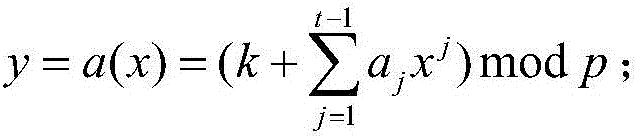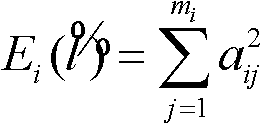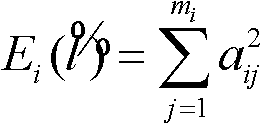Patents
Literature
68results about How to "Avoid refactoring" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
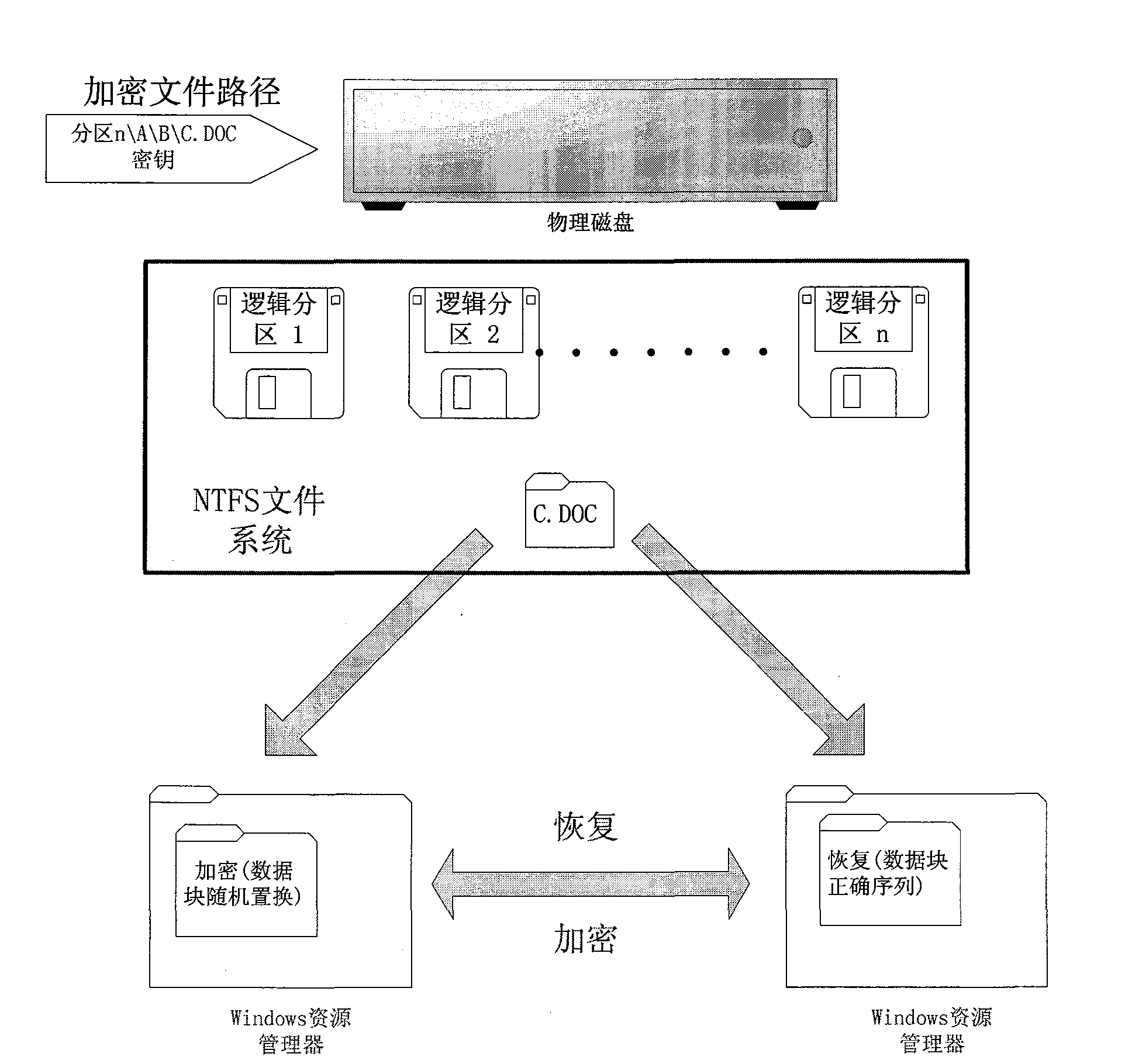
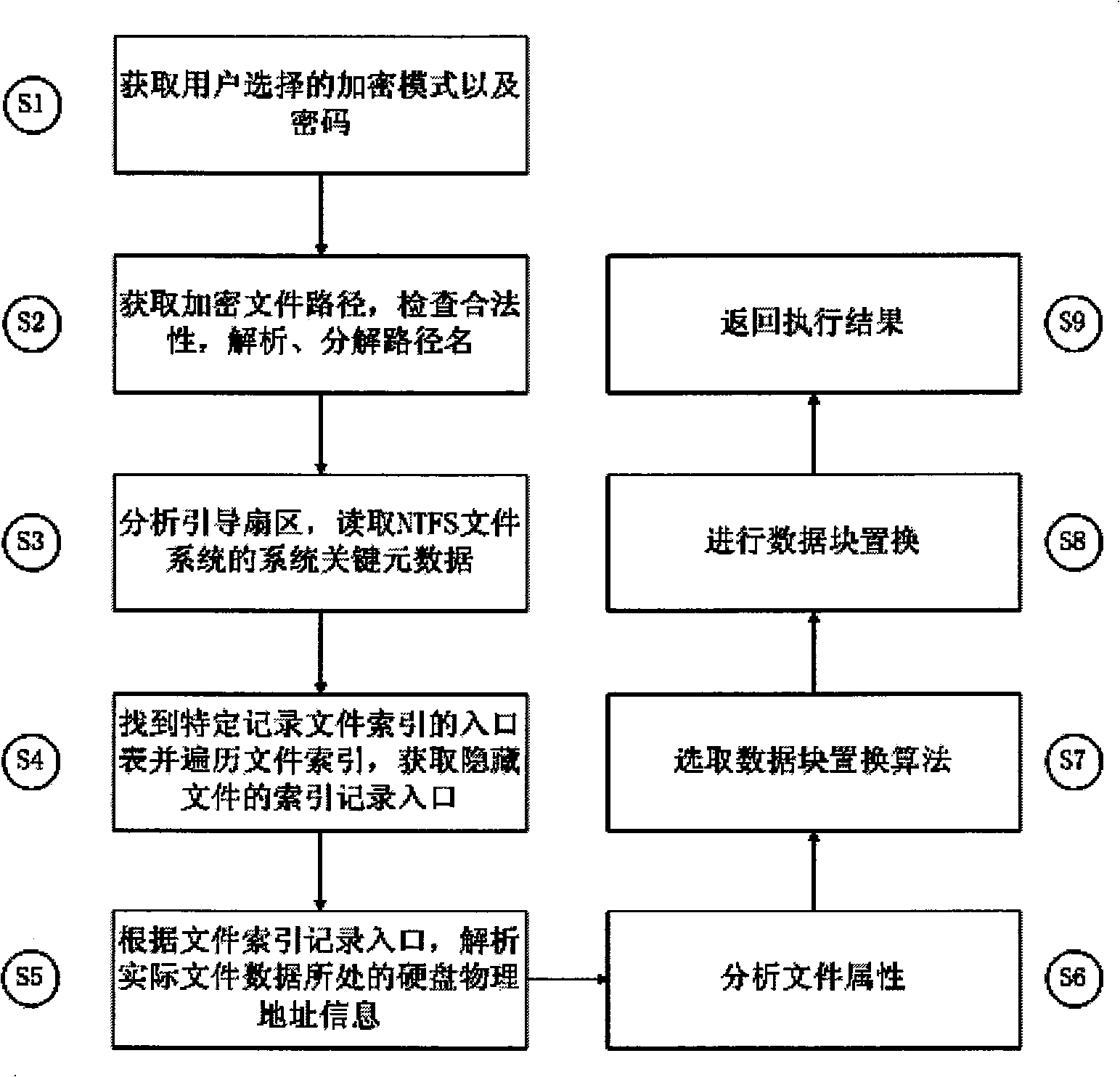
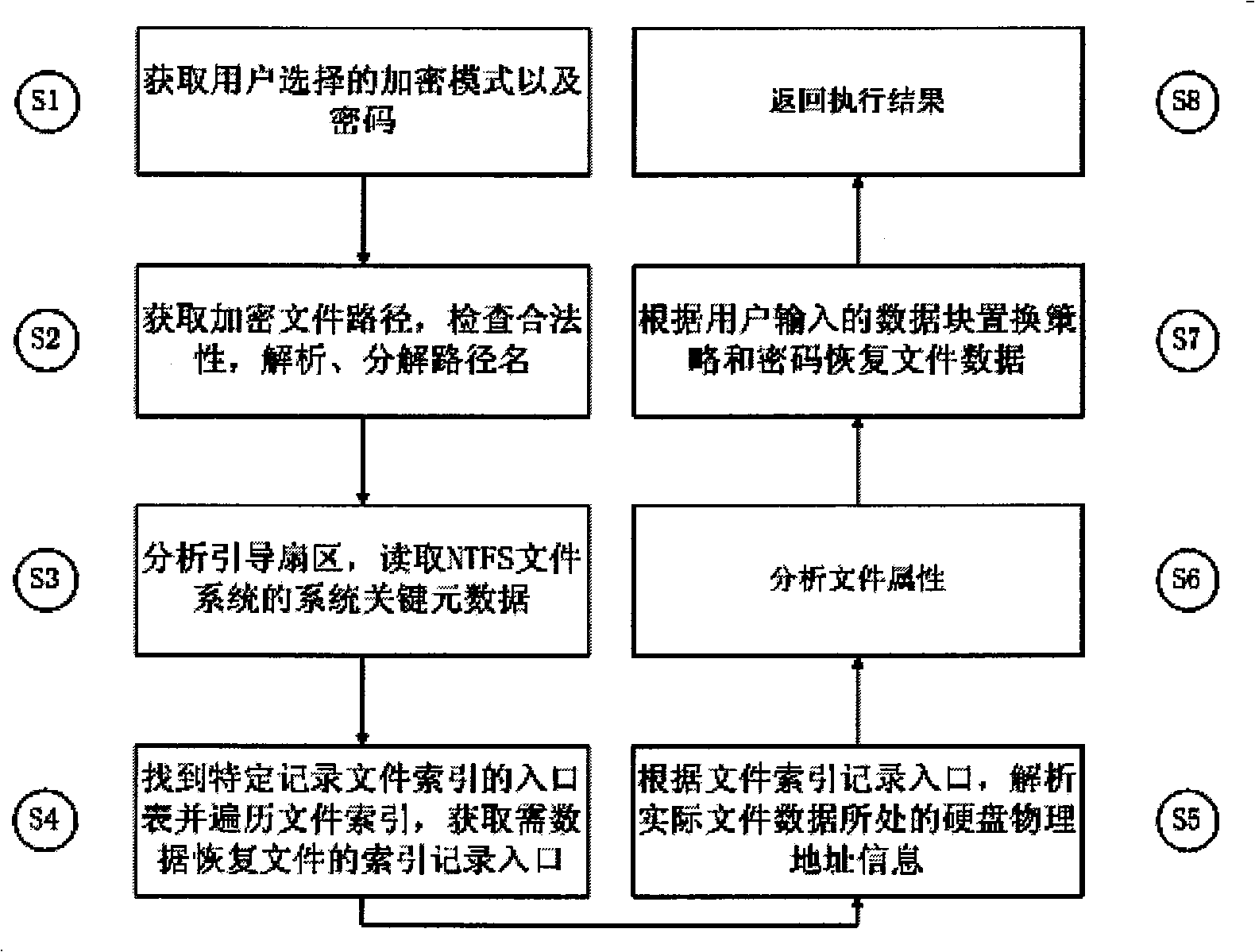
Light-weight file encryption and decrypting and recovering method in NTFS file system
InactiveCN101634992AImprove efficiencySystem friendlySpecial data processing applicationsRaw dataComputer hardware
A light-weight file encryption and decrypting and recovering method in an NTFS file system belongs to the technical field of information security. The method comprises the following steps: selecting a proper data block replacement method to overwrite data following the attribute of a file referred to by a legal file path according to encryption options selected by a user, and storing a seed generating a random data block replacement sequence; then generating a reverse replacement sequence according to the seed generating the random data block replacement sequence to overwrite the data of a file referred to by a legal file path, thus recovering raw data. The method helps achieve the purposes of encrypting light-weight files and preventing file reconstruction and data intrusion by optimally selecting random replacement file data blocks according to structural properties of the NTFS file system.
