Authentication method, device and electronic device
An identity verification method and a technology to be verified are applied in the field of devices, electronic equipment, and identity verification methods to achieve the effects of reducing consumption, reducing transmission to a server, and improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
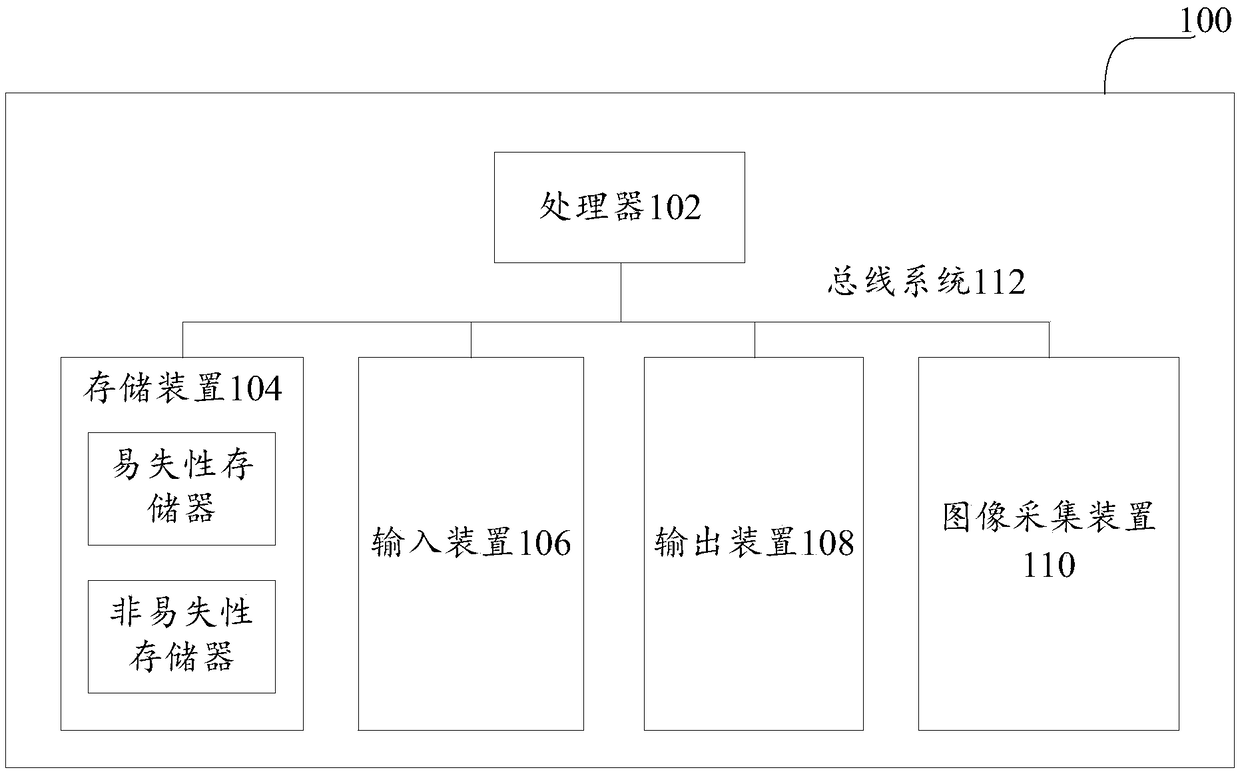
[0061] First, refer to figure 1 An example electronic device 100 for implementing the identity verification method of the embodiment of the present invention will be described. The example electronic device 100 may be a computer, or a mobile terminal such as a smart phone or a tablet computer.
[0062] Such as figure 1 As shown, the electronic device 100 includes one or more processors 102 and one or more storage devices 104. Optionally, the electronic device 100 may further include an input device 106, an output device 108, and an image acquisition device 110, and these components are interconnected by a bus system 112 and / or other forms of connection mechanisms (not shown). It should be noted that figure 1 The components and structures of the electronic device 100 shown are only exemplary and not restrictive. The electronic device may also have other components and structures as required.
[0063] The processor 102 may be a central processing unit (CPU), a graphics processing un...
Embodiment 2
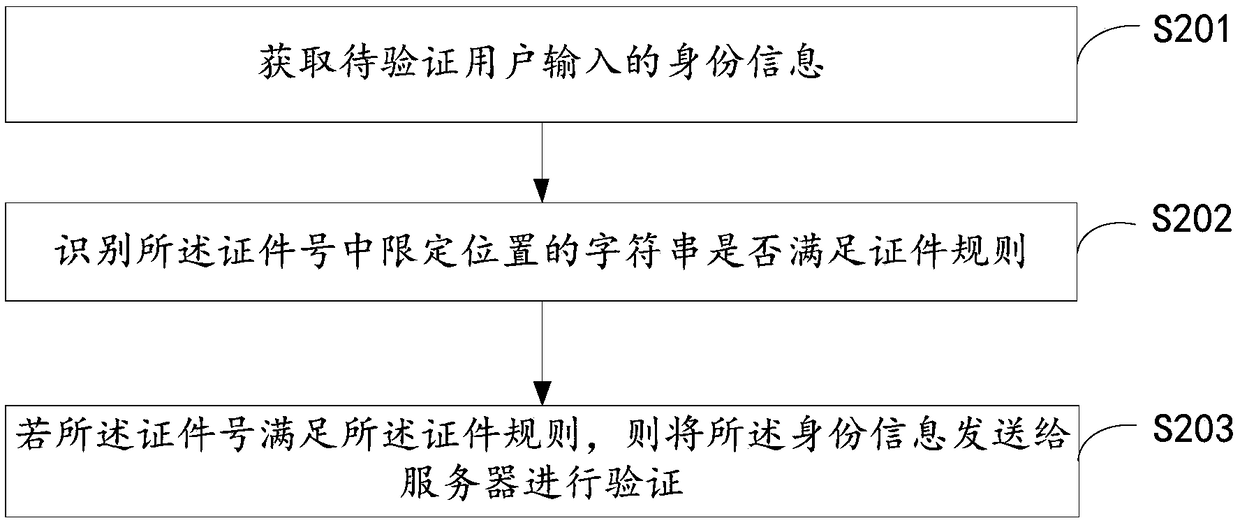
[0071] See figure 2 , Is a flowchart of a data encryption method provided by an embodiment of the present invention. The following will figure 2 The specific process shown is elaborated.
