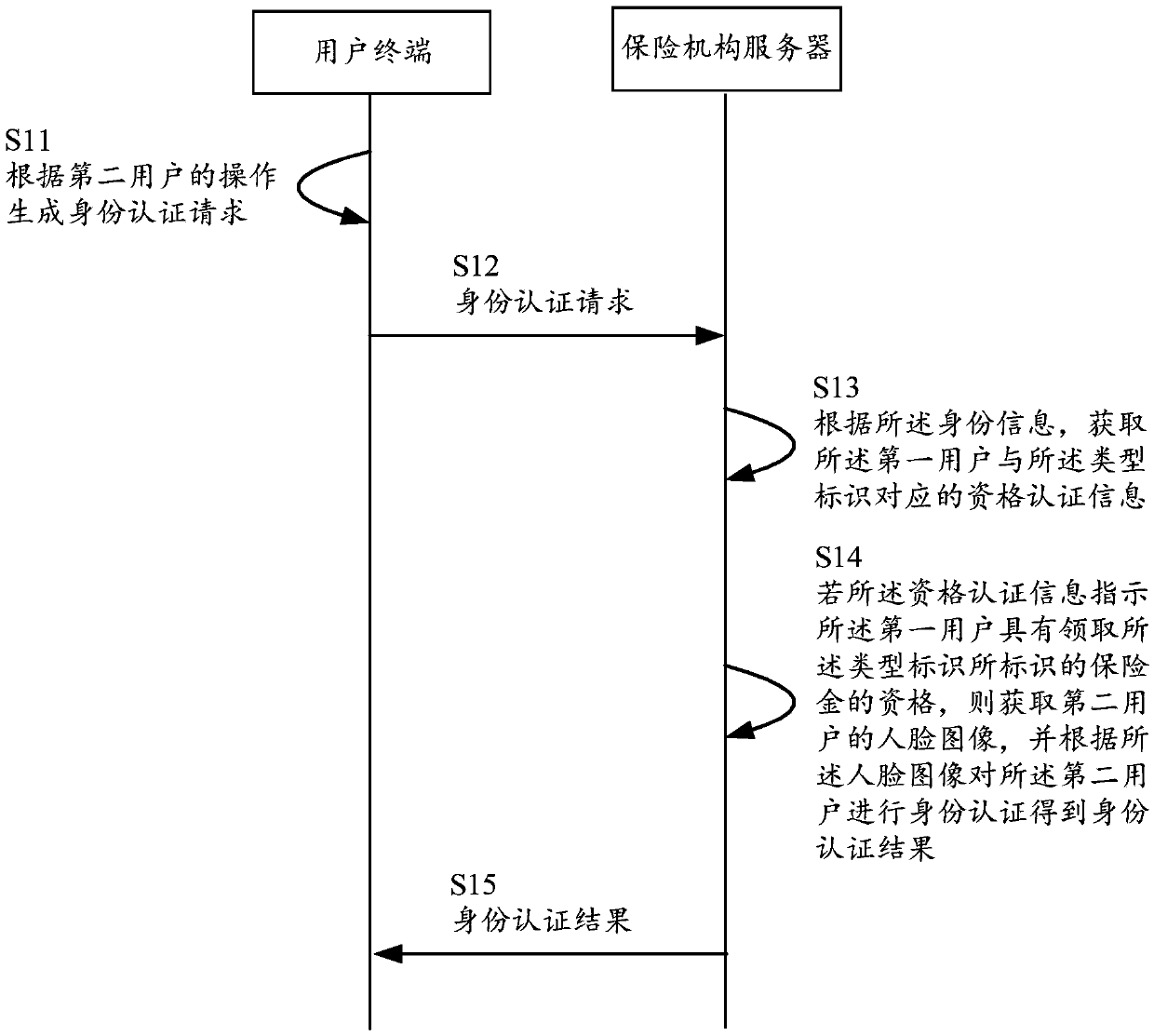
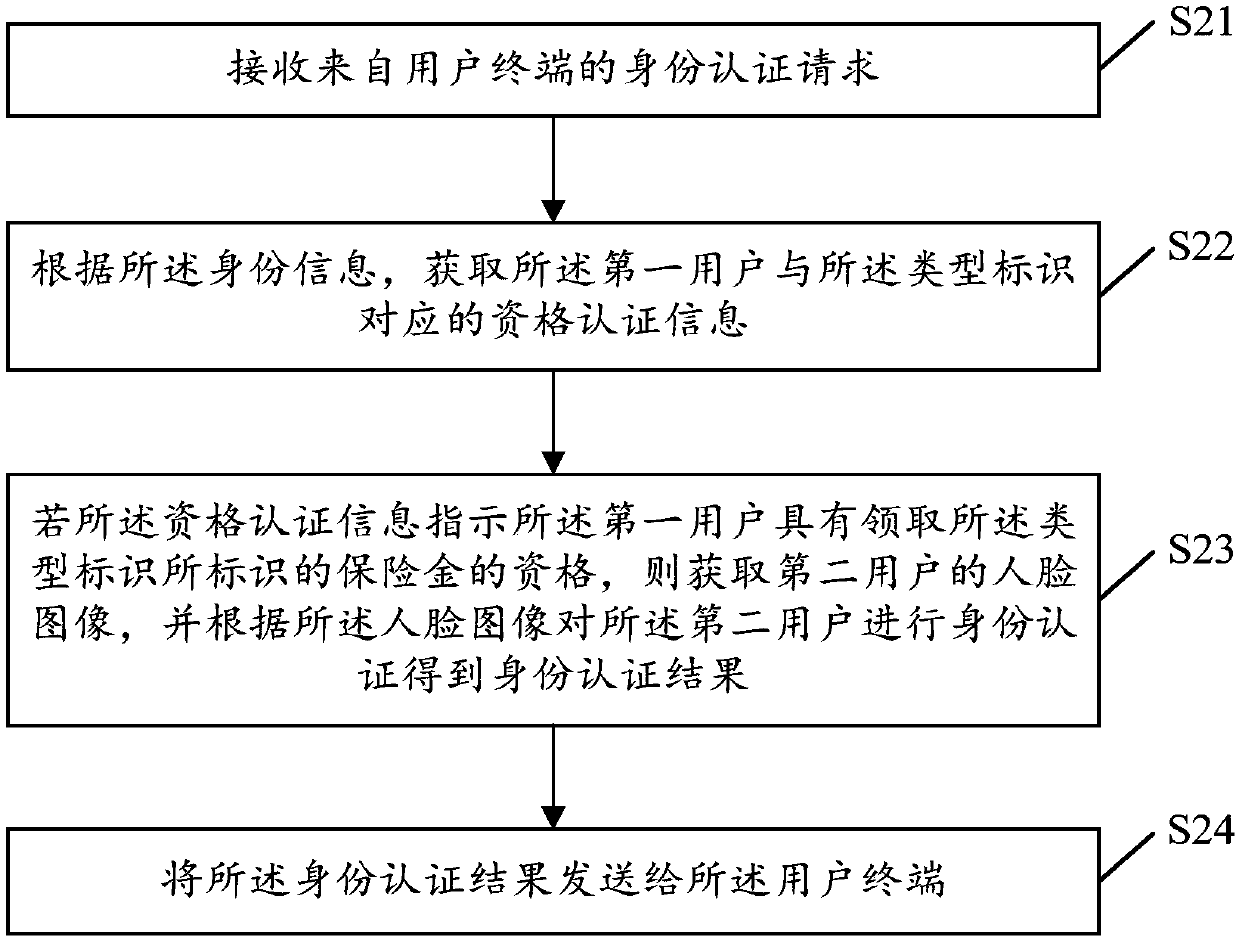
Method for authenticating identity of insured person, server of insurance institution and user terminal
PendingCN109523408ASave yourself the pain of running aroundShorten the timeFinanceDigital data authenticationInternet privacy
An embodiment of the present application discloses an identity authentication method of an insured person, The method comprises the following steps: receiving an identity authentication request from auser terminal, wherein the identity authentication request includes identity information of a first user and a type identification of insurance money to be collected by the first user; the identity authentication request is generated by the user terminal according to an operation of a second user; and a user terminal. Obtaining qualification authentication information corresponding to the type identification of the first user according to the identity information, if the qualification authentication information indicates that the first user is eligible for the insurance premium identified bythe type identification, then obtaining a face image of a second user, performing identity authentication on the second user according to the face image to obtain an identity authentication result, and sending the identity authentication result to the user terminal, wherein the identity authentication result is used for indicating whether the second user and the first user are the same user or not. Embodiments of the present application can improve the efficiency of identity authentication for insured persons.
