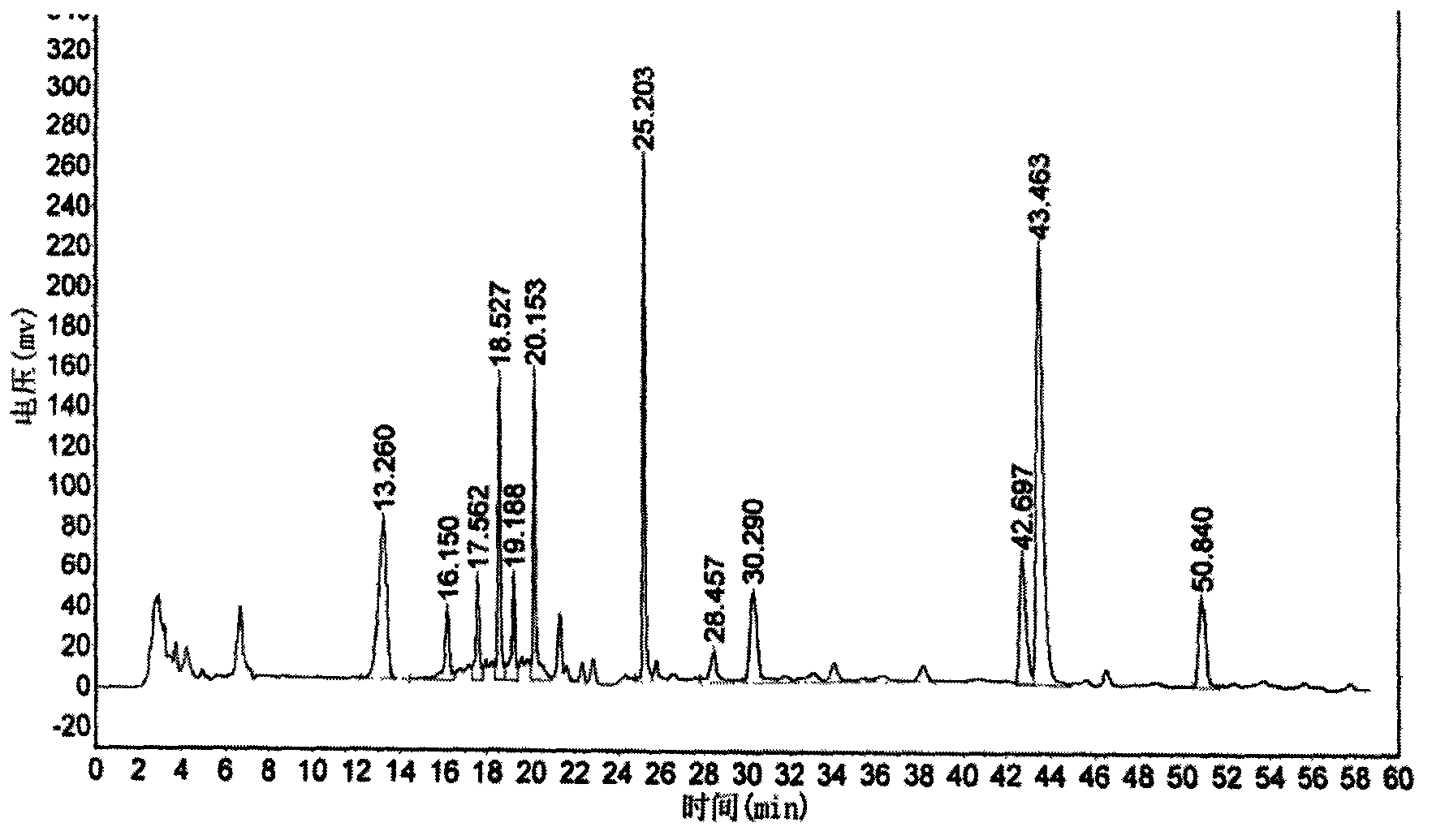
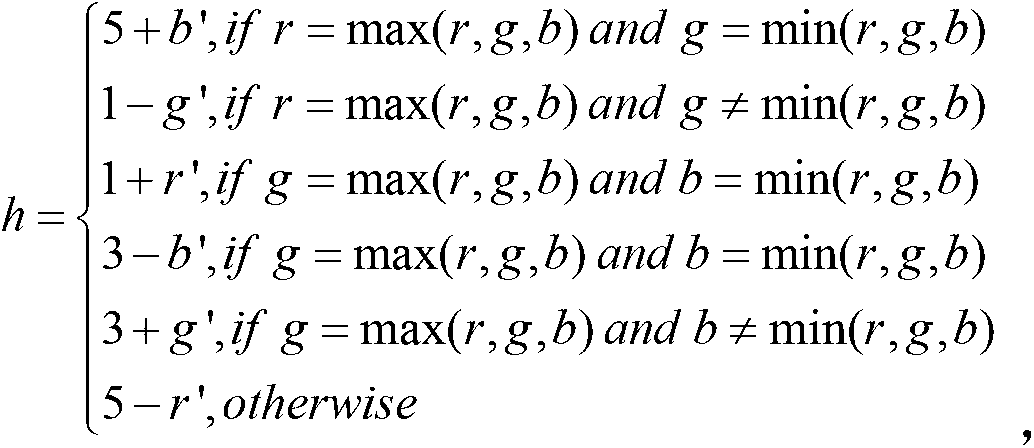Patents
Literature
223results about How to "Realize authentication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
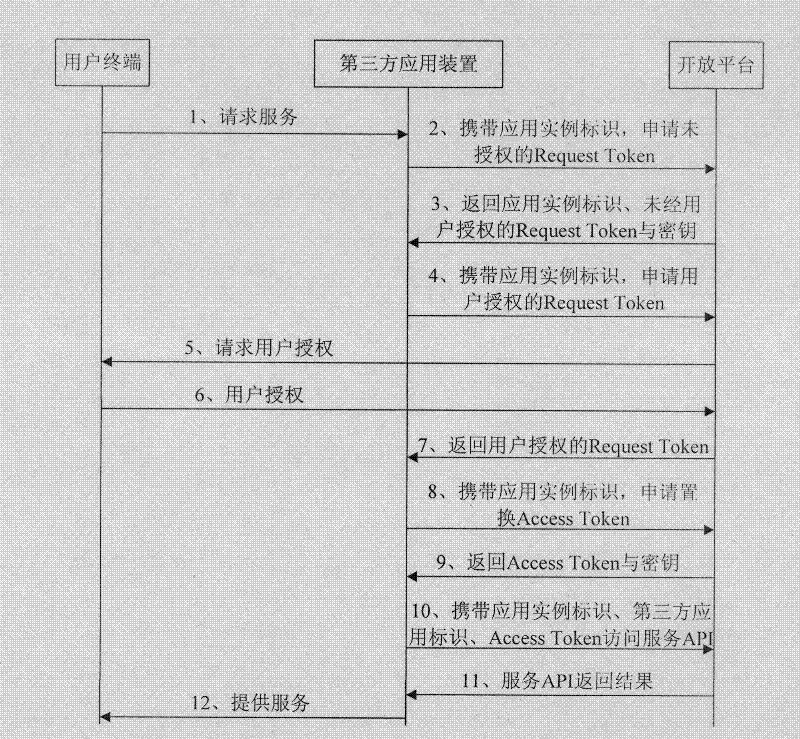
OAuth protocol-based safety certificate method of open platform and system thereof
InactiveCN102394887AFlexible Billing CapabilityRealize authenticationUser identity/authority verificationProtocol for Carrying Authentication for Network AccessWeb technology
The invention relates to an OAuth protocol-based safety certificate method of an open platform and a system thereof. The method comprises the following steps that: an open platform checks whether an application example identifier that is consistent with the platform is carried in an access request for application of an unauthorized Request Token, wherein the access request is sent by a third part application apparatus; if not, a new application example identifier is distributed; and the application example identifier, a Request Token that is not authorized by a user and a corresponded token secret key are returned to the third part application apparatus; and the third part application apparatus updates the application example identifier to the local and continuously carries the application example identifier to carry out a subsequent OAuth certificate request; the open platform utilizes the application example identifier to guide the user authorization; and then, an Access Token and a corresponded secret key are issued to the third part application apparatus. According to the invention, the method and the system belong to the network technology field; and accurate certificate and authentication can be carried out on service scenes of a plurality of third part application operation examples; and moreover, flexible charging can be realized.
Owner:EB INFORMATION TECH
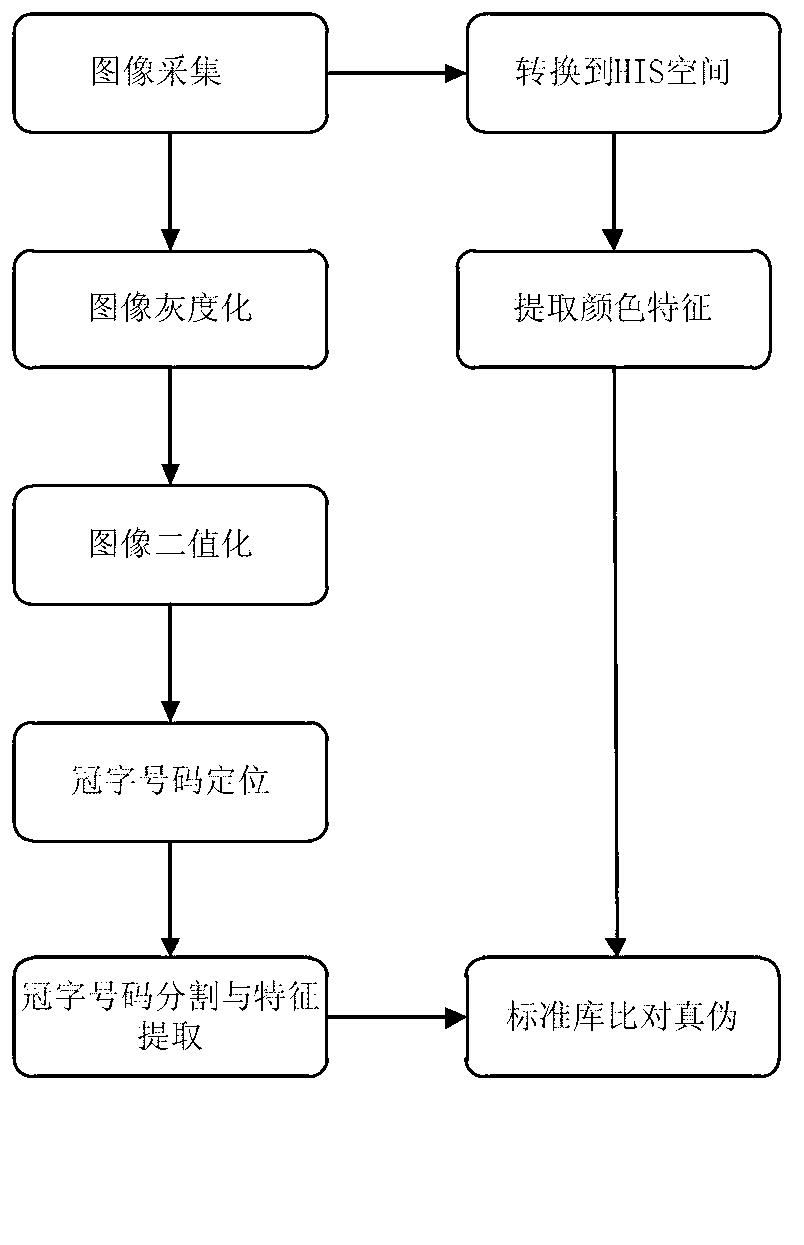
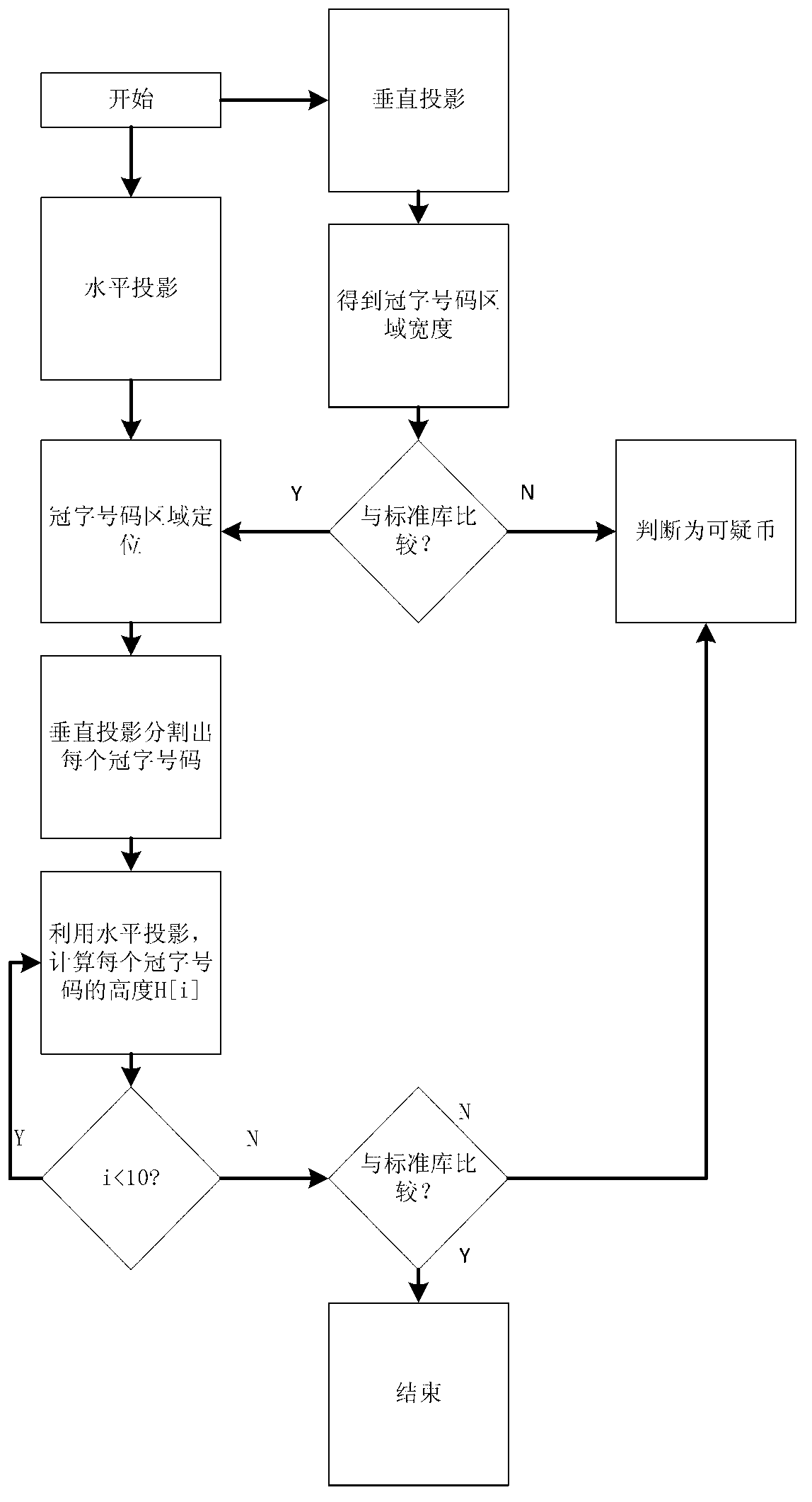
Renminbi (RMB) counterfeit identifying method based on crown-word image characters
ActiveCN103136845ARealize authenticationCombating Counterfeit Money CrimePaper-money testing devicesCharacter and pattern recognitionEngineeringIdentification rate
The invention discloses a renminbi (RMB) counterfeit identifying method based on crown-word image characters. The method includes the steps of locating based on a repeated projection method, extracting based on divisional RMB crown-word characters, carrying out identifying on crown-word images so as to achieve division and extraction of crown-word numbers, and then judging whether a piece of RMB is a piece of suspicious paper money according to the color of the crown-word numbers, the width of a crown-word number area and the font sizes. The RMB counterfeit identifying method based on the crown-word image characters is capable of improving the identification rate of the current RMB paper money and makes a contribution to striking crimes in counterfeit money and protecting national currency security.
Owner:ZHEJIANG UNIV
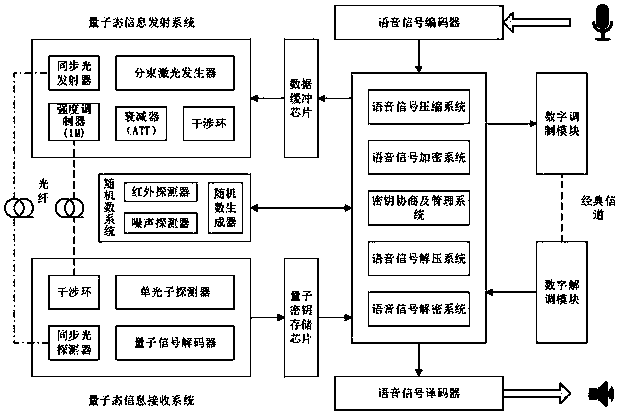
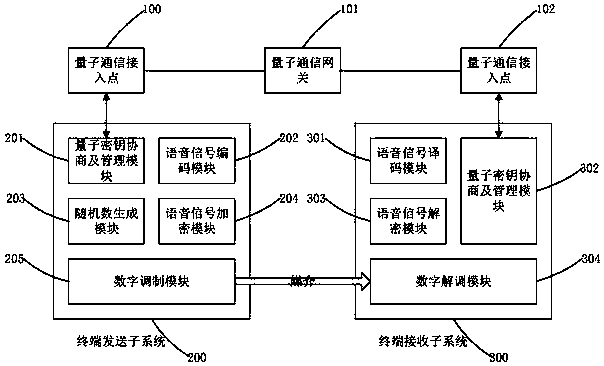
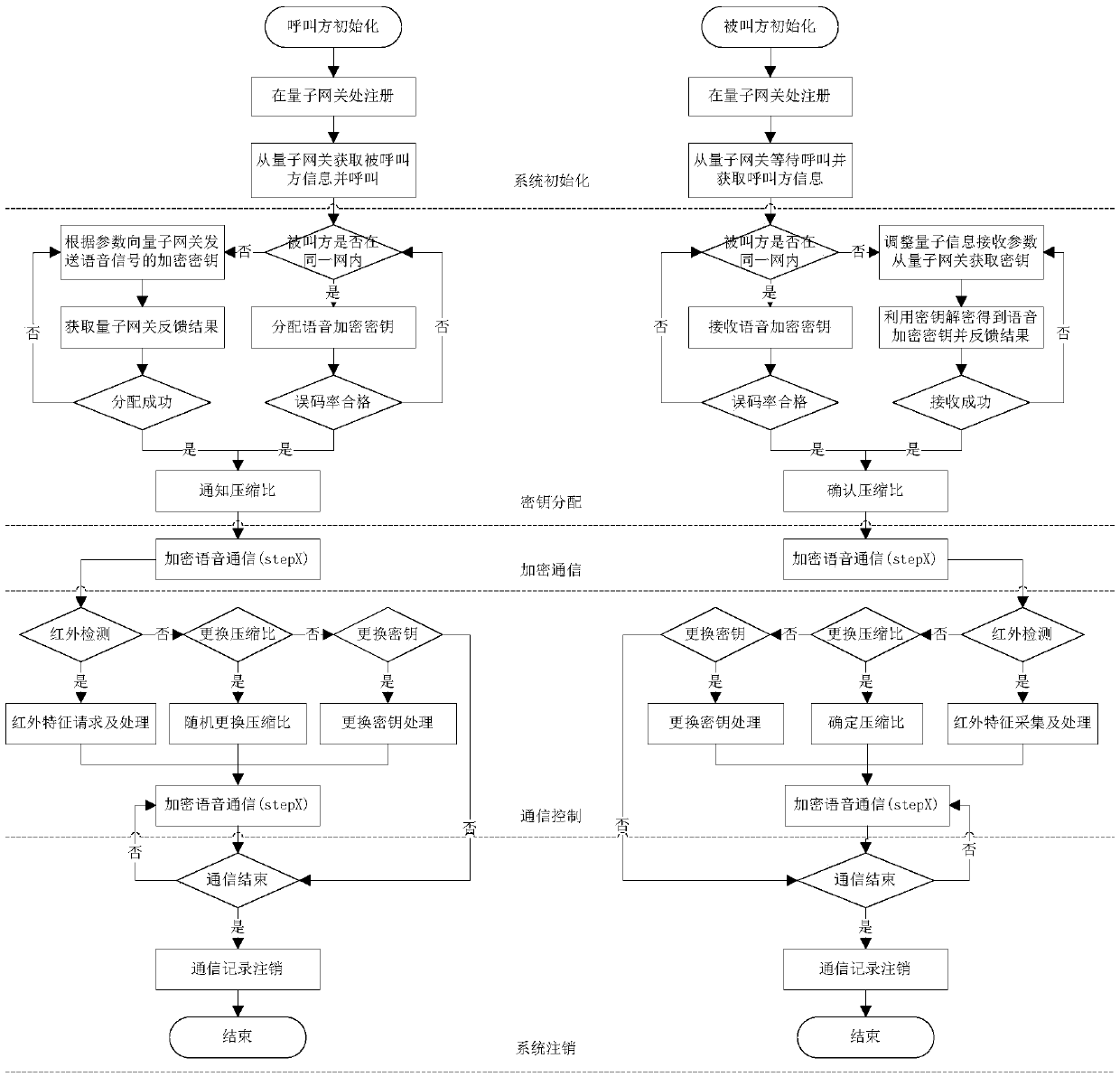
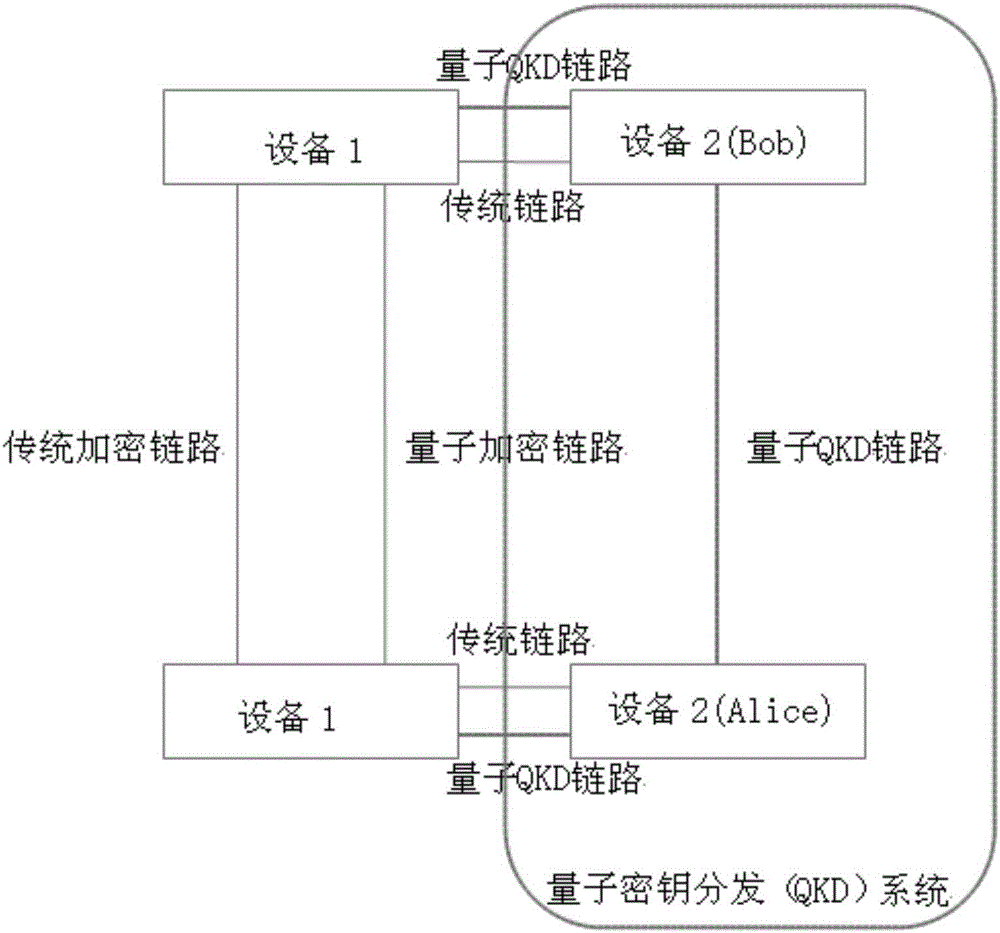
Voice signal quantum encryption communication system based on random number
ActiveCN108768542ARandomUnpredictableKey distribution for secure communicationSpeech analysisSignal encodingSignal decoding
The invention relates to a voice signal quantum encryption communication system based on a random number, which comprises terminal equipment, a quantum communication access point, a quantum communication gateway and a quantum communication access point, wherein the terminal equipment consists of a terminal sending subsystem and a terminal receiving subsystem; the terminal sending subsystem comprises a quantum key agreement and management module, a voice signal encoding module, a random number generation module, a voice encryption module and a digital modulation module; and the terminal receiving subsystem comprises a voice signal decoding module, a quantum key agreement and management module, a voice decryption module and a digital demodulation module. One piece of terminal equipment simultaneously comprises the terminal sending subsystem and the terminal receiving subsystem. According to the invention, the terminal sending subsystem is applied to send a voice signal with good encryption performance and high anti-interference performance and meanwhile, the terminal receiving subsystem is utilized to receive and reduce the voice signal, so that safety and integrity in the communication process are ensured.