Owner:SHANGHAI JIAO TONG UNIV
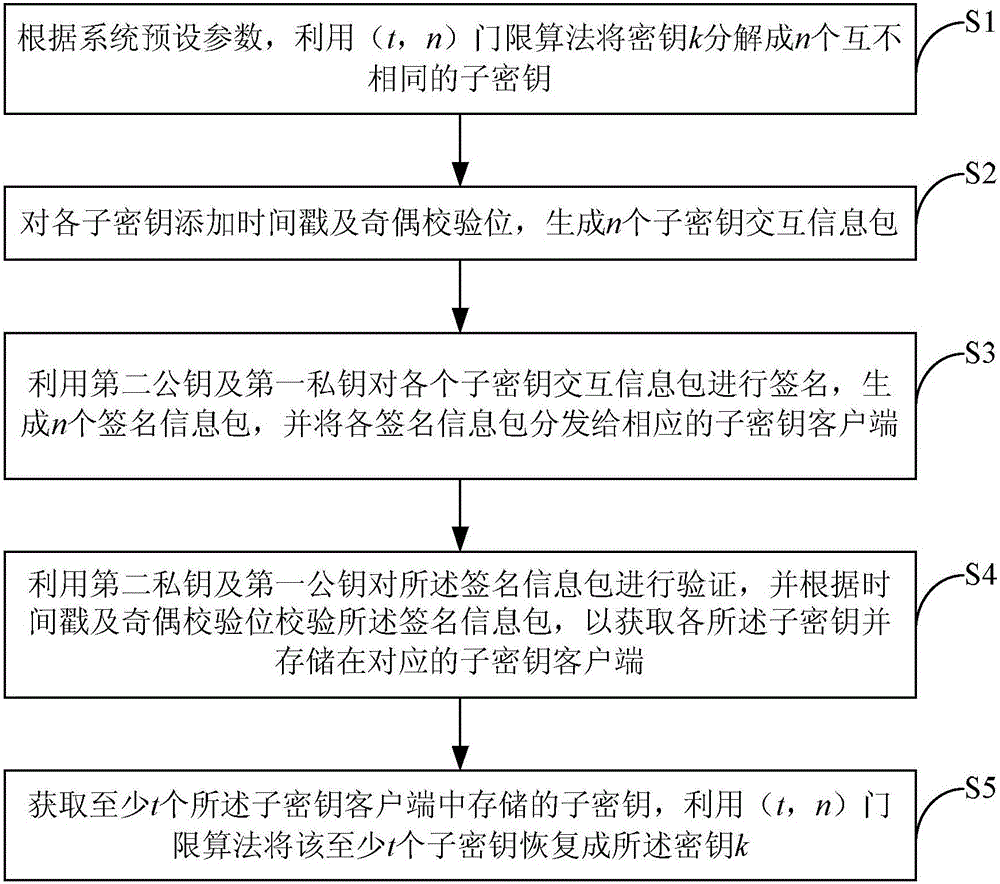
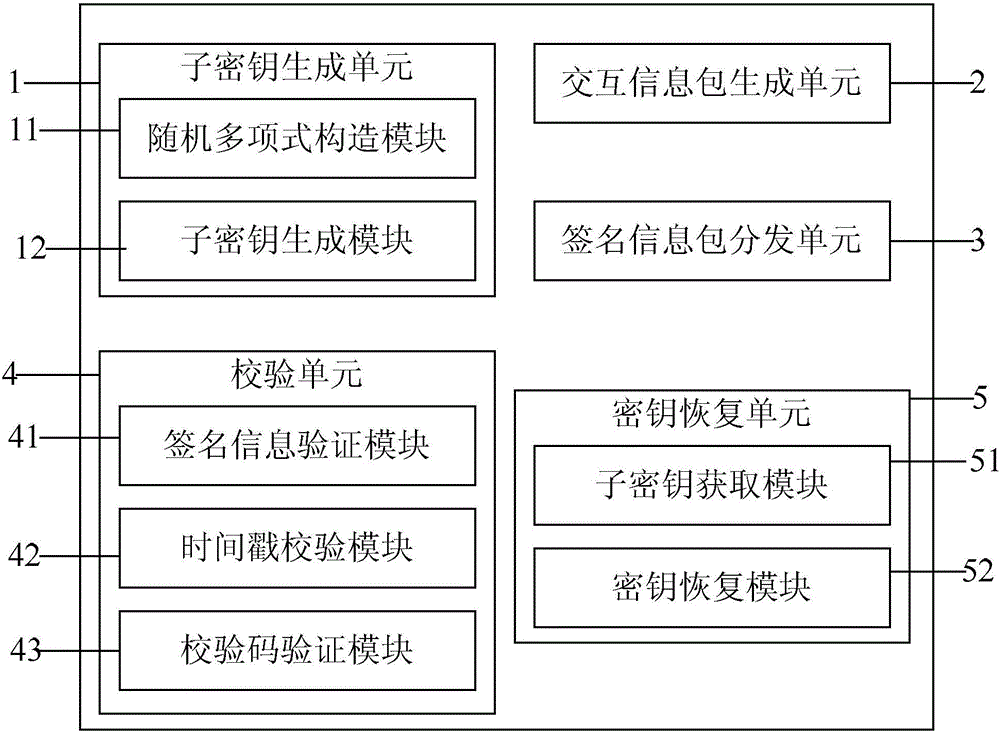
Key sharing method and device
ActiveCN106027245AGuaranteed correctnessEnsure safetyKey distribution for secure communicationKey sharingParity bit
The invention provides a key sharing method and device. The method comprises the steps of decomposing a key k into n mutually different sub-keys by employing a (t, n) threshold algorithm according to preset parameters of a system; adding time stamps and parity check bits to the sub-keys, thereby generating n sub-key interaction information packets; signing the sub-key interaction information packets by employing a second public key and a first private key, thereby generating n signed information packets, and distributing the signed information packets to corresponding sub-key clients; verifying the signed information packets by employing a second private key and a first public key and checking the signed information packets according to the time stamps and the parity check bits, thereby obtaining the sub-keys, and storing the sub-keys in the corresponding sub-key clients; and obtaining the sub-keys stored in at least t sub-key clients, restoring the at least t sub-keys to the key k by employing the (t, n) threshold algorithm, wherein the first private key and the first public key are a mutually matching key pair, and the second private key and the second public key are a mutually matching key pair.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
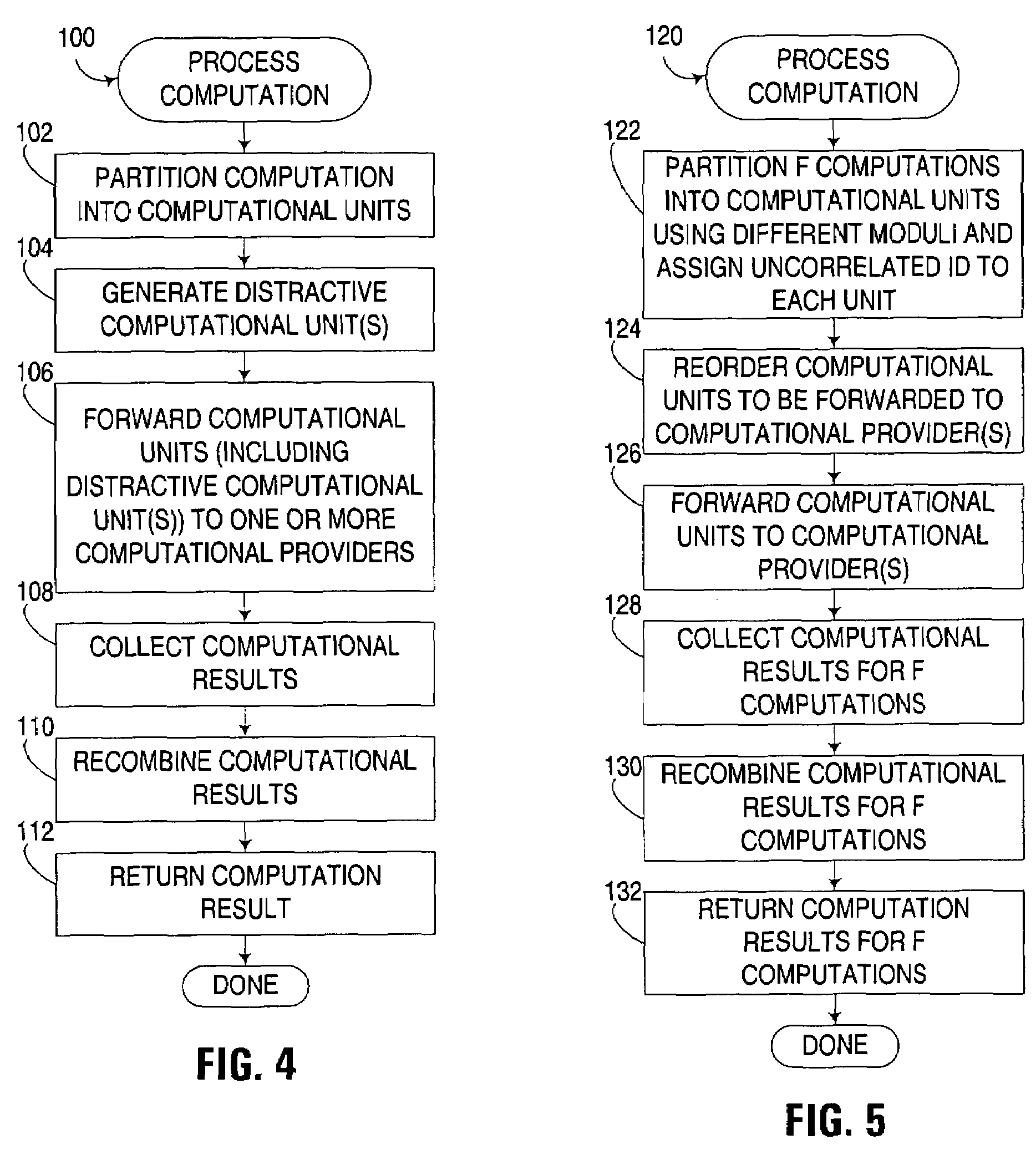
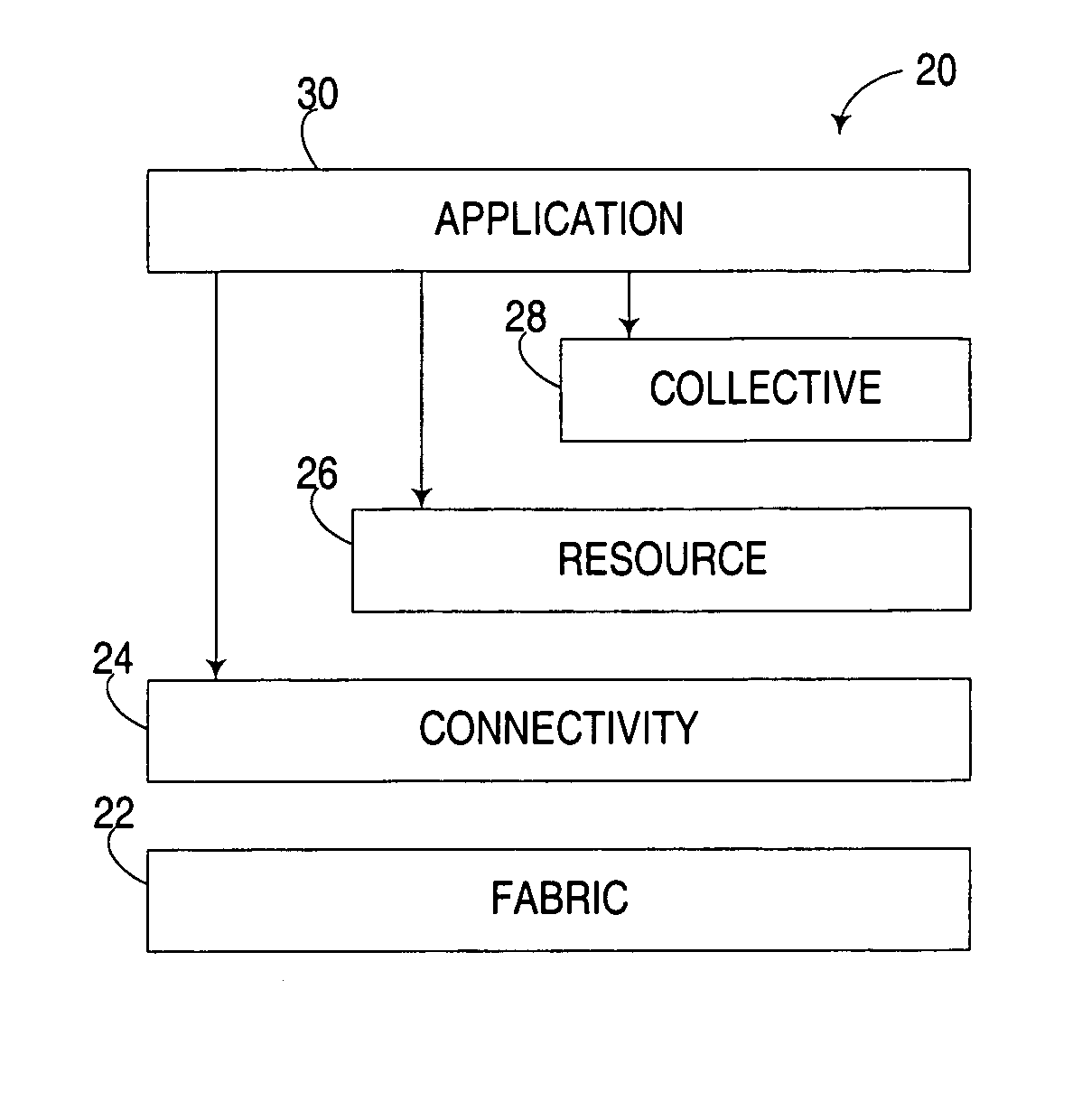
Distributed computation in untrusted computing environments using distractive computational units
InactiveUS7426749B2Complicate detectionComplicate reconstitutionResource allocationMemory loss protectionTrustworthy computingParallel computing
Owner:INT BUSINESS MASCH CORP
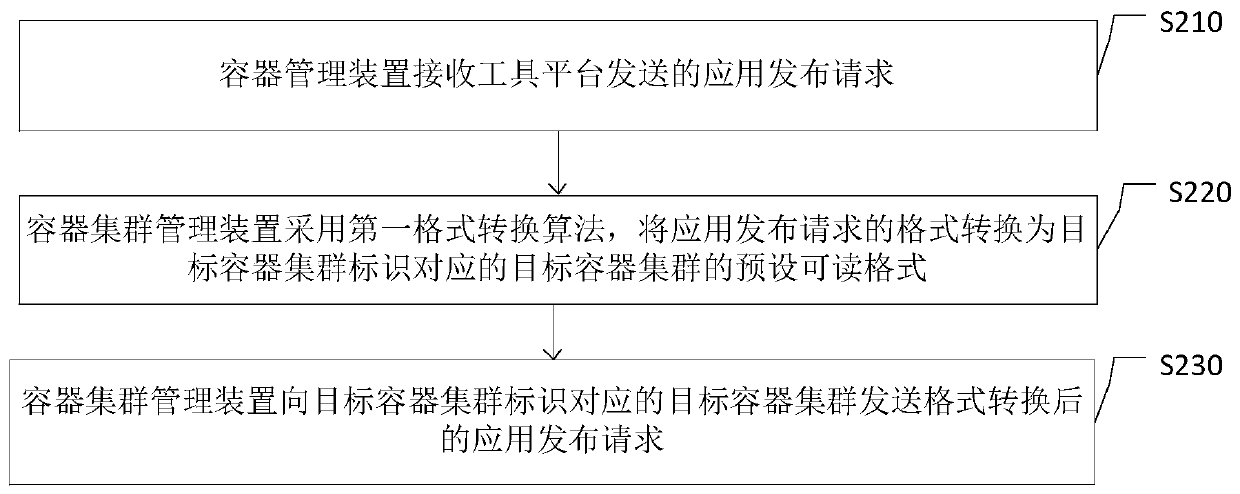
Container cluster management method, device and system
ActiveCN110290189AReduce management costsAvoid refactoringData switching networksContainerizationOperating system
The invention discloses a container cluster management method, device and system, and relates to the technical field of finance. The method comprises the following steps: receiving an application publishing request sent by a tool platform, wherein the application publishing request comprises a program file of an application to be published, an identifier of the application to be published, a target container cluster identifier corresponding to the application to be published and a server identifier in a target container cluster; converting the format of the application release request into a readable format of a target container cluster corresponding to the target container cluster identifier by adopting a first format conversion algorithm to obtain the application release request after format conversion; and sending the application publishing request after format conversion to a target container cluster corresponding to the target container cluster identifier, wherein the application publishing request is used for indicating the target container cluster to execute a publishing operation on the program file of the application to be published in the server corresponding to the server identifier. According to the method, reconstruction and reconstruction of a non-containerization system architecture are avoided, and the management cost of the container cluster is reduced.
Owner:WEBANK (CHINA)
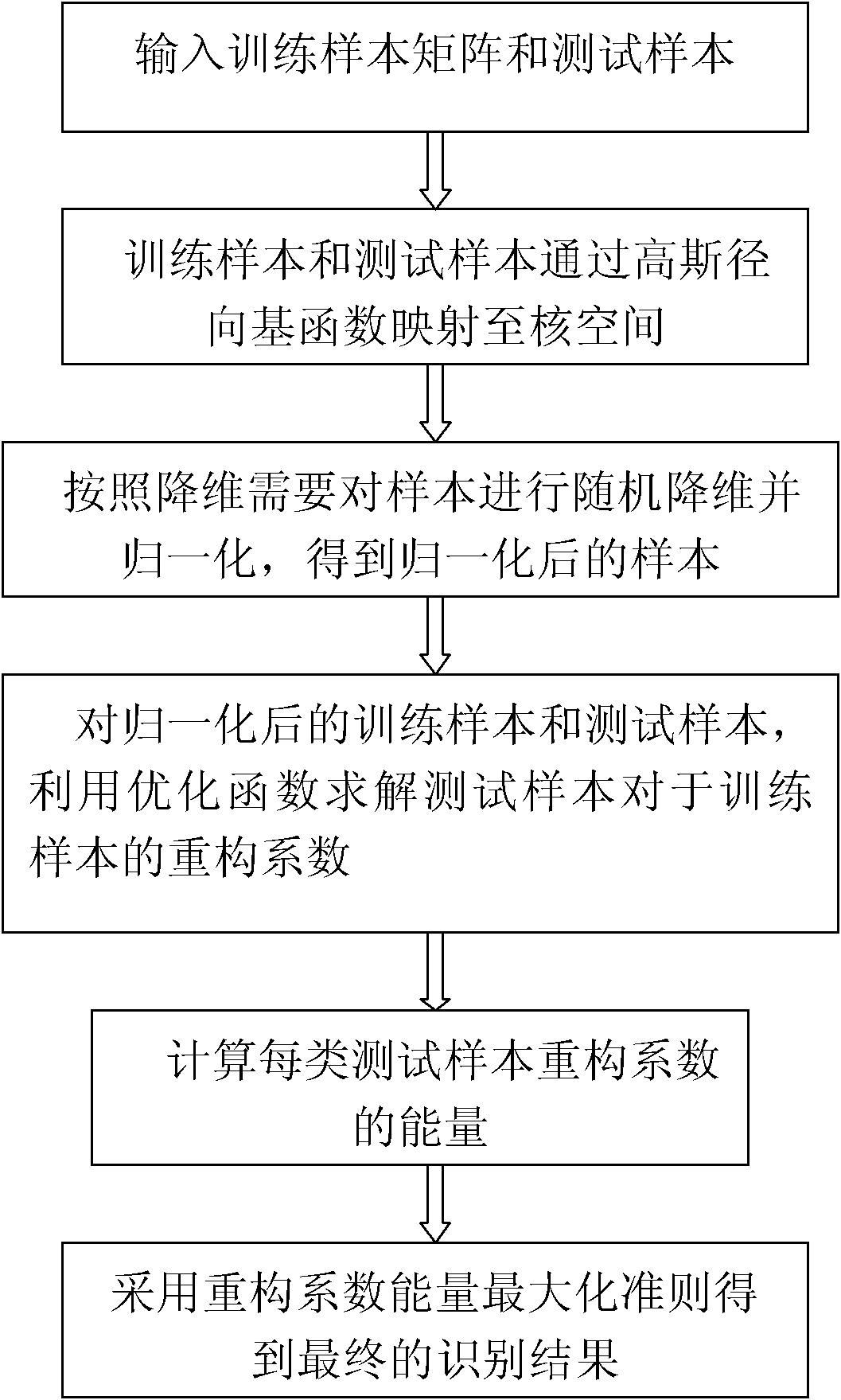
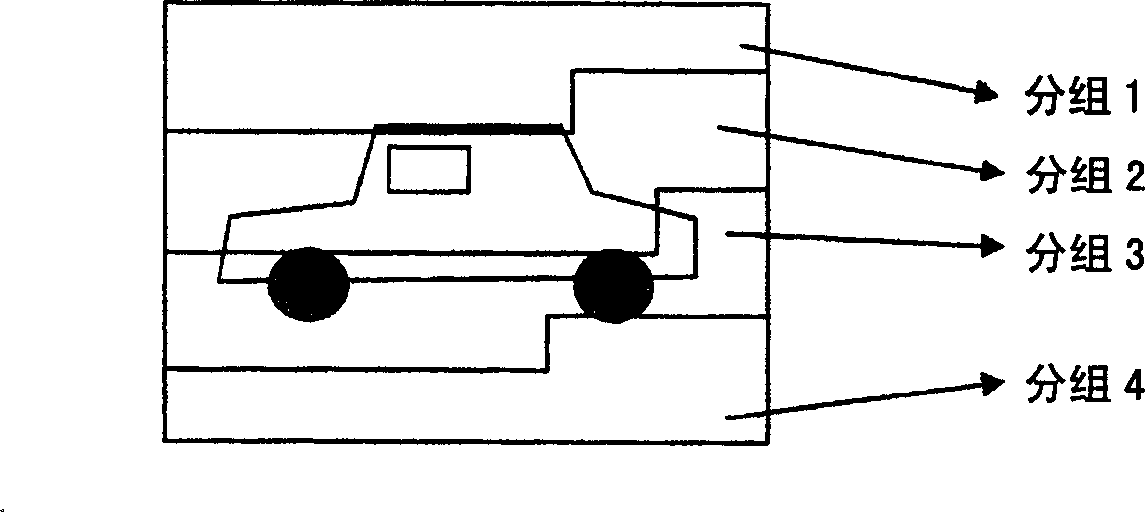
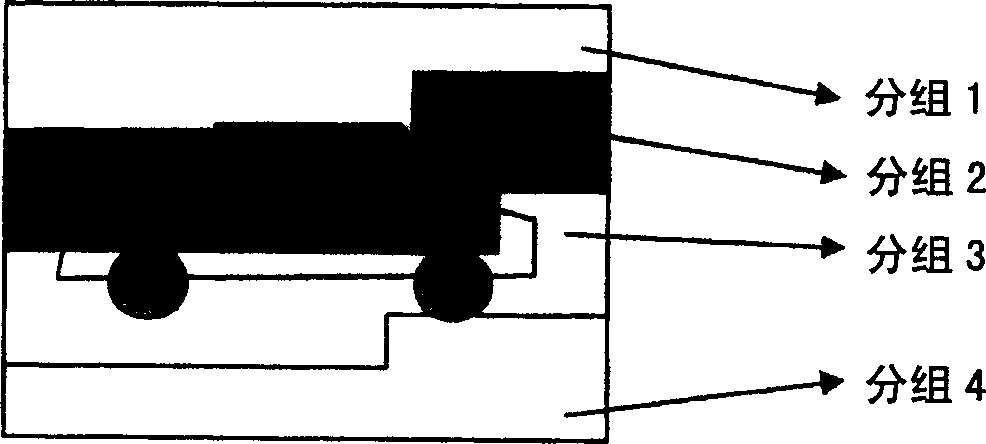
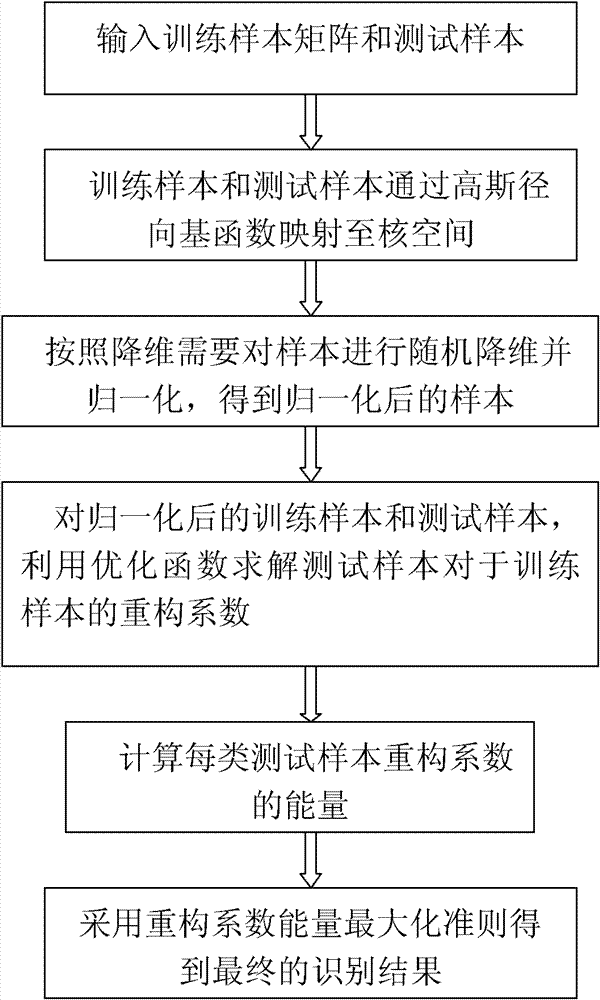
SAR (synthetic aperture radar) target identification method based on nuclear sparse representation
InactiveCN102122355AAvoid refactoringImprove fault toleranceCharacter and pattern recognitionTest sampleAlgorithm
The invention discloses an SAR (synthetic aperture radar) target identification method based on nuclear sparse representation, mainly solving the problem of low error tolerance in the prior art. The method comprises the following realization steps: (1) respectively mapping a training sample matrix and a test sample to a nuclear space, randomly reducing the dimension of the mapped sample to the required dimension, and normalizing the dimension; (2) solving a reconstructed coefficient vector between the normalized test sample and the training sample matrix; and (3) solving the energy of the reconstructed coefficient of the test sample in each class, and substituting the energy into a class judging formula to obtain a final identification result. Compared with the prior art, the SAR target identification method is characterized by improving the error tolerance of the algorithm, so that the SAR target identification method has higher identification precision and high arithmetic speed in the SAR target identification application; and meanwhile, an application range is popularized to a low-dimensional sample, thus having better universality.
