Identification authentication method of open network base on dynamic credible third-party
A technology of identity authentication and open network, applied in user identity/authority verification, public key for secure communication, special data processing applications, etc. The effect of controlling identity authentication, improving reliability, and enhancing controllability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] In order to illustrate the implementation scheme of authentication described in the present invention, we give the following best example, and describe in more detail the implementation scheme of identity authentication based on a dynamic trusted third party in an open network.
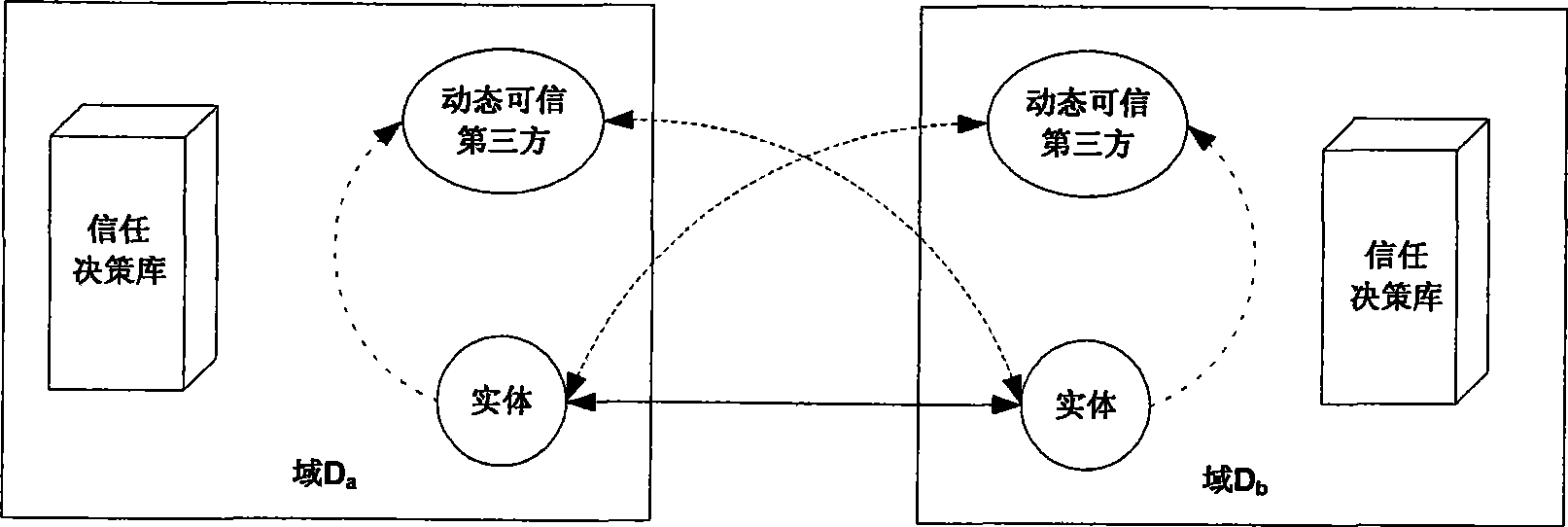
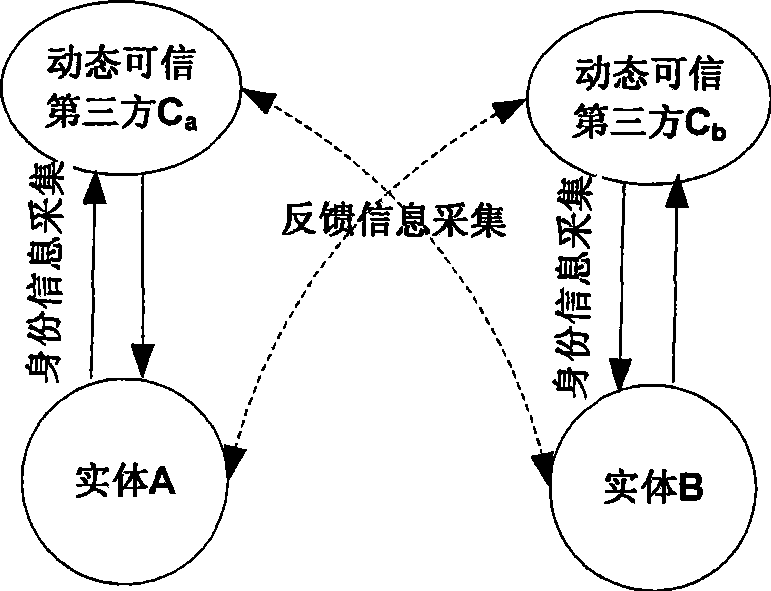
