Patents
Literature
227 results about "IP tunnel" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
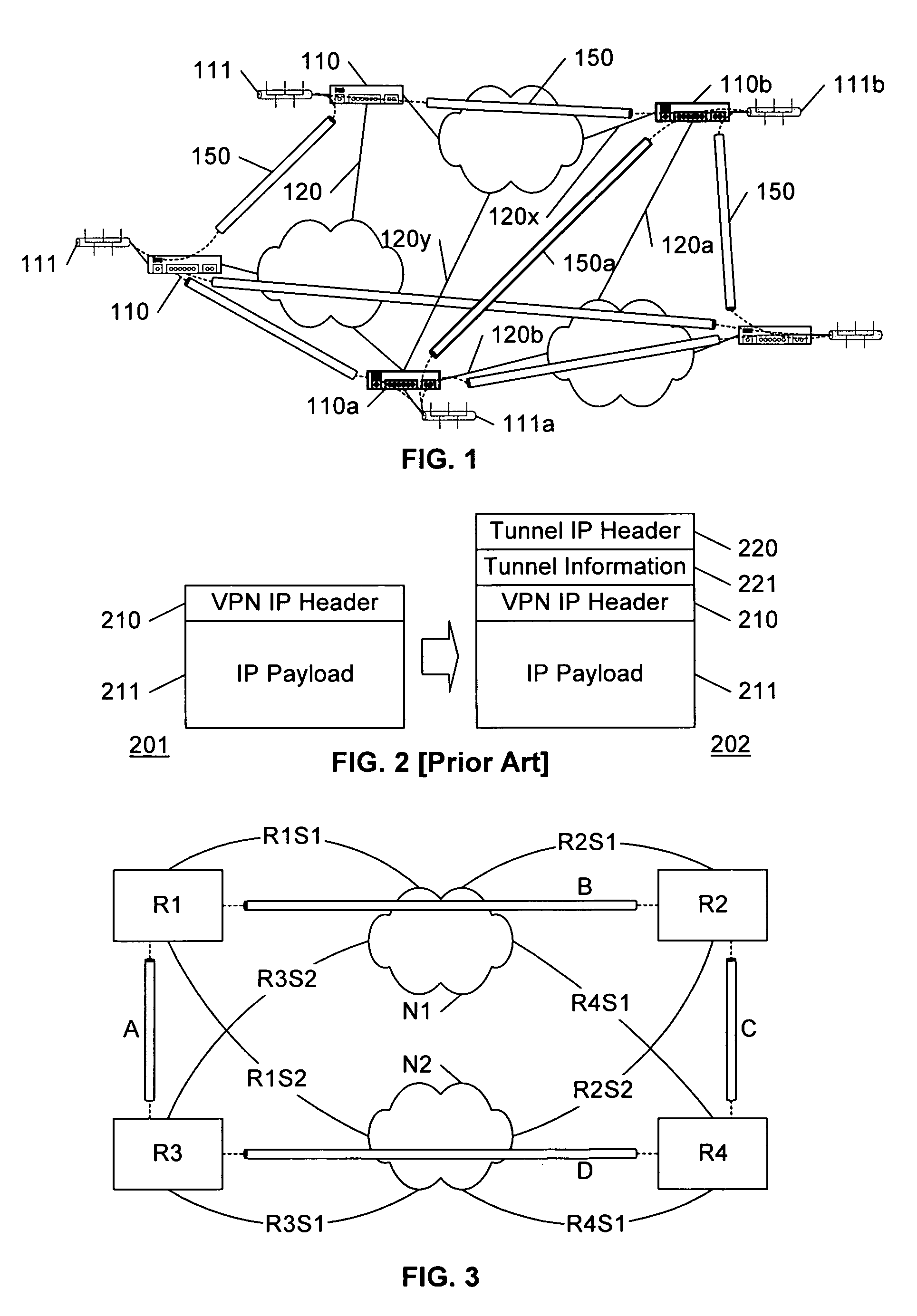
An IP tunnel is an Internet Protocol (IP) network communications channel between two networks. It is used to transport another network protocol by encapsulation of its packets. IP tunnels are often used for connecting two disjoint IP networks that don't have a native routing path to each other, via an underlying routable protocol across an intermediate transport network. In conjunction with the IPsec protocol they may be used to create a virtual private network between two or more private networks across a public network such as the Internet. Another prominent use is to connect islands of IPv6 installations across the IPv4 Internet.
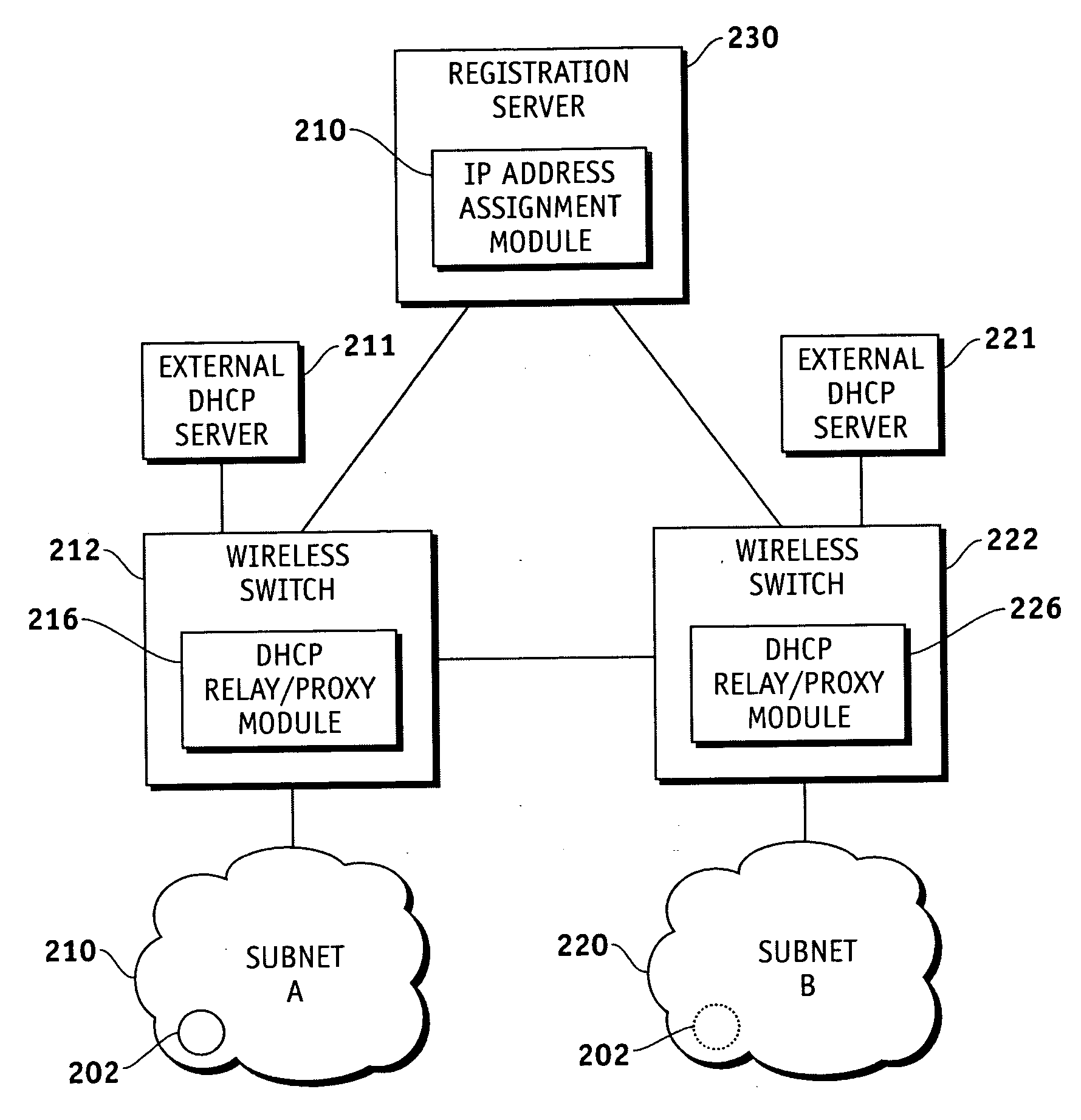
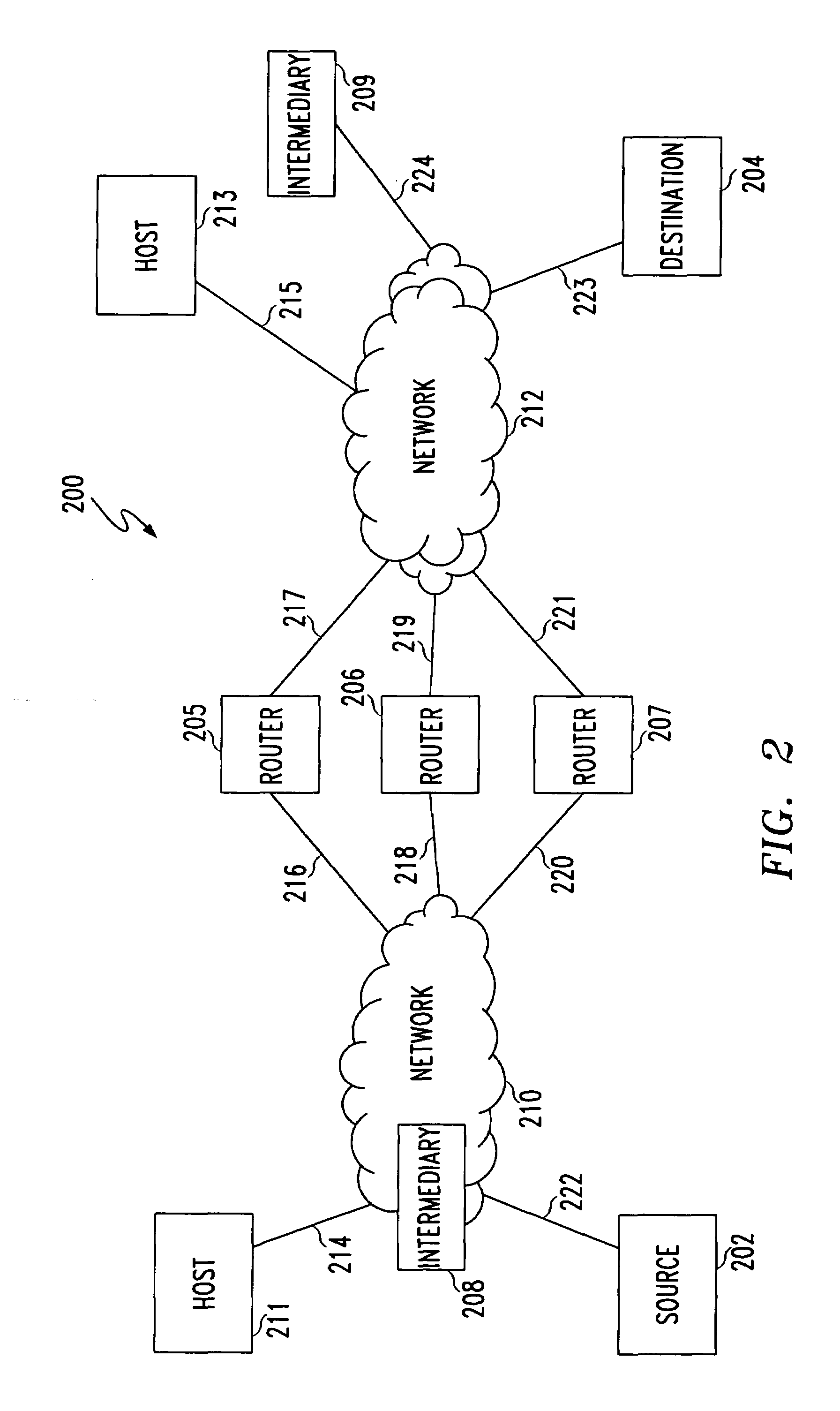
Method, system and apparatus for assigning and managing IP addresses for wireless clients in wireless local area networks (WLANs)
Techniques are provided IP address assignment and management in a wireless network. Such a wireless network can comprise a plurality of wireless clients, a registration server, a plurality of wireless switches each being configured to support a particular subnet. Each wireless client can generate a Dynamic Host Configuration Protocol (DHCP) request for an Internet Protocol (IP) address when the client either powers up in of moves to a new subnet, 802.11 authenticates and associates and 802.1x authenticates. The wireless switches can communicate with the registration server over an IP tunnel. For example, each wireless switch can receive the DHCP requests from wireless clients associated with the subnet of the wireless switch, and forward the DHCP requests to the registration server. The registration server can receive the forwarded DHCP requests, and assign IP addresses to the wireless clients based on the forwarded DHCP requests.
Owner:SYMBOL TECH INC
Agile digital communication network with rapid rerouting
ActiveUS7362709B1Low reliabilityImprove reliabilityError preventionFrequency-division multiplex detailsUser deviceBackup path
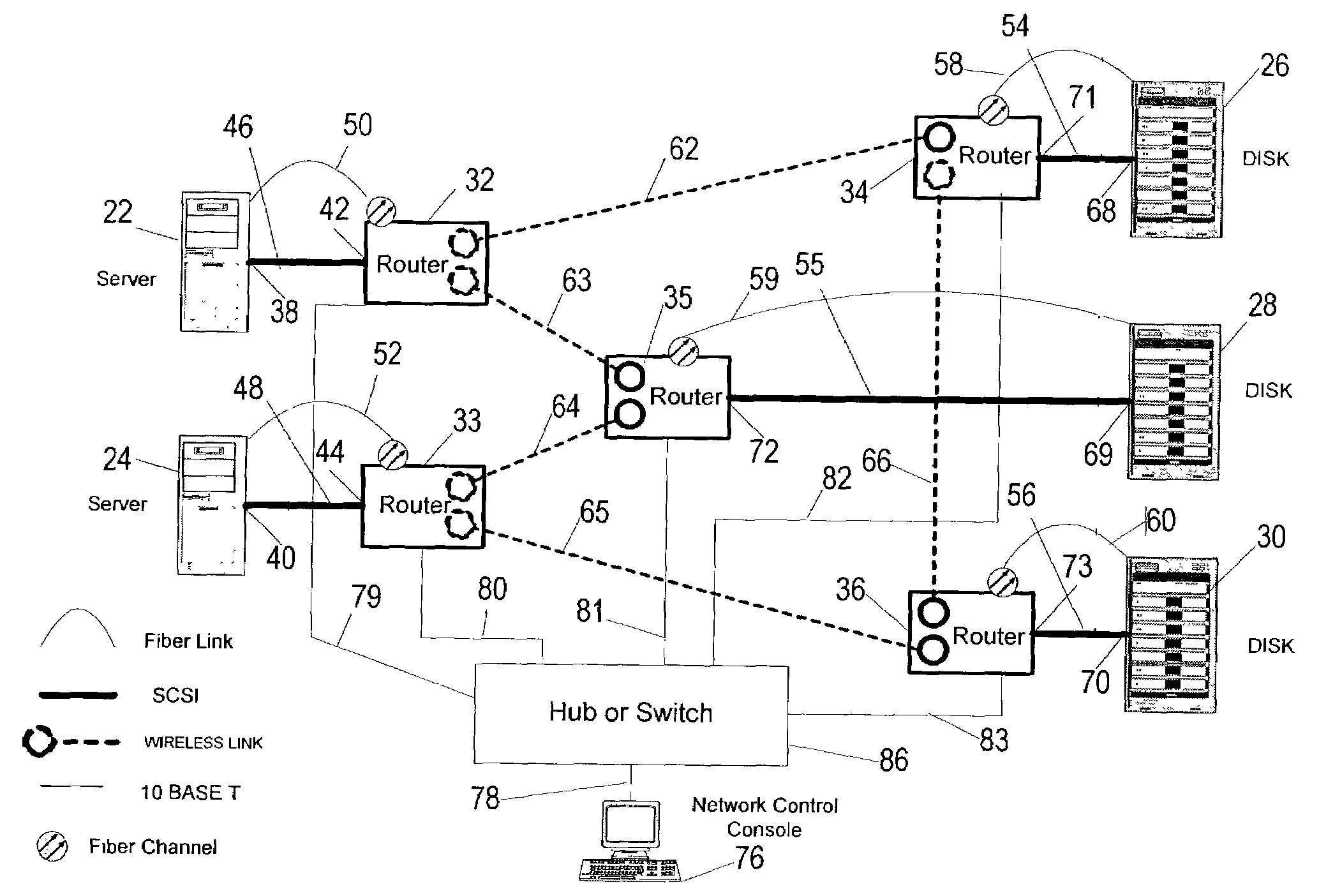
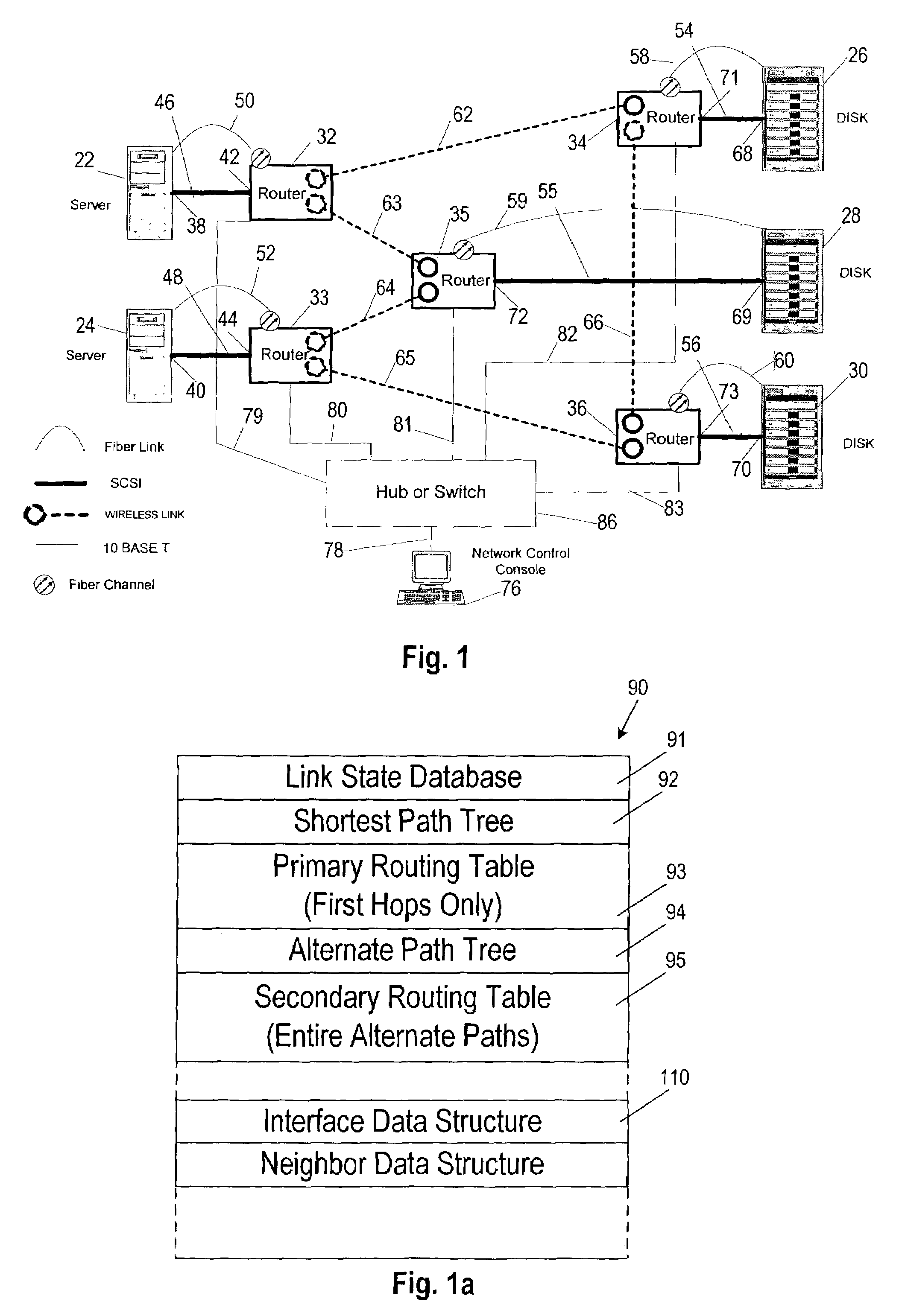
An agile digital communications network has a number of routers that serve as nodes in a mesh network communicating between a user device (e.g., computer, server, etc.) and a target device (e.g., disc storage cabinets, tape, jukebox, etc.). The routers operate on an open shortest path first protocol, each router having two or more interfaces or links to other routers. When a link connected to a router is down and is in the shortest path to another router identified in a communication packet, the packet is forwarded to the identified router on a precalculated alternate route that does not use the unavailable link. IP tunneling assures that routing loops do not occur and send the packet back to the router with the unavailable link because it would have been in the shortest path of an intermediate router. A tunneling technique is provided that maximizes the levels of encapsulation needed at two, regardless of the size or configuration of the network. An unavailable link is not broadcast immediately throughout the network, giving the link an opportunity to be restored before all of the routers are called on to recalculate the shortest paths and alternate paths. During a short interval following the discovery of an unavailable link, then, a router connected to that link is in a state identified as the Use Alternate Path state, and the link is repeatedly checked for availability. Each router calculates and stores the alternative paths to each other router after first calculating the shortest path to each other router. The alternate paths are pulled up and used when an unavailable link is detected. Dijkstra's algorithm is used to calculate the shortest paths. A new algorithm called the iterative dynamic Dijkstra's algorithm is used to calculate the alternative routes.
Owner:THE ARIZONA BOARD OF REGENTS ON BEHALF OF THE UNIV OF ARIZONA
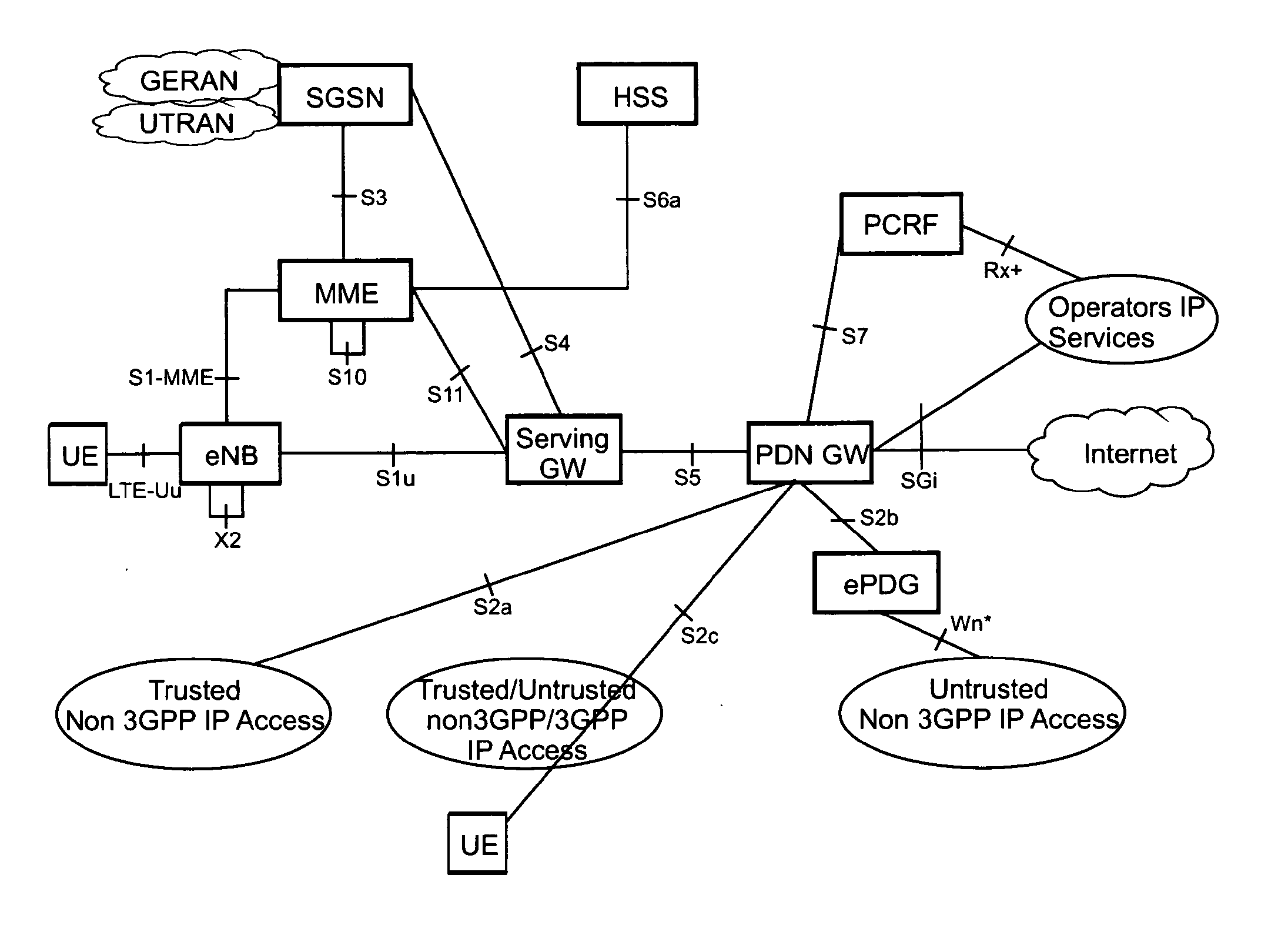
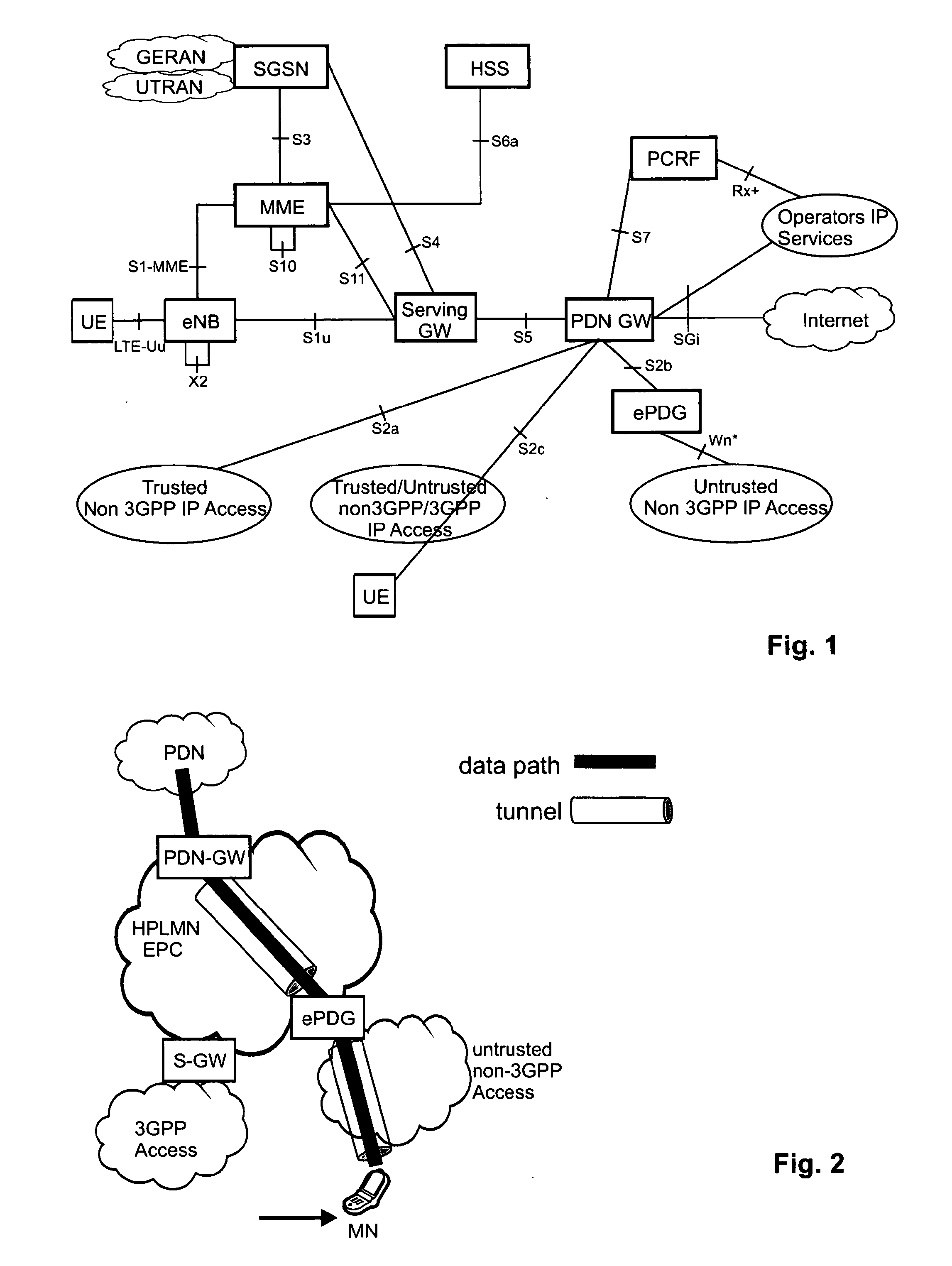
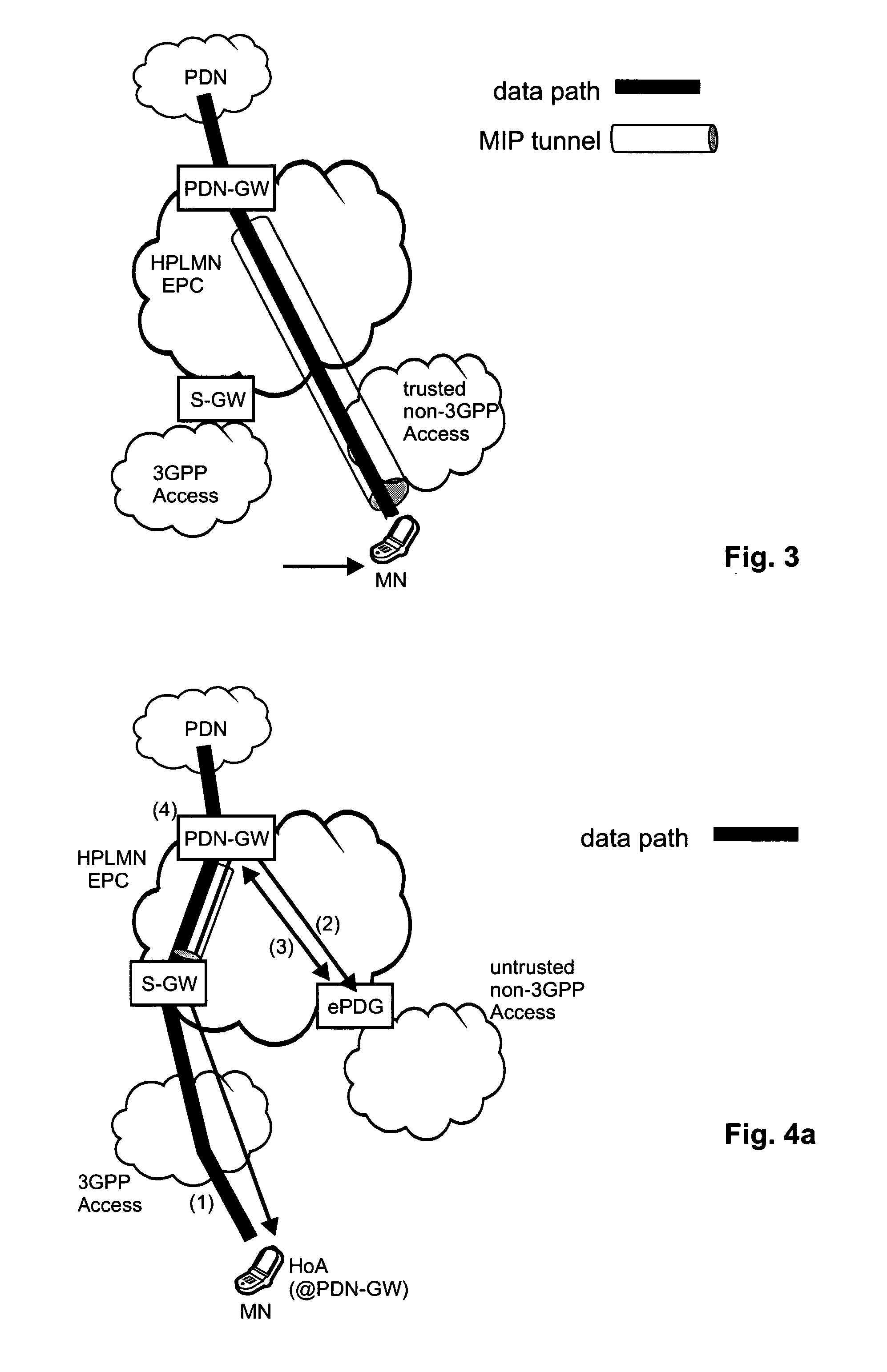
Optimization of handovers to untrusted non-3gpp networks
The invention relates to a method for ensuring IP session continuity upon a handover of a mobile node to a non-3GPP network, wherein an ongoing IP session of the mobile node goes via a packet data network gateway. For non-3GPP networks it is necessary to discover a security gateway and to then establish the corresponding tunnels to the ePDG to form the new data path; a security tunnel between the mobile node and the security gateway, and an IP tunnel between the packet data network gateway and the security gateway. In order to prepare the handover to possible non-3GPP accesses, the two tunnels are pre-established, however maintained deactivated until their use is actually needed. Accordingly, when handing over to the non-3GPP network, the IP session may be continued without any significant interruption by activating the already established tunnels.
