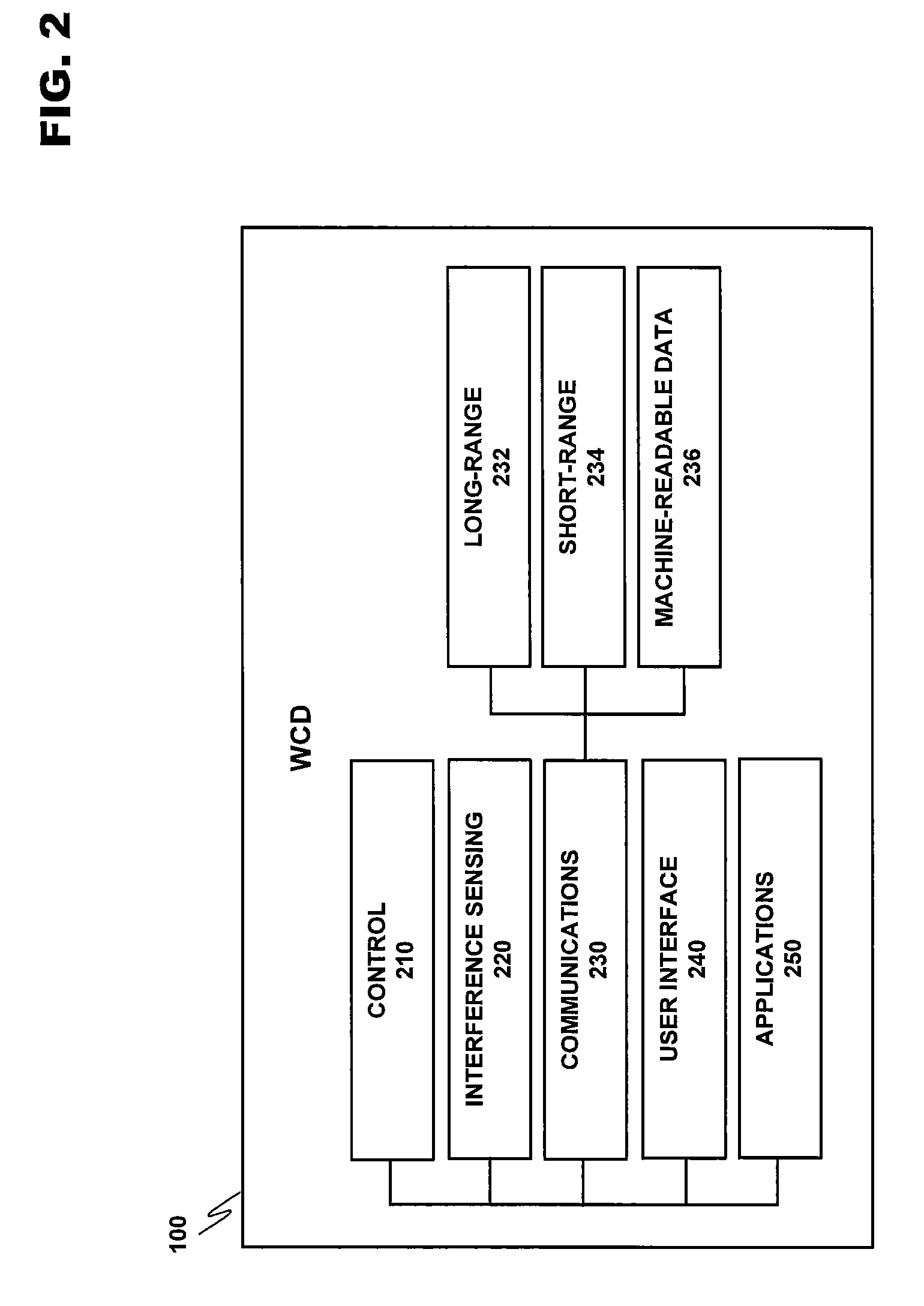
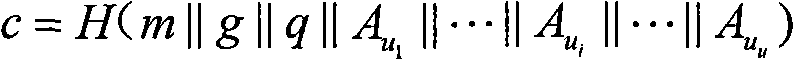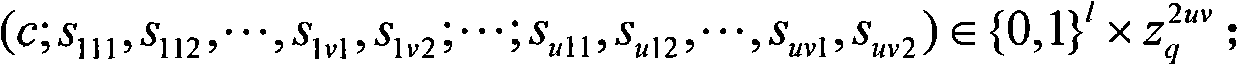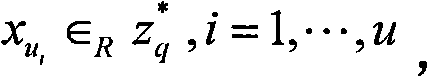Patents
Literature
80 results about "Key establishment" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
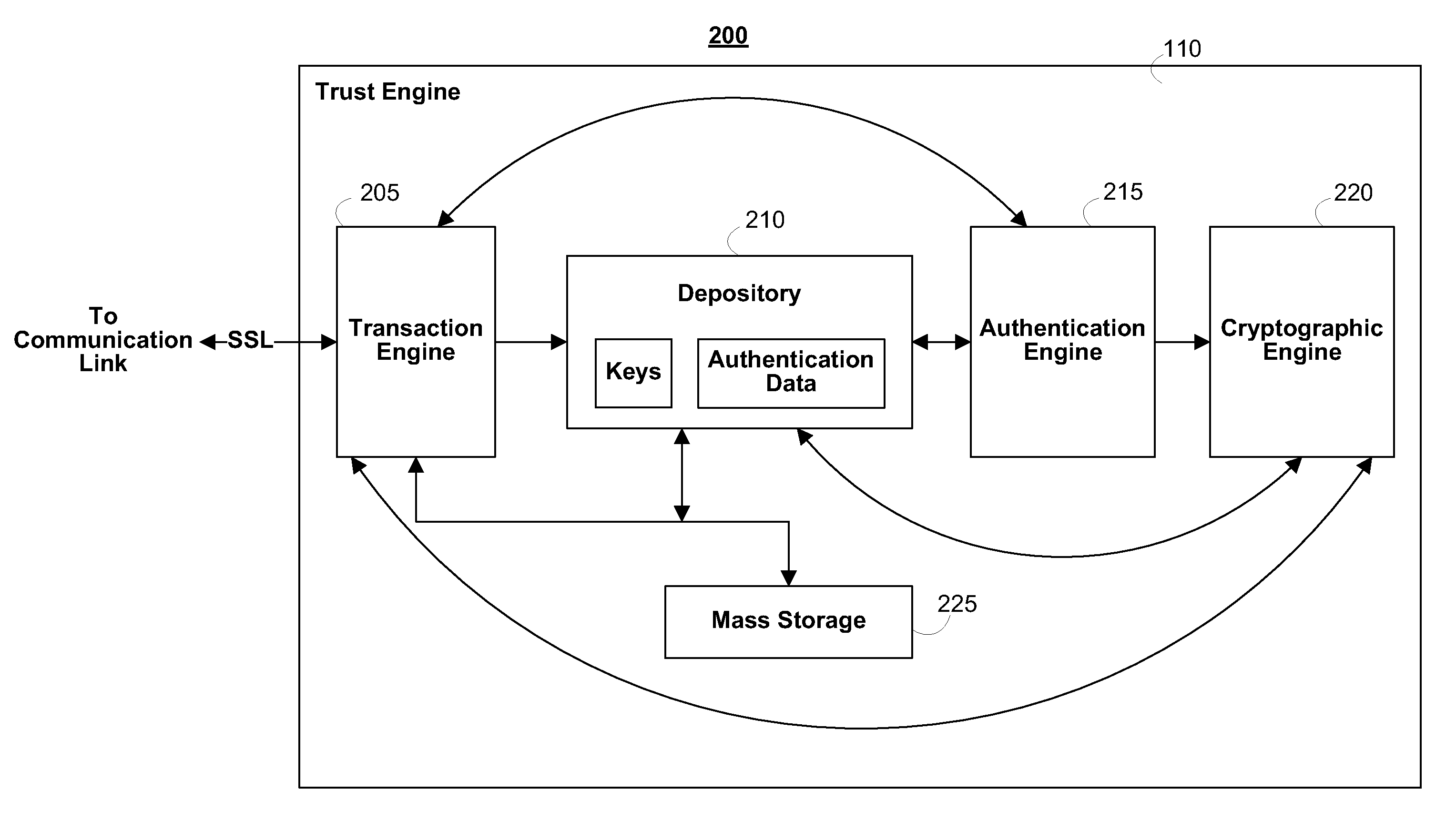
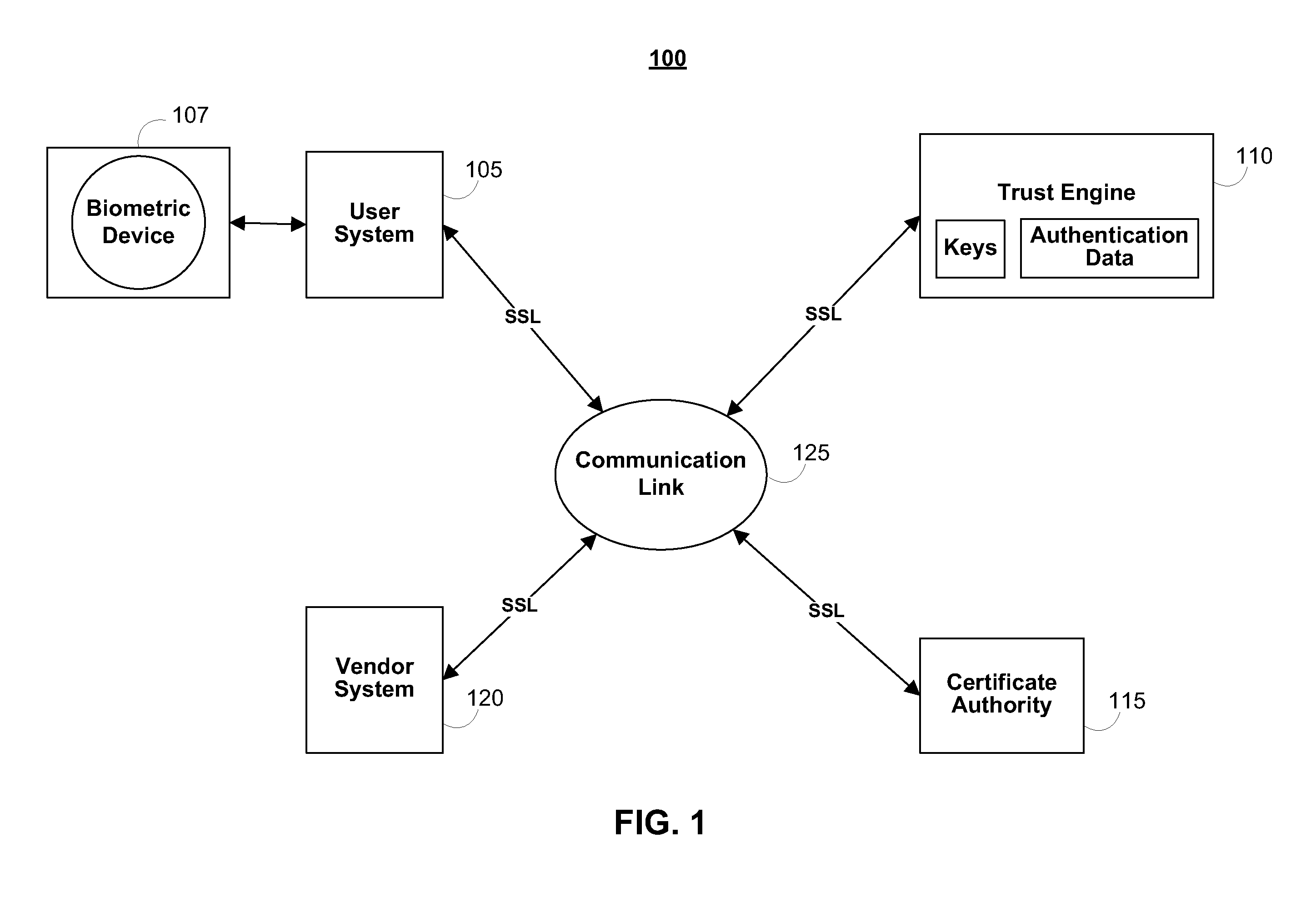
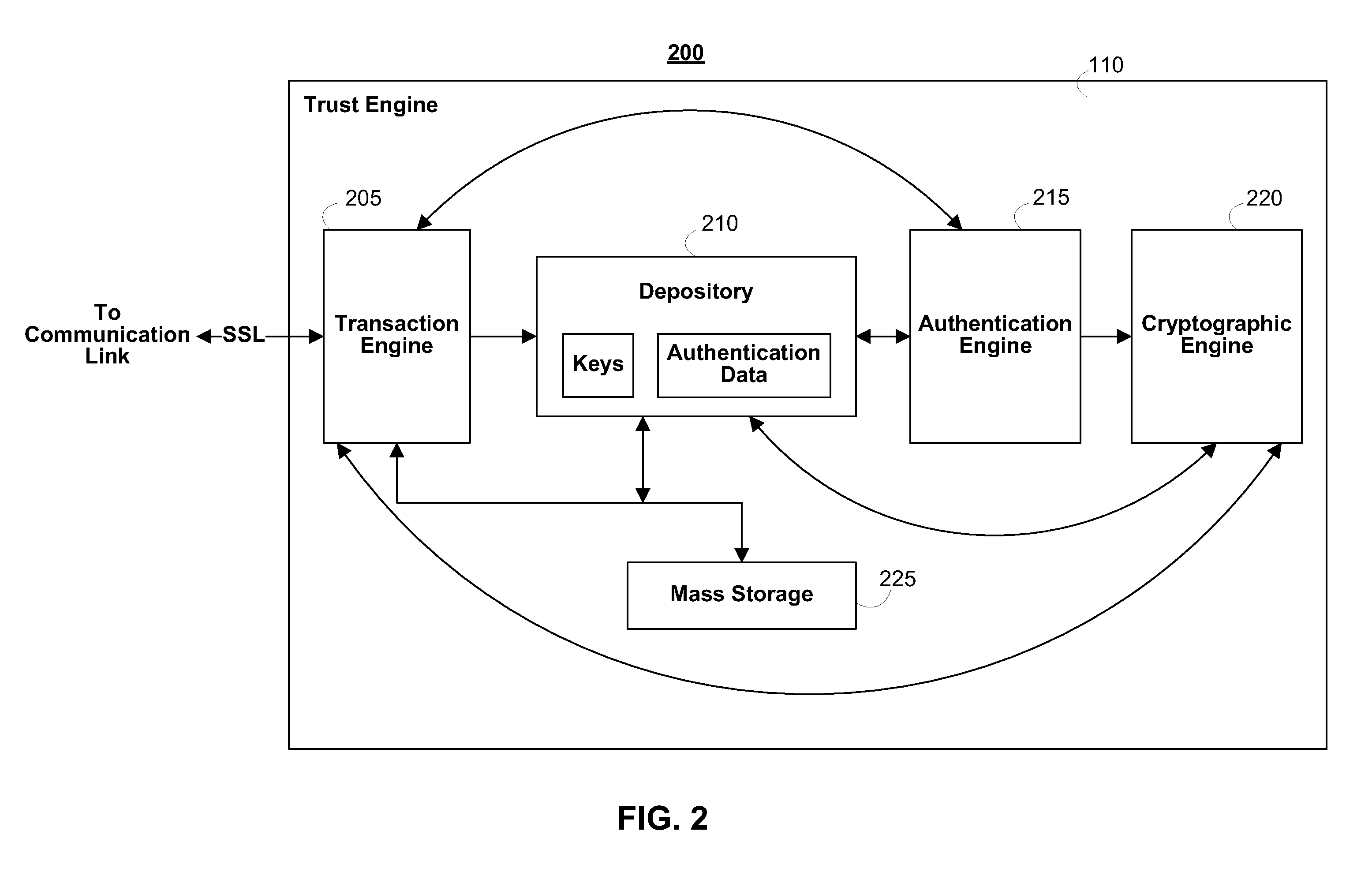
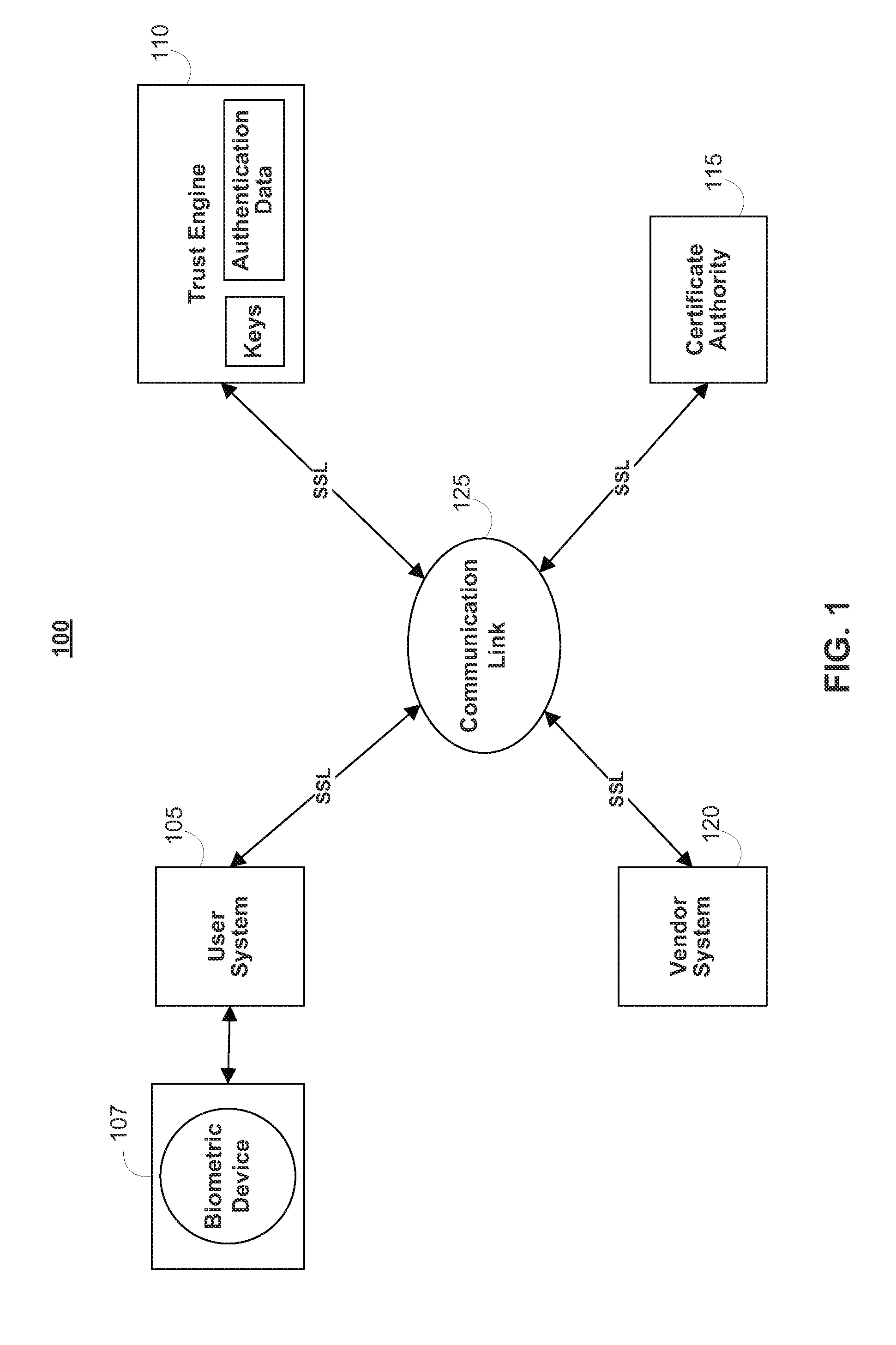
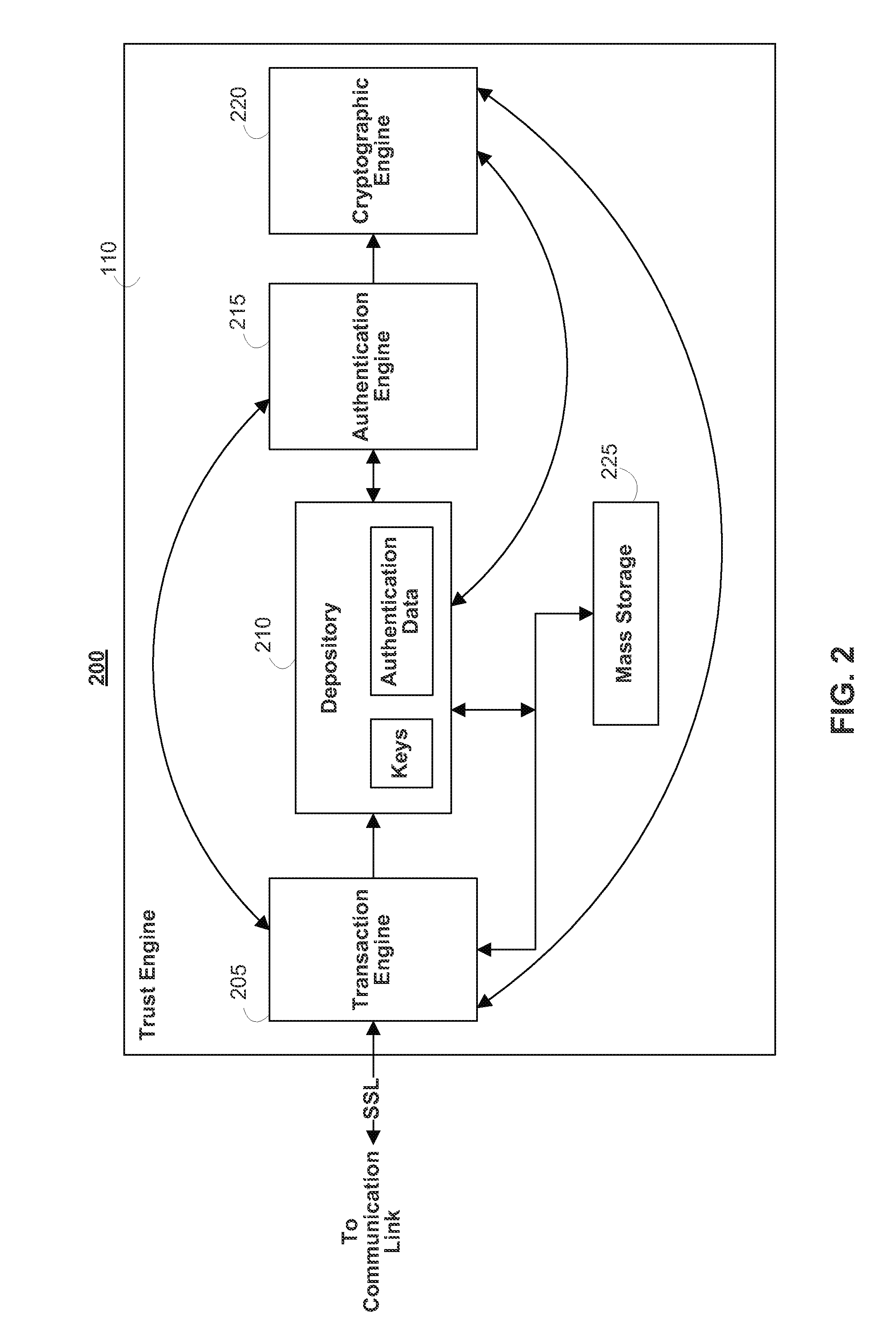
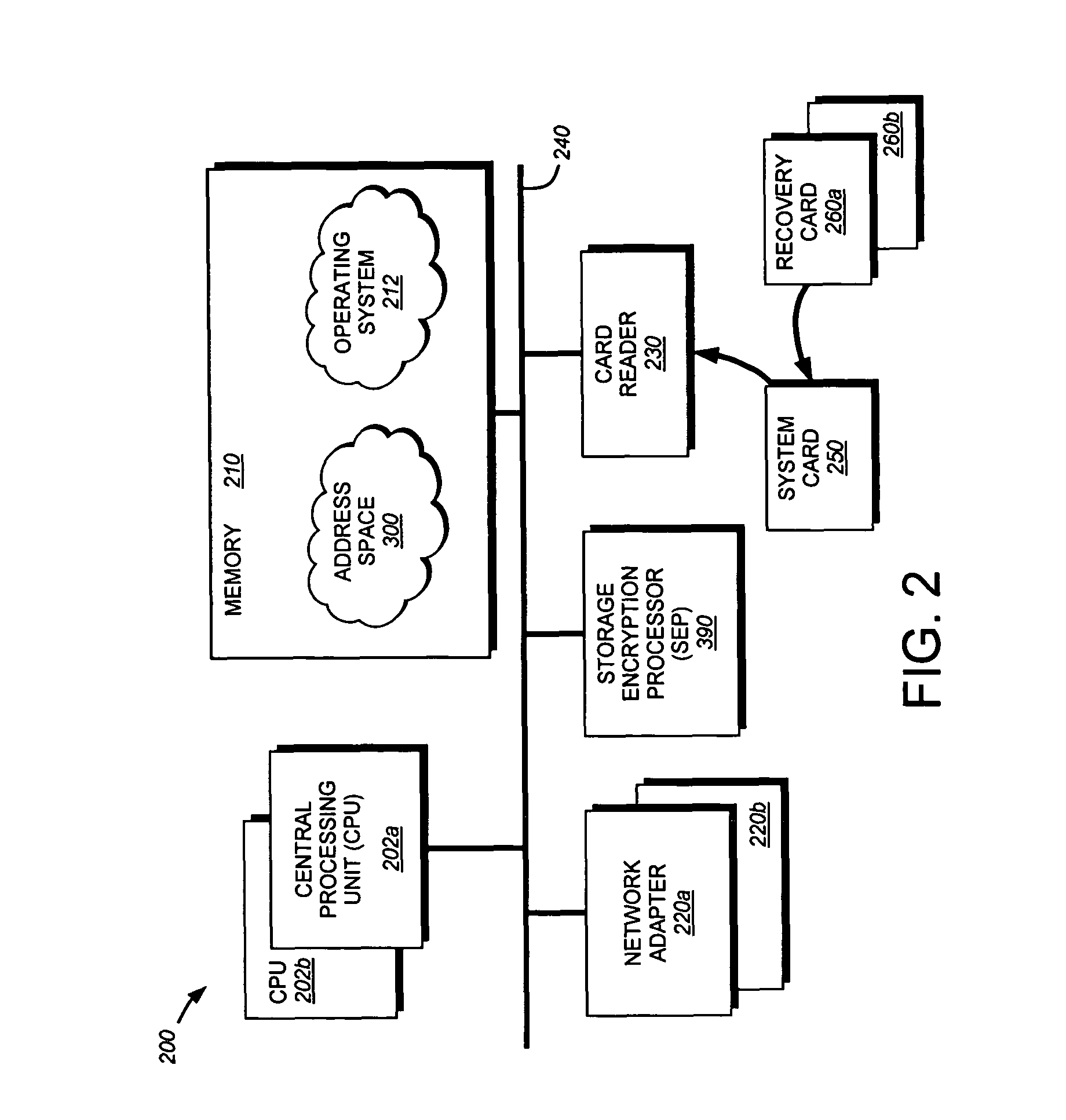
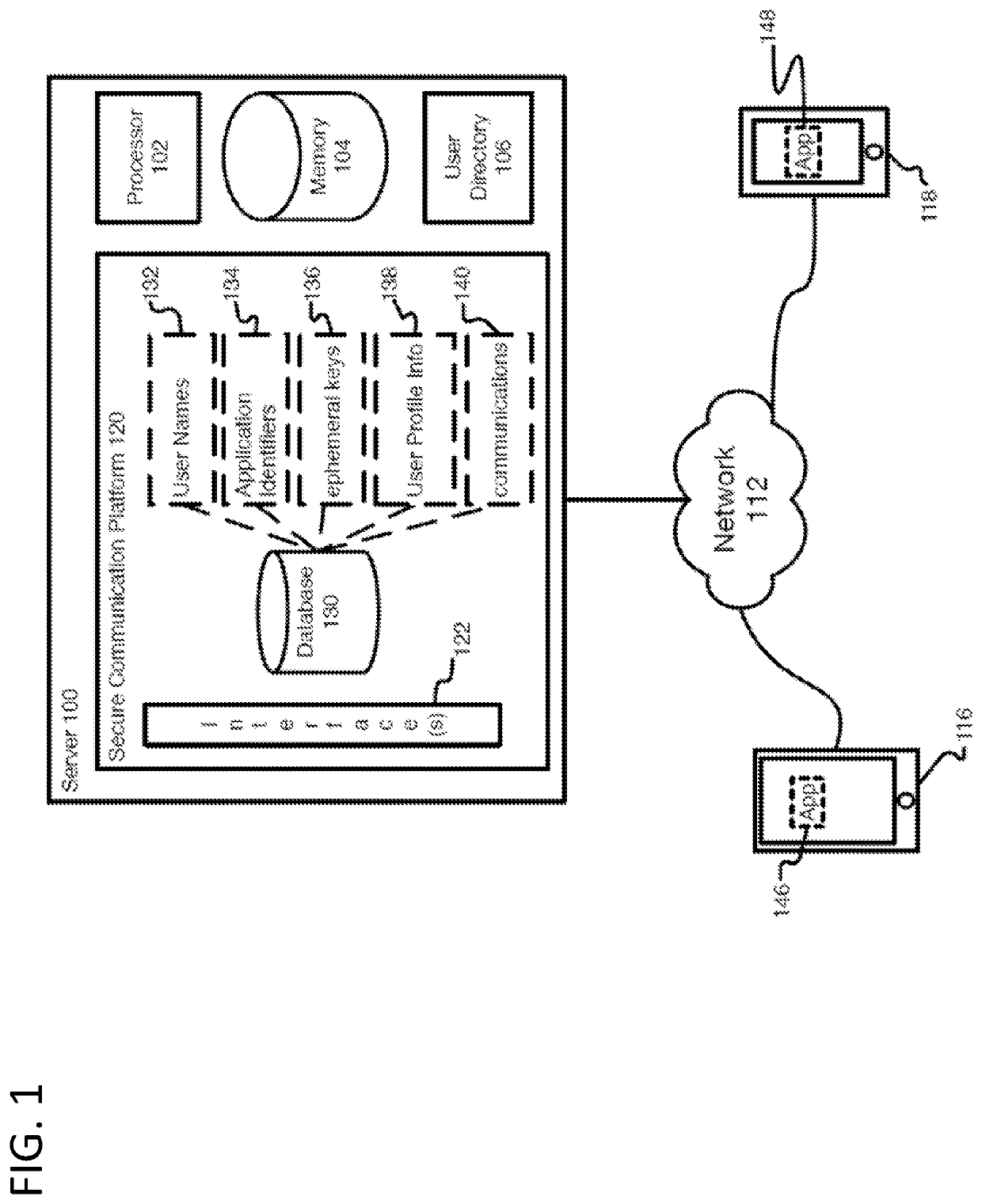
Systems and methods for securing data in motion
ActiveUS20110202755A1Computer security arrangementsData switching networksCertificate authorityKey establishment
Two approaches are provided for distributing trust among a set of certificate authorities. Both approaches are equally secure. In each approach, a secure data parser is integrated with any suitable encryption technology. Each approach may be used to secure data in motion. One approach provides methods and systems in which the secure data parser is used to distribute trust in a set of certificate authorities during initial negotiation (e.g., the key establishment phase) of a connection between two devices. Another approach of the present invention provides methods and systems in which the secure data parser is used to disperse packets of data into shares. A set of tunnels is established within a communication channel using a set of certificate authorities, keys developed during the establishment of the tunnels are used to encrypt shares of data for each of the tunnels, and the shares of data are transmitted through each of the tunnels. Accordingly, trust is distributed among a set of certificate authorities in the structure of the communication channel itself.
