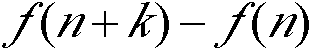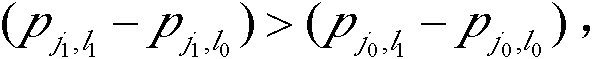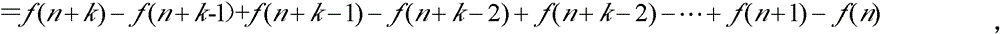Patents
Literature
42results about How to "Reduce storage complexity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
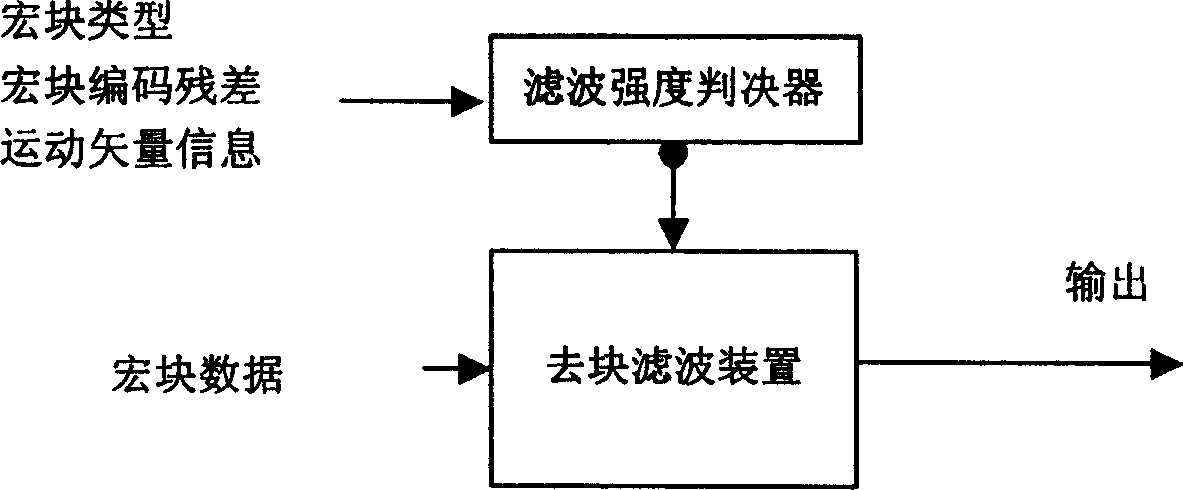
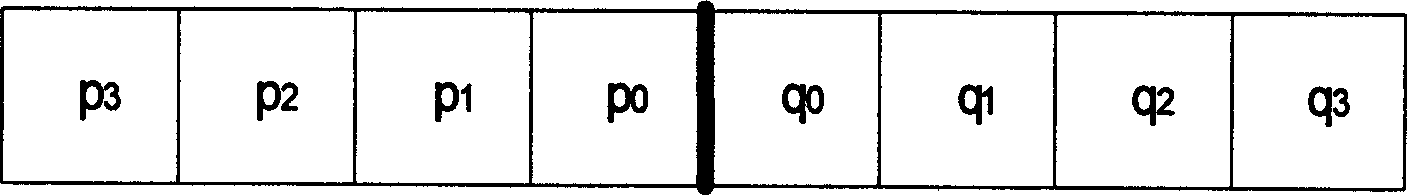
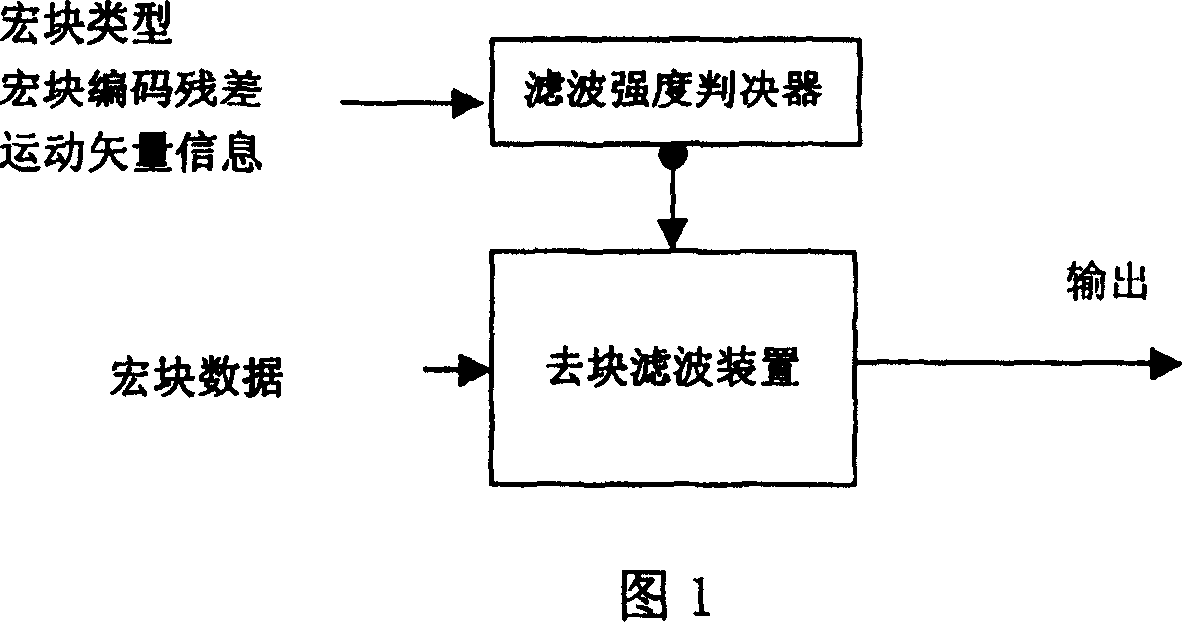
Deblocking filtering method and apparatus of video frequency or image
ActiveCN1652610AReduce computational complexityReduce storage complexityTelevision systemsDigital video signal modificationRound complexitySelf adaptive
Using macro block type and quantized parameters, the disclosed method determines whether de-block filtering is carried out or not, and determine what kind of macro block filtering mode is selected or adopted in case of de-block filtering is needed. The method does not use residual information of coded macro or information of motion vector to determine whether de-block filtering is needed or not. Based on macro block filtering mode adopted and content of image, de-block filtering procedure is determined in self-adaption. Under precondition of possessing considerable objective and subjective decoded image quality, the disclosed method reduces computation complexity and storage complexity greatly. The invention can be extended to application of other signal processes, not limited in area of video frequency or encoding and decoding images.
Owner:XFUSION DIGITAL TECH CO LTD
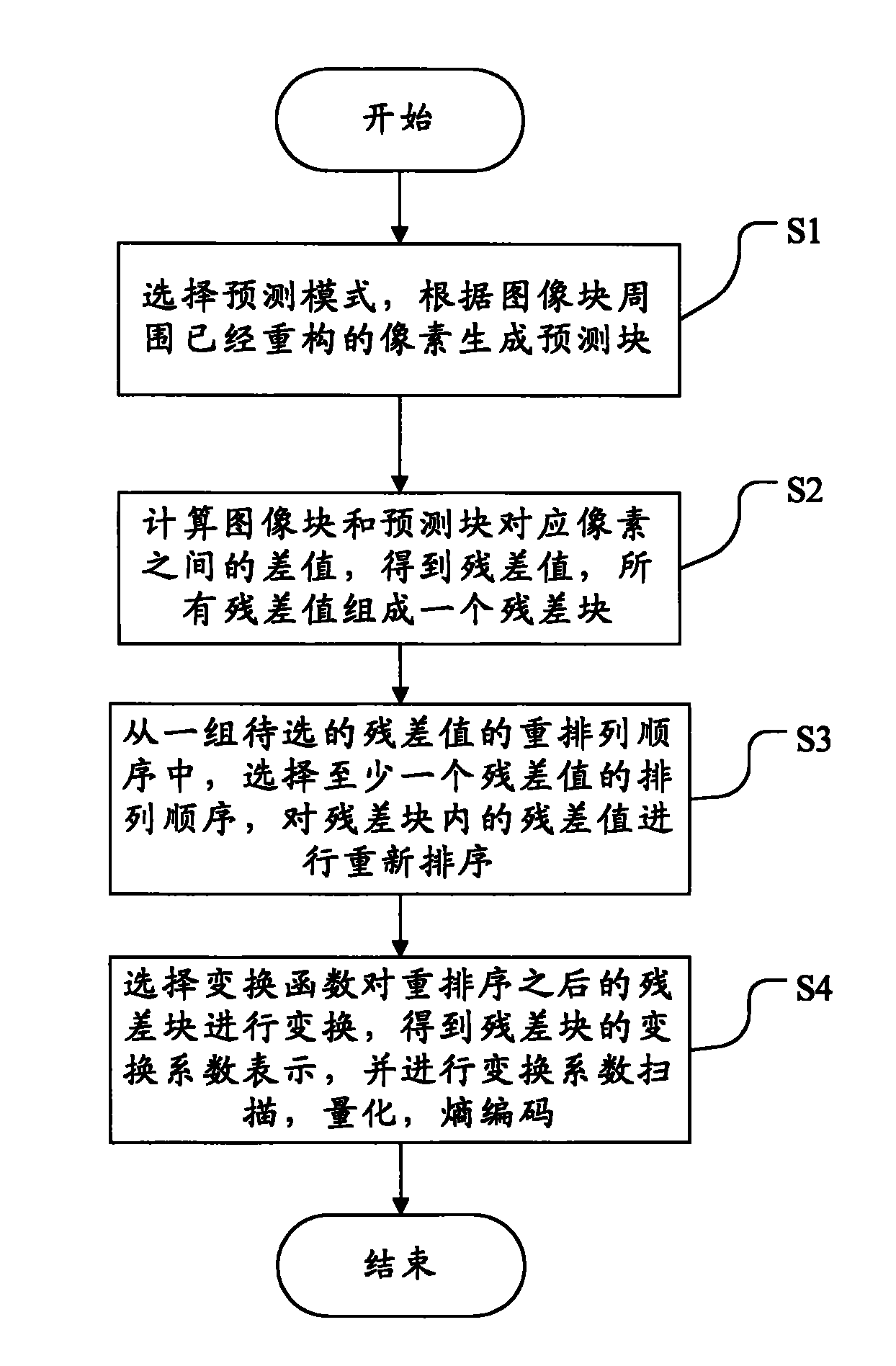
Method and system for coding, decoding and reconstructing video image blocks
ActiveCN101895756AReduce storage complexityTelevision systemsDigital video signal modificationPattern recognitionResidual value
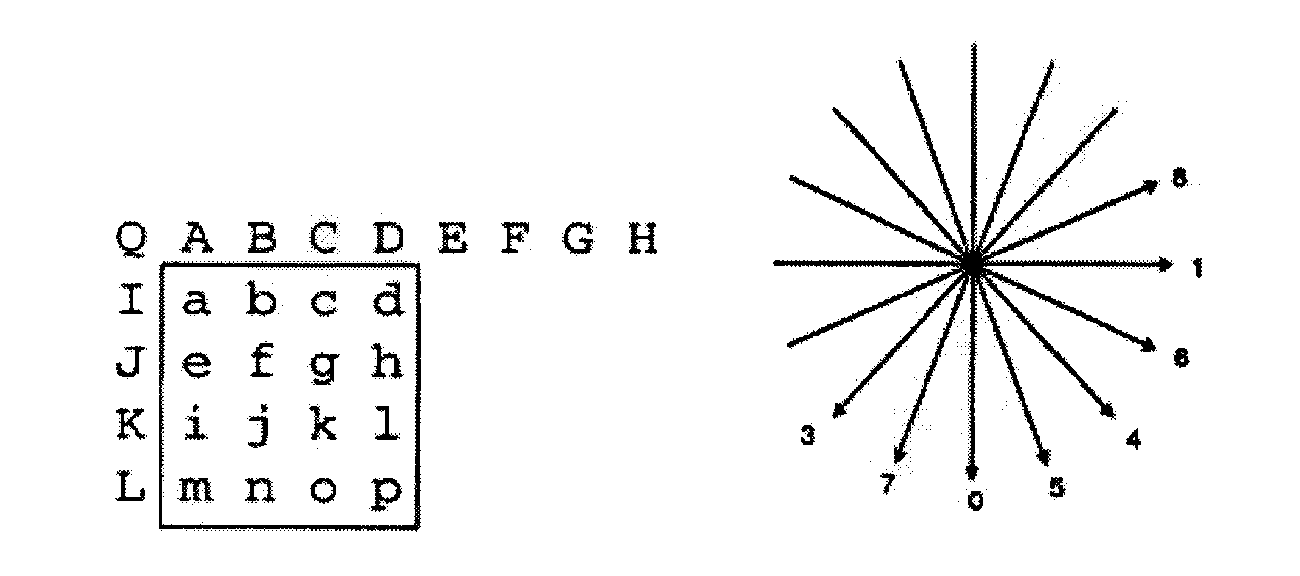
The invention discloses a method and a system for coding, decoding and reconstructing video image blocks, wherein the coding method comprises the following steps: selecting a prediction mode, and generating predicted blocks according to the reconstructed pixels around image blocks; calculating the difference between the pixels corresponding to the image blocks and the predicted blocks to obtain residual values, wherein all the residual values constitute a residual block; selecting the arrangement sequence of at least one residual value from a group of rearrangement sequences of the residual values to be selected, and rearranging the residual values in the residual block; transforming the rearranged residual block by selecting a transformation function to obtain the indication of the transformation coefficient of the residual block; and further scanning, quantifying and carrying out entropy-coding on the transformation coefficient. By rearranging the residual sampling values in the residual block in a null field, the characteristics of residual statistics in different modes can be similar or identical, thus achieving the performance similar to the transformation related to the modes by using fewer transformation functions and reducing the storage complexity of a coder and a decoder at the same time.
Owner:PEKING UNIV
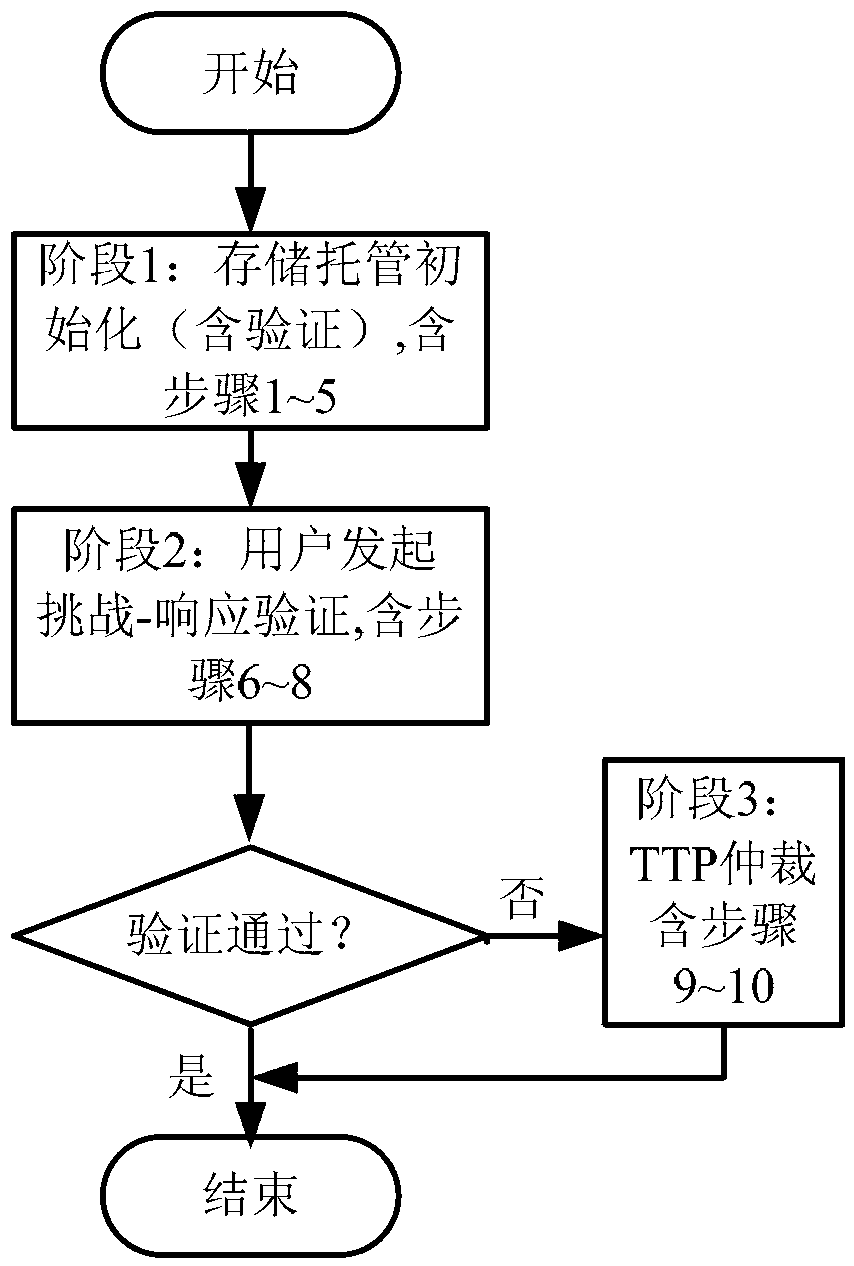
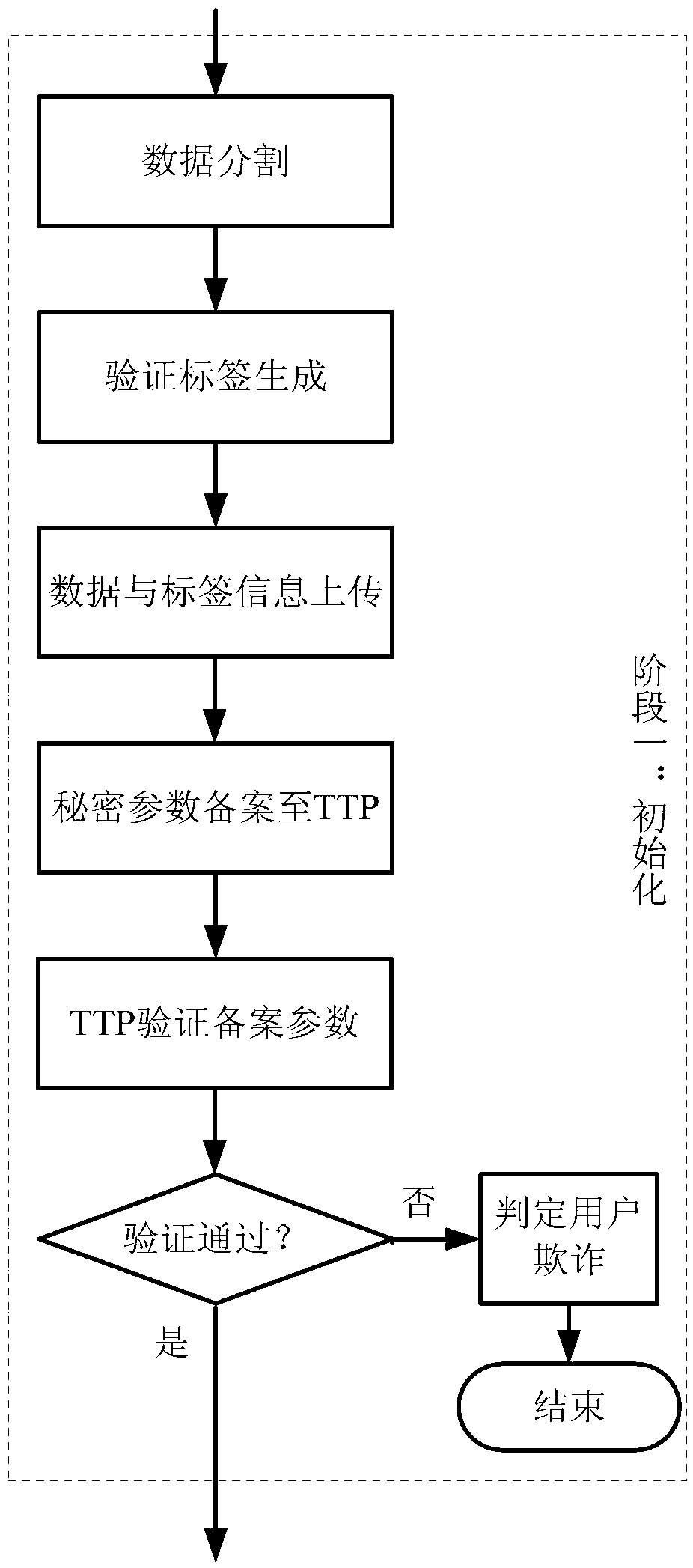
Publicly-verifiable cloud data possession checking method
ActiveCN103414690AReduce storage complexityReduce computational complexityTransmissionComputation complexityRelevant information
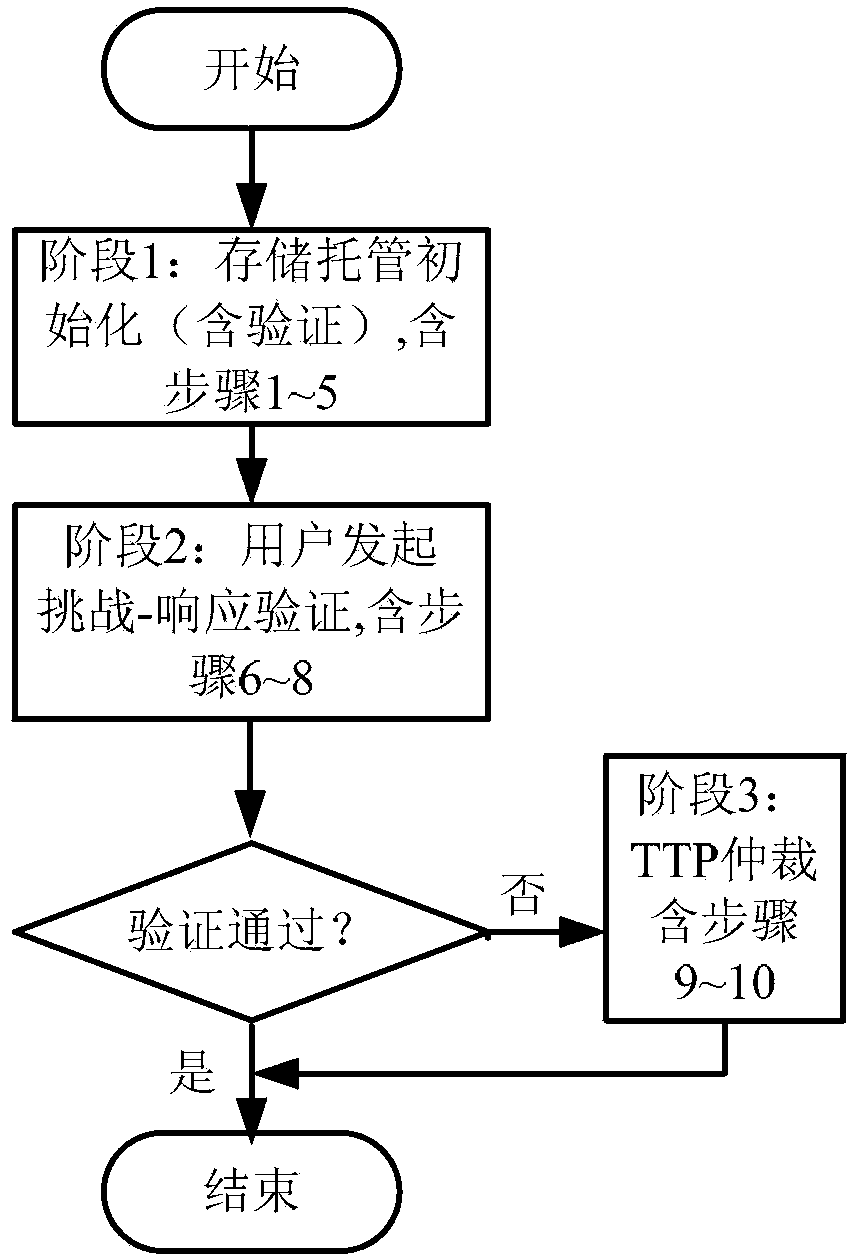
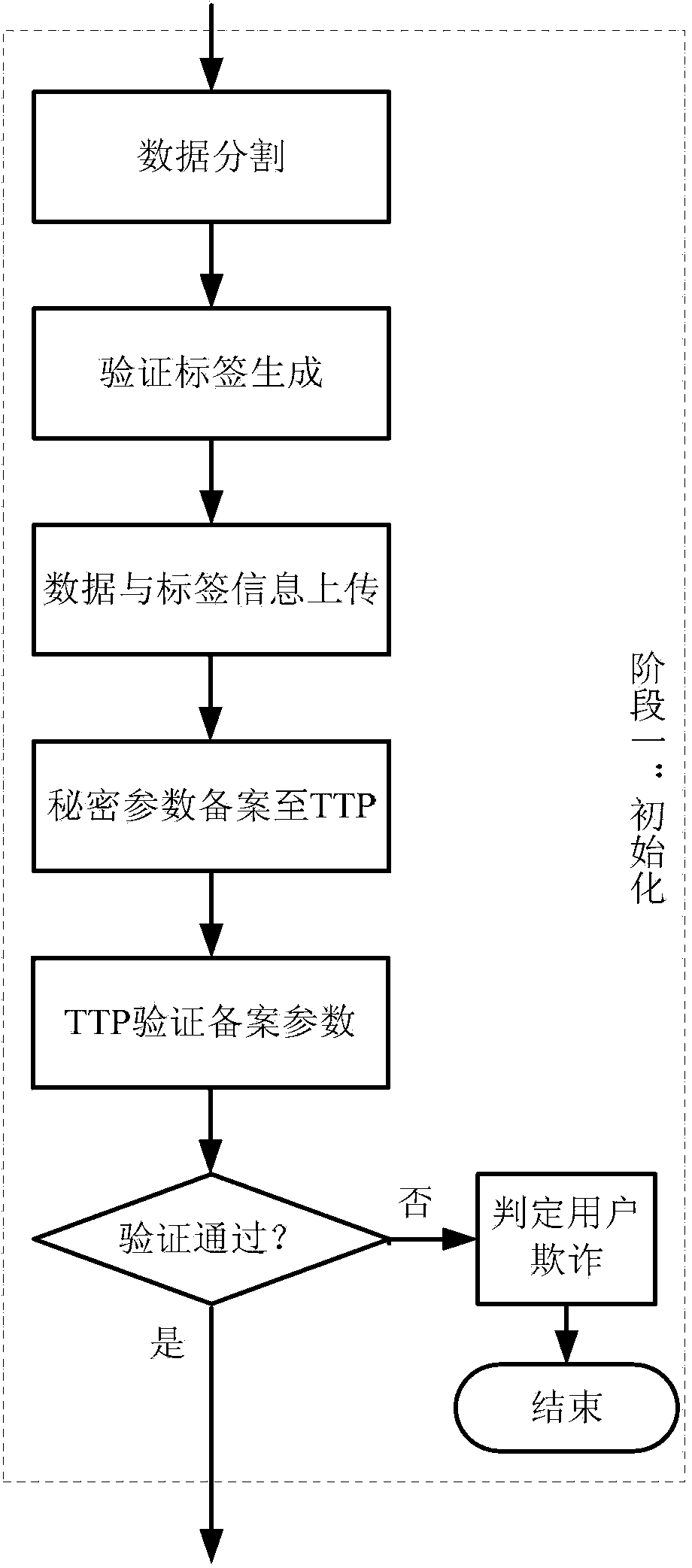
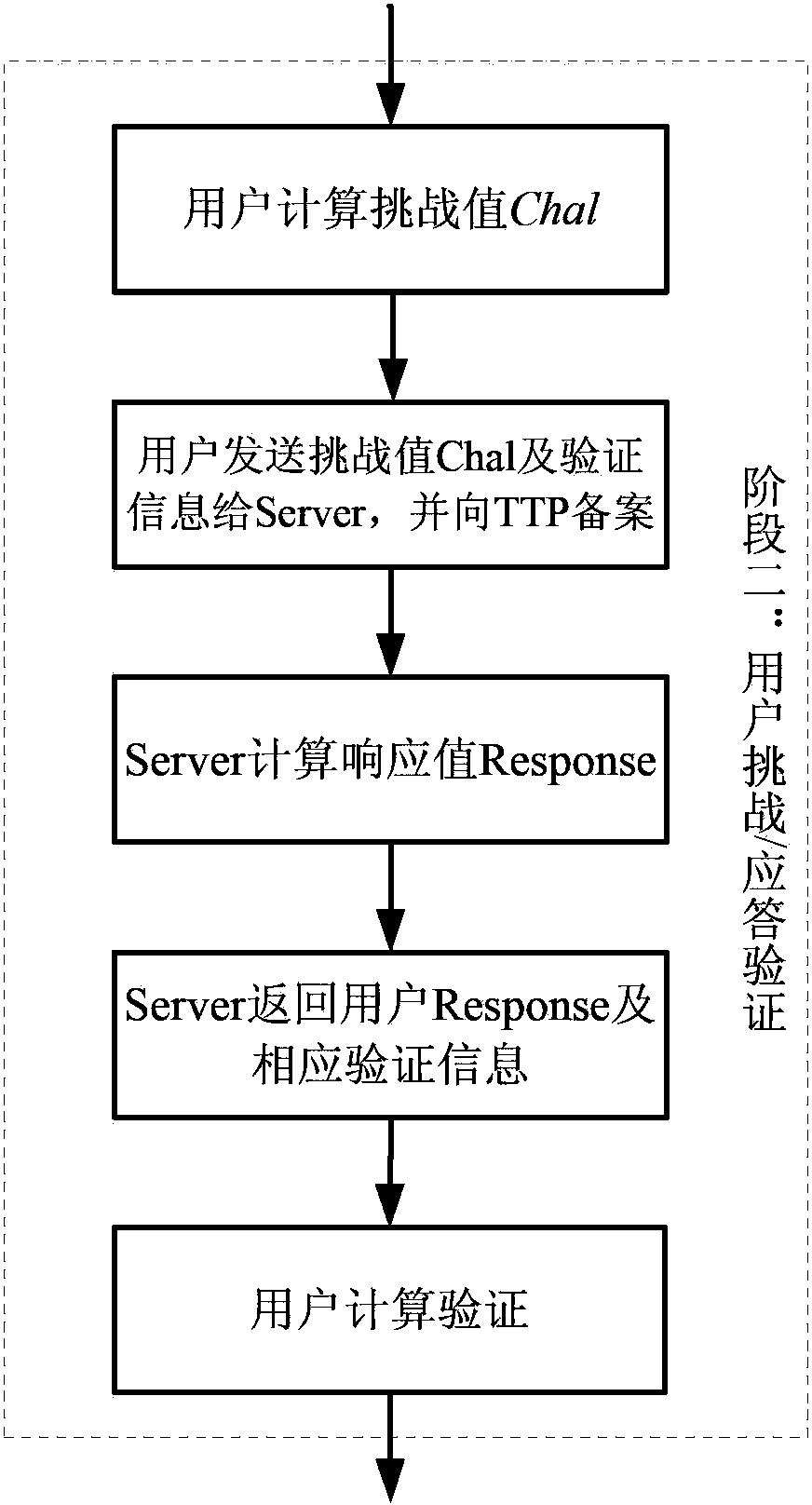
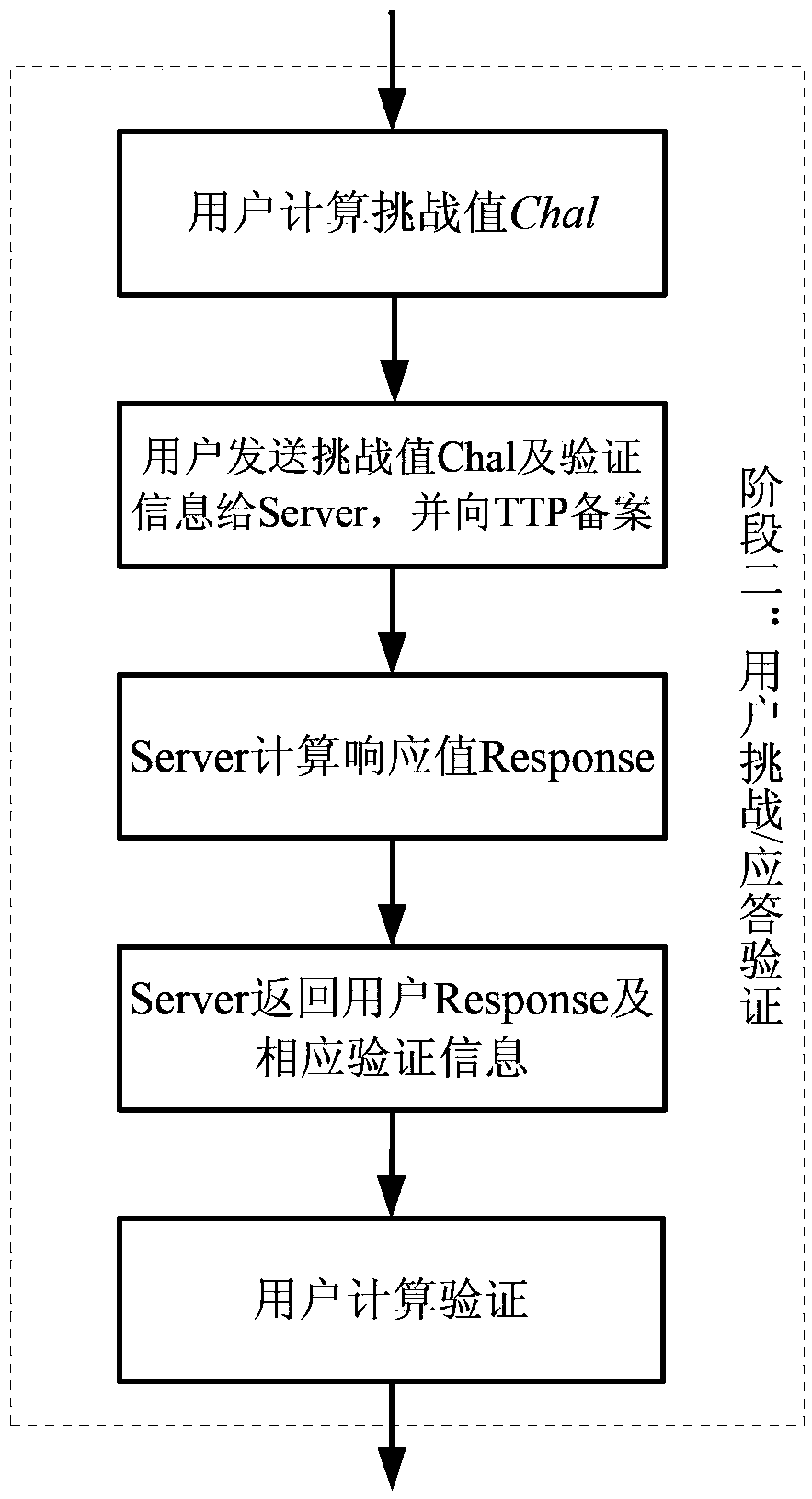
