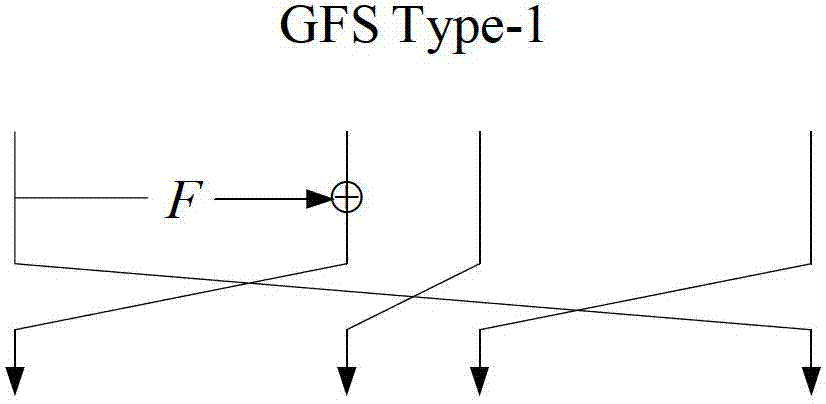
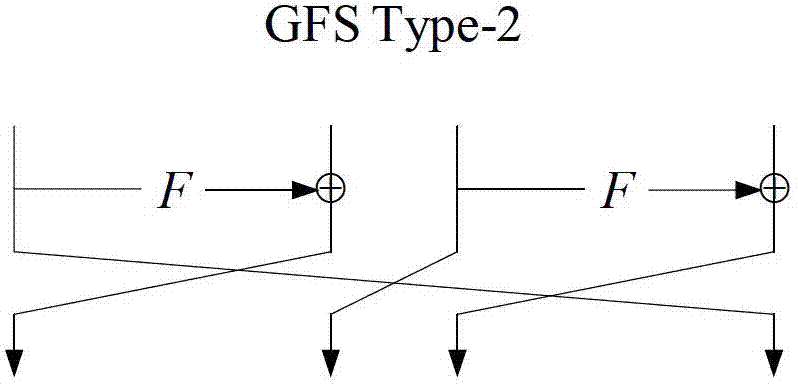
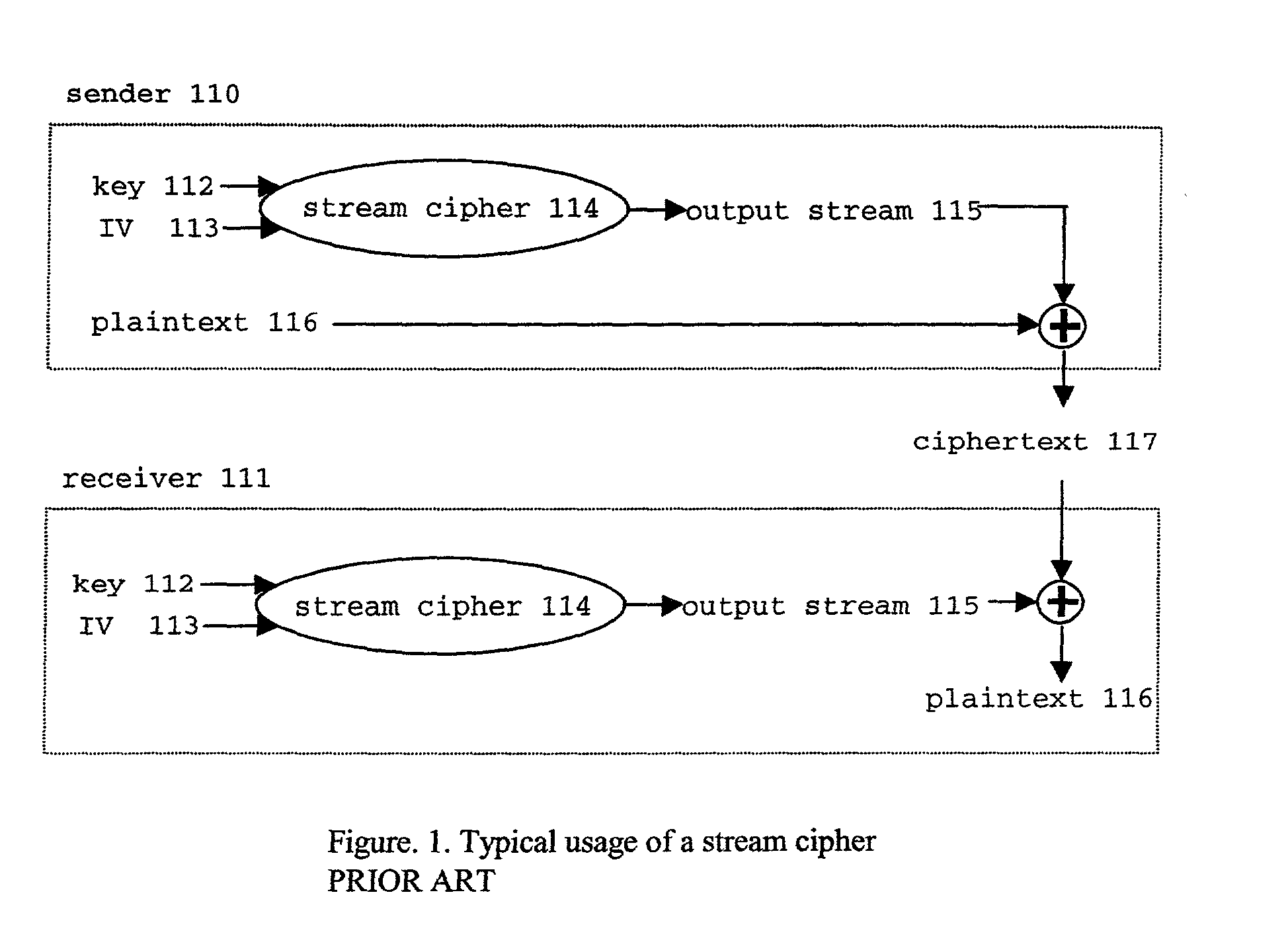
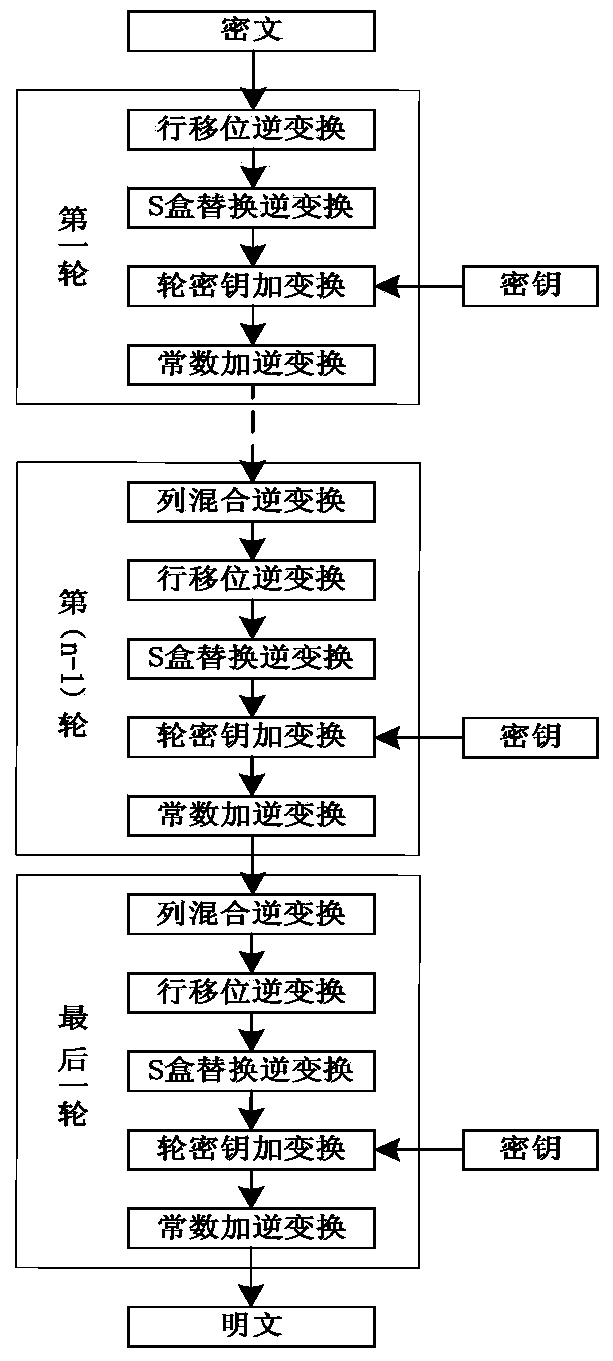
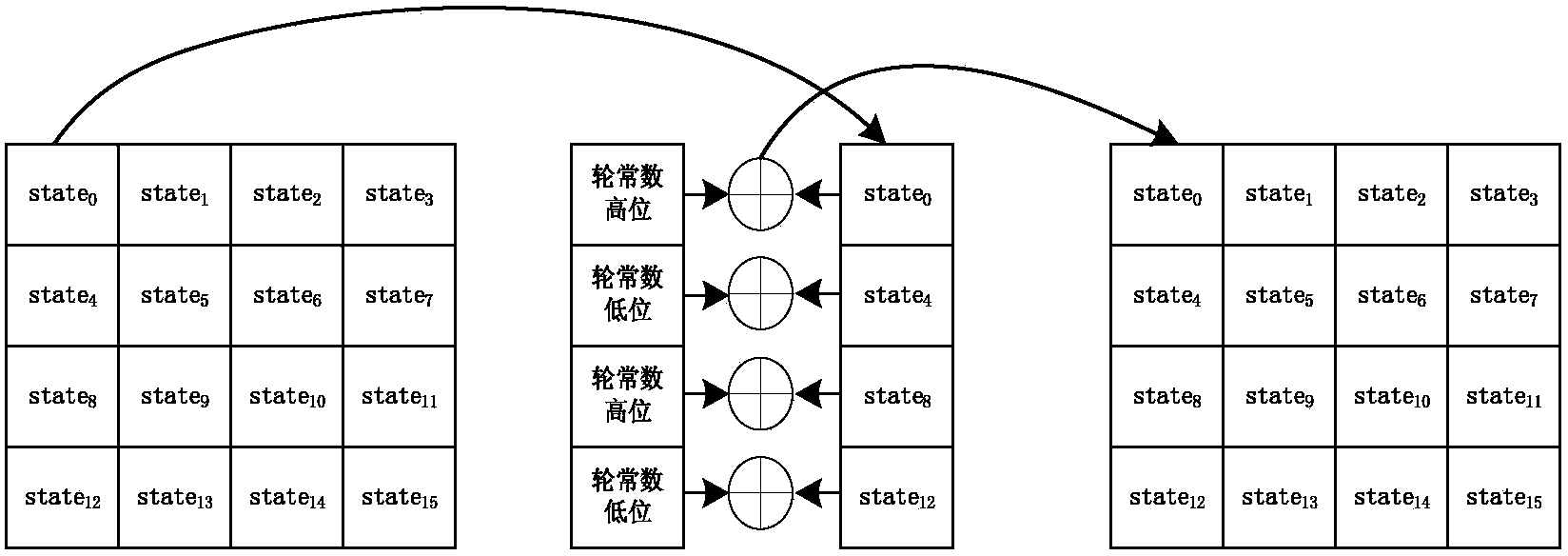
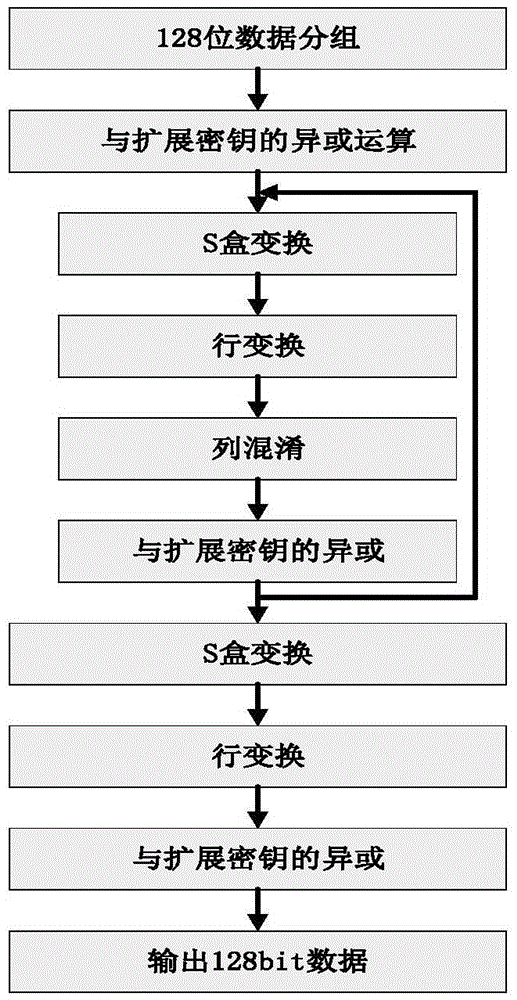
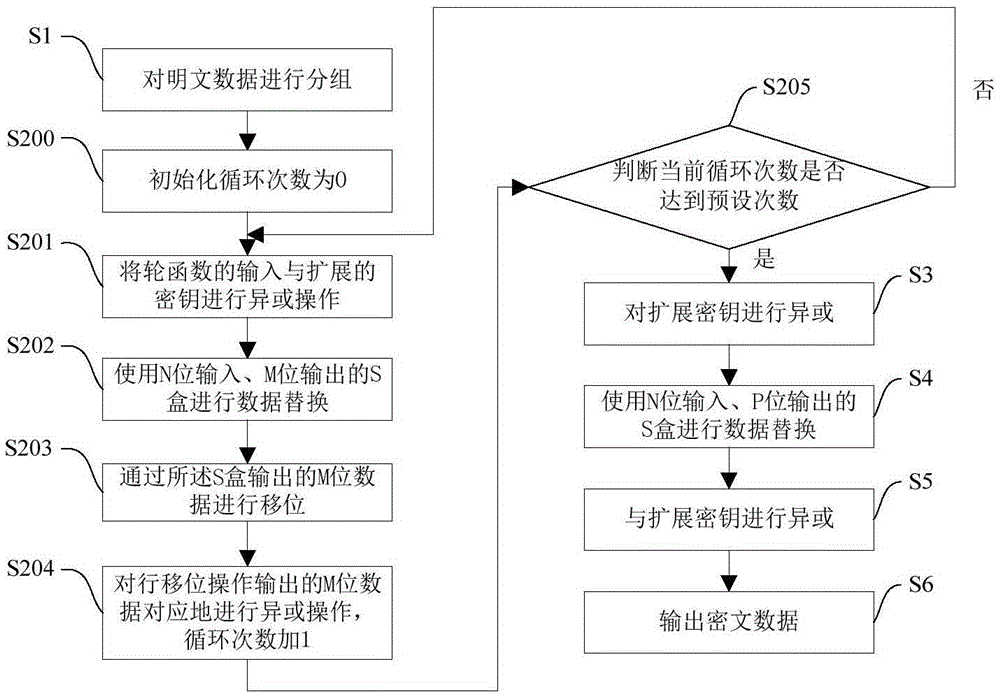
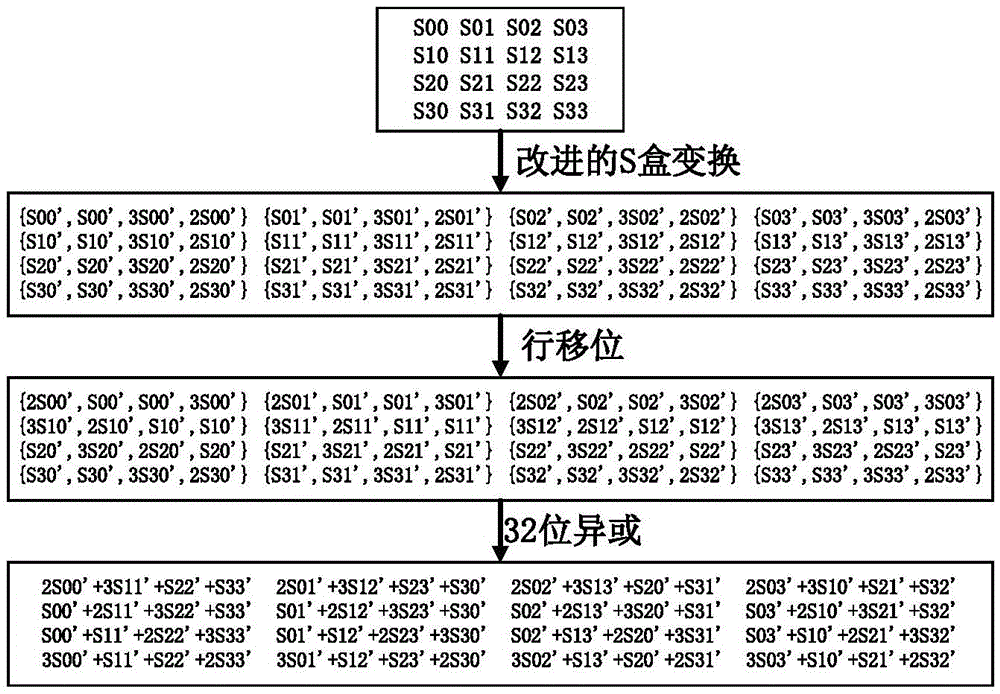
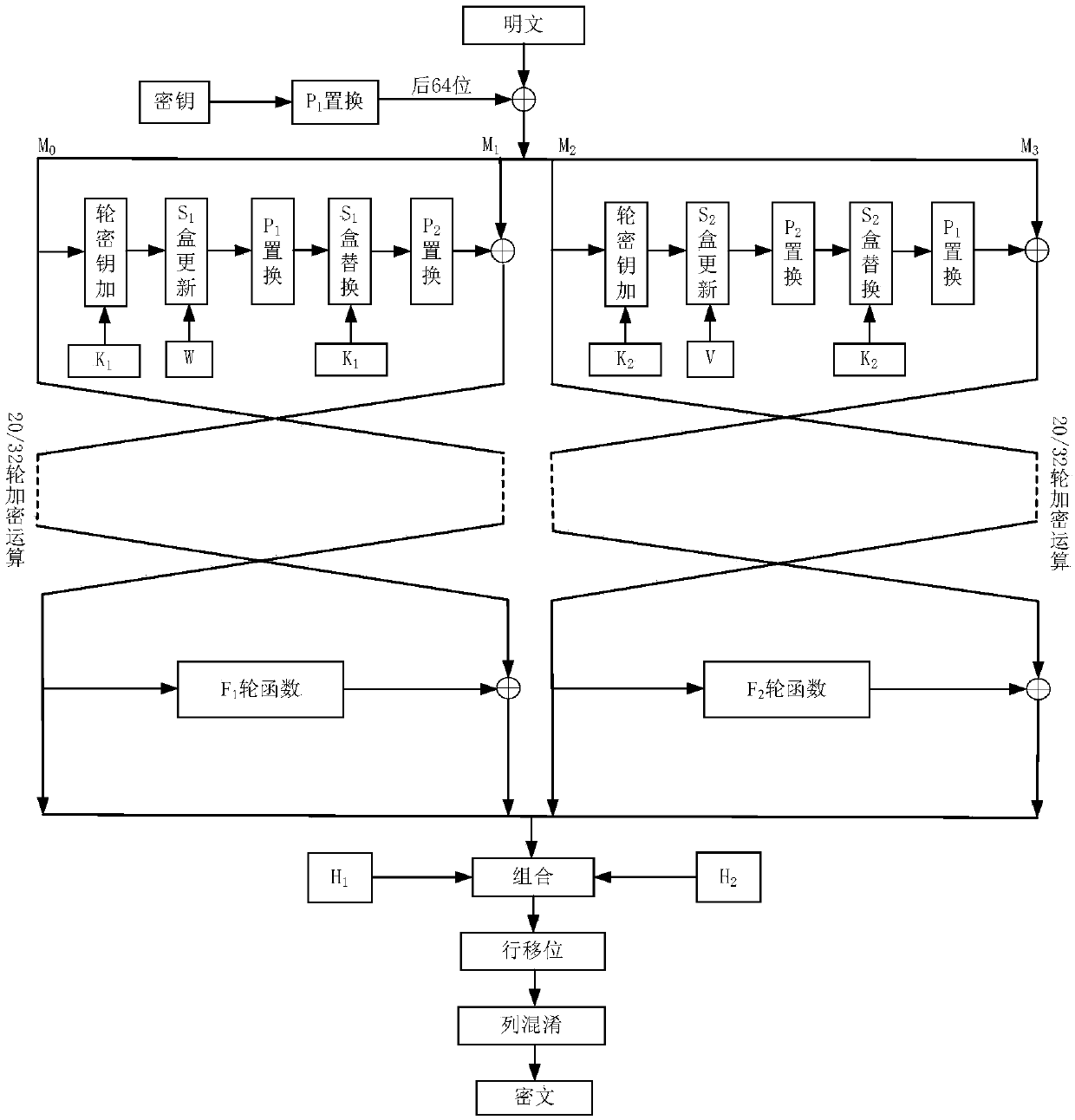
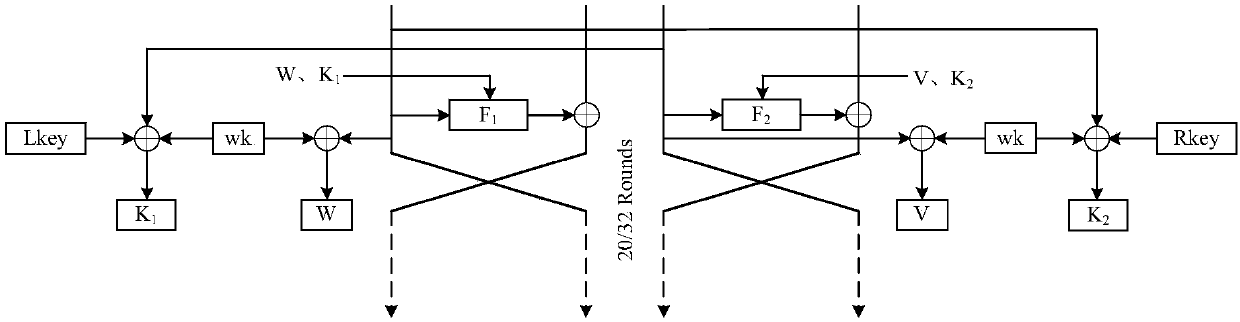
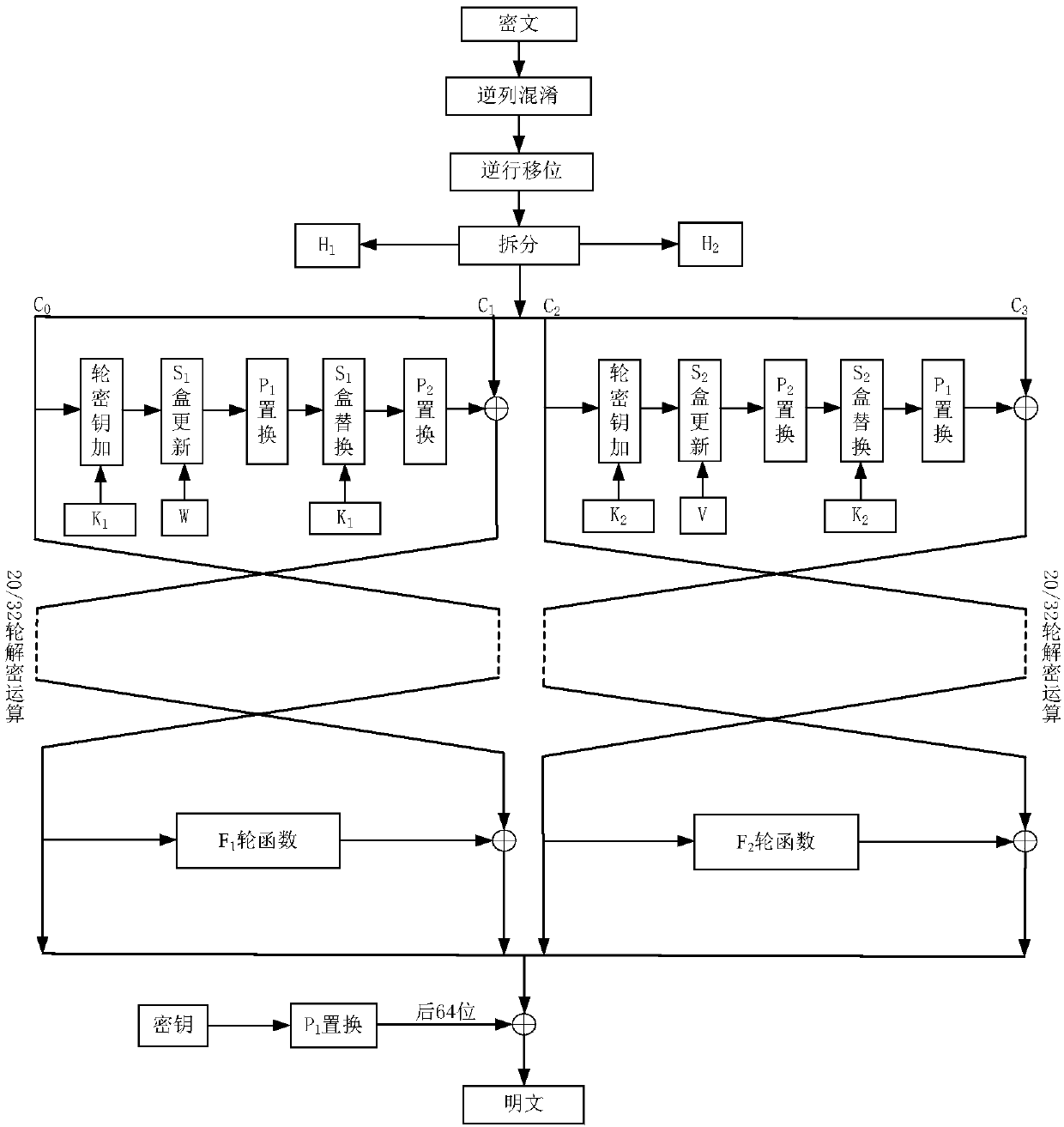
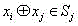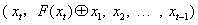Patents
Literature
163 results about "Round function" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
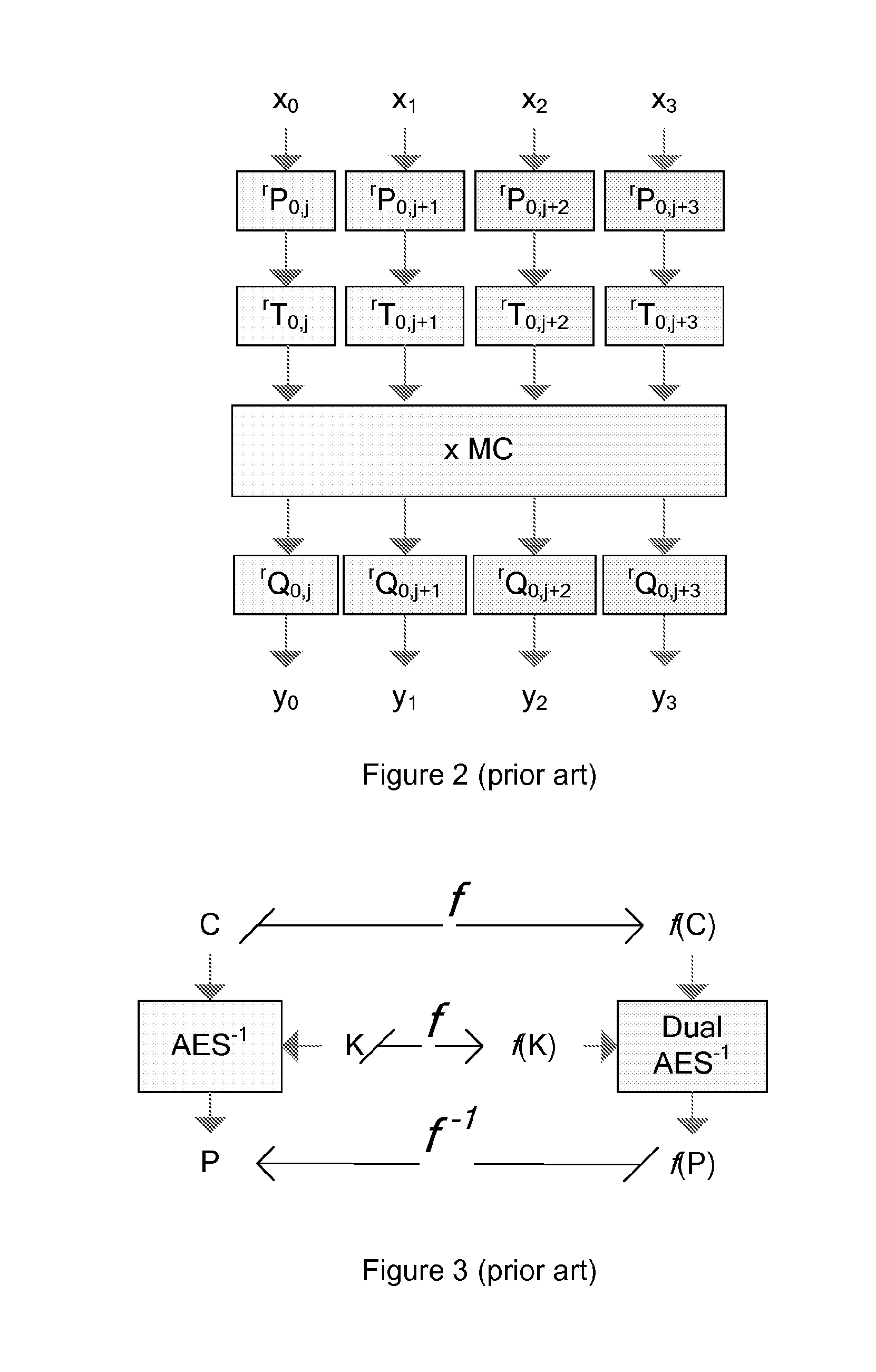
In topology and in calculus, a round function is a scalar function , over a manifold , whose critical points form one or several connected components, each homeomorphic to the circle , also called critical loops. They are special cases of Morse-Bott functions.
