Patents
Literature
76 results about "Node deletion" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
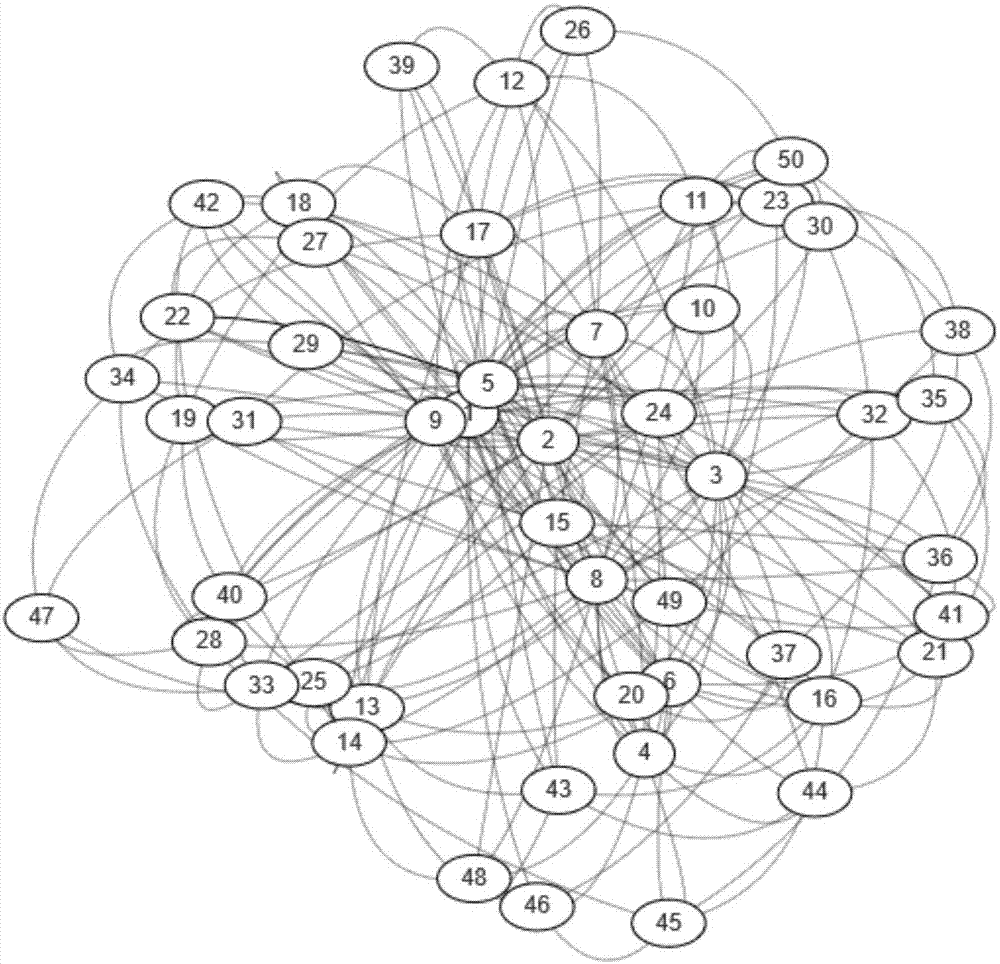
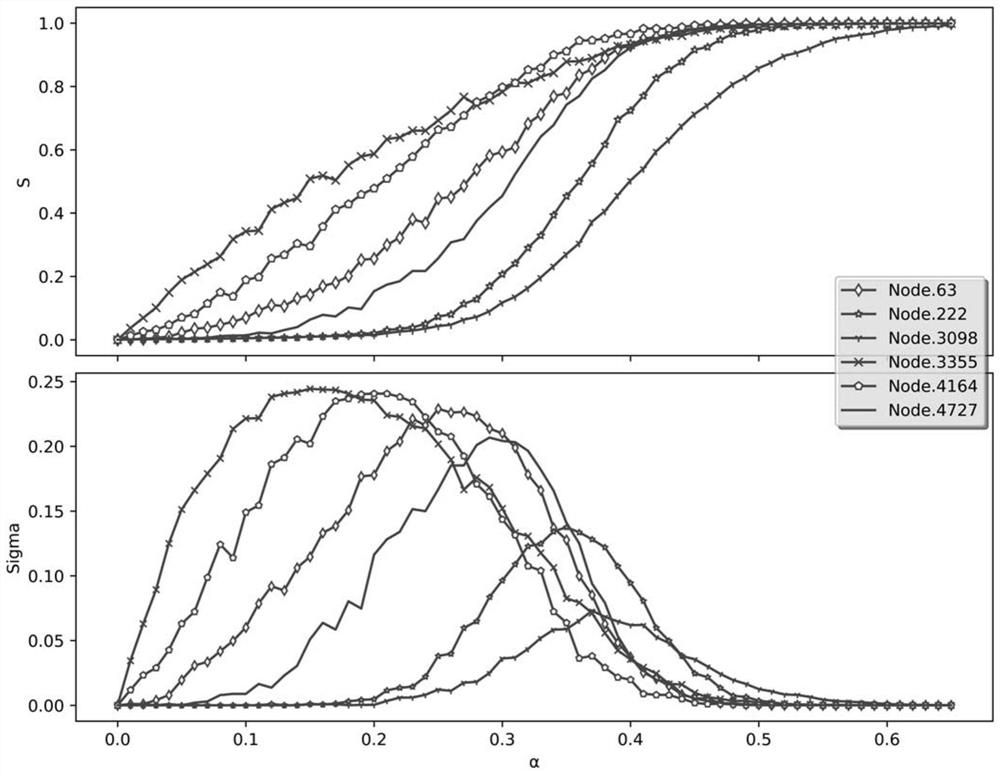
Node deletion is the procedure of removing a node from a network, where the node is either chosen randomly or directly. Node deletion is used to test the robustness and the attack tolerance of networks. Understanding how a network changes in response to node deletion is critical in many empirical networks. Application varies across many fields, including the breakdown of the World Wide Web via router removal, elimination of epidemics or fighting against criminal organizations.
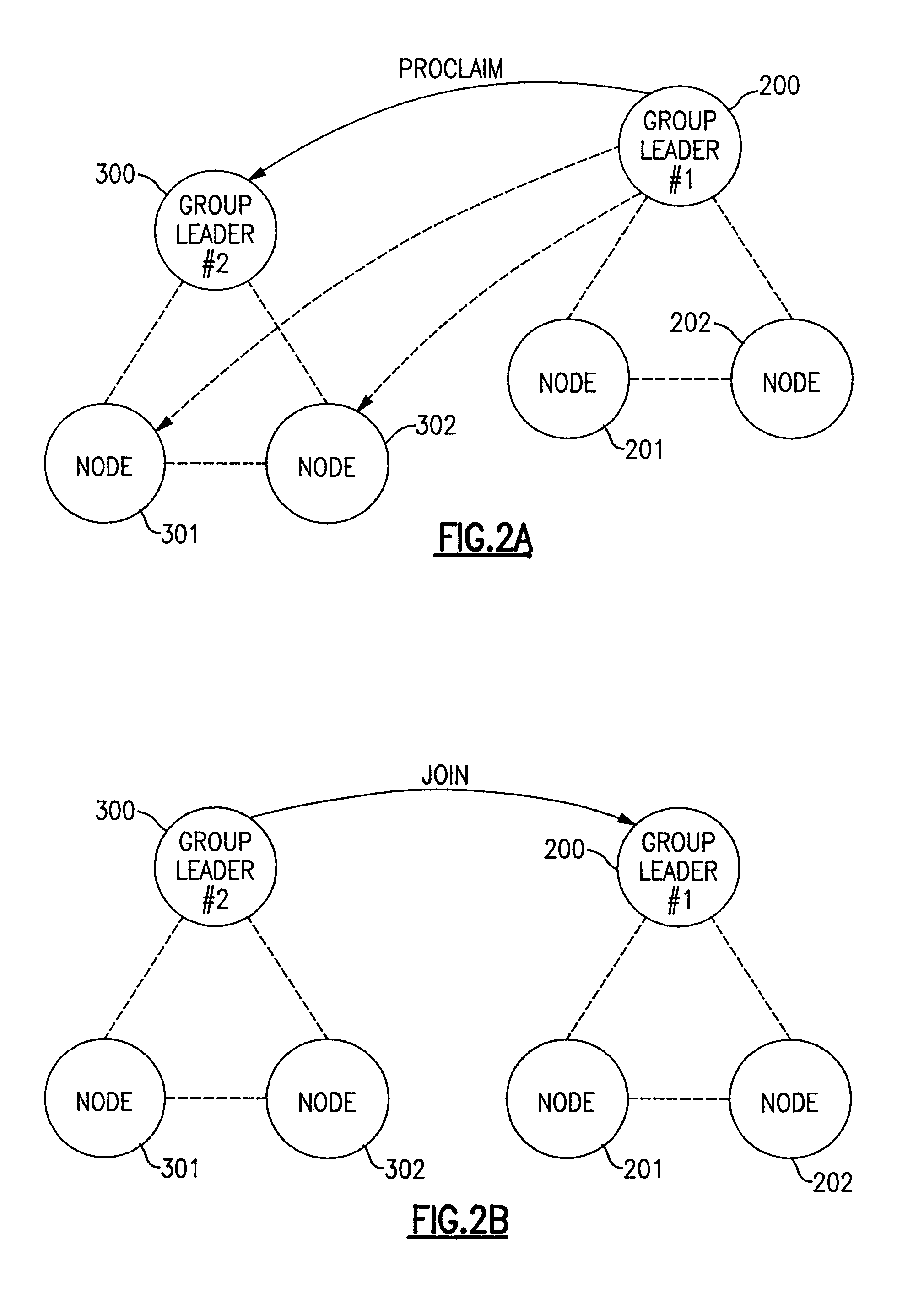
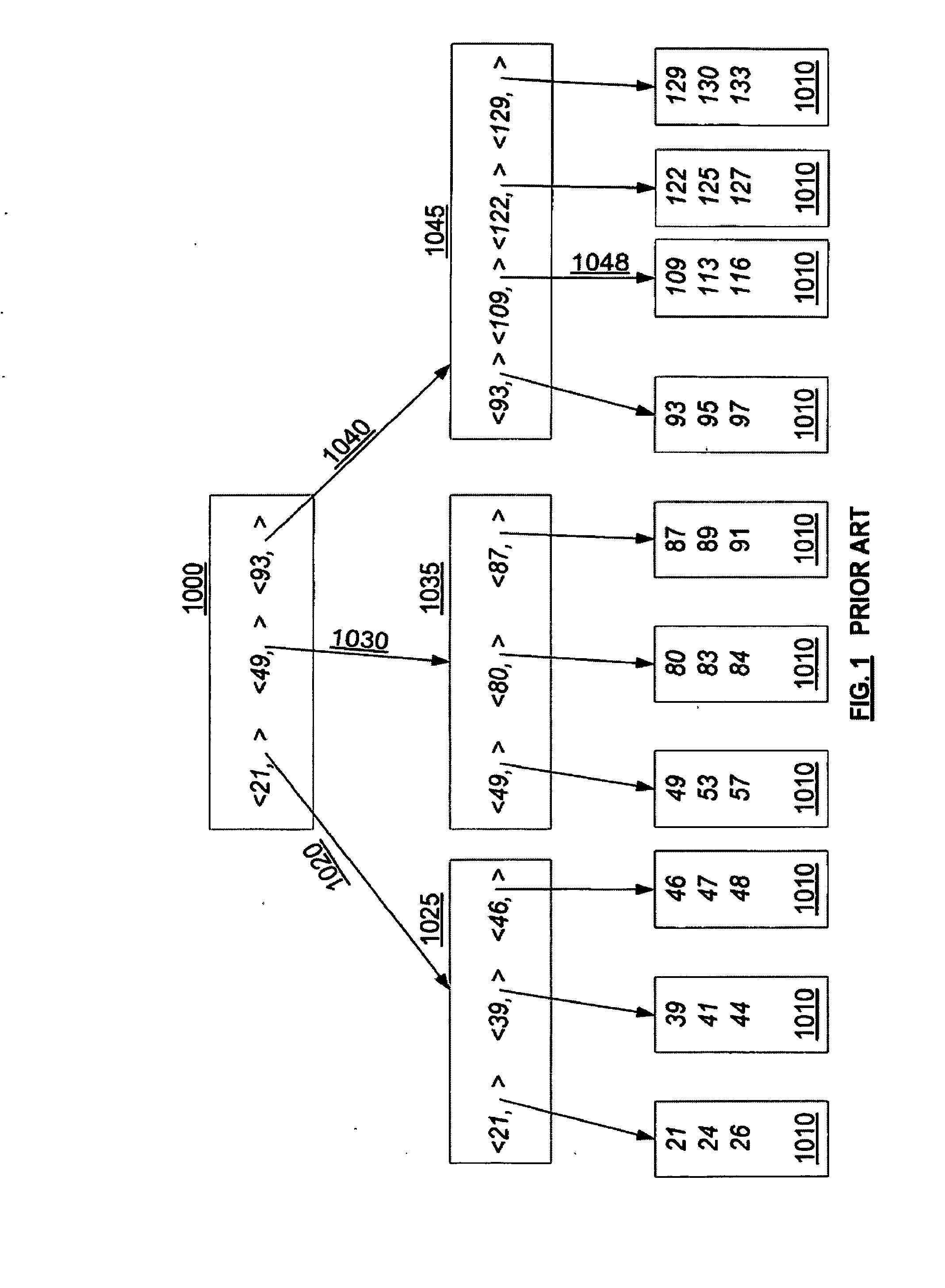
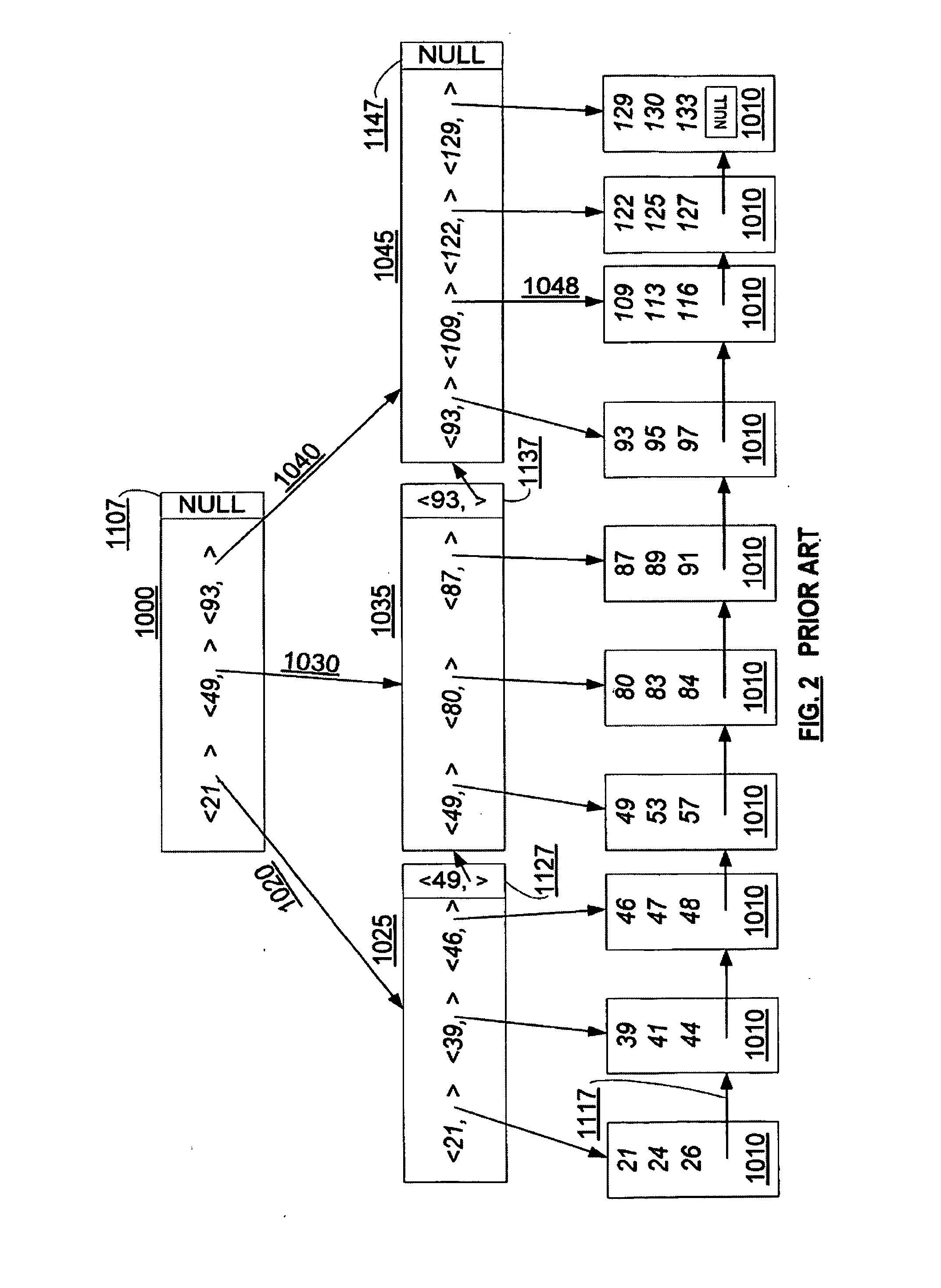
Concurrency control for B-trees with node deletion
InactiveUS20050171960A1Highly concurrent access of dataEasy to solveData processing applicationsDigital data information retrievalConcurrency controlTree (data structure)
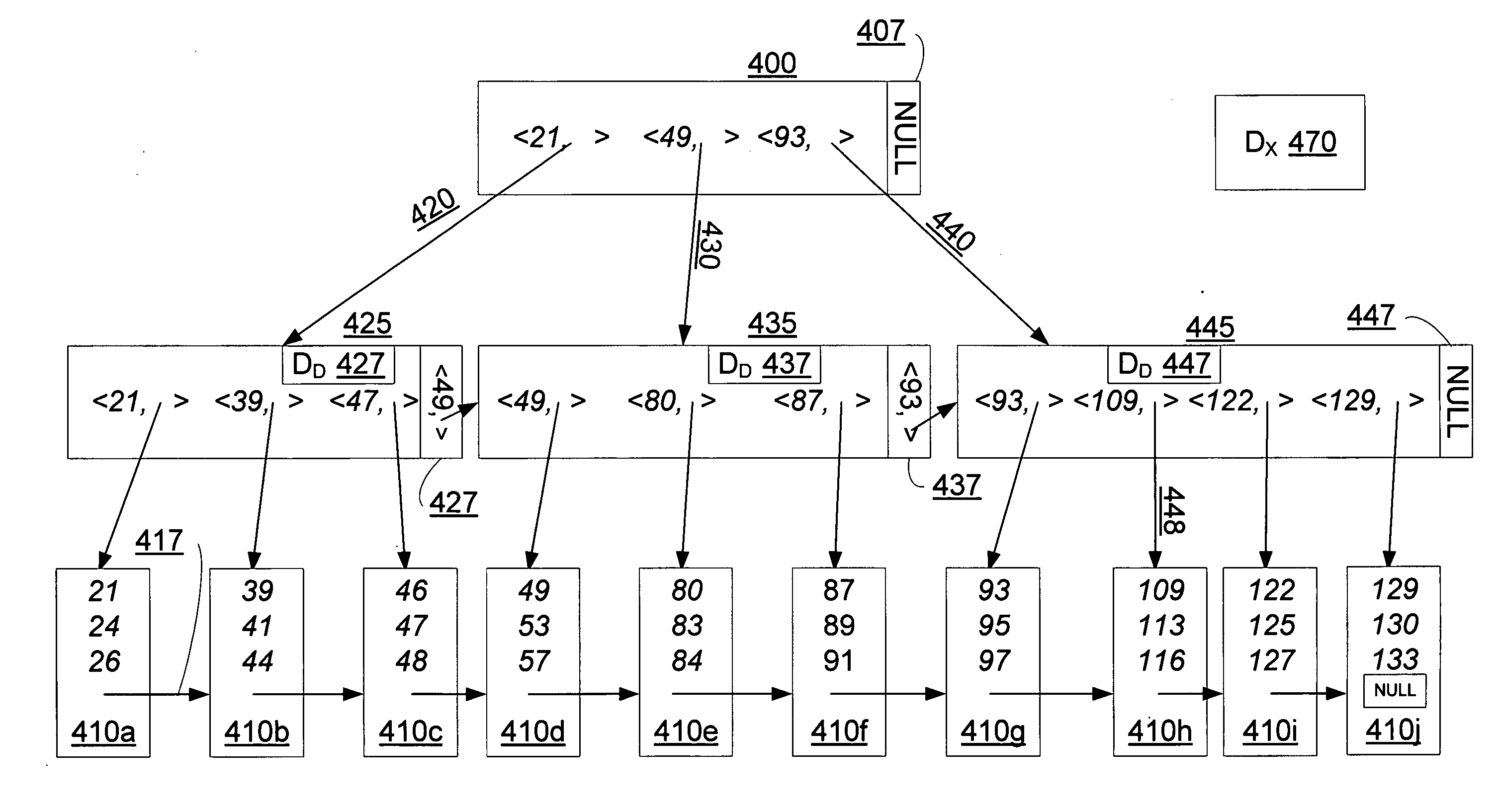
A data structure, added to a modified form of the Blink-tree data structure, tracks delete states for nodes. The index delete state (DX) indicates whether it is safe to directly access an index node without re-traversing the B-tree. The DX state is maintained globally, outside of the tree structure. The data delete state (DD) indicates whether it is safe to post an index term for a new leaf node. A DD state is maintained in each level 1 node for its leaf nodes. Delete states indicate whether a specific node has not been deleted, or whether it may have been deleted. Delete states are used to remove the necessity for atomic node splits and chains of latches for deletes, while not requiring retraversal. This property of not requiring a retraversal is exploited to simplify the tree modification operations.