A publicly-verifiable cloud data possession checking method is provided. The method includes the three stages of initialization, user challenge-response verification and TTP arbitration; the three stages comprise the following ten steps that: step 1, data segmentation [F->F'] is performed; step 2, verification tag generation [(SK, F)-> HVT] is performed; step 3, data and tag information upload [(F, HVT)->S] is performed; step 4, secret parameters are recorded to a TTP (trusted third party); step 5, the TTP verifies recorded parameters; step 6, [chal] is initiated by a user, and the chal and the verification information of the chal are handed over to the TTP so as to be record; step 7, a server makes a response; step 8, [(R, sk)->(' success', 'failure')] is verified; step 9, relevant information acquisition is verified; and step 10, the trusted third party performs verification publicly. With the publicly-verifiable cloud data possession checking method of the invention adopted, the user can verify the existence and integrity of data in a cloud storage server. The publicly-verifiable cloud data possessions checking method is advantageous in no limitation on the number of user authentication times as well as small storage capacity and low computational complexity of a client, and has great practical value and broad application prospect.
Owner:BEIHANG UNIV
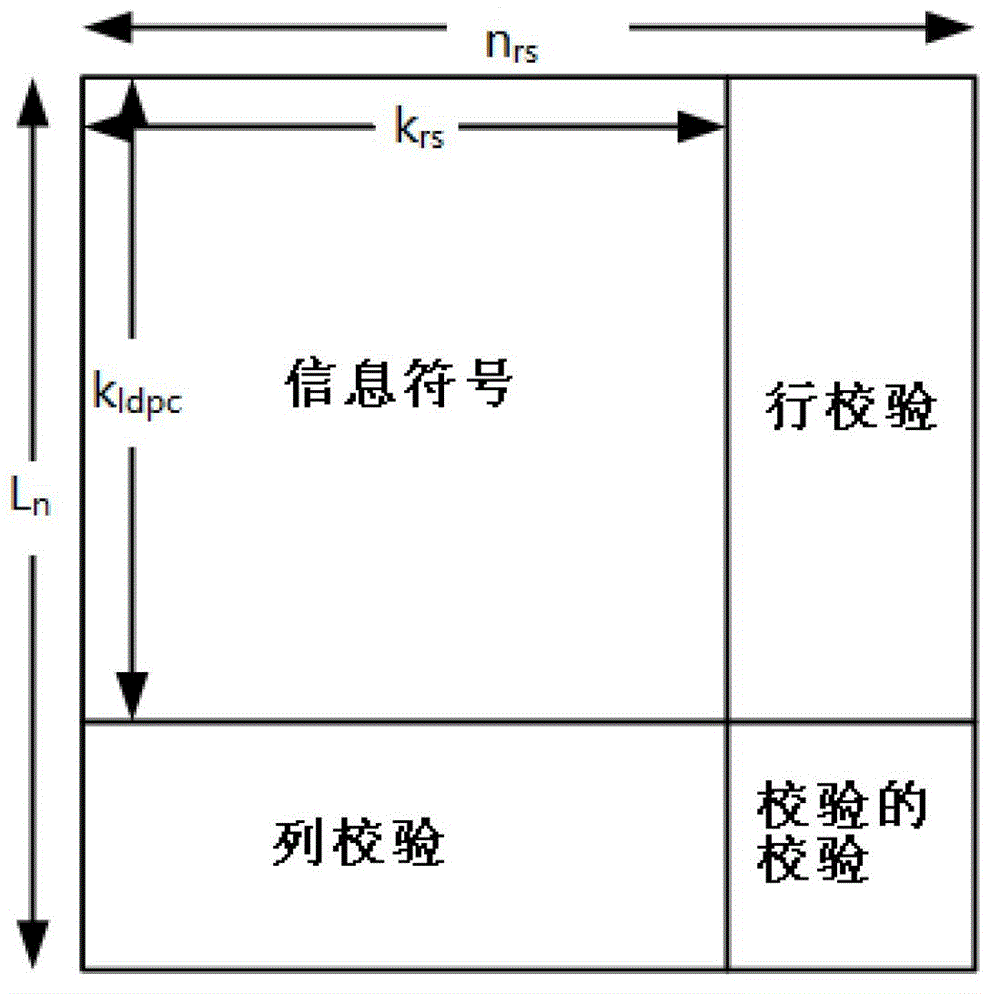
Encoding and decoding method of LDPC-RS (Low Density Parity Check-Reed-Solomon) two-dimensional product code with compatible code rate
InactiveCN103338046AReduce storage complexityLower latencyError correction/detection using multiple parity bitsCommunications systemComputation complexity
The invention provides an encoding and decoding method of an LDPC-RS (Low Density Parity Check-Reed-Solomon) two-dimensional product code with compatible code rate and belongs to the technical field of channel encoding and decoding in a communication system. The method comprises the followings: adopting LDPC code words with compatible code rate as ingredient code words; constructing LDPC-RS two-dimensional product code words with compatible code rate; realizing a function of partial decoding by combining characteristics of the compatible code rate, so that the storage complexity, receiving delay and decoding complexity of a receiving end are reduced. A corresponding decoding scheme and an initial decoding receiving code rate can be selected by a decoding framework according to estimated channel quality information on one hand; various decoding methods are skillfully combined by the decoding framework on the other hand, so that a most applicable decoding method is adopted at different stages of decoding, so as to achieve the purposes of optimizing decoding performance and reducing the computational complexity.
Owner:SHANGHAI JIAO TONG UNIV
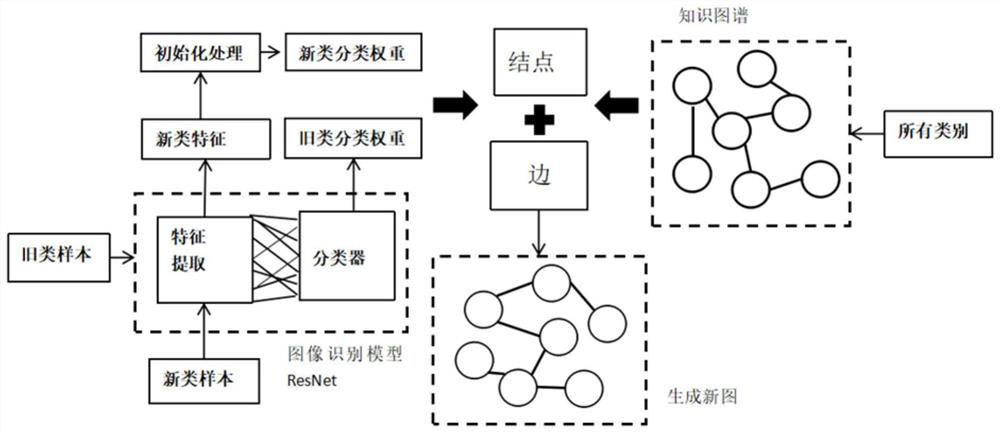
Development method and system of small sample classification model based on graph convolutional neural network
ActiveCN112183620AVisual transfer is fast and preciseReduce the cost of trainingCharacter and pattern recognitionNeural architecturesGraph spectraUndirected graph
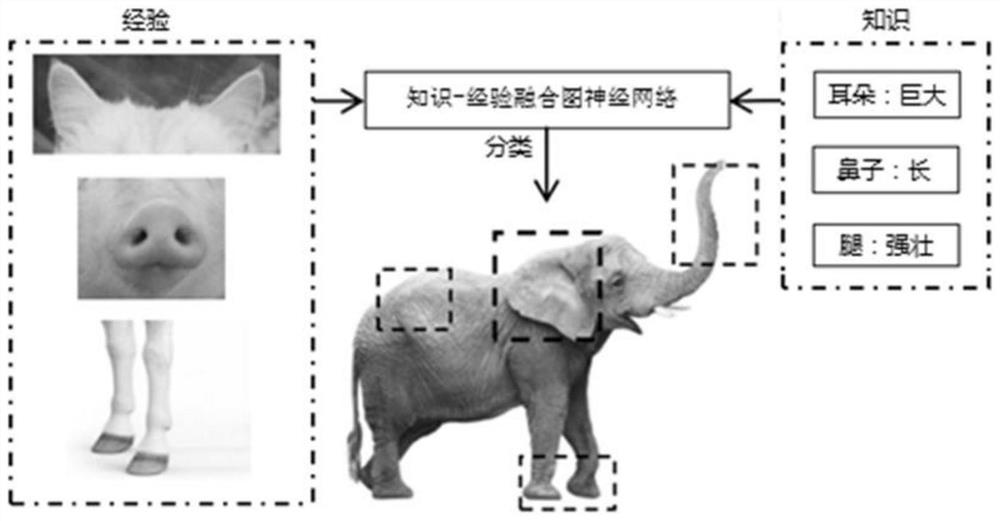
The invention belongs to the field of computer vision, particularly relates to a development method and system of a small sample classification model based on a graph convolutional neural network, andaims to solve the problems that an existing model is poor in performance and needs a large number of training samples with labels when applied to a new task. The method comprises the steps of extracting a knowledge graph formed by an undirected graph, and obtaining knowledge information related to a task; extracting experience information of the original model in the training process of the old task; fusing the knowledge information and the empirical information to form a new fusion graph; and obtaining a new task-oriented cognitive developed classification model by establishing a relationship between a new task category and an old task category and carrying out model training. According to the method, in the task migration process, a new task can achieve rapid and accurate visual migration without providing a large number of samples with labels, the utilization rate of the model is greatly increased, the cost of training the model is reduced, and the time of training the model is shortened.