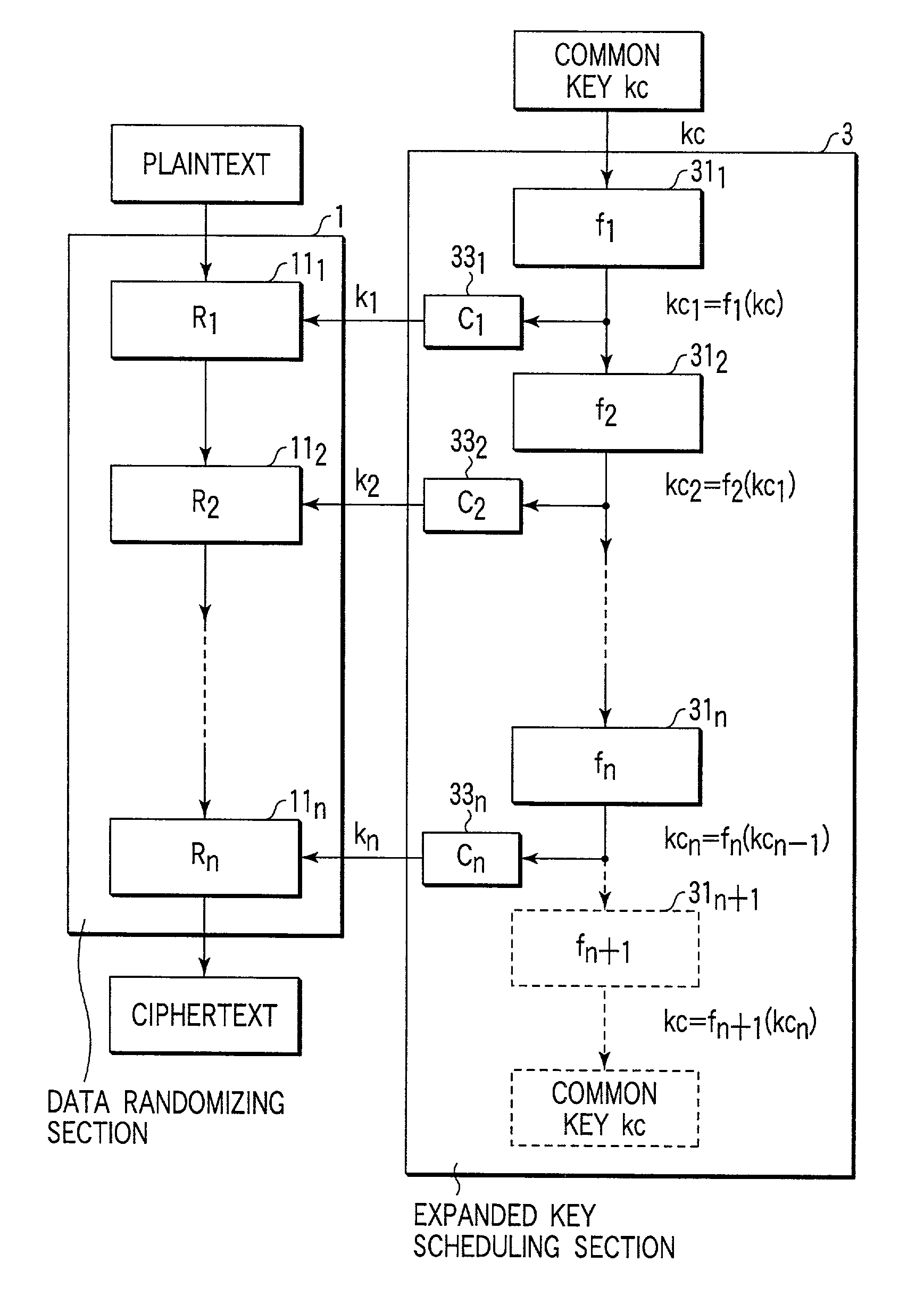
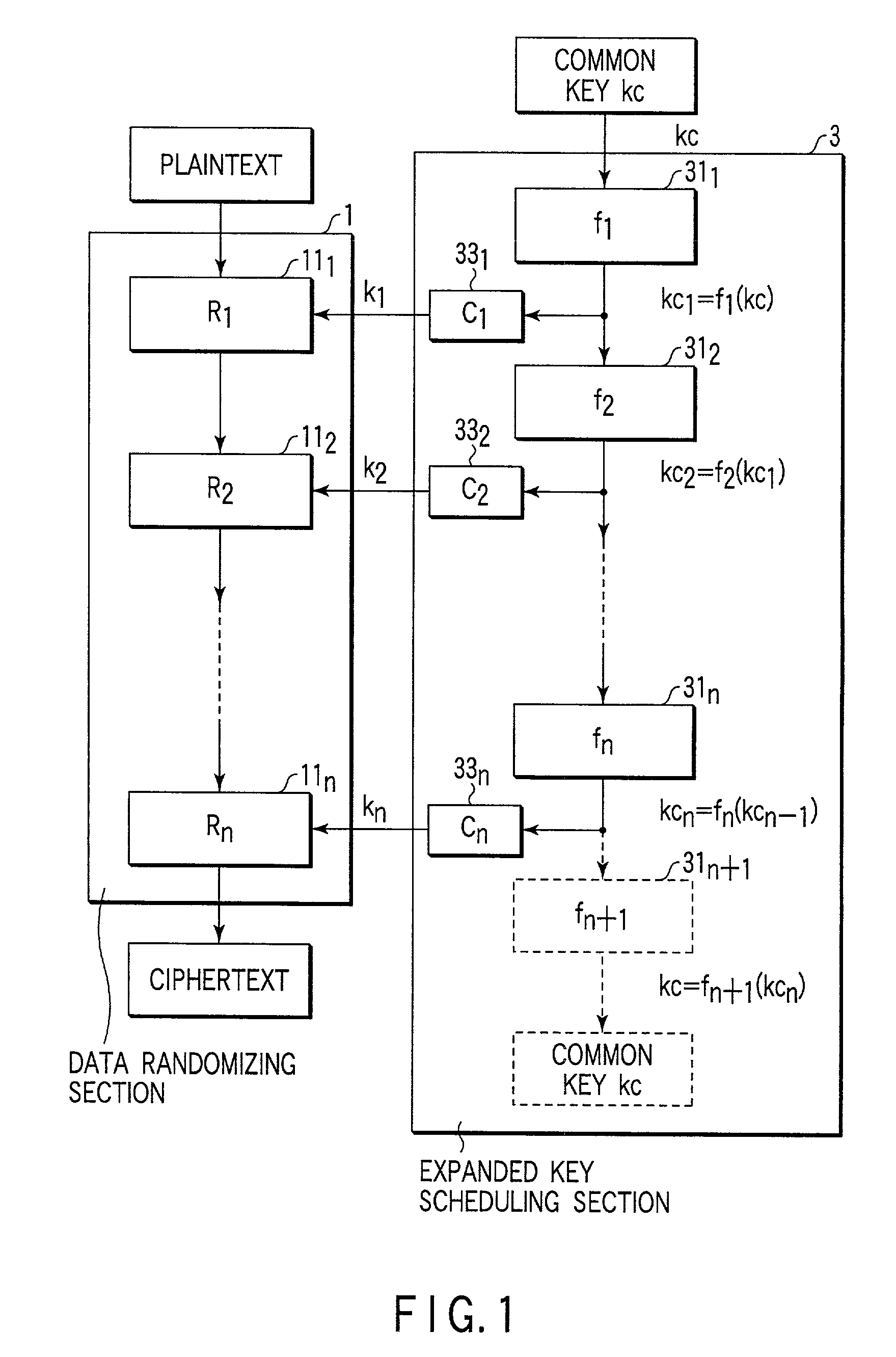
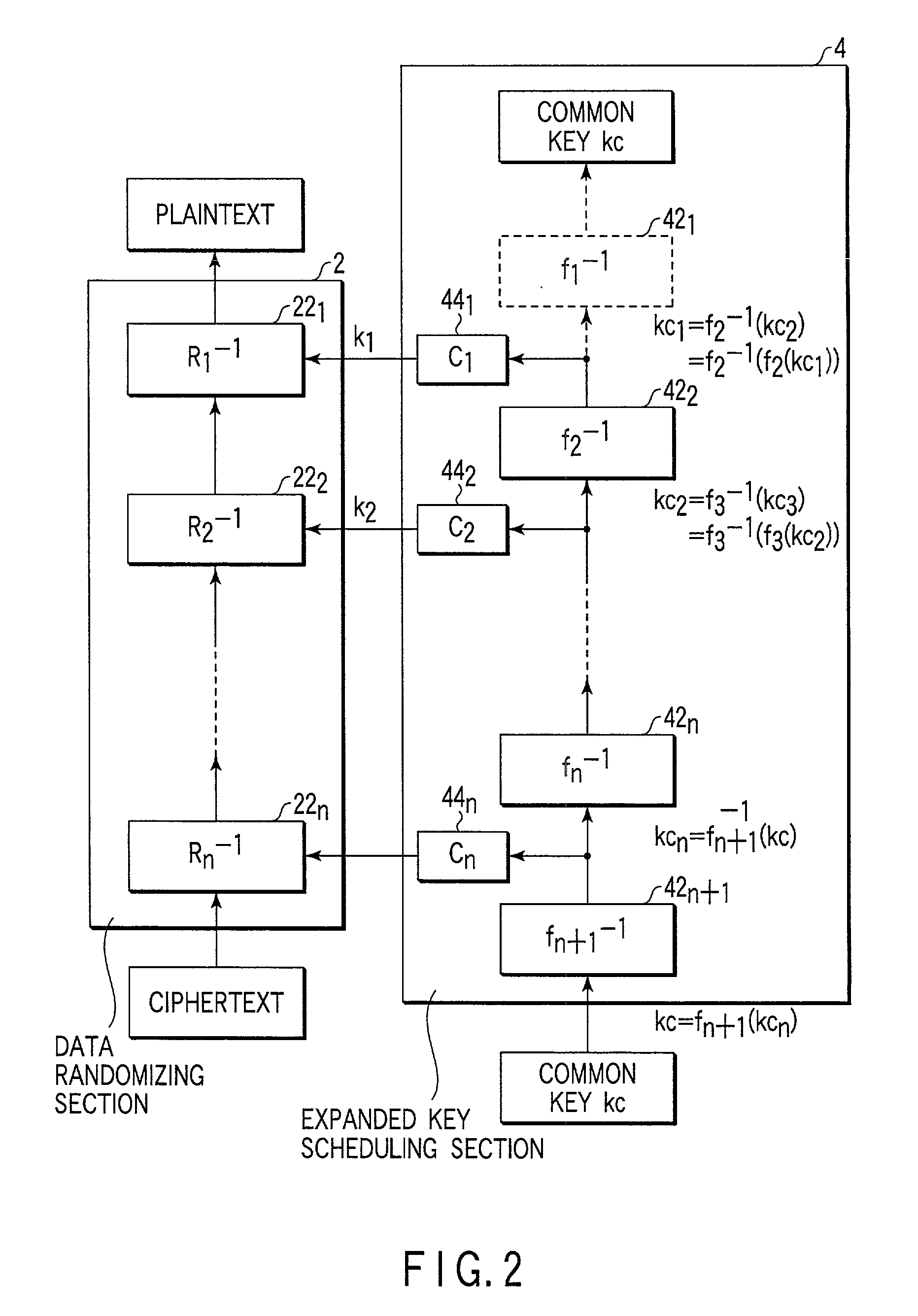
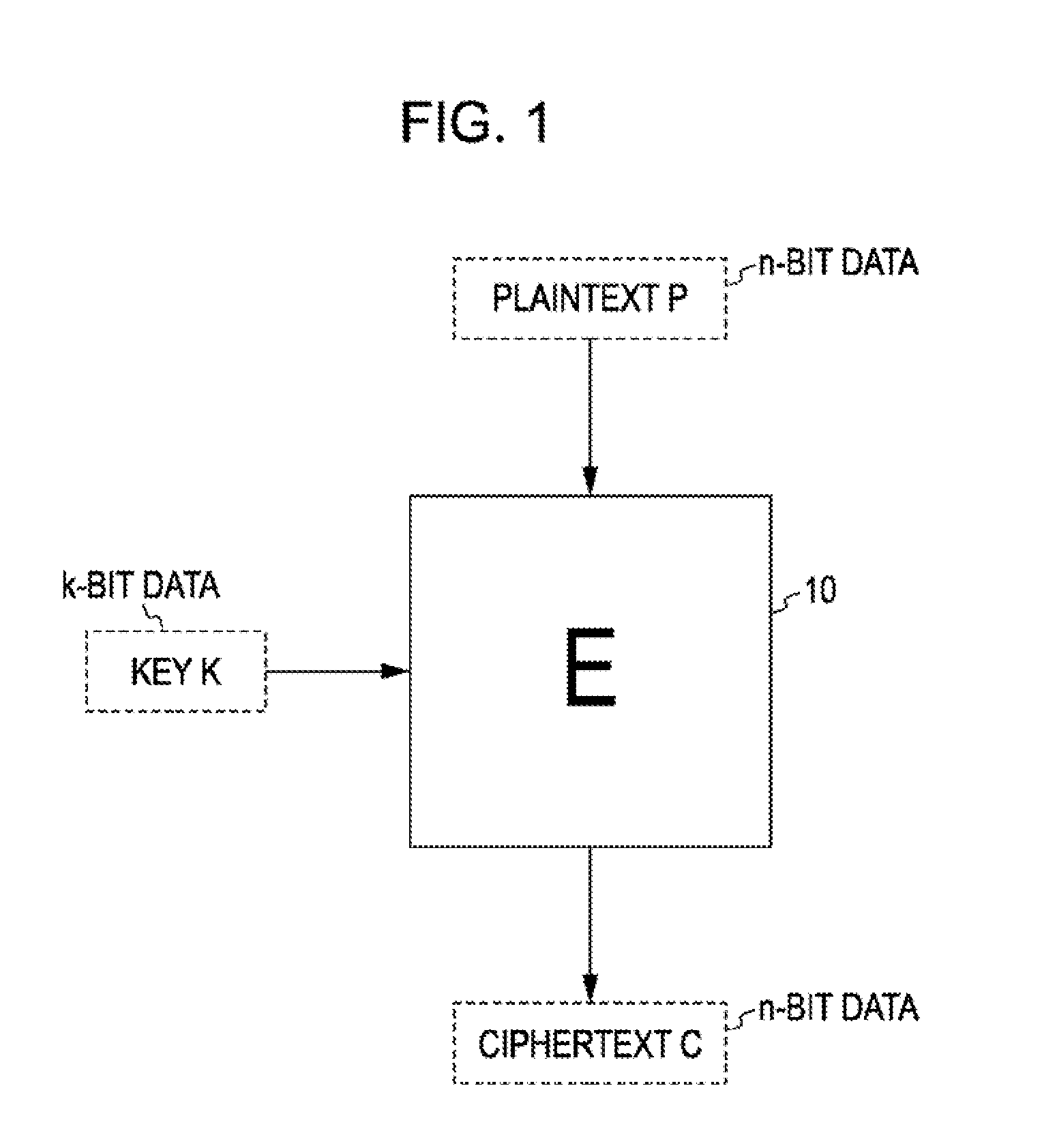
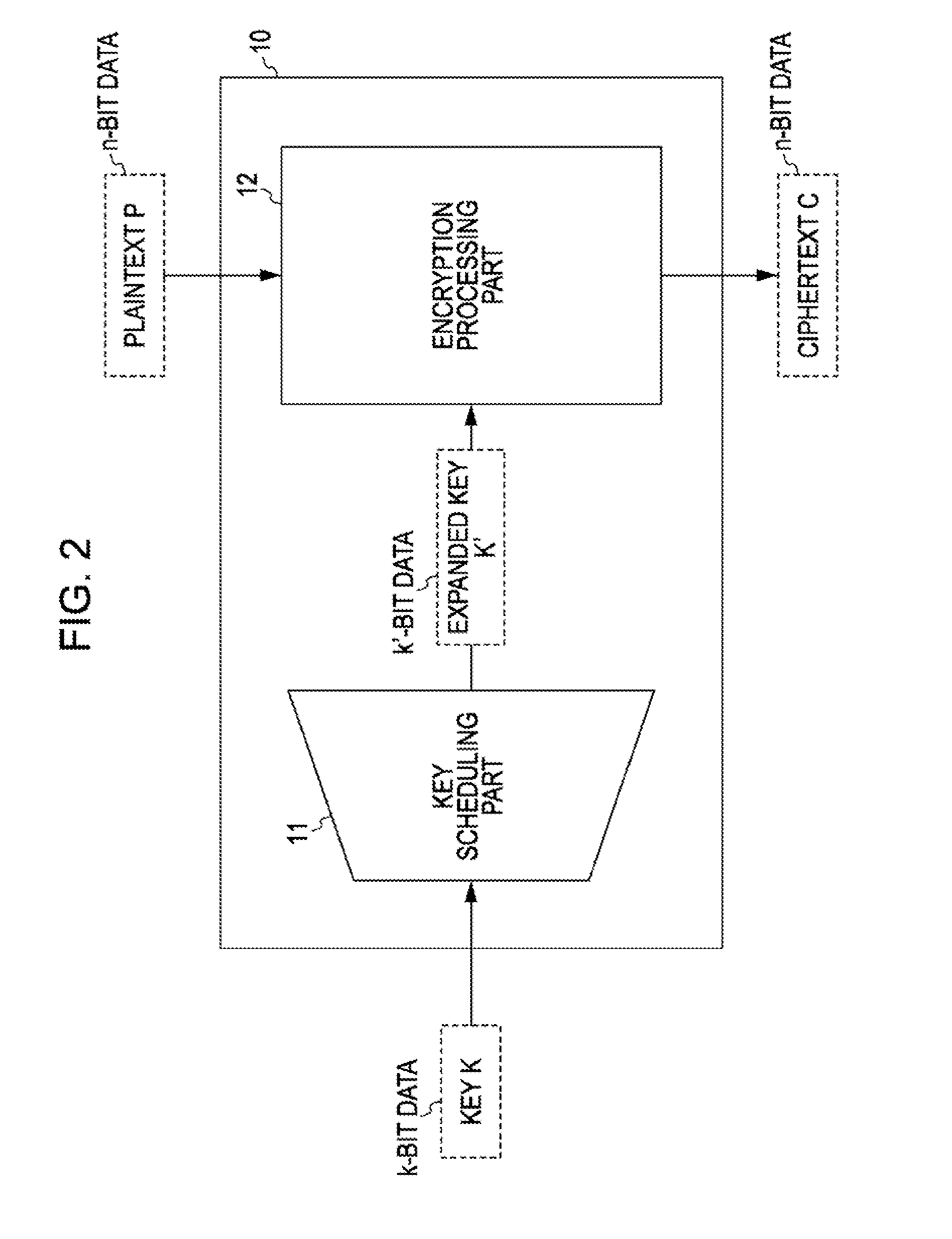
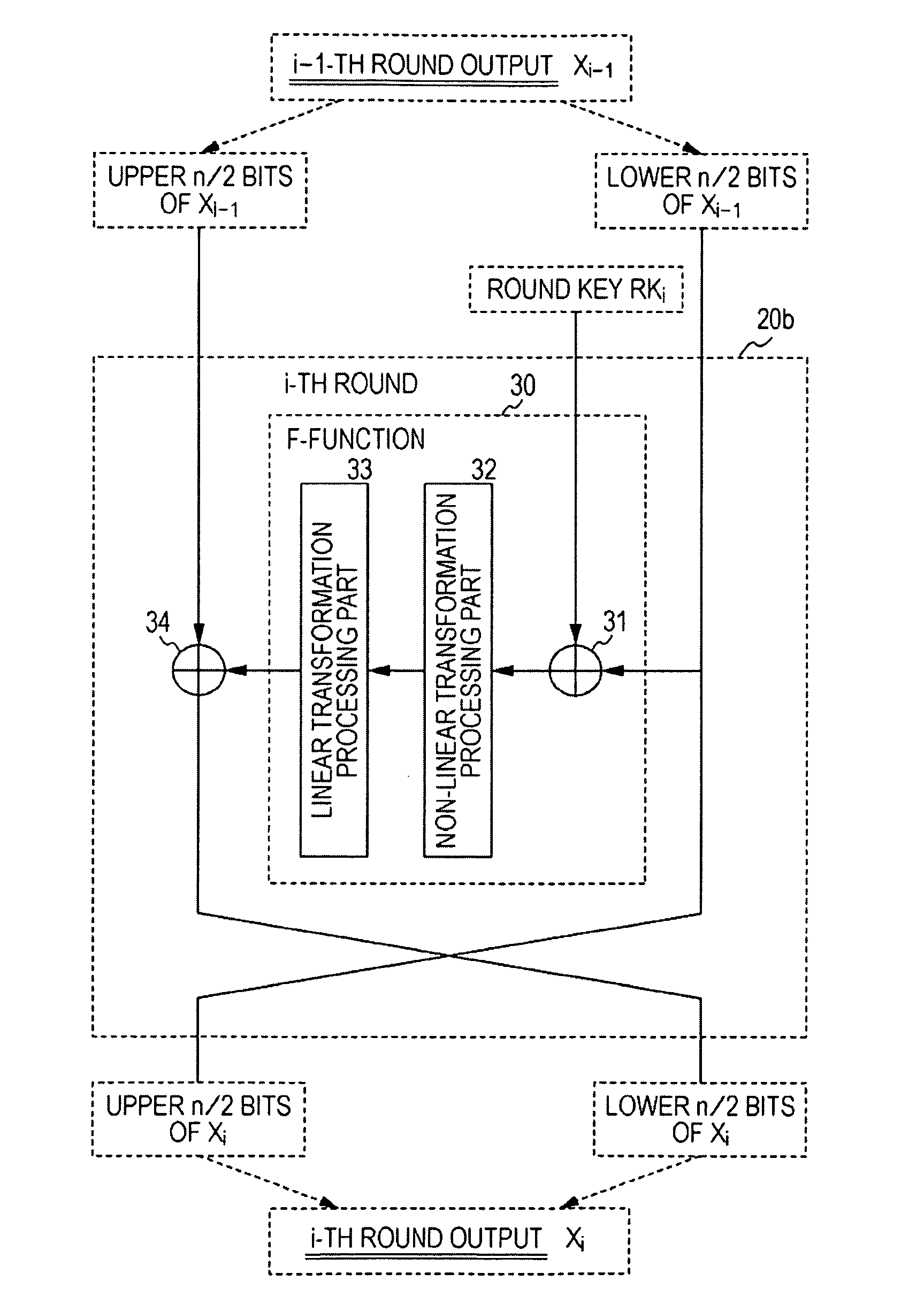
Encryption apparatus, decryption apparatus, expanded key generating apparatus and method therefor, and recording medium
InactiveUS7194090B2Avoids and reduces delay timeEncryption apparatus with shift registers/memoriesSecret communicationComputer hardwareKey schedule
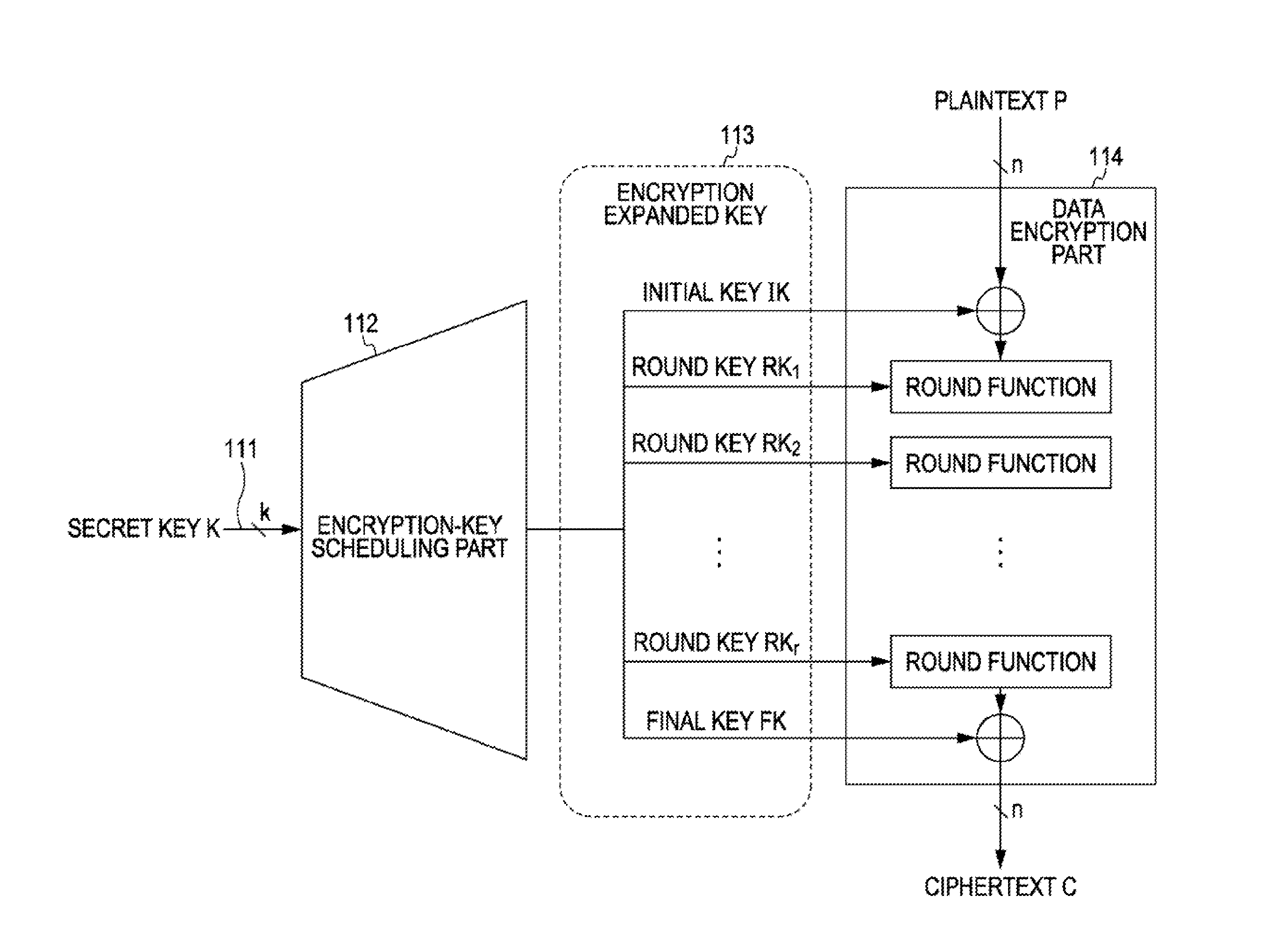
Expanded key schedule circuit for common key encryption system in which expanded keys are used in a predetermined order in data randomizing process for encryption and in a reversed order in data randomizing process for decryption, comprises round processing circuits connected in series. The round processing circuits subject the common key or sub key of a previous stage to a round function to output a sub key. The sub key of the last stage is equal to the common key. The expanded keys are generated from the sub keys.
Owner:KK TOSHIBA
Application method of Hamming distance model on SM4 cryptographic algorithm lateral information channel energy analysis and based on S box input
ActiveCN103138917AExtended Side Channel Energy Analysis MethodEfficient analysisEncryption apparatus with shift registers/memoriesPower analysisS-box
The invention discloses an application method of a Hamming distance model on SM4 cryptographic algorithm lateral information channel energy analysis and based on S box input. The application method is characterized in that the Hamming distance model is established by selecting an S box or a round function as an attacking point in the process that the SM4 cryptographic algorithm lateral information channel energy analysis is carried out, the input of the S box is used as an initial state v1 of the Hamming distance model, the output of the S box is used as subsequent state v2 of the Hamming distance (HD (v1, v2)) model when the S box is attacked, and the output / input of the round function is used as the subsequent state v2 of the Hamming distance (HD (v1, v2)) model when the round function is attacked. The method can be applied to CPA / DPA lateral information channel energy analysis of the SM4 cryptographic algorithm. Correlation between a correct guess secret key and energy information is improved, and validity and success rate of the analysis are enhanced.
