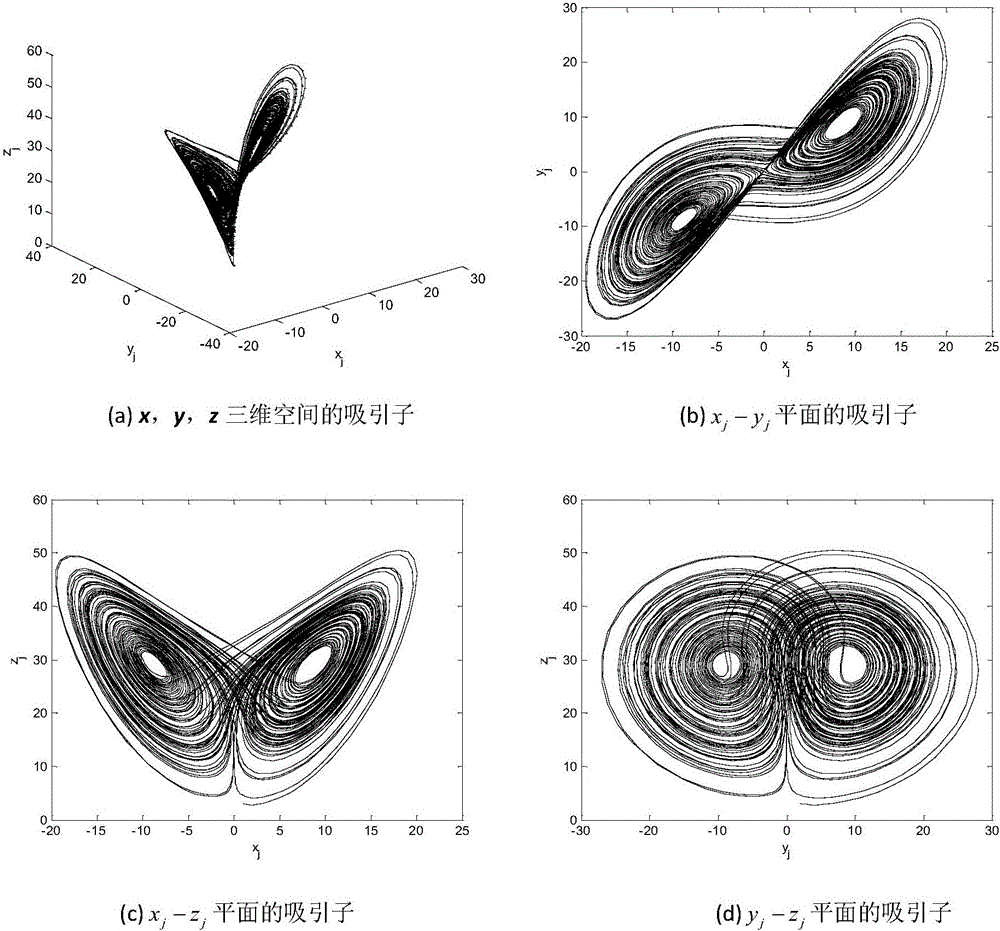
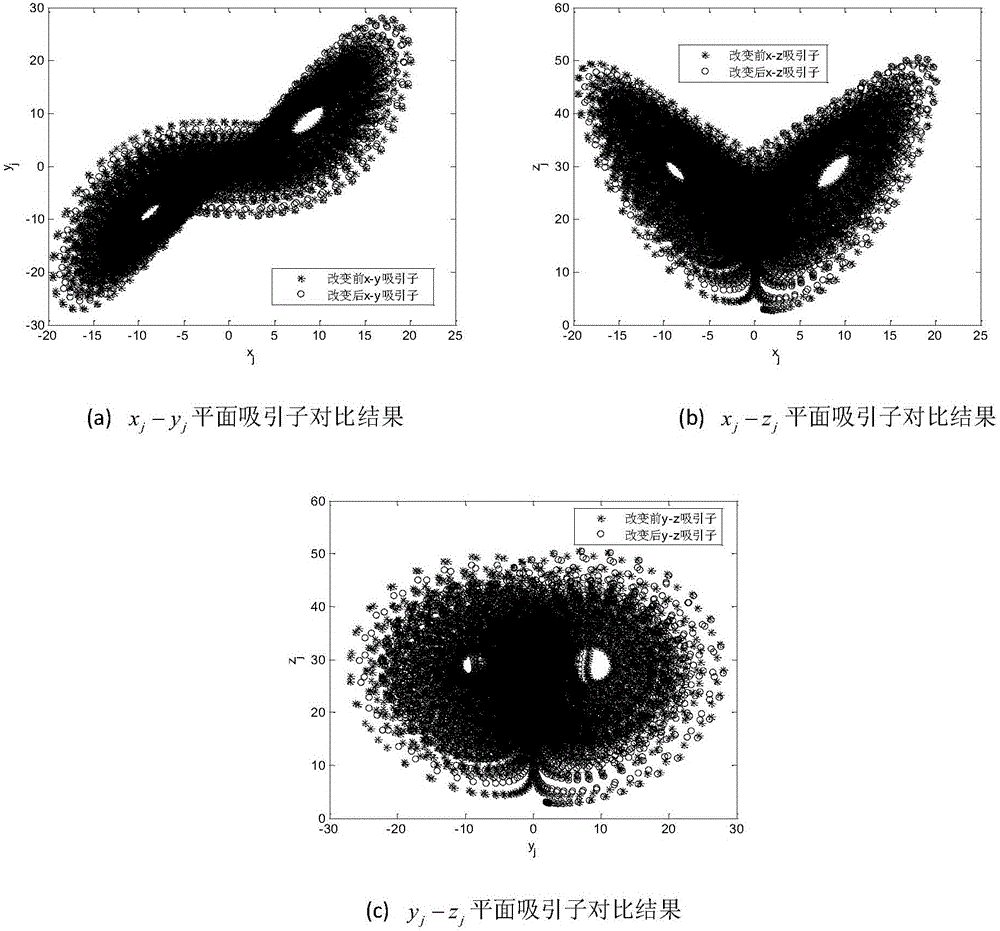
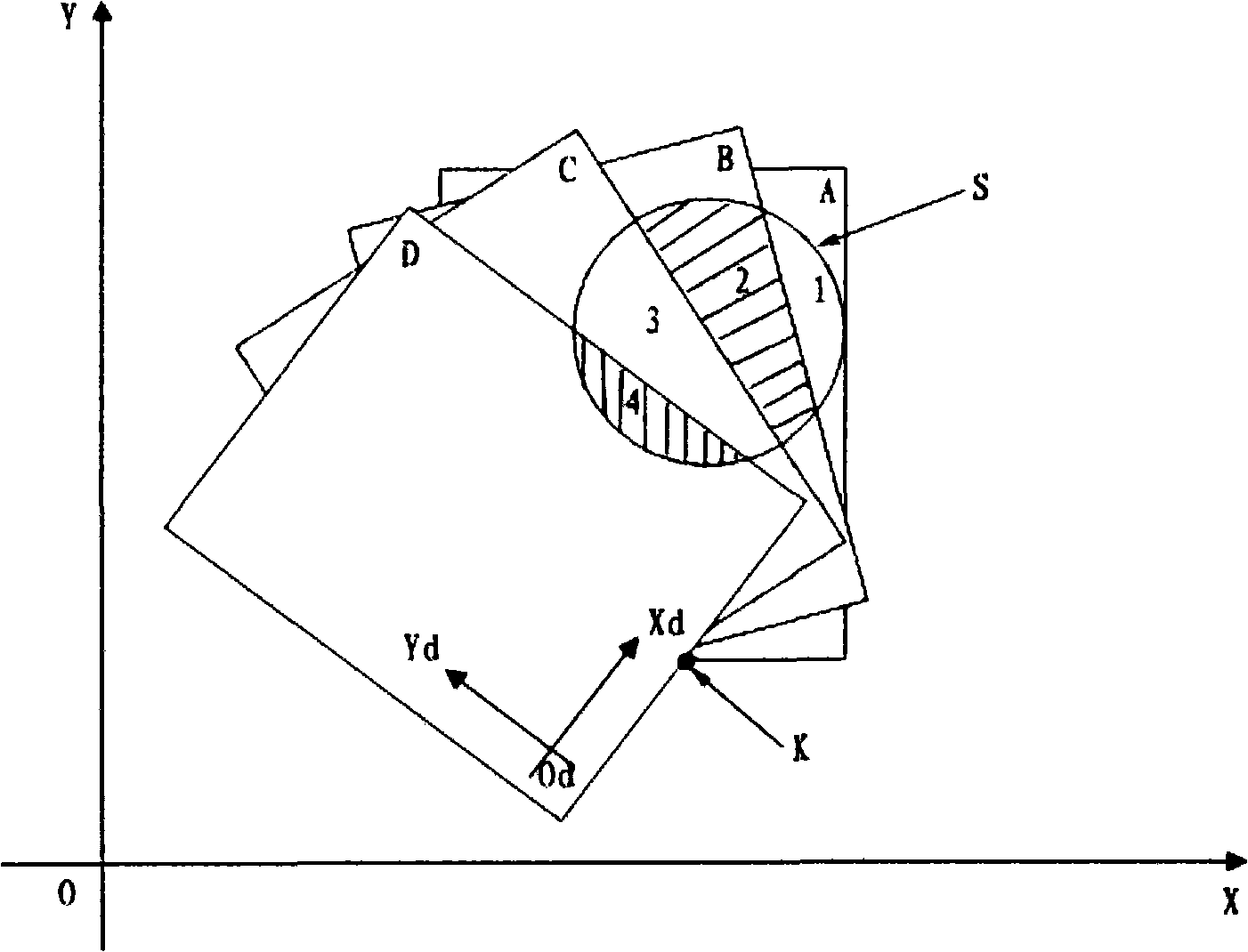
Patents
Literature
57results about How to "Unpredictable" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
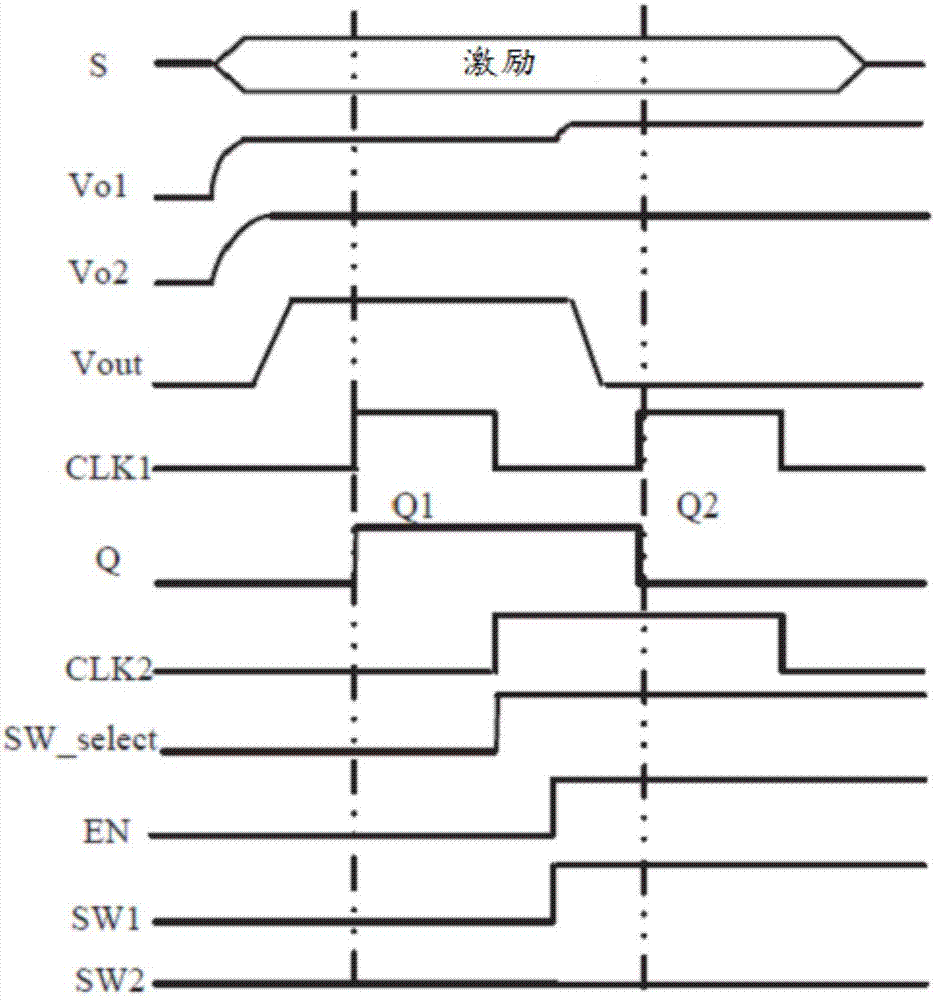
Voice signal quantum encryption communication system based on random number
ActiveCN108768542ARandomUnpredictableKey distribution for secure communicationSpeech analysisSignal encodingSignal decoding
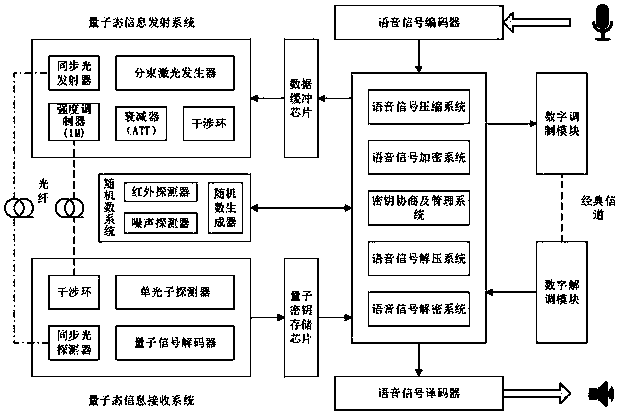
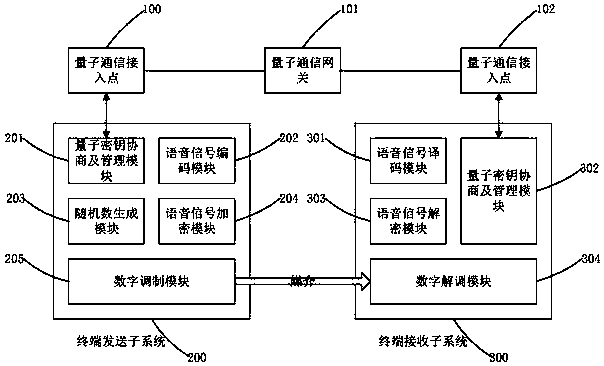
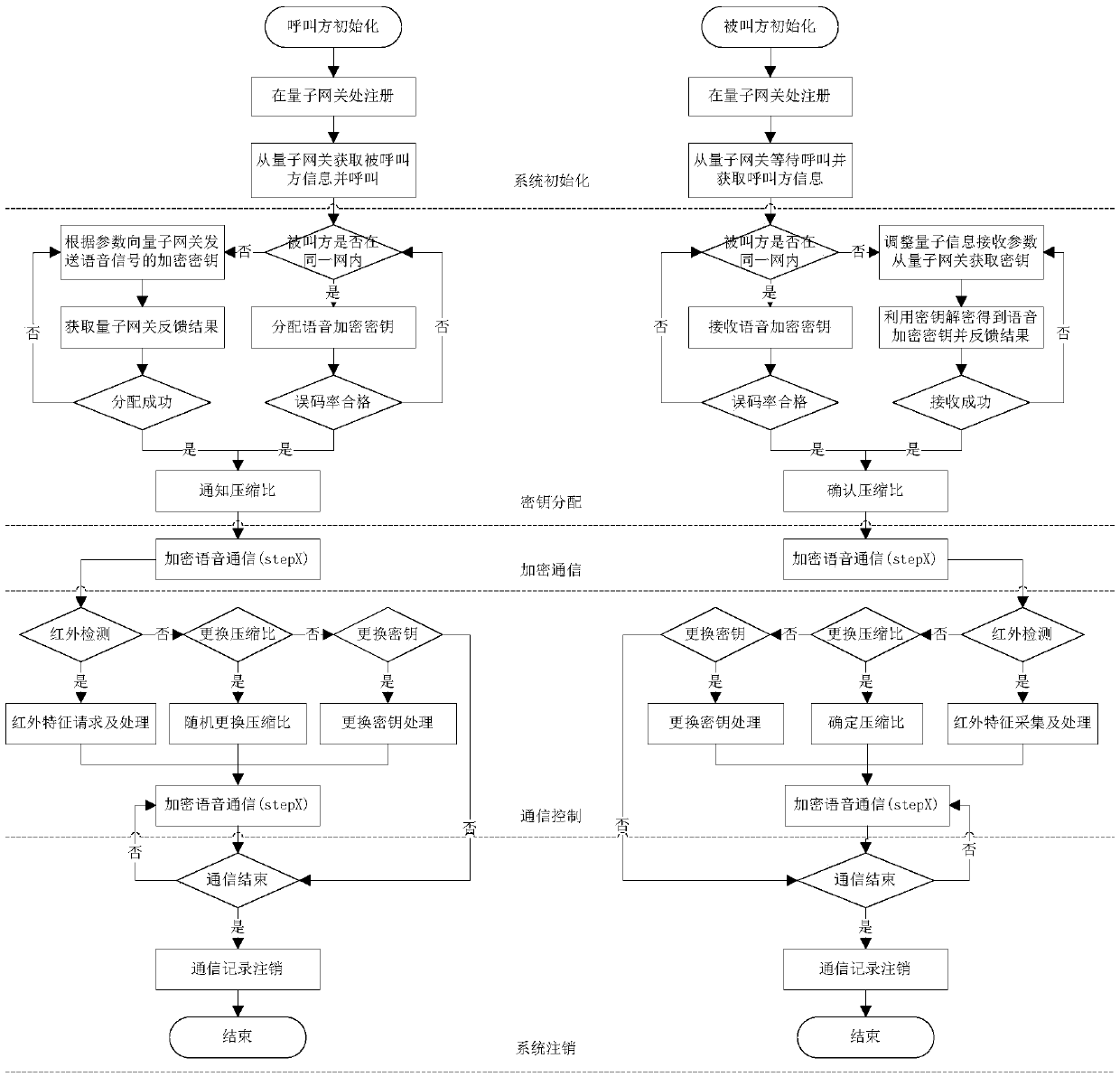
The invention relates to a voice signal quantum encryption communication system based on a random number, which comprises terminal equipment, a quantum communication access point, a quantum communication gateway and a quantum communication access point, wherein the terminal equipment consists of a terminal sending subsystem and a terminal receiving subsystem; the terminal sending subsystem comprises a quantum key agreement and management module, a voice signal encoding module, a random number generation module, a voice encryption module and a digital modulation module; and the terminal receiving subsystem comprises a voice signal decoding module, a quantum key agreement and management module, a voice decryption module and a digital demodulation module. One piece of terminal equipment simultaneously comprises the terminal sending subsystem and the terminal receiving subsystem. According to the invention, the terminal sending subsystem is applied to send a voice signal with good encryption performance and high anti-interference performance and meanwhile, the terminal receiving subsystem is utilized to receive and reduce the voice signal, so that safety and integrity in the communication process are ensured.