Owner:深圳平安医疗健康科技服务有限公司
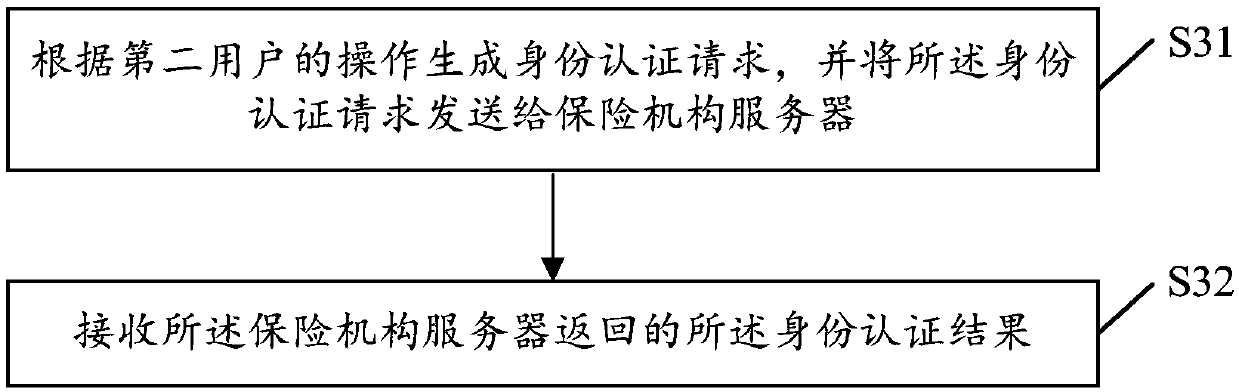
Identity authentication method and device
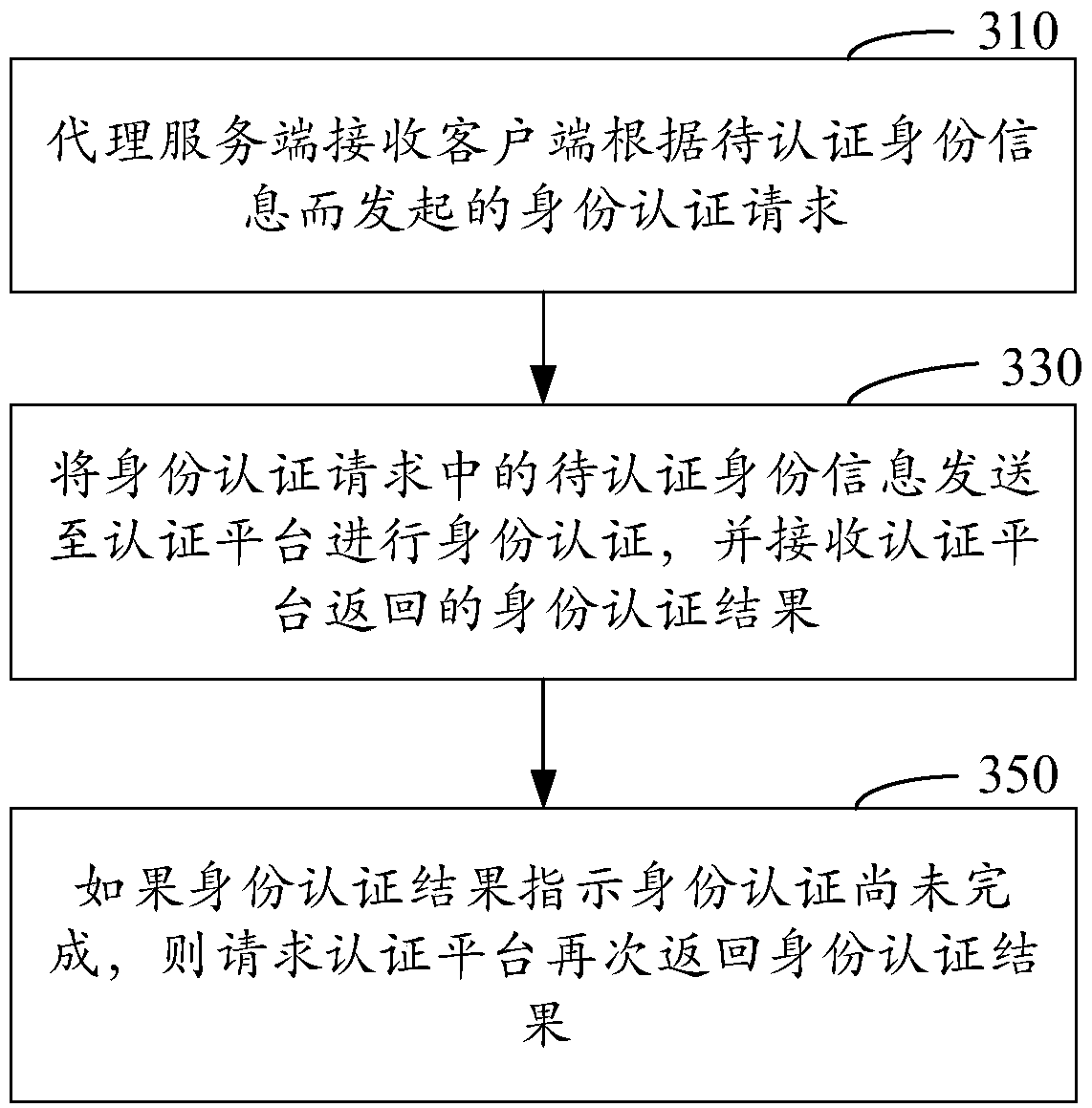
ActiveCN108809927AIdentity authentication process is complicatedAvoid multiple interactionsTransmissionClient-sideProxy server
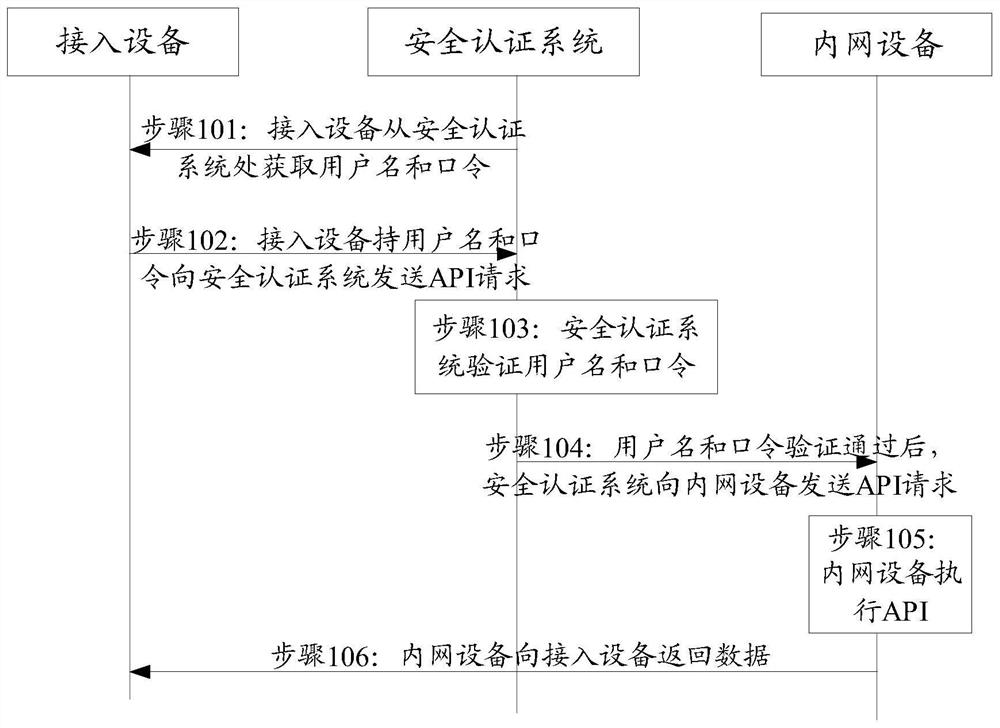
The invention relates to an identity authentication method and device. The identity authentication method comprises the following steps that: a proxy server side receives an identity authentication request initiated by a client according to identity information to be authenticated; the identity information to be authenticated in the identity authentication request is sent to an authentication platform for identity authentication, and an identity authentication result returned by the authentication platform is received; and if the identity authentication result indicates that the authenticationis not completed yet, the authentication platform is requested to return the authentication result again. Through adoption