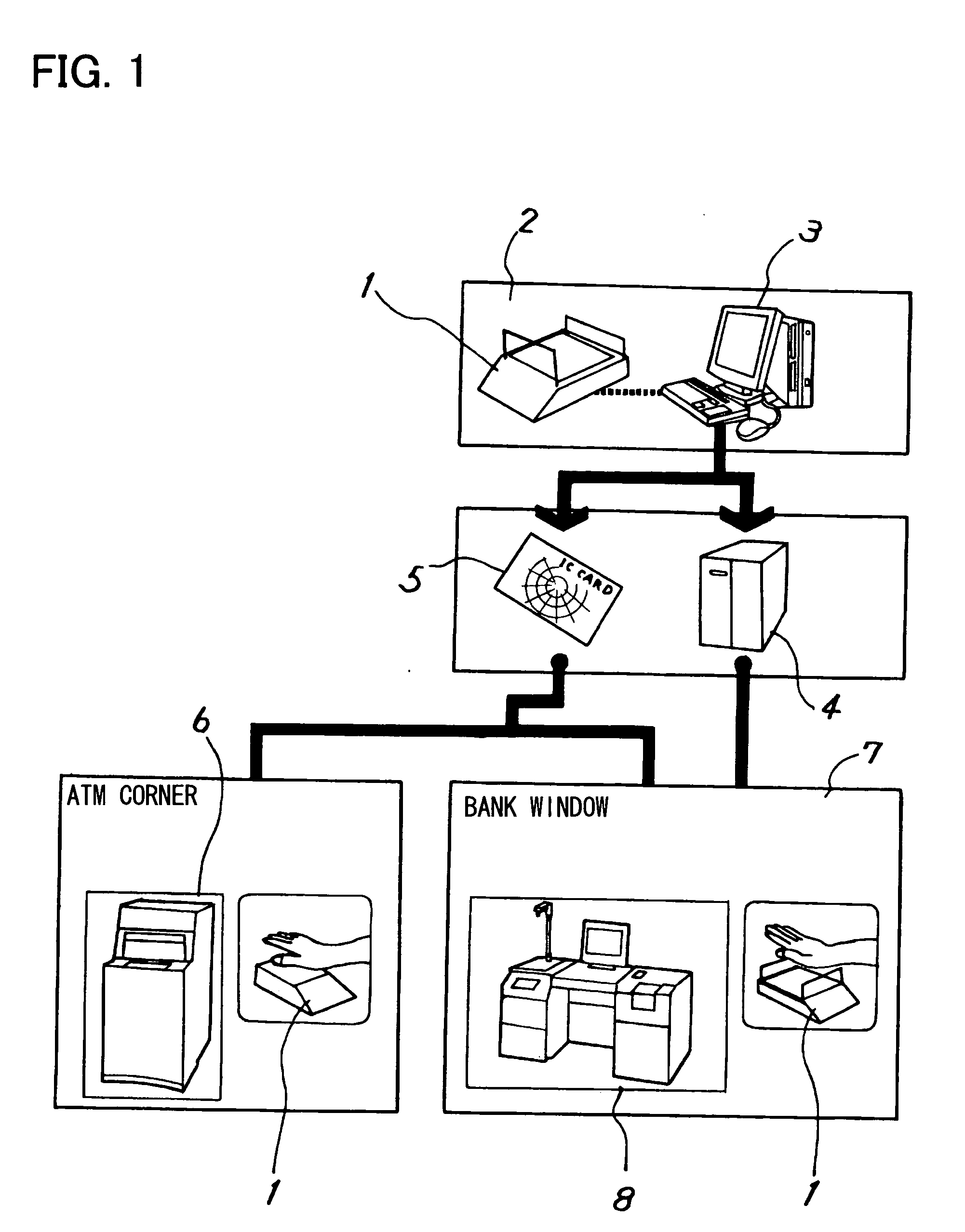
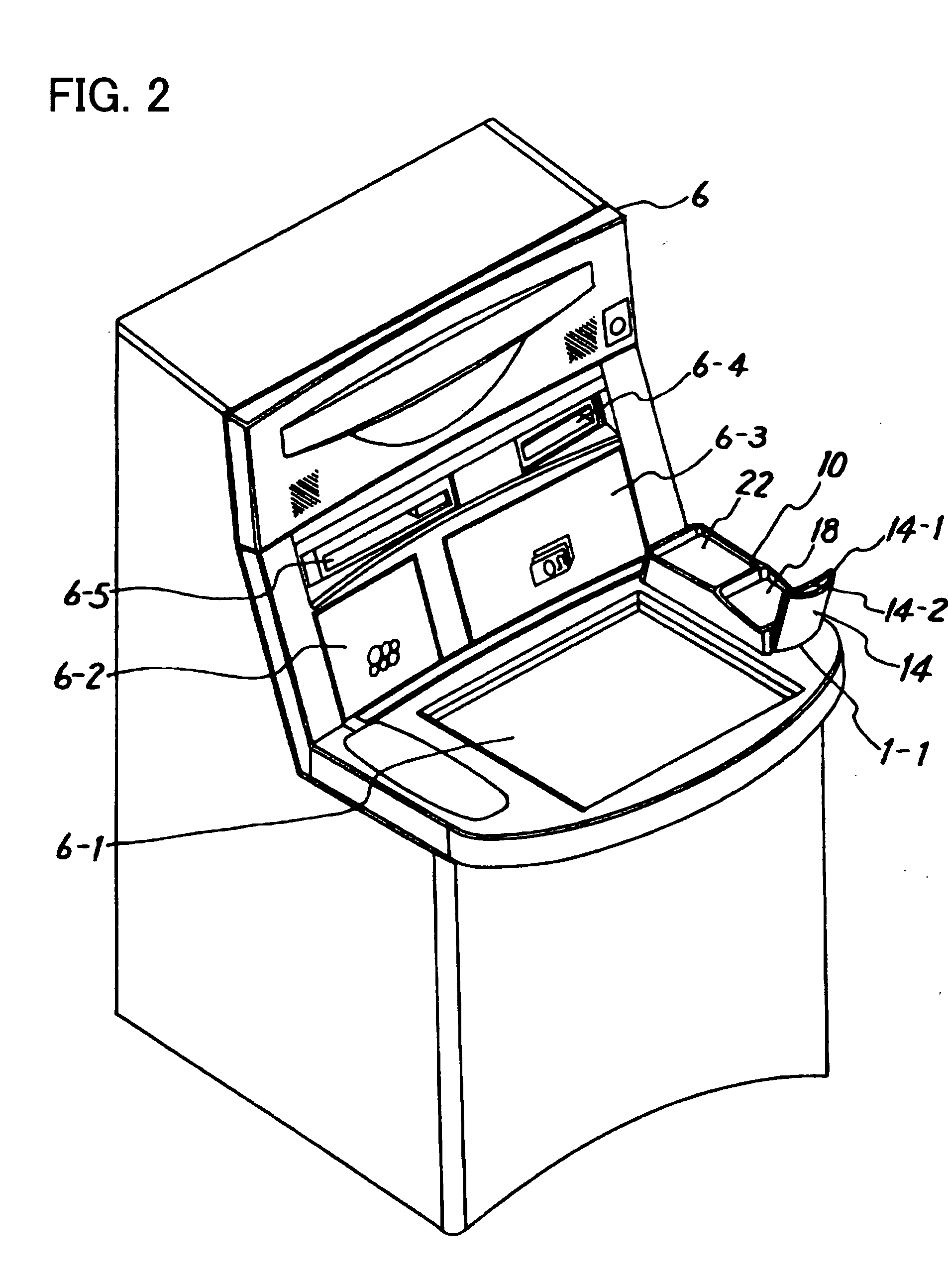
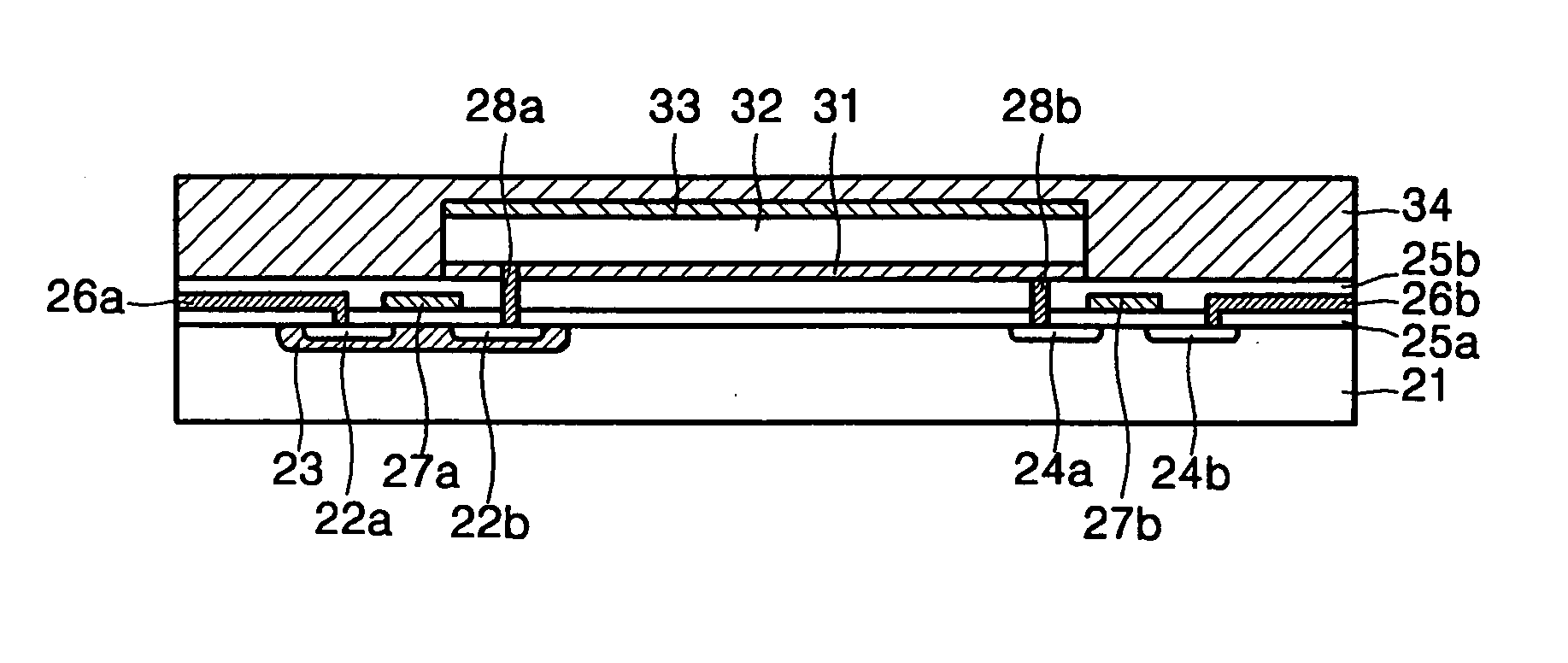
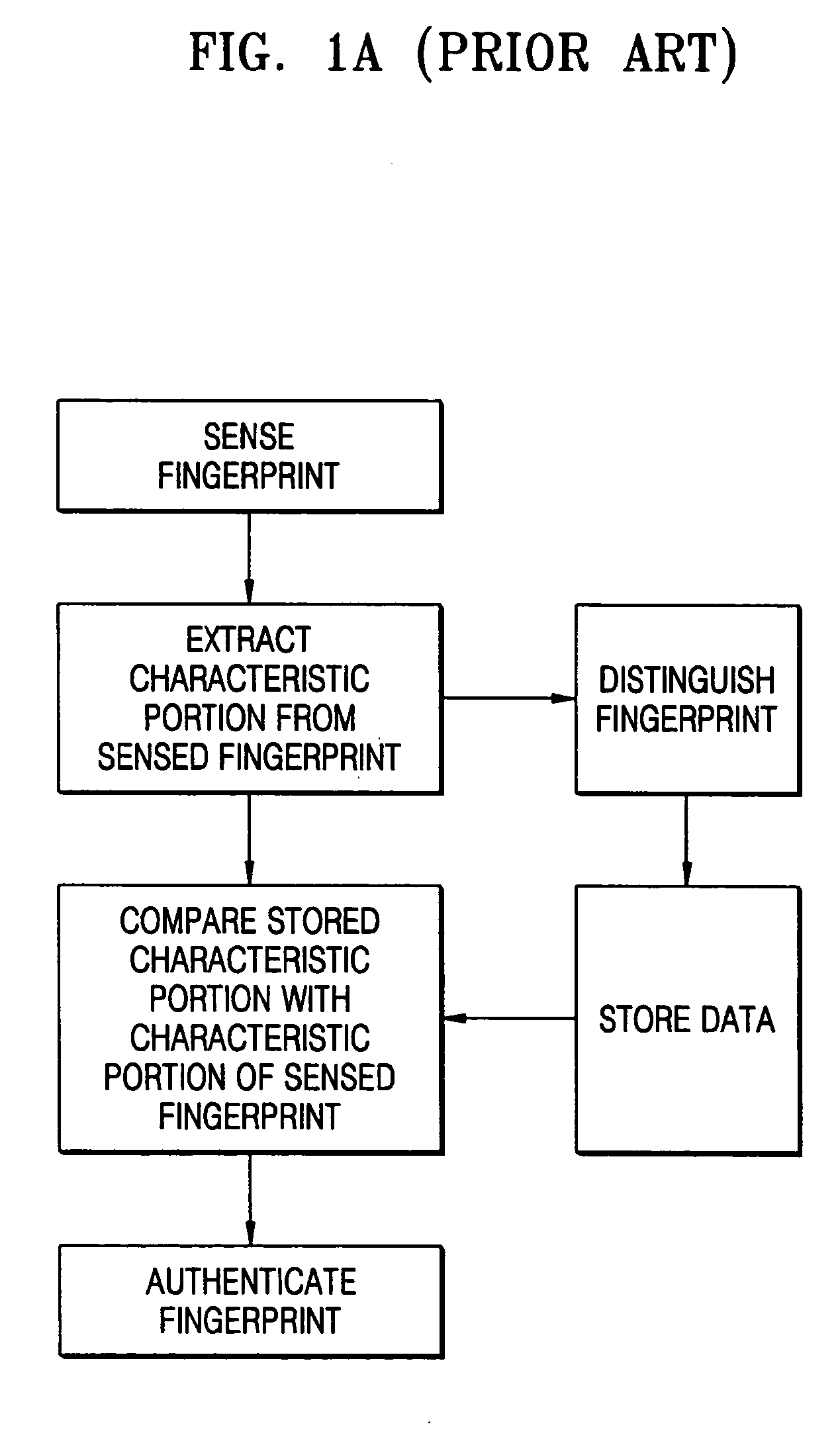
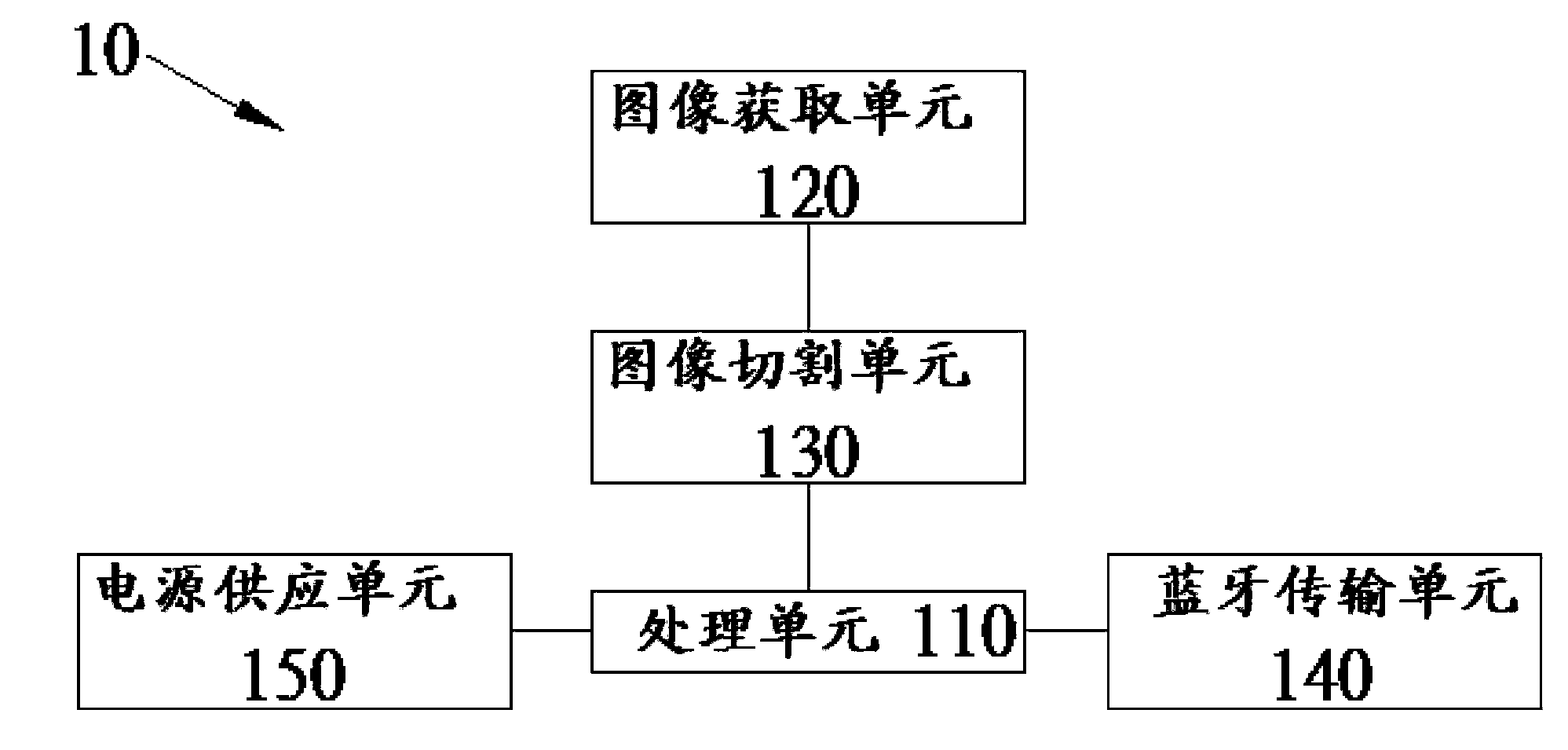
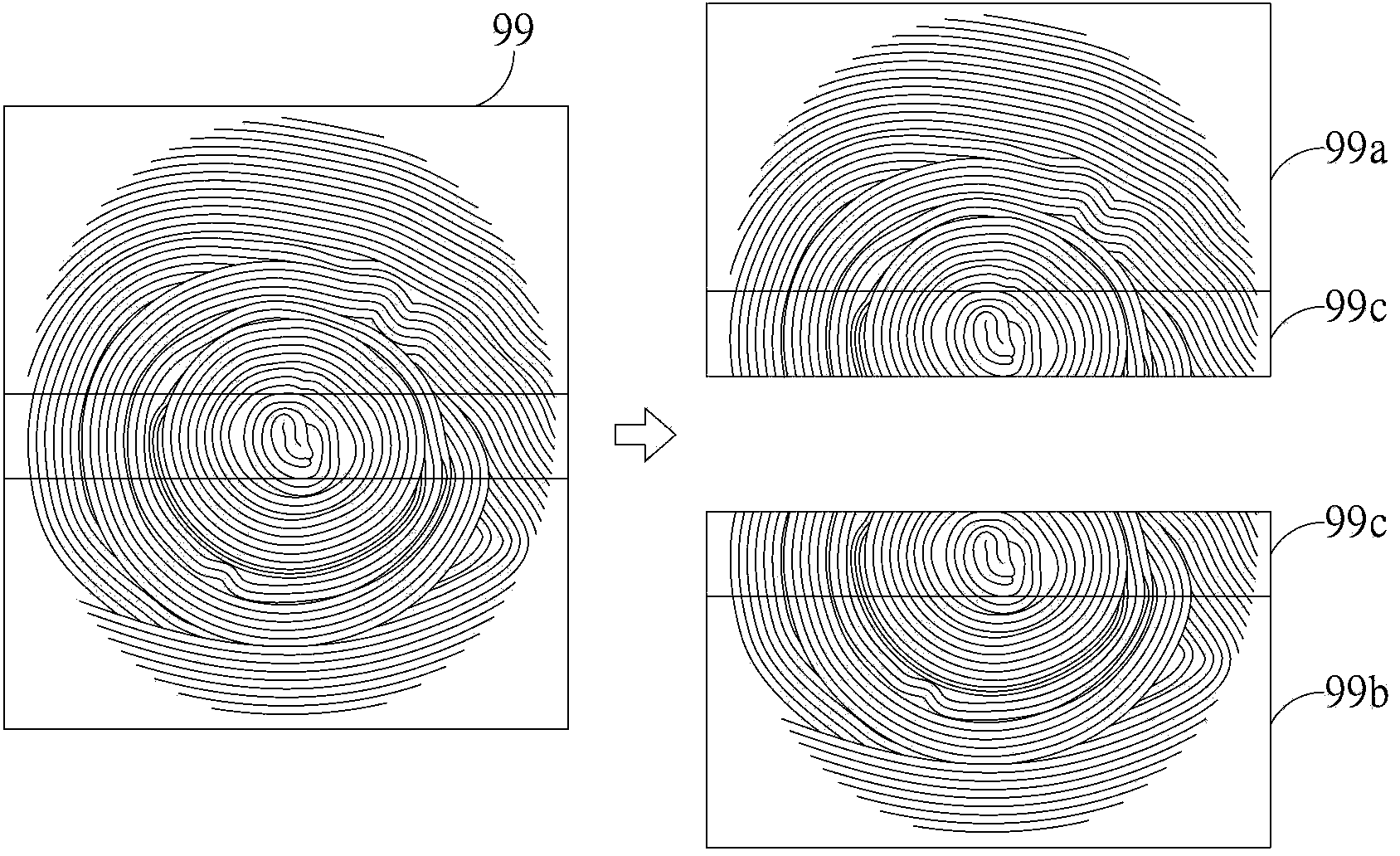
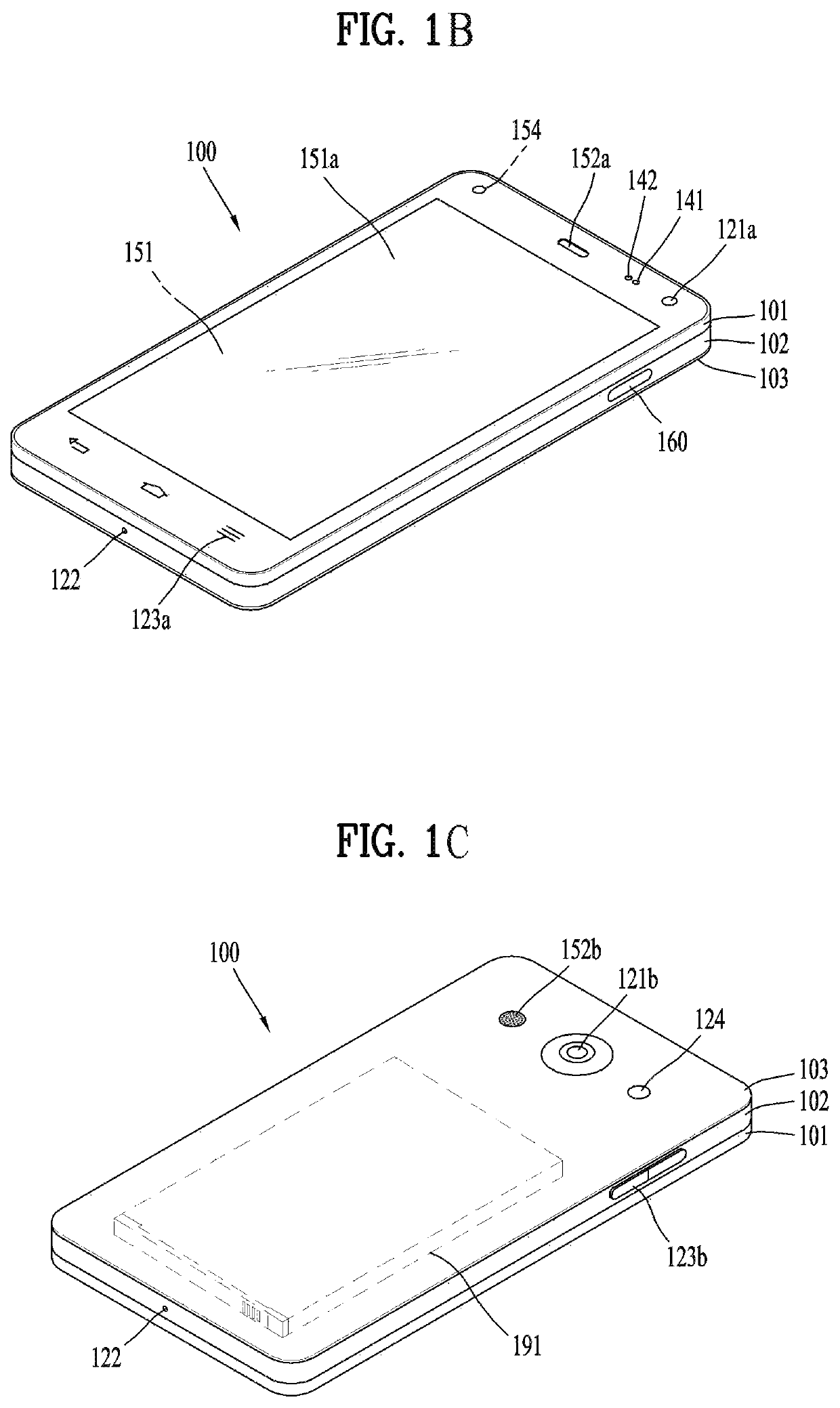
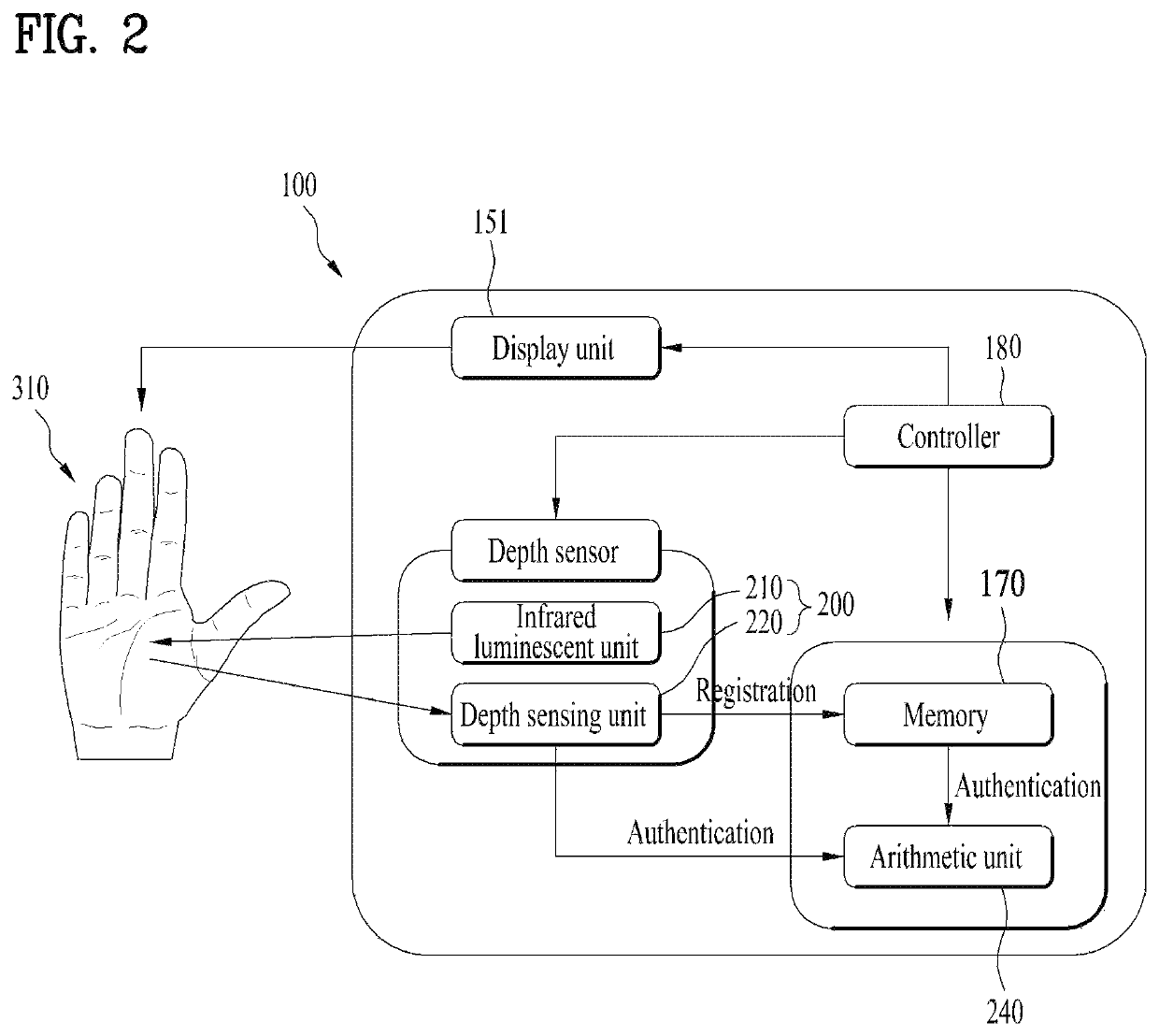
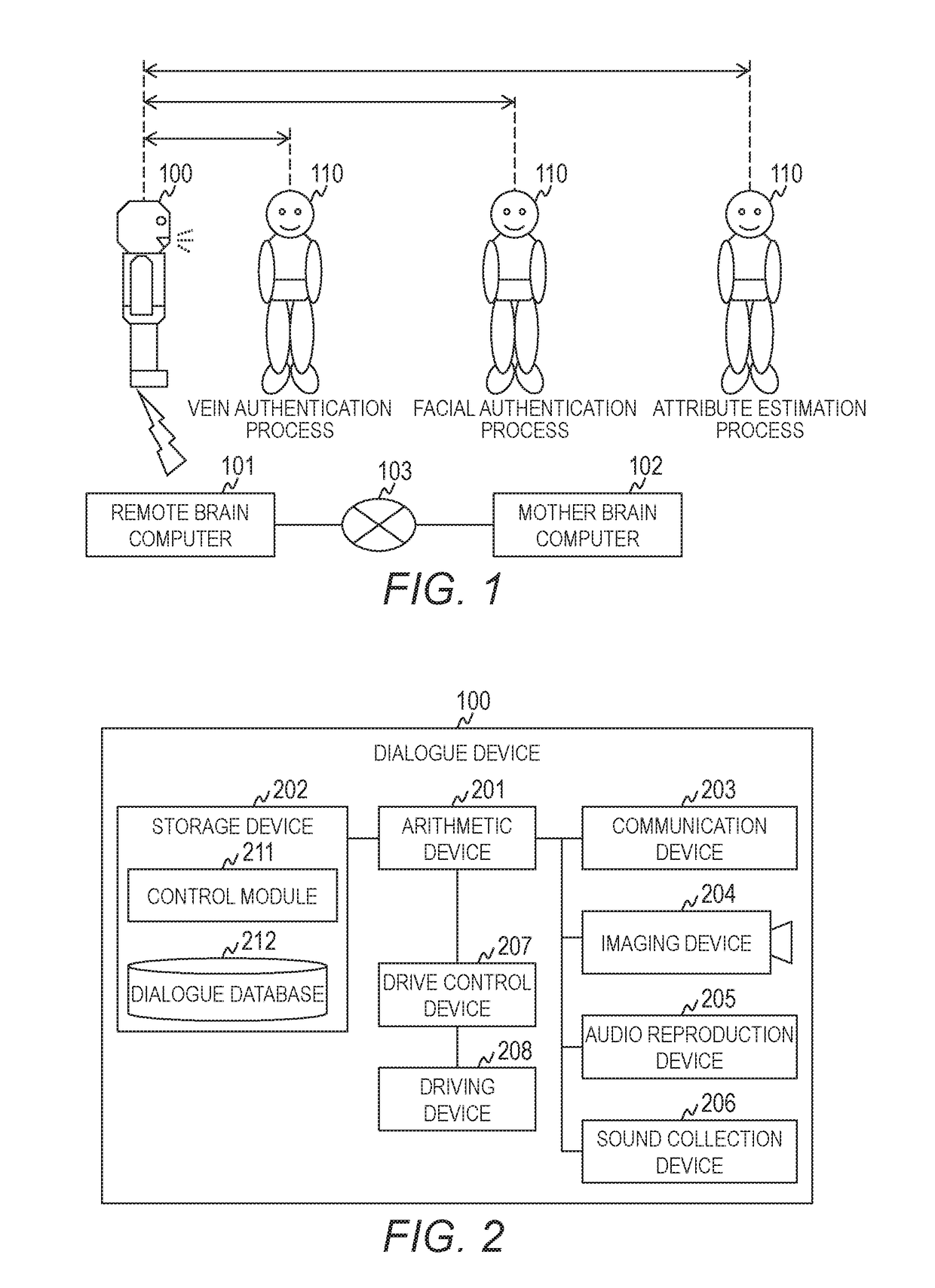
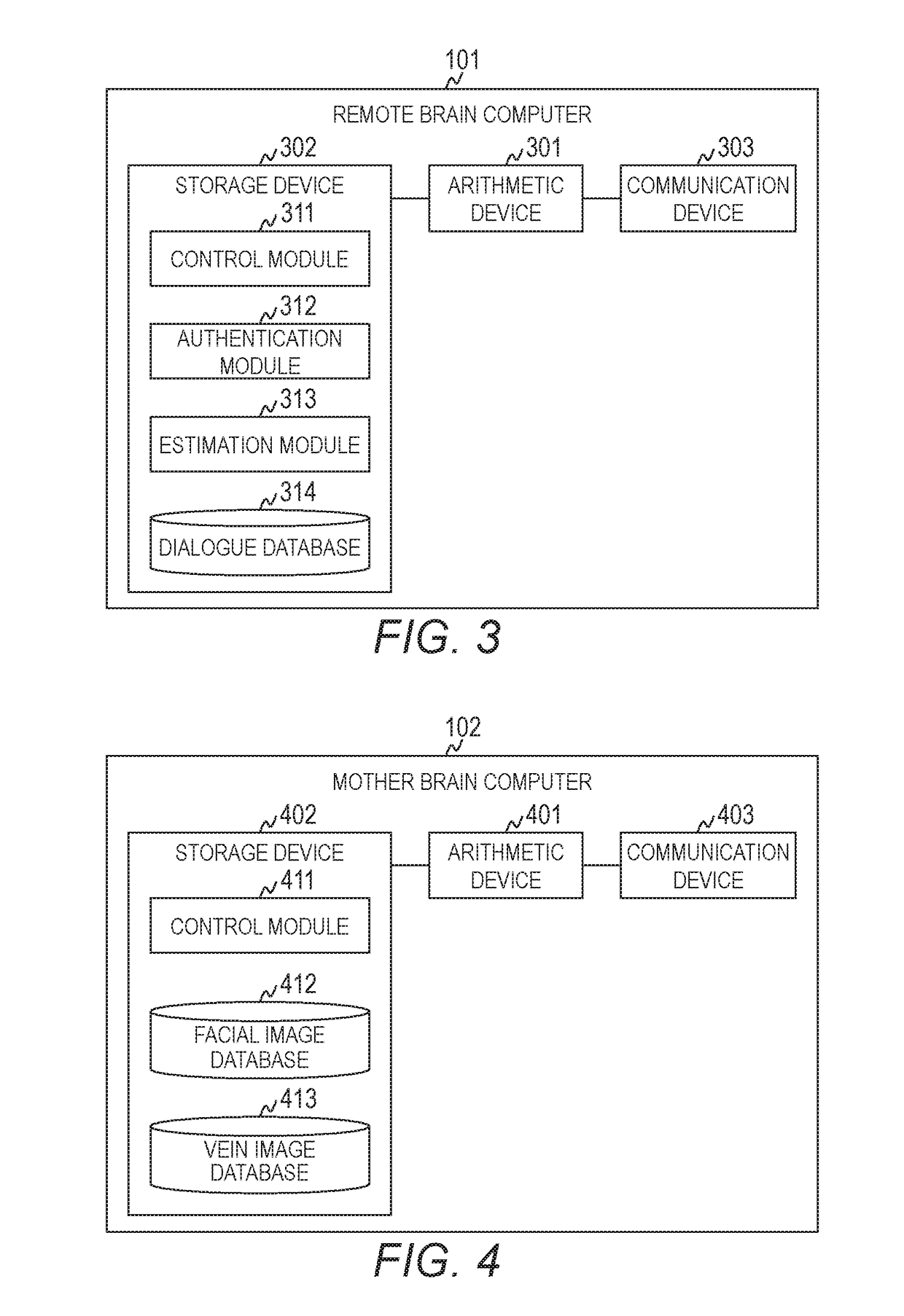
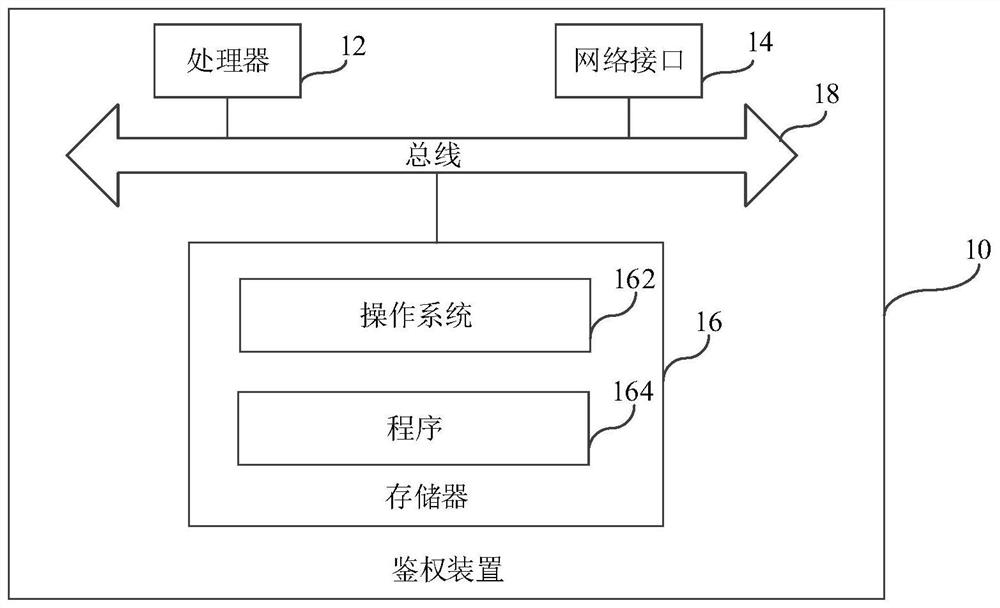
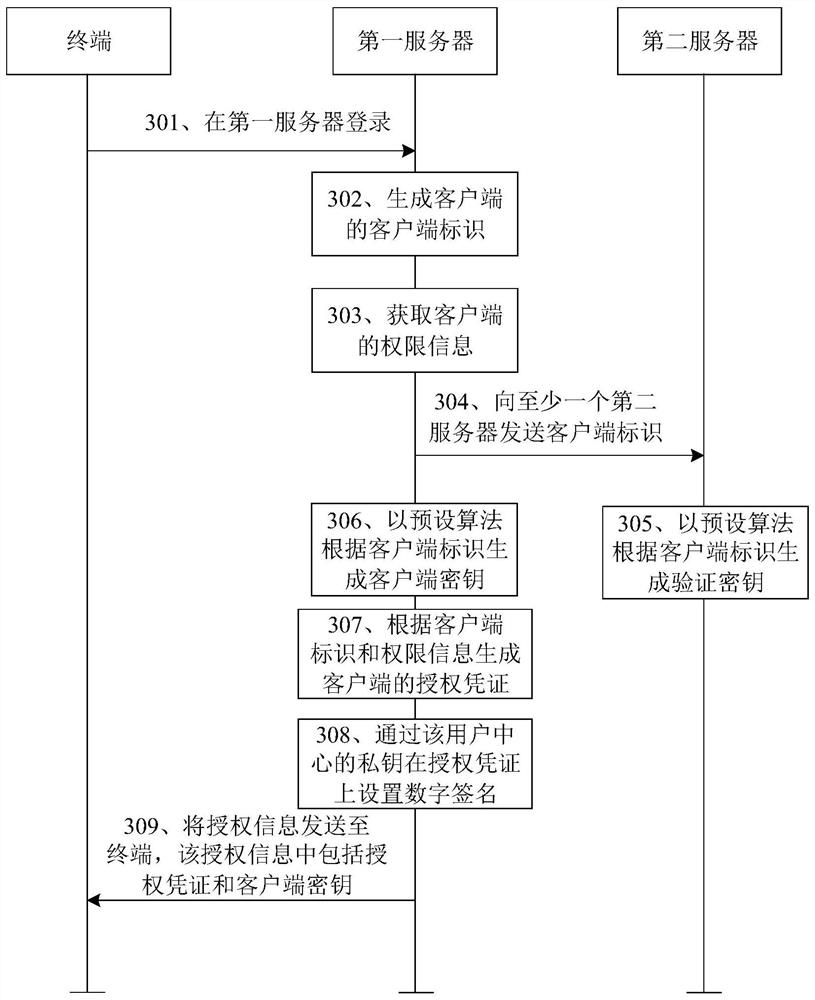
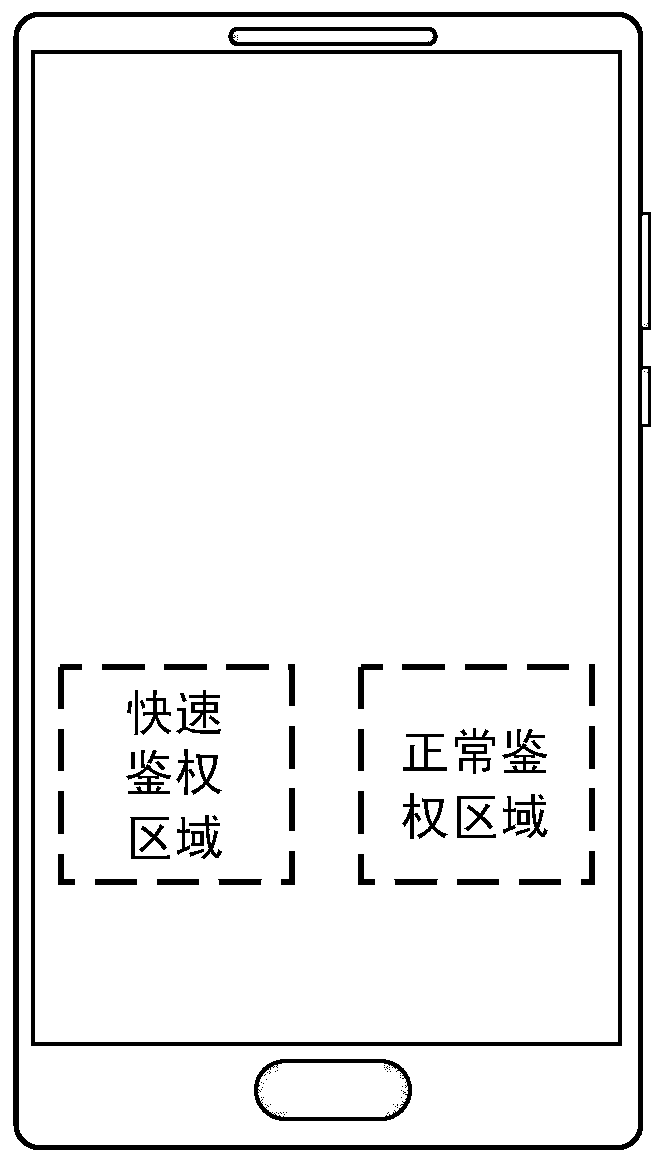
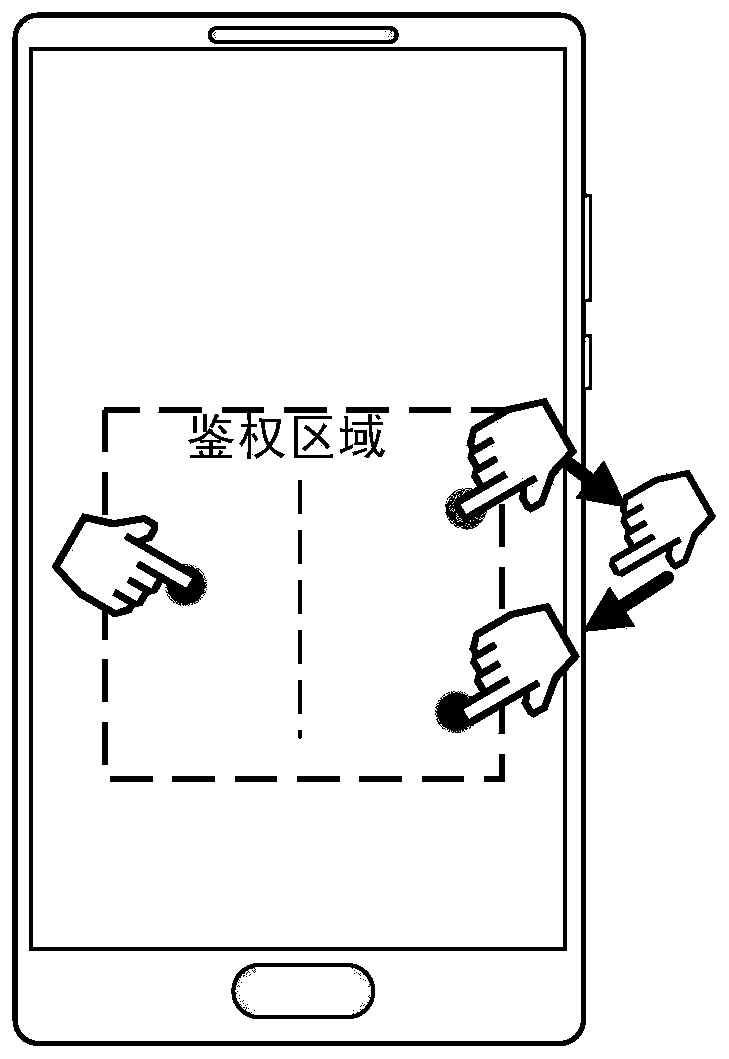
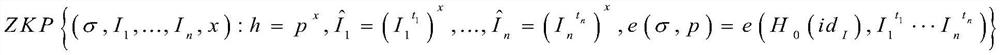Patents
Literature
37results about How to "Improve authentication speed" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
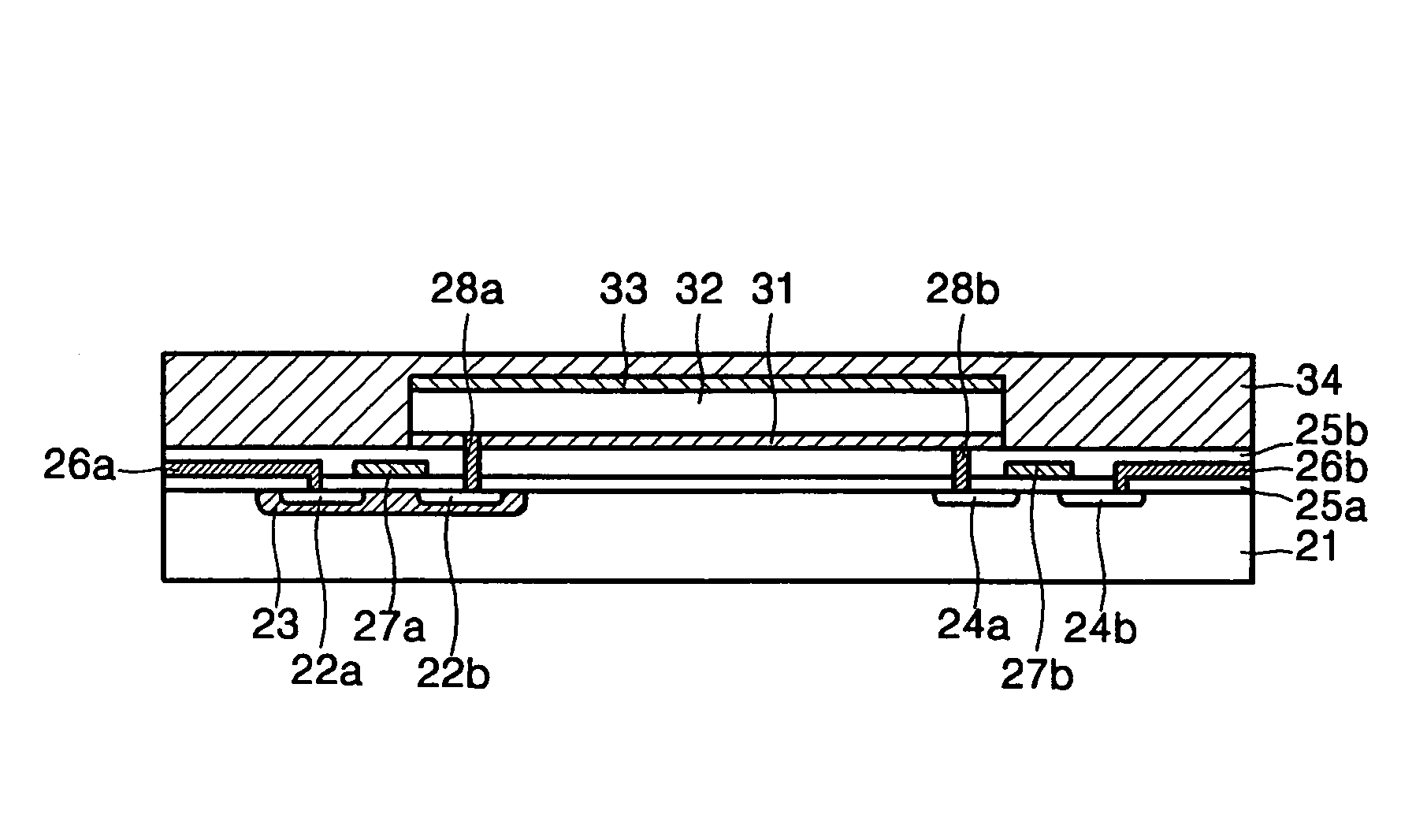
Fingerprint sensor and fabrication method thereof
InactiveUS7400750B2Improve authentication speedTransistorPiezoelectric/electrostrictive device manufacture/assemblyDopantEngineering
Provided are a fingerprint sensor and a fabrication method thereof. The fingerprint sensor includes: a complementary metal-oxide semiconductor structure which is formed on a substrate that is doped with a first type dopant; an insulating layer which is formed on the complementary metal-oxide semiconductor structure; a lower electrode which is formed in a central portion of the insulating layer; a piezoelectric region which is formed on the lower electrode; an upper electrode which is formed on the piezoelectric layer; and a fingerprint contact layer which is formed to cover a portion of an upper surface of the insulating layer on which the lower electrode has not been formed, the lower electrode, the piezoelectric region, and the upper electrode.
