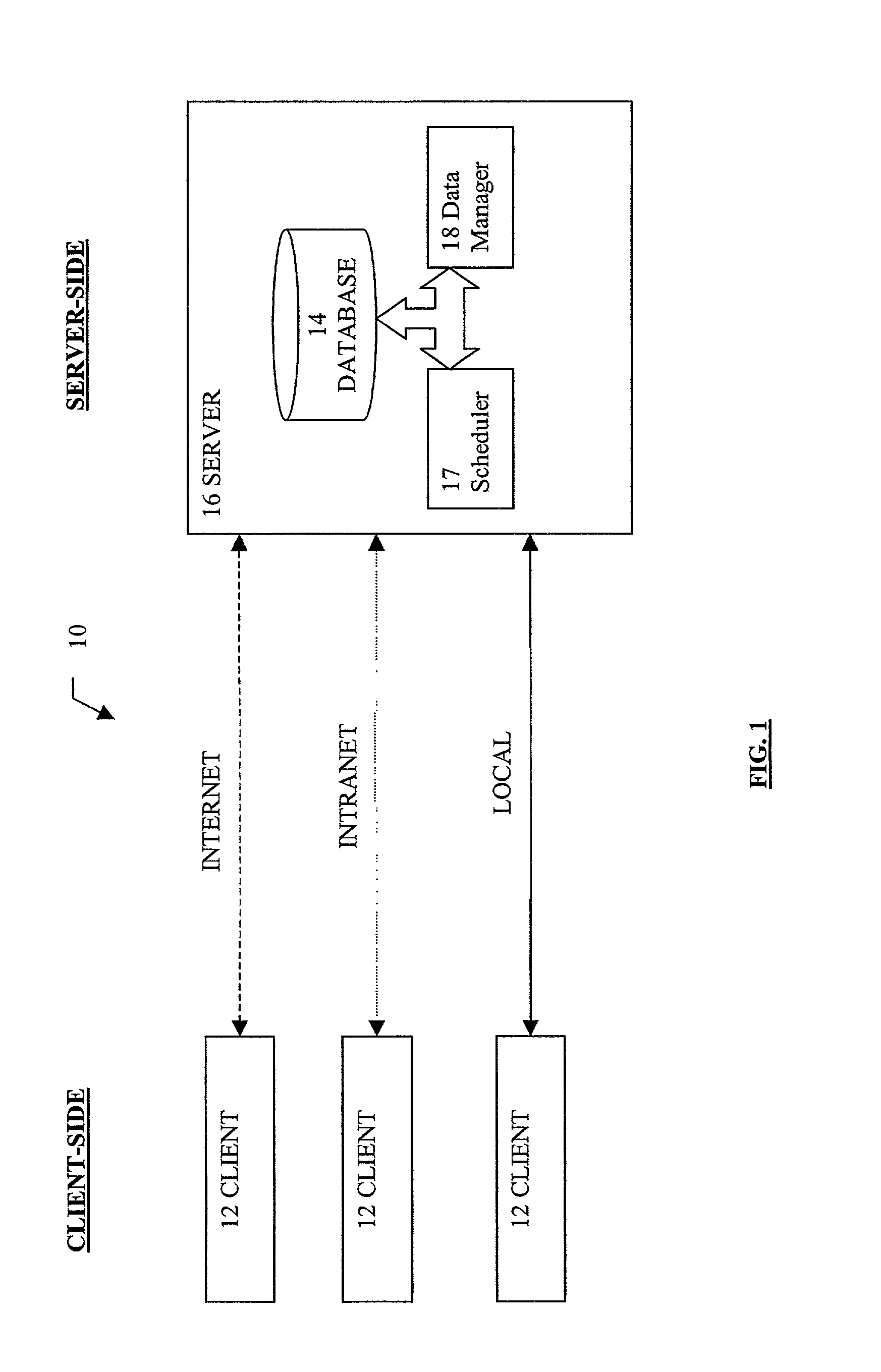
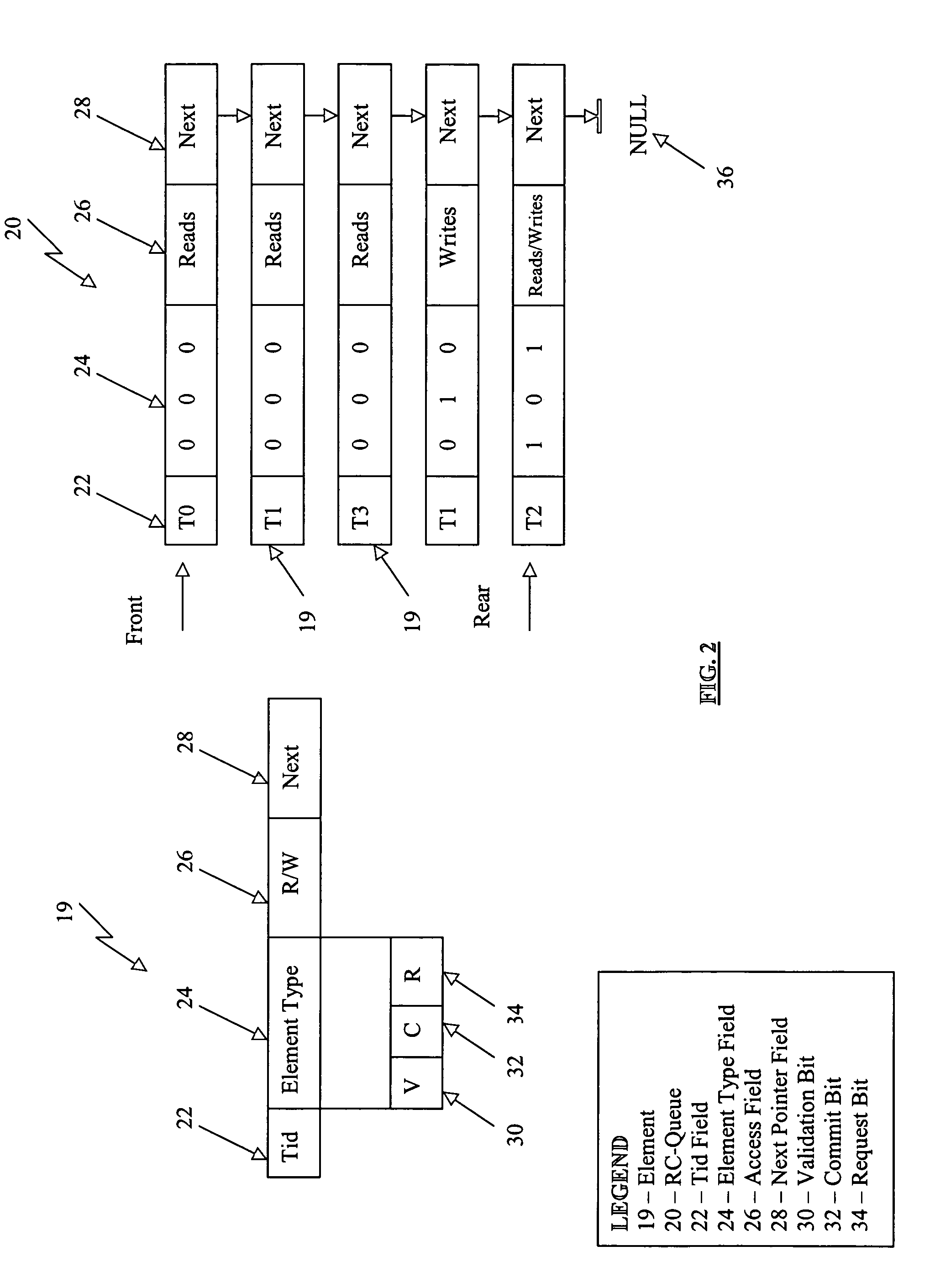
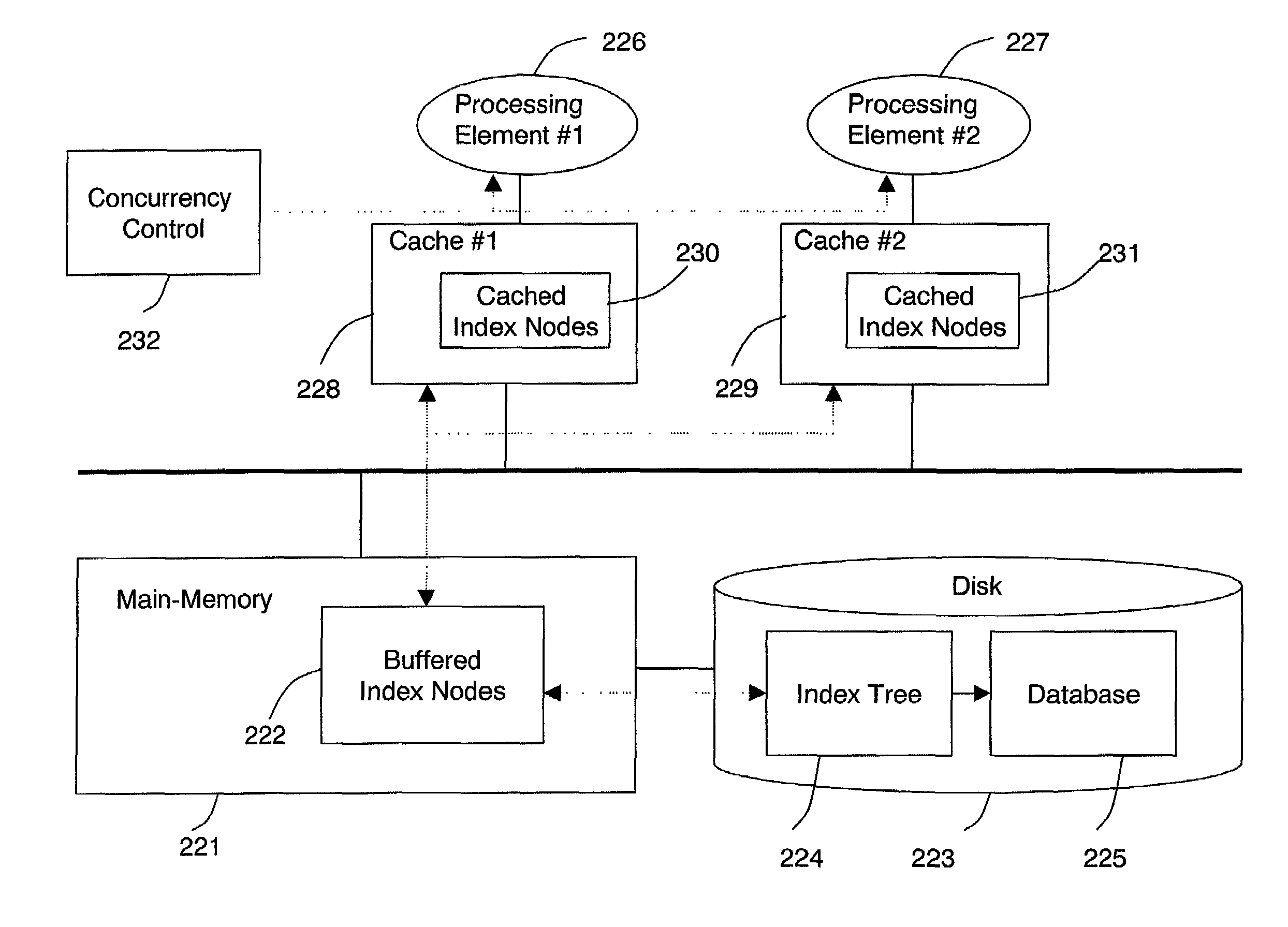
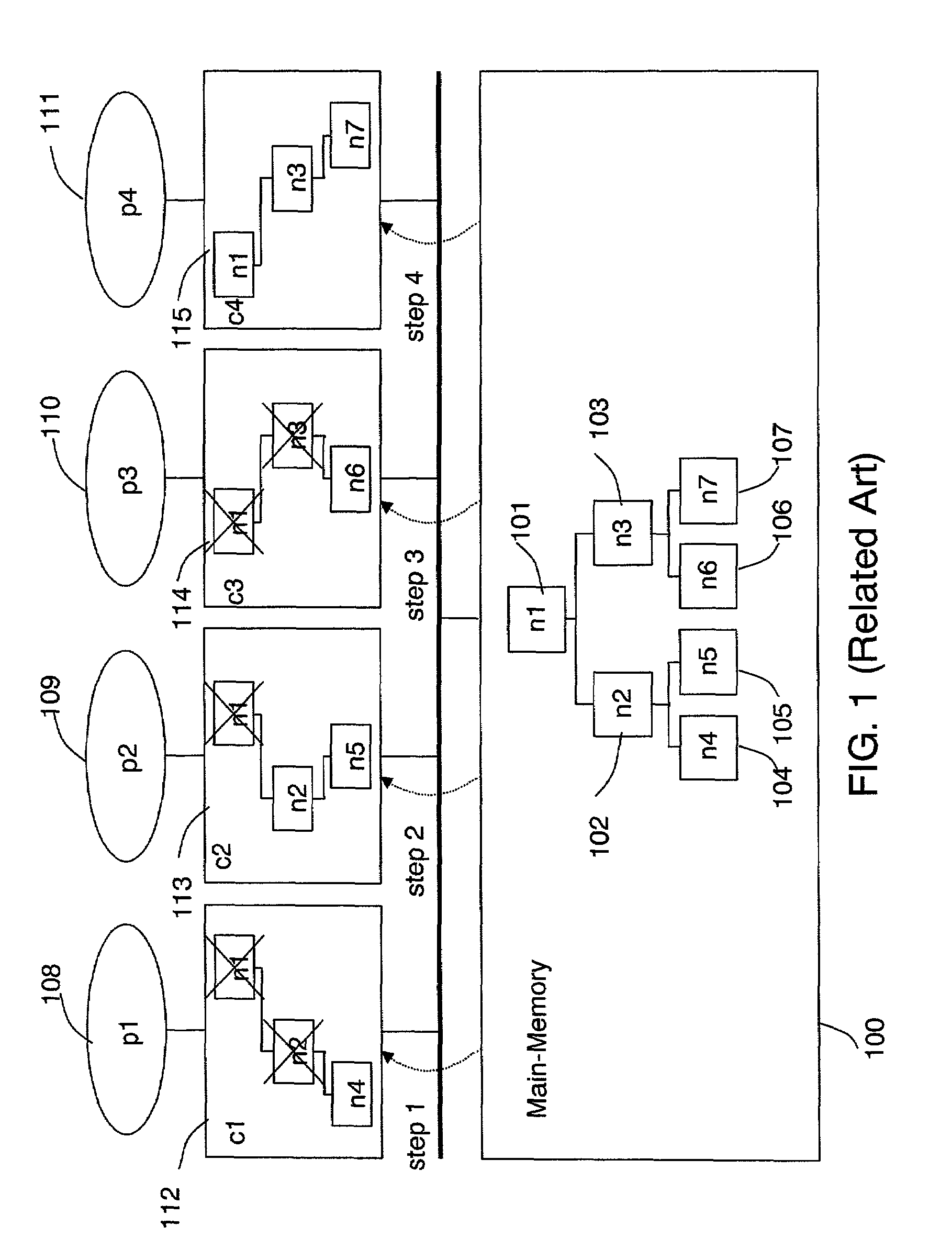
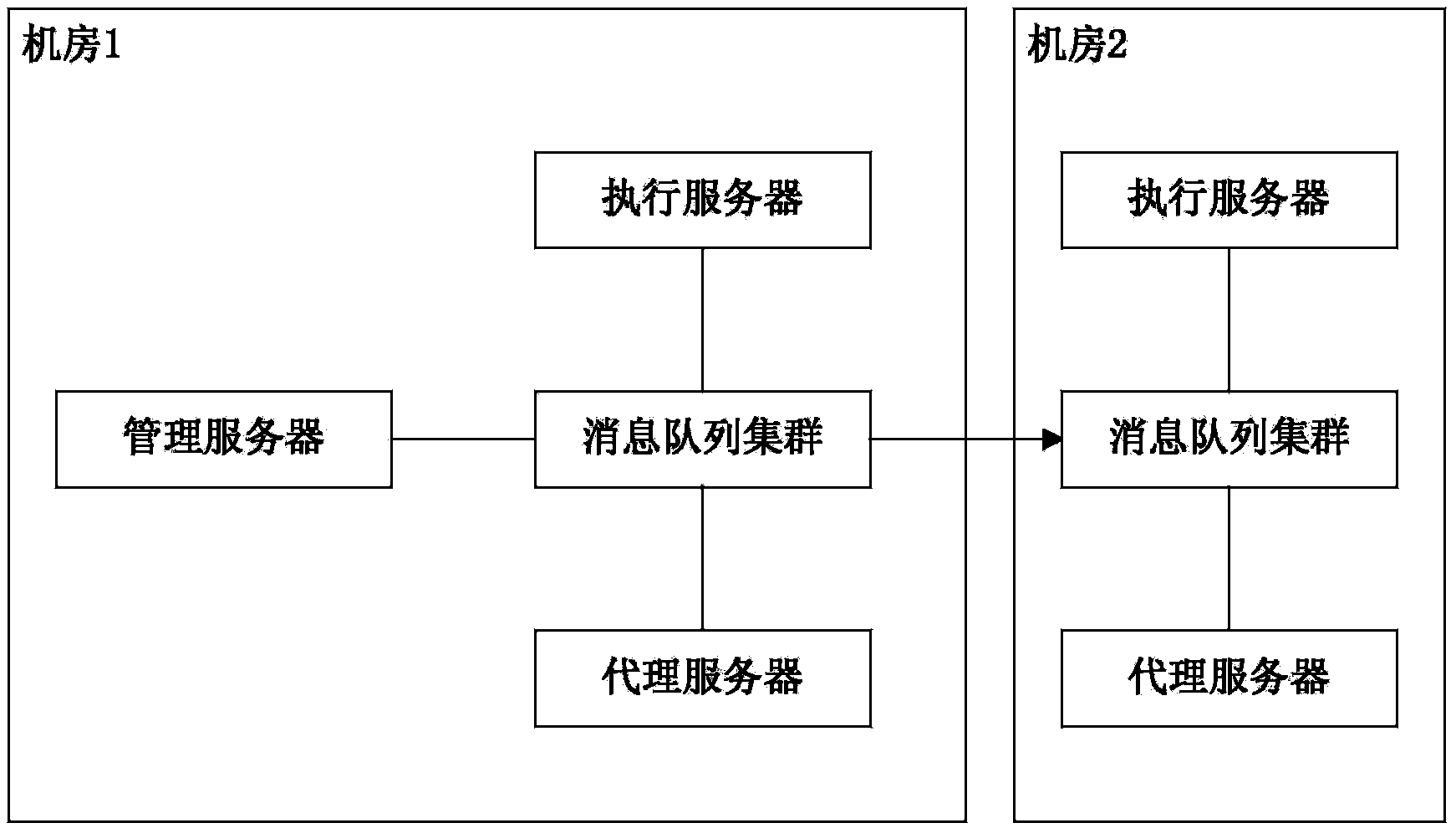
Patents
Literature
335 results about "Concurrency control" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
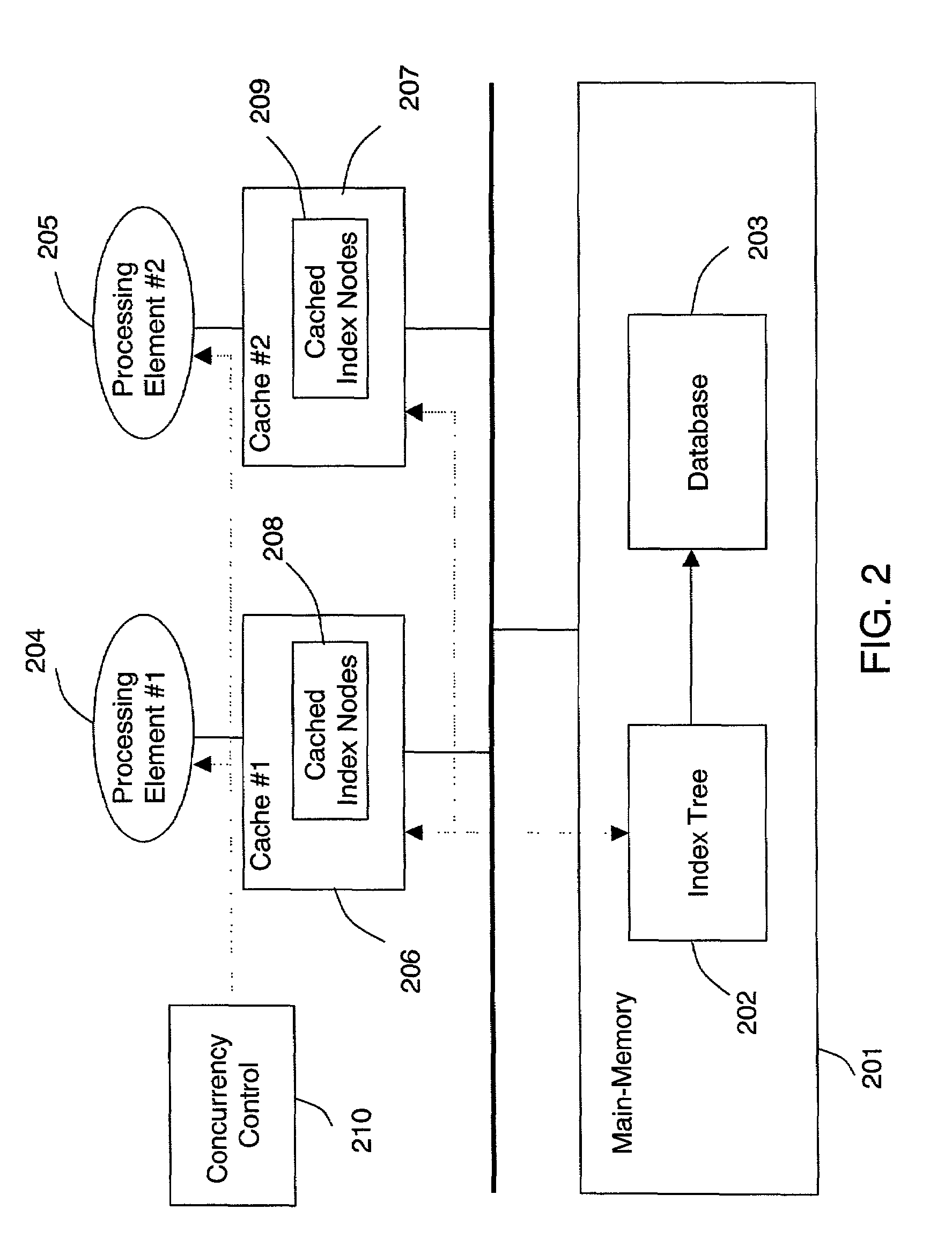
In information technology and computer science, especially in the fields of computer programming, operating systems, multiprocessors, and databases, concurrency control ensures that correct results for concurrent operations are generated, while getting those results as quickly as possible.
