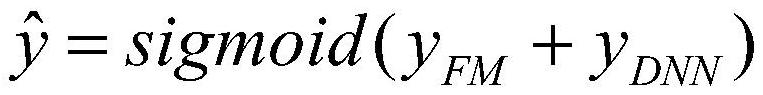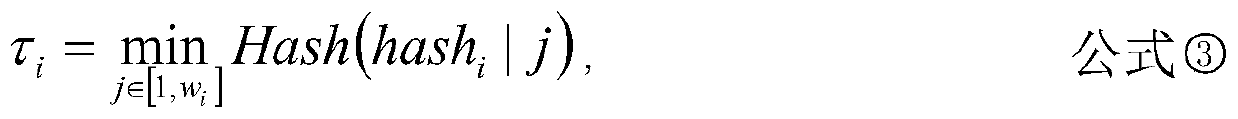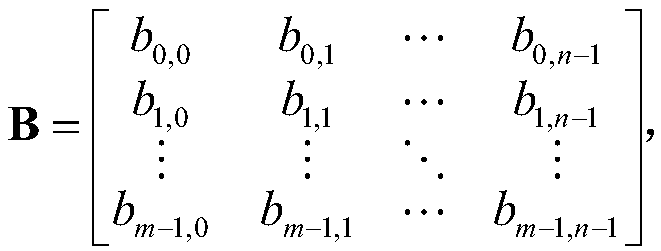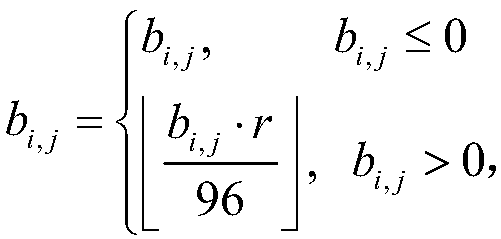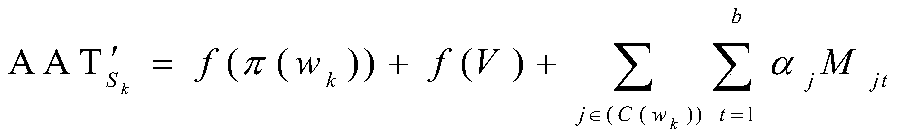Patents
Literature
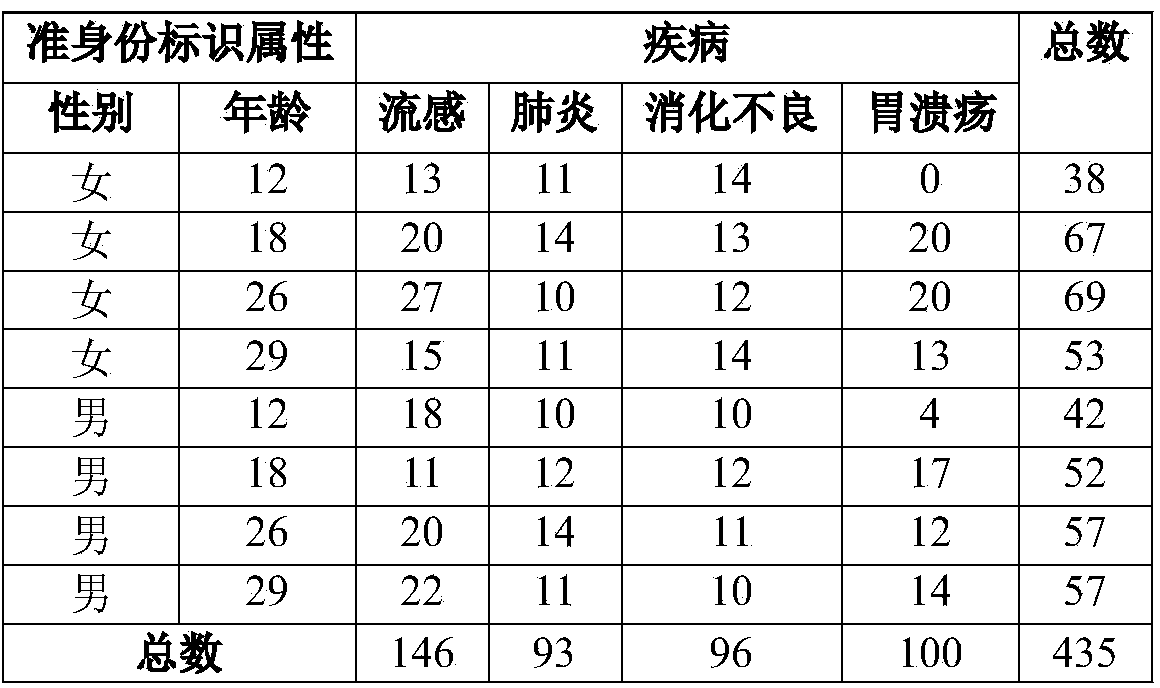
36 results about "Random replacement" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Random replacement generator for a cache circuit
InactiveUS6643740B1Memory architecture accessing/allocationEnergy efficient ICTRandom replacementParallel computing
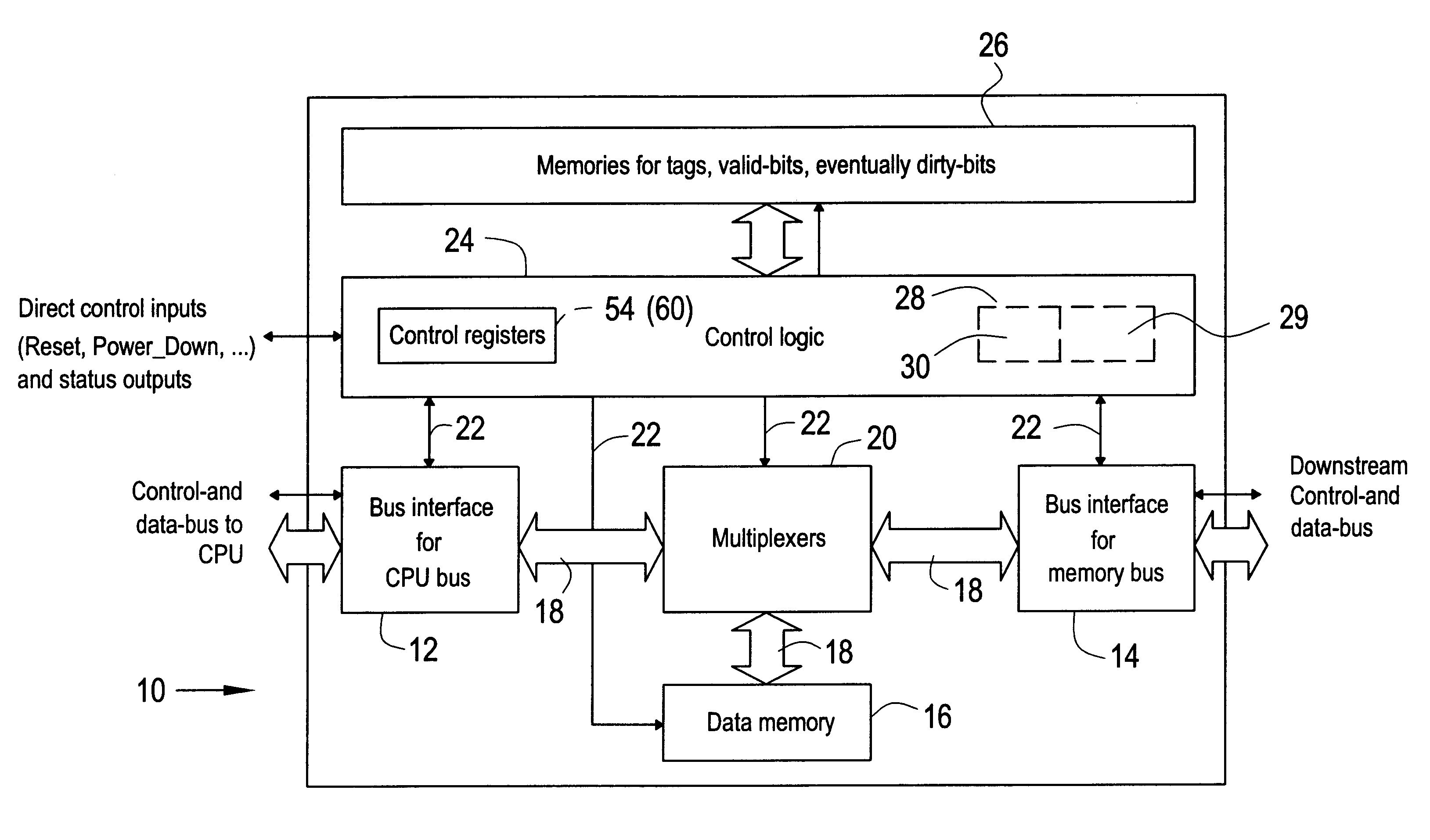
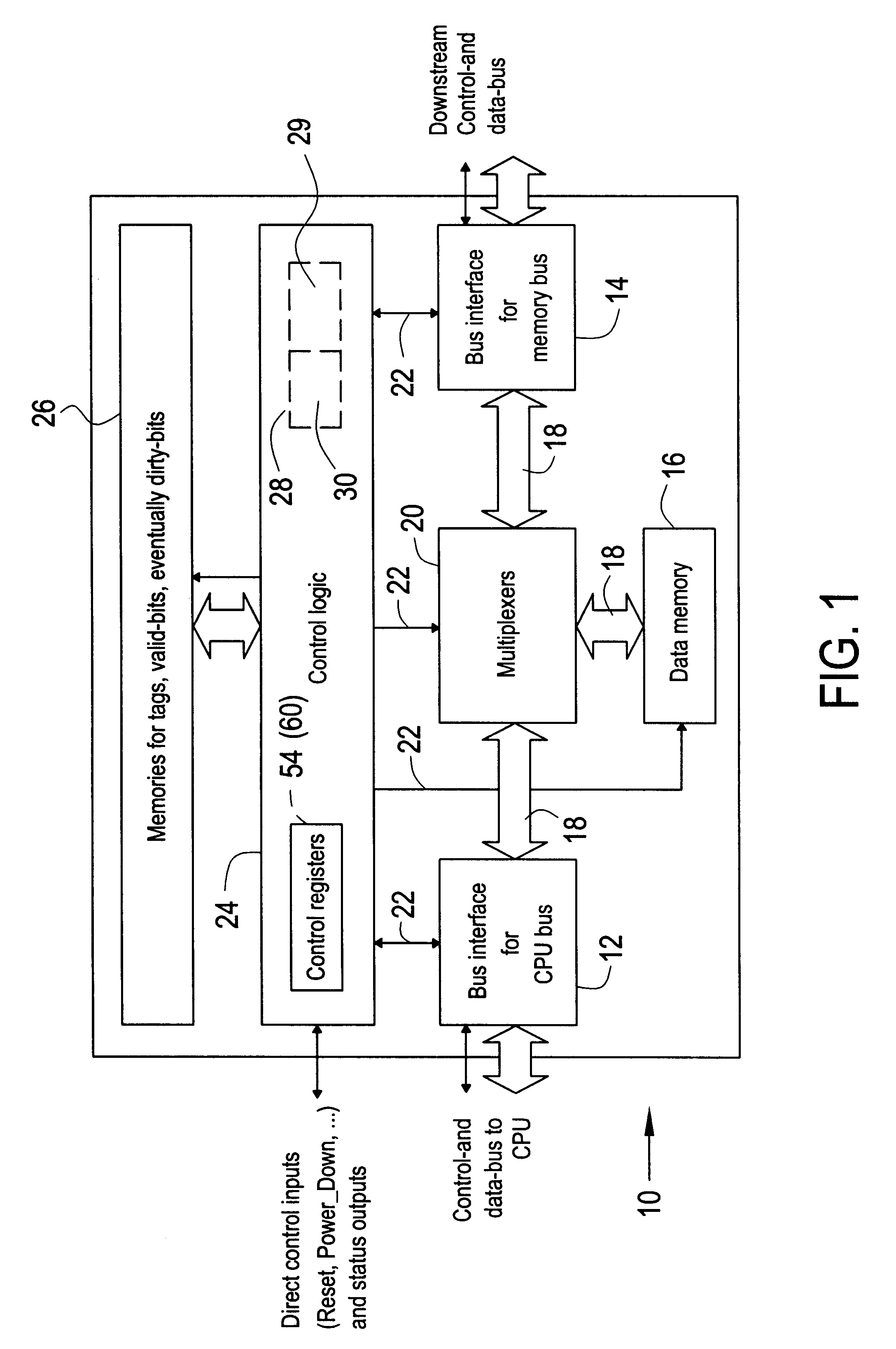
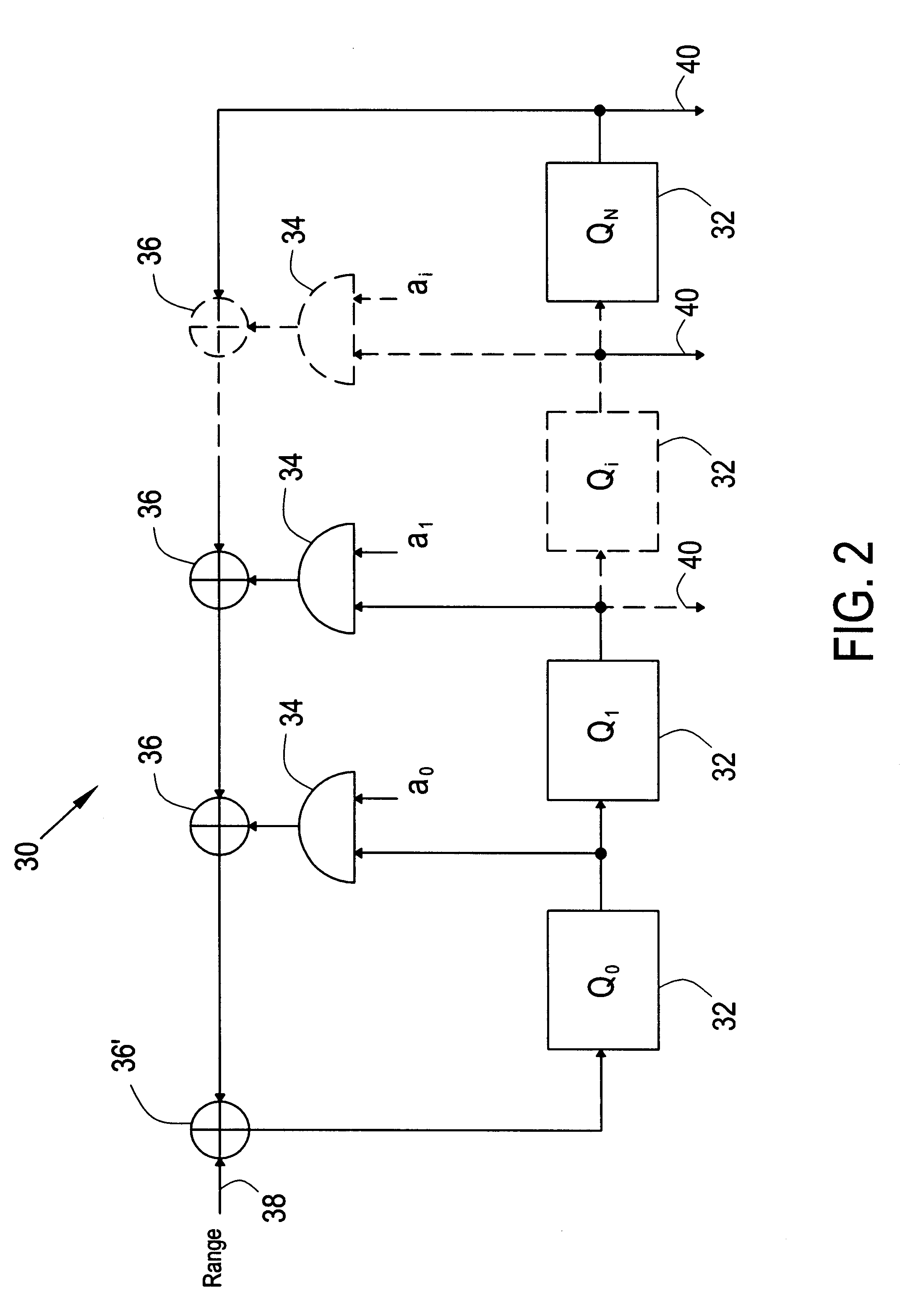
A cache may comprise a memory and control logic. The memory may be configured for storing data buffered by the cache. The control logic may be configured controlling accesses to the memory. The control logic may comprise a pseudo-noise generator and a trigger device. The pseudo-noise generator may be configured for generating a pseudo-random number representing, for a miss access requiring allocation, which of a plurality of possible addresses in the memory to use for the allocation. The trigger device may be configured for controlling a cycle of the pseudo-noise generator to output the pseudo-random number therefrom.
Owner:AVAGO TECH INT SALES PTE LTD
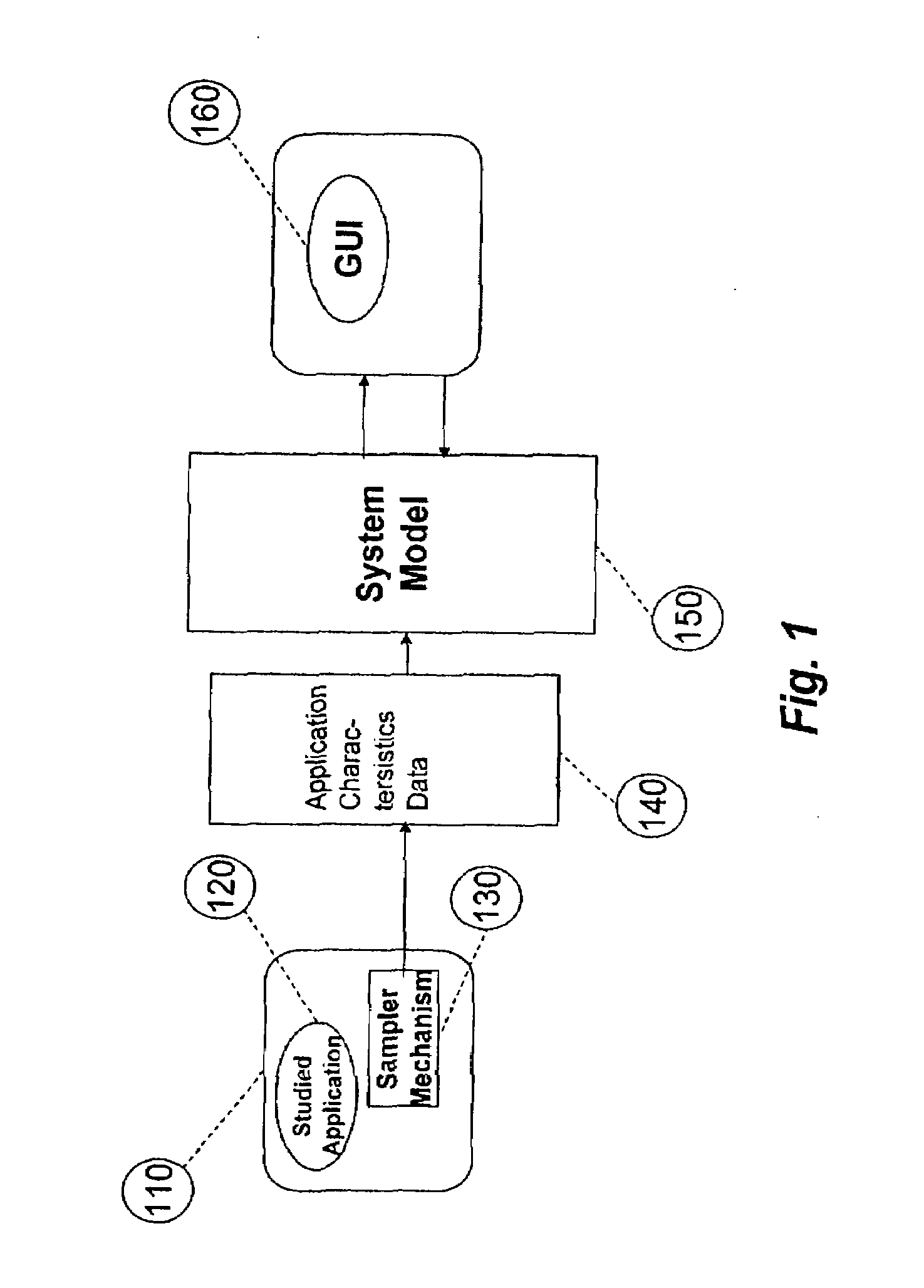
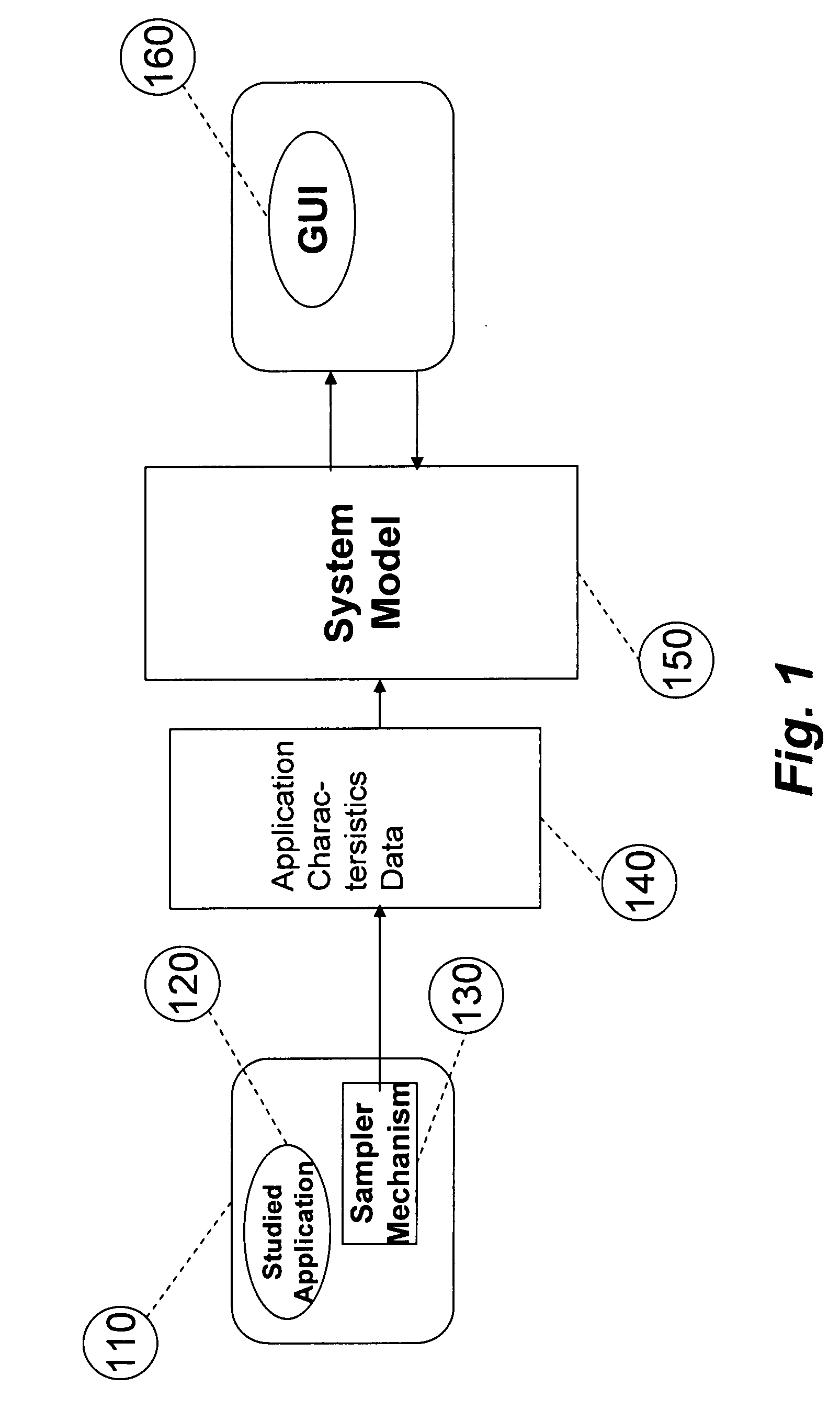
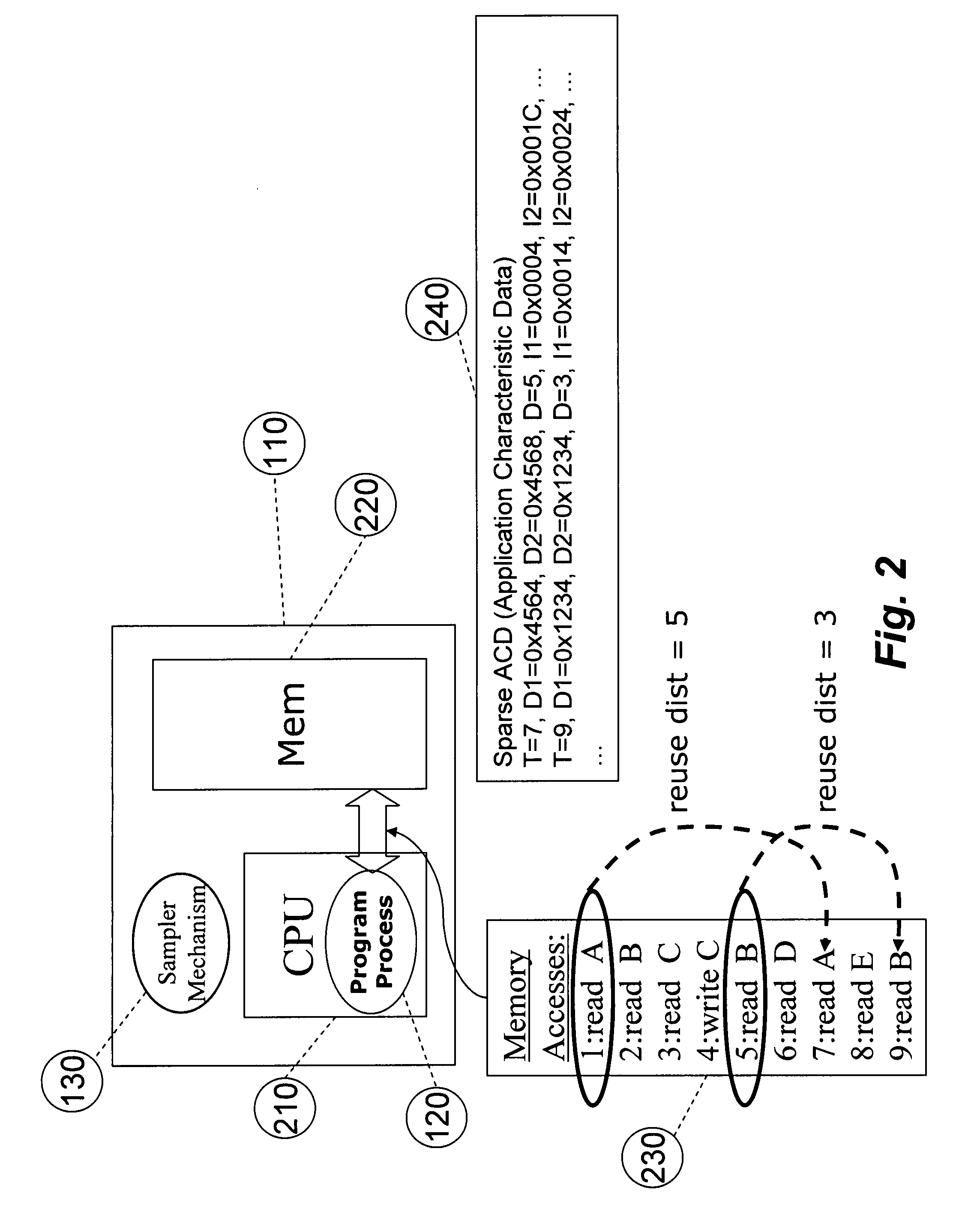
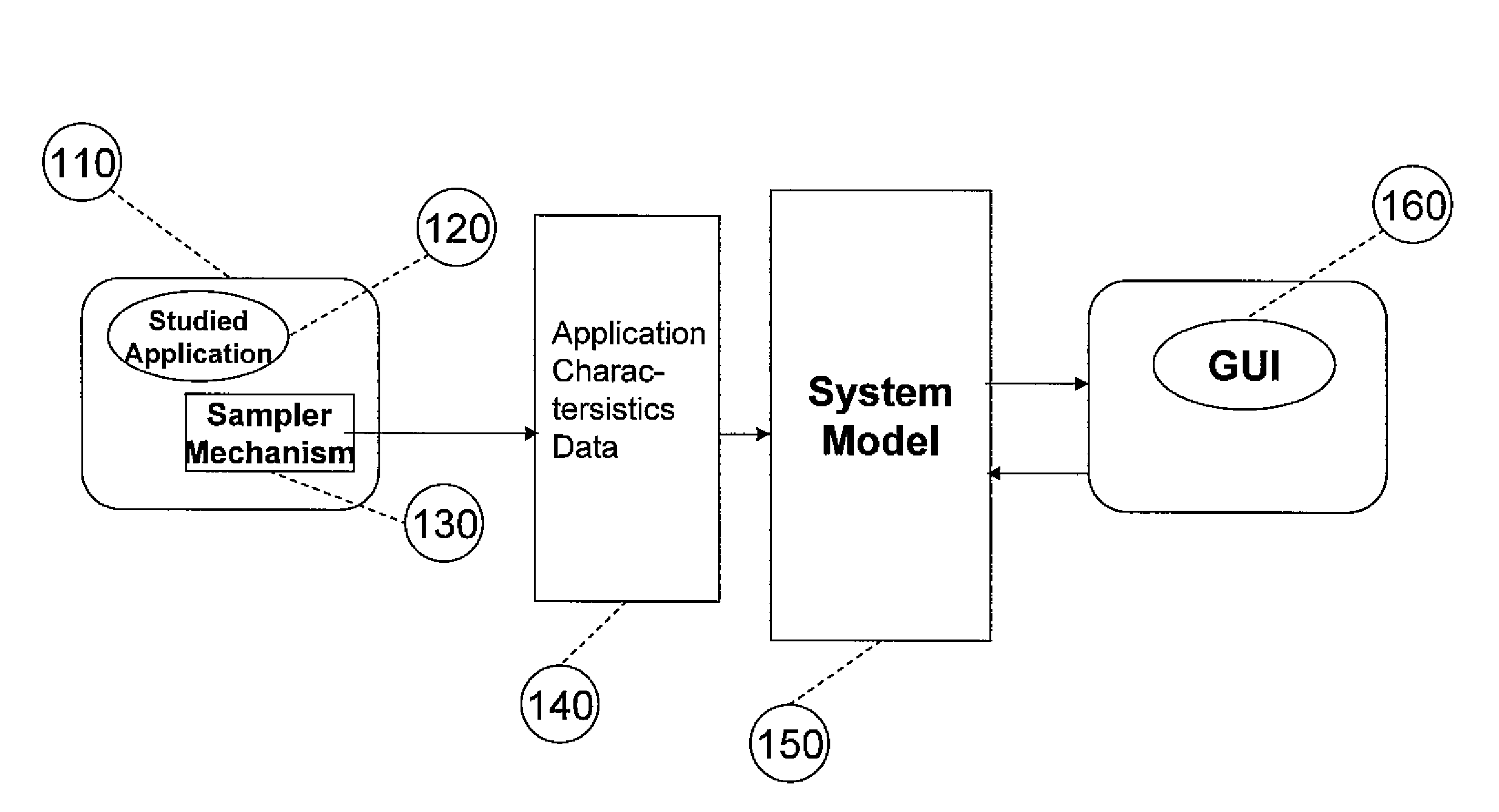
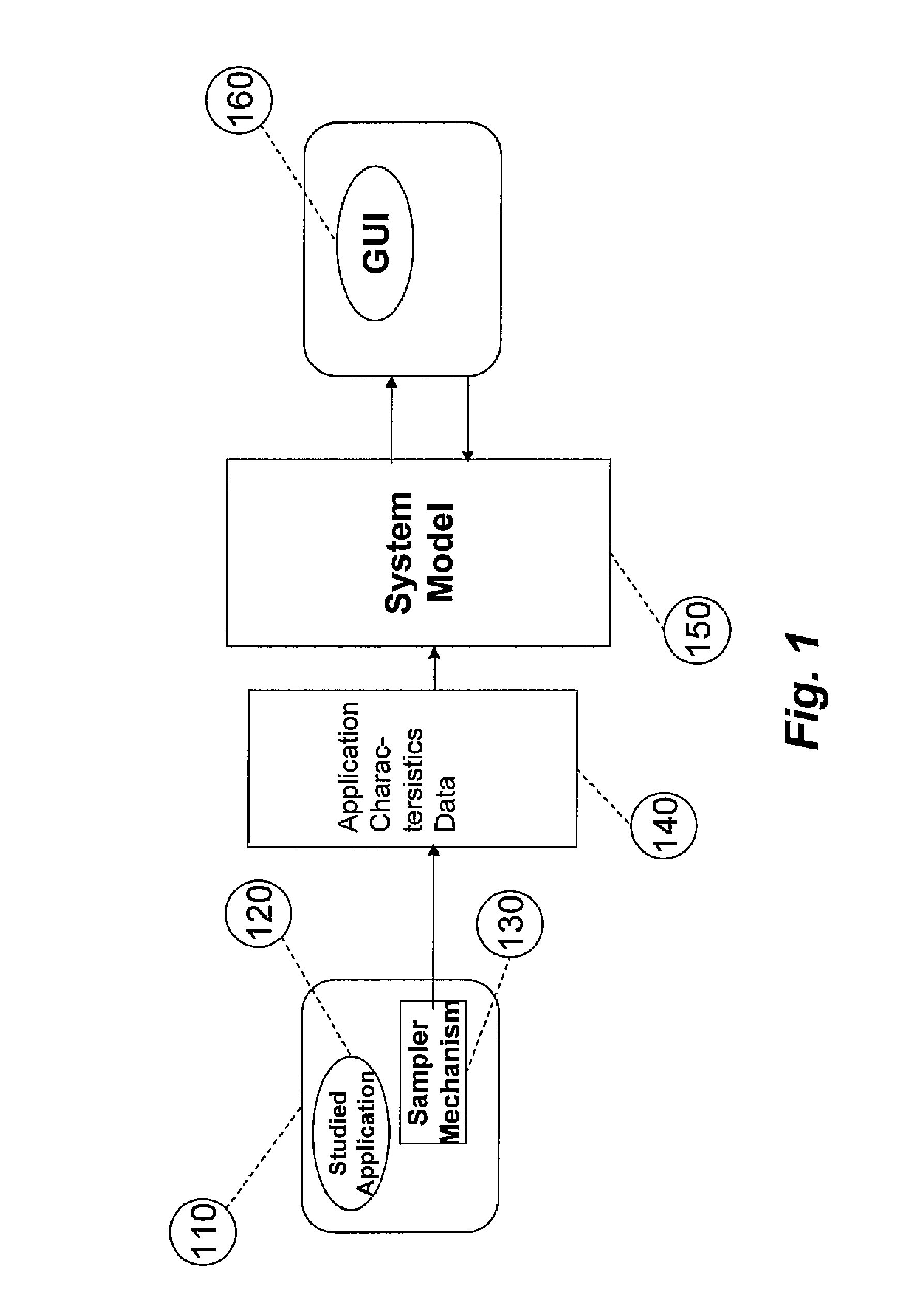
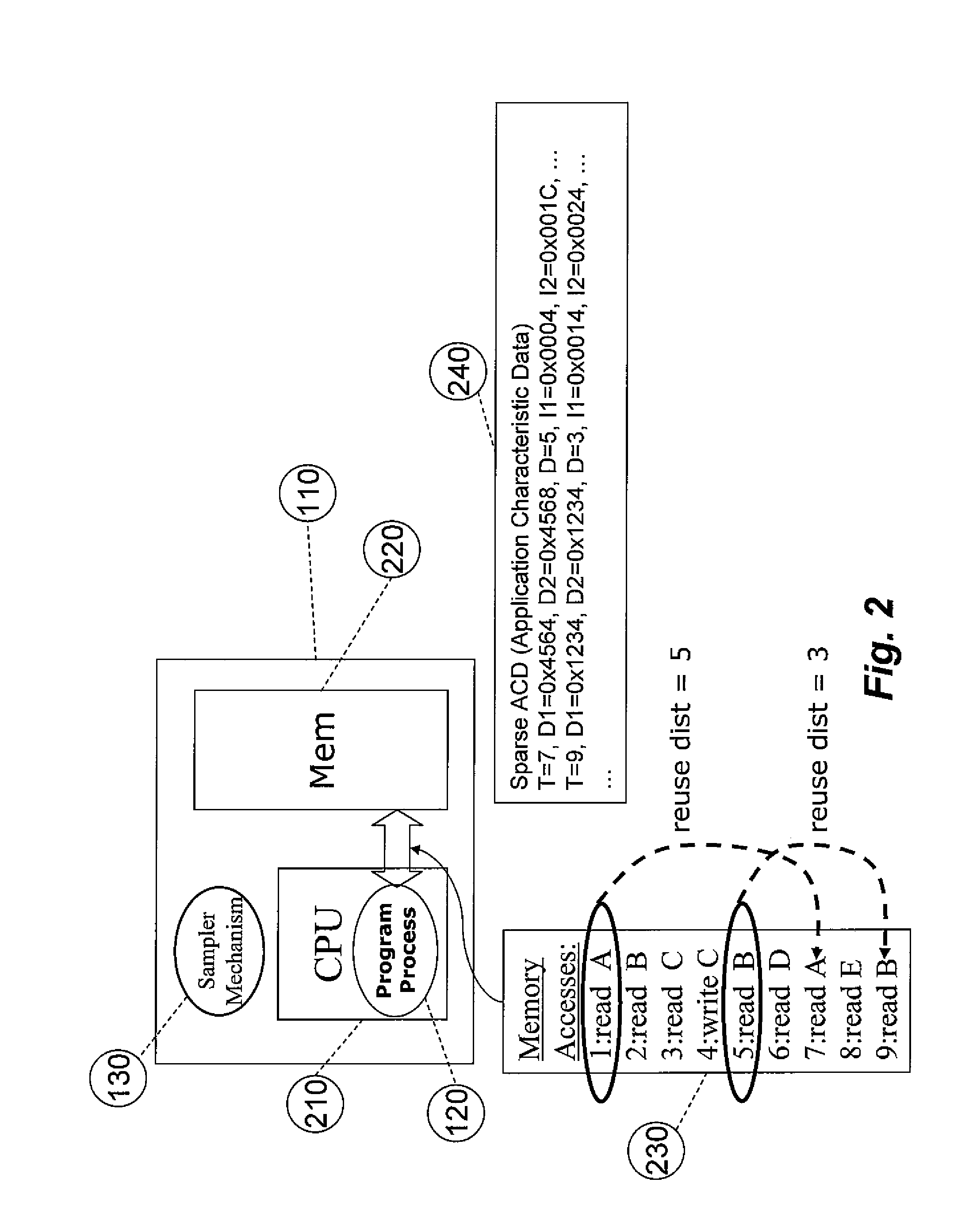
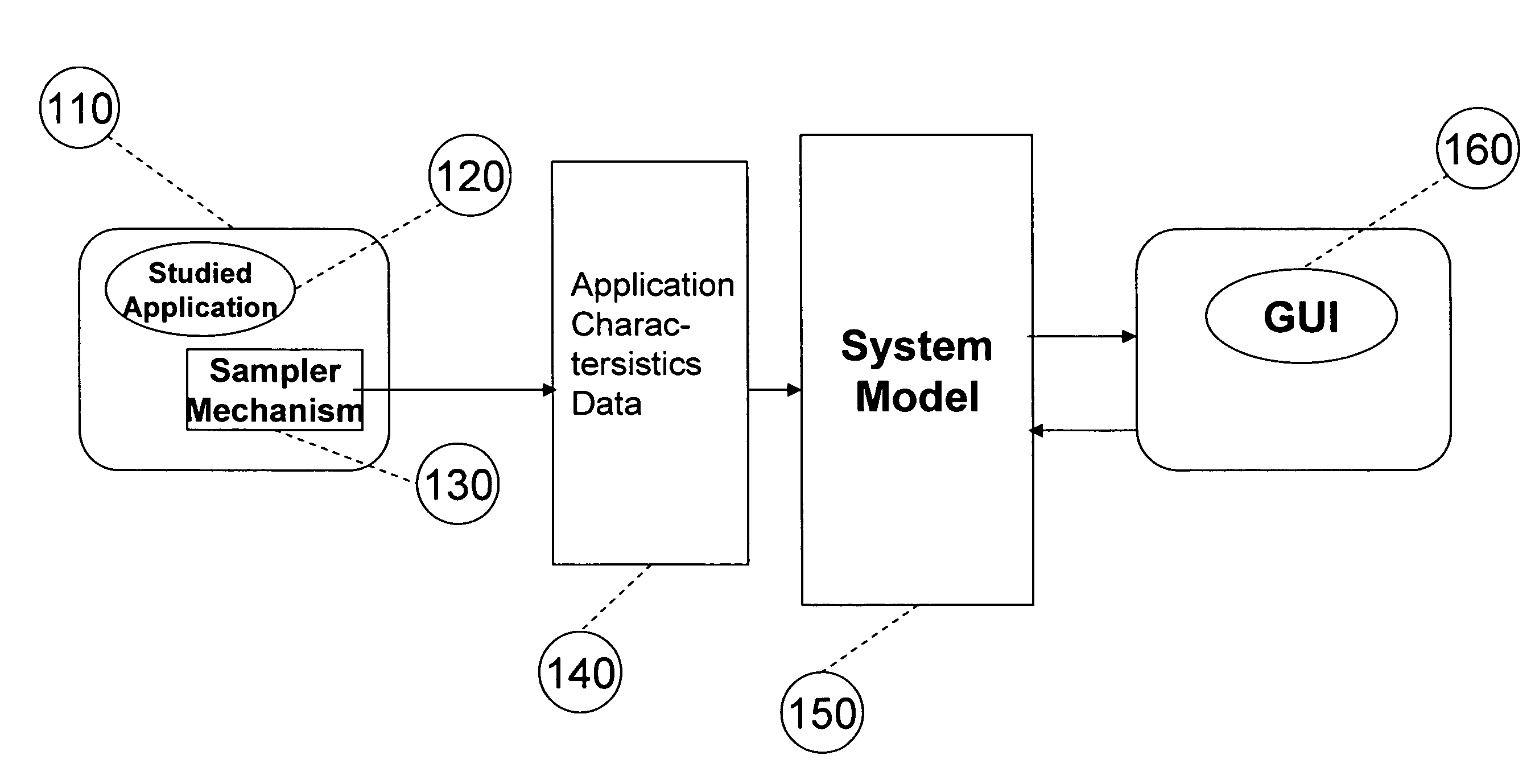
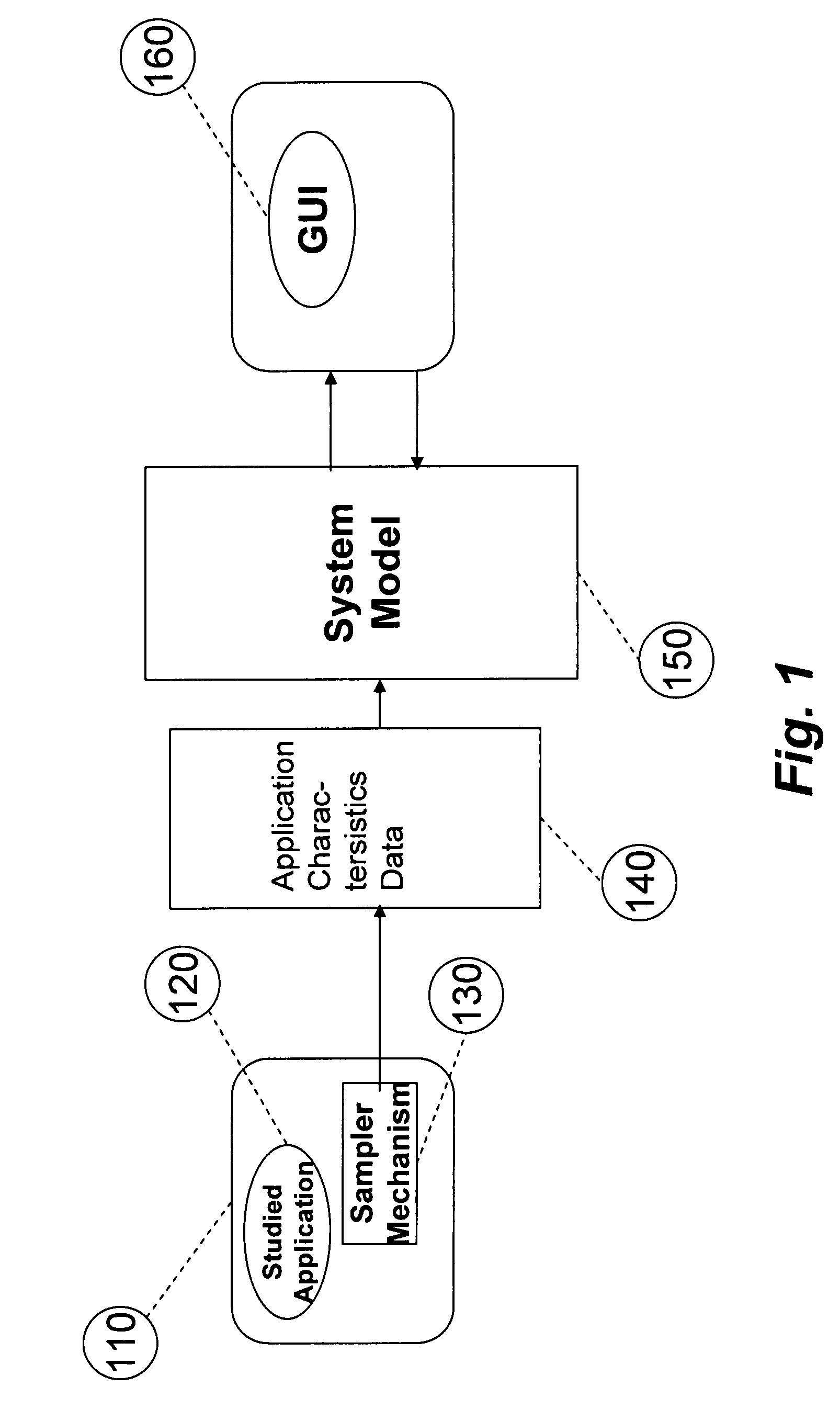
System for and method of capturing performance characteristics data from a computer system and modeling target system performance
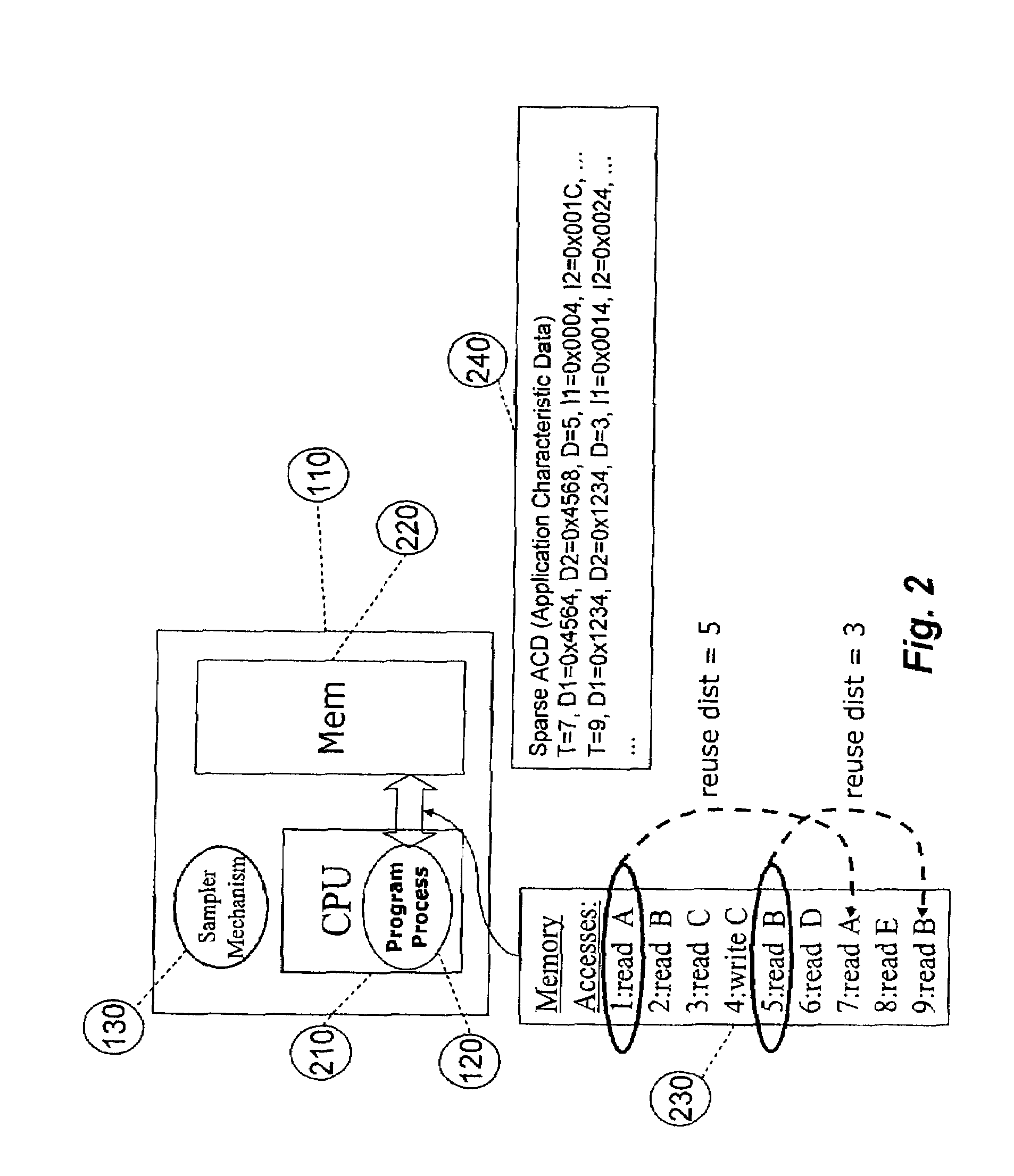
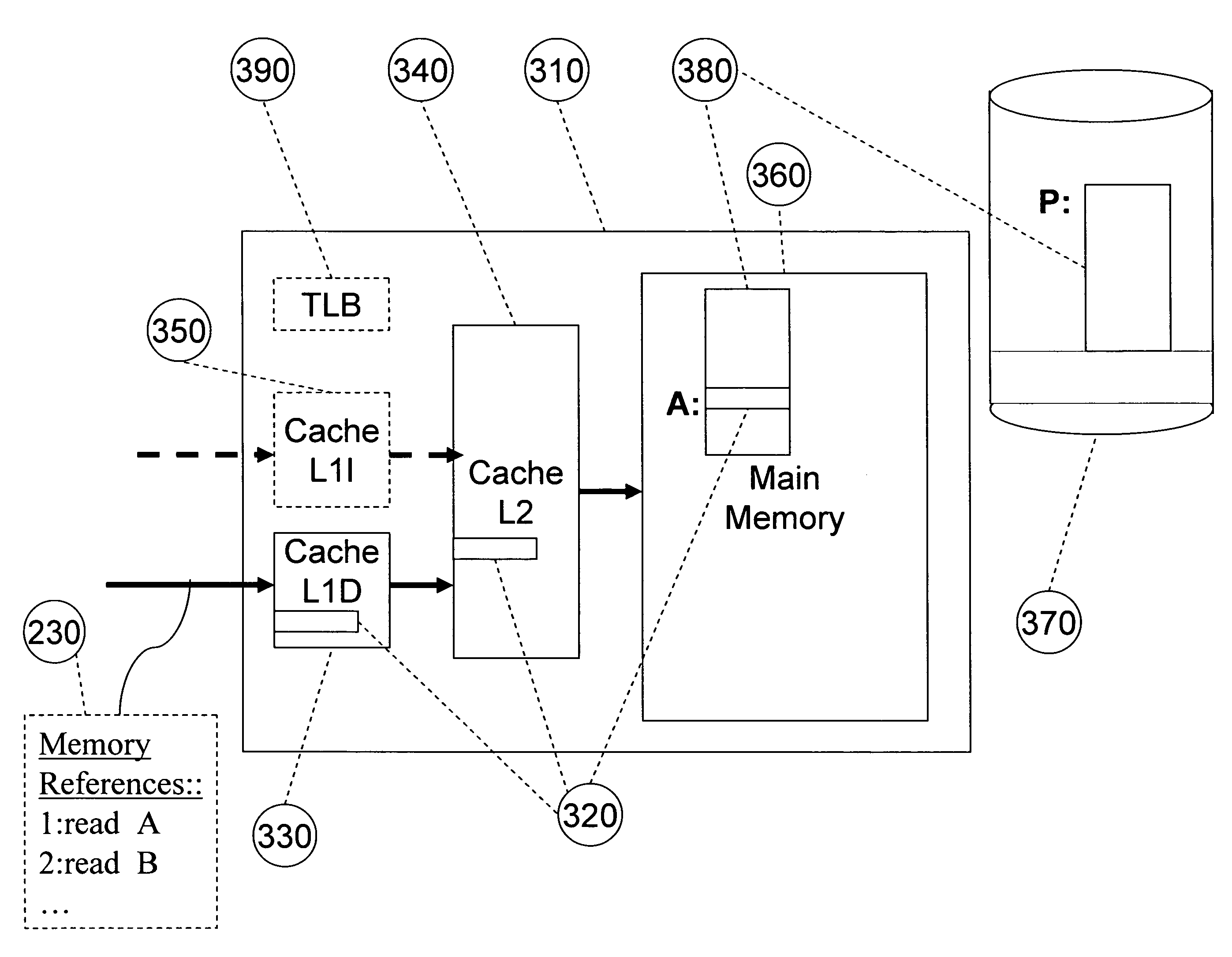
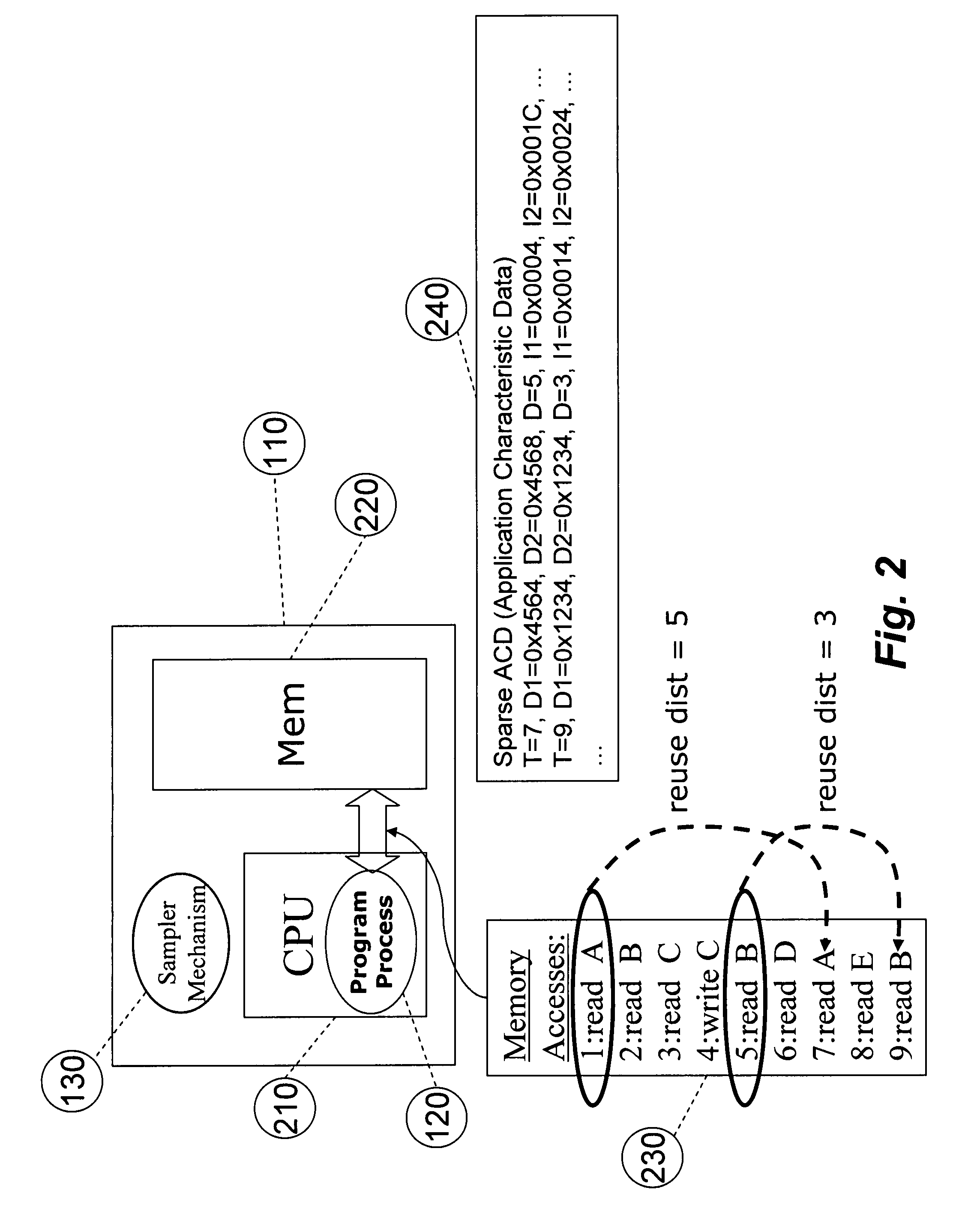
ActiveUS8539455B2Satisfy speedSimple and efficient user environmentError detection/correctionDigital computer detailsData modelingRandom replacement
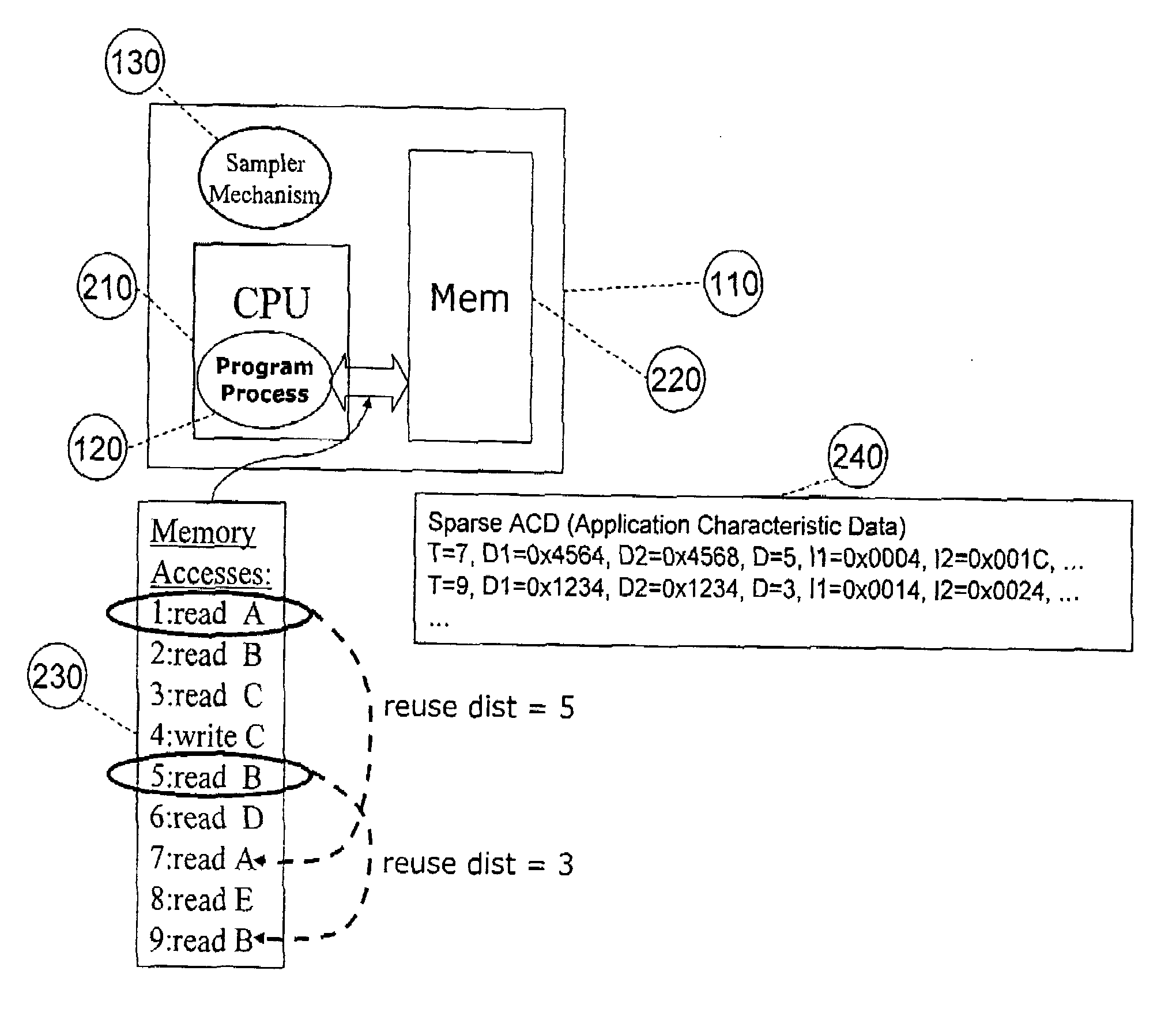
A system, method, and computer program product that captures performance-characteristic data from the execution of a program and models system performance based on that data. Performance-characterization data based on easily captured reuse distance metrics is targeted. Reuse distance for one memory operation may be measured as the number of memory operations that have been performed since the memory object it accesses was last accessed. Separate call stacks leading up to the same memory operation are identified and statistics are separated for the different call stacks. Methods for efficiently capturing this kind of metrics are