Owner:SAMSUNG ELECTRONICS CO LTD
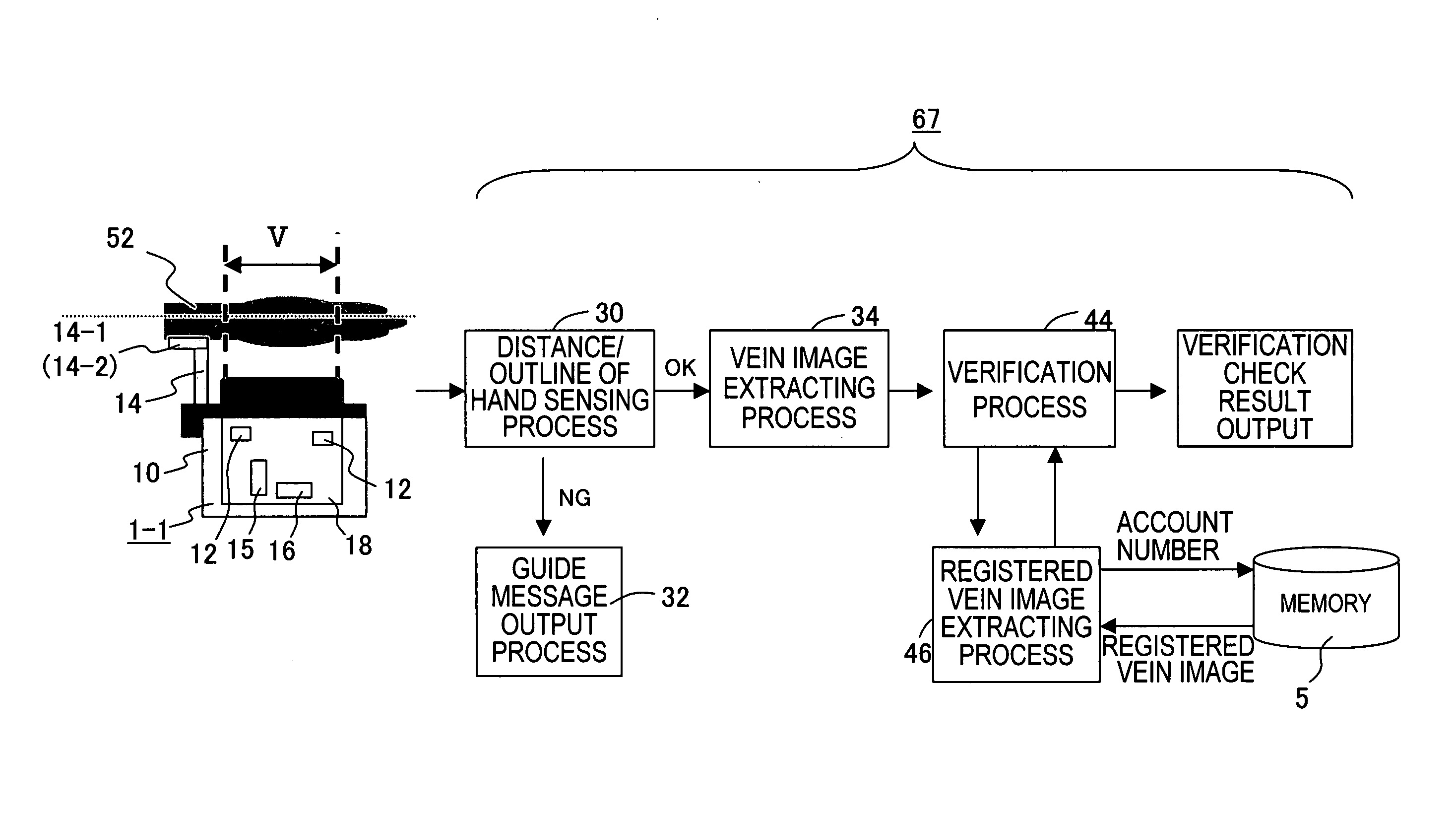
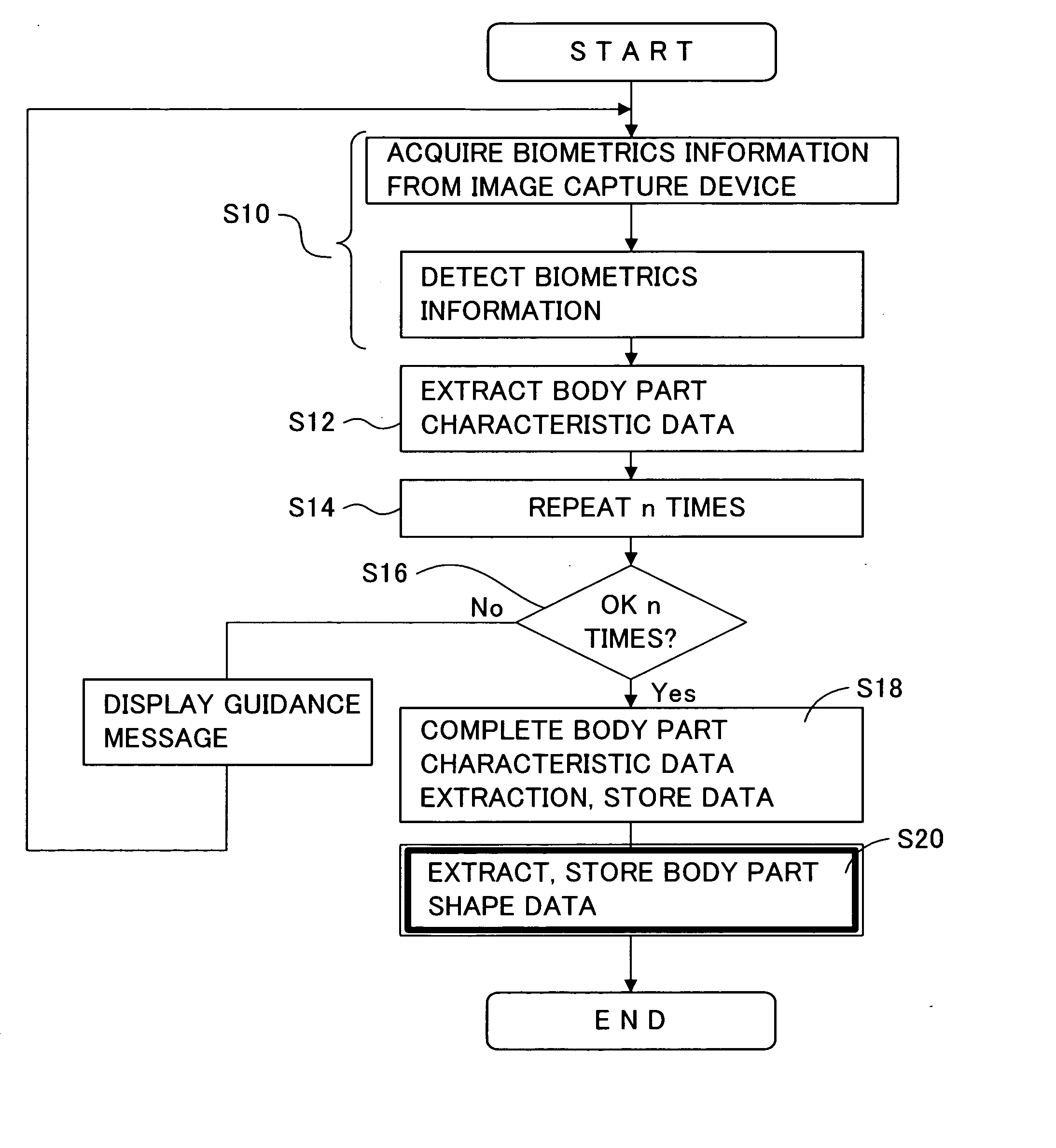
Guidance screen control method of biometrics authentication device, biometrics authentication device, and program for same
ActiveUS20060023919A1Avoid partialImprove authentication speedImage analysisPerson identificationComputer hardwareDisplay device
In a biometrics authentication device which uses biometrics information to authenticate individuals, guidance is provided such that image capture of biometrics information is performed appropriately. An image capture device is caused to perform a plurality of image capture operations (including distance measurement) at short intervals. And when image capture NG occurs frequently, a control unit stacks the NG results, and if image capture NGs are not resolved even after a prescribed number of image capture operations, judges that the relation between the body part and the image capture device must be corrected, analyzes the stacked image capture NG causes, and displays a guidance screen on a display device according to the analysis result.
Owner:FUJITSU LTD +1
Fingerprint sensor and fabrication method thereof
InactiveUS20050105784A1Increase fingerprint authentication speedImprove authentication speedTransistorPiezoelectric/electrostrictive device manufacture/assemblyDopantContact layer
Provided are a fingerprint sensor and a fabrication method thereof. The fingerprint sensor includes: a complementary metal-oxide semiconductor structure which is formed on a substrate that is doped with a first type dopant; an insulating layer which is formed on the complementary metal-oxide semiconductor structure; a lower electrode which is formed in a central portion of the insulating layer; a piezoelectric region which is formed on the lower electrode; an upper electrode which is formed on the piezoelectric layer; and a fingerprint contact layer which is formed to cover a portion of an upper surface of the insulating layer on which the lower electrode has not been formed, the lower electrode, the piezoelectric region, and the upper electrode.
Owner:SAMSUNG ELECTRONICS CO LTD
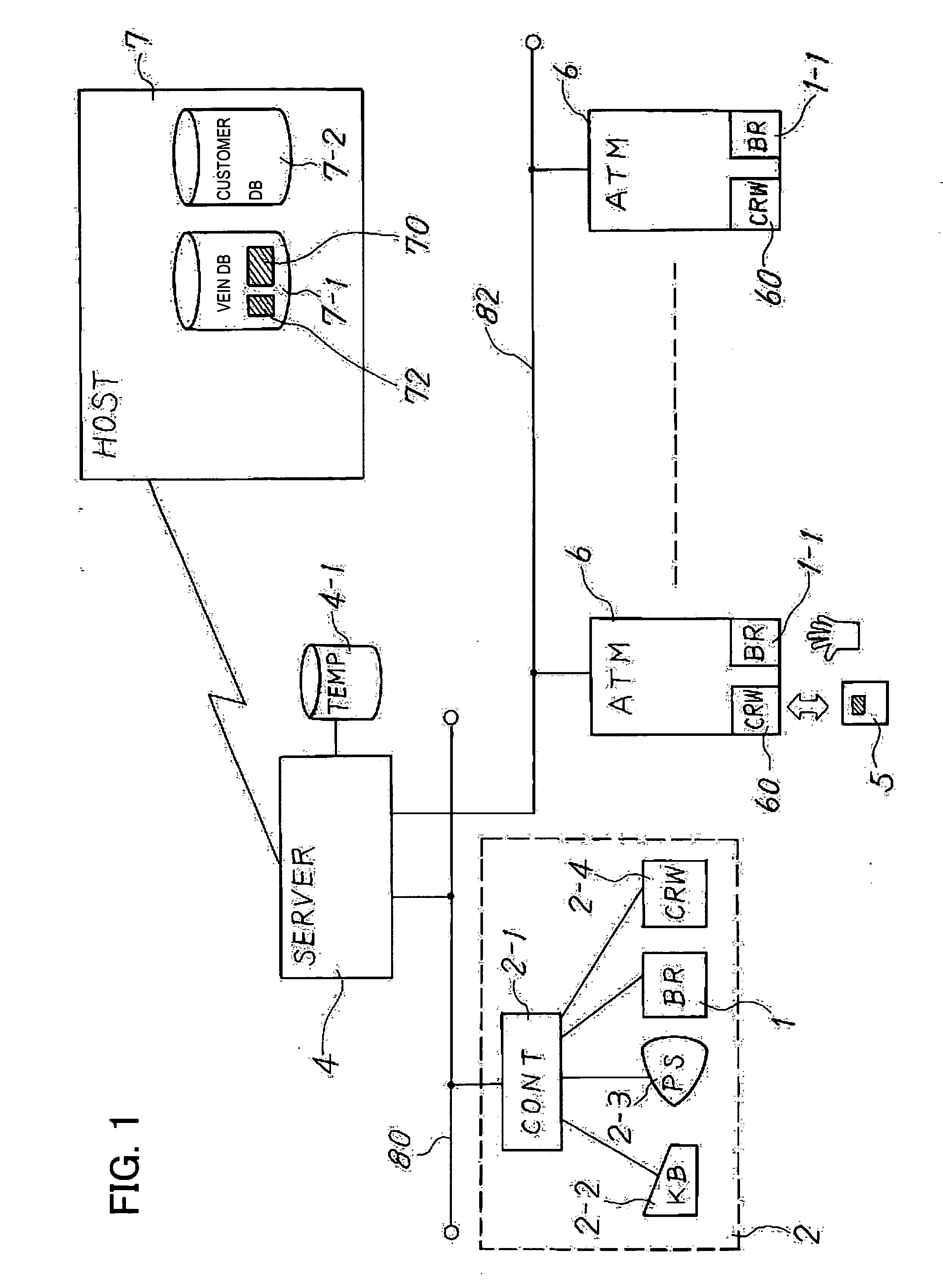
Biometrics system and biometrics method
InactiveUS20070098223A1Improve authentication speedImprove conveniencePerson identificationIndividual entry/exit registersAuthentication systemBody region
A biometrics authentication system that performs individual authentication in use of biometrics information facilitates authentication operation and reduces authentication errors. A storage unit stores therein the shape of the body part of the user, of which is captured at the time of registration of biometrics data, and a display unit displays the body part shape from the time of registration when authenticating the user for directly identifying the state of image capture of the body part at the time of registration and for guiding into a state of image capture of the body part similar to the state at the time of registration. The body part can be guided effectively such that the circumstances of body part image capture at the time of authentication and at the time of registration are in agreement, for improved verification efficiency.
Owner:FUJITSU LTD +1
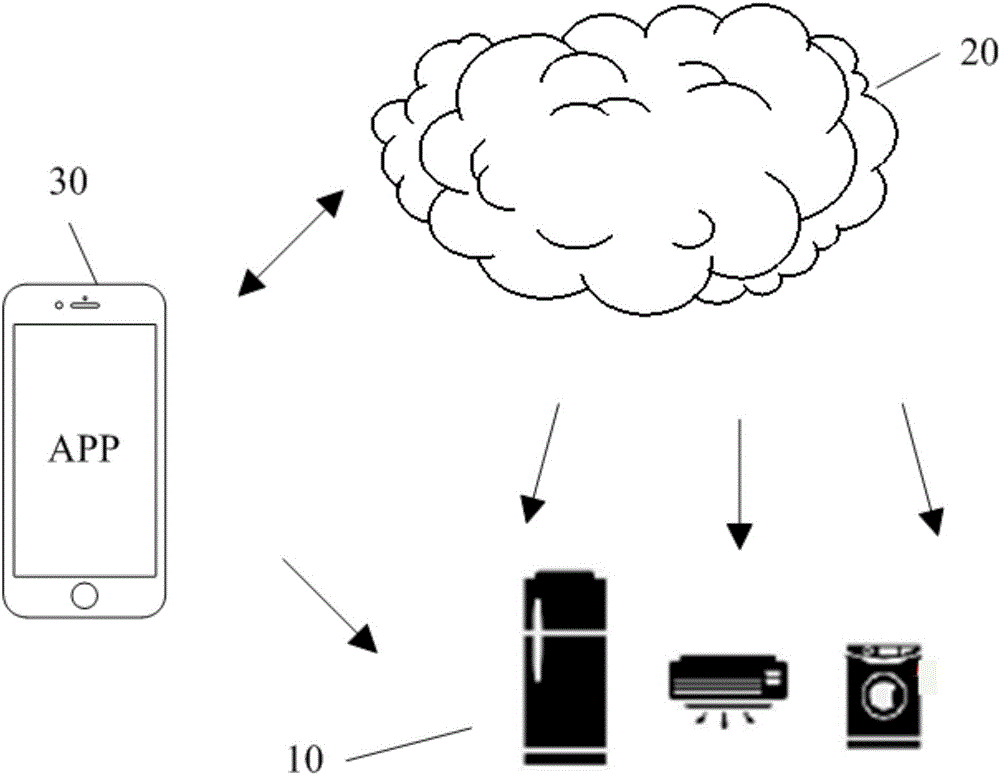
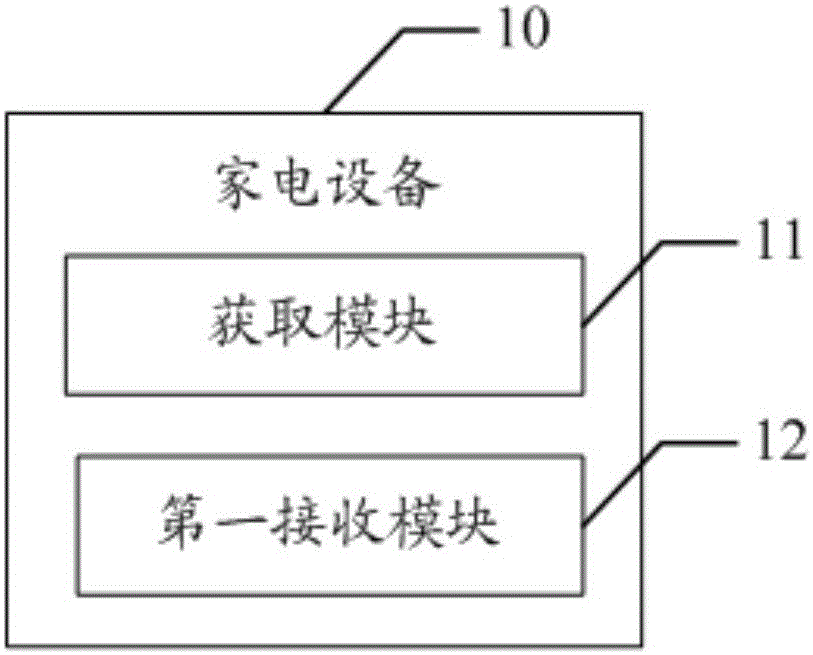
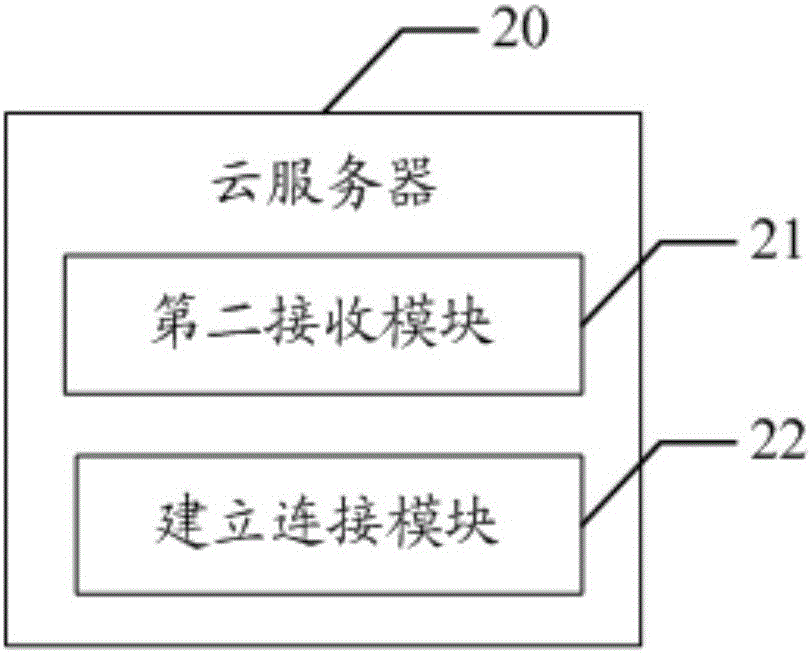
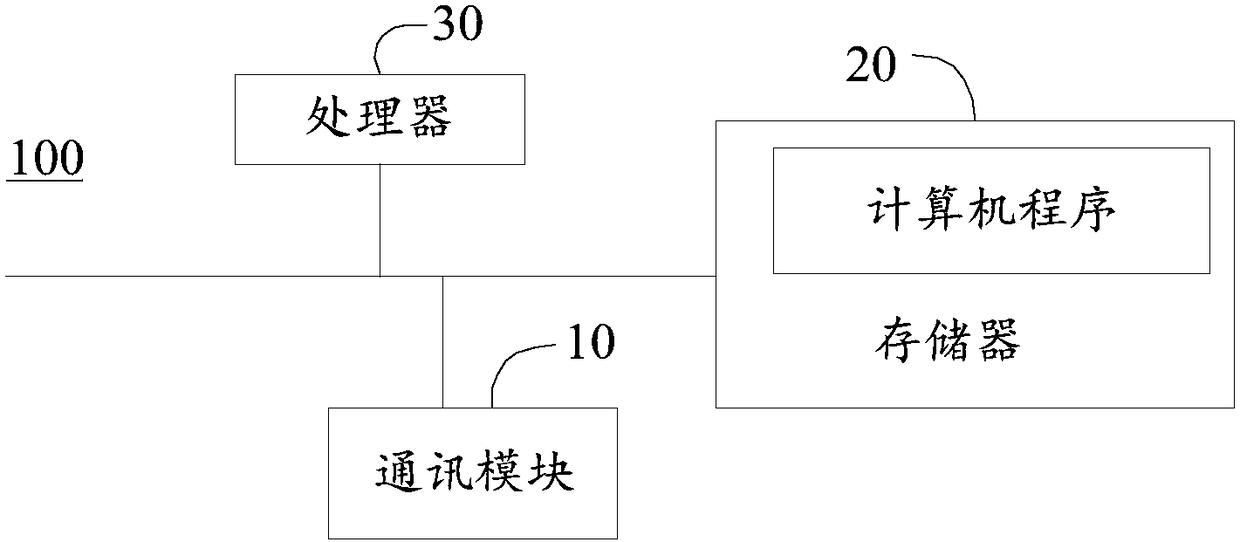
Household appliance, communication system and method for household application and cloud server and cloud server
InactiveCN106101097AImprove securityImprove authentication speedTransmissionCommunications systemCiphertext
The invention discloses a household appliance, a communication system and method for the household appliance and a cloud server, and the cloud server. The method comprises the following steps that: the household appliance acquires a first cyphertext encrypted by a cloud server public key in an authorization module, and transmits the first cyphertext to the cloud server; the cloud server receives the first cyphertext, decrypts the first cyphertext through a cloud server private key, encrypts the decrypted first cyphertext through a household appliance public key to obtain a second cyphertext, and transmits the second cyphertext to the household appliance; the household appliance receives the second cyphertext, determines the cloud server as a legal cloud server according to the second cyphertext, encrypts a generated confirmation message through a preset encryption algorithm, and sends the encrypted confirmation message to the cloud server; and the cloud server receives the confirmation message, and establishes a connection with the household appliance when the household appliance is determined as the legal household appliance according to the confirmation message. Through adoption of the household appliance, the communication system and method and the cloud server, the security of communication information between the household appliance and the cloud server is improved, and the identity authentication speed is increased.