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI
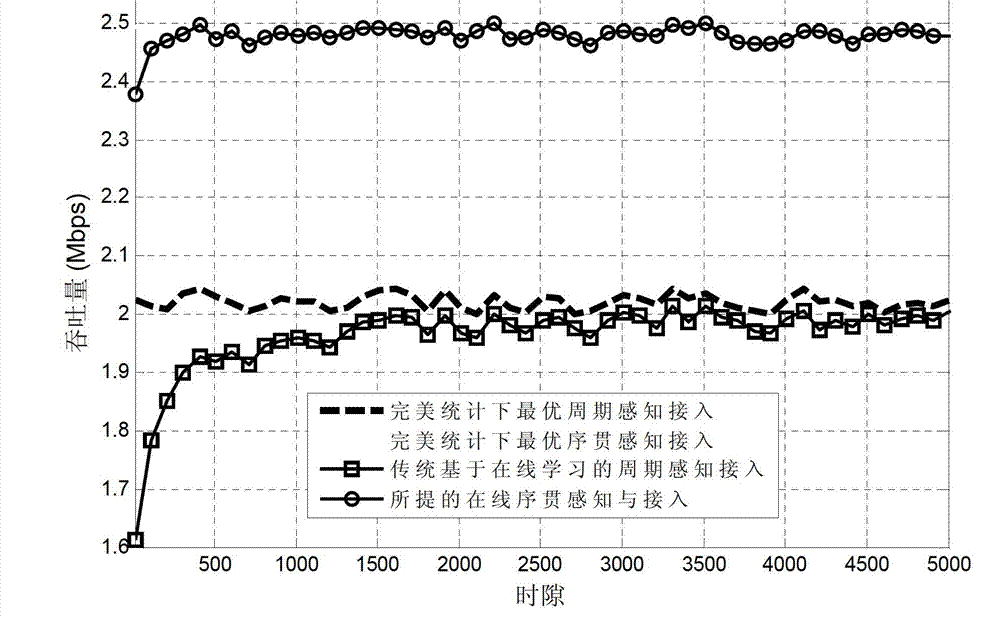
Epsilon-greed based online sequential perceiving and opportunity accessing method
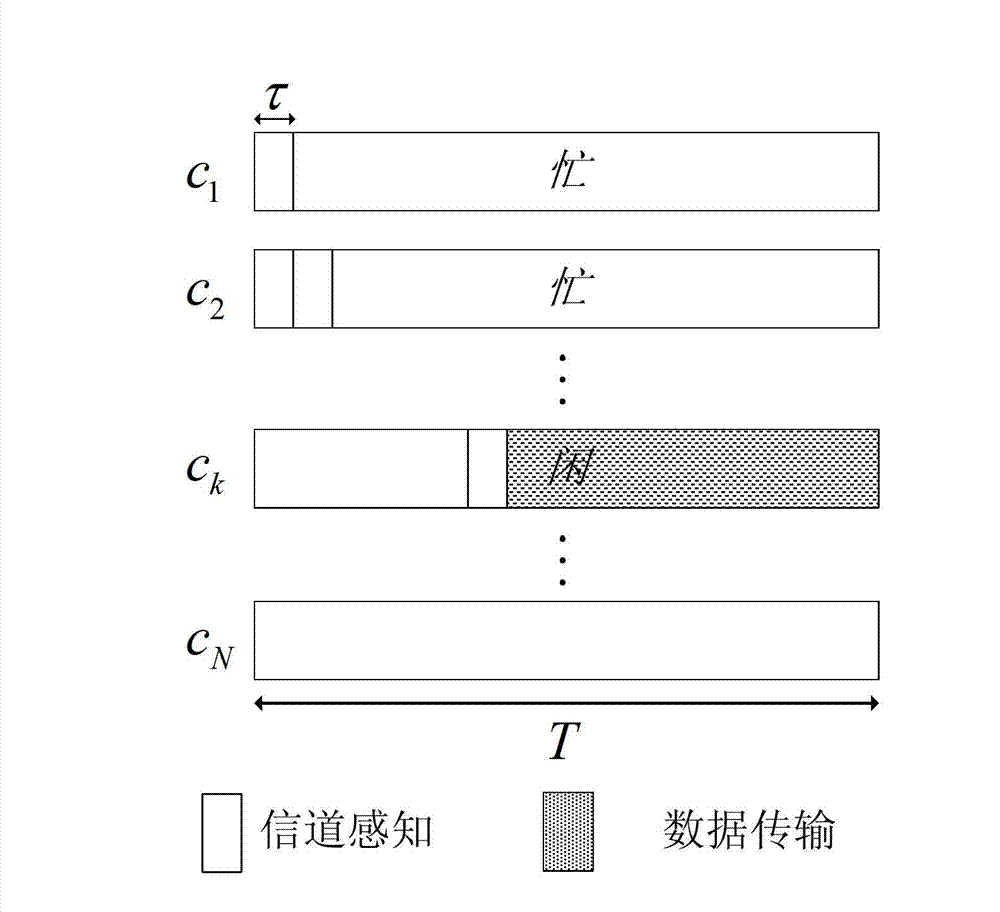
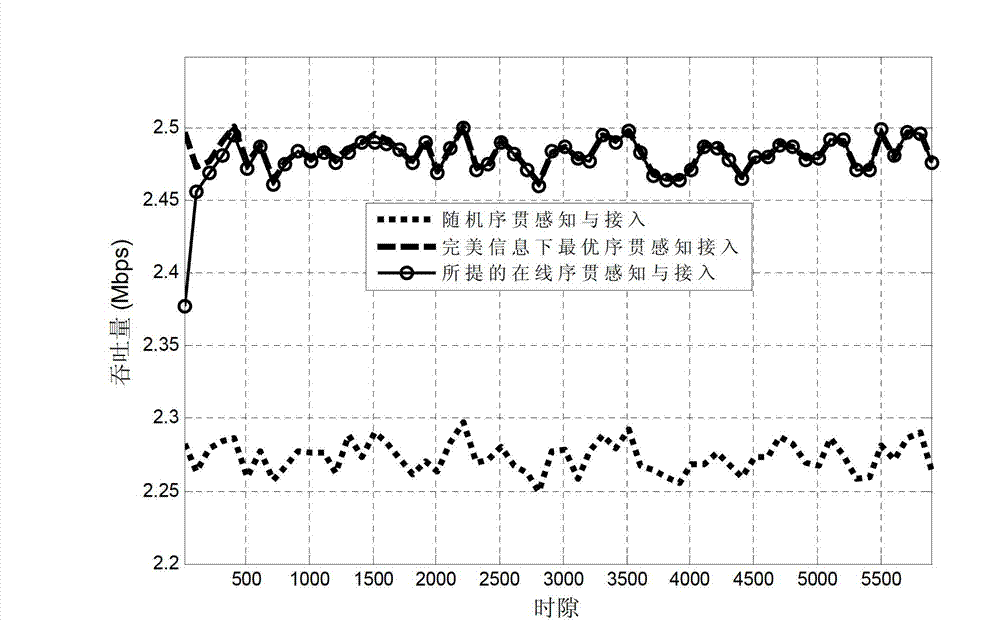
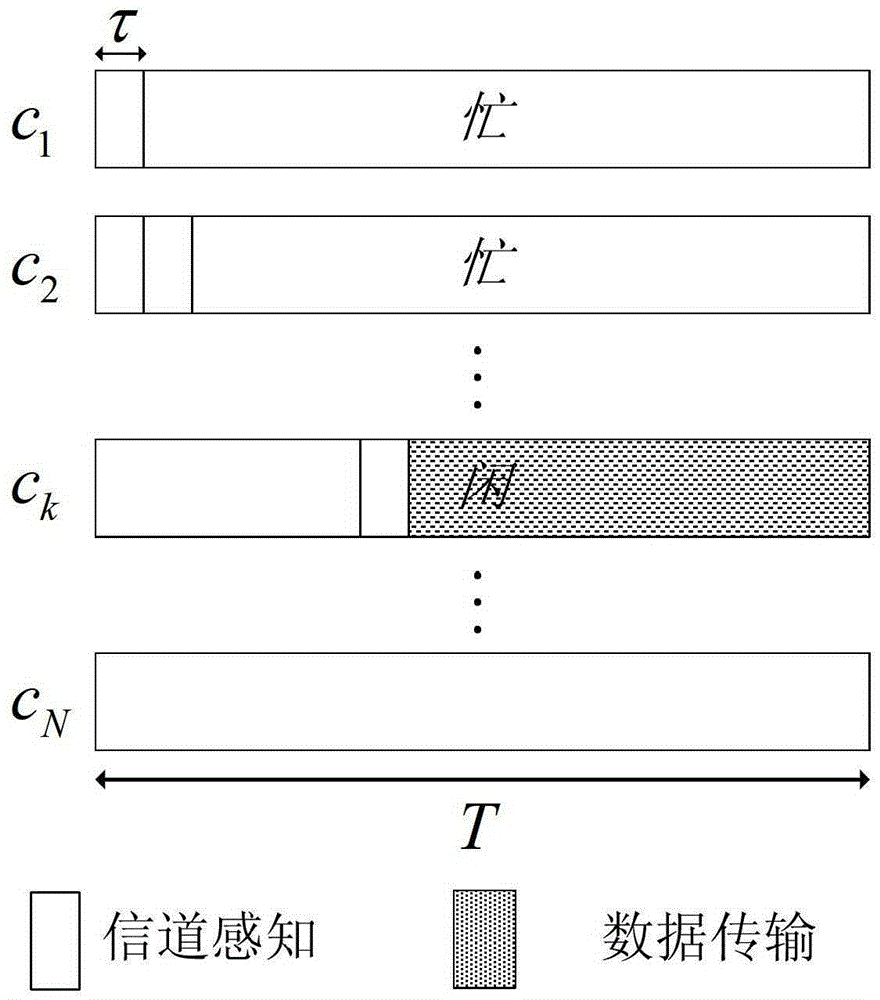
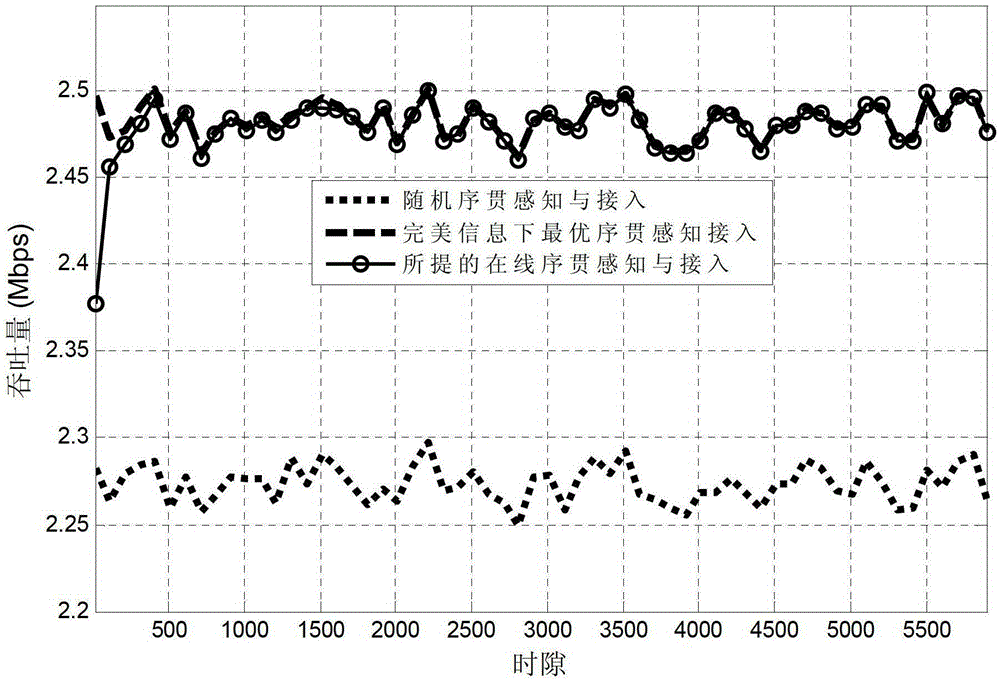
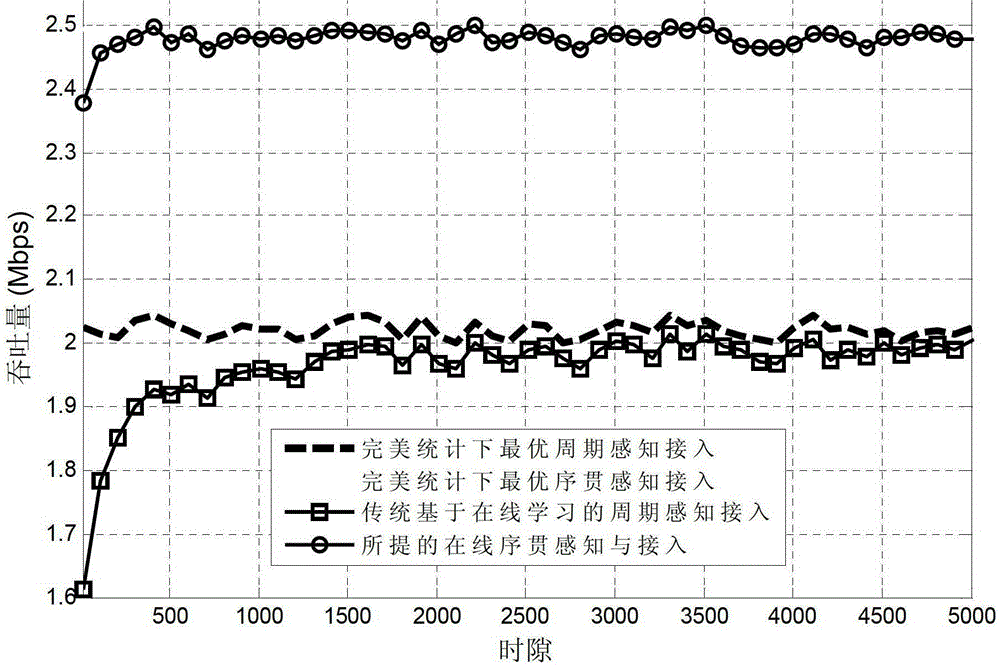
ActiveCN103179675AMaximize long-term cumulative throughput gainsIncrease the speed of learningWireless communicationDecision takingOnline learning
Disclosed is an epsilon-greed based online sequential perceiving and opportunity accessing method. In each time slot, users perceive channels sequentially and get access opportunistically to realize transmission. The method includes a step of initializing relative parameters and making access decisions based on online learning in each time slot, and has capabilities of learning environments actively and adapting to dynamic changes of environments. In addition, the method is an online decision implementing method, and the next decision is adjusted in real time according to each decision and feedback by systems, so that long-term accumulated throughput gain of the systems is maximized.
Owner:COMM ENG COLLEGE SCI & ENGINEEIRNG UNIV PLA
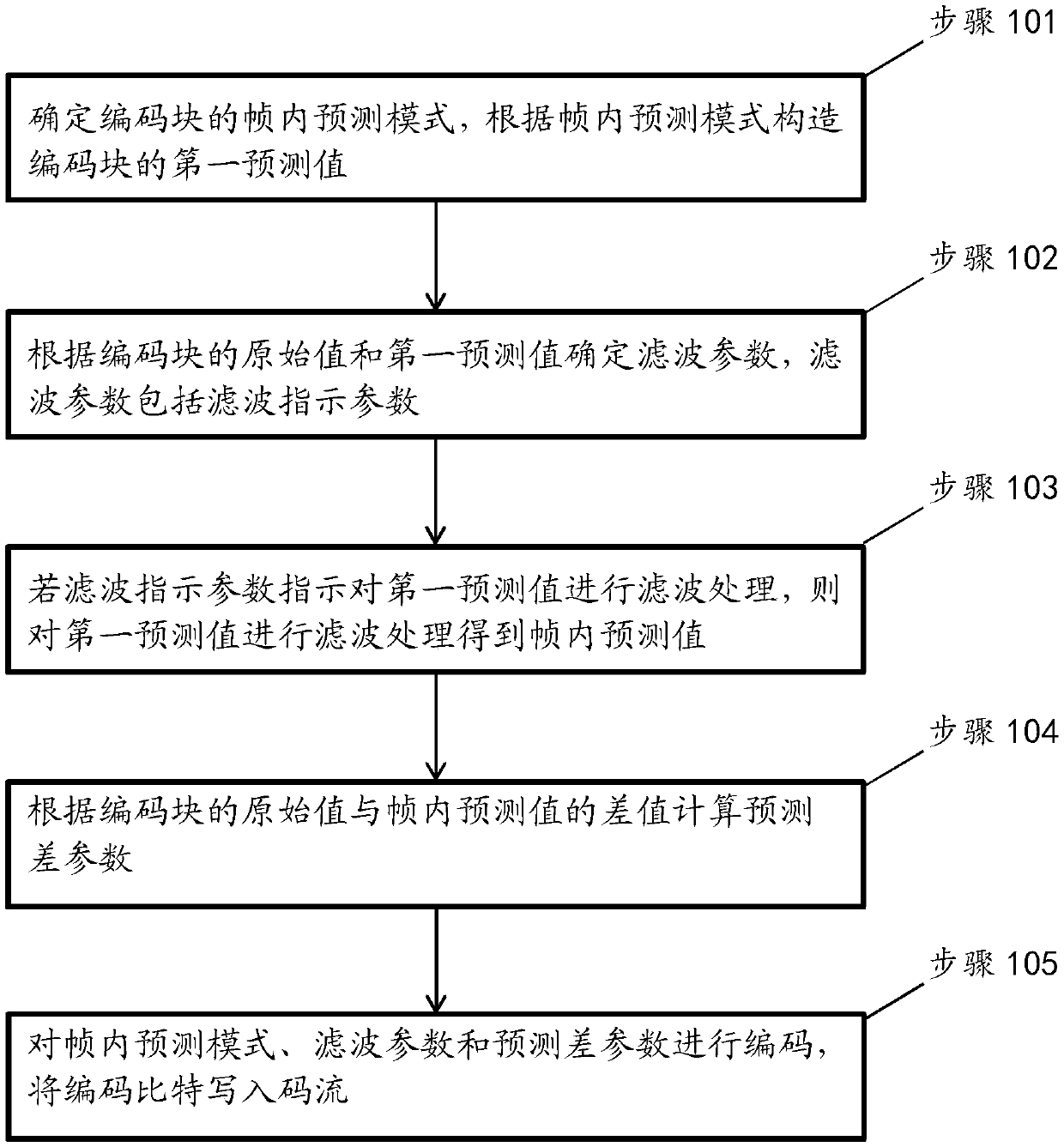
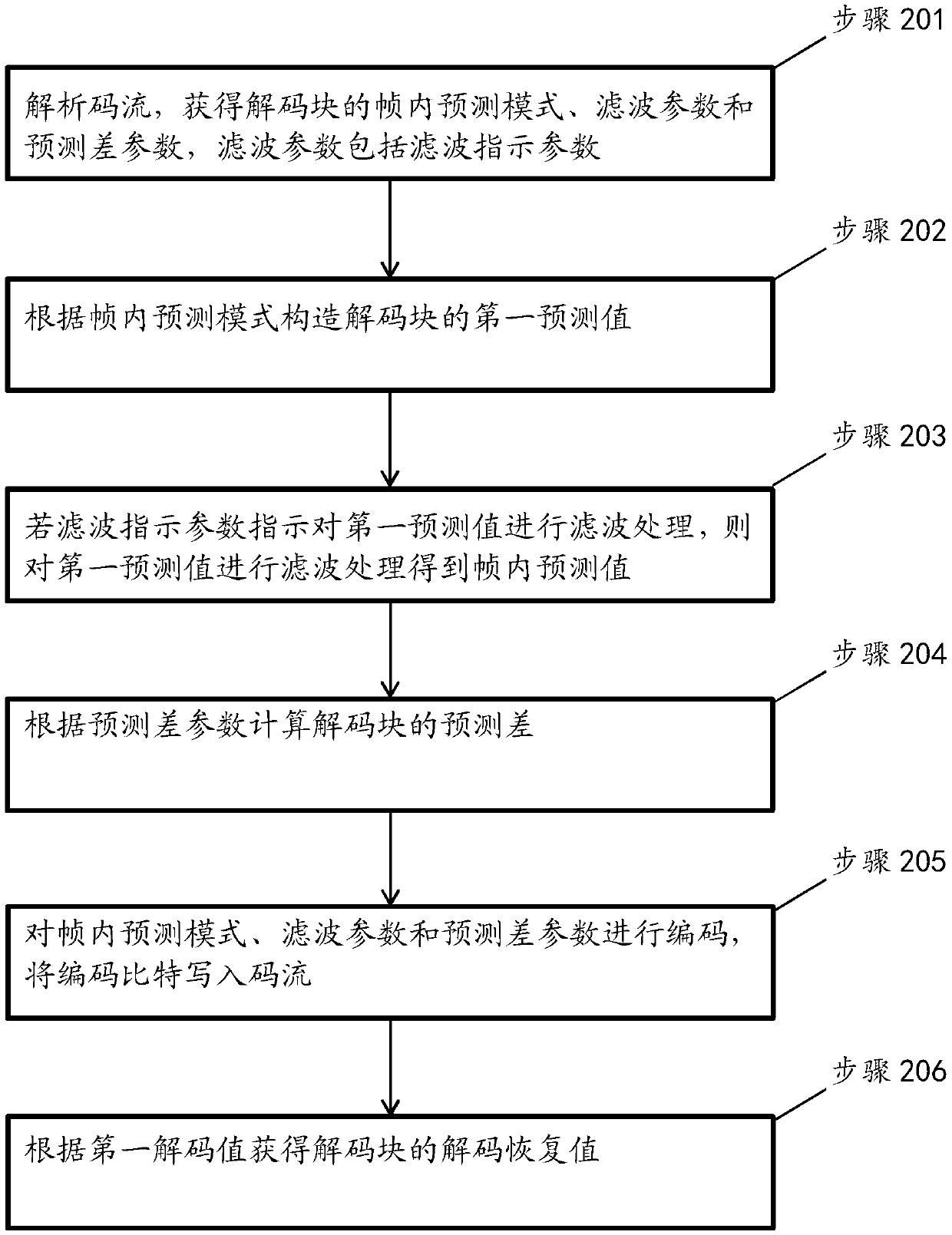
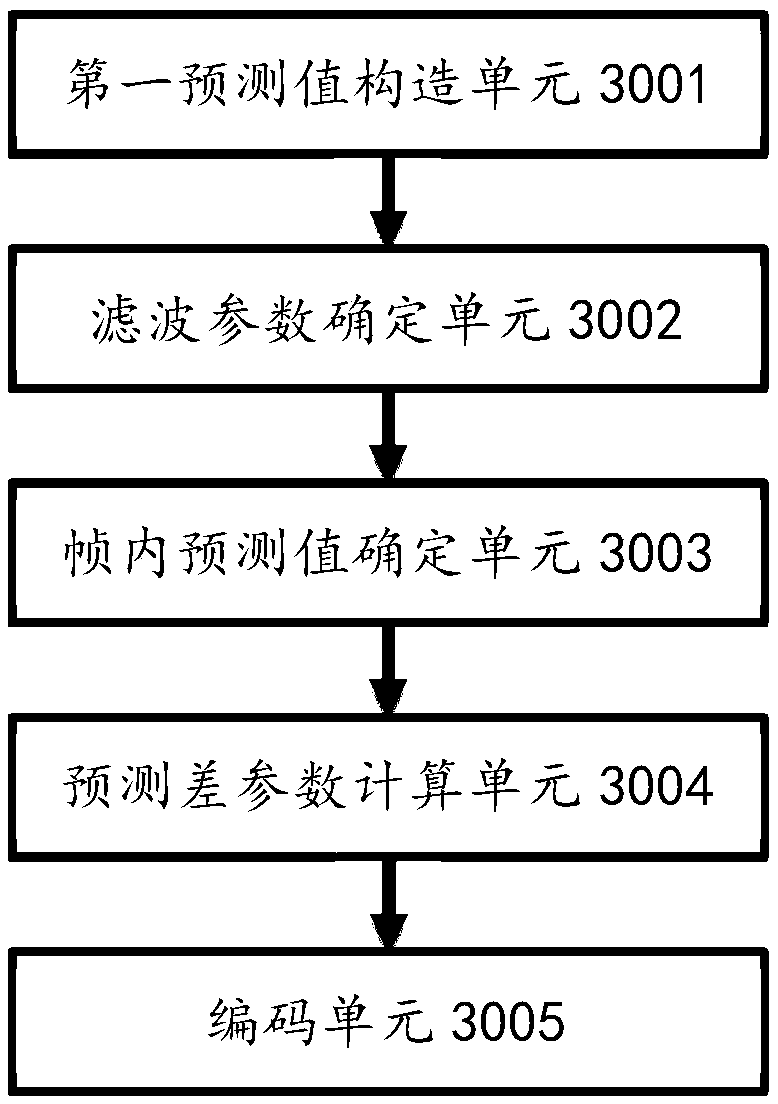
Image encoding method, image decoding method, encoder, decoder and storage medium
PendingCN110650349AReduce in quantityReduce overheadDigital video signal modificationCoding blockEncoder decoder
Provided in an embodiment of the present invention is an image encoding method, comprising: determining an intra prediction mode of an encoded block, and constructing a first prediction value of the encoded block according to the intra prediction mode; determining a filtering parameter according to the original value of the coding block and the first prediction value, wherein the filtering parameter comprises a filtering indication parameter; if the filtering indication parameter indicates to perform filtering processing on the first prediction value, performing filtering processing on the first prediction value to obtain an intra-frame prediction value; calculating a prediction difference parameter according to the difference between the original value of the coding block and the intra-frame prediction value; and encoding the intra-frame prediction mode, the filtering parameter and the prediction difference parameter, and writing encoding bits into a code stream. The invention furtherprovides an image decoding method, an encoder, a decoder and a computer storage medium.