Owner:CHINA THREE GORGES UNIV
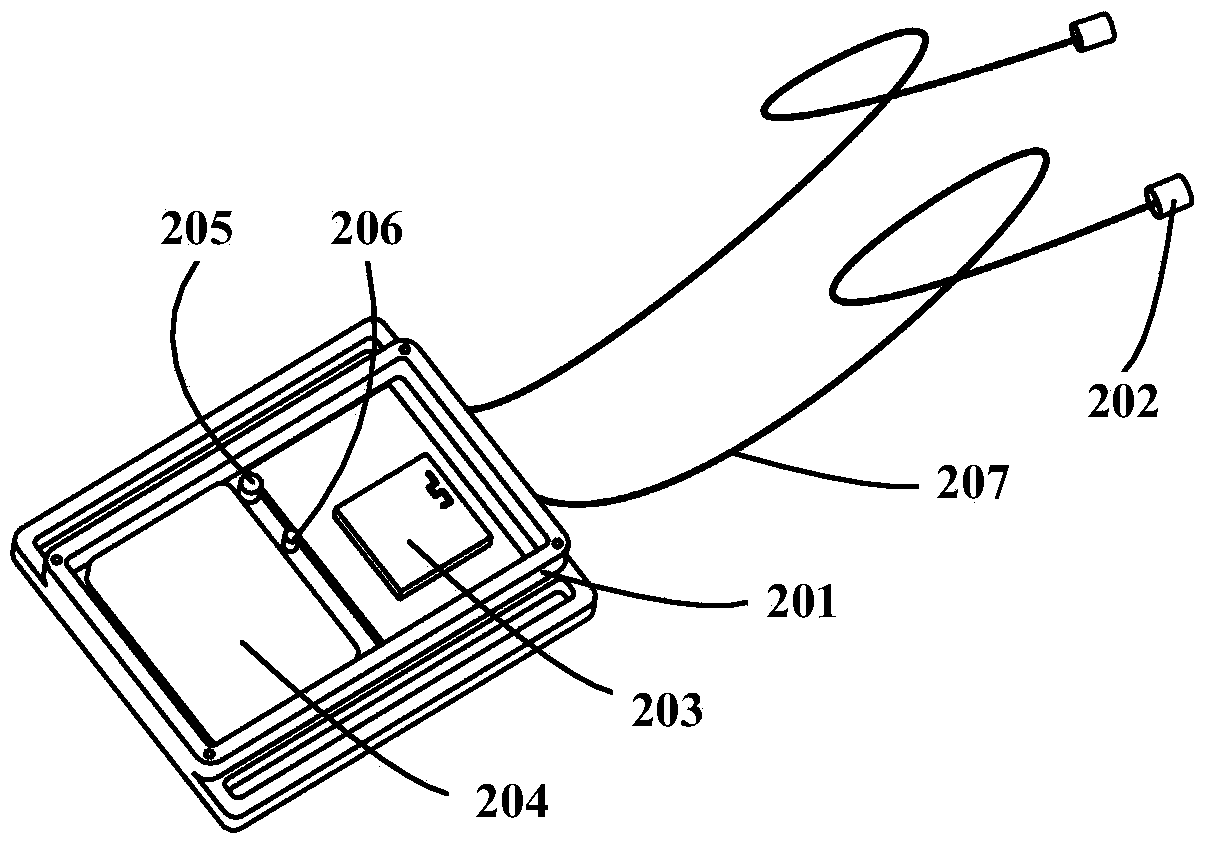
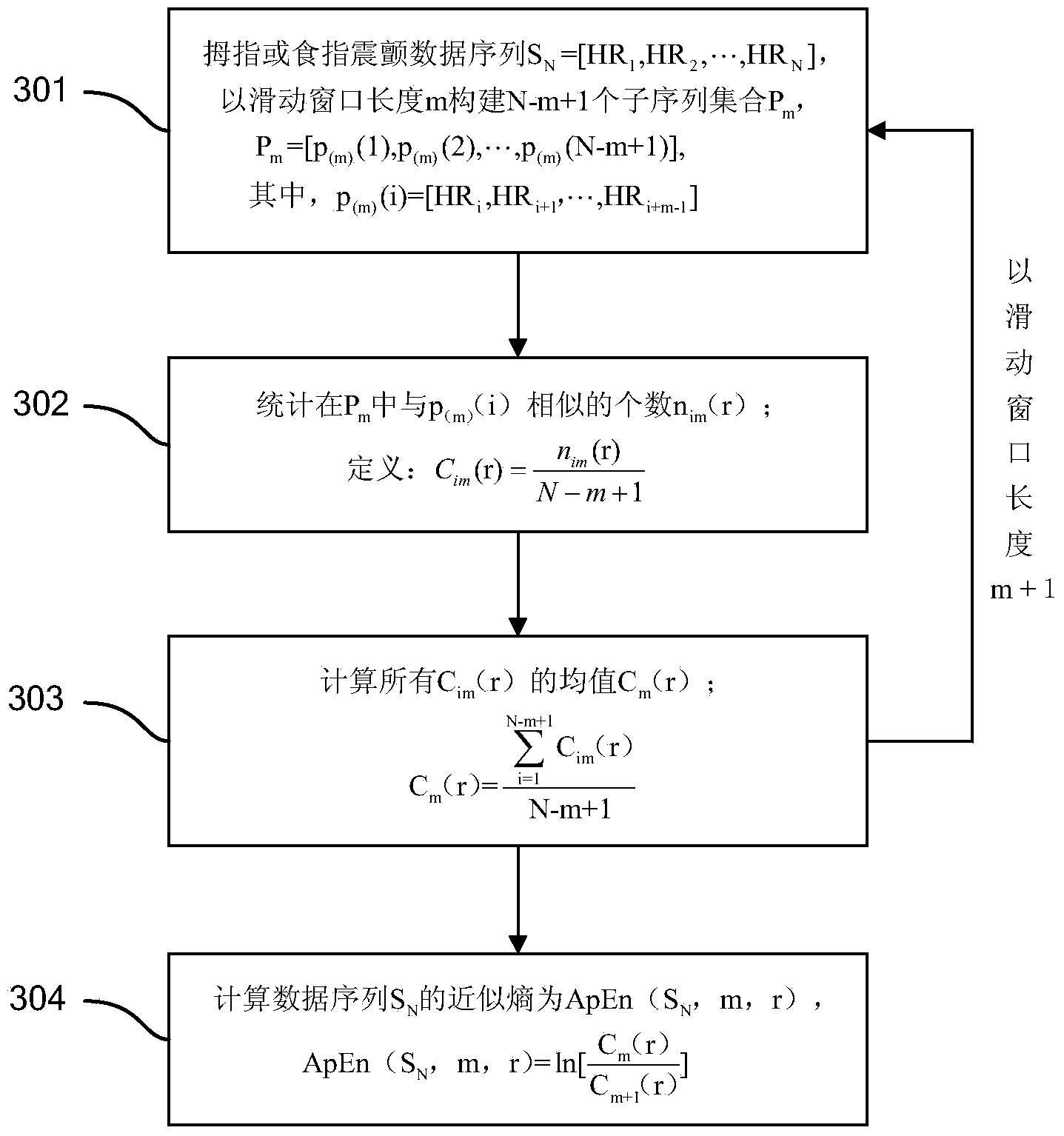
Method for quantitatively evaluating symptoms of tremor of patient with Parkinson's disease according to approximate entropy and cross approximate entropy
ActiveCN104398263ANo damageUnpredictableDiagnostic recording/measuringSensorsTremor amplitudeMedicine
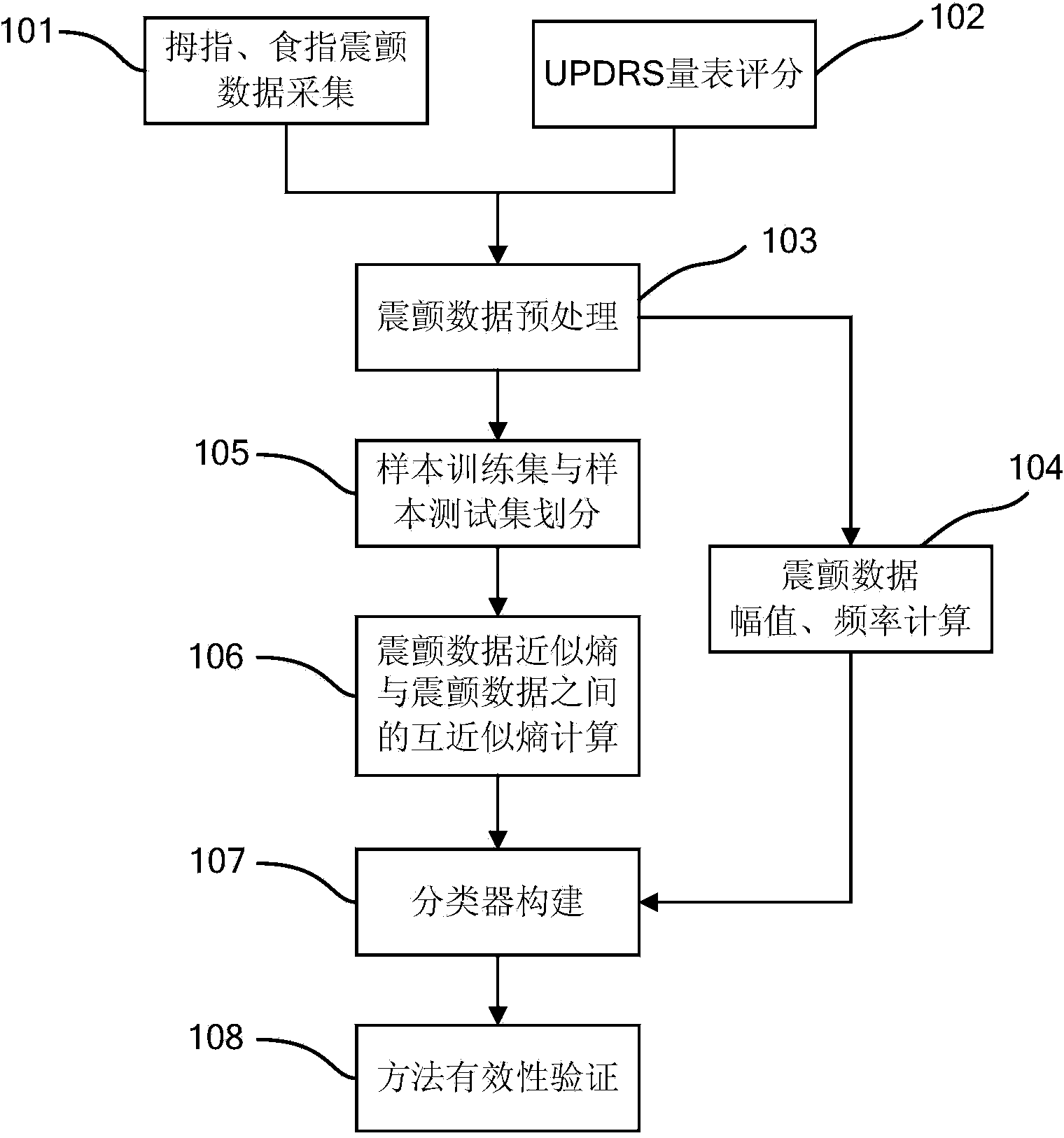
The invention provides a method for quantitatively evaluating the symptoms of tremor of a patient with Parkinson's disease according to the approximate entropy and the cross approximate entropy, belonging to the fields of health care and pattern recognition. The method is characterized by comprising the following steps of: collecting the data of specified tremor of the thumb, collecting the data of specified tremor of the index finger, and grading the specified tremor of the thumb and the specified tremor of the index finger according to a UPDRS (unified Parkinson's disease rating scale); preprocessing the data of tremor; separating a sample training set from a sample testing sample; calculating the approximate entropy and the cross approximate entropy of the data of tremor; constructing the model of a classifier, and verifying the effectiveness of a method. The regularity and the synchronization of the tremor of the patient with Parkinson's disease are disclosed effectively according to the approximate entropy and the cross approximate entropy, and the symptoms of tremor can be accurately and quantitatively classified according to the tremor amplitude, the tremor frequency and other characteristics of the patient. The method is used for objectively evaluating the symptoms of tremor of the patient with Parkinson's disease, and can be applied to the fields of treatment and rehabilitation assessment of the patient with Parkinson's disease and the like.
Owner:HEFEI INSTITUTES OF PHYSICAL SCIENCE - CHINESE ACAD OF SCI +1
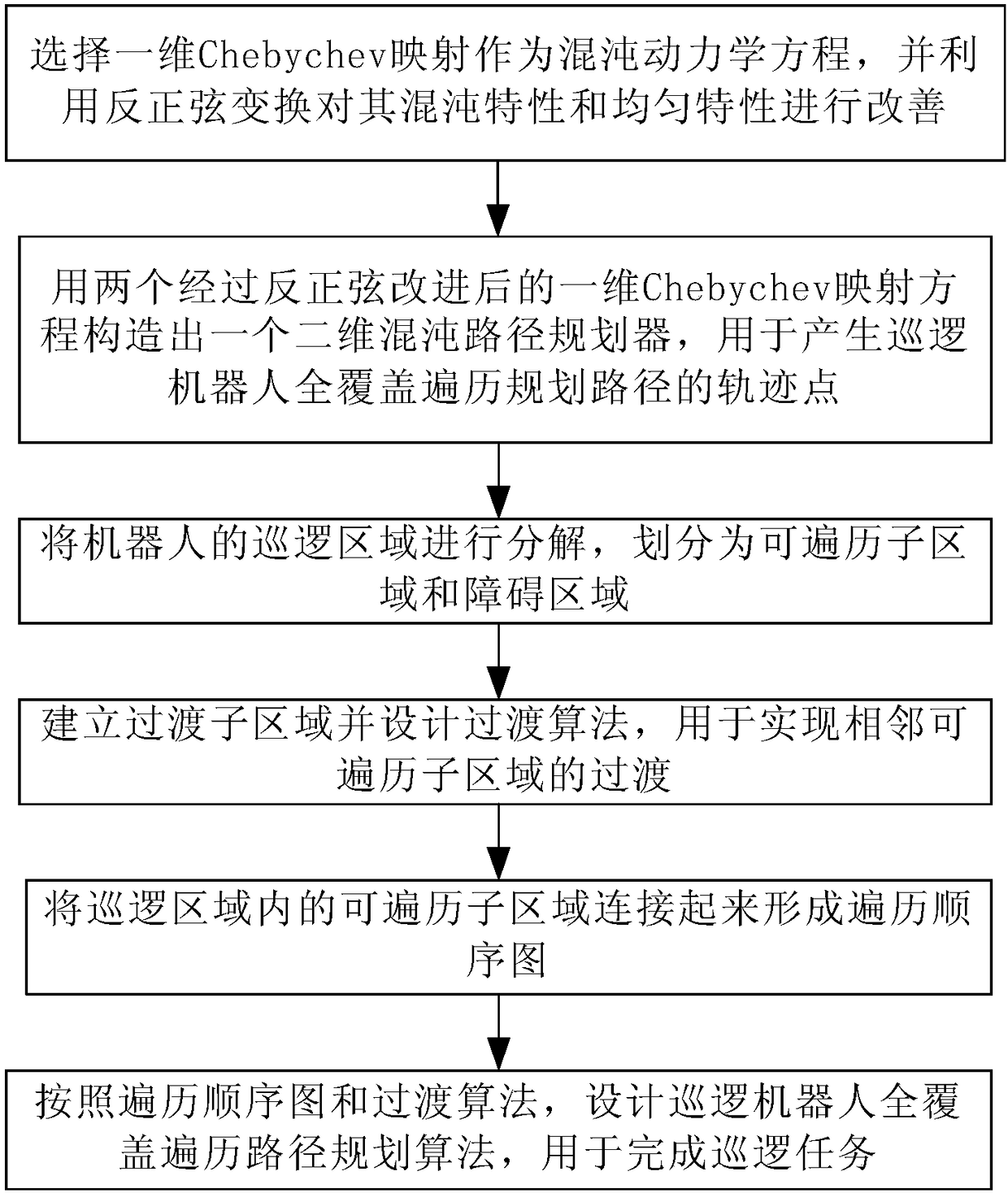
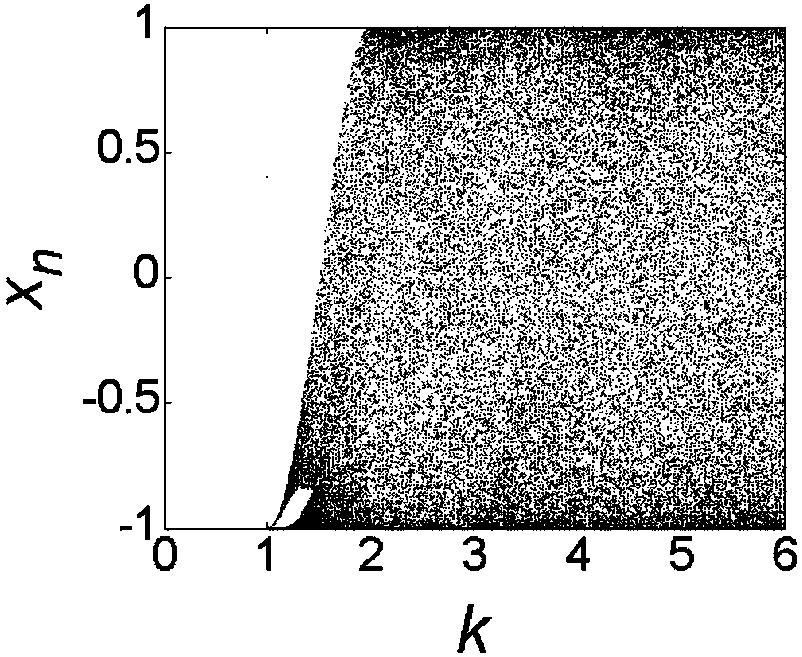
Design method of patrol robot full-coverage traversal path planning algorithm
InactiveCN108255178AIncrease coverageImprove work efficiencyPosition/course control in two dimensionsDynamic equationSequence diagram
The invention discloses a design method of a patrol robot full-coverage traversal path planning algorithm. The method includes the following steps that: a one-dimensional Chebychev mapping is selectedas a chaotic dynamic equation, and inverse sine transformation is utilized to improve the chaotic characteristic and uniform characteristic of the chaotic dynamic equation; two inverse sine-improvedone-dimensional Chebychev mapping equations are adopted to construct a two-dimensional chaotic path planner; the patrol area of a robot is decomposed into traversable sub-regions and obstacle regions;transition sub-regions re established, and a transition algorithm is designed; the traversable sub-regions in the patrol area are connected to form a traversal sequence diagram; the patrol robot full-coverage traversal path planning algorithm is designed according to the traversal sequence diagram and the transition algorithm, and the patrol robot full-coverage traversal path planning algorithm can be used for completing a patrol task. The algorithm of the invention has the advantages of simplicity, low repetition rate and high coverage rate, and can ensure the randomness and unpredictabilityof the patrol task while ensuring full coverage of the patrol area.
Owner:SHANDONG UNIV OF TECH
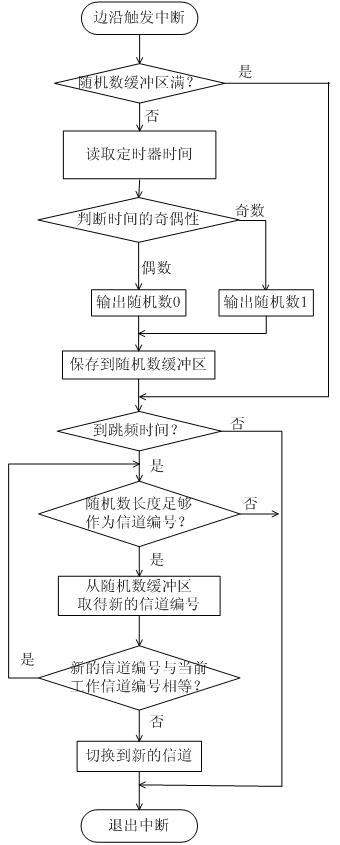
Ultrahigh frequency passive radio frequency identification reader and frequency hopping method thereof
InactiveCN101620665AAvoid collisionSimple circuit designSensing record carriersTransmissionDown conversion mixerUltrahigh frequency
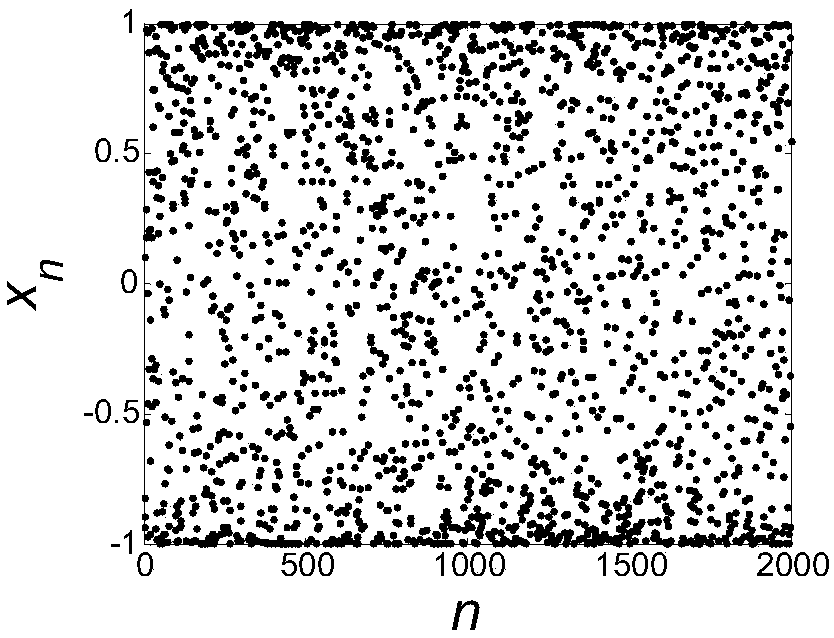
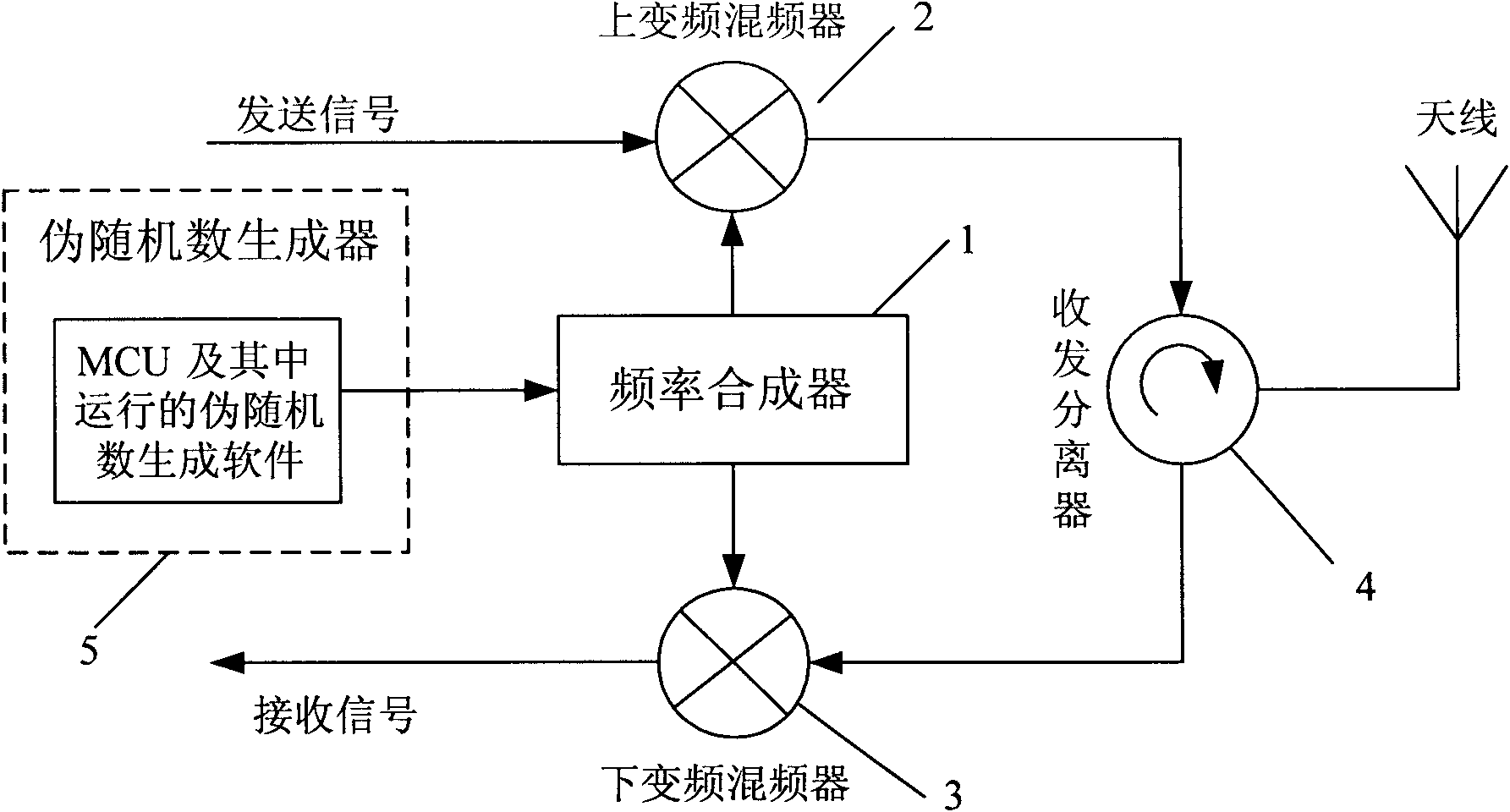
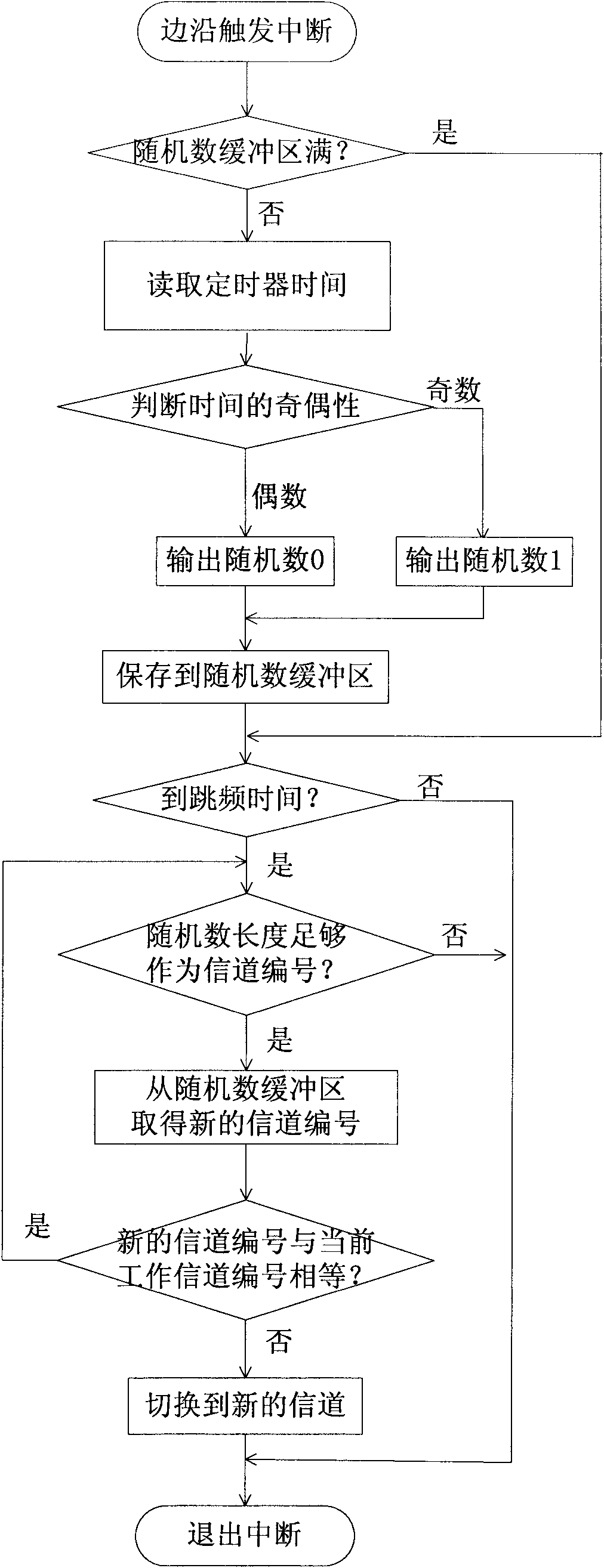
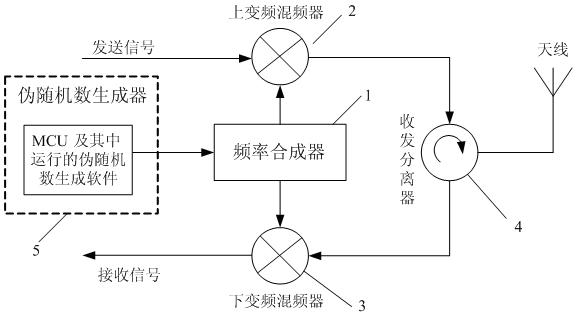
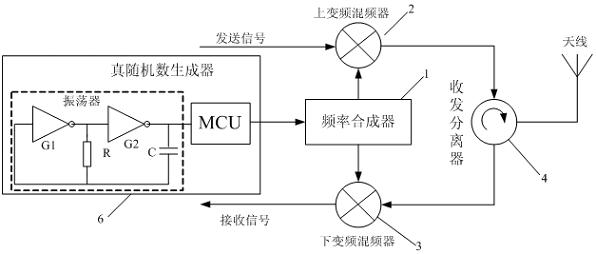
The invention discloses an ultrahigh frequency passive radio frequency identification reader which mainly comprises a frequency synthesizer, an up-conversion mixer, a down-conversion mixer and a receiving-transmitting separator, wherein the up-conversion mixer and the down-conversion mixer are connected with the frequency synthesizer; the receiving-transmitting separator is respectively connected with the up-conversion mixer and the down-conversion mixer. The ultrahigh frequency passive radio frequency identification reader is characterized in that the frequency synthesizer is also connected with a true-random number generator. The invention also discloses a frequency hopping method of the ultrahigh frequency passive radio frequency identification reader. The true-random number generator is used for controlling frequency hopping, and a working channel of each frequency hopping is decided by the true-random number generator. Because a true-random number is not generated by calculating by an algorithm but comes from physical randomness, the true-random number has unpredictability. The invention effectively overcomes the defect that an ordinary ultrahigh frequency passive radio frequency reader adopting a pseudo-random number frequency hopping is easy to be inimically tracked and interfered.