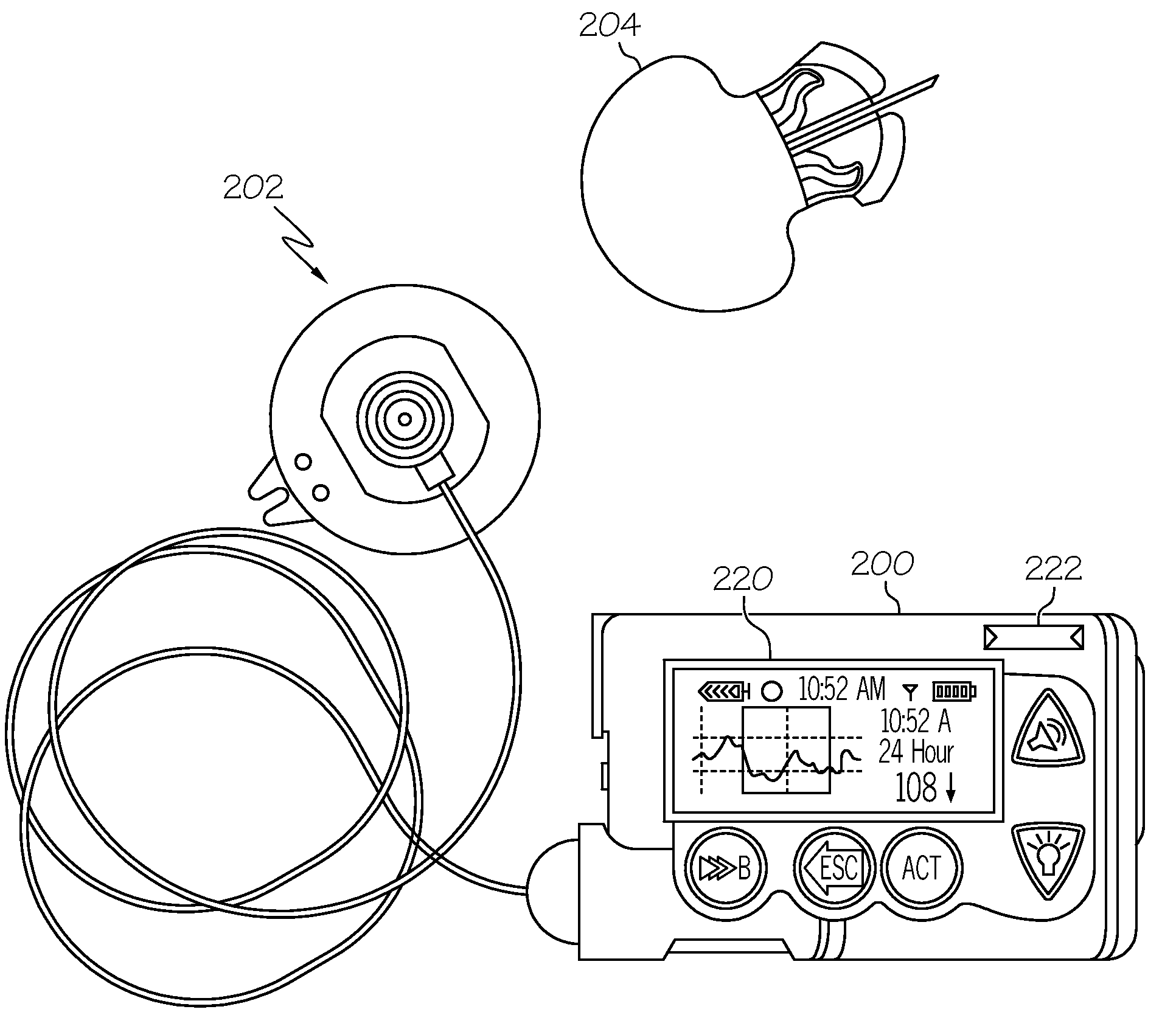
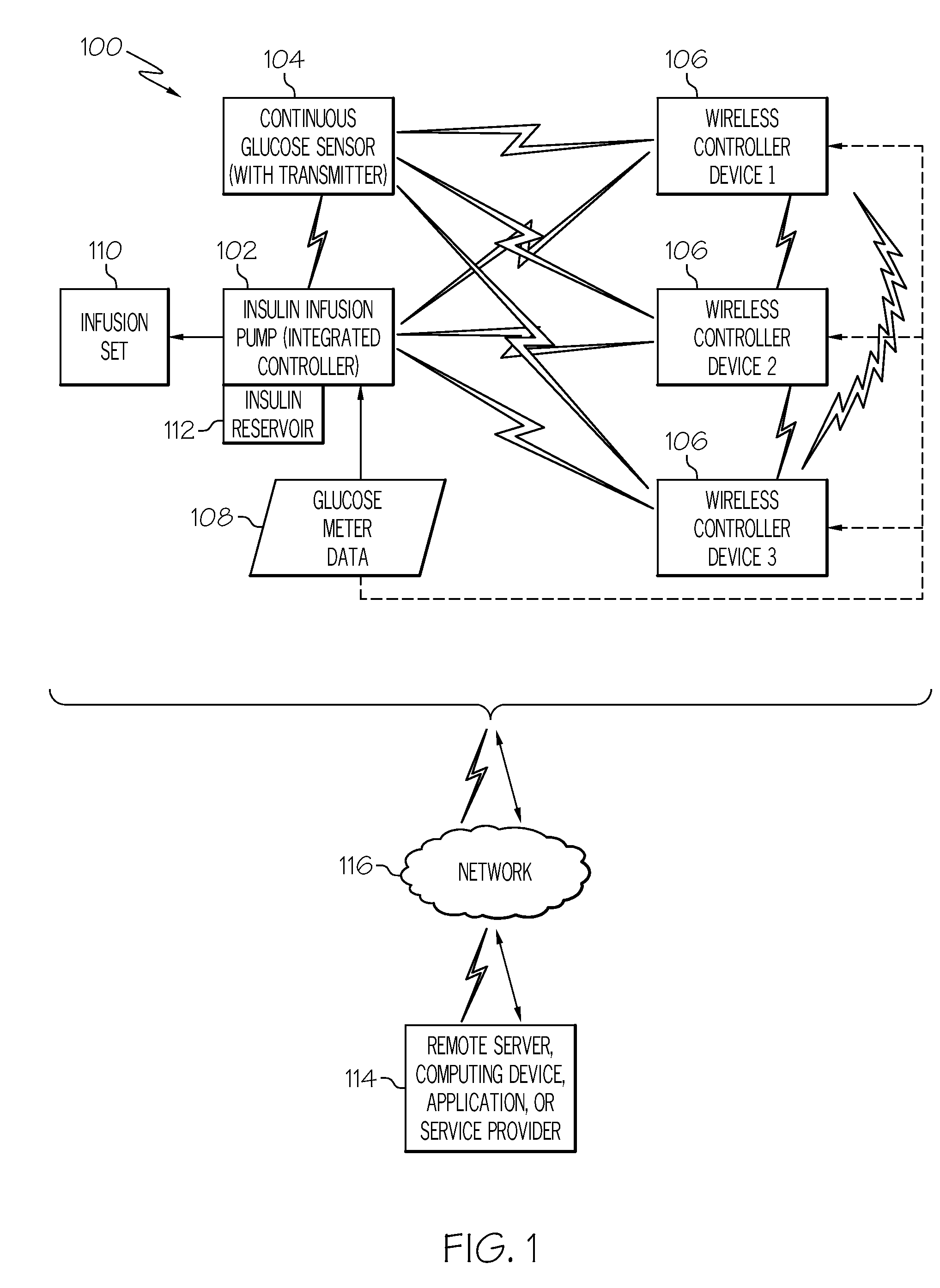
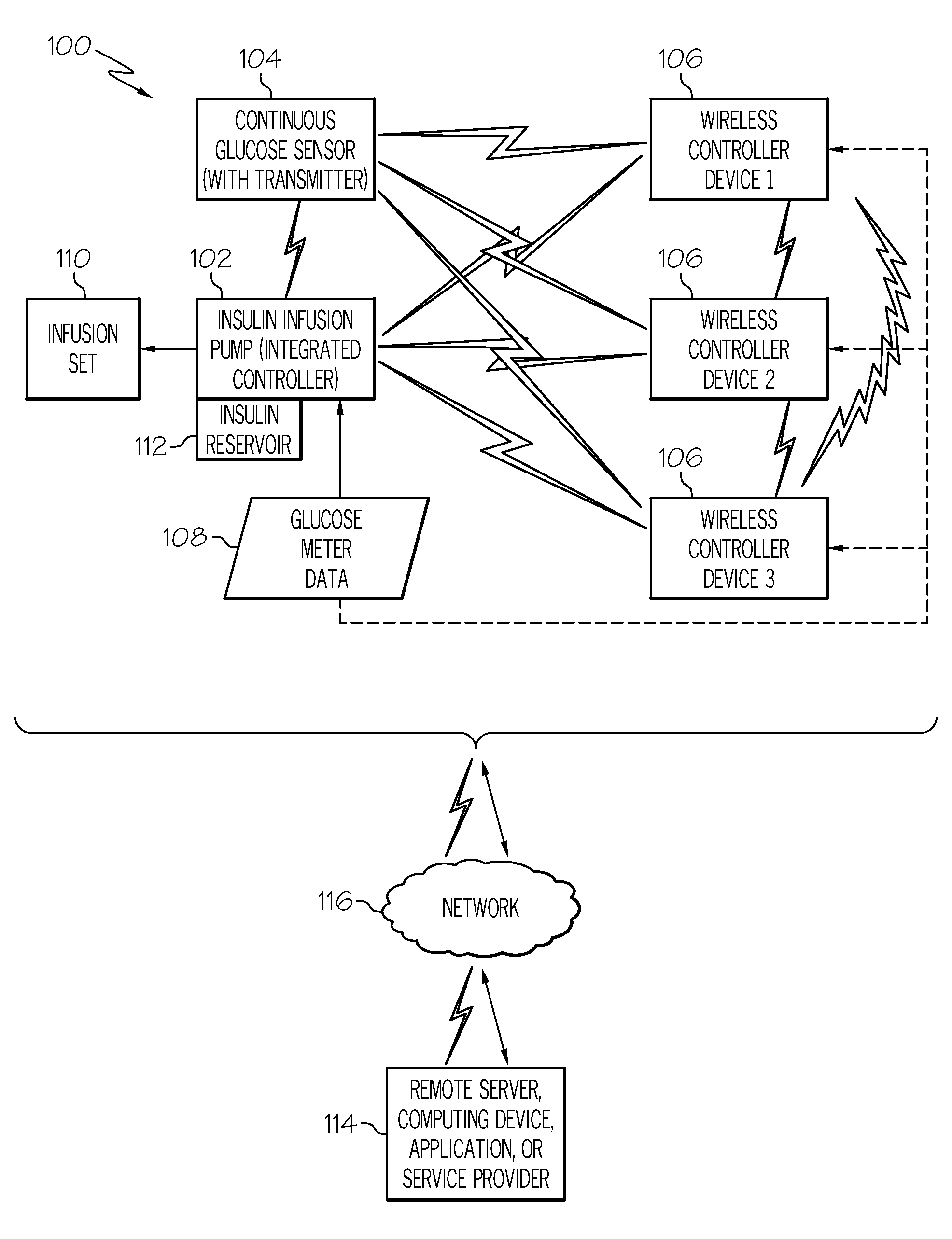
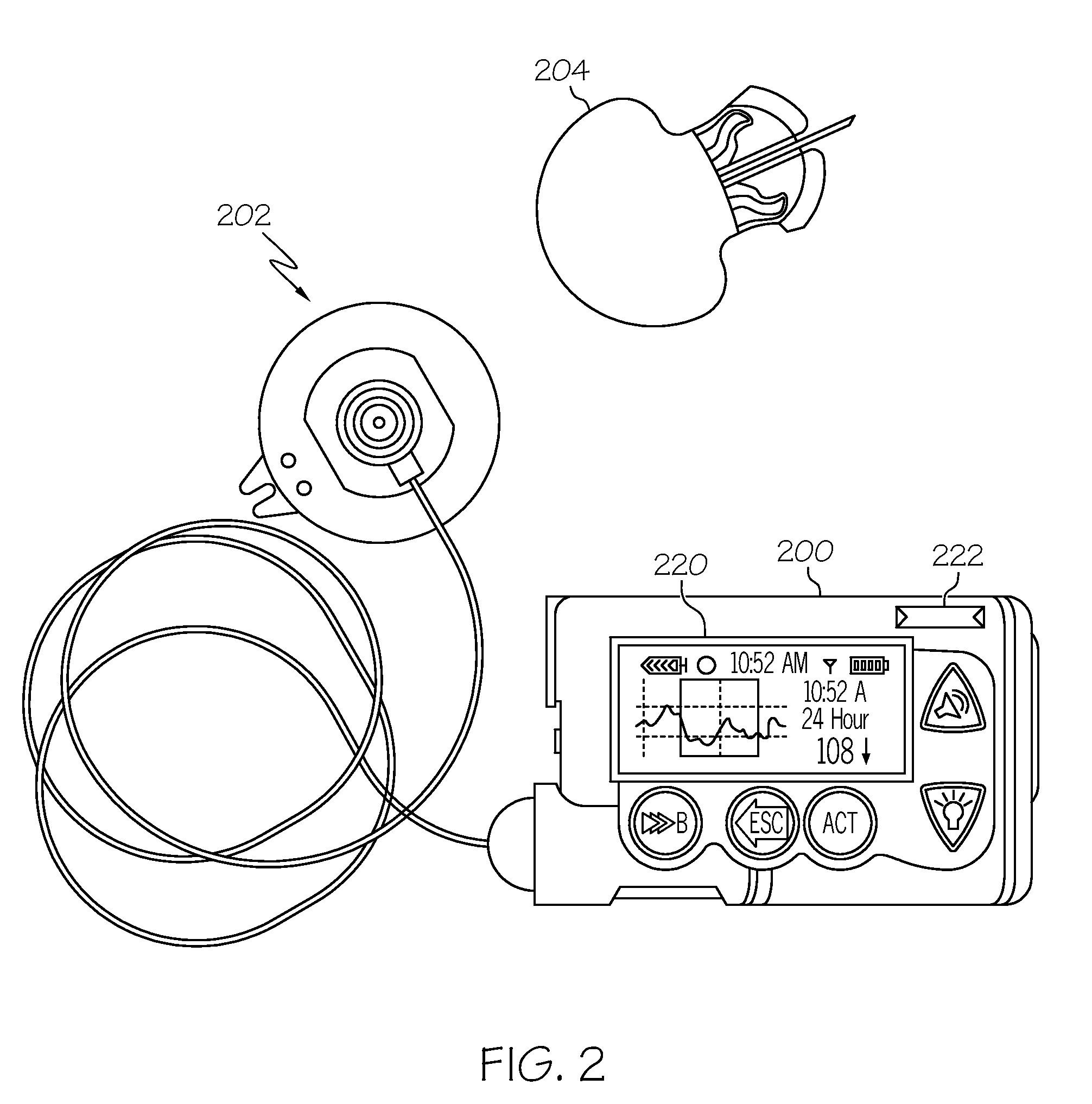
Coordination of control commands in a medical device system having at least one therapy delivery device and at least one wireless controller device
ActiveUS20110006876A1ElectrotherapyMechanical/radiation/invasive therapiesConcurrency controlEngineering
A medical device system includes at least one controllable patient-worn or patient-carried medical device, and a plurality of controller devices that are capable of independently controlling features or functions of the patient medical device. Control commands and other data is wirelessly communicated among the patient medical device and the multiple controller devices. A number of techniques, protocols, and other measures are provided to coordinate wireless communication between the various devices in a medical device system. These control command coordination processes address situations where conflicting, redundant, or concurrent control commands might be independently issued by the multiple controller devices.
Owner:MEDTRONIC MIMIMED INC
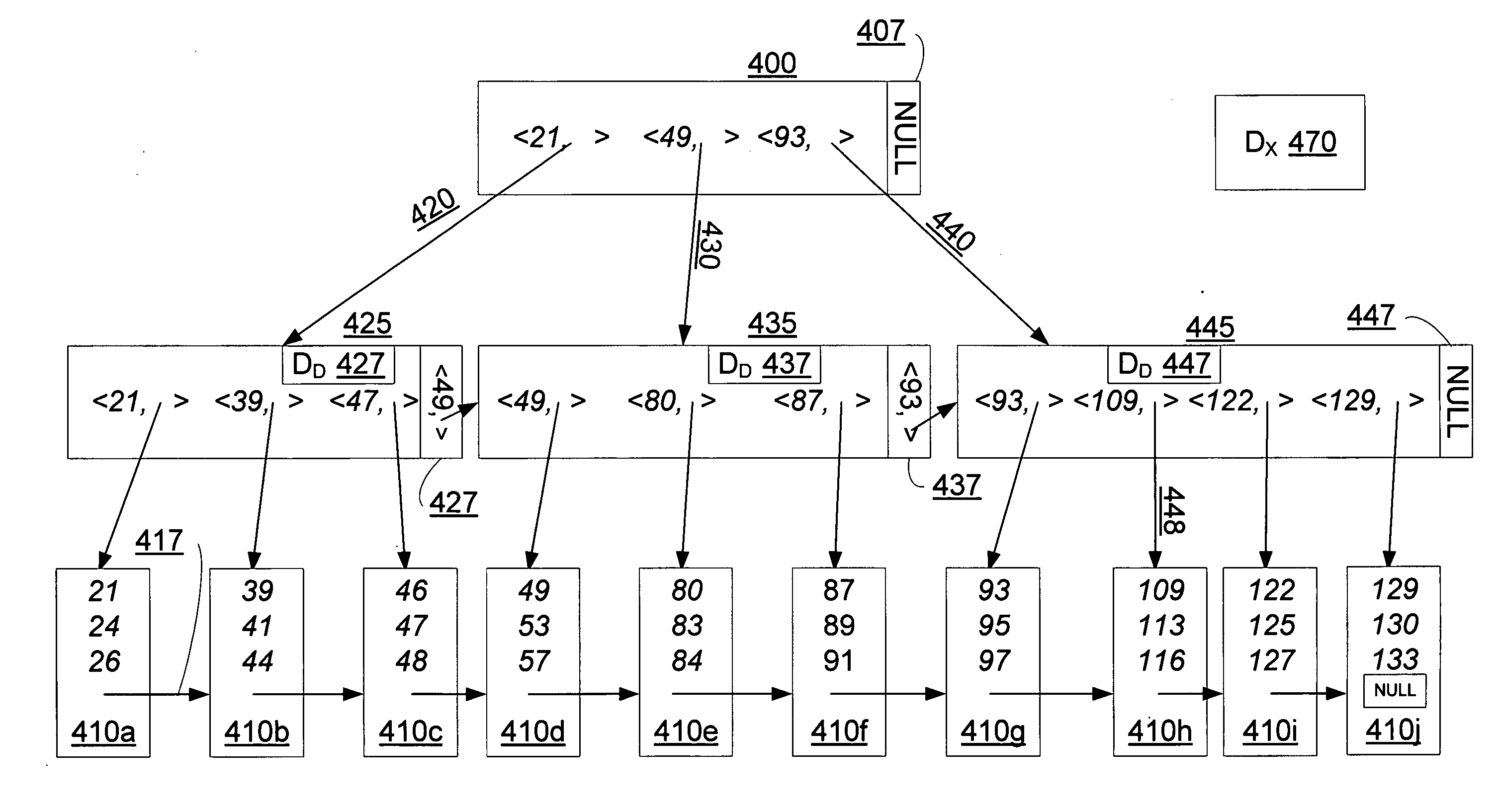
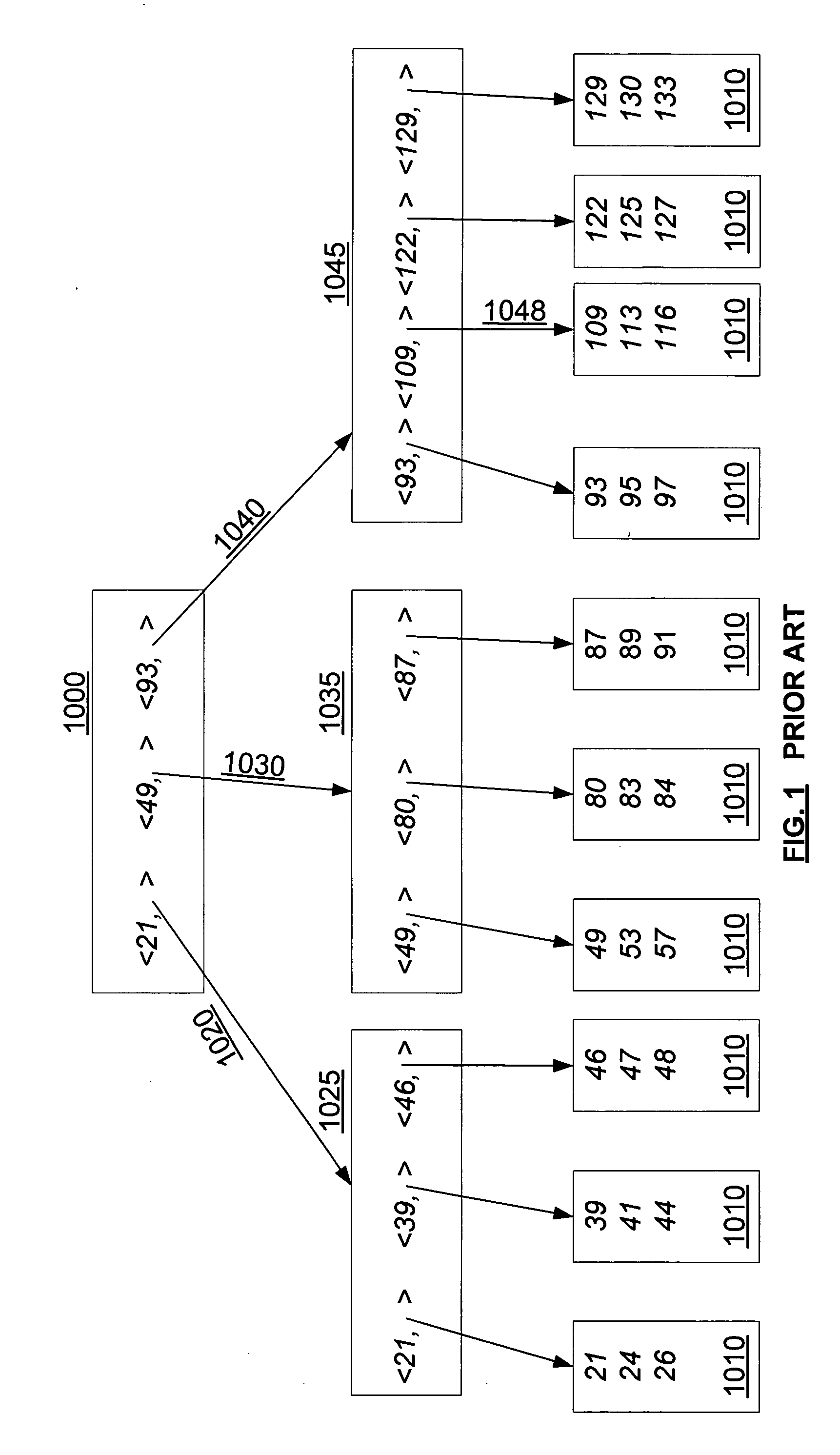
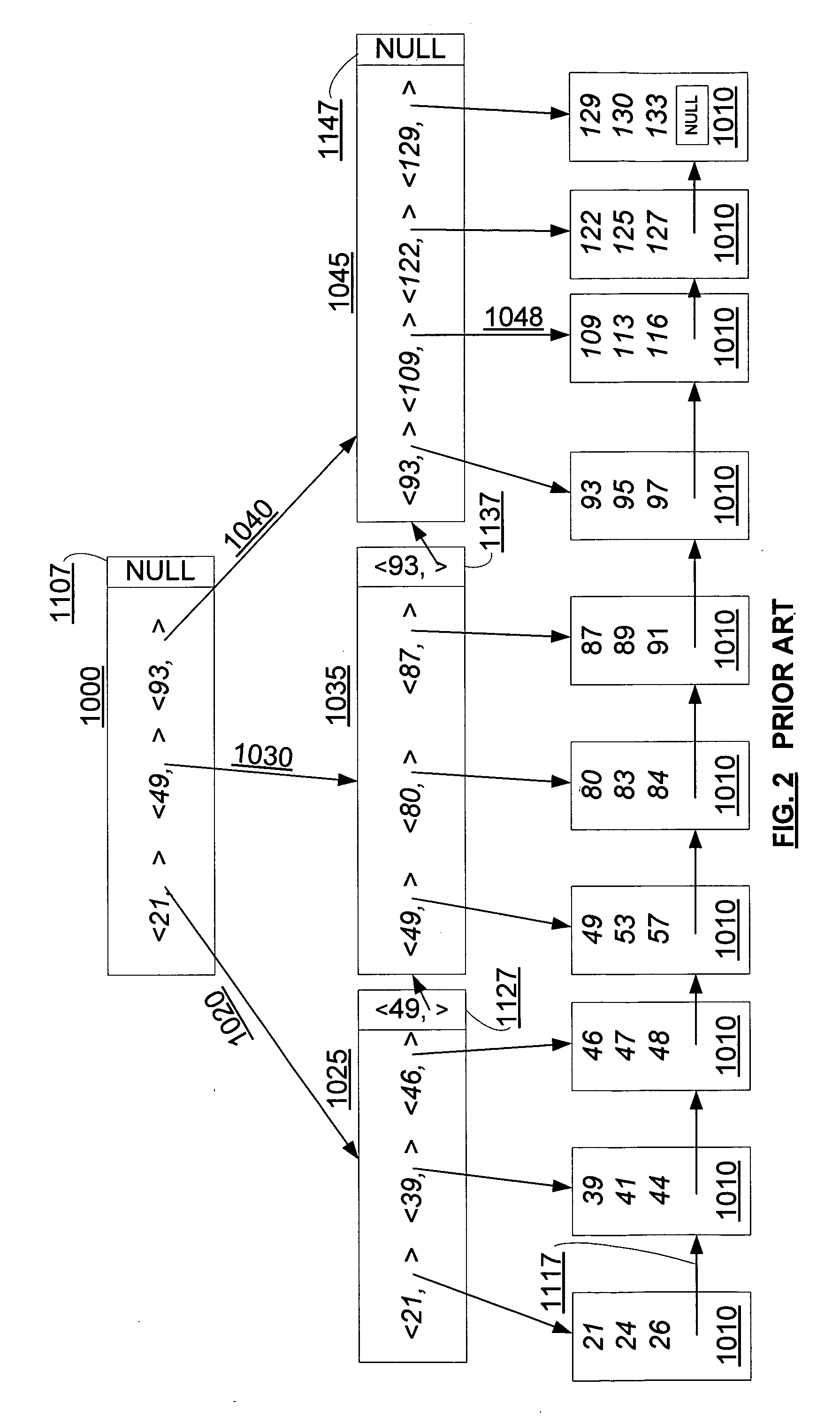
Concurrency control for B-trees with node deletion
InactiveUS20050171960A1Highly concurrent access of dataEasy to solveData processing applicationsDigital data information retrievalConcurrency controlTree (data structure)
A data structure, added to a modified form of the Blink-tree data structure, tracks delete states for nodes. The index delete state (DX) indicates whether it is safe to directly access an index node without re-traversing the B-tree. The DX state is maintained globally, outside of the tree structure. The data delete state (DD) indicates whether it is safe to post an index term for a new leaf node. A DD state is maintained in each level 1 node for its leaf nodes. Delete states indicate whether a specific node has not been deleted, or whether it may have been deleted. Delete states are used to remove the necessity for atomic node splits and chains of latches for deletes, while not requiring retraversal. This property of not requiring a retraversal is exploited to simplify the tree modification operations.