of the identity authentication method and device provided by the invention,the problem that the flow of identity authentication in the prior art is too complicated is solved, and the efficiency of identity authentication is increased effectively.
Owner:PING AN TECH (SHENZHEN) CO LTD
Gun and bullet getting and returning and vein self-service authentication management system
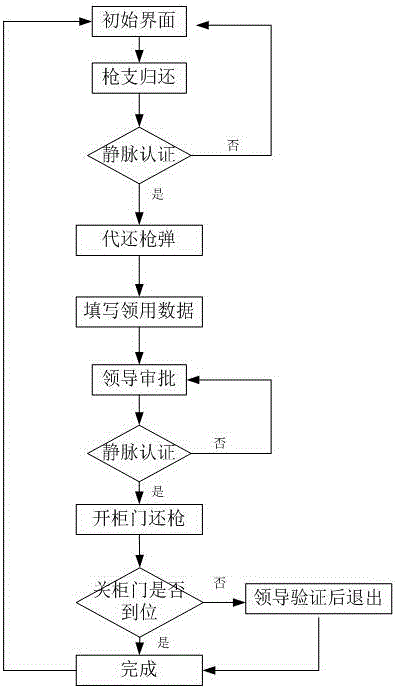
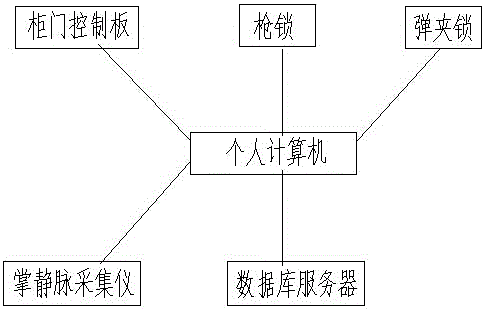
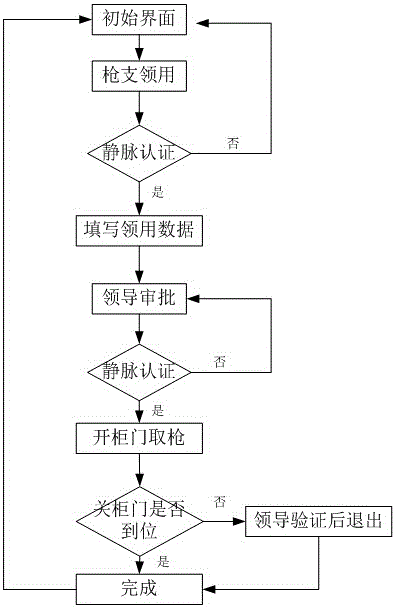
The invention relates to a gun and bullet getting and returning and vein self-service authentication management system. The system is characterized by comprising a computer arranged in a gun cabinet, wherein the computer is connected with a palm vein acquisition instrument; the computer is further connected with a database server through a network line; the computer is further connected with a cabinet door control board of the gun cabinet, a cartridge clip lock and a gun lock through serial ports; and when personnel are