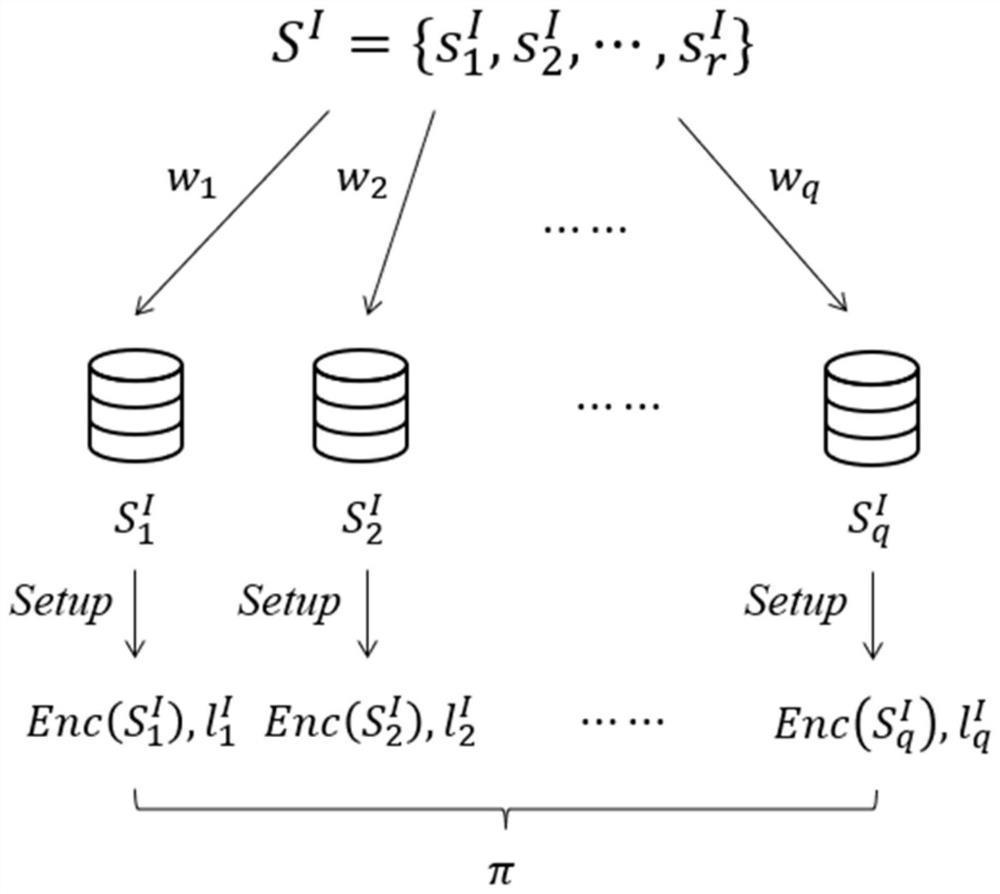
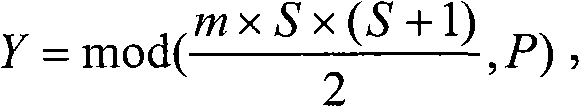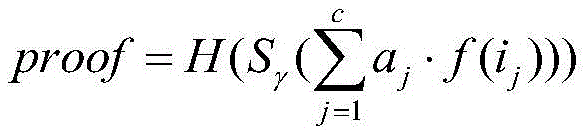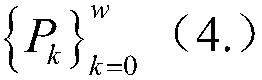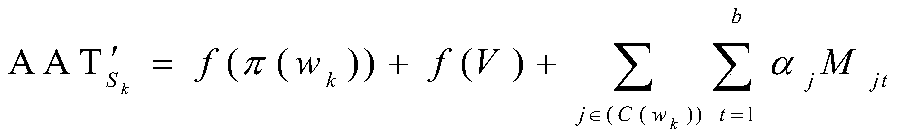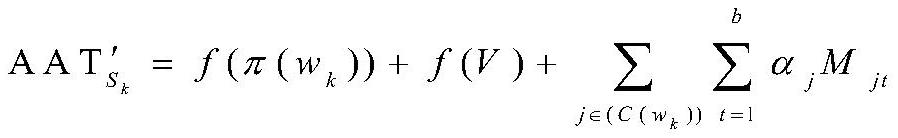Patents
Literature
31 results about "Pseudorandom permutation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In cryptography, a pseudorandom permutation (PRP) is a function that cannot be distinguished from a random permutation (that is, a permutation selected at random with uniform probability, from the family of all permutations on the function's domain) with practical effort. An unpredictable permutation (UP) Fₖ is a permutation whose values cannot be predicted by a fast randomized algorithm. Unpredictable permutations may be used as a cryptographic primitive, a building block for cryptographic systems with more complex properties.
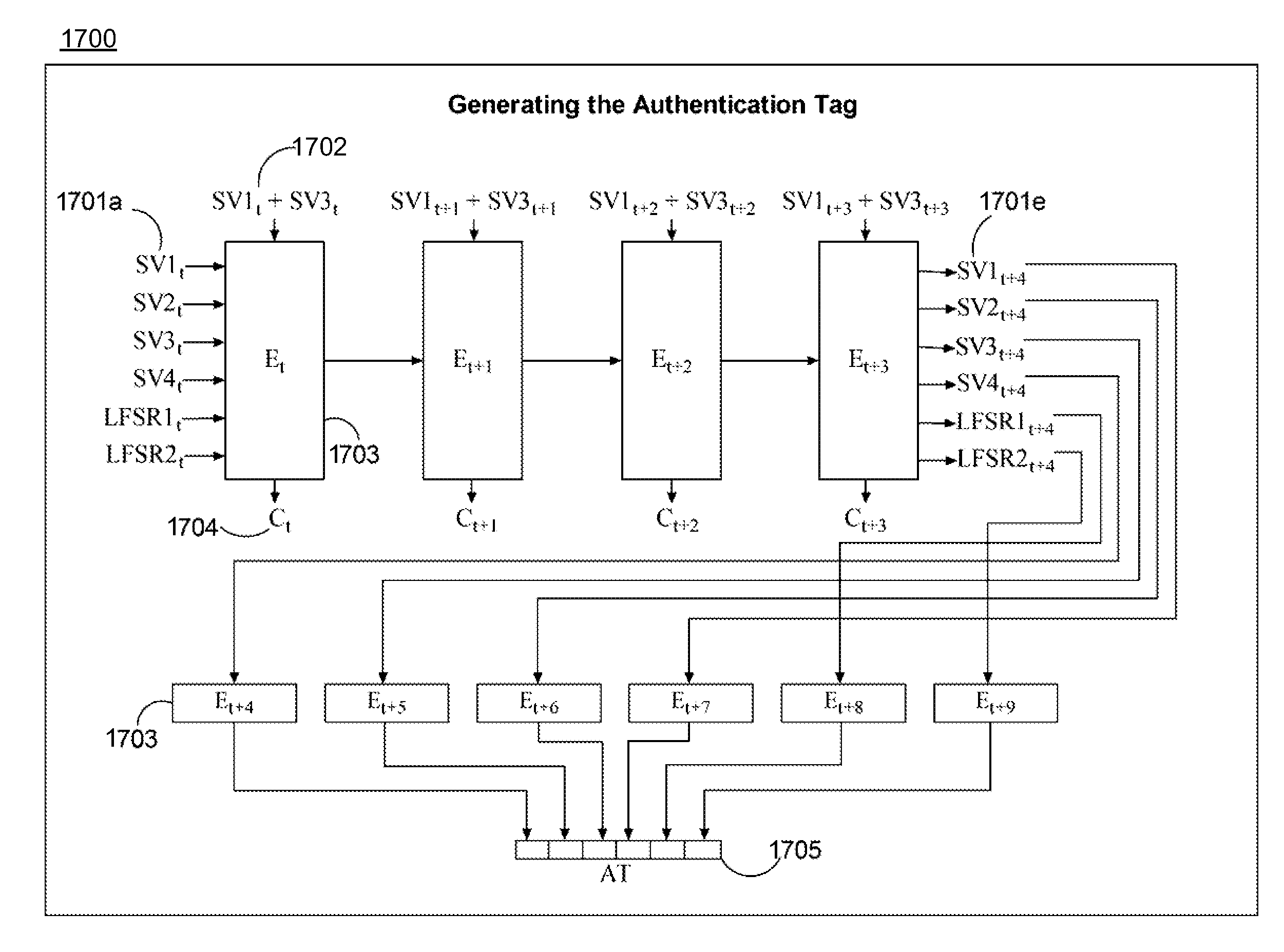
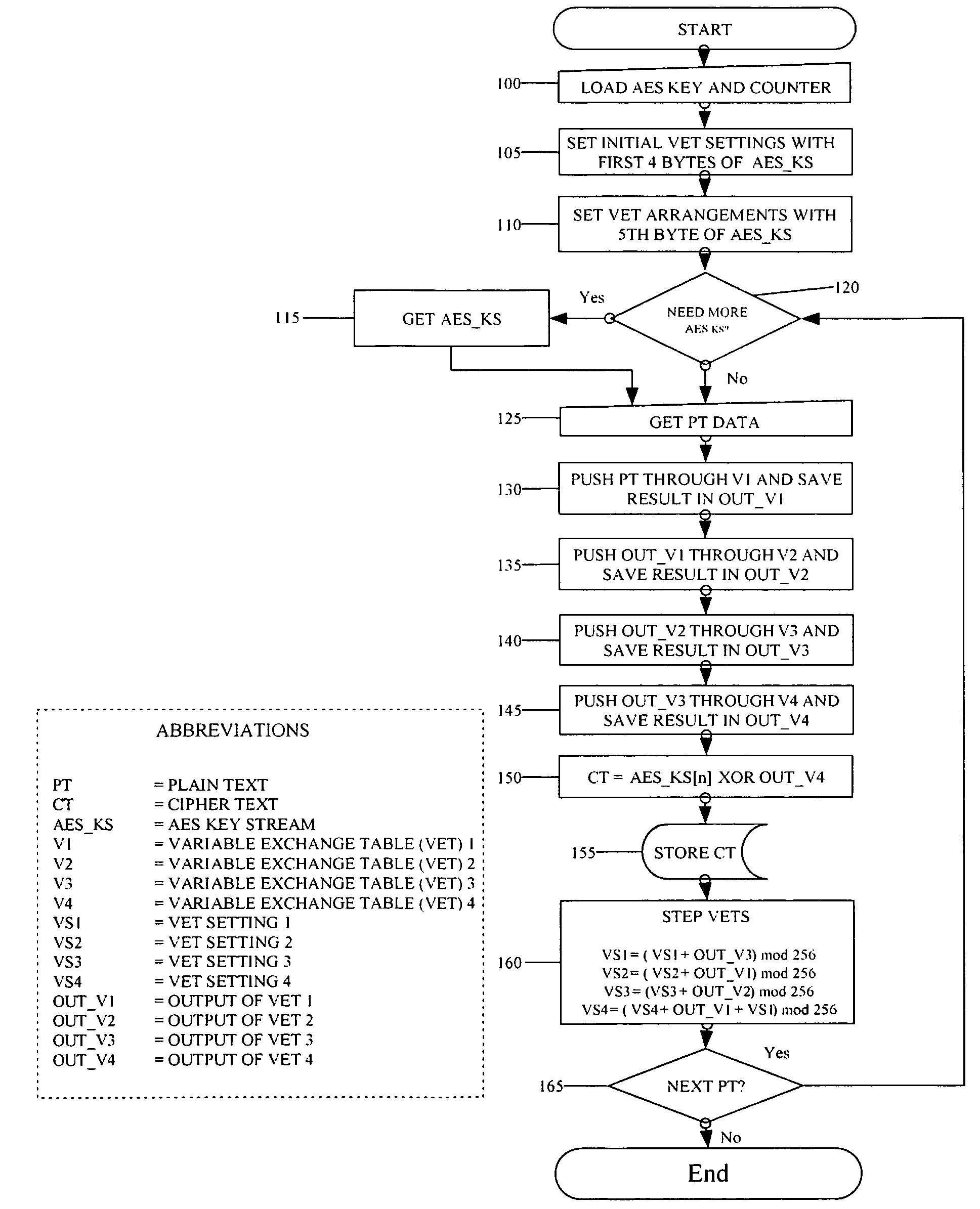
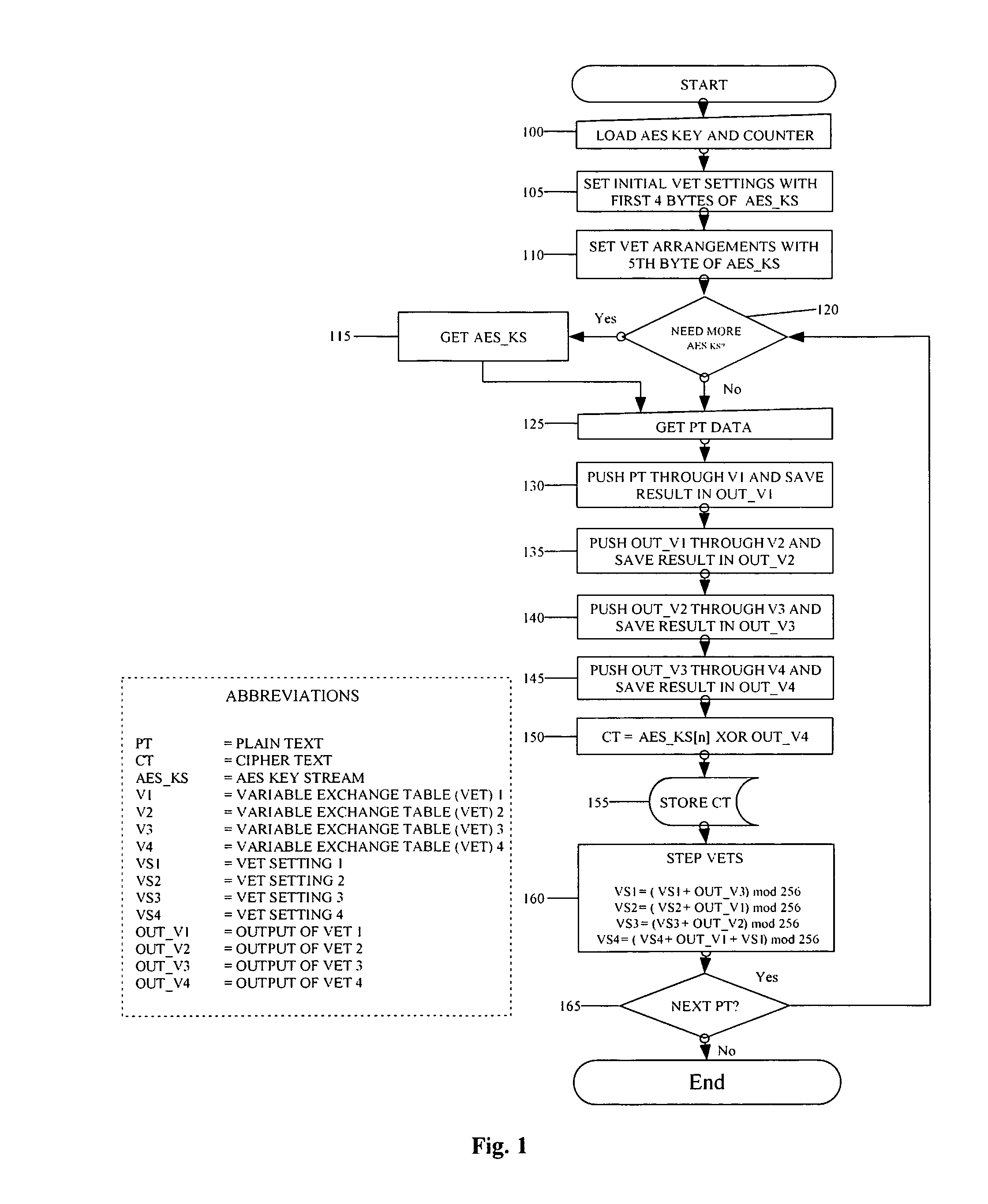
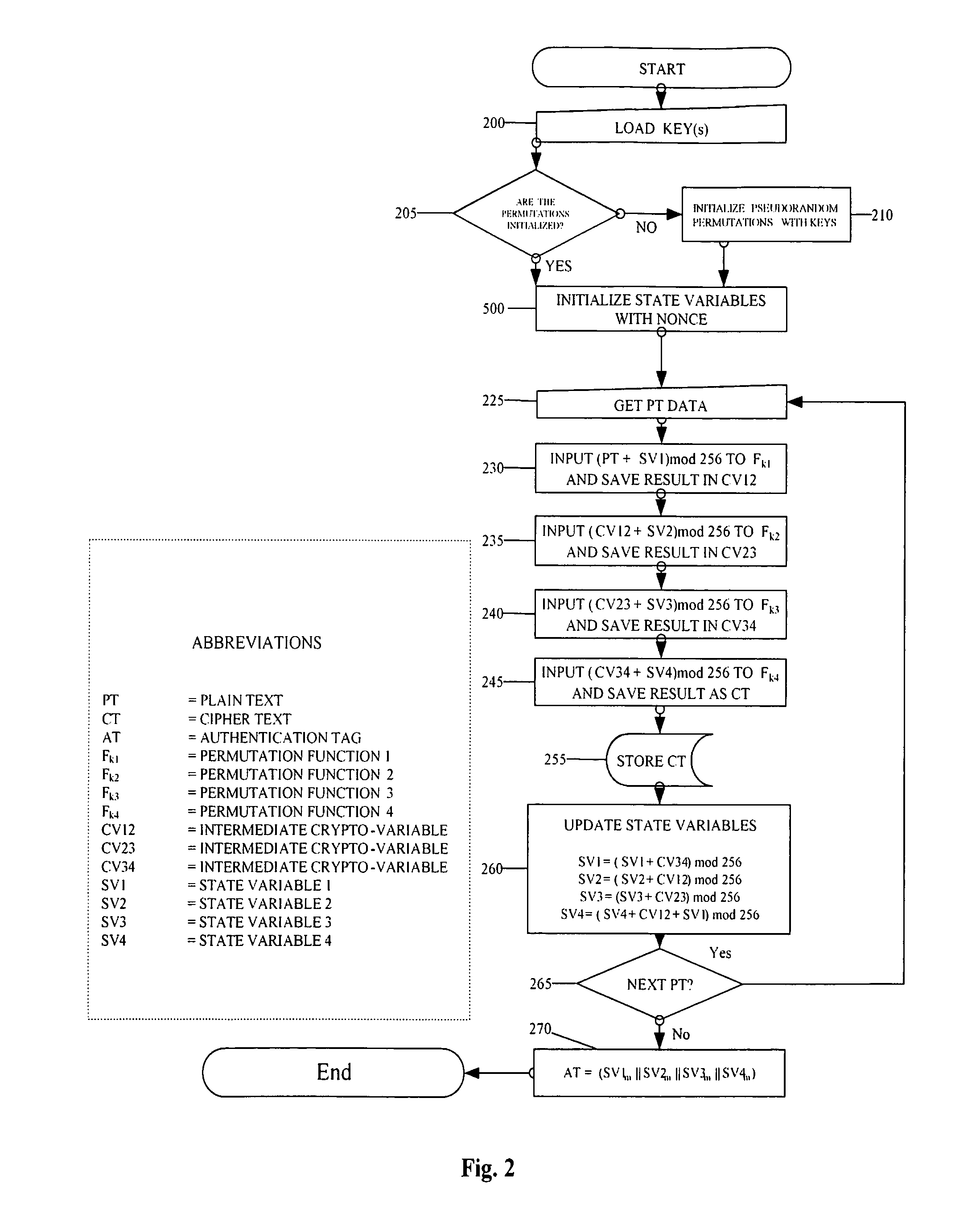
System for encrypting and decrypting a plaintext message with authentication
InactiveUS20120008767A1Lower levelLow levelSecret communicationSecuring communicationComputer hardwarePlaintext
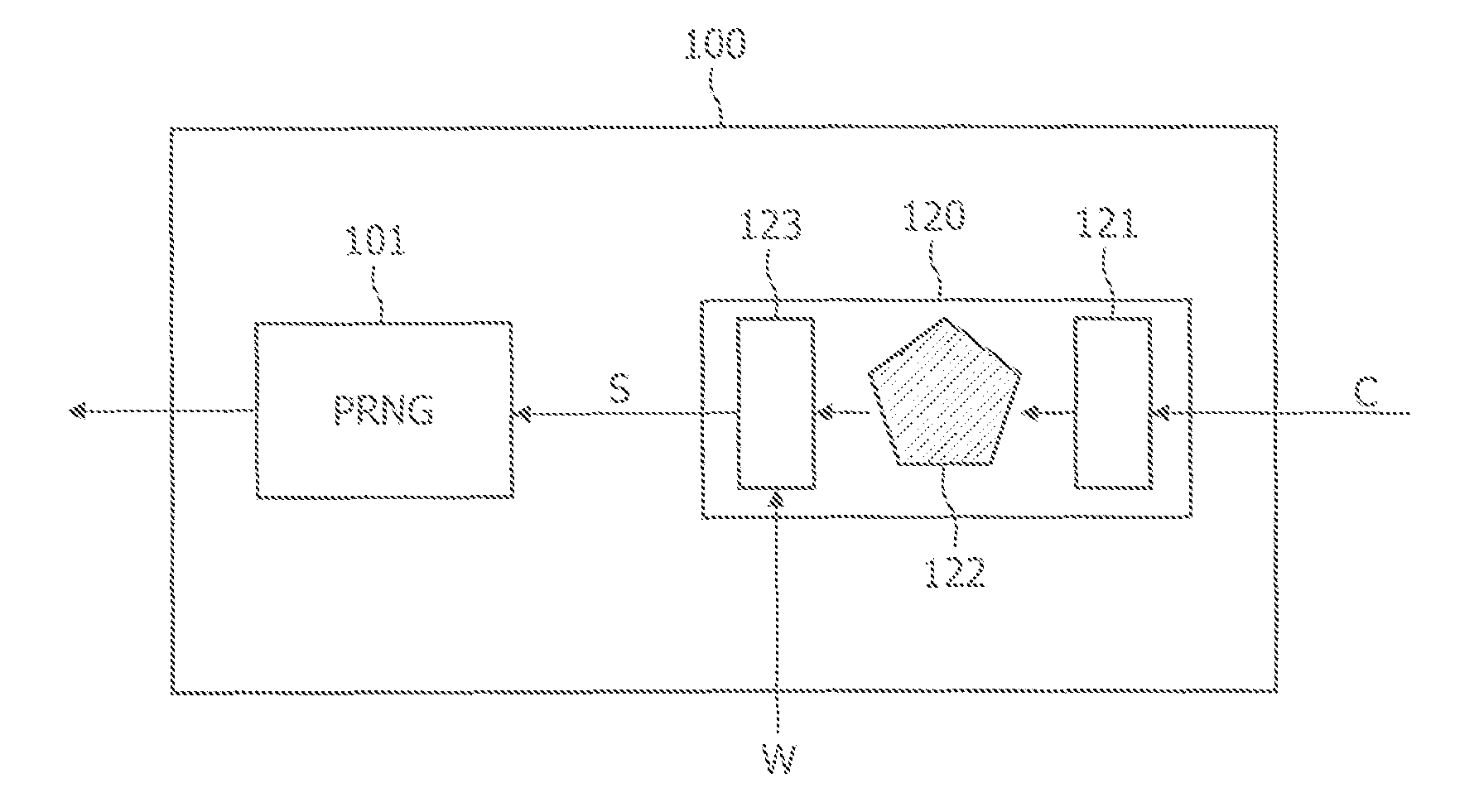
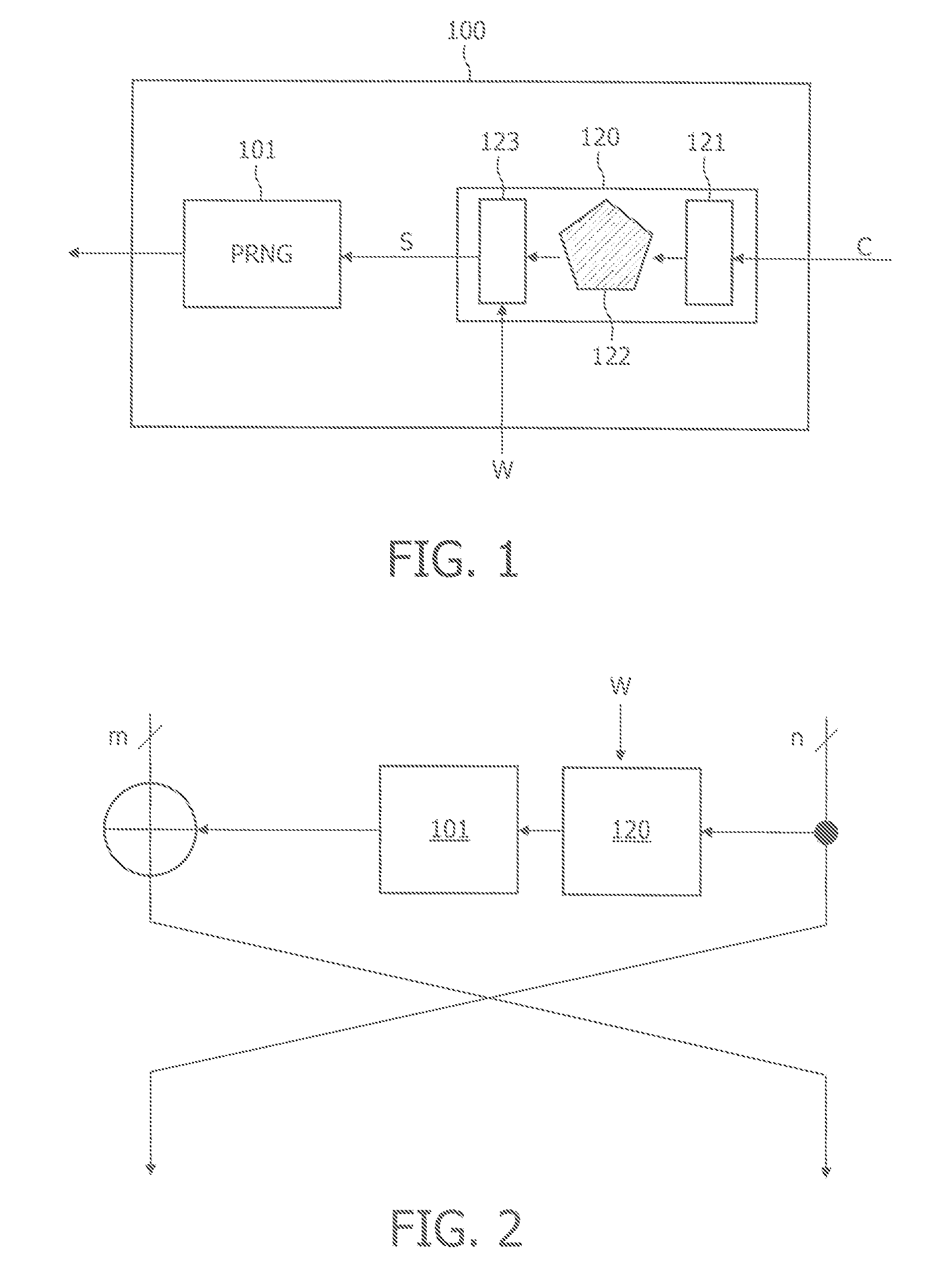
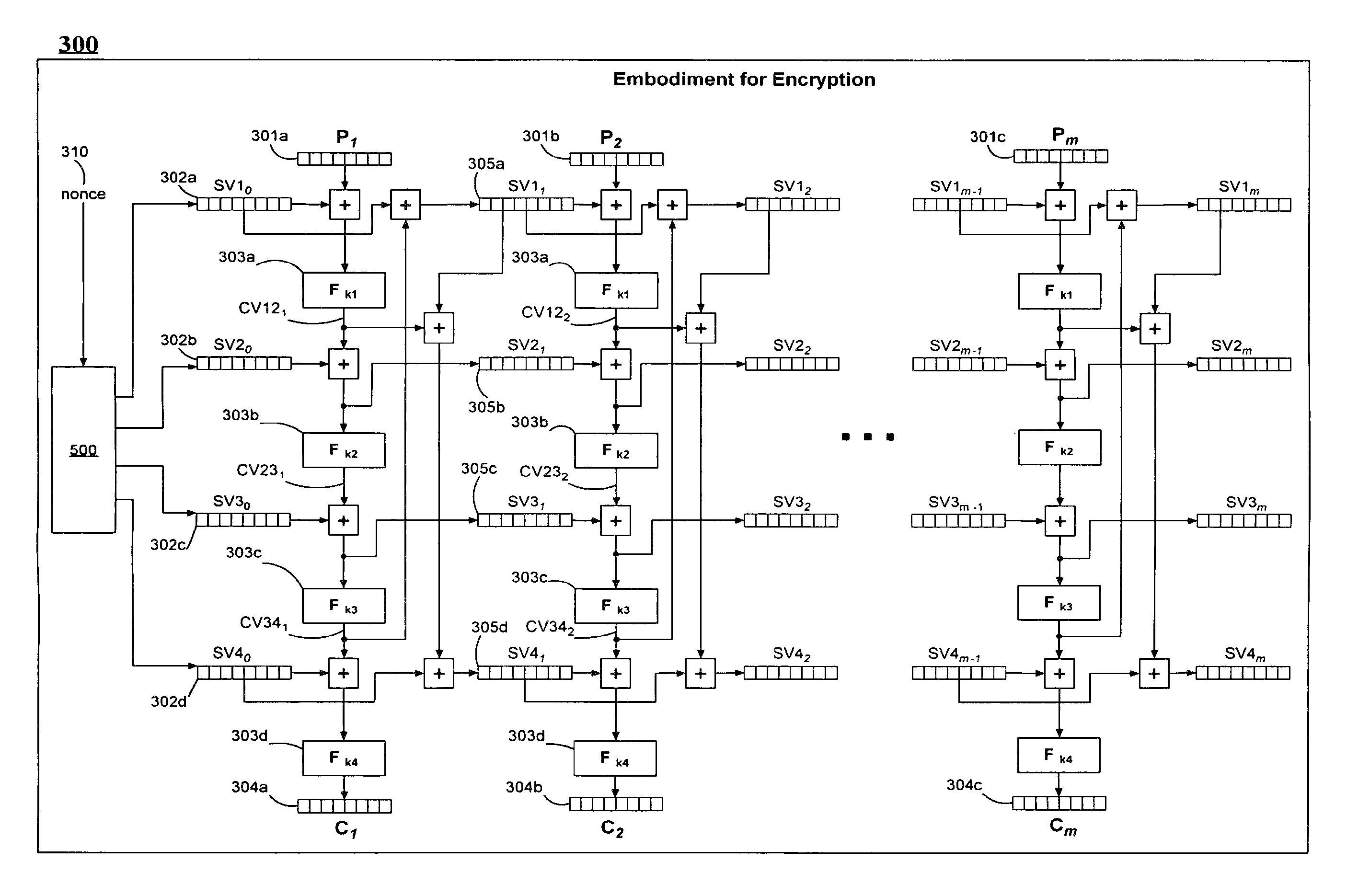
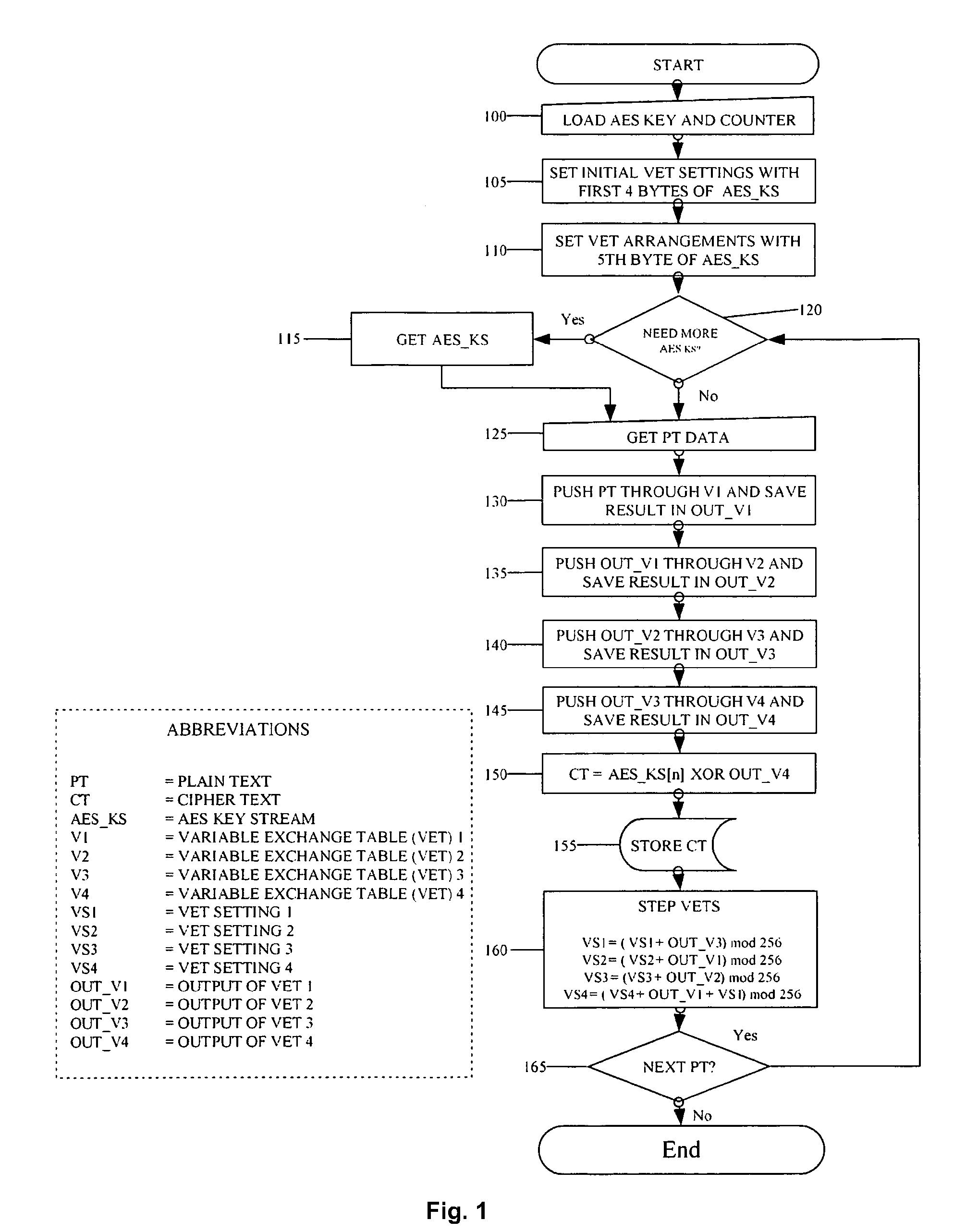
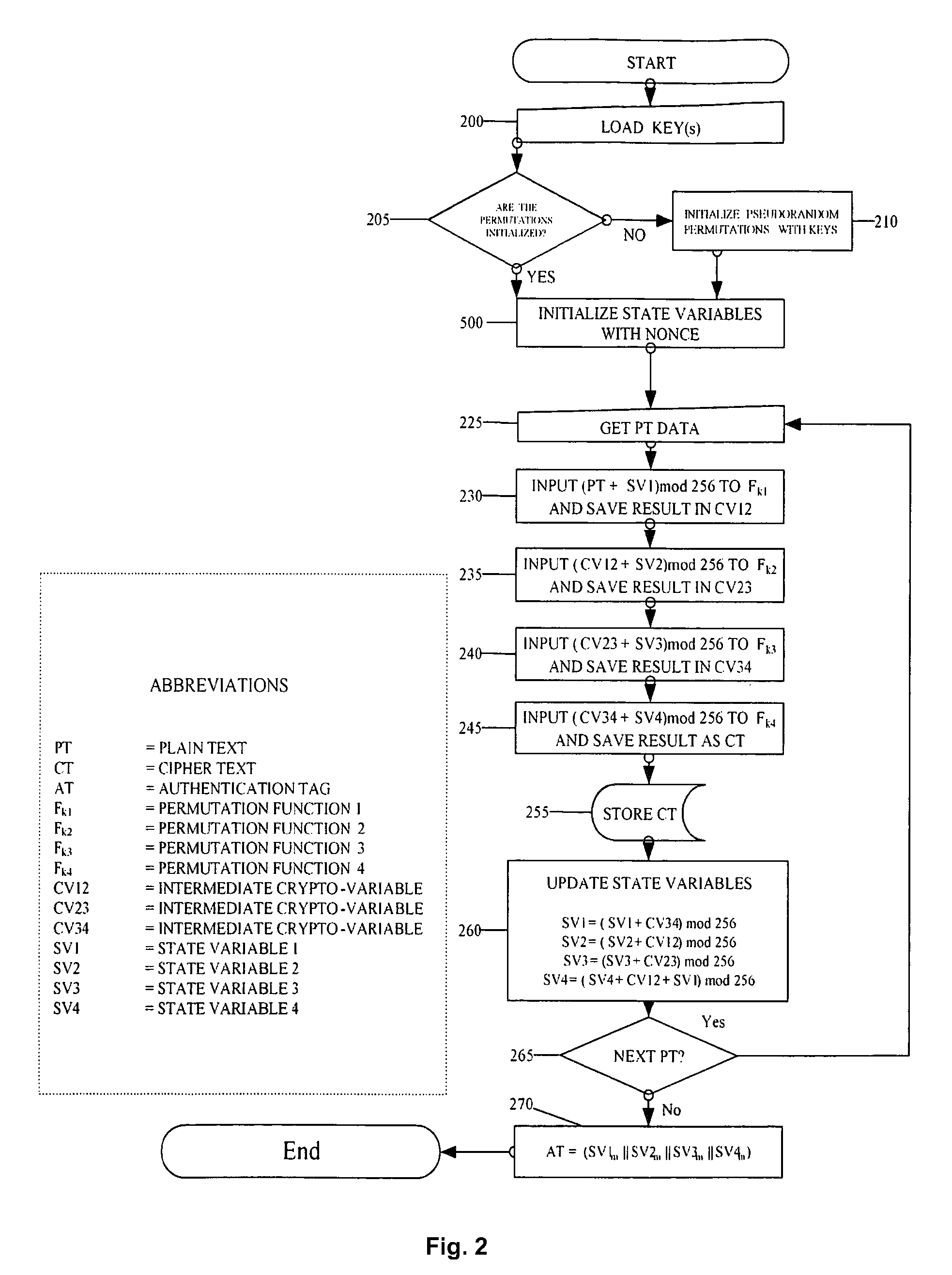
The described system and method provide for an encryption and authentication technique that achieves enhanced integrity verification through assured error-propagation using a multistage sequence of pseudorandom permutations. The method generates intermediate data-dependent