Owner:MICROSOFT TECH LICENSING LLC
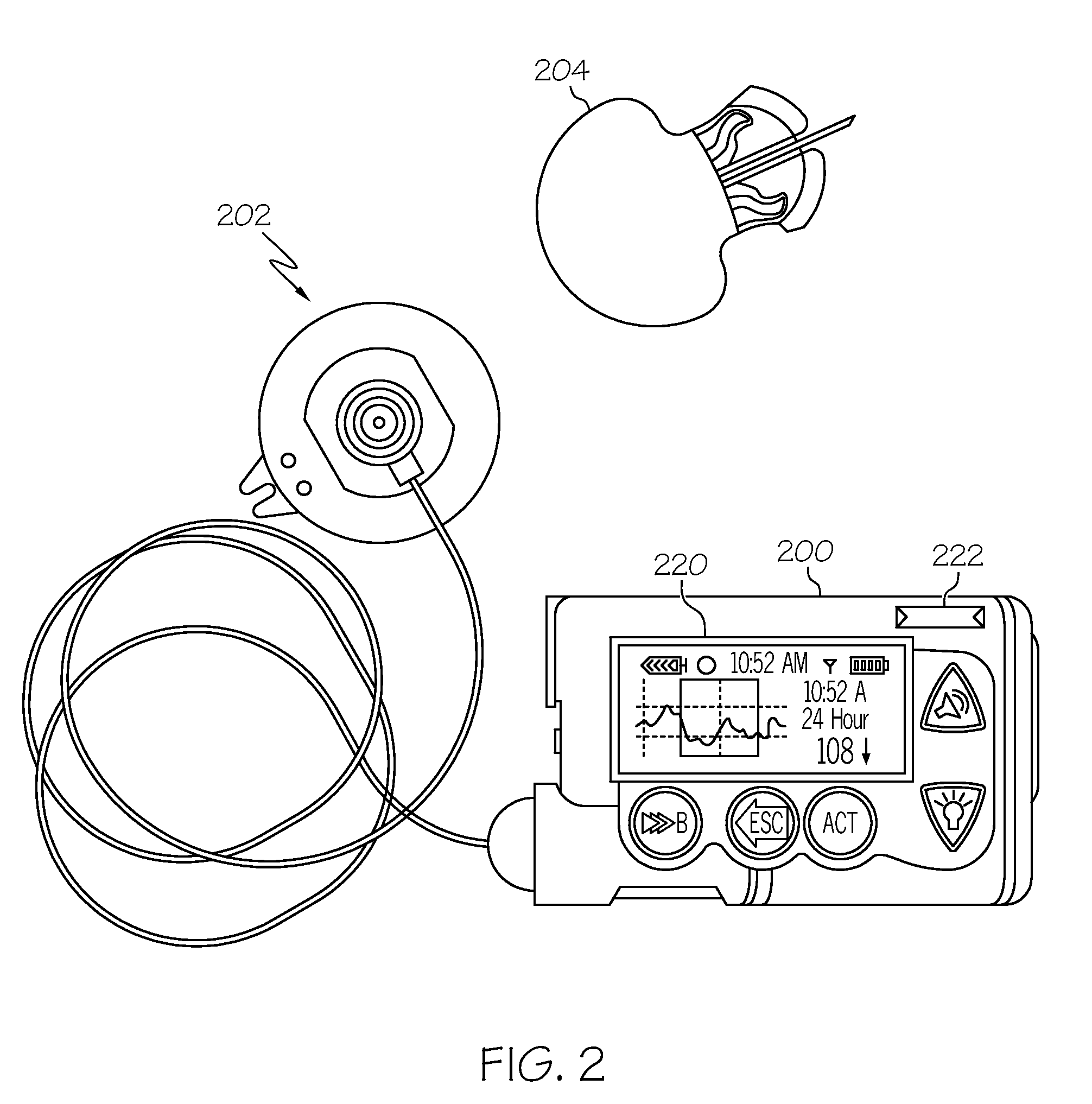
Coordination of control commands in a medical device system having at least one therapy delivery device and at least one wireless controller device
ActiveUS8344847B2Convenient treatmentElectrotherapyMechanical/radiation/invasive therapiesWireless controlConcurrency control
A medical device system includes at least one controllable patient-worn or patient-carried medical device, and a plurality of controller devices that are capable of independently controlling features or functions of the patient medical device. Control commands and other data is wirelessly communicated among the patient medical device and the multiple controller devices. A number of techniques, protocols, and other measures are provided to coordinate wireless communication between the various devices in a medical device system. These control command coordination processes address situations where conflicting, redundant, or concurrent control commands might be independently issued by the multiple controller devices.
Owner:MEDTRONIC MIMIMED INC
Dual access to concurrent data in a database management system
ActiveUS20090070330A1Digital data information retrievalDigital data processing detailsConcurrency controlRelational database management system
Various embodiments include one or more of systems, methods, software, and data structures that allow dual access to concurrent data in a database management system including uncommitted updated data. Some embodiments include a dual snapshot of data in a multi-version concurrency control style database, but the embodiments described herein are equally applicable to virtually any other type of database and database management system.
Owner:SAP AG
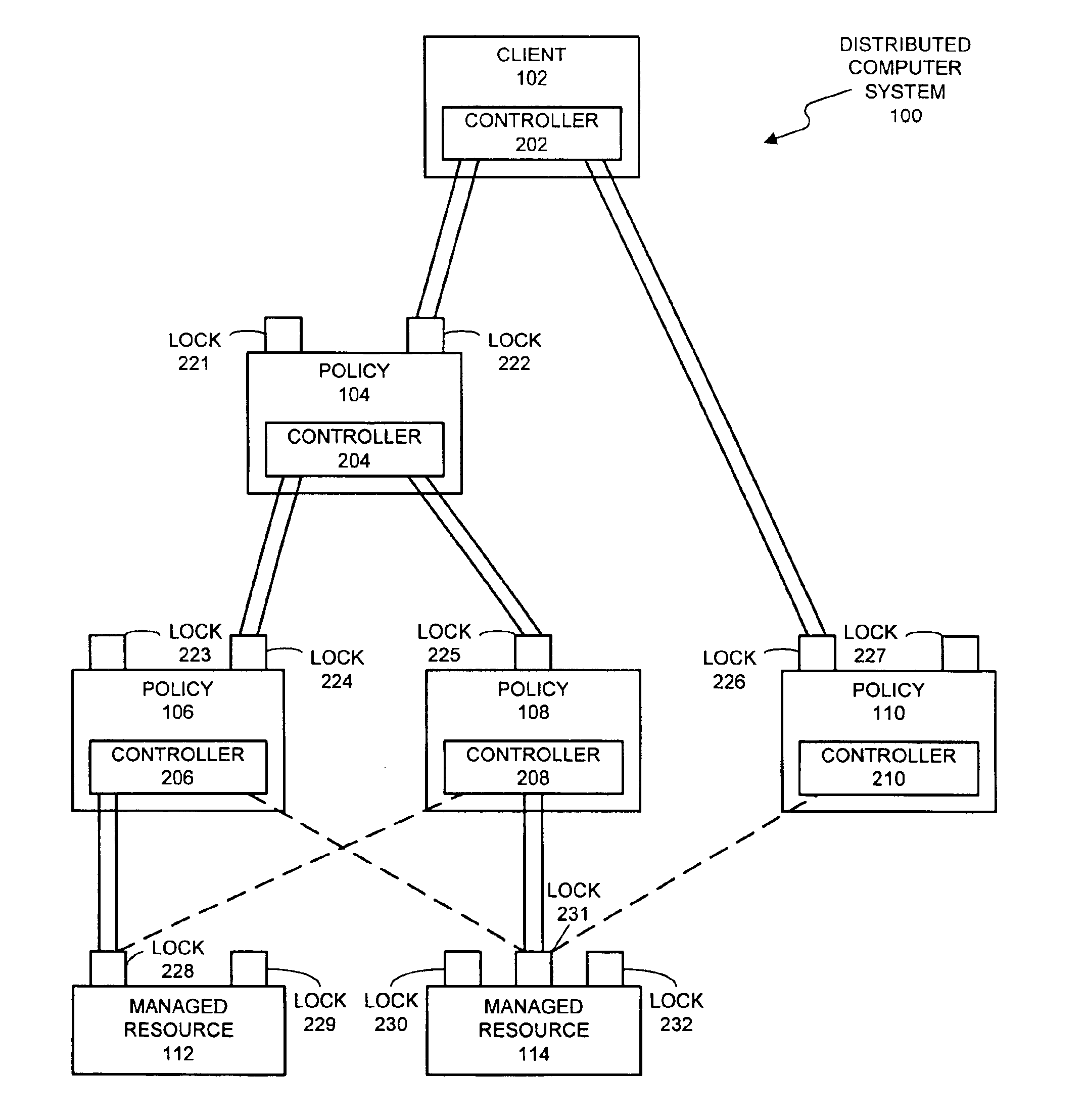
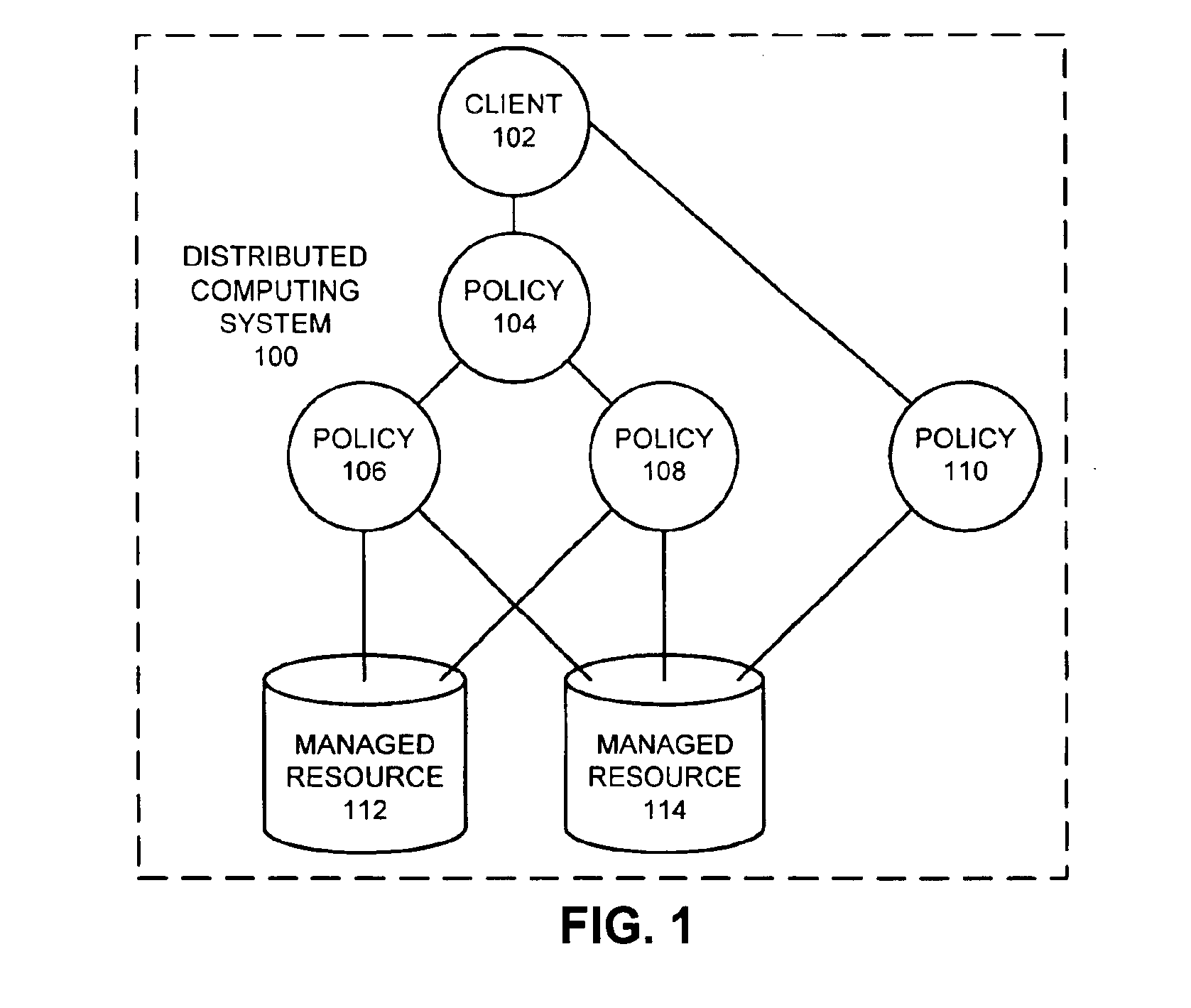
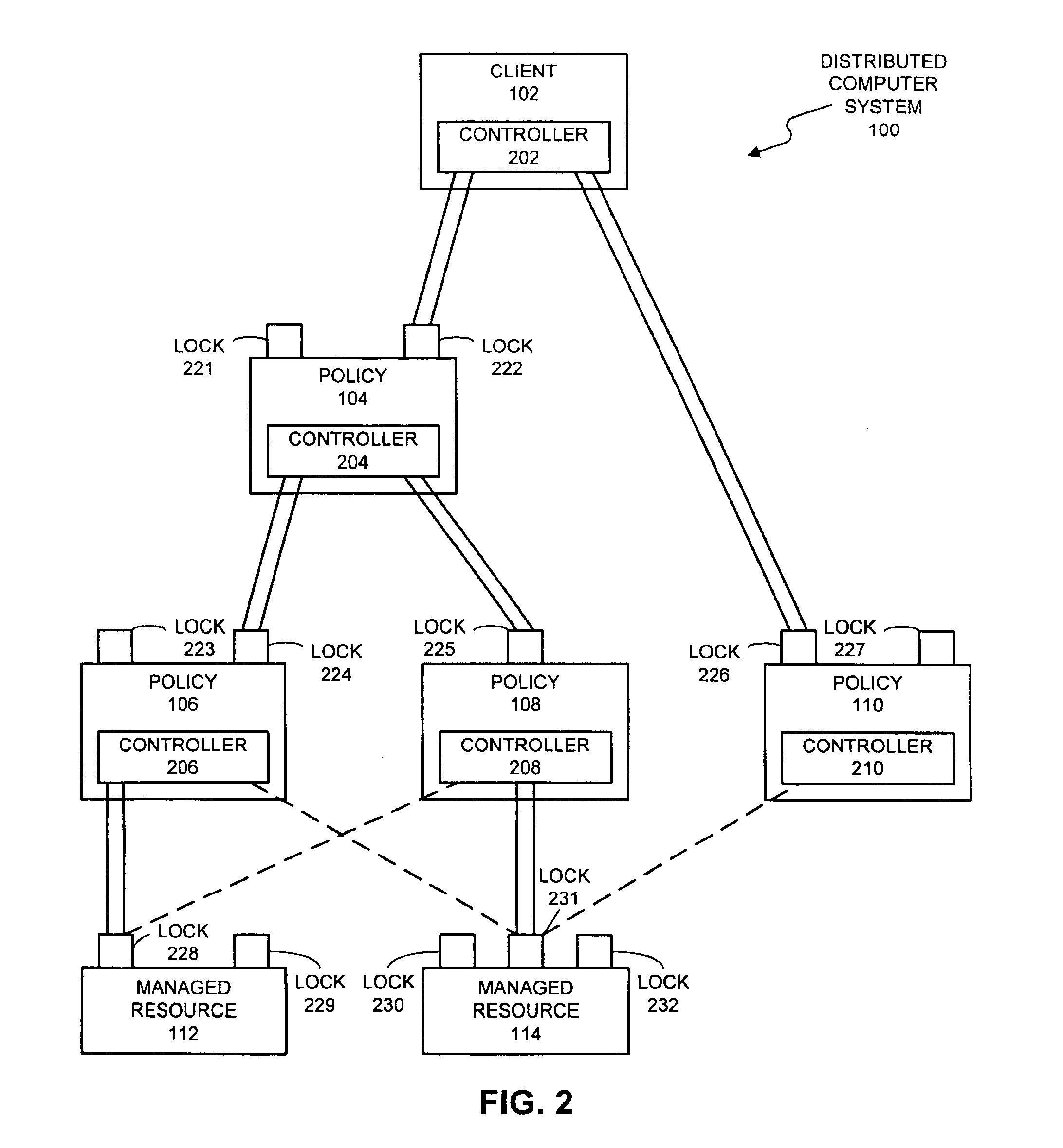
Method and apparatus for concurrency control in a policy-based management system
InactiveUS6865549B1Facilitates concurrency controlData processing applicationsProgram synchronisationConcurrency controlPolicy-based management
A system that facilitates concurrency control for a policy-based management system that controls resources in a distributed computing system. The system operates by receiving a request to perform an operation on a lockable resource from a controller in the distributed computing system. This controller sends the request in order to enforce a first policy for controlling resources in the distributed computing system. In response the request, the system determines whether the controller holds a lock on the lockable resource. If so, the system allows the controller to execute the operation on the lockable resource. If not, the system allows the controller an opportunity to acquire the lock. If the controller is able to acquire the lock, the system allows the controller to execute the operation on the lockable resource.
Owner:ORACLE INT CORP
Hierarchical locking in b-tree indexes
ActiveUS20080086470A1Easy to appreciateData processing applicationsDigital data information retrievalConcurrency controlComputer science
Portions of a B-tree index in a database are locked for concurrency control. In one example, hierarchical lock modes are provided that permit locking a key, a gap between the key and the next key, and a combination of the key and the gap. In another example, key range locking may be applied to the B-tree index using locks on separator keys of index nodes. In another example, key range locking may be applied to the B-tree index using locks on key prefixes.
Owner:MICROSOFT TECH LICENSING LLC
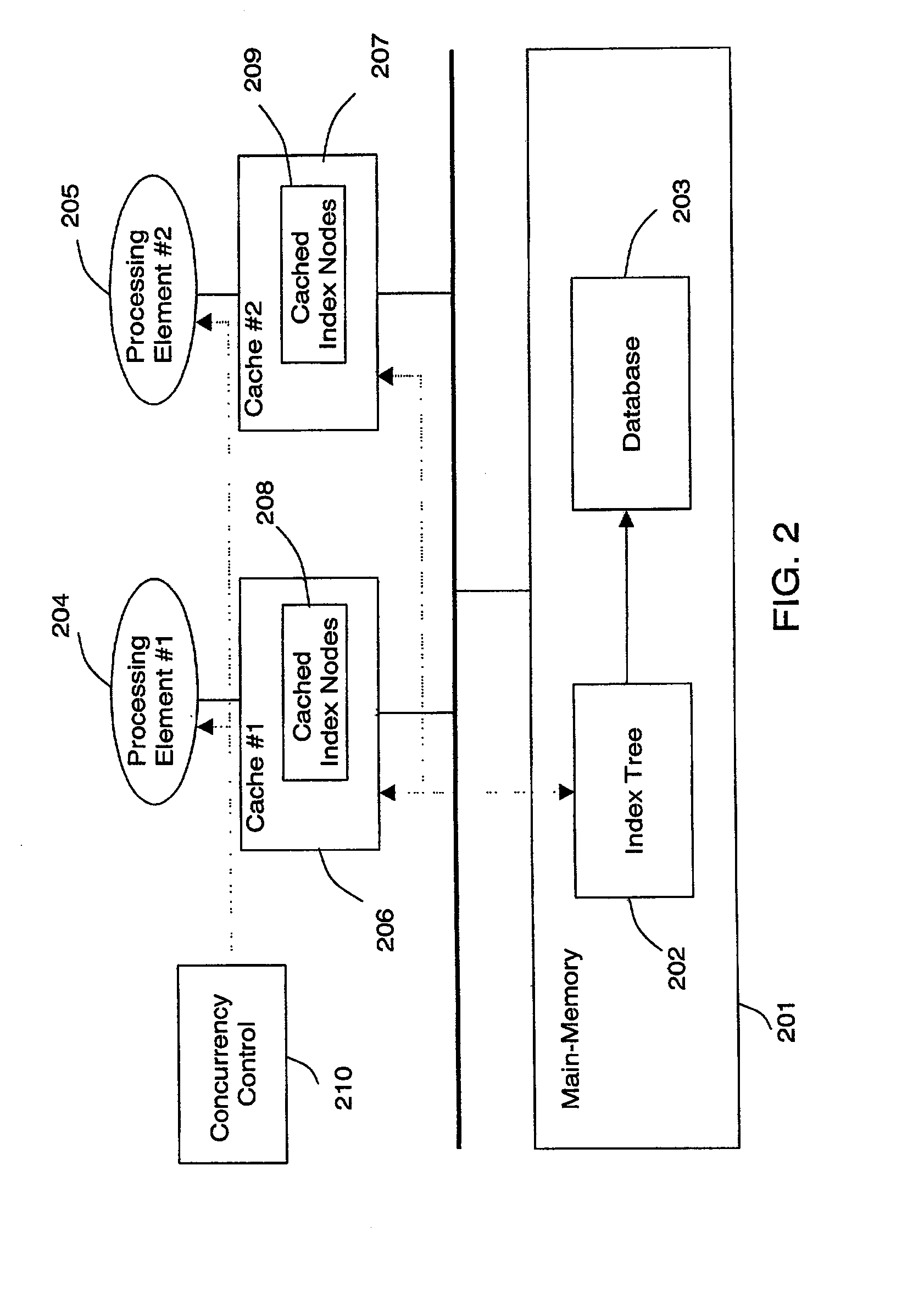
Cache-conscious concurrency control scheme for database systems
ActiveUS20080065670A1Data processing applicationsDigital data information retrievalConcurrency controlDatabase
An optimistic, latch-free index traversal (“OLFIT”) concurrency control scheme is disclosed for an index structure for managing a database system. In each node of an index tree, the OLFIT scheme maintains a latch, a version number, and a link to the next node at the same level of the index tree. Index traversal involves consistent node read operations starting from the root. To ensure the consistency of node read operations without latching, every node update operation first obtains a latch and increments the version number after update of the node contents. Every node read operation begins with reading the version number into a register and ends with verifying if the current version number is consistent with the register-stored version number. If they are the same, the read operation is consistent. Otherwise, the node read is retried until the verification succeeds. The concurrency control scheme of the present invention is applicable to many index structures such as the B+-tree and the CSB+-tree.
Owner:SAP AG
Dual access to concurrent data in a database management system
ActiveUS7930274B2Digital data information retrievalDigital data processing detailsConcurrency controlDual access
Various embodiments include one or more of systems, methods, software, and data structures that allow dual access to concurrent data in a database management system including uncommitted updated data. Some embodiments include a dual snapshot of data in a multi-version concurrency control style database, but the embodiments described herein are equally applicable to virtually any other type of database and database management system.
Owner:SAP AG
Concurrency control in high performance database systems
InactiveUS7051028B2Data processing applicationsDigital data information retrievalConcurrency controlComputer science
A system and method for concurrency control in high performance database systems. Generally includes receiving a database access request message from a transaction. Then, generating an element that corresponds to the access request message. The element type is that of a read element, commit element, validated element, or restart element. The element is then posted to a read-commit (RC) queue. If the element is a commit element, an intervening validation of the transaction is performed. Upon the transaction passing validation the requested database access is performed.
Owner:NORTH DAKOTA STATE UNIV RES FOUND
Cache-conscious concurrency control scheme for database systems
ActiveUS7293028B2Efficient index structureEffective structureData processing applicationsDigital data information retrievalProcessor registerConcurrency control
An optimistic, latch-free index traversal (“OLFIT”) concurrency control scheme is disclosed for an index structure for managing a database system. In each node of an index tree, the OLFIT scheme maintains a latch, a version number, and a link to the next node at the same level of the index tree. Index traversal involves consistent node read operations starting from the root. To ensure the consistency of node read operations without latching, every node update operation first obtains a latch and increments the version number after update of the node contents. Every node read operation begins with reading the version number into a register and ends with verifying if the current version number is consistent with the register-stored version number. If they are the same, the read operation is consistent. Otherwise, the node read is retried until the verification succeeds. The concurrency control scheme of the present invention is applicable to many index structures such as the B+-tree and the CSB+-tree.
