Application of selecting round key XOR input to perform side-channel power analysis of SM4 cryptographic algorithm
A cryptographic algorithm and energy analysis technology, which is applied in the application field of selecting round key XOR input for SM4 cryptographic algorithm side channel energy analysis, and can solve the problems affecting the success rate of SM4 cryptographic algorithm analysis.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
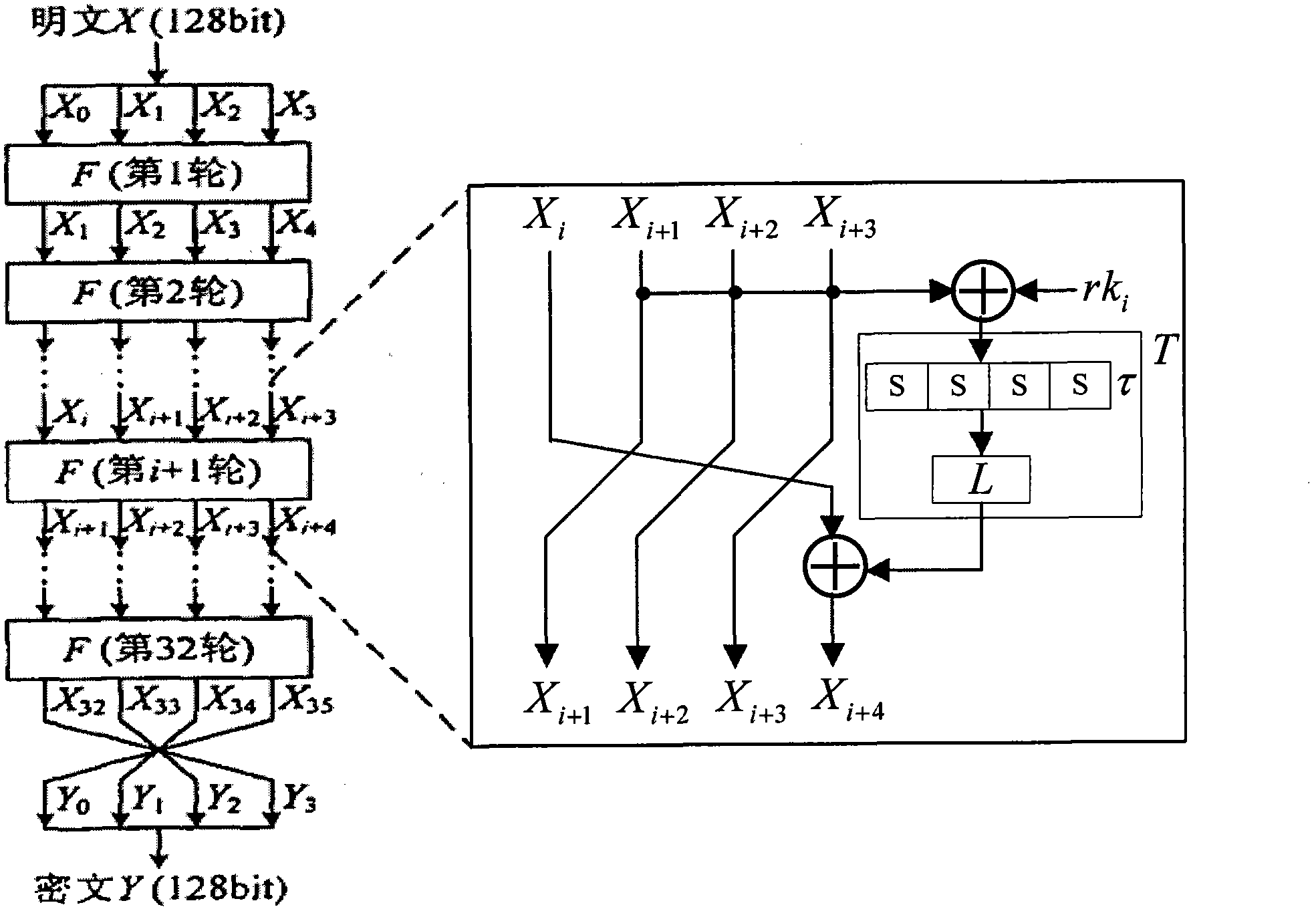
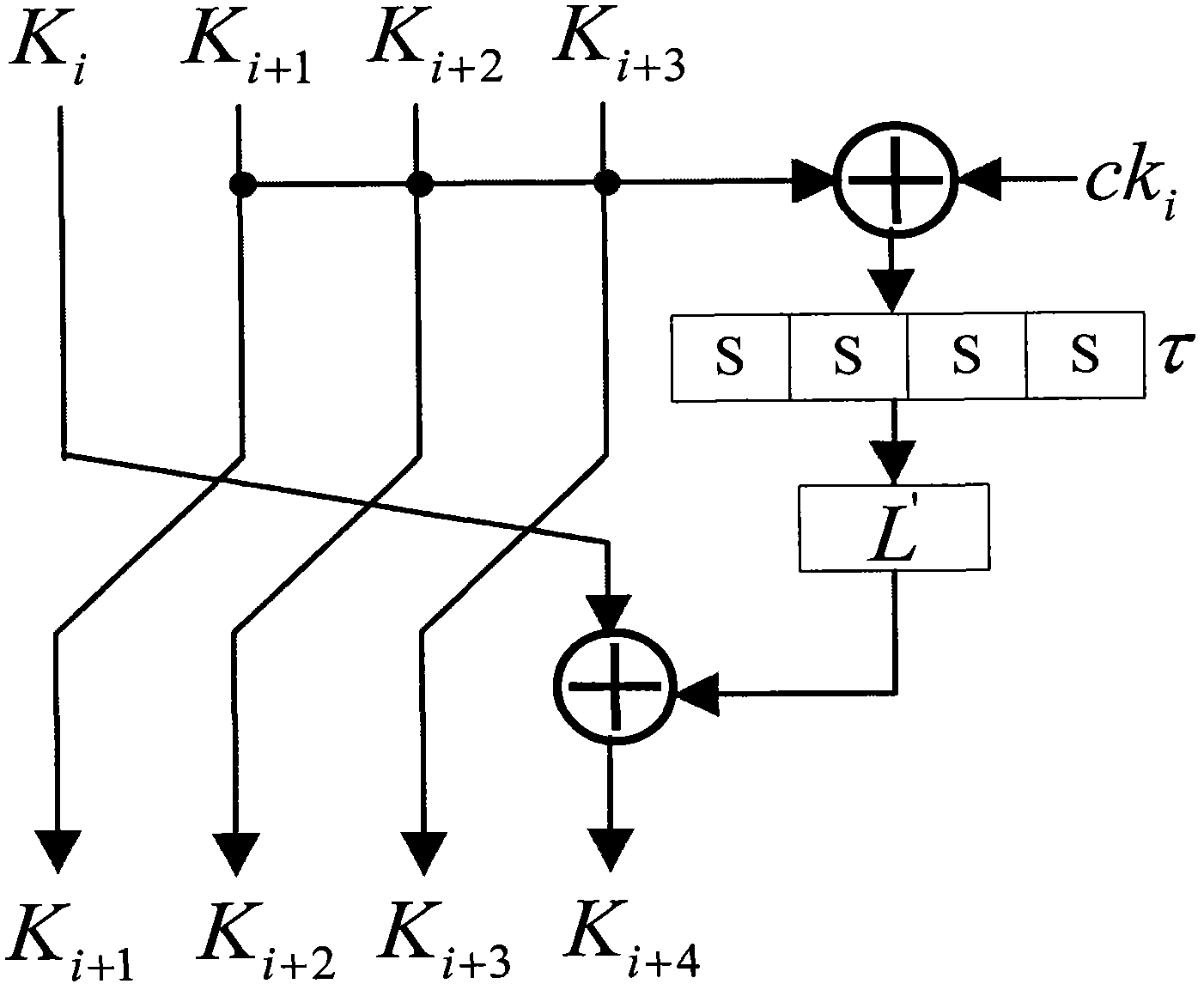