Owner:MICROSOFT TECH LICENSING LLC
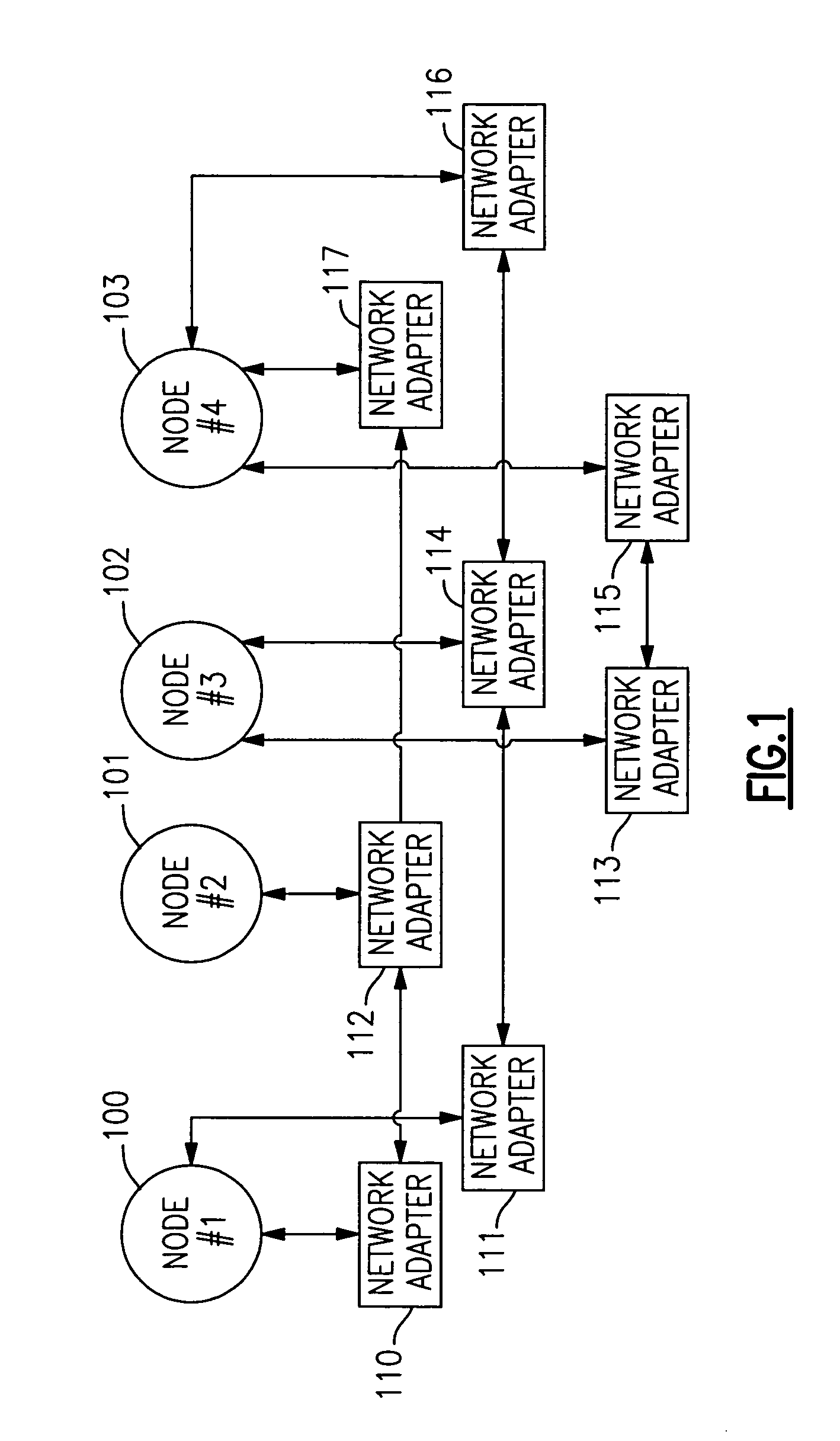
Method using two different programs to determine state of a network node to eliminate message response delays in system processing
InactiveUS7120693B2Increase elasticityImprove usabilityProgram initiation/switchingBroadband local area networksData processing systemLiveness
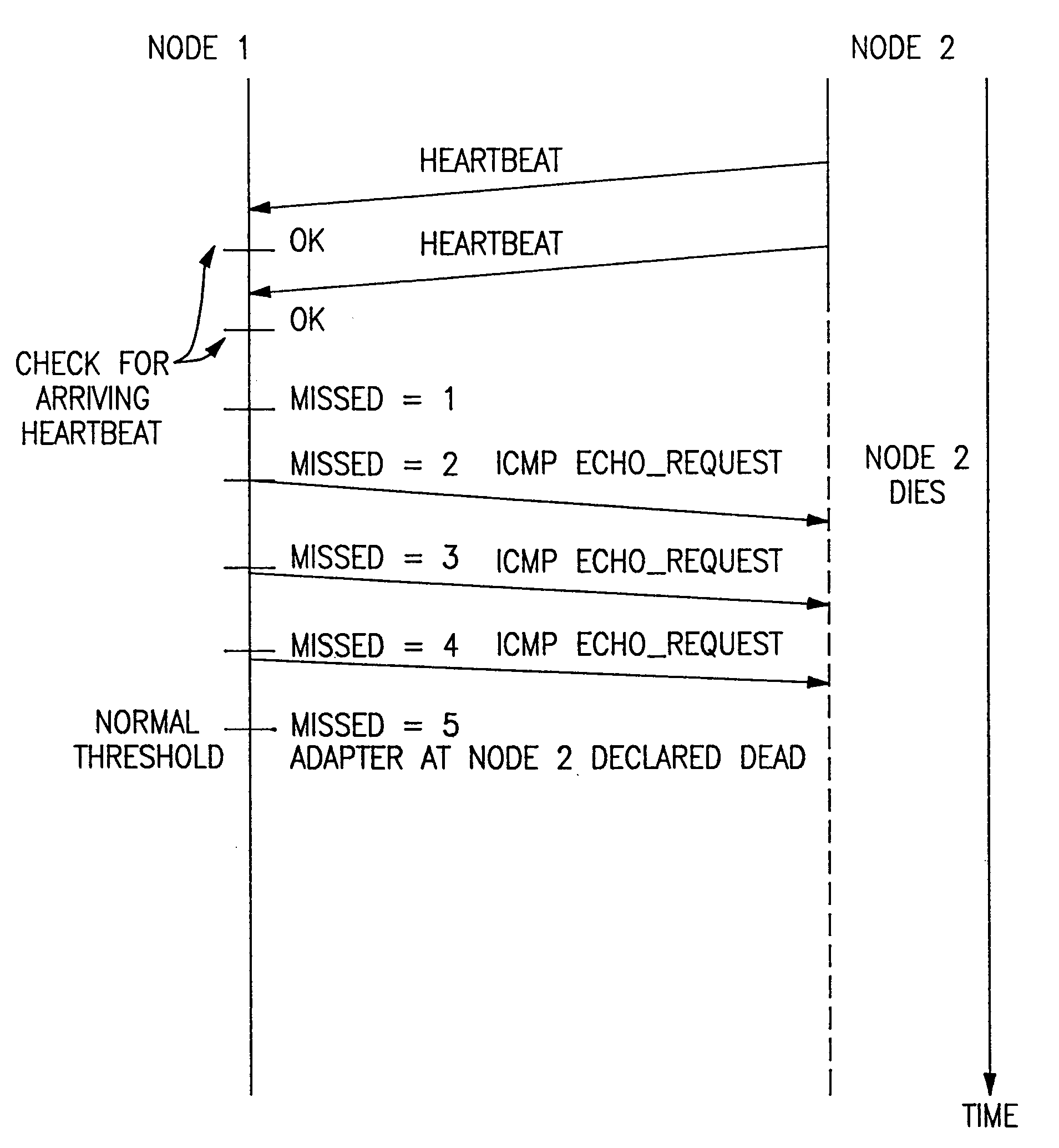
The determination of node and / or adapter liveness in a distributed network data processing system is carried out via one messaging protocol that can be assisted by a second messaging protocol which is significantly less susceptible to delay, especially memory blocking delays encountered by daemons running on other nodes. The switching of protocols is accompanied by controlled grace periods for needed responses. This messaging protocol flexibility is also adapted for use as a mechanism for controlling the deliberate activities of node addition (birth) and node deletion (death).
Owner:IBM CORP
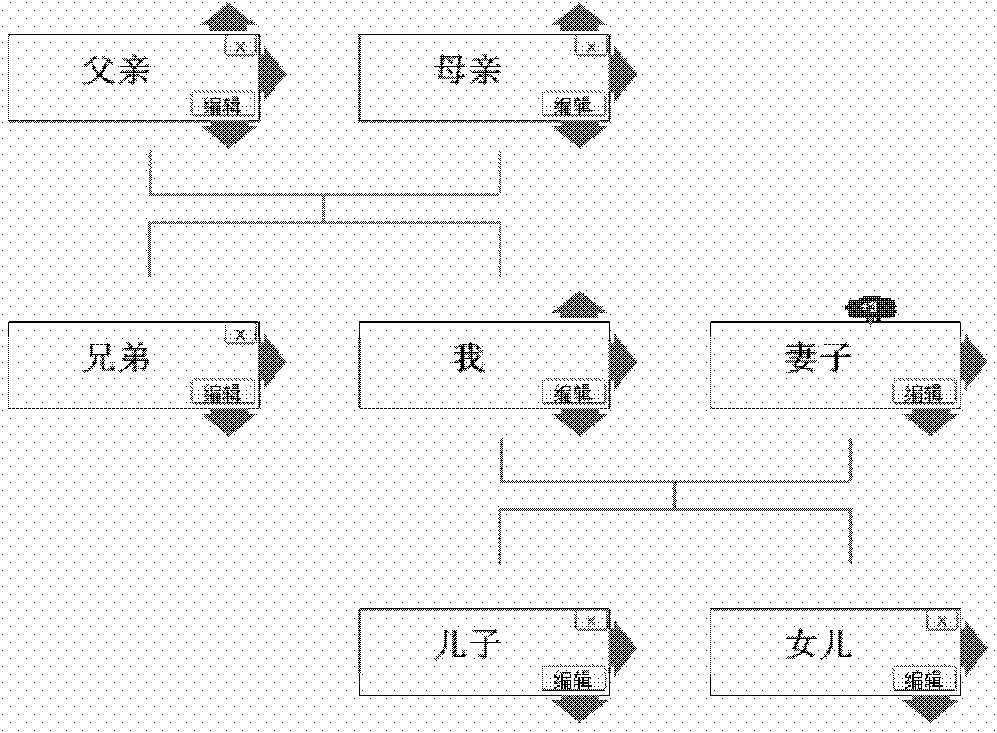
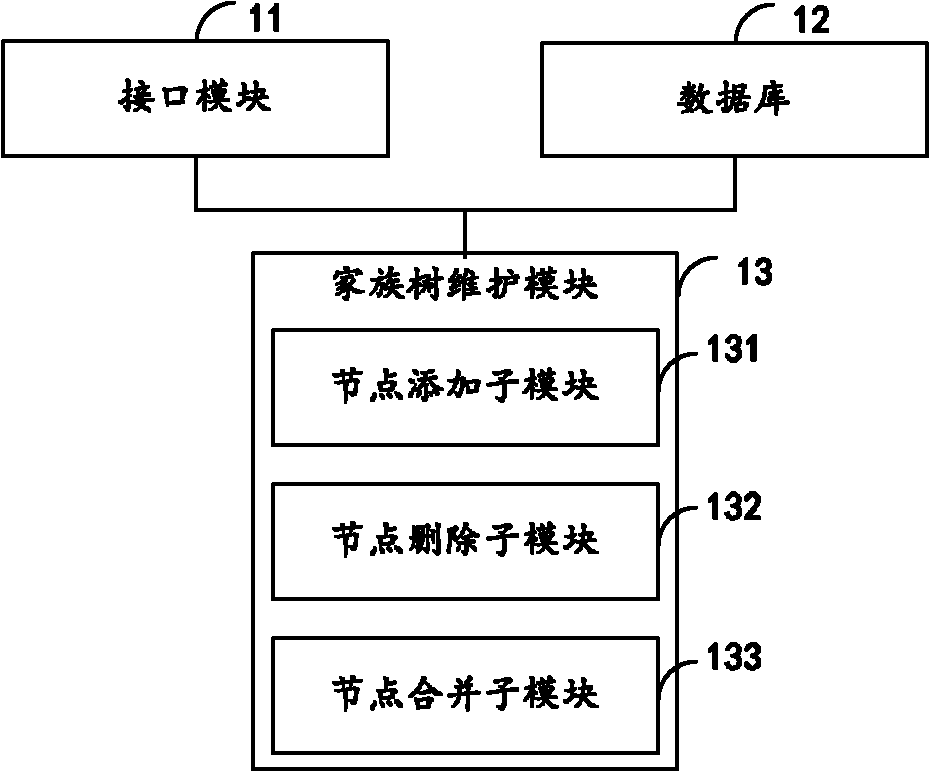
Processing system and processing method for nodes in family tree
InactiveCN102142015AIncrease reflectionEasy to useSpecial data processing applicationsData informationTheoretical computer science
The invention discloses a processing system and a processing method for nodes in a family tree. The processing system for the nodes in the family tree comprises an interface module, a database and a family tree maintenance module, wherein the interface module is used for providing an input interface and an output interface for users; the database is used for storing the data information of the family tree; the family tree maintenance module is used for maintaining the nodes in the family tree and a connection relation among the nodes according to the operation of the users and comprises a node addition submodule, a node deletion submodule and a node merging submodule; the node addition submodule is used for adding the nodes and the connection relation among the nodes; the node deletion submodule is used for deleting the nodes and the connection relation relevant to the nodes according to a preset deletion rule; and the node merging submodule is used for merging relevance nodes according to a preset merging rule, wherein the relevance nodes comprise common nodes in different family trees and relevant nodes in one family tree. By the processing system and the processing method, the blood relationships of various complex families in the actual world can be expressed accurately and integrally to the greatest extent, the openness of maintaining the family trees is ensured, and the user experience is improved.
Owner:唐凌遥
Concurrency control for b-trees with node deletion
InactiveUS20080071809A1Highly concurrent access of dataEasy to solveData processing applicationsDigital data information retrievalConcurrency controlTree (data structure)
Owner:MICROSOFT TECH LICENSING LLC
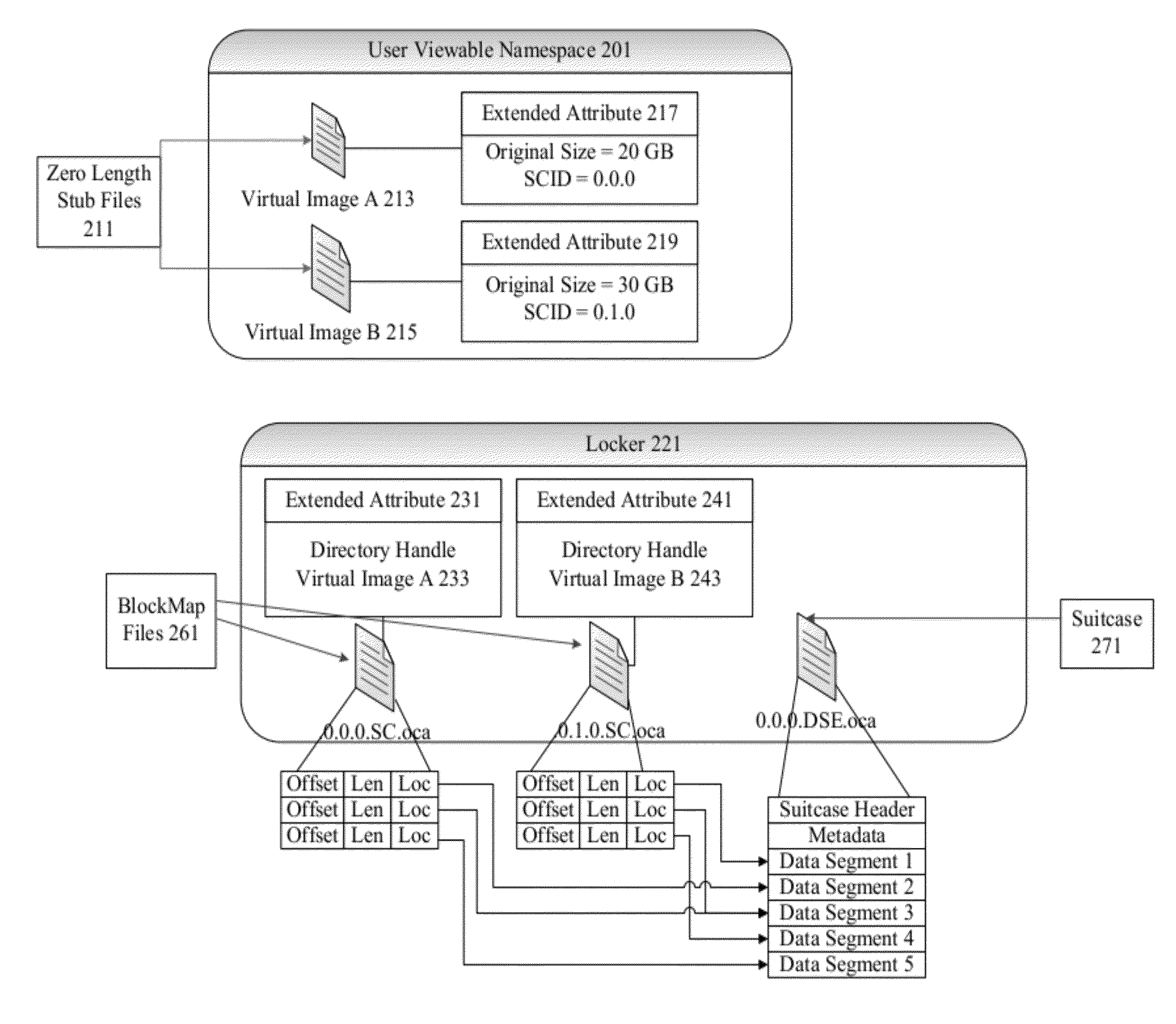
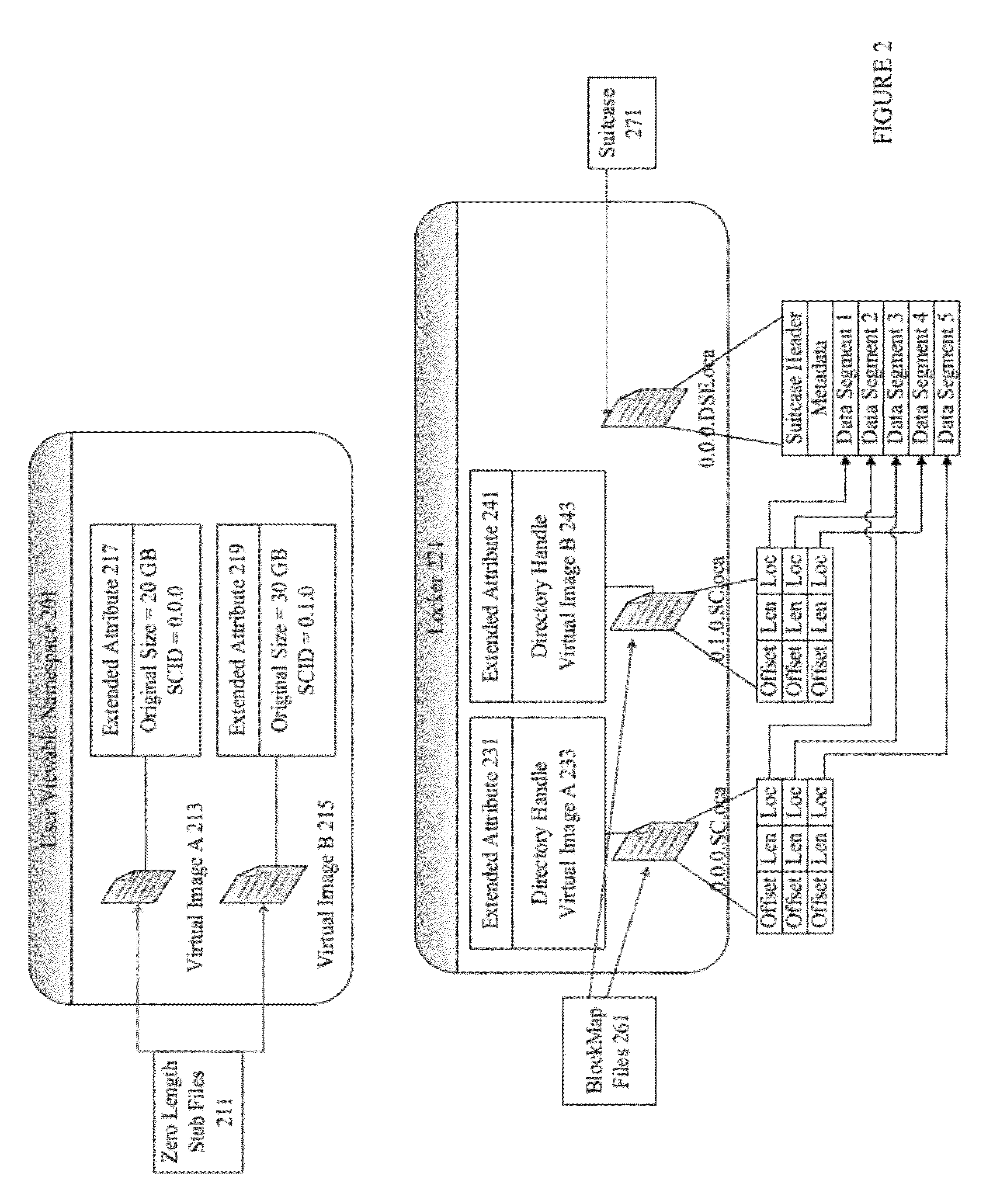
Data block migration
ActiveUS20120084527A1Digital data information retrievalMemory adressing/allocation/relocationDowntimeData deduplication
Techniques and mechanisms are provided for migrating data blocks around a cluster during node addition and node deletion. Migration requires no downtime, as a newly added node is immediately operational while the data blocks are being moved. Blockmap files and deduplication dictionaries need not be updated.