Owner:国家密码管理局商用密码检测中心
Application of selecting round key XOR input to perform side-channel power analysis of SM4 cryptographic algorithm
ActiveCN103227717AExtended Side Channel Energy Analysis MethodEfficient analysisEncryption apparatus with shift registers/memoriesComputer hardwareChannel power
The invention discloses an application of selecting round key XOR input to perform side-channel power analysis of an SM4 cryptographic algorithm. The application is characterized in that in the process of the side-channel power analysis of the SM4 cryptographic algorithm, S boxes or round functions are selected to serve as attack points to establish a Hamming distance (HD) model, the round key XOR input is taken as a preceding state v1 of the HD model, and when the S boxes are attacked, the subsequent state v2 of the HD (v1, v2) model is S box output; and when the round functions are attacked, the subsequent state v2 of the HD (v1, v2) model is output / input of the round functions. The method can be applied to the side-channel power analysis of a CPA (correlation power analysis) and DPA (differential power analysis) of the SM4 cryptographic algorithm. With the adoption of the method, the correlation between a right guessing secret key and a power message is improved, the effectiveness of the analysis is enhanced, and the success rate is increased.
Owner:国家密码管理局商用密码检测中心
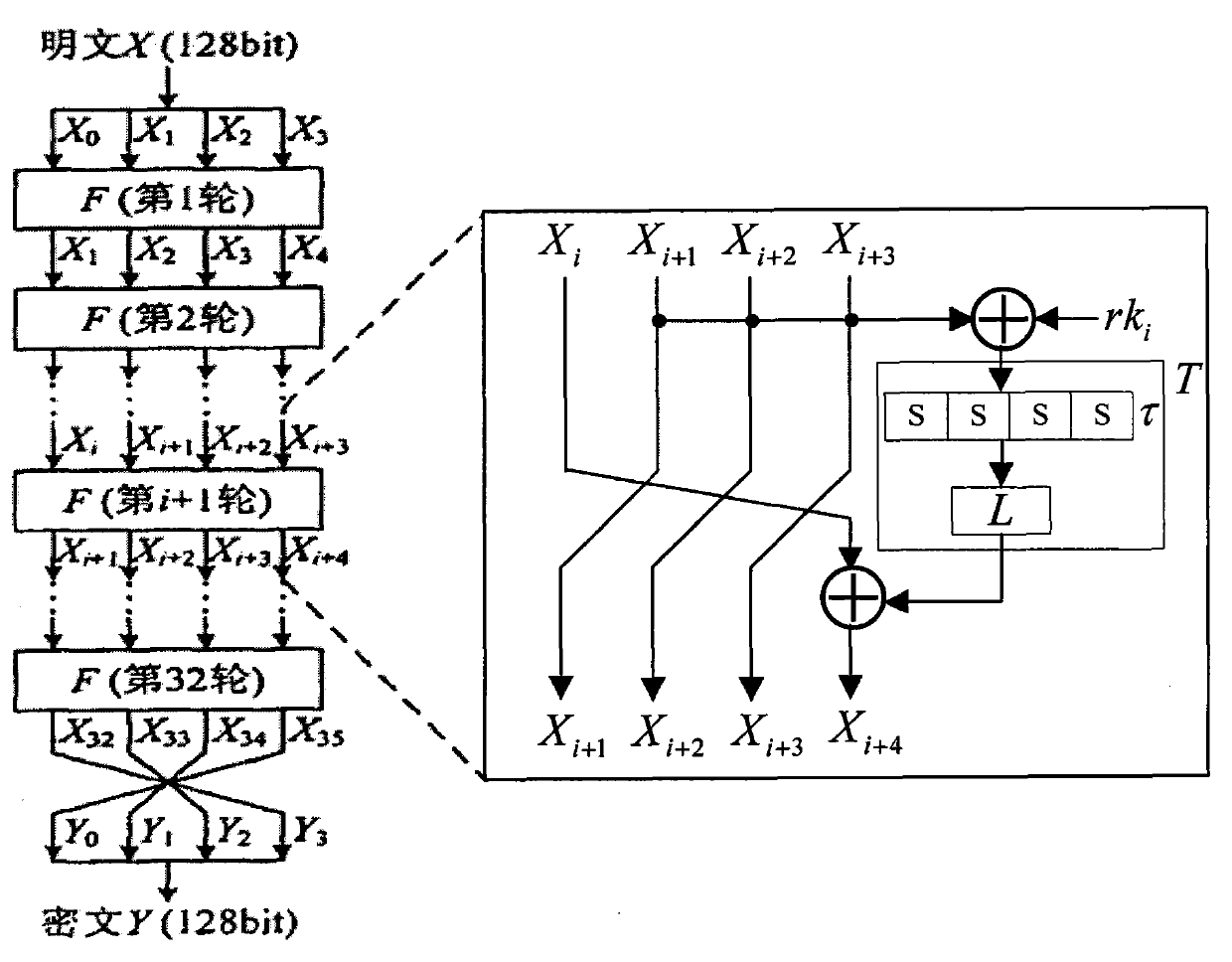
Plaintext or ciphertext selection based side channel power analysis attack method on round function output of SM4 cipher algorithm
InactiveCN104202145APractical applicabilityIncrease flexibilityEncryption apparatus with shift registers/memoriesComputer hardwarePlaintext
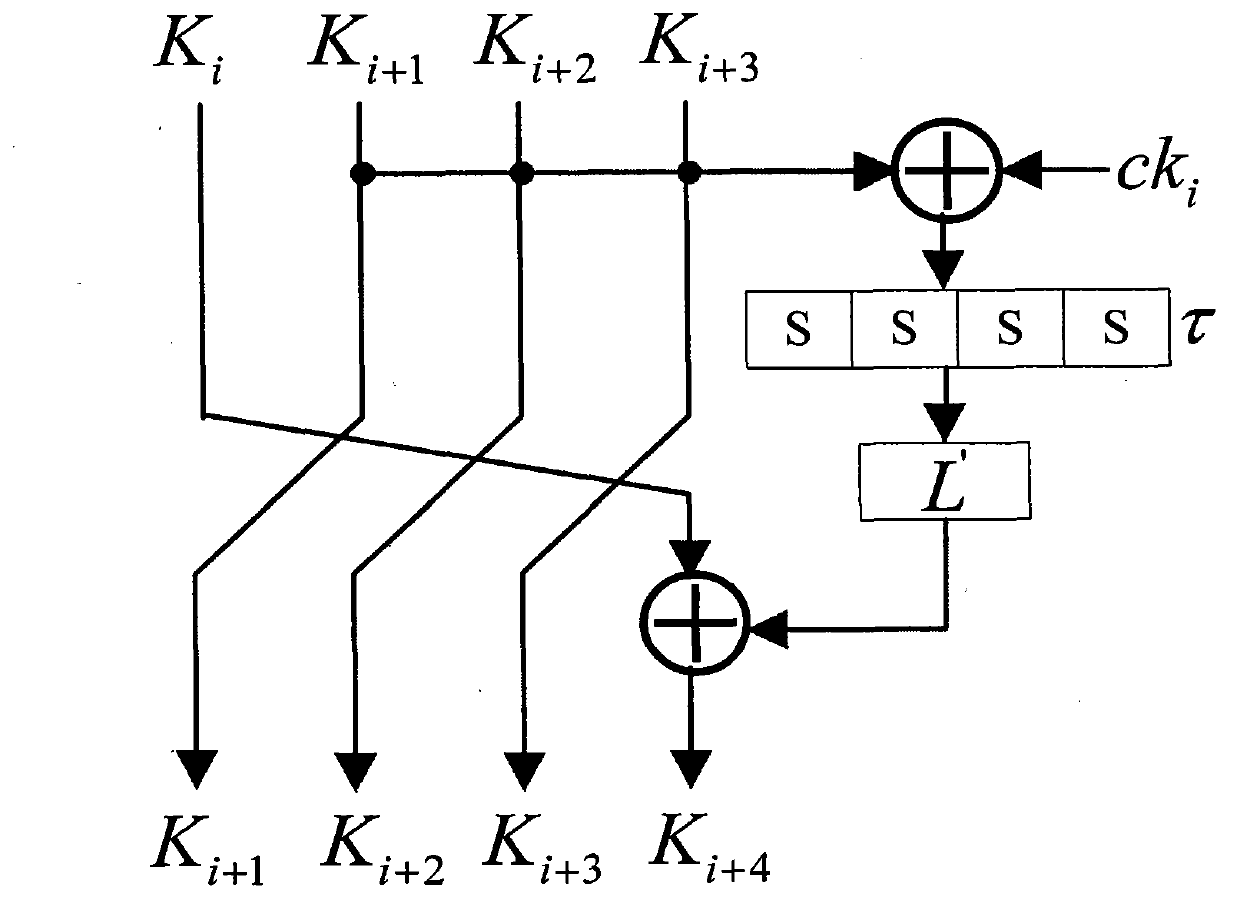
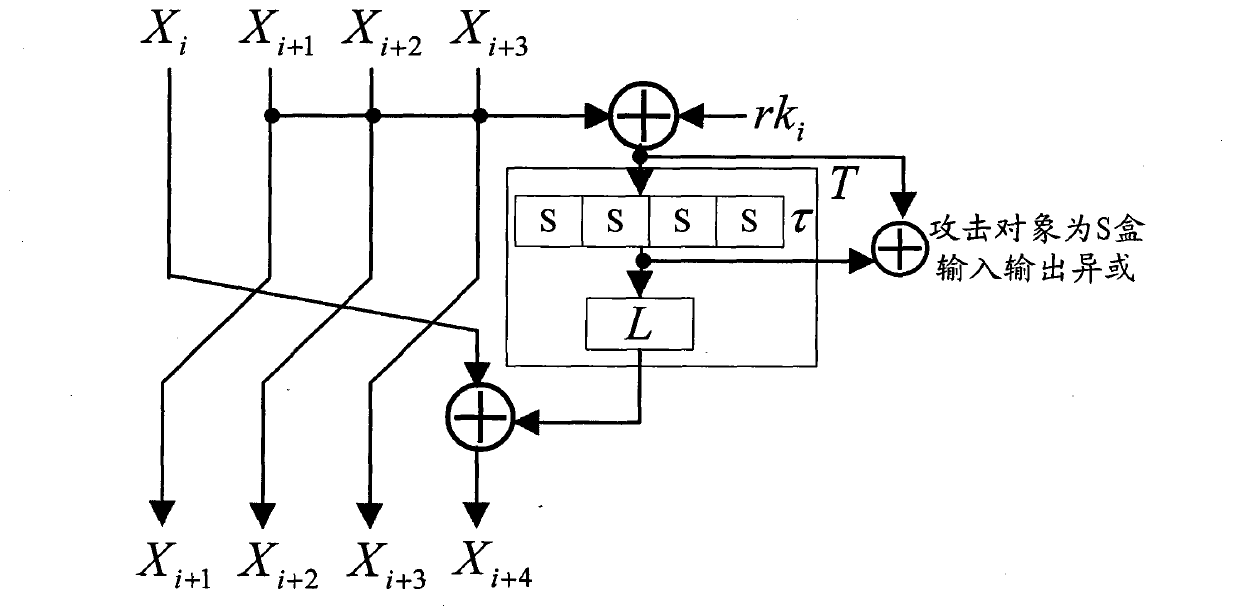
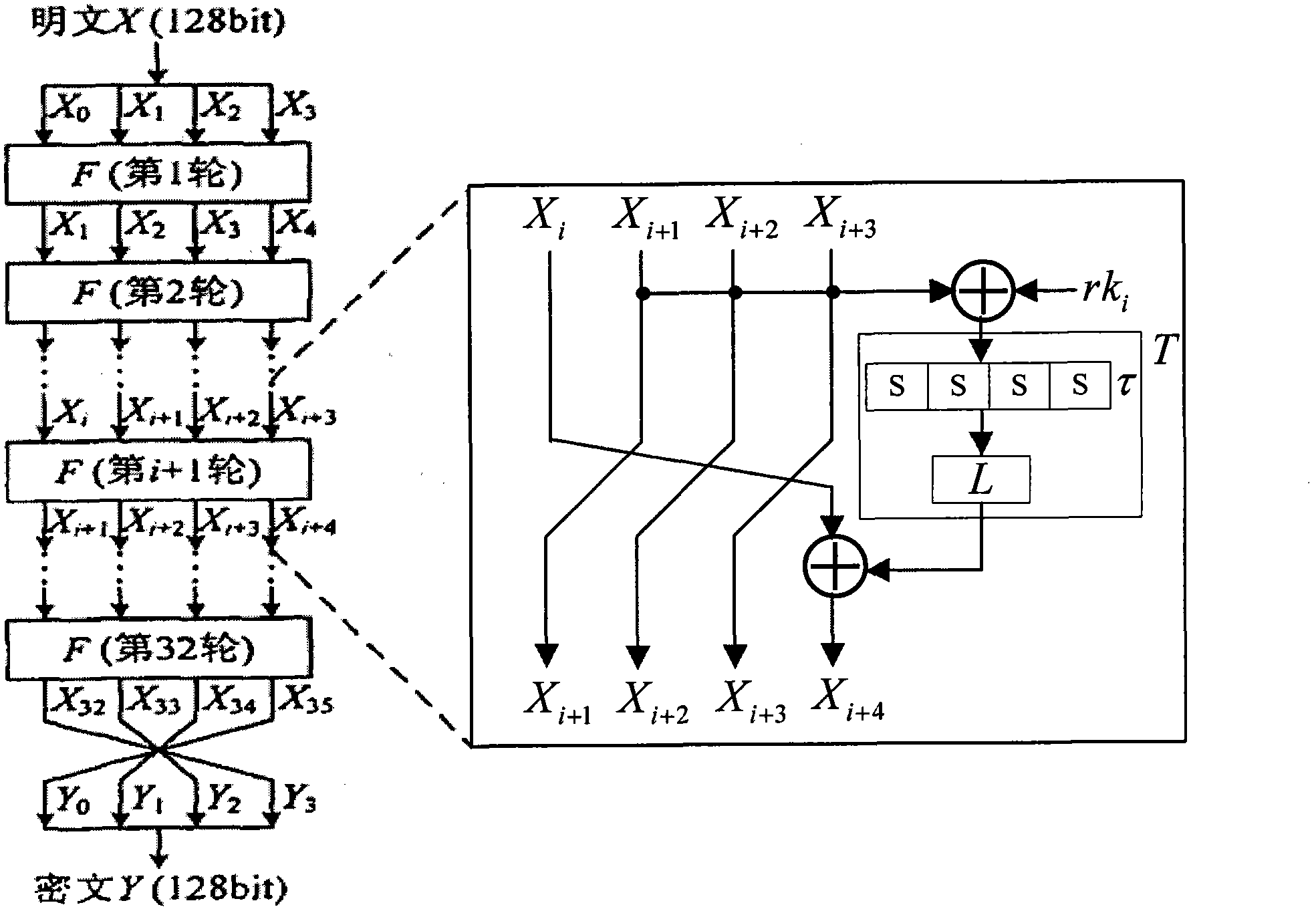
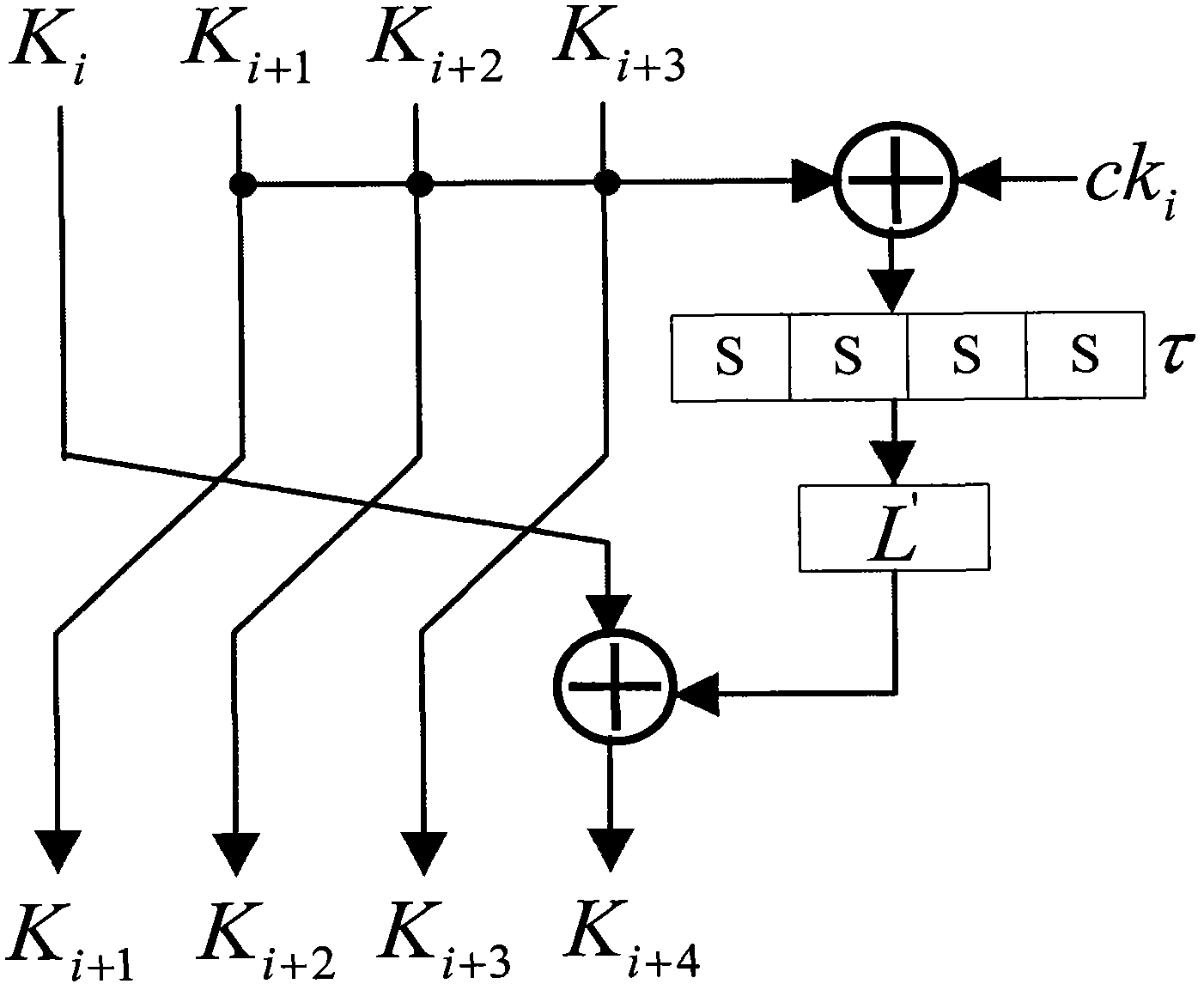
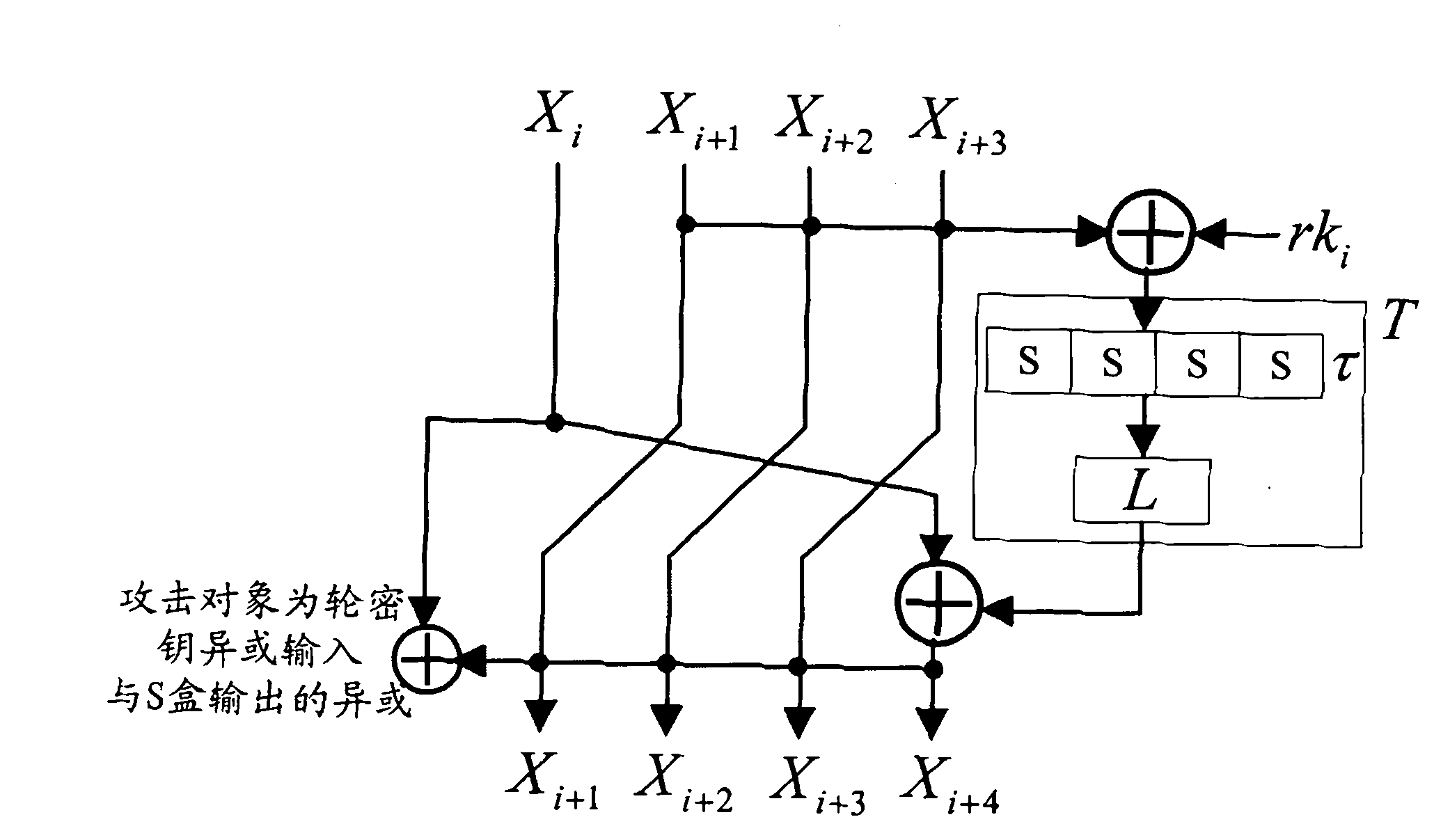
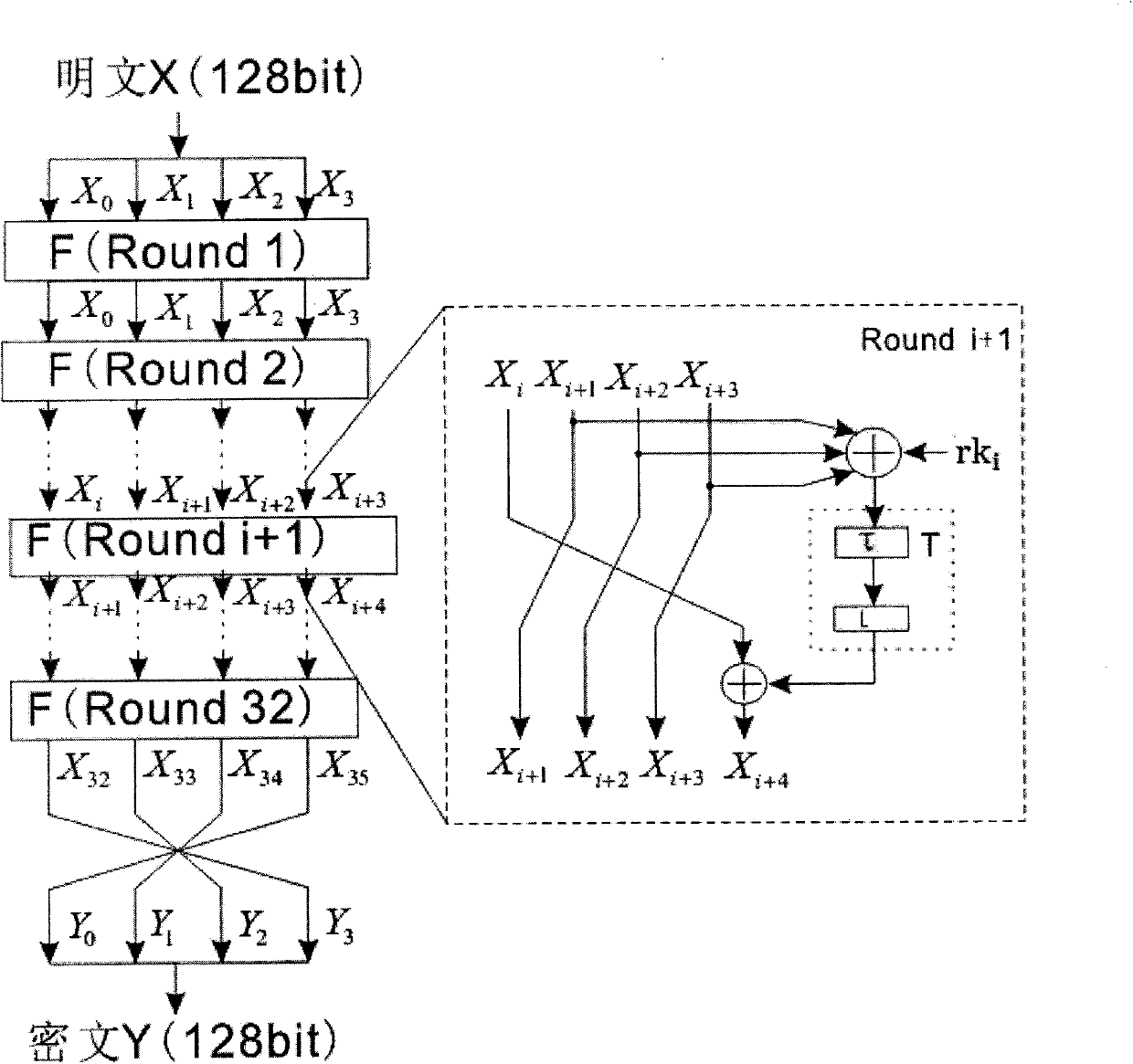
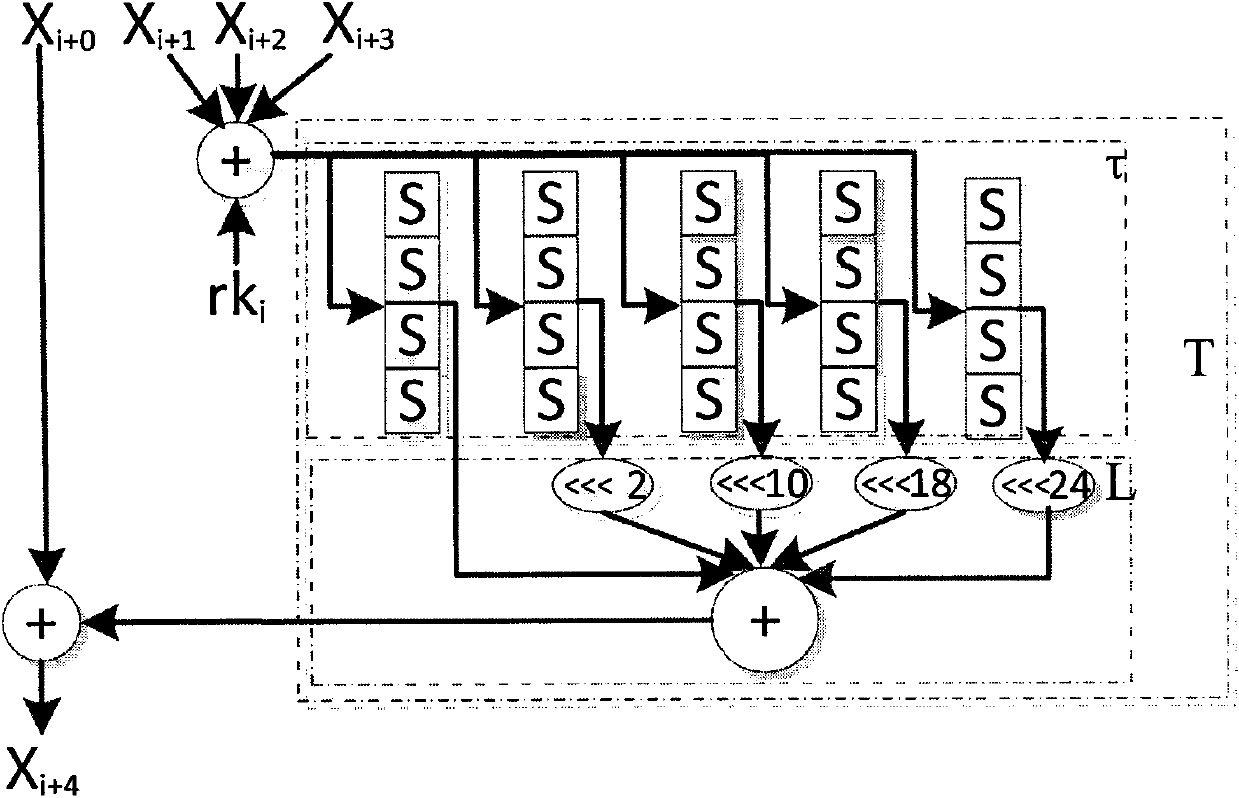
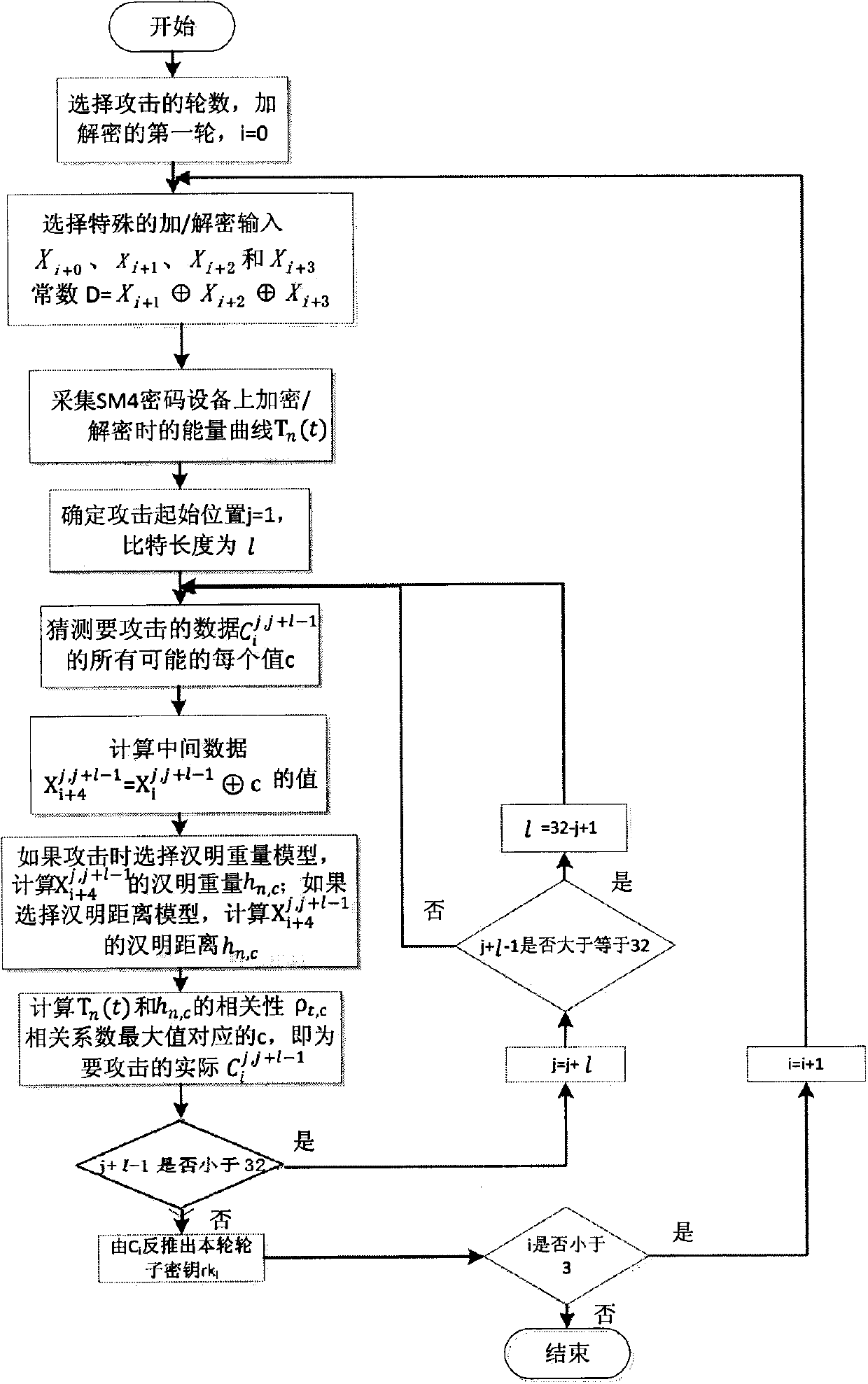
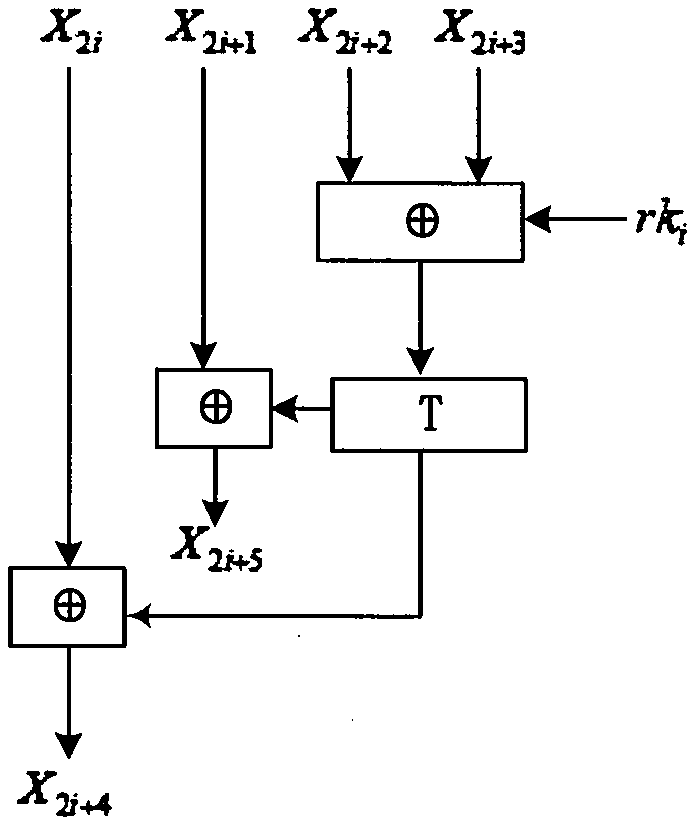
The invention discloses a plaintext or ciphertext selection based side channel power analysis attack method on round function output of the SM4 cipher algorithm. The method includes the steps of S1, selecting plaintext or ciphertext to input X<i+0>, X<i+1>, X<i+2> and X<i+3> on the condition of allowing the exclusive OR result of the X<i+1>, X<i+2> and X<i+3> to be a constant value and guaranteeing randomness of the X<i+0>, utilizing side channel power attack processes to attack the output C of linear transform L of each round of the first four round functions, and deducing inversely to acquire the round key rk of the first four round functions in encryption or decryption according to the output C; S2, according to the round keys rk<0>, rk<1>, rk<2> and rk<3> of the first four found functions, inversely calculating the initial key by a key expansion algorithm. The method can realize power analysis attack by means of multiple attacks and can attack with selection of proper-length bits according to actual computing capacity, thus flexibility, effectiveness and success rate of analysis are improved.