cryptographic variables at each stage, which are systematically combined into feedback loops. The encryption technique also generates an authentication tag with minimal post processing that is the size of the state. The size of the state is dependent on the number of pseudorandom permutations and the size of the LFSR. The authentication tag provides a unique mapping to the plaintext for any number of plaintext blocks that is less than or equal the size of the state. In addition to being a stand alone encryption algorithm, the disclosed technique is applicable to any mode that uses pseudorandom permutations such as, key dependent lookup tables, S-Boxes, and block ciphers such as RC5, TEA, and AES.
Owner:SMITH ERIC MYRON +3
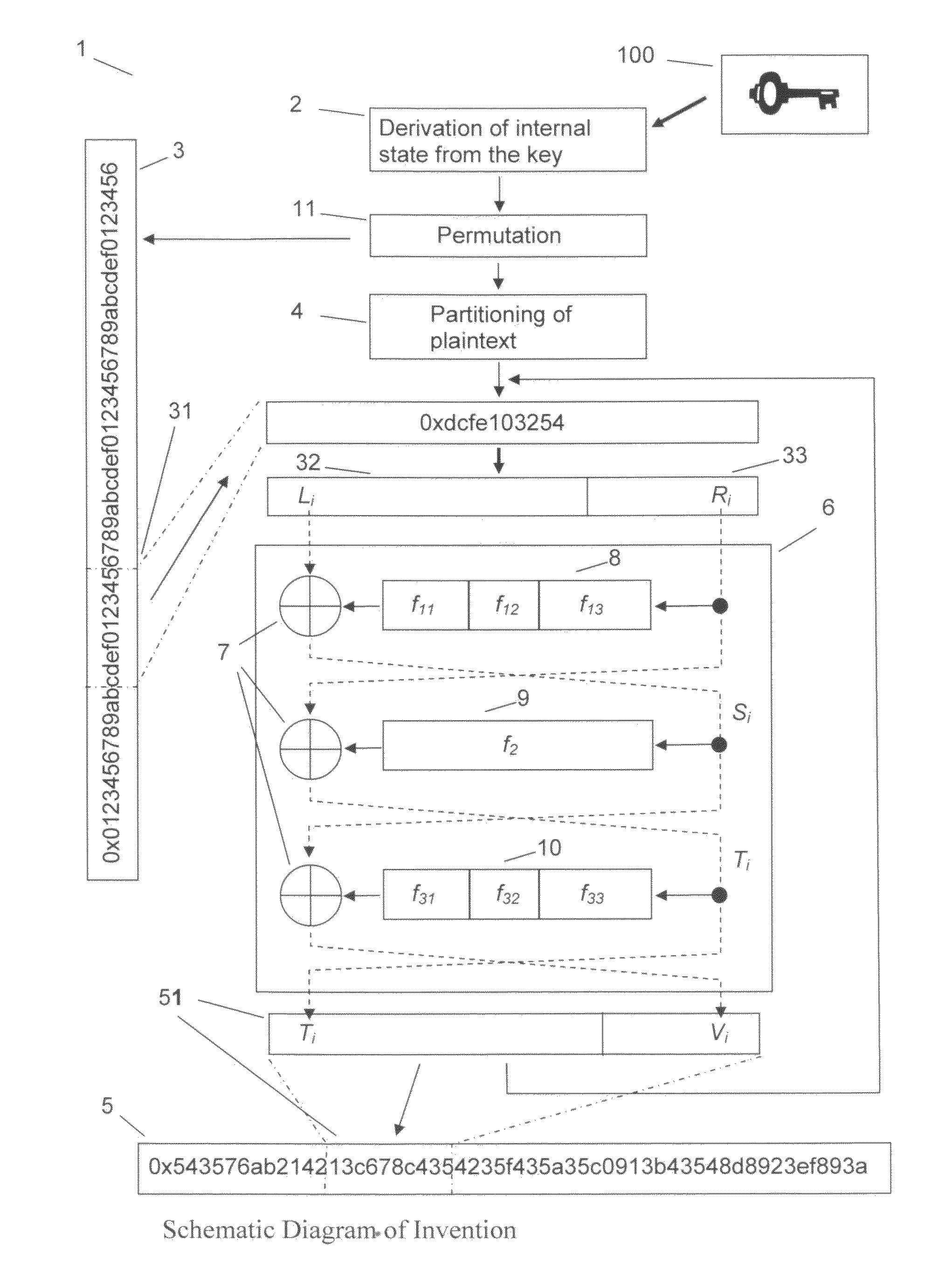
Block cipher
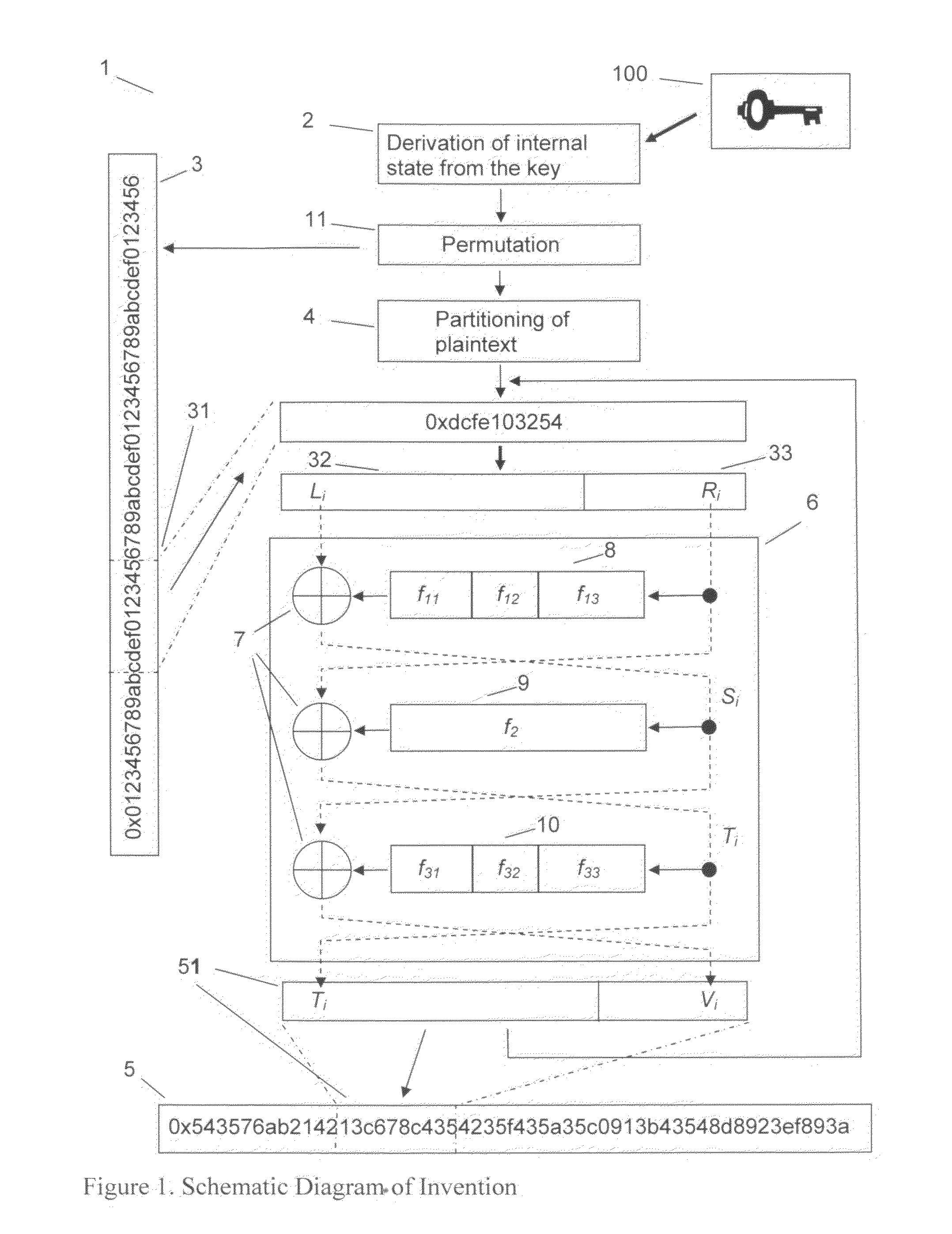
The method provided is for the encryption of data block by block, but unlike conventional methods like DES or AES, with a variable and substantially greater block length. The enciphering operations depend not only on the key, but also on the length of the plaintext blocks. The method meets the Strict Avalanche Criterion much better than conventional ciphers and blocks do not need to be padded. The method that additionally partitions outsized blocks executes the following steps:Derivation of the internal state of the method from the key, pseudorandom permutation of plaintext bits or groups of plaintext bits, partitioning of outsized plaintext data blocks, execution of at least three unbalanced Feistel network rounds with round functions having the ability to output results with variable length and bit-by-bit exclusive-or combination with output of round functions within the Feistel rounds.
