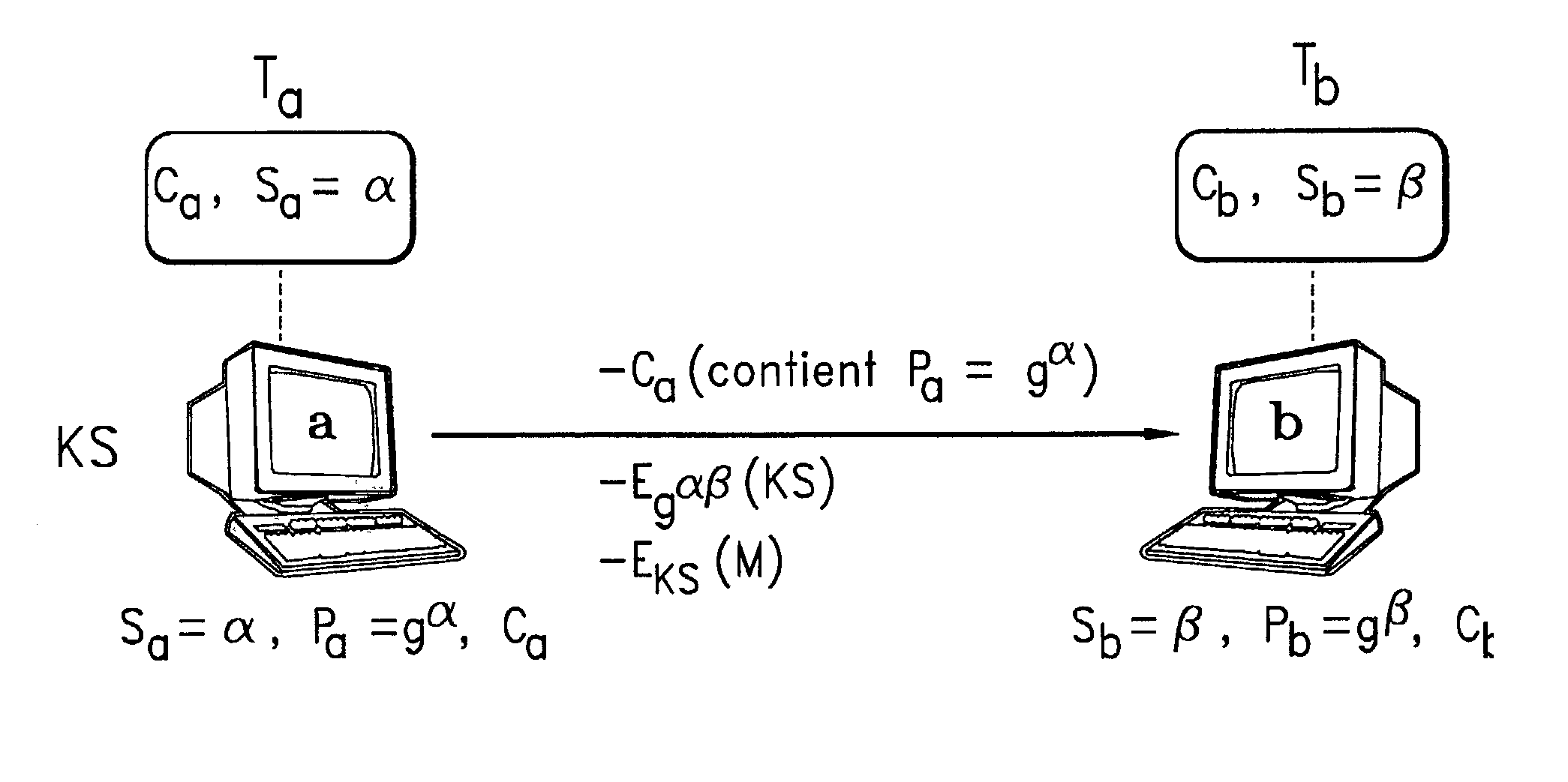Patents
Literature
302 results about "Secure communication system" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
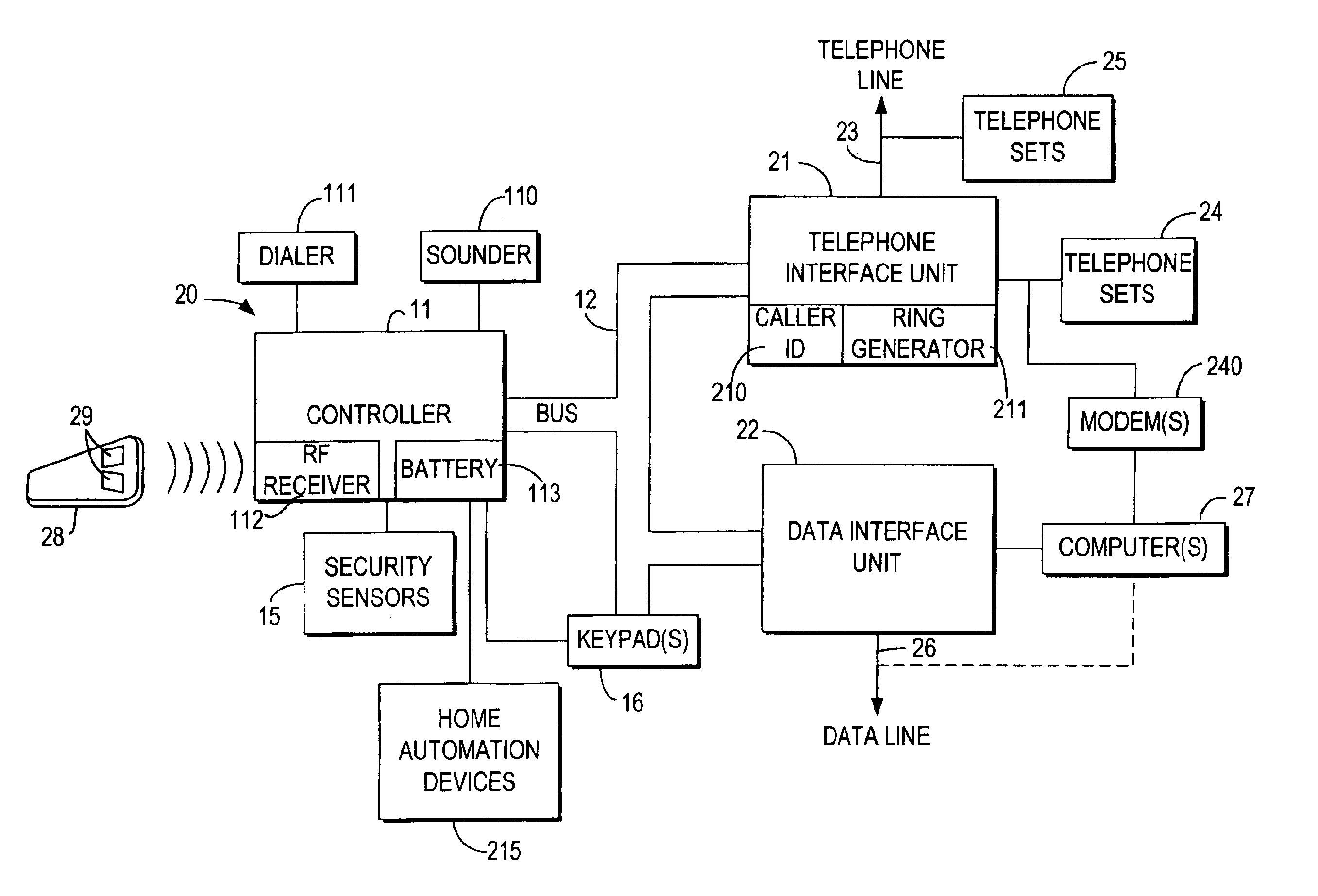
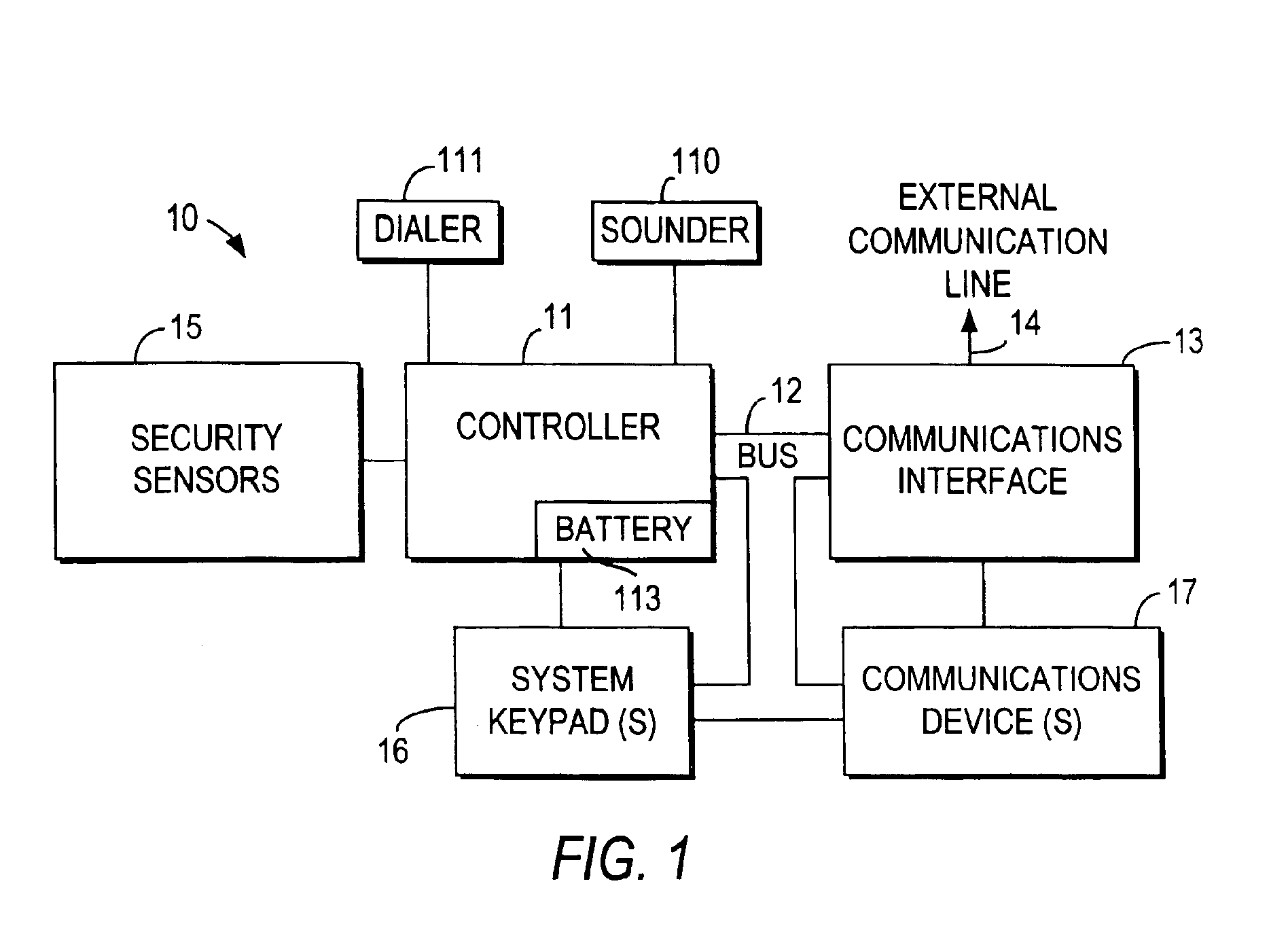
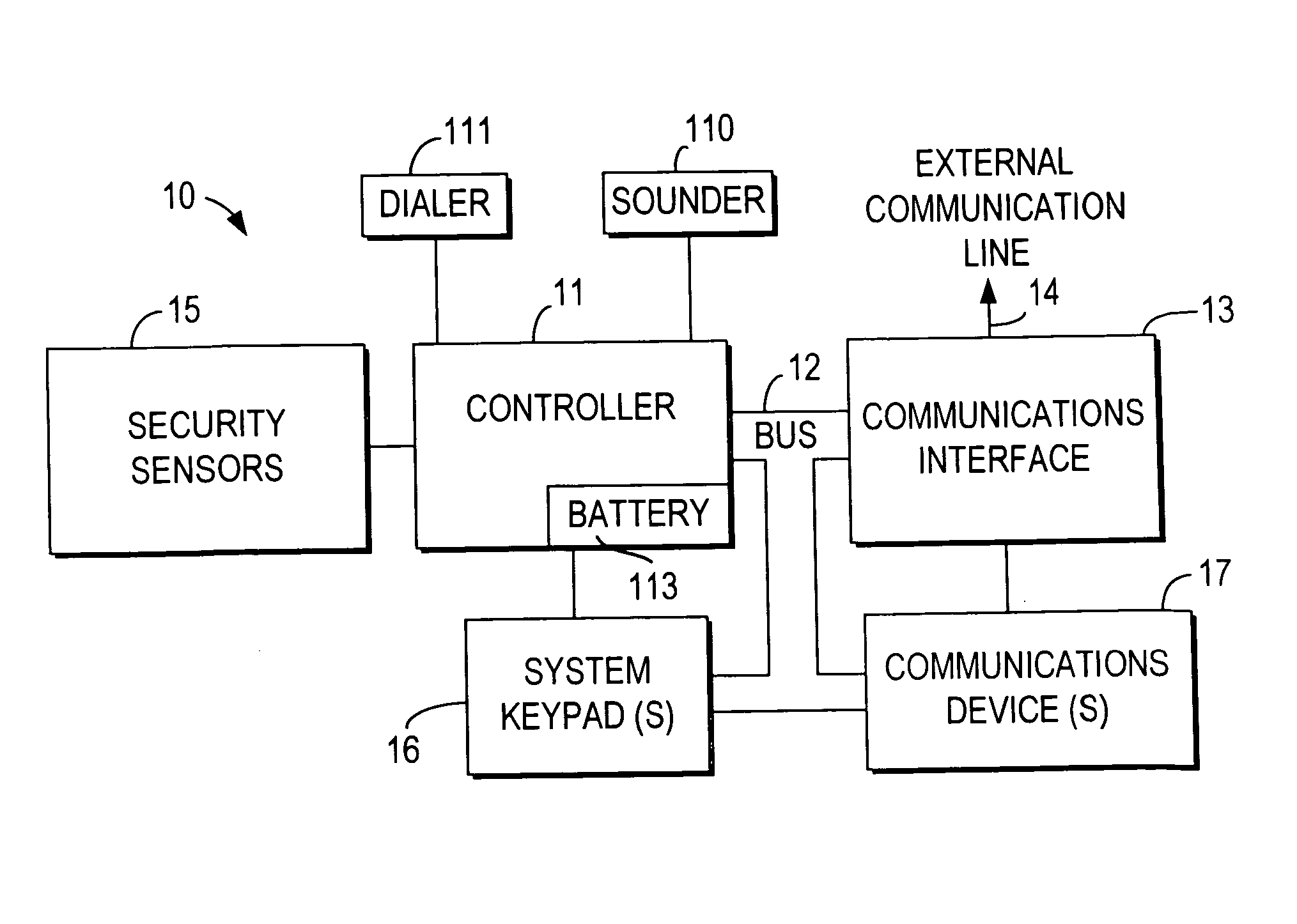
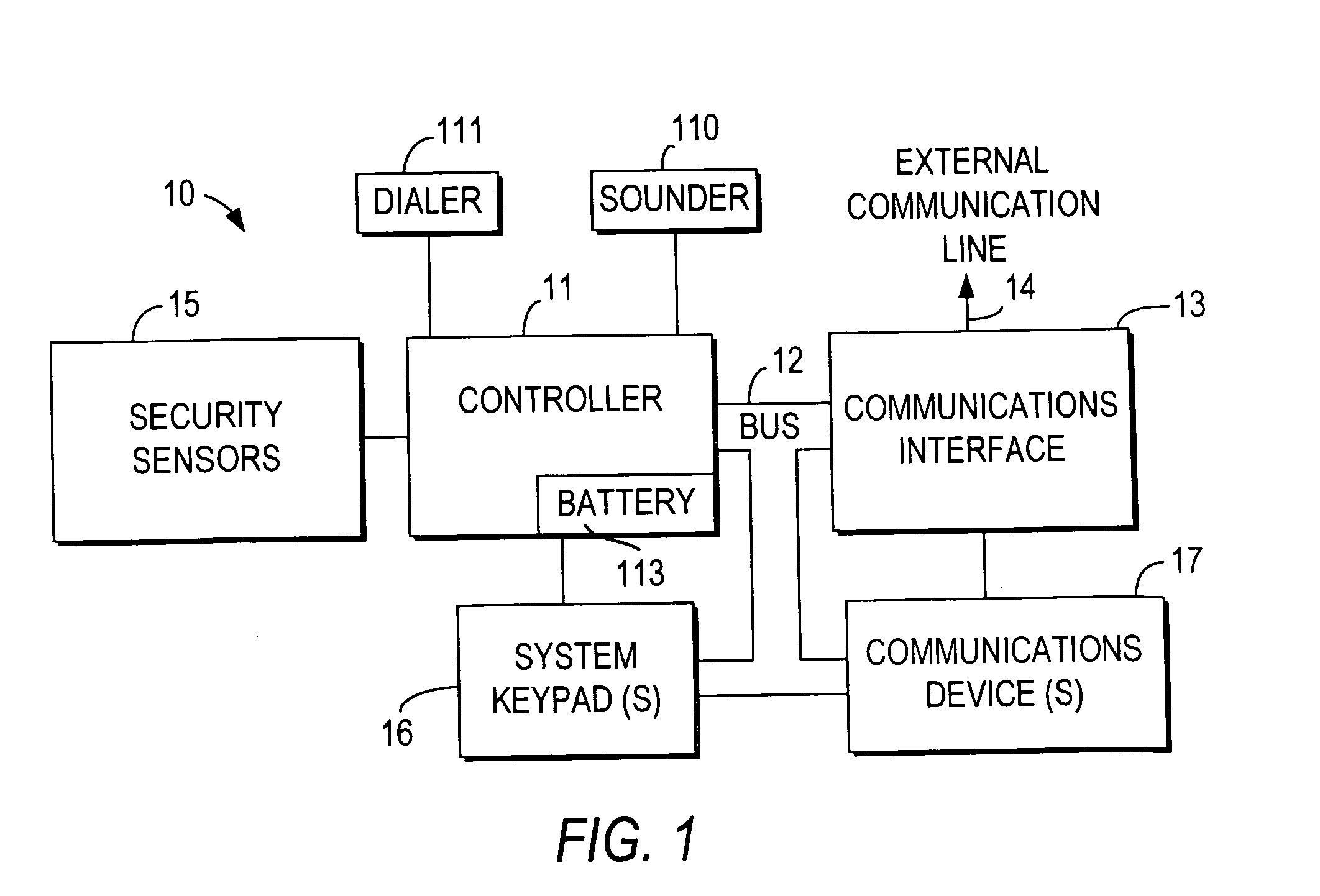
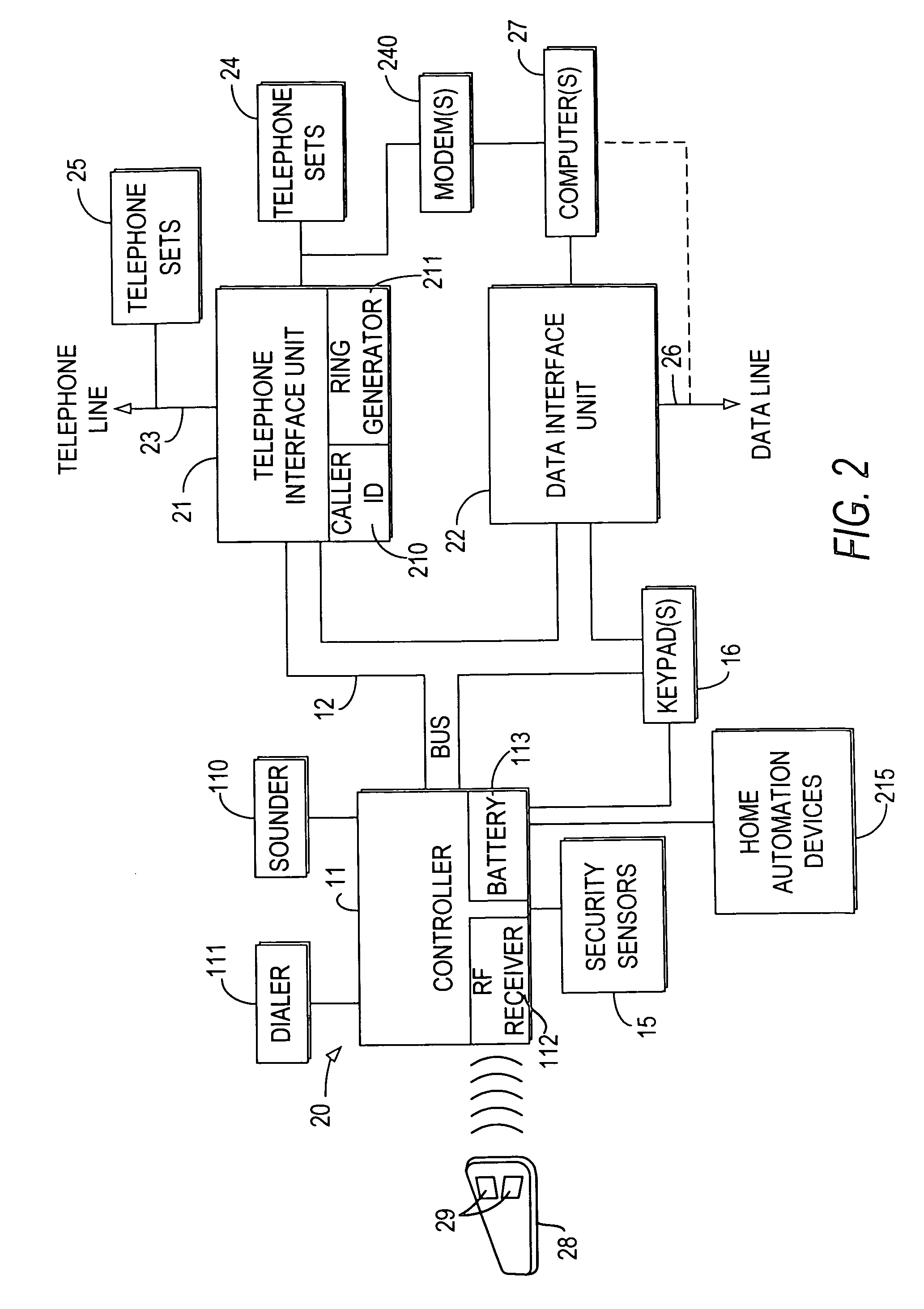
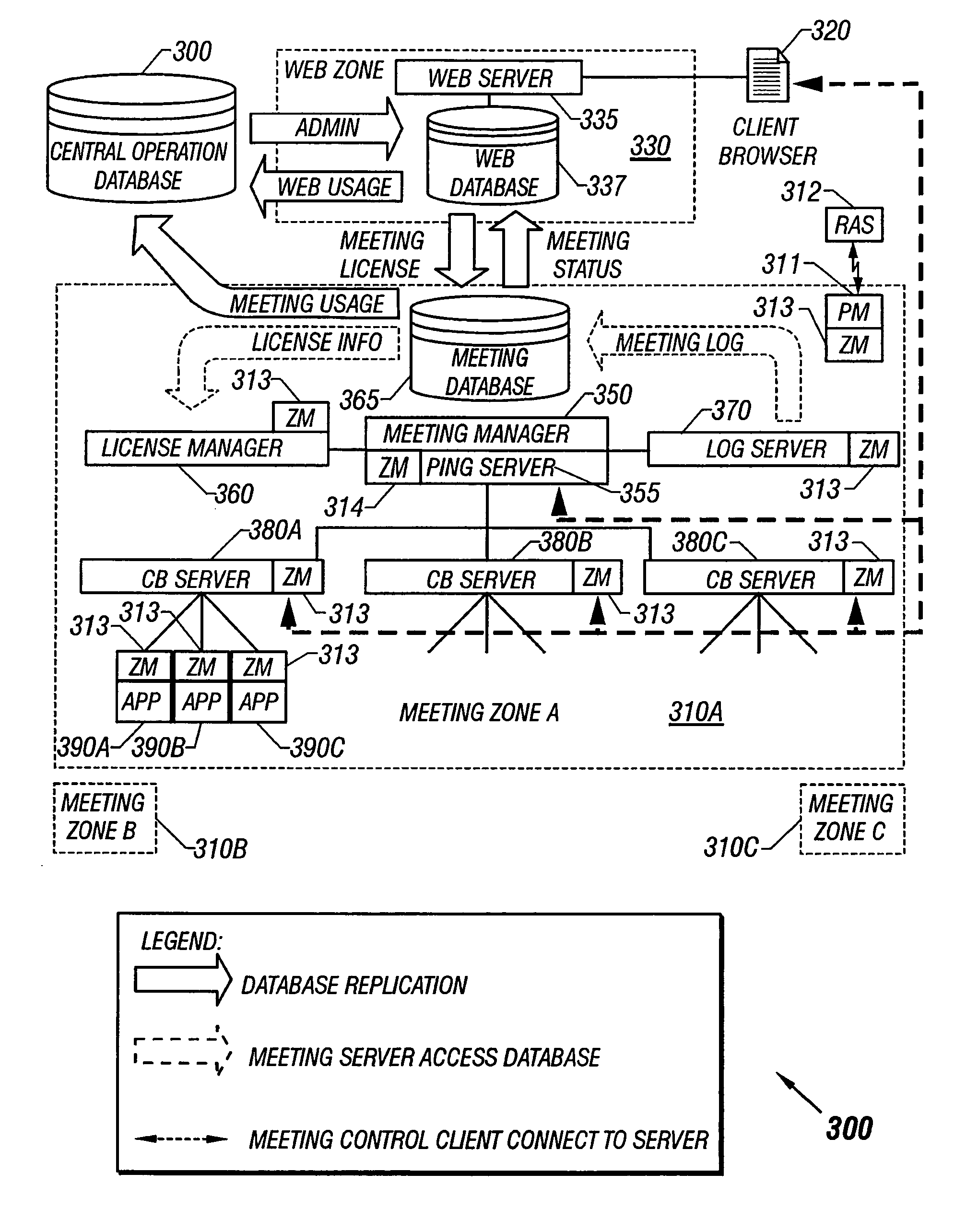
Integrated security and communications system with secure communications link
InactiveUS6928148B2Minimize the numberImprove securitySpecial service for subscribersCalled number recording/indicationData interfaceSecurity system
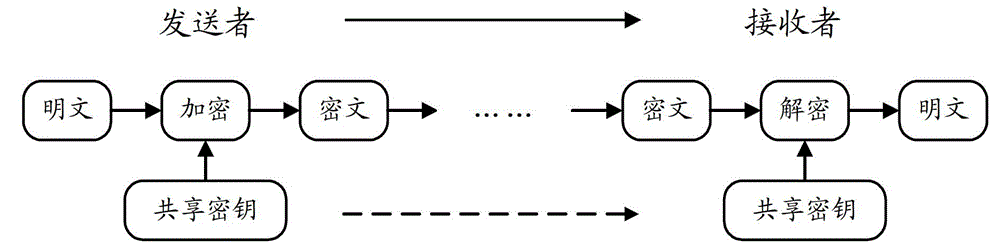
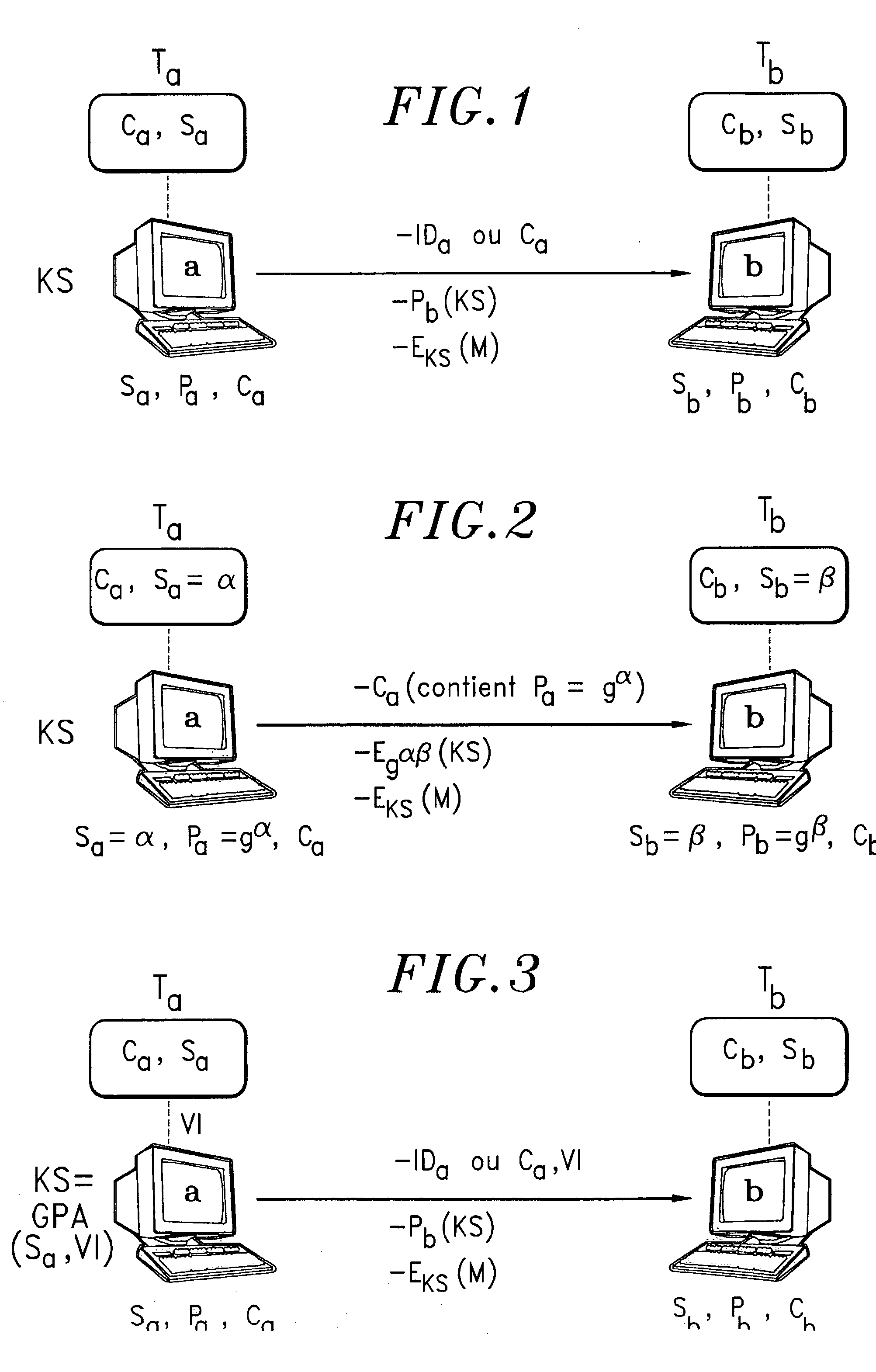
An integrated security and communications system combines a security system to either or both of a telephone system interface and a data interface. Users have access to voice-mail or other PBX-type telephone functions, many or all of which can be accessed not only at telephone sets, but also at keypads of the security system. Data functions such as electronic mail and possible partial or full World Wide Web access may also be provided at the keypads, as well as at connected personal computers or computer terminals. The system keypads may be enhanced to better accommodate some of the added functions. A central communications station could be used to maintain secure, shared private key encrypted communications with each premises system, using a redirector arrangement or relay to allow each premises system to communicate securely with a central monitoring station and with other systems. The secure communications system could be used without a security system to allow secure computer-to-computer communications.