Owner:成都三零盛安信息系统有限公司
On-chip true random number generator
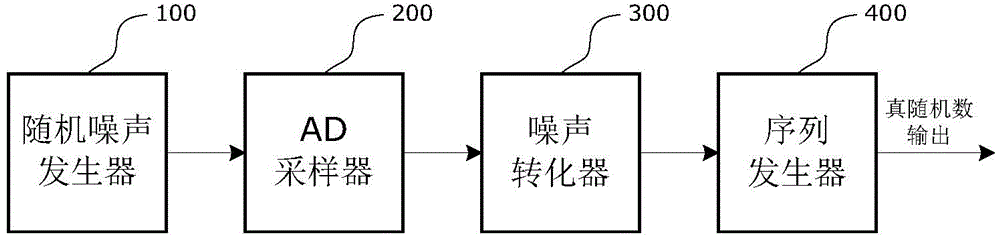
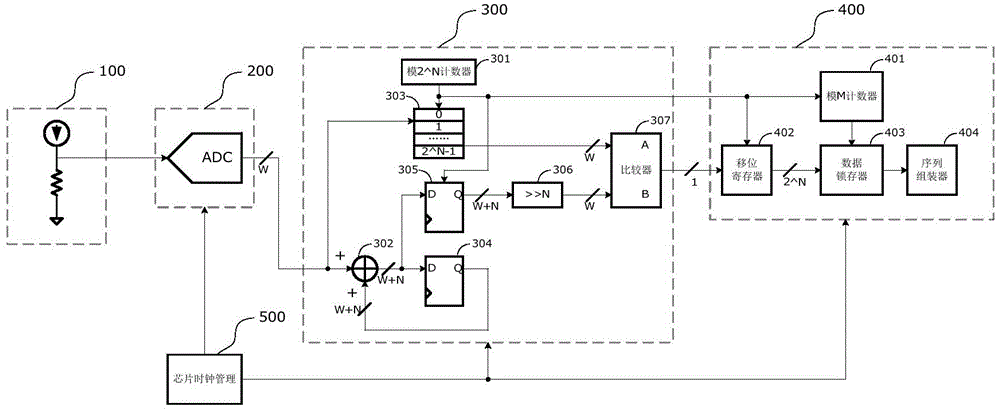
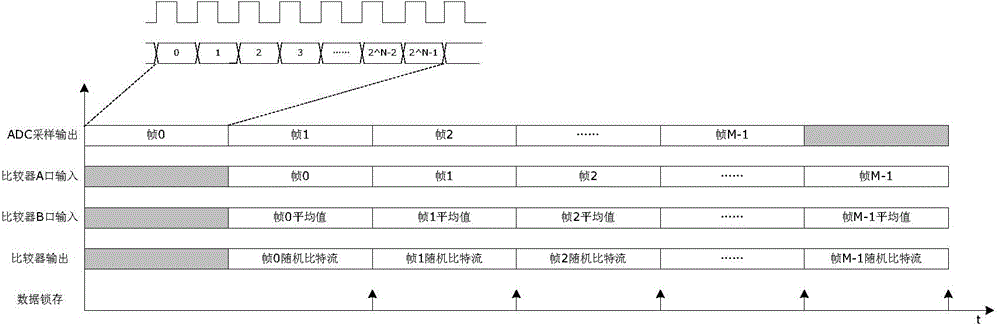
InactiveCN104133658AEvenly distributedQuality improvementRandom number generatorsProduction lineRandom noise
The invention relates to an on-chip true random number generator, which comprises a random noise generator, an AD (Analog to Digital) sampler, a noise converter and a sequence generator. The on-chip true random number generator is characterized in that an on-chip temperature sensor is used as a noise source of the true random number generator; a temperature value is converted into a digital signal through AD sampling; the digital signal obtained through sampling is subjected to noise extraction conversion, and a group of true random sequences is obtained; and finally, a plurality of groups of random sequences are assembled through the sequence generator, and true random numbers in any bit are generated. An on-chip noise signal is used as a signal source of the true random number, so the characteristics of randomness, unpredictability and the like are realized, and the generated random numbers are in uniform distribution, comfort to the characteristics of irrelevance and the like and belongs to high-quality true random numbers. The on-chip true random number generator belongs to an on-chip true random number generator realized by using an integrated circuit; the technologies of chip design production line, synchronous processing, resource reuse and the like are utilized; and the on-chip true random number generator has the advantages that the cost is low, the stability is good, the velocity is high, the realization is easy, and the like.
Owner:JIANGSU HONGYUN TECH
Safe binary arithmetic encoding method for three-dimensional Lorenz mapping control based on weighted processing
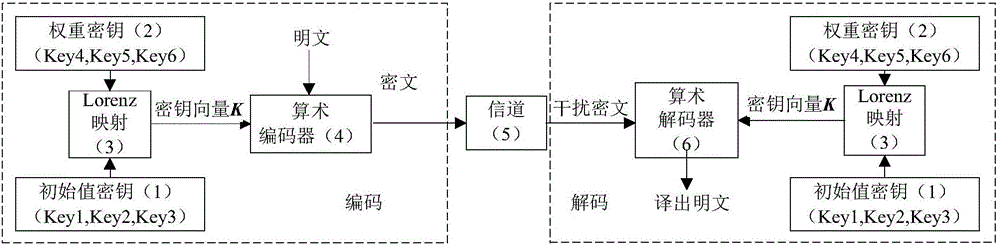
ActiveCN106230578AUnpredictableIncrease the difficulty of crackingKey distribution for secure communicationError preventionBinary-safeData compression
The invention aims at providing a safe binary arithmetic encoding method for three-dimensional Lorenz mapping control based on weighted processing. The method is composed of an initial value key (1), a weight key (2), a Lorenz mapping (3), an arithmetic encoder (4), a channel (5) and an arithmetic decoder (6). An encryption vector is generated by a three-dimensional Lorenz chaotic system, the idea of weight is imported to increase the operation space of the key, and the unpredictability of the encryption vector is stronger than that of a chaotic system with a lower dimension. Meanwhile, by adopting the safe binary arithmetic encoding method provided by the invention, data compression and encryption are integrated without losing the encoding efficiency, thereby simplifying the structure of a communication system.
Owner:HARBIN ENG UNIV
Apparatus for drafting perforated rider bill by WYSWYG manner and drafting method
InactiveCN101493950AConvenient to show againImprove anti-counterfeiting performanceEditing/combining figures or textElectronic documentDocumentation
The invention relates to the computer application field, in particular to a device which is applied to conduct special processing over electronic documents when an electronic seal system conducts the e-signature and a method thereof. The invention provides a device applied to drawing seals on the perforation in a 'what you see is what you get' manner, which comprises the following parts: an electronic document module, an electronic seal module, a drawing module and a control module. The electronic document module completes the management function of an electronic document page; the electronic seal module completes the generating function of an electronic seal face; the drawing module complete the function of drawing seals on the perforation; and the control module completes the function of rotating an electronic document page in accordance with a certain parameter in the 'what you see is what you get' manner, seals on the perforation, partially draws the divided seal on the perforation to the corresponding position on the electronic document page and then saves relevant parameter for future use. The device and the method provided by the invention significantly improve relevant functions of the electronic seal system.
Owner:沈前卫
Oscillator and true random number generating circuit formed by same
ActiveCN104182202ASolve the problem of poor randomnessUnpredictableRandom number generatorsLow speedRandom Number Seed
The invention discloses an oscillator and a true random number generating circuit formed by the same in the field of design of an integrated circuit. The oscillator adopts a novel structure; a main loop can adopt a quadrilateral, octagonal or dodecagonal structure or other structures, i.e. a 4n-gonn structure, wherein n is an integer greater than zero. The true random number generating circuit comprises a high-speed oscillator, a low-speed oscillator, an xor circuit, a clock circuit, a system clock circuit and a sampling circuit. The oscillator provides a random source for the true random number generating circuit, forms the high-speed oscillator and the low-speed oscillator and is controlled by two external enable signals a and b; signals at the output ends of the high-speed oscillator and the low-speed oscillator are different or the high-speed oscillator and the low-speed oscillator output primary random number seeds; the clock circuit and the system clock circuit control the sampling circuit to carry out sampling on the primary random number seeds for twice so as to generate a true random number sequence; the true random number generating circuit solves the problems of poor randomness and periodic generation of the true random number sequence.
Owner:泰芯智能科技(昆山)有限公司
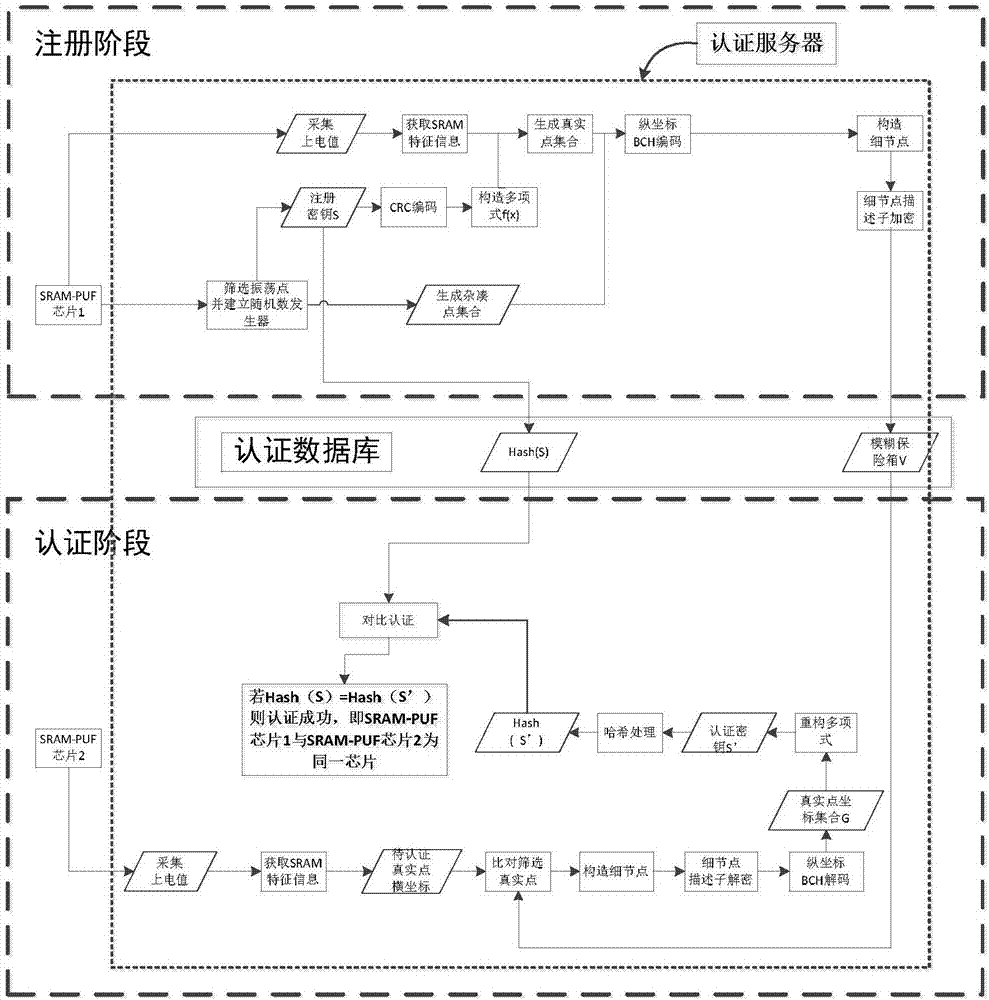
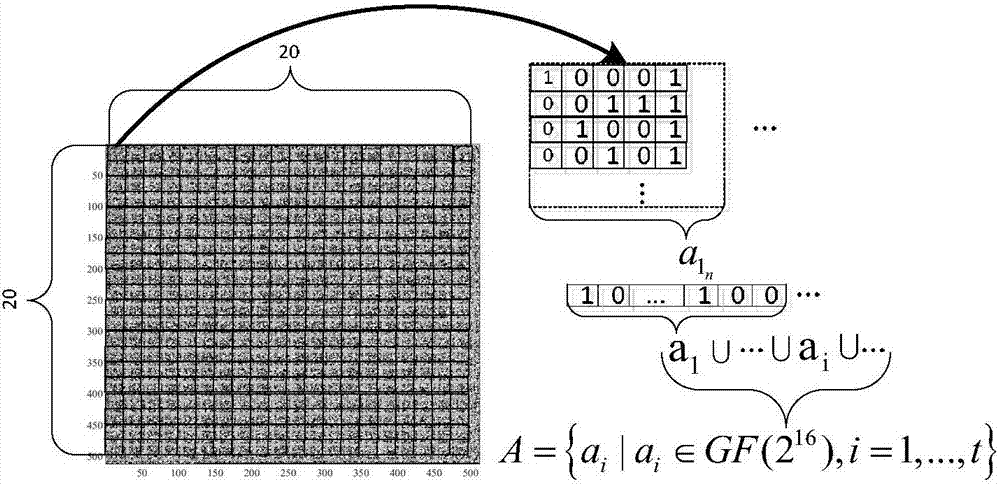
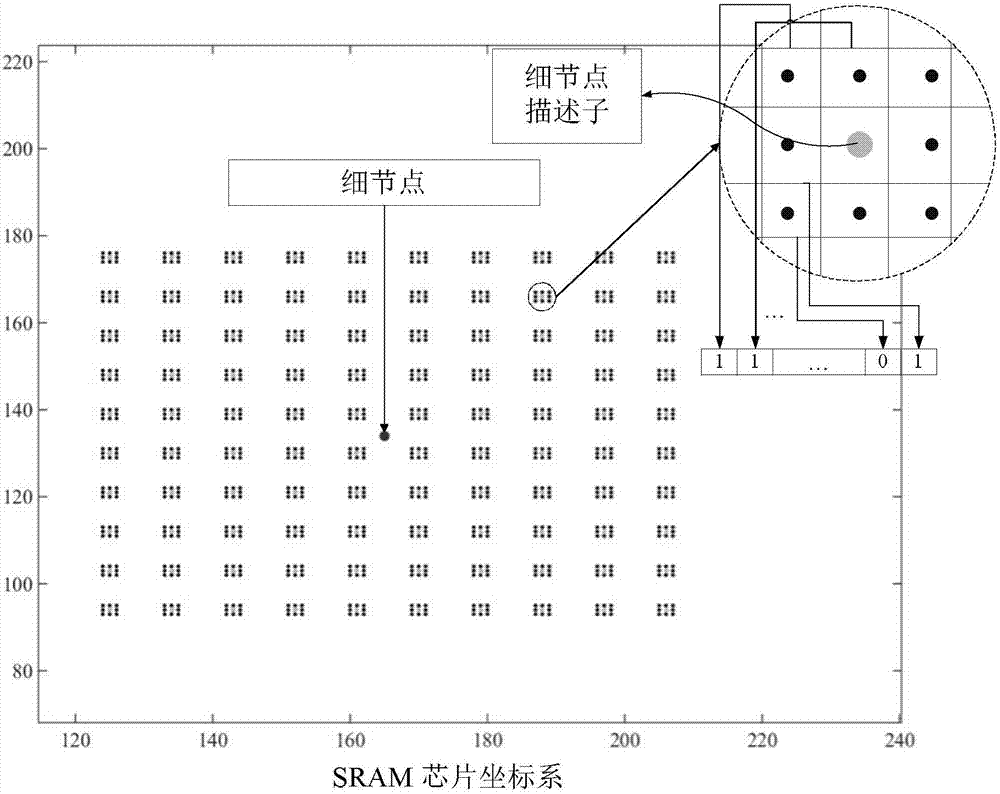
SRAM-PUF-based fuzzy safe box authentication method
ActiveCN106941400AUnpredictableThe distribution is completely randomKey distribution for secure communicationUser identity/authority verificationAmbiguityFeature data
The present invention discloses an SRAM-PUF-based fuzzy safe box authentication method. According to the method, during the registration phase, the feature data of SRAM-PUF are extracted and a secret key S is constructed. Meanwhile, the hash value of the secret key S is calculated. According to the feature data of SRAM-PUF and the secret key S, a fuzzy safe box V is generated for encryption. A corresponding authentication method is provided cooperatively, wherein the fuzzy safe box technology is introduced to the SRAM-PUF-based authentication system. According to the invention, the polynomial reconstruction and the error correction coding are conducted to generate the secret key S. based on the above manner, the reconstruction and authentication of the secret key can still be accurately realized with the presence of a certain error rate PUF. The ambiguity of the PUF and the accuracy of the secret key are organically combined, and an encryption authentication system having the error correction function is provided. As a result, the safety and the reliability in the authentication process are improved. Meanwhile, the method is easy to implement, and can resist various current mainstream attack modes to the fuzzy safe box.
Owner:SOUTHEAST UNIV
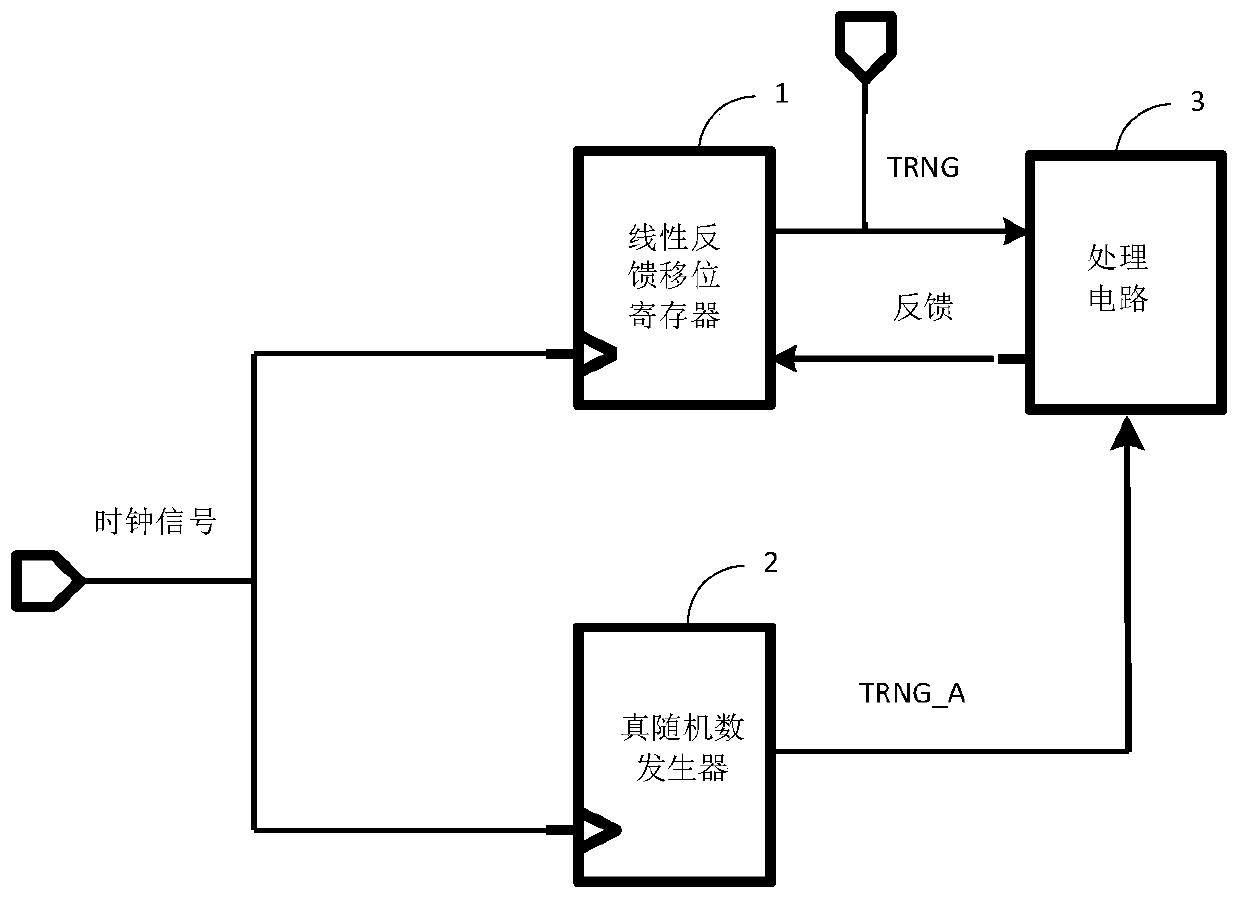
Random number generation circuit
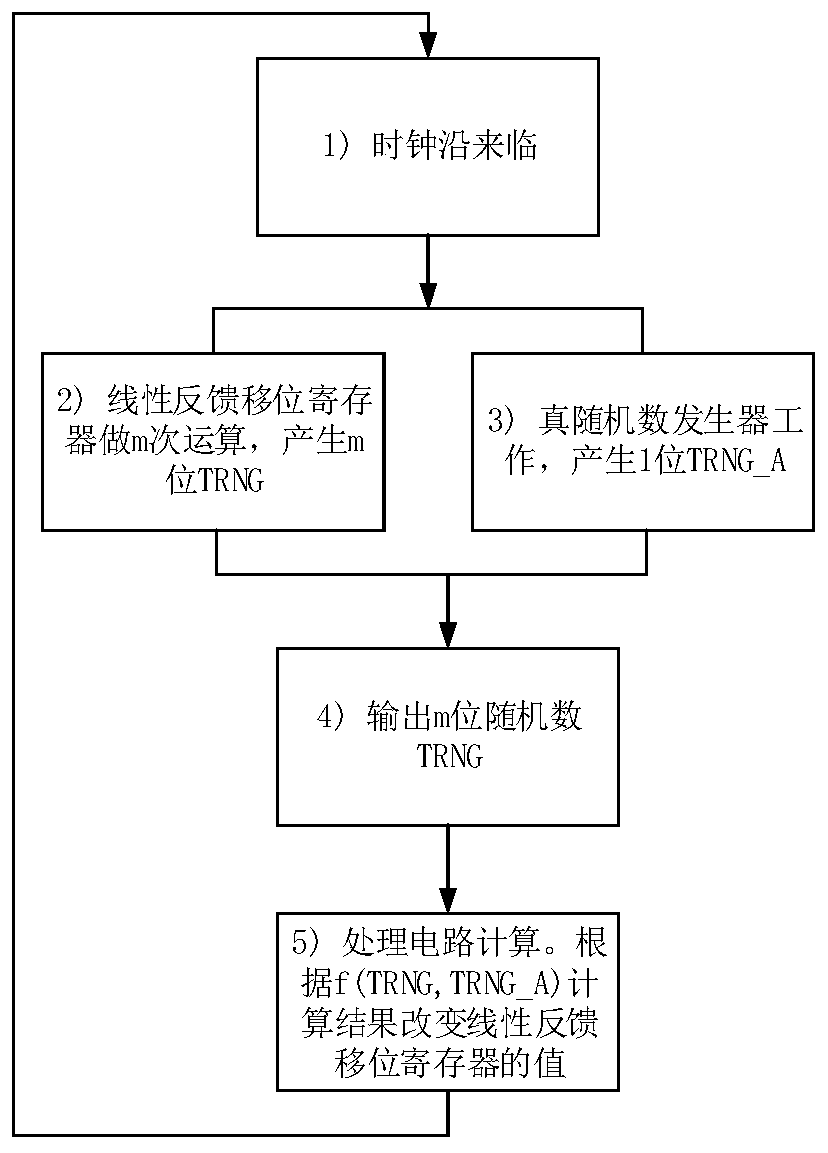
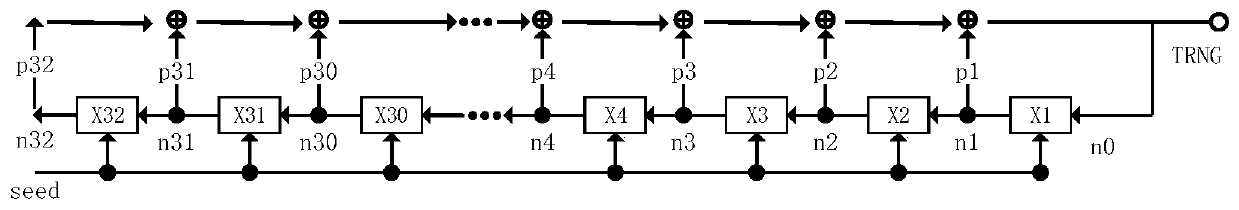
ActiveCN110413257AHigh security requirementsUnpredictableRandom number generatorsRandom number generationClock signal
The invention discloses a random number generation circuit, which comprises a true random number generator used for receiving a first clock signal and generating a one-bit true random number under thecontrol of the first clock signal; a linear feedback shift register used for receiving a second clock signal, generating m-bit pseudo-random numbers under the control of the second clock signal, andoutputting the m-bit pseudo-random numbers as an output result of the random number generation circuit; and a processing circuit respectively connected with the linear feedback shift register and thetrue random number generator, and used for calculating according to the true random number and the m-bit pseudo random number and feeding back a calculation result to the linear feedback shift register. According to the random number generation circuit provided by the invention, the true random number TRNG _ A is introduced, so that the output m-bit TRNG random number has unpredictability, and therequirement of high safety of the random number is met.