Owner:MIDEA GRP CO LTD
Authentication method for obtaining interface access authority, server and storage medium
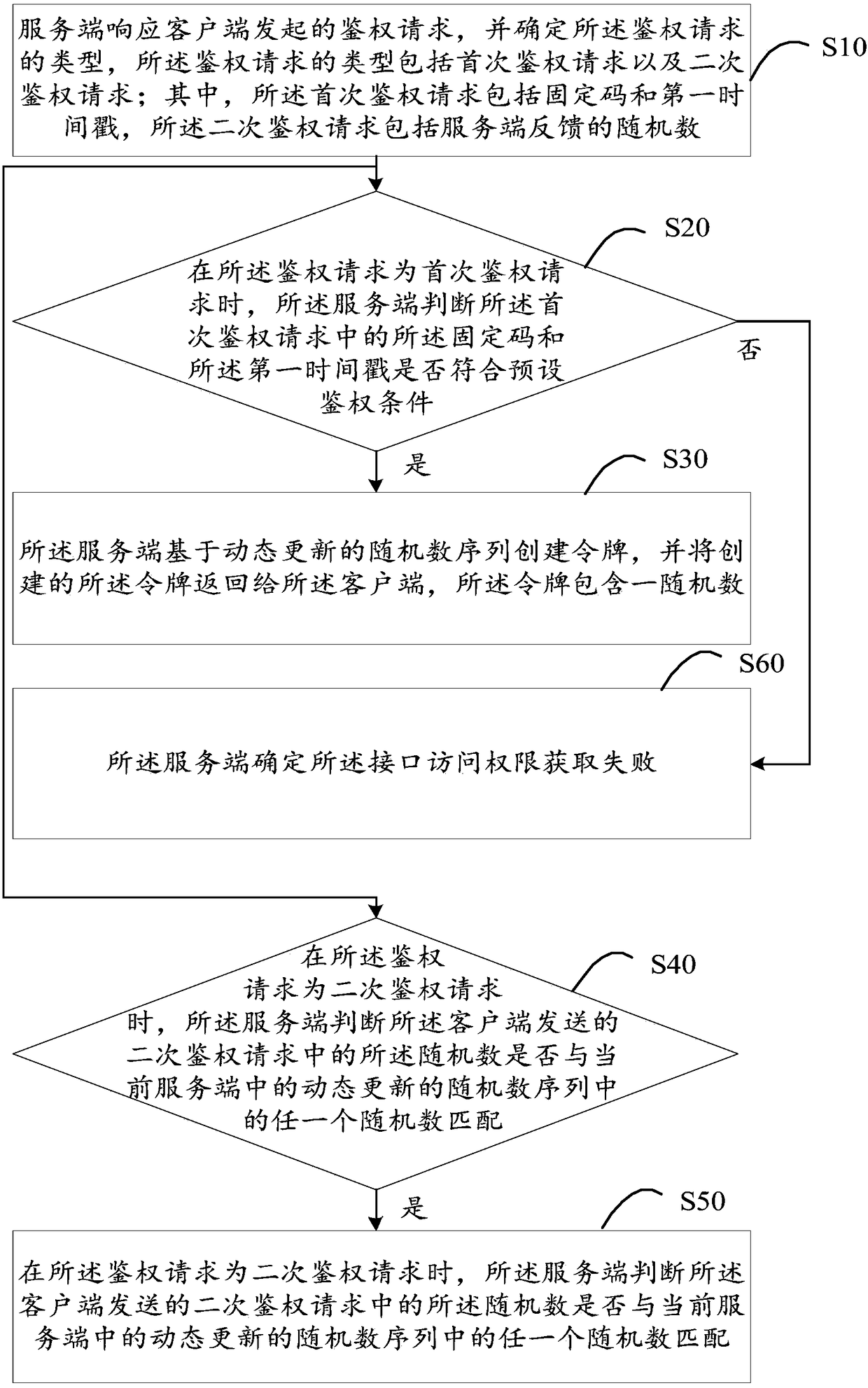
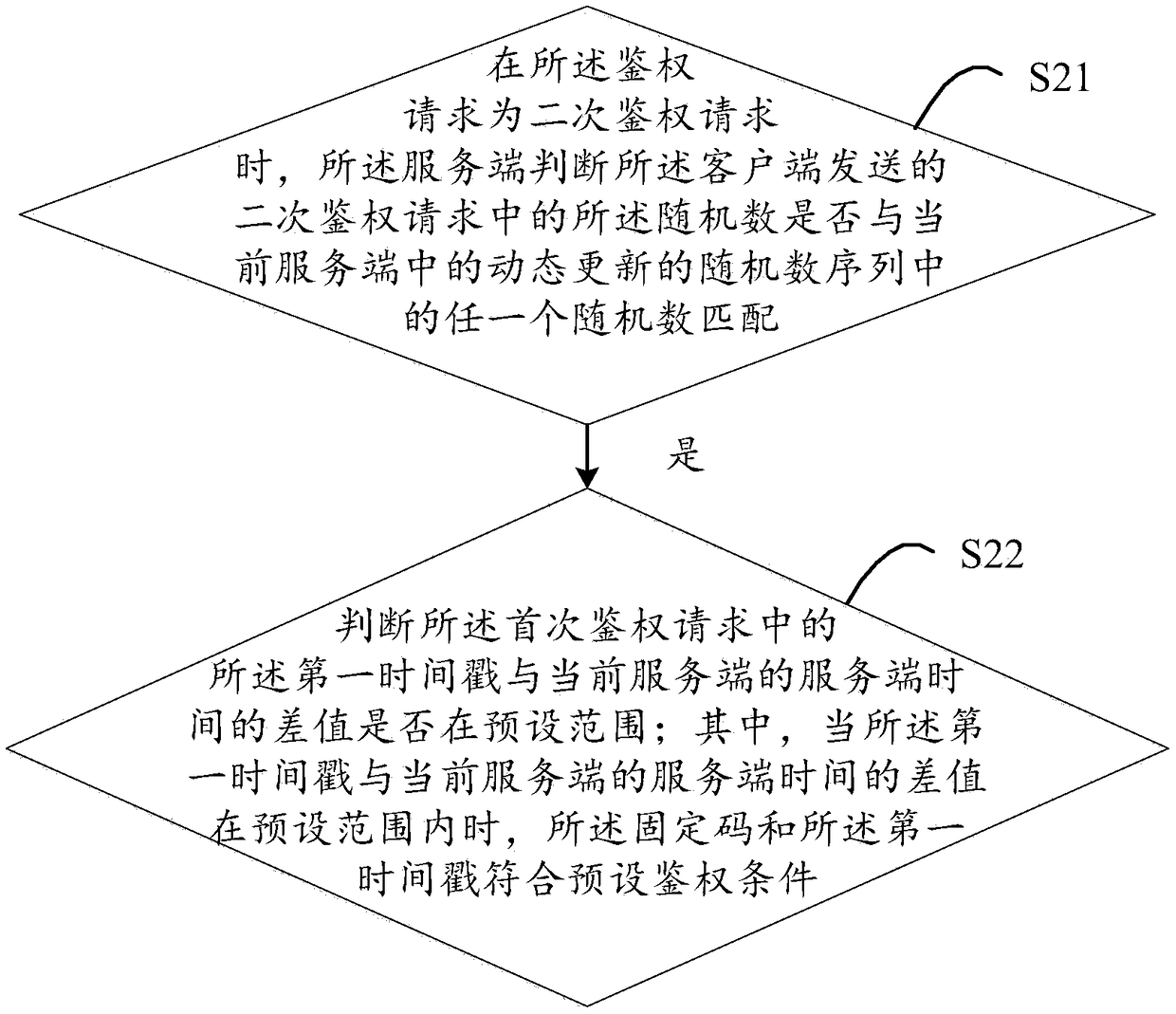
The invention discloses an authentication method for obtaining interface access authority, a server and a storage medium. The method comprises the following steps: responding to an authentication request initiated by a client, and determining a request type, wherein the type is a primary authentication request comprising a fixed code and a first timestamp, and a secondary authentication request comprising a feedback random number; when the authentication request is the primary authentication request, judging whether the fixed code and the first timestamp in the request meet a preset authentication condition; when the authentication request is the secondary authentication request, judging whether the random number in the request matches the random number in a dynamically updated random number sequence in the current server; when the fixed code and the first timestamp meet the preset authentication condition, or when the random number in the secondary authentication request matches the random number in the random number sequence in the current server, and when the interface access authority is successfully obtained, creating a token containing the random number based on the random number sequence, and returning the token to the client. The authentication method disclosed by the invention is high in authentication speed.
Owner:PINGAN PUHUI ENTERPRISE MANAGEMENT CO LTD
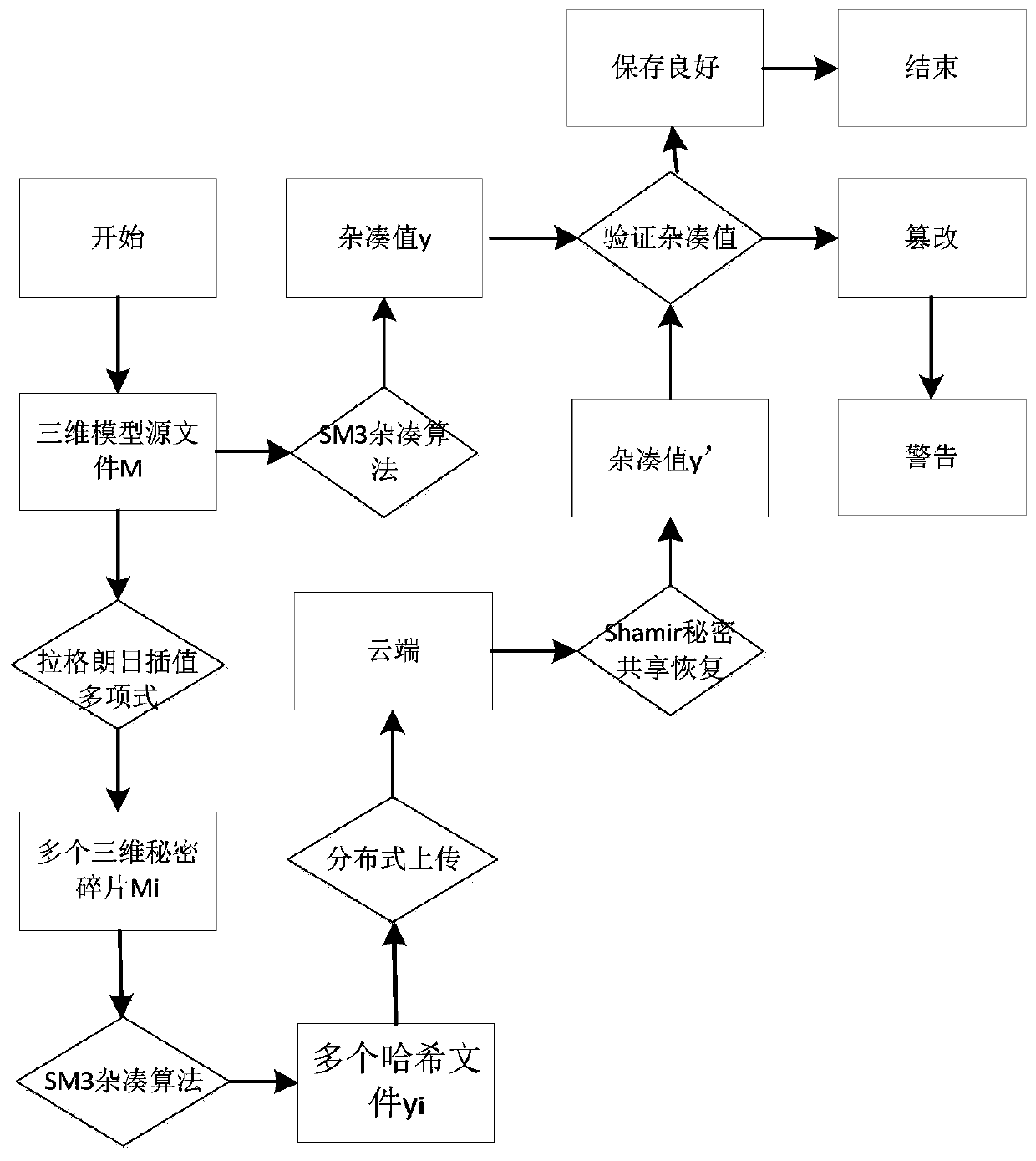
Authentication method of three-dimensional model file based on secret sharing in cloud environment
ActiveCN110610105AEnsure consistencyGuaranteed accuracyDigital data protectionThree dimensional modelEncryption
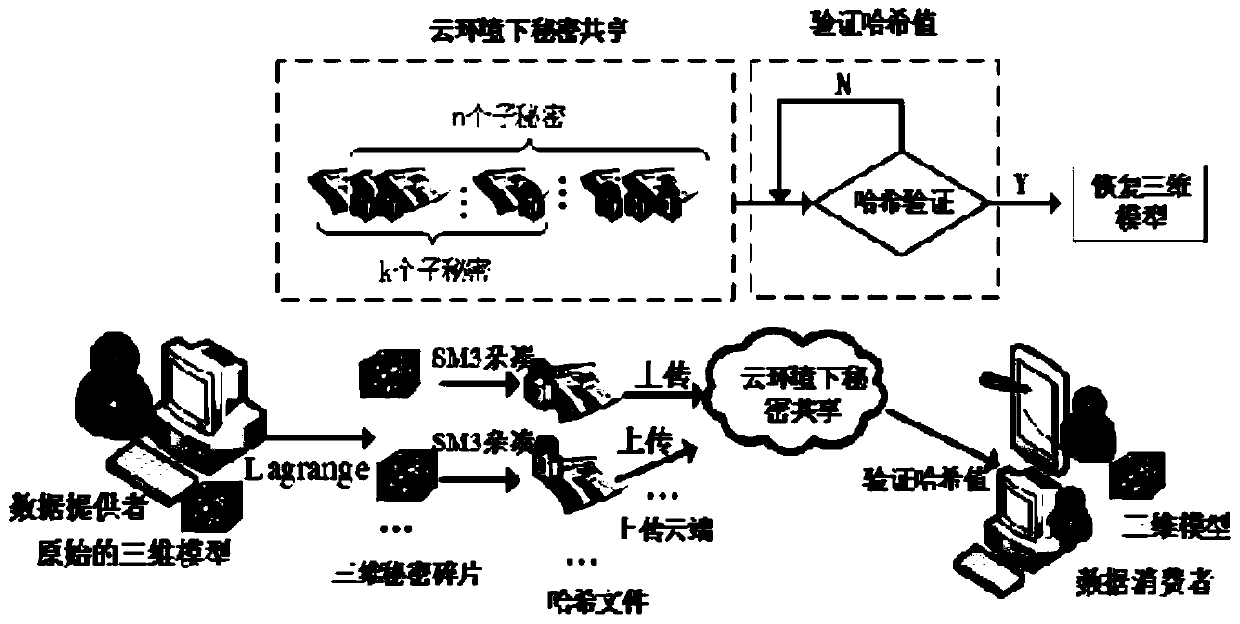
The invention provides an authentication method for a three-dimensional model file based on secret sharing in a cloud environment, which comprises the following steps of constructing a secret polynomial by adopting a Lagrange interpolation polynomial, generating the secret fragments from a source file, and transmitting and storing the secret fragments in a plurality of secret participants in a distributed manner; taking the source file and the secret fragments as the original structure carriers, respectively generating the digital abstracts from the secret fragments of the source file by utilizing an SM3 hash algorithm, and uploading the digital abstracts generated by the secret fragments to a cloud in a distributed manner; and recovering the digital digest of the three-dimensional model file based on a (k, n) threshold secret sharing method of Shamir, and performing consistency verification on the digital digest of the three-dimensional model file before encryption and after recovery.The invisibility, robustness and analysis resistance of the method are improved, and the fraudulent behaviors during the secret sharing process are effectively prevented. The method has the good performance at the aspect of protecting the integrity of the file, and particularly has the obvious advantages at the aspect of efficiency.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
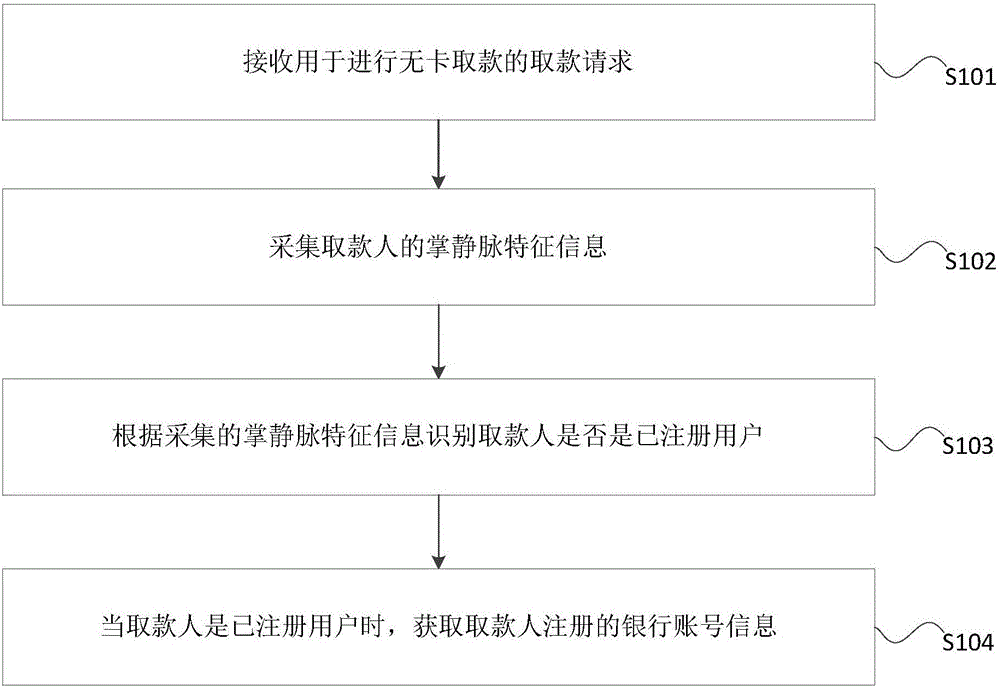
Card-free withdrawal method and apparatus
InactiveCN106651566ARealize cardless withdrawalEasy withdrawalComplete banking machinesFinanceBank accountWithdrawal Request
The invention discloses a card-free withdrawal method and apparatus. The method comprises the steps of receiving a withdrawal request used for performing card-free withdrawal; acquiring palm vein feature information of a payee; identifying whether the payee is a registered user or not according to the acquired palm vein feature information; and when the payee is the registered user, obtaining bank account information registered by the payee, wherein the bank account information is used for the payee to perform withdrawal operation. According to the method and the apparatus, the palm vein feature information of the payee is acquired, whether the current payee is the registered user or not by utilizing the palm vein feature information, and if yes, the bank account information registered by the payee is obtained and used for the payee to perform the withdrawal operation, so that the user can perform card-free withdrawal without carrying any device, a magnetic card or the like, and the withdrawal is convenient.
Owner:JIANGSU FUJITSU COMM TECH
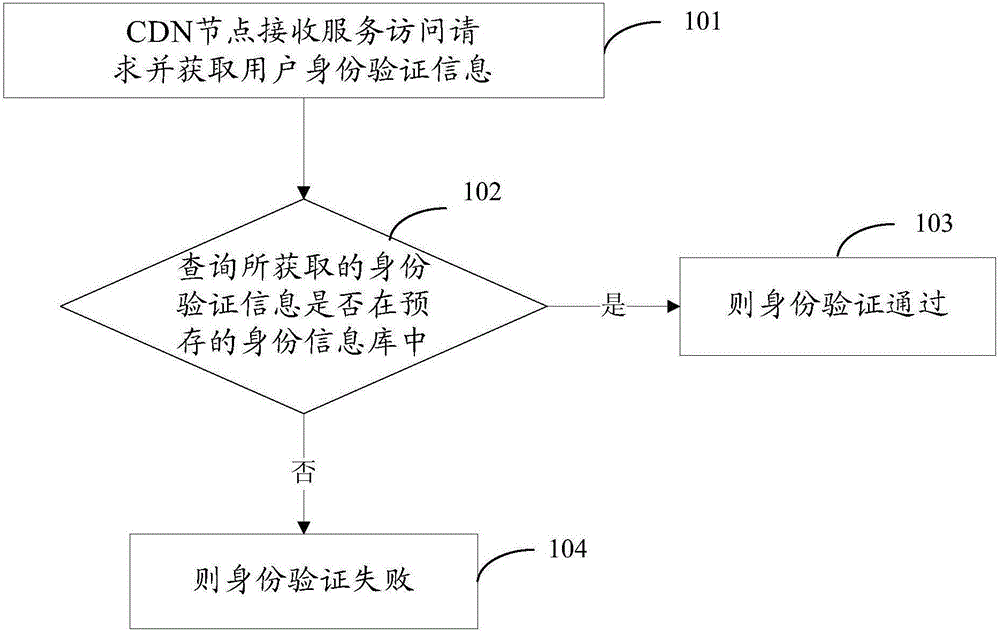
Identity authentication method, device and system
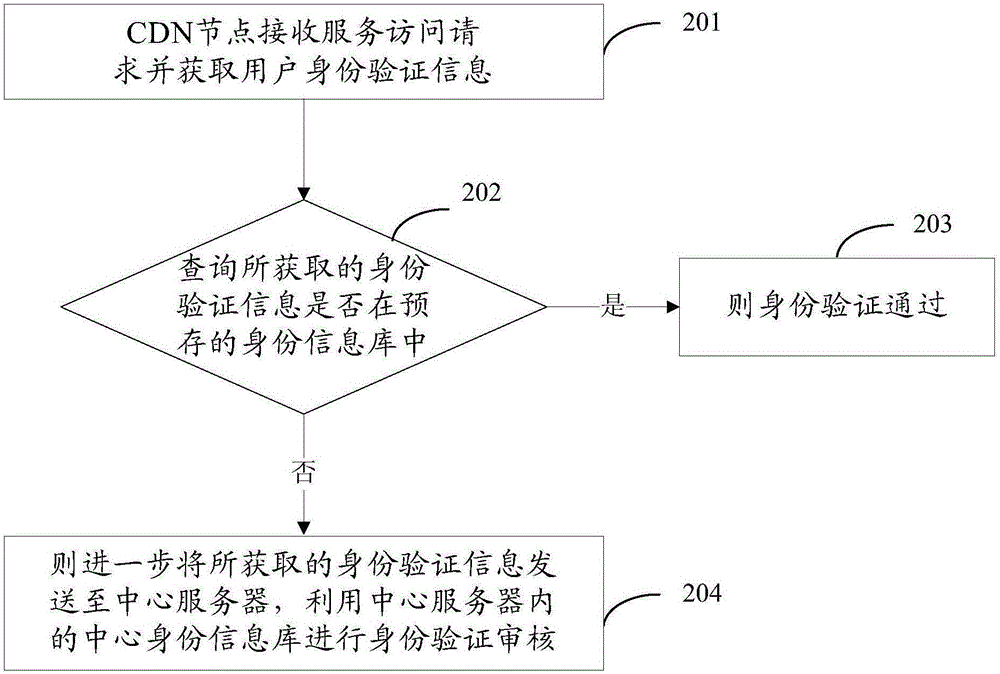
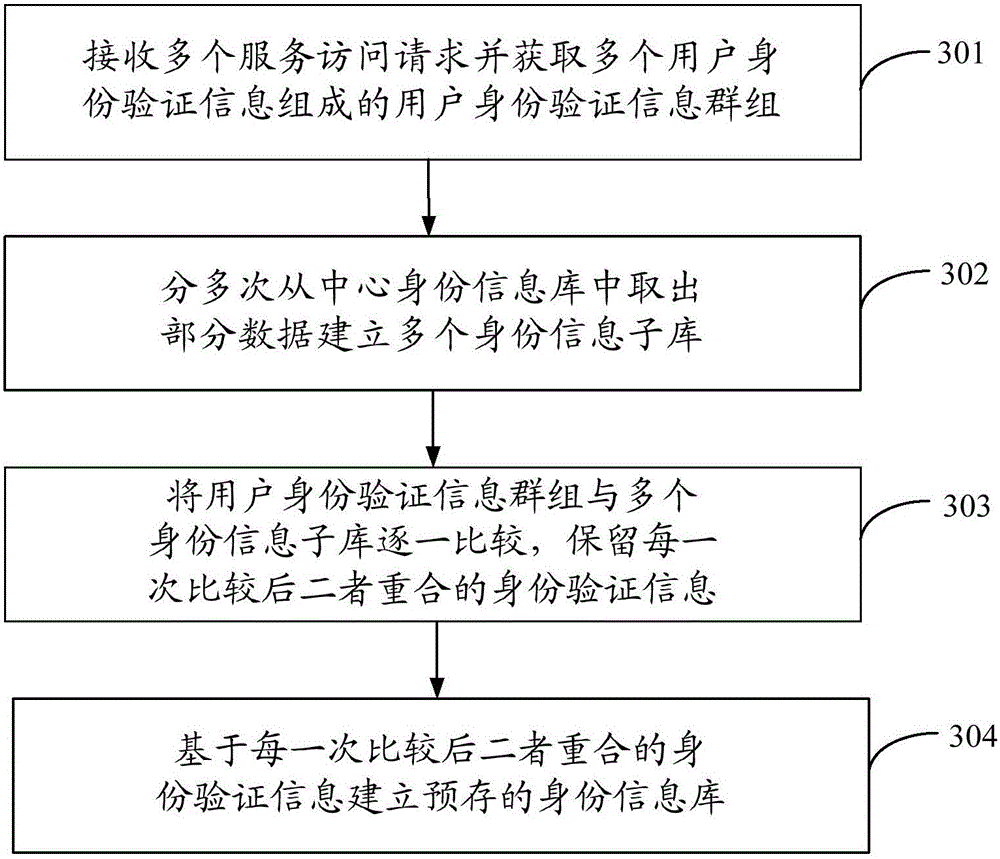
InactiveCN105871888AImprove authentication speedHigh speedTransmissionInformation repositoryUser authentication
The embodiment of the invention provides an identity authentication method, device and system. The method comprises the steps that CDN nodes receive a service access request and acquire identification authentication information of users; whether the acquired identity authentication information is in a prestored identity information base or not is queried; if yes, identity authentication succeeds; if not, identity authentication fails, or the acquired identity authentication information is further sent to a center service for identity authentication auditing through a central identity information base. Accordingly, by authenticating the user identity through the CDN nodes, the user identity authentication speed can be significantly increased, the crowded condition of a network can be relieved, and the resource access efficiency of the users is improved. In addition, the CDN nodes can be regionally arranged in a distributed mode to authenticate the identity information of the users in the regional range of the CDN nodes, the user identity authentication speed can be further increased, the resource access efficiency of the users is improved, and the user experience is improved.
