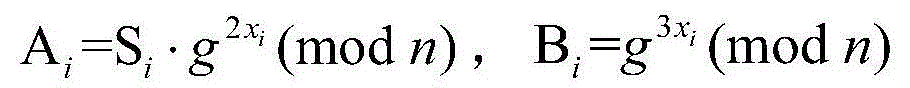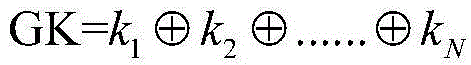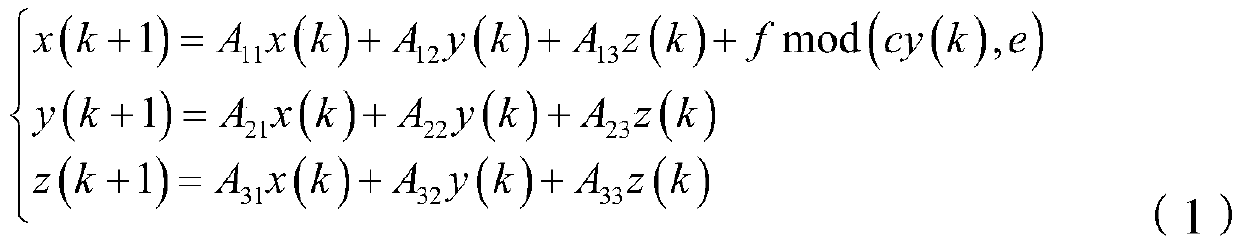Patents
Literature
40results about How to "Realize confidential communication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
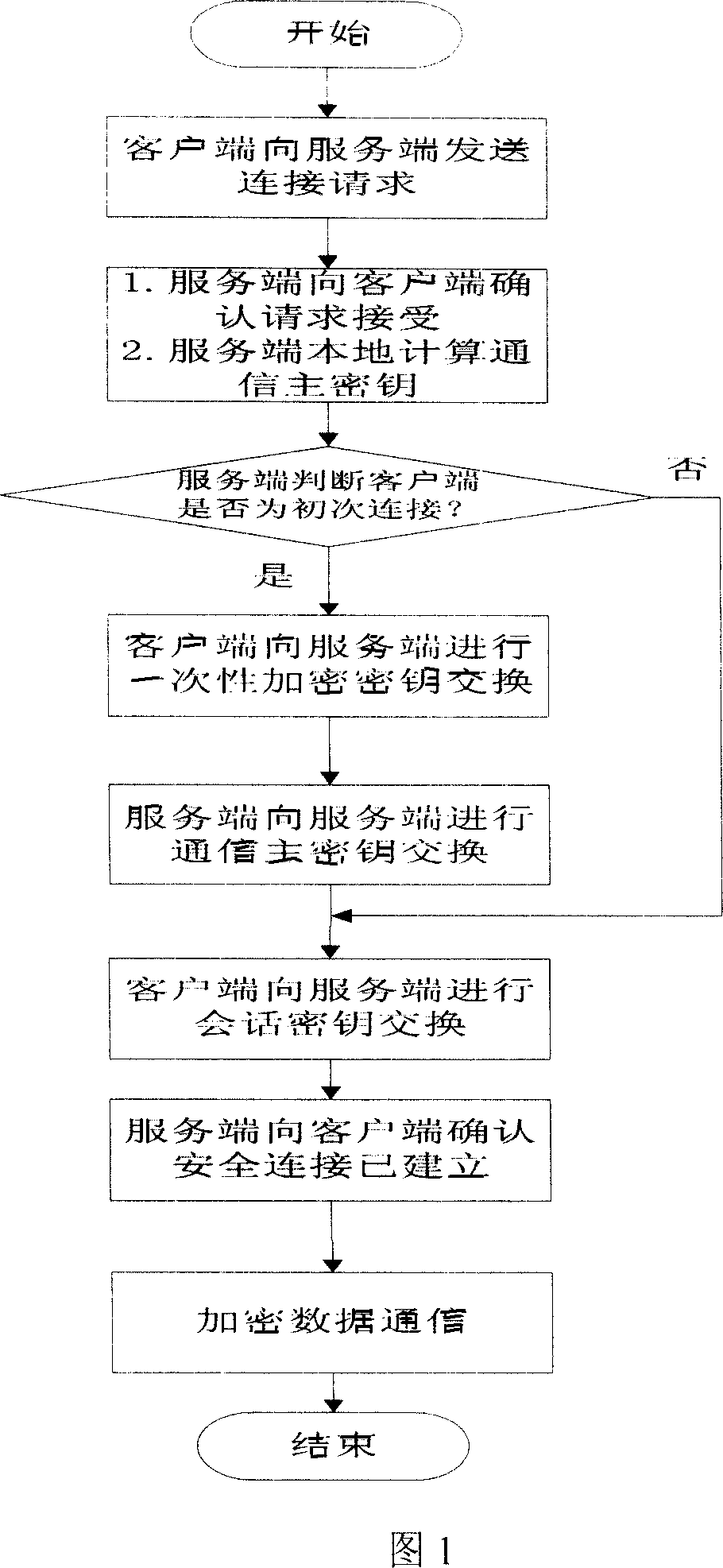
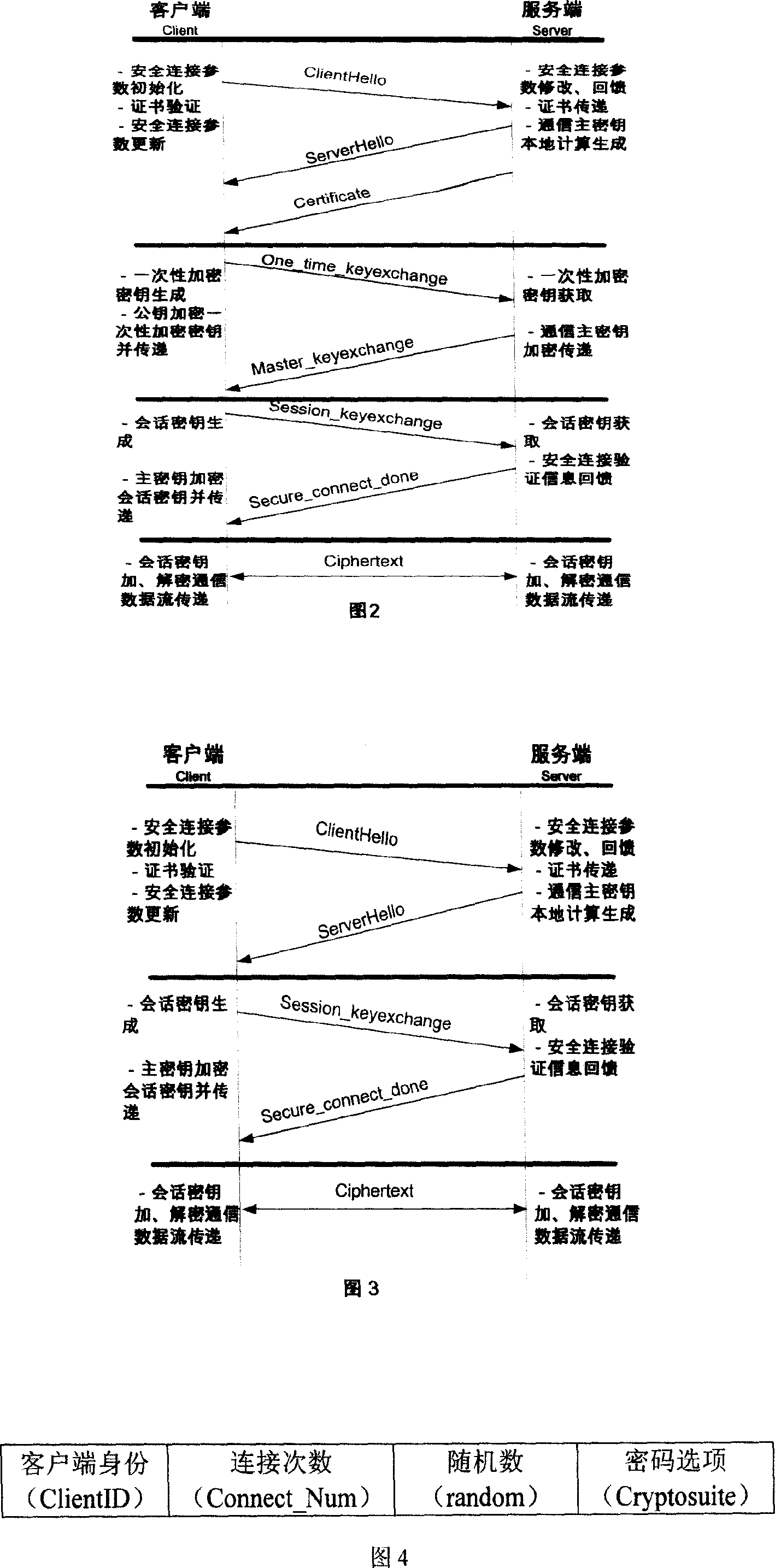
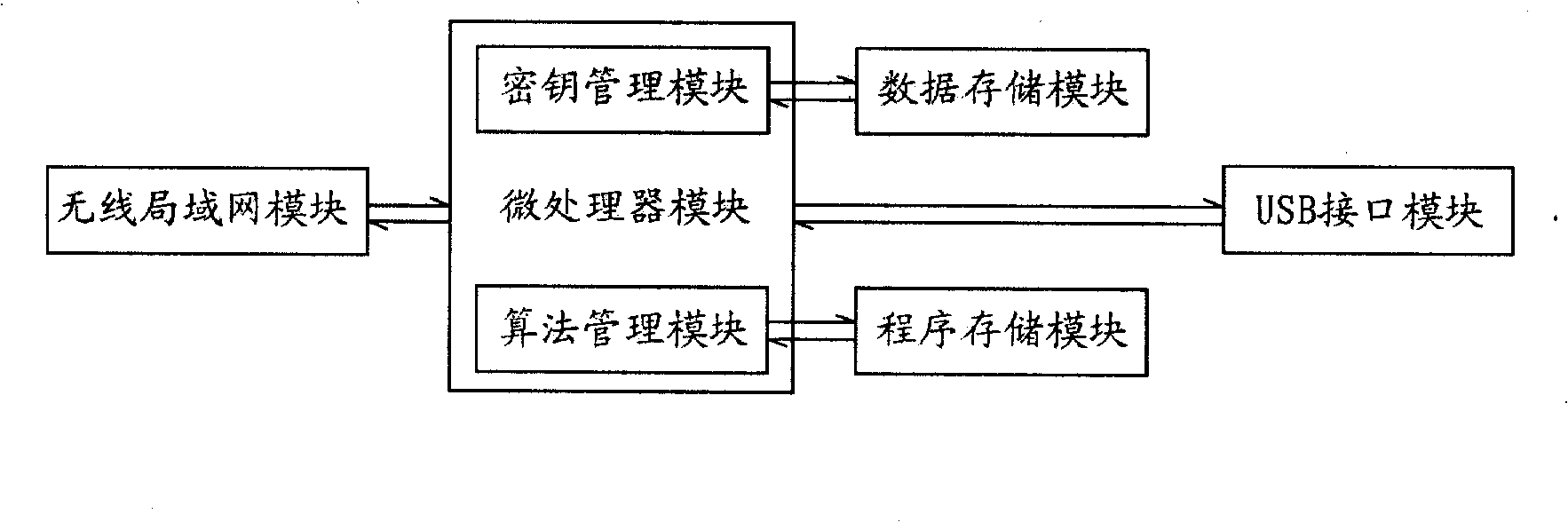
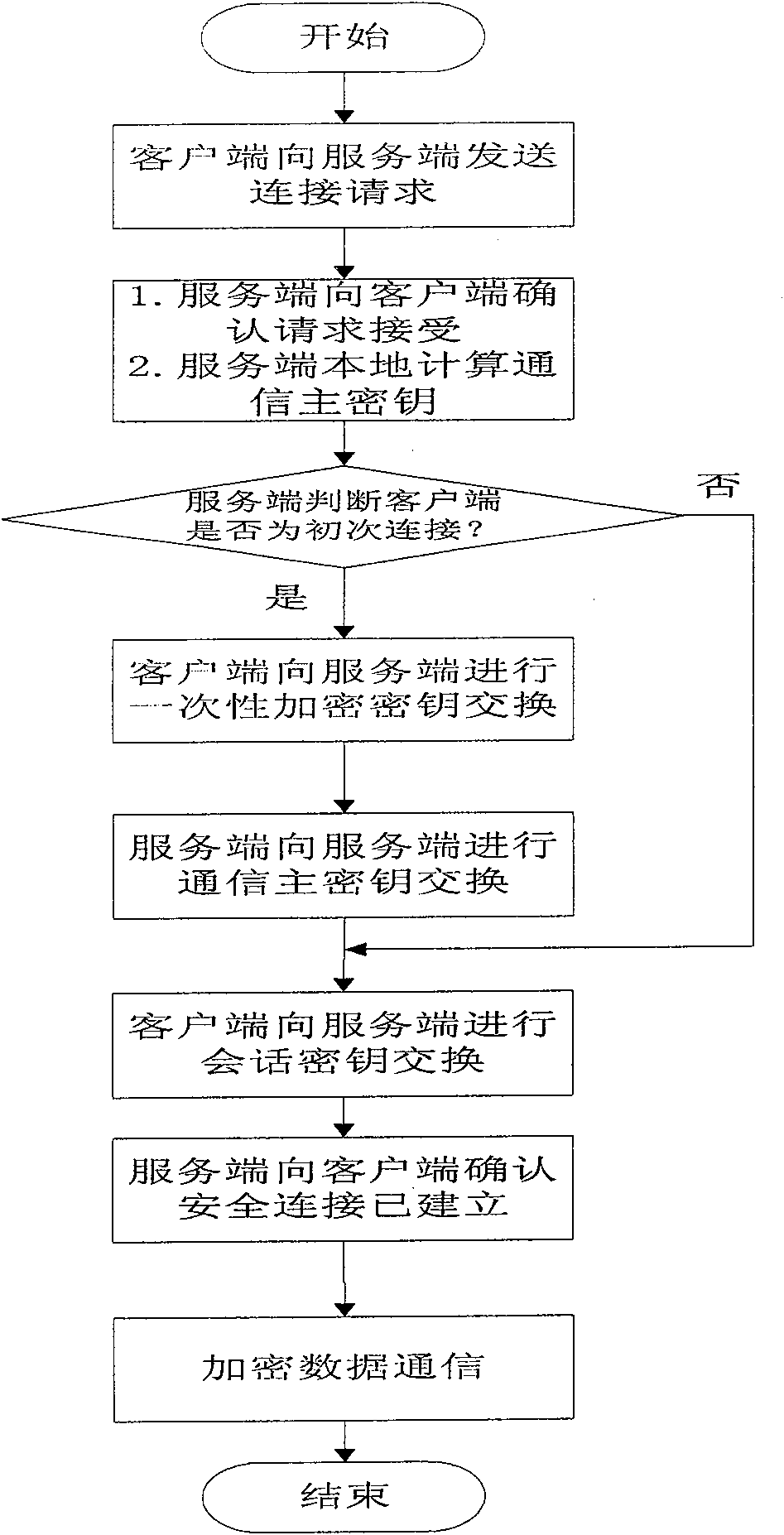
Web communication encrypting method
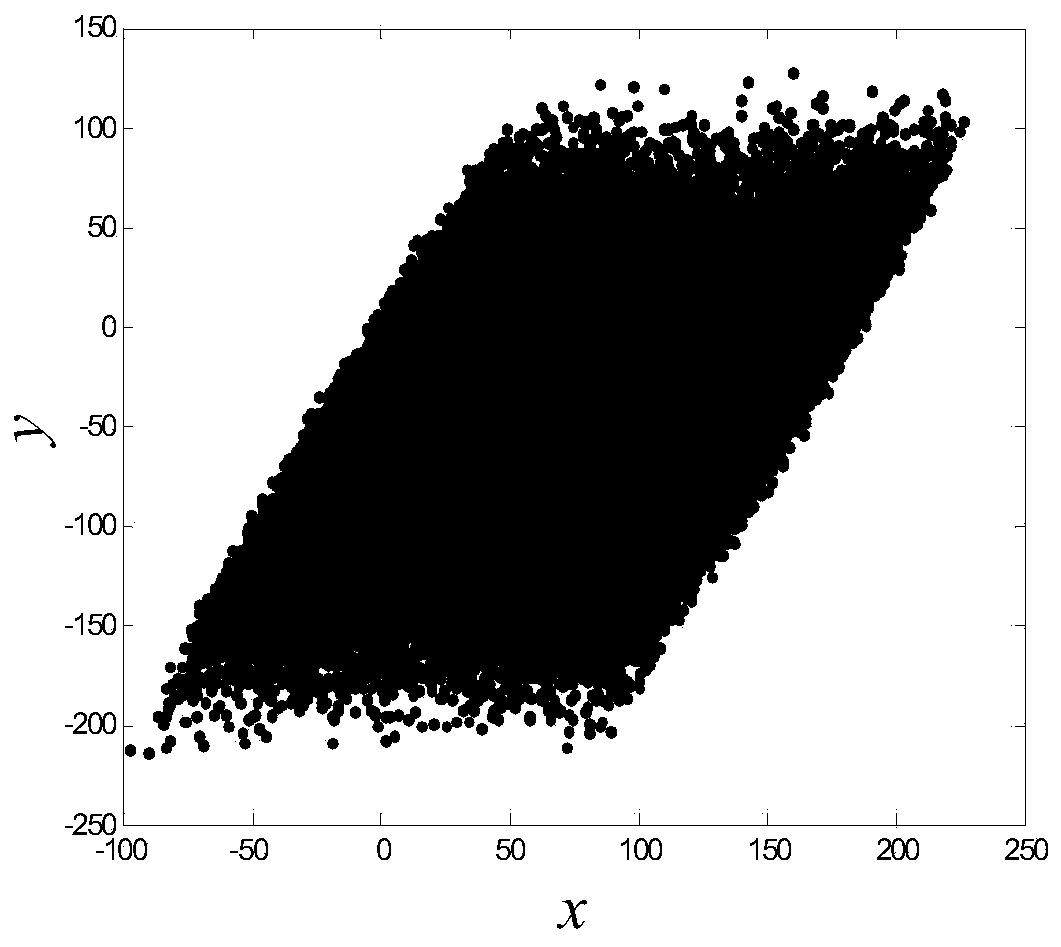
InactiveCN101022455AReduce the amount of key storageAvoid monitoringSynchronising transmission/receiving encryption devicesComputer hardwareKey exchange
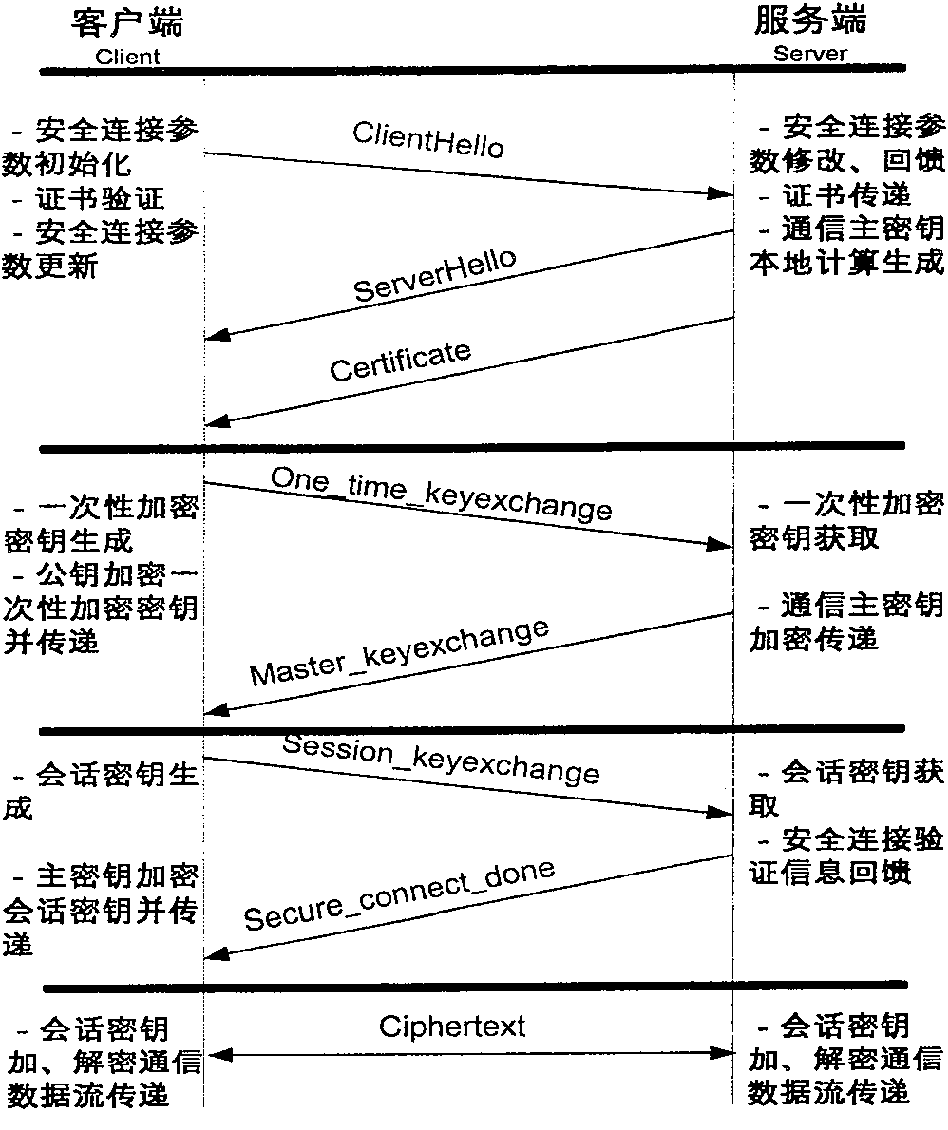
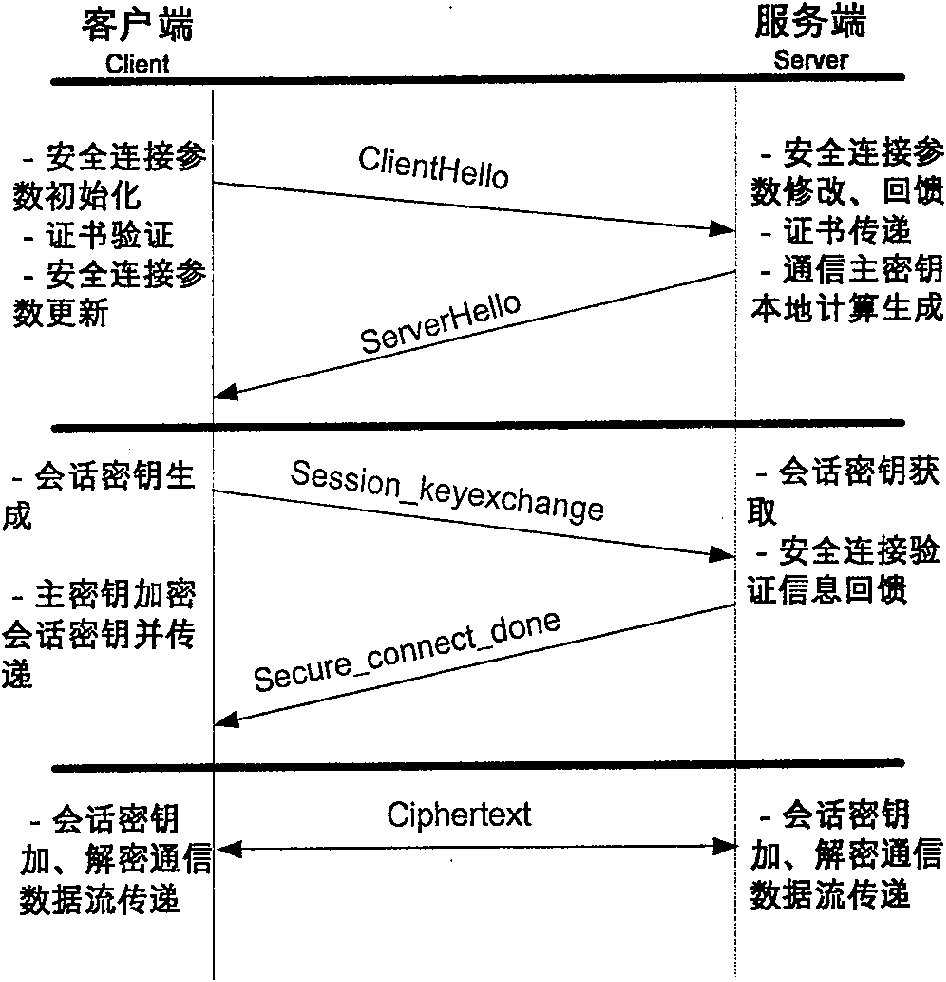
A method for enciphering web-communication includes obtaining communication master cipher key provided from service end an storing said communication master cipher key by client end when first communication is carried out, only requiring to generate cipher key locally by calculation at service end when communication is carried out again, utilizing locally stored communication master cipher key to realize transmission of conversation cipher key by client end then using said conversation cipher key to carry out enciphering / deciphering on communication data by both parties for realizing secret communication.