Owner:TRANSACT & MEMORY
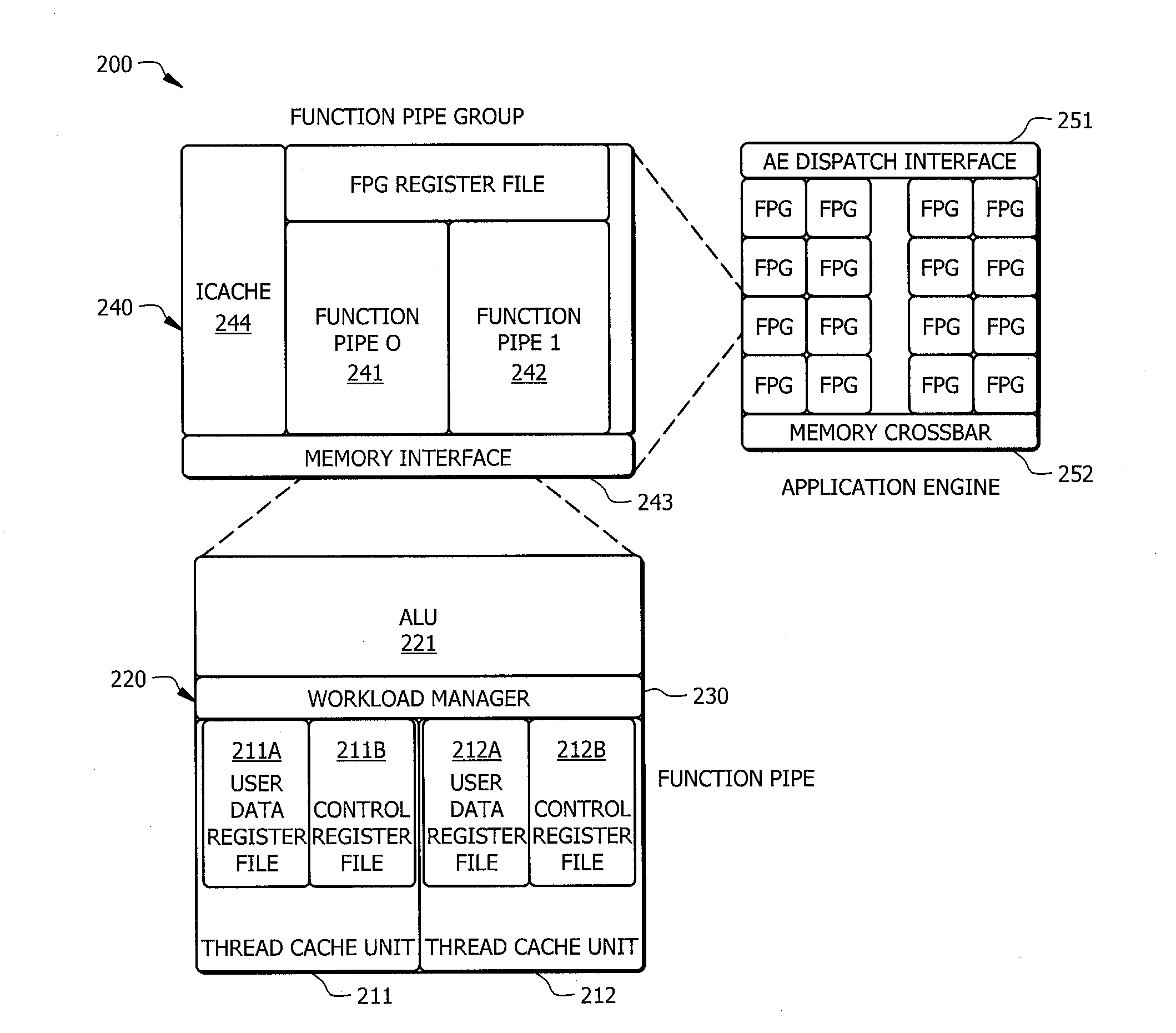
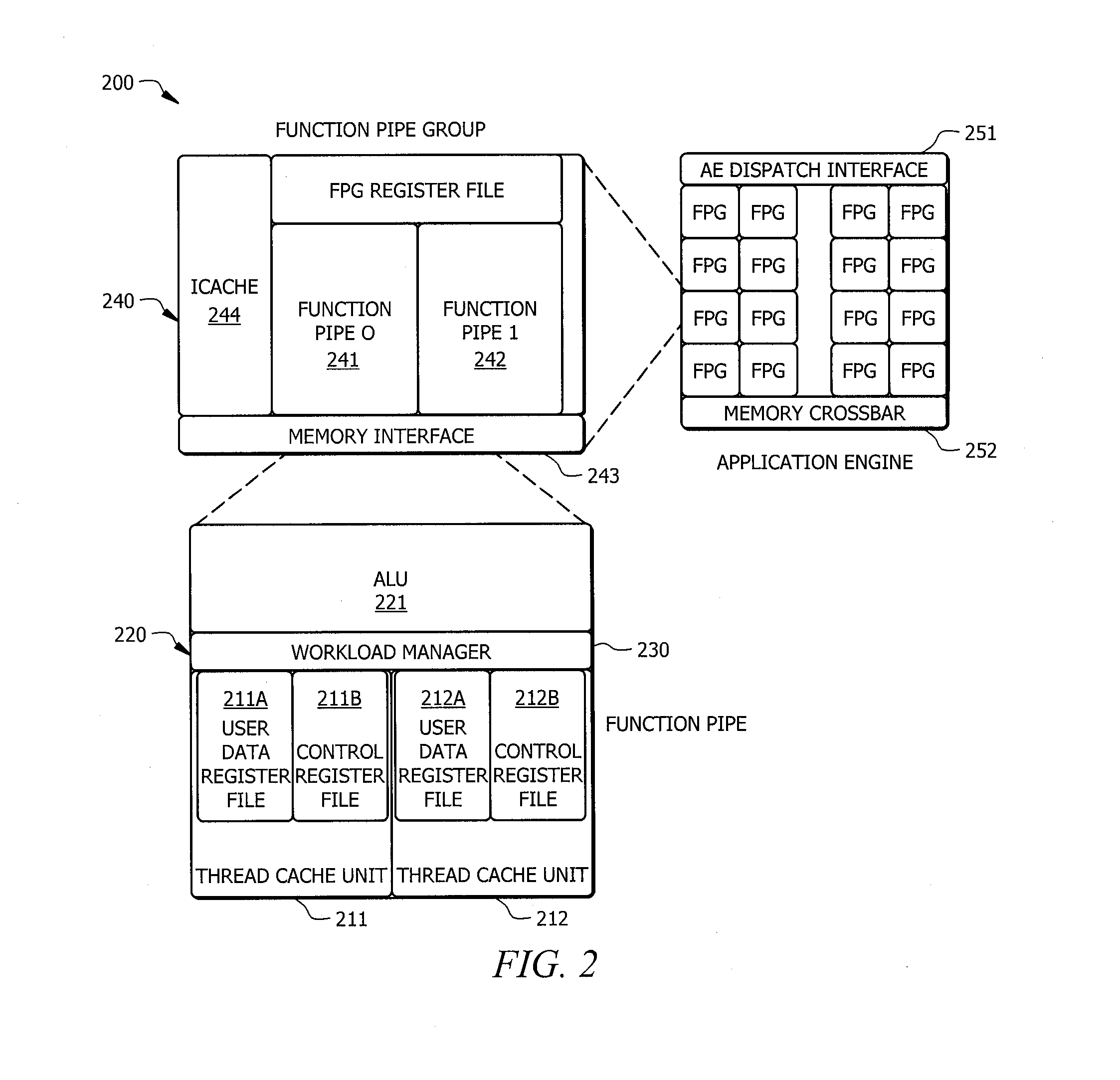
Systems and methods for efficient scheduling of concurrent applications in multithreaded processors
ActiveUS20130332711A1Efficient executionEasy to addInstruction analysisDigital computer detailsInstruction set designConcurrency control
Systems and methods which provide a modular processor framework and instruction set architecture designed to efficiently execute applications whose memory access patterns are irregular or non-unit stride as disclosed. A hybrid multithreading framework (HMTF) of embodiments provides a framework for constructing tightly coupled, chip-multithreading (CMT) processors that contain specific features well-suited to hiding latency to main memory and executing highly concurrent applications. The HMTF of embodiments includes an instruction set designed specifically to exploit the high degree of parallelism and concurrency control mechanisms present in the HMTF hardware modules. The instruction format implemented by a HMTF of embodiments is designed to give the architecture, the runtime libraries, and / or the application ultimate control over how and when concurrency between thread cache units is initiated. For example, one or more bit of the instruction payload may be designated as a context switch bit (CTX) for expressly controlling context switching.
Owner:MICRON TECH INC
Concurrency control using an effective change stack and tenant-based isolation
ActiveUS8341128B1Digital data information retrievalDigital data processing detailsConcurrency controlBase isolation
Transaction processing is disclosed. A first transaction associated with a first system tenant is received. The first transaction is associated with a transaction effective time. It is determined whether the first transaction modifies data. In the event that the first transaction modifies data, it is determined whether a second transaction is executing that modifies data associated with the first system tenant. In the event that there is not a second transaction executing, the first transaction is executed with respect to the transaction effective time.
Owner:WORKDAY INC
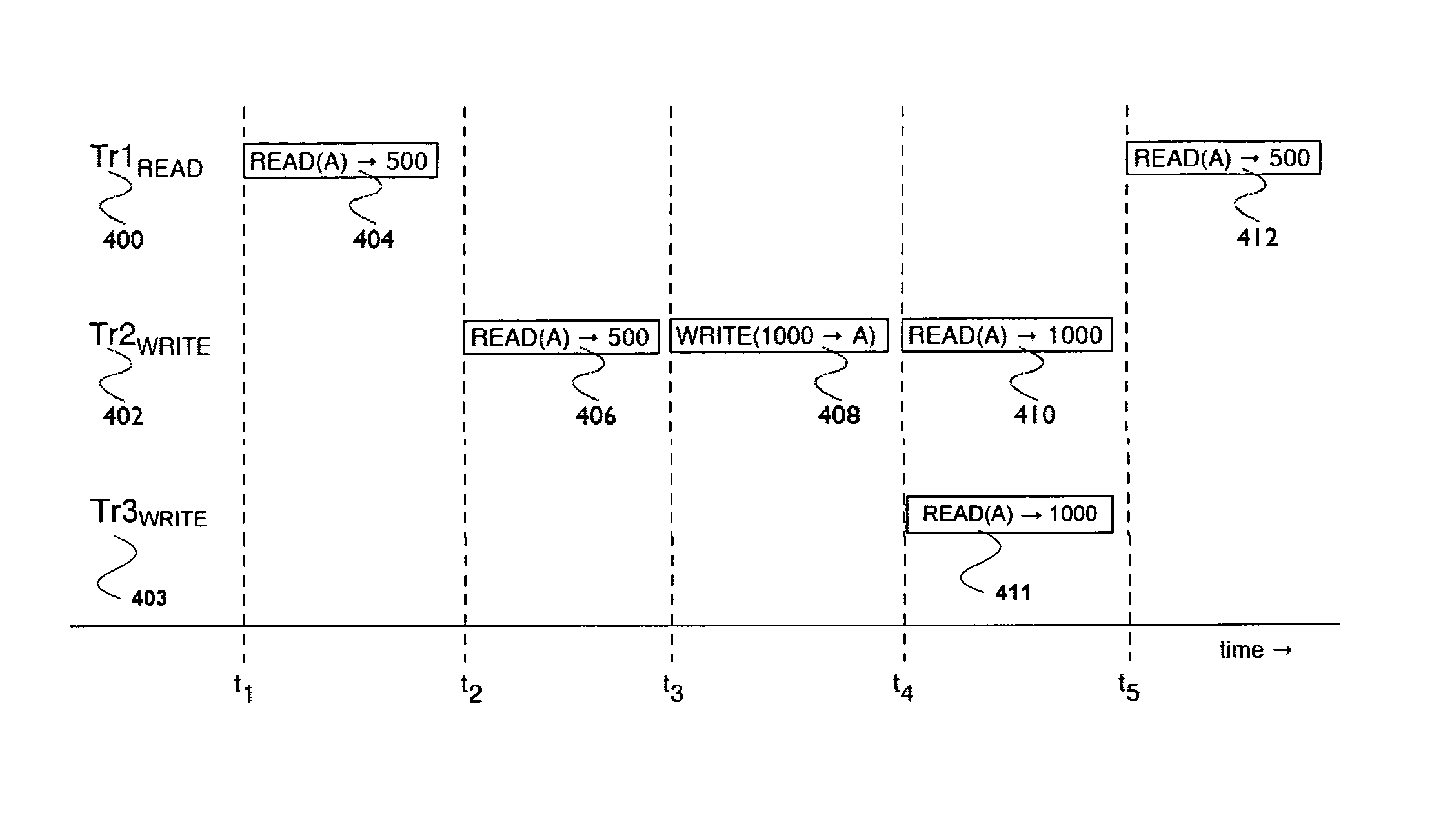
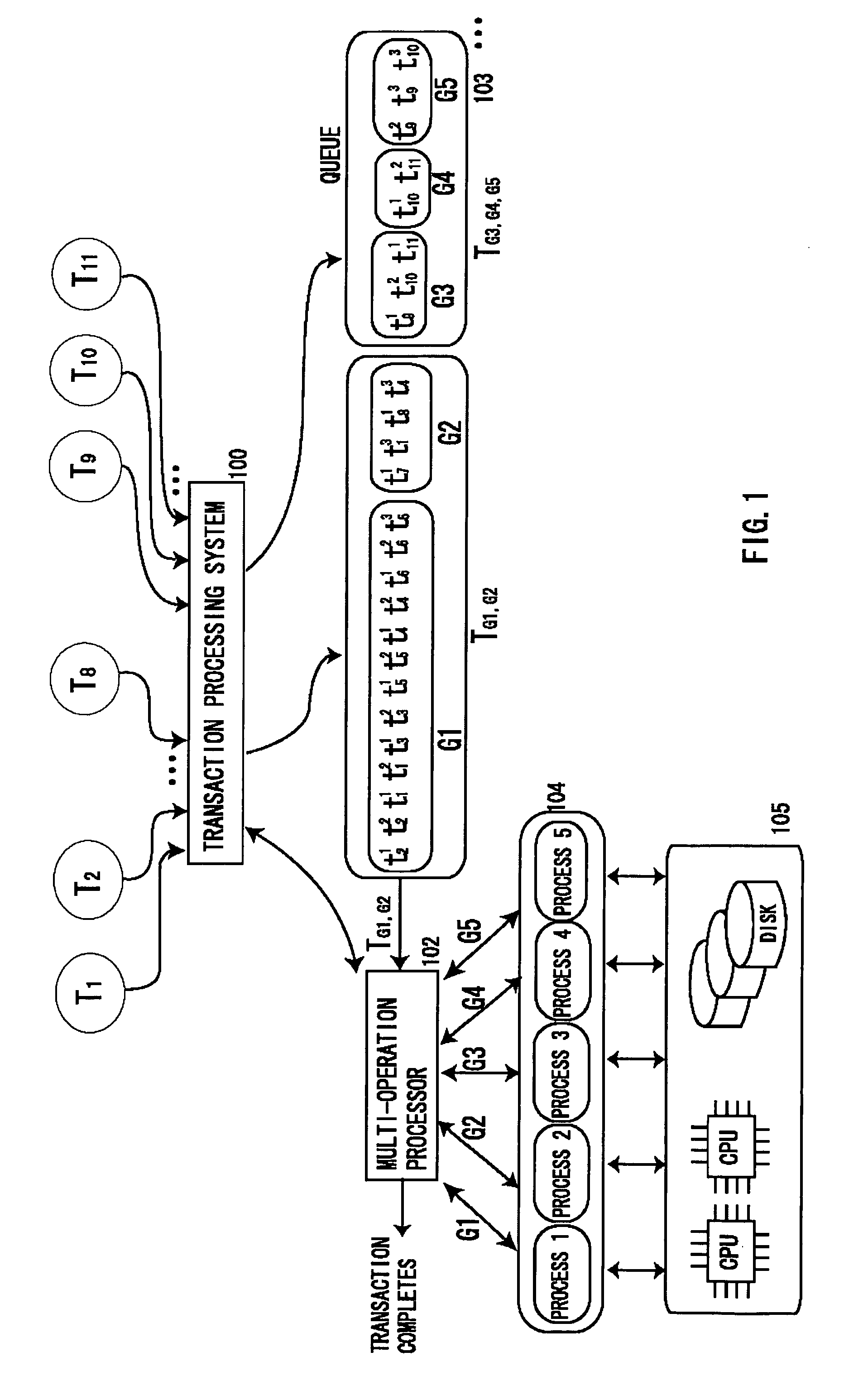
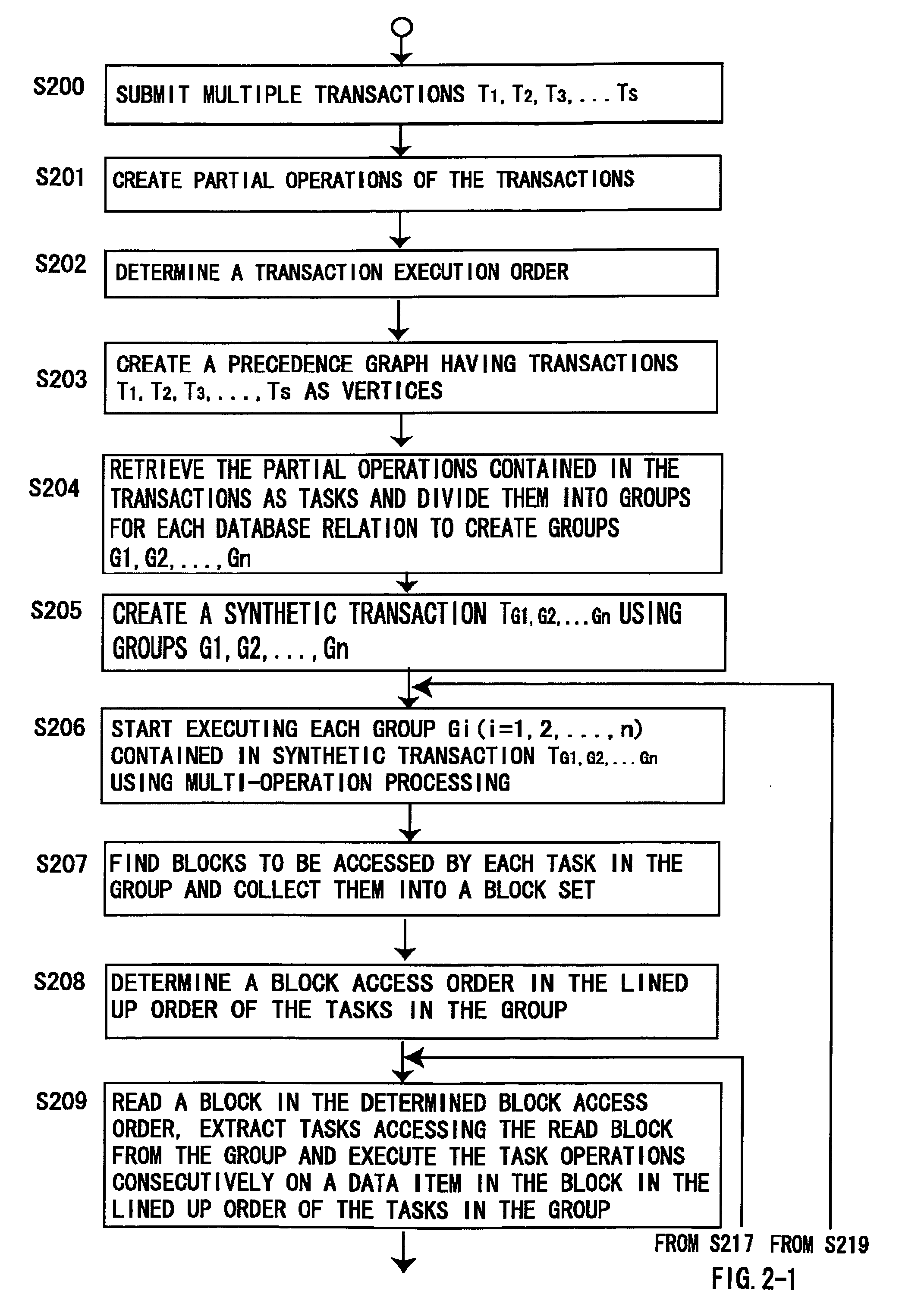
Transaction processing system of database using multi-operation processing providing concurrency control of transactions
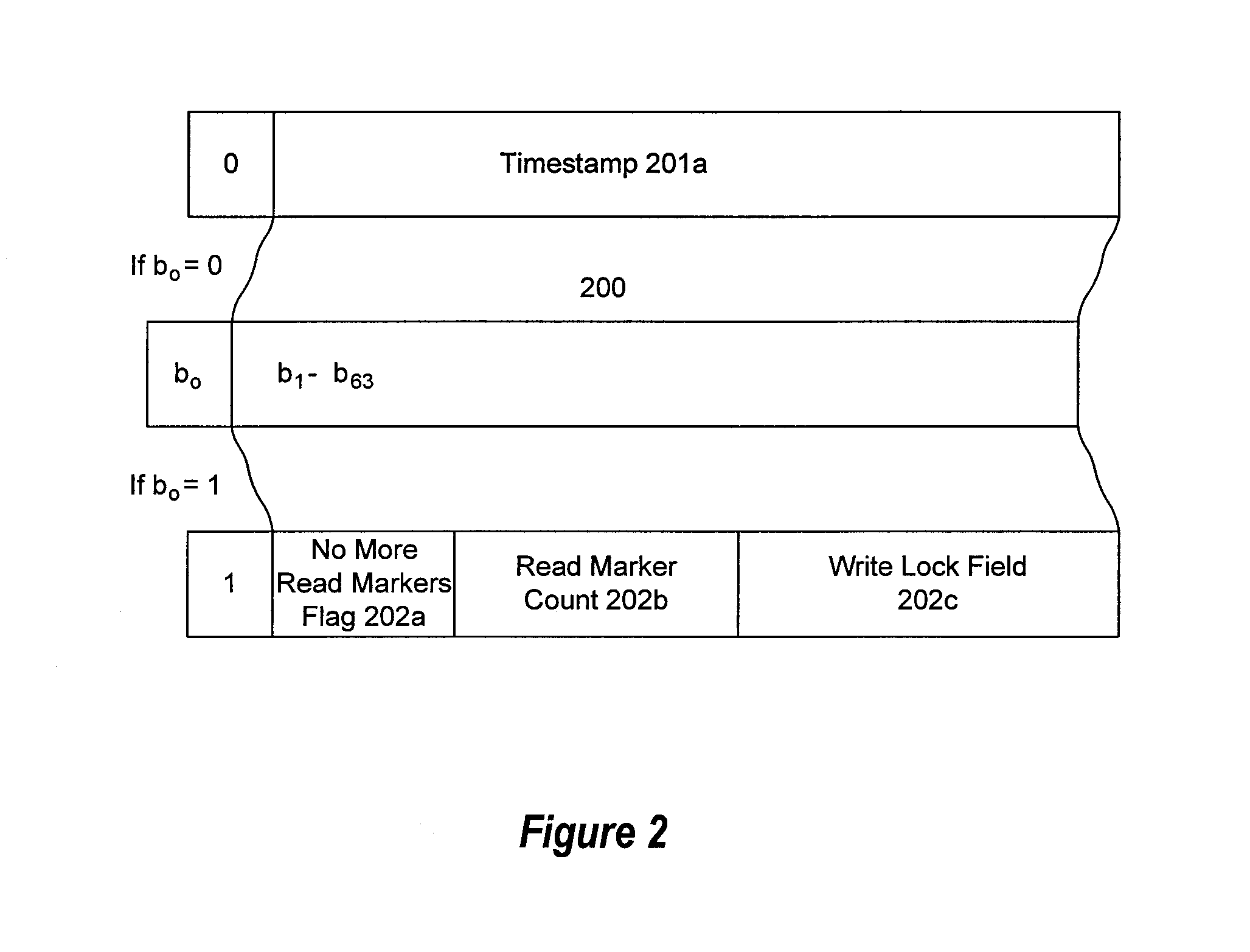
ActiveUS20090287703A1Digital data information retrievalDigital data processing detailsTimestampConcurrency control
Instead of executing a plurality of submitted transactions separately, each data item to be processed by the plurality of submitted transactions is retrieved only once, update operations of the plurality of transactions are executed consecutively on the retrieved data item in main memory, and only the last updated result is written in a database once.Two-phase locking technique and timestamp technique are used for multi-operation processing providing concurrency control of transactions in order to execute multiple synthetic transactions concurrently.