Owner:QUEST SOFTWARE INC
Complex network node importance assessment method and system thereof
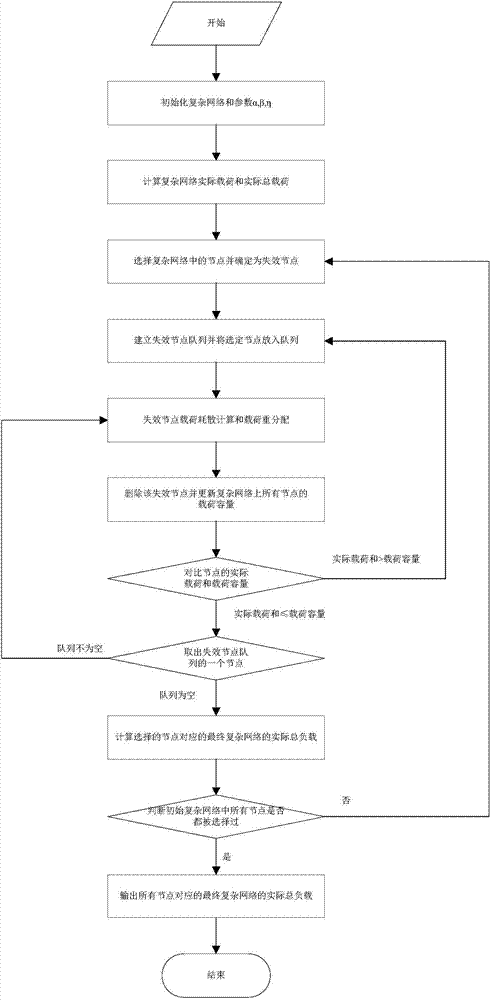
ActiveCN107453919ATrue importance assessmentMateriality assessment scienceData switching networksCascading failureLoad capacity
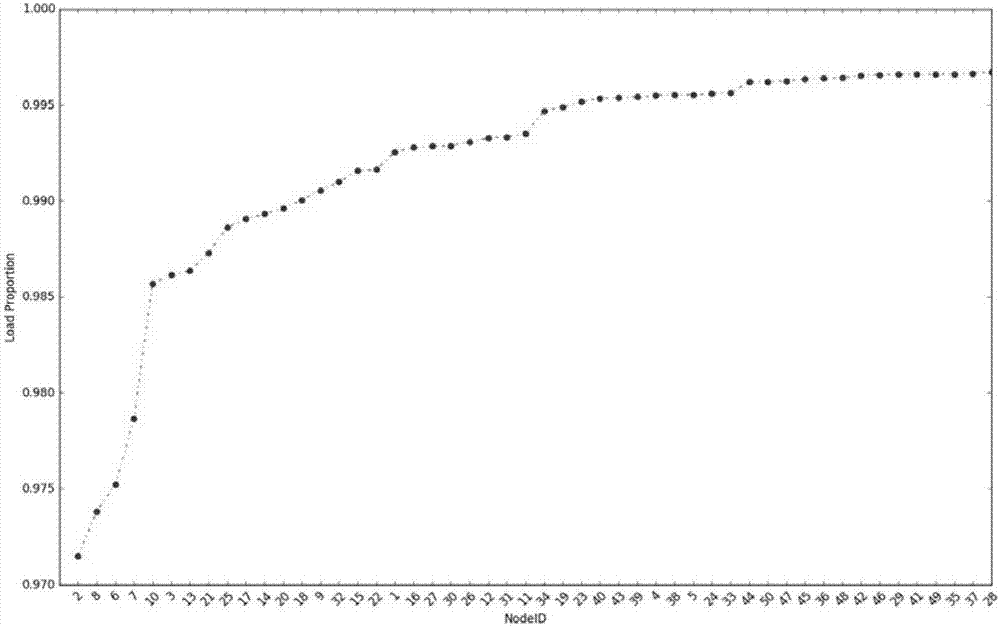
The invention discloses a complex network node importance assessment method and a system thereof. The method comprises the following steps of S1, initializing an actual load of each node in a complex network and calculating an initial total load of the complex network; S2, successively carrying out failure investigation on each node of the complex network and carrying out cascade failure simulation; during a cascade failure simulation process, after a failure node is deleted, adjusting and updating an actual load of a neighbor node, updating a load capacity of each complex network node, according to the updated load and the updated load capacity, carrying out a new round of failure determination on the complex network till that the complex network is stable, and calculating a residual total load of the complex network; and S3, according to the initial total load and the residual total load, assessing importance of each node. The method and the system possess a dynamic deepening characteristic of fully considering the complex network cascade failure, an inherent property of an important node can be prompted, and node importance in the complex network can be really and accurately assessed.
Owner:NAT UNIV OF DEFENSE TECH
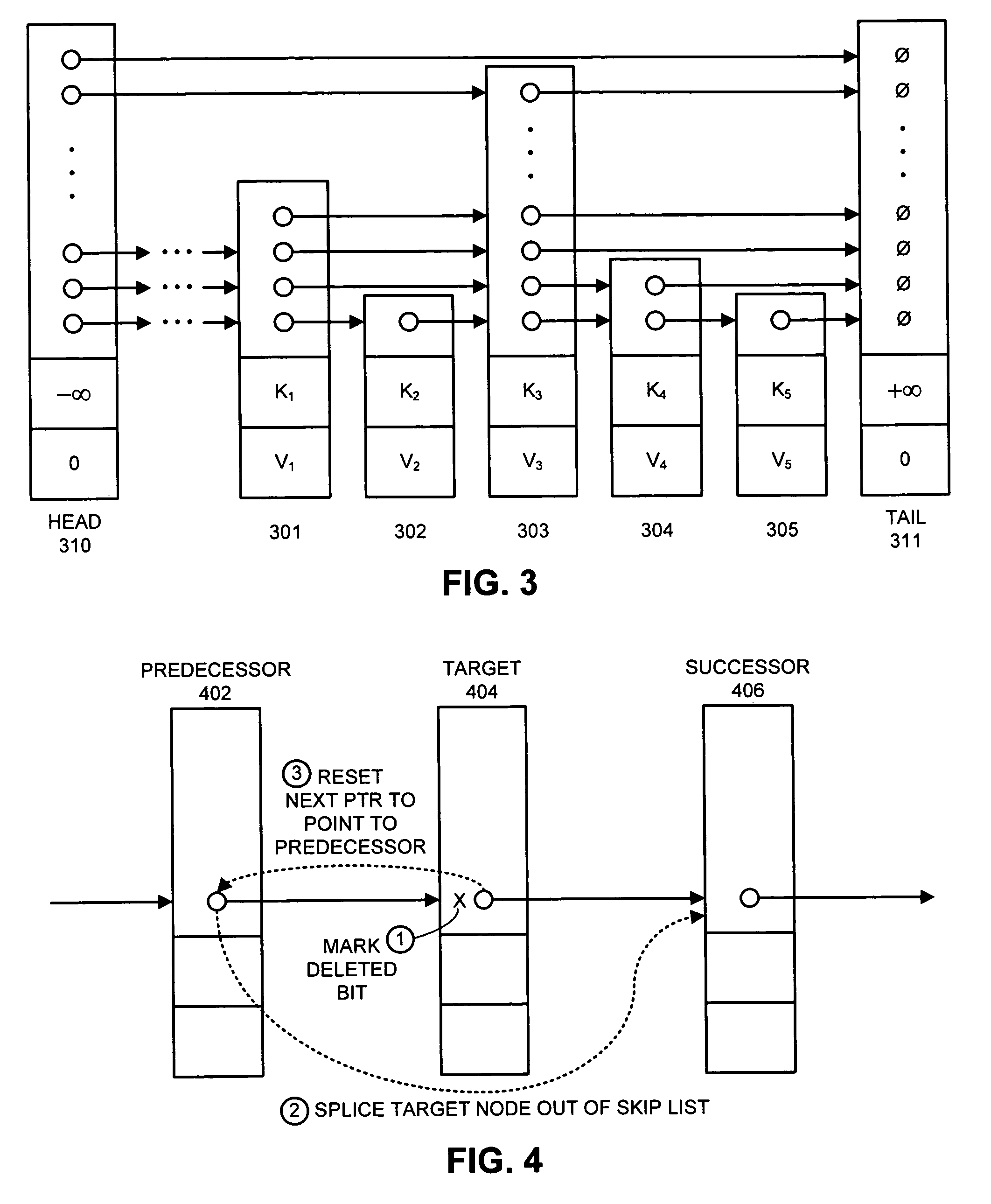
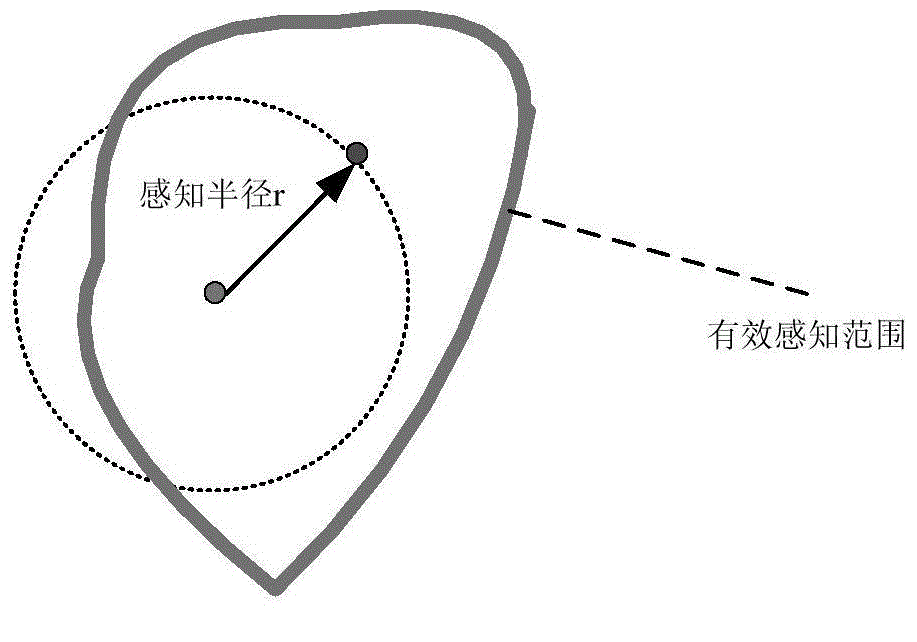
Method and apparatus for implementing a lock-free skip list that supports concurrent accesses
ActiveUS7308448B1Guaranteed progressData processing applicationsProgram synchronisationSkip listComputer science
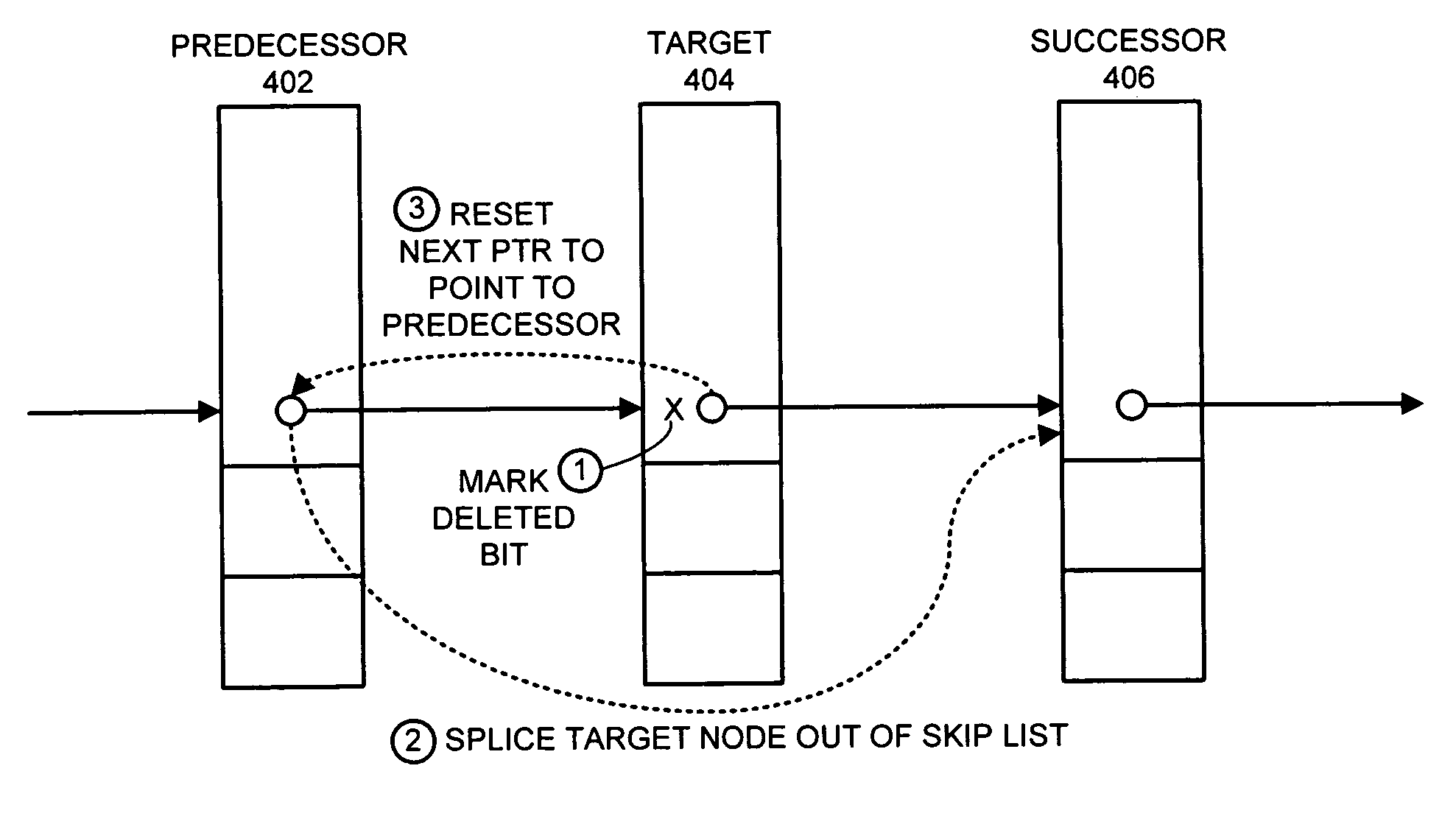
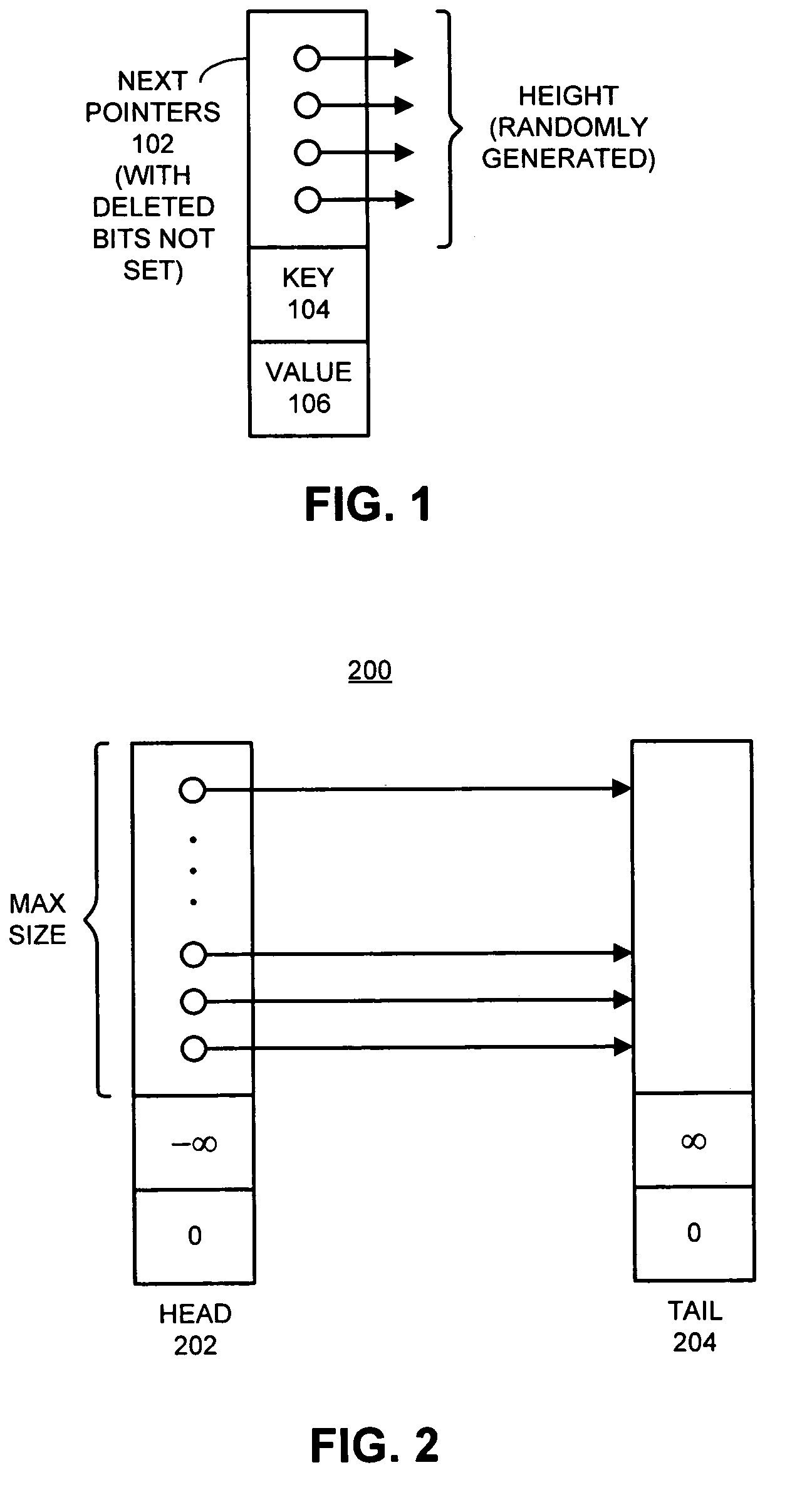
One embodiment of the present invention provides a system that supports concurrent accesses to a skip list that is lock-free, which means that the skip list can be simultaneously accessed by multiple processes without requiring the processes to perform locking operations. During a node deletion operation, the system receives reference to a target node to be deleted from the skip list. The system marks a next pointer in the target node to indicate that the target node is deleted, wherein next pointer contains the address of an immediately following node in the skip list. This marking operation does not destroy the address of the immediately following node, and furthermore, the marking operation is performed atomically and thereby without interference from other processes. The system then atomically modifies the next pointer of an immediately preceding node in the skip list to point to an immediately following node in the skip list, instead of pointing to the target node, thereby splicing the target node out of the skip list.
Owner:ORACLE INT CORP
Blackspot-prediction farmland time-varying heterogeneous network node deployment and interactive dispatching method
ActiveCN104378771AIncrease coverageExtend the life cycleNetwork topologiesNetwork planningNODALCoverage ratio
The invention discloses a blackspot-prediction farmland time-varying heterogeneous network node deployment and interactive dispatching method. The node deployment includes acquiring attribute of nodes according to path loss, node sensing probability, effective node sensing area and surplus node energy in the process of signal transmission; acquiring significance of the nodes according to the attribute and the node degree of the nodes; deploying the nodes by a constraint tightening method according to the significance of the nodes. The node interactive-dispatching includes determining a redundant node set according to the surplus node energy and the network coverage rate; according to a farmland time-varying heterogeneous network node set, determining a triangulation graph corresponding to the node set; according to the redundant node set, deleting non-redundant nodes and relevant sides in the triangulation graph to obtain a subdivision graph; determining dormant nodes in the redundant node set to obtain a dormant node set according to the redundant node set; deleting the nodes in the dormant node set in the farmland time-varying heterogeneous network node set to obtain a communication coverage set.