Owner:PEKING UNIV
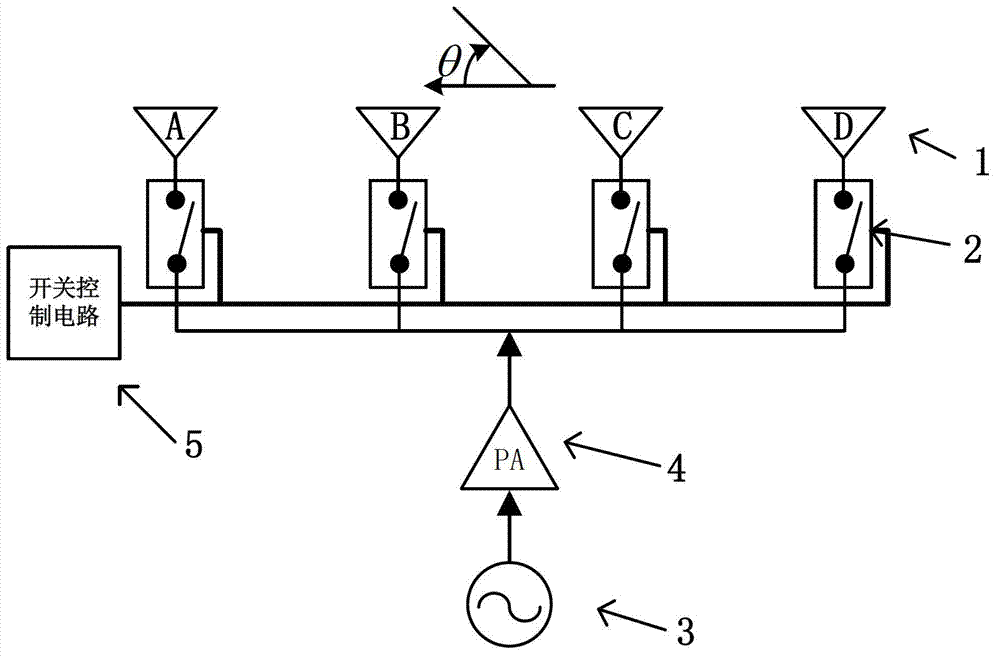
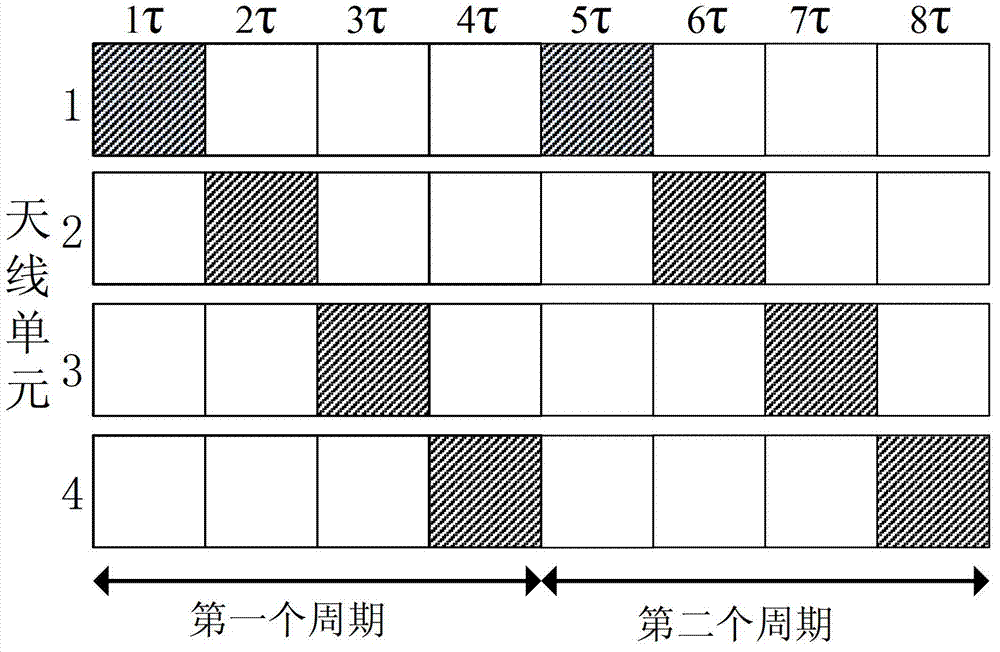
Four-dimensional antenna array based secret communication system and method thereof
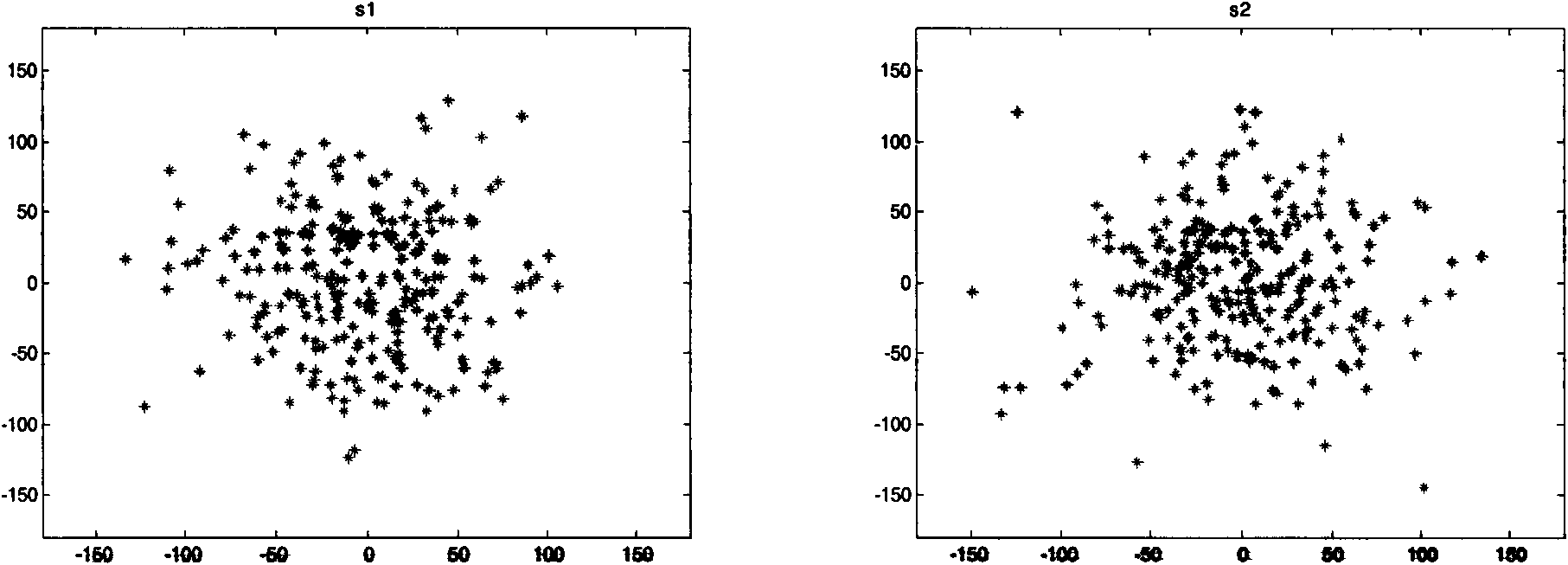
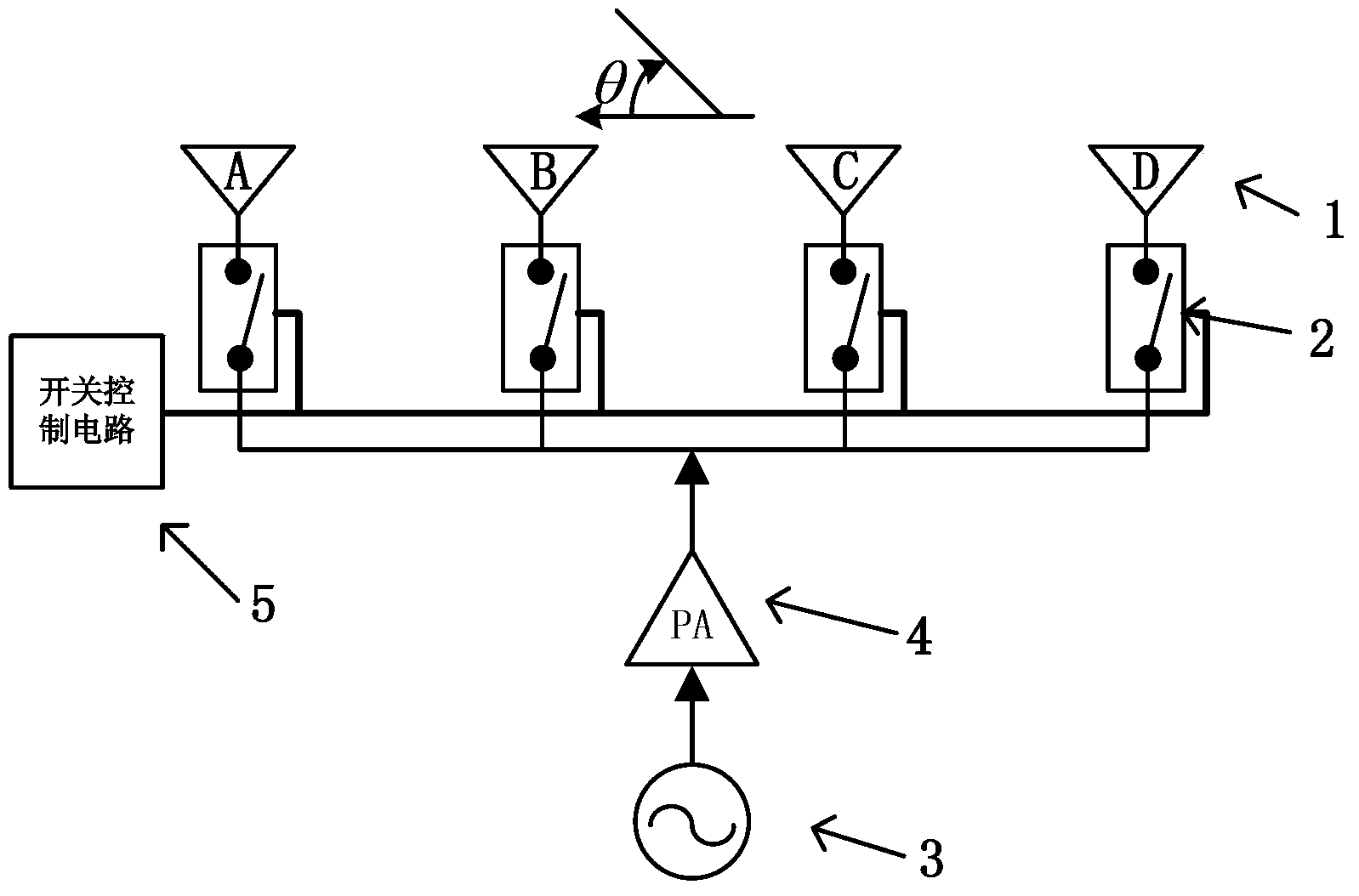
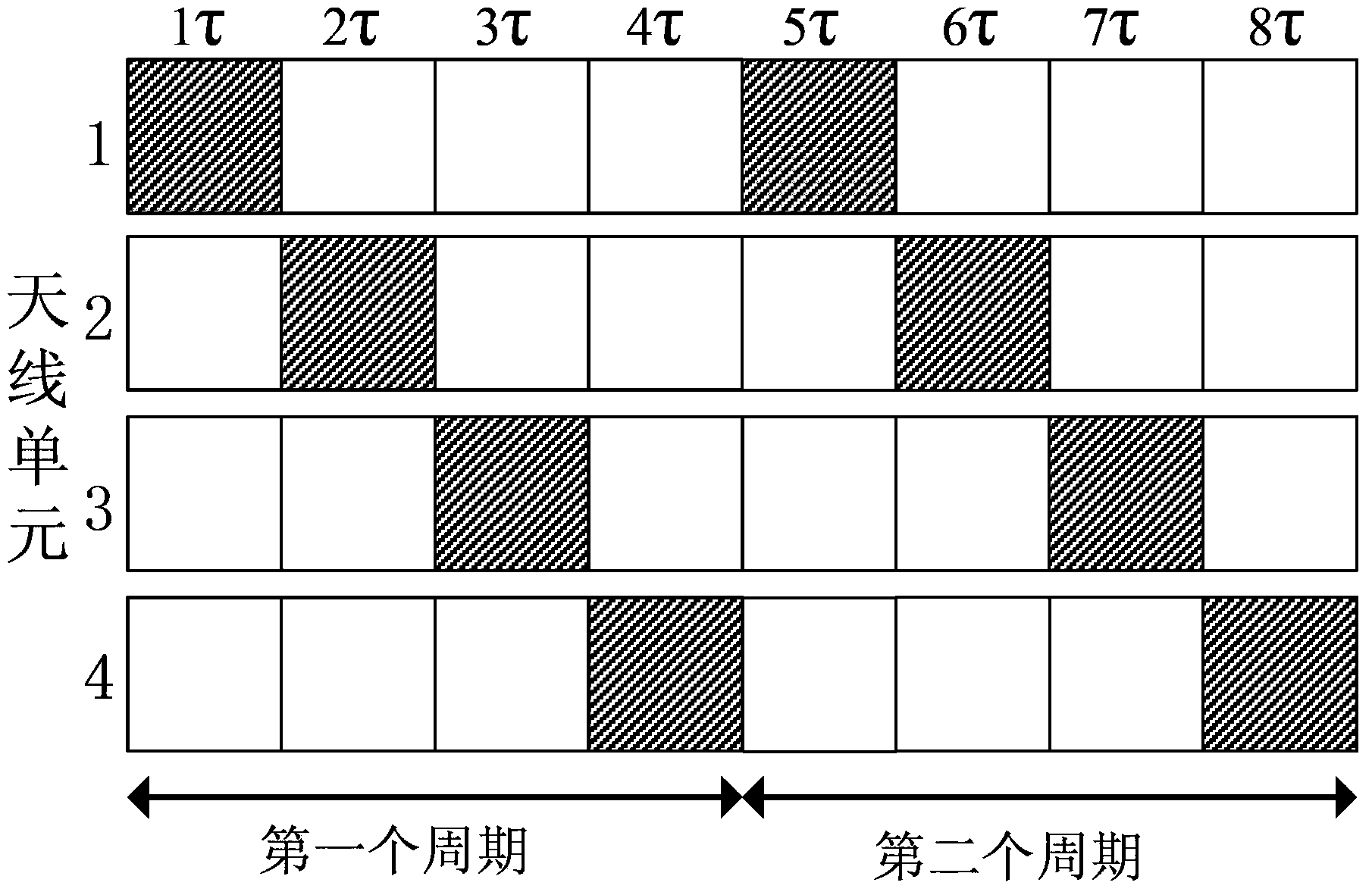
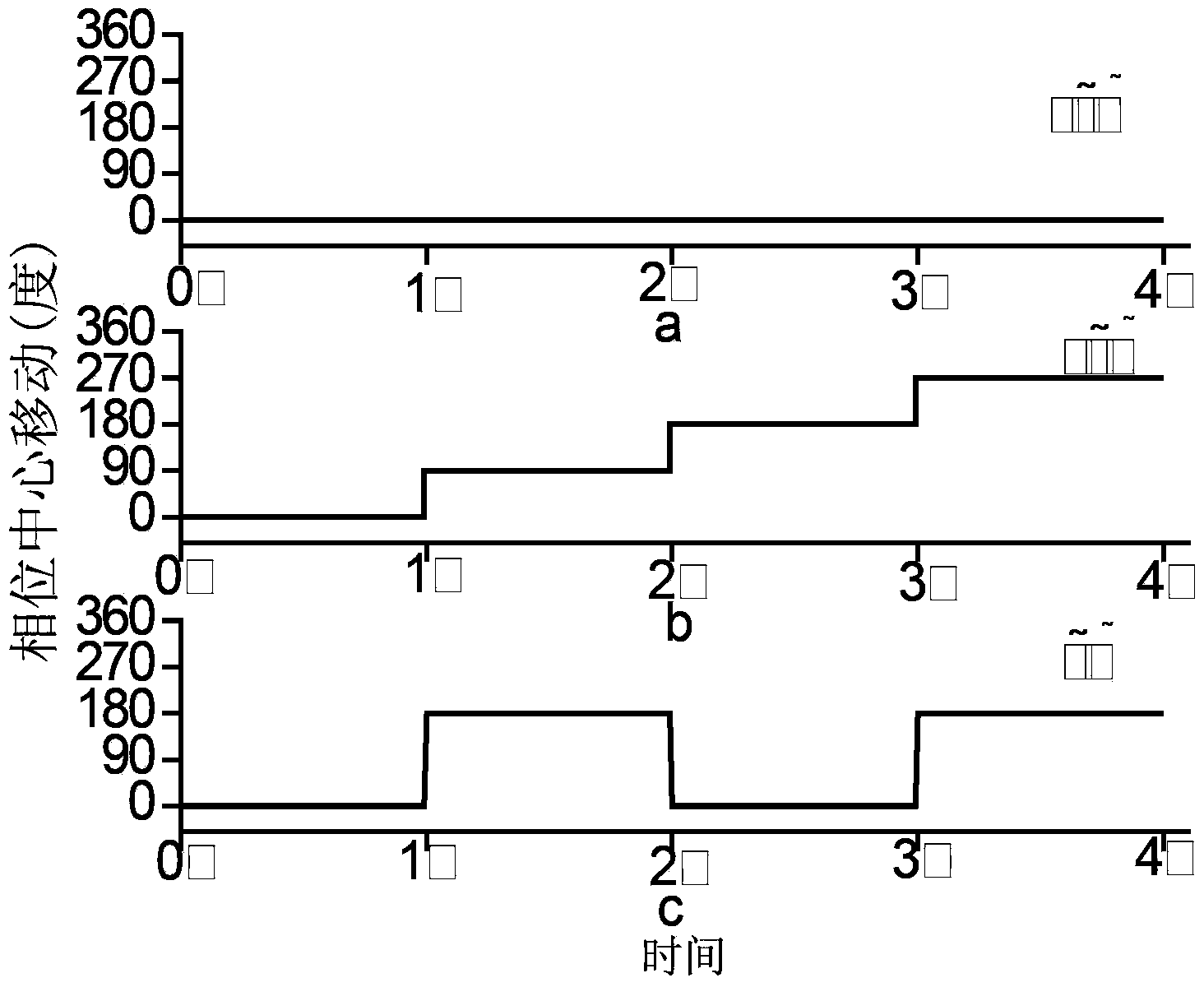
ActiveCN102857280ARealize confidential communicationAvoid lostSpatial transmit diversitySecret communicationEngineeringArray element
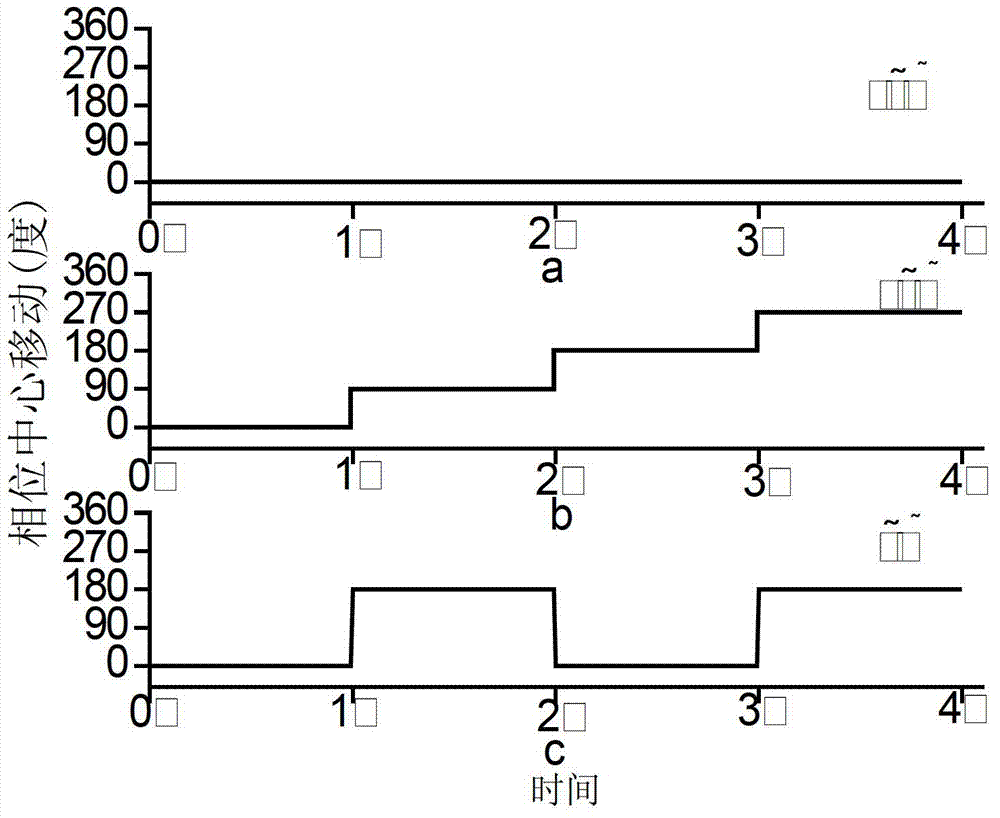
The invention discloses a four-dimensional antenna array based secret communication system and a method thereof. The system basically comprises an antenna unit, a high-speed radio frequency switch, a high-precision local oscillation source, a power amplifier, a switch control circuit and the like. The system and the method are characterized in that a phase center of an array is moved by controlling of working time sequences of all array elements (or subarrays) in the antenna array, modulation of information is finished at an antenna end, signals which are required to be transmitted are synthesized in a specific direction only, signals which are required to be transmitted can not be synthesized in other directions, a plurality of modulation methods, such as quadrature phase shift keying (QPSK), binary phase shift keying (2PSK) and M spread spectrum sequences, can be achieved, and the structure of a transmitter can be simplified. Compared with traditional secret communication methods, the method is a novel physical layer encryption method and can effectively resist eavesdropping receivers in side lobe directions. The system and the method are applied to wireless communication systems.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Method for key management and node authentication of sensor network
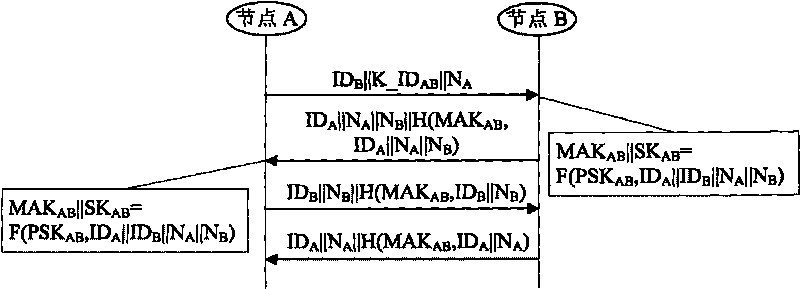
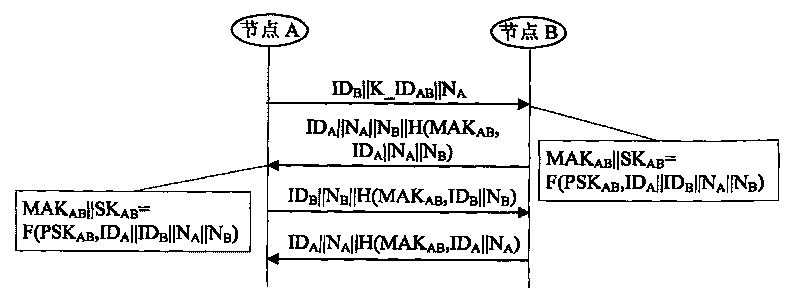
ActiveCN101699891ARealize confidential communicationSave resourcesKey distribution for secure communicationUser identity/authority verificationSecure communicationNetwork deployment
Owner:CHINA IWNCOMM
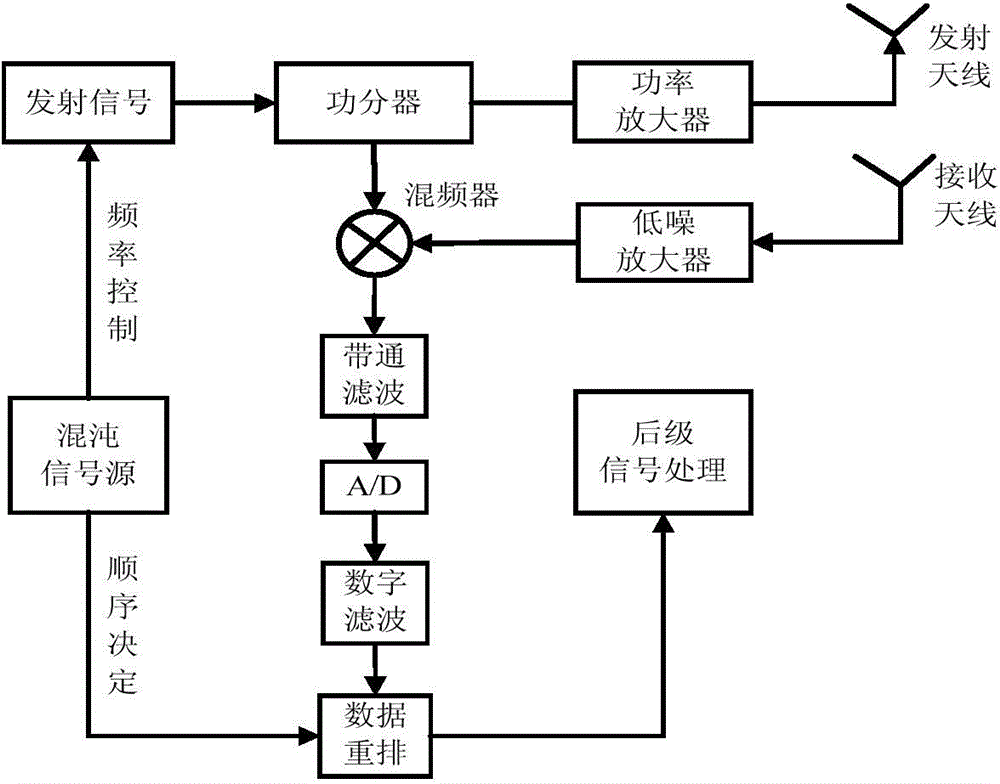
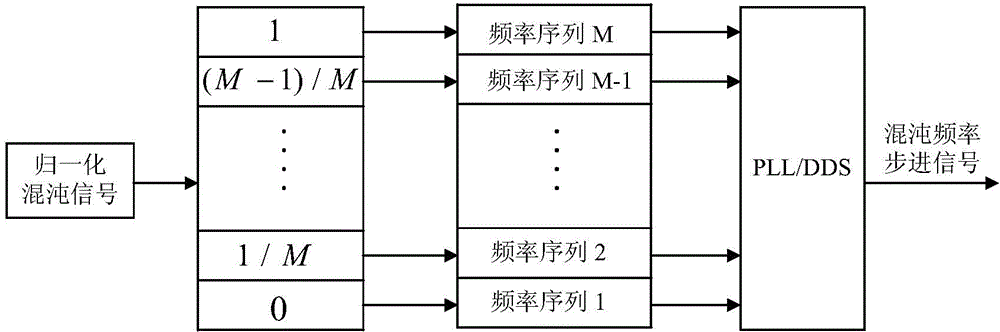
Stepping frequency radar system based on chaotic signal source, and channel construction method thereof
InactiveCN103954959AImprove anti-interference abilityLow probability of interceptRadio wave reradiation/reflectionImpulse frequencyRadar systems
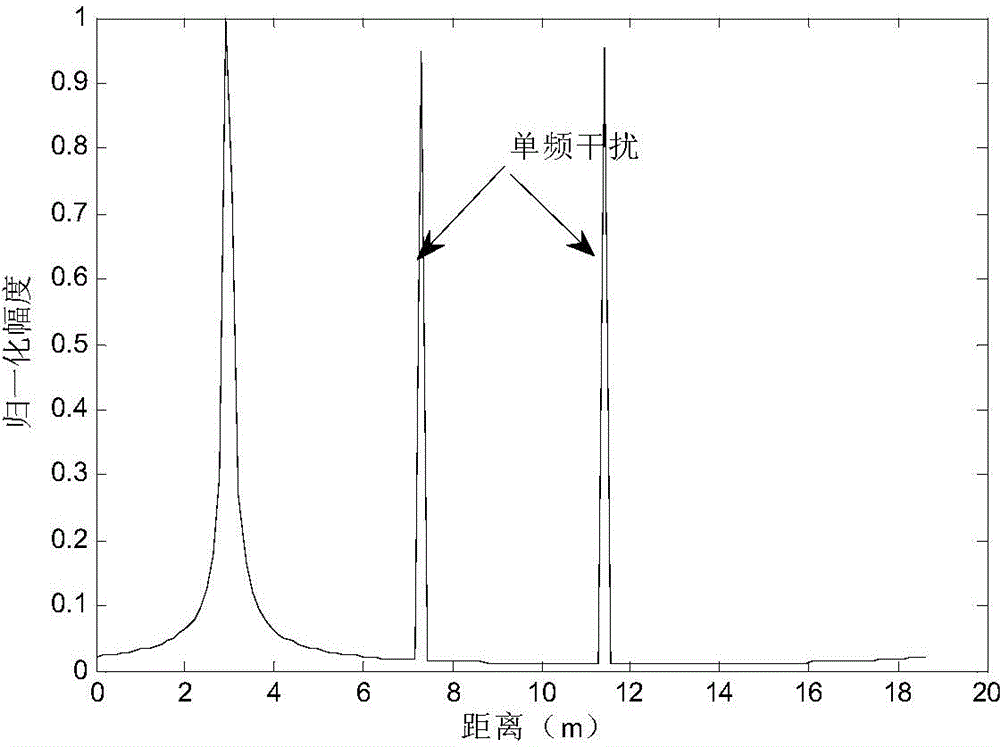