Owner:ADEMCO INC
Secure communications system for collaborative computing
InactiveUS6901448B2Improve scalabilityEliminate points of failureSpecial service provision for substationMultiple digital computer combinationsCommunications systemPrivate network
A method of distributed collaborative computing is provided. The method includes: partitioning a collaboration function into sub-functions; assigning at least one said sub-function to each of a plurality of logical processes; associating a respective management process with each of said plurality of logical processes, said logical processes configured so that each said logical process is capable of communicating with every other said logical process through said respective management process; communicating between said logical processes using said respective management processes; and monitoring said respective management processes with a single supervisor process; wherein said communicating employs a secure protocol on a dedicated network.
Owner:CISCO TECH INC
Secure Communication Systems, Methods, and Devices
InactiveUS20110302408A1Facilitates secure communicationUser identity/authority verificationSecurity arrangementData validationCommunications system
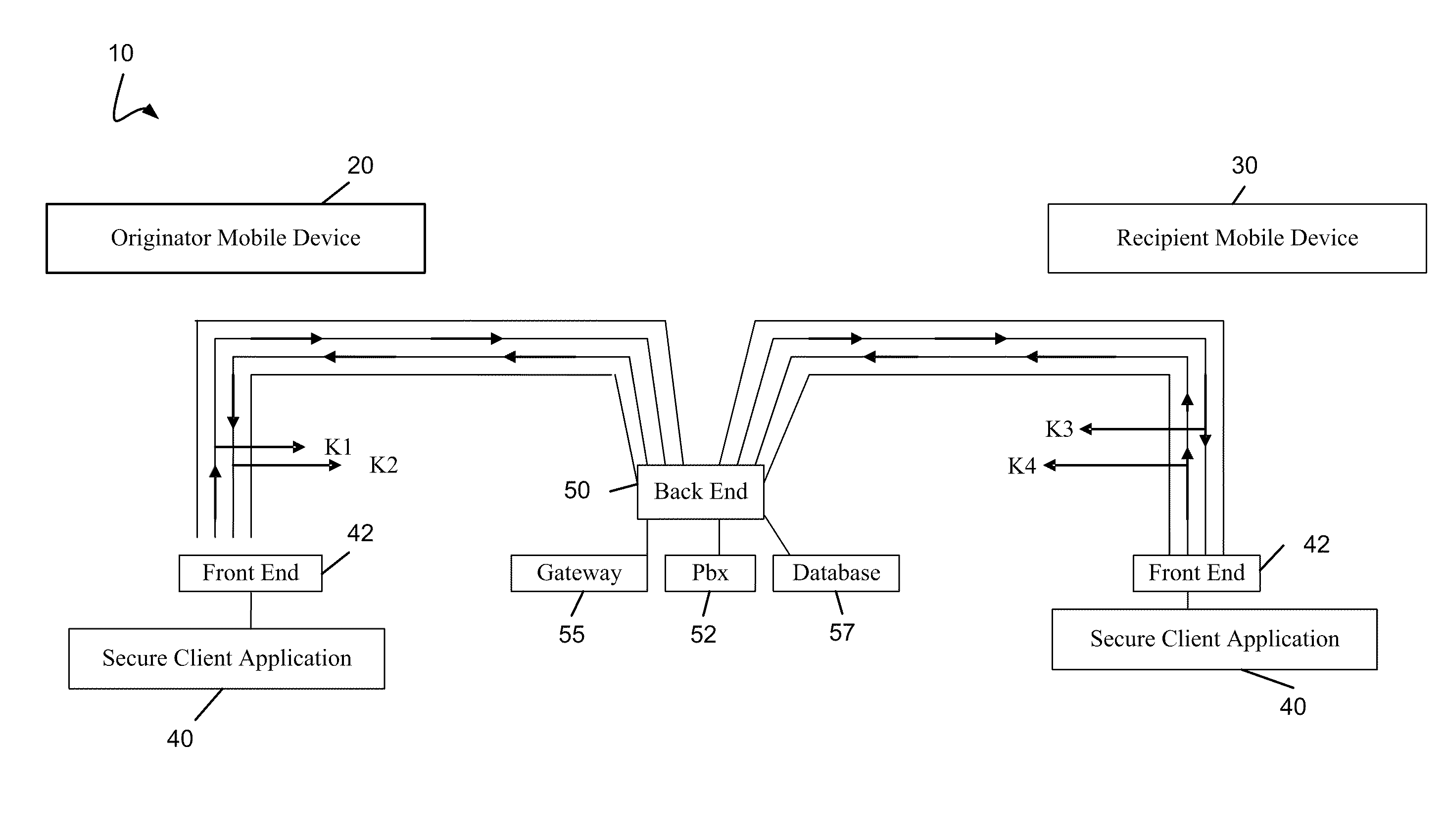
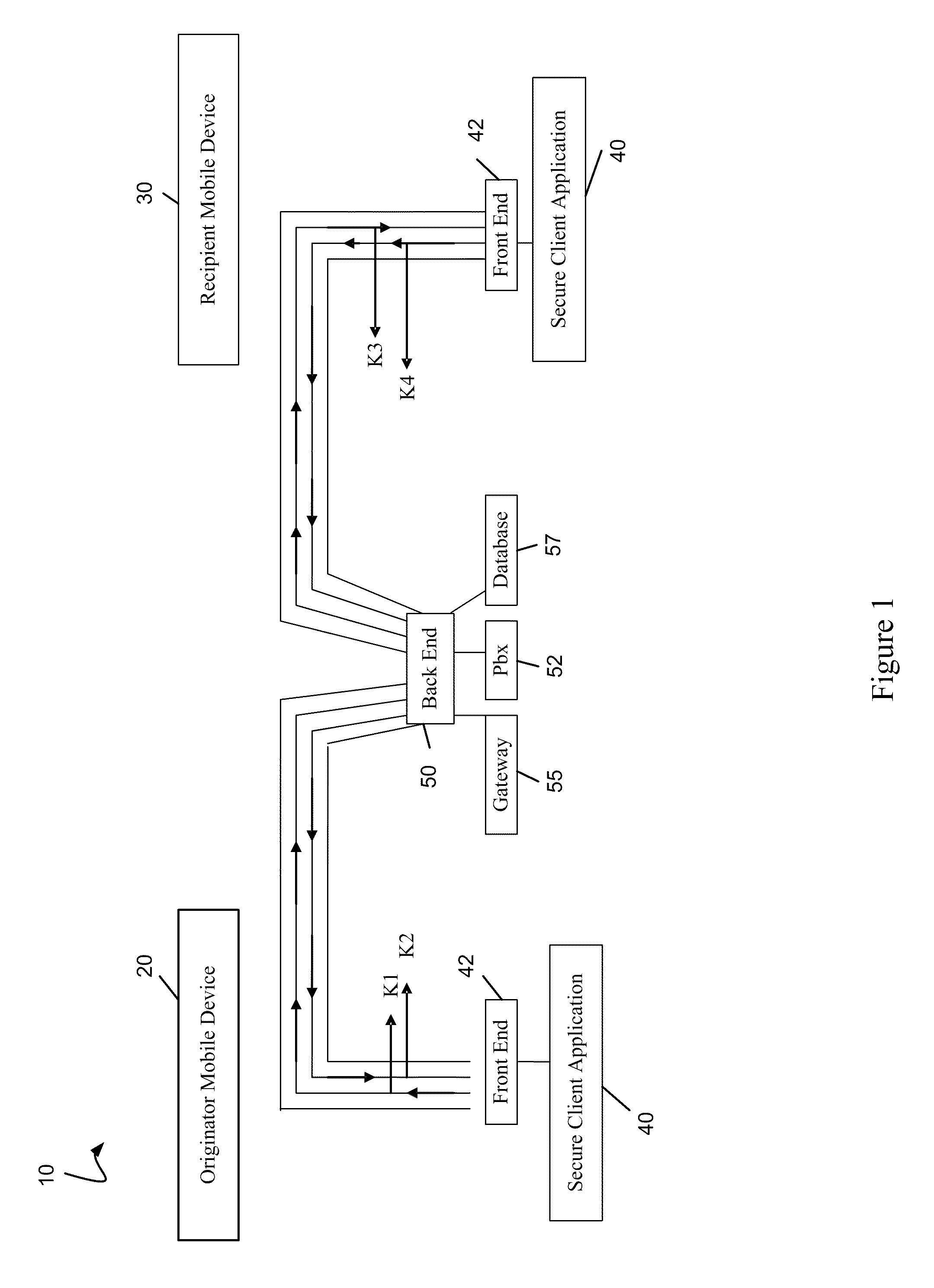
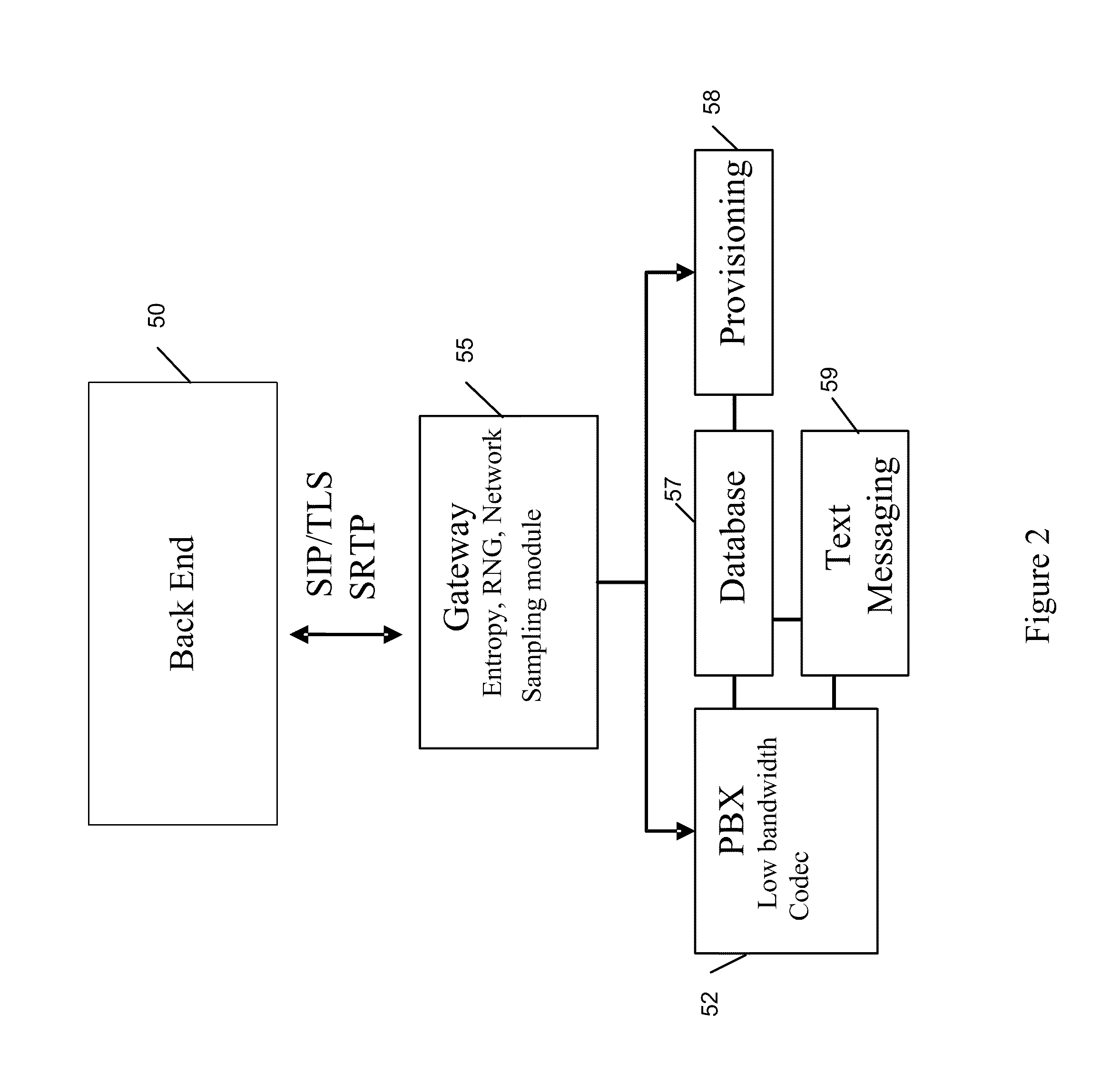
In par, the invention relates to a secure communication system. The system includes a voice call processing server; a user database in communication with the server; and a security gateway in communication with the server and the database, wherein the gateway transmits an encrypted signaling key and at least one encrypted media key in response to validating a mobile device using configuration data stored in the database, wherein the server tracks call traffic encrypted using the at least one media key, the call traffic routed using the Internet.
