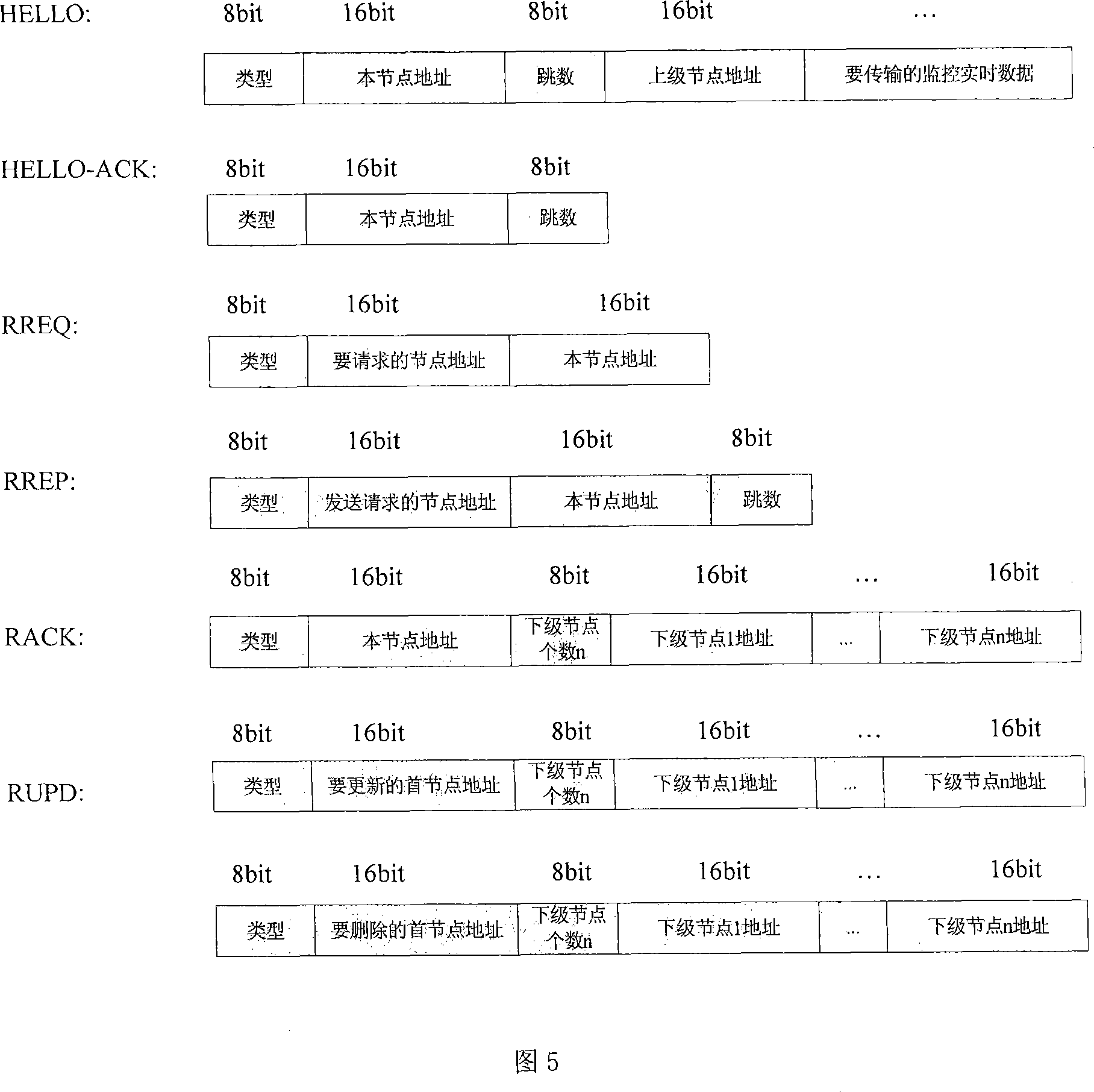Patents
Literature
309 results about "Network formation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
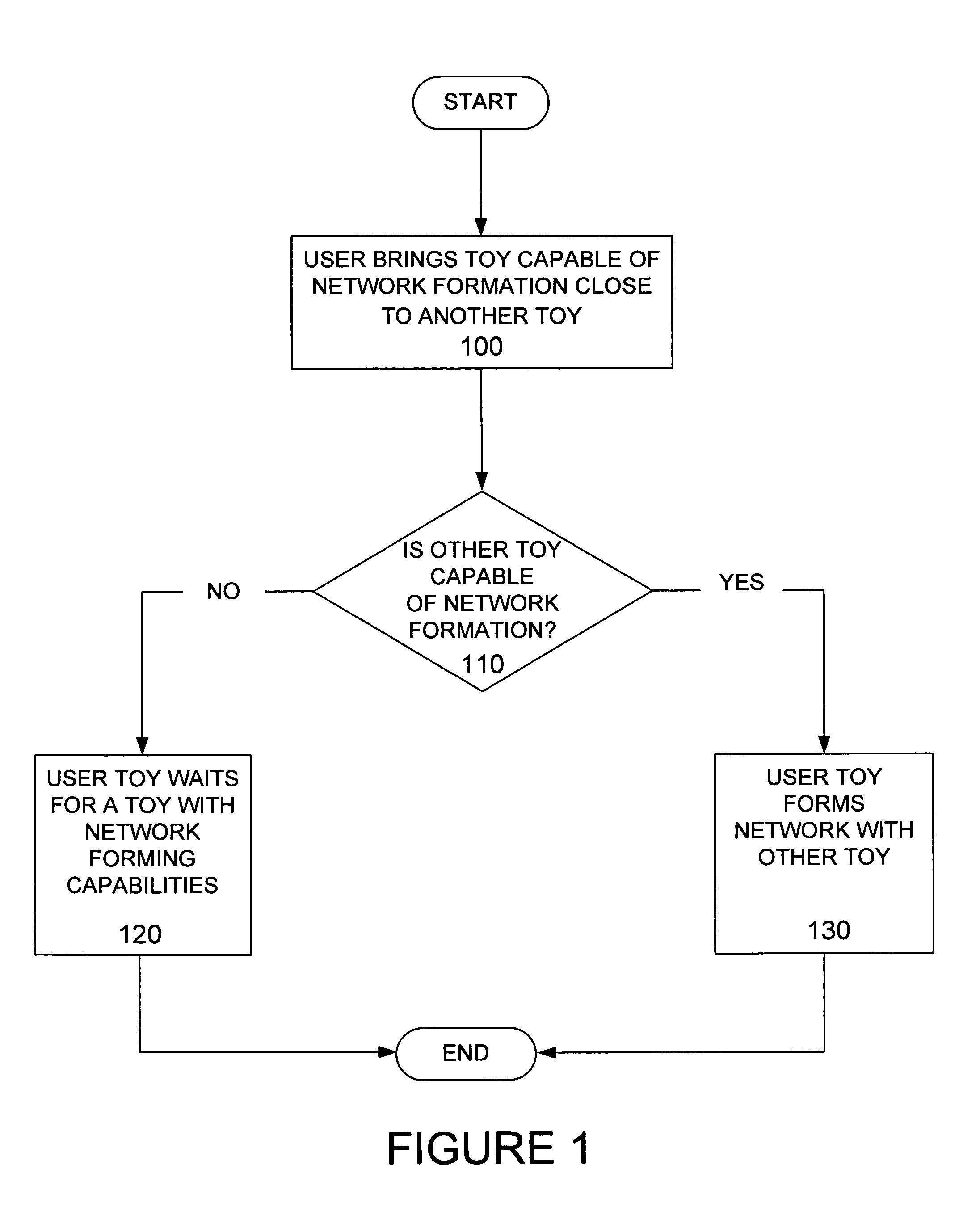
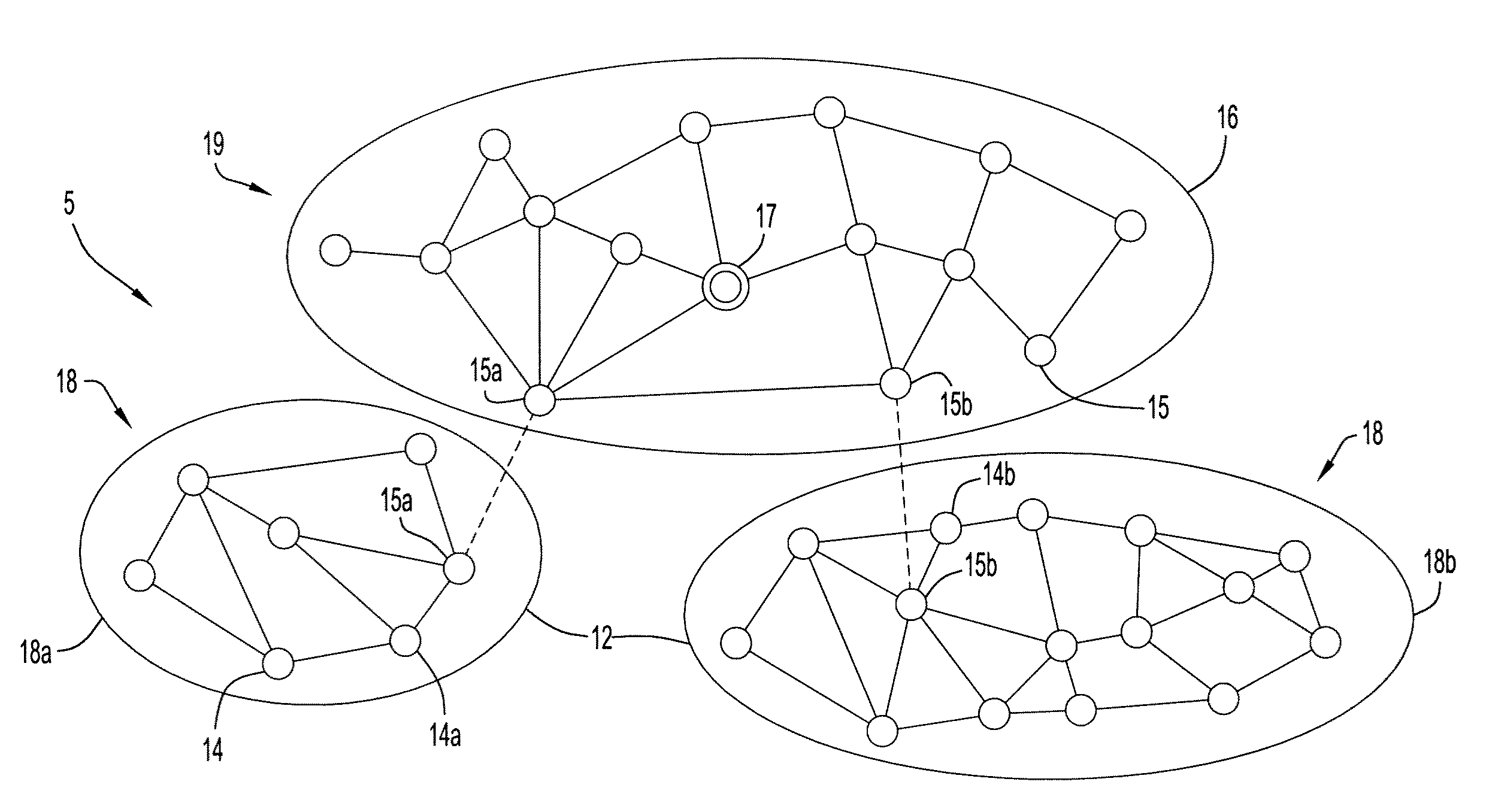
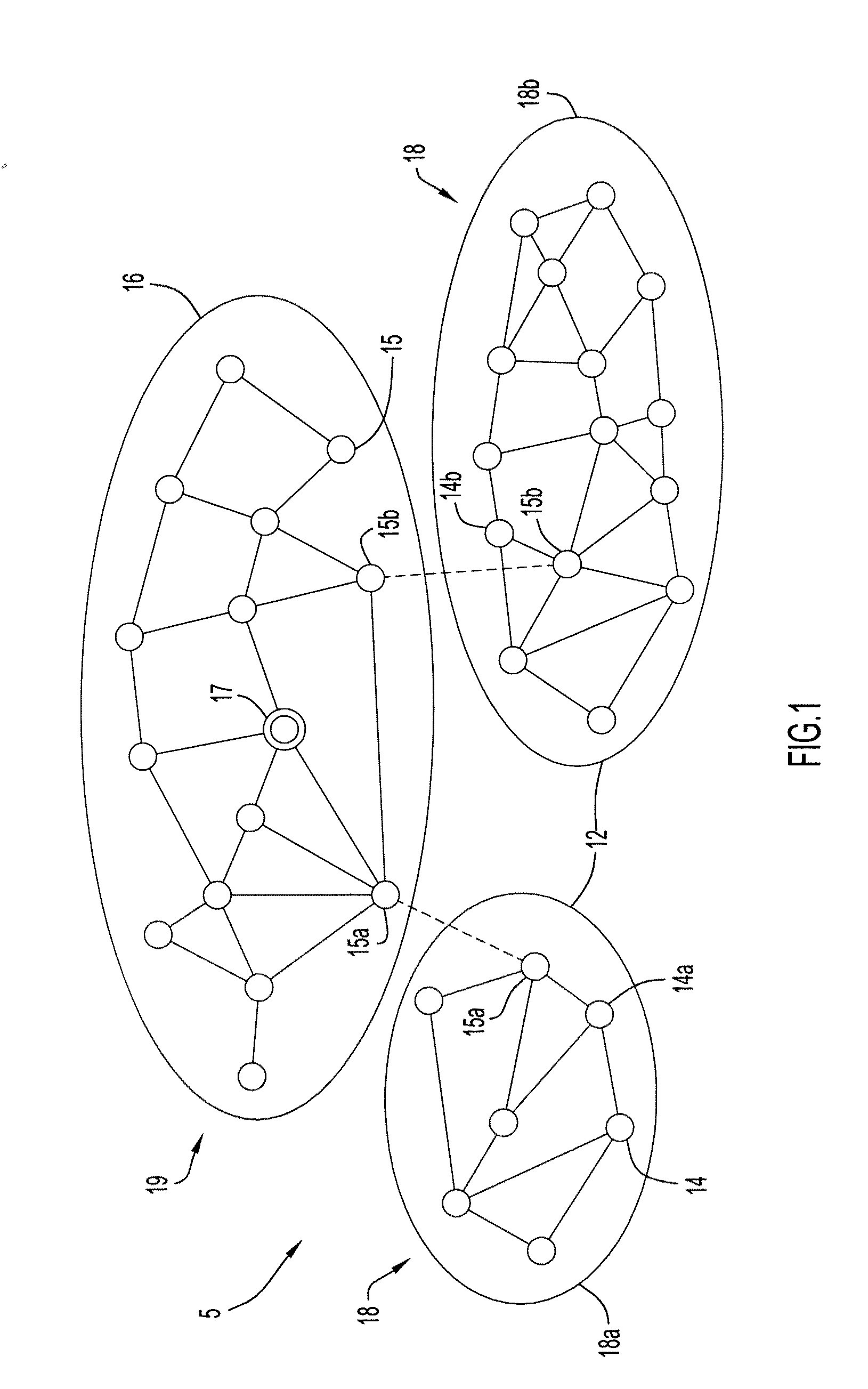
Network formation is an aspect of network science that seeks to model how a network evolves by identifying which factors affect its structure and how these mechanisms operate. Network formation hypotheses are tested by using either a dynamic model with an increasing network size or by making an agent-based model to determine which network structure is the equilibrium in a fixed-size network.
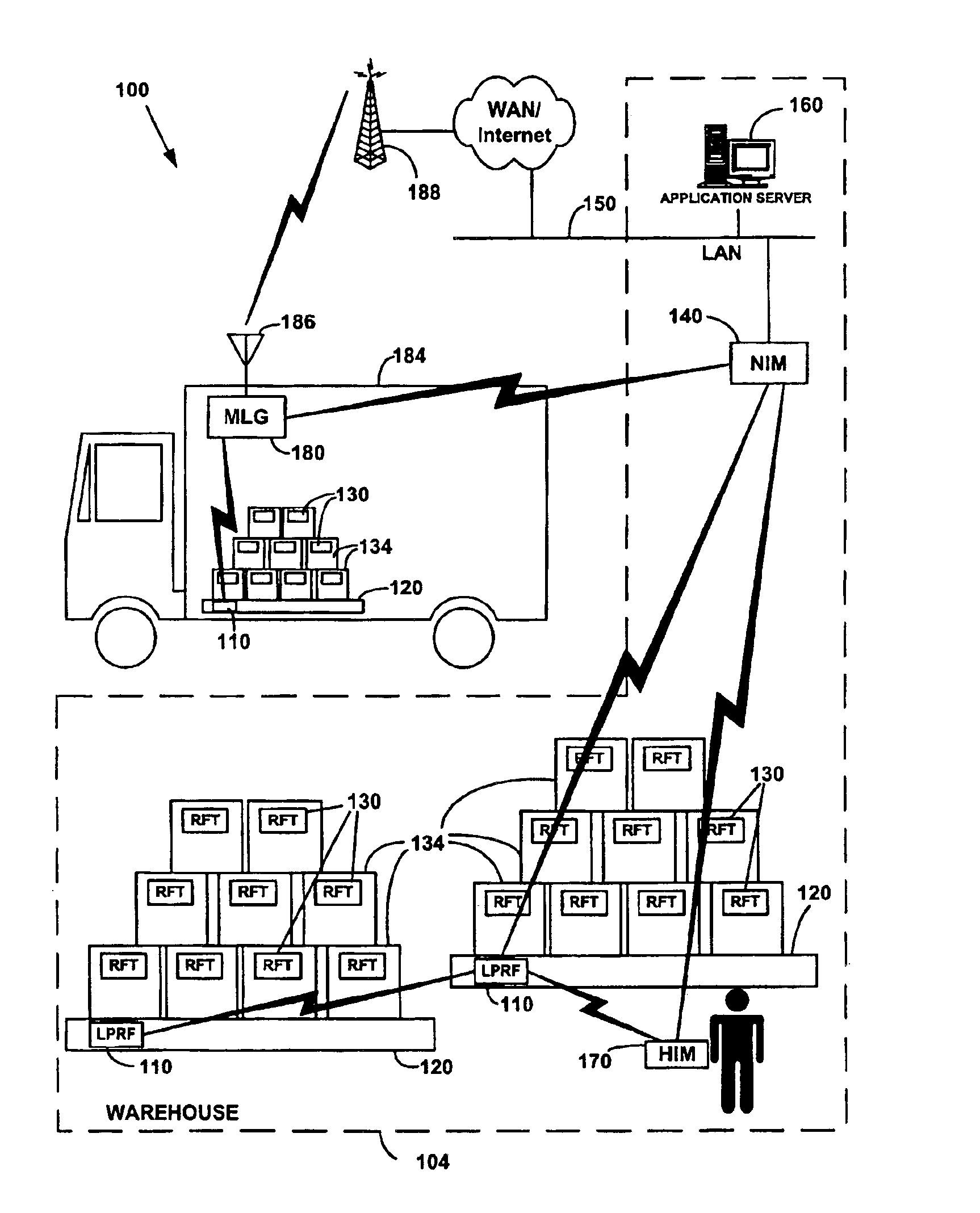
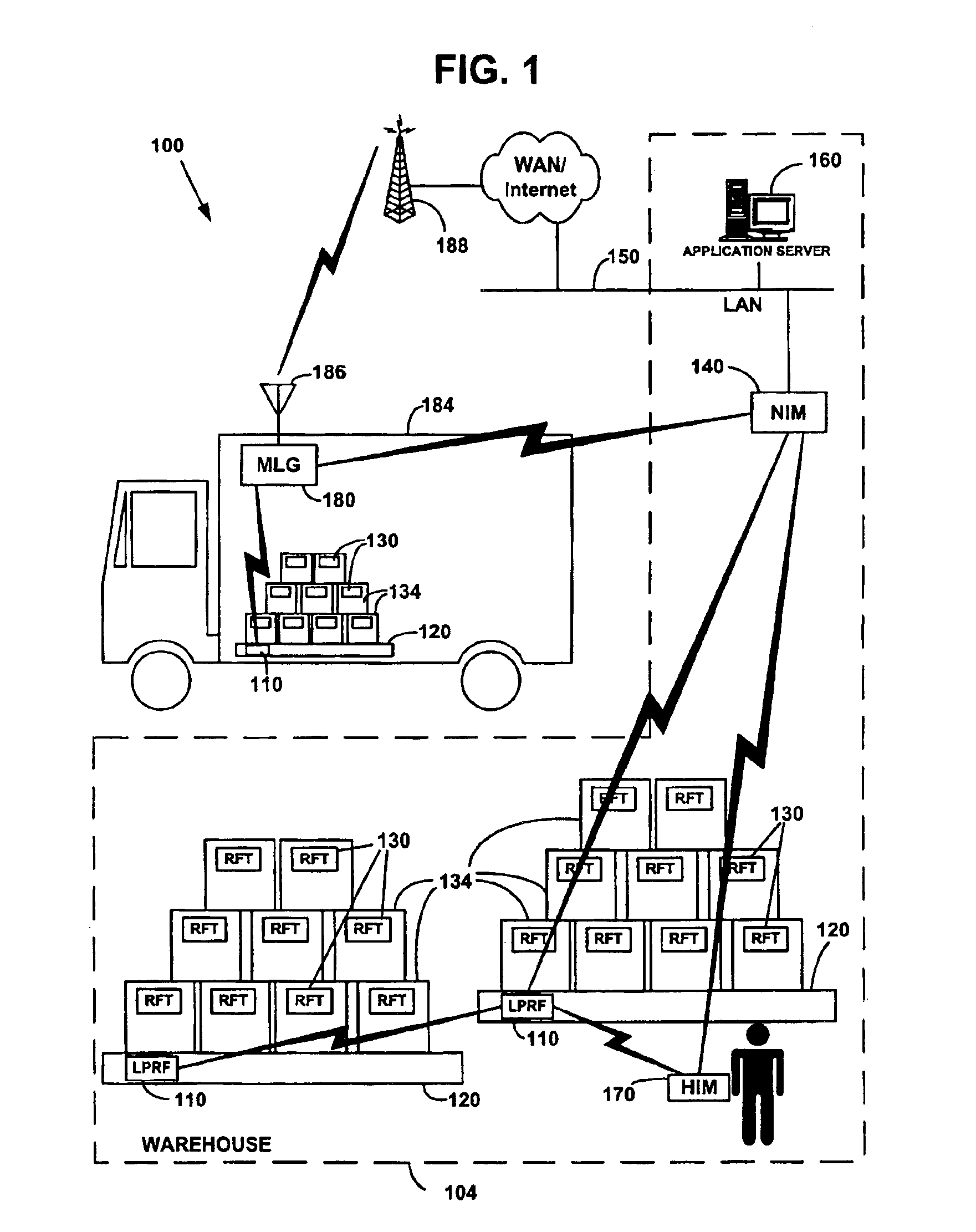
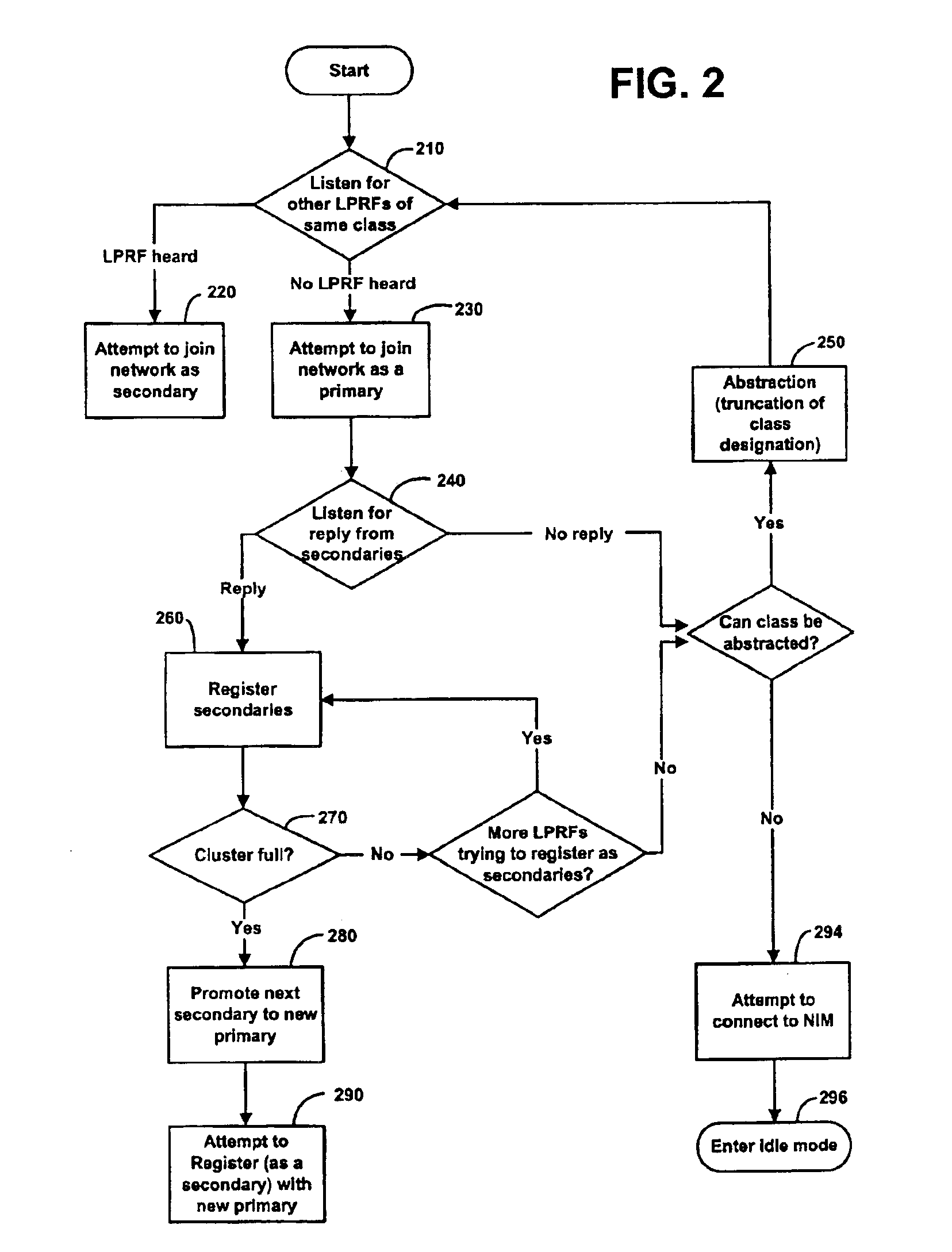
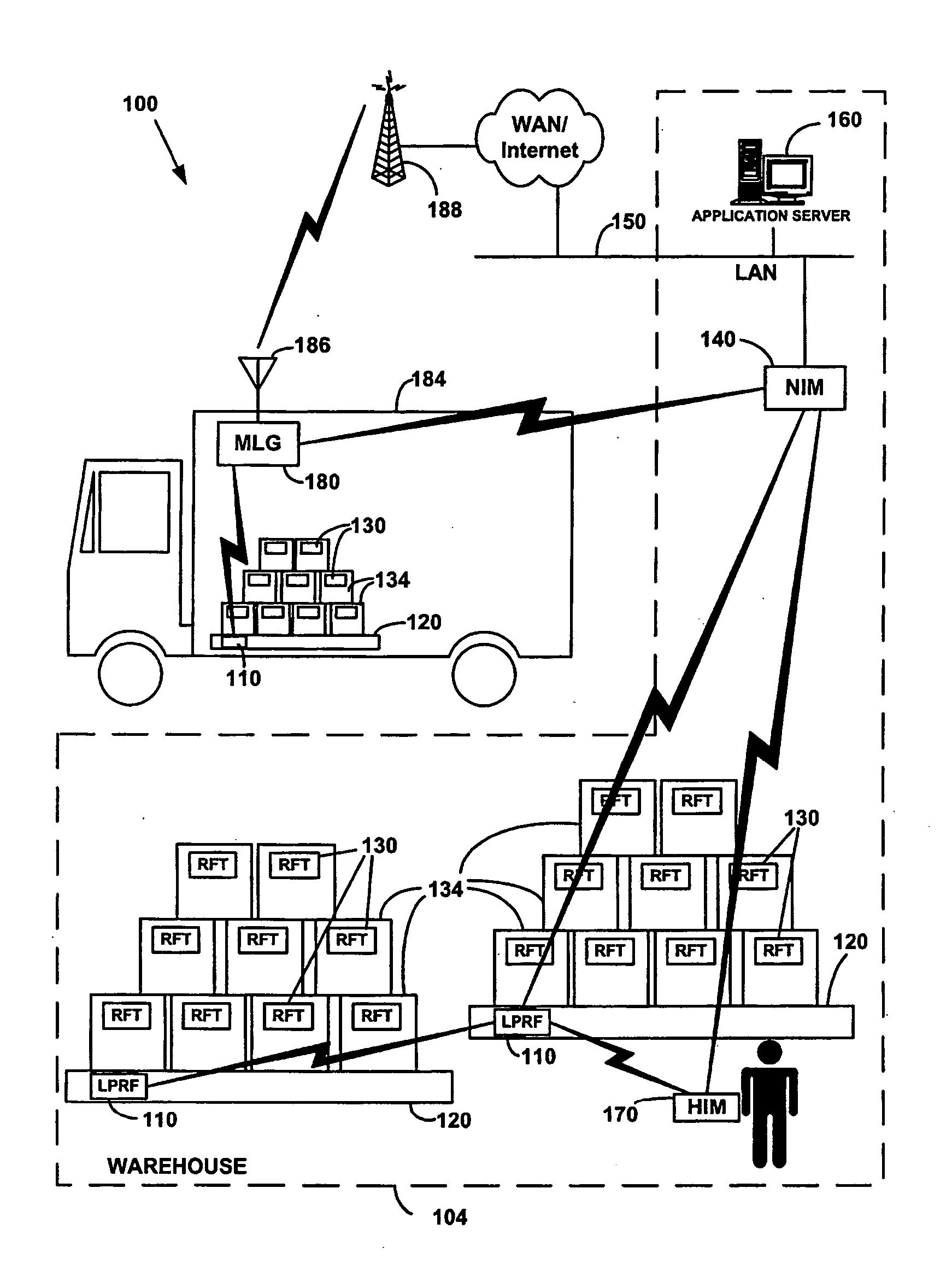
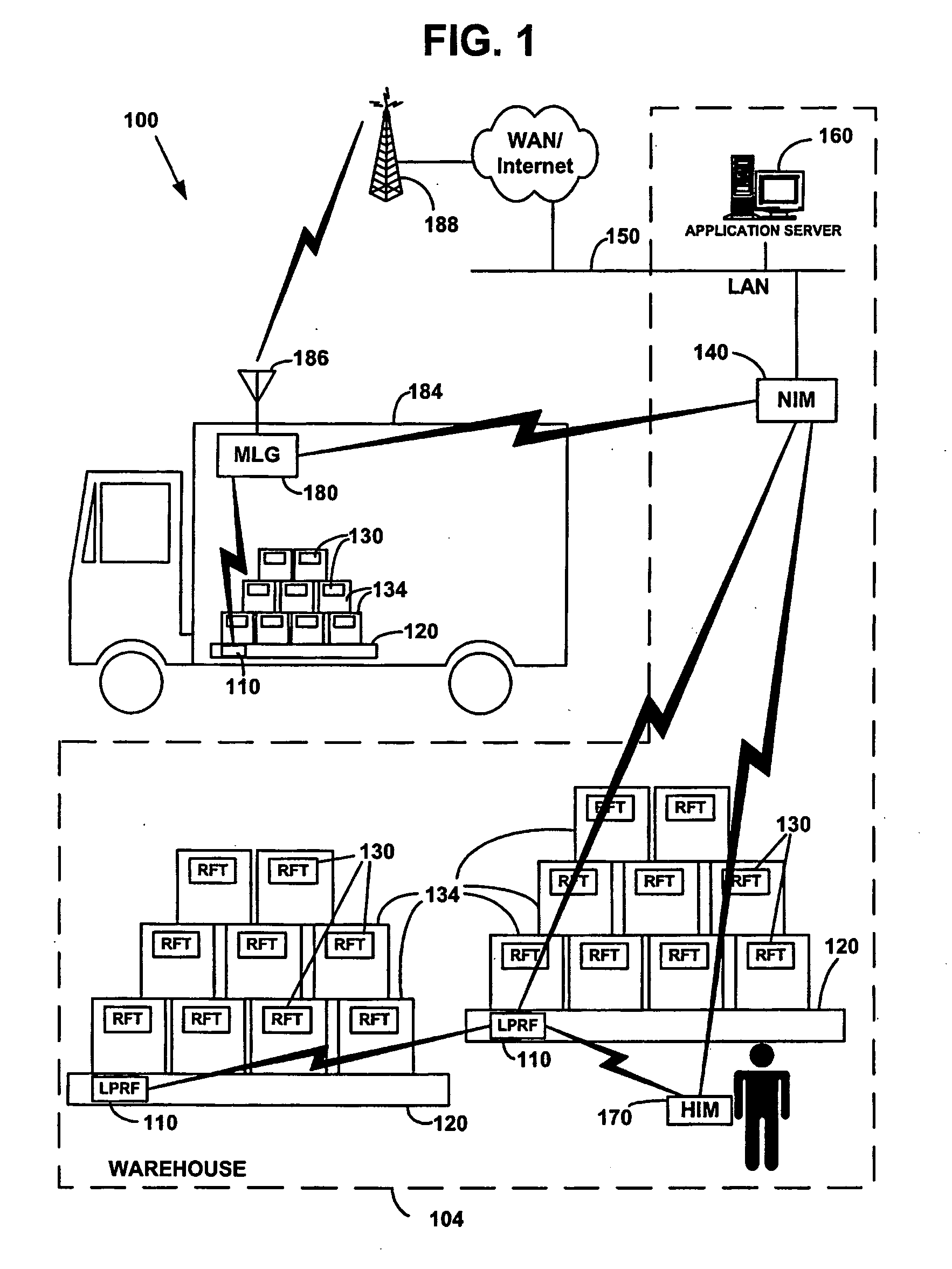
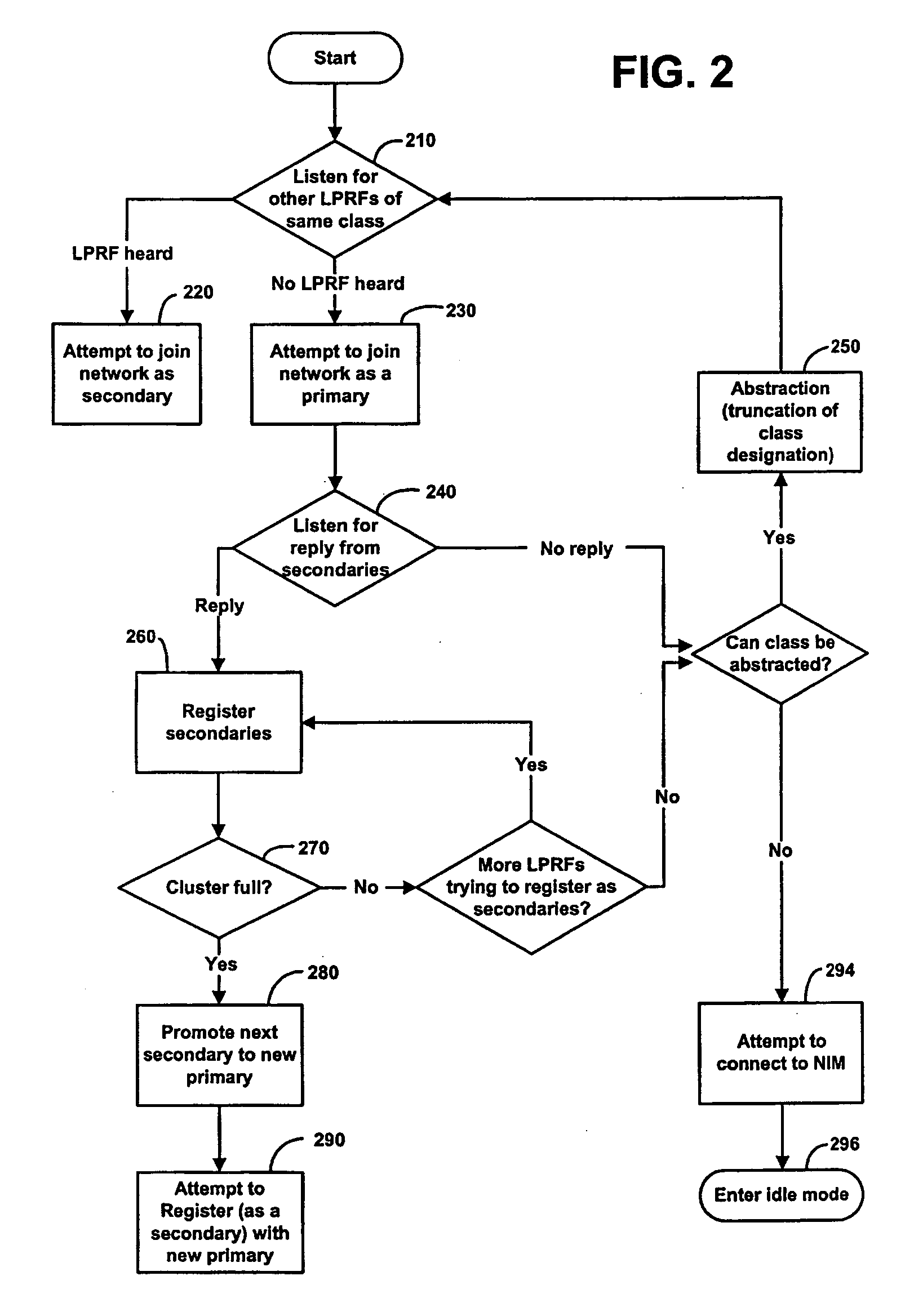
Network formation in asset-tracking system based on asset class
InactiveUS6934540B2Special service provision for substationEnergy efficient ICTTransceiverWireless transceiver
A plurality of wireless transceivers are associated with assets and each transceiver is assigned a class designation representative of an attribute, characteristic, relation, or behavior of its respective asset. Class based network formation routines are utilized to establish hierarchical networks based on asset classes, and the asset class is used by each transceiver to screen communications intended for receipt by transceivers of the same class. The overall wireless data communication network results in reduced power consumption and signal interference in asset-tracking applications. The transceivers may include a query handling routine for forming a dynamically distributed hierarchical database system. Furthermore, a recipient transceiver selectively receives communications from other local transceivers by transmitting at incrementally stronger power levels to successive groups of transceivers, and receiving reply transmissions only from a limited number of the transceivers that excludes those transceivers from which communications already are received.
