Secret communication method based on fraction order Fourier transform order-multiplexing
A fractional Fourier, secure communication technology, applied in the field of information security, can solve the problem that the fractional Fourier transform order is not fully utilized and so on
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] The present invention will be described in detail below in conjunction with the accompanying drawings and embodiments.
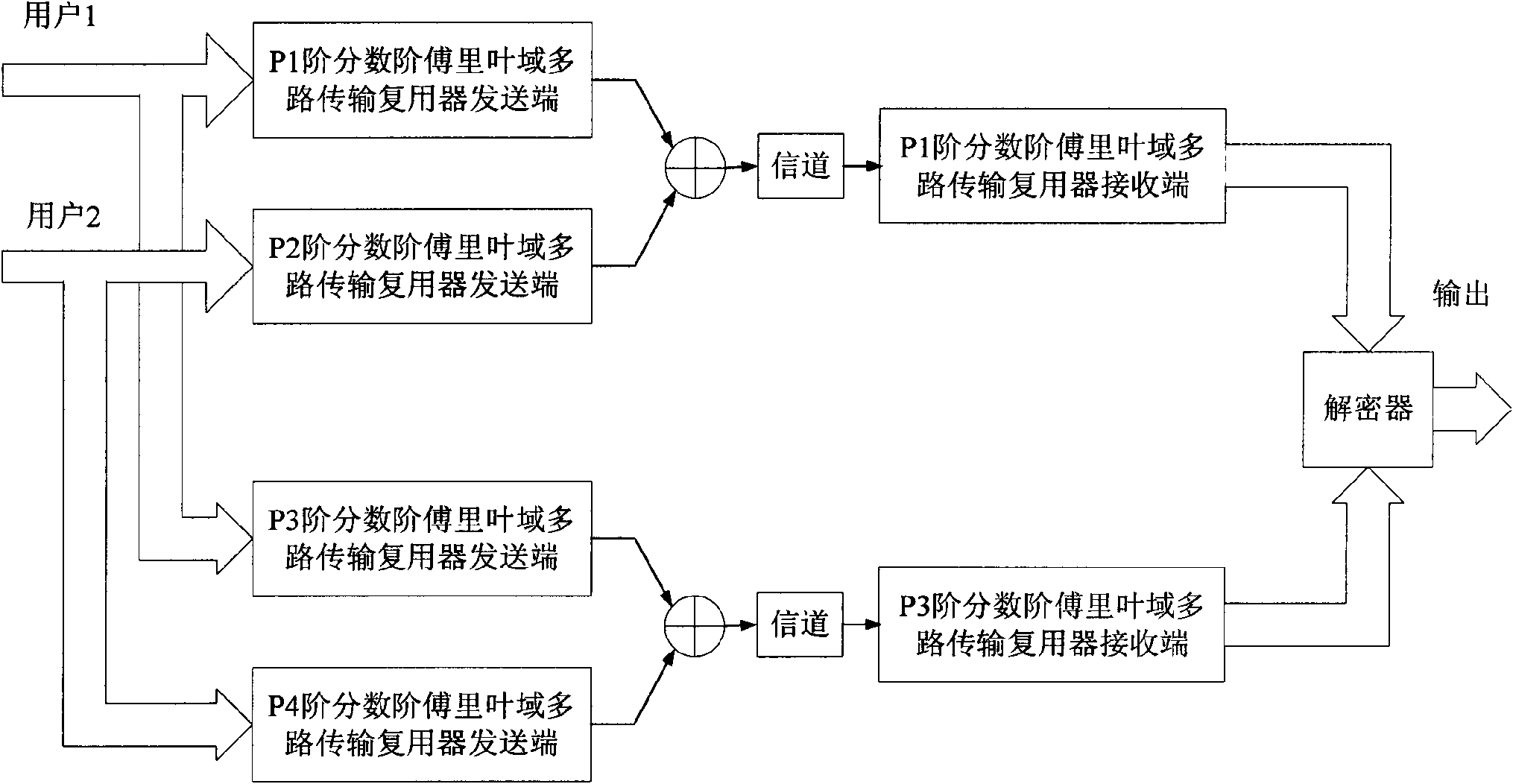
[0037] The secure communication technology based on fractional Fourier transform proposed by the present invention comprises the following steps