Owner:MORRIGAN PARTNERS
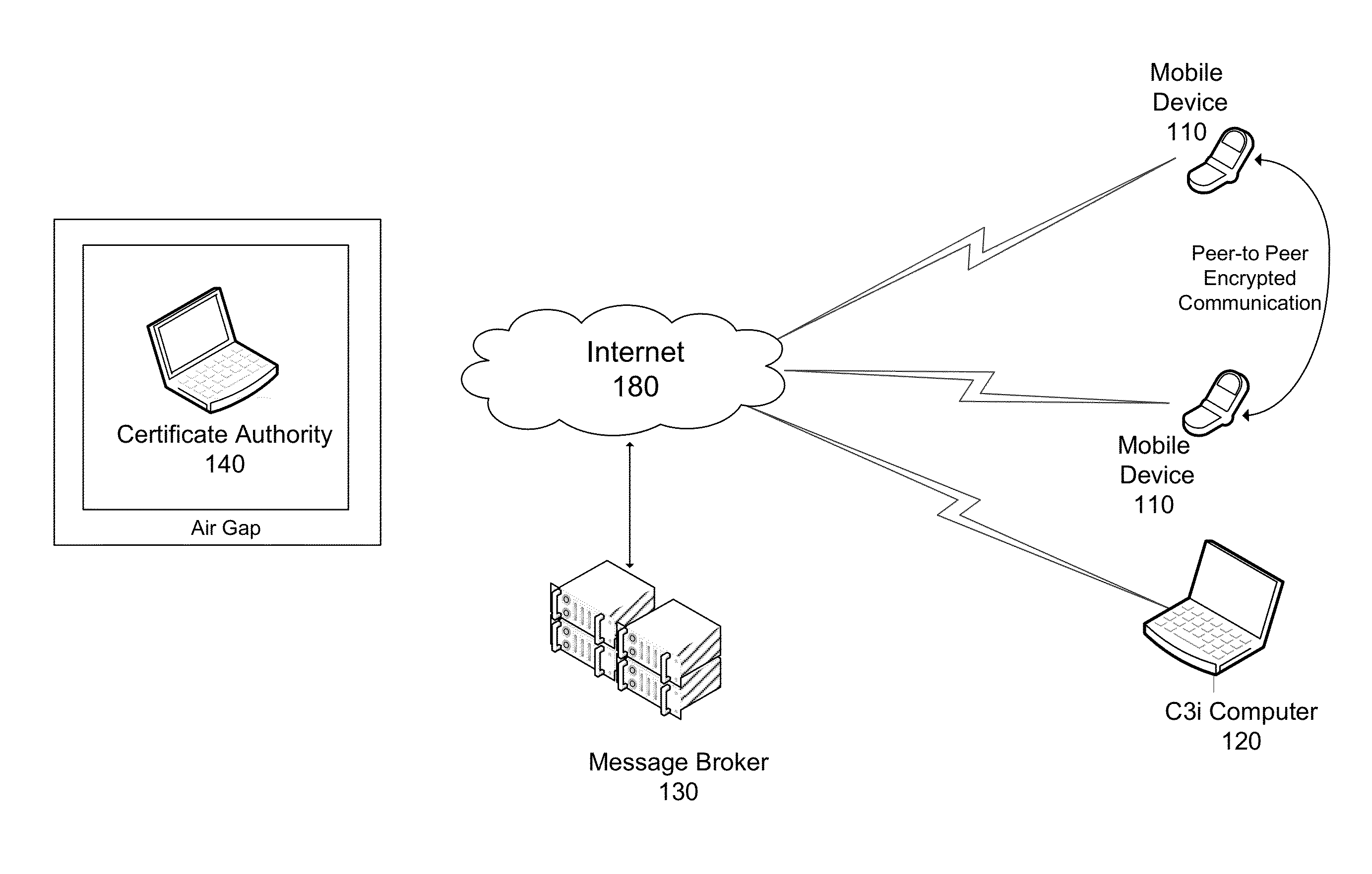
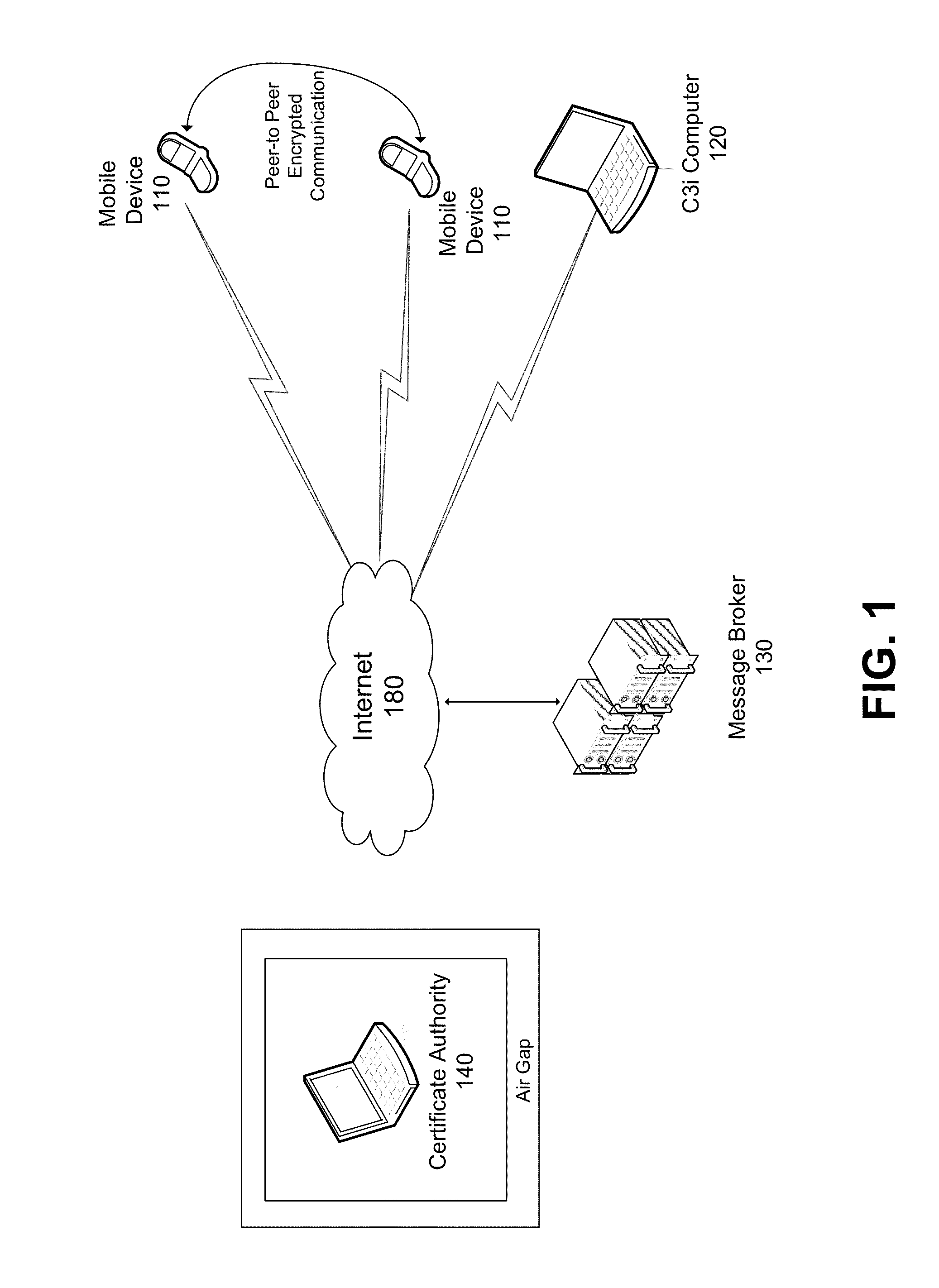
Secure Communication System For Mobile Devices
ActiveUS20110131406A1Multiple keys/algorithms usageSecret communicationControl communicationsChain of trust
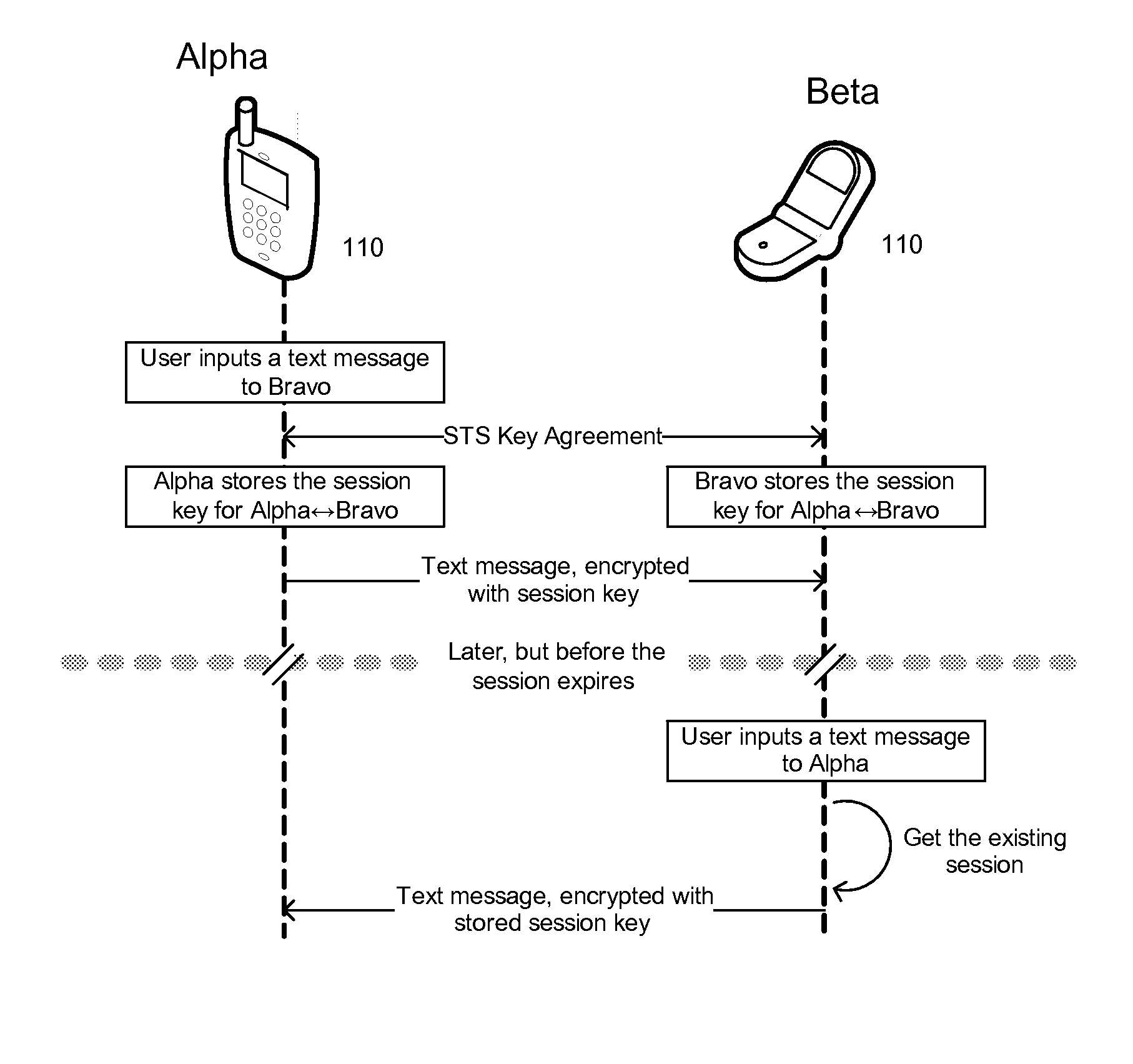
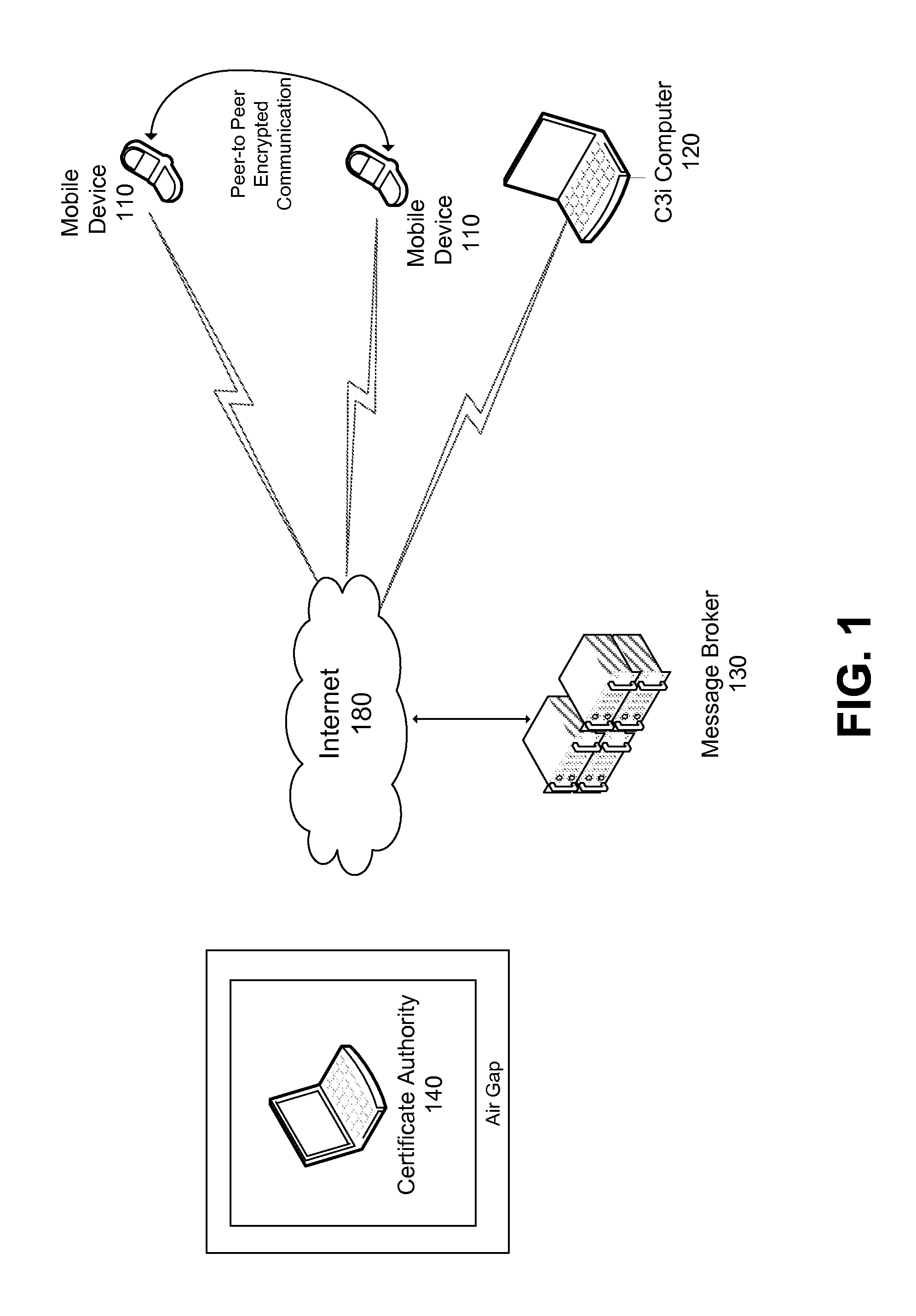
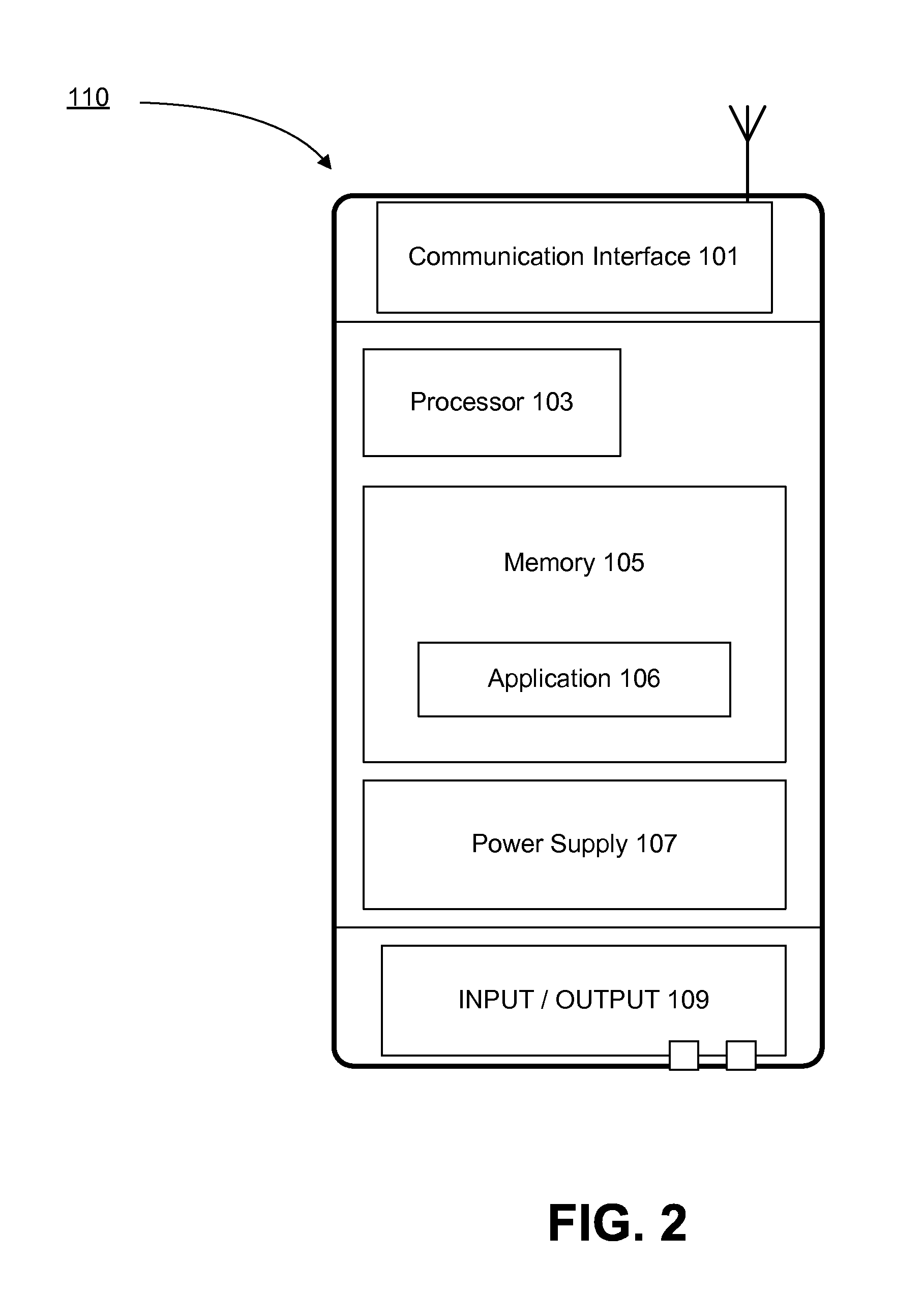
A comprehensive solution for providing secure mobile communication is provided. The system includes techniques for authentication and control of communication end-points; chain of trust to ensure devices are certified as authentic; contact list management; peer-to-peer encrypted voice, email, and texting communication; and a technique for bypassing an IP PBX to ensure high levels of security. The system is able to support use of commodity mobile communication devices (e.g., smart phones, laptops) over public carrier networks.