Owner:GOOGLE LLC
Network Formation in Asset-Tracking System Based on Asset Class
InactiveUS20040082296A1Improve reliabilityFacilitates monitoring and controlling and queryingSpecial service provision for substationEnergy efficient ICTWireless transceiverTransceiver
A plurality of wireless transceivers are associated with assets and each transceiver is assigned a class designation representative of an attribute, characteristic, relation, or behavior of its respective asset. Class based network formation routines are utilized to establish hierarchical networks based on asset classes, and the asset class is used by each transceiver to screen communications intended for receipt by transceivers of the same class. The overall wireless data communication network results in reduced power consumption and signal interference in asset-tracking applications. The transceivers may include a query handling routine for forming a dynamically distributed hierarchical database system. Furthermore, a recipient transceiver selectively receives communications from other local transceivers by transmitting at incrementally stronger power levels to successive groups of transceivers, and receiving reply transmissions only from a limited number of the transceivers that excludes those transceivers from which communications already are received.
Owner:GOOGLE LLC
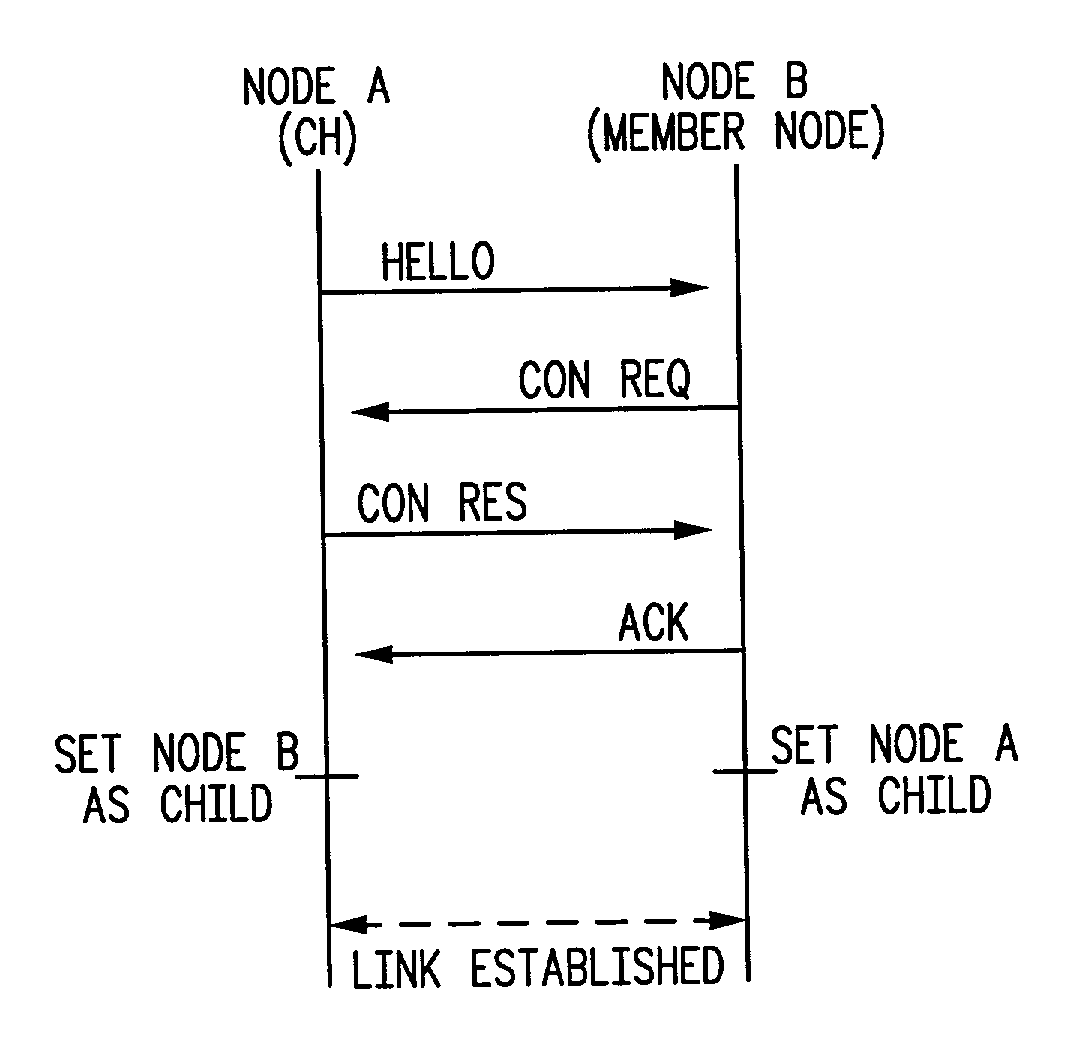
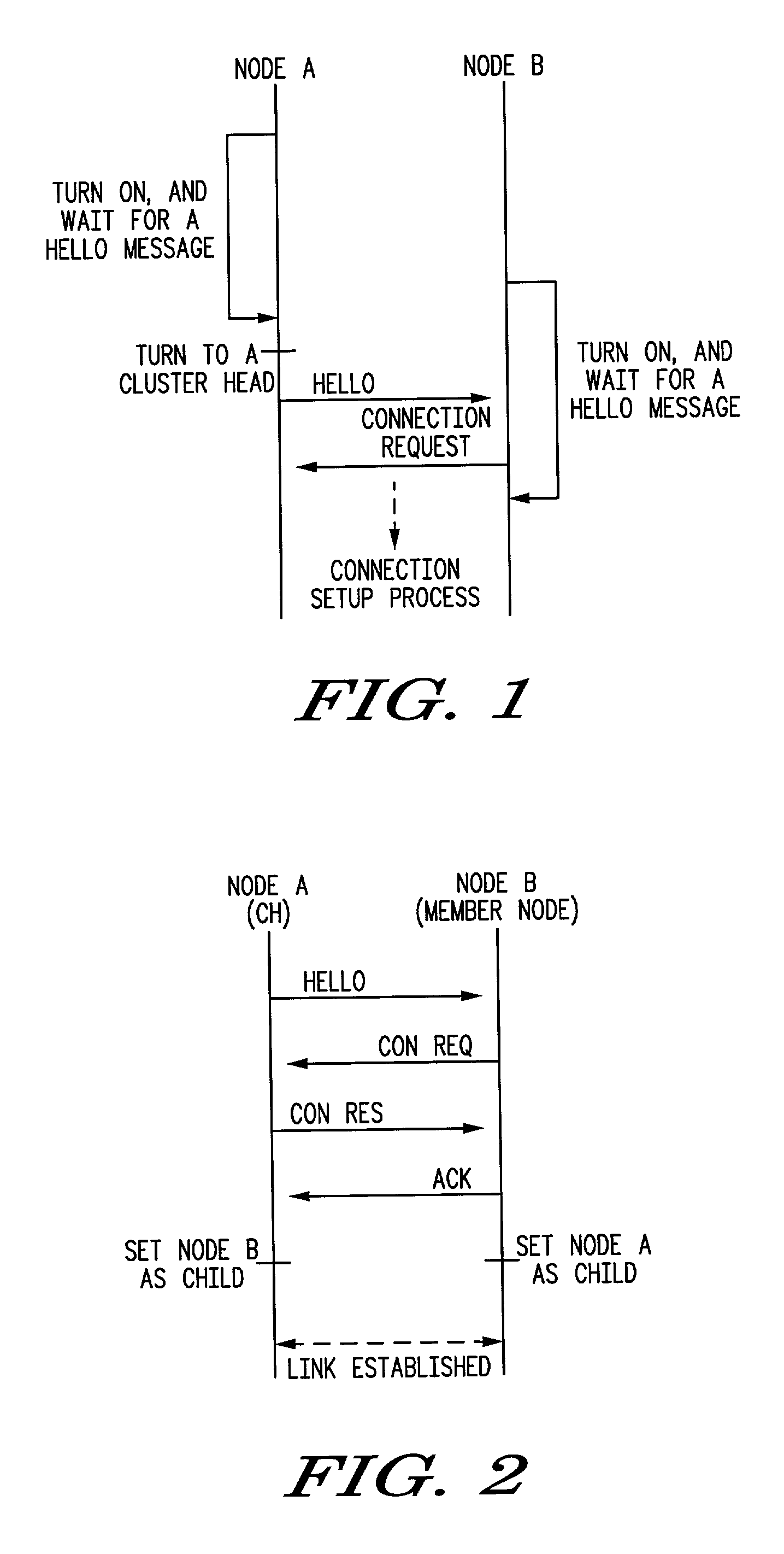
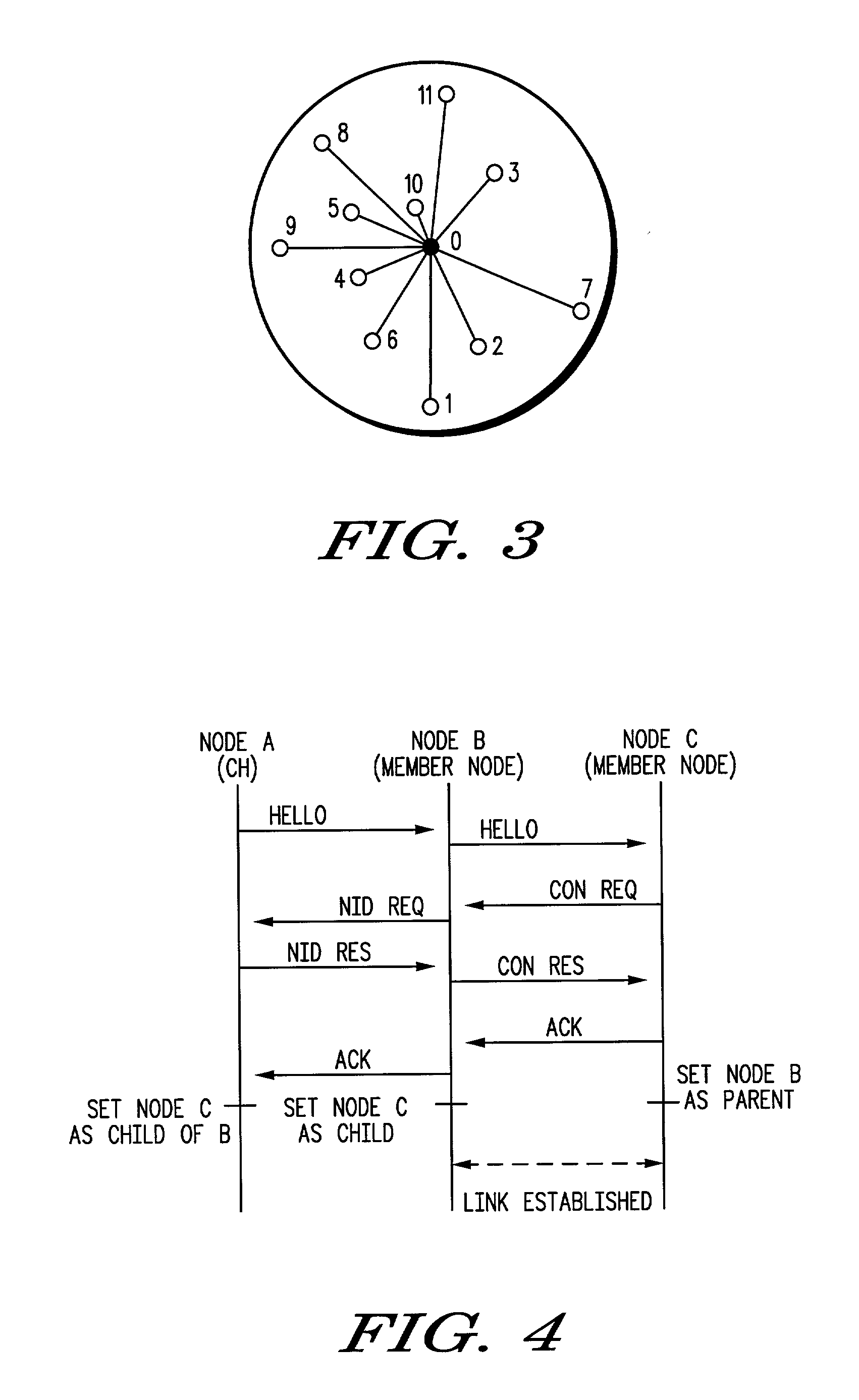
Protocol and structure for self-organizing network
InactiveUS7171476B2Error prevention/detection by using return channelNetwork topologiesTelecommunications linkMulti cluster
A cluster tree network formed by self-organization of a number of nodes. The method of self-organization includes processes for cluster formation, cluster network maintenance, intra-cluster communication. In the cluster formation process, each node discovers if any neighboring node is a cluster head or if any node is already a member of a cluster (thus making it a networked node), and if a cluster head or a networked node is discovered, each node establishes a communication link with the cluster head or the networked node. If no cluster head or networked node is discovered, the node itself becomes a cluster head. The network is maintained by each node periodically broadcasting a HELLO message to neighboring nodes, receiving responses to the HELLO message and updating a neighbor list in accordance with responses to the HELLO message. Multi-cluster networks are also provided using the processes of inter-cluster network formation, inter-cluster network maintenance, and inter-cluster communication. The resulting network has one or more clusters of nodes, each with a cluster head and a number of member nodes, each assigned a node identifier by the cluster head. In a multi-cluster network, a designated device assigns identifies to each cluster head in the network. Border nodes, which are members of at least two clusters, act as routers connecting the clusters and relaying information packets between the clusters.
Owner:ARRIS ENTERPRISES LLC
Secure authentication and network management system for wireless LAN applications
InactiveUS20060072527A1Efficient and effectiveProtect healthDigital data processing detailsUser identity/authority verificationWi-FiNetwork management
An authentication and network management system for Wi-Fi local area networks includes a network management device and a plurality of Wi-Fi local area networks coupled to the network management device. Each local network includes at least one access point device having a Wi-Fi radio. A plurality of end user devices are attachable to the network forming nodes thereof, and each end user device has input plugs, such as USB ports and the like, for coupling accessories thereto. An authentication device is provided in the network for authenticating the end user devices attached to the network. A plurality of authenticating keys is provided, with each key attachable to an input plug of an end user device. Each key contains a validation certificate therein, wherein the authentication device verifies the presence of a current validation certificate on a key coupled to the end users device prior to granting access to the network.
Owner:DIRECTPOINTE
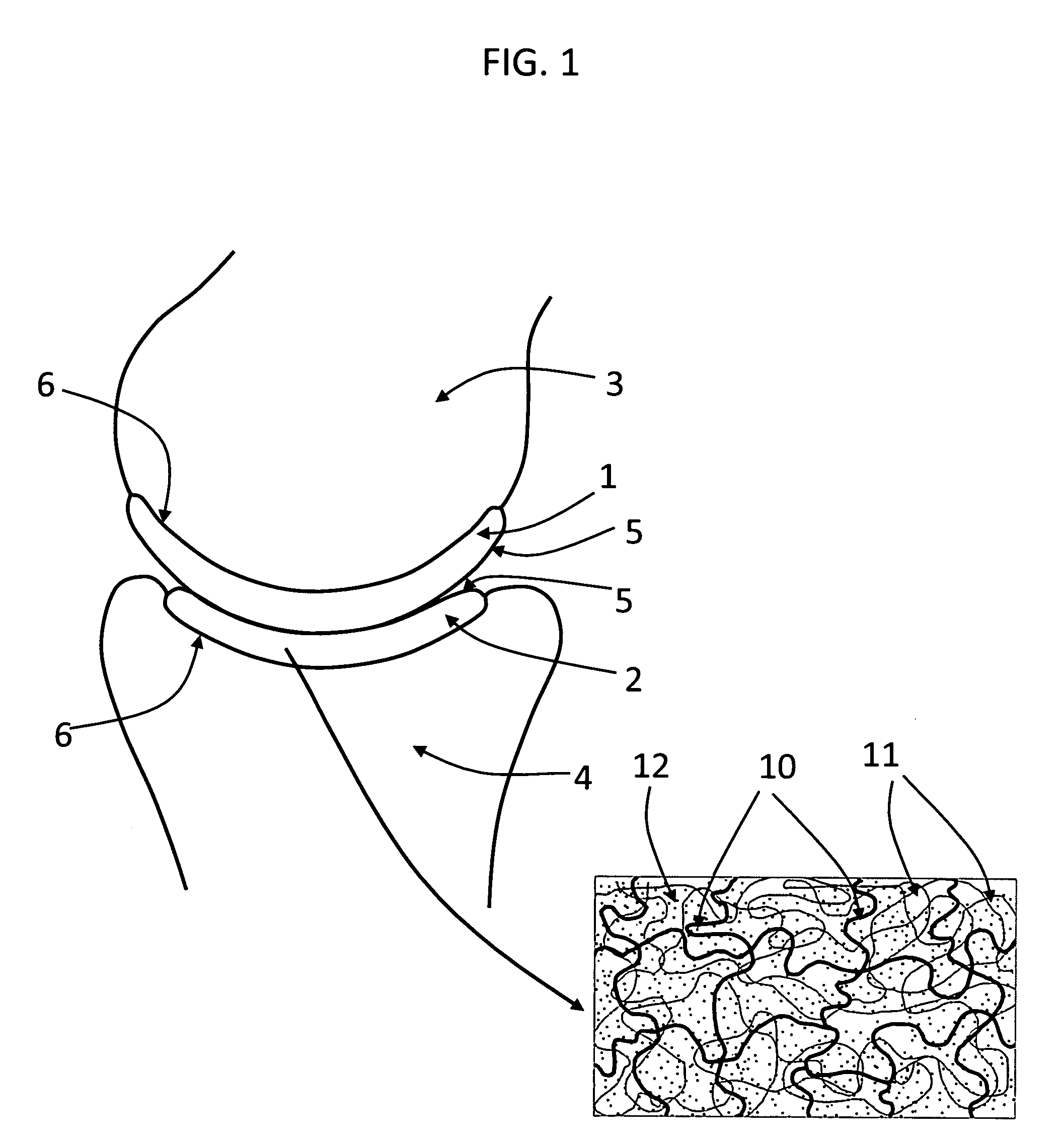
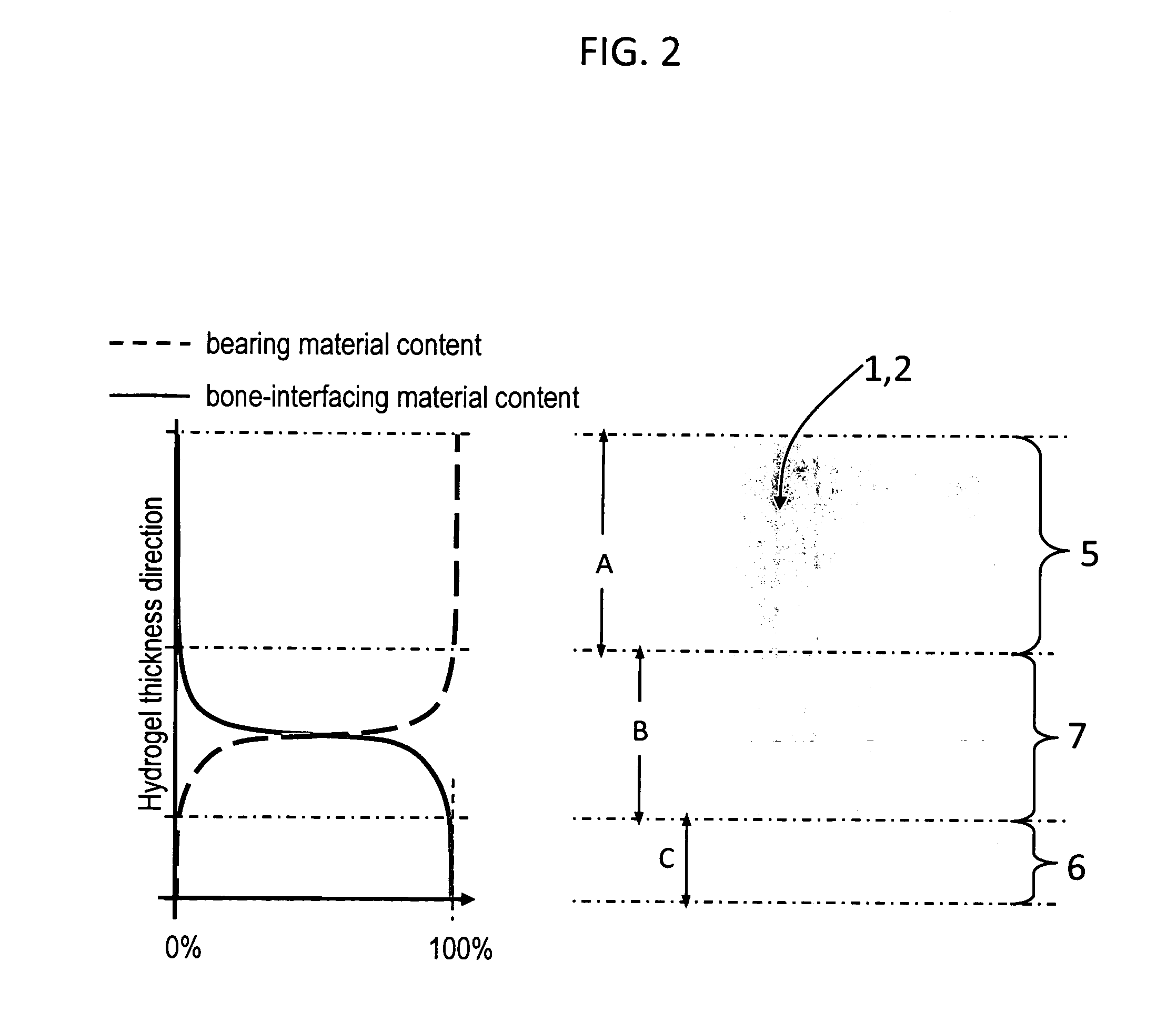
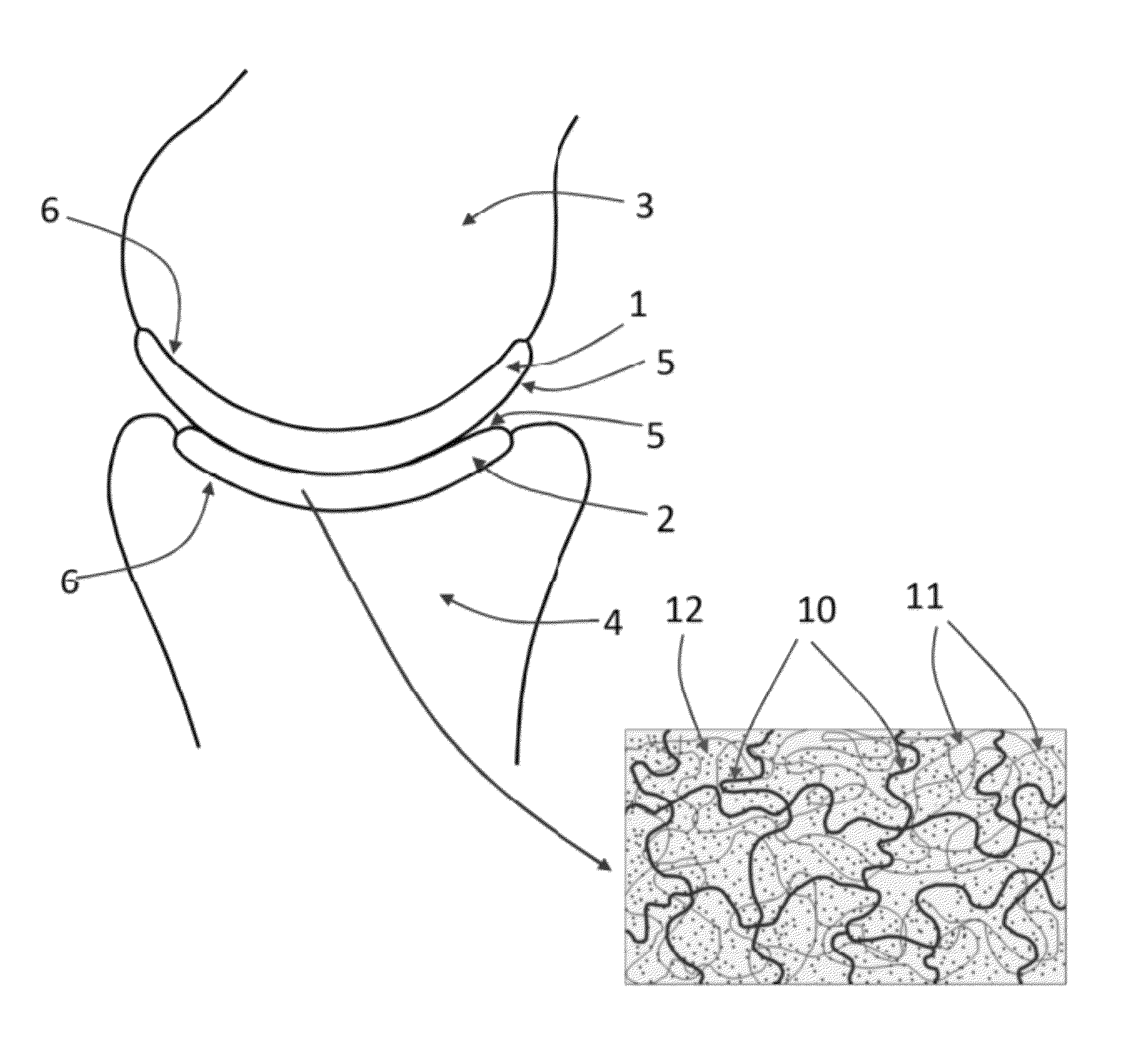
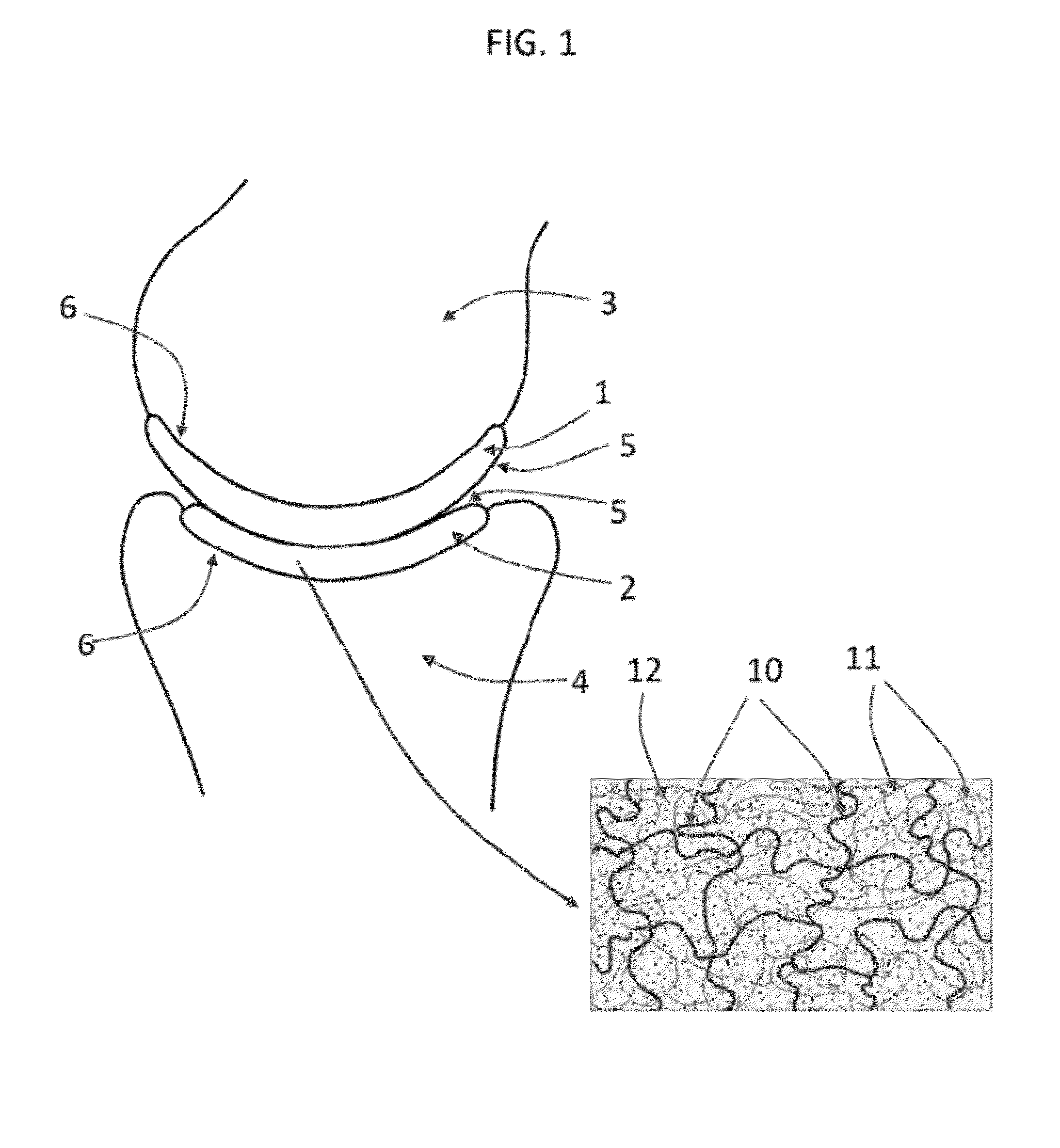
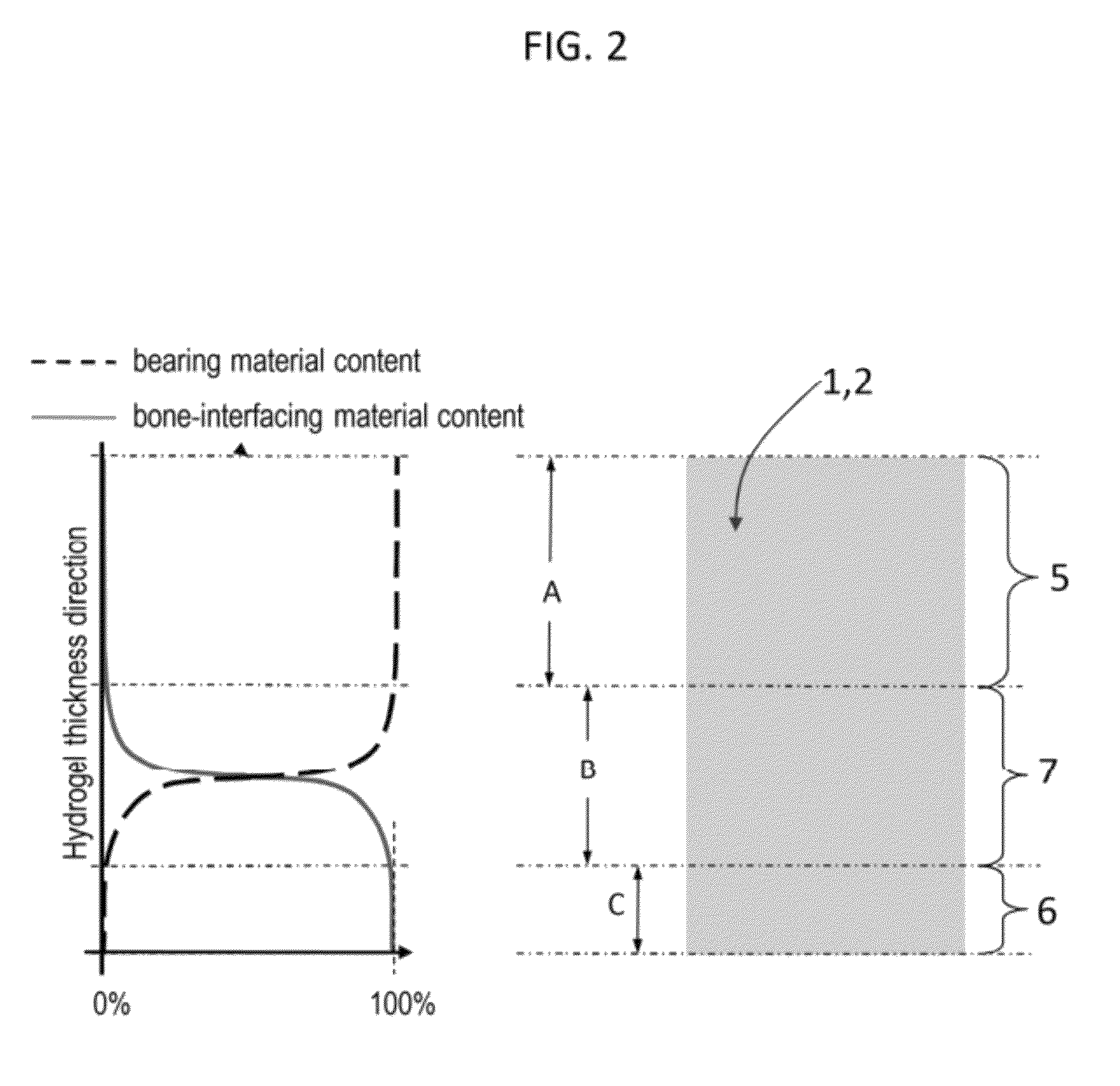
Hydrogel arthroplasty device
InactiveUS20090088846A1Stimulate bone cell growthEasy adhesionFinger jointsPowder deliveryCross-linkNeutral ph
An arthroplasty device is provided having an interpenetrating polymer network (IPN) hydrogel that is strain-hardened by swelling and adapted to be held in place in a joint by conforming to a bone geometry. The strain-hardened IPN hydrogel is based on two different networks: (1) a non-silicone network of preformed hydrophilic non-ionic telechelic macromonomers chemically cross-linked by polymerization of its end-groups, and (2) a non-silicone network of ionizable monomers. The second network was polymerized and chemically cross-linked in the presence of the first network and has formed physical cross-links with the first network. Within the IPN, the degree of chemical cross-linking in the second network is less than in the first network. An aqueous salt solution (neutral pH) is used to ionize and swell the second network. The swelling of the second network is constrained by the first network resulting in an increase in effective physical cross-links within the IPN.
