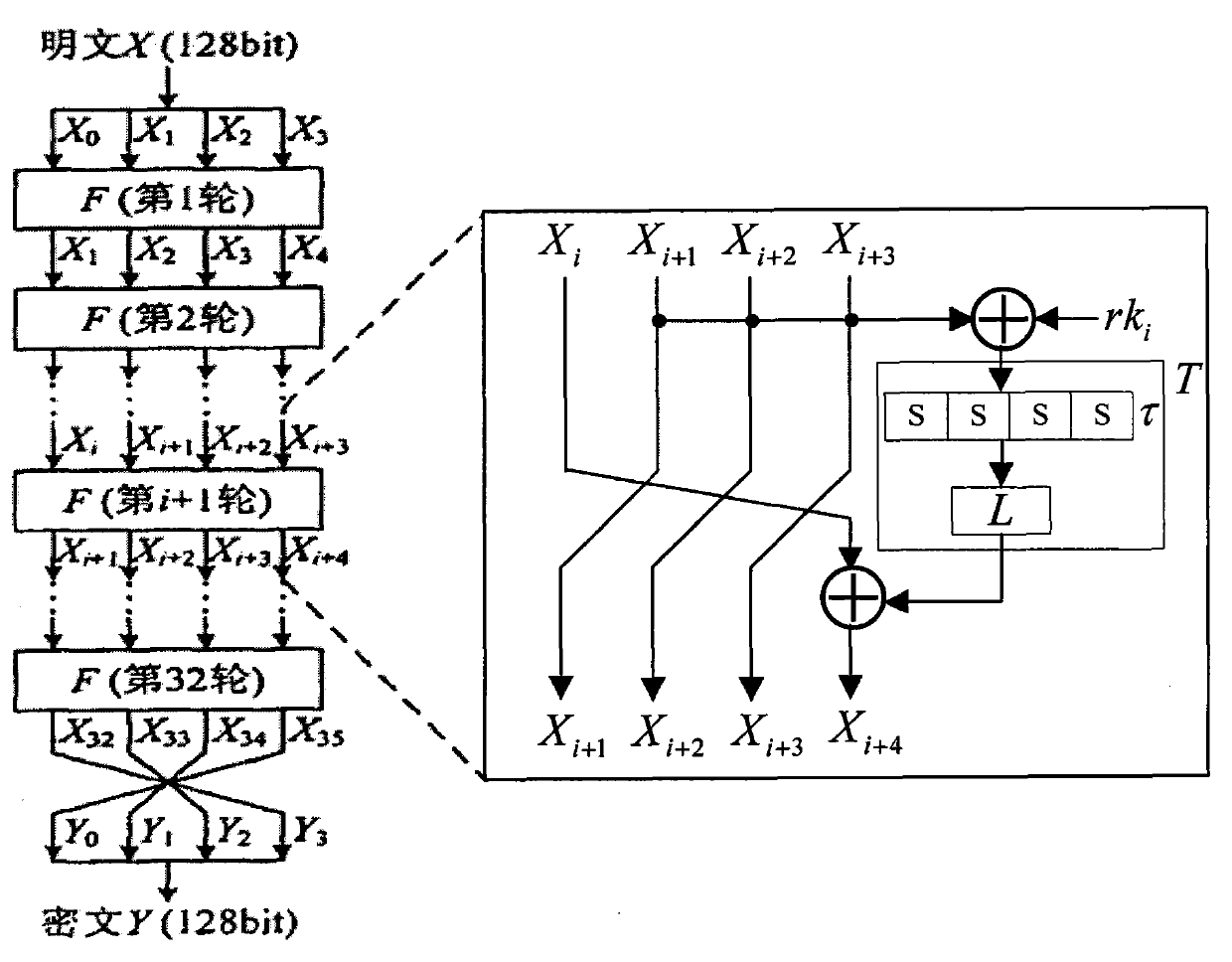
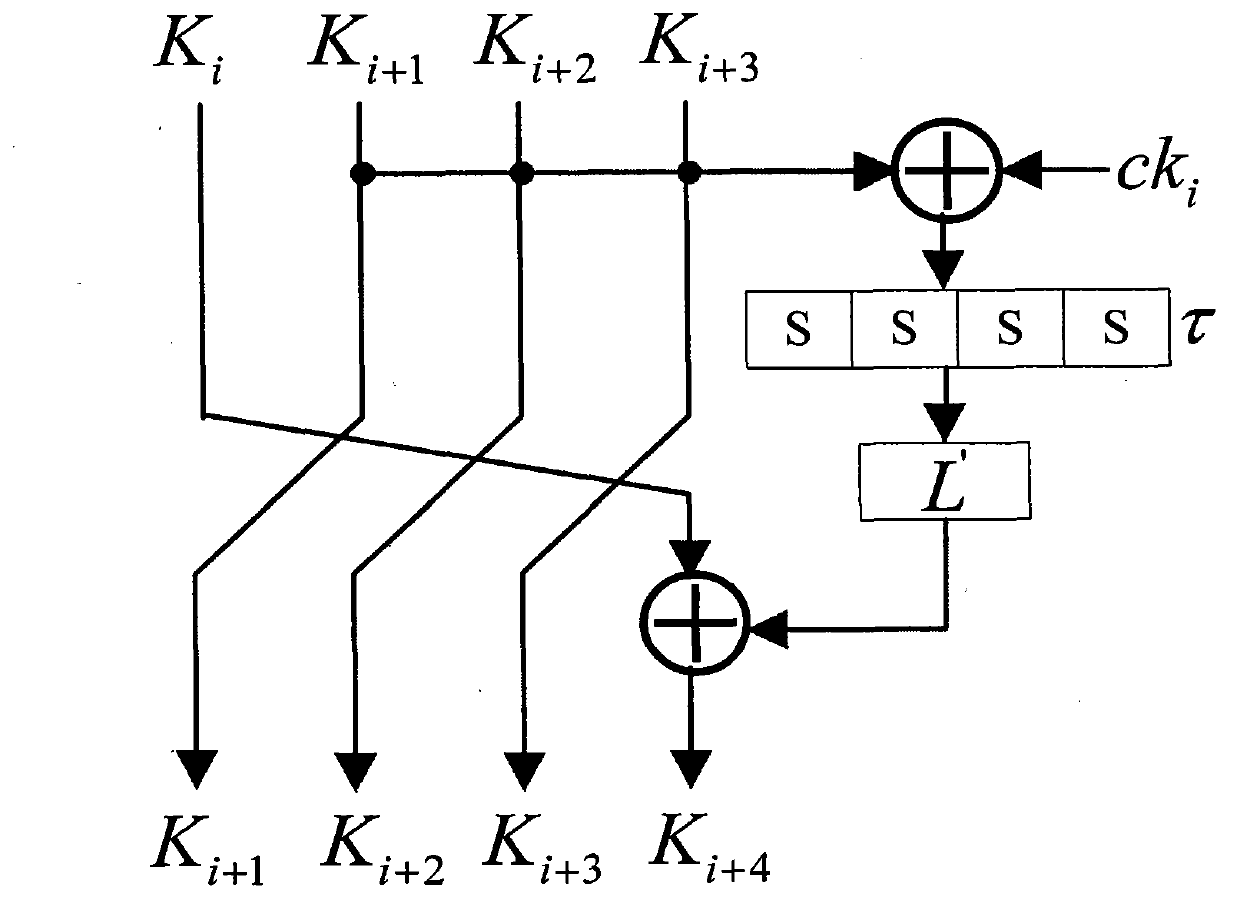
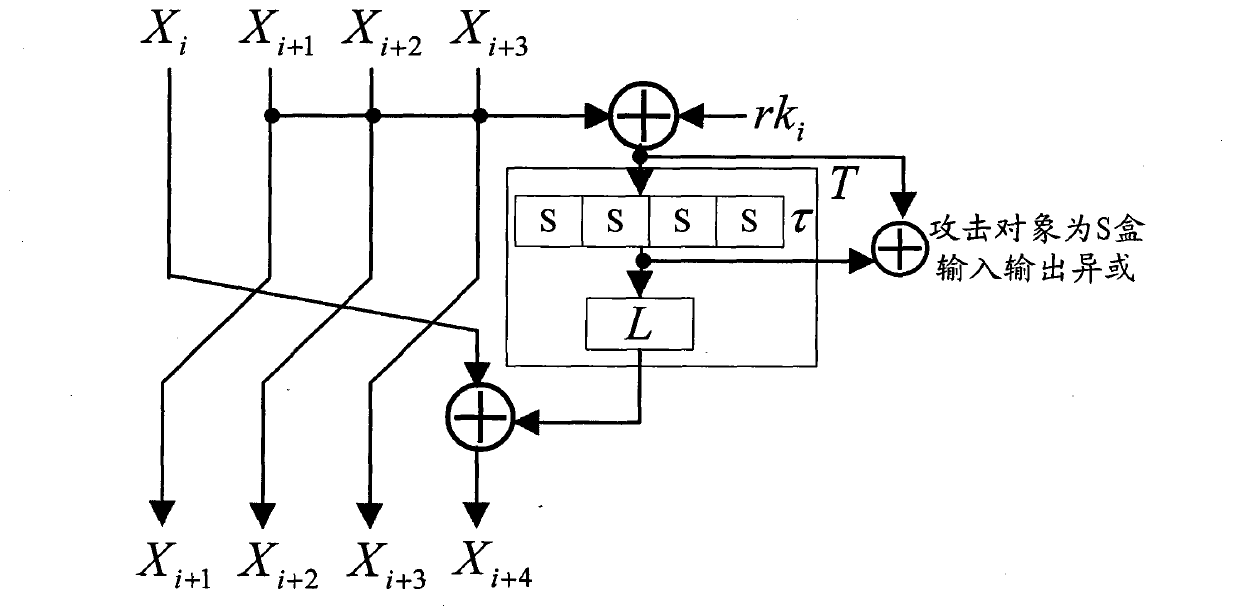
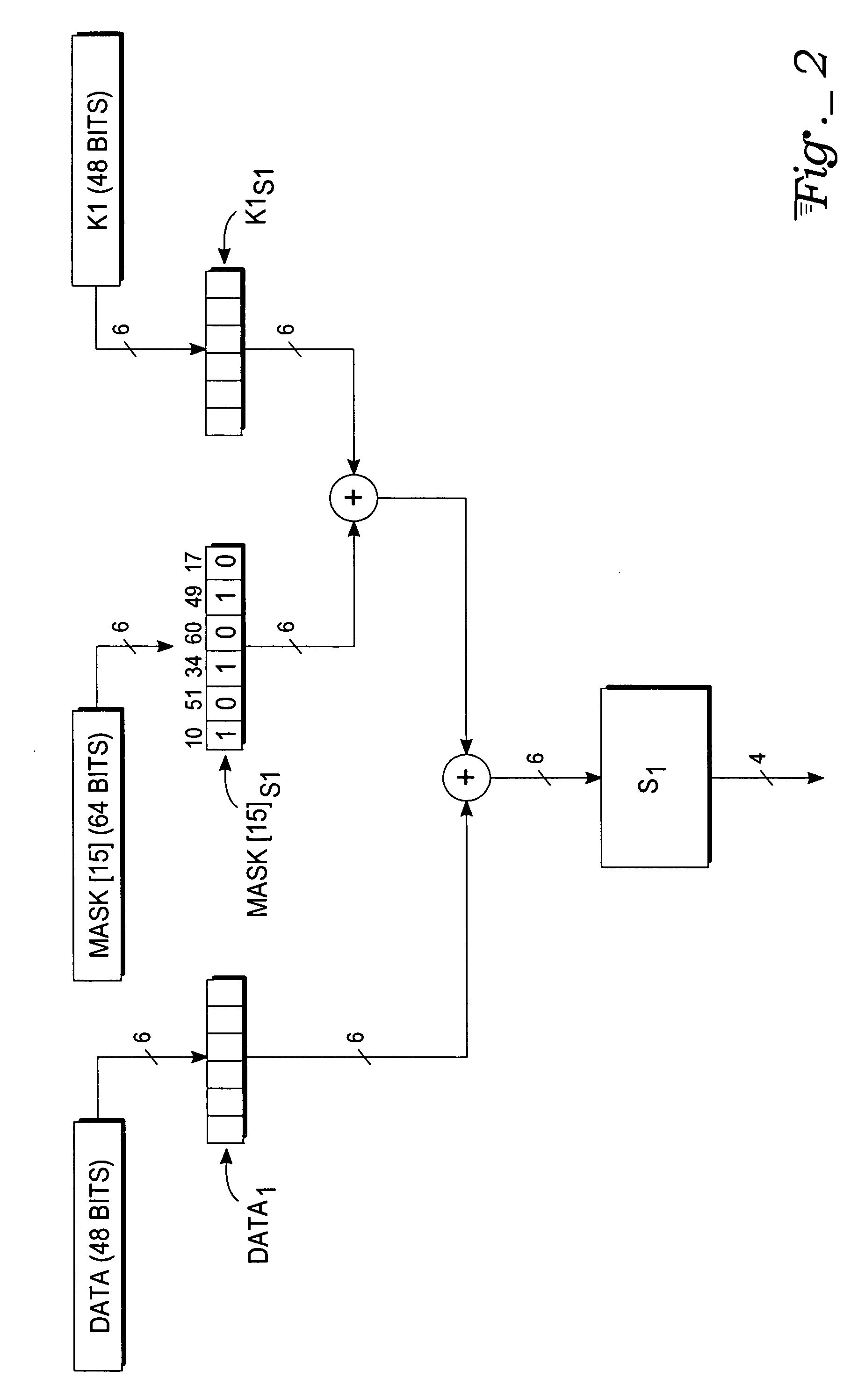
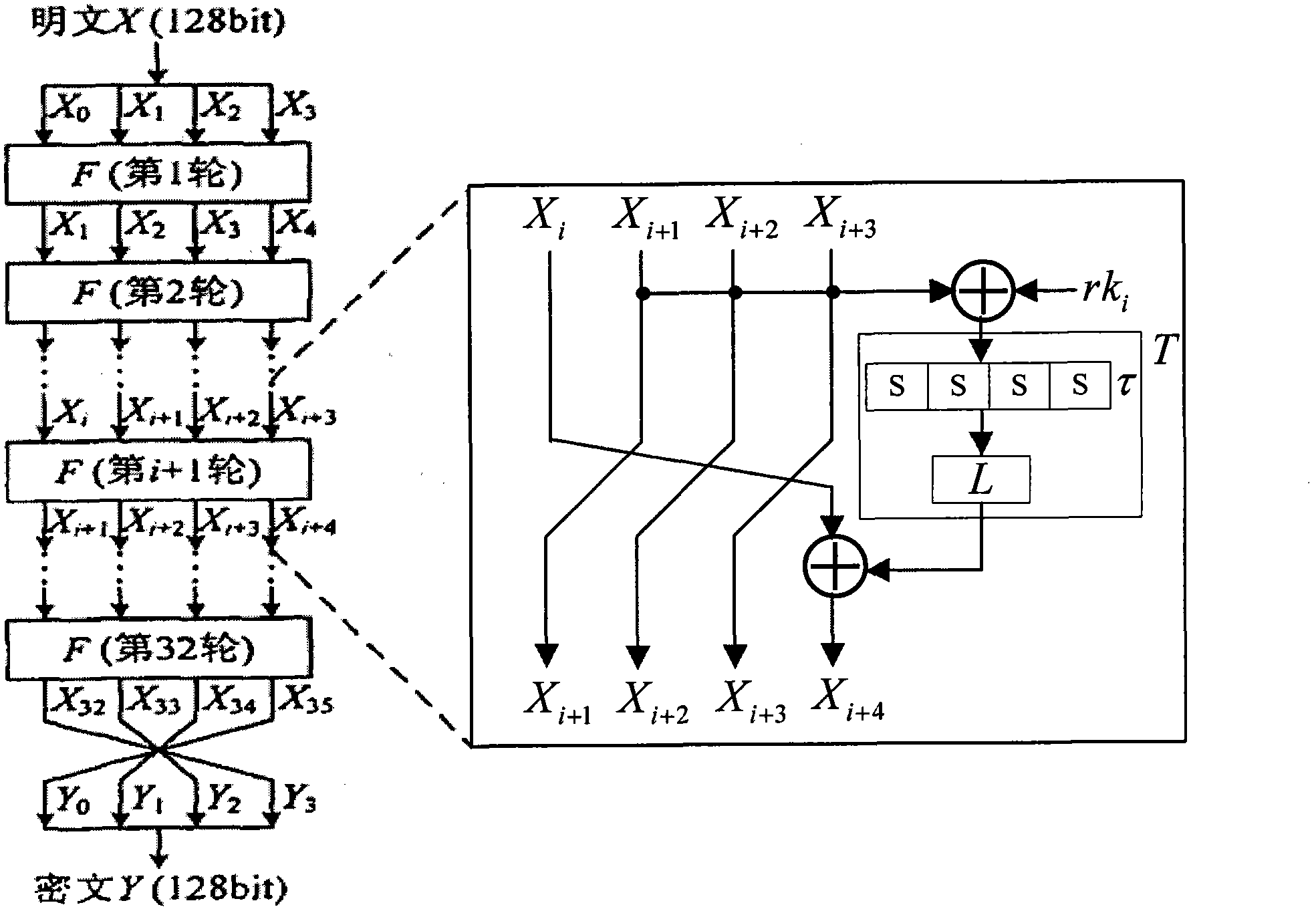
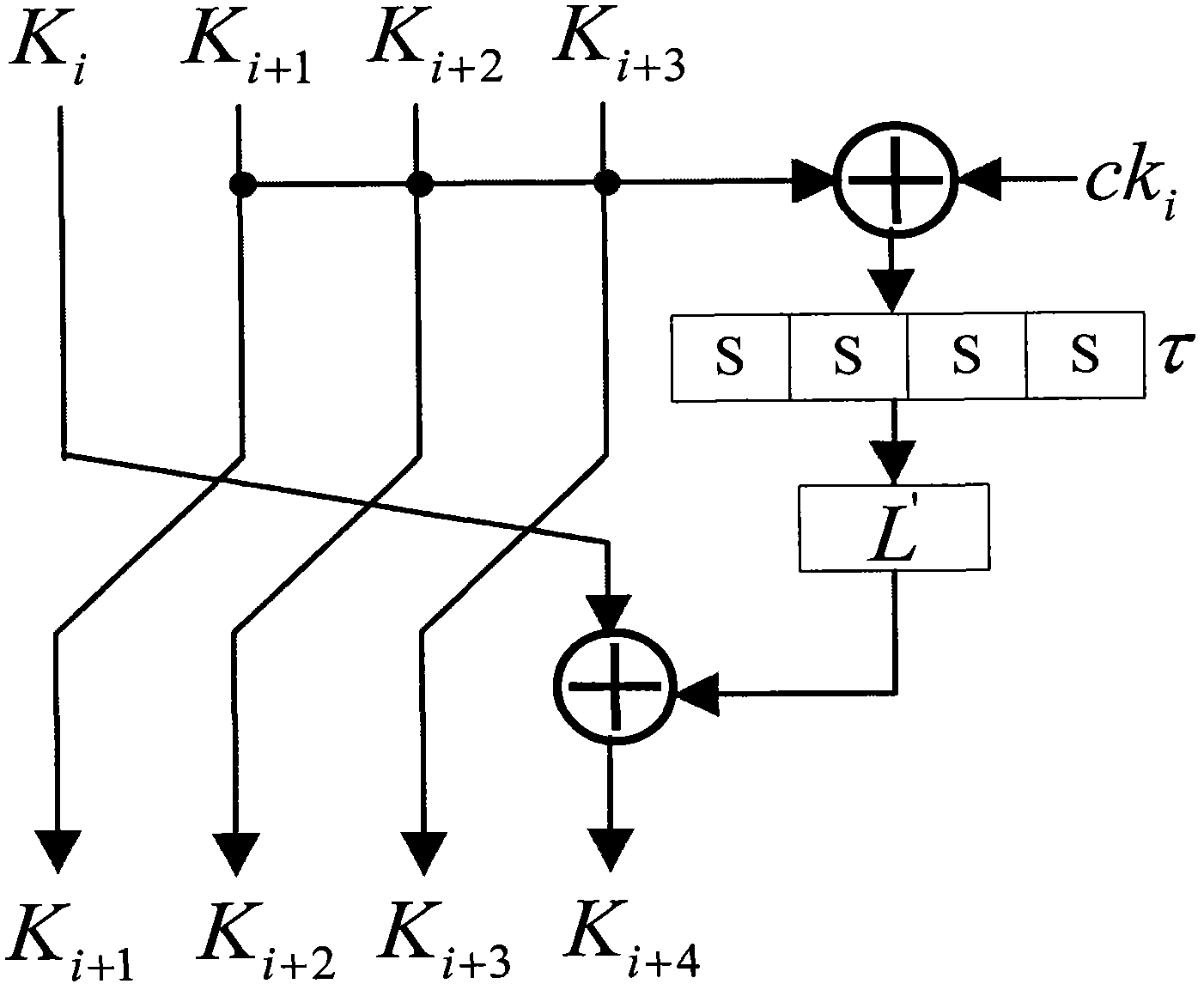
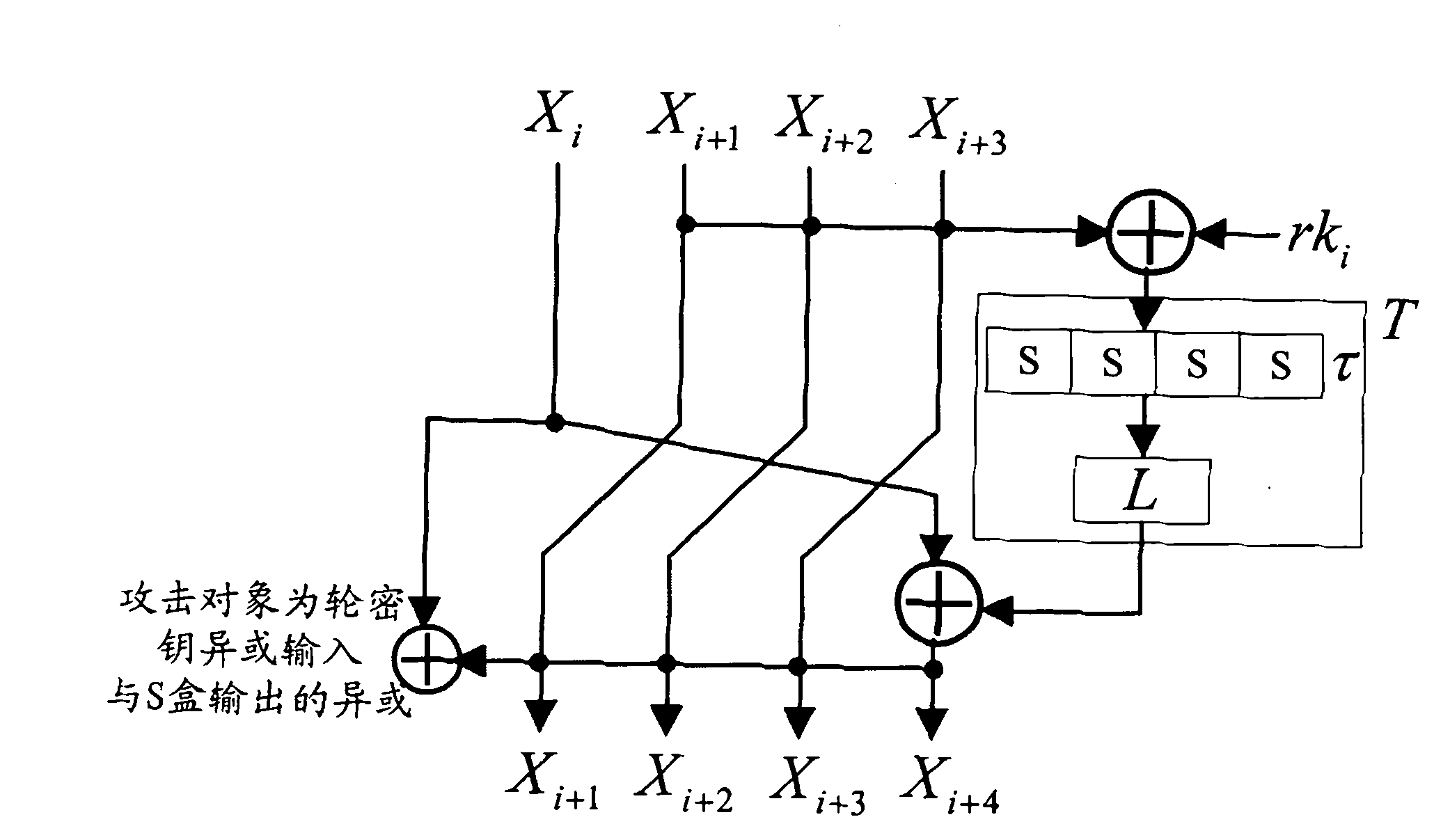
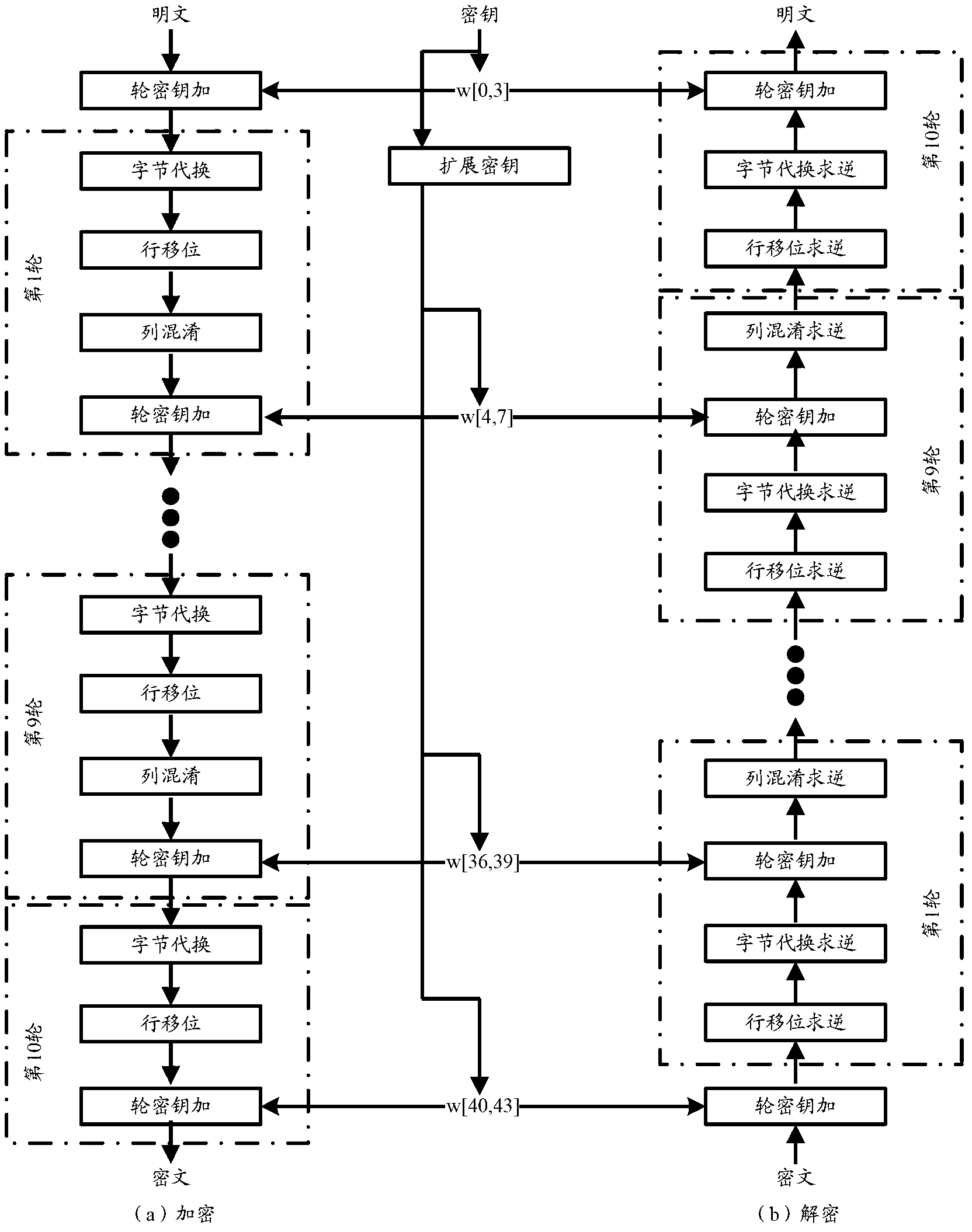
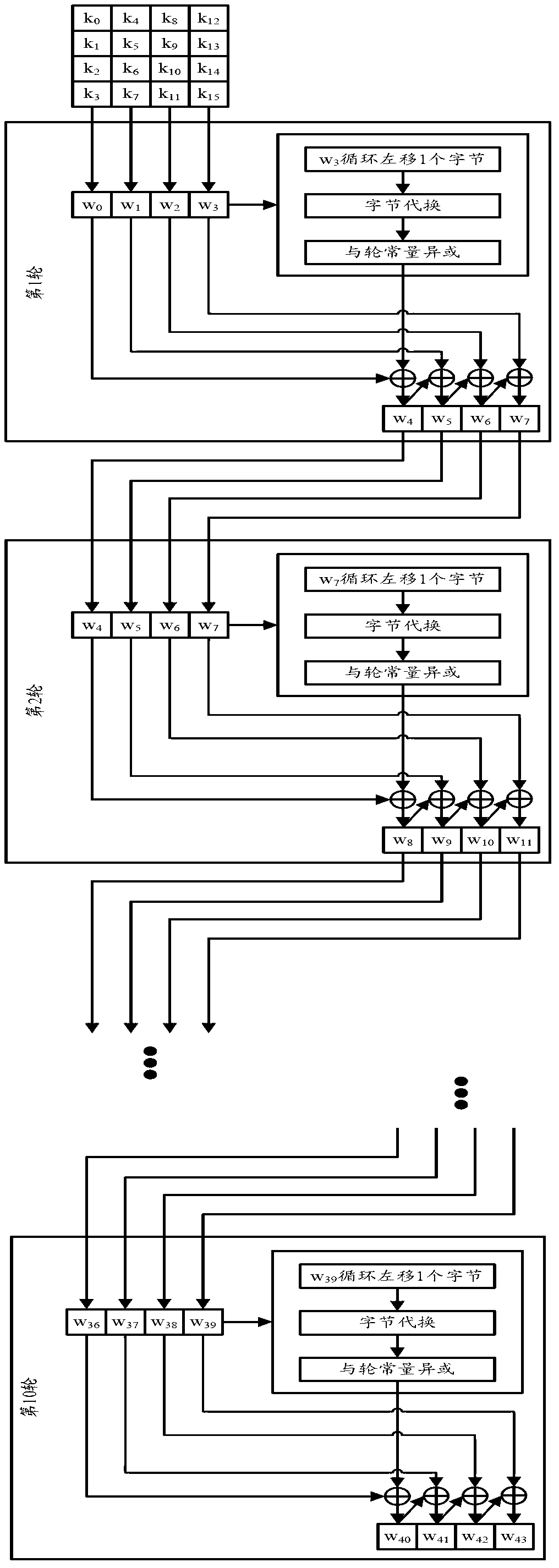
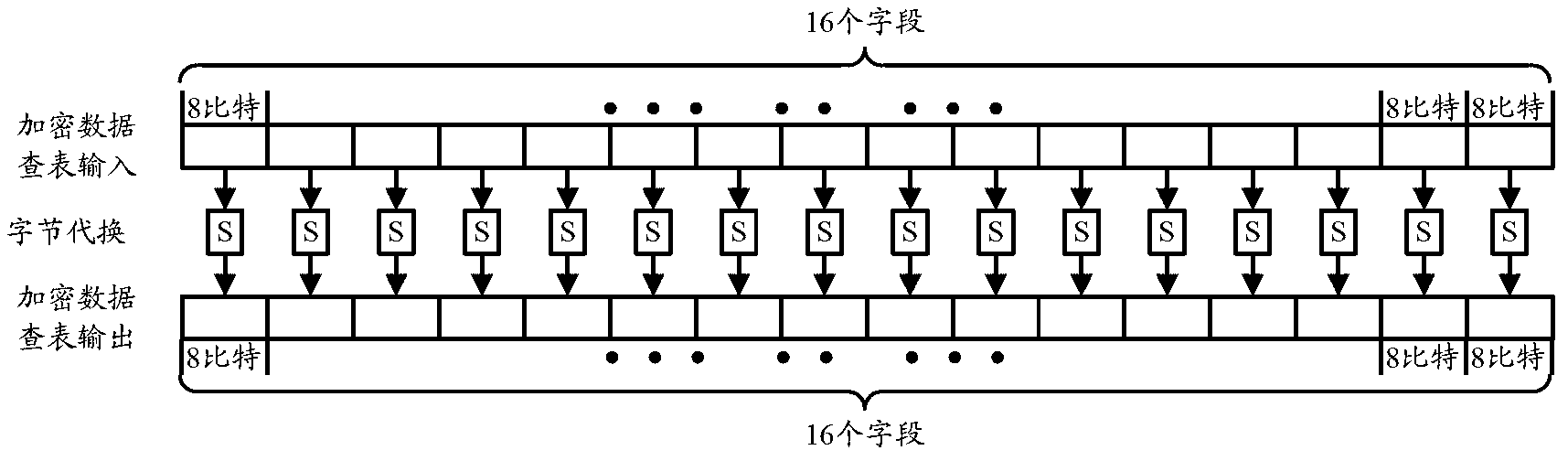
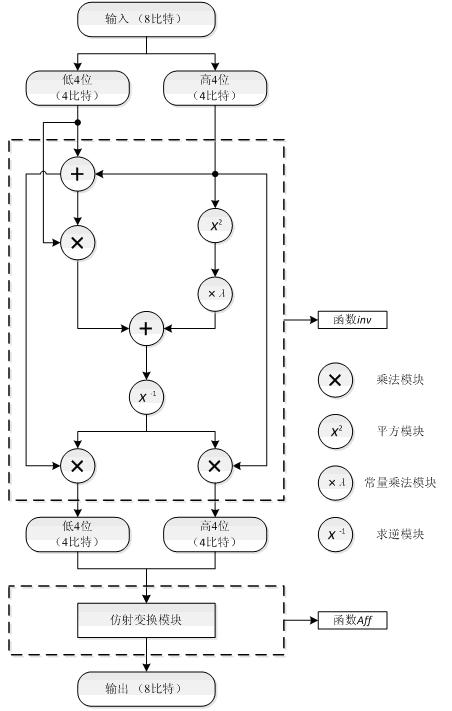
Patents
Literature
298 results about "S-box" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
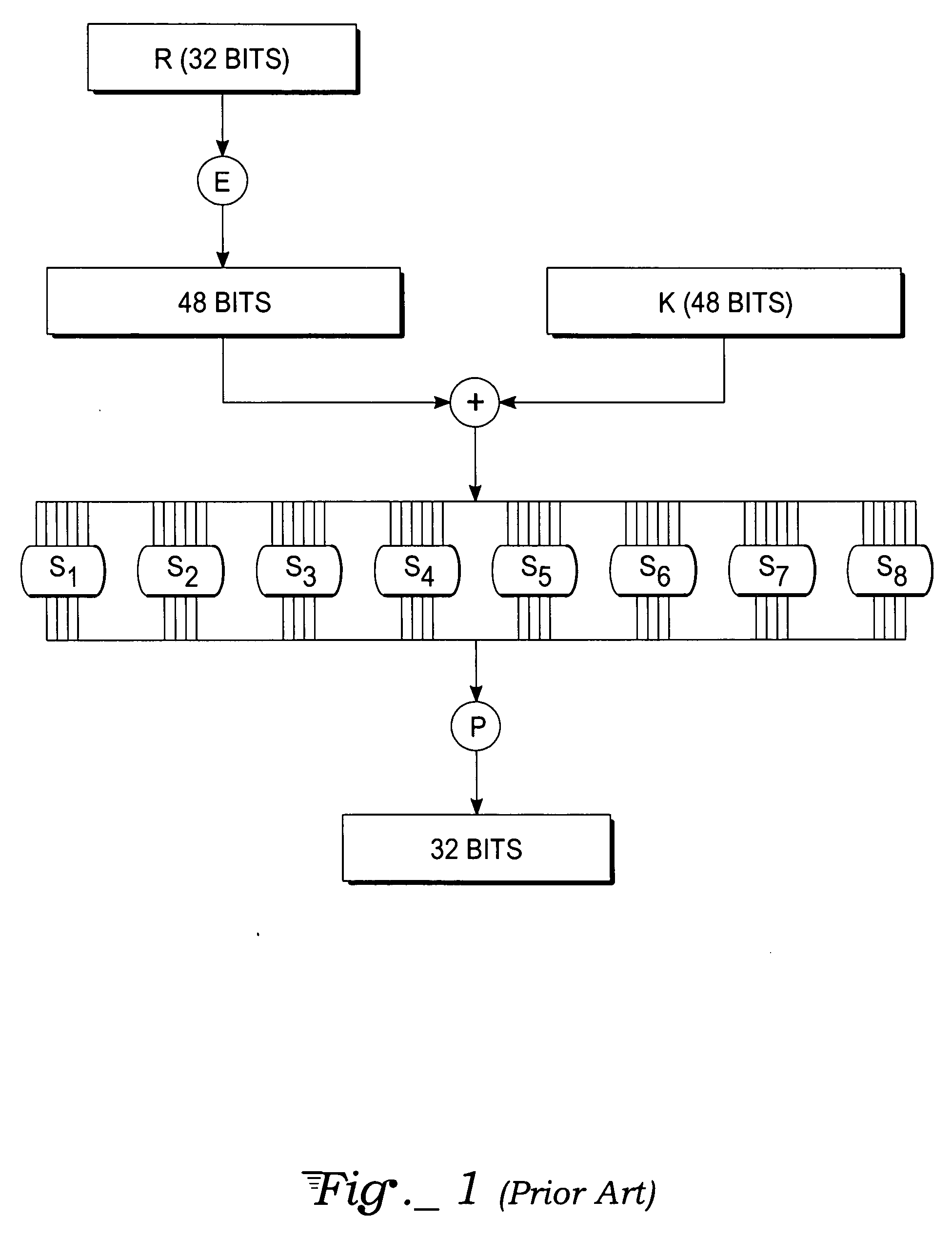