Owner:LETV HLDG BEIJING CO LTD +1
Authentication method, device and system, and storage medium
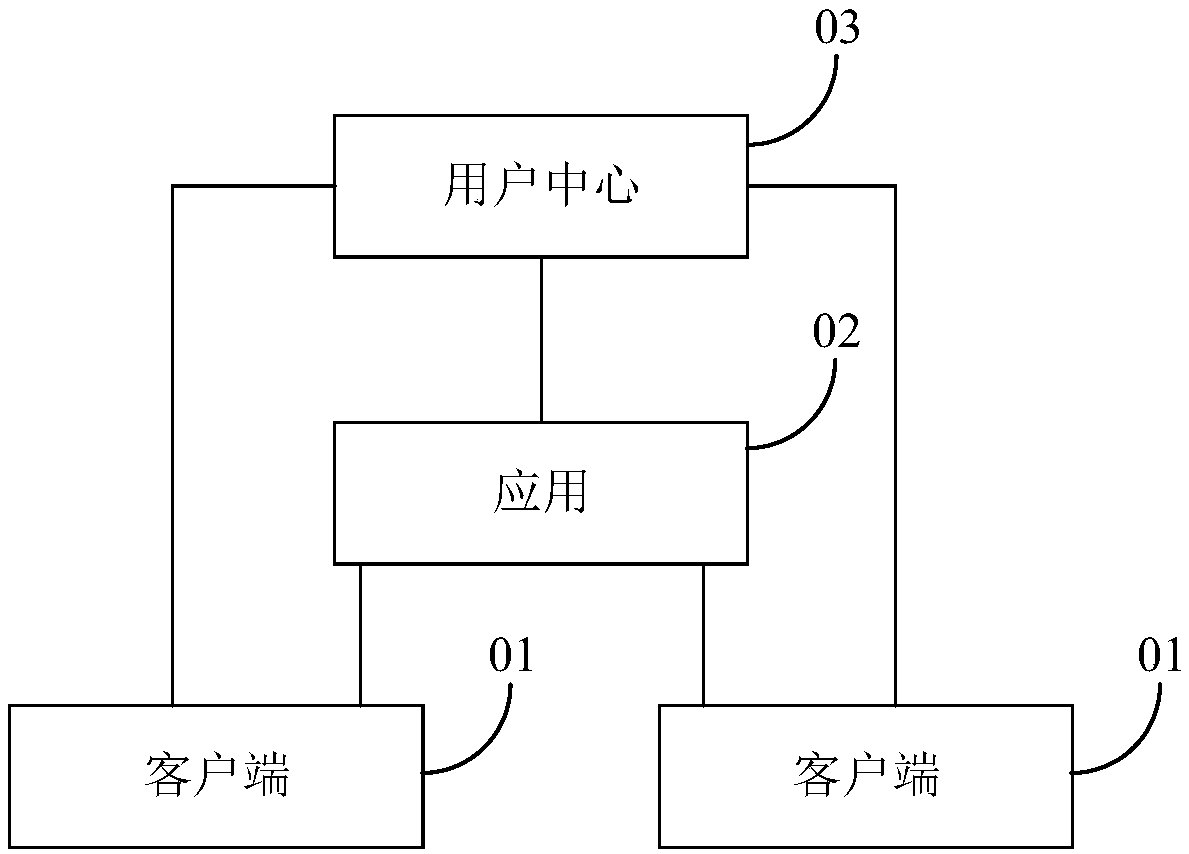
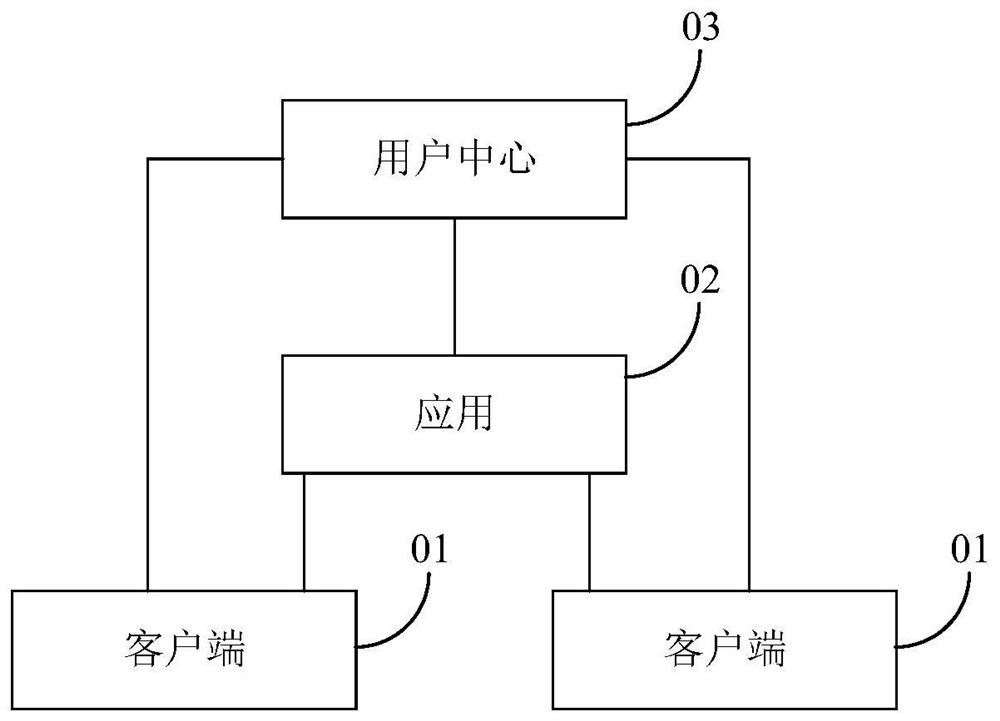
ActiveCN108964885AImprove authentication speedKey distribution for secure communicationUser identity/authority verificationAuthorization certificateAuthentication server
The invention discloses an authentication method, an authentication device, an authentication system and a storage medium, which belong to technical field of security. The authentication method comprises the steps of: acquiring, by means of an application, a client identifier of a client generated by a user center, wherein the client identifier is an identifier of the client allocated by the usercenter after the client logs in at the user center; performing authority validation on an authentication certificate by means of the client identifier when the application receives authentication information comprising the authentication certificate transmitted by the client, wherein the authentication certificate is a certificate transmitted from the user center to the client and used for cooperating with the client identifier so as to verify the authority of the client; and allowing the client to access by means of the application when the authentication certificate passes authority validation. Through performing authentication operation by using authority information in the authentication certificate by means of the applications locally, a user do not need to go to the user center for using an authentication service provided by the user center to perform centralized authentication. Compared to a centralized authentication method in the related art, the authentication method, the authentication device, the authentication system and the storage medium accelerates the authentication speed by adopting a discrete authentication method.
Owner:HUAWEI TECH CO LTD
Method and electronic device for authenticating user by using voice command
PendingUS20210097158A1Improve authentication speedImprove securityCharacter and pattern recognitionDigital data authenticationEngineeringSpeech sound
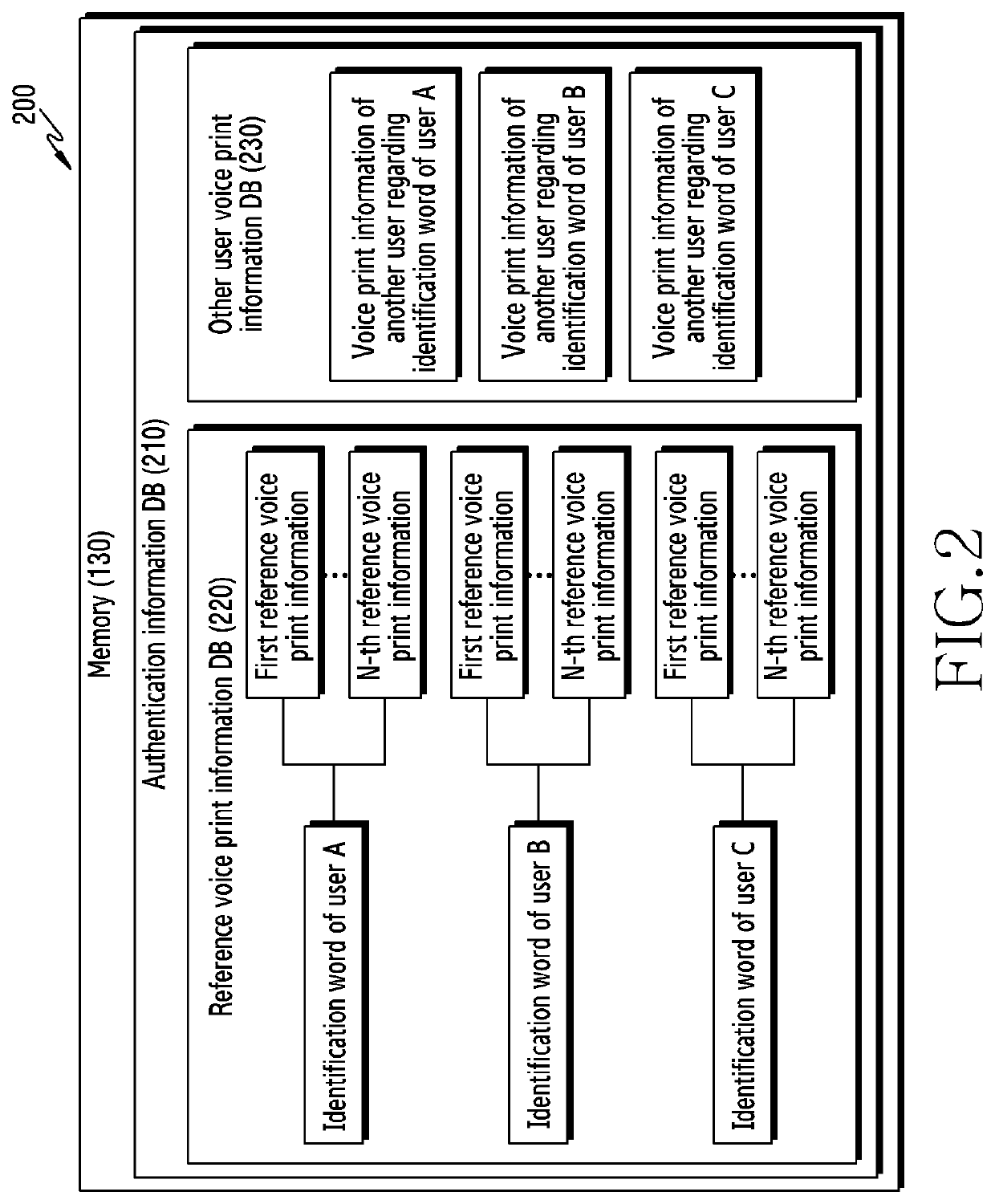
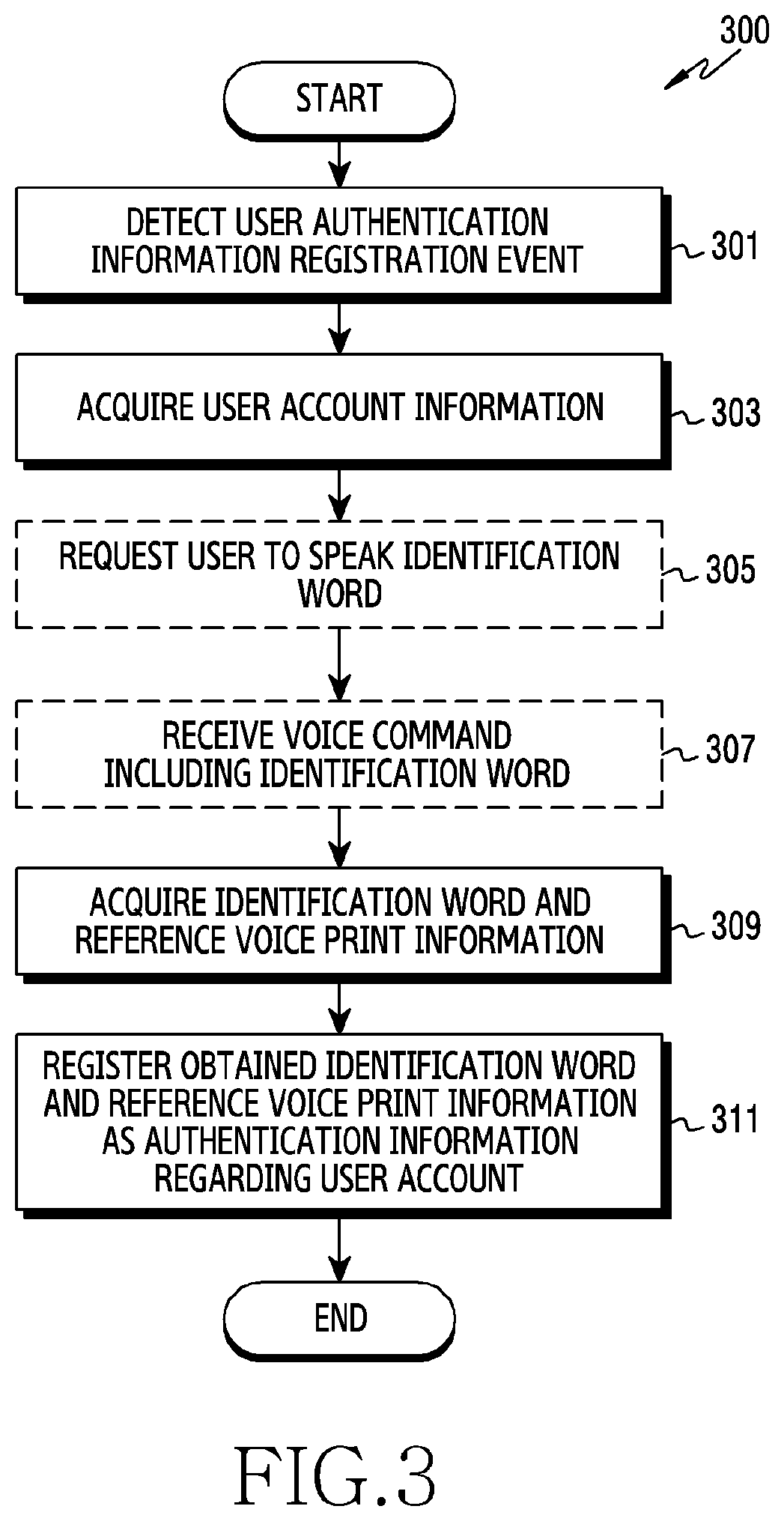
Various embodiments of the present invention relate to a method and an electronic device for authenticating a user by using a voice command. Here, the electronic device may comprise a memory, an input apparatus, and a processor, wherein the processor is configured to: receive a voice command from the input apparatus; acquire user identification information and voice print information from the voice command; search reference voice print information of each of multiple users stored in the memory, for reference voice print information corresponding to the acquired user identification information; and perform authentication on the basis of the acquired voice print information and the reference voice print information. Other embodiments are also possible.
Owner:SAMSUNG ELECTRONICS CO LTD
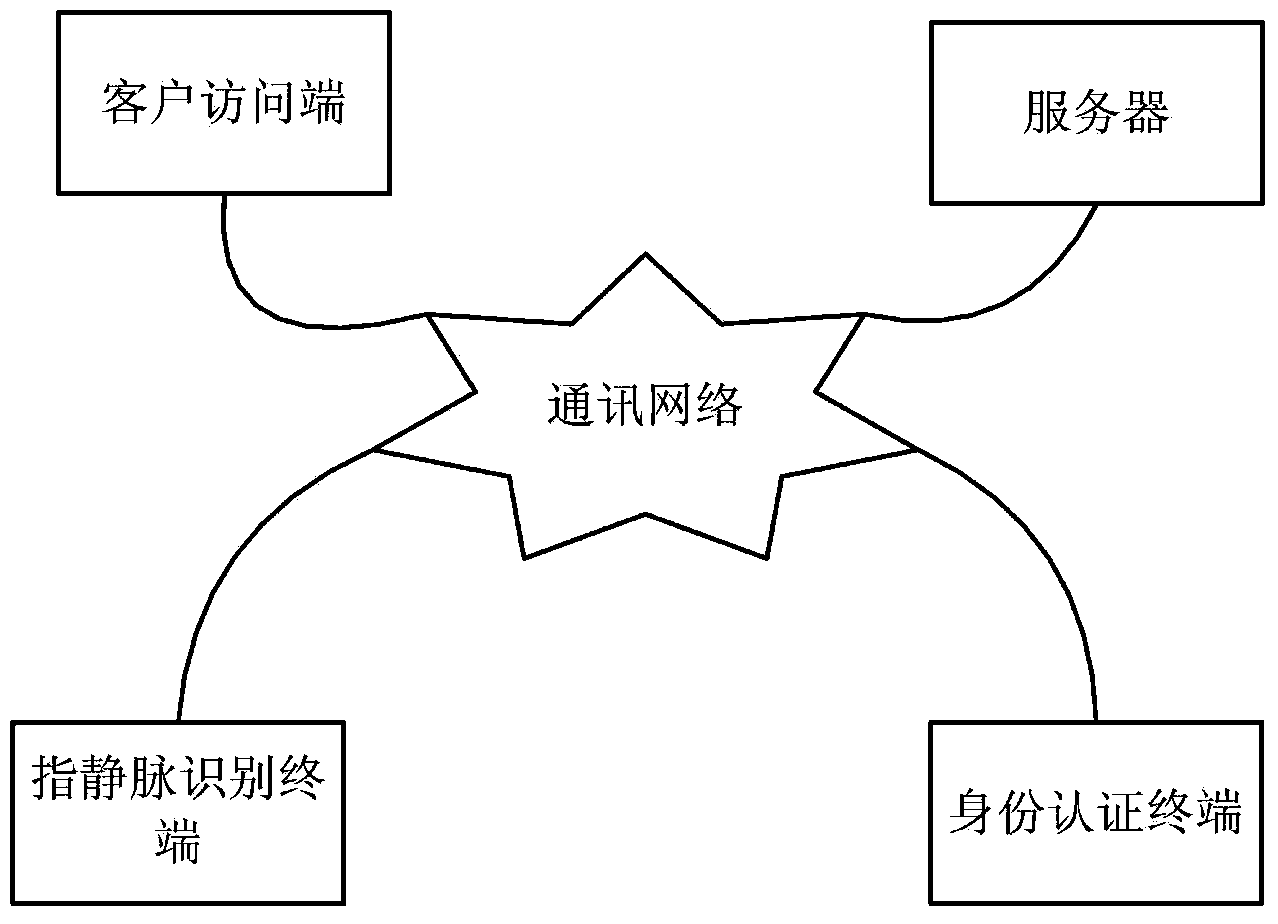
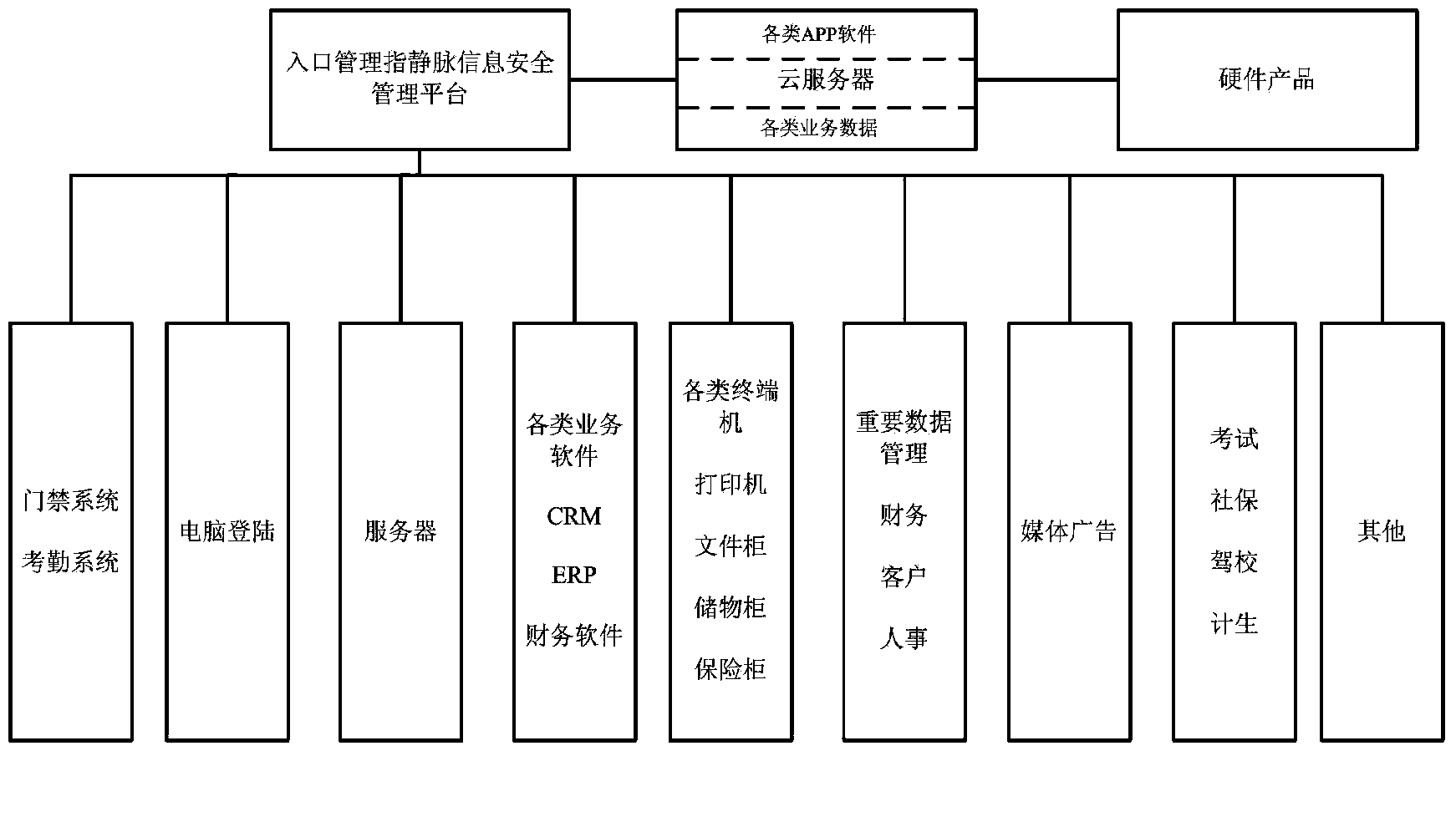
Finger vein information security management platform
ActiveCN104394173AAvoid inconvenienceEnhanced authenticationTransmissionSubcutaneous biometric featuresInformation security managementLocal memories
A finger vein information security management platform comprises a finger vein intelligent terminal, a communication network, a server, a client access port and an identity authentication terminal, wherein the finger vein intelligent terminal is connected with the server through the communication network; the client access port is connected with the server through the communication network; the identity authentication terminal is connected with the server through the communication network; the server is a cloud server; the finger vein intelligent terminal comprises a finger vein recognizing device and a shell; the finger vein recognizing device comprises a control main board; the control main board is connected with a finger vein collector, a voice player, an audio collector, a video collector, a capacitive touch screen, a wireless communication module, an LED display lamp and an RFID (radio frequency identification device) reader-writer; a local memory module and an alarm card are arranged on the control main board; the alarm card is connected with the voice player. The finger vein information security management platform has the advantages of high security and good convenience and quickness.
Owner:宁波锐智汇峰智能科技有限公司
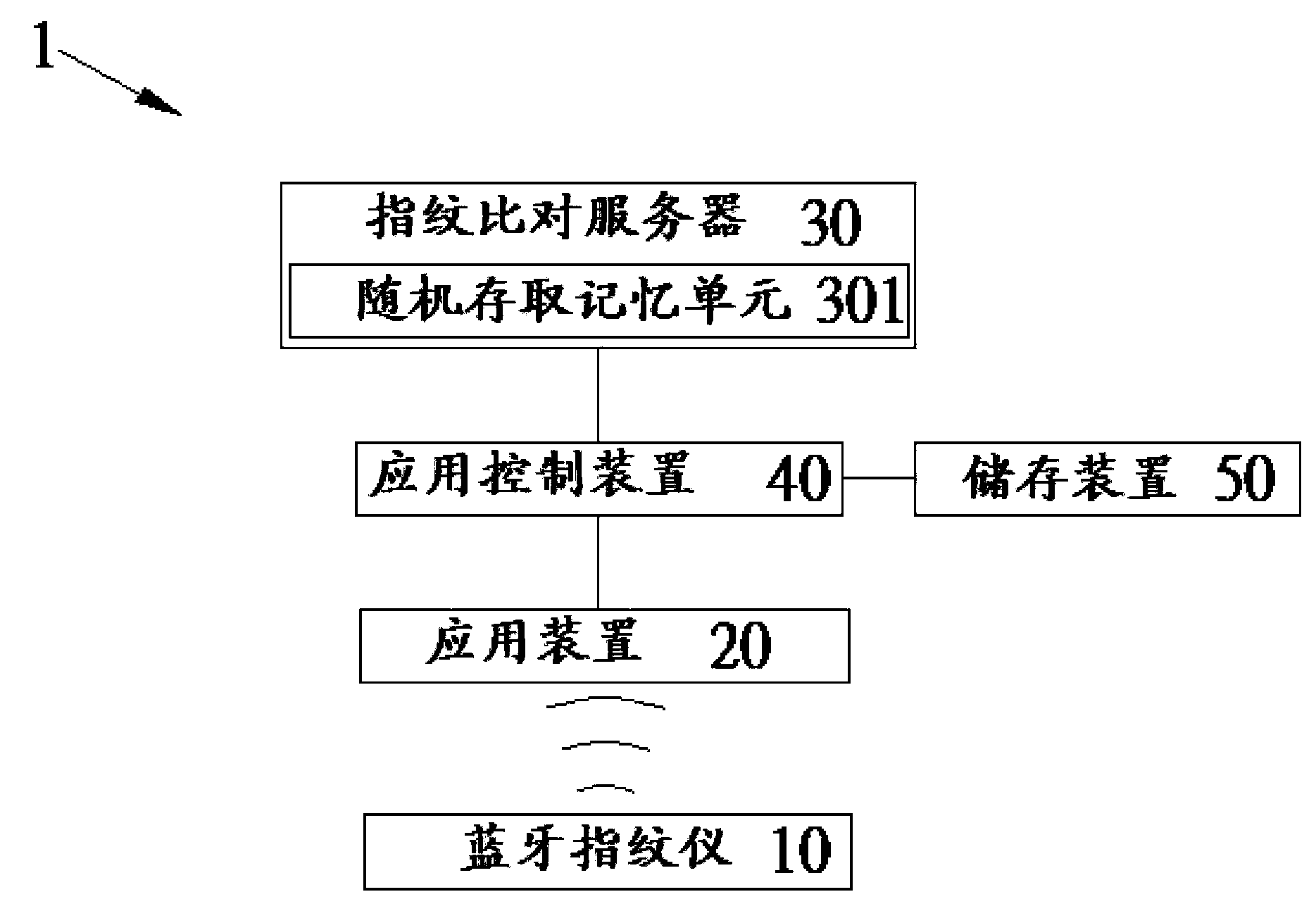
Fingerprint identification and verification system and method thereof
InactiveCN103678978AShorten the timeFaster thanCharacter and pattern recognitionDigital data authenticationComputer hardwareBluetooth
The invention provides a fingerprint identification and verification system and a method thereof. The fingerprint identification and verification system includes a Bluetooth fingerprint device, an application device, a fingerprint identification server, and an application control device. The Bluetooth fingerprint device captures a fingerprint image, extracts the minutiae data from the fingerprint image, and sends the minutiae data to the application device. The application device transmits the minutiae data and a verification request to the application control device and the application control device transmits the minutiae data to the fingerprint identification server to perform the fingerprint identification process. The fingerprint identification server sends a verification result on which the application control device depends to accept or refuse the verification request from the application device. As a result, the speed of the user's identification process can be increased by using the Bluetooth fingerprint device to derive the minutiae data.