Owner:CUMMINGS ENG CONSULTANTS
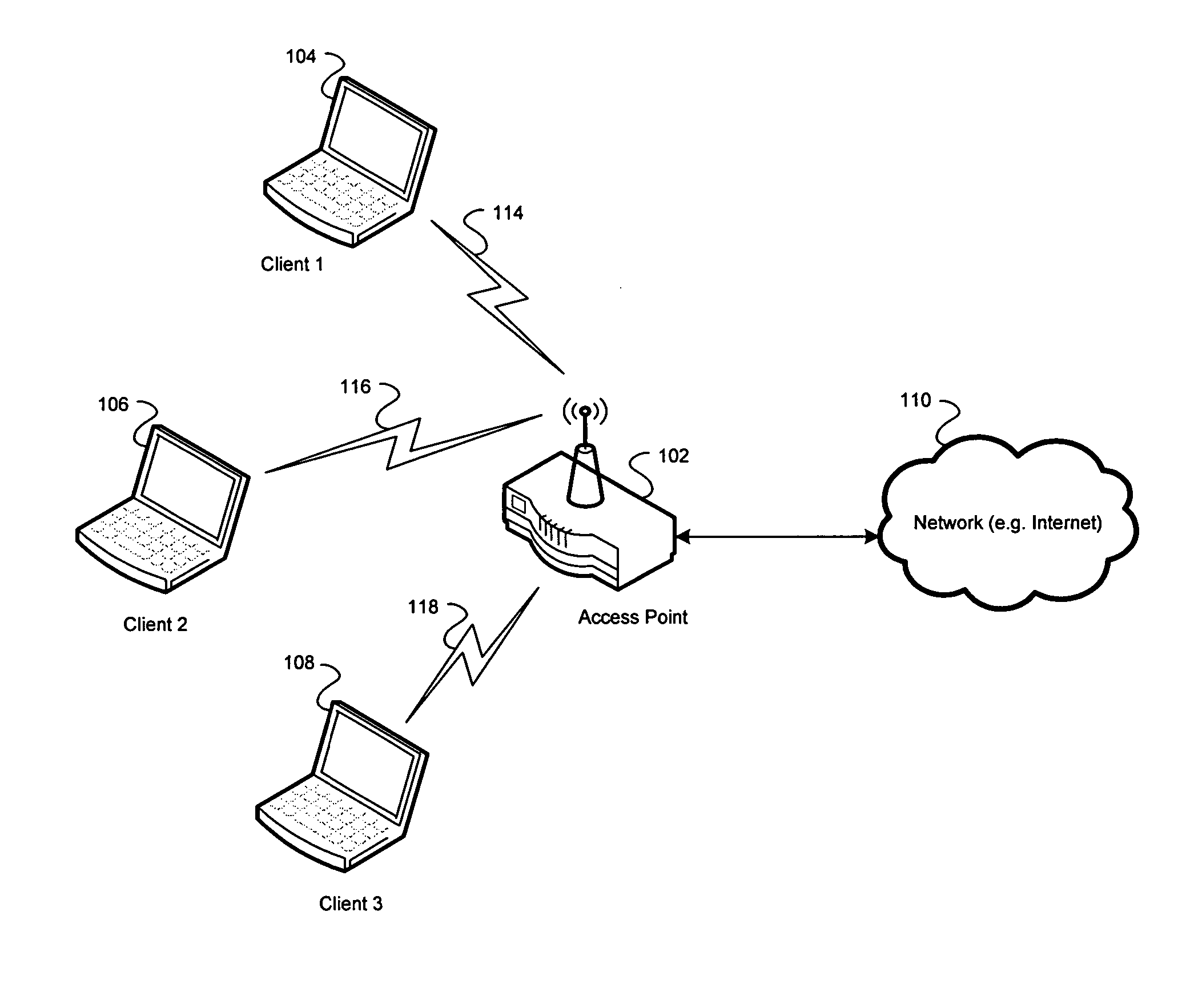
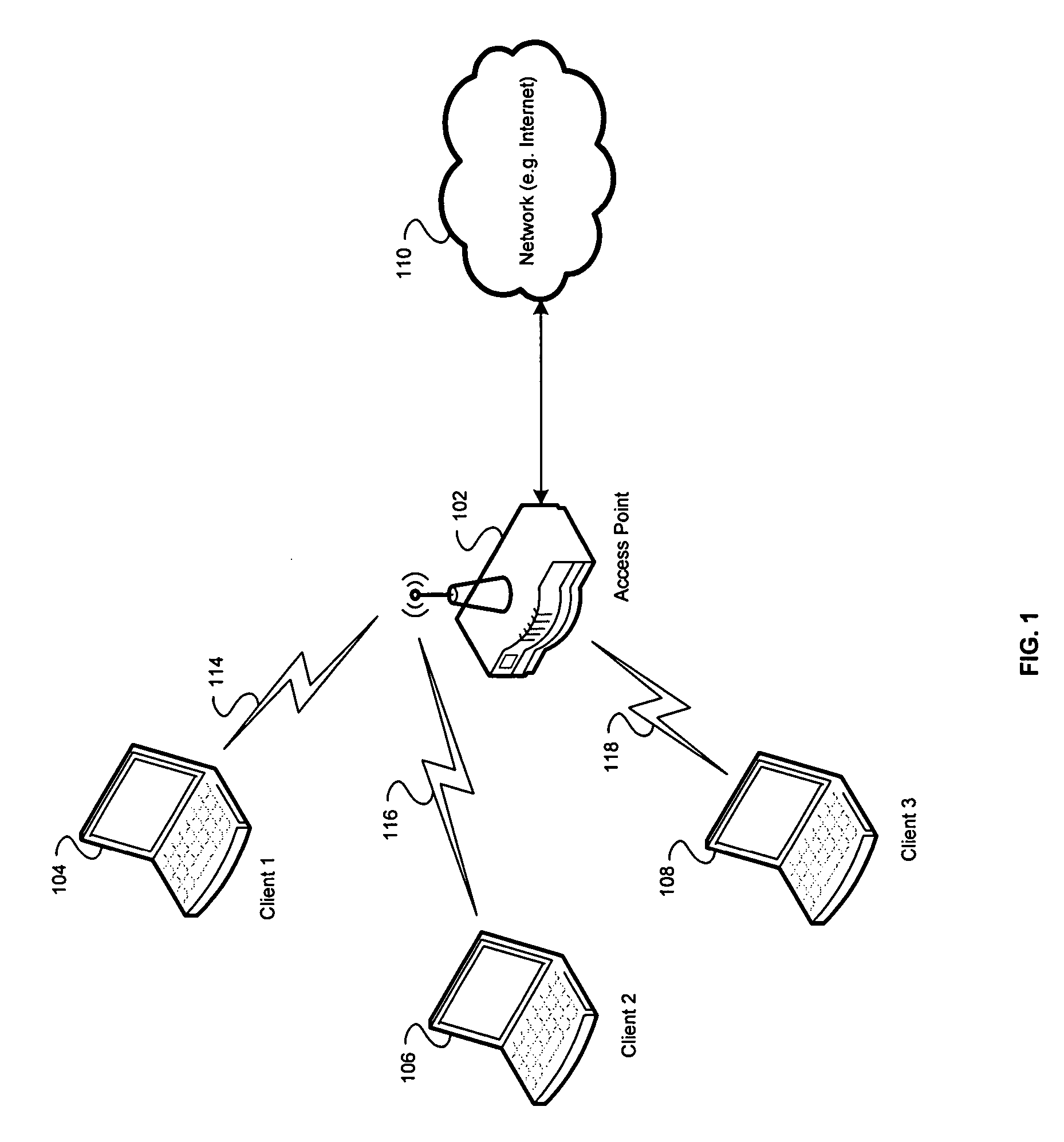
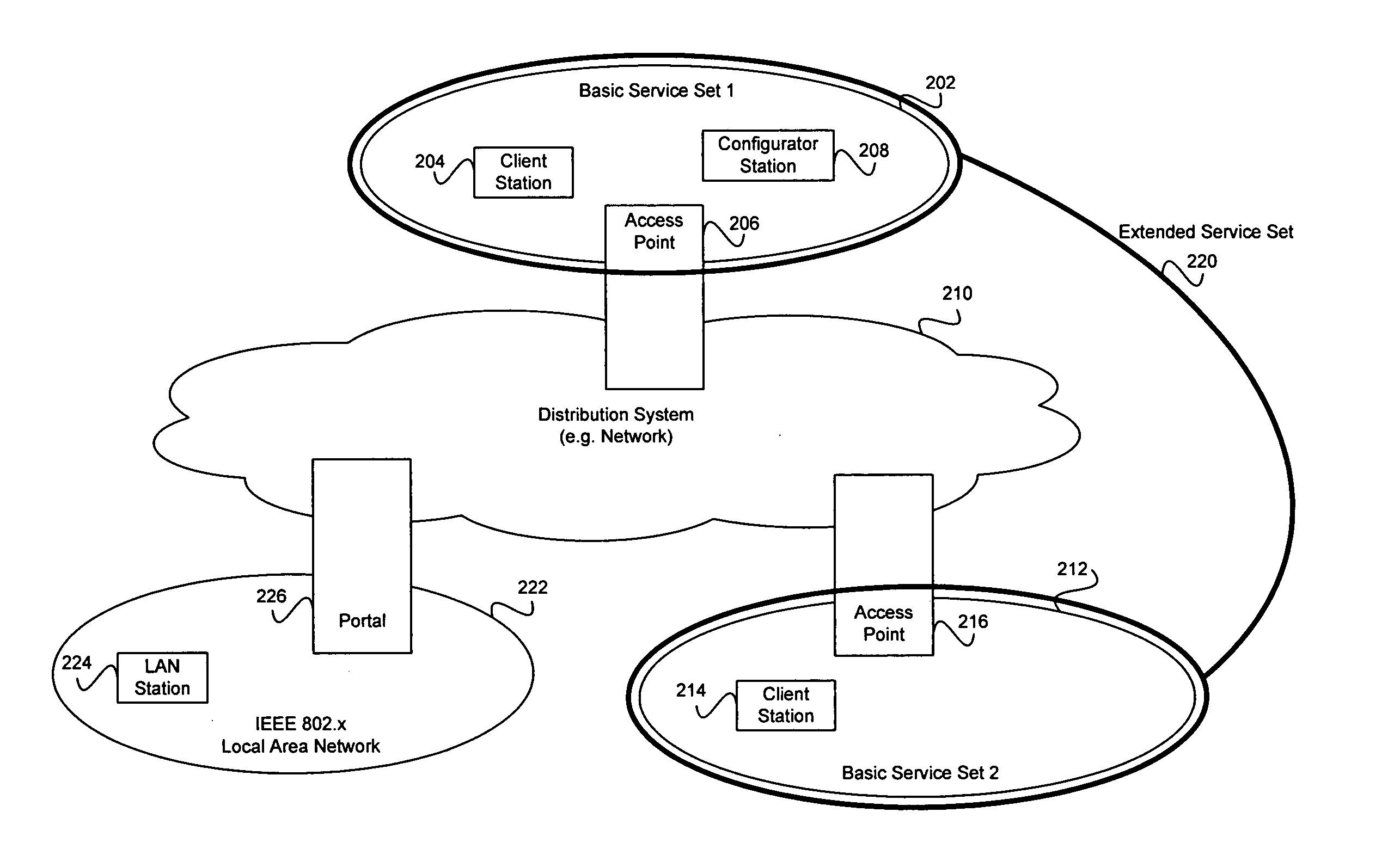
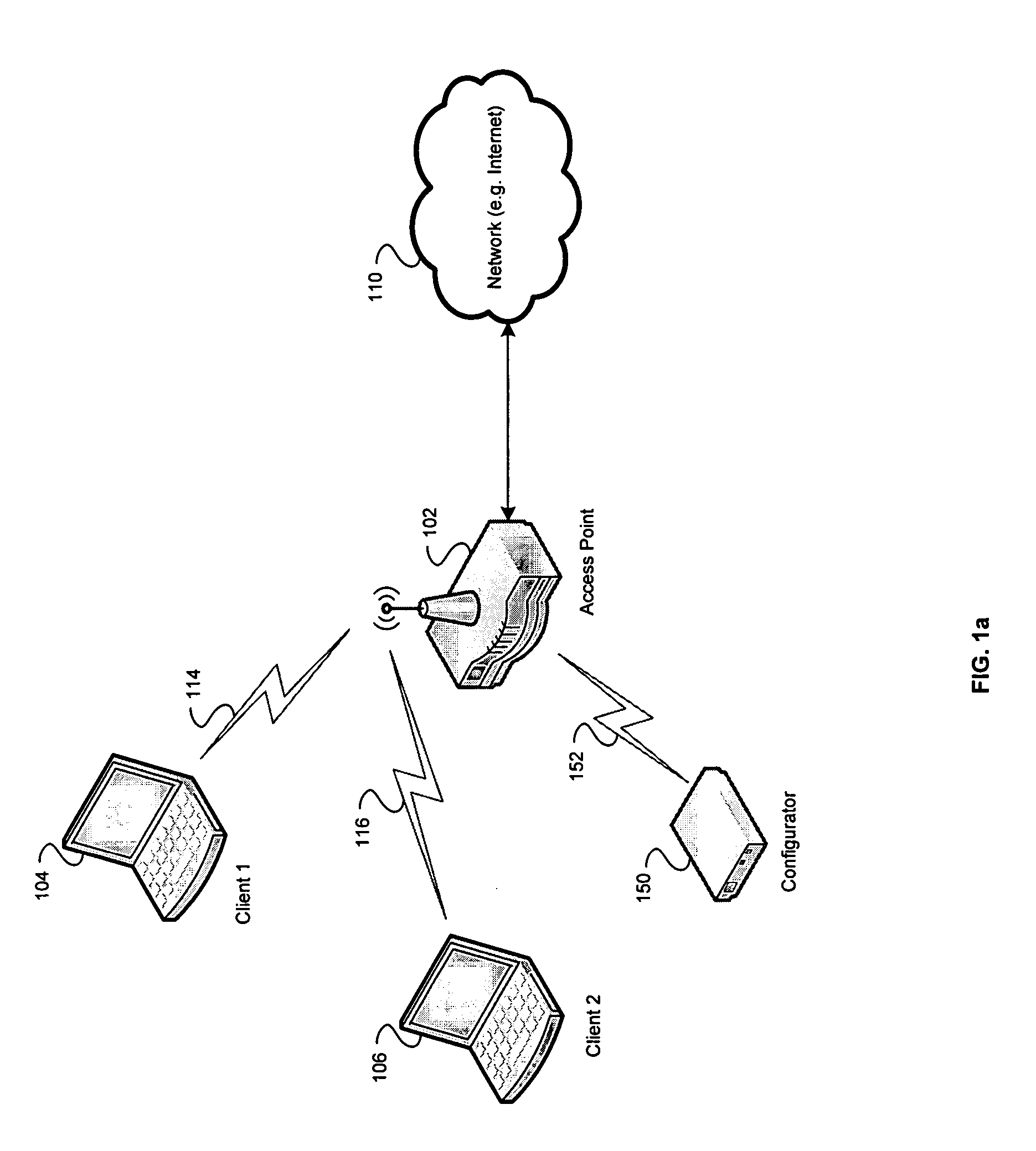
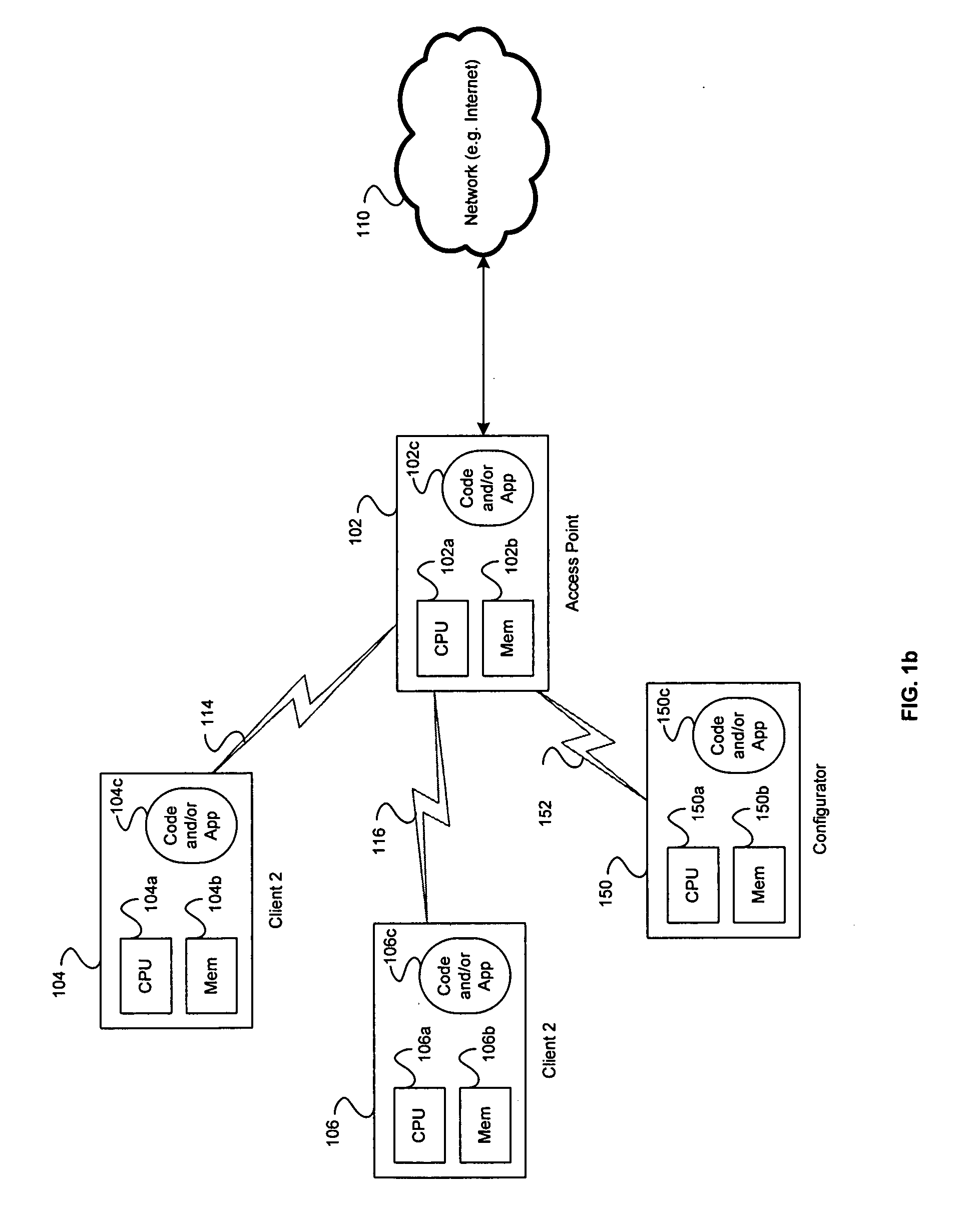
Method and system for exchanging setup configuration protocol information in beacon frames in a WLAN
InactiveUS20060039341A1Digital data processing detailsMultiple digital computer combinationsBeacon frameClient-side
Certain aspects of a method for enabling exchange of information in a secure communication system may comprise configuring at least one 802.11 client station via authentication enablement information comprising data that specifies a time period during which configuration is allowed. The data that specifies a time period during which configuration is allowed may comprise a configuration window open field, which indicates a period when a configuration setup window is open. At least one client station may be configured via the authentication enablement information comprising recently configured data, which indicates whether at least one configurator has configured at least one other client station within the time period during which the configuration is allowed.