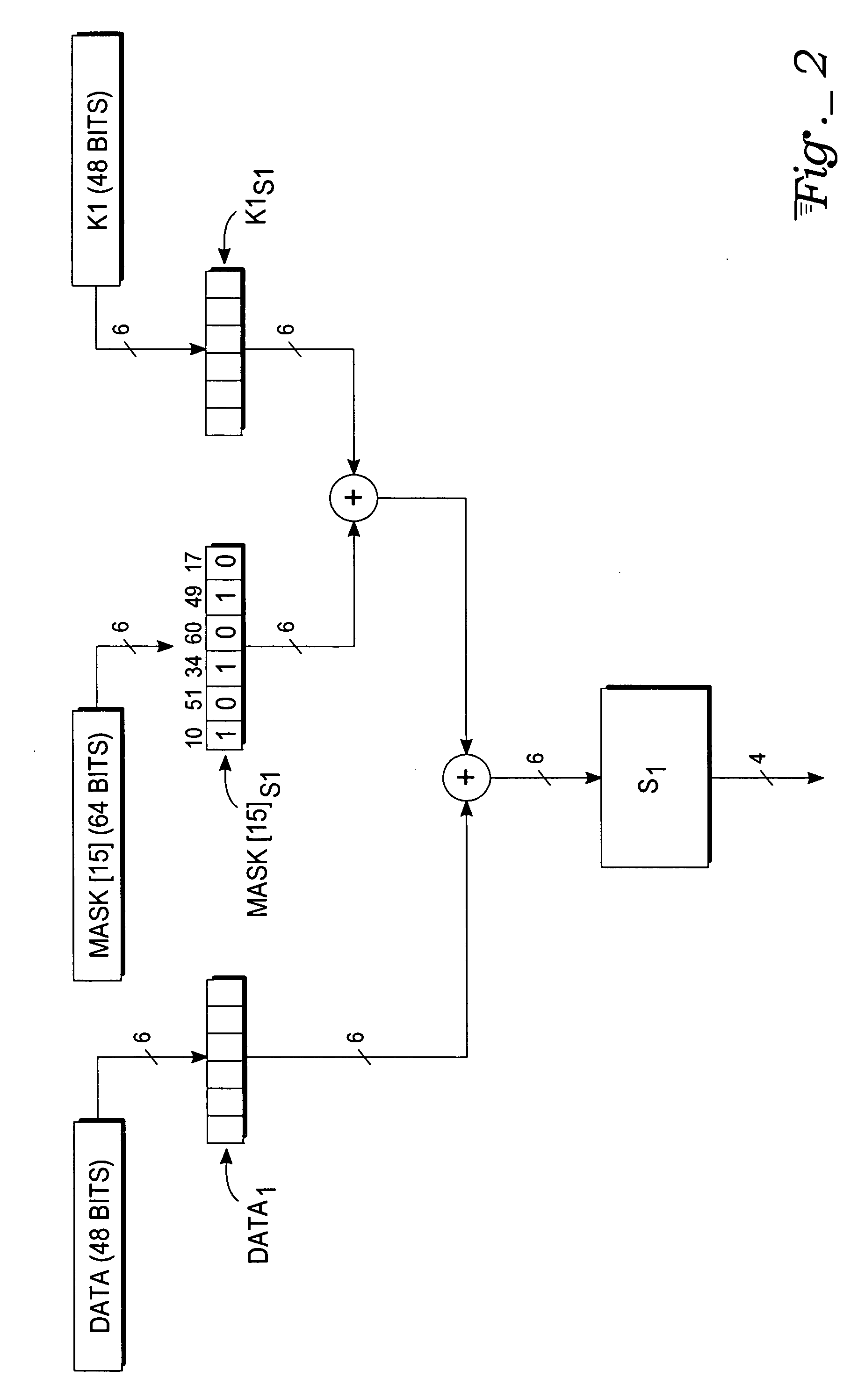
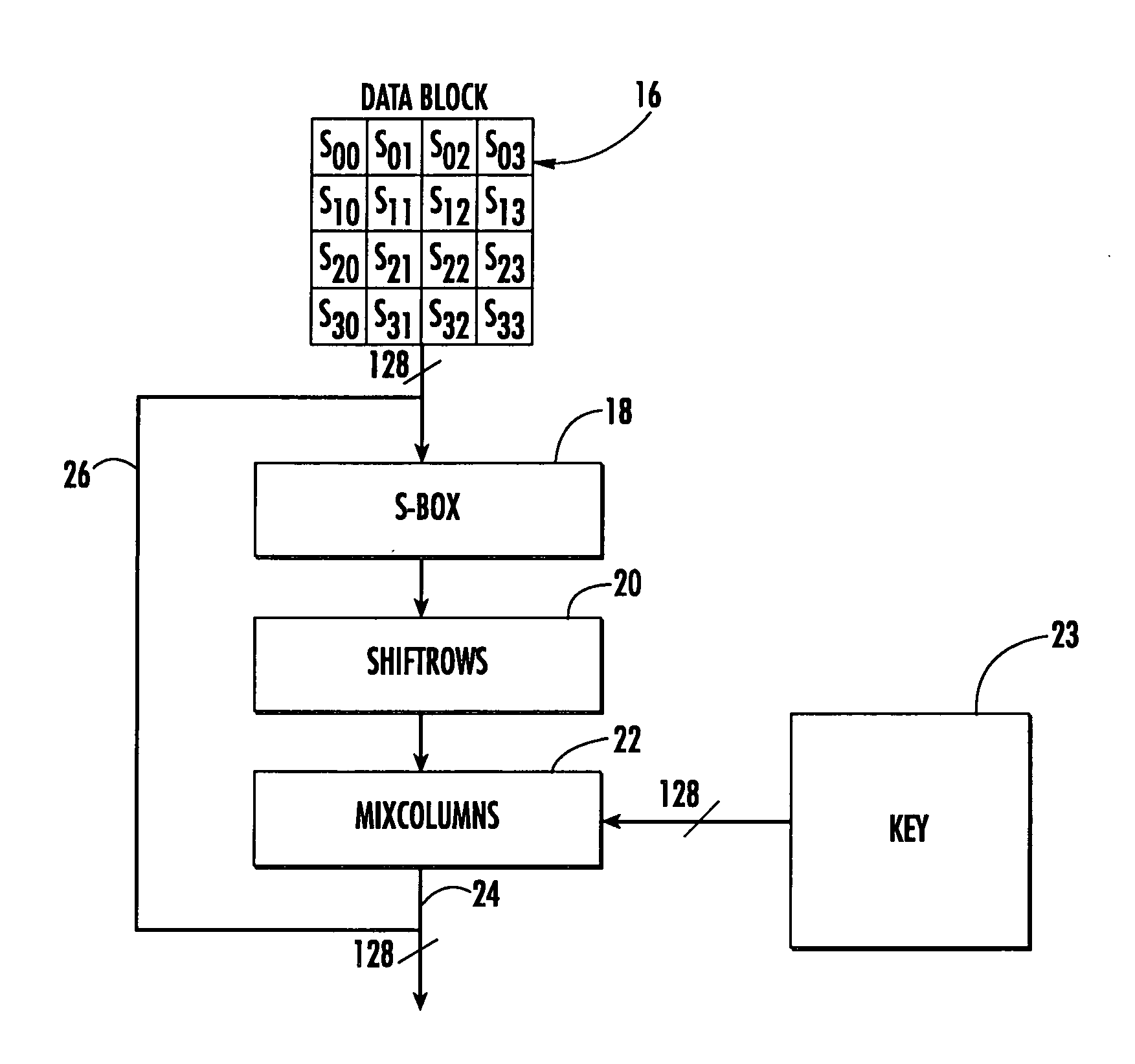
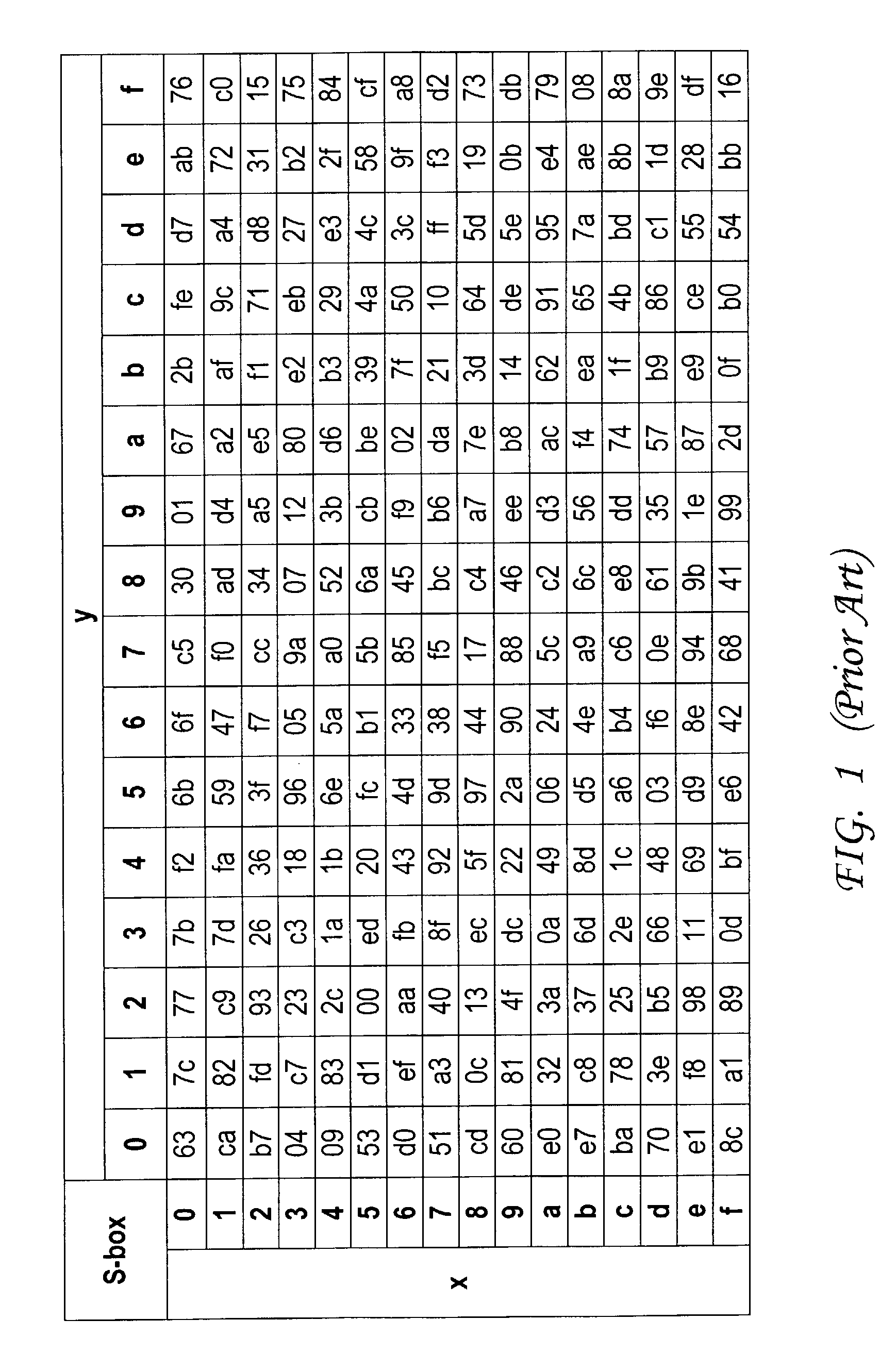
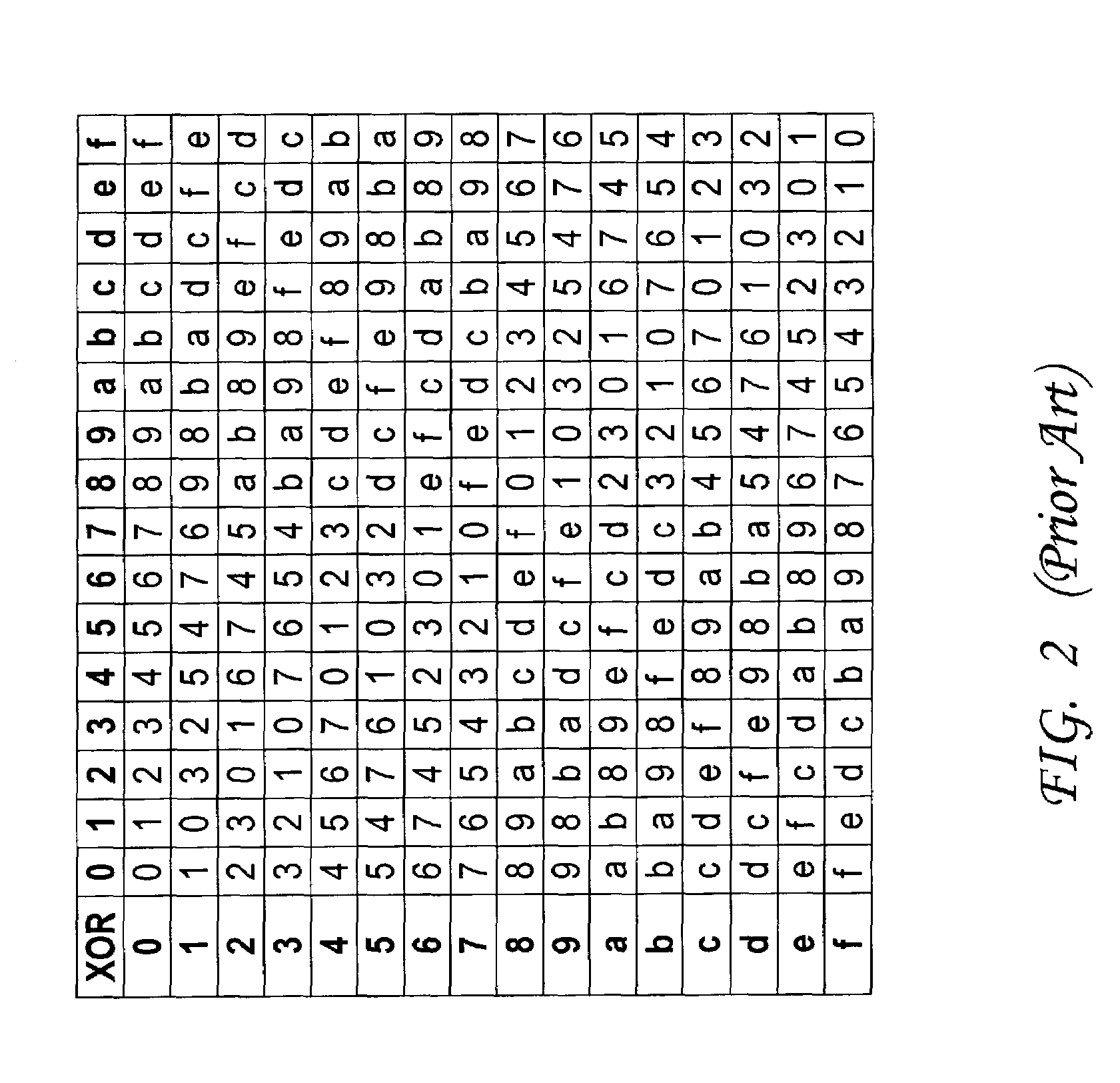
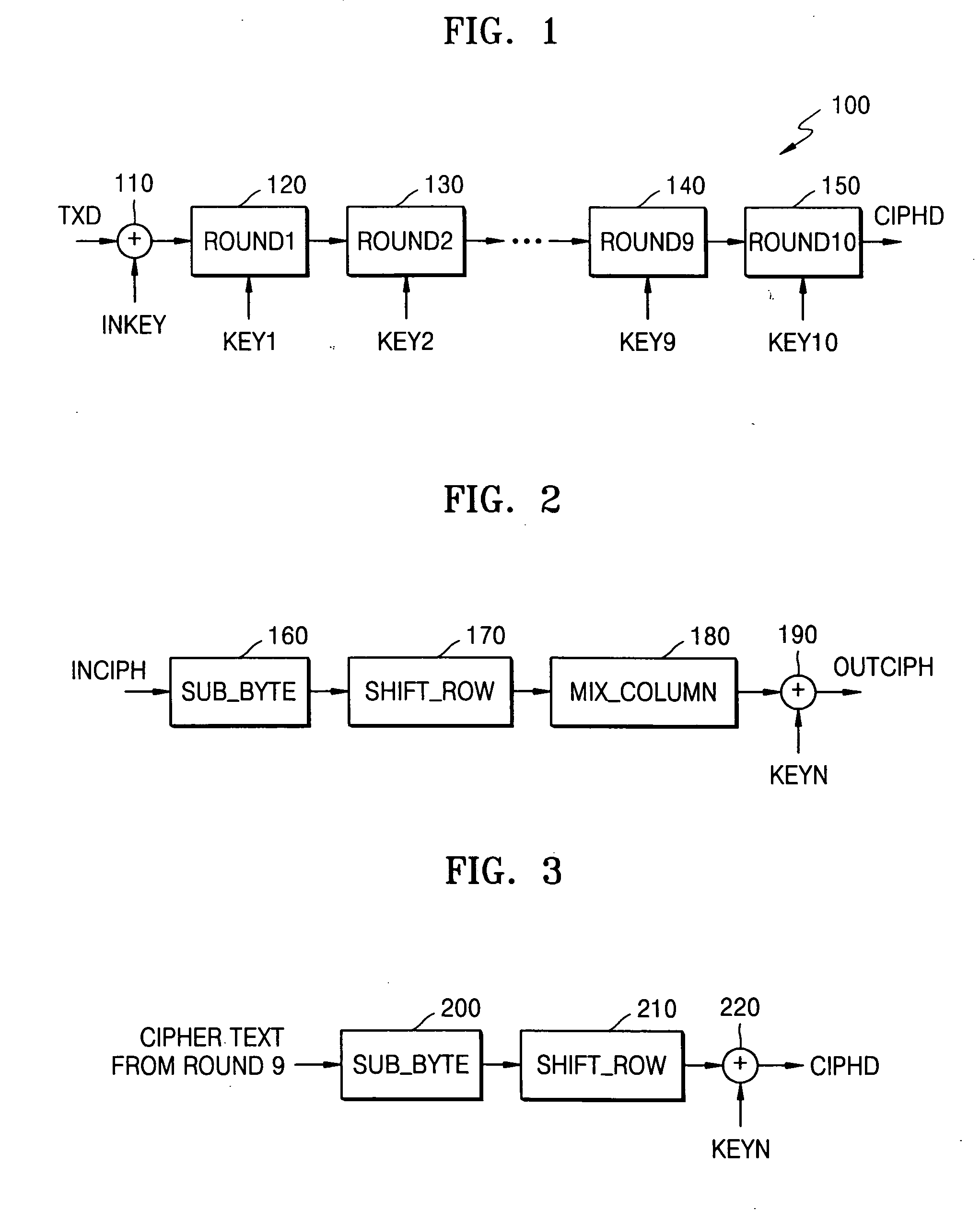
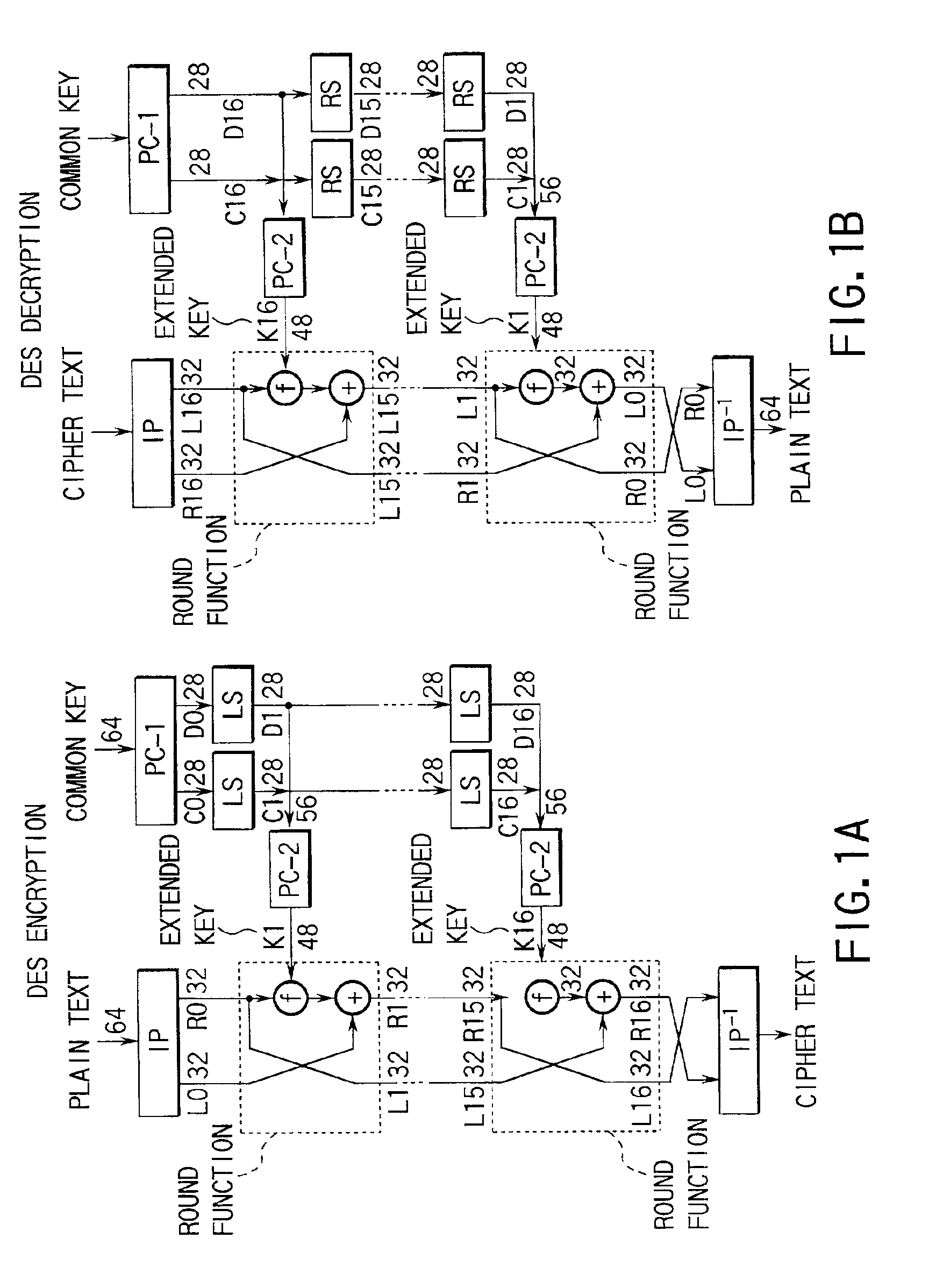
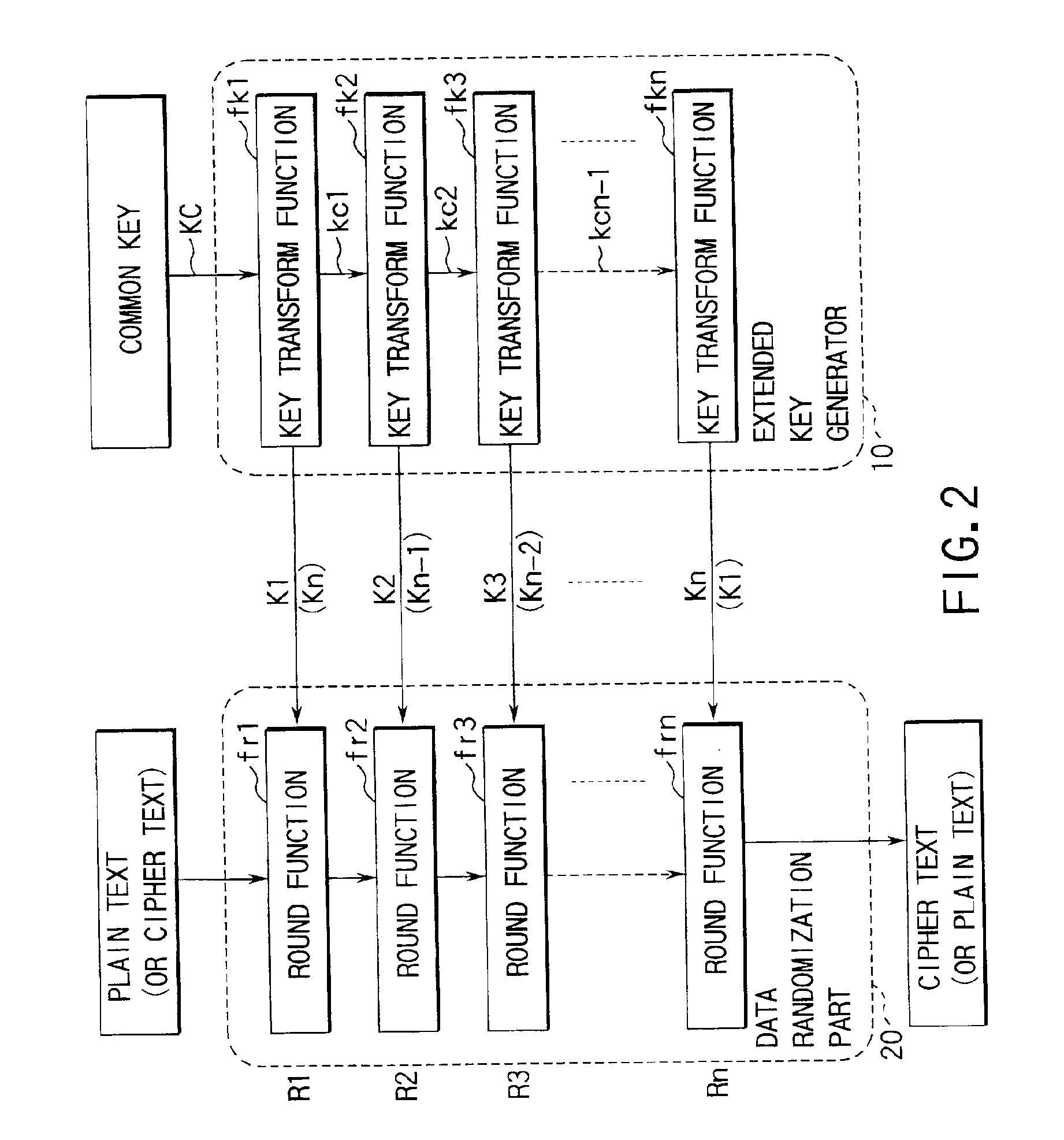
In cryptography, an S-box (substitution-box) is a basic component of symmetric key algorithms which performs substitution. In block ciphers, they are typically used to obscure the relationship between the key and the ciphertext — Shannon's property of confusion.