Owner:BEIJING SMARTCHIP MICROELECTRONICS TECH COMPANY +2
Ultrahigh-frequency passive radio-frequency identification reader
InactiveCN102117398AUnpredictableOvercoming the Predictability FlawTransmissionSensing by electromagnetic radiationFrequency conversionFrequency frogging
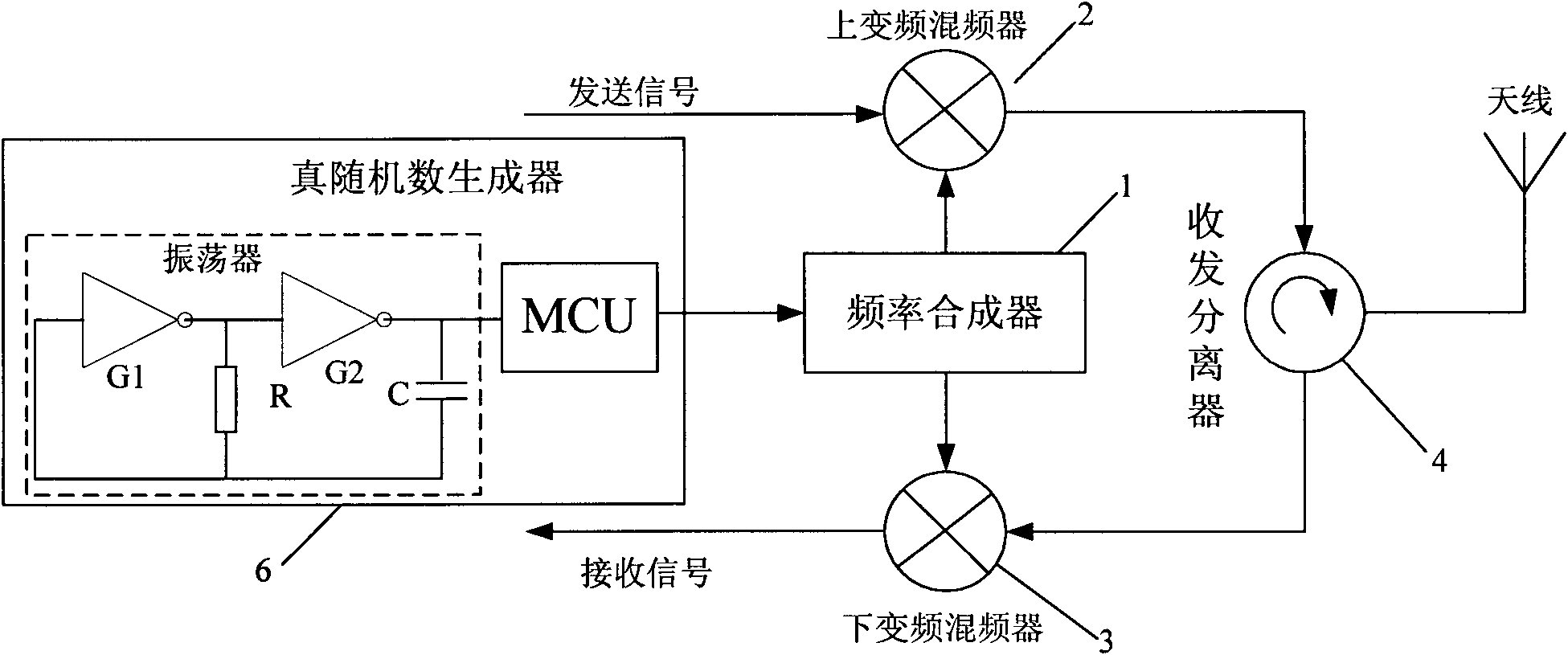
The invention discloses an ultrahigh-frequency passive radio-frequency identification reader, which mainly comprises a frequency synthesizer, an upper frequency conversion mixer, a lower frequency conversion mixer, a receiving separator and a transmitting separator, wherein the upper frequency conversion mixer and the lower upper frequency conversion mixer are connected with the frequency synthesizer respectively; and the receiving separator and the transmitting separator are connected with the frequency conversion mixer and the lower upper frequency conversion mixer respectively. The ultrahigh-frequency passive radio-frequency identification reader is characterized in that the frequency synthesizer is also connected with a real random number generator. According to the invention, the frequency hopping is controlled by the real random number generator and a work channel of each frequency hopping is decided by the real random number. The real random number is not generated by an algorithm but originates from the physical randomness, so that the random number has the unpredictability. By using the invention, the defect that the general ultrahigh-frequency passive radio-frequency identification reader adopting the frequency hopping of the pseudo random number is easy to collide in the same area is overcome. Meanwhile, the defects that the general radio-frequency identification reader adopting the frequency hopping of the pseudo random number is tracked and intervened with hostility easily are overcome.
Owner:成都三零盛安信息系统有限公司
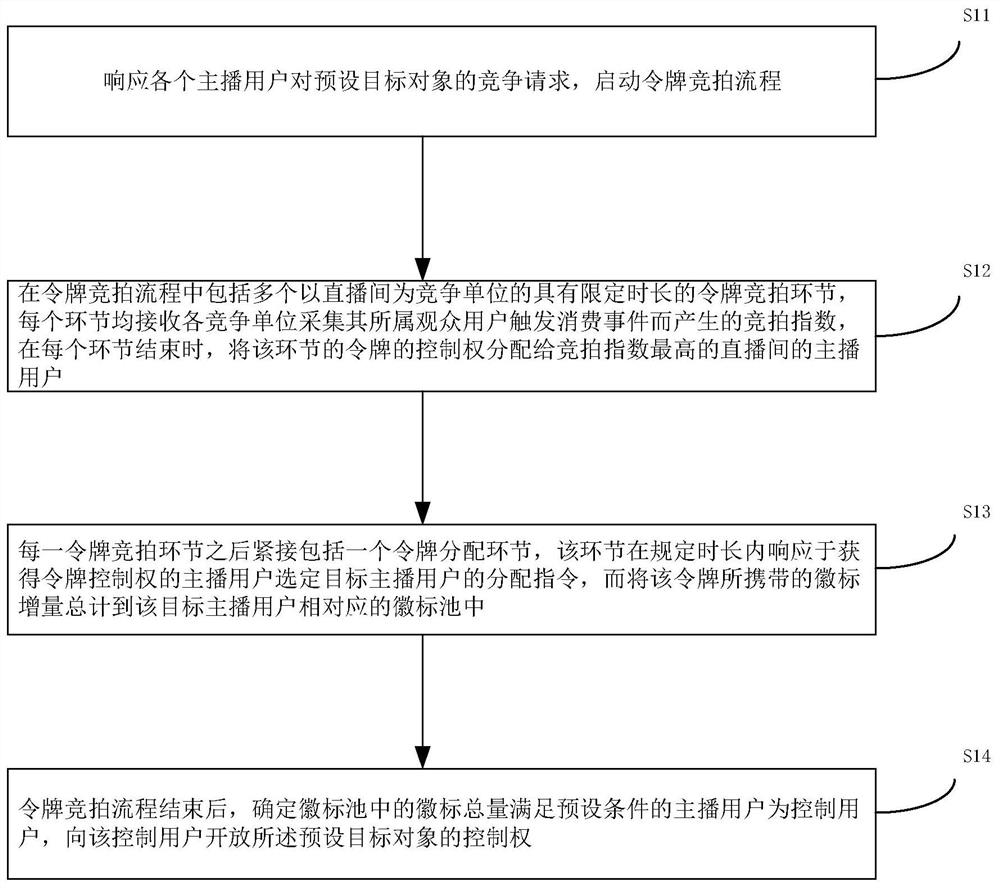
Multi-anchor user connection coordination control method and device, equipment and storage medium
ActiveCN111757134AGood for stimulating interactive trafficPlay efficientlyCommerceSelective content distributionComputer networkOperations research
The invention discloses a multi-anchor user connection coordination control method and device, equipment and a storage medium, and the method comprises the steps when the anchor users of a plurality of live broadcast rooms are in a connection live broadcast state: in response to a competition request of each anchor user for a preset target object, starting a token auction process, the token auction process comprises a plurality of token auction links with limited duration, each link receives an auction index generated by each live broadcast room, and allocates the control right of the token tothe anchor user with the highest auction index; in response to an allocation instruction of the anchor user obtaining the token control right within a specified duration, summing up the logo increment of the token into a logo pool of the target anchor user; and after the token auction process is finished, opening the control right of the preset target object to the anchor user of which the totallogo meets the preset condition. According to the invention, cheating behaviors of online activities in the online live broadcast state can be prevented, and the utilization rate of background resources of the live broadcast platform can be improved.
Owner:广州方硅信息技术有限公司
Random number generation method and system based on interactive curve
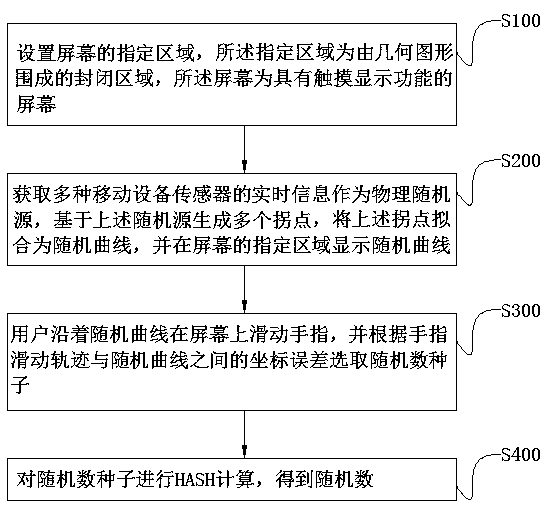
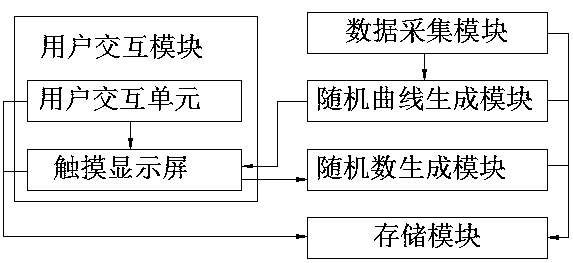
ActiveCN108804011AAvoid Malicious OperationsRandomKey distribution for secure communicationInput/output processes for data processingData acquisitionMobile device
The invention discloses a random number generation method and system based on an interactive curve, and belongs to the field of information security technology. The technical problem to be solved is how to generate random numbers of mobile equipment on the premise of ensuring security and convenience. The method comprises the following steps: generating a random curve by an acquired physical random source; making a user draw a screen along the random curve; and performing HASH calculation on coordinate errors between a screen drawing track and the random curve to generate a random number. Thesystem comprises a user interaction module, a data acquisition module, a random curve generation module, a random number generation module and a storage module. Through adoption of the method and thesystem, random and unpredictable random numbers of the mobile equipment can be generated.
Owner:北京信任度科技有限公司
Data link anti-quantum computing communication method and system based on ID cryptography and symmetric key pool
ActiveCN111698095AUnpredictableEnabling Quantum Computing Resistant CommunicationsKey distribution for secure communicationPublic key for secure communicationKey (cryptography)Syncword
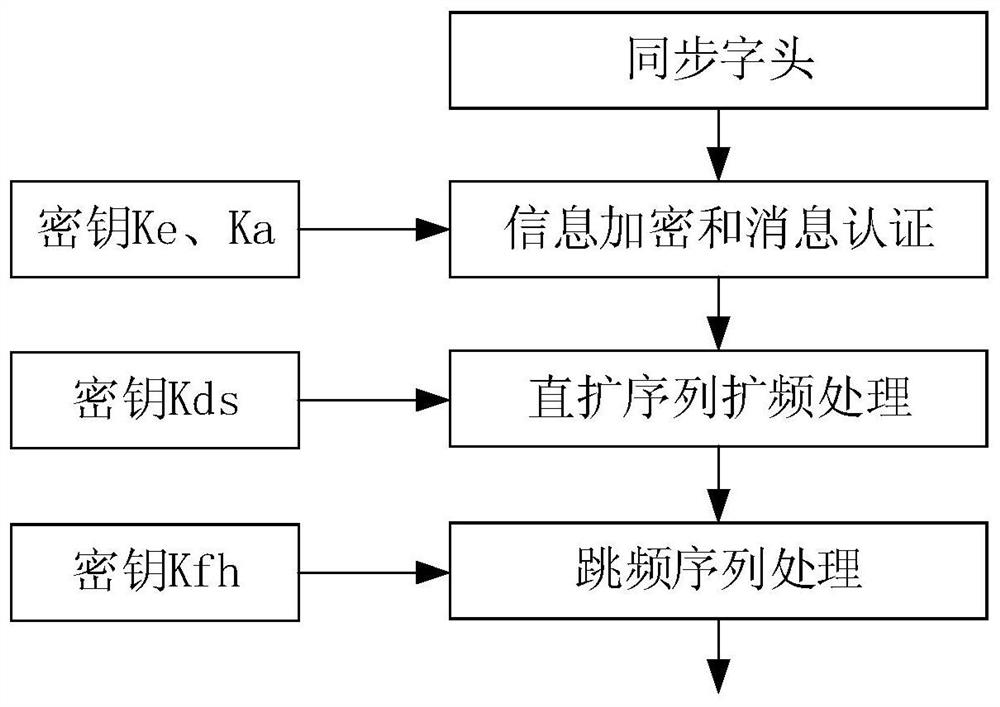
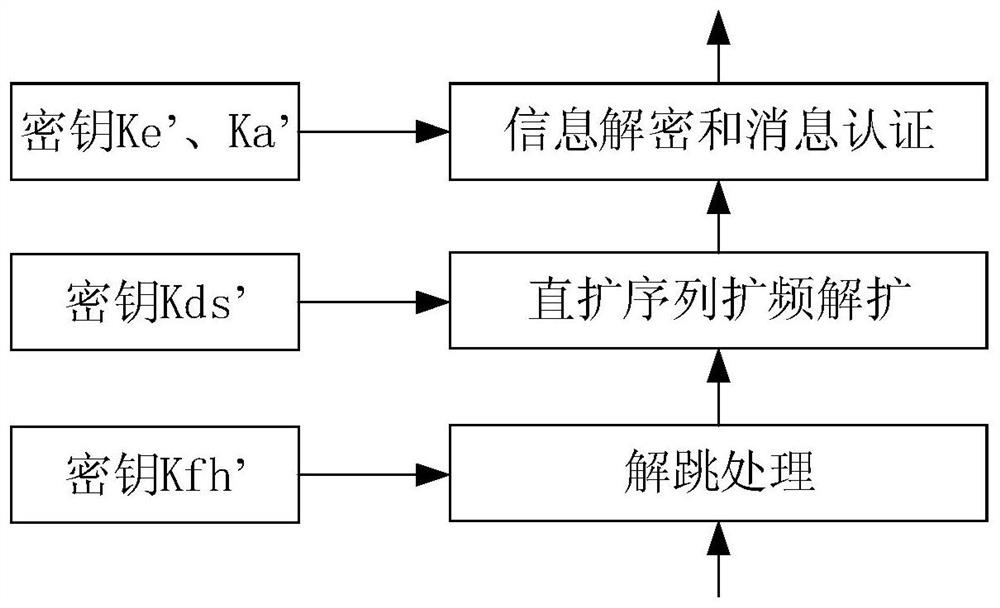
The invention provides a data link anti-quantum computing communication method and system based on ID cryptography and a symmetric key pool. The method comprises the following steps: firstly, allocating respective identity IDs and private keys to two communication parties through an ID cryptography mechanism, calculating opposite side public keys by the two communication parties respectively by utilizing the IDs disclosed by the opposite sides, and calculating symmetric keys according to the own private keys and the opposite side public keys; when the two parties with the symmetric key communicate with each other, enabling asender and areceiver to perform frequency hopping synchronization through adoption of a synchronization header method, and appoint to select at least one part of information in the synchronization header as initial information; enabling the initial information to besubjected to root key transformation by a key pool, so that the initial information acquired by the enemy becomes useless information; and then, based on a true random number key sequence in three links of root key calculation information encryption and message authentication, direct sequence spread spectrum and frequency hopping which cannot be obtained by an enemy, achieving anti-quantum calculation of data transmission, and therefore the security of the whole data link system is greatly improved.
Owner:南京如般量子科技有限公司 +1
Image encryption method based on chaotic mapping and chaotic S-box substitution
ActiveCN112906043AImprove relevanceAvoid crackingDigital data protectionImage data processing detailsColor imageS-box
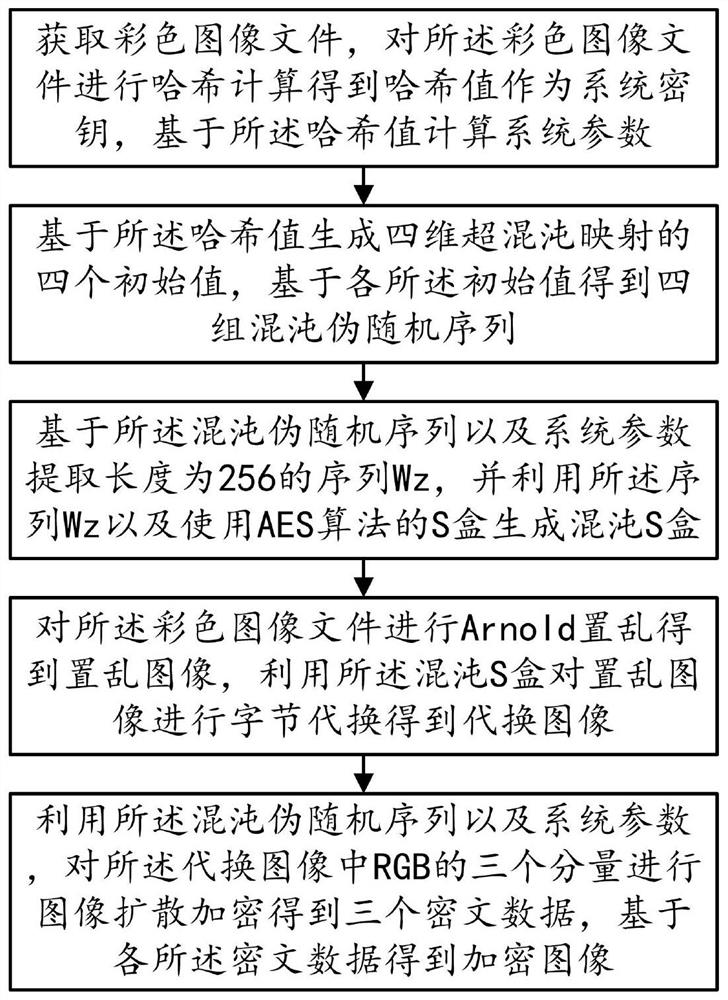
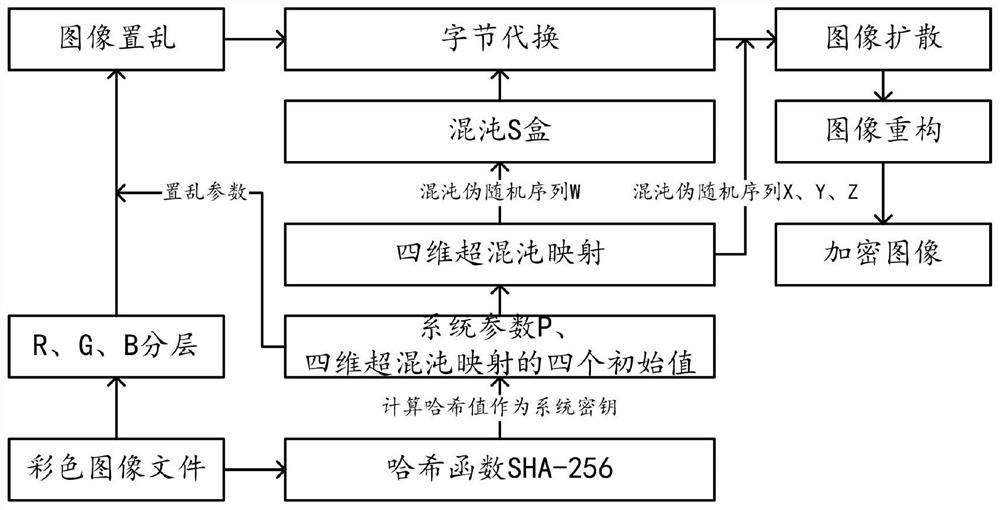
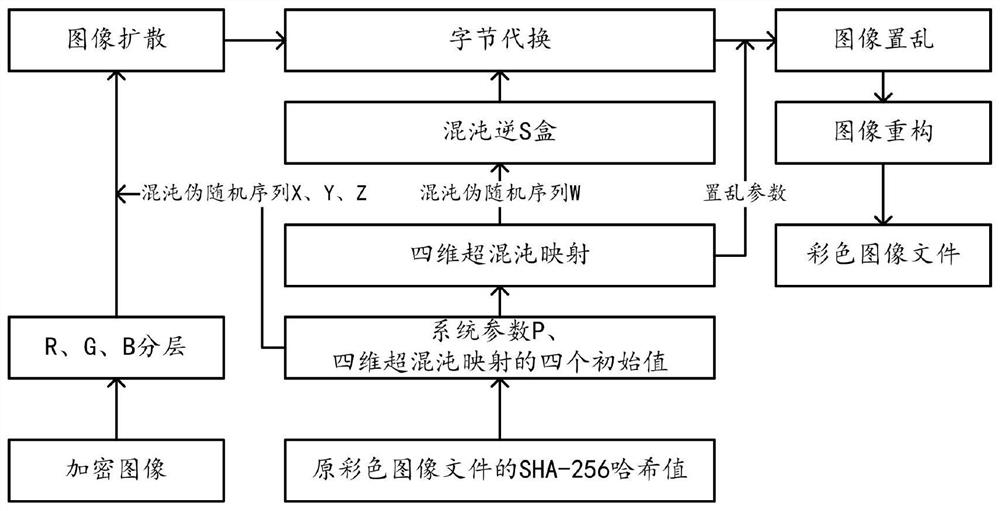
The invention provides an image encryption method based on chaotic mapping and chaotic S-box substitution in the technical field of image encryption, and the method comprises the steps: S10, obtaining a color image file, carrying out the Hash calculation, obtaining a Hash value, and calculating a system parameter based on the Hash value; step S20, generating four initial values of four-dimensional hyper-chaotic mapping based on the Hash values, and further obtaining four groups of chaotic pseudo-random sequences; s30, extracting a sequence Wz based on the chaotic pseudo-random sequence and system parameters, and generating a chaotic S box by using the sequence Wz and the S box using the AES algorithm; step S40, performing Arnold scrambling on the color image file to obtain a scrambled image, and performing byte substitution on the scrambled image by using a chaos S box to obtain a substituted image; and S50, performing image diffusion encryption on the three components of the RGB in the substitution image by using the chaos pseudo-random sequence and the system parameters to obtain three pieces of ciphertext data, and obtaining an encrypted image based on each piece of ciphertext data. The method has the advantage that the security of image encryption is greatly improved.