Owner:AVAGO TECH INT SALES PTE LTD
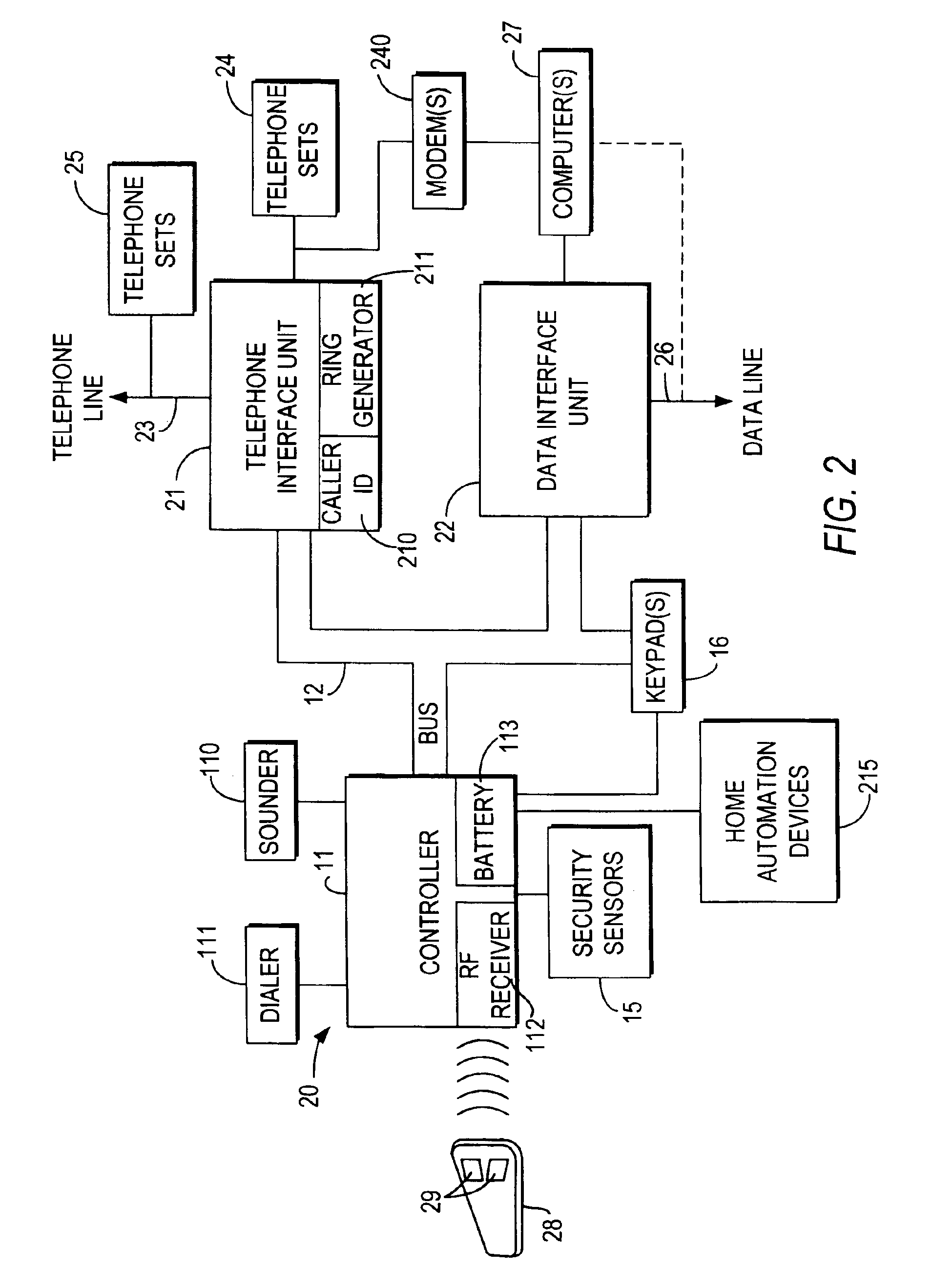
Integrated security and communications system with secure communications link
InactiveUS20050213715A1Minimize the numberImprove securitySpecial service for subscribersCalled number recording/indicationData interfaceSecurity system
An integrated security and communications system combines a security system to either or both of a telephone system interface and a data interface. Users have access to voice-mail or other PBX-type telephone functions, many or all of which can be accessed not only at telephone sets, but also at keypads of the security system. Data functions such as electronic mail and possible partial or full World Wide Web access may also be provided at the keypads, as well as at connected personal computers or computer terminals. The system keypads may be enhanced to better accommodate some of the added functions. A central communications station could be used to maintain secure, shared private key encrypted communications with each premises system, using a redirector arrangement or relay to allow each premises system to communicate securely with a central monitoring station and with other systems. The secure communications system could be used without a security system to allow secure computer-to-computer communications.
Owner:ADEMCO INC
Reoccuring Keying System
ActiveUS20130054967A1Avoid Security CompromiseReduce inconvenienceUser identity/authority verificationRolloverSecure communication system
A secure communication system or method are disclosed that may employ a constant level of trust between participants and a security management entity. As part of the constant level of trust, a communication policy may cause participants to request key validation every time the participant wishes to take an action that requires use of a key. In this manner, the participant may regularly communicate with the security management, and this regular communication can be further used to implement key renewal and / or rollover procedures.
Owner:COMCAST CABLE COMM LLC
Secure communication system for mobile devices
ActiveUS8392699B2Multiple keys/algorithms usageSecret communicationControl communicationsChain of trust
Owner:CUMMINGS ENG CONSULTANTS
Safe and trusted block chain of data in traceability system and management method
InactiveCN108804928AQuick shareTransparent sharingDigital data protectionPlatform integrity maintainanceHuman–machine interfaceChain system
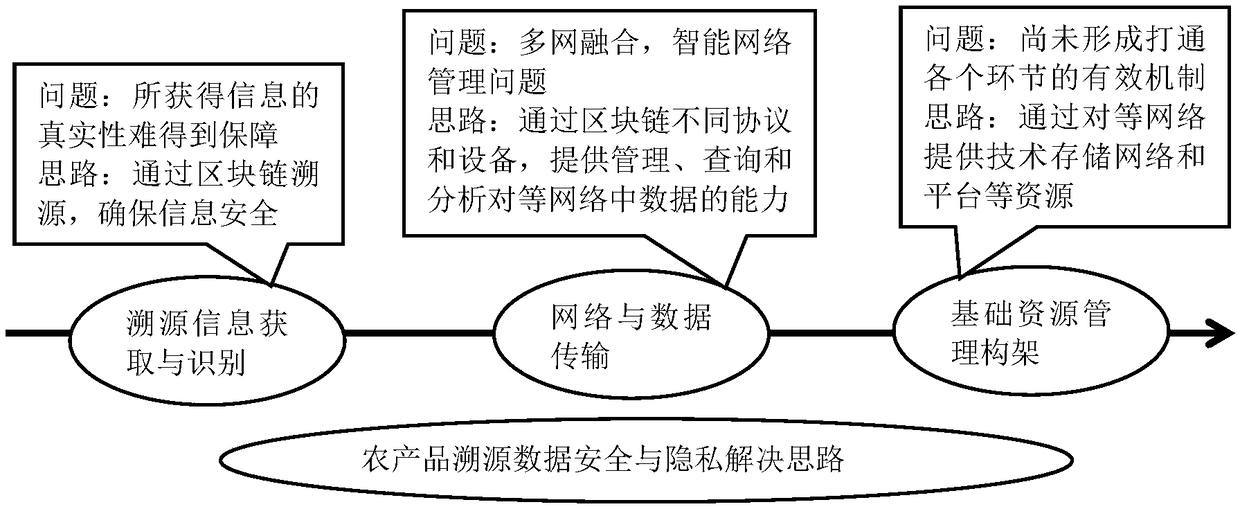
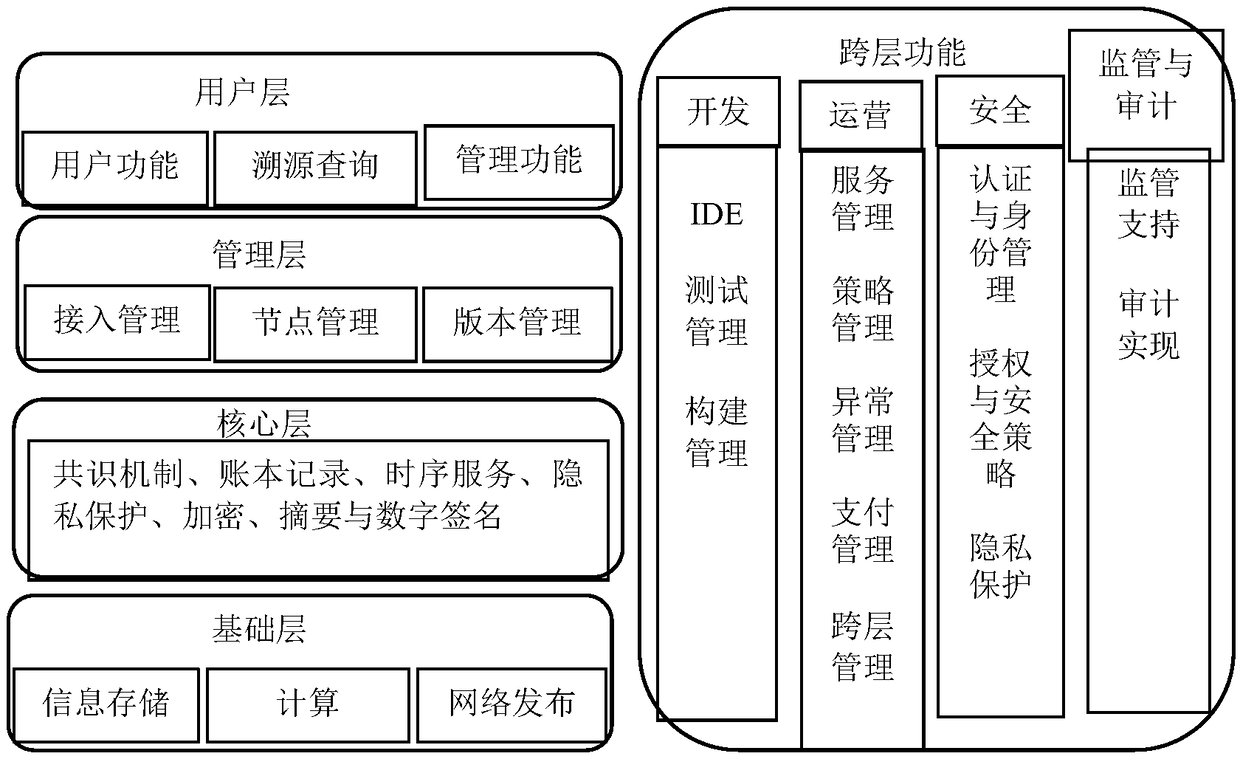
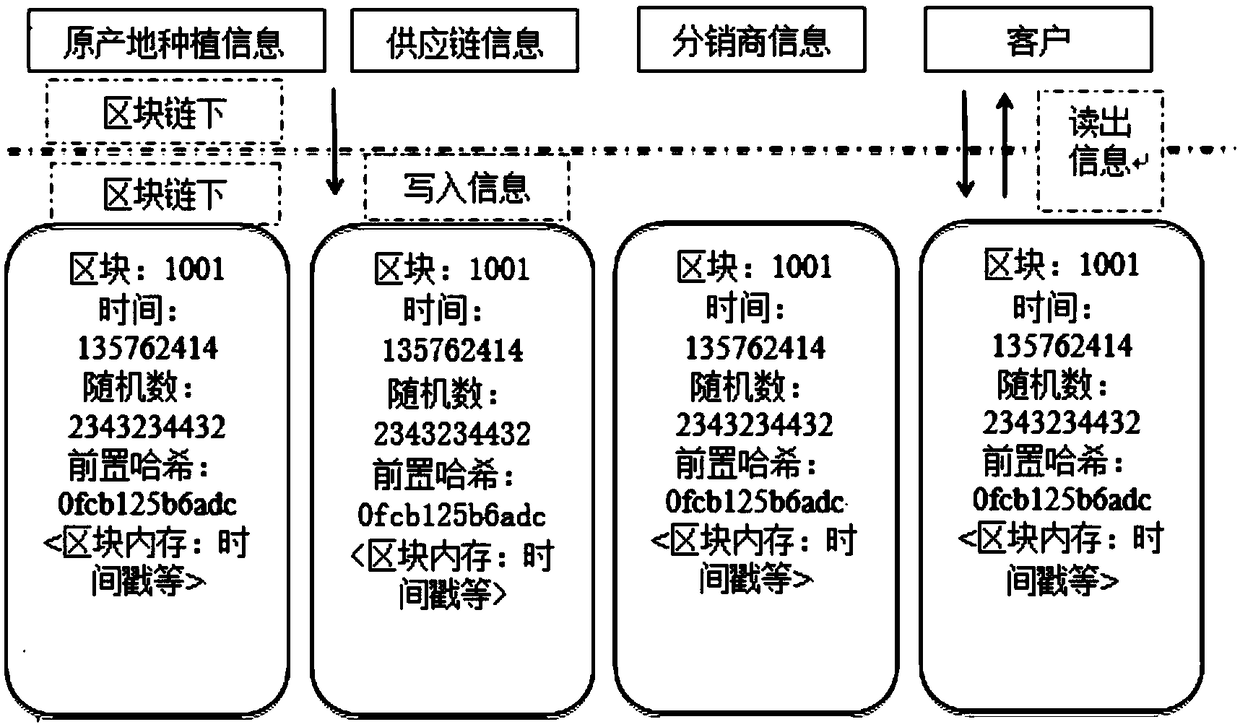
The invention belongs to the technical field of agricultural product data processing, and discloses a safe and trusted block chain of data in a traceability system and a management method, wherein a user layer is a user-oriented interface and performs human-machine interface information interaction with agricultural product consumers; the user layer outputs the block chain service to other resource layers; a management / service layer provides uniform access and management service of nodes of participant parties of agricultural product traceability; a core layer is the core functional layer of the block chain system and provides reliable and efficient service capability for the safety traceability system; a basic layer provides the basic operation environment and components required by normal operation of the block chain system; a cross-layer functional layer provides service for the communication and infrastructure of the agricultural product traceability system. The system transplant the secure communication systems of the block chain into a platform and allows for faster and more transparent information sharing. The specification information communication is the encryption mechanism of strong security, and the asymmetric encryption system / public key system is used to ensure the information interaction security.