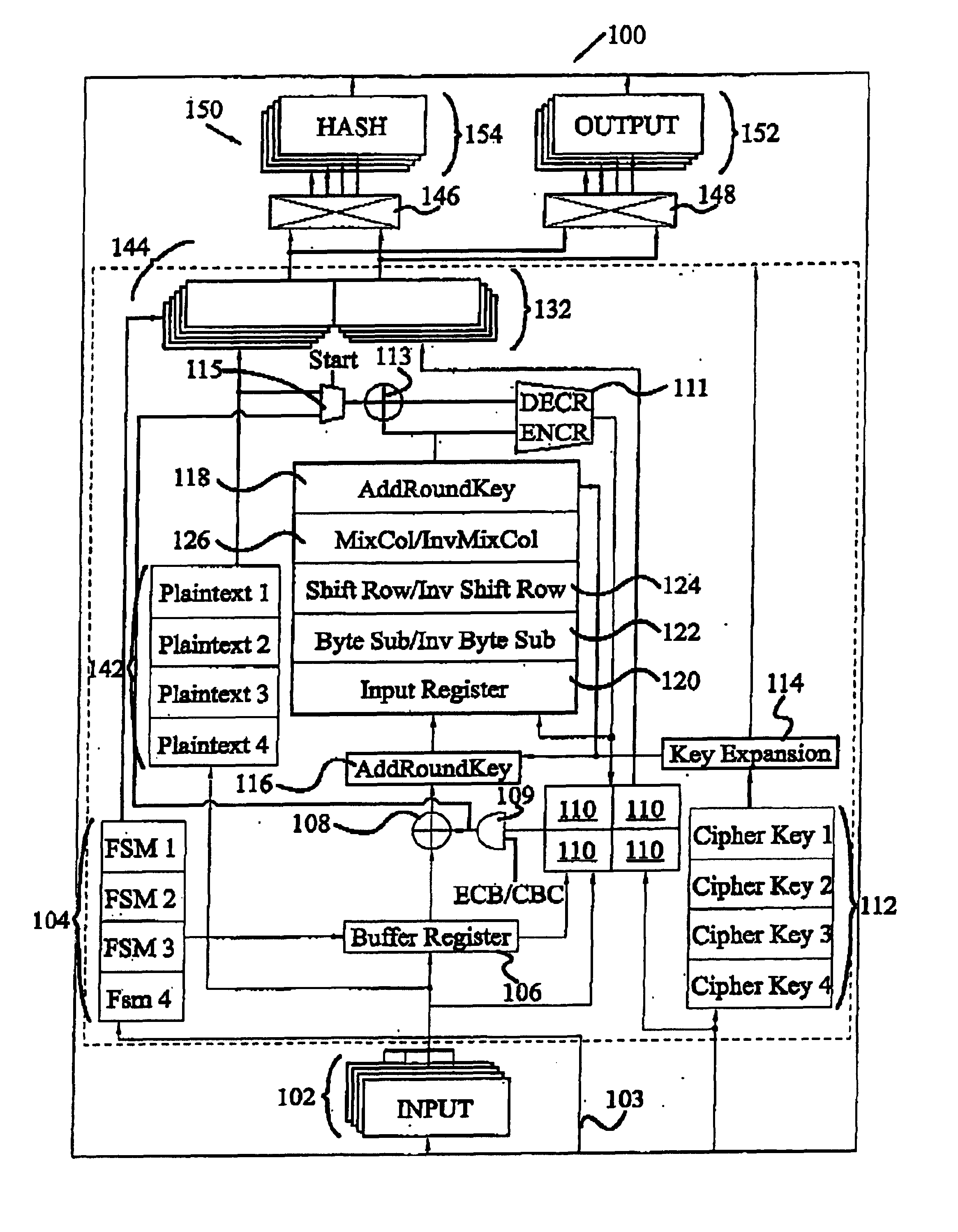
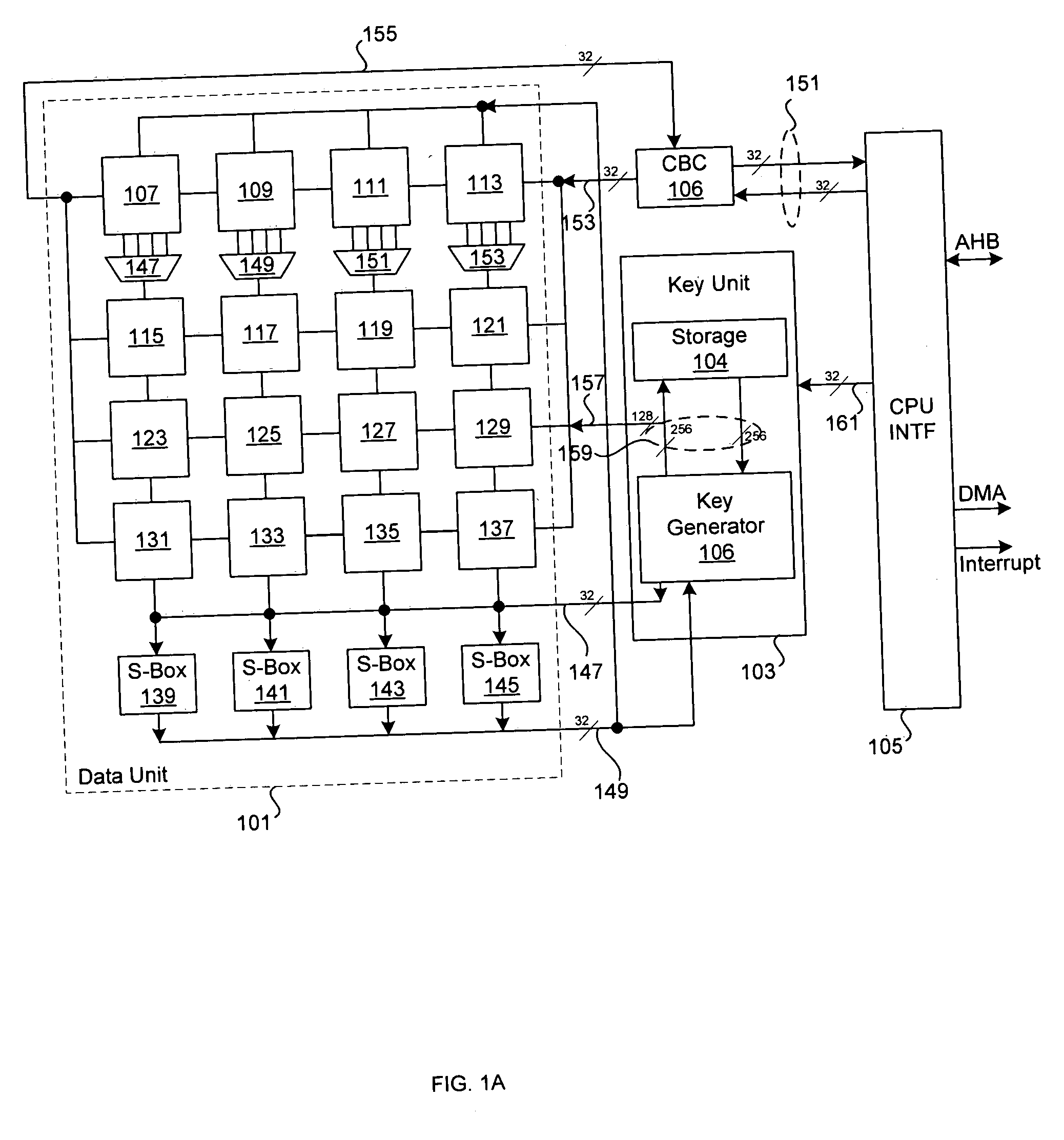
Circuit and method for implementing the advanced encryption standard block cipher algorithm in a system having a plurality of channels
InactiveUS6937727B2Efficient implementationGenerate efficientlyEncryption apparatus with shift registers/memoriesUser identity/authority verificationS-boxAdvanced Encryption Standard
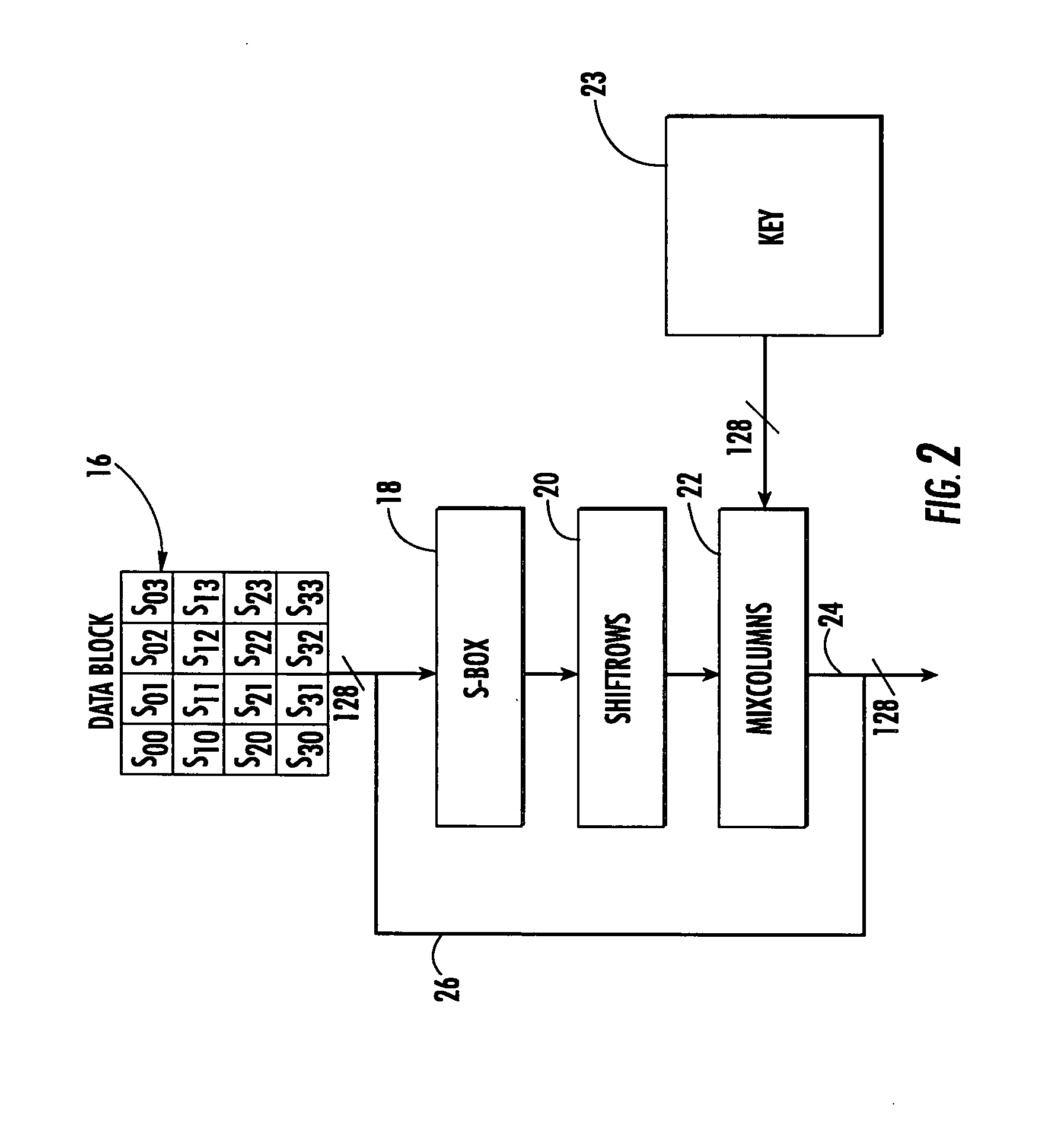
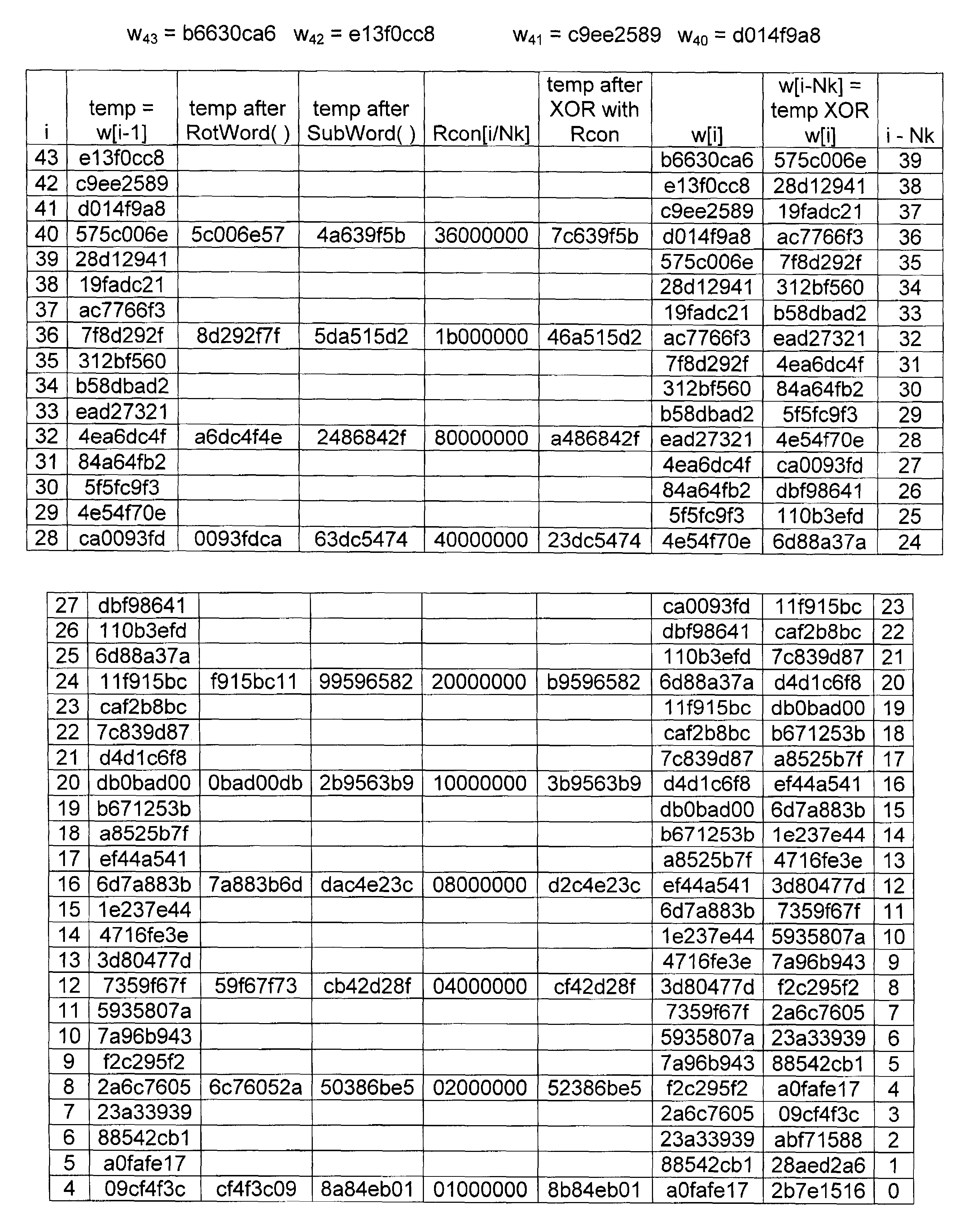
A circuit includes a single circuit portion for implementing the Advanced Encryption Standard (AES) block cipher algorithm in a system having a plurality of channels. The circuit portion includes a circuit for individually generating, on the fly, the round keys used during each round of the AES block cipher algorithm. The circuit portion also includes shared logic circuits that implement the transformations used to encrypt and decrypt data blocks according to the AES block cipher. The single circuit portion encrypts or decrypts data blocks from each of the plurality of system channels in turn, in round-robin fashion. The circuit portion also includes a circuit for determining S-box values for the AES block cipher algorithm. The circuit additionally implements an efficient method for generating round keys on the fly for the AES block cipher decryption process.
Owner:EXCELIS INC
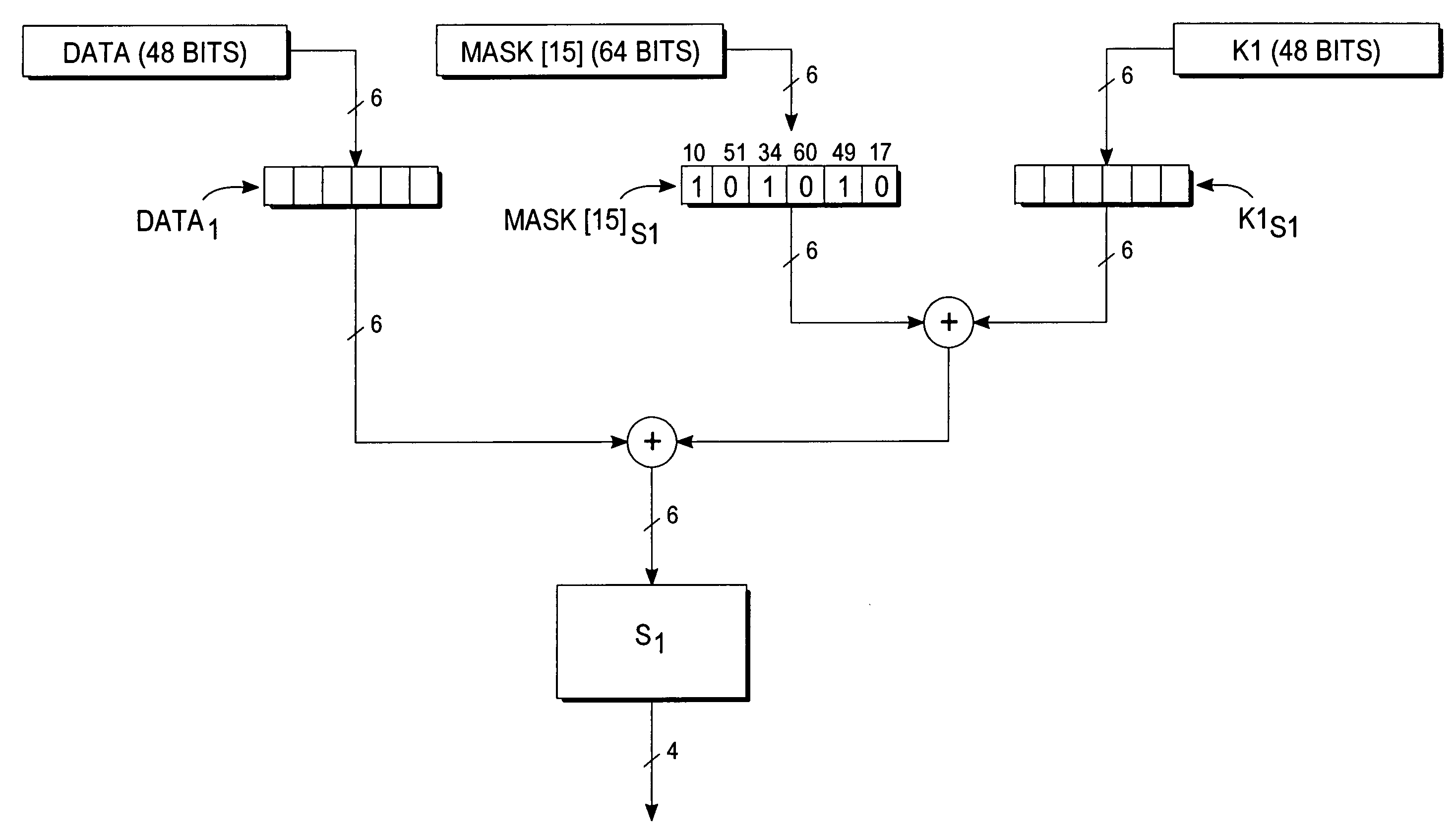
Encryption protection method
InactiveUS20080019503A1Encryption apparatus with shift registers/memoriesSecret communicationComputer hardwareS-box
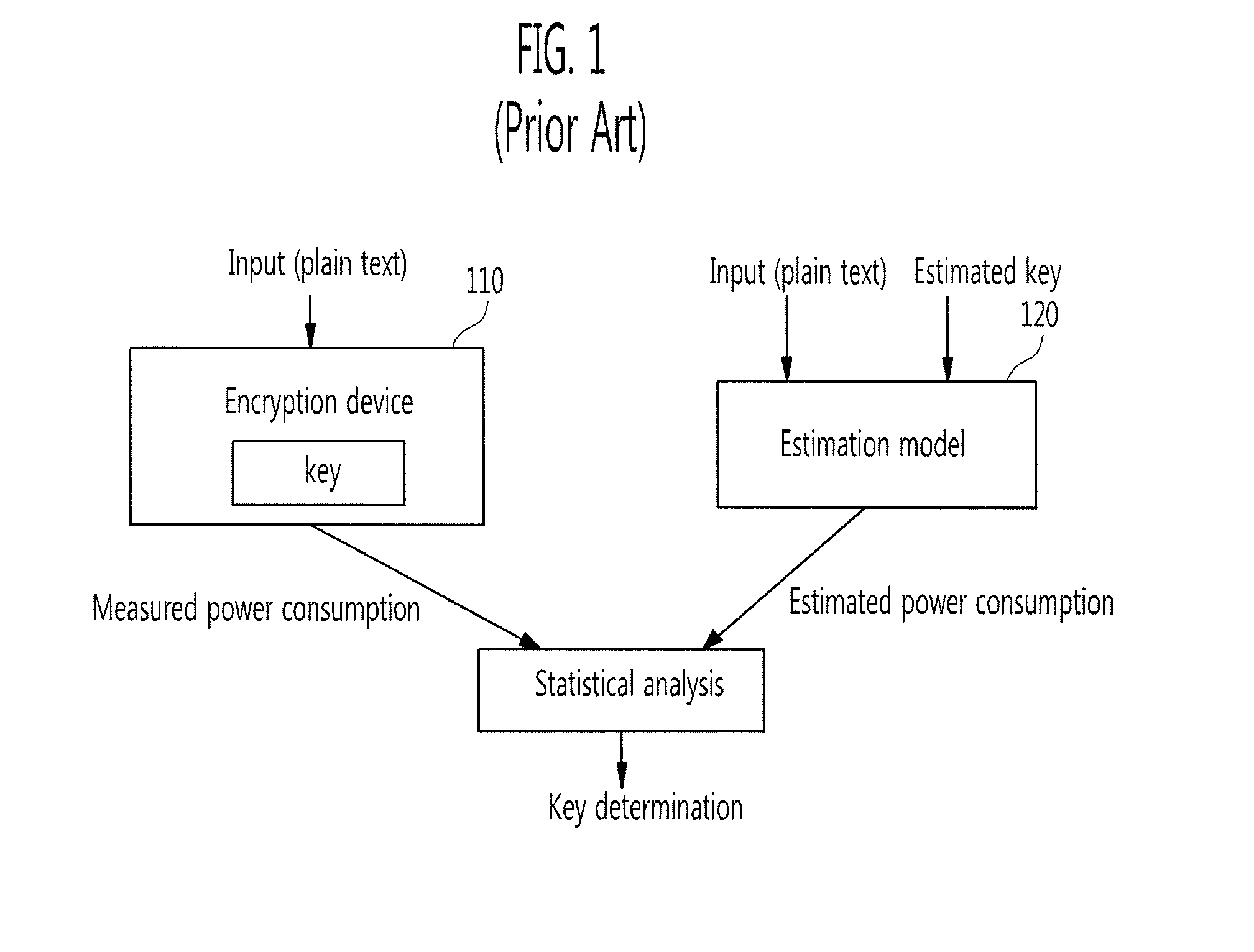
A deterministic blinding method for cipher algorithms that employ key-mixing and substitution (S-box) operations uses a masking table constructed with a true mask and a plurality of dummy masks corresponding to every possible S-box input. Each mask is applied in the key-mixing operation (e.g., bitwise XOR) to the cipher key or to round subkeys to generate true and dummy keys or subkeys that are applied to the data blocks within the overall cipher algorithm or within individual cipher rounds. The mask values prevent side-channel statistical analyses from determining the true from the dummy keys or subkeys. The true mask is identifiable to the cipher but not by external observers.
Owner:CRYPTOGRAPHY RESEARCH
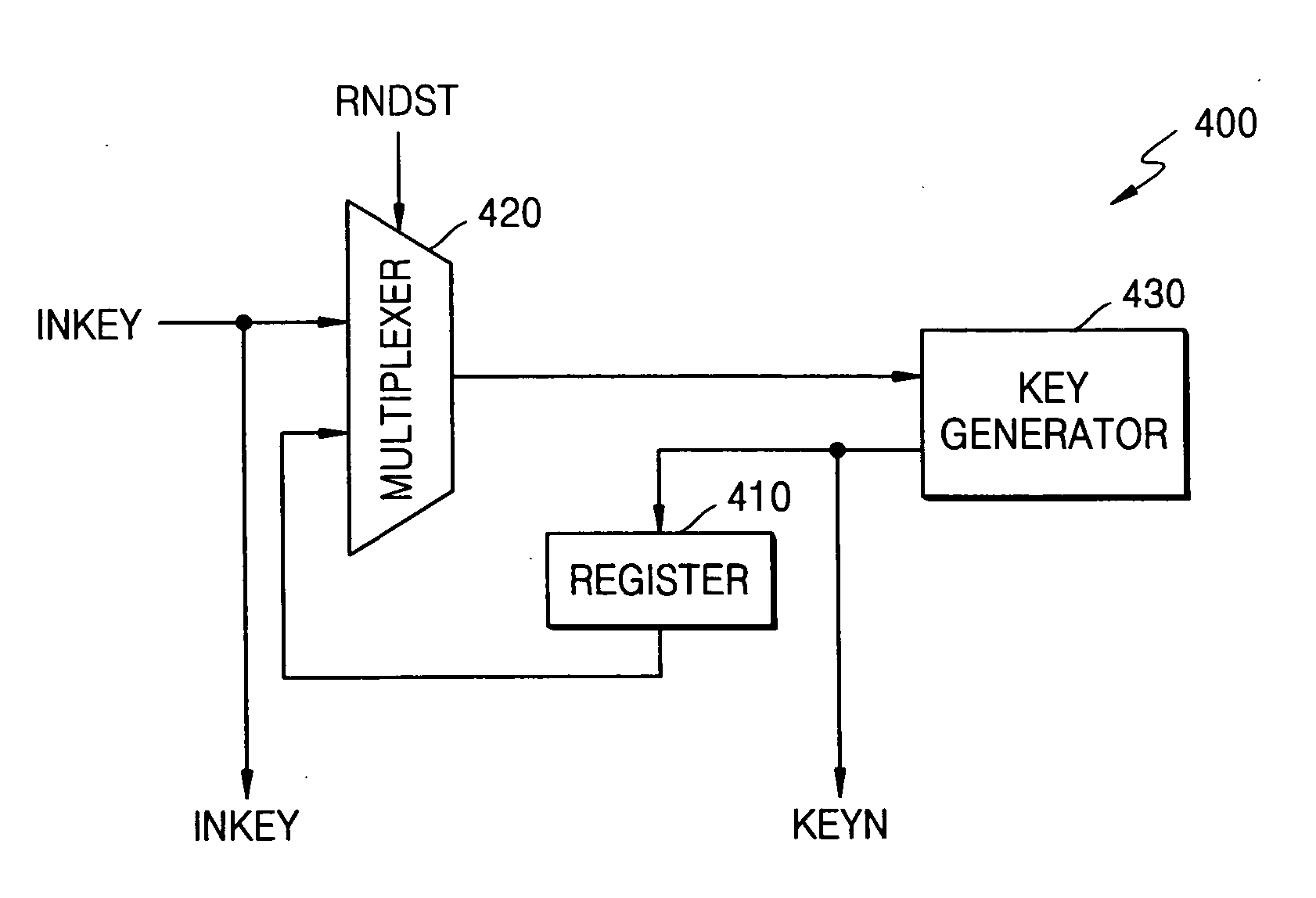
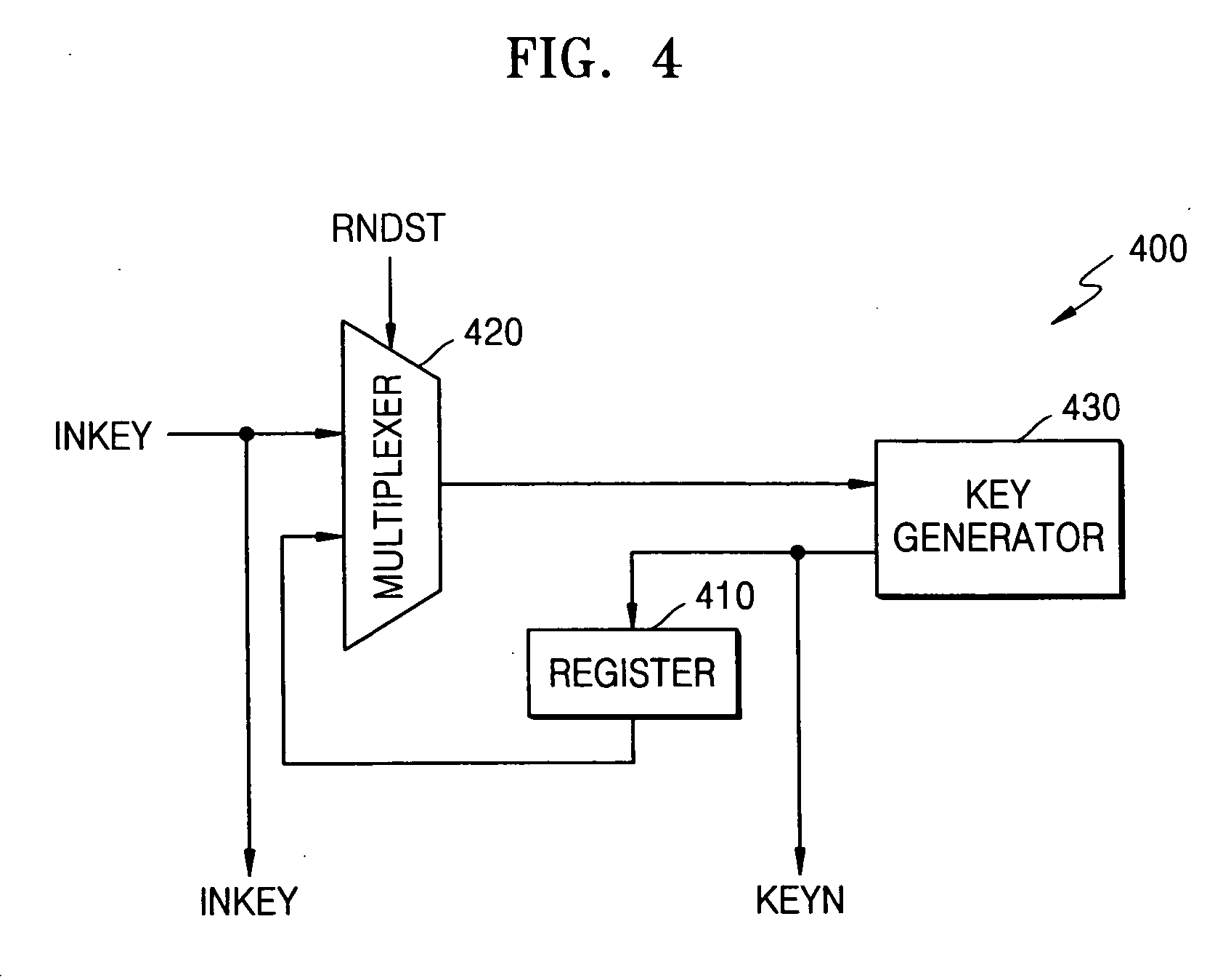
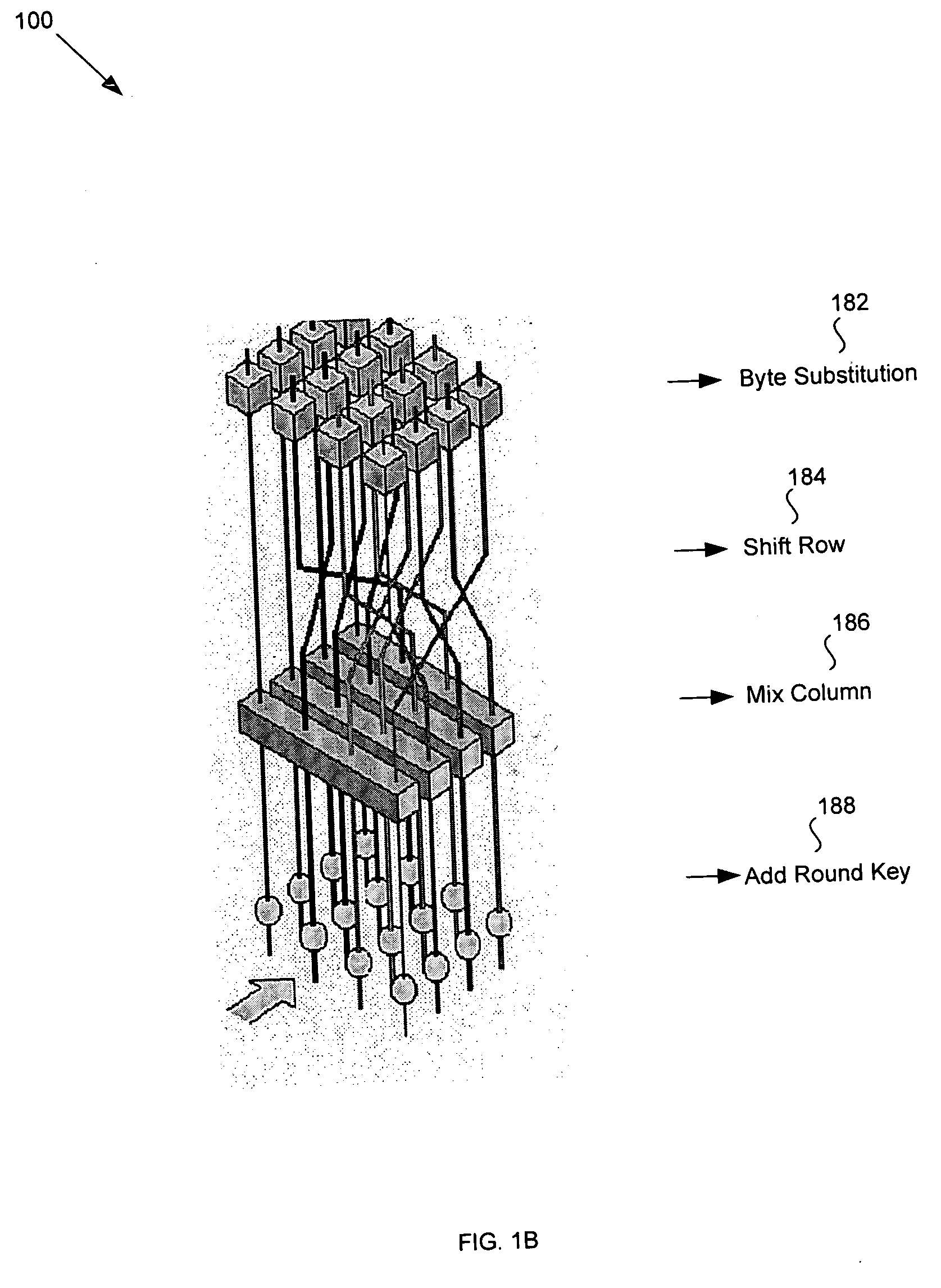
Advanced encryption standard (AES) engine with real time S-box generation
ActiveUS20050058285A1Good encryptionDifferent operationalEncryption apparatus with shift registers/memoriesSecret communicationShift registerS-box
An advanced encryption standard (AES) engine with real time S-box generation includes a Galois field multiplier system in a first mode responsive to a first data block for generating an AES selection (S-box) function by executing the multiplicative increase in GF1(2m) and applying an affine over GF(2) transformation to obtain a subbyte transformation; and a shift register system for transforming the subbyte transformation to obtain a shift row transformation; the Galois field multiplier system is responsive in a second mode to the shift row transformation to obtain a mix column transformation and add a round key for generating in real time an advanced encryption standard cipher function of the first data block.
Owner:ANALOG DEVICES INC +1
Advanced encryption standard (AES) hardware cryptographic engine
ActiveUS7295671B2Reduce in quantityKey distribution for secure communicationMultiple keys/algorithms usageS-boxAdvanced Encryption Standard
A cryptographic method and related implements the Rijndael—AES encryption standard. In one improvement, the decryption round keys are generated on a round by round basis from the final Nk round keys saved from a previous encryption key scheduling operation. Latency and memory requirements are thereby minimized. S-boxes for the AES key generation and cipher operation itself, may be implemented multiple times in different ways with different power signatures, with a pseudo-random selection of the pathway for the different bytes to be substituted. The premix operation occurs simultaneously with the generation of first round keys, and a dummy circuit with substantially identical timing as the real premix circuitry adds power consumption noise to the premix.
Owner:ATMEL CORP
Hardware cryptographic engine and hardware cryptographic method using an efficient S-BOX implementation
InactiveUS20050169463A1Efficient use ofLow powerMultiple keys/algorithms usageEncryption apparatus with shift registers/memoriesComputer hardwareAdvanced encryption standard algorithm
A hardware cryptographic engine implementing an Advanced Encryption Standard (AES) algorithm is disclosed. The hardware cryptographic engine comprises a plurality of modules corresponding to rounds of AES. Each of the plurality of modules comprises an S-BOX computing a multiplicative inverse of each element in an input vector over GF(28) using an operation over GF(((22)2)2), and replacing each element of the input vector with a substitute element obtained using a result of the operation.