The invention discloses a stepping frequency radar system based on a chaotic signal source. The system comprises a signal emission module, a signal receiving module, the chaotic signal source and a data rearrangement module. The chaotic signal source generates chaotic signals, on one hand, controls the emission frequency sequence of an emission pulse string, and on the other hand, performs reordering control on echo signals received by the signal receiving module. The invention also discloses a channel construction method of a stepping frequency radar system. The method enables each chaotic signal sampling value to be corresponding to a group of frequency modulation sequences after normalization processing is performed on each chaotic signal sampling value, controls the signal emission module to emit pulse strings corresponding to the group of frequency modulation sequences, and controls the signal receiving module to rearrange signal echo vectors according to pulse frequencies in an increasing order. The method, on one hand, enables emission signals to be provided with higher anti-interference capability and lower interception probability, and at the same time, solves the problem of quite poor clutter inhibition capability of stepping frequency signals in a conventional stepping frequency system.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
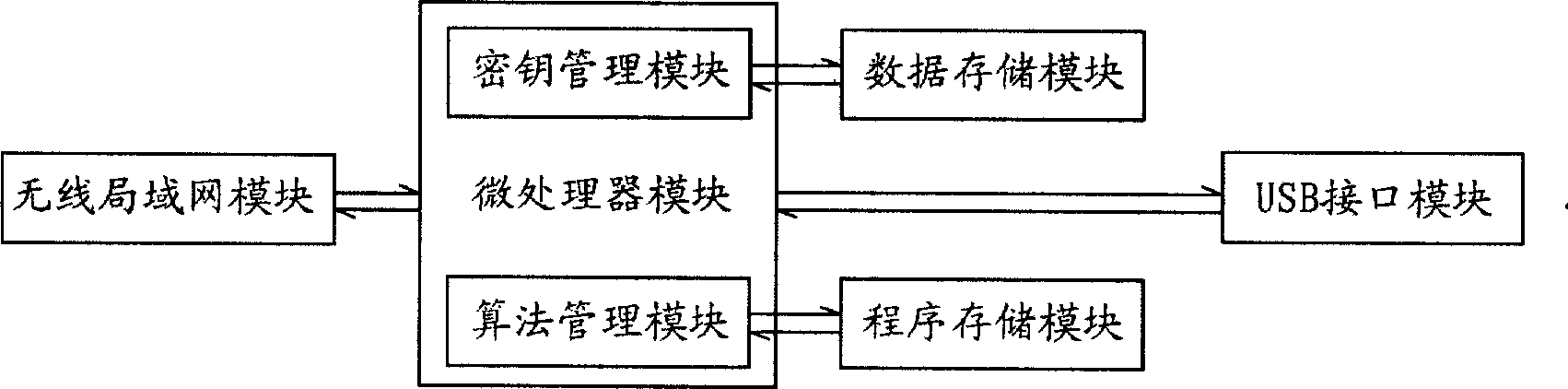
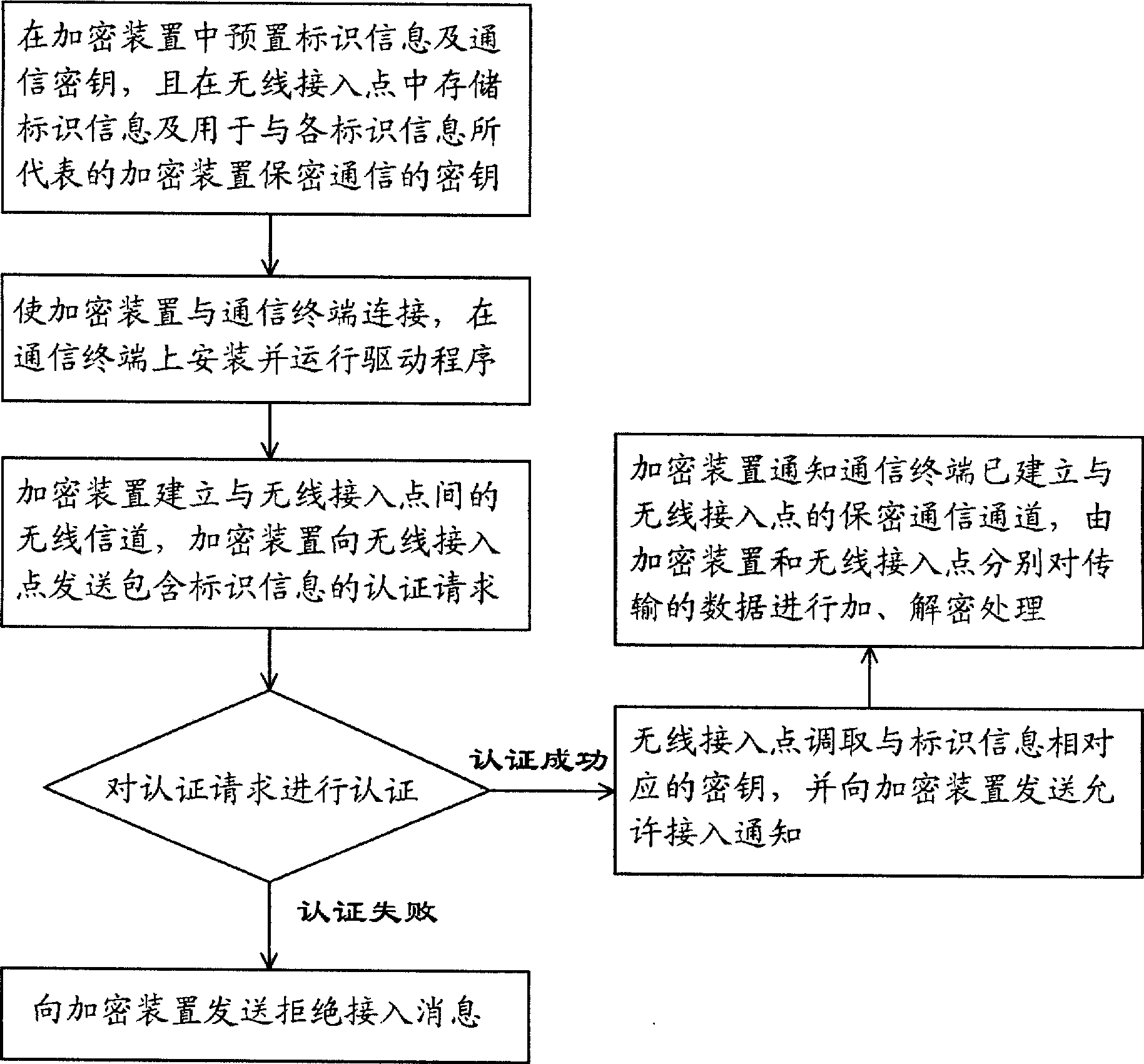
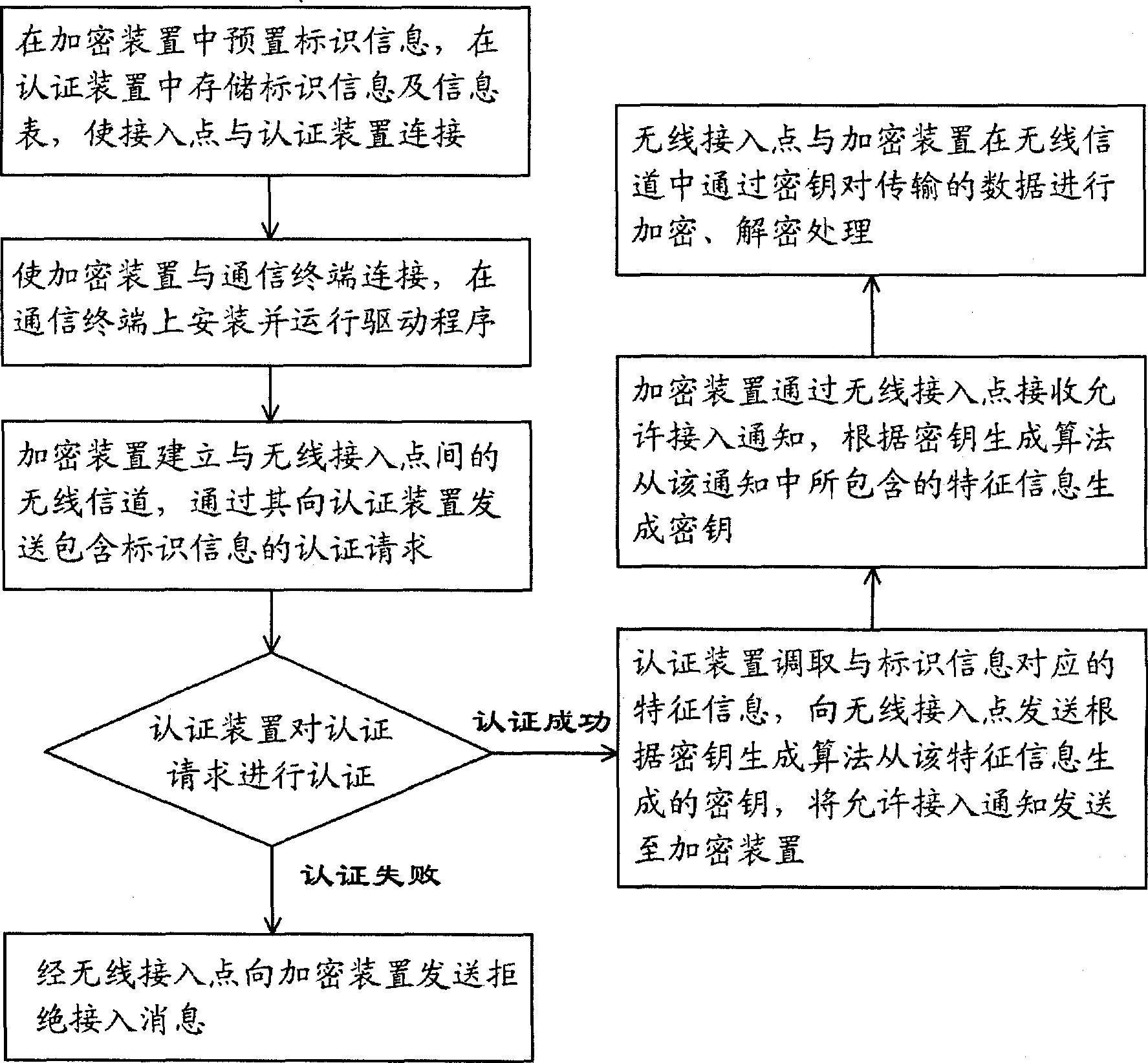
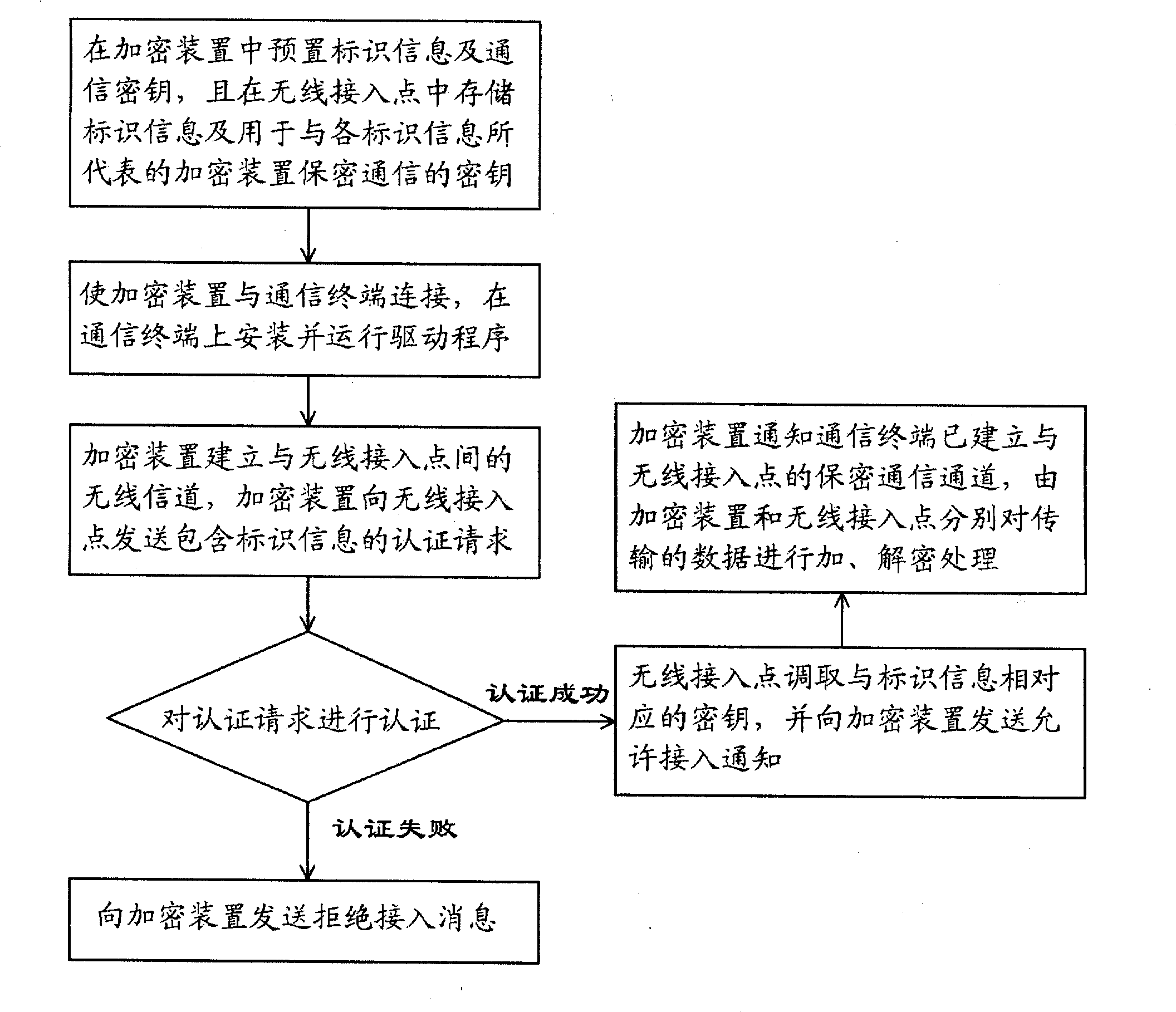
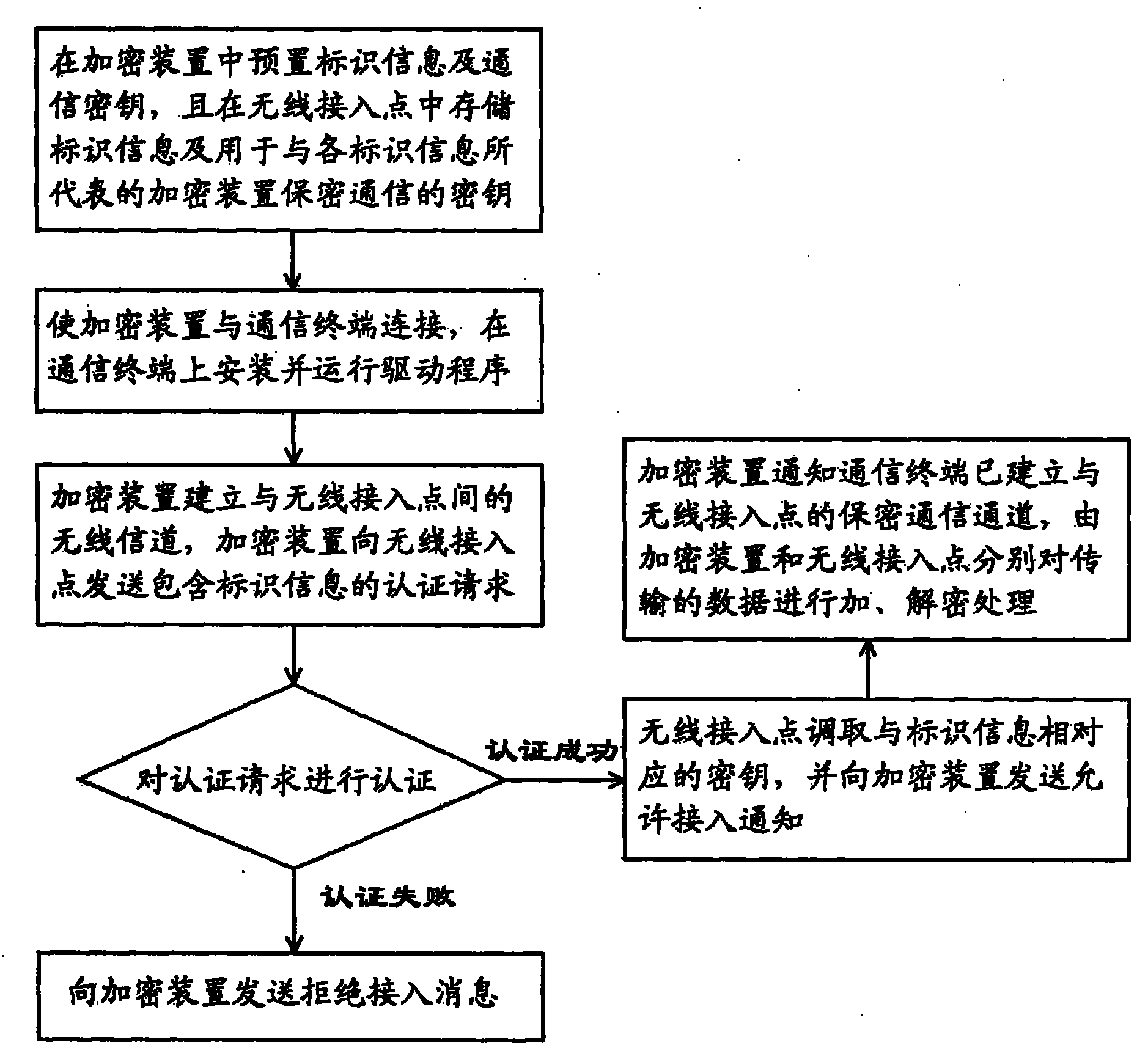
Method for implementing secret communication between communication terminal and wireless access point
InactiveCN101431453AEasy accessImprove securityKey distribution for secure communicationData switching by path configurationCommunication interfaceWireless access point
The invention relates to a method for secret communication between communication terminal and wireless access point comprising following steps: (1) presetting unique identification information and communication key in encryption device, storing authenticated identification information and key of encryption device at wireless access point; (2)connecting encryption device and communication terminal via communication interface and acquiring power supply, installing and operating dedicated drive program on communication terminal; (3) the encryption device sending authentication request including identification information to wireless access point; (4) wireless access point authenticating the encryption device according to identification information included in authentication request, if authentication being successful, then fetching corresponding key and sending notice of permission for access; (5) the encryption device notifying communication terminal of the established connection with wireless access point after receiving permission for access, encrypting, deciphering the transmitted data by communication key; wireless access point encrypting and deciphering the transmitted data via key.