Owner:XIDIAN UNIV
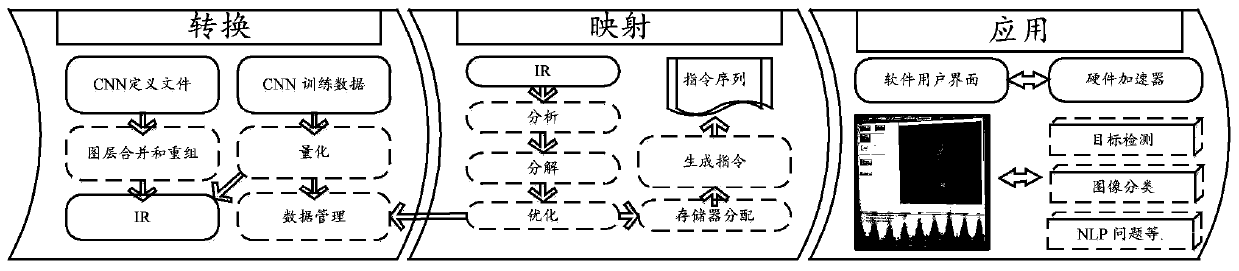
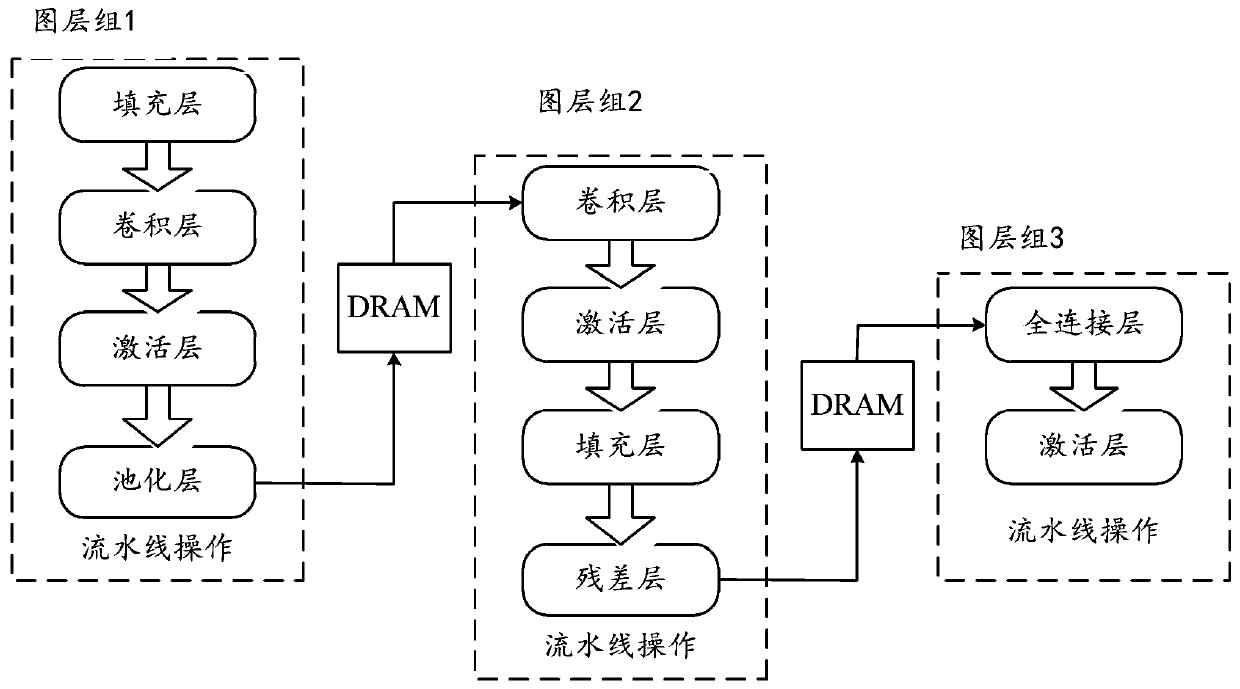
CNN acceleration method and system based on OPU
ActiveCN110058883AOvercoming universality issuesOvercome the inability to accurately predict the order of instructionsKernel methodsNeural architecturesGranularityInstruction set
The invention discloses a CNN acceleration method and system based on OPU, and relates to the field of CNN acceleration methods based on FPGA. The method includes that an OPU instruction set is defined; the compiler converts the CNN definition files of different target networks, selects an optimal accelerator to configure mapping according to the defined OPU instruction set, and generates instructions of different target networks to complete mapping; the OPU reads the compiled instruction, operates the instruction according to a parallel computing mode defined by the OPU instruction set, and completes acceleration of different target networks. According to the method, the instruction type is defined, the instruction granularity is set, network recombination optimization is carried out, a mapping mode for guaranteeing the maximum throughput is obtained by searching a solution space, and hardware adopts a parallel computing mode; the problem that an existing FPGA acceleration work aims at generating specific independent accelerators for different CNNs is solved, and the effects that the FPGA accelerator is not reconstructed, and acceleration of different network configurations is rapidly achieved through instructions are achieved.
Owner:梁磊
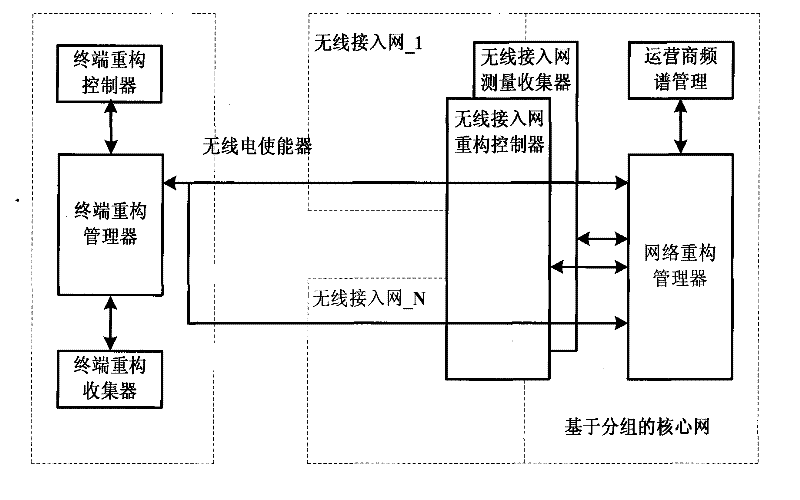
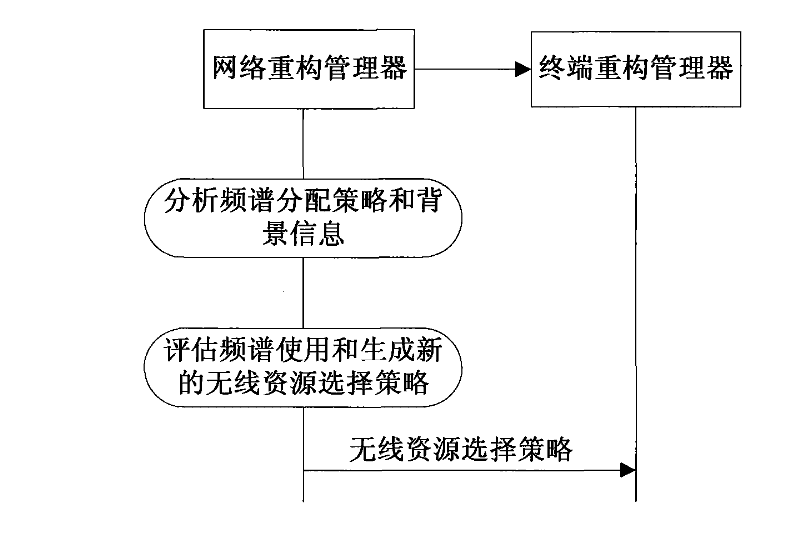
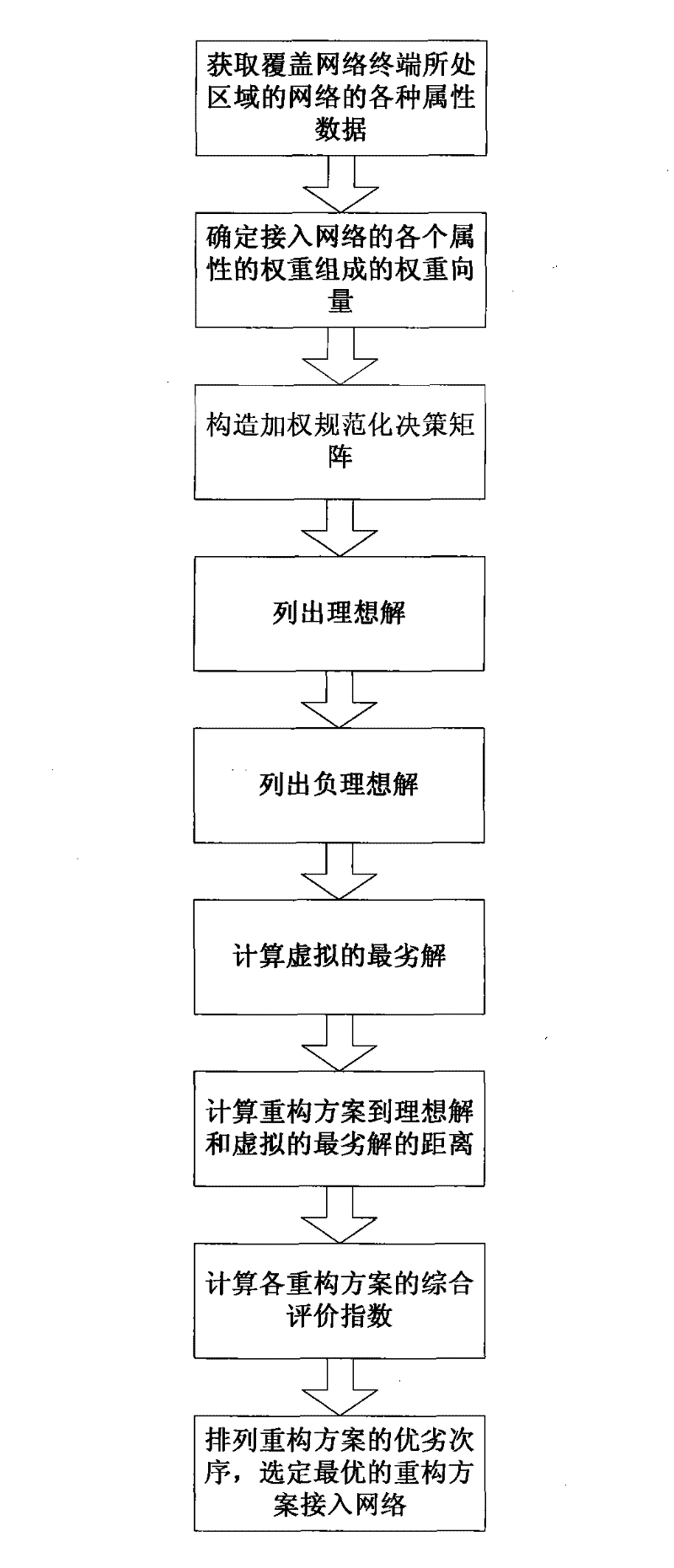
Reconstruction method of terminal under environment of cognitive radio network
InactiveCN101754226AResolve contradictionsScientific sortNetwork planningFeature vectorAccess network
The invention discloses a reconstruction method of a terminal under the environment of a cognitive radio network and belongs to the communication technology field. The invention mainly solves the problem that the terminal is frequently reconstructed and can not effectively make a decision. The reconstruction method comprise the specific processes: firstly, acquiring various attribute data of the network for covering an area where the network terminal is positioned; secondly, determining the weights of all attributes of an access network by applying an eigenvector method; thirdly, constructing a weighted and specified decision array according to the various attributes of reconfiguration schemes; fourthly, listing an ideal solution and a negative-ideal solution; fifthly, calculating a virtual worst solution; sixthly, calculating distances from each reconstruction scheme to the ideal solution and from the reconstruction scheme to the negative-ideal solution; seventhly, calculating comprehensive evaluation indexes of each reconstruction scheme; and eighthly, arranging good and bad sequences of each reconstruction scheme and selecting the optimal scheme access network. The invention not only can effectively determine the weights of various attributes in each reconstruction scheme and select the optimal scheme access network, but also can be used for the reconstruction of the terminal under environment of the cognitive radio network.