Owner:THE GOVERNMENT OF THE UNITED STATES OF AMERICA AS REPRESENTED BY THE DEPT OF VETERANS AFFAIRS +1
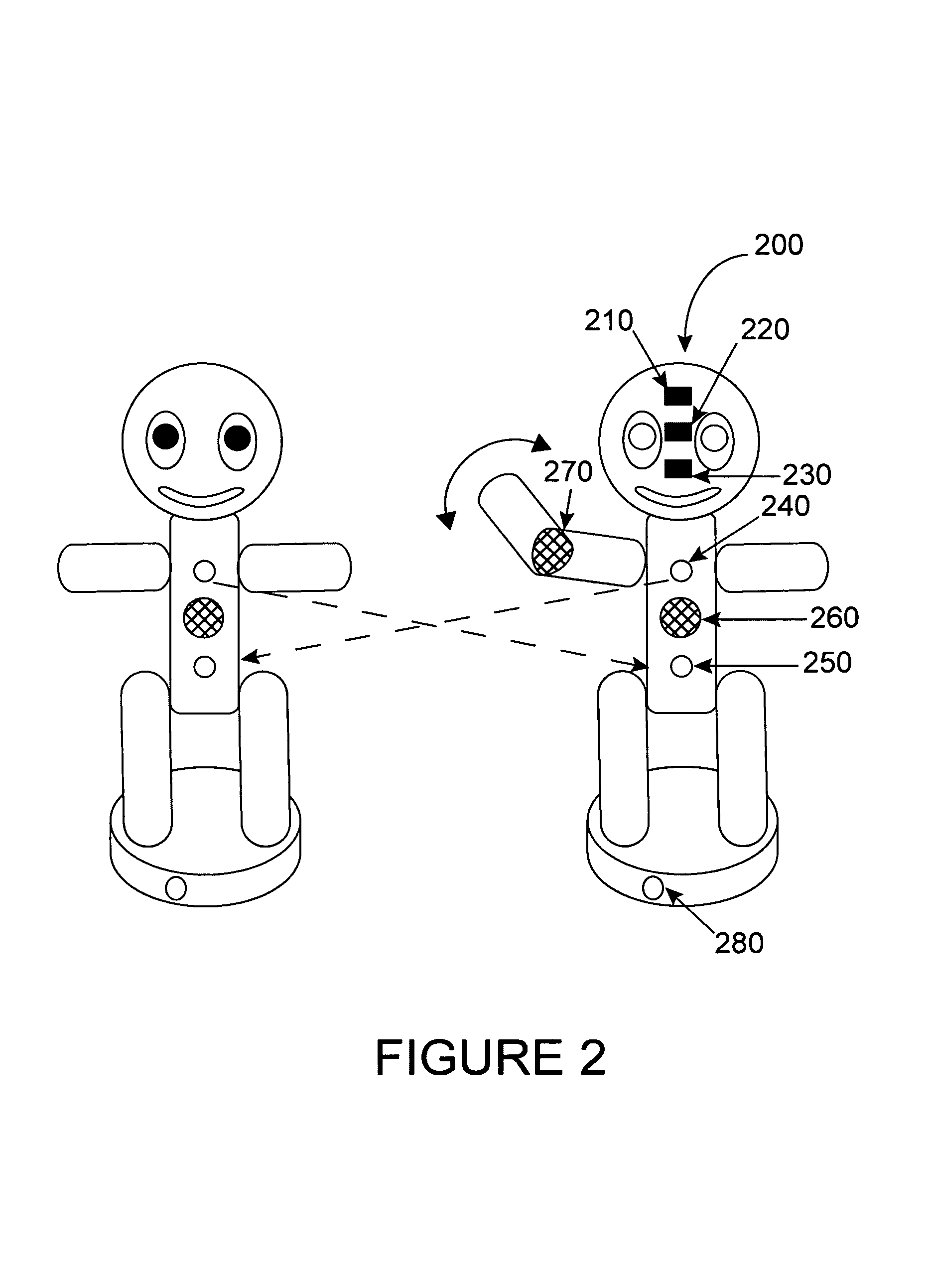
Figurines having interactive communication
Owner:STUPID FUN CLUB LLC A DELAWARE LIMITED LIABILITY
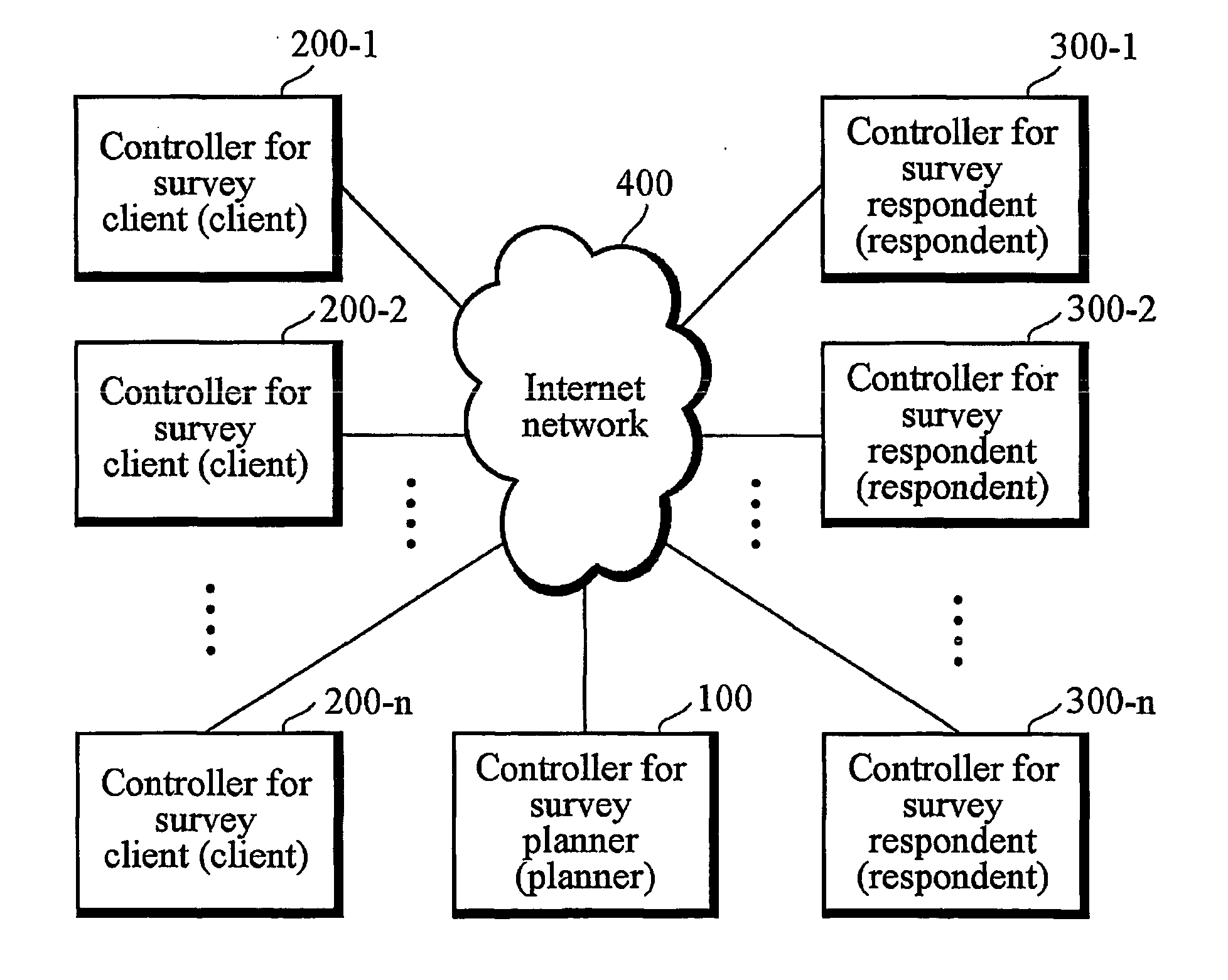
Method for respondent-based real-time survey
Owner:KIM JEONG UK
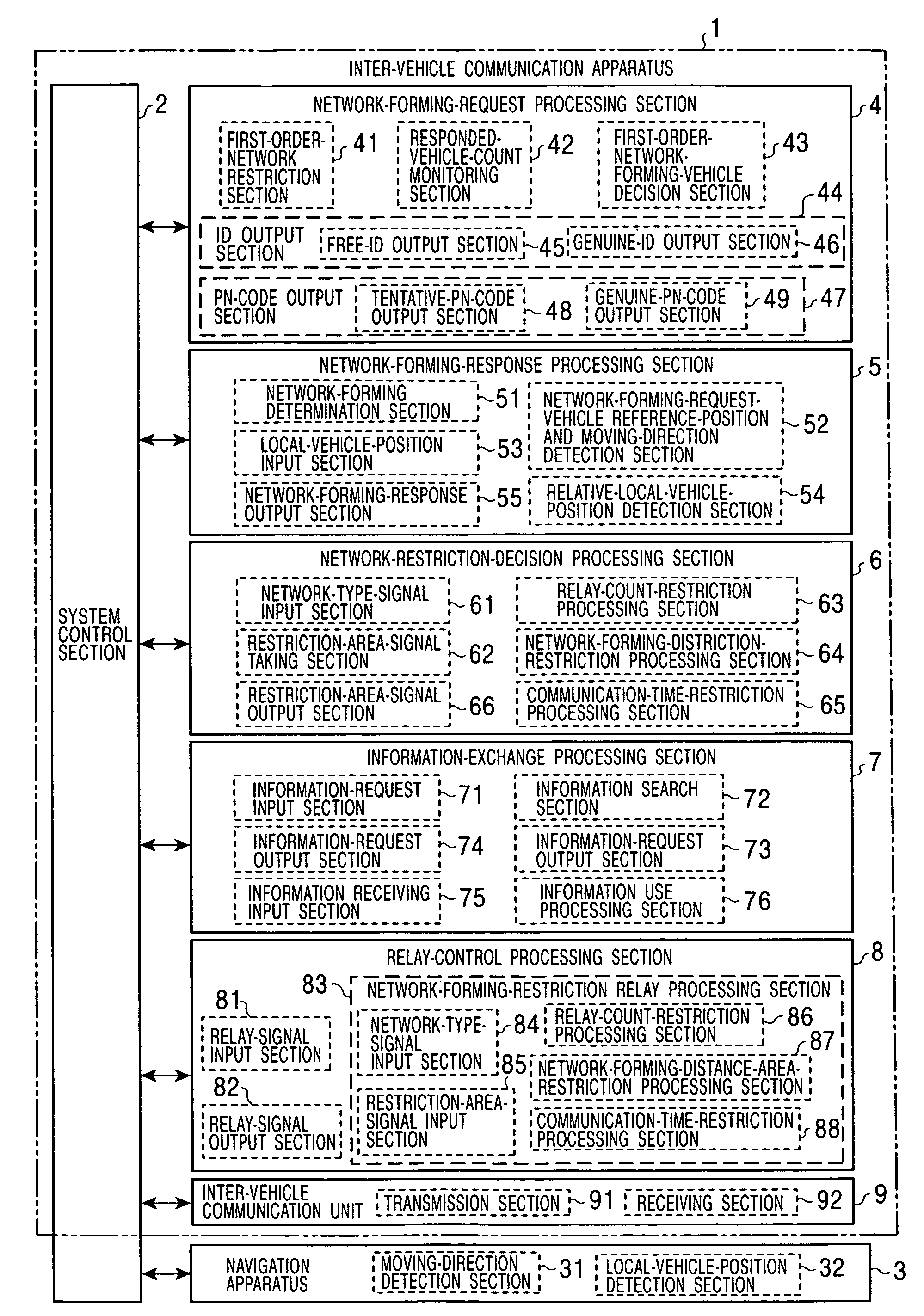
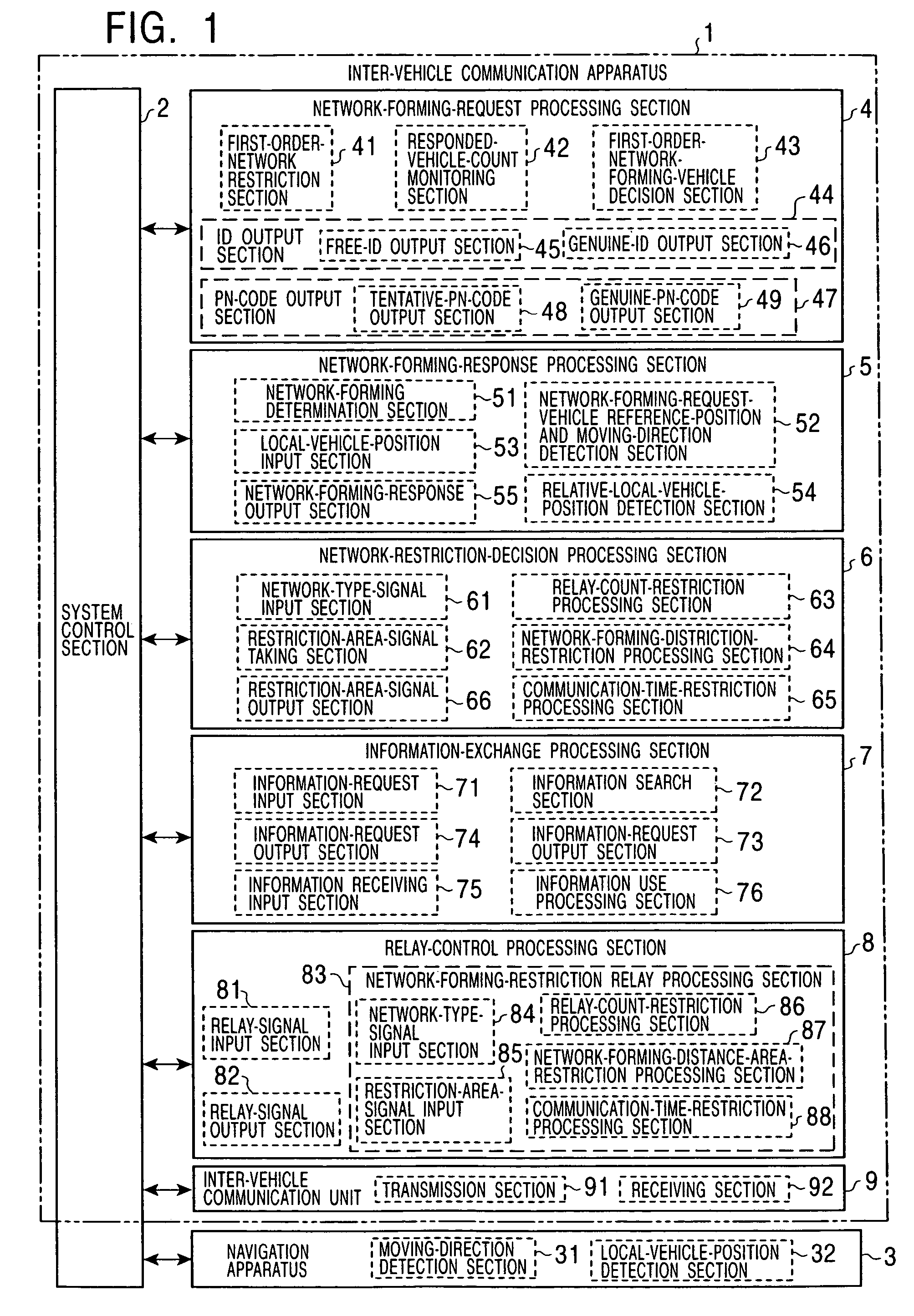
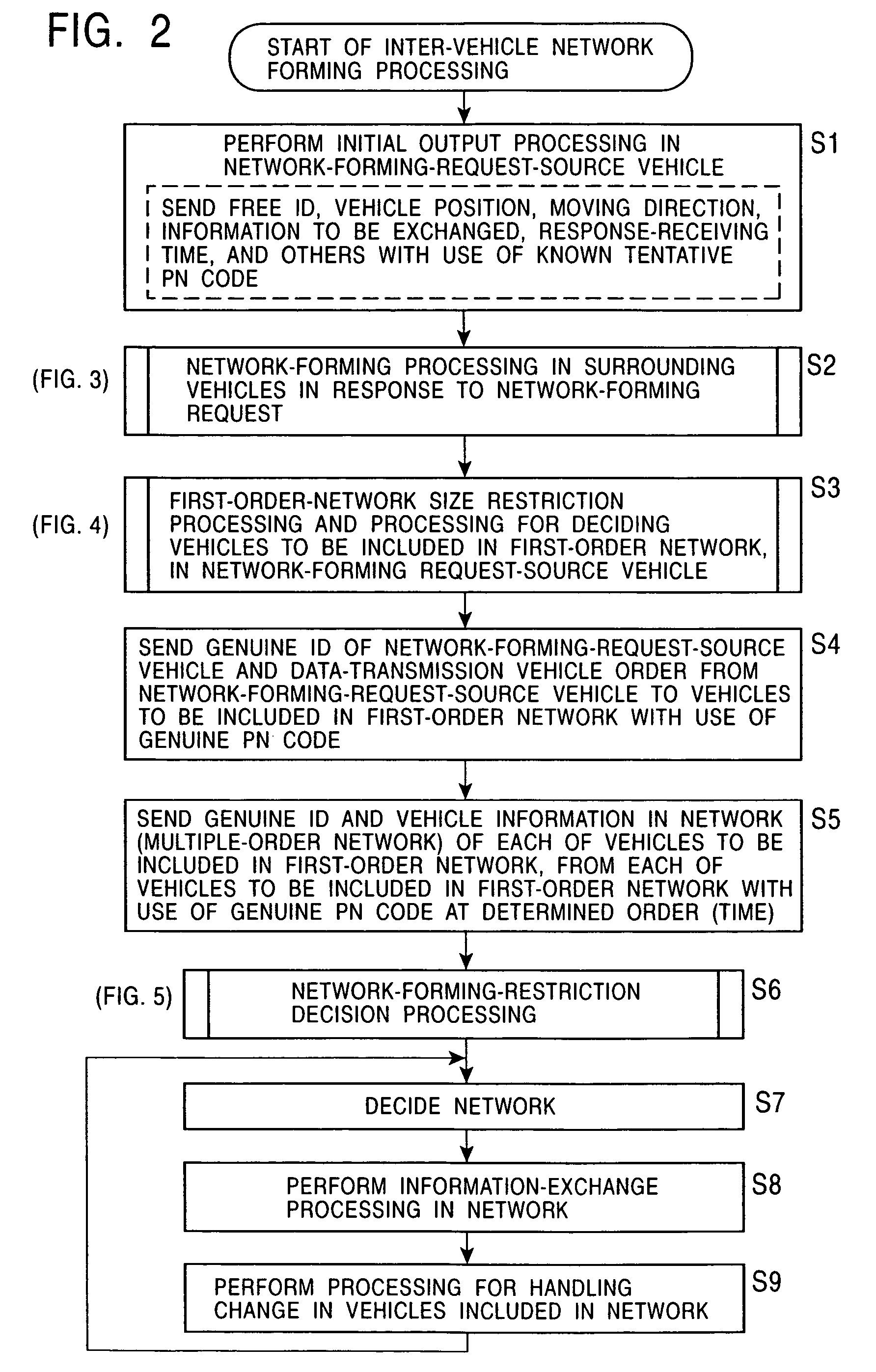
Inter-vehicle communication apparatus and method with restrictions on size of network
InactiveUS7272357B2Avoid interferenceRestrict formArrangements for variable traffic instructionsAssess restrictionArea networkInter vehicle communication
Owner:ALPINE ELECTRONICS INC
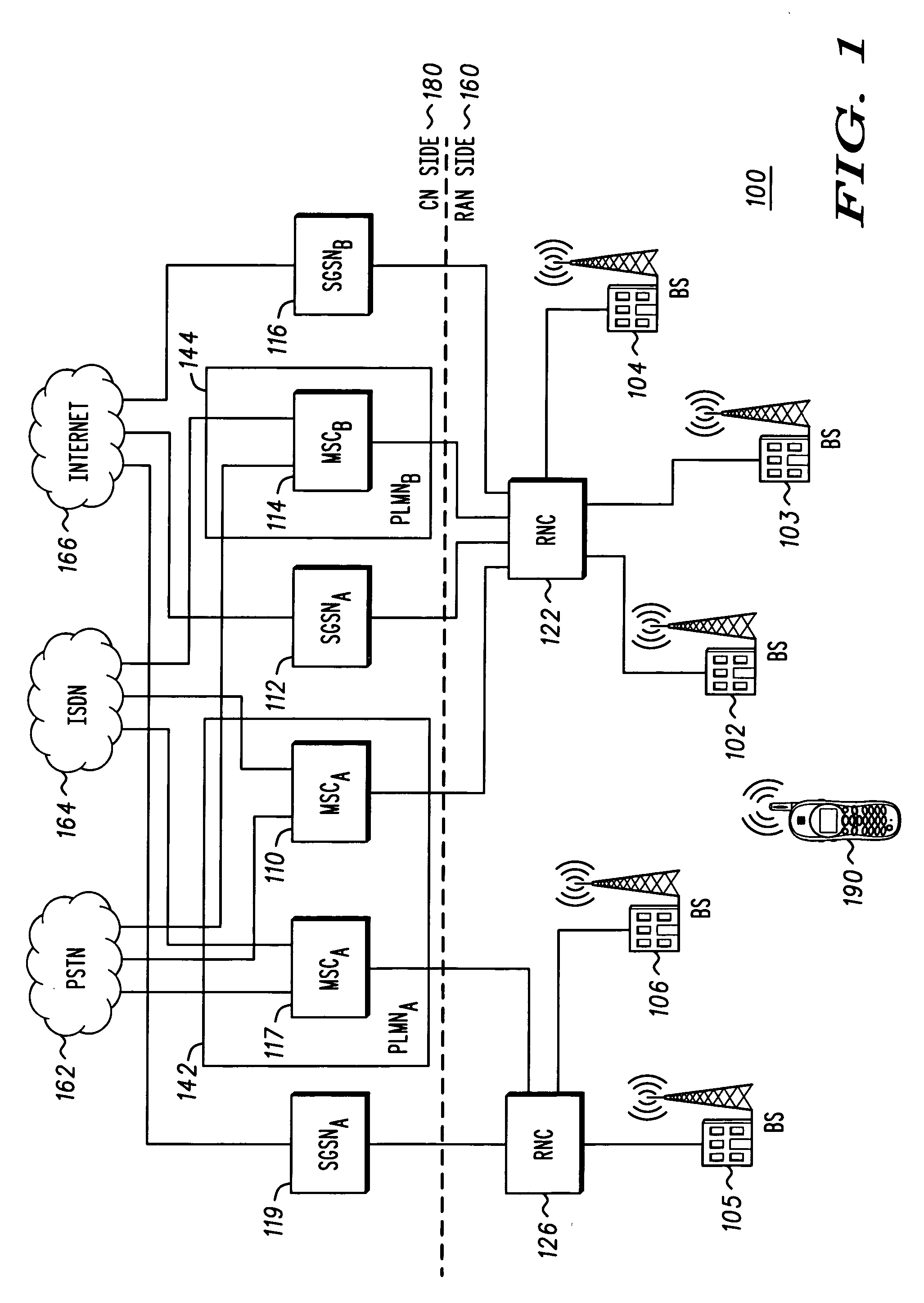
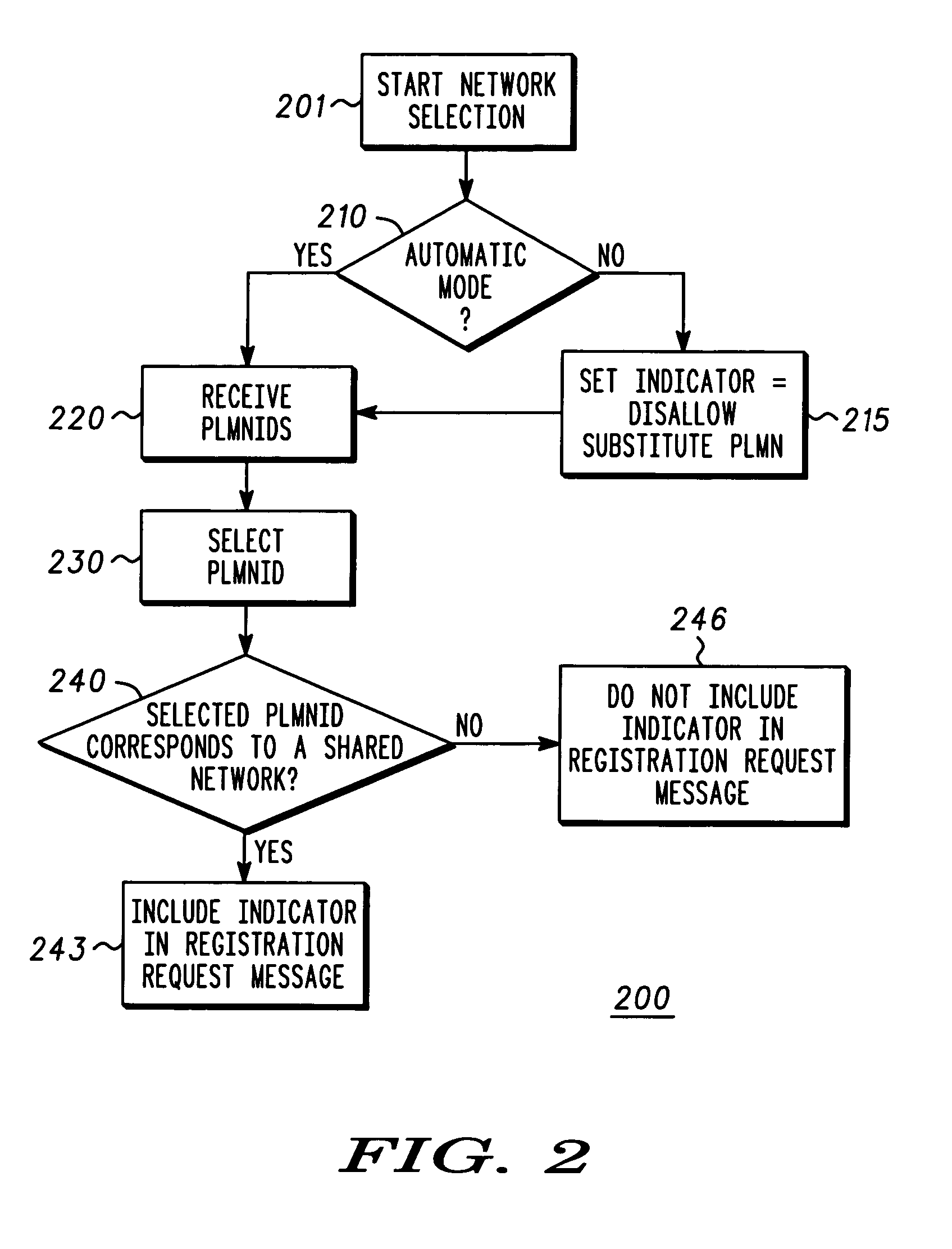
Method for selecting a core network
ActiveUS20050075129A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsCommunication deviceCore network
A method (200) for selecting a core network for a communication device includes the steps of: receiving (220) at least one core network identifier; selecting (230) a core network identifier; setting (215) an indicator to indicate whether a substitute core network is allowed; determining (240) whether the selected core network identifier corresponds to a shared network; forming a registration request message containing the selected core network identifier; including (243) the indicator in the registration request message; and transmitting the registration request message.