Owner:FURUYA TORU
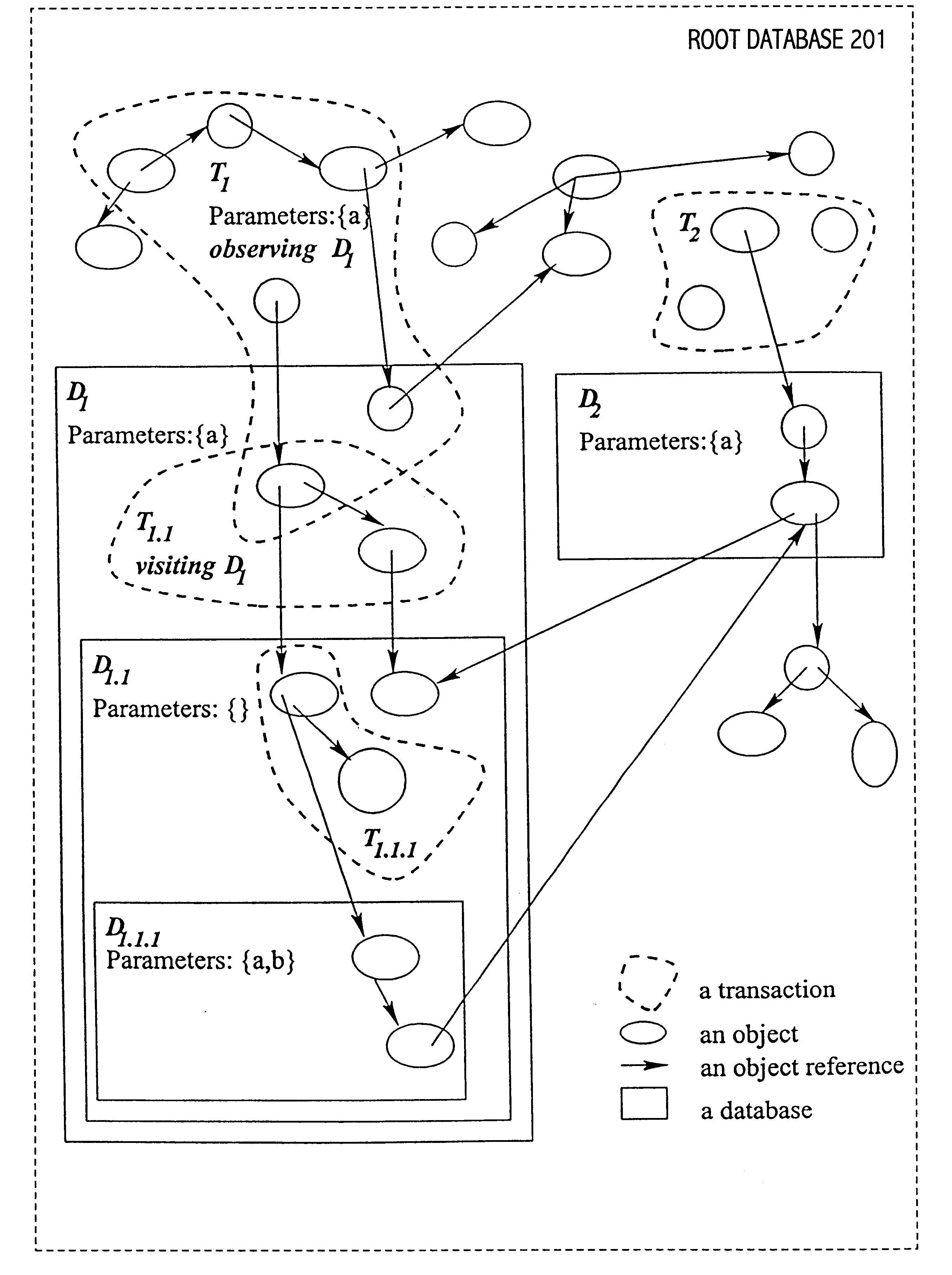
Implementation of nested databases using flexible locking mechanisms
InactiveUS6772154B1Easy to updateFacilitating adoptionData processing applicationsDigital data information retrievalConcurrency controlLocking mechanism
Techniques have been developed whereby concurrency control mechanisms such as nested databases can be expressed in terms of operations implemented by various flexible transaction processing systems. For example, one such implementation of nested databases is particularly suitable for transaction processing systems that provides a lock delegation facility and which allow specification of ignore-conflict relationships between locking capabilities. By providing techniques that support movement of objects from a database to a subdatabase thereof, as well as termination (e.g., commit or abort) of transactions and databases (including subdatabases), transaction processing systems can provide advanced transaction models with unconventional concurrency control mechanisms. Some realizations allow specification of uses of parameters with lock modes and facilitate transformation of such uses into a form suitable for utilization in execution environments that support ignore-conflict relationships.
Owner:ORACLE INT CORP
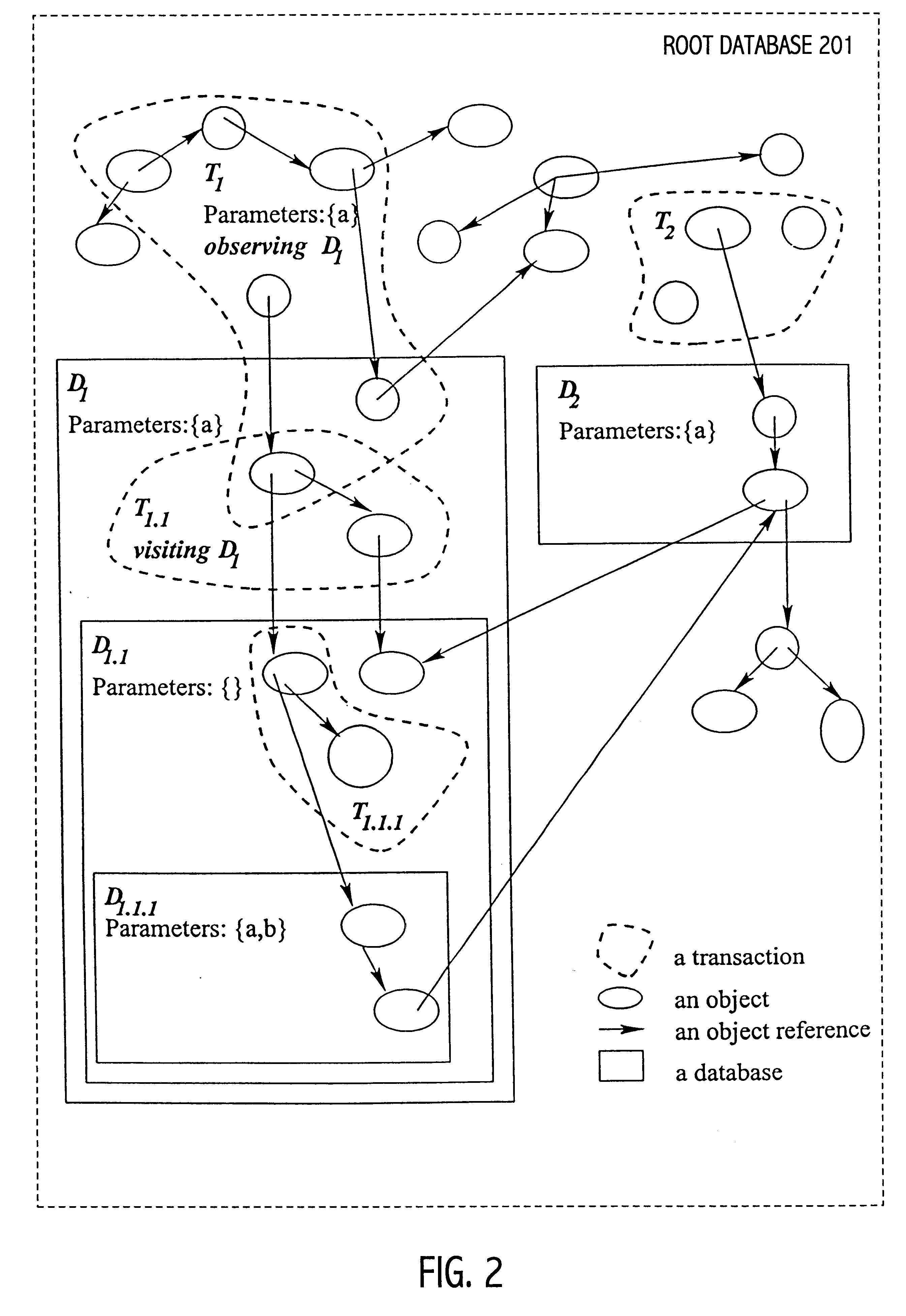
Self-Adaptive Prefix Encoding for Stable Node Identifiers
InactiveUS20060004858A1Improve efficiencyEasy to exportDigital data processing detailsSemi-structured data retrievalConcurrency controlTheoretical computer science
A variable-length binary string is utilized to encode node identifiers in a tree for an XML document object model. A general prefix encoding scheme is followed; a node identifier is generated by the concatenation of encodings at each level of a tree along a path from a root node to another particular node. Arbitrary insertions are supported without change to existing node identifier encodings. In addition, the method provides for document order when unsigned binary string comparison is used to compare encoded node identifiers. In support of sub-document concurrency control, prefix encoding provides a way to derive ancestor-descendant relationships among nodes in a tree. Lastly, the encoding method provides a natural pre-order clustering sequence, also known as depth-first clustering. If a prefix is applied to an encoding with a level number, starting with zero at the root, width-first clustering will result. A mixed clustering can also be supported.
Owner:IBM CORP
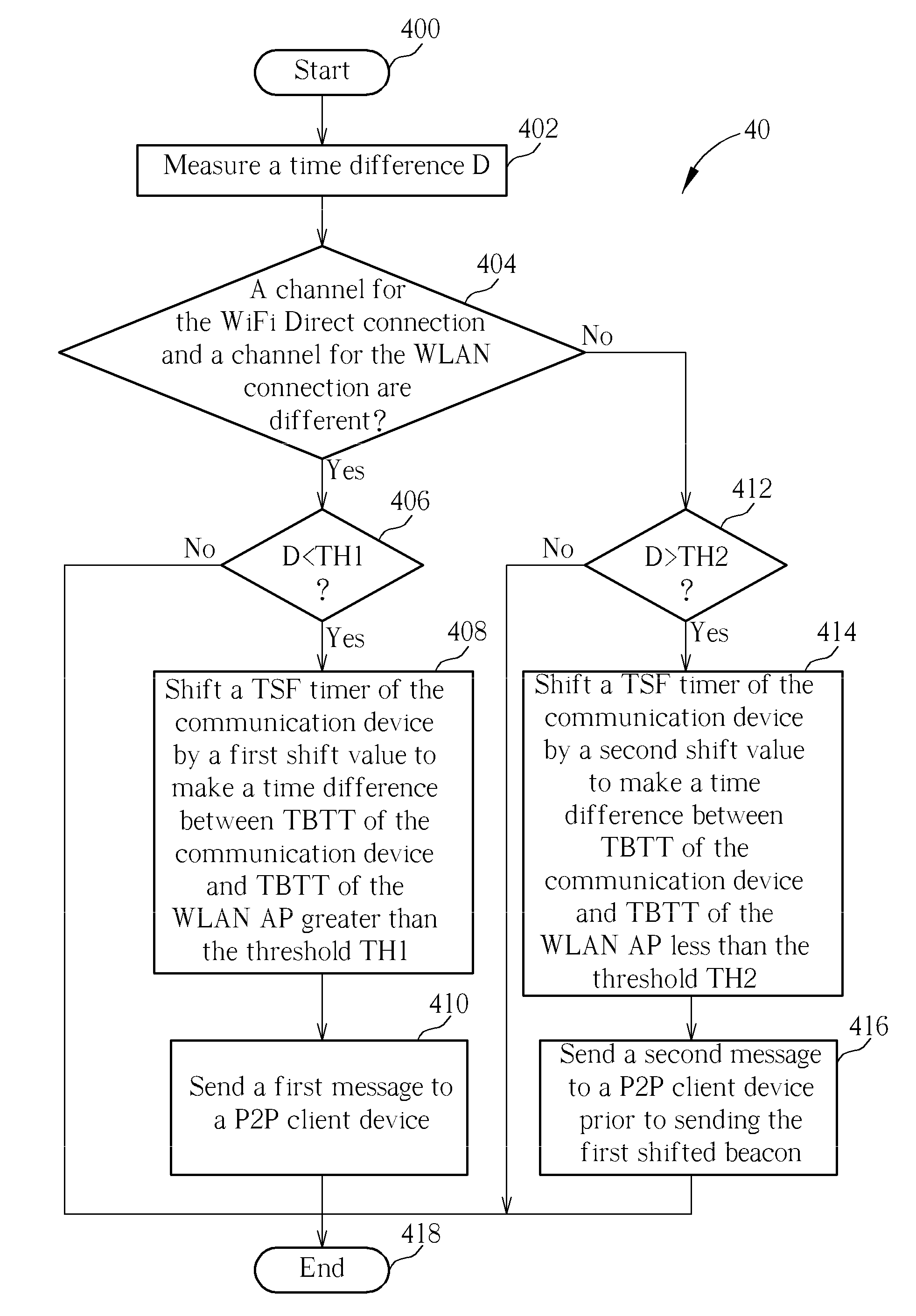
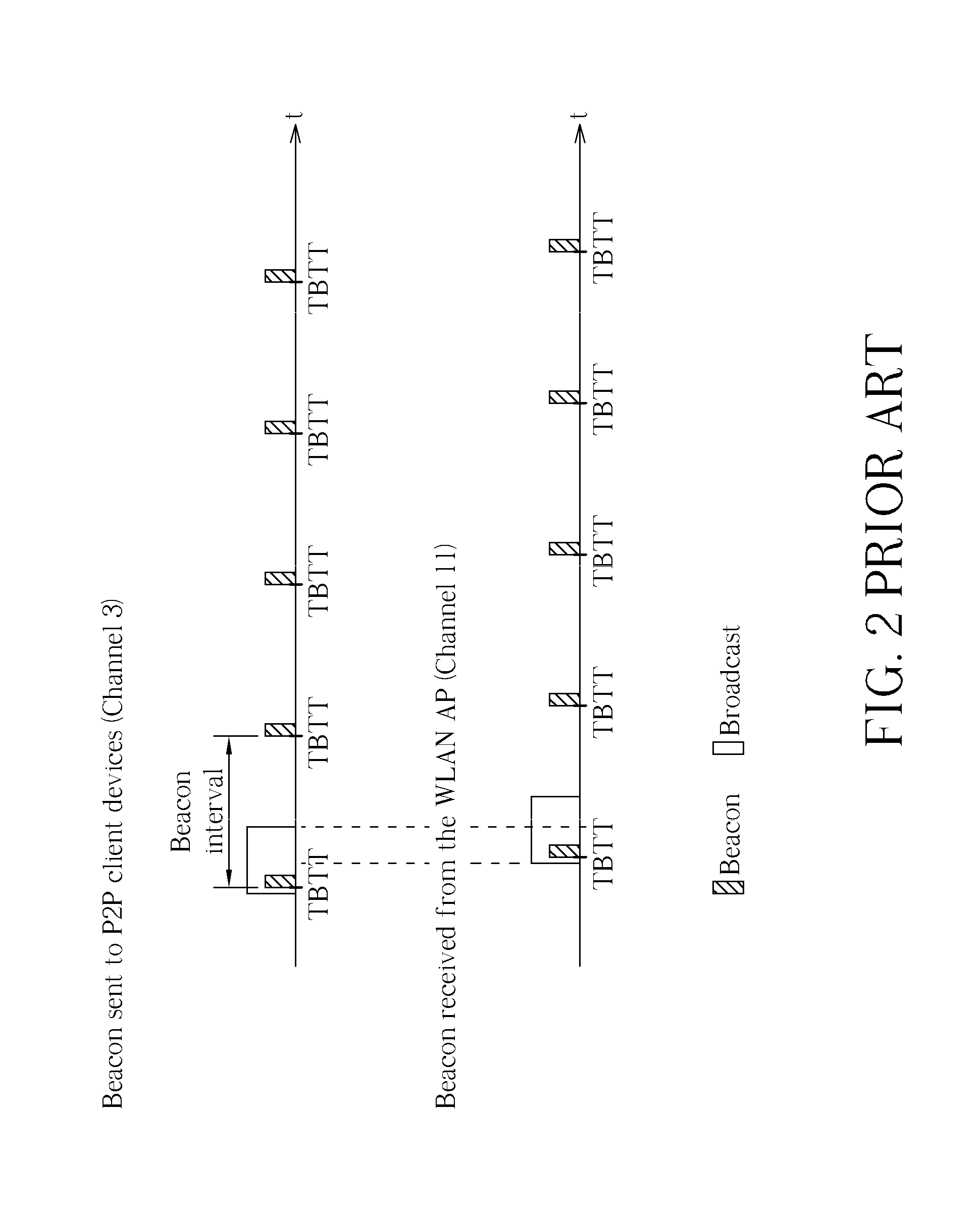
Concurrent control method for a communication device embedded with wi-fi direct
A concurrent control method for a communication device embedded with Wi-Fi Direct includes dynamically adjusting a target beacon transmission time (TBTT) of a Wi-Fi Direct connection according to a time difference between the TBTT of the communication device and a nearest TBTT of a wireless local area network access point (WLAN AP) and whether a channel for the Wi-Fi Direct connection and a channel for the WLAN connection are different.
Owner:MEDIATEK INC
Method and system for managing a multi-focus remote control session
InactiveUS20090085871A1Input/output for user-computer interactionCathode-ray tube indicatorsRemote controlConcurrency control
A method and system for managing a multi-focus remote control session (RCS) within a computer system. A unique identifier (UserID) of each user and associated input devices are registered to the RCS. The users have shared concurrent control of a computer screen via the input devices. Responsive to selection of windows within the computer screen by the input devices, concurrently operative focus is provided to each selected window and is specific to the UserID associated with the input device that selected the window. Each selected window having focus may be accessed and manipulated by only the input devices associated with the UserID to which the focus provided to each selected window is specific. The selected windows to which focus has been provided are recording in a computer readable medium in association with the UserID specific to the selection of the windows.
Owner:IBM CORP
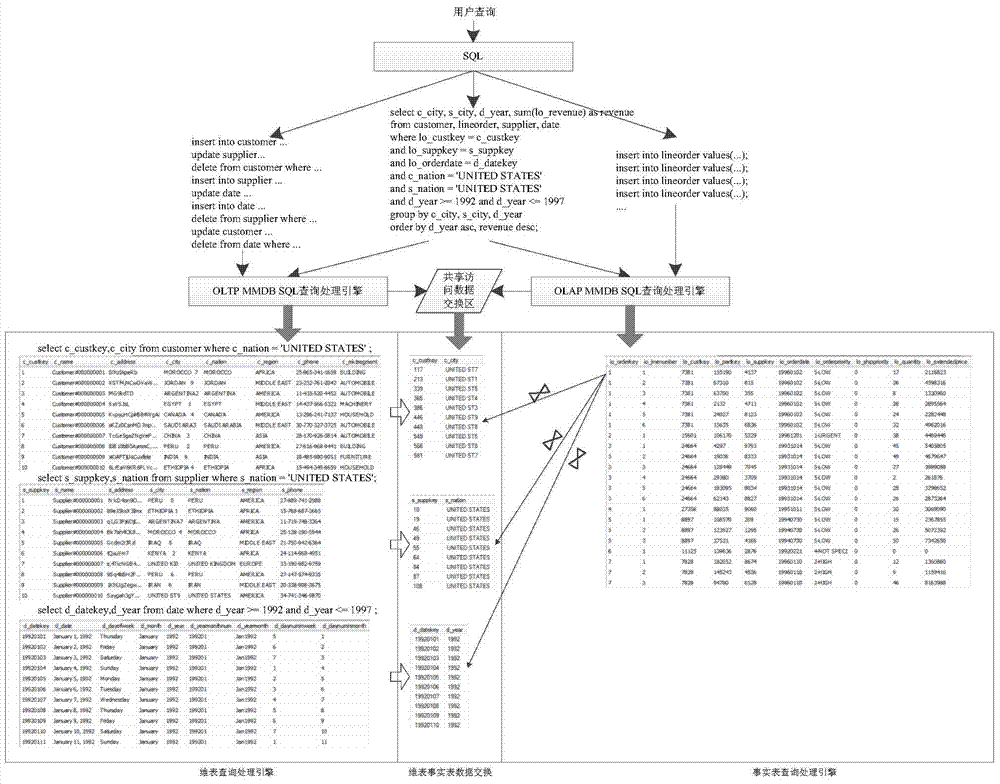
Memory database OLTP and OLAP concurrency query optimization method
ActiveCN103942342AIncrease the probability of concurrent access conflictsEasy to handleMulti-dimensional databasesSpecial data processing applicationsData compressionArray data structure
The invention relates to a memory database OLTP and OLAP concurrency query optimization method. The method includes the steps that (1) by means of two query processing engines, independent storage engines are adopted to a dimension table and a fact table; (2) the dimension table is updated through an embedded concurrency control mechanism of the independent storage engines, the fact table is equivalent to multiple continuous arrays in logic and maintains two dynamic data structures, namely a read record pointer and a write record pointer, the read record pointer records the position of the last record inquired through OLPA currently, and the write record pointer records the insert position of a new record; (3) an OLTP transactional queue and an OLAP transactional queue are independently executed with the read pointer and the write pointer as boundaries, the fact table adopts a column storage horizontal fragmentation model based on the fixed number of columns, N columns of storage records serve as an independent column storage container, and each column storage container adopts an independent data compression mechanism; (4) an access function on compressed data or non-compressed data is provided through access interfaces of the column storage containers when OLAP query has access to the column storage containers.
Owner:RENMIN UNIVERSITY OF CHINA
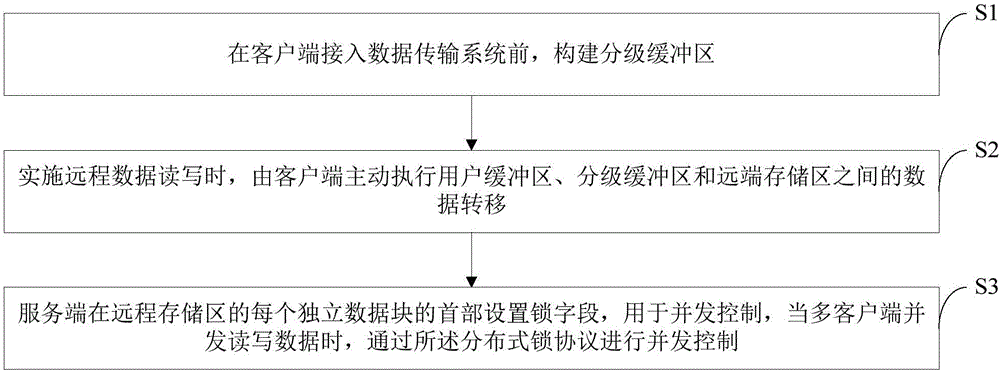
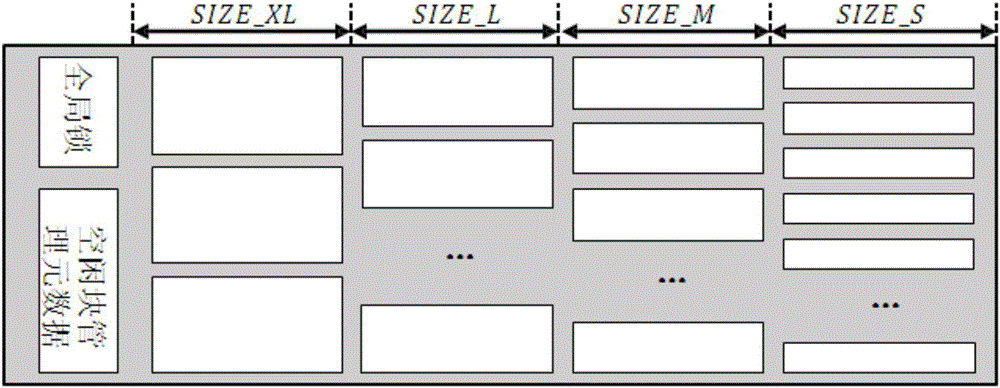
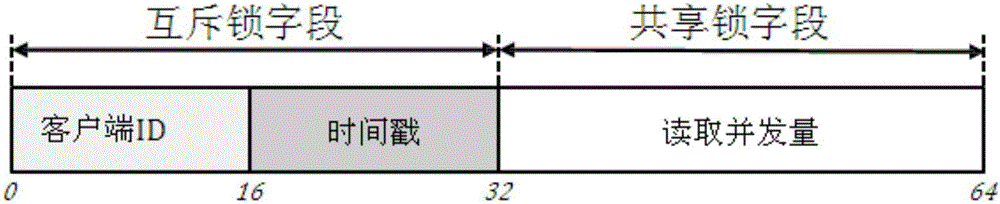
High concurrent data transmission method based on RDMA (Remote Direct Memory Access)
ActiveCN106657365AReduce data duplicationRelieve stressTransmissionConcurrency controlRemote direct memory access
The invention discloses a high concurrent data transmission method based on RDMA (Remote Direct Memory Access). The method comprises the steps of establishing a graded buffer area before a client accesses a data transmission system; actively carrying out data transfer among a user buffer area, the graded buffer area and a remote memory area by the client when remote data read / write is carried out; and setting a lock field at the head part of each independent data block of the remote memory area by a server, wherein the lock field is used for concurrent control, when a plurality of clients concurrently read / write data, the concurrent control is carried out through a distributed lock protocol that the server locks locally and the clients unlock remotely. The method has the advantages that the data replication is reduced when a file is read / written, the processing pressure of the server is reduced, and the efficient concurrent control is provided.