Owner:XIAN QIANGJUN INFORMATION TECH
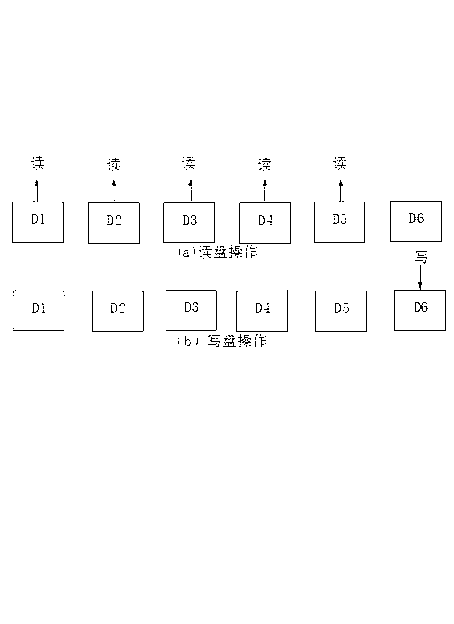
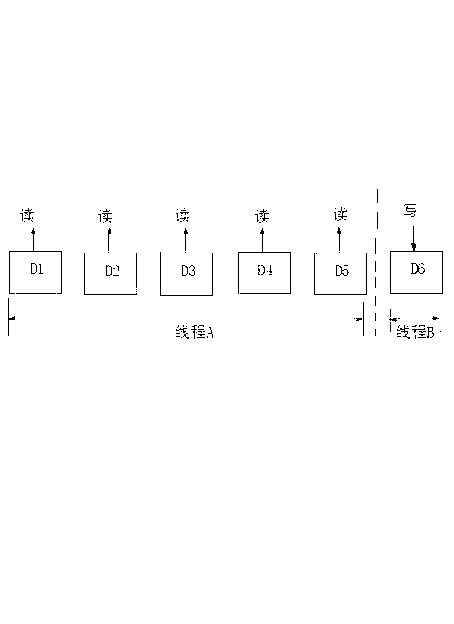
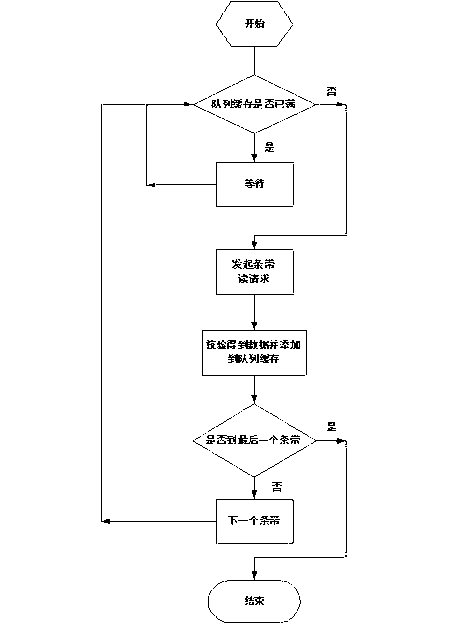
Method of improving disk array data reconstruction efficiency
InactiveCN103186438AAvoid refactoringInput/output to record carriersRedundant hardware error correctionDisk arrayData reconstruction
The invention provides a method of improving the disk array data reconstruction efficiency. The method is characterized in that a reconstruction process of treating a same stripe is carried out in two threads, as for one thread, disk reading operation is carried out only, as for the other thread, disk writing operation is carried out, and the amount of data blocks of a buffer queue is limited and is larger than that of stripe buffer so as to asynchronously write data without influencing the disk reading operation; the data of an original data disk is read and is checked, and the data obtained by checking is added into the buffer queue; and the other thread used for disk writing acquires the data from the buffer queue. With the adoption of the method, the position of writing the data per time needs to be marked and recorded and can be updated into super block information, thus preventing reconstruction starting anew after restart due to power off.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Compositions for disrupting and inhibiting reconstitution of wound biofilm
InactiveUS20070116750A1Facilitate topical administration of MDPP-AAvoid refactoringHeavy metal active ingredientsBiocideAcute woundBiofilm
Disclosed are compositions and methods for wound care, especially for treatment of chronic wounds. Compositions are methods are described for inhibiting reconstitution of biofilm in a chronic wound or preventing expansion of a biofilm in a chronic or acute wound.
Owner:WOLCOTT RANDALL
Ship turning motion simulation method
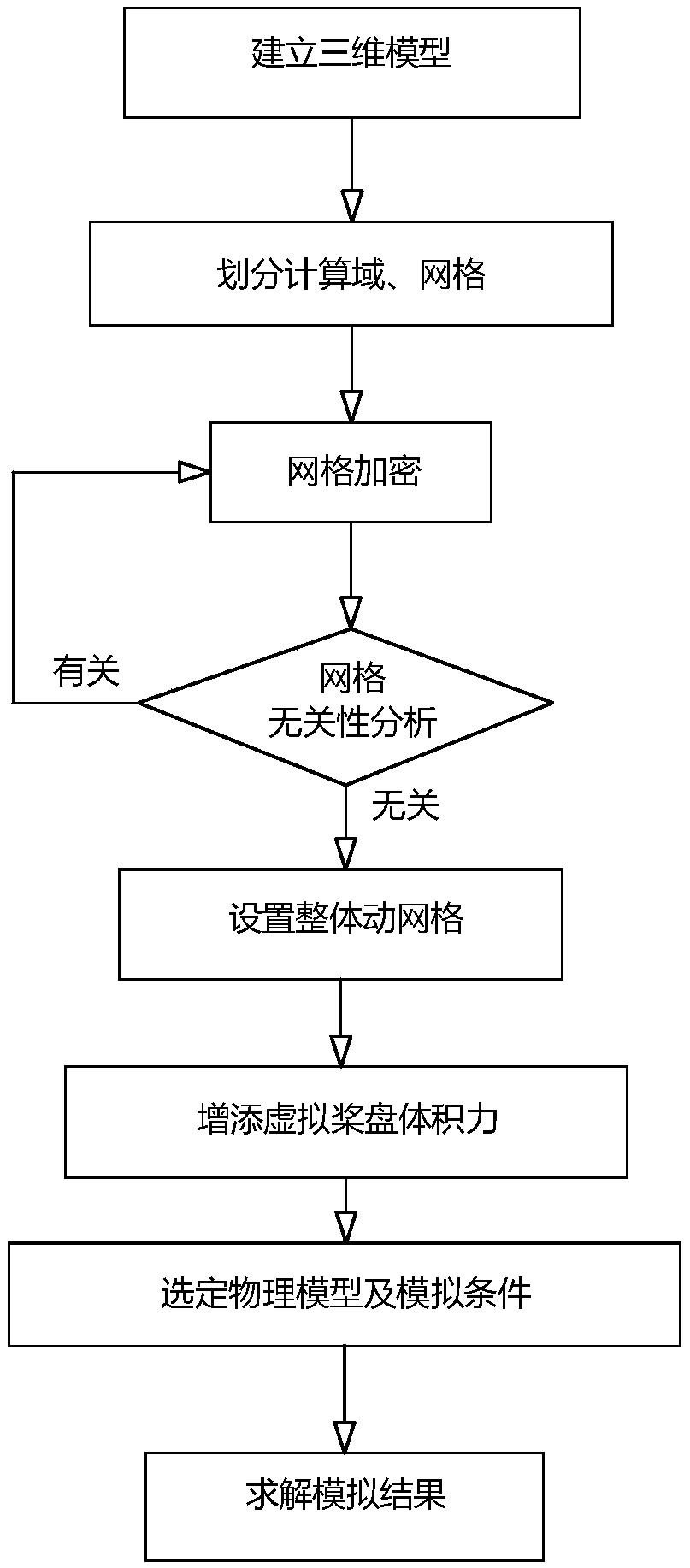
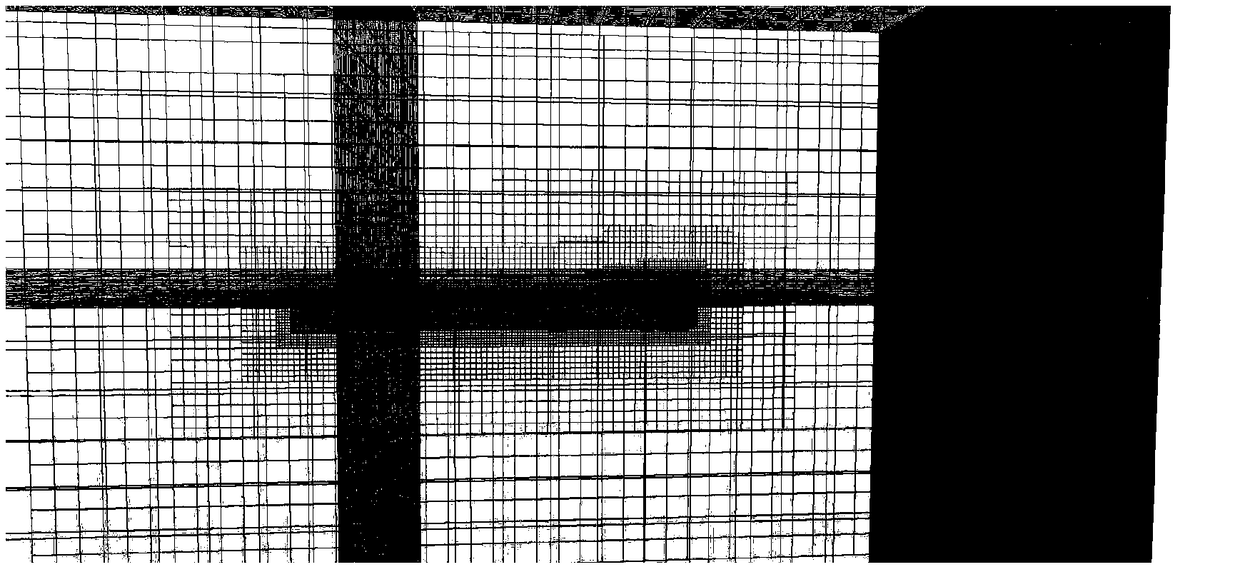
ActiveCN109325303ASave workloadSave the amount of calculationSustainable transportationDesign optimisation/simulationGyrationPropeller
The invention belongs to the technical field of ship motion measurement, in particular to a ship turning motion simulation method. The method does not model a propeller, but simulates propeller thrustwith virtual paddle volume force, and simulates ship or submarine rotating motion in water with integral dynamic mesh, so that the simulation precision is improved and the modeling difficulty is simplified, and accordingly designers and testers can quickly and accurately predict the hydrodynamic performance of the ship 's gyration.
Owner:NAVAL UNIV OF ENG PLA
Multi-focusing image fusion method based on multi-dimensional image analysis and block consistency verification
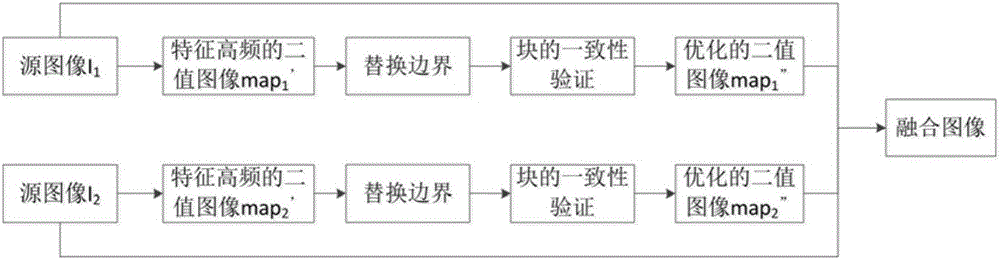
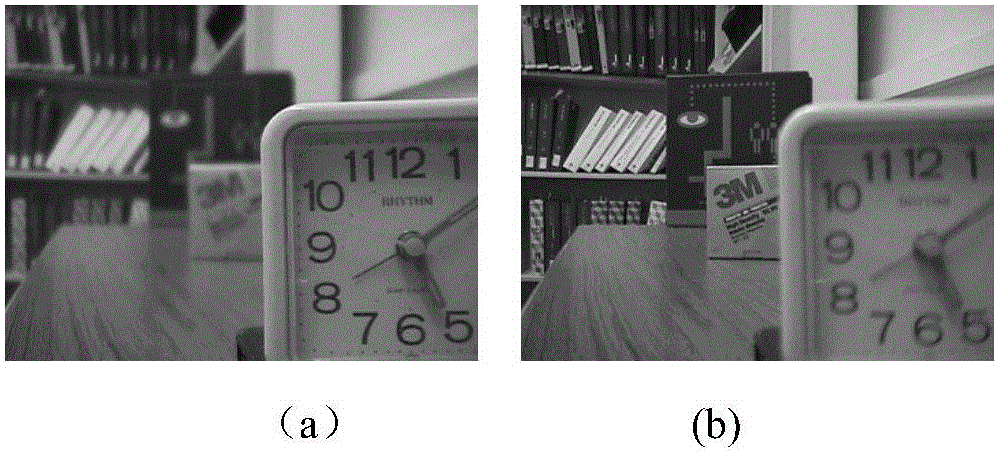
ActiveCN105894483AAvoid decompositionAvoid refactoringImage enhancementImage analysisPattern recognitionMultiscale decomposition
The invention relates to a multi-focusing image fusion method based on multi-dimensional image analysis and block consistency verification. The method includes the steps of conducting multi-dimensional decomposition for a down-sampled multi-focusing source image, calculating the definition of characteristic high frequency sub-band coefficient and conducting bi-side filtering to obtain an initial binary image, conducting up-sampling after processing isolated small areas in areas in the initial binary image, replacing the up-sampled binary image boundaries with original boundaries of a source image, conducting partitioning processing and block consistency verification to finally optimize the binary image boundaries, and conducting fusion for the source image accordingly. Optimal boundaries of focusing areas and non-focusing areas of a source image are obtained based on multi-dimensional image analysis and block consistency verification, so as to guarantee direct and accurate fusion of source image focusing areas. The algorithm is simple. The focusing information of a multi-focusing image can be effectively maintained on the premise of introducing no error information.
Owner:云南联合视觉科技有限公司
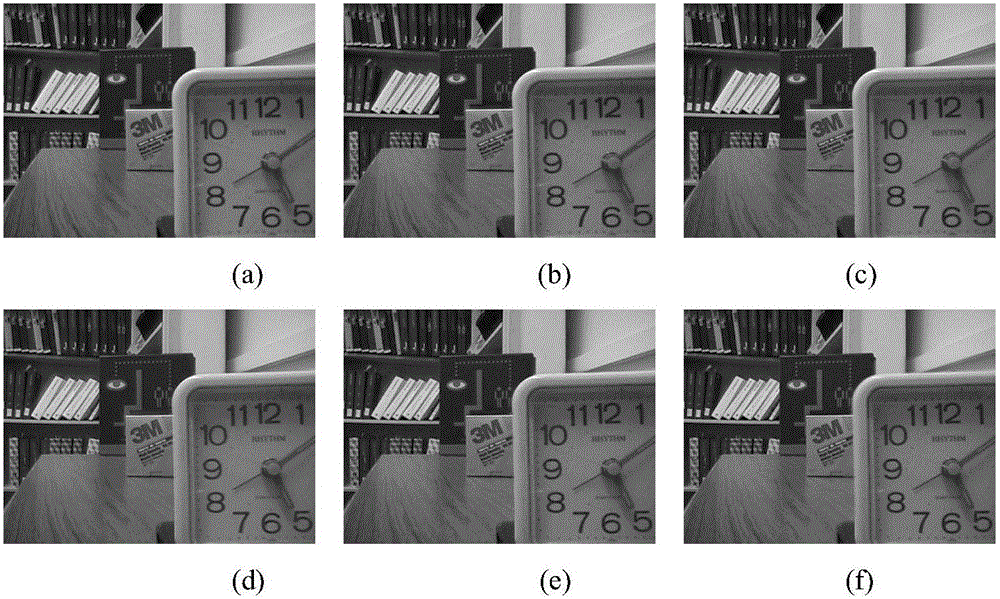
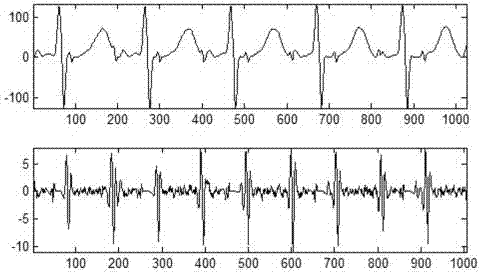
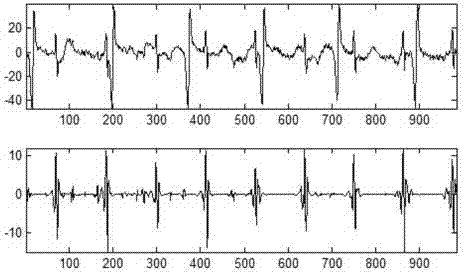
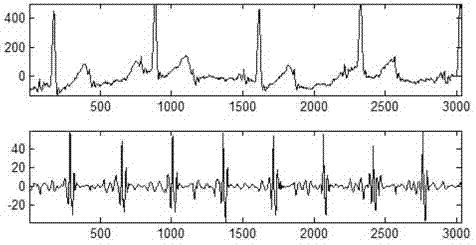
Fetal electrocardiogram signal extracting method based on wavelet threshold denoising
InactiveCN102783945ASuppress heart rateEfficient and accurate extractionDiagnostic recording/measuringSensorsEcg signalDenoising algorithm
The invention discloses a fetal electrocardiogram signal extracting method based on wavelet threshold denoising. The method comprises the following steps of: carrying out stationary wavelet transform processing on a maternal abdomen signal, and decomposing to obtain each layer of wavelet coefficient; independently processing each layer of wavelet detail coefficient, removing fetal electrocardiogram wavelet coefficients, reconstructing remained maternal electrocardiogram wavelet coefficients, and obtaining maternal electrocardiogram in the abdomen signal; removing the reconstructed maternal electrocardiogram from the abdomen signal to obtain a fetal electrocardiogram signal; and denoising the extracted fetal electrocardiogram by utilizing a wavelet correlation denoising algorithm to obtain a clear fetal electrocardiogram signal. Due to the method, the accurate extraction of the fetal electrocardiogram signal can be realized. The method is based on a single channel, the computation of wavelet transform modulus maxima is avoided, and better instantaneity is realized.
Owner:BEIJING UNIV OF TECH
Excitation system negative damping detection method based on oscillation energy injection
InactiveCN104101805AAvoid refactoringAvoid errorsElectrical testingExcitation currentElectric power system
The invention discloses an excitation system negative damping detection method based on oscillation energy injection and relates to the technical field of power system dynamic stability. The method includes calculating the excitation system oscillation energy injection through a formula of Wex=integral (t2, t1) delta mu f (t) delta i f (t) d t; only extracting the oscillation component of the concerned oscillation frequency through an identification algorithm for calculation; determining the negative and positive of the damping of the excitation system according to the positive and negative of the oscillation energy injection. The excitation system damping is detected through the directly measured generator excitation voltage mu f and excitation current i f for avoiding the reconstruction of generator internal variables, so that the calculation is simple; the generator internal parameters are not used for avoiding errors caused by inaccurate generator parameters, so that the calculation is accurate. The excitation voltage and the excitation current during oscillation can be extracted from a generator monitoring system database for being used for the analysis of excitation system damping characteristics; the method can also be programmed as a subroutine to be integrated into the generator monitoring system for application.
