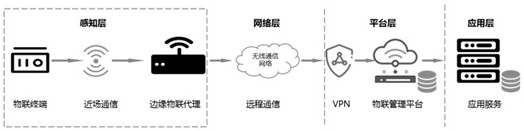
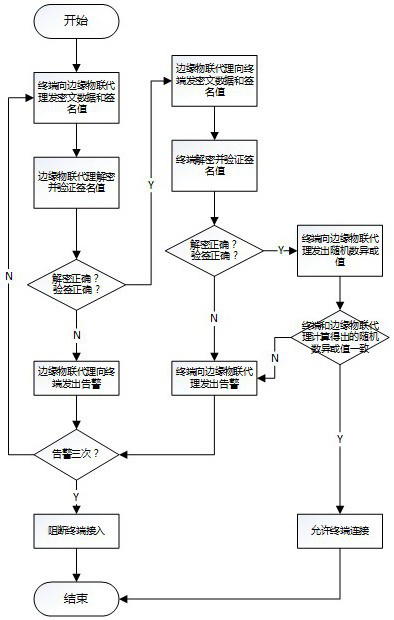
A method for lightweight identity authentication of power Internet of Things sensing terminals
A technology of power Internet of Things and IoT terminals, applied in the field of identity authentication, can solve problems such as the inapplicability of PKI, or public key infrastructure authentication system, so as to make up for its own low efficiency, facilitate large-scale popularization, and reduce the interaction between communication parties. link effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0066] The following examples are only used to illustrate the technical solution of the present invention more clearly, but not to limit the protection scope of the present invention.
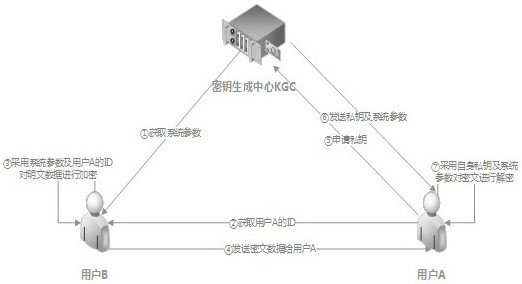
[0067] There are two application scenarios of the IBC logo authentication system, one is encryption-decryption, and the other is signature-verification. The following two application scenarios are analyzed and explained.
[0068] (1) Encryption-decryption
[0069] In the encryption-decryption application scenario, user B uses the system parameters of the key generation center KGC and the public key of user A to encrypt the data, and user A enters the private key matching the public key obtained from the key generation center KGC and system parameters, the ciphertext data sent by user B can be decrypted, that is, the ciphertext data can be decrypted, so as to ensure the security of data transmission. The specific process is as follows: figure 1 shown. Different from the traditional PKI authent...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com