[0036] according to figure 1 Given the identity authentication architecture diagram in , it is assumed that the interactive entities participating in identity authentication in the open network are A and B, where: A is the resource requester, B is the resource provider, and their domains are D a and D b . And, suppose that within a certain period of time, domain D a The selected dynamic trusted third party is denoted as C a , domain D b The selected dynamic trusted third party is denoted as C b , the specific implementation scheme of identity authentication between entities A and B described in the present invention is:
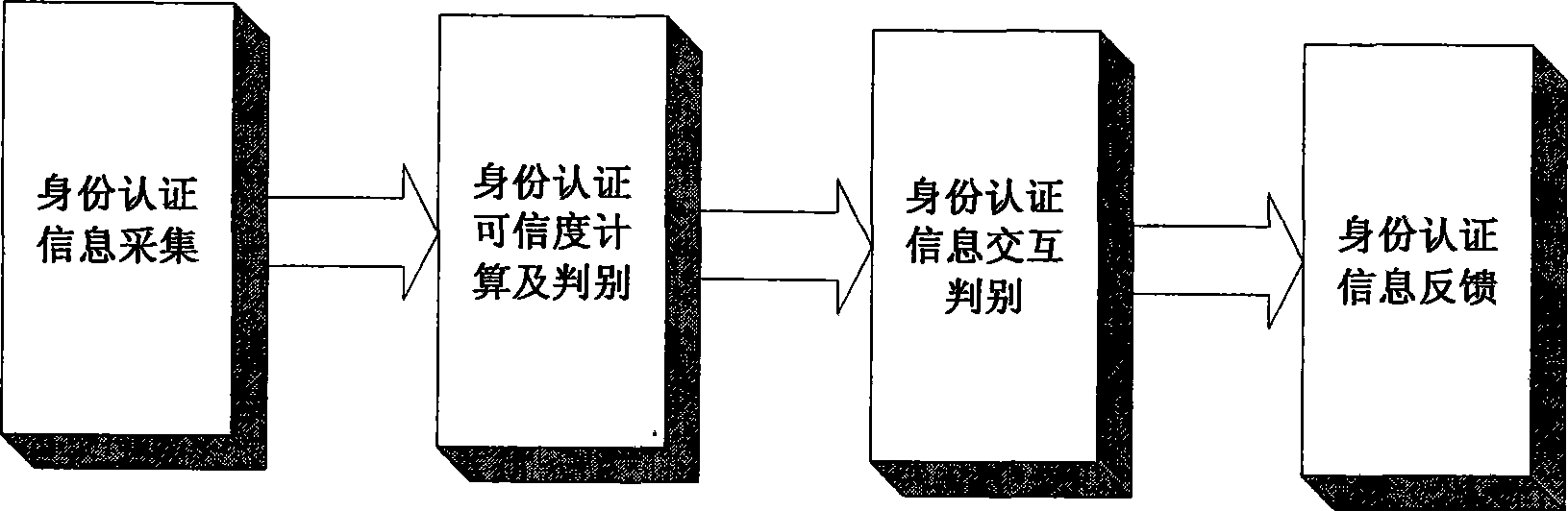
[0037] The first stage: identity authentication information collect...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com