Owner:BEIJING RES CENT FOR INFORMATION TECH & AGRI
Digital addressing-based method for structured storage and rapid processing of command relation tree
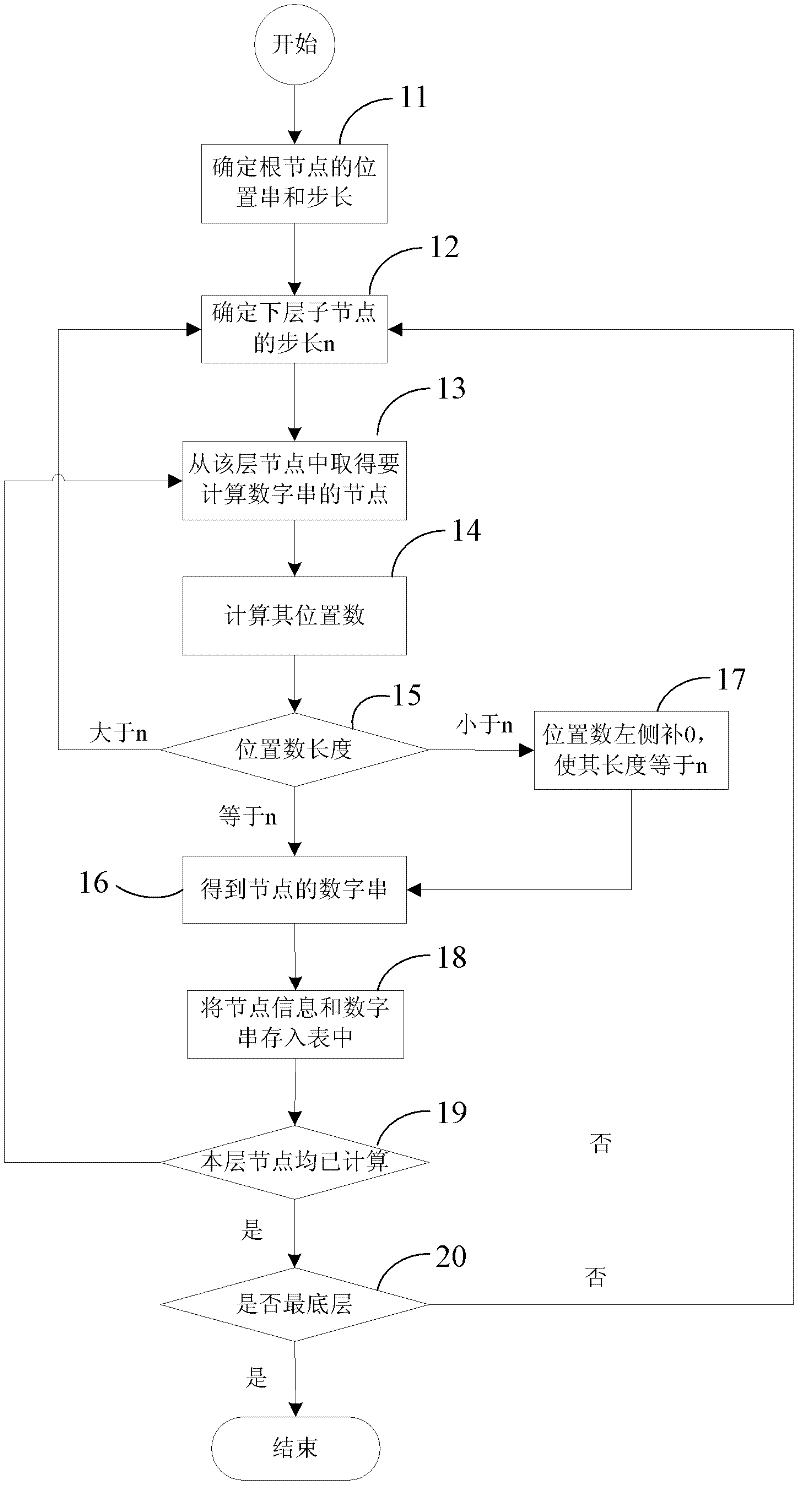
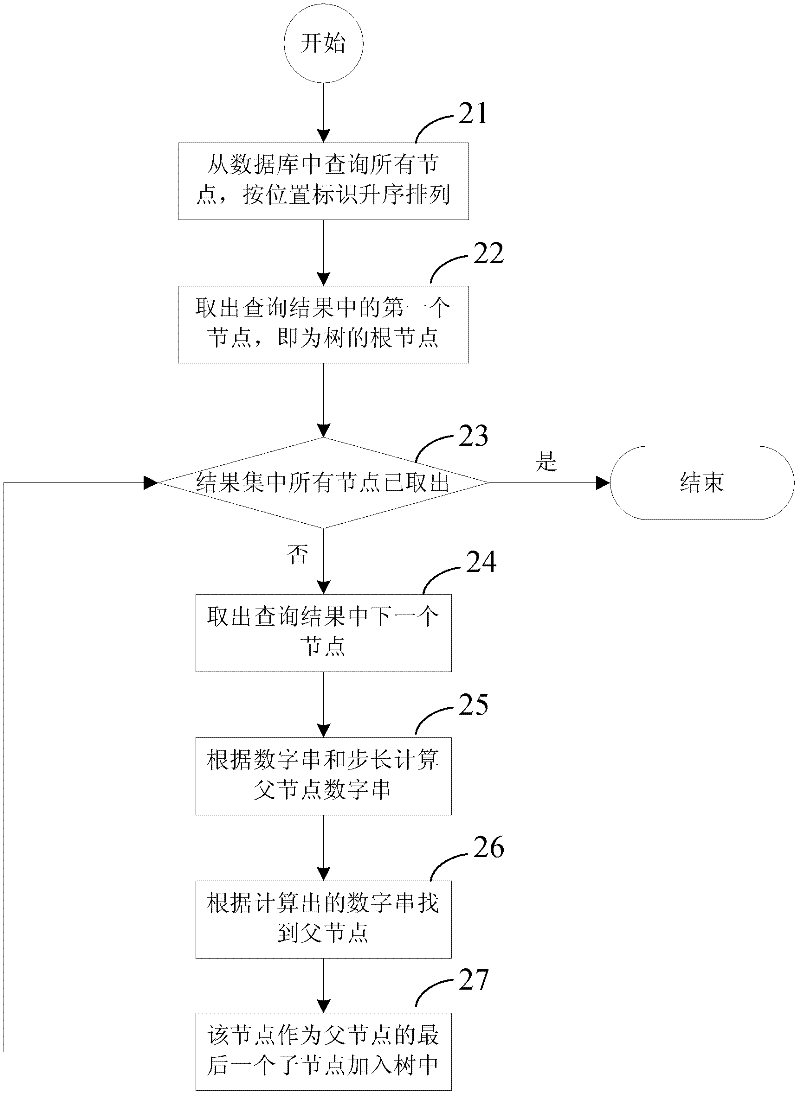
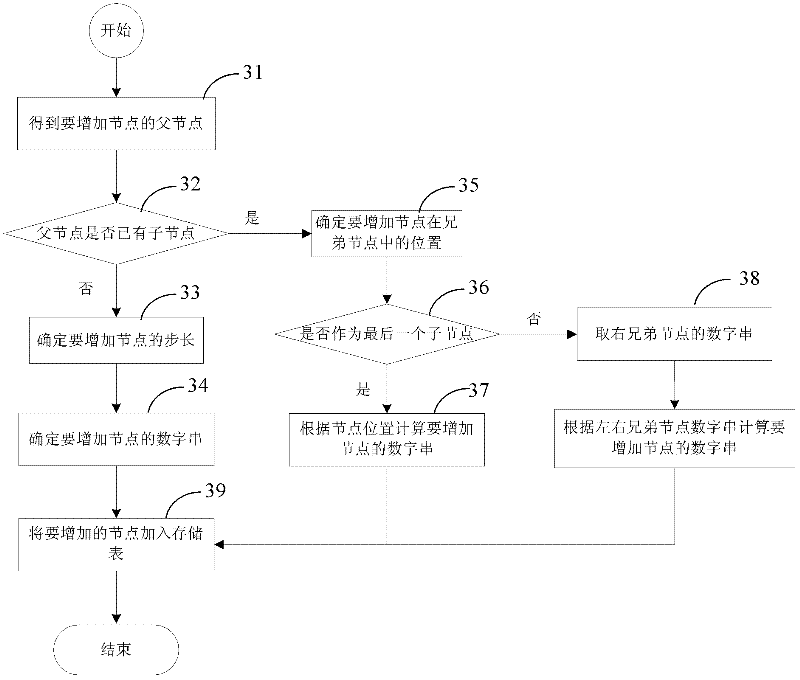
ActiveCN102508866AImprove operational efficiencyCutting costsSpecial data processing applicationsTable (database)Theoretical computer science
The invention discloses a digital addressing-based method for structured storage and rapid processing of a command relation tree. The method comprises the following steps of: 1, marking all nodes on the command relation tree by numeric strings with node positional information; 2, storing node identifiers, the numeric strings, step length and node information of all the nodes serving as a record into a database, and storing the structure information of one tree by a two-dimensional table; and 3, managing the structure information of the tree, wherein the management comprises the following operation of: reading the structure information of the tree, increasing nodes and deleting nodes. According to the method, the tree structure can be rapidly stored and read, ergodic search with low efficiency can be avoided according to the numeric strings identified with the node position, the system and the step length of the numeric strings can be flexibly configured, and the processing efficiency,the flexibility and the stability are improved.
Owner:THE 28TH RES INST OF CHINA ELECTRONICS TECH GROUP CORP
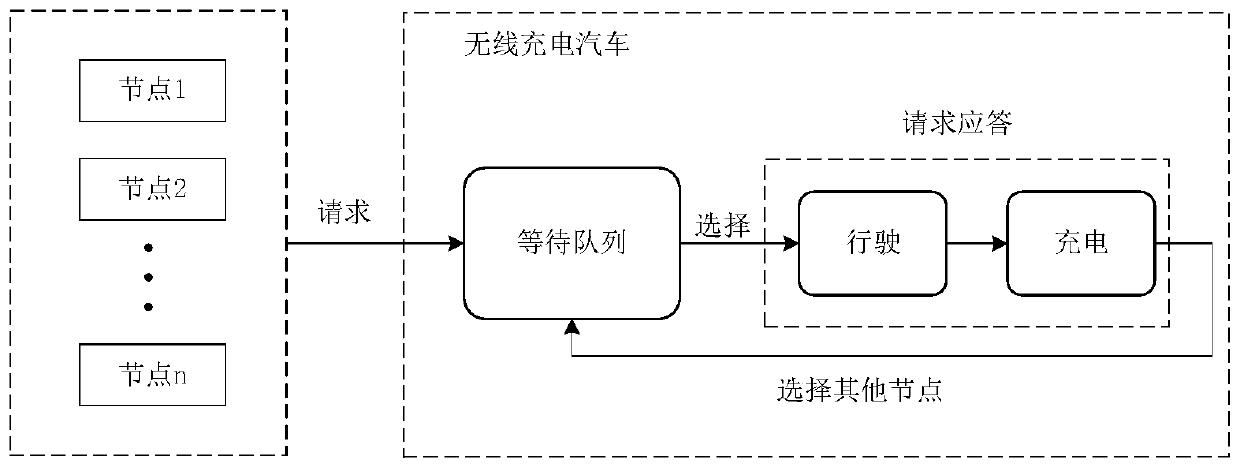
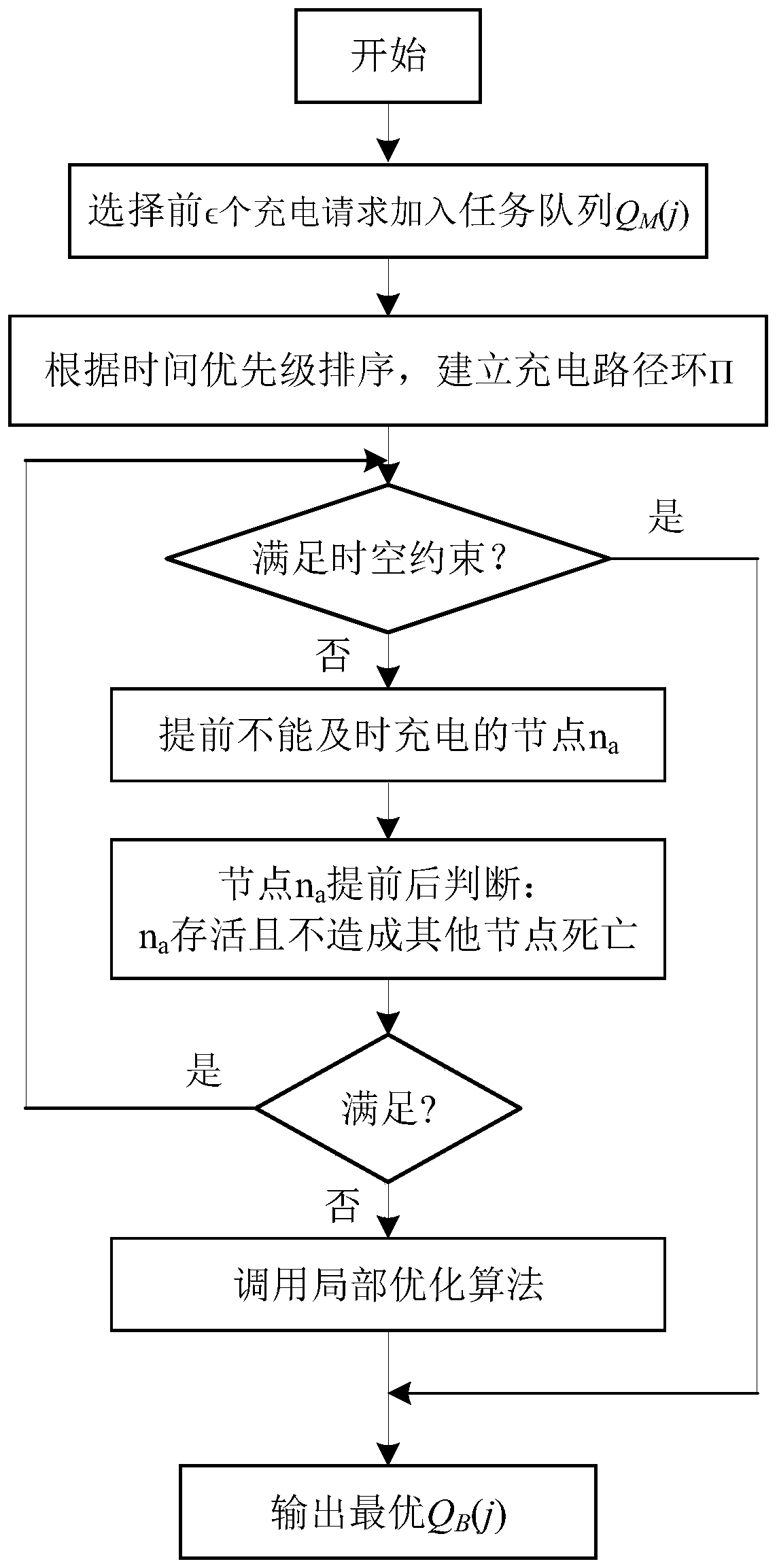
Space-time scheduling algorithm for on-demand charging in wireless rechargeable sensor network
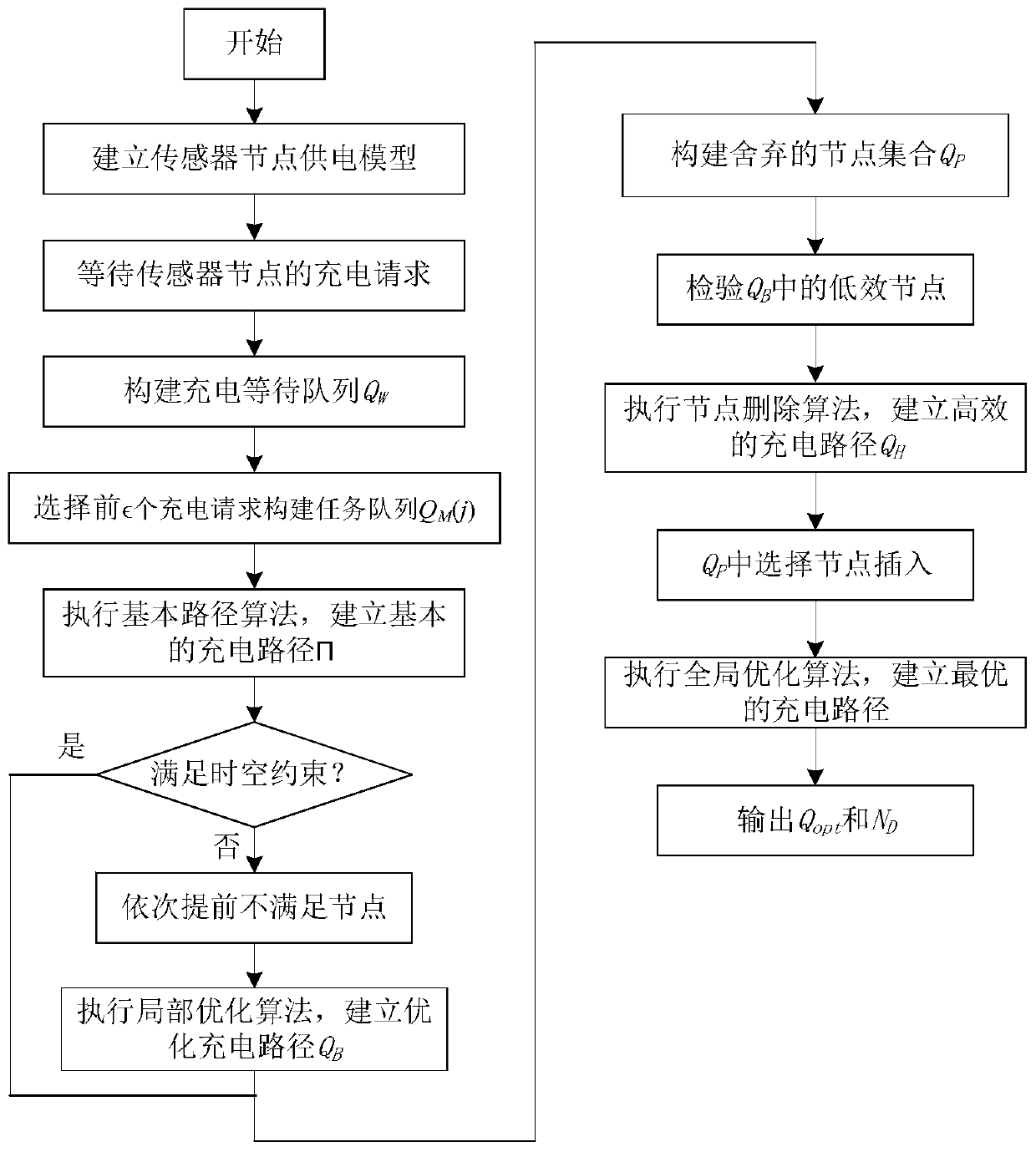
The invention provides a space-time scheduling algorithm for on-demand charging in a wireless rechargeable sensor network. The space-time scheduling algorithm comprises steps of establishing a sensornode wireless power supply model; executing a basic path algorithm according to the sensor node wireless power supply model to obtain a basic charging path; executing a local optimization algorithm tofurther enlarge the charging remaining time by optimizing the basic charging path; executing a node deletion algorithm to reduce the driving time by adjusting a charging queue on the premise of keeping the sensor nodes alive, and reducing the number of endangered dead nodes by deleting low-efficiency nodes in a charging path; and executing a global optimization algorithm to globally optimize theefficient charging path to obtain an output optimal charging path and the number of dead nodes. According to the invention, local and global optimization is carried out on the basic charging path, sothat the number of dead nodes is minimized and the system energy efficiency is maximized.
Owner:云南电网有限责任公司丽江供电局
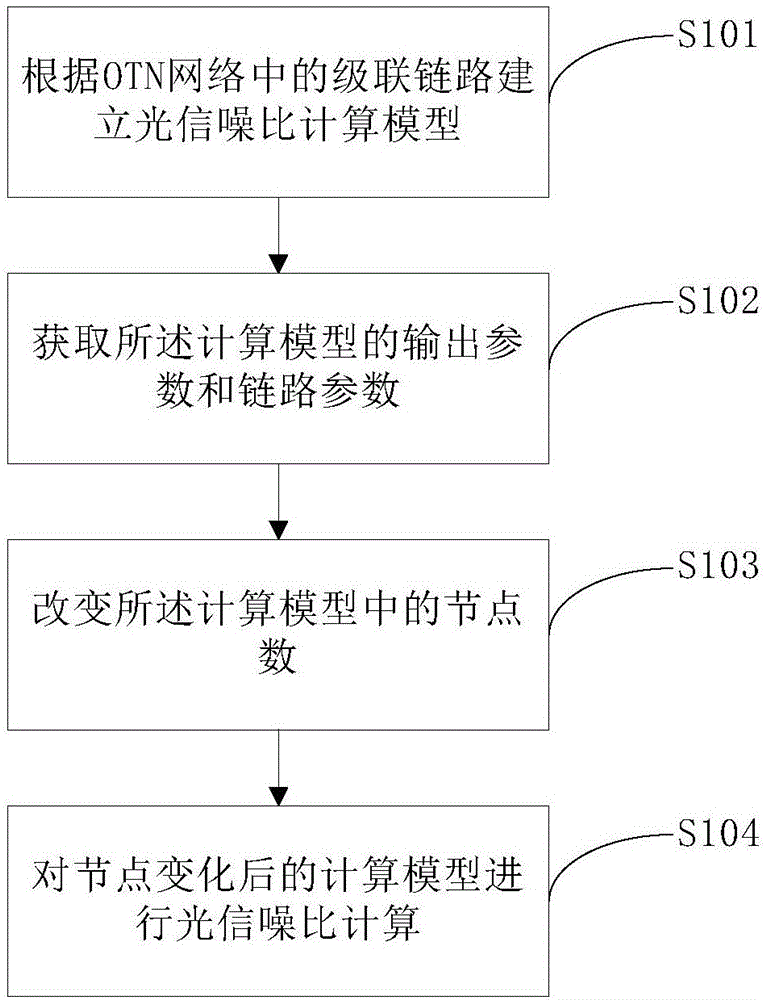
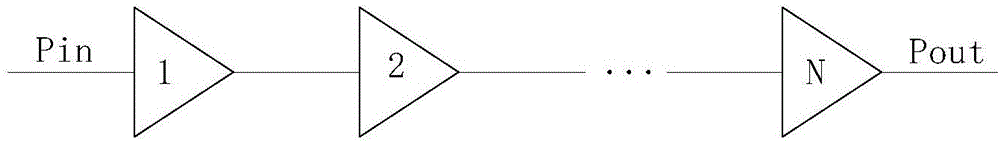
Optical signal-to-noise ratio calculation method for OTN
The embodiment of the invention discloses an optical signal-to-noise ratio calculation method for an OTN. The method comprises the following steps of: establishing an optical signal-to-noise ratio calculation model according to a cascade link in the OTN; obtaining an output parameter and a link parameter of the calculation model; changing the node number in the calculation model; and performing optical signal-to-noise ratio calculation of the calculation model having changed nodes. According to the embodiment of the invention, the corresponding optical signal-to-noise ratio calculation model is established; the optical signal-to-noise ratio of the calculation model is obtained through the calculated output parameter and link parameter of the calculation model; then, operations, such as node increasing and node deletion, are carried out based on the calculation model; therefore, the network topology of the OTN is changed; the OTN topology change problem and the problem whether transmission also can be continuously carried out after topology is changed are considered; and it judges that the optical signal-to-noise ratio after network topology is changed is calculated if the topology changed OTN satisfies the continuous transmission condition.