Owner:GOOGLE TECH HLDG LLC
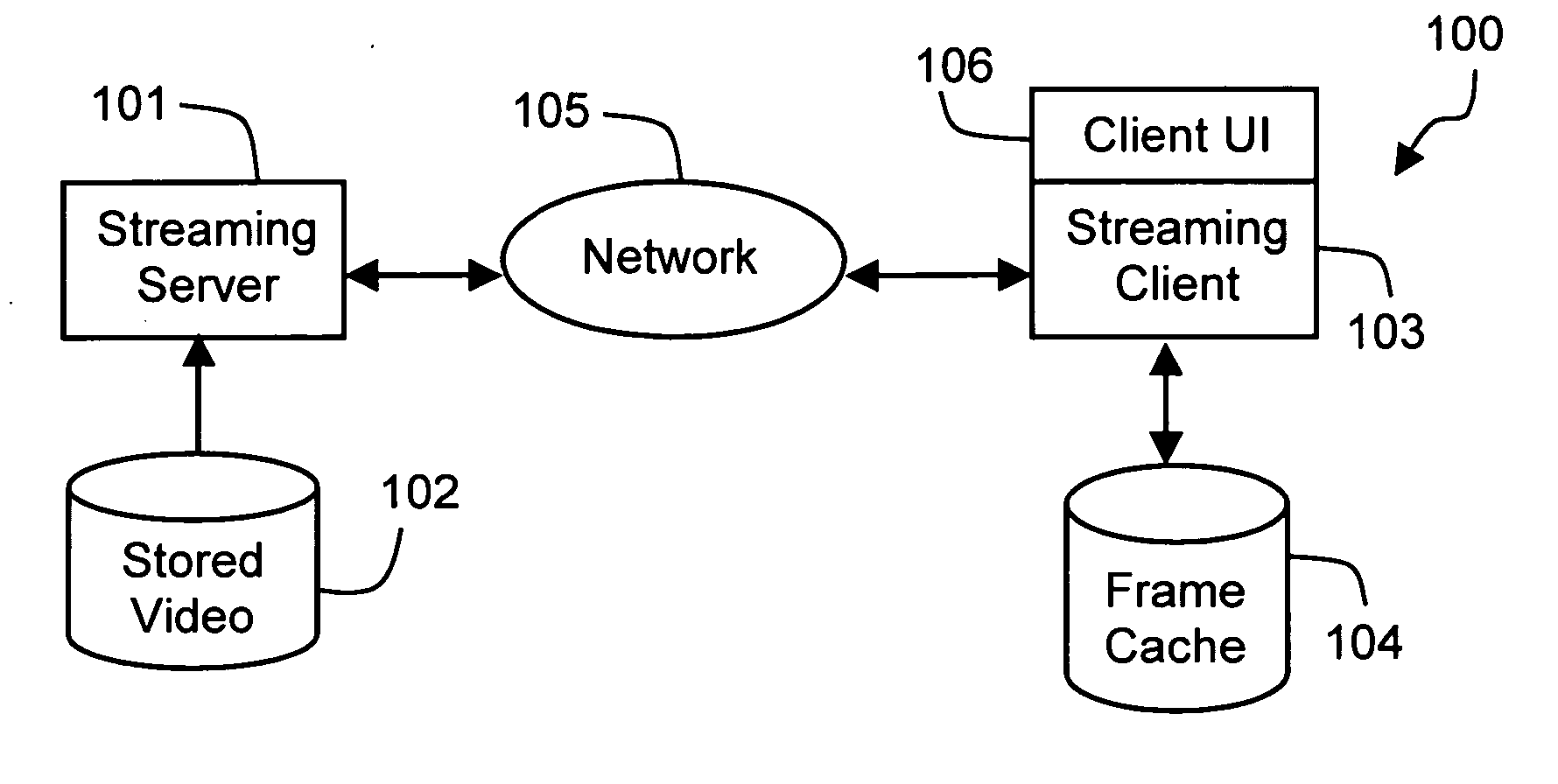
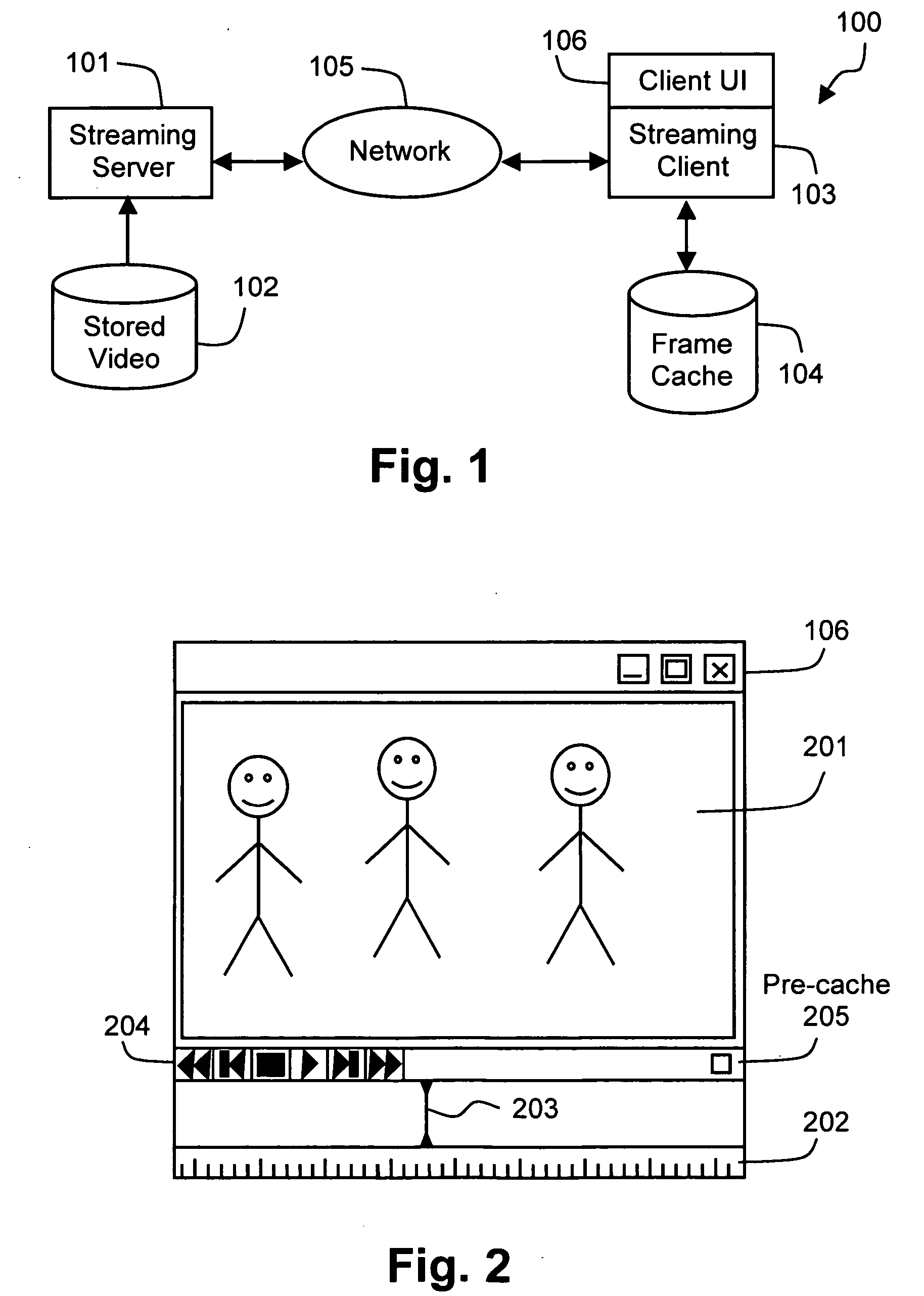
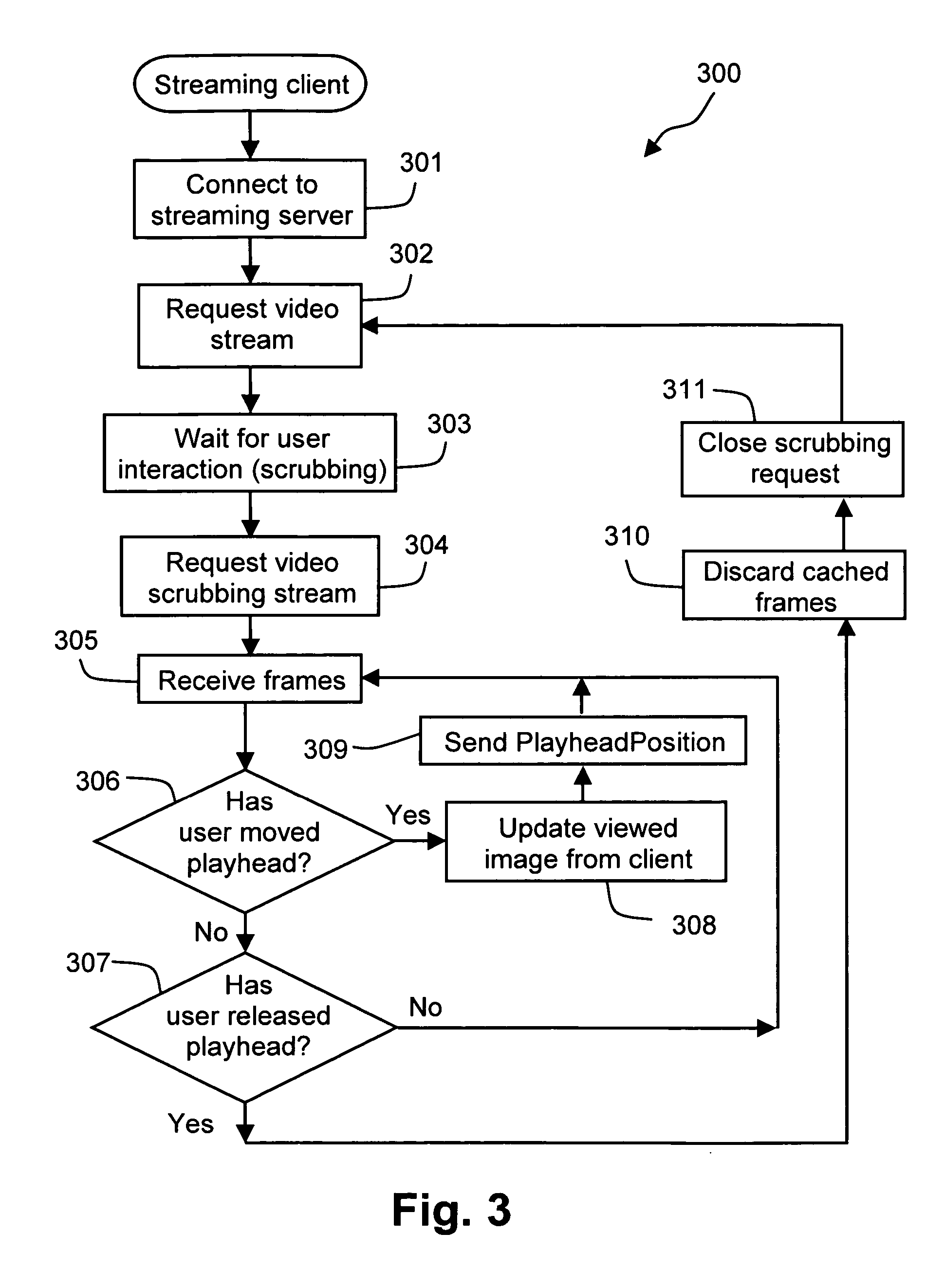
Frame scattering for video scrubbing
ActiveUS20060288392A1Overcome problemsTelevision system detailsAnalogue secracy/subscription systemsComputer graphics (images)Time line
Disclosed is a method of retrieving video frames over a network for subsequent display. A user interaction (303) with a timeline (202) represented by a client (103) coupled to the network (105) is detected. From the detected interaction, a request (304) for video to be retrieved from a server (101) across the network is formed. A series of non-contiguous (scattered) sample frames (FIGS. 13-16) received in response to the request are then cached (104) for subsequent display. This method permits efficient handling of video scrubbing requests for streamlining video as only selected ones of the cached sample frames close to a GUI play head position (203) need be reproduced. Since the frames are non-contiguous, the scope of the source video is quickly sampled permitting improved user response and, where desired, adjustment of the play head position.
Owner:CANON KK
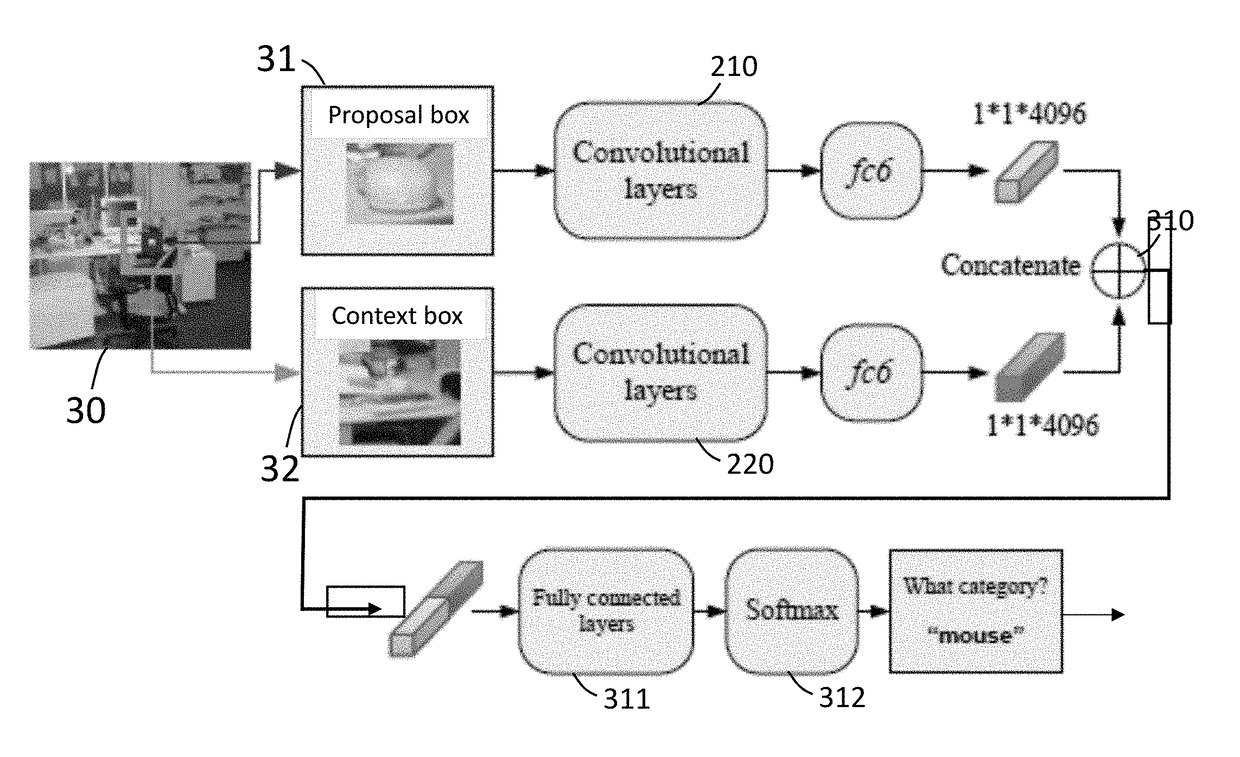
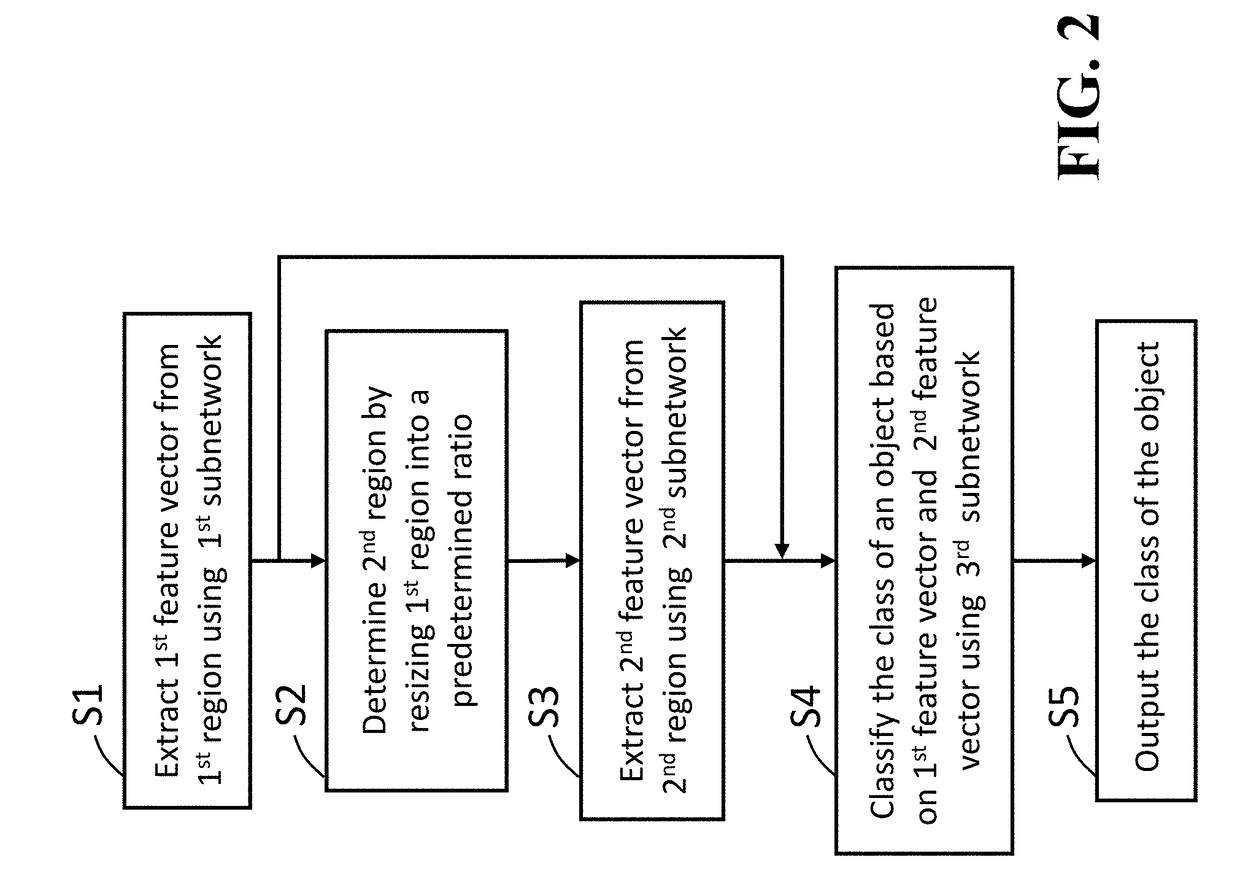
Object Detection System and Object Detection Method
A method for detecting an object in an image includes extracting a first feature vector from a first region of an image using a first subnetwork, determining a second region of the image by resizing the first region into a fixed ratio using a second subnetwork, wherein a size of the first region is smaller than a size of the second region, extracting a second feature vector from the second region of the image using the second subnetwork, classifying a class of the object using a third subnetwork on a basis of the first feature vector and the second feature vector, and determining the class of object in the first region according to a result of the classification, wherein the first subnetwork, the second subnetwork, and the third subnetwork form a neural network, wherein steps of the method are performed by a processor.
Owner:MITSUBISHI ELECTRIC RES LAB INC
Secure authentication and network management system for wireless LAN applications
InactiveUS7565529B2Efficient and effective toolProtect healthRandom number generatorsUser identity/authority verificationEngineeringNetwork management
An authentication and network management system for Wi-Fi local area networks includes a network management device and a plurality of Wi-Fi local area networks coupled to the network management device. Each local network includes at least one access point device having a Wi-Fi radio. A plurality of end user devices are attachable to the network forming nodes thereof, and each end user device has input plugs, such as USB ports and the like, for coupling accessories thereto. An authentication device is provided in the network for authenticating the end user devices attached to the network. A plurality of authenticating keys is provided, with each key attachable to an input plug of an end user device. Each key contains a validation certificate therein, wherein the authentication device verifies the presence of a current validation certificate on a key coupled to the end users device prior to granting access to the network.
Owner:DIRECTPOINTE
Gene specifically expressed in postmitotic dopaminergic neuron precursor cells
InactiveUS20070122882A1Efficient separationEasy to prepareFungiBacteriaNeuro-degenerative diseaseNovel gene
A novel gene 65B13 expressed specifically and transiently in dopaminergic neuron precursor cells immediately after cell cycle exit was obtained by the present invention. The cellular expression of 65B13 can be used as an index to select cells that are suitable in terms of their safety, survival rate, and network formation ability, for transplant therapy of neurodegenerative diseases such as Parkinson's disease.
Owner:EISIA R&D MANAGEMENT CO LTD
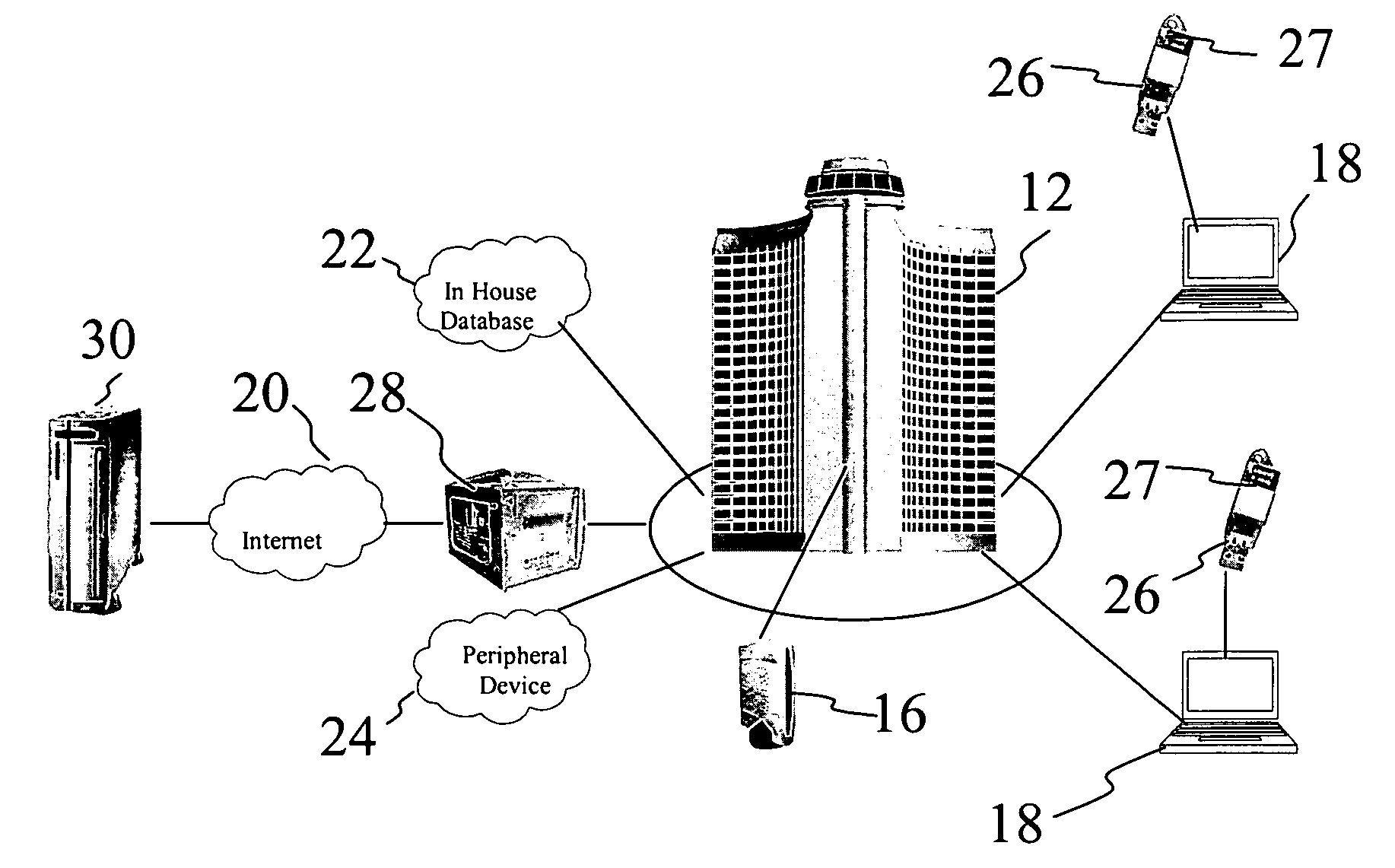
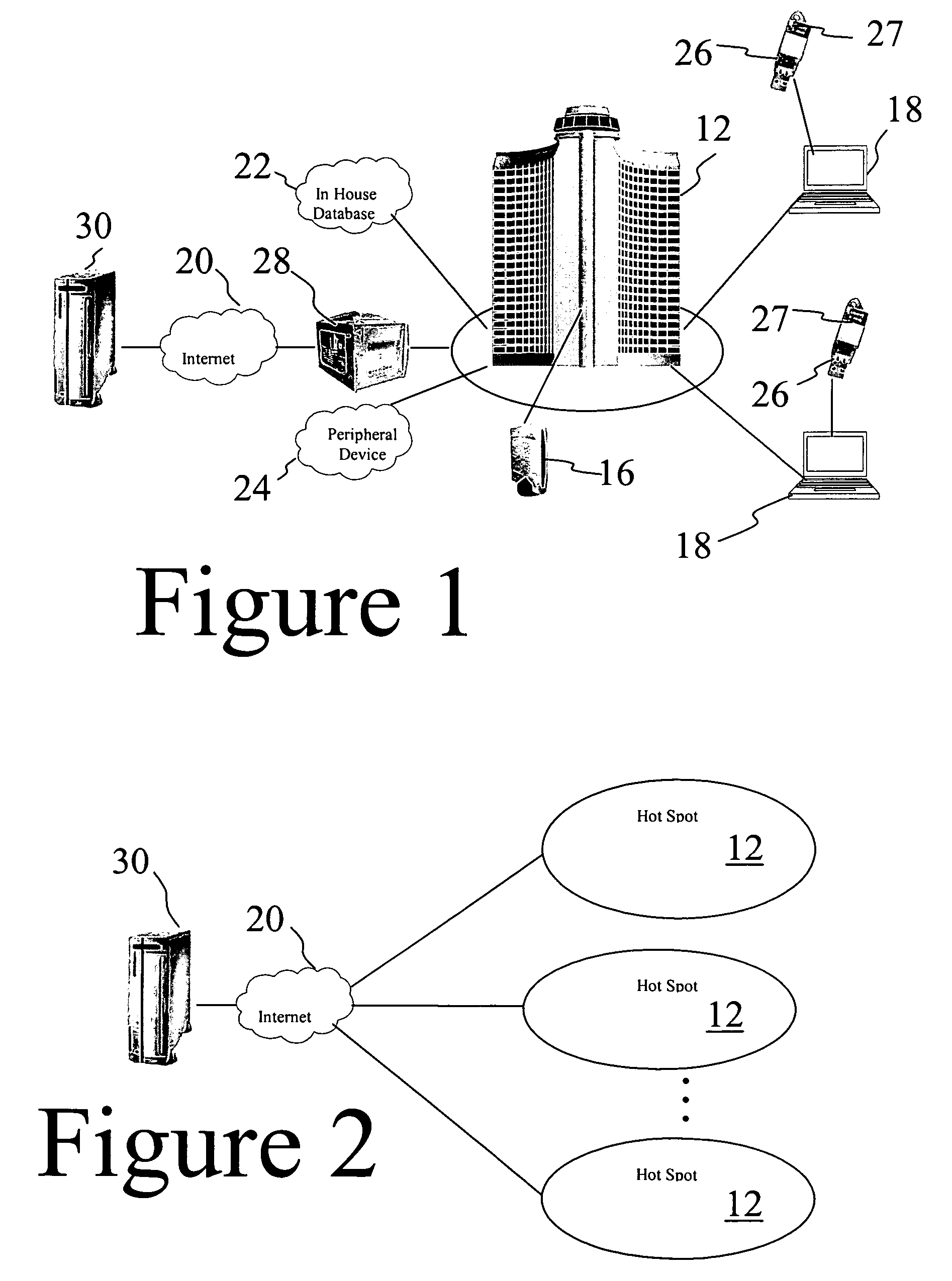
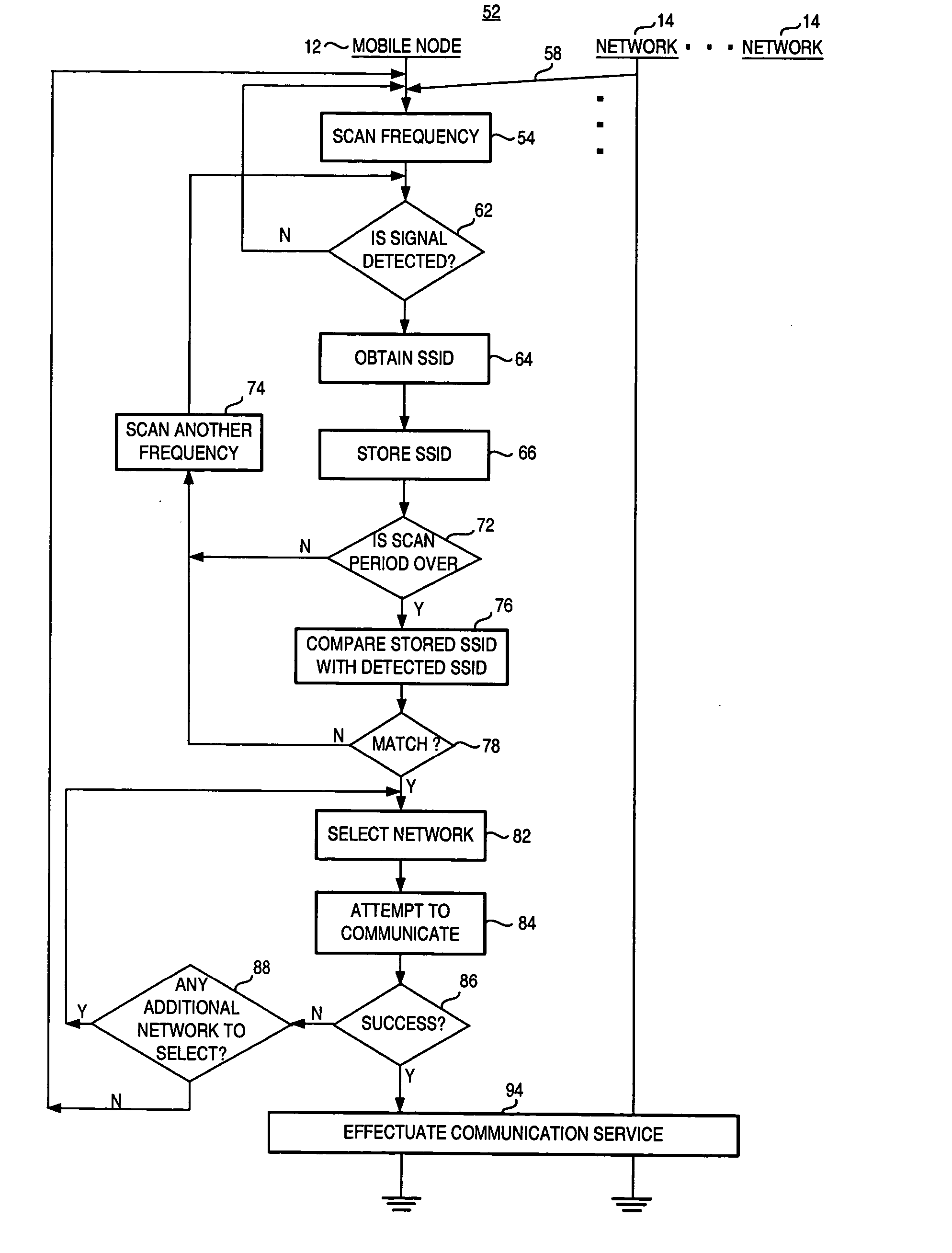
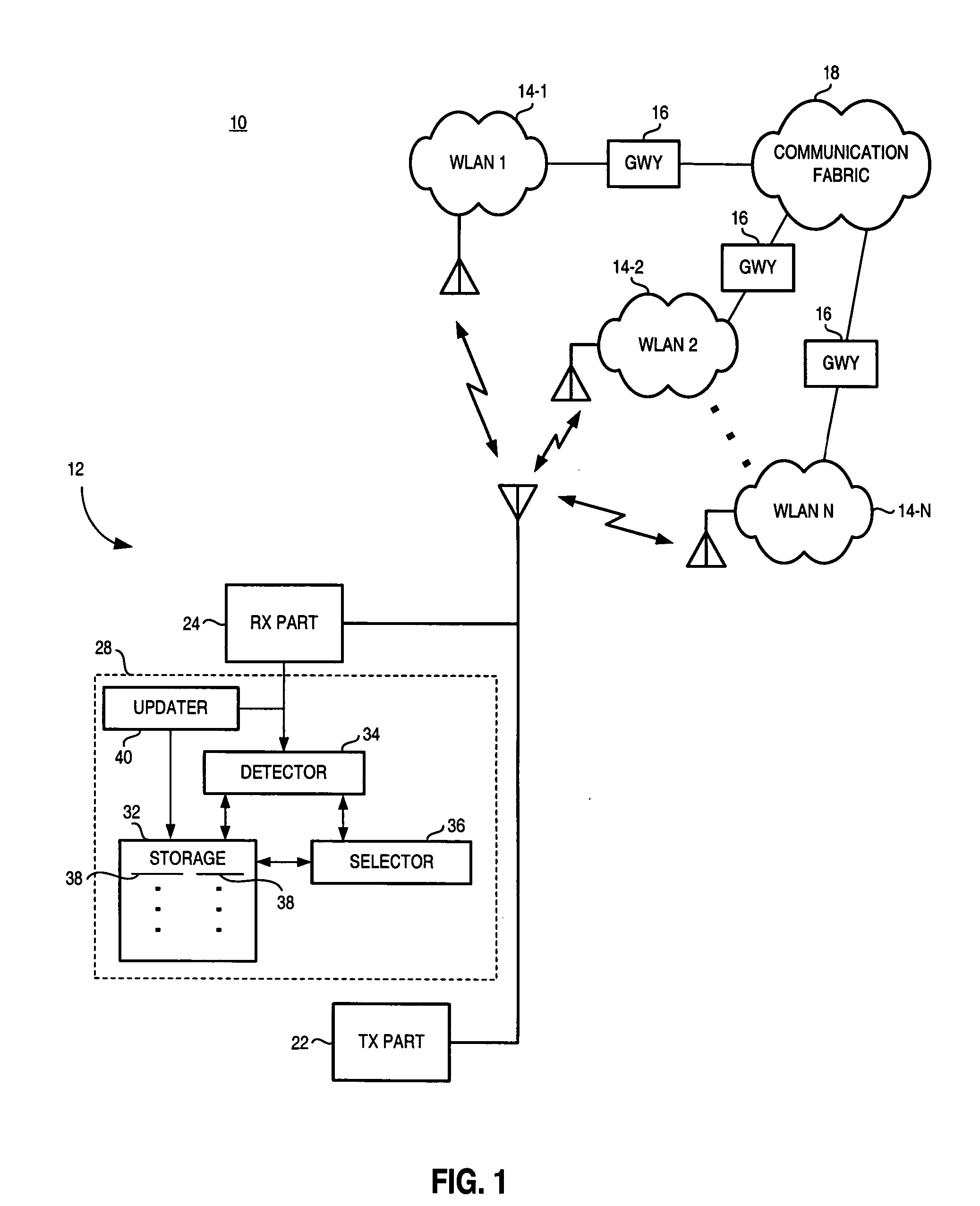
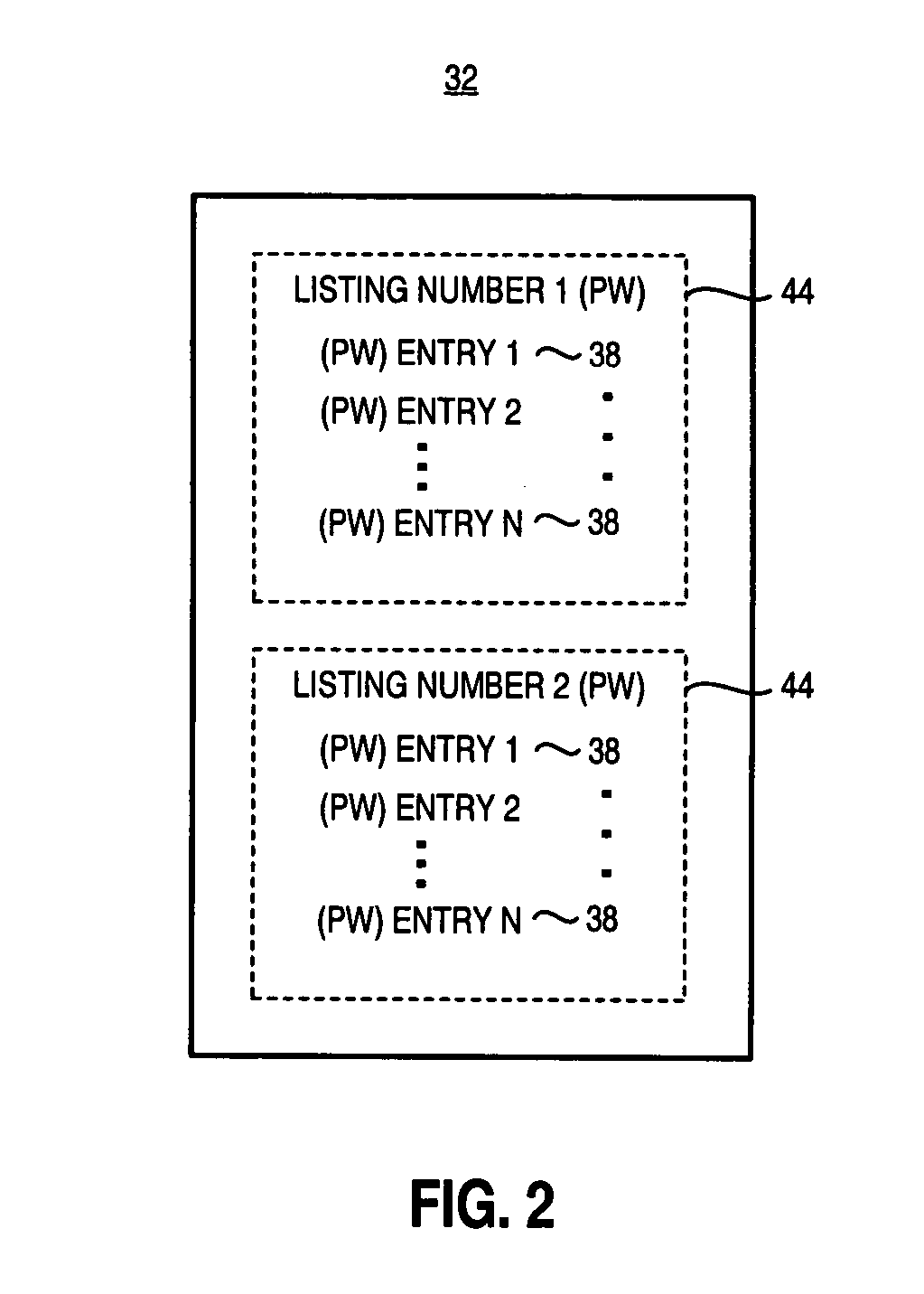
Apparatus, and associated method, for facilitating selection by a mobile node of a network through which to communicate
InactiveUS20050147060A1Good choiceError preventionFrequency-division multiplex detailsCommunications systemCorrelation method
Apparatus, and an associated method, for a mobile node operable in a radio communication system formed of multiple networks. A listing is maintained at the mobile node containing entries that identify which networks with which the mobile node is permitted to communicate. A detector detects networks within communication range of the mobile node. Identities of the networks are obtained, and selection of one or more networks for which the mobile node to attempt to communicate is made based upon the stored entries and the detected networks.