Owner:SAMSUNG ELECTRONICS CO LTD
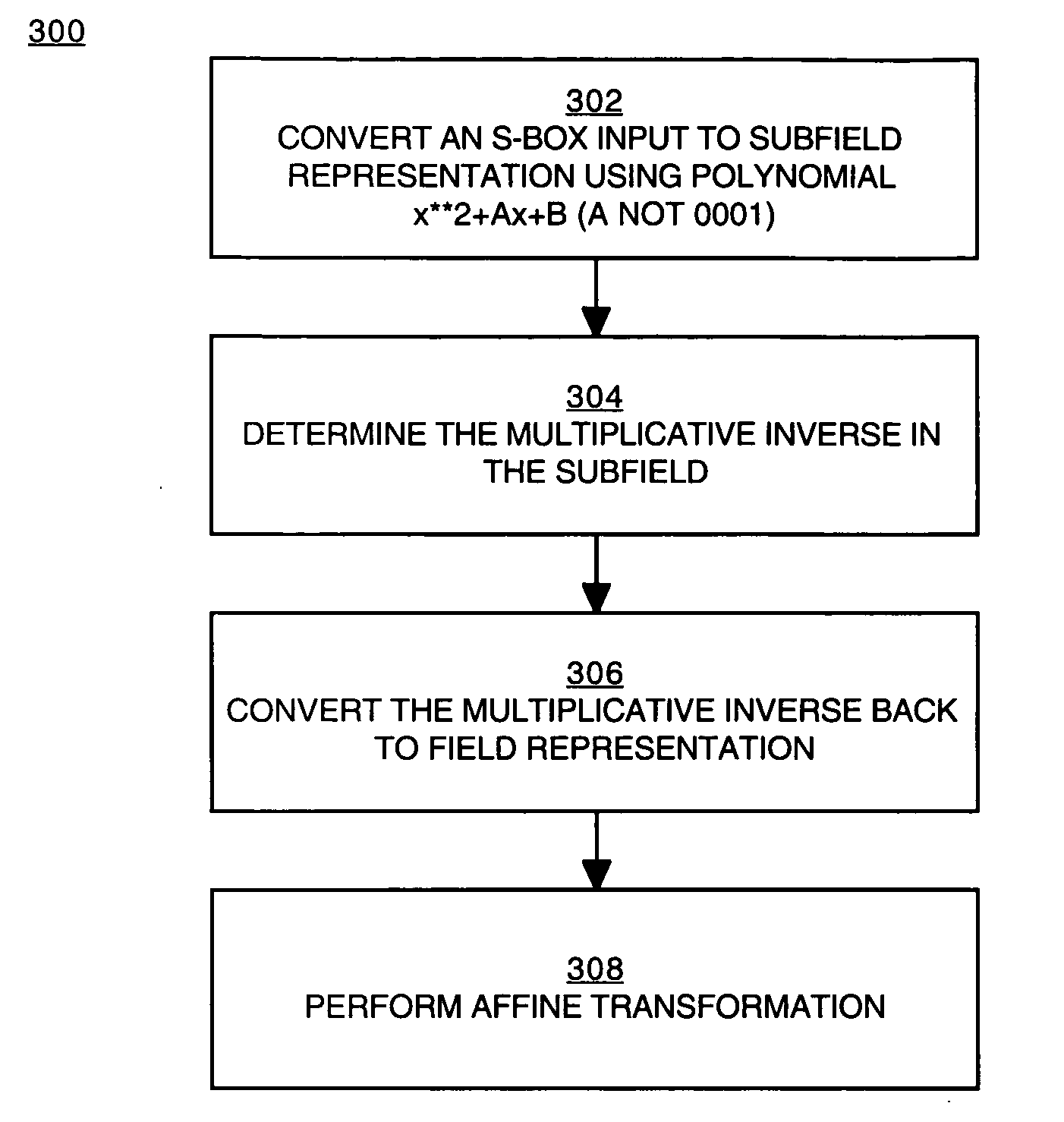
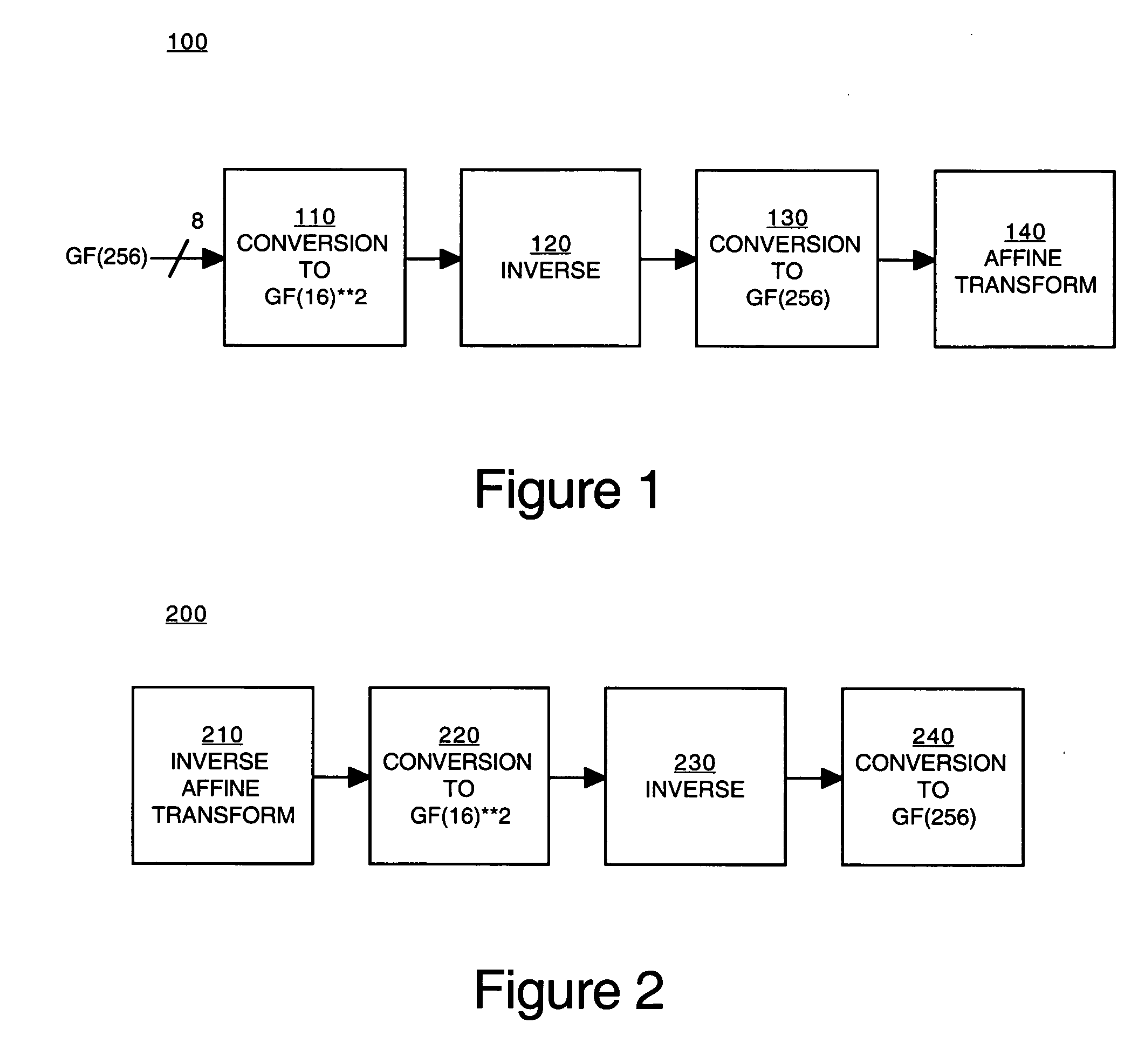
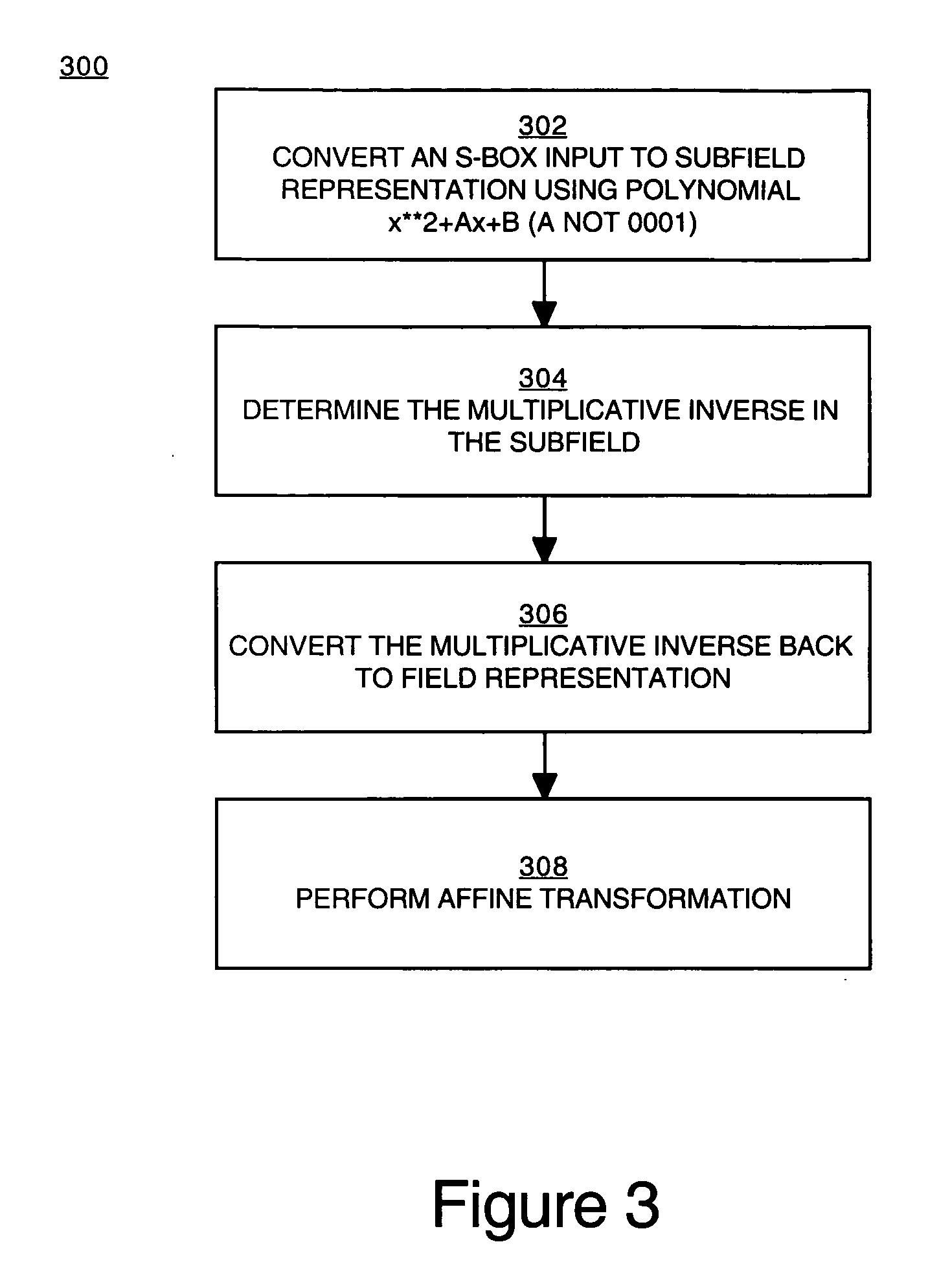
Implementation of a switch-box using a subfield method
InactiveUS20060093136A1Improve S-box implementationLess silicon areaEncryption apparatus with shift registers/memoriesDigital data processing detailsS-boxSwitch box
Methods and systems for implementing a switch box (S-box) in a cryptographic application are described. An input to the S-box is converted from a Galois field representation GF(N2) to a Galois subfield representation GF(N)2. The input is converted using a generating polynomial of the form x2+Ax+B, where A and B are elements in GF(N) and where A has a value other than unity. The multiplicative inverse of the Galois subfield representation GF(N)2 is determined. The multiplicative inverse is converted back to the Galois field representation GF(N2). An affine transformation of the multiplicative inverse is then performed.
Owner:CISCO TECH INC
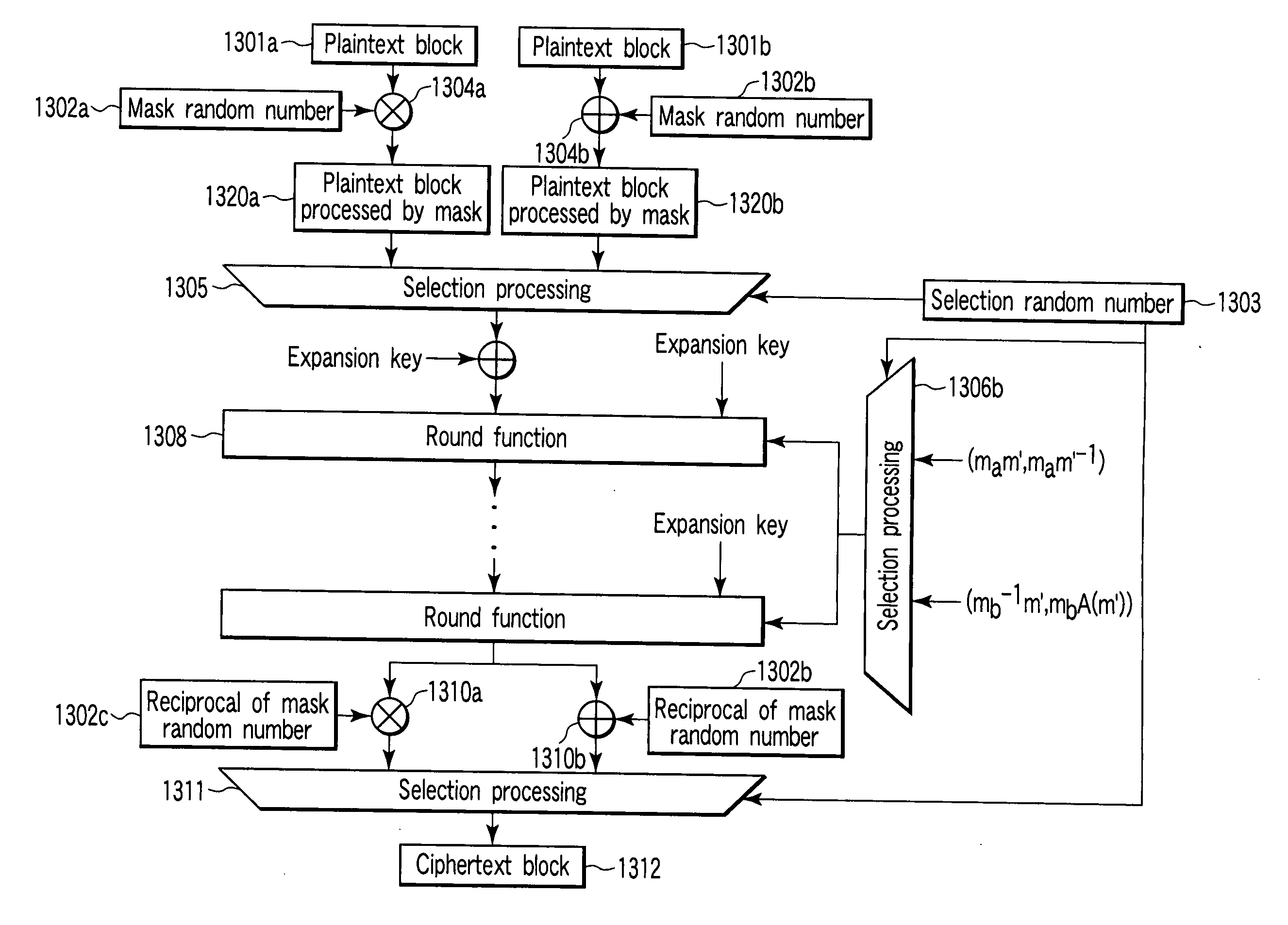
Encryption apparatus and encryption method
An encryption apparatus for generating a ciphertext block from a plaintext block is disclosed. A selector selects at random one mask random number from a plurality of random numbers generated by a random number generator. A mask processing unit executes mask processing of a plaintext block by using the mask random number selected by the selector. A storage unit stores a first table representing an initial S-box. A converter converts the first table into a second table representing a deformed S-box on the basis of the mask random number selected by the selector. An encryption unit generates a ciphertext block by shuffling the mask-processed plaintext block using the second table.
Owner:KK TOSHIBA
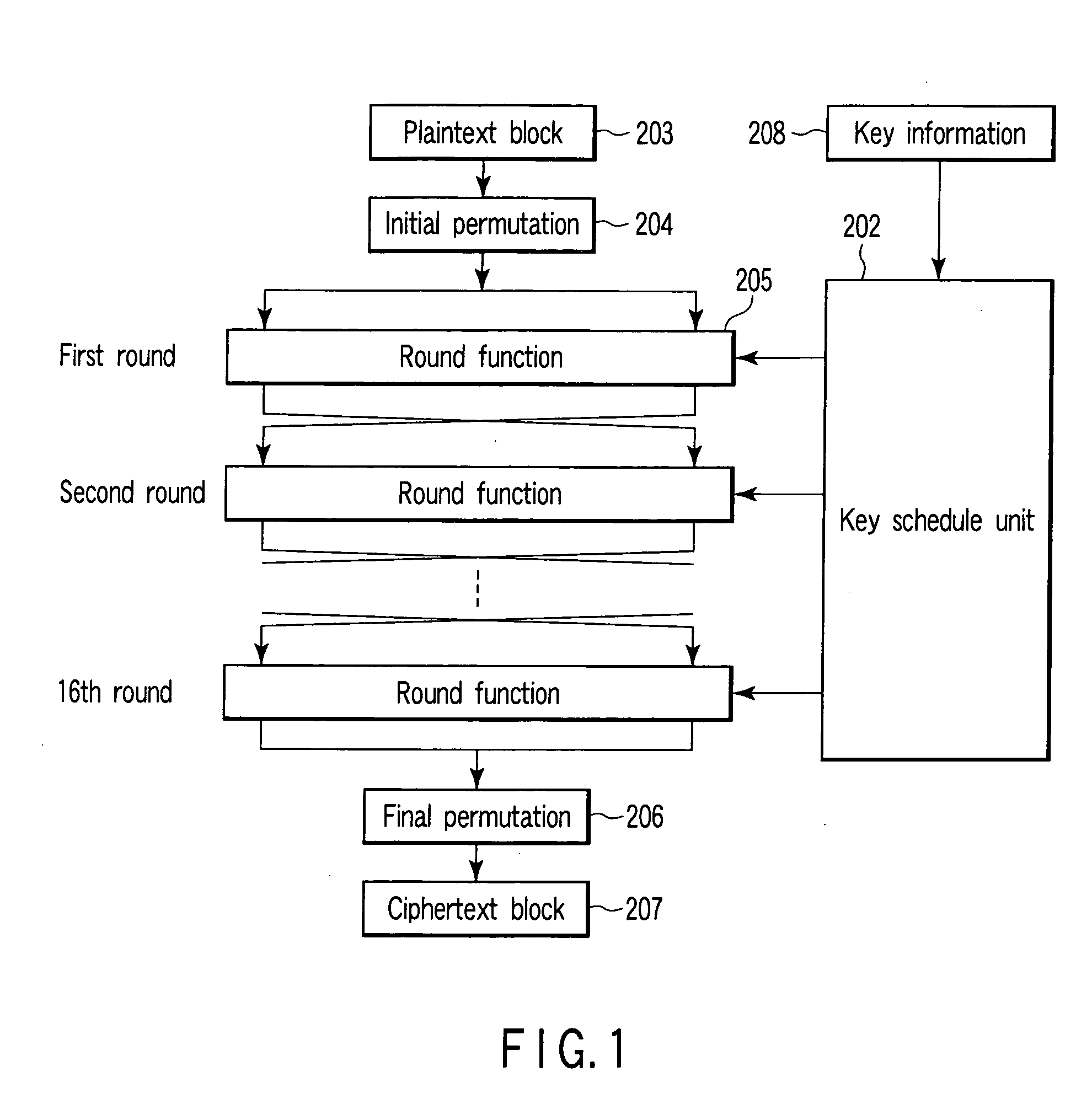
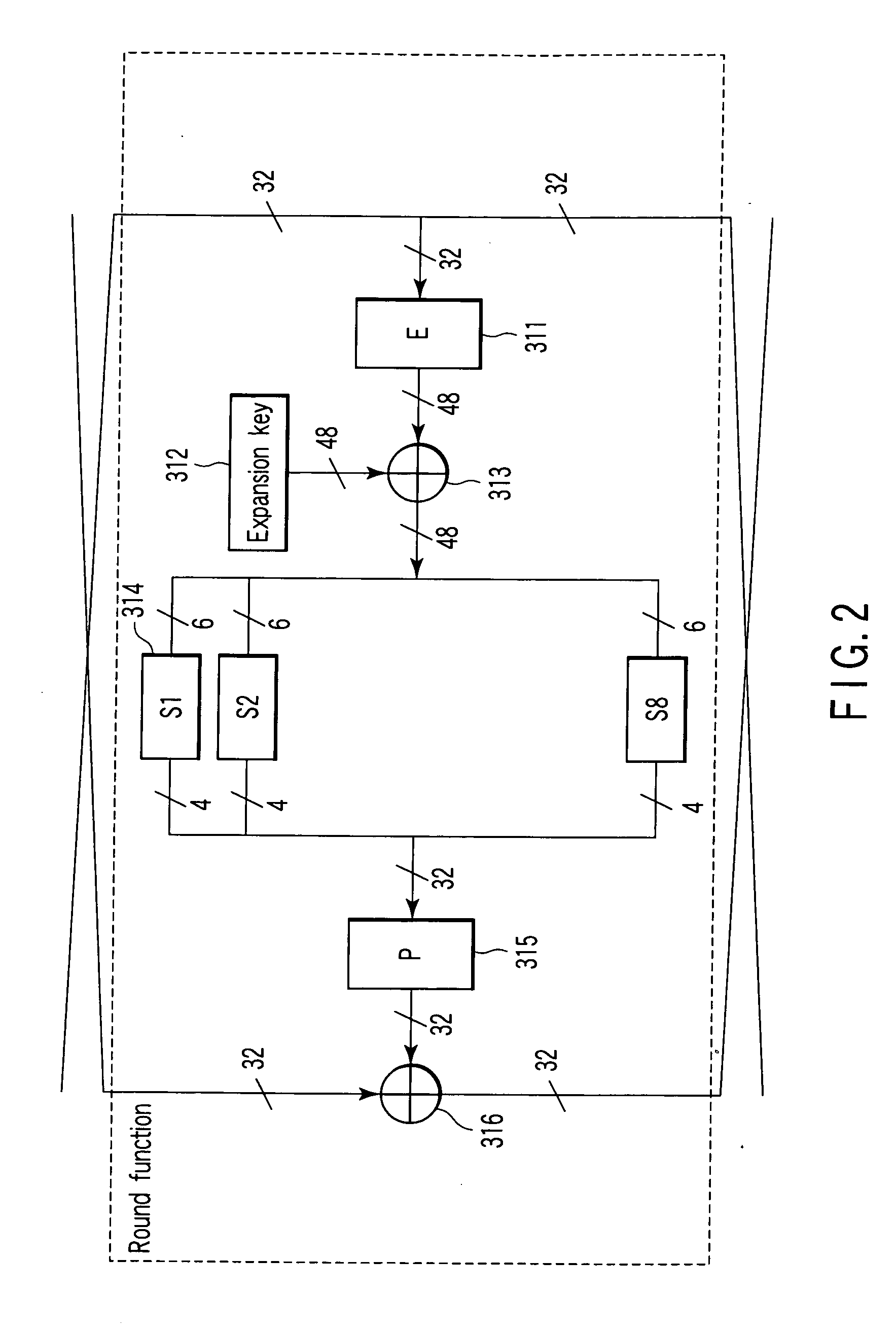
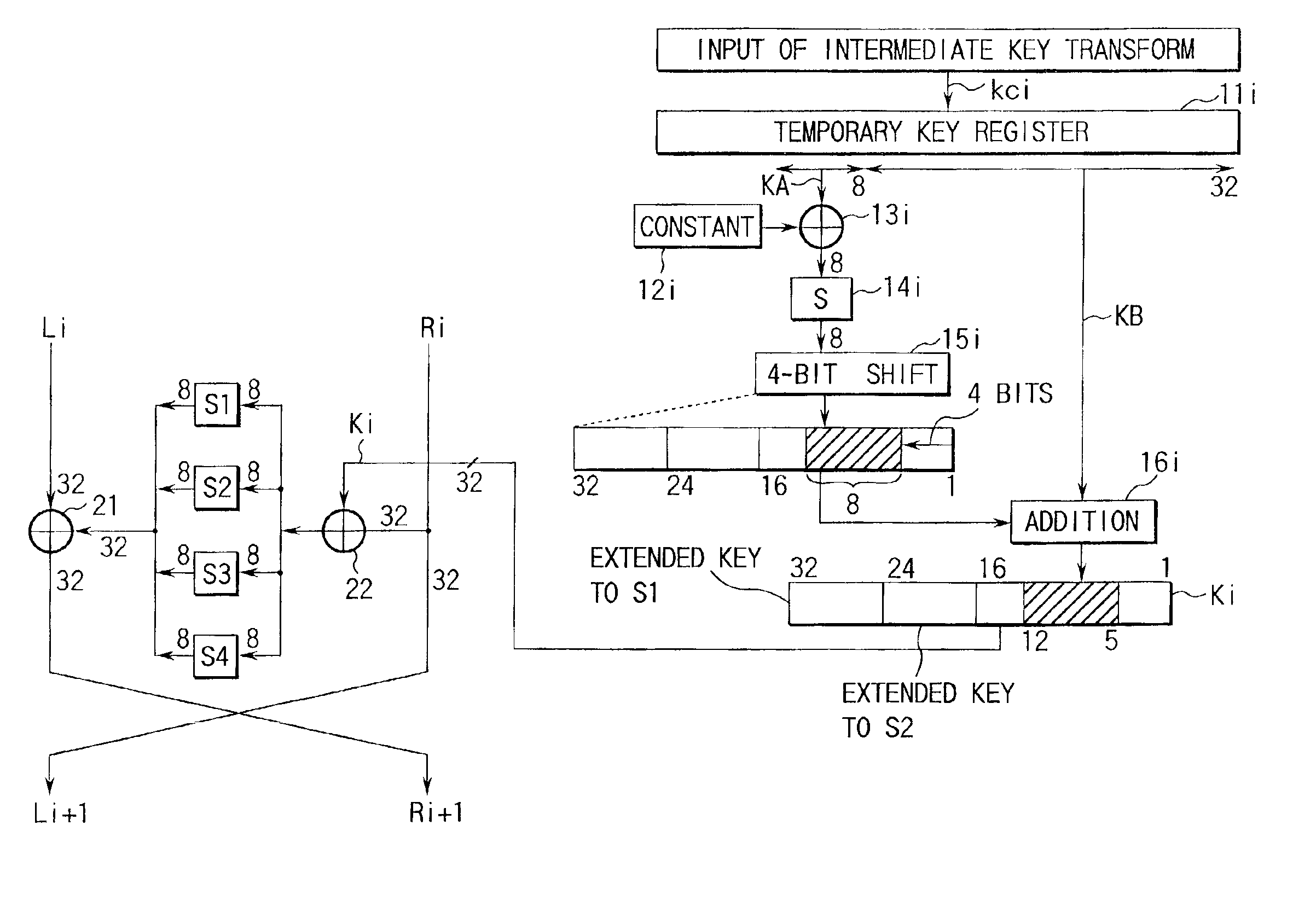
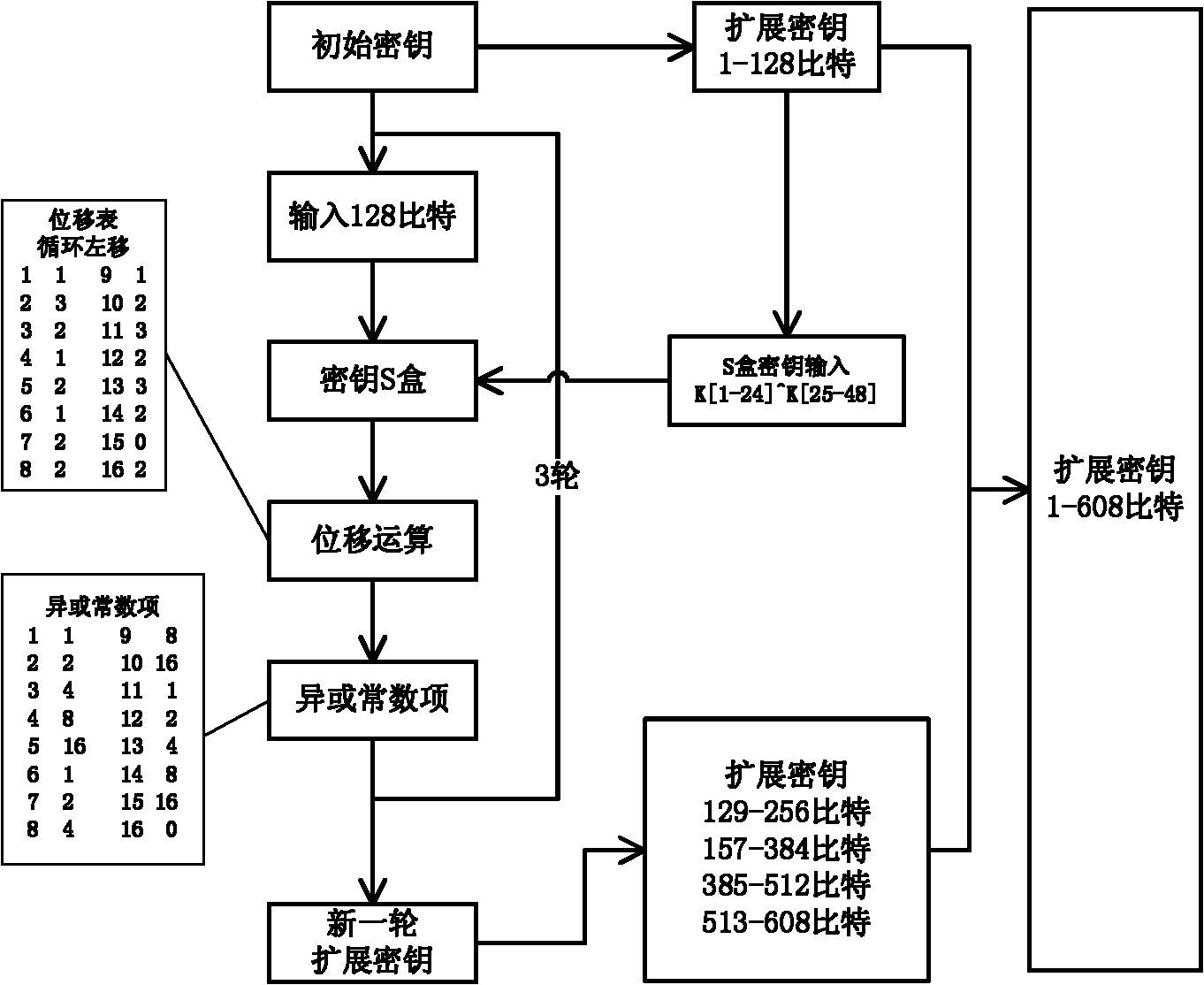
Extended key generator, encryption/decryption unit, extended key generation method, and storage medium
InactiveUS6891950B1Avoid it happening againImproving cryptological robustnessEncryption apparatus with shift registers/memoriesDigital data processing detailsComputer hardwareS-box
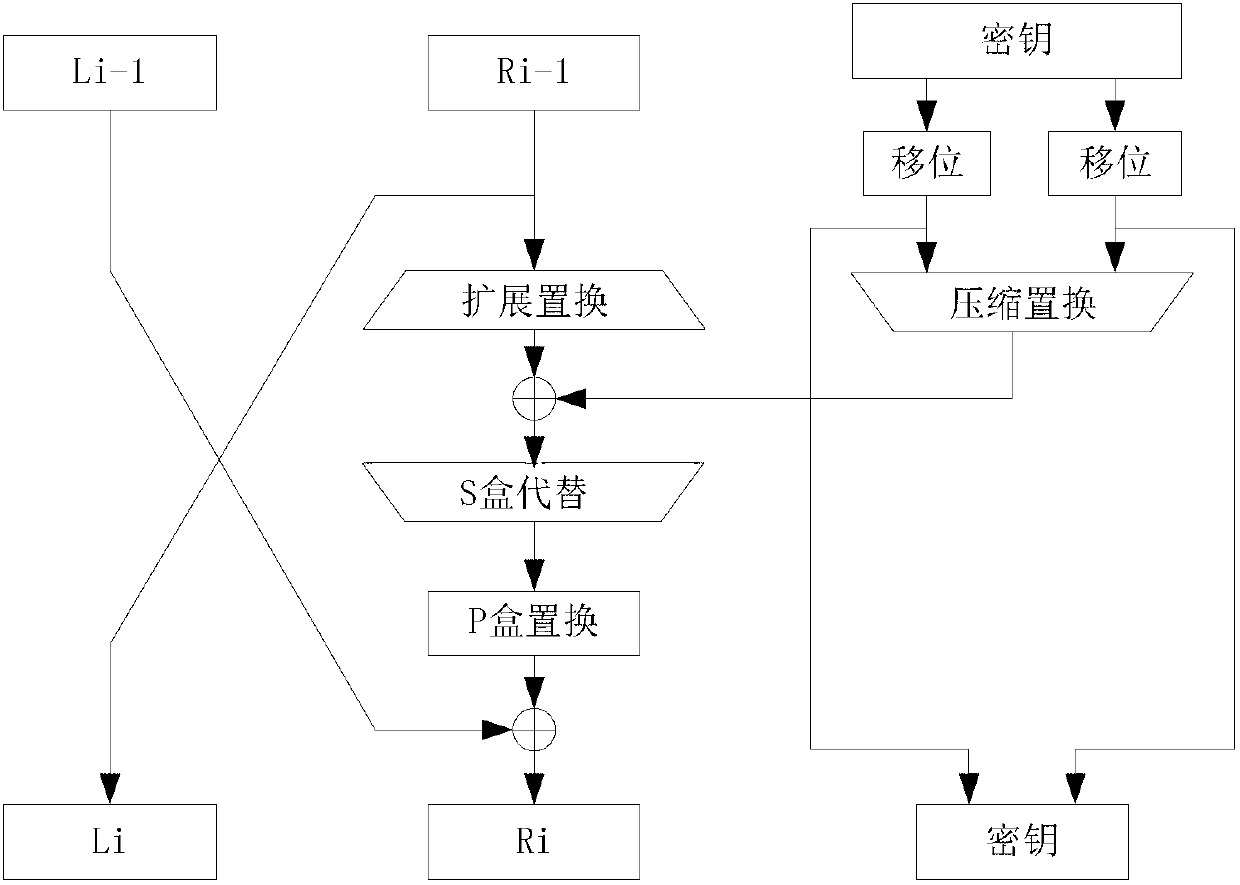
There are disclosed an extended key generator, encryption / decryption unit, and storage medium, in which as each of key transform functions, a transform process is done by an S box (substitution table) on the basis of a first key obtained from the inputted key, and an adder computes a corresponding one of extended keys on the basis of a value obtained by shifting the transformed result of the S box to the left, and a second key obtained from the inputted key.