Owner:ZTE CORP
Monitorable privacy communication method based on secret sharing scheme
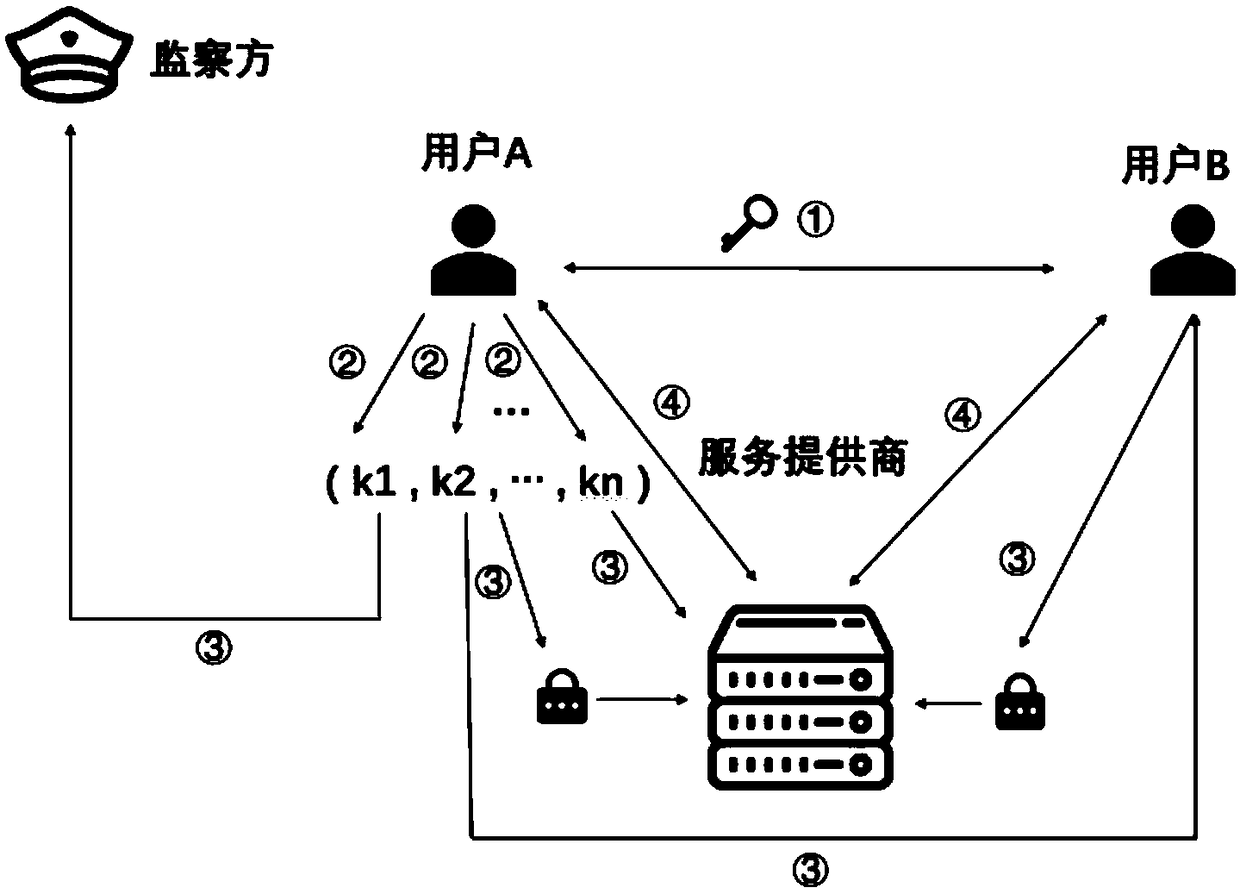
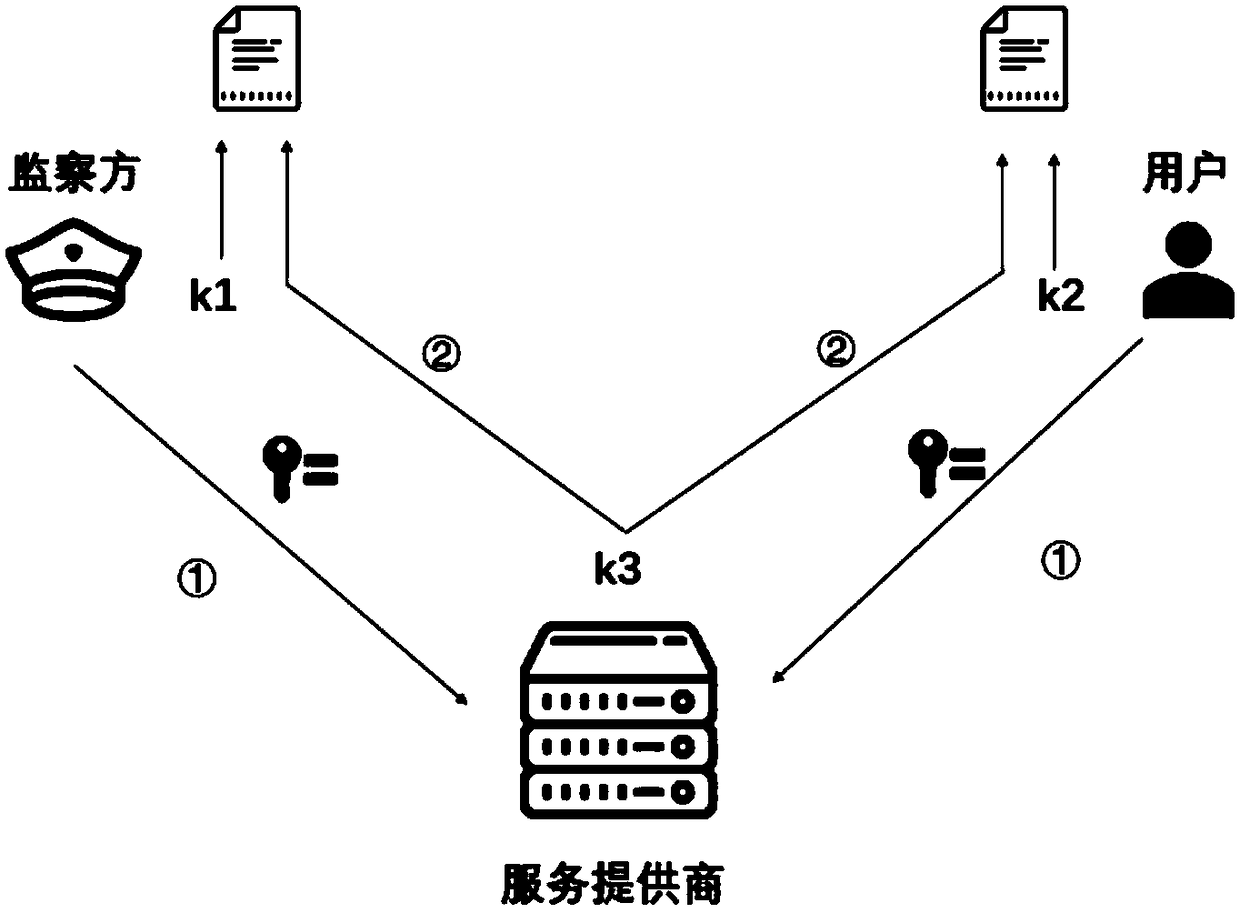
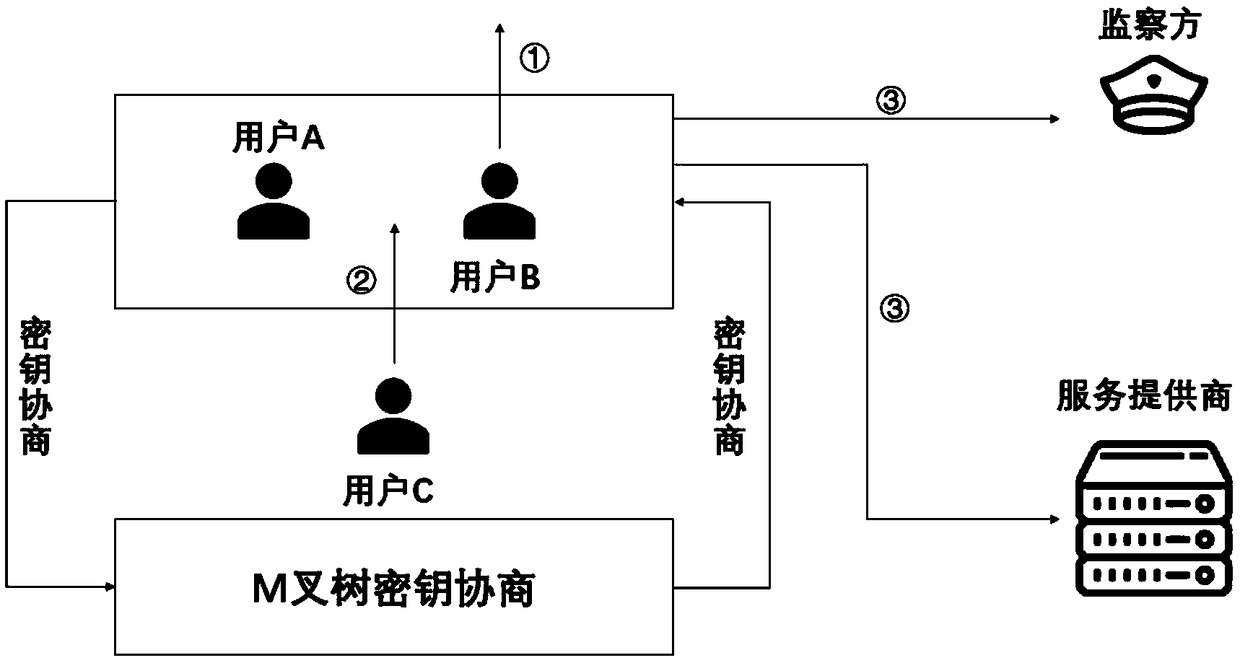
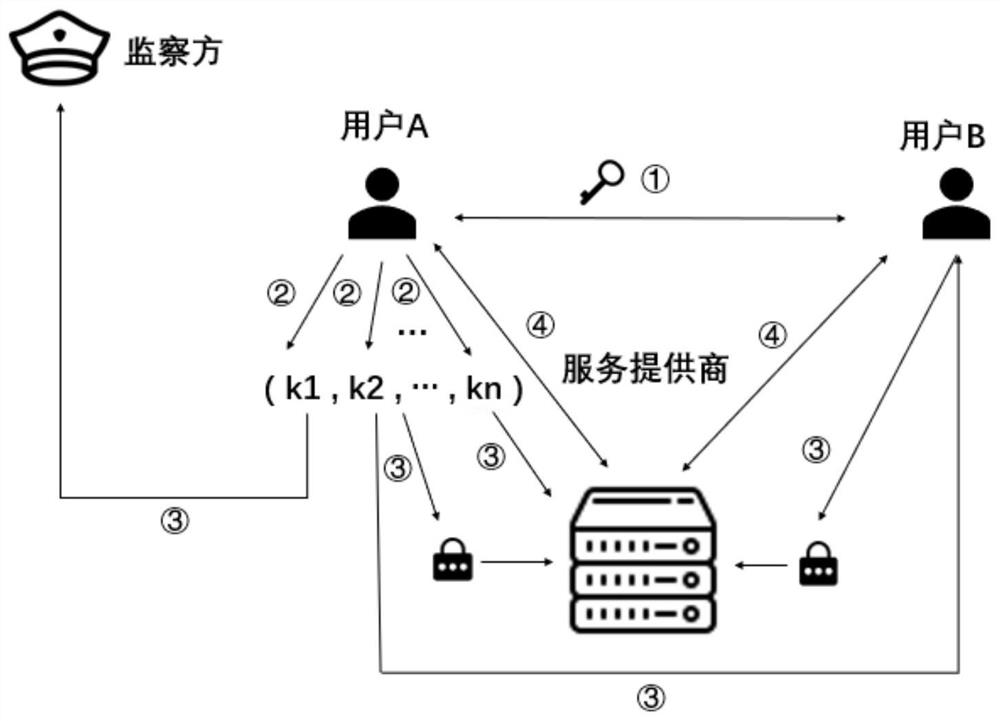
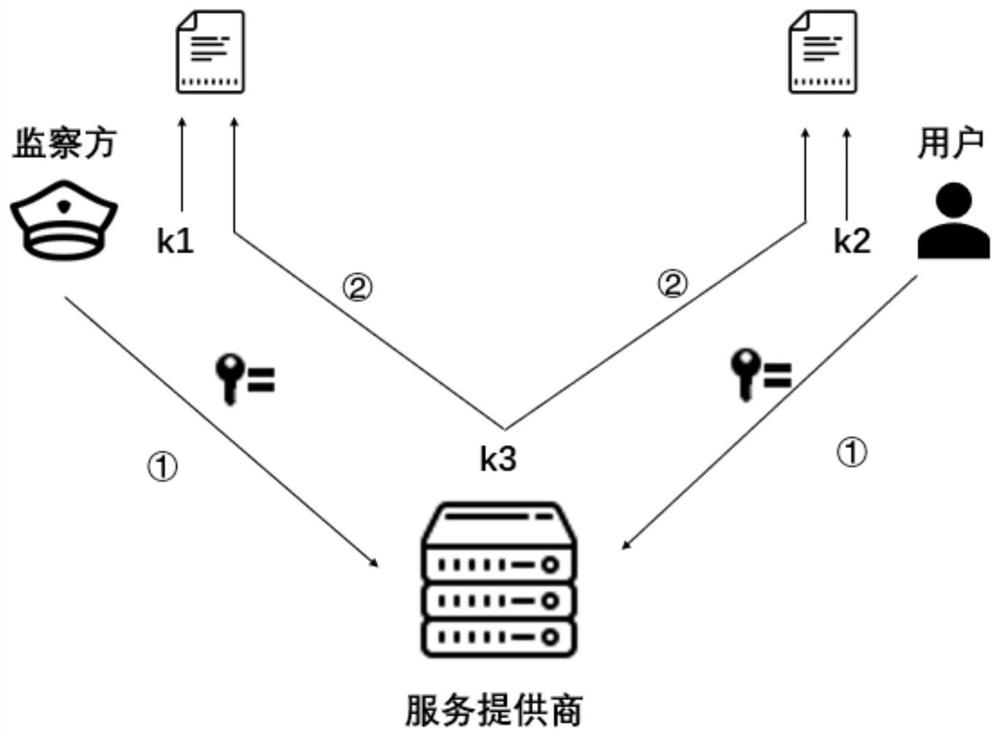
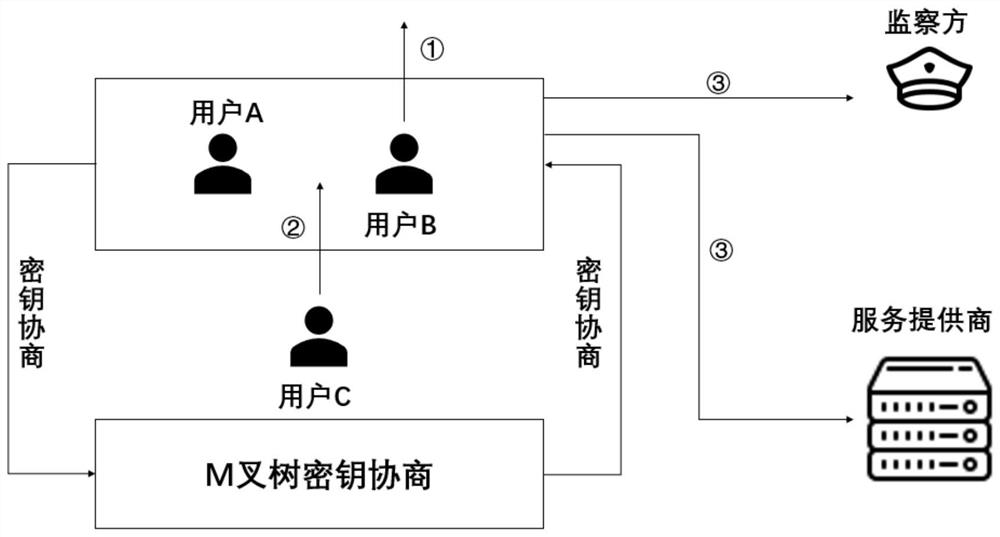
ActiveCN109495248ARealize functionGuaranteed private communicationsKey distribution for secure communicationData switching networksInternet privacySession key
The invention discloses a monitorable privacy communication method based on a secret sharing scheme. The privacy communication method comprises a user side, a service provider, and an monitor side. The user side comprises a sender and a receiver. Point-to-point communication or many-to-many communication between the sender and the receiver is adopted. A key agreement is performed between the sender and the receiver through a DH protocol. After the key agreement is completed, a session key formed is divided according to the number of the sender, the receiver, the service provider, and the monitor side, and the divided key is assigned to the sender, the receiver, the service provider, and the monitor side. Then, a group member encrypts the received divided key. The service provider receivesthe encrypted key and the assigned divided key. The monitor side receives the assigned divided key. According to the monitorable privacy communication method based on a secret sharing scheme, the contradiction between the privacy communication of users and the content monitoring from the service provider in the prior art can be solved; privacy communication of users can be protected to the greatest extent; and point-to-point and many-to-many monitorable privacy communication can be achieved.
Owner:曹鸣佩
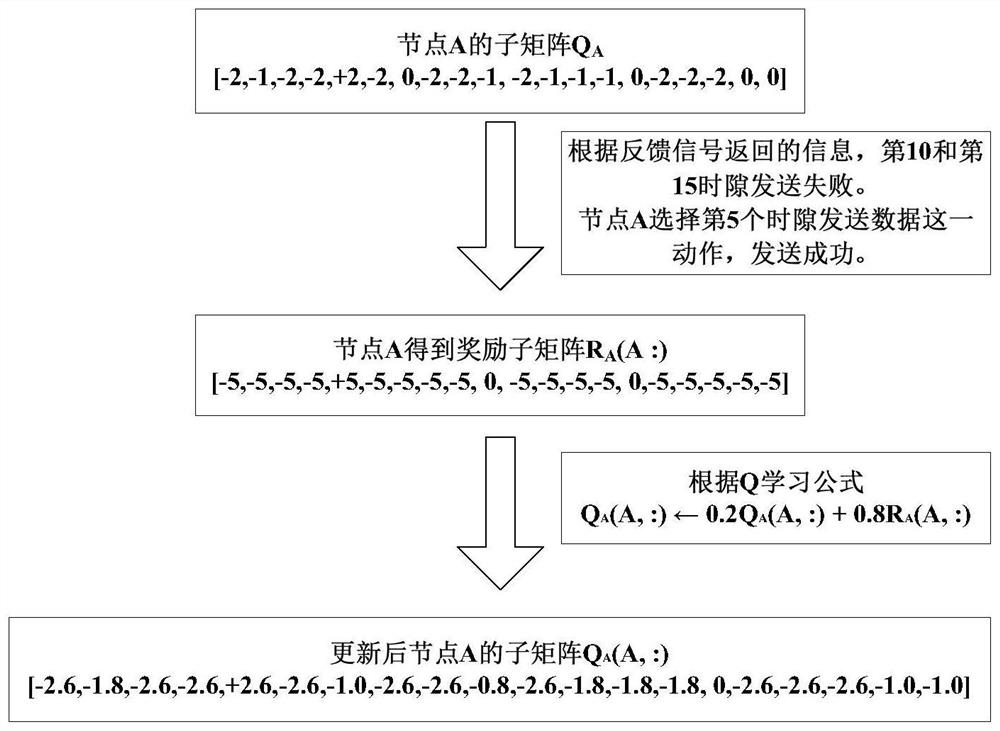
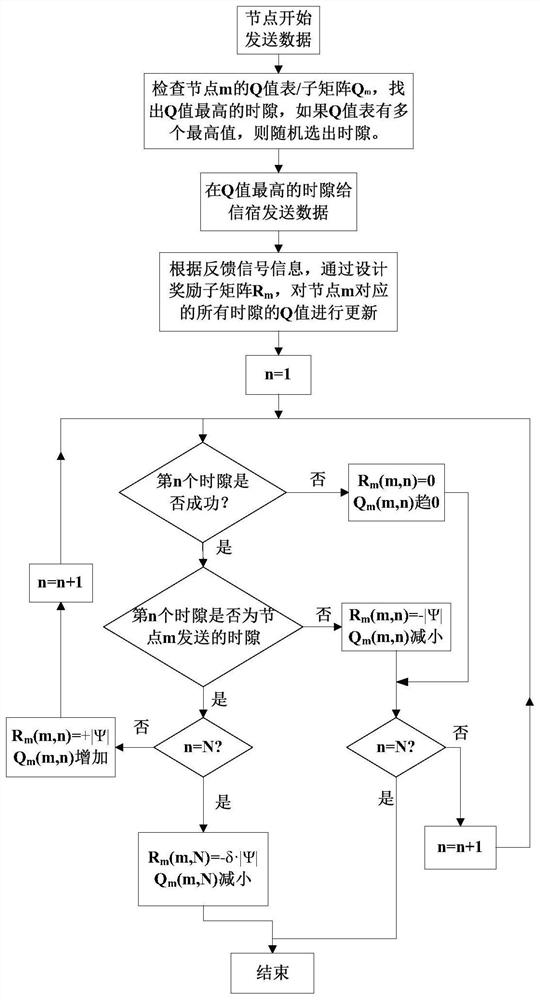
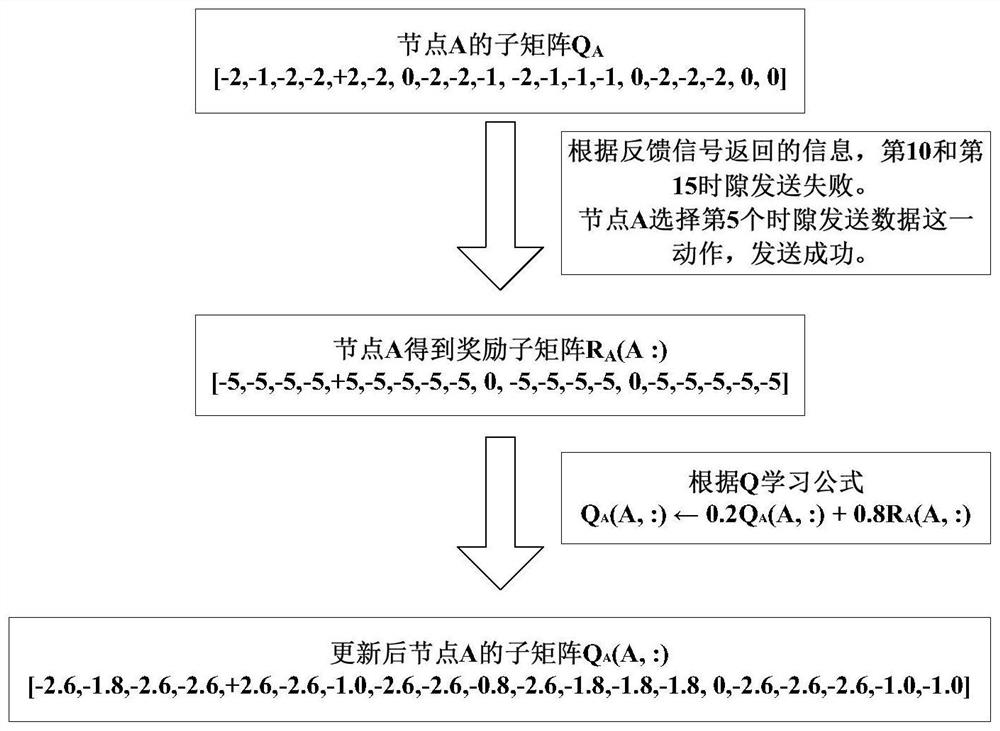
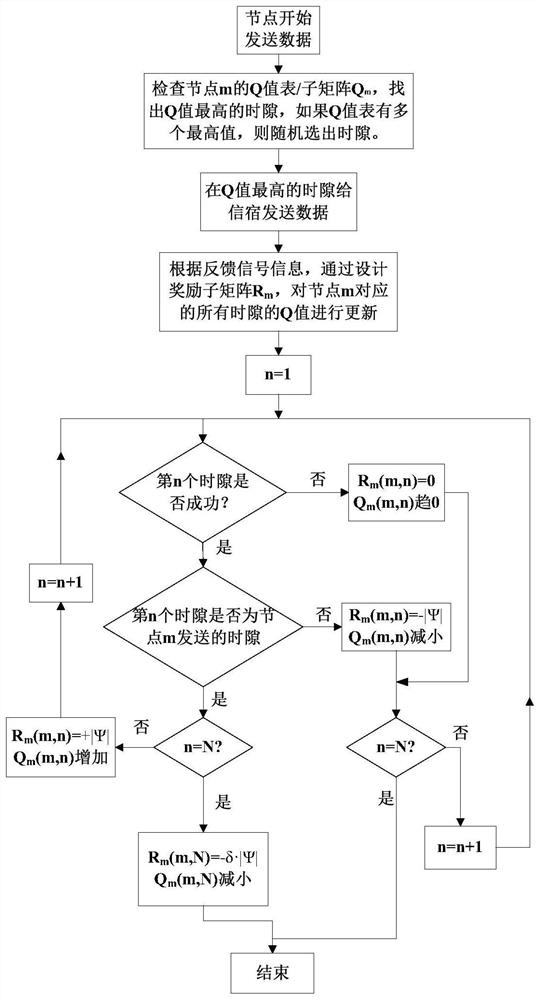
Q learning-based medium access control method for underwater acoustic network with variable number of nodes
ActiveCN113691391AImprove network throughputImprove throughputError prevention/detection by using return channelSonic/ultrasonic/infrasonic transmissionData transmissionUnderwater acoustics
The invention discloses a node number variable underwater acoustic network medium access control method based on Q learning, and relates to an underwater acoustic network. The method comprises the following steps: dividing a transmission process of collecting data sensed by underwater acoustic sensor nodes by aggregation nodes into a plurality of time slots, applying a Q learning algorithm, combining feedback signals of the aggregation nodes and the quantity change condition of the sensor nodes, reasonably setting an award mechanism, and carrying out integral award sub-matrix design on a whole line (namely, a sub-matrix) of a Q matrix, not updating the Q matrix element by element, and reasonably distributing the time slot to each sensor node, so the data is not influenced by other sensor nodes in the transmission process, and the data collection conflict of the aggregation node is avoided. The method provided by the invention has the characteristics of high learning speed, high throughput, low energy consumption and strong anti-interference capability, can solve the problem of time slot redundancy when nodes are reduced or the problem of insufficient time slot when nodes are increased due to node death or position drift, and ensures the success rate of underwater acoustic data transmission and high throughput of an underwater acoustic network.
Owner:XIAMEN UNIV +1
A publicly verifiable cloud data possession verification method
ActiveCN103414690BImplement presence/integrity verificationImplement remote storage service verification fairnessTransmissionComputation complexityRelevant information
A publicly-verifiable cloud data possession checking method is provided. The method includes the three stages of initialization, user challenge-response verification and TTP arbitration; the three stages comprise the following ten steps that: step 1, data segmentation [F->F'] is performed; step 2, verification tag generation [(SK, F)-> HVT] is performed; step 3, data and tag information upload [(F, HVT)->S] is performed; step 4, secret parameters are recorded to a TTP (trusted third party); step 5, the TTP verifies recorded parameters; step 6, [chal] is initiated by a user, and the chal and the verification information of the chal are handed over to the TTP so as to be record; step 7, a server makes a response; step 8, [(R, sk)->(' success', 'failure')] is verified; step 9, relevant information acquisition is verified; and step 10, the trusted third party performs verification publicly. With the publicly-verifiable cloud data possession checking method of the invention adopted, the user can verify the existence and integrity of data in a cloud storage server. The publicly-verifiable cloud data possessions checking method is advantageous in no limitation on the number of user authentication times as well as small storage capacity and low computational complexity of a client, and has great practical value and broad application prospect.