Owner:MALIKIE INNOVATIONS LTD
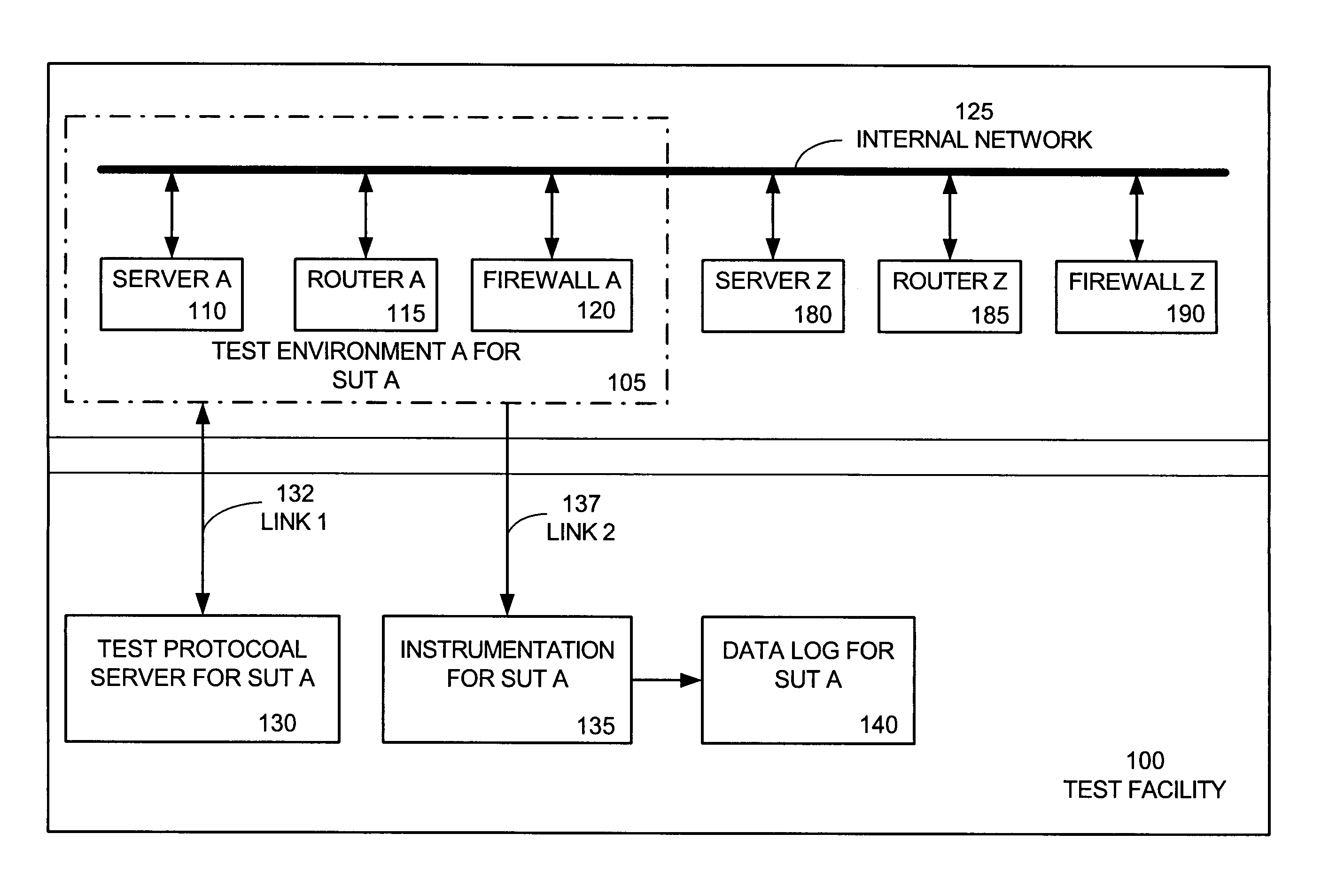
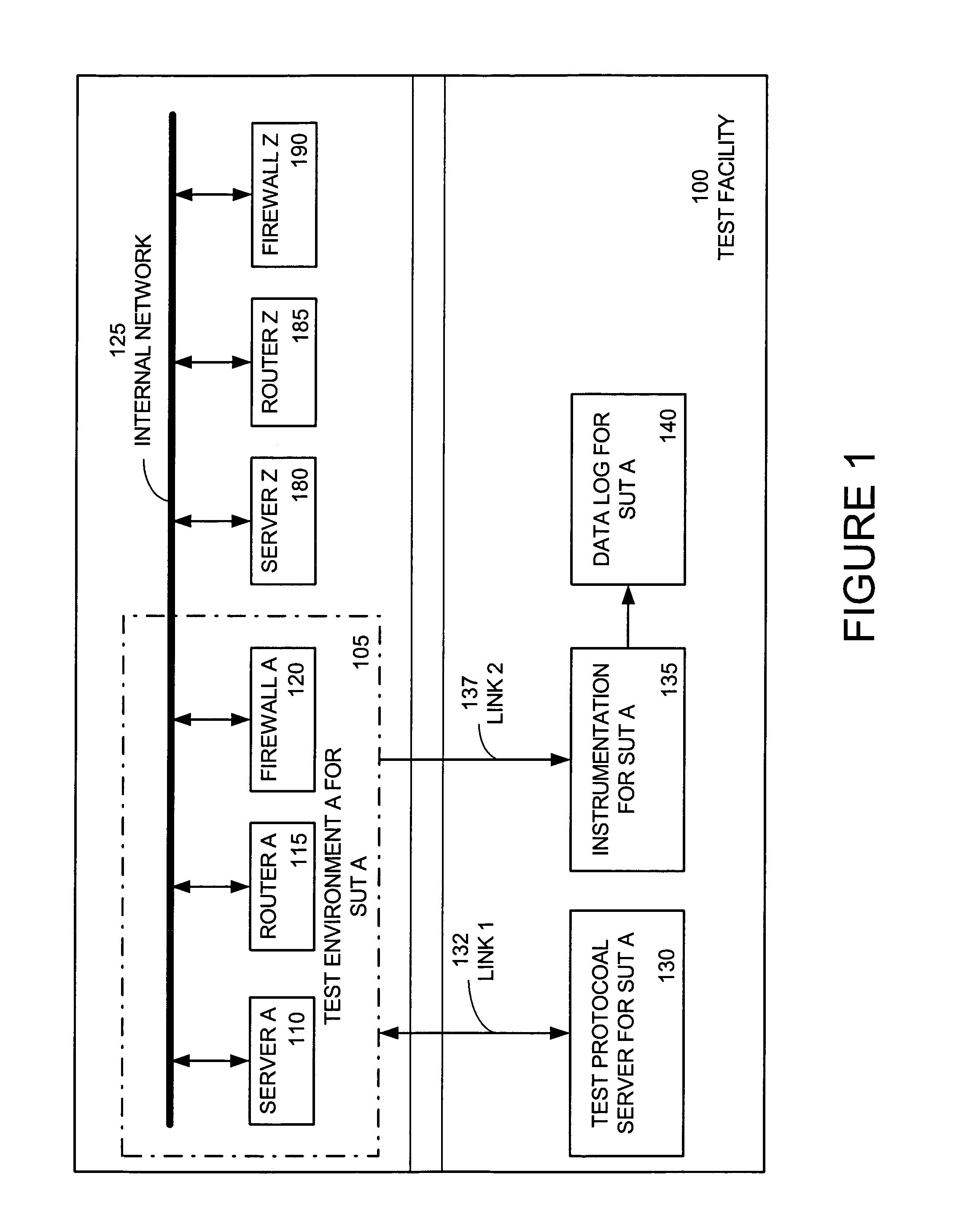
System and method of testing software and hardware in a reconfigurable instrumented network
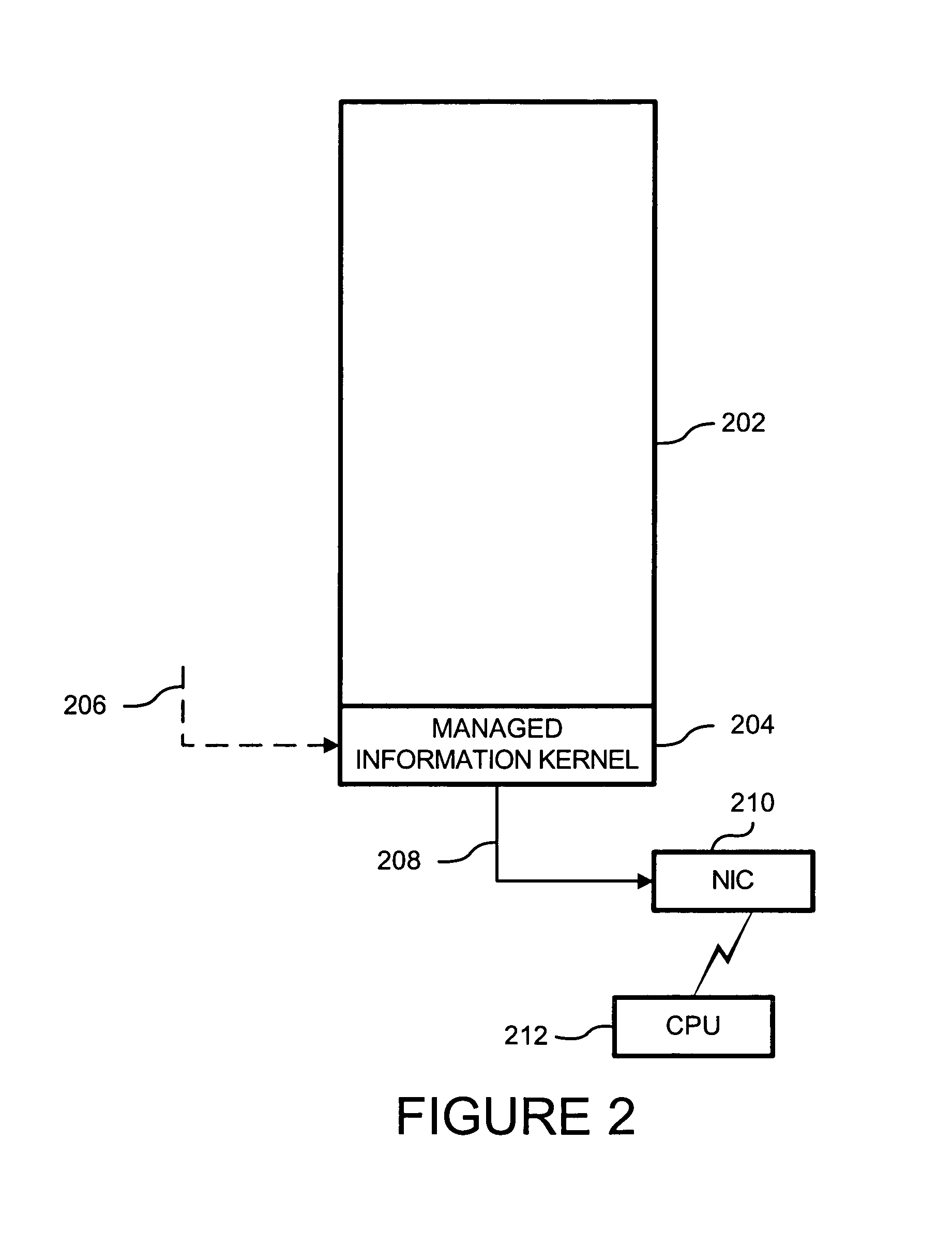
A method of testing a computer system in a testing environment formed of a network of routers, servers, and firewalls. Performance of the computer system is monitored. A log is made of the monitored performance of the computer system. The computer system is subjected to hostile conditions until it no longer functions. The state of the computer system at failure point is recorded. The performance monitoring is done with substantially no interference with the testing environment. The performance monitoring includes monitoring, over a sampling period, of packet flow, hardware resource utilization, memory utilization, data access time, or thread count. A business method entails providing a testing environment formed of a network of network devices including routers, servers, and firewalls, while selling test time to a customer on one or more of the network devices during purchased tests that test the security of the customer's computer system. The purchased tests are conducted simultaneously with other tests for other customers within the testing environment. Customer security performance data based on the purchased tests is provided without loss of privacy by taking security measures to ensure that none of the other customers can access the security performance data. The tests may also be directed to scalability or reliability of the customer's computer system. Data about a device under test is gathered using a managed information kernel that is loaded into the devices operating memory before its operating system. The gathered data is prepared as managed information items.
Owner:AVANZA TECH
Method for wireless self-organizing of monitoring system to form tree-shaped routing
InactiveCN101179499AAdaptableReduce overheadError prevention/detection by using return channelData switching by path configurationStructure of Management InformationNetwork communication
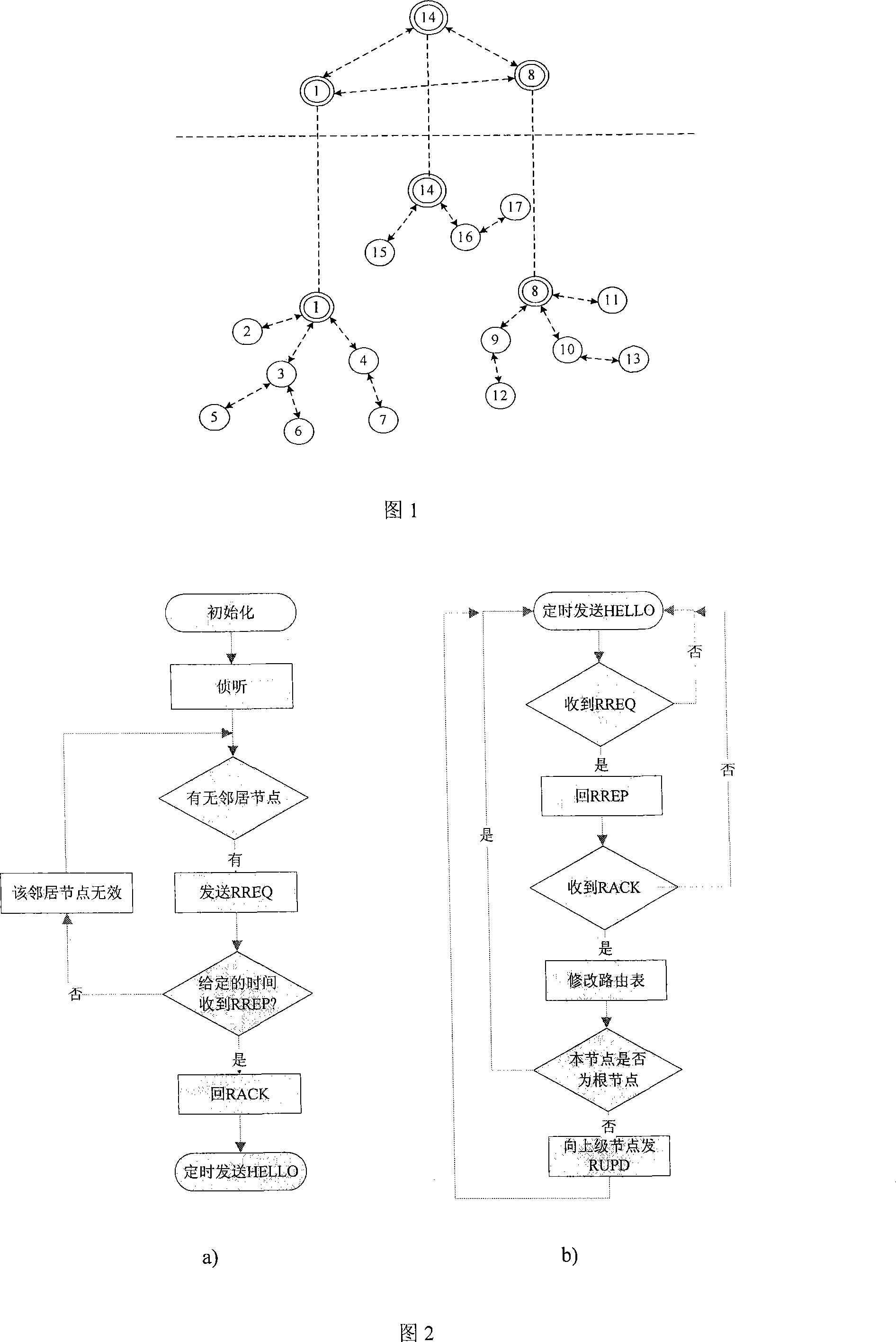
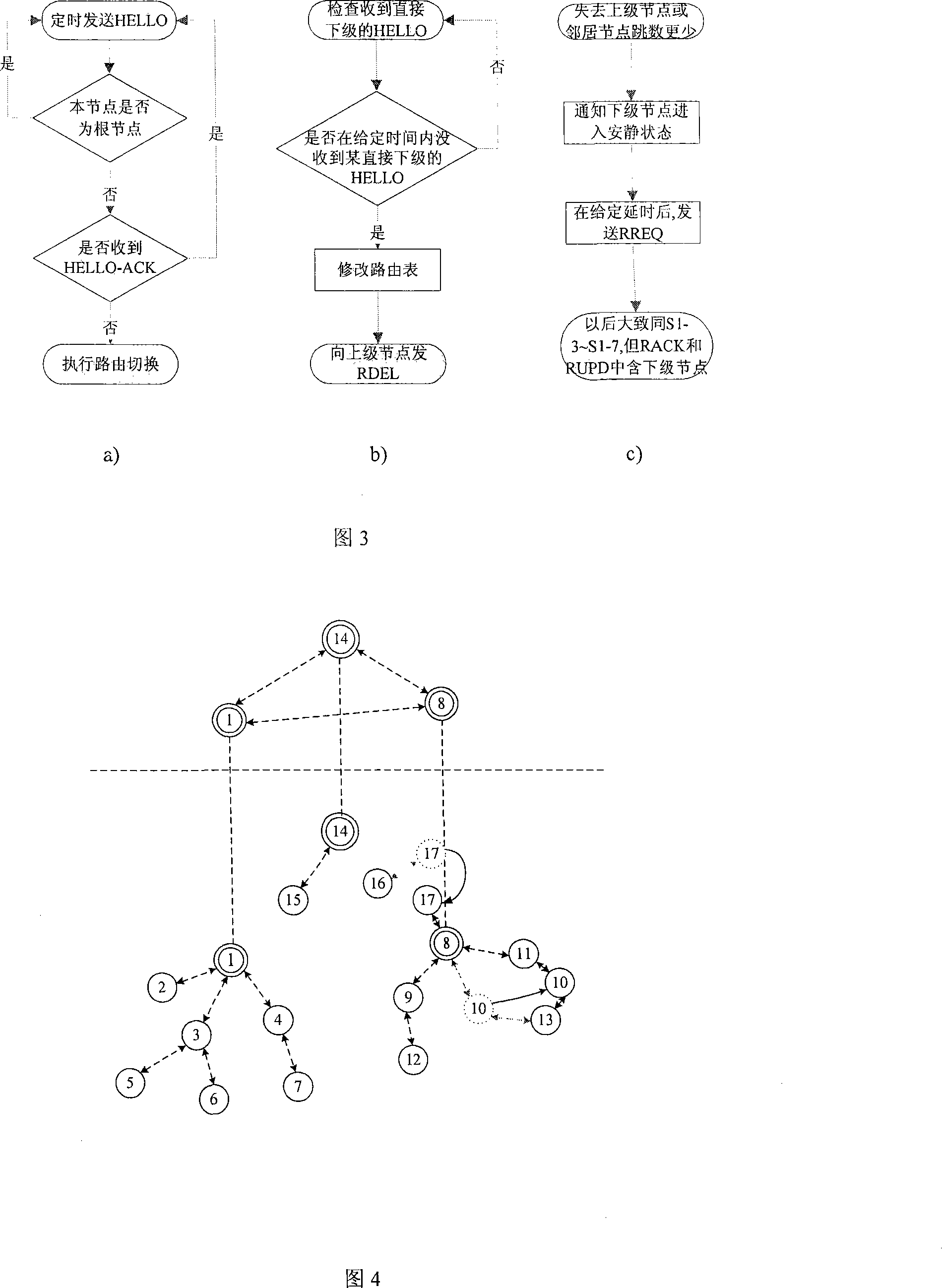
The invention relates to a method for routing a queue tree in a wireless self-organization network applicable to a monitoring system. The invention includes a routing generation process, a dynamic maintenance of the routing and a monitoring data amalgamation transmission based on routing arithmetic. A network node selects the neighboring node with a small hot count to send a routing establishment request, and according to a handshaking mechanism, a routing relationship between an upper level and a lower level is established, and the whole network is formed a plurality of tree routing structures; according to ways of a connection detection, a past-due detection and upper node switching, a dynamic maintenance of the routing is realized, changes in network communication topology caused by factors such as the motion of the node and power change are adapted; by using the network structure of the tree routing, the node is able to inosculate the a communication desire to monitor the data in due time at the same time of maintaining the route. The method of the invention has the advantages of low spending on the communication, small delay of transmission and steady and reliable network.
Owner:SHANGHAI UNIV +1
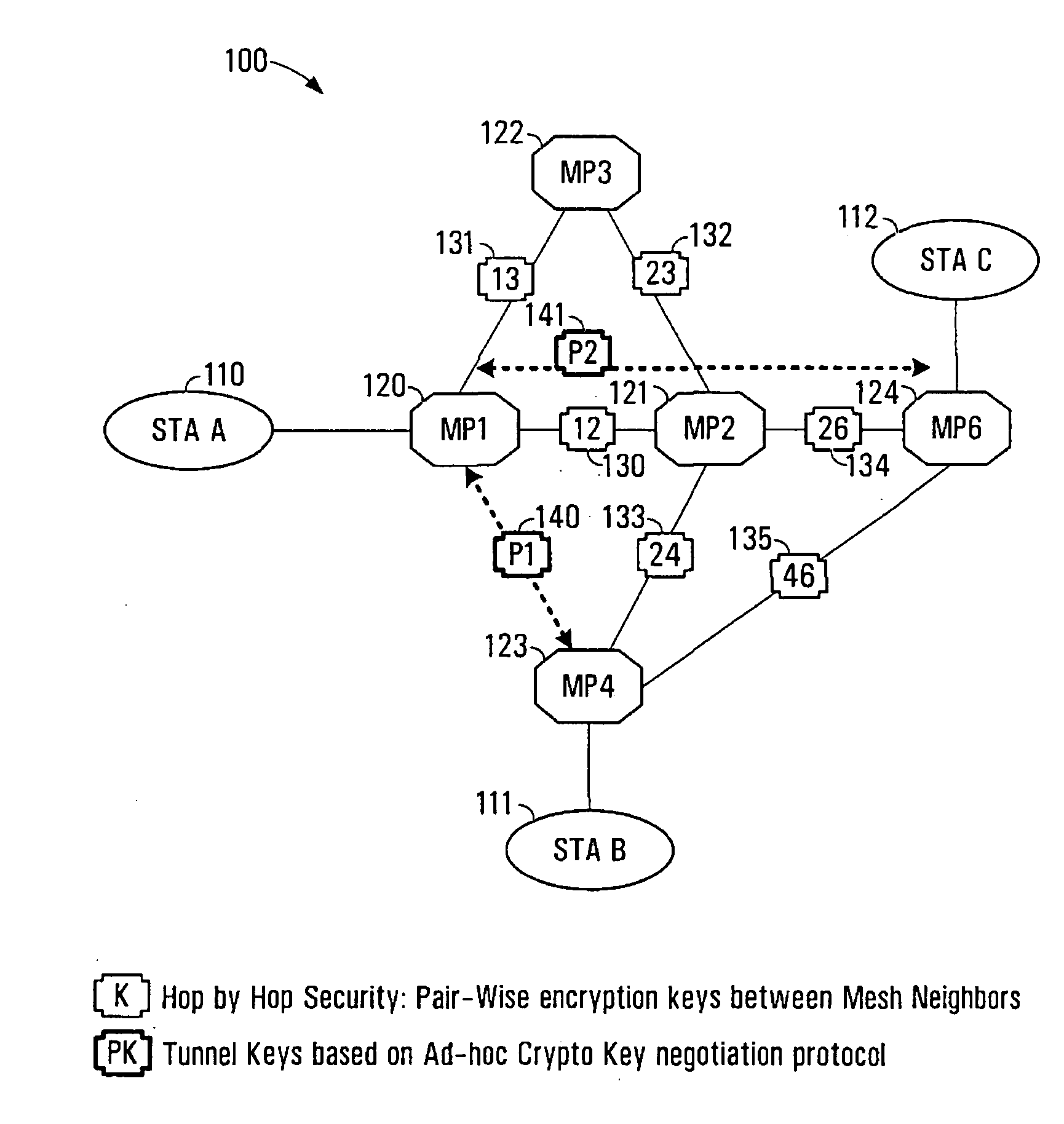
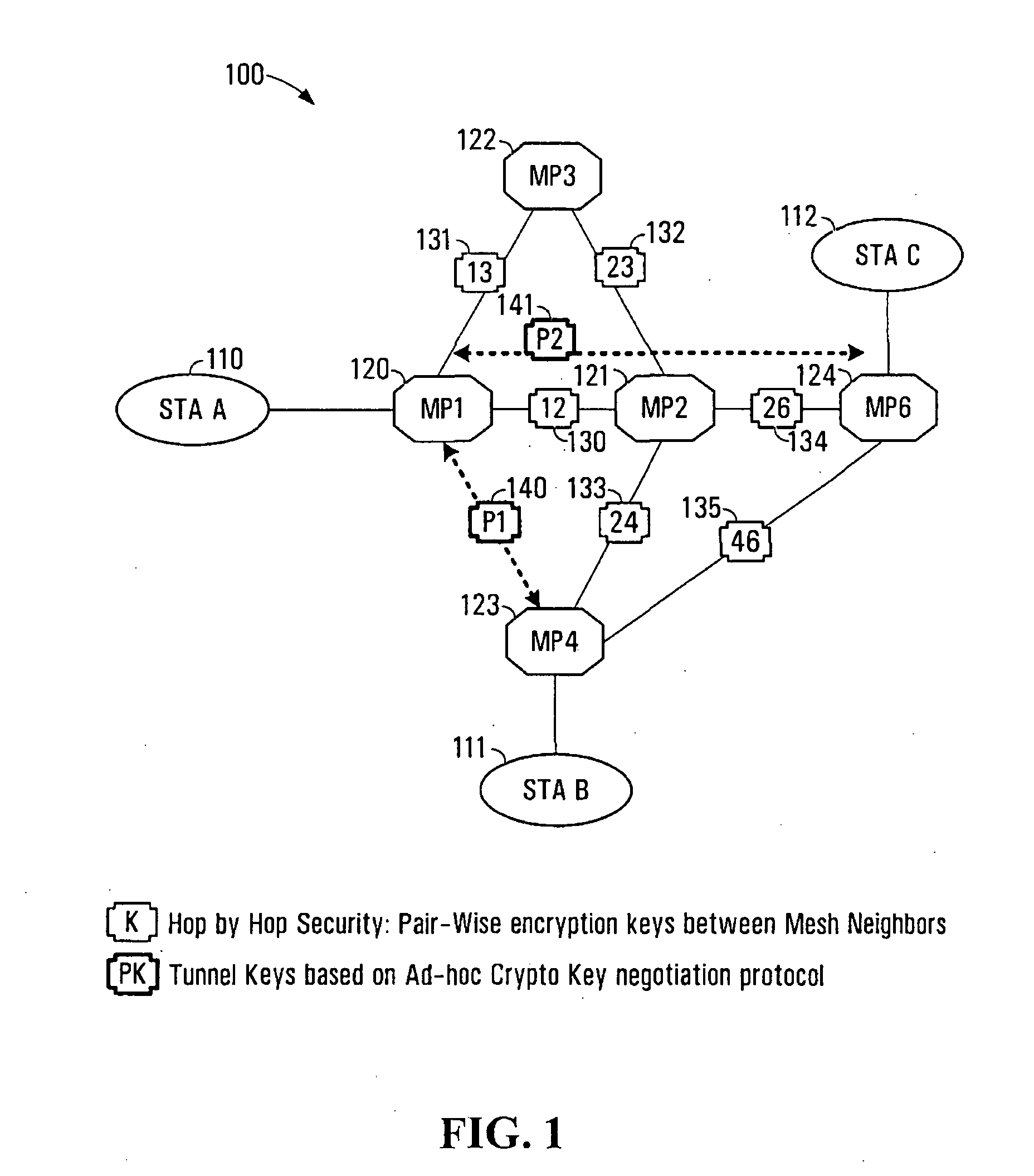
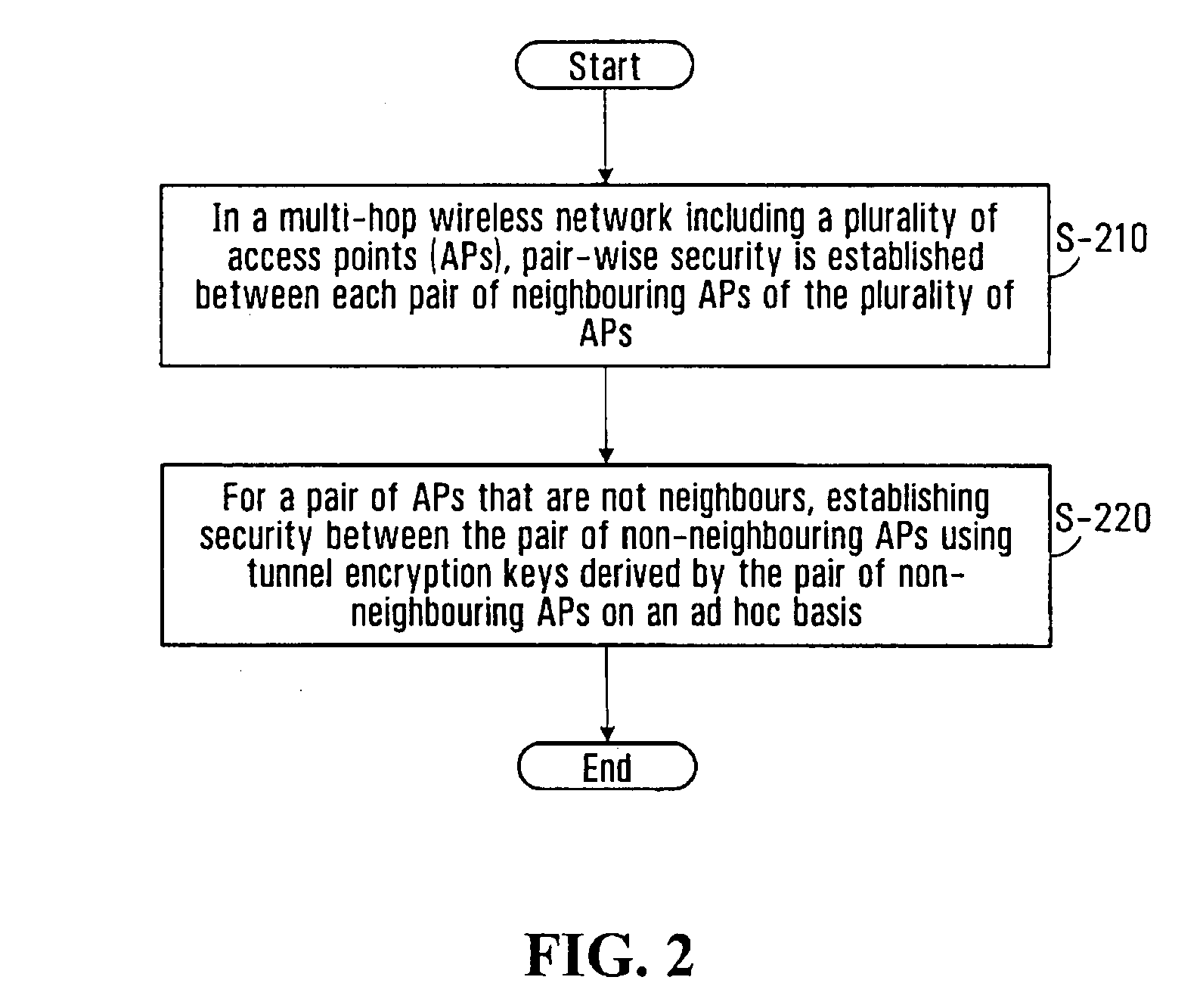
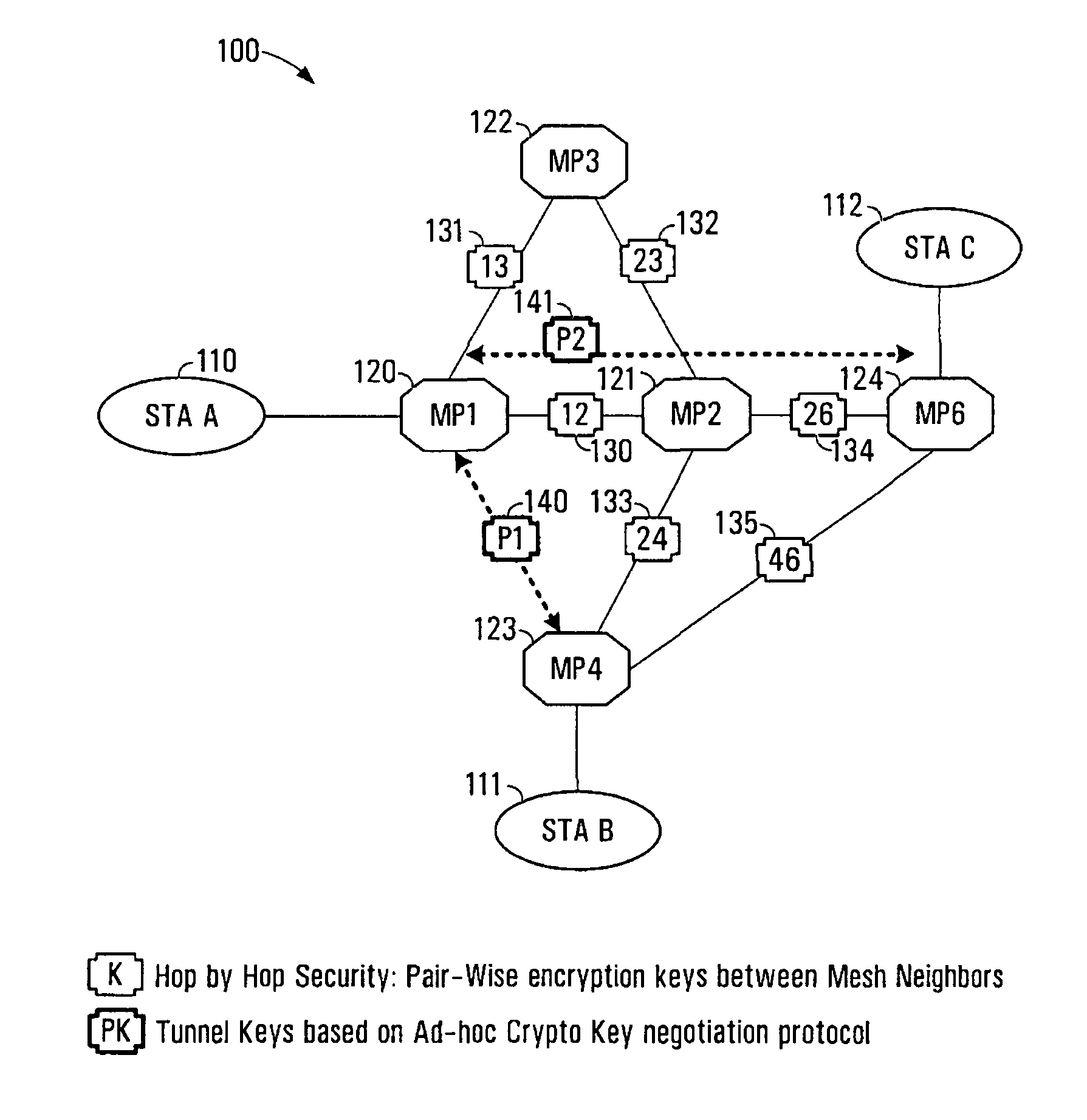
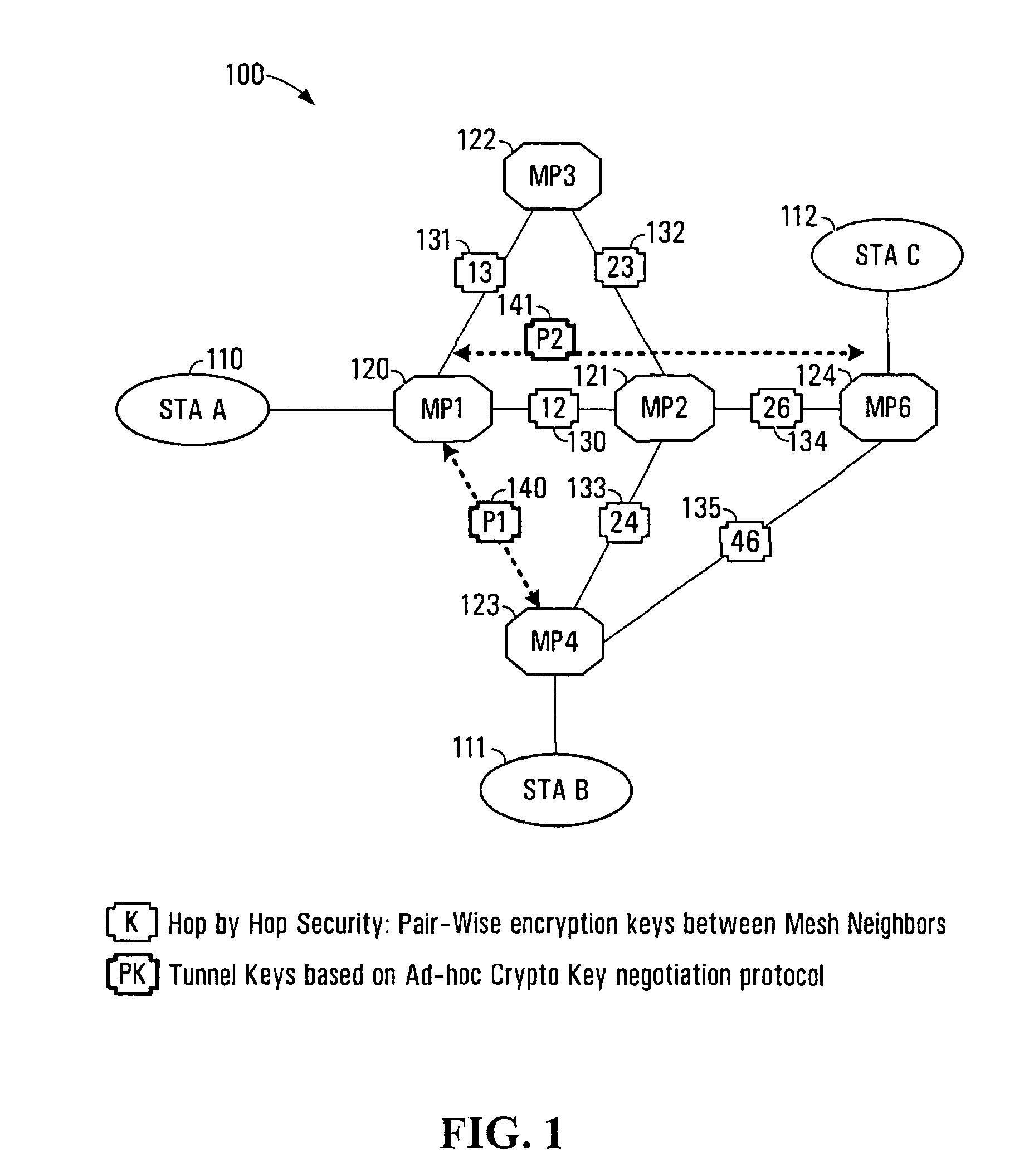
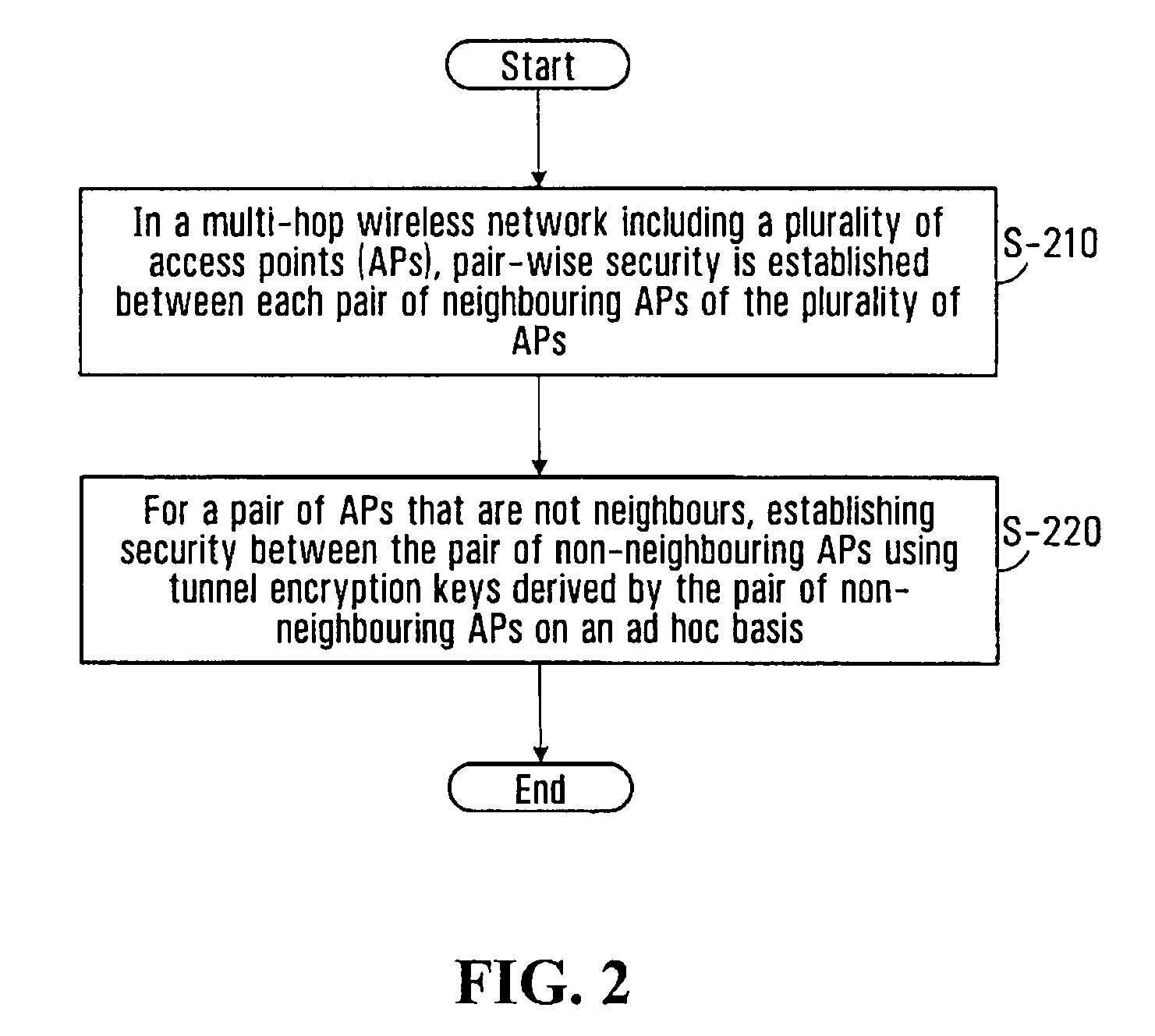
System and method for secure wireless multi-hop network formation
ActiveUS20080016338A1Synchronising transmission/receiving encryption devicesUser identity/authority verificationNode authenticationEncryption
The present invention provides methods and devices for a security architecture for use in wireless multi-hop networks. A method for implementing pair-wise encryption key establishment, network node authentication and determining tunnel encryption keys is provided in a following manner. In a multi-hop wireless network including a plurality of network nodes, pair-wise security is established between pairs of neighbouring network nodes of the plurality of network nodes. For example, pair-wise security is established in the form of temporal pair-wise encryption keys. Following establishment of pair-wise security between pairs of neighbouring network nodes, for a pair of network nodes that are not neighbours, tunnel security is established between the pair of network nodes using tunnel encryption keys derived by the pair of network nodes on an ad hoc basis. The tunnel encryption keys are used to form the connection between non-neighbouring network nodes so as to avoid the hop-by-hop encryption / decryption used in conventional multi-hop wireless systems.