Owner:SECURITY FIRST INNOVATIONS LLC
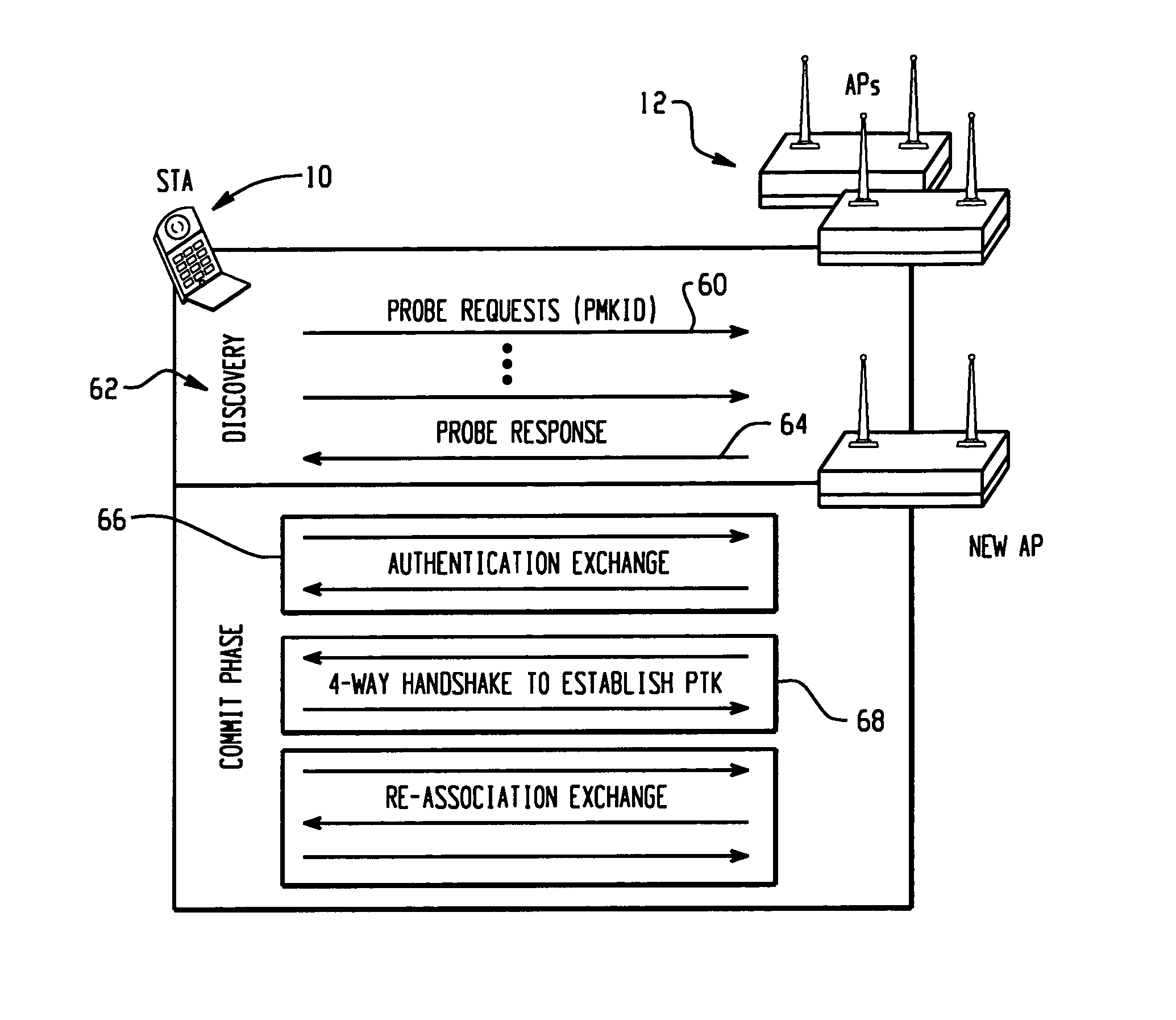
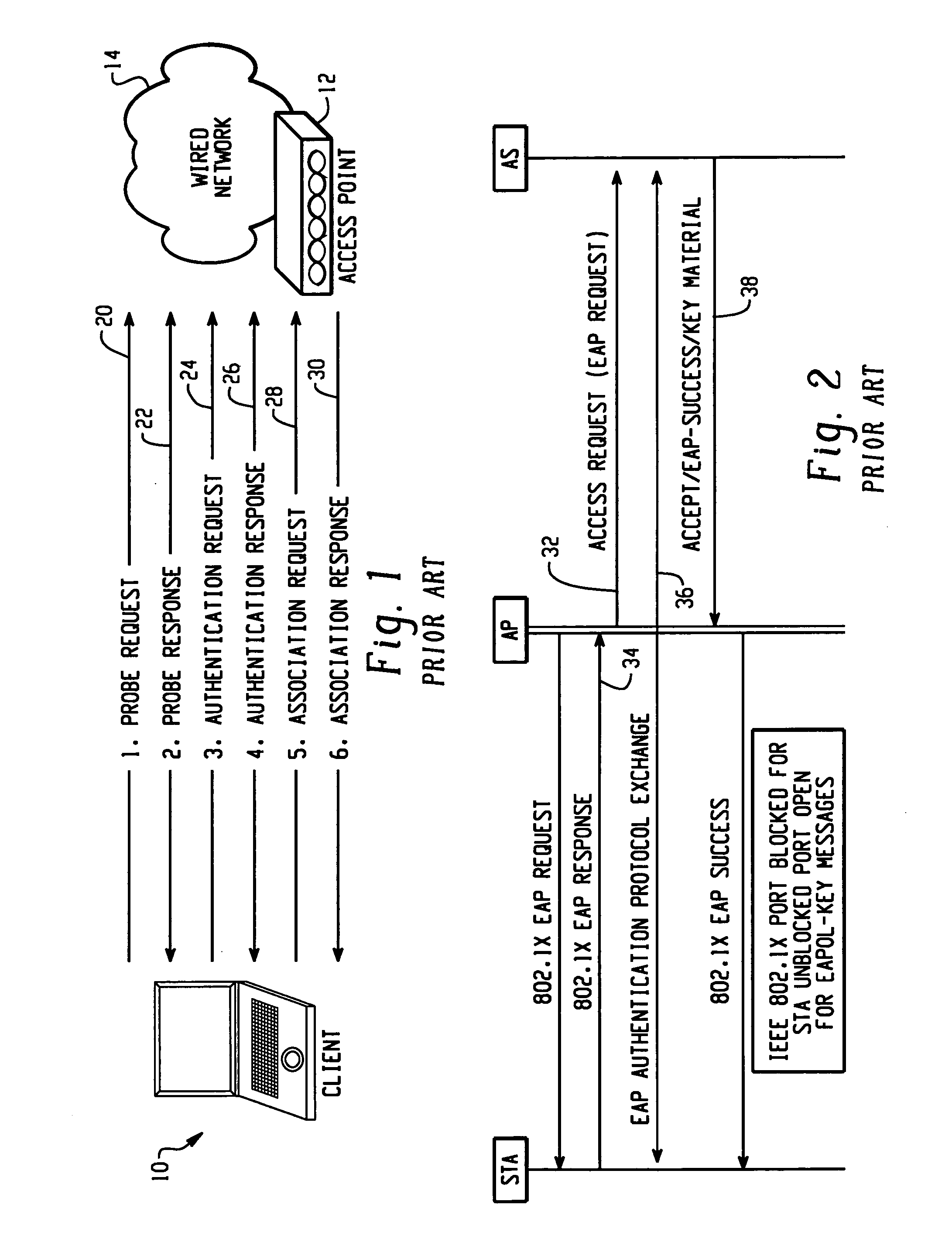
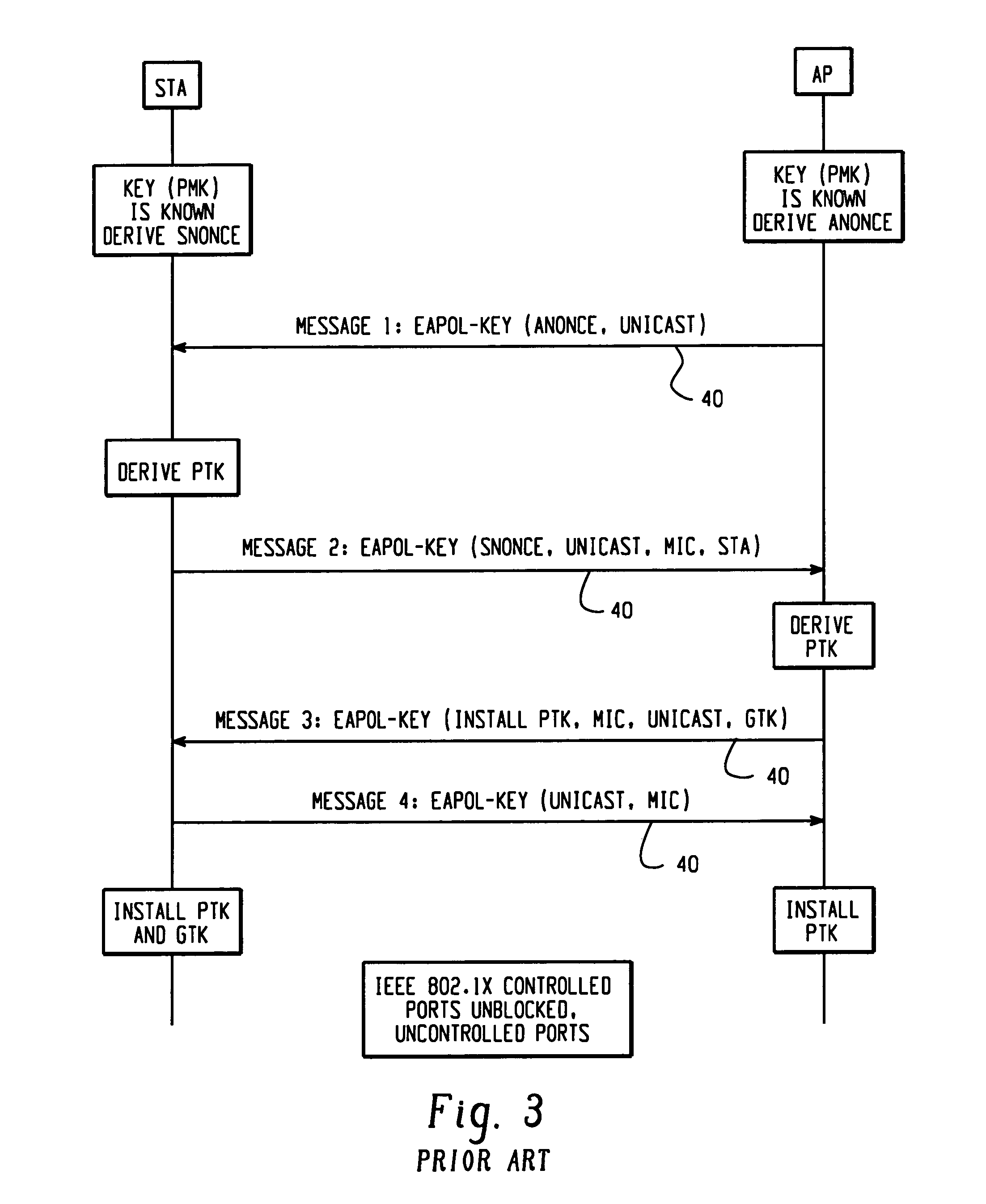
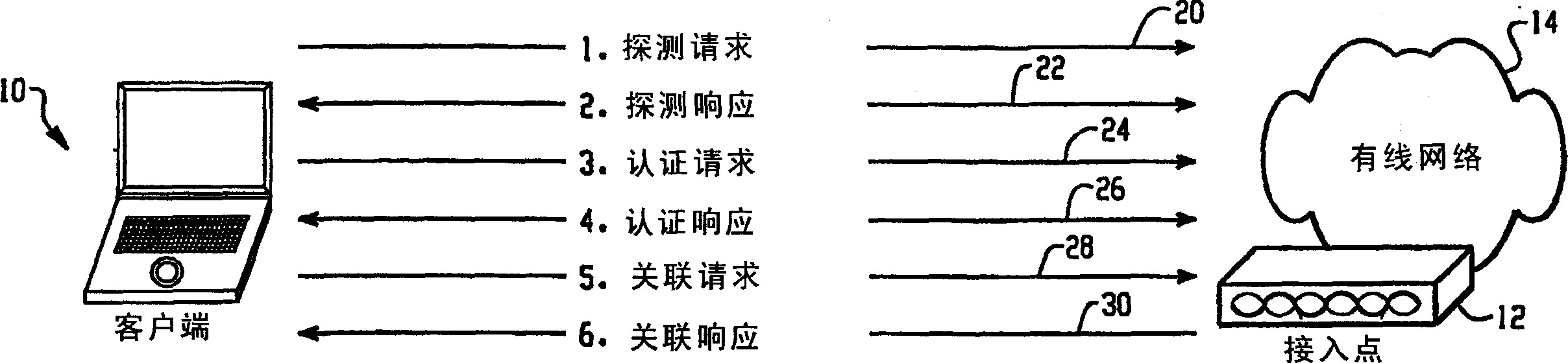
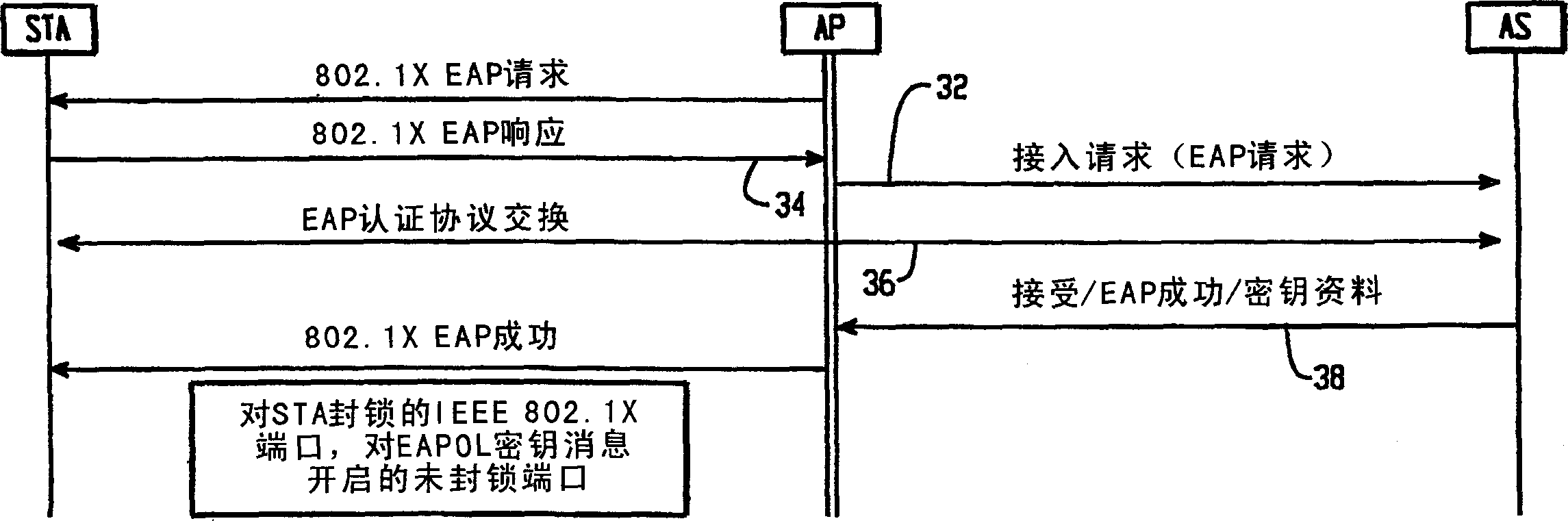
Facilitating 802.11 roaming by pre-establishing session keys
InactiveUS7275157B2Reduce switching delayCommunication securityUser identity/authority verificationNetwork topologiesTelecommunicationsKey establishment
A method and system for pre-authenticating a pre-establishing key management on a roaming device prior to reassociation to facilitate fast hand-off in a wireless network is described. For enhanced mobility, both authentication and key establishment is performed prior to reassociation of the roaming device between access points. When the roaming device enters in contact with one of the access points, a local authentication is performed between the access point and the roaming device prior to reassociation with the access point to allow for fast hand-offs of the device between access points within the network.
Owner:CISCO TECH INC
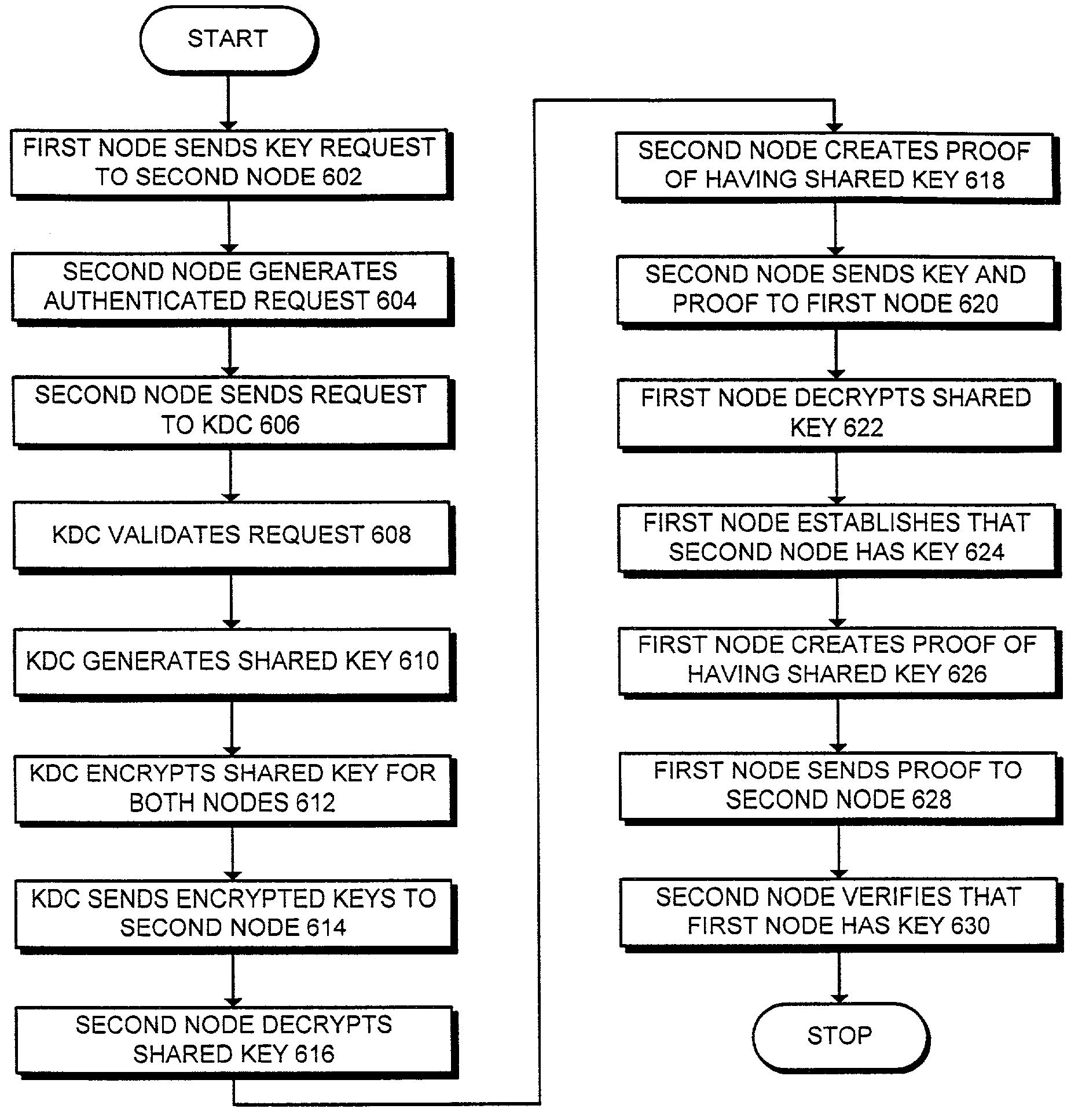
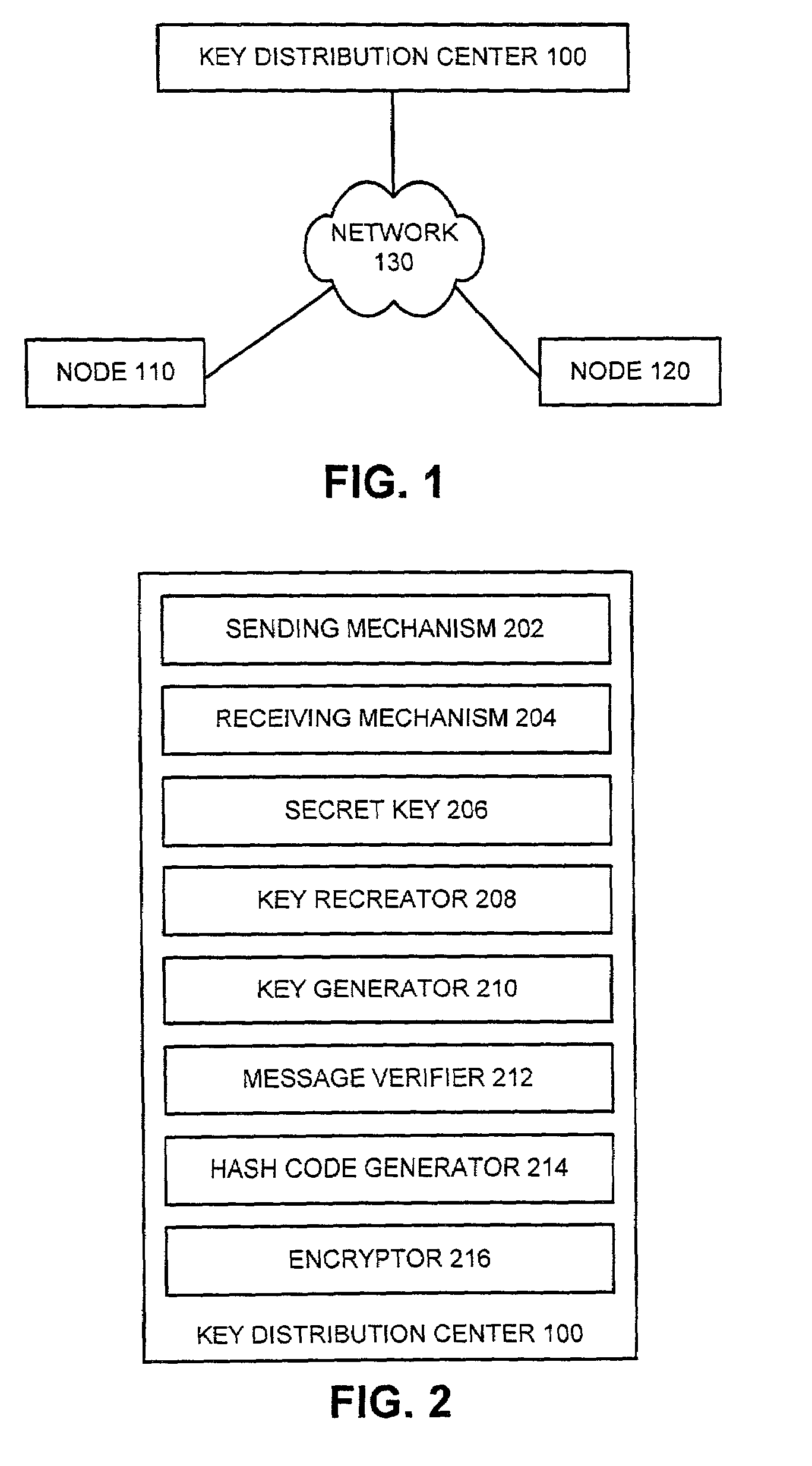
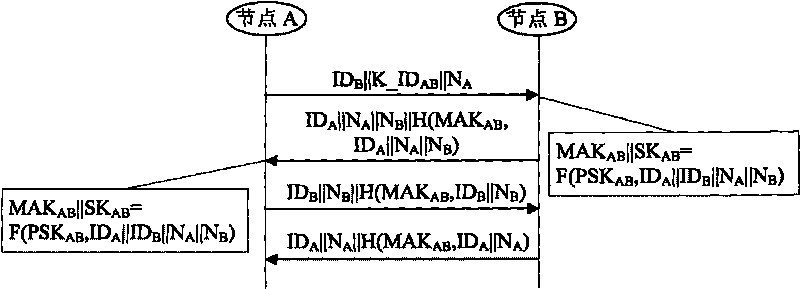
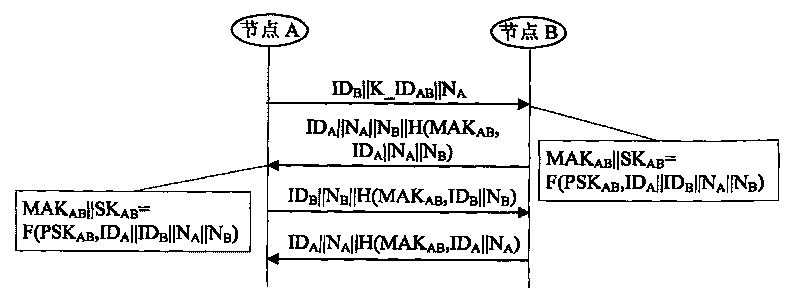
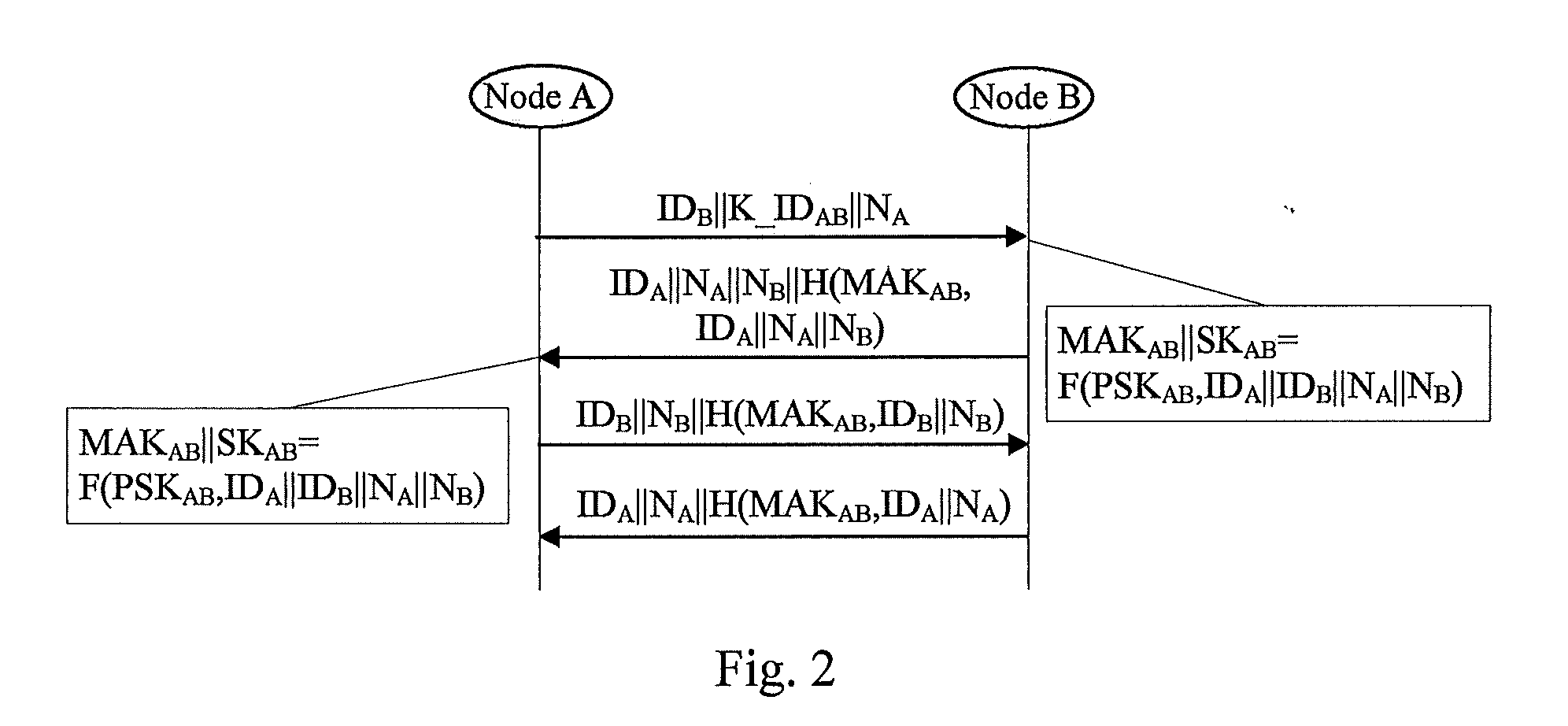
Method and apparatus for cryptographic key establishment using an identity based symmetric keying technique
One embodiment of the present invention provides a system for establishing a shared cryptographic key between participating nodes in a network. The system operates by sending a first message from the first node to the second node requesting establishment of a shared key. The second node sends a second message containing identifiers and a message authentication code to a key distribution center (KDC). The authentication code is generated using a second node key belonging to the second node. The KDC recreates the previously created second node key