Owner:TSINGHUA UNIV
Cache-conscious concurrency control scheme for database systems
InactiveCN1522409ADigital data information retrievalMemory adressing/allocation/relocationConcurrency controlProcessor register
An optimistic, latch-free index traversal (''OLFIT') concurrency control scheme is disclosed for an index structure for managing a database system. In each node of an index tree, the OLFIT shceme maintains a latch, a version number, and a link to the next node at the same level of the index tree. Index traversal involves consistent node read operations starting from the root. To ensure the consistency of node read operations without latching, every node update operation first obtains a latch and increments the version number after update of the node contents. Every node read operation begins with reading the version number into a register and ends with verifying if the current version number is consistent with the register-stored version number. If they are the same, the read operation is consistent. Otherwise, the node read is retried until the verification succeeds. The concurrency control scheme of the present invention is applicable to many index structures such as the B+-tree and the CSB+-tree.
Owner:SAP AG
Event dispatching method and system
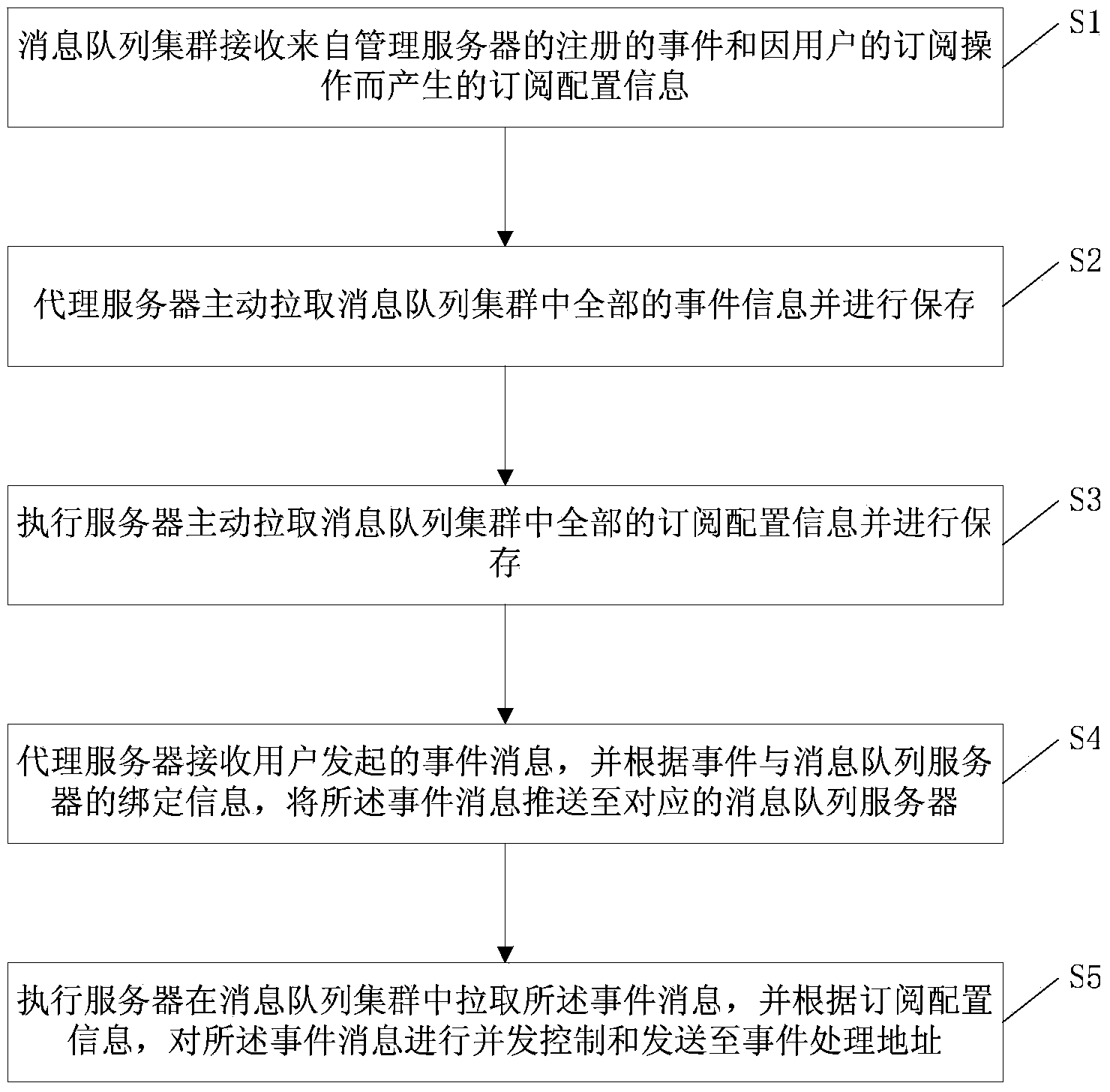
ActiveCN103927218AImprove processing efficiencyImprove development efficiencySoftware simulation/interpretation/emulationMessage queueConcurrency control
The invention relates to an event dispatching method and system. The method includes the steps that a message array cluster receives registered events from a management server and subscription configuration information caused by subscription operation of users; a proxy server actively draws and stores all event information in the message array cluster; an execution server actively draws and stores all subscription configuration information in the message array cluster; the proxy server receives event messages initiated by the users and pushes the event messages to a corresponding message array server according to the binding information of the events and the message array server; the execution server draws the event messages in the message array cluster, conducts concurrence control over the event messages and sending the event messages to an event processing address. By the adoption of the event dispatching method and system, development of cross-system event message transfer is simplified, concurrence sending of the event messages can be achieved, and therefore processing efficiency of the event messages is improved.
Owner:GUANGZHOU PINWEI SOFTWARE
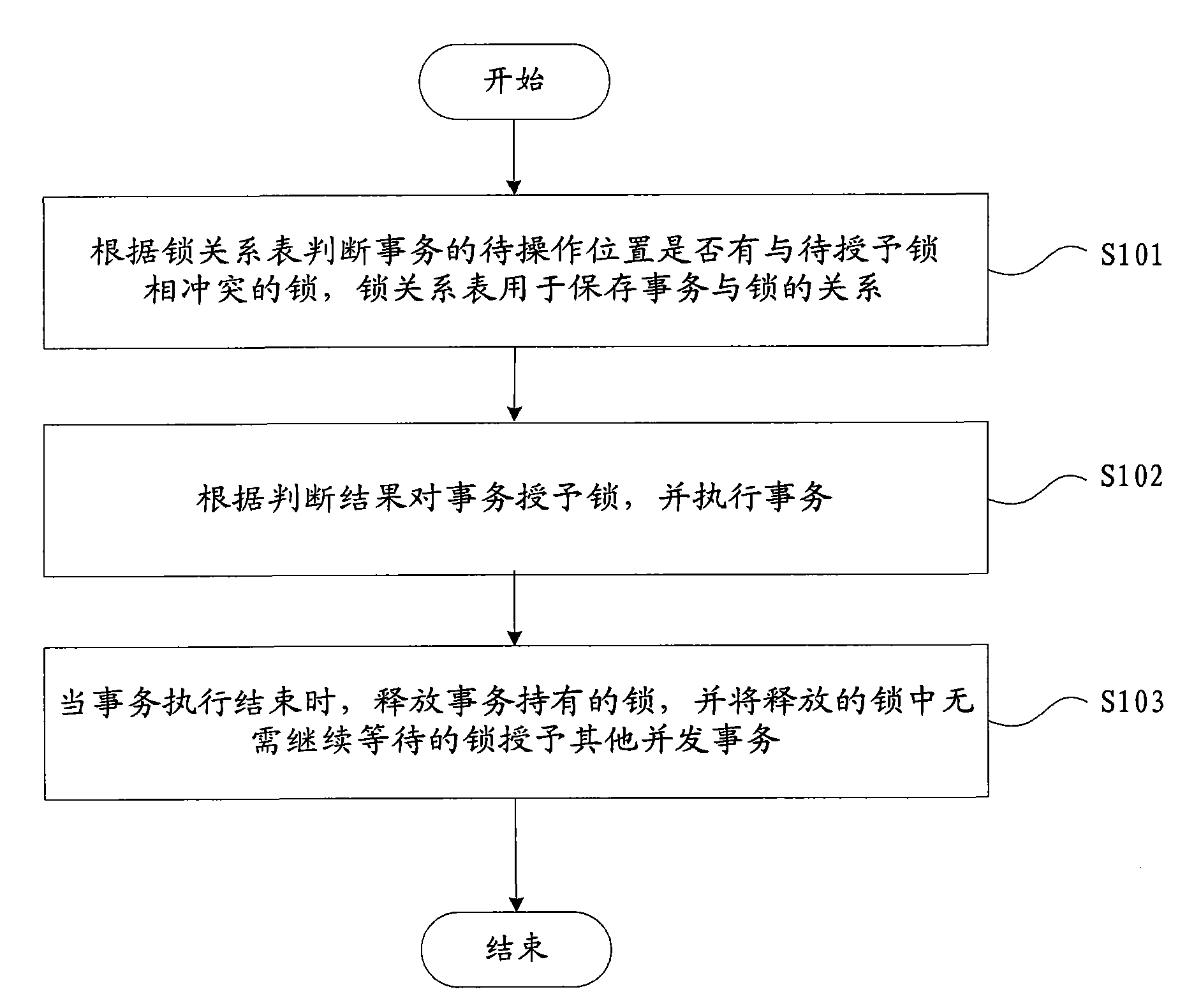
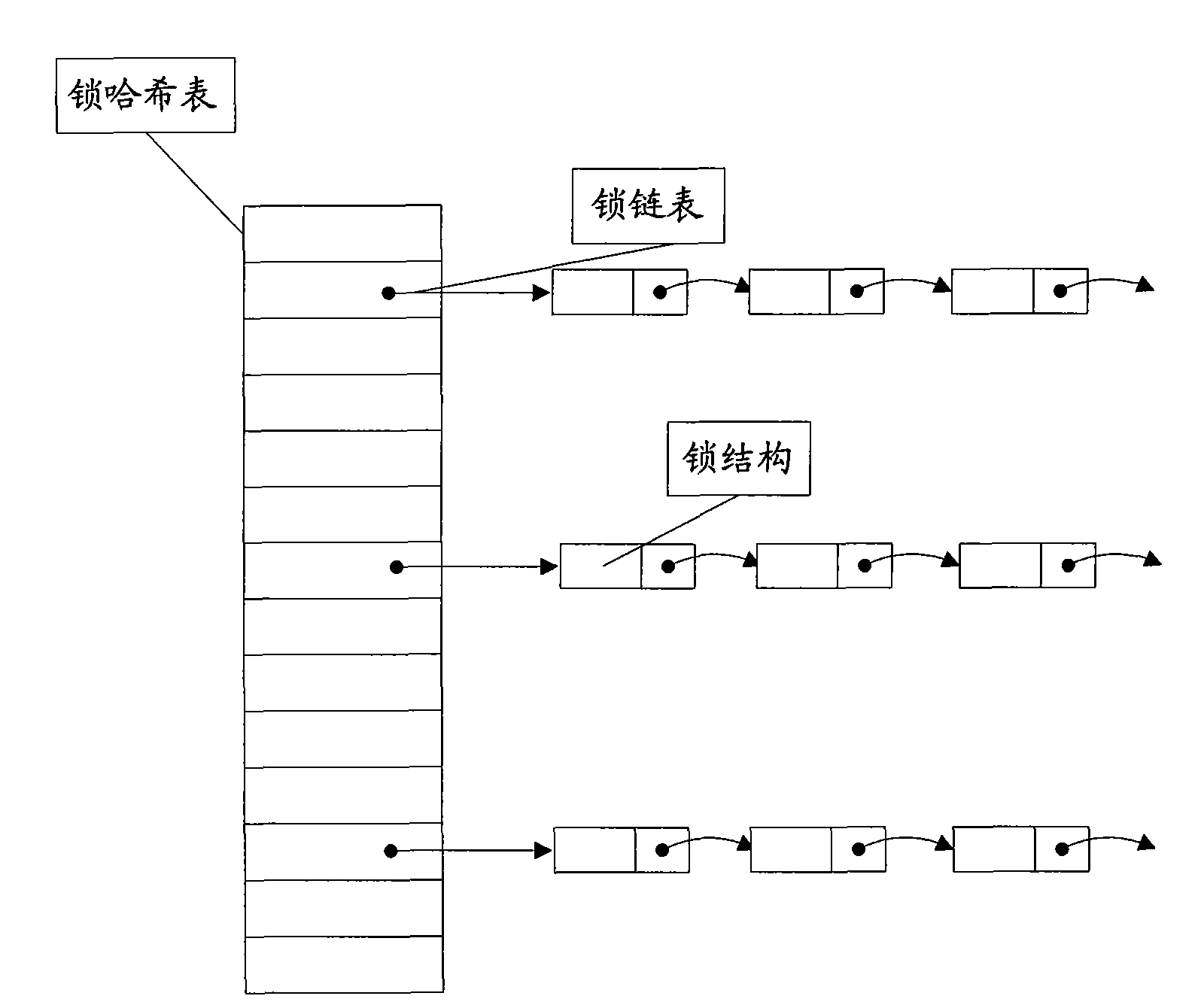
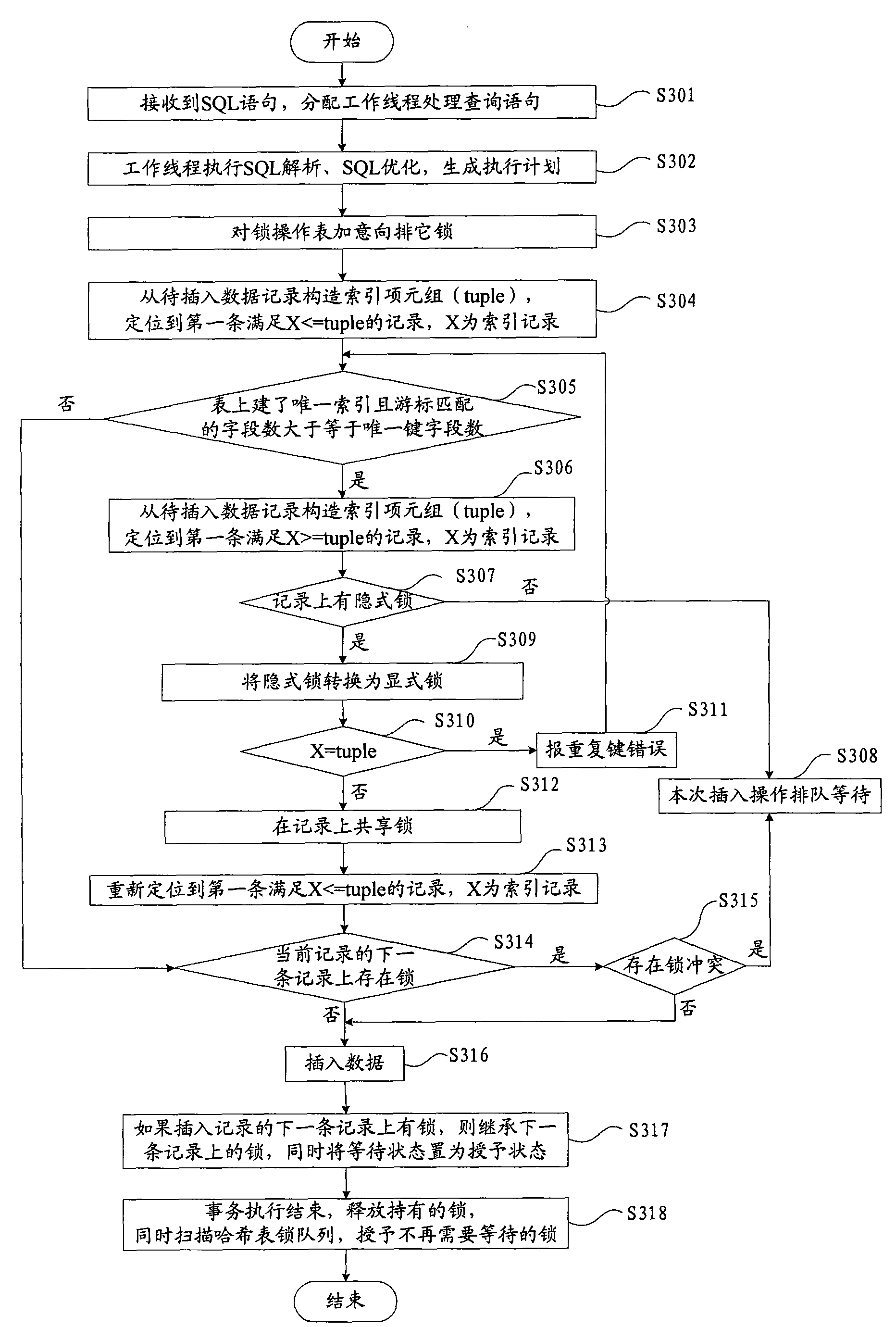
Concurrency control method and device
ActiveCN101615203AOvercome the problems of low concurrency and poor system performanceImprove concurrencyDigital data information retrievalProgram controlConcurrency controlDistributed computing
The invention provides a concurrency control method, which comprises the following steps: judging whether locks conflicted with locks to be granted exist at a position of a transaction to be operated according to a lock relation table which is used for storing the relation of the transaction and the locks; granting the locks to the transaction according to a judgment result, and executing the transaction; and when the execution of the transaction is finished, releasing the locks held by the transaction, and granting the locks not needing continuously waiting in the released locks to other concurrency transactions. The invention also provides a concurrency control device, which comprises a judgment module, an execution module and a release module. The method solves the problems of low concurrency and poor system performance of transaction control by a concurrency method in related technology so as to improve the concurrency of the transaction control and concurrency control effect.
Owner:ZTE CORP
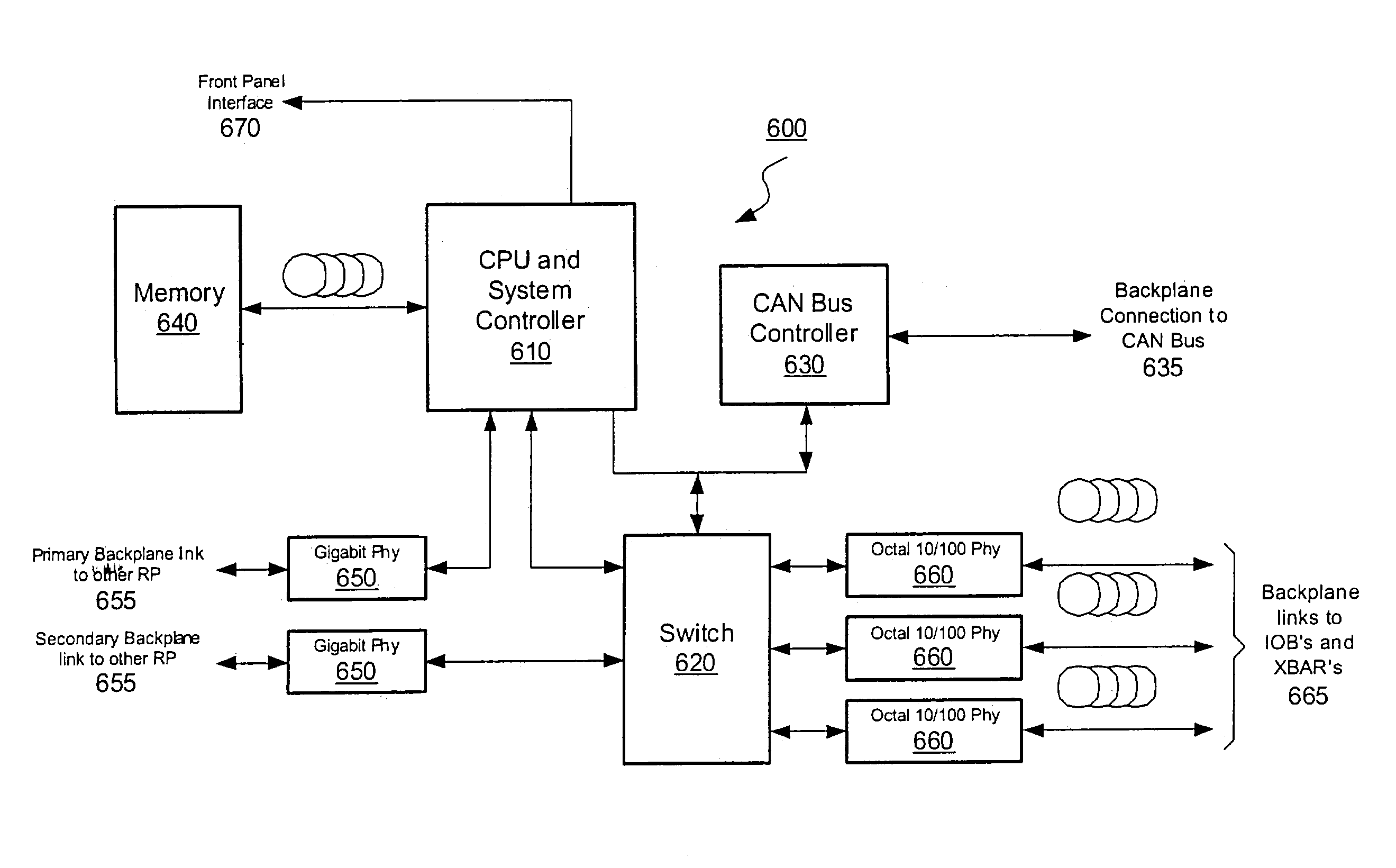
Method and apparatus for a control communication channel in a packet-forwarding device
ActiveUS7245629B1Improve scalabilityReduce congestionNetwork connectionsElectric digital data processingControl communicationsConcurrency control
A control backplane replaces the traditional shared bus with a dedicated communication channel using a high-speed protocol, such as Ethernet. The resulting system may conduct several concurrent control sessions with clients and devices associated with the network switch. Removing the shared bus from the control plane also improves the reliability of the new system, because it is no longer susceptible to a single point of failure.