Owner:SOVEREIGN PEAK VENTURES LLC
Unmanned-gyroplane system used for automatic-inspection of bridges and tunnels and navigation method
ActiveCN104843176AFlexibleEffective dodgeNavigation by speed/acceleration measurementsSatellite radio beaconingUncrewed vehicleNavigation system
The invention provides an unmanned-gyroplane system used for automatic inspection of bridges and tunnels and a navigation method, belonging to the field of automatic detection of bridge and tunnel diseases. According to the invention, aimed at the characteristics of bridge and tunnel areas, the unmanned gyroplane inspection system which realizes autonomous navigation in virtue of GPS, laser radar and IMU is designed; and the system realizes autonomous inspection of an open bridge area by using a GPS navigation system and autonomous inspection of a closed tunnel area by using a laser radar navigation system, dodging of bridges, tunnels and motor vehicles via an automatic evadible system, and shooting of images of key areas, wherein the images are sent back to a ground station, and thematic pictures of diseases of bridge and tunnels are generated by the ground station and provided to related personnel for use. The unmanned-gyroplane system provided by the invention has the characteristics of mobility and flexibility in the process of inspection and has the advantages of a wide inspection coverage area, unblocking of traffic, real-time returning of live shots, etc.
Owner:恒华数元科技(天津)有限公司
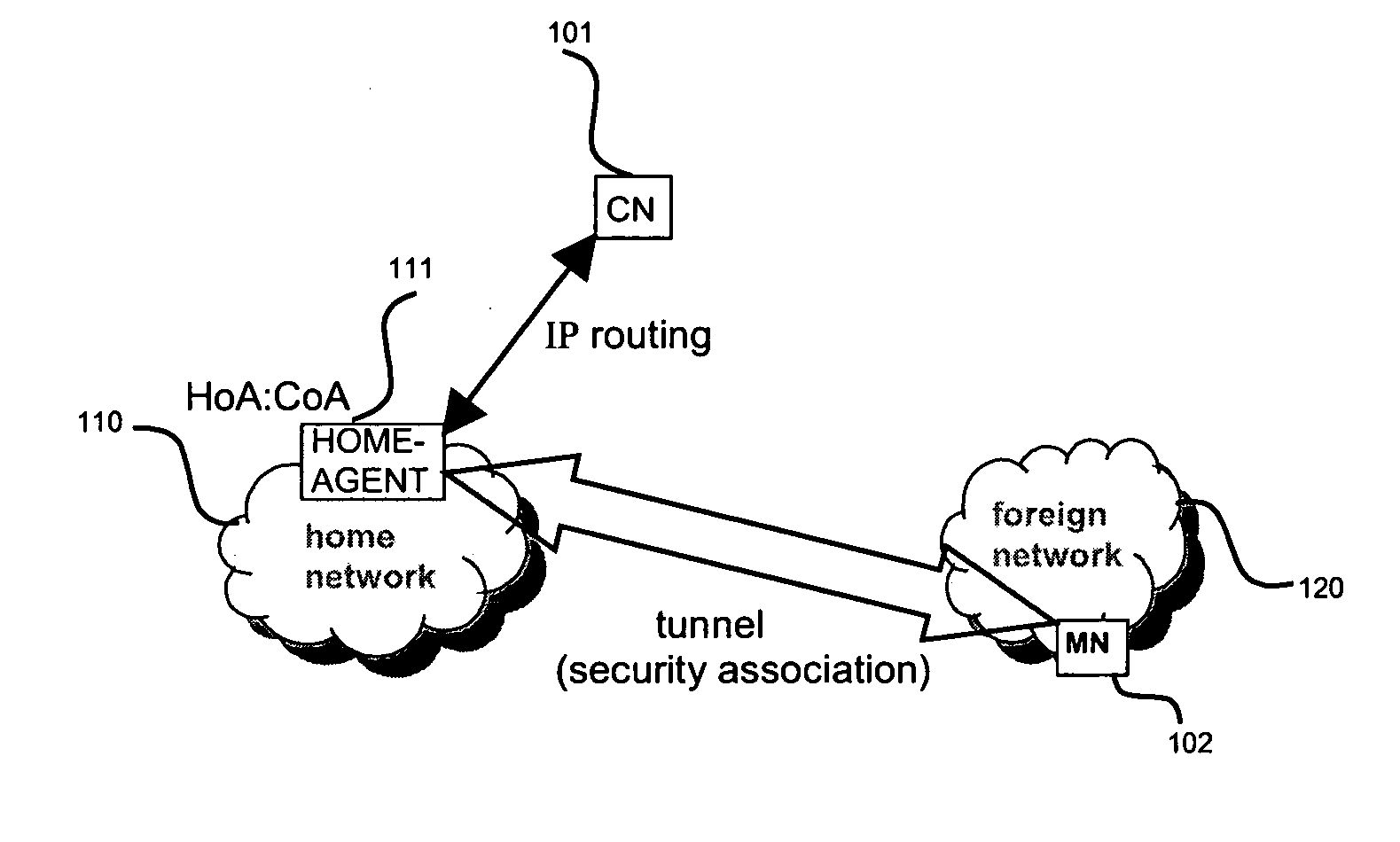
Route optimization of a data path between communicating nodes using a route optimization agent
InactiveUS20120044949A1Easy to optimizeImprove directionAssess restrictionData switching by path configurationSecurity associationDatapath
The invention relates to optimizing a data path between two communication nodes. A route optimization agent (ROA) is determined in the current network of the second communication node, preferably on the data path between the two communication nodes. Then, an IP tunnel is established between the first communication node and the ROA, the IP tunnel and the corresponding security association of said IP tunnel being based on the home address of the first communication node in its home network. The first communication node may have two IP tunnels based on the same home address, one to its home agent and one to the ROA. Corresponding routing entries and binding cache entries need to be established in the ROA and the first communication node so that all data packets between the two communication nodes are exchanged via the established IP tunnel over the ROA.
Owner:OPTIS WIRELESS TECH LLC
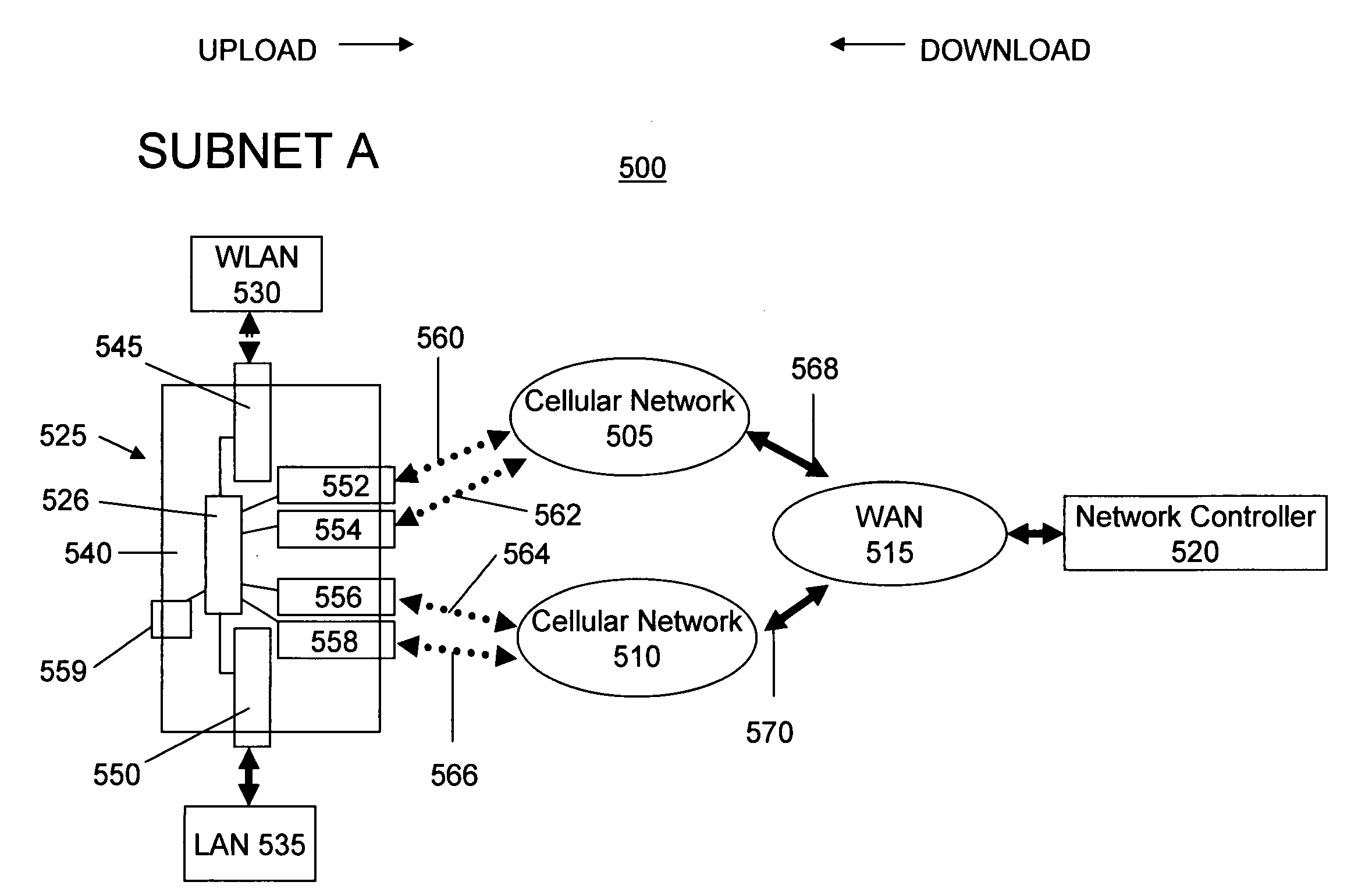
Mobile network configuration and method
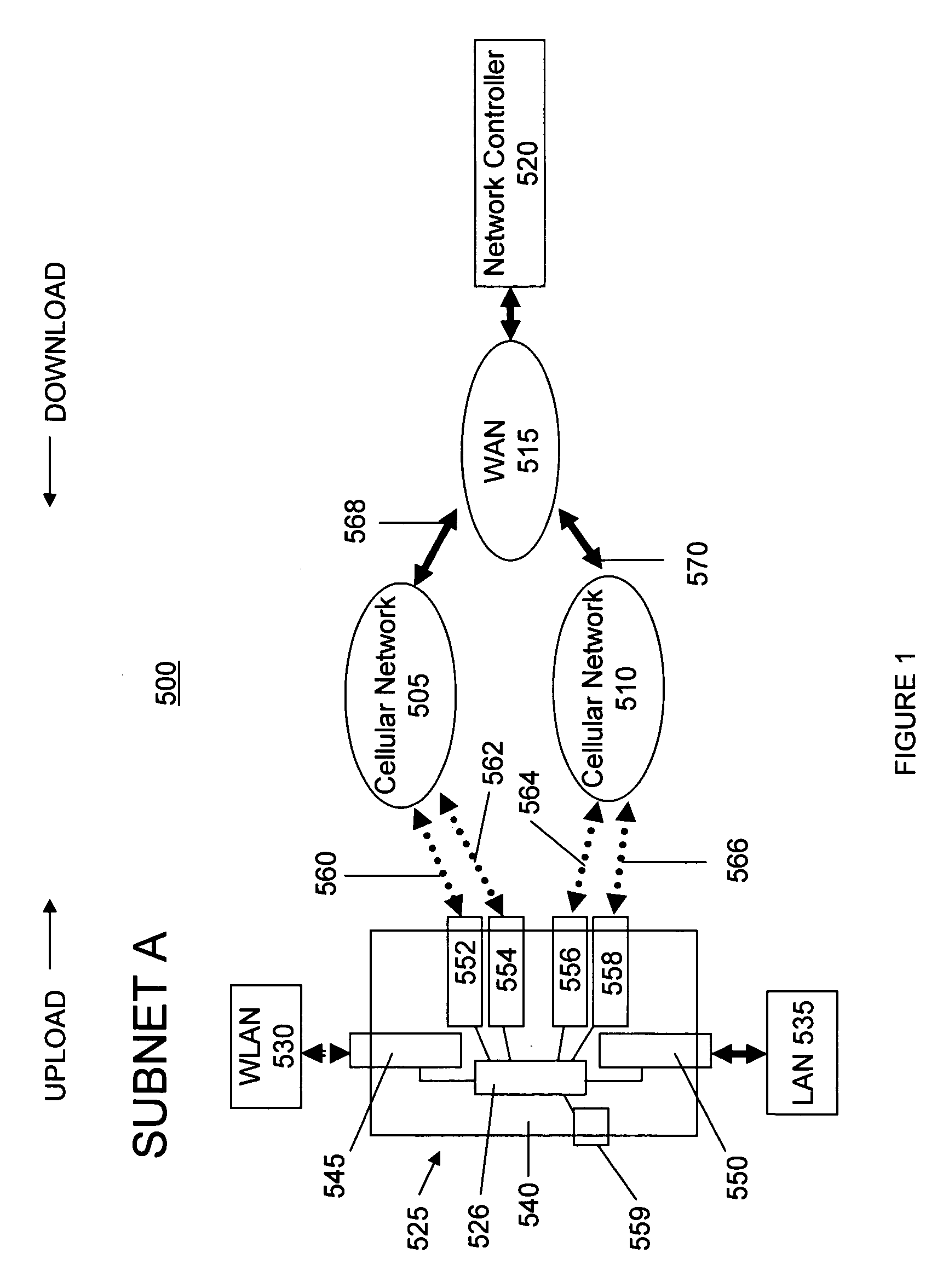
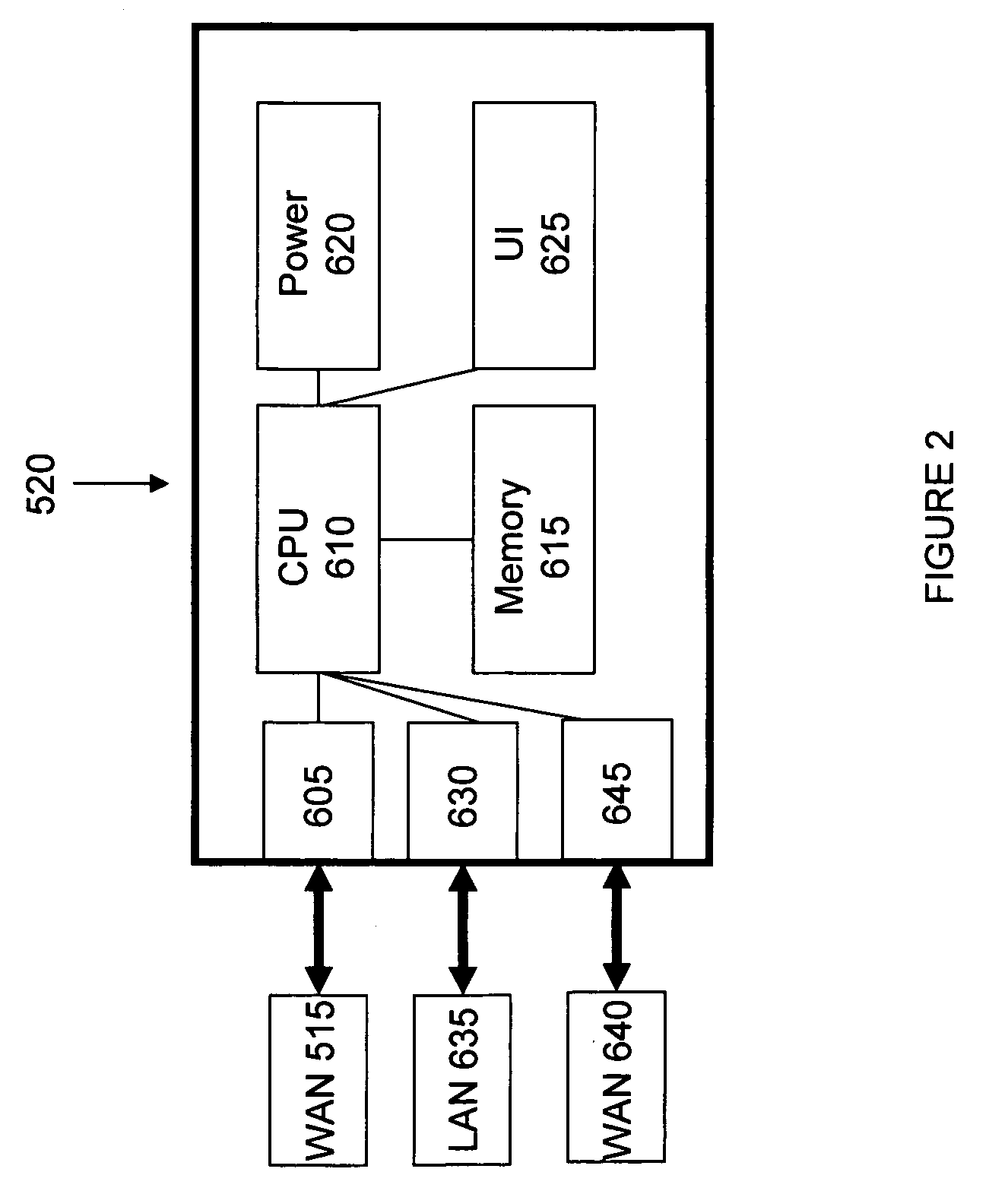
A mobile network configuration 500 includes a mobile router 525 forming one or more mobile subnets and including a plurality of cellular network interface devices 552, 554, 556, 558 installed thereon. The mobile network 500 further includes a network controller 520 installed as a node on a WAN 515. The mobile network 500 utilizes one or more cellular networks 505, 510 to provide network access to the WAN 515 via gateways 568, 570. The mobile router 525 provides a network interface between one or more local subnets 530, 535 and the at least one cellular network 505, 510. The mobile network 500 operates to establish an IP tunnel between the mobile router 525 and the network controller 520 for each of the plurality of cellular network interface devices 552, 554, 556, 558 installed on the mobile router 525 and to exchange network traffic between the mobile router and the network controller over any one of the IP tunnels.