authenticated, palm vein information is read through the palm vein acquisition instrument and sent to the database server to perform identity comparison, a cabinet door opening command is sent through a serial port when the identity is legal, a gun cabinet door is opened, and the corresponding cartridge clip lock and gun lock are opened. The system has the beneficial effects of simple structure, convenient use, high accuracy and strict management; and automatic control and vein authentication technologies are adopted, so that the problems of slow getting and returning, low authentication efficiency and the like of existing bullets are solved and the efficiency of gun and bullet getting and returning process and personnel identity authentication is improved.
Owner:山东登云智能科技有限公司
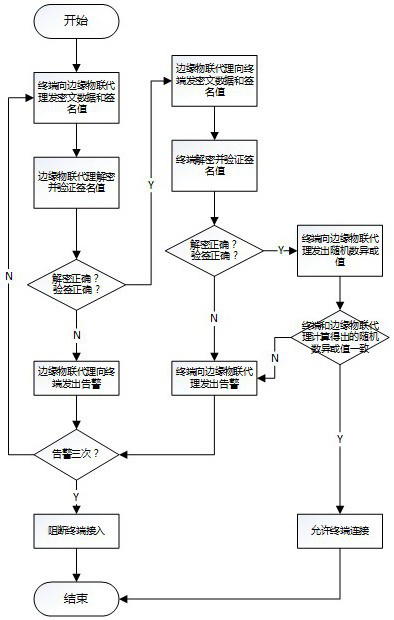
A method for lightweight identity authentication of power Internet of Things sensing terminals
ActiveCN111083131BEasy to manageEasy to popularize on a large scaleUser identity/authority verificationCiphertextThe Internet
The invention discloses a method for light-weight identity authentication of electric power Internet of Things sensing terminals. In step 1, the IoT terminal sends ciphertext data and signature values to the edge IoT agent, and enters into step 2; in step 2, the edge IoT The agent decrypts the ciphertext data and verifies the signature value, and enters step 3; step 3, judges whether the edge IoT agent decrypts the ciphertext data is correct, and judges whether the edge IoT agent verifies the signature value is correct: if the edge IoT agent decrypts the ciphertext data correctly and the edge object If the conditions for the correct signature value of the joint agent verification signature are met at the same time, then enter step 4; if the edge IoT agent decrypts the ciphertext data is incorrect or the edge IoT agent verifies the signature value is incorrect, the edge IoT agent sends an alarm to the terminal and enters step 5, define Number of alarms N, N is an integer, N=N+L, L is a constant not equal to 0.