Owner:AIGO DIGITAL TECHNOLOGY CO LTD
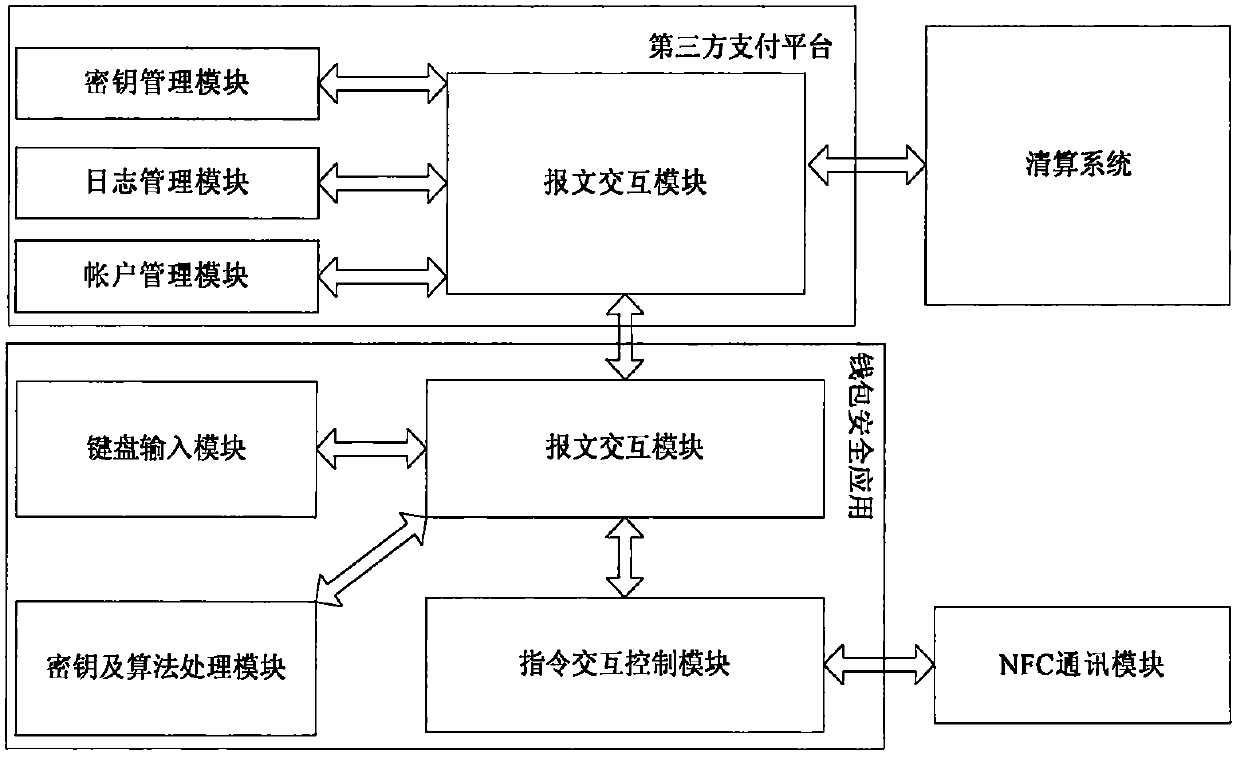
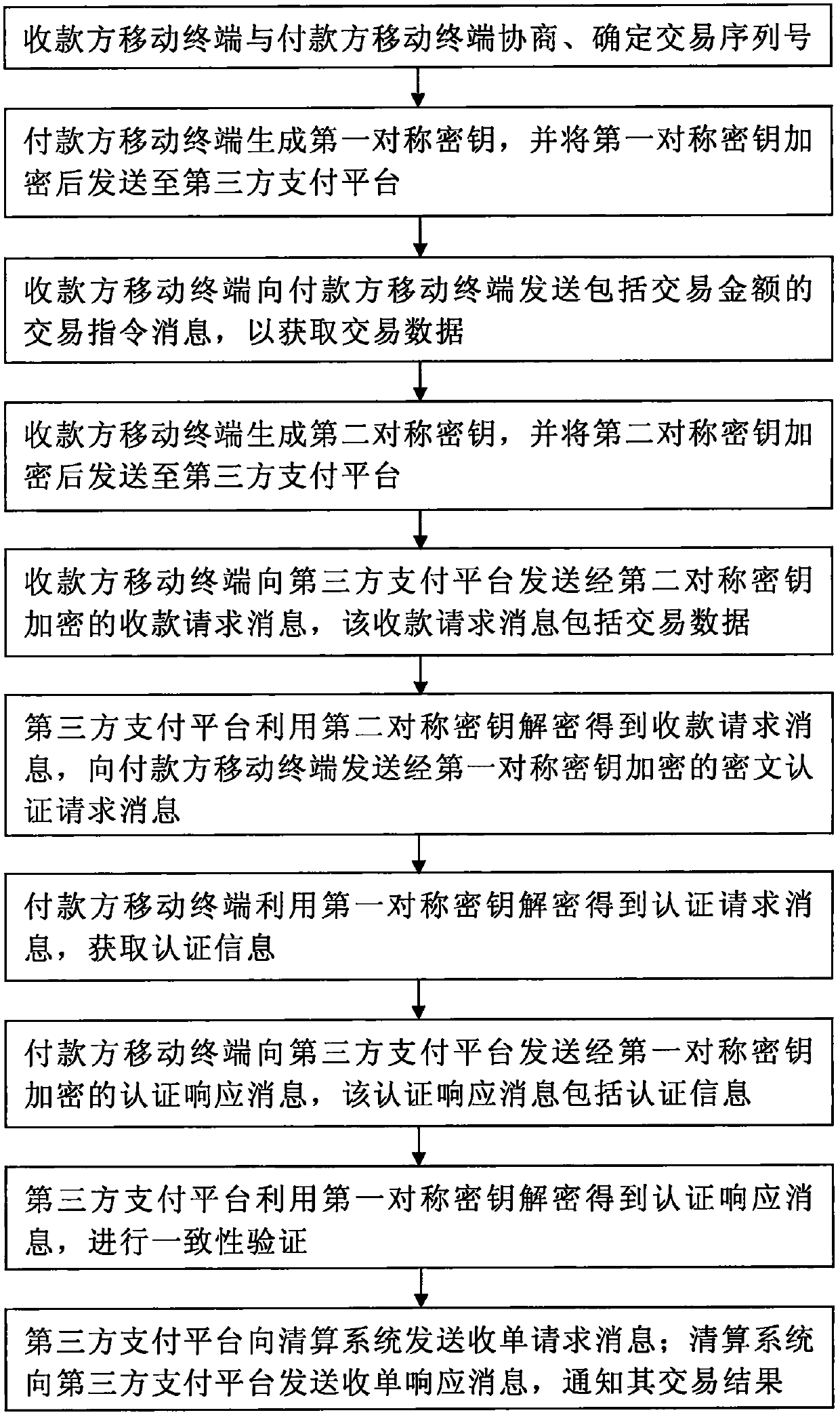
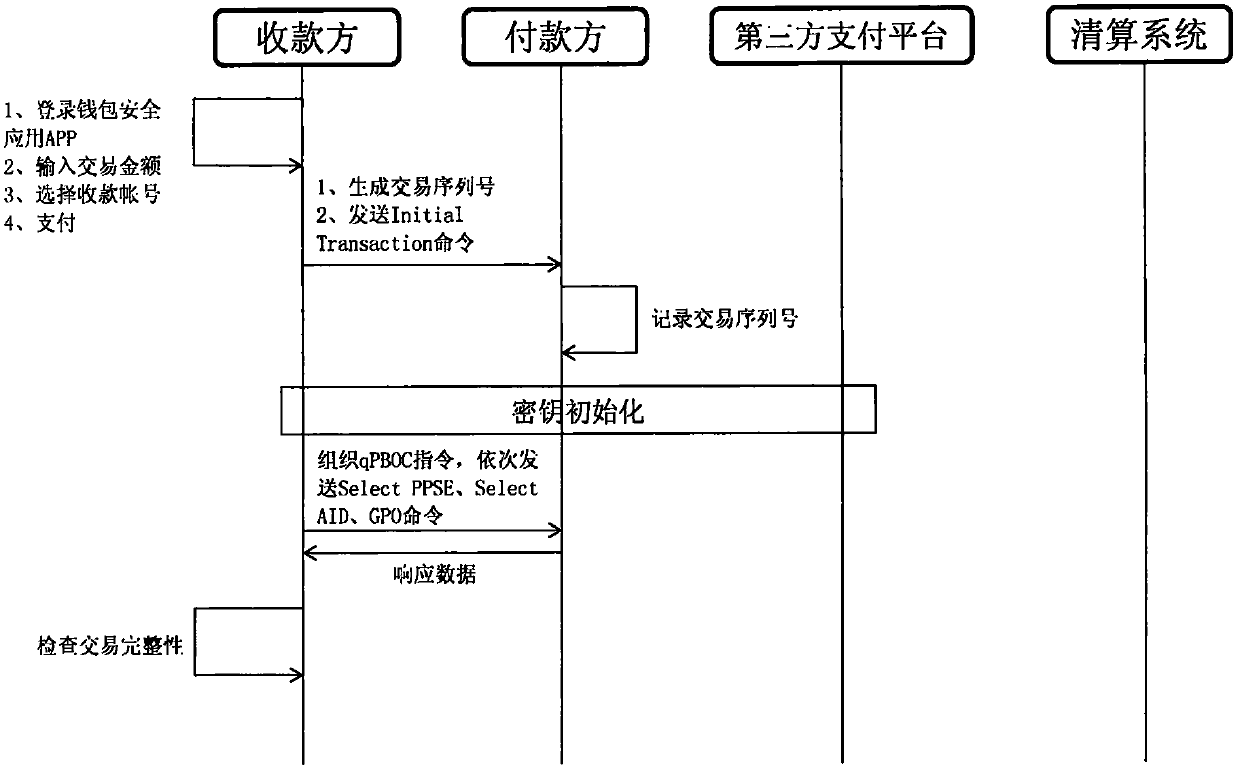
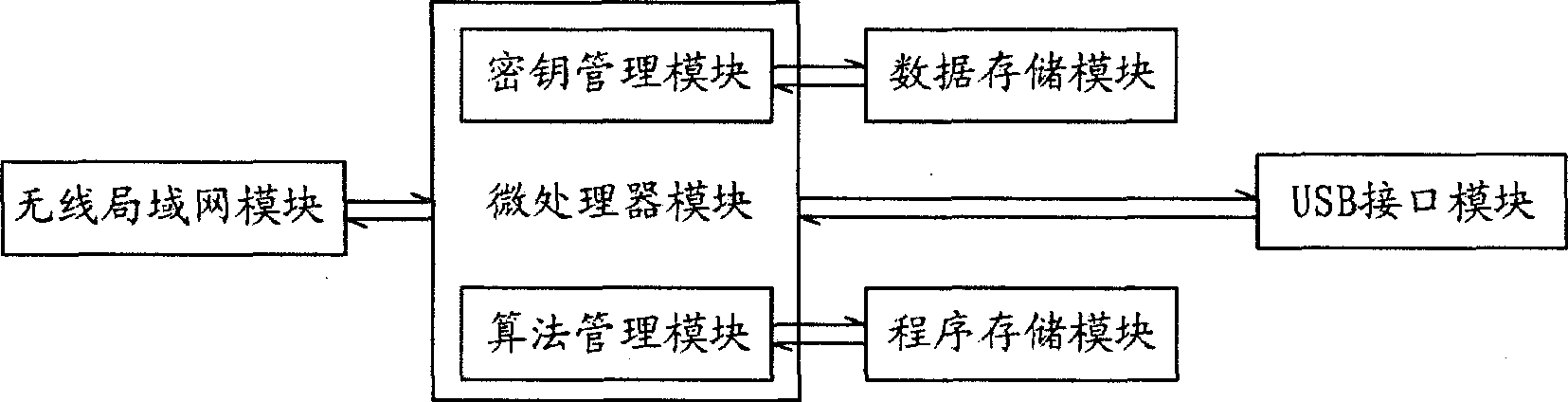
Security payment system and method for near field communication mobile terminal
ActiveCN107784499ARealize confidential communicationImprove safety and reliabilityProtocol authorisationPayments involving neutral partySecure communicationThird party
The invention provides a security payment system and a method for a near field communication mobile terminal. The mobile terminals of two trading parties send respective symmetric keys to a third party payment platform for preservation, the interacted data between the mobile terminals of two trading parties and the third party payment platform use the corresponding symmetric keys for encryption and decryption subsequently, secure communication between the mobile terminals of two trading parties and the third party payment platform is realized, a payer completes authentication operation on themobile terminal during the payment process, and the process is secure and reliable. Through carrying out integrity verification on the trading data, verification is carried out through a random numberto avoid a replay attack, and the security and the reliability of the whole payment process are enhanced further; the payment system supports a fast payment function based on the JR / T 0025 Chinese financial integrated circuit (IC) card specification series standard, and the security is high; and payment functions such as acquiring and transfer can be completed only by installing a wallet securityapplication in the near field communication mobile terminal, the user experience is improved, and promotion and application are facilitated.
Owner:北京银联金卡科技有限公司
Method for implementing secret communication of wireless local area network
InactiveCN101431455ARealize confidential communicationEnsure safetyPublic key for secure communicationUser identity/authority verificationWireless lanWireless access point
The invention relates to a method for implementing encrypted communication for wireless LAN comprising (1) presetting identification information in encryption device, storing identification information in authentication device, establishing information table of corresponding relation of identification information and characteristic information in authentication device, connecting the access point and authentication device; (2) installing and operating dedicated drive program; (3) encryption device sending authentication request to authentication device; (4) the authentication device authenticating according to identification information, if the authentication being successful, then fetching corresponding characteristic information, transmitting the first key created from the characteristic information by the authentication device according to the algorithm to wireless access point, and transmitting to encryption device; (5) the encryption device acquiring characteristic information via wireless access point, and creating a key from the characteristic information according to same key creation algorithm; (6) wireless access point and encryption device encrypting and deciphering the transmitted data via the first key in wireless channel.
Owner:AIGO DIGITAL TECHNOLOGY CO LTD
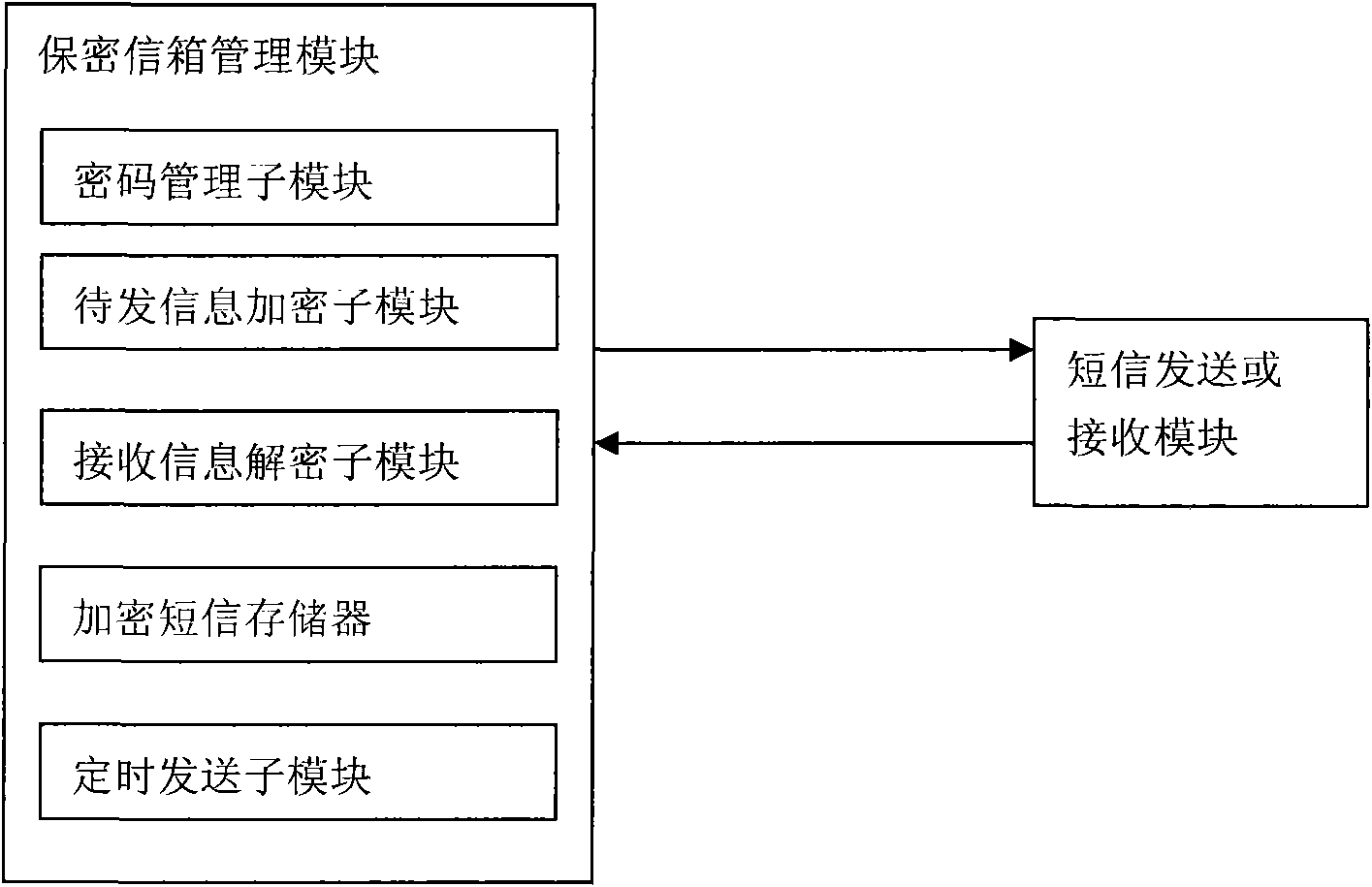
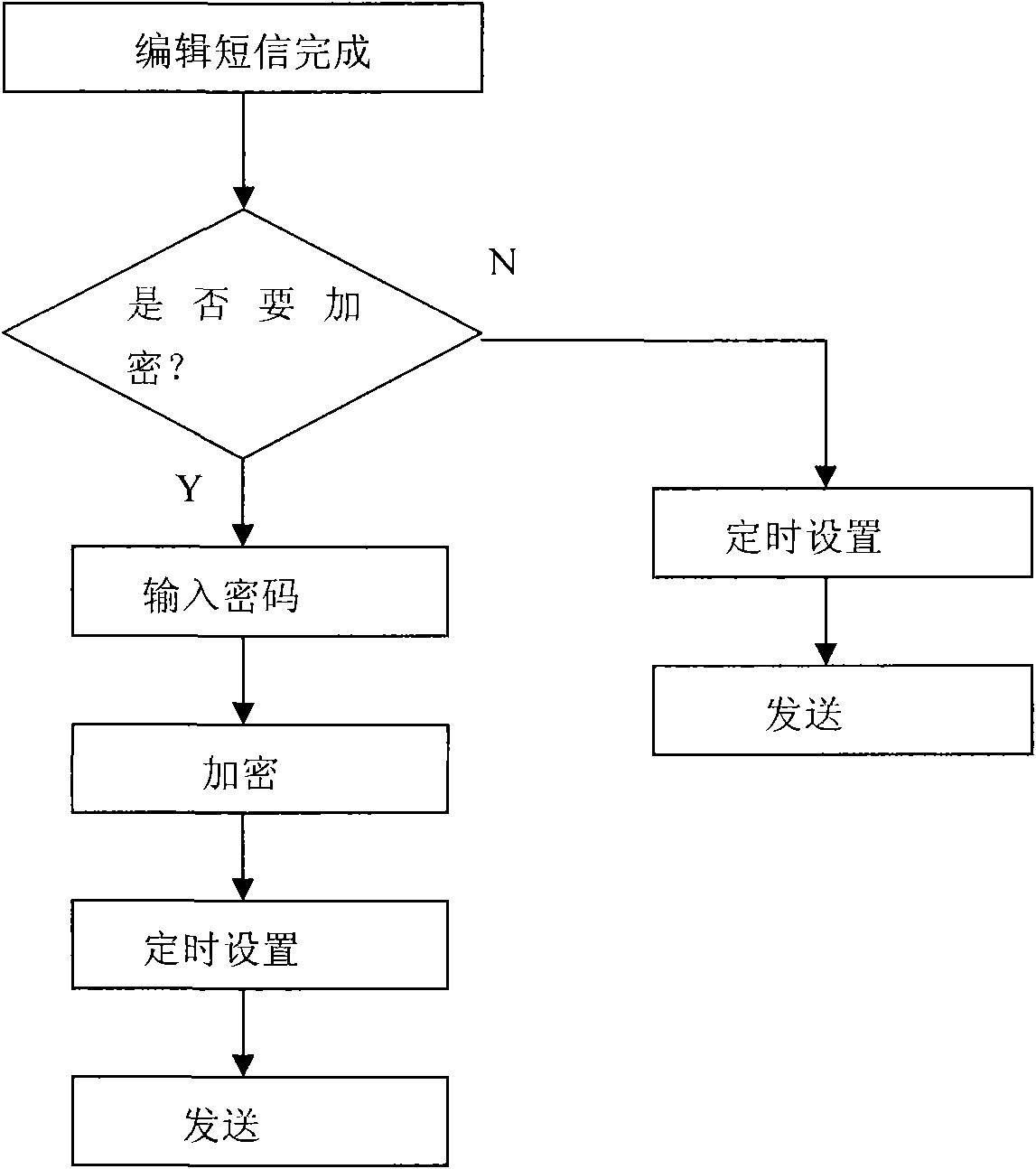
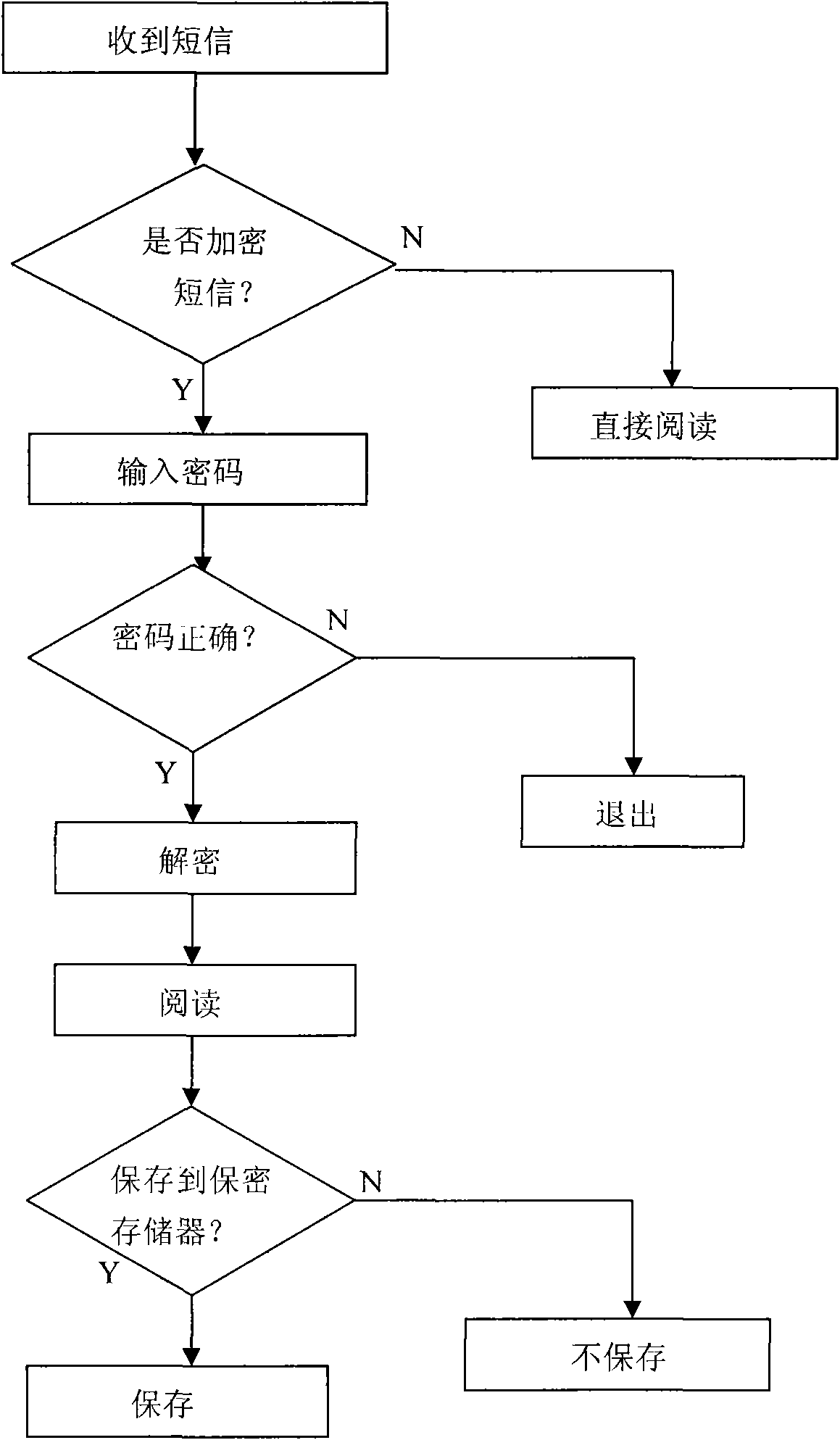
System and method for encrypting short messages by using mobile phone terminal
InactiveCN101795315ASolve the leakage problemRealize confidential communicationSubstation equipmentSecurity arrangementSecure communicationSecret code
The invention discloses a system and a method for encrypting short messages by using a mobile phone terminal. The system comprises a secret mail box management module arranged on a main board of the mobile phone, wherein the secret mail box management module comprises a password management sub-module used for setting, modifying, deleting and verifying short a message password of a user, an information-to-be-sent encryption sub-module used for encrypting the short messages edited by the user and a received information decryption sub-module used for decrypting the encrypted short messages received by the user. The system has the advantages of solving the problem of information content reveal existing in the communication process, realizing one-to-many secure communication, and having a function of sending the edited short messages at a scheduled time.