Owner:CHINA THREE GORGES UNIV
Safety access method of wireless metropolitan area network
InactiveCN101272616AReduces the possibility of crackingRealize AuthenticationUser identity/authority verificationRadio/inductive link selection arrangementsDigest access authenticationAccess method
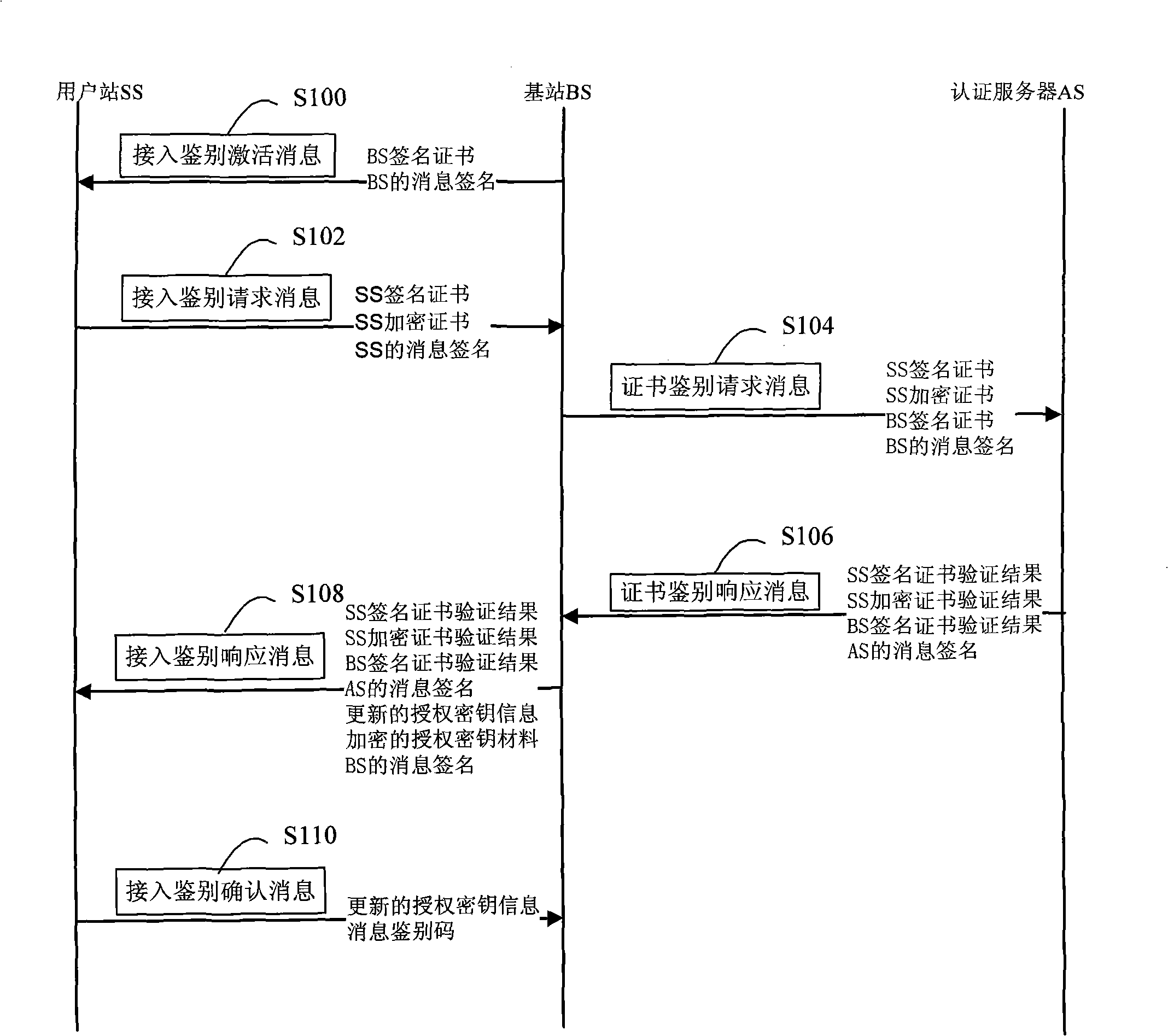
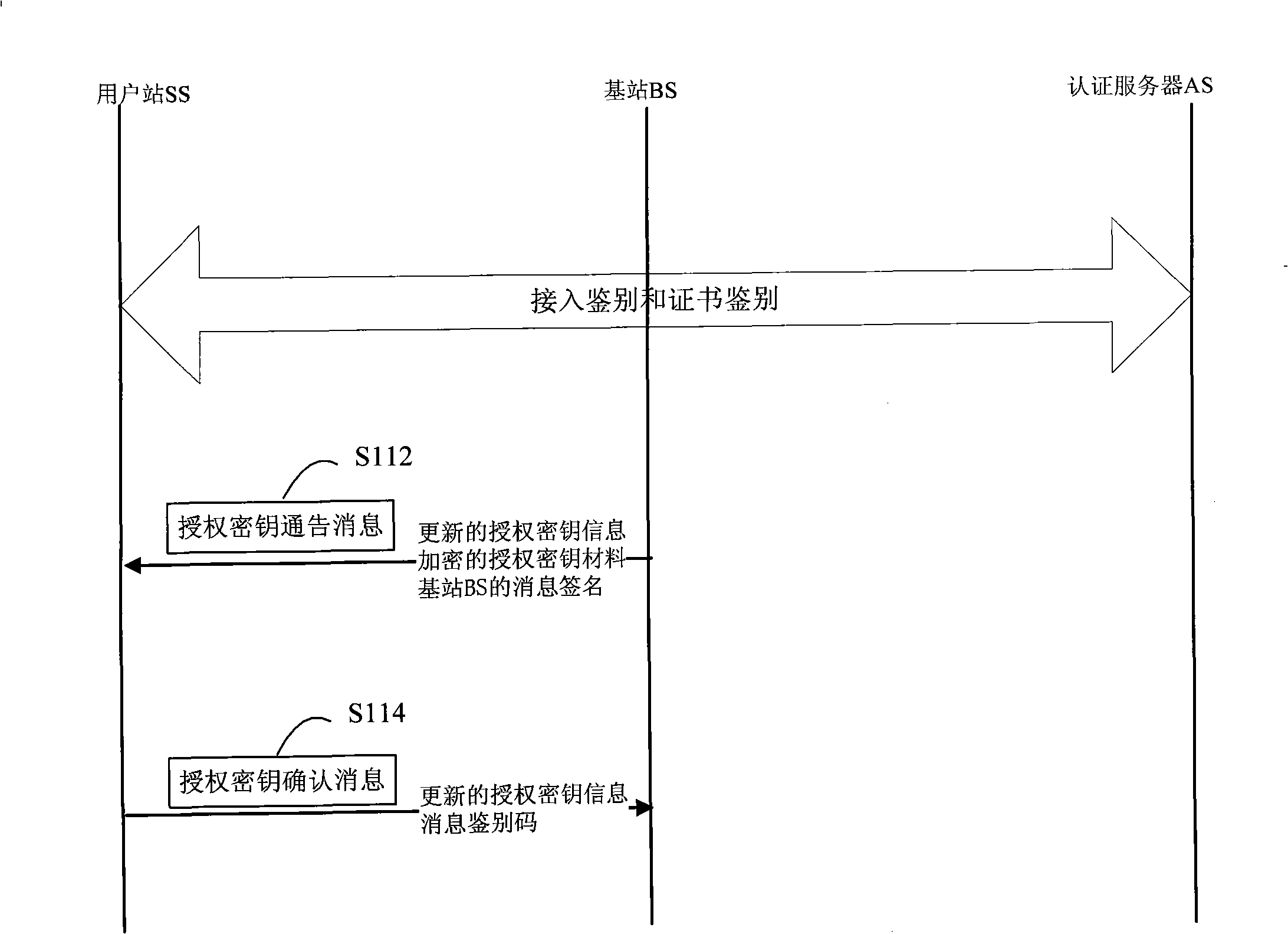
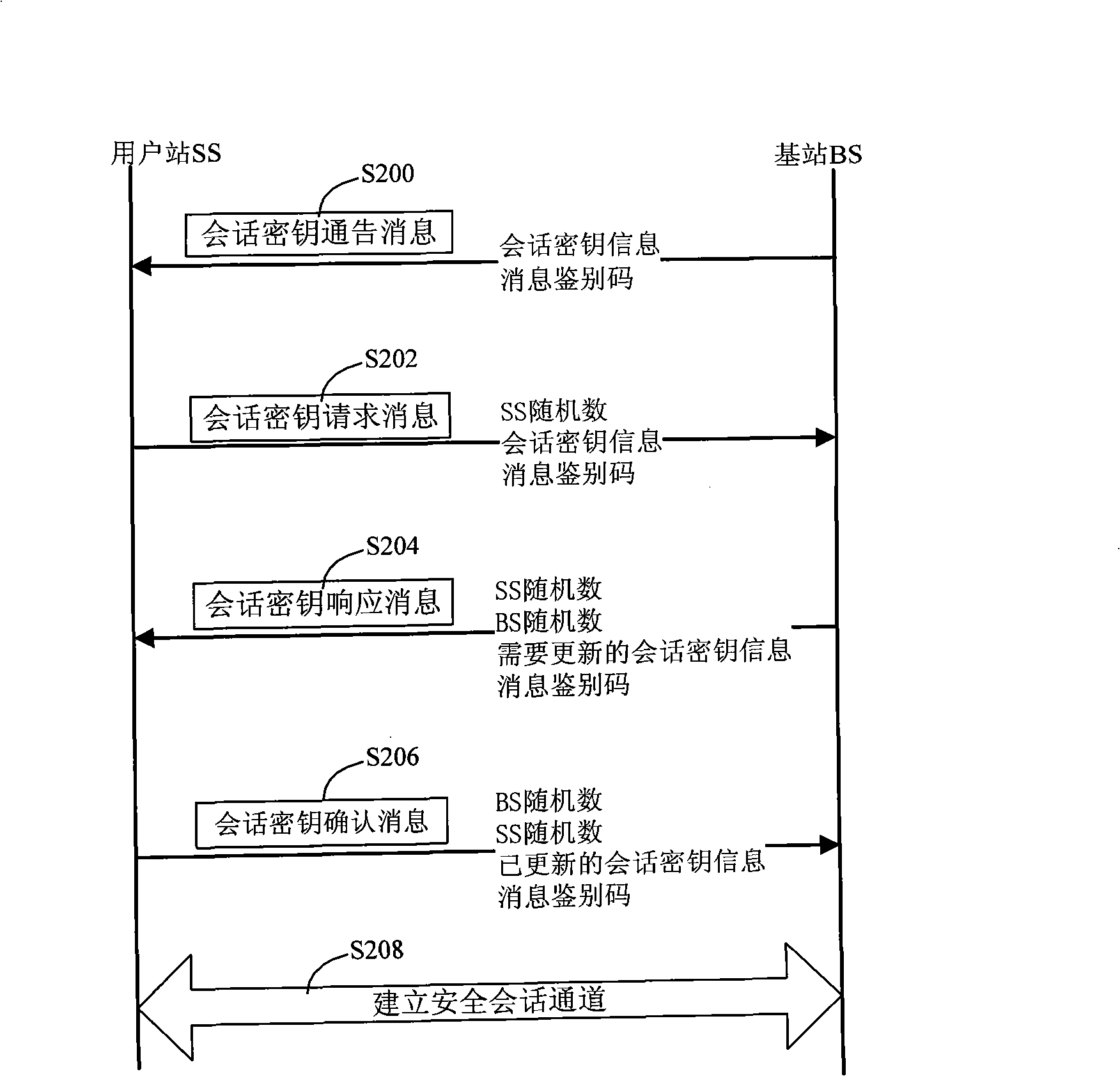
The invention relates to a method for safe accessing of a wireless metropolitan area network, which comprises an authenticating step and a session key negotiating step. The authenticating step comprises that: a subscriber station SS sends a request message for access authentication to a base station BS; the BS sends a request message for certificate authentication to an authentication server AS; the AS verifies the request message for certificate authentication and sends a response message for certificate authentication to the BS; the BS verifies the validity of the identity of the SS according to the response message for certificate authentication; if the SS is valid, the BS sends the response message for access authentication to the SS; the SS verifies the validity of the BS according to the response message for access authentication; if the BS is valid, the SS uses the encryption certificate key of the SS to decrypt the material of authentication key. The SS signing certificate in the proposal is used for stating the identity and the SS encrypting certificate is used for encrypting and decrypting the material of authentication key so as to reduce the risk that the key is decrypted; through verifying the certificates of the BS and the SS by the AS, authentication for the subscriber station SS and the base station BS is realized and security level is improved.
Owner:GCI SCI & TECH
Cloud service-based community access control system and door opening method
ActiveCN107492168AImplement authorizationWide range of servicesIndividual entry/exit registersTransmissionAccess timeMarine navigation
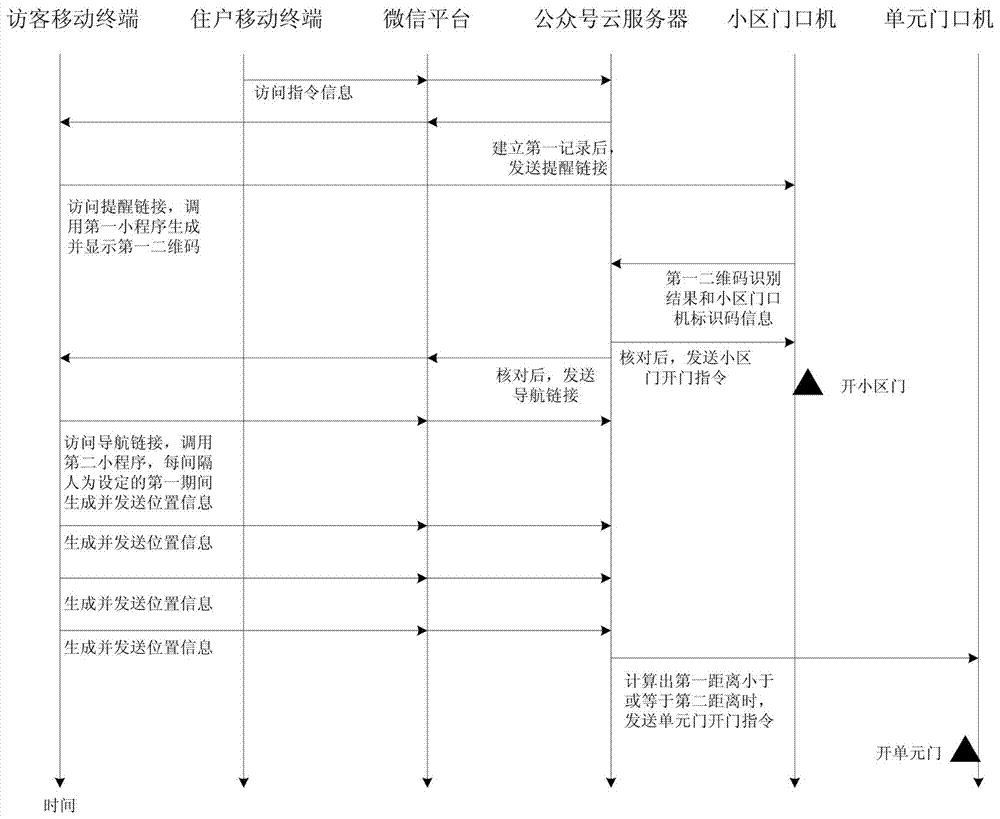
The invention discloses a cloud service-based community access control system and a door opening method. The cloud service-based community access control system comprises a WeChat platform, a resident mobile terminal platform, a visitor mobile terminals, an official account cloud server, a community entrance machine and an apartment entrance machine, an access control cloud service WeChat official account is followed through the resident mobile terminal and the visitor mobile terminal to realize the communication of the official account cloud server with the resident mobile terminal and the visitor mobile terminal. In the relevant door opening method, a resident can pre-authorize and restrict the access time of visitors; and the check of the visitor's identity can be realized, navigation from the community entrance machine to the apartment entrance machine is provided for the visitor, and an apartment door is automatically opened when the visitor is close to the apartment door.
Owner:XIAMEN DNAKE INTELLIGENT TECH CO LTD
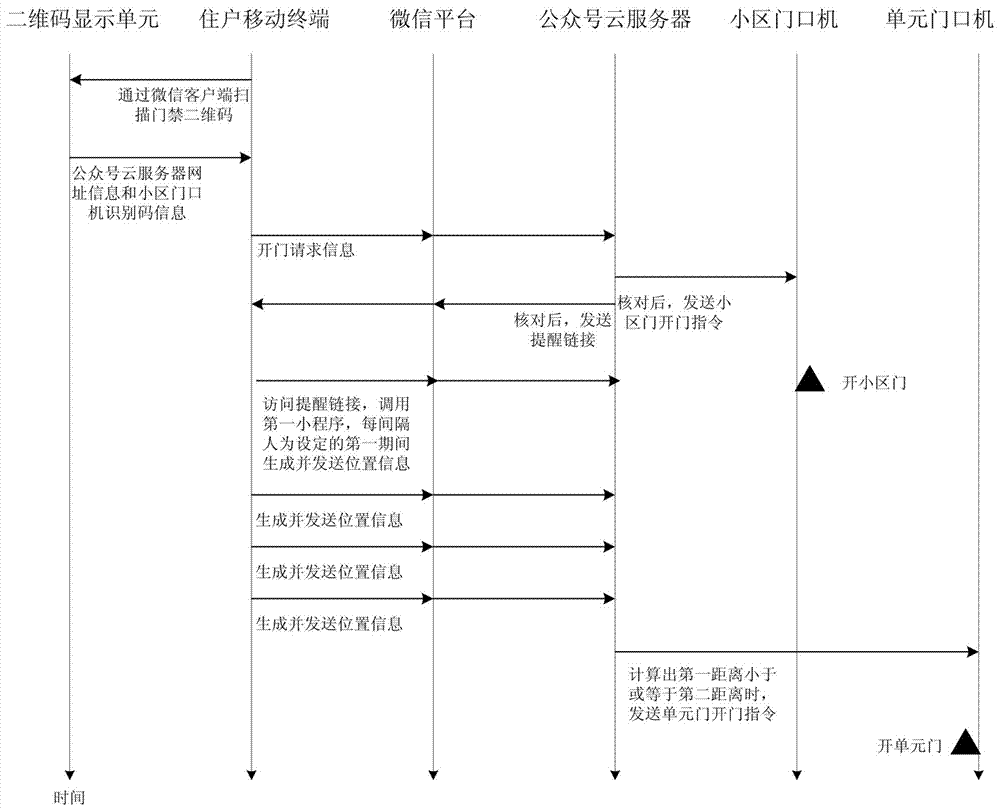
Community access control system based on WeChat and door opening method
ActiveCN107507305AWide range of servicesLow costIndividual entry/exit registersData switching networksAccess timeComputer terminal
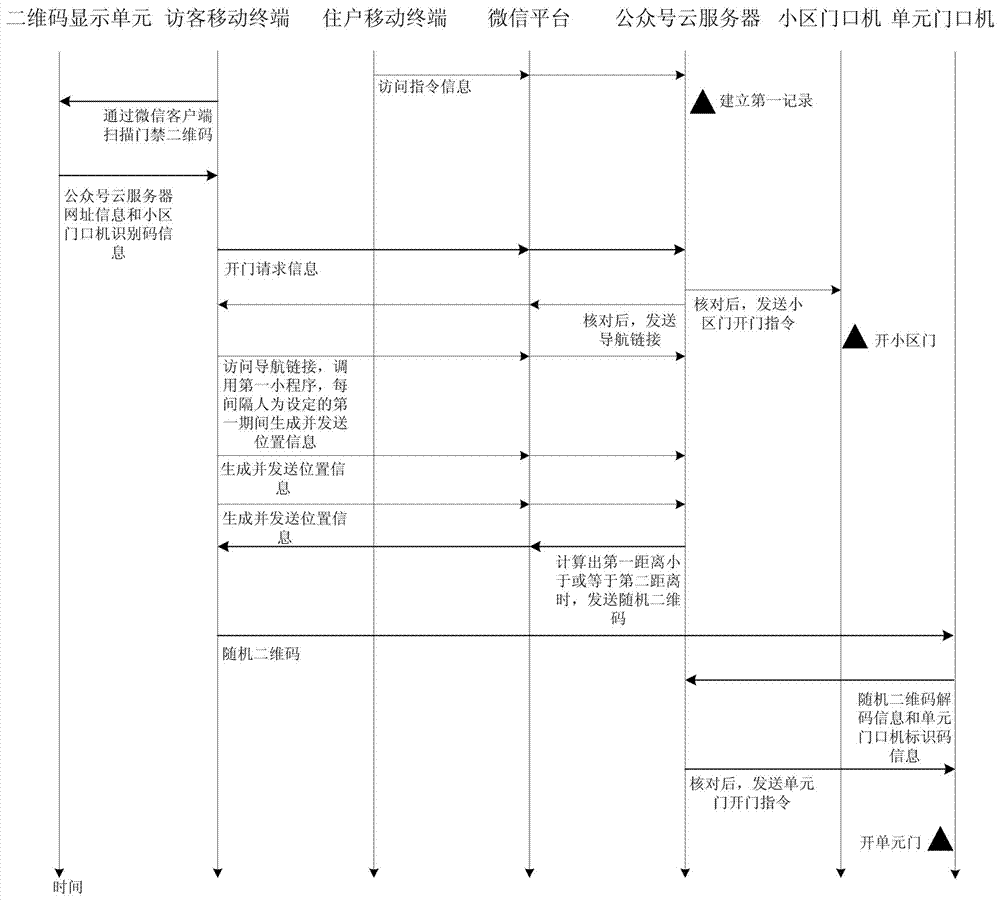
The invention discloses a community access control system based on WeChat and a door opening method. The community access control system based on WeChat comprises a two-dimensional code display unit, a WeChat platform, a household mobile terminal, a visitor mobile terminal, an official account cloud server, a community entrance machine and a unit entrance machine. By subscribing an access control cloud service WeChat official account through the household mobile terminal and the visitor mobile terminal, communication of the official account cloud server and the household mobile terminal with the visitor mobile terminal can be realized. In the relevant door opening method, the household can carry out pre-authorization and limit the access time of a visitor, also the method can achieve identity verification of the visitor, also can provide navigation for the visitor from the community entrance machine to the unit entrance machine, and enhances the door opening experience of the household and visitor.