Owner:BEIHANG UNIV
Local differential number dynamic BP decoding method for LDPC code
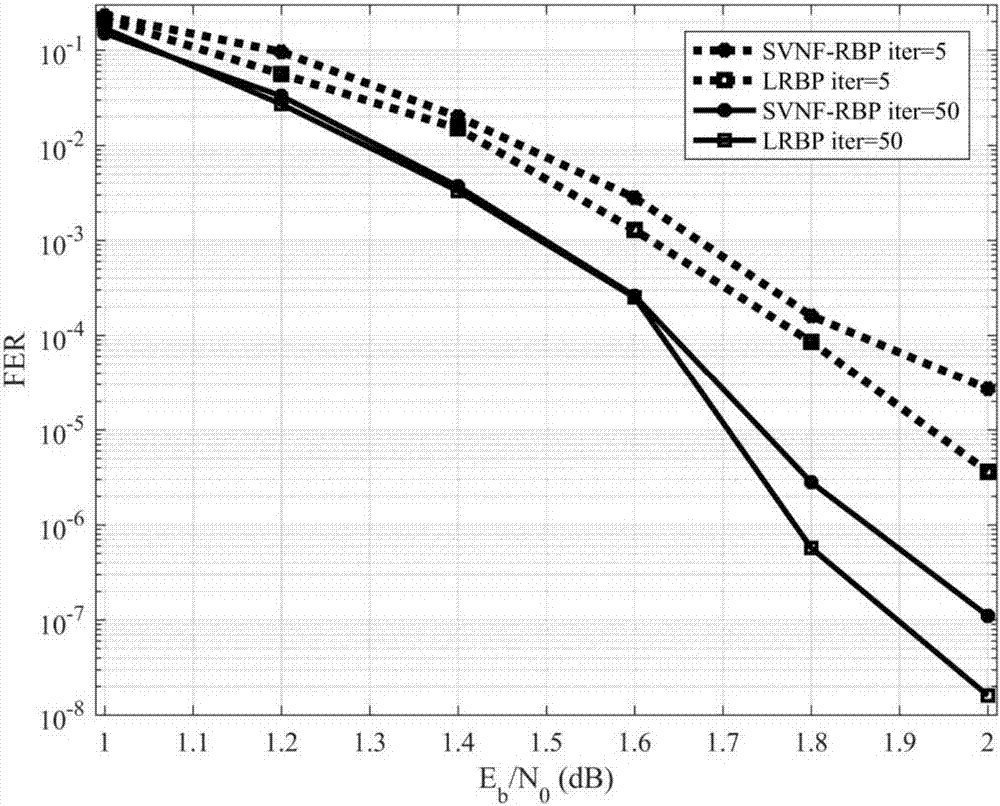
ActiveCN107241104AReduce complexityQuick flipError correction/detection using multiple parity bitsCode conversionDecoding methodsSignal-to-noise ratio (imaging)
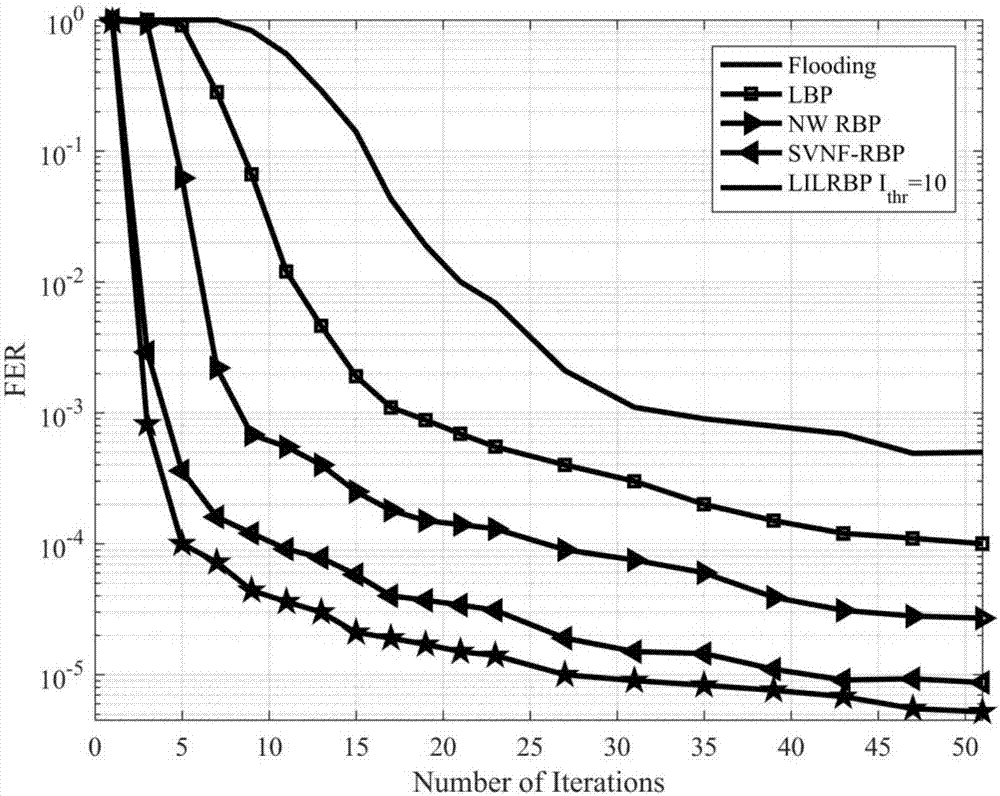
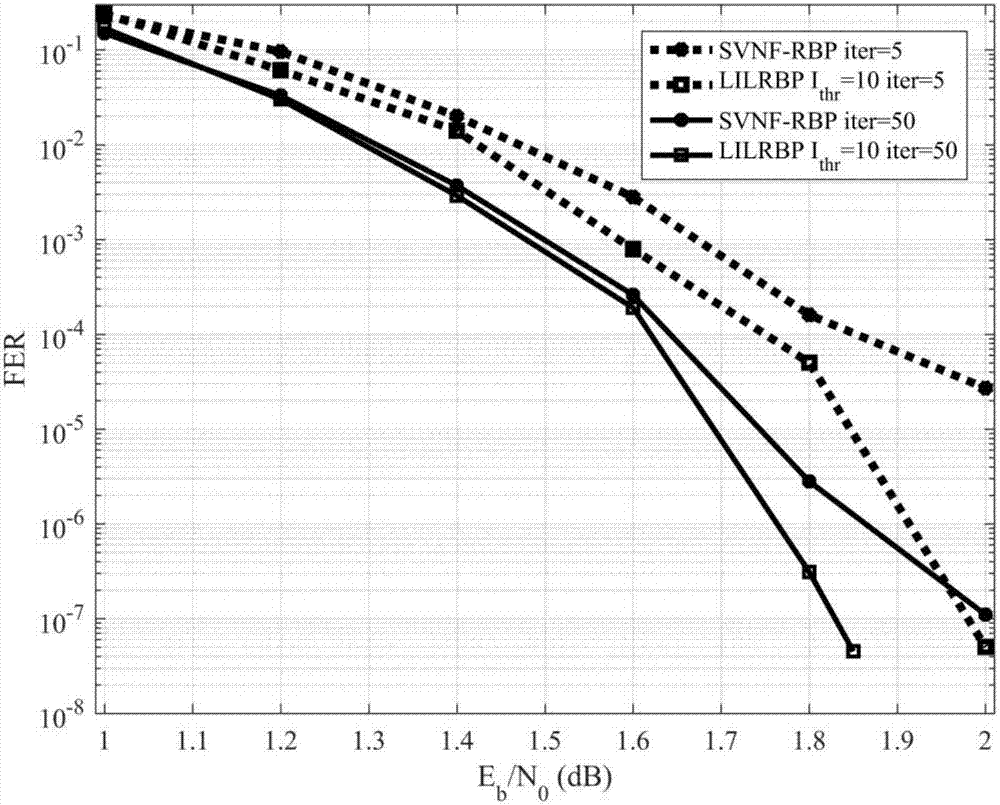
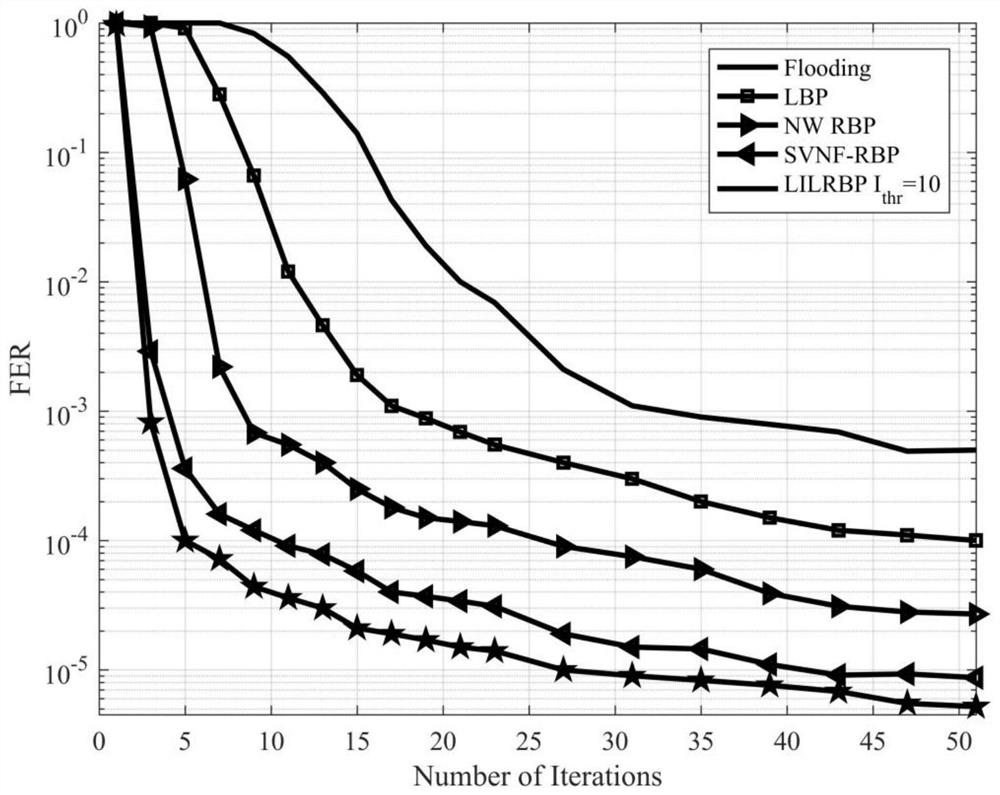
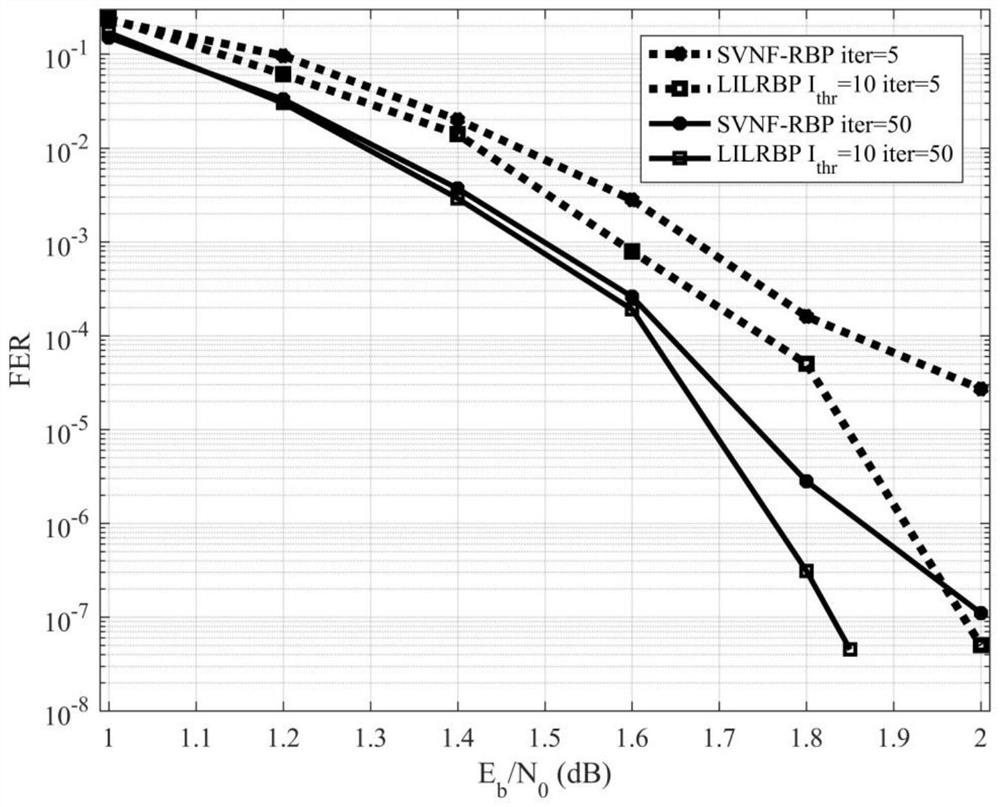
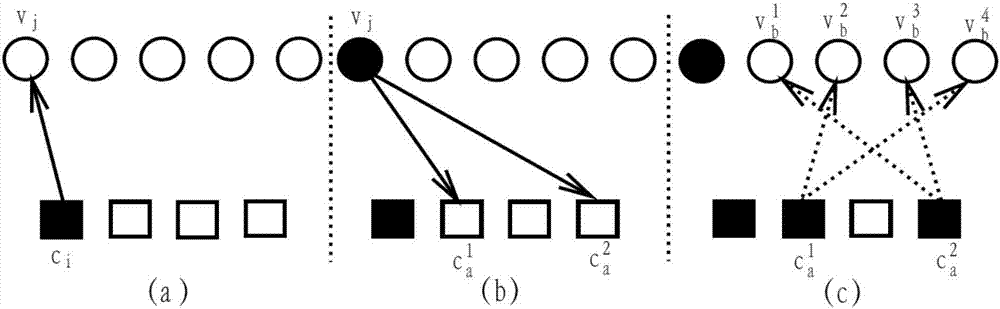
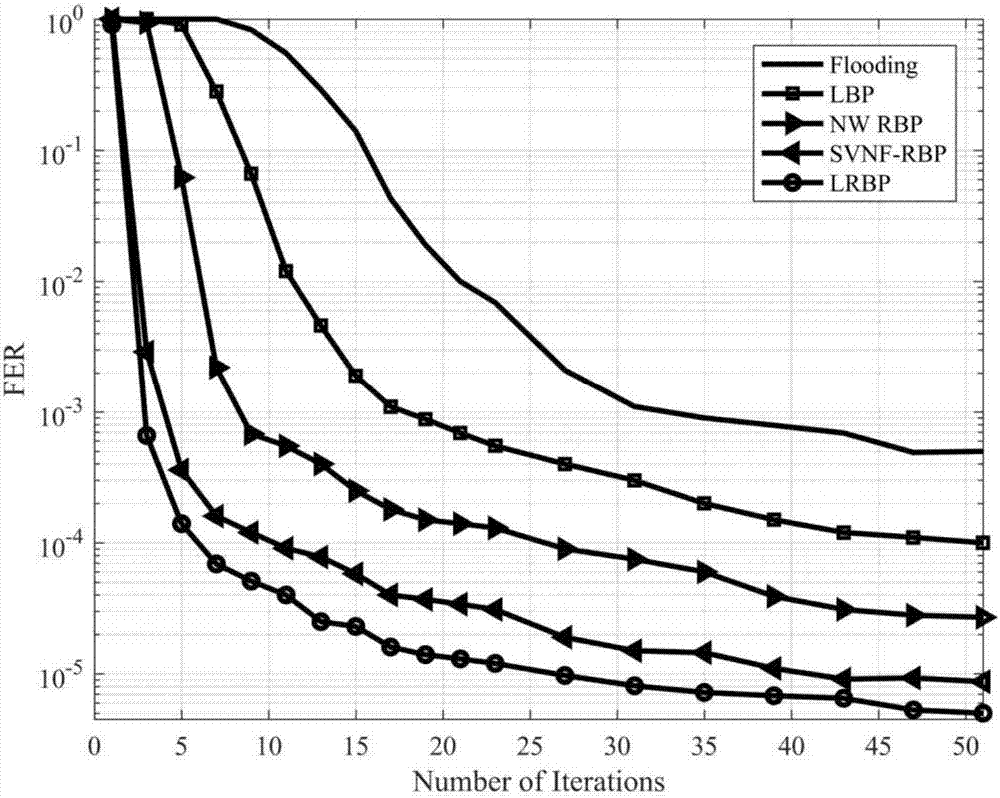
The invention provides a local dynamic update decoding method (LILRBP) based on an LDPC code aiming at a dynamic BP decoding algorithm of the LDPC code. According to the method, the local residual based message update is adopted, the BP decoding performance including a small number of iterations under high signal-to-noise ratio can be effectively improved, and other dynamic BP decoding algorithms can be surpassed. Different from the previous dynamic BP decoding methods, the LILRBP method considers that residuals have time validity, and therefore, the LILRBP method only focuses on the recent part of the residuals, sets an iteration times threshold, then filters the local residuals according to the change of likelihood ratio symbols of a correlation variable node below the threshold, and then determines the next message to be updated according to the filtered residual; and above the threshold, the next message to be updated is directly determined based on the local residual. The advantages of the method are as follows: the message update can always be performed by using the latest messages, the role of accelerating the algorithm convergence speed can be played, and the local residuals are re-filtered below the threshold, the algorithm convergence can be further accelerated, the convergence of the algorithm can be influenced by the combination of the two operations, the convergence speed of the BP decoding algorithm can be effectively improved, and the purpose of improving the decoding performance can be achieved.
Owner:GUANGDONG UNIV OF TECH
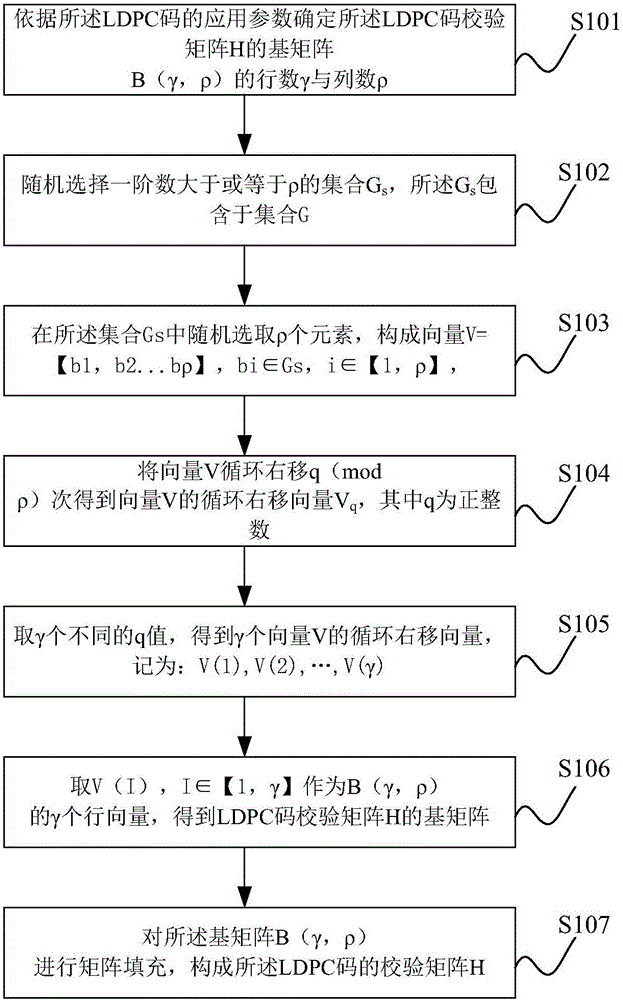
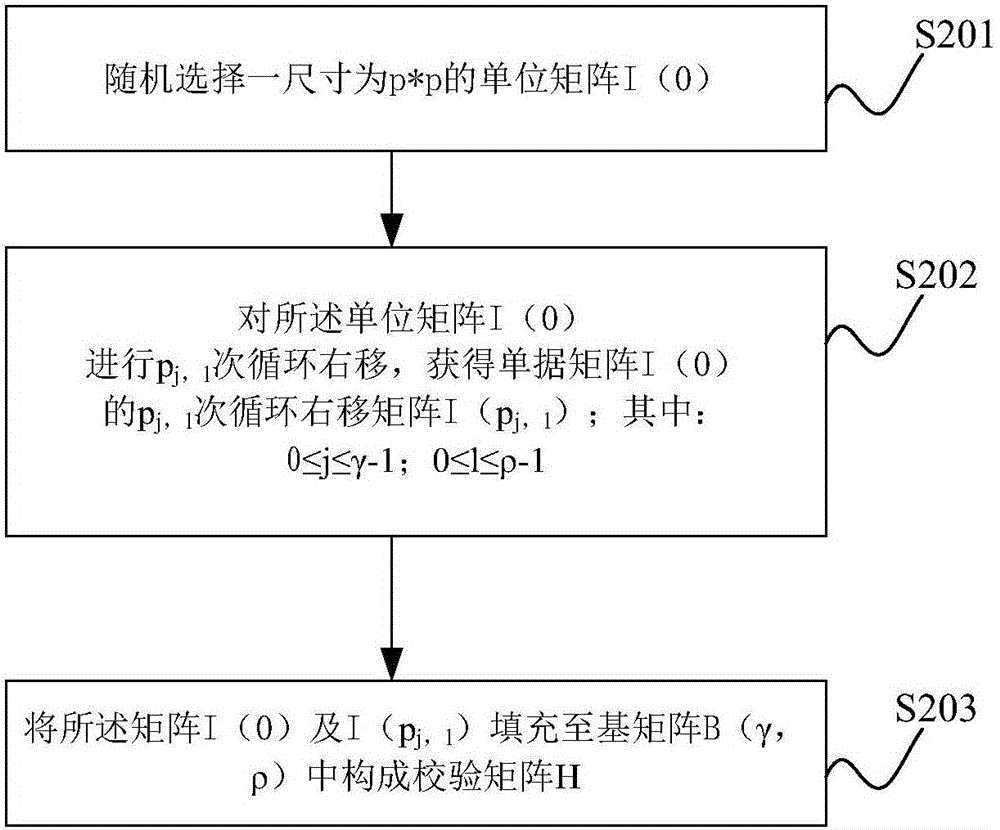
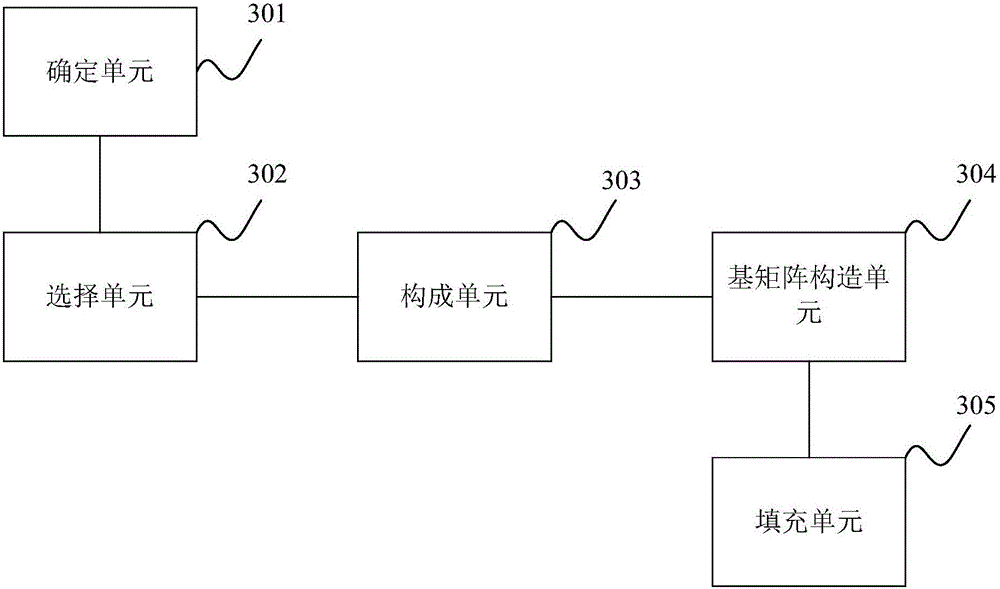
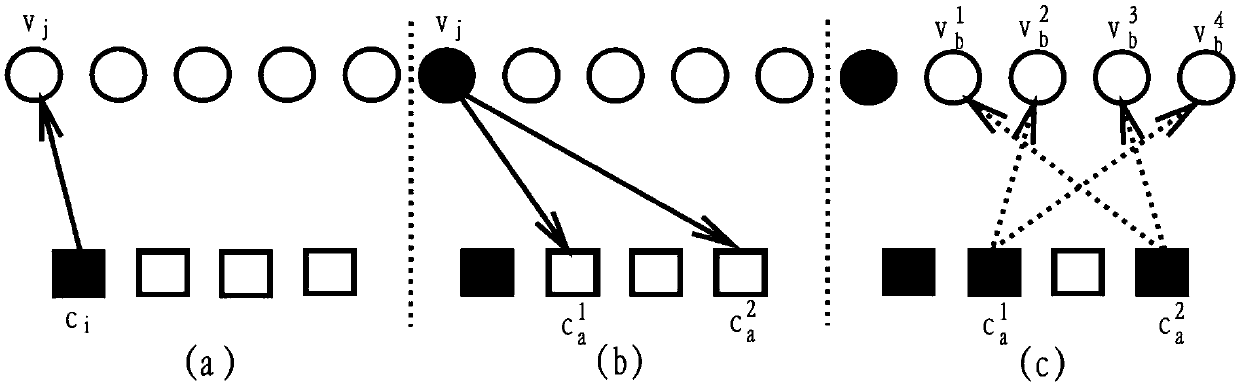
Construction method for quasi-cyclic low density parity check (LDPC) code check matrix
ActiveCN102386933BImprove performanceReduce storage complexityError correction/detection using multiple parity bitsTheoretical computer scienceLow-density parity-check code
The invention relates to a construction method for a quasi-cyclic low density parity check (LDPC) code check matrix. The construction method for the quasi-cyclic LDPC code check matrix comprises the following steps of: determining a line parameter J and a column parameter L of a basis matrix of the check matrix to be designed; after the line and column parameters are determined, traversing all columns by the line, and for the given position of the jth line and the lth column of the basis matrix, sequentially obtaining terms of each Hanoi tower array according to the definitions of the Hanoi tower array that f(1)=1 if n is 1 and that f(n+1)=s*f(n)+1 if n is more than 1; obtaining a circulant permutation matrix offset value pj,l according to a formula pj,l=f(j+1)+j, adding a digital value jof a corresponding line to each f(j+1) value obtained by the second step to obtain a circulant permutation matrix offset value pi,j and arranging the pi,j at the position of the jth line and the lth column of the basis matrix to be constructed; and constructing the basis matrix to be designed by using all the pj,l values. By the method, the performance of a quasi-cyclic LDPC code is improved, and simultaneously storage complexity is decreased.