described. These data can be refined into easily interpreted performance metrics, such as performance data related to caches with LRU replacement and random replacement strategies in combination with fully associative as well as limited associativity cache organizations. Methods for assessing cache utilization as well as parallel execution are covered. The method includes modeling multithreaded memory systems and detecting false sharing coherence misses.
Owner:ROGUE WAVE SOFTWARE
System for and method of capturing application characteristics data from a computer system and modeling target system
InactiveUS20090055594A1Satisfy demand flexibilitySatisfy speedError detection/correctionMemory adressing/allocation/relocationData simulationRandom replacement
A system for, method of and computer program product captures performance-characteristic data from the execution of a program and models system performance based on that data. Performance-characterization data based on easily captured reuse distance metrics is targeted, defined as the total number of memory references between two accesses to the same piece of data. Methods for efficiently capturing this kind of metrics are described. These data can be refined into easily interpreted performance metrics, such as performance data related to caches with LRU replacement and random replacement strategies in combination with fully associative as well as limited associativity cache organizations.
Owner:ROGUE WAVE SOFTWARE
System for and method of capturing application characteristics data from a computer system and modeling target system
ActiveUS8443341B2Satisfy speedSimple and efficient user environmentError detection/correctionDigital computer detailsData simulationRandom replacement
Owner:ROGUE WAVE SOFTWARE
System for and method of capturing application characteristics data from a computer system and modeling target system
InactiveUS8141058B2Satisfy speedSimple and efficient user environmentError detection/correctionSpecific program execution arrangementsData simulationRandom replacement
A system for, method of and computer program product captures performance-characteristic data from the execution of a program and models system performance based on that data. Performance-characterization data based on easily captured reuse distance metrics is targeted, defined as the total number of memory references between two accesses to the same piece of data. Methods for efficiently capturing this kind of metrics are described. These data can be refined into easily interpreted performance metrics, such as performance data related to caches with LRU replacement and random replacement strategies in combination with fully associative as well as limited associativity cache organizations.