Owner:XIAMEN DNAKE INTELLIGENT TECH CO LTD
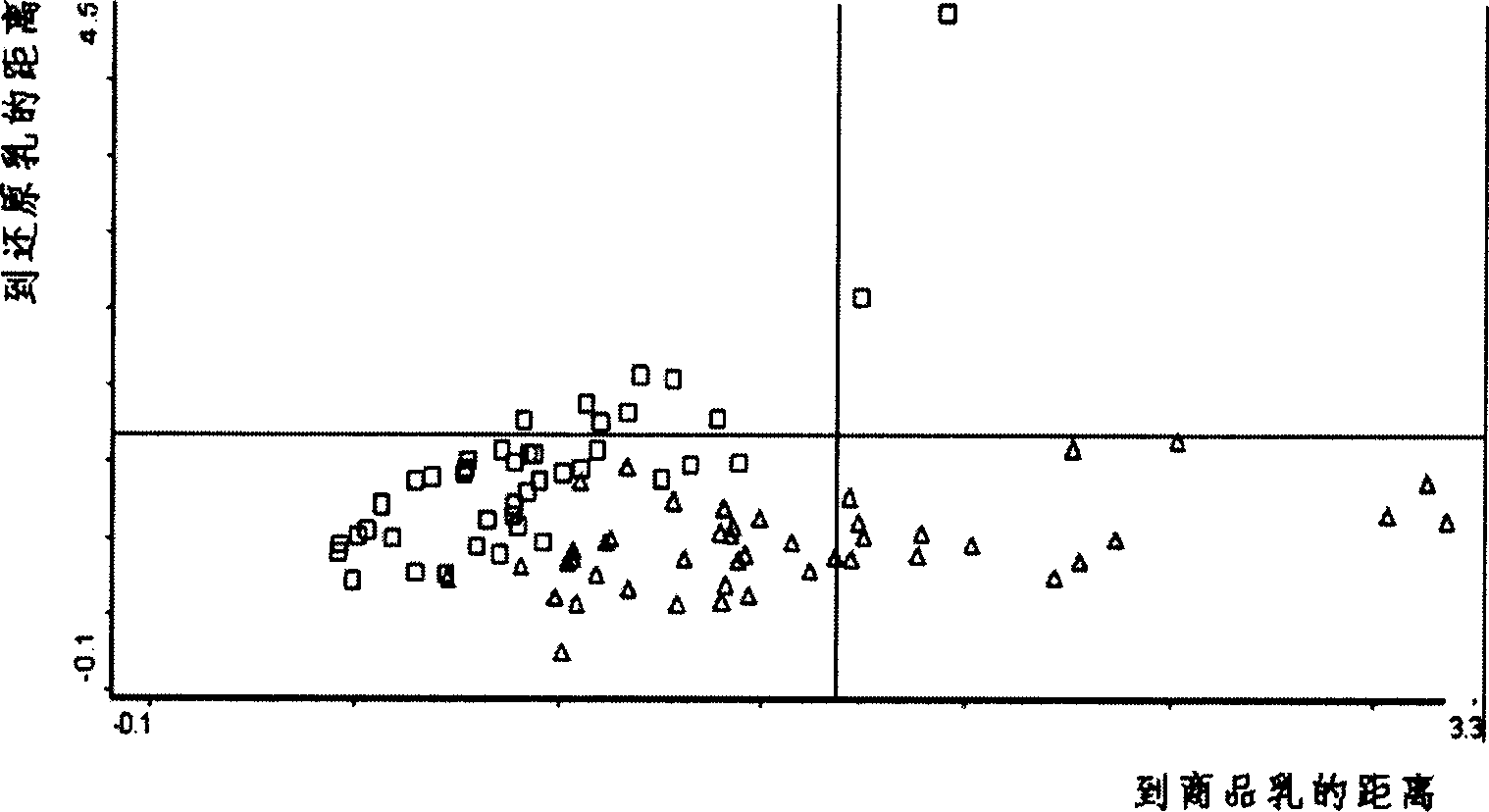
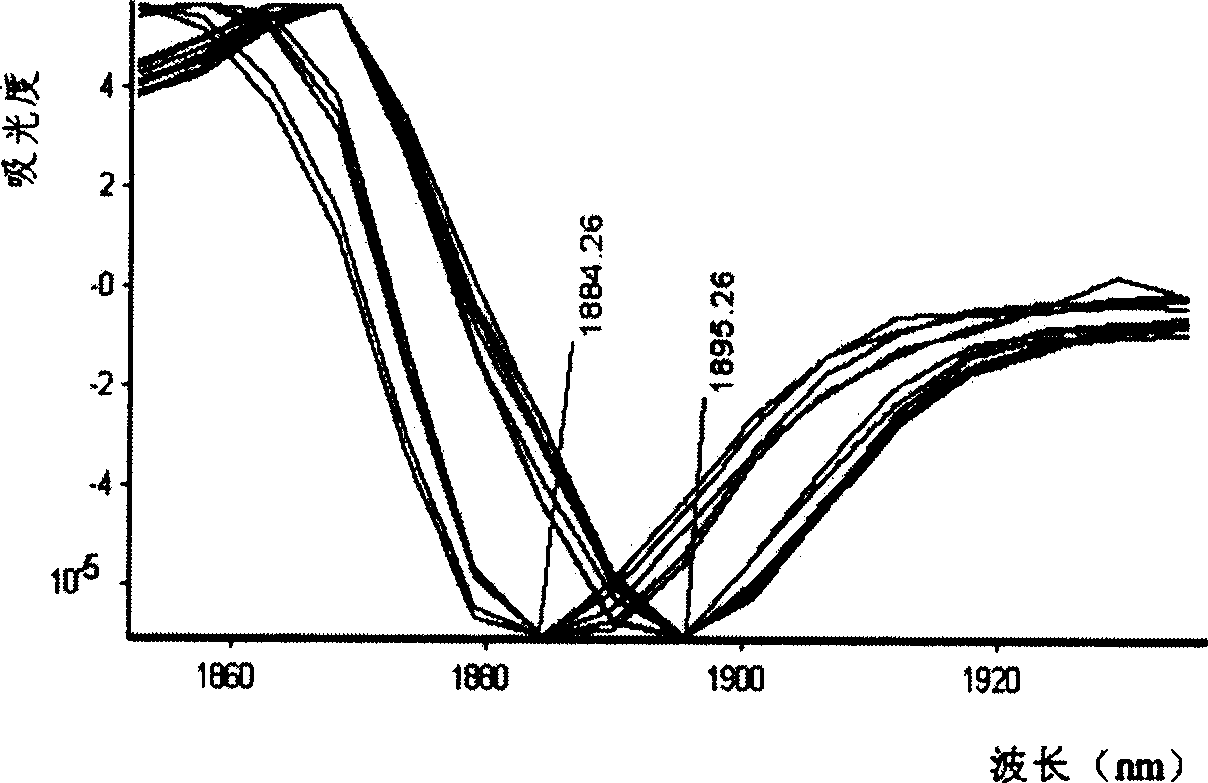
Method for identifying reductive milk in fresh milk and commodity milk by using near infrared spectrum
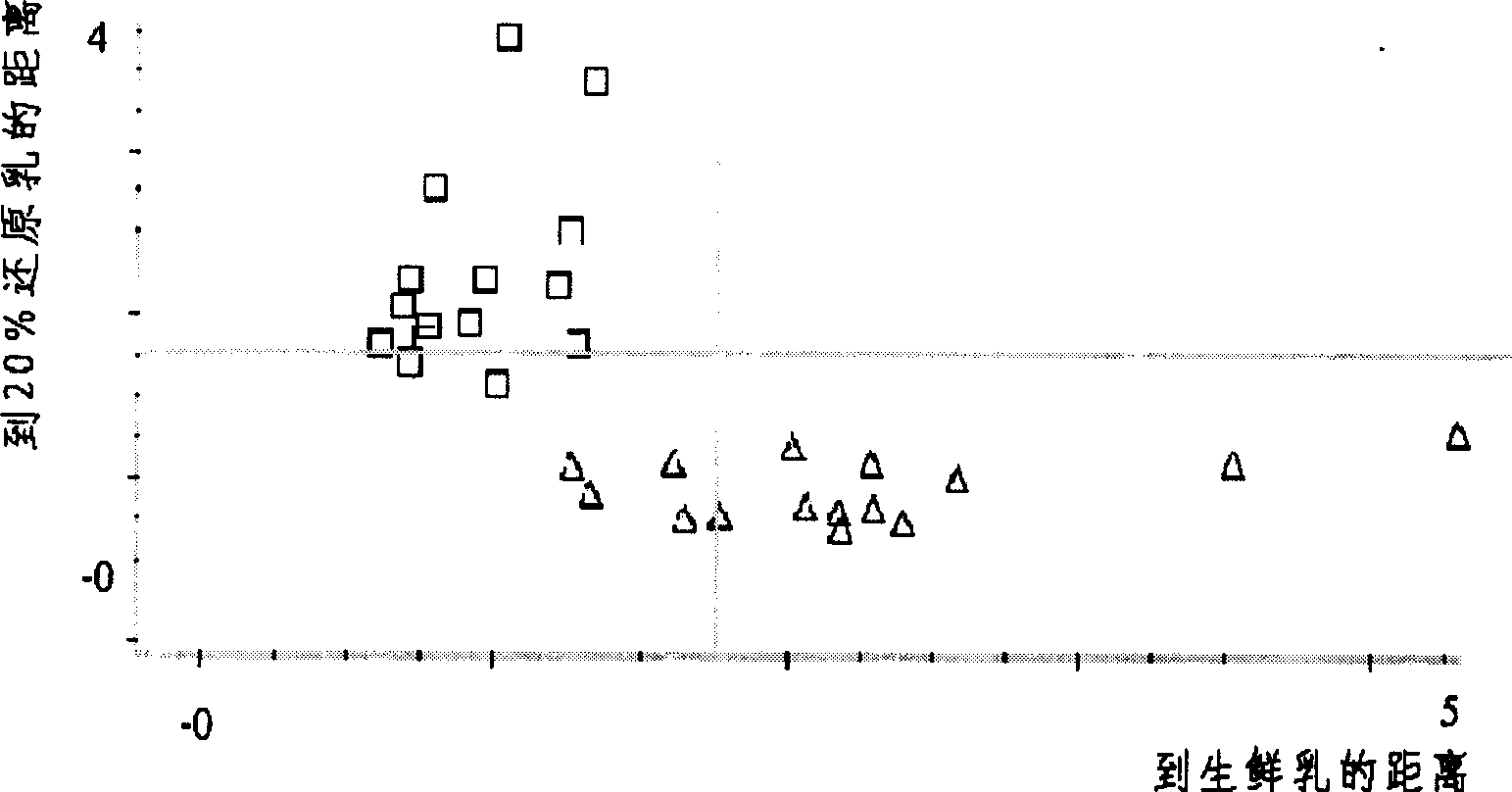
InactiveCN1804582ARealize authenticationImprove accuracyTesting dairy productsColor/spectral properties measurementsNear infrared spectraData treatment
The invention provides a method for using near infrared spectra to identify the reduction milk-like liquid of fresh milk and product milk, which comprises the following steps: first doing front process to the sample with known reduction milk-like liquid content, collecting the sample's near infrared spectra, establishing the qualitative or quantitative identifying model, collecting the near infrared spectra of the unknown sample to do data process and doing qualitative or quantitative identifying.
Owner:CHINA AGRI UNIV
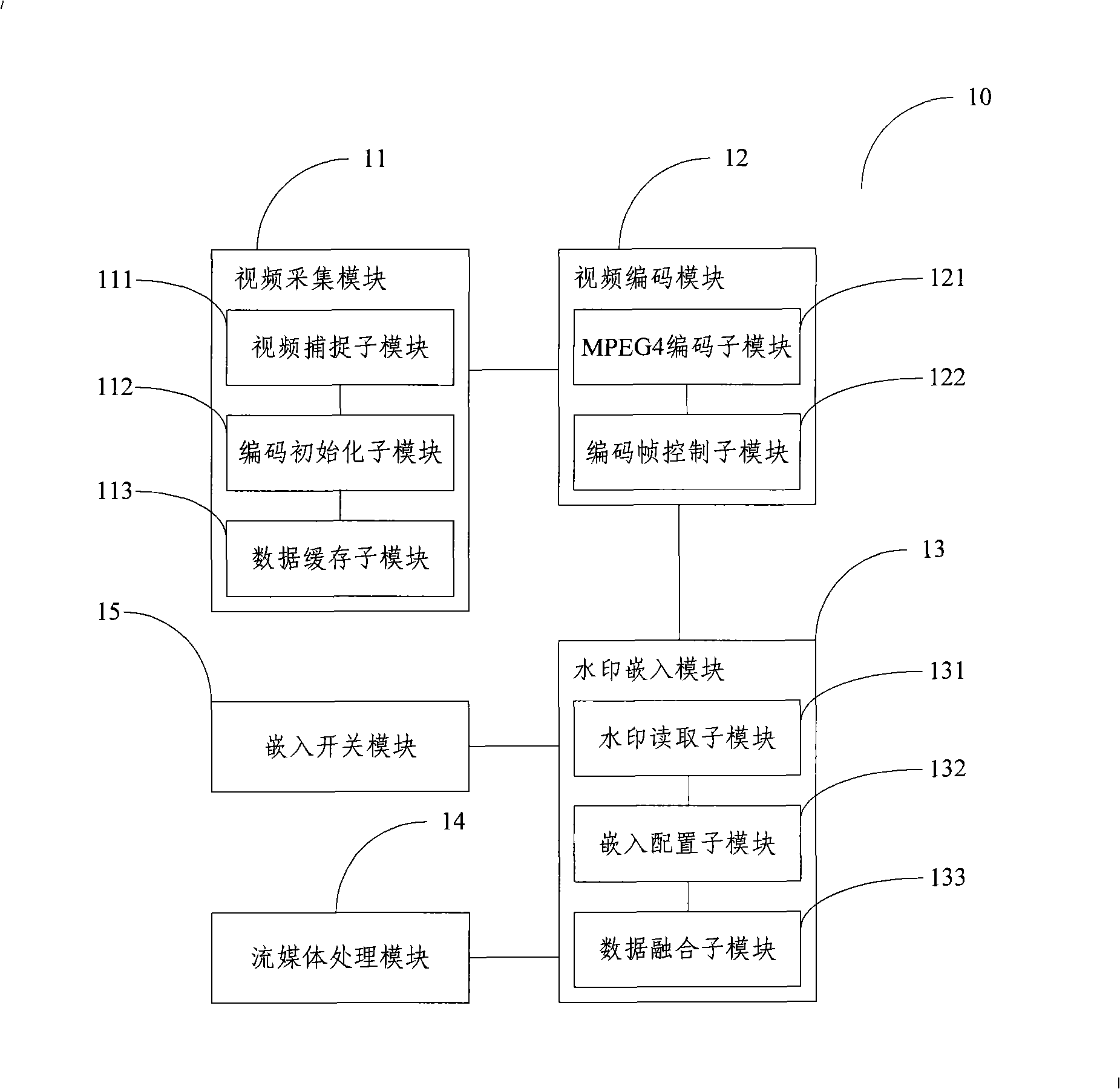
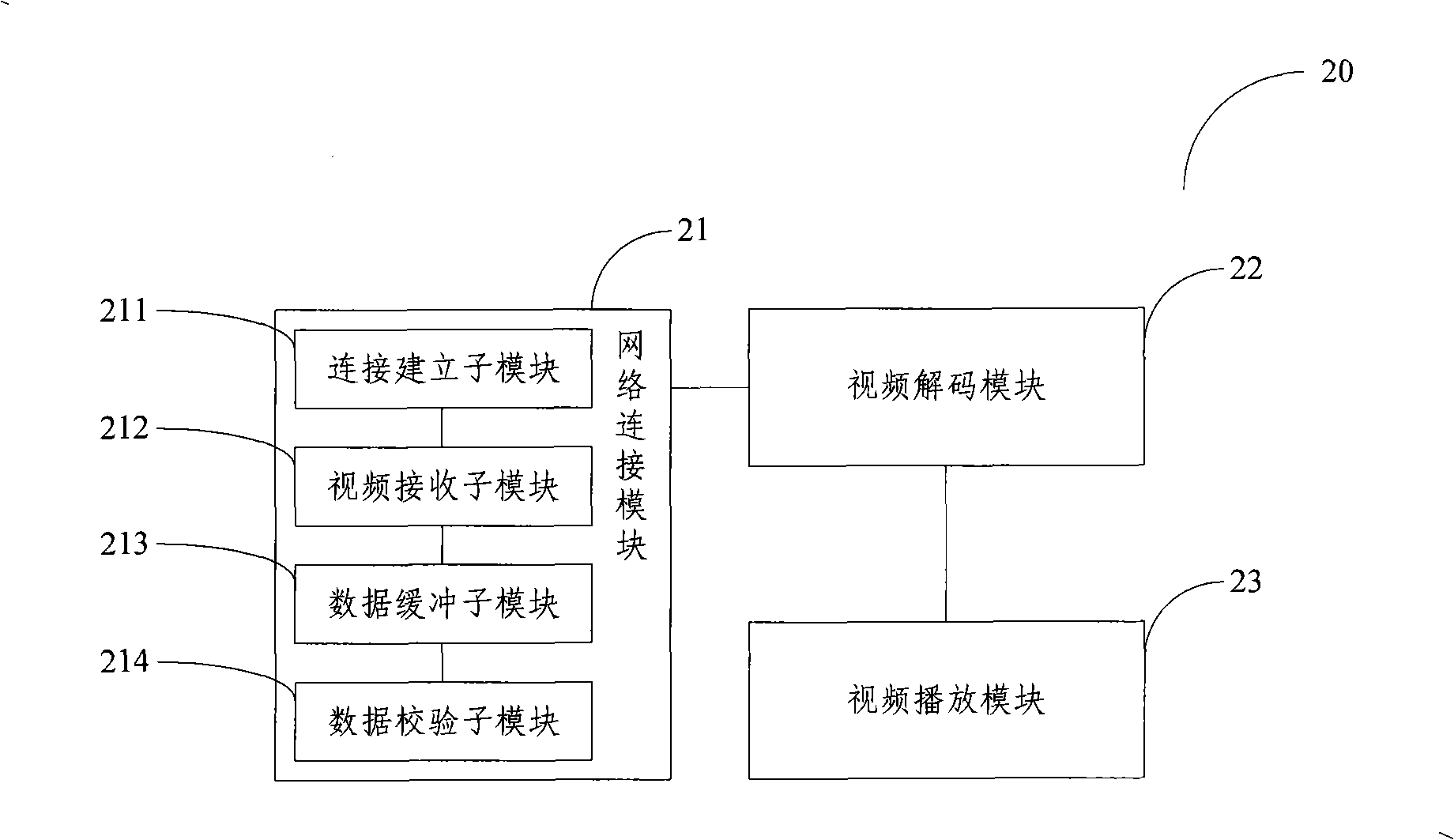
System for real time embedding visible watermark into flow medium as well as server terminal and client terminal thereof
ActiveCN101325702AAchieve protectionRealize authenticationPulse modulation television signal transmissionImage data processing detailsVideo encodingTransfer procedure
The invention relates to a server side of a stream media visible watermark real-time embedding system, comprising: a video collecting module for real-time collection of video data; a video decoding module for compressive coding of the video data; a watermark embedding module for embedding information of the digital watermark into a code stream output after the video decoding module compresses and codes the video data in order to acquire the video data comprising the watermark; a stream media processing module for storing the video data comprising the watermark and output by the watermark embedding module and transferring the video data in accordance with a connection request from a client side. The invention also comprises a corresponding client and a stream media visible watermark real-time embedding system composed by the server side and the client side. The embodiment of the inventive stream media visible watermark real-time embedding system integrates the digital watermark with coding of the video data, which accomplishes real-time embedding for the watermark in the process of transmission of the stream media so as to achieve protection and authentication for copyright of the stream media information in the process of visiting.