Owner:YUNNAN POWER GRID
Self-adaptive multi-injection waiting routing method based on social circle
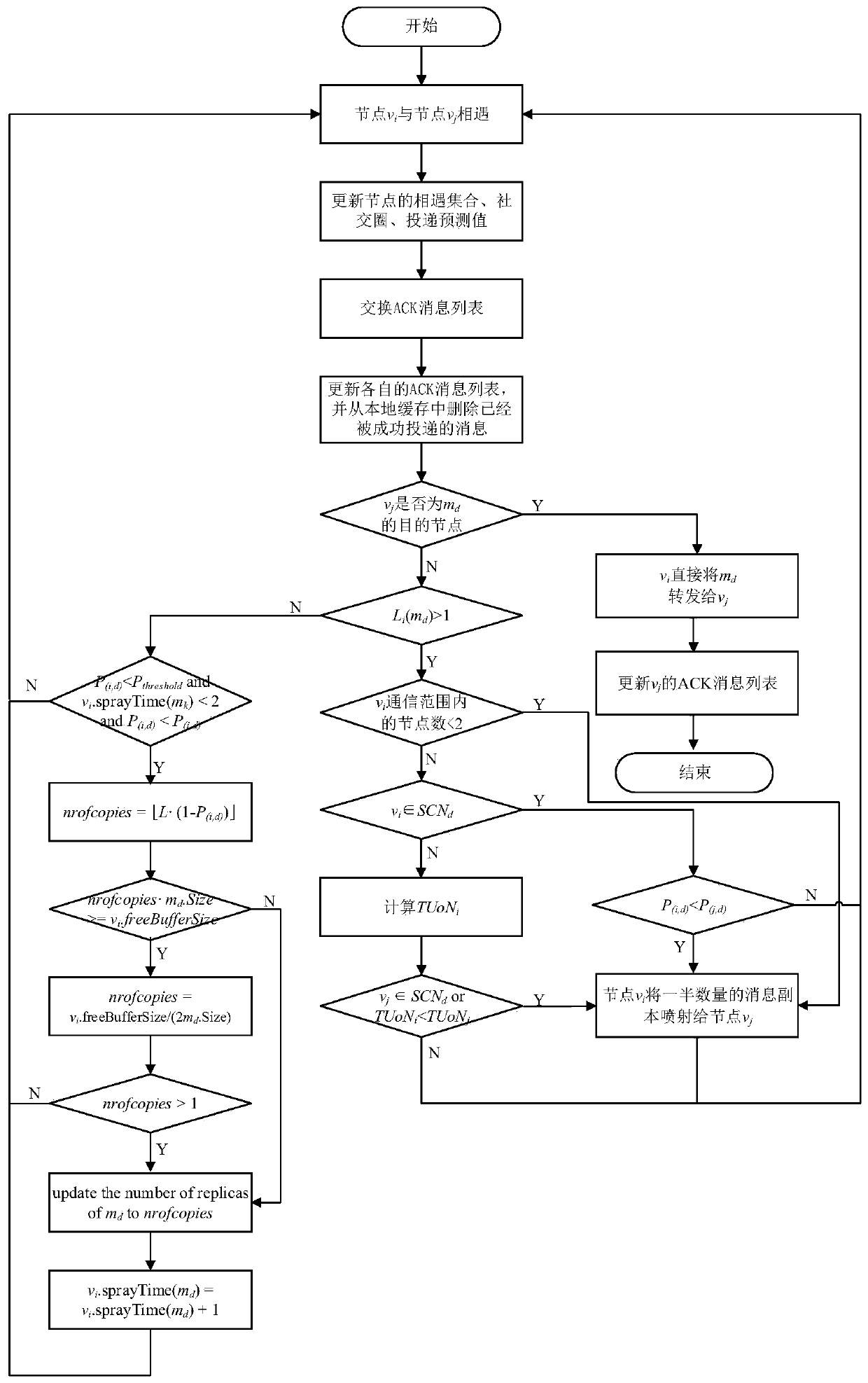
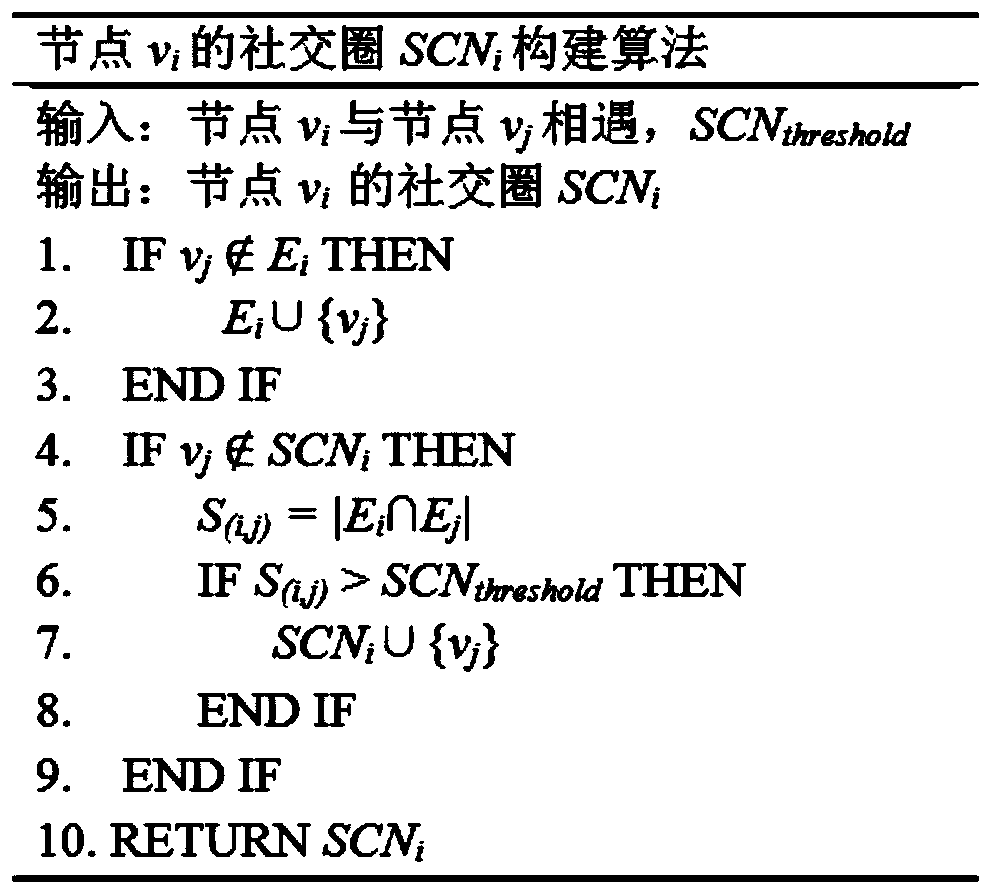
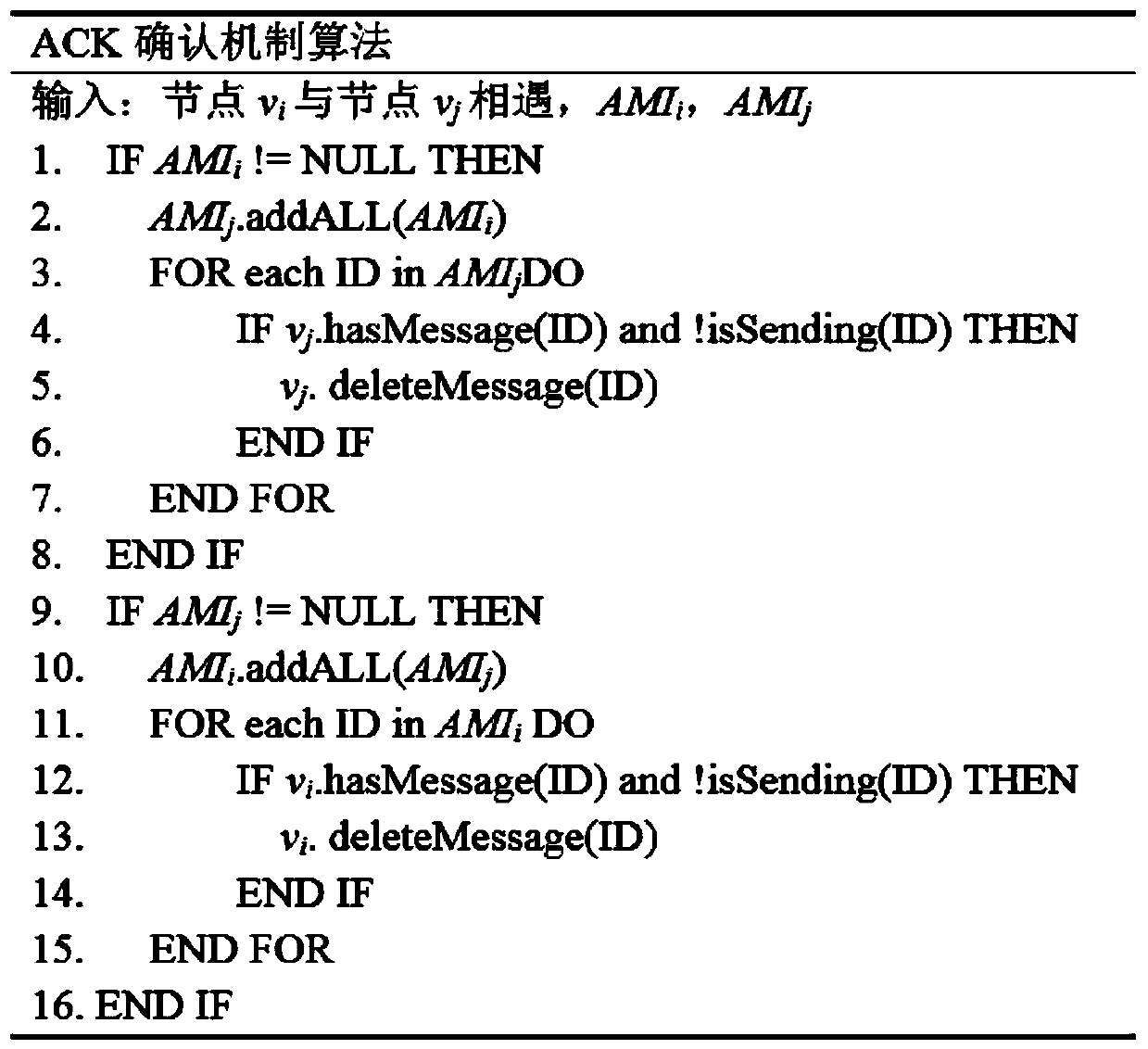
ActiveCN110809302AFast deliveryImprove performanceError prevention/detection by using return channelData switching networksSocial circleTrunking
The invention discloses a self-adaptive multi-injection waiting routing method based on a social circle. The self-adaptive multi-injection waiting routing algorithm based on the social circle comprises an injection stage and a waiting stage, according to the method, a message carried by a node vi is forwarded to a destination node vd, a social circle of the node is constructed based on similarityin an injection stage, and different relay node selection strategies are adopted according to whether the node carrying the message is in the social circle of the destination node or not. In the waiting stage, an adaptive multi-injection strategy based on the delivery prediction value is carried out, and the strategy selectively carries out multi-injection on some messages with the copy number being 1. And after a certain message in the network is successfully delivered to the destination node, the node in the network is notified to delete the message successfully delivered to the destinationnode by using an ACK confirmation mechanism algorithm. The self-adaptive multi-injection waiting routing method based on the social circle is an efficient routing algorithm of a delay tolerant network.
Owner:HUAZHONG NORMAL UNIV
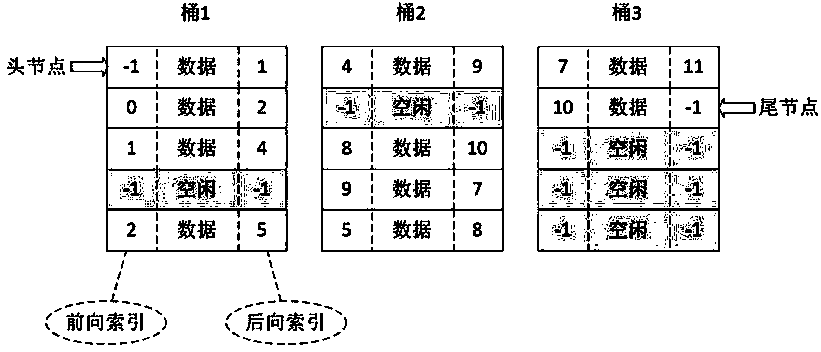
Implementation method of barrel type linked list structure
InactiveCN104199966ASolving inefficienciesImprove operational efficiencySpecial data processing applicationsDatabase indexingInternal memorySoftware system
The invention provides an implementation method of a barrel type linked list structure. The method is characterized in that a linked list uses barrel type structures as unit organization nodes, the positions of the previous node and the next node are pointed out by digital indexes among the nodes, and the linked list can be serially connected by multiple barrel type structures; during node adding, the idle positions in the barrel type structure are searched, and if the barrel type structure is full, another barrel type structure is created and data is saved into the barrel type structure; during node deletion, the corresponding positions of the barrel type structure is set to be idle. Compared with traditional linked list structure, the barrel type linked list has the advantages that the barrel type linked list can be managed by using the barrel type structure as unit, bidirectional connection in a pointer manner is avoided, node adding and deleting are quite fast and convenient, and during linked lift node traversing, internal memory cache hit ratio is increased while the operation efficiency of the a software system is increased evidently due to the fact that the nodes are internal memory continuous.
Owner:HANGZHOU ELECTRONICS SOUL NETWORK TECH
Personal file permission chain management system and method based on improved multi-layer PBFT
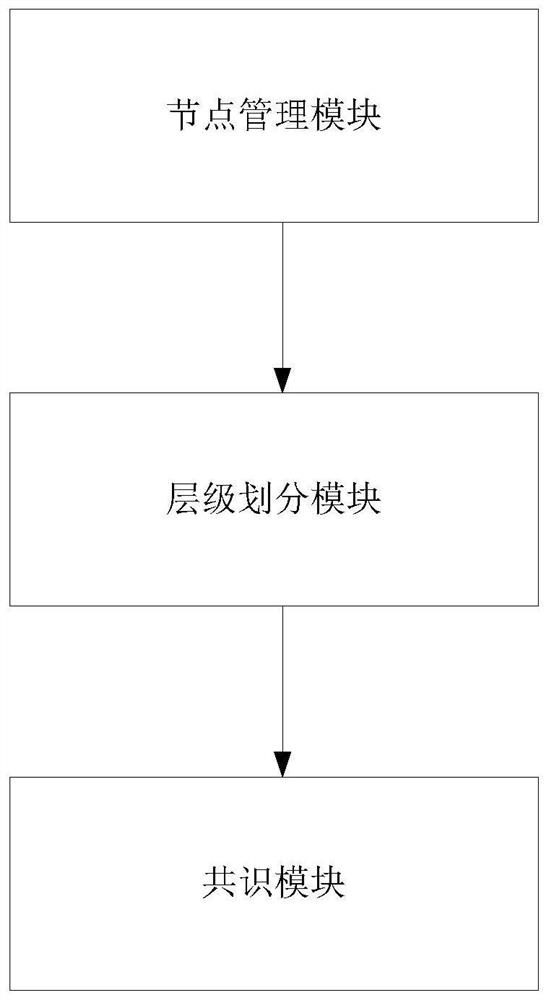
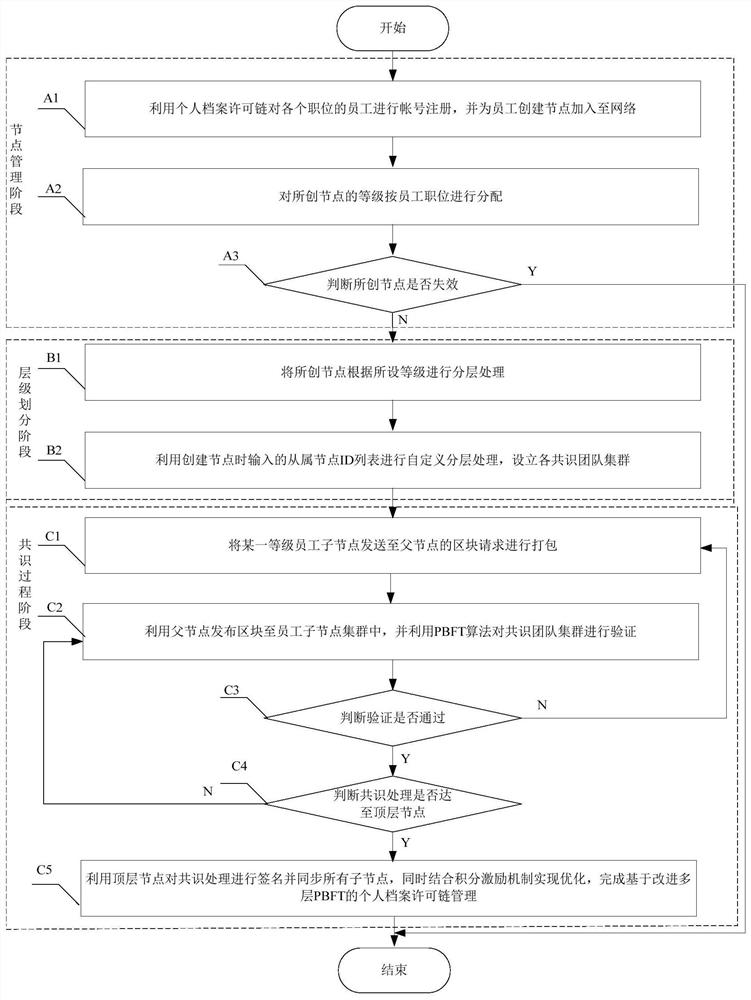
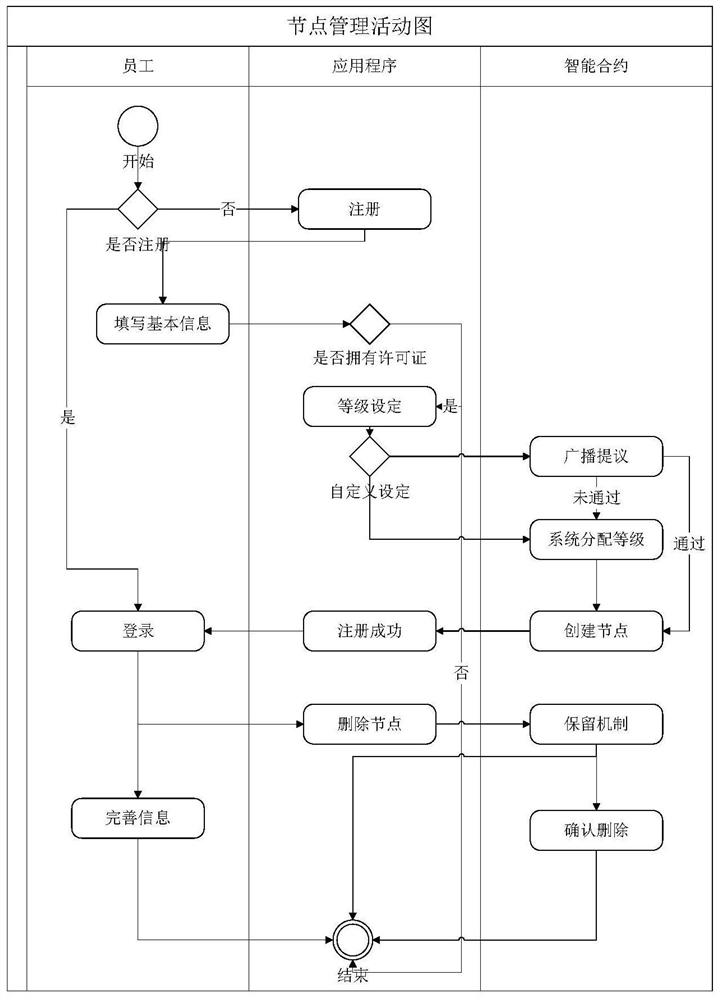
ActiveCN111858105AClear hierarchySolve scalabilityInterprogram communicationDatabase distribution/replicationDistributed computingManagement system
The invention provides a personal file permission chain management system and method based on improved multi-layer PBFT, belongs to the technical field of block chains, and comprises a node managementmodule, a hierarchical division module and a consensus module which are connected in sequence. The node management module is used for performing node creation, grade allocation and node deletion management on participated nodes by utilizing a personal file permission chain; the hierarchical division module is used for carrying out hierarchical division on all the nodes according to the levels ofthe nodes and carrying out user-defined hierarchical processing through the node levels and the slave node ID list; and the consensus module is used for realizing optimization in combination with a PBFT consensus algorithm, the multi-layer nodes and an excitation mechanism. Through the design, the problems that a license chain system is poor in node expansibility, high in inter-node communicationcomplexity, low in system efficiency after the number of nodes is increased and the like are solved, the total single consensus communication duration of the license chain management system is effectively shortened, and the single consensus communication frequency is greatly reduced.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA +1
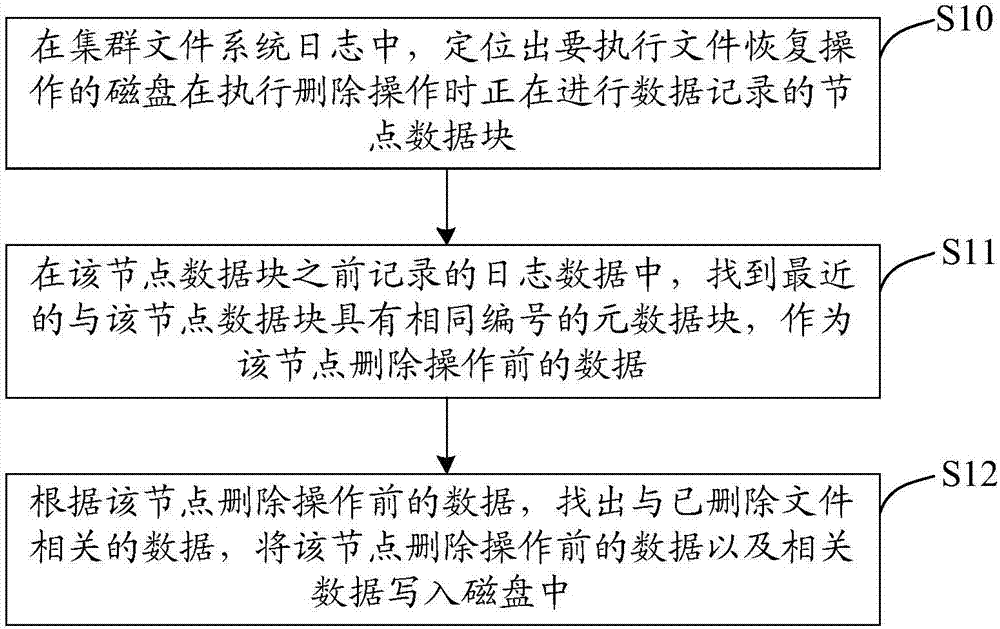
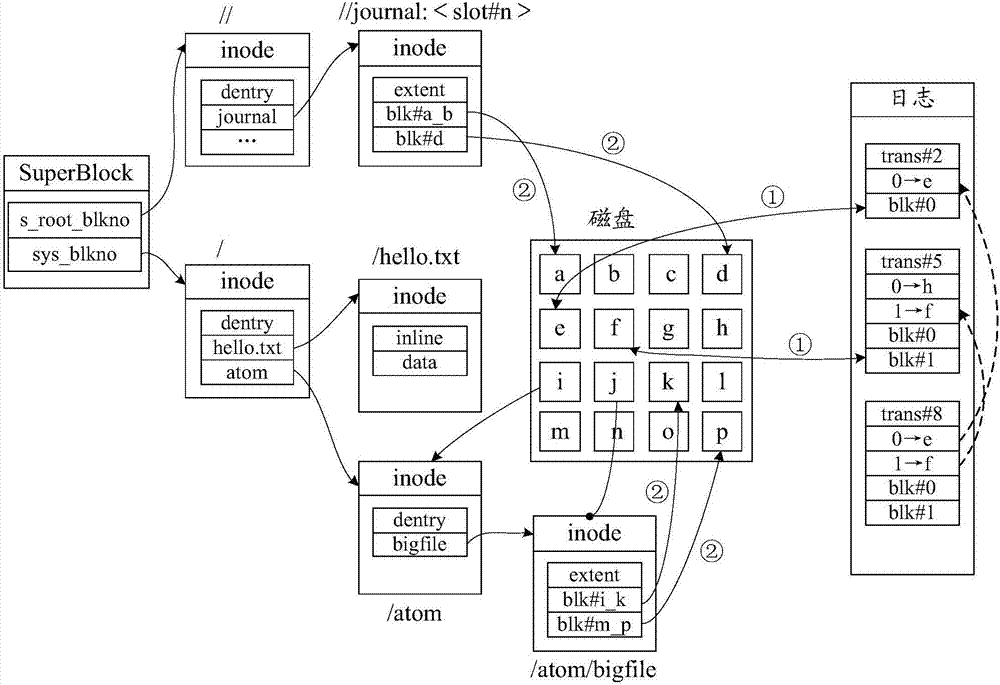
Recovery method and device for deleted file in cluster file system
ActiveCN107315661AImprove performanceAchieve the purpose of recoveryRedundant operation error correctionRecovery methodFile system
The invention discloses a recovery method and device for a deleted file in a cluster file system. The method comprises the following steps that: in a cluster file system log, positioning the node data block which records data when a disk which executes a file recovery operation executes a deletion operation; in log data recorded previously by the node data block, searching a latest metadata block which has the same index number with the node data to serve as data before a node deletion operation; and according to the data before the node deletion operation, searching data related to the deleted file, and writing the data before the node deletion operation and the related data into other disks. By use of the method and the device, under a situation that a system does not have extra expenditures, a purpose of recovering deleted file can be achieved, and file data recovery is realized in a non-invasion way so as to be favorable for keeping that a file system owns good performance.