using the second node identifier and a secret key known only to the key distribution center. The KDC then verifies the message authentication code using the second node key. If the message authentication code is verified, the KDC creates a shared key for the nodes to use while communicating with each other. The KDC securely communicates this shared key to the participating nodes
Owner:MCAFEE LLC
System and method for secure wireless multi-hop network formation
ActiveUS20080016338A1Synchronising transmission/receiving encryption devicesUser identity/authority verificationNode authenticationEncryption
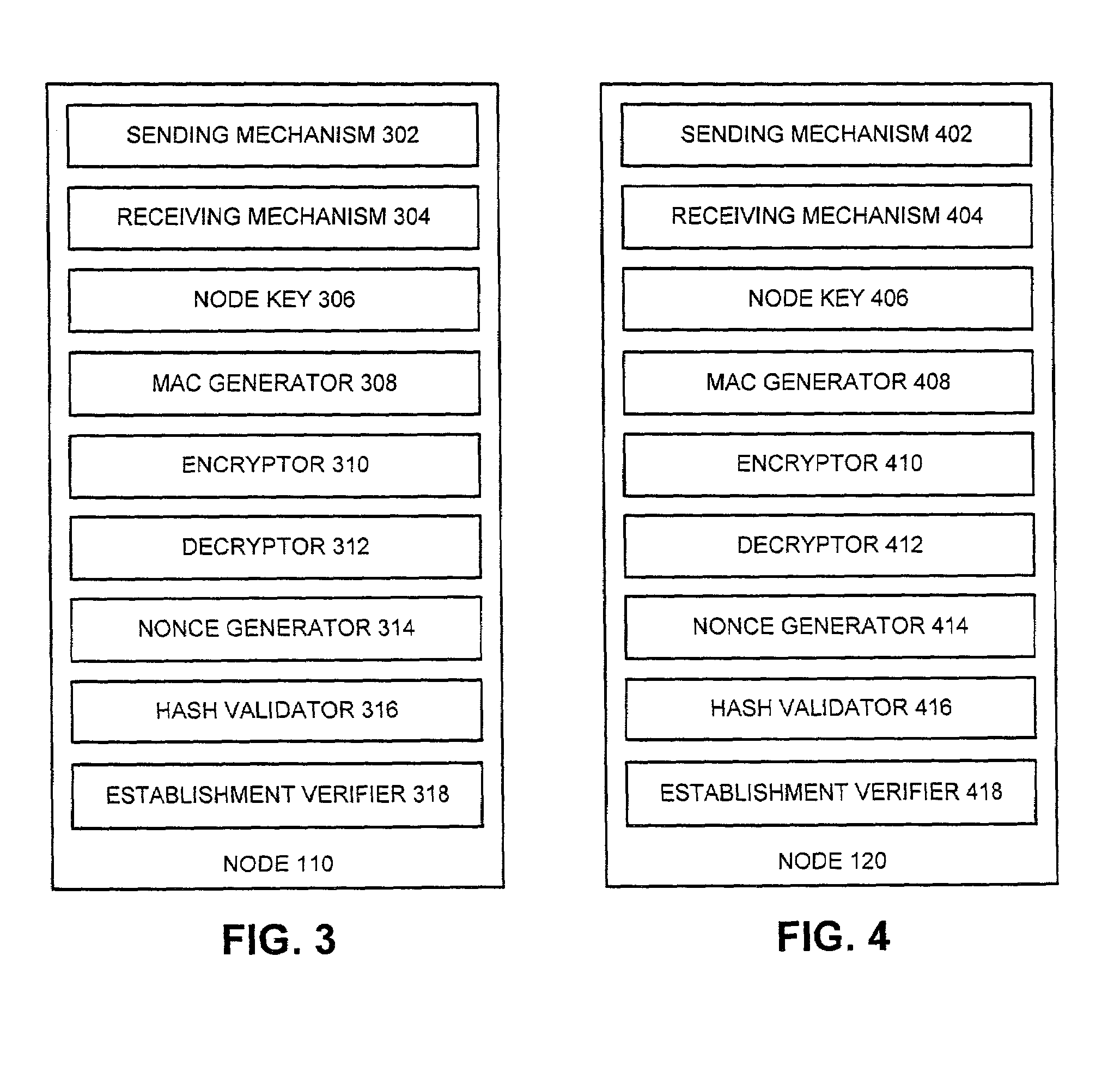
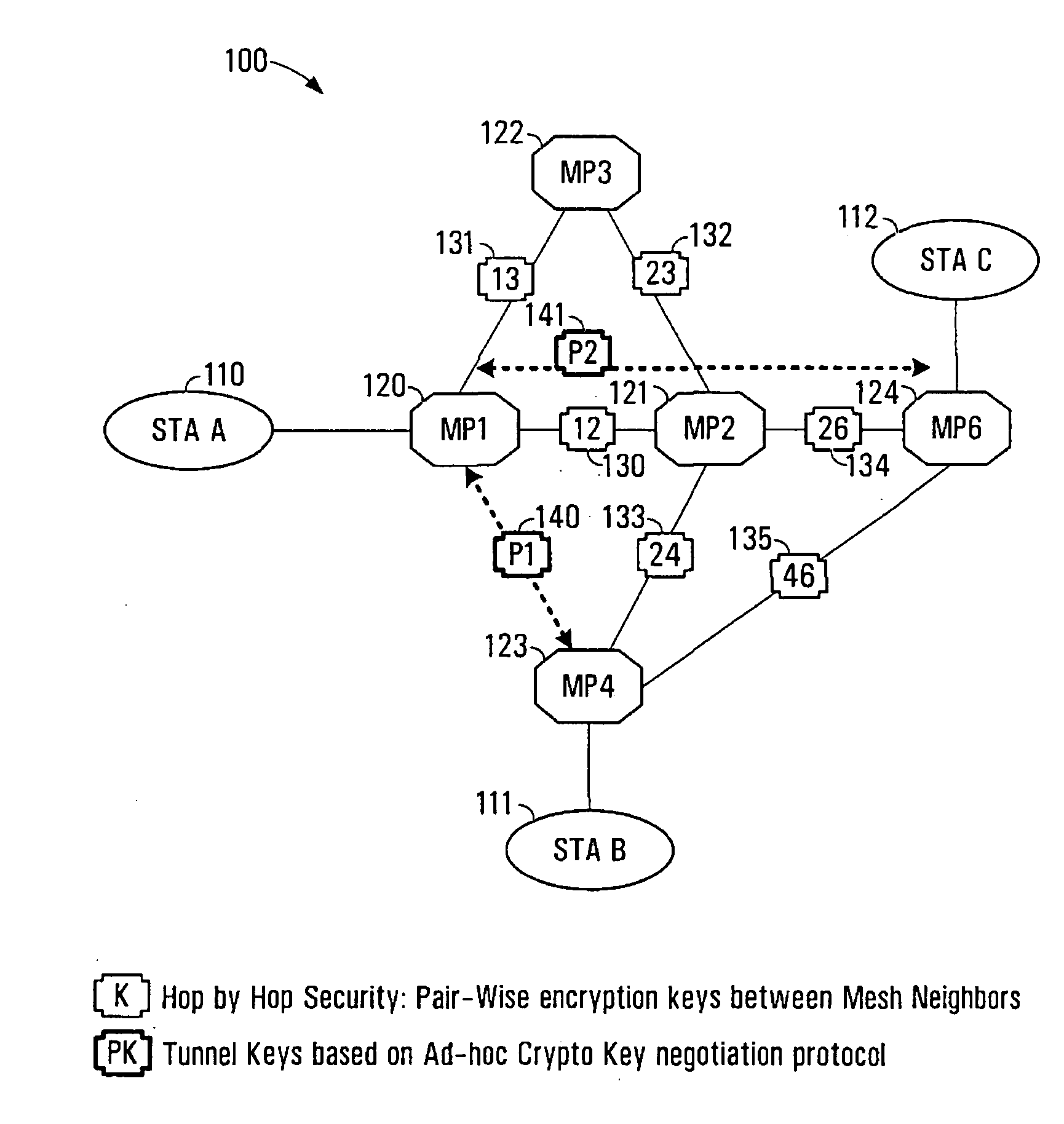
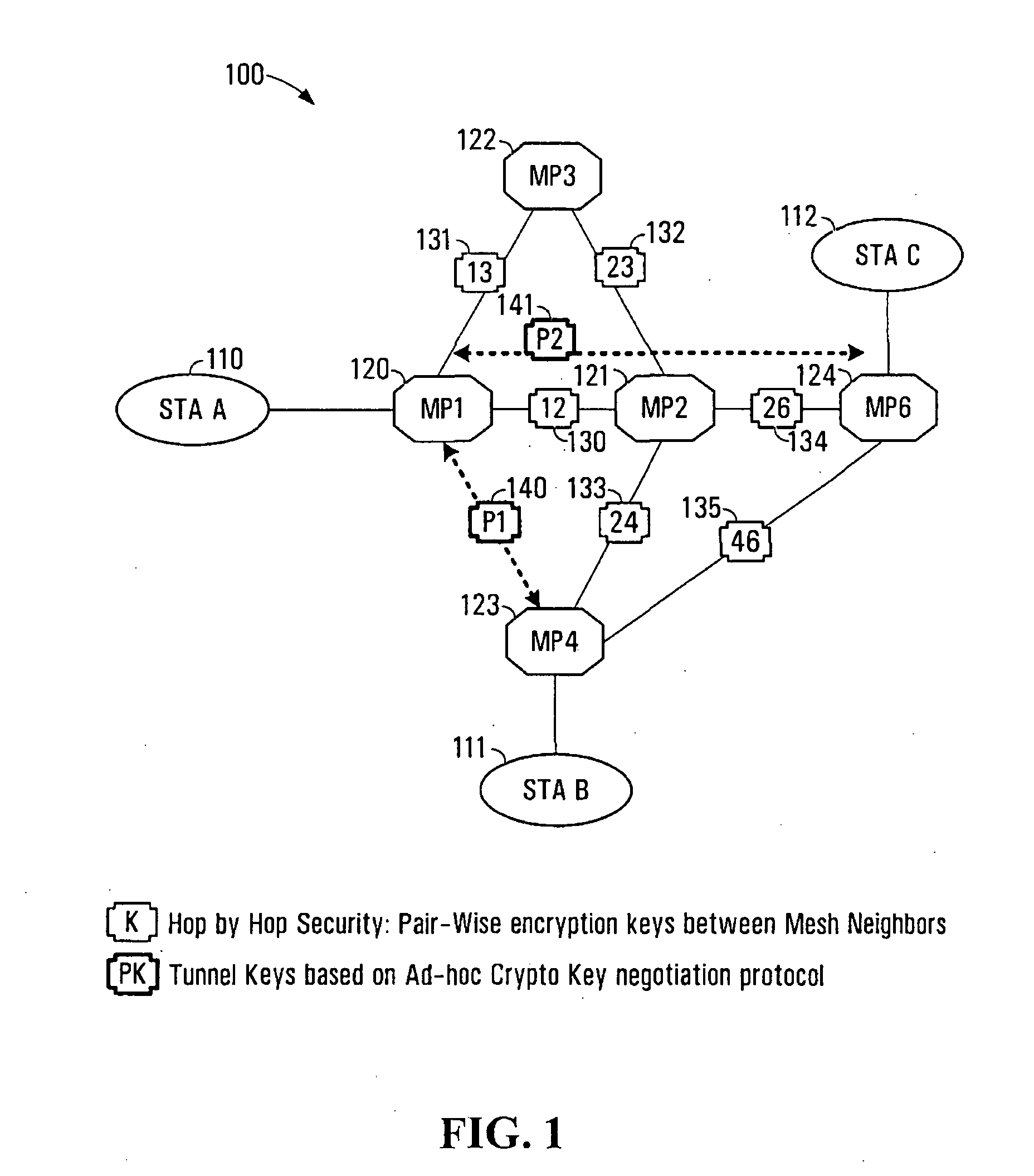
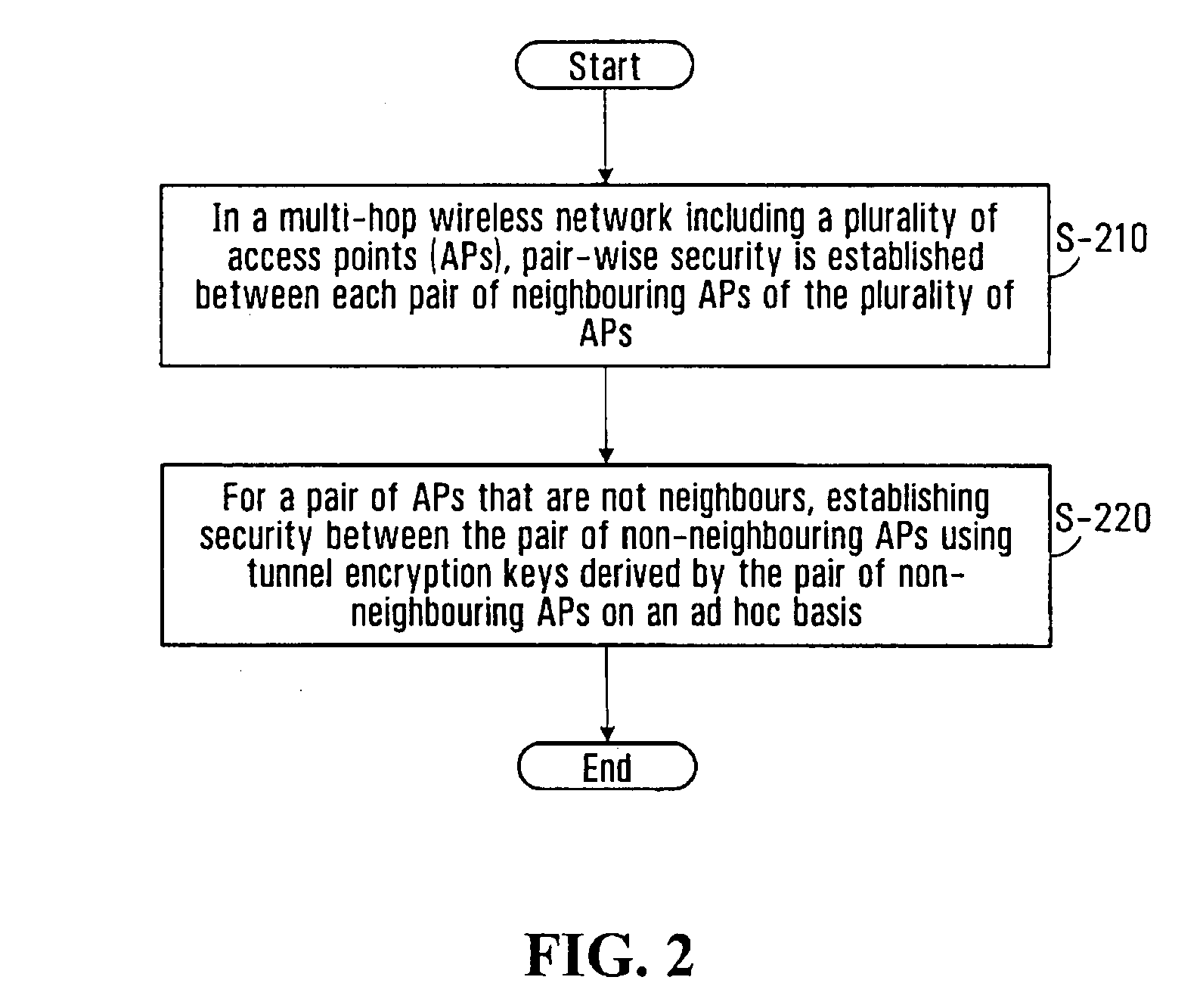
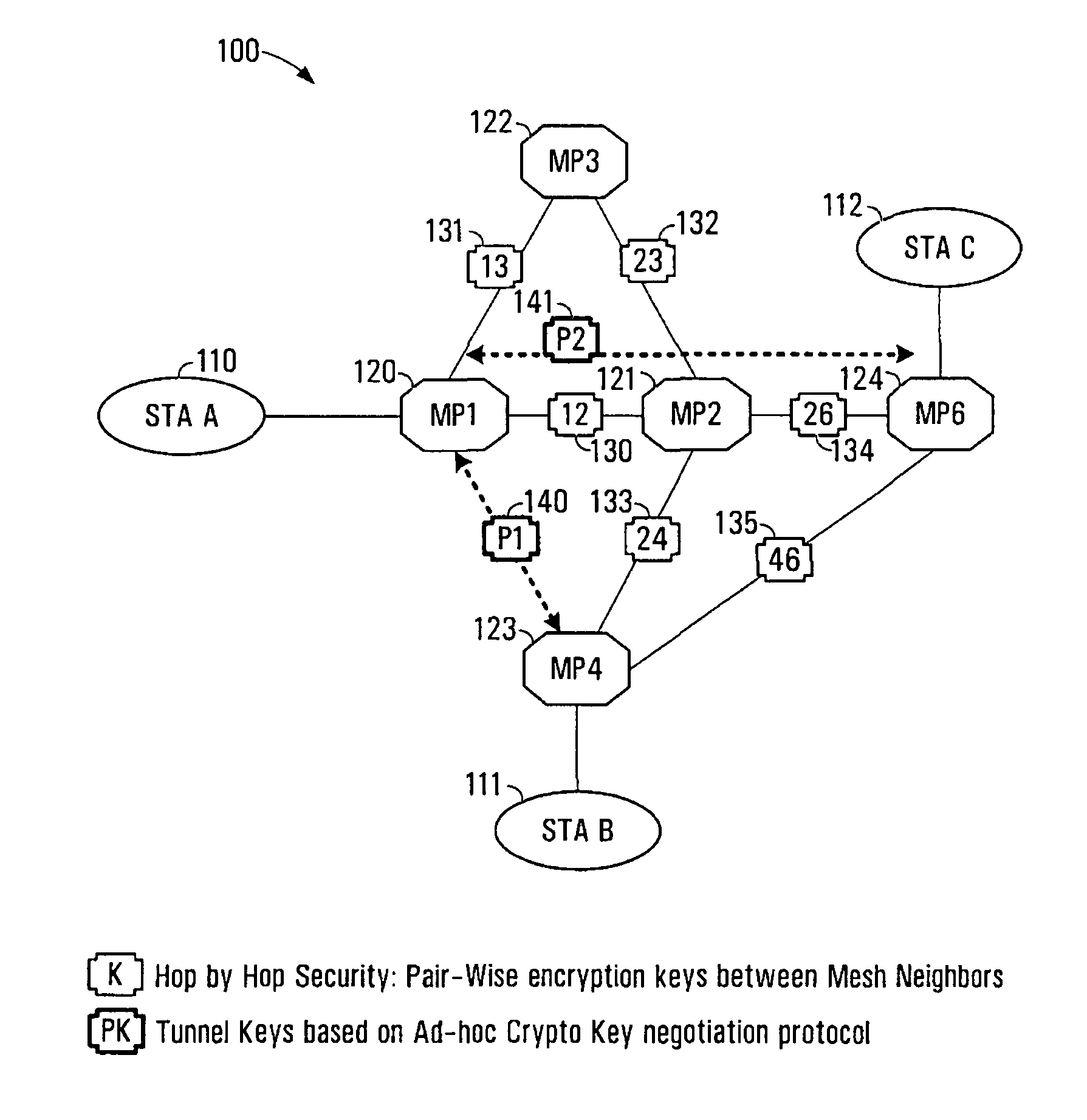
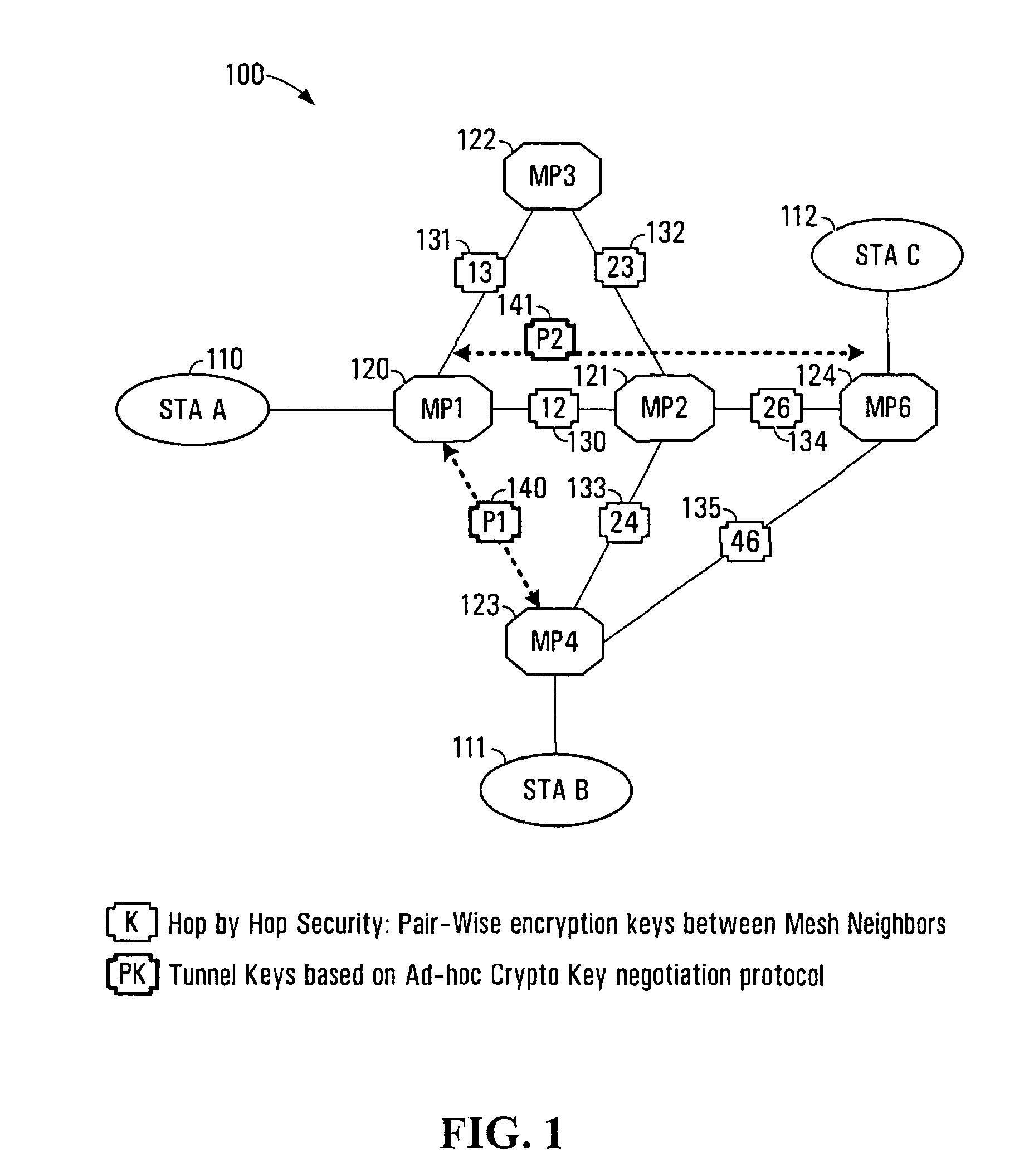
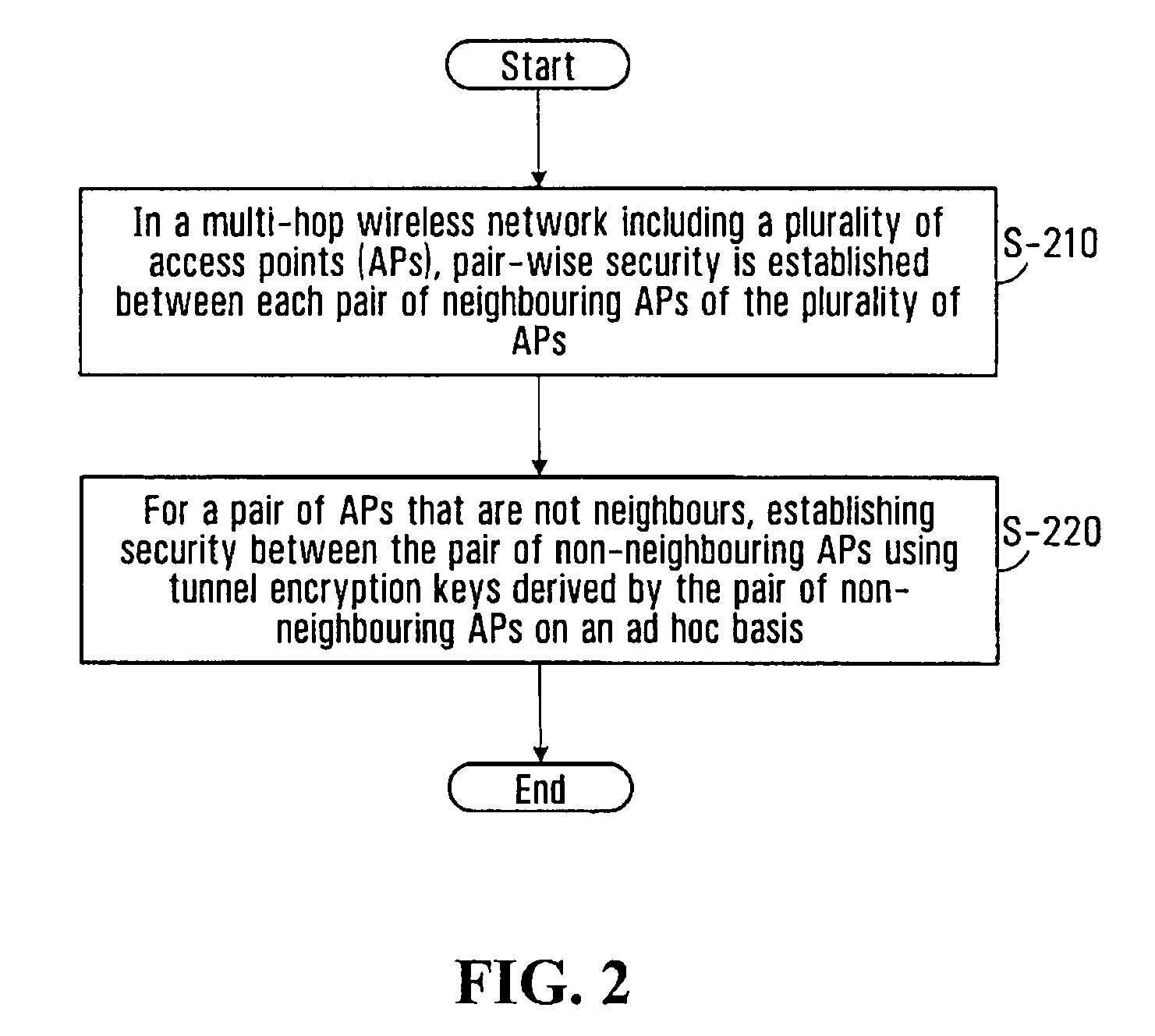
The present invention provides methods and devices for a security architecture for use in wireless multi-hop networks. A method for implementing pair-wise encryption key establishment, network node authentication and determining tunnel encryption keys is provided in a following manner. In a multi-hop wireless network including a plurality of network nodes, pair-wise security is established between pairs of neighbouring network nodes of the plurality of network nodes. For example, pair-wise security is established in the form of temporal pair-wise encryption keys. Following establishment of pair-wise security between pairs of neighbouring network nodes, for a pair of network nodes that are not neighbours, tunnel security is established between the pair of network nodes using tunnel encryption keys derived by the pair of network nodes on an ad hoc basis. The tunnel encryption keys are used to form the connection between non-neighbouring network nodes so as to avoid the hop-by-hop encryption / decryption used in conventional multi-hop wireless systems.