Owner:WAAV INC
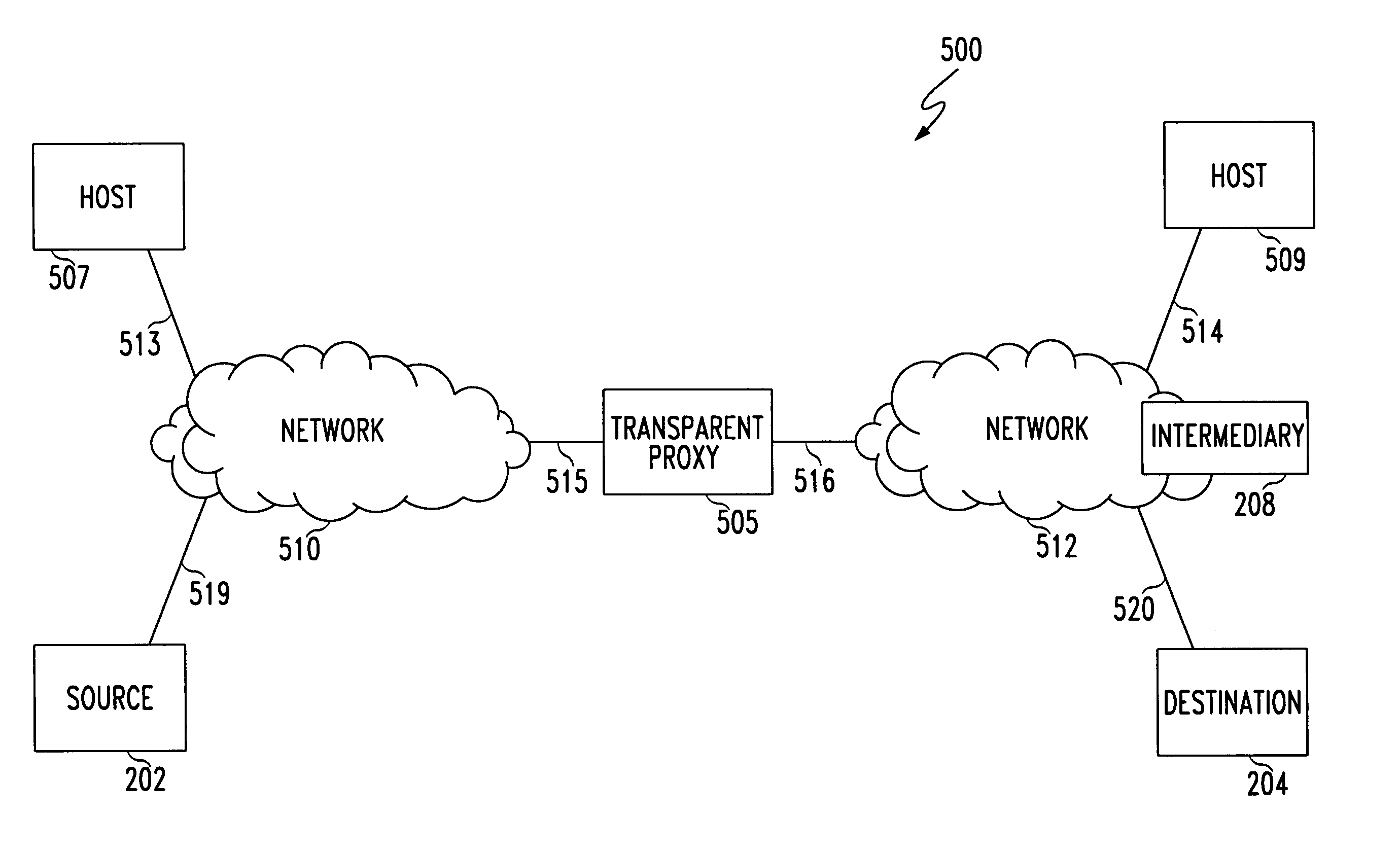
Apparatus and methods for providing translucent proxies in a communications network
InactiveUS7016973B1Improve throughputMultiple digital computer combinationsTransmissionData packIP tunnel
The Translucent Proxying of TCP (TPOT) device and methods use TCP-OPTIONS and IP tunneling to guarantee that all IP packets belonging to a specific TCP connection will traverse the proxy which intercepts the first packet of data. This guarantee allows the ad-hoc deployment of TPOT devices anywhere within the communication network, and does not restrict the placement of proxy devices at the edge of the network. Furthermore, no extra signaling support is required for the TPOT device to properly function while the addition of TPOT devices to communication networks significantly improves the throughput of intercepted TCP packets of data.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
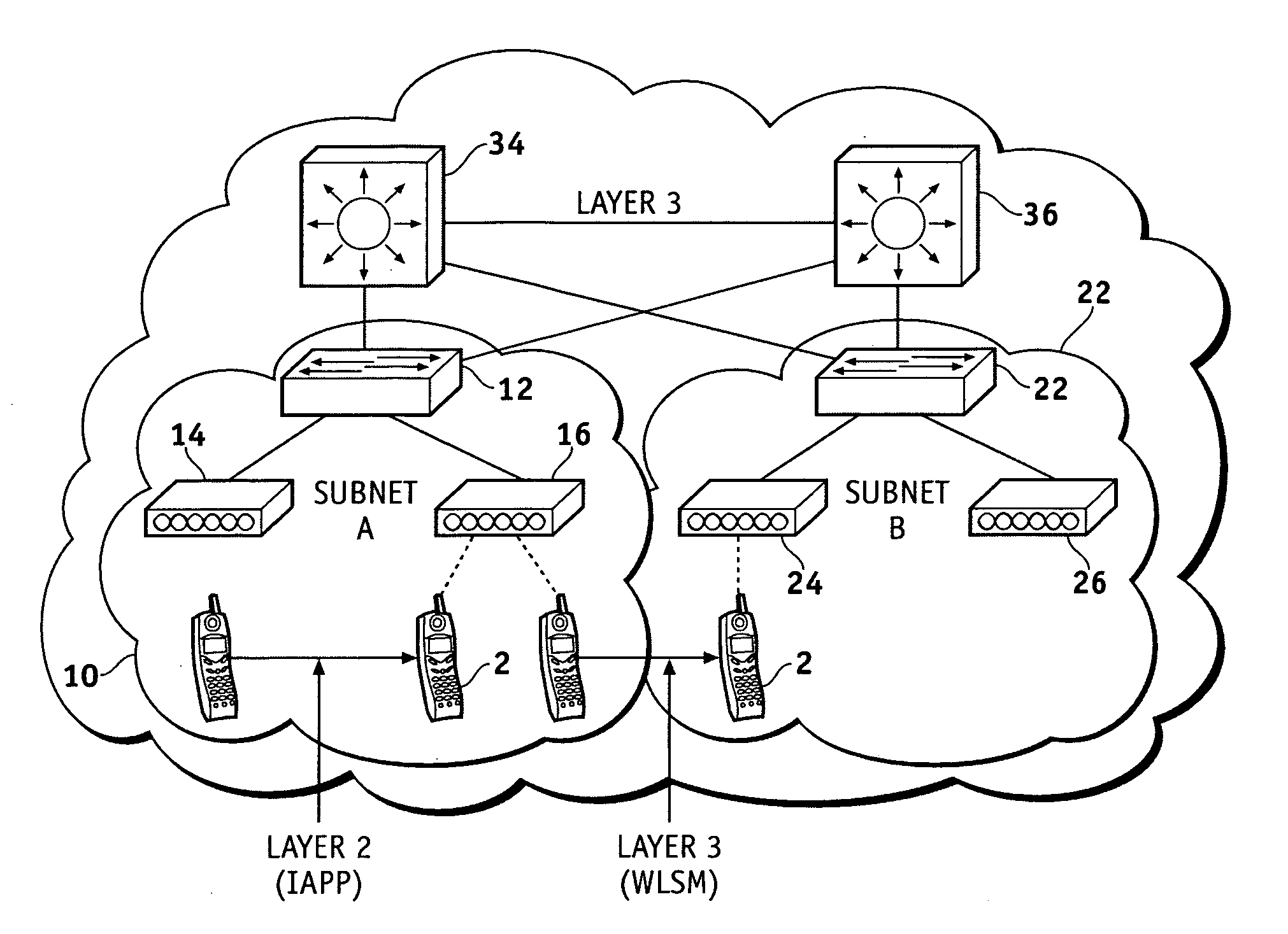
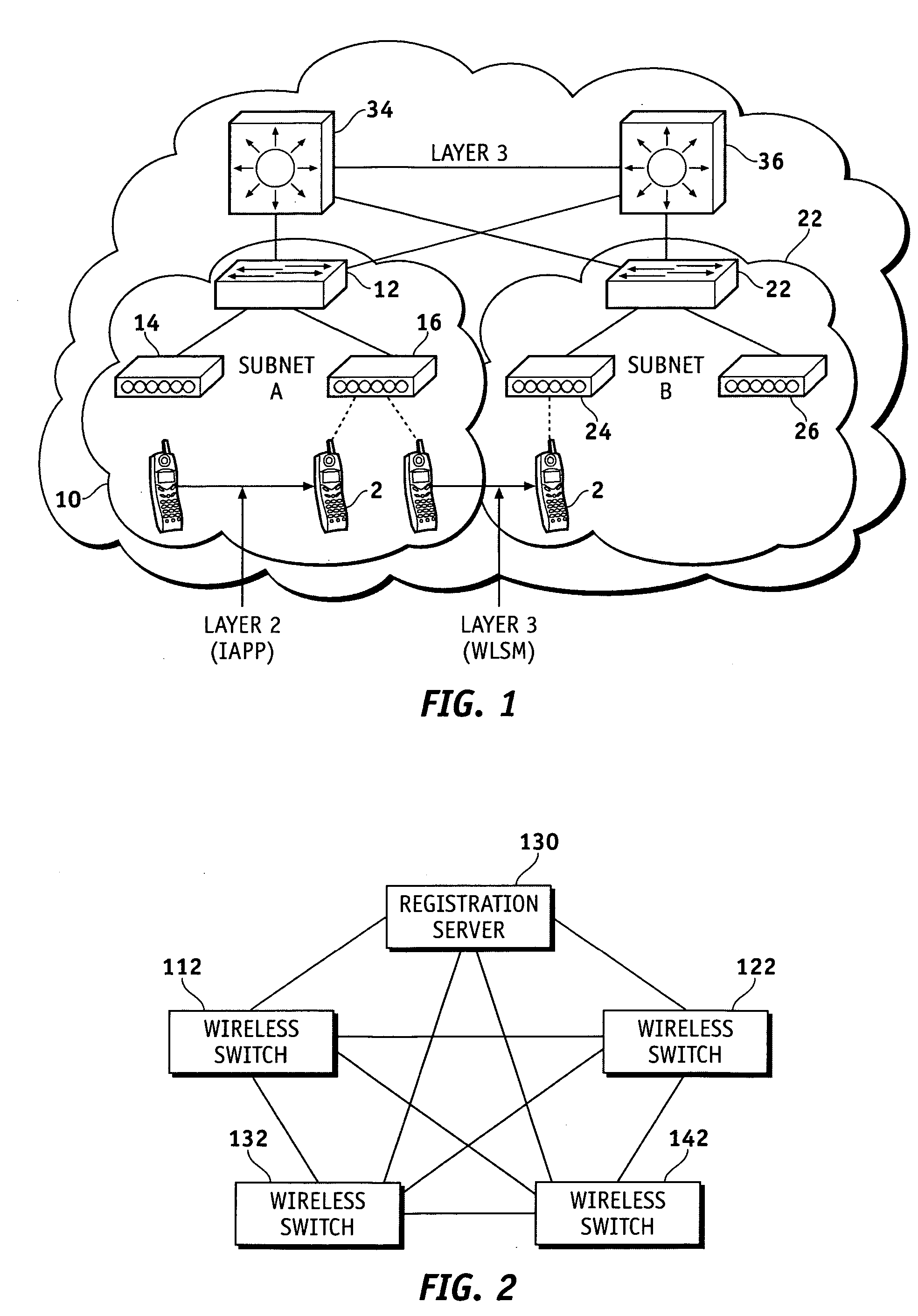
Method, system and apparatus for creating an active client list to support layer 3 roaming in wireless local area networks (WLANs)
ActiveUS20060245404A1Network topologiesData switching by path configurationTelecommunicationsIp address
Owner:EXTREME NETWORKS INC
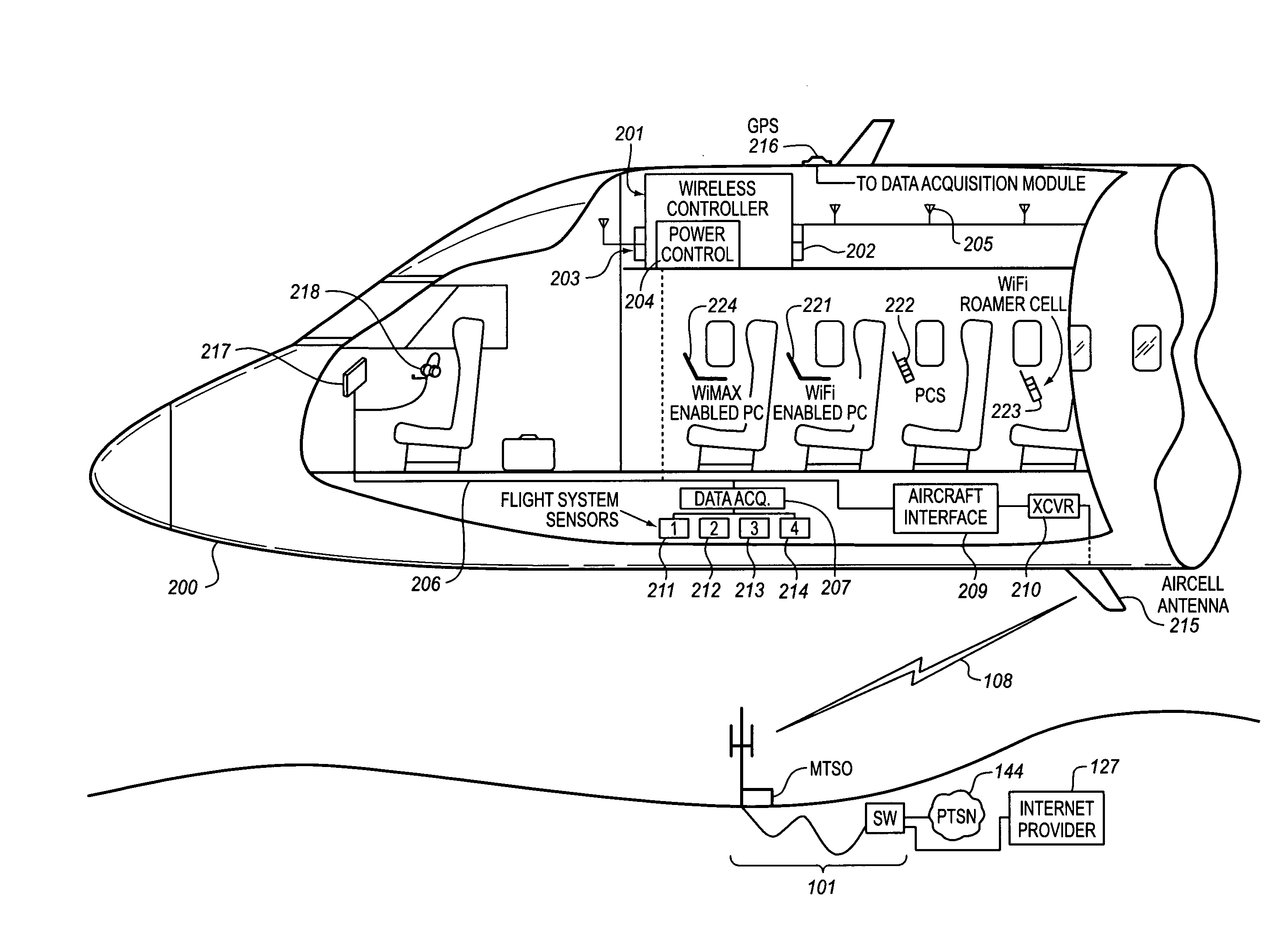
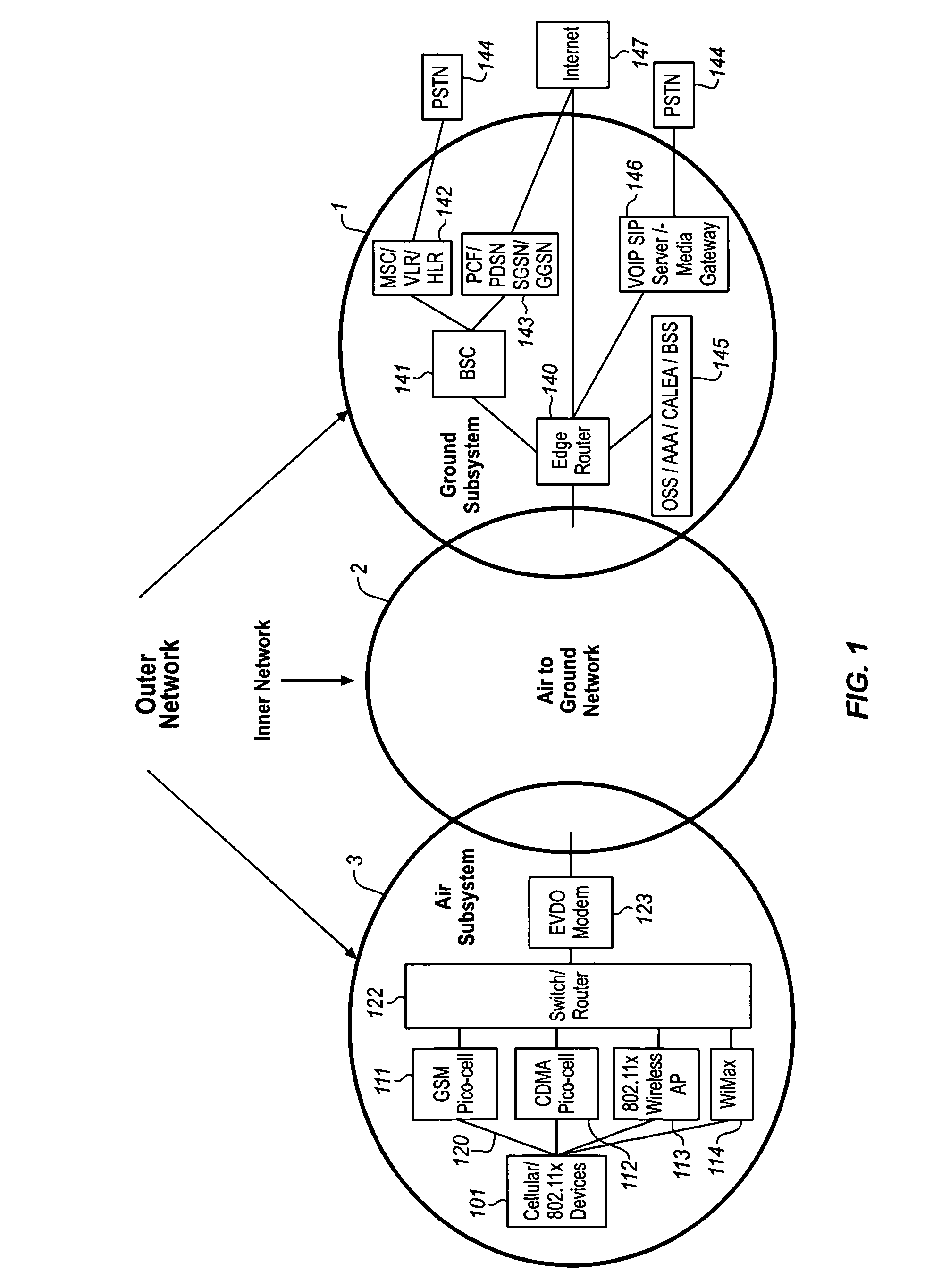
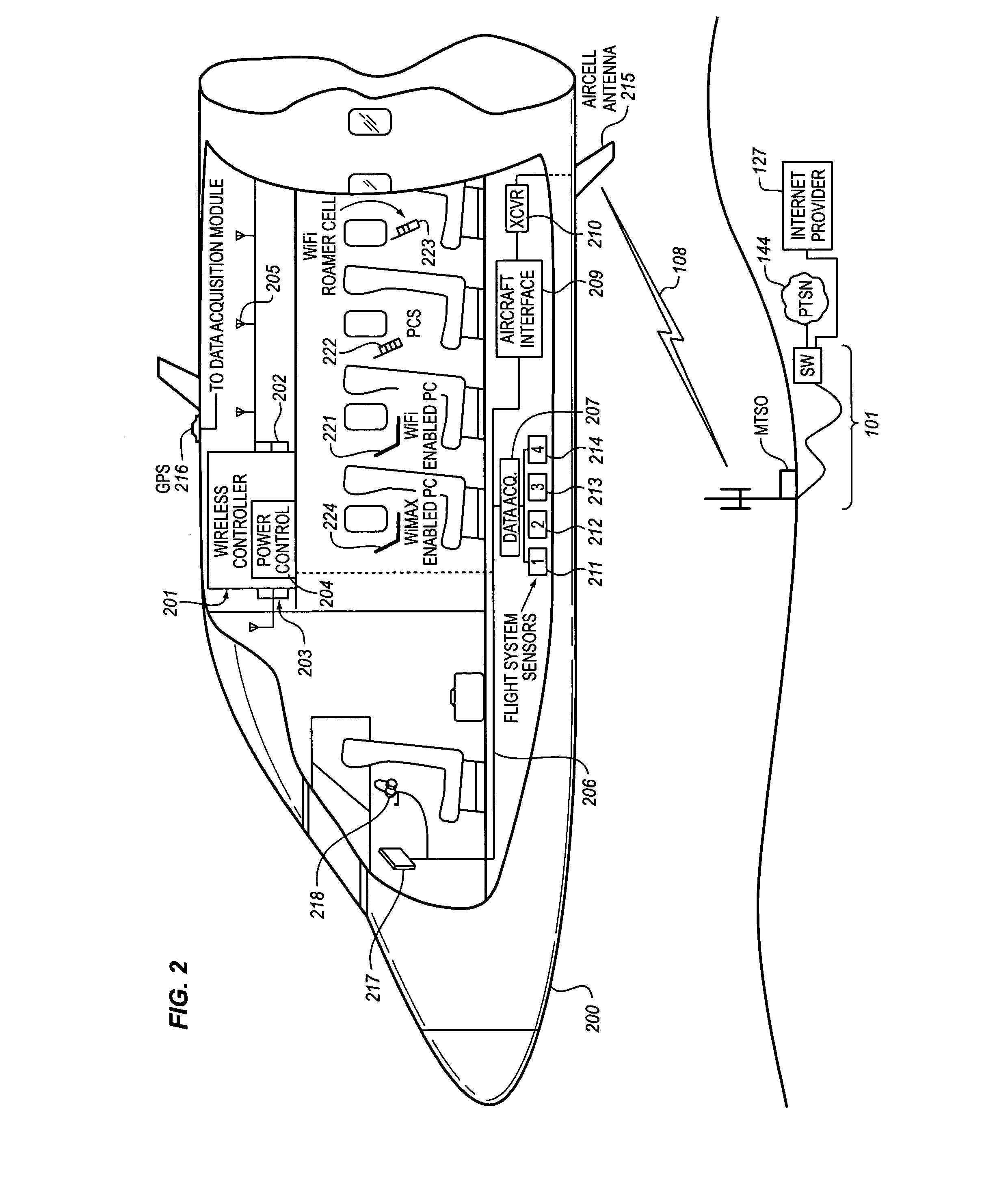
System for creating an air-to-ground IP tunnel in an airborne wireless cellular network to differentiate individual passengers
InactiveUS20090010200A1Improve travel experienceSimplifies provision of serviceNetwork topologiesConnection managementPoint-to-Point ProtocolIp address
The Aircraft Air-To-Ground IP Tunnel System provides wireless communication services to passengers located onboard an aircraft by storing data indicative of the individually identified passenger wireless devices located onboard the aircraft. The Aircraft Air-To-Ground IP Tunnel System assigns a single IP address to each Point-to-Point Protocol link connecting the aircraft network to the ground-based communication network and creates an IP subnet onboard the aircraft. The IP subnet utilizes a plurality of IP addresses for each Point-to-Point link, enabling each passenger wireless device to be uniquely identified with their own IP address. This is enabled since both Point-to-Point Protocol IPCP endpoints have pre-defined IP address pools and / or topology configured, so each Point-to-Point Protocol endpoint can utilize a greater number of IP addresses than one per link. Such an approach does not change IPCP or other EVDO protocols / messaging but allows this address to be directly visible to the ground-based communication network.
Owner:GOGO BUSINESS AVIATION LLC
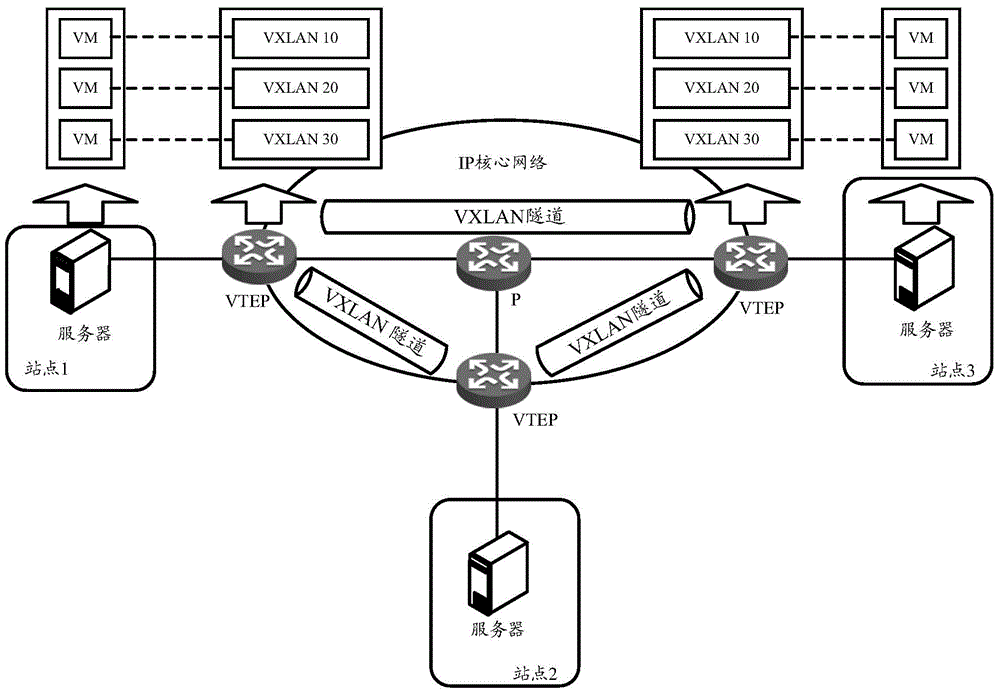
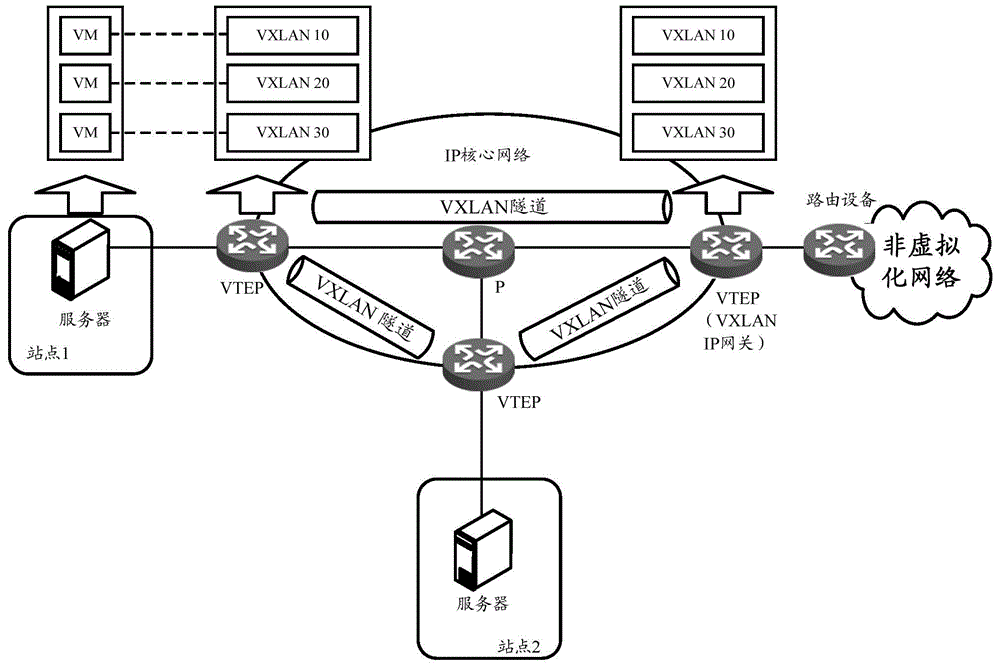
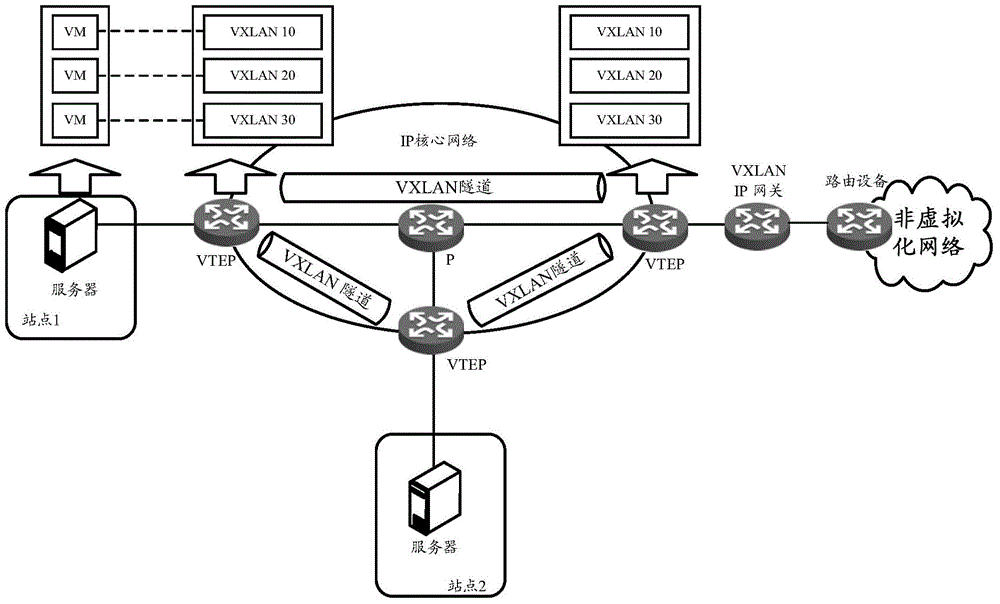
VXLAN (virtual extensible local area network)-based massage forwarding method and device
The invention discloses a VXLAN (virtual extensible local area network)-based massage forwarding method and device. The method includes the following steps that: when a current device is an opposite-end VTEP (VXLAN tunnel end point) of a main VTEP (VXLAN tunnel end point) and a standby VTEP (VXLAN tunnel end point), a tunnel between the current device and the main VTEP is established and is configured as a main tunnel, and a tunnel between the current device and the standby VTEP is established and is configured as a standby tunnel; after a user message to be sent to a non-virtual network is received, and the outgoing interface of the user message is determined as a tunnel; if the tunnel state of the tunnel in a tunnel table is active, the destination IP address of the tunnel is used, and the user message is encapsulated to form a VXLAN message, and the VXLAN message is forwarded through the tunnel; and if the tunnel state of the tunnel in the tunnel table is inactive, the destination IP address of an association tunnel of the tunnel is used, and the user message is encapsulated to form a VXLAN message, and the VXLAN message is forwarded through the association tunnel. According to the method, when the tunnel is the main tunnel, the association tunnel is the standby tunnel, and if the tunnel is the standby tunnel, the association tunnel is the main tunnel.