Owner:ROLLGEN CLEMENS KARL BERHARD
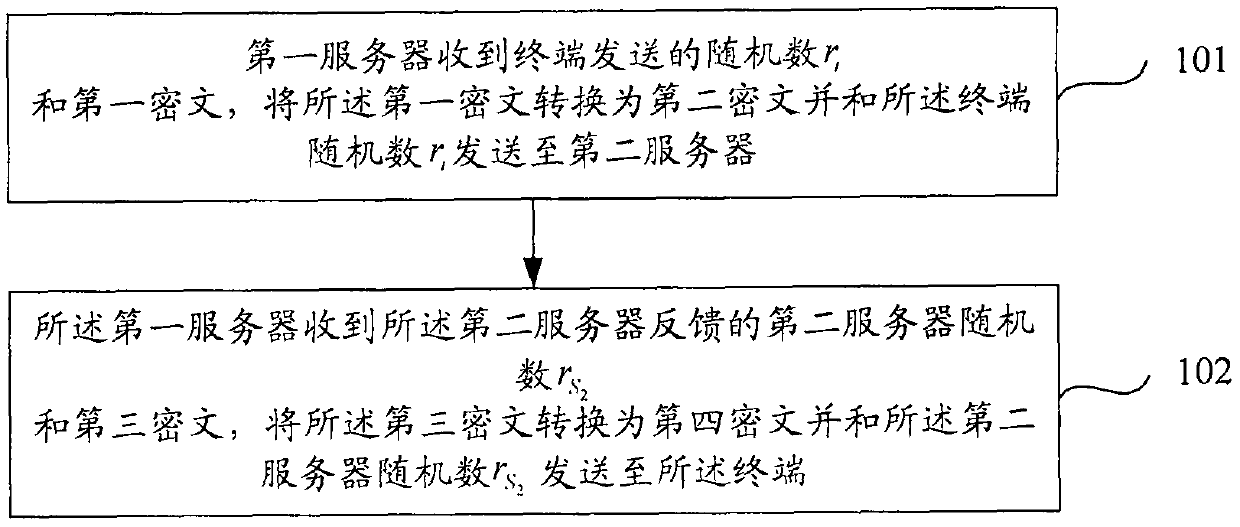
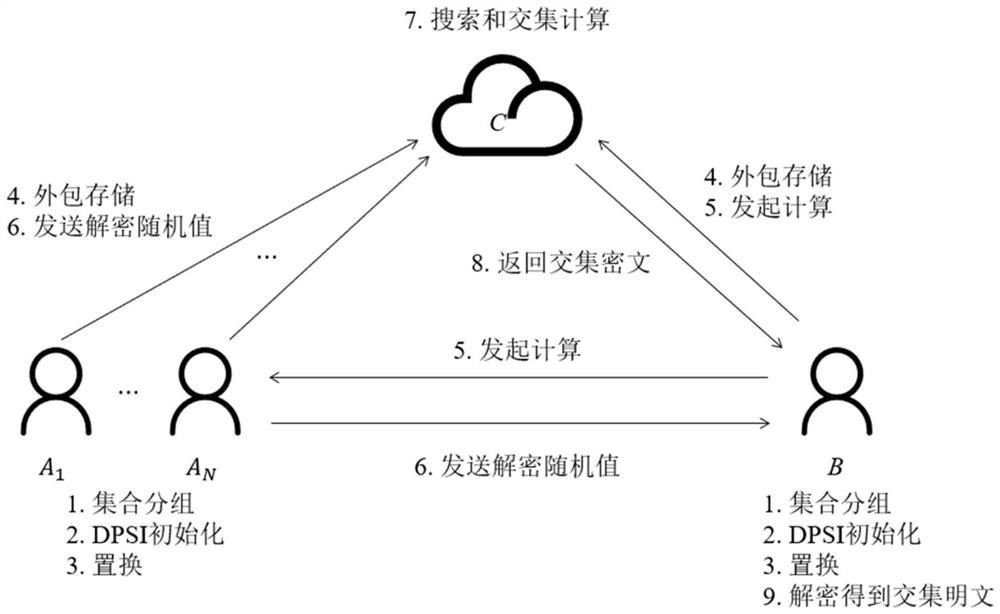
Cloud outsourcing privacy set comparison method and device
InactiveCN107196926AImprove securityImproving the efficiency of private collection comparisonsTransmissionCiphertextPseudorandom permutation
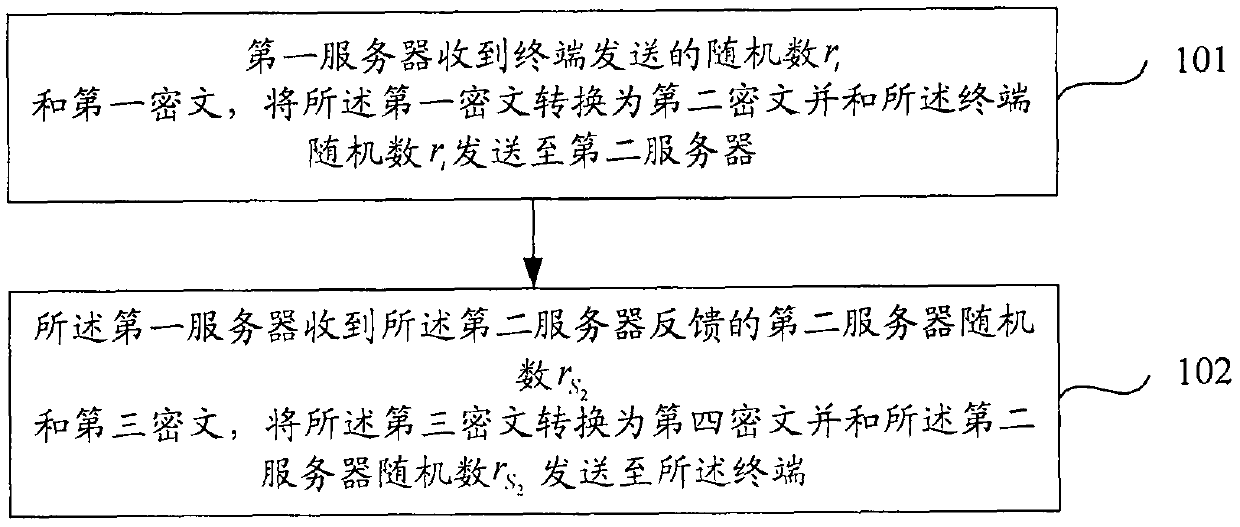
The invention discloses a cloud outsourcing privacy set comparison method and a cloud outsourcing privacy set comparison device, which relate to the field of communication technologies, and are used for solving the problems that security cannot be guaranteed, and the practicality and extendibility are not high existing in the existing outsourcing privacy set comparison protocol. The cloud outsourcing privacy set comparison method comprises the steps that: a first server receives a random number ri and a first ciphertext sent by a terminal, converts the first ciphertext into a second ciphertext and sends the second ciphertext and the random number ri to a second server; and the first server receives a second server random number r<S2> and a third ciphertext fed back by the second server, converts the third ciphertext into a fourth ciphertext and sends the fourth ciphertext and the second server random number r<S2> to the terminal, wherein the second server adopts a second server secret key K<S2> to obtain a pseudo-random permutation of a terminal set and calculates an intersection set of the pseudo-random permutation, the third ciphertext comprises the intersection set of the pseudo-random permutation of the terminal set and a pseudo-random function of the second server secret key K<S2>, and the fourth ciphertext comprises the intersection set of the pseudo-random permutation of the terminal set and a pseudo-random function of a terminal secret key Ki.
Owner:HENAN NORMAL UNIV
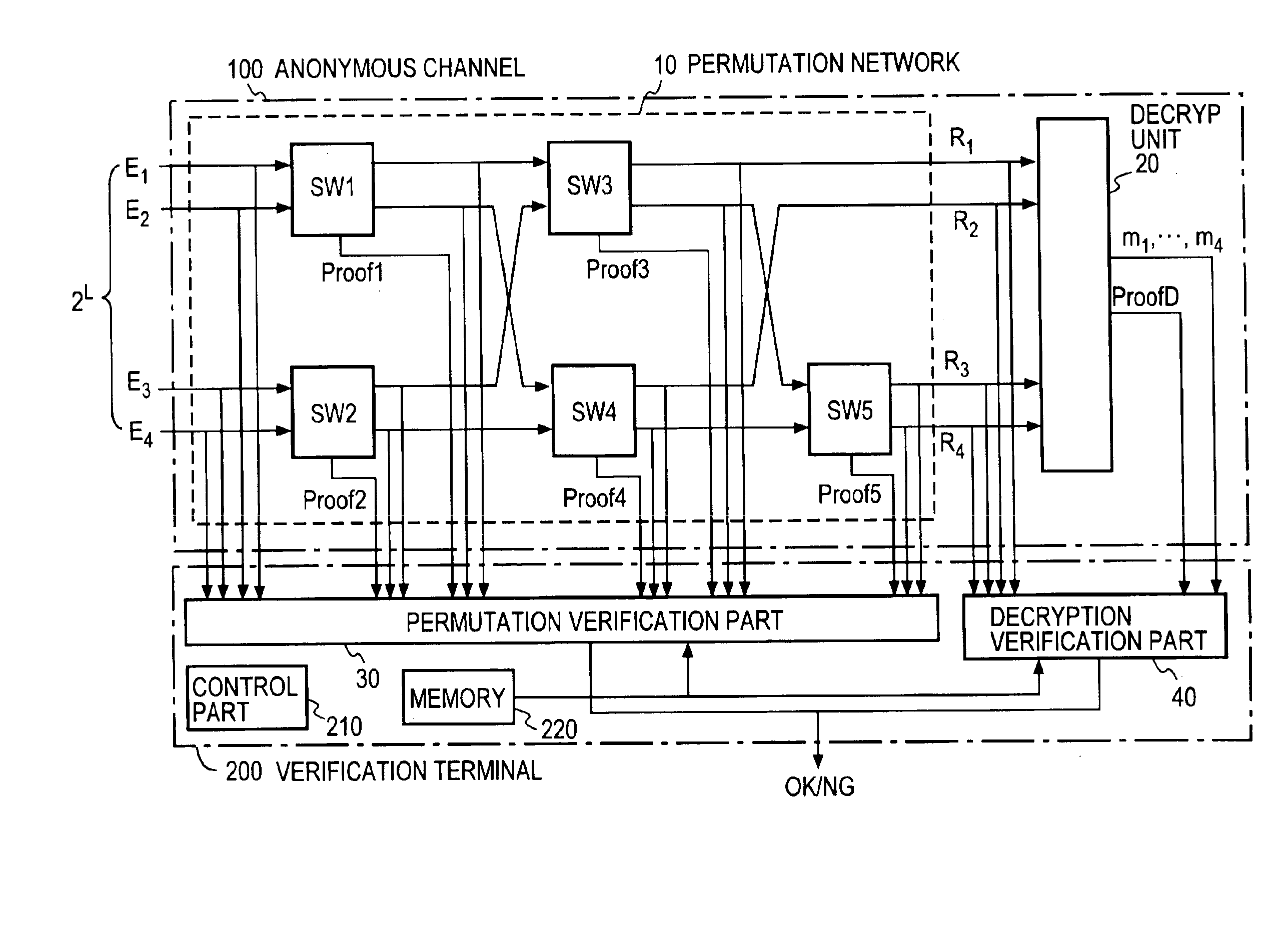
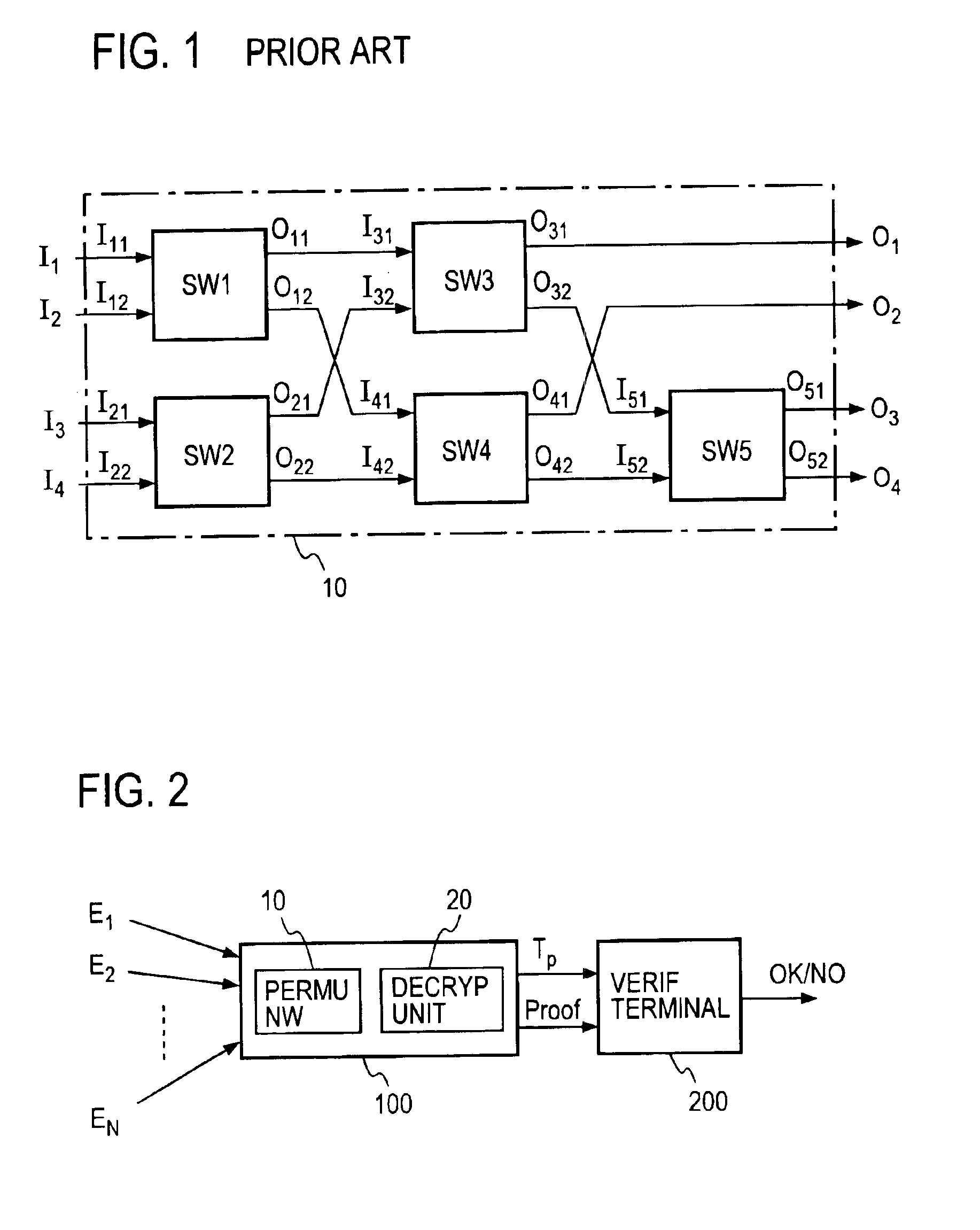
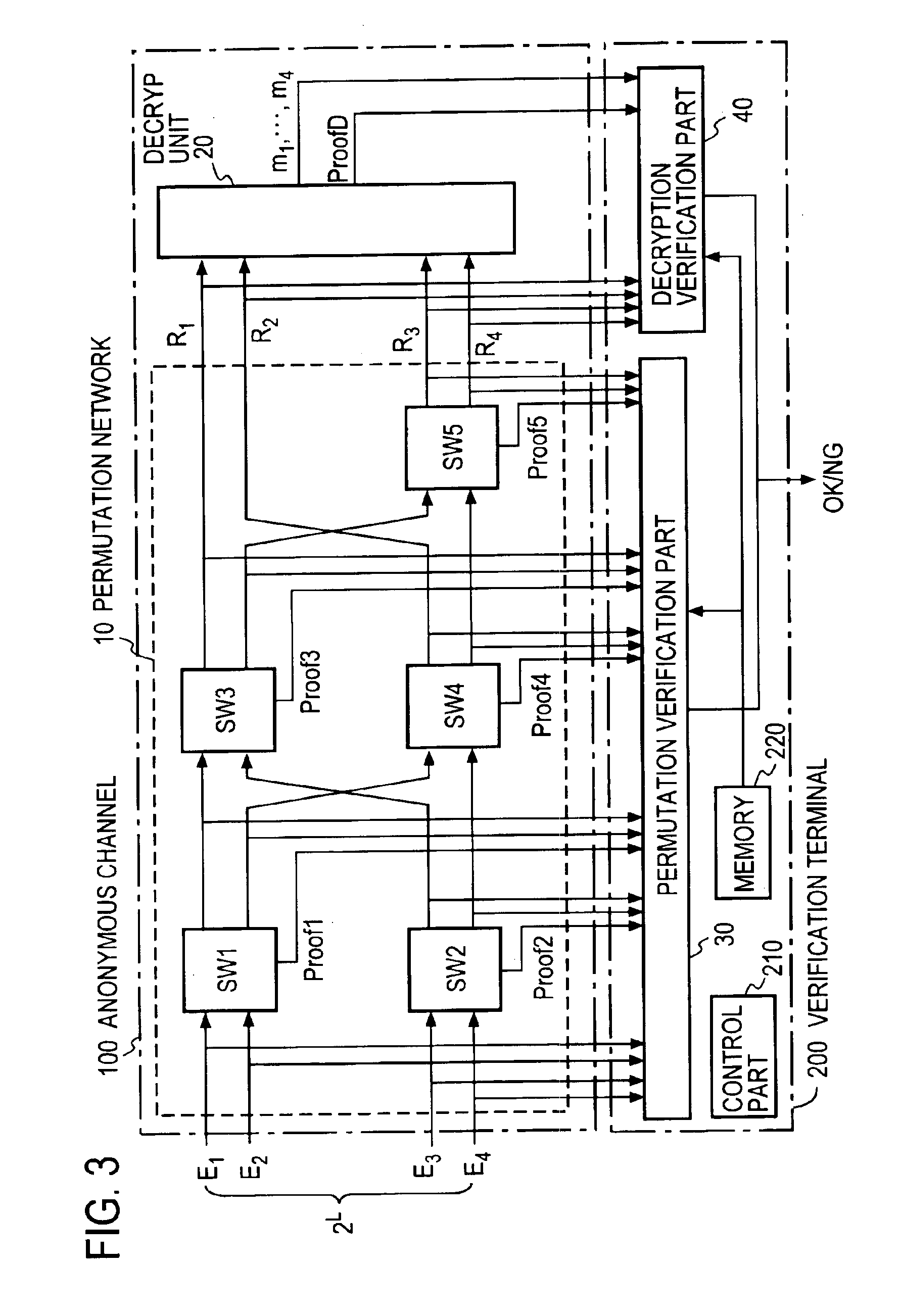
Verifiable anonymous channel
InactiveUS6937728B1Efficiently proveEfficient verificationPublic key for secure communicationUser identity/authority verificationPseudorandom permutationValidator
Two El Gamal ciphertexts, which are input to a two-input two-output unit switching gates SW forming a permutation network, are randomized with a random number and randomly permuted, and a zero-knowledge proof, which proves the correspondence between the inputs and outputs of the switching gates SW, is output to a verifier without revealing the random number and the random permutation. A decryption unit decrypts ciphertexts from a unit switching gate SW in he last column through the use of a secret key, and proves in zero-knowledge the validity of the decryption without revealing the secret key. A verification unit verifies the proof of each unit switching gate and the proof of the decryption unit.