Owner:TSINGHUA UNIV
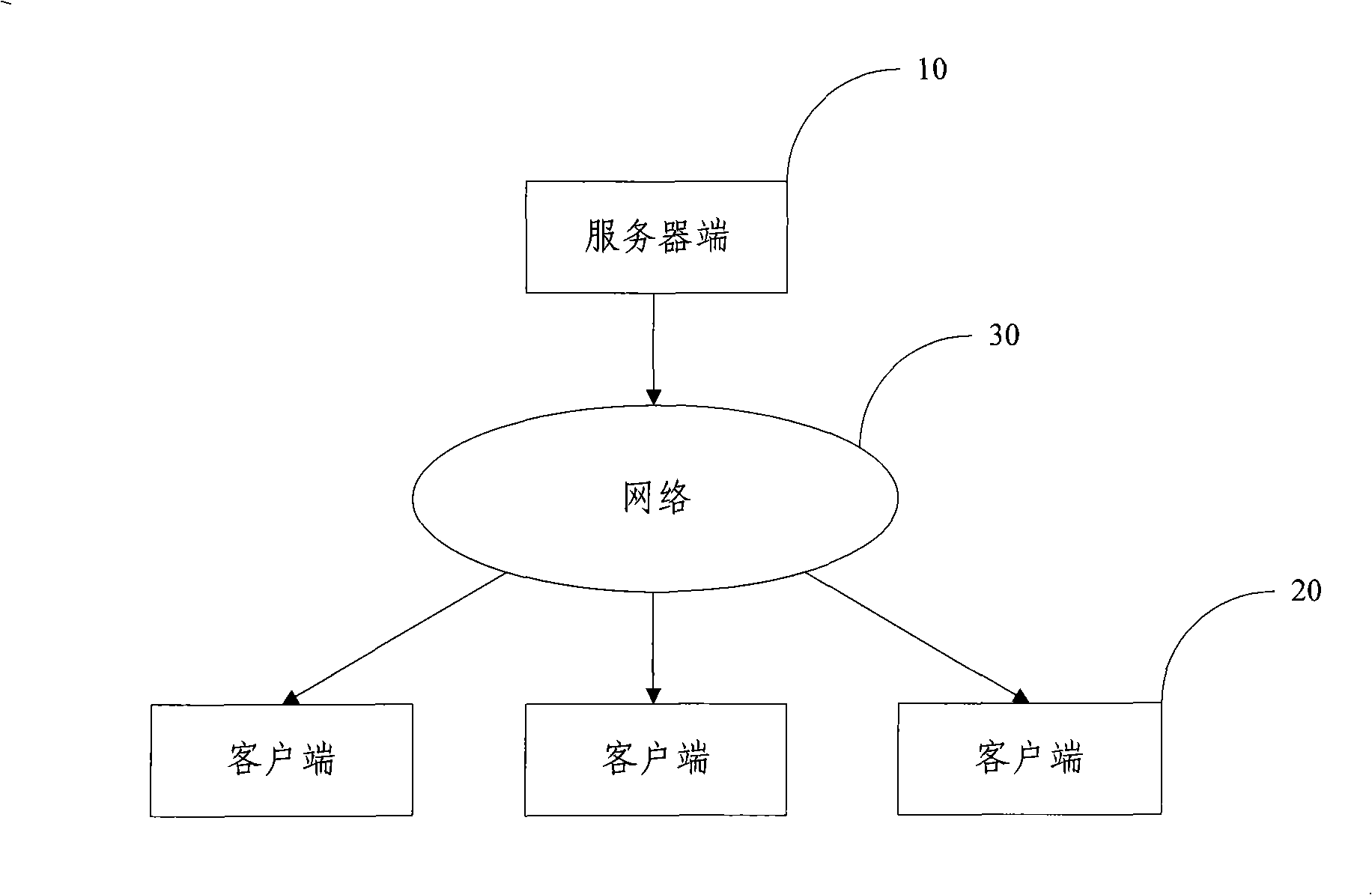
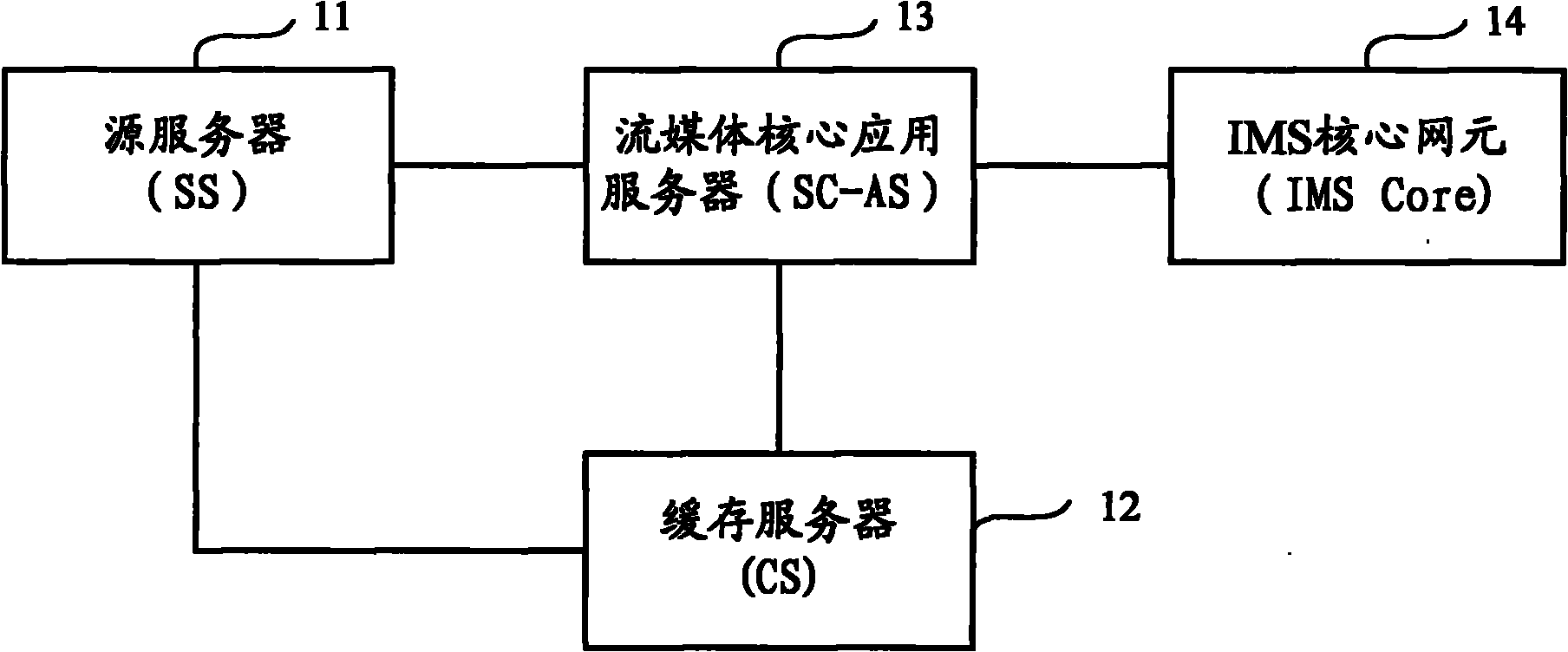
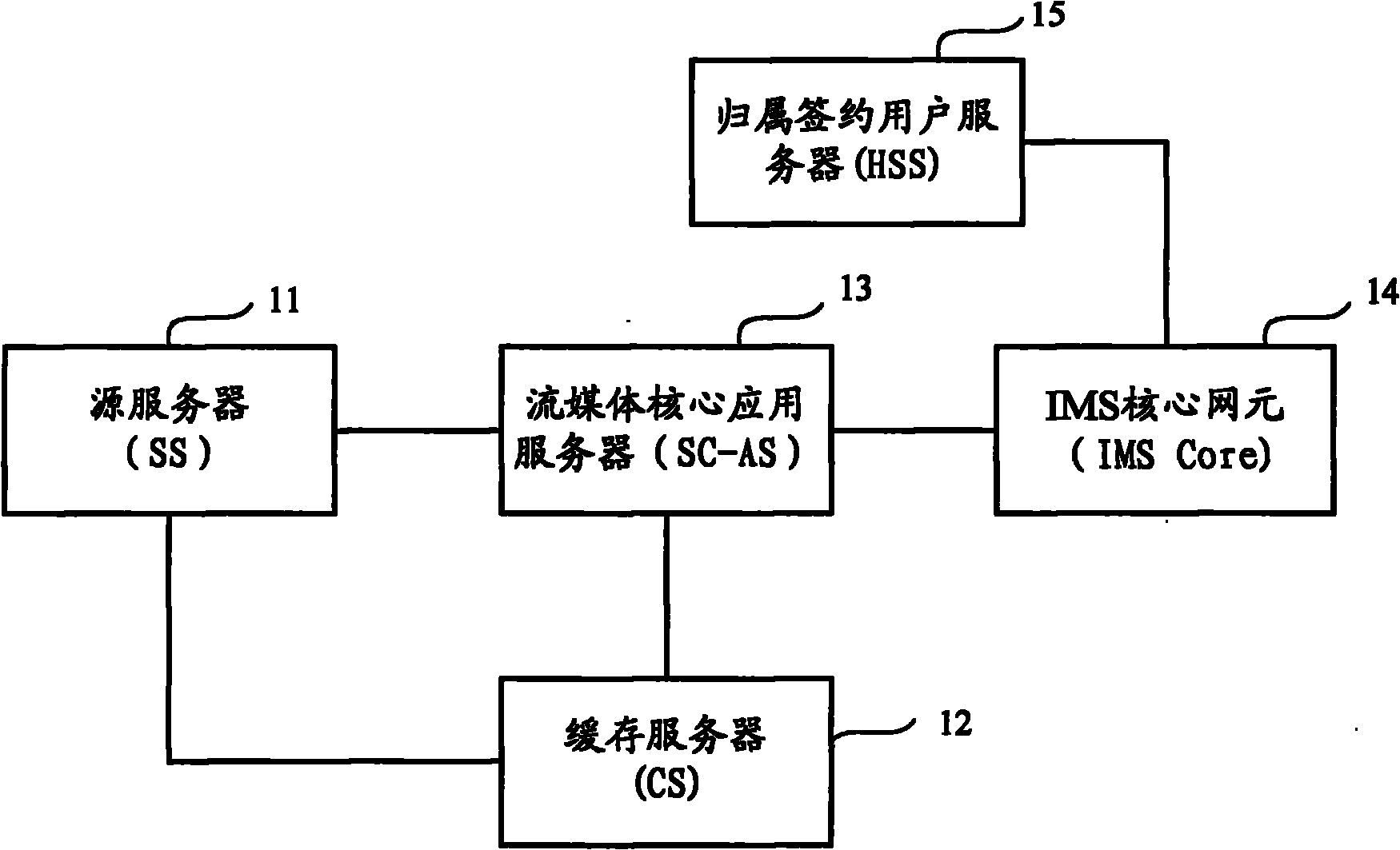
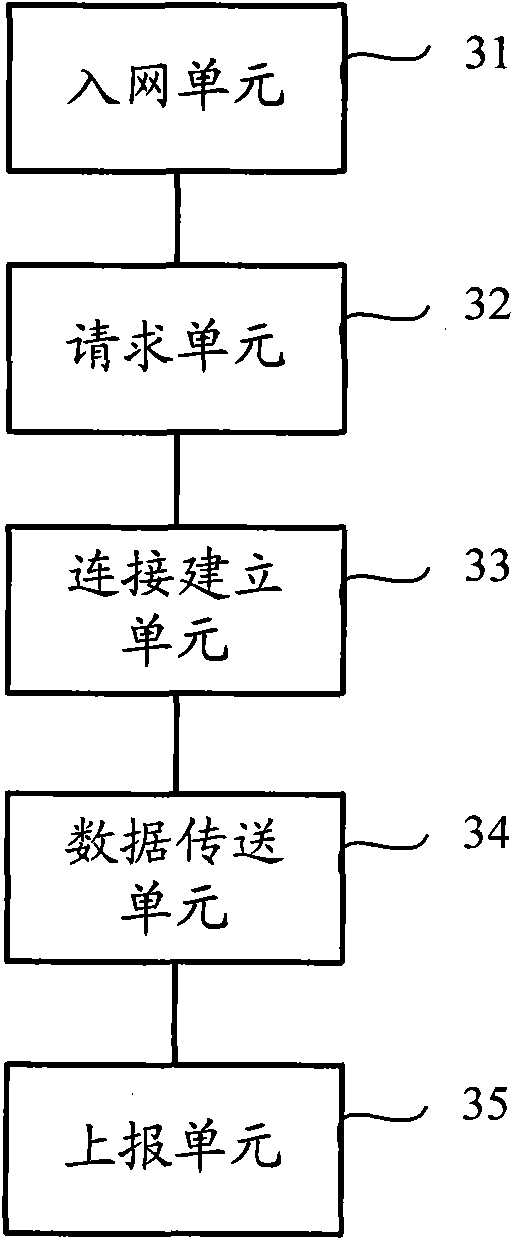
P2P (Point-to-Point) streaming media system, P2P user equipment and streaming media data transmitting method
InactiveCN101924778ACopyright protectionRealize managementData switching networksApplication serverData information
The invention discloses a P2P (Point-to-Point) streaming media system which comprises a source server, a caching server, a streaming media key application server and an IMS (IP Multimedia Subsystem) key network element, wherein the source server stores streaming media contents; the caching server caches streaming media data and sends to P2P user equipment; the streaming media key application server is interacted with the caching server to generate program information, obtains owned streaming media data information and current state information reported by the P2P user equipment through the IMS key network element, and provides corresponding program information and resource information for the P2P user equipment requesting streaming media service; and the IMS key network element accesses the P2P user equipment into an IMS network and controls the connection negotiation among the P2P user equipment, the caching server providing the downloading of the corresponding streaming media data and other P2P user equipment. The invention also provides the P2P user equipment and a streaming media data transmitting method. The invention realizes that the P2P user equipment is accessed into the IMS network through the IMS key network element for controlling the streaming media service.
Owner:CHINA MOBILE COMM GRP CO LTD
Identification log-on method and device for access non IMS mobile terminal into IMS field
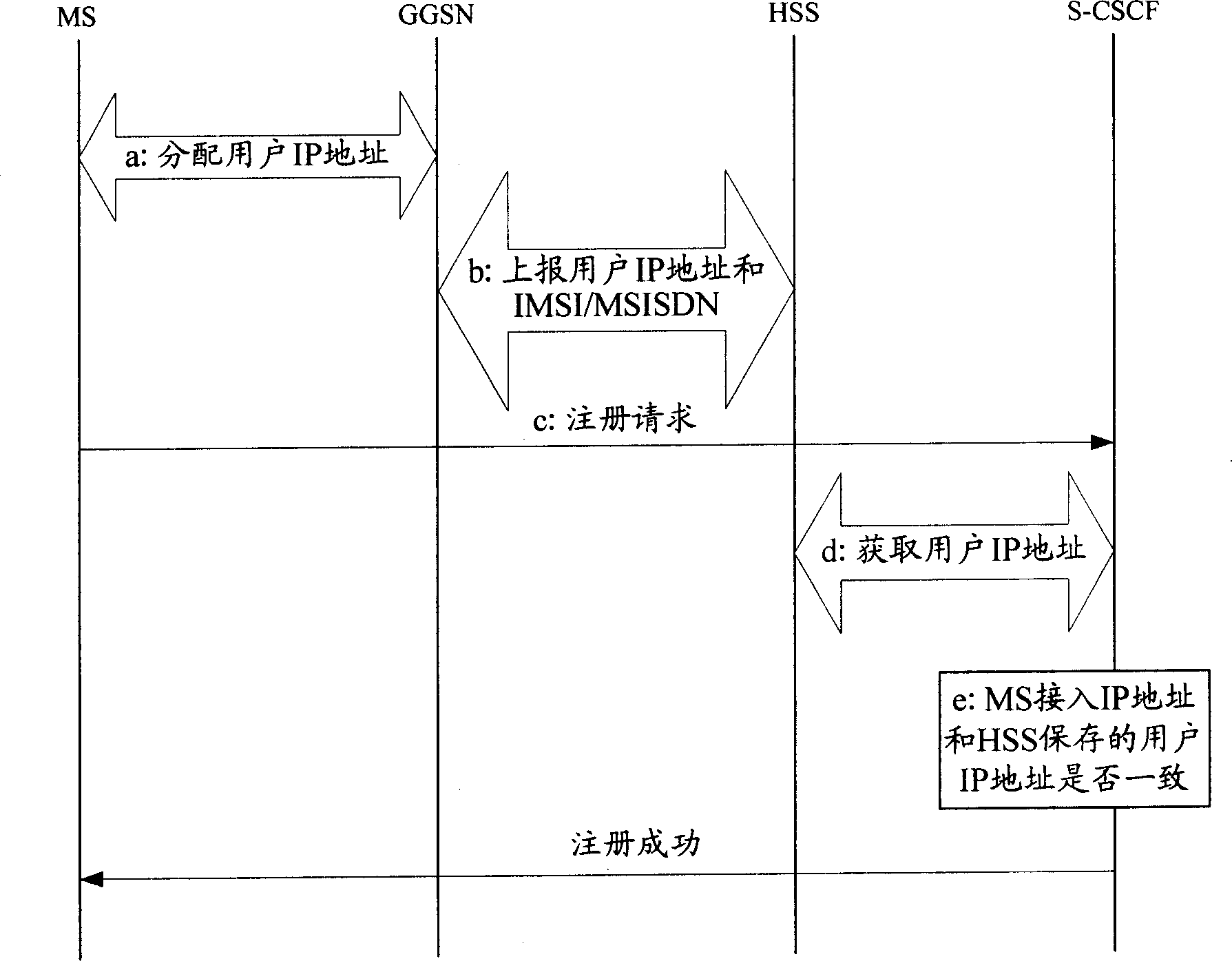
InactiveCN1870822AGuaranteed reliabilityGuaranteed successful registrationUser identity/authority verificationRadio/inductive link selection arrangementsAuthenticationSignaling process
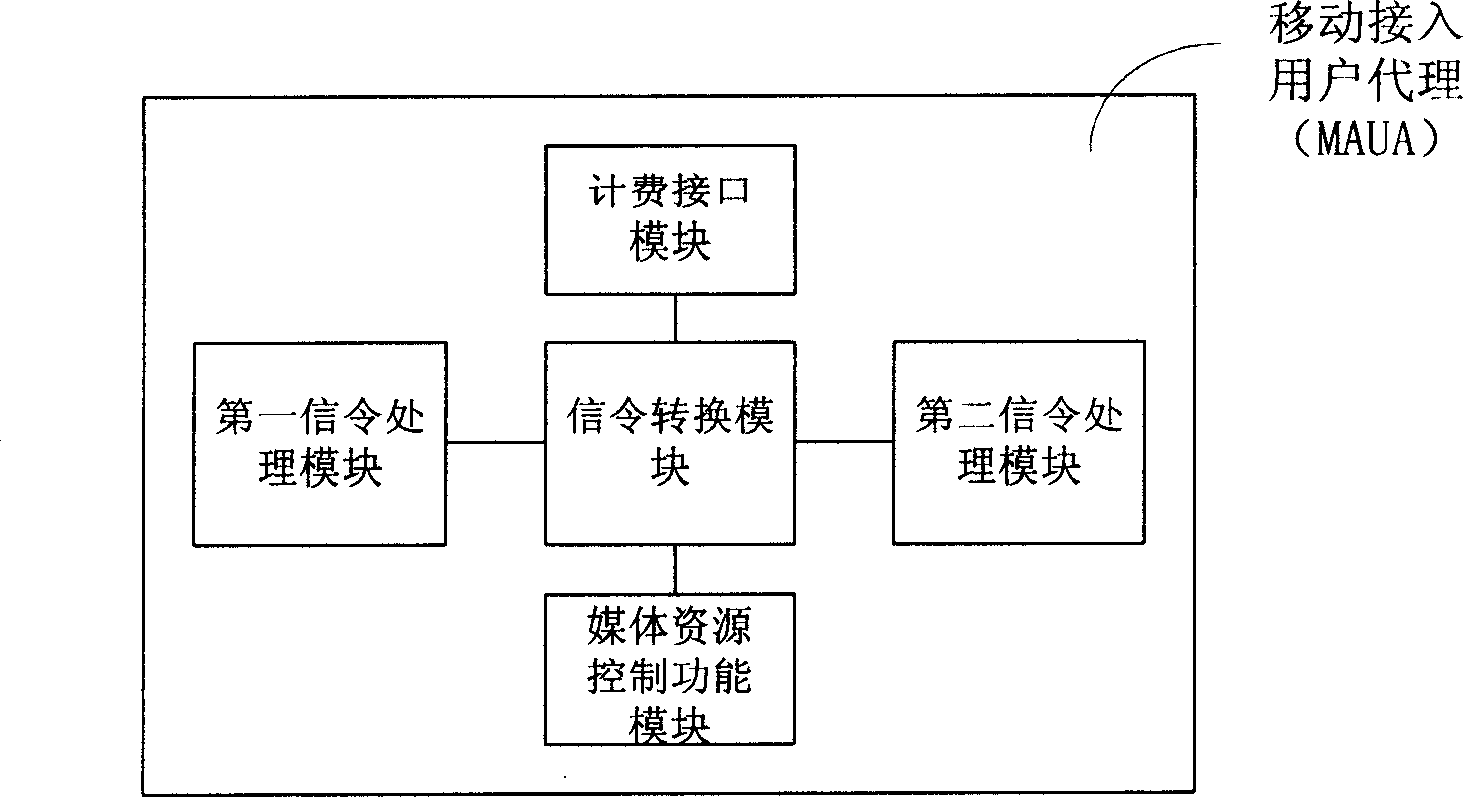
The invention discloses a log-on authentication method for a non-IMS mobile terminal access IMS domain including: a non-IMS mobile terminal user accesses mobile agent initiates registration request and receives the authentication random number from IMS domain by the access mobile user agent, carries out calculation on authentication according to the random number and then transmits the result to the IMS domain by the mobile access user agent for authentication. The invention also discloses a mobile access user agent device including: a first signaling process module, a signaling conversion module and a second signaling process module to interact between the non-IMS terminal and the IMS domain to realize format conversion between information from the IMS domain and non-IMS terminal supported information.