Owner:武汉工商学院
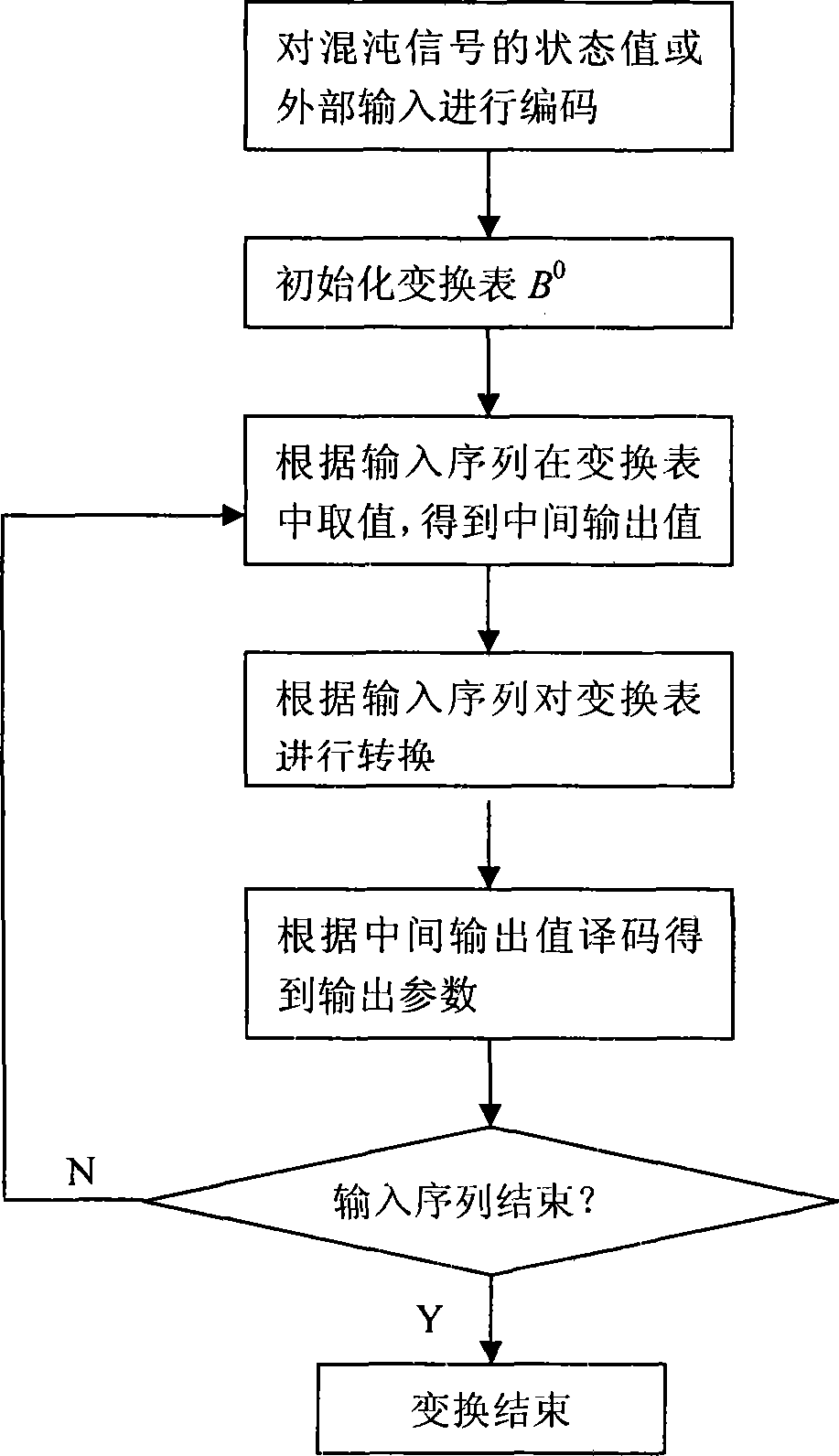
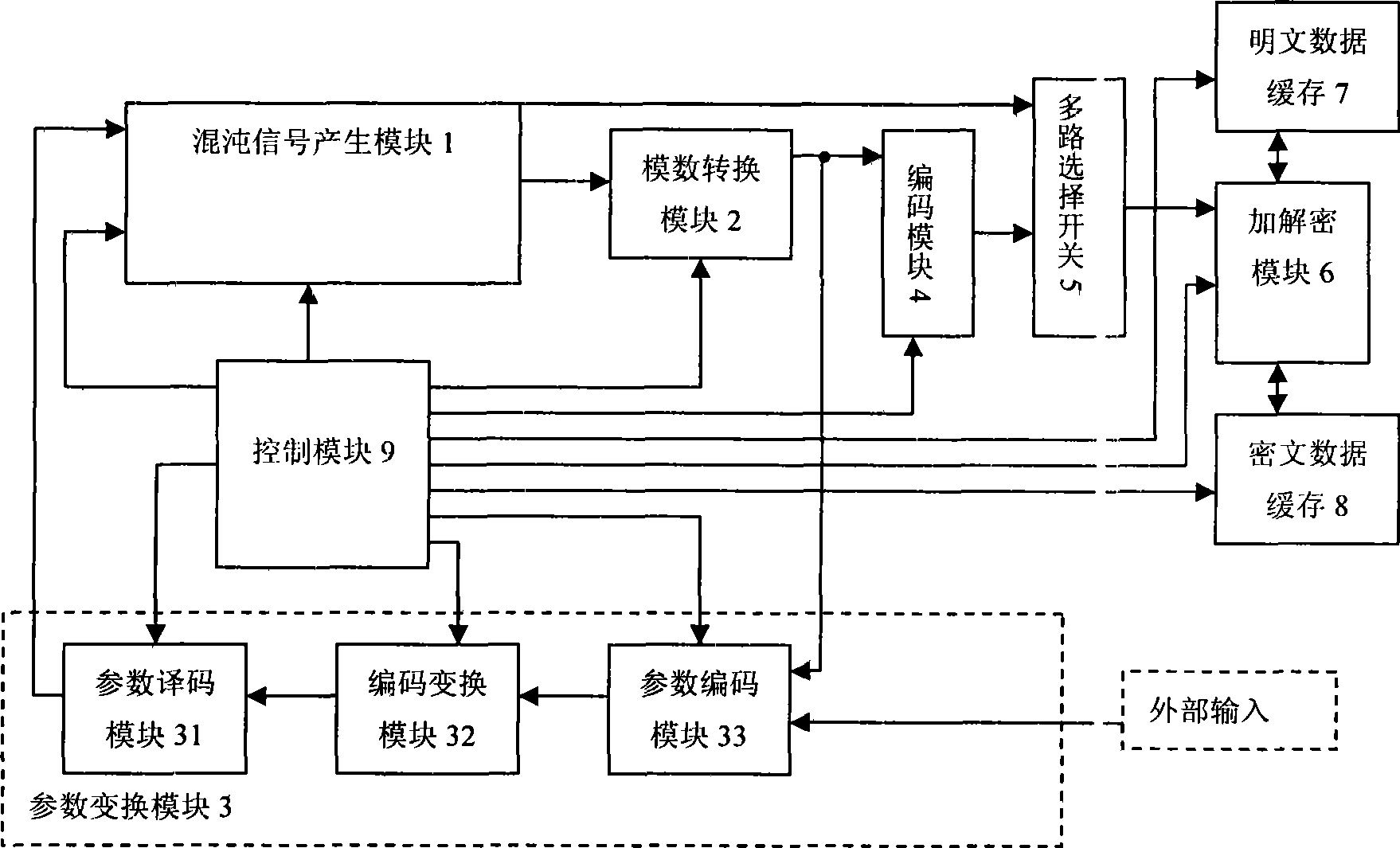
Method for generating variable parameter chaos signal and chaos secret communication system
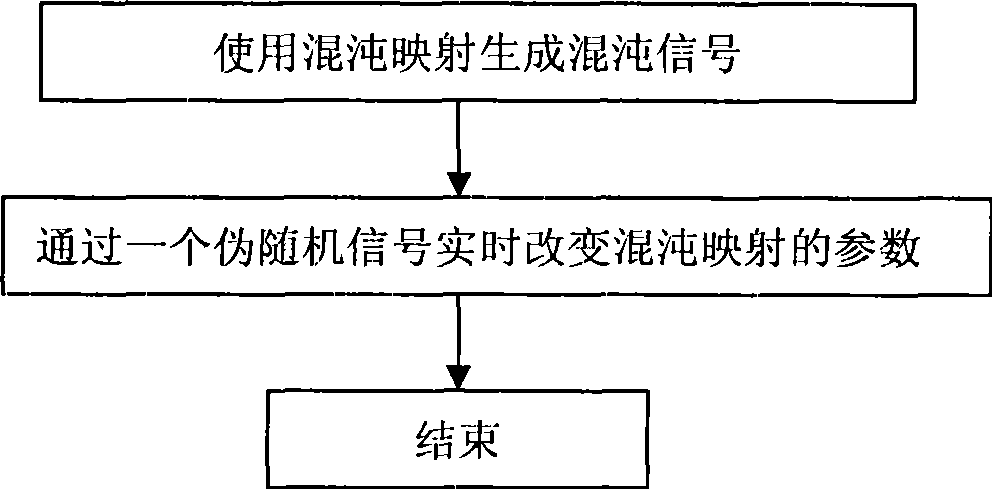
InactiveCN101394266AIncreased complexityDefense analysisSecuring communicationComplex mathematical operationsCiphertextNonlinear prediction
The invention discloses a method for generating a variable parameter chaotic signal, and a chaotic secure communication system. The method comprises the following steps: firstly, chaotic mapping is used to generate the chaotic signal; then a parameter set of the chaotic mapping is determined in advance, so as to process any pseudorandom signal, and enable the state of the pseudorandom signal and the elements of the parameter set to be in one-to-one correspondence; and a corresponding parameter is chosen to generate the variable parameter chaotic signal by chaotic mapping according to the state of the pseudorandom signal. The system comprises a chaotic signal generating module, an analog-to-digital conversion module, a parameter transformation module, a coding module, a multi-path choice switch, an encryption / decryption module, an encrypted message data cache, a plaintext data cache and a control module. The invention can increase the complexity of the output of the chaotic signal or a chaotic sequence, and effectively resist the analysis of the nonlinear prediction technology based on phase-space reconstruction. The output digital chaotic sequence can be taken as a pseudorandom number sequence or key stream to encrypt data; the output continuous chaotic signals can be used for designing a secret communication system based on chaos synchronization .