Owner:SUZHOU LANGCHAO INTELLIGENT TECH CO LTD
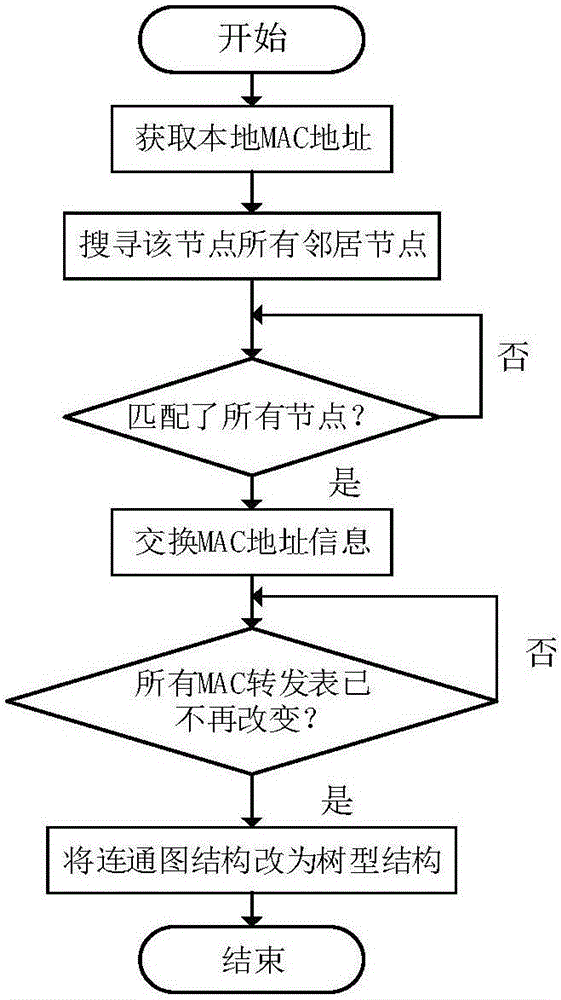
Automatic networking and data forwarding method utilizing MAC address in Android mobile terminal
ActiveCN107528721AUniqueness guaranteedAvoid broadcast stormsNetwork topologiesStar/tree networksTransmission protocolBroadcast packet
The invention provides an automatic networking and data forwarding method utilizing an MAC address in an Android mobile terminal, and belongs to the technical field of data transmission, network formation and MAC address acquisition. The method comprises the following steps: step 1, a networking module establishes a local area network of wireless mobile; step 2, a new node adding module adds a new mode; step 3, a node deletion module deletes the node; step 4, a packet sending environment establishment module establishes a packet sending environment; and step 5, a data forwarding module forwards data. According to the automatic networking and data forwarding method, no additional algorithm or cost is needed to maintain and ensure the address uniqueness of each mobile device in the network; the broadcast storm caused by copy and forwarding of broadcast data packets in the loop is avoided; and no high level transmission protocol is depended on, so that the transmitted data packet has a simpler structure, and the used protocol is simpler, and the transmission overhead is reduced.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
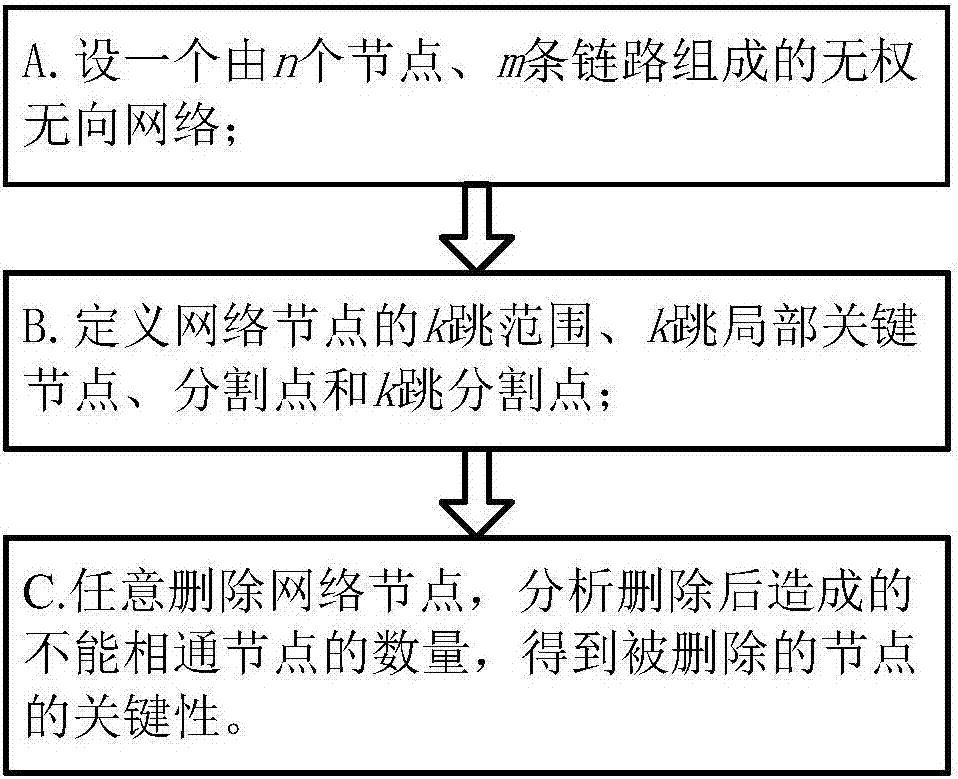
Grid structure vulnerability node identification method
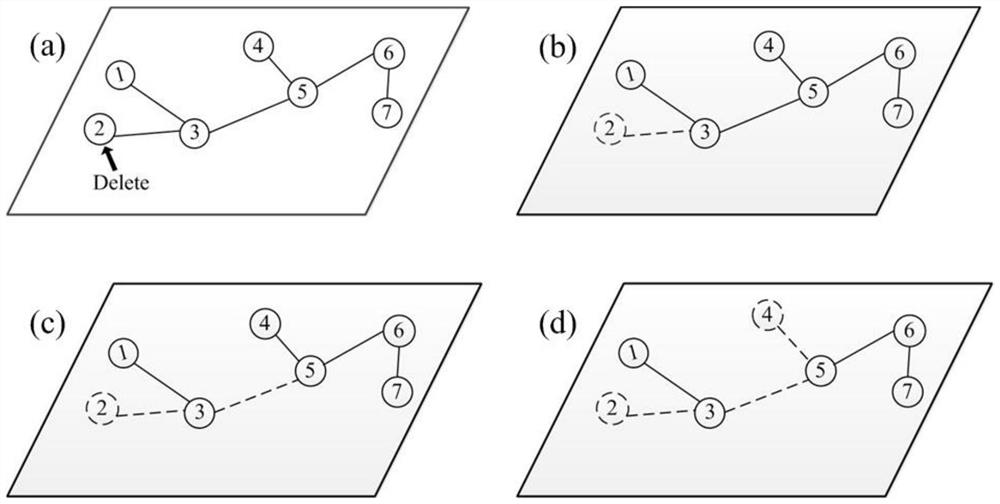
The invention discloses a method for identifying vulnerable nodes of a grid structure, which includes: 1) reading in the node connection relationship data of the grid topology structure, and configuring the number k of pre-attacked or destroyed nodes; 2) calculating two nodes based on the network topology structure The shortest path between and the average path length L of the network; 3) Calculate the network efficiency E; 4) Delete the relevant path connected to the node and recalculate the network efficiency Ei of the point; 5) Calculate the network efficiency Ei of each node based on the network efficiency Ei 6) Based on the node vulnerability index, use the original input node connection relationship data to obtain the network topology diagram; 7) Remove the node with the largest node vulnerability value Vi, and loop through steps 2)-6) to obtain the second vulnerability node; 8) loop k times, and finally complete the identification of N-k vulnerability points. The vulnerability node identification method described above can dynamically identify the node vulnerability, taking into account the change of the node vulnerability under the changed network topology after the node is deleted.
Owner:杭州创云一智科技有限公司
Location optimization method for intelligent roadside unit
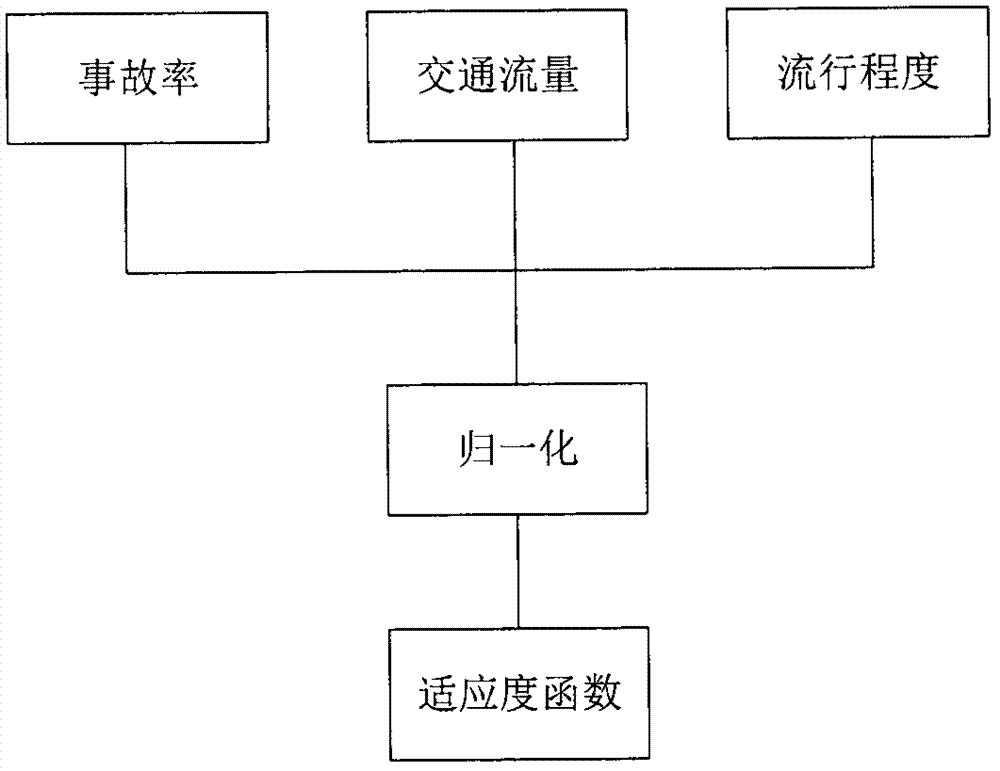
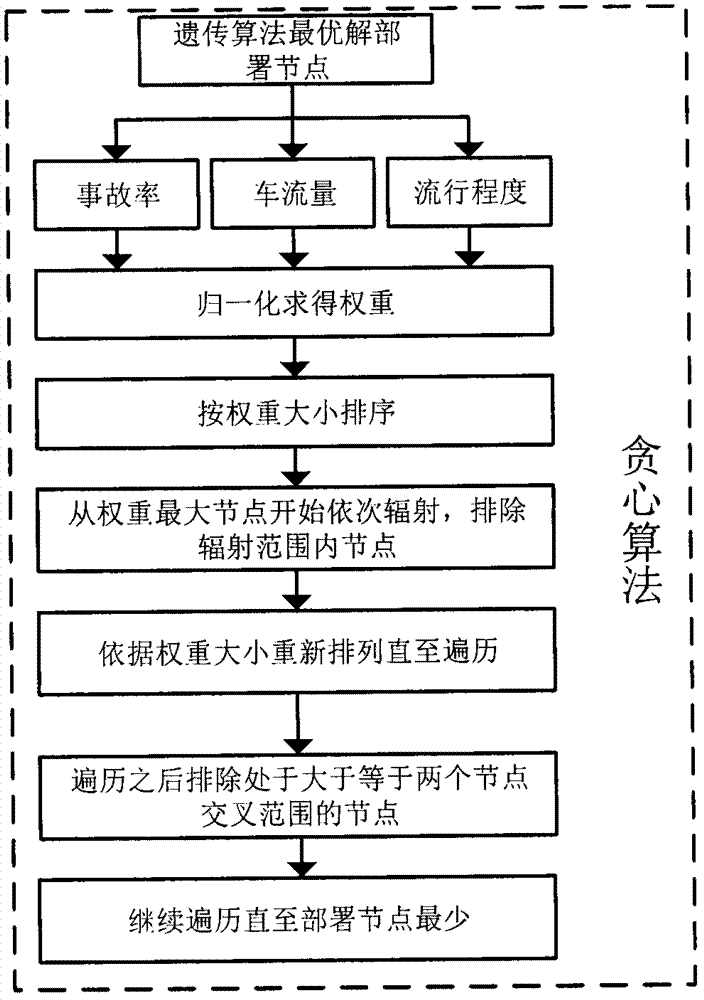
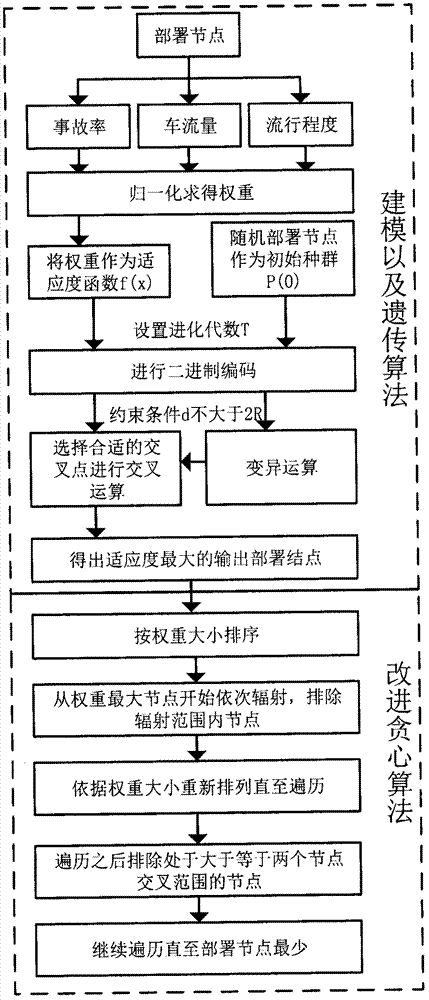
The invention provides a mixed algorithm-based intelligent traffic system roadside unit deployment optimization method. A business district is selected as a research object; normalization is performed according to vehicle flow, popularity, accident rate and the like of an initial deployment point position; and calculation is performed to obtain a weight value of a deployment point. Based on an index, namely, a weight value of an initial node, modeling analysis is performed by utilizing a genetic algorithm and a greedy algorithm, and node deletion is performed to obtain an optimal deployment scheme.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
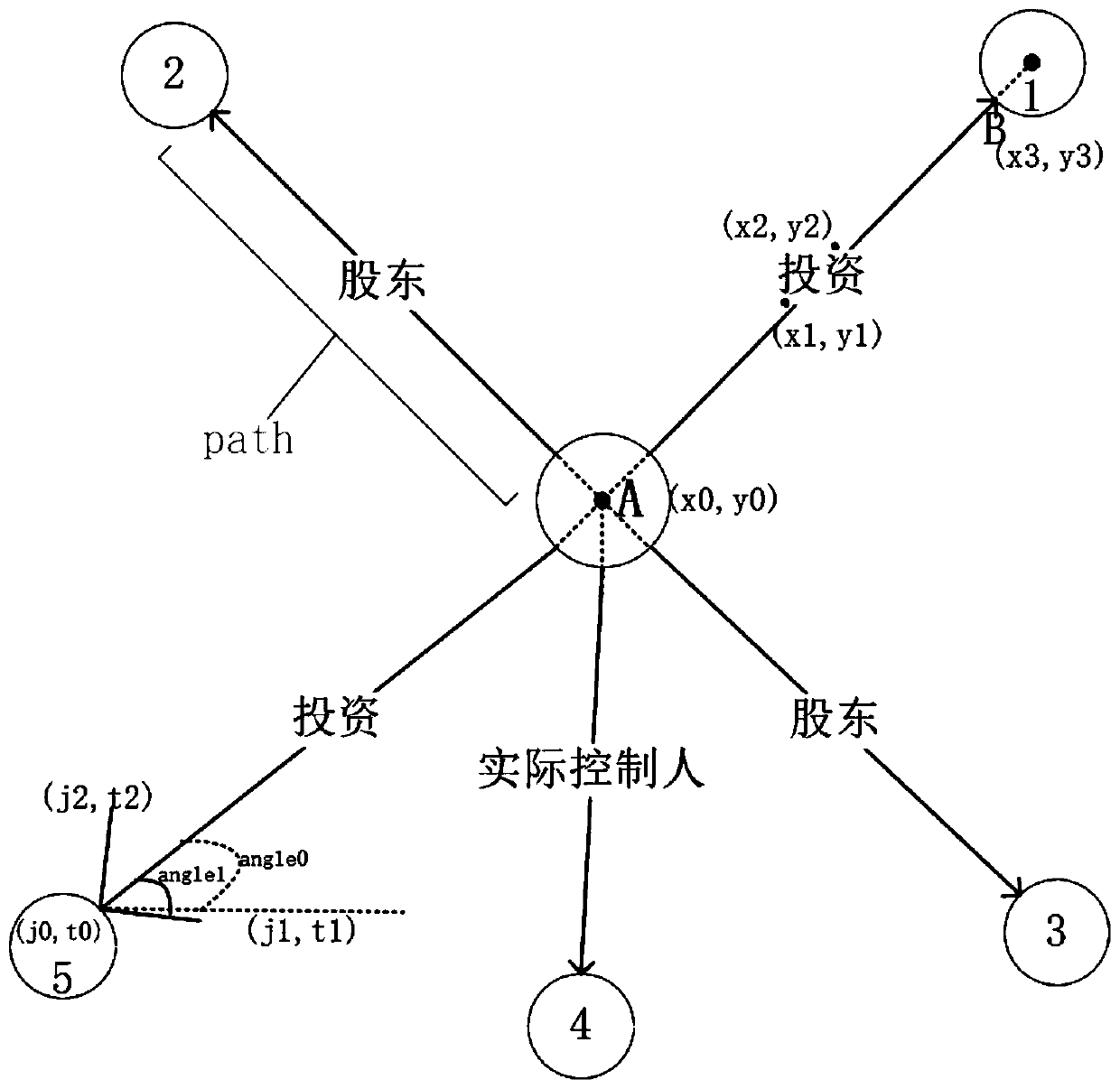
Method for displaying enterprise association relationship graph based on d3
ActiveCN110889014ATo achieve the recovery effectOther databases indexingOther databases browsing/visualisationData displayAlgorithm
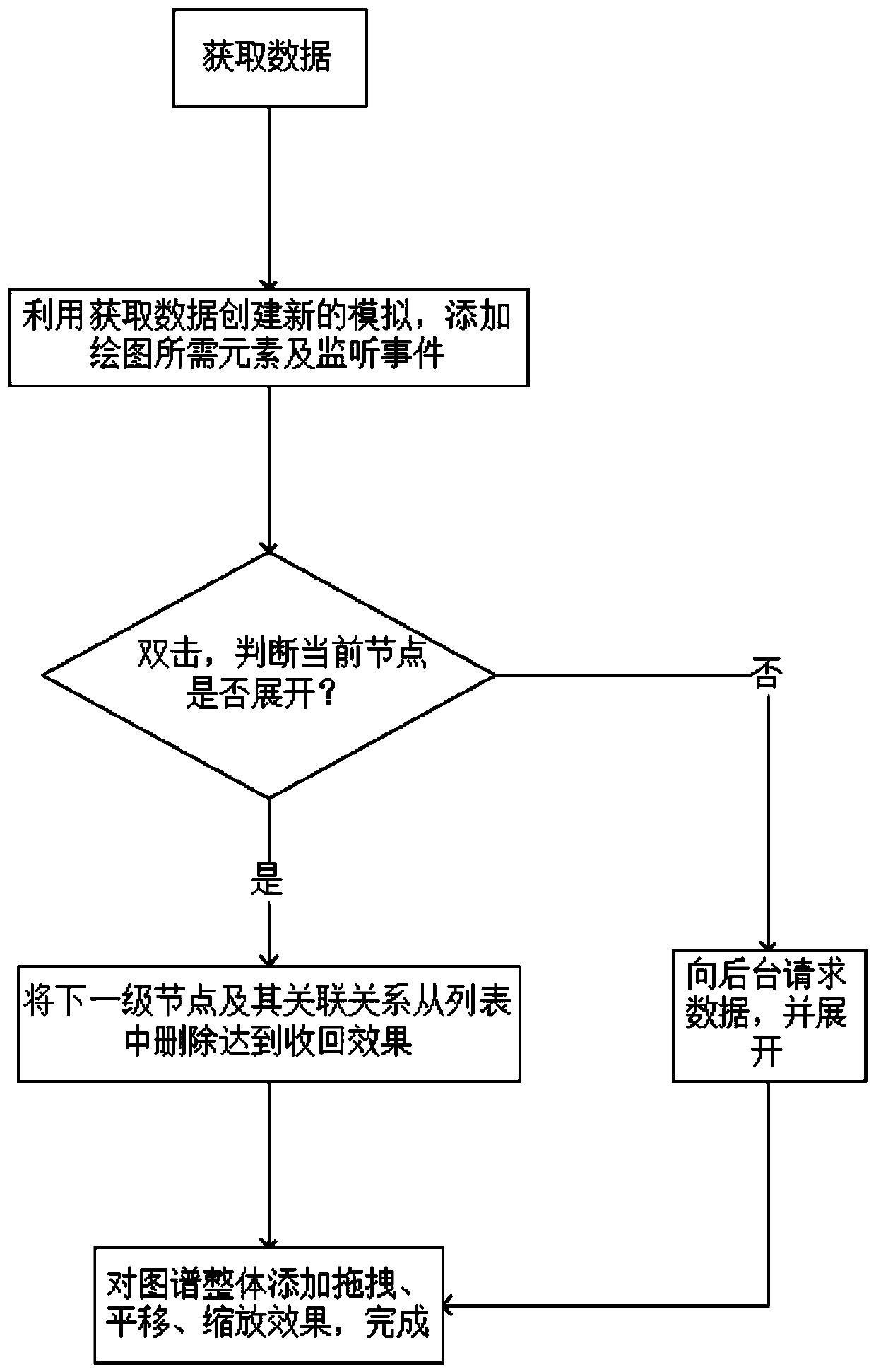
The invention discloses a method for displaying an enterprise association relationship graph based on d3, which comprises the following steps of S1, obtaining relationship data D required for drawing,performing serialization operation by a fastjson package after the obtained data D is packaged into an object through a tool class, and returning a json file; S2, creating a new forceSimulation by utilizing the D, defining an svg canvas, calling a tick method to obtain node coordinates (x, y) in real time, based on a node array N and an edge array E of the layout, adding three graphic elements required for drawing: line, circle and text, and binding attributes in the data N and the data E with the three graphic elements; and S3, realizing functions of double-click node expansion and double-click node deletion for an existing map, updating page data in real time according to operation, and only retaining data displayed on a page. The method is good in user experience and good in page fluency.