Owner:NEW H3C TECH CO LTD
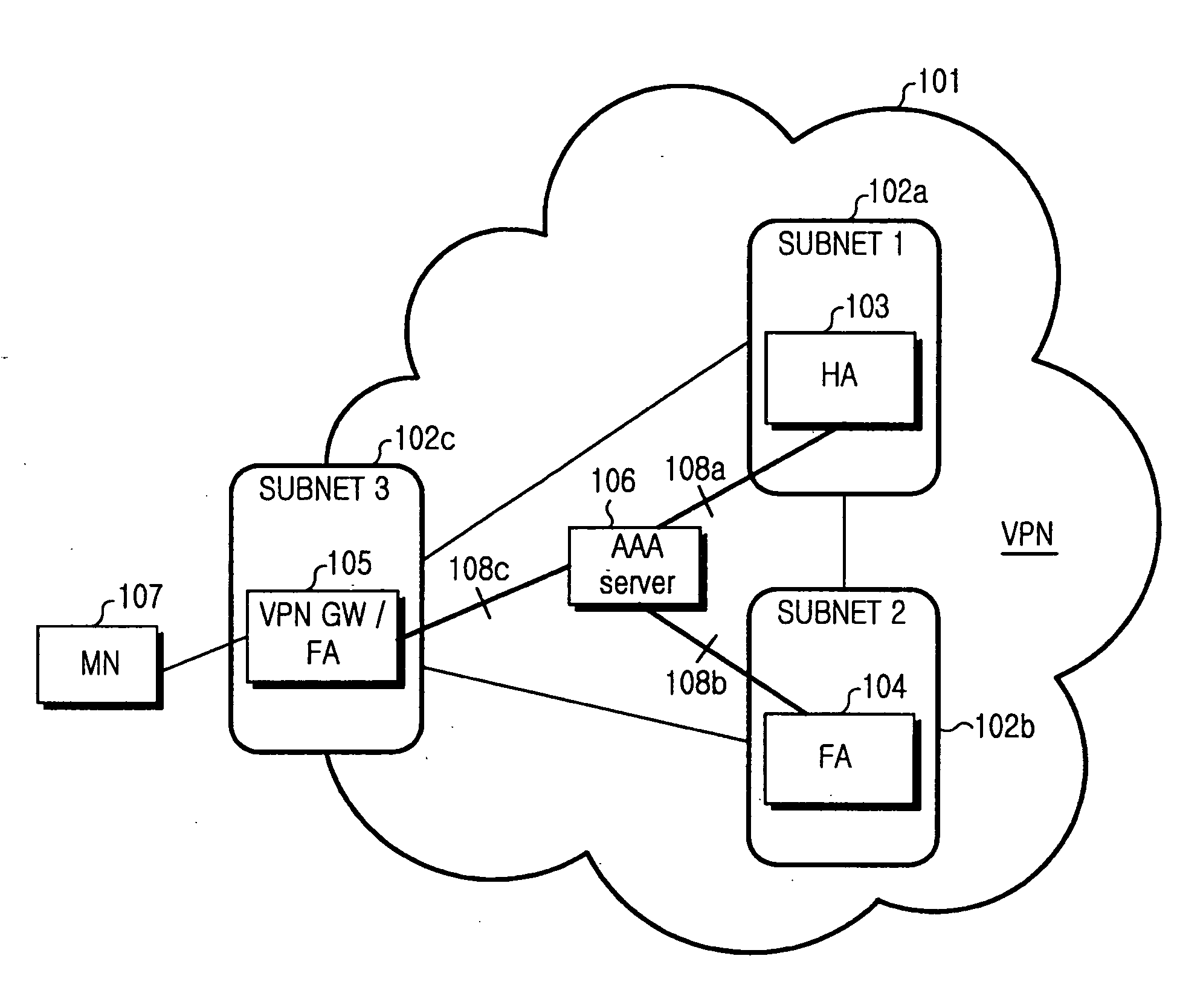
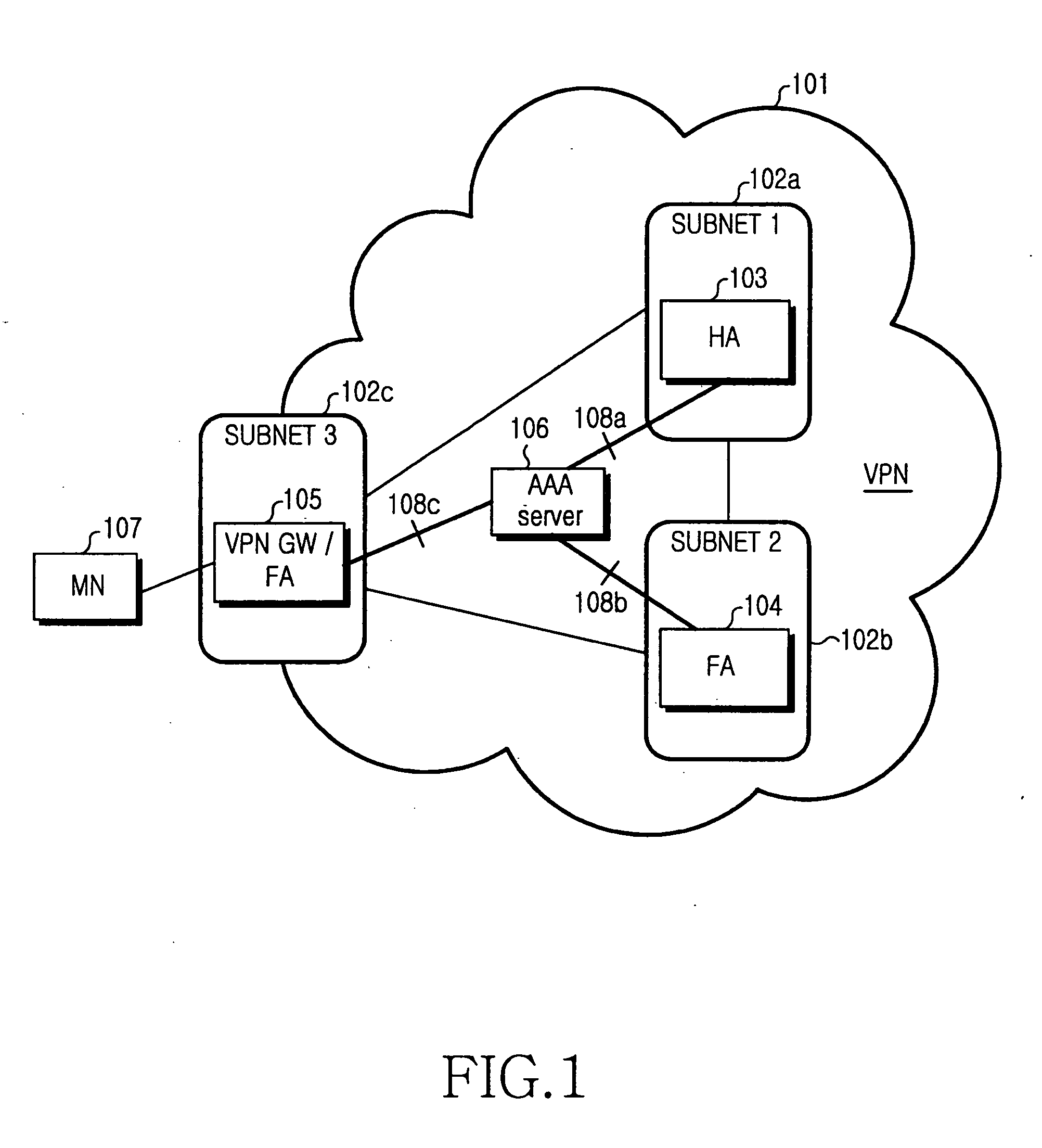
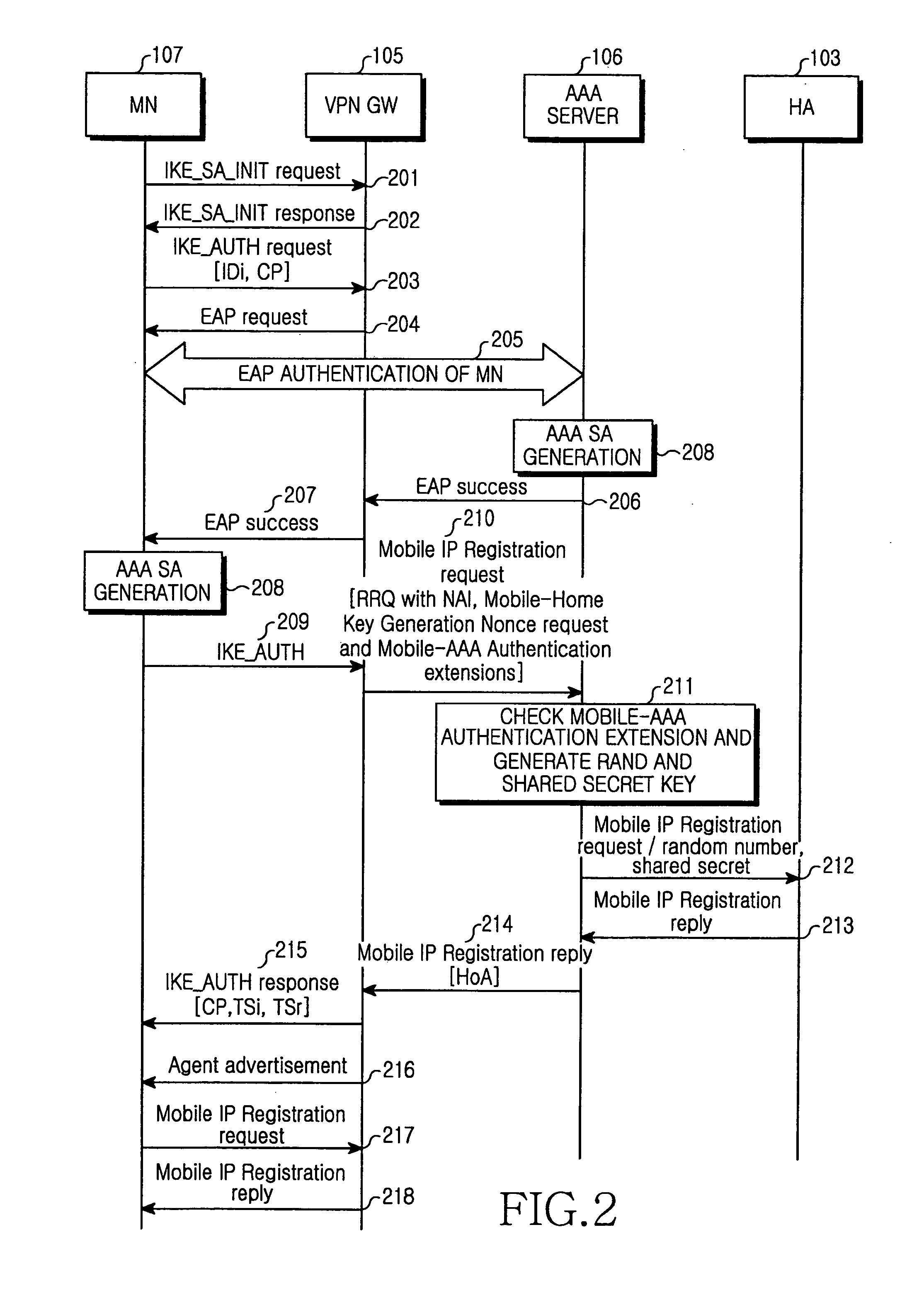
Communication method and apparatus using IP address of VPN gateway for mobile node in a VPN
ActiveUS20060104252A1Avoid overlapDigital data processing detailsMultiple digital computer combinationsTelecommunicationsIp address
A communication method and apparatus using the IP address of a gateway for an MN in a VPN are provided. When the MN is to access the VPN, the gateway acting an FA in the VPN performs a Mobile IP registration on behalf of the MN and is allocated a HoA for the MN from an HA. Therefore, the number of addresses required for the Mobile IP registration of the MN is reduced and overlap between an IP-in-IP tunnel for Mobile Internet and an IPsec tunnel for the VPN is avoided. As a result, packet transmission overhead is reduced.
Owner:SAMSUNG ELECTRONICS CO LTD +1
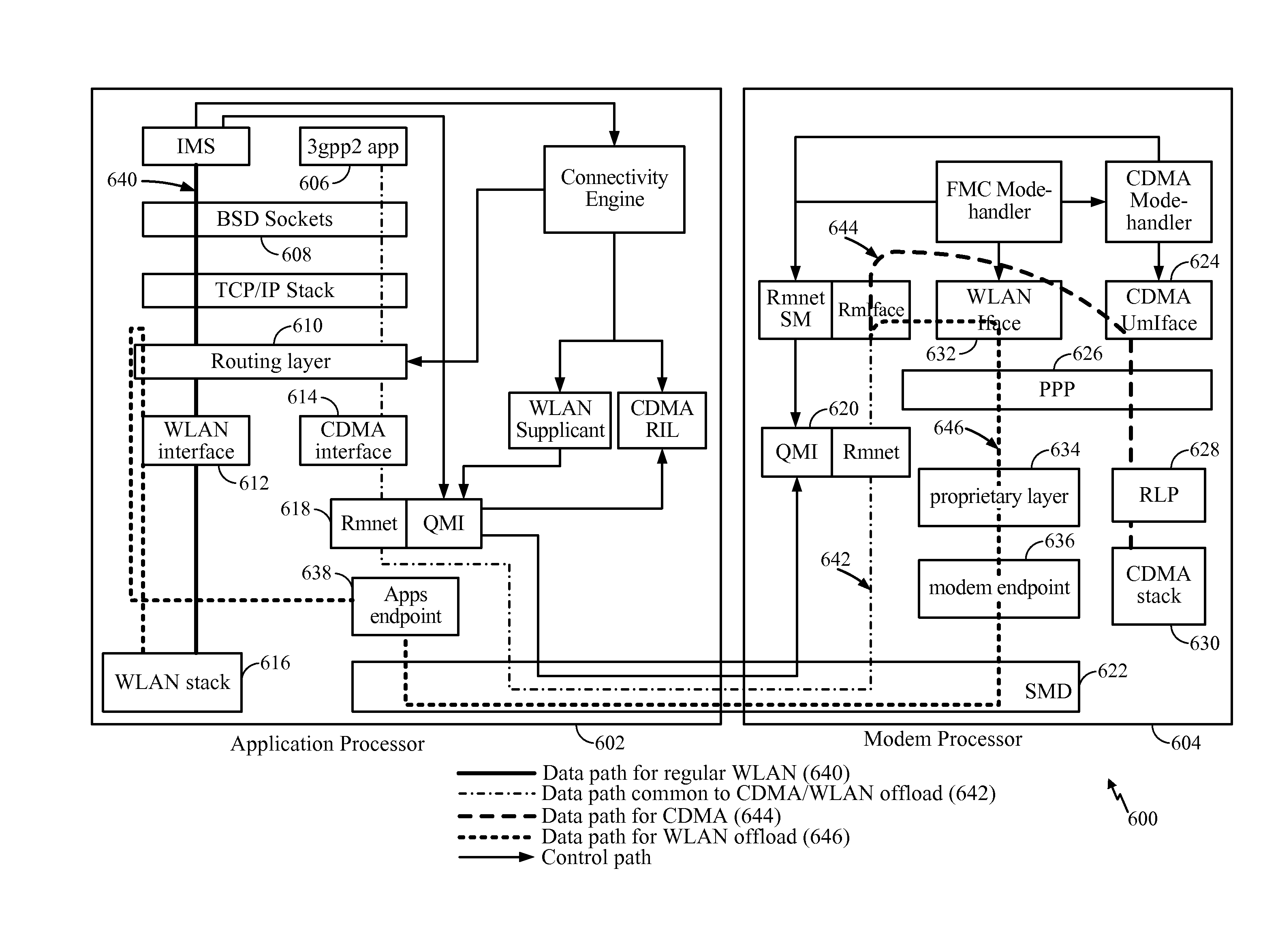
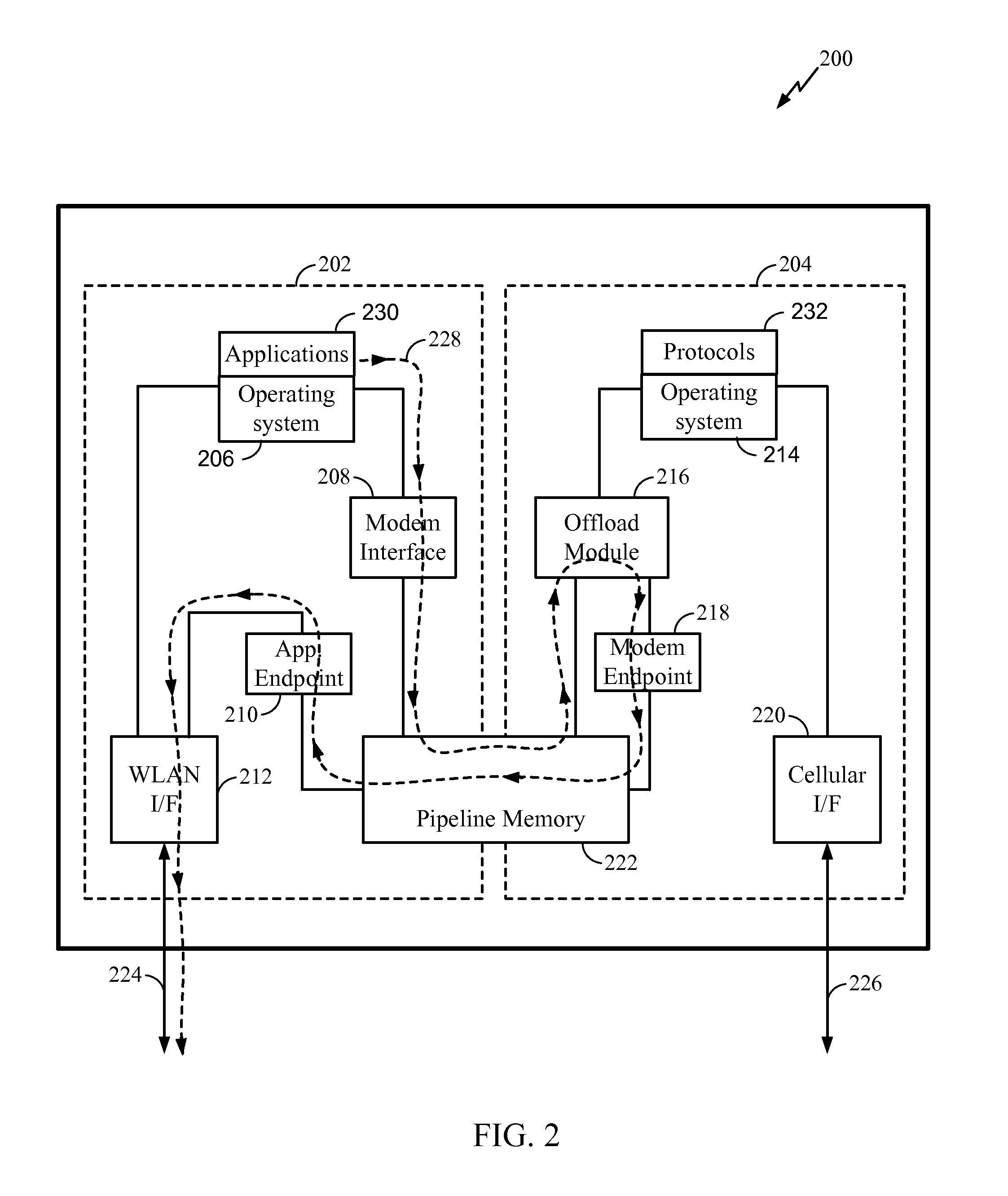
Architecture for WLAN offload in a wireless device
Architecture for performing WLAN offload in a wireless device is disclosed. In an exemplary embodiment, an apparatus includes an application section configured to form IP packets from data to be transmitted, a modem section configured to apply a cellular protocol to the IP packets to form cellular protocol packets, an endpoint configured to encapsulate the cellular protocol packets to form outer IP tunnel packets, and a WLAN interface configured to transmit the outer IP tunnel packets over a WLAN communication channel. In another exemplary embodiment, an apparatus includes a WLAN interface configured to receive outer IP tunnel packets over a WLAN communication channel, an endpoint configured to extract cellular protocol packets from the outer IP tunnel packets, a modem processor configured to remove a cellular protocol from the cellular protocol packets to form IP packets, and an application processor configured to extract received data from the IP packets.
Owner:QUALCOMM INC
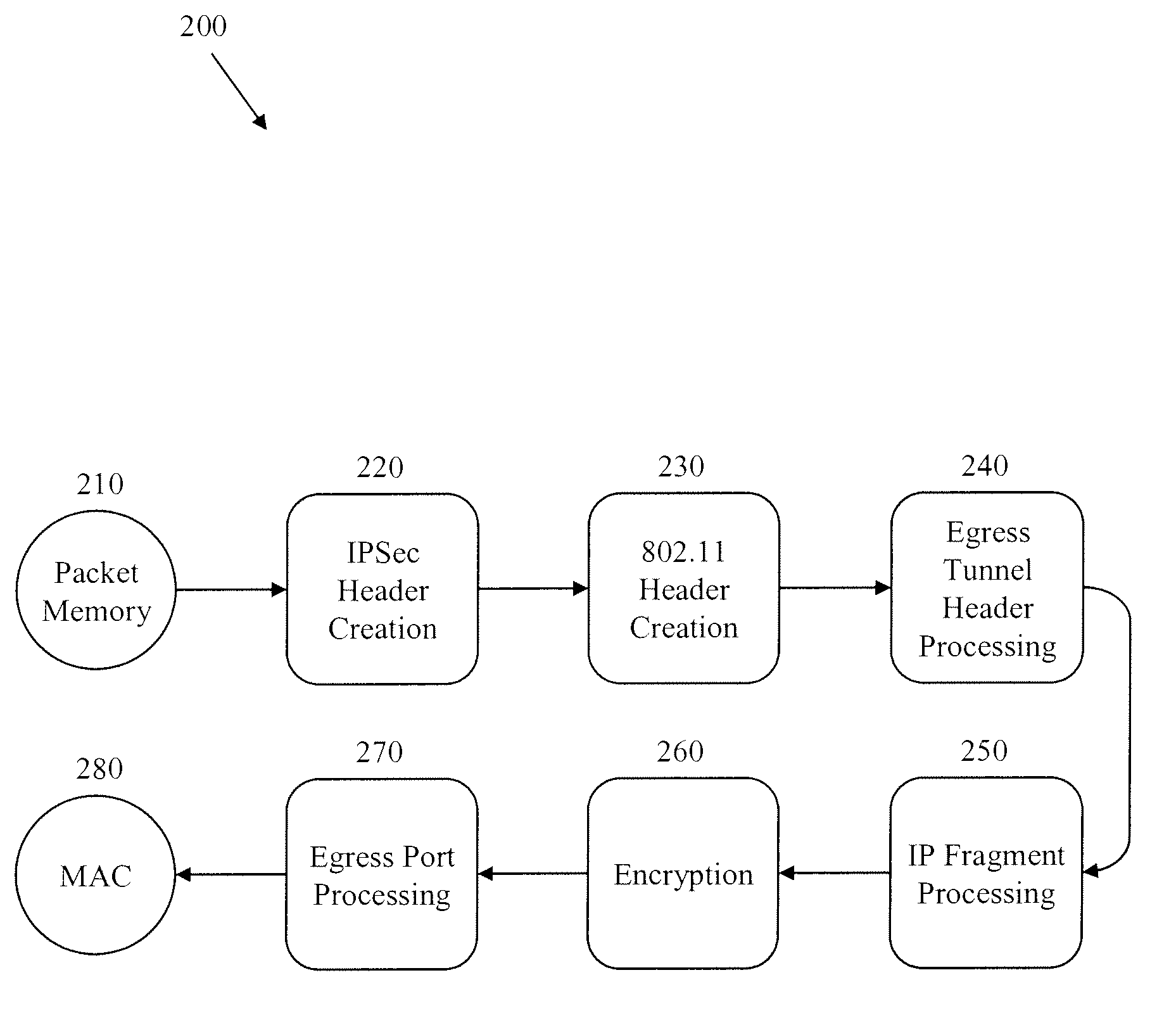
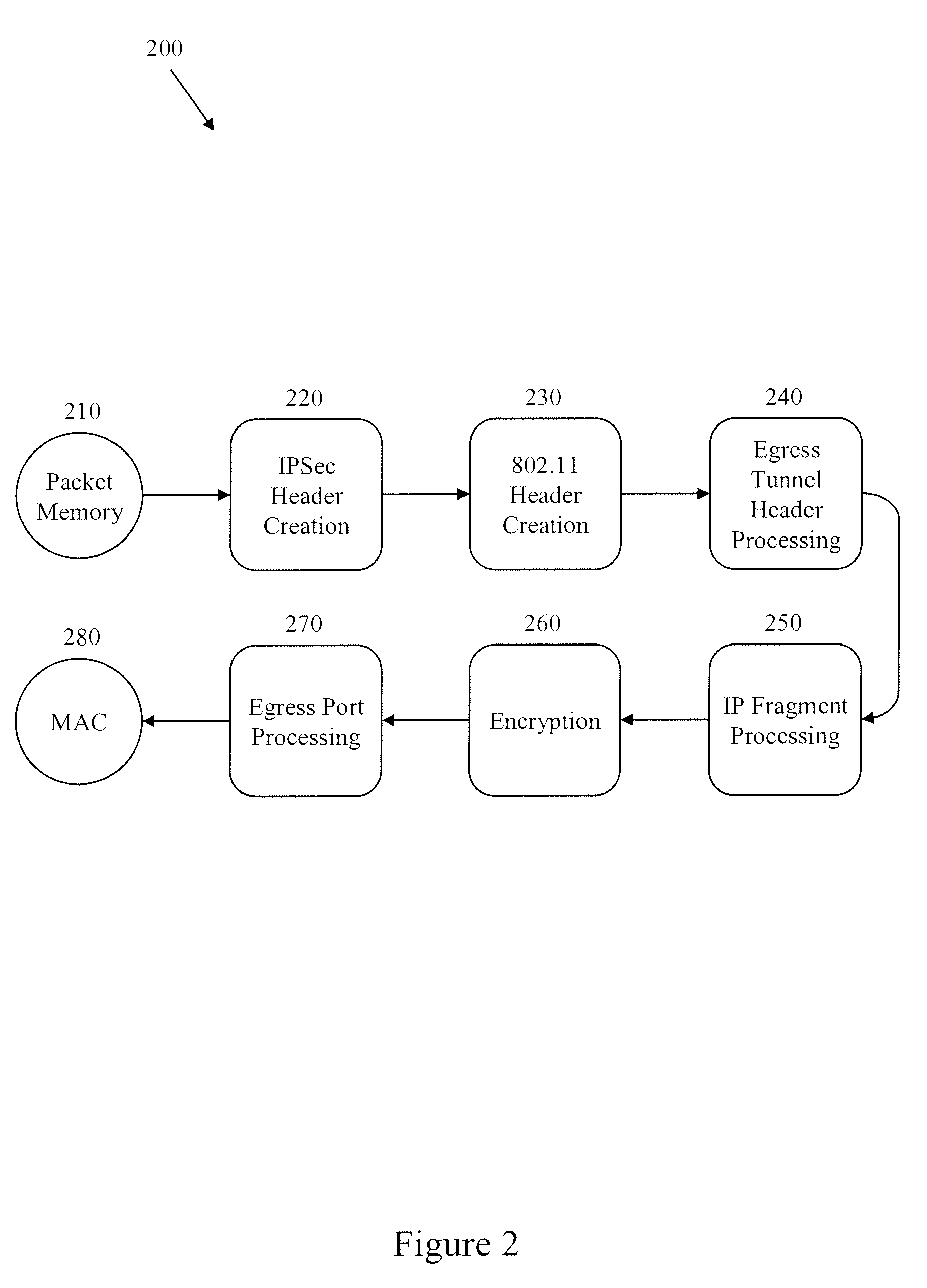
Methods and Systems for Fragmentation and Reassembly for IP Tunnels in Hardware Pipelines
A novel flow-through architecture for fragmentation and reassembly of tunnel packets in network devices is presented. The fragmentation and reassembly of tunneled packets are handled in the hardware pipeline to achieve line-rate processing of the traffic flow without the need for additional store and forward operations typically provided by a host processor or a co-processor. In addition, the hardware pipeline may perform fragmentation and reassembly of packets using encrypted tunnels by performing segment-by-segment crypto. A network device implementing fragment reassembly can include an ingress hardware pipeline that reassembles fragmented packets between a media access control (MAC) of the device and an output packet memory of the device, where the incoming fragmented packets can be encrypted and / or tunneled. A network device implementing packet fragmentation can include an egress hardware pipeline that fragments packets between an input packet memory of the device and the MAC, where the outgoing fragments can be encrypted and / or tunneled.
Owner:SINETT CORP
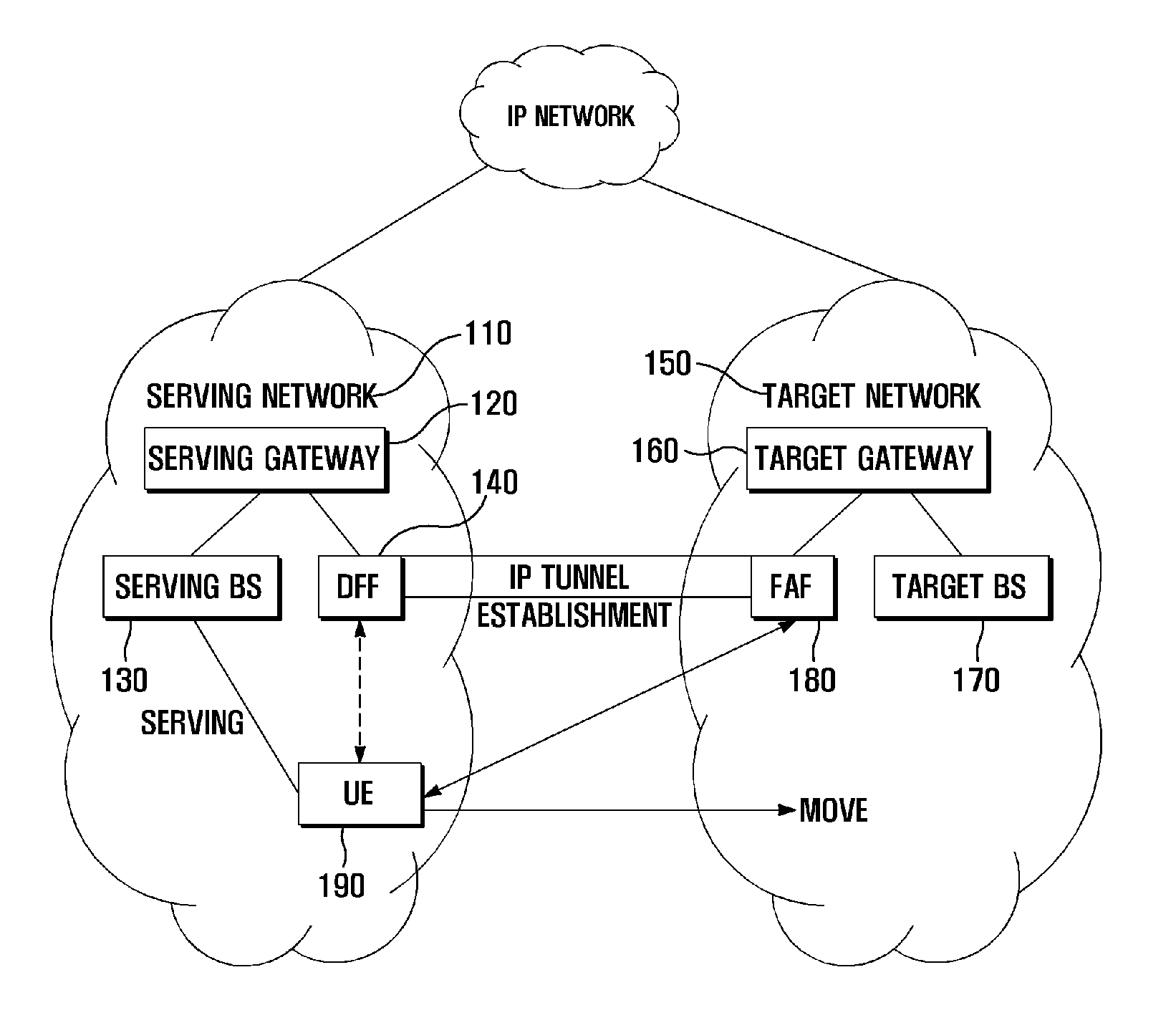
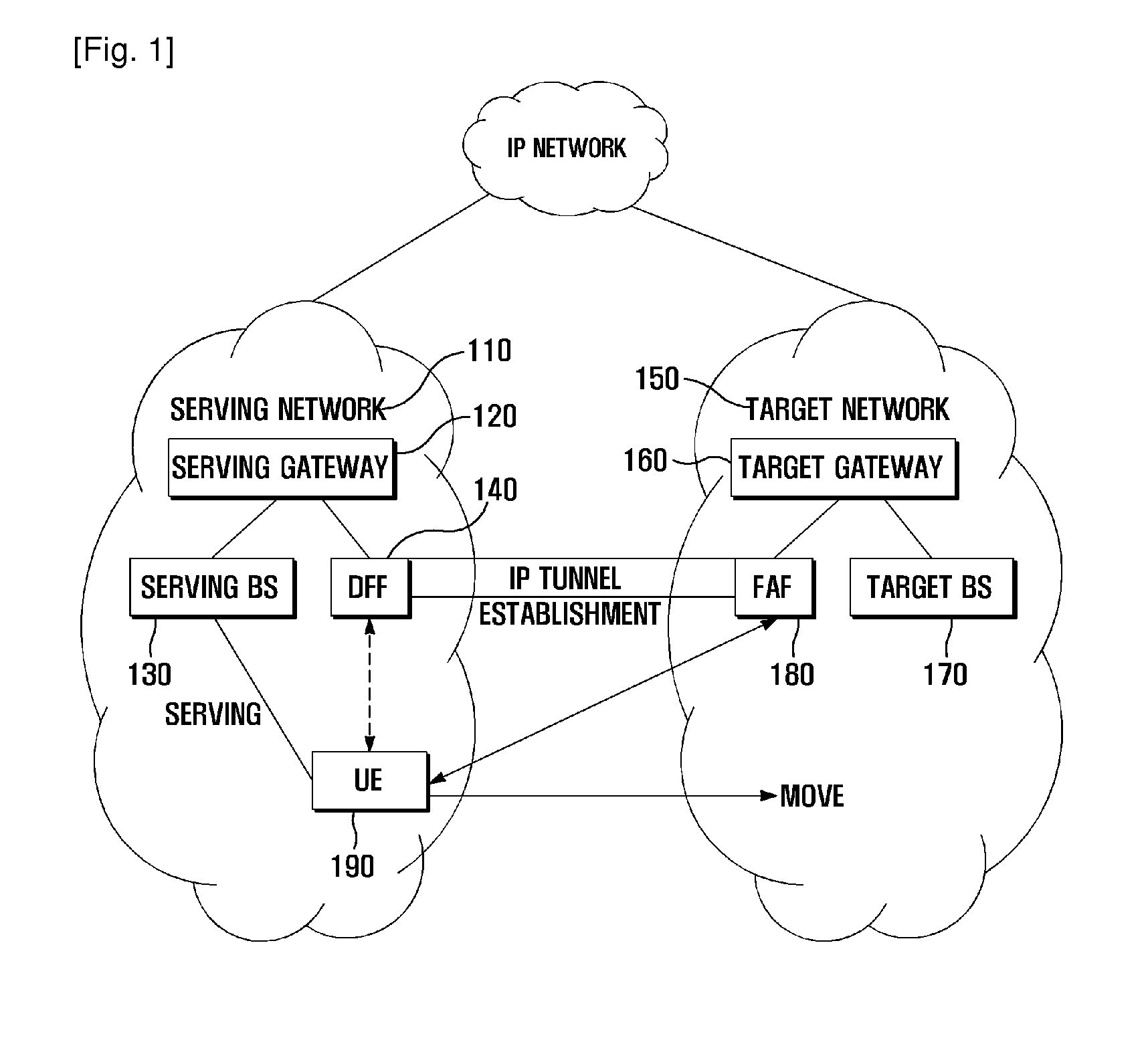
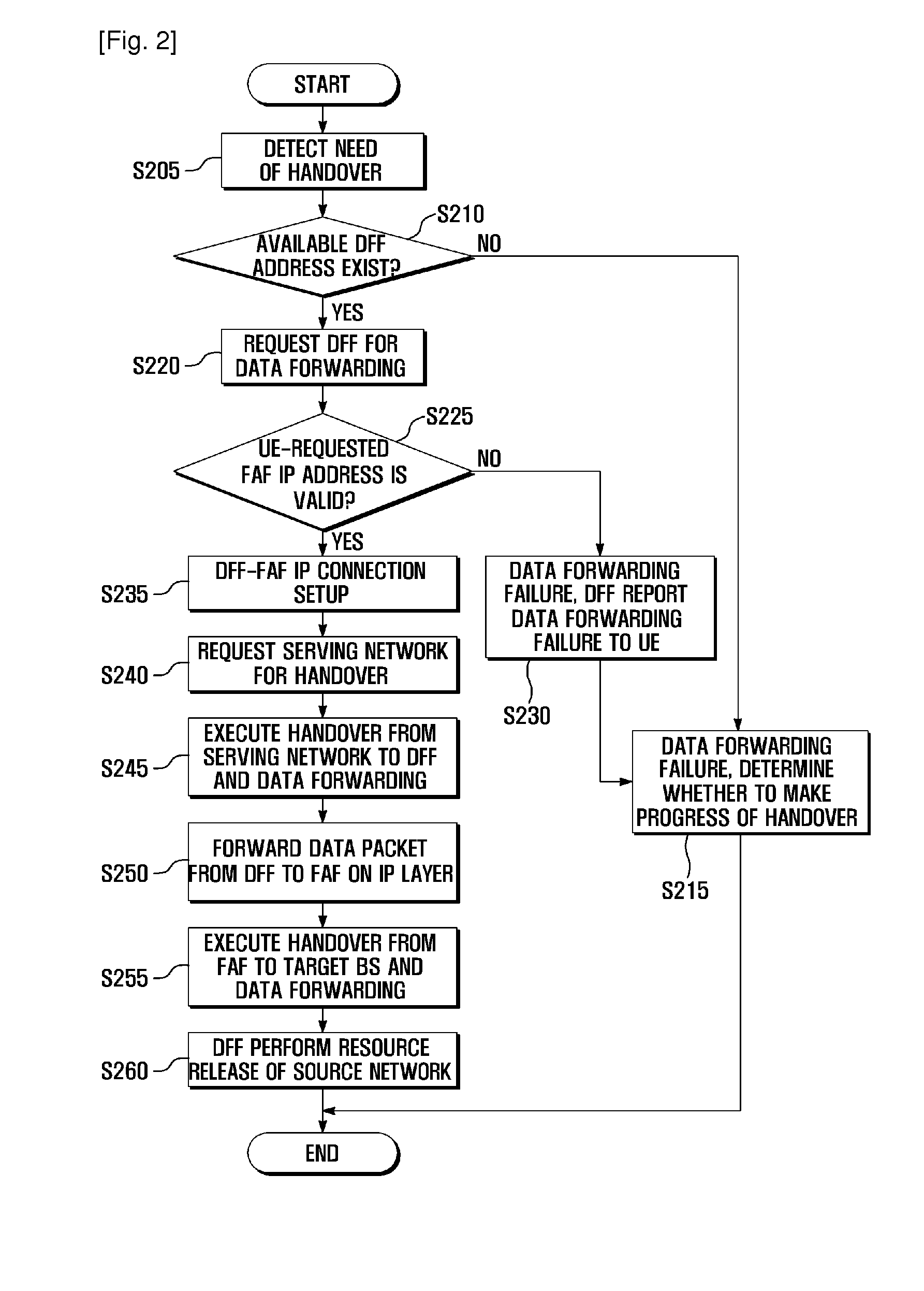
Data forwarding method and system for vertical handover
ActiveUS20110211559A1Minimize data lossWireless commuication servicesSecuring communicationIP tunnelData loss
A data forwarding method and system is provided for avoiding data loss during a vertical handover by forwarding data through an IP tunnel established between a newly introduced network entity called a Data Forwarding Function of the serving network and a Forward Attachment Function of a target network. A data forwarding method of a data forwarding unit located in a serving network for a vertical handover according to the present invention includes receiving an address of a forwarding attachment unit located in a target network and a data forwarding preparation request that are transmitted by a user equipment; establishing an Internet Protocol (IP) tunnel to the forwarding attachment unit according to the data forwarding preparation request; and forwarding, when a vertical handover is initiated, handover packets to the forwarding attachment unit through the IP tunnel.