Owner:KK TOSHIBA +1
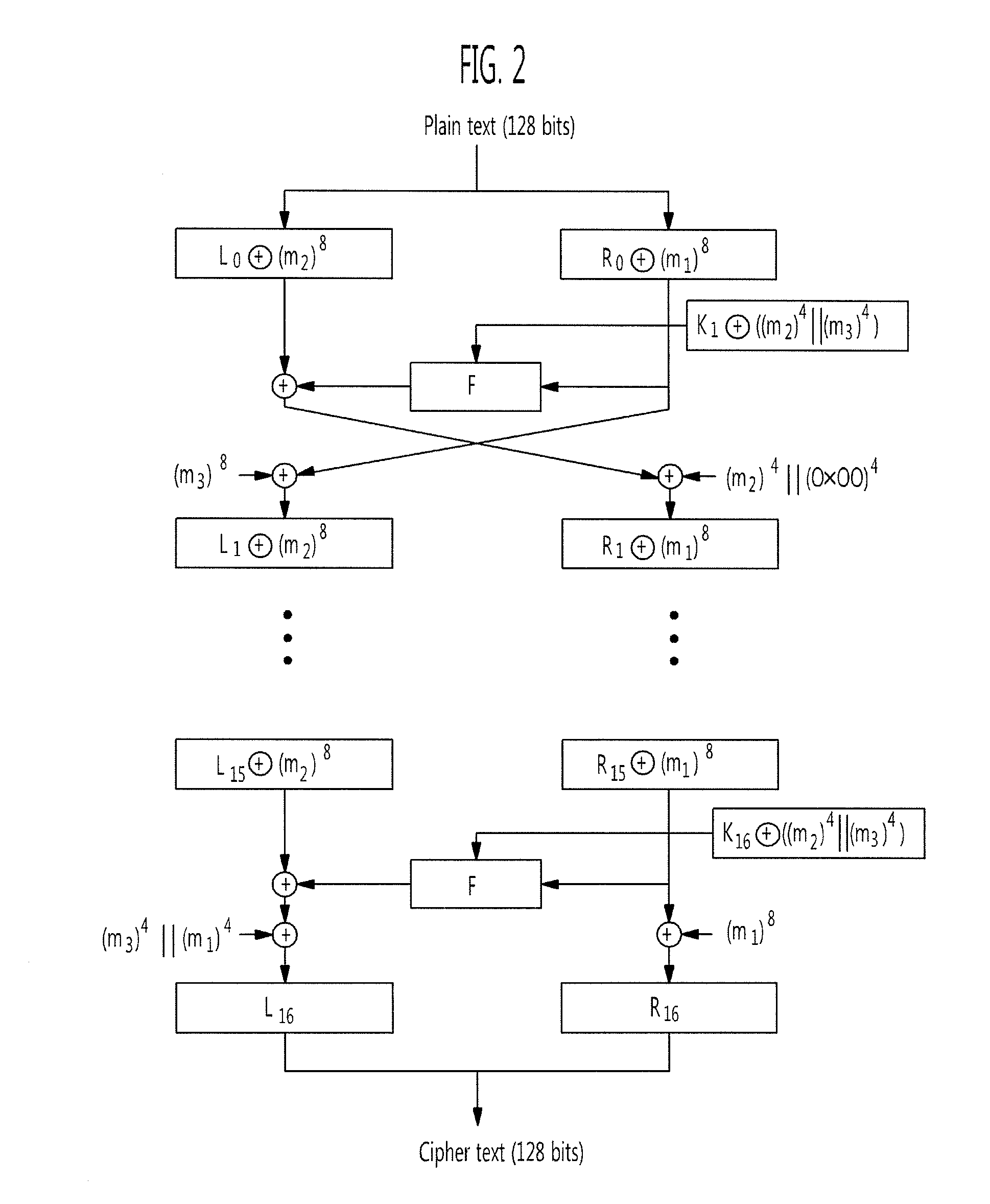
Application method of Hamming distance model on SM4 cryptographic algorithm lateral information channel energy analysis and based on S box input
ActiveCN103138917AExtended Side Channel Energy Analysis MethodEfficient analysisEncryption apparatus with shift registers/memoriesPower analysisS-box
The invention discloses an application method of a Hamming distance model on SM4 cryptographic algorithm lateral information channel energy analysis and based on S box input. The application method is characterized in that the Hamming distance model is established by selecting an S box or a round function as an attacking point in the process that the SM4 cryptographic algorithm lateral information channel energy analysis is carried out, the input of the S box is used as an initial state v1 of the Hamming distance model, the output of the S box is used as subsequent state v2 of the Hamming distance (HD (v1, v2)) model when the S box is attacked, and the output / input of the round function is used as the subsequent state v2 of the Hamming distance (HD (v1, v2)) model when the round function is attacked. The method can be applied to CPA / DPA lateral information channel energy analysis of the SM4 cryptographic algorithm. Correlation between a correct guess secret key and energy information is improved, and validity and success rate of the analysis are enhanced.
Owner:国家密码管理局商用密码检测中心
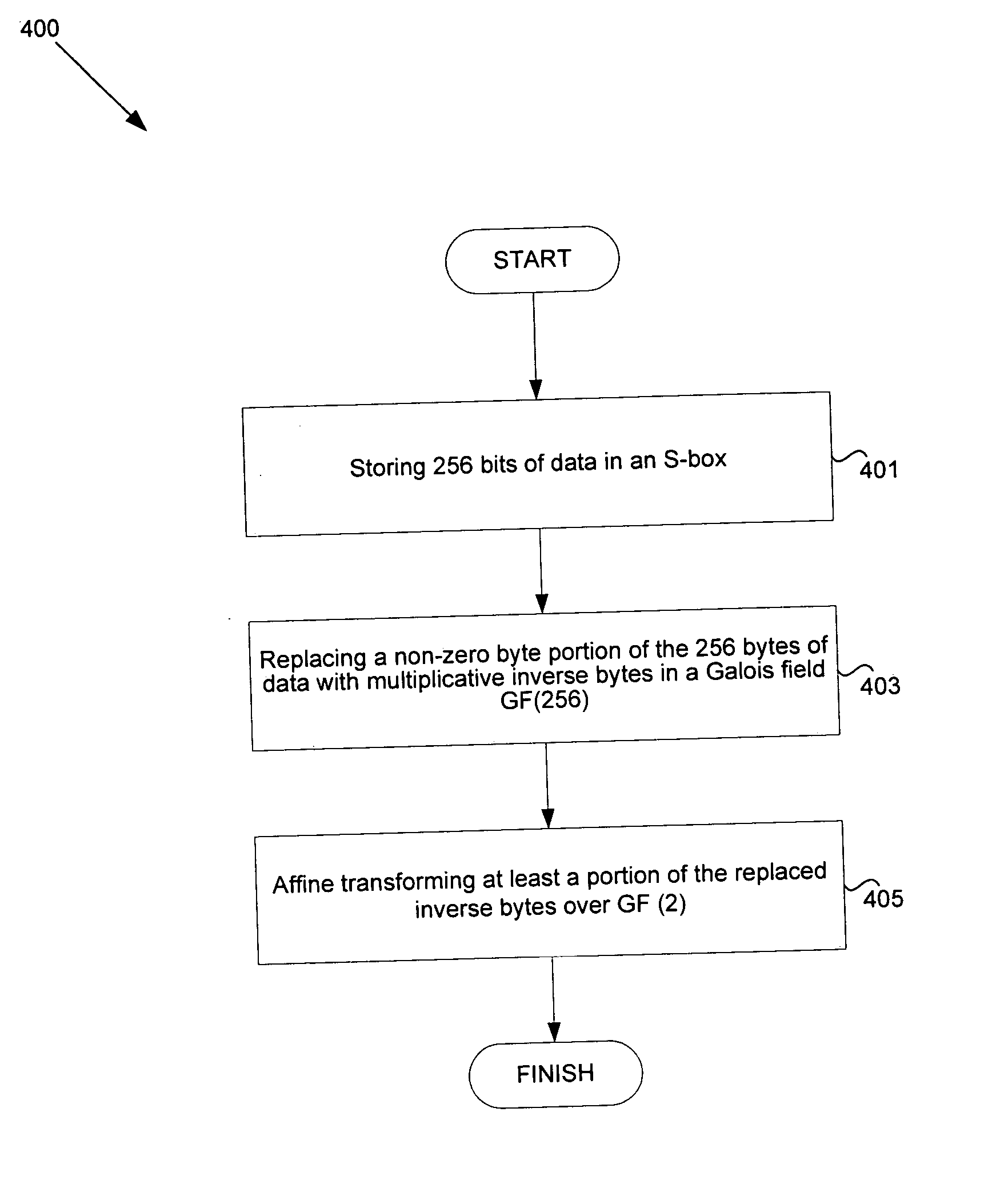
Method and system for implementing substitution boxes (S-boxes) for advanced encryption standard (AES)
Systems and methods for implementing Advanced Encryption Standard (AES) are disclosed herein. Aspects of the method may comprise storing 256 bytes of data. A non-zero byte portion of the 256 bytes of data may be replaced with multiplicative inverse bytes in a Galois field GF(256) and the replaced inverse bytes may be affine transformed over GF (2). The affine transformed bytes may be affine inverse transformed, and the affine inverse transformed bytes may be multiplicatively inversed over GF(256). The affine transformation over GF(2) may be determined as a matrix multiplication and addition of (1 1 0 0 0 1 1 0). If the 256 bytes comprise a zero byte, the zero byte from the 256 bytes of data may be mapped to the zero byte portion of the 256 bytes of data.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
Encryption protection method
InactiveUS7848515B2Encryption apparatus with shift registers/memoriesSecret communicationS-boxStatistical analysis
A deterministic blinding method for cipher algorithms that employ key-mixing and substitution (S-box) operations uses a masking table constructed with a true mask and a plurality of dummy masks corresponding to every possible S-box input. Each mask is applied in the key-mixing operation (e.g., bitwise XOR) to the cipher key or to round subkeys to generate true and dummy keys or subkeys that are applied to the data blocks within the overall cipher algorithm or within individual cipher rounds. The mask values prevent side-channel statistical analyses from determining the true from the dummy keys or subkeys. The true mask is identifiable to the cipher but not by external observers.
Owner:CRYPTOGRAPHY RESEARCH INC
Application of selecting round key XOR input to perform side-channel power analysis of SM4 cryptographic algorithm
ActiveCN103227717AExtended Side Channel Energy Analysis MethodEfficient analysisEncryption apparatus with shift registers/memoriesComputer hardwareChannel power
The invention discloses an application of selecting round key XOR input to perform side-channel power analysis of an SM4 cryptographic algorithm. The application is characterized in that in the process of the side-channel power analysis of the SM4 cryptographic algorithm, S boxes or round functions are selected to serve as attack points to establish a Hamming distance (HD) model, the round key XOR input is taken as a preceding state v1 of the HD model, and when the S boxes are attacked, the subsequent state v2 of the HD (v1, v2) model is S box output; and when the round functions are attacked, the subsequent state v2 of the HD (v1, v2) model is output / input of the round functions. The method can be applied to the side-channel power analysis of a CPA (correlation power analysis) and DPA (differential power analysis) of the SM4 cryptographic algorithm. With the adoption of the method, the correlation between a right guessing secret key and a power message is improved, the effectiveness of the analysis is enhanced, and the success rate is increased.
Owner:国家密码管理局商用密码检测中心
Encryption method for network and information security
ActiveCN101764686AHigh speedDiffusion is fastKey distribution for secure communicationEncryption apparatus with shift registers/memoriesComputer hardwareKey size
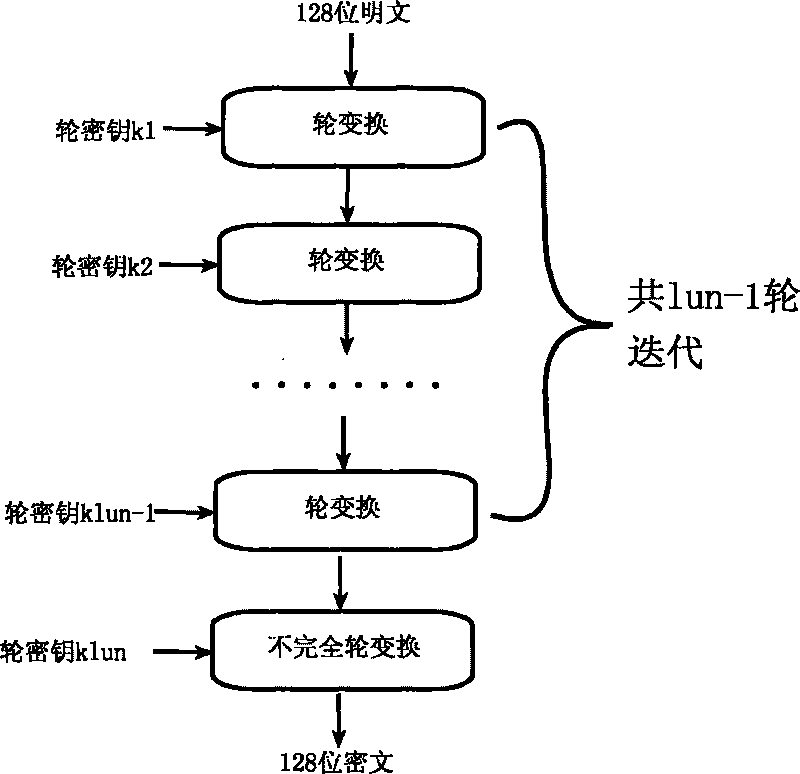
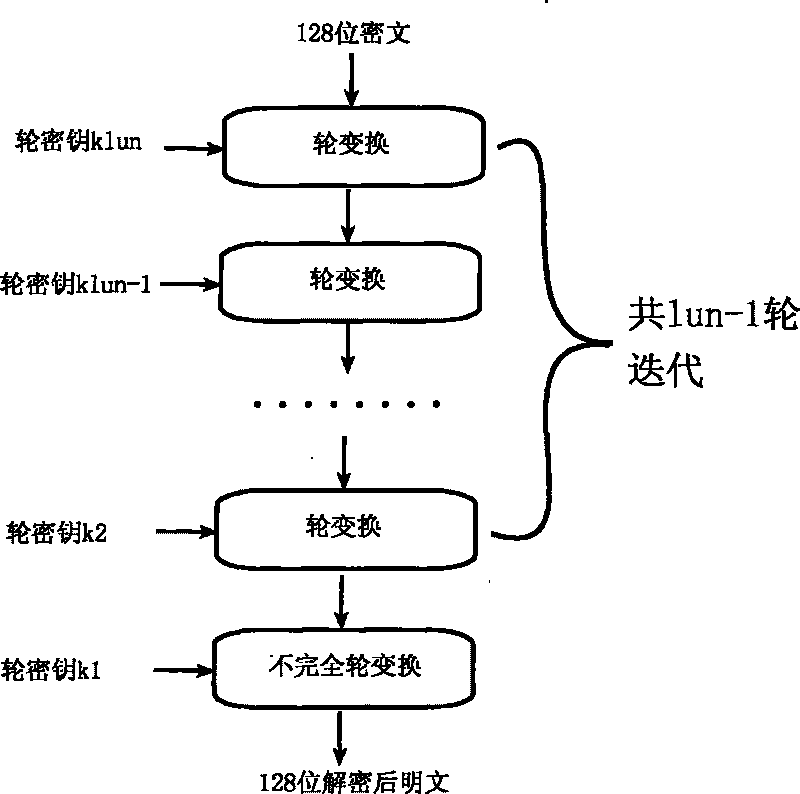
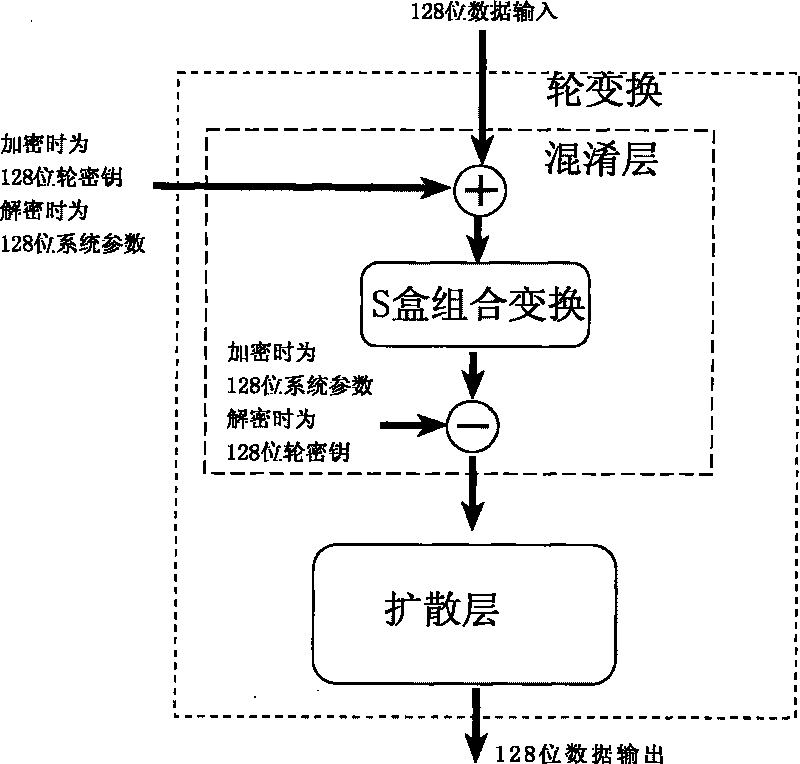
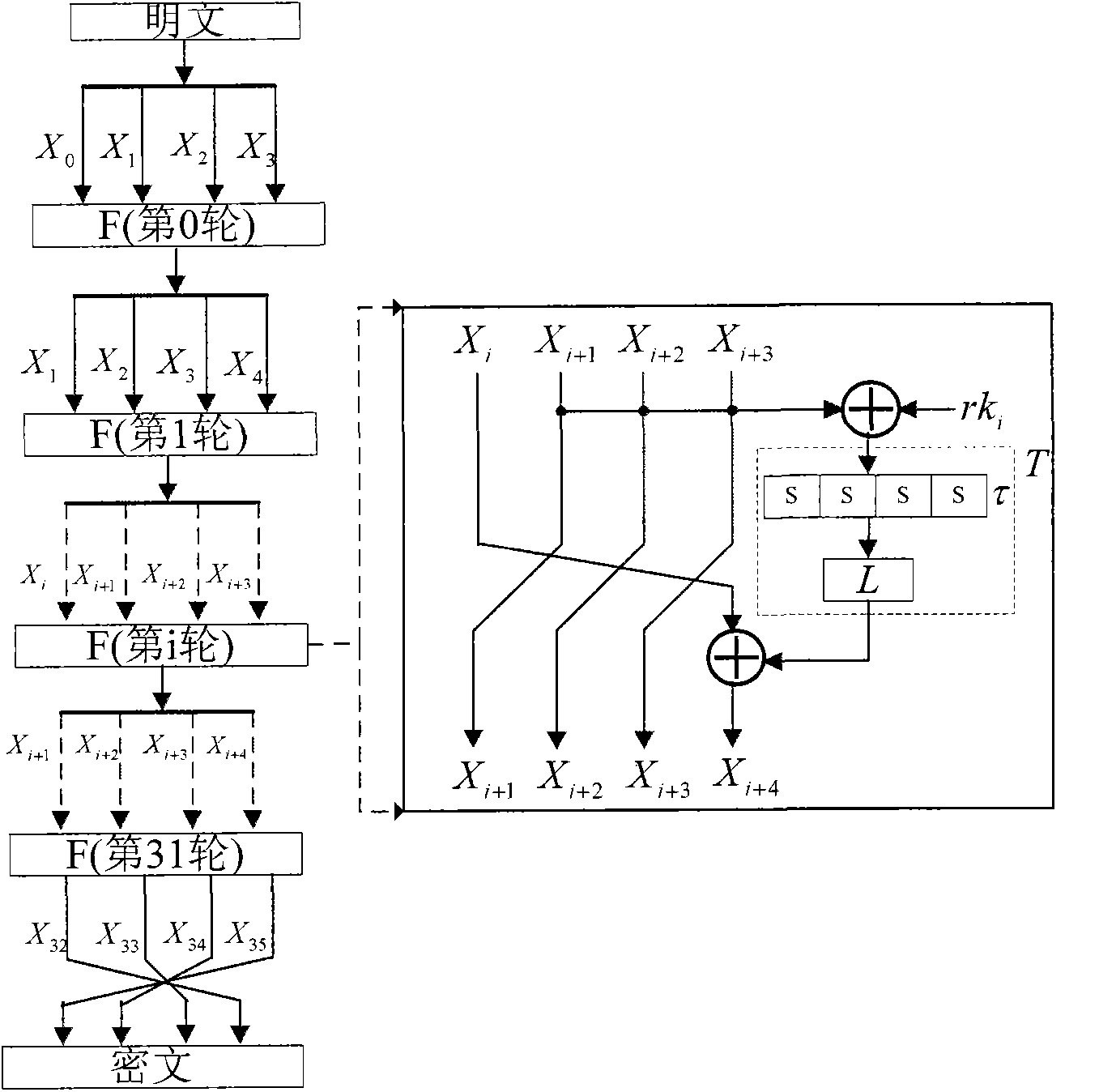
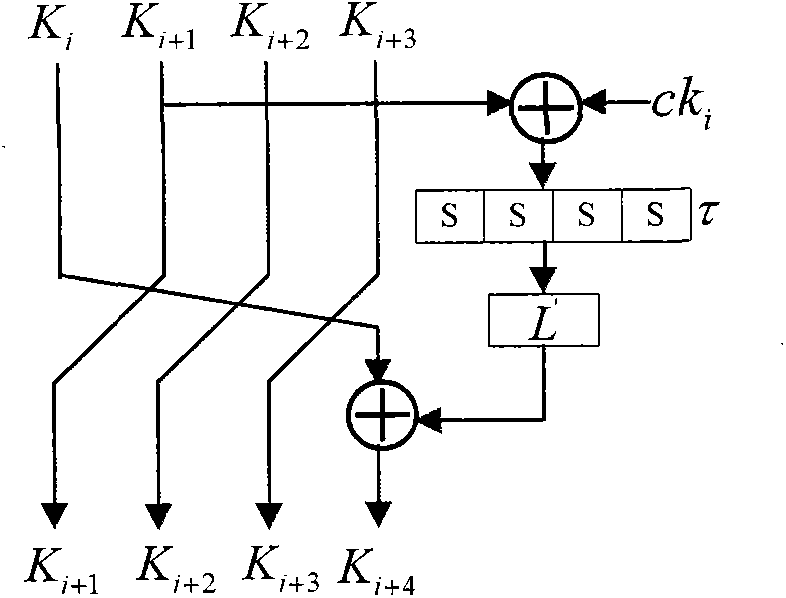
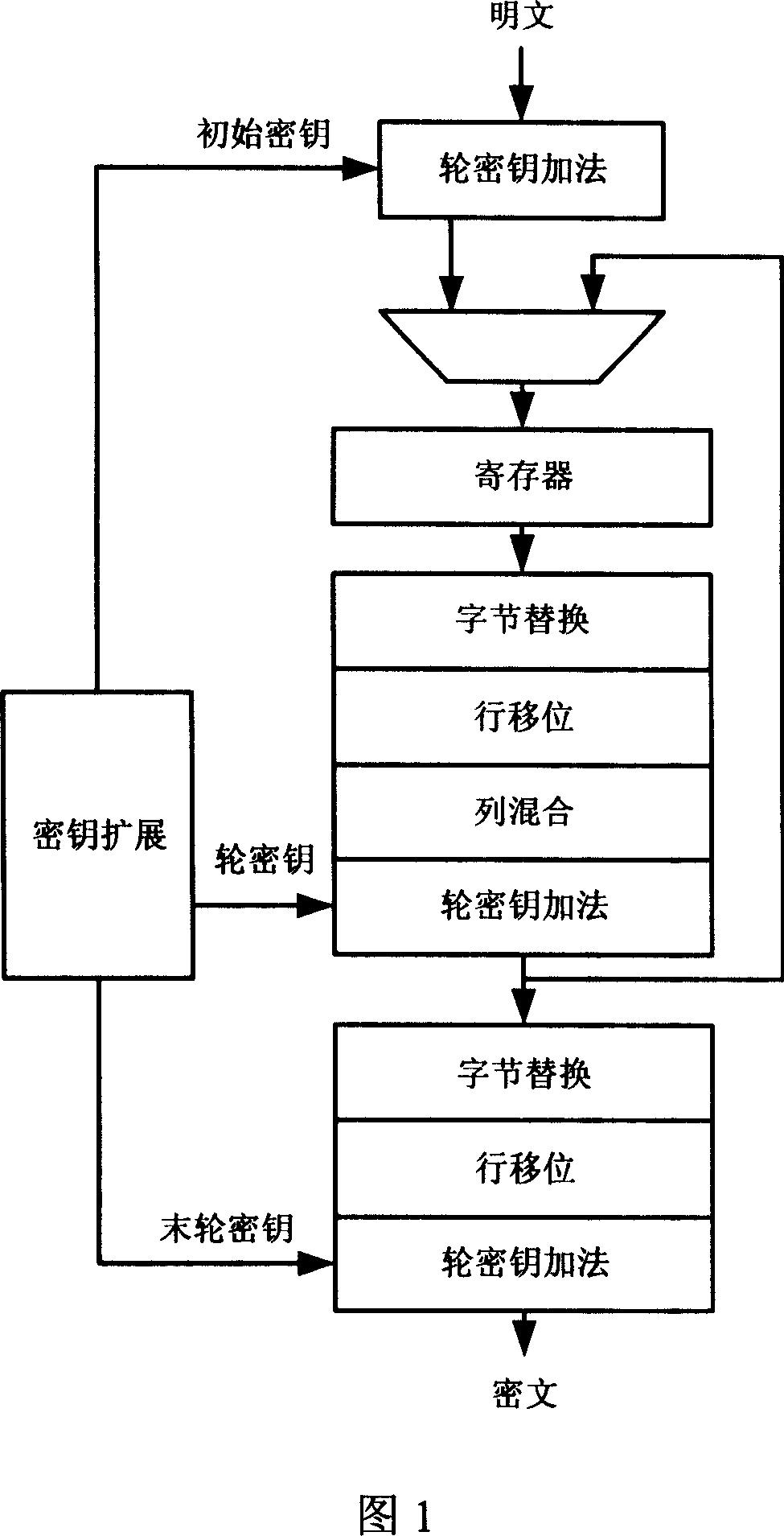
The invention relates to an encryption method for network and information security; the adopted packet length and key length are 128 bits, and a 128-bit system parameter is added; encryption algorithm comprises a plurality of rounds of round transform iteration consisting of mixed layers and diffusion layers, wherein the last round is incomplete round transformation, and the incomplete round transformation consists of the mixed layer; the mixed layer comprises key plus, S box portfolio transform and system parameter minus; the S box portfolio transform comprises 8-input 8-output reversible S box transform and inverse S box transform in the same number which are output by parity exchange; the diffusion layer can construct linear transformation with a reversible re-model polynomial matrix; an encryption round key is generated by an encryption key through encryption round transformation; and decryption algorithm is the inverse transformation of encryption algorithm. The encryption methodfor network and information security has the advantages of high diffusion speed, good security strength, hardware resource saving, and very high speed when being realized by hardware and on a software platform.
Owner:INST OF APPLIED MATHEMATICS HEBEI ACADEMY OF SCI
Block cipher encryption and decryption method
InactiveCN102025484AIncreased confusionImprove throughputEncryption apparatus with shift registers/memoriesS-boxAdvanced Encryption Standard
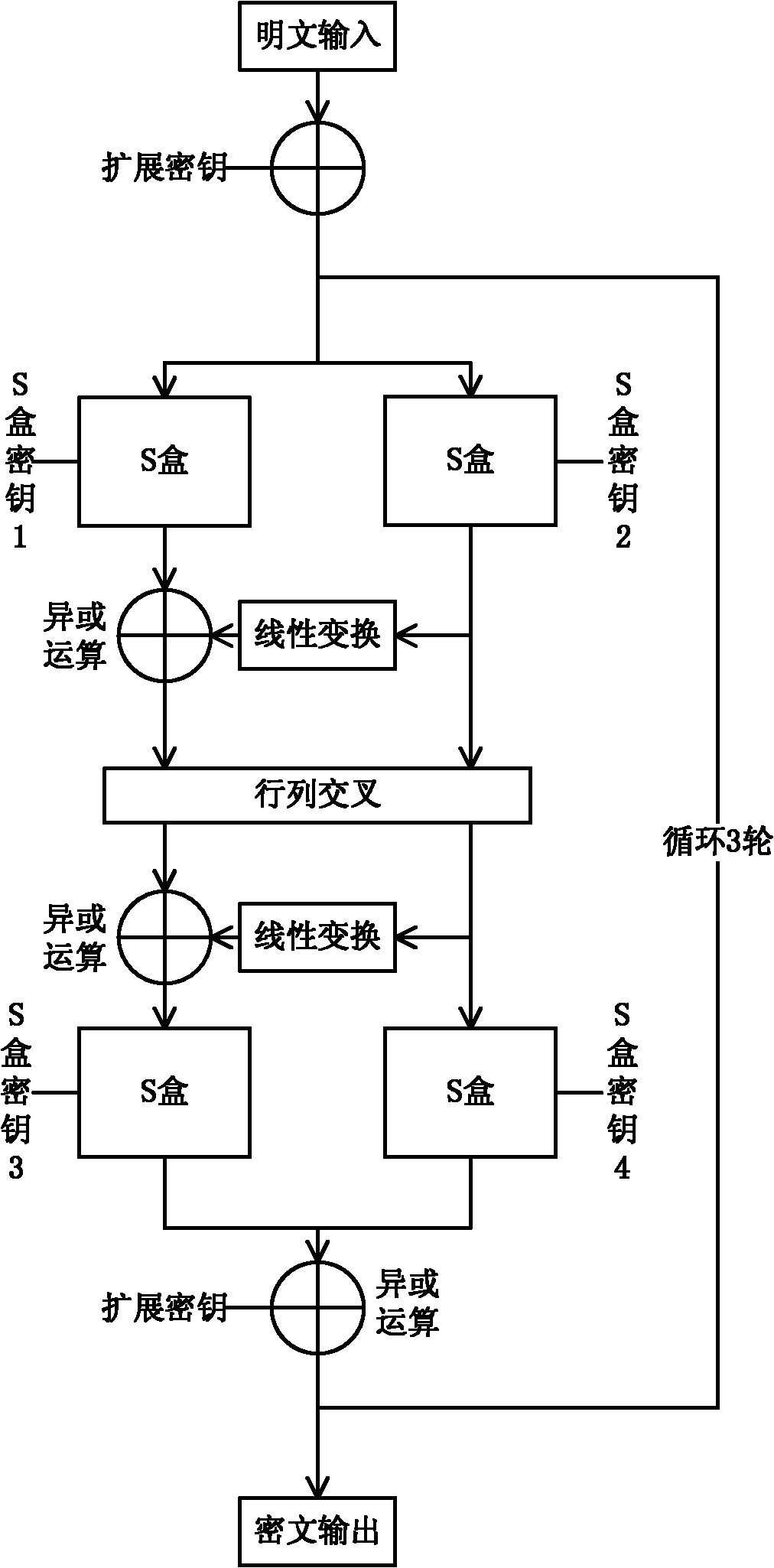
The invention provides a block cipher encryption and decryption method belonging to the field of data encryption and decryption. The algorithm of the invention designs a symmetric encryption structure, especially the S-box design in the invention can configure S transformation required for encryption and S inverse transformation required for decryption without additional circuit resources, thereby being beneficial to the implementation of an encryption / decryption integrated hardware circuit and consuming fewer area resources compared with the AES (advanced encryption standard) encryption / decryption integrated circuit. The complicated S box structure of the algorithm can resist the traditional known attack methods. In case of a small number of encryption rounds (three rounds), a high encryption speed can be provided, and decryption can be carried out at the same speed by using the same encryption and decryption hardware. The algorithm is especially suitable for realizing an ASIC (application specific integrated circuit), and can realize an ASIC chip based on the encryption and decryption special-purpose algorithm. Besides, the invention can be also used for the design of IP cores on FPGA (field programmable gate array). Compared with the AES algorithm, the invention consumes fewer resources on FPGA and has higher speed.