Owner:APPLE INC
Open protocol for authentication and key establishment with privacy
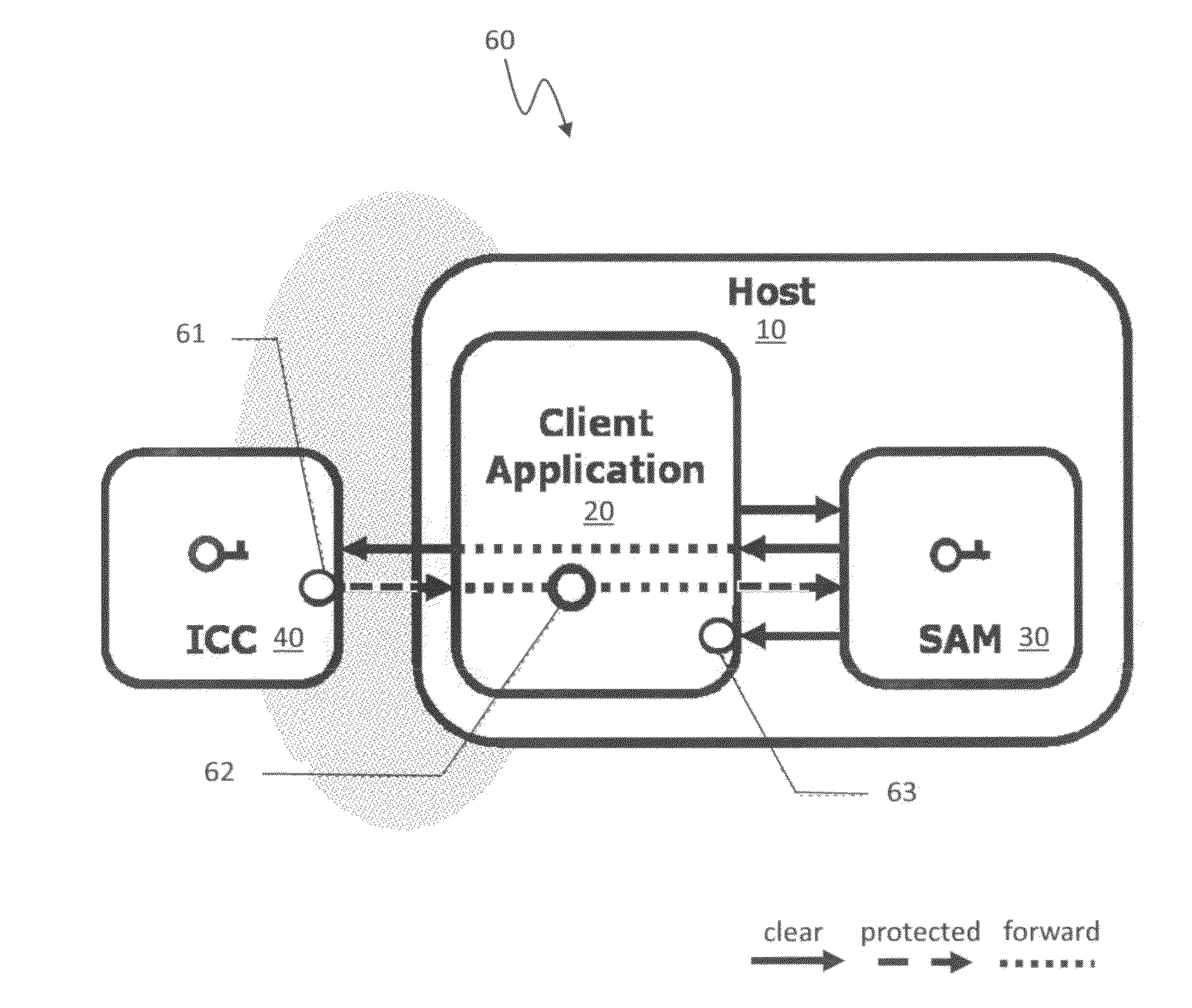
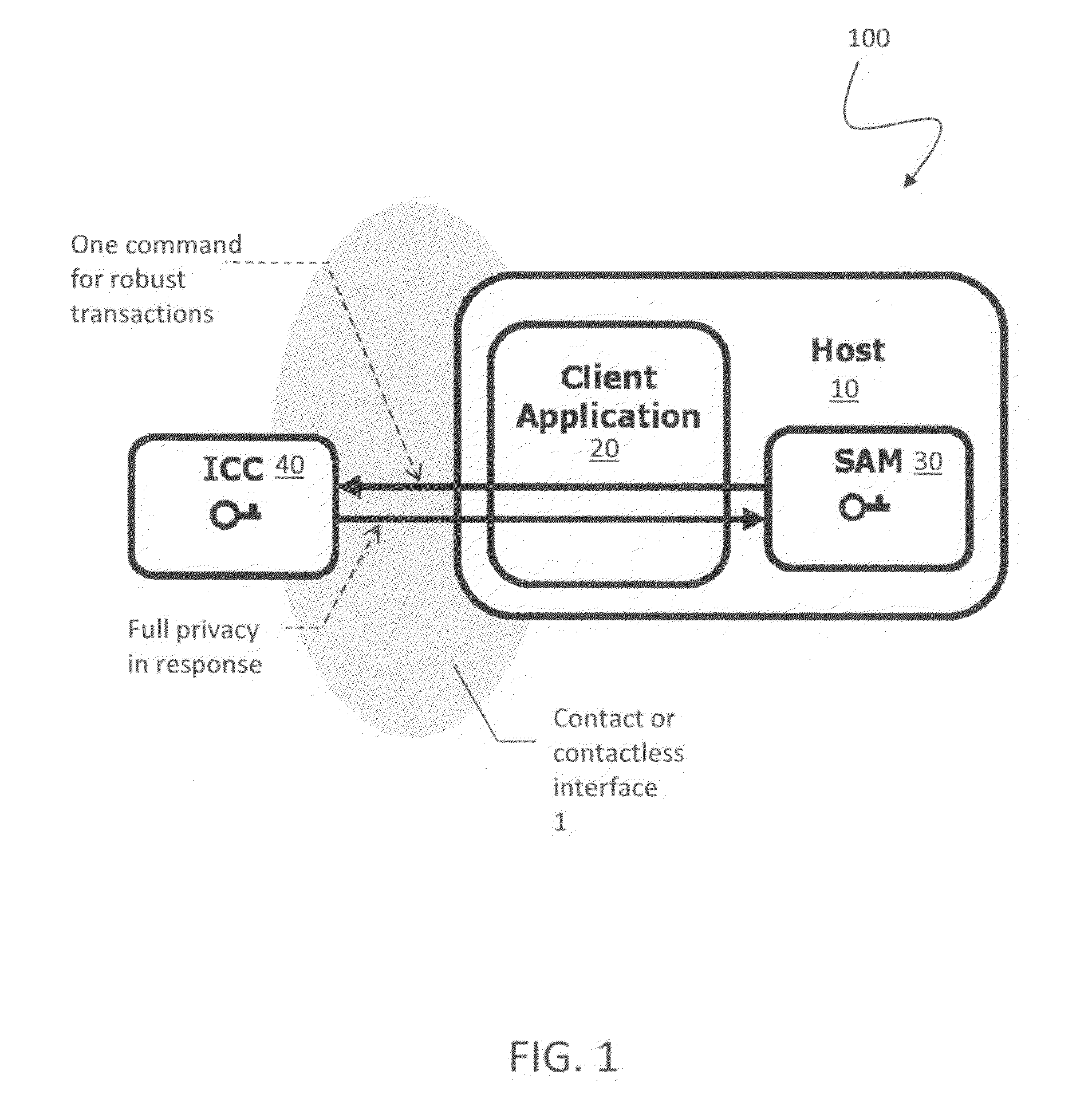
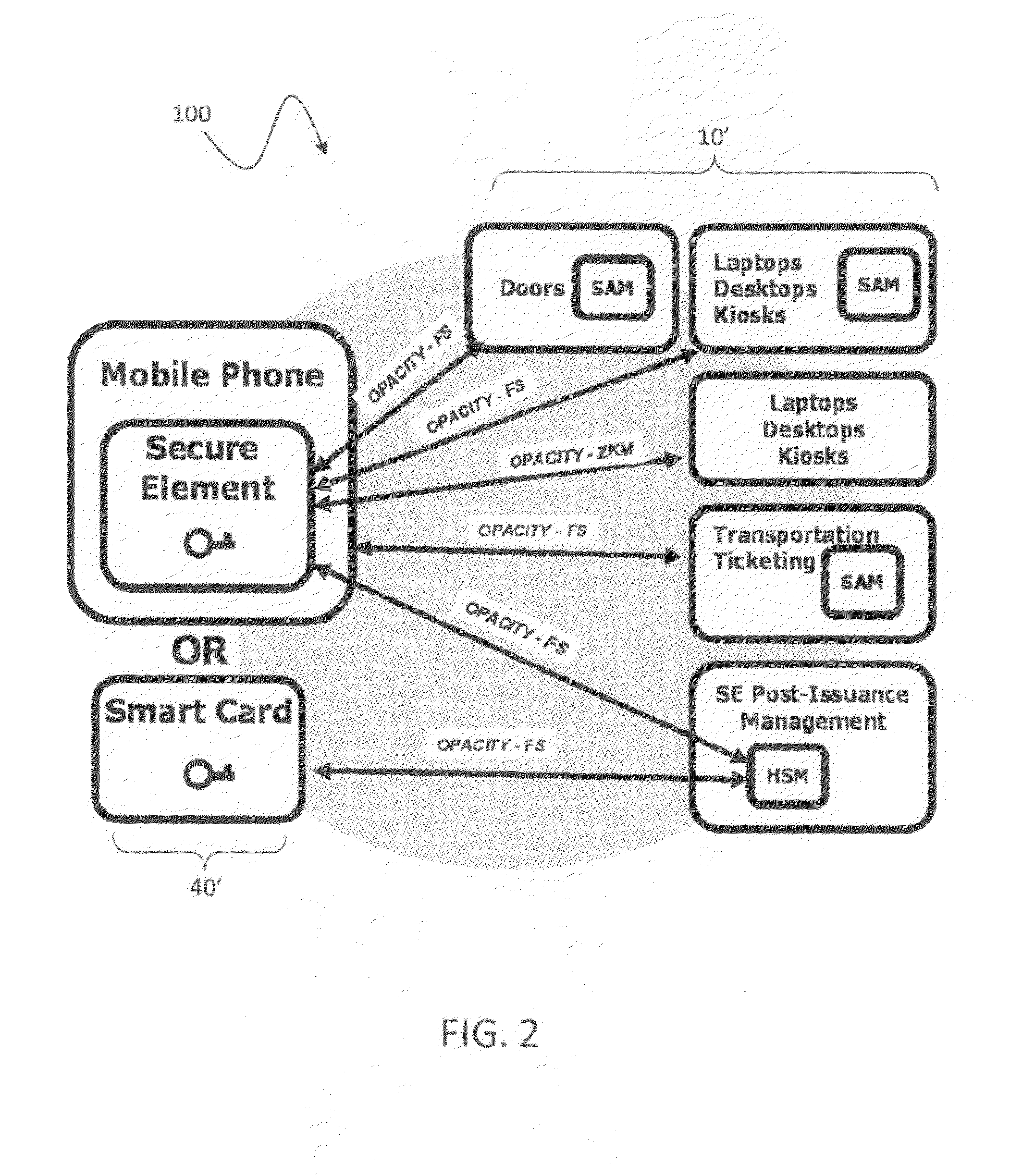
ActiveUS20120144193A1Public key for secure communicationUser identity/authority verificationSmart cardPhysical access
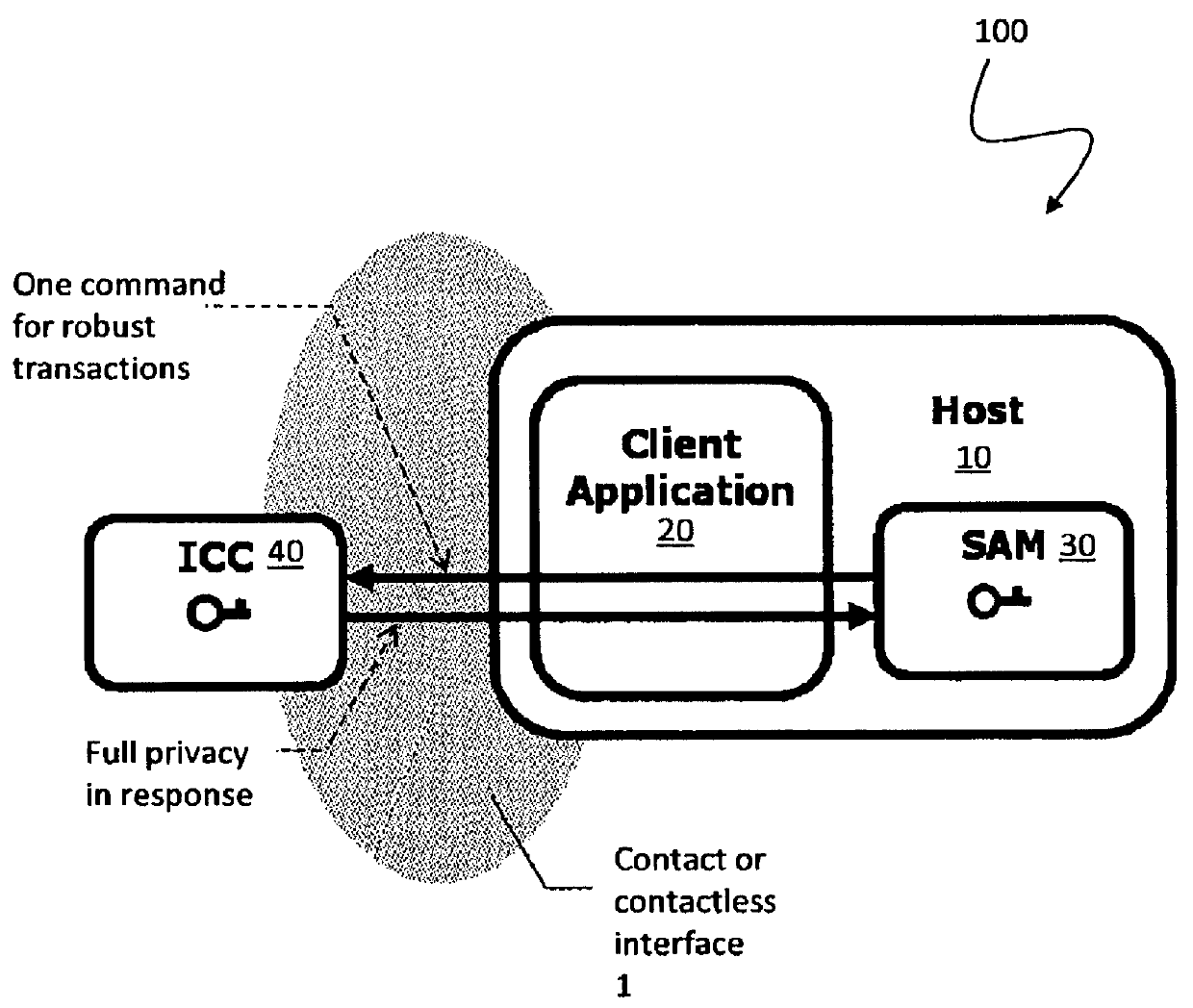
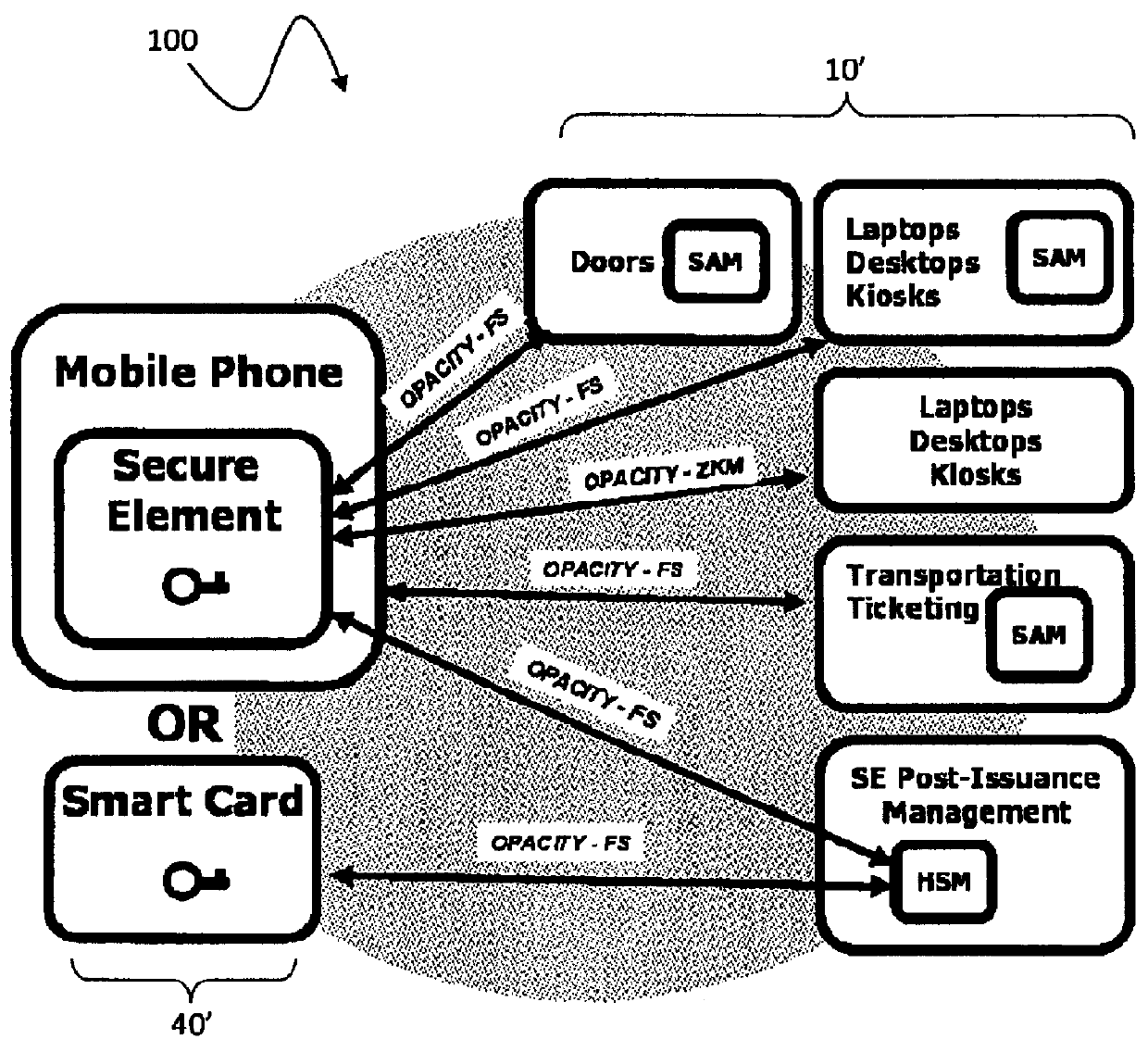
A suite of efficient authentication and key establishment protocols for securing contact or contactless interfaces between communicating systems. The protocols may be used in secure physical access, logical access and / or transportation applications, among other implementations. The system authenticates a mobile device such as a smart card and / or mobile phone equipped with a secure element presented to one or more host terminals and establishes shared secure messaging keys to protect communications between the device and terminal. Secure messaging provides an end-to-end protected path of digital documents or transactions through the interface. The protocols provide that the device does not reveal identification information to entities different from a trusted host. The terminal may be a contactless reader at a door for controlling physical access, a desktop, laptop or kiosk for controlling logical access, and / or an access point for obtaining an encrypted digital ticket from an authenticated mobile device used for transit applications.
Owner:ASSA ABLOY AB
Systems and methods for securing data in motion
ActiveUS20130042105A1Public key for secure communicationComputer security arrangementsStructure of Management InformationComputer science
Owner:SECURITY FIRST INNOVATIONS LLC
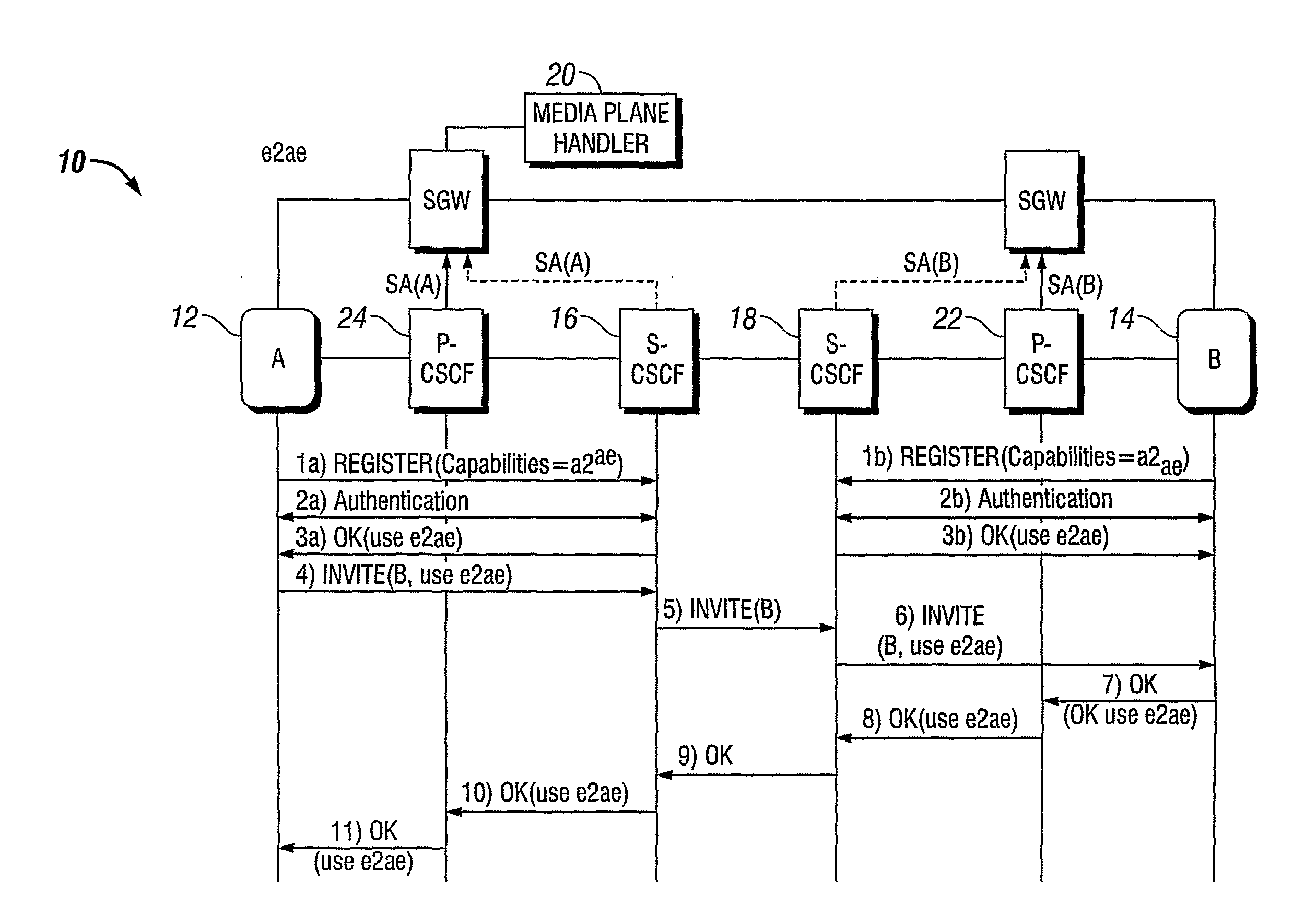
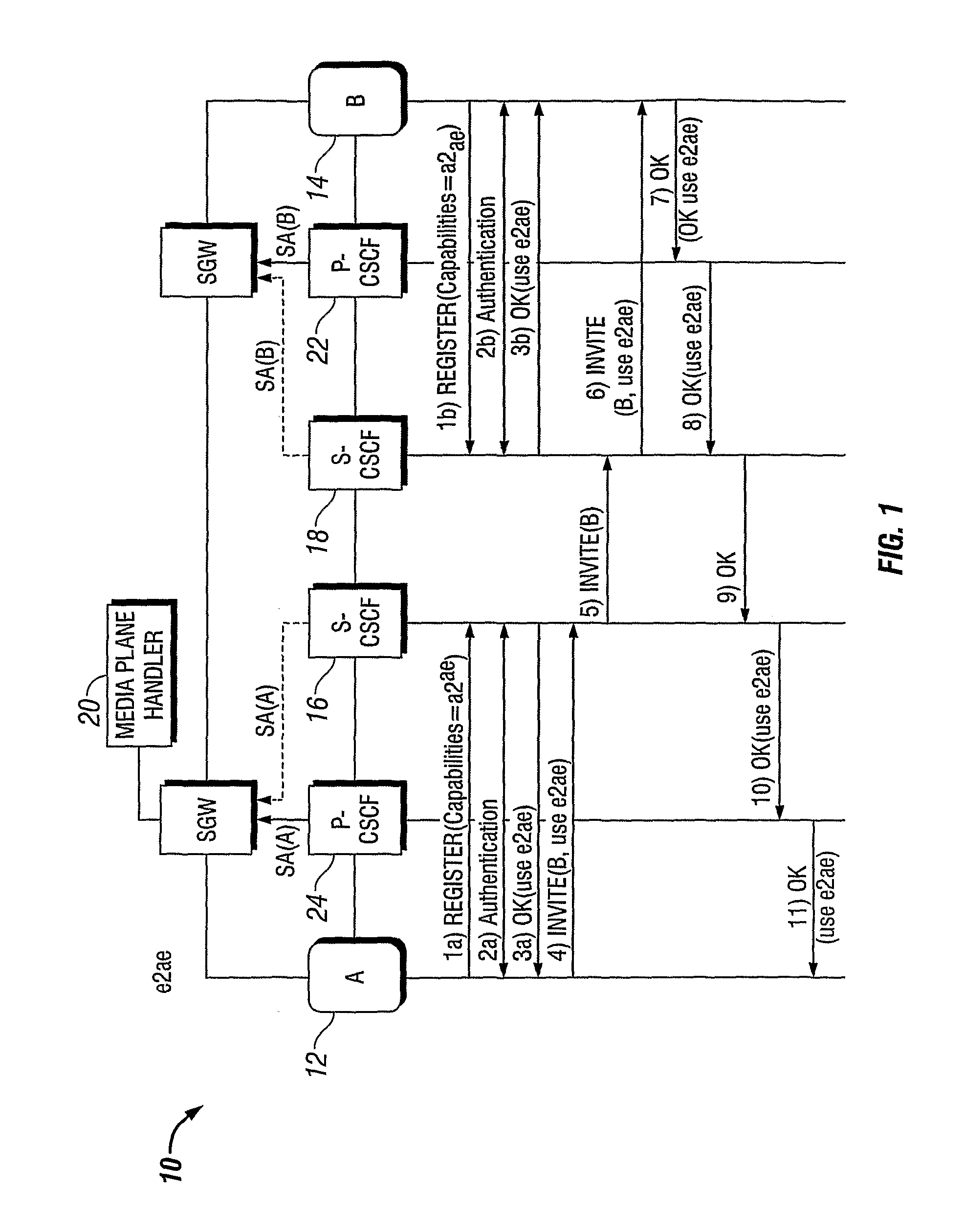
Method and Apparatuses for End-to-Edge Media Protection in ANIMS System
An IMS system includes an IMS initiator user entity. The system includes an IMS responder user entity that is called by the initiator user entity. The system includes a calling side S-CSCF in communication with the caller entity which receives an INVITE having a first protection offer and parameters for key establishment from the caller entity, removes the first protection offer from the INVITE and forwards the INVITE without the first protection offer. The system includes a receiving end S-CSCF in communication with the responder user entity and the calling side S-CSCF which receives the INVITE without the first protection offer and checks that the responder user entity supports the protection, inserts a second protection offer into the INVITE and forwards the INVITE to the responder user entity, wherein the responder user entity accepts the INVITE including the second protection offer and answers with an acknowledgment having a first protection accept. A method for supporting a call by a telecommunications node.
Owner:TELEFON AB LM ERICSSON (PUBL)
Method and apparatus for key management in distributed sensor networks
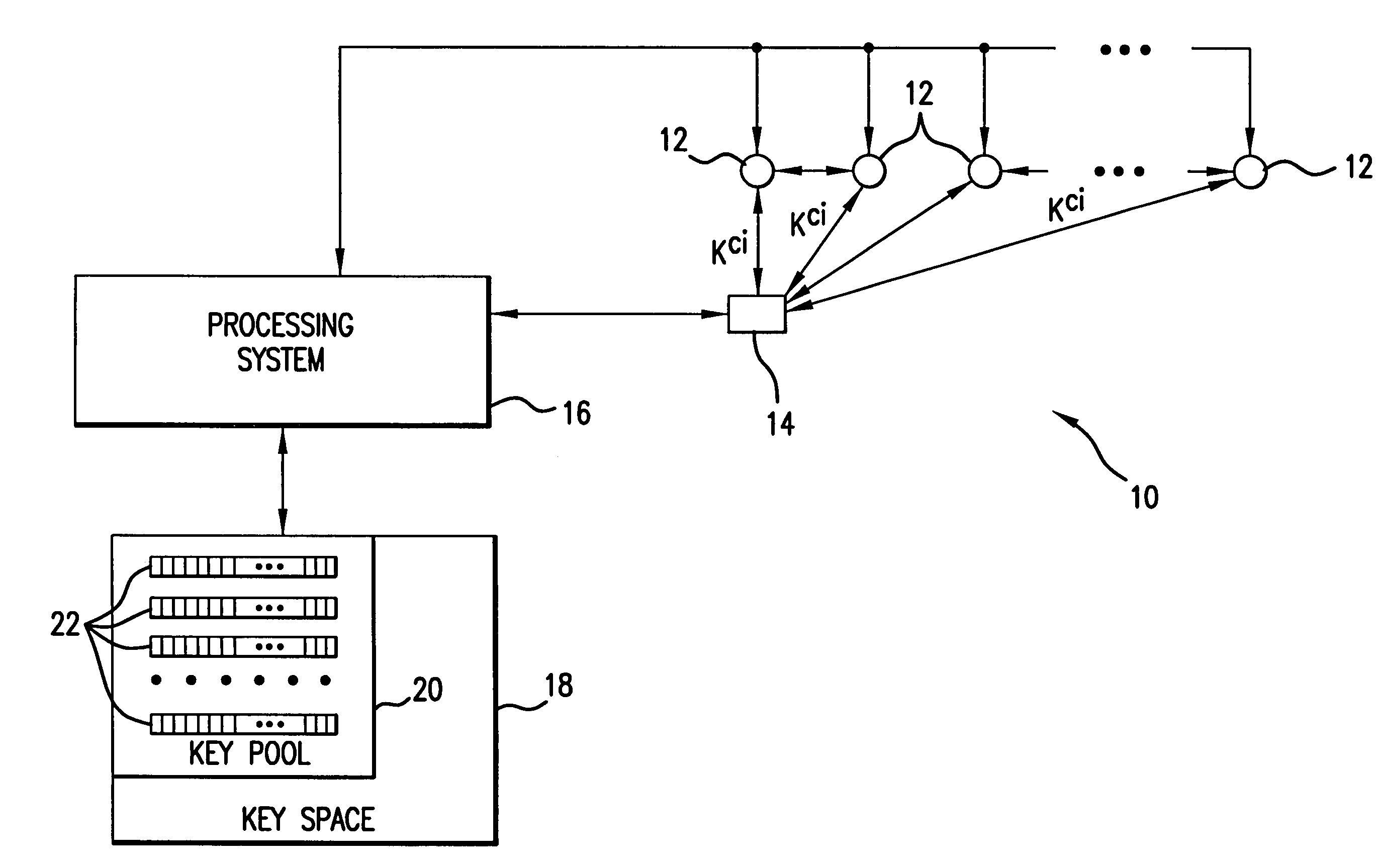
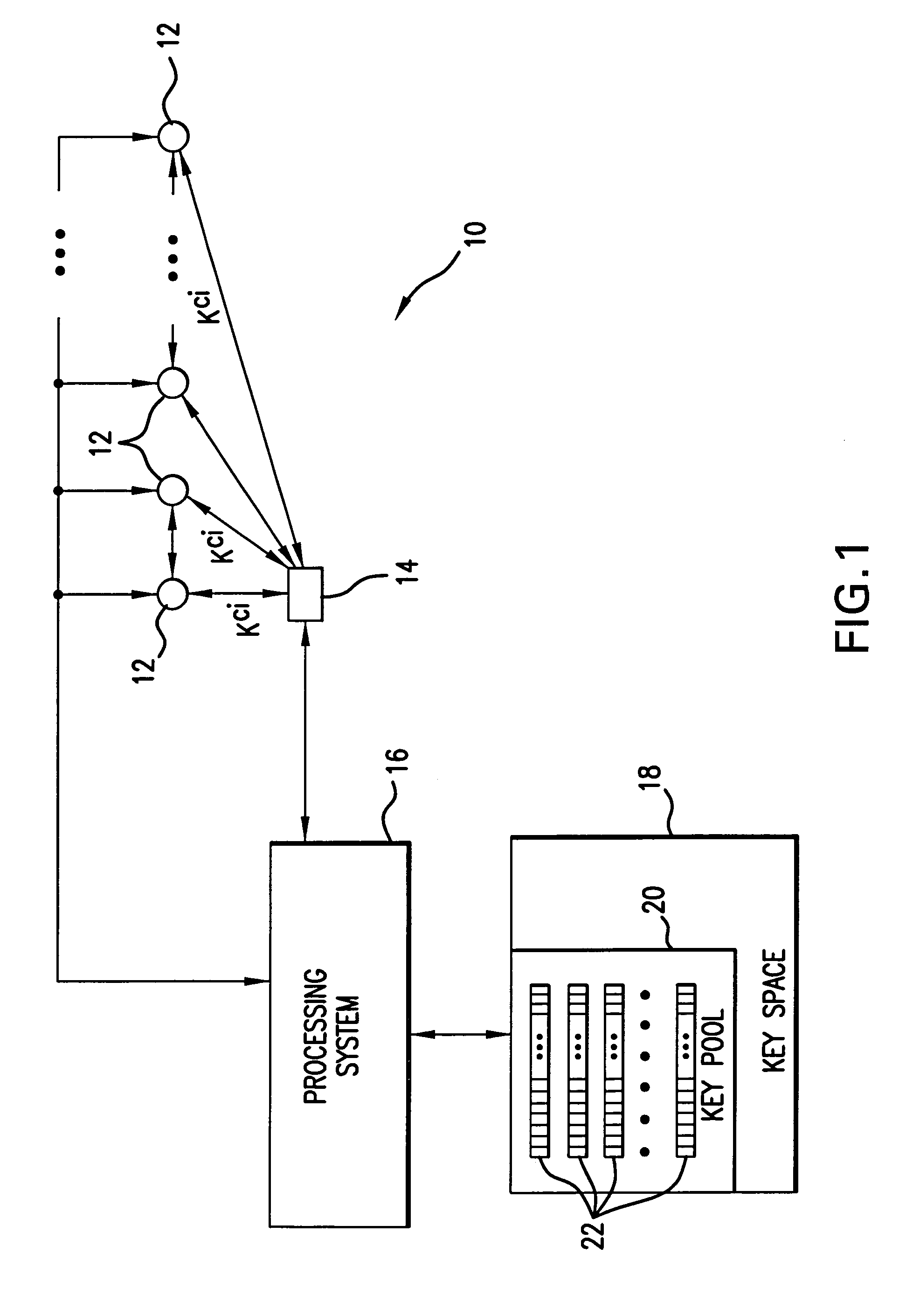
InactiveUS7486795B2Key distribution for secure communicationOptical rangefindersSensor arraySecure communication
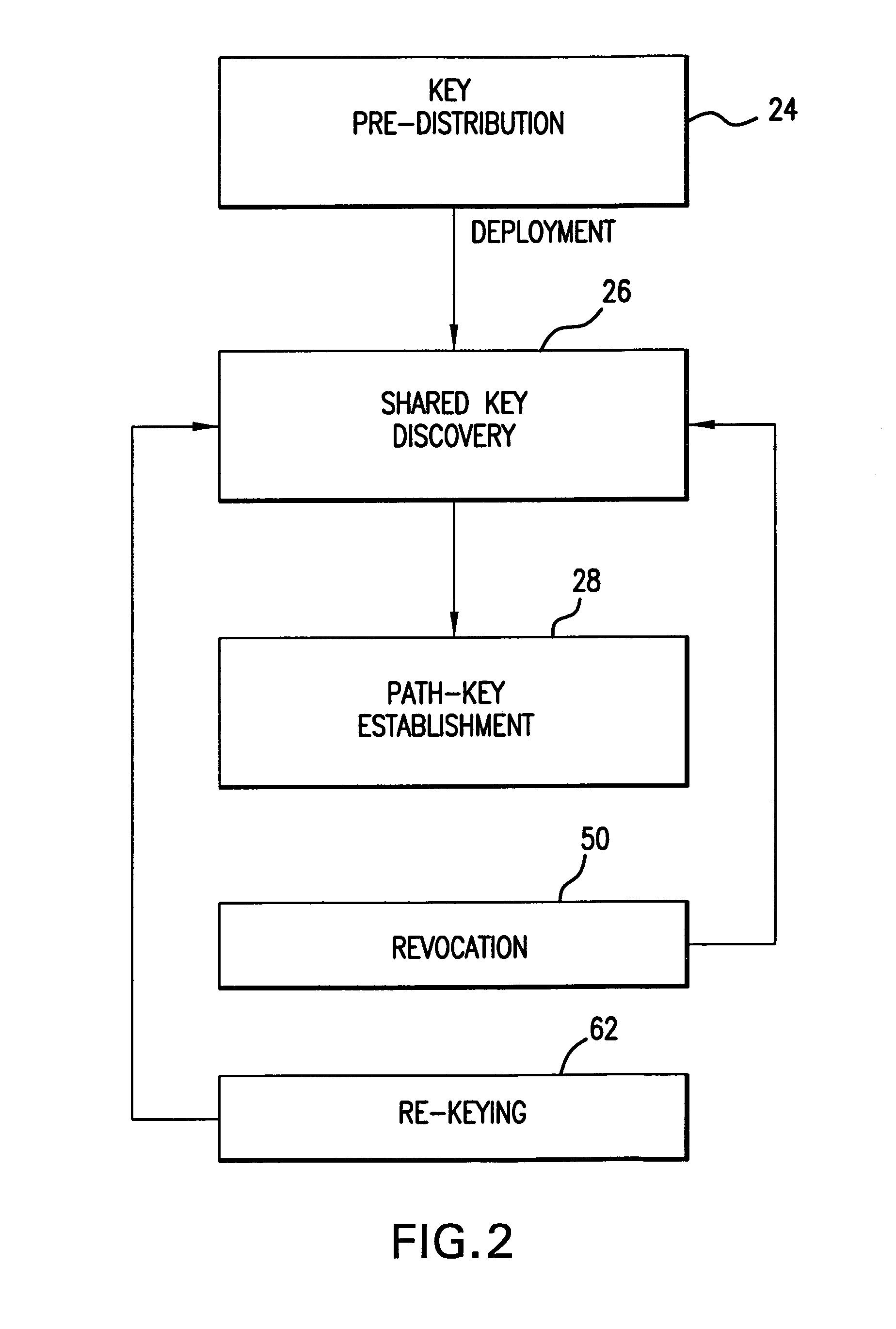
In a distributed sensor network, a method of key management is carried out in several phases, particularly key pre-distribution phase, shared key discovery phase, and as needed, a path key establishment phase. In the key pre-distribution phase, prior to DSN deployment, a ring of keys is distributed to each sensor node, each key ring consisting of randomly chosen keys from a large pool of keys which is generated off-line. A shared key exists between each two key rings with a predetermined probability. In the shared key discovery phase, which takes place upon deployment of the DSN, every sensor node discovers its neighbors in wireless communication range with which it shares keys, and the topology of the sensor array is established by forming secure communication links between respective sensor nodes. The path key establishment phase assigns a path key to selected pairs of sensor nodes in wireless communication range that do not share a key but are connected by two or more links at the end of the shared key discovery phase. The key management scheme also assumes a revocation phase for removal of the key ring of the compromised sensor node from the network. Also, re-keying phase is assumed for removal of those keys with the expired lifetime.