Owner:HUAWEI TECH CO LTD
Terminal of selecting access to mobile network or wireless LAN
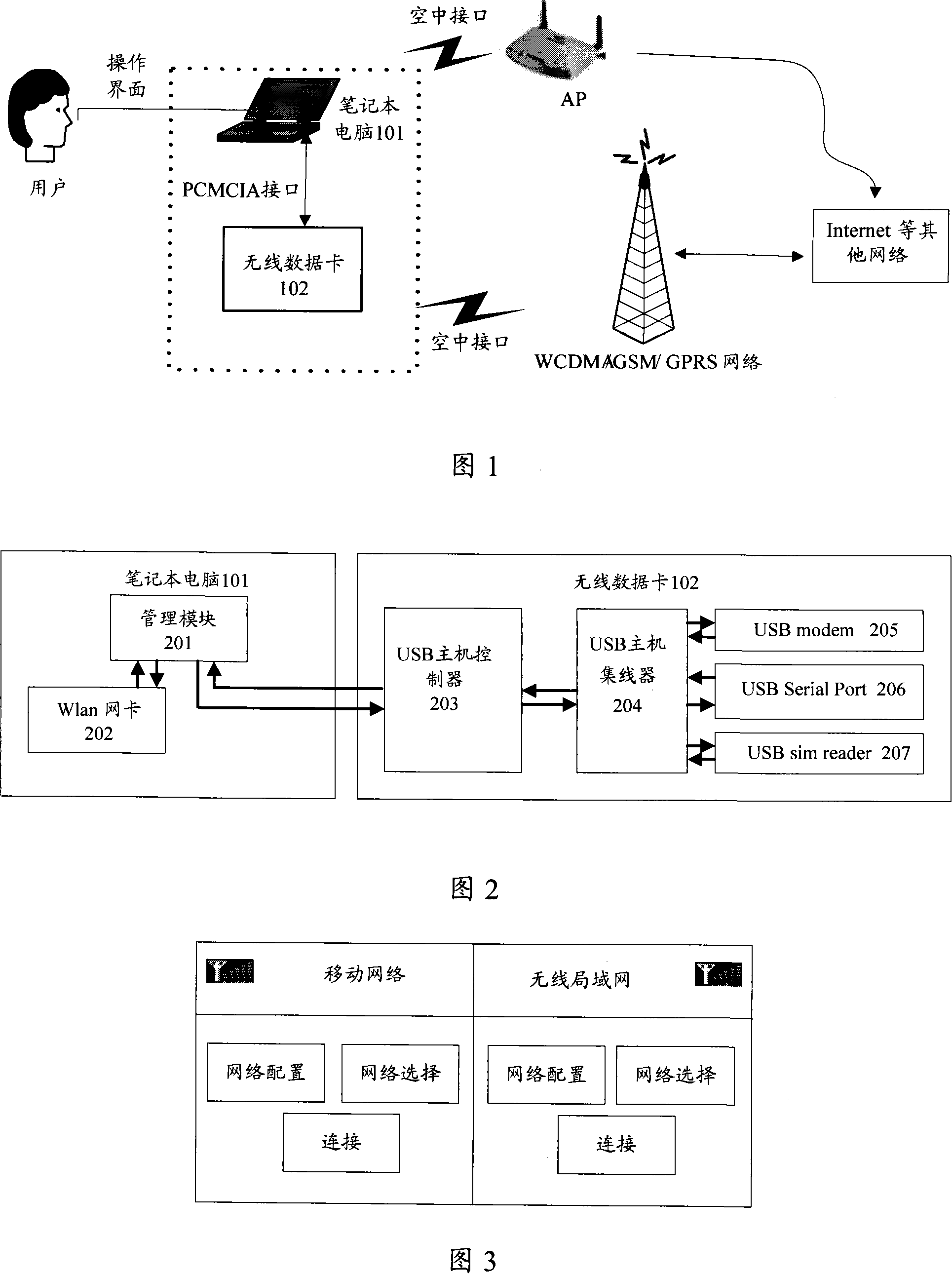
InactiveCN101141354AExpand business scopeRealize authenticationData switching detailsData switching by path configurationThird generationWireless data
The utility model discloses a terminal used to access the mobile network or wireless local area networks. The terminal comprises a PC's Wlan network card which is used to connect the wireless local area networks. The PC is also provided with the wireless data card and the management module; the wireless data card is used to connect the mobile network as well as authorize and certify the Wlan network card's access to the wireless local area networks; the control module is respectively connected with the wireless data card and the Wlan network card, so as to conduct relevant control. The Wlan network card is also initialized and the network information from the Wlan network card and the wireless data card can be sent to the operating interface of the PC. The utility model can help the user selectively access 3G mobile network and Wlan network, so as to not only provide the users with convenience, but branch out the service scope of the mobile carriers.
Owner:ZTE CORP
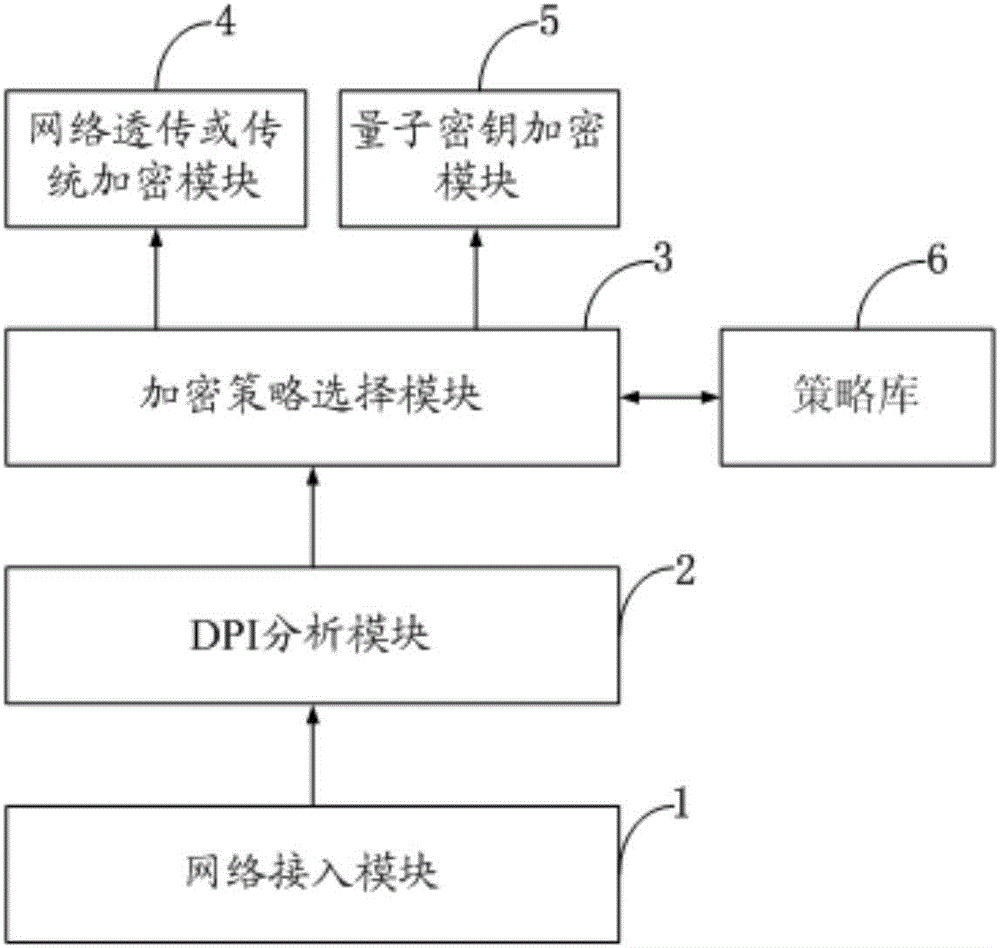
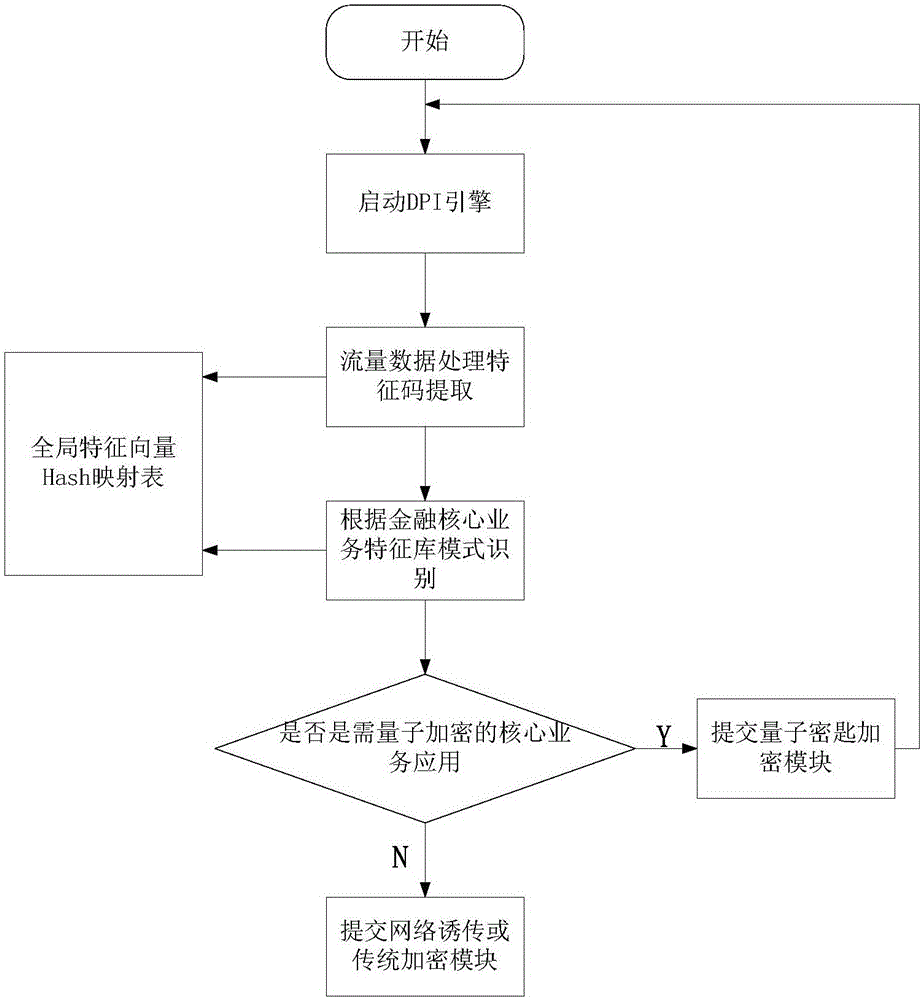
Quantum secrete key distribution method based on DPI
InactiveCN106161015ARealize authenticationRealize quantum secure communicationKey distribution for secure communicationTraffic volumeKey distribution
The invention discloses a quantum secrete key distribution method based on a DPI. The quantum secrete key distribution method based on the DPI comprises the steps that a DPI analysis module of a system carries out application layer analysis on a network data stream, and service types of various applications are recognized and submitted to an encryption strategy selecting module; the encryption strategy selecting module carries out quantum secrete key encryption or traditional secrete key encryption or selects transparent transmission on services with different safety levels according to priorities; a network transparent transmission or traditional secrete key encryption module carries out unencrypted transparent transmission or carries out encryption based on a traditional encryption algorithm based on algorithm safety; a quantum secrete key encryption module carries out quantum encrypted transmission. According to the quantum secrete key distribution method based on the DPI, network core service flows are distinguished and identified, different service flows are encrypted in a graded mode, a quantum secrete key distribution encryption mode or a traditional encryption mode is selected according to encryption strategies, quantum secrete communication of the core service flow of the network is achieved, and the transmission efficiency of the network services is considered.
Owner:CHANGCHUN UNIV
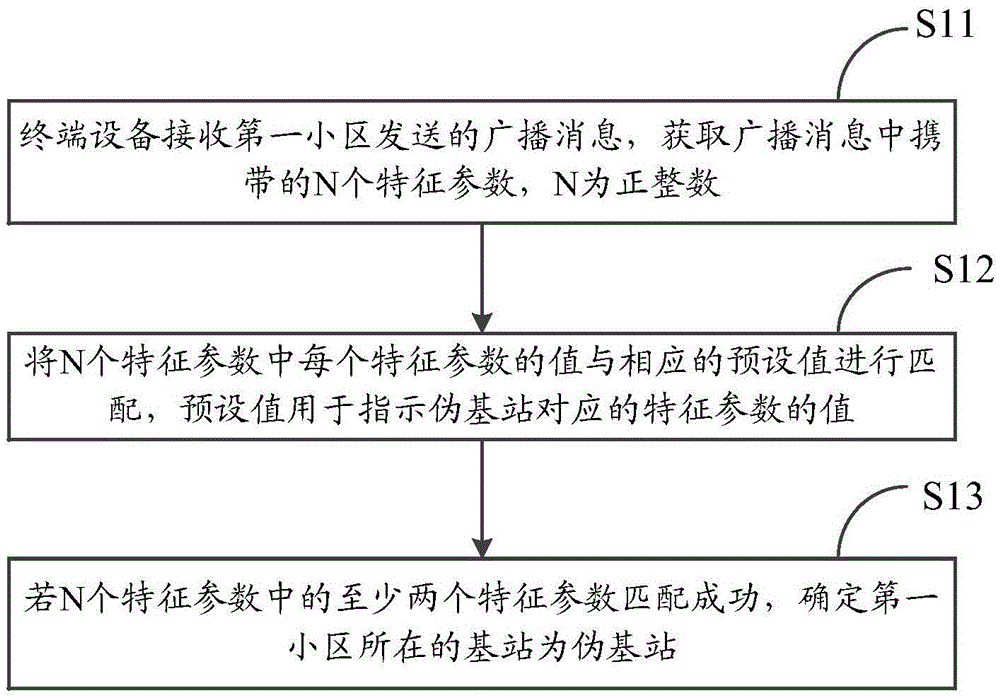
Information processing method and terminal device
InactiveCN105554764ARealize authenticationImprove efficiencySecurity arrangementInformation processingTerminal equipment
The invention provides an information processing method and a terminal device, aiming to improve the effect of verifying pseudo base stations by the terminal device. The method comprises the steps that the terminal device receives a broadcast message sent from a first cell, and acquires N characteristic parameters carried in the broadcast message, wherein N is a positive integer; the value of each of the N characteristic parameters is matched with a corresponding preset value, wherein the preset value is used for indicating the value of the characteristic parameter corresponding to the pseudo base station; and if at least two of the N characteristic parameters are matched successfully, it is determined that the base station in which the first cell is is the pseudo base station.
Owner:LENOVO (BEIJING) CO LTD
Method for determining multiple kinds of animal origin meat based on liquid chromatographic-tandem mass spectrometric technology
The invention provides a method for determining multiple kinds of animal origin meat based on the liquid chromatographic-tandem mass spectrometric technology. The method includes the steps of pretreating samples, screening multiple standard meat sample feature polypeptides, and detecting feature polypeptides in meat samples to be detected through the liquid chromatographic-tandem mass spectrometric technology and the like. Components of the multiple kinds of animal origin meat can be identified by adopting the method, the scanning function of liquid chromatography-tandem mass spectrometry is brought into full play in the technology, the selected ion monitoring mode is monitored to collect signals in real time, second-level daughter ion intensity triggering is used, corresponding parent ion second-level fragmentation full-scanning spectrograms are collected to obtain a more exact qualitative information function, interference of a complex matrix is avoided, and the false positive possibility is reduced. In addition, the method is simple in pretreatment and facilitates operation on samples in batches.
Owner:CHINA MEAT RES CENT
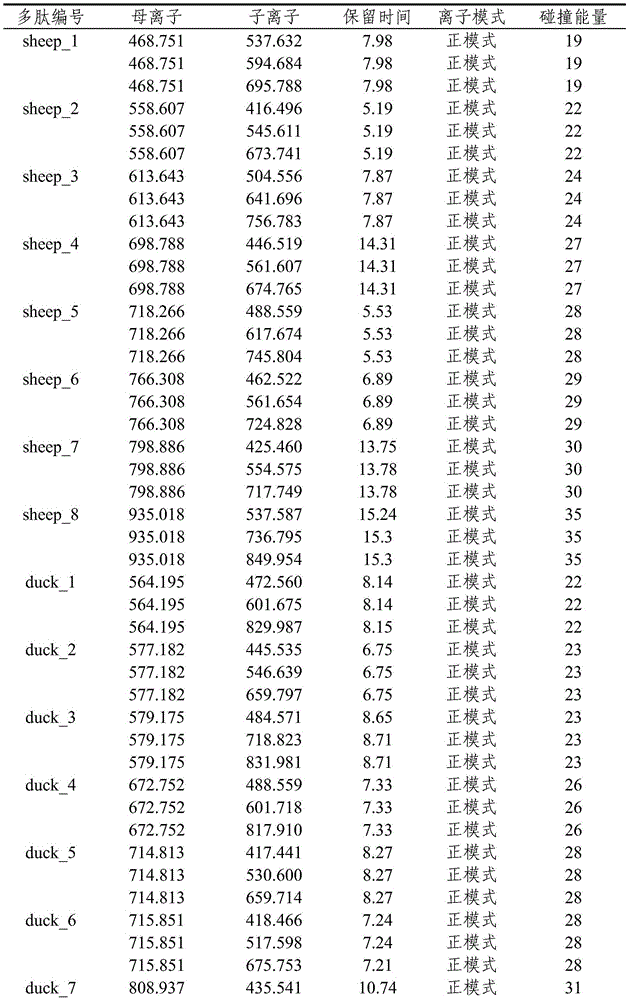
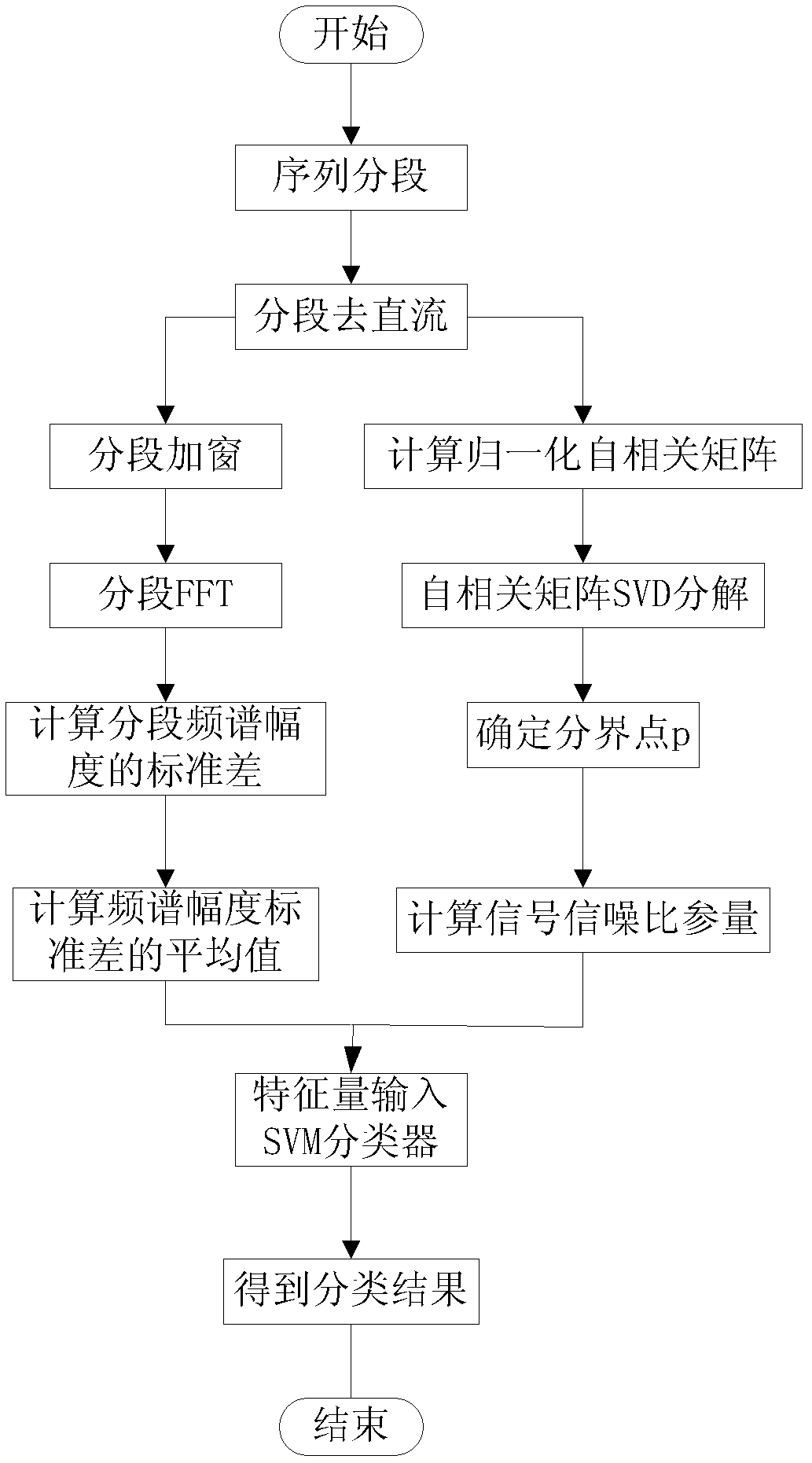
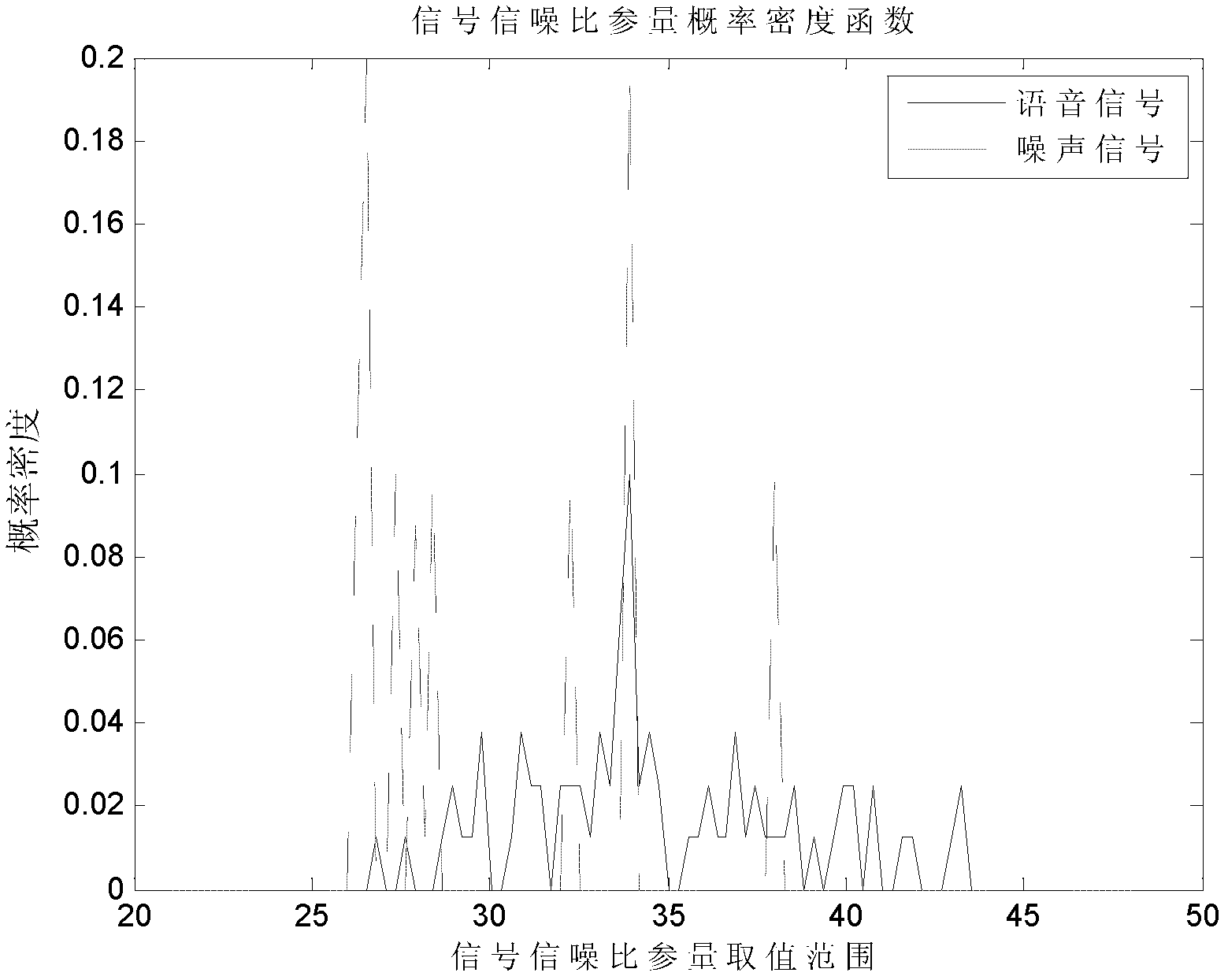
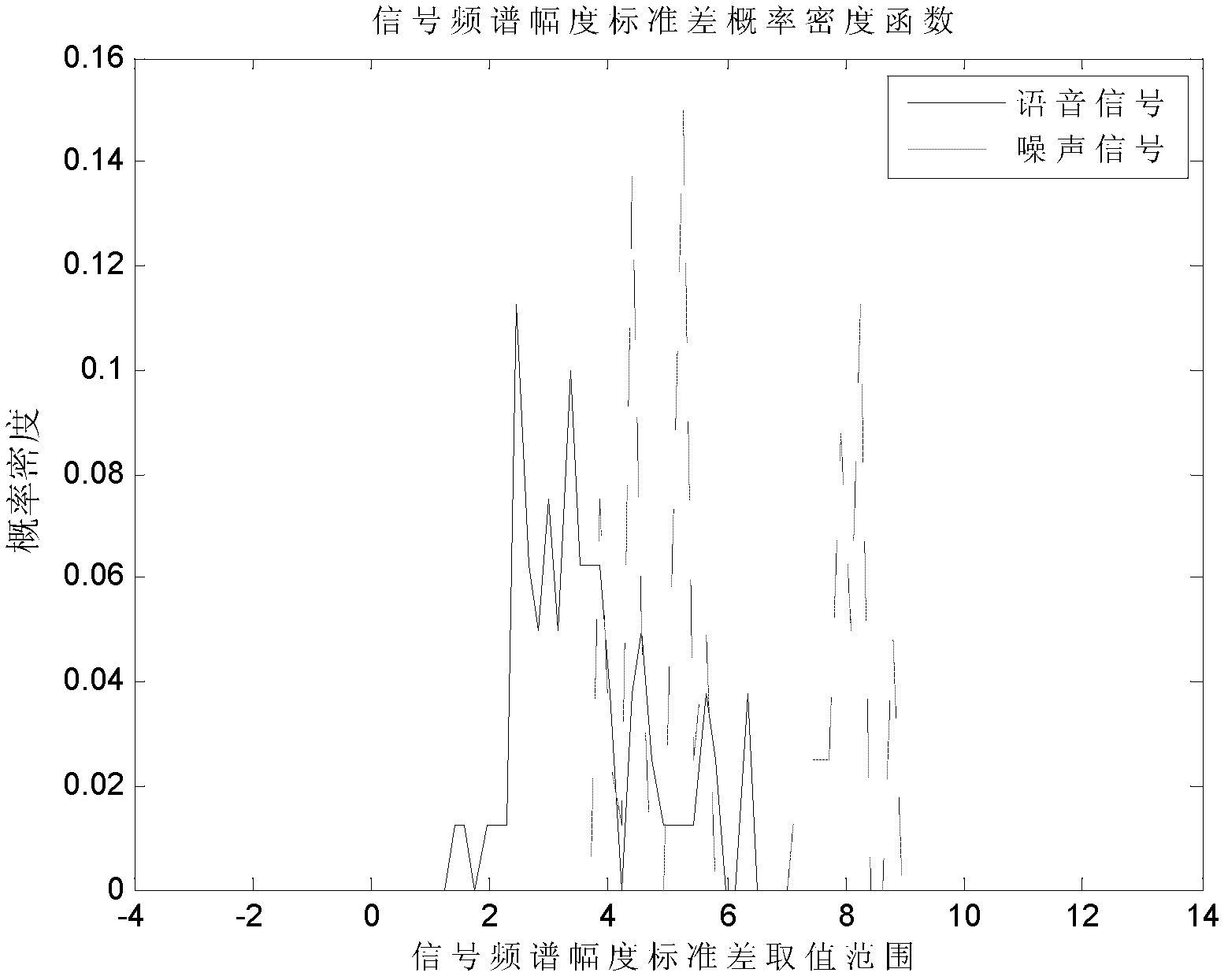
Support vector machine based classification method of base-band time-domain voice-frequency signal
InactiveCN102760444ARealize authenticationImplement classificationSpeech recognitionSingular value decompositionFrequency spectrum
The invention relates to a support vector machine based classification method of base-band time-domain voice-frequency signals, comprising the following steps of: firstly segmenting a base-band time-domain voice-frequency signal sequence to obtain initial segmented subsequences; then respectively subtracting respective mean value from each initial segmented subsequence to obtain zero-mean-value segmented subsequences; then carrying out windowing treatment on each zero-mean-value segmented subsequence, respectively carrying out Fourier transformation treatment on results to obtain the spectrum amplitudes of the zero-mean-value segmented subsequences, and respectively solving the standard difference of each spectrum amplitude to obtain a characteristic quantity; sequentially combining the zero-mean-value segmented subsequences into a long subsequence according to an order; then calculating a normalized autocorrelation matrix of the long subsequence, and carrying out singular value decomposition on the normalized autocorrelation matrix to obtain a demarcation point of a subspace; then calculating the signal to noise ratio parameter of an other characteristic quantity; and finally sending an input vector composed of the two characteristic quantities into a trained SVM (Support Vector Machine) classifier to identify the classification of base-band time-domain voice-frequency signals and distinguish a voice signal and a noise signal.