Owner:NIPPON TELEGRAPH & TELEPHONE CORP
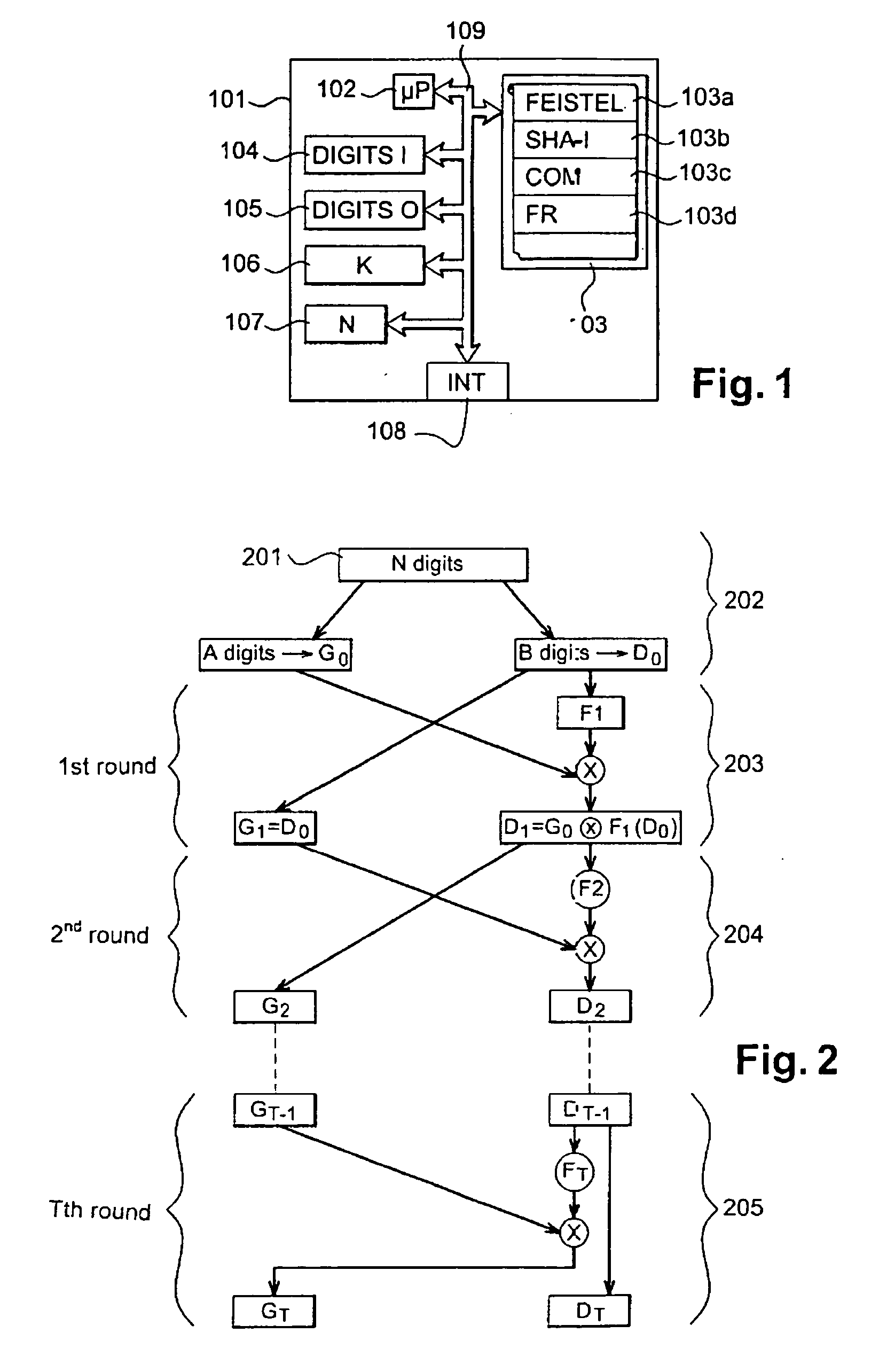
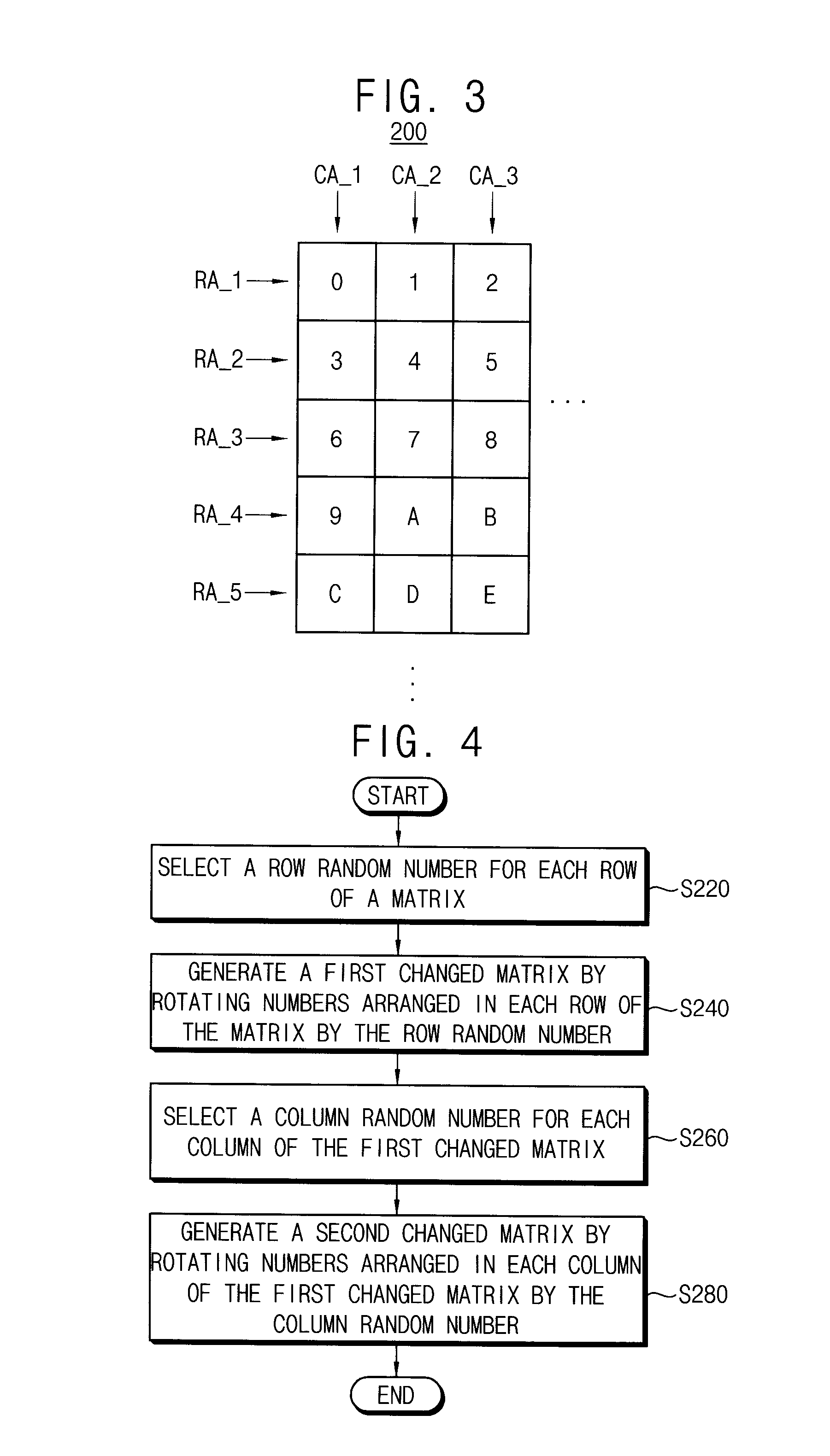
Method for the generation of pseudo-random permutation of an N-digit word
InactiveUS20040208321A1Encryption apparatus with shift registers/memoriesCoding/ciphering apparatusOne-way functionPseudorandom permutation
Owner:WARY JEAN PHILIPPE
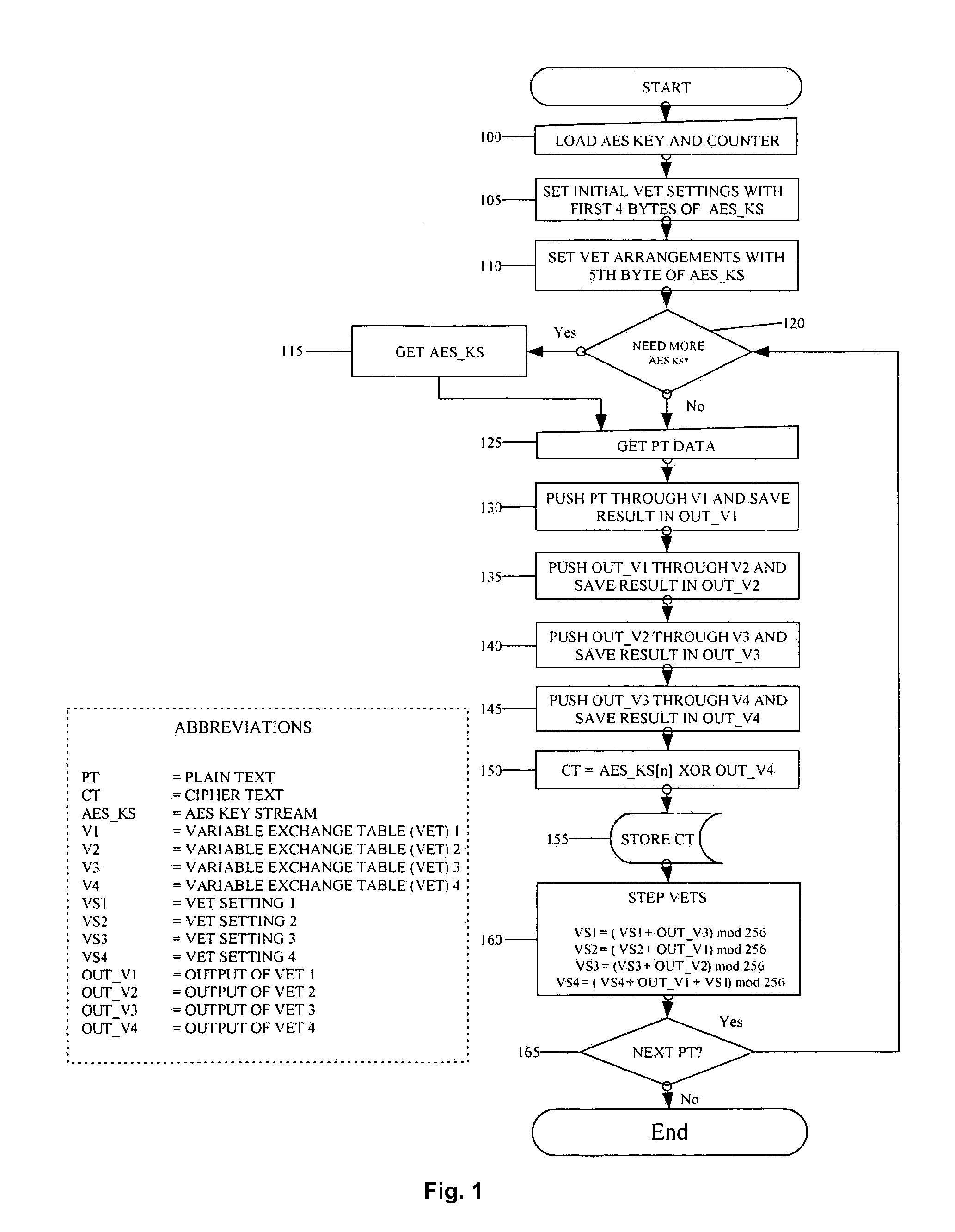
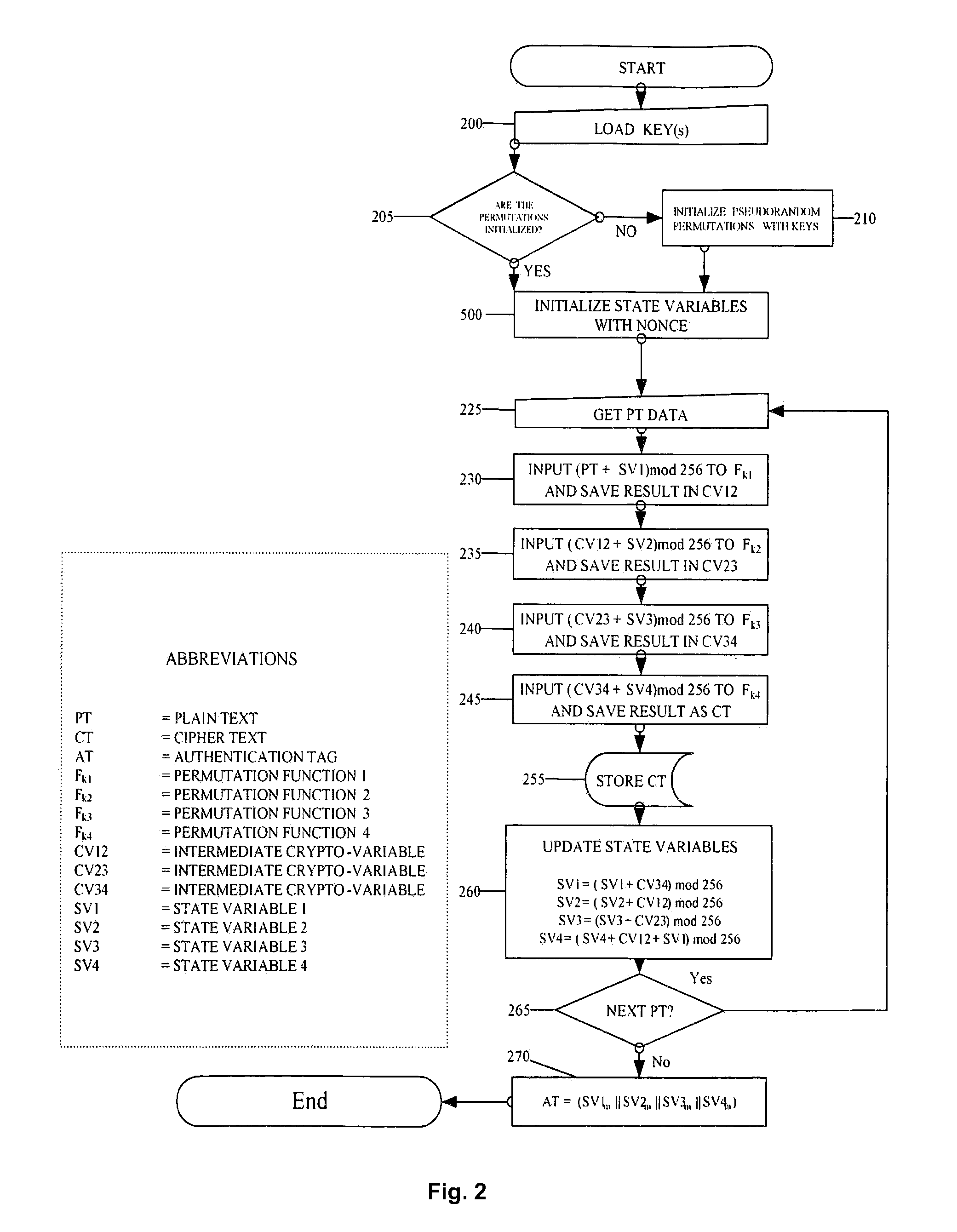
Encrypting a plaintext message with authentication
InactiveUS7715553B2Low levelEfficiently integrityUser identity/authority verificationDigital data protectionPlaintextComputer hardware
An encryption and authentication technique that achieves enhanced integrity verification through assured error-propagation using a multistage sequence of pseudorandom permutations. The present invention generates intermediate data-dependent cryptographic variables at each stage, which are systematically combined into feedback loops. The encryption technique also generates an authentication tag without any further steps that is N times longer than the block size where N is the number of pseudorandom permutations used in the encipherment of each block. The authentication tag provides a unique mapping to the plaintext for any number of plaintext blocks that is less than or equal to N. In addition to being a stand alone encryption algorithm, the disclosed technique is applicable to any mode that uses pseudorandom permutations such as, key dependent lookup tables, S-Boxes, and block ciphers such as RC5, TEA, and AES.
Owner:DUPRE DURWARD D
Method of generating arbitrary numbers given a seed
ActiveUS20100054466A1Improve protectionSignificant comprehensive benefitsRandom number generatorsEncryption apparatus with shift registers/memoriesNumber generatorPseudorandom permutation
The invention provides a method of generating arbitrary numbers given a seed, characterized by providing a challenge derived from the seed to a physical token, receiving an initial response from the physical token, combining the initial response with helper data associated with the challenge to produce a stable response, and generating the arbitrary numbers using a pseudo-random number generator using the stable response as a seed for the generator. Preferably one or more of these pseudo-random permutations are used as one or more round function(s) in a Feistel block cipher. The generated arbitrary numbers may also be used to create a cryptographic key.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
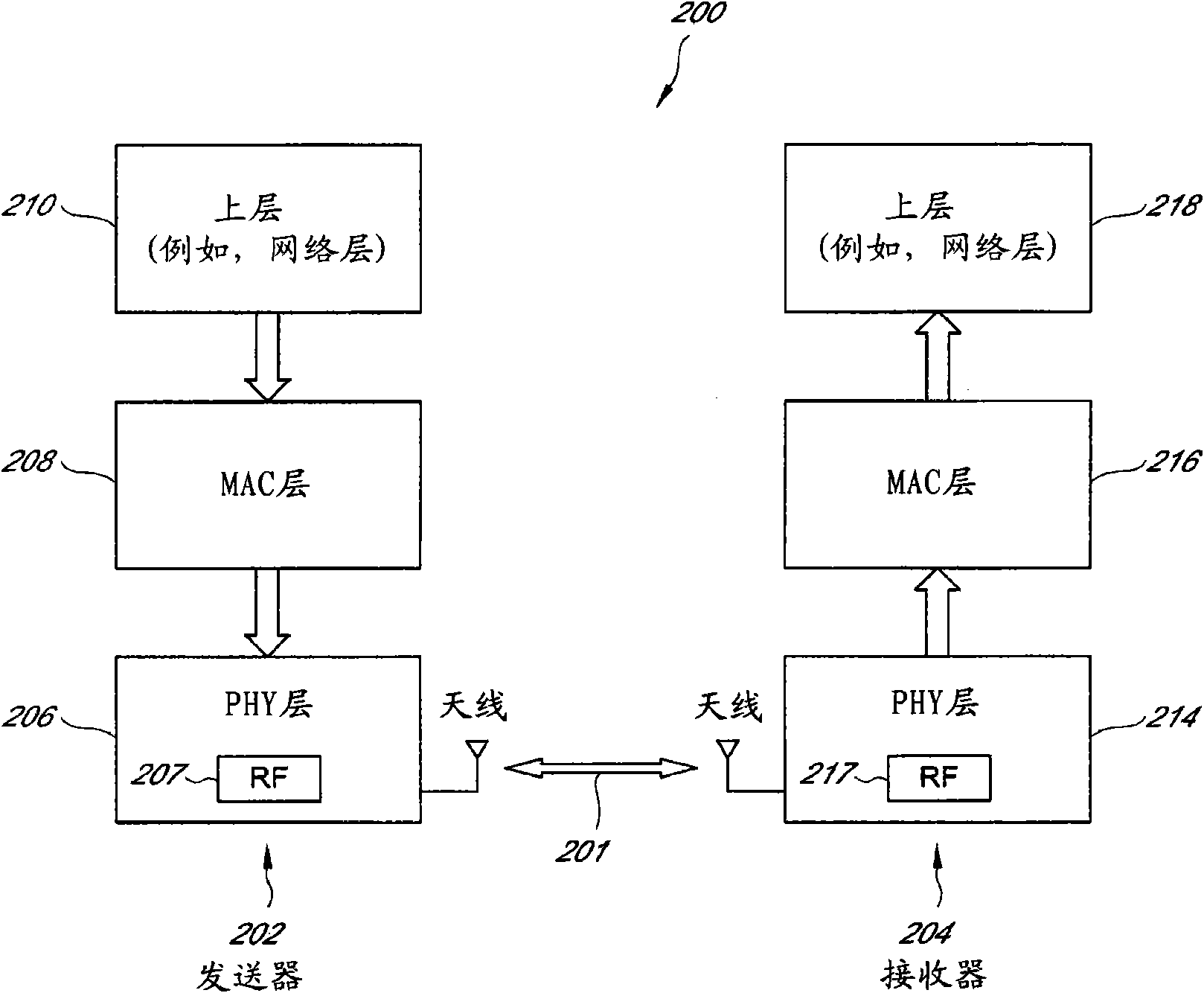
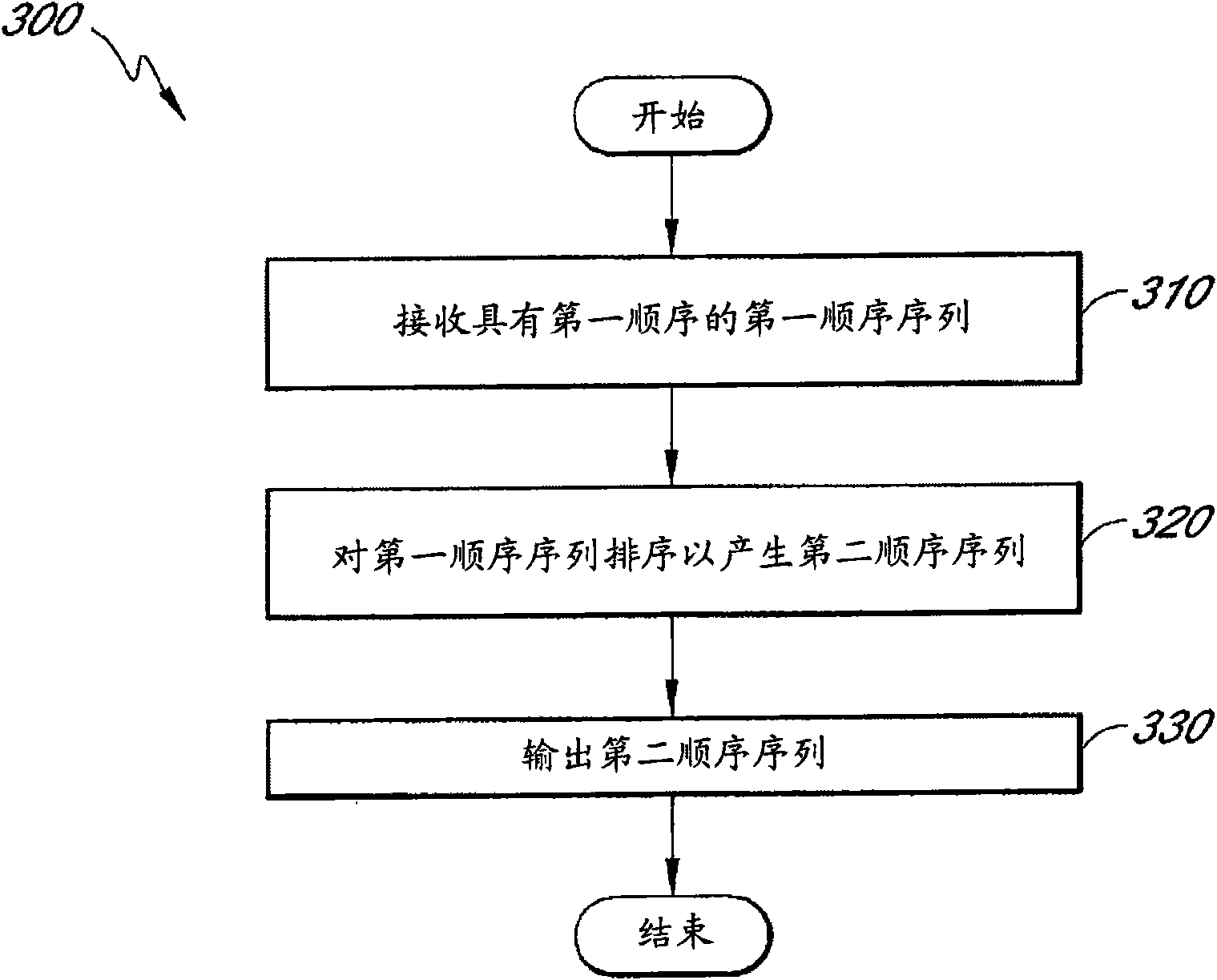
System and method for pseudorandom permutation for interleaving in wireless communications
InactiveCN101926095ANetwork topologiesCode conversionSymbol of a differential operatorPseudorandom permutation
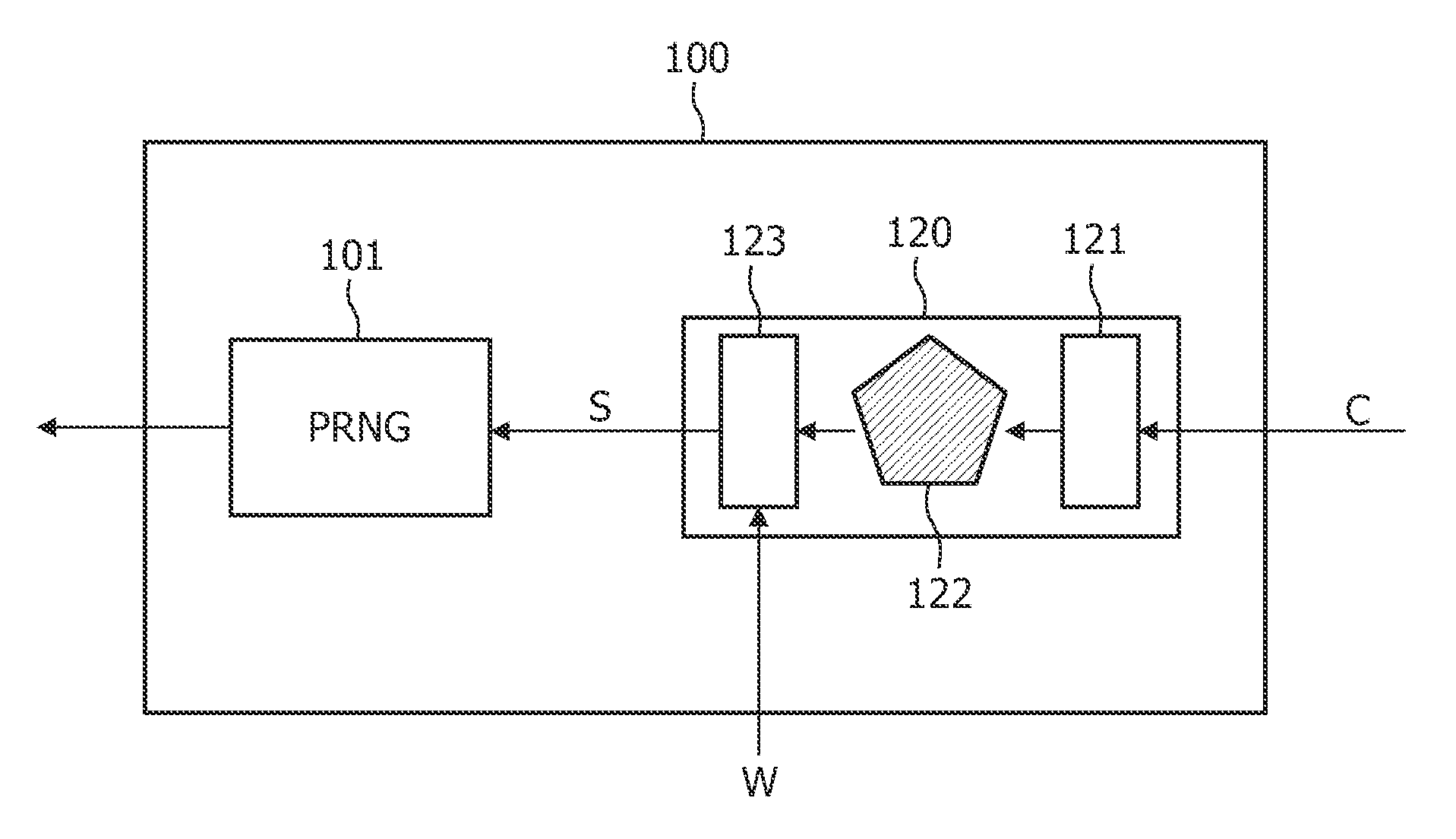
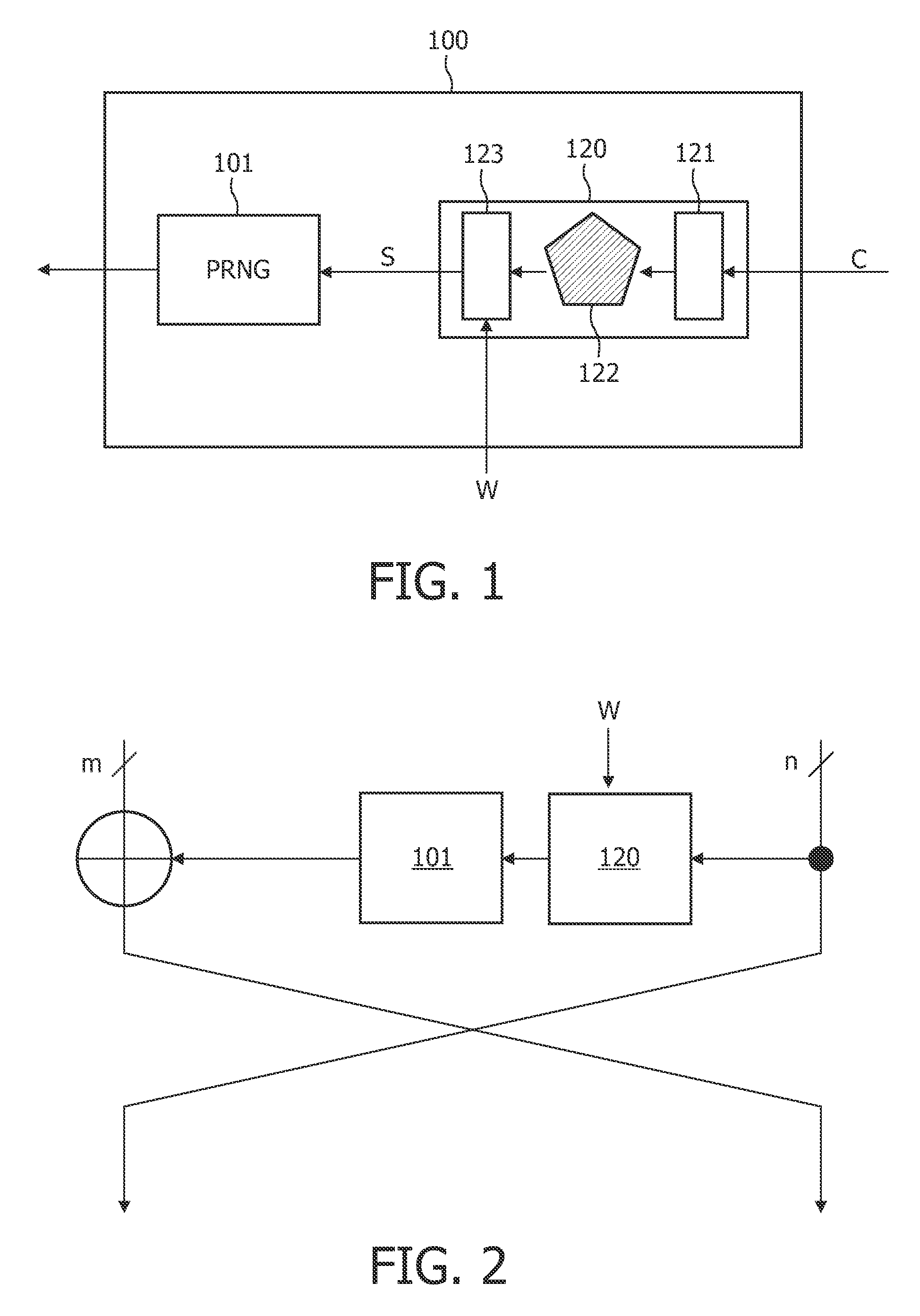
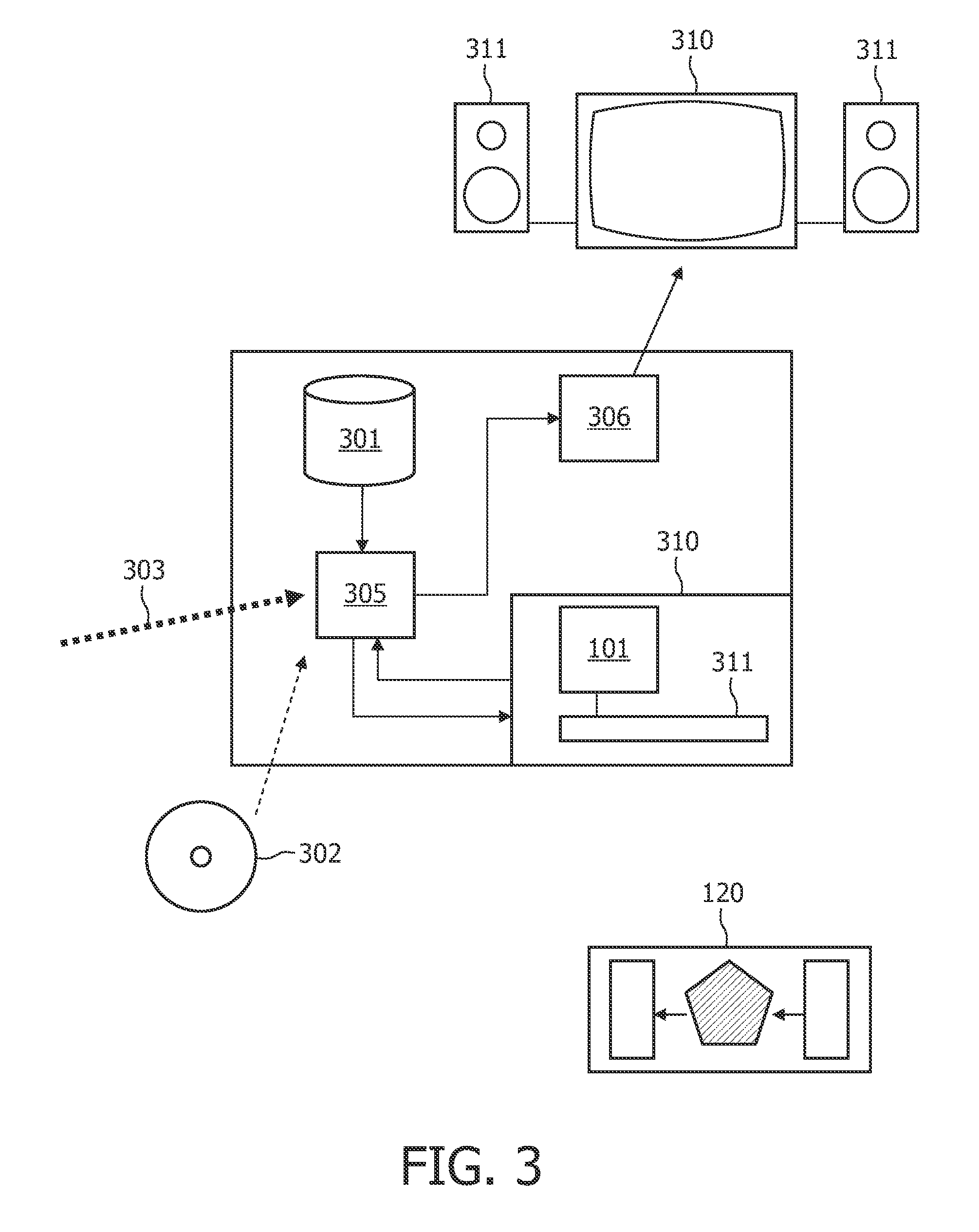
A system and method for pseudorandom permutation for interleaving in wireless communication are disclosed. In one embodiment, the method comprises receiving a first ordered sequence of communication symbols having a first order, permuting the first ordered sequence of communication symbols to generate a second ordered sequence of communication symbols having a second order, and outputting the second ordered sequence of communication symbols, wherein the second order is based, at least in part, on a third order having a greater size than the second order, the third order being a pseudorandom permutation defined by the input-output relationship Y=mod((m*S*(S+1)) / 2,P),,wherein P is the smallest power of two not less than the number of elements in the first ordered sequence, S is an input order represented by a sequence of consecutive integers from zero to P-1 in increasing order, Y is an output order represented as a sequence of integers, and m is an integer.