Owner:MARYLAND UNIV OF
System and method for secure wireless multi-hop network formation
ActiveUS7881474B2Synchronising transmission/receiving encryption devicesUser identity/authority verificationSelf-organizing networkNode authentication
The present invention provides methods and devices for a security architecture for use in wireless multi-hop networks. A method for implementing pair-wise encryption key establishment, network node authentication and determining tunnel encryption keys is provided in a following manner. In a multi-hop wireless network including a plurality of network nodes, pair-wise security is established between pairs of neighboring network nodes of the plurality of network nodes. For example, pair-wise security is established in the form of temporal pair-wise encryption keys. Following establishment of pair-wise security between pairs of neighboring network nodes, for a pair of network nodes that are not neighbors, tunnel security is established between the pair of network nodes using tunnel encryption keys derived by the pair of network nodes on an ad hoc basis. The tunnel encryption keys are used to form the connection between non-neighboring network nodes so as to avoid the hop-by-hop encryption / decryption used in conventional multi-hop wireless systems.
Owner:APPLE INC
Open protocol for authentication and key establishment with privacy
ActiveUSH2270H1Public key for secure communicationUser identity/authority verificationSmart cardPhysical access
A suite of efficient authentication and key establishment protocols for securing contact or contactless interfaces between communicating systems. The protocols may be used in secure physical access, logical access and / or transportation applications, among other implementations. The system authenticates a mobile device such as a smart card and / or mobile phone equipped with a secure element presented to one or more host terminals and establishes shared secure messaging keys to protect communications between the device and terminal. Secure messaging provides an end-to-end protected path of digital documents or transactions through the interface. The protocols provide that the device does not reveal identification information to entities different from a trusted host. The terminal may be a contactless reader at a door for controlling physical access, a desktop, laptop or kiosk for controlling logical access, and / or an access point for obtaining an encrypted digital ticket from an authenticated mobile device used for transit applications.
Owner:ASSA ABLOY AB
System and method for initial key establishment using a split knowledge protocol
ActiveUS8245050B1Key distribution for secure communicationDigital data processing detailsComputer hardwareKey establishment
Owner:NETWORK APPLIANCE INC
Method for key management and node authentication of sensor network
ActiveCN101699891ARealize confidential communicationSave resourcesKey distribution for secure communicationUser identity/authority verificationSecure communicationNetwork deployment
Owner:CHINA IWNCOMM
Facilitating 802.11 roaming by pre-establishing session keys
InactiveCN1836404ANetwork topologiesData switching by path configurationTelecommunicationsKey establishment
Owner:CISCO TECH INC
Key establishment utilizing link privacy
InactiveUS20080220746A1Network topologiesSpecial service for subscribersSecure communicationSecurity information
A system for allowing two or more wireless devices to form a secure relationship despite any other device that may be attempting to intercept information exchanged between the devices. The process may be performed automatically by the devices, yielding security information that may be used to authenticate information believed to have been sent from a known device. The security information may include at least an encryption key utilized to identify previously encountered known devices and for securing communication with these devices. The security key may be computed by analyzing the transmission and receipt of advertising messages, or by analyzing the contents of pseudorandom information contained in advertising message payloads.
Owner:NOKIA CORP
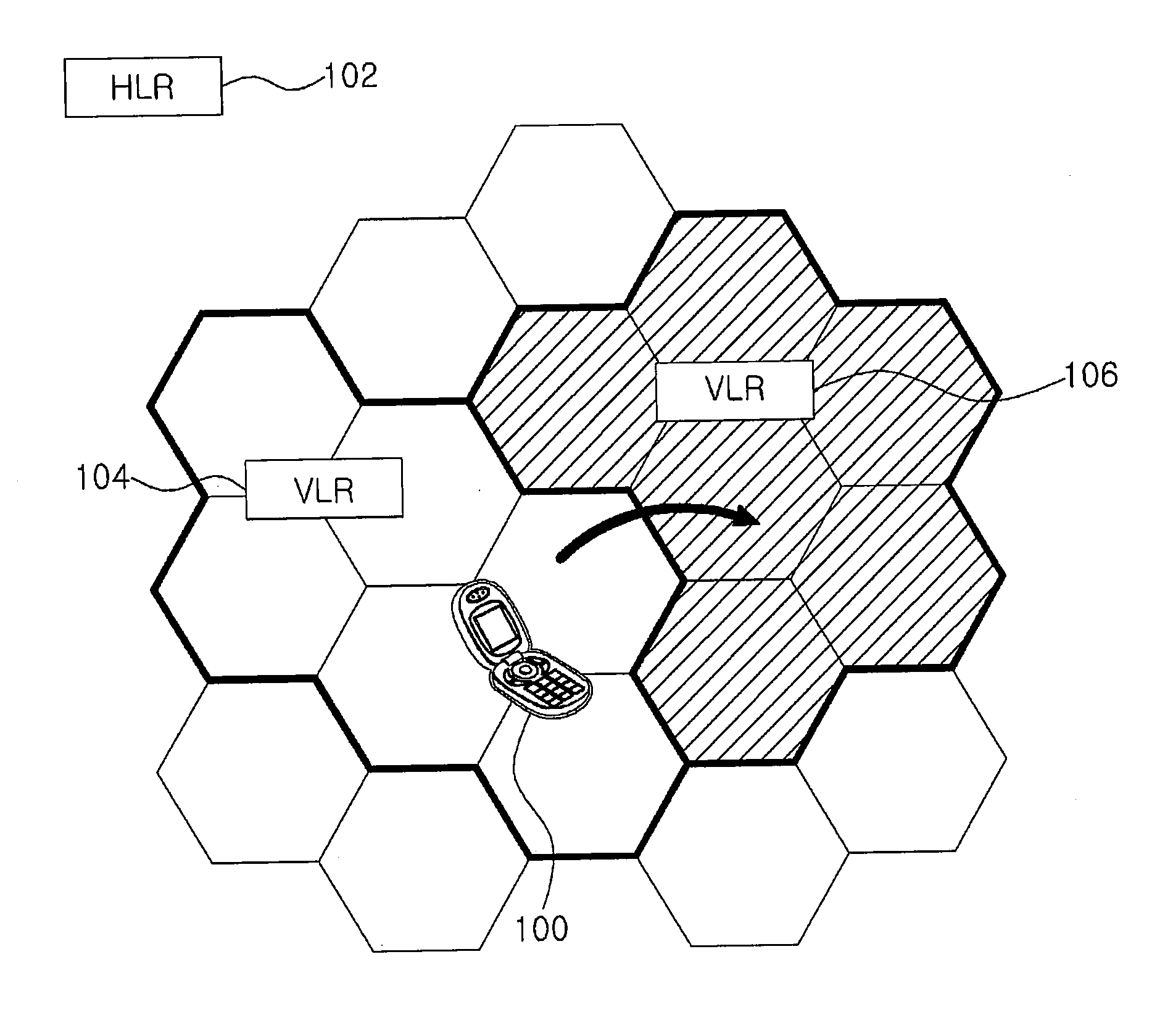
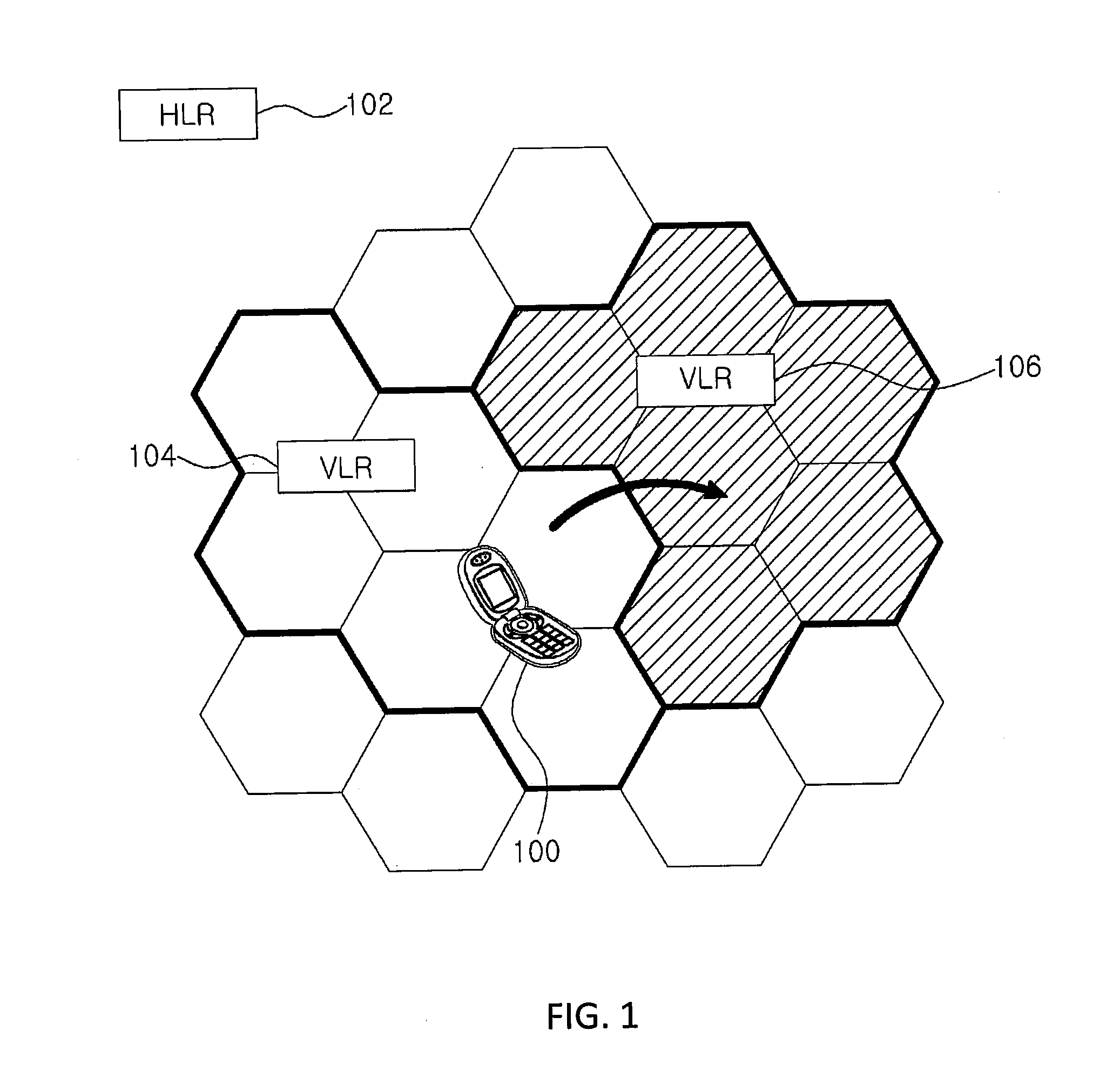
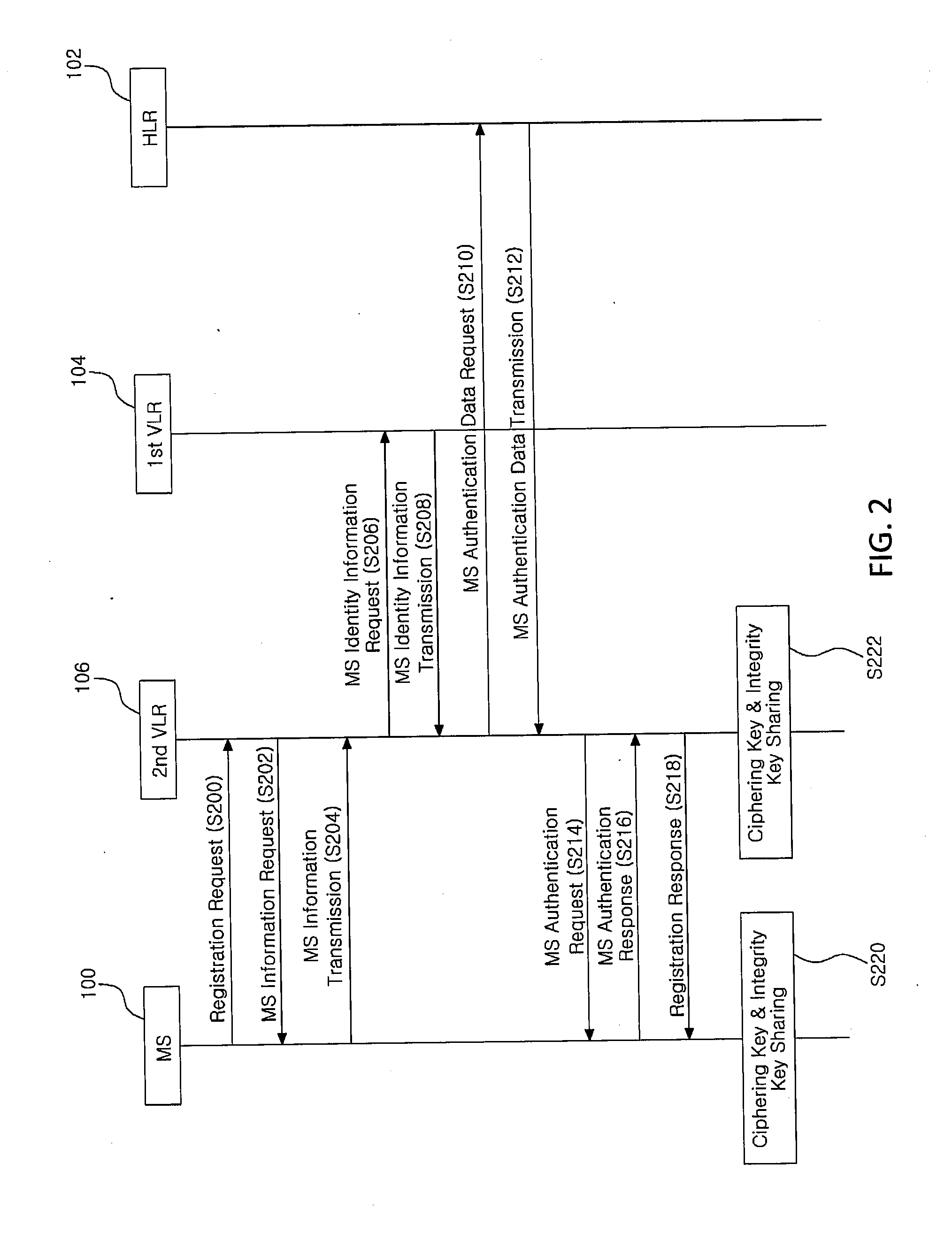
Method for authentication and key establishment in a mobile communication system and method of operating a mobile station and a visitor location register
InactiveUS20120142315A1Simplify the authentication processConsume bandwidthUnauthorised/fraudulent call preventionEavesdropping prevention circuitsTelecommunicationsProcessor register
The present invention relates to a method whereby the mobile station and a visitor location register create and share a ciphering key and an integrity key in order to directly authenticate each other. The communication method in a mobile communication system such as this includes registering the mobile station with the home location register; and having the mobile station and the visitor location register directly authenticate each other and mutually share a ciphering key and an integrity when the mobile station moves to the visitor location register.
Owner:IND ACADEMIC CORP FOUND YONSEI UNIV
Smart community home gateway-based safety payment method
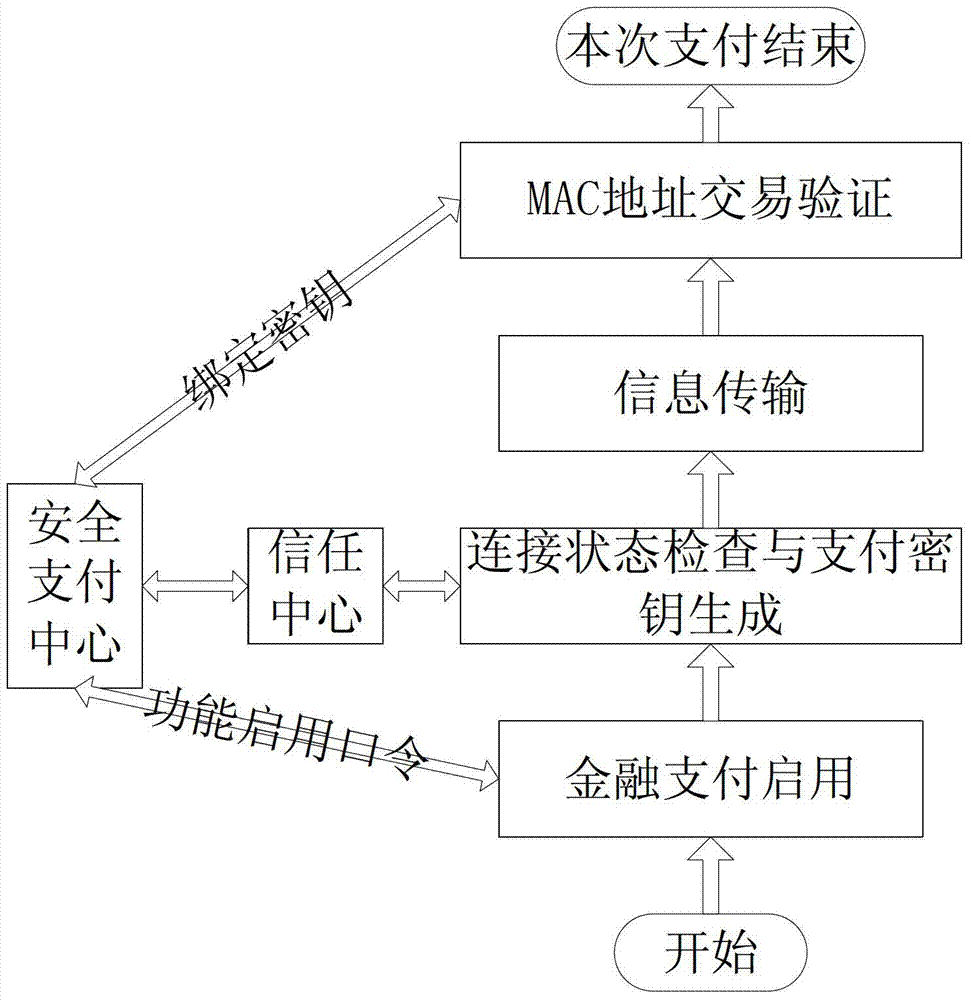
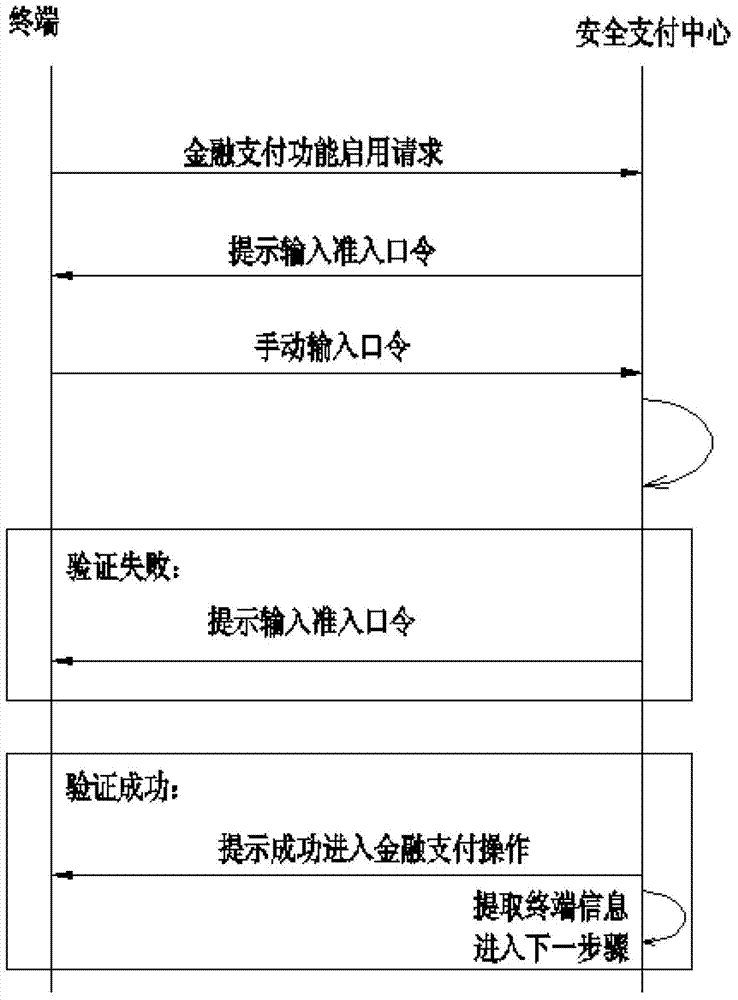
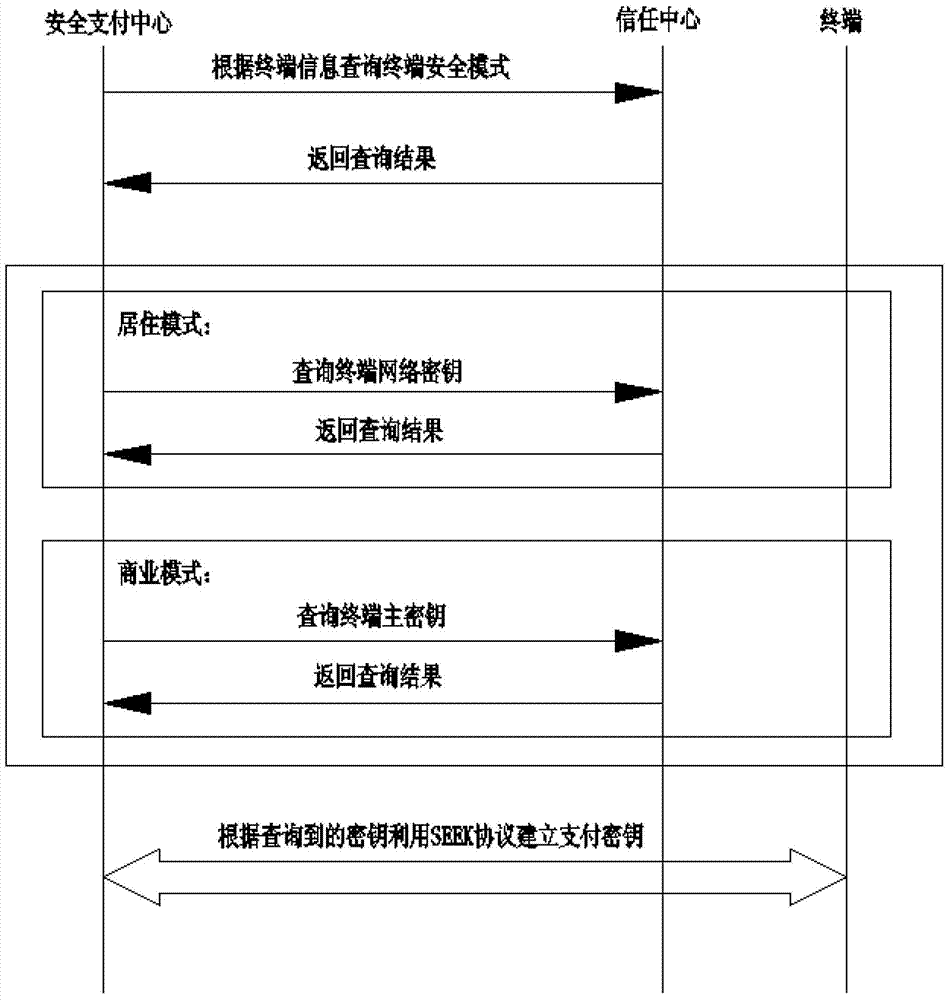
InactiveCN103400269ADoes not affect functionEfficiency is not affectedPayment protocolsPaymentPassword
The invention relates to a smart community home gateway-based safety payment method. The smart community home gateway-based safety payment method comprises the following steps: a, wirelessly connecting a home gateway with a terminal through a Zigbee mode and establishing a safety payment center in the home gateway; b, submitting a financial payment enabling request by the terminal and prompting the terminal to input a payment admission password by the home gateway; c, establishing a payment key by the safety payment center by using an SKKE (Symmetric-key Key Establishment) protocol; d, encrypting an MAC (Media Access Control) address of the home gateway by the safety payment center by using a binding key and transmitting to a bank server together with corresponding financial payment account and password; and e, checking the transmitted financial payment account, the password, the decrypted MAC address and the MAC address extracted in the transmitted information by the bank server, and performing payment operation when the financial payment account, the password, the decrypted MAC address and the MAC address extracted in the transmitted information are correspondingly consistent. The smart community home gateway-based safety payment method is convenient in payment operation, and the safety and the reliability of payment are improved.
Owner:JIANGSU HILLSUN INFORMATION IND
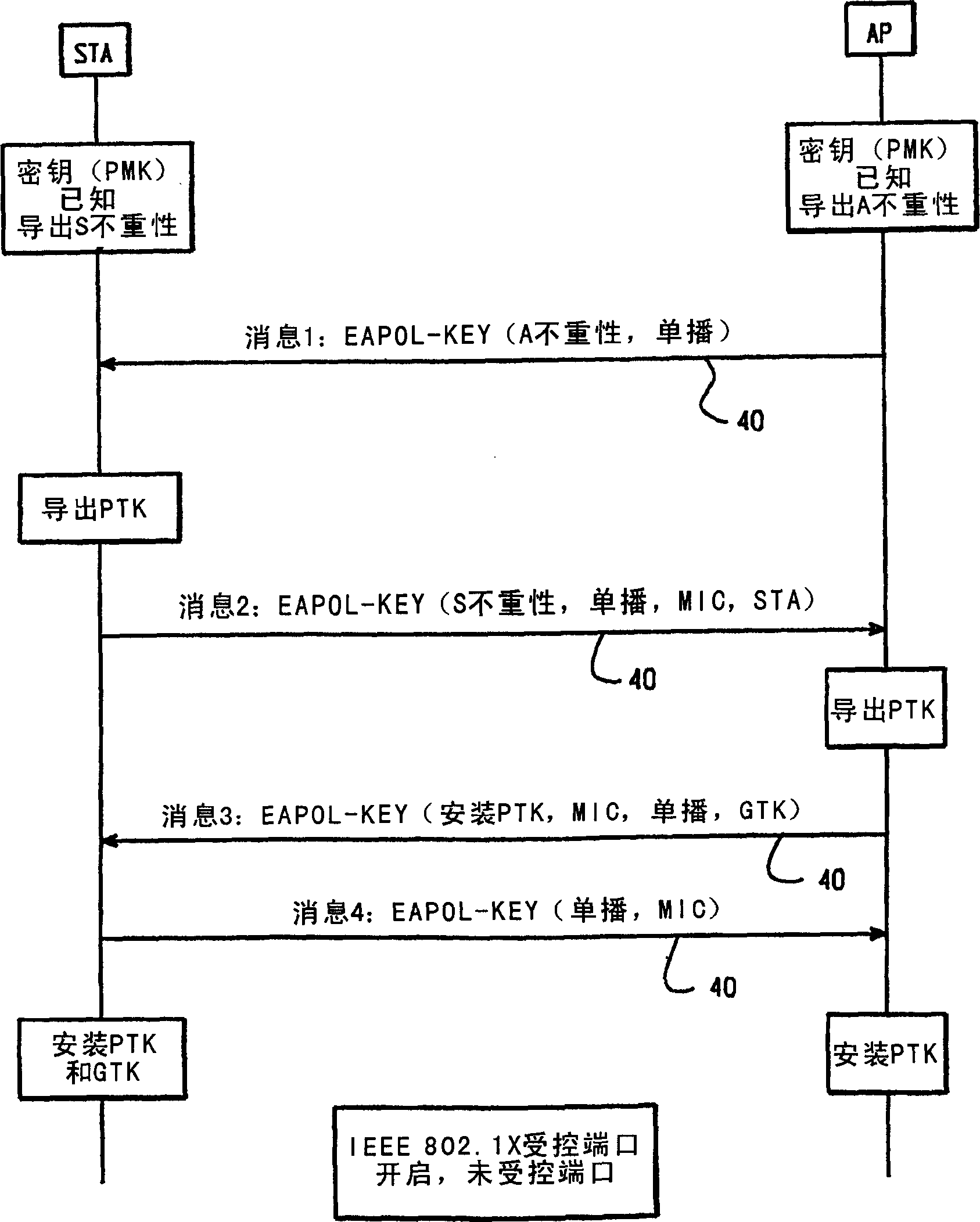
Efficient key establishment for wireless networks
ActiveUS8510560B1Verify integrityDigital data processing detailsUser identity/authority verificationWireless mesh networkTelecommunications
A method and apparatus for deriving an encryption key for use between two stations in a wireless network using information intrinsic to one of the stations, without exchanging pairwise transient keys.