Owner:ROGUE WAVE SOFTWARE
Privacy protection method for contingency table data dissemination
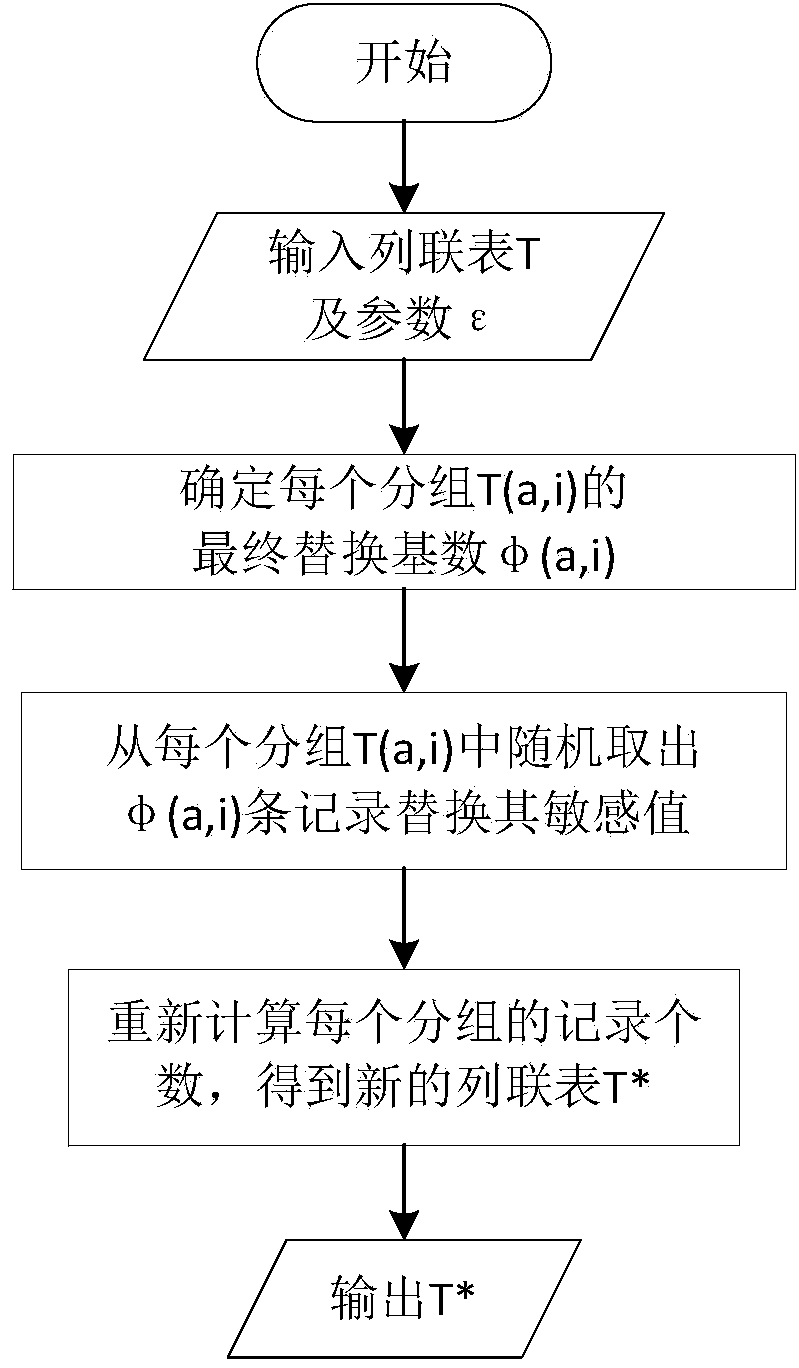
ActiveCN104216994AMeet security needsHigh precisionDigital data protectionSpecial data processing applicationsData privacy protectionRandom replacement
The invention discloses a privacy protection method for contingency table data dissemination and belongs to the field of privacy protection of computer data. The privacy protection method comprises the following steps: determining an initial replacement base number and a final replacement base number of each group in a contingency table; recording random replacement of a sensitive value based on an index mechanism; repeatedly calculating each replaced group and outputting a new contingency table. According to the privacy protection method, the processed contingency table meets safety requirements of epsilon-difference privacy; meanwhile, inquires supported by any meta-data are supported; processed data errors are small and the accuracy is high so that the data availability is stronger.
Owner:HUAZHONG UNIV OF SCI & TECH
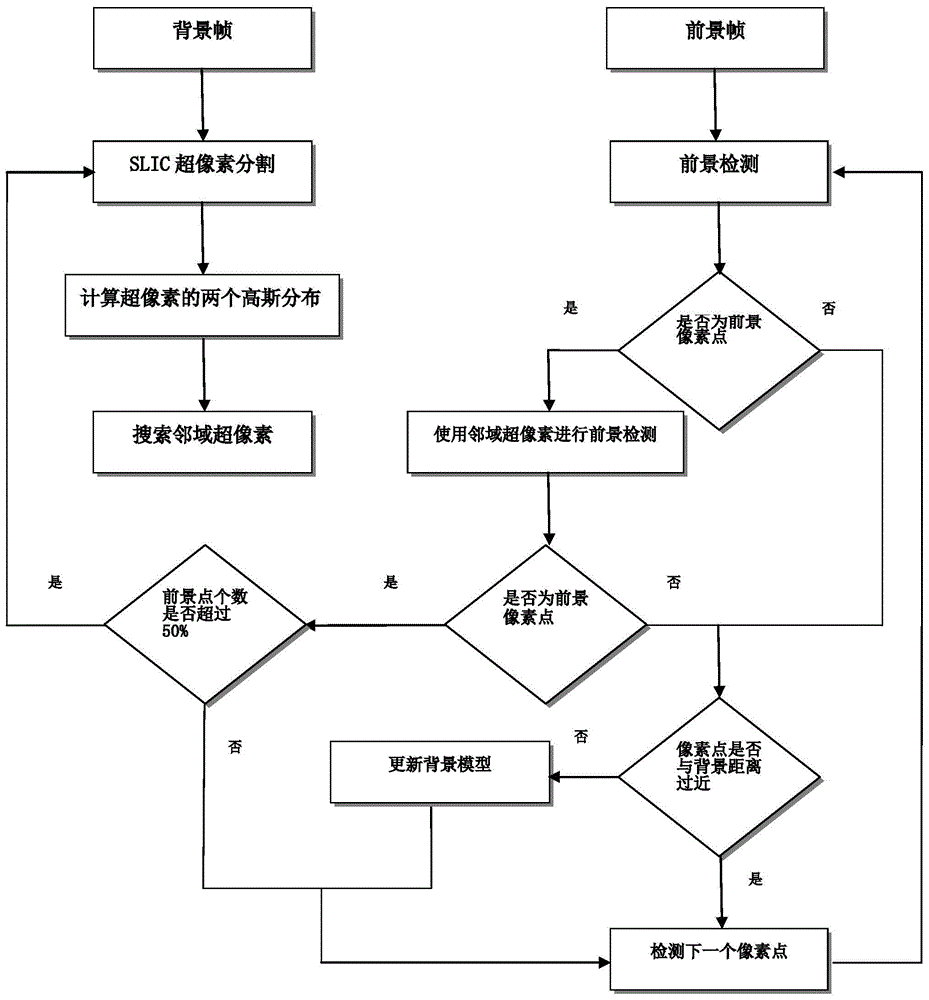
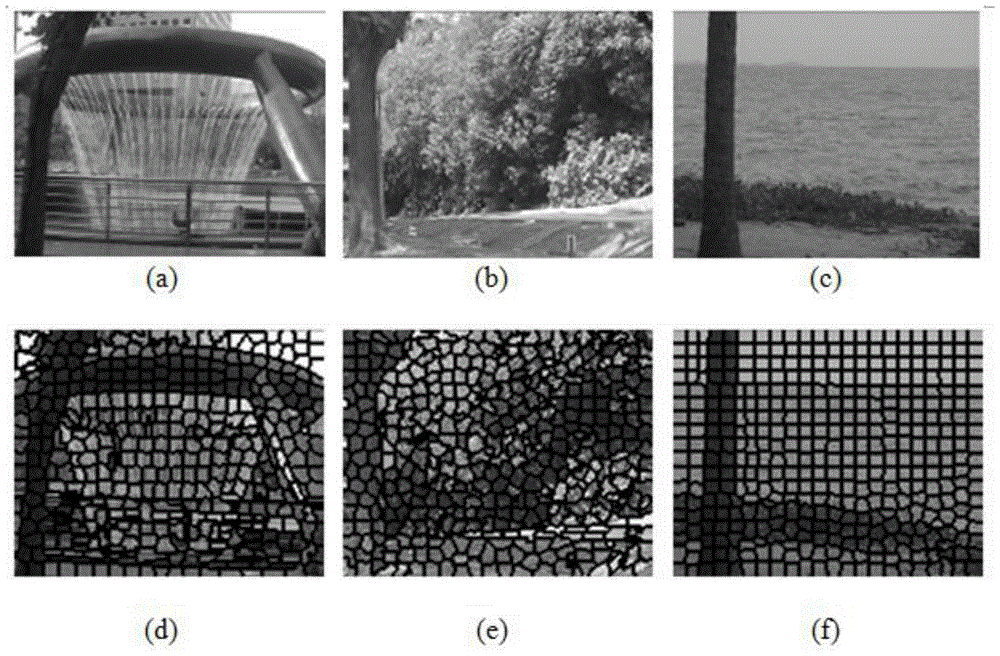
ViBe (Visual Background Extractor) algorithm and SLIC (Simple Linear Iterative Cluster) superpixel based background difference method
InactiveCN105741277AHigh precisionMake full use of spatial correlationImage enhancementImage analysisData setImaging processing
A background difference method based on ViBe algorithm and SLIC superpixel belongs to the technical field of image processing. The invention comprises the following steps: background modeling based on superpixel segmentation, foreground detection and background update. The invention proposes a background modeling foreground detection algorithm combined with SLIC superpixels under the ViBe algorithm framework. While effectively utilizing the advantages of the ViBe algorithm, it expands the neighborhood range of pixels by combining with SLIC superpixels, and makes full use of the spatial correlation of background pixels so that it can better deal with phenomena such as wind and grass and camera shake. The background update method of ViBe algorithm for random replacement of the background library is changed to the update method of Gaussian distribution, which avoids the instability caused by the random replacement strategy to the algorithm. In the experimental part, three sets of frame sequences in the I2R dataset are used for background modeling and foreground detection experiments, and the GMM algorithm and ViBe algorithm are used to compare with our algorithm.