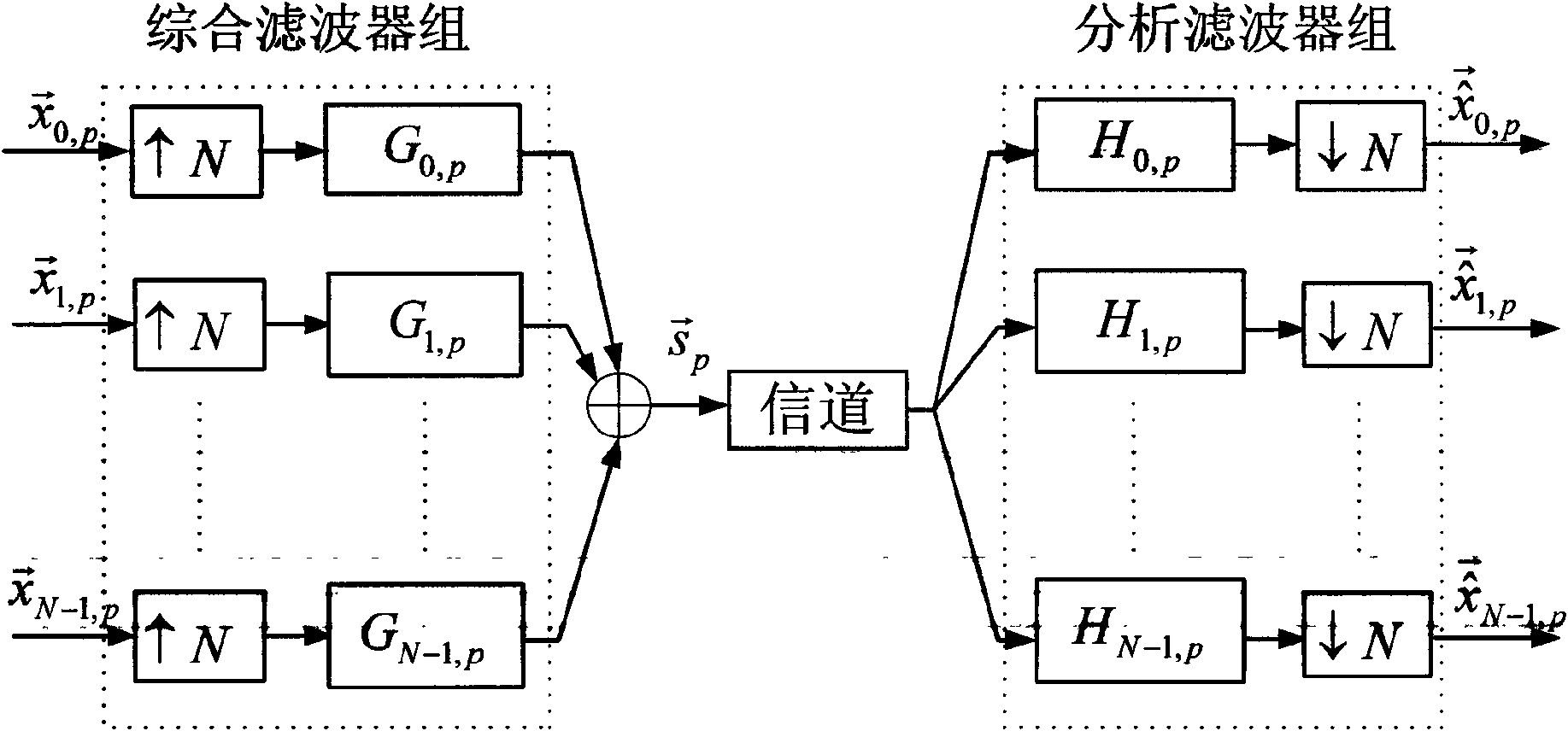
[0038] 1. Design of Fractional Fourier Domain Multiplexer
[0039] (1) According to the number M of users in the designed system, select M that satisfies the invertibility condition of matrix C in formula (3) 2 a fractional Fourier transform order, below, we briefly discuss the multiplexing order p i The selection method of , the determinant value of matrix C in formula (3) can be expressed as the form shown in formula (8)
[0040] | C | = Π i = 0 M - 1 e - j ·...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com