Owner:MARVELL ASIA PTE LTD
Key management and node authentication method for sensor network
ActiveUS20120300939A1Lower capability requirementsReduce storageKey distribution for secure communicationUser identity/authority verificationNetwork communicationNode authentication
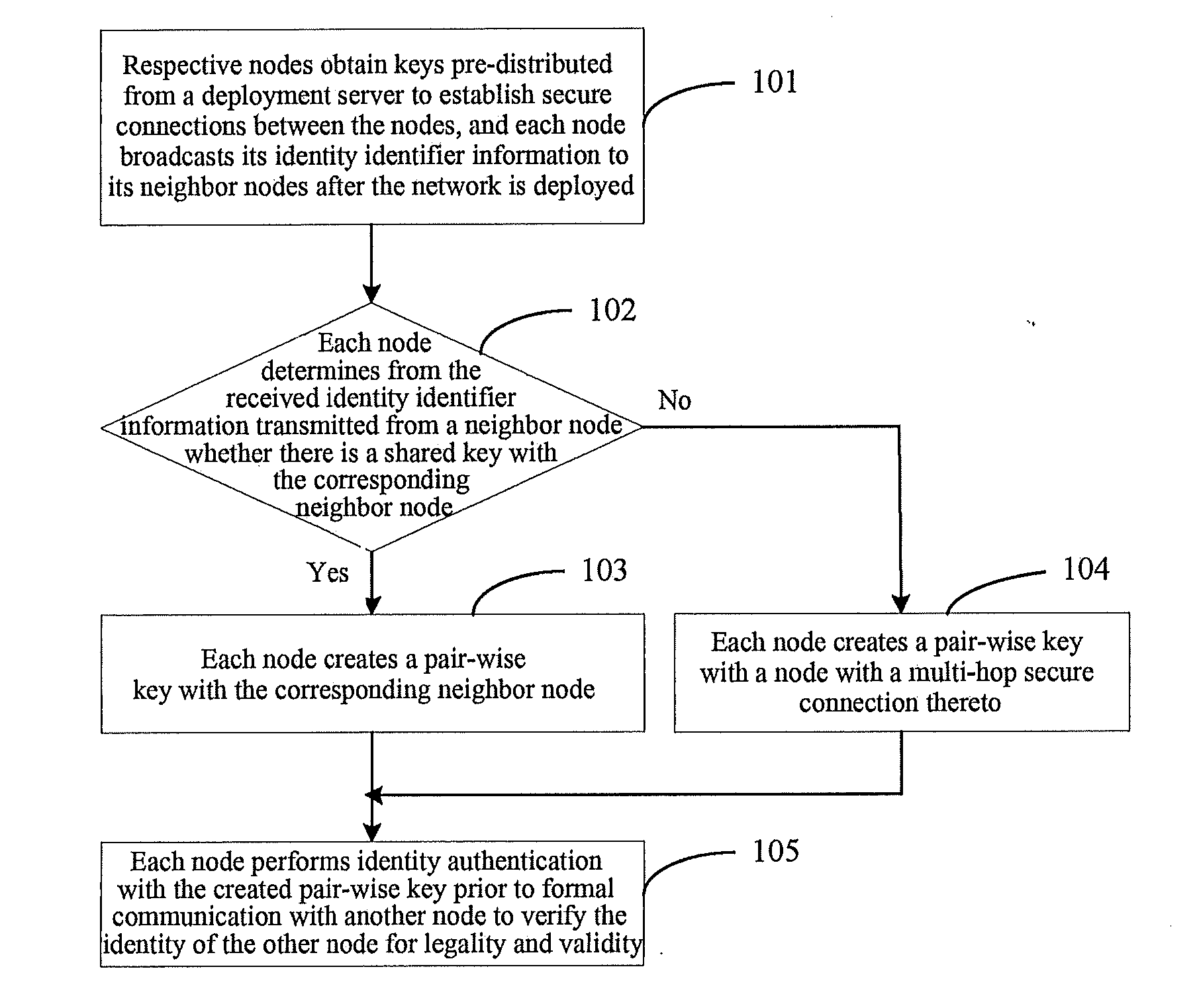
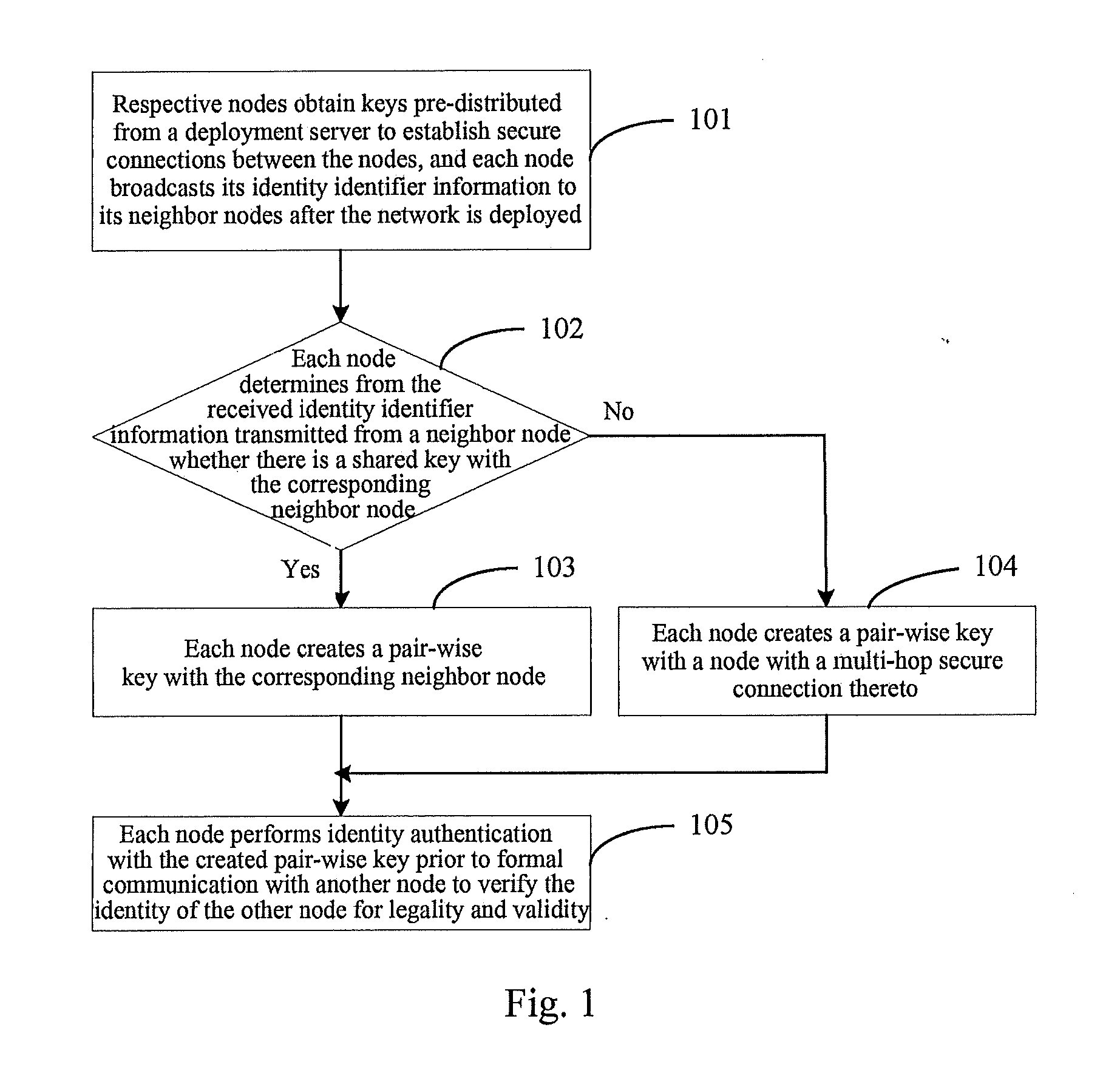
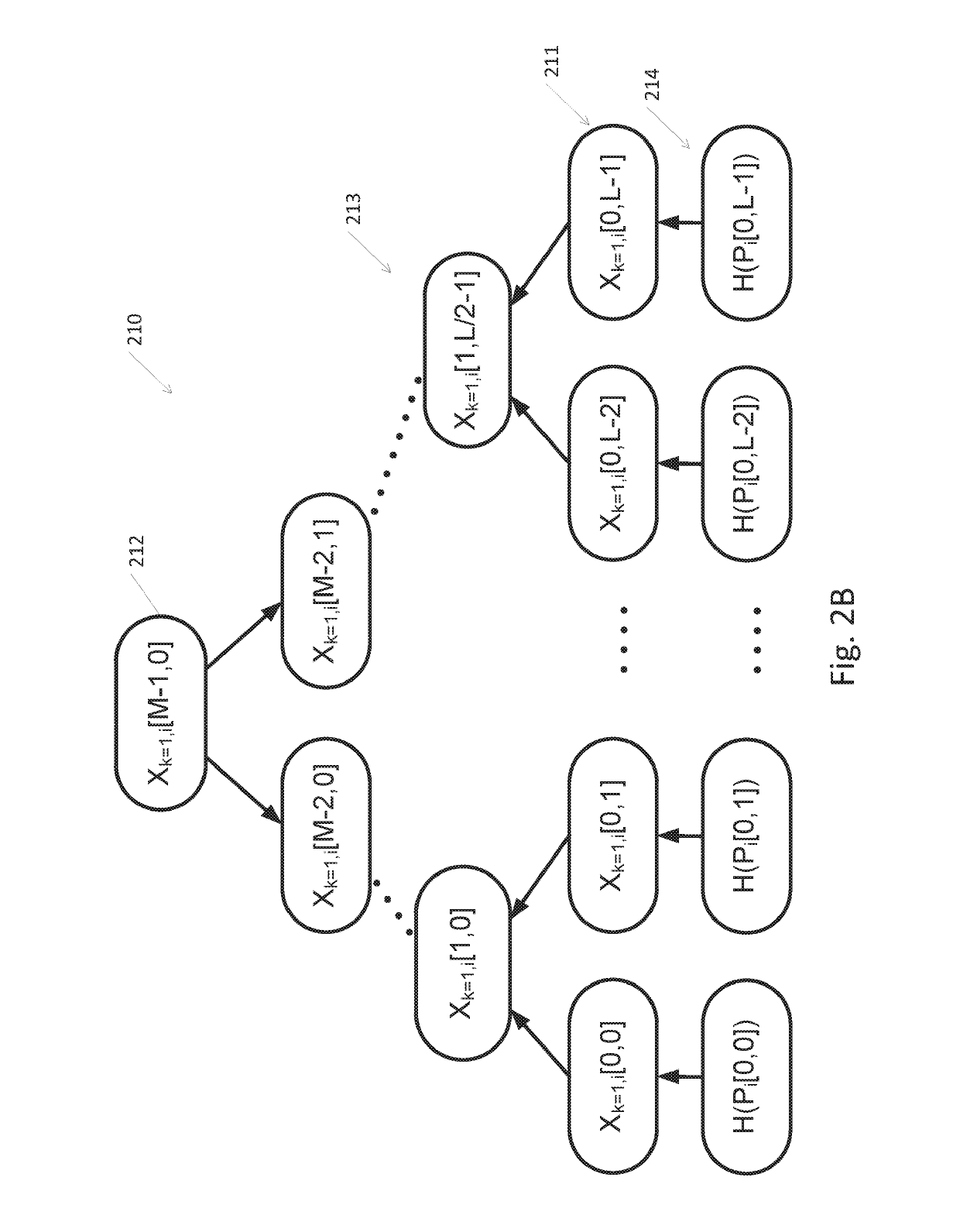
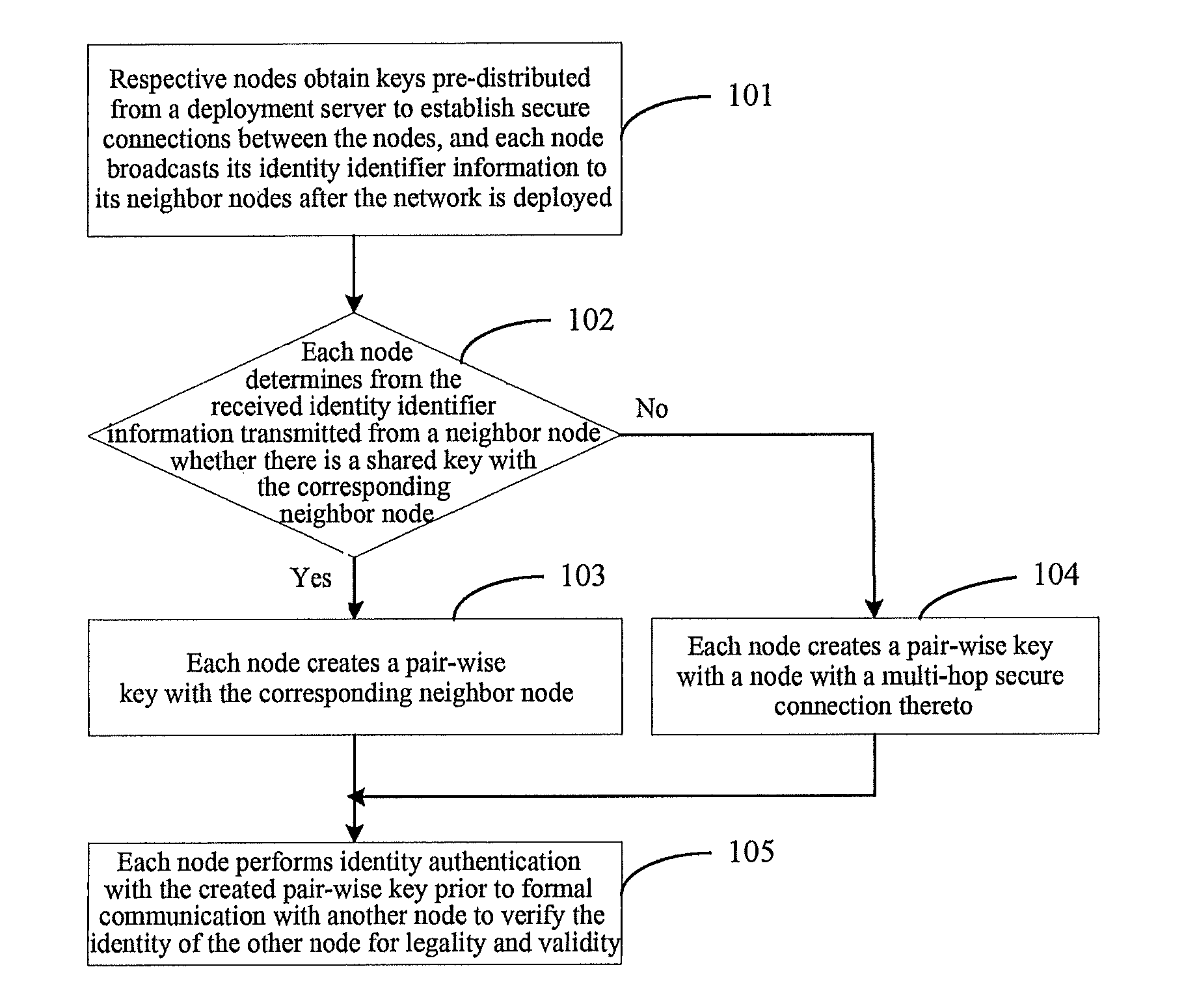
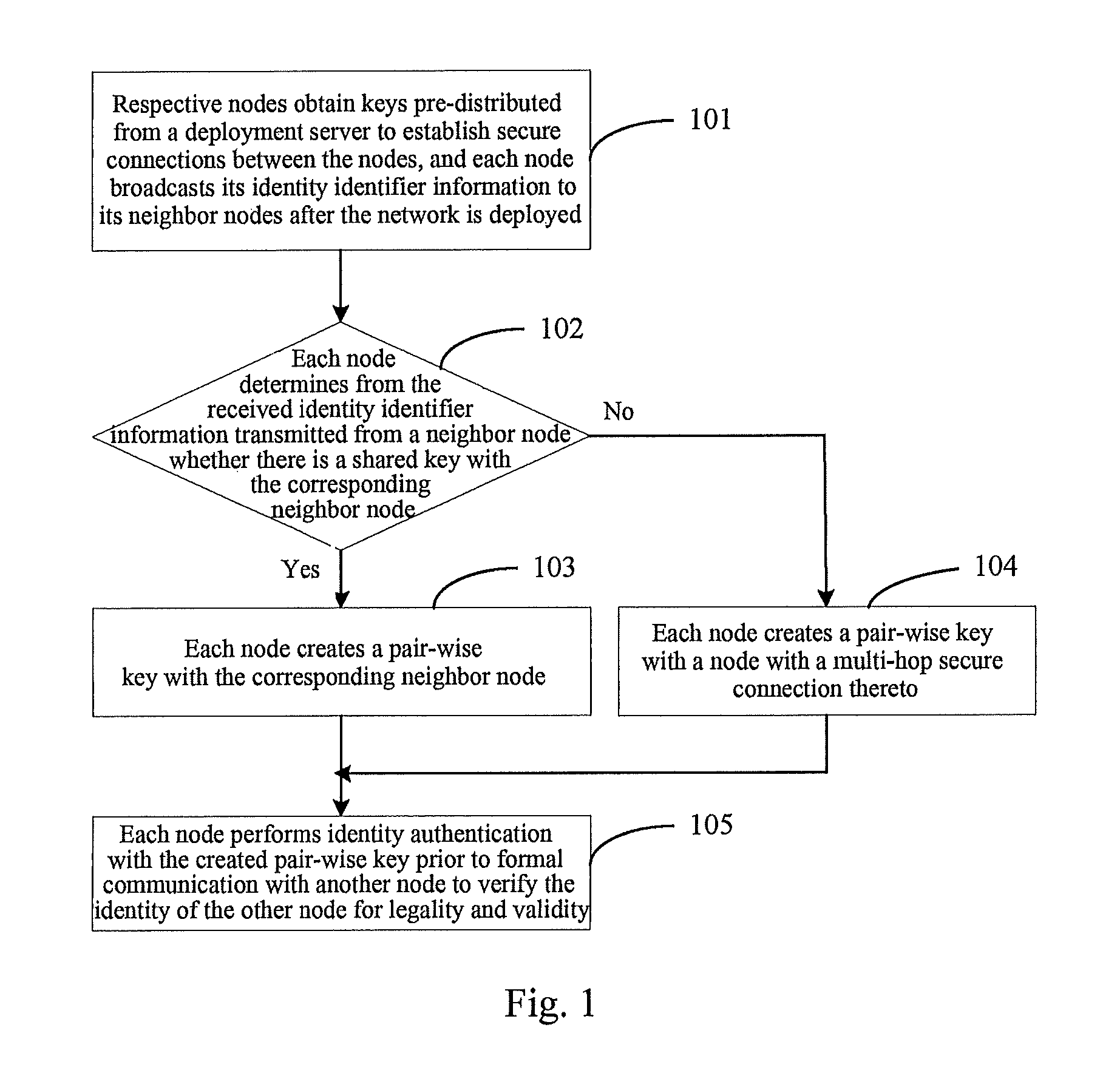
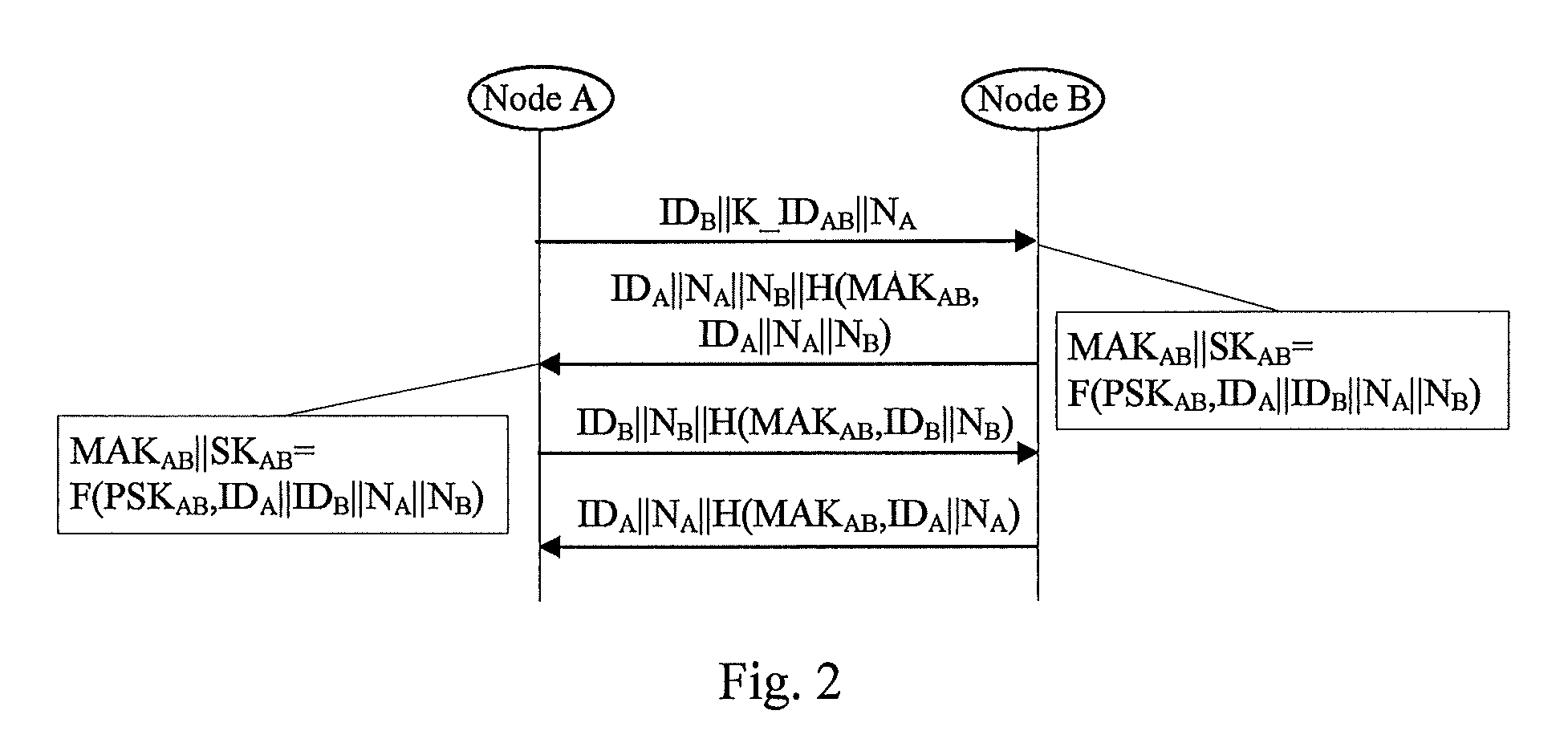
A key management and node authentication method for a sensor network is disclosed. The method comprises the following steps of: 1) keys pre-distribution: before deploying the network, communication keys for establishing security connection between nodes are pre-distributed to all of nodes by a deployment server. 2) Keys establishment: after deploying the network, a pair key for the security connection is established between nodes, which includes the following steps of: 2.1) establishment of shared keys: the pair key is established between neighbor nodes in which the shared keys are existed; 2.2) path keys establishment: the pair key is established between the nodes in which there is no shared keys but there is a multi-hop security connection. 3) Node identity (ID) authentication: before formally communicating between nodes, the identity is authenticated so as to determine the legality and the validity of the identity of the other. It is possible for effectively resisting attacks such as wiretapping, tampering, and replaying and the like for the network communication, realizing the secret communication between the nodes, effectively saving resources of the nodes of the sensor network, and prolonging the service lift of the sensor network in the method.
Owner:CHINA IWNCOMM
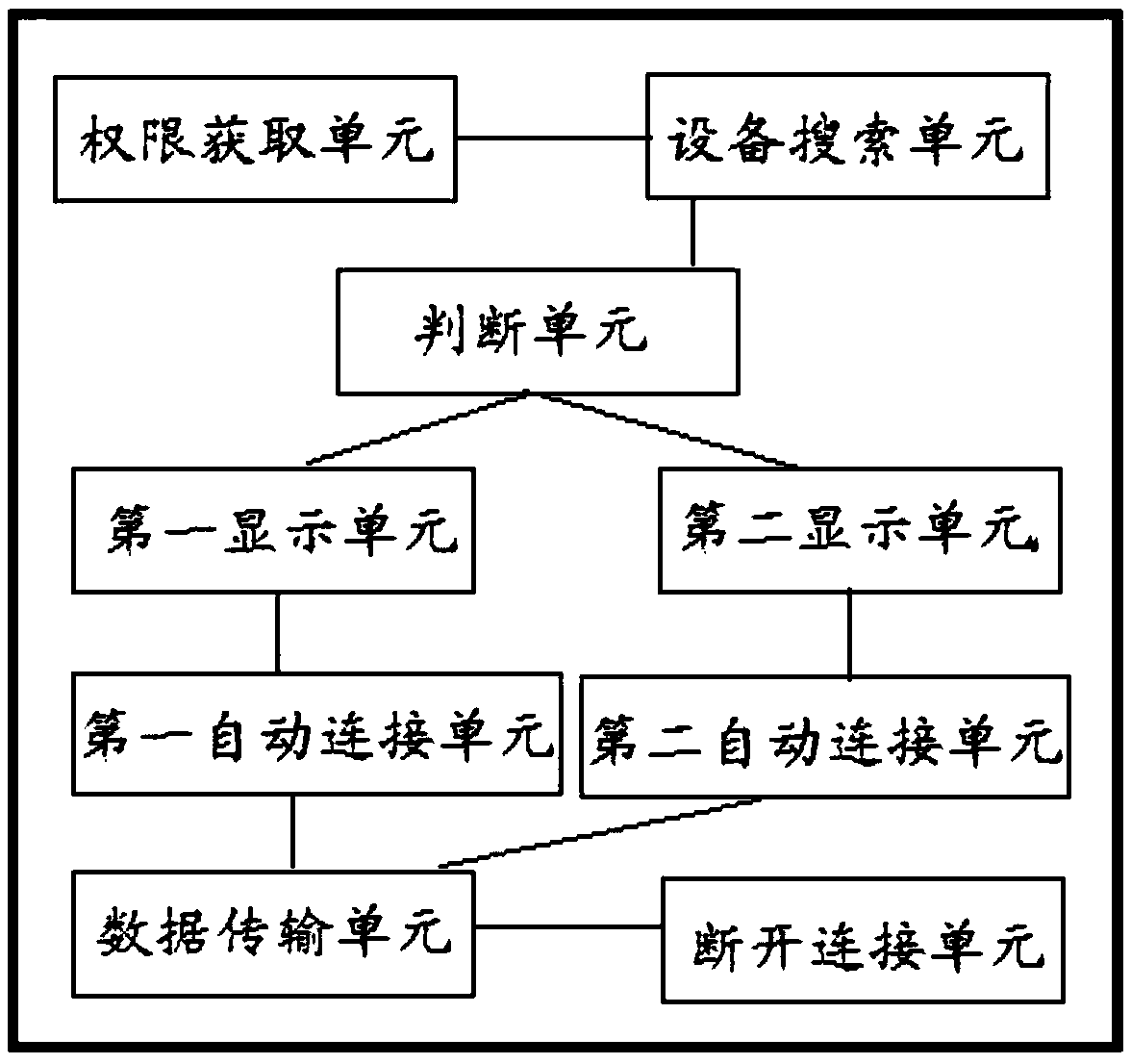
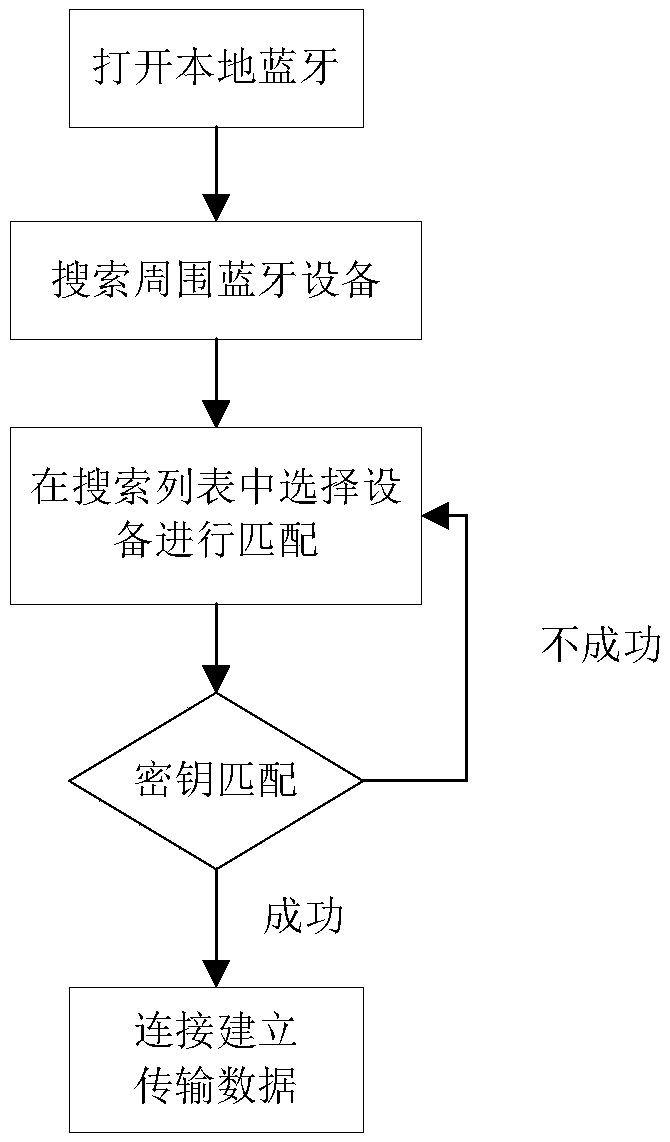
Method and device for one-key establishment of communication connection between Bluetooth devices
InactiveCN105516897AThe connection is automatically establishedFirmly connectedConnection managementSubstation equipmentBluetoothEmbedded system
The invention provides a method and a device for one-key establishment of communication connection between Bluetooth devices. The method is realized by installing an application program in a smart phone and comprises the steps of obtaining Bluetooth authority and opening a Bluetooth function of the smart phone to enable that the smart phone can be searched by surrounding Bluetooth devices; controlling a Bluetooth adapter to search all the surrounding Bluetooth devices; judging whether a bound Bluetooth device exists; if the bound Bluetooth device exists uniquely, automatically connecting the Bluetooth device; otherwise, displaying the names of the multiple bound Bluetooth devices in a screen and automatically connecting the Bluetooth device which is selected by a user based on the selection of the user; and if no bound Bluetooth device exists, displaying the names of the searched Bluetooth devices in the screen one by one and then automatically connecting the Bluetooth device which is selected by the user based on the selection of the user. According to the method and the device for one-key establishment of communication connection between the Bluetooth devices, communication connection between two Bluetooth devices can be established automatically through one key, and the user can connect the smart phones by using the Bluetooth devices conveniently.