Owner:CHENGDU UNIV OF INFORMATION TECH +2
Encryption processing apparatus, encryption method, and computer program
ActiveUS20100008498A1Unauthorized memory use protectionRecord information storageComputer hardwareExclusive or
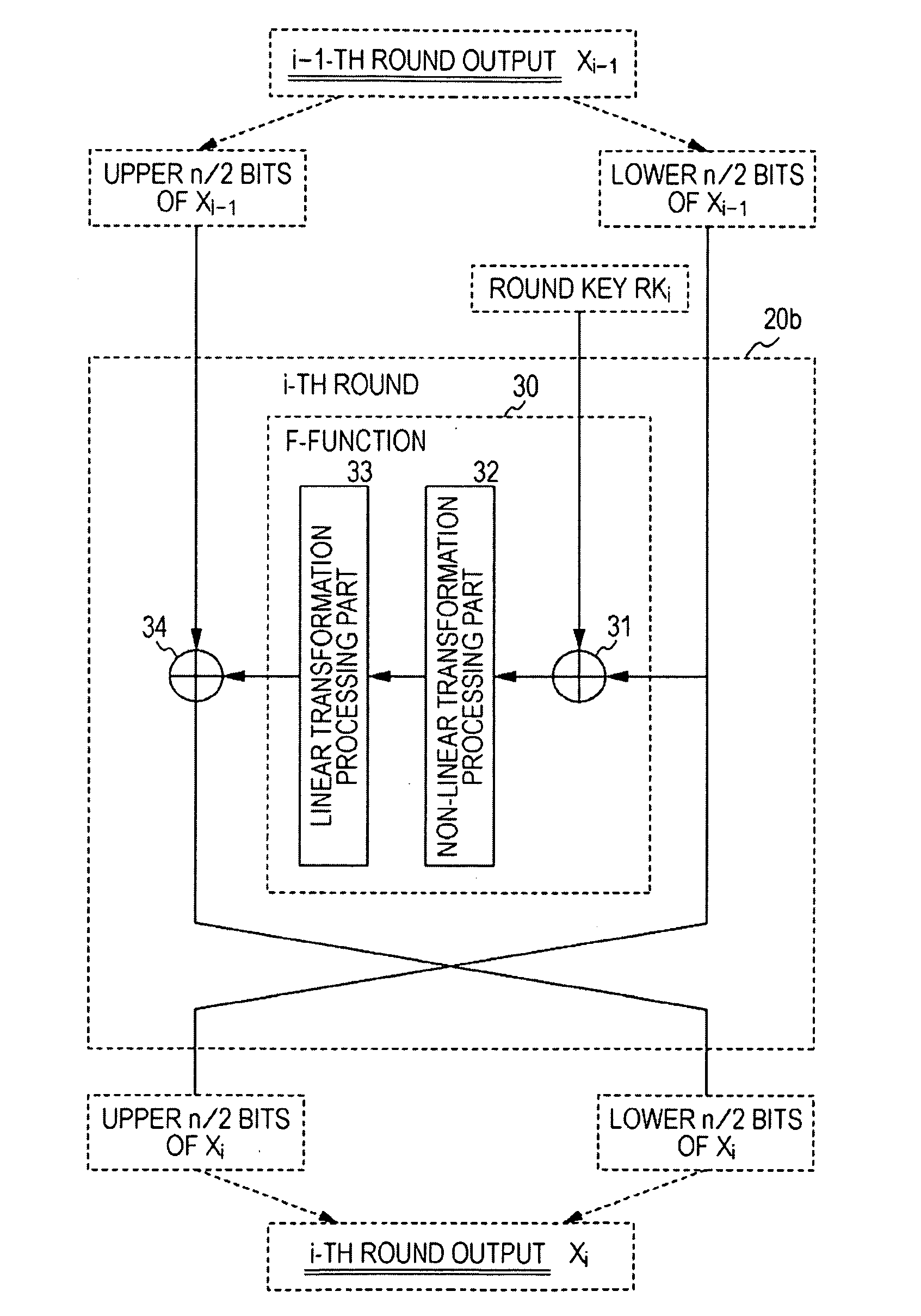
A common-key blockcipher processing structure that makes analysis of key more difficult and enhances security and implementation efficiency is realized. In a key scheduling part in an encryption processing apparatus that performs common-key blockcipher processing, a secret key is input to an encryption function including a round function employed in an encryption processing part to generate an intermediate key, and the result of performing bijective transformation based on the intermediate key, the secret key, and the like and the result of performing an exclusive-OR operation on the bijective-transformed data are applied to round keys. With this structure, generation of round keys based on the intermediate key generated using the encryption function whose security has been ensured is performed, thereby making it possible to make analysis of the keys more difficult. The structure of the key scheduling part can be simplified, thereby making it possible to improve the implementation efficiency.
Owner:SONY CORP
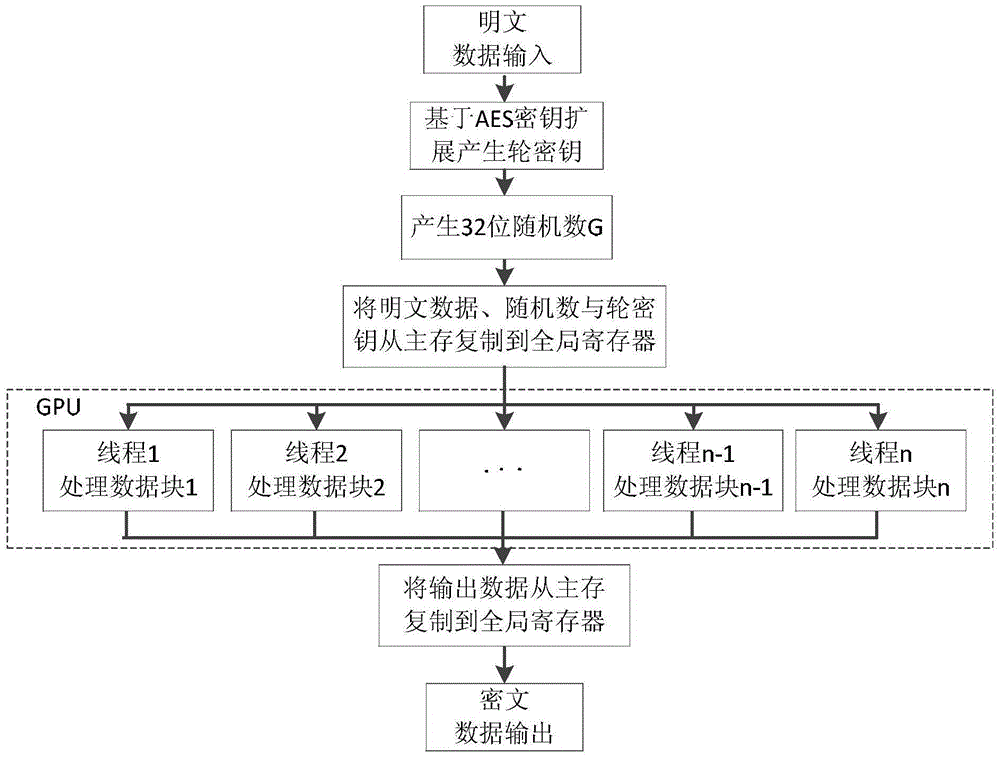
Improved SM4 parallel encryption and decryption communication method based on GPU (Graphics Processing Unit)
ActiveCN105490802AFast implementationImprove securityEncryption apparatus with shift registers/memoriesComputer hardwareData stream
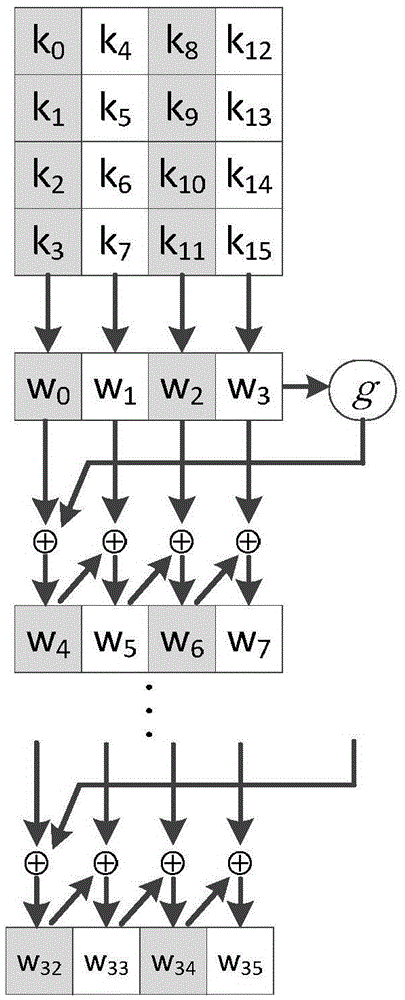
The invention discloses an improved SM4 parallel encryption and decryption communication method based on a GPU (Graphics Processing Unit). The encryption and decryption method comprises the following steps: using an AES (Advanced Encryption Standard)-128 key expansion algorithm to generate an expanded subkey needed by an SM4 encryption algorithm; improving a round function in the SM4 encryption algorithm; and using the parallel computing power of the GPU, improving the SM4 encryption algorithm into a form of parallel encryption. By adopting the encryption and decryption communication method of the invention, the security and the speed of implementation can be effectively improved, real-time and parallel encryption can be performed on data, and the encryption speed can be improved, so that normal transmission of data flow can be guaranteed and the processing delay can be reduced.
Owner:桂林蓝港科技有限公司
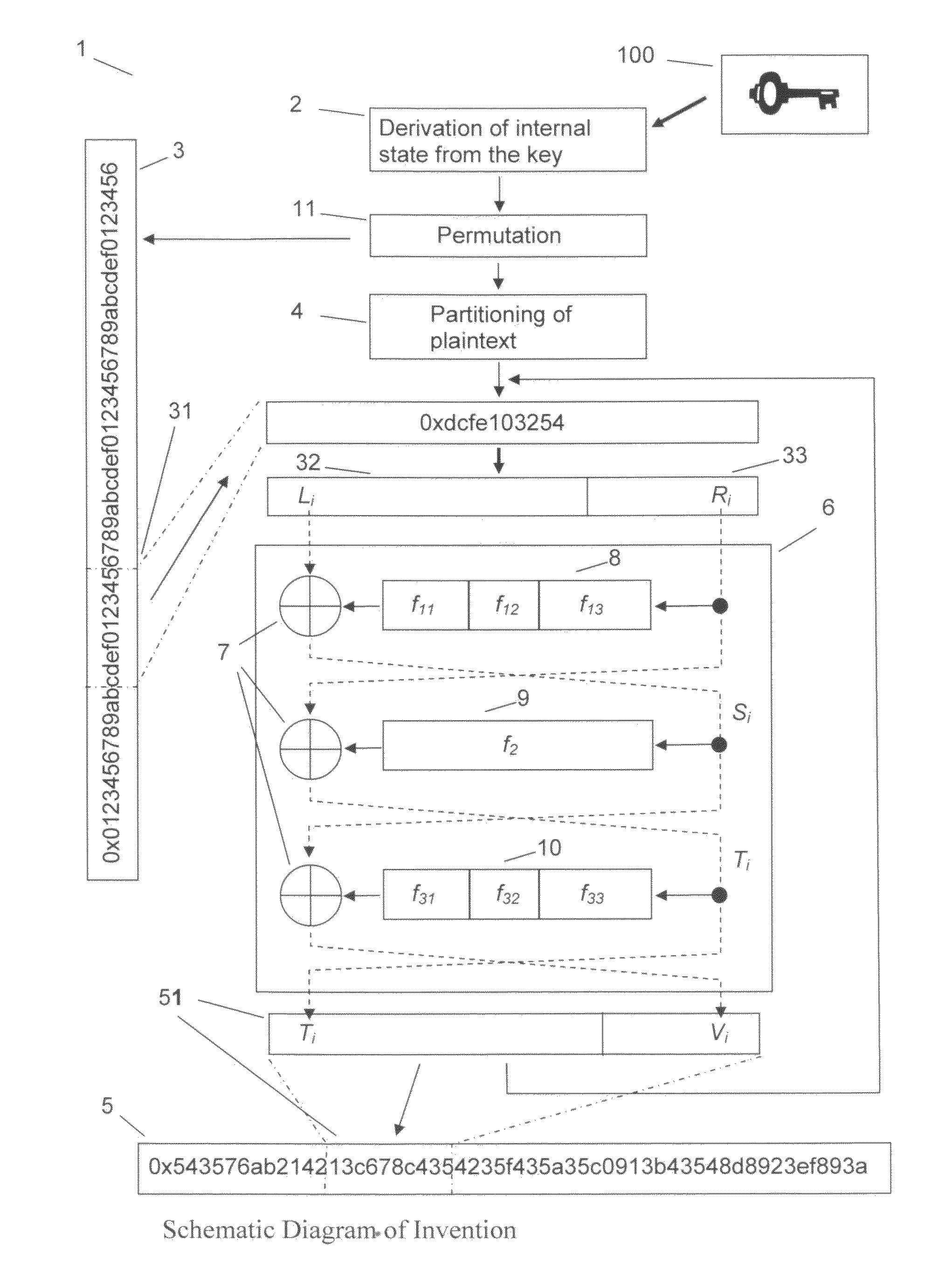
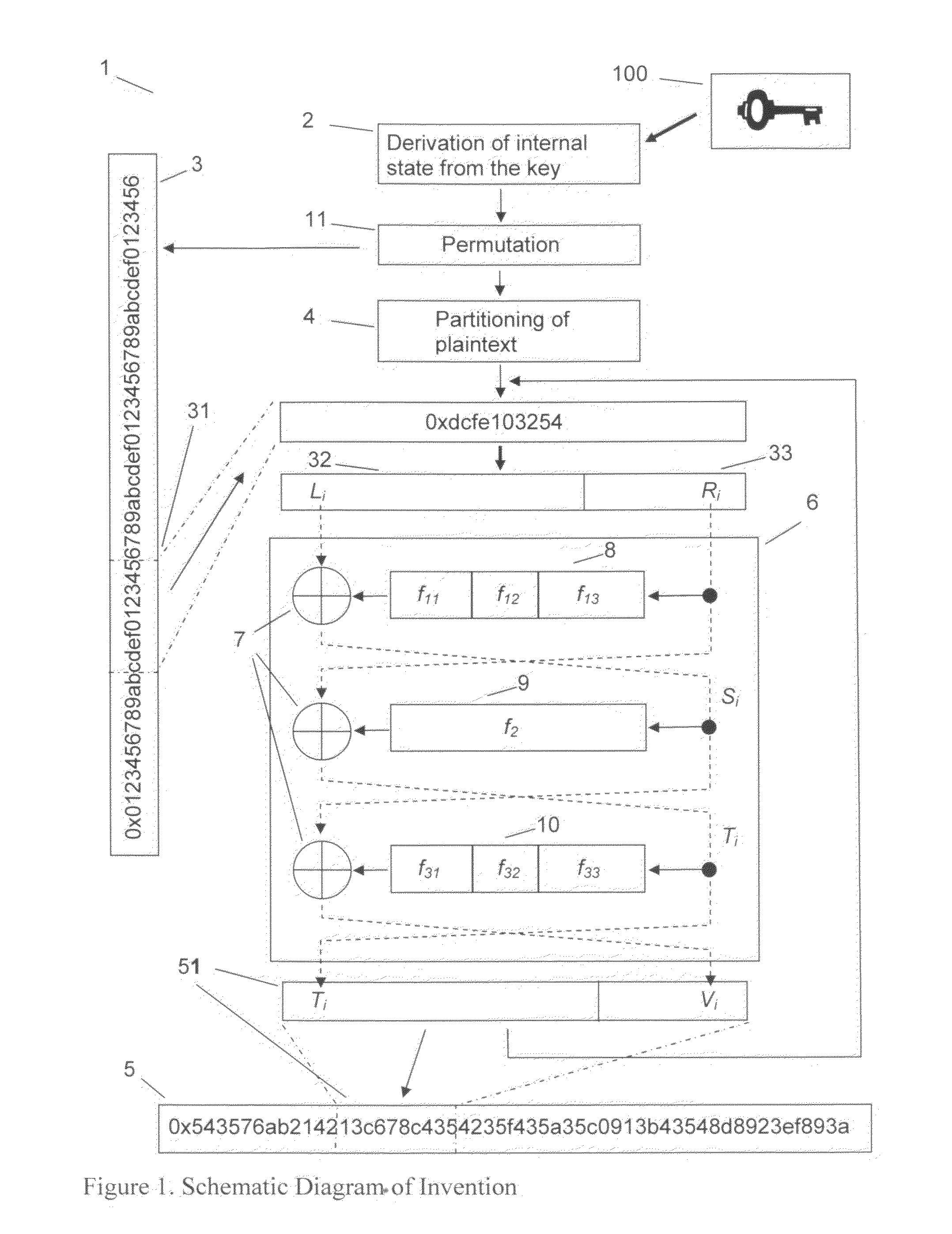
Block cipher
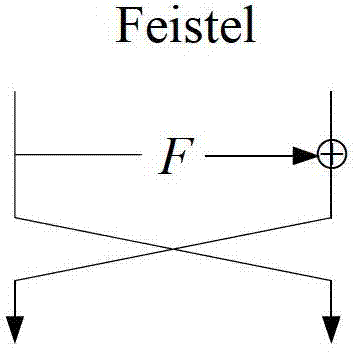
The method provided is for the encryption of data block by block, but unlike conventional methods like DES or AES, with a variable and substantially greater block length. The enciphering operations depend not only on the key, but also on the length of the plaintext blocks. The method meets the Strict Avalanche Criterion much better than conventional ciphers and blocks do not need to be padded. The method that additionally partitions outsized blocks executes the following steps:Derivation of the internal state of the method from the key, pseudorandom permutation of plaintext bits or groups of plaintext bits, partitioning of outsized plaintext data blocks, execution of at least three unbalanced Feistel network rounds with round functions having the ability to output results with variable length and bit-by-bit exclusive-or combination with output of round functions within the Feistel rounds.
Owner:ROLLGEN CLEMENS KARL BERHARD
Method and system for a symmetric block cipher using a plurality of symmetric algorithms
InactiveUS20110069834A1Increase the difficultyImprovement effortsMultiple keys/algorithms usageSecret communicationKey sizeComputer hardware
A method and system for hybrid encryption wherein all of the round function variables including the encryption algorithm change for each round. This permits the generation of block sizes and key sizes of any length and use standard block sizes and key sizes for the respective symmetric algorithm for each round function.
Owner:URBANIK JERZY HENRYK +1
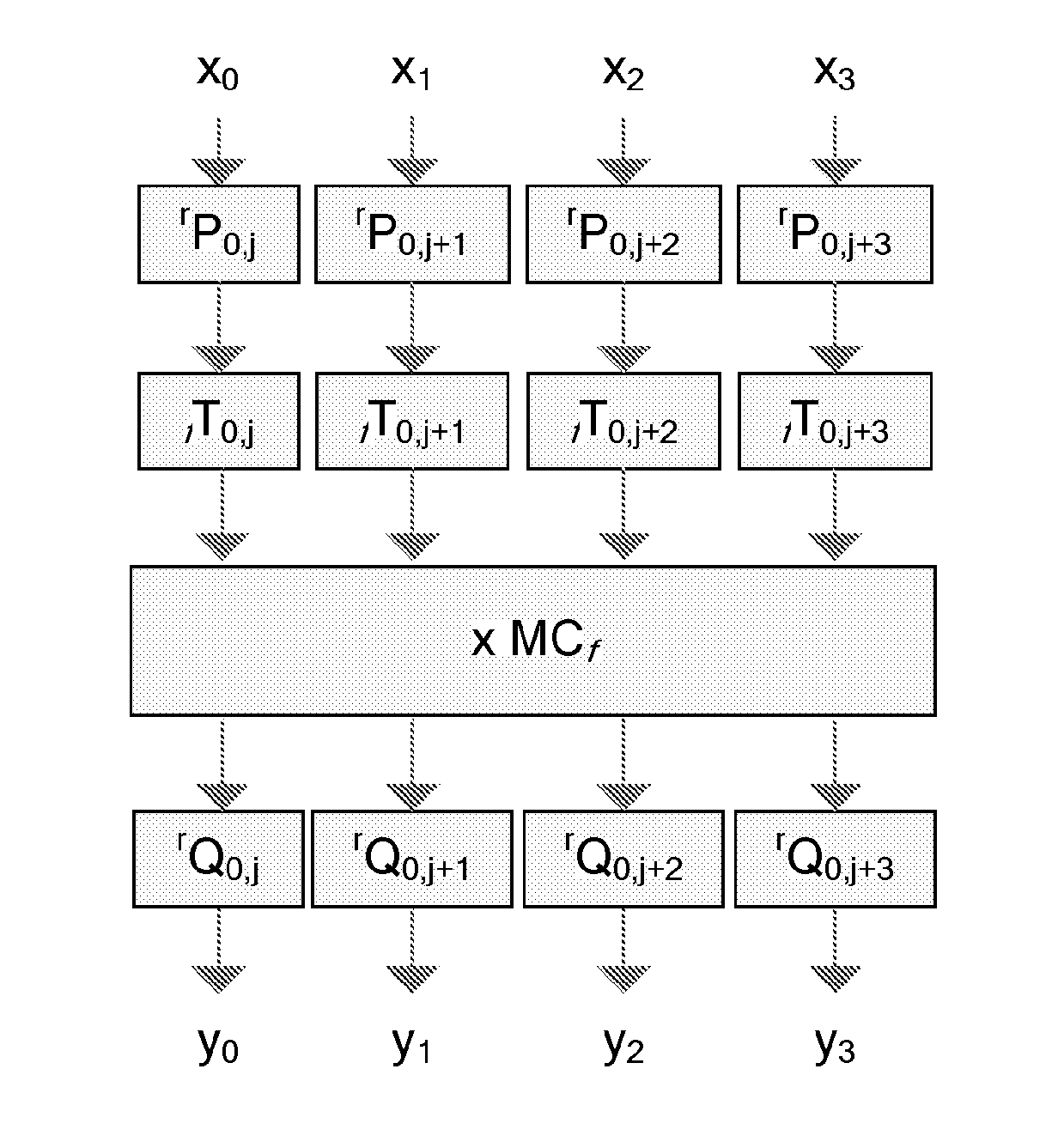
Encryption Processing Apparatus, Encryption Processing Method, and Computer Program
InactiveUS20080056490A1Great difficulty of key analysisGreat difficulty of cryptanalysisSecret communicationCryptographic attack countermeasuresRound functionData transformation
An encryption processing apparatus for performing common-key blockcipher processing, the encryption processing apparatus includes an encryption processing part that performs data transformation in which a round function is iterated for a plurality of rounds; and a key scheduling part that generates round keys used to execute the round function. The key scheduling part is configured to repeatedly apply an xs times multiplication over an extension field GF( 2m), generated by an m-th order irreducible polynomial f(x) defined over GF(2), to an m-bit intermediate key generated by transformation of a secret key to generate a plurality of different round intermediate keys serving as data for generating a plurality of different round keys.