Owner:APPLE INC
Dynamic modeling and control technology for independent mobile sensor network
InactiveCN101127657ASolving Dispersion ProblemsTroubleshoot Tracking Control IssuesEnergy efficient ICTData switching by path configurationSimulationSensor node
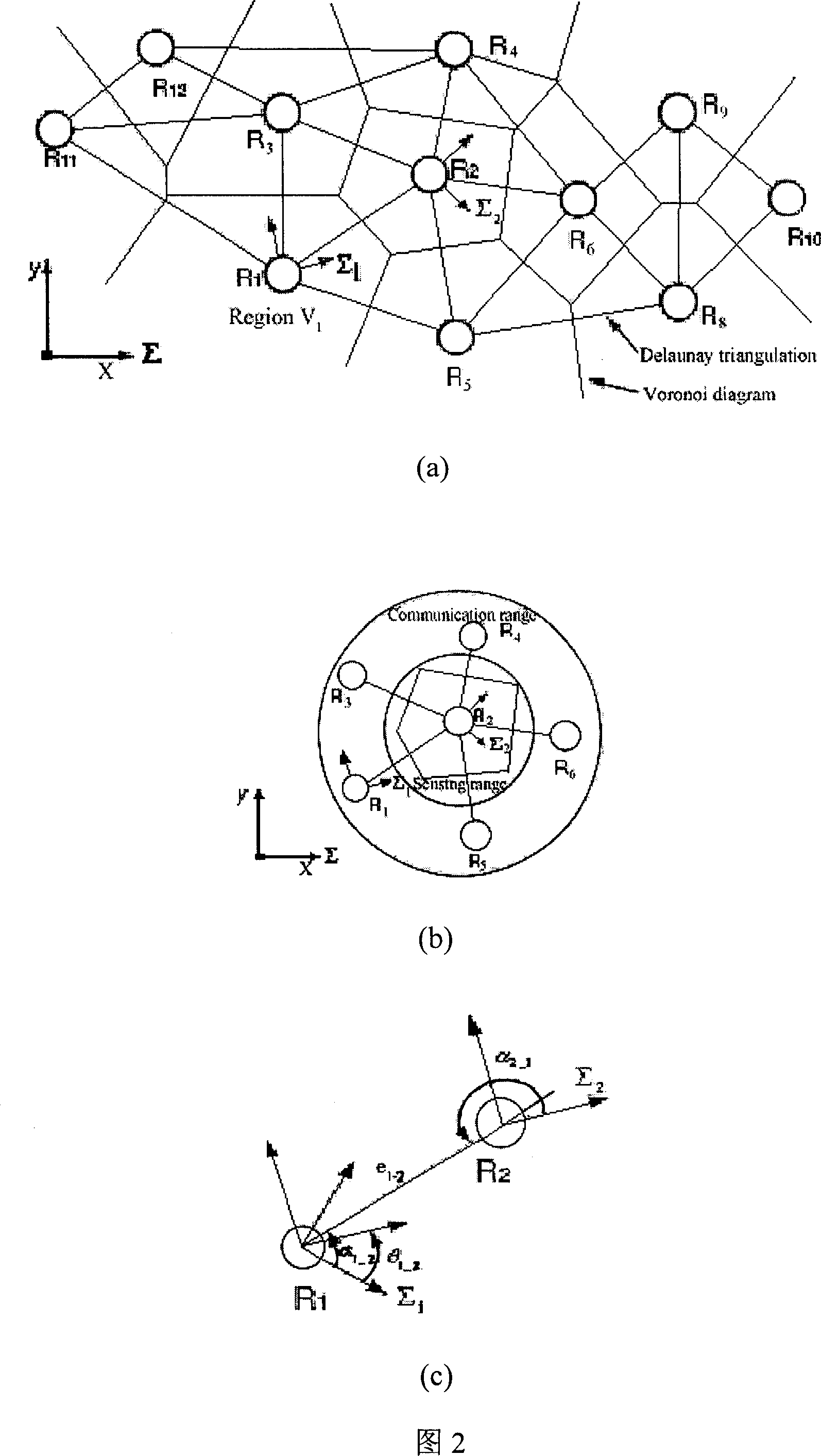
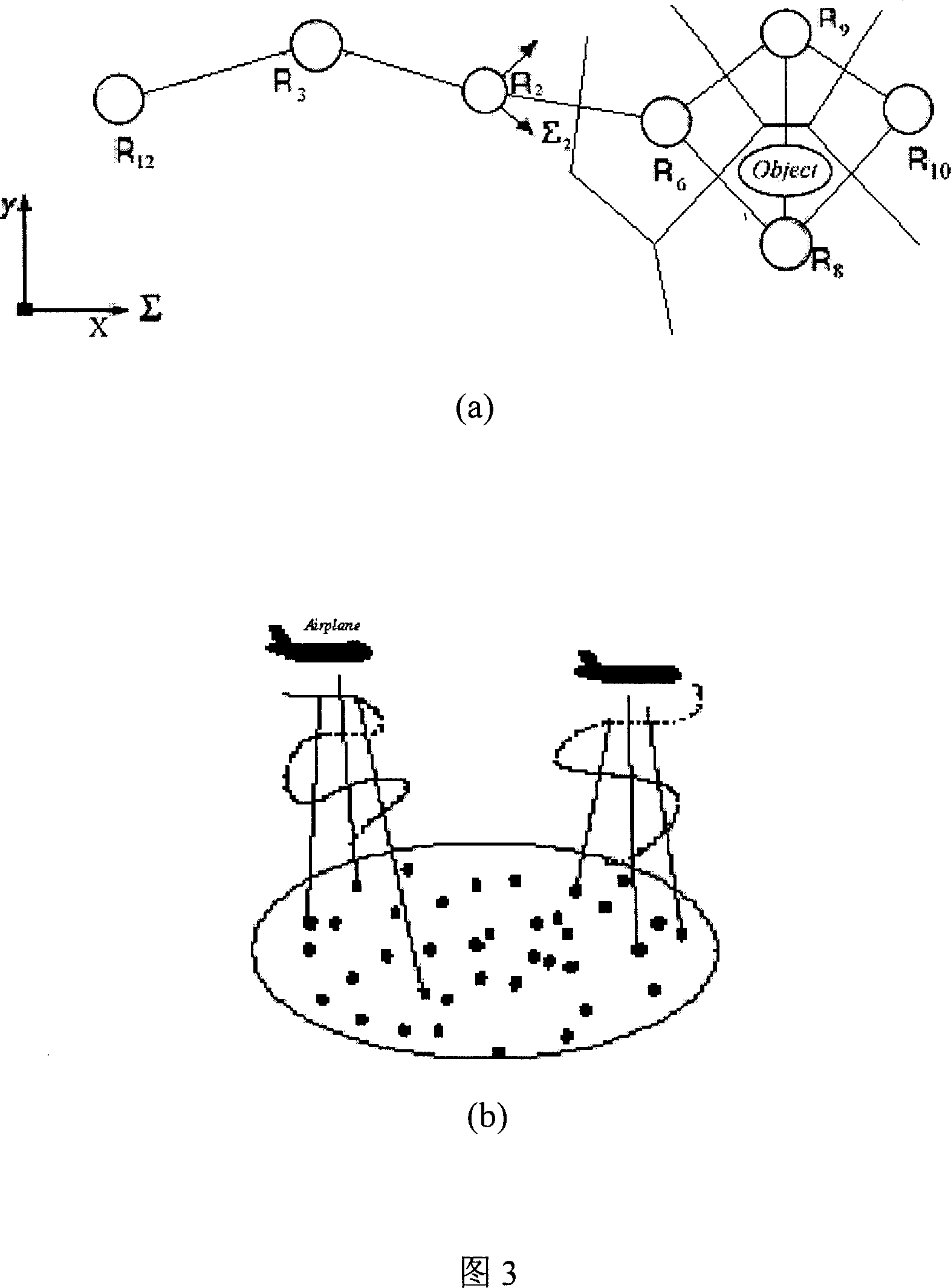
The utility model relates to a dynamic modeling and control technique of a self-moving sensor network and belongs to the sensor network technology. According to the technical proposal provided by the utility model, the dynamic modeling and controlling technology of a self-moving sensor network comprises the steps: the step I: build a distributed moving sensor network model based on the local Delaunay triangulation and other applicable diagram; the step II: use two methods to perform the distributed self-arrangement and the self-organization in the network for the sensor controlling node of each region in the distributed moving sensor network model; the step III: use the formation algorithm to control the network node formation and the node cooperation to achieve the purpose of fully energy-saving; the step IV: build the ad-hoc route data transmission protocol of the self-organization network of the distributed mobile robots to realize the stable work of the entire self-moving sensor network. The utility model can provide an algorithm for the repeatable configuration, cooperation, route development and verification of the sensor network with a plurality of moving sensor nodes.
Owner:无锡青起长升智能科技有限公司
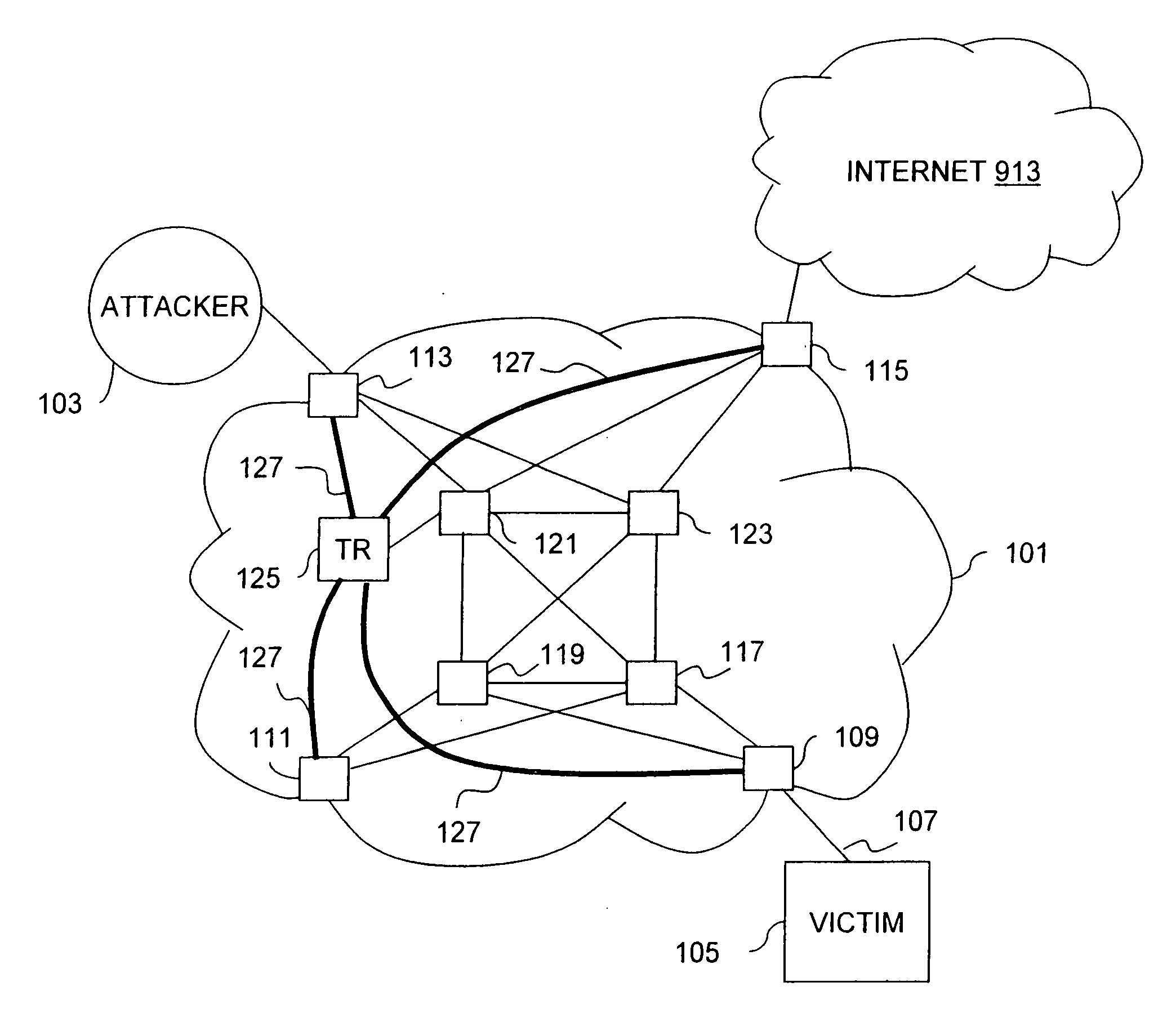
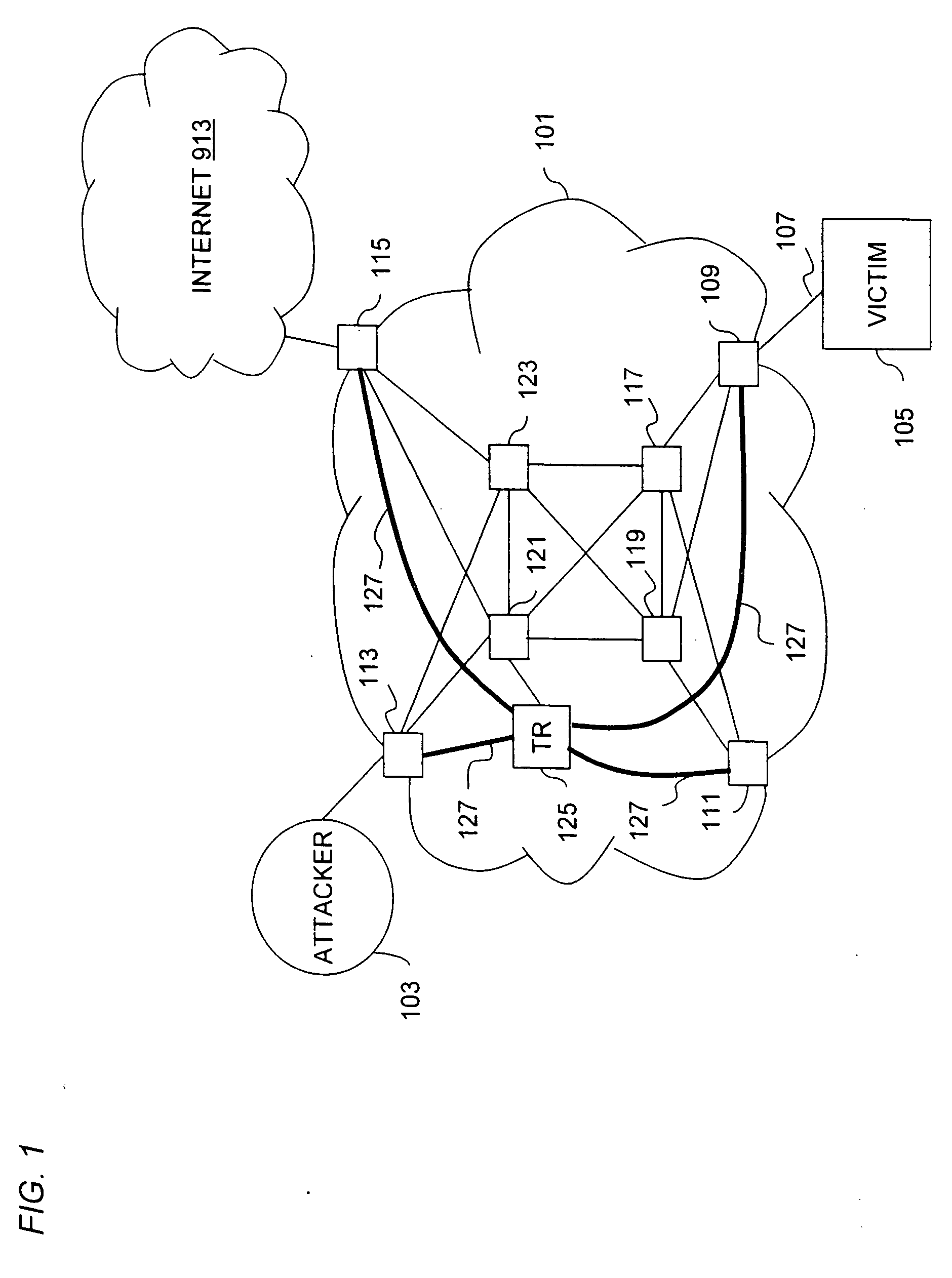
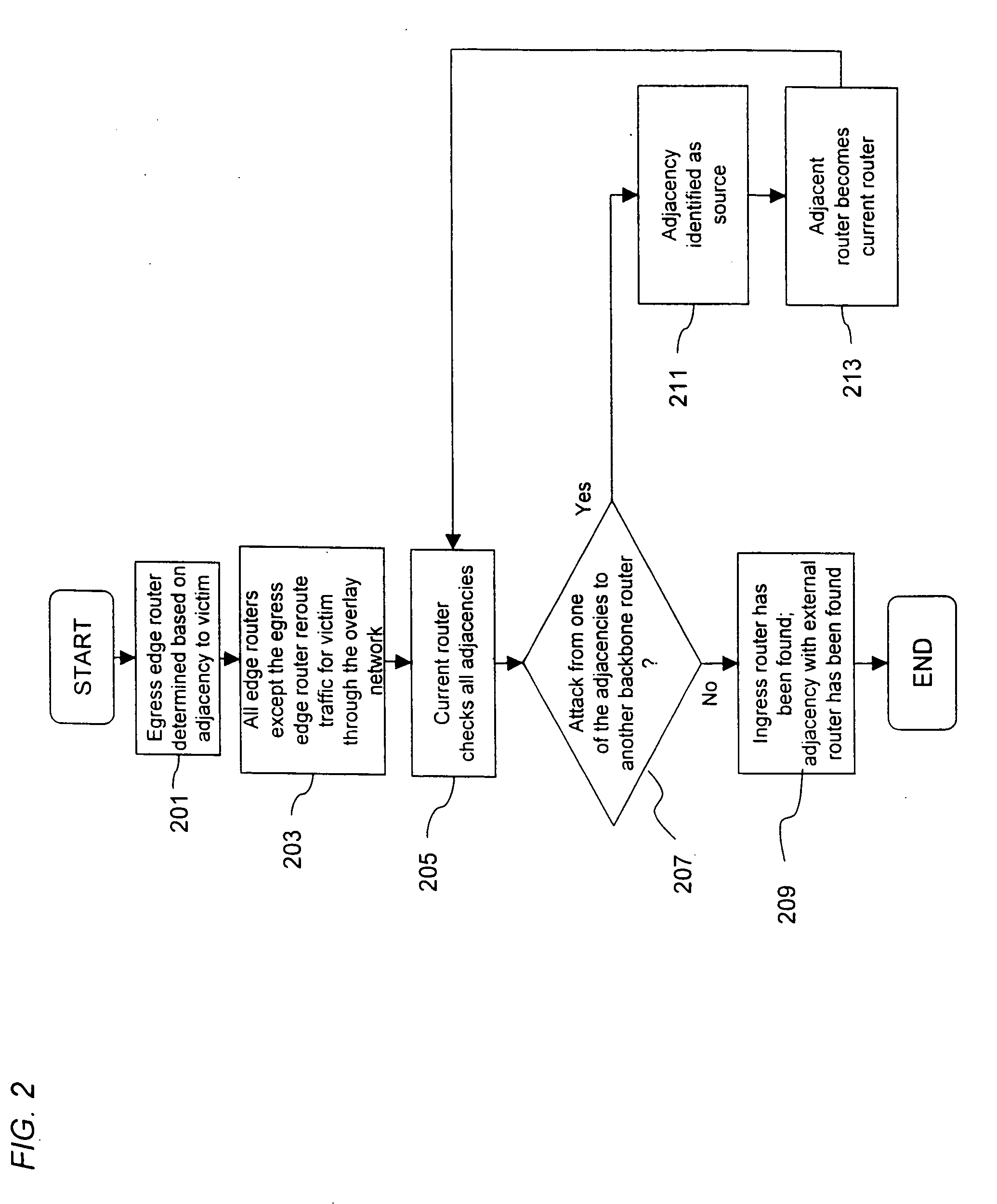
Overlay network for tracking denial-of-service floods in unreliable datagram delivery networks
ActiveUS20060156402A1Low costDeployment to minimizedMemory loss protectionUser identity/authority verificationService provisionIP tunnel
An approach for tracking denial-of-service (DoS) flood attacks using an overlay IP (Internet Protocol) network is disclosed. One or more tracking routers form an overlay tracking network over the network of an Internet Service Provider (ISP). The ISP network includes numerous transit routers and edge routers. The tracking routers communicate directly with all the edge routers using IP tunnels. The edge routers within the ISP network perform security diagnostic functions, in part, to identify a DoS flood attack that has been launched by one or more attackers. To track down an attacker, an egress edge router identifies the DoS flood attack datagrams, rerouting these datagrams to the overlay tracking network. The tracking routers perform hop-by-hop input debugging to identify the ingress edge router associated with the source of the DoS flood attack.