Owner:SAMSUNG ELECTRONICS CO LTD +1
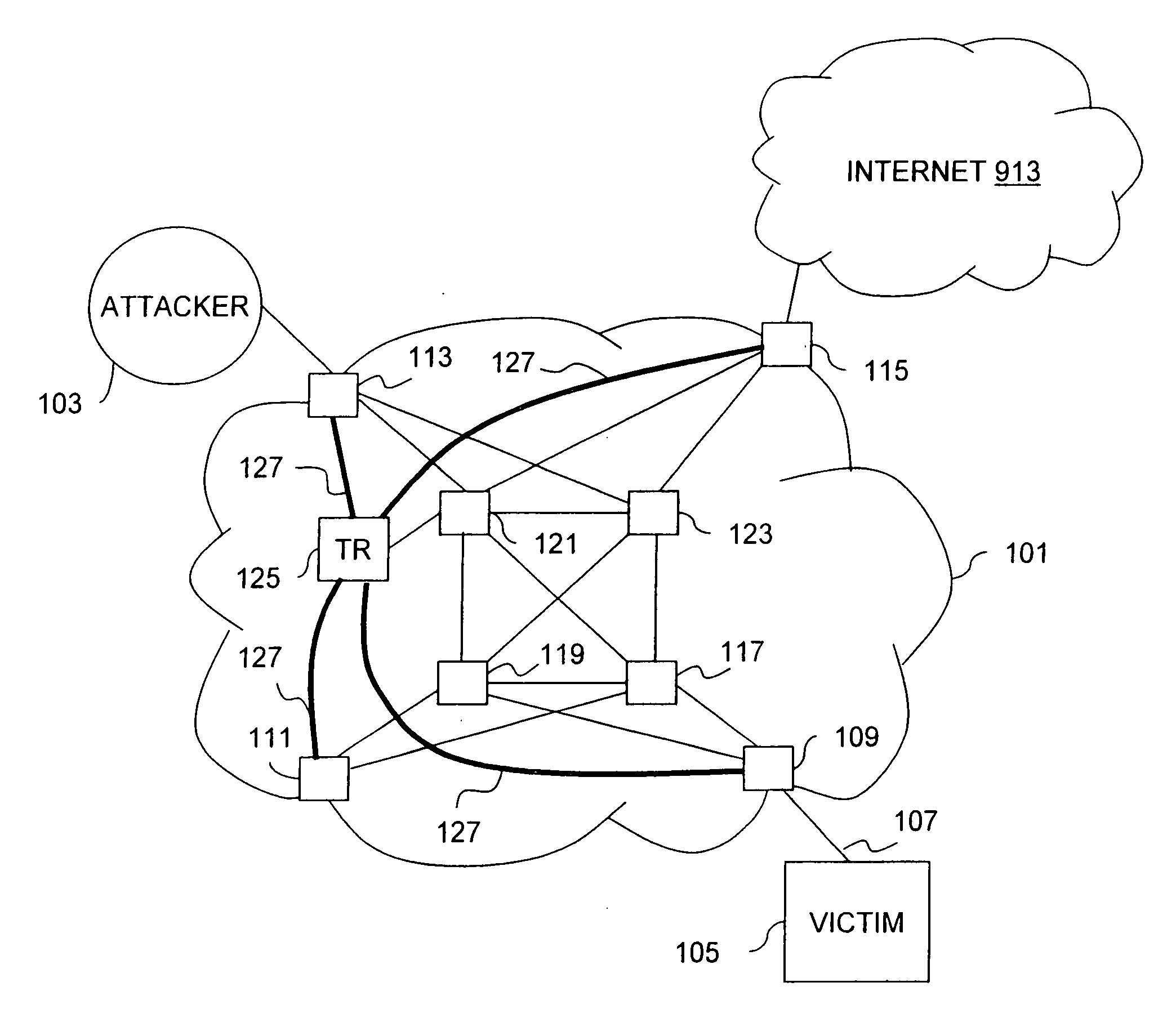
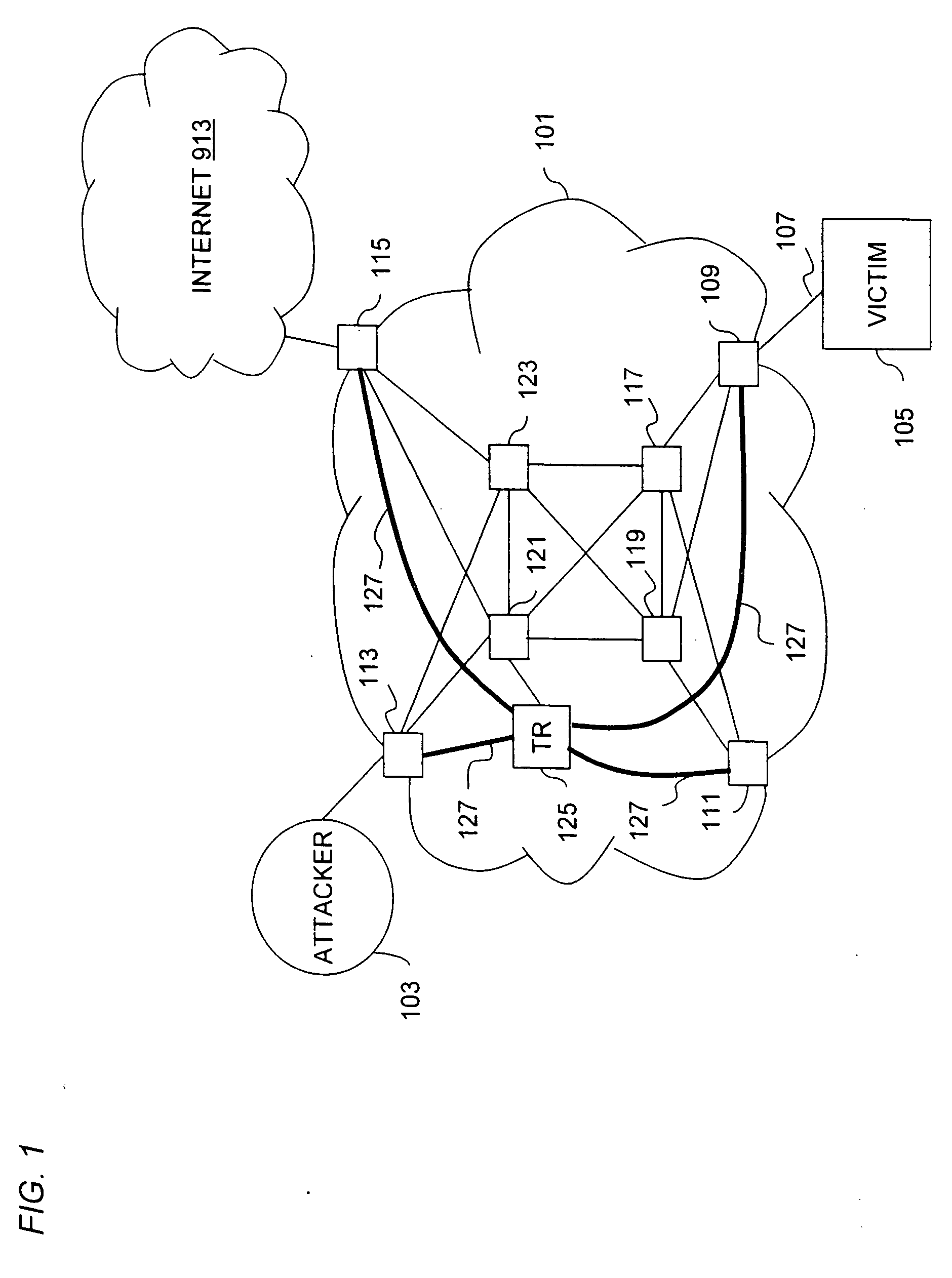
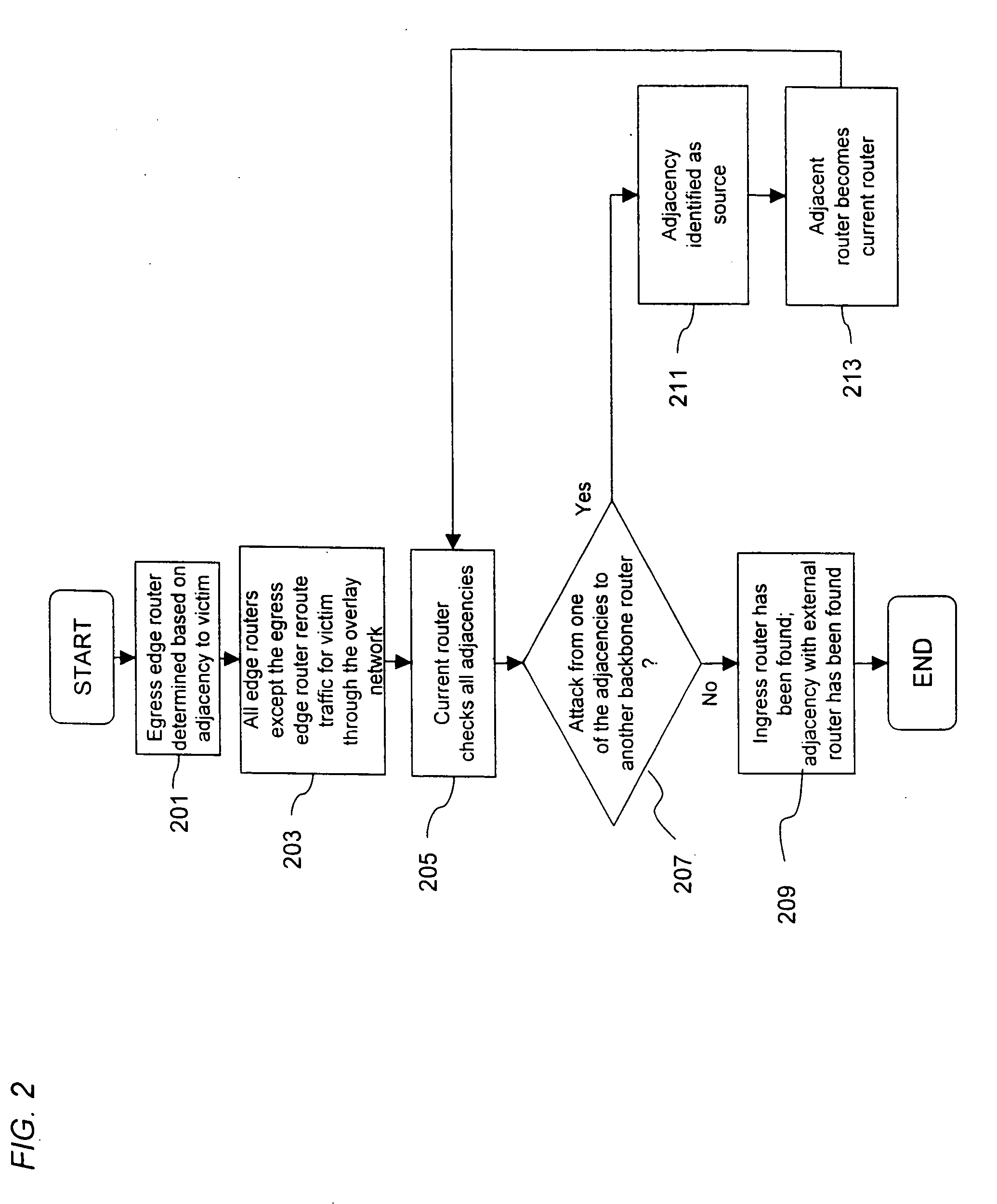
Overlay network for tracking denial-of-service floods in unreliable datagram delivery networks
ActiveUS20060156402A1Low costDeployment to minimizedMemory loss protectionUser identity/authority verificationService provisionIP tunnel
An approach for tracking denial-of-service (DoS) flood attacks using an overlay IP (Internet Protocol) network is disclosed. One or more tracking routers form an overlay tracking network over the network of an Internet Service Provider (ISP). The ISP network includes numerous transit routers and edge routers. The tracking routers communicate directly with all the edge routers using IP tunnels. The edge routers within the ISP network perform security diagnostic functions, in part, to identify a DoS flood attack that has been launched by one or more attackers. To track down an attacker, an egress edge router identifies the DoS flood attack datagrams, rerouting these datagrams to the overlay tracking network. The tracking routers perform hop-by-hop input debugging to identify the ingress edge router associated with the source of the DoS flood attack.
Owner:PALO ALTO NETWORKS INC
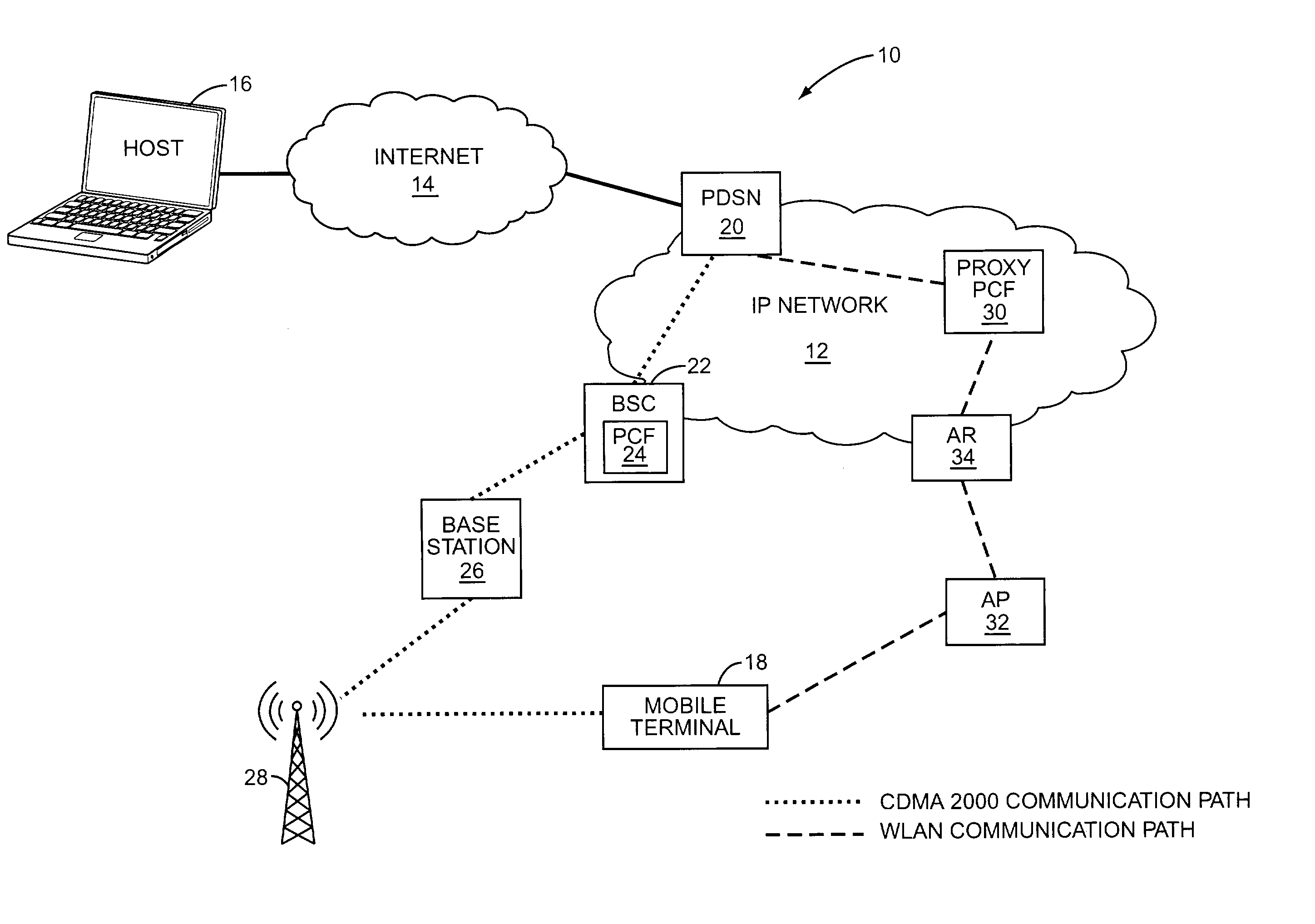
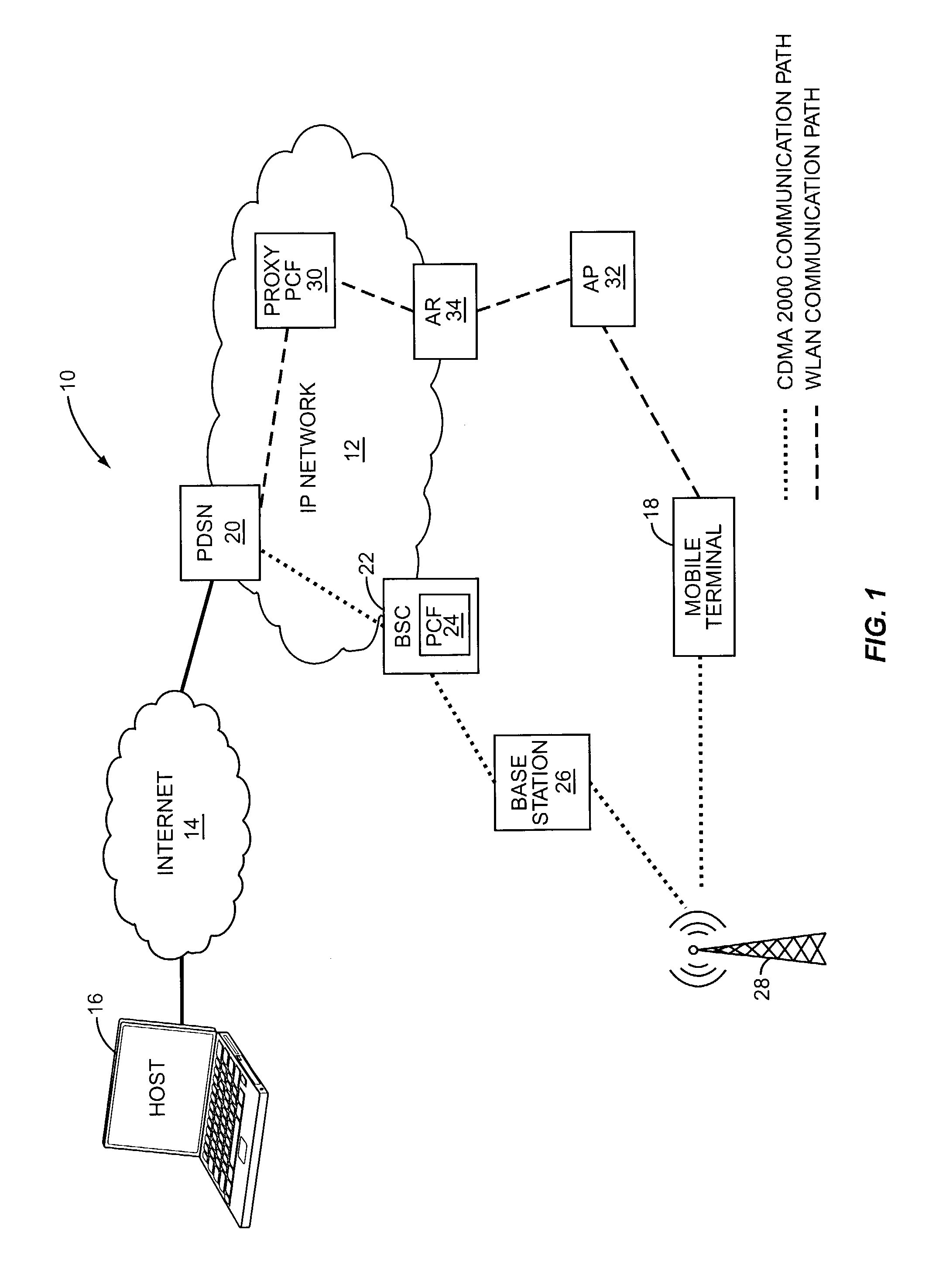
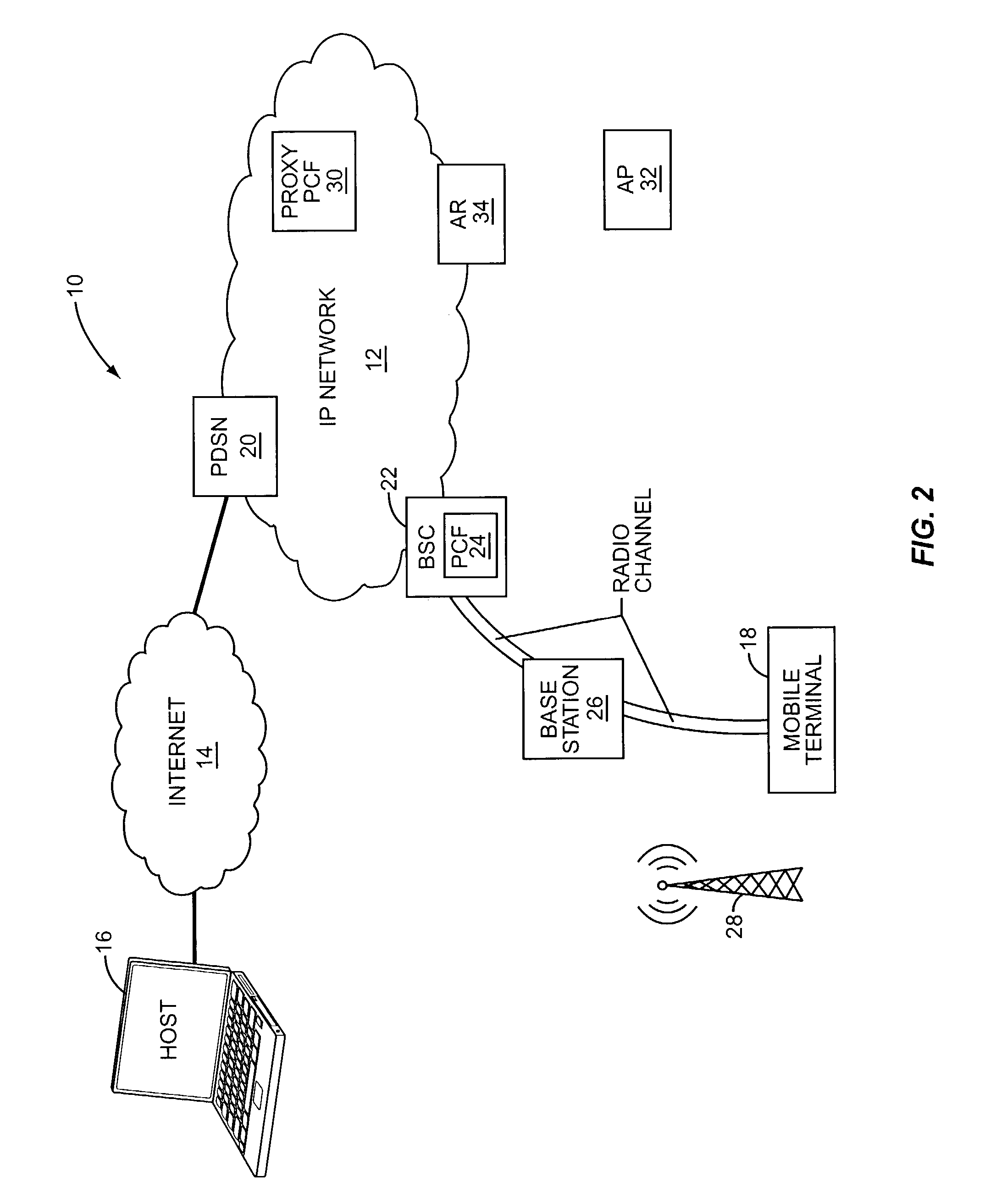
Efficient handoffs between cellular and wireless local area networks
InactiveUS7583632B2Convenient handoverOptimize networkData switching by path configurationWireless commuication servicesPacket data serving nodeIP tunnel
The present invention facilitates a handoff between cellular and wireless local area networks (WLANs). To facilitate a WLAN interface with the cellular network, a proxy packet control function (P-PCF) establishes a data tunnel to a packet data serving node (PDSN), as well as a WLAN association with a mobile terminal. The WLAN association is a tunnel, and is preferably implemented via an Access Router acting as a liaison between the proxy PCF and an Access Point. The Access Router and the proxy PCF establish an IP tunnel, which carries the WLAN user's PPP traffic. Handoffs between the cellular and WLAN networks are facilitated by effecting a same-PDSN, inter-PCF handoff wherein the communication session with the mobile terminal is effectively changed from between the PDSN and the proxy PCF to between the PDSN and a PCF associated with a base station controller facilitating the cellular access, and vice versa.