Owner:SICHUAN UNIV
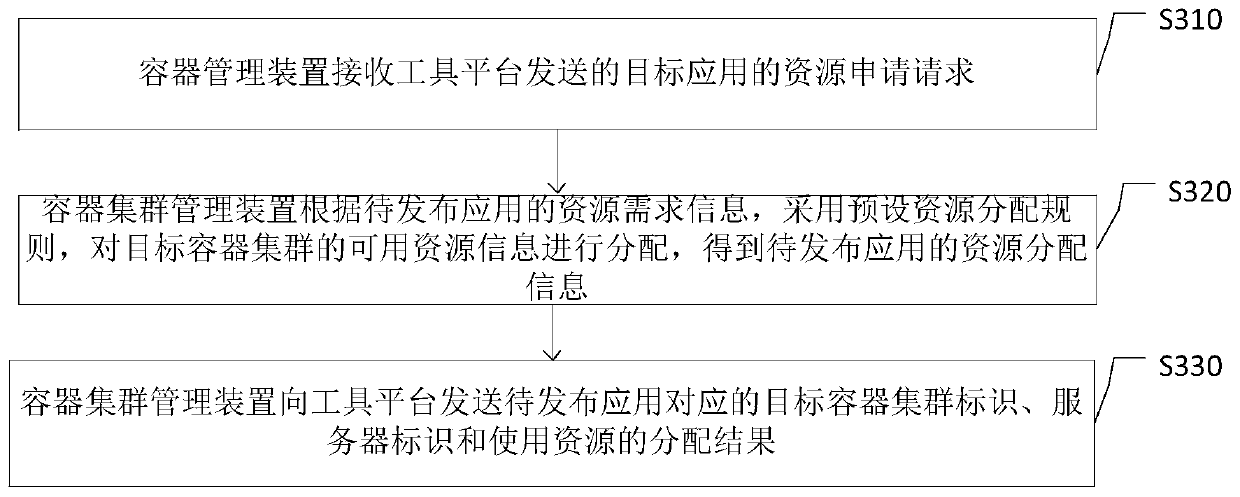
Tenant resource invading-oriented cloud application resource dynamic scheduling method
PendingCN109960591ASolve the isolation problemSolve resource problemsProgram initiation/switchingResource allocationConcurrency controlCloud server
The invention relates to a tenant resource invading-oriented cloud application resource dynamic scheduling method. The method comprises the following steps: binding tenant applications and componentswith a task manager so as to perceive the whole tenant and the local units; according to the technical scheme, reusing the cloud server task thread in the one-time request processing process while performing the concurrent control on the tenant request, so that the problem of interactive protocol reconstruction is avoided, the maximum concurrent scale of the tenant is adjusted to adapt to the performance fluctuation generated when the tenant load dynamically changes, and the problems of tenant isolation and resource occupation are solved.
Owner:DIGITAL CHINA INFORMATION SYST
Method for realizing neural network model splitting by using multi-core processor and related product
PendingCN110689121AAvoid modificationAvoid refactoringNeural architecturesPhysical realisationAlgorithmTheoretical computer science
The embodiment of the invention discloses a method for realizing neural network model splitting by using a multi-core processor and a related product. When operators capable of being split exist in the neural network model, the operators are split, the optimal splitting combination is selected to obtain the optimal splitting result of the whole neural network model, then the sub-operators corresponding to the optimal splitting result are executed in parallel through multiple cores, and the purpose of reducing resource consumption of computer equipment is achieved.
Owner:ANHUI CAMBRICON INFORMATION TECH CO LTD
Distributed computation in untrusted computing environments using distractive computational units
InactiveUS20050160288A1Complicate detection and reconstitutionComplicate detectionResource allocationMemory loss protectionTrusted ComputingParallel computing
Owner:IBM CORP
Compressed domain video watermark embedding and extracting methods based on moving object
ActiveCN108521613AGood anti-heavy compression performanceFlexible embeddingDigital video signal modificationSelective content distributionMotion vectorObject label
The invention discloses a compressed domain video watermark embedding method based on a moving object. The compressed domain video watermark embedding method based on the moving object is characterized by comprising the steps of: performing scrambling encryption on binary watermark information to obtain encrypted binary watermark information, obtaining a moving object labelling graph of each frameof image of a video by using a video object tracking method based on a compressed domain, obtaining a corresponding moving object in each frame of image according to the moving object labelling graph, furthermore, obtaining a corresponding motion vector from the extracted moving object in each frame of image, obtaining module values of all motion vectors of the moving object in each frame of image by calculation, and furthermore, performing cycle watermark embedding operation on the motion vector corresponding to the module value, which is greater than or equal to a pre-set threshold value inall the module values, by using the obtained binary watermark information, so that a video embedded with the watermark is obtained. By means of the compressed domain video watermark embedding and extracting methods based on the moving object disclosed by the invention, the technical problem that the watermark can be damaged after the video with the watermark is re-coded in the existing video digital watermark embedding method based on the compressed domain can be solved.
Owner:SOUTH CENTRAL UNIVERSITY FOR NATIONALITIES
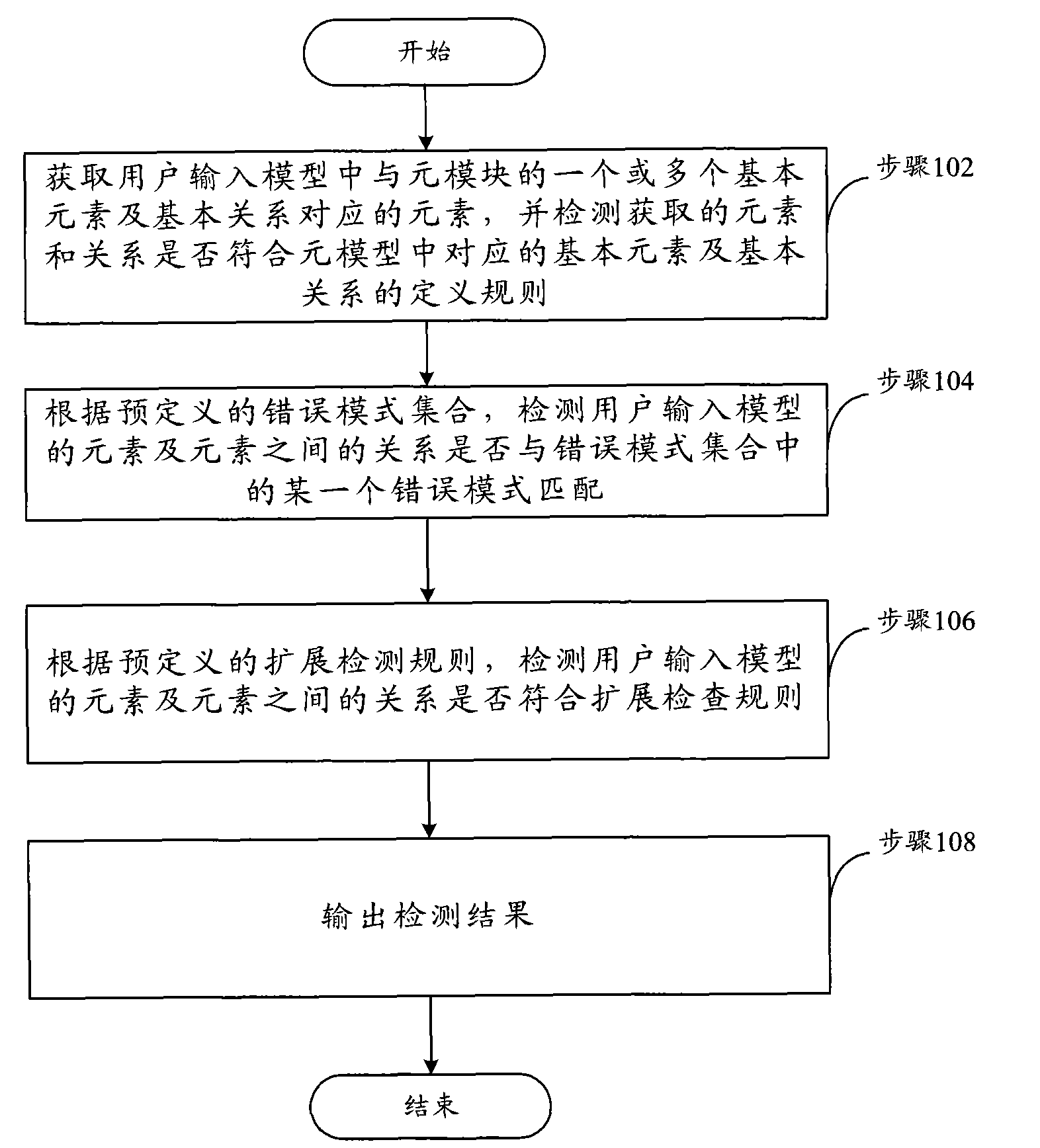
Method and device for detecting user input model
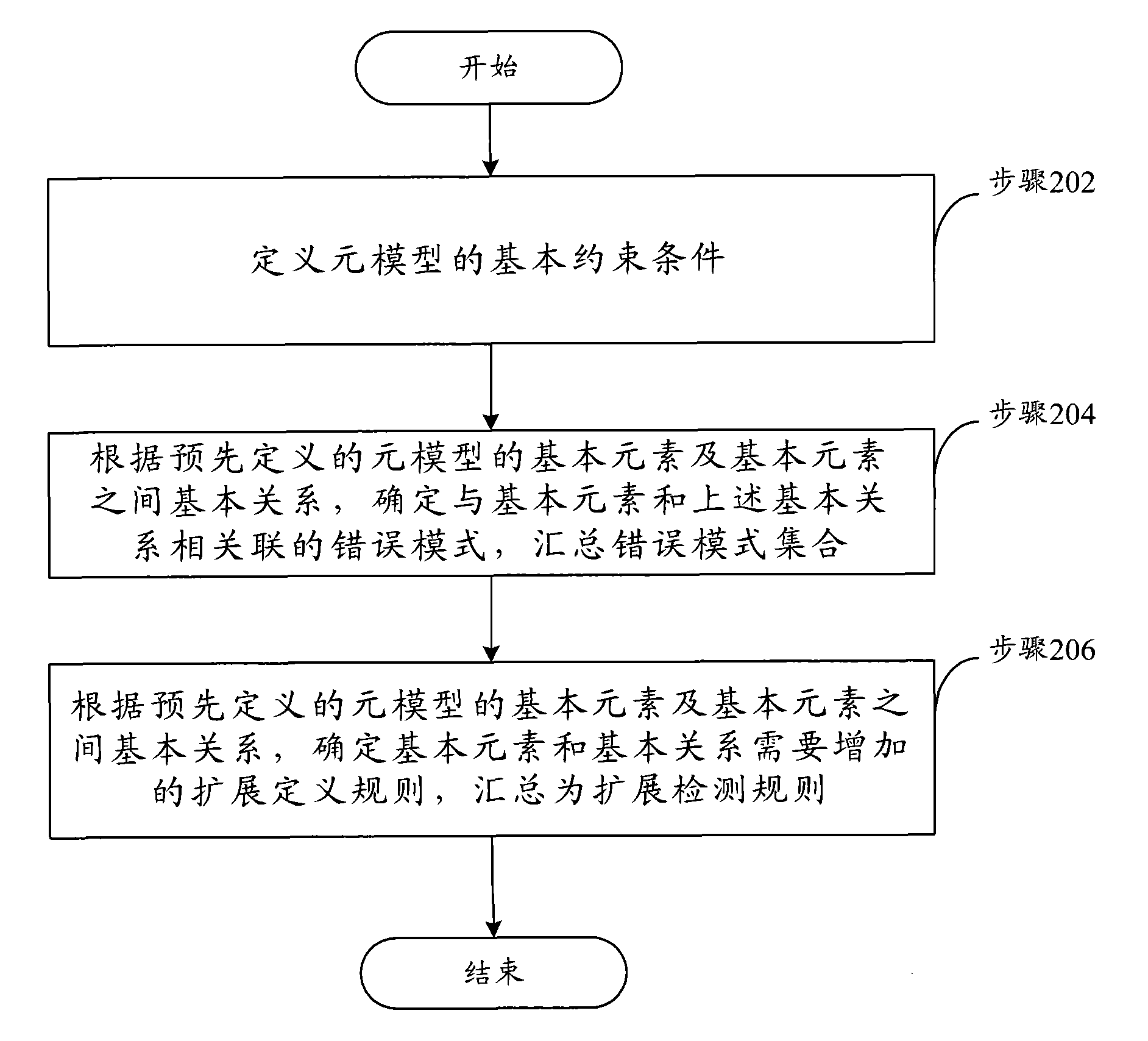
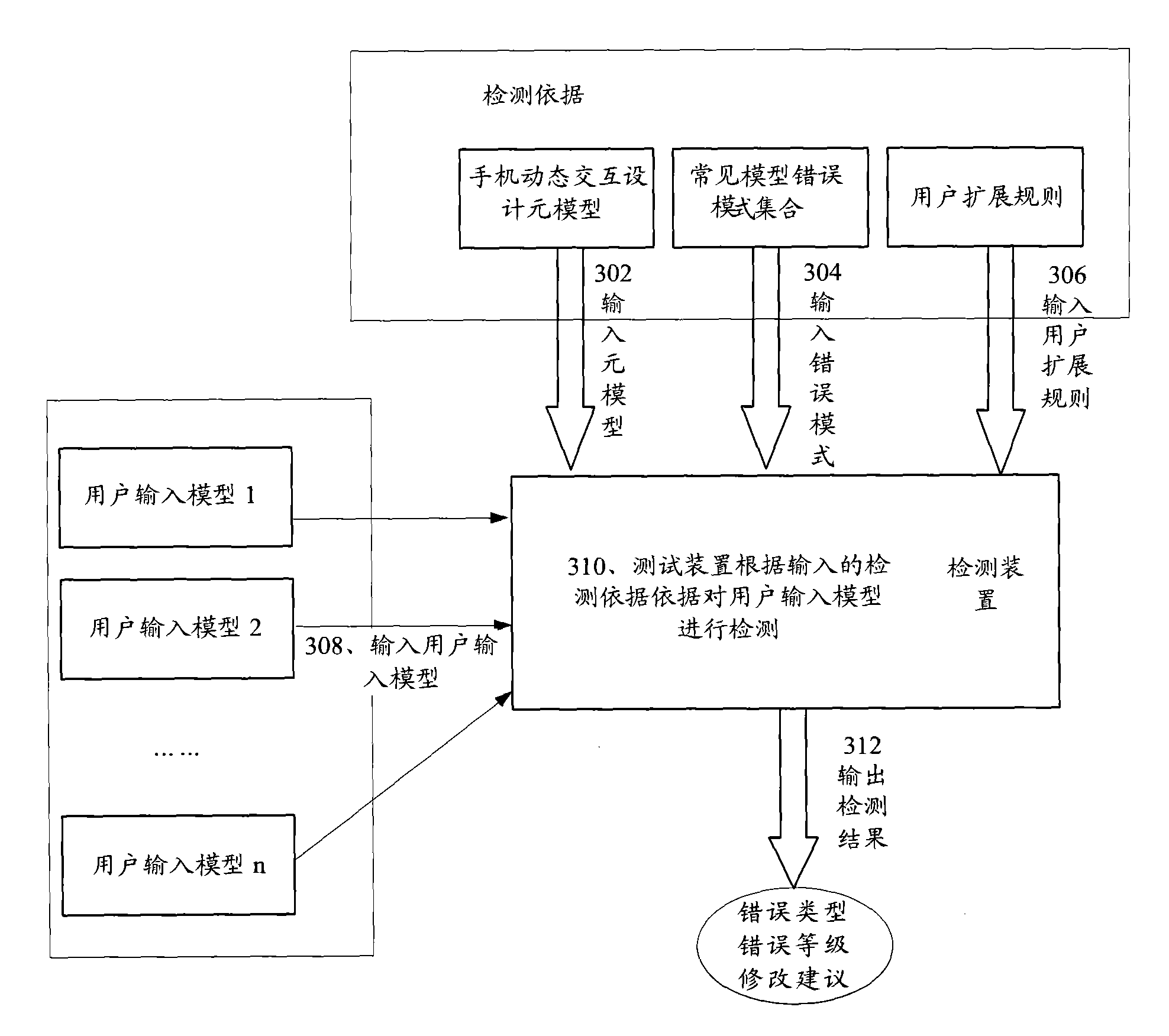
ActiveCN101673200AAvoid refactoringShorten the timeSoftware testing/debuggingExecution for user interfacesSystem reconfigurationUser input
The invention discloses a method and a device for detecting a user input model. The device comprises a user input model storage module, a meta-model storage module, a meta-module detection module andan output module, wherein, the user input model storage module is used for saving and analyzing the input user input model; the meta-model storage module is used for saving and analyzing a predefinedmeta-model basic constraint condition; the meta-module detection module is used for detecting whether the relationship between elements of the user input model conforms to the meta-model basic constraint condition according to the above basic constraint condition; the output module is used for displaying the output detection results on a file or a view corresponding to the user input model. According to the technical scheme provided by the invention, users can find the problem of the model at the earlier stage of modeling and design, thus system reconfiguration caused by the error of model design in the development and verification process can be avoided, and the time of development and verification is greatly reduced.