Owner:BEIHANG UNIV
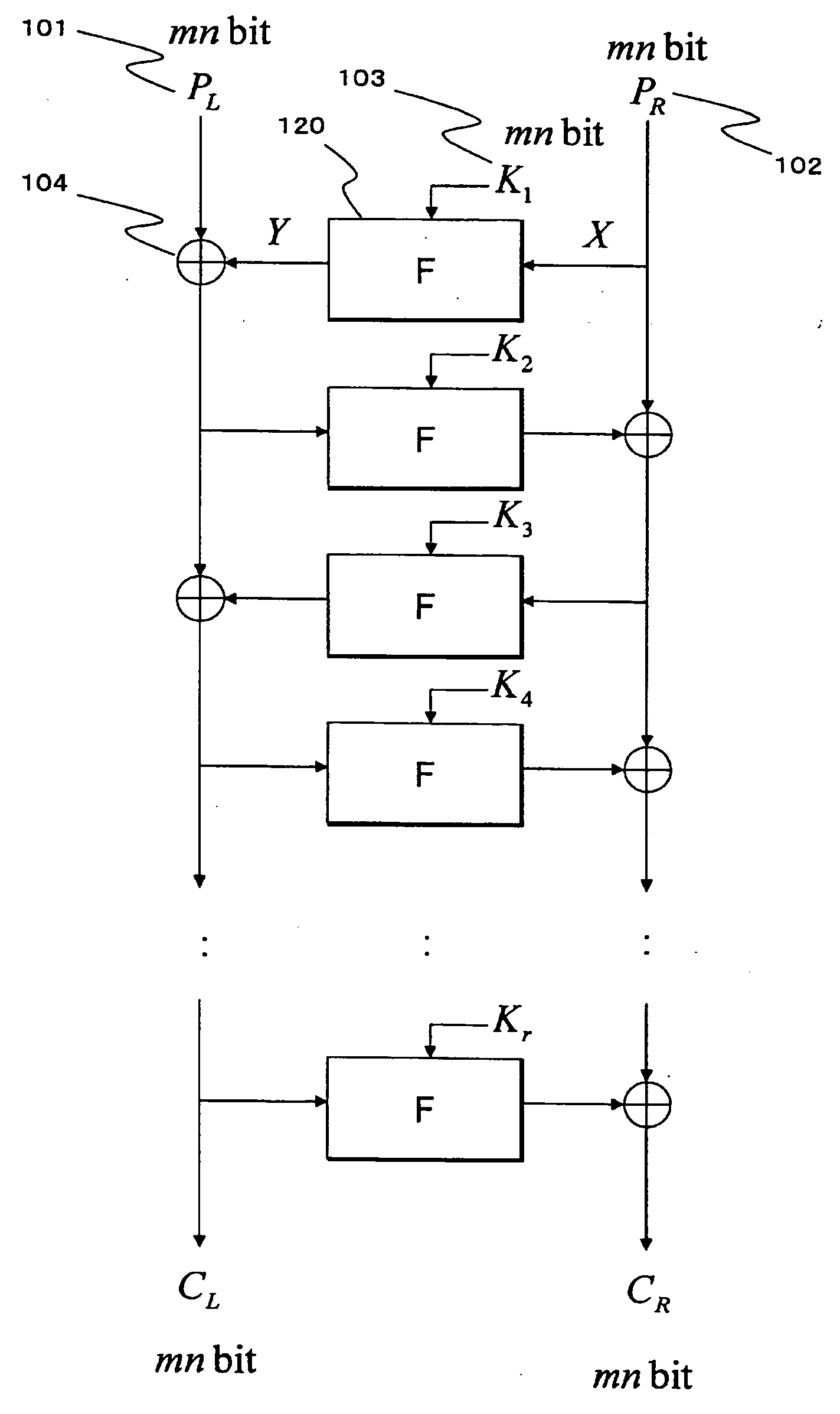
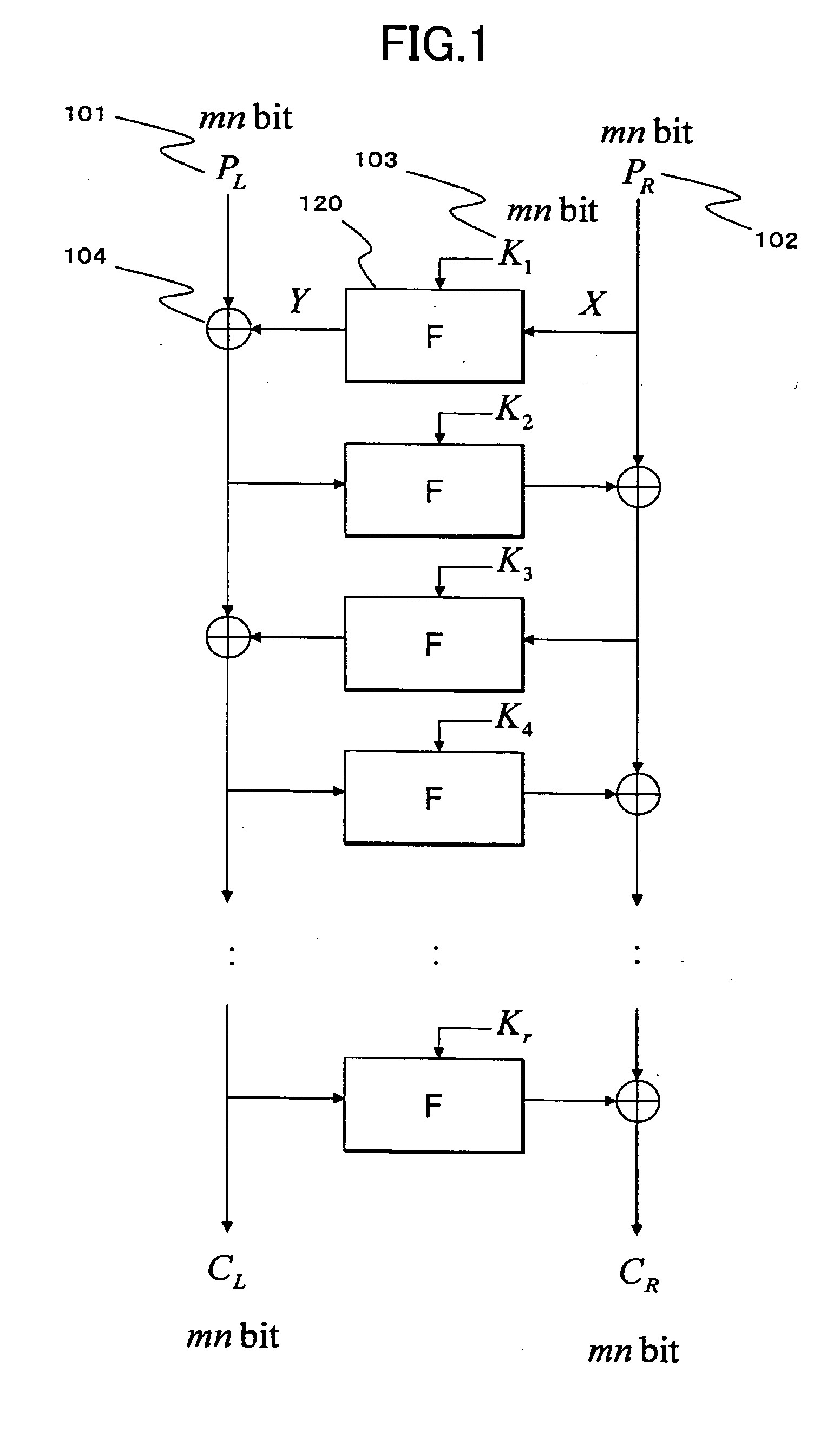
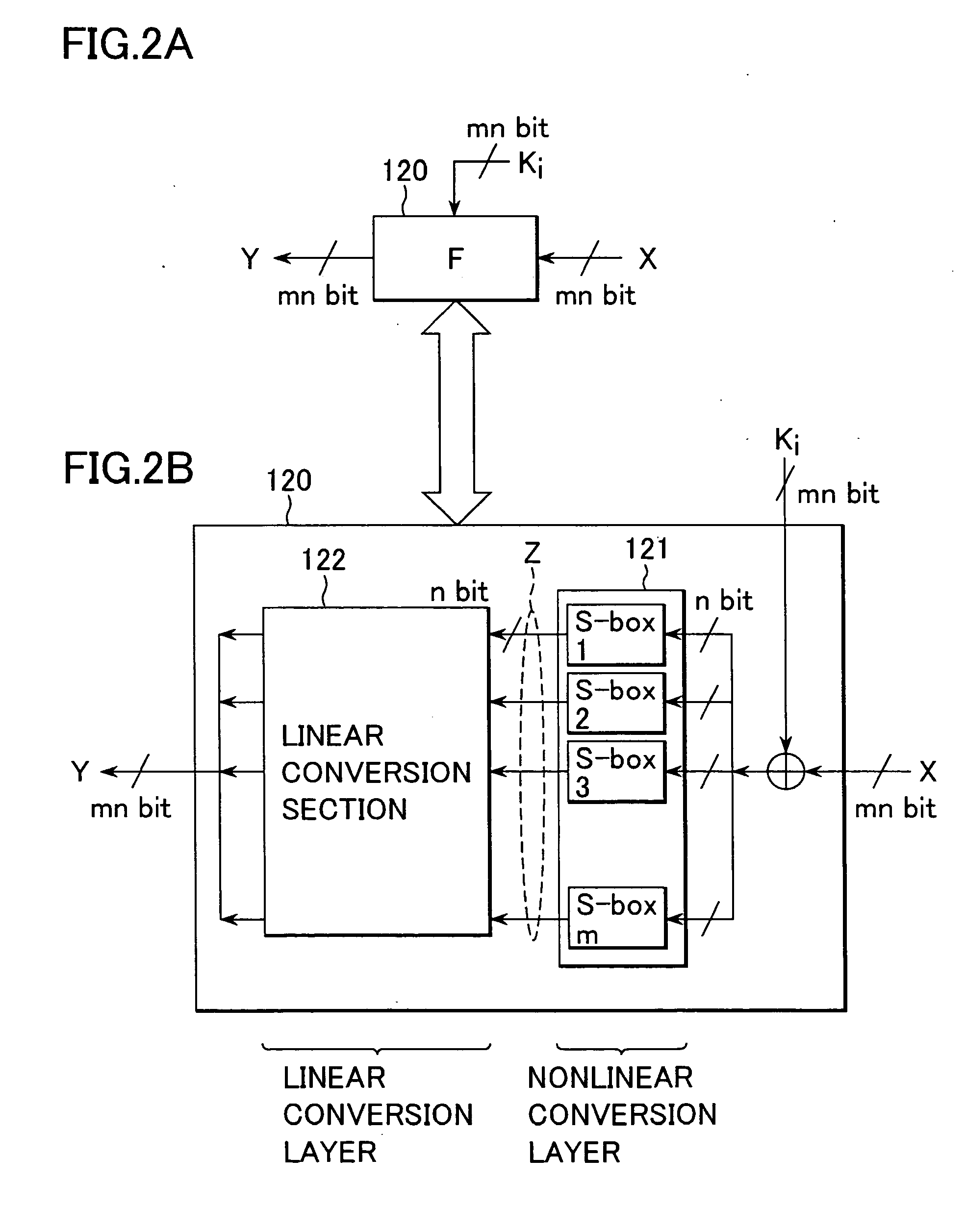
Cryptographic processing apparatus and cryptographic processing method, and computer program
ActiveUS20050111659A1Highly secure encryption processingHigh analysisEncryption apparatus with shift registers/memoriesSecret communicationComputer hardwareS-box
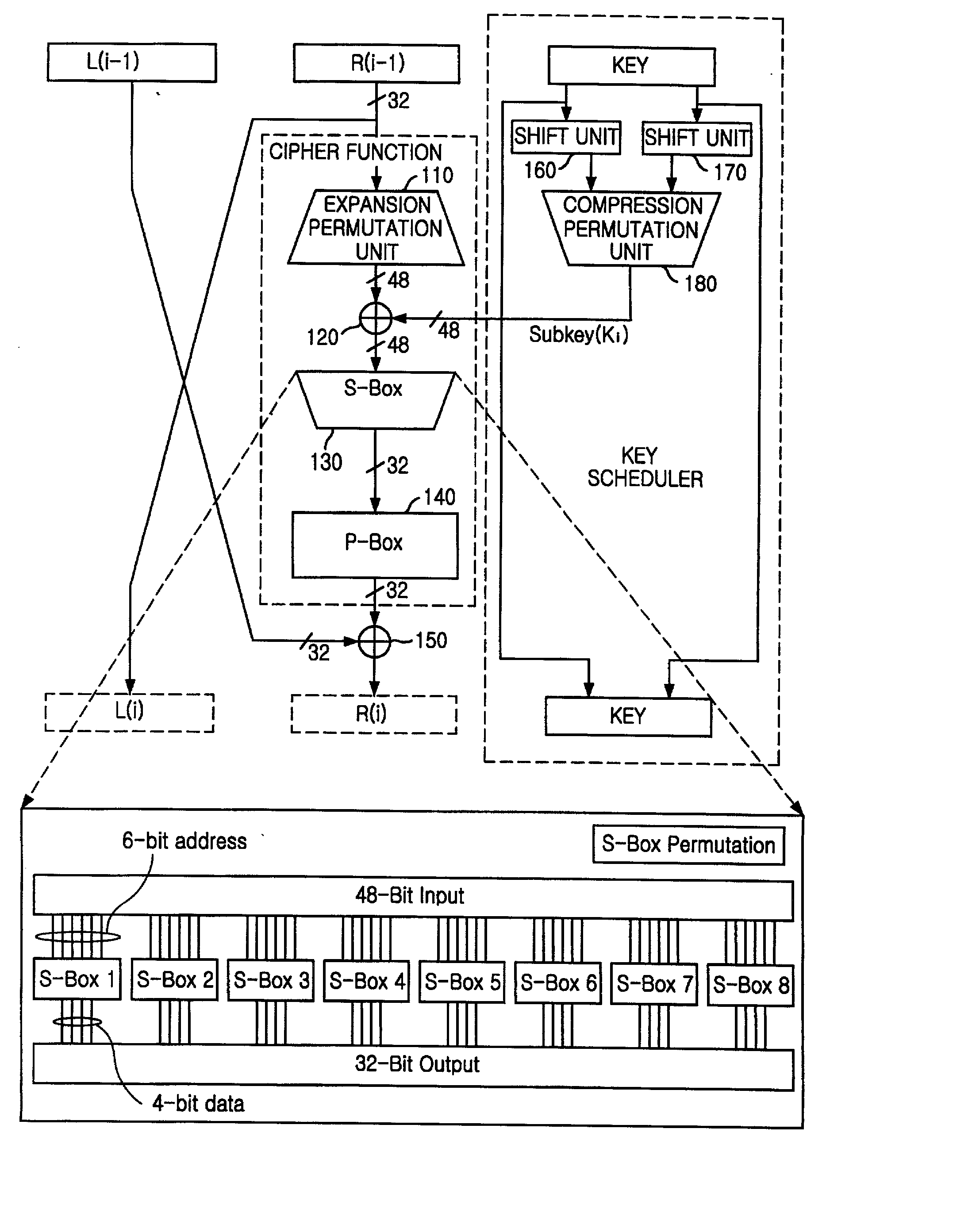
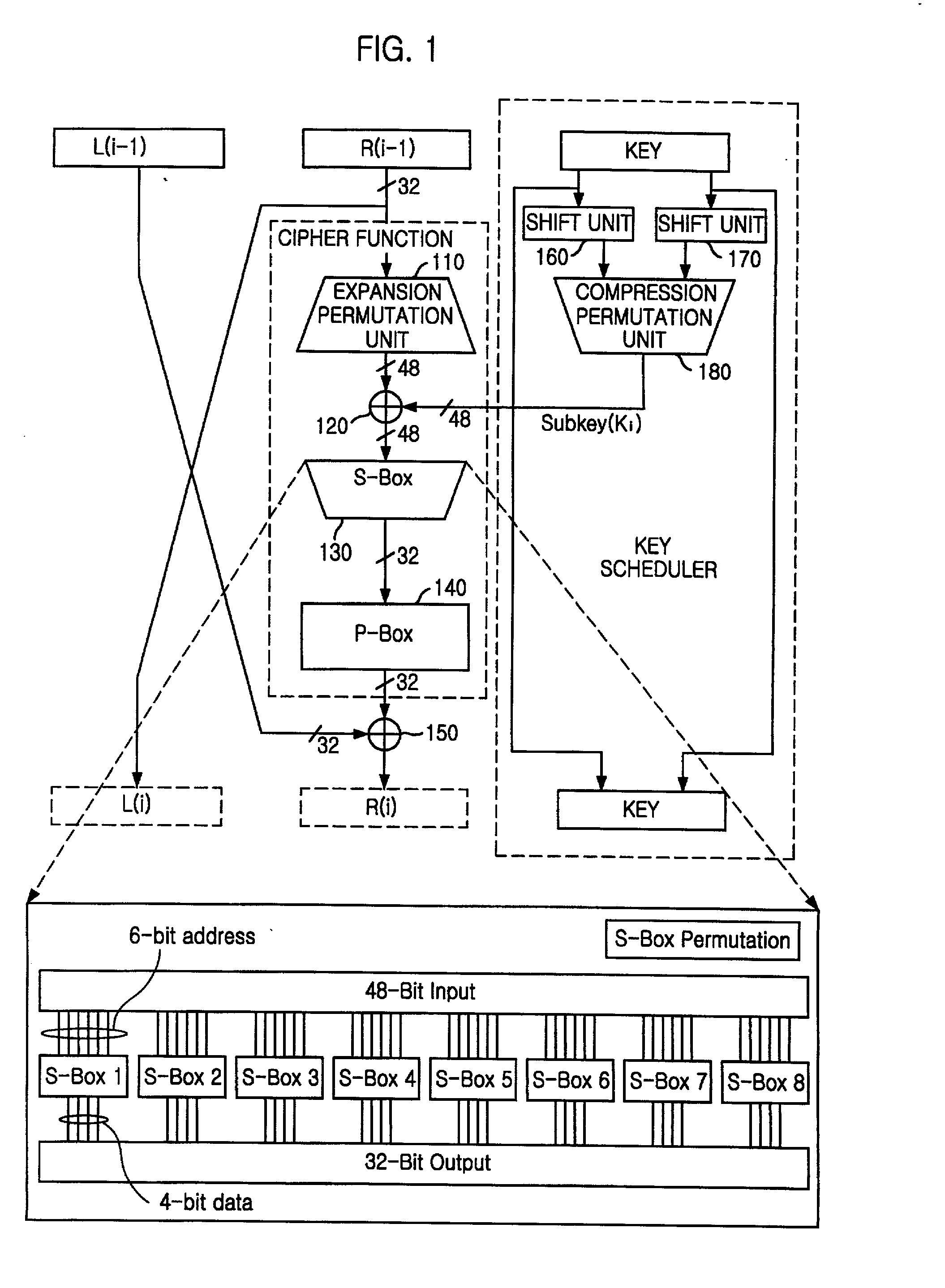
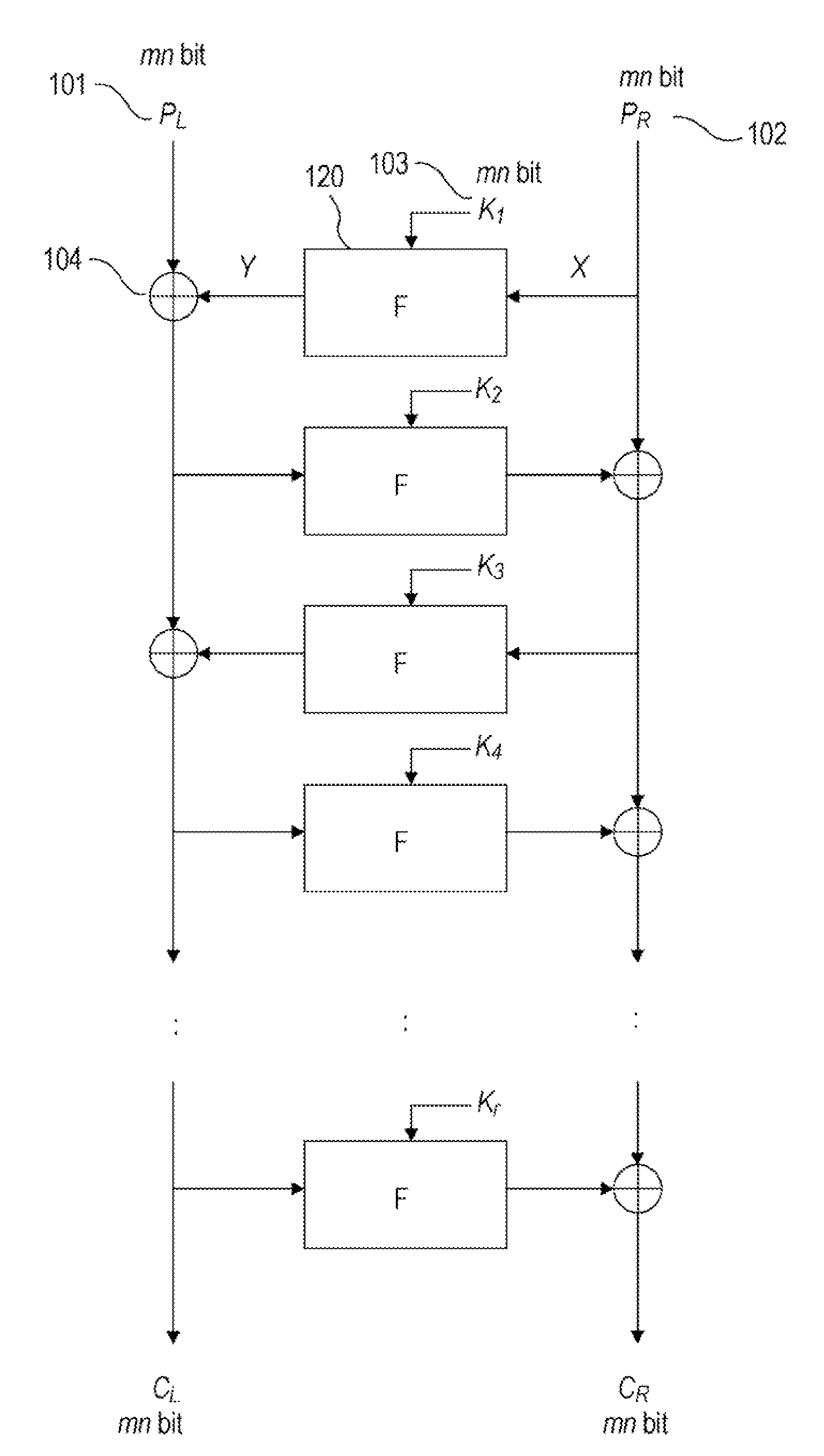
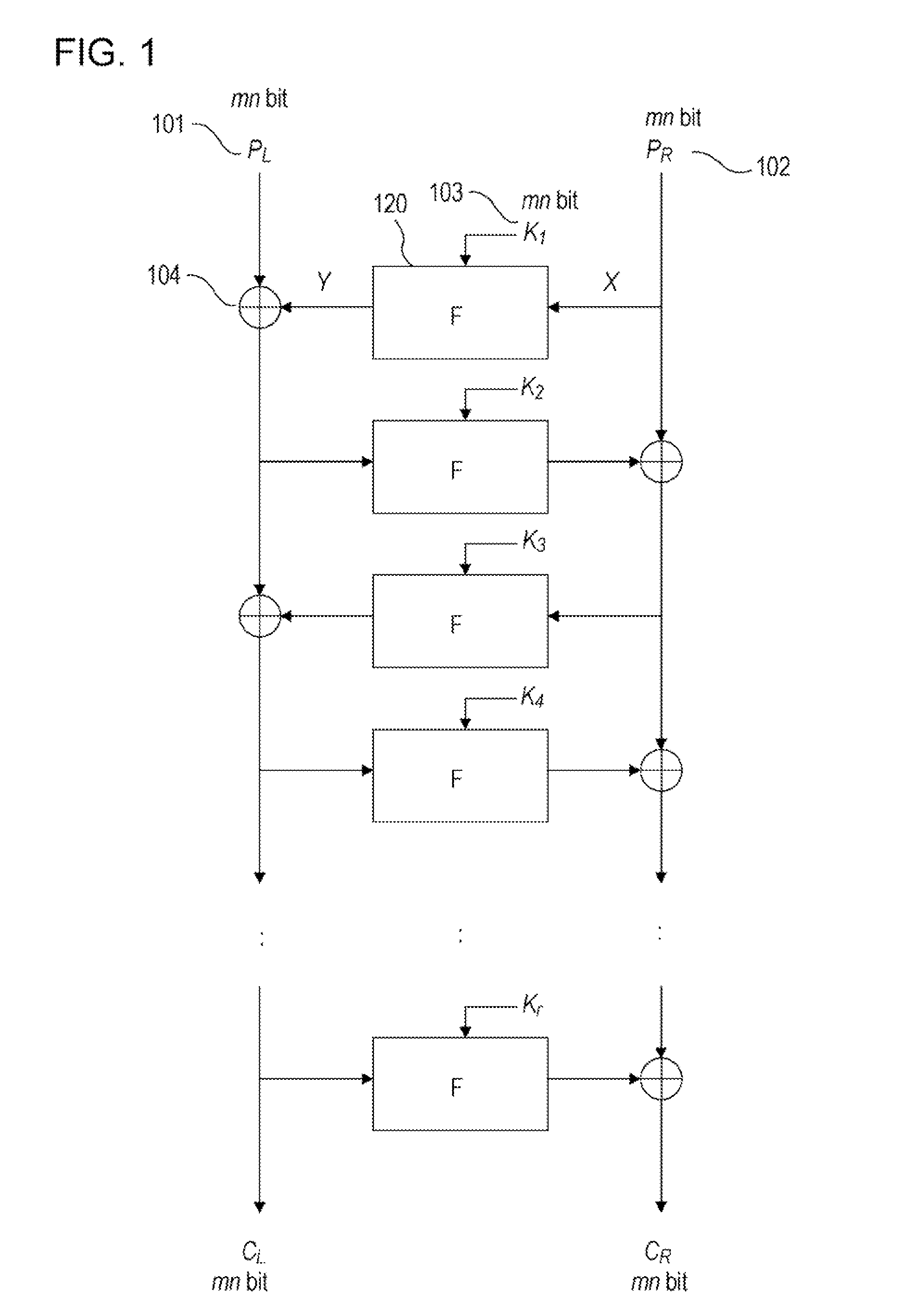
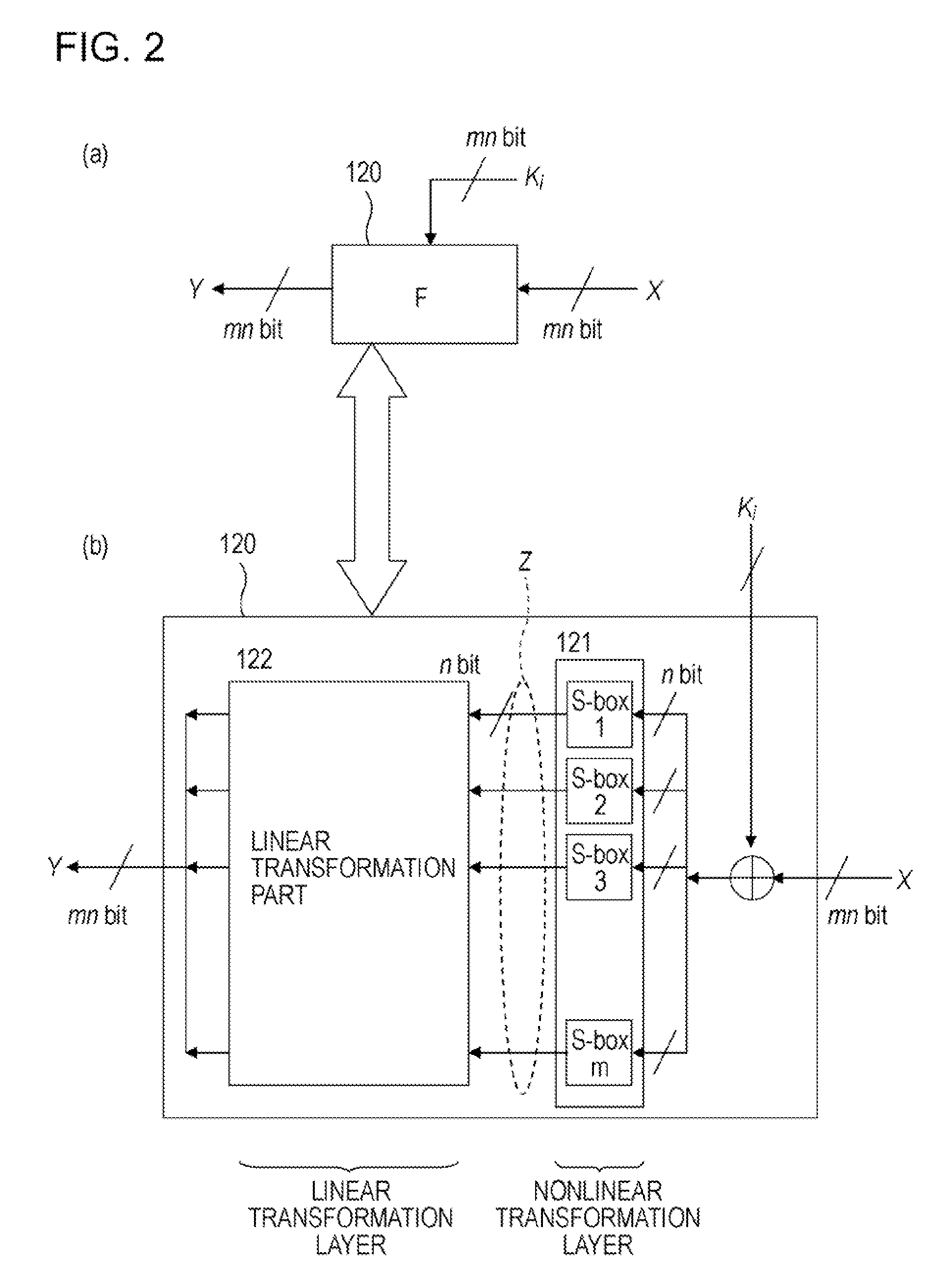
There is provided a highly secure cryptographic processing apparatus and method where an analysis difficulty is increased. In a Feistel type common key block encrypting process in which an SPN type F function having a nonlinear conversion section and a linear conversion section is repeatedly executed a plurality of rounds. The linear conversion process of an F function corresponding to each of the plurality of rounds is performed as a linear conversion process which employs an MDS (Maximum Distance Separable) matrix, and a linear conversion process is carried out which employs a different MDS matrix at least at each of consecutive odd number rounds and consecutive even number rounds. This structure makes it possible to increase the minimum number (a robustness index against a differential attack in common key block encryption) of the active S box in the entire encrypting function.