Owner:TSINGHUA UNIV
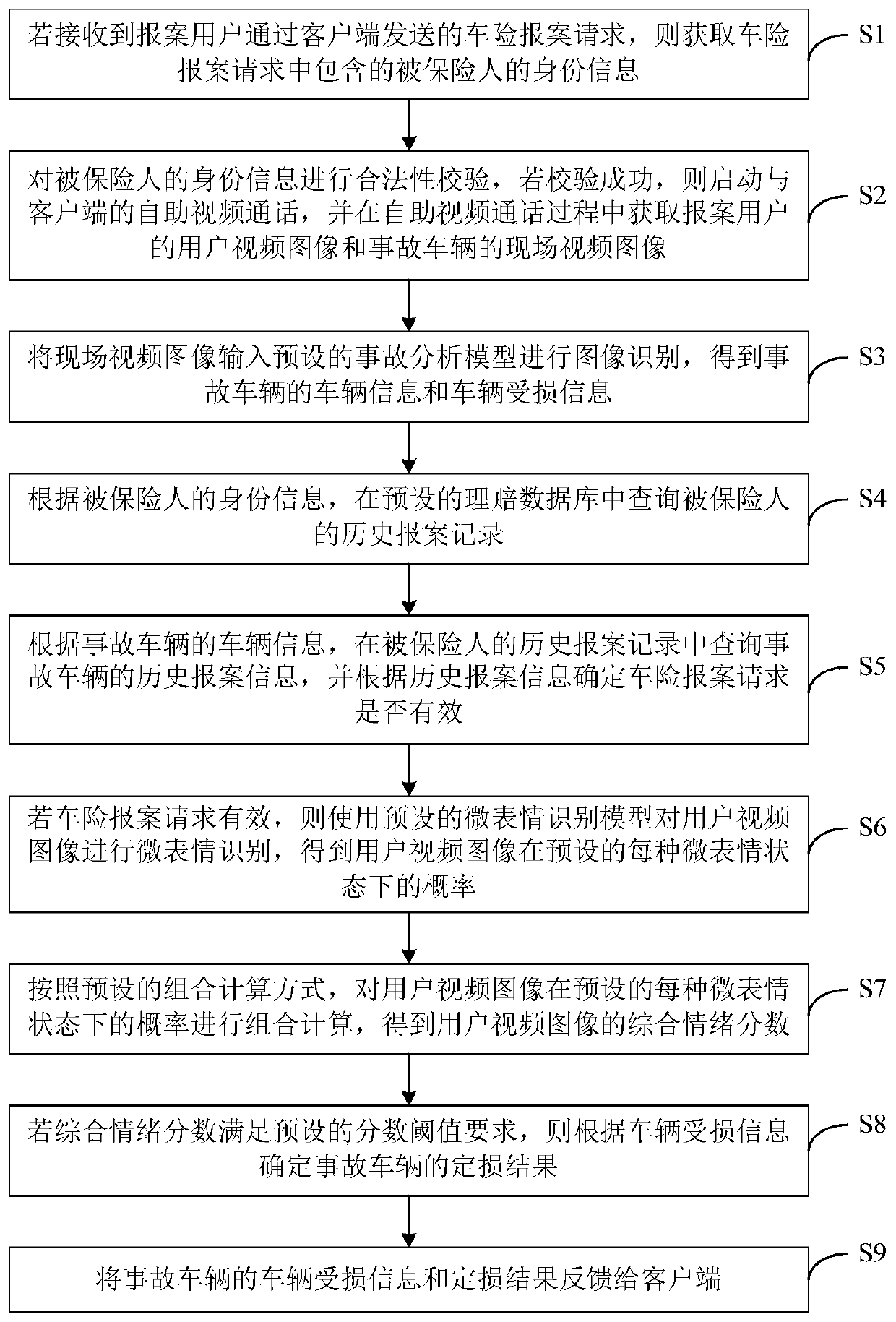
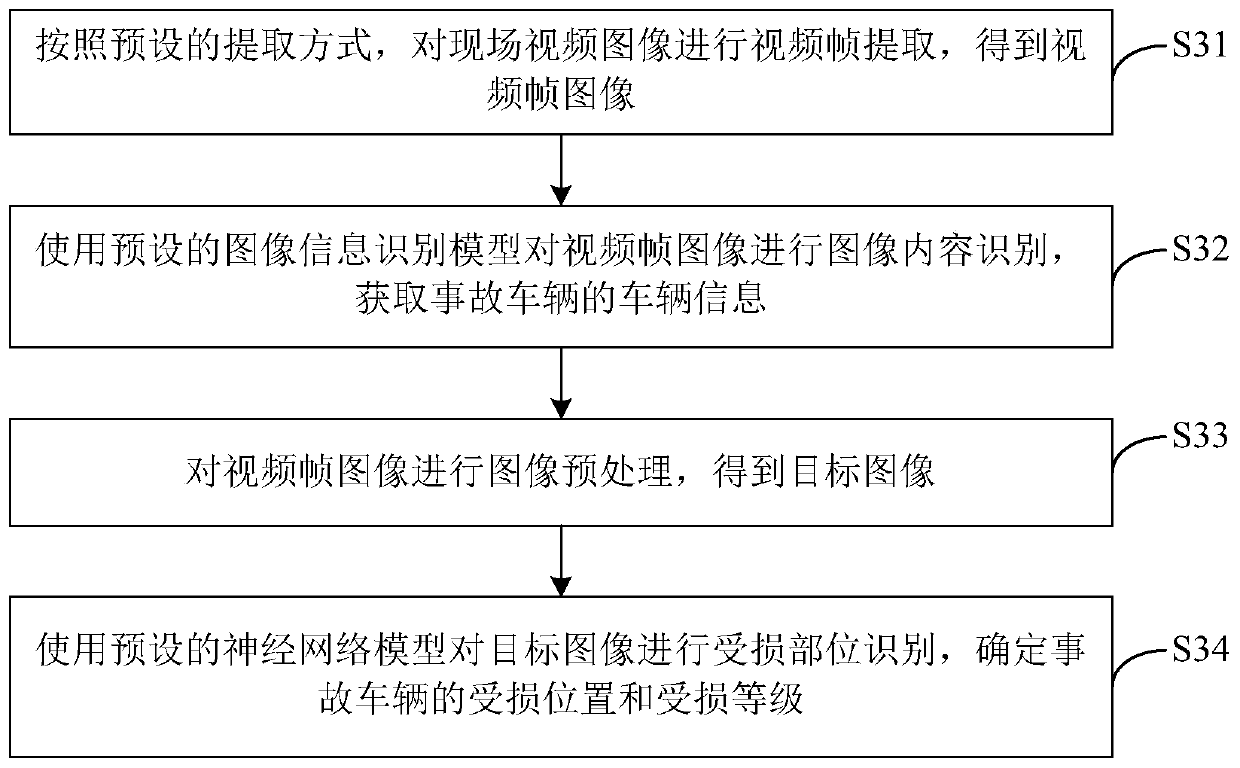
Vehicle insurance loss assessment method, device and equipment based on image recognition and storage medium
PendingCN109784170AImprove accuracyImprove processing efficiencyFinanceCharacter and pattern recognitionPattern recognitionAccidents vehicle
The invention discloses a vehicle insurance loss assessment method, device and equipment based on image recognition and a storage medium. The method comprises the steps of obtaining a user video imageof a case reporting user and an on-site video image of an accident vehicle through a self-service video call; Inputting the on-site video image into an accident analysis model for image recognition to obtain vehicle information and vehicle damage information of the accident vehicle; If it is determined that the vehicle insurance case reporting request is valid according to the historical case reporting information of the accident vehicle, performing micro-expression recognition on the user video image by using a micro-expression recognition model to obtain a comprehensive emotion score of theuser video image; And if the comprehensive emotion score satisfies a preset score threshold requirement, determining a damage assessment result of the accident vehicle according to the vehicle damageinformation. According to the technical scheme, automatic loss assessment is achieved, manual intervention is not needed, the vehicle insurance processing efficiency and timeliness are improved, theauthenticity of vehicle insurance reporting is effectively identified, the risk of false video reporting is reduced, and the insurance processing accuracy is improved.
Owner:PING AN TECH (SHENZHEN) CO LTD
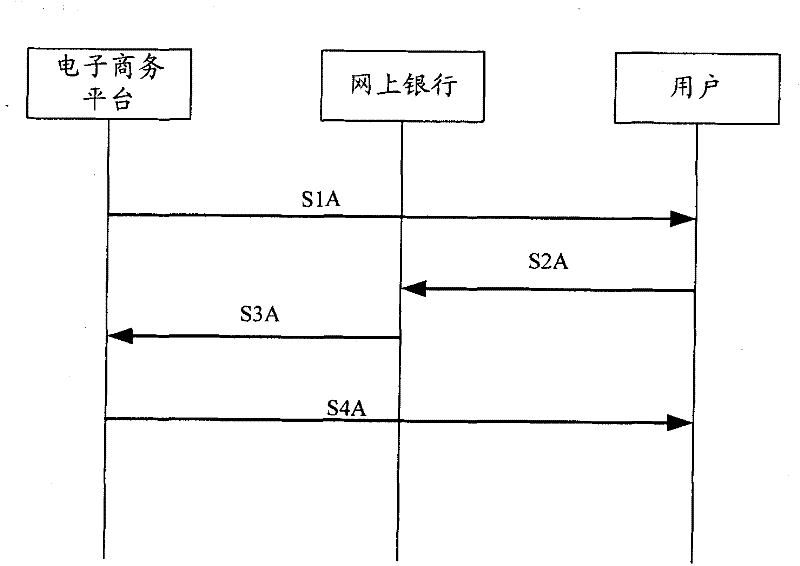
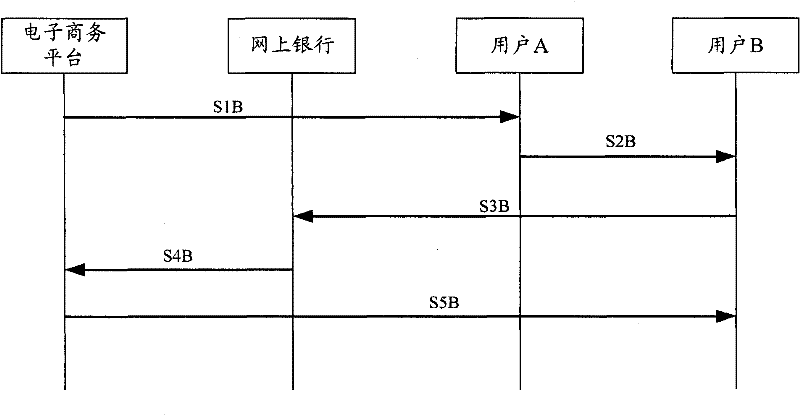
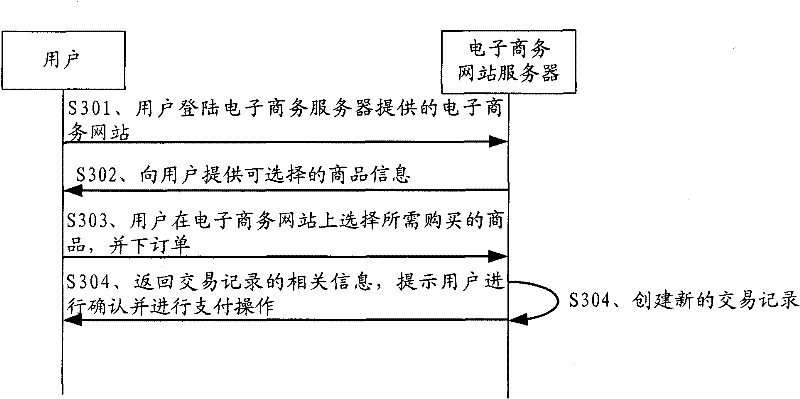
Network payment authentication method, server and system
ActiveCN102223354AEnsure safetyRealize authenticationUser identity/authority verificationPayment architectureInternet bankPhishing
The application discloses a network payment authentication method, a server and a system. The method comprises the following steps that an e-commerce website server receives online bank identification selected by a user and identity authentication identification information which is input by the user and corresponds to the online bank identification; the e-commerce website server sets up a payment request and returns the payment request to the user, wherein the payment request contains the identity authentication identification information; and the e-commerce website server receives the authentication result returned by an online bank server, wherein the authentication result is obtained in the way that according to the identity authentication information contained in the payment request transmitted by the user, and the online bank server carries out authentication to the identity authentication information input by the user in the payment operation. The application completely eradicates illegal actions that phishing is carried out by an online bank payment interface, so as to protect the safety of the transaction by utilizing the network payment of the e-commerce website server.
Owner:ADVANCED NEW TECH CO LTD
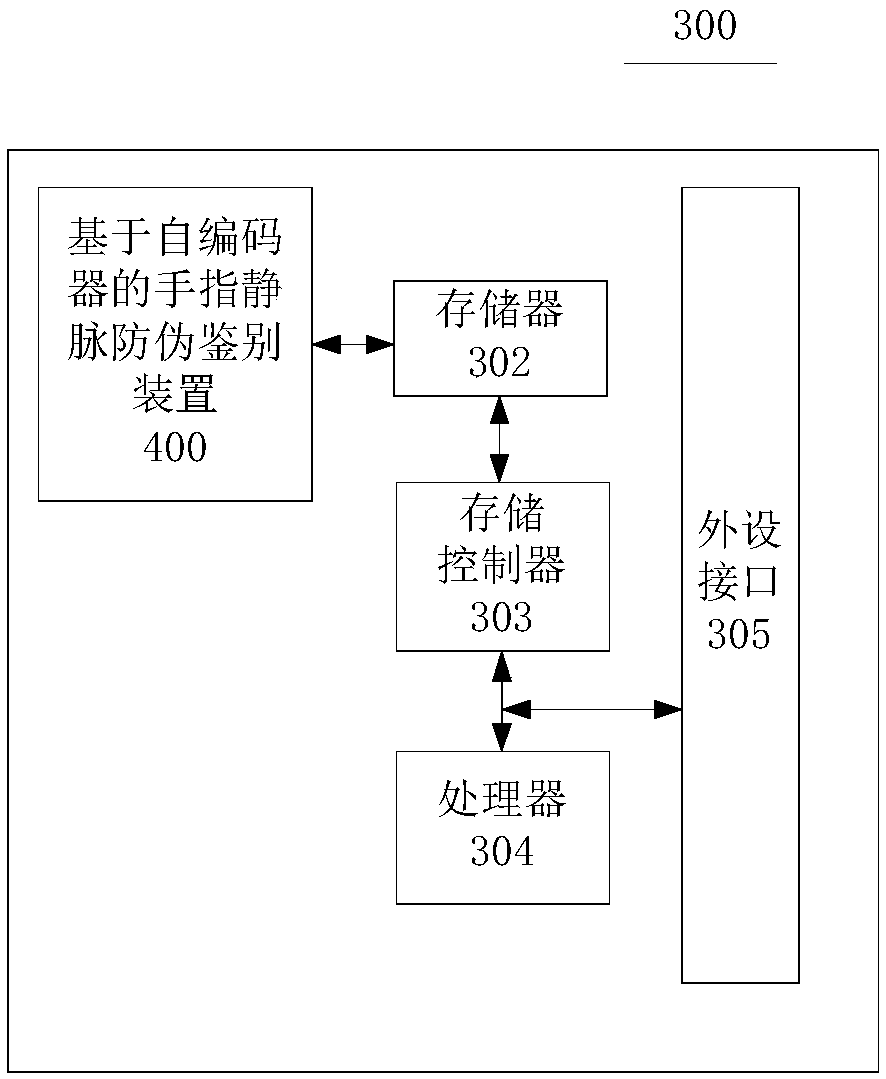
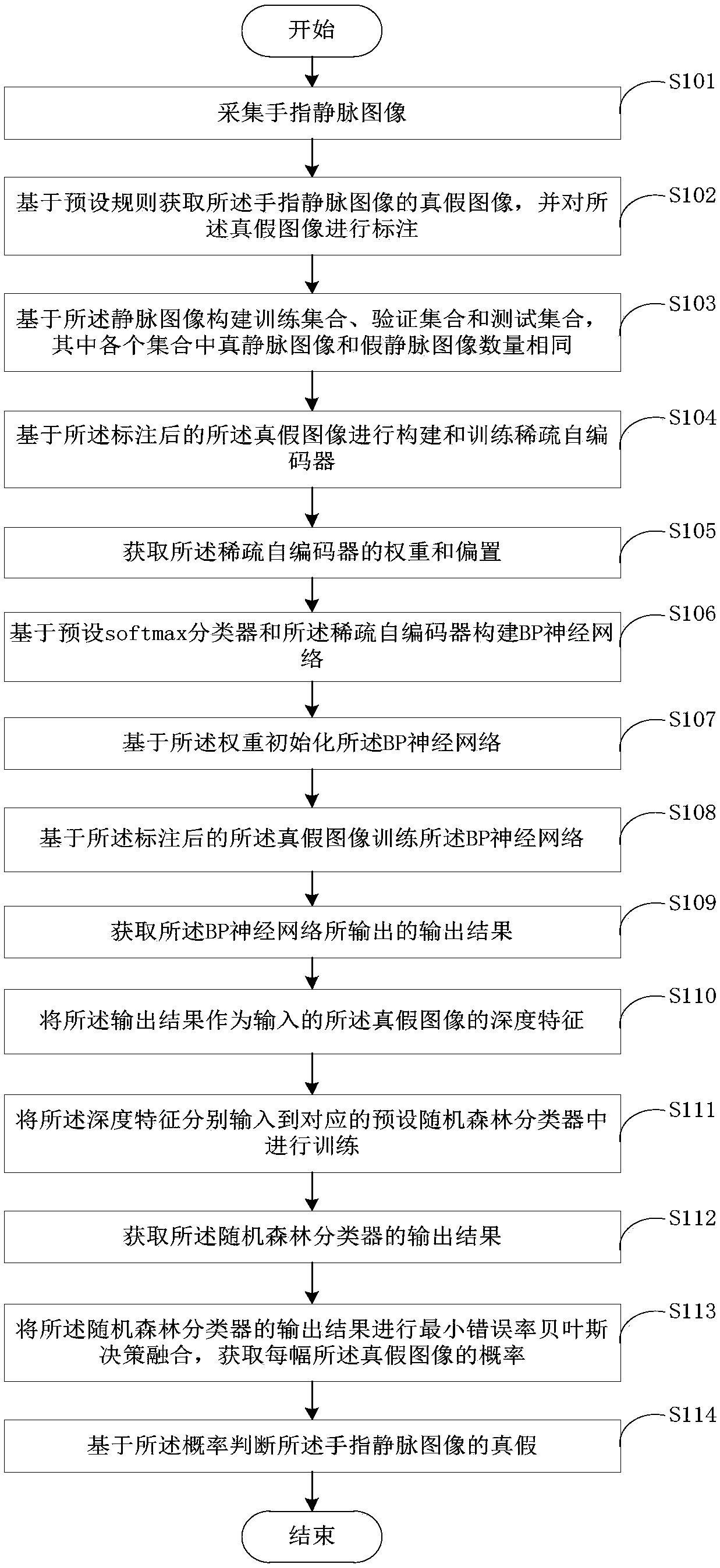
Method and system for finger vein anti-counterfeiting discriminating based on autoencoder
ActiveCN107832718ARealize authenticationDetecting live finger characterNeural learning methodsFeature vectorHidden layer
The embodiment of the invention provides a method and a system for finger vein anti-counterfeiting discriminating based on an autoencoder, belonging to the field of biometric identification technology. The method comprises the steps of: establishing a training set according to collected finger vein images and corresponding tags; constructing a sparse autoencoder model and employing a gray-level image training set to perform training of a sparse autoencoder; employing the weight of the trained SAE (sparse autoencoder) to initialize a neural network, and performing training of the neural network; taking output of each hidden layer of the neural network as one extracted feature vector; and finally, respectively inputting each feature vector to one corresponding random forest classifier, employing a Bayesian model to perform decision fusion of output results, and achieving finger vein anti-counterfeiting discriminating.