Owner:SONY CORP
Method of diversification of a round function of an encryption algorithm
InactiveUS20120170739A1Secret communicationCryptographic attack countermeasuresComputer hardwareAdvanced Encryption Standard
A method of diversification of an iterative function of an encryption algorithm. During an iteration at least one parameter other than an encryption key and an input message is modified. It is particularly advantageous that the encryption algorithm is the Advanced Encryption Standard.
Owner:THOMSON LICENSING SA
Format-reserved encryption algorithm based on multi-segmented Feistel network
InactiveCN105959098ADoes not affect compatibilityEncryption apparatus with shift registers/memoriesPlaintextComputer hardware
A format-preserving encryption algorithm based on a multi-segmented Feistel network, the method includes the following steps: S According to its own format, it is divided into t part: S 1 ,S 2 ,…,S t . where set S i is of size n i . Set the number of rounds for the Feistel network r and the key used by the round function k , where the number of rounds r for the number of divisions t associated even numbers; for a given plaintext m , format it as: m=x 1 || x 2 || … || x t ,in: x 1 ∈ S 1 ,x 2 ∈ S 2 ,…,x t ∈ S t ;Will x 1 ,x 2 ,…,x n as t Segmentation of the Feistel network t input, or input as ;Execute r rounds of round operations, and the final output ciphertext is c=y 1 || y 2 || … || y t ,in: y 1 ∈ S 1 ,y 2 ∈ S 2 ,…,y t ∈ S t , the advantages of the present invention are: by segmenting the sensitive data and defining the value domains of different segments, using self-defined pseudo-random functions, modulus addition and modulus subtraction operations, and using Feistel network to perform even-numbered rounds of round operations to achieve Encryption that preserves the format can support numerical data encryption schemes that retain any given format. After encryption, the data and database will not be affected, which provides the possibility for the encryption protection of numerical personal identification information in existing database application systems.
Owner:东港股份有限公司 +1
Authenticated encryption device, authenticated encryption method, and program for authenticated encryption
ActiveUS20160173276A1Encryption apparatus with shift registers/memoriesUser identity/authority verificationPlaintextAlgorithm
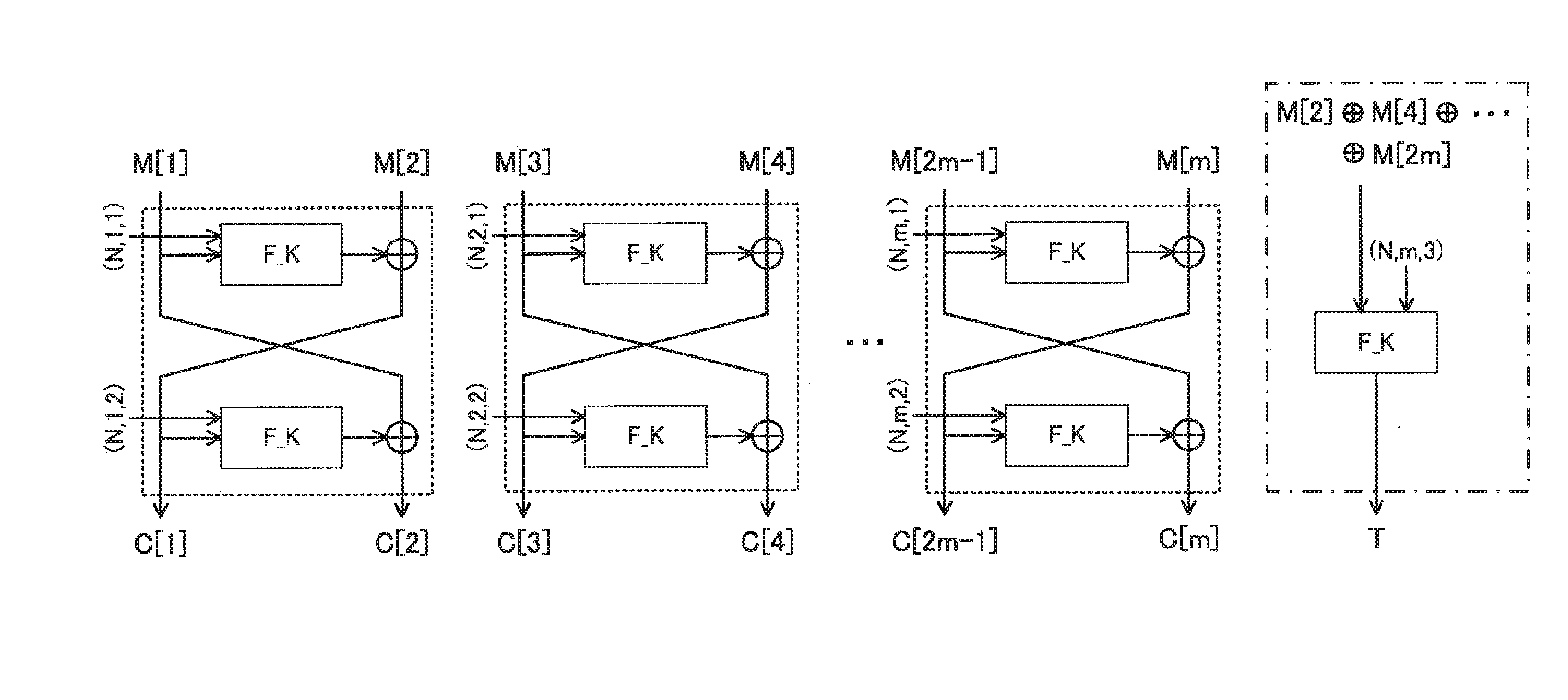
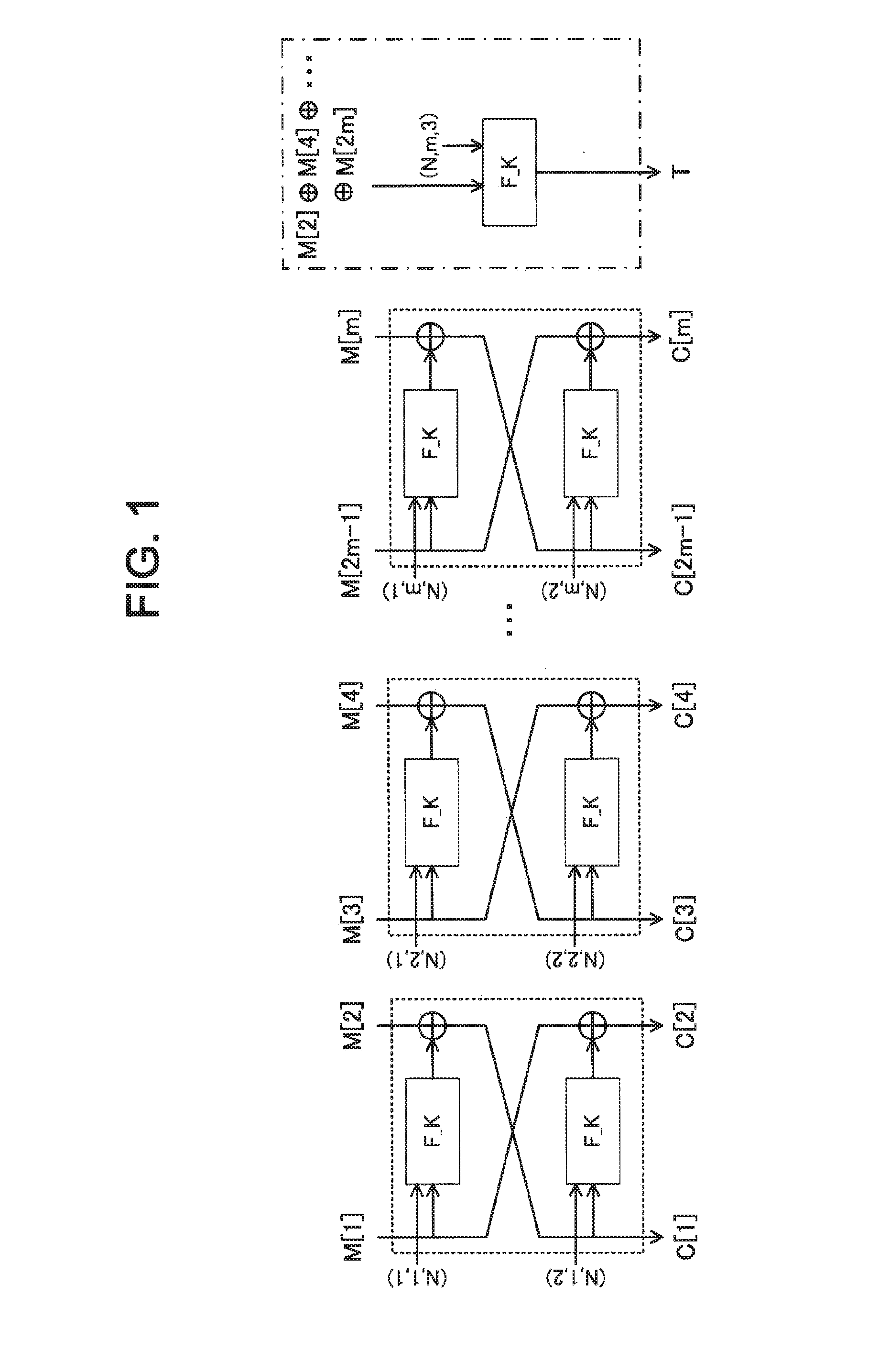
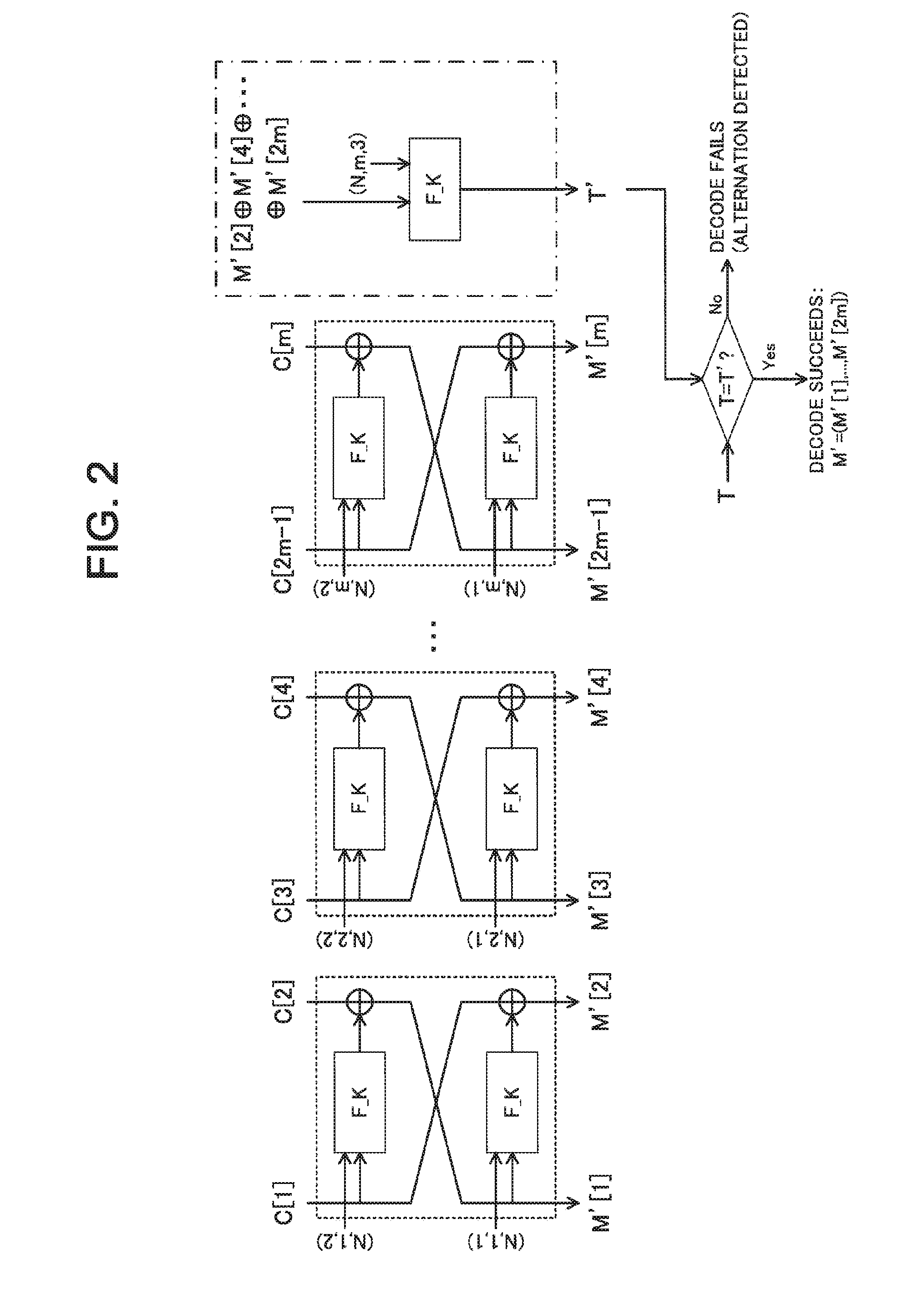
To achieve one-pass and one-rate authenticated encryption capable of performing parallel processings and totally performing encryption and decode processings by only one encryption function. An authenticated encryption device comprises an authenticated encryption means for applying a two-round Feistel structure using an encryption function assigned with an auxiliary variable for a round function per two blocks to an input plaintext or encrypted text thereby to generate an encrypted text or decoded plaintext. The authenticated encryption means finds an encrypted text chunk CC[i]=(C[i_1], C[i_2]) corresponding to an i-th plaintext chunk MC[i]=(M[i_1], M[i_2]) when dividing a plaintext into chunks per two blocks as:C[i_1]=F_K((N,Tw_i_1),M[i_1]) xor M[i_2],C[i_2]=F_K((N,Tw_i_2),C[i_1]) xor M[i_1].
Owner:NEC CORP
Cipher device adopting Feistel-PG structure and encryption method
InactiveCN103051442AIncrease flexibilityImprove implementation efficiencyEncryption apparatus with shift registers/memoriesComputer hardwarePlaintext
The invention discloses a cipher device adopting a Feistel-PG structure and an encryption method. The Feistel-PG structure consists of a round function F, the round function F maps a t*k*m bit string into a t*k*m bit string, the input X is mapped into U through linear conversion P and nonlinear conversion G, the linear conversion P is displacement based on the t*k*m bit string and is the position conversion of t*m k bit characters, the nonlinear conversion G is concatenation of t nonlinear conversions based on t*k bit string, the nonlinear conversion T is nonlinear conversion based on k*m bit string, and T converts (um-1 to u1, u0) into A (S(um-1 to u1, u0)) through S box layer and linear conversion A, wherein the S box layer is formed by m k*k s boxes through concatenation, and the linear conversion A is linear conversion based on k*m bit string. The encryption method adopting the Feistel-PG encryption structure comprises round key addition, linear conversion P and nonlinear conversion G, the output of plaintext W after the r-round iteration is used as ciphertext. Through the device and the method provided by the invention, the cipher algorithm design is more flexible, and in addition, lower realization cost can be realized at the same security intensity.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
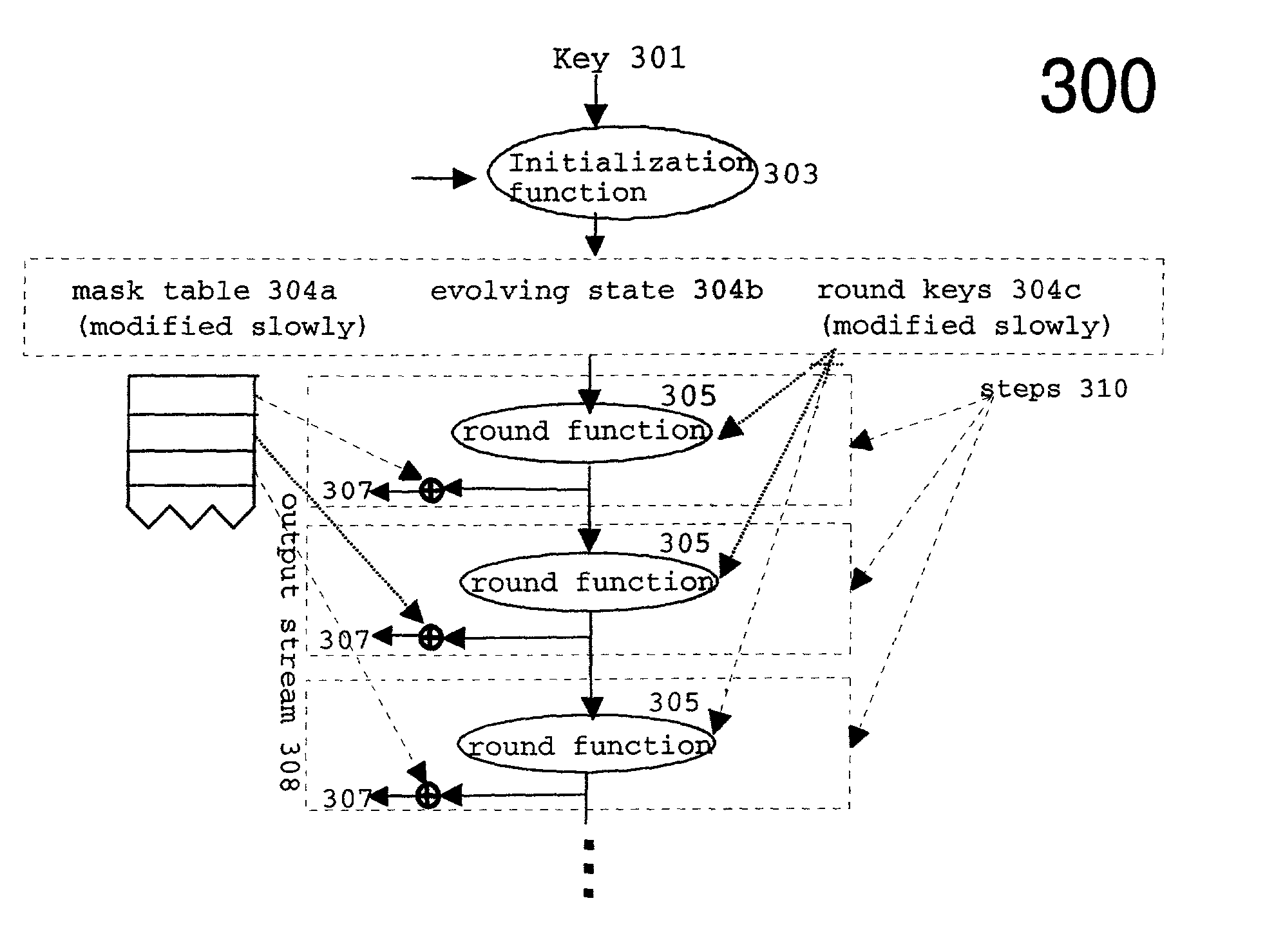
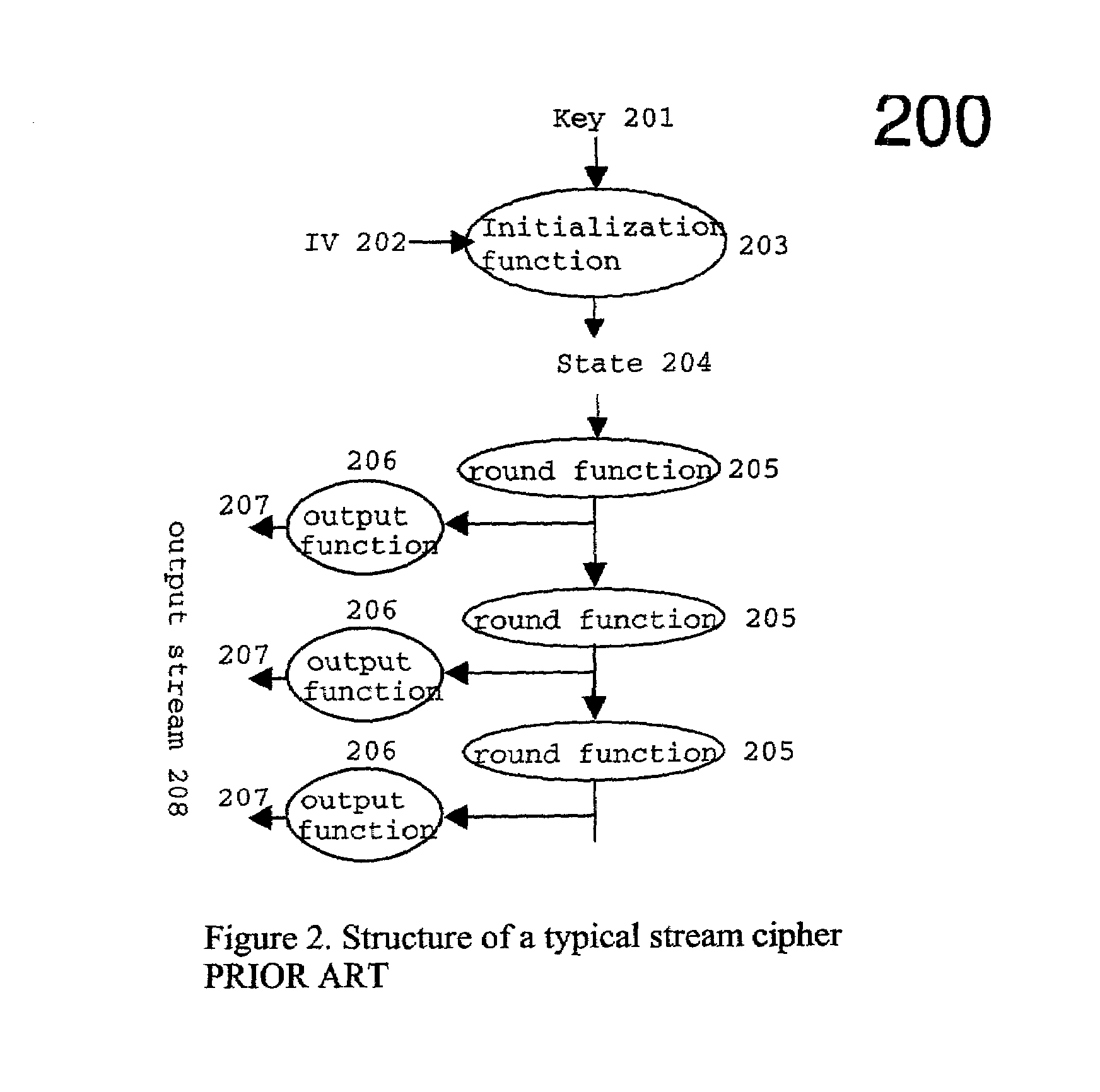
Efficient stream cipher system and method
InactiveUS7236592B2Quick implementationSecret communicationSecuring communicationComputer hardwareComputerized system
A computer system and method generates a random output stream of bits. The system comprises an initial evolving state produced from one or more initial keys, one or more round functions, and one or more mask tables. Each round function is part of a step in a sequence of steps. Each step applies the respective round function to a current evolving state to produce a respective new evolving state for processing by the next step in the sequence. The first step in the sequence starts b processing the initial evolving state. The mask tables are produced from one or more of the initial keys. Each of the mask tables has one or more masks. The masks are combined, in each respective step, with the respective new evolving state in a combination operation to create a respective step output. The random output stream bits is a concatenation of each of the respective step outputs. In one preferred embodiment, one or more of the masks in the mask tables are replaced by one or more replacement masks after a number of combination operations. The replacement masks not being linear combinations of prior masks. In an alternative embodiment, there are two or more mask tables produced from one or more of the initial keys. One or more of the masks from each table is combined, in each respective step, with the respective new evolving state in a combination operation to create a respective step output. There may or may not be replacement of the masks in this embodiment.
Owner:GOOGLE LLC
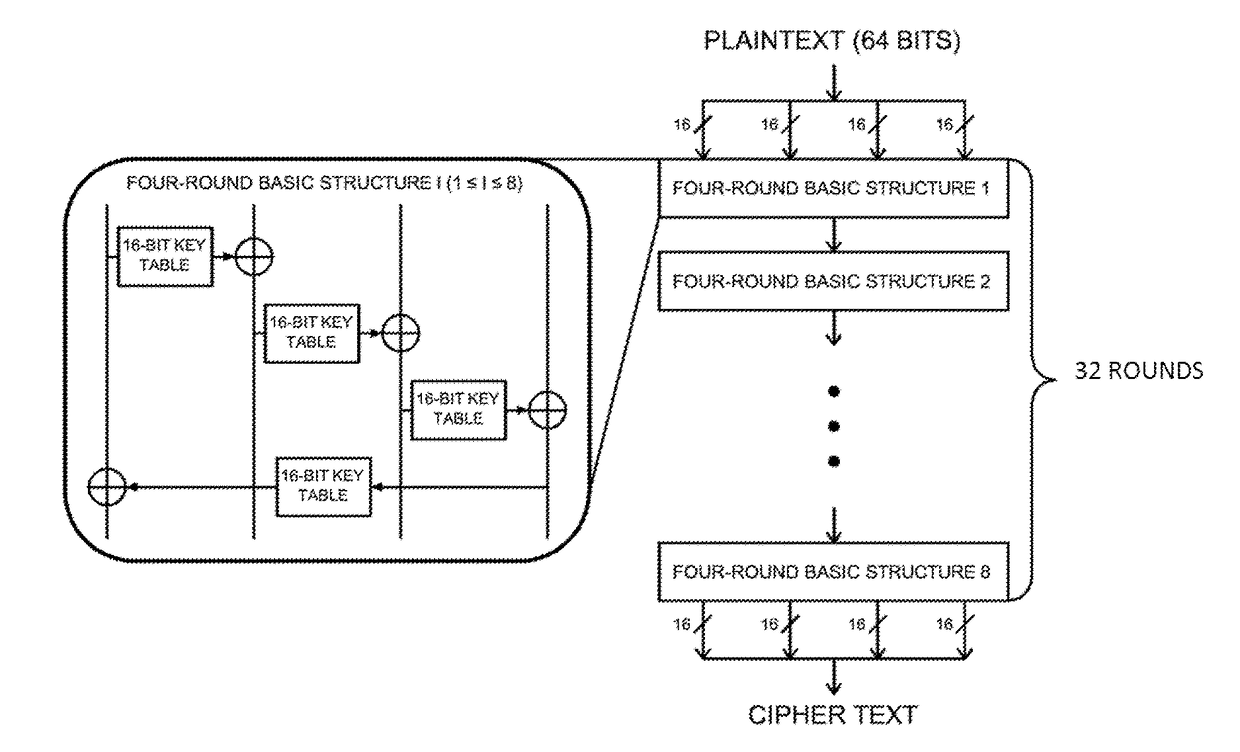
Method of implementing the data encryption standard with reduced computation
InactiveUS7103180B1Reduce in quantityShorten the lengthSecret communicationSecuring communicationComputer hardwareGeneral purpose
An efficient software implementation of the round function of the Data Encryption Standard (DES) involves mathematical transformations performed on the DES round function and the DES round key computation function that reduce the computation required to complete a DES round on general-purpose, embedded, and cryptographic processors. These transformations shift computation associated with the Expansion Permutation from the DES round function to the DES round key computation function. As a result, fewer instructions are required to compute the inputs of the DES S-boxes in the round function.
