Method for key management and node authentication of sensor network
一种传感器网络、密钥管理的技术,应用在传感器网络密钥管理和节点鉴别领域,能够解决传感器网络无法抵抗攻击、密钥网络节点鉴别服务等问题
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
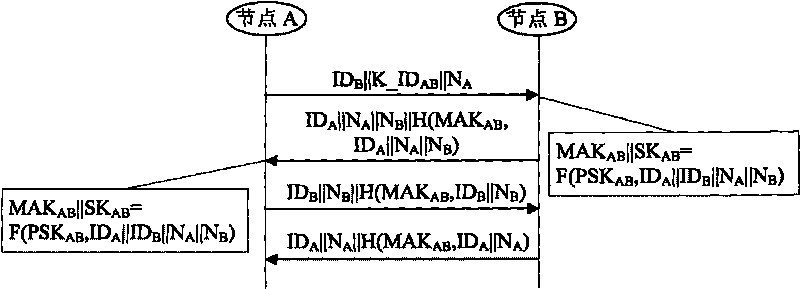
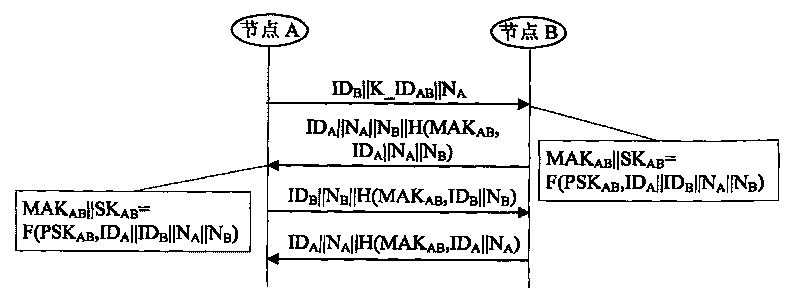
[0041] The invention provides a sensor network key management and node authentication method, the method includes the following steps:
[0042] 1) Key pre-distribution. Before network deployment, the deployment server pre-distributes the communication key used to establish a secure connection between nodes to all nodes. The specific implementation method is:
[0043] 1.1) Before network deployment, the deployment server initializes the key pool to generate the key pool KP, which contains multiple keys and their key identifiers. The number of keys in the key pool is recorded as |KP|, |KP| is large enough, and it is assumed that the deployment server is safe;
[0044] 1.2) Assume that the preset network connectivity is P c , the number of nodes in the network is n, and each node has a corresponding identification ID. According to the classical random graph theory, calculate the degree d=(n-1)*(lnn-ln(-lnP c )) / n. In order to ensure good scalability, usually the preset number...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com