Owner:HUAQIAO UNIVERSITY
Highly encrypted RFID authentication system for chip fingerprints
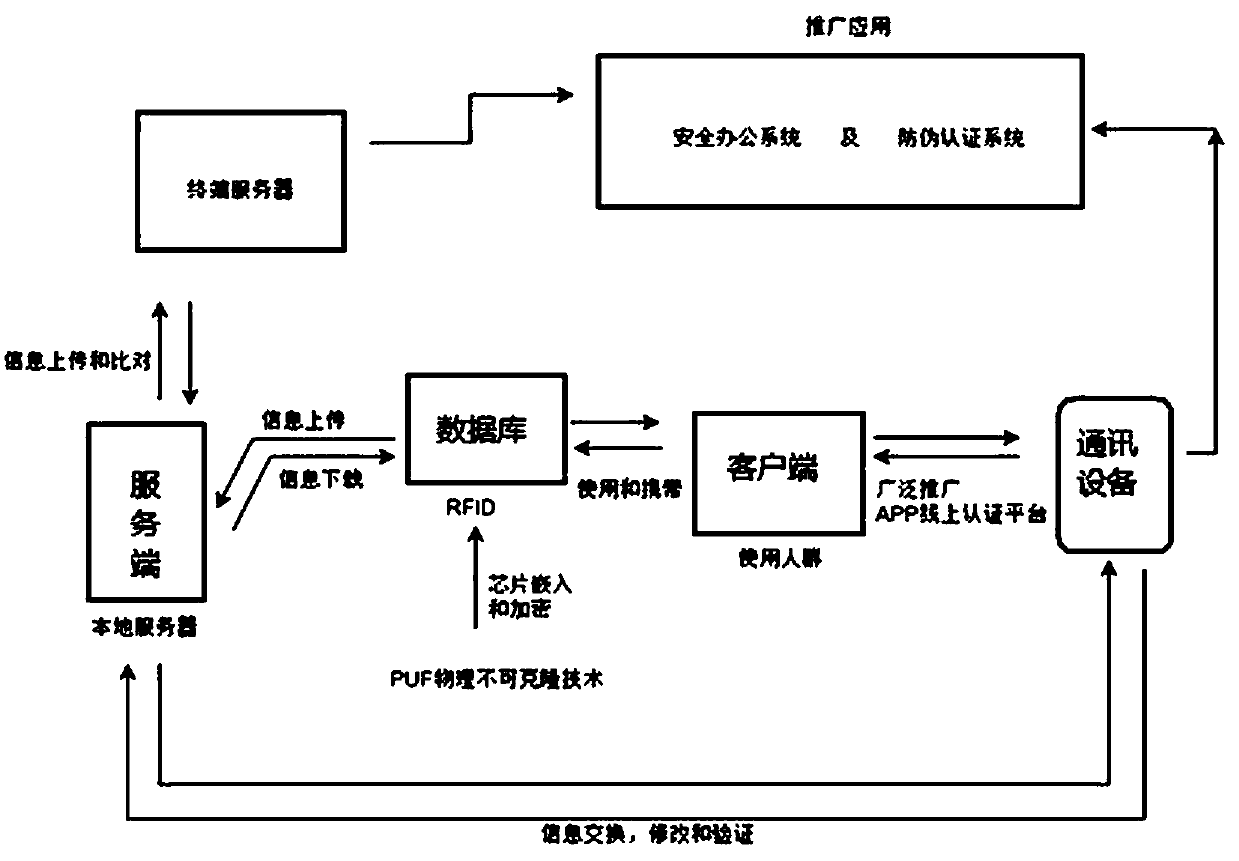
PendingCN110276423ARobustNon-clonableCo-operative working arrangementsInternal/peripheral component protectionRfid authenticationTerminal server
The invention discloses a highly encrypted RFID authentication system for chip fingerprints. The highly encrypted RFID authentication system comprises a server, a terminal server, a popularization and application module, communication equipment, a client and a database, wherein the server is in control connection with the terminal server; the server is in control connection with the communication equipment and used for achieving information exchange, modification and verification; the server is in control connection with the database, the client and the communication equipment in sequence; and the server and the database are used for controlling information uploading and downloading. In this way, the highly encrypted RFID authentication system for chip fingerprints utilizes the internal physical structure of the physical entity to uniquely identify a single physical entity to realize an effective authentication thought, fully utilizes the RFID of the PUF (Physical Unclonable Function), and utilizes the characteristics of robustness, unclonability and unpredictability of the PUF at the same time, so that the highly encrypted RFID authentication system for the chip fingerprint is widely applied to the field of authentication.
Owner:苏州因缇格电子科技有限公司
Automatic music lottery drawing machine and lottery drawing method
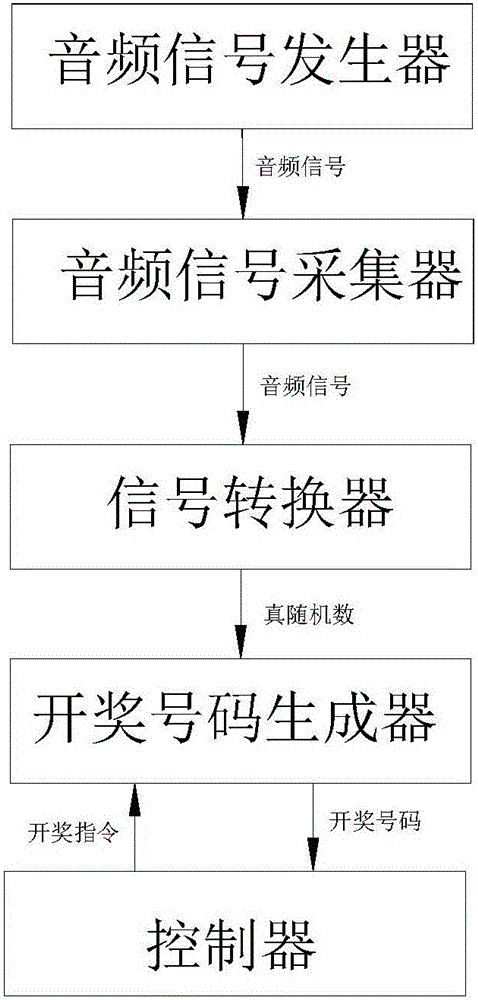
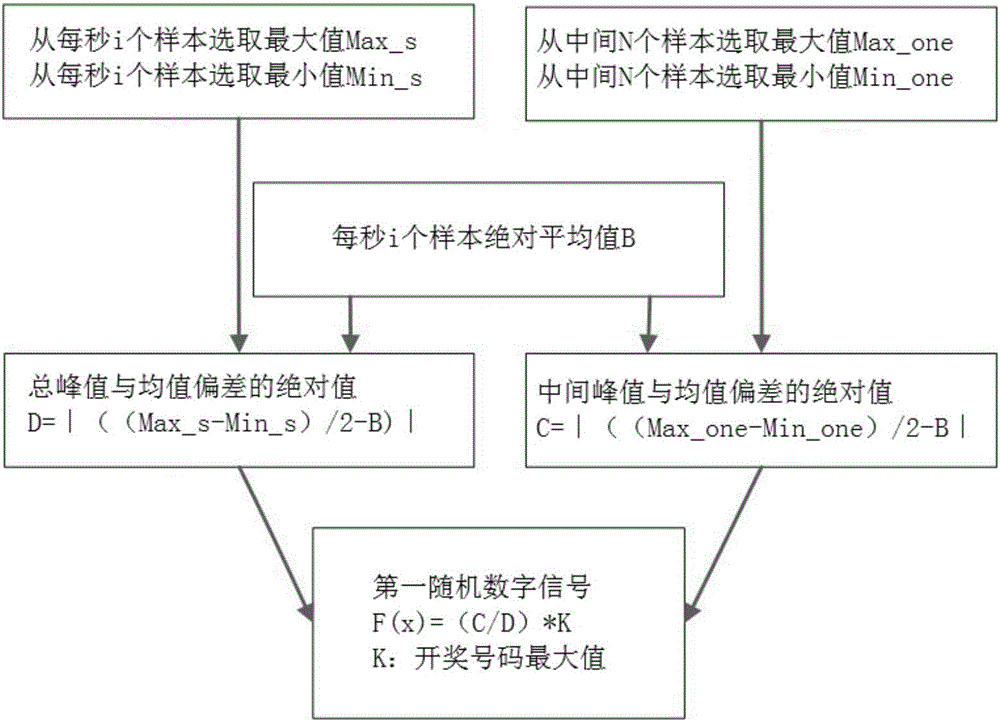
InactiveCN105913536AIncrease randomnessStrong randomnessLottery apparatusNumber generatorBase sequence
The invention discloses an automatic music lottery drawing machine and a lottery drawing method. The lottery drawing machine comprises an audio signal generator for sending a random audio signal, an audio signal acquisition unit for acquiring a random audio signal sent by the audio signal generator, a signal converter for converting the acquired random audio signal into a first random digital signal, a controller for sending a lottery drawing control instruction, and a lottery drawing number generator for putting the first random digital signal into a pseudorandom number base sequence to generate a real random number base sequence, and generating a lottery drawing number from the real random number base sequence according to the lottery drawing control instruction sent by the controller. The automatic music lottery drawing machine is high in automation degree, strong in randomness and high in unpredictability and requirements on modern rapid and automatic lottery drawing are met.
Owner:上海申彩信息系统有限公司
Internet of vehicles trust management method based on double-layer block chain
ActiveCN112862311AAbility to improve reliabilityUnpredictableInterprogram communicationResourcesEvaluation resultAttack
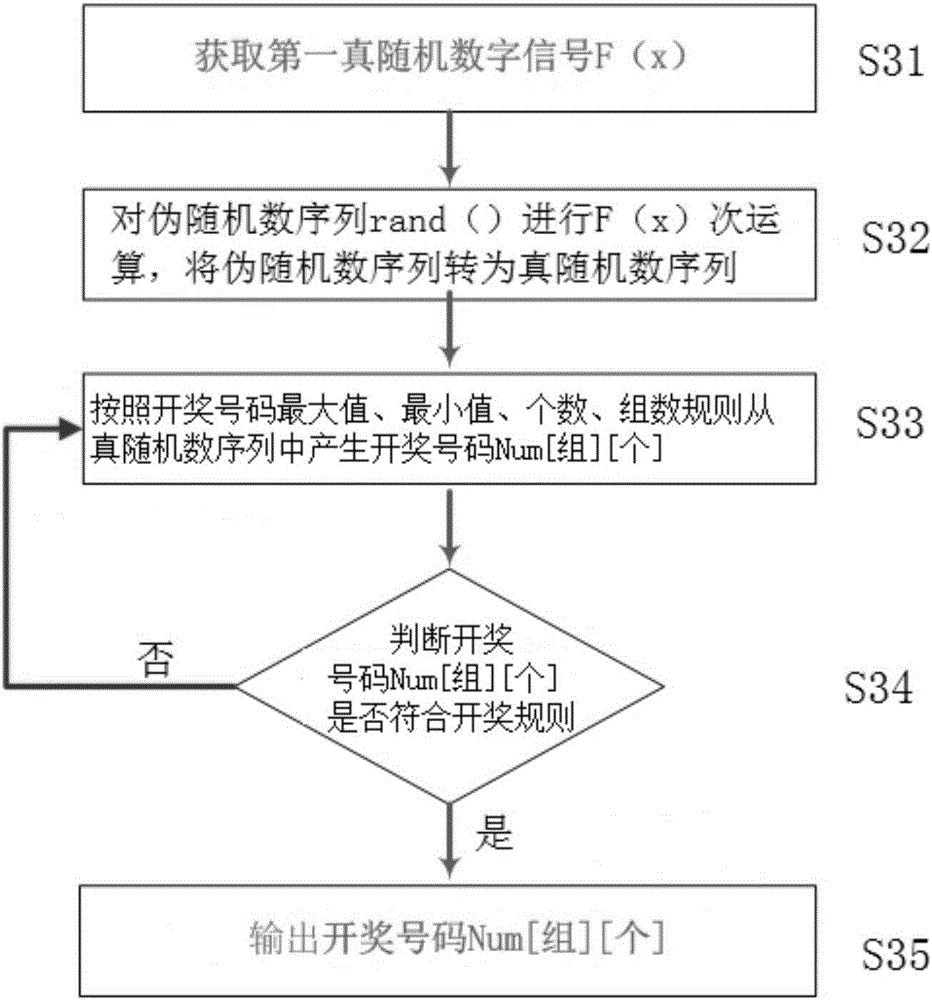
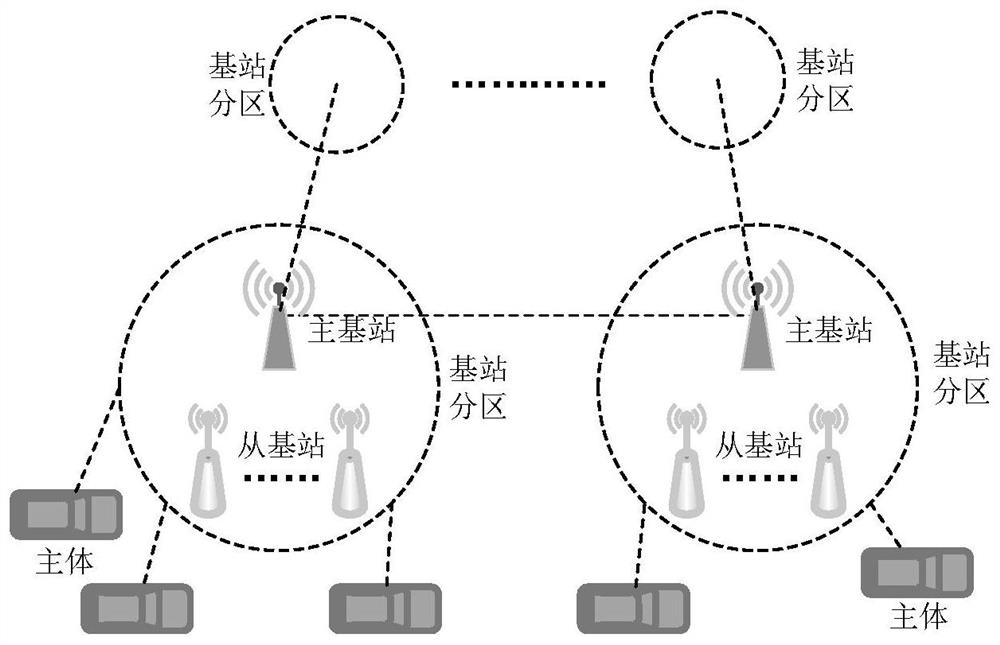
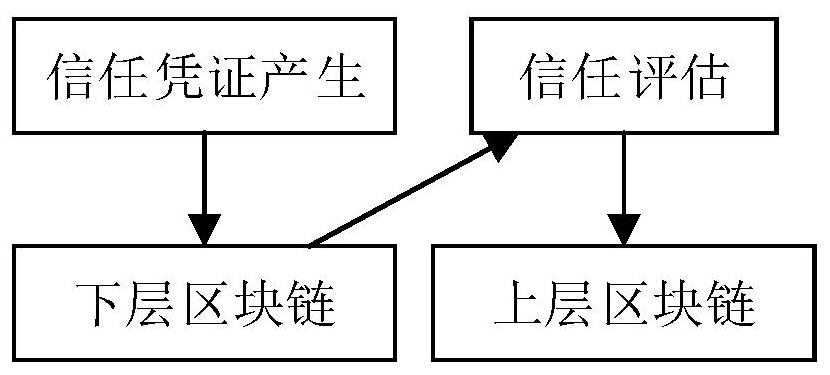
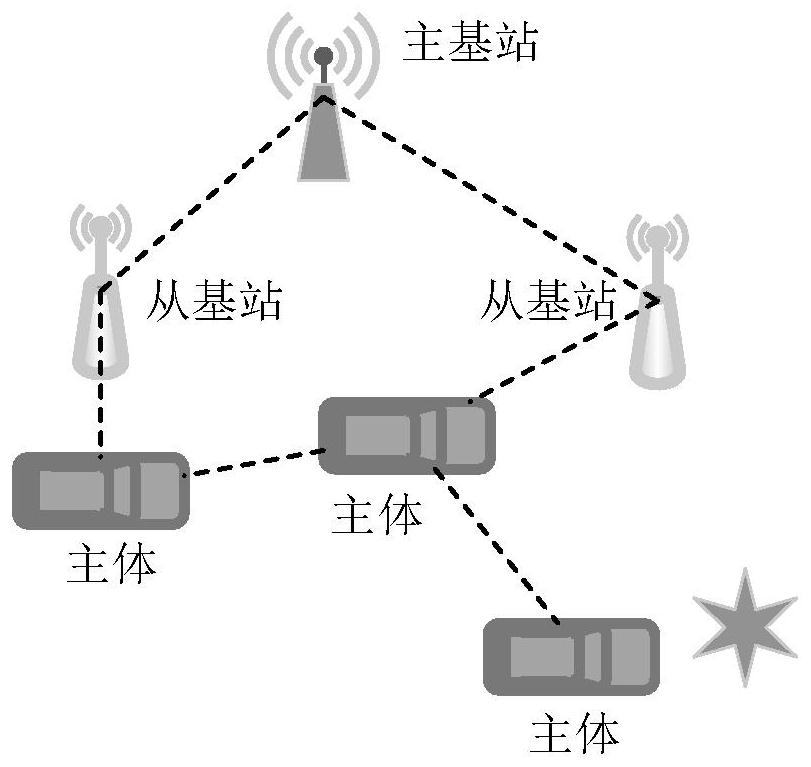
The invention discloses an Internet of Vehicles trust management method based on a double-layer block chain, which constructs a new trust voucher and evaluation system, and reflects the behavior trend of a subject through the behavior frequency and trust value acceleration change of the Internet of Vehicles subject, thereby effectively improving the ability of a trust index set to evaluate the reliability of the subject. A double-layer block chain structure is adopted, trust evaluation data and trust voucher data are stored at the same time, and the two types of data are mutually independent logically. Therefore, the trust evaluation system has the capability of accommodating dual-granularity data, and auditing performance and traceability of trust evaluation results are guaranteed. For node characteristics of a trust management system, an accounting right distribution algorithm based on a pseudo-random number is provided, the consensus efficiency can be effectively improved, and calculation power consumption caused by consensus can be avoided. According to the method, the accounting node sequence can be unpredictable, so that a collusion attack is effectively prevented.