Owner:EGIS TECH
User authentication method and device, server and storage medium
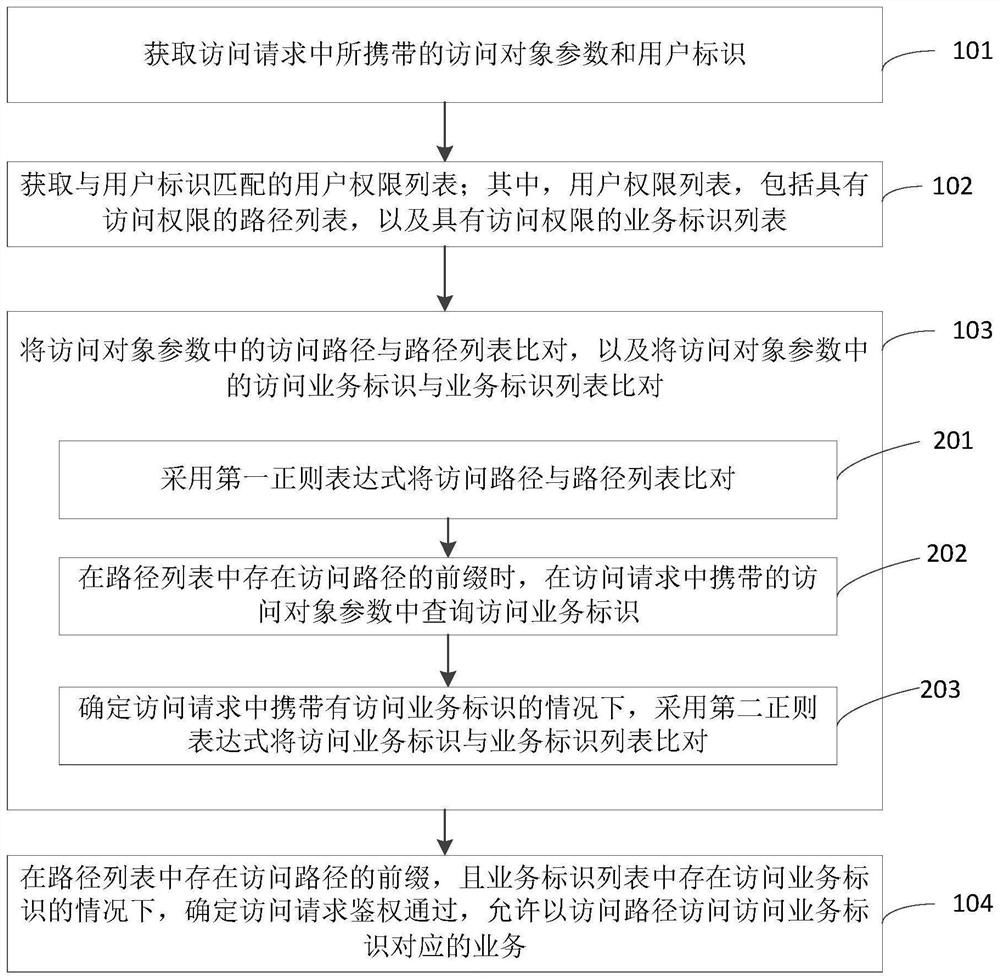
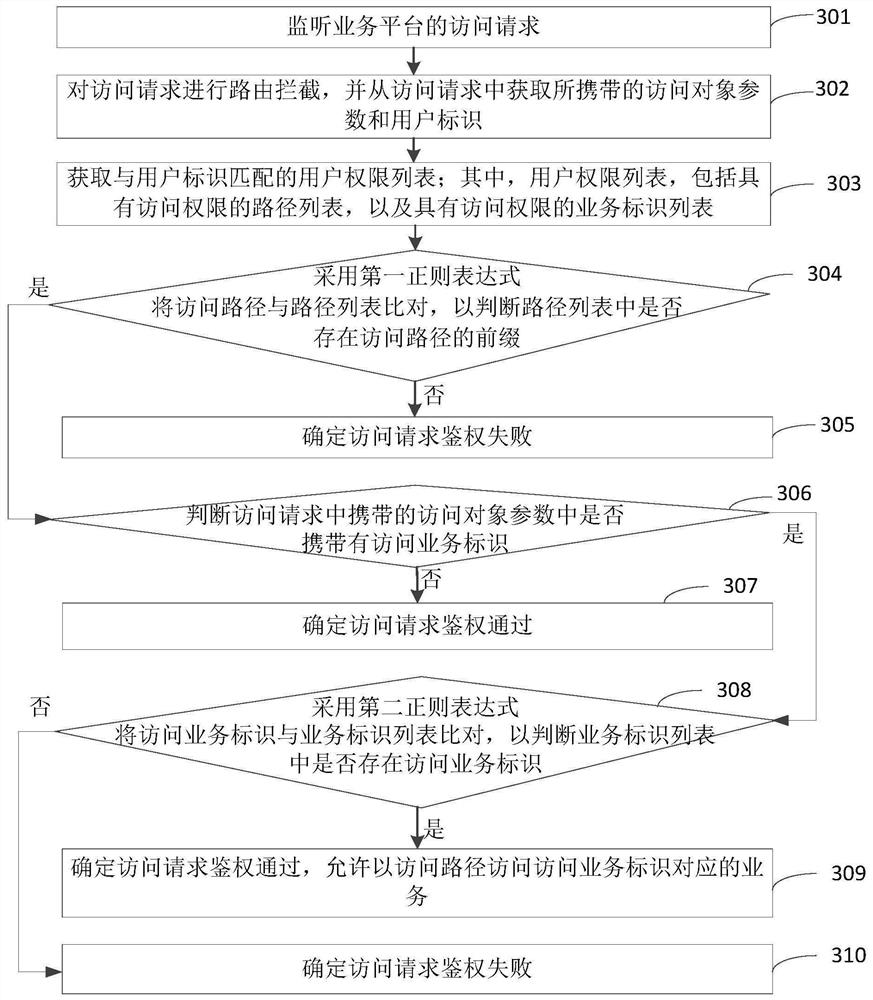
PendingCN112507298ARealize authenticationImprove authentication speedDigital data authenticationOther databases queryingPathPingUser Privilege
The invention relates to a user authentication method and device, a server and a storage medium, and relates to the technical field of computers, and the method comprises the steps of obtaining an access object parameter and a user identification carried in an access request; obtaining a user permission list matched with the user identifier, wherein the user permission list comprises a path list with access permission and a service identifier list with access permission; comparing an access path in the access object parameter with a path list, and comparing an access service identifier in theaccess object parameter with a service identifier list; and under the condition that the prefix of the access path exists in the path list and the access service identifier exists in the service identifier list, determining that the access request passes the authentication, and allowing the access path to access the service corresponding to the access service identifier. The authentication of theaccess request of the user is realized, the authentication speed is improved, and the workload of authority maintenance is reduced.
Owner:BEIJING DAJIA INTERNET INFORMATION TECH CO LTD
A wireless local area network access authentication method, device and system
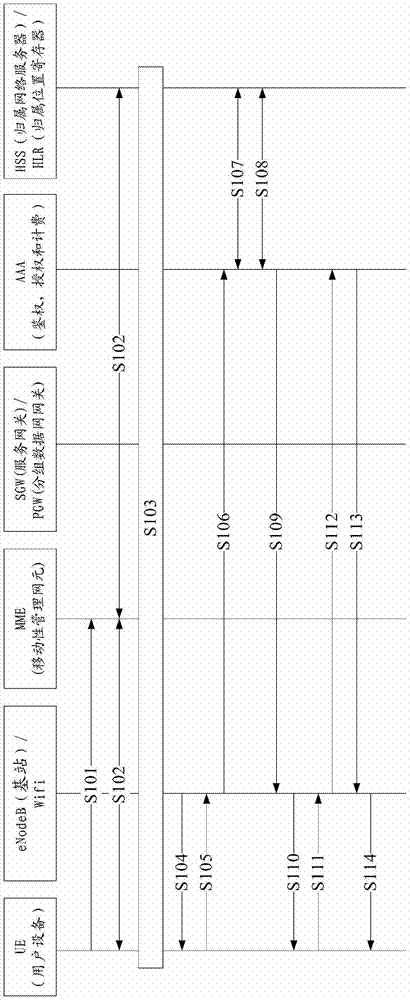
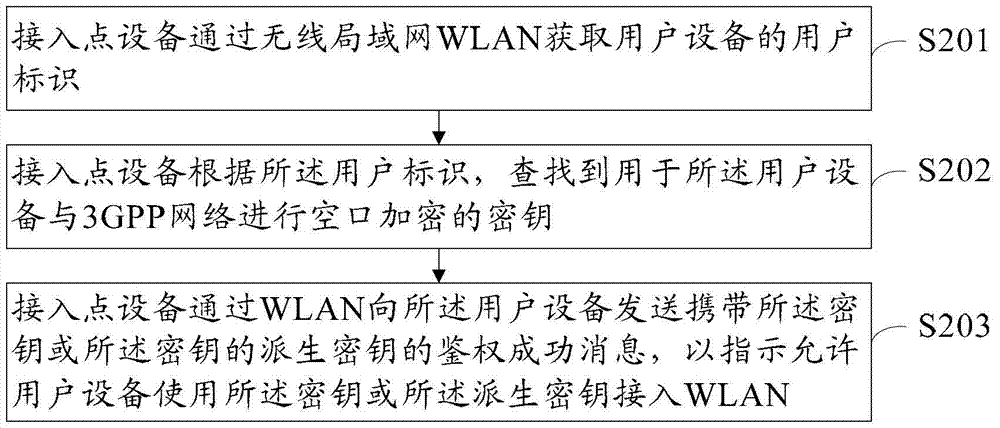
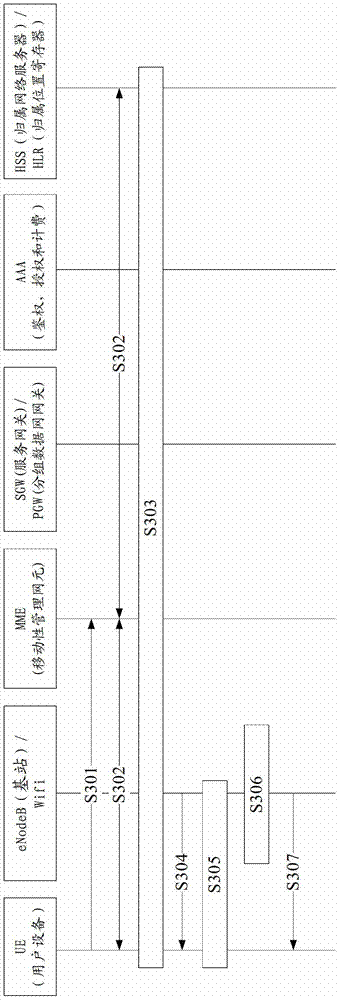
ActiveCN103609154BImprove authentication speedReduce connection establishment delayNetwork topologiesSecurity arrangementAccess networkAir interface
Embodiments of the present invention provide a wireless local area network access authentication method, device, and system, which relate to the communication field, and can Realize quick authentication when UE accesses 3GPP core network successively from 3GPP and WLAN. The wireless local area network access authentication method includes: an access point device obtains a user identification of a user equipment through a wireless local area network WLAN; An air interface encrypted key; the access point device sends an authentication success message carrying the key or a derived key of the key to the user equipment through the WLAN, to indicate that the user equipment is allowed to use The key or the derived key accesses the WLAN. The embodiment of the invention is used for wireless local area network access.
Owner:HUAWEI TECH CO LTD
Controlled secure code authentication
ActiveCN107086981AImprove securityEliminate needUser identity/authority verificationInternal/peripheral component protectionAuthentication system
Owner:ATMEL CORP
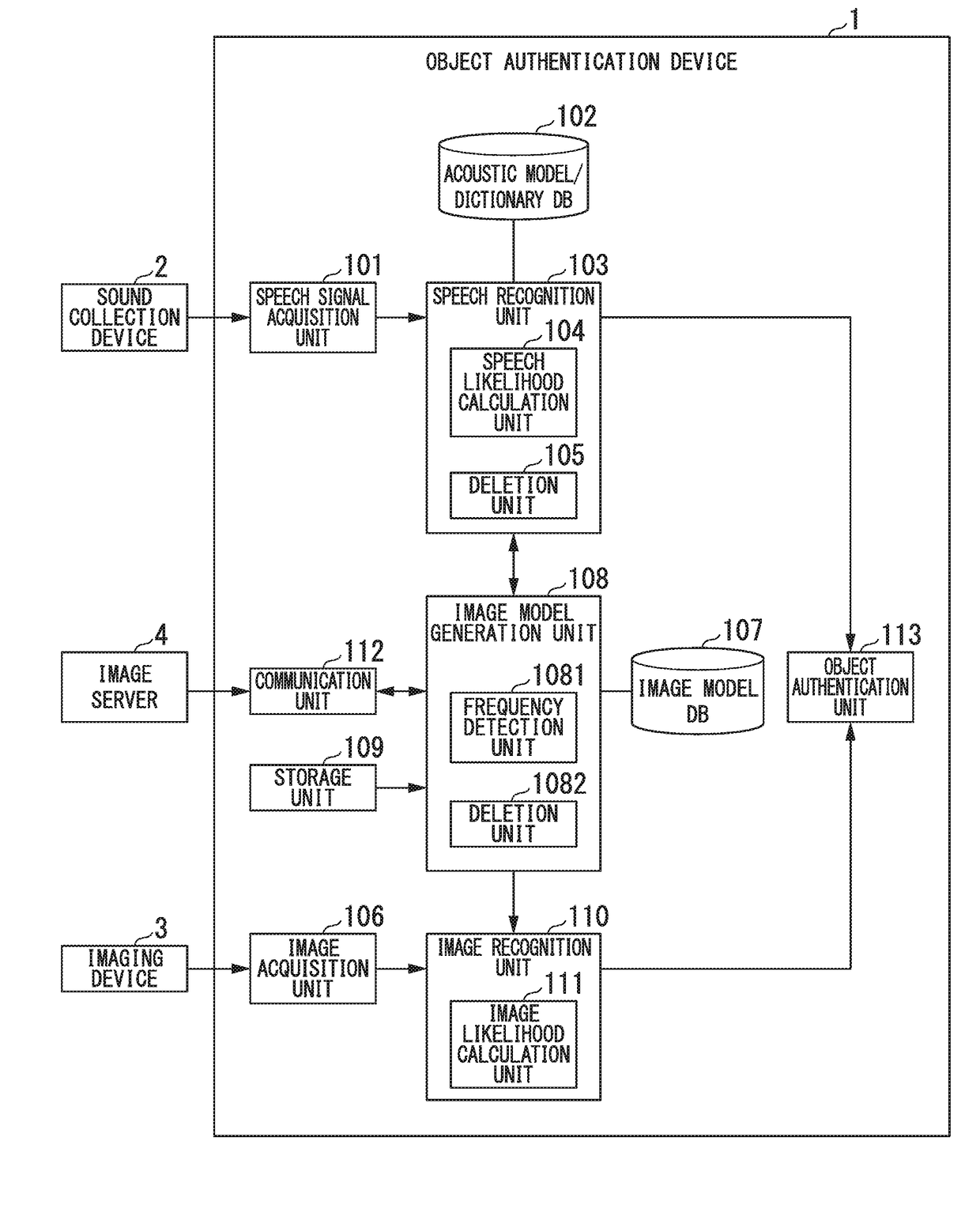
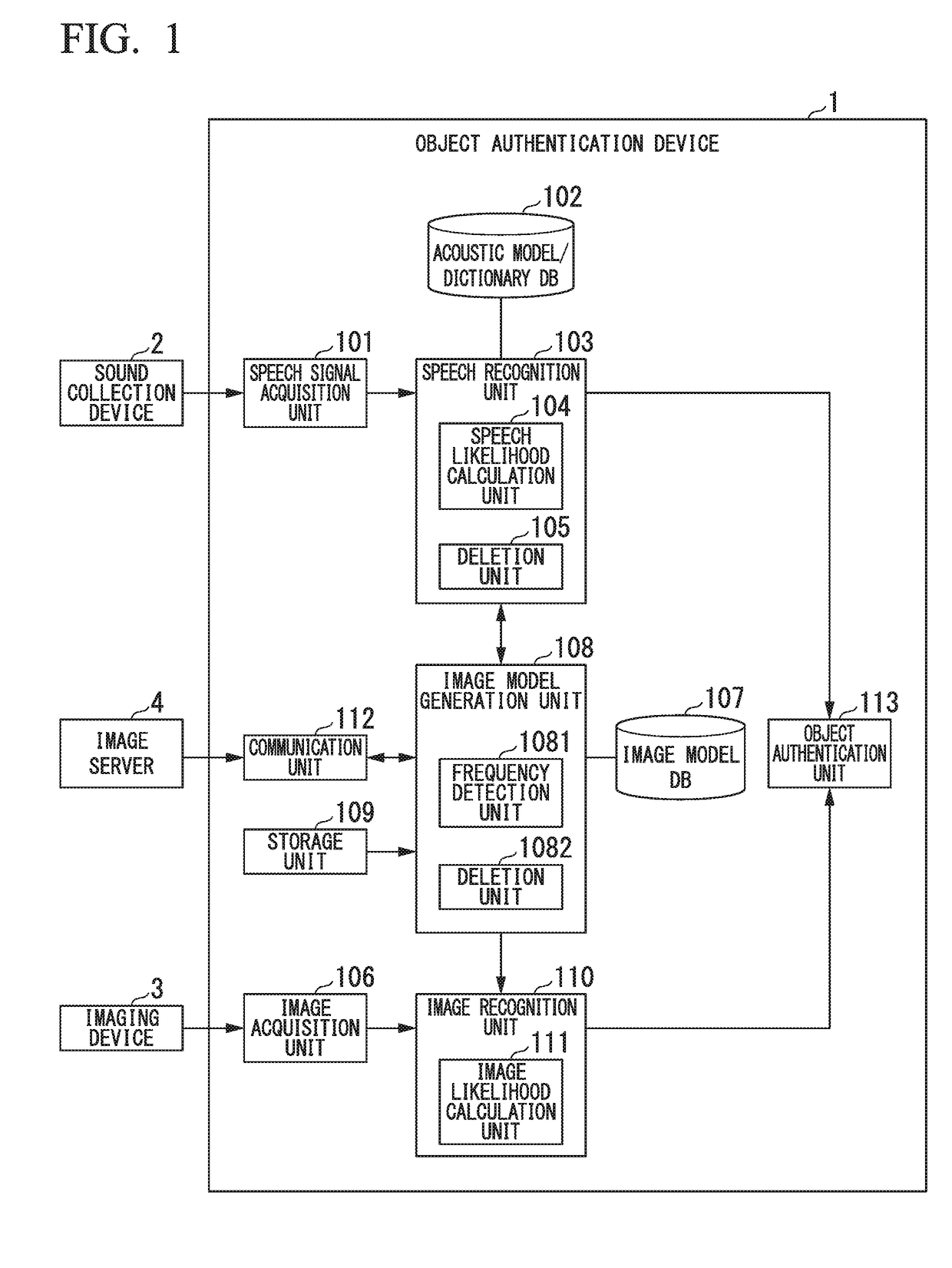
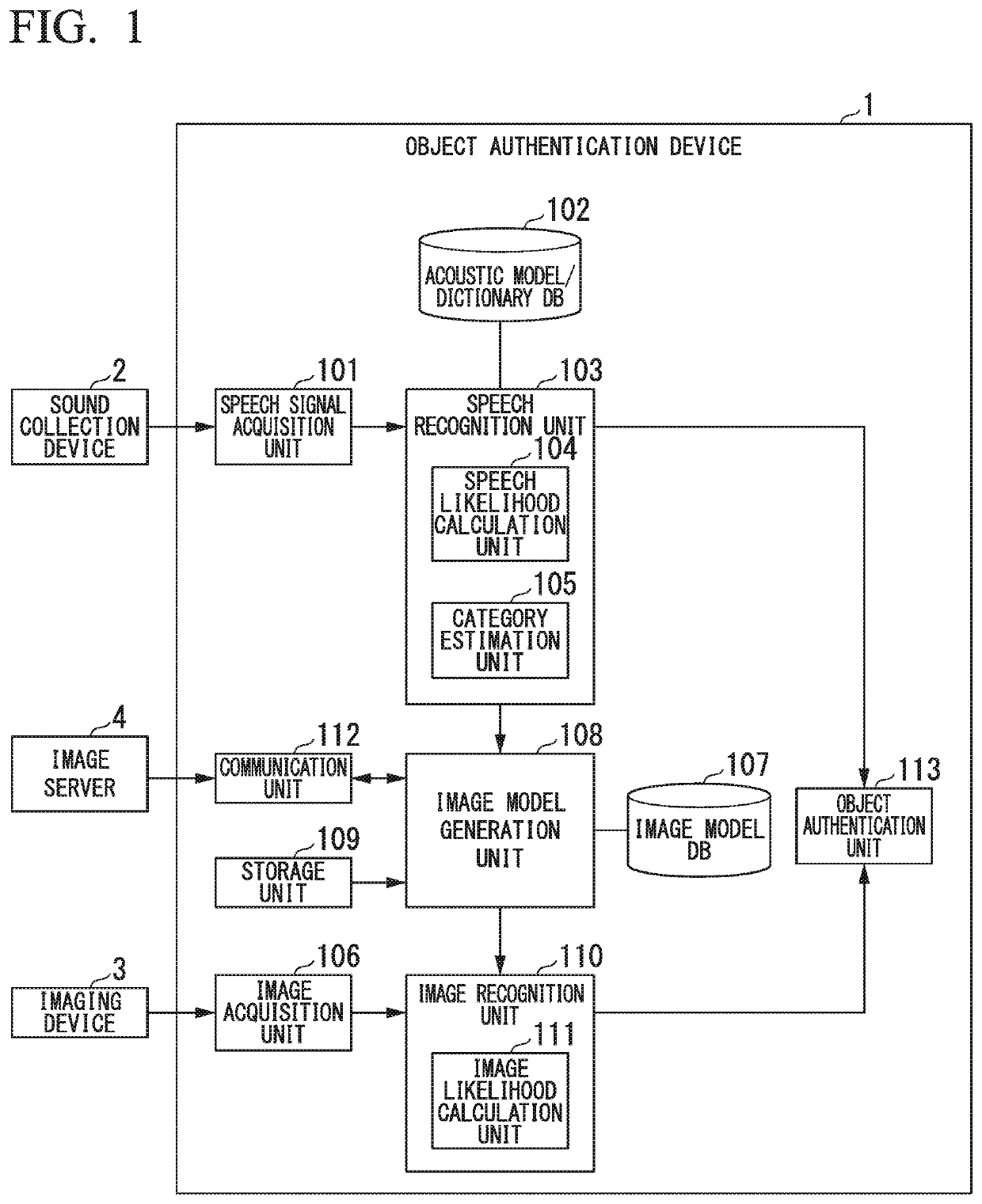
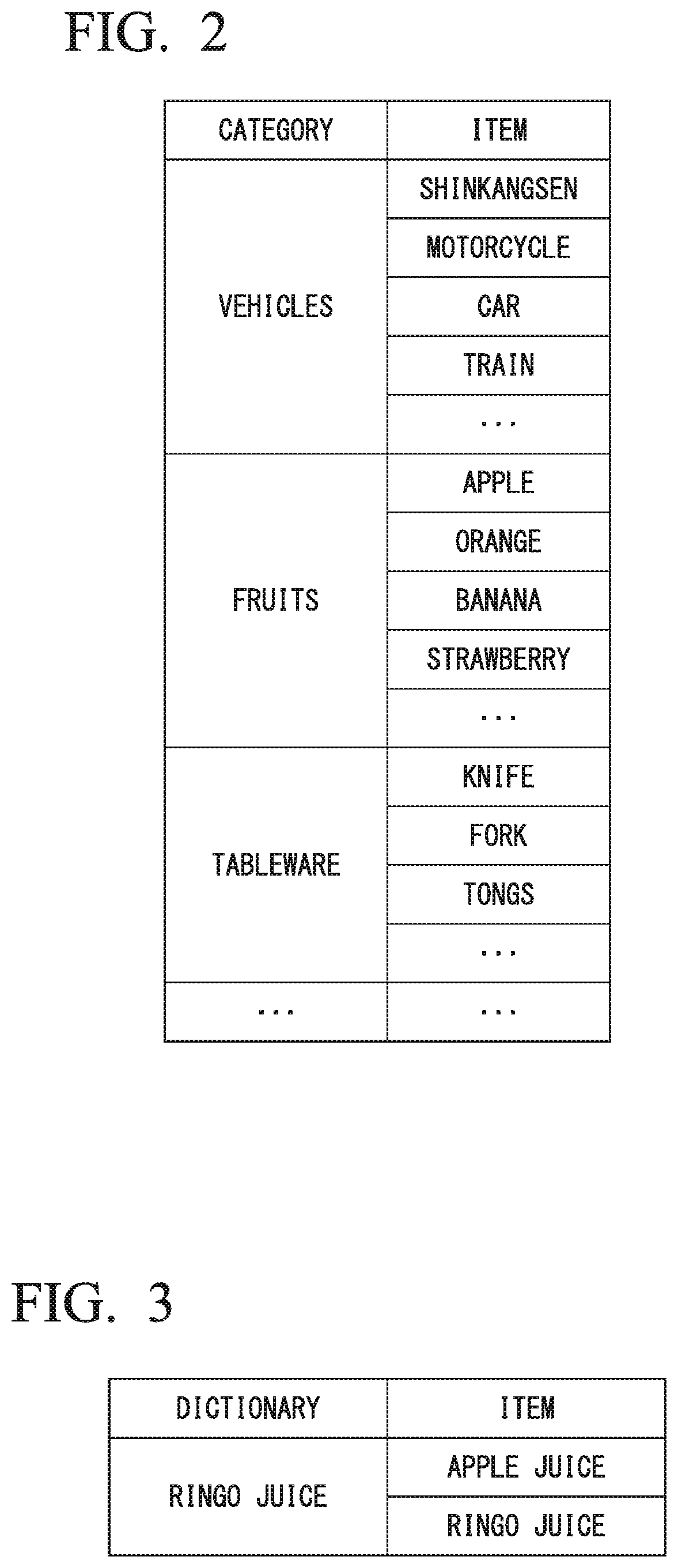
Object authentication device and object authentication method
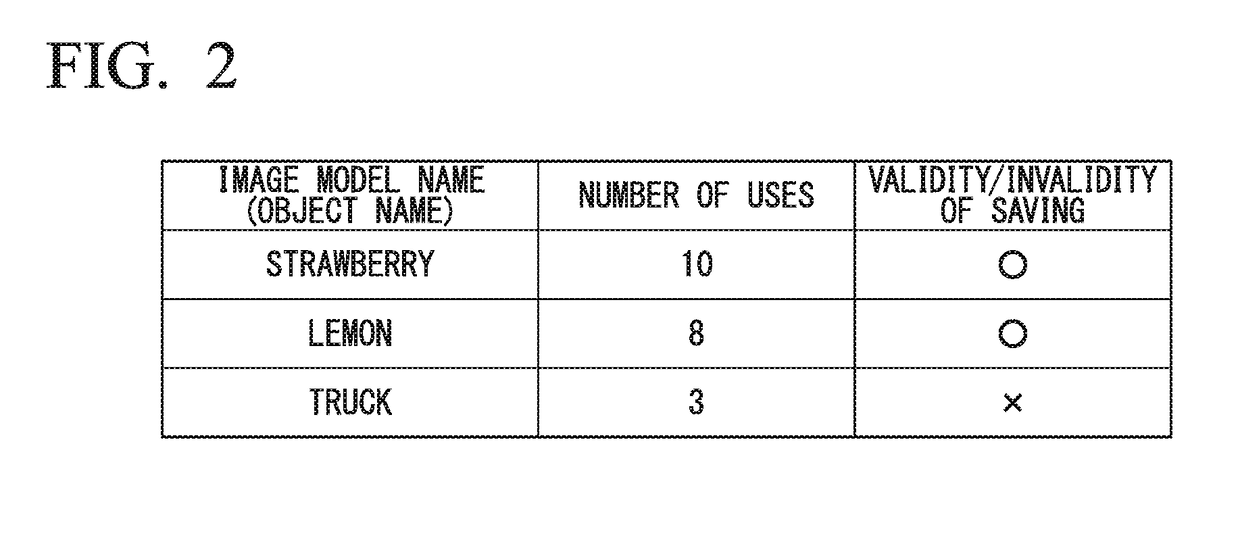
ActiveUS20180286398A1Improve authentication speedIncrease speedStill image data retrievalCharacter and pattern recognitionSpeech soundAuthentication
An object authentication device includes a speech recognition unit configured to obtain candidates for a speech recognition result for an input speech and a likelihood of the speech as a speech likelihood and an image model generation unit configured to obtain image models of a predetermined number of candidates for the speech recognition result in descending order of speech likelihoods, wherein the image model generation unit initially performs retrieval from an image model database storing the image models when the image models for the candidates for the speech recognition result are generated and generates an image model from information acquired from a network if the image model is not stored in the image model database.