Owner:深圳市杰普林数码科技有限公司
Secure communication system based on random time sequence four-dimensional circular ring array
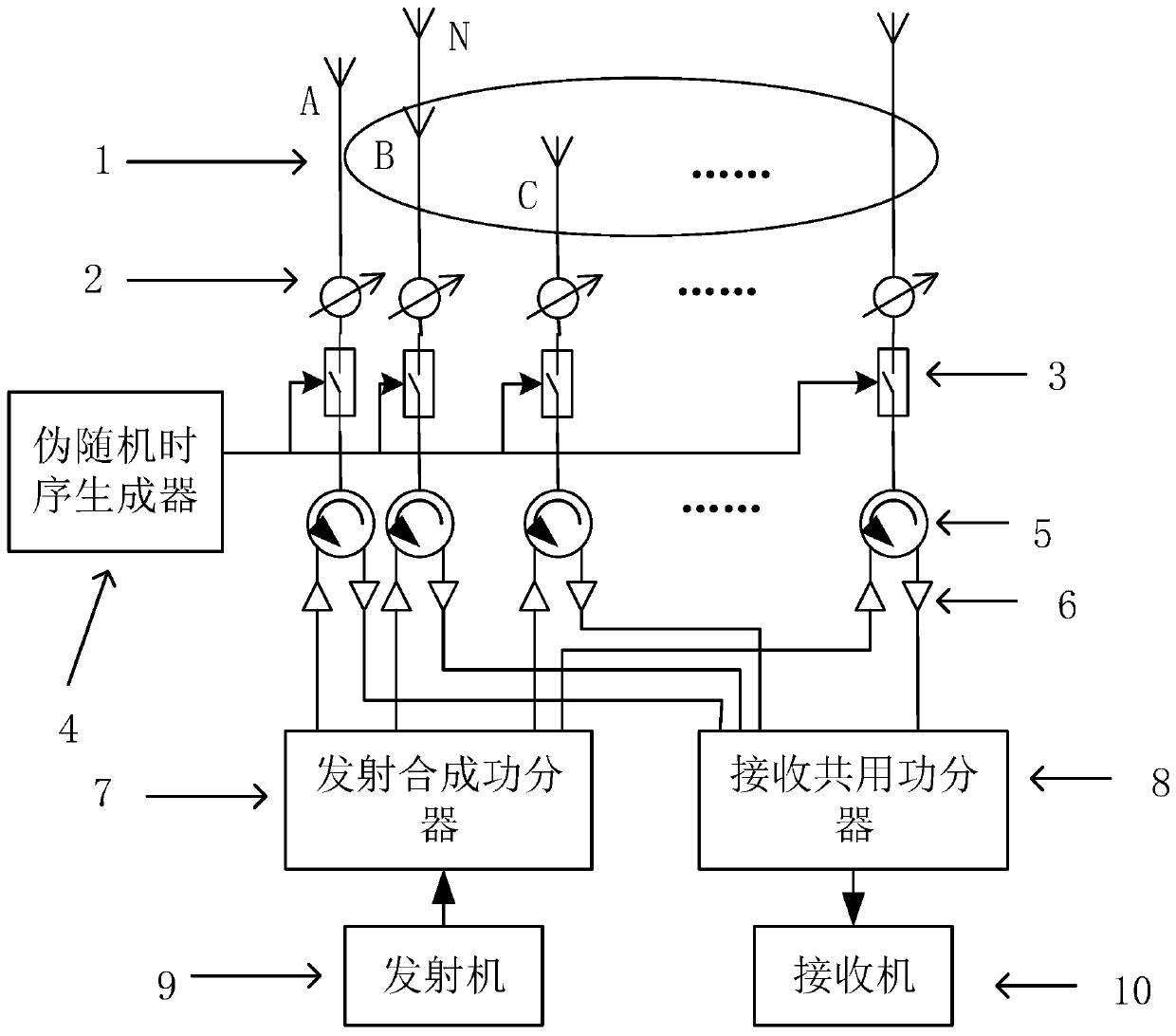
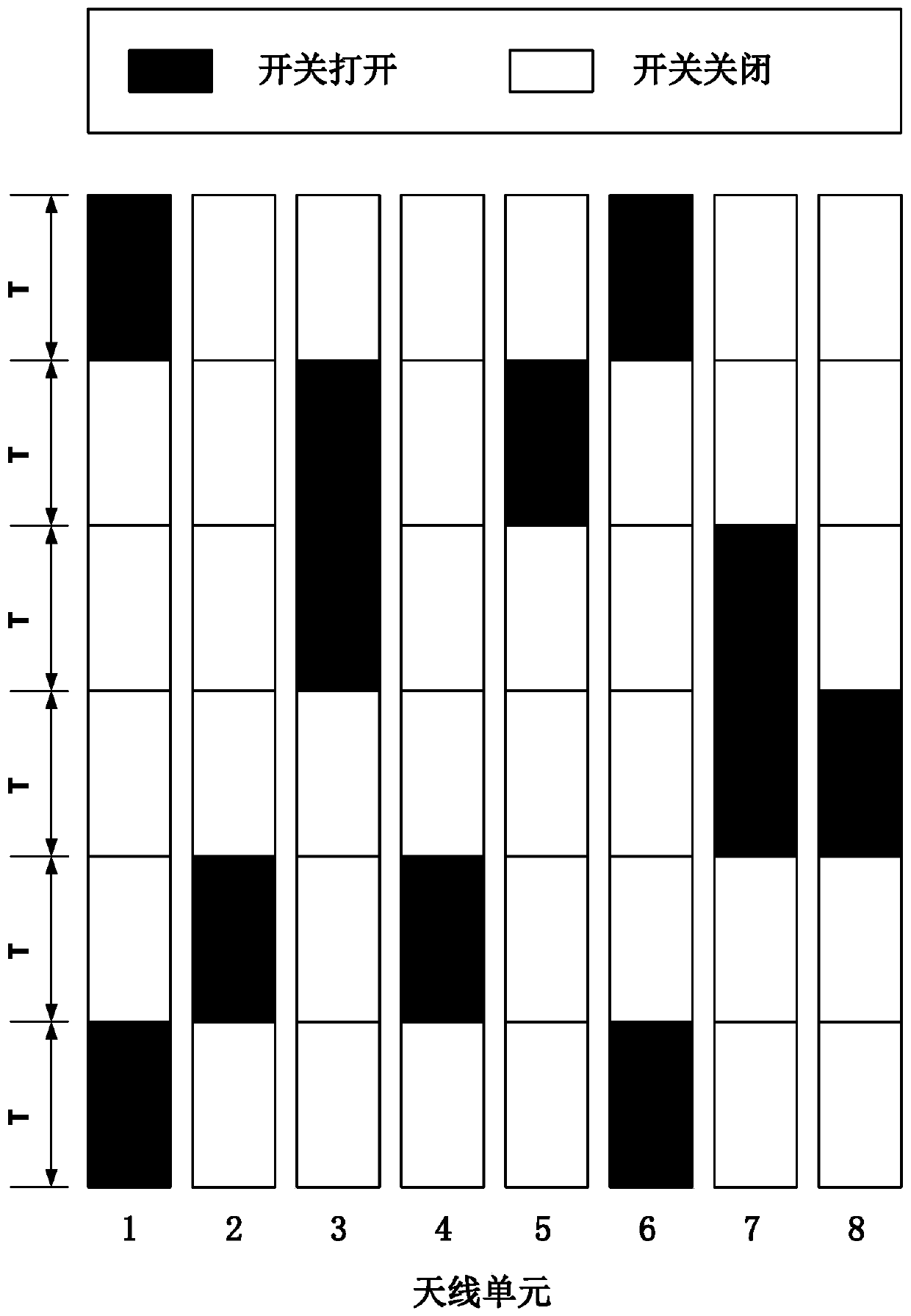
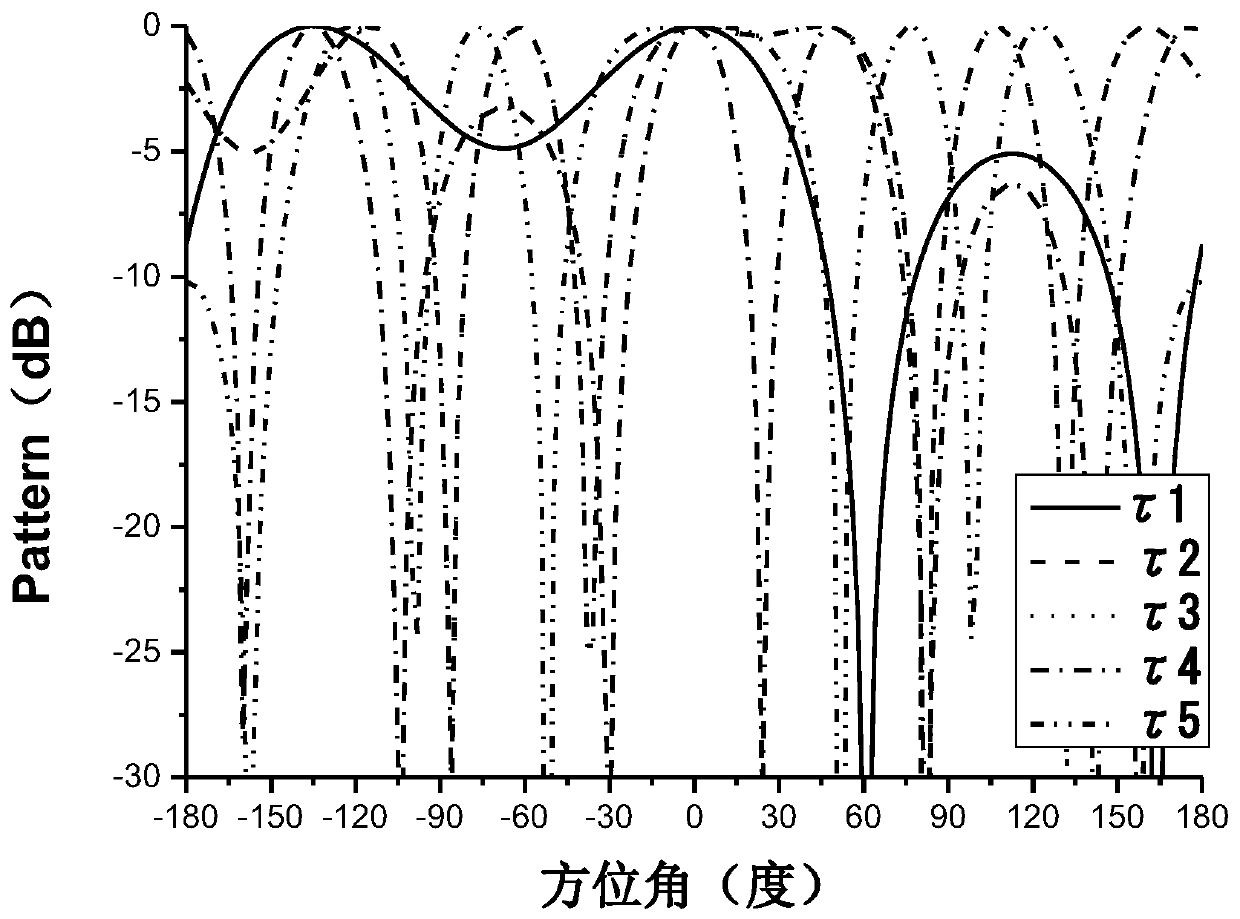
InactiveCN110139272AIncrease the number ofNarrow confidential communication widthPhase-modulated carrier systemsSecurity arrangementCommunications systemAntenna gain
The invention discloses a secure communication system based on random time sequence four-dimensional circular ring array. The basic structure comprises a circular ring antenna array, a phase shifter,a time modulator, a pseudo-random time sequence generator, a circulator, a power amplifier, a transmitting combination success divider, a receiving common power divider, a transmitter, a receiver andthe like. The biggest innovation of the invention lies in that random time modulation is used, so that the antenna gain in a desired direction is not changed and the antenna gain in an undesired direction is not changed randomly. The method can be applied to all modulation systems based on amplitude and phase, such as BPSK, QPSK and the like. The circular ring array is introduced, so that omnidirectional secure communication can be realized. Compared with an existing secure communication mode based on a four-dimensional antenna array, the method provides a new random time modulation mode, onlyrandom and messy signals can be received in the unexpected direction, the problem that an existing system is insufficient in safety is solved, and full-airspace secure communication can be achieved.The present invention is used in a wireless communication system.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
Message authentication and group key negotiation method based on vehicle-mounted short distance communication network
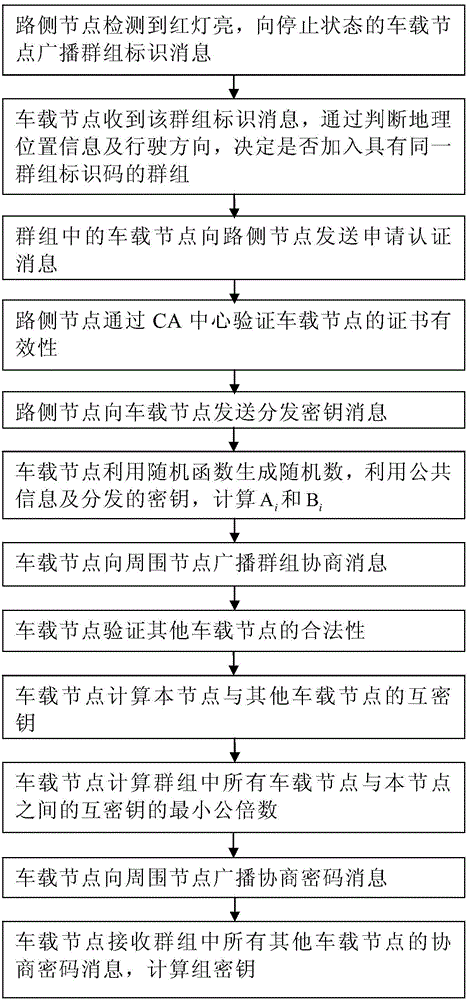
ActiveCN105812133AImprove securityRealize confidential communicationUser identity/authority verificationShortest distanceIn vehicle
The invention discloses a message authentication and group key negotiation method based on a vehicle-mounted short distance communication network, comprising steps of utilizing a road side node arranged at a crossroad to detect the state of a signal lamp, constituting vehicles having same geographic position information and same driving directions into a cluster during the red light, performing verification on the vehicle-mounted node in the cluster through a certificate authorization center, and distributing a secret key to the vehicle-mounted node passing through the verification, wherein the vehicle-mounted node in the cluster utilizes the distributed secret key to generate a group code through a cluster code negotiation process and thus utilizes the group code to realize the confidential communication between the vehicle-mounted nodes. The message authentication and group key negotiation method utilizes the V2X network characteristics, like the characteristics of the road side node, that the vehicle-mounted node is in the halted state when the red light is on and the status of all vehicle-mounted nodes are equal, realizes the information verification of the vehicle-mounted nodes and the cluster secret key negotiation process in the V2X network, and improves the safety of the V2X network.
Owner:DATANG GOHIGH INTELLIGENT & CONNECTED TECH (CHONGQING) CO LTD
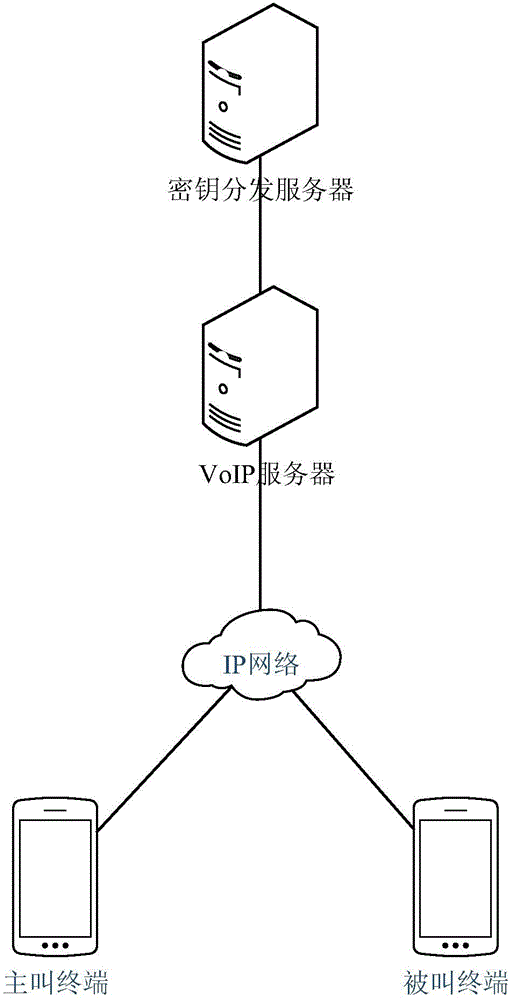
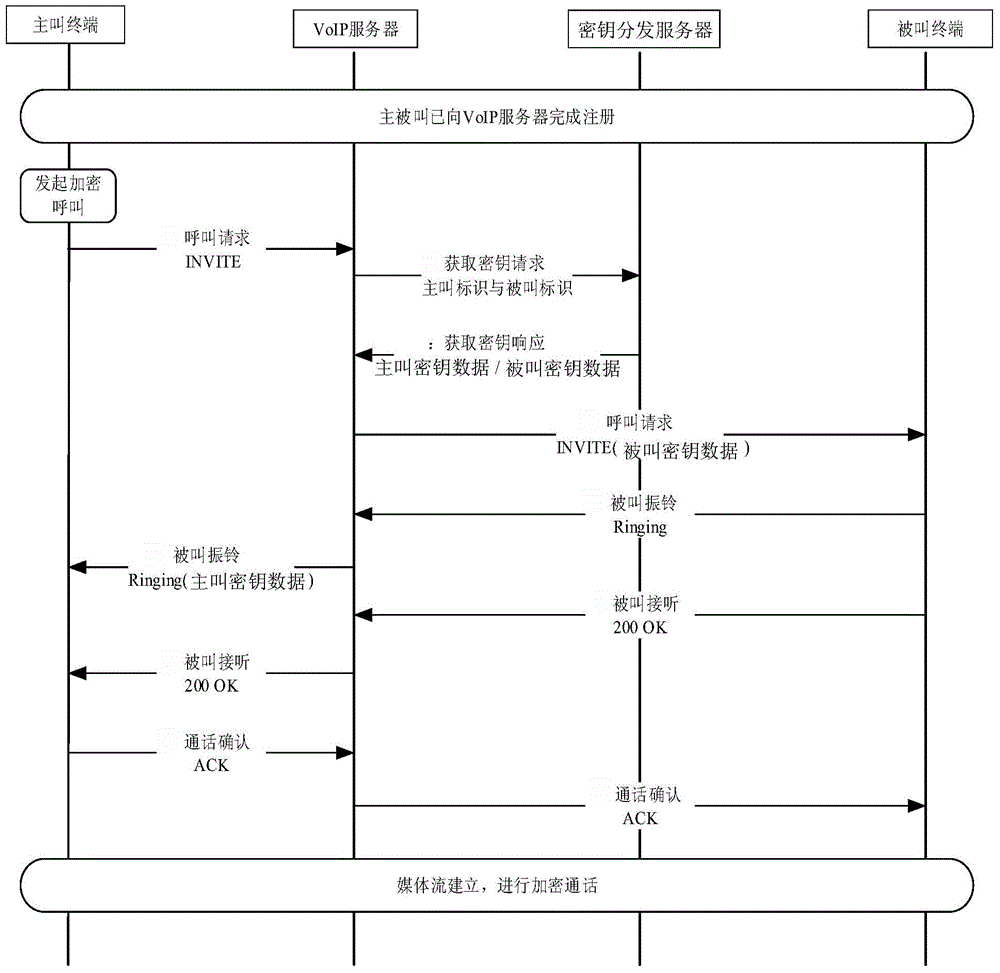
Secret key distribution method based on session initiation protocol (SIP) communication system
ActiveCN105991277ASimplify the distribution processRealize confidential communicationKey distribution for secure communicationInterconnection arrangementsComputer hardwareSession Initiation Protocol
The present invention discloses a secret key distribution method based on an SIP communication system. The secret key distribution method is realized based on a communication system composed of a VOIP server, a secret key distribution server and a plurality of terminals, and is characterized in that the terminals send the calling request messages to the VOIP server, the VOIP server sends a secret key obtaining request message to the secret key distribution server, and the secret key distribution server utilizes the public keys of the terminals to generate the secret key data of the terminals and distributes the secret key data to the terminals via the VOIP server; after receiving the corresponding secret key data, the terminals utilizes the own private keys to decrypt the secret key data to obtain the session keys, and the calling and called terminals utilize the session keys to realize the secret communication. According to the present invention, a secret key distribution process is simplified, the secret key data is transmitted to the terminals by the SIP messages in communication connection without needing to increase the message number additionally, the real-time performance is stronger, and the secret communication of the terminals can be realized.
Owner:BEIJING DATANG GOHIGH DATA NETWORKS TECH CO LTD
Communication method for encrypted equipment and unencrypted equipment hybrid networking
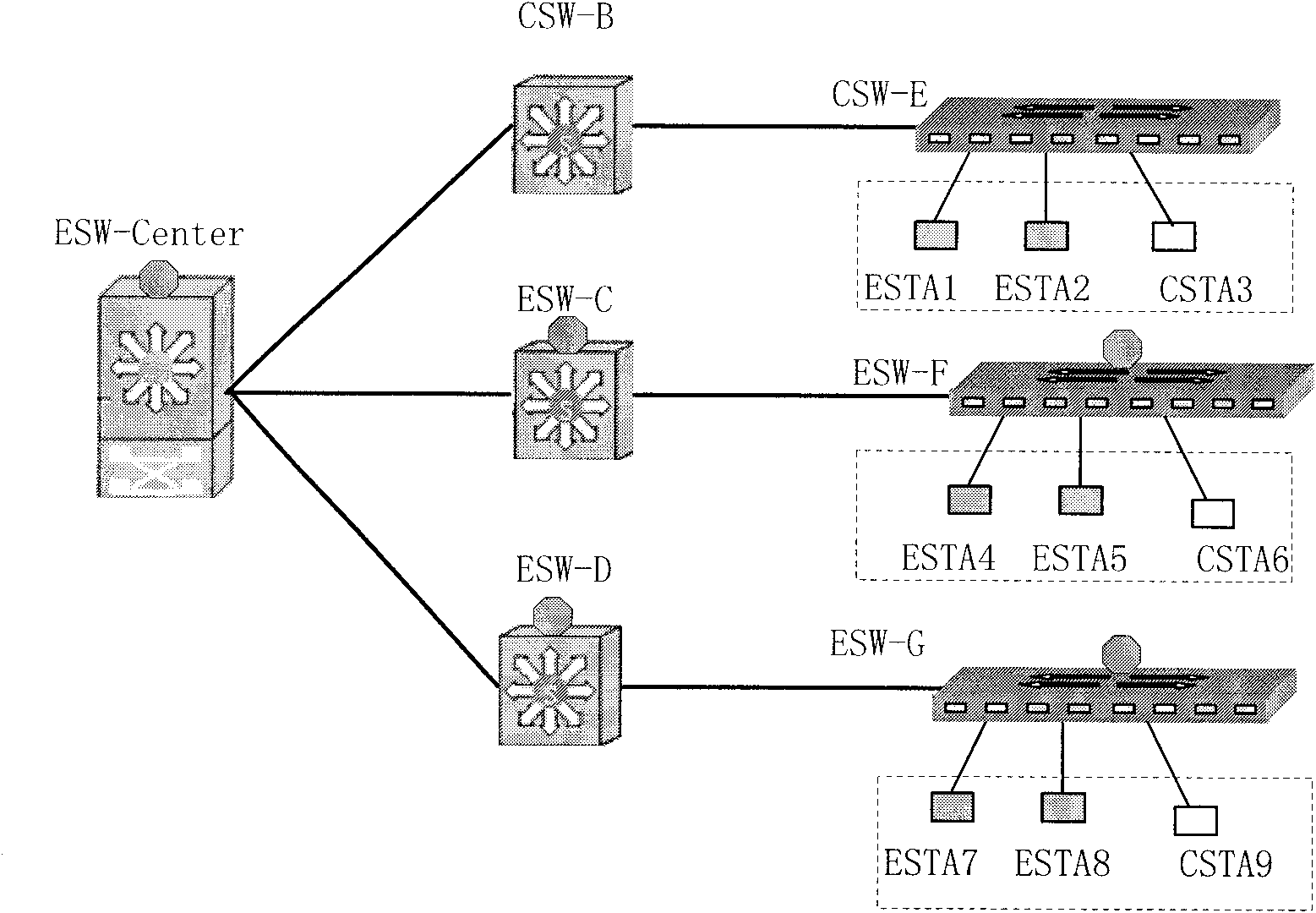
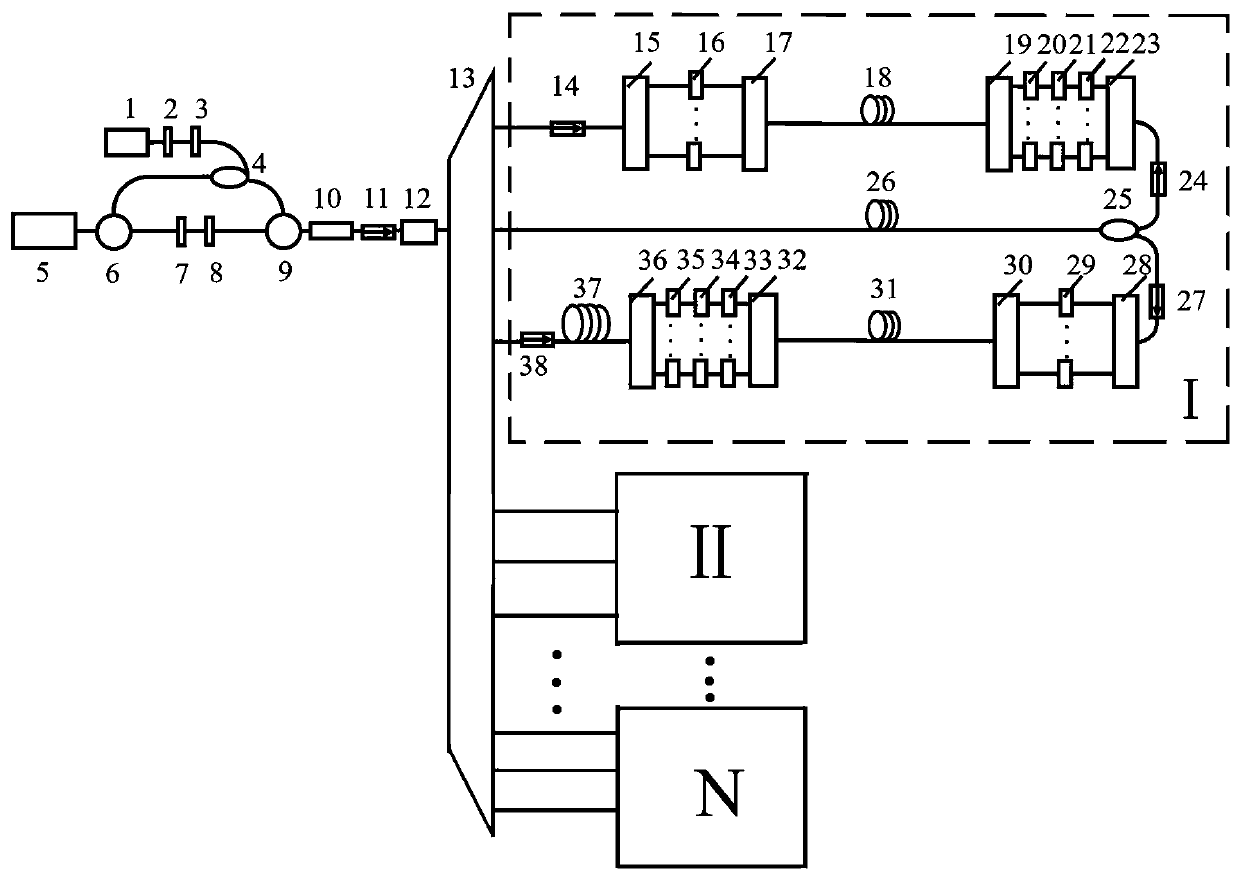
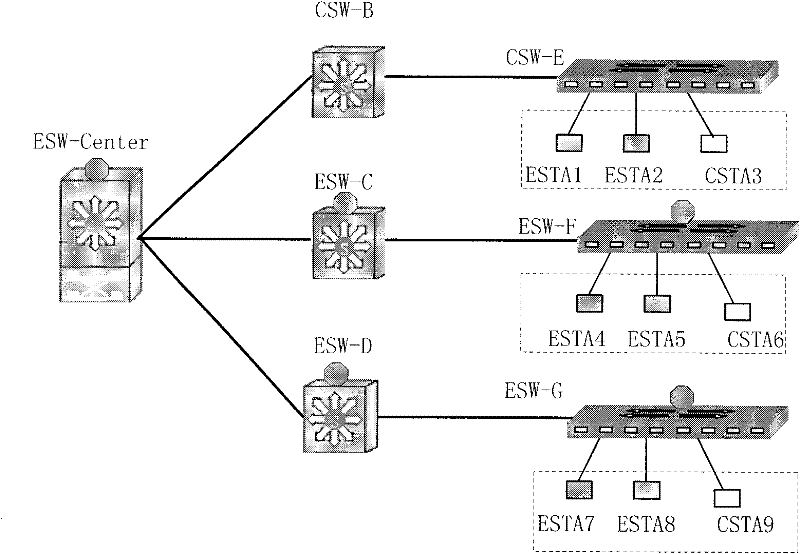
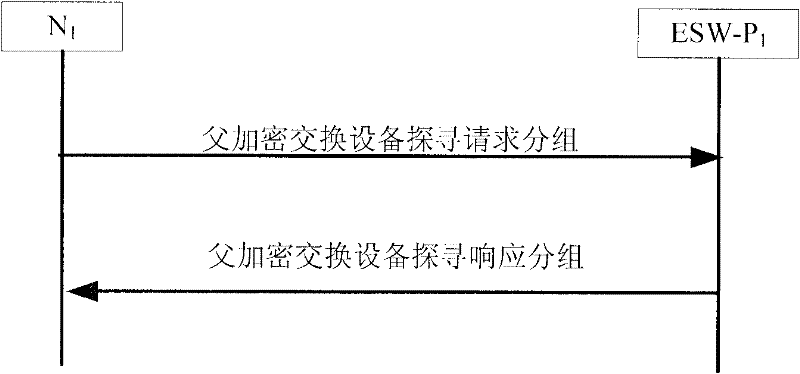
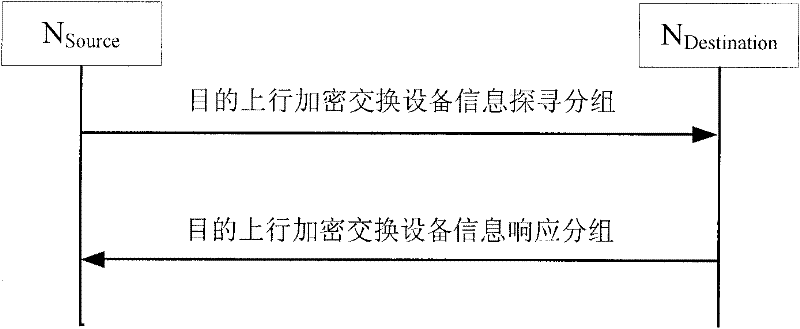
InactiveCN101834722ARealize Hybrid NetworkingRealize unencrypted communicationSpecial service provision for substationMultiple keys/algorithms usageNetwork packetData link layer
The invention discloses a communication method for encrypted equipment and unencrypted equipment hybrid networking, which is characterized in that: all unencrypted switching equipment directly forwards all protocol packets and user packets in the network, and all encrypted switching equipment adopts the following three steps to process the protocol packets: seeking father encrypted switching equipment, identifying and establishing a unicast key, and establishing a key between nodes. The communication method for encrypted equipment and unencrypted equipment hybrid networking has the advantages of solving the technical problem that the communication method in the prior art is large in potential safety hazard, high in upgrade cost and low in transmission efficiency, realizing the compatibility of the encrypted equipment and the unencrypted equipment, simultaneously ensuring the secrecy transmission of a data link layer of a local area network, and realizing the unencrypted communication between the traditional nodes, and the secret communication between the encrypted equipment.