Owner:FUJIAN UNIV OF TECH
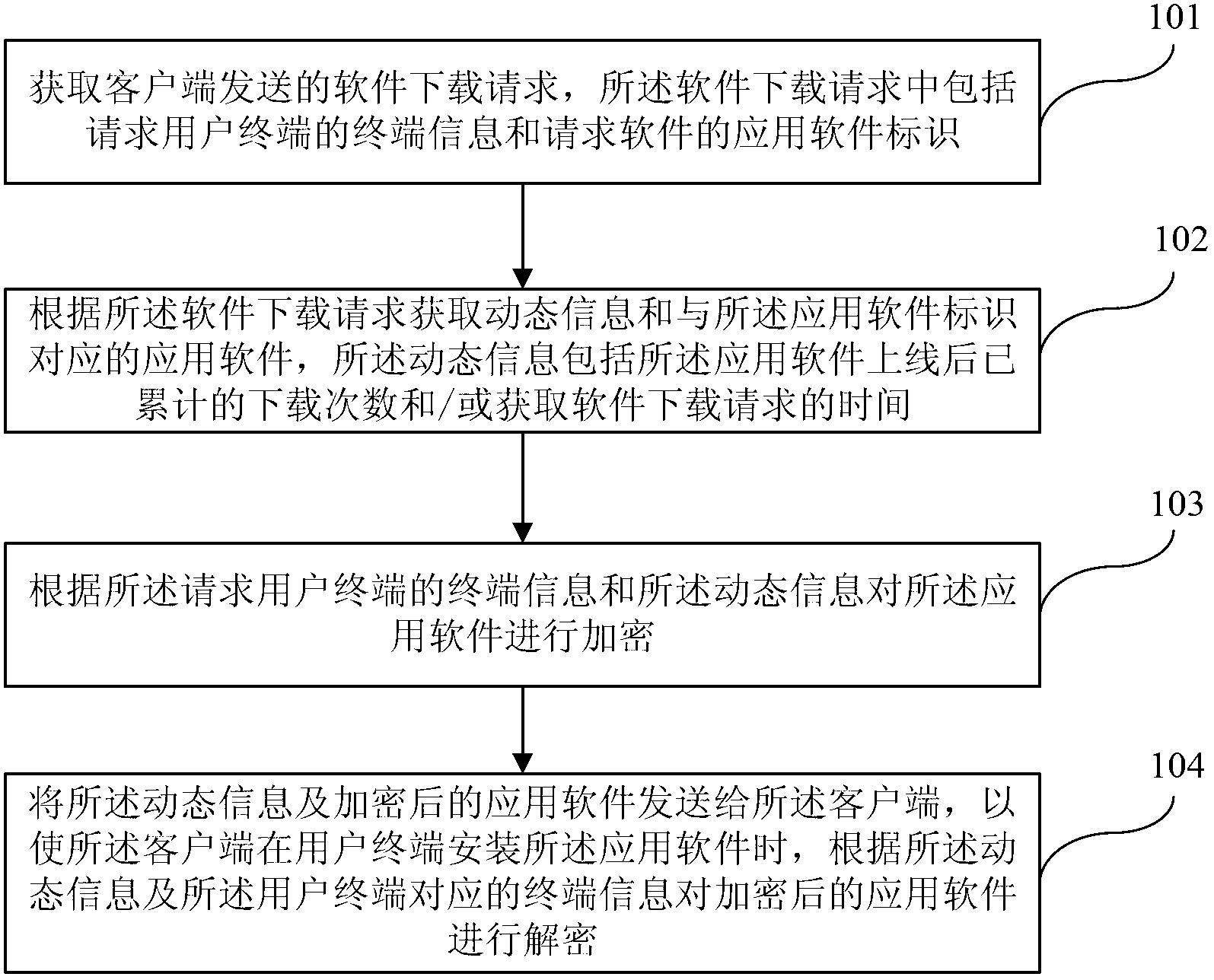
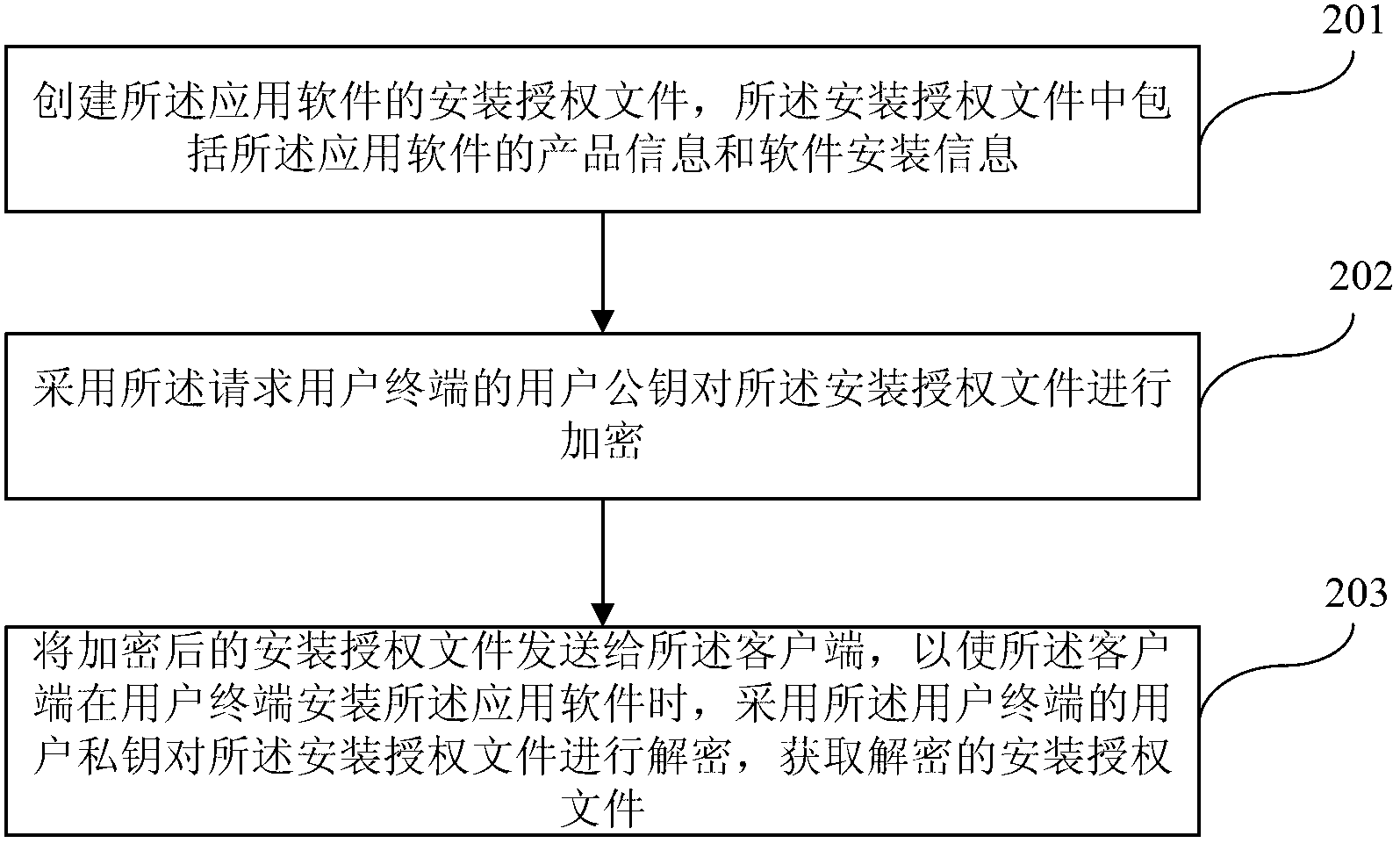
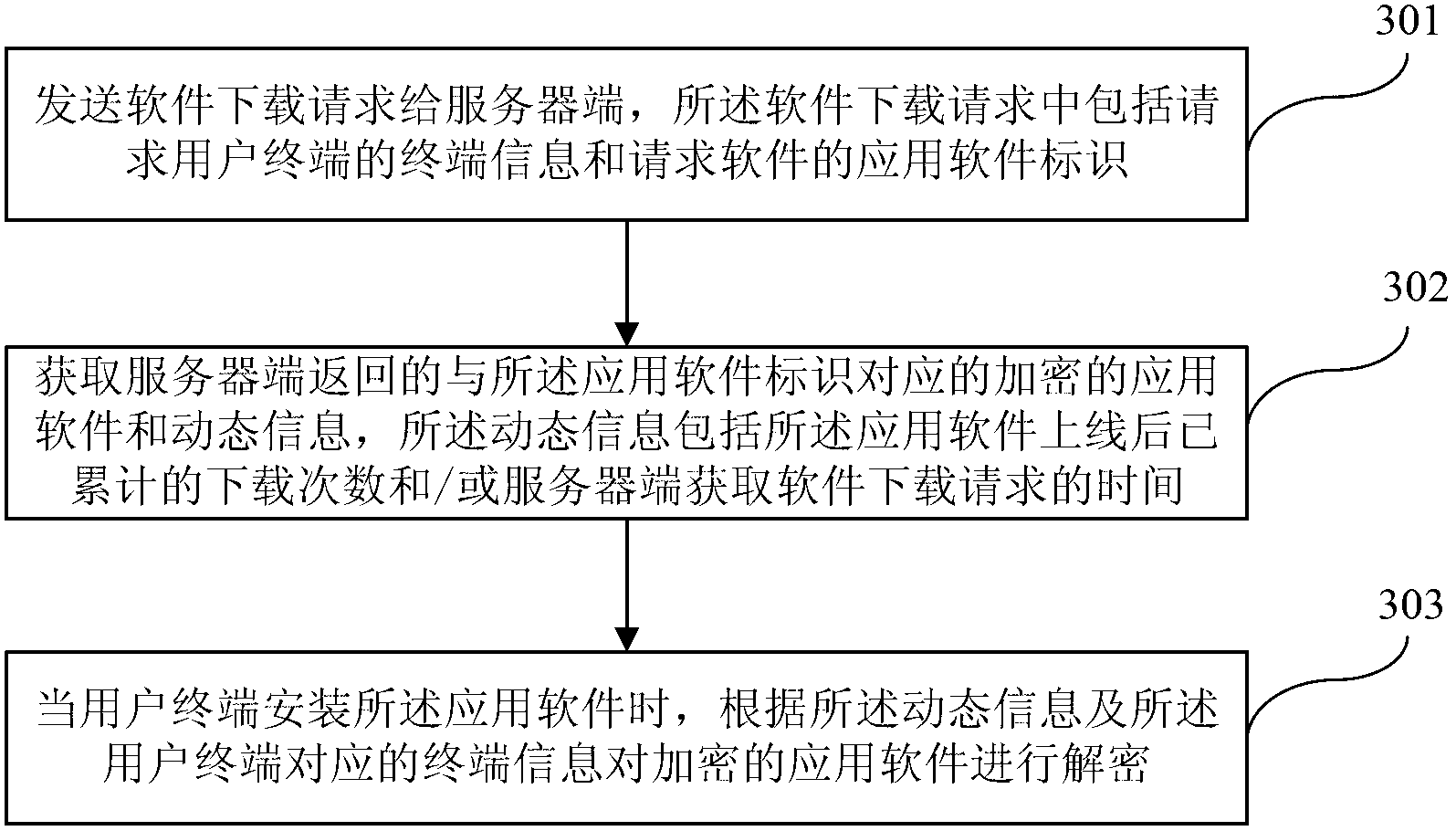
Application software digital right management method, device and system
ActiveCN103235904AImprove effectivenessUniqueProgram/content distribution protectionSoftware engineeringComputer terminal
The invention discloses an application software digital right management method, device and system. The application software digital right management method includes obtaining a software downloading request sent by a client side, wherein the software downloading request includes terminal information of a request user terminal and application software identification of request software; obtaining dynamic information and application software corresponding to the application software identification according to the software downloading request, wherein the dynamic information includes accumulated downloading times of the application software after online and / or software downloading request obtaining time; encrypting the application software according to the terminal information of the request user terminal and the dynamic information; and sending the dynamic information and the encrypted application software to the client side so that when the client side installs the application software on the user terminal, the encrypted application software can be decrypted according to the dynamic information and the terminal information corresponding to the user terminal. The application software digital right management method, device and system can effectively improve application software digital right management strength.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
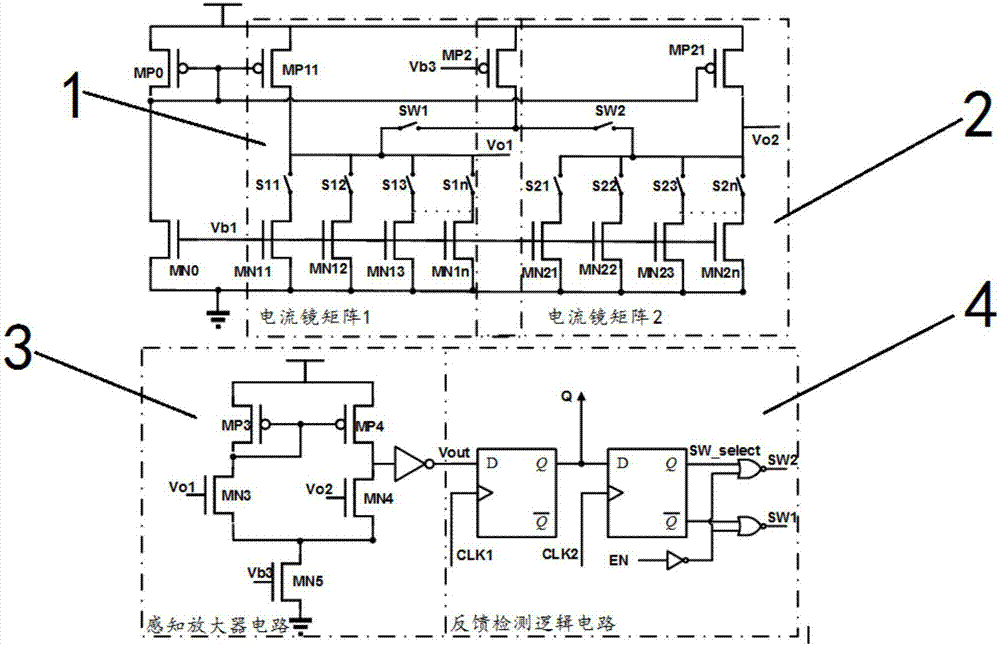
Physical non-clonable circuit referring to fake resistance, authentication and secret keys and implement method
InactiveCN107491704AImprove stabilityLow costReliability increasing modificationsInternal/peripheral component protectionSense amplifierLogical circuit
The invention discloses a physical non-clonable circuit referring to fake resistance, authentication and secret keys and an implement method. The circuit comprises current mirror matrixes, a sensing amplifier circuit and a feedback detection logic circuit, wherein each current mirror matrix comprises two PMOS transistors, the PMOS transistors are used for forming two identical mirrors at the same time, the physical non-clonable circuit further comprises a set of NMOS transistors in each current mirror matrix, aiming at different excitation, one NMOS transistor in one set of NMOS transistors in each current mirror matrix is chosen to constitute one current mirror, the sensing amplifier circuit is used for receiving voltage output by the current mirror matrixes as input and generating response, and the feedback detection logic circuit is used for detecting and / or labeling unstable output.
Owner:大家传承网络科技(深圳)有限公司
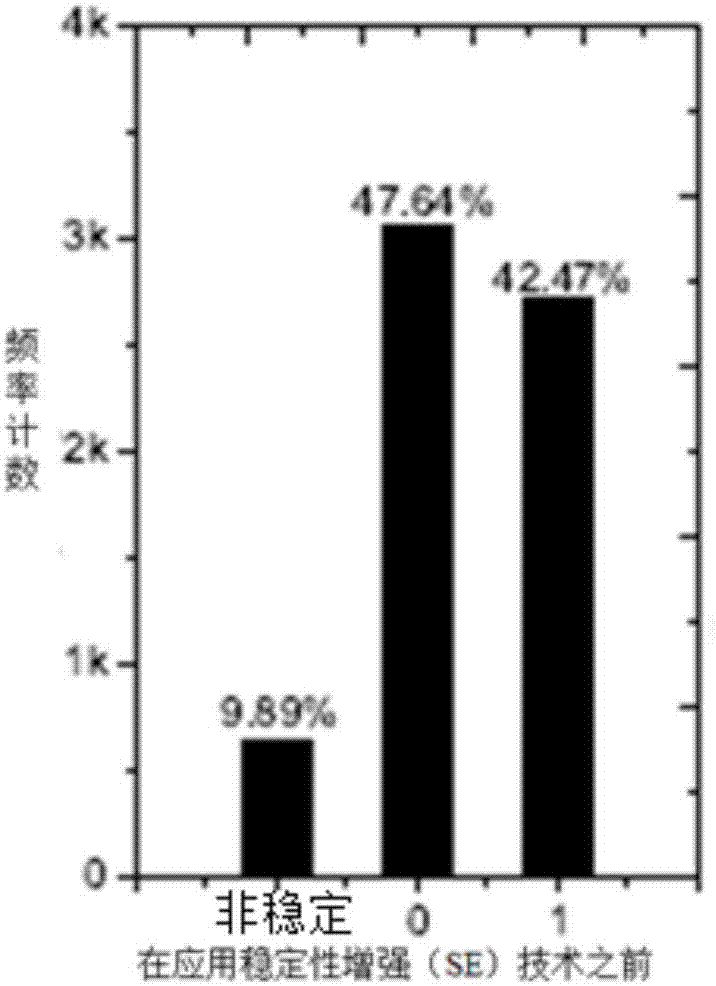
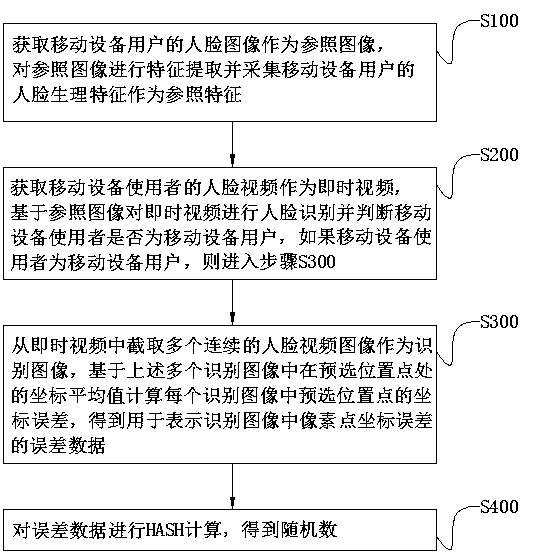
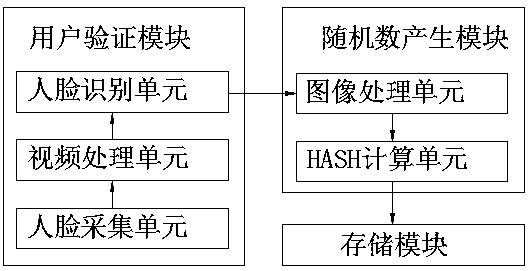
Random number generation method and system based on face image recognition
ActiveCN108921036AAvoid Malicious OperationsAvoid lostRandom number generatorsCharacter and pattern recognitionUser verificationPattern recognition
The invention discloses a random number generation method and system based on face image recognition, belongs to the field of an information security technology and aims to solve the technical problemof how to generate a random number of a mobile device on the premise of guaranteeing security and convenience. According to the method, whether a mobile device user is a mobile device owner or not isconfirmed by acquiring a face video of the mobile device user and performing face recognition, and a random number is generated by performing error calculation on the face video of the mobile deviceuser. The system comprises a user verification module, a random number generation module and a storage module, wherein the user verification module comprises a face collection unit, a video processingunit and a face recognition unit, and the random number generation module comprises an image processing unit and a HASH calculation unit. Through the random number generation method and system, a random and unpredictable random number can be generated, and loss caused by mobile device losing can be avoided.
Owner:北京信任度科技有限公司
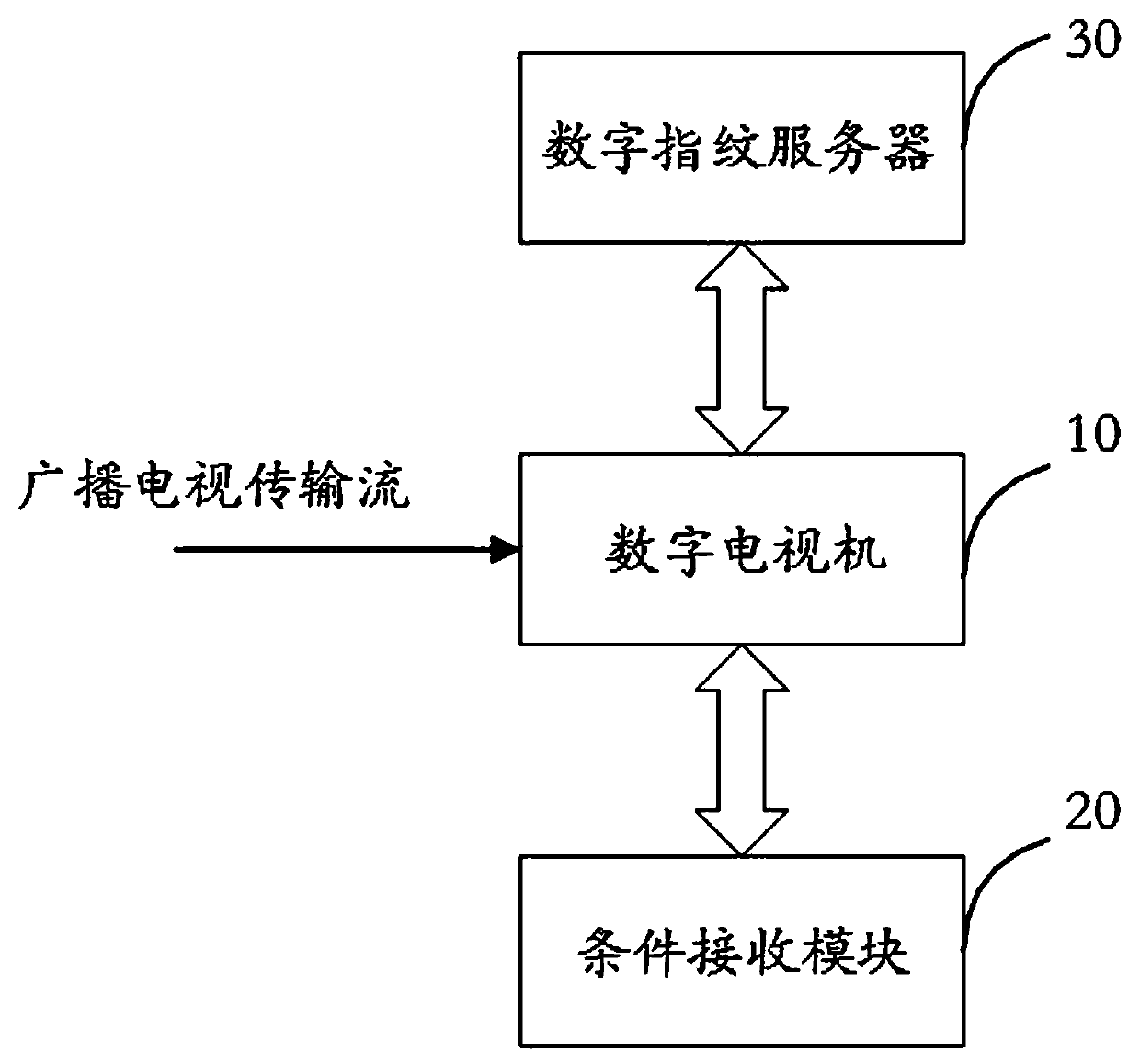
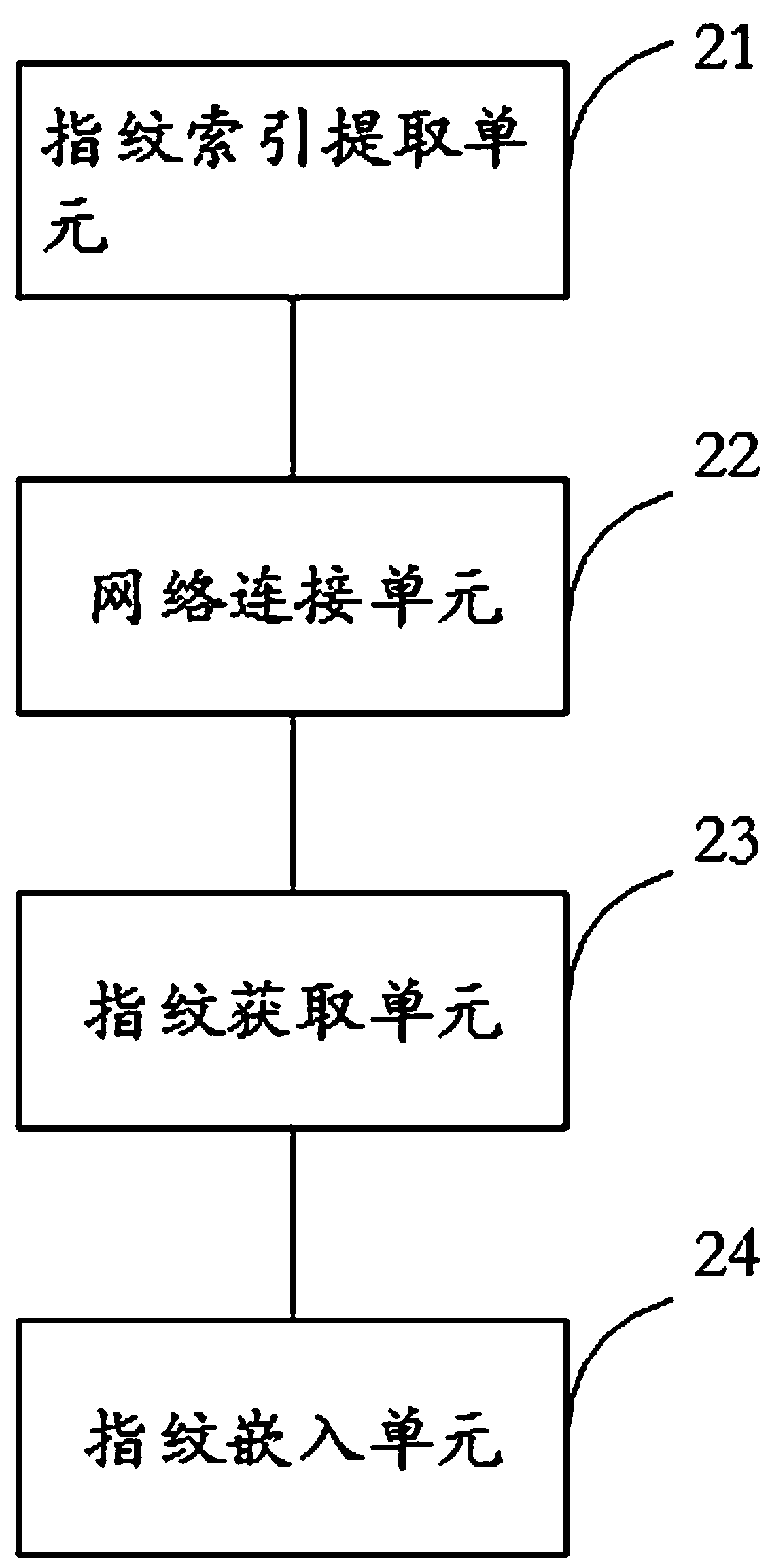
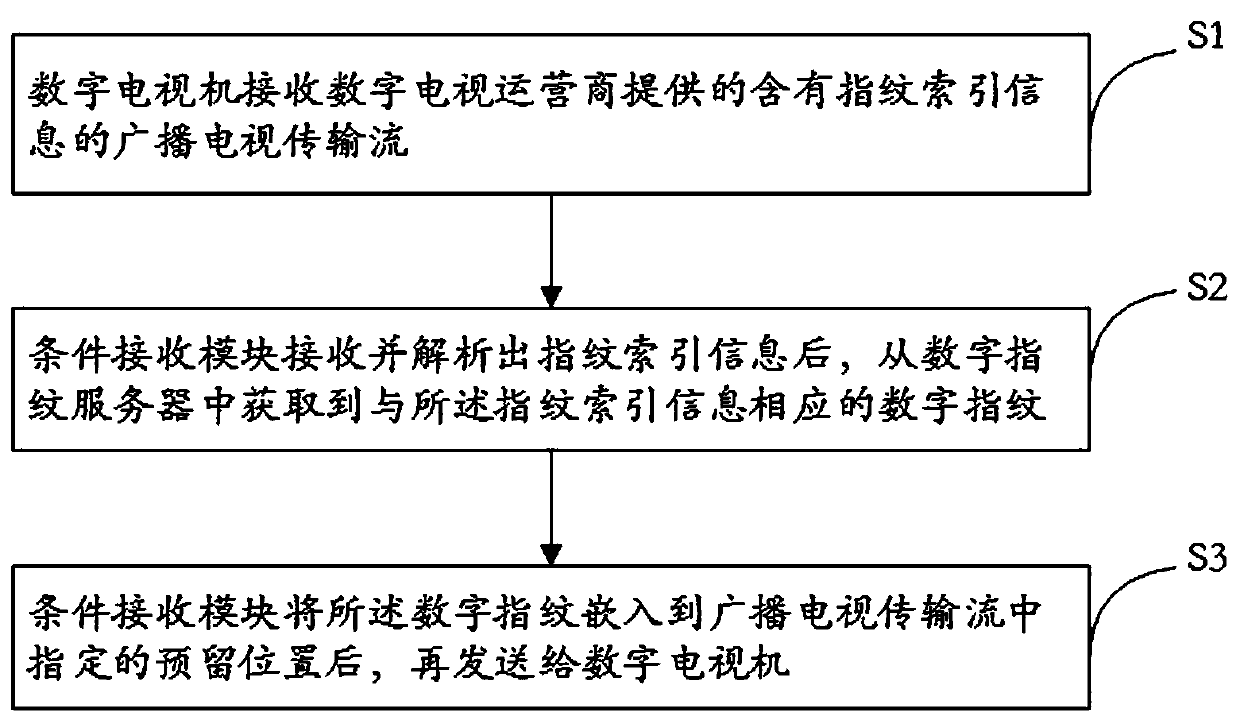
Digital television fingerprint embedding system and method and conditional access module
InactiveCN108040271AStrong correlationImprove real-time performanceSelective content distributionConditional accessDigital fingerprint
The invention discloses a digital television fingerprint embedding system and method and a conditional access module. The digital television fingerprint embedding system comprises a digital televisionhost, a conditional access module and a digital fingerprint server, wherein the conditional access module is connected with the digital television host; the digital fingerprint server is arranged ata cloud; the digital television host is used for receiving broadcast television transmission streams including fingerprint indexing information provided by a digital television operator; and the conditional access module is used for acquiring digital fingerprinting corresponding to the fingerprint indexing information from the digital fingerprint server, embedding the digital fingerprinting into specified reserved positions in the broadcast television transmission streams and transmitting the broadcast television transmission streams embedded with the digital fingerprinting to the digital television host. The digital television fingerprint embedding system disclosed by the invention is excellent in dynamic real-time property of the digital fingerprinting and has high relation to the program content.