Owner:HARBIN INST OF TECH SHENZHEN GRADUATE SCHOOL
Electronic key management using pki to support group key establishment in the tactical environment
ActiveUS20140226821A1Key distribution for secure communicationPublic key infrastructure trust modelsComputer hardwareSupport group
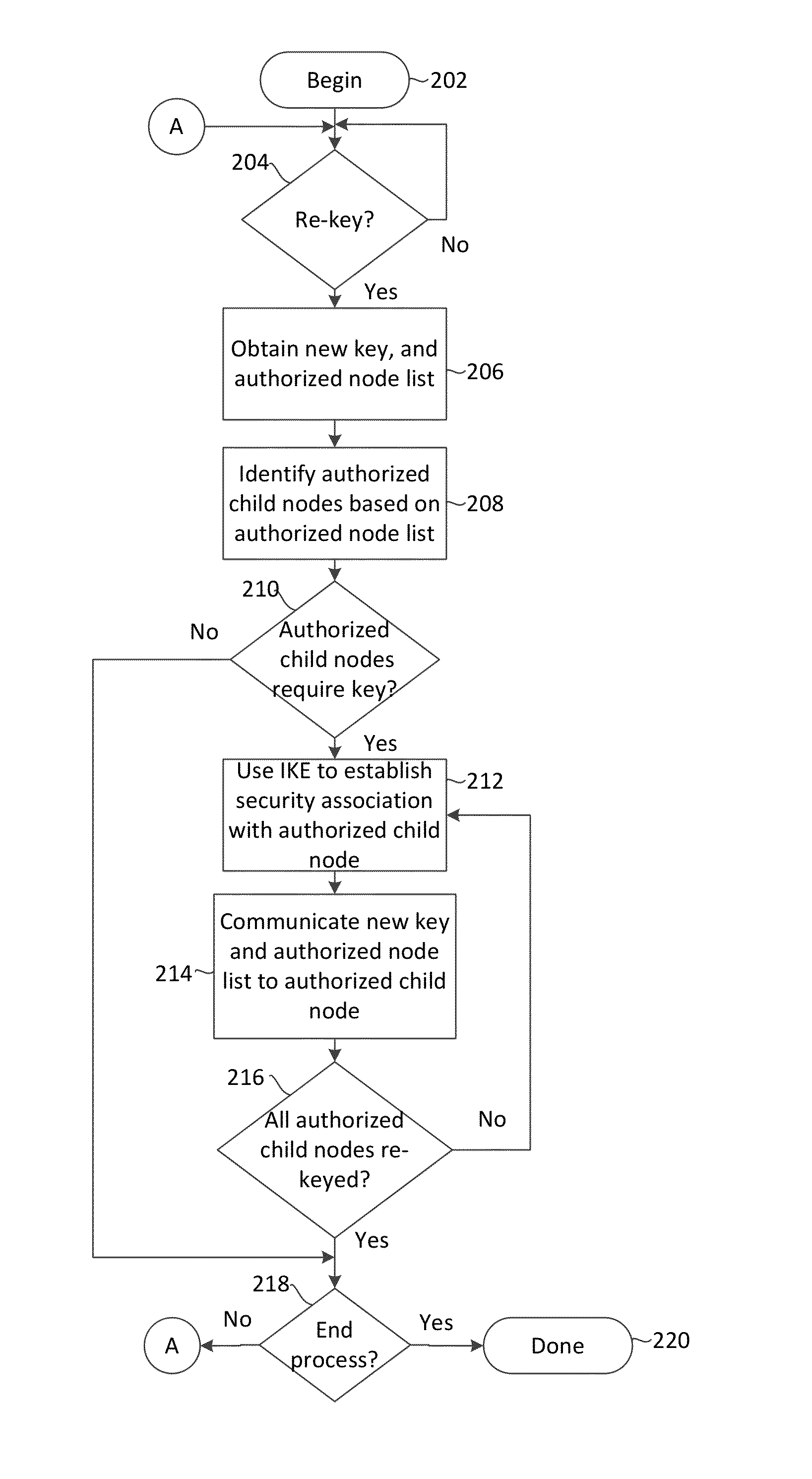
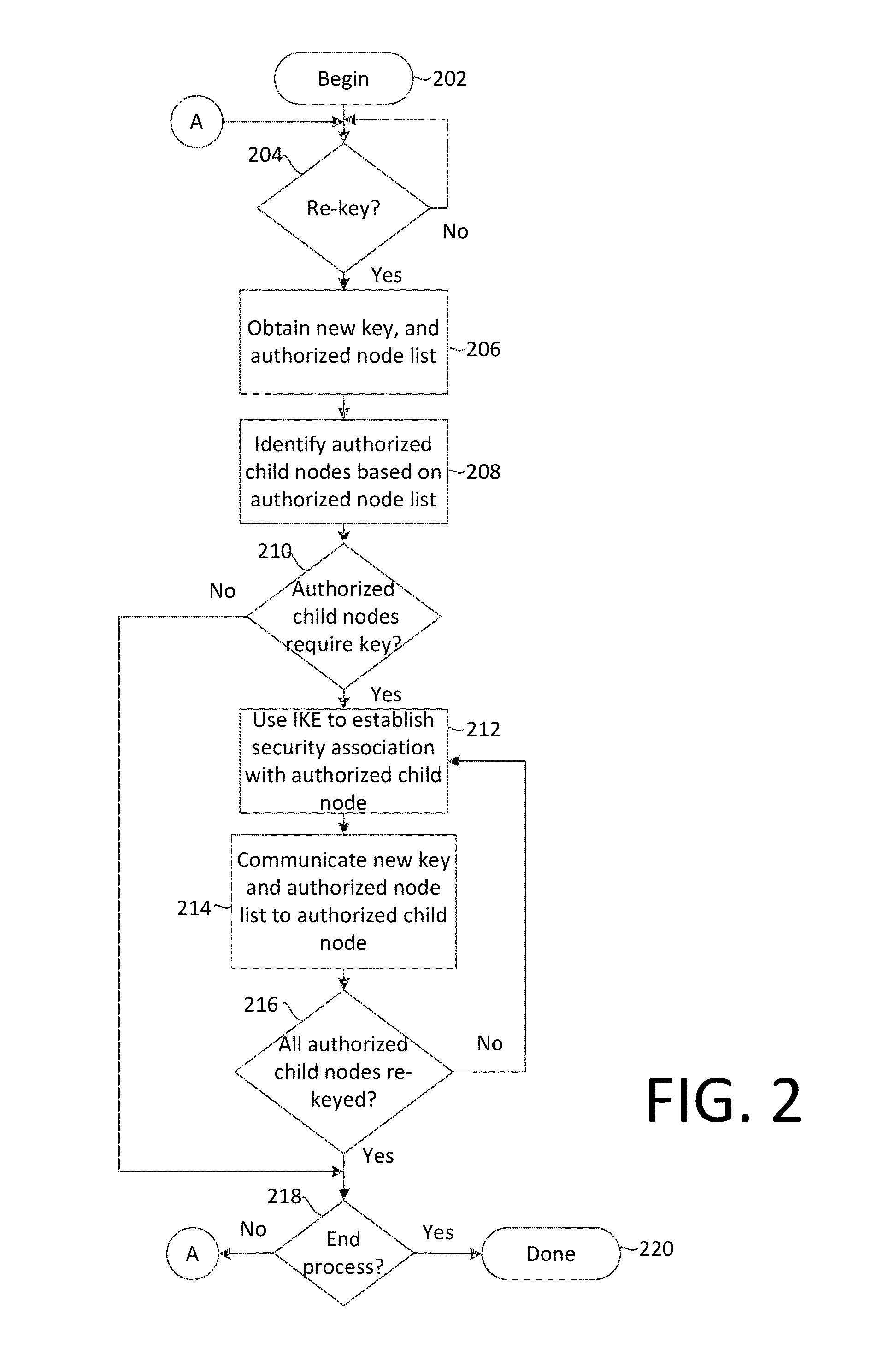
Method for distributing a group session cryptographic key includes initiating at least one pairwise key distribution session including a root node (100) and at least one communication node (101-107). The method further includes performing at a communication node which has received the group session cryptographic key a propagated pairwise key distribution session with at least one of the communication nodes which has not previously received said group session cryptographic key. The propagated pairwise key distribution sessions are performed at each of the communication nodes which subsequently receives the group session cryptographic key until the group session cryptographic key has been securely provided to all authorized communication nodes.
Owner:HARRIS GLOBAL COMMUNICATIONS INC
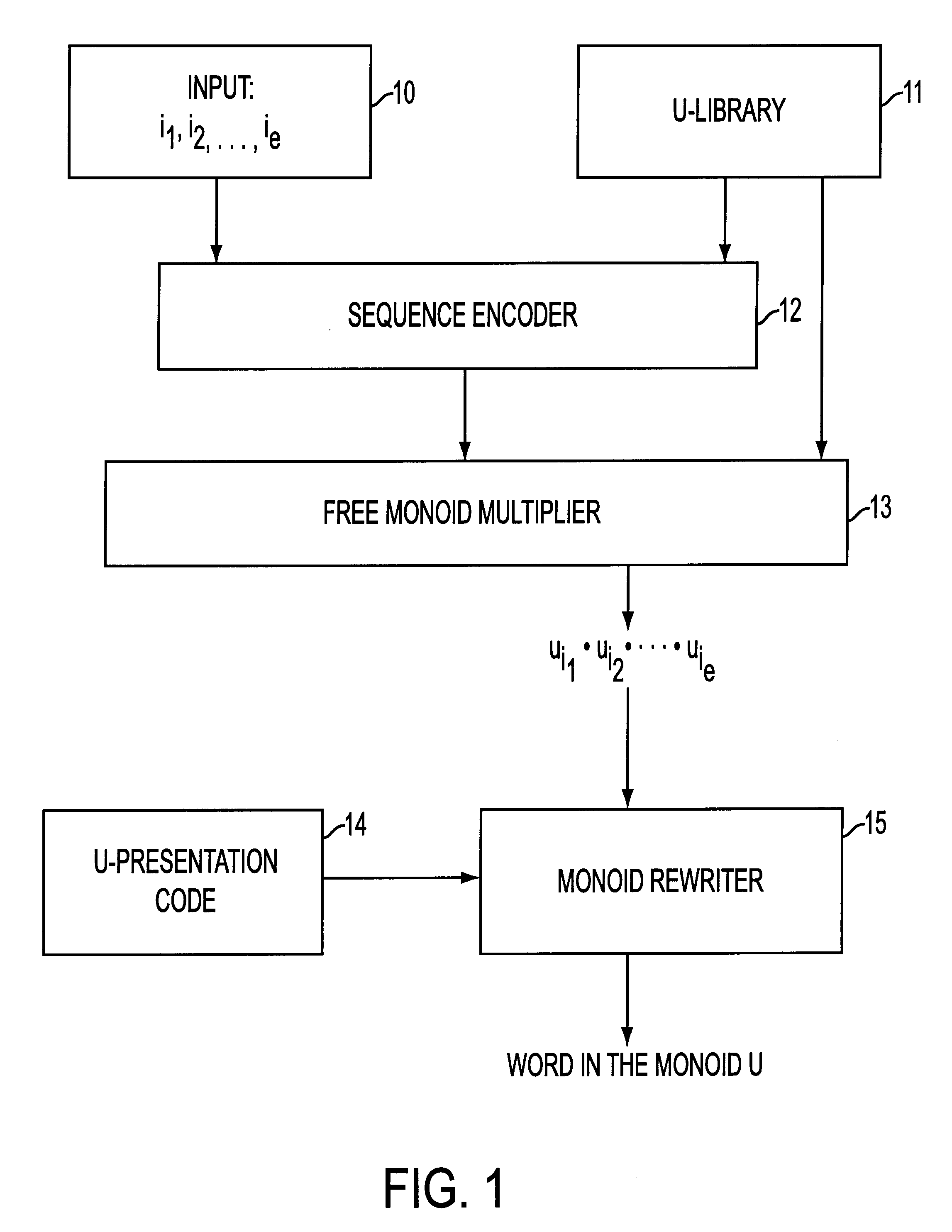
Method and apparatus for cryptographically secure algebraic key establishment protocols based on monoids
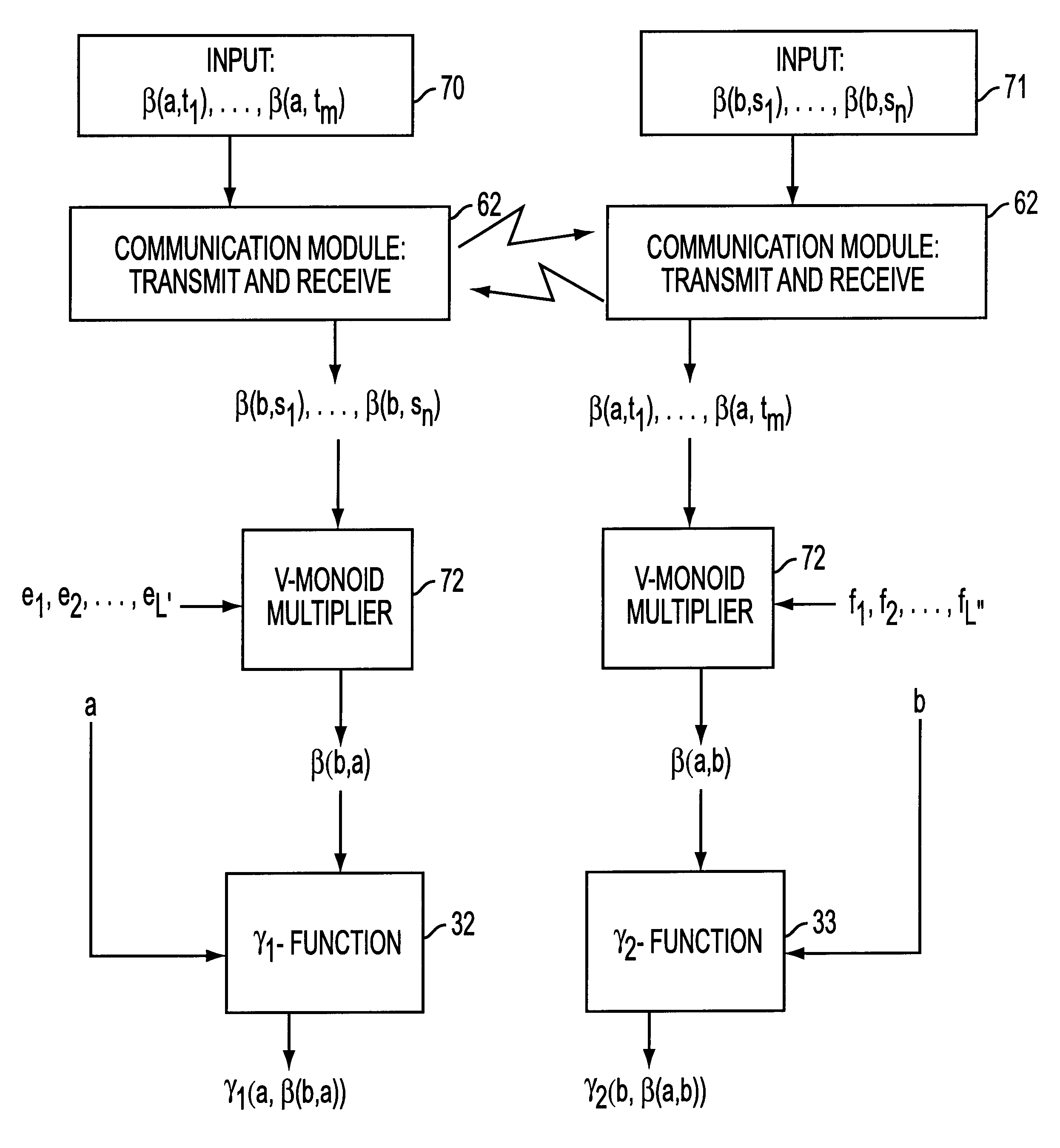
InactiveUS6493449B2Reducing step and calculationEasy to implementKey distribution for secure communicationPublic key for secure communicationFast algorithmKey establishment protocol
The present invention is a method and apparatus for providing cryptographically secure algebraic key establishment protocols that use monoids and groups possessing certain algorithmic properties. Special fast algorithms associated with certain monoids and groups are used to optimize both key agreement and key transport protocols. The cryptographic security of the algorithms is based on the difficulty of solving the conjugacy problem in groups and other known hard algebraic problems. Braid groups and their associated algorithms are the basis for highly rapid key agreement and key transport protocols which employ modest computational resources.
Owner:ARITHMETICA INC
System and method for mekle puzzles symeteric key establishment and generation of lamport merkle signatures
InactiveUS20190140819A1Encryption apparatus with shift registers/memoriesUser identity/authority verificationLamport signatureTheoretical computer science
A system and method for signing a message and establishing a symmetric key between two entities. A plurality of leaves are generated, each including public and private values of a Lamport signature; a plurality of trees are generated each including a subgroup of leaves; leaves of a first nested tree are used for signing messages sent to a second entity. If a first nested tree is exhausted, then a leaf of a following tree is used for signing and a root of the following tree together with an auxiliary value are published, the auxiliary value enabling the second entity to verify that the root of the following tree was generated by the first entity. The symmetric key is generated using a modified Merkel puzzle including a plurality of rows, each including a plurality of hashed values. The modified Merkel puzzle may be signed using a leave of a nested tree.
Owner:SECRET DOUBLE OCTOPUS LTD
Key management and node authentication method for sensor network
ActiveUS8913751B2Improve abilitiesConserve effectively resourceKey distribution for secure communicationUser identity/authority verificationNetwork communicationNode authentication
A key management and node authentication method for a sensor network is disclosed. The method comprises the following steps of: 1) keys pre-distribution: before deploying the network, communication keys for establishing security connection between nodes are pre-distributed to all of nodes by a deployment server. 2) Keys establishment: after deploying the network, a pair key for the security connection is established between nodes, which includes the following steps of: 2.1) establishment of shared keys: the pair key is established between neighbor nodes in which the shared keys are existed; 2.2) path keys establishment: the pair key is established between the nodes in which there is no shared keys but there is a multi-hop security connection. 3) Node identity (ID) authentication: before formally communicating between nodes, the identity is authenticated so as to determine the legality and the validity of the identity of the other. It is possible for effectively resisting attacks such as wiretapping, tampering, and replaying and the like for the network communication, realizing the secret communication between the nodes, effectively saving resources of the nodes of the sensor network, and prolonging the service lift of the sensor network in the method.
Owner:CHINA IWNCOMM
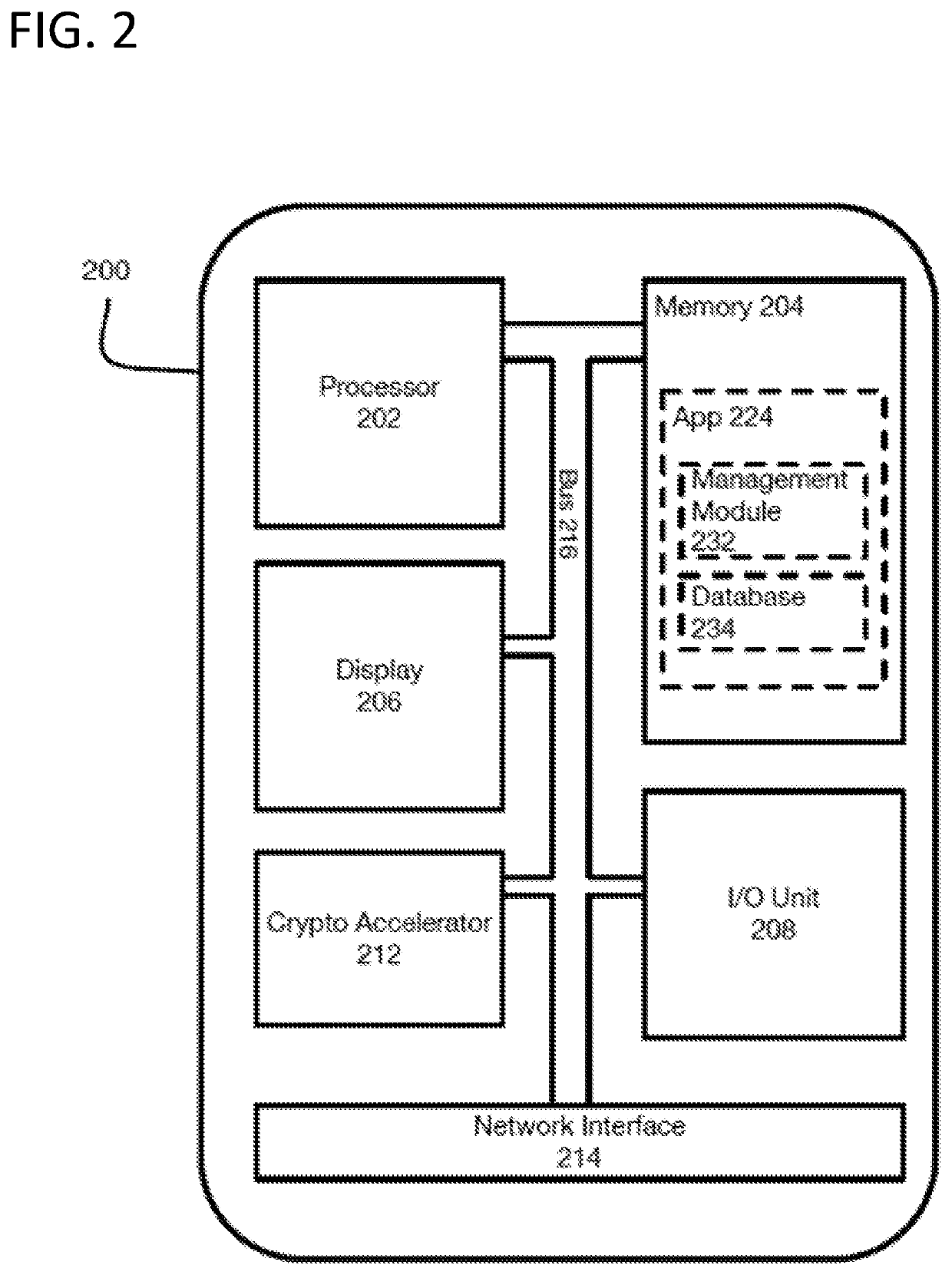
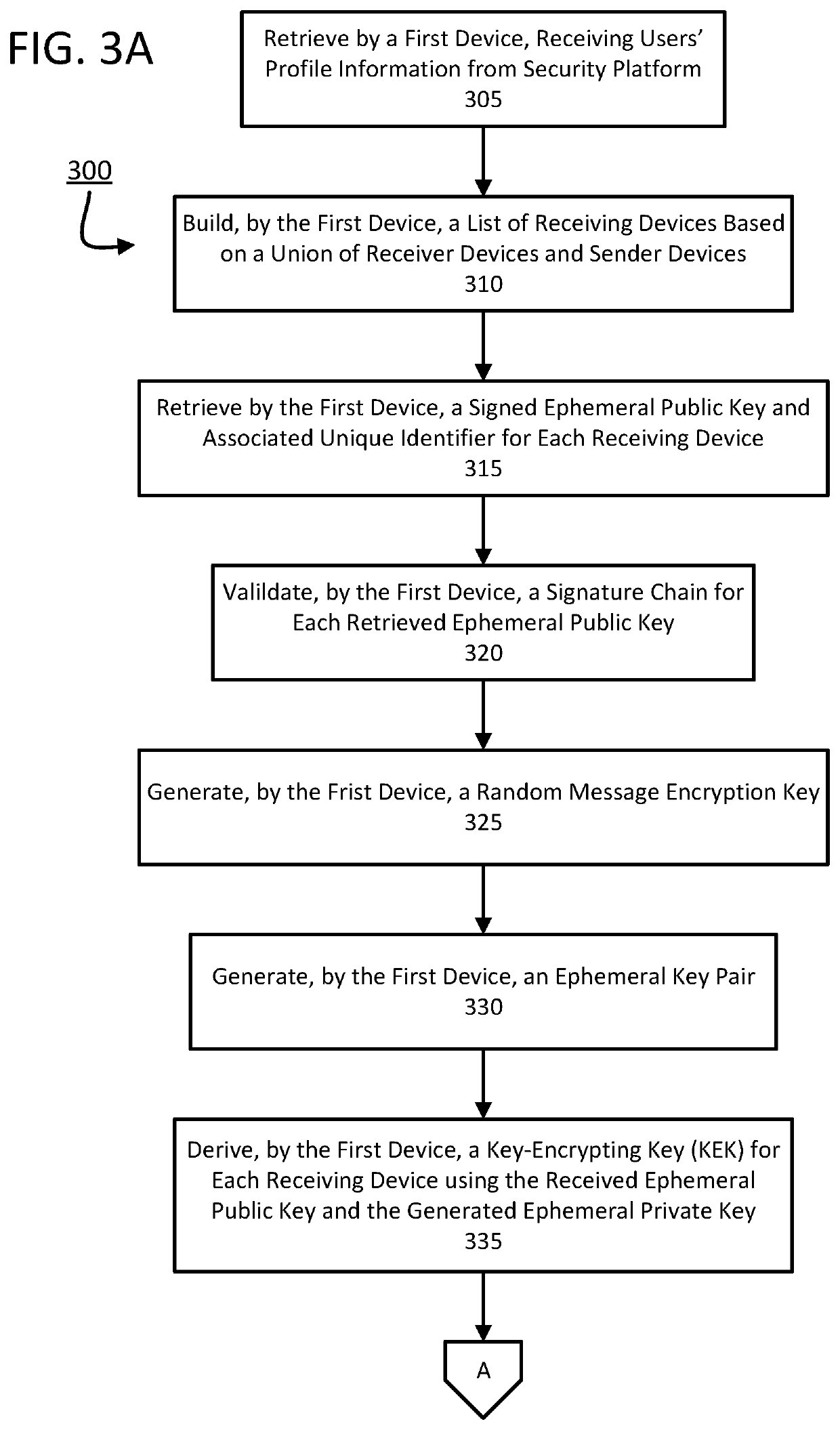
Two-Way Handshake for Key Establishment for Secure Communications
ActiveUS20200213111A1Speed up the processMultiple keys/algorithms usageUser identity/authority verificationSecure communicationEnd-to-end encryption
The present application describes a method, system, and non-transitory computer-readable medium for end-to-end encryption during a secure communication session. According to the present disclosure, a first device initializes a secure communication session with at least one second device. Initializing the secure communication session includes transmitting an invitation to a secure communication session to the at least one second device. The at least one second device may generate a transmission root key, which may be used to derive a first key for encrypting data transmitted to the first device and a second key for decrypting received data from the first device. The at least one second device may transmit the transmission root key to the first device, which may use the transmission root key to derive a first key to encrypt data transmitted to the at least one second device and a second key to decrypt data received from the at least one second device.
Owner:AMAZON TECH INC +1
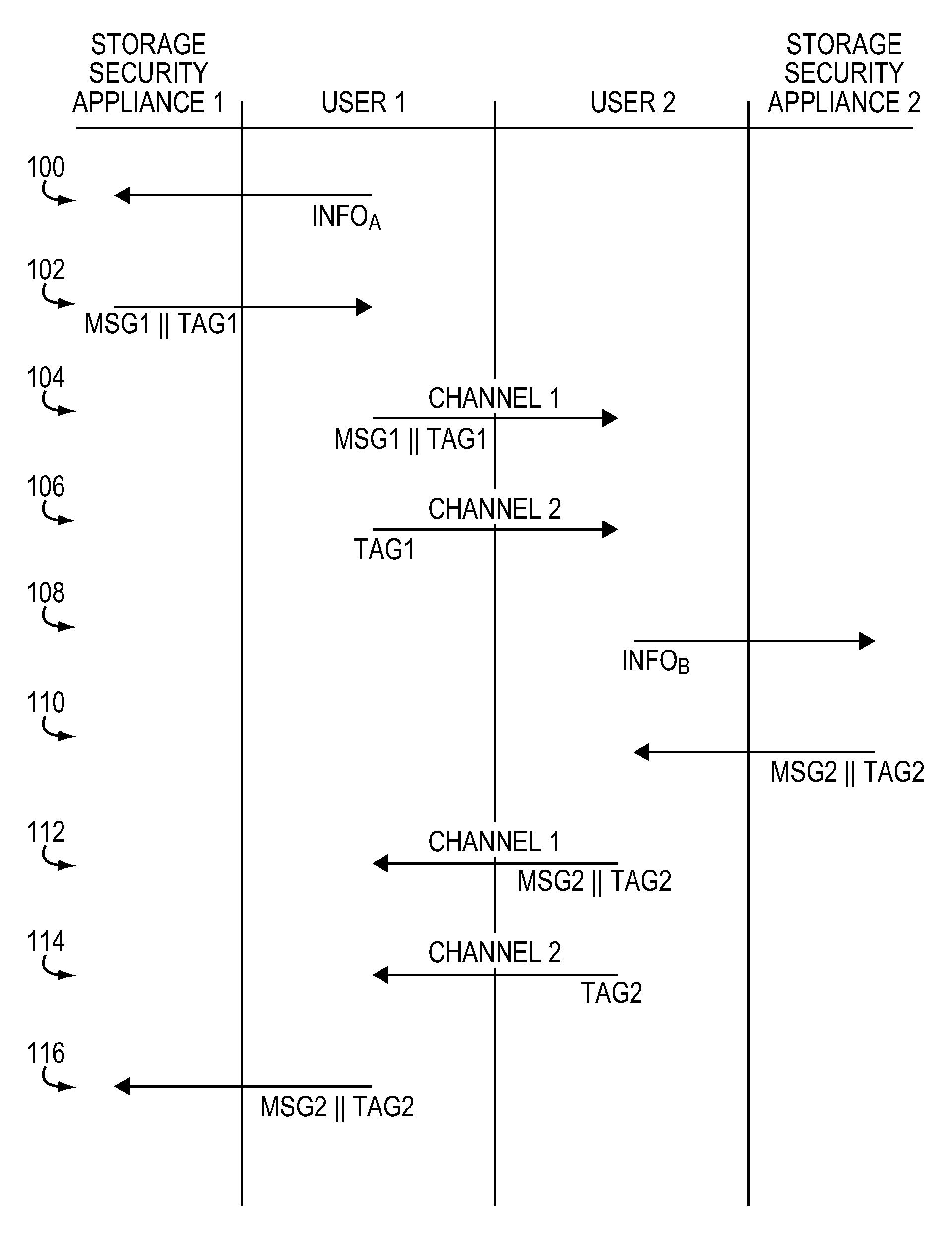
Method and apparatus for offline cryptographic key establishment
InactiveUS7971234B1Digital data processing detailsUser identity/authority verificationKey exchangeNetwork connection
The invention provides an authentication scheme that allows networked devices to establish trust in connection with the exchange of keys pursuant to an asymmetrical cryptographic technique, such as Diffie-Hellman. The invention provides a technique, referred to as offline key establishment, that establishes a trust relationship between two networked devices that use Diffie-Helman. Offline key sharing provides for the exchange of authentication information using a separate channel which, in the preferred embodiment does not constitute an IP connection. Thus, while communications between networked devices may ultimately proceed via a network connection, trust between the networked devices is established via a separate, offline channel, such as a telephone call or email message. The use of offline key establishment allows for such features as one way key sharing; and addresses situations where one party to the exchange does not want to share all of his keys, but just one or two keys.