Owner:DALIAN UNIV OF TECH
Entity-programming building block with separation type ID module
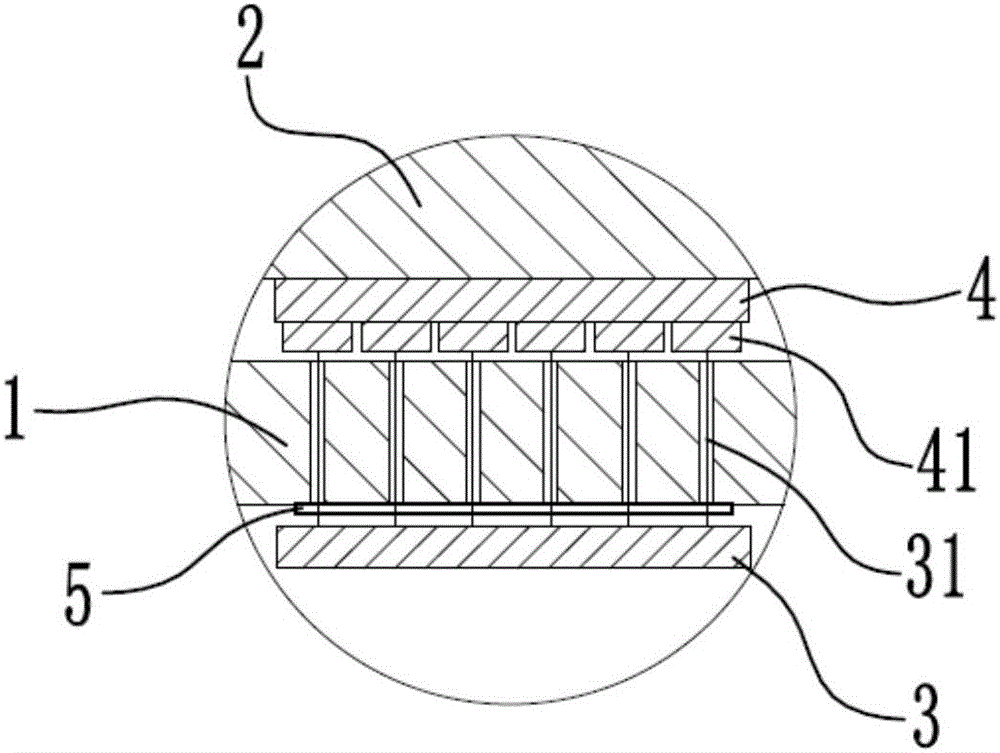
ActiveCN106334323AWide range of usesFunction increaseToysProgramme control in sequence/logic controllersRandom replacementArchitectural engineering
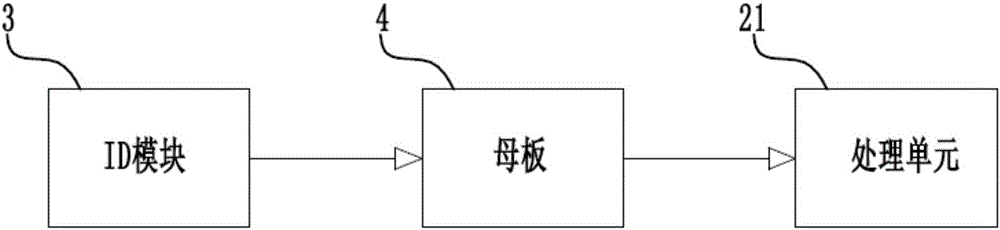
The invention provides an entity-programming building block with a separation type ID module. The entity-programming building block comprises a building block main body, a circuit board, the ID module and a mother board, wherein the circuit board is arranged in the building block main body and is provided with a processing unit; the ID module is independent from the building block main body and the circuit board; the mother board is arranged on the circuit board and is in signal connection with the ID module. Compared with the prior art, the entity-programming building block provided by the invention has the following advantages that (1) random replacement of ID of the entity-programming building block can be realized, so that the application of the entity-programming building block is wider and the function is diversified; (2) the operation difficulty in replacement of the ID of the entity-programming building block is reduced, the implementation mode is simplified and convenience is brought for operation of groups such as children; (3) the cost for replacement of the ID of the entity-programming building block is reduced; (4) a user can more conveniently replace the ID, and can define the type of the entity-programming building block by self; and (5) when the type of the entity-programming building block is developed, the replacement of the ID can be realized faster.
Owner:SUZHOU LEPAITE ROBOT CO LTD
Image compression sensing method based on perceptual and random displacement
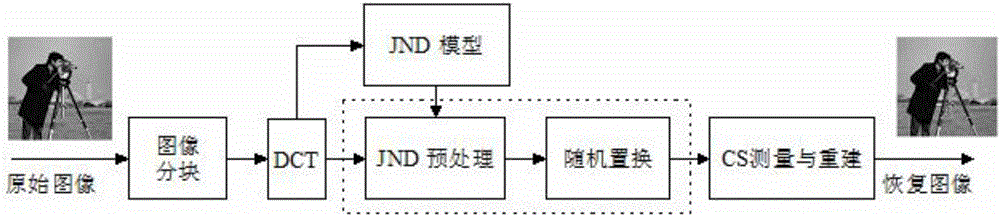
InactiveCN106534856AReduce complexityResistant to data lossDigital video signal modificationRandom replacementImage compression
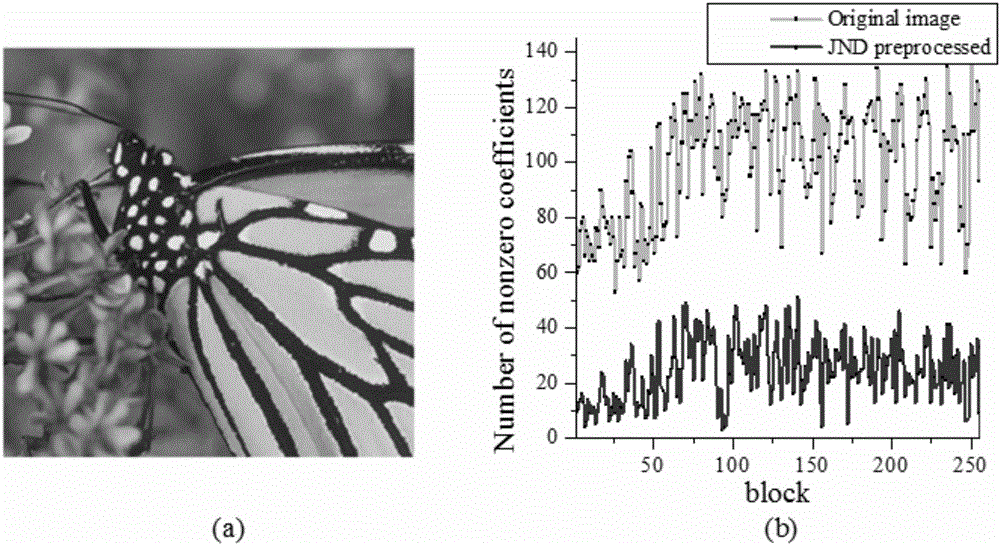
The invention discloses an image compression sensing method based on perceptual and random displacement. The method comprises the following steps: segmenting an image into nXn image blocks; conducting DCT transformation to each image block; utilizing a JND module to calculate the JND value in the DCT domain; utilizing the JND value to process the original DCT coefficient wherein the DCT value smaller than the JND value is reset as zero and the DCT value greater than the JND value stays unchanged; after that, conducting random replacement to the processed data; using a random matrix to observer for a measurement value of compression sensing; and finally, restoring the received data. With the method of the invention, the complexity of the coding end can be reduced and the coding end is enabled to have the ability to prevent data loss, making it applied in areas where the coding end has a poor computing ability but a strong decoding end and remarkably improving the compression efficiency.
Owner:SHANGHAI UNIV
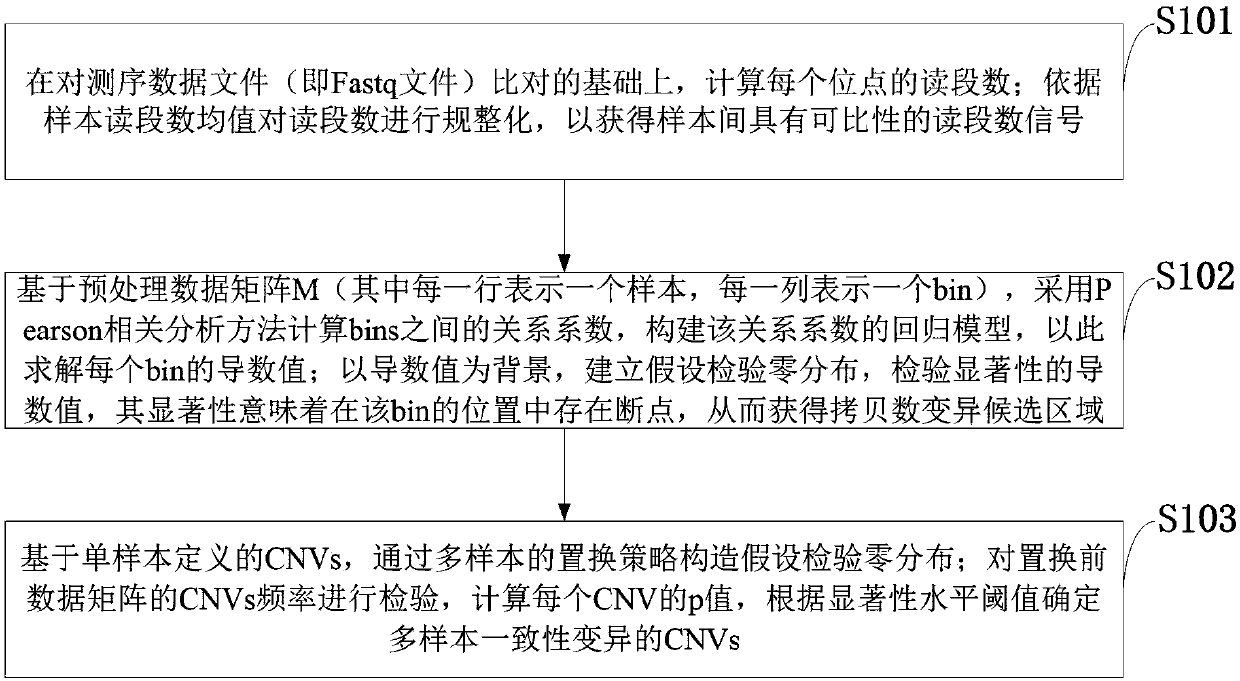
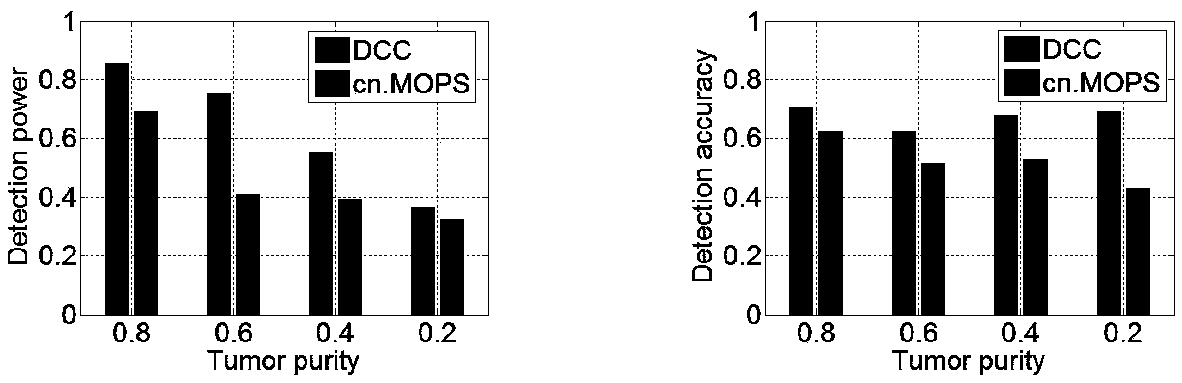
Statistical testing method of copy number consistency variation region in multiple samples
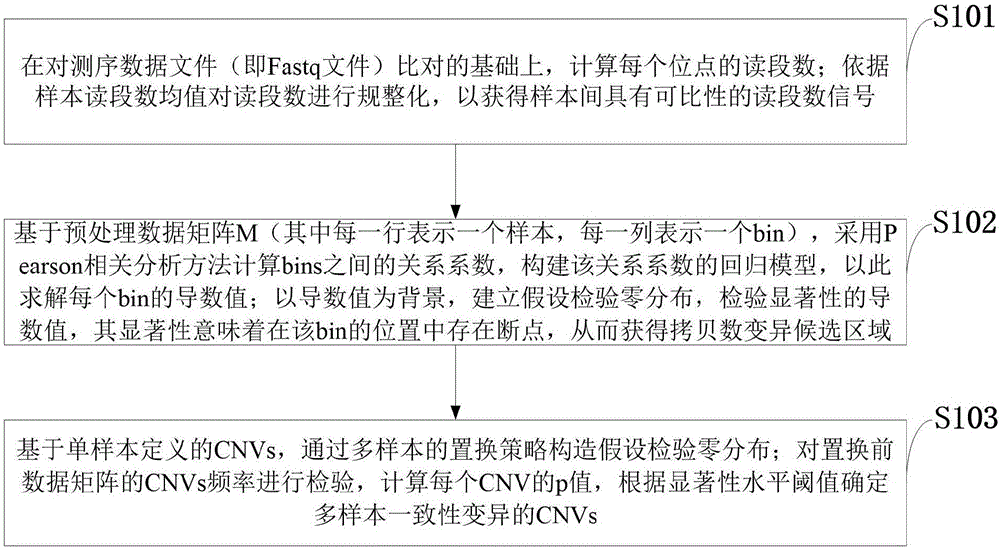
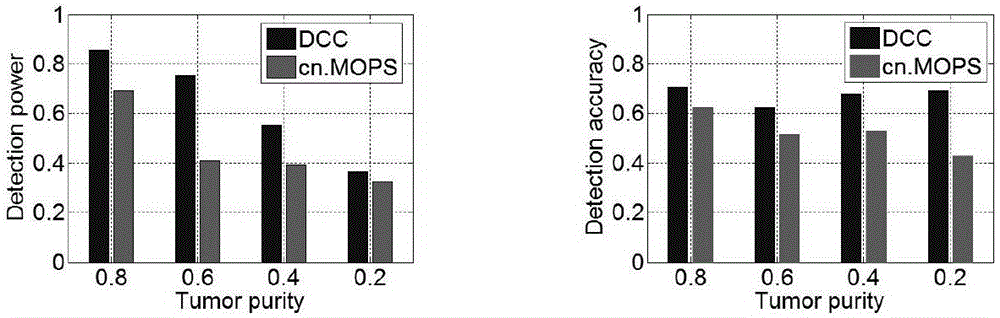
ActiveCN106682455AConvenient inspectionAvoid using sequencing read counts directlyBiostatisticsProteomicsHypothesisRandom replacement
The invention discloses a statistical testing method of copy number consistency variation region in multiple samples. The method comprises the steps that a quasi synthetic curve is constructed based on the relation coefficients of the copy digital points, the derivative value of each digital point is calculated, significant derivative values are tested through the hypothesis test method, and a variable candidate region for the copy numbers is built from the determination of the breakpoint of the copy numbers; a hypothesized null distribution is constructed through the method of randomly replacing the CNVs on the two directions of the whole genome group and the samples, and the copy number consistency variable region in multiple samples is tested. According to the method, directly using the read number of sequence is avoided, certain sequence mistakes and noises can be accommodated, and a boundary of the variable region for the copy numbers can be relatively accurately located;based on the random replacements of the CNVs on the two directions of the whole genome group and the samples, compared to the replacements on a single direction, more real head distribution of the hypothesis test can be obtained by the method; meanwhile the test of the diversified consistency variable CNVs, namely, the variable region of the copy number consistency existed in multiple sample subclasses, is facilitated.
Owner:XIDIAN UNIV
Punching device for handmade leather manufacturing
PendingCN110273030AEasy to replaceFeel free to adjust spacingLeather clicking/perforating/clickingSkins/hides/leather/fur manufacturing apparatusPunchingRandom replacement
The invention relates to a handmade leather manufacturing punching tool, in particular to an assembly type punching device for handmade leather manufacturing. The punching device comprises a knocking handle and a hole-shaped mould positioned on the head position of the knocking handle, wherein a slide rail is arranged on the head position of the knocking handle; the slide rail is positioned on the inner plate surface of a fixed plate; the lower end of the fixed plate and one side of the top end surface of the knocking handle are fixed into an integer; a slide plate is arranged on the slide rail; a slide slot which is matched with the slide rail is formed in the inner plate surface of the slide plate; the slide rail is positioned in the slide slot; at least three bearing table holes are formed in the top of the slide plate; hole-shaped moulds are inserted into the bearing table holes; three slide surfaces of the slide rail and three slide surfaces of the slide slot are integrally formed into a wedge-shaped locking slide surface; and under action of external force, the slide slot only can transversely slide on the slide rail. The punching device improves working efficiency, reduces use cost, realizes free random replacement of hole-shaped moulds and convenient later-stage maintenance, and realizes a self-adaptive punching design.
Owner:王洲
Recommendation system recommendation method and device, recommendation system and storage medium
ActiveCN112069396AIncrease the probability of finding "surprises"Digital data information retrievalNeural architecturesRandom replacementPrediction probability
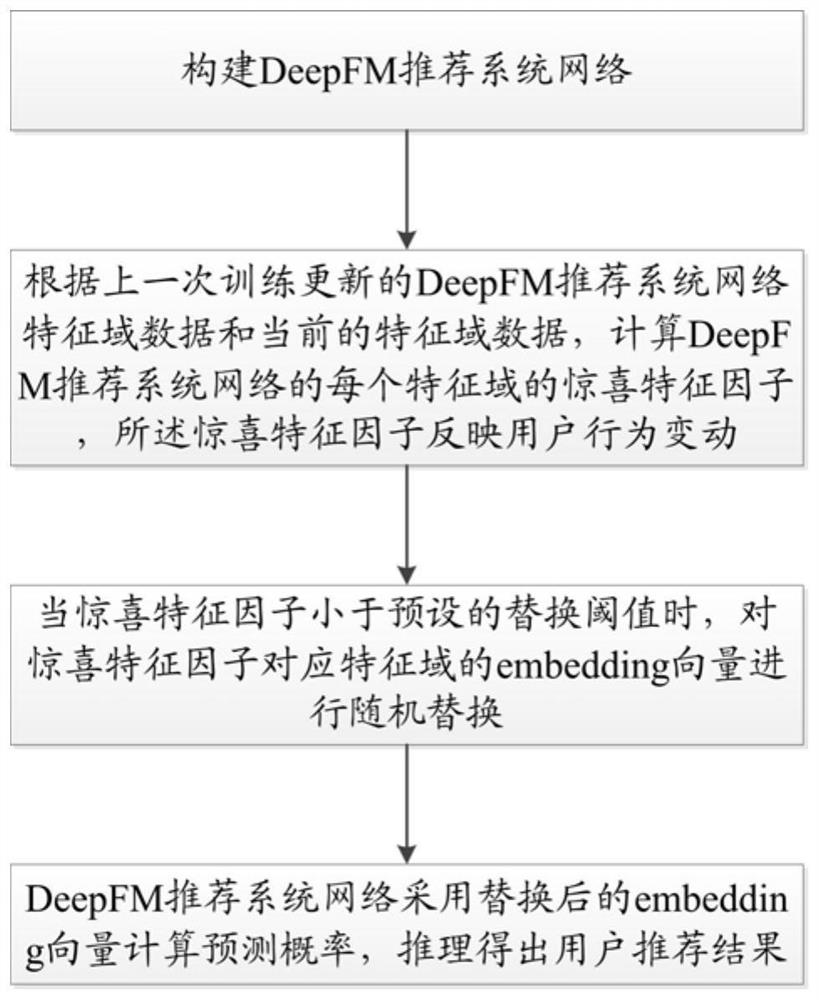
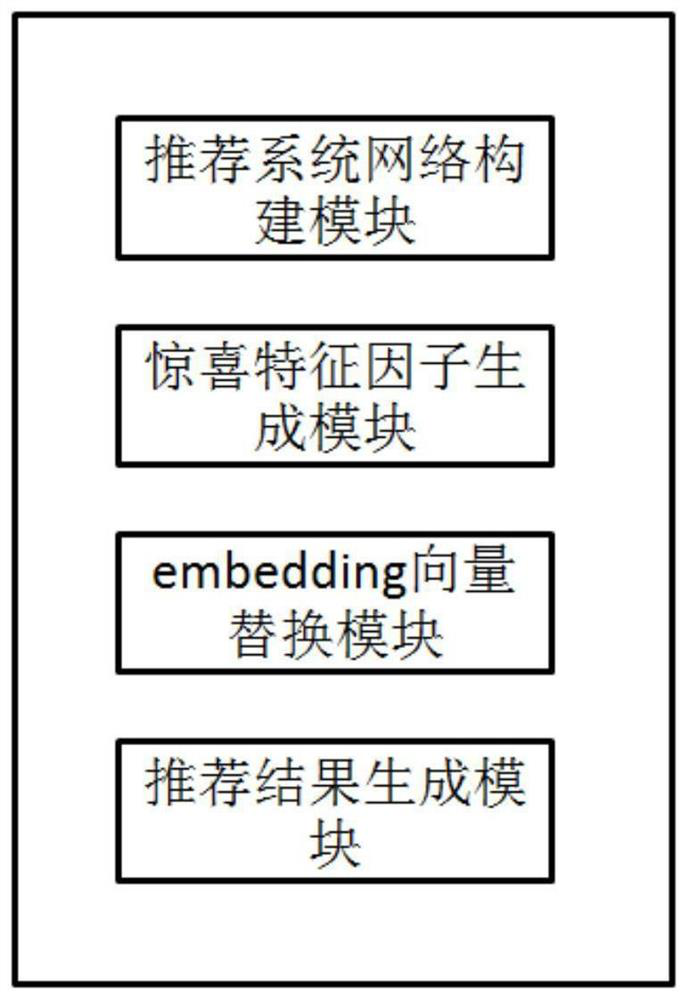
The invention discloses a recommendation system recommendation method and device, a recommendation system and a storage medium. The method comprises the steps of constructing a DeepFM recommendation system network; calculating a surprise characteristic factor of each characteristic domain of the DeepFM recommendation system network according to the characteristic domain data of the DeepFM recommendation system network updated in the last training and the current characteristic domain data, the surprise characteristic factor reflecting user behavior changes; when the surprise characteristic factor is smaller than a preset replacement threshold, carrying out random replacement on the embed vector of the characteristic domain corresponding to the surprise characteristic factor; and the DeepFMrecommendation system network calculates a prediction probability by adopting the replaced embed vector, and obtains a user recommendation result by reasoning. The recommendation system comprises a recommendation system network construction module, a surprise characteristic factor generation module, an embed vector replacement module and a recommendation result generation module. According to themethod, the probability of discovering surprises is improved on the basis that the memory ability and the generalization ability of a recommendation system are reserved.