Owner:CHINA IWNCOMM
Secret communication method based on fraction order Fourier transform order-multiplexing
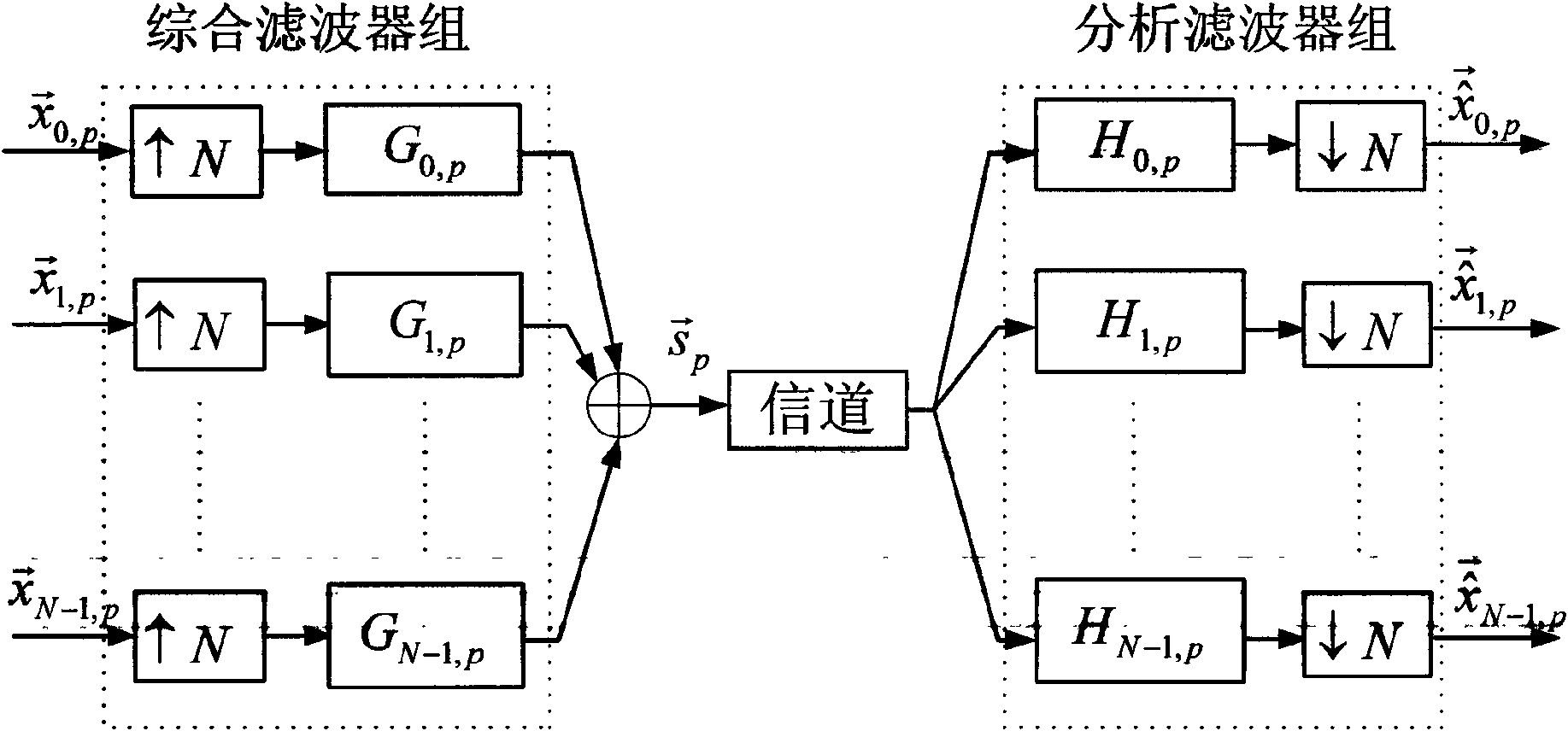
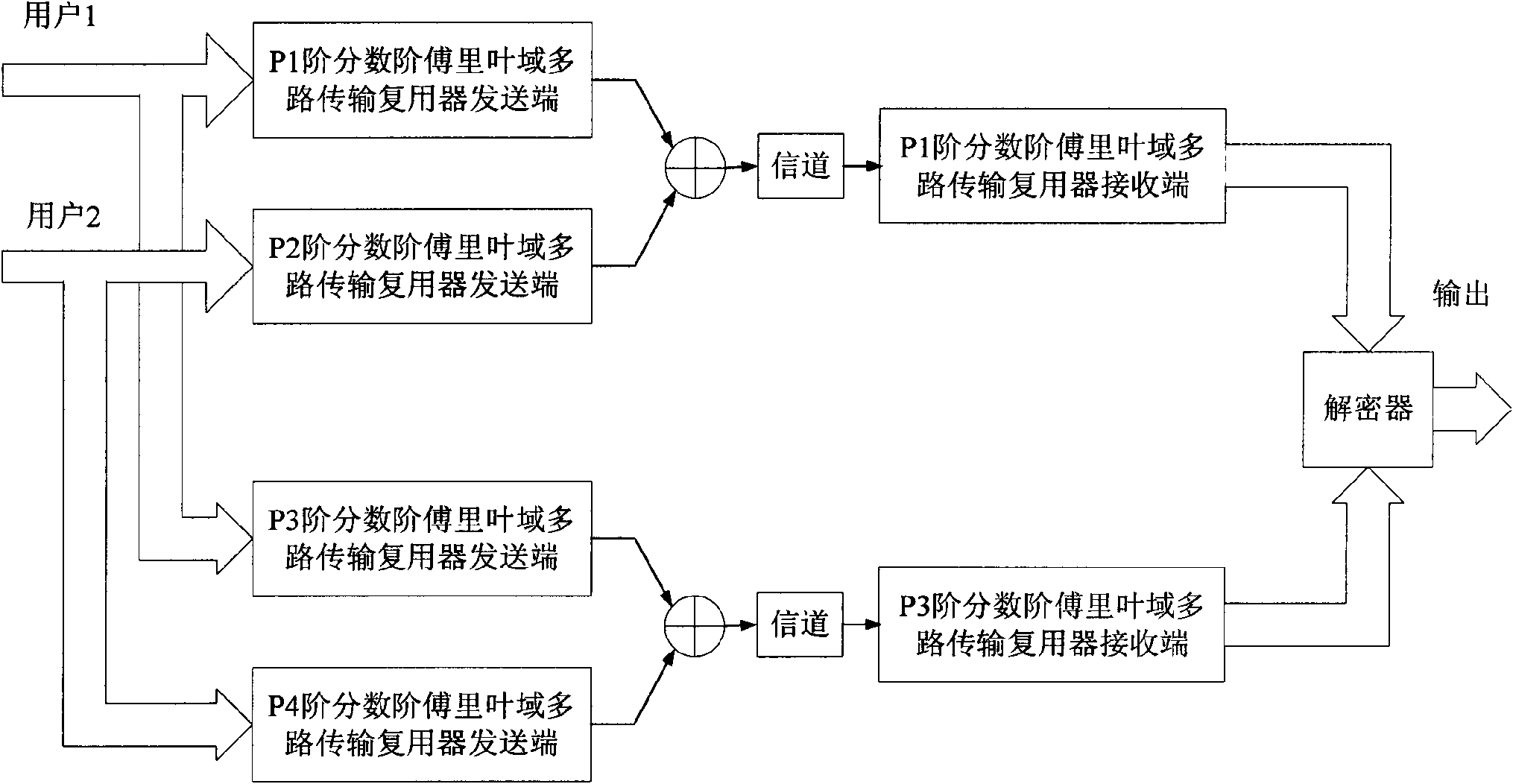
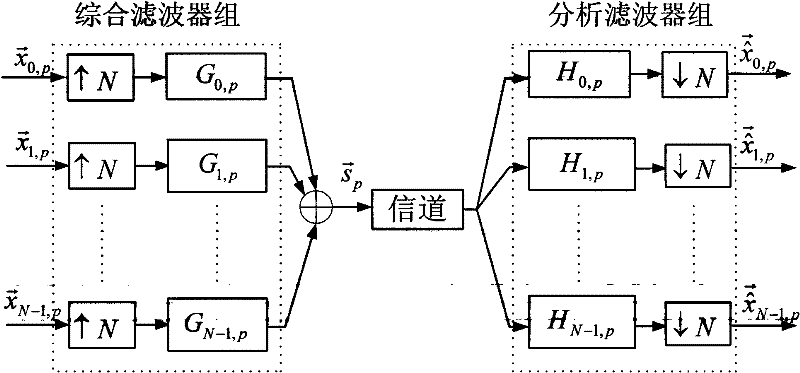
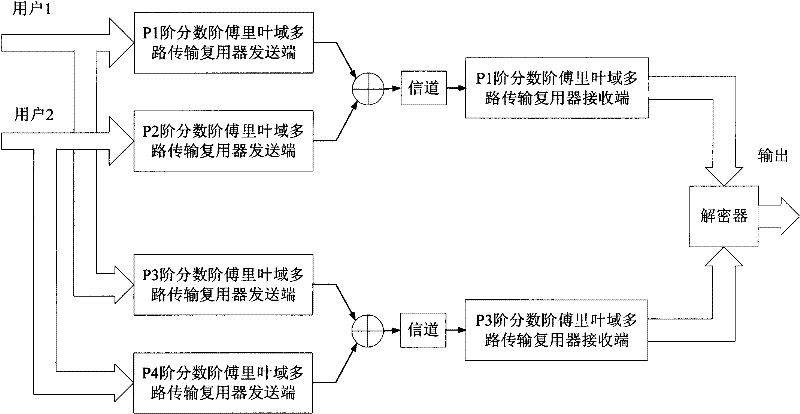
InactiveCN101667911ALarge key spaceImprove securityKey distribution for secure communicationMultiple keys/algorithms usageMultiplexingCommunications system
The invention relates to a secret communication method based on fraction order Fourier transform order-multiplexing, belonging to the information safety field. The secret communication method comprises the following steps: establishing linear equations by using the relation among filters in a multiplex transmission multiplexer accurately reestablished by fraction order Fourier domains with different orders and selecting discrete-sampling discrete fraction order Fourier transform as a basic tool, realizing the demodulation of the fraction order Fourier transform order-multiplexing; and realizing effective recovery of transmission information by using the multiplexed fraction order Fourier transform order as a secret in the information decryption. The secret communication method based on thefraction order Fourier transform order-multiplexing completely utilizes the order change characteristic of the fraction order Fourier transform, enlarges the secret space relative to the traditionalsecret communication method based on fraction order Fourier transform, improves the safety of the system, can realize secret communication under a multi-carrier mode, and can provide a new way for thedesign of a multi-user communication system.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Four-dimensional antenna array based secret communication system and method thereof
ActiveCN102857280BRealize confidential communicationAvoid lostSpatial transmit diversitySecret communicationArray elementEngineering
The invention discloses a four-dimensional antenna array based secret communication system and a method thereof. The system basically comprises an antenna unit, a high-speed radio frequency switch, a high-precision local oscillation source, a power amplifier, a switch control circuit and the like. The system and the method are characterized in that a phase center of an array is moved by controlling of working time sequences of all array elements (or subarrays) in the antenna array, modulation of information is finished at an antenna end, signals which are required to be transmitted are synthesized in a specific direction only, signals which are required to be transmitted can not be synthesized in other directions, a plurality of modulation methods, such as quadrature phase shift keying (QPSK), binary phase shift keying (2PSK) and M spread spectrum sequences, can be achieved, and the structure of a transmitter can be simplified. Compared with traditional secret communication methods, the method is a novel physical layer encryption method and can effectively resist eavesdropping receivers in side lobe directions. The system and the method are applied to wireless communication systems.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
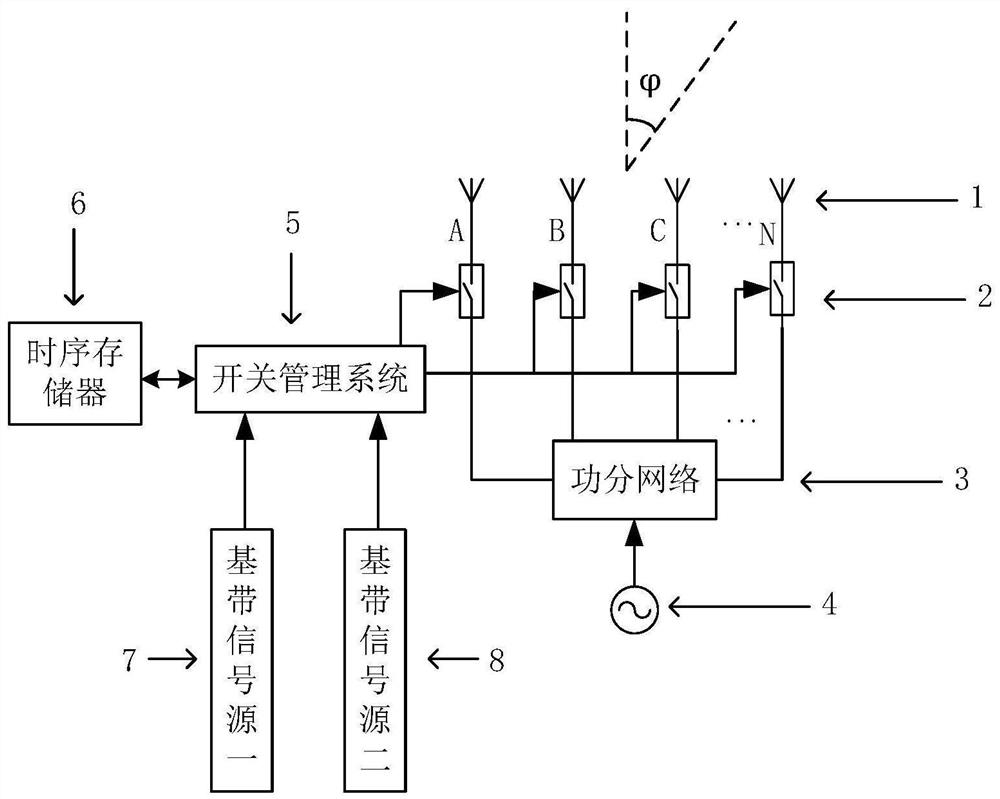
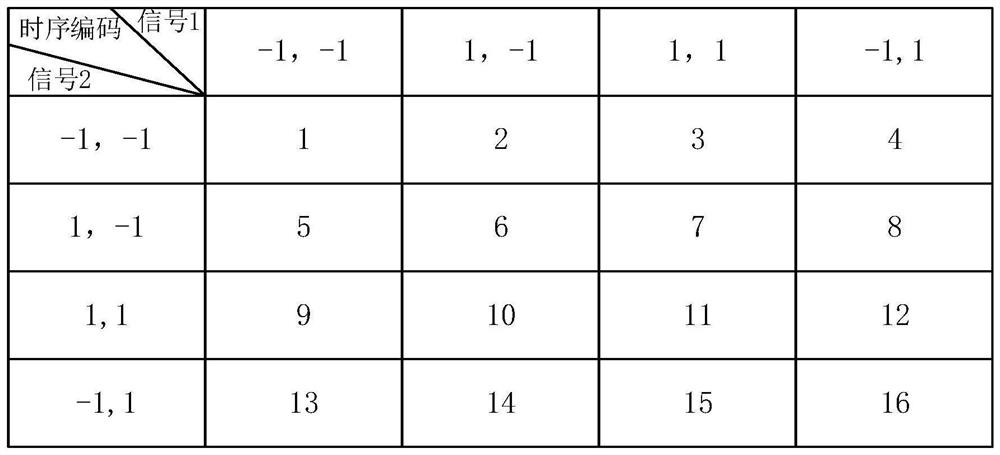
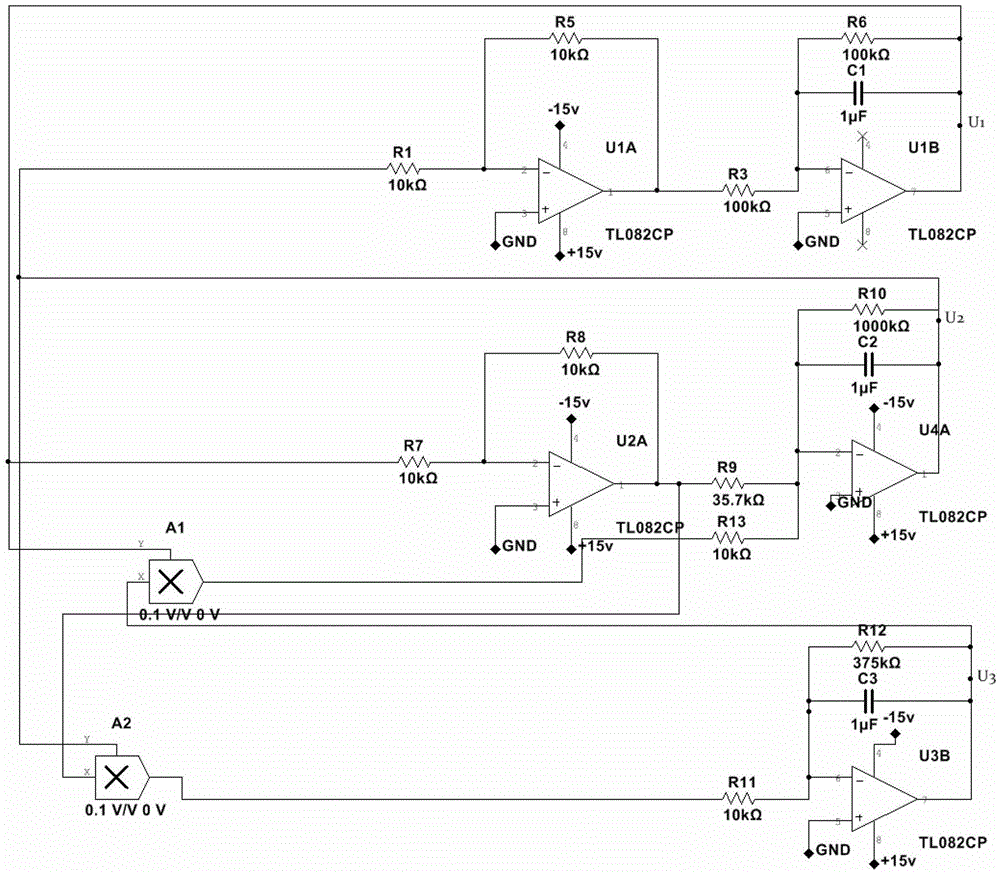
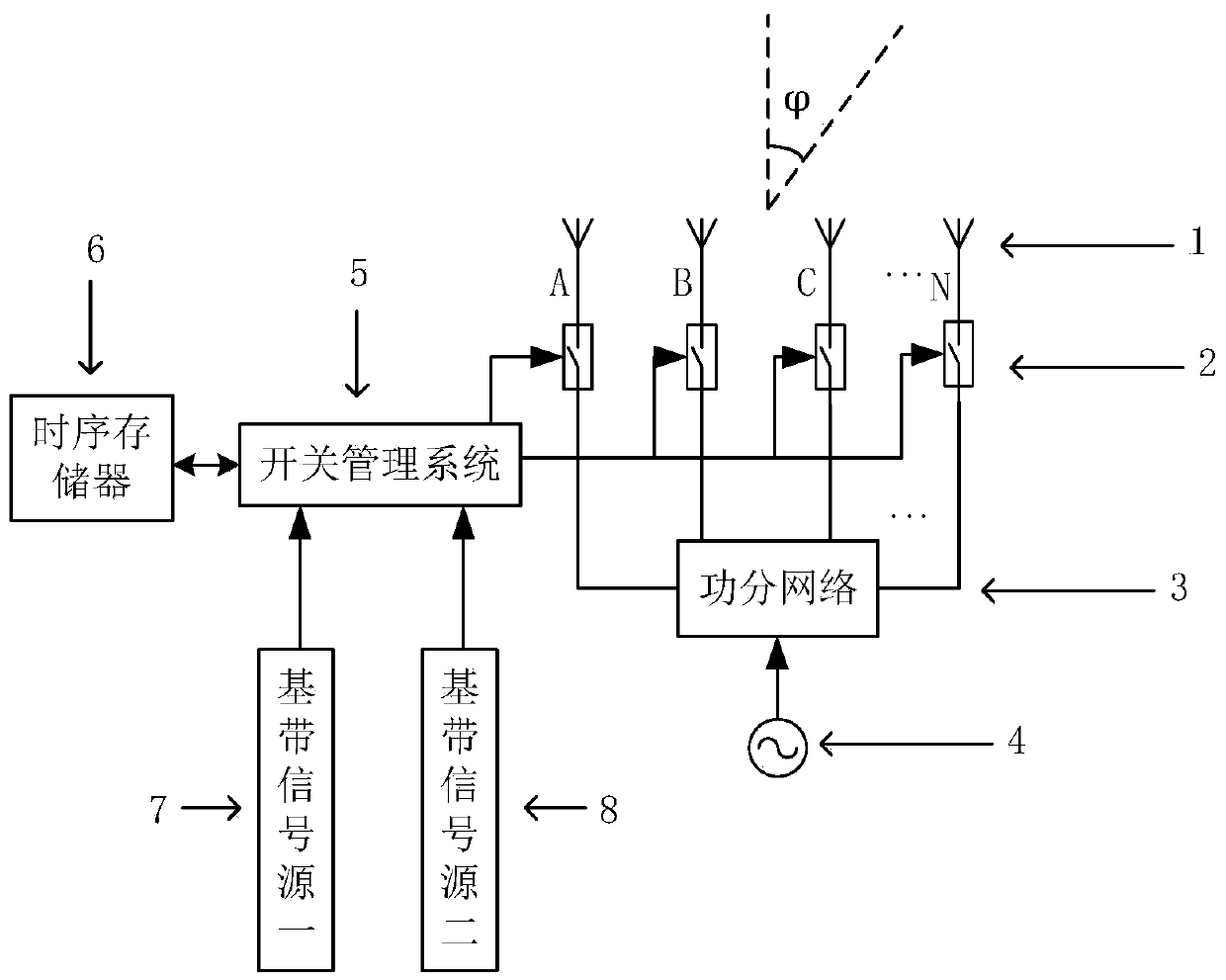
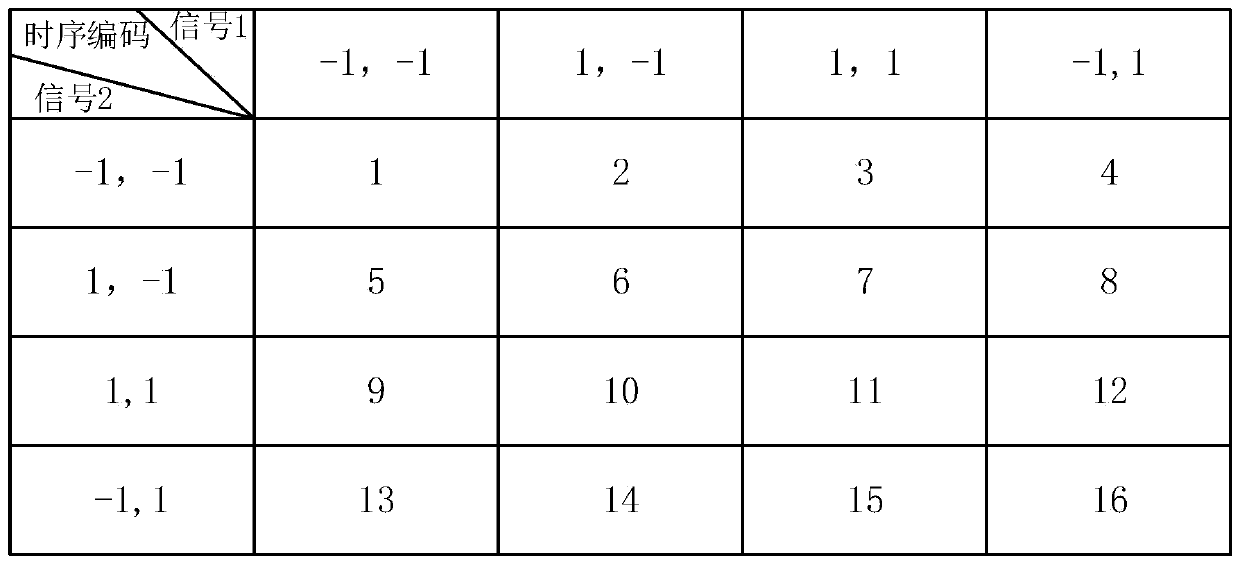
A Dual-Channel Directional Modulation System Based on Four-Dimensional Antenna Array
ActiveCN110224960BRealize confidential communicationAdjustable emission directionSpatial transmit diversityPhase-modulated carrier systemsRadio frequencySecurity system
The invention discloses a dual-channel directional modulation system based on a four-dimensional antenna array. Its basic structure includes antenna array, radio frequency modulation switch, power division network, local oscillator source, switch management system, sequential memory, baseband signal source 1, baseband signal source 2 and other devices. The biggest innovation of the present invention is that in the absence of a phase shifter, only using a radio frequency modulation switch, the directional modulation and secure communication of two signals in space at the same time are realized, and the transmission direction of the signal can be adjusted by changing the switch sequence . The present invention can use BPSK, QPSK, QAM and other modulation modes, and has good secret communication effect. Compared with the existing security system based on four-dimensional antenna array, this method has the characteristics of simple structure, lower cost, and flexible and convenient adjustment. The invention is used in a wireless communication system.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
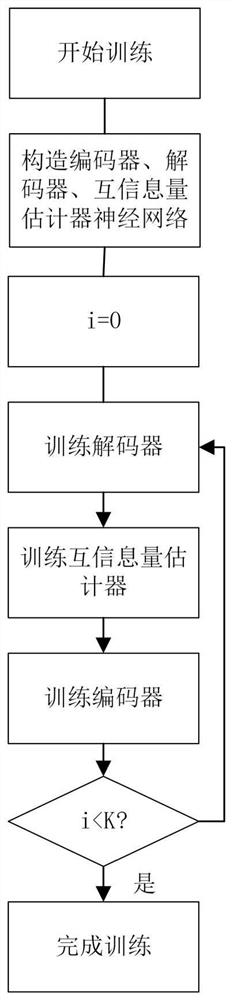
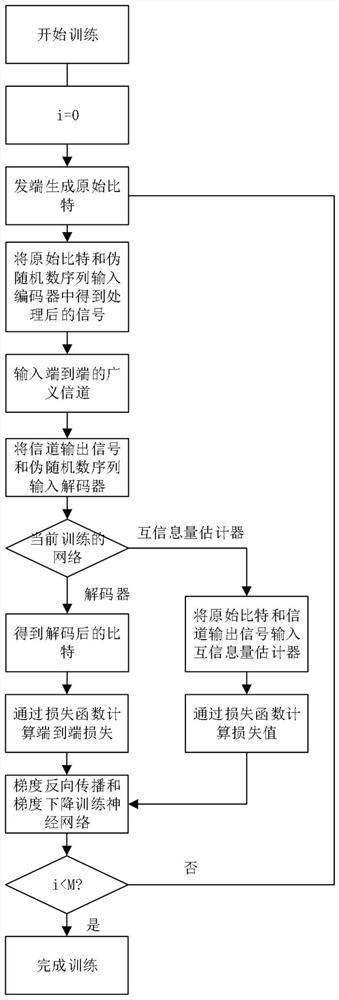
Physical layer secrecy method and system based on mutual information estimation neural network
ActiveCN114337849ALoud noiseMaximize the amount of mutual informationElectromagnetic transmission optical aspectsNeural learning methodsCommunications systemAlgorithm
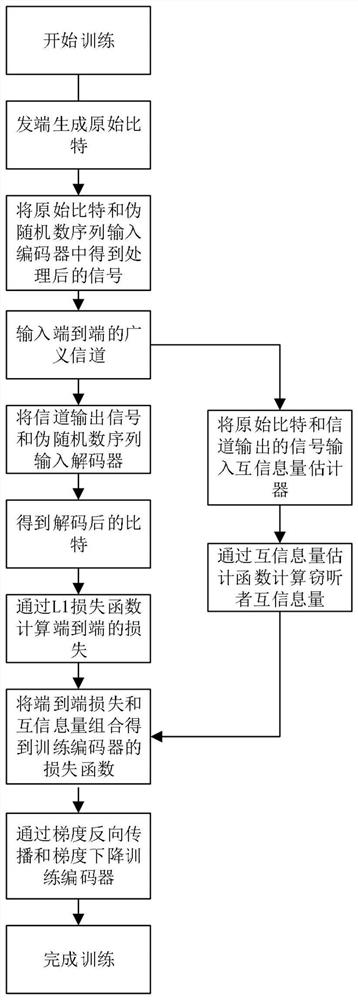
The invention provides a physical layer secrecy method and system based on a mutual information estimation neural network, and the method comprises the steps: S1, carrying out the training of an encoder and a decoder based on mutual information estimation and end-to-end deep learning, and obtaining a trained encoder and a trained decoder; and S2, physical layer confidential transmission is carried out by using the trained encoder and the trained decoder. According to the method, mutual information estimation and end-to-end deep learning methods are introduced, a confidentiality system for minimizing the mutual information of eavesdropper channels is realized through mutual information estimation, a reliable communication system for realizing the maximum mutual information of legal user channels is realized through end-to-end deep learning, the scheme gives consideration to confidentiality and reliability, and the method is suitable for popularization and application. The method is suitable for a long-distance high-speed optical communication transmission system.