Owner:NANJING NARI GROUP CORP +3
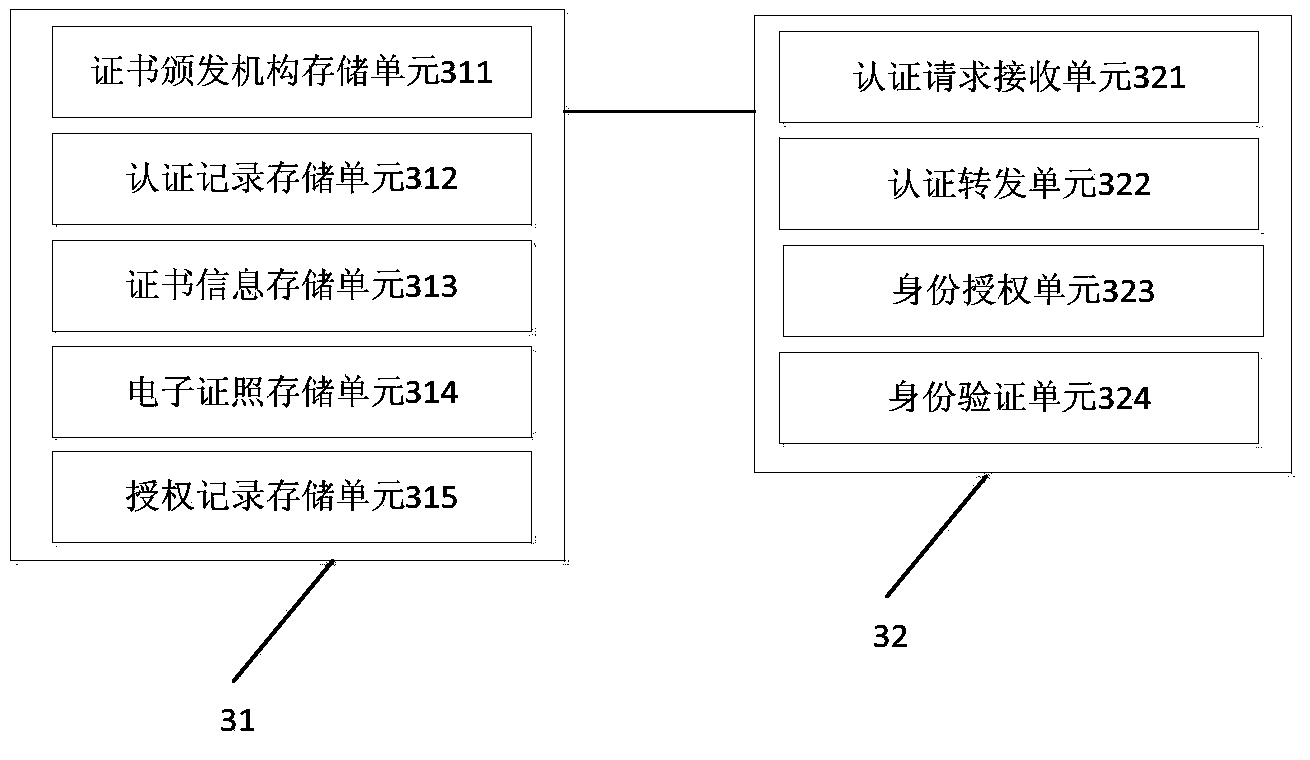
Identity authentication support platform and authentication method based on digital certificate interconnection
ActiveCN103475485BImprove docking efficiencySimplify the identity verification processUser identity/authority verificationDigital data authenticationInterconnectionAuthentication scheme
The invention discloses an identity authentication supporting platform and an authentication method based on digital certificate interconnection and interworking to solve the problems that an existing digital certificate is repeatedly issued and approved, and the using cost of a user is high and the using process is complex and to enable the identity of the virtual network to be relevant to the identity of the real world. The requests that digital certificate authentication needs to be carried out on application systems are centralized to the identity authentication supporting platform based on the digital certificate interconnection and interworking to be processed in a unified mode, the application systems are high in communicating efficiency, and the identity authentication procedures are simple and reliable. The identity authentication information based on the digital certificate interconnection and interworking can be shared, the digital certificate authentication does not need to be carried out on all application systems, and the identity authentication efficiency is improved.
