Image encryption method based on chaotic mapping and chaotic S-box substitution
A technology of chaotic mapping and encryption method, applied in image data processing, image data processing, instruments, etc., can solve the problems of unsuitable digital image encryption, hidden dangers of digital image security, and high redundancy, so as to increase the cost of cracking and improve security. Sexuality, the effect of enhancing relatedness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
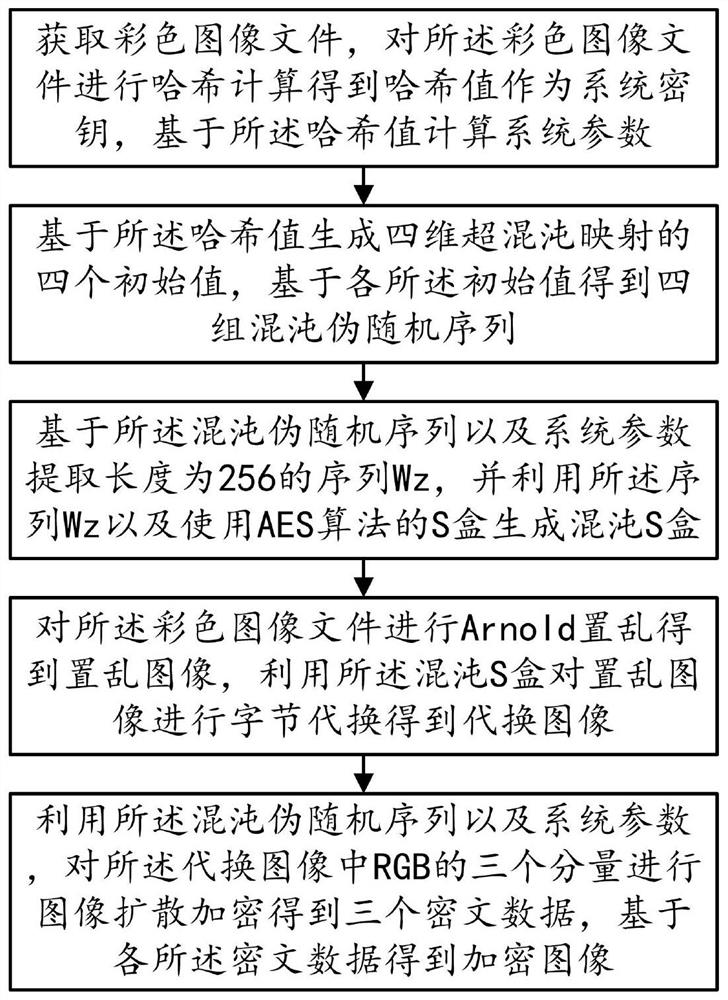
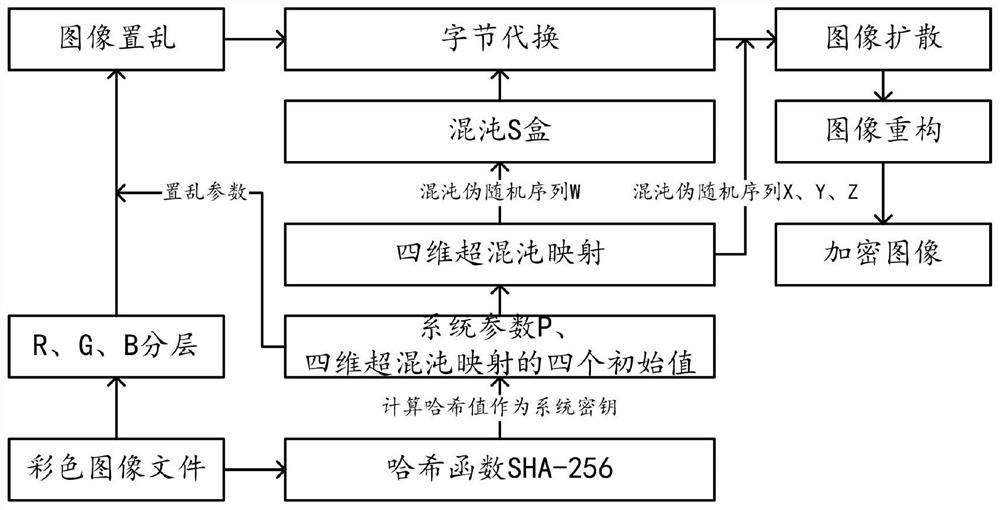
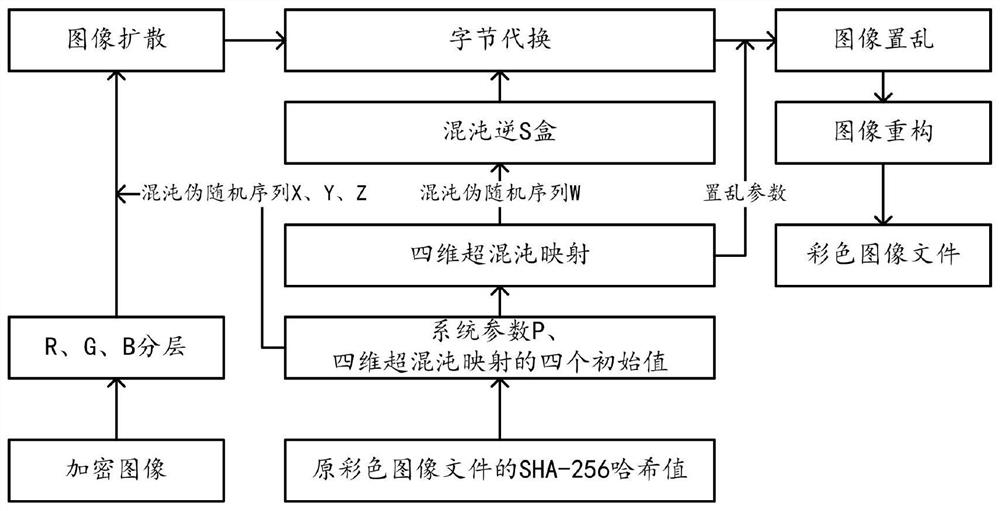
[0063] The general idea of the technical solution in the embodiment of the application is as follows: the hash value is obtained by performing hash calculation on the color image file, the system parameter P is obtained based on the hash value, and four initial values of the four-dimensional hyperchaotic map are generated based on the hash value , the hash value is used as the system key, and the color image is encrypted by combining the four-dimensional hyperchaotic map and the chaotic S-box to improve the security of image encryption.
[0064] Please refer to Figure 1 to Figure 8 As shown, one of the preferred embodiments of an image encryption method based on chaotic mapping and chaotic S-box substitution of the present invention comprises the following steps:
[0065] Step S10, acquiring a color image file, performing a hash calculation on the color image file to obtain a hash value as a system key, and calculating a system parameter P based on the hash value;
[006...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com