Owner:SHANGHAI JIAO TONG UNIV
Secret communication system based on double chaotic modulation
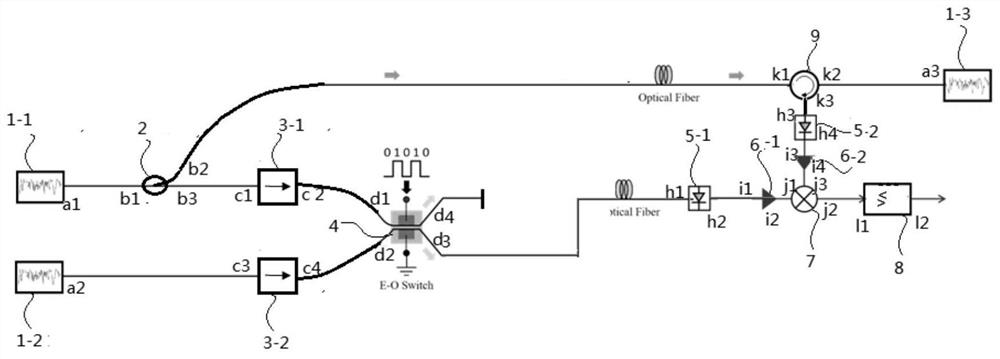
ActiveCN112600661ARealize demodulationRealize confidential communicationElectromagnetic transmission optical aspectsSecuring communication by chaotic signalsPhotoswitchIsolator
The invention relates to a secret communication system based on double chaotic modulation, and the system comprises: a transmitting end which comprises a first chaotic laser which is connected with acoupler, wherein the coupler is connected with a first isolator, the first isolator is connected with a photoelectric switch, a second chaotic laser is connected with a second isolator, and the secondisolator is connected with the photoelectric switch; a receiving end which comprises a third chaotic laser which is in communication connection with a circulator, wherein the circulator is in communication connection with a second photoelectric detector, the second photoelectric detector is in communication connection with a cross-correlator, the cross-correlator is in communication connection with a first radio frequency amplifier and a decision device, and the first radio frequency amplifier is in communication connection with the first photoelectric detector; and a circulator which is in communication connection with the coupler, wherein the photoelectric switch is in communication connection with the first photoelectric detector. According to the invention, double chaos is utilized tospread spectrum of digital information, identical chaotic sequences are synchronously generated, and after the sending end receives information modulation, the receiving end utilizes synchronous local signals to demodulate the information, so that secret communication is realized.
Owner:深圳立专技术转移中心有限公司
Method for implementing secret communication between communication terminal and wireless access point
InactiveCN101431453BEasy accessImprove securityKey distribution for secure communicationData switching by path configurationCommunication interfaceComputer terminal
The invention relates to a method for secret communication between communication terminal and wireless access point comprising following steps: (1) presetting unique identification information and communication key in encryption device, storing authenticated identification information and key of encryption device at wireless access point; (2)connecting encryption device and communication terminalvia communication interface and acquiring power supply, installing and operating dedicated drive program on communication terminal; (3) the encryption device sending authentication request including identification information to wireless access point; (4) wireless access point authenticating the encryption device according to identification information included in authentication request, if authentication being successful, then fetching corresponding key and sending notice of permission for access; (5) the encryption device notifying communication terminal of the established connection with wireless access point after receiving permission for access, encrypting, deciphering the transmitted data by communication key; wireless access point encrypting and deciphering the transmitted data viakey.
Owner:AIGO DIGITAL TECHNOLOGY CO LTD
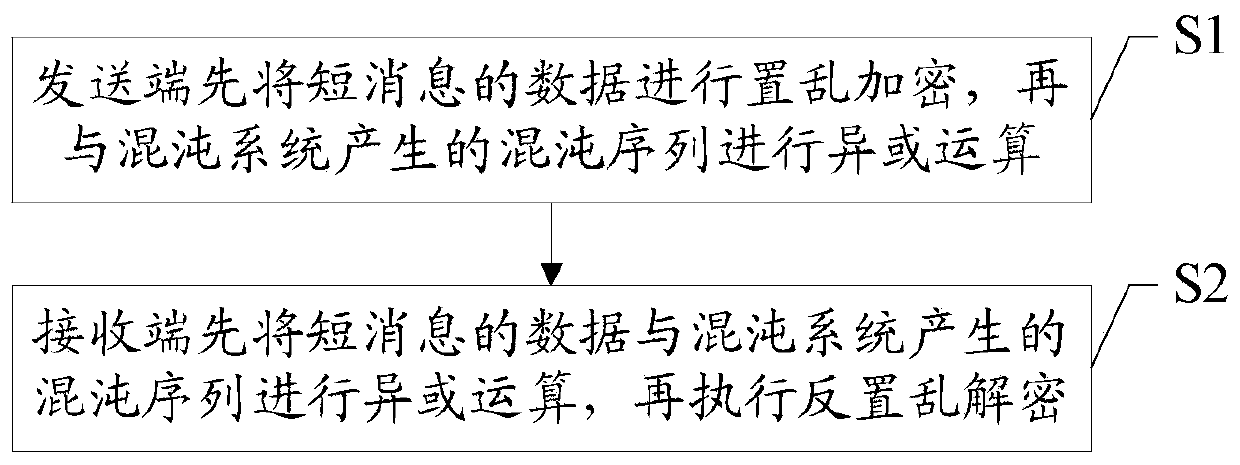
A short message secure communication method and system based on chaotic algorithm
ActiveCN106658487BRealize confidential communicationGood encryptionMessaging/mailboxes/announcementsSecuring communication by chaotic signalsSecure communicationAlgorithm
The invention discloses a short message secret communication method and system based on a chaos algorithm. The short message secret communication method comprises the steps that A, a sending terminal firstly performs scrambling encryption on data of a short message, and then performs an exclusive-or operation with a chaos sequence generated by a chaos system; and B, a receiving terminal firstly performs an exclusive-or operation on the data of the short message and the chaos sequence generated by the chaos system, and then executes anti-scrambling decryption. Encryption processing is performed on the short message according to combination of a short message protocol and the chaos system so as to realize secret communication of the short message. Meanwhile, an excellent encryption effect of the short message is ensured by combining inherent randomness, irregular orderliness and sensitivity for an initial value of the chaos system.
Owner:HUIZHOU TCL MOBILE COMM CO LTD
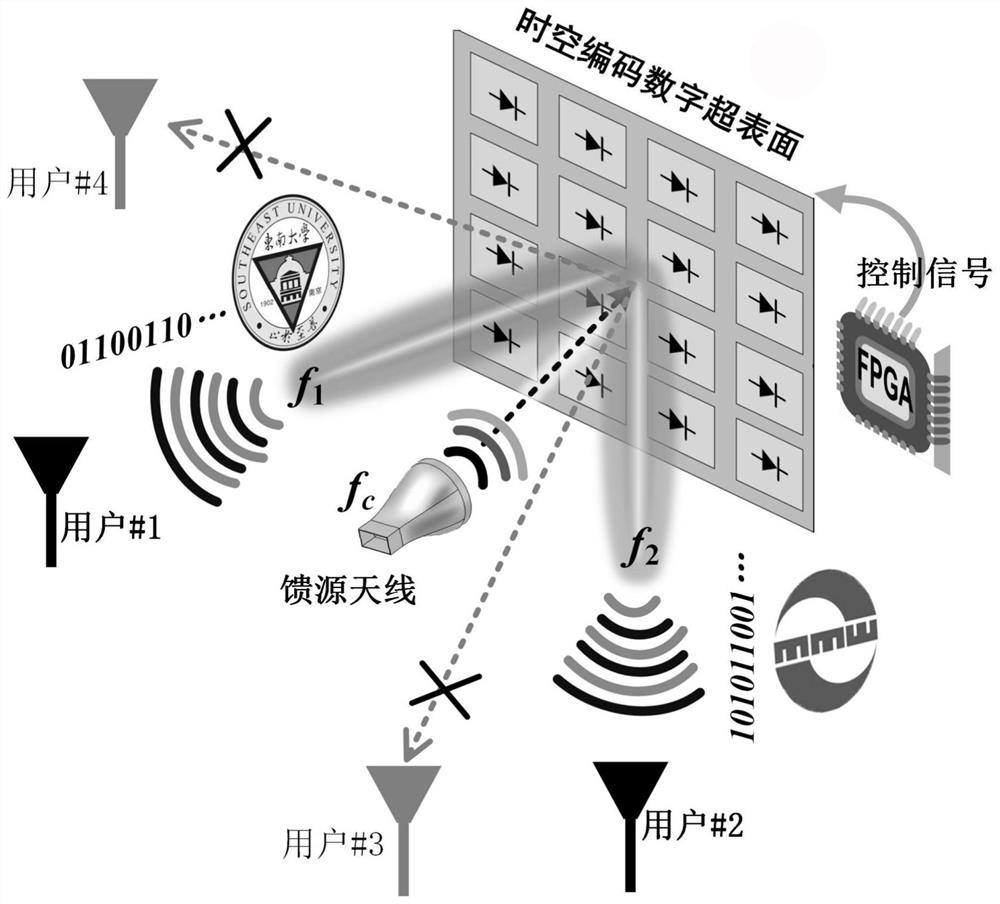
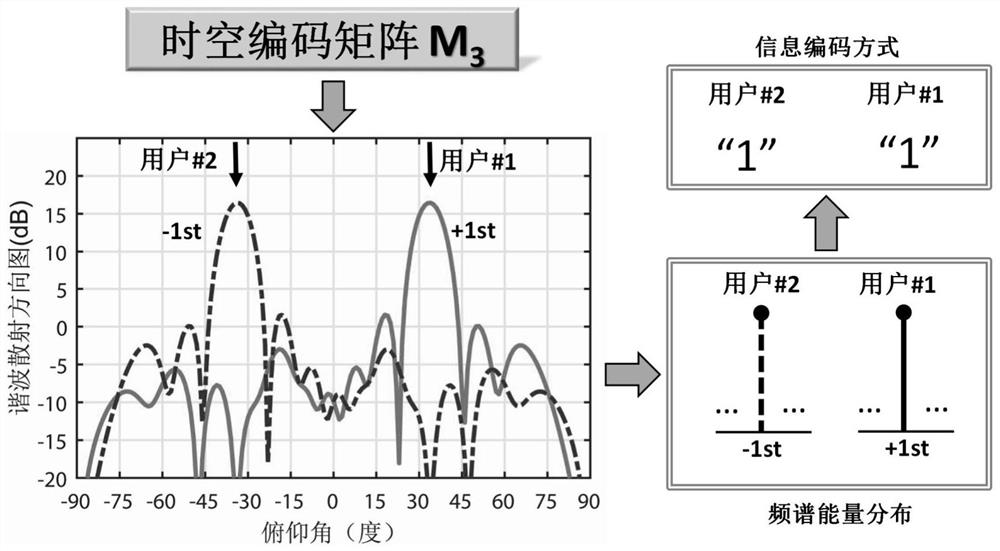
Multi-user wireless communication system and method based on space-time coding metasurface
ActiveCN110365616BSimple structureEliminate the RF moduleMultiple modulation transmitter/receiver arrangementsAmplitude-modulated carrier systemsInterference (communication)RF module
The invention discloses a multi-user wireless communication system based on a time-space coded supersurface. The transmitting end mainly includes a time-space coded metasurface, a feed antenna, and a digital control module; the receiving end is a traditional demodulation device. The invention also discloses the wireless communication method of this system. The feed antenna transmits a single-tone signal to the metasurface, and uses an algorithm to optimize the space-time encoding matrix, and jointly controls the energy distribution of the reflected signal in the space domain and the frequency domain, so that different harmonics The spatial beam of the system points to users in a specific direction for direct encoding of information; through the digital control module, different space-time encoding matrices are switched in real time, and different information is transmitted to multiple designated users simultaneously and independently, while users in other directions cannot demodulate. The transmitter has the characteristics of directional modulation, which can realize confidential communication and anti-interference; it also acts as a space mixer and antenna radiation, eliminating the need for digital-to-analog conversion, mixing and amplification RF modules, simplifying the communication transmitter architecture.
Owner:SOUTHEAST UNIV
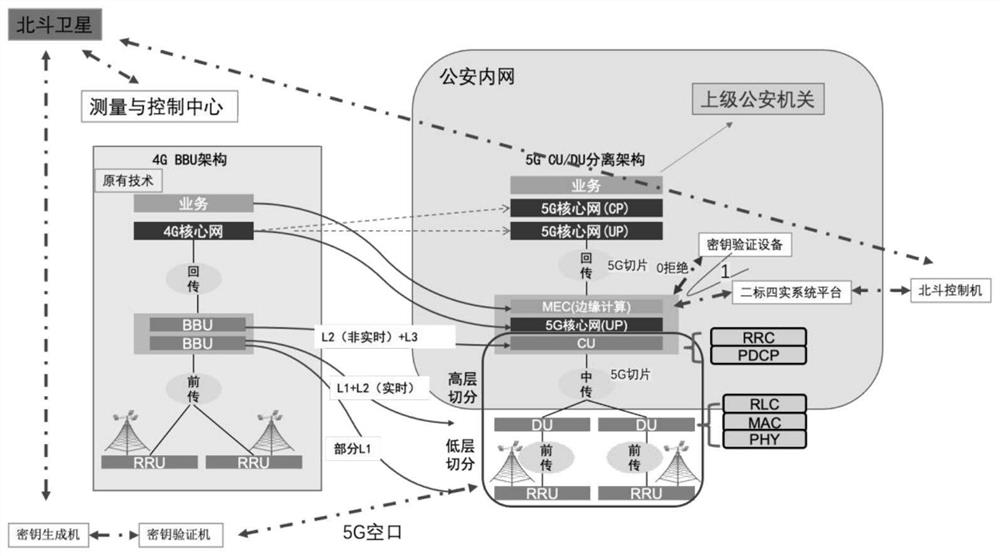
Two-standard four-real data security access system based on 5G edge computing
ActiveCN113301566ARealize confidential communicationEfficient collectionNetwork topologiesSecurity arrangementPrivate networkAir interface
The invention relates to a two-standard four-real data security access system based on 5G edge computing, and the system comprises the following parts: a key generator which is used for verifying the identity of a user, and obtaining a key transmitted by a Beidou controller after the verification succeeds; a key verifier which is associated with the key generator and is used for acquiring a key obtained by a user through the key generator; a 5G edge computing system which comprises a key verification device that interacts with a 5G base station through a 5G air interface and further interacts with the key verifier through a 5G slicing technology, and which is used for obtaining the key and verifying the key through the key verification device to obtain a verification result; the two-standard four-real system platform which is deployed in a public security internal network and is used for storing two-standard four-real data and allowing the key verifier to get access when the verification result obtained by the 5G edge computing system passes. According to the invention, the key generator and the key verifier can be used outside the public security private network to provide preconditions for an extranet user to access the public security intranet two-standard four-real platform data.
Owner:广州瀚信通信科技股份有限公司
Secret communication method based on fraction order Fourier transform order-multiplexing
InactiveCN101667911BLarge key spaceImprove securityKey distribution for secure communicationMultiple keys/algorithms usageMultiplexingCommunications system
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
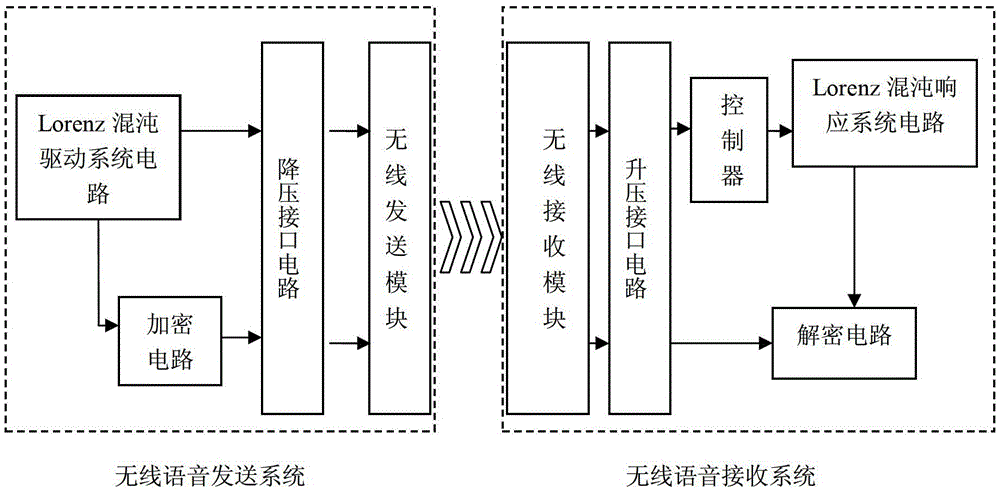
A two-way wireless voice security communication system and method based on lorenz chaotic circuit
A two-way wireless voice secure communication system and method based on Lorenz chaos circuit. The system includes a first wireless voice secure communication system and a second wireless voice secure communication system; the wireless voice secure communication system includes a wireless voice sending system and a wireless voice receiving system. System; the wireless voice sending system includes Lorenz chaos drive system circuit, buck interface circuit, wireless sending module and encryption circuit; the wireless voice receiving system includes Lorenz chaos response system circuit, boost interface circuit, controller, wireless receiving module and decryption circuit ; Wireless communication is performed between the wireless voice sending system and the wireless voice receiving system of the first wireless voice secure communication system, and between the wireless voice sending system and the wireless voice receiving system of the second wireless voice secure communication system. Chaotic signals have noise-like characteristics and are concealable. The extreme sensitivity of chaotic signals to initial conditions makes them unpredictable in the long term and extremely resistant to interception.
