Bidirectional identity authentication method based on lightweight CA, computer program and storage medium
A two-way identity authentication and lightweight technology, which is applied in the field of two-way identity authentication based on lightweight CA, computer programs and storage media, can solve the problems of high communication transmission overhead, identity privacy leakage, and resource consumption, etc., to reduce Occupies storage resources, transmits less information, and has the effect of security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
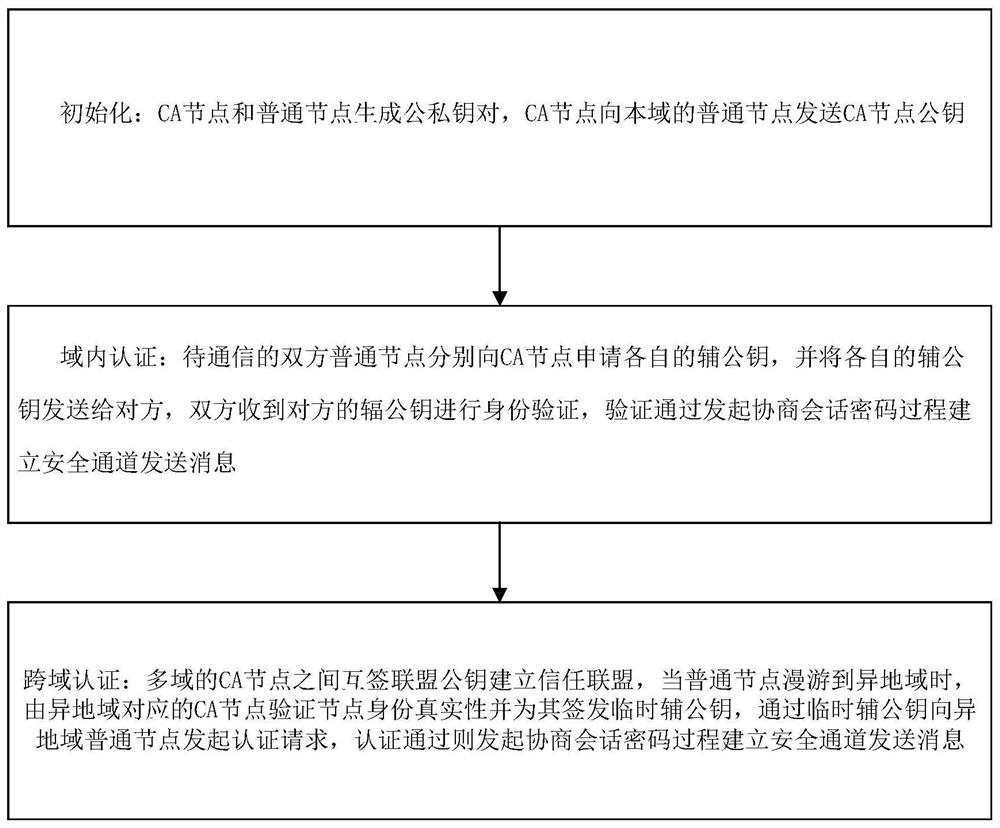
[0039] Such as figure 1 , a two-way identity authentication method based on a lightweight CA, including:
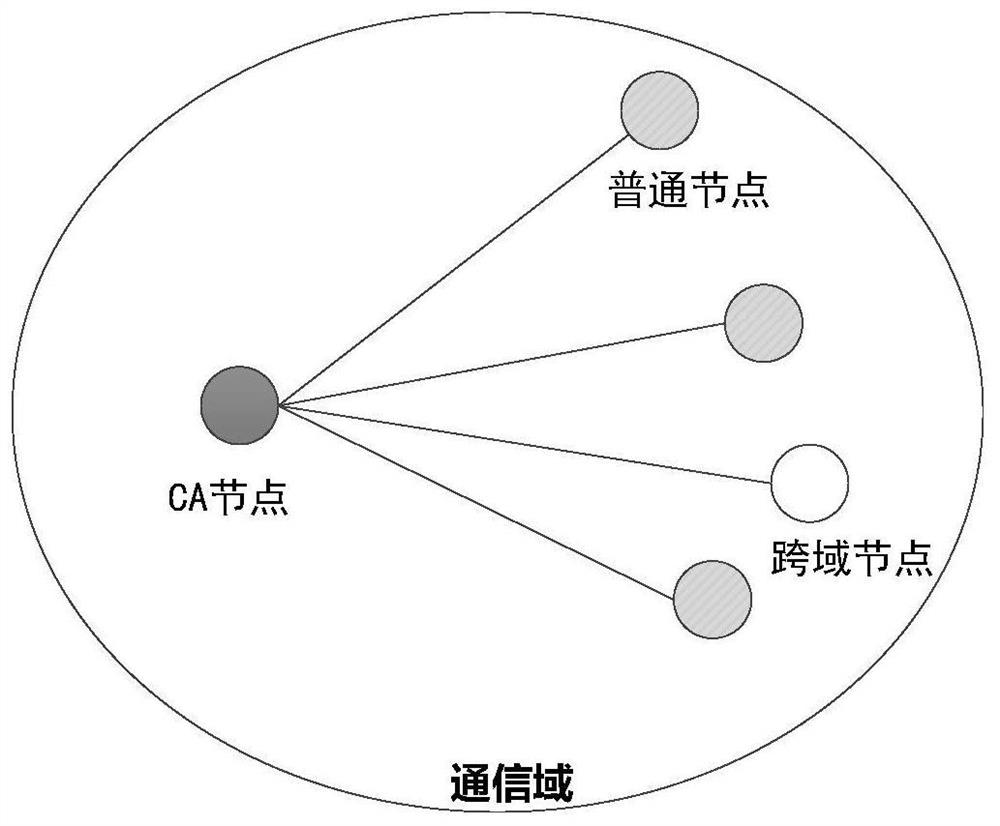
[0040] Initialization: CA node and ordinary node generate a public-private key pair, and the CA node sends the public key of the CA node to the ordinary node in the domain;
[0041] Intra-domain authentication: The ordinary nodes of both parties to be communicated apply for their respective secondary public keys from the CA node, and send their respective secondary public keys to the other party. Both parties receive the secondary public key of the other party for identity verification, and the verification process initiates the negotiation session password process Establish a secure channel to send messages;