Owner:上海新微科技发展有限公司
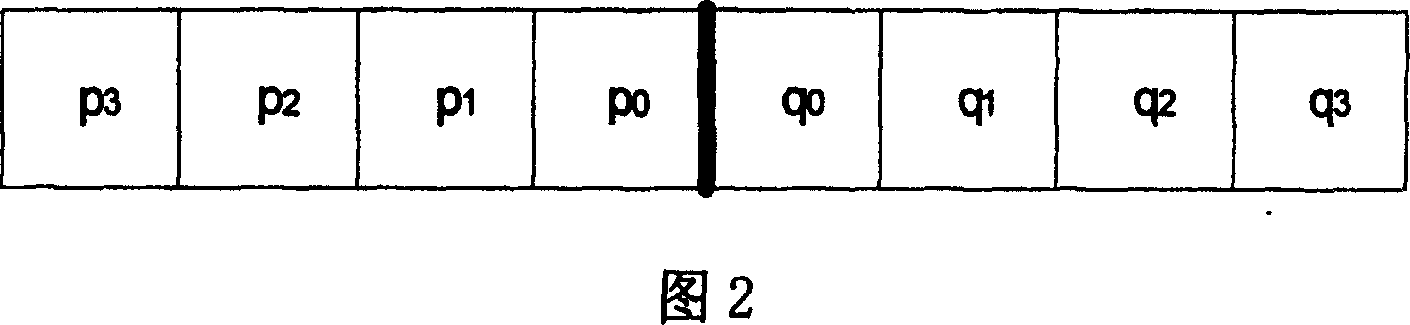
Method and system for reordering and inversely reordering predicted residual blocks
InactiveCN101895757AReduce storage complexityTelevision systemsDigital video signal modificationResidual BlocksAmplitude distribution
The invention discloses a method and a system for reordering and inversely reordering predicted residual blocks. The method comprises that: according to the amplitude distribution of the predicted residual blocks obtained by statistics, methods for ordering the predicted residual blocks are set, and all possible methods for ordering the predicted residual are two or more than two; and according to the methods for ordering the residual blocks, residuals in the residual blocks are reordered before the residual blocks are converted. By reordering the residual sampling values in the residual blocks in a null field, statistical characteristics of residuals in different modes are approximately same, so the performance approximate to mode related transformation is realized by only using a small number of transformation functions, and the storage complexity of a coder decoder is simultaneously reduced.
Owner:PEKING UNIV
Method and device for qrasi-energy convervation change in vide frequency image cornpression
ActiveCN1589015AReduce computational complexityReduce storage complexityTelevision systemsDigital video signal modificationImage compressionImage code
This invention discloses a quasi-energy conservation and transformation method and the device used in video or image compact by applying two-dimension transformation of not accurate energy conservation, data of different positions adopt a same orthonormalization process to reduce computation complexity and storage complexity for a code / decode device, which is not only used in video or image code / decode field but also used in other signal processes.
Owner:XFUSION DIGITAL TECH CO LTD
Efficient duplicate removal auditing method for cloud storage data
PendingCN114666349AEnsure safetyIntegrity guaranteedKey distribution for secure communicationUser identity/authority verificationEngineeringBlind signature
The invention discloses a cloud storage data efficient deduplication auditing method, which belongs to the technical field of cloud storage, and comprises the following steps: S1, establishing a cloud storage system, generating parameters of the cloud storage system, and initializing various parameters of the cloud storage system; according to the method, the convergence key is encrypted by using the idea of blind signature and uploaded to the cloud server, the storage and management problems of the convergence key are solved, the data uploaded by the user is subjected to de-duplication operation by using file-level and file-block-level de-duplication modes, the de-duplication granularity is lower, and the de-duplication efficiency is improved. Meanwhile, a file management directory is introduced to manage contents of files and file blocks, convergence keys and legal users, and the efficiency of data deduplication label query is improved by using a Bloom filter.
Owner:XIDIAN UNIV
Coding method, coding apparatus, and communications apparatus
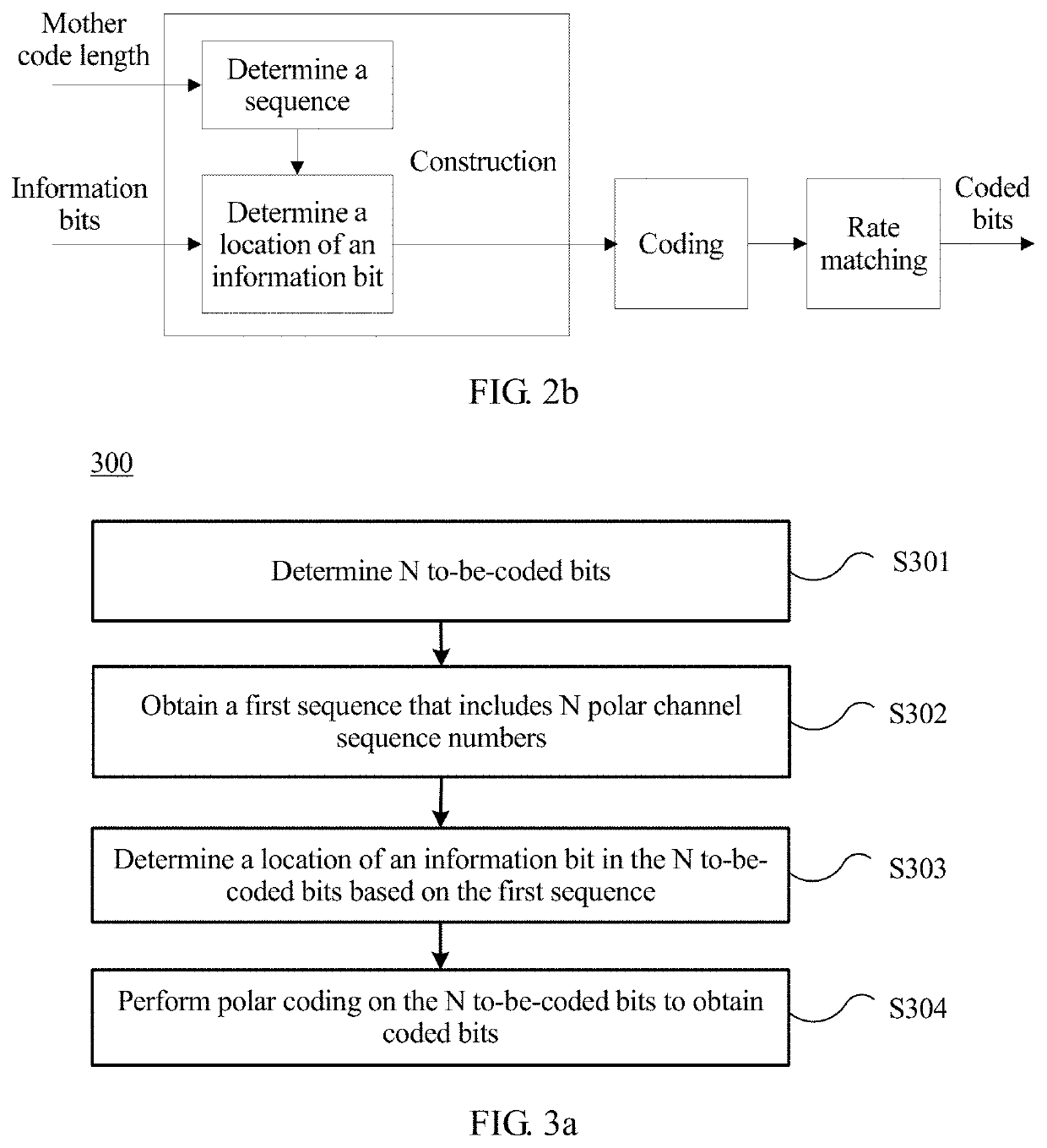
ActiveUS20190349220A1Reduce storage complexityImprove performance of polarError preventionCode conversionCommunication deviceComputer science
Embodiments can provide a coding method, a coding apparatus, and a communications apparatus. The method includes: determining N to-be-coded bits, where N is a positive integer; obtaining a first sequence that includes N polar channel sequence numbers; determining a location of an information bit in the N to-be-coded bits based on the first sequence; and performing polar coding on the N to-be-coded bits to obtain coded bits. The location of the information bit in the to-be-coded bits is determined based on the obtained first sequence that includes N polar channel sequence numbers, so that performance of a polar code can be improved.
Owner:HUAWEI TECH CO LTD
RC-LDPC code construction method based on matrix expansion and Fibonacci sequence
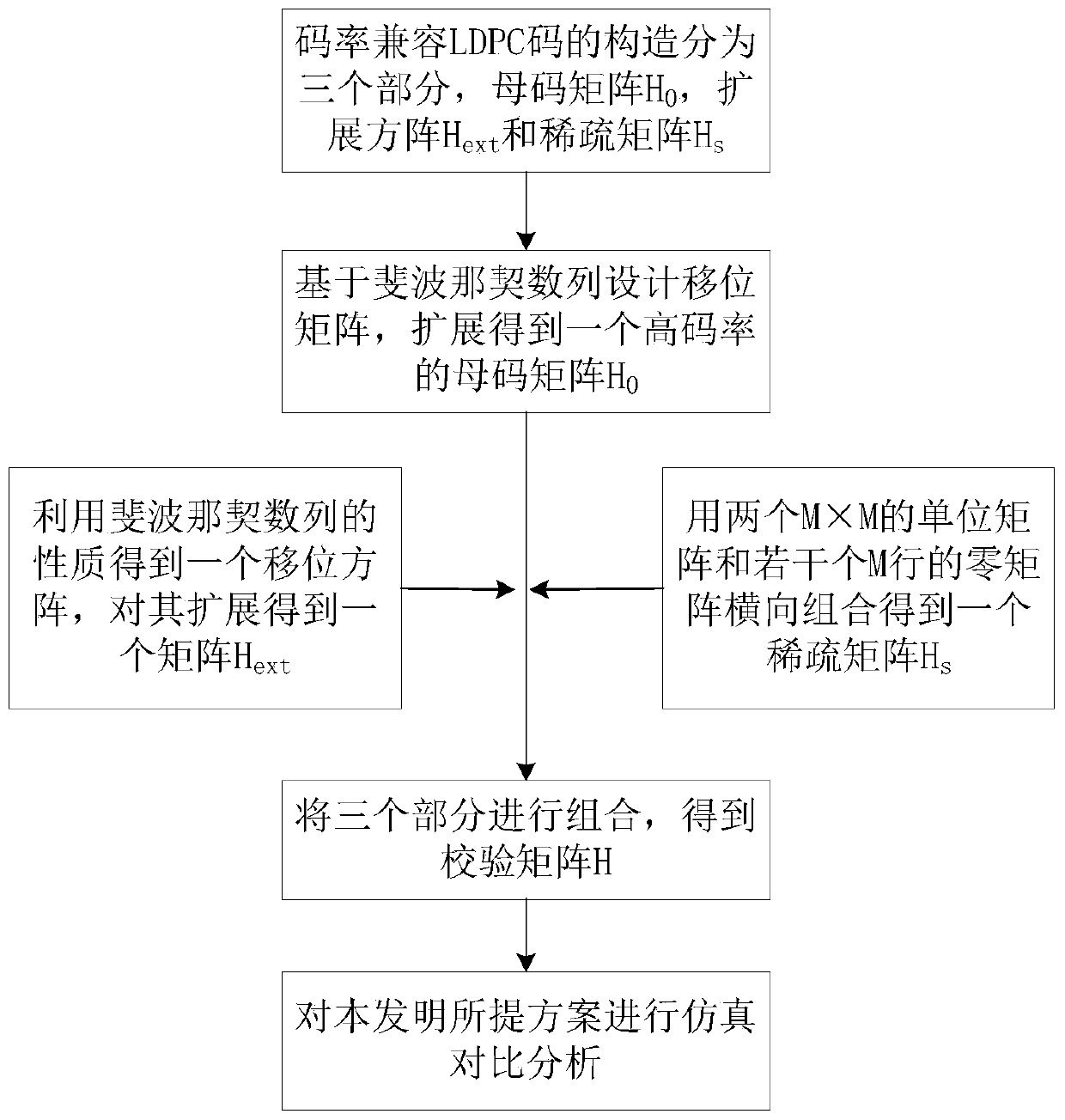
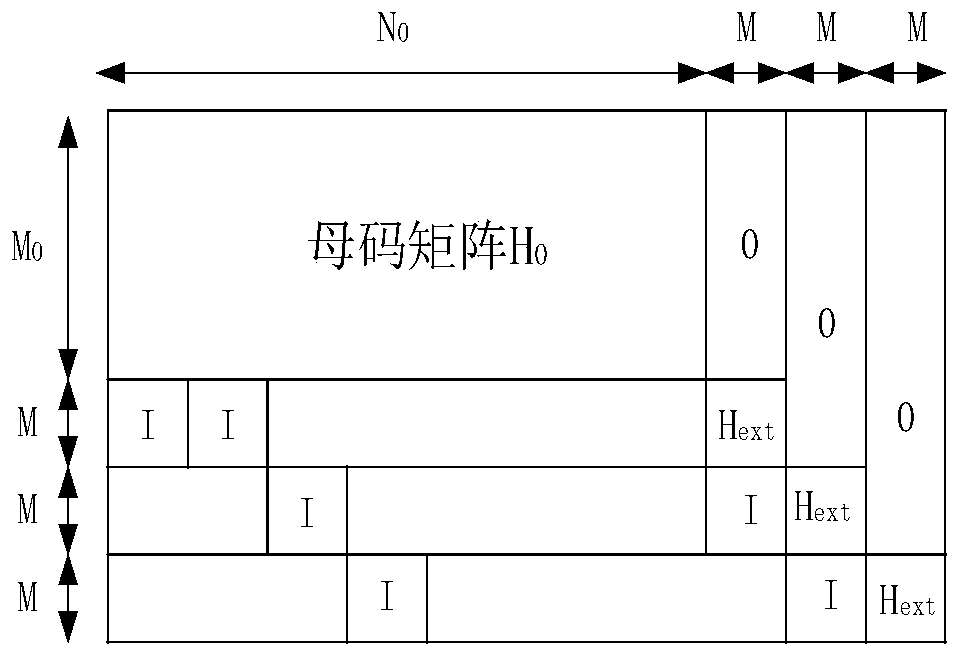
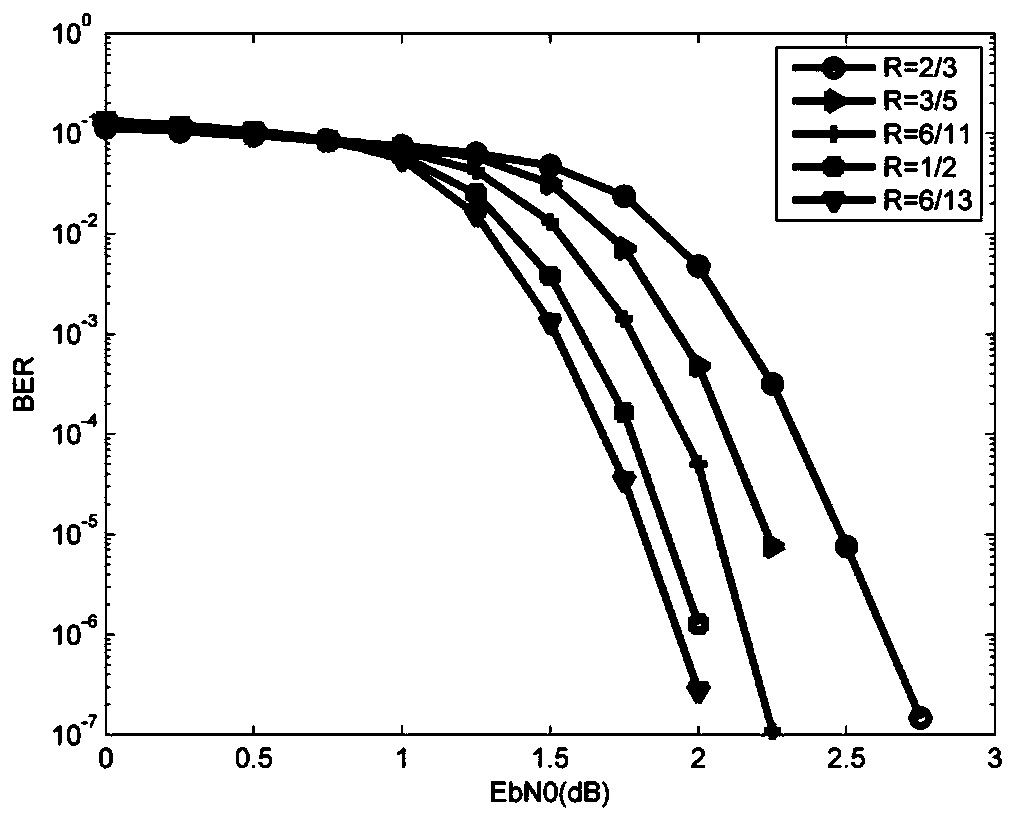
PendingCN111464191AEasy to implementAvoid formingOther error detection/correction/protectionComputation complexityCommunications system
The invention relates to an RC-LDPC code construction method based on matrix expansion and a Fibonacci sequence. According to the method, check bits are expanded on the basis of a mother code matrix to obtain a group of RC-LDPC codes with the same information bit length and different code rates. The shift matrix of a mother code matrix and the extension matrix is constructed by utilizing a Fibonacci sequence with special properties, and a final check matrix is obtained after the shift matrix is combined with a sparse matrix. The construction method is simple in construction and low in calculation complexity. Simulation results show that the constructed F-RC-LDPC code has good waterfall zone performance in a large code rate range and has no obvious error floor. Moreover, when the bit errorrate is 10<-6>, the net coding gain of the constructed F-RC-LDPC code is improved to a certain extent compared with other LDPC code patterns with the same code length and code rate. Therefore, the scheme has a practical application value in a communication system.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
A dynamic bp decoding method for local different signs for ldpc codes
ActiveCN107241104BReduce complexityQuick flipError correction/detection using multiple parity bitsCode conversionDecoding methodsTheoretical computer science
The invention provides a local dynamic update decoding method (LILRBP) based on an LDPC code aiming at a dynamic BP decoding algorithm of the LDPC code. According to the method, the local residual based message update is adopted, the BP decoding performance including a small number of iterations under high signal-to-noise ratio can be effectively improved, and other dynamic BP decoding algorithms can be surpassed. Different from the previous dynamic BP decoding methods, the LILRBP method considers that residuals have time validity, and therefore, the LILRBP method only focuses on the recent part of the residuals, sets an iteration times threshold, then filters the local residuals according to the change of likelihood ratio symbols of a correlation variable node below the threshold, and then determines the next message to be updated according to the filtered residual; and above the threshold, the next message to be updated is directly determined based on the local residual. The advantages of the method are as follows: the message update can always be performed by using the latest messages, the role of accelerating the algorithm convergence speed can be played, and the local residuals are re-filtered below the threshold, the algorithm convergence can be further accelerated, the convergence of the algorithm can be influenced by the combination of the two operations, the convergence speed of the BP decoding algorithm can be effectively improved, and the purpose of improving the decoding performance can be achieved.