Owner:NORTHEASTERN UNIV LIAONING
Two-channel directional modulation system based on four-dimensional antenna array
ActiveCN110224960AAdjustable emission directionAchieving Directional ModulationSpatial transmit diversityPhase-modulated carrier systemsEngineeringRadio frequency
The invention discloses a two-channel directional modulation system based on a four-dimensional antenna array. The basic structure comprises an antenna array, a radio frequency modulation switch, a power division network, a local oscillation source, a switch management system, a time sequence memory, a baseband signal source 1, a baseband signal source 2 and the like. The biggest innovation of thetwo-channel directional modulation system lies in that under the condition of no phase shifter, directional modulation and secure communication of two paths of signals in space can be realized only by using a radio frequency modulation switch, and the transmitting direction of the signals can be adjusted by changing a switch sequence. Modulation modes of BPSK, QPSK, QAM and the like can be used,and a good secret communication effect is achieved. Compared with an existing security system based on a four-dimensional antenna array, the method has the advantages of being simple in structure, lower in cost, flexible and convenient to adjust and the like. The present invention is used in a wireless communication system.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
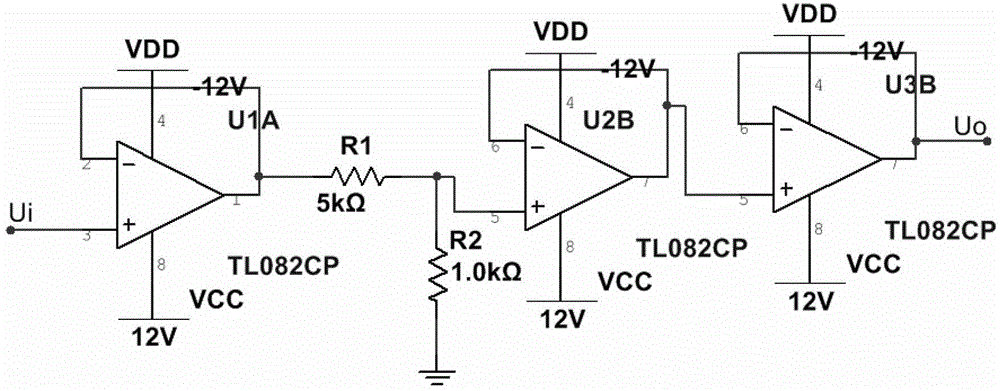
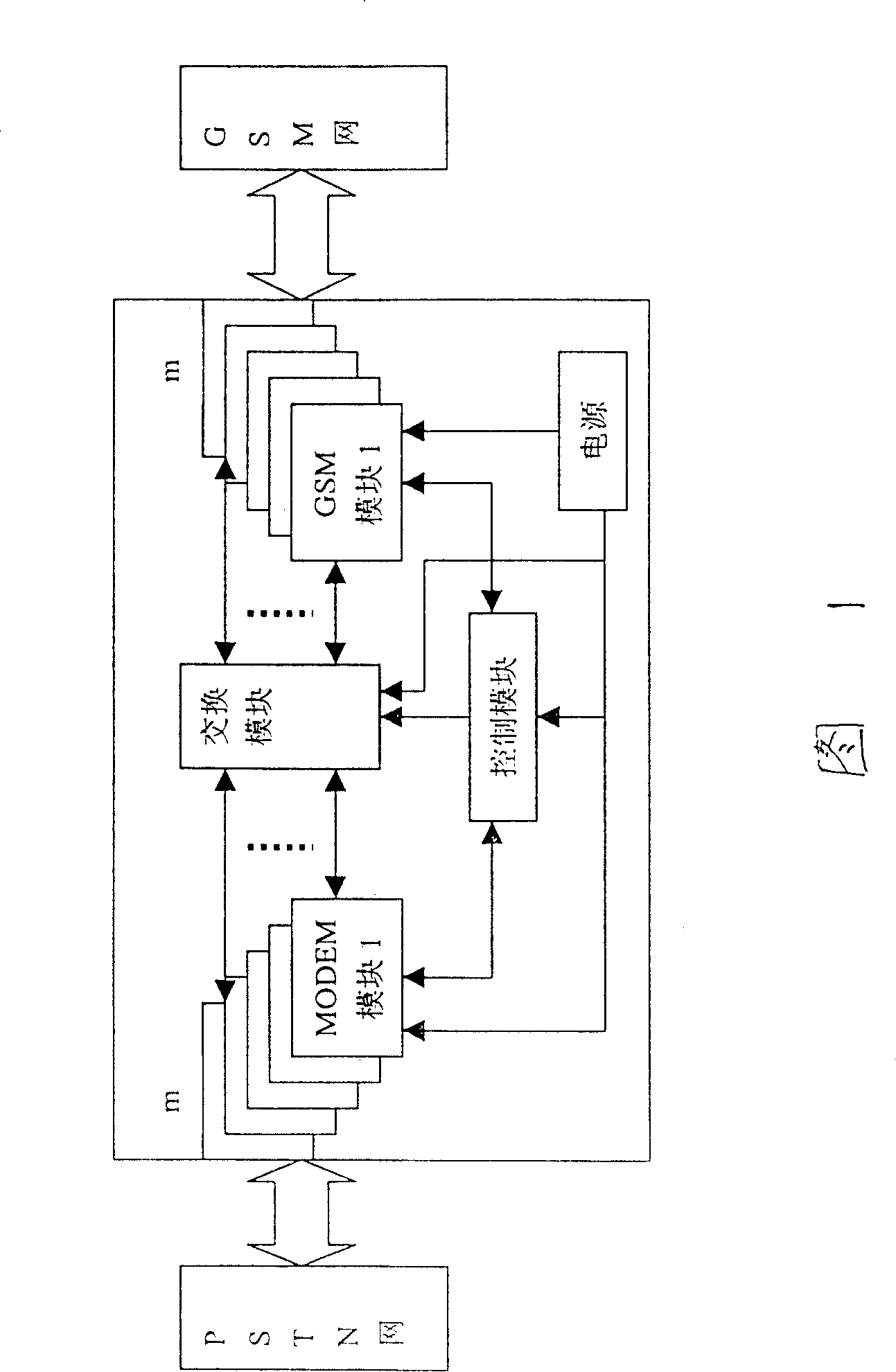
Apparatus and method for implementing end-to-end encrypted communication between line telephone and GSM handset
InactiveCN100388728CEnsure safetyNo lossAutomatic exchangesNetwork connectionsEnd-to-end encryptionSecure communication
This invention discloses a device and a method for end-to-end ciphered communication between wire telephones and cell phones. A MODEM module of the device is connected with the wire phone net, GSM module is connected with GSM net, the exchange module is connected with MODEM and GSM module, a control module is connected with the MODEM, exchange and GSM, a power supply module provides working supply to the modules. The secure communication is realized by the following steps taking the wire phone secure set as the calling party: 1, the calling party dials the gateway access number and a called cell phone number, 2, PSTN exchange provides the dial number to the gate, its MODEM extracts the number to the control module, 3, the control module calls the cell phone by GSM net, 4, the cell phone sends a response to GSM module to set up GSM communication, 5, the control sends the response to the server set to set up PSTN communication connection, 6, the control module controls the exchange module to connect MODEM and GSM modules for secure communication.
Owner:成都三零瑞通移动通信有限公司
Web communication encrypting method
InactiveCN100574325CAvoid encryption and decryption operationsRealize confidential communicationSynchronising transmission/receiving encryption devicesSecure communicationKey exchange
The invention provides a Web communication encryption method, which distinguishes between the first communication and the second communication between the client and the server. When the client accessing for the first time communicates with the server on the Web, it needs to negotiate to determine the communication encryption algorithm, and there is no need to negotiate again when communicating again; when communicating for the first time, the client obtains the communication master key provided by the server and saves the communication master key , when communicating again, the server only needs to calculate and generate the key locally, and the client uses the locally stored communication master key to transmit the session key, and then the two parties use the session key to encrypt and decrypt the communication data to realize confidential communication. The communication encryption method of the present invention greatly reduces the key storage capacity of the server, and the reduction of the key exchange calculation load of the server is also obvious.
Owner:PEKING UNIV
Radar communication integrated signal generating and receiving method based on random step frequency OFDM (Orthogonal Frequency Division Multiplexing)
PendingCN113965441AGuaranteed low peak-to-average power ratio characteristicsGuaranteed high peak sidelobe ratio characteristicsCode division multiplexMulti-frequency code systemsRadarDemodulation
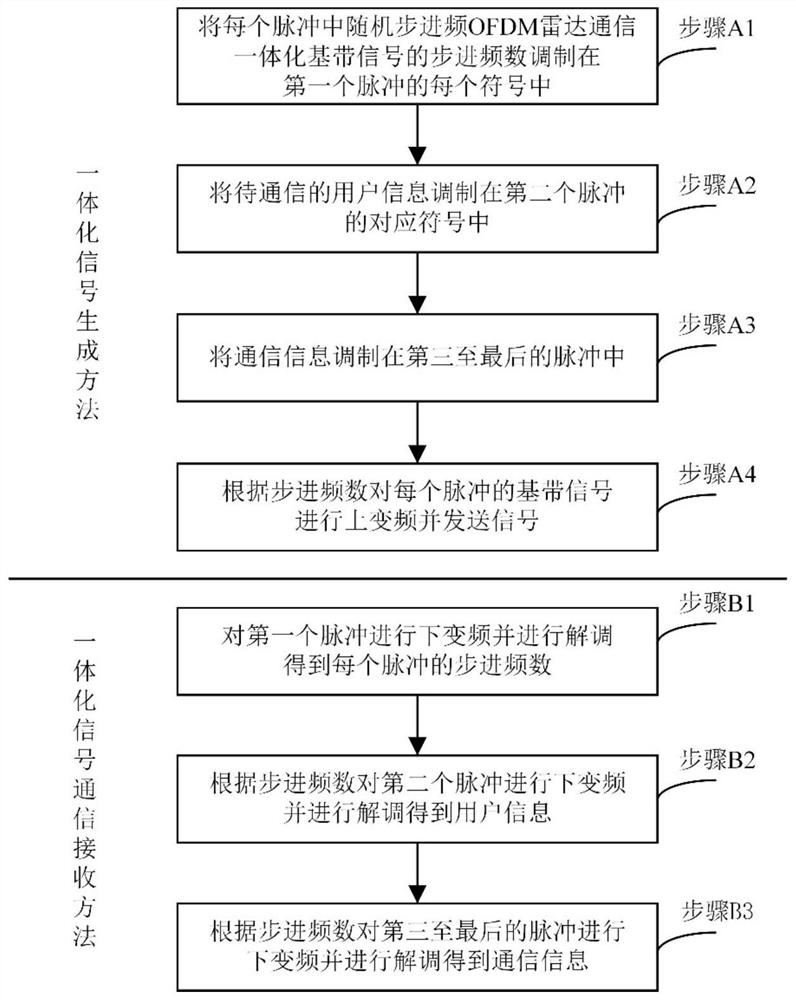
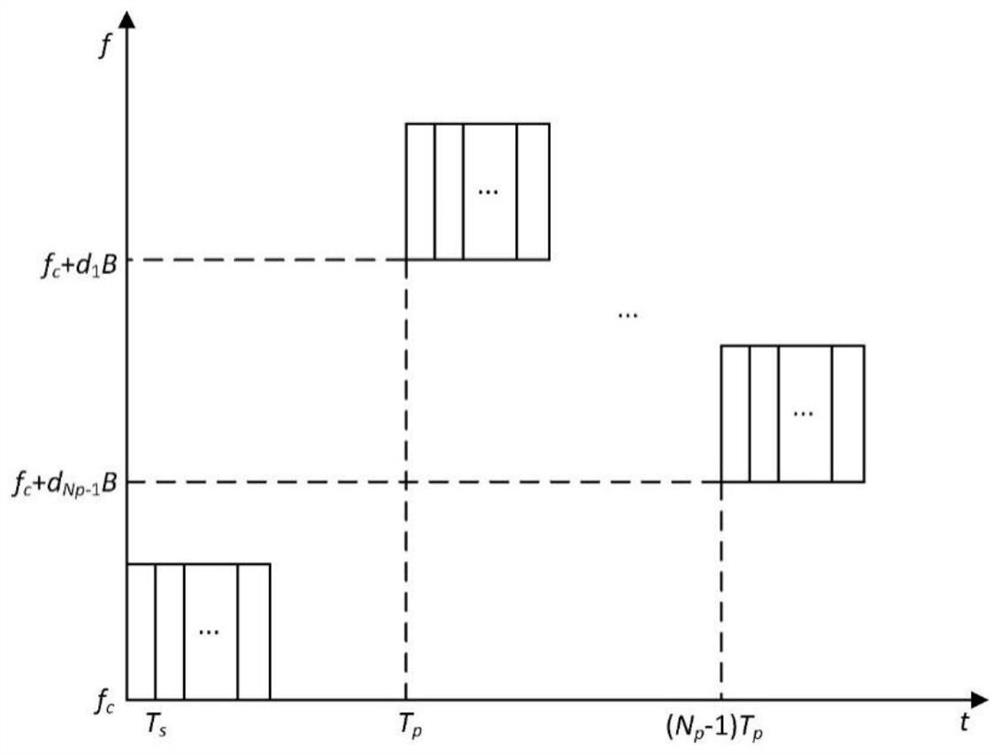
The invention discloses a radar communication integrated signal generating and receiving method based on random step frequency OFDM (Orthogonal Frequency Division Multiplexing). The radar communication integrated signal generating and receiving method comprises the following steps: generating a radar communication integrated signal; modulating the step frequency number of each pulse in each symbol of a first pulse; modulating user information to be communicated in a corresponding symbol of the second pulse; modulating the communication information in the third to last pulses; performing up-conversion on the baseband signal of each pulse according to the stepping frequency number, and sending the signal; receiving a radar communication integrated signal; performing down-conversion and demodulation on the first pulse to obtain the step frequency number of each pulse; performing down-conversion on the second pulse according to the stepping frequency number, and demodulating to obtain user information; and performing down-conversion on the third to last pulses according to the stepping frequency number, and performing demodulation to obtain communication information. According to the invention, one-point-to-multipoint communication in a radar communication integrated system can be realized, and confidential communication in a special system is realized by using the random step frequency of each pulse.
Owner:JIANGSU UNIV OF SCI & TECH
Authentication and encryption method for wireless network
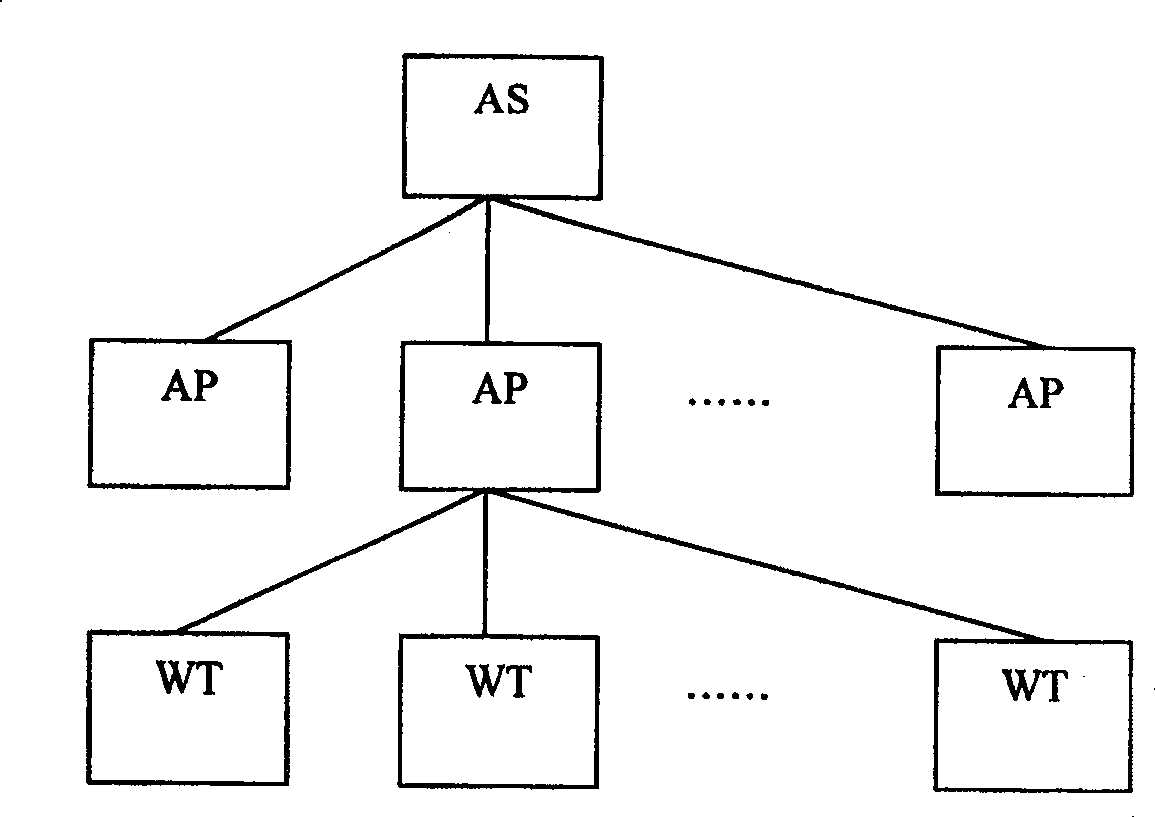
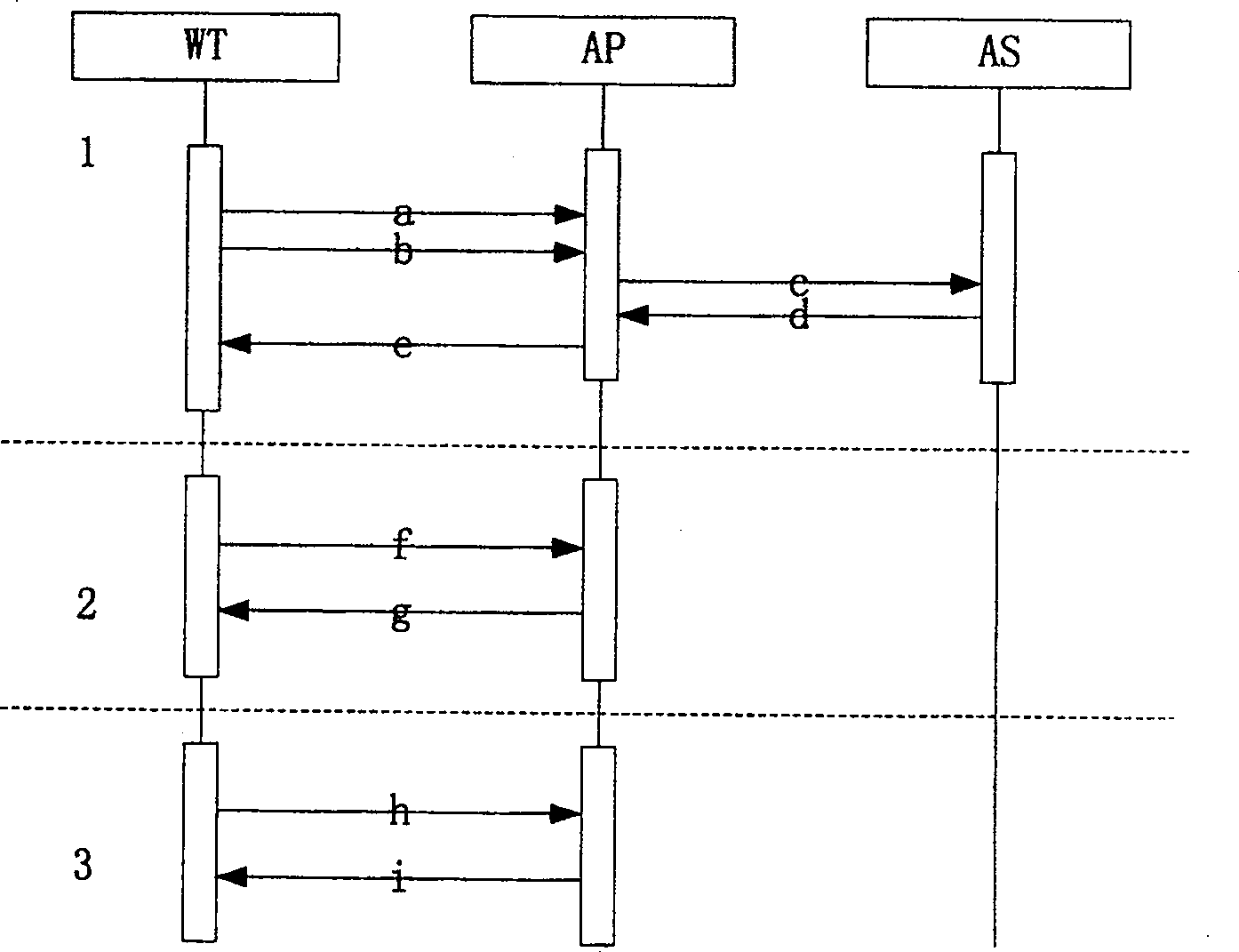
ActiveCN100525182COvercoming confidentiality limitationsRealize two-way authenticationMultiple keys/algorithms usageSecure communicationBroadcast data
An authentication and security method for a wireless network. When a wireless terminal communicates with a wireless access point, a two-way certificate authentication is performed by an authentication server; after the two-way certificate authentication is successful, a unicast key negotiation is performed to realize secure communication of unicast data ; After the unicast key negotiation is successful, the wireless access point notifies the wireless terminal of the multicast / broadcast key to realize the secure communication of the multicast / broadcast data; the present invention solves the problem of security access control in the wireless network and overcomes the wireless Due to the limitation of confidentiality of data communication on the link, using public key cryptography technology, the two-way certificate authentication between the wireless terminal and the wireless access point is realized through the authentication server, which improves the security of access control; through dynamic unicast key negotiation The multicast / broadcast key notification completes the identification of each unicast key by each wireless terminal and the dynamic update of the unicast key and the multicast / broadcast key during the communication process, which realizes the confidential communication of data and increases the The difficulty of cracking.
Owner:CHINA IWNCOMM
Two-way chaos security communication system and communication method based on twdm-pon
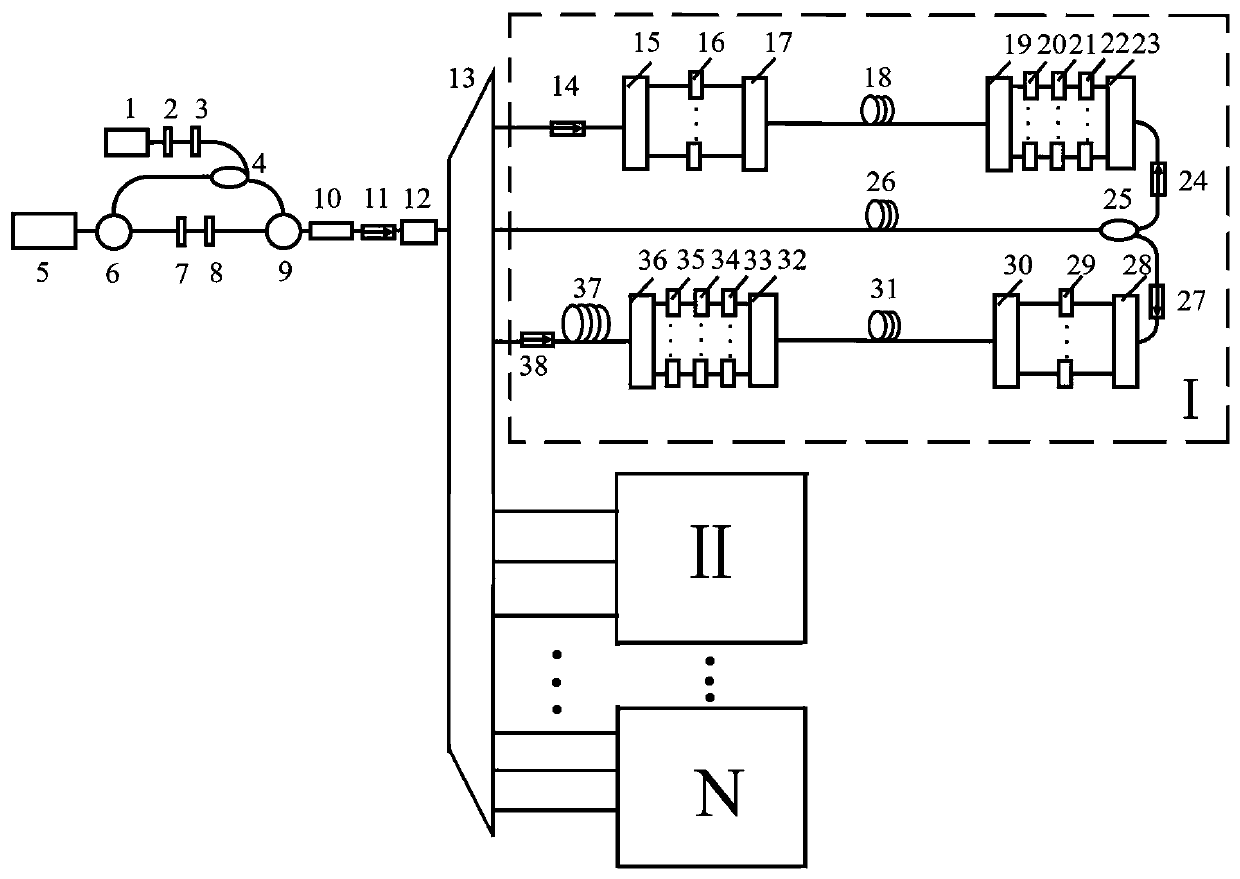
ActiveCN109547151BRealize demodulationHigh speed loadingMultiplex system selection arrangementsTime-division optical multiplex systemsGratingCarrier signal
The invention discloses a bidirectional chaotic secure communication system based on TWDM-PON and a communication method. A beam of continuous laser is injected into an isolator-free multi-longitudinal mode semiconductor laser with external cavity random grating feedback, thereby realizing spectrum broadening of multi-mode chaotic laser without delay feature; the light is divided into multiple paths through a multipath light splitter, three paths form one group, each group is connected with a forward multipath information loading transmission demodulation part and a backward multipath information loading transmission demodulation part; the chaotic laser is separated according to the longitudinal-mode wavelength by using a wave-division multiplexer so as to be used as the chaotic laser carrier of multipath communication; three paths of each group form two closed-loop structures for realizing forward multipath information loading transmission demodulation and backward multipath information loading transmission demodulation. The multiuser directional secure communication can be realized, and the high-speed information can be loaded, the user amount is greatly improved, and the user demand is satisfied.
Owner:TAIYUAN UNIV OF TECH
Communication method for encrypted equipment and unencrypted equipment hybrid networking
InactiveCN101834722BRealize Hybrid NetworkingRealize unencrypted communicationSpecial service provision for substationMultiple keys/algorithms usageRelationship - FatherNetwork packet
The invention discloses a communication method for encrypted equipment and unencrypted equipment hybrid networking, which is characterized in that: all unencrypted switching equipment directly forwards all protocol packets and user packets in the network, and all encrypted switching equipment adopts the following three steps to process the protocol packets: seeking father encrypted switching equipment, identifying and establishing a unicast key, and establishing a key between nodes. The communication method for encrypted equipment and unencrypted equipment hybrid networking has the advantagesof solving the technical problem that the communication method in the prior art is large in potential safety hazard, high in upgrade cost and low in transmission efficiency, realizing the compatibility of the encrypted equipment and the unencrypted equipment, simultaneously ensuring the secrecy transmission of a data link layer of a local area network, and realizing the unencrypted communication between the traditional nodes, and the secret communication between the encrypted equipment.
Owner:CHINA IWNCOMM
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com