Owner:ZTE CORP
Reconstruction system and reconstruction method applied to time-triggered communication of avionics system
ActiveCN110413426AAvoid refactoringImprove the immunityFault responseInterprogram communicationEnd systemConfiguration generation
The invention discloses a reconstruction system and a reconstruction method applied to time-triggered communication of an avionics system. The reconstruction system is characterized in that an end system fault recording module, a resource checking module, a configuration generation module and a reconstruction execution module are additionally arranged in a traditional avionics system. The reconstruction method comprises the steps of selecting a reconstruction strategy after an end system fails, executing migration type reconstruction according to backup resources of a redundant end system, executing preemptive type reconstruction according to available idle resources, and executing degradation type reconstruction if resources are insufficient. According to the reconstruction method, on thebasis of application migration, association from applications to messages is established, and for different resource constraint conditions, the fault problem of application failure on an end system module is solved in a mode of designing message secondary scheduling. The reconstruction method is based on a satisfiability model theory scheduling method, and can recover faults of the support end system when the avionics system operates.
Owner:BEIHANG UNIV
Spectrum sensing method based on non-refactoring framework
InactiveCN103986540AAvoid refactoringSmall amount of calculationTransmission monitoringData vectorCompressed sampling
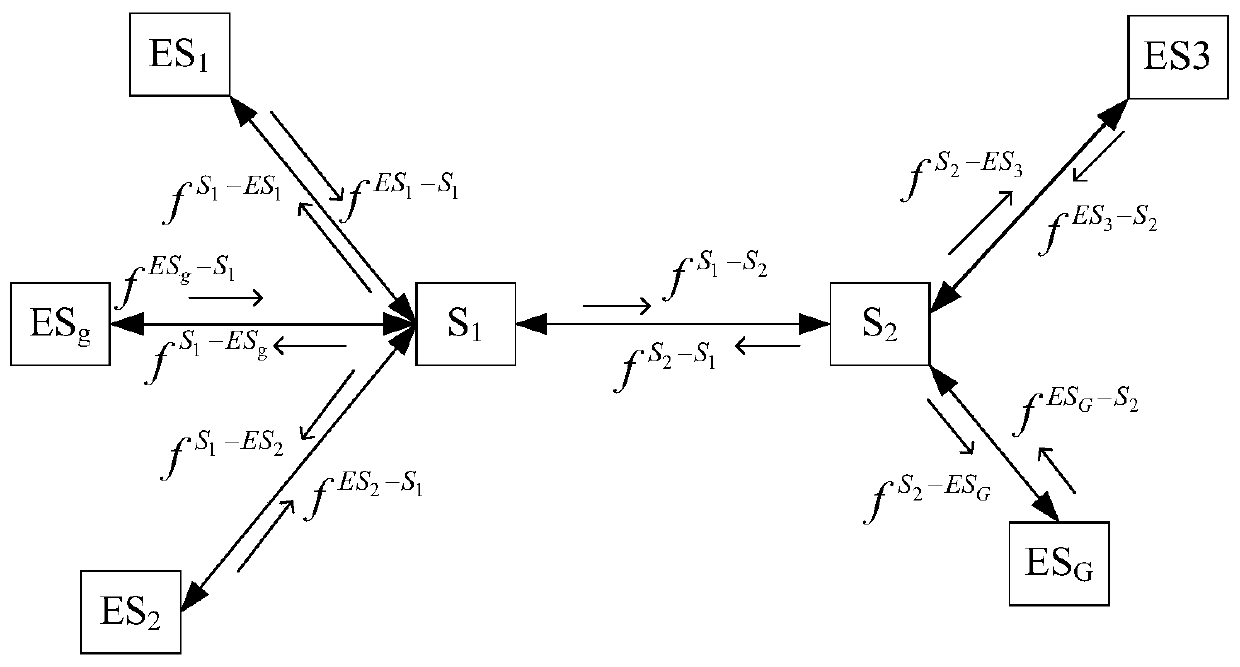
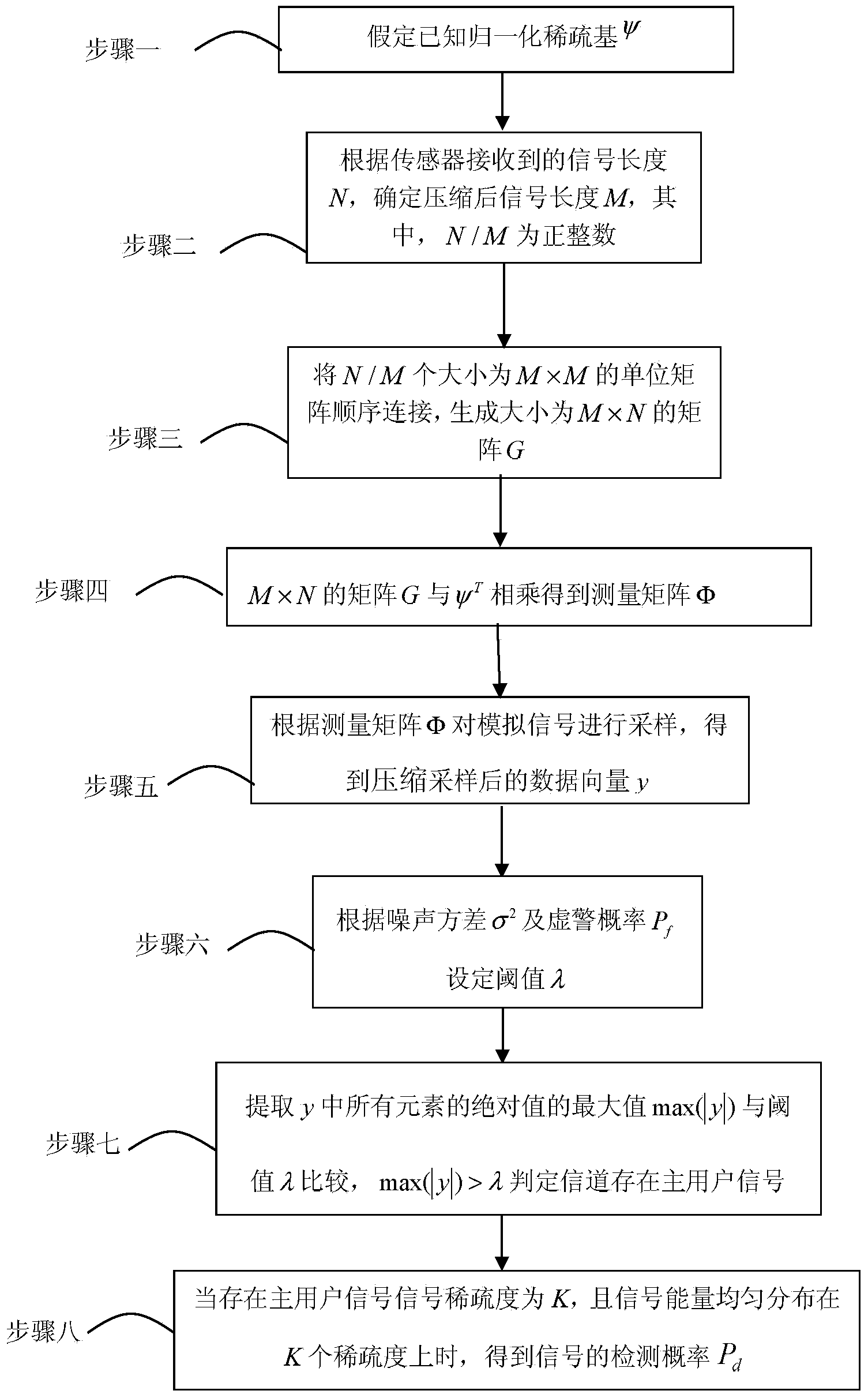
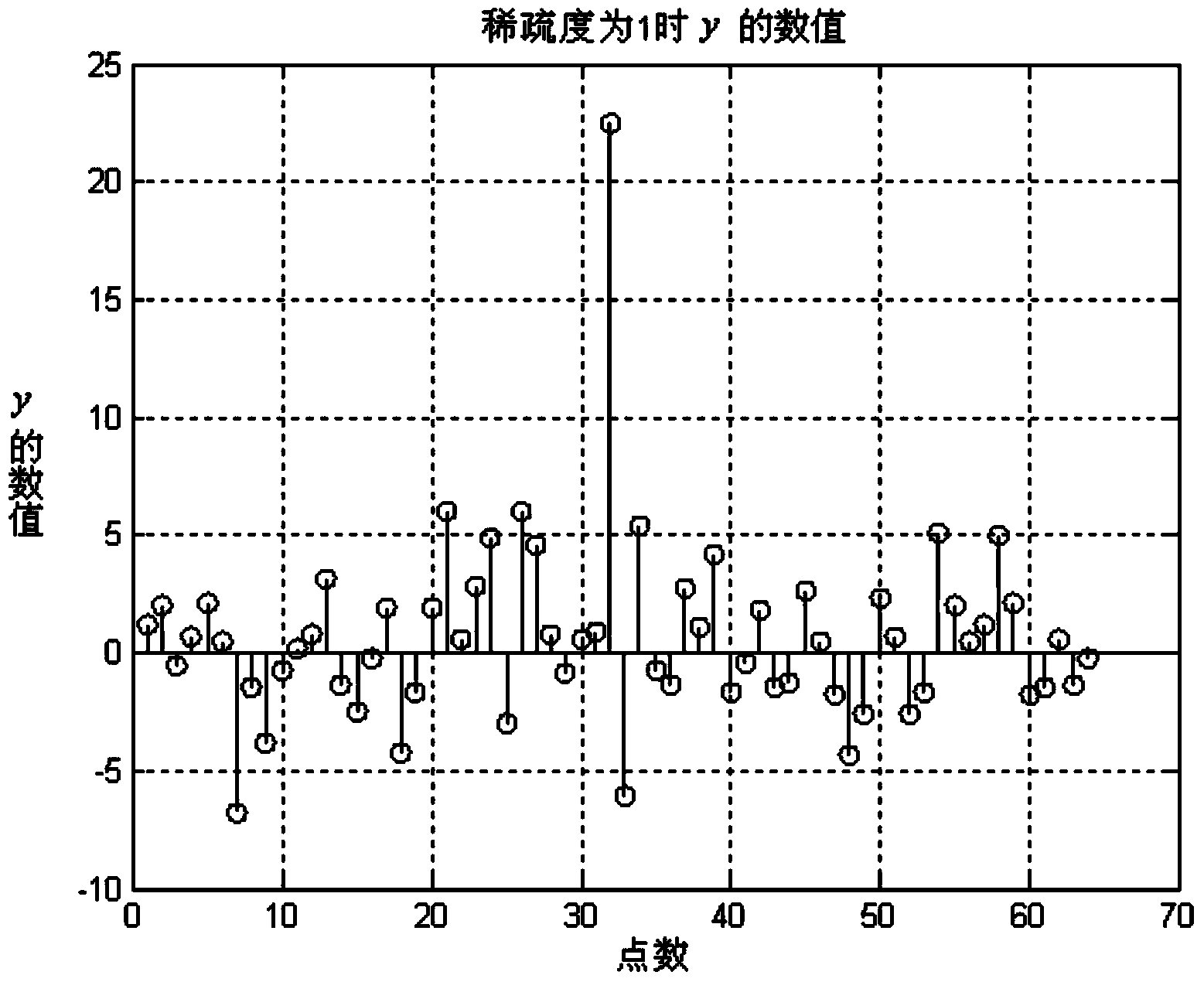
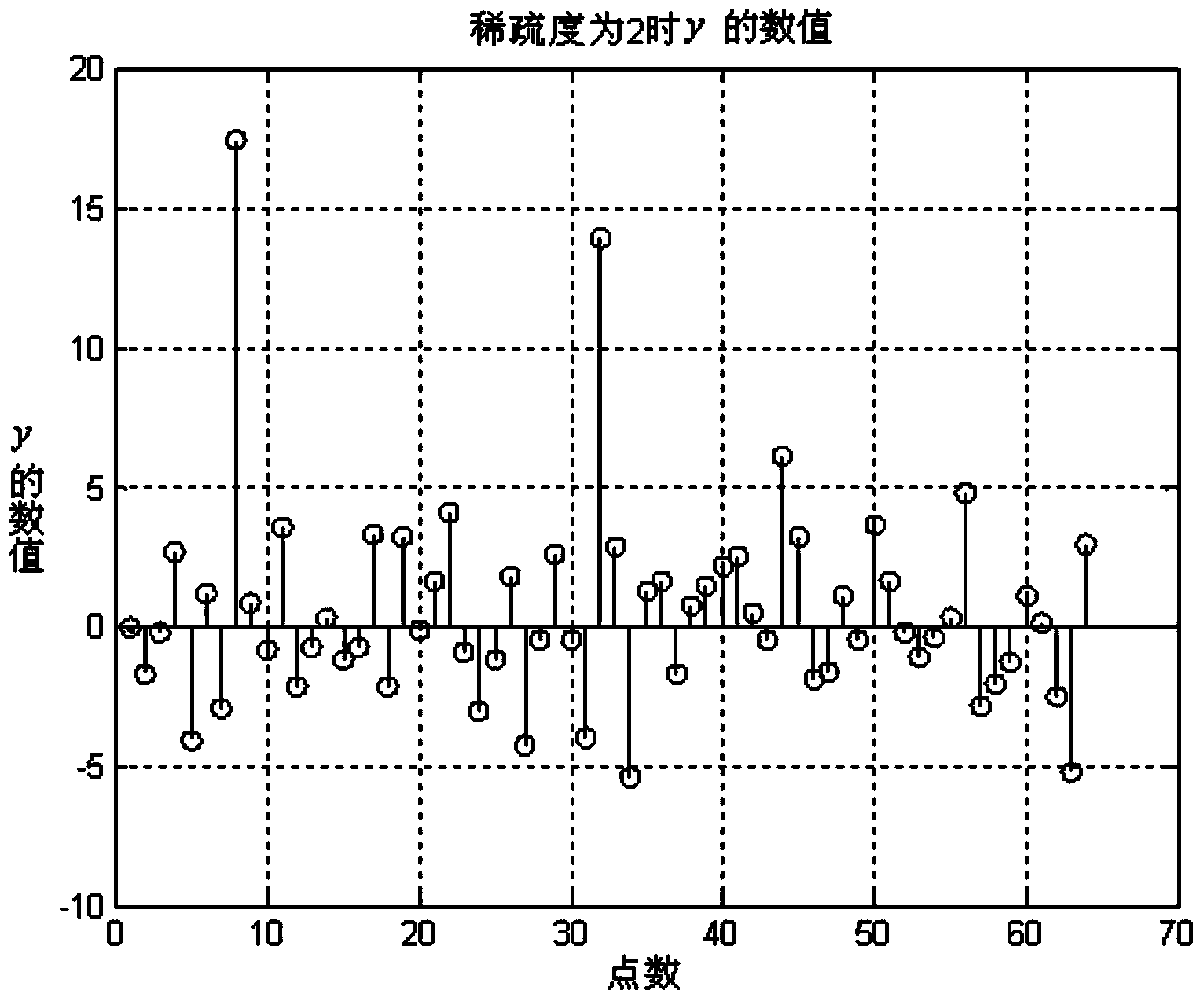
The invention relates to a spectrum sensing method based on a non-refactoring framework and aims at solving the problems that the utilization ratio of a spectrum resource authorized by a wireless communication technology is low, a conventional compressed sensing spectrum sensing algorithm is complex, and spectrum sensing can not be carried out by directly utilizing a data matrix which is in compressed sampling under the non-refactoring framework. The spectrum sensing method comprises the steps of 1, determining normalized sparse-group psi; 2, according to the signal length N, determining the signal length M after compressing; 3, generating an M*N matrix G; 4, multiplying the M*N matrix G and psi<T> to obtain a measuring matrix phi; 5, obtaining a data vector y after compressed sampling; 6, setting a threshold value lambda according to a noise variance sigma<2> and a false alarm probability Pf; 7, determining that a main user signal exists in a channel according to that max(|y|) is larger than lambda; 8, obtaining the detection probability Pd of the signal and the like. The spectrum sensing method is applied to the spectrum sensing field of the non-refactoring frameworks.
