An anti-counterfeiting method based on RFID and physical unclonable function
A technology of RFID tags and functions, which is applied in the field of anti-counterfeiting based on RFID and physical unclonable functions, can solve the problems of high server calculation and high server storage complexity, and achieve the effects of high query efficiency, reduced calculation complexity, and low price
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
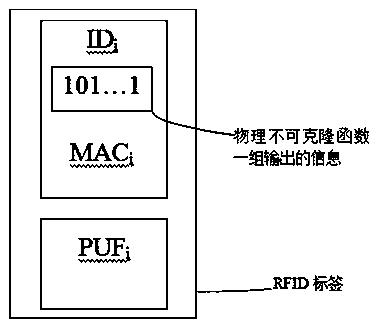
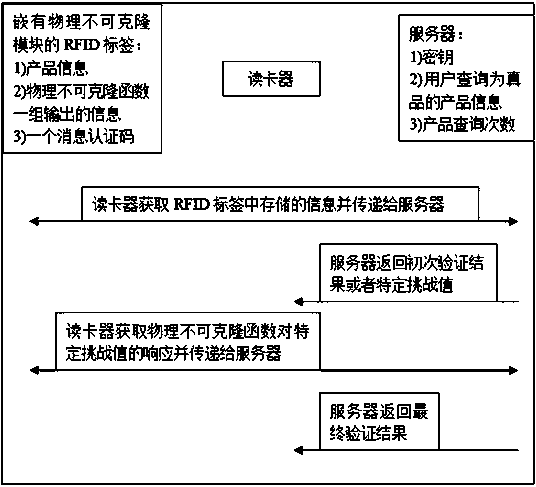
[0044] The invention adopts physical unclonable function (PUF) technology to fight against cloning attacks of RFID tags, uses message verification code technology to complete product legality authentication, and uses Bloom filter technology to reduce storage complexity of RFID tag end. Each RFID tag contains at least two parts: a storage unit and a PUF module, wherein the storage unit mainly stores product information, a set of output information of the PUF and a message authentication code. The PUF module is an anti-cloning module, which is embedded in the RFID tag and cannot be separated.
[0045] The anti-counterfeiting method of the present invention includes three participants: an RFID tag embedded with a PUF module, a card reader and a server. The server only stores the key and the product information and query times that have been queried as genuine products. Product information, a set of output information of the PUF embedded therein and a message authentication code ...
Embodiment 2
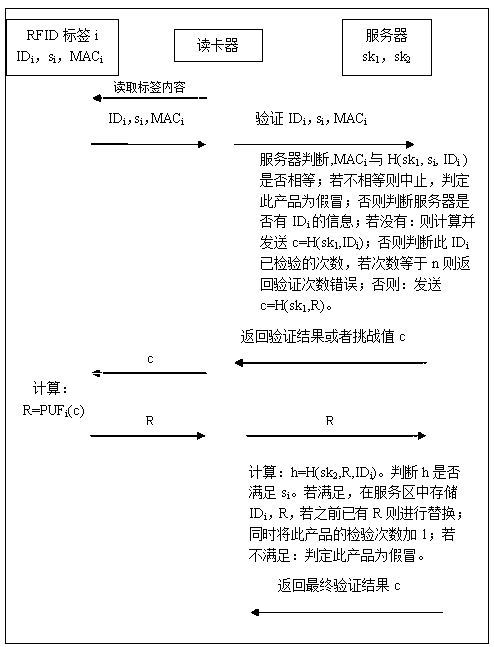
[0064] The above anti-counterfeiting method can be described more clearly by the symbols defined below.
[0065] ID i : The product information in the RFID tag i, which can include information such as the unique code of the product;
[0066] PUFs i (z): When the input is z, PUF i The output of the module, where the PUF i The module is embedded in the RFID tag i;
[0067] m: safety parameters;
[0068] sk 1 and sk 2 : The key generated and stored by the server, which belongs to the set of m-length 0 and 1 bit strings {0,1} m ;
[0069] n: the maximum number of times each product can be queried;
[0070] x i : The number of times that the product identified by the RFID tag i is verified to be genuine during the query;
[0071] k: Bloom filter length parameter;
[0072] t: the number of hash functions that need to be used in the Bloom filter;
[0073] H(): hash function, mapped to the interval {0,1} l , the value of l can be 160;
[0074] h 1 ( ),…,H t ( ): T has...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com