Owner:HEWLETT PACKARD DEV CO LP
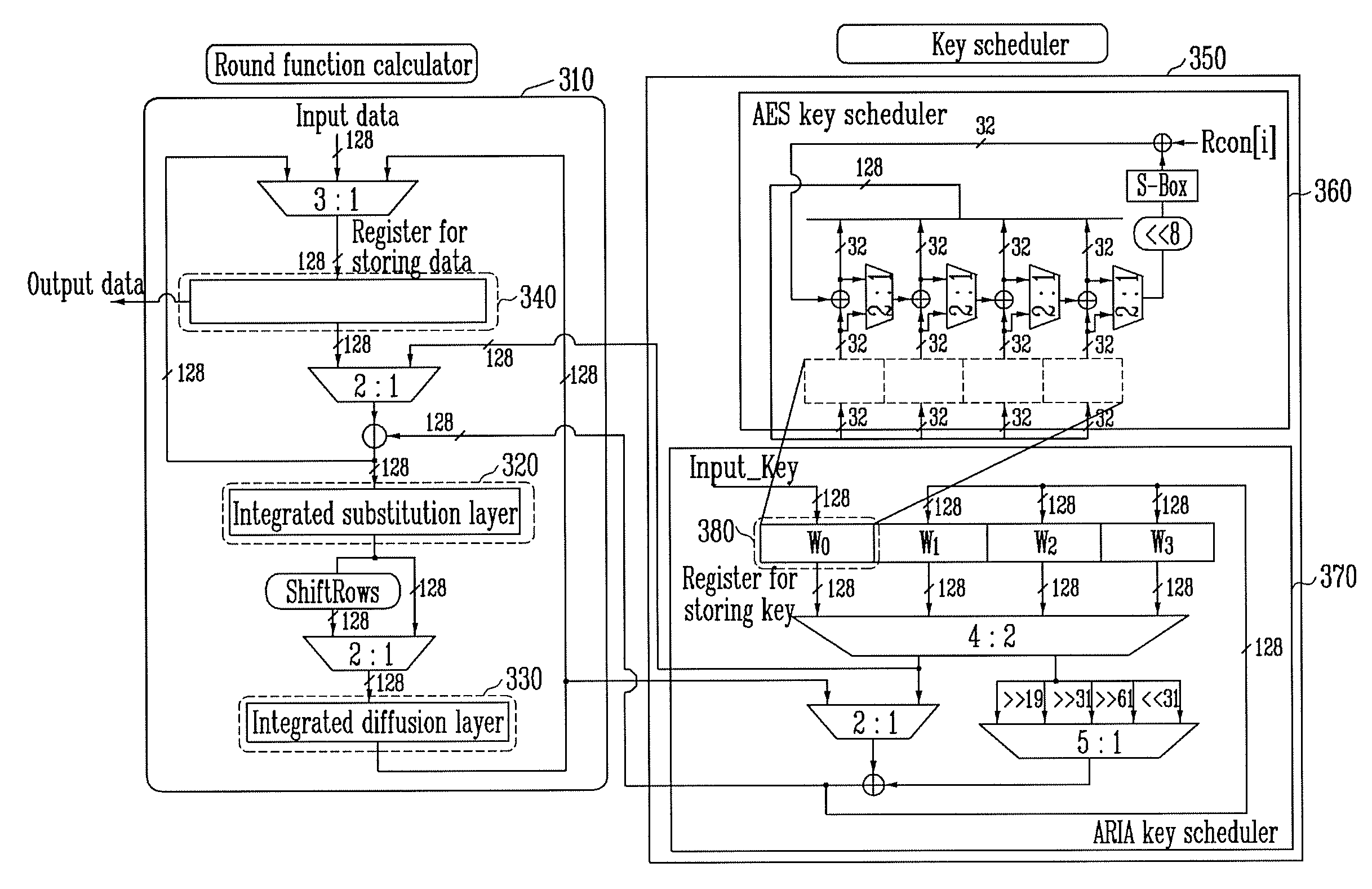
Arithmetic method and apparatus for supporting aes and aria encryption/decryption functions
ActiveUS20080112560A1Encryption apparatus with shift registers/memoriesSecret communicationDisk encryptionRound function
Provided are an arithmetic method and apparatus for supporting Advanced Encryption Standard (AES) and Academy, Research Institute and Agency (ARIA) encryption / decryption functions. The apparatus includes: a key scheduler for generating a round key using an input key; and a round function calculator for generating encrypted / decrypted data using input data and the round key. Here, the round function calculator includes an integrated substitution layer and an integrated diffusion layer capable of performing both AES and ARIA algorithms.
Owner:ENERGY MACHINES +1
Novel low-resource efficient lightweight Surge block cipher implementation method
ActiveCN104065474AClear structureImprove performanceEncryption apparatus with shift registers/memoriesKey sizeComputer hardware
The invention discloses a novel low-resource efficient lightweight Surge block cipher implementation method. The method comprises the steps that the Surge block length is designed to be of a 64-bit type, and the secrete key length is designed to be of the 64-bit type, the 80-bit type and the 128-bit type on the basis of the SPN structure; a secrete key is in a non-extensible mode; five modules of a round function are combined in a new mode, the encryption sequence is constant addition, round key addition, S-box replacement, row shifting and column mixing transformation, and column mixing transformation does not exist in the last round; a constant addition transformation module operates a round constant in each round; according to the round constant selection combination, 0, 1, 2 and 3 are selected as the high bits, the combination of one odd number, one even number, one even number and one add number from 0 to 15 is selected as the low bits, and the obtained combinatorial numbers are randomly fixed into a permutation; a column mixing transformation module utilizes the (0,1,2 and 4) combination which facilitates hardware implementation for forming a matrix, and hardware is constructed on a galois field GF (24) to obtain the friendly matrix. The experimental result shows that the occupied area resources are smaller, meanwhile, the encryption performance is good and the known attacks can be resisted compared with existing lightweight ciphers of the SPN structure.
Owner:HENGYANG NORMAL UNIV
AES (Advanced Encryption Standard) encryption method and power attack resisting method based on the same
The invention discloses an AES (Advanced Encryption Standard) encryption method and a power attack resisting method based on the same; the AES encryption method comprises the following steps: grouping clear data; carrying out XOR operation on an input and an expanded secret key of a round function; carrying out data replacement with an S box having an 8-bit input and a 32-bit output; shifting 32-bit data output by the S box; carrying out the XOR operation correspondingly on the 32-bit data output by row shifting operation; carrying out the XOR operation on the expanded secret key; carrying out the data replacement with the S box having the 8-bit input and the 8-bit output; carrying out the XOR operation with the expanded secret key; and outputting encrypted data. The invention has the following advantages: the operations needed by each of the steps in the encryption method only have table look-up, shifting and XOR, so the logic implementation is relatively simple and efficient; and the power attack resisting method has mixcolumn, so the power attack resisting effect is good.
Owner:WUXI RES INST OF APPLIED TECH TSINGHUA UNIV
Method and apparatus for implementing lightweight block cipher SCS
ActiveCN108123791AImprove securityIncrease flexibilityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesComputer hardwareDiffusion
The invention discloses a method and apparatus for implementing a lightweight block cipher SCS. A turn key and a control key are divided in keys, the round key participates in a round key adding operation, the control key controls the generation of each turn of S box to obtain a random S box, the update of the control key and the turn key is related to the operation result of the last turn, the Sbox used in each turn is random, the operation result of each turn is also random, so that the degree of confusion can be increased; in a round function, a high pseudo-random P permutation is generated by the Mason rotation algorithm in each round to achieve the diffusion, and after the end of the round function iteration, row shift and the column confusion transform are executed, so that the diffusion effect is enhanced by using the dual diffusion mode, and the security is improved. Compared with the situation that the difference between the resource consumption of fixed cipher structures isnot large, the internal structure of the device has the advantages of greatly improving the security of the scheme, and increasing the defense coefficients of linear attack, differential attack and the like to a certain extent.
Owner:HENGYANG NORMAL UNIV
Method of generating arbitrary numbers given a seed
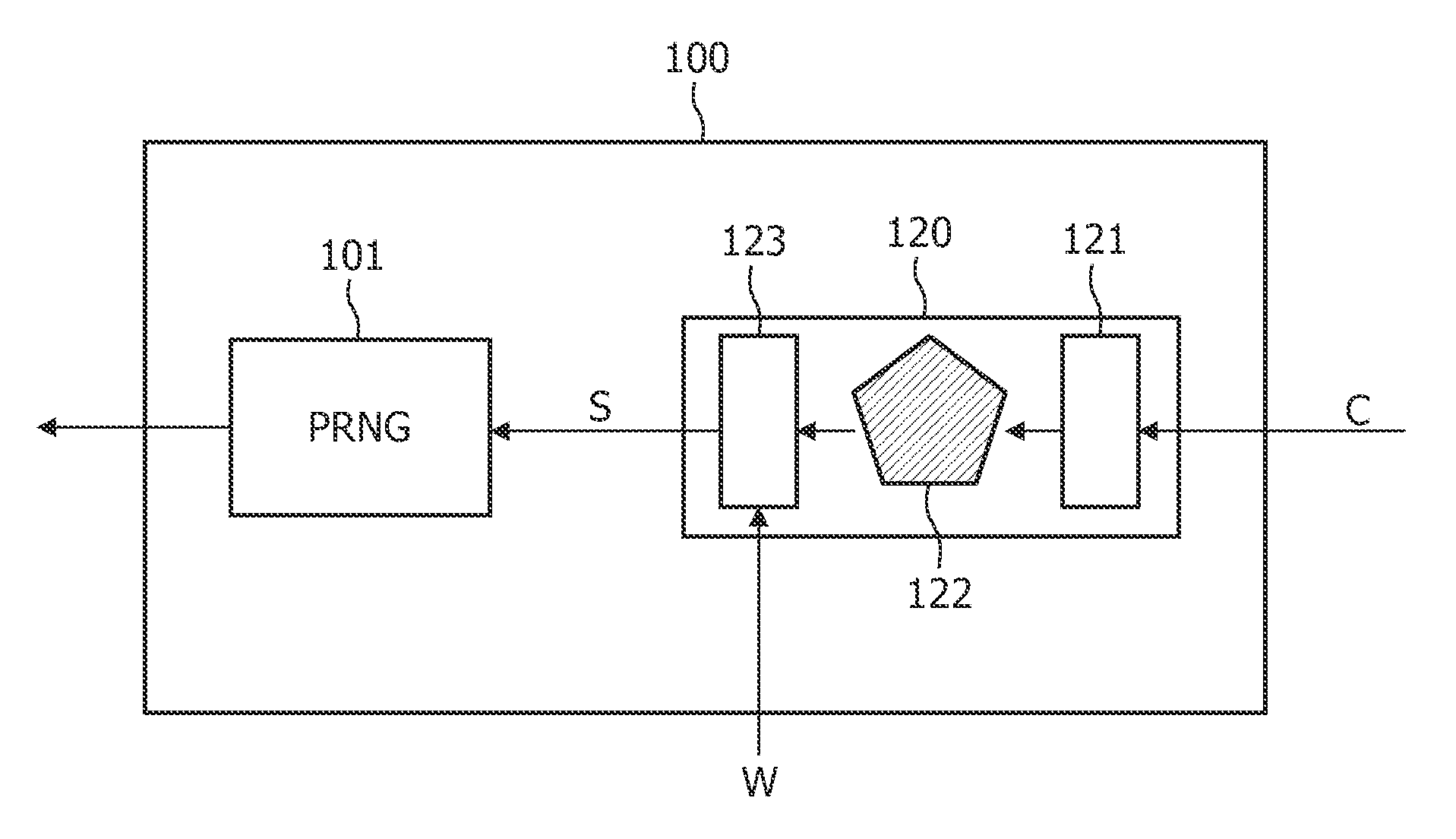
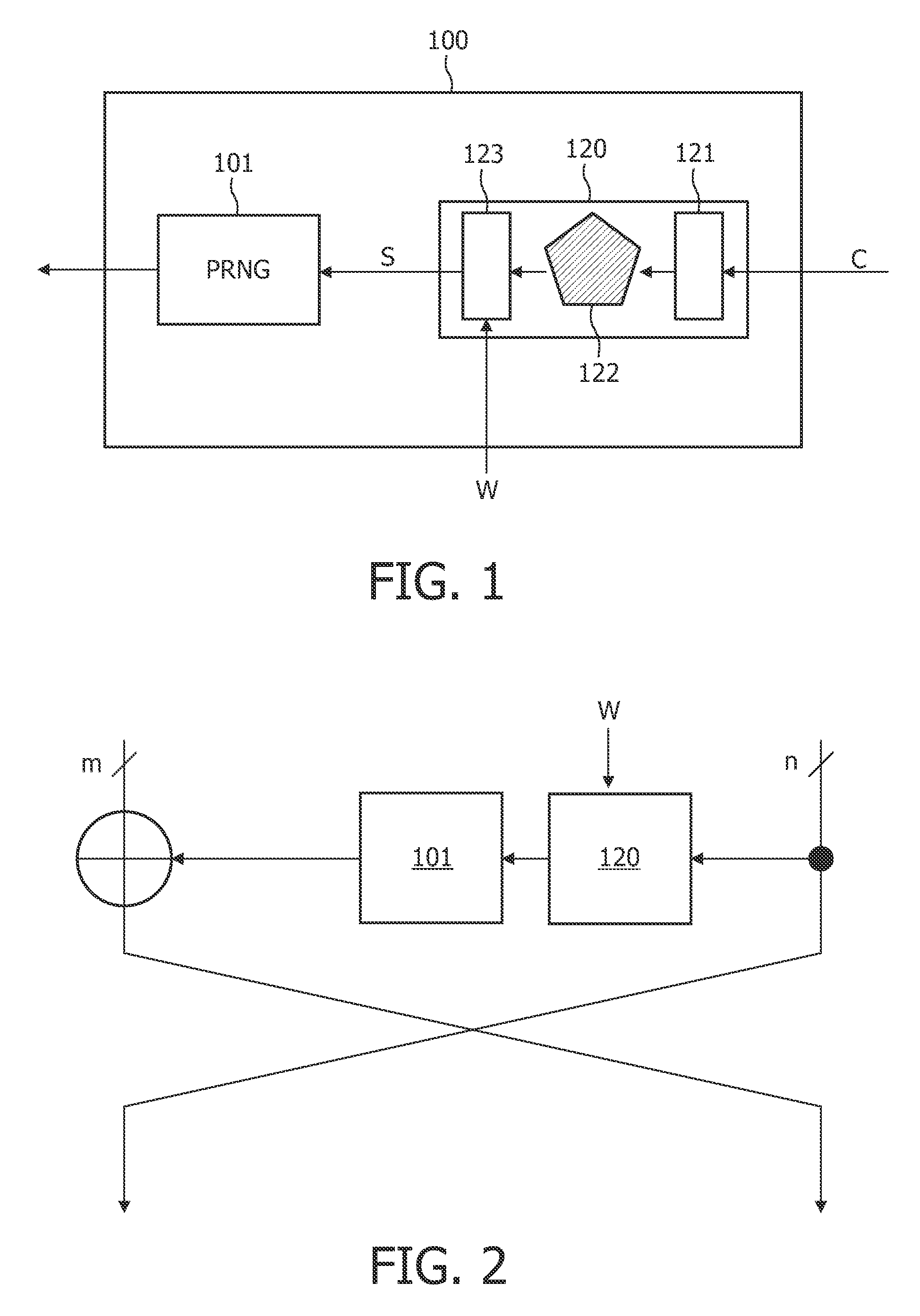
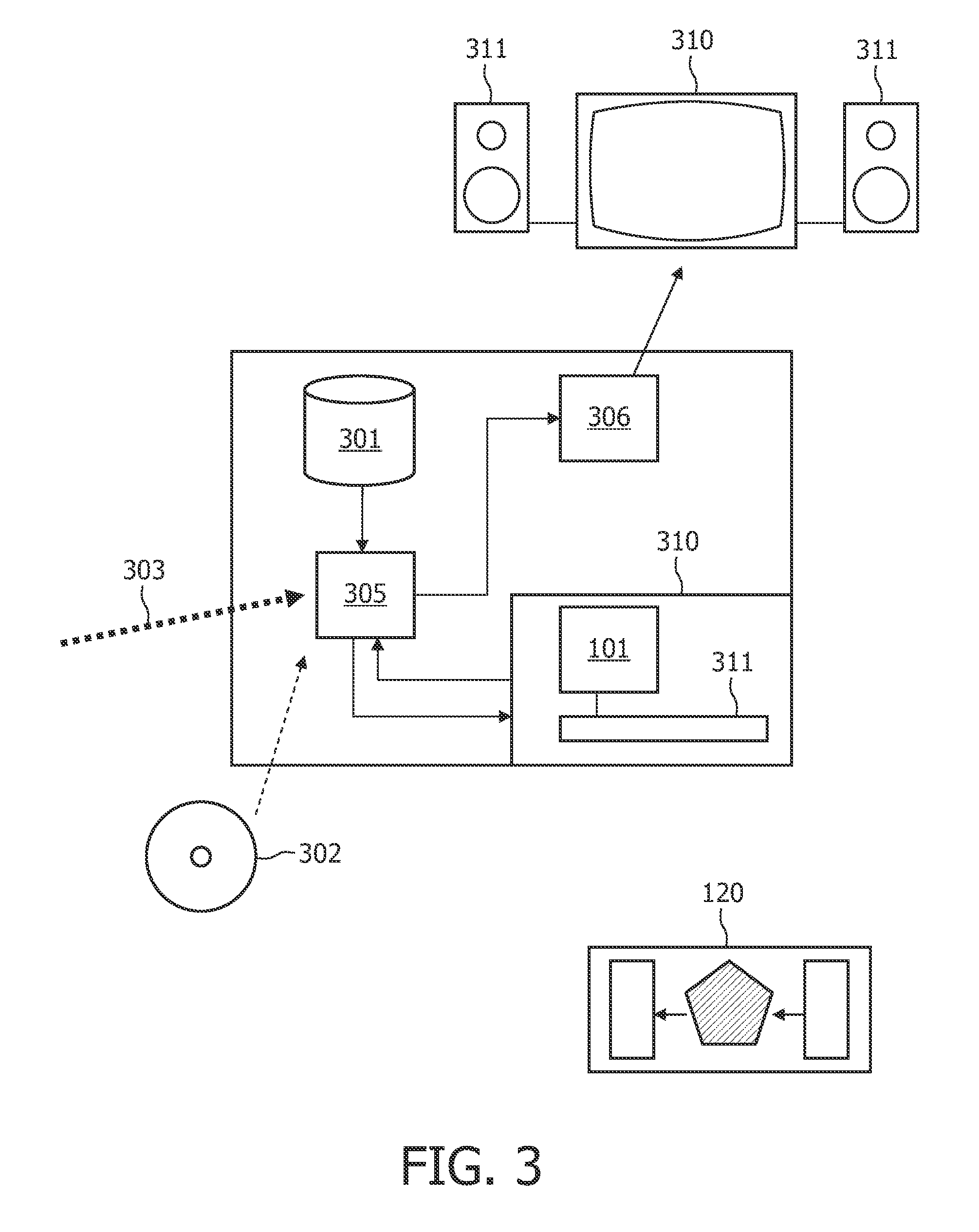
ActiveUS20100054466A1Improve protectionSignificant comprehensive benefitsRandom number generatorsEncryption apparatus with shift registers/memoriesNumber generatorPseudorandom permutation
The invention provides a method of generating arbitrary numbers given a seed, characterized by providing a challenge derived from the seed to a physical token, receiving an initial response from the physical token, combining the initial response with helper data associated with the challenge to produce a stable response, and generating the arbitrary numbers using a pseudo-random number generator using the stable response as a seed for the generator. Preferably one or more of these pseudo-random permutations are used as one or more round function(s) in a Feistel block cipher. The generated arbitrary numbers may also be used to create a cryptographic key.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
Apparatus and method for encryption
ActiveUS20170126396A1Key distribution for secure communicationEncryption apparatus with shift registers/memoriesComputer hardwarePlaintext
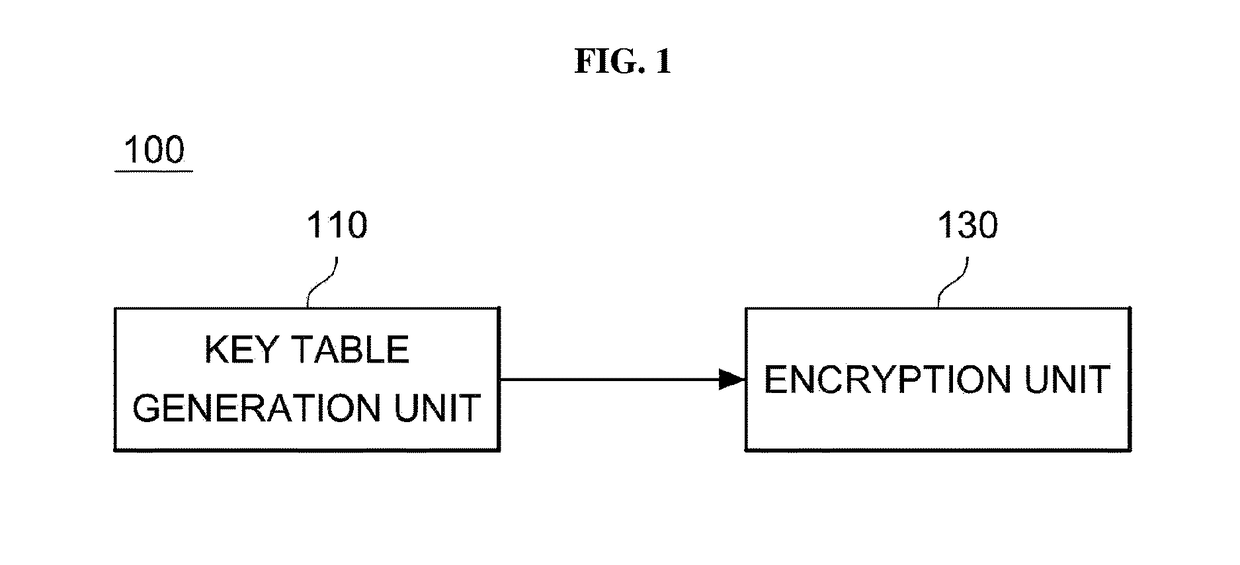
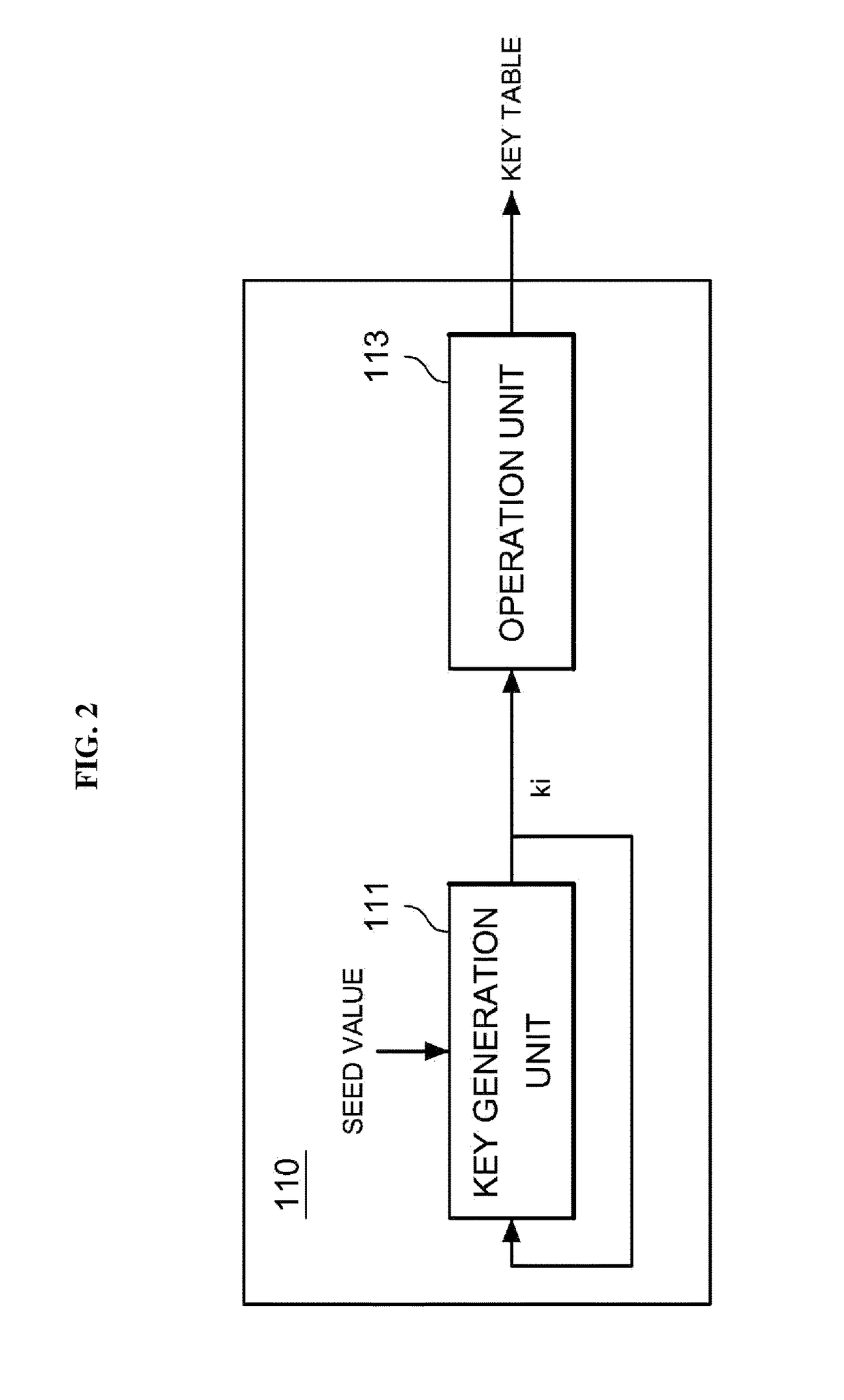
Disclosed are an apparatus and a method for encryption. The apparatus includes a key table generator configured to generate random values based on a seed value and generate a key table including the generated random values; and an encryptor configured to apply the generated key table to a round function, generate a block encryption algorithm having a Feistel structure based on the round function, and encrypt a plaintext data block based on the generated block encryption algorithm.
