Monitorable privacy communication method based on secret sharing scheme
A communication method and secret sharing technology, applied in the field of monitoring privacy communication, can solve problems such as methods that do not have content censorship
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0094] The implementation of the present invention will be illustrated by specific specific examples below, and those skilled in the art can easily understand other advantages and effects of the present invention from the contents disclosed in this specification.
[0095]Those skilled in the art know that the technical scheme of the present invention adopts a mature encryption scheme. For the field of cryptography, the encryption algorithm that has been verified and widely used is mature and effective. Using these mature encryption schemes, it can be realized in the ciphertext Protect the security of the original text in case of leakage.
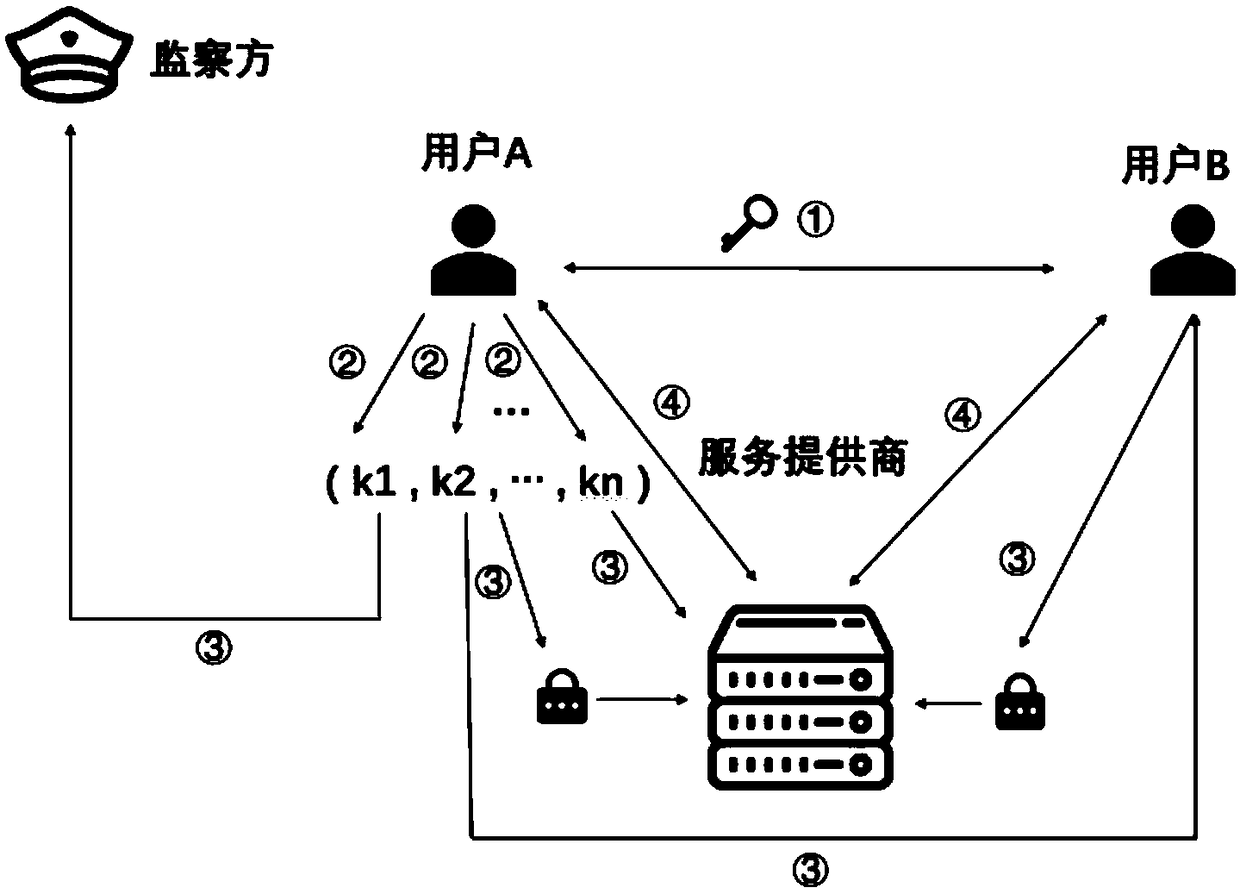
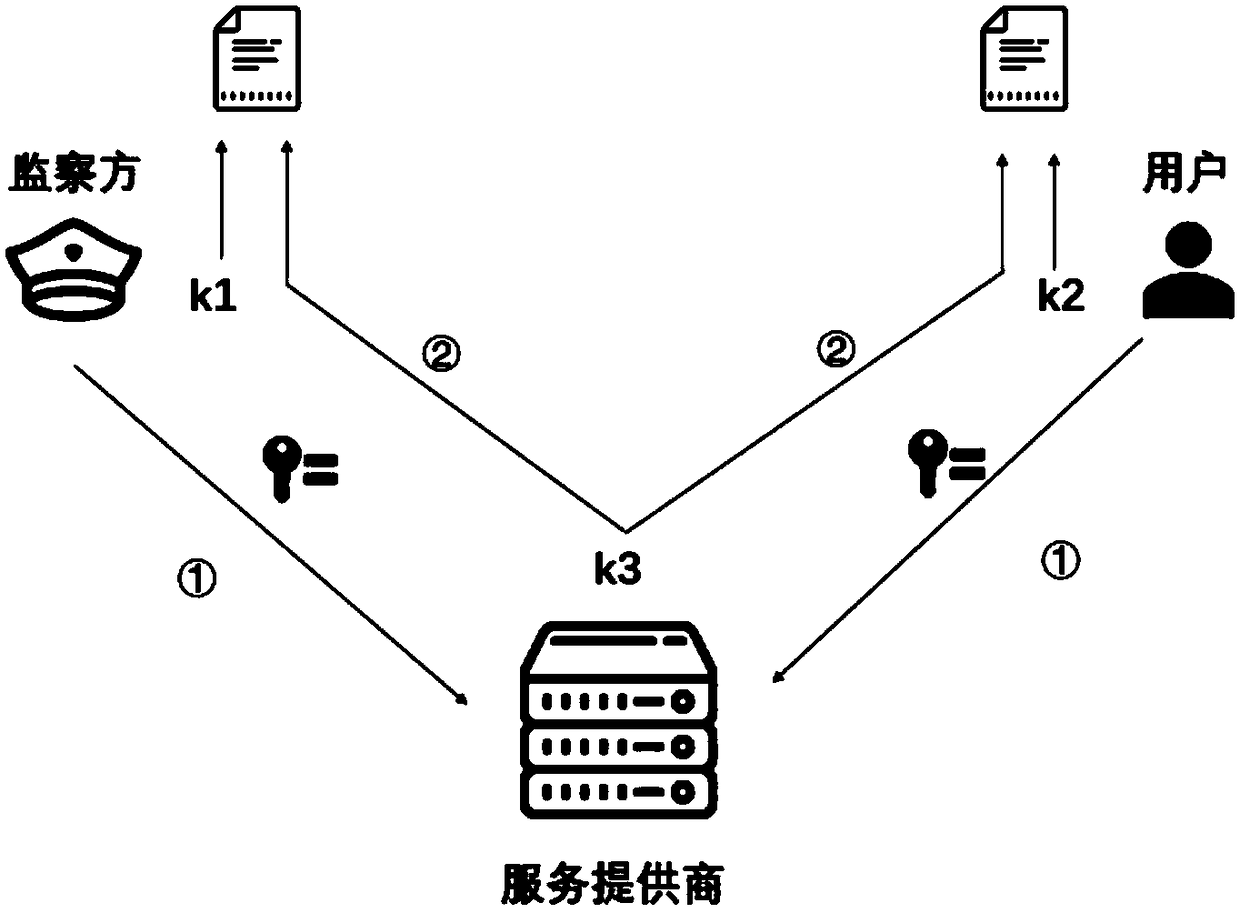
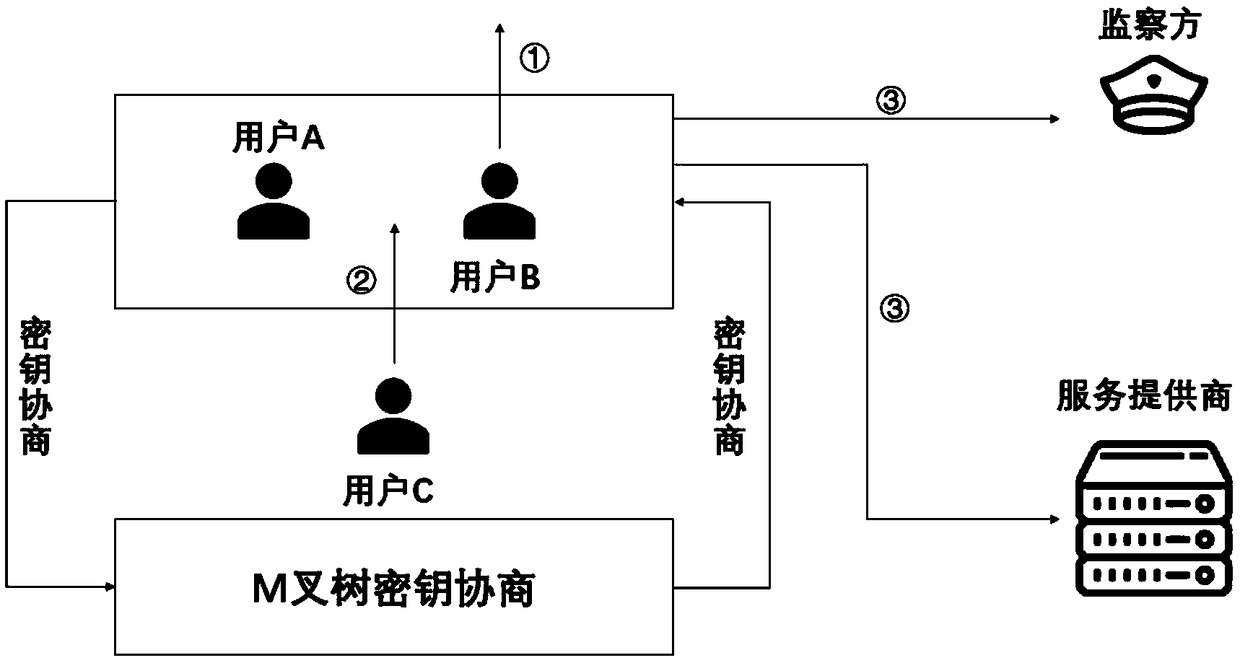
[0096] In reality, the user side, service provider, and supervisory side do not trust each other, that is, the interaction between the three parties is based on an untrusted model, and any two parties cannot form an offensive and defensive alliance. Therefore, in the process of cooperative decryption by multiple parties, each party is unwill...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com