Owner:HUAZHONG UNIV OF SCI & TECH
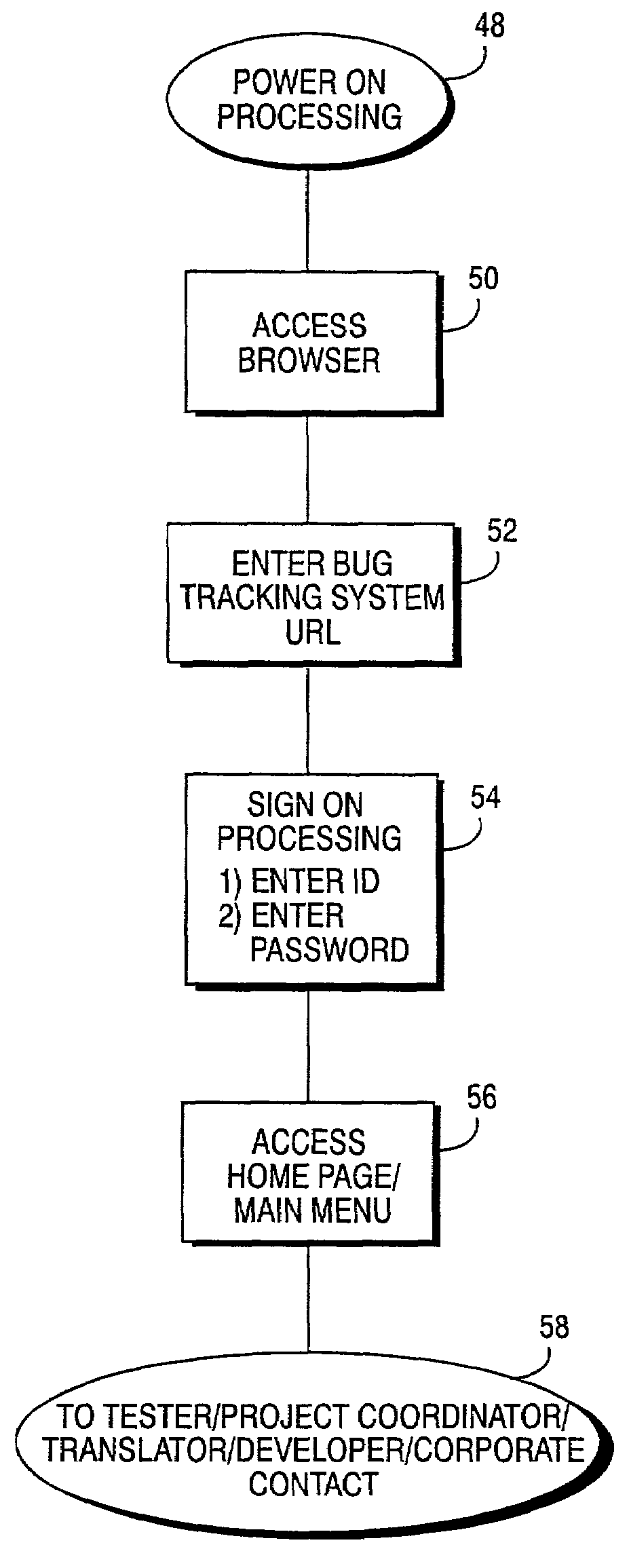
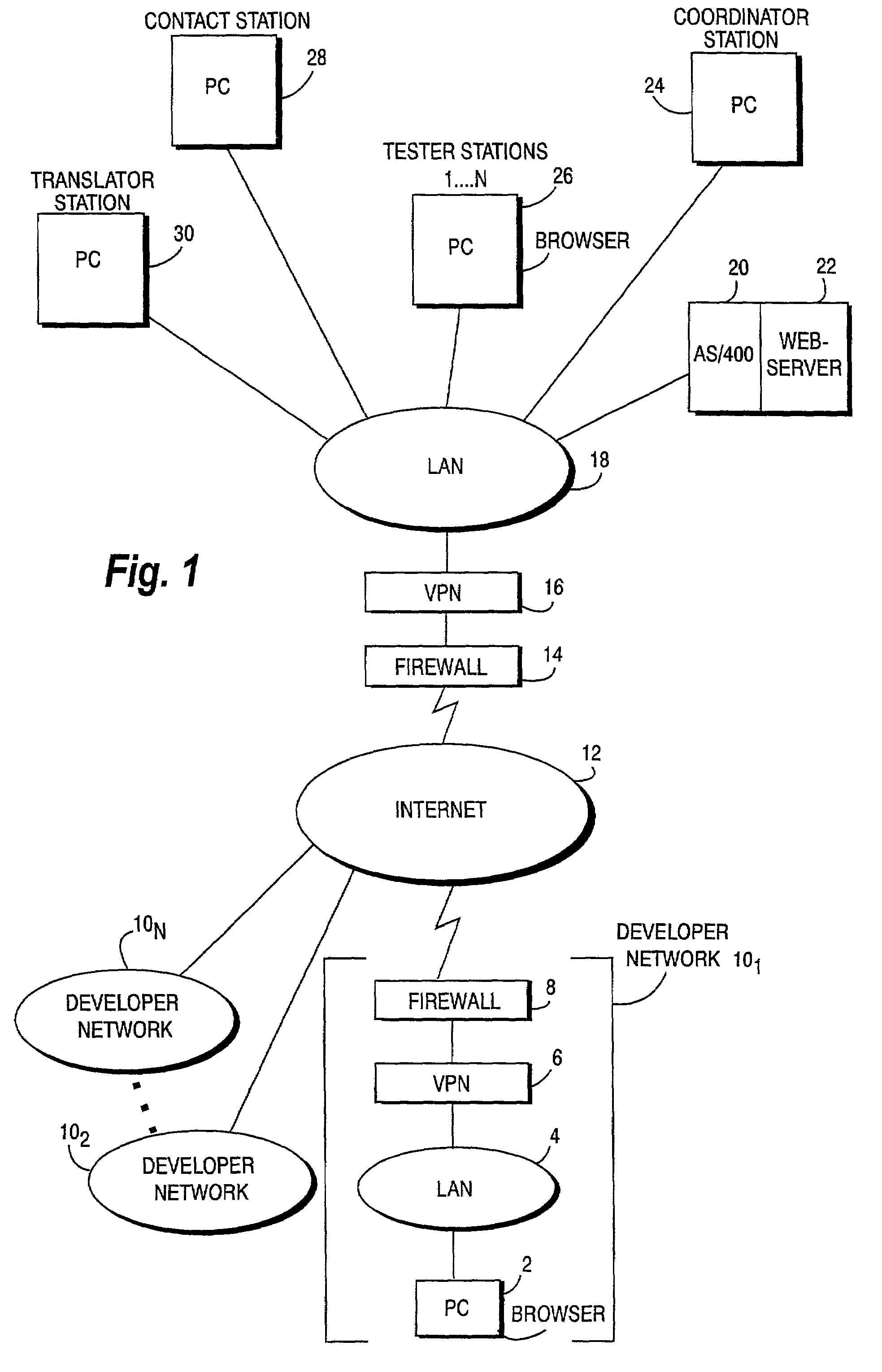
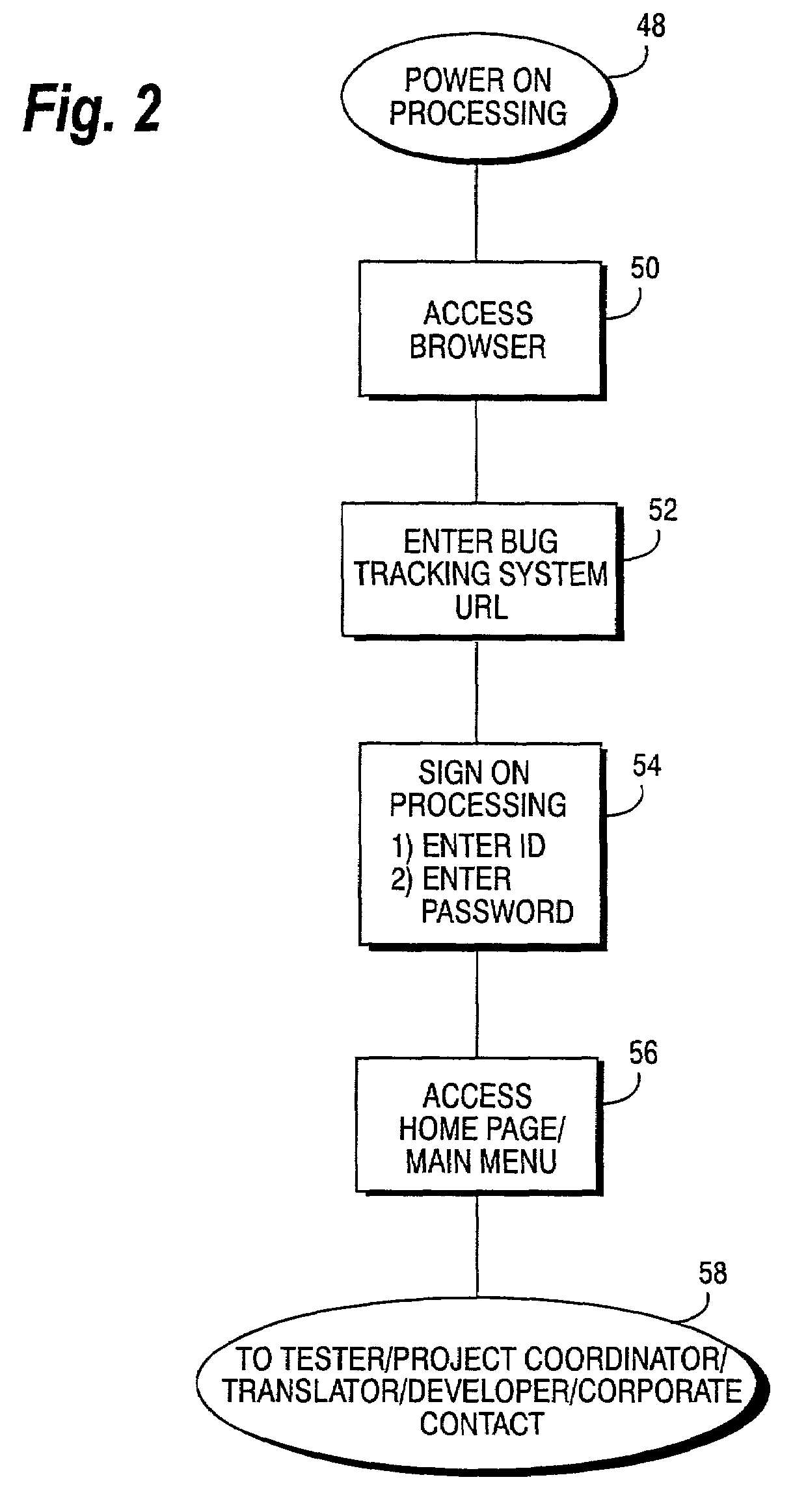
Product testing and bug tracking system
InactiveUS7657872B2Software testing/debuggingSpecific program execution arrangementsProduct testingCommunications system
An Internet-based, secure communications system is utilized for enabling communications between a video game tester, project coordinator and others with a game developer. A master bug log which compiles all uncovered bugs is accessible by a game developer and other authorized system users via a web server, which stores bug tracking system applications programs and associated data bases. Such a master bug log includes a file attachment capability permitting a digitized image file replicating a video game display screen sequence depicting the bug, to be attached for downloading to, for example, a game developer. Bugs may be sorted, for example, so that a game developer can retrieve only those bugs having a digitized file attachment. Game and debugging related messages may be exchanged between testers, project coordinators, and corporate contacts.
Owner:NINTENDO OF AMERICA
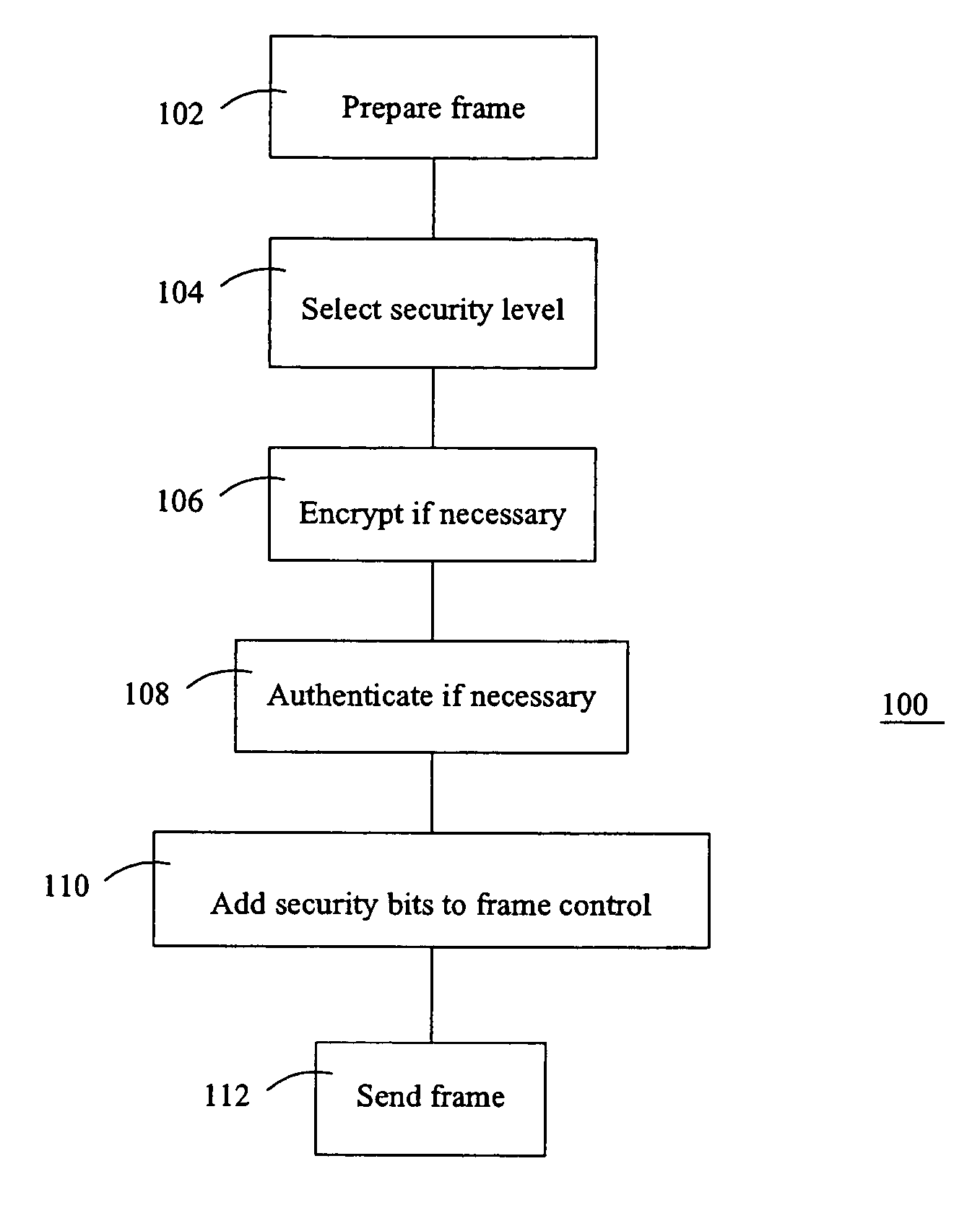
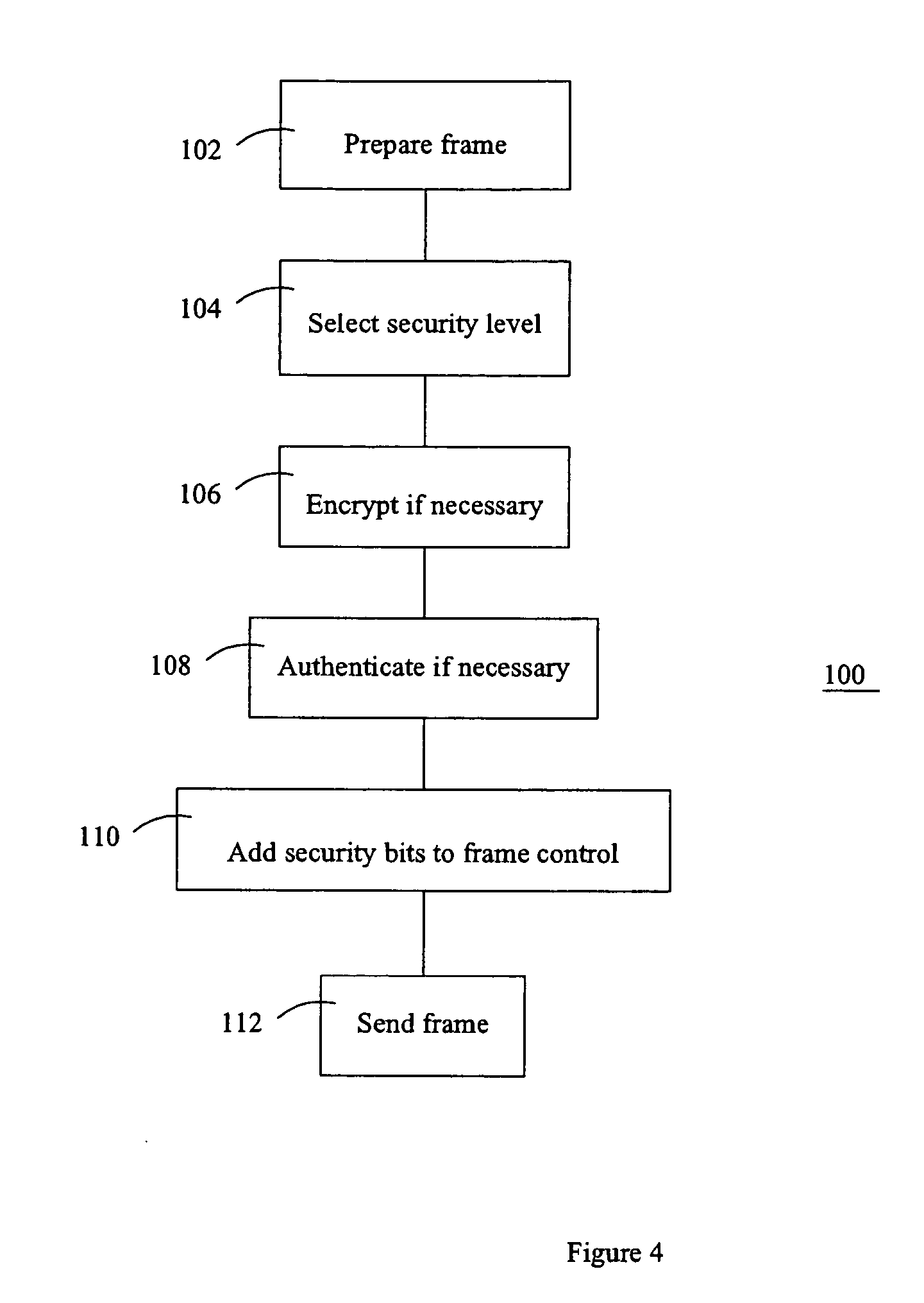