Owner:RPX CLEARINGHOUSE
Tunnel setup method and tunnel setup device
ActiveCN104243270AReduce configuration requirementsAdd control functionNetworks interconnectionTelecommunicationsIp address
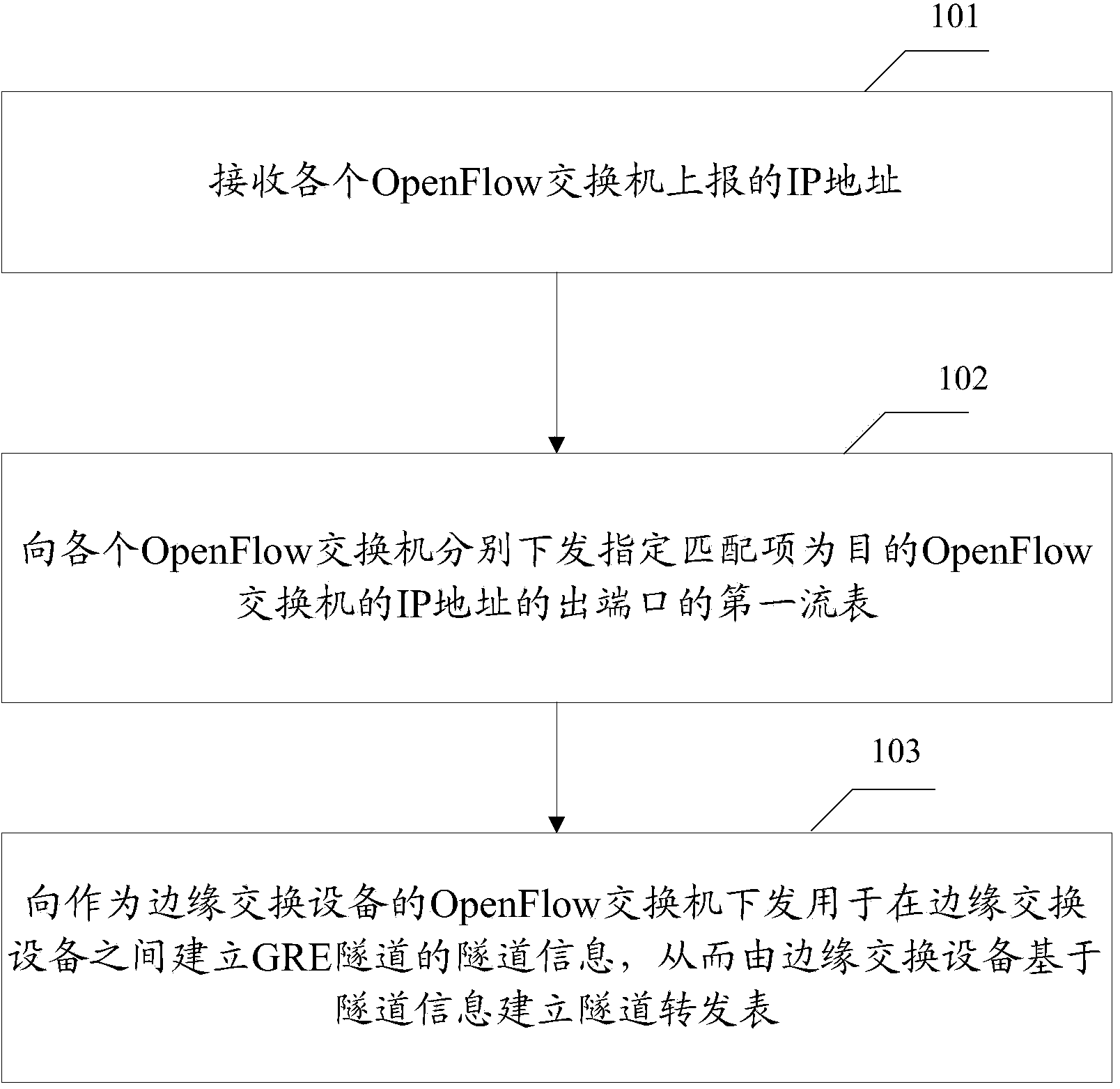
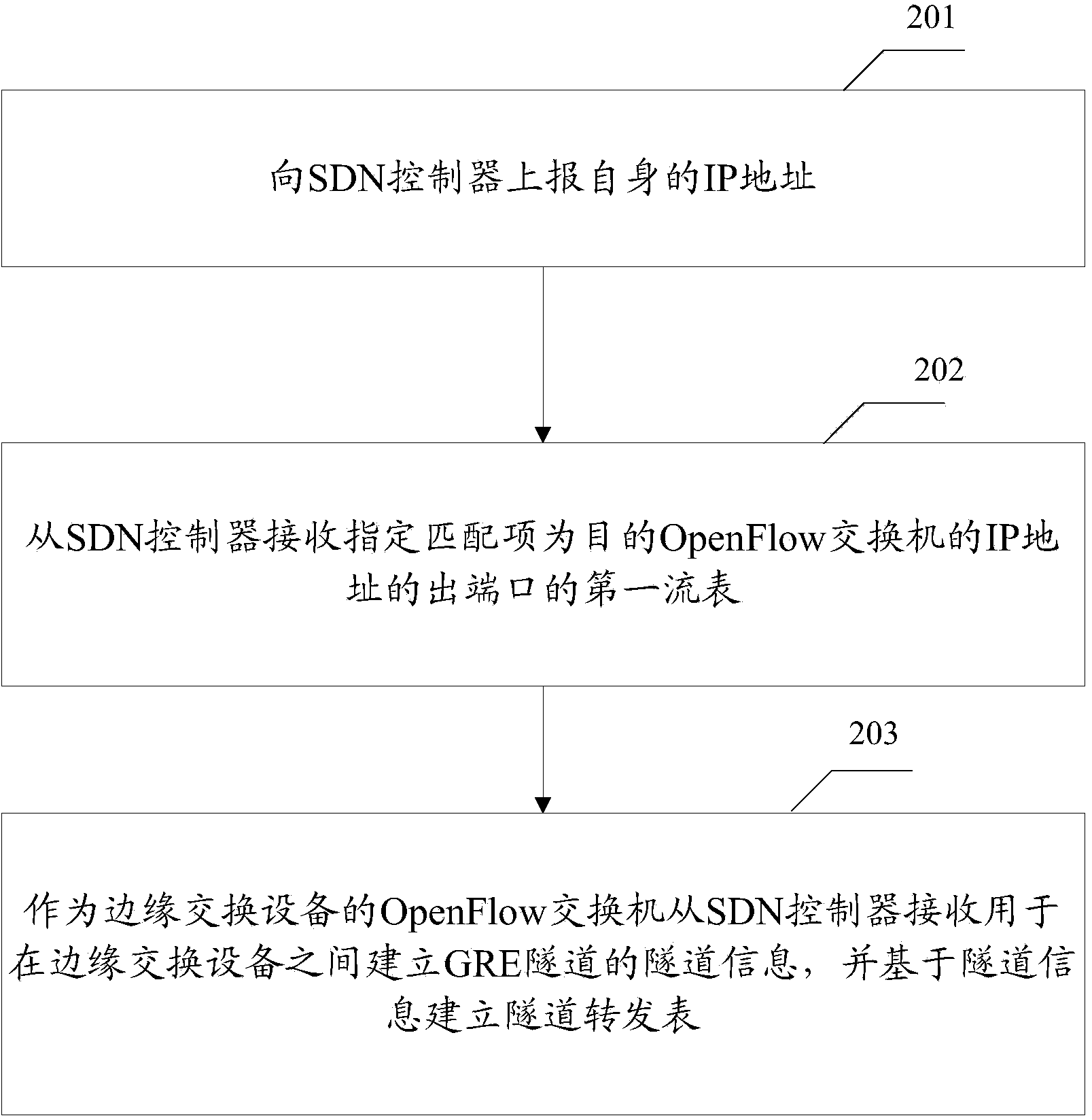
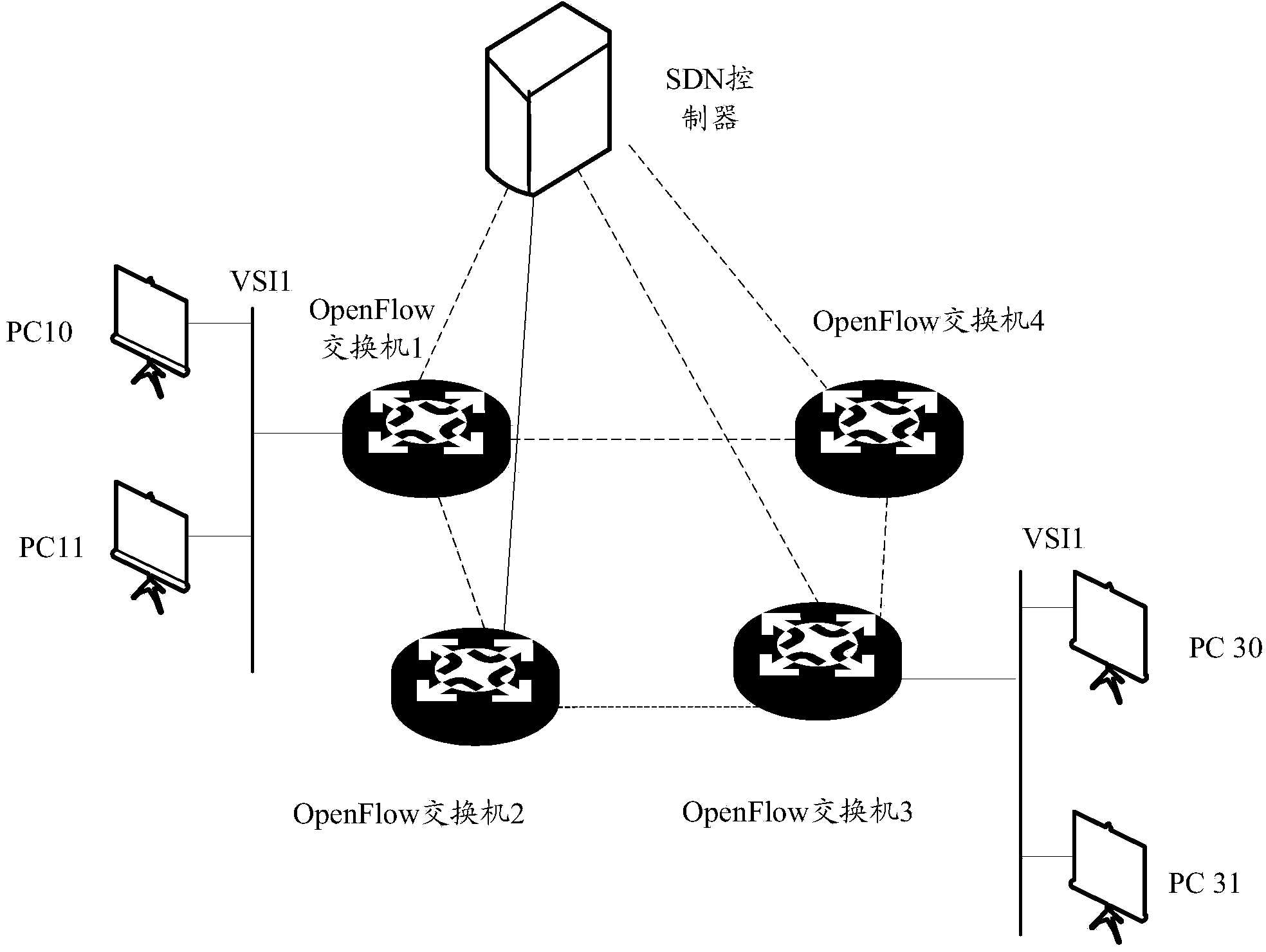
The invention provides a tunnel setup method and a tunnel setup device. The tunnel setup method includes steps executed by an SDN (software defined network) controller in SDN architecture. The steps include: receiving an IP (internet protocol) address reported by each OpenFlow switch; respectively issuing a first flow table with an assigned matching item being an outlet interface of the IP address of a target OpenFlow switch; issuing tunnel information used for setup of GRE (general route encapsulation) tunnels among edge switch equipment to the OpenFlow switches serving as the edge switch equipment, and enabling the edge switch equipment to set up a tunnel forwarding table on the basis of the tunnel information. A function of controlling the SDN by the SDN controller is enhanced while configuration demands on the OpenFlow switches are lowered, and network resources are saved.
Owner:NEW H3C TECH CO LTD
Apparatus and methods for providing translucent proxies in a communications network
InactiveUS7386631B1Improve throughputMultiple digital computer combinationsTransmissionNetwork packetIP tunnel
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
Handover method for mobile station having mobile IP address in mobile communication system
InactiveCN1394397AWireless network protocolsRadio transmission for post communicationIp addressMobile communication systems
Owner:SAMSUNG ELECTRONICS CO LTD
Method for establishing IP tunnel and device for distributing IP address
InactiveCN101188542ARealize communicationRadio/inductive link selection arrangementsNetworks interconnectionIp addressThe Internet
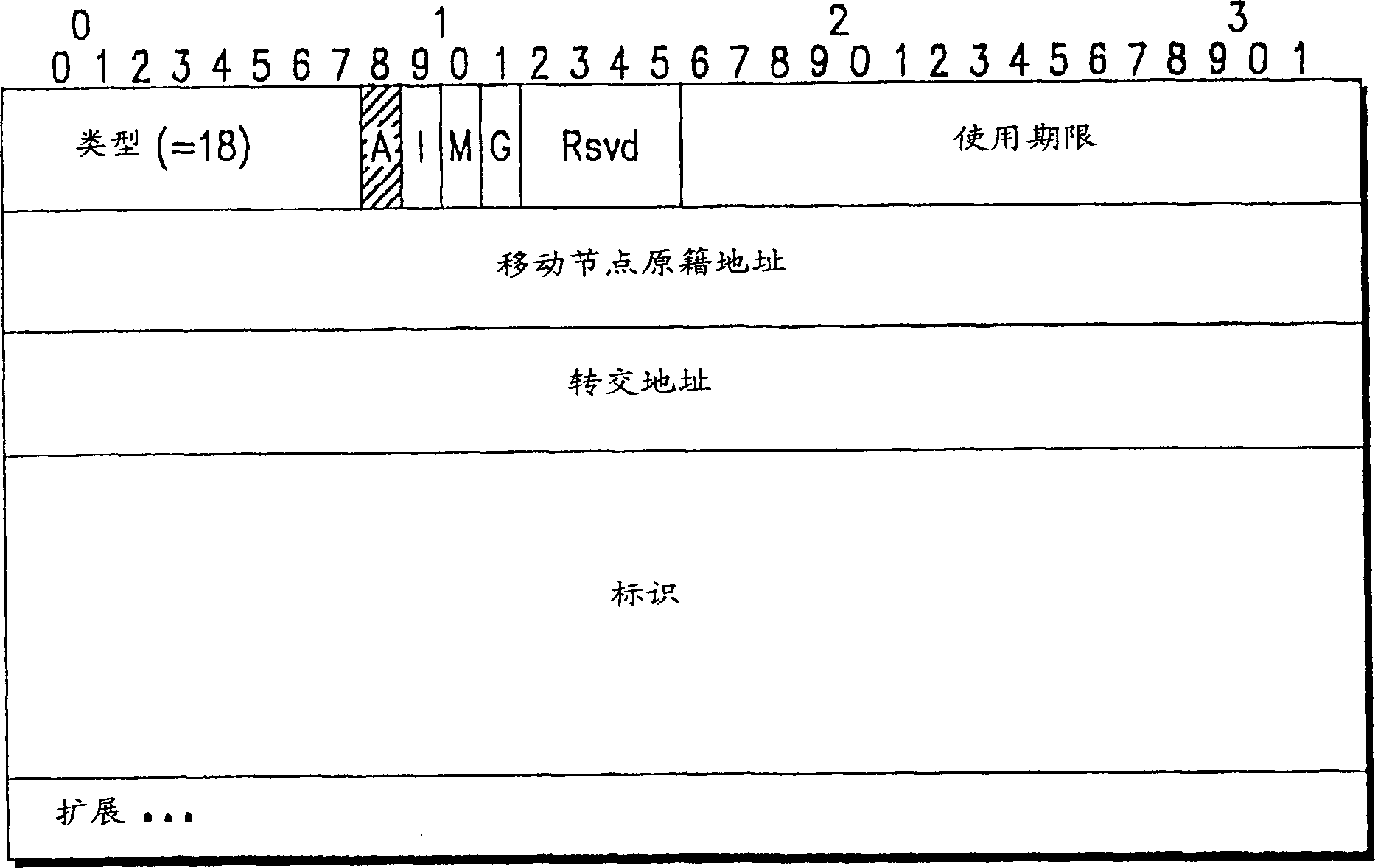
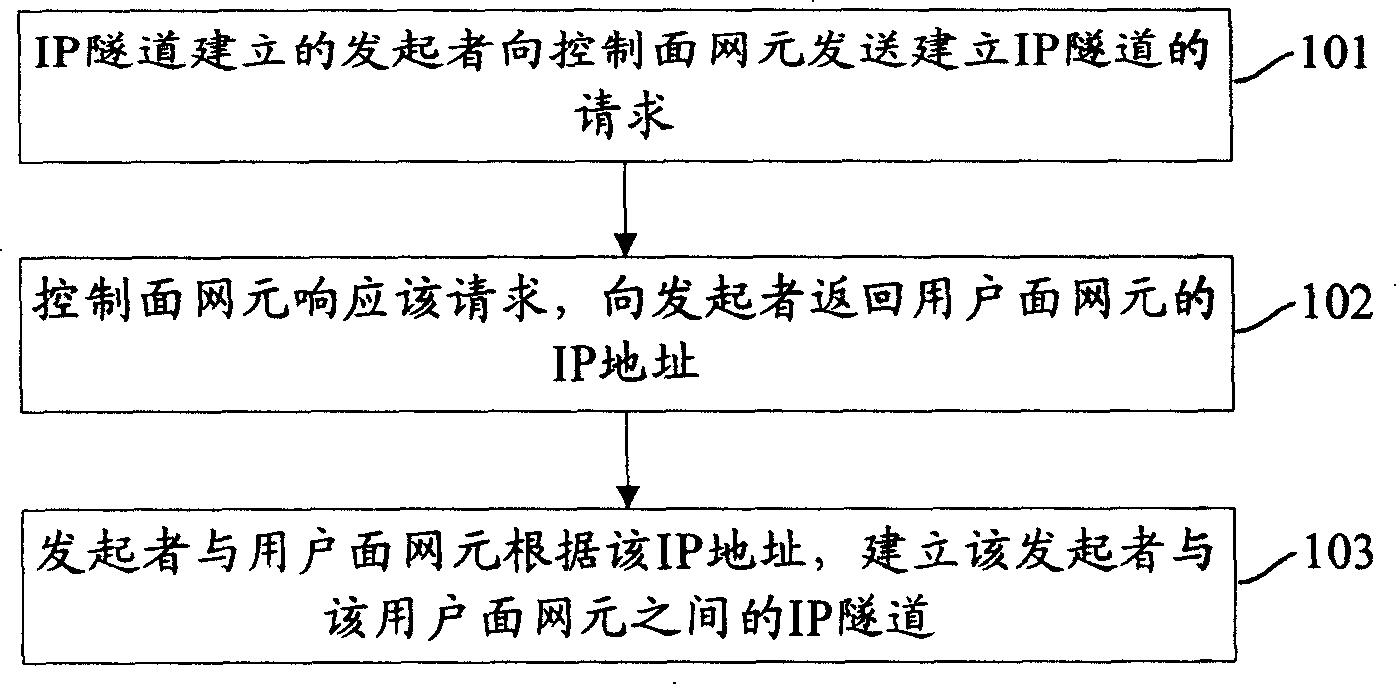
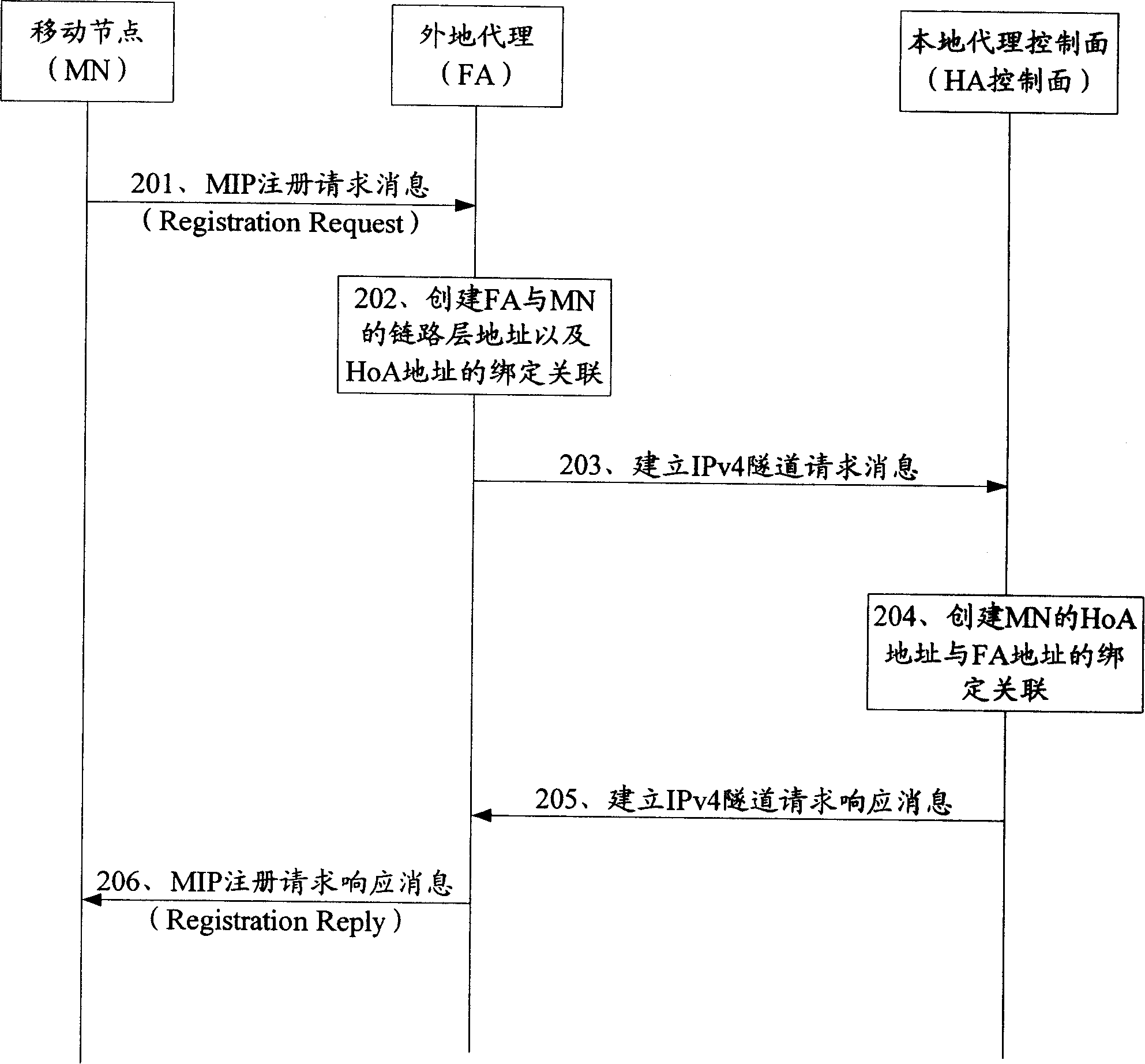
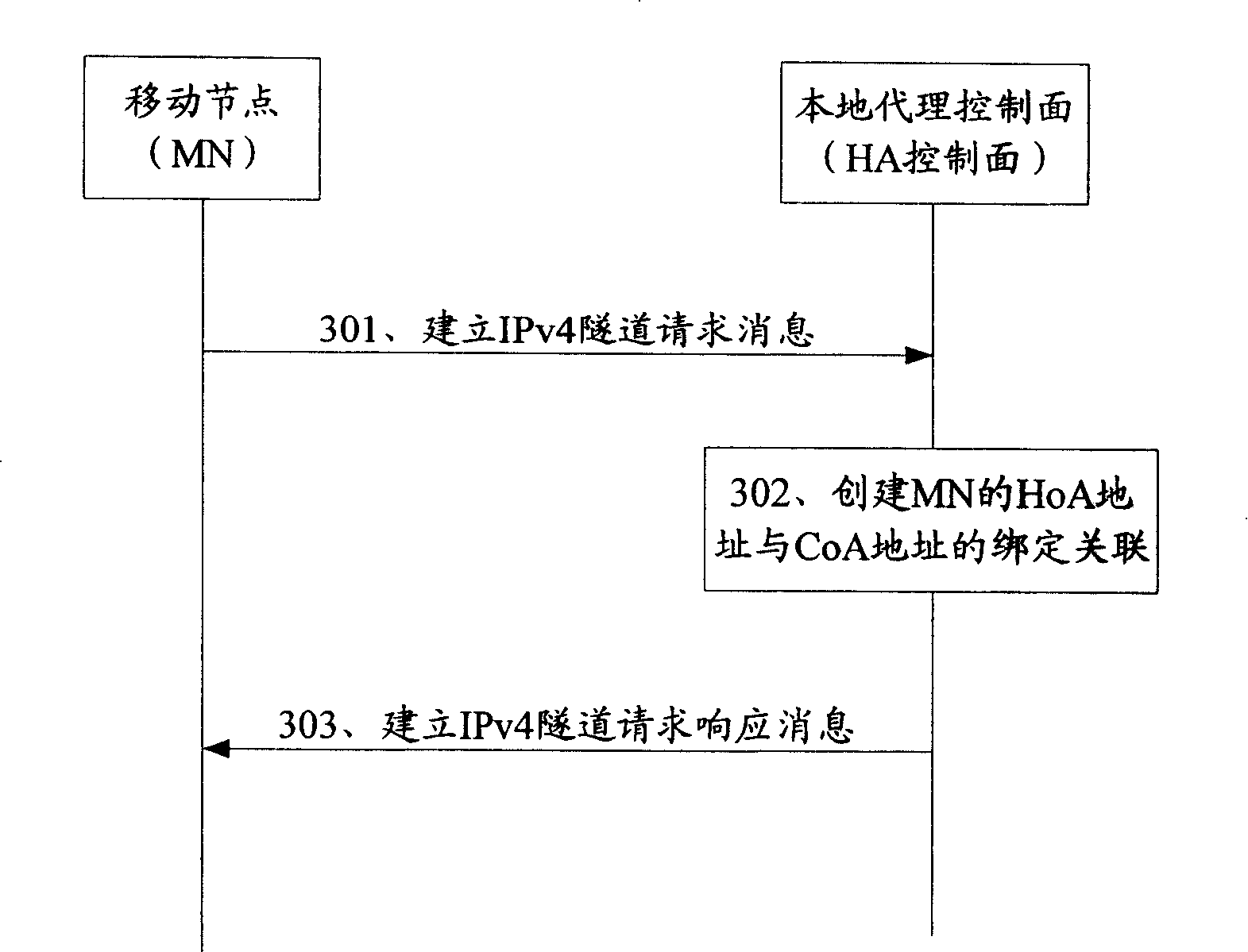
The embodiment of the invention discloses a method to establish an internet agreement IP tunnel. The method comprises the steps that a tunnel-established initiator sends a tunnel-established request to a control face element location; the control face element location responds to the request, and sends back the IP address of a user face element location to the initiator; the initiator and the user face element location use the IP address to establish an IP tunnel between the initiator and the user face element location. Based on the method, the invention also discloses a system to establish the internet agreement IP tunnel and a device to distribute the IP address. Through the IP tunnel established between the initiator and the user face element location, the technical proposal which is provided by the invention can realize the communications between the tunnel-established initiator and the user face element location in the IP-based moving management technology.