Owner:SONY CORP
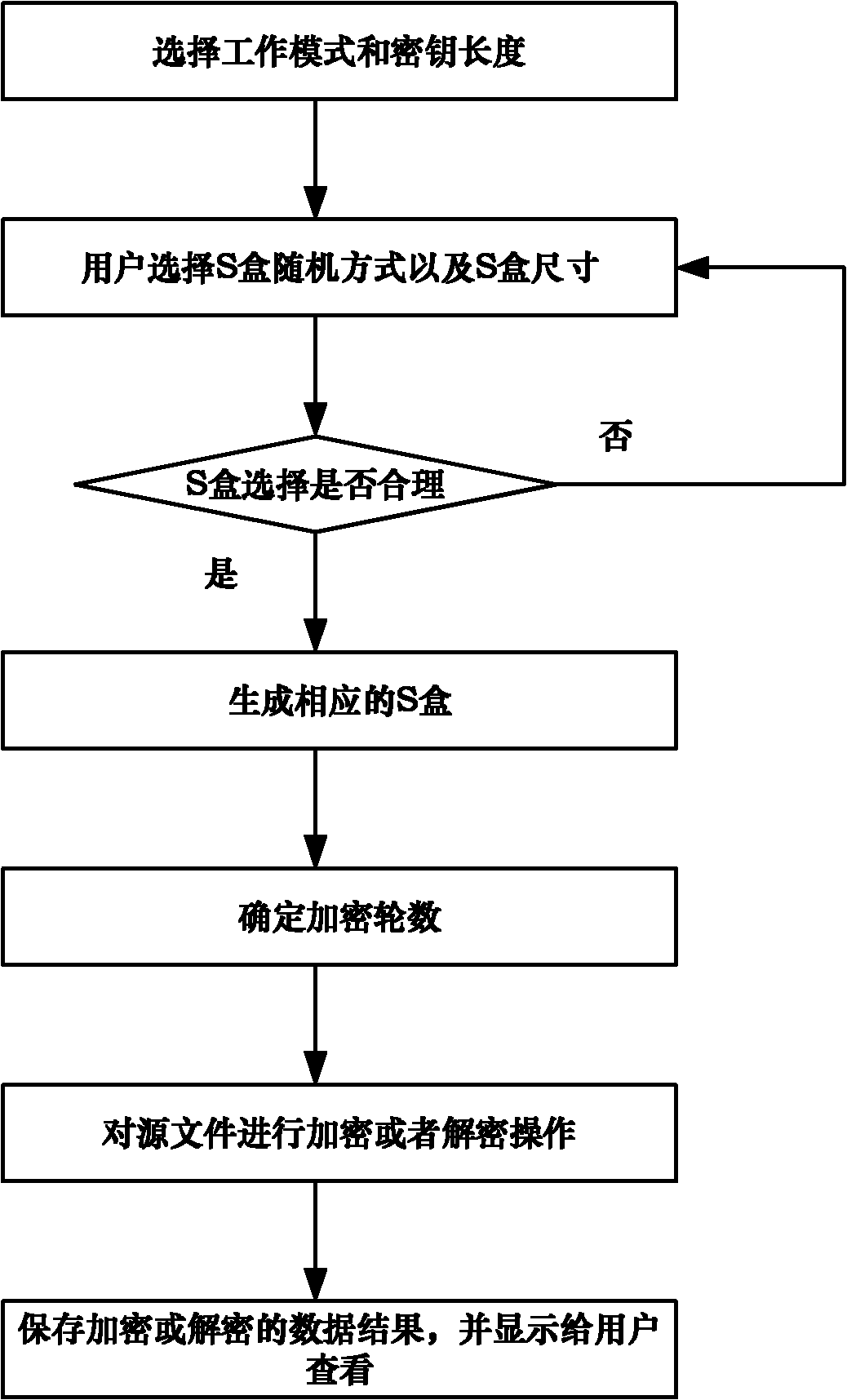
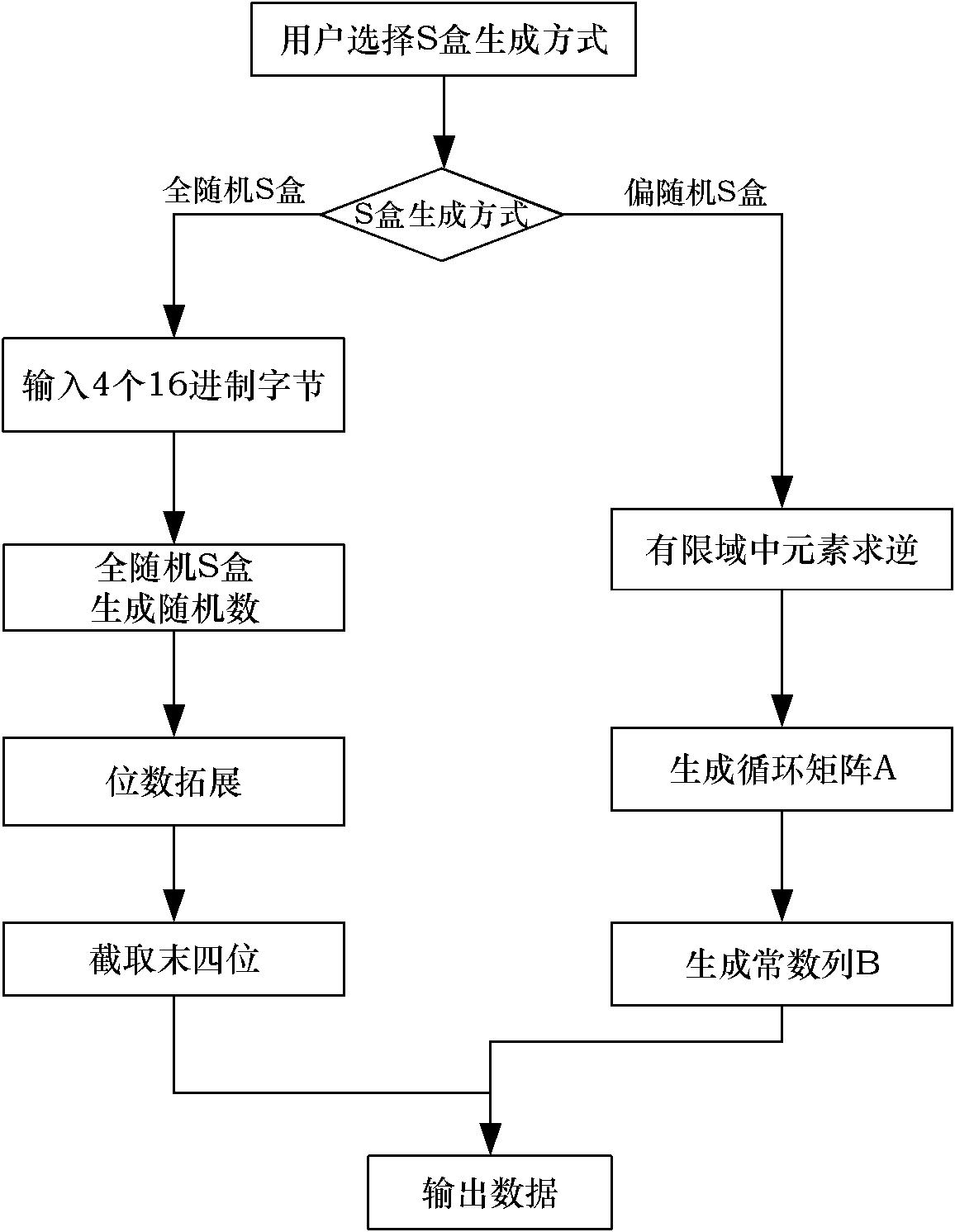
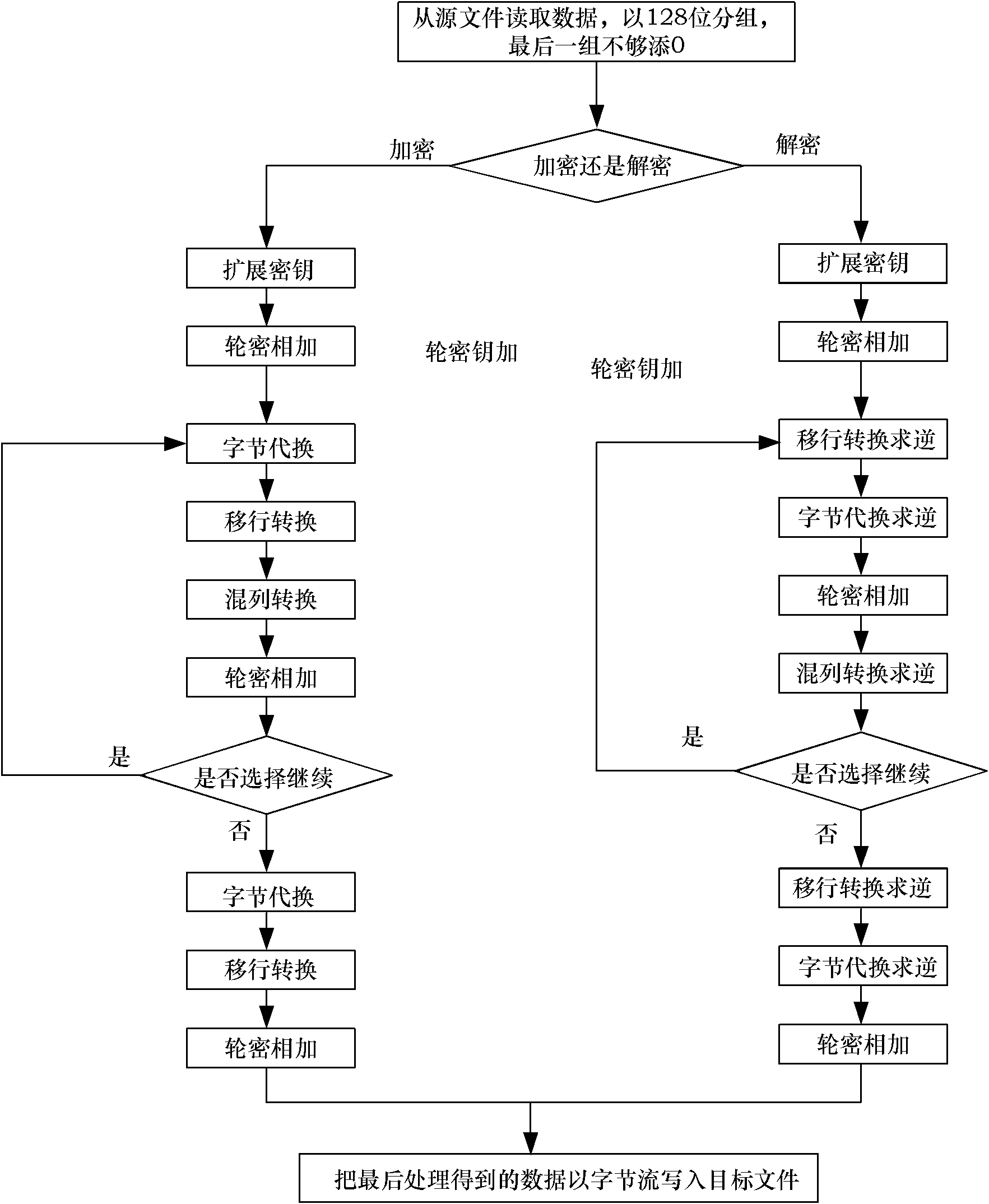
Multimode reconfigurable encryption method based on advanced encryption standard (AES) encryption algorithm
InactiveCN102185692AAvoid Side Channel AttacksEasy to operateEncryption apparatus with shift registers/memoriesComputer hardwareS-box
The invention discloses a multimode reconfigurable encryption method based on an advanced encryption standard (AES) encryption algorithm. In the method, five operating modes are provided for a user to select, and an all-random S box generation way and a biased random S box generation way are provided. The method comprises the following steps of: judging whether the operating mode and an S box selected by the user are rational or not; if the selected operating mode and the selected S box are irrational, prompting the user to perform reselection; if the selected operating mode and the selected S box are rational, further calculating the smallest encryption round number according to the differential uniformity and nonlinearity of the generated S box, and determining a final encryption round number according to the requirements of the user; selecting a source file for an encryption or decryption operation; and finally storing the encrypted or decrypted data file, and providing the encrypted or decrypted data file for the user to view. By the method, side channel attacks possibly on encryption realized by adopting hardware are effectively avoided, and an operating way of the reconfigurable encryption method is optimized; the method is applied to the configuration of a set of reconfigurable software encryption system, and the reconfiguration and integration of block ciphers into the same software system; and convenience is brought to operations and management.
Owner:BEIHANG UNIV
Method and device for improving digital encryption standard resisting differential power analysis
InactiveCN102983964ADestroy correlationTo achieve the purpose of resisting power analysisEncryption apparatus with shift registers/memoriesPlaintextPower analysis
The invention discloses a method and a device for improving a digital encryption standard resisting differential power analysis. In an S-box function processing step of standard 16-time operation for digital encrypting a 64-bit plaintext, a new S-box function represented by SM-Box is set in the following way. According to the invention, through the adoption of the S-box function transformed by different random numbers, relevance between real key information and a power curve is destroyed and great difficulty is caused in information obtaining of power analysis so as to achieve a purpose of resisting the power analysis. According to the invention, by using a covering technology, the plaintext is pre-covered before encryption operation and the random numbers are covered in each operation, so that attack caused by information leakage is effectively prevented, and the capacity of resisting differential power analysis attack is enhanced.
Owner:DATANG MICROELECTRONICS TECH CO LTD
Encryption device, decryption device, encryption method, and integrated circuit
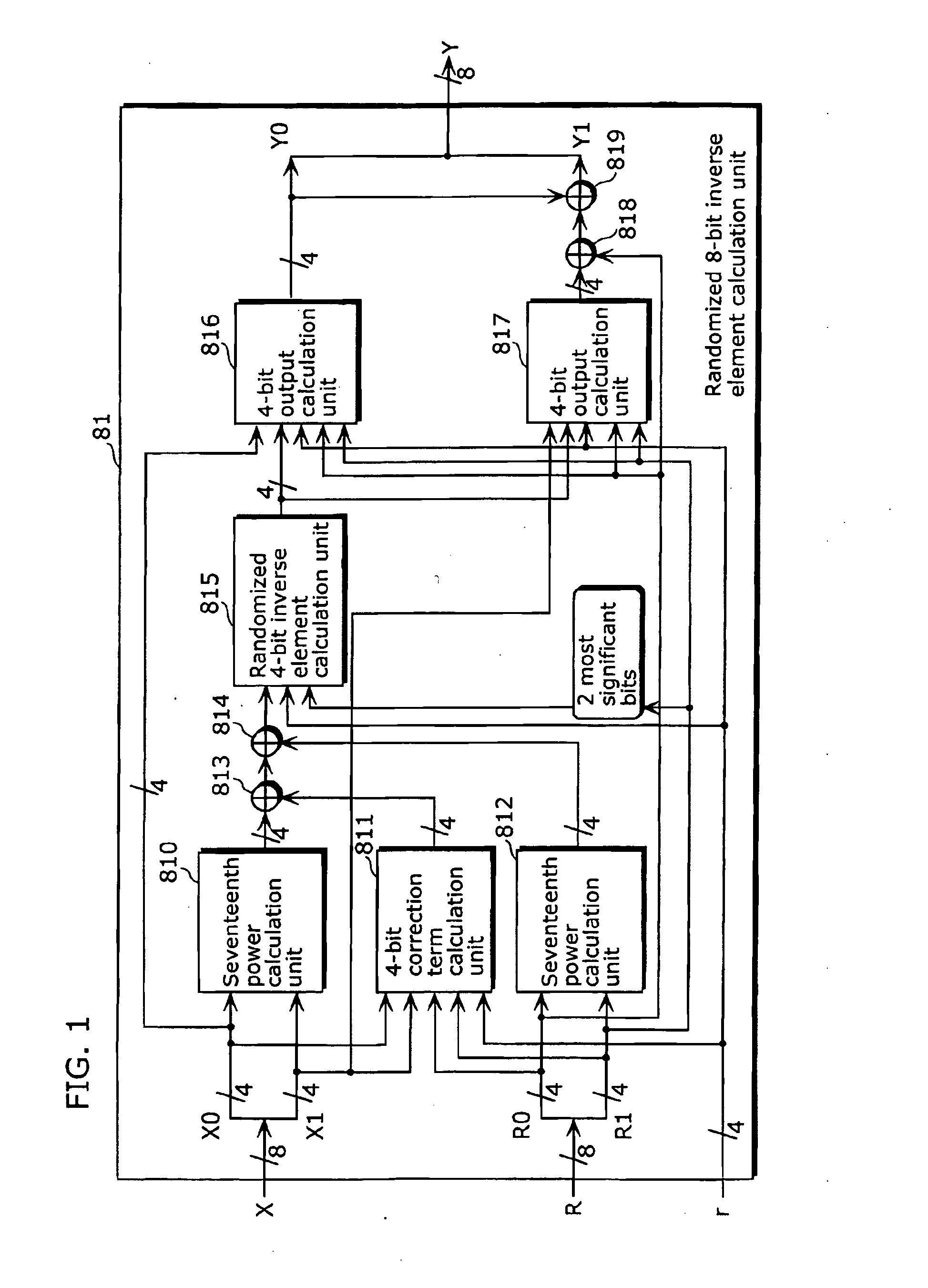
ActiveUS20100086126A1Simple structureReduce the numberRandom number generatorsSecret communicationPower analysisS-box
There has been a problem that the maximum number of logical steps increases and processing speed decreases when a masking method in which S-Box is implemented using an inverse element calculation in a composite field as a countermeasure for power analysis attack on an AES cipher.An encryption device (1) which generates encrypted text from plain text using a key, the encryption device (1) includes a randomized 8-bit inverse element calculation unit (101) which receives randomized input data that is obtained by adding, to input data on which predetermined processing is performed with the key, a predetermined input mask value determined depending on a random number, and which generates randomized output data that is obtained by adding, to an inverse element of the input data, an output mask value that is an inverse element of the input mask value, wherein the encryption device generates the encrypted text from the generated randomized output data.
Owner:PANASONIC CORP
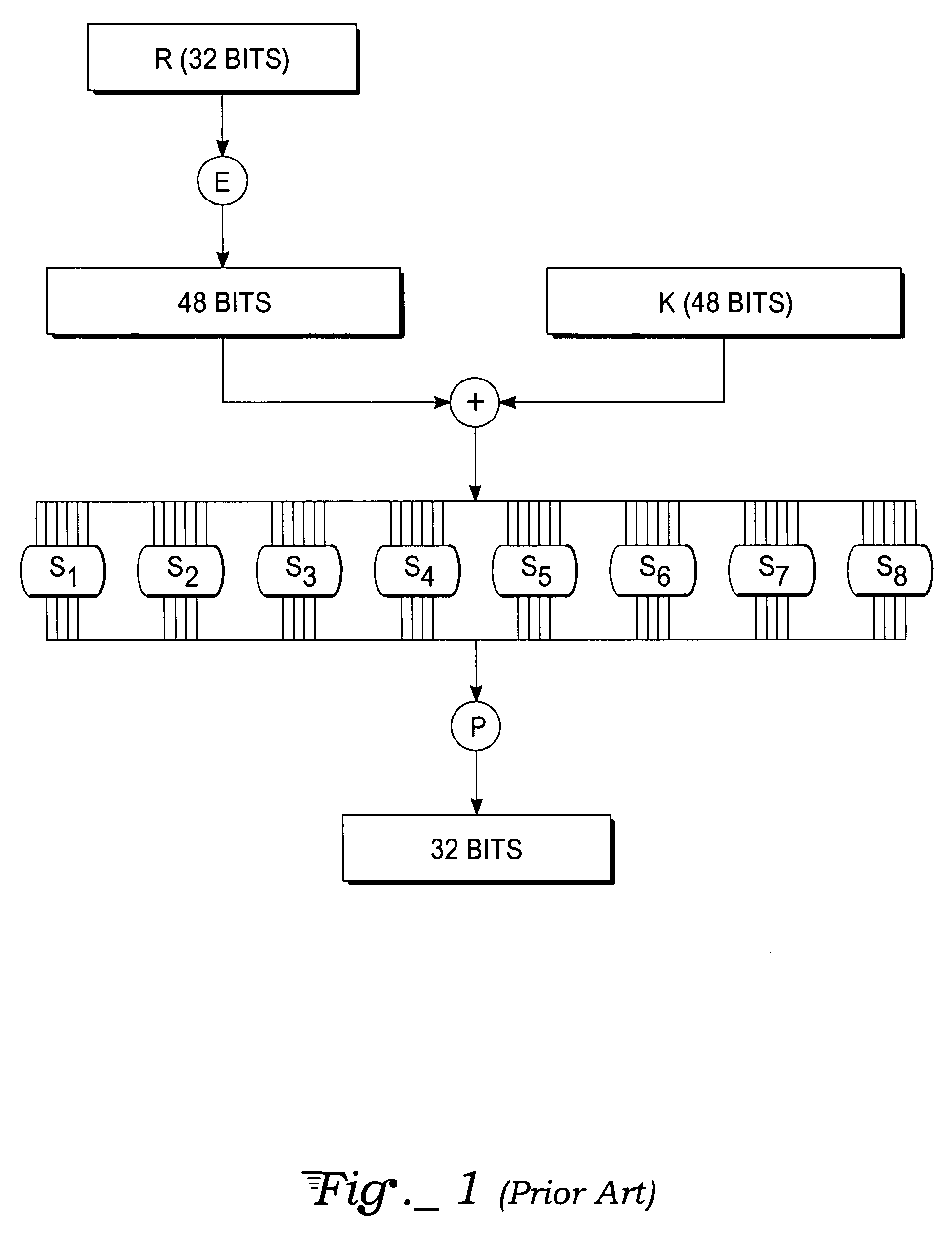
Encryption apparatus using data encryption standard algorithm
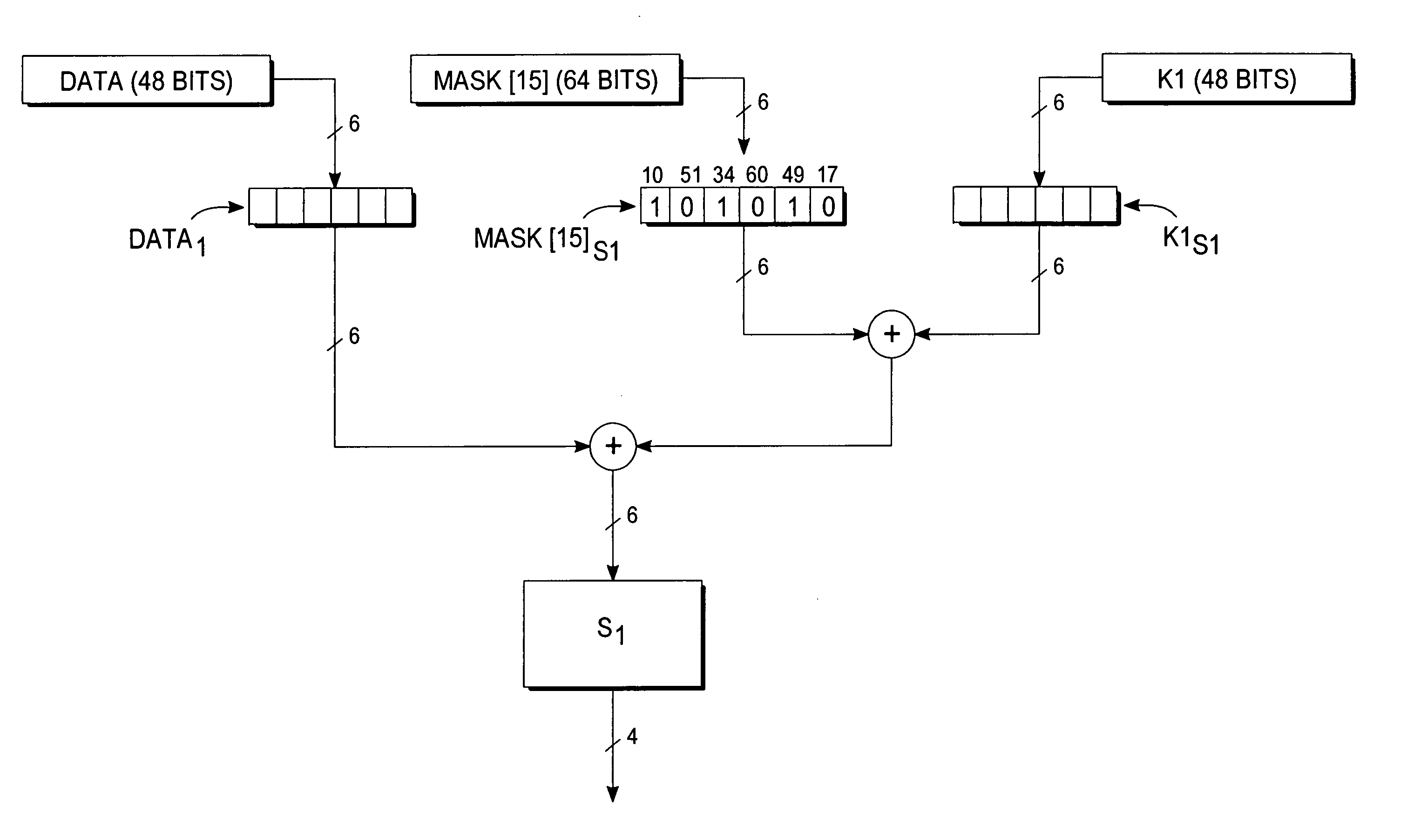
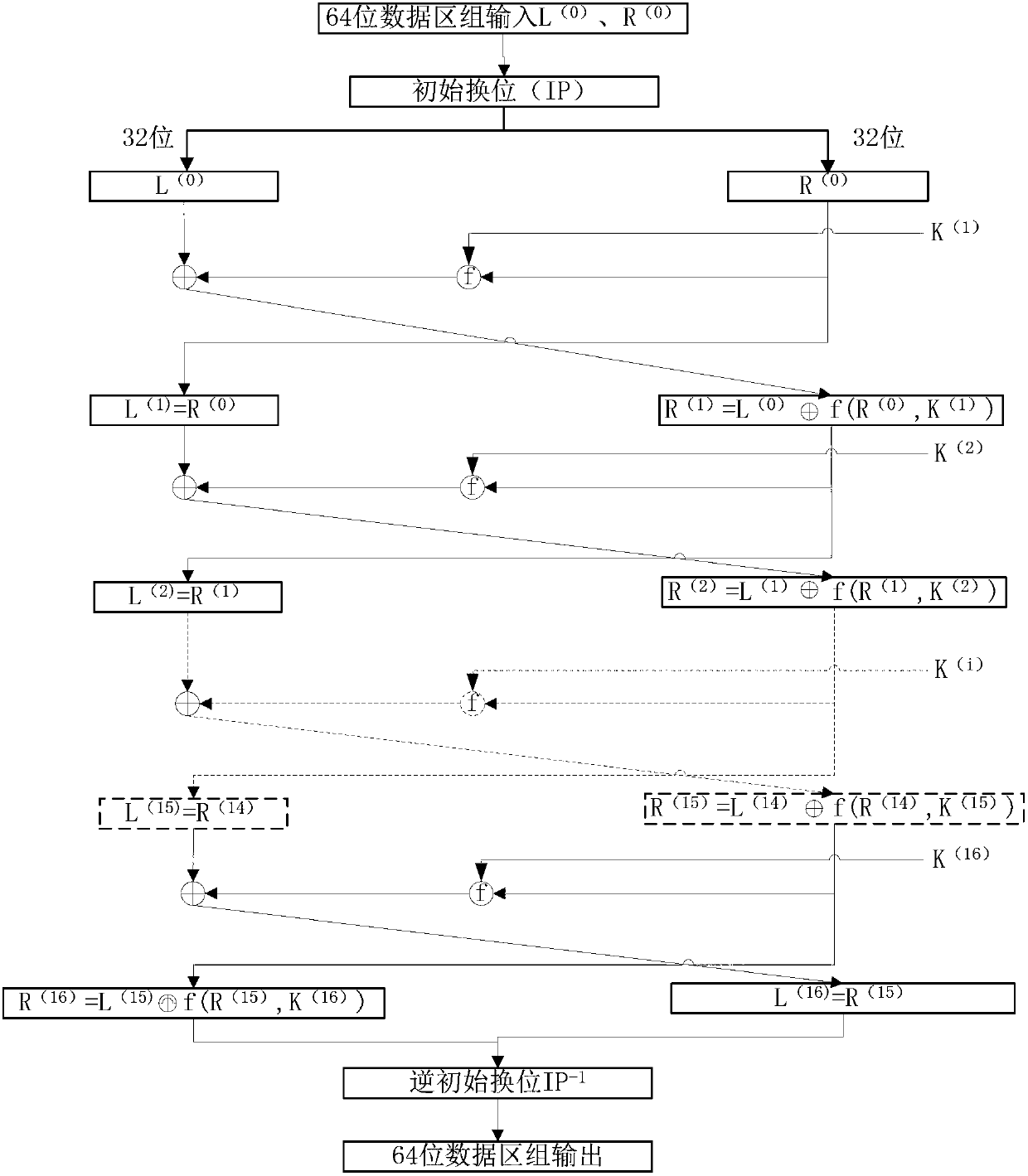
InactiveUS20020003876A1Improve process capabilityEncryption apparatus with shift registers/memoriesSecret communicationS-boxMultiplexer
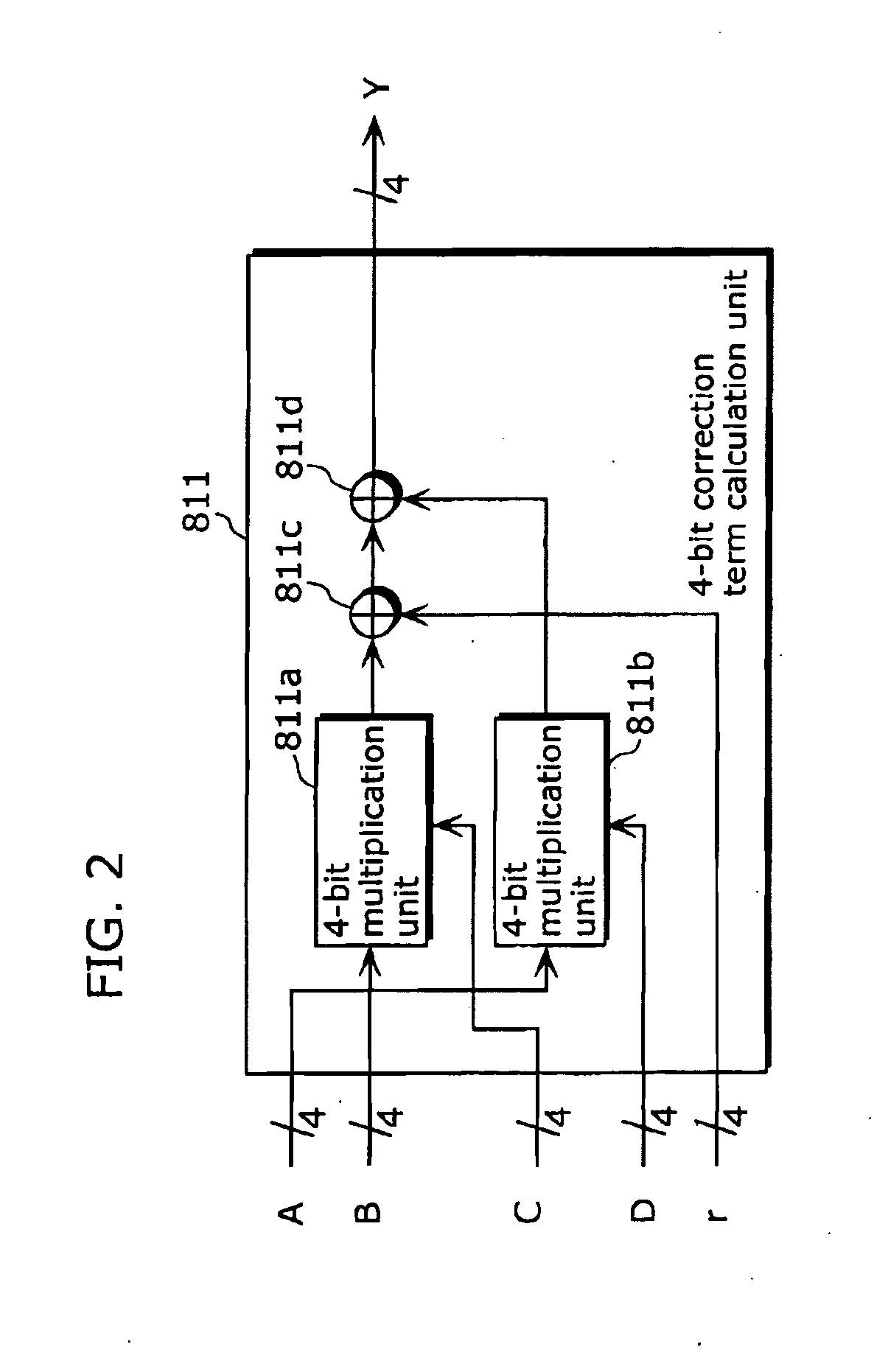
An encryption device eliminates data contention and minimizes area by accessing twice data for a given time by using a memory device of two times faster access time. The encryption device for performing encryption of plain text blocks using data encryption standard algorithm, wherein the encryption device includes an initial permutation unit, a data encryption unit having n-stage (n is an even number) pipeline structure using a first clock, a second clock and a third clock, and an inverse initial permutation unit, the encryption device includes: a multiplexer for selecting one of n / 3 48-bit inputs; 8 S-Boxes, each for receiving 6-bit address among the selected 48-bit and outputting 4-bit data; a demultiplexer for distributing 32-bit data from the S-Boxes to n / 3 outputs; and a controller for control the multiplexer and the demultiplexer with a fourth clock and a fifth clock, wherein the fourth and the fifth clock are faster than the first, the second and the third clocks by n / 3 times.
Owner:ABOV SEMICON
System for encrypting and decrypting a plaintext message with authentication
InactiveUS20120008767A1Lower levelLow levelSecret communicationSecuring communicationComputer hardwarePlaintext
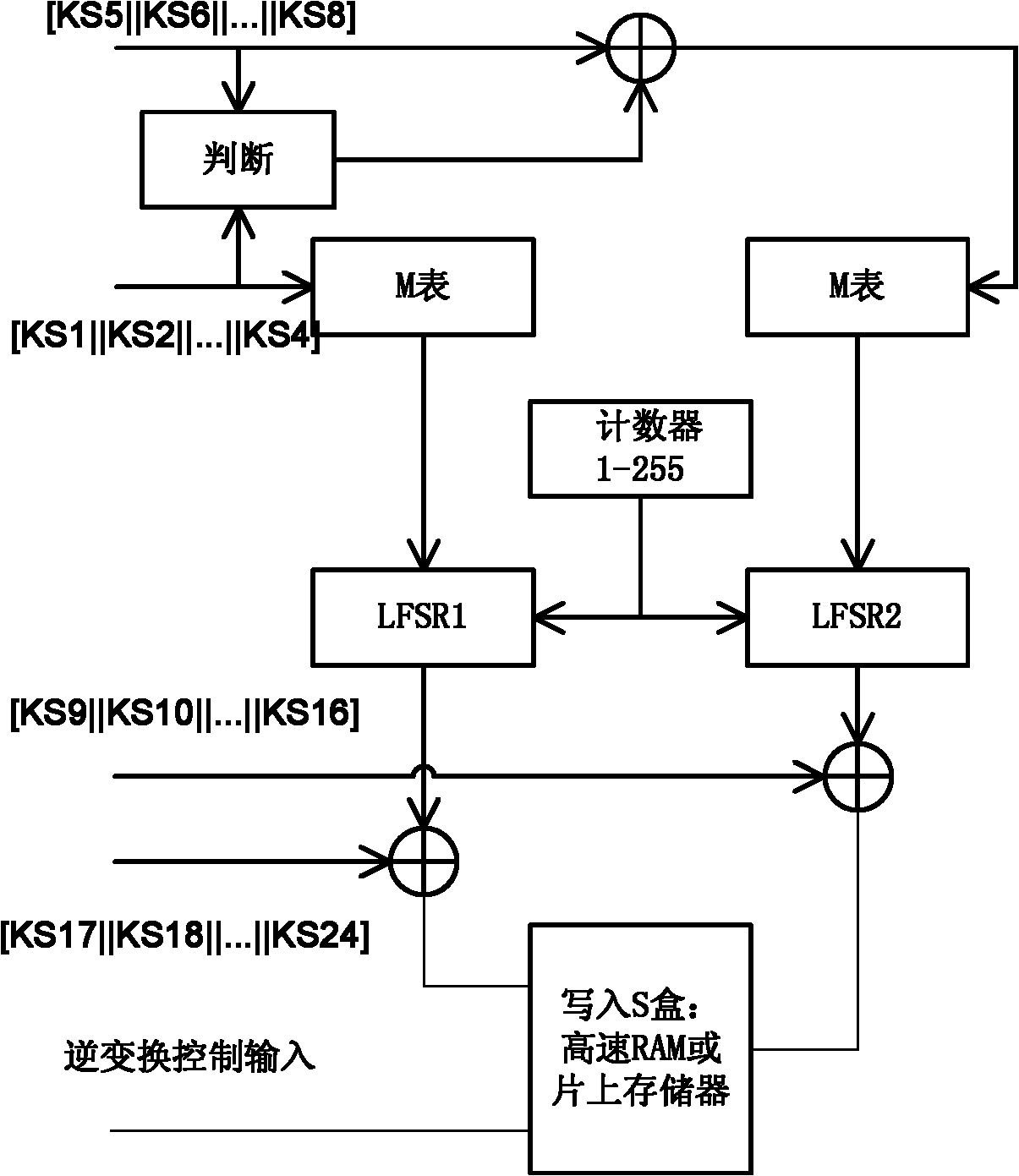
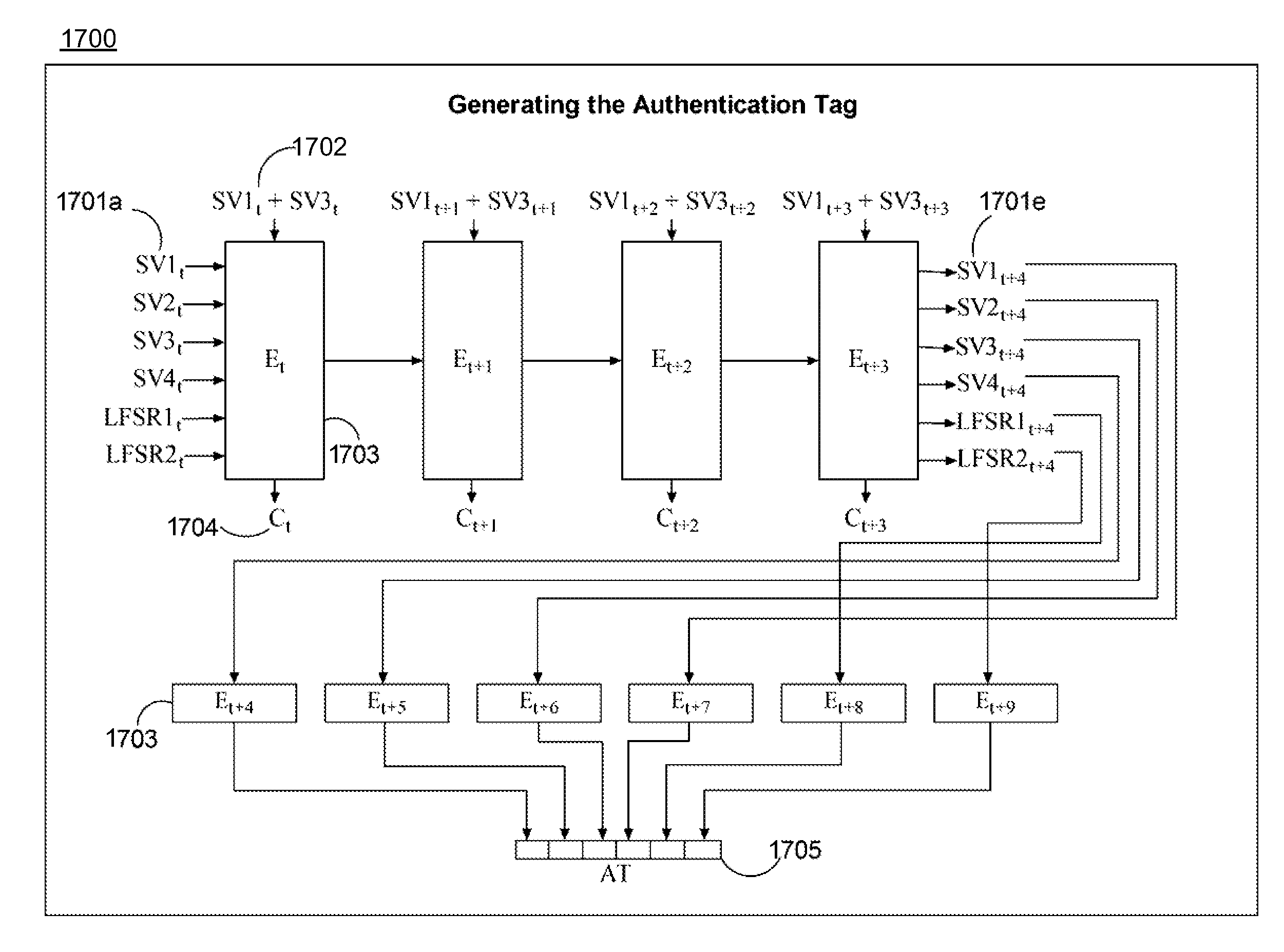
The described system and method provide for an encryption and authentication technique that achieves enhanced integrity verification through assured error-propagation using a multistage sequence of pseudorandom permutations. The method generates intermediate data-dependent cryptographic variables at each stage, which are systematically combined into feedback loops. The encryption technique also generates an authentication tag with minimal post processing that is the size of the state. The size of the state is dependent on the number of pseudorandom permutations and the size of the LFSR. The authentication tag provides a unique mapping to the plaintext for any number of plaintext blocks that is less than or equal the size of the state. In addition to being a stand alone encryption algorithm, the disclosed technique is applicable to any mode that uses pseudorandom permutations such as, key dependent lookup tables, S-Boxes, and block ciphers such as RC5, TEA, and AES.