Owner:PALO ALTO NETWORKS INC
Inter-vehicle communication apparatus
InactiveUS20050003844A1Easily apply appropriate restrictionPrevent PN codeArrangements for variable traffic instructionsAssess restrictionArea networkTrunking
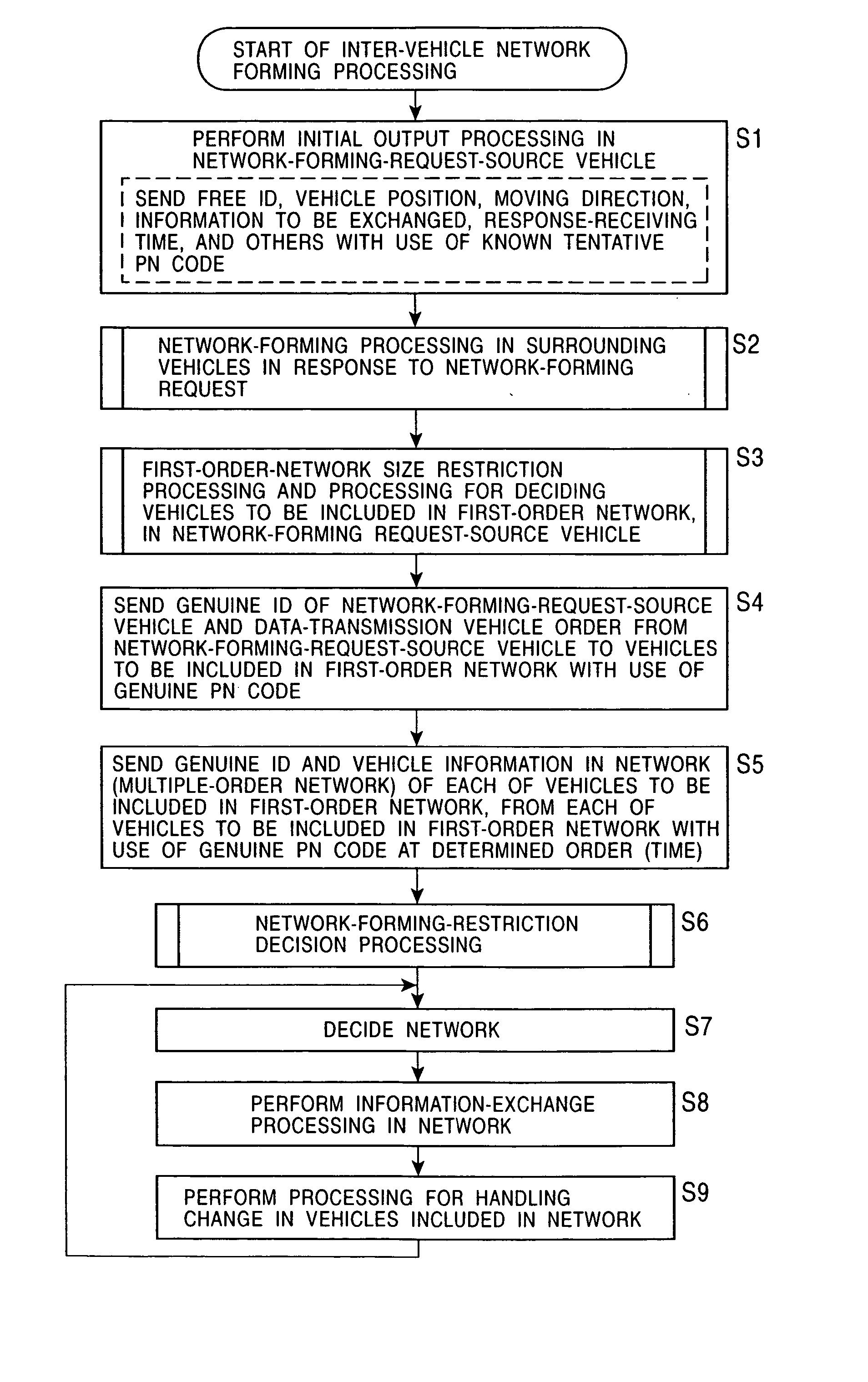
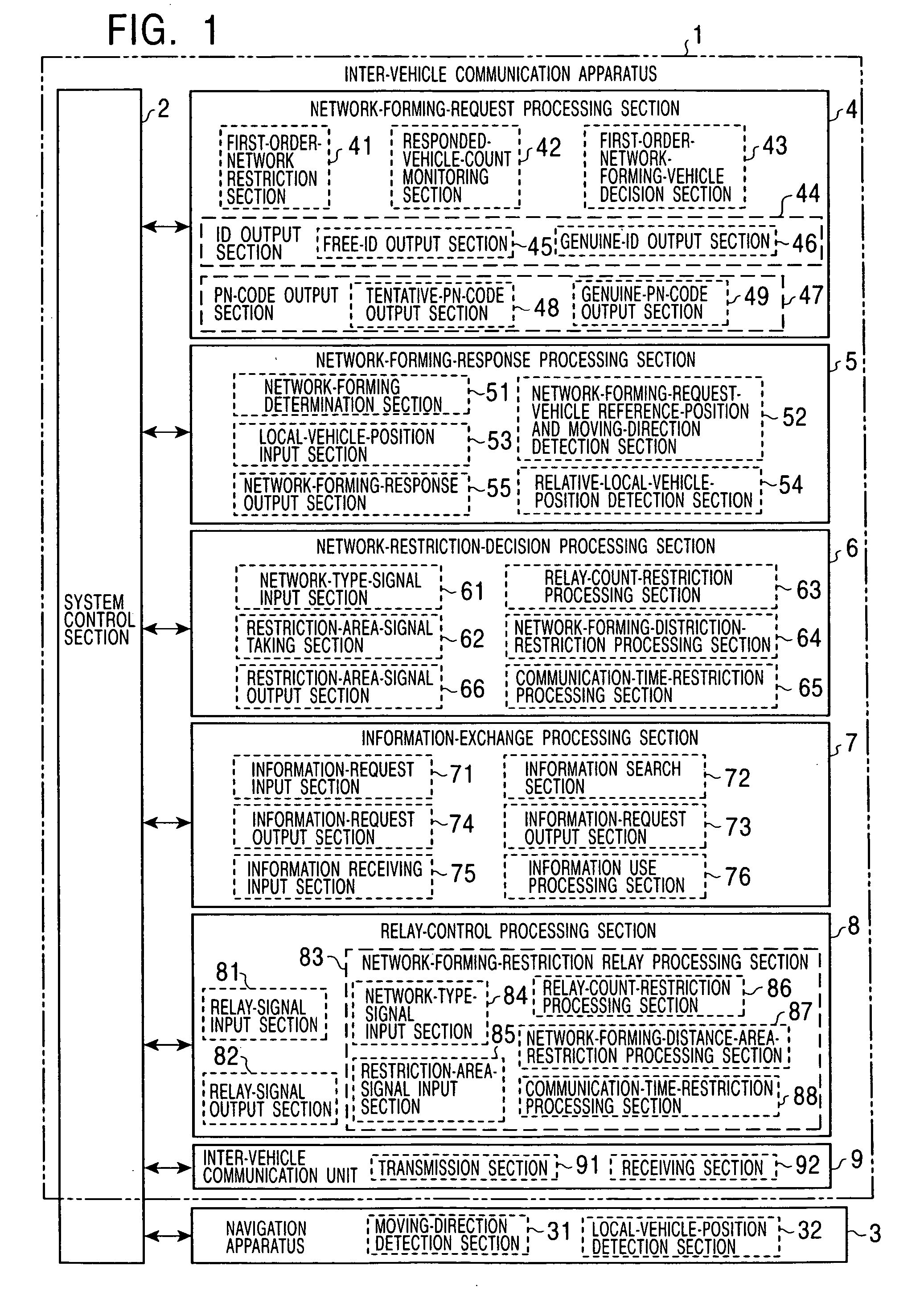
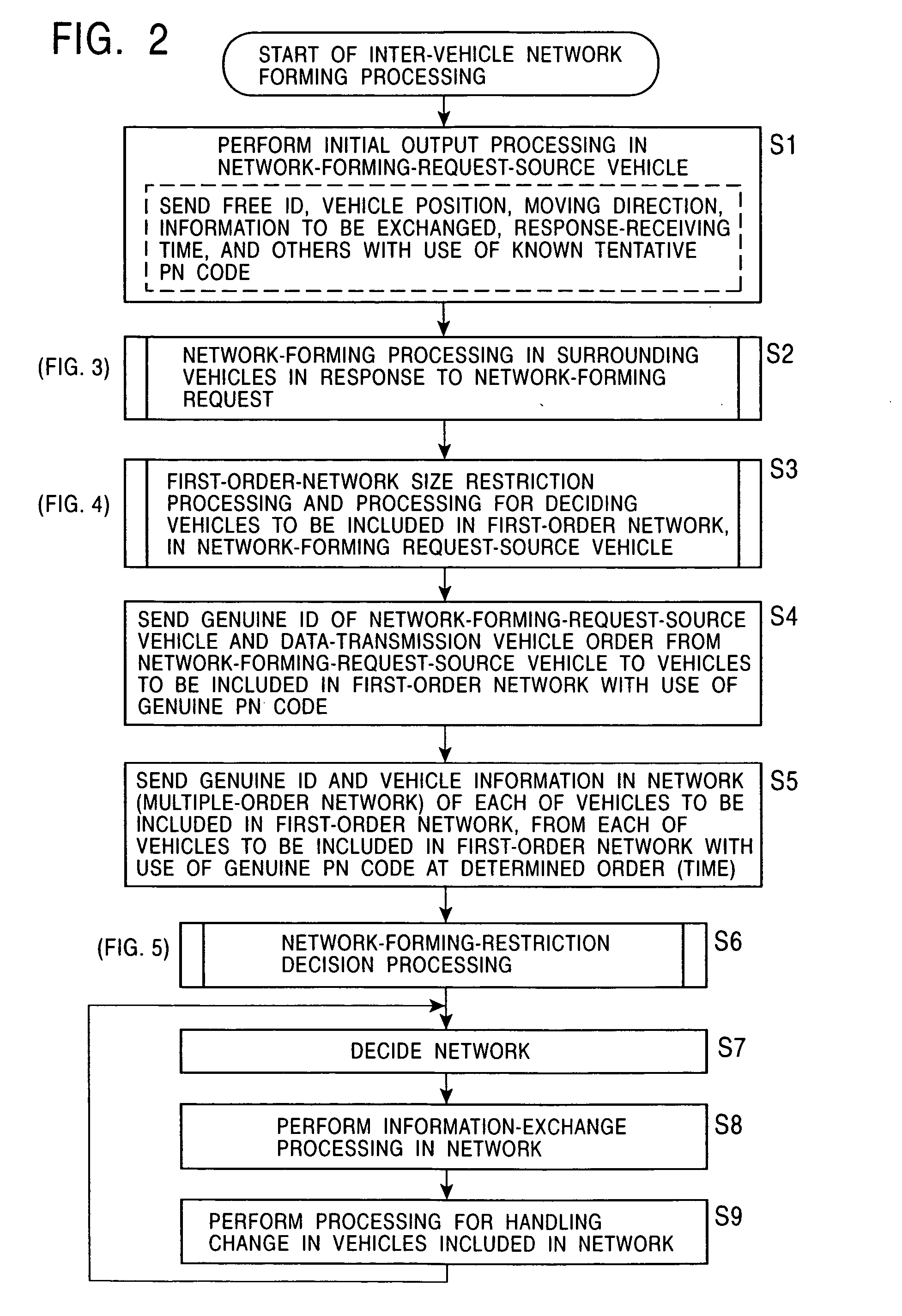
When a network is formed among vehicles with the use of inter-vehicle communication units, a network-forming-request-source vehicle sends its position serving as a reference position, its moving direction, and requested information to surrounding vehicles by the use of a free ID. Among the surrounding vehicles, vehicles which are to subscribe to the network receive the position, the moving direction, and the requested information, determine where the vehicles are positioned among positions specified in advance relative to the reference position, and respond at a timing corresponding to their positions by the use of free IDs. The network-forming-request-source vehicle receives the responses, stops receiving responses when the number of responded vehicles reaches an appropriate number of vehicles, and sends its genuine ID and a vehicle communication order. Then, a restriction, such as a restriction based on the number of times relay processes are allowed, a restriction based on a predetermined-distance area from the center of balance or the center, or a restriction based on a communication period equal to a predetermined time or shorter from when the network is formed, all of which correspond to the type of network, is applied to form an appropriate-area network.
Owner:ALPINE ELECTRONICS INC
Industrial control network redundancy fault-tolerant system
ActiveCN101907879AAvoid network conflictSolve redundancyError preventionTotal factory controlComputer monitorComputer monitoring
The invention discloses an industrial control network redundancy fault-tolerant system, belonging to the industrial control field. The system of the invention comprises four parts, namely a main controller redundancy system, a slave redundancy system, a fault log system and a host computer monitoring interface, wherein the main controller redundancy system is composed of two main controllers which provide redundancy; each main controller carries a control network to form network redundancy or the two main controllers share one control network; the slave redundancy system is composed of a main controller and a pair of slaves; the main controller monitors the communication condition of the current line and selects the best communication path in real time; the fault log system records the fault message of the device; and the host computer monitoring interface provides communication response for a monitoring computer and processes input operation to control the operation of the redundancy system. The system of the invention can ensure that the resources of the control network of the two redundancies synchronize automatically; the fault can be judged automatically; and when the network has a failure, the network can be switched to a backup control network within 300 milliseconds to operate continuously.
Owner:DALIAN UNIV OF TECH
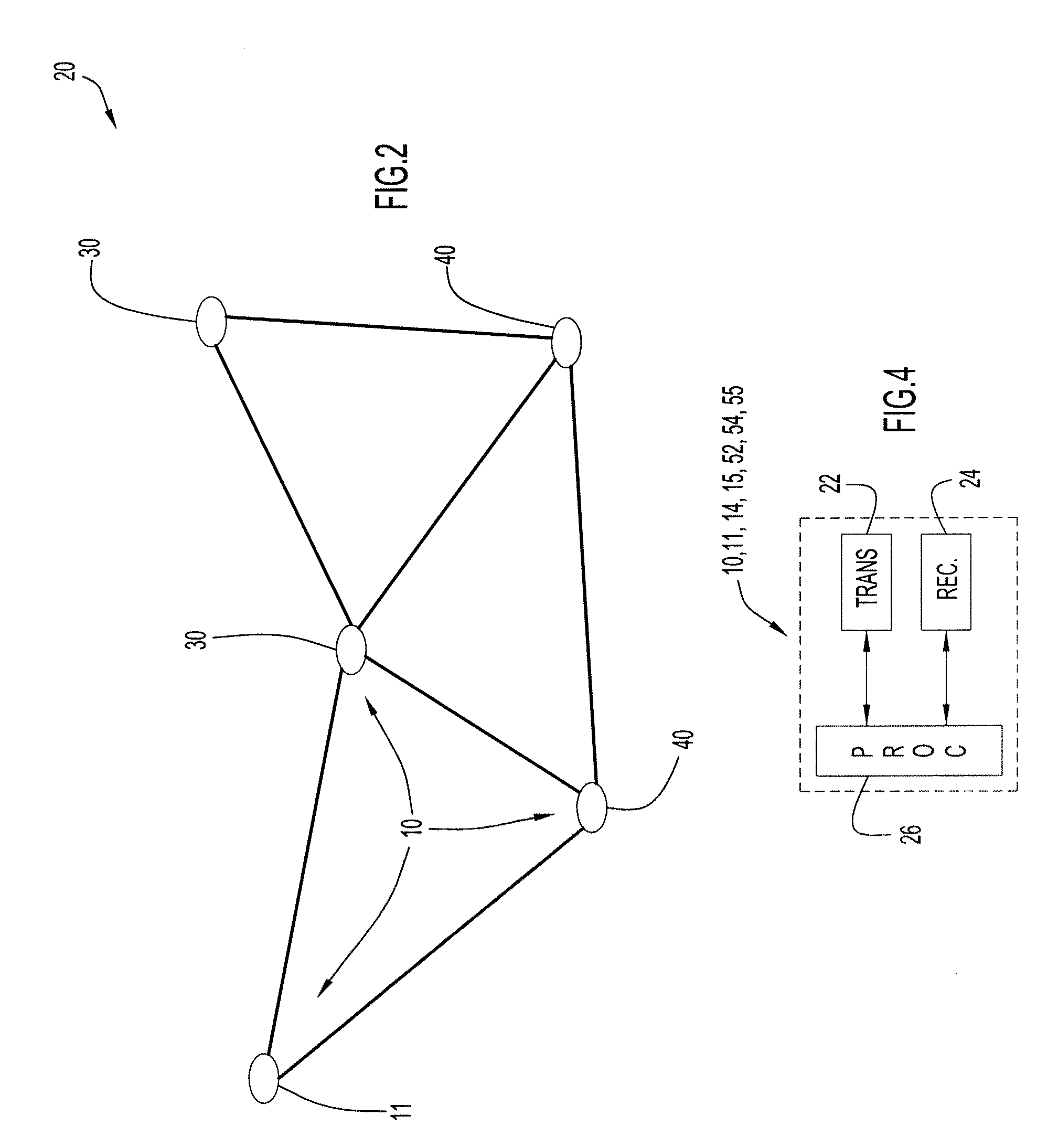
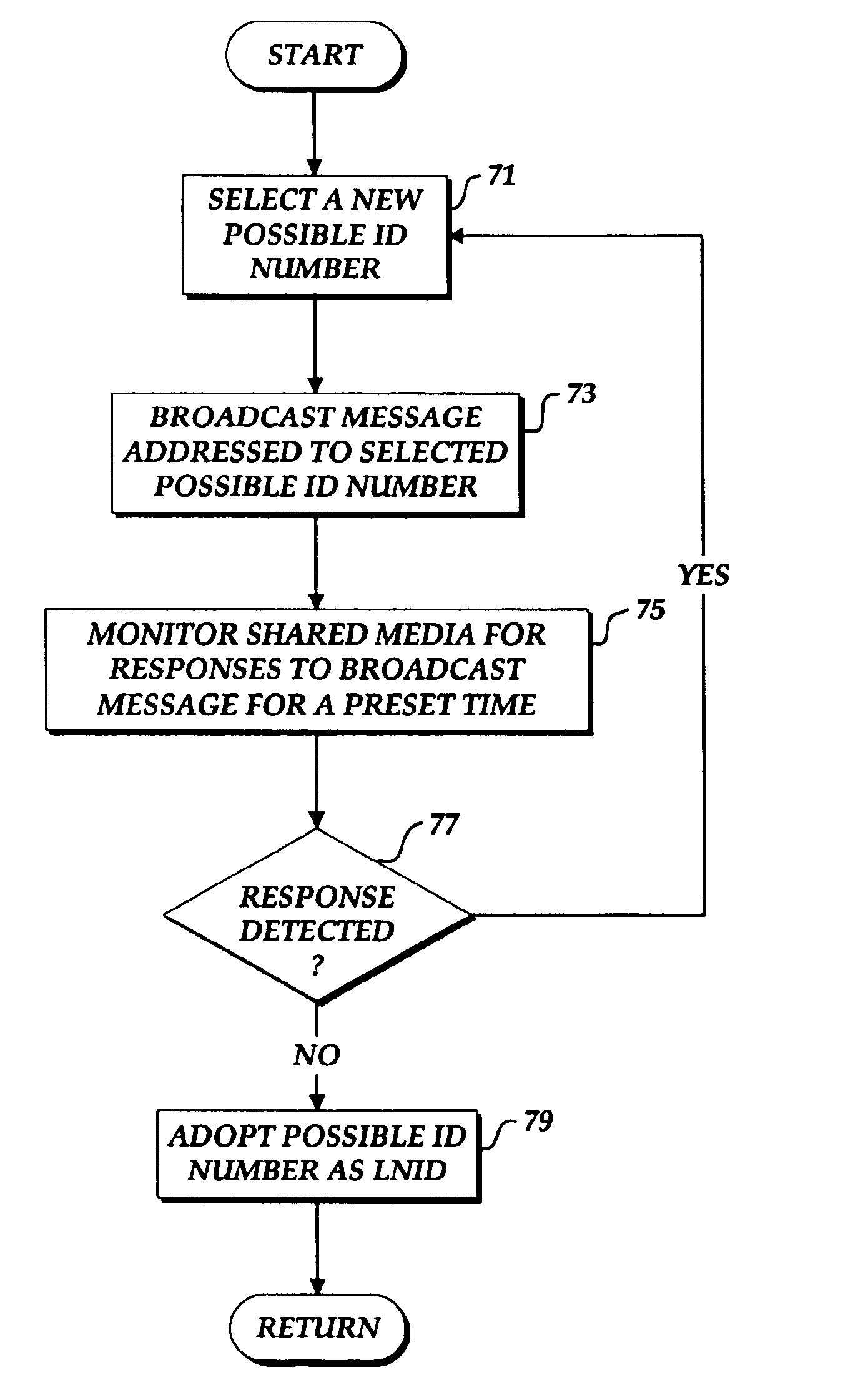
Method and Apparatus for Controlling Packet Transmissions Within Wireless Networks to Enhance Network Formation
ActiveUS20110007669A1Small sizeReduce the amount requiredNetwork topologiesData switching by path configurationWireless mesh networkSteady state
Network formation in wireless networks according to an embodiment of the present invention is enhanced based on control of network formation packet transmissions (e.g., Packet Radio Organizational Packet (PROP) transmissions). A source-initiated approach controls re-transmission of inquiry / reply PROP packets based on the presence of a neighboring node. This reduces the size and amount of PROP packets transmitted during neighbor discovery. In addition, the source-initiated approach controls re-transmission of PROP packets indicating a change in an upstream or control type node (e.g., LNC PROP). In this case, the node determines the presence of steady-state conditions (e.g., maintenance of conditions for the original LNC PROP transmission), and enables a single re-transmission of the LNC PROP packet, thereby reducing the transmission of unnecessary or duplicate LNC PROP packets (e.g., containing substantially the same information as previously transmitted packets since conditions have remained the same).
Owner:HARRIS GLOBAL COMM INC
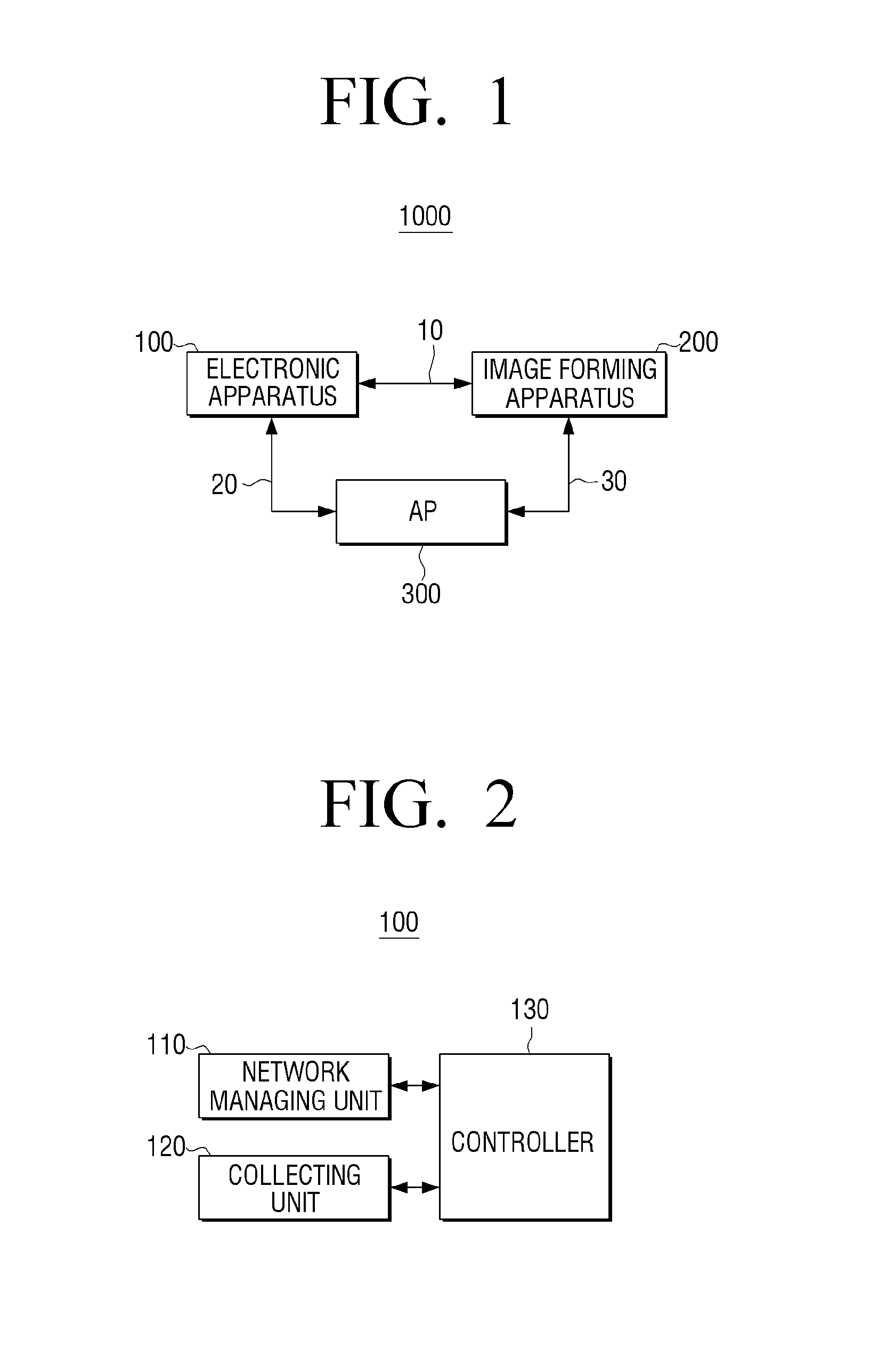
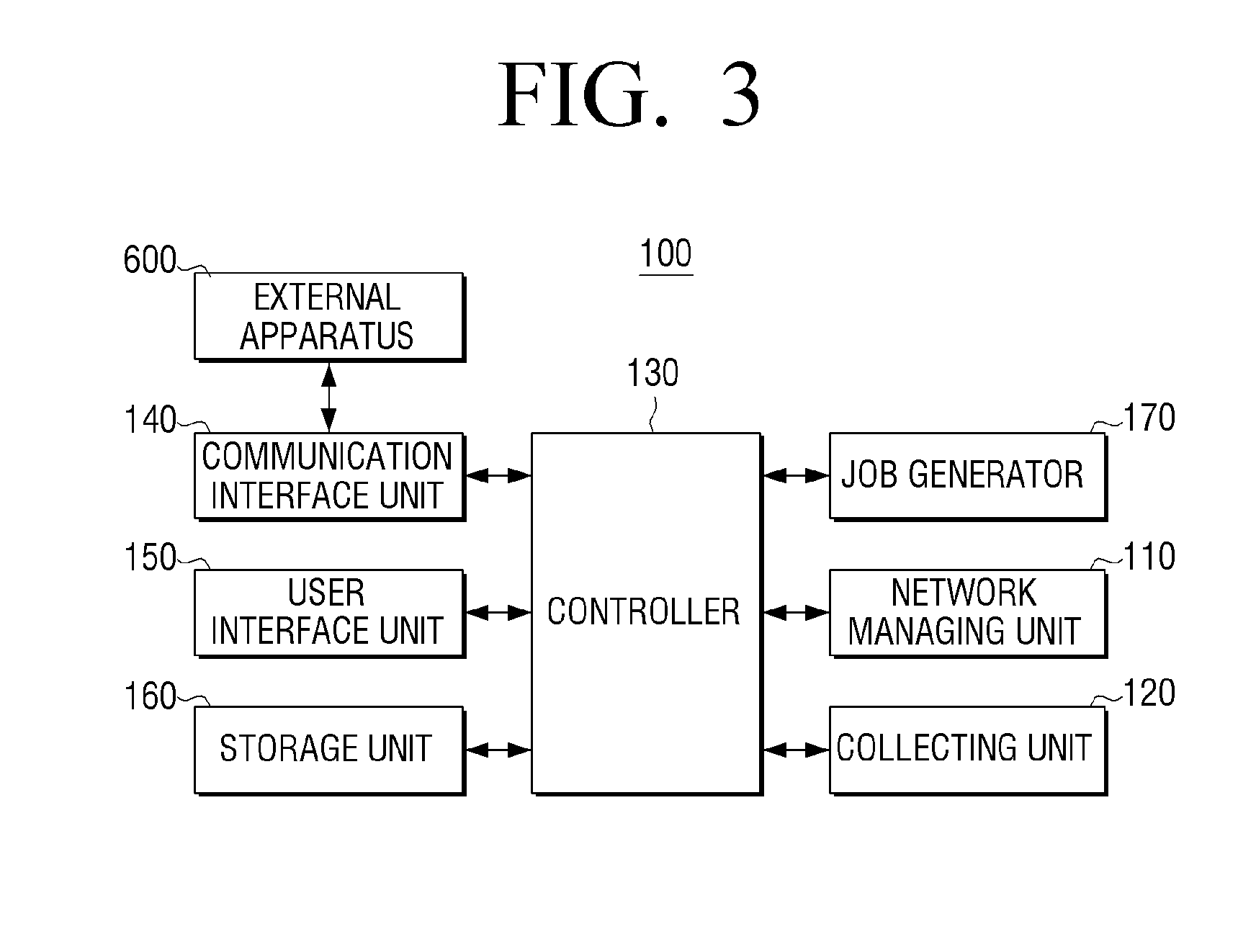
Electronic apparatus, image forming apparatus, image forming system, wireless connection method, image forming method, and computer-readable recording medium
InactiveUS20140118778A1Easy to set upAssess restrictionConnection managementImage formationNetwork management
An electronic apparatus includes a network managing unit configured to form a link to an access point through a first communication network and form a link to an image forming apparatus through a second communication network different from the first communication network, a collecting unit configured to collect wireless setting information of the access point, and a controller configured to transmit the collected wireless setting information to the image forming apparatus using the second communication network to form a link with the image forming apparatus via the access point.
Owner:S PRINTING SOLUTION CO LTD
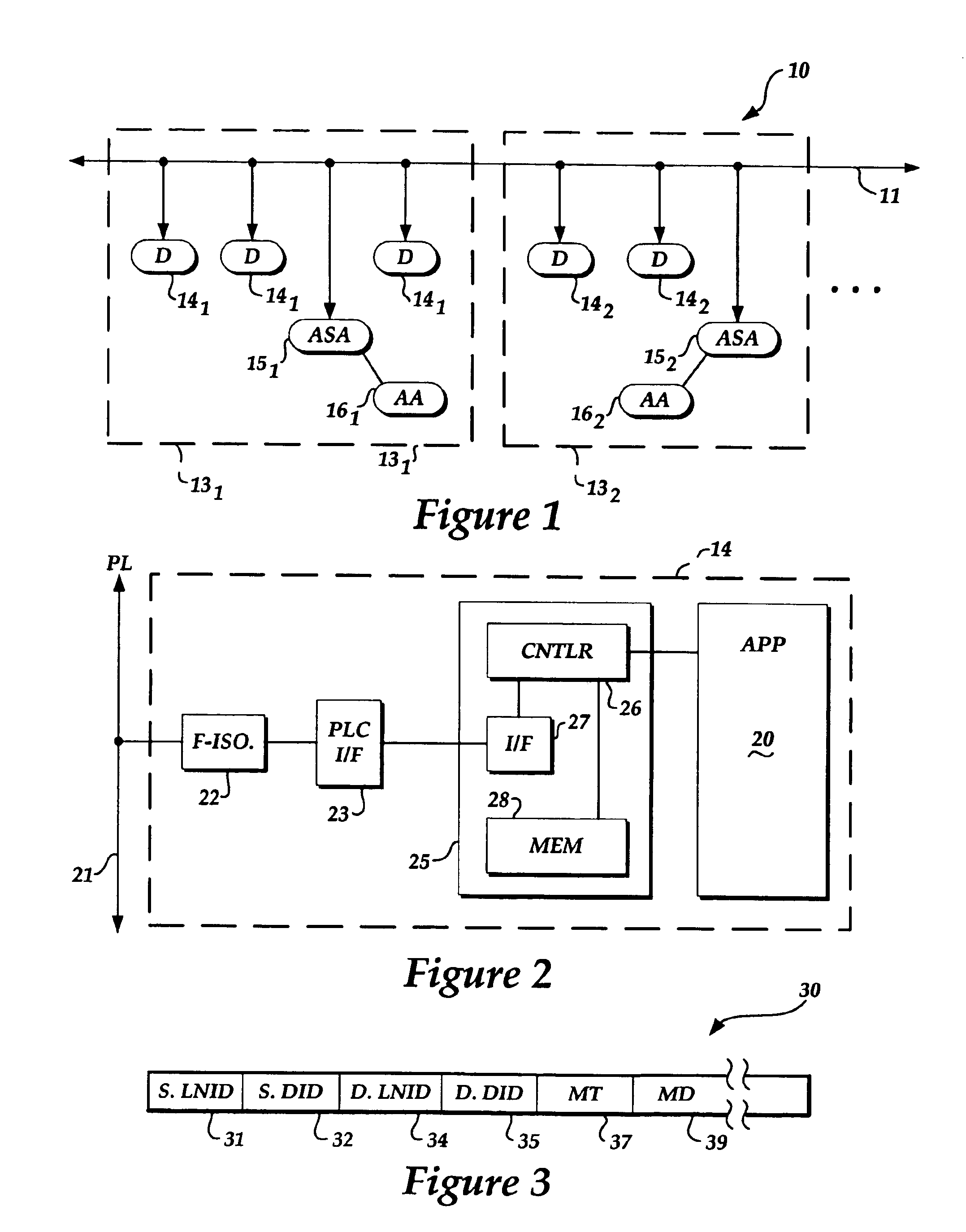
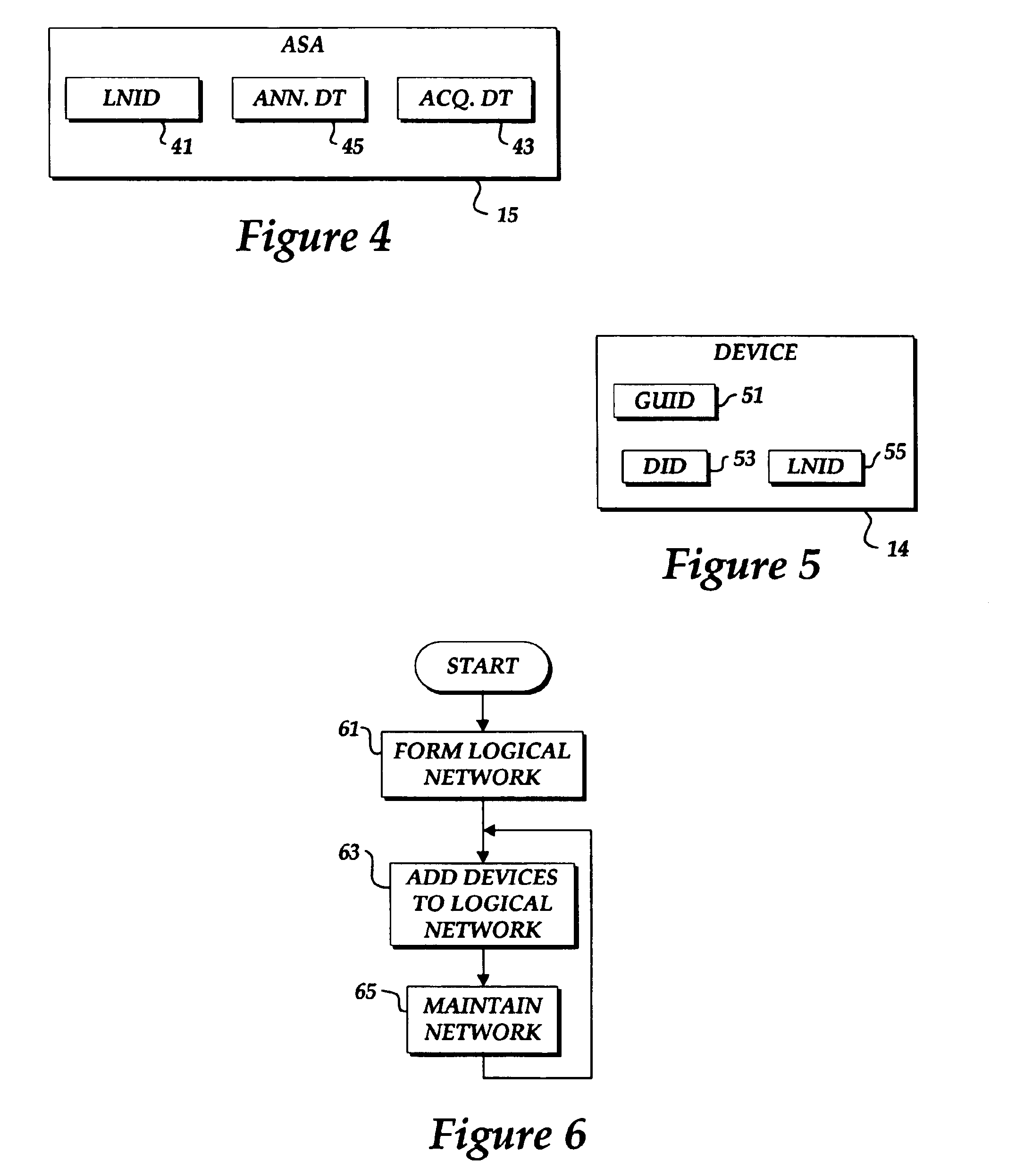
System for networked component address and logical network formation and maintenance
InactiveUS6934269B1Optimization mechanismBroadcast transmission systemsTime-division multiplexMessage typeLogical network
A system for forming and maintaining one or more networks of devices connected to a shared includes processes for: (a) forming a logical network on the shared media; (b) discovering devices connected to the shared medium; (c) assigning (or acquiring) devices to a logical network; and (d) maintaining a logical network. The system also defines a message format and protocol for communication over the shared media. The protocol uses a two-level address scheme (e.g., a logical network ID and a device ID) and defines several message types used to support the above processes and other useful features. A logical network includes an address space arbiter (ASA) and, typically, one or more devices attached to the shared media. An acquisition authority (AA), interacting with the ASA, is required to complete acquisition of a device by a logical network.
Owner:MICROSOFT TECH LICENSING LLC
Discontinuously laminated film
ActiveUS8603609B2Increase speedOrnamental structuresSpecial ornamental structuresEngineeringProcess conditions
Polymer films may be discontinuously laminated by processes such as adhesive bonding, ultrasonic bonding, embossing, ring rolling, and strainable network formation. The films may be prestretched under cold process conditions before lamination. The laminates have superior properties such as tear strength. The laminates may be incorporated into bags, such as trash bags.