Owner:HUAWEI TECH CO LTD
Synchronous data acquisition system used in wind tunnel based on stable dynamic pressure control
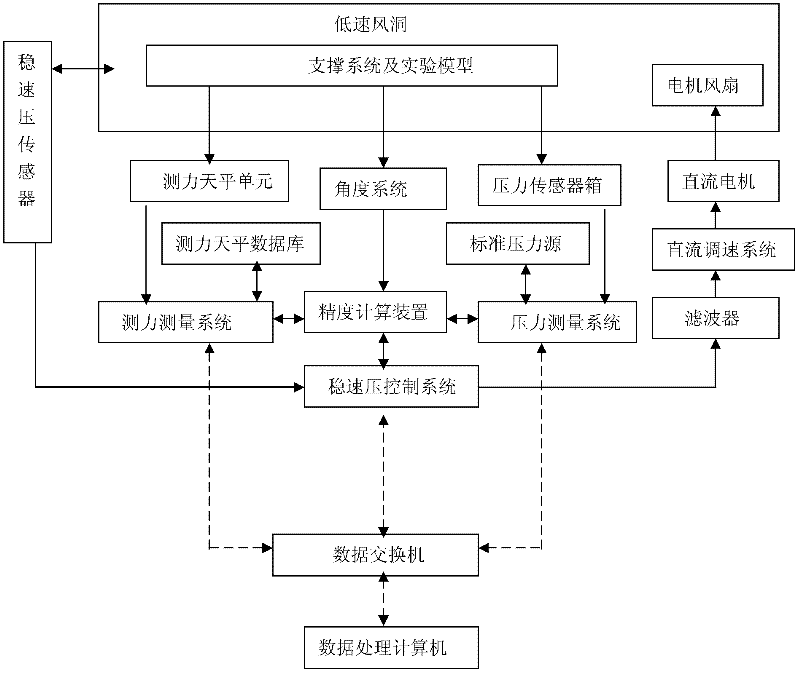
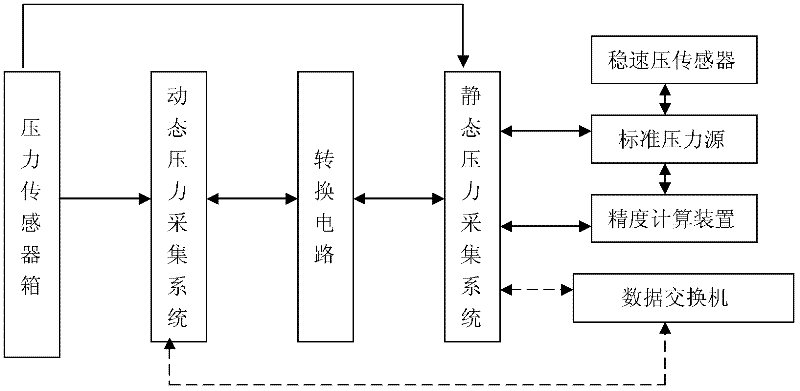
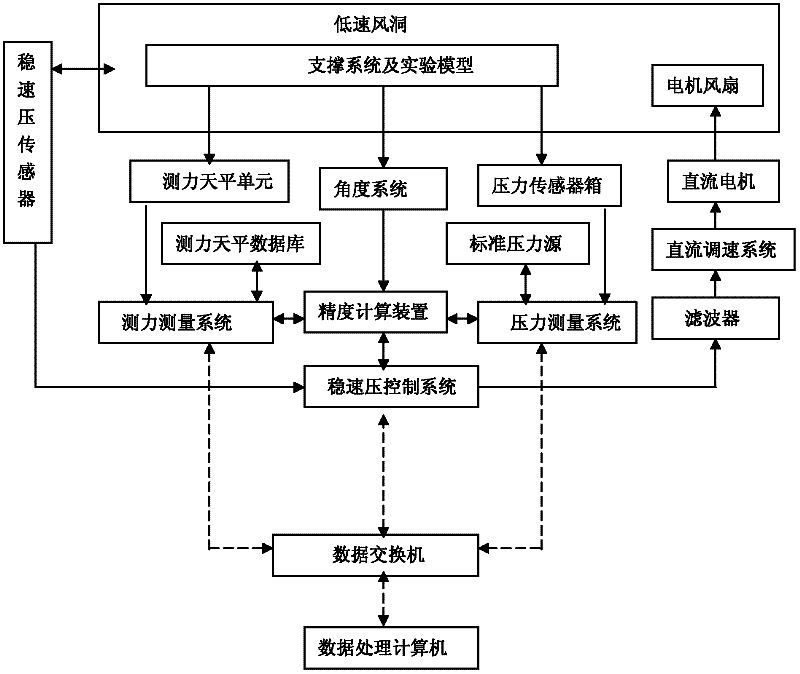
InactiveCN102393638ASave human effortSimple methodAerodynamic testingAdaptive controlLow speedMathematical model
The invention discloses a synchronous data acquisition system used in a wind tunnel based on stable dynamic pressure control. The data acquisition system comprises a pressure sensor, a pressure acquisition system, an aerodynamic force balance unit, an aerodynamic force acquisition system, a standard pressure source, an industrial personal computer (IPC), a stable dynamic pressure sensor, an accuracy control device, an aerodynamic parameter system and a motor fan, wherein, the pressure sensor measures the pressure in the low-speed wind tunnel and transmits the measured pressure value to the pressure acquisition system; the aerodynamic force balance unit measures aerodynamic force on an experimental model and outputs the measured aerodynamic force value to the aerodynamic force acquisition system; the standard pressure source respectively calibrates the pressure sensor, the pressure acquisition system and the stable dynamic pressure sensor so as to obtain calibration factors, the calibration factors are transmitted to the IPC so as to obtain a controlled process mathematical model for stable dynamic pressure control, and then the controlled process mathematical model is transmitted to the accuracy control device; the accuracy control device drives the pressure acquisition system, the aerodynamic parameter system and the aerodynamic force acquisition system to perform synchronousdata acquisition; the stable dynamic pressure sensor acquires variation of a flow field in the low-speed wind tunnel, and then the variation value is transmitted to the IPC; and the IPC controls the motor fan to rotate. The data acquisition system disclosed by the invention has the advantages that manpower is saved, high-accuracy data can be obtained, the operating method is simple and practical,the cost is low and the application prospect is wide.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
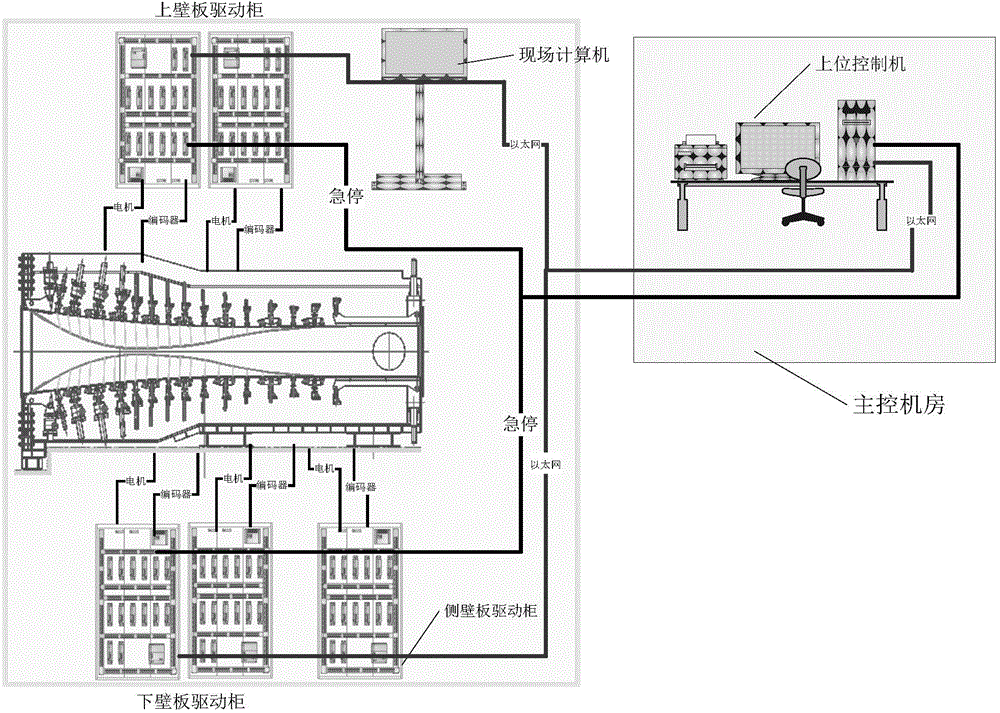
Synchronous control system and method for all flexible plate nozzle of wind tunnel
InactiveCN104655392AReduce test costsImprove flexibilityAerodynamic testingSynchronous motorControl system
The invention discloses a synchronous control system and method for an all flexible plate nozzle of a wind tunnel. The synchronous control system comprises a left wall plate, a right wall plate, flexible plates, a front end plate, a rear end plate and drive mechanisms, wherein the left wall plate and the right wall plate are arranged in parallel in the horizontal direction; the two flexible plates are arranged symmetrically in the longitudinal direction and form a column body with the left wall plate and the right wall plate, and the side surfaces of the column body are sealed; multiple hinge supporting points are arranged on the surfaces, backing to airflow, of the flexible plates, and the flexible plates are connected with the drive mechanisms through the hinge supporting points; the front end plate and the rear end plate are vertically arranged at two ends of the column body. The structure with a round outside and a square inside is formed, airflow of the wind tunnel goes in from one end of the column body and goes out from the other end of the column body, and the front end plate and the rear end plate can be used for fixing and mounting the flexible plates.
Owner:北京瑞赛长城航空测控技术有限公司 +2
Method and device for forwarding MPLS data packages
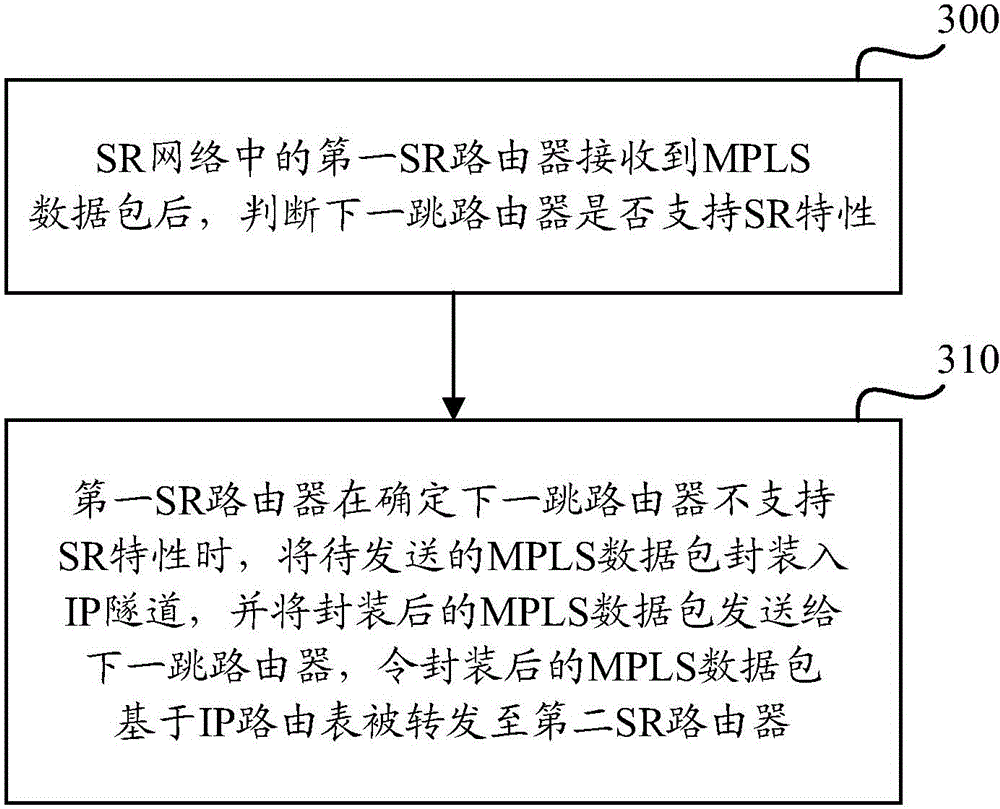
ActiveCN104378292AMeet the requirements for incremental deploymentData switching networksIP tunnelIP forwarding algorithm
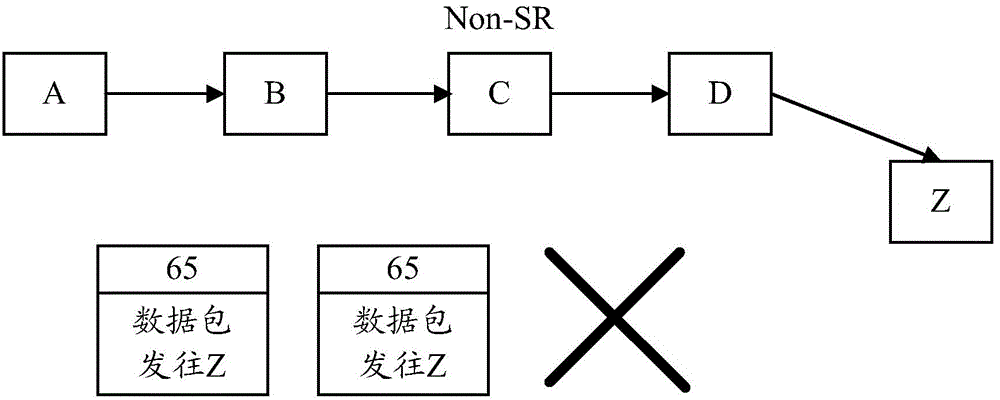
Disclosed are a method and device for forwarding an MPLS data packet, which are used for realizing the correct forwarding of an MPLS data packet in a mixed networking environment of an SR network and a non-SR network. The method comprises: when obtaining an MPLS data packet to be sent, a first SR router in an SR network judging whether a next-hop router supports an SR characteristic or not; and if it is determined that the next-hop router does not support the SR characteristic, the first SR router encapsulating the MPLS data packet into an IP tunnel, and sending the encapsulated MPLS data packet to the next-hop router, so that the encapsulated MPLS data packet is forwarded to a second SR router based on an IP routing table. In this way, the correct forwarding of an MPLS data packet can be completed in a mixed networking environment of an SR network and a non-SR network, thereby meeting the requirements of SR network incremental deployment.
Owner:HUAWEI TECH CO LTD
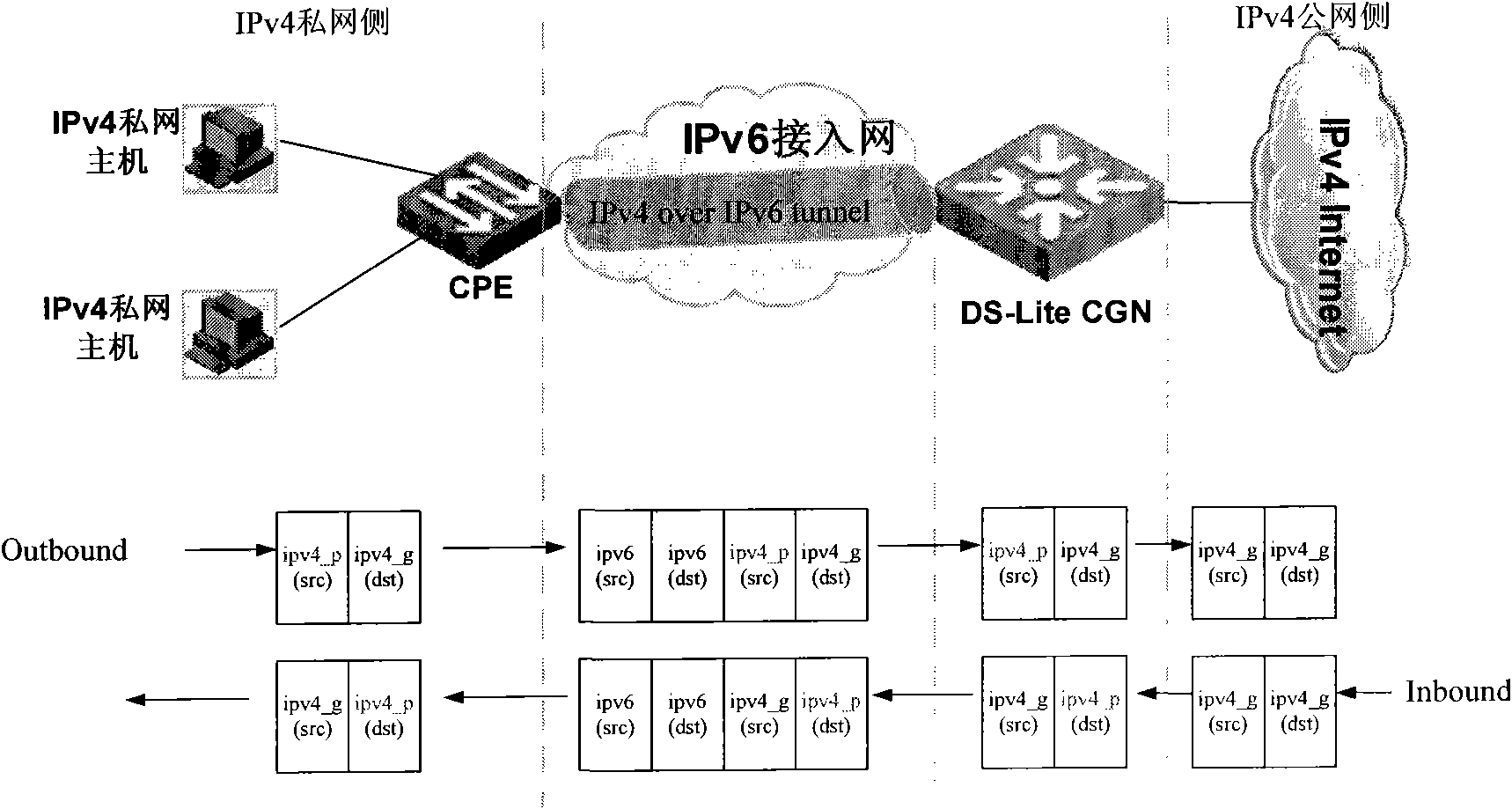
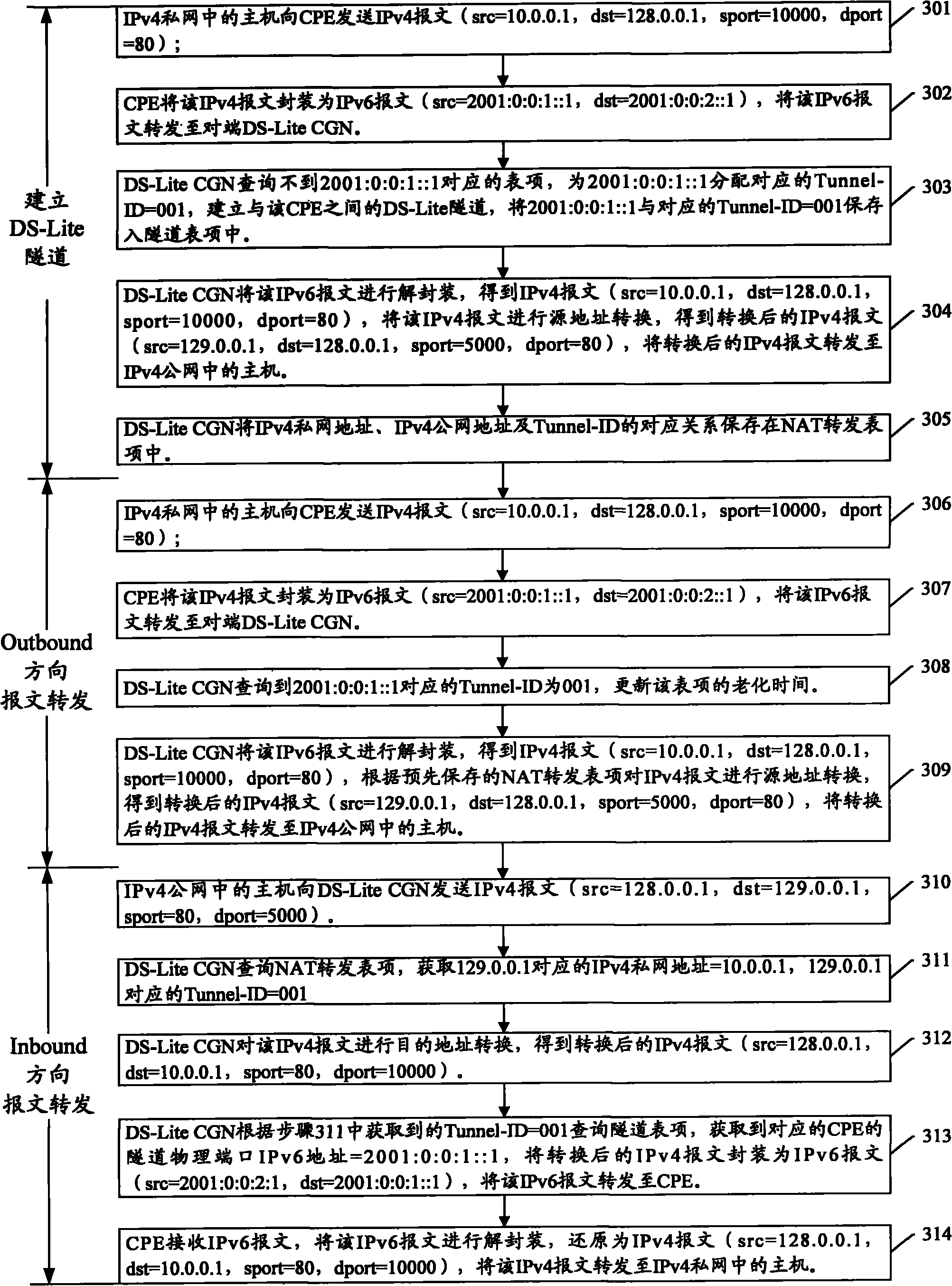
Method for establishing DS-Lite tunnel and DS-Lite CGN
InactiveCN102377628ASolve the problem of heavy renovation workNetworks interconnectionCarrier gradeTerminal equipment
The invention provides a method for establishing a dual-stack lite (DS-Lite) tunnel and a DS-Lite carrier-grade network address translation (DS-Lite CGN) device. The method comprises the following steps that: when a DS-Lite CGN has received an IPv6 message from customer premise equipment (CPE), if an item corresponded to an IPv6 address of a tunnel physical port of the CPE can not be queried in a tunnel item, a tunnel identifier corresponded to the IPv6 address of the tunnel physical port of the CPE is distributed and a DS-Lite tunnel between the CPE and the tunnel identifier is established; and moreover, the tunnel identifier is recorded in a network address translation (NAT) forwarding item. According to the invention, a problem on a large working load for transformation of a traditional NAT technology can be solved; and moreover, tedious configuration on a DS-Lite tunnel is avoided.
Owner:NEW H3C TECH CO LTD
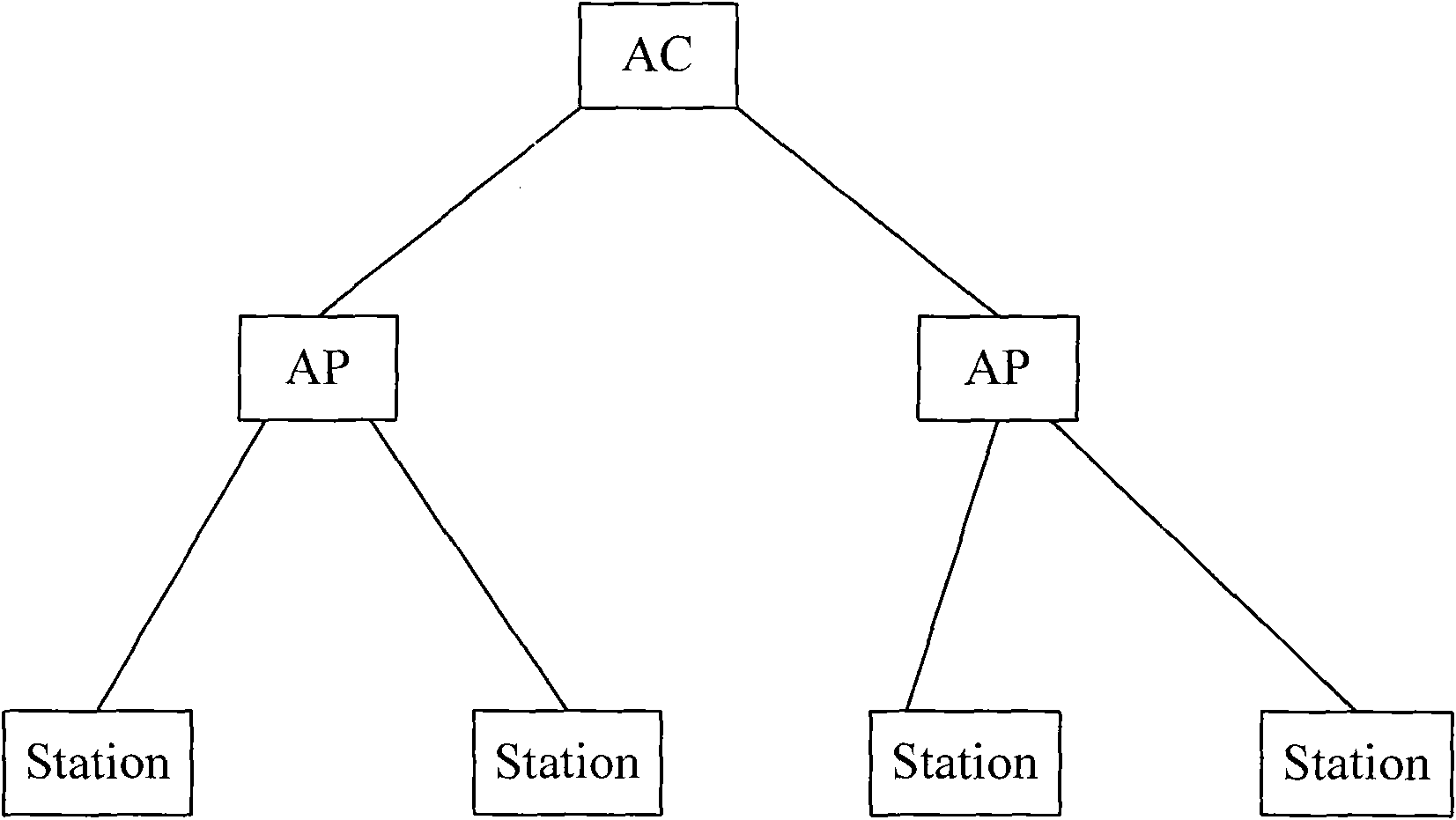
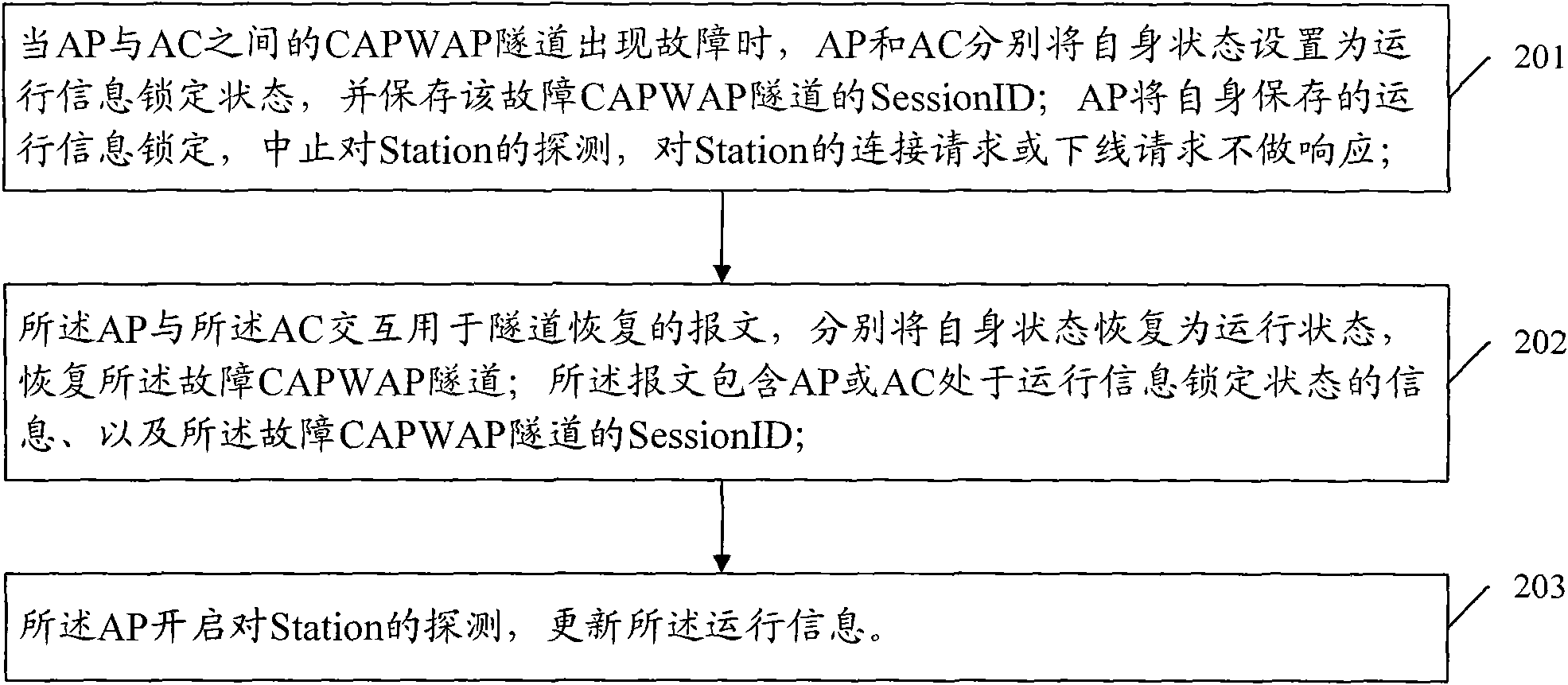
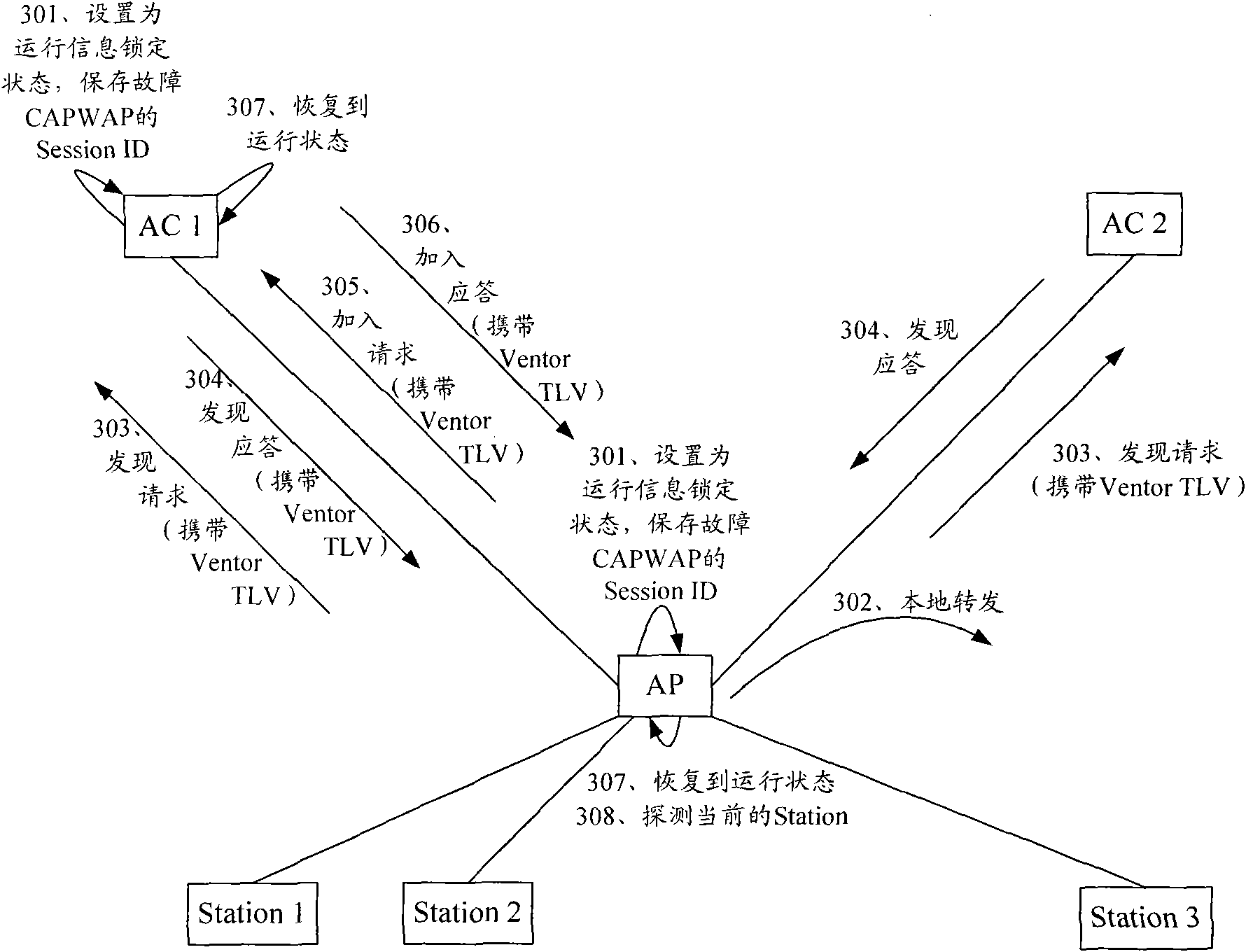
Method, system and device for recovering control and provisioning for wireless access point (CAPWAP) tunnel
ActiveCN102143604AUninterrupted serviceWireless network protocolsData switching networksIP tunnelCAPWAP
The invention discloses a method, a system and a device for recovering control and provisioning for wireless access point (CAPWAP) tunnel. The method comprises the steps that: when the CAPWAP tunnel between an access point (AP) and an access controller (AC) fails, the AP and AC set states as operating information locking states respectively and save the session identifier (ID) of the failed CAPWAP tunnel; the AP locks the saved operating information, aborts the detection for a station and does not respond to the connection request or offline request of the station; the AP interacts with the AC for the tunnel recovery message, the AP and the AC recover states as operating sates respectively to recover the failed CAPWAP tunnel; the message comprises the information about the AP and the AC being in the operation information locked state and the session ID of the failed CAPWAP tunnel; the AP starts the detection for the station to update the operating information. According to the invention, the AP still can keep the service for the station uninterrupted during the recovery of the CAPWAP tunnel.