Owner:HARBIN INST OF TECH
Cross-view gait recognition method combining LSTM and CNN
PendingCN112232224ASimplify preprocessing stepsAvoid refactoringCharacter and pattern recognitionNeural architecturesFeature vectorData set
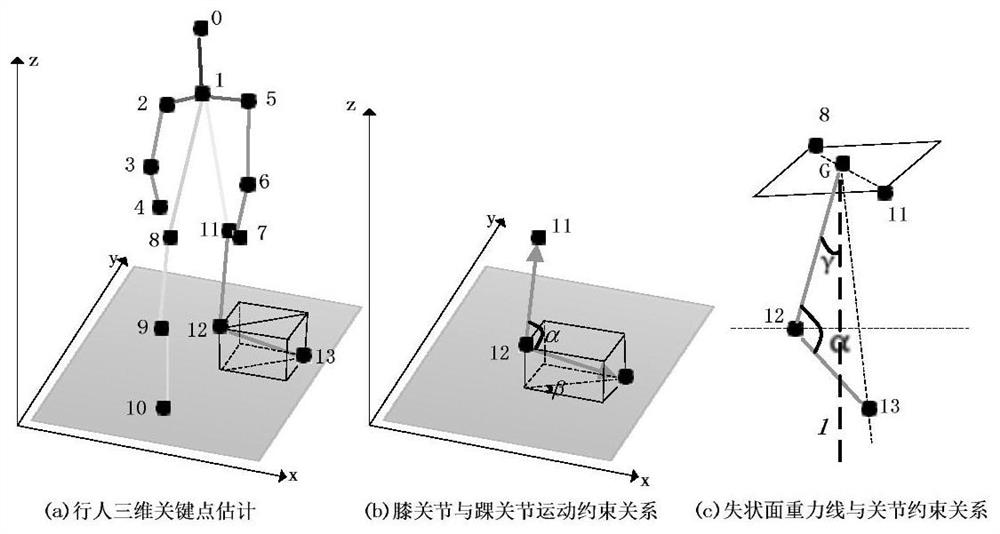
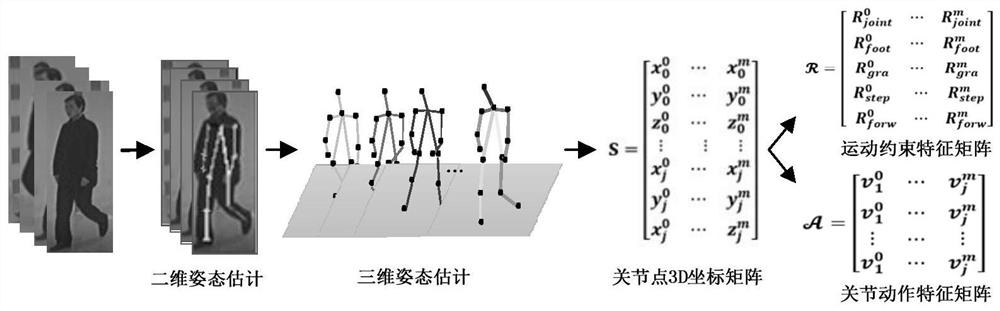
The invention discloses a cross-view gait recognition method combining LSTM and CNN, which comprises the following steps of: 1) extracting 3D (Three-Dimensional) attitude data of pedestrians in a video by adopting OpenPose3D from a CASIA-B gait video data set; 2) extracting motion constraint data and joint action data of video pedestrian joint points from the 3D attitude data obtained in the step1), constructing a pedestrian gait constraint matrix, and establishing a sample set; (3) constructing a 3D gait recognition network LC-POSEGAIT; 4) training a 3D gait recognition network LC-POSEGAIT by using the training set sample obtained in the step 2); and 5) utilizing the trained 3D gait recognition network LC-POSEGAIT to extract gait feature vectors of the video pedestrians, and completing cross-view gait recognition combining LSTM and CNN. The method can realize cross-view gait recognition, avoids preprocessing work of pedestrian detection and tracking, and can alleviate the influence of factors such as shooting angles, carried articles and illumination on gait recognition.
Owner:XI'AN UNIVERSITY OF ARCHITECTURE AND TECHNOLOGY
Method for verifying feasibility of inserting CRISPR-Cas9 system mediated target gene into candida utilis
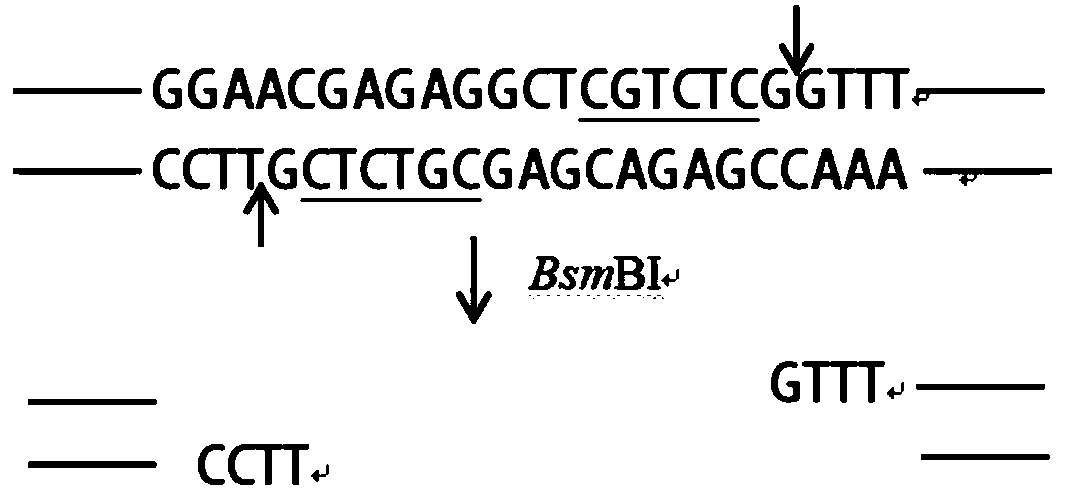
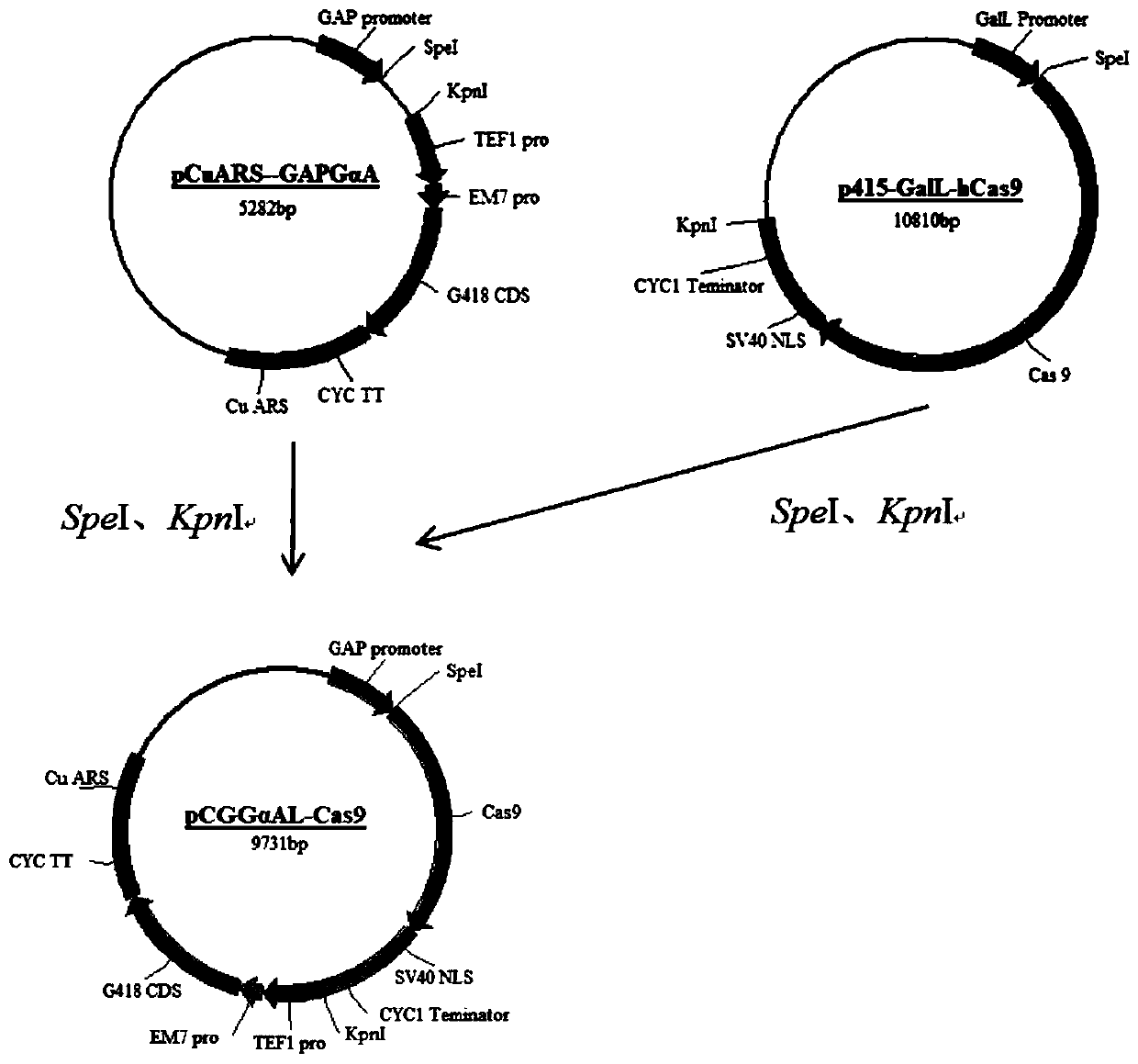
ActiveCN110305892AImprove gene editing efficiencyEnable overlapping PCR ligationVectorsStable introduction of DNAEnzyme digestionInsertion sequence
The invention discloses a method for verifying the feasibility of inserting a CRISPR-Cas9 system mediated target gene into candida utilis. The method includes the following steps that S1, an expression vector of the candida utilis containing Cas9 segments is constructed; S2, tRNAGlu genes and downstream expression units of sgRNA are amplified, PCR link is overlapped and a restriction enzyme cutting site is introduced, and after connection, the amplified tRNAGlu genes and downstream expression units of the sgRNA are combined with the vector of the candida utilis to obtain sgRNA initial recombinant plasmid; S3, pre-insertion and target sequences are selected, a sticky tail end is added to the 5' end of a target and complementary sequence, and double chain segments are formed by annealing andthen connected with the initial recombinant plasmid after enzyme digestion to obtain sgRNA mature recombinant plasmid; S4, a recombinant donor segment containing a left homologous arm and a right homologous arm of a pre-insertion sequence is constructed; and S5, the sgRNA recombinant plasmid and the recombinant donor segment are used for transforming the candida utilis carrying Cas9. The feasibility of inserting the CRISPR-Cas9 system mediated target gene into the candida utilis is verified by identifying the expression of the donor segment.
Owner:GUANGDONG QIZHI BIOTECHNOLOGY CO LTD +2
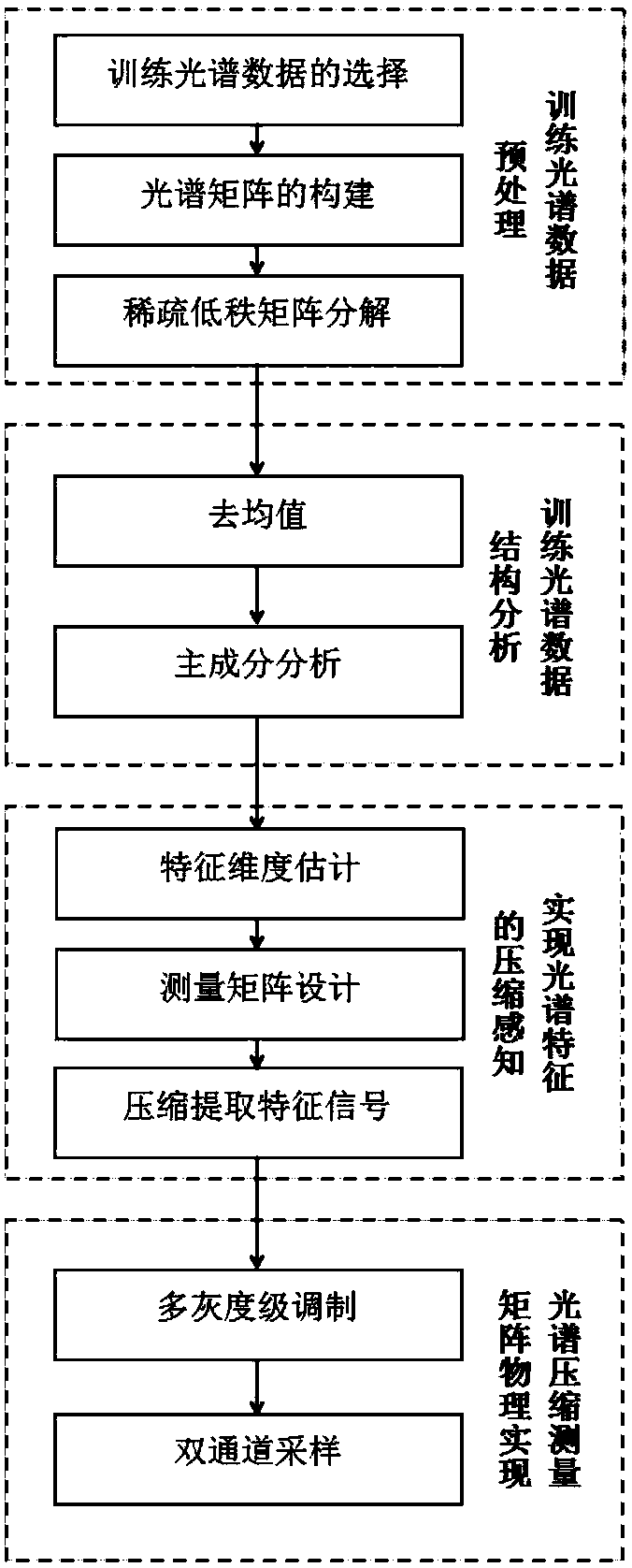
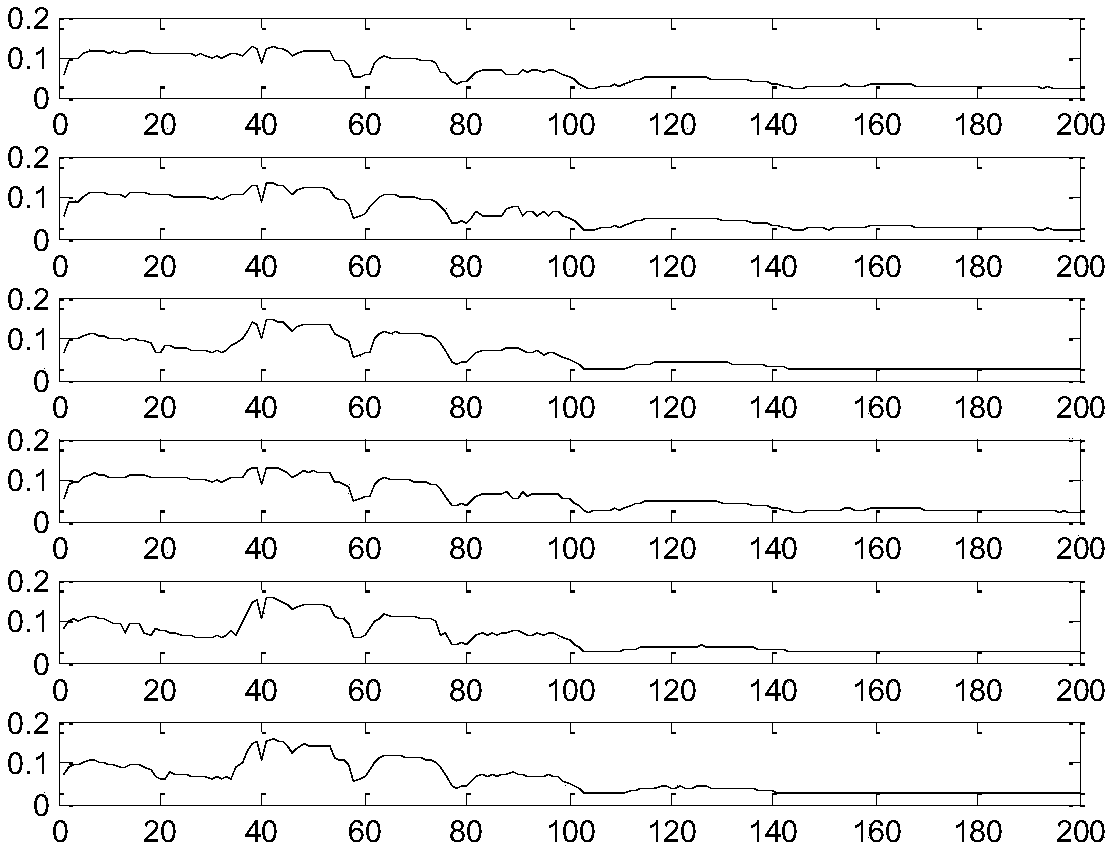
Method for compressed sensing features of spectrum
ActiveCN108520235AAvoid refactoringImprove acquisition efficiencyCharacter and pattern recognitionFeature extractionDigital micro mirror device
The invention discloses a method for compressed sensing of the features of a spectrum, and the method can achieve the compressed extraction of a feature signal of a spectrum signal based on a constructed spectrum compression measurement matrix, and achieves the compressed sensing of the spectrum features. In addition, the method also proposes a physical implementation method for a spectrum compression measurement matrix Phi based on a DMD (digital micro-mirror device). The method can effectively avoid the signal reconstruction and feature extraction, and the measurement data can be directly used for classification and recognition, thereby greatly reducing the calculating and storage expenditure, and improving the obtaining efficiency of the spectrum information. Because the dimensions of aspectrum feature signal are smaller than the dimensions of a spectrum signal, the measurement data obtained through the method will be smaller than the measurement data of a conventional compressed spectrum imaging method.