Owner:SMITH ERIC MYRON +3
Masking method of defending differential power analysis attack in seed encryption algorithm
ActiveUS20110013767A1Improve efficiencyIncrease speedError preventionUnauthorized memory use protectionPower analysisS-box
A plurality of S-boxes is masked by one masking inverse table. Therefore, the computation cost and the use amount of the RAM necessary for masking at the time of a masking operation for defending a differential power analysis attack in a SEED encryption algorithm can be effectively reduced.
Owner:ELECTRONICS & TELECOMM RES INST
Second-order side channel energy analysis method for SM4 algorithm of simple mask
ActiveCN103647637ABreaking new ground for attackExtended side channel energy analysis methodEncryption apparatus with shift registers/memoriesPower analysisS-box
The invention discloses a second-order side channel energy analysis method for an SM4 algorithm of a simple mask. To achieve mask protection for the SM4 algorithm with the output of four S boxes carrying the same mask value, the method comprises the steps of (1) acquiring energy traces and establishing a sampling energy consumption matrix; (2) preprocessing the energy consumption matrix in the previous step; (3) selecting attack points to conduct CPA or DPA to obtain rki, 0; (4) re-selecting an S-box operation part and following the steps (2) and (3) to obtain rki, u through analysis; and (5) carrying out the steps (2), (3) and (4) on previous / next four rounds to obtain a round key and obtaining an initial key through a key inverse expansion operation. The technical scheme of the invention innovatively provides the new second-order energy analysis method, develops a new situation of SM4 cryptographic algorithm attack, extends the side channel power analysis method for the SM4 algorithm, and can fully and effectively conducts side channel energy analysis on the SM4 cryptographic algorithm; and the method of the technical scheme is highly practical for common mask protection measures.
Owner:国家密码管理局商用密码检测中心
Information Processing Apparatus
ActiveUS20090103716A1Increase resistanceIncrease the number ofKey distribution for secure communicationEncryption apparatus with shift registers/memoriesHigh resistanceInformation processing
A high-security cryptanalysis-resistant cryptographic processing apparatus and a cryptographic processing method are provided. A Feistel common key block cipher is produced by repeatedly performing an SPN-type F-function including a nonlinear transformation part and a linear transformation part over a plurality of rounds. In each round, a linear transformation process is performed according to an F-function using a matrix determined so as to satisfy a relatively loose constraint whereby high resistance to differential attacks and / or linear attacks is achieved. The relatively loose constraint allows an increase in the number of candidates for usable matrices, and it is possible to maintain the number of active S-boxes to a sufficiently large level. This makes it possible to increase the minimum number of active S-boxes, which is one of measures indicating the degree of robustness of ciphers, and thus it is possible to realize an algorithm of encrypting data in a highly secure manner so that high resistance to attacks is achieved.
Owner:SONY CORP
Method and table look-up device for encrypting and decrypting data by using symmetric cryptographic algorithm
ActiveCN102710415AMeet the requirements in terms of realization areaMeet area requirementsMultiple keys/algorithms usageData stream serial/continuous modificationComputer hardwareMultiplexing
The invention discloses a method and a table look-up device for encrypting and decrypting data by using a symmetric cryptographic algorithm. The method comprises the following steps of: determining all types of S boxes required to be used when the S boxes are required to be used for table look-up in the symmetric cryptographic algorithm; determining the total amount Ni of the S boxes of each type, and when Ni is more than 1, determining that the S boxes of the type satisfy a multiplexing condition; and when the data are encrypted and decrypted by using the symmetric cryptographic algorithm, multiplexing the S boxes of at least one type satisfying the multiplexing condition. By the method and the device, occupation of the symmetric cryptographic algorithm on hardware resources can be reduced under the condition that the hardware resources are relatively constrained.
Owner:CHINA IWNCOMM
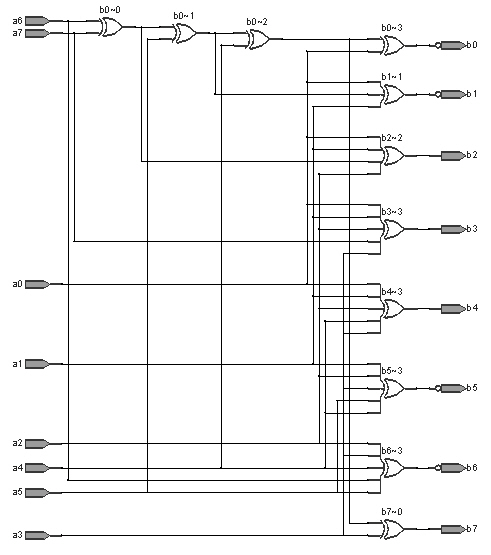
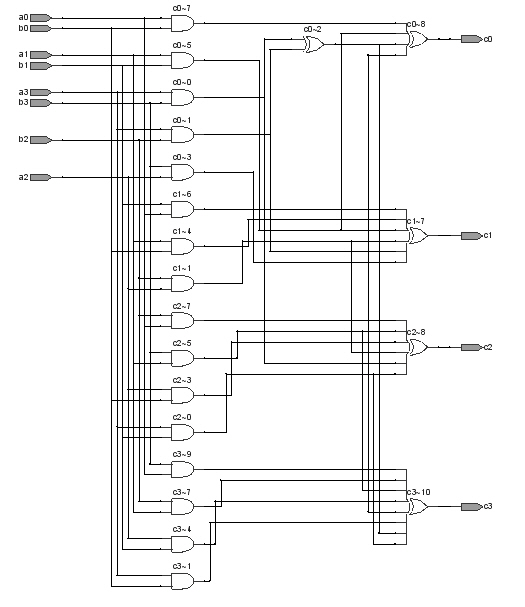
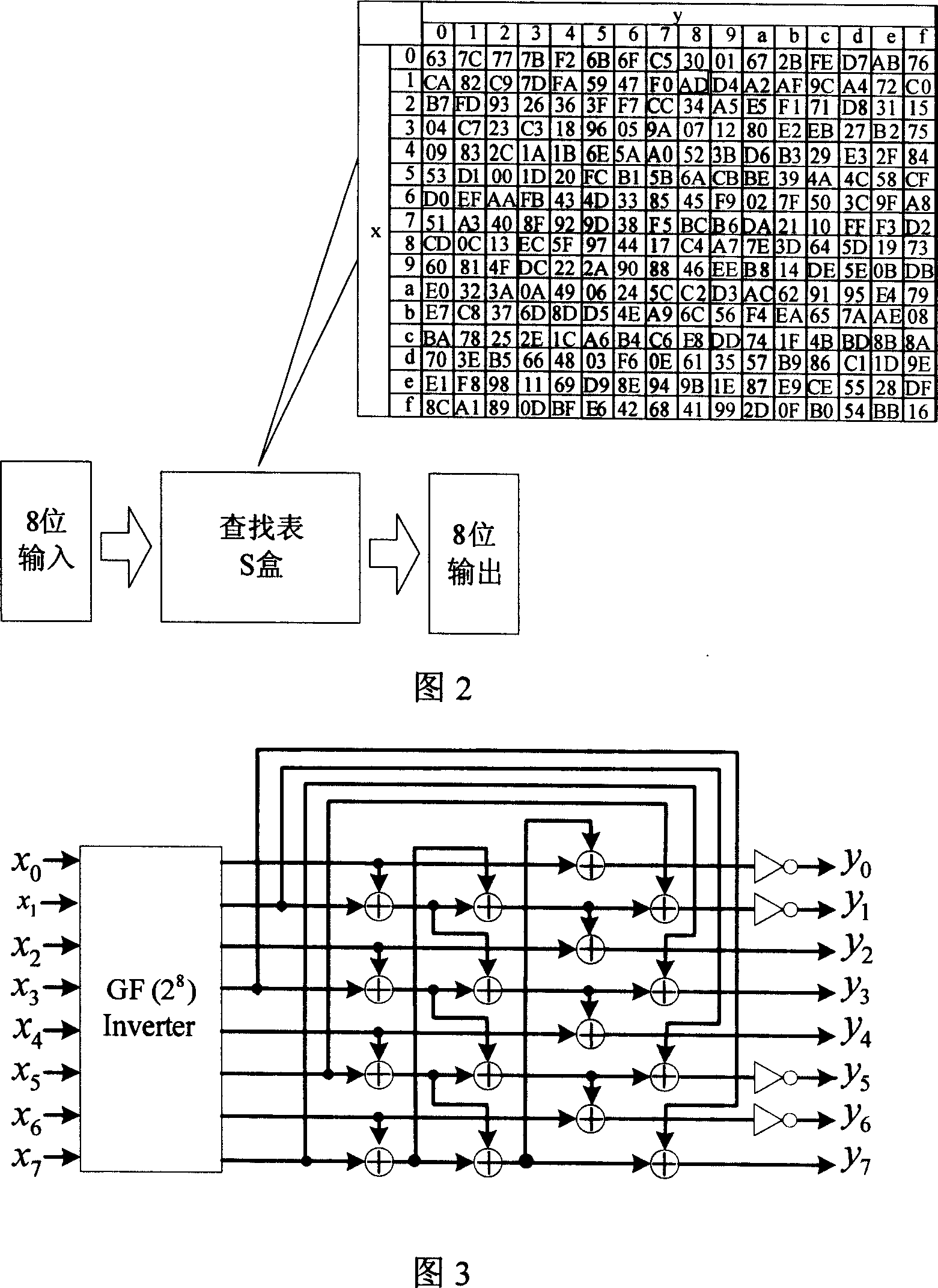
S box applicable to hardware realization and circuit realization method thereof
InactiveCN101938349AStrong nonlinearityStrongly Differential Propagation ProbabilitySecuring communicationS-boxNegation
The invention provides an 8*8 S box applicable to hardware realization and a circuit realization method thereof. The S box is compounded by using an inversion operation on a finite field GF (((22)2)2) and affine transformation of GF (2)8 and has stronger nonlinearity, difference transmission probability, snowslide performance, algebra complexity and other cryptological properties. Compared with other Galois fields comprising 28 elements, the field GF (((22)2)2) selected by the invention can reduce the complexity of the inversion operation, and the selection of polynomials generated by various levels of field extension further reduces the expense of subfield operations. The invention also provides a hardware realization mode of the S box, the entire calculation process of the S box can be fully converted into the operations of XOR, AND and negation of bits, and the hardware realization mode can be realized by using a simple logic gate circuit. The entire process does not require table lookup, so that the overall realization expense of hardware is reduced.
Owner:BEIHANG UNIV
A byte replacement circuit for power consumption attack prevention
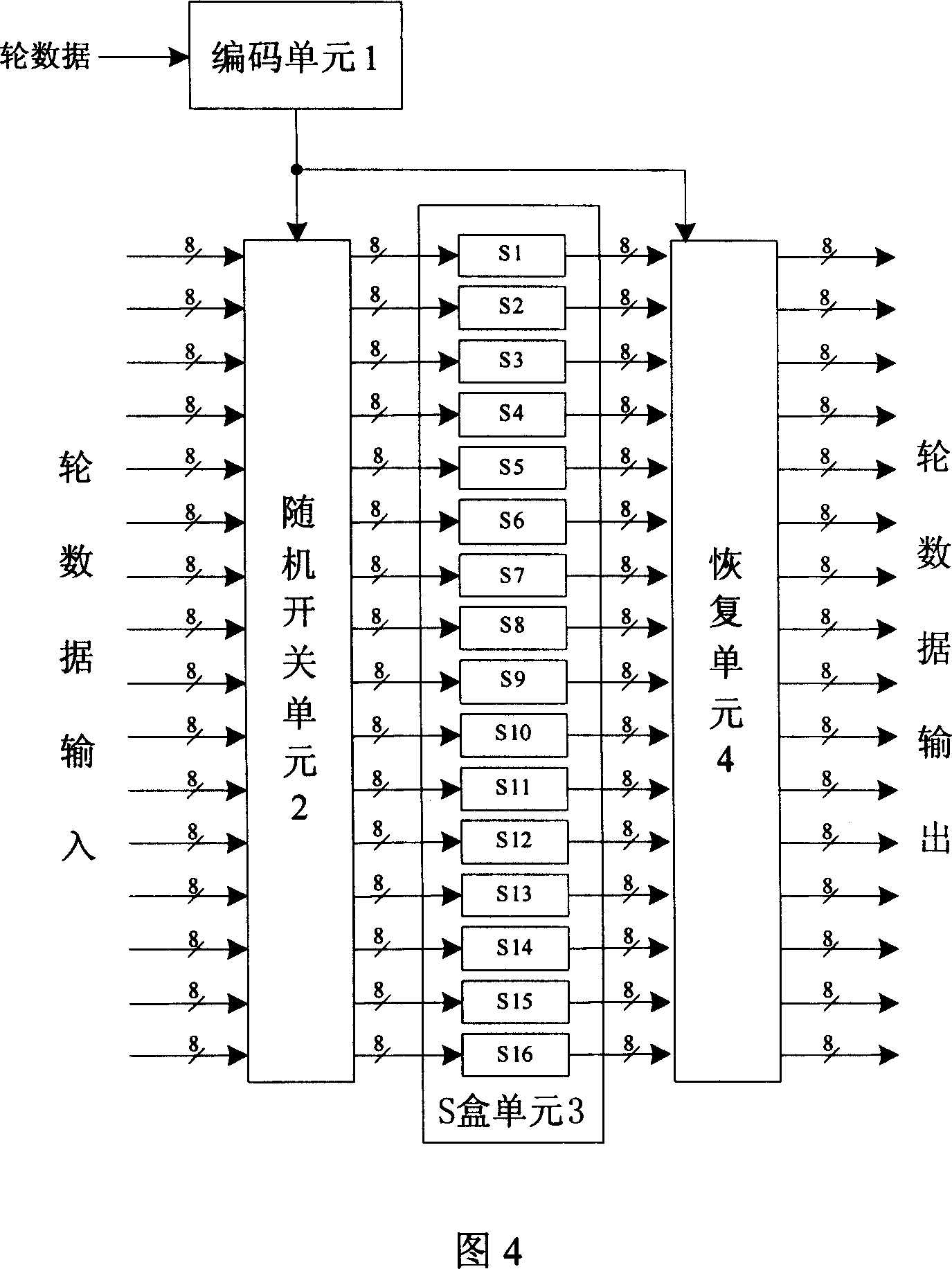
InactiveCN101009554AEnhanced anti-power attack featuresEncryption apparatus with shift registers/memoriesPlaintextS-box
The invention discloses a byte alternative circuit of anti power consumption attack that includes coding unit, random switching unit, S-box unit, and recovery unit. The S-box unit consists of 4-16 isomerous S-boxes. The invention adopts isomerous S-box unit to replace the traditional signal S-box, the switching unit is inserted in the input end of S-box unit, and the recovery unit is added behind the output end. When it is been attracting, the invention can select according to the input data of attack, and no need the additional random number generator. On the other hand, the method which adds the number of random plaintext is invalid for the circuit which is provided by the invention. The invention don't need to apply the special circuit and logical mode, and can be compatible with the presexisting AES enciphering circuit. The invention can improve the anti power consumption attack greatly with less expense, and it can cover the key when the hardware of AES is encrypting and decrypting to make the power attack not get the correct key.
Owner:HUAZHONG UNIV OF SCI & TECH
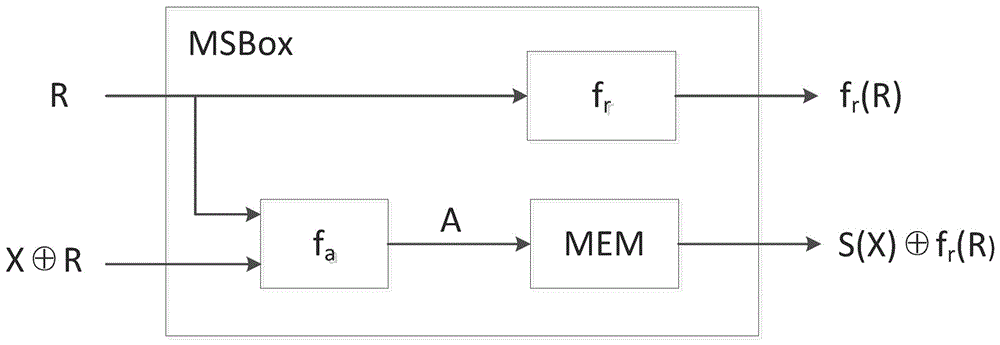
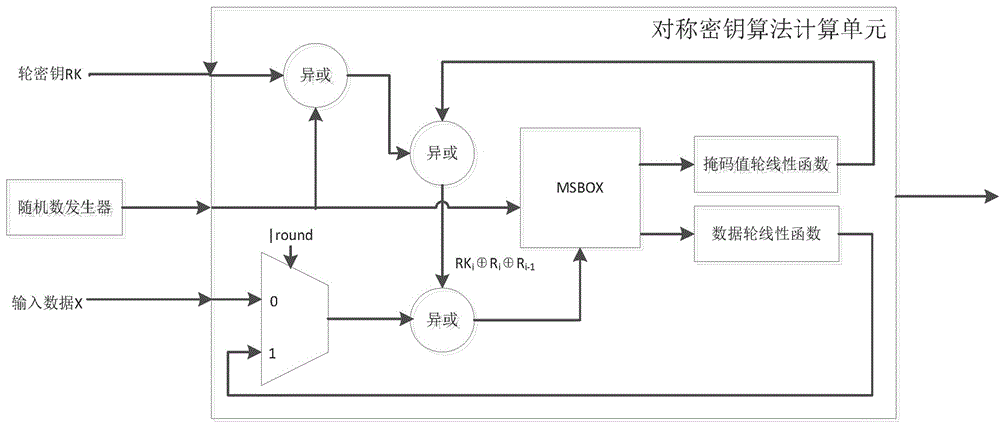
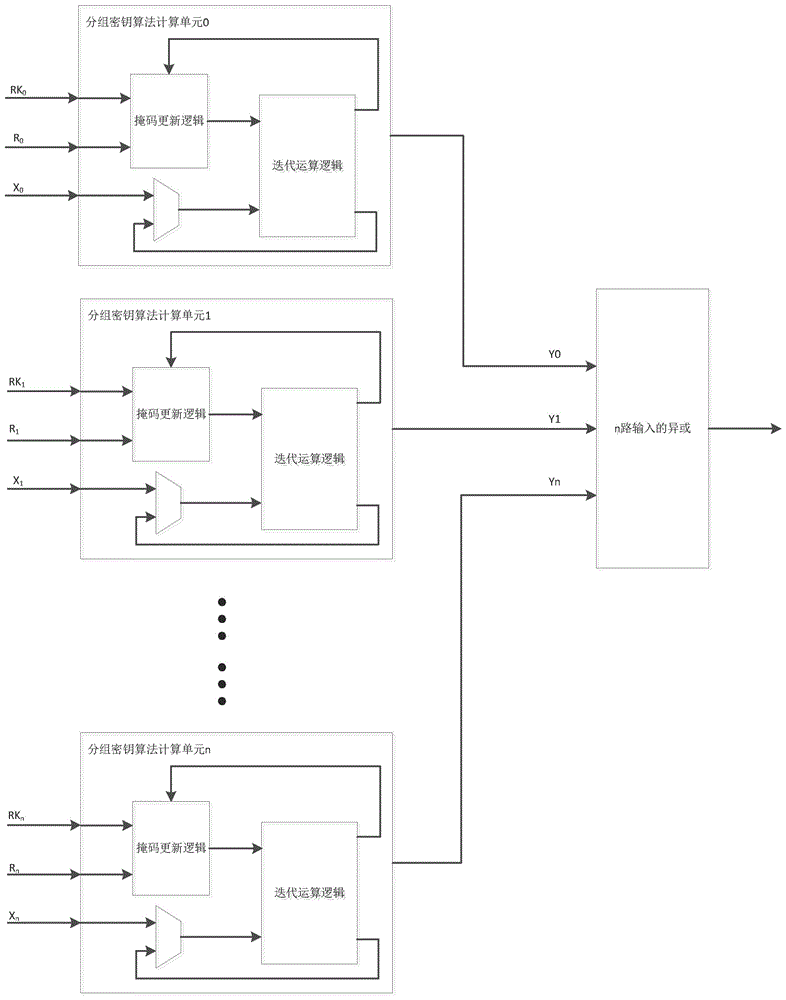
Mask S box, packet key calculation unit, apparatus and corresponding construction method
ActiveCN106788974AHigh reusabilityIncreased complexityEncryption apparatus with shift registers/memoriesDigital data processing detailsS-boxComputer module
The present invention discloses a mask S box, a packet key calculation unit, an apparatus and corresponding construction method. The mask S box comprises an input module, an address mapping processing module, and an output module. The input module receives and uses a random number and input data masked by the random number as two inputs of the mask S box. The address mapping processing module performs one-to-one mapping on the two inputs and corresponding storage addresses in a memory of the mask S box. The output module performs linear processing on the random number by using a linear equation so as to obtain and uses the random number after linear conversion as one output of the mask S box. The storage address is obtained after the random number undergone linear conversion masks the output of the original S box, and is used as another output of the mask S box. The mask S box is safe, and further, the mask S box is easy to implement, is low in power consumption and small in area, and is optimized and expanded to realize the anti-high order DPA encryption device.
Owner:SHENZHEN STATE MICRO TECH CO LTD
Logistics distribution bill generating method based on two-dimension code and encryption technology
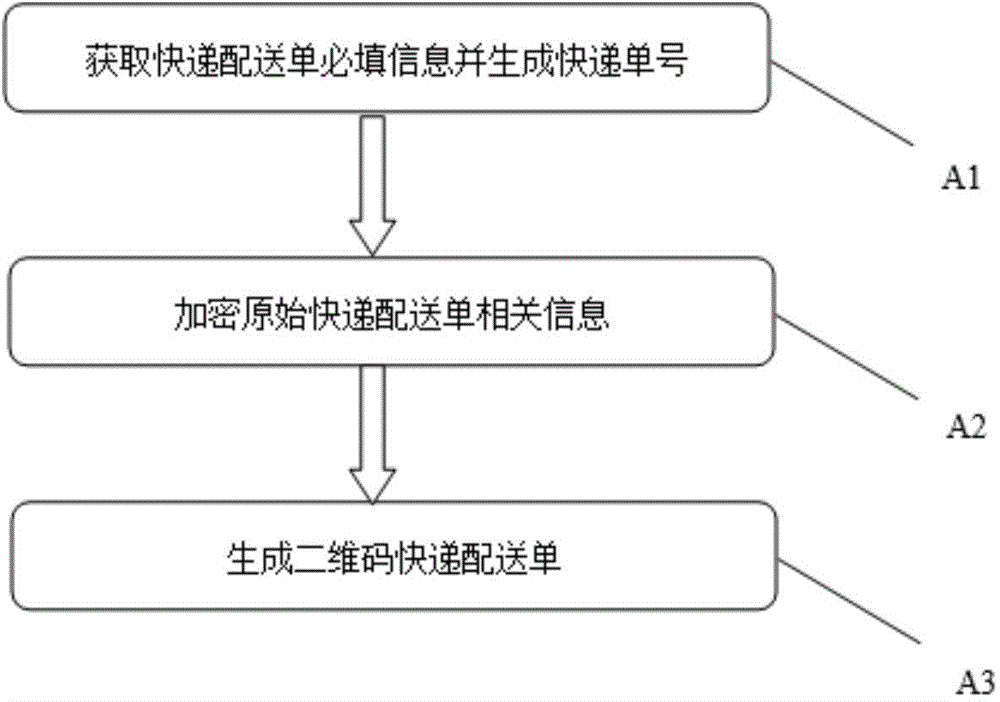
InactiveCN104463529AEncryption/decryption okImprove protectionEncryption apparatus with shift registers/memoriesLogisticsLogistics managementS-box
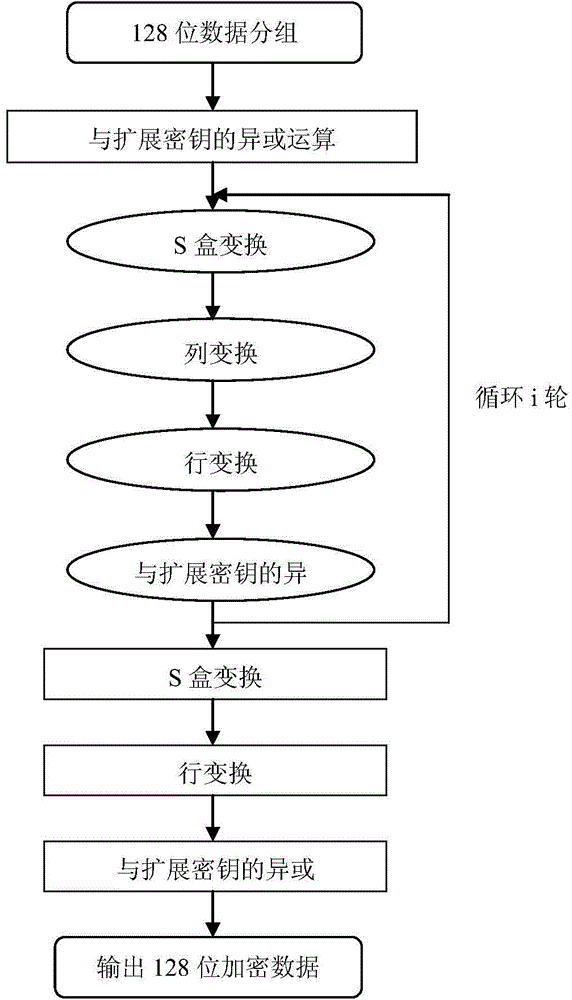
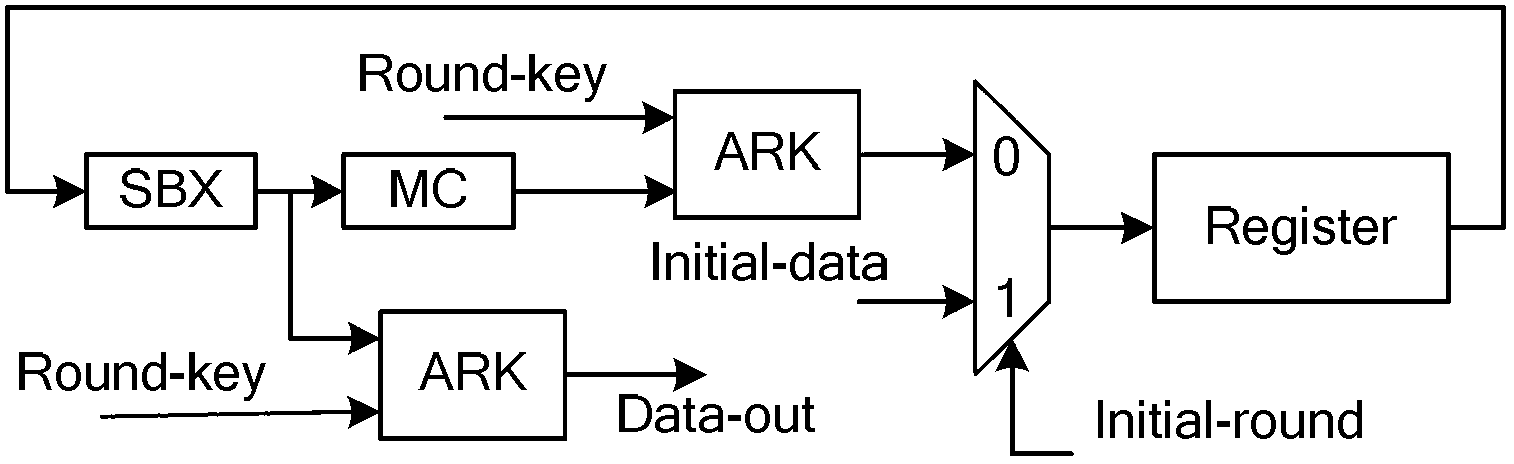
A logistics distribution bill generating method based on a two-dimension code and an encryption technology includes the following steps that A1, required basic information of an original express distribution bill is obtained, and an express bill number is automatically generated; A2, the symmetric encryption algorithm AES algorithm is adopted for encrypting the related information of the original express distribution bill, and the process includes the steps that (1), 128-bit data are grouped; (2), xor calculation of an and expansion secrete key is performed; (3), S box transformation is performed; (4), row transformation is performed; (5), column transformation is performed; (6), xor is performed in the and expansion secrete key; (7), S box transformation is performed; (8), row transformation is performed; (9), xor is performed on the and expansion secrete key; (10), the 128-bit data are output; A3, a two-dimension code express distribution bill is generated through a two-dimension code generator. The distribution efficiency and safety degree of logistics can be improved.
Owner:ZHEJIANG UNIV OF TECH
Method and device for implementing AES (Advanced Encryption Standard) enciphering and deciphering
InactiveCN102801519AReduce areaReduce power consumptionEncryption apparatus with shift registers/memoriesKey sizeComputer hardware
The invention provides a method and a device for implementing AES (Advanced Encryption Standard) enciphering and deciphering. The method comprises the following steps: loading data to be enciphered / deciphered to a register; outputting the data to be enciphered / deciphered to an S box multiplex unit for Nr round operation, wherein Nr is determined by the key length; performing enciphering / deciphering S box operation by the S box multiplex unit on data sent by the register according to an enciphering / deciphering control signal; performing enciphering / deciphering column mixing operation and round key addition operation on the data output by the S box multiplex unit, and caching an operation result to the register; and in the Nrth round operation, performing round key addition operation on output of the S box multiplex unit and then outputting an result to complete enciphering / deciphering. Thus, the method and the device for implementing AES enciphering and deciphering can cache the results of enciphering and deciphering round operations by using the same register, and realize S box and inverse S box operations by using the same logic, and thereby achieving the aim of reducing chip area and power consumption.
Owner:RAMAXEL TECH SHENZHEN
Cipher device adopting Feistel-PG structure and encryption method
InactiveCN103051442AIncrease flexibilityImprove implementation efficiencyEncryption apparatus with shift registers/memoriesComputer hardwarePlaintext
The invention discloses a cipher device adopting a Feistel-PG structure and an encryption method. The Feistel-PG structure consists of a round function F, the round function F maps a t*k*m bit string into a t*k*m bit string, the input X is mapped into U through linear conversion P and nonlinear conversion G, the linear conversion P is displacement based on the t*k*m bit string and is the position conversion of t*m k bit characters, the nonlinear conversion G is concatenation of t nonlinear conversions based on t*k bit string, the nonlinear conversion T is nonlinear conversion based on k*m bit string, and T converts (um-1 to u1, u0) into A (S(um-1 to u1, u0)) through S box layer and linear conversion A, wherein the S box layer is formed by m k*k s boxes through concatenation, and the linear conversion A is linear conversion based on k*m bit string. The encryption method adopting the Feistel-PG encryption structure comprises round key addition, linear conversion P and nonlinear conversion G, the output of plaintext W after the r-round iteration is used as ciphertext. Through the device and the method provided by the invention, the cipher algorithm design is more flexible, and in addition, lower realization cost can be realized at the same security intensity.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com