Owner:GUANGDONG UNIV OF TECH
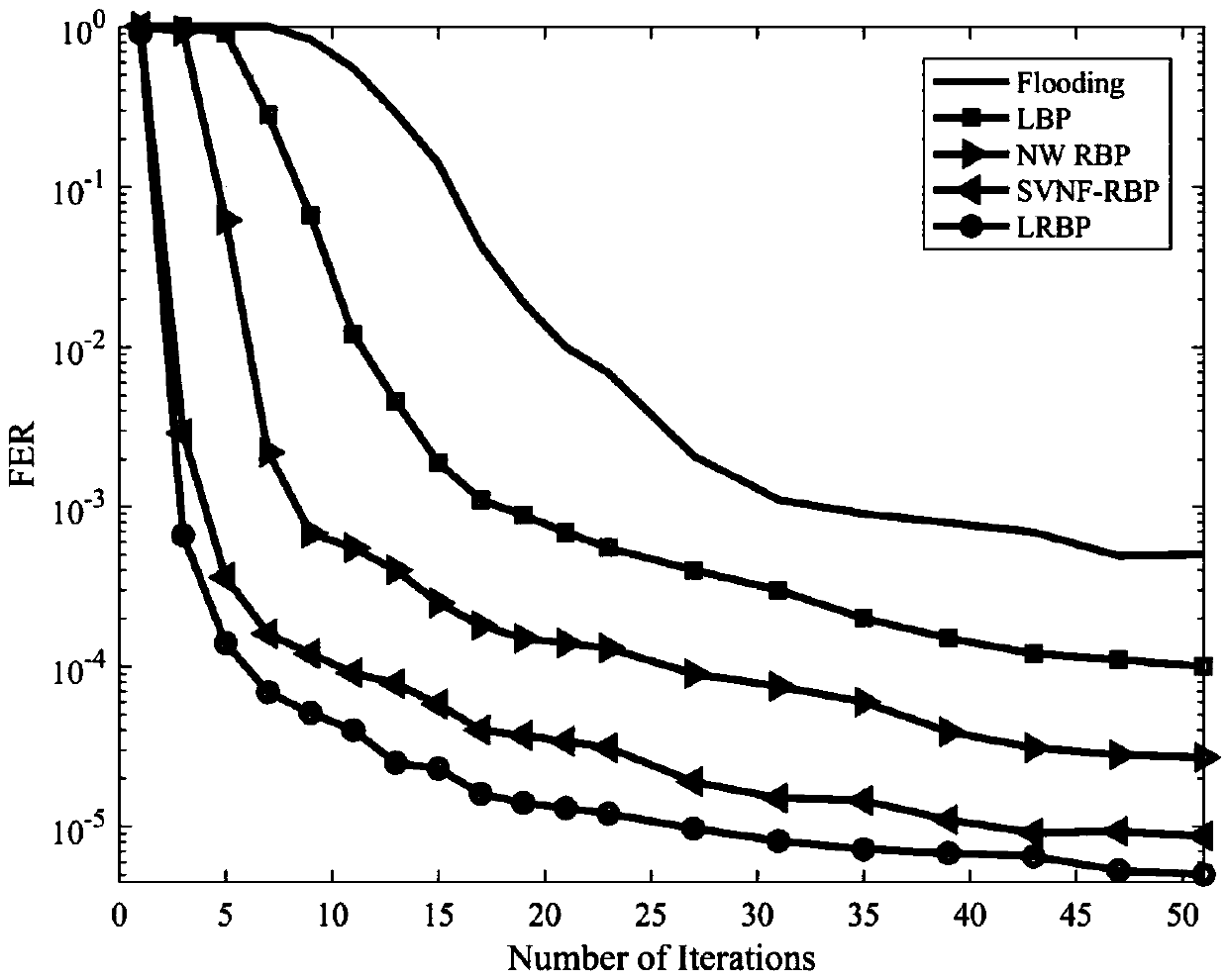
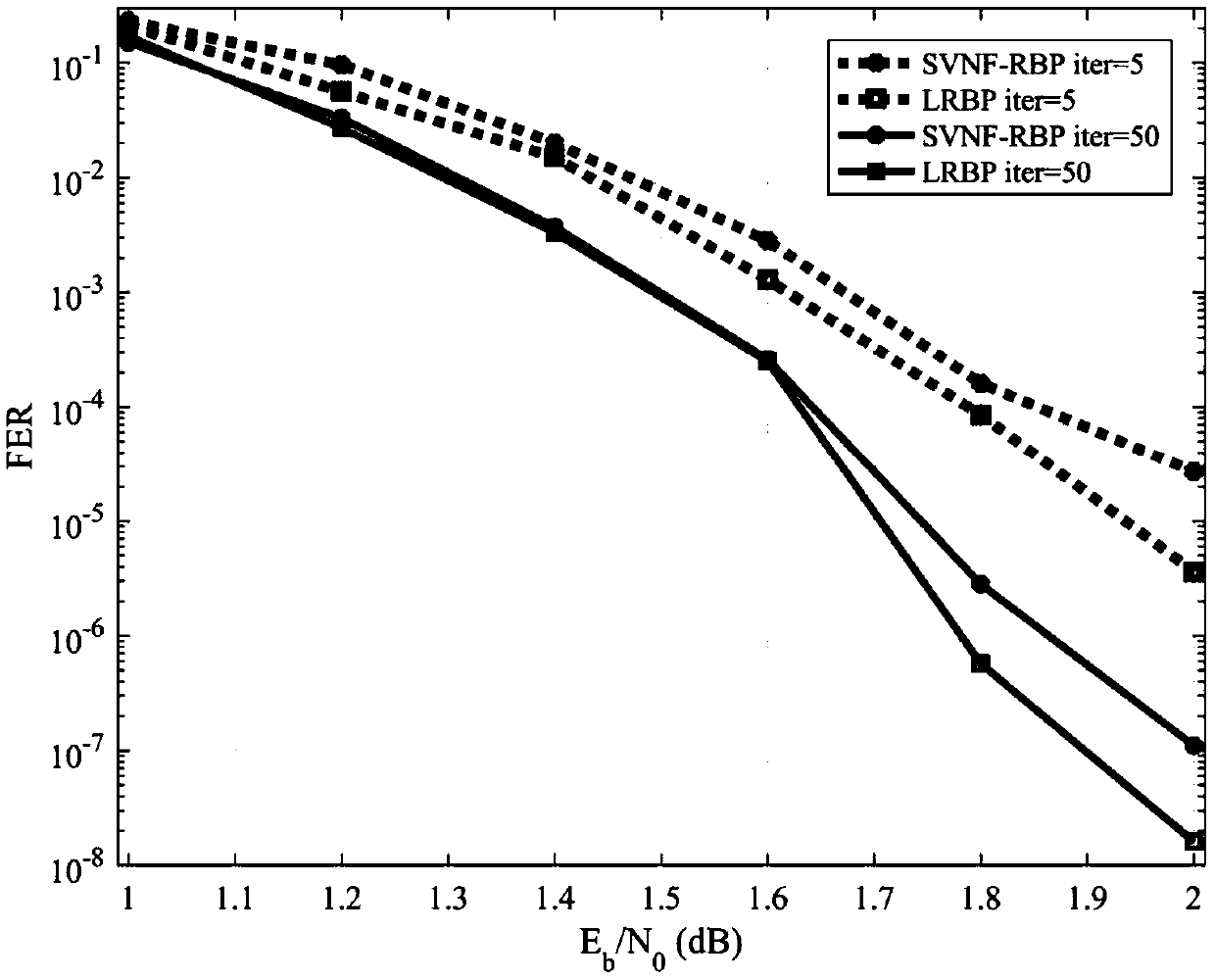
Local dynamic BP decoding method for LDPC code
ActiveCN107241103AImprove decoding performanceReduce complexityError correction/detection using multiple parity bitsCode conversionDecoding methodsRate of convergence
The invention discloses a dynamic BP decoding algorithm for an LDPC code and provides a local dynamic updating decoding method LRBP (Local Residual BP) based on the LDPC code. According to the method, through local residual based message updating, the BP decoding performance comprising little iteration times is effectively improved, and the method surpasses other dynamic BP decoding algorithms. Different from the traditional dynamic BP decoding method, the LRBP method considers that residuals have time validity, so close attention only paid to the time close residuals, a next to-be-updated message is determined according to the time close residuals, the advantage to to this is that the message updating is always carried out through utilization of the newest message, the convergence of the algorithm can be influenced, and the convergence speed of the BP decoding algorithm is effectively improved.
Owner:GUANGDONG UNIV OF TECH
Online sequential perception and opportunistic access method based on ε-greedy
ActiveCN103179675BMaximize long-term cumulative throughput gainsIncrease the speed of learningWireless communicationAccess methodDecision taking
Disclosed is an epsilon-greed based online sequential perceiving and opportunity accessing method. In each time slot, users perceive channels sequentially and get access opportunistically to realize transmission. The method includes a step of initializing relative parameters and making access decisions based on online learning in each time slot, and has capabilities of learning environments actively and adapting to dynamic changes of environments. In addition, the method is an online decision implementing method, and the next decision is adjusted in real time according to each decision and feedback by systems, so that long-term accumulated throughput gain of the systems is maximized.
Owner:COMM ENG COLLEGE SCI & ENGINEEIRNG UNIV PLA
An Inspectable Privacy Communication Method Based on Secret Sharing Scheme
ActiveCN109495248BRealize functionGuaranteed private communicationsKey distribution for secure communicationData switching networksPrivate communicationInternet privacy
A monitorable privacy communication method based on a secret sharing scheme. The privacy communication method includes the user side, the service provider and the monitoring side. The user side includes the sender and the receiver. The sender and the receiver use point-to-point communication or In many-to-many communication, the sender and receiver conduct secret key negotiation through the DH protocol; after the secret key negotiation is completed, the session key will be formed according to the sender, receiver's team members, service provider and monitoring Split the secret key according to the number of parties; distribute the split secret key to the sender, receiver team members, service provider and supervisor, and the team members encrypt the received split secret key; the service provider Receive the encrypted key of the group members and the assigned split key; the monitoring party receives the assigned split key. The invention solves the contradiction between the existing user's private communication and the service provider's content monitoring, protects the user's private communication to the greatest extent, and realizes point-to-point and many-to-many private communications that can be monitored.
Owner:曹鸣佩
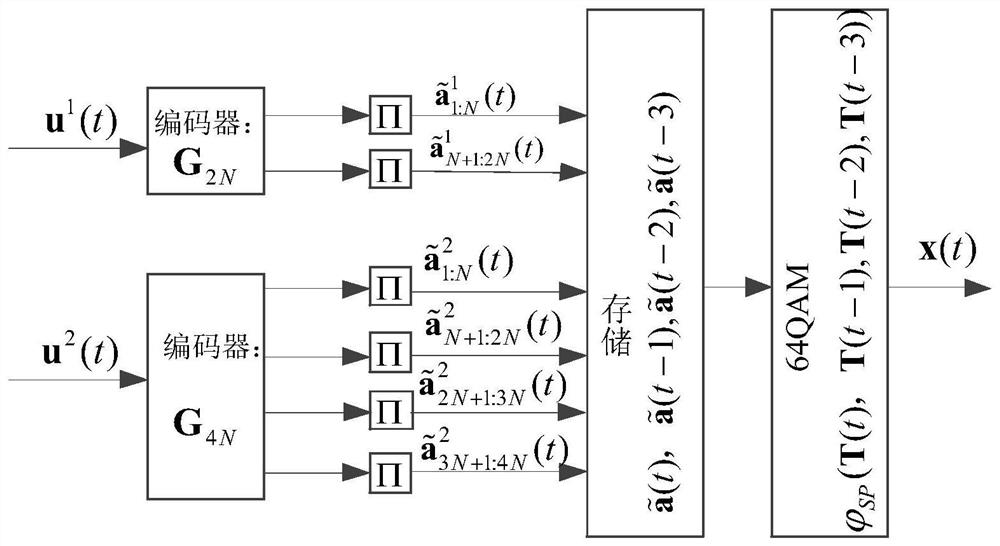
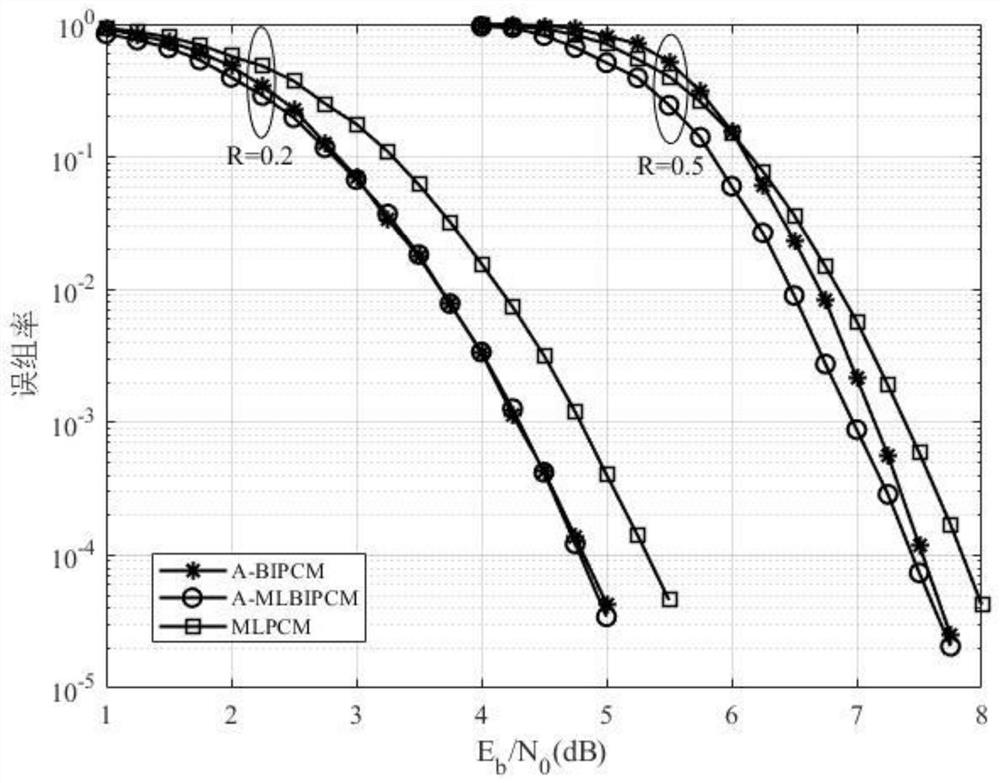
A Polar Code-Based Asynchronous Multi-Level Bit Interleaved Coding and Modulation Method
ActiveCN113556211BImprove polarization performanceHigh error rate performanceChannel coding adaptationForward error control useModulation patternEngineering
The invention discloses a polar code-based asynchronous multi-level bit interleaving coding and modulation method, which includes the following steps: firstly obtain the best coding mode and modulation mode for system coding and modulation through traversal search, and then use the Gaussian approximation method to obtain The transmission position of information bits; polar code encoding; interleaving the encoded data; data storage at the sending end; modulation; receiving signals at the receiving end; calculating and storing symbol likelihood ratios; decoding and code reconstruction; storing bit sequences . The invention reduces the complexity of storage and decoding under the condition that the group error rate performance is not damaged, and is suitable for practical communication applications.
Owner:SOUTHEAST UNIV +1
Method and device for constructing check matrix of ldpc code
ActiveCN102904581BReduce storage complexityError correction/detection using multiple parity bitsTheoretical computer scienceLow density
The invention discloses an LDPC (low density parity check) code check matrix constructing method which is used for constructing check matrix of LDPC codes on the basis of property of a Golomb-Ruler set. Only one row vector of a basis matrix is required to store when in a process of constructing the basis matrix of the check matrix, each row of the basis matrix can be acquired by means of cyclic shift of the row vector, and accordingly storage complexity of the basis matrix of the check matrix of the LDPC codes is reduced, and storage complexity of the check matrix of the LDPC codes is reduced equivalently.
Owner:无锡感知金服物联网科技有限公司
Local dynamic BP decoding method for LDPC codes
InactiveCN111181571AImprove decoding performanceReduce complexityError correction/detection using multiple parity bitsCode conversionDecoding methodsComputer engineering
Aiming at the dynamic BP decoding algorithm of the LDPC code, the invention provides a local dynamic update decoding method (LRBP) based on the LDPC code, and the method adopts the message update based on the local residual error, thereby effectively improving the BP decoding performance within a small number of iterations, and surpassing other dynamic BP decoding algorithms. Different from the conventional dynamic BP decoding method, the LRBP method considers that the residual error has timeliness, so that only the nearest residual error in time is paid attention to, and the next message to be updated is determined. The method has the advantages that the latest message can be always used for updating the message, the convergence of the algorithm can be influenced, and the convergence speed of the BP decoding algorithm is effectively improved.
Owner:王海林
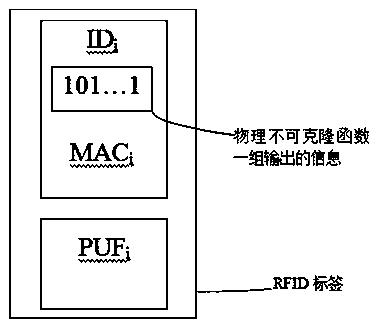
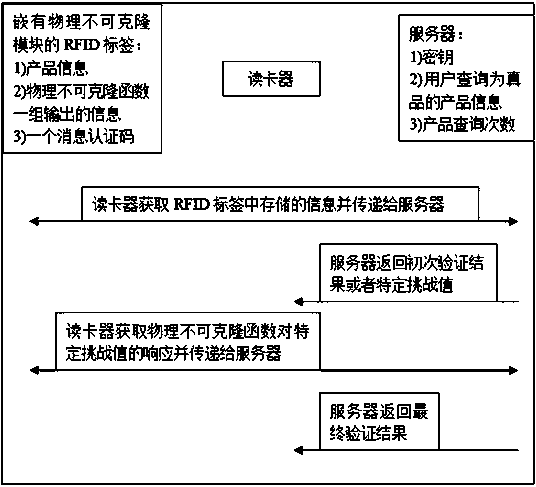
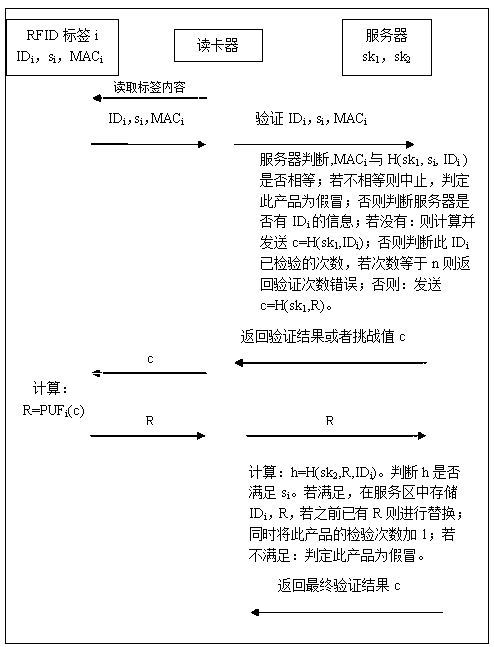
An anti-counterfeiting method based on RFID and physical unclonable function
InactiveCN103345690BReduce storage complexityRealize authenticity verificationUser identity/authority verificationCo-operative working arrangementsComputation complexityPhysical unclonable function
Owner:SUN YAT SEN UNIV
Medium access control method for underwater acoustic network with variable number of nodes based on q-learning
ActiveCN113691391BImprove learning efficiencyIncreased energy expenditureError prevention/detection by using return channelSonic/ultrasonic/infrasonic transmissionSimulationSensor node
The invention discloses a Q-learning-based medium access control method for an underwater acoustic network with a variable number of nodes, involving the underwater acoustic network. Divide the transmission process of the sink node collecting the perceived data of the underwater acoustic sensor nodes into several time slots, use the Q learning algorithm, combine the feedback signal of the sink node, the change of the number of sensor nodes, and set the reward mechanism reasonably, aiming at a Q matrix The entire row (that is, the sub-matrix) is designed for the overall reward sub-matrix instead of updating the Q matrix element by element, and the time slots are reasonably allocated to each sensor node, so that the data will not be affected by other sensor nodes during transmission and avoid aggregation Node data collection conflict. The method proposed in the present invention has the characteristics of fast learning speed, high throughput, energy saving, and strong anti-interference ability, and can solve the problem of time slot redundancy when nodes are reduced or time slots when nodes are increased caused by node death or position drift Insufficient problems, to ensure the success rate of underwater acoustic data transmission and high throughput of underwater acoustic network.
Owner:XIAMEN UNIV +1
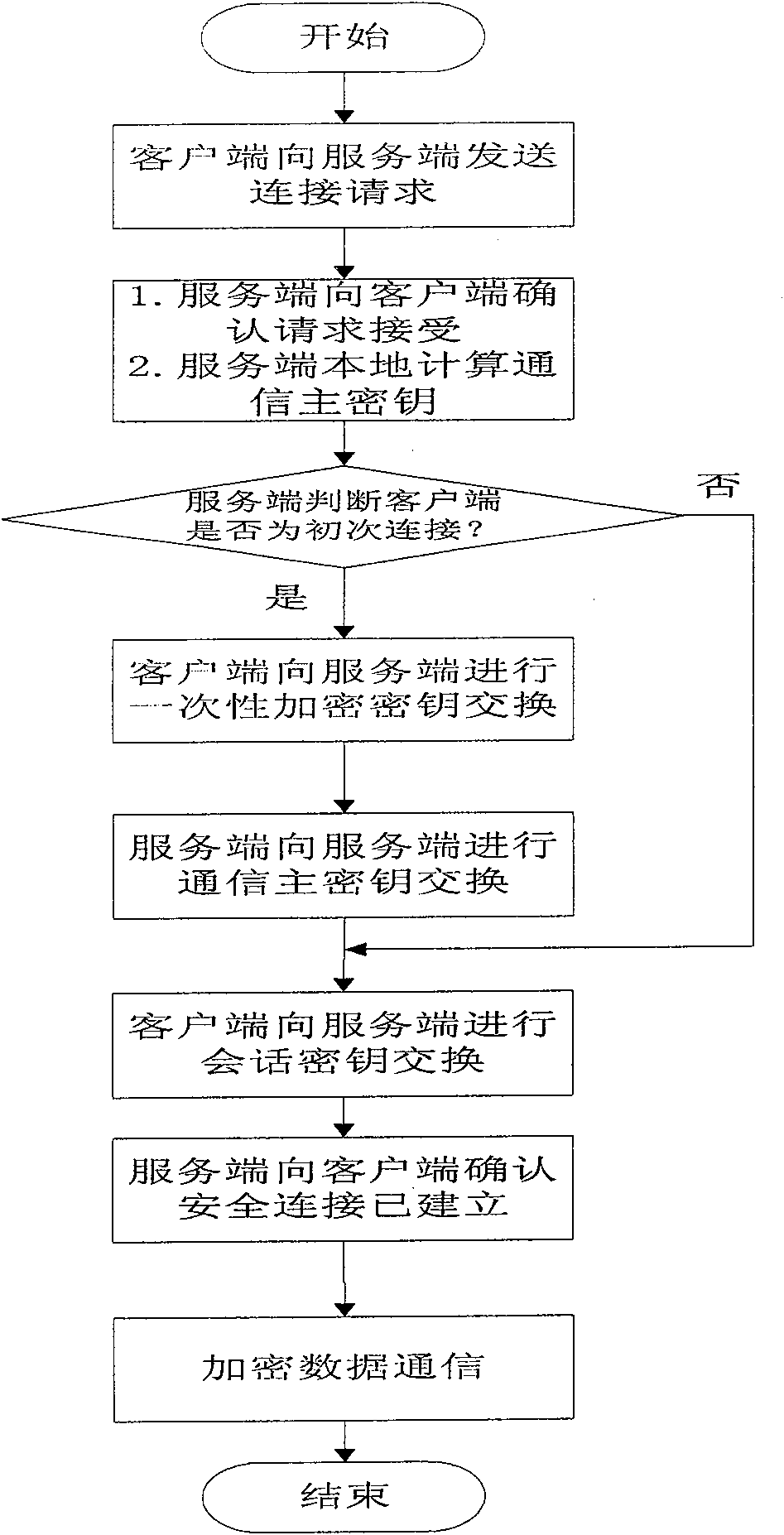
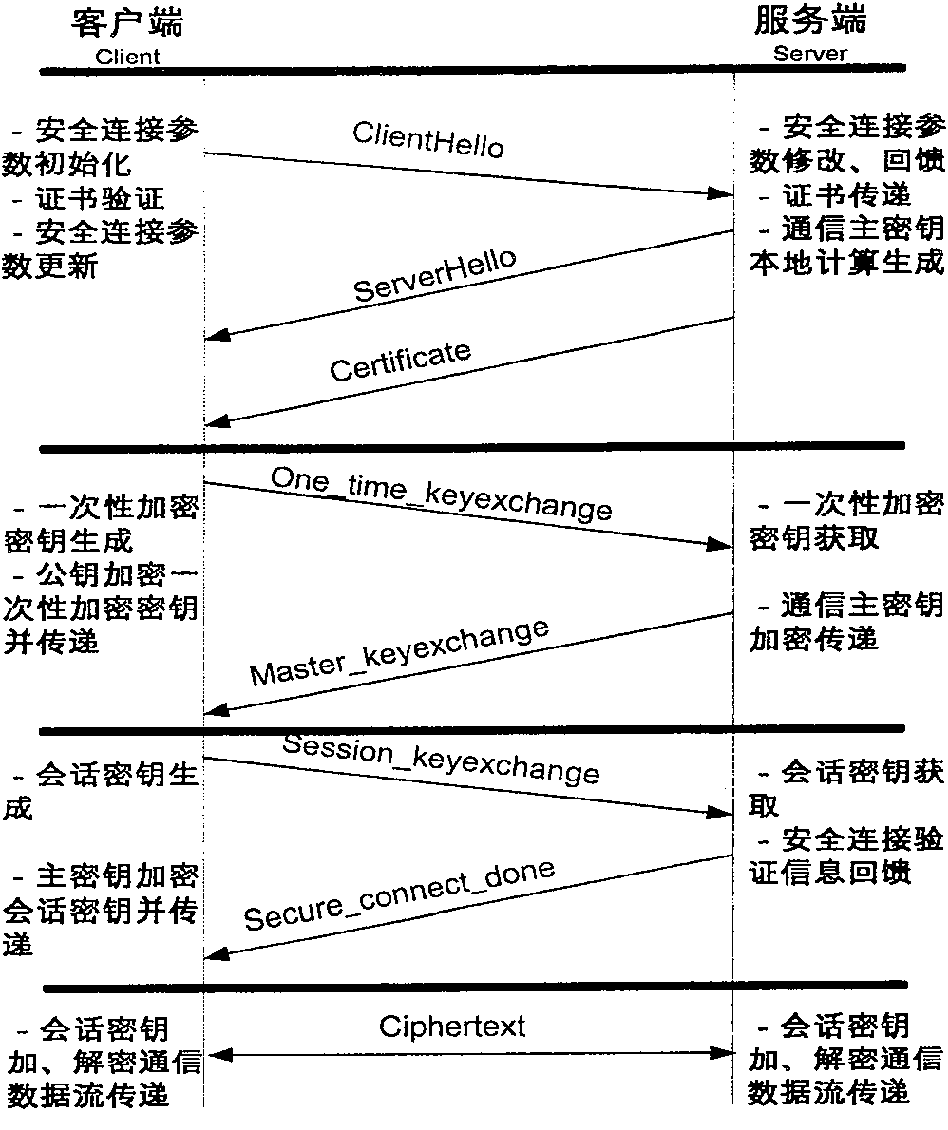
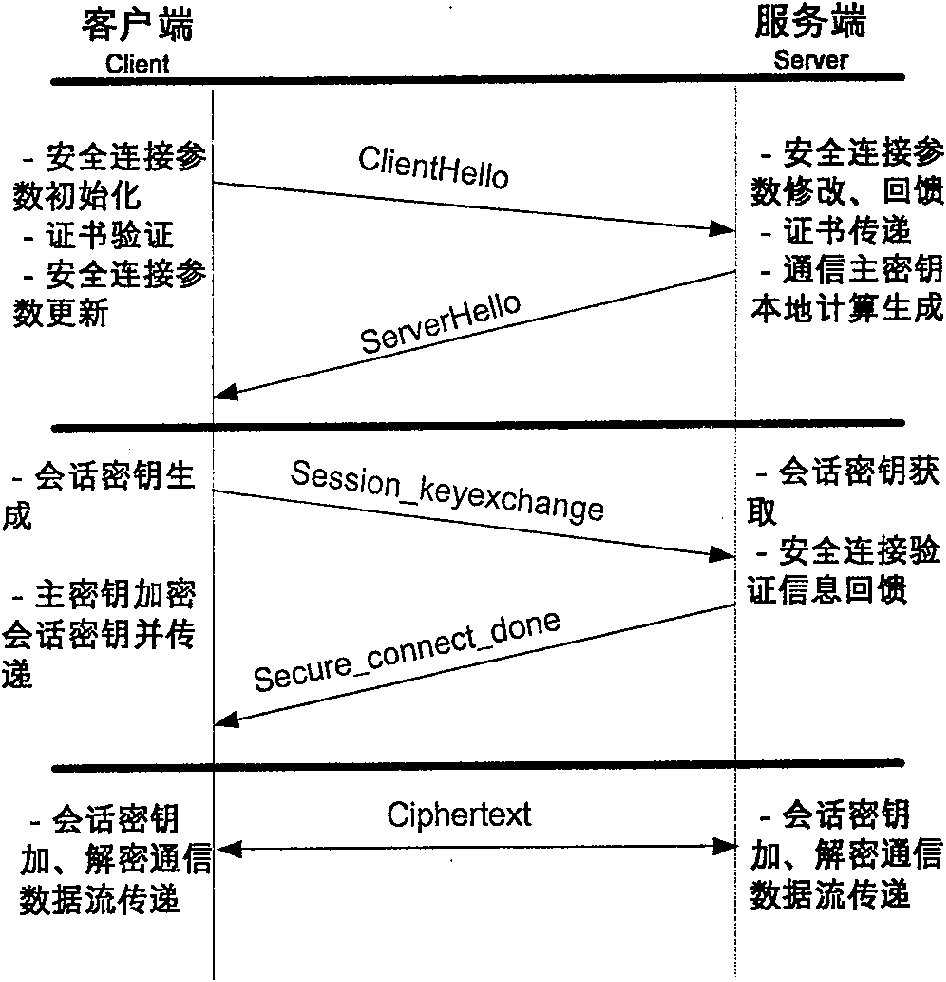
Web communication encrypting method
InactiveCN100574325CAvoid encryption and decryption operationsRealize confidential communicationSynchronising transmission/receiving encryption devicesSecure communicationKey exchange
The invention provides a Web communication encryption method, which distinguishes between the first communication and the second communication between the client and the server. When the client accessing for the first time communicates with the server on the Web, it needs to negotiate to determine the communication encryption algorithm, and there is no need to negotiate again when communicating again; when communicating for the first time, the client obtains the communication master key provided by the server and saves the communication master key , when communicating again, the server only needs to calculate and generate the key locally, and the client uses the locally stored communication master key to transmit the session key, and then the two parties use the session key to encrypt and decrypt the communication data to realize confidential communication. The communication encryption method of the present invention greatly reduces the key storage capacity of the server, and the reduction of the key exchange calculation load of the server is also obvious.