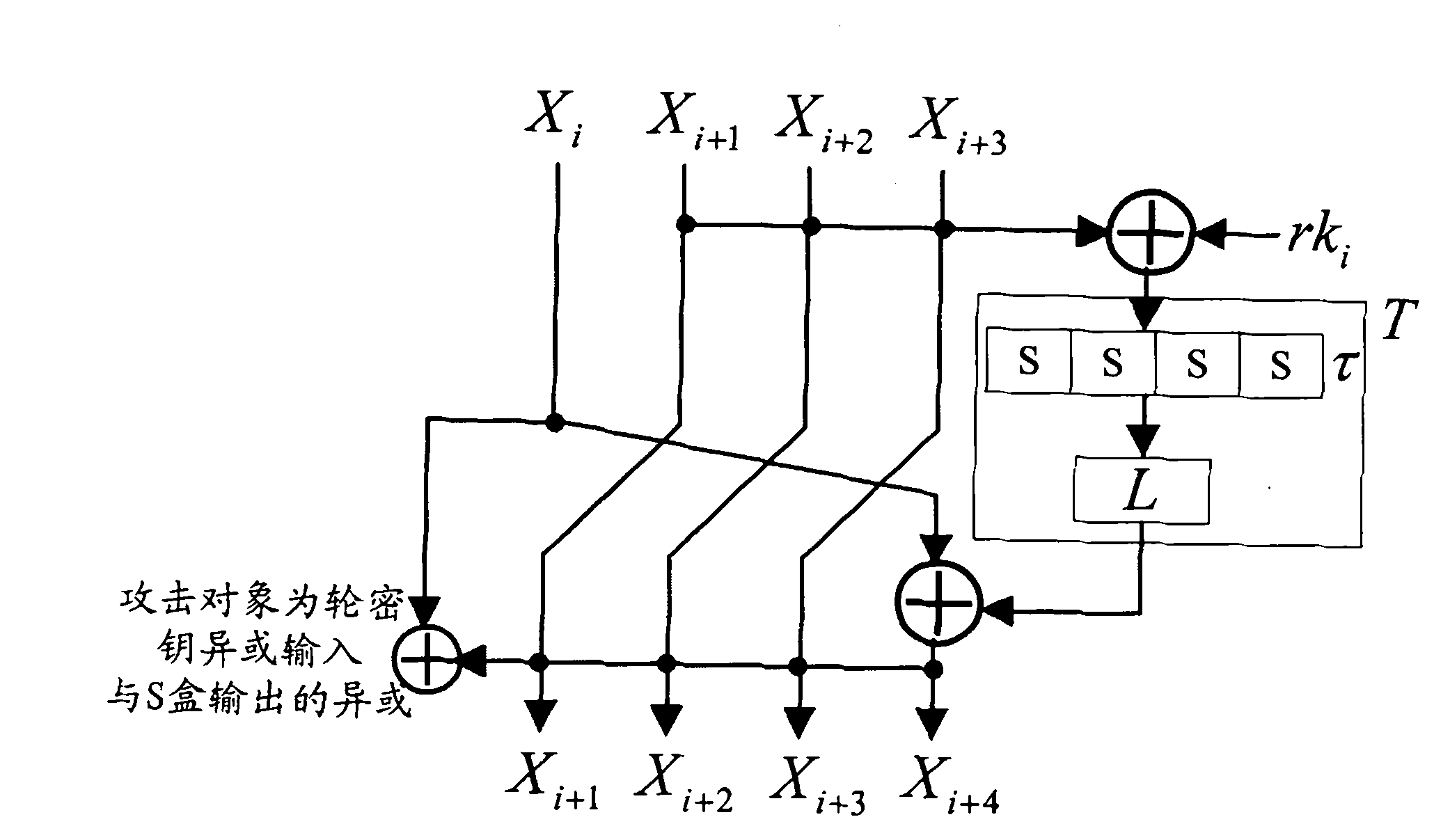
[0064] The technical solution of the present invention is described in detail below. First, the CPA analysis of the round function of the SM4 encryption algorithm is taken as an example to illustrate the technical solution of the present invention. Image 6 Is the CPA analysis flow chart,. For the encryption operation of the SM4 cipher algorithm, if the encrypted plaintext is known, analyze the first 4 rounds of the cipher algorithm. Assuming that the encryption operation of N groups of plaintexts is performed, the input of the kth group of plaintexts is k ∈ {0,...,N-1}, the round input of round i is i is 0, 1, 2, 3 in turn, and the steps are as follows: (1) collect energy traces, perform encryption operations on each group of plaintext, collect energy consumption information corresponding to the measurement time point, which is the energy trace, and establish a sampling energy consumption matrix W(N×T):
[0065]
[0066] in, Expressed as the sampling energy consumpt...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com