Owner:INSPUR SUZHOU INTELLIGENT TECH CO LTD
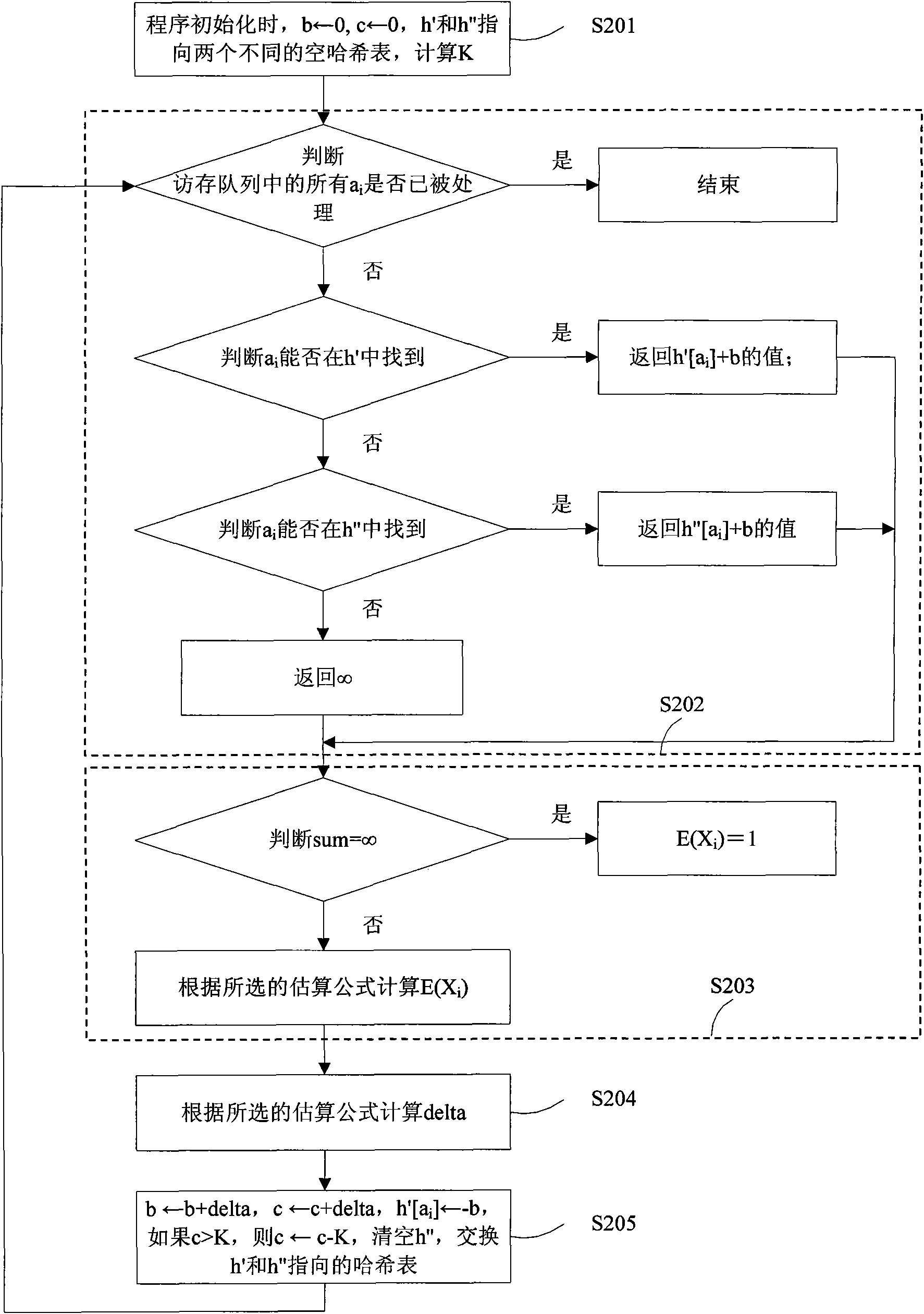
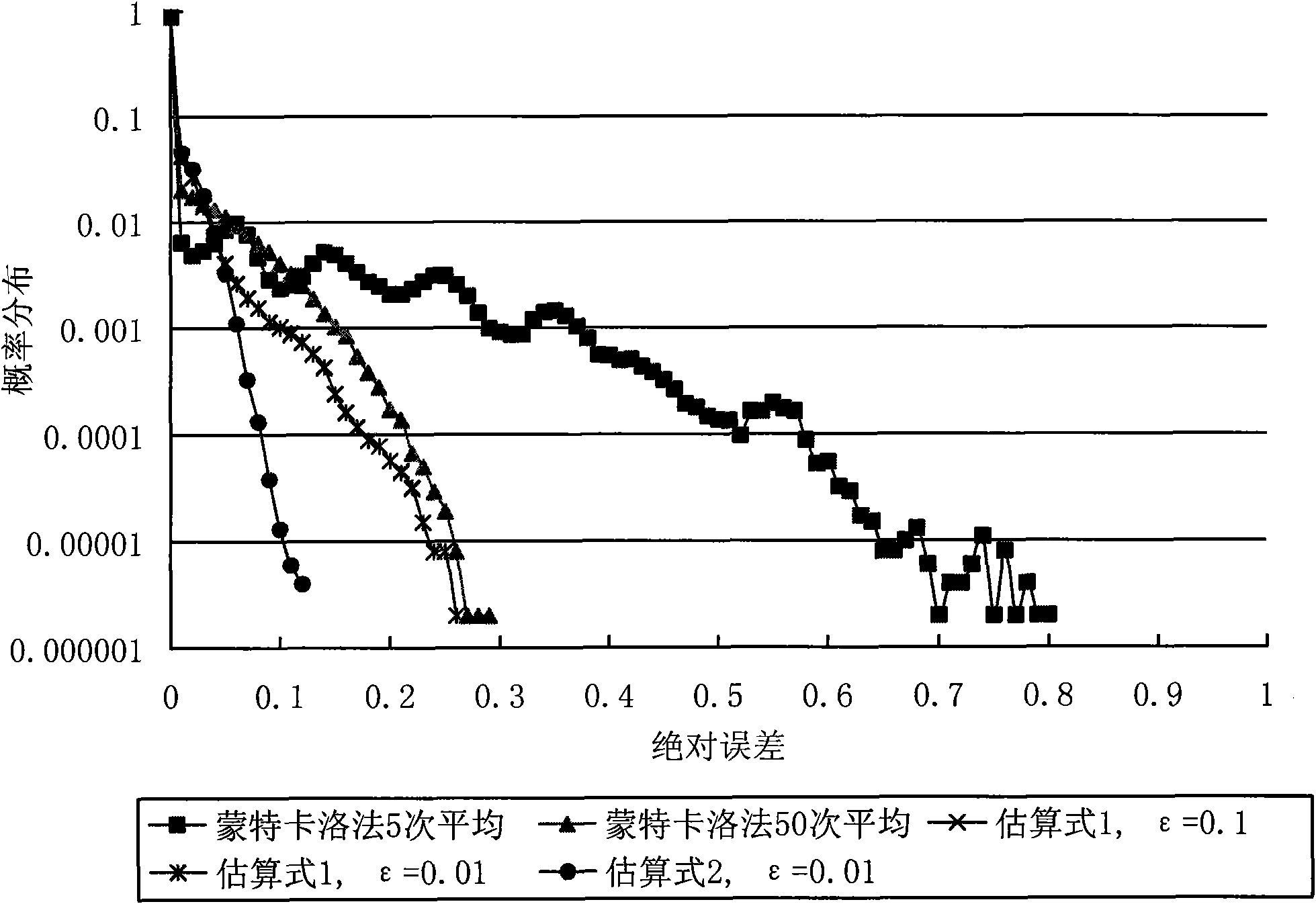
Efficient analogy method for replacing cache randomly
ActiveCN101916229ASolve the problem that the hit probability of each point in the access sequence cannot be givenMemory adressing/allocation/relocationAlgorithmRandom replacement
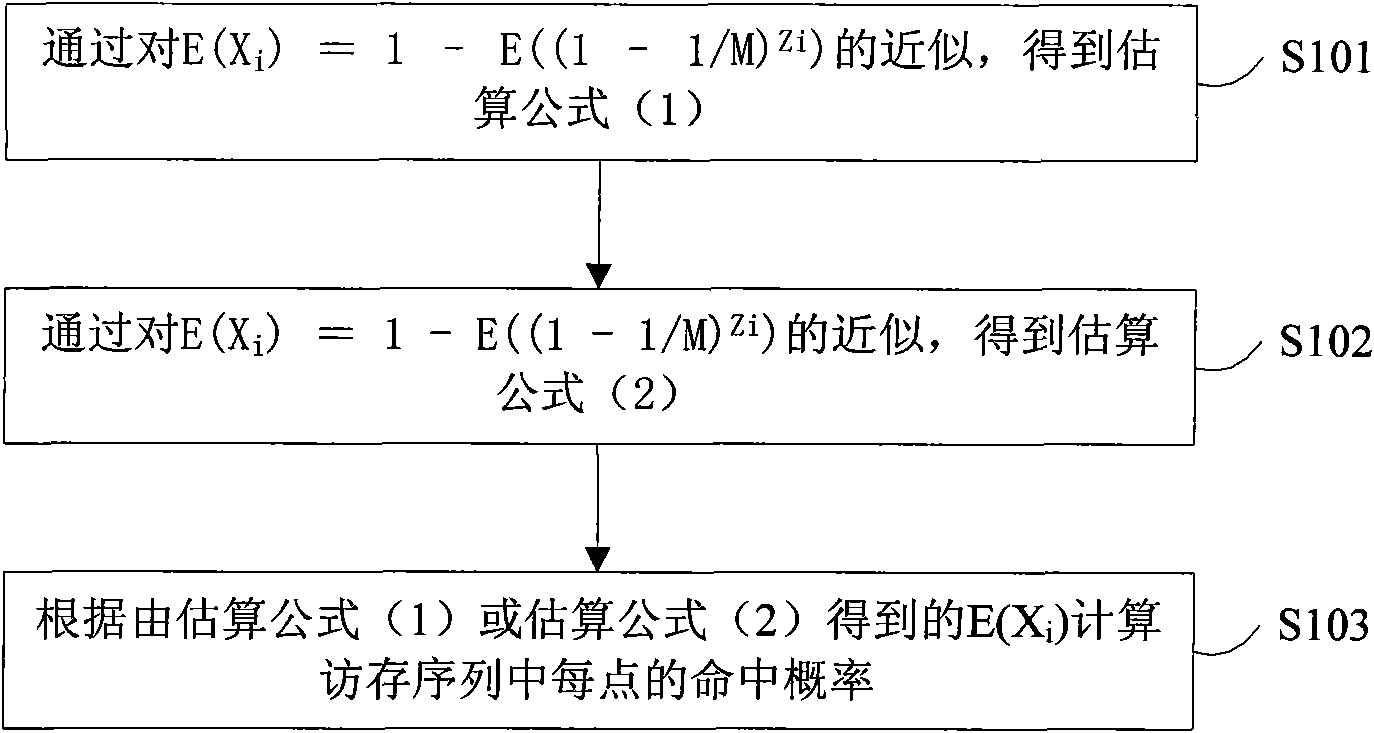
The invention relates to an efficient analogy method for replacing a cache randomly, comprising the following steps of: firstly, obtaining an estimating formula (1) or (2): E(Xi)is approximate to 1-(1-1 / M)E(Zi)(1)E(Xi) is approximate to 1-Pij(1+E(Xj) / (M-1))-1(2) by approximating E(Xi)=1-E((1-1 / MZi); and secondly, calculating the hit probability 1-E(Xi) of each point in a memory array according to E(Xi) obtained by the estimating formula (1) or (2), wherein Xi is an index random variable of a depletion event, E(Xi) is a mathematic expectation, M is the degree of association of the cache, Xj belongs to a reusing window of Xi, namely all depletion events during the period from value of ai appearing previously to i. If the value of the point ai in the memory array does not appear before, Zi is infinite; if the value of the point ai appears before, Zi is equal to time of depletion events during the period from value of ai appearing previously to i. The invention can obtain an estimation of the hit probability of each point in the memory array through one analogue round by using the estimating formula of a probability model.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
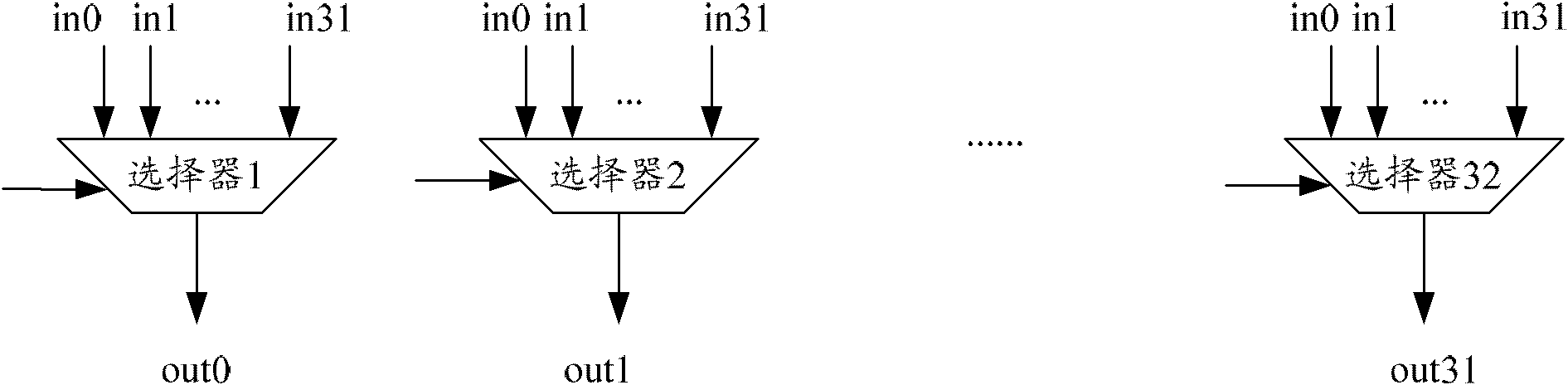
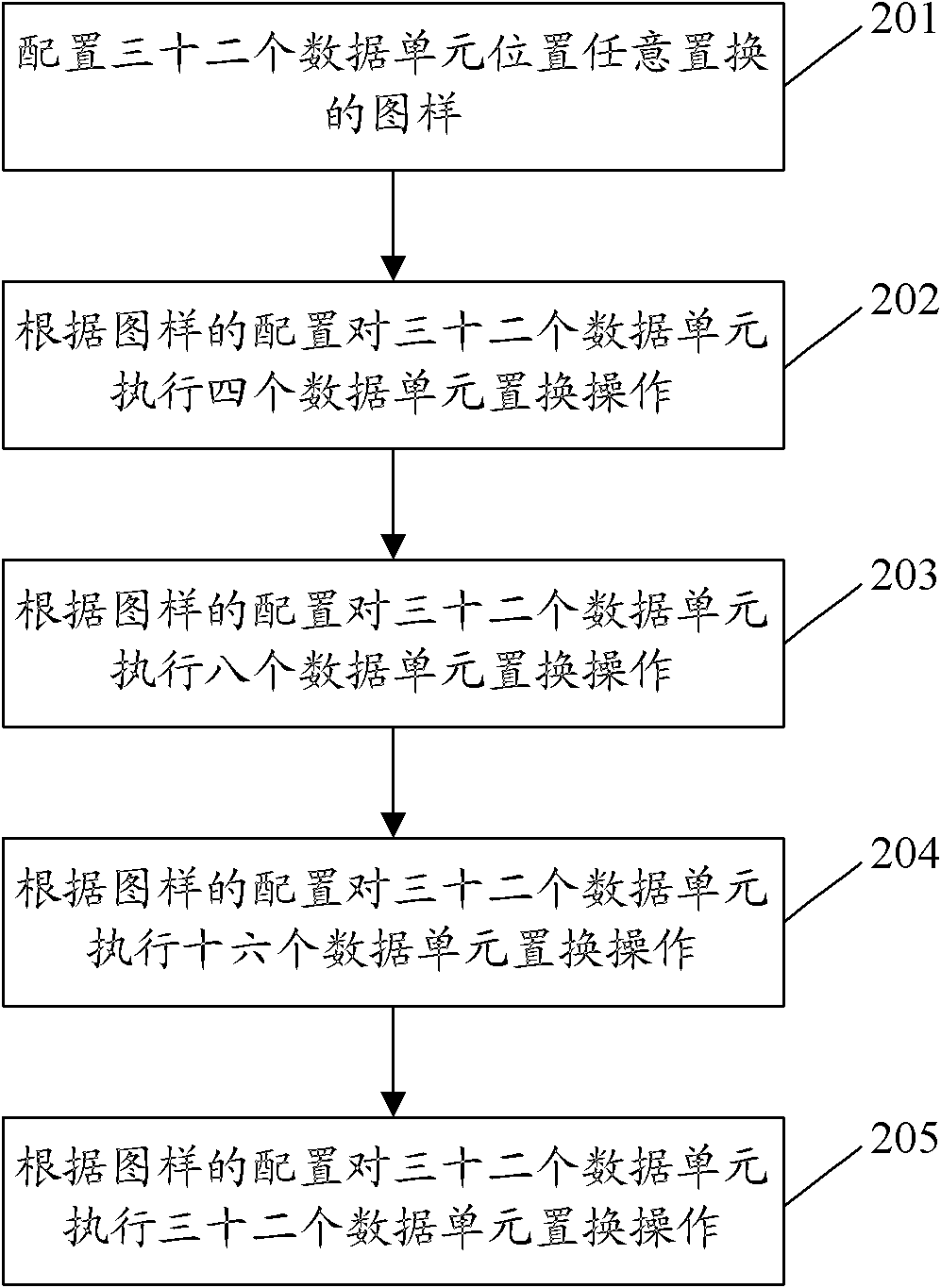
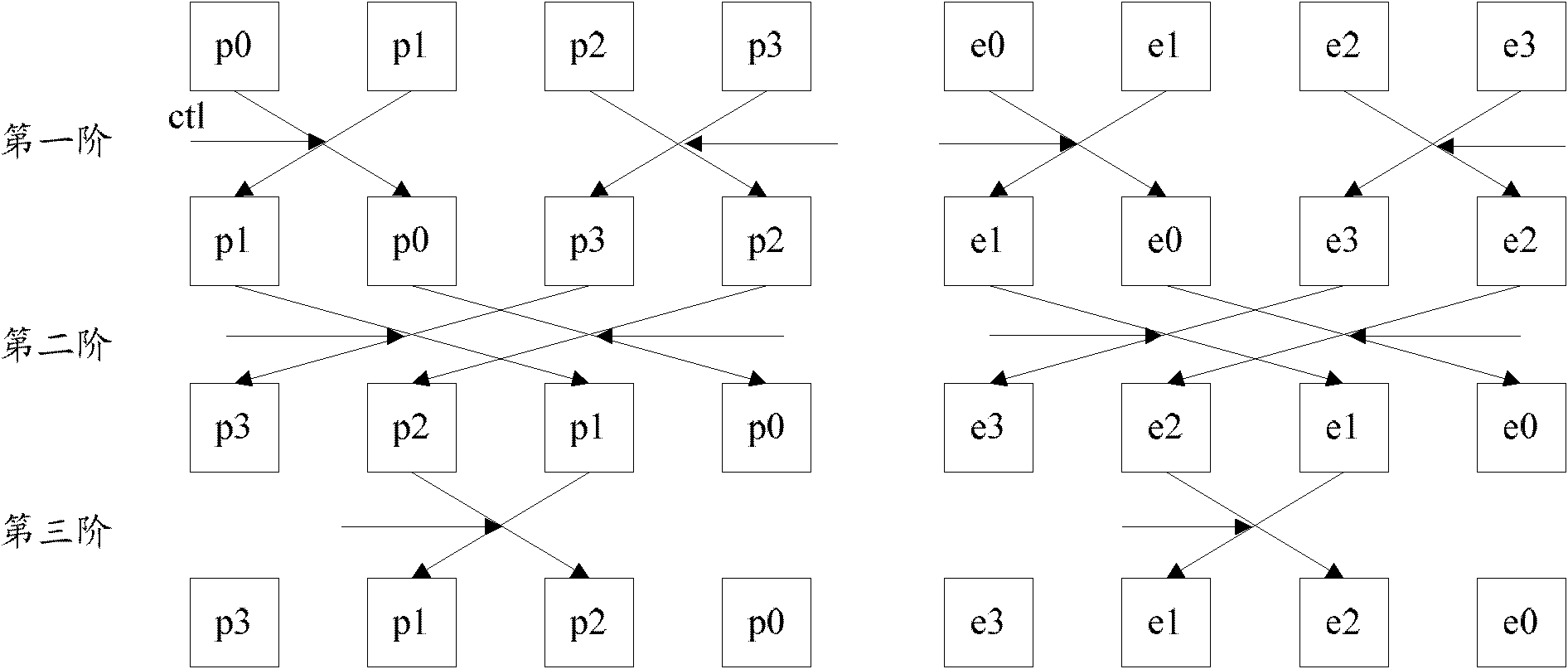
Method and device supporting random replacement of plurality of data units
InactiveCN102737007ASmall footprintReduce areaEnergy efficient ICTPower managementPower consumptionRandom replacement
The invention discloses a method supporting random replacement of a plurality of data units and comprises the steps of configuring patterns for random replacement of N data units; and performing replacement operation on the N date units according to configuration of the patterns in a data unit replacement process. The invention further disclosed a device supporting random replacement of a plurality of data units. By means of the method and the device, occupied space of data unit replacement circuits in a chip can be reduced, and simultaneously power consumption is lowered.
Owner:ZTE CORP
Guardrail lock
ActiveCN103556891AEasy to installEasy to replaceConstruction fastening devicesRandom replacementFastener
The invention belongs to the field of guardrails, and concretely relates to a children's guardrail lock. The children's guardrail lock comprises a lock bracket and a lock structure which are mutually matched, the lock structure comprises a lock shell, a lock pin part arranged at the front end of the lock shell and a switch part used for controlling the back-and-forth sliding of the lock pin part, and the lock pin part is connected with the switch part through a linkage part. The lock pin part comprises a pin body inserted to the front end of the lock shell and a lock pin fixedly arranged at the front end of the pin, the lock bracket is provided with a pinhole matched with the lock pin, and the switch part comprises a switch sliding block inserted to the front end of the lock shell and positioned over the lock pin part, a button fixedly arranged at the top of the switch sliding block and a fastener used for preventing the switch sliding block from separating from the lock shell. The lock pin part and the switch part are simply inserted into the lock shell to realize assembling and lock joint fixing, and the lock pin is driven by the back-and-forth sliding of the switch part to realize unlocking, so the guardrail lock has the advantages of simple structure, convenient assembling and dismounting, difficult dead locking, realization of random replacement of all parts, convenient maintenance, difficult damage of all the parts, and long service life.
Owner:浙江丽童家居有限公司
Out-of-block consensus method under asynchronous network condition
ActiveCN110535629ASolve the problem of high synchronization requirementsFast implementation of block consensusKey distribution for secure communicationEncryption apparatus with shift registers/memoriesHash functionRandom replacement
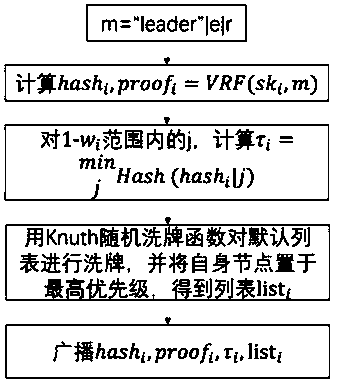
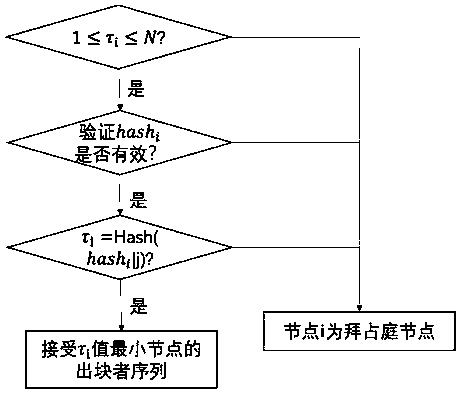
The invention discloses an out-of-block consensus method under an asynchronous network condition. The method comprises the following steps: generating a consensus and verifying the consensus; whereinthe list passing the verification is an out-of-block list obtained by consensus; the method for generating the consensus comprises the following steps: establishing a spliced character string; obtaining a hash value and a corresponding proof through a verifiable random function; calculating a hash function for j in each range of 1-wi, and selecting a minimum value: taking tau i obtained in the step III as a priority, and inversely deriving corresponding j according to tau i; performing random replacement on the default list by using a random shuffling function; placing the user i at the highest priority position of the list after replacement to obtain a list; broadcasting. According to the consensus method provided by the invention, the consensus problem in the asynchronous network can besolved, if the consensus node cannot output the block, the block is output by the node arranged at the second bit, and so on, so that the requirement on network synchronization is greatly reduced; meanwhile, the method does not need to know the share information of the whole network, and can reduce the calculation and communication expenditure.