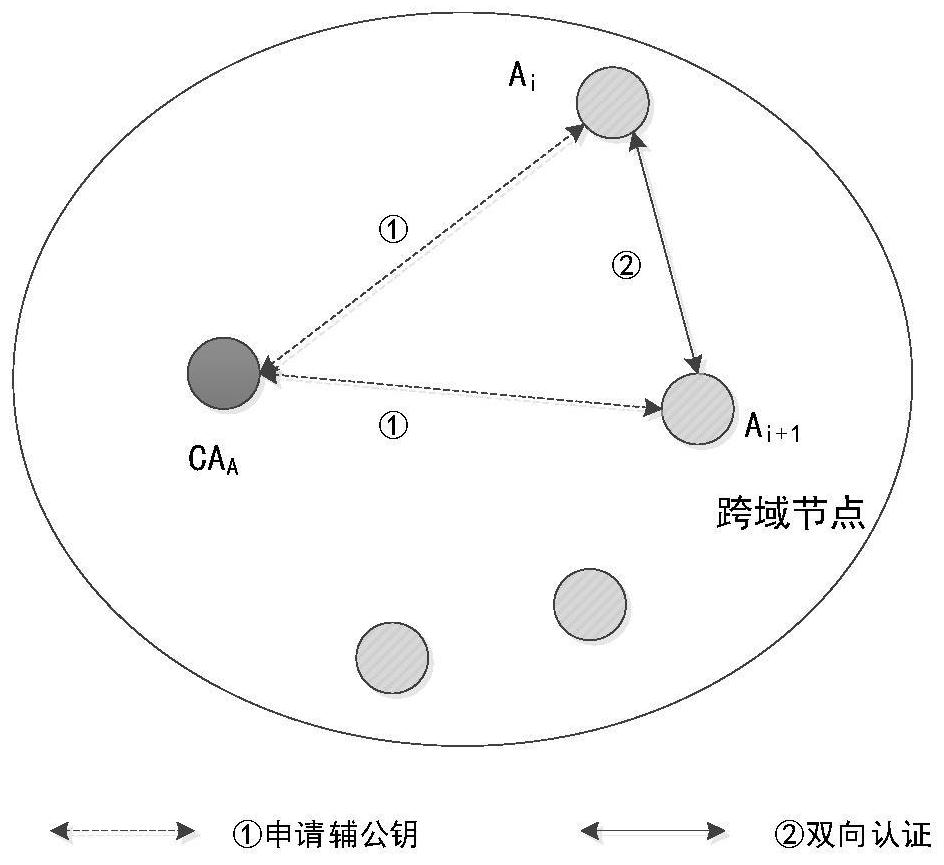
[0042] Cross-domain authentication: Multi-domain CA nodes sign the alliance public key to establish a trust alliance. When a common node roams to a different region, the CA node corresponding to the different region verifies the authenticity of the node's identity...
Embodiment 2
[0092] On the basis of Embodiment 1, a computer program is provided, which includes computer program instructions, wherein, when the program instructions are executed by a processor, they are used to implement the lightweight CA-based two-way identity authentication in Embodiment 1 The process corresponding to the method.
Embodiment 3
[0094] On the basis of Embodiment 1, a computer-readable storage medium is provided, on which computer program instructions are stored, wherein, when the program instructions are executed by a processor, they are used to implement the lightweight CA-based The process corresponding to the two-way authentication method.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com