Owner:SAMSUNG SDS CO LTD +2
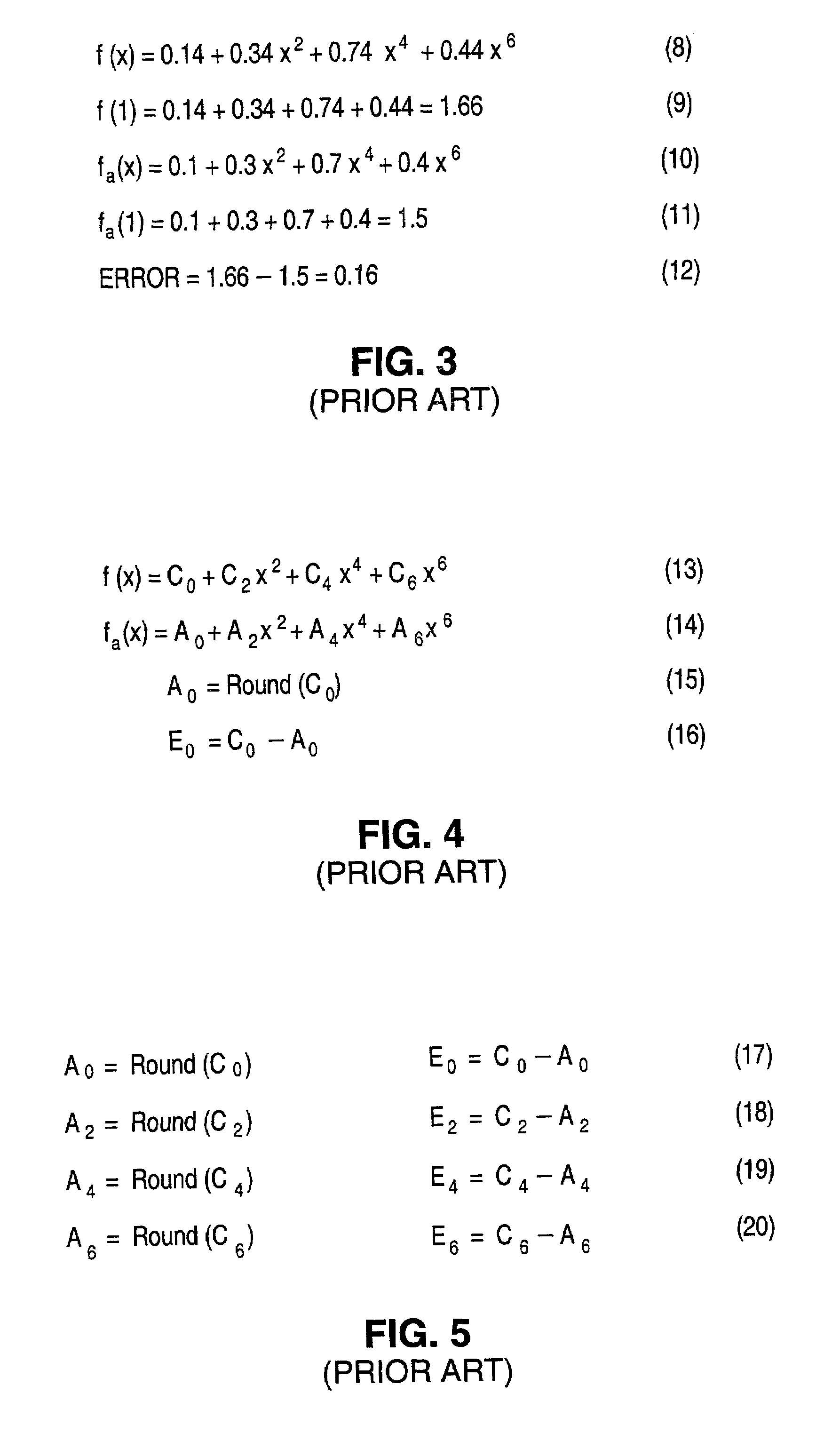
Apparatus and method for minimizing accumulated rounding errors in coefficient values in a lookup table for interpolating polynomials
InactiveUS6978289B1Error minimizationDigital function generatorsComplex mathematical operationsComputer hardwareLookup table
Owner:ADVANCED MICRO DEVICES INC
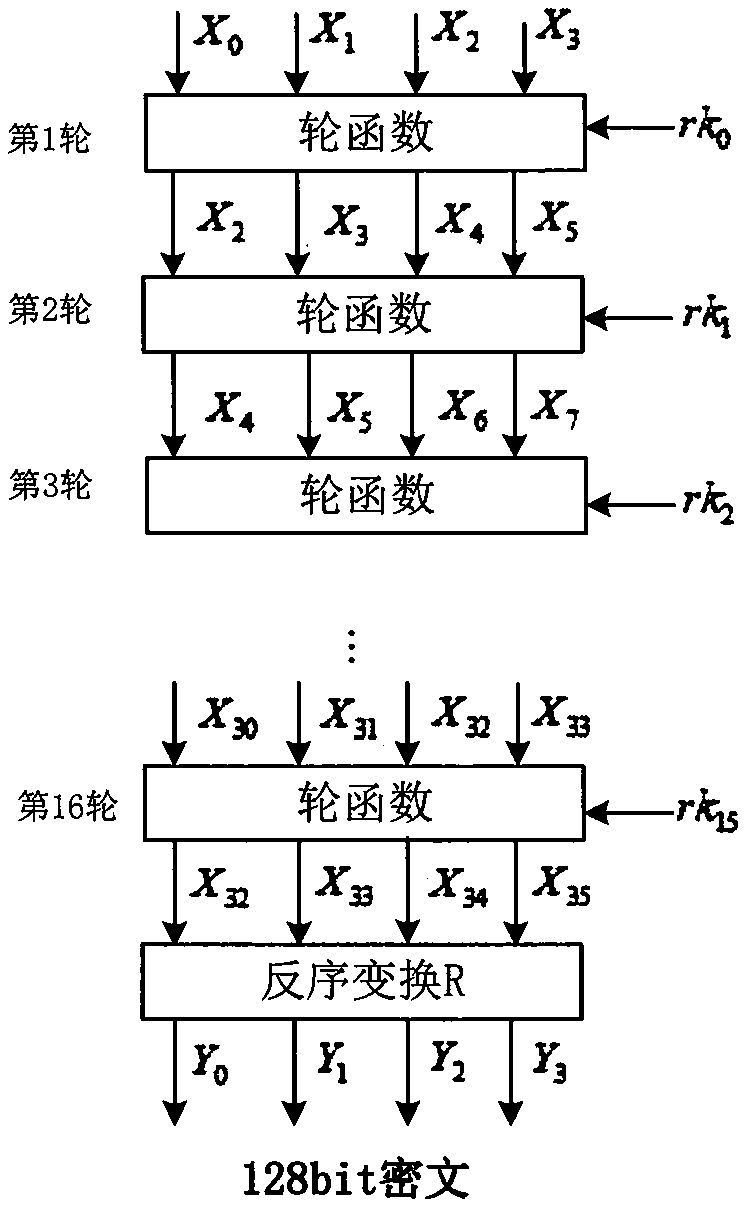
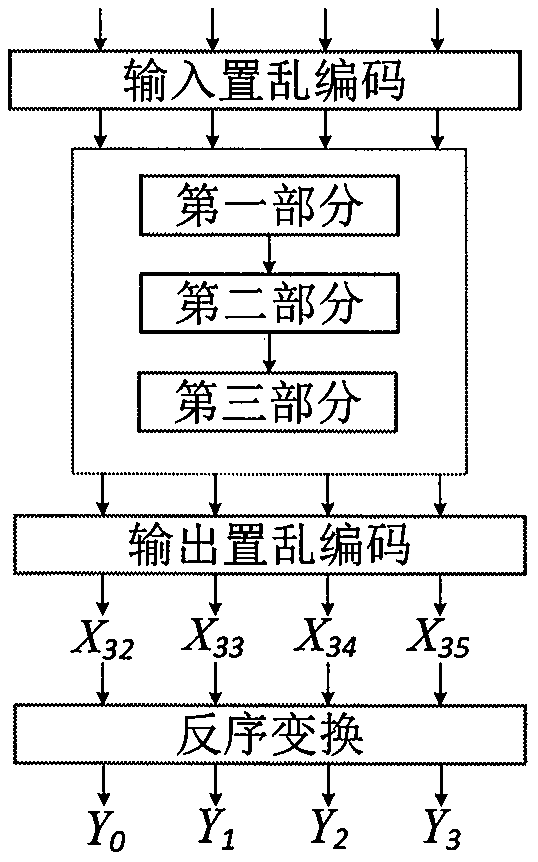
16-wheel SM4-128/128 white box password implementation method
InactiveCN110278072AImprove computing efficiencyIntegrity guaranteedEncryption apparatus with shift registers/memoriesComputer hardwarePassword
In an unsafe environment, a cryptographic analyzer can implement attacks on an algorithm and a secret key by tracking a binary system operated by a program, reading the secret key in a memory and a program execution intermediate result, carrying out static analysis and the like, and a white-box cryptographic algorithm can protect the secret key in the unsafe environment. The invention discloses a 16-round SM4-128 / 128 white box password implementation method, which describes a new mode of improving an SM4 password algorithm when the encryption round number is 16, and the mode improves the structure of a round function, namely the iterative process of the encryption algorithm. An improved SM4 white-box cryptographic algorithm is provided, and the whole encryption and decryption process can be converted into a form of calculating randomly selected affine transformation and lookup tables. The principle is that the internal state of a coding hiding algorithm is input and output scrambled, the secret key is embedded into a lookup table in a coding mode, and meanwhile, a block matrix is used for reducing the scale of the lookup table.
Owner:BEIJING ELECTRONICS SCI & TECH INST
Housing case flanger and use method thereof
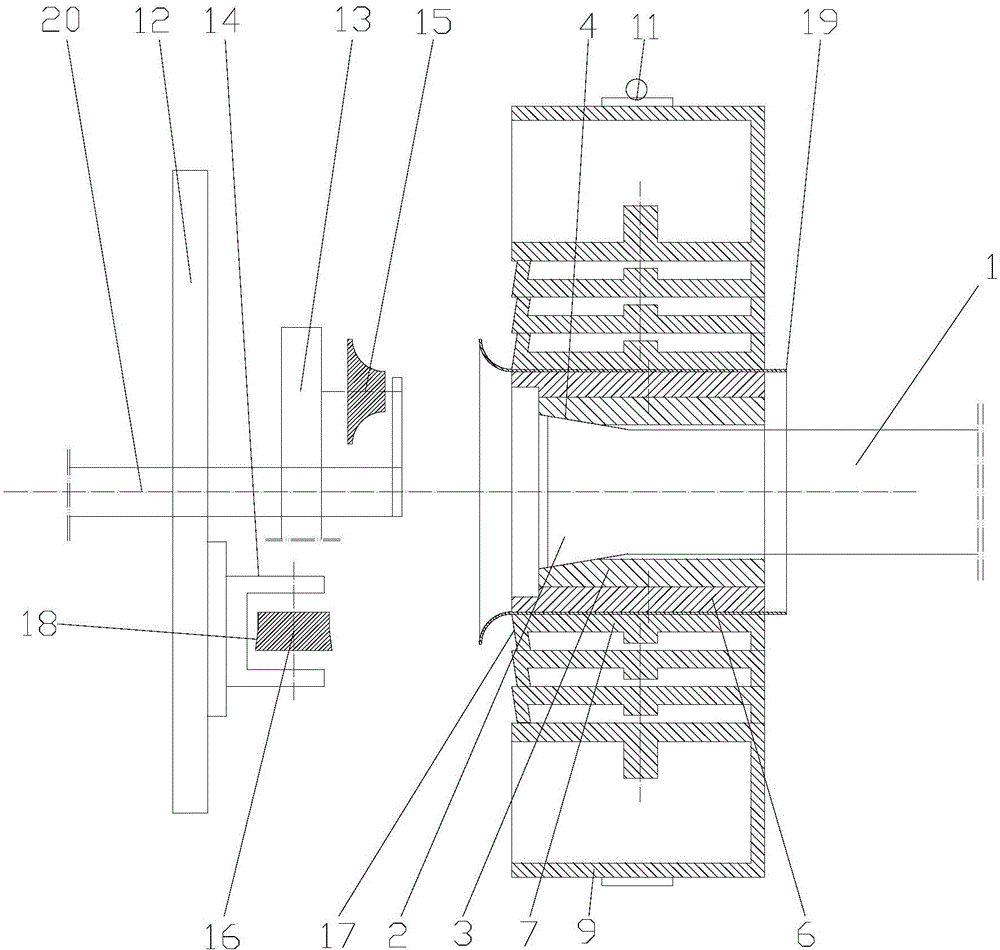
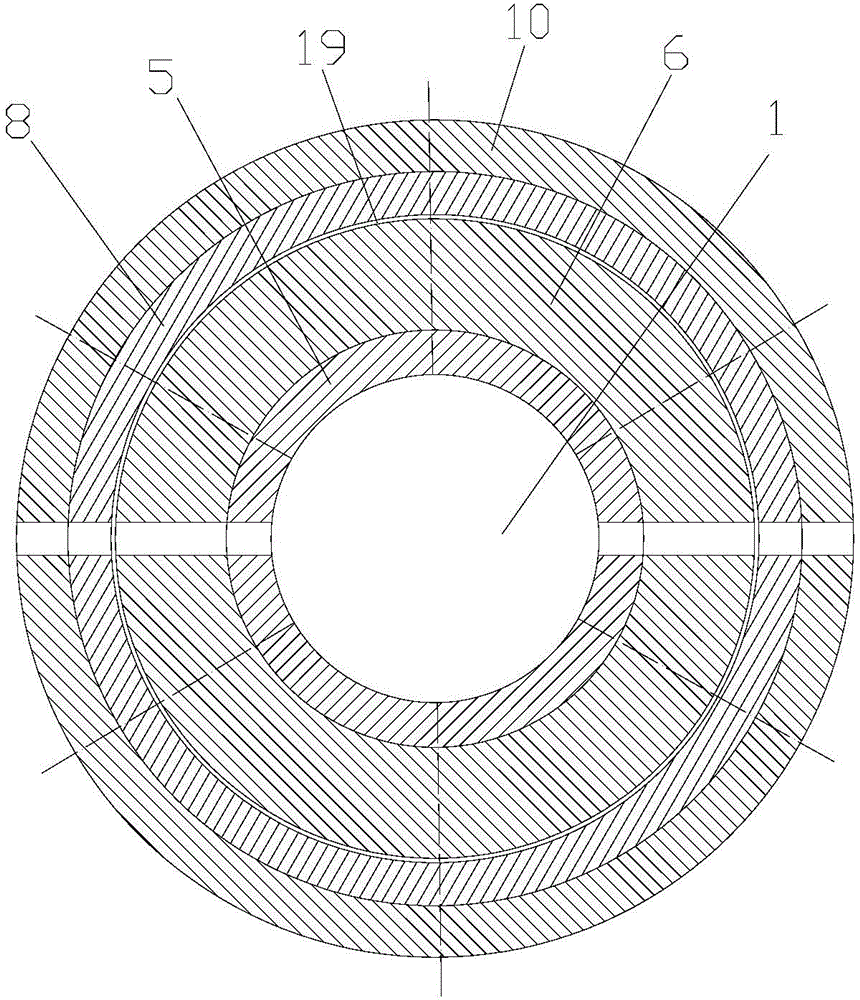
ActiveCN104985041AImprove aerodynamic performanceImprove efficiencyMetal-working feeding devicesPositioning devicesImpellerEngineering
The invention discloses a housing case flanger, which comprises an axial feed mechanism, a main shaft box, a clamp device and a rotary pressing device, wherein the clamp device is fixed to the axial feed mechanism; and the rotary pressing device is in transmission connection with the main shaft box. The use method of the housing case flanger comprises the steps of fixing a housing case, rotary pressing a horn mouth, rotary pressing a right-angle side and the like. The housing case flanger and the use method thereof are adopted; through the autorotation of main rotating wheels and auxiliary rotating wheels and the rotation of a turnplate, a horn side and a right-angle side flange of the housing case are subjected to rotary pressing; since the clamp device which internally expands and externally holds is used for fixing the housing case, and the clamp device has an automatic centring rounding function, a necking-down phenomenon cannot happen to an opening of the housing case in the rotary pressing process, an assembling clearance between the impeller outer diameter of a draught fan which is finally assembled and the inner wall of the housing case can be reduced, and the aerodynamic performance and the efficiency of the draught fan are improved.
Owner:ZHEJIANG SHANGFENG SPECIAL BLOWER IND CO LTD
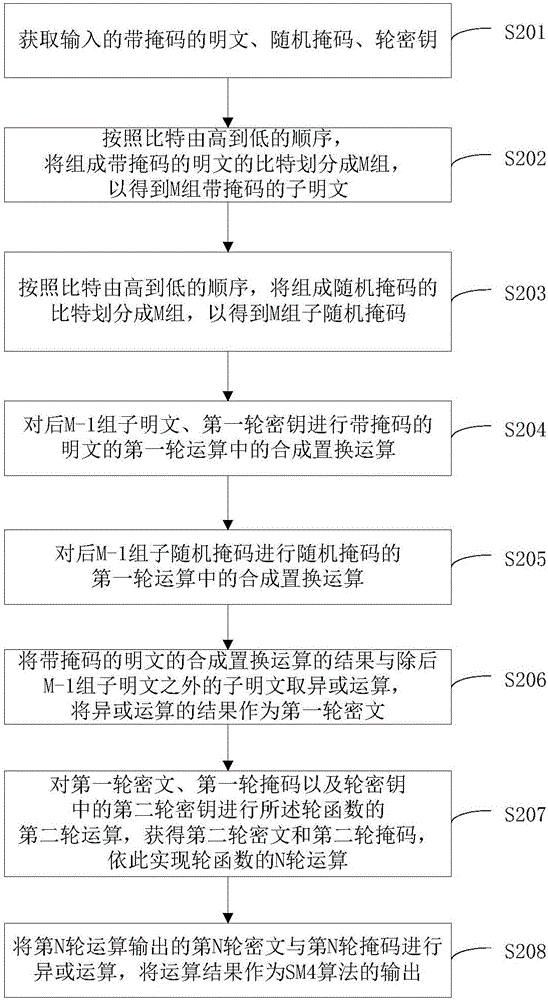
Mask method and mask device for SM4 algorithm
The invention discloses a mask method and a mask device for an SM4 algorithm. The mask method comprises the following steps: acquiring an inputted masked plain text, a random mask and round keys; carrying out a first round operation of a round function on the masked plain text, the random mask and a first round key in the round keys, to obtain a first round ciphertext and a first round mask; carrying out a second round operation of the round function on the first round ciphertext, the first round mask and a second round key in the round keys, to obtain a second round ciphertext and a second round mask, so as to realize N rounds of operation of the round function in turn; and carrying out an XOR operation an N round ciphertext and an N round mask outputted from the N round operation, wherein the operation result is taken as an output of the SM4 algorithm. Namely, except for the first round operation in the N rounds of operation of the round function, masks required for each round operation are all obtained by the output of the last round operation next to the current round operation, and therefore a demask on an intermediate value of the N rounds of operation is not required by adopting the technical solution disclosed by the invention, so that a resistance to an energy attack is realized.
Owner:CHINA INFORMATION TECH SECURITY EVALUATION CENT
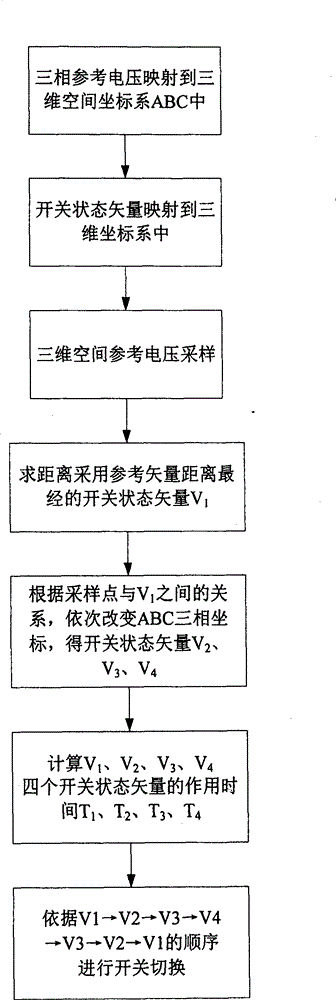
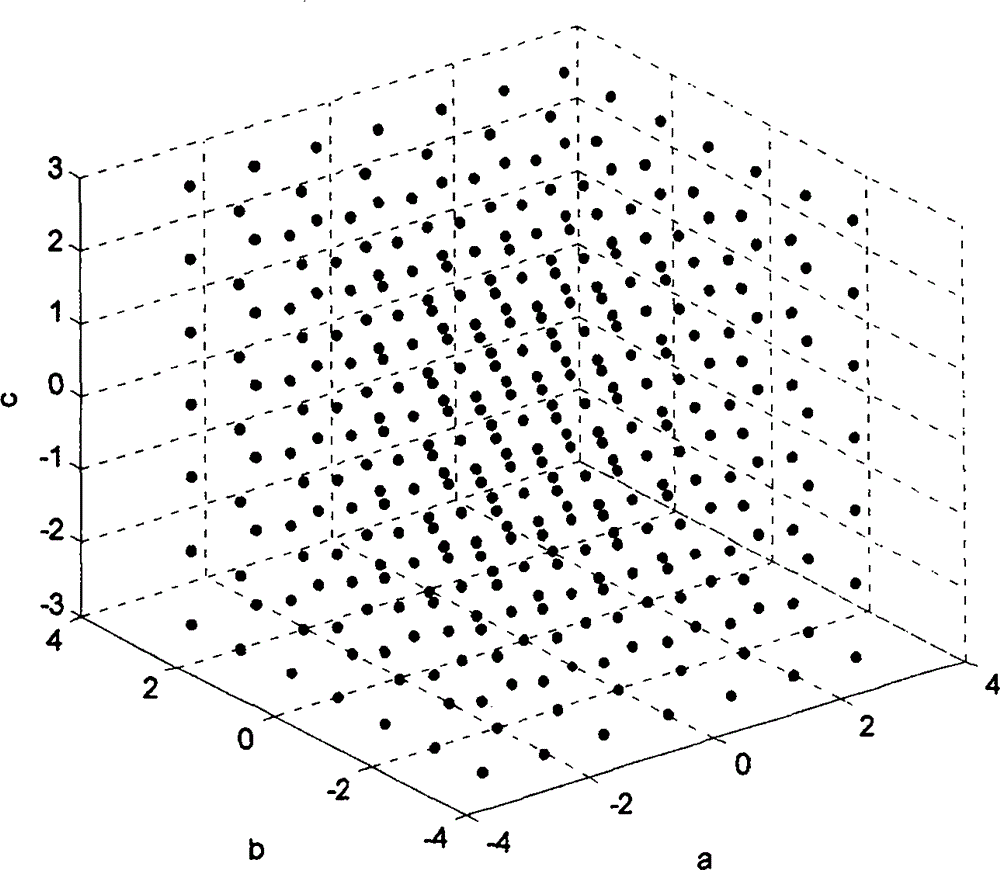
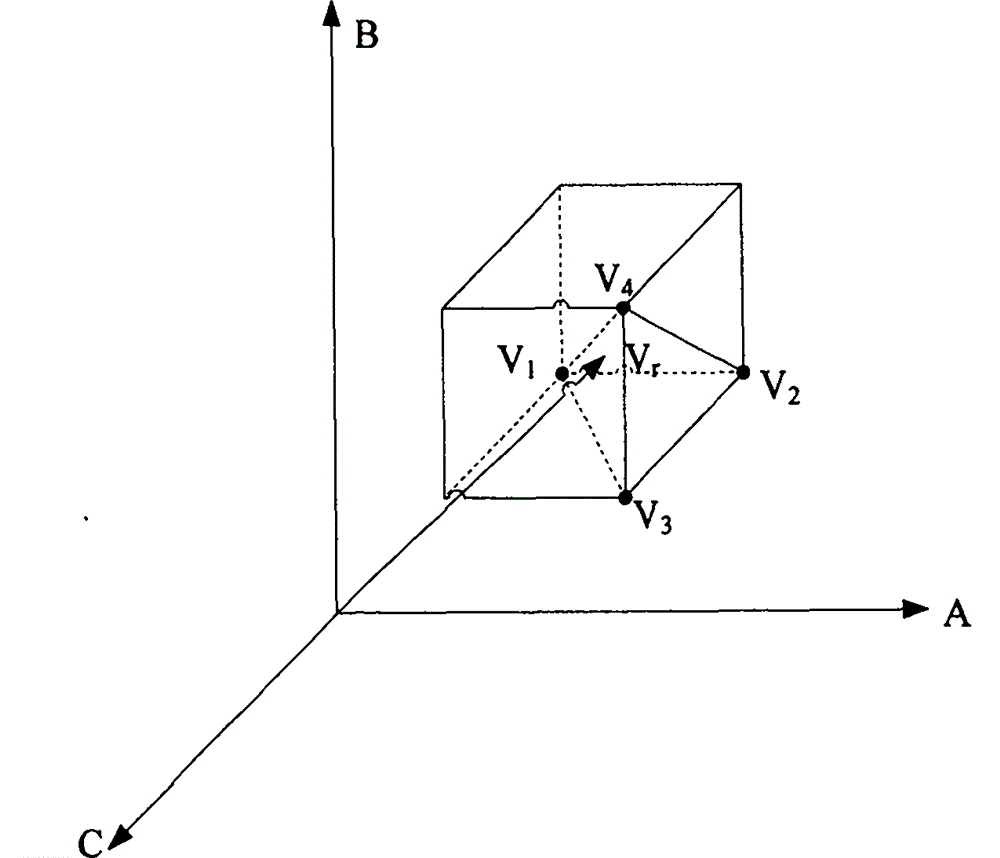
Three-dimensional space vector modulation algorithm of multi-level inverter
ActiveCN104467496AQuick responseReduce switching frequencyAc-dc conversionVoltage vectorThree-dimensional space
The invention discloses a three-dimensional space vector modulation algorithm of a multi-level inverter. According to the algorithm, coordination transformation and trigonometric function operation are avoided, a three-phase reference voltage is directly mapped to a three-dimensional space coordinates system and sampled, the switching state vector closest to the sampled reference voltage vector is obtained through a round function, three coordinate components of the switching state vector are changed in sequence with the switching state vector as the starting point according to the relation between the switching state vector and the reference voltage vector, four switching state vectors are obtained, the reference voltage vector is combined through the four switching state vectors, and switching among the four switching state vectors is achieved. According to the algorithm, the space vector modulation algorithm of the multi-level inverter is simplified and is suitable for any multi-level inverter, and the output voltage zero-sequence component is controlled within the range shown in the specification, and the space vector modulation algorithm can be applied and popularized in the multi-level inverter.
Owner:NANCHANG INST OF TECH
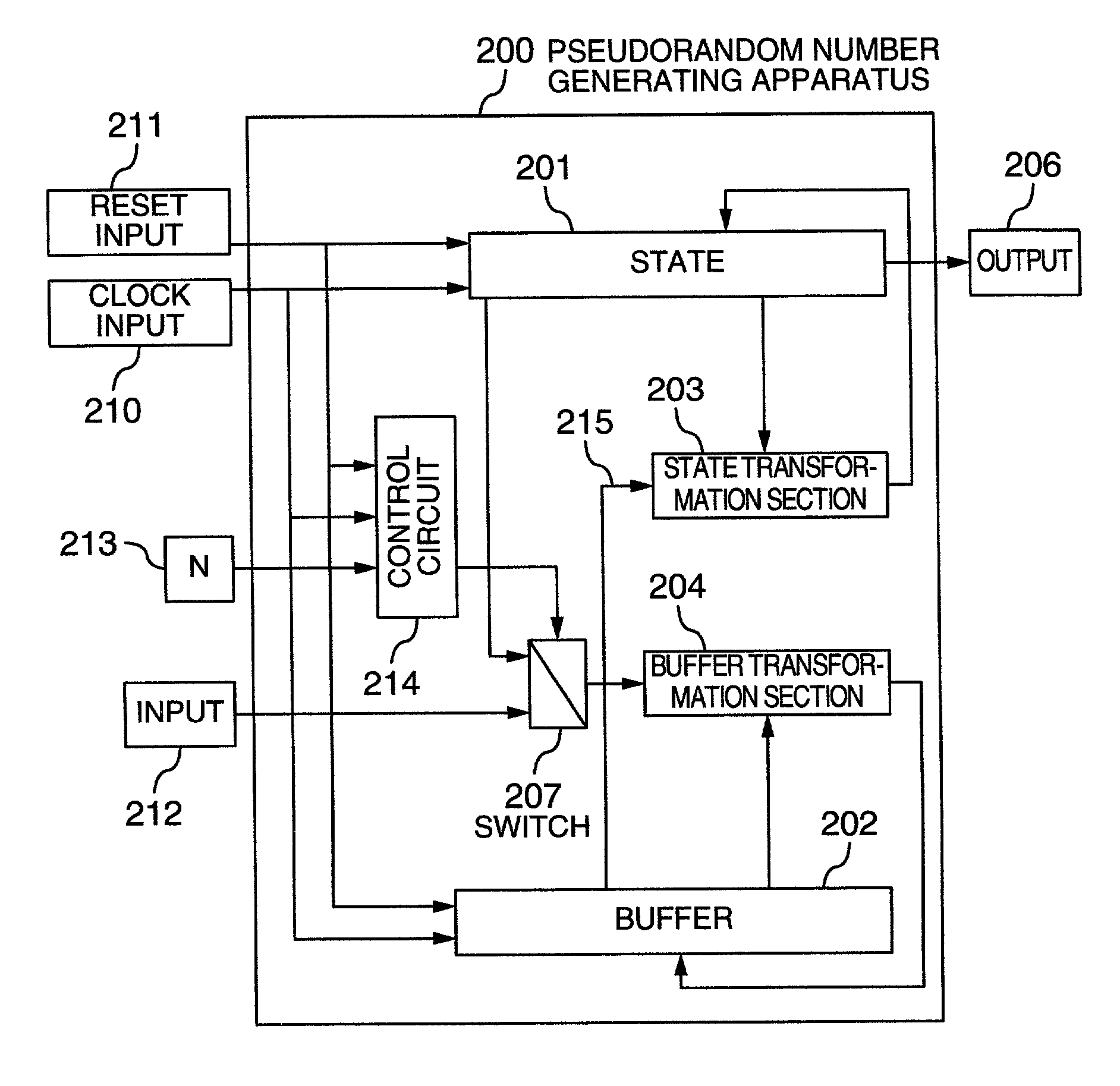
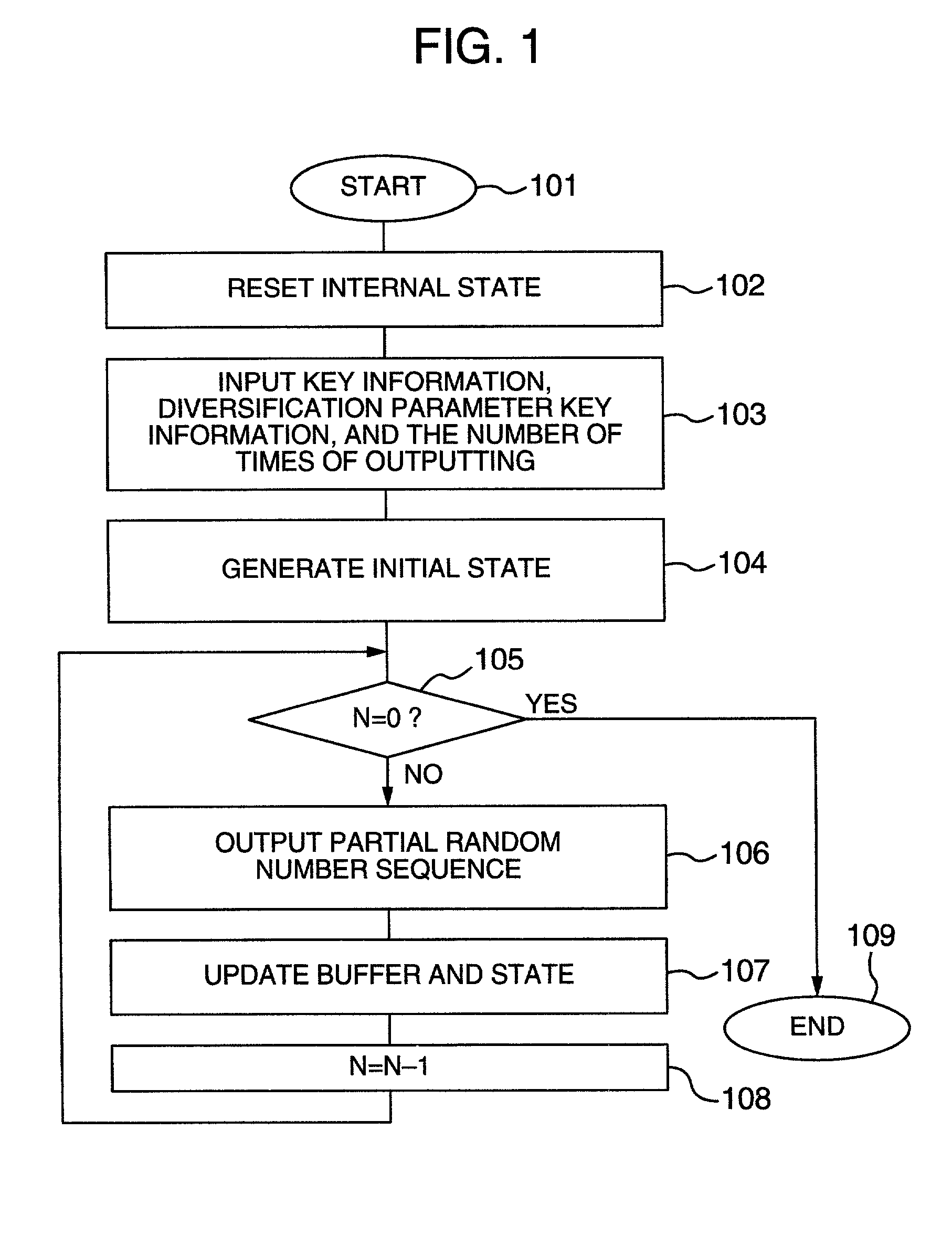
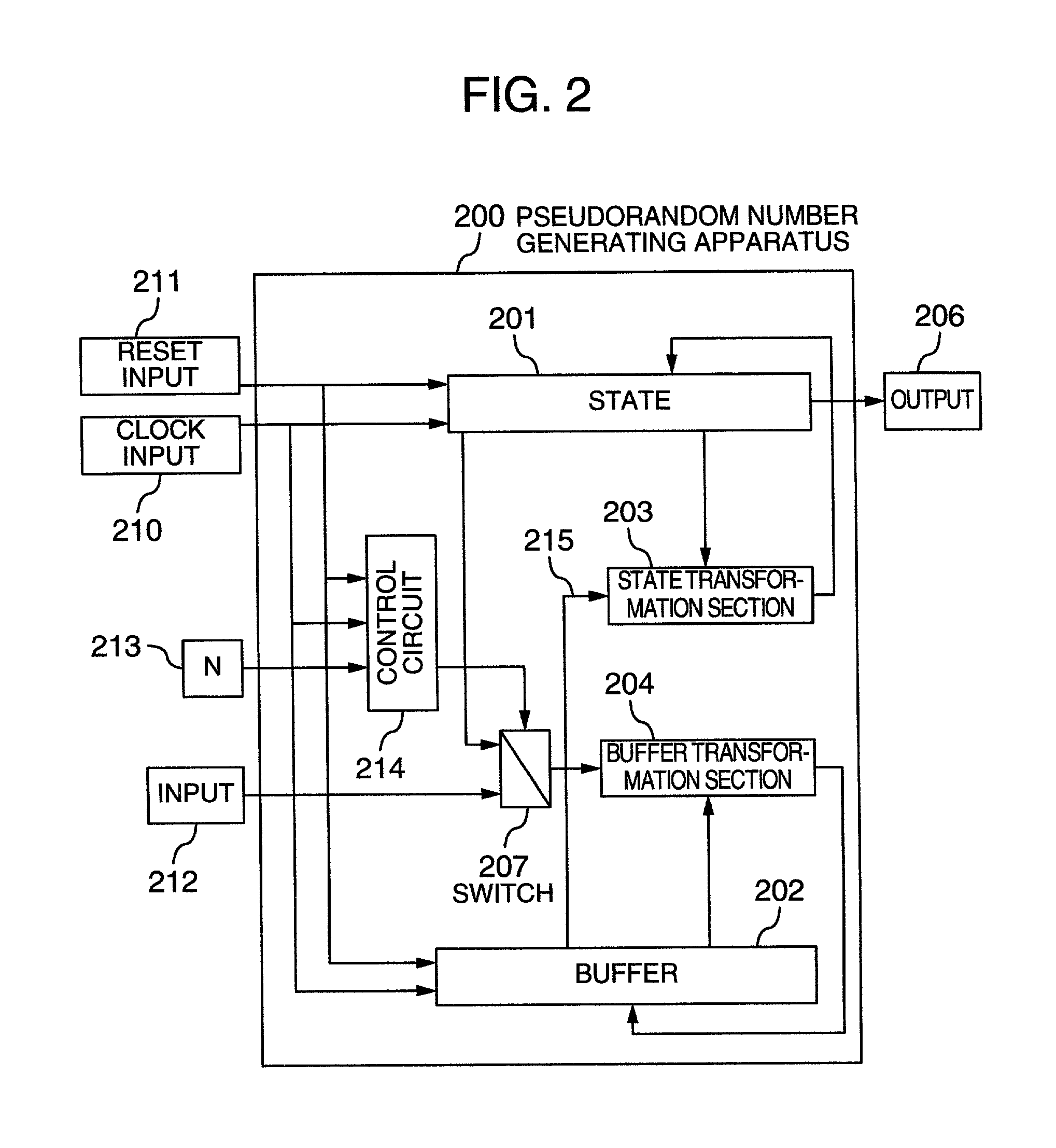
Pseudorandom number generating apparatus or encryption or decryption apparatus using the same
ActiveUS7224796B2Improve securityHigh speed machiningRandom number generatorsSecret communicationComputer hardwarePseudo random number generation
In a buffer and a state included in a pseudorandom number generating apparatus, the state has the configuration of assuming that the unit length of data processing is n, the state has a size of 3×n bits, and the buffer has a capacity of 32×n bits, and according to clock control, a state transformation section (state transformation function) for conducting a state alteration from time t to time t+1 uses a nonlinear function F (having an n-bit input and an n-bit output) twice, or two different nonlinear functions F and G respectively once. The state transformation section has such a configuration that a nonlinear function such as a round function of a block cipher sufficiently evaluated as to the cryptographic security and implementation.