Owner:重庆金融科技研究院 +1
Second-generation ID card anti-counterfeiting verification system
InactiveCN104820814AIncreased handling securityRealize authenticationDigital data authenticationSensing record carriersVerification systemComputer hardware
An embodiment of the invention provides a second-generation ID card anti-counterfeiting verification system. A card reading module reads identification information of a chip in a second-generation ID card to be verified and user information stored in the chip, and a control module verifies the identification information and / or the user information according to ID card anti-counterfeiting verification information stored in a storage module to determine whether the second-generation ID card is authenticated successfully. Thus, ID card authentication is realized, and the safety of processing is improved under the condition of ensuring the efficiency of related service.
Owner:熊小军
Chiral sensor and preparation method thereof
InactiveCN101788525AReduce volumeRealize detectionSolid-state devicesMaterial analysis by electric/magnetic meansInsulation layerSemiconductor materials
The invention discloses a chiral sensor and a preparation method thereof. The chiral sensor provided with an organic field effect transistor as the basic structure thereof comprises a substrate, a gate insulation layer, an active layer, a gate electrode, a source electrode and a drain electrode, wherein the chiral sensor is characterized in that the active layer of the organic field effect transistor is made of organic semiconductor materials having the functions of chiral recognition and detection, more particularly, the component of the active layer can be a single chiral semiconductor material or alternatively an organic semiconductor material doped with a chiral material. By improving the materials of the active layer, the chiral sensor and the preparation method of the invention based on the organic field effect transistor can achieve the flexible detection of various chiral substances within a wide range and the identification of the corresponding isomers; and besides, the organic field effect transistor is small-sized, thus reducing the size and cost of detection components in application.
Owner:SUZHOU INST OF NANO TECH & NANO BIONICS CHINESE ACEDEMY OF SCI
Six-flavor hematinic capsule, its quality control method and application thereof
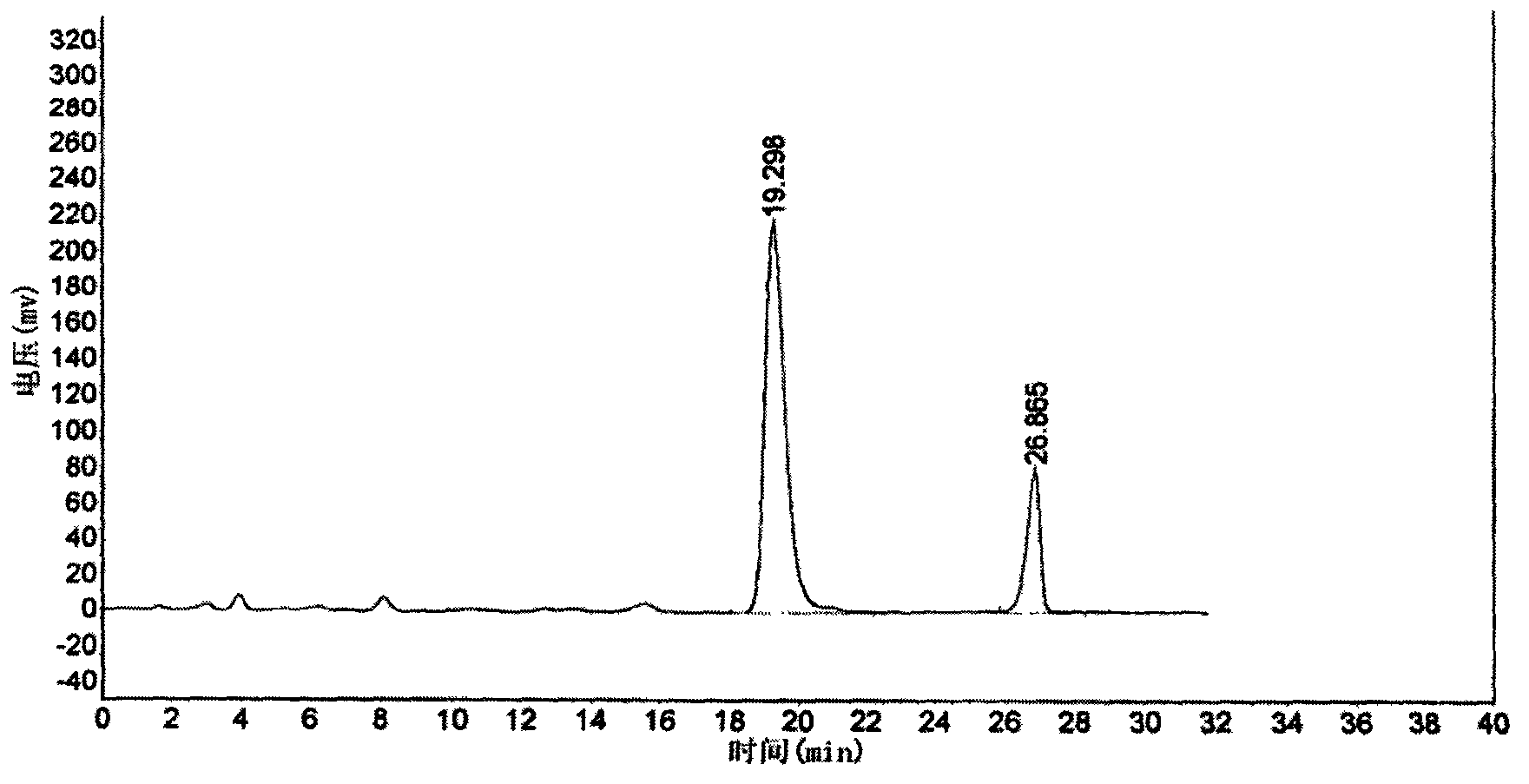
ActiveCN103381217ARealize authenticationAccurate measurementSenses disorderComponent separationBlurred visionLithospermum
The invention discloses a six-flavor hematinic capsule, its quality control method and an application thereof. The six-flavor hematinic capsule is prepared by adding auxiliary materials into raw materials consisting of Chinese angelica, Ligusticum wallichii, Radix Astragali, prepared rehmannia root, lithospermum and white peony root. According to the quality control method of the six-flavor hematinic preparation, whether the six-flavor hematinic capsule contains white peony root, Chinese angelica, Radix Astragali, prepared rehmannia root, lithospermum, Ligusticum wallichii and components is identified by thin layer chromatography; by high-performance liquid chromatography, in vitro dissolution behavior of the six-flavor hematinic capsule is determined, and effective component groups are identified by fingerprint; verbascoside and calycosin glucoside are used as reference substances to simultaneously determine contents in the six-flavor hematinic capsule; and the content of a volatile component ligustilide in the six-flavor hematinic capsule is determined by a gas chromatographic method. The method provided by the invention is simple to operate, is accurate and advanced, has good linear relation, reappearance, precision, stability and recovery rate, can be adopted to effectively control product quality and guarantee curative effect of the product. The invention also provides an application in the preparation of a medicine for treating eye damage and blurred vision.
Owner:GUANGDONG GUOYUAN GUOYAO PHARMA CO LTD
Automatic access control system based on real-time geographic coordinates, and door opening method
ActiveCN107403491AWide range of servicesLow costIndividual entry/exit registersData switching networksAutomatic controlAutomatic train control
The invention discloses an automatic access control system based on real-time geographic coordinates, and a door opening method. The automatic access control system based on the real-time geographic coordinates comprises a two-dimensional code display unit, a WeChat platform, resident mobile terminals, an official account cloud server, a residential community doorphone and unit doorphones; the communication between the official account cloud server and the resident mobile terminals can be realized by using the resident mobile terminals to concern the access control cloud service WeChat official account. According to the related door opening method, a resident scans an access control two-dimensional code of a residential community door, so that the identity of the resident can be verified; if the resident passes through verification of identity, the residential community door can be opened, and a unit door can be automatically opened when the resident gets close to the unit door. According to the automatic access control system and the door opening method, the resident only needs to be verified for once at the residential community door and then does not need to be verified anymore, so that the door opening of the resident is facilitated.
Owner:XIAMEN DNAKE INTELLIGENT TECH CO LTD
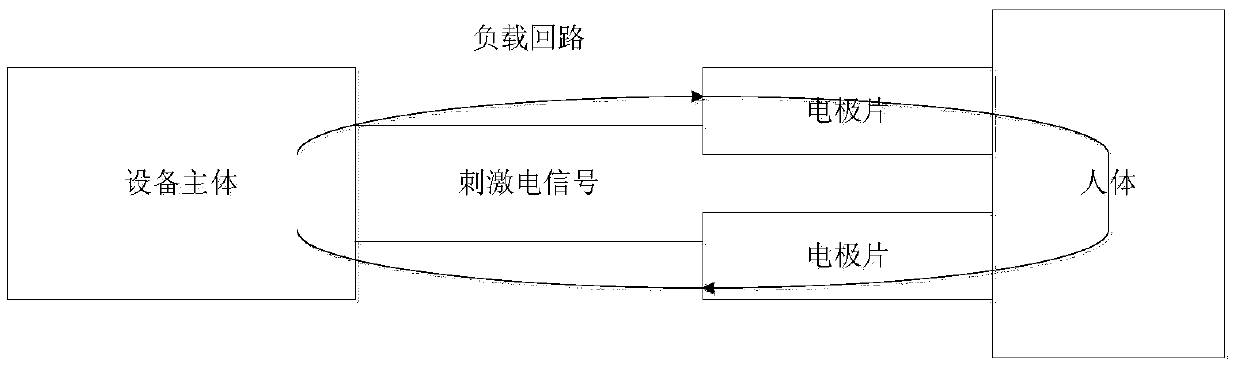
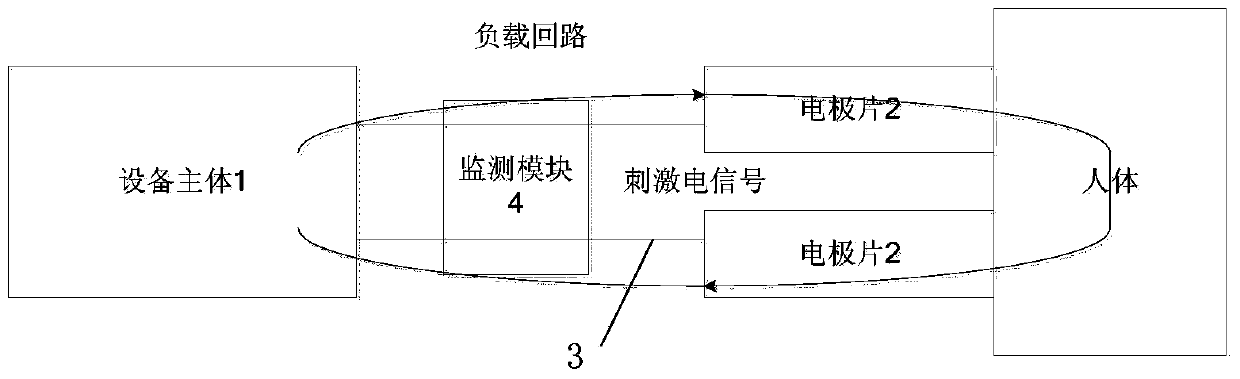
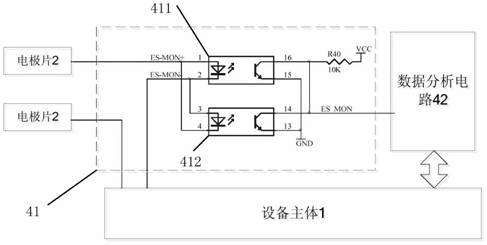
Electrical stimulation treatment device capable of conducting electrode contact state monitoring
ActiveCN104001264ARealize authenticationBreaking the status quo of "blind treatment"Artificial respirationVoltage amplitudeElectricity
The invention relates to an electrical stimulation treatment device capable of conducting electrode contact state monitoring. As a monitoring module is additionally arranged between a device body and an electrode plate to judge the contact state of the electrode plate, and whether the electrode plate is unloaded or not can be identified. In other words, information of current stimulation signals collected and converted by a signal pick-up circuit is read by a data analysis circuit in the monitoring module, and whether the current electrode plate is connected to an effective load or not is judged according to the current amplitude and / or the voltage amplitude of output electric signals. By means of the electrical stimulation treatment device, based on identification of unloaded conditions of the electrode plate, the contact state of the electrode plate and the human body can be dynamically monitored in the treatment process of a patient, an unloaded warning is given out under the conditions of dropping and poor contact caused by looseness of the electrode plate, and a medical worker can be assisted to find abnormities and correct the abnormities.
Owner:BEIJING RUAO MEDICAL TECH
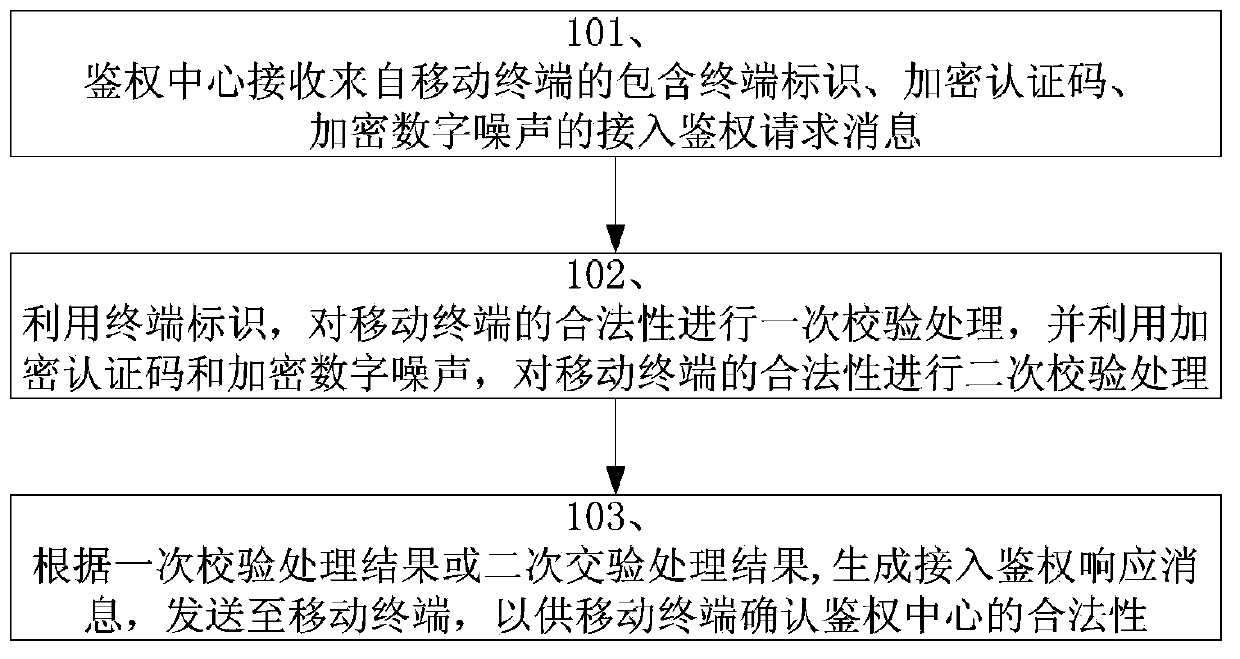
Method and device for authentication of mobile terminal
InactiveCN104185178ARealize authenticationPrevent counterfeitingSecurity arrangementCommunications securityEncryption
The invention discloses a method and device for authentication of a mobile terminal and relates to the technical field of mobile-communication security. The method includes the following steps: an authentication center receives an access authentication request message which comes from the mobile terminal and includes a terminal identification, an encryption verification code, and an encryption digital noise; using the terminal identification in the access authentication request message to carry out verification processing on the legality of the mobile terminal and using the encryption verification code and the encryption digital noise in the access authentication request to carry out second verification processing on the legality of the mobile terminal; and according to the result of the first verification processing and the result of the second verification processing, generating an access authentication response message and sending the message to the mobile terminal so as to allow the mobile terminal to confirm the legality of the authentication center according to the access authentication response message. The method and device are capable of effectively preventing use of a fake mobile terminal.
Owner:NO 61 INST OF GENERAL STAFF
Method and system for obtaining user terminal authentication information by data service center
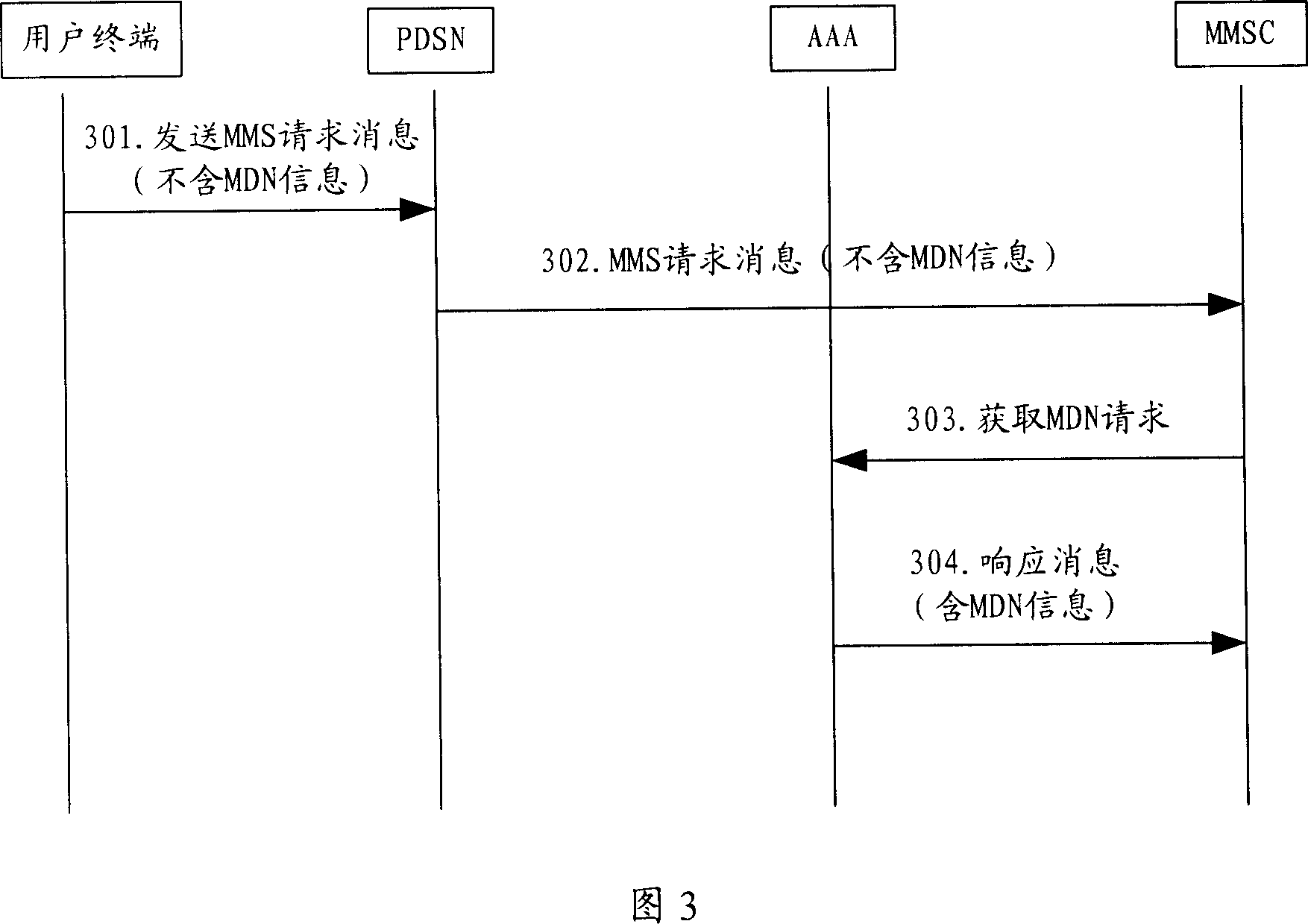
InactiveCN1968090ARealize authenticationSolve the problem of authentication failureUser identity/authority verificationCode division multiplexIp addressAuthentication information
The invention relates to a method for using data service center to obtain the user terminal identification information, and a relative system, wherein said method comprises that: setting IMSI, user terminal IP address, and projection with MDN on the system network unit; the center via communication with PDSN and system network unit. And the system comprises PDSN, network unit, and data service center. With said invention, user terminal can use data service center to identify the user terminal, without special order.