Owner:SHENZHEN STATE MICRO TECH CO LTD
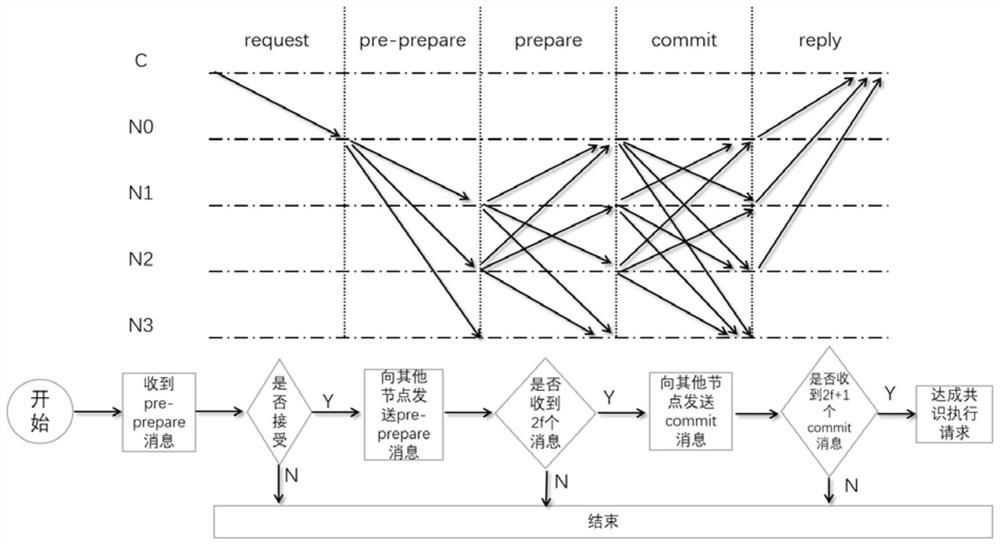
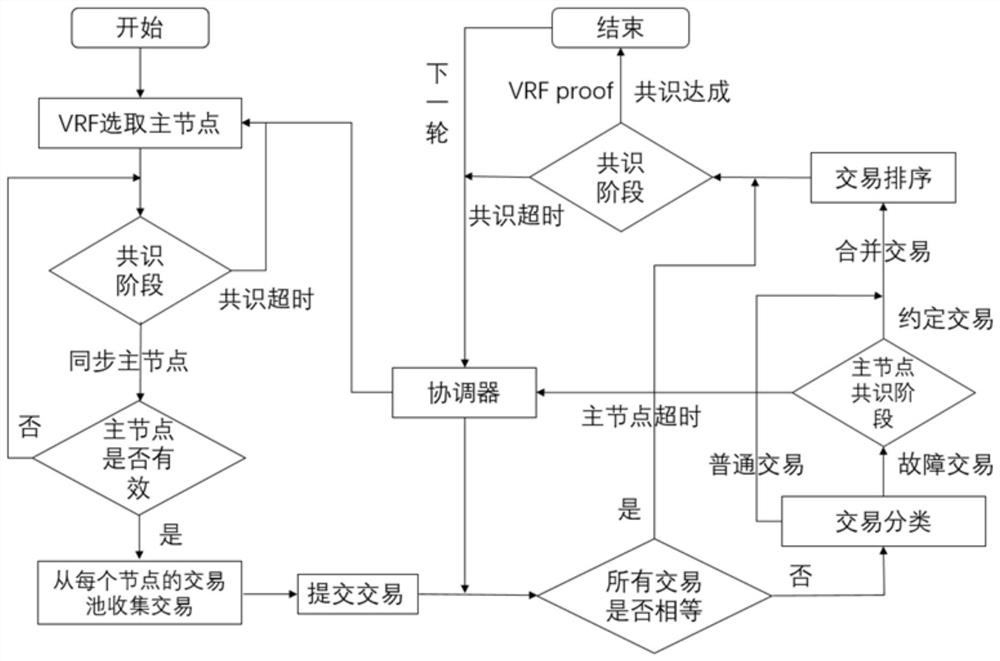
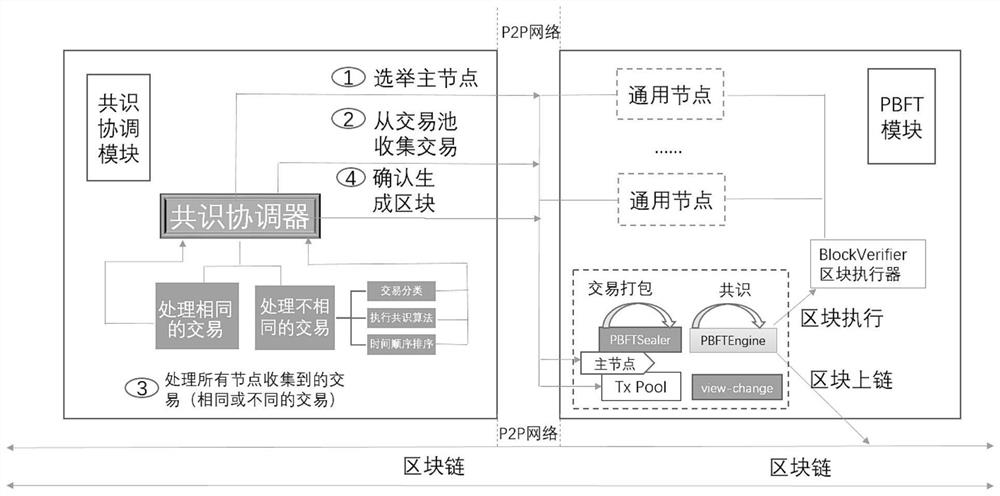
Method and device for improving PBFT consensus expandability, computing equipment and storage medium
PendingCN113746635AImprove scalabilityExtended run timeKey distribution for secure communicationFinanceConsensusFinancial transaction
The invention discloses a method and device for improving PBFT consensus expandability, computing equipment and a storage medium. The method comprises the steps that a consensus coordinator is introduced, a main node is selected to execute a consistency algorithm based on PBFT, and the main node communicates with the consensus coordinator; the consensus coordinator collects transactions from the transaction pool of each node, classifies the transactions according to equality of the collected transactions, and decides whether to execute a consistency algorithm. The invention aims to enable the system to still provide good service after a plurality of nodes are added into the system.
Owner:HUBEI UNIV OF ARTS & SCI
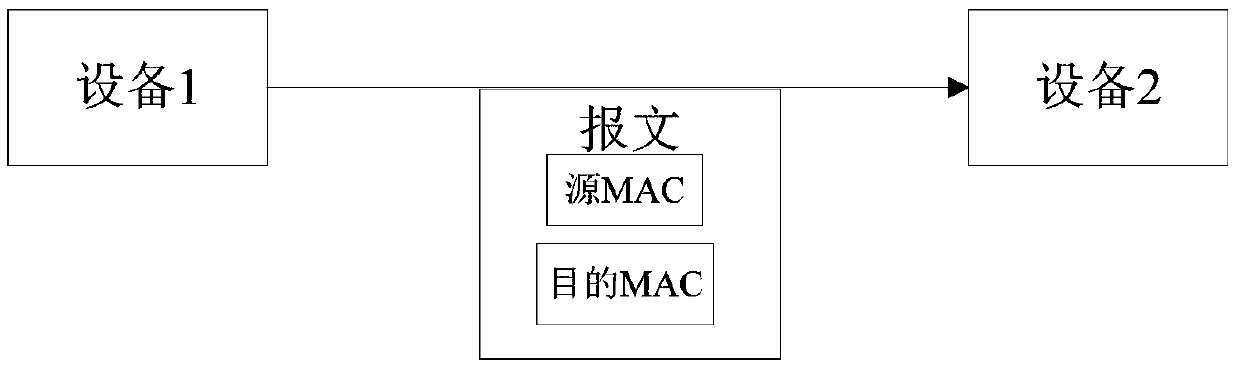
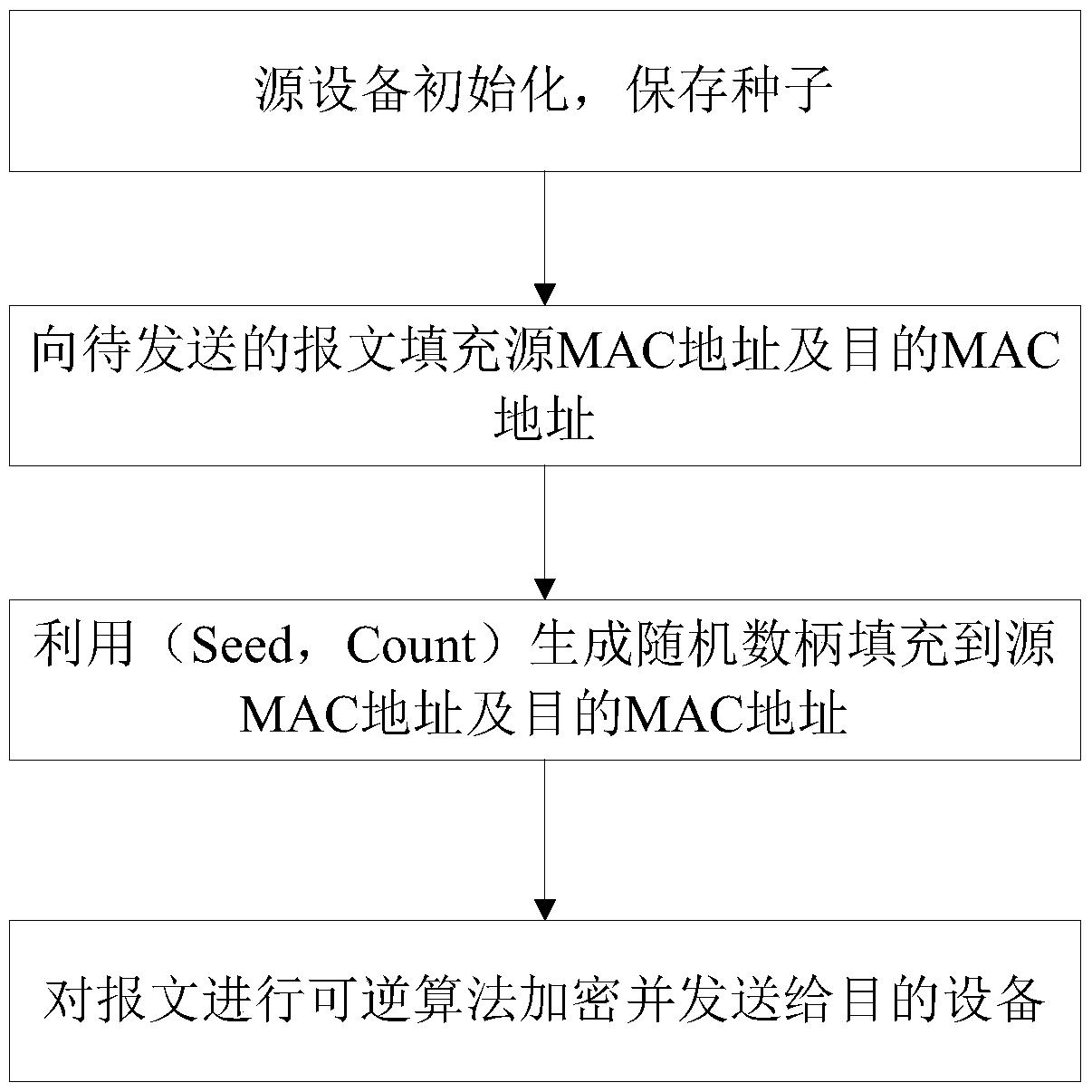
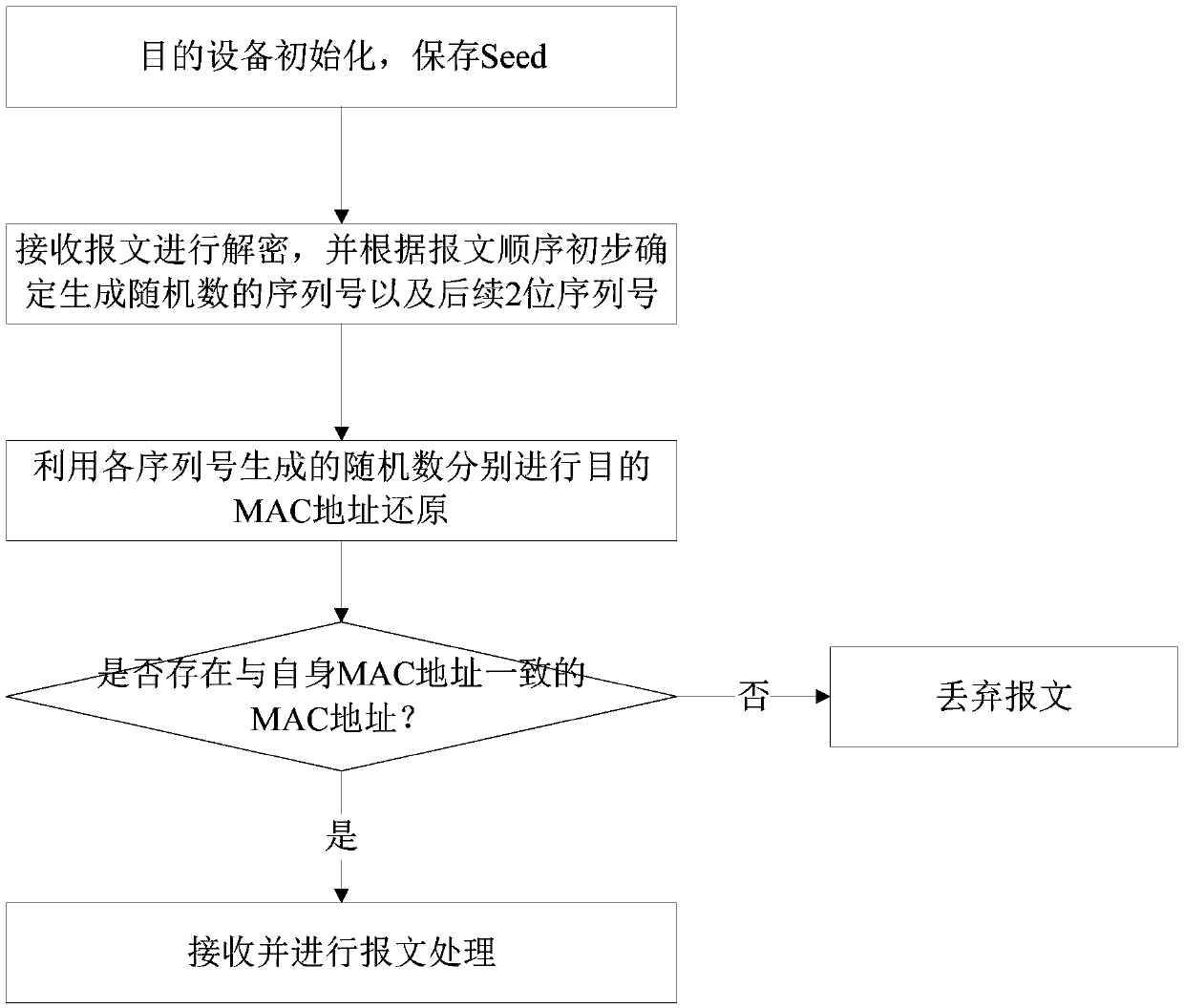
Method and system for safely accessing to target device by changing hardware identifiers
The invention discloses a method for safely accessing to a target device by changing hardware identifiers. The method is used for sending messages from a source device to the target device, comprising that: the source device obtains a corresponding first sequence number according to the sending sequence of the messages, generates random numbers based on the first sequence number and a first seed and adds the generated random numbers to the hardware identifiers of the target device of corresponding messages; after receiving the messages, the target device obtains a second sequence number according to the receiving sequence of the messages, generates corresponding random numbers based on the second sequence number and a second seed stored in the target device so as to reduce the hardware identifiers in the messages, compares the reduced hardware identifiers with own hardware identifiers, receives the messages when the reduced hardware identifiers are in accord with own hardware identifiers, and discards the messages when the reduced hardware identifiers are not in accord with own hardware identifiers. The invention also discloses a corresponding system for safety accessing to the target device. In application of the invention, the illegal monitoring difficulty is increased by adding random numbers to the hardware identifier so as to hidden the hardware identifiers; and the device accessing safety is ensured.
Owner:ZHEJIANG UNIVIEW TECH CO LTD
Hanging dyeing and colorful Ling dyeing process manufacture method for cashmere products
The invention discloses a hanging dyeing and colorful Ling dyeing process manufacture method for cashmere products. The method is characterized by including the steps: firstly, hanging dyeing: (1) washing a fabric by clear water, pressing and sizing, enabling the cashmere products to be smooth, and detecting and repairing defects; (2) soaking the cashmere products into dyeing liquid, slowly lifting the cashmere products from bottom to top, and enabling the products to be gradually dyed to form a graduated color; (3) firstly hanging and dyeing the cashmere products at the temperature of 85 DEGC for 35 minutes, and secondly fixing the color of the products at the temperature of 36 DEG C; (4) dyeing; (5) fixing the color for 20 minutes after hanging and lifting are completed; (6) washing andshrinkage washing the products after fixing is completed, adding quantitative softening agent, and washing, drying and pressing; secondly, colorful Ling dyeing: (1) horizontally placing the productsaccording to nature states, dyeing the products; (2) spraying dyes on the product at random to form a flying cloud effect. The method has the characterized that the products are clear in layer, unpredictable, high in pattern stereoscopic feeling, elegant in color, noble and rich, and patterns quickly change.
Owner:赤峰东黎羊绒设备有限公司
Preparation method of spice with nut fragrance and hay fragrance, spice and application thereof
InactiveCN112220099AUnpredictableImprove coordinationTobacco preparationEssential-oils/perfumesBiotechnologyMaillard reaction
The invention relates to a preparation method of cigarette flavors and fragrances, in particular to a preparation method of a spice with nut fragrance and hay fragrance, the spice and an application thereof. The preparation method of the spice comprises the following steps: uniformly mixing serine and fructose in the presence of a solvent containing tobacco stem powder, adding a FeCl3 catalyst at90-120 DEG C under the condition that the pH value is 6-10, carrying out a Maillard reaction in a closed system, reacting for 1-5 hours, freeze-drying, and extracting to obtain a tobacco stem Maillardreaction product, namely the spice. On the premise of not adding nuts and other substances with corresponding characteristic fragrance, the tobacco stems, serine and fructose are directly used as theraw materials, and the Maillard reaction is performed to generate the unexpected technical effects that the prepared tobacco stem Maillard reaction product has pleasant and obvious nut fragrance andhay fragrance, and has favorable harmony.
Owner:CHINA TOBACCO YUNNAN IND
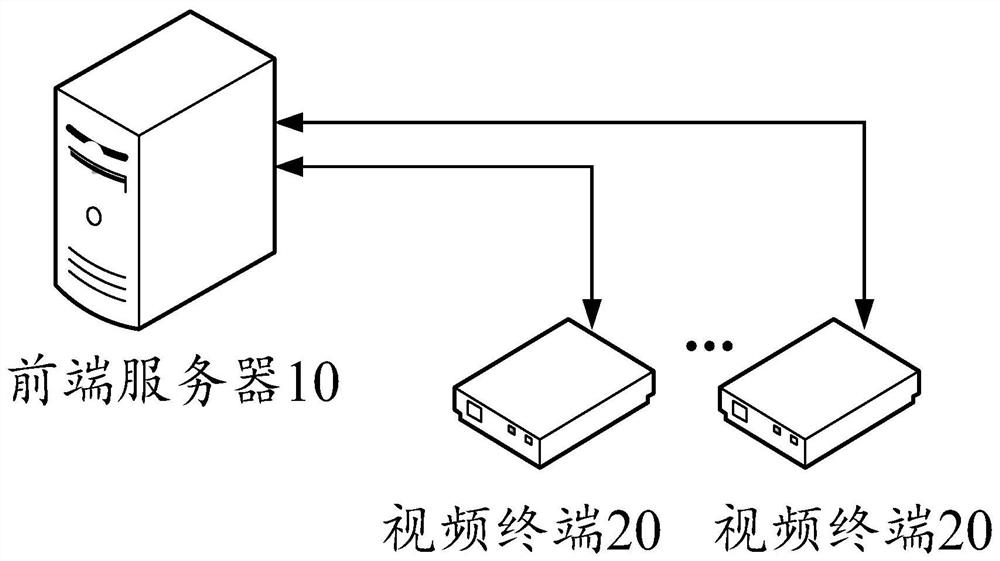
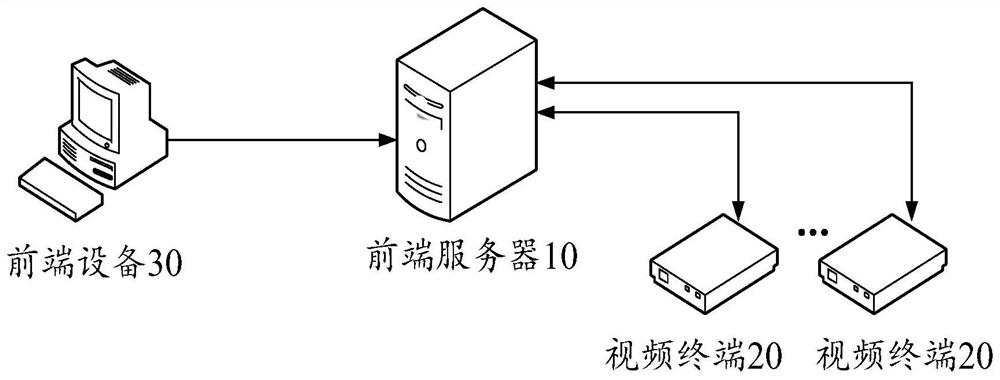
Video verification system and method
ActiveCN112383836AIncrease the difficultyImprove securitySelective content distributionVerification systemEngineering
The invention belongs to the technical field of video anti-counterfeiting, and discloses a video verification system and method. The system comprises a front-end server and a video terminal, the videoterminal obtains current video identification information of video information, anti-counterfeiting node information is searched in the front-end server according to the current video identificationinformation and sent to the video terminal, the video terminal finds anti-counterfeiting information in a video according to the anti-counterfeiting node information, and the video terminal sends theanti-counterfeiting information to the front-end server according to the anti-counterfeiting node information. The current anti-counterfeiting information is sent to a front-end server for verification. Through the mode, the anti-counterfeiting information is arranged in the anti-counterfeiting node, and the anti-counterfeiting node is set according to different video information, so that the anti-counterfeiting information is unpredictable, the difficulty of finding the anti-counterfeiting information by a thief is increased, and the safety is improved.