Owner:HONDA MOTOR CO LTD
Information interaction method, device and system
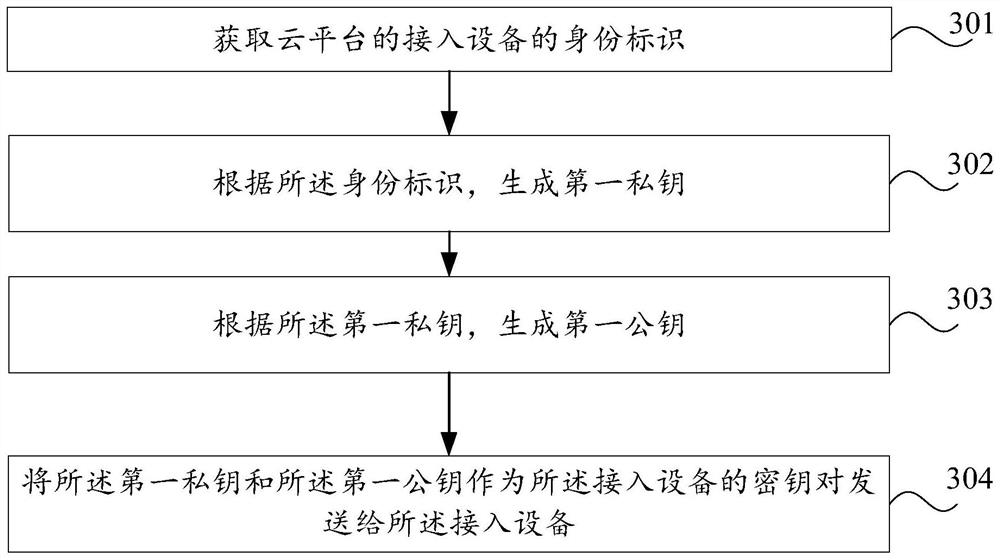
PendingCN113204757AImprove identity authentication efficiencyImprove authentication speedDigital data protectionDigital data authenticationEngineeringCommon key
The embodiment of the invention provides an information interaction method, device and system. The method applied to a cloud platform comprises the following steps: acquiring an identity label of access equipment of the cloud platform; generating a first private key according to the identity label; generating a first public key according to the first private key; and sending the first private key and the first public key to the access equipment as a key pair of the access equipment. Therefore, the embodiment of the invention can improve the authentication efficiency.
Owner:北京明朝万达科技股份有限公司
Video stream address authentication method and system based on TLS, and storage medium, storage medium and equipment
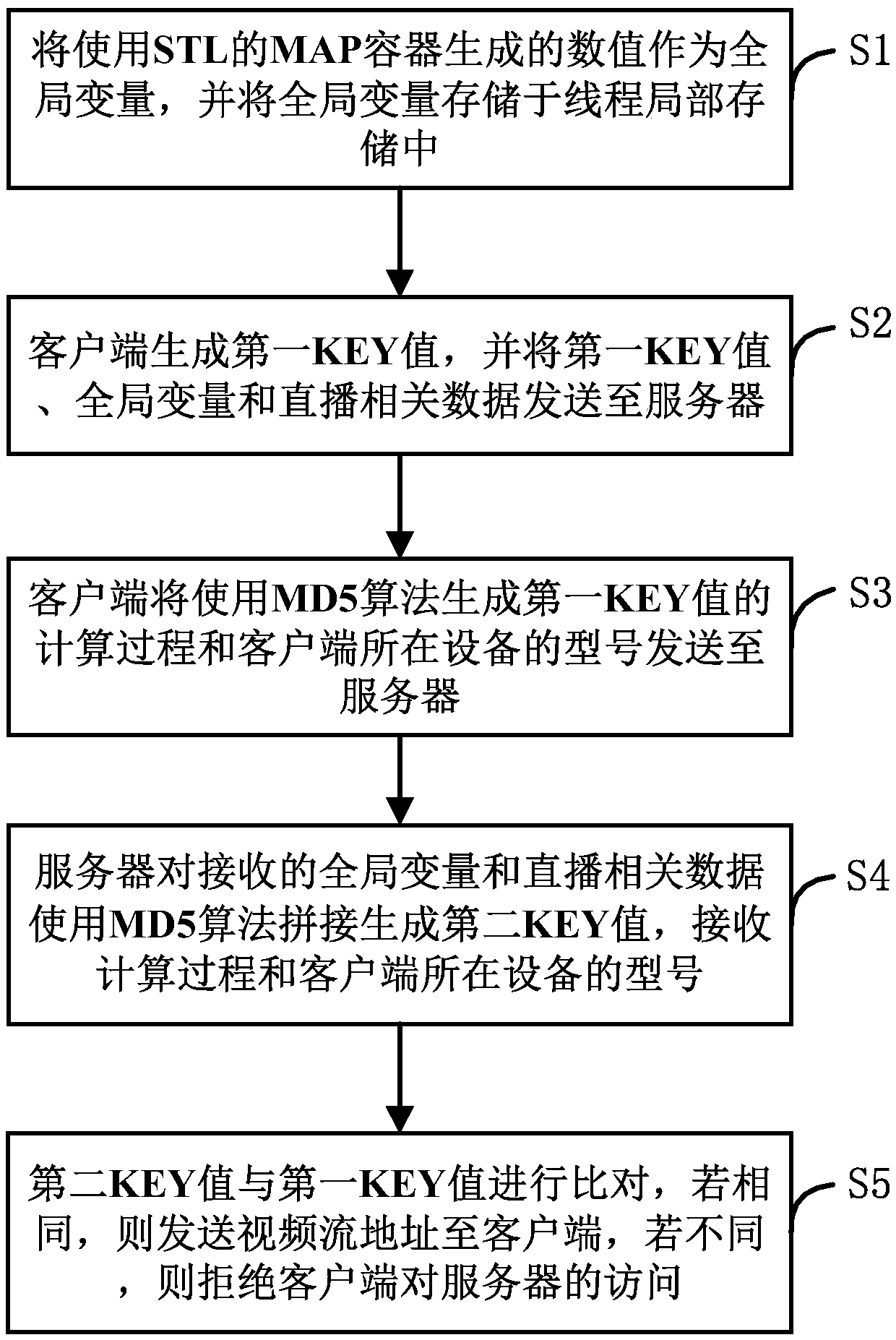
ActiveCN110691267AImprove authentication speedAvoid gettingSelective content distributionThird partyMD5
The invention discloses a video stream address authentication method and system based on TLS, a storage medium and equipment, and relates to the technical field of live video stream playing. The method comprises the following steps: a numerical value generated by an MAP container using an STL is used as a global variable, and the global variable is stored in a thread local storage; the client usesan MD5 algorithm to splice the global variable and the live broadcast related data to generate a first KEY value, and sends the first KEY value, the global variable and the live broadcast related data to the server; the server splices the received global variable and the live broadcast related data by using an MD5 algorithm to generate a second KEY value; and the second KEY value is compared withthe first KEY value, if the second KEY value and the first KEY value are the same, the video stream address is sent to the client, and if the second KEY value and the first KEY value are different, the client is refused to access the server. According to the invention, the video stream address can be effectively prevented from being acquired by the third-party platform, and the legitimate rightsand interests of the live broadcast platform are ensured.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
Biometric authentication device
ActiveUS10592721B2Shorten speedConveniently performedDigital data authenticationPrint image acquisitionEngineeringComputer vision
Owner:LG ELECTRONICS INC
Computer system, dialogue control method, and computer
ActiveUS20190005311A1Quick responseQuick identificationDigital data information retrievalDigital data authenticationDatabase machineComputer vision
A computer system that performs in dialogue with a user and provides a prescribed service, comprising: an imaging device; a computer; and a generation device generating dialogue content on a basis of an algorithm for generating dialogue content. The computer couples to a database that stores an authentication image used for an authentication process that uses an image. The computer calculates a distance between the user and the imaging device; executes an attribute estimation process in a case where the distance is larger than a threshold, selects the algorithm on the basis of results of the attribute estimation process, and issues a notification of the selected algorithm to the generation device.
Owner:HITACHI LTD
Face recognition method and system applied to bank business processing
InactiveCN105426880ARelieve pressureReduce workloadCharacter and pattern recognitionSimulationTechnical standard
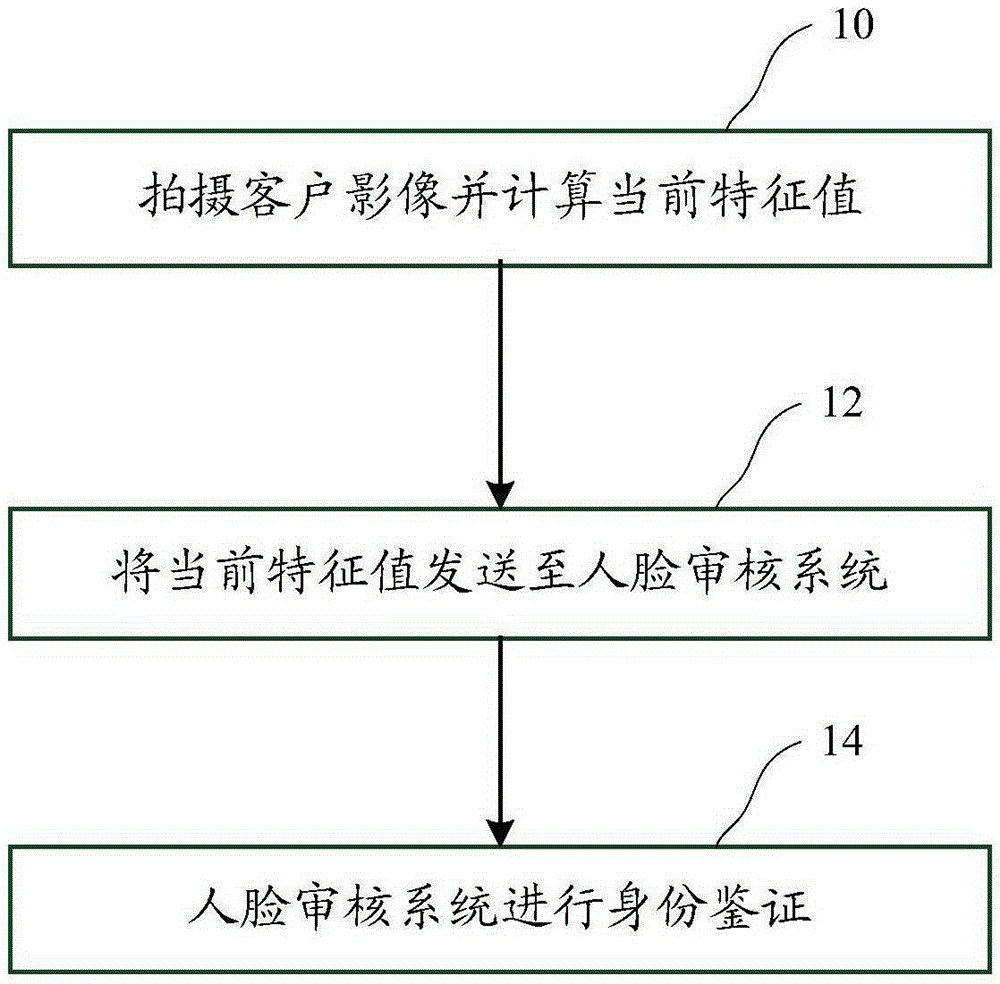
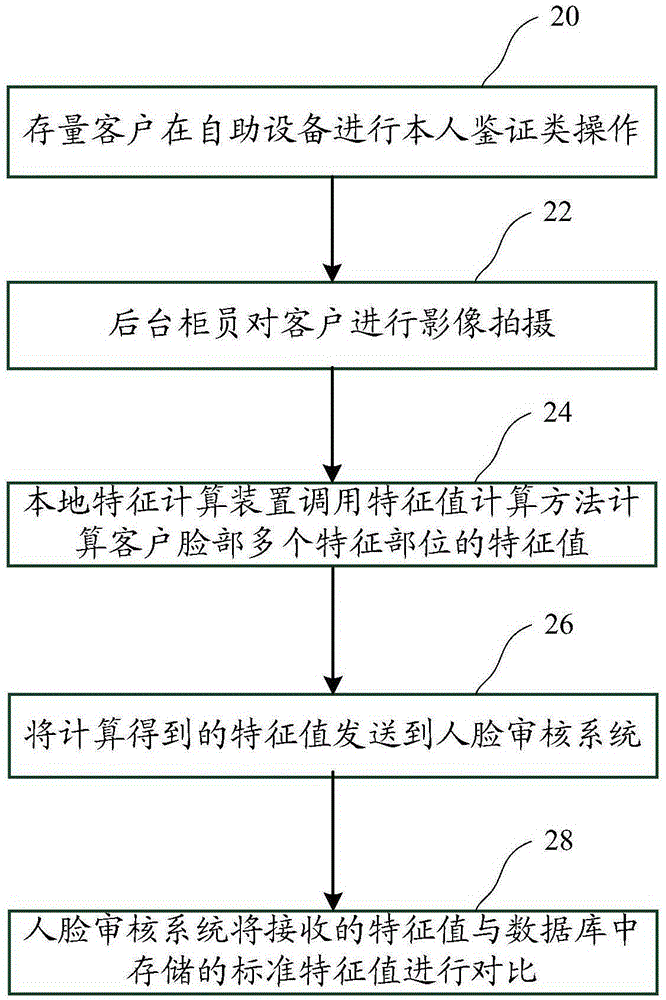
The invention discloses a face recognition method and system applied to bank business processing. The method comprises the steps that a client image is photographed by image photographing equipment of self-service equipment at the self-service equipment side, and the current characteristic values of a client face are calculated according to the client image; and the current characteristic values are transmitted to the face checking system of a server side, and the face checking system performs comparison according to the current characteristic values and the standard characteristic values of the client so as to determine authenticity of the client. With application of the face recognition method and system applied to bank business processing, pressure of bandwidth and the server in mass concurrent processing can be effectively reduced so that authentication speed can be enhanced and workload of a background system (e.g. the face checking system) can be reduced.
Owner:CHINA CONSTRUCTION BANK
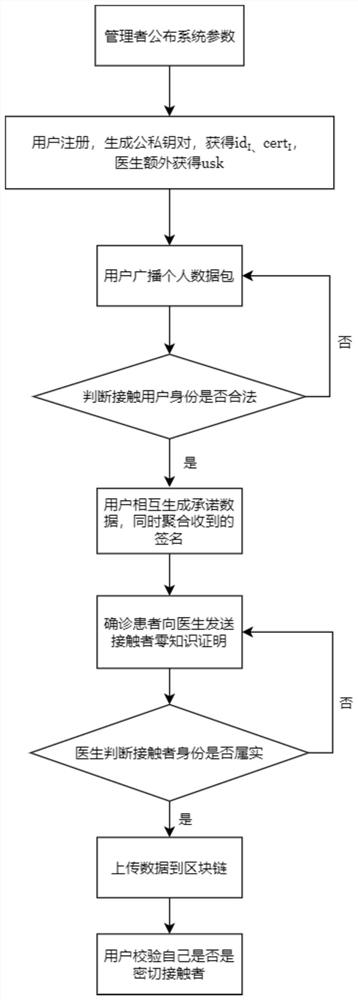
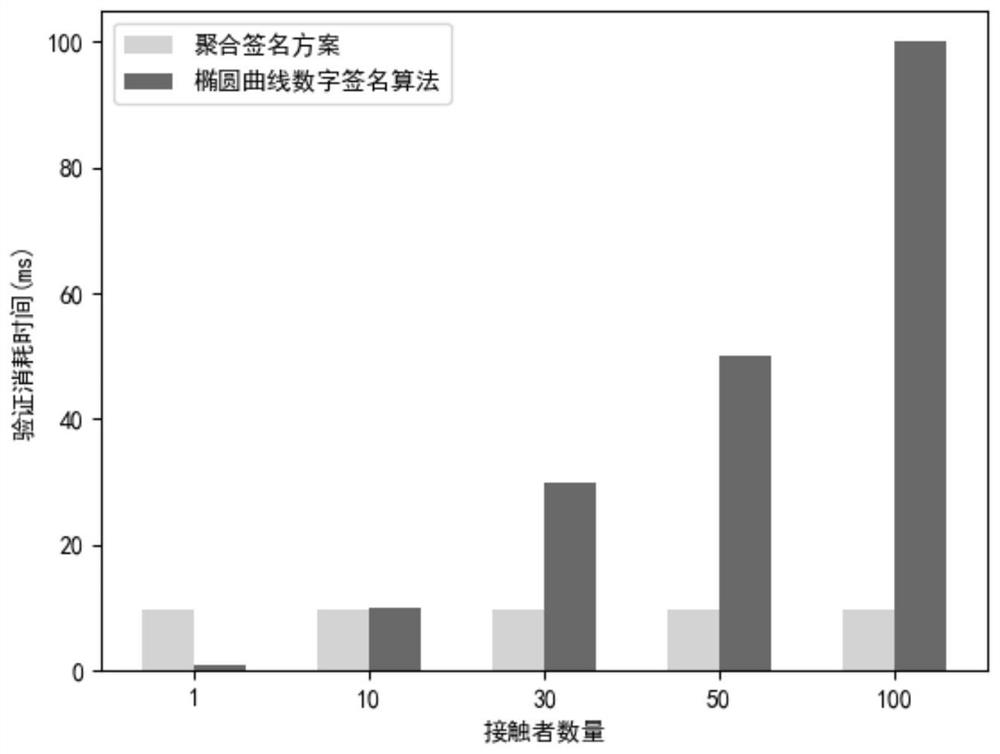
Contact person tracking privacy protection method based on aggregation signature
ActiveCN113395691ASave storage spacePrevent Identity LeakageUser identity/authority verificationSecurity arrangementData packPrivacy protection
The invention discloses a contact person tracking privacy protection method based on an aggregation signature. The method specifically comprises the steps: firstly, generating public and private key pairs of a manager, a user and a doctor; the user broadcasts the hash value of the personal data packet, and when the users meet, whether the opposite side is a legal user is authenticated; after the authentication succeeds, mutual commitments are generated among the users; the user aggregates the signatures of the data packets of other users stored in the commitment process into a single short signature; then, the diagnosers create respective false identities for the contact persons of the diagnosers; the diagnoser sends the false identity information to the doctor, and after the doctor verifies the identity of the contact person, a group signature is generated, and the data packet is uploaded to the block chain; the doctor reports a definite diagnosis state of the user to a manager; and finally determining a close contact person. By adopting the aggregation signature technology, the local storage space of the user is saved, the privacy of the contact person can be protected by the aggregation zero-knowledge proof generated by the diagnoser to the contact person. Meanwhile, the identity authentication speed of the doctor to the contact person can be increased.
Owner:XI'AN POLYTECHNIC UNIVERSITY
Authentication method, device, system and storage medium
ActiveCN108964885BImprove authentication speedKey distribution for secure communicationUser identity/authority verificationAuthorization certificateInternet privacy
The application discloses an authentication method, device, system and storage medium, belonging to the field of security technology. The method includes: the application obtains the client ID of the client generated by the user center, and the client ID is an ID assigned by the user center after the client logs in at the user center; when the application receives the authentication information including the authorization certificate sent by the client , verify the authority of the authorization certificate through the client ID, the authorization certificate is sent to the client by the user center, and is used to cooperate with the client ID to prove the client's authority; when the authorization certificate passes the authority verification, the application allows the client to perform access. In this application, each application locally uses the authority information in the authorization certificate to perform the authentication operation, without going to the authentication service provided by the user center for centralized authentication. Compared with the centralized authentication method in the related art, the authentication speed is improved by a discrete authentication method.
Owner:HUAWEI TECH CO LTD
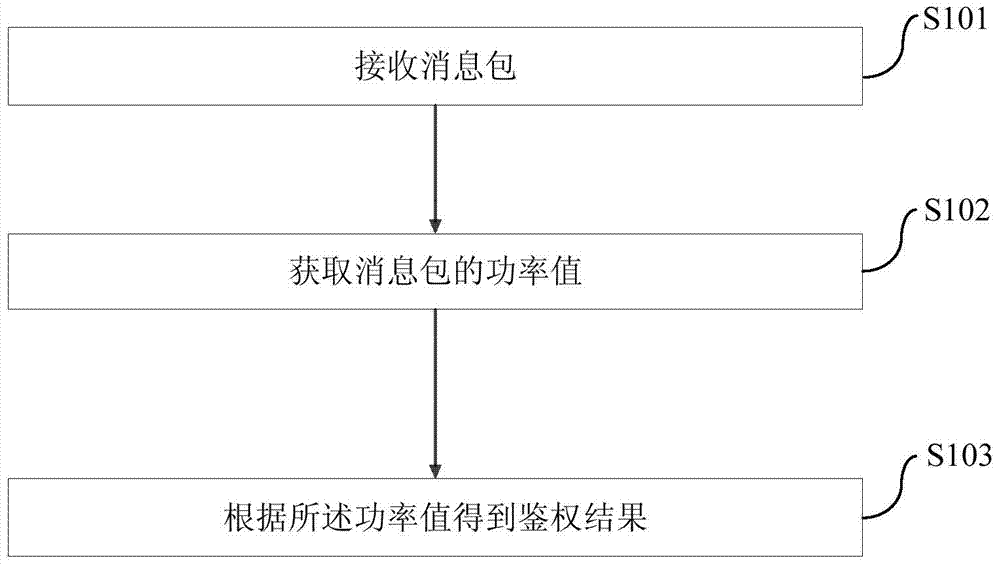
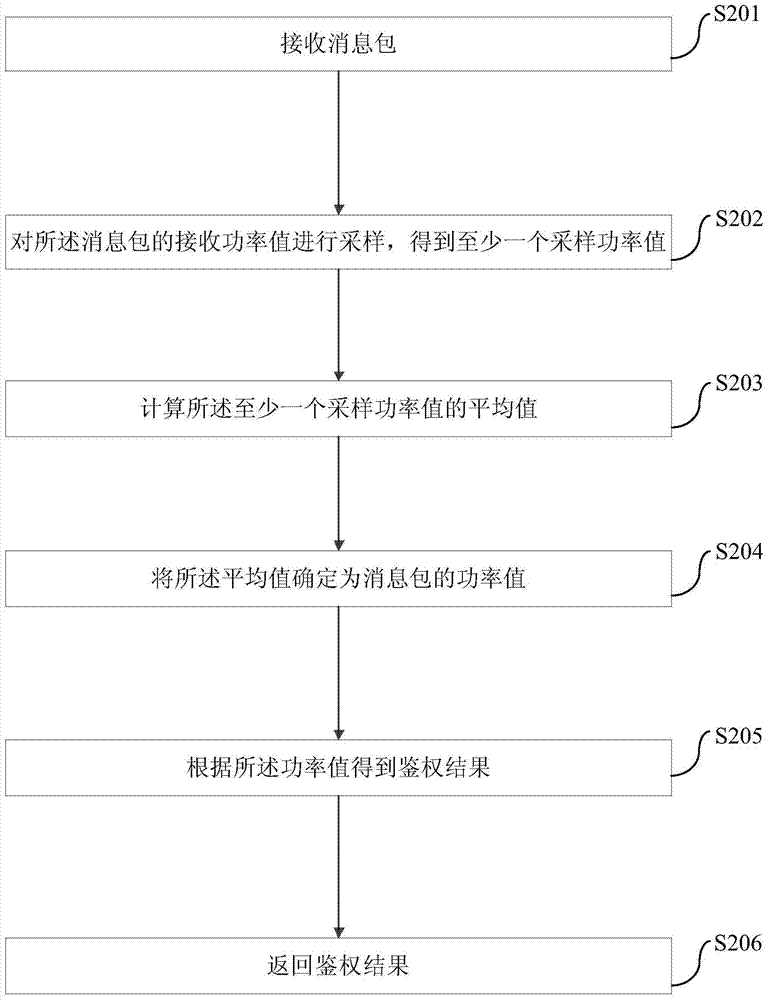
Electronic device authentication method and device
ActiveCN104680057BImprove experienceEasy to operateDigital data authenticationComputer hardwareAuthentication
The invention provides an electronic equipment authentication method and device. The electronic equipment authentication method comprises the following steps that a message packet is received; a power value of the message packet is obtained; and authentication results are obtained according to the power value. The method can realize fast authentication of electronic equipment.