Owner:SAMSUNG ELECTRONICS CO LTD
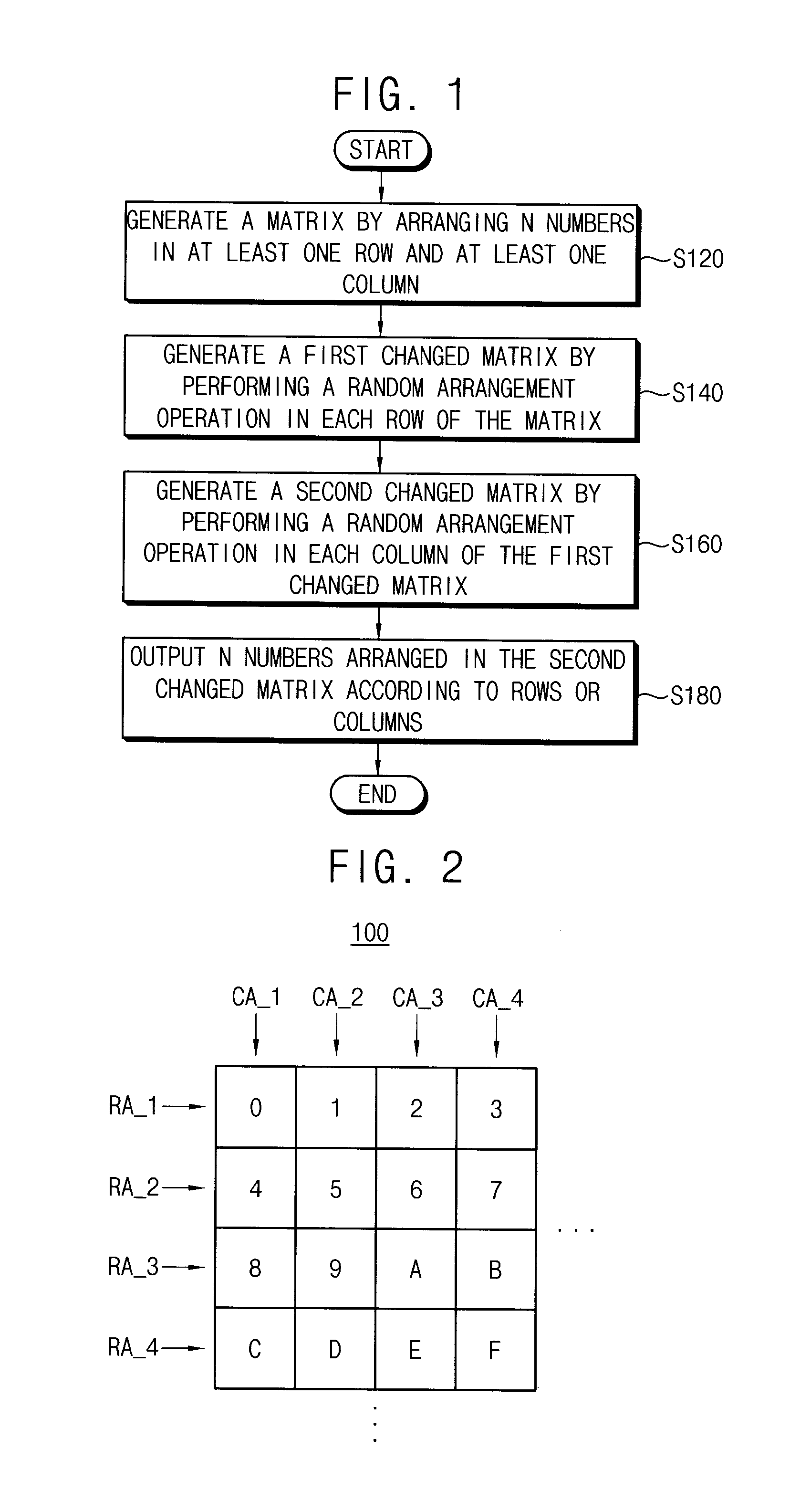
Method of generating a random permutation, random permutation generating device, and encryption/decryption device having the same
ActiveUS20130259224A1Reduce complexityEasy to useSynchronising transmission/receiving encryption devicesRandom number generatorsPseudorandom permutationComputer science
Owner:SAMSUNG ELECTRONICS CO LTD
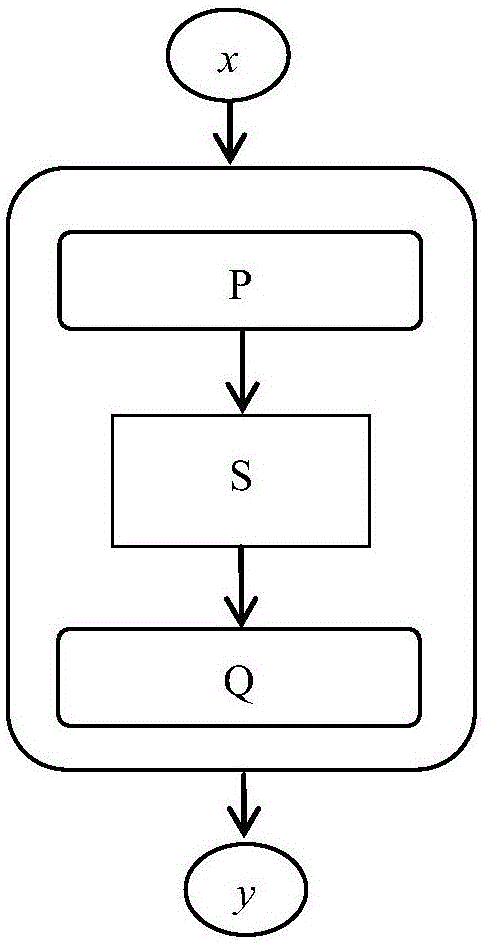
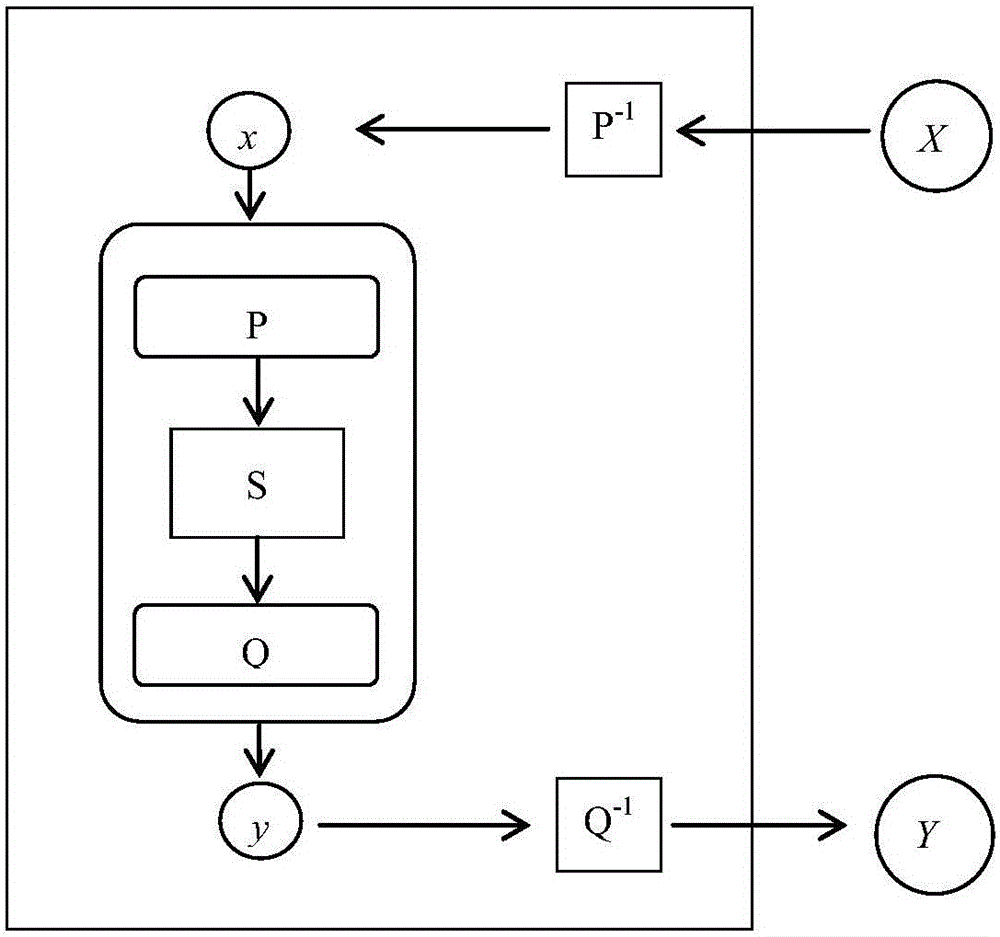
Method for encrypting white box password based on random permutation
InactiveCN106452729AEnsure safetyEncryption apparatus with shift registers/memoriesCryptographic attack countermeasuresEncrypted functionPassword
The invention discloses a method for encrypting a white box password based on random permutation. The method comprises the following steps: inputting a confusion function P; performing random permutation on S; and outputting a confusion function Q. By adoption of the method disclosed by the invention, more other information cannot be acquired except that a lookup table is observed, the entire encryption of the encryption scheme can be guaranteed to be not restored by an attacker due to white box attack, namely, an algorithm having the same encryption function is not copied, and thus the security of operating the encryption algorithm on an untrusted terminal is guaranteed.
Owner:SHANGHAI JIAO TONG UNIV
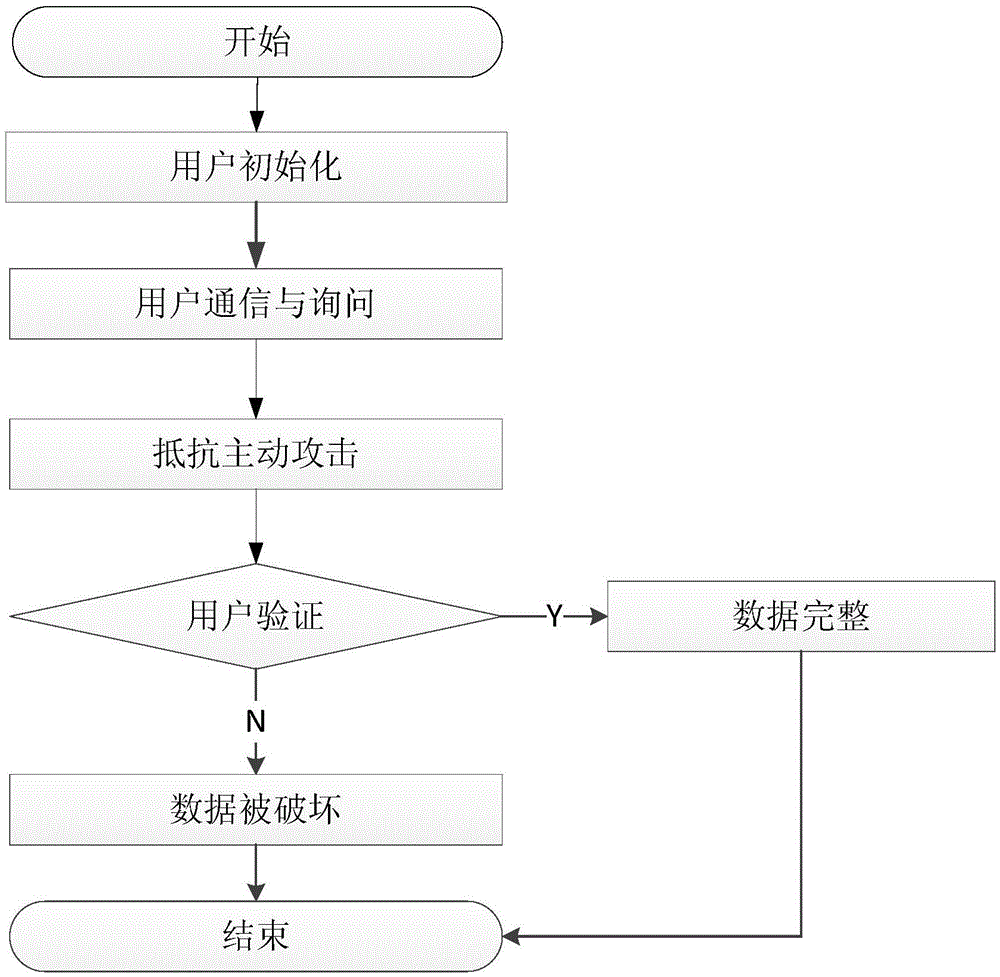
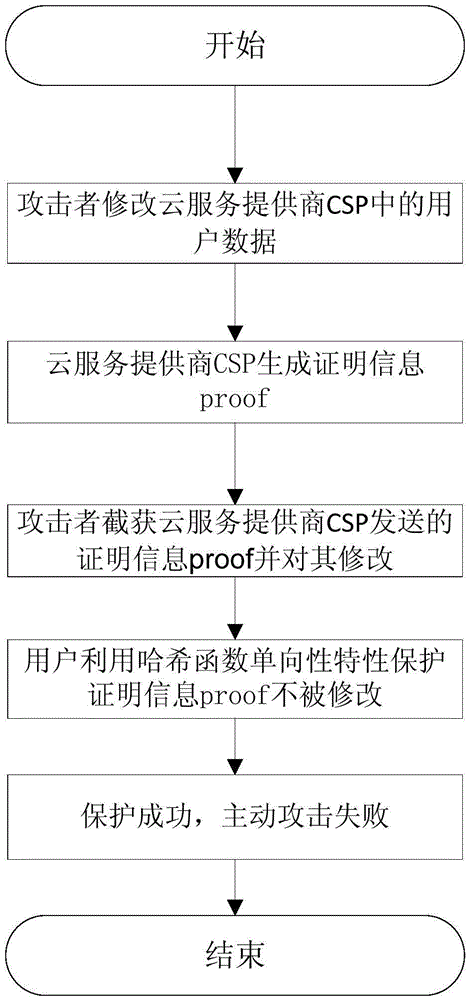
Integrity verification method based on active attack resistance in cloud storage
The invention discloses an integrity verification method with an active attack resistance, wherein the integrity verification method mainly settles a problem of incapability of resisting active attacks in prior art. The integrity verification method comprises the steps of 1, uniformly blocking a file by a user, generating a main label and an auxiliary label, selecting a cryptographic Hash function, a pseudo random function and a pseudo random substitution function; 2, transmitting file sub-blocks to a cloud service provider by the user, deleting a local file, generating inquiry information by the user and transmitting the inquiry information to the cloud service provider; 3, generating proving information by the cloud service provider, and resisting the active attack by the user through the proving information and unidirectionality of the Hash function; and 4, verifying the proving information by the user through locally generating verification information, wherein the proving information is transmitted by the cloud service provider, if verification passes, determining a fact that the user data are complete, and otherwise, determining a fact that the data are damaged. The integrity verification method has advantages of reducing communication traffic and improving active attack resistance. The integrity verification method can be used for data integrity verification under a precondition that a client which is supported in cloud storage loses a data ownership.