Owner:SHENZHEN JIUZHOU ELECTRIC
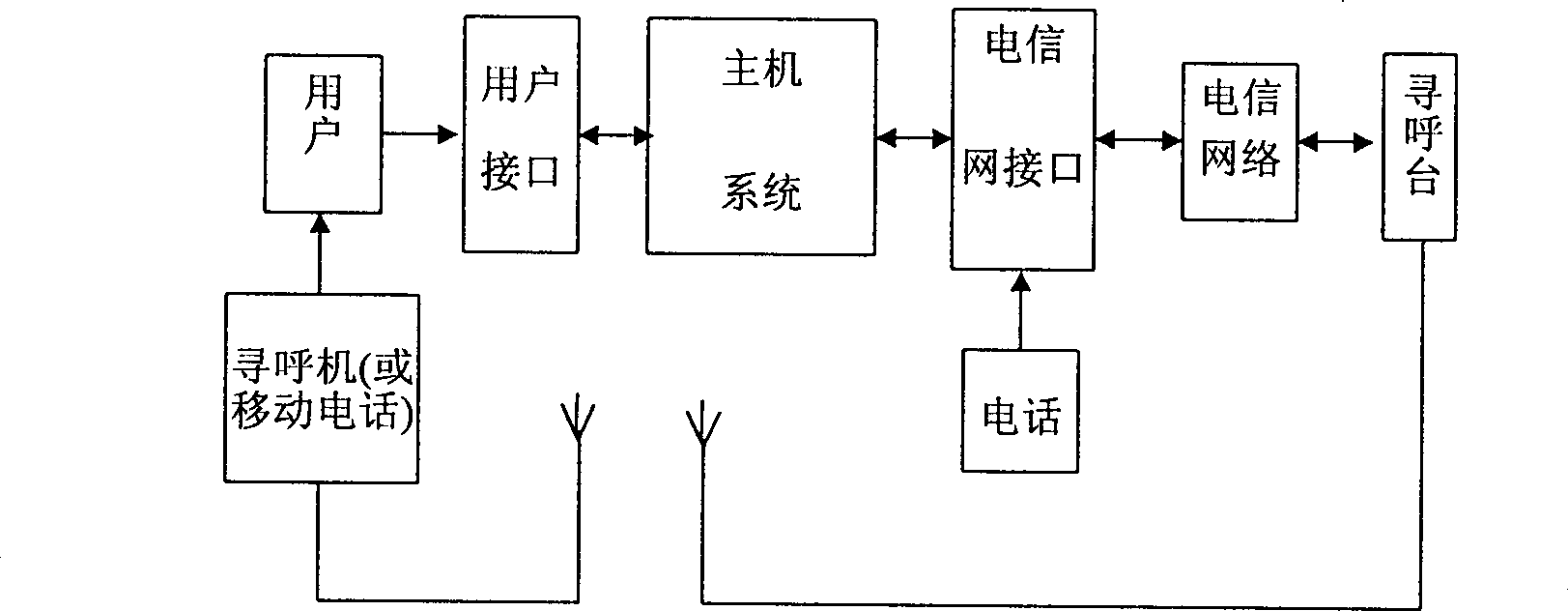
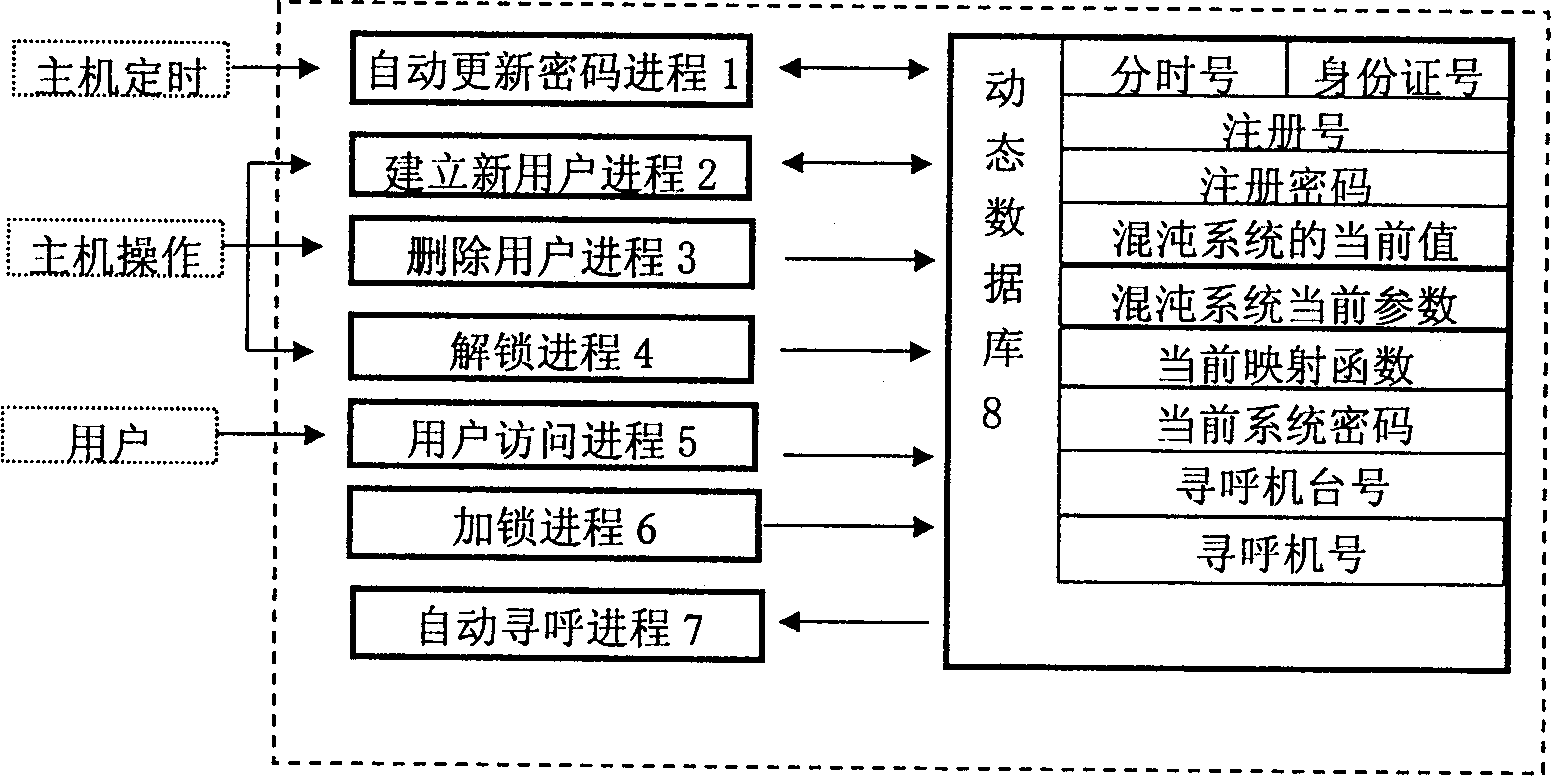
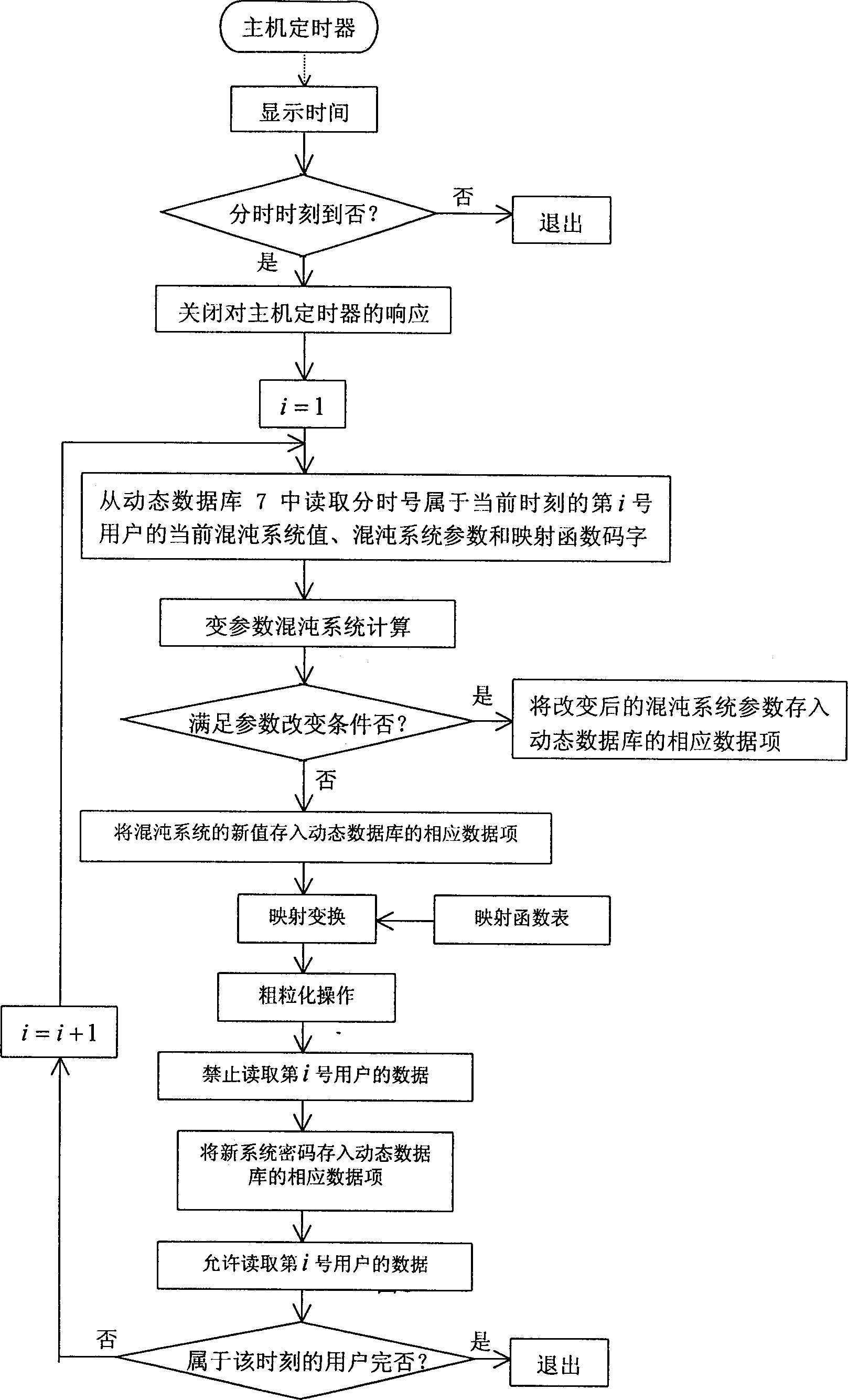
Dynamic cipher wireless transmission method
InactiveCN1110212CUnpredictableImprove confidentialitySynchronising transmission/receiving encryption devicesRadio/inductive link selection arrangementsPagerUser information
A dynamic cipher system for wireless paging is disclosed. The function of its main system is implemented by software, including dynamic database, creating new user process, automatic updating new cipher process, user access process and automatic paging process. User information is input via user interface. The main system inquires relative number of pager or mobile telephone in dynamic database and transmits dynamic cipher to user via telecommunication network interface and paging station. Said dynamic cipher is generated by parameter-changing chaotic calculation, mapping and coarse granularity operation. Its advantages are high security and efficacy. Said system can be used in network communication and electric lock.
Owner:HUAZHONG UNIV OF SCI & TECH
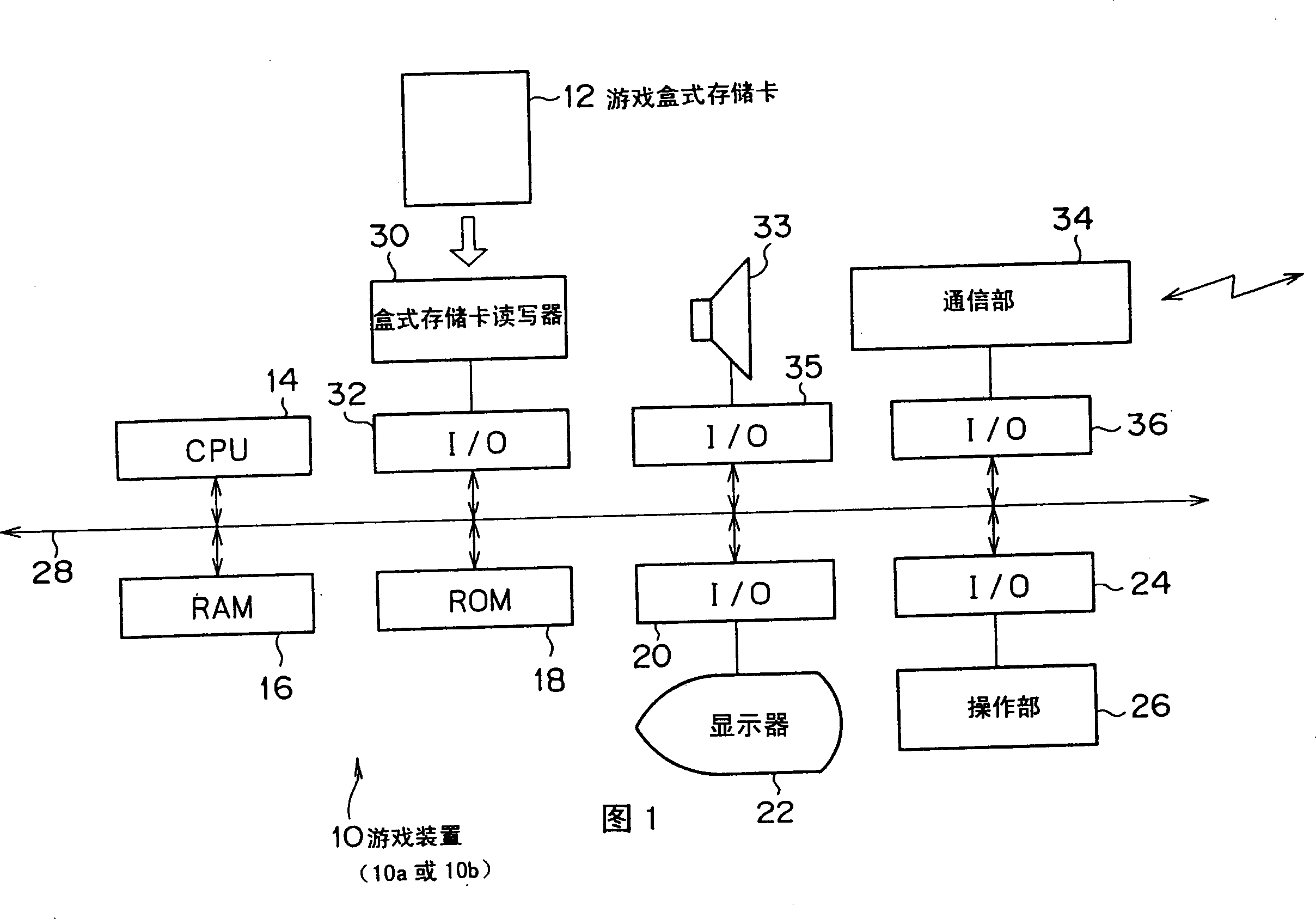
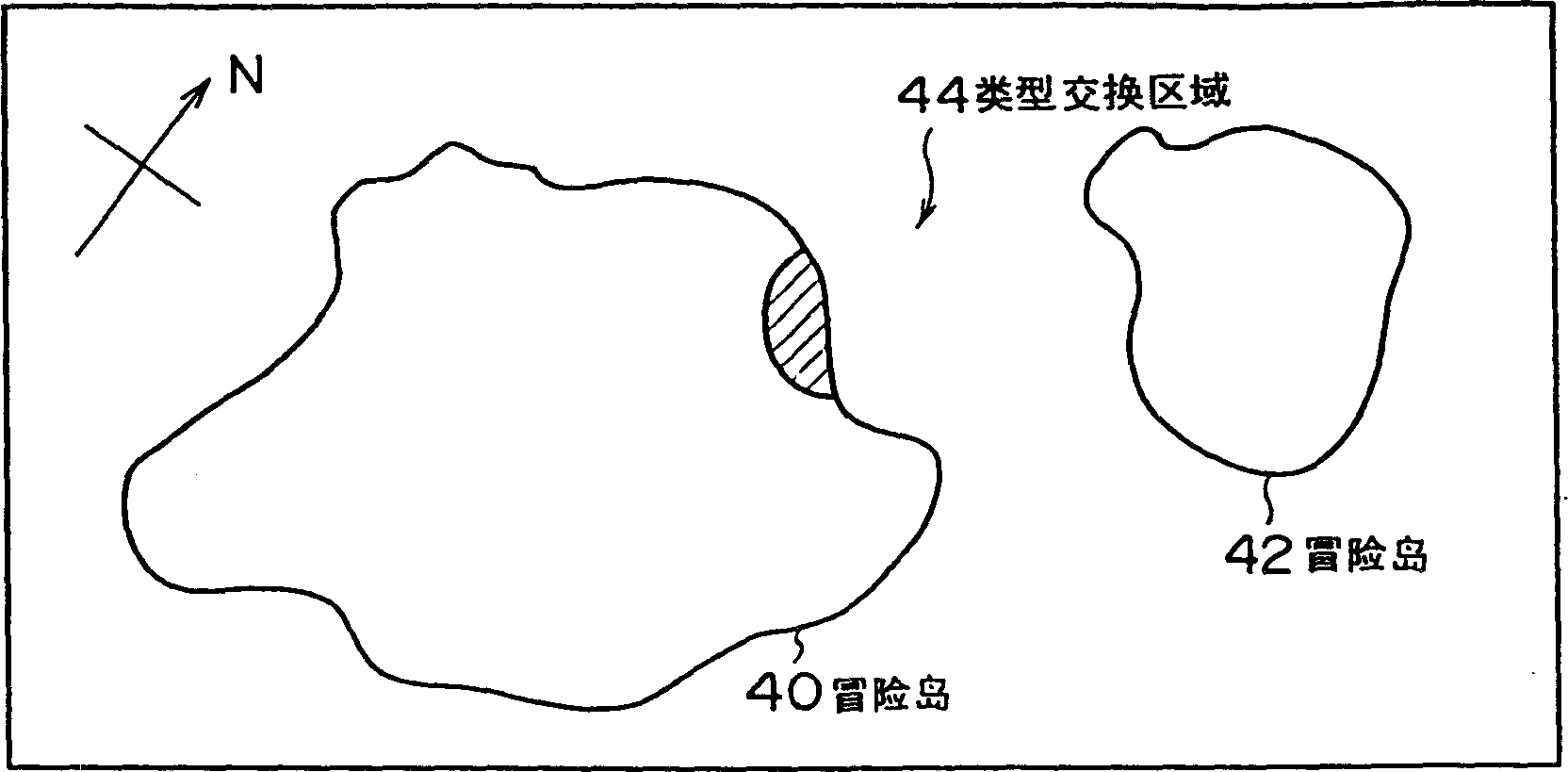
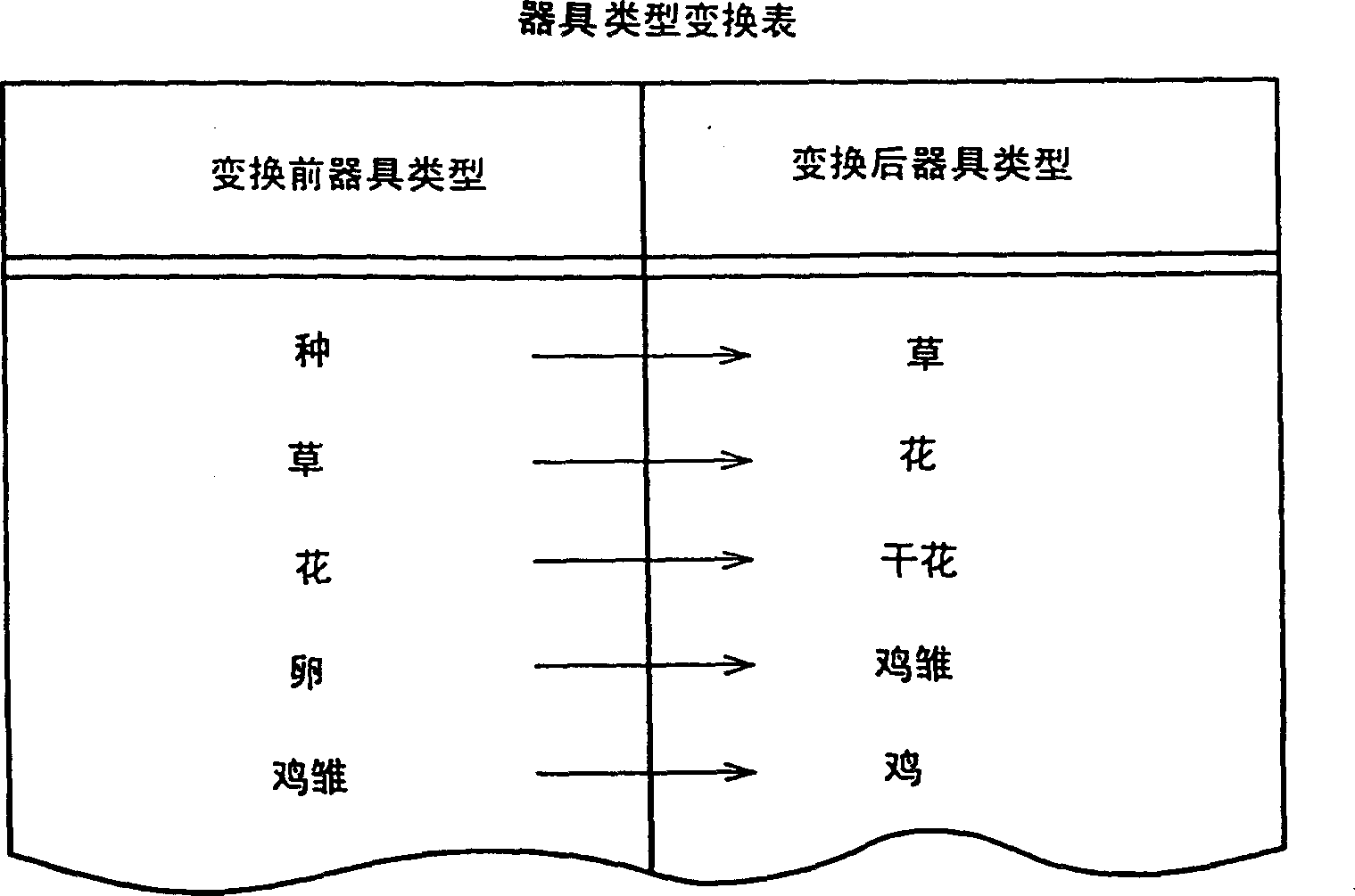
Game apparatus and its control method
A game apparatus is provided with a bottle mail function for converting the game item. In the bottle mail function, two game apparatuses are connected to communicate with each other by a communication cable, or the like, one of game items possessed by own game character is designated, and game item specifying information for specifying the game item can be exchanged between both game apparatuses. The game item specified by the game item specifying information obtained from the opponent's game apparatus is taken as a converting game item, and the converting destination game item corresponding thereto is read out from an item converting table. The read out game item is possessed by the player character instead of the former game item.
Owner:KONAMI DIGITAL ENTERTAINMENT CO LTD
High efficiency safety radio frequency label searching method
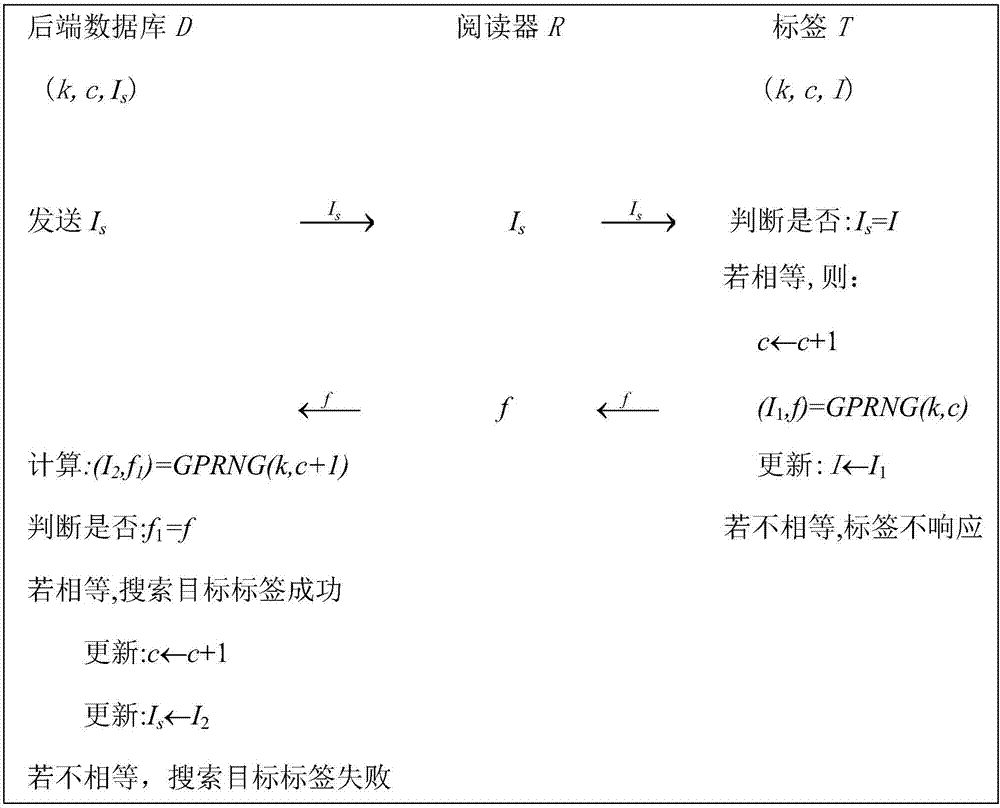
ActiveCN107294957AWith privacy and security featuresLeak will notCo-operative working arrangementsTransmissionCommunications securityData mining
The invention discloses a high efficiency safety radio frequency label searching method, and relates to the radio frequency identification communication safety technical field; the method comprises the following steps: a rear database forwards index information Is to a reader; the reader broadcasts the Is to all labels in a magnetic field scope; each label receives information, compares self-stored index information I with received Is, thus determining whether the label is the target label or not; the rear database receives confirm information f forwarded by the reader, uses self secret key k and a pointer value c to calculate and compare with f, thus determining whether the searching has succeeded or not. The method uses a pseudorandom number generator to safely calculate labels with low cost, uses the pointer value to synchronize a server with labels, and uses an index information updating method to protect label privacy and authentication; in the whole process, the rear database and labels only need to have the pseudorandom number generator capability, so the searching method is efficient and safe.
Owner:SOUTH CHINA NORMAL UNIVERSITY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com