Owner:ZHEJIANG ICINFO TECH
Multi-layer blockchain cross-domain authentication method in the application scenario of the Internet of Things
ActiveCN112637189BAvoid Privacy LeakageImprove space utilizationSecuring communicationInternet privacyThe Internet
The invention relates to a multi-layer blockchain cross-domain authentication method under the application scenario of the Internet of Things, belonging to the technical fields of the Internet of Things and the blockchain. This method uses the blockchain identity registration protocol, cross-domain identity authentication protocol, and node trust evaluation method based on entrusted proof of rights and interests to perform distributed node management and security protection on the blockchain in IoT application scenarios. When different blocks When the nodes of the chain need to perform cross-chain identity authentication and data exchange, the public blockchain is used for cross-chain credible identity authentication to ensure user privacy and data security. Programs include etc. Compared with the original centralized identity authentication method, the present invention improves the efficiency of identity authentication in the distributed application scenario of the Internet of Things, solves the problem of certificate management in heterogeneous networks, and has better security and usability.
Owner:CHONGQING UNIV +1
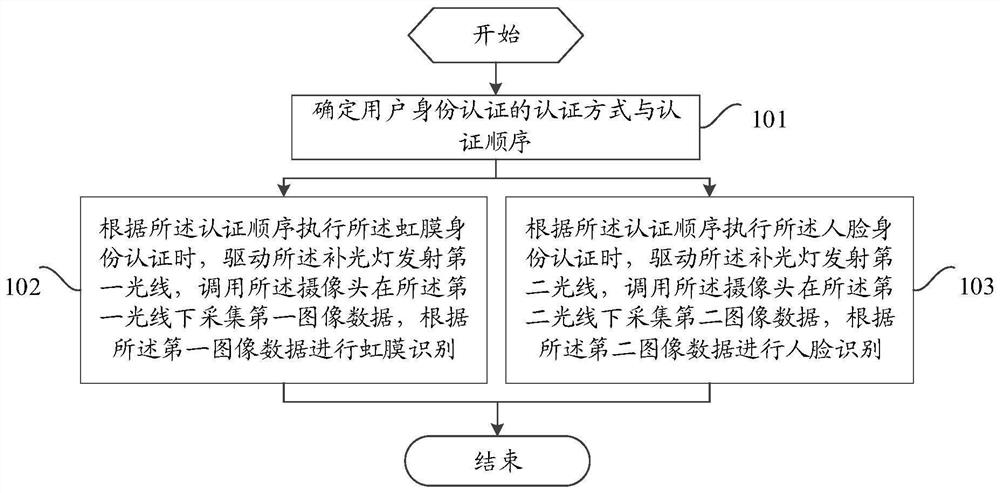
A user identity authentication method and mobile terminal
ActiveCN108734001BImprove identity authentication efficiencyIncrease diversityAcquiring/recognising eyesDigital data authenticationComputer visionIris recognition
Owner:VIVO MOBILE COMM CO LTD
Identification preprocessing, identification method and device
ActiveCN110765842BReduce in quantityImprove identity authentication efficiencyCharacter and pattern recognitionTransmissionInternet privacyIdentity recognition
Disclosed are an identification preprocessing, identification method and equipment. After any user brings his mobile device into the preset nearby area of the biometric feature collection device, the user's mobile device will receive the wireless signal broadcast by the biometric feature collection device, and the wireless signal will trigger the mobile device to identify the owner user. The group ID of the user group is provided to the identification server. The identification server will determine the registered biometrics associated with each user in the user group corresponding to the group identifier from the set of registered biometrics, and send the determined registered biometrics to the biometrics collection device, and the biometrics collection device will Add the registered biometrics issued by the identification server to the locally established screening feature set. In this way, the biometric feature collection device will use each registered biometric feature in the screening feature set to compare with the collected biometric feature of the user to be identified (ie, collect the biometric feature) to identify the user.
Owner:ADVANCED NEW TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com