Owner:HITACHI LTD
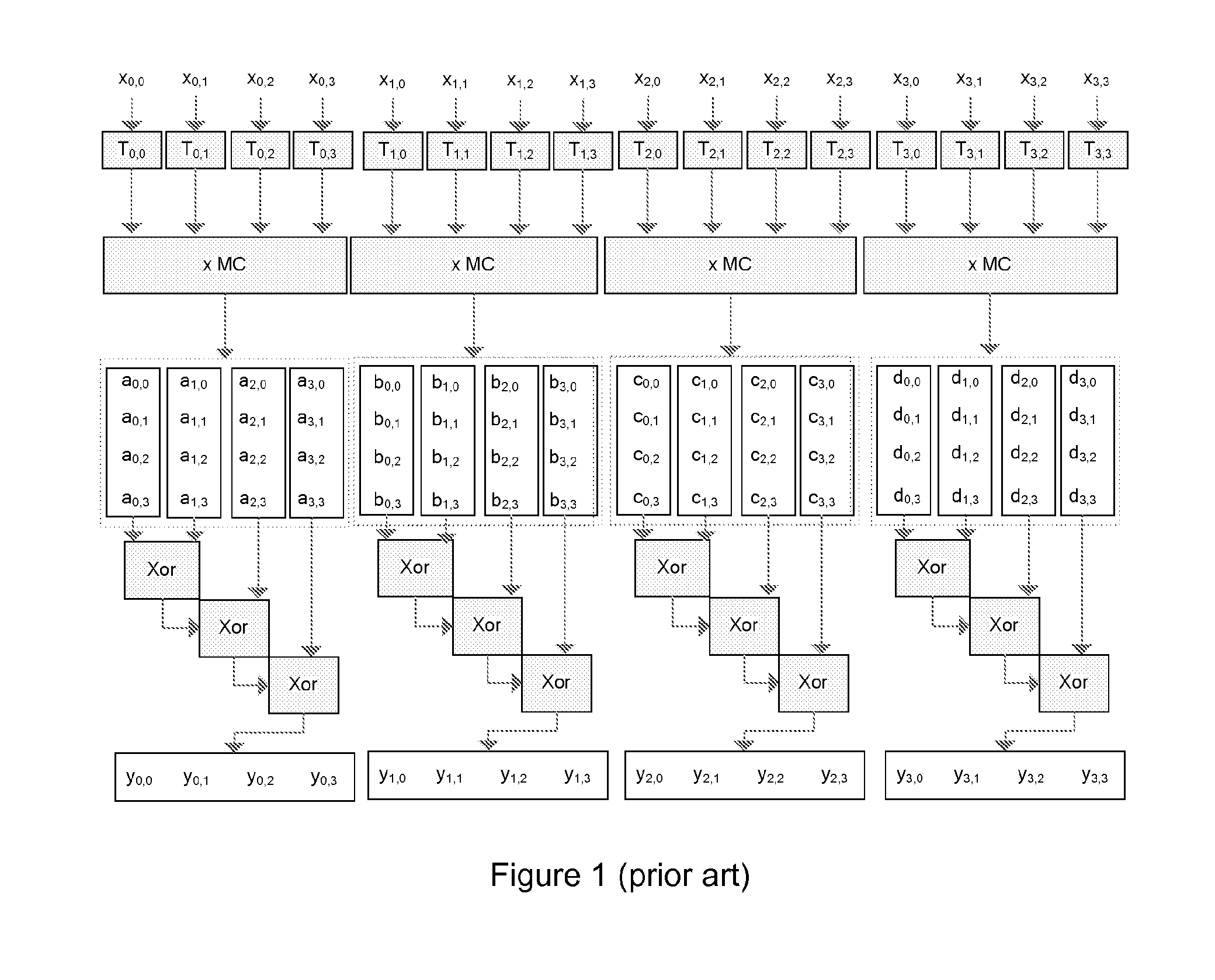
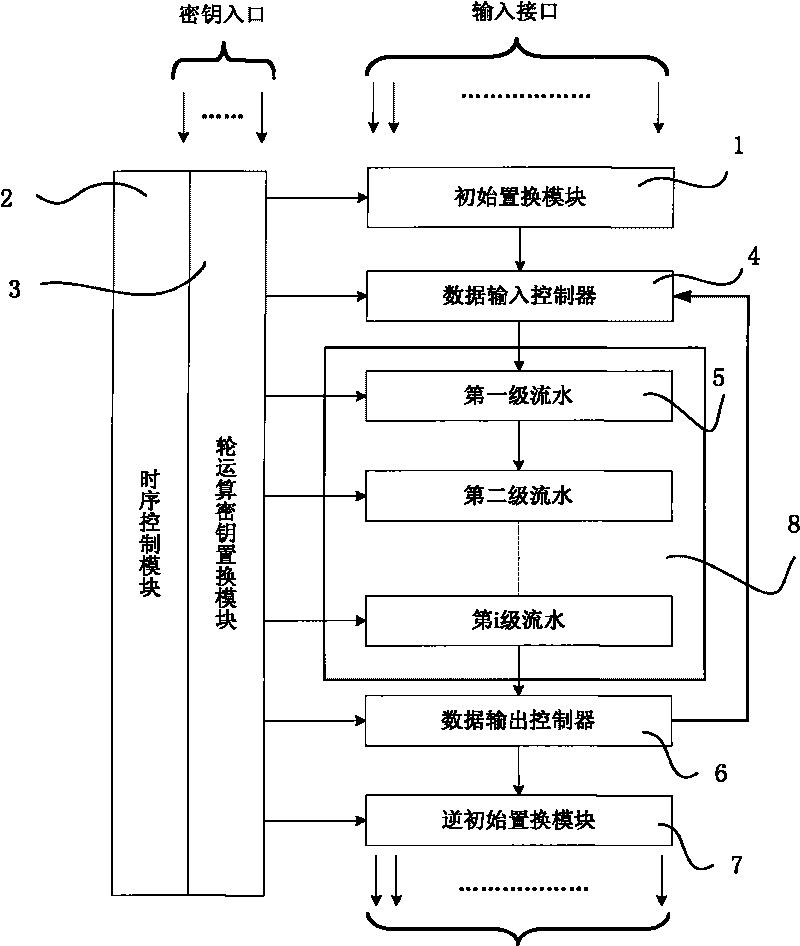
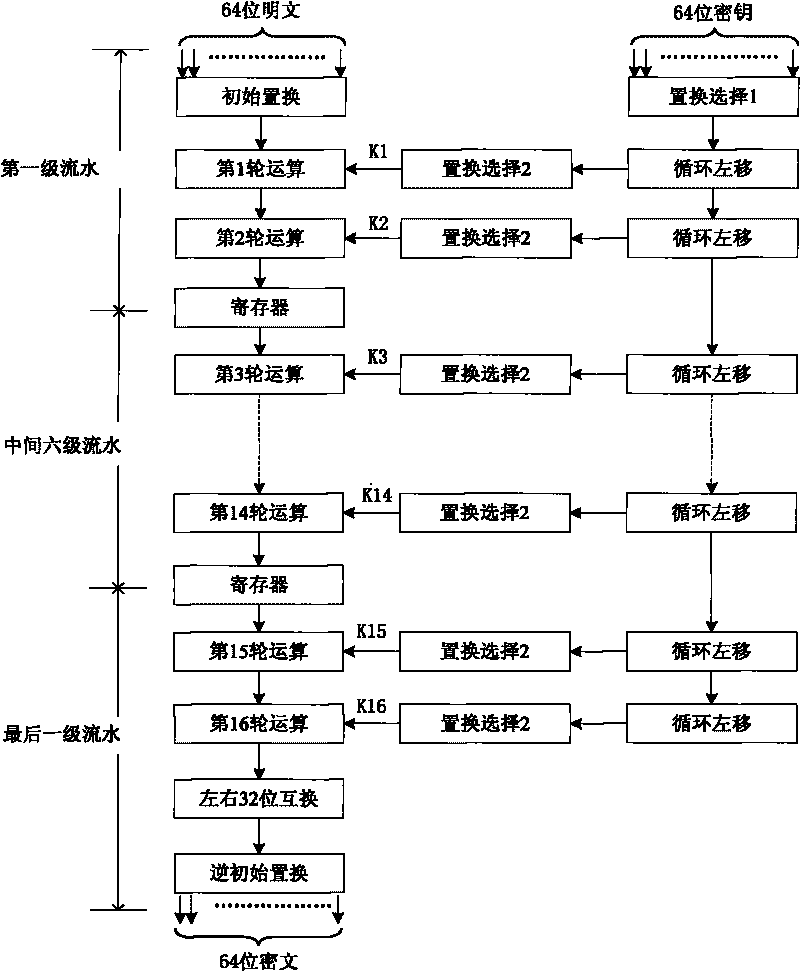
Method and device for generating symmetric block ciphers
InactiveCN101729242AReduce areaReduce power consumptionKey distribution for secure communicationPublic key for secure communicationParallel computingRound function
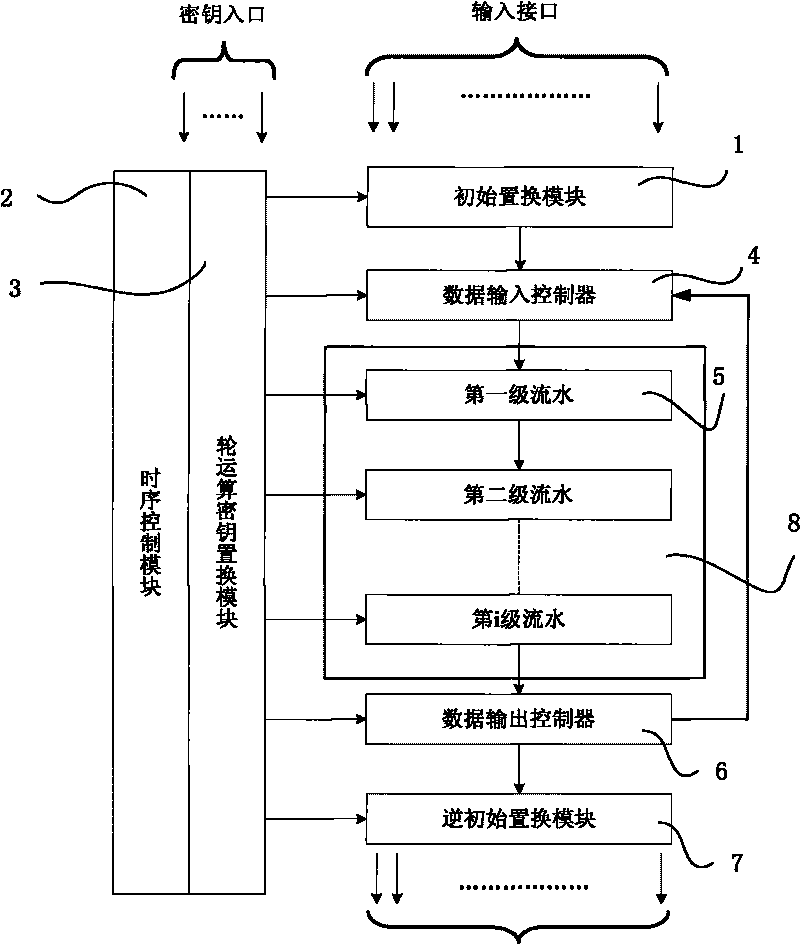
The invention relates to a method and device for generating symmetric block ciphers. The device adopts chips for symmetric block ciphers. The method is characterized in that initial replacement is carried out on the input data; all the round function operations in the first-stage pipeline are carried out on the input data; the data after undergoing operations in the first-stage pipeline are input into the second-stage pipeline, and the second group of data are input into the first-stage pipeline; when a group of data in one batch finish all the round function operations, the data are transmitted to an inverse initial replacement module by a data output controller under the control of a sequential control module to finish encryption and decryption operations; simultaneously, when a group of data in the above step are output, a group of data in the next batch are output to the pipeline and the rest can be done in the same manner to finish all the encryption and decryption operations. After adopting the method, under the premise of not reducing the number of rounds of cipher algorithm iteration, the area of the chips is reduced by a specific method of module reuse.
Owner:苏州中科集成电路设计中心有限公司
Lightweight cryptographic algorithm HBcipher implementation method and device
ActiveCN108206736AAchieve efficiency and flexibilityIncrease confusionEncryption apparatus with shift registers/memoriesComputer hardwareControl signal
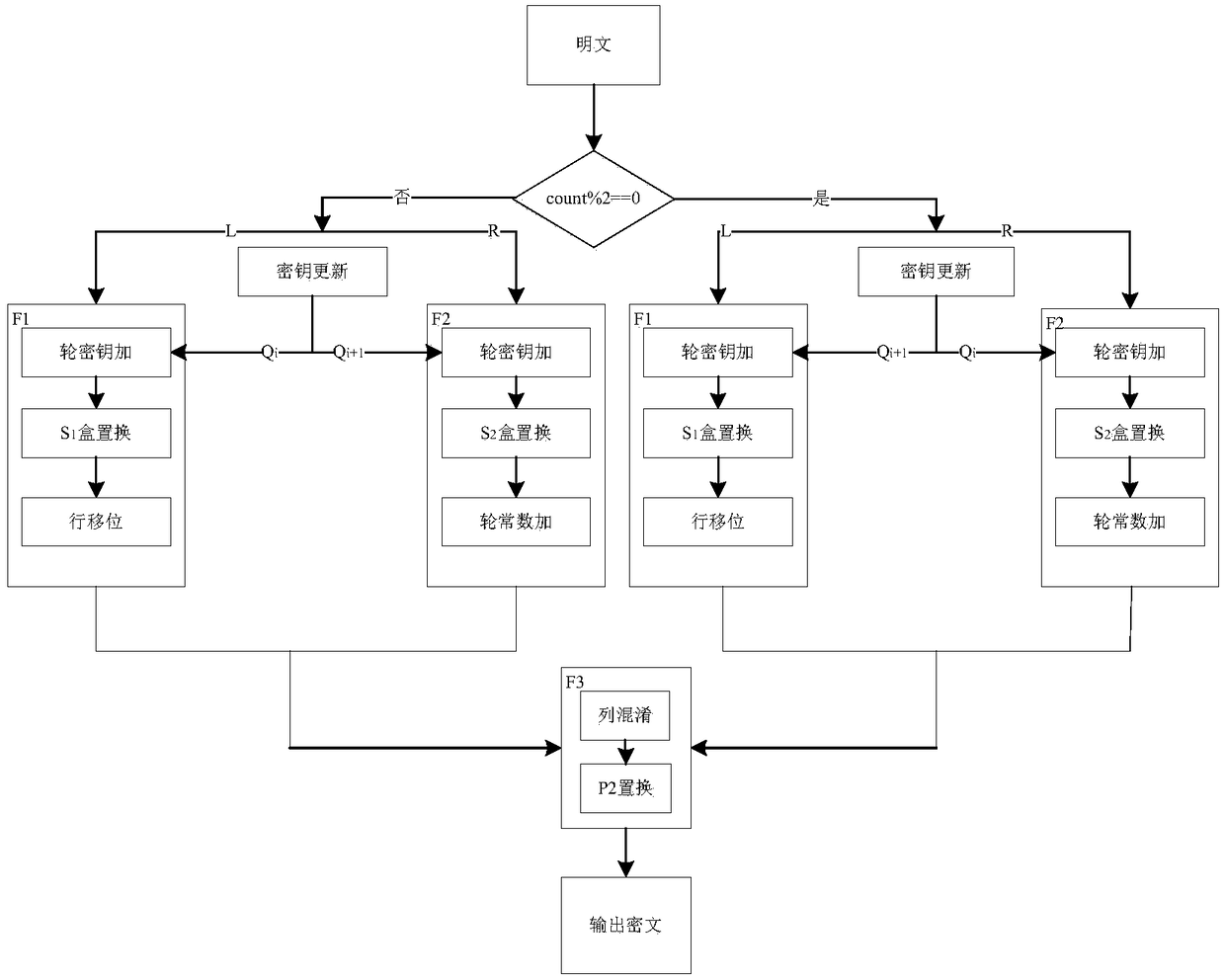
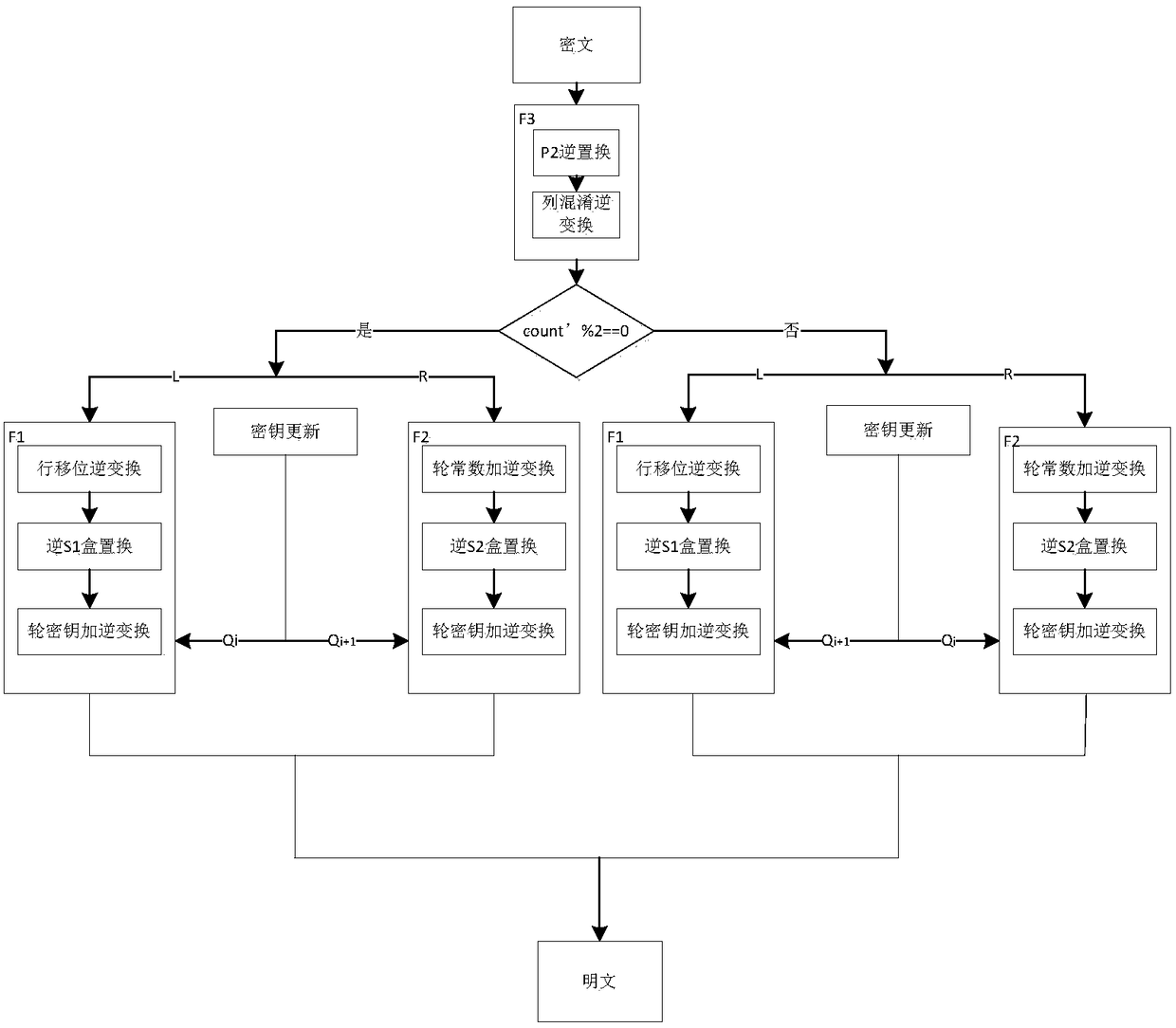
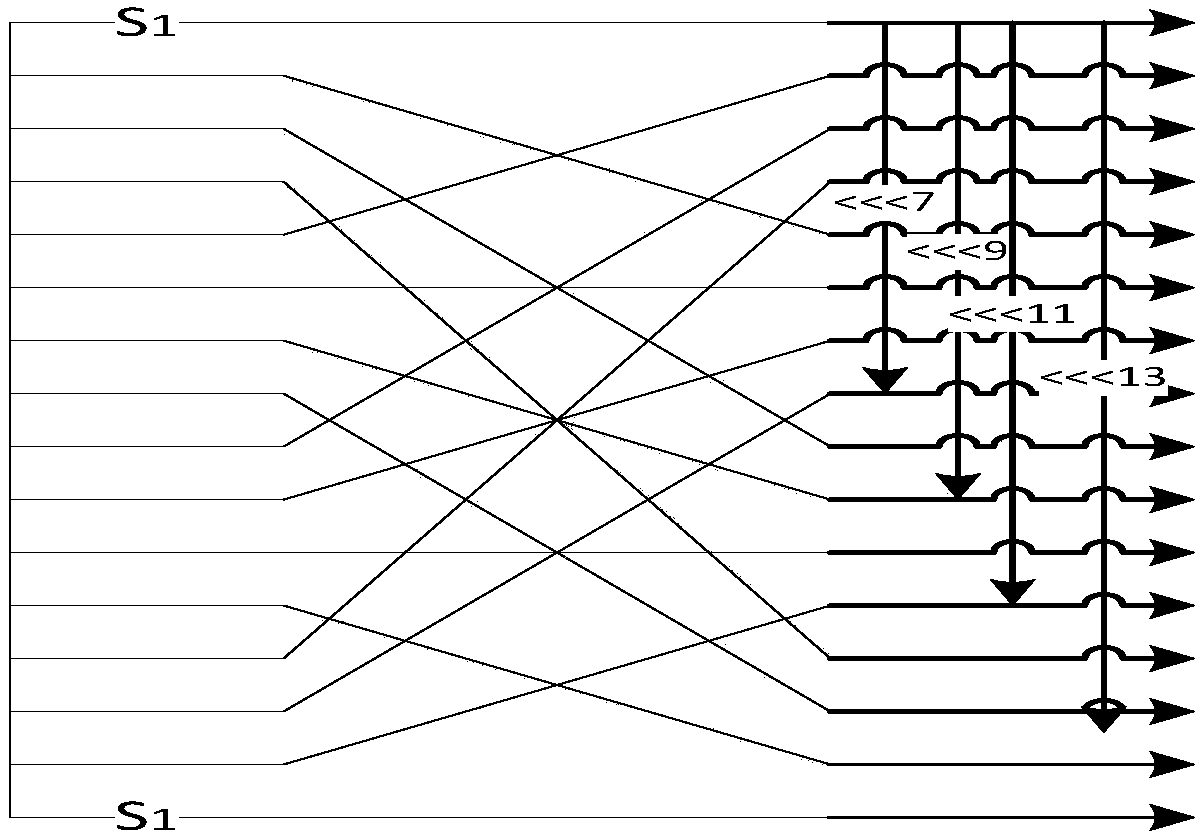
The invention provides a lightweight cryptographic algorithm HBcipher implementation method and device. In the method, a round function used in the encryption or decryption process is an F function adopting three groups of SPN structures, and a novel P2 substitution mode is proposed in the round function. By selecting a round constant count as a round operation control signal, two different operation modes are designed according to the parity of count; when the algorithm is implemented by Xilinx ISE Design Suite 13.2 hardware, the throughput rate of HBcipher-64 is 511.38 Mbps, the throughput rate of HBcipher-128 is 716.6848 Mbps, and compared with a current lightweight cryptographic algorithm, the algorithm has high encryption efficiency.
Owner:HENGYANG NORMAL UNIV
Encryption processing apparatus, encryption method, and computer program
ActiveUS8369522B2Unauthorized memory use protectionRecord information storageComputer hardwareExclusive or
A common-key blockcipher processing structure that makes analysis of key more difficult and enhances security and implementation efficiency is realized. In a key scheduling part in an encryption processing apparatus that performs common-key blockcipher processing, a secret key is input to an encryption function including a round function employed in an encryption processing part to generate an intermediate key, and the result of performing bijective transformation based on the intermediate key, the secret key, and the like and the result of performing an exclusive-OR operation on the bijective-transformed data are applied to round keys. With this structure, generation of round keys based on the intermediate key generated using the encryption function whose security has been ensured is performed, thereby making it possible to make analysis of the keys more difficult. The structure of the key scheduling part can be simplified, thereby making it possible to improve the implementation efficiency.
Owner:SONY CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com