Owner:HUAWEI TECH CO LTD
Coin distinguishing apparatus and its method for distinguishing
InactiveCN1787017AHigh identification accuracyWidely usedCoin testingEngineeringIdentification device
The invention relates to a coin identifying or discriminating device and method, especially relating to the discrimination of the true coins from the false coins. The method vertically slides the tested coin along a guiding groove down onto a substrate, collects a sound signal emitted by the coin as striking the substrate through sound sensor, directly sends the sound signal or sends the sound signal amplified by a power amplifier to a frequency spectrum analyzing device for making frequency spectrum analysis so as to obtain an inherent frequency of the tested coin, and compares the inherent frequency with a standard data in a frequency spectrum standard memory for making frequency spectrum discrimination; then uses a pressure sensor to measure the weight of the tested coin and sends the generated force signal amplified by a power amplifier into a weight analyzing device and calculates to obtain the weight of the tested coin and compares it with a standard data in a weight standard memory for making weight discrimination; then by an operational policy maker, synthetically analyzes and obtains the final discrimination result. The discriminating device has simple structure, lower manufacturing cost, and high identifying accuracy, applied to identification of various coins and having a wide application prospect.
Owner:UNIV OF SCI & TECH OF CHINA
Biological identity authentication and payment system based on hand vein identification and identity authentication method
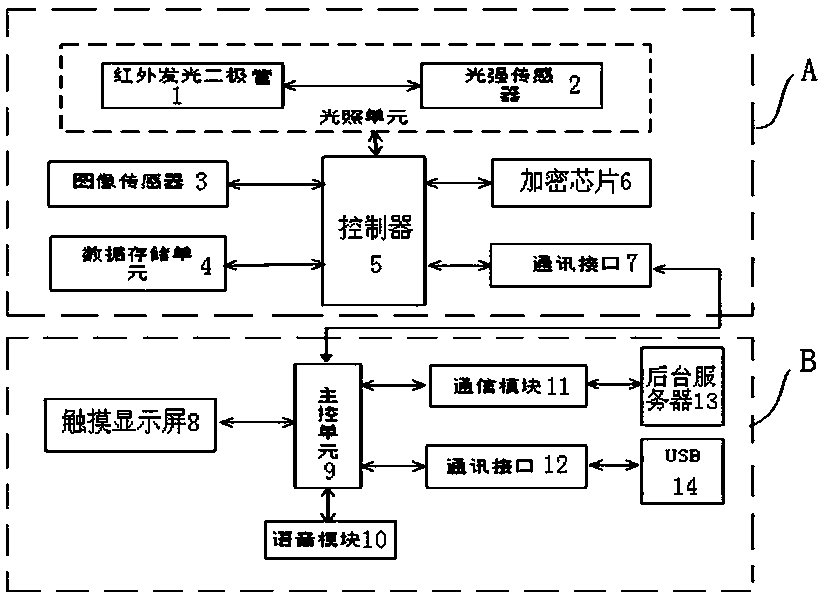
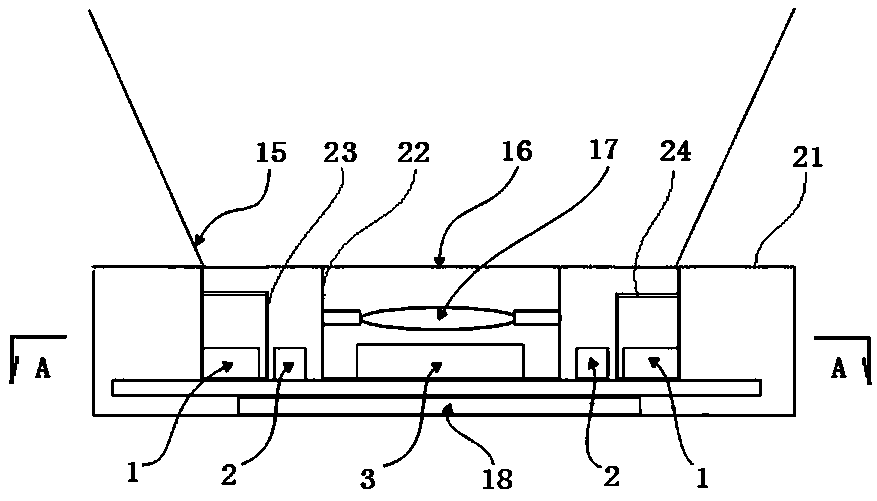
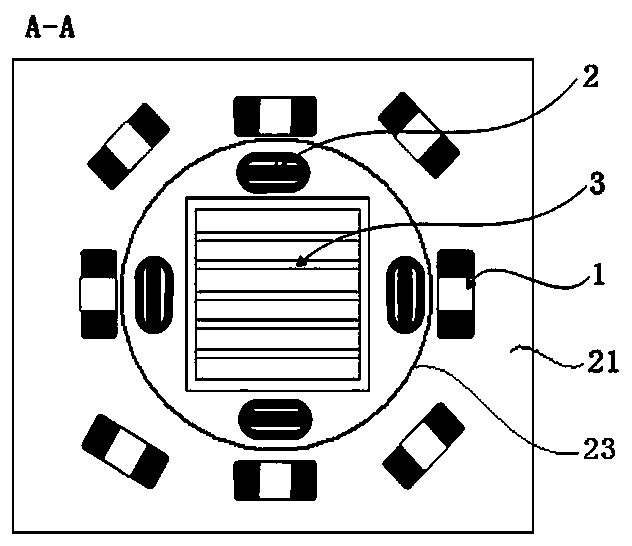
PendingCN108319911ANo need to worry about the risk of being stolenRealize authenticationImage analysisSubcutaneous biometric featuresElectrical connectionLight-emitting diode
A biological identity authentication and payment system based on hand vein identification and an identity authentication method are disclosed. A palm vein acquisition unit and a display interaction unit are included and are connected through a data line. The palm vein acquisition unit comprises a hand vein palm holding body, a lens module group, an image sensor, an infrared light emitting diode array, a light intensity sensor, a controller, a data storage unit, an encryption chip, and a communication interface which is connected with the display interaction unit. The electrical connection relationship of the palm vein acquisition unit is that the image sensor, the infrared light emitting diode array, the light intensity sensor, the data storage unit, the encryption chip, and the communication interface are connected with the corresponding interfaces of the controller respectively. The system and the method have advantages that a user only needs to register one-time hand vein information and bind a personal payment account to a hand vein identification biological identity authentication device for one time so that the binding of personal property account information and personal biological authentication information can be completed; and compared with other biological identification technology, the technology in the invention possesses high safety.
Owner:DEEPBLUE TECH (SHANGHAI) CO LTD
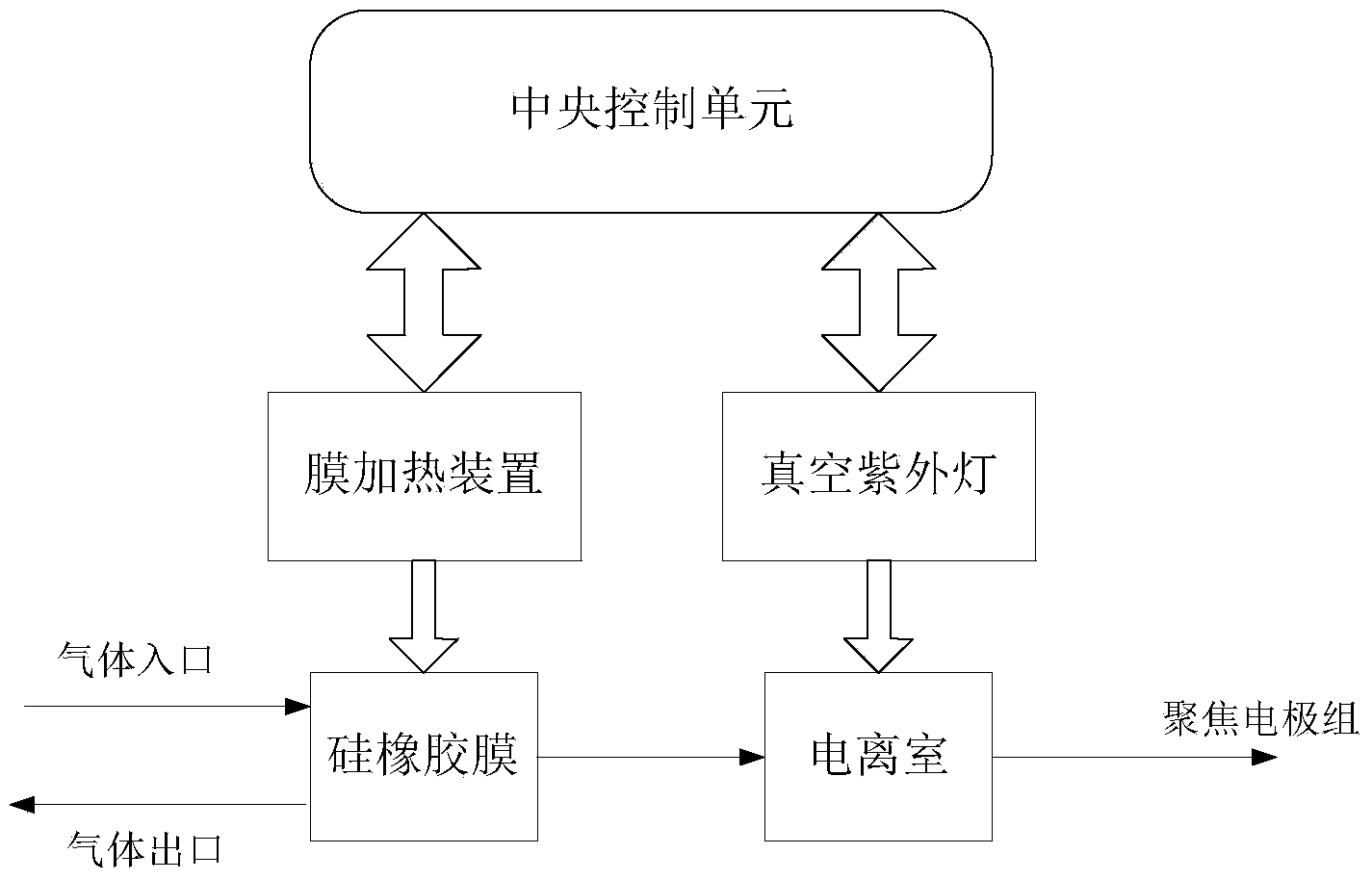
Device and method for on-line rapid analysis of volatile organic compound
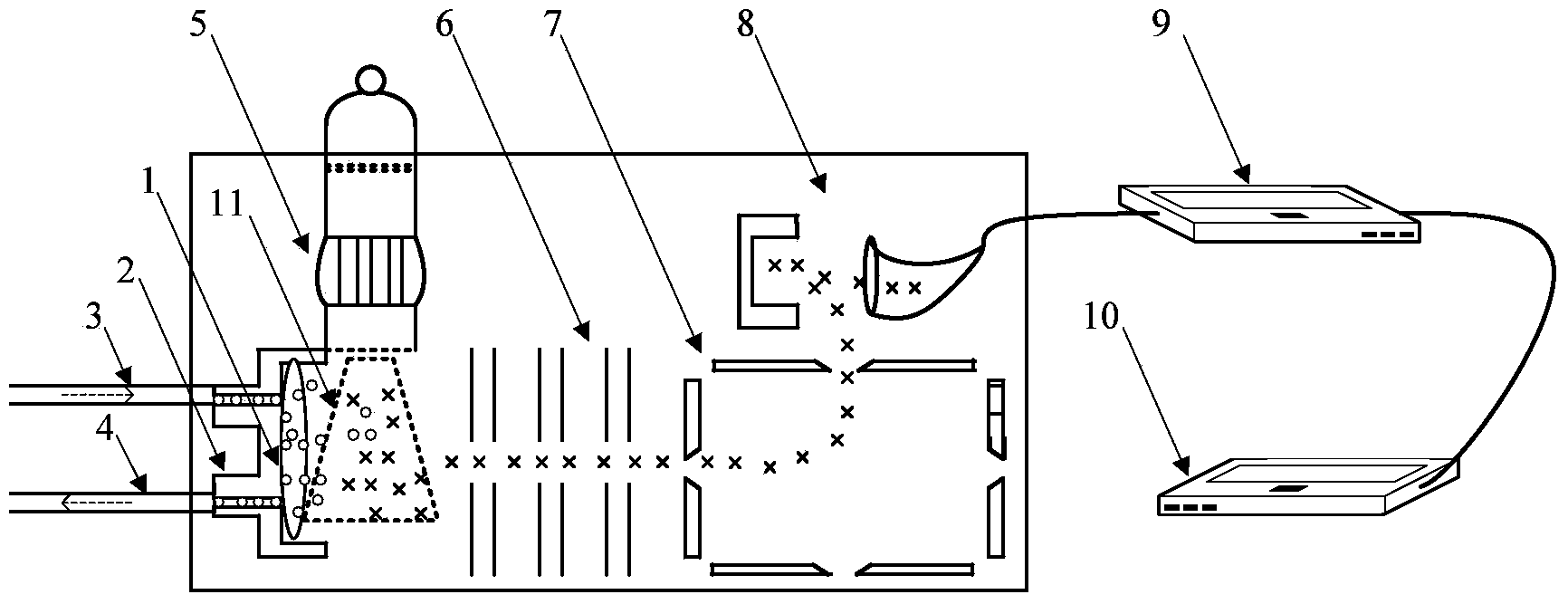
InactiveCN103730325ASimple structureShort response timeMaterial analysis by electric/magnetic meansMass spectrometersPhysicsIonization
The invention discloses a device and method for on-line rapid analysis of a volatile organic compound. The device comprises a film sample feeding device, a film heating device, a vacuum ultraviolet light single-photon ionization source, a focusing electrode assembly, a digital linear ion trap, an ion detection device, a data collecting device, a central control unit and the like. According to the device and method for on-line rapid analysis of the volatile organic compound, the vacuum ultraviolet light single-photon ionization source is adopted, a molecular ion peak is mainly generated after sample molecules are ionized, a spectrogram is greatly simplified, and the vacuum ultraviolet light single-photon ionization source is combined with the digital linear ion trap with the second-level mass spectrum function so that the compound can be rapidly and accurately analyzed and the components of a complex sample can be rapidly analyzed and identified; in addition, a silicon rubber film structure is used without the requirement for complex sample pretreatment, the responding time is short, sample feeding is rapid, and the device and method satisfy the requirement for on-line analysis. The device and method for on-line rapid analysis of the volatile organic compound can be widely applied to the technical field of analytical instrument detection.
Owner:KUSN HEXIN MASS PECTRUM TECH +1
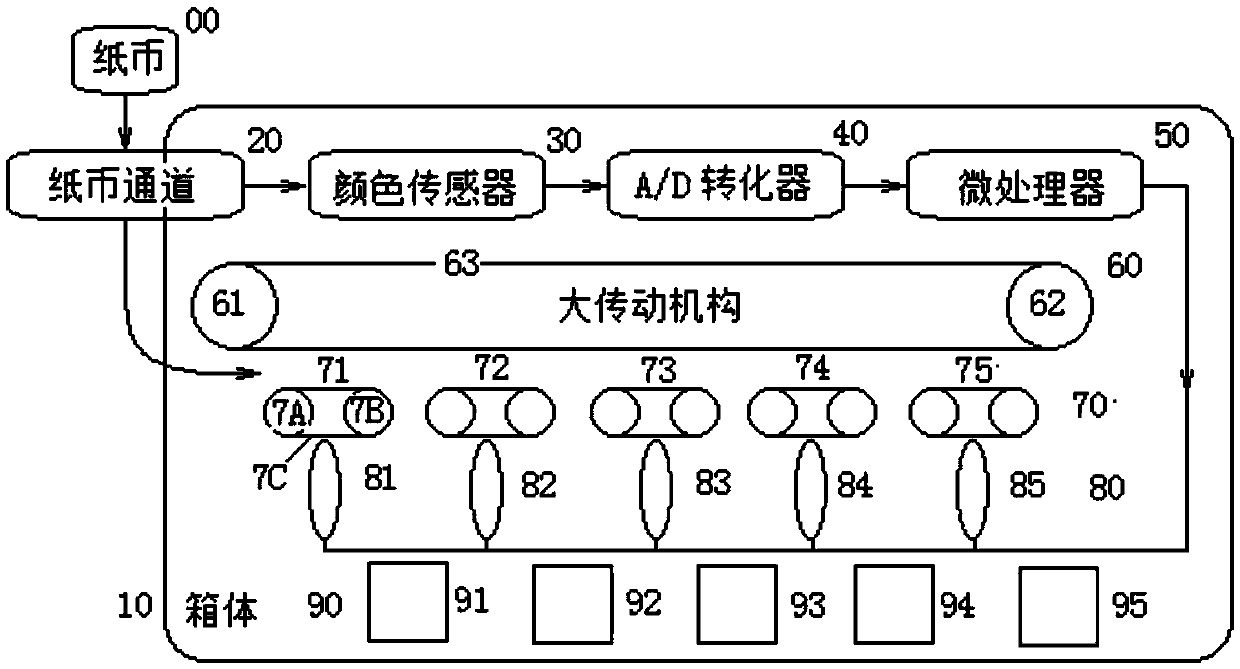
Banknote-receiving device based on voltage-controlled rotating speed
InactiveCN105513198ARealize authenticationRealize the separationCoin/currency accepting devicesEngineeringColor signal
The invention discloses a banknote-receiving device based on voltage-controlled rotating speed and relates to a device for identifying and receiving banknotes. A banknote channel body, a color sensor, an A / D converter, a microprocessor, a large transmission mechanism, small transmission mechanisms, tensioning mechanisms, and receiving boxes are disposed in a box body. The color sensor is disposed on the inlet of a banknote channel and rightly faces the banknotes. The large transmission mechanism, the small transmission mechanisms, the tensioning mechanisms, and the receiving boxes are successively and correspondingly arranged under the banknote channel. The color sensor, the A / D converter, the microprocessor, and the tensioning mechanisms are successively connected, measure color signals of the banknotes, and gather different banknotes in different receiving boxes according to classifications. The banknote-receiving device may fast and accurately identify, classify, and count the banknotes, is simple in structure and low in cost, and can be widely used in small-profit enterprise. The receiving method based on voltage-controlled rotating speed and the color-based identifying principle are suitable for any apparatuses requiring identification and reception.
Owner:HUAZHONG AGRI UNIV
Gas sensor array for detecting indoor gas pollution
InactiveCN1542444AEasy to identifyRealize authenticationMaterial analysis by electric/magnetic meansPhysicsIndium
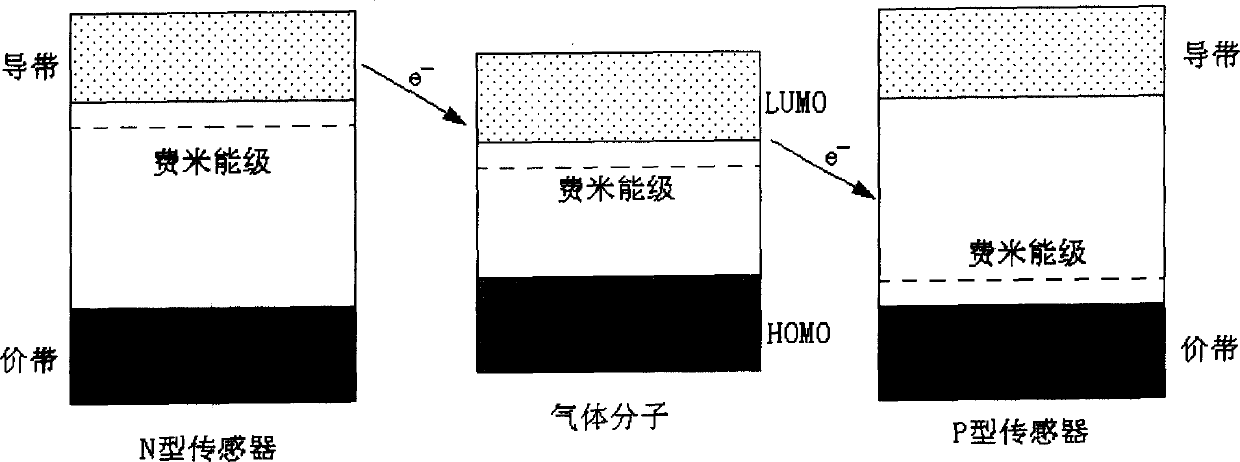
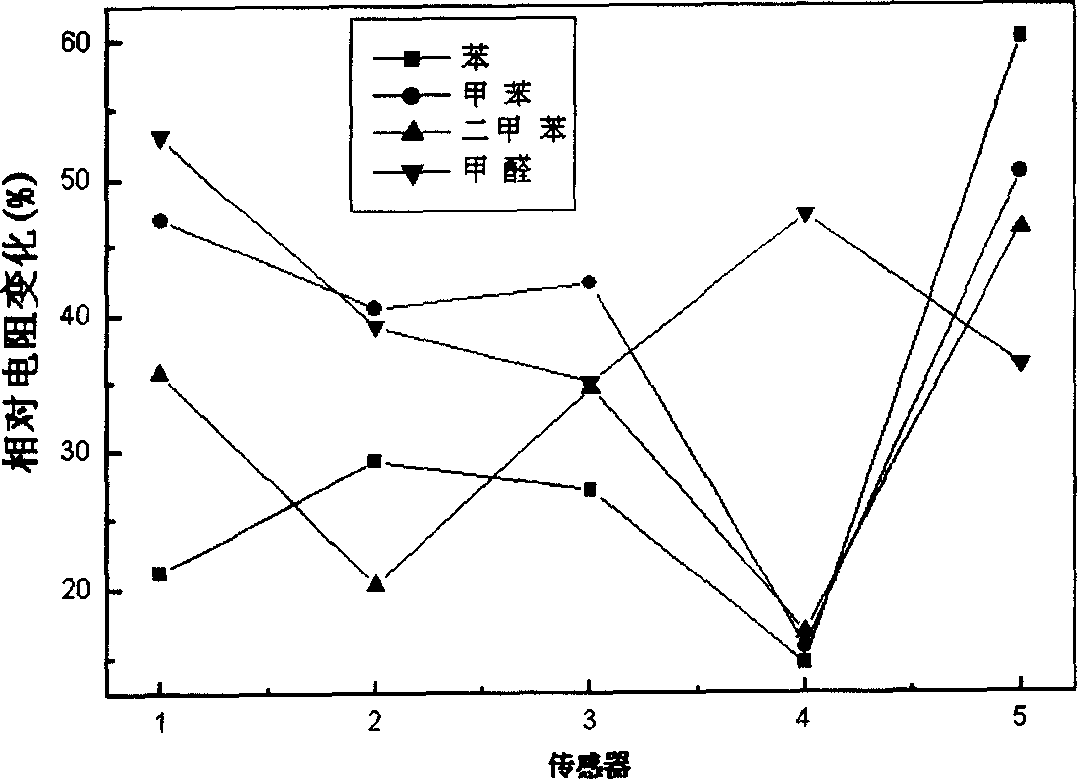
The gas sensor array for detecting indoor gaseous pollutant consists of several In-Sn oxide film gas sensors with different In / Sn atom ratio within 0-1.0. The sensors with different In / Sn atom ratio have different response to gases, so that the gas sensor array has greatly raised gas selectivity and may be used in identifying benzene, toluene, xylene, formaldehyde and other common indoor pollutant gases.
Owner:ZHEJIANG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com