Owner:THE GLAD PROD CO
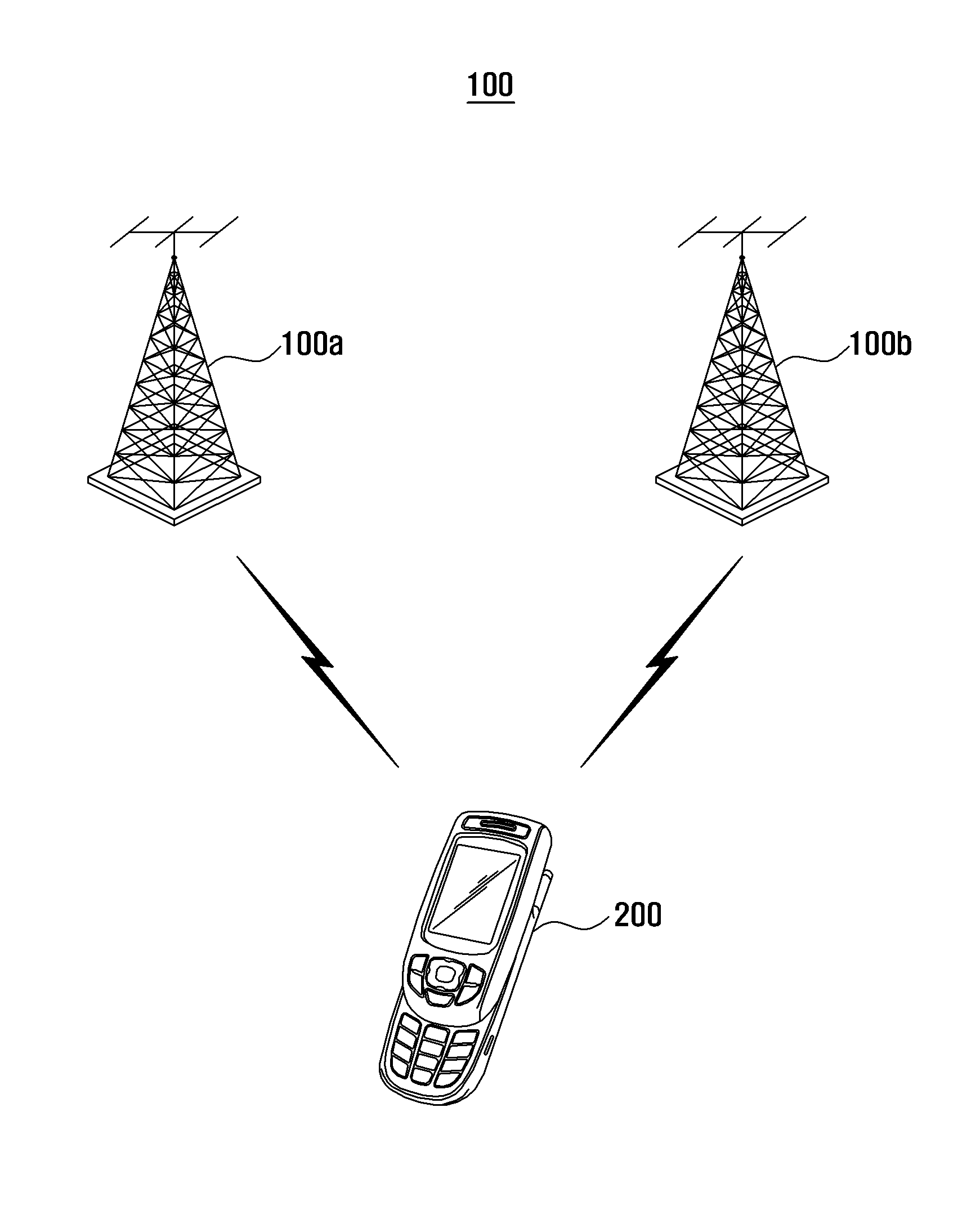
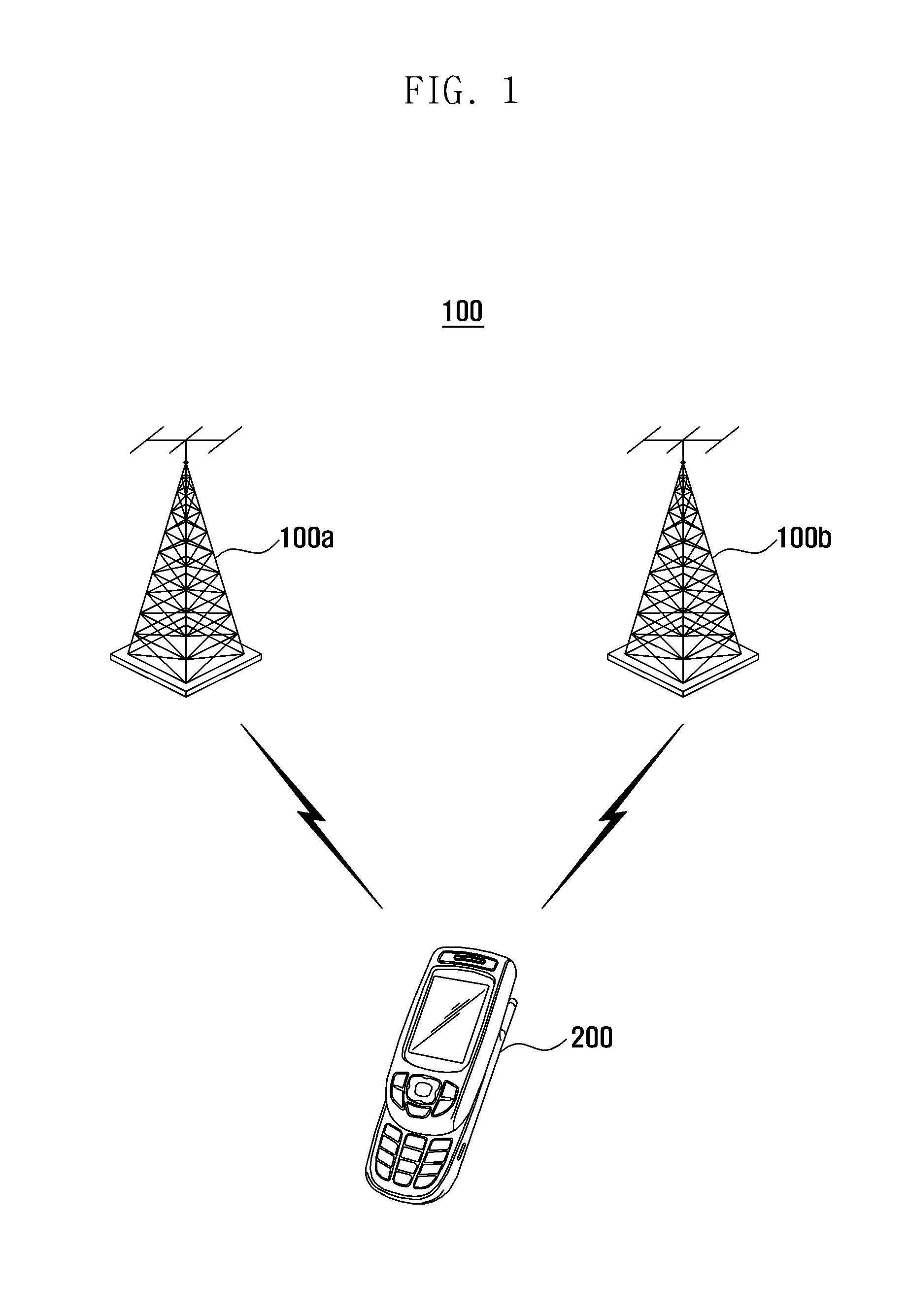
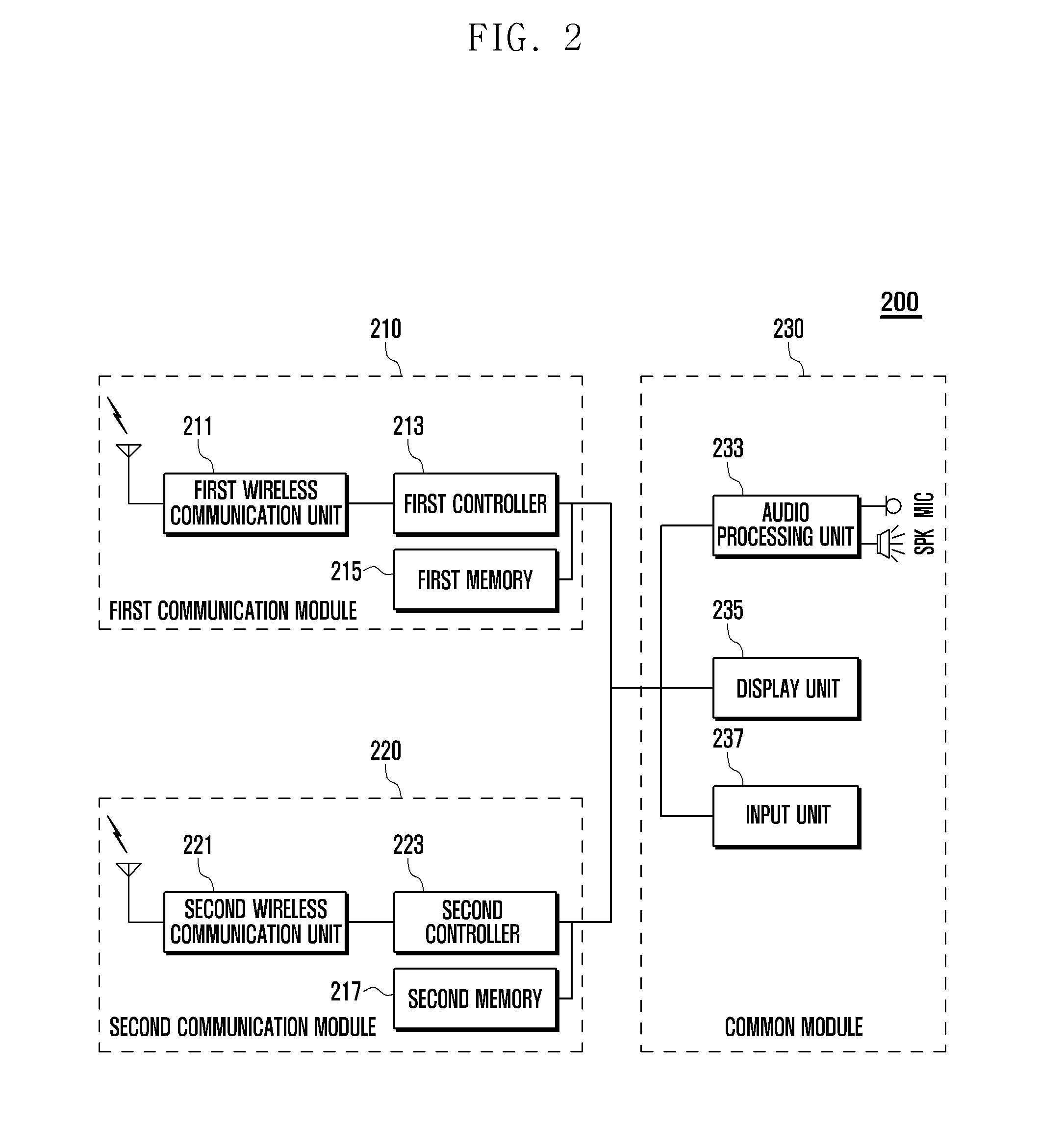
Communication operating method for dual standby mobile terminal and dual standby mobile terminal supporting the same
ActiveUS20120149419A1Quick and easy recoveryReduce power consumptionAssess restrictionRadio transmissionBase stationNetwork formation
A communication operating method and a dual standby mobile terminal including a first communication module and a second communication module are provided. The first communication module supports forming a first communication channel with a first wireless communication network. A second communication module supports forming a second communication channel with a second wireless communication network. When the first communication module transitions from an abnormal service state to a normal service state, the first communication module performs a base station search based on base station channel information of the second communication module and camps on a found base station.
Owner:SAMSUNG ELECTRONICS CO LTD
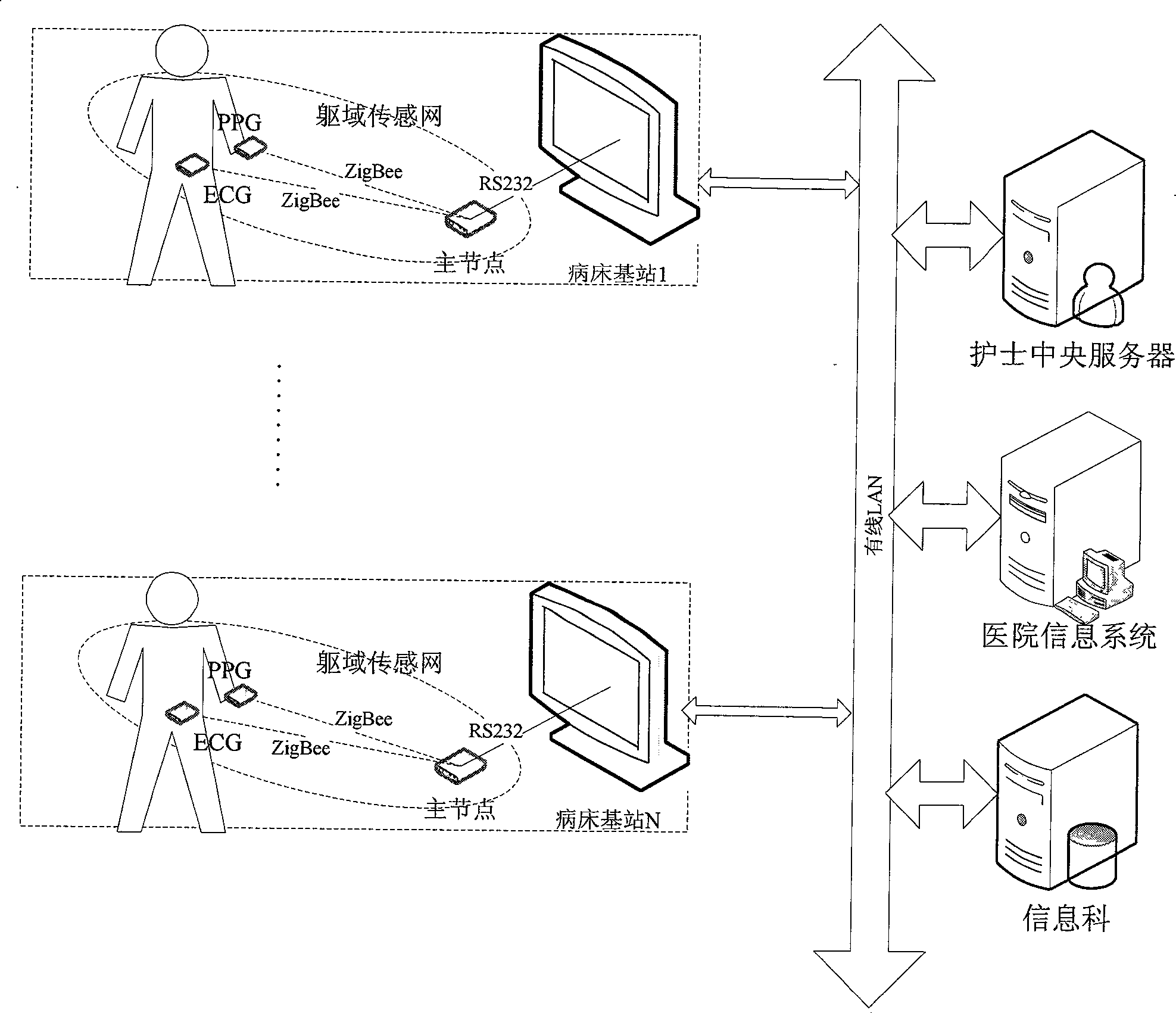
Sickroom wireless monitoring system based on ZigBee
InactiveCN101371801ARealize supervision and alarmRealize information storageNear-field transmissionTransmission systemsEcg signalPatient's room
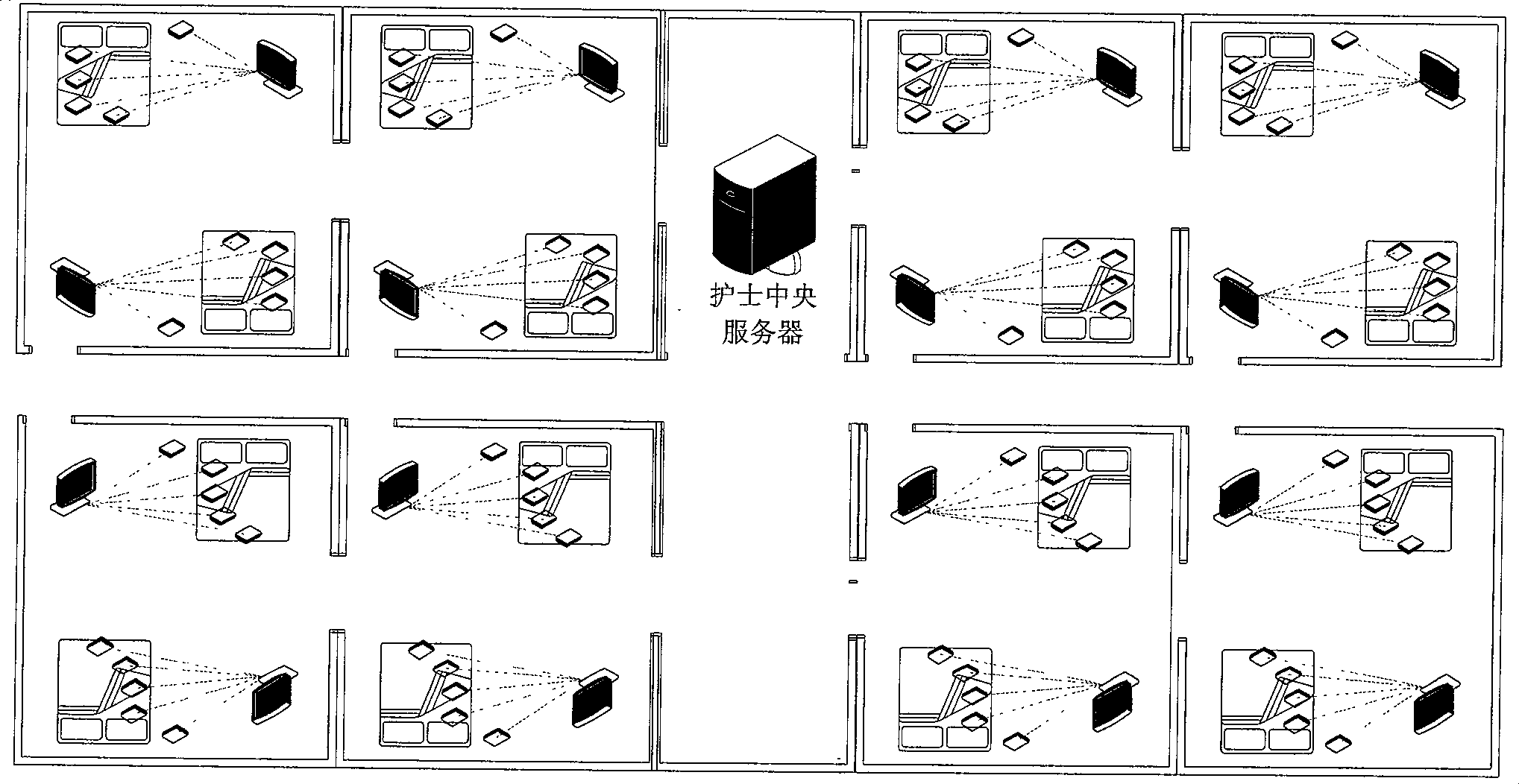
The invention discloses a ward wireless monitoring system based on ZigBee and consists of a plurality of wireless physiological parameter miniaturization modules, a monitoring base station and a nurse central server. The invention also discloses the application of the ward wireless monitoring system based on ZigBee to ward centralized wireless monitoring and patient random movement monitoring. The ward wireless monitoring system can collect a variety of physiological parameters such as electrocardiosignals, heart rate, heart sound, oxygen saturation of blood, body temperature, and the like, and adopt ZigBee technology for wireless transmission of data so as to realize ward centralized wireless monitoring and patient random movement monitoring and facilitate the medical staff monitoring the disease process of patients and taking protection measures. The system of the invention has the advantages of low power consumption, miniaturization, low cost, convenient network formation, capability of detecting a variety of parameters, good extending and interactive ability and high reliability; the system can reflect the physiological status of the body more veritably and can greatly reduce the electric cable connection on critical patients, thus facilitating the wearing of patients as well as the diagnosis and treatment operation of doctors and nurses.
Owner:SOUTH CHINA UNIV OF TECH
Hydrogel arthroplasty device
An arthroplasty device is provided having an interpenetrating polymer network (IPN) hydrogel that is strain-hardened by swelling and adapted to be held in place in a joint by conforming to a bone geometry. The strain-hardened IPN hydrogel is based on two different networks: (1) a non-silicone network of preformed hydrophilic non-ionic telechelic macromonomers chemically cross-linked by polymerization of its end-groups, and (2) a non-silicone network of ionizable monomers. The second network was polymerized and chemically cross-linked in the presence of the first network and has formed physical cross-links with the first network. Within the IPN, the degree of chemical cross-linking in the second network is less than in the first network. An aqueous salt solution (neutral pH) is used to ionize and swell the second network. The swelling of the second network is constrained by the first network resulting in an increase in effective physical cross-links within the IPN.
Owner:THE BOARD OF TRUSTEES OF THE LELAND STANFORD JUNIOR UNIV +1
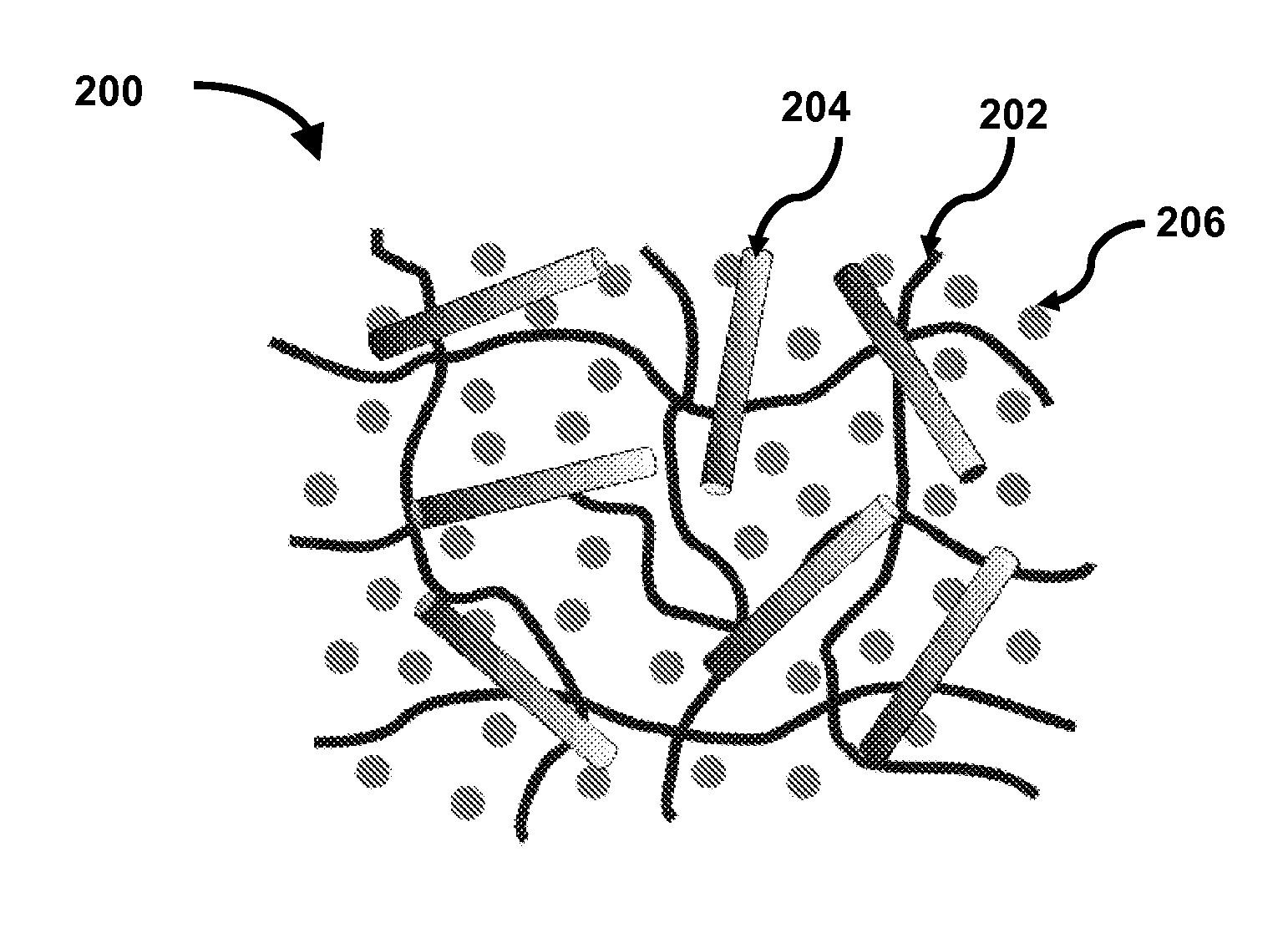
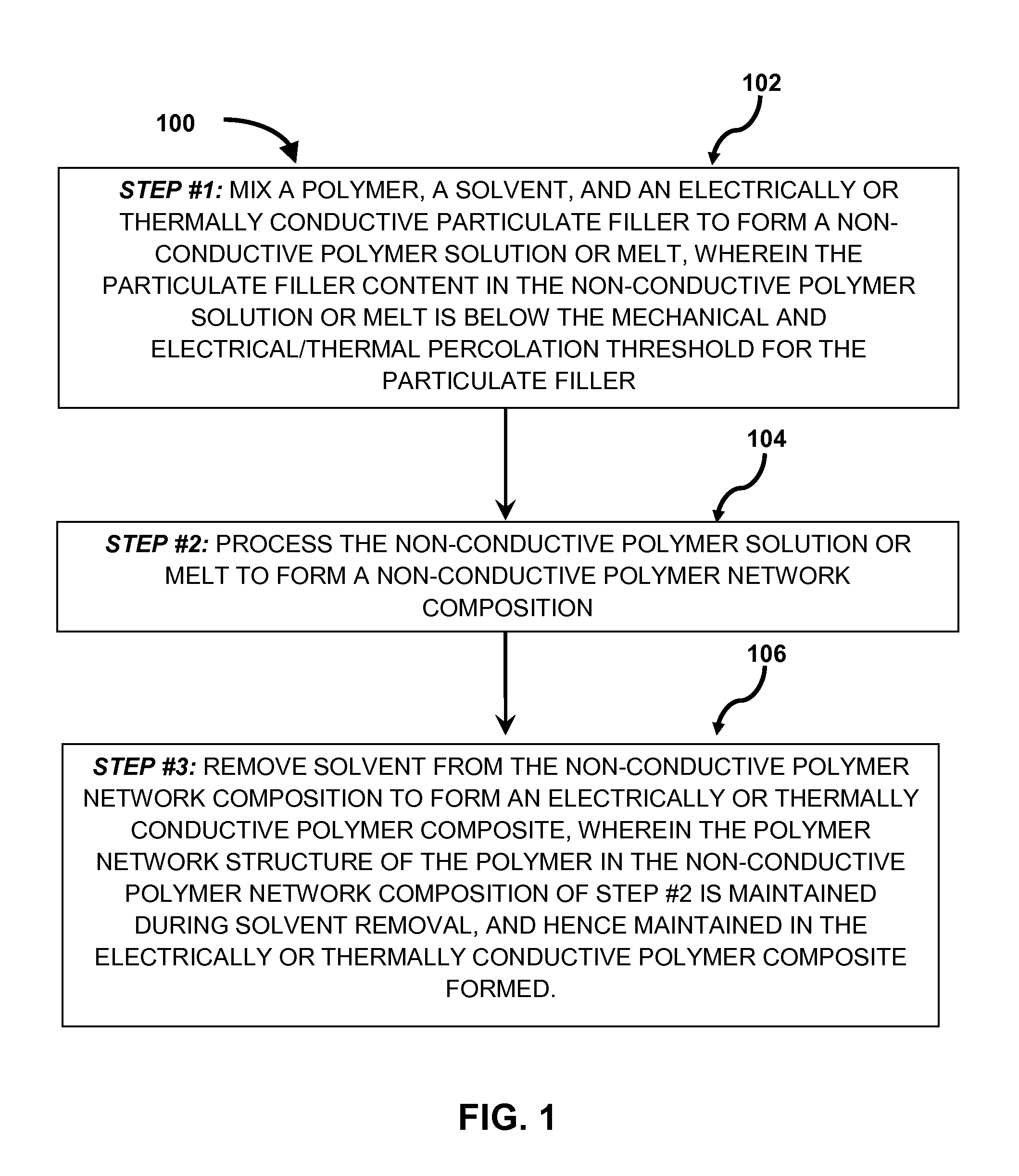
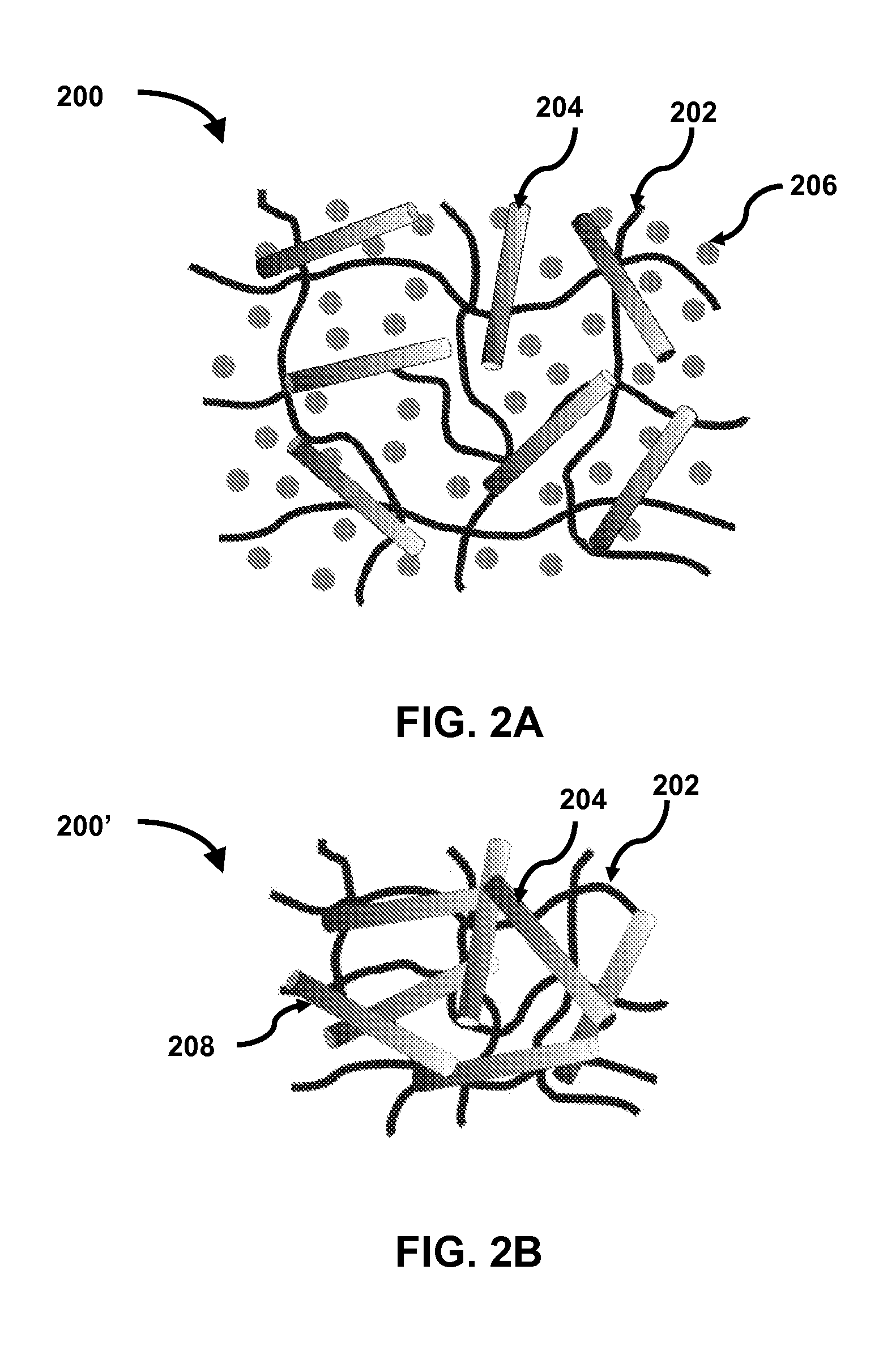
Solvent assisted processing to control the mechanical properties of electrically and/or thermally conductive polymer composites
ActiveUS20150083961A1Conductive materialNon-conductive material with dispersed conductive materialParticulatesElectricity
Electrically and / or thermally conductive polymer composites and methods of preparing same are provided. In some embodiments, a method for preparing an electrically and / or thermally conductive polymer composite may include (1) mixing a polymer, a conductive particulate filler, and a solvent compatible with the polymer to form a non-conductive polymer solution or melt; (2) processing, the non-conductive polymer solution or melt to form a non-conductive polymer network composition; wherein the presence of solvent during three-dimensional network formation manipulates the polymer network structure; and (3) removing the solvent from the non-conductive polymer network composition to form an electrically and / or thermally conductive polymer composite. The altered polymer chain structure present in the non-conductive polymer network composition is maintained in the composite, and offsets the impact of particulate filler addition including increased modulus, decreased elasticity, and decreased elongation at break. This method enables development of composite materials with electrical / thermal and mechanical performance that can be tailored independently.
Owner:US SEC THE ARMY THE
System and method for secure wireless multi-hop network formation
ActiveUS7881474B2Synchronising transmission/receiving encryption devicesUser identity/authority verificationSelf-organizing networkNode authentication
The present invention provides methods and devices for a security architecture for use in wireless multi-hop networks. A method for implementing pair-wise encryption key establishment, network node authentication and determining tunnel encryption keys is provided in a following manner. In a multi-hop wireless network including a plurality of network nodes, pair-wise security is established between pairs of neighboring network nodes of the plurality of network nodes. For example, pair-wise security is established in the form of temporal pair-wise encryption keys. Following establishment of pair-wise security between pairs of neighboring network nodes, for a pair of network nodes that are not neighbors, tunnel security is established between the pair of network nodes using tunnel encryption keys derived by the pair of network nodes on an ad hoc basis. The tunnel encryption keys are used to form the connection between non-neighboring network nodes so as to avoid the hop-by-hop encryption / decryption used in conventional multi-hop wireless systems.
Owner:APPLE INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com