Owner:XIDIAN UNIV
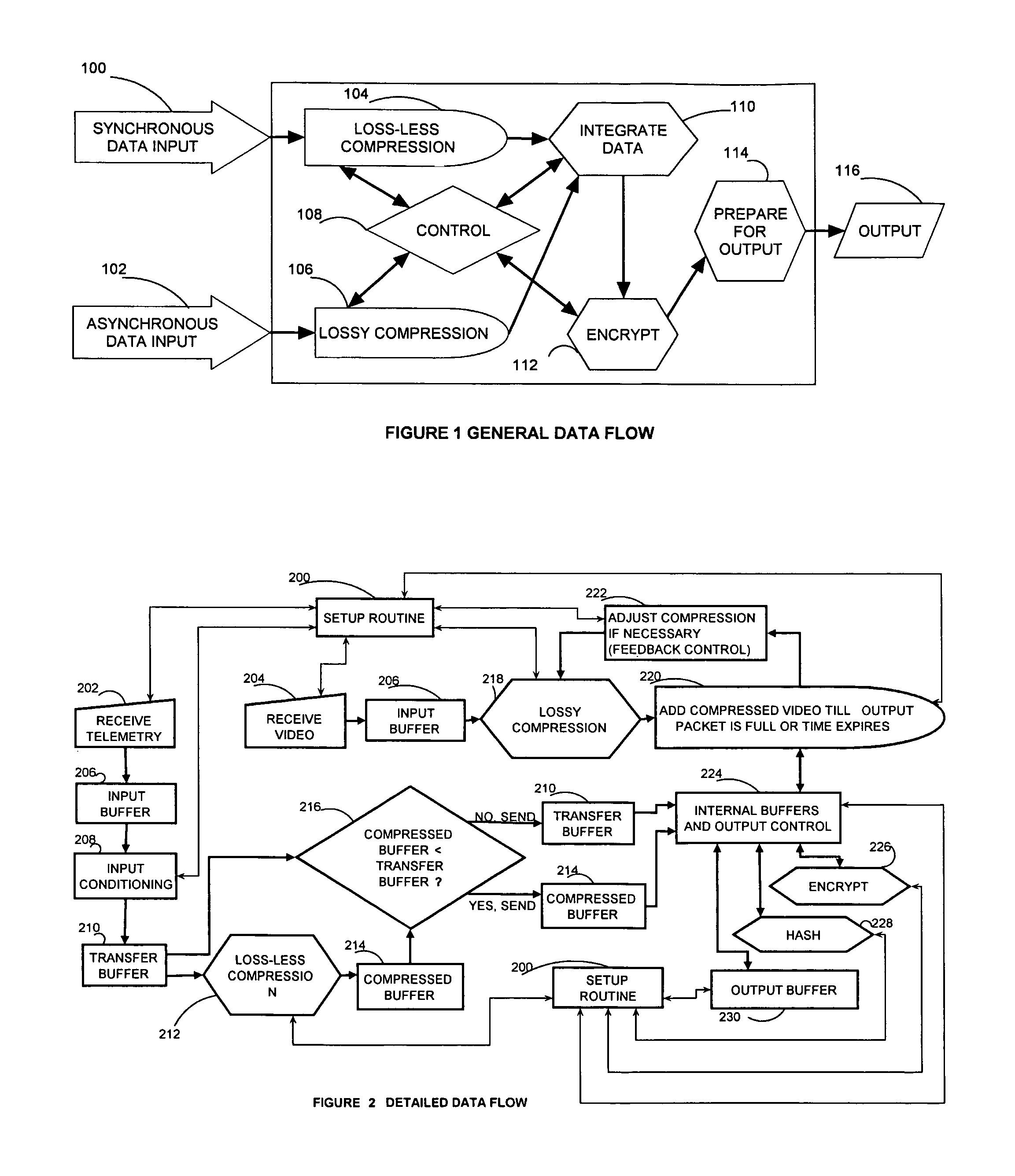
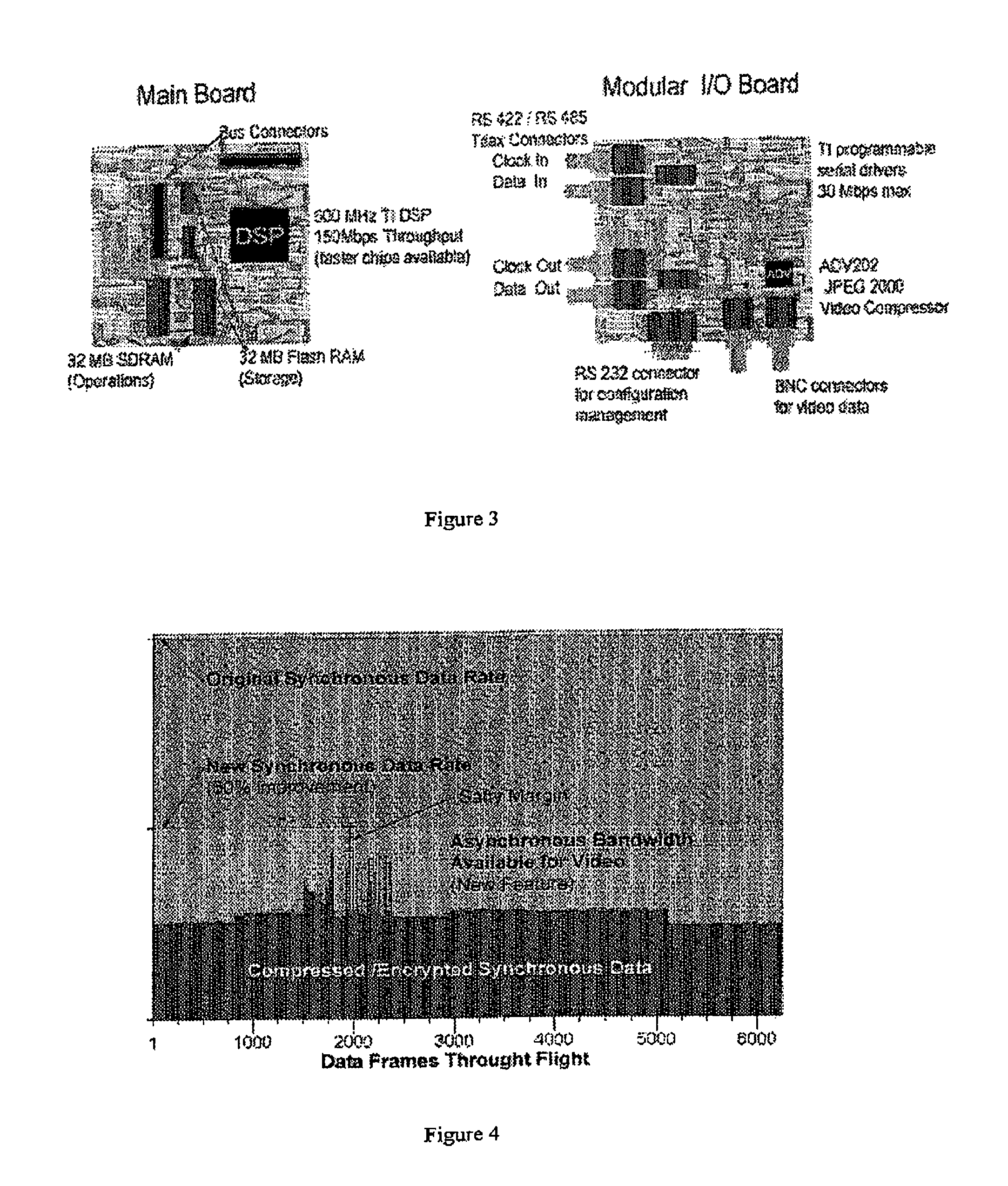
Managing telemetry bandwidth and security
InactiveUS8184691B1Attenuation bandwidthLoss-less compressionPicture reproducers using cathode ray tubesCode conversionPseudorandom permutationTelemetry Equipment
An encryption and authentication technique that achieves enhanced integrity verification through assured error-propagation using a multistage sequence of pseudorandom permutations. The present invention generates intermediate data-dependent cryptographic variables at each stage, which are systematically combined into feedback loops. The encryption technique also generates an authentication tag without any further steps that is N times longer than the block size where N is the number of pseudorandom permutations used in the encipherment of each block. The authentication tag provides a unique mapping to the plaintext for any number of plaintext blocks that is less than or equal to N. In addition to being a stand alone encryption algorithm, the disclosed technique is applicable to any mode that uses pseudorandom permutations such as, key dependent lookup tables, S-Boxes, and block ciphers such as RC5, TEA, and AES.
Owner:DUPRE DURWARD D
Pseudo random permutation based data encryption method in OPC UA edge computation
InactiveCN109586894ASmall memory capacityImplement lightweight encryptionSecuring communication by chaotic signalsComputer hardwareChaotic systems
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Random modulation-based combined channel and secure coding and decoding design method
InactiveCN103475462AImplement the encryption functionReduce coding complexityError preventionEncryption apparatus with shift registers/memoriesSecure codingPseudorandom permutation
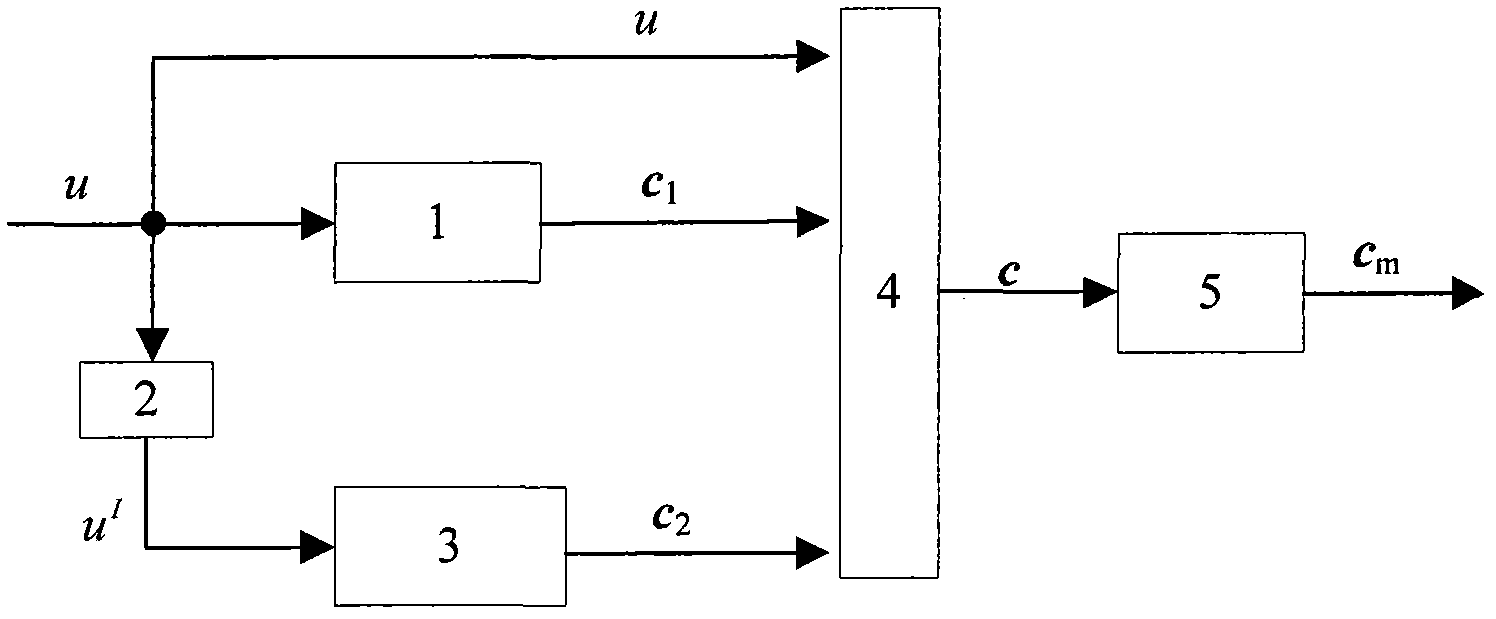
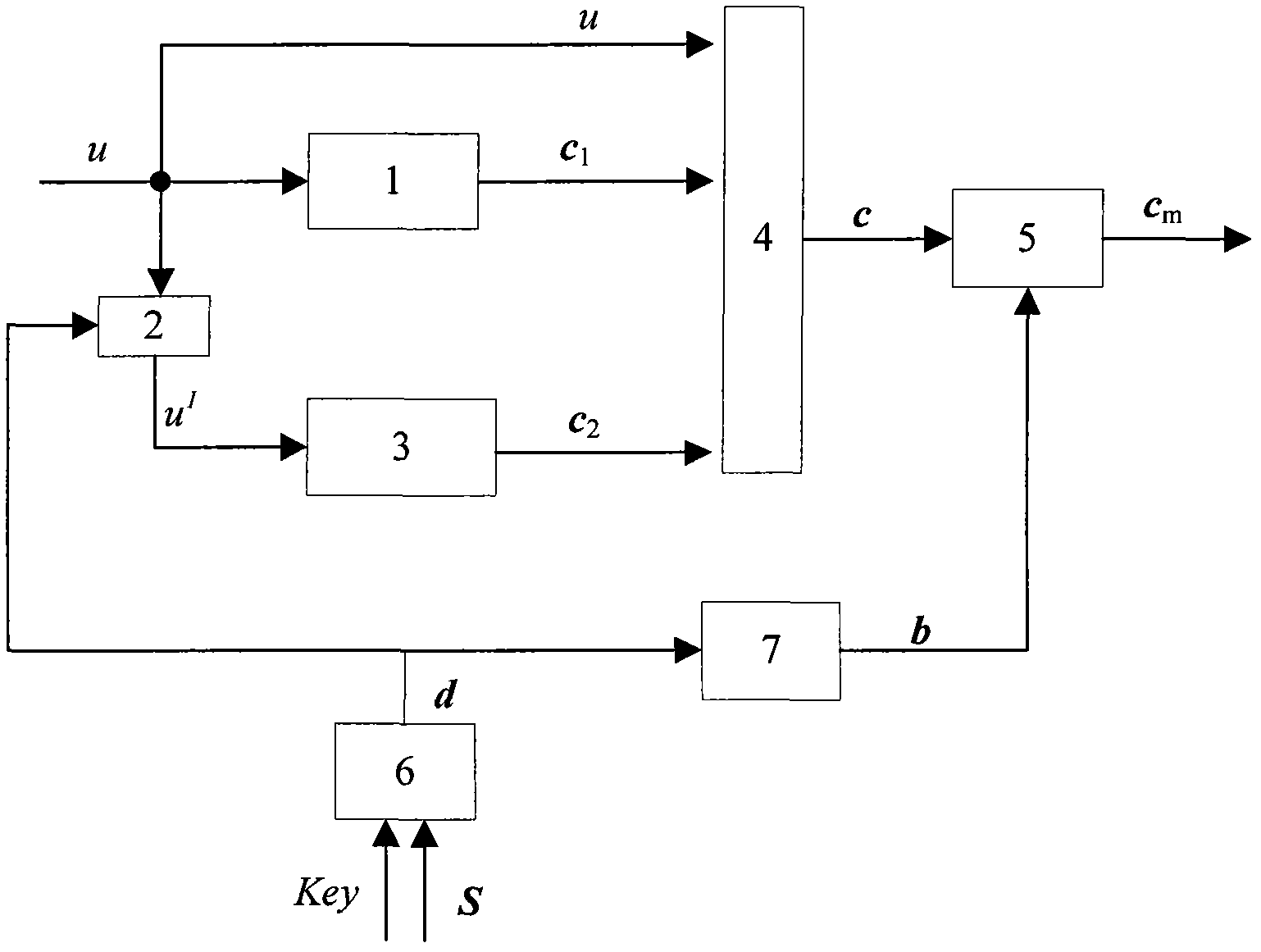
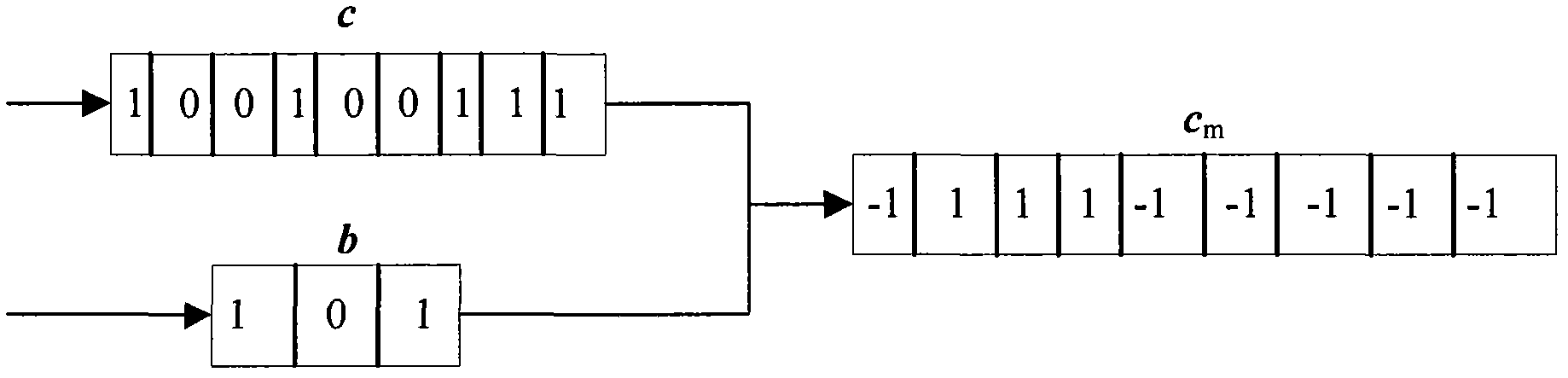
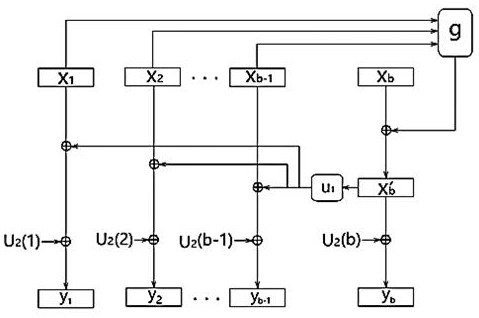
In allusion to the problem that a modulator of a routine Turbo code stream has no encryption function, a modulation and encryption method based on key control is designed according to a random modulation-based combined channel and secure coding and decoding design method. By the method, an interleaver is associated with a modulator. Firstly, length of the interleaver is set as N; S is natural sequence of the length N; a Key is adopted to generate a random permutation d of natural numbers having the length N, wherein d=f(S,Key), and f is a random permutation function; mod-2 operation is carried out on d to generate a binary sequence b having the length N; and finally, random modulation is carried out on a reused coded bit sequence c, and a modulation sequence cm is outputted. During demodulation, a receiving end adopts the same Key and random function f with a coding end to generate the binary sequence b having the length N, and demodulation is carried out to output the correct bit sequence c.
Owner:GRADUATE SCHOOL OF THE CHINESE ACAD OF SCI GSCAS
Method of generating arbitrary numbers given a seed
ActiveUS8594326B2Quality improvementImprove protectionDigital data processing detailsSecret communicationPseudorandom permutationNumber generator
The invention provides a method of generating arbitrary numbers given a seed, characterized by providing a challenge derived from the seed to a physical token, receiving an initial response from the physical token, combining the initial response with helper data associated with the challenge to produce a stable response, and generating the arbitrary numbers using a pseudo-random number generator using the stable response as a seed for the generator. Preferably one or more of these pseudo-random permutations are used as one or more round function(s) in a Feistel block cipher. The generated arbitrary numbers may also be used to create a cryptographic key.
Owner:KONINK PHILIPS ELECTRONICS NV
Sequence cipher based search encryption method in cloud storage environment
ActiveCN107454059AImprove protectionImprove securityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesComputer hardwareCiphertext
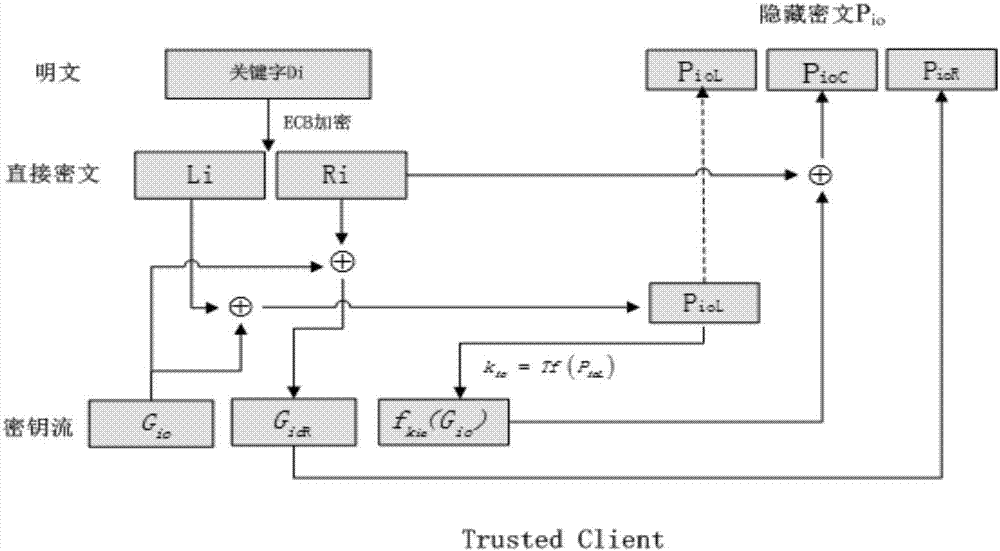
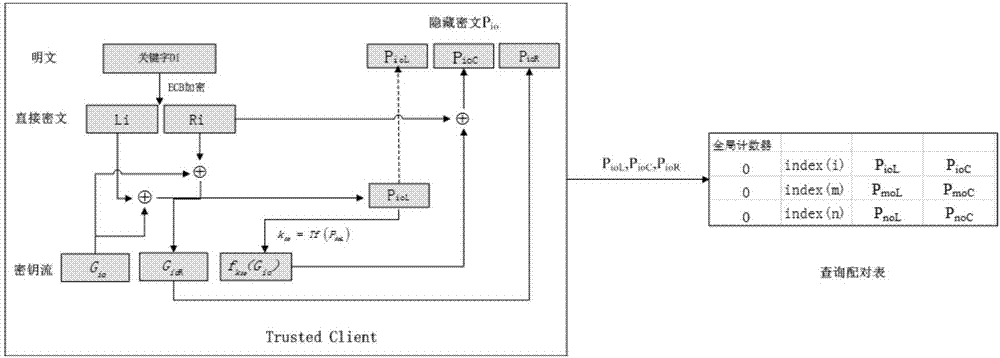
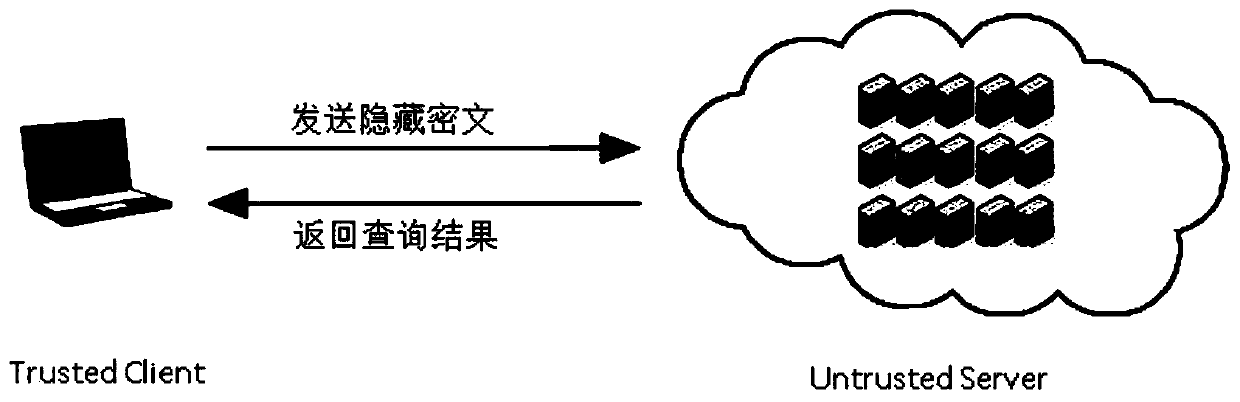
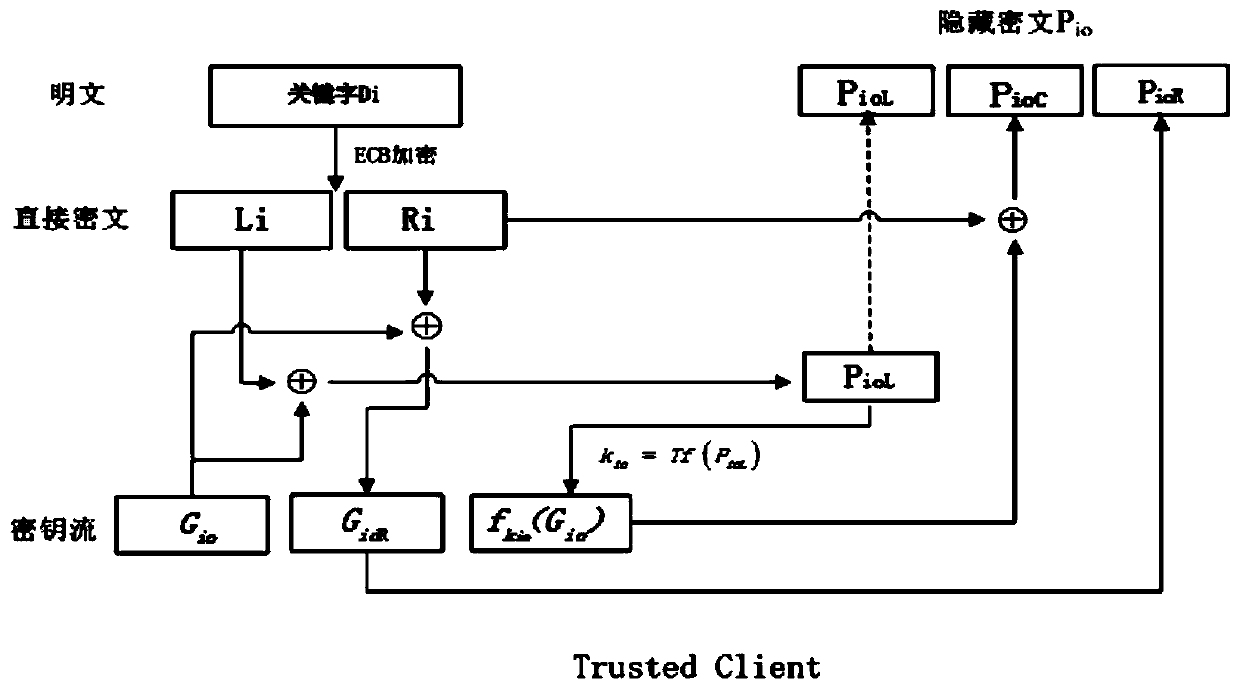
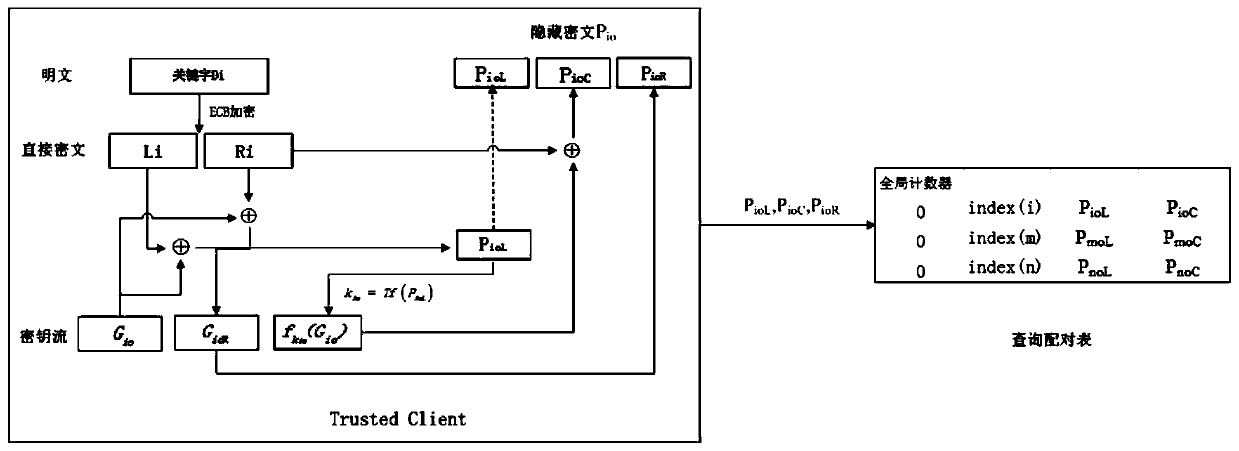
The invention relates to a sequence cipher based search encryption method in a cloud storage environment. The sequence cipher based search encryption method in the cloud storage environment comprises the steps of realizing data security search by improving a key stream generation mode in sequence cipher encryption, and carrying out ECB encryption for a searched keyword to form a direct ciphertext; generating a random number by a pseudorandom generator, and generating a key stream by using the random number and the direct ciphertext through a pseudorandom replacement function; and finally carrying out XOR operation for the key stream and the direct ciphertext to obtain a concealed ciphertext, storing the concealed ciphertext at a server and accordingly building a query matching table; when a new search query occurs, firstly calculating a replacement key and then comparing data in the query matching table with the equality relationship among the concealed ciphertext of the current query session, and accordingly confirming the returned query result. The sequence cipher based search encryption method in the cloud storage environment can realize efficient data search of users, can increase the verification efficiency and can guarantee privacy security.