Owner:ZHEJIANG UNIV OF TECH
Ad Hoc network key node identification method fused with deletion method
InactiveCN106912040AStrong computing powerReduce time complexityNetwork topologiesSecurity arrangementNetwork keyNetwork model
The invention discloses a dynamic Ad Hoc network key node identification method. The dynamic Ad Hoc network key node identification method comprises the following steps of: constructing an Ad Hoc network model, defining the connectivity of an Ad Hoc network, defining the connectivity of the Ad Hoc network after nodes are deleted, defining the key degree of Ad Hoc network nodes, dynamically identifying Ad Hoc network key nodes, and determining the key performance sequence of the Ad Hoc network nodes. The dynamic Ad Hoc network key node identification method disclosed by the invention solves the following problems in the existing algorithm: key nodes of a network are difficultly given; the key performances of the identified key nodes cannot be distinguished; the existing algorithm is not suitable for key node identification of a large-scale network or a dynamic network, etc. Thereby, the identification efficiency of the Ad Hoc network key nodes is further increased; and the security and the reliability of the Ad Hoc network are improved.
Owner:ELECTRONICS ENG COLLEGE PLA
Hello message exchange method for greedy geographical routing protocol
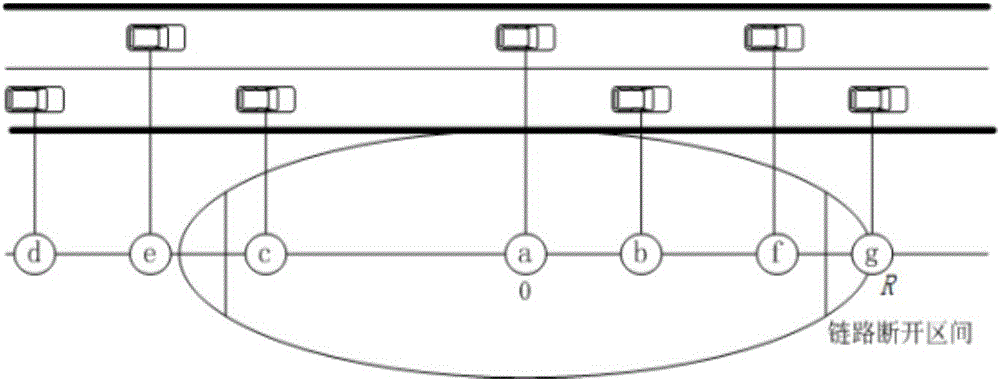
ActiveCN106101000AReflect on-offTimely on and offData switching networksTransfer probabilityTransition probability matrix
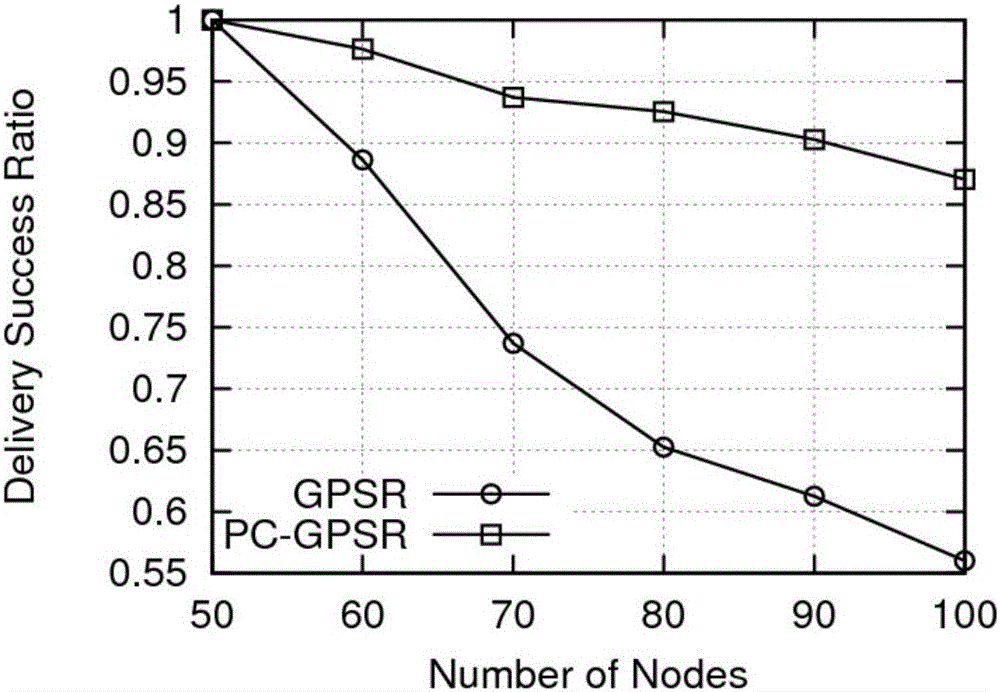
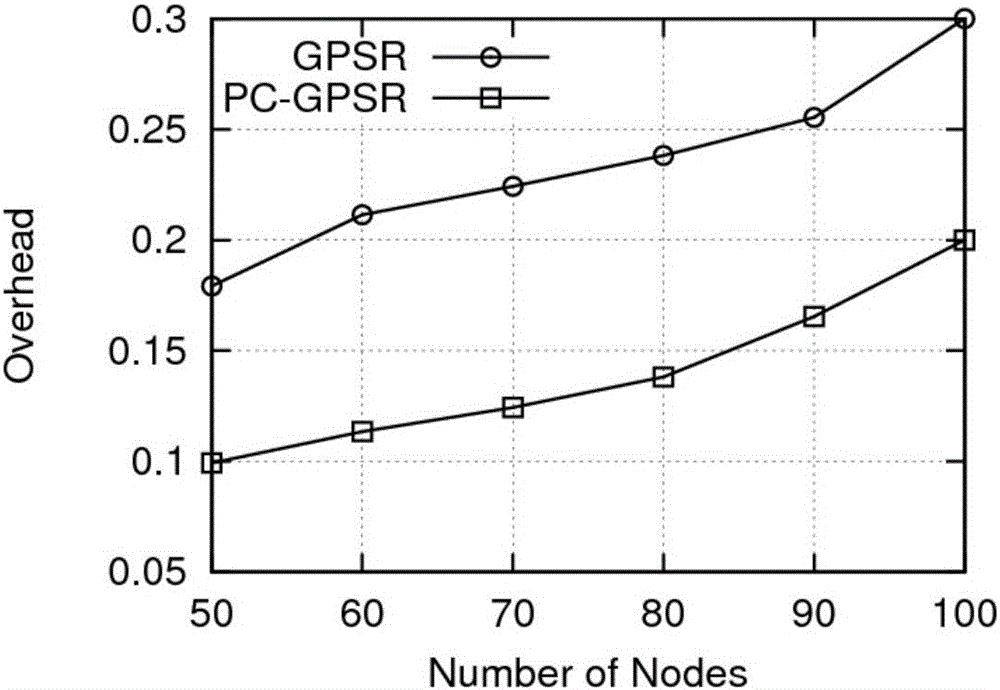
The invention discloses a hello message exchange method for a greedy geographical routing protocol. The realization scheme of the method is that the road width is considered to be far smaller than communication radiuses of vehicles; the vehicles on a road are approximately taken as a one-dimensional network; the communication ranges of nodes are discretized; mathematical modeling is carried out on link states by employing a Markov process; links are described as Markov links with absorption boundaries; link connection probabilities are calculated according to a first arrival probability and a one-step transfer probability matrix; corresponding relationships can be established between the link communication probabilities and beacon exchange periods according to statistic properties; the width of a link disconnection interval in the minimum hello message exchange period of the vehicles can be designed; and neighbor nodes in the link disconnection interval will be deleted by forwarding nodes. Compared with the greedy geographical routing protocol, the method has the advantages that the data packet delivery success rate is improved, the relatively low control overhead is obtained, and the method can be applied to a vehicular ad-hoc network.
Owner:JIANGXI UNIV OF SCI & TECH
Linked list management system based on structured language and method
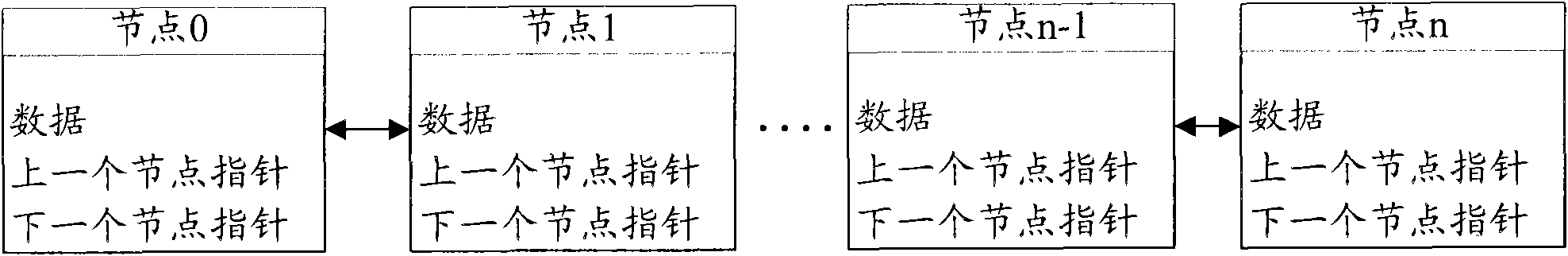
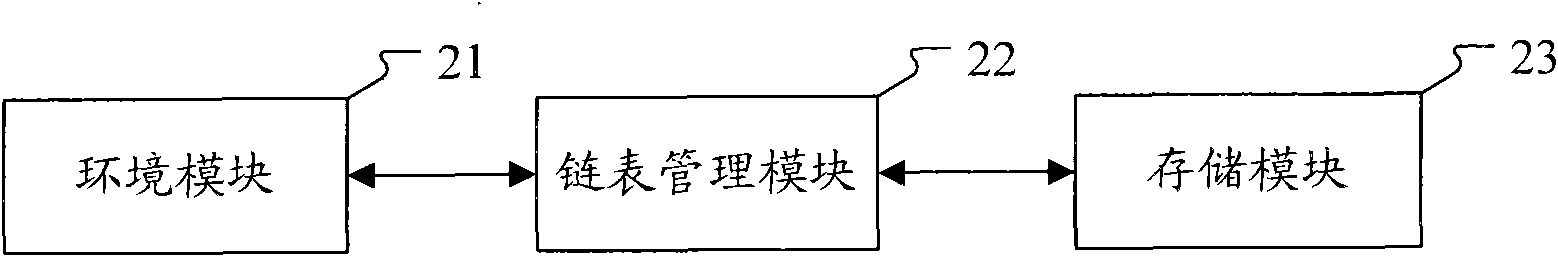
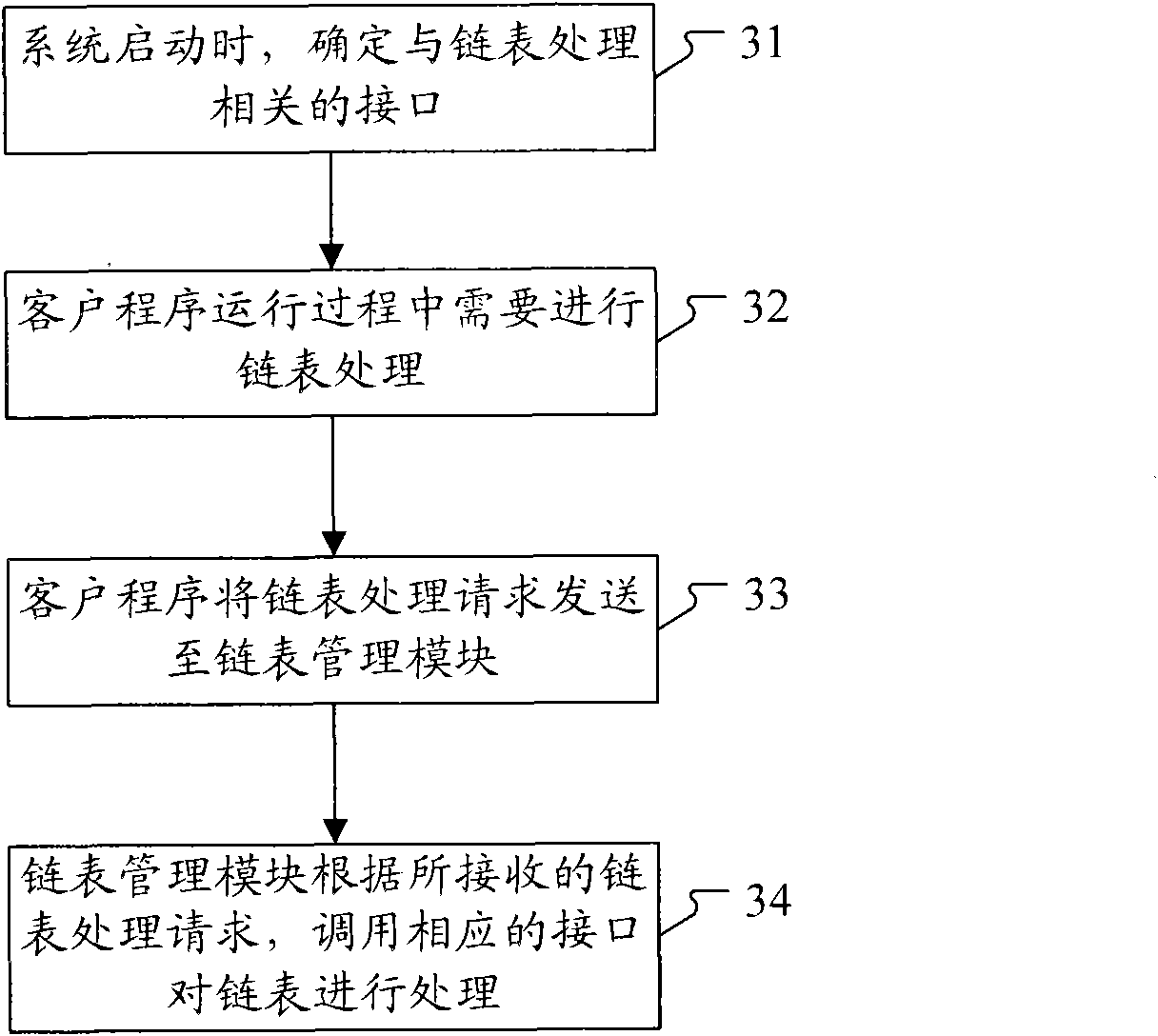
InactiveCN101582031AImprove maintainabilityImprove acceleration performanceMemory adressing/allocation/relocationSpecific program execution arrangementsOperational systemMaintainability
The invention discloses a linked list management method based on structured language, which comprises the steps of determining an interface related to the linked list processing according to the operating system when an operating system; sending a linked list processing request from a client program to a linked list management module; calling an interface and / or a comparison interface related to the linked list processing and carrying out the processing operation on the linked list by the linked list management module according to a received linked list creation request, a linked list deletion request, a node creation request, a node query request, a node update request or a node deletion request. In different projects, by calling corresponding interfaces, the method can realize linked list management according to the set processing flow, and does not need to respectively compile codes to realize linked list management, thus being capable of obviously simplifying codes, improving the maintainability and expansibility of the codes and further improving the software development efficiency.
Owner:GLOBAL INNOVATION AGGREGATORS LLC
GIS data editing method
ActiveCN110554820AAvoid position deviationRealize seamless splicing2D-image generationInput/output processes for data processingGraphicsAnchor point
The invention belongs to the technical field of geographic information methods and discloses a GIS data editing method which comprises the translation steps that a geometric figure needing translationis selected, an anchor point and an anchor point range are displayed after a translation tool is clicked, a finger clicks the geometric figure needing translation, and if the clicking position of thefinger is within the anchor point range, the anchor point is pressed, and a geometric object is moved; otherwise, nodes in the graph are reselected as anchor points, and the finger clicking positionis continuously judged until the finger clicking position is within the range of the anchor points. According to the method, surveyors can conveniently edit and correct drawn geometric figures on sitein field work, and the field work data editing efficiency is improved. According to the method, editing operation of point, line and surface graphic objects can be carried out through the functions of node movement, node addition, node deletion, trimming, line segmentation, surface segmentation, combination, public edge automatic tracking, cutting and the like.
Owner:XIAN REMOTE SENSING SCI & TECH OF INFORMATION CO LTD
A node importance evaluation method for urban public transport network
InactiveCN109214656AQuantitative results are reasonableSimple algorithmResourcesTransit networkOperability
The invention discloses a node importance evaluation method for urban public transport network, which comprises the following steps: calculating the composite degree of all nodes; the nodes are deleted one by one to form a new network, and the difference between the new network and the original network is calculated. Fusion of the dynamic attributes of the node, to obtain quantitative results. According to the dynamic attribute and the static attribute of the node in the complex network, based on the node importance evaluation method based on node deletion, this paper proposes a node importance evaluation method for urban public transport network, combining the static attributes of nodes in the network topology and the dynamic attributes of nodes given by human activities, and taking intoaccount the relationship between nodes, it can reflect the changes of the importance of nodes with time, making the quantization results more reasonable, and the algorithm is simple and operable.
Owner:四川唯新电子科技有限公司
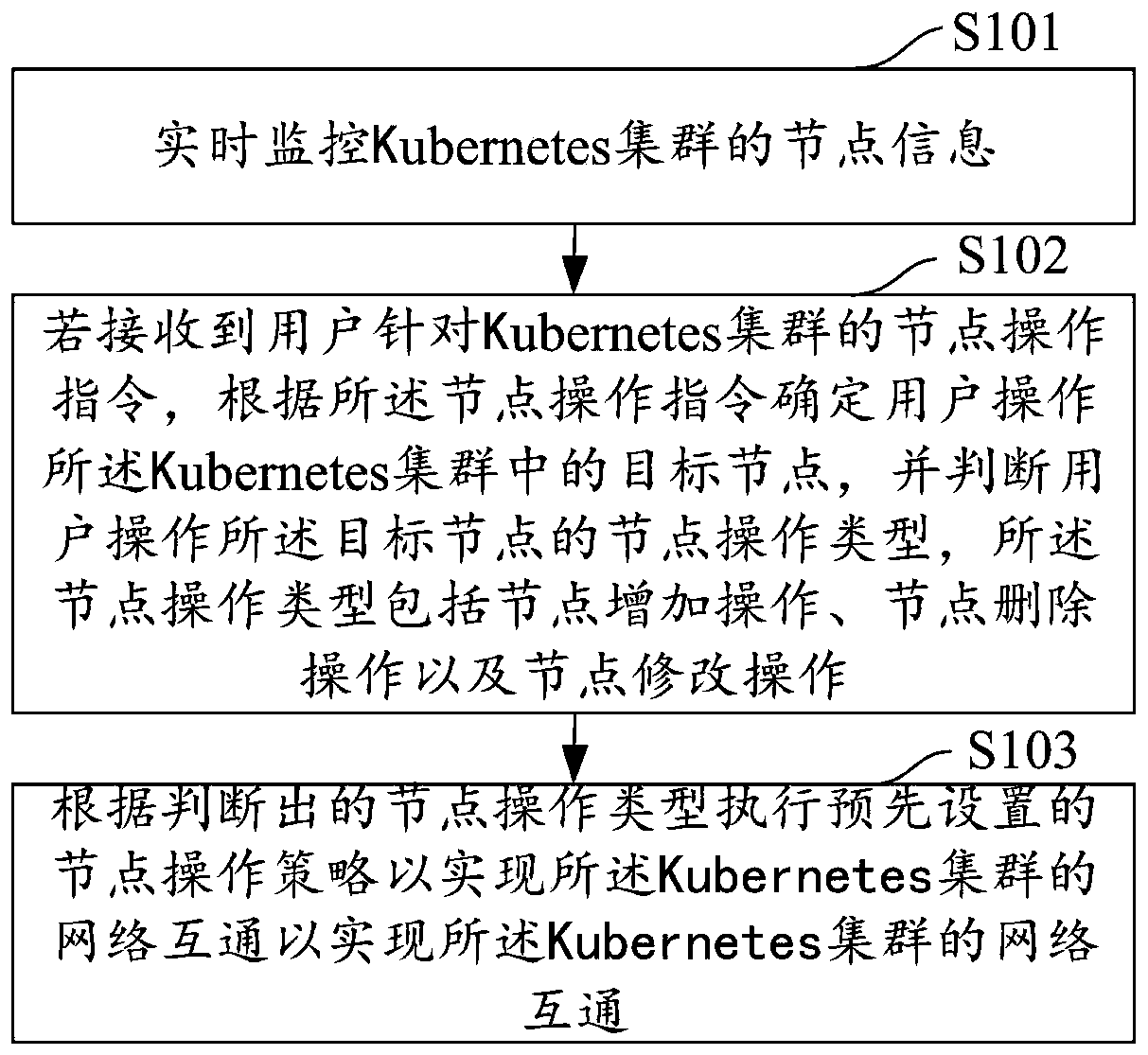
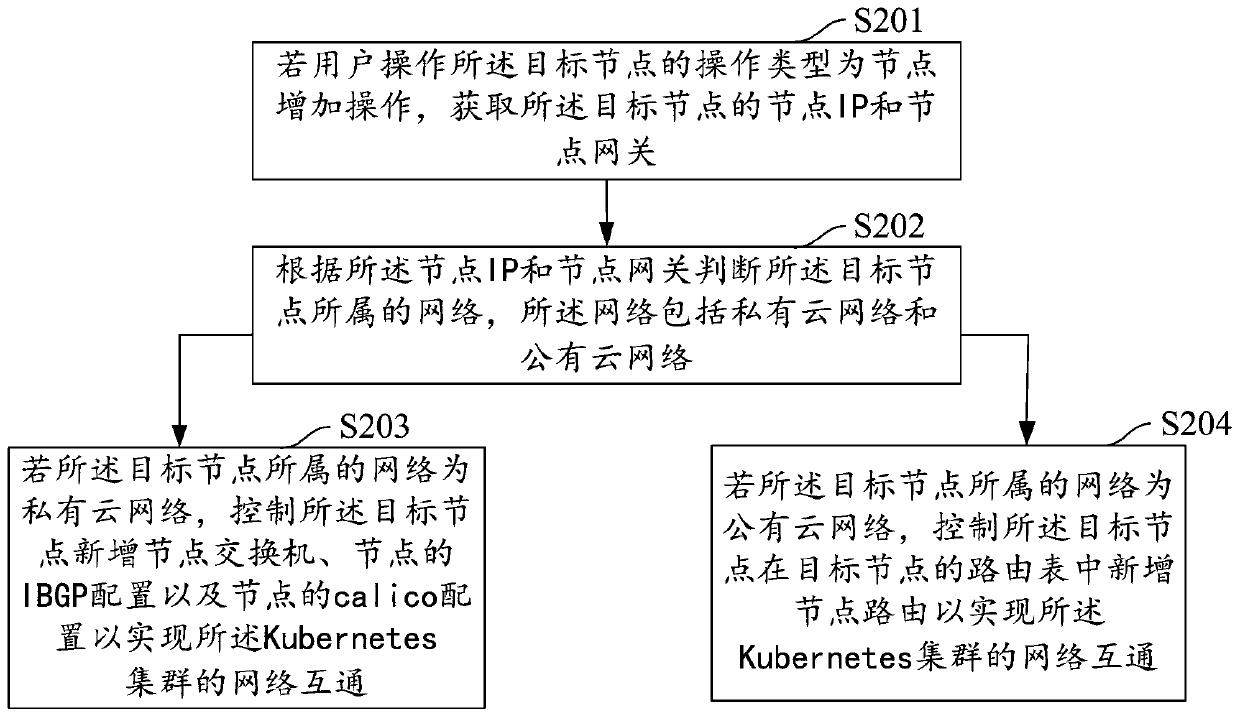
Network intercommunication method and device for realizing Kubernetes cluster, equipment and storage medium
ActiveCN110808857AImplement configuration operationsImprove the efficiency of adding, deleting and modifying operationsData switching networksNode deletionComputer equipment
The embodiment of the invention discloses a network intercommunication method and device for realizing a Kubernetes cluster, computer equipment and a storage medium. The method comprises the followingsteps: monitoring node information of the Kubernetes cluster in real time; if a node operation instruction of a user for the Kubernetes cluster is received, sending the Kubernetes cluster to the server; determining a target node in a user operation Kubernetes cluster according to the node operation instruction, and judging a node operation type of the user operation target node, the node operation type comprising a node addition operation, a node deletion operation and a node modification operation; and executing a preset node operation strategy according to the judged node operation type soas to realize network intercommunication of the Kubernetes cluster. According to the method, internal and external network intercommunication of the Kubernetes cluster can be realized, network intercommunication can be realized for private clouds and public clouds, and network intercommunication can also be realized under the condition of mixing the private clouds and the public clouds.