Owner:EXTREME NETWORKS INC
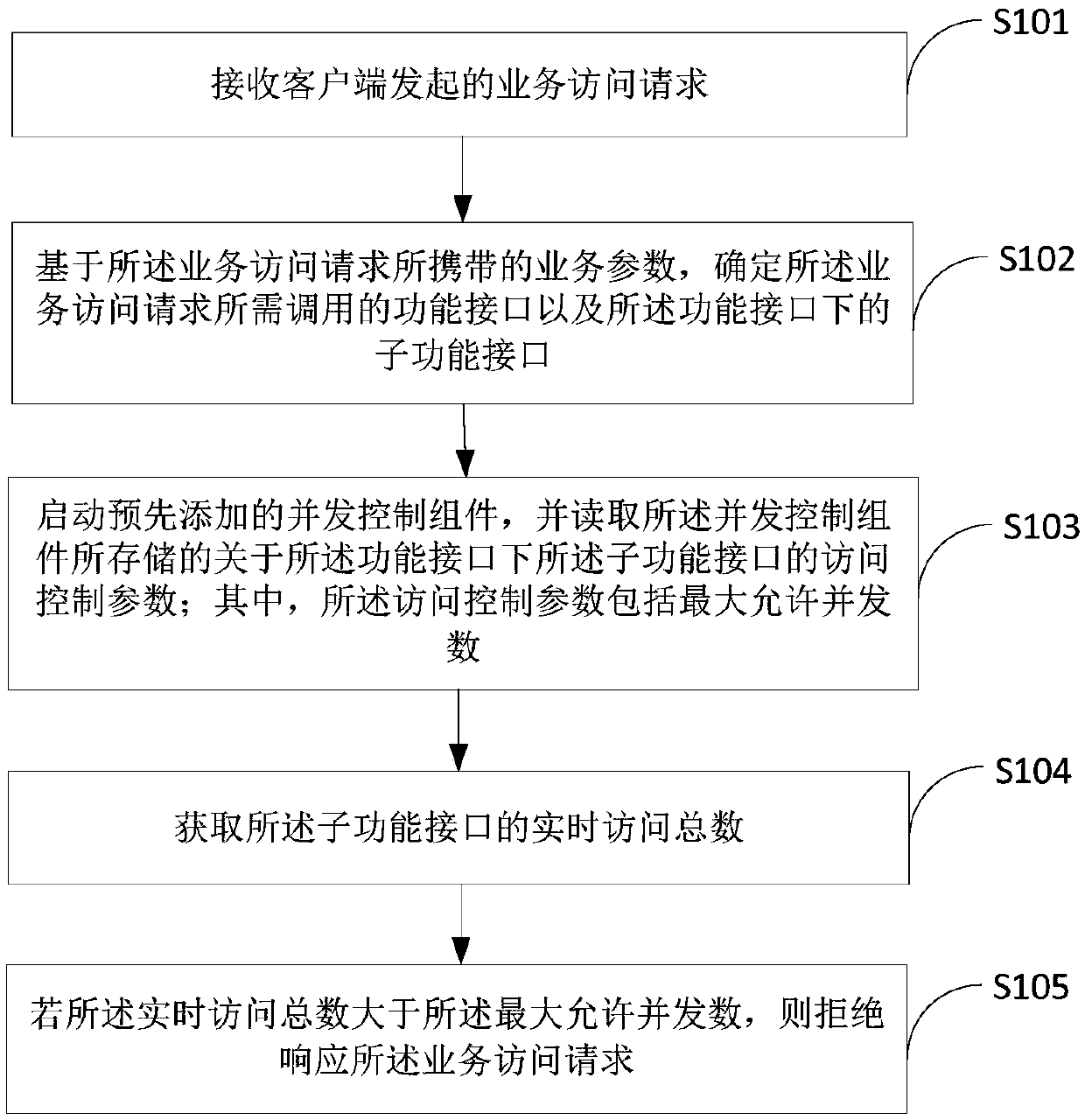
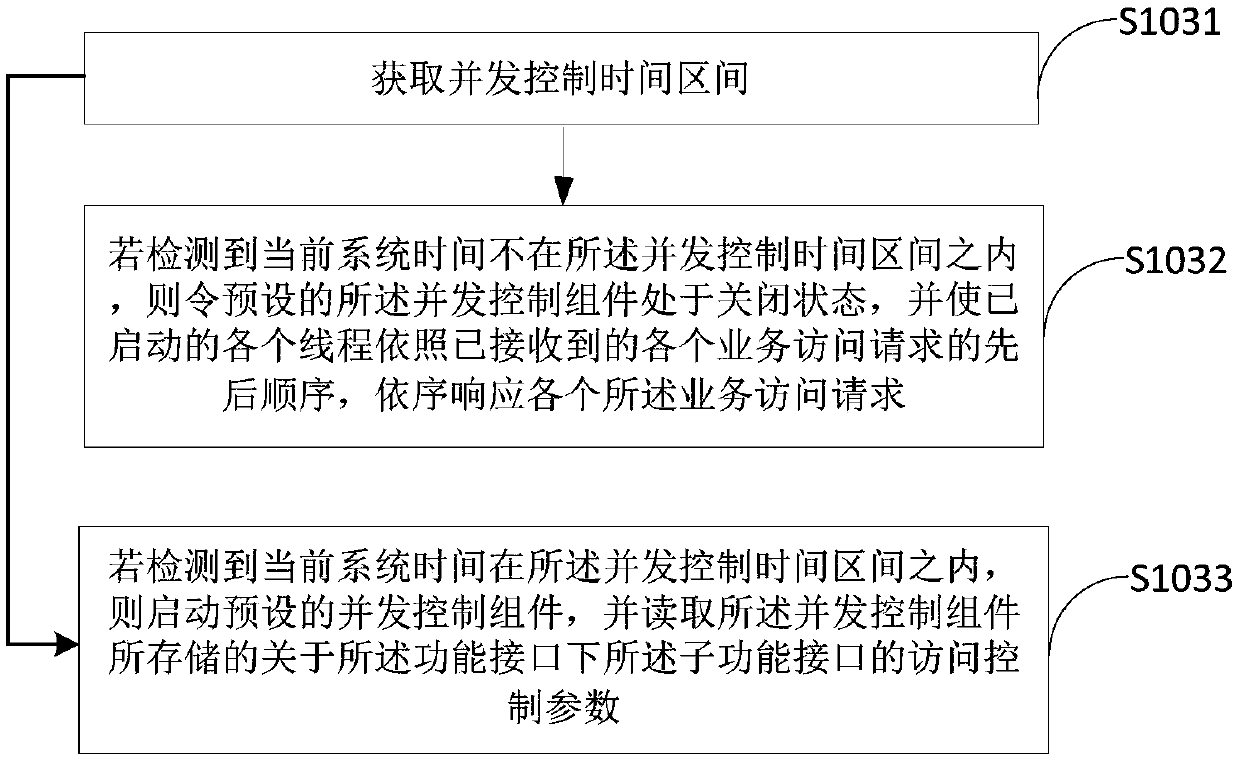
Concurrent access control method, terminal device and medium
ActiveCN108683604AAvoid paralyzing situationsImprove stabilityResource allocationProgram synchronisationConcurrency controlTerminal equipment
The present invention belongs to the computer technological field and provides a concurrent access control method, a terminal device, and a medium. The method includes the following steps that: a service access request initiated by a client is received; a function interface required to be called by the service access request and sub-function interfaces subordinated to the function interface are determined according to service parameters carried by the service access request; a pre-added concurrency control component is started, and the access control parameters of the sub-function interfaces subordinated to the function interface which are stored by the concurrency control component are read, wherein the access control parameters include a maximum allowed concurrent number; and the total number of the real-time accesses of the sub-function interfaces is obtained; and the service access request is rejected if the total number of the real-time accesses is greater than the maximum allowedconcurrent number. With the concurrent access control method, the terminal device, and the medium of the invention adopted, the possibility of the paralysis of a whole system can be decreased; the normal access of other sub-function interfaces is not affected; and the stability and reliability of the service system can be improved.
Owner:PING AN TECH (SHENZHEN) CO LTD
Controlling workload of a computer system through only external monitoring
InactiveUS20080301696A1Error detection/correctionMultiprogramming arrangementsTraffic capacityConcurrency control
Owner:INT BUSINESS MASCH CORP
Multi-version concurrency control method in database and database system
ActiveCN103744936AError detection/correctionSpecial data processing applicationsConcurrency controlMultiversion concurrency control
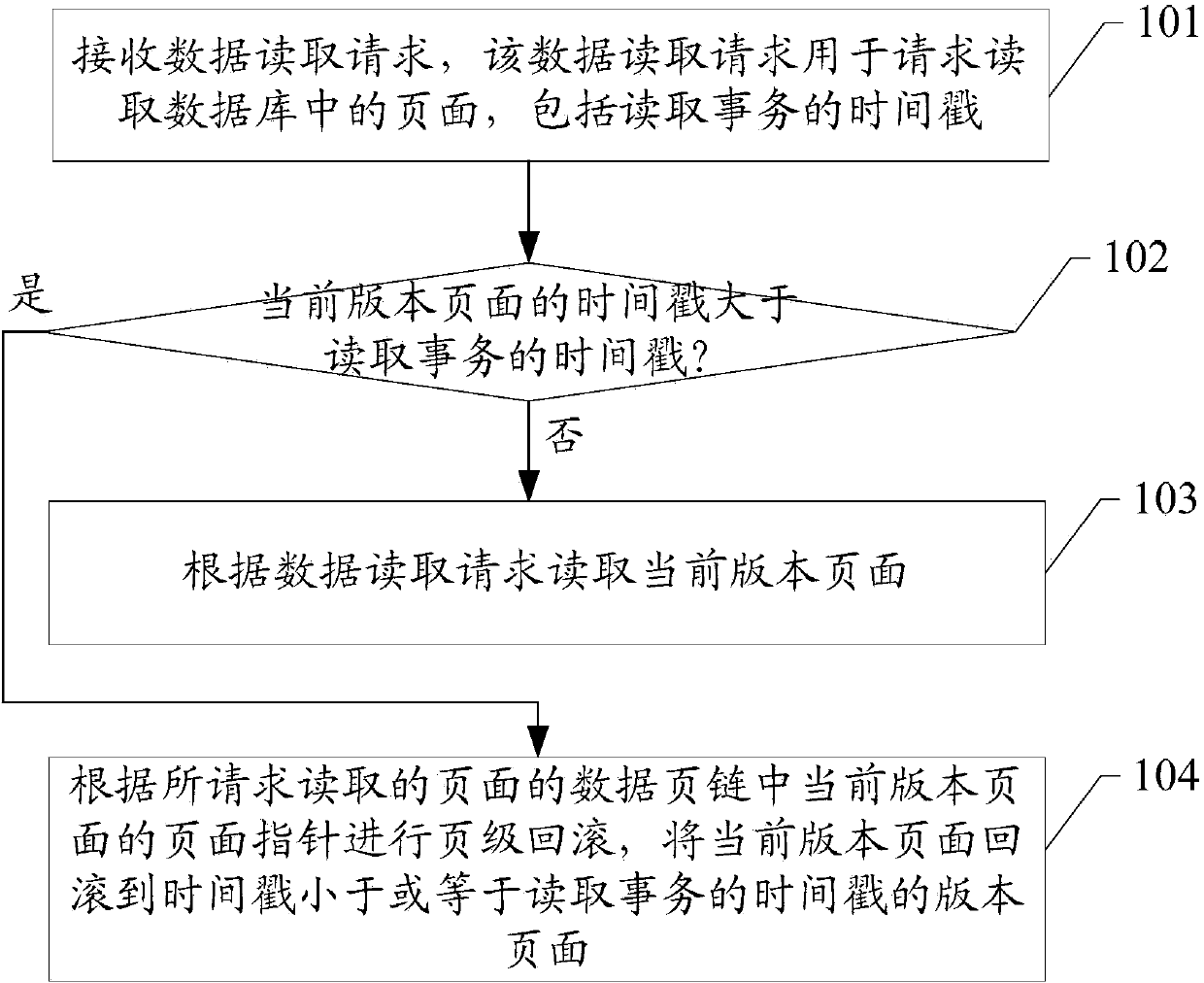
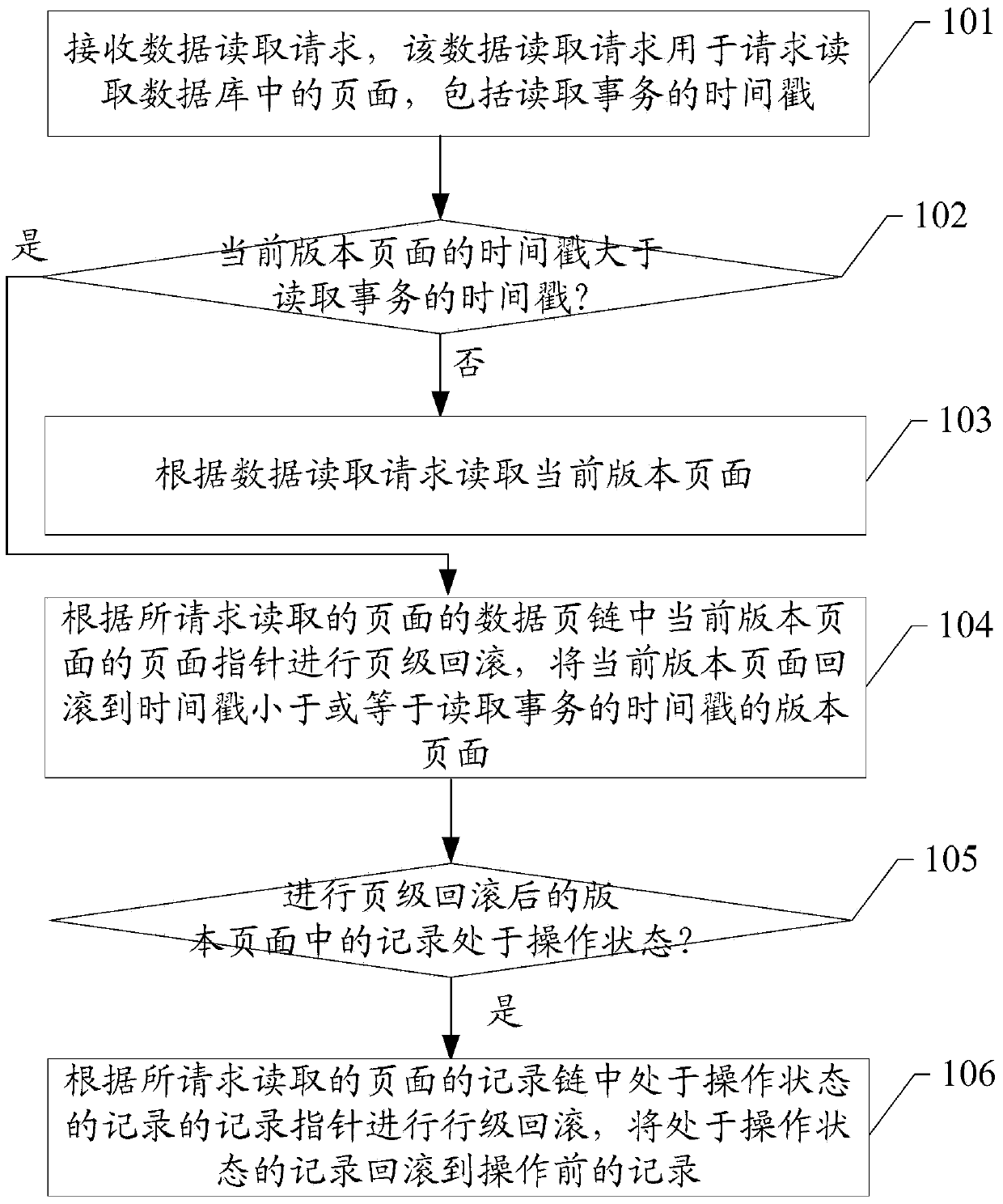
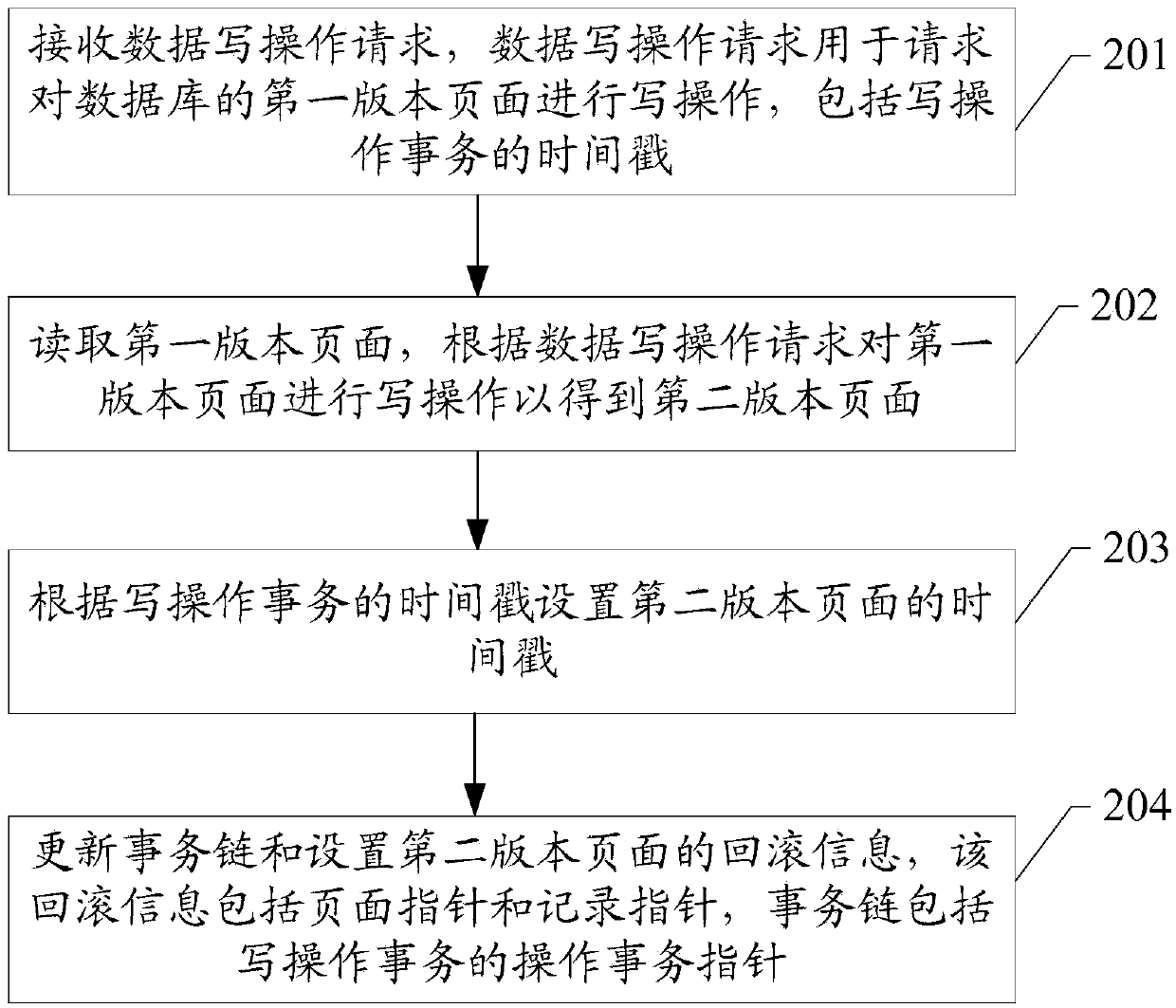
The embodiment of the invention discloses a multi-version concurrency control method in a database and a database system, which are mainly applied to the technical field of databases. The database system is provided with a data page chain of a page; the data page chain comprises a page compass of each version of the page; the page compass of one version of the page is used for pointing to another version of the page before last operation of the version of the page, so that the page can be directly rolled back to the page which needs to be read based on the data page chain of the page which is requested to be read if the time stamp of the current version of the page is greater than the time stamp including a reading service in a data reading request when pages in the database are read, a user is convenient to know the page in the database at any time and is convenient to inquire data of each version of the page in the database. Furthermore, the database system can realize roll-back of records efficiently through combination of the data page chain and a record chain, and can realize reading consistency.
Owner:HUAWEI TECH CO LTD
End to End Multicast
ActiveUS20140095924A1Improve bandwidth efficiencyData switching networksRedundant hardware error correctionSource encodingComputer network
IP multicast enabled devices, systems and methods for use on an end-to-end IP multicast-enabled network are disclosed. An IP multicast system, device and method operable on the network includes an IP multicast-engine, and storage for storing instruction sets to instruct the engine to send messages according to a select multicast application. A plurality of devices become members of an IP multicast group such that sending a message to a single multicast address can provide for the concurrent control of, and the delivery of the multicast message to, the devices of the group. Error conditions in a multicast source may be handled by preserving the multicast session resources, and reassigning a multicast source address from a faulty source encoding device to an alternate device.
