Method, system and equipment for traversing firewall
A firewall and node technology, applied in the field of communication, can solve problems such as inability to communicate with each other
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
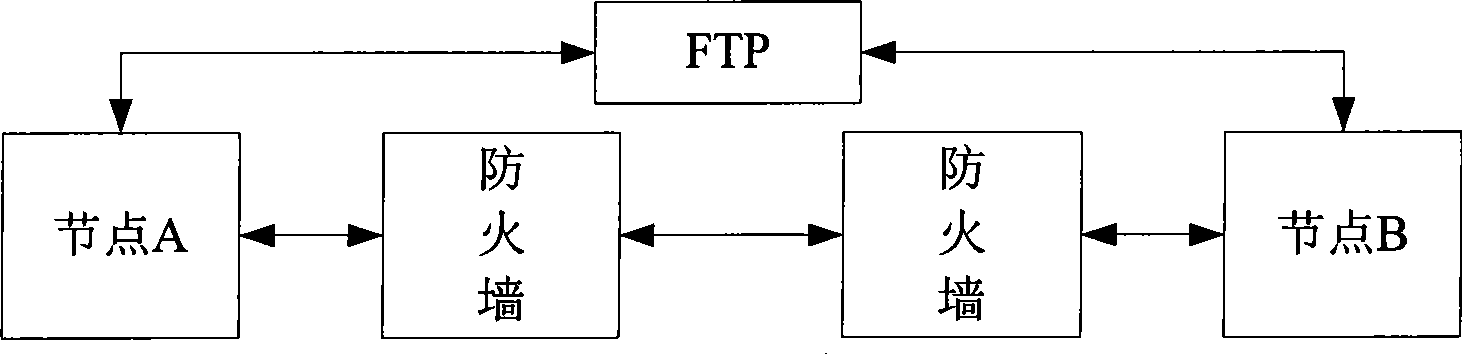
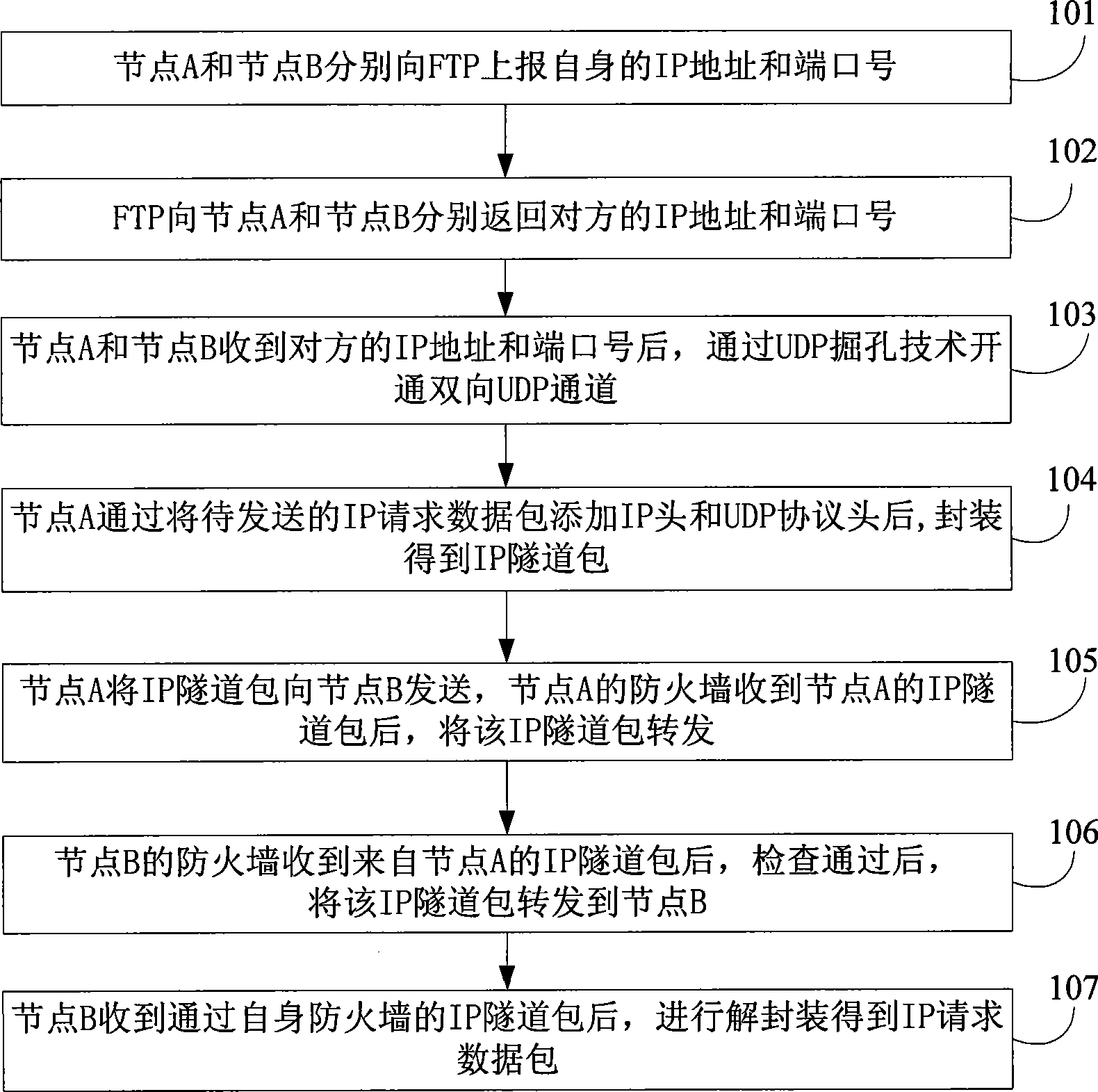
[0038] see figure 1 , is a schematic diagram of a network for firewall traversal provided by an embodiment of the present invention. by figure 1 In this example, node A as the visitor and node B as the visited party communicate with each other as an example. For convenience, this embodiment pre-sets a firewall traversal proxy (FTP, Firewall Traversal Proxy) between node A and node B. Node A and Node B obtain the IP address and port number of the opposite end through FTP. Among them, FTP only needs to have a static and global IP address, which can be specifically a separate server or router with a public IP address; Its functions are integrated on existing servers or routers in the network, but barrier-free communication with the visiting party and the visited party must be guaranteed. see figure 2 , the present embodiment takes the IP request packet as the data to be sent as an example, and the specific steps of the method are as follows:
[0039] Step 101: Node A and Nod...
Embodiment 2
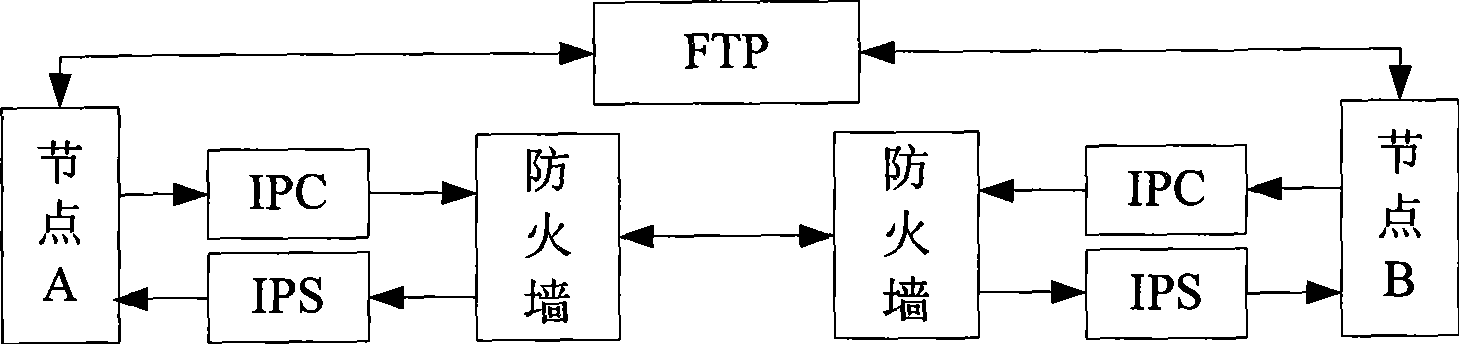
[0062] see image 3 , is a schematic diagram of a network for firewall traversal provided by an embodiment of the present invention. and figure 1 Compared with the provided networking structure, image 3 IPC (IP Tunnel Client, IP Tunnel Client) and IPS (IP Tunnel Server, IP Tunnel Proxy Server) are respectively deployed near Node A and Node B in , taking Node A and Node B for mutual communication as an example, see Figure 4 , the present embodiment takes the IP request packet as the data to be sent as an example, and the specific steps of the method are as follows:
[0063] Step 201: Node A and Node B report their IP addresses and port numbers to FTP respectively.
[0064] Step 202: After FTP receives the IP addresses and port numbers reported by node A and node B, save them, and return the IP addresses, port numbers and session identifiers of the peers to node A and node B respectively.
[0065] Wherein, the session identifier SID is pre-stored by FTP, and is used for mu...
Embodiment 3
[0091] see Figure 5 , the firewall traversal system provided by the embodiment of the present invention, the system includes:
[0092] The first node is used to obtain the IP address and port number of the second node; according to the IP address and port number of the peer node, the data to be sent is encapsulated into an IP tunnel packet, and the IP tunnel packet is sent;
[0093] The second node is configured to receive the IP tunnel packet sent by the first node, and decapsulate the IP tunnel packet to obtain data to be sent.
[0094] Among them, the first node includes:
[0095] An acquisition module, configured to acquire the IP address and port number of the second node;
[0096] The encapsulation module is used to add an IP header and a user datagram protocol header to the data to be sent according to the IP address and port number obtained by the acquisition module, and encapsulates it into an IP tunnel packet, and the IP header and the user datagram protocol heade...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com