Owner:GUANGDONG UNIV OF TECH
Data security protection method based on granulation
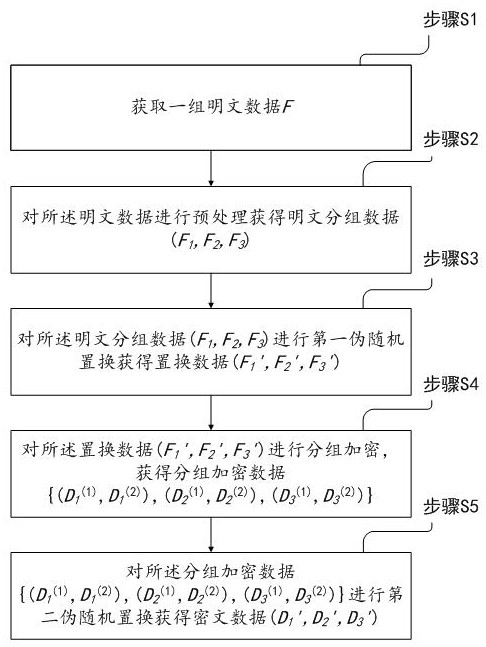
ActiveCN111769943AMultiple keys/algorithms usageEncryption apparatus with shift registers/memoriesPlaintextAlgorithm
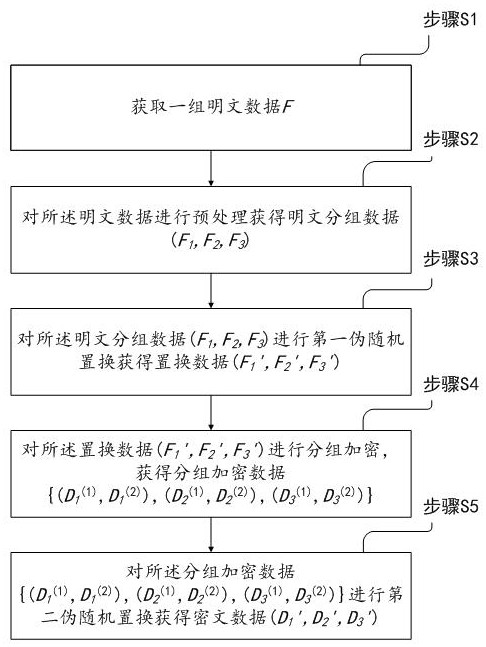
The invention provides a data security protection method based on granulation. The data security protection method comprises the following steps: S1, acquiring a group of plaintext data; Ss2, preprocessing the plaintext data to obtain plaintext grouped data; Ss3, performing first pseudo-random replacement on the plaintext grouped data to obtain replacement data; Ss4, performing grouping encryptionon the replacement data to obtain grouping encryption data; and S5, performing second pseudo-random replacement on the block encryption data to obtain ciphertext data. According to the data securityprotection method based on granulation, the probability that a secret stealer steals and restores effective information is reduced, and the security of data transmission is improved.
Owner:BEIJING CHERILEAD TECH
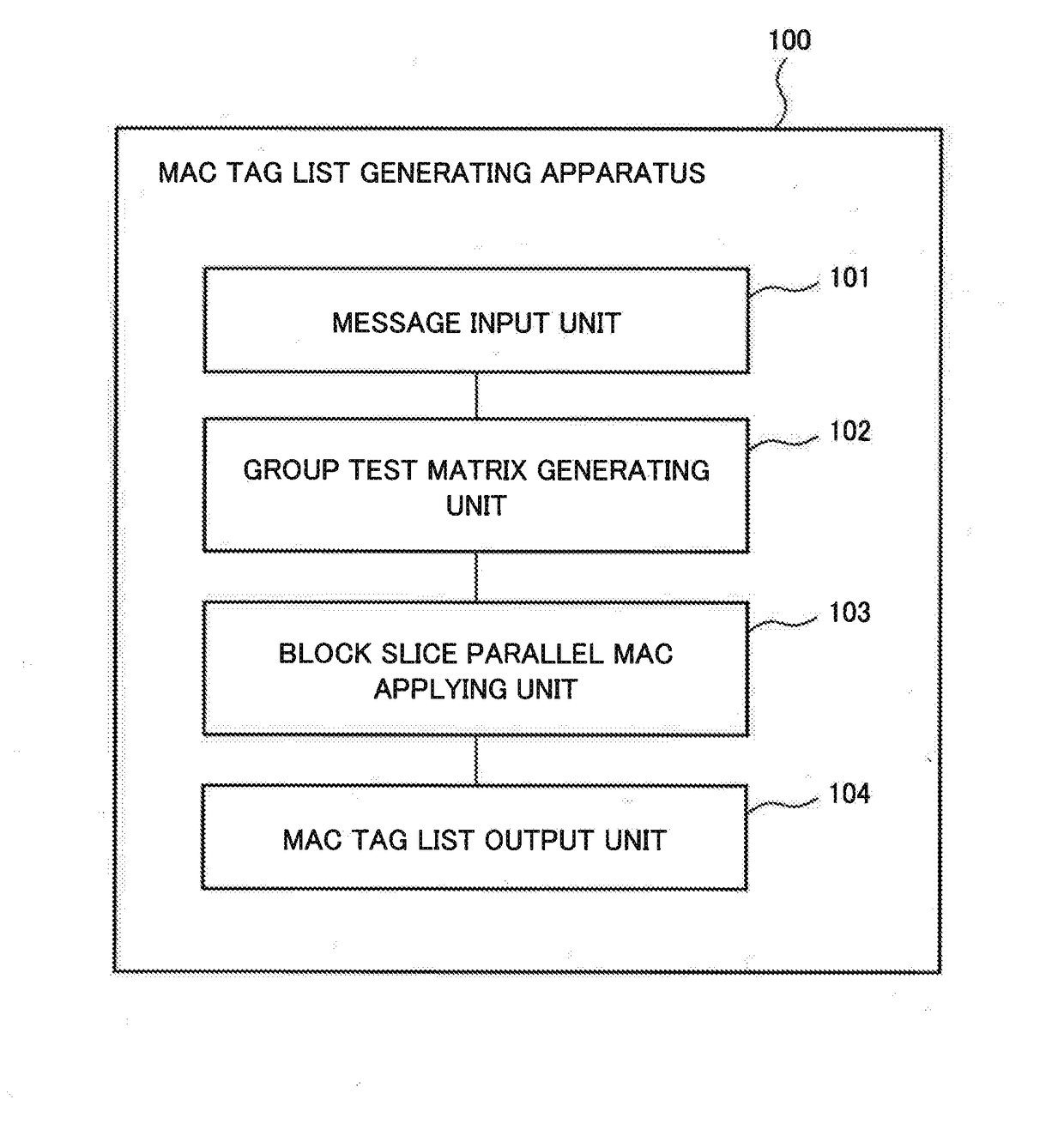
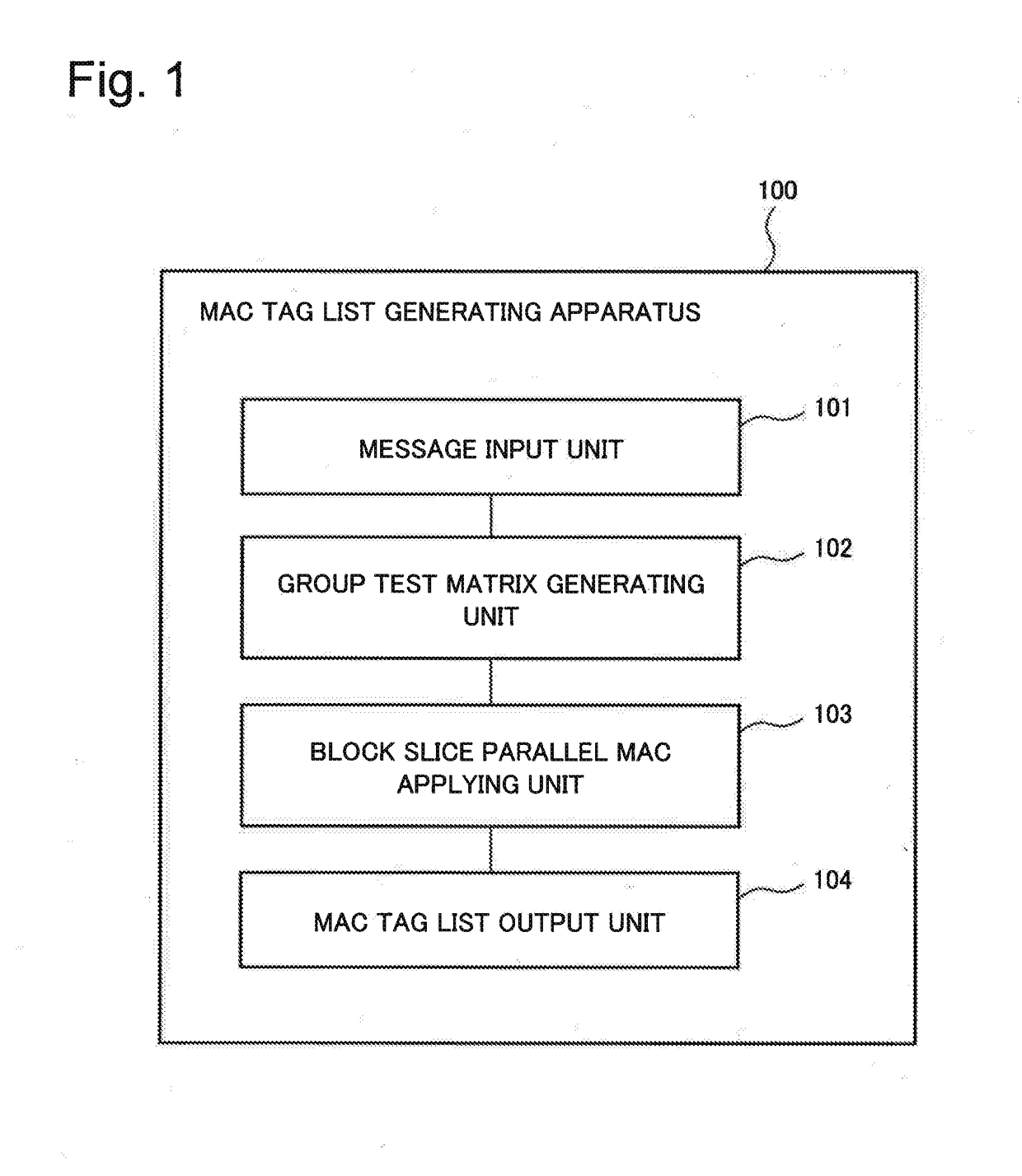
Mac tag list generating apparatus, mac tag list verifying apparatus, mac tag list generating method, mac tag list verifying method and program recording medium
ActiveUS20180013550A1Efficiently performing message authenticationEfficient executionKey distribution for secure communicationEncryption apparatus with shift registers/memoriesComputer hardwarePseudorandom permutation
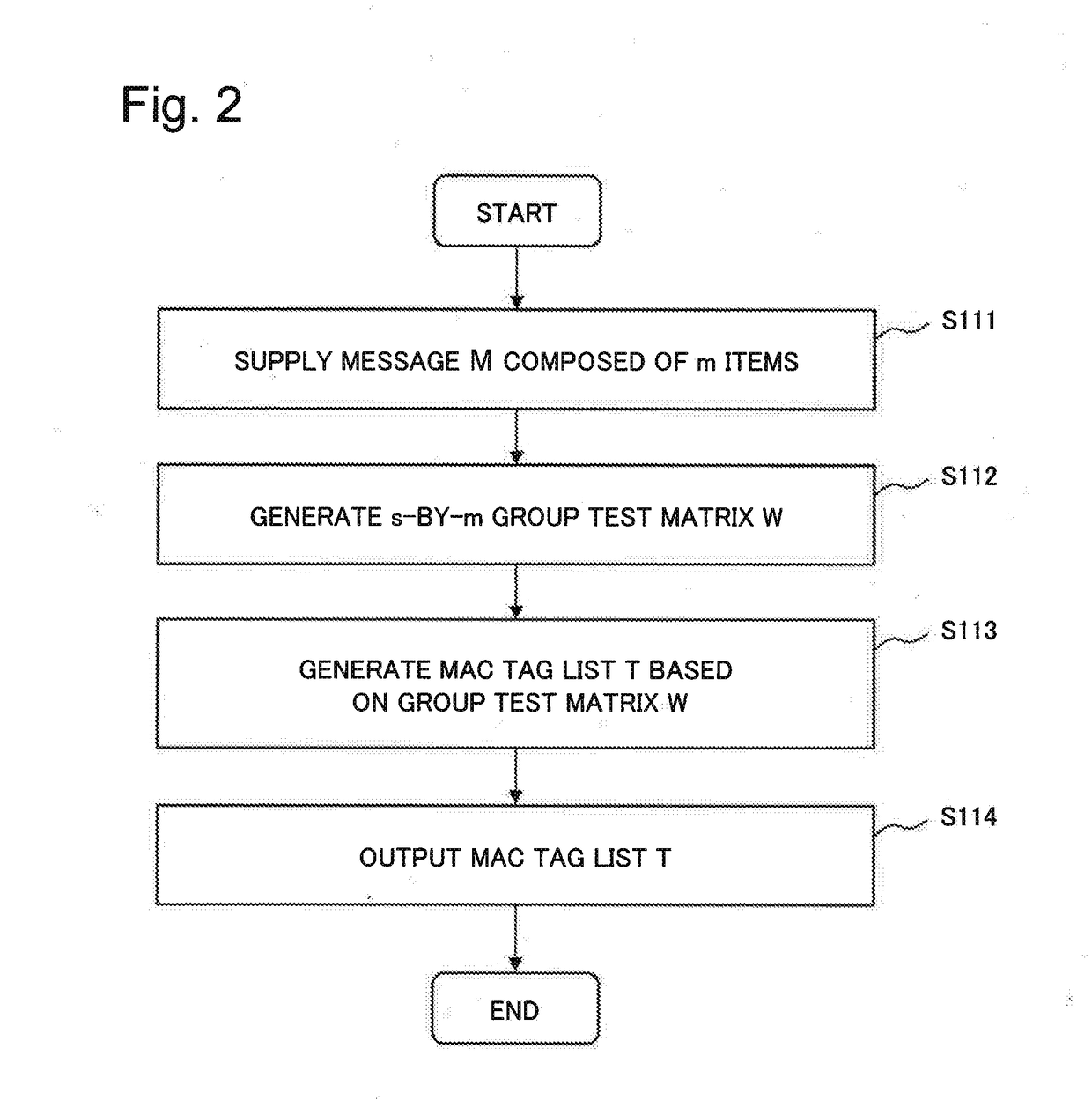
Disclosed is a MAC tag list generating apparatus capable of efficiently performing message authentication through which information pertaining to a falsified position as well as existence of falsification can be obtained. This MAC tag list generating apparatus is provided with: a group test matrix generating means for generating a group test matrix W, which is a parameter of a combined group test, on the basis of a plurality of items obtained by dividing an obtained message M; and a MAC tag list generating means that, while sharing results obtained by applying a pseudo random function to the items forming each row of the generated group test matrix W, sums the results, and then applies the summed results to pseudo random permutation to generate a MAC tag list T, which is a MAC tag list pertaining to the message M.
Owner:NEC CORP
System for encrypting and decrypting a plaintext message with authentication
InactiveUS8712036B2Low levelEfficiently integrityUser identity/authority verificationSecret communicationComputer hardwarePlaintext
The described system and method provide for an encryption and authentication technique that achieves enhanced integrity verification through assured error-propagation using a multistage sequence of pseudorandom permutations. The method generates intermediate data-dependent cryptographic variables at each stage, which are systematically combined into feedback loops. The encryption technique also generates an authentication tag with minimal post processing that is the size of the state. The size of the state is dependent on the number of pseudorandom permutations and the size of the LFSR. The authentication tag provides a unique mapping to the plaintext for any number of plaintext blocks that is less than or equal the size of the state. In addition to being a stand alone encryption algorithm, the disclosed technique is applicable to any mode that uses pseudorandom permutations such as, key dependent lookup tables, S-Boxes, and block ciphers such as RC5, TEA, and AES.
Owner:SMITH ERIC MYRON +3
Efficient searchable proxy privacy set intersection method and device
PendingCN114491613AWill not affect online efficiencyEnsure safetyKey distribution for secure communicationDigital data protectionIndex mappingData set
The invention discloses an efficient searchable agent privacy set intersection method and device, and the method comprises the steps: grouping user data sets according to keywords, generating an index for each sub-set after grouping based on a pseudo-random function, encrypting the sub-set corresponding to each keyword, and generating an encrypted sub-set; the encrypted subset and the index are replaced and then uploaded to a cloud server; sending the to-be-searched keyword of the user initiating intersection calculation and the pseudo-random permutation key to other users, so that the other users find index values of the same keyword subsets of the two users through calculation, and generating an index-to-index mapping to be sent to a cloud server, and finding subsets corresponding to the keywords to be searched in the data of different users according to the mapping, carrying out intersection on the subsets corresponding to the keywords to be searched, and returning an intersection result to the user initiating intersection calculation. According to the embodiment of the invention, a searchable function is added in agent privacy set intersection, and meanwhile, the security and the efficiency are ensured.
Owner:BEIHANG UNIV
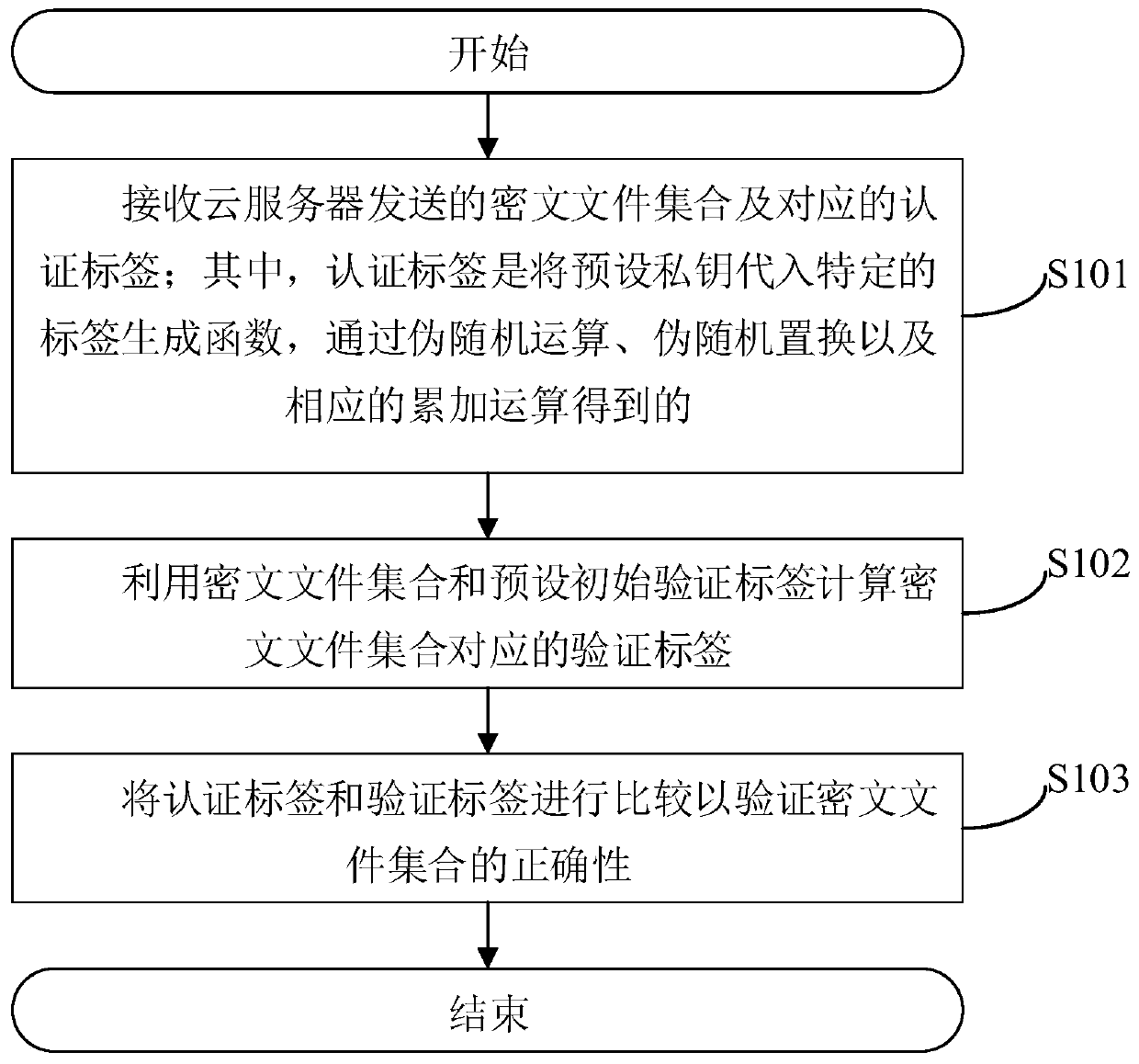
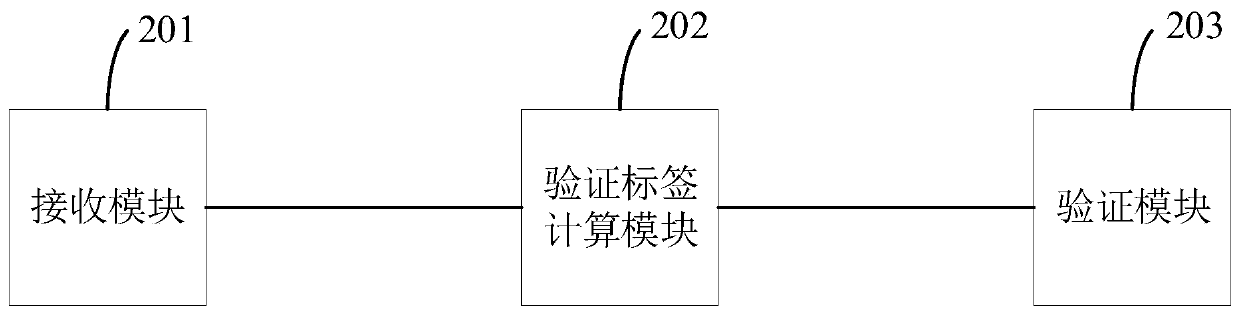
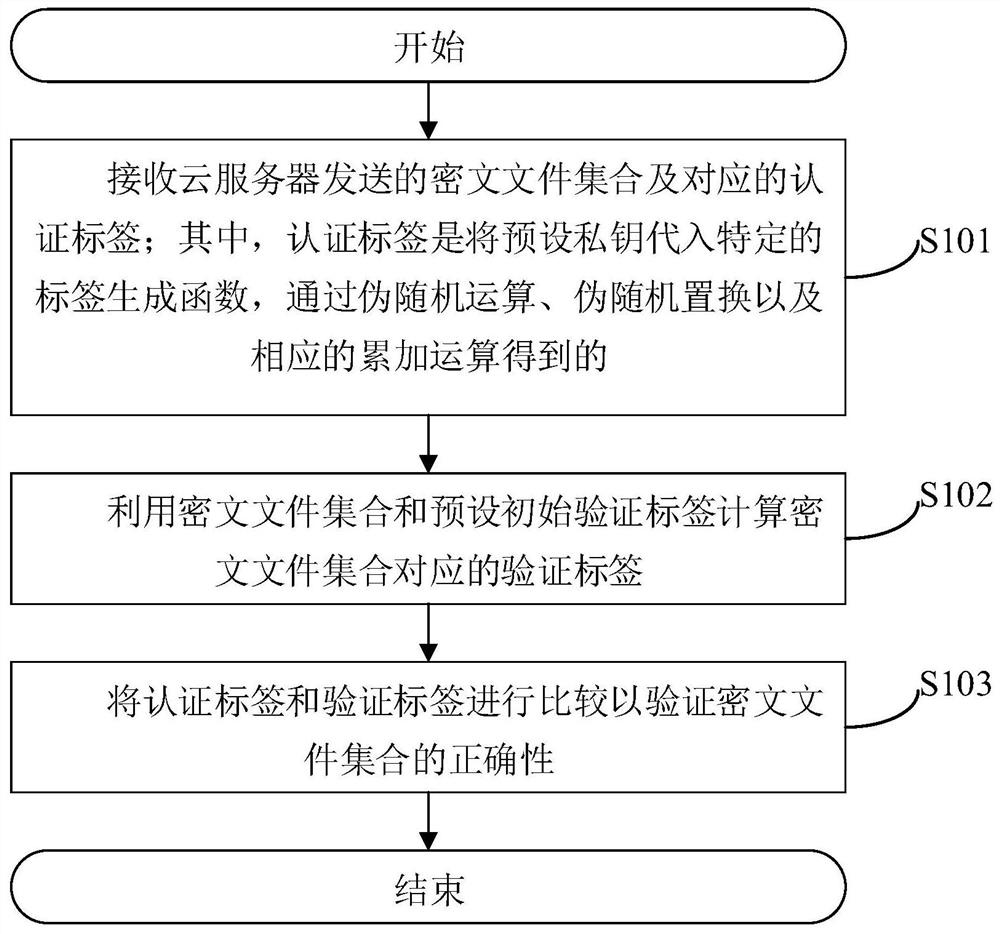
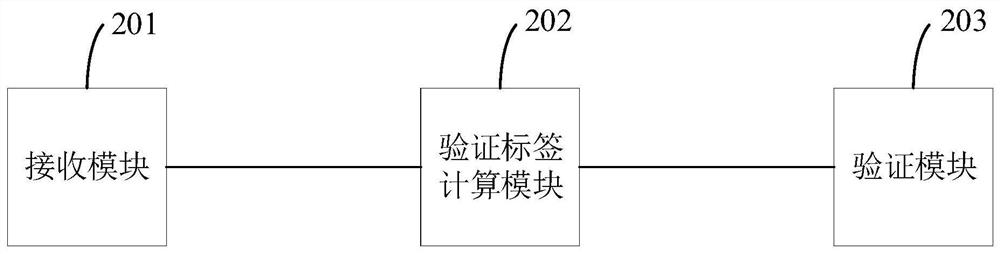
Ciphertext file set correctness verification method and system and related device
ActiveCN110061994AAvoid computational overheadReduce verification burdenSecuring communicationCiphertextRandom replacement
The invention provides a ciphertext file set correctness verification method. The method comprises the following steps: receiving a ciphertext file set sent by a cloud server and a corresponding authentication label; wherein the authentication label is obtained by substituting a preset private key into a specific label generation function and carrying out pseudo-random operation, pseudo-random replacement and corresponding accumulation operation; calculating a verification label corresponding to the ciphertext file set by using the ciphertext file set and a preset initial verification label; and comparing the authentication tag with the verification tag to verify the correctness of the ciphertext file set. According to the method, the authentication label is obtained by substituting the preset private key into the specific label generation function through the pseudo-random operation, the pseudo-random replacement and the corresponding accumulation operation, so that a large amount ofcalculation expenditure can be avoided, and the verification burden is reduced. The invention further provides a ciphertext file set correctness verification system and device and a computer readablestorage medium which all have the above beneficial effects.