Owner:奥科塞尔控股公司
Attack model library establishment method in quantum cryptographic protocol
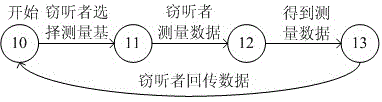
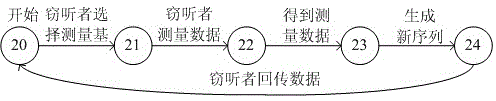
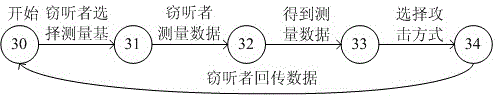
InactiveCN105049197ADetect wiretappingEnsure communication securityKey distribution for secure communicationCommunications securityAttack model
The invention discloses an attack model library establishment method in a quantum cryptographic protocol. An attack model library comprises an interception retransmission attack model, a random replacement attack model, a general attack model, a Trojan Horse attack model and an invisible photon attack model. The interception retransmission attack model is as follows: a transmitter transmits a sequence Ai to an information channel; an eavesdropper completely intercepts sequence and randomly selects a measurement basis to measure each photon and record a result Ei; the eavesdropper obtains a new sequence Ei' while all photons are measured and transmits the sequence to a receiver, and the receiver obtains a result Bi. The model library established by the method comprises the interception retransmission attack model, the random replacement attack model, the general attack model, the Trojan Horse attack model and the invisible photon attack model. By accurately describing the process of the five attack manners, the method is suitable for the communication protocol with similar property and could effectively detect the wiretap to ensure the communication safety.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
Method for constructing multi-system LDPC code check matrix
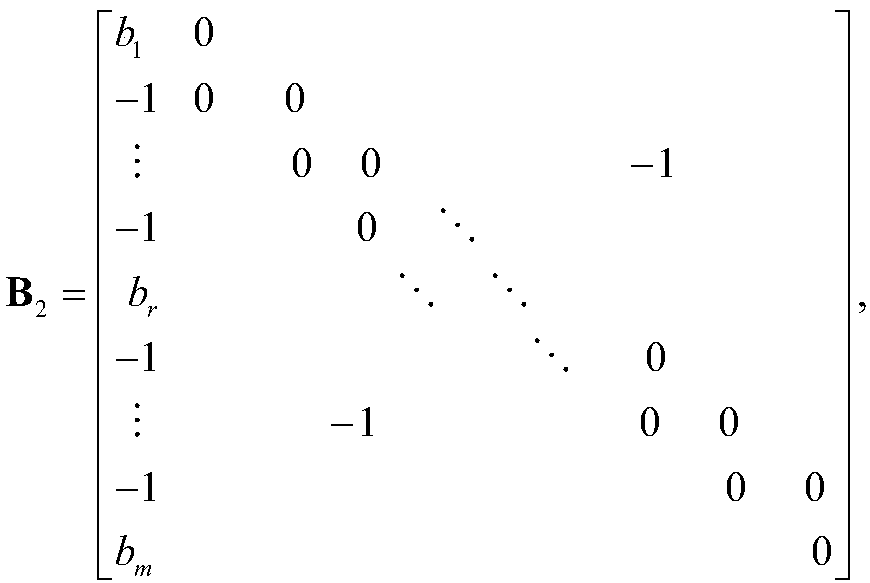
ActiveCN108494411AStable and good error correction effectError correction/detection using multiple parity bitsCode conversionEssential matrixAlgorithm
The invention provides a method for constructing a multi-system LDPC code check matrix based on the IEEE802.16e standard, and belongs to the field of methods for constructing channel coding check matrixes. The method for constructing the multi-system LDPC code check matrix based on the IEEE802.16e standard provided by the invention is a QC-LDPC construction method for the multi-system, and the main idea is to obtain a cyclic permutation matrix by using non-1 elements in a basic matrix of the standard as shift values, and then replace the corresponding non-1 elements in the basic matrix with the cyclic permutation matrix to obtain the multi-system check matrix. In general, the method has stable and good error correction performance compared with the method of performing multi-system numberrandom replacement on non zero elements in a binary matrix in the IEEE 802.16e standard.
Owner:SHANDONG UNIV
Mobile phone and structure thereof for preventing SIM card from being taken out
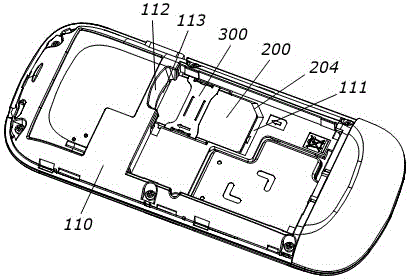
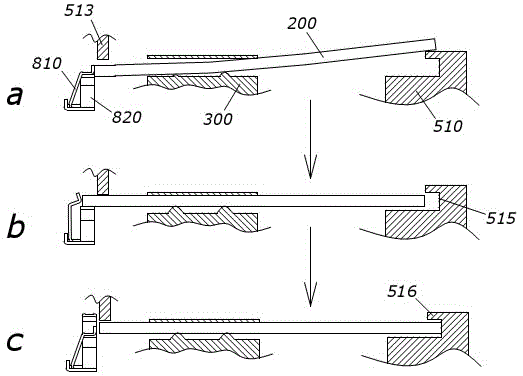
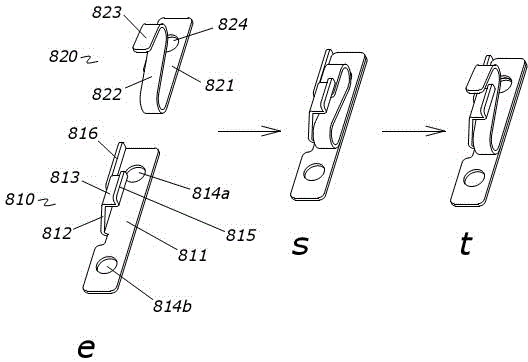
The invention discloses a mobile phone and a structure thereof for preventing an SIM card from being taken out. The structure comprises a first elastic sheet, a second elastic sheet and a first baffle plate which are positioned at the front end of an SIM card notch on the bottom case of the mobile phone, wherein before an SIM card is inserted into the second elastic sheet, the first elastic sheet is compressed, the SIM card is inserted from the bottom of the first baffle plate to replace the first elastic sheet so as to restrict the popping out of the second elastic sheet, and the second elastic sheet pops out after the SIM card goes back. Because the first elastic sheet for restricting the popping out of the second elastic sheet and the first baffle plate in an original nail buckling position are adopted, the SIM card is utilized to push away the first elastic sheet, and the second elastic sheet is popped out when the SIM card goes back; and the side surface of the second elastic sheet is utilized to block the front end of the SIM card, and the first baffle plate is used for pressing the front end of the SIM card to cooperate with an SIM card base and the SIM card notch to block the side wall of the rear end of the SIM card so as to block the SIM card together, thereby effectively preventing users from randomly taking out the SIM card first inserted for random replacement, and satisfying requirements of customers.
Owner:HUIZHOU TCL MOBILE COMM CO LTD
Rapid grouping method for precise elements
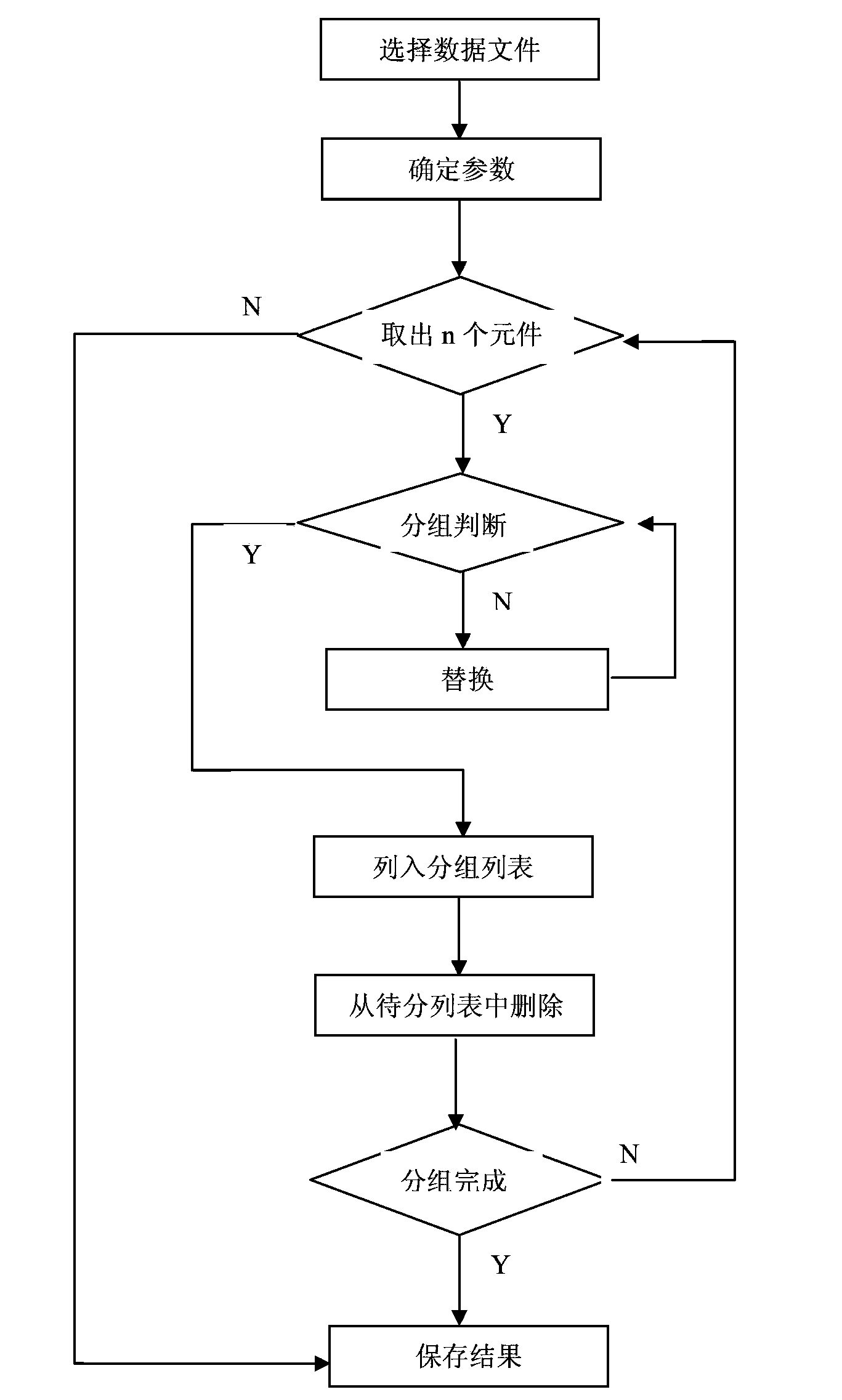
InactiveCN103810366AIncrease workloadHigh probability of errorSpecial data processing applicationsAviationRandom replacement
The invention belongs to the field of precise instruments for aviation and particularly relates to a rapid grouping method for precise elements. With the adoption of the rapid grouping method for the precise elements, provided by the invention, the automation of a grouping process can be realized. Data can be processed by using a strong computing capacity of a computer, so that the work, which needs to be finished for some hours originally, can be immediately finished; a result can be automatically stored. With the adoption of the rapid grouping method for the precise elements, the precise elements failing to meet the requirements can be randomly replaced, so that the grouping work can be finished in a maximum and optimal manner; an optimal scheme can be rapidly found out through random selection and random replacement by using the strong computing capacity of the computer, so that not only can the human resources can be released, but also the grouping quality and the grouping stability can be improved. Meanwhile, the working efficiency can be greatly improved.
Owner:FLIGHT AUTOMATIC CONTROL RES INST
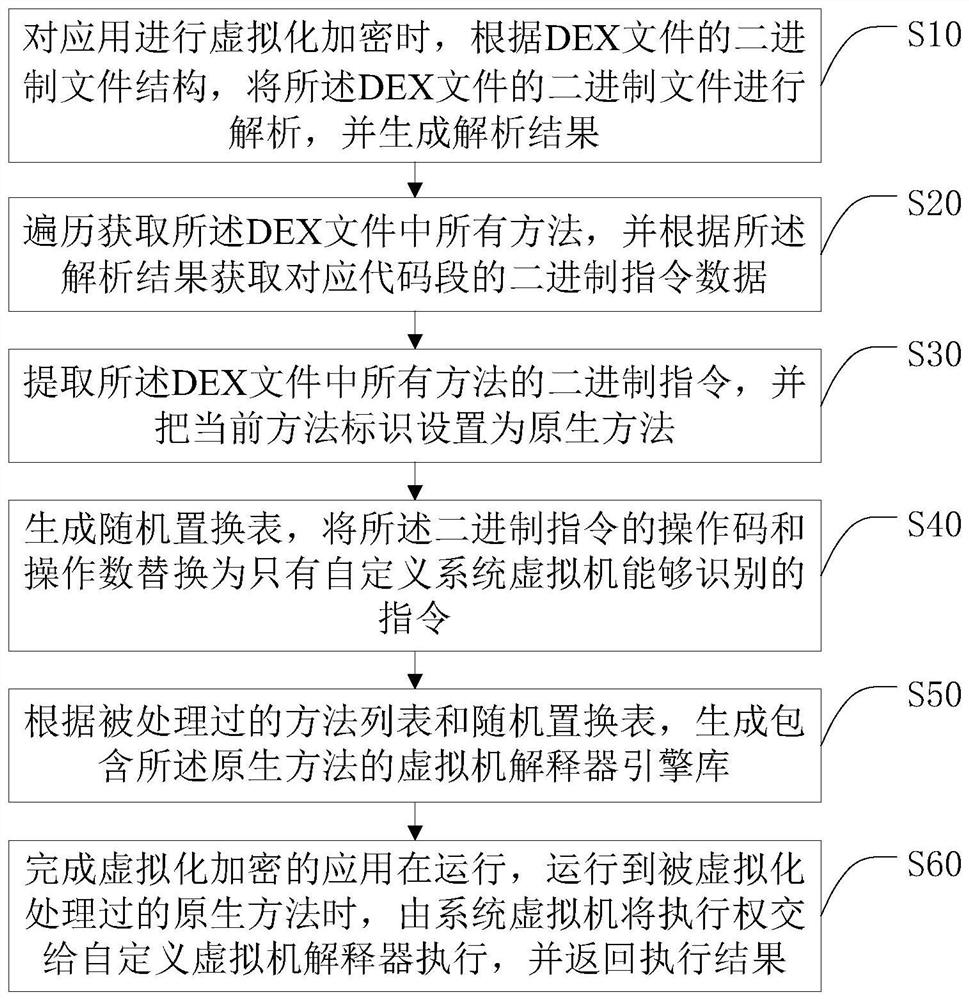
Code virtualization encryption method, terminal and storage medium
PendingCN112052459ADigital data protectionPlatform integrity maintainanceVirtualizationData ingestion
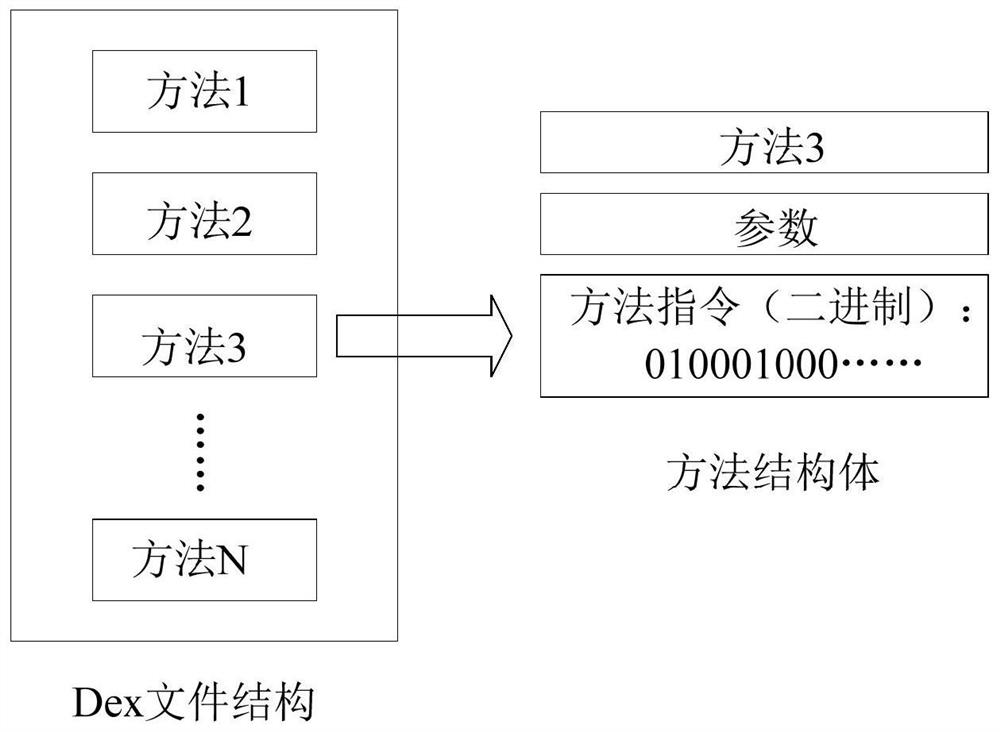
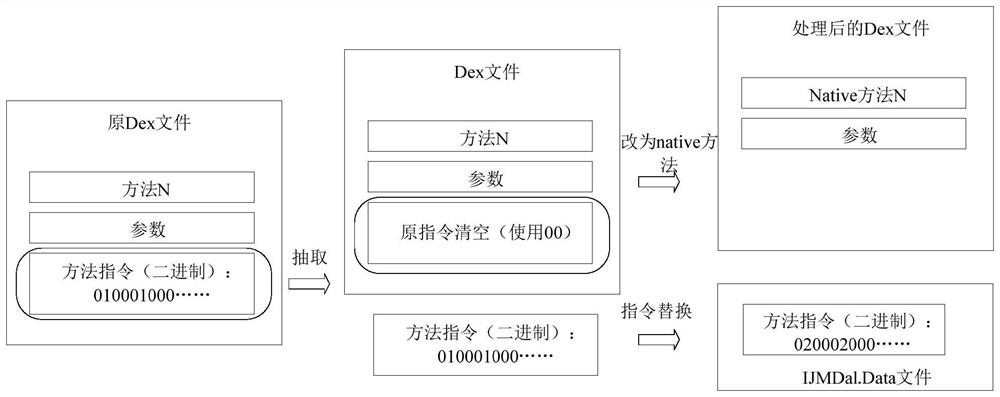
The invention discloses a code virtualization encryption method, a terminal and a storage medium, and the method comprises the steps: analyzing a binary file of a DEX file according to the structure of the binary file of the DEX file during encryption, and generating an analysis result; traversing to obtain all methods in the DEX file, and obtaining binary instruction data of corresponding code segments according to an analysis result; extracting binary instructions of all methods in the DEX file, and setting a current method identifier as a native method; generating a random replacement table, and replacing an operation code and an operand of the binary instruction with an instruction which can only be recognized by a custom system virtual machine; generating a virtual machine interpreterengine library containing the native method according to the processed method list and the random replacement table; and when the virtualized and encrypted application runs to the virtualized and processed native method, enabling a system virtual machine to deliver the execution right to a custom virtual machine interpreter for execution, and return an execution result.
Owner:北京智游网安科技有限公司
Ciphertext file set correctness verification method and system and related device
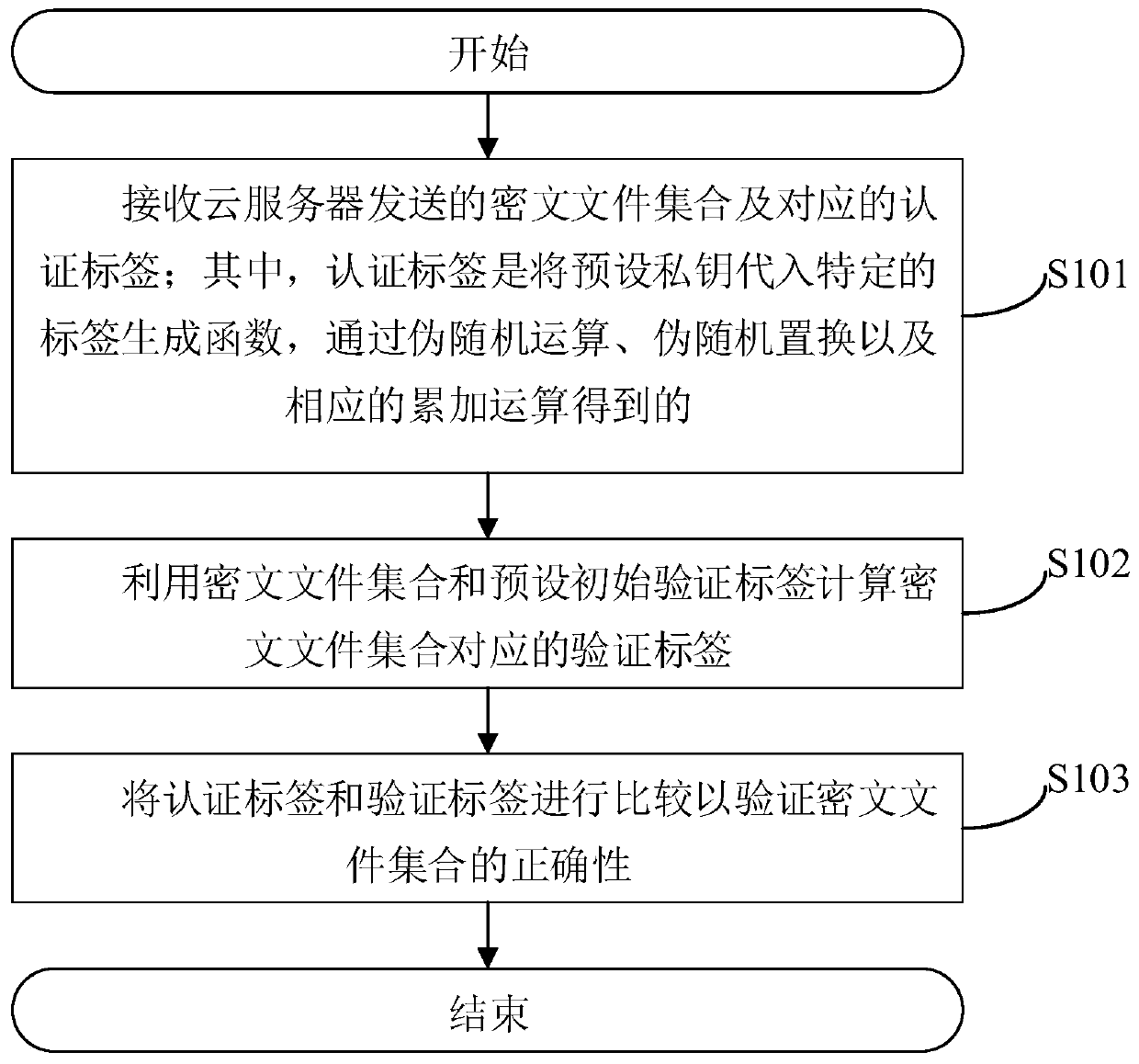
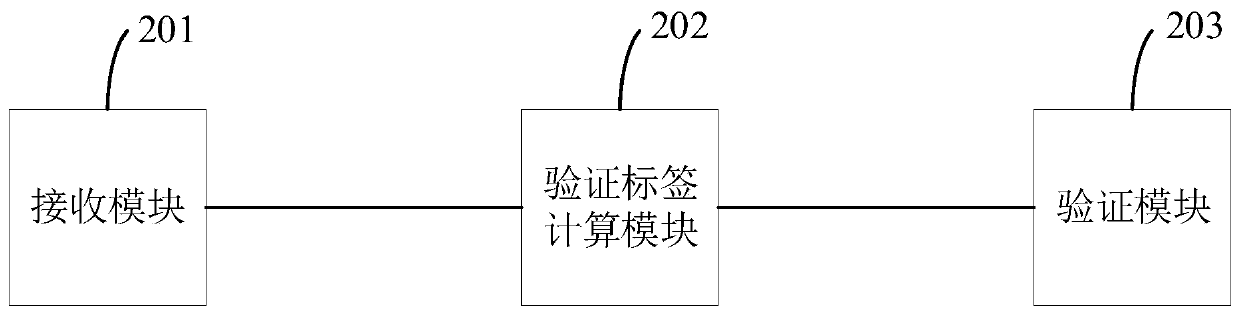
ActiveCN110061994AAvoid computational overheadReduce verification burdenSecuring communicationCiphertextRandom replacement
The invention provides a ciphertext file set correctness verification method. The method comprises the following steps: receiving a ciphertext file set sent by a cloud server and a corresponding authentication label; wherein the authentication label is obtained by substituting a preset private key into a specific label generation function and carrying out pseudo-random operation, pseudo-random replacement and corresponding accumulation operation; calculating a verification label corresponding to the ciphertext file set by using the ciphertext file set and a preset initial verification label; and comparing the authentication tag with the verification tag to verify the correctness of the ciphertext file set. According to the method, the authentication label is obtained by substituting the preset private key into the specific label generation function through the pseudo-random operation, the pseudo-random replacement and the corresponding accumulation operation, so that a large amount ofcalculation expenditure can be avoided, and the verification burden is reduced. The invention further provides a ciphertext file set correctness verification system and device and a computer readablestorage medium which all have the above beneficial effects.