Owner:COMCAST CABLE COMM LLC
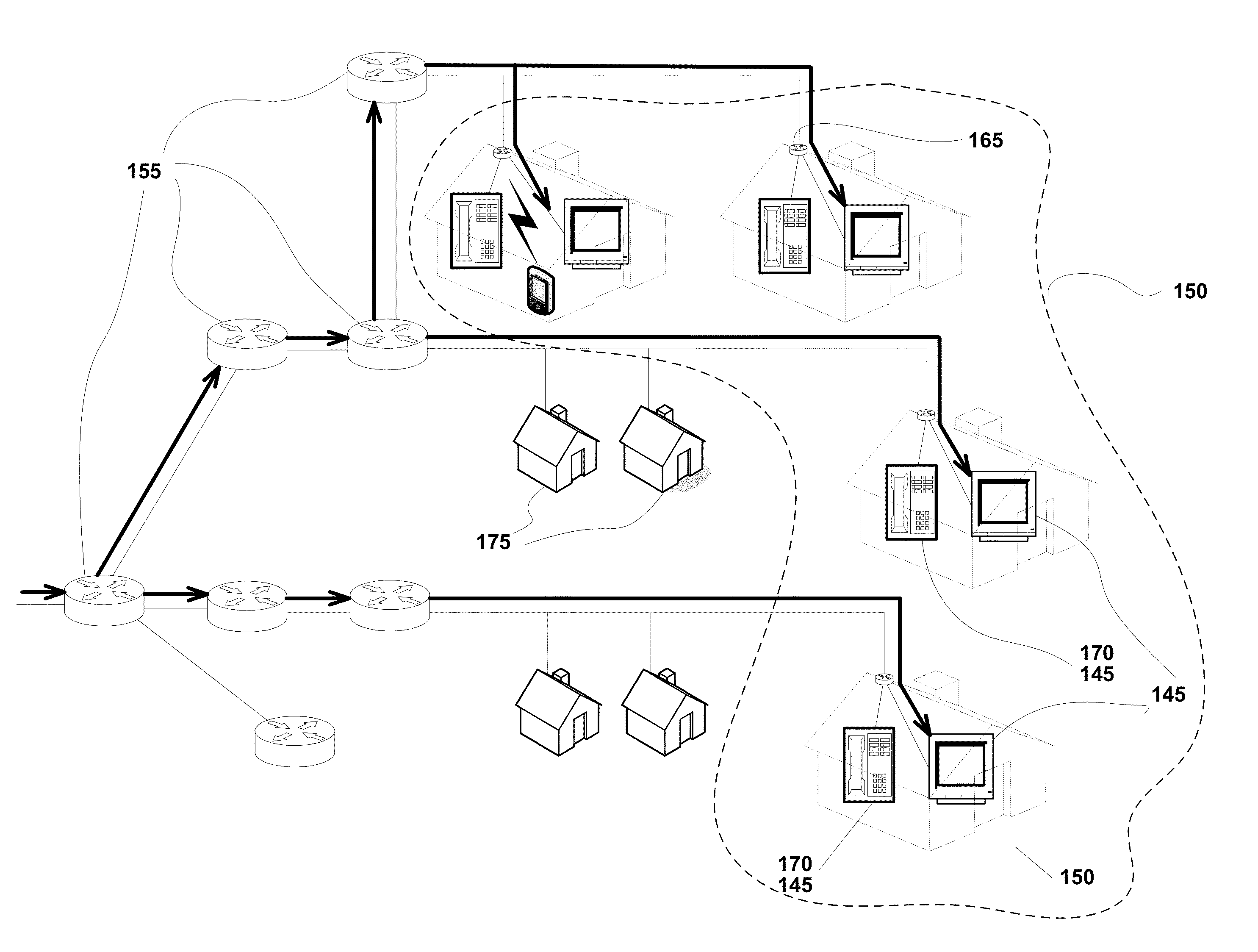
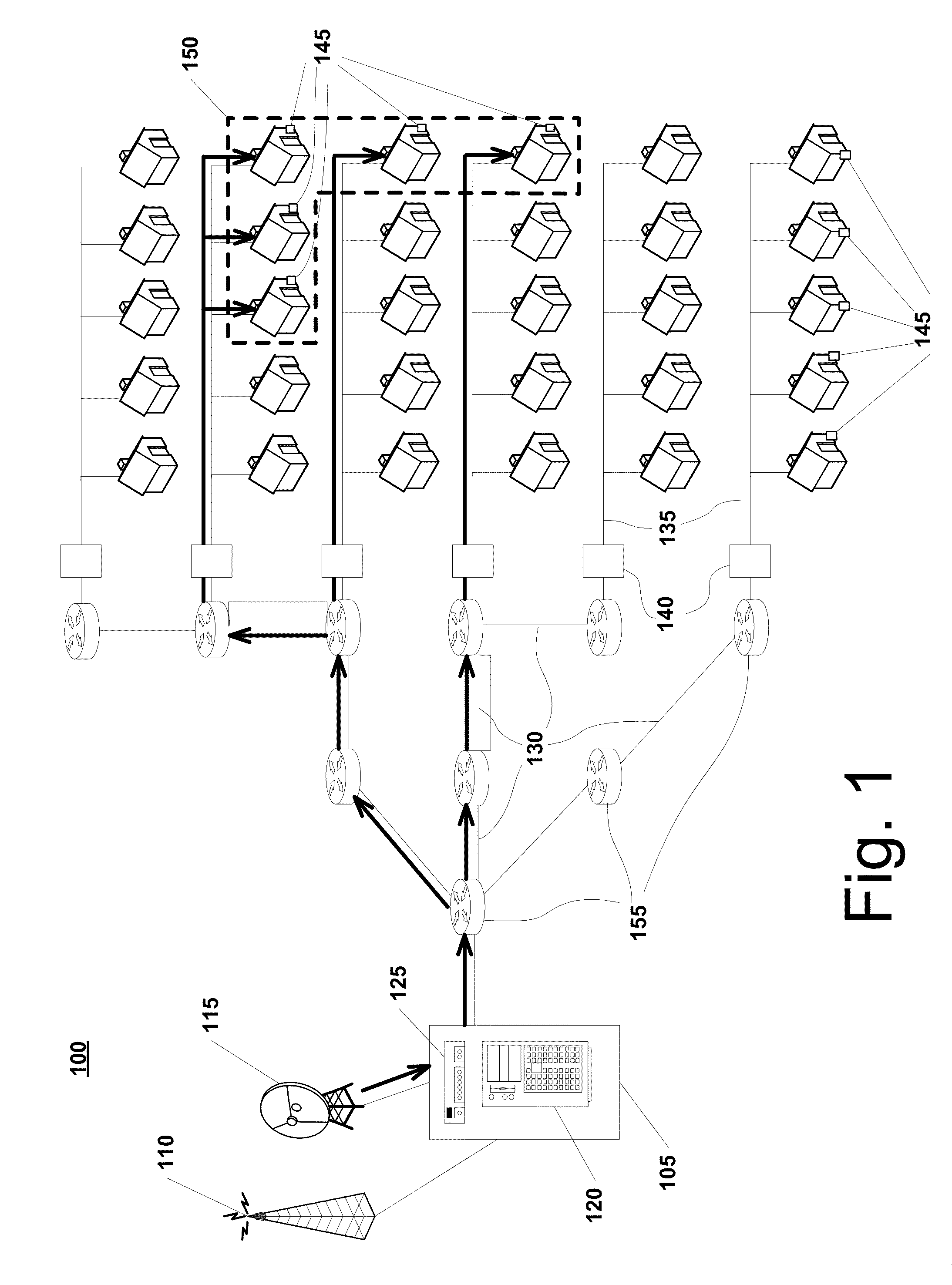
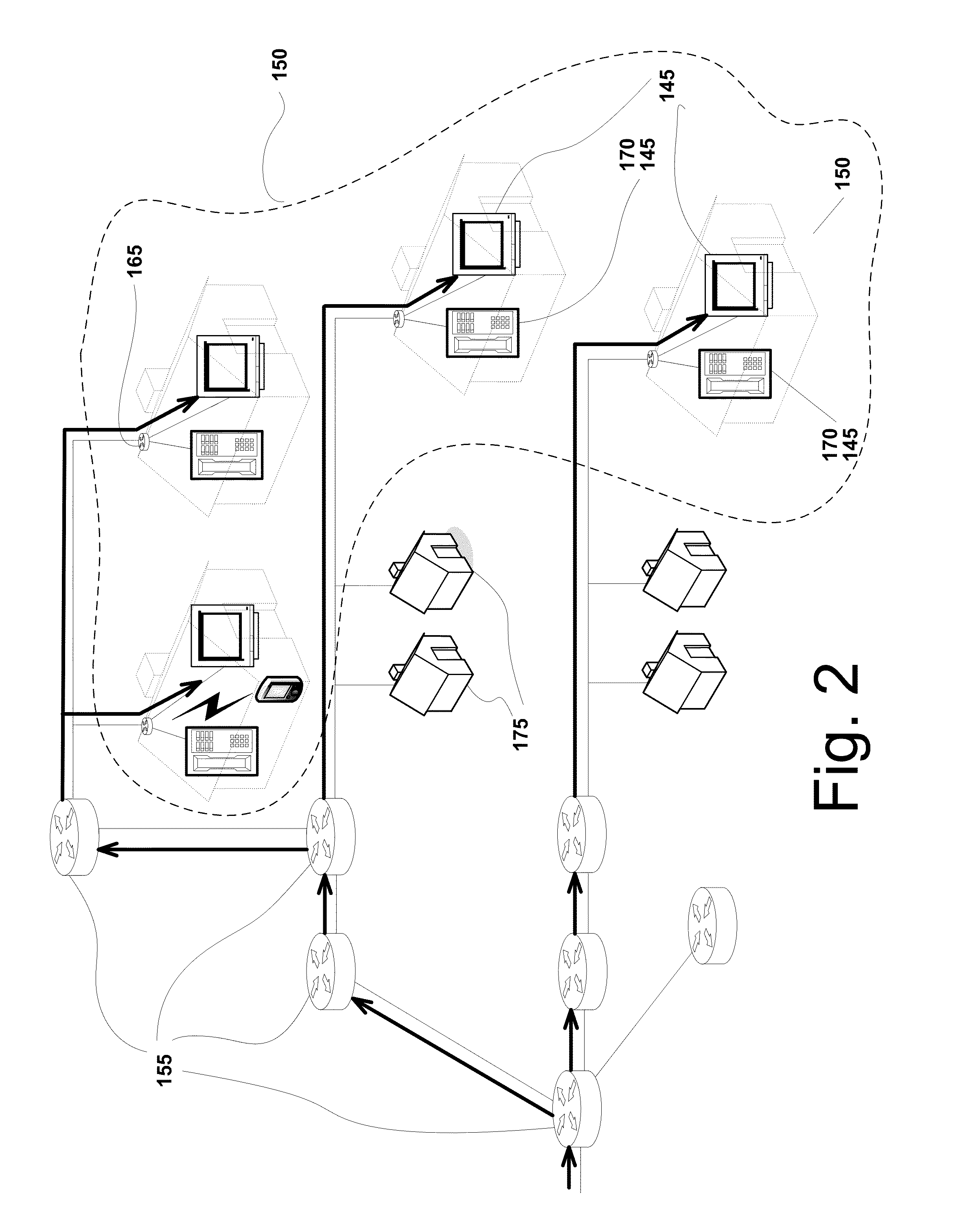
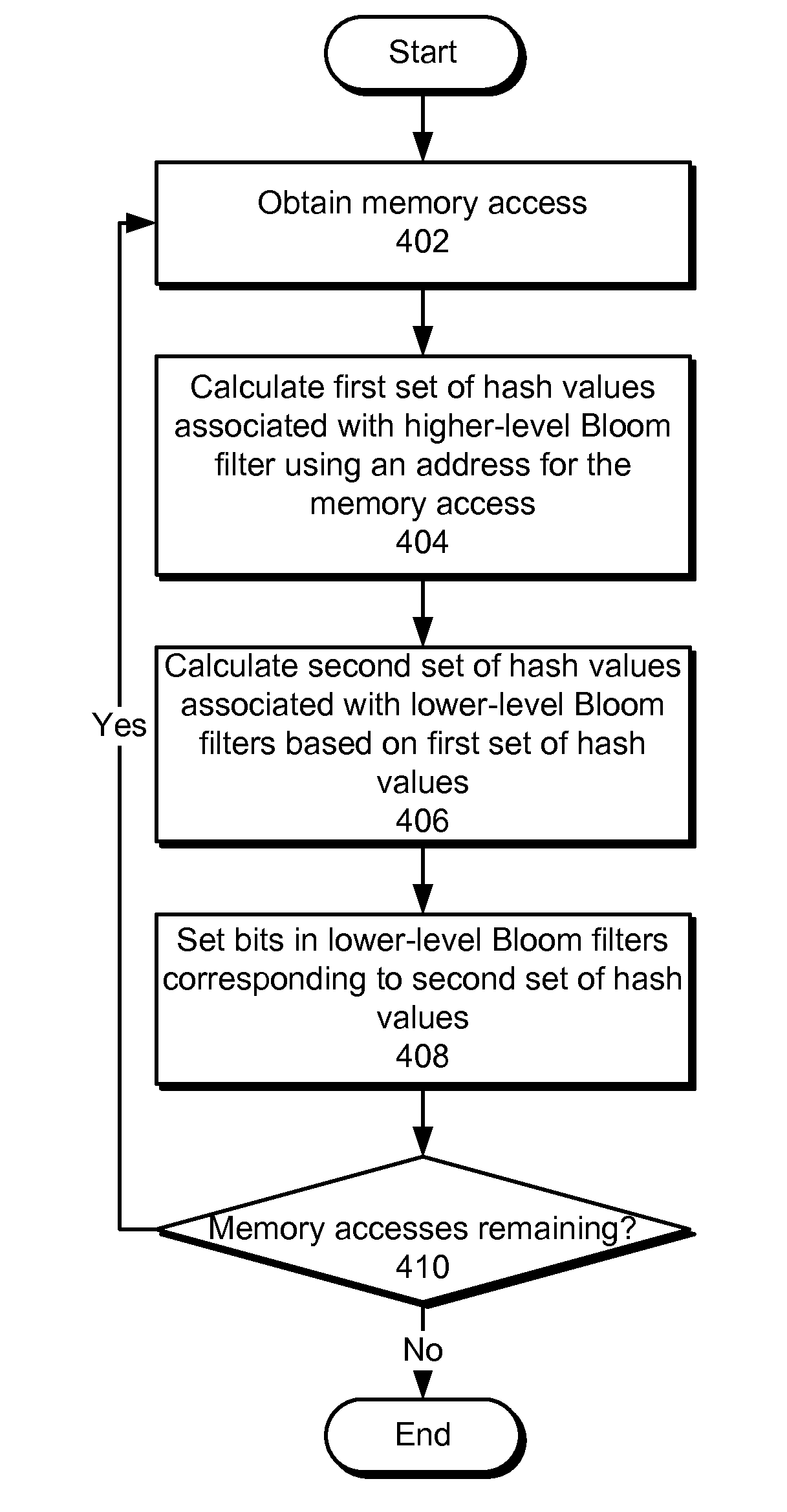
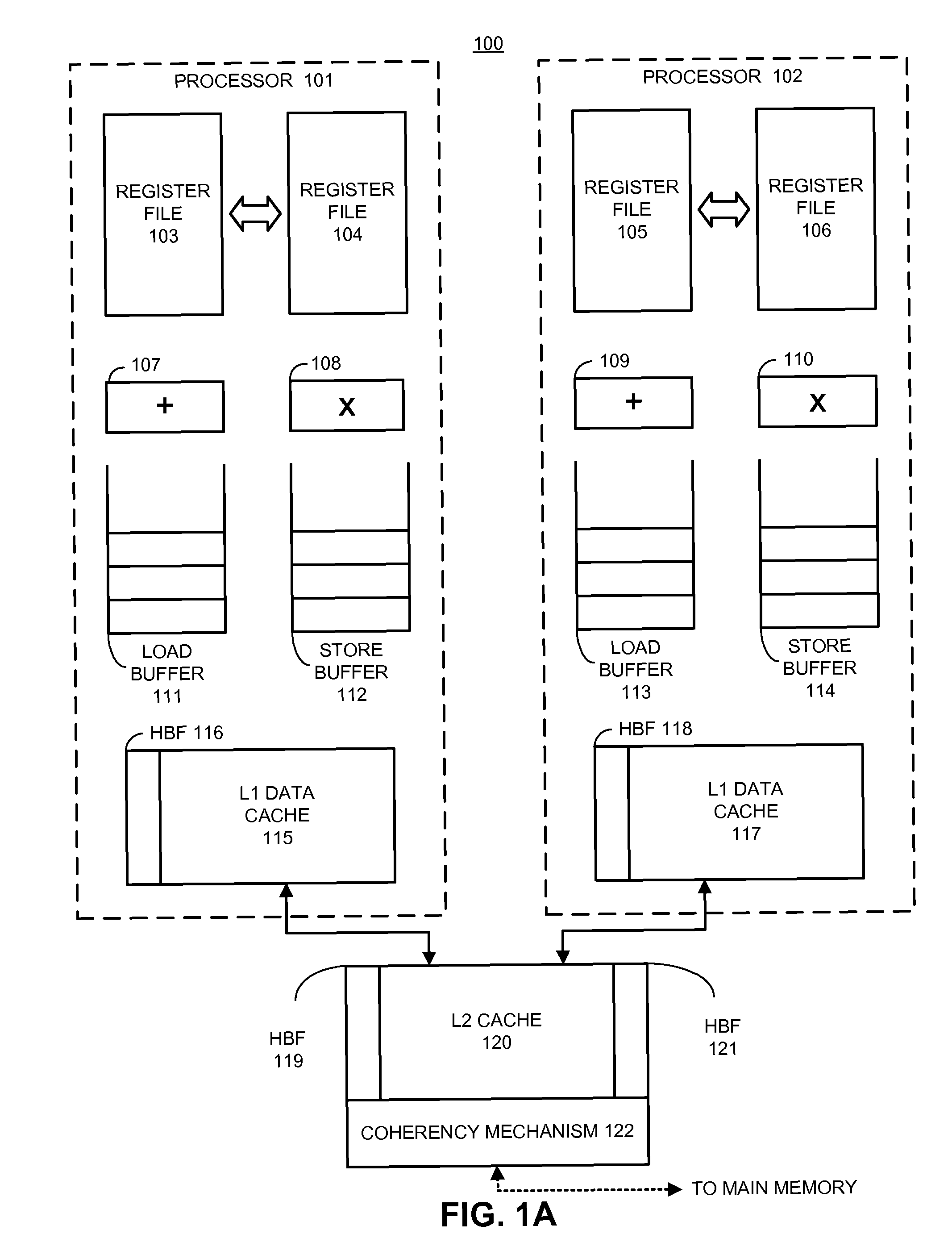
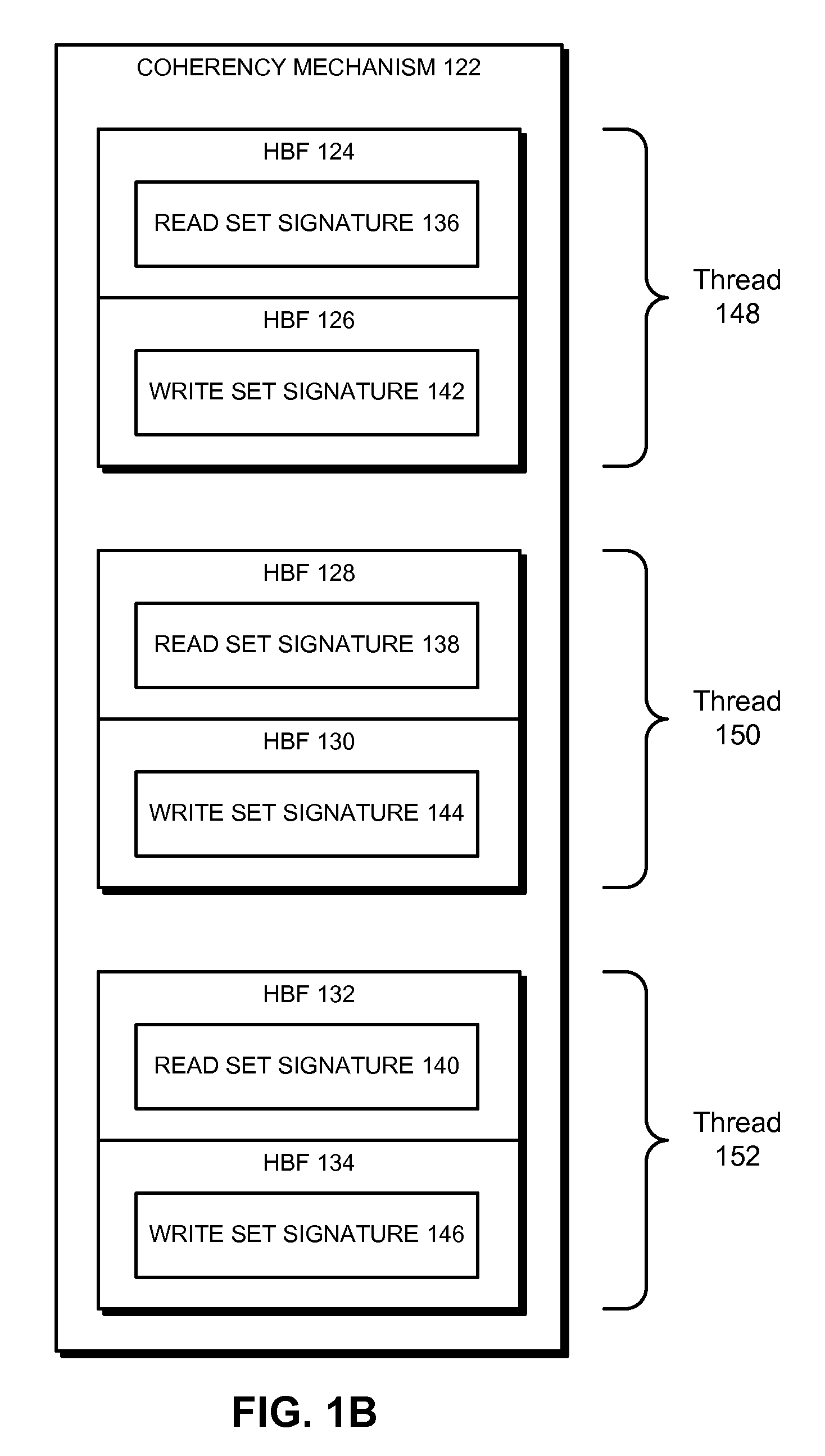
Hierarchical bloom filters for facilitating concurrency control
ActiveUS8484438B2Facilitates concurrency controlDigital data processing detailsSpecial data processing applicationsConcurrency controlComputerized system
Some embodiments provide a system that facilitates concurrency control in a computer system. During operation, the system generates a set of signatures associated with memory accesses in the computer system. To generate the signatures, the system creates a set of hierarchical Bloom filters (HBFs) corresponding to the signatures, and populates the HBFs using addresses associated with the memory accesses. Next, the system compares the HBFs to detect a potential conflict associated with the memory accesses. Finally, the system manages concurrent execution in the computer system based on the detected potential conflict.
Owner:ORACLE INT CORP
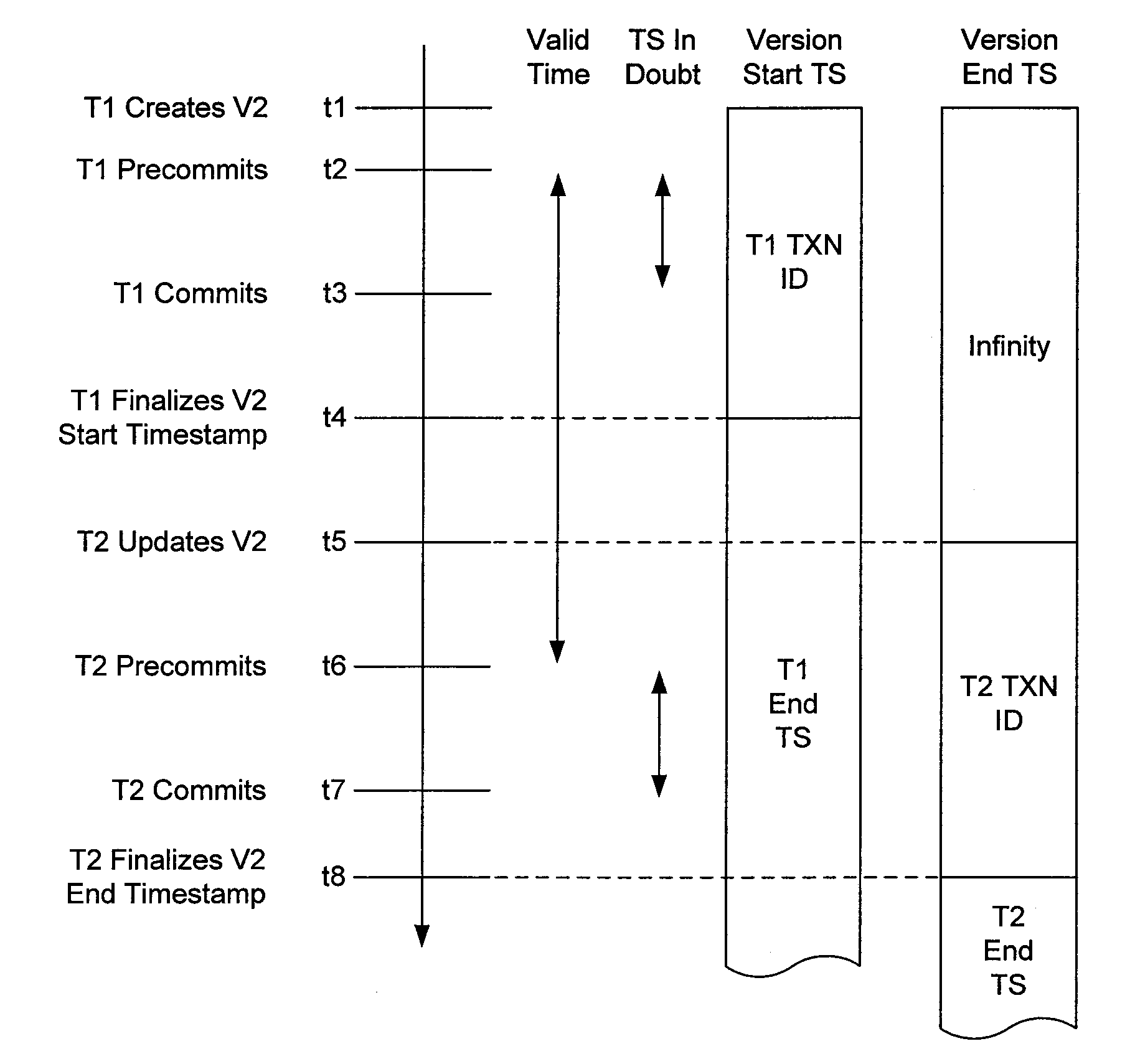
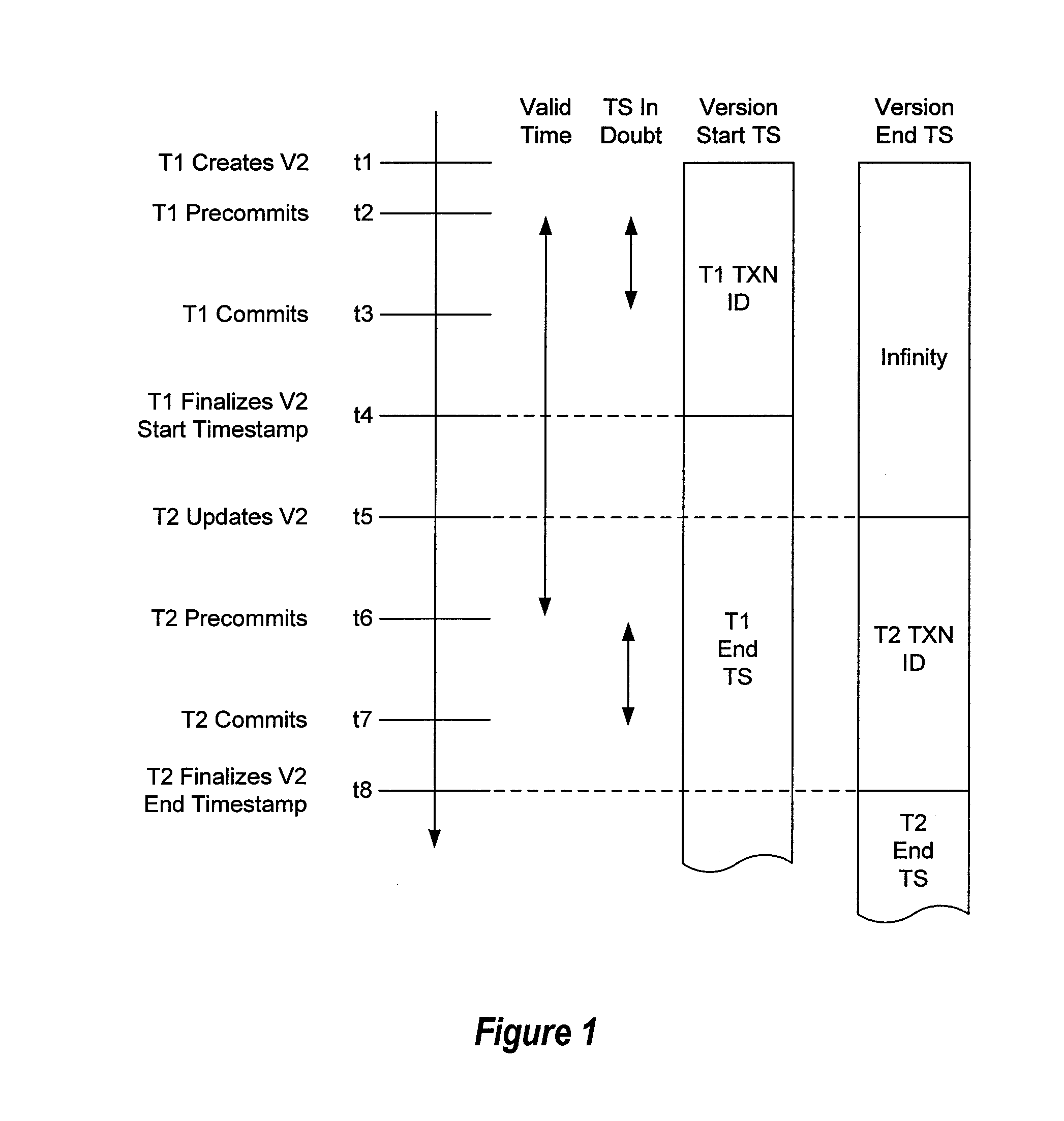
Efficient multi-version locking for main memory databases
ActiveUS20120233139A1Correct orderDigital data information retrievalDigital data processing detailsConcurrency controlMultiversion concurrency control
A transaction creates a wait for dependency on a version in a main memory database implementing a multi-version concurrency control scheme. The wait for dependency allows the transaction to update the version while other transactions are reading the version. The multi-version concurrency control scheme also allows commit dependencies to be implementing concurrently with wait for dependencies. Commit dependencies allow a transaction to read an updated version before the updated version is committed.
Owner:MICROSOFT TECH LICENSING LLC
Method and system for concurrency control in log-structured merge data stores
InactiveUS20160179865A1Program synchronisationDigital data processing detailsConcurrency controlStructure of Management Information
The present teaching relates to concurrency control in log-structured merge (LSM) data stores. In one example, a call is received from a thread for writing a value to a key of LSM components. A shared mode lock is set on the LSM components in response to the call. The value is written to the key once the shared mode lock is set on the LSM components. The shared mode lock is released from the LSM components after the value is written to the key.
Owner:YAHOO INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com