Owner:NAT UNIV OF DEFENSE TECH
RAID reconstruction method and device
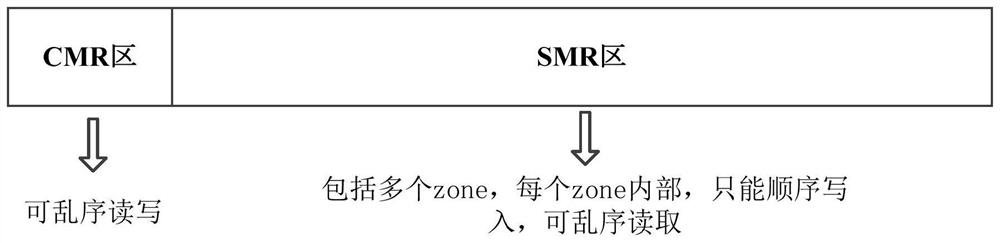
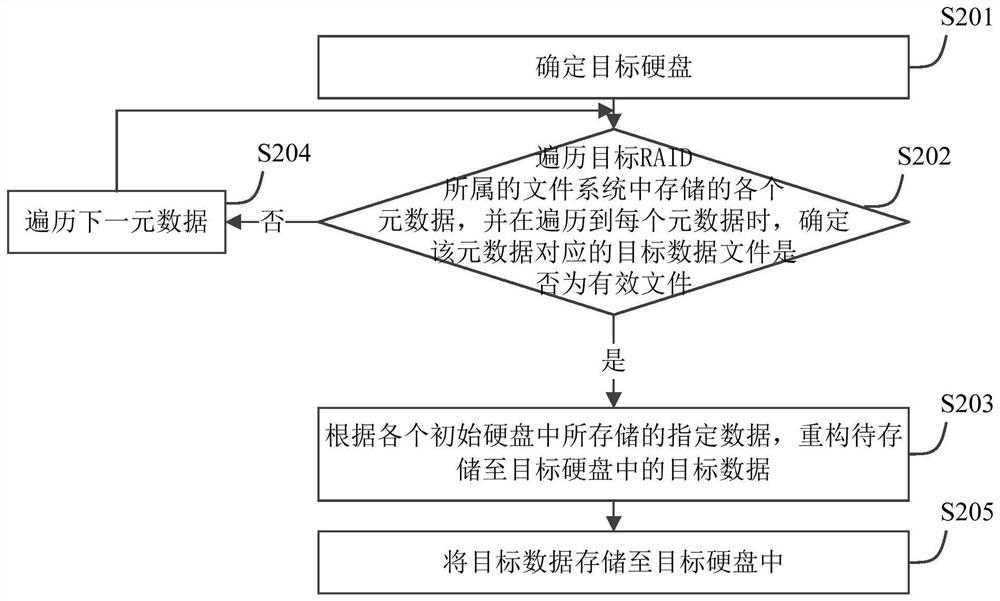
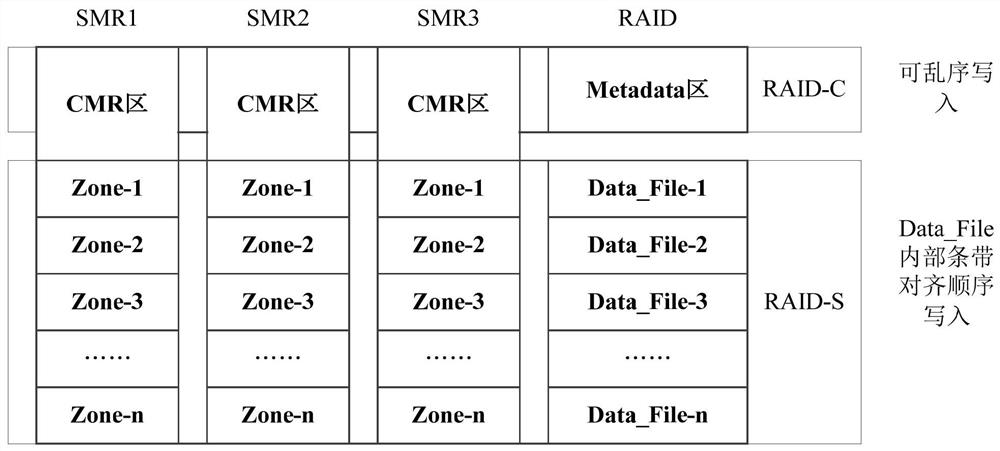
PendingCN113419686AAvoid refactoringFast and efficient refactoringInput/output to record carriersRAIDFile system
The embodiment of the invention provides an RAID reconstruction method and device, and relates to the technical field of data storage. The reconstruction method is applied to the RAID drive. The method comprises the following steps: determining a target hard disk, wherein the target hard disk is used for reconstructing a target RAID; traversing each metadata stored in a file system to which the target RAID belongs, and when each metadata is traversed, determining whether a target data file corresponding to the metadata is a valid file; if yes, reconstructing target data to be stored in the target hard disk according to specified data stored in each initial hard disk; and storing the target data into the target hard disk. Compared with the prior art, by applying the scheme provided by the embodiment of the invention, on the premise of ensuring the integrity of the data stored in the RAID and the data security of the RAID and improving the security level of the RAID, the RAID after the hard disk with the read-write exception is removed can be quickly and efficiently reconstructed.
Owner:HANGZHOU HIKVISION DIGITAL TECH
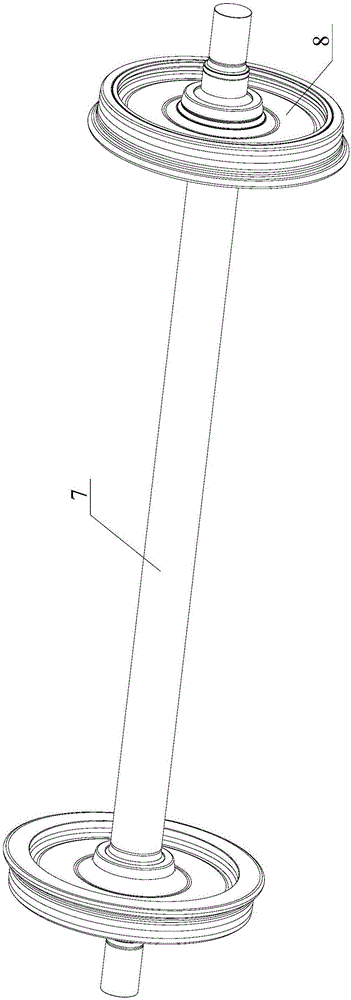
Auxiliary process shaft used for spraying paint on wheels of railway vehicles
The invention belongs to the field of auxiliary devices for spraying paint on wheels of railway vehicles and discloses an auxiliary process shaft used for spraying paint on wheels of railway vehicles. According to the auxiliary process shaft, a wheel positioning mechanism with opposite conical slopes is used for axially positioning a naked piece of a novel wheel with a noise reduction ring in a rolling mode, so that the rapid and even paint spraying procedure of the naked piece of the novel wheel is completed through an existing mature paint spraying chamber device, the tedious and complex procedures such as paint spraying protection of components like brake discs and noise reduction rings are avoided, and furthermore, reconstitution and optimization design of the technological process are achieved. In addition, the auxiliary process shaft used for spraying paint on wheels of railway vehicles has the advantages of being simple and practical in structure, convenient to assemble and disassemble, low in cost, convenient to popularize and the like.
Owner:CRRC CHANGCHUN RAILWAY VEHICLES CO LTD
Method and device for compressing video-packet coded video data
InactiveCN1606881ALittle deterioration in qualityReduce the degree of deteriorationCode conversionTelevision systemsAlgorithmTheoretical computer science
Owner:INTERDIGITAL CE PATENT HLDG
SAR (synthetic aperture radar) target identification method based on nuclear sparse representation
InactiveCN102122355BAvoid refactoringImprove fault toleranceCharacter and pattern recognitionTest sampleAlgorithm
Owner:XIDIAN UNIV
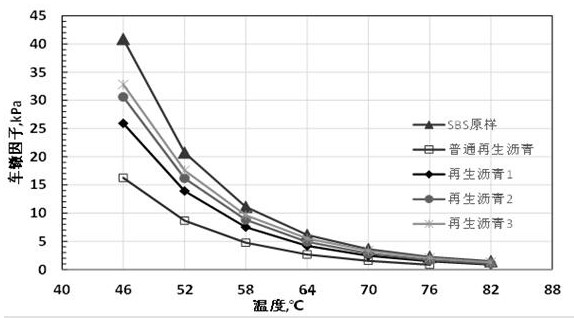
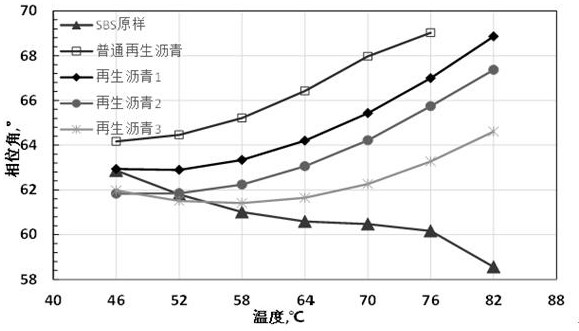
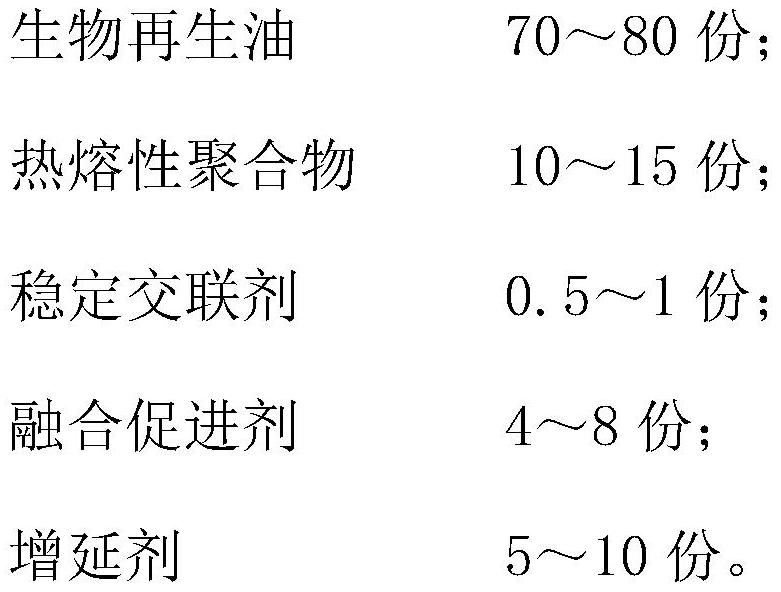
Stable modified asphalt regenerant based on epoxy bio-oil and preparation method of stable modified asphalt regenerant
PendingCN112063189AImprove viscoelastic propertiesImprove low temperature and fatigue performanceBuilding insulationsProcess engineeringAsphalt
The invention discloses a stable modified asphalt regenerant based on epoxy bio-oil and a preparation method of the stable modified asphalt regenerant. The stable modified asphalt regenerant is mainlyprepared by oxidizing, heating, stirring and mixing 70-80 parts of bio-reclaimed oil, 10-15 parts of a hot melt polymer, 0.5-1 part of a stable cross-linking agent, 4-8 parts of a fusion promoter and5-10 parts of a ductility improver. The stable modified asphalt regenerant has the advantages of economy, environmental friendliness, good regeneration effect, capability of effectively ensuring stable performance of the regenerated asphalt mixture and the like.
Owner:江苏宝利路面材料技术有限公司 +1
GR reinforced magnesium alloy-based composite material wire and preparation method
The invention discloses a GR reinforced magnesium alloy-based composite material wire. The GR reinforced magnesium alloy-based composite material wire comprises the following raw materials in percentage by weight: 0.5-1.5% of GR powder and the balance magnesium alloy powder, and the sum of the weight percentages of the components is 100%. The problems of multiple stratification and burning loss ofGR are avoided, the problem of the interface between single-layer graphene GR and magnesium alloy grains is solved, the reinforcing effect of the GR on a matrix is fully exerted, and interface microcracks are avoided. The invention also provides a preparation method of the composite material wire. The method comprises the following steps: 1, high-energy ball milling; and 2, extrusion forming, specifically, extrusion forming is carried out on the GR powder and the magnesium alloy powder subjected to ball milling in the step 1 in two steps, firstly reciprocating extrusion is carried out, and then normal forward extrusion is carried out, so that the graphene-reinforced magnesium alloy-based composite material wire is prepared.
Owner:西安诺高镁新材料科技有限公司
Soft tissue deformation simulation method based on coupling of mesh-free Galerkin and mass spring
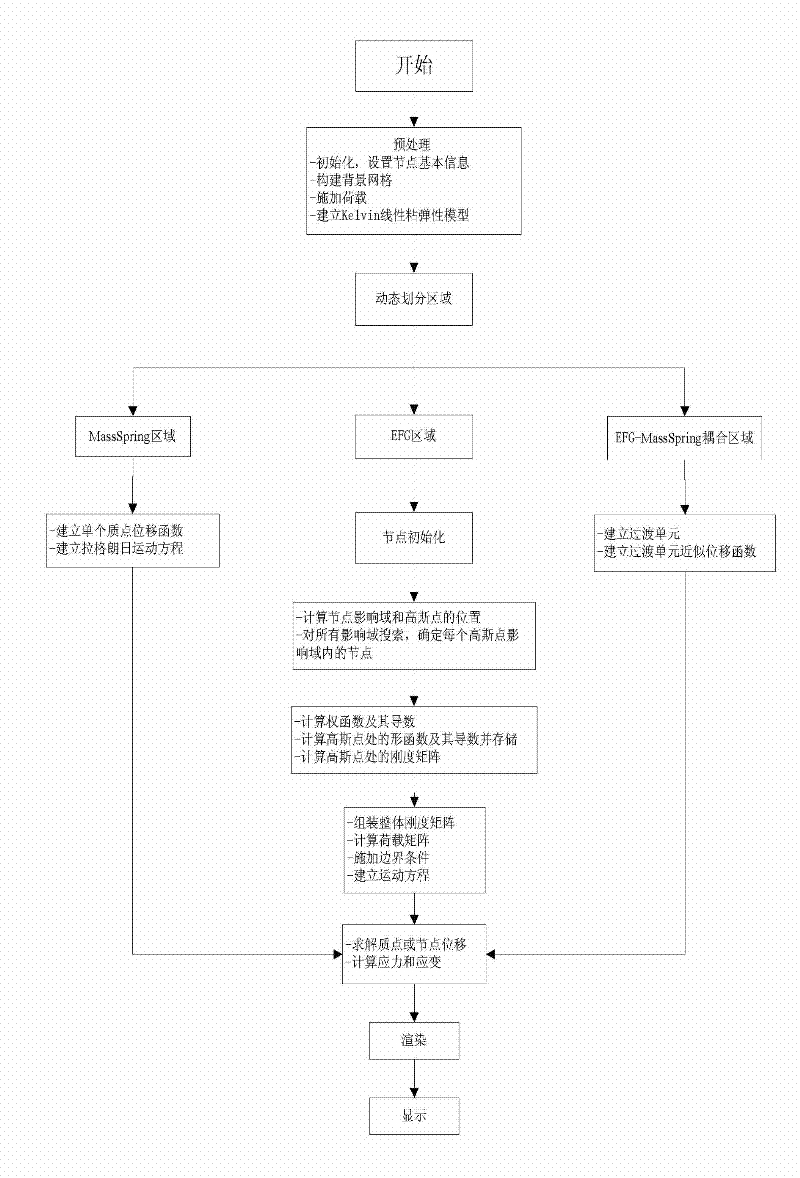
InactiveCN102262699BImprove continuityImprove stabilitySpecial data processing applicationsComputation complexitySoft tissue deformation
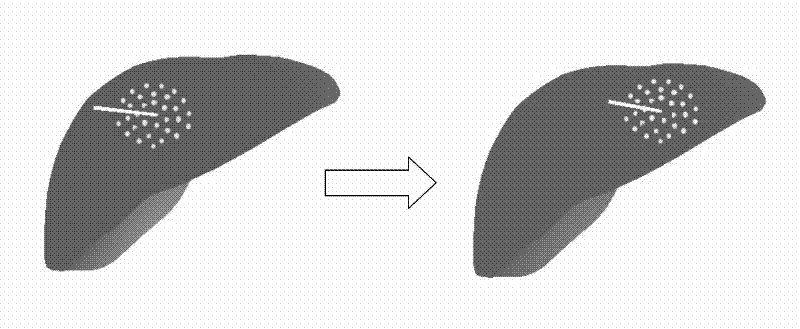
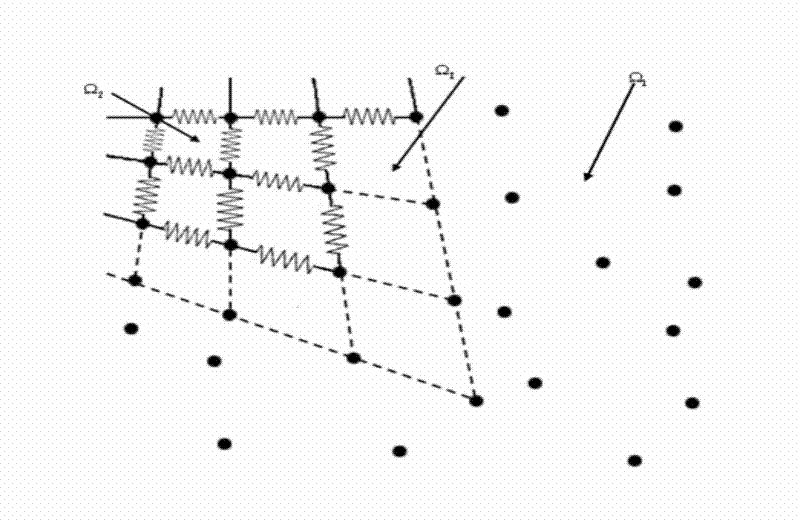
The invention relates to an object deformation real-time simulation graphic processing technique, particularly a soft tissue deformation simulation method based on coupling of mesh-free Galerkin and mass spring, which comprises the following steps: in the pretreatment process, establishing a linear viscoelasticity biomechanical model for soft tissues; in the deformation computation process, dynamically partitioning a mesh-free region and a mass spring region according to the load carried by the soft tissues, establishing a transitional unit of the connection region between the mesh-free region and mass spring region, and constructing a transitional unit approximation displacement function, thereby implementing self-adapting coupling of a mesh-free Galerkin method and a mass spring method;and in the after-treatment process, outputting the state of the mass or node of each time step in the deformation process onto a screen, carrying out illumination rendering, and finally displaying the real-time deformation process of the soft tissue organ under stressed conditions on the screen, thereby implementing visualization effect of dynamic deformation. By utilizing the advantage of high efficiency in the mass spring method and the advantages of high precision and no need of mesh reconstruction in the mesh-free Galerkin method, the invention overcomes the defect that the Galerkin method is not suitable for solving a large-scale problem, thereby effectively lowering the complexity of computation in the soft tissue deformation simulation and enhancing the operation efficiency.
Owner:NORTH CHINA UNIV OF WATER RESOURCES & ELECTRIC POWER
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com