Owner:QINGDAO UNIV
File processing method, electronic equipment and storage medium
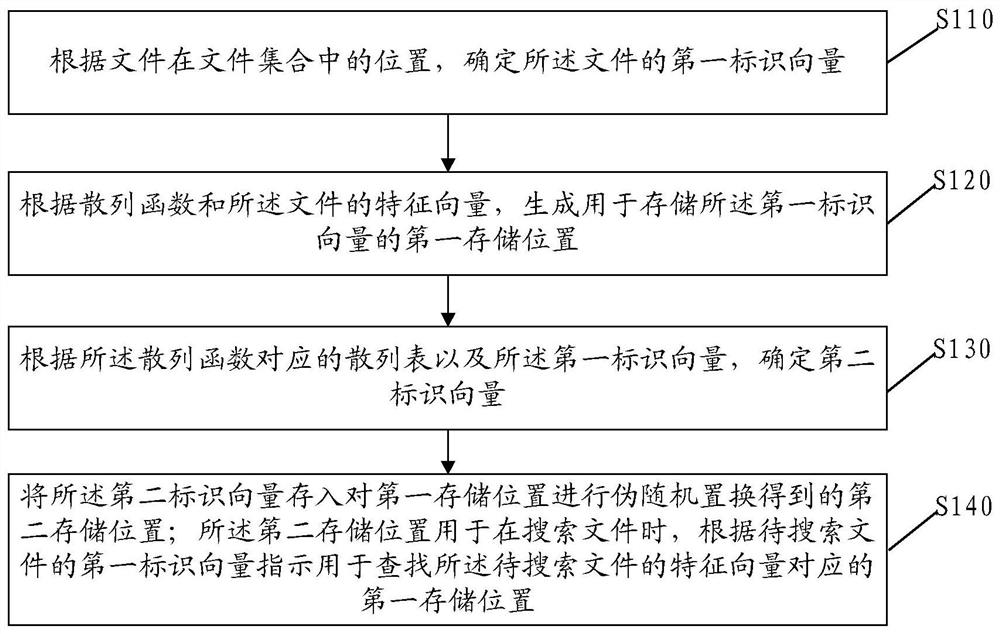
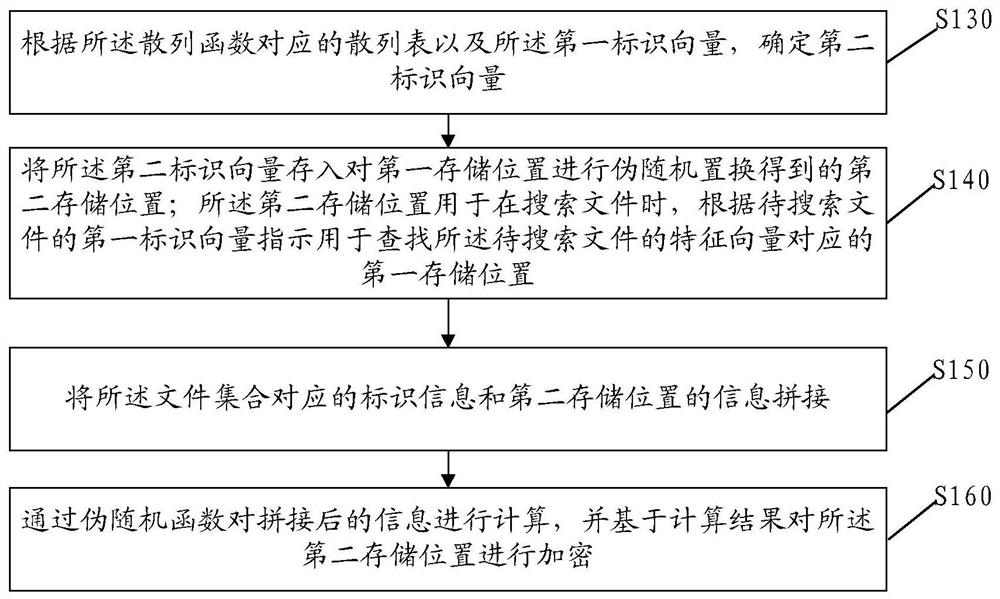
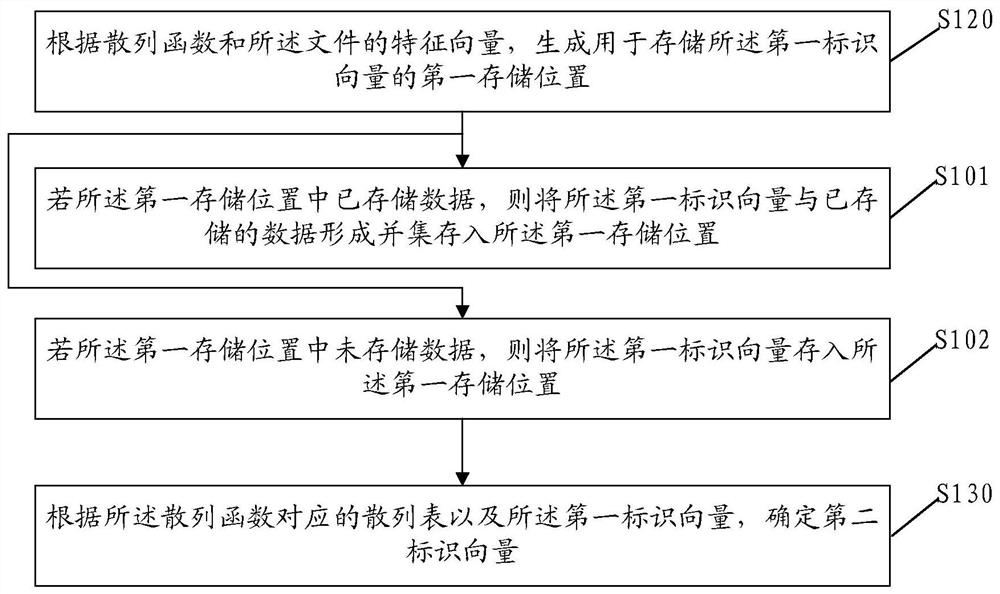
PendingCN113868441AImprove search efficiencyImprove privacyMultimedia data indexingMultimedia data queryingDocument handlingEngineering
The embodiment of the invention discloses a file processing method, electronic equipment and a storage medium, and the file processing method comprises the steps: determining a first identification vector of a file according to the position of the file in a file set; generating a first storage position for storing a first identification vector according to the hash function and the feature vector of the file; determining a second identification vector according to a hash table corresponding to the hash function and the first identification vector; and storing the second identification vector into a second storage position obtained by performing pseudo-random permutation on the first storage position; wherein the second storage position is used for indicating the first storage position corresponding to the feature vector for searching the to-be-searched file according to the first identification vector of the to-be-searched file when the file is searched. Therefore, according to the second storage position, the corresponding file can be searched based on the position of the to-be-searched file in the file set, and a user does not need to provide an accurate keyword for searching, so that the file searching efficiency is improved.
Owner:卓尔智联(武汉)研究院有限公司
Method for detecting randomicity of pseudorandom sequence based on random permutation
InactiveCN101697533BAddress limitationsSolve one-sidednessTransmissionAutomatic controlInterleave sequence
The invention discloses a method for detecting the randomicity of a pseudorandom sequence based on random permutation, which belongs to the field of detection and mainly solves the problems of limitation and onesidedness existing in the traditional randomicity detection method. A series of random permutation processing, such as inversion or negative or random interleaving, is carried out on a sequence to be detected; statistics is carried out on an inverse sequence or a negative sequence or a random interleaving sequence obtained after the random permutation processing by a Cramer-von Mises detection method, a statistical value corresponding to the sequence is obtained, and the statistical value corresponding to the sequence is compared with a selected standard statistical value; if the statistical value is smaller than the standard statistical value, the sequence to be detected meets random properties; and contrarily, the sequence to be detected does not have the random properties. The invention enables the randomicity detection of the pseudorandom sequence to be more comprehensive in a detection result and can be applied to the fields of secret communication, aerospace, distance measurement, cryptography and automatic control.
Owner:XIDIAN UNIV
A Particle-Based Data Security Protection Method
ActiveCN111769943BMultiple keys/algorithms usageEncryption apparatus with shift registers/memoriesCiphertextData transmission
Owner:BEIJING CHERILEAD TECH
A cloud outsourcing privacy set comparison method and device
InactiveCN107196926BImprove securityImproving the efficiency of private collection comparisonsTransmissionCiphertextEngineering
Owner:HENAN NORMAL UNIV
Message identification method and electronic device
ActiveCN105207978AGuaranteed accuracyImprove production efficiencyData switching networksComputer hardwarePassword
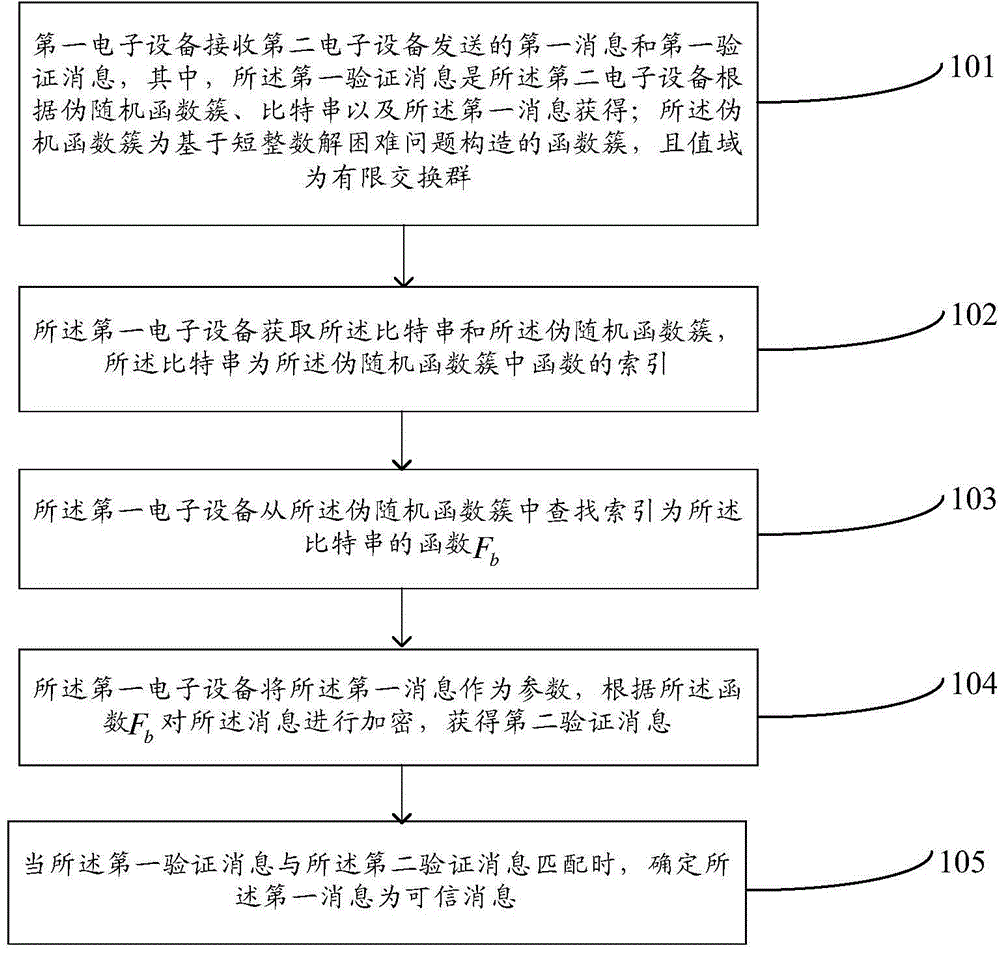
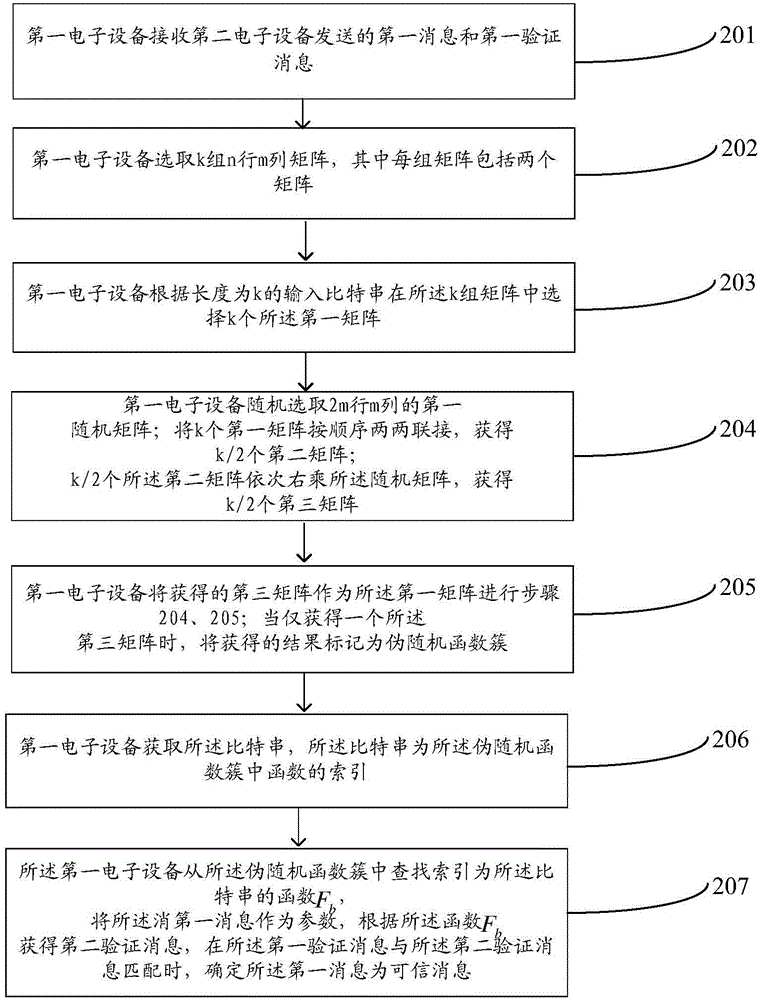
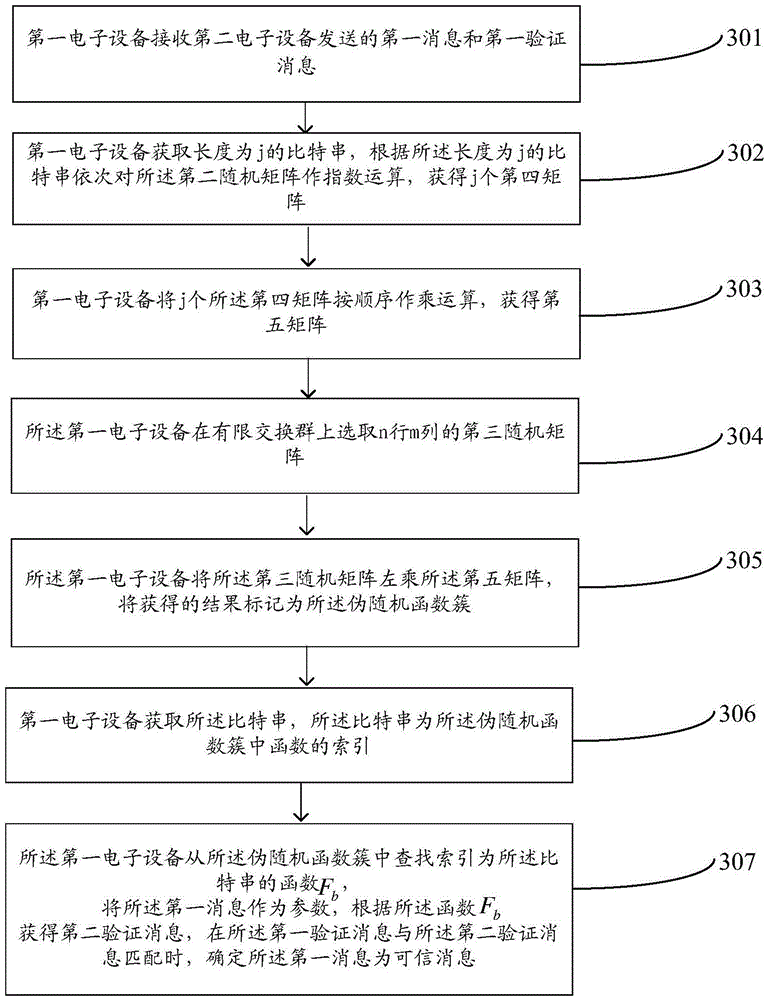
The embodiment of the invention provides a message identification method and an electronic device and belongs to the information security and password. According to the method, pseudorandom functions are constructed based on a short integer difficulty-solving problem, so that computational complexity and modulus can be reduced, and security and the accuracy of message identification can be improved. The message identification method includes the following steps that: a first electronic device receives a first message and a first authentication message which are transmitted by a second electronic device, and the cluster value domain of the pseudorandom functions is a finite abelian group; the first electronic device obtains bit strings and a pseudorandom function cluster, wherein the bit strings are the indexes of functions in the pseudorandom function cluster; the first electronic device searches a function Fb from the pseudorandom function cluster, the index of the function Fb being the bit string; the first electronic device adopts the first message as a parameter, and obtains a second authentication message according to the function Fb; and when the first authentication message is matched with the second authentication message, the first message is determined as a credible message.
Owner:HONOR DEVICE CO LTD
System and method for pseudorandom permutation for interleaving in wireless communications
Owner:SAMSUNG ELECTRONICS CO LTD
Message authentication code pre-computation with applications to secure memory
InactiveCN102138300BEncryption apparatus with shift registers/memoriesUser identity/authority verificationGreek letter epsilonMessage authentication code
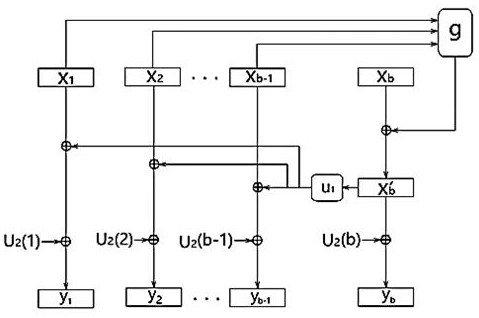
A method comprising the steps of creating a random permutation of data from a data input by executing at least one of a Pseudo-Random Permutation (PRP) and a Pseudo-Random Function (PRF), creating a first data block by combining the random permutation of data with a received second data block and executing an epsilon-differentially uniform function on the result of the combination, XORing the result of the epsilon-DU function evaluation with a secret key, and reducing the first data block to a first message authentication code.
Owner:PROVENANCE ASSET GRP LLC
A search encryption method based on sequence cipher in cloud storage environment
ActiveCN107454059BImprove protectionImprove securityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesCiphertextKeystream
The invention relates to a sequence cipher based search encryption method in a cloud storage environment. The sequence cipher based search encryption method in the cloud storage environment comprises the steps of realizing data security search by improving a key stream generation mode in sequence cipher encryption, and carrying out ECB encryption for a searched keyword to form a direct ciphertext; generating a random number by a pseudorandom generator, and generating a key stream by using the random number and the direct ciphertext through a pseudorandom replacement function; and finally carrying out XOR operation for the key stream and the direct ciphertext to obtain a concealed ciphertext, storing the concealed ciphertext at a server and accordingly building a query matching table; when a new search query occurs, firstly calculating a replacement key and then comparing data in the query matching table with the equality relationship among the concealed ciphertext of the current query session, and accordingly confirming the returned query result. The sequence cipher based search encryption method in the cloud storage environment can realize efficient data search of users, can increase the verification efficiency and can guarantee privacy security.
Owner:GUANGDONG UNIV OF TECH
A method, system and related device for verifying the correctness of a set of ciphertext files
ActiveCN110061994BAvoid computational overheadReduce verification burdenSecuring communicationAlgorithmCiphertext
A method for verifying the correctness of a ciphertext file set provided by this application includes: receiving the ciphertext file set and the corresponding authentication label sent by the cloud server; wherein, the authentication label is to substitute a preset private key into a specific label generation function, Obtained by pseudo-random operation, pseudo-random permutation and corresponding accumulation operation; use the ciphertext file set and the preset initial verification label to calculate the verification label corresponding to the ciphertext file set; compare the authentication label and the verification label to verify the ciphertext file The correctness of the collection. In this method, the authentication label is obtained by substituting the preset private key into a specific label generation function through pseudo-random operation, pseudo-random permutation and corresponding accumulation operation, which can avoid a large amount of calculation overhead and reduce the verification burden. The present application also provides a system, device and computer-readable storage medium for verifying the correctness of a set of ciphertext files, all of which have the above beneficial effects.
Owner:QINGDAO UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com