Owner:NEW H3C TECH CO LTD
Method for establishing traffic engineering-over-label switch path tunnel and equipment
ActiveCN107306222AAchieve optimizationRealize business protectionNetworks interconnectionTraffic capacityIP tunnel
The invention discloses a method for establishing a traffic engineering-over-label switch path (TE-over LSP) tunnel and equipment. The embodiment of the invention provides a TE-over LSP tunnel establishment method and equipment. The method comprises: a forwarding device receives a control message sent by a domain controller, wherein the control message includes a TE-over LSP tunnel identifier ID, an input label, an output label, and an output interface identifier; the forwarding device establishes a TE-over LSP tunnel corresponding to the TE-over LSP tunnel ID based on the control message, so that the forwarding device forwards a message by using a TE tunnel or a physical interface as an output interface based on the indication of the output interface identifier when the TE-over LSP tunnel is used for forwarding a message. According to the method disclosed by the invention, TE-over LSP tunnels iterated to different TE tunnels can be established for different services and thus different services are carried at different TE-over LSP tunnels for forwarding, so that resources optimization and service protection are realized.
Owner:HUAWEI TECH CO LTD
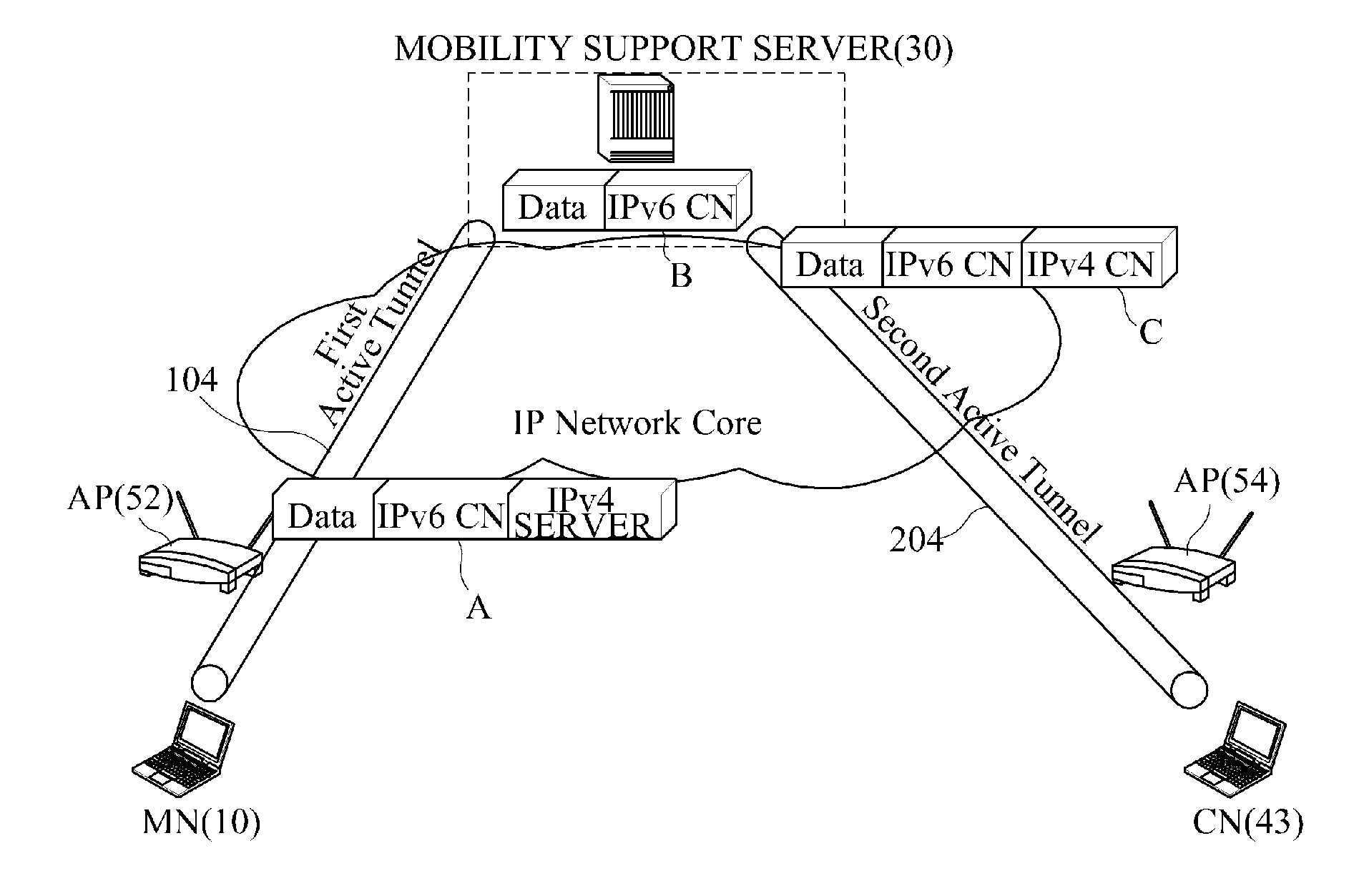
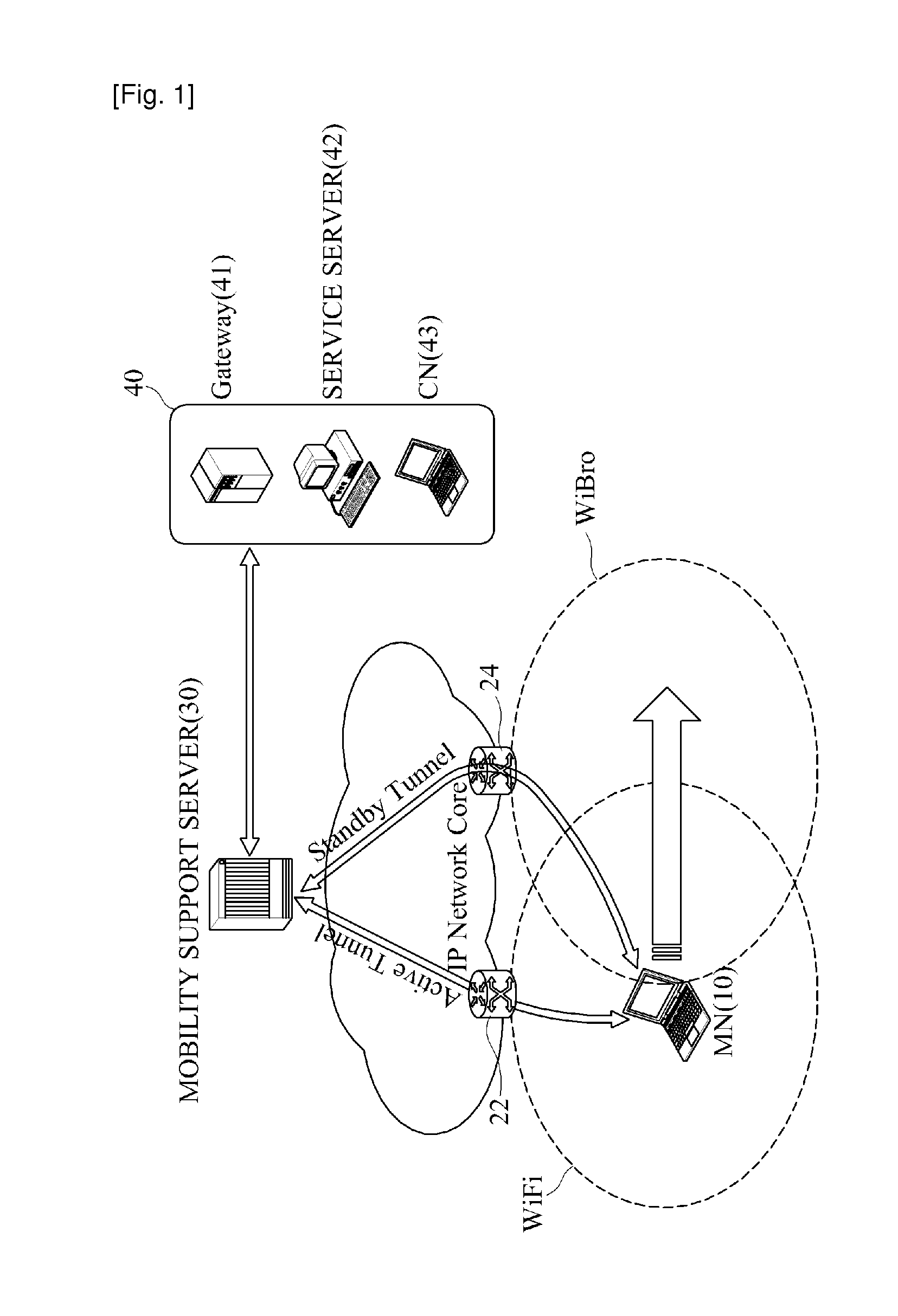
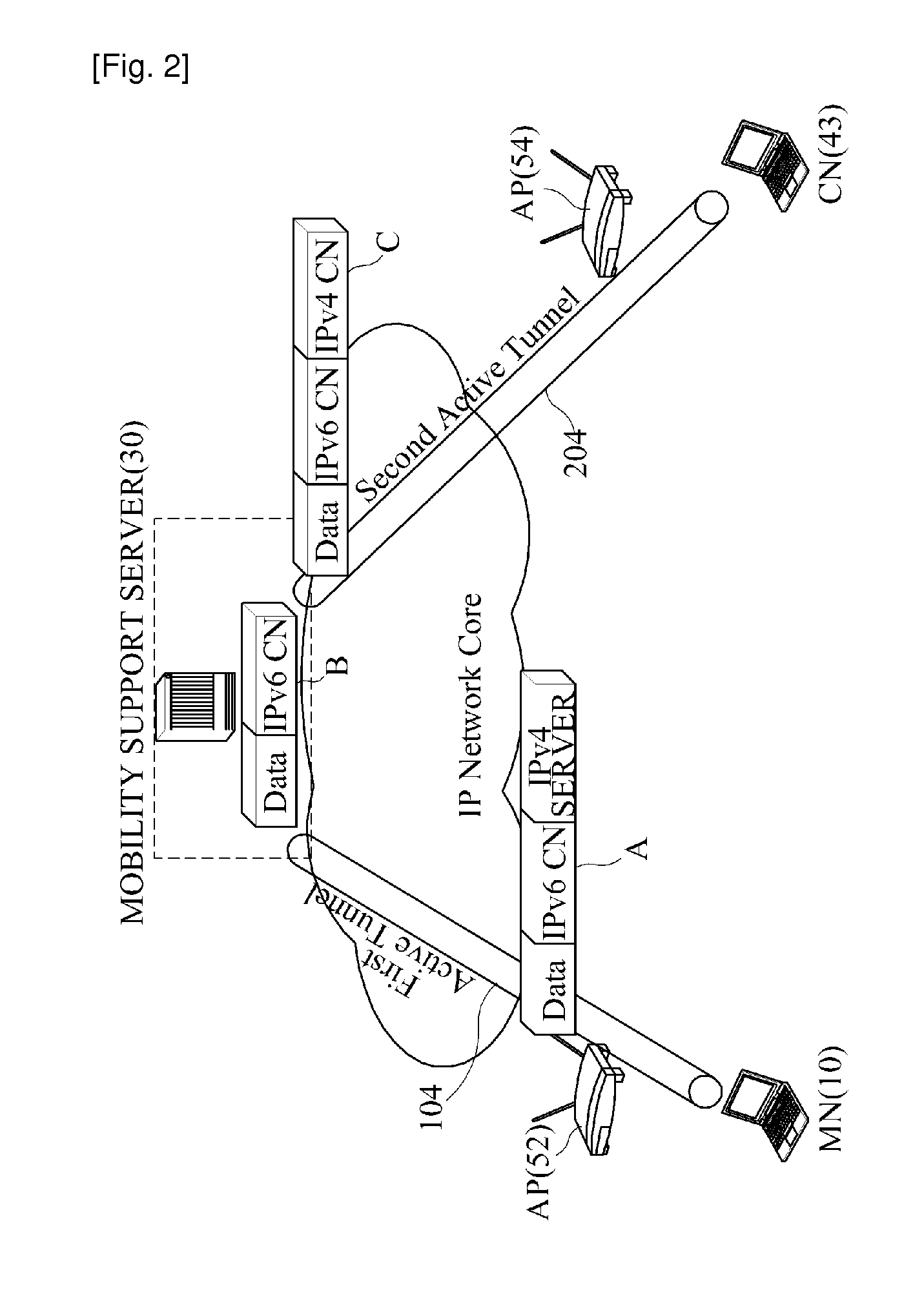
Tunneling-based mobility support equipment and method
InactiveUS20110002220A1Reduce the burden onEasy to addMultiplex system selection arrangementsError preventionTelecommunicationsHeterogeneous network
A tunneling-based mobility support method and apparatus is provided which supports a mobility of a mobile node in a heterogeneous network regardless of IP versions (IPv4 / IPv6). The mobility support apparatus includes a load balancer, a plurality of mobility support servers, and a plurality of end routers each being TCP connected to each of the mobility support servers. When receiving a tunnel establishment request message from the mobile node, the load balancer selects one mobility supports server from a plurality of mobility support servers to control a mobility service for the mobile node. The selected mobility support server selects a plurality of tunnel end addresses of one end router from the plurality of end routers to establish an IP tunnel with the mobile node according to a predetermined criterion, forwards the tunnel establishment request message to the end router, and sends the mobile node a tunnel establishment response message including the tunnel end address of the selected end router.
Owner:ELECTRONICS & TELECOMM RES INST
Method for establishing a multi-link access between a local network and a remote network, and corresponding appliance
ActiveUS20090313690A1Computer security arrangementsMultiple digital computer combinationsMulti linkIP tunnel
Owner:INTERDIGITAL CE PATENT HLDG
Network physical connection inference for IP tunnels
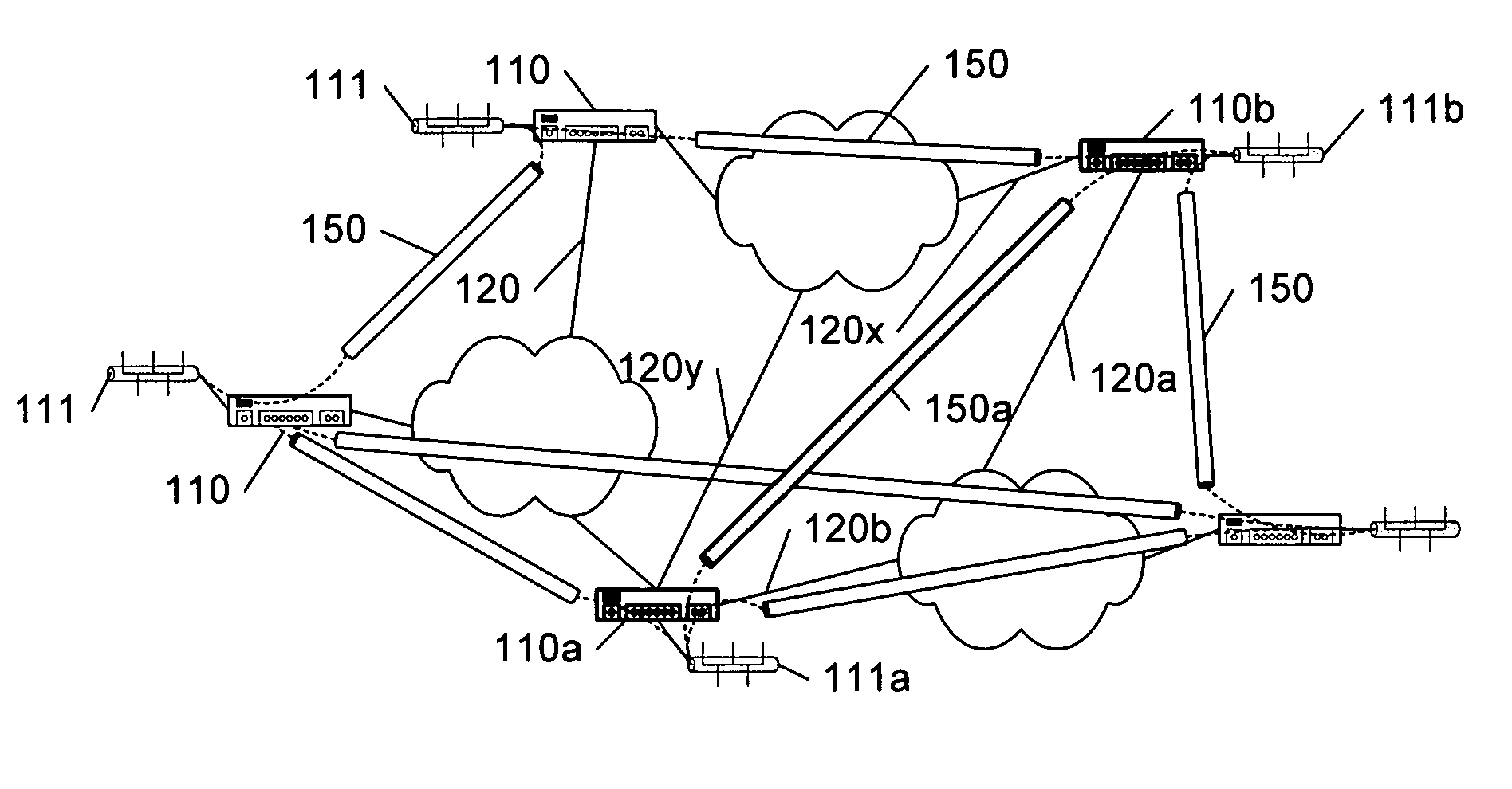
The physical connection corresponding to IP tunnels in a network are found by tracing through the device configuration and routing tables at the routers in the network to determine the outbound interface associated with each tunnel endpoint, and then inferring a likely return interface associated with the opposite tunnel endpoint. Depending upon the particular configurations, a variety of tests can be applied to validate the inference. Patricia trees are preferably used to store and process the configuration data for efficient tracing through the routing tables at each router.
Owner:RIVERBED TECH LLC
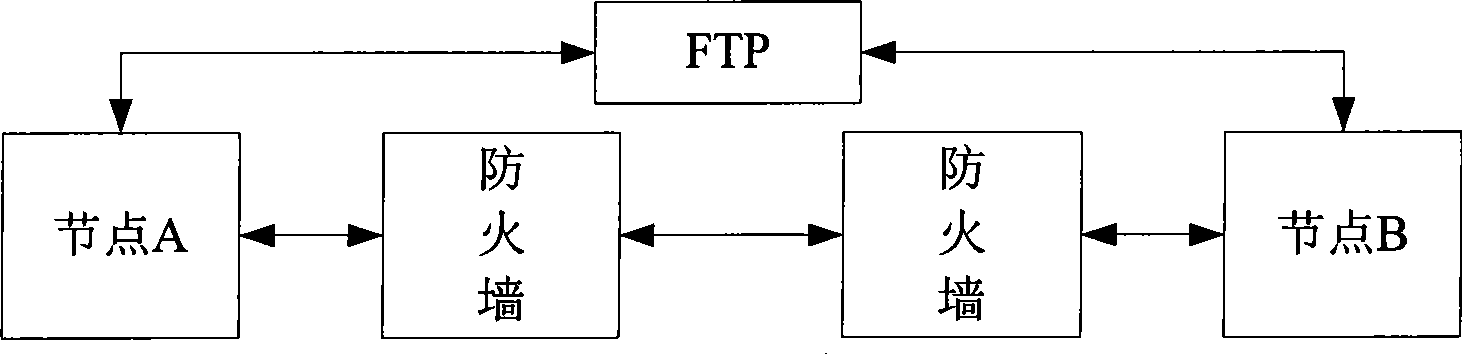
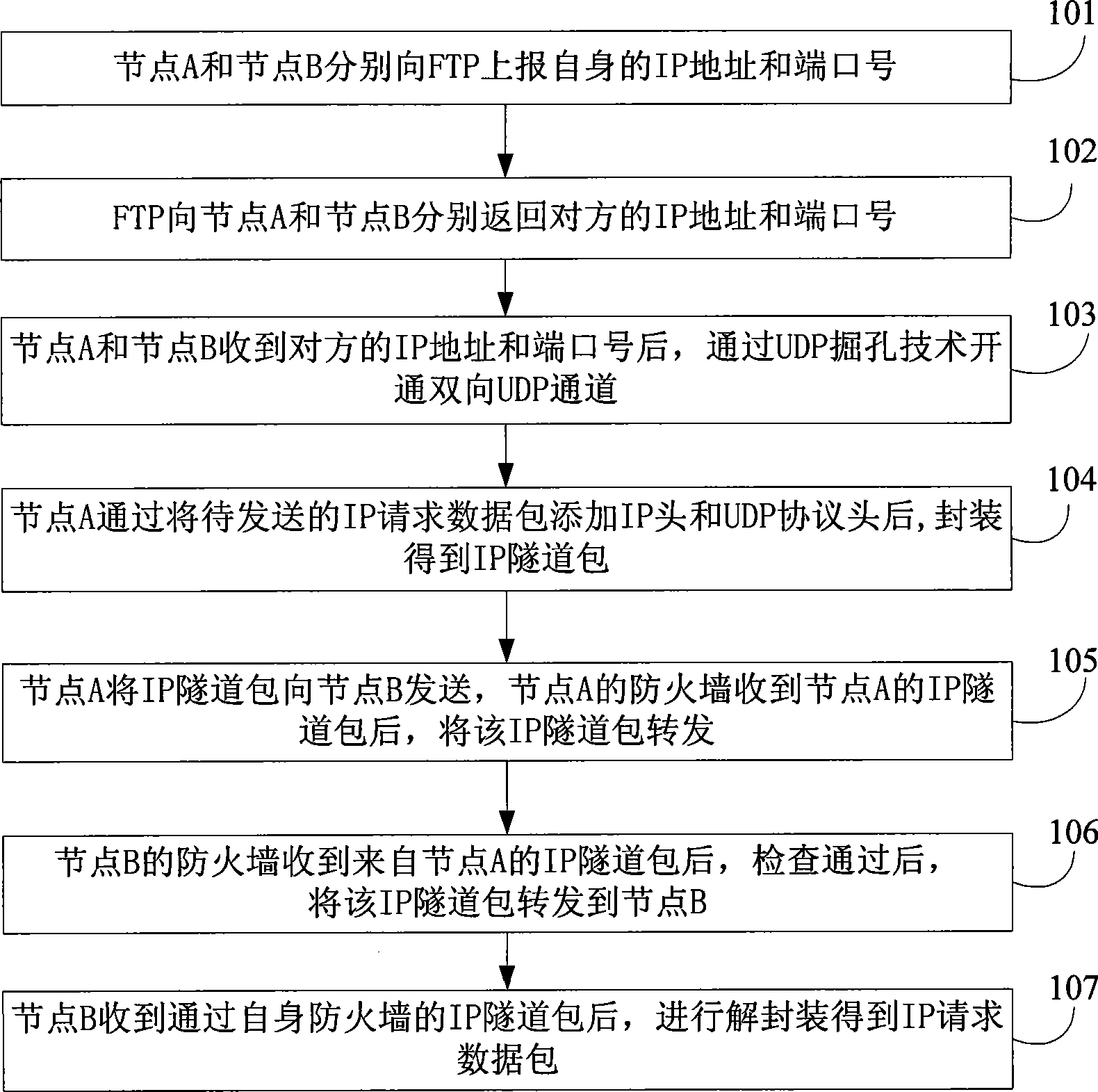
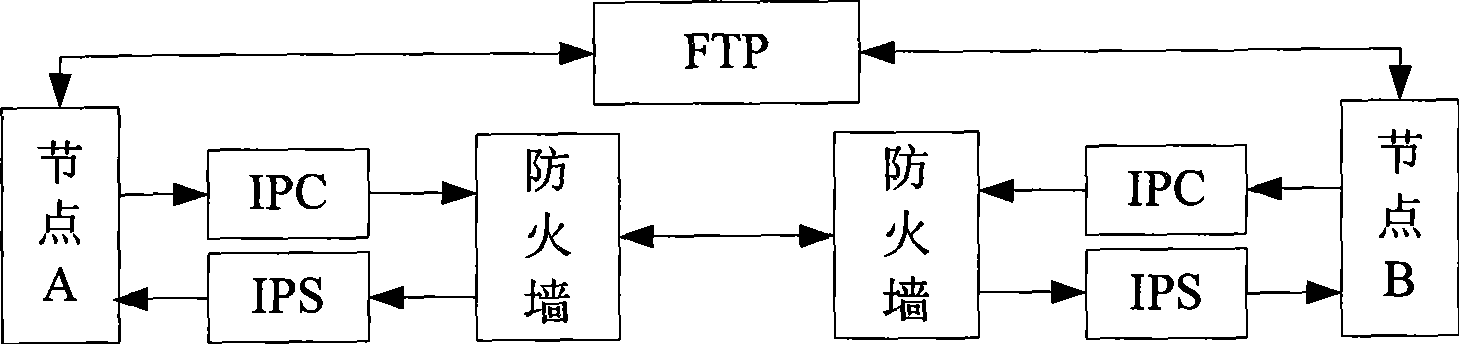
Method, system and equipment for traversing firewall
The invention discloses a firewall penetration method, a system and a device thereof, belonging to communication field. The method includes the following steps: acquiring the IP address and the port number of a correspondent node; encapsulating the data to be sent into an IP tunnel packet according to the IP address and the port number of the correspondent node and enabling the IP tunnel packet to penetrate the firewall of the correspondent node; and sending the IP tunnel packet to the correspondent node. The system comprises a first node and a second node; or a first node, a first node proxy client, a second node and a second node proxy server. The node device comprises an acquisition module, an encapsulating module and a sending module. The method, the system and the device encapsulate the data to be sent and add an IP header and an UDP header to obtain the IP tunnel packet which can penetrate the firewall of the correspondent node, thus achieving connection and communication among the communication nodes.
Owner:HUAWEI TECH CO LTD +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com