Owner:PEKING UNIV
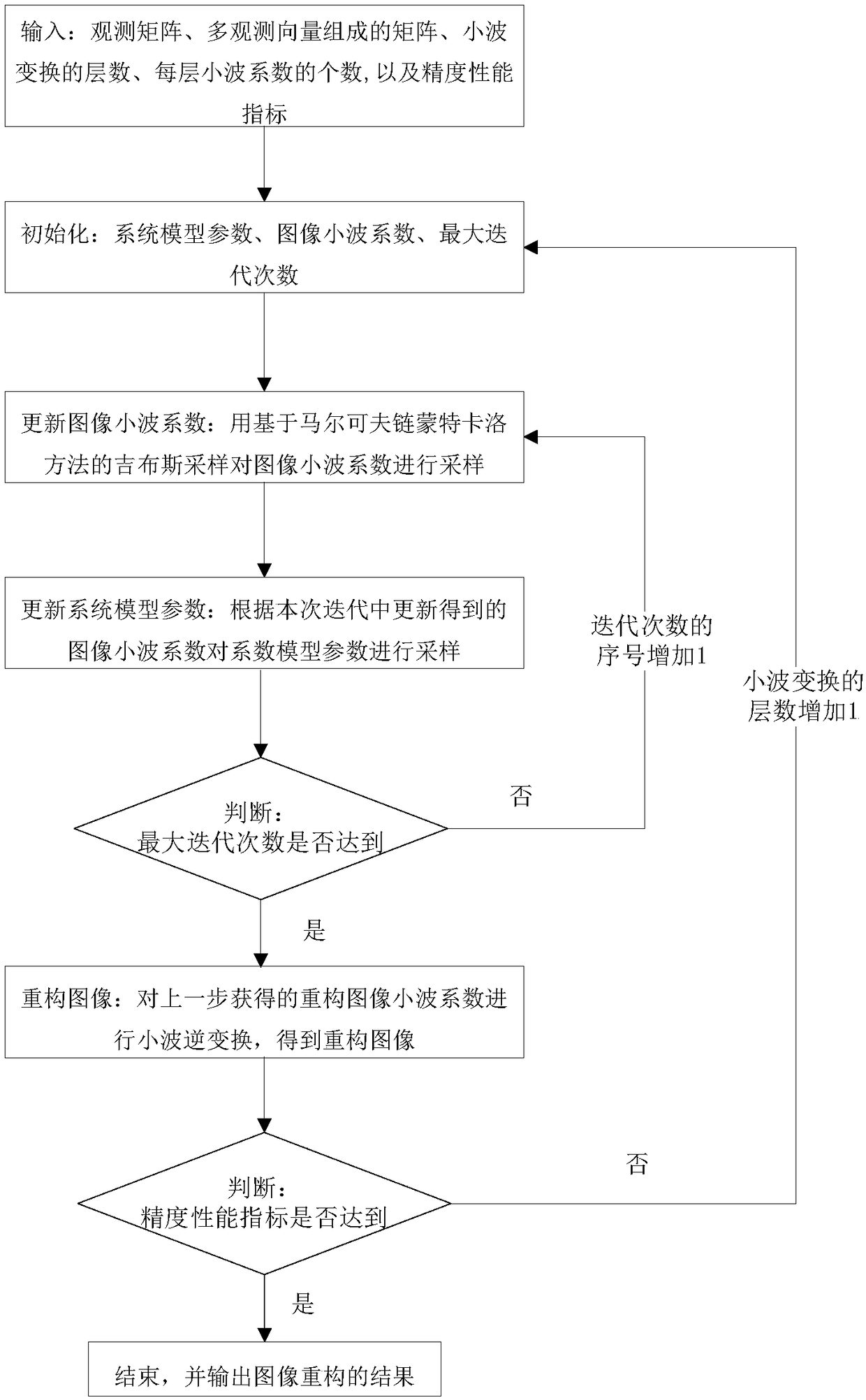
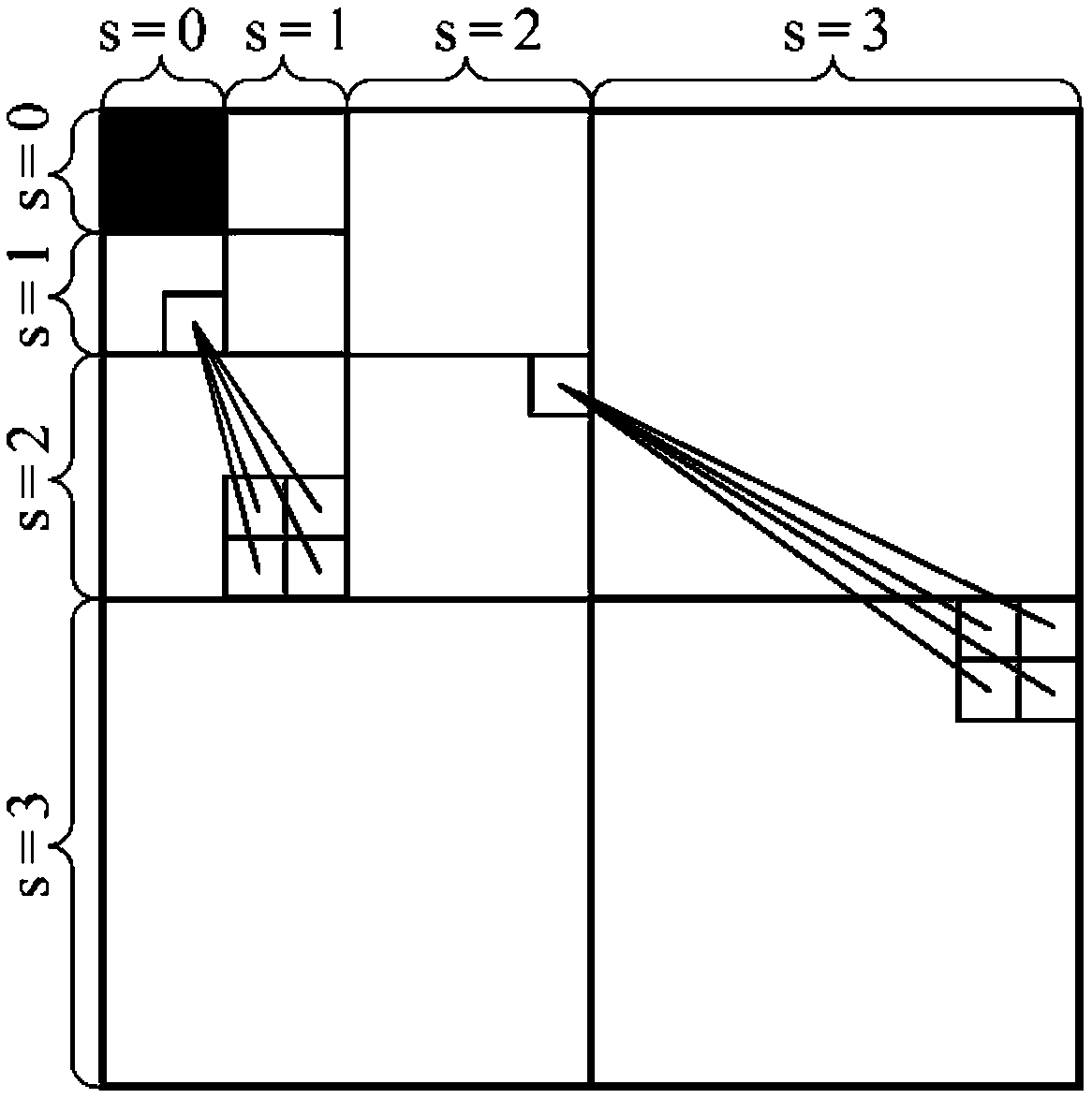
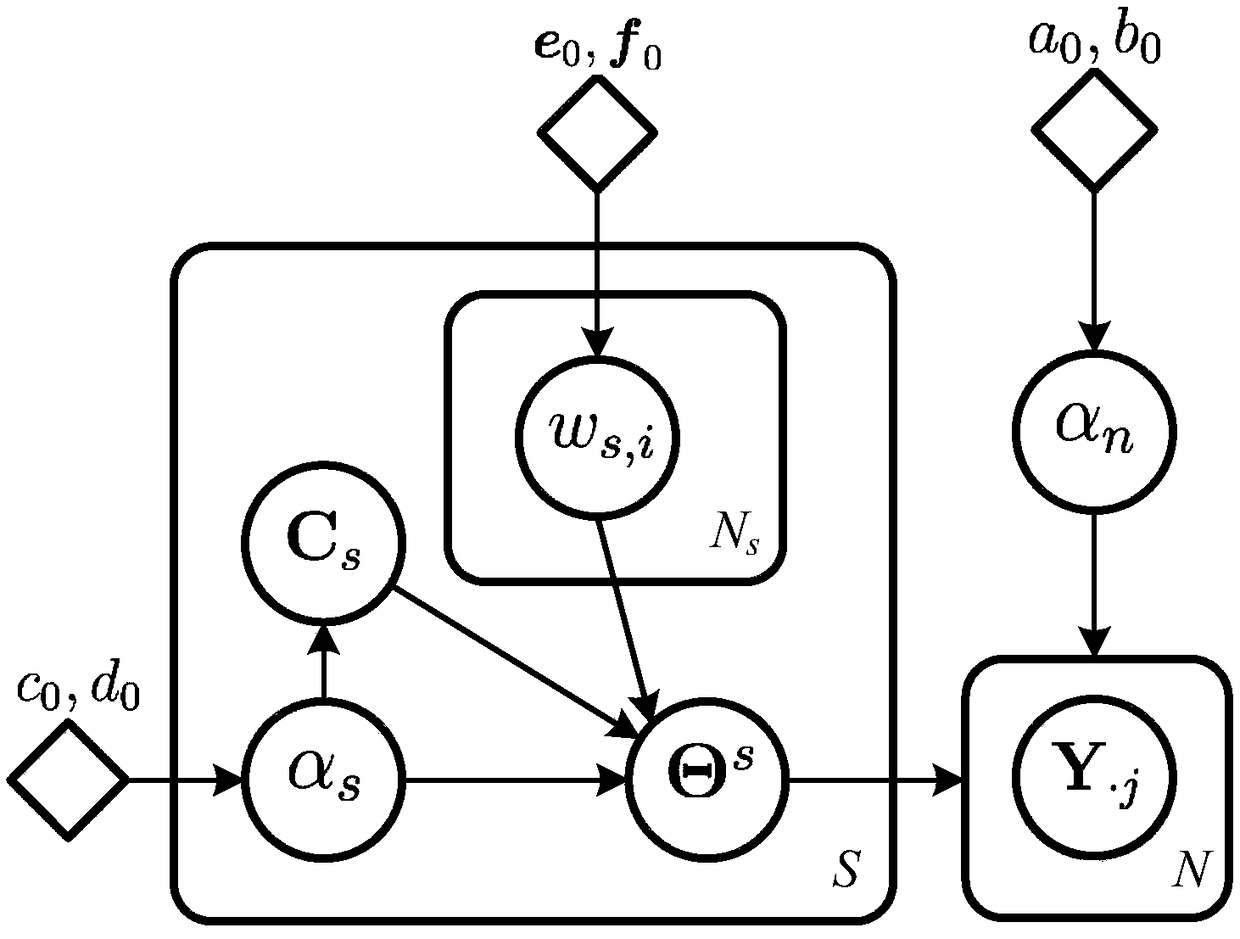
Improving Accuracy and Reducing Complexity of Sparse Image Reconstruction Using Structural Prior Constraint
ActiveCN107784278BHigh precisionImprove reconstruction accuracyCharacter and pattern recognitionObservation matrixGibbs sampling
A method for improving sparse image reconstruction accuracy and reducing complexity by using structured prior constraints, belonging to the field of remote sensing image compression technology, is characterized in that it is a method of introducing image information on the basis of a multi-observation vector model to improve accuracy and reduce complexity , including the following steps in turn: input observation matrix, matrix composed of multi-observation vectors, number of wavelet transform layers, number of wavelet coefficients in each layer; initialize system model parameters, image wavelet coefficients, maximum number of iterations, precision performance index; use Markov-based The Gibbs sampling of the chain Monte Carlo method reconstructs the wavelet coefficients of the image, and then performs wavelet inverse transform on the reconstructed wavelet coefficient matrix to obtain the reconstructed image. The present invention can apply the required accuracy performance index to the actual reconstructed image, utilize the multi-observation vector model to reduce the complexity, and at the same time adjust the reconstruction accuracy by adjusting the number of wavelet transform layers, so that the quality of the reconstructed image meets the performance index requirements .
Owner:TSINGHUA UNIV
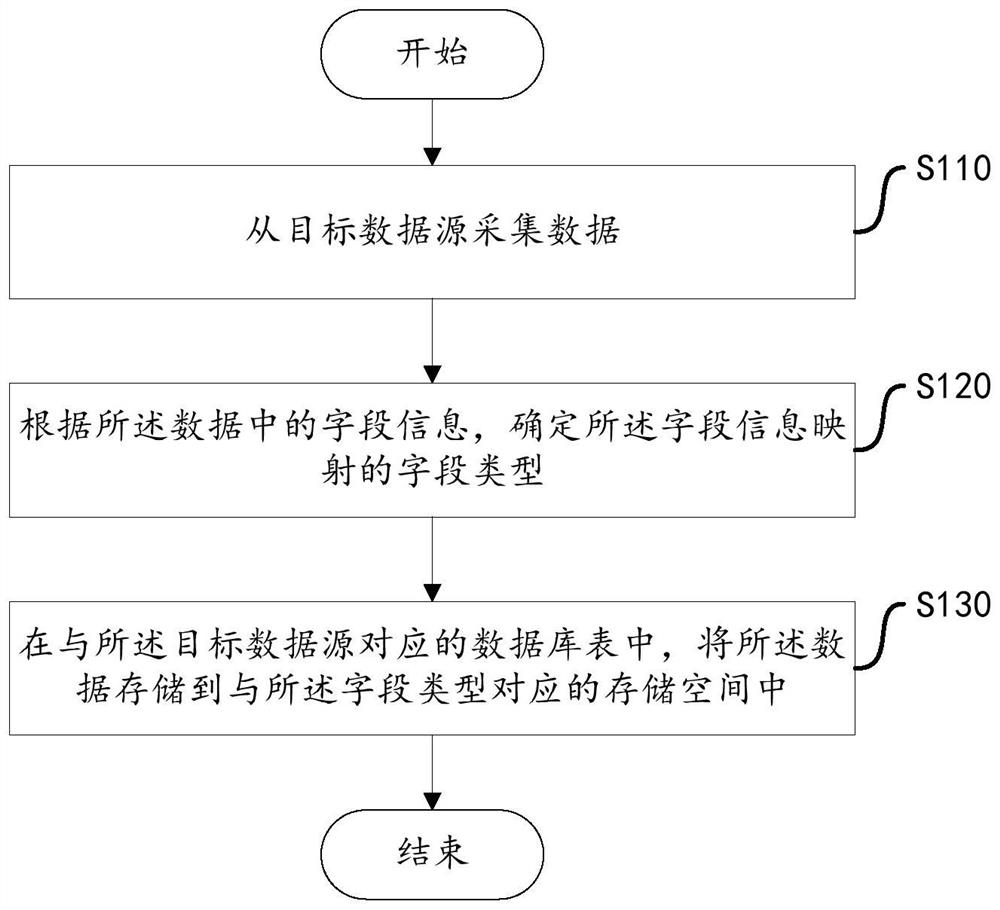
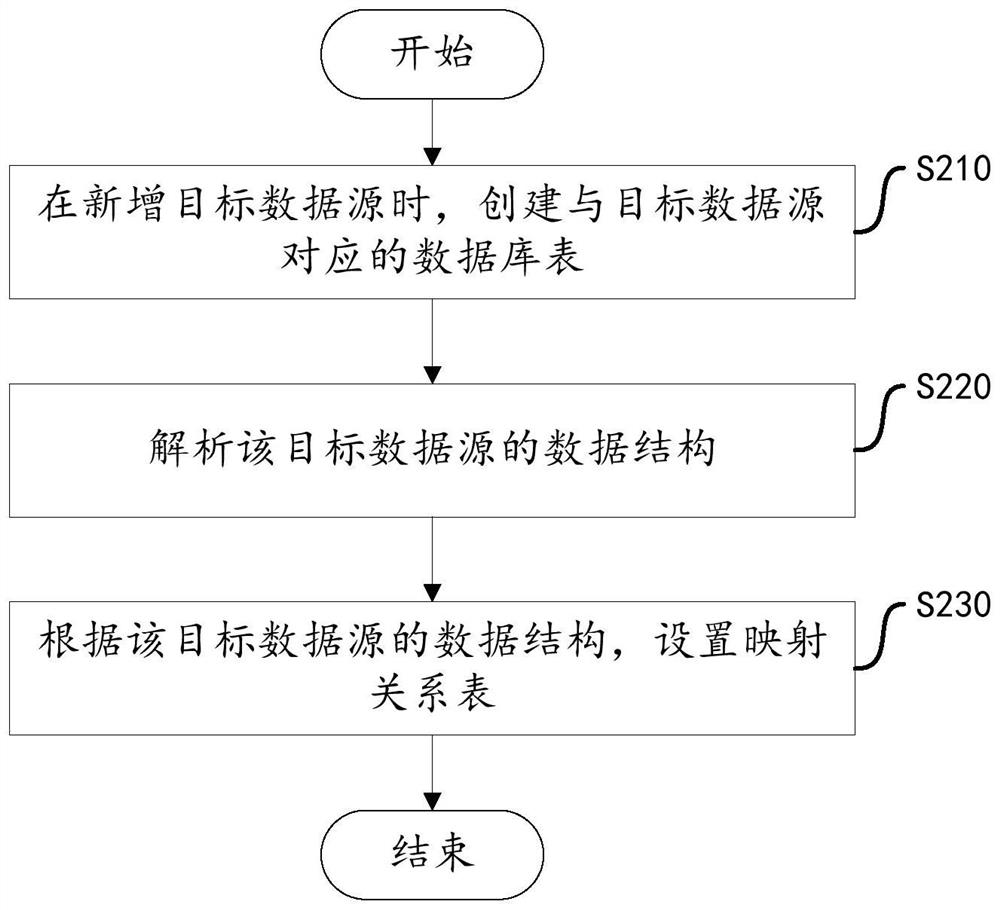
Data storage method and device, equipment and storage medium
PendingCN112527792AReduce storage complexitySimplify data storage stepsSpecial data processing applicationsDatabase indexingStorage efficiencyInformation mapping
The invention discloses a data storage method and device, equipment and a storage medium. The method comprises the steps of collecting data from a target data source; determining a field type mapped by the field information according to the field information in the data; and storing the data into a storage space corresponding to the field type in a database table corresponding to the target data source. By setting different field types for the storage space of the database table, a unified storage structure is provided for the data sources with different data structures, the situation that different data storage structures are set for the data sources with different data structures is avoided, the storage complexity of different target data sources is reduced. The data storage steps are simplified, the data storage efficiency is improved, the target data sources of different data structures can reuse the storage logic, and unified storage of the data of the target data sources of different data structures is facilitated.
Owner:BEIJING GRIDSUM TECH CO LTD
Deblocking filtering method and apparatus of video frequency or image
ActiveCN100345450CReduce computational complexityReduce storage complexityTelevision systemsDigital video signal modificationPattern recognitionComputation complexity
Using macro block type and quantized parameters, the disclosed method determines whether de-block filtering is carried out or not, and determine what kind of macro block filtering mode is selected or adopted in case of de-block filtering is needed. The method does not use residual information of coded macro or information of motion vector to determine whether de-block filtering is needed or not. Based on macro block filtering mode adopted and content of image, de-block filtering procedure is determined in self-adaption. Under precondition of possessing considerable objective and subjective decoded image quality, the disclosed method reduces computation complexity and storage complexity greatly. The invention can be extended to application of other signal processes, not limited in area of video frequency or encoding and decoding images.
Owner:XFUSION DIGITAL TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com