Owner:SHENZHEN QIANHAI HUANRONG LIANYI INFORMATION TECH SERVICES CO LTD
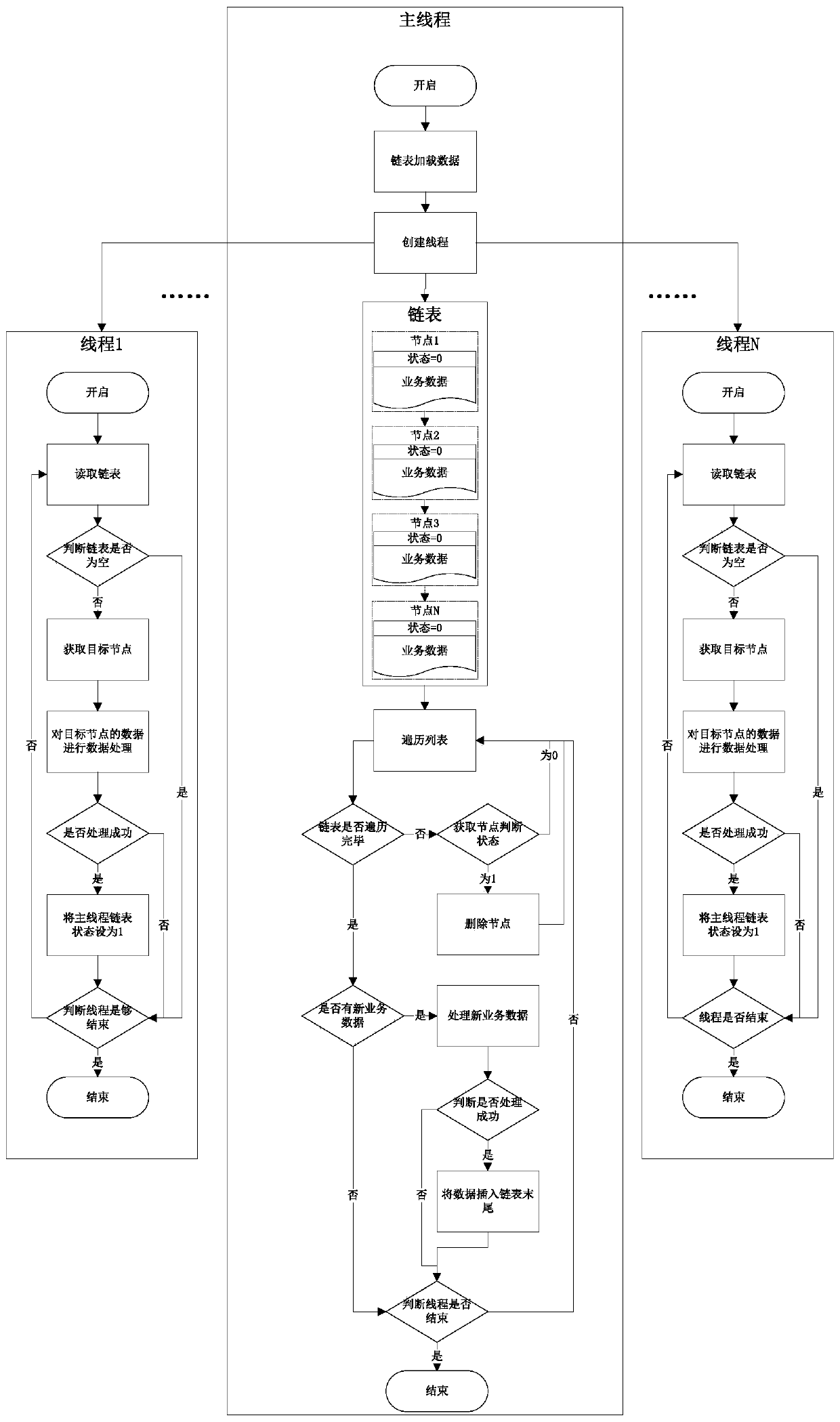
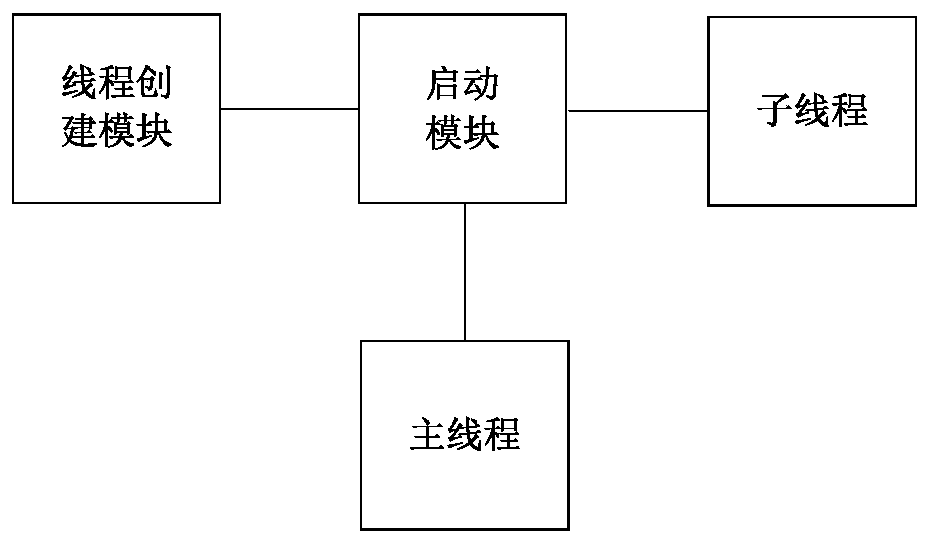
Multi-thread linked list processing method and device and computer readable storage medium
InactiveCN110598054AImprove processing efficiencyNot easy to breakProgram synchronisationOther databases indexingProcess identificationComputer science
The invention provides a multi-thread linked list processing method and device and a computer readable storage medium. The multi-thread linked list processing method comprises the steps: building a main thread and a plurality of sub-threads, enabling a linked list to be loaded into the main thread, and enabling state information to comprise a processed identification and an unprocessed identification; after the sub-thread is started, obtaining a target node with an unprocessed identifier from the linked list, carrying out data processing on the data of the target node, if the processing succeeds, updating the state information of the target node into a processed identifier in the linked list, and obtaining the next node from the linked list again; and traversing each node in the updated linked list by the main thread, and deleting the node of which the state information is the processed identifier in the traversing process. According to the multi-thread linked list processing method, the main thread and the plurality of sub-threads are adopted to process the data together, and the state information of the nodes is added into the data of the linked list, and the plurality of sub-threads process the data of the nodes in the linked list in parallel, and the influence on other sub-threads does not need to be considered, and the data processing efficiency is improved, and the linkedlist is not easy to damage.
Owner:GUILIN CHANGHAI DEV
M2M node deletion and registration methods and M2M node
InactiveCN105636241AEasy maintenanceSolve the lossConnection managementMachine-to-machine/machine-type communication serviceComputer networkNode deletion
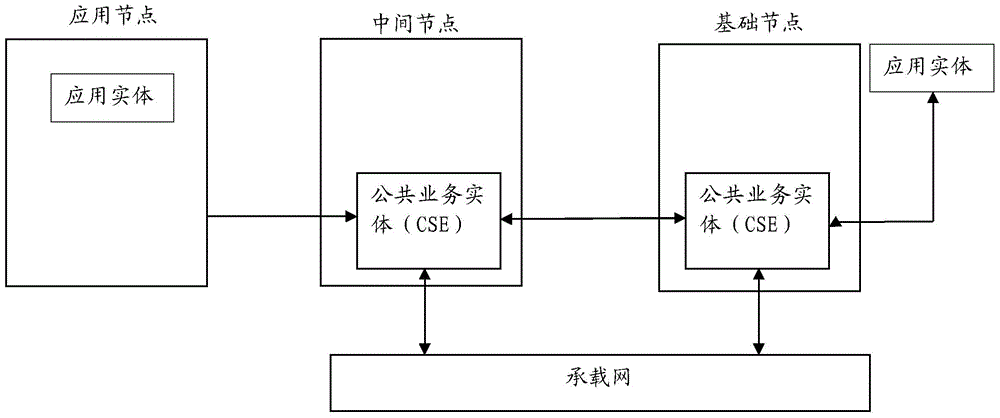
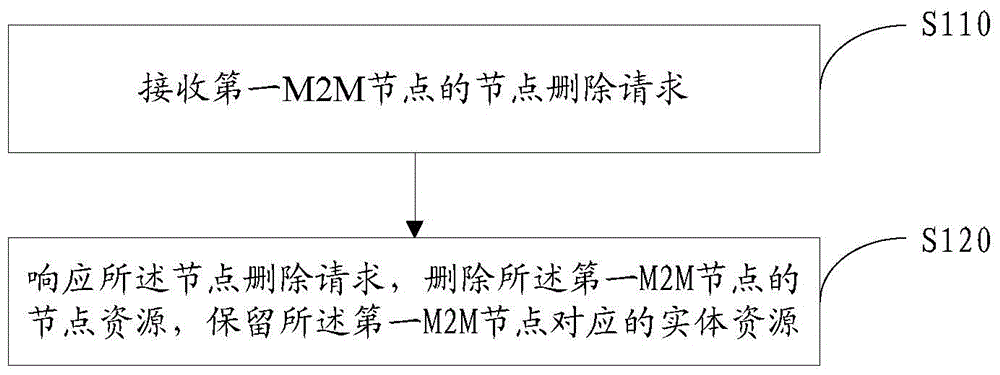
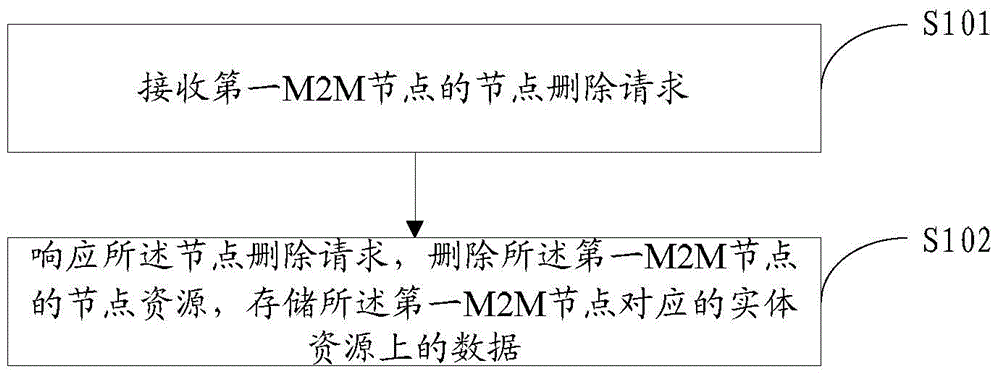
The invention discloses M2M node deletion and registration methods and an M2M node. The deletion method comprises a receiving step of receiving a node deletion request from a first M2M node; and a response step of responding to the node deletion request, deleting node resources of the first M2M node, and reserving entity resources corresponding to the first M2M node, wherein the entity resources comprise at least one of application entity (AE) resources and common service entity (CSE) resources.
Owner:ZTE CORP
Method and device for searching soft sphere decoding in single-tree mode
ActiveCN103326813AGuaranteed performanceGuaranteed performance lossError prevention/detection by diversity receptionDecoding methodsRound complexity
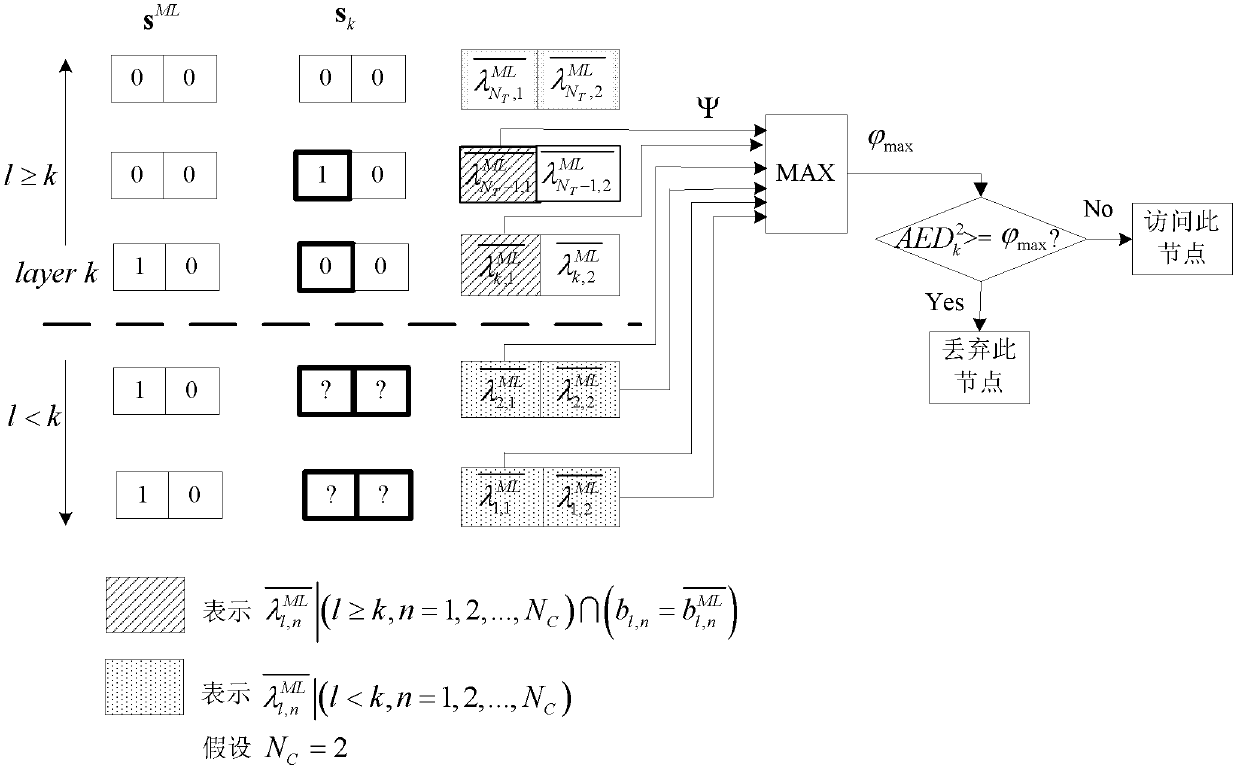
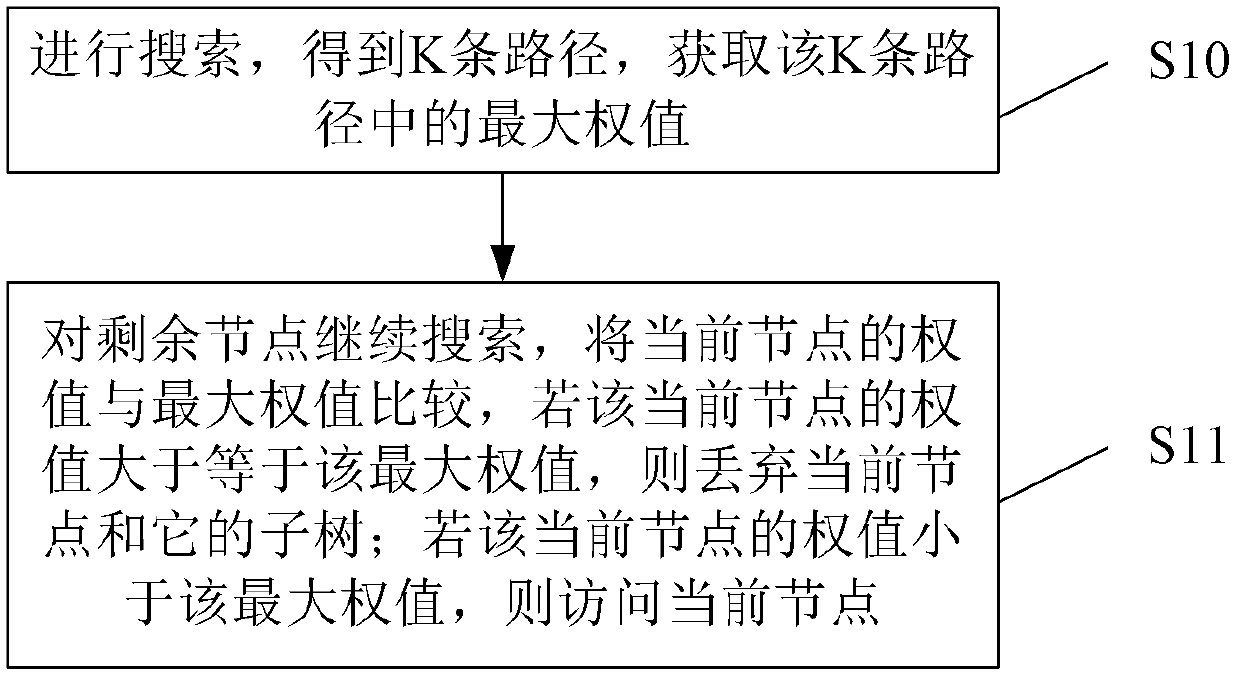
The invention provides a method and device for searching soft sphere decoding in a single-tree mode. Comparison is carried out through the weight of a current node and the maximum weight of the obtained K routes, namely, a comparison level which can be definitely obtained is introduced, and the maximum weight of the comparison level is used as a single-tree node to conduct deletion. Therefore, under the premise that the performance loss can be received, node deletion is further carried out, the performance of searching the soft sphere decoding in the single-tree mode is ensured, and complexity is further reduced.
Owner:MORNINGCORE TECH CO LTD
Node importance identification method based on complex network dependent seepage model
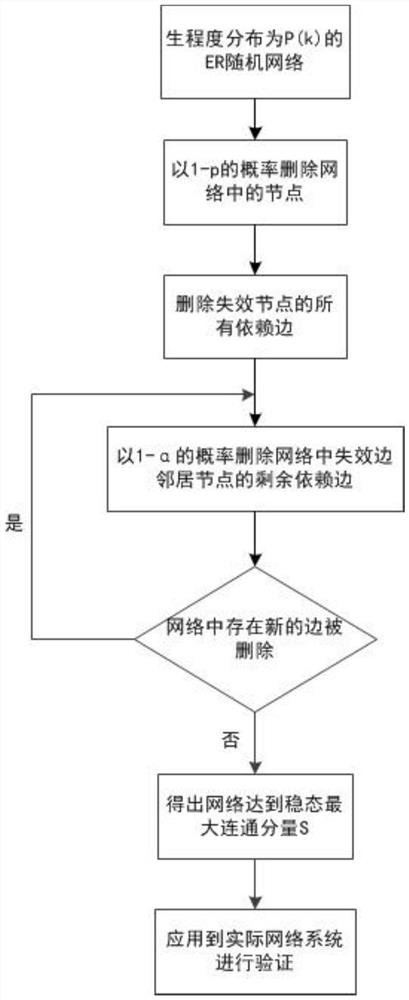
PendingCN111881545AEnsure safety and stabilityEnsure social stabilityDesign optimisation/simulationSpecial data processing applicationsEngineeringNetwork model
The invention provides a node importance identification method based on a complex network dependent seepage model, and aims to determine the influence of nodes in a network according to seepage characteristics and a cascade dynamic process when the network fails. The method comprises an edge-dependent network modeling module and a real network verification module, and the edge-dependent network modeling module comprises the following steps: (1) constructing a network model based on an edge-dependent mechanism, and introducing a weak-dependent seepage model to adjust the dependence intensity between connected edges in the network model; (2) performing failure investigation on the nodes in the network model in the step (1), setting adjustable parameters to control the dependency strength among the nodes, performing a new round of failure judgment according to whether a new dependency edge failure exists in the network model or not, and obtaining a final value of the maximum communicationcomponent of the network model until the network model is stable; (3) evaluating the importance of the node according to the edge dependence intensity critical value and the maximum communication component causing the network crash when the node is deleted.
Owner:HANGZHOU NORMAL UNIVERSITY
Forwarding entry deletion method and root node
The invention discloses a forwarding entry deletion method and a root node. The method comprises the following steps: a root node of a multicast tree sends first multicast tree cutoff messages to part of or all nodes in primary downstream multicast neighbor nodes of the root node respectively after detecting cutoff of the multicast flow, so as to enable the primary downstream multicast neighbor nodes receiving the first multicast tree cutoff messages to delete the forwarding entries of the multicast tree maintained by the primary downstream multicast neighbor nodes per se; and the root node deletes the forwarding entries of the multicast tree maintained by the root node per se after detecting cutoff of the multicast flow. The invention has the advantage that as the root node deletes the forwarding entries of the multicast tree maintained by the root node per se, and part of or all nodes in the primary downstream multicast neighbor nodes of the root node delete the forwarding entries of the multicast tree maintained by the primary downstream multicast neighbor nodes per se, a plurality of multicast entries on the multicast tree are quickly deleted based on a notification mechanism.
Owner:HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com