Owner:QINGDAO UNIV
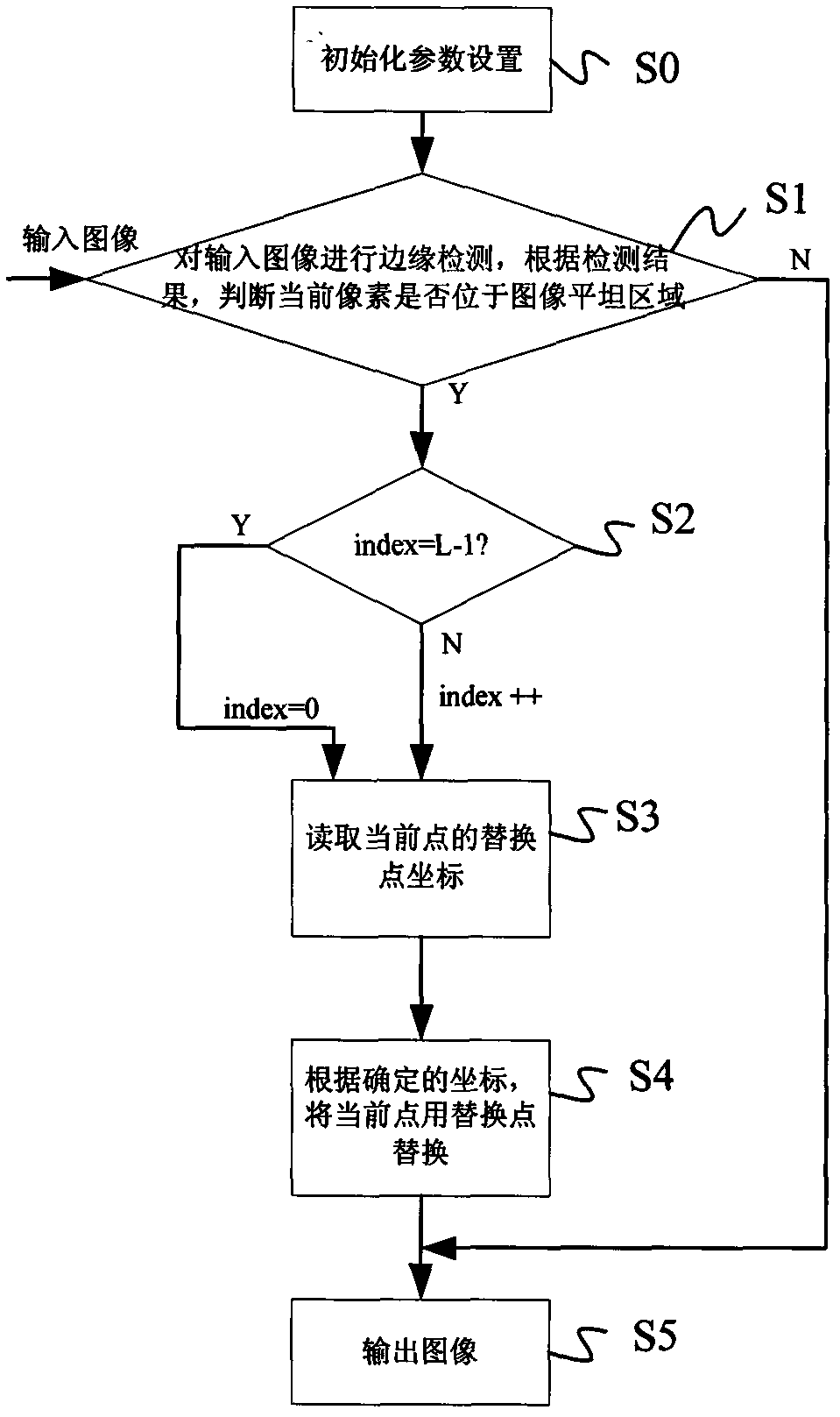
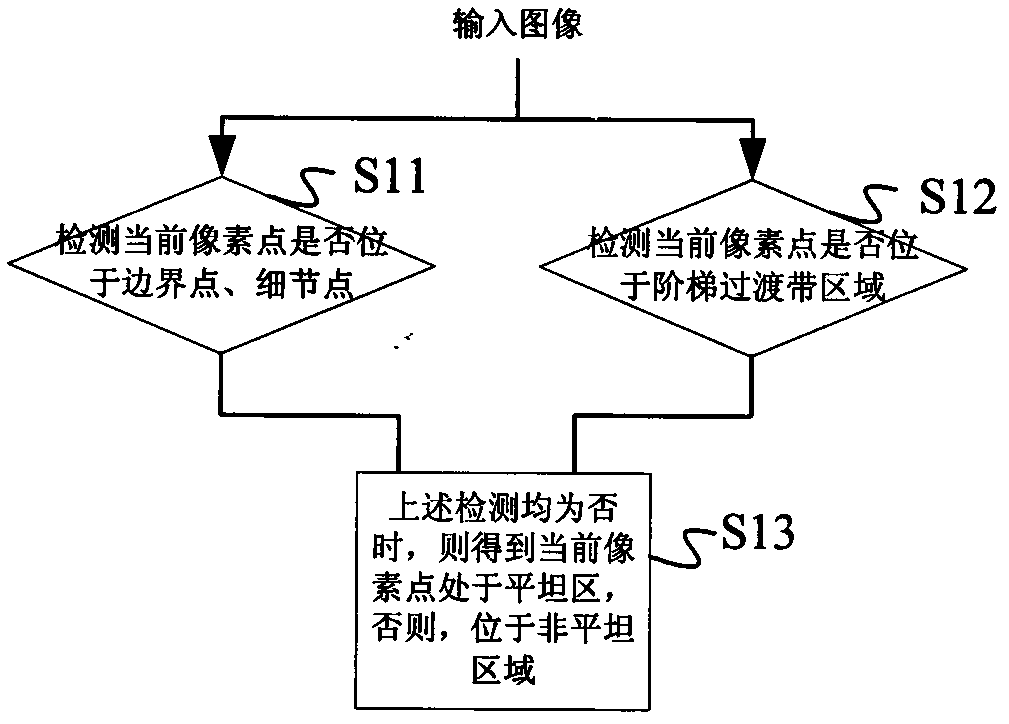
Noise reducing method and noise reducing system based on random replacement
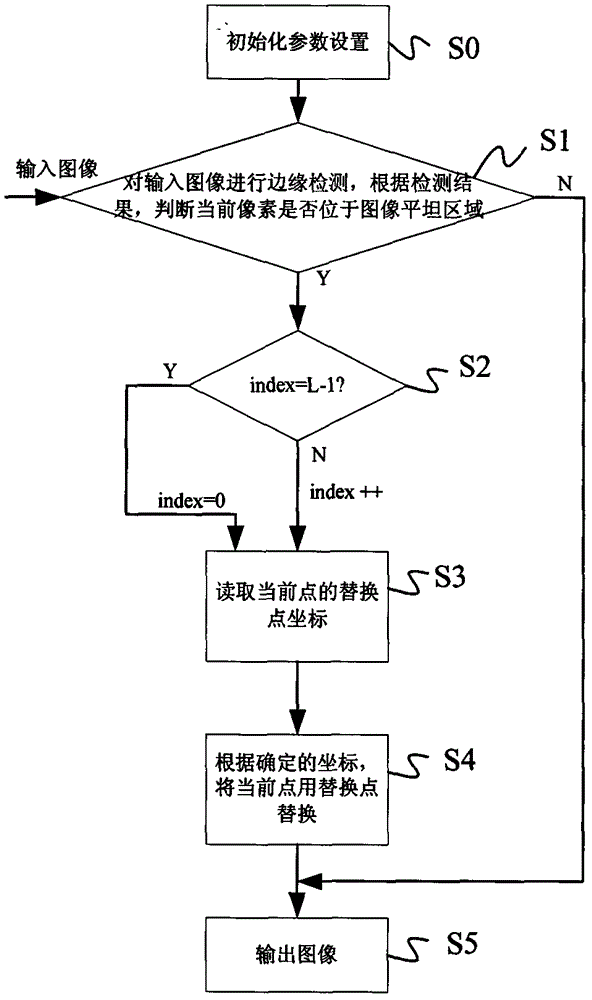
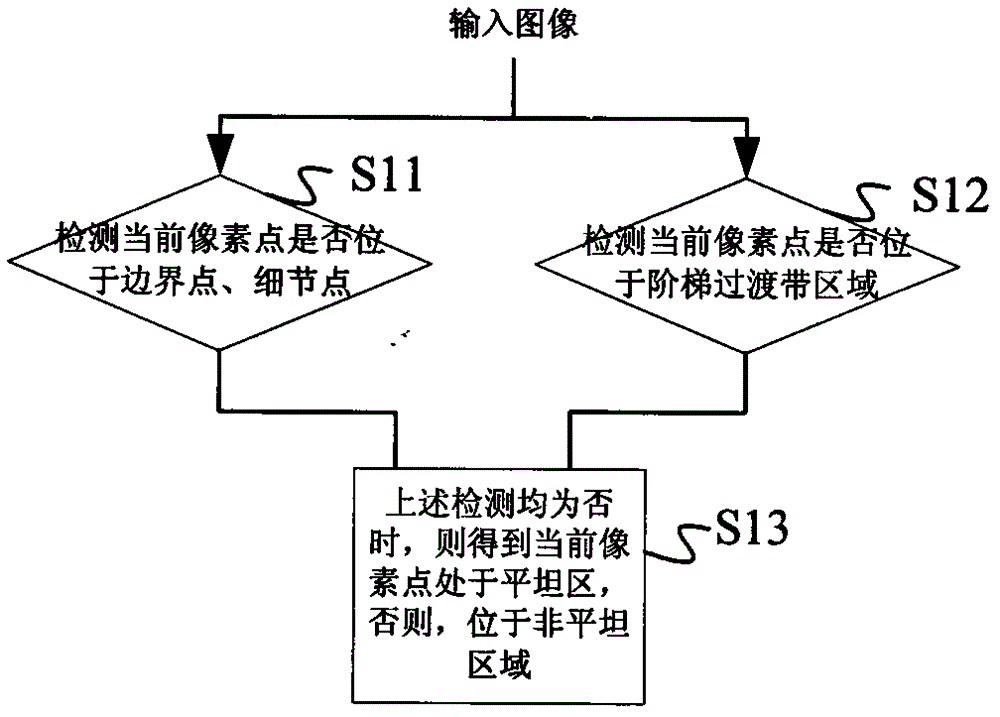
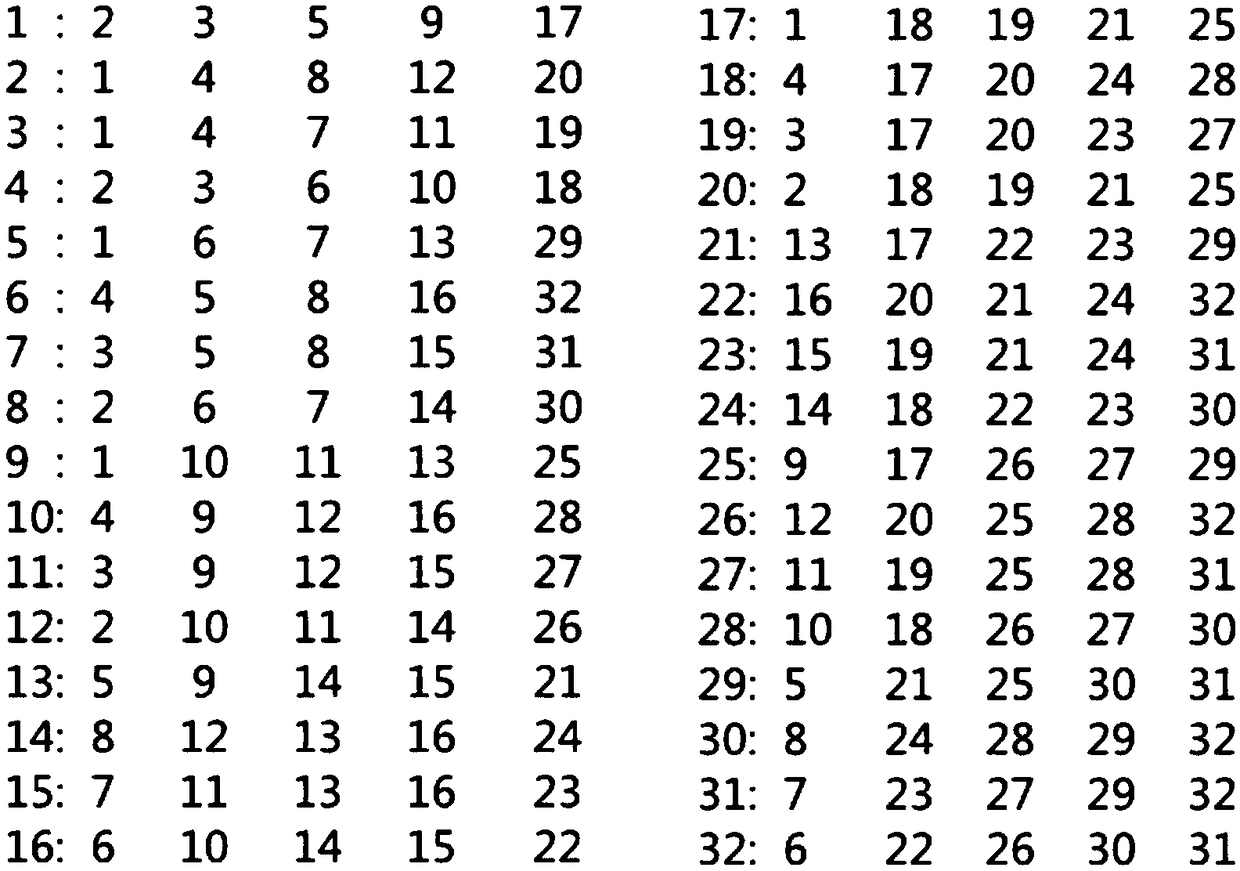
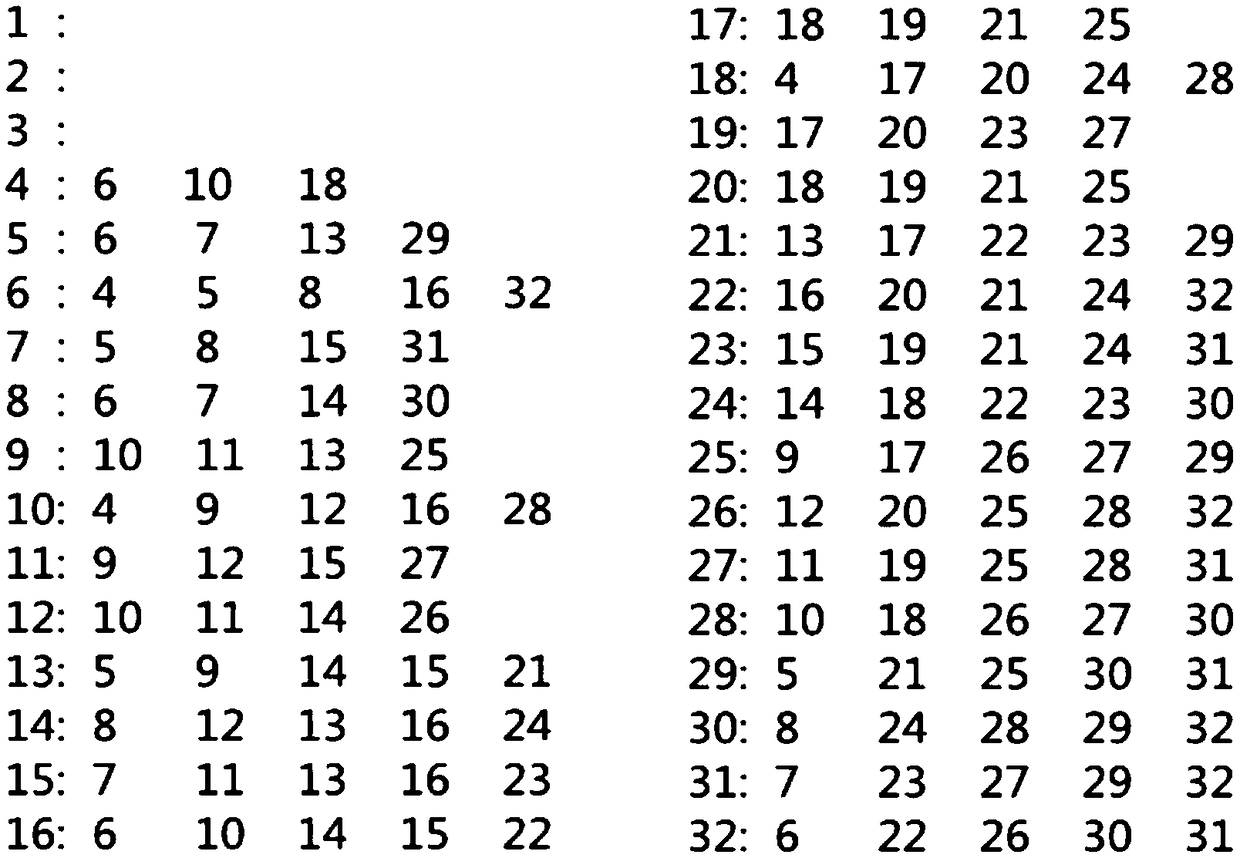
ActiveCN102999882AImperceptibleEasy to implementImage enhancementPattern recognitionRandom replacement
An embodiment of the invention discloses a noise reducing method and a noise reducing system based on random replacement. The noise reducing method includes steps of setting initialized parameters; performing edge detection to input images, judging whether current pixels are in flat areas or not according to detection results; if so, then calculating substitution point identity values; reading substitution point coordinates of current points from a substitution template according to the substitution point identity values, and then substituting the substitution points for the current points. The invention further discloses a noise reducing system based on random replacement. The noise reducing system comprises an initialized parameter setting unit, an edge detection unit, a substitution point identity calculating unit, a substitution point coordinate reading unit and a substitution unit. By the noise reducing method and the noise reducing system based on random substitution, noise signals in images are 'scattered' to the surrounding areas, and render noises and most Gaussian noises are reduced effectively.
Owner:ARKMICRO TECH
A statistical test method for multiple-sample copy number consistent variation regions
ActiveCN106682455BConvenient inspectionAvoid Sequencing ReadsBiostatisticsProteomicsRandom replacementComputer science
The invention discloses a statistical testing method of copy number consistency variation region in multiple samples. The method comprises the steps that a quasi synthetic curve is constructed based on the relation coefficients of the copy digital points, the derivative value of each digital point is calculated, significant derivative values are tested through the hypothesis test method, and a variable candidate region for the copy numbers is built from the determination of the breakpoint of the copy numbers; a hypothesized null distribution is constructed through the method of randomly replacing the CNVs on the two directions of the whole genome group and the samples, and the copy number consistency variable region in multiple samples is tested. According to the method, directly using the read number of sequence is avoided, certain sequence mistakes and noises can be accommodated, and a boundary of the variable region for the copy numbers can be relatively accurately located;based on the random replacements of the CNVs on the two directions of the whole genome group and the samples, compared to the replacements on a single direction, more real head distribution of the hypothesis test can be obtained by the method; meanwhile the test of the diversified consistency variable CNVs, namely, the variable region of the copy number consistency existed in multiple sample subclasses, is facilitated.
Owner:XIDIAN UNIV
A noise reduction method and system based on random replacement
ActiveCN102999882BImperceptibleEasy to implementImage enhancementPattern recognitionRandom replacement
An embodiment of the invention discloses a noise reducing method and a noise reducing system based on random replacement. The noise reducing method includes steps of setting initialized parameters; performing edge detection to input images, judging whether current pixels are in flat areas or not according to detection results; if so, then calculating substitution point identity values; reading substitution point coordinates of current points from a substitution template according to the substitution point identity values, and then substituting the substitution points for the current points. The invention further discloses a noise reducing system based on random replacement. The noise reducing system comprises an initialized parameter setting unit, an edge detection unit, a substitution point identity calculating unit, a substitution point coordinate reading unit and a substitution unit. By the noise reducing method and the noise reducing system based on random substitution, noise signals in images are 'scattered' to the surrounding areas, and render noises and most Gaussian noises are reduced effectively.
Owner:ARKMICRO TECH
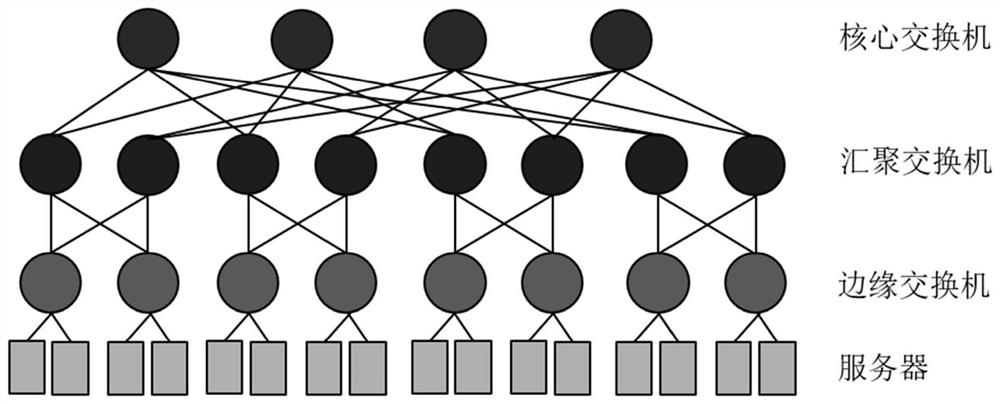
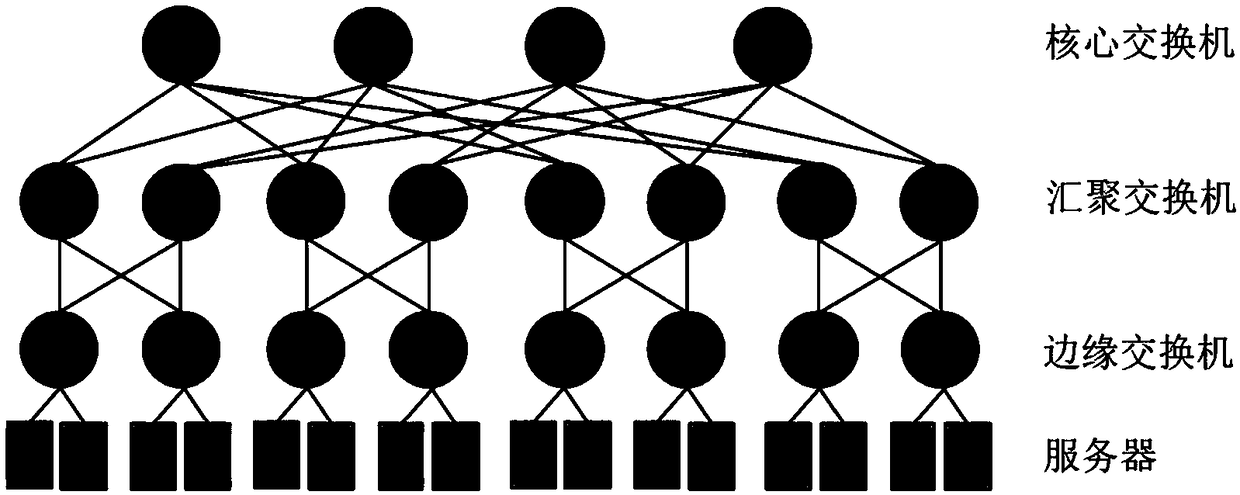
Method of Constructing Data Center Network Fault Tolerance Based on Cross Cube Network
InactiveCN105871714BGuaranteed uptimeImprove fault toleranceData switching networksFault tolerancePattern recognition
The invention discloses a fault-tolerant method for constructing a data center network based on a cross-cube network, which belongs to the cross-technical field of computer and mathematics. The present invention comprises the following steps: according to the definition rule of CQn, generates the association matrix code of CQn, obtains the adjacency point of each vertex of CQn, saves the adjacency relation between the vertices in the association matrix, generates error set afterwards, eliminates in the association matrix Error set, and finally perform depth-first traversal on the remaining sub-matrix to find the required path, that is, to judge whether there is a cycle of a specified length in the matrix and record a qualified cycle. The remaining sub-matrix is the part of CQn after removing the error subset. The present invention adopts the cross cube network CQn to construct an efficient, fault-tolerant and scalable data center network, and its fault-tolerant capability is n-2, that is, when n-2 errors occur in the network, the rest of the system can still be guaranteed to operate normally , which improves the fault tolerance capability of the system, and also improves the topological performance such as scalability and reliability of the data center network.
