Method for authenticating identity of insured person, server of insurance institution and user terminal
An identity authentication and user terminal technology, applied in the medical field, can solve the problems of unfavorable physical recovery of the wounded, low authentication efficiency, waste of the insured's time, etc., to prevent someone from falsely claiming insurance money, improve efficiency, and save time.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0051] The embodiments of the present application will be described below with reference to the drawings in the embodiments of the present application.
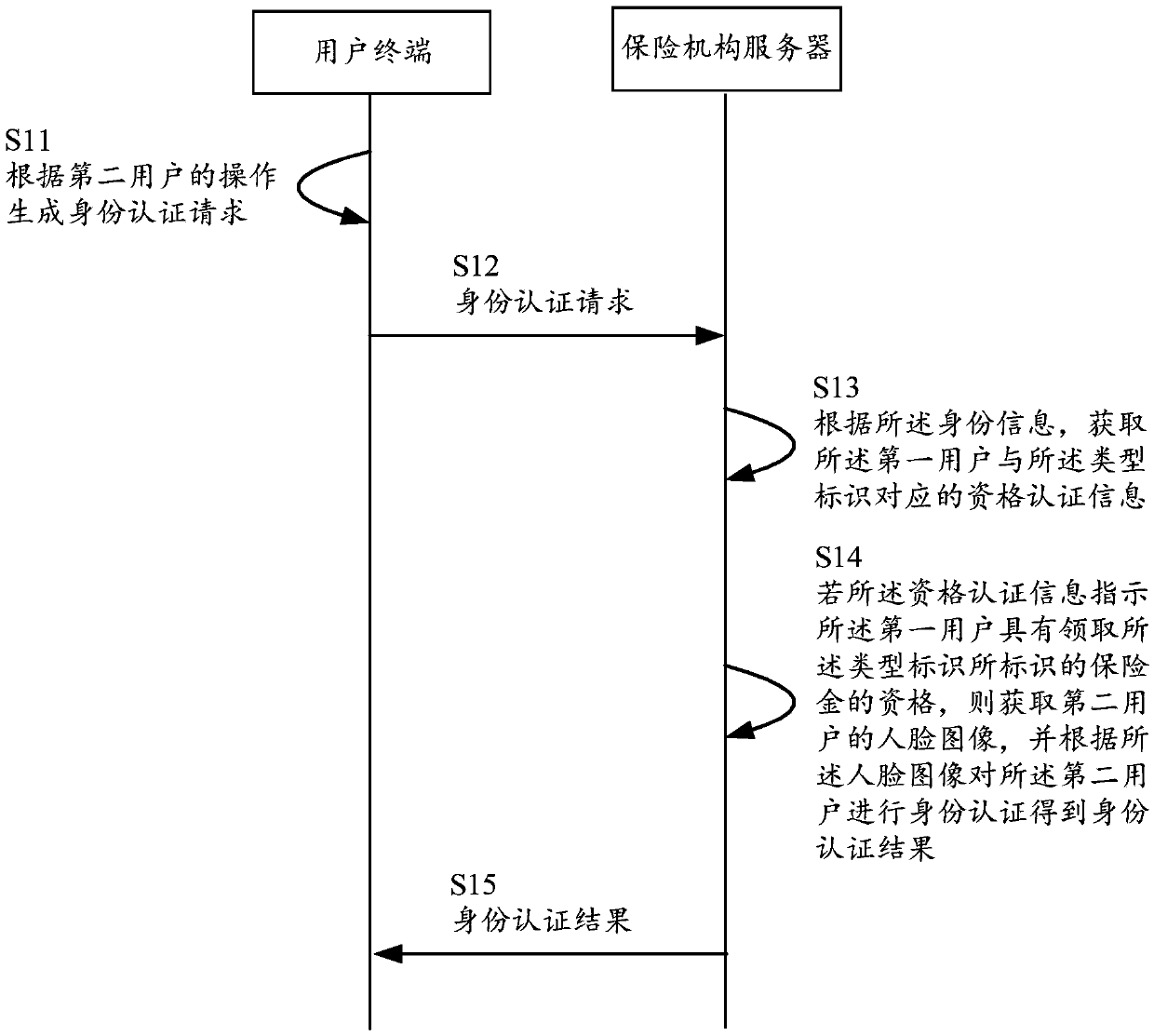
[0052] see first figure 1 , figure 1 It is a schematic flowchart of an identity authentication method for an insured person provided in the embodiment of this application. Such as figure 1 Indicated methods of identifying the enrollee may include:
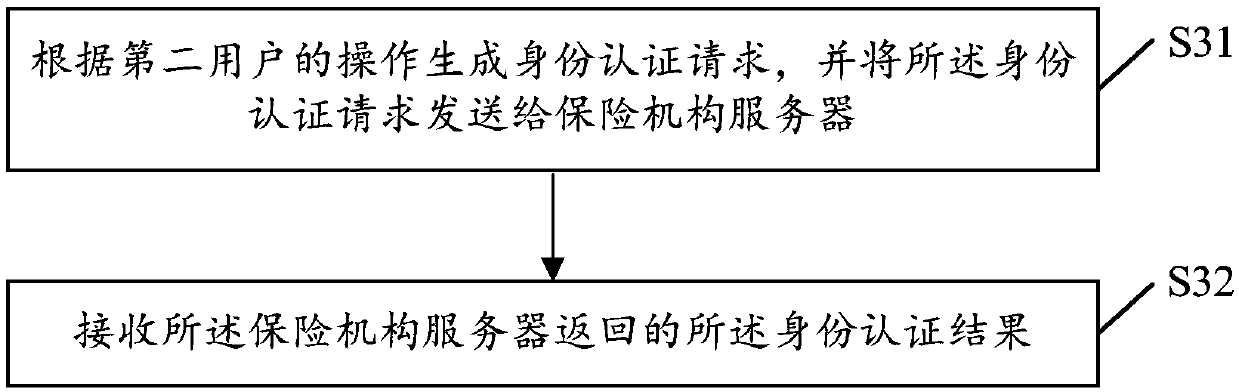
[0053] S11. The user terminal generates an identity authentication request according to an operation of the second user.