[0072] Step S201: Obtain the identity information input by the user to be verified.
[0073] In this embodiment, the identity information may include a certificate number.
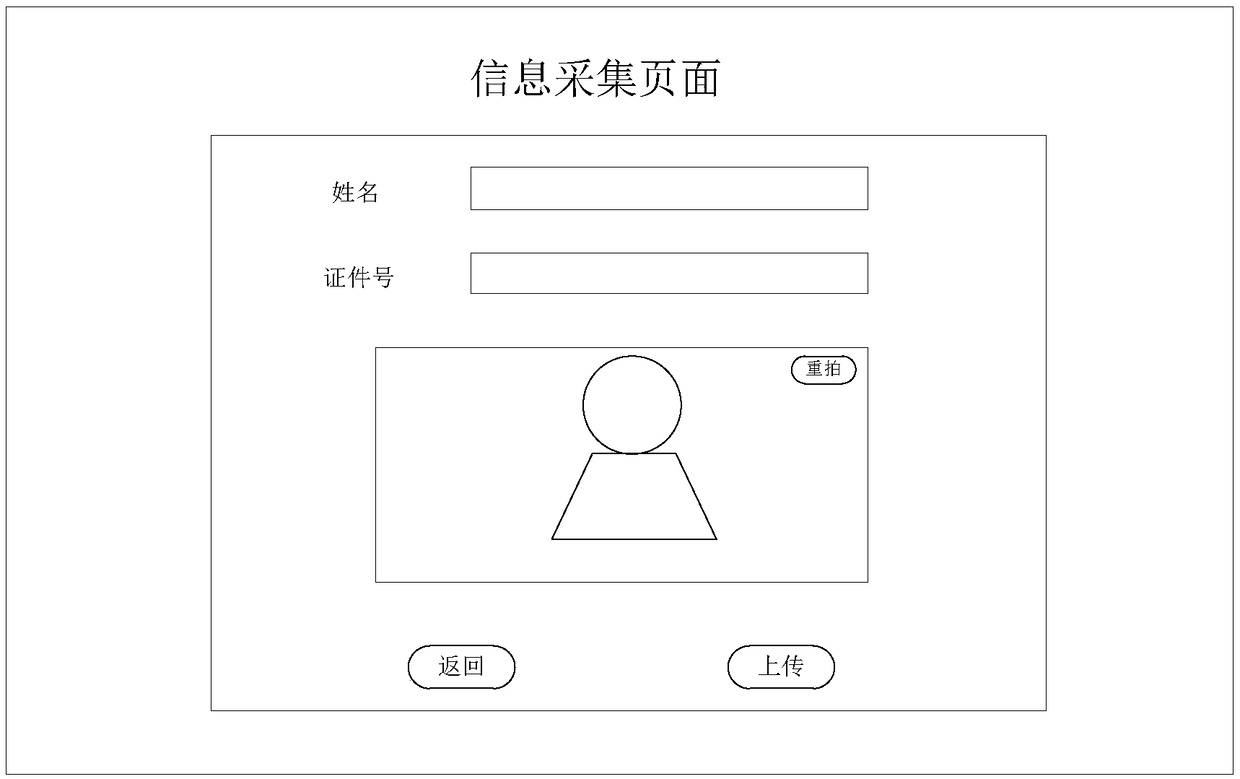
[0074] In one embodiment, an information collection page can be provided, and the identity information of the user to be verified can be obtained by receiving a character string entered by the user in the information collection page. Such as image 3 As shown, image 3 A schematic diagram of the information collection page in an example is shown. The figure shows multiple input boxes for receiving user input data, including a name input box and a certificate number input box. further, image 3 There is also a "return" button in it, and the "return" button is configured to return to the previous page.
[0075] In another imp...
Embodiment 3
[0133] See Figure 5 , Is a schematic diagram of functional modules of the identity verification device provided by the embodiment of the present invention. Each module in the identity verification device in this embodiment is used to execute each step in the method provided in the second embodiment. The identity verification device includes the following modules.
[0134] The obtaining module 301 is configured to obtain the identity information of the user to be verified, and the identity information includes a certificate number.
[0135] The first identification module 302 is used to identify whether the character string at the position limited by the certificate number meets the certificate rules.
[0136] The sending module 303 is configured to send the identity information to the server for verification if the certificate number meets the certificate rules.
[0137] Optionally, the identity verification device further includes:
[0138] The collection module 304 is configured t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com