Owner:NETWORK APPLIANCE INC
Real-time communication security for automation networks
ActiveUS20100217967A1Provide securitySpecial service provision for substationKey distribution for secure communicationCommunications securitySecure communication
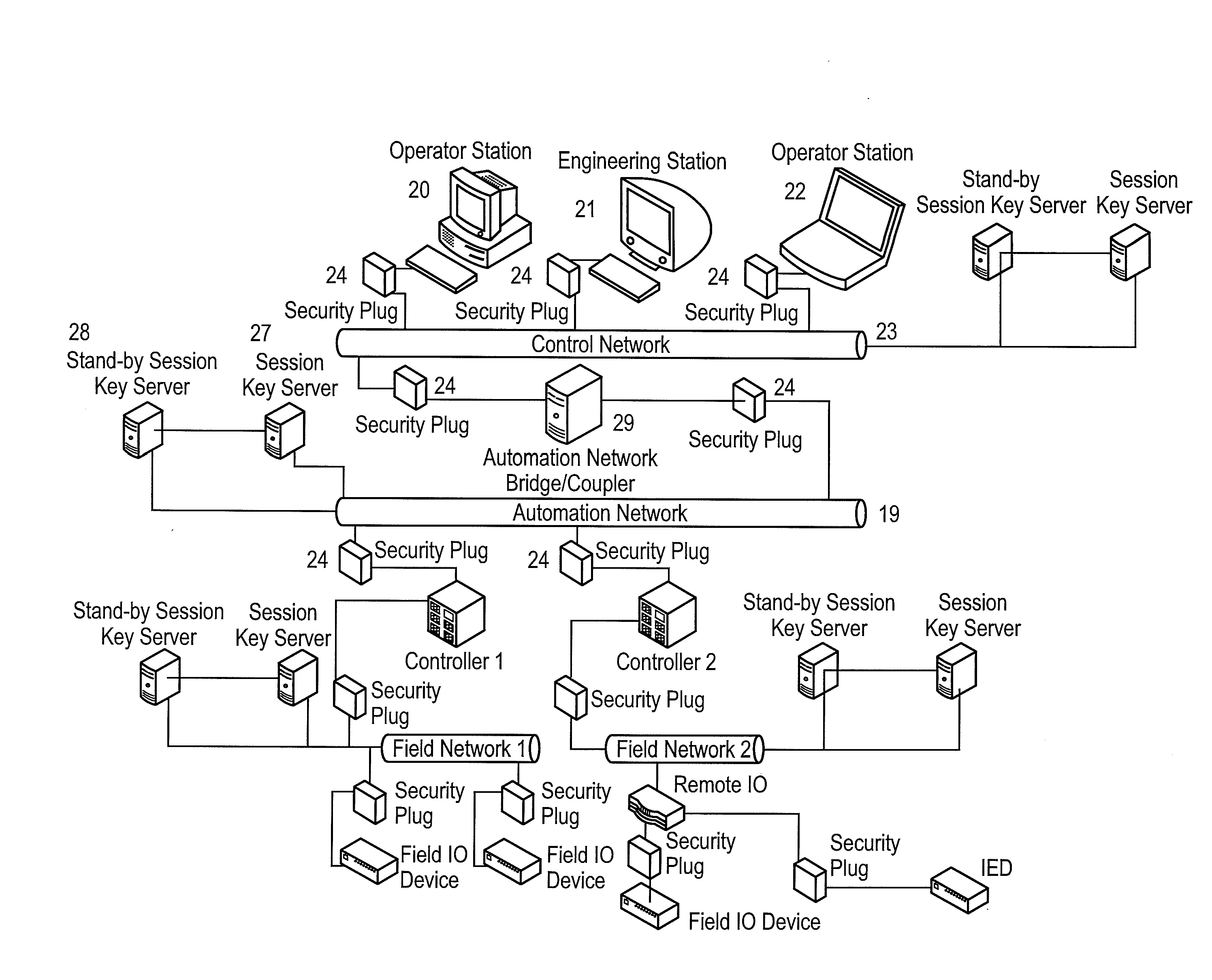
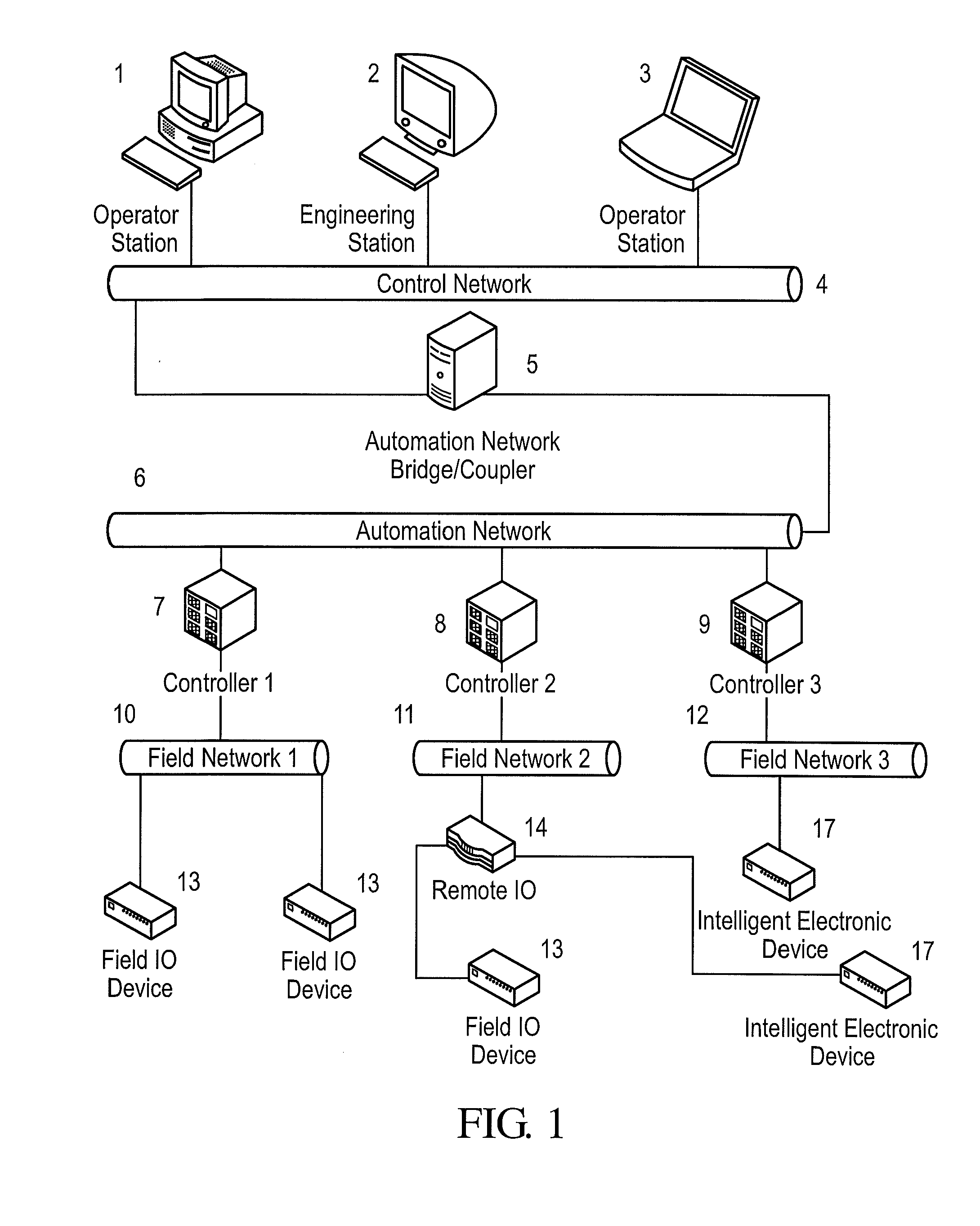
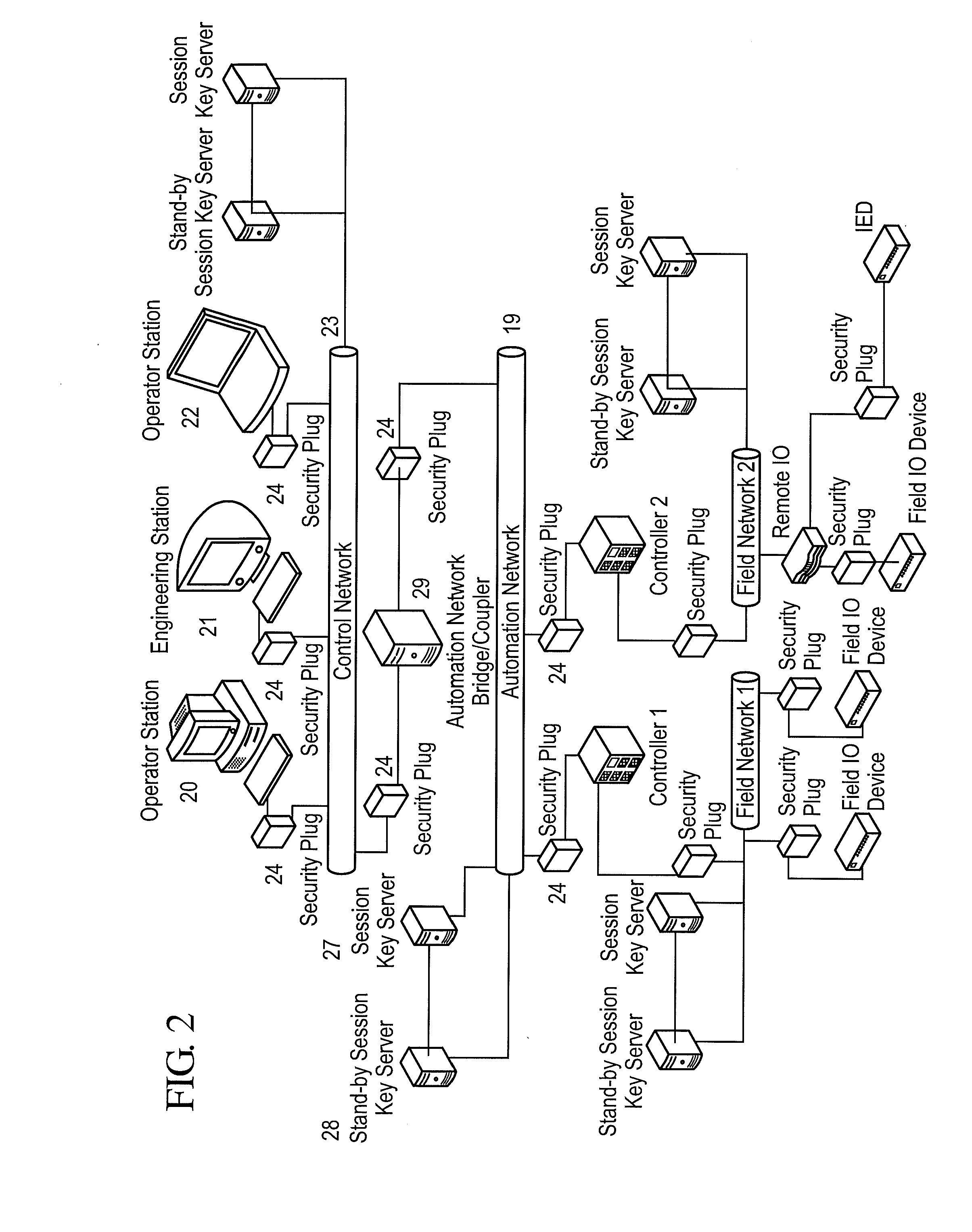
A framework, device and method are disclosed for providing broadcast communication security over Ethernet within an automation system, wherein a security plug provides secure working of the automation system. The security plug can be implemented using ASIC / FPGA technology to provide compatibility with existing systems and an intuitive plug-and-play model. An exemplary system can address jitter-sensitivity by providing a real-time architecture, with minimal transmission latencies. The security plug can have separate security and communication modules that make provisions for protocol independent working of the security plug, within these networks. The method can include bootstrapping, secret key establishment and secure communication, for providing real-time guarantees.
Owner:HITACHI ENERGY SWITZERLAND AG
Method for protecting security of digital signature documents of multiple verifiers strongly designated by multiple signers.
InactiveCN101651542AImprove securityEnsure safetyUser identity/authority verificationInstrumentsElectronic documentHash function
The invention discloses a method for protecting the security of digital signature documents of multiple verifiers strongly designated by multiple signers. The method is implemented according to the following steps: step 1, system parameter generation: selecting a cyclic group the order of which is prime number and a one-way Hash function of cryptography; step 2, user secret key establishment: selecting private keys for the multiple signers secretly, distributing by a secret channel, generating public keys for each signer ,selecting private keys for multiple designated verifier secretly and distributing the private keys by a secret channel; step 3, signature process: calculating digital signatures of strongly designated verifiers on information m through operation by the multiple signers; step 4, verifying process: verifying whether the equation is valid by digit operation; if so, the verification is successful; if not, the verification fails. The method of the invention has highly operation efficiency and can provide security protection of completeness, authenticity and non-repudiation of the electronic documents in storage process or transmission process.
Owner:XIAN UNIV OF TECH
Method and system for controlling car key
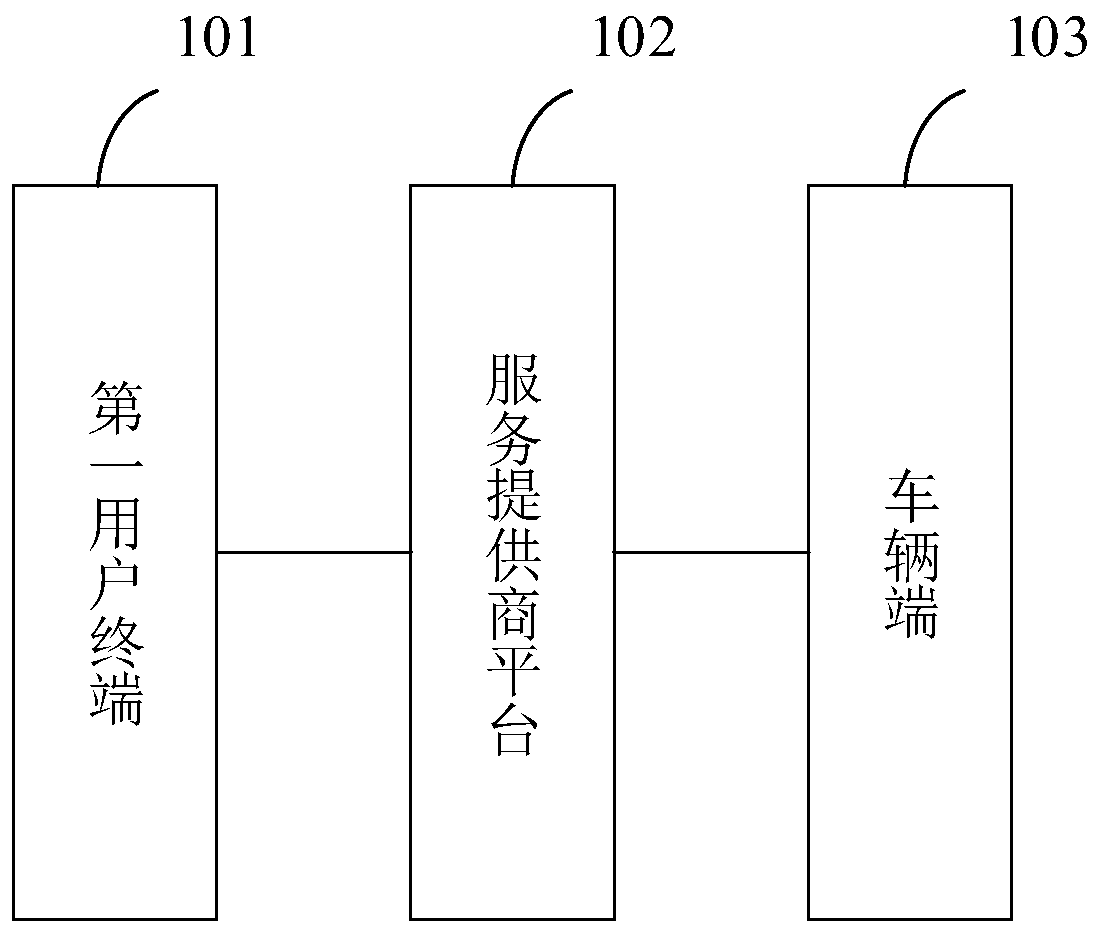
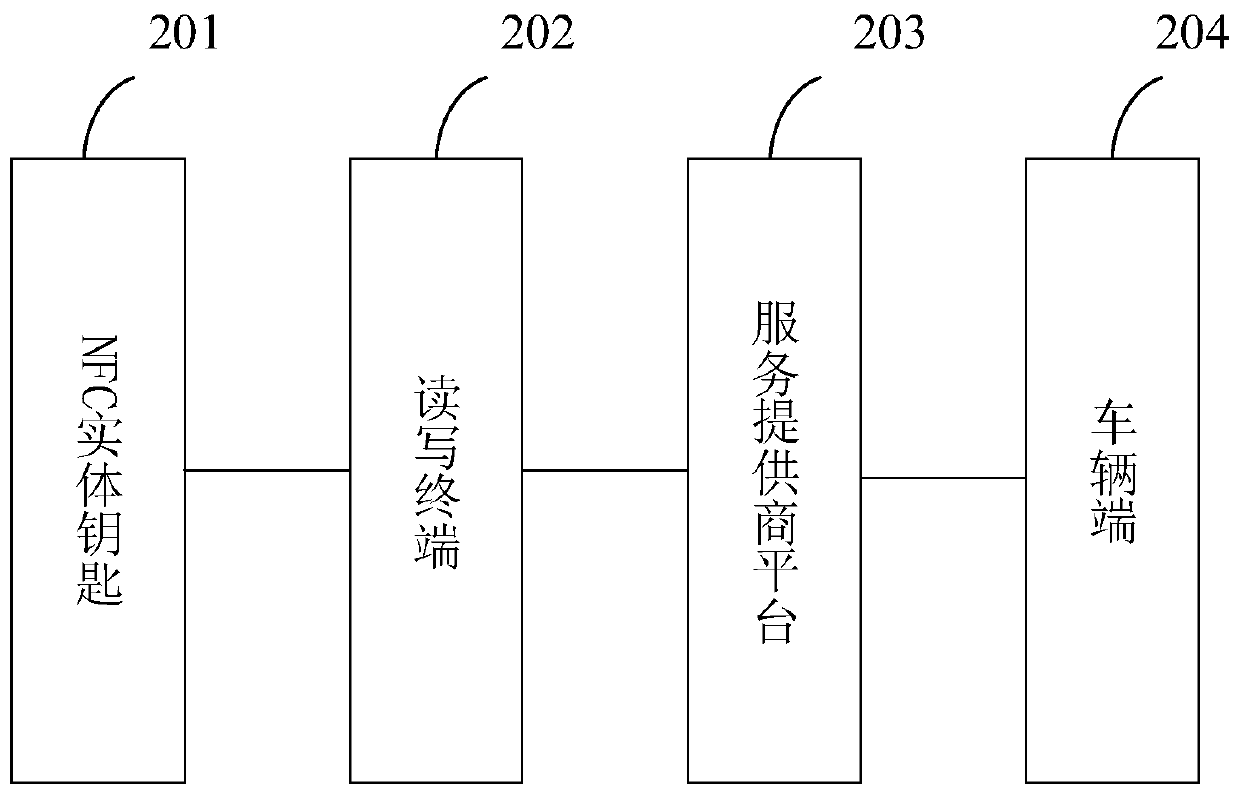
ActiveCN110136306AEasy to controlImprove convenienceIndividual entry/exit registersService provisionComputer terminal
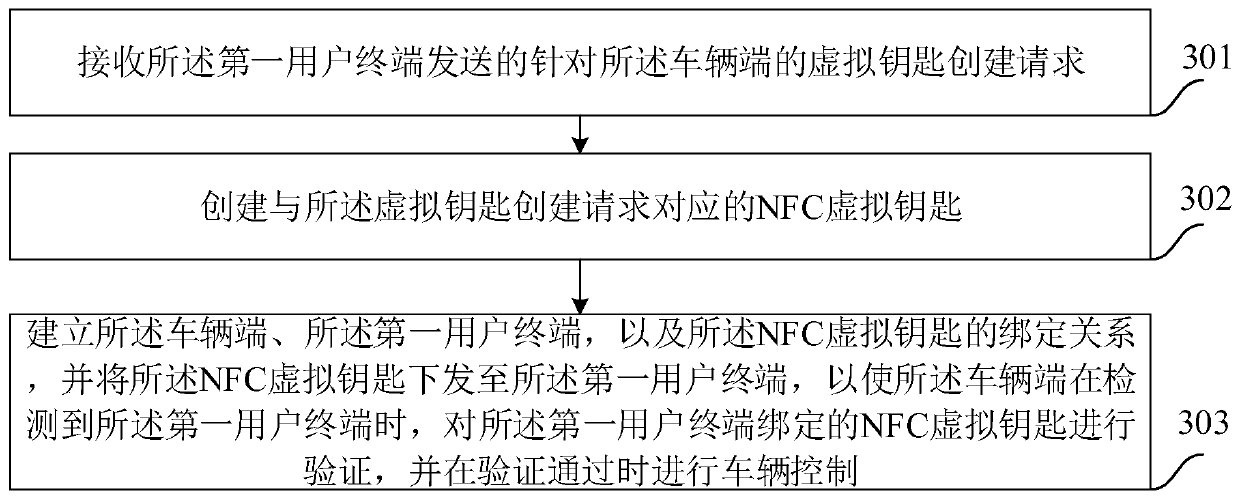
The embodiment of the invention provides a method and a system for controlling a car key. The system comprises a first user terminal, a service provider platform and a vehicle side, wherein the firstuser terminal is used for responding user operation, generating a virtual key establishment request for the vehicle side and sending the request to the service provider platform; the service providerplatform is used for creating an NFC virtual key corresponding to the virtual key establishment request, and establishing a binding relation among the vehicle side, the first user terminal and the NFCvirtual key so as to issue the NFC virtual key to the first user terminal; and the vehicle side is used for carrying out verification on the NFC virtual key bond by the first user terminal when the first user terminal is detected and carrying out vehicle control when the verification is realized. According to the method and the system, the control for the NFC car key is realized, and the convenience and safety for controlling the car key are promoted.
Owner:GUANGZHOU XIAOPENG MOTORS TECH CO LTD
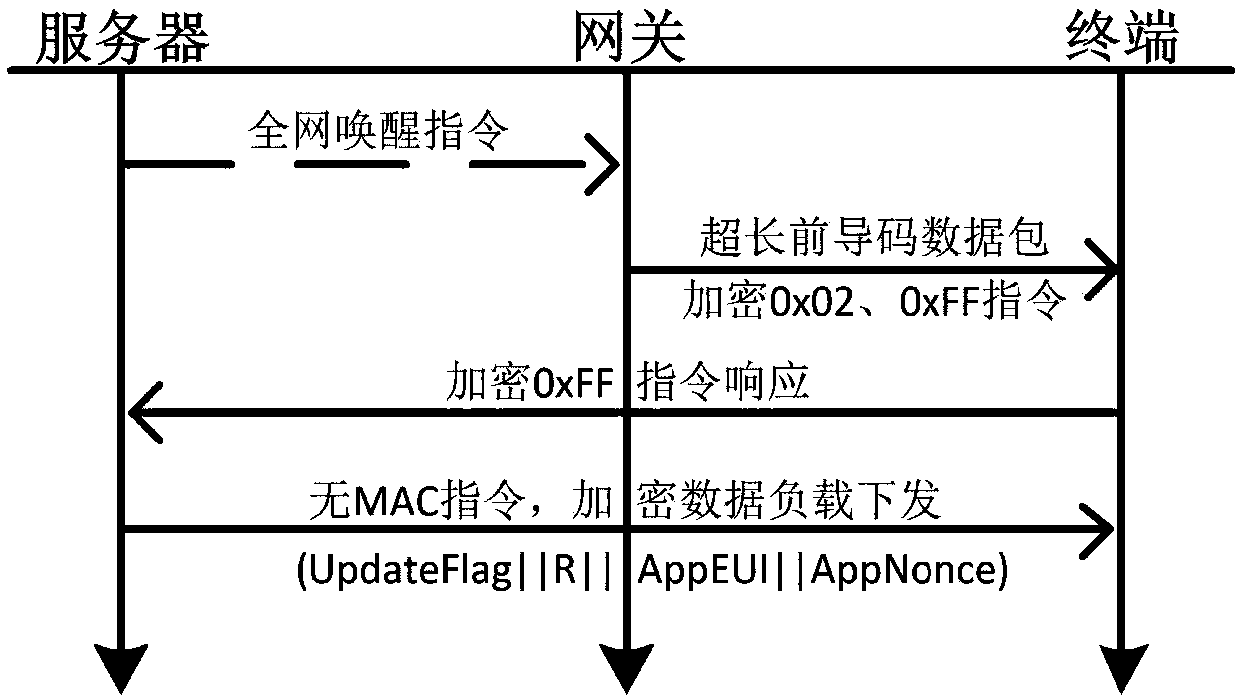
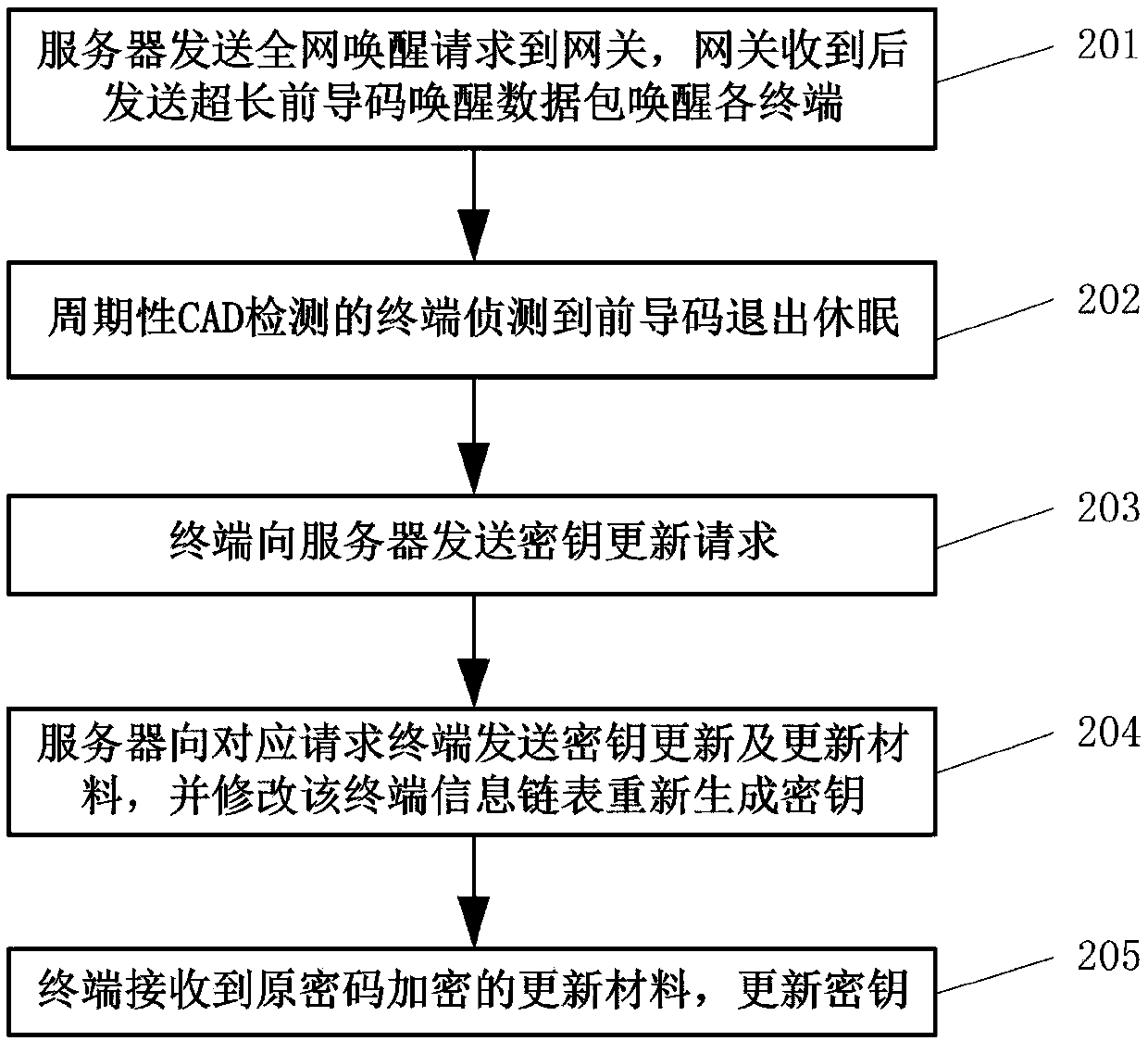
Matrix type key management method for LoRaWAN
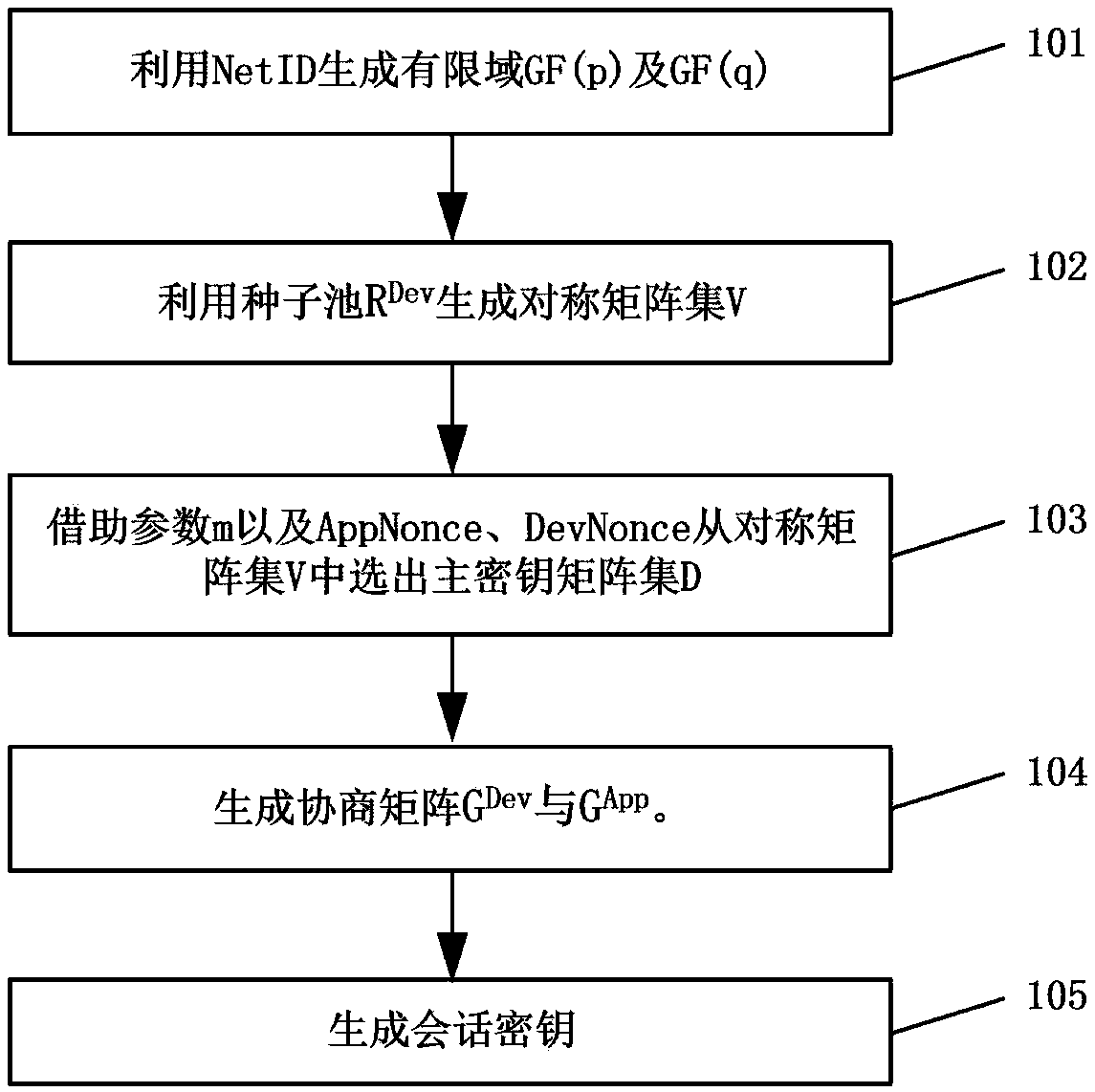
ActiveCN107846280AImprove securityGuaranteed CompatibilityPower managementKey distribution for secure communicationRandom Number SeedRadio frequency
The invention relates to a matrix type key management method for LoRaWAN, and belongs to the field of the wireless wide area network. The method comprises the following steps: generating a symmetrix matrix of the key computation by using a random number seed pool R and a line limit number M, and accomplishing the negotiation in the key establishment with the help of the existing AppEUI, AppNonce and DevNonce in the LoRa access interaction message; generating the auxiliary material required by the individual key by using the specific message content of the LoRa and the character thereof; computing by using the matrix type matrix to obtain the AppSKey and NwkSKey required by the LoRa; and realizing the key update based on the WOR function by using the specific CAD mode of the LoRa radio frequency chip. Through the method disclosed by the invention, the conflict between the improved Blom key management key and the LoRa protocol is solved, and the security of the LoRa network has a certainimprovement.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Shared secret key establishment method between wireless equipment based on receiving signal intensity
ActiveCN105187203AResist attackImprove applicabilityKey distribution for secure communicationComputer hardwareCommunications security
The invention discloses a shared secret key establishment method between wireless equipment based on receiving signal intensity. The method comprises the steps that 1) a security isolation environment is created for two sets of wireless equipment; 2) initiation equipment transmits multiple authentication requests to response equipment according to the set transmitting power and the set time interval; 3) the response equipment calculates the standard deviation of the receiving signal intensity; and if the standard deviation of the receiving signal intensity is less than a threshold value, an authentication passing message is replied to the initiation equipment, or authentication is not passed; 4) the initiation equipment generates a secret key K of which length is m bits, and then transmits m data packets to the response equipment; 5) the response equipment records the signal receiving intensity of the m data packets and recovers a secret key K' of which length is m bits according to m receiving signal intensity, and then replies a message encrypted by the secret key K'; and 6) the initiation equipment performs decryption by using the secret key K, and replies an authentication success message if decryption is successful so that secret key sharing is completed. Communication security is greatly enhanced by the shared secret key establishment method between the wireless equipment based on the receiving signal intensity.
Owner:INST OF INFORMATION ENG CAS +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com