Owner:MIDEA INTELLIGENT LIGHTING & CONTROLS TECH CO LTD
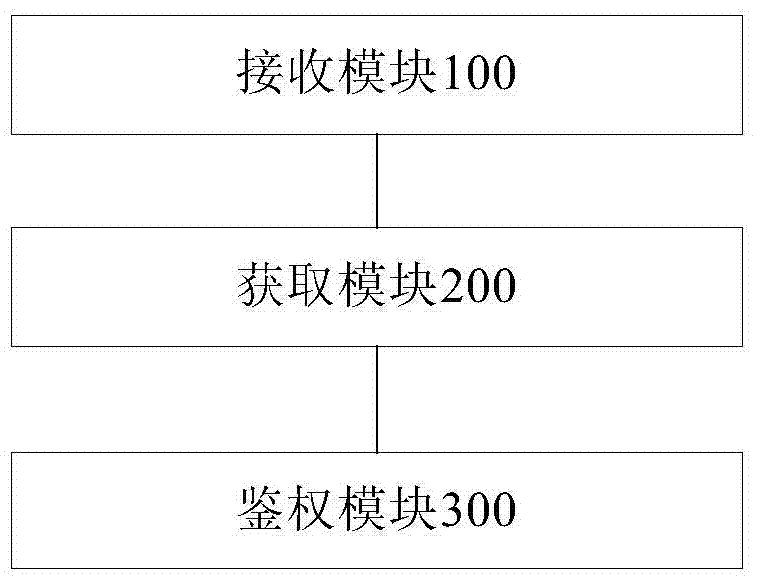
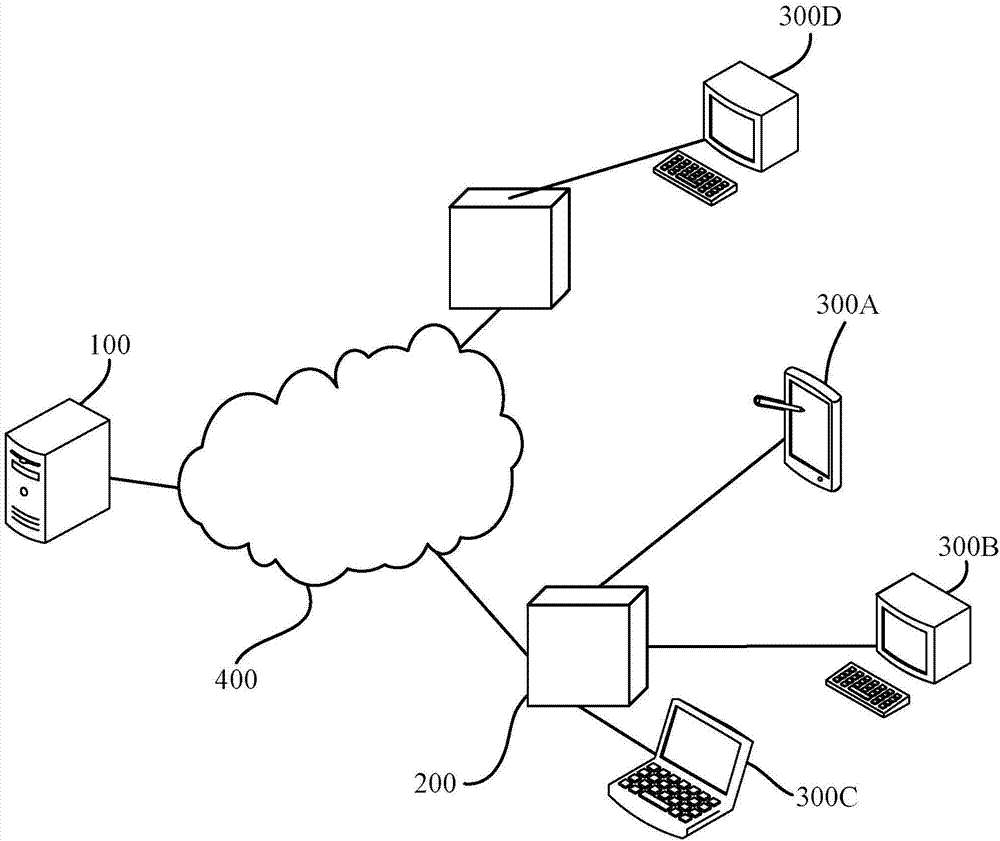
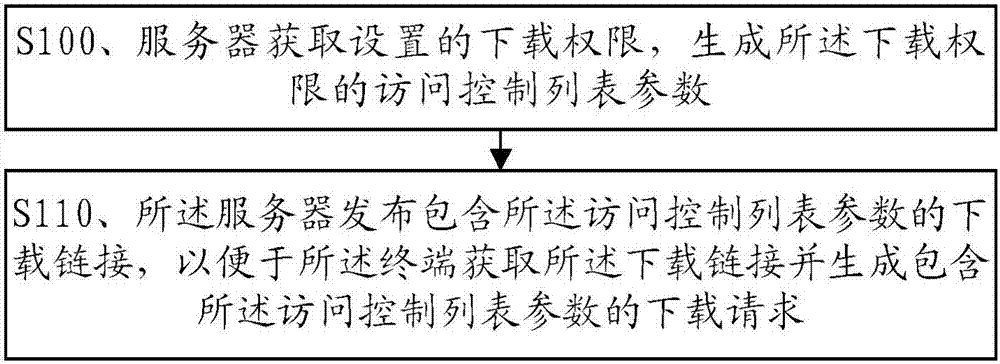
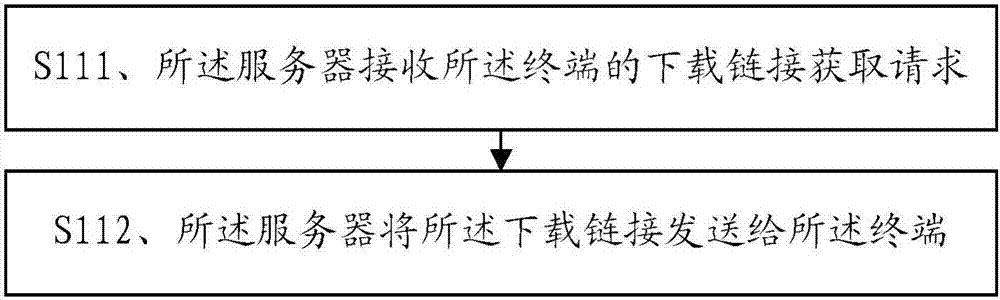
File download method, device and system
ActiveCN104471918BQuick responseReduce loadDigital data authenticationSecuring communicationAccess control listServer
The present invention discloses a file downloading method, a server, a download access node, and a distributed storage system, which pertains to the field of communications technologies, and is designed to resolve a problem in the prior art that load on the server increases, and an authentication speed and a response speed for downloading a file are reduced. The file downloading method includes: acquiring, by a server, download permission that is set, and generating an access control list parameter of the download permission; and releasing, by the server, a download link that includes the access control list parameter, so that a terminal acquires the download link and generates a download request that includes the access control list parameter.
Owner:HUAWEI TECH CO LTD
Authentication device and electronic equipment
InactiveCN110704824AImprove experienceImprove authentication speedDigital data authenticationMatching and classificationEmbedded systemControl electronics
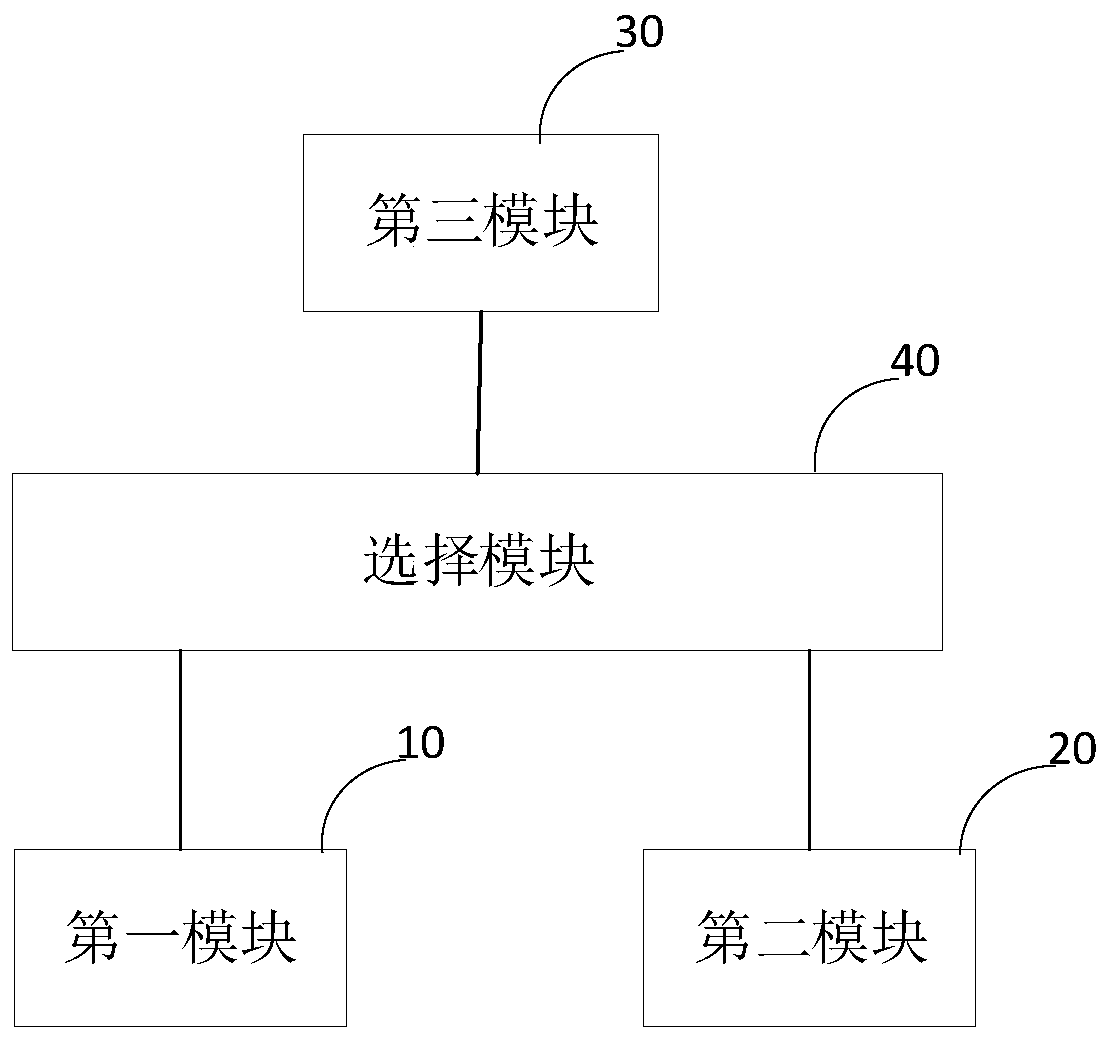
The invention relates to an authentication device and electronic equipment. The device comprises a first module, a second module, a third module and a selection module, the first module is used for outputting a first control signal to the selection module under the condition that a received trigger signal is a first trigger signal, so that an electric connection relationship between the first module and the second module is established through the selection module; controlling a second module to collect first fingerprint information; outputting a second control signal to the selection module so as to establish an electrical connection relationship between the third module and the second module through the selection module; the third module is used for acquiring first fingerprint information of the second module under the condition that the third module is electrically connected with the second module; performing fingerprint identification on the first fingerprint information, and outputting an identification result; and under the condition that the identification result of the third module is successful identification, controlling the electronic equipment to change the state. According to the invention, the authentication speed can be greatly improved, the authentication time is reduced, and the user experience is improved.
Owner:CHIPONE TECH BEIJINGCO LTD
Authentication device and electronic device
PendingCN110717440AImprove authentication speedReduce authentication timeCharacter and pattern recognitionDigital data authenticationEmbedded systemComputer hardware
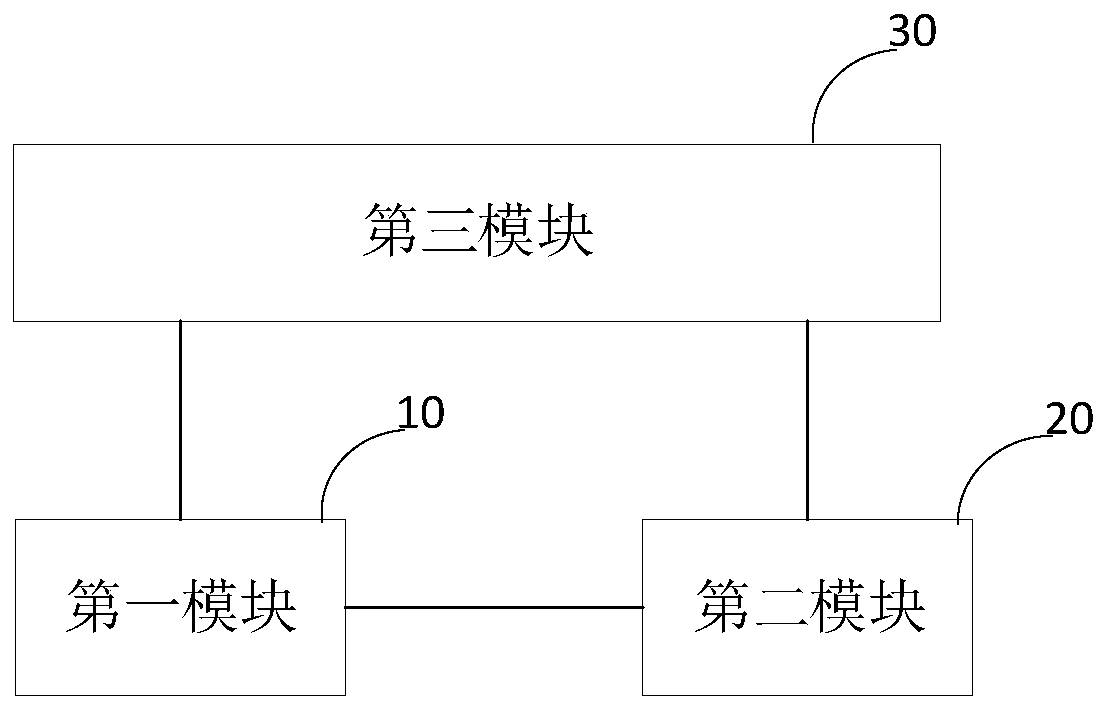
The invention relates to an authentication device and an electronic device, and the device comprises a first module which is used for determining the type of a received triggering signal, and outputting a first control signal under the condition that the triggering signal is a first authentication signal; a second module electrically connected to the first module and used for acquiring first fingerprint information according to the first control signal, performing fingerprint identification on the first fingerprint information by utilizing a first fingerprint identification algorithm and outputting an identification result; and a third module electrically connected to the first module and the second module, and used for controlling the electronic device to change the state under the condition that the identification result of the second module is that the identification is successful. According to the invention, when a user triggers the first authentication signal, in response to the first authentication signal, the second module is used to rapidly carry out fingerprint information acquisition and fingerprint identification, and in the case of successful identification, rapid authentication is carried out, so that the authentication speed can be greatly improved, the authentication time is reduced, and the user experience is improved.
Owner:CHIPONE TECH BEIJINGCO LTD
Object authentication device and object authentication method
ActiveUS10861452B2Improve authentication speedImprove accuracySpeech recognitionThree-dimensional object recognitionSpeech soundSubvocal recognition
Owner:HONDA MOTOR CO LTD
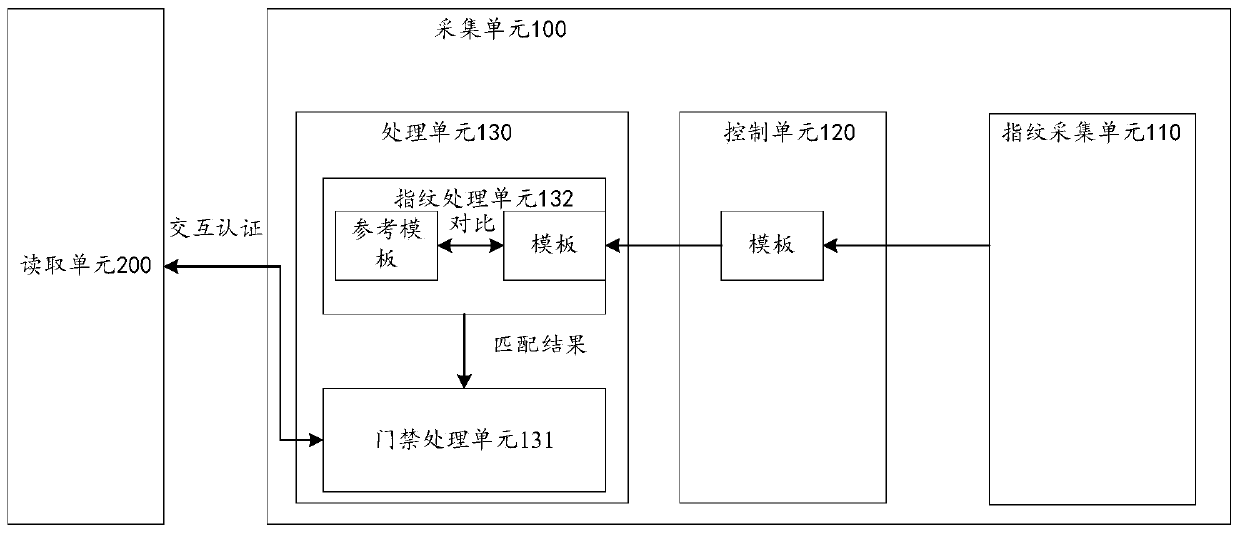
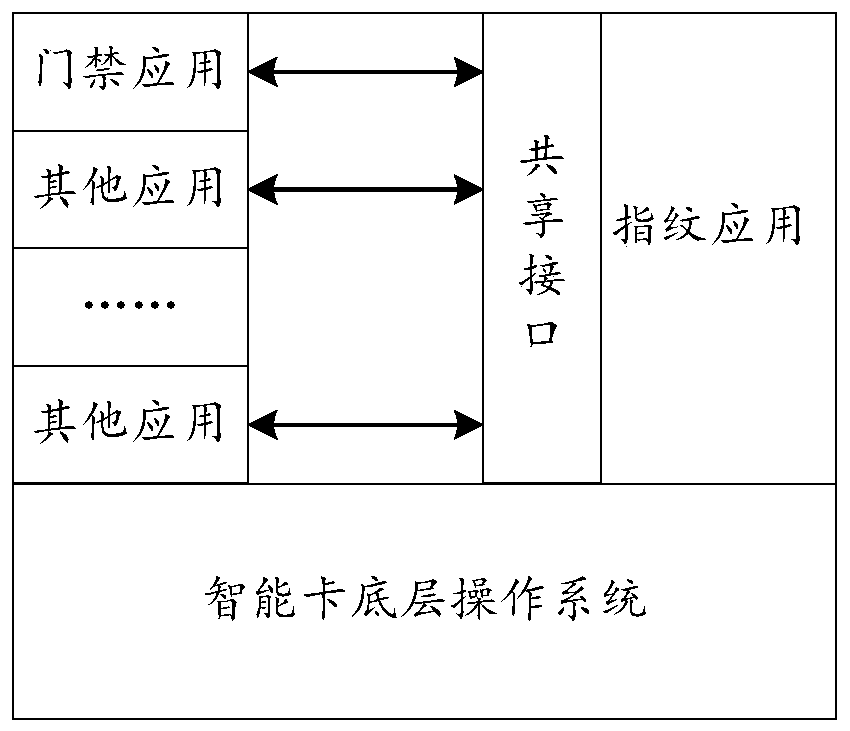
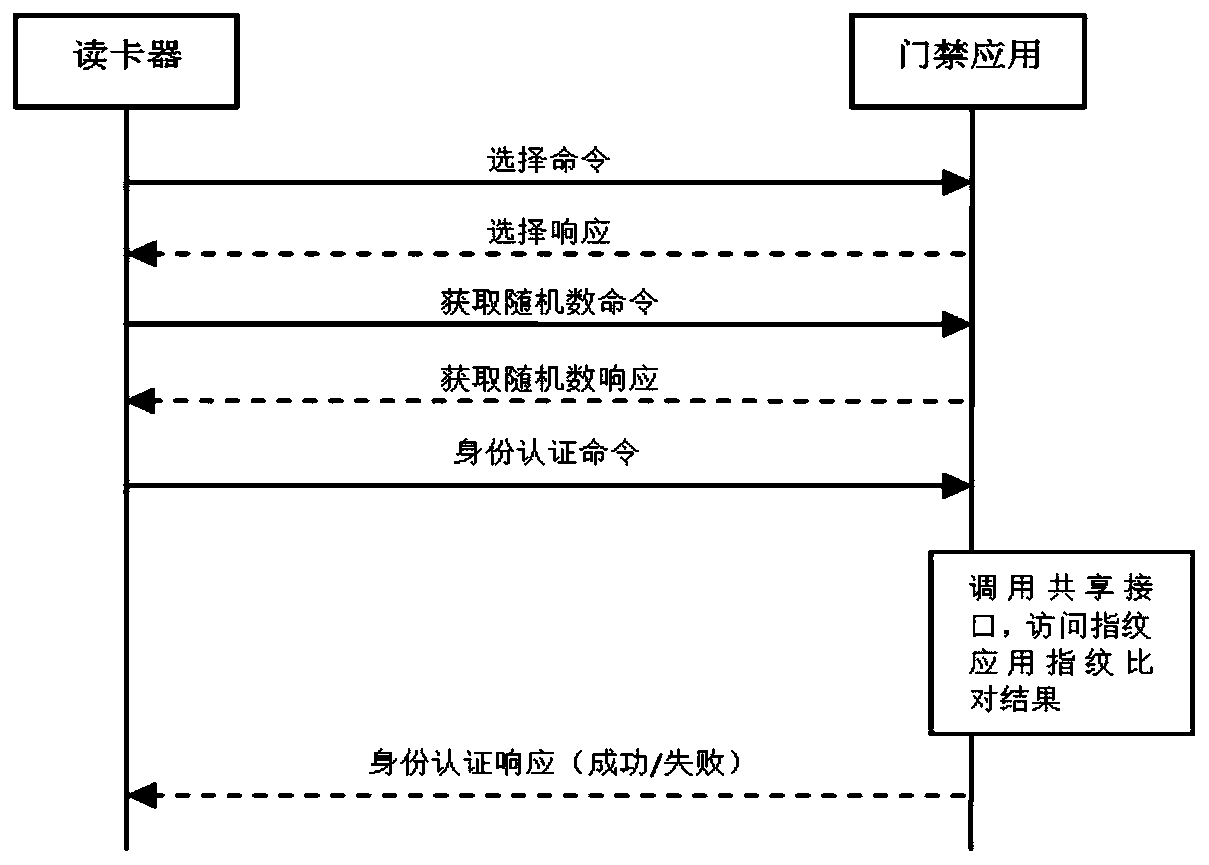
Identity recognition device and method
InactiveCN110969749AReduce verification timeImprove authentication speedIndividual entry/exit registersMatching and classificationEmbedded systemIdentification device
The invention relates to an identity recognition device and method, and the method comprises the steps: enabling a collection unit to enter a field for power-on, and carrying out the parallel execution of fingerprint collection and interaction verification, comprising the steps: collecting the fingerprint information of a user, carrying out the templating, and comparing the templated fingerprint information with a stored fingerprint template, thereby obtaining a fingerprint comparison result; and performing interactive authentication by a reading unit and an access control processing unit through a random number and a secret key. According to the invention, the identity recognition device and method have the beneficial effects that the parallel access mechanism is adopted, and the identity recognition process and the fingerprint acquisition and comparison process are carried out at the same time, so that the verification time is shortened, and the identity verification speed of the fingerprint card is increased.
Owner:EASTCOMPEACE TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com