Owner:DALIAN UNIV OF TECH
A data center scheduling system and method
Owner:HUAZHONG UNIV OF SCI & TECH
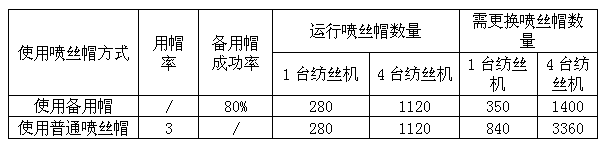
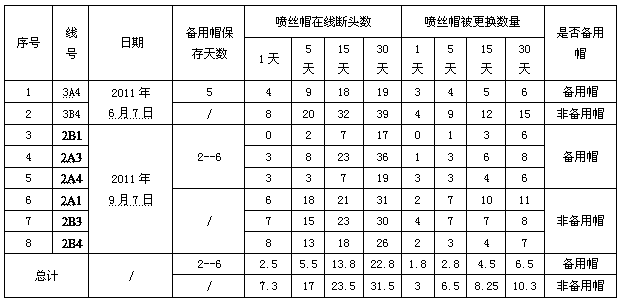
Manufacturing method of backup spinning nozzle
ActiveCN102514821BHigh success rateEasy to preparePackaging under vacuum/special atmosphereProduction lineRandom replacement
The invention relates to a manufacturing method of a backup spinning nozzle. A debugged spinning nozzle is removed from a spinning machine, and a silica gel plug is used for quickly sealing the serum inlet of the spinning nozzle; low-viscosity synthetic ester is applied on the surface of the spinning nozzle; the spinning nozzle is wrapped by a freshness preservation film, and put into a vacuum packaging bag to be vacuumized; and the spinning nozzle which is packaged under a vacuum condition is put into a spinning nozzle box to be stored at room temperature. The manufacturing method of the backup spinning nozzle has a higher spinning nozzle use success rate. The manufacturing method and the operation are simple, no acetone or low temperature is used for storage, no hidden safety hazard exists, and the cost is low. The manufacturing method of the backup spinning nozzle can be widely applied to production startup, the operation of replacing the spinning nozzle due to the replacement of tow specification and the random replacement of abnormal spinnerets of the spinning nozzle on a production line, significantly the broken head recovery time and the startup time or the time for replacing the spinning nozzle due to the replacement of the tow specification is reduced, the product quality can be improved, the cost can be reduced, and the production efficiency can be improved.
Owner:KUNMING CELLULOSE FIBERS CO LTD
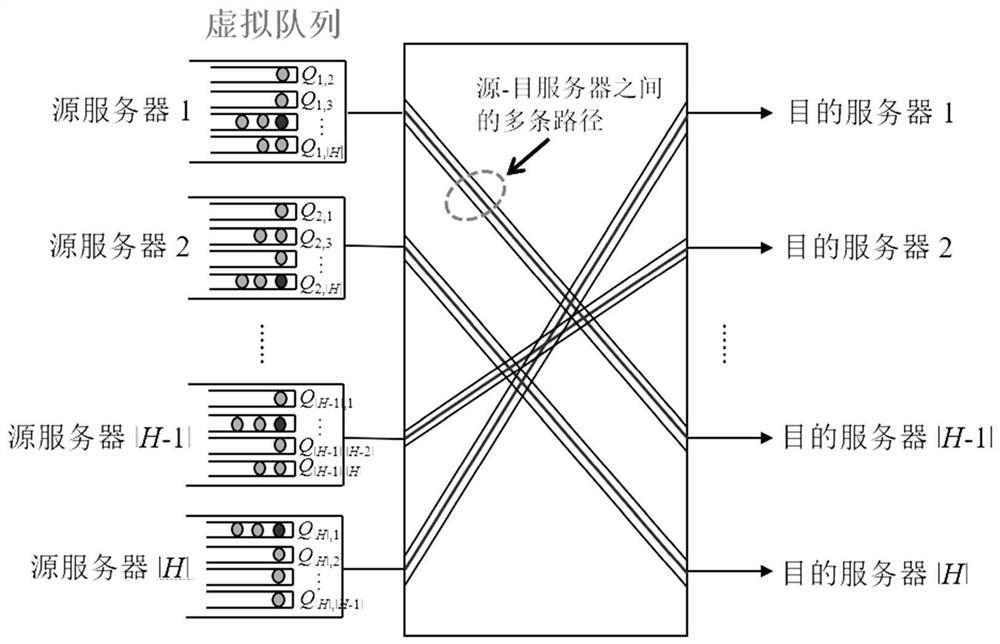
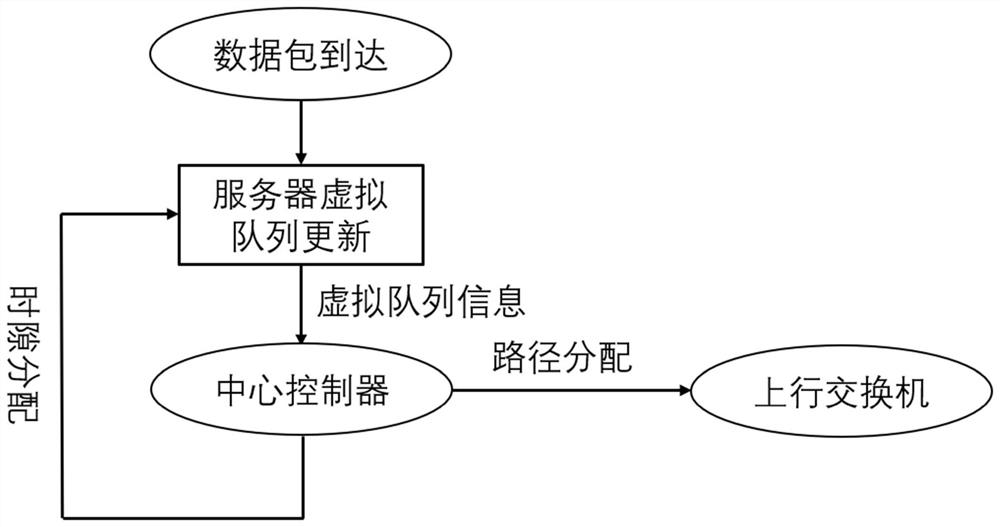
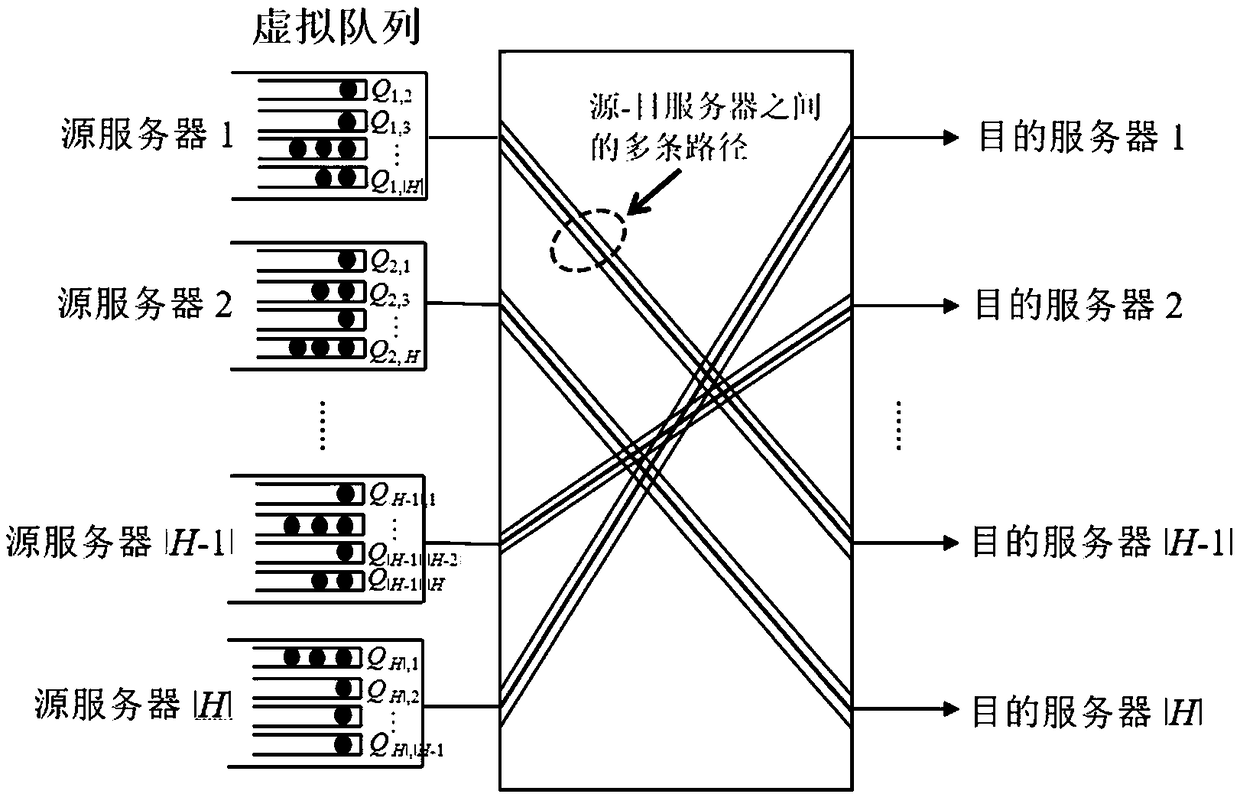
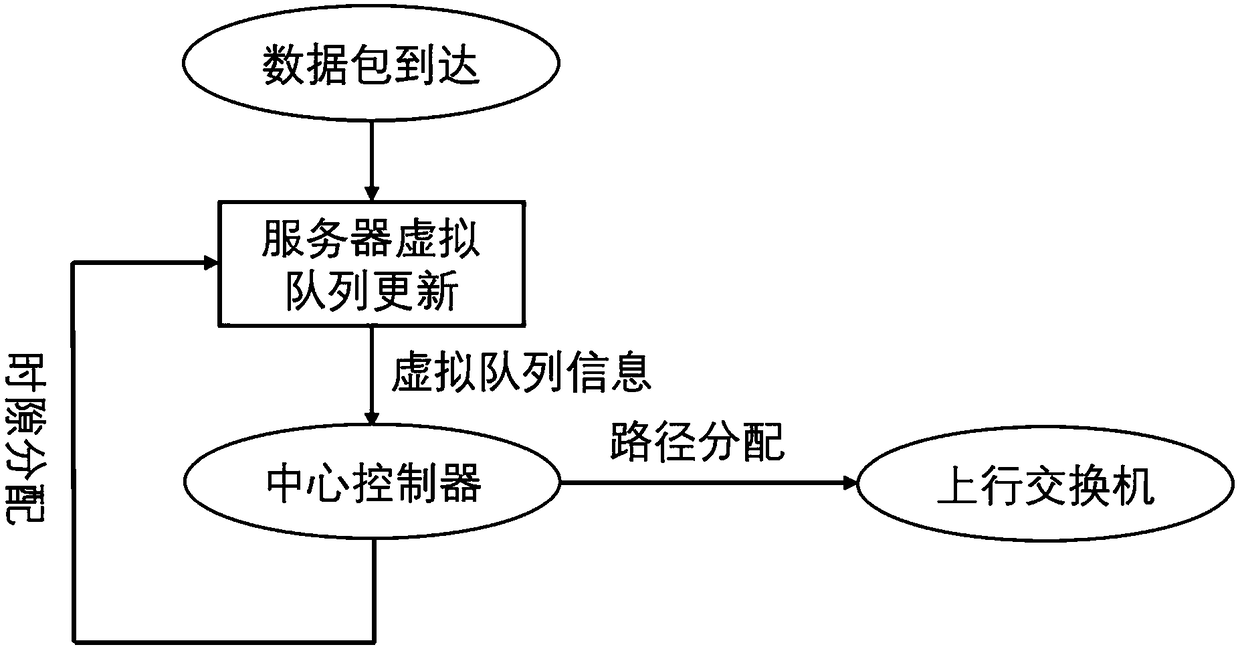
Data center scheduling system and method
The invention discloses a data center scheduling system and method. The scheduling system can determine a moment and path allocation scheme by generating conflict-free path sets of a fat tree to ensure the unity of moment allocation and path allocation. The method comprises the steps: information interaction between a center controller and a data layer and a scheduling strategy of the center controller, wherein the center controller needs to collect virtual queue length information from servers, determines a scheduling scheme according to the virtual queue length information and a randomly-selected conflict-free data set and then feeds back scheduling scheme information to the servers and uplink switches. The designed scheduling system only needs the virtual queue length of a current moment and information of the conflict-free path set used at a previous moment, the conflict-free path set used at the current moment is generated by randomly replacing part of paths, and in-network transmission zero delay can be achieved; and an adopted path replacement strategy is only related to the virtual queue length, and the optimal throughput can be achieved by reasonably designing the replacement probability.
Owner:HUAZHONG UNIV OF SCI & TECH
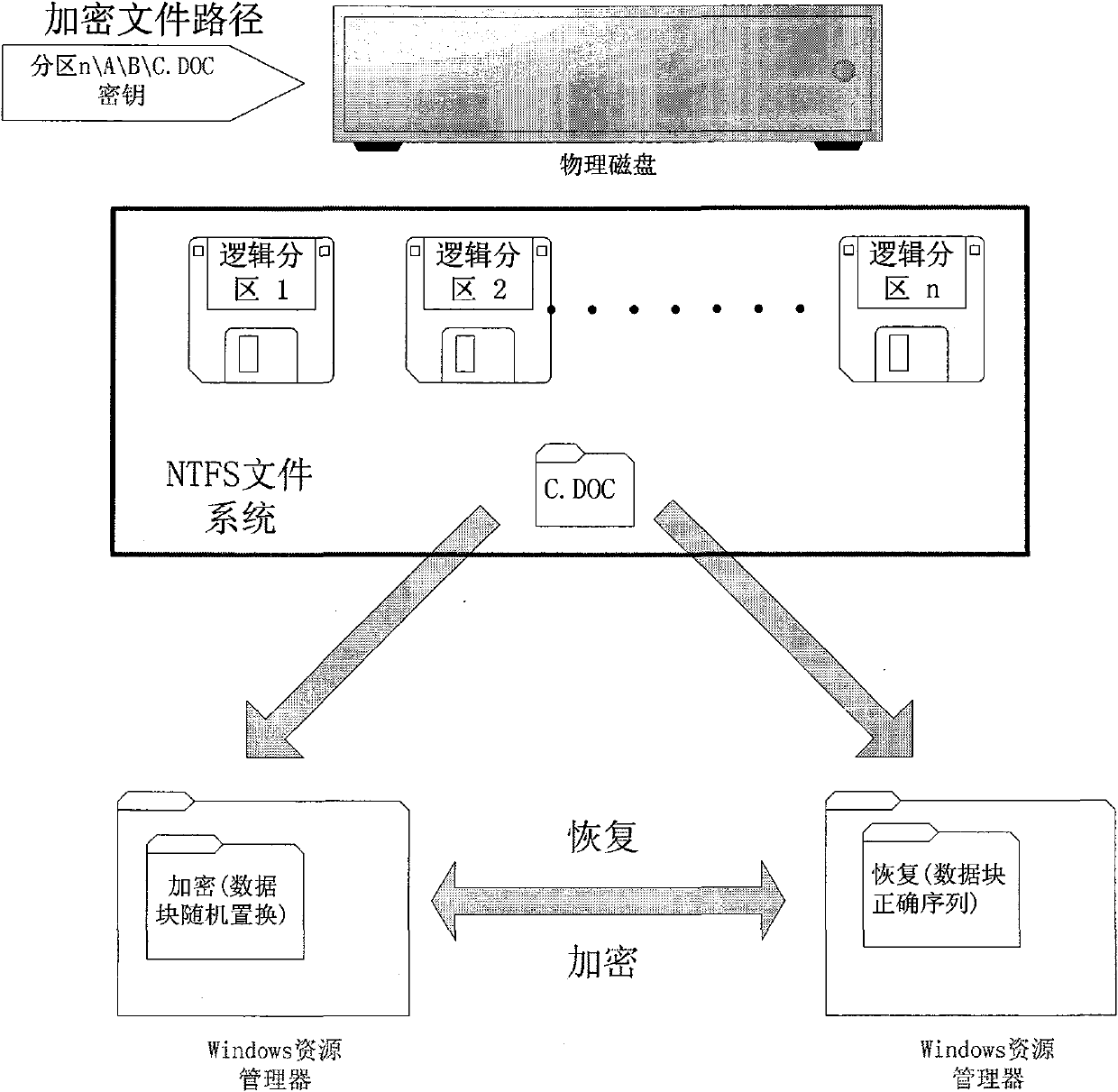
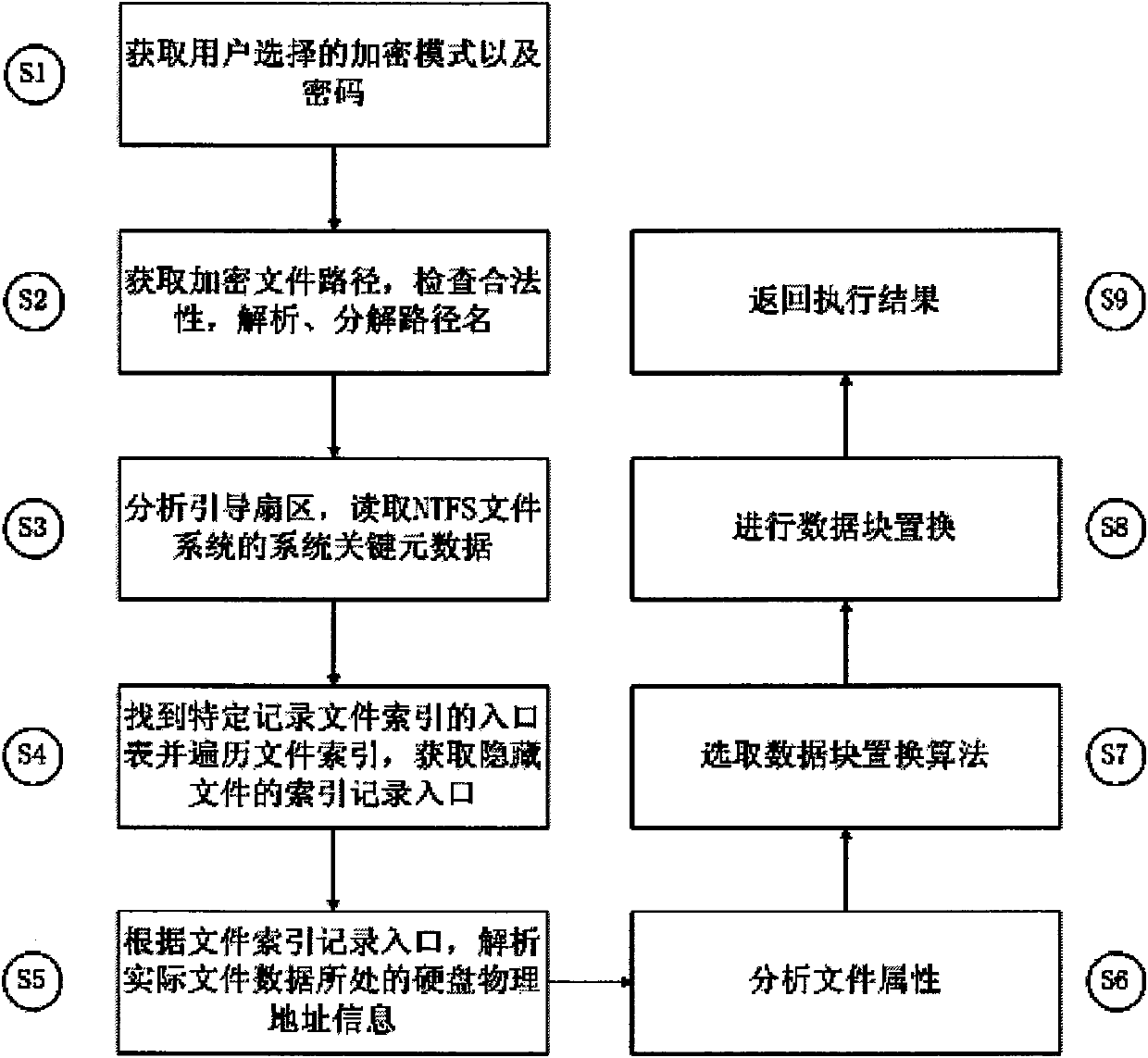
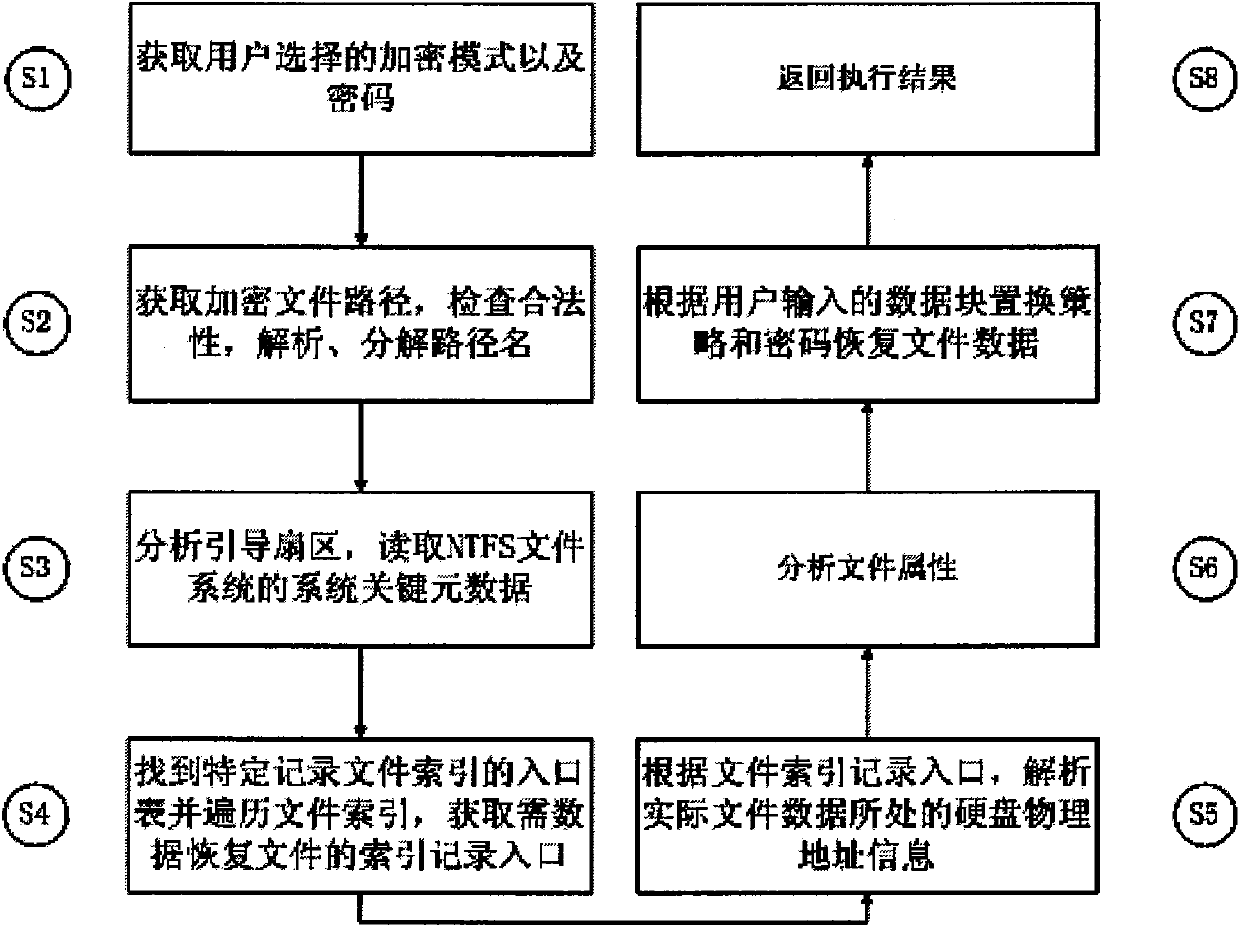
Light-weight file encryption and decrypting and recovering method in NTFS file system
InactiveCN101634992BAvoid refactoringPrevent intrusionSpecial data processing applicationsComputer hardwareOriginal data
Owner:SHANGHAI JIAOTONG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com