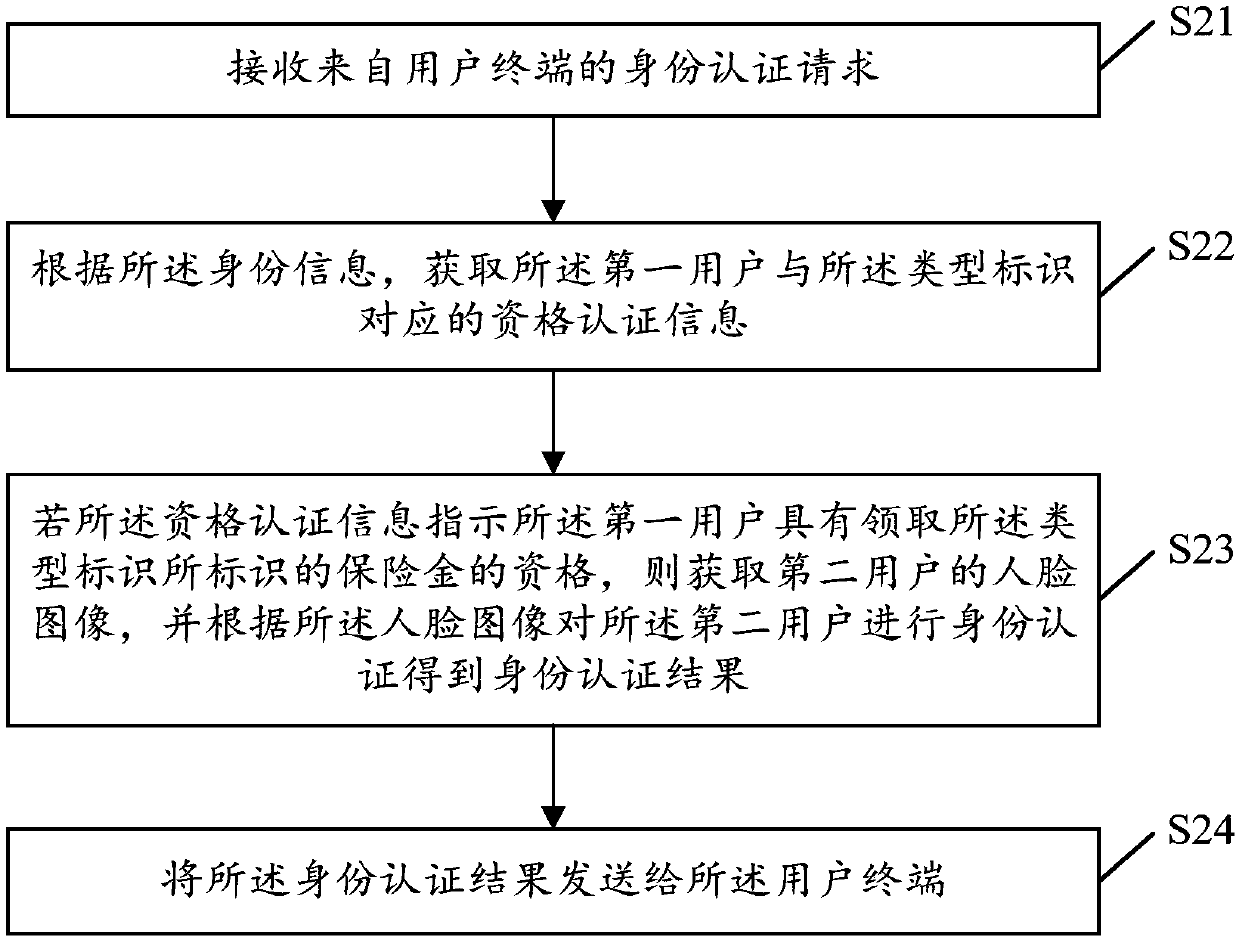
[0054] Specifically, the operation of the above-mentioned second user may open a client installed in the user terminal for the second user, and input an identity authentication instruction in the client. Wherein, the identity authentication instruction includes the identity information of the first user, the type identification of the insurance money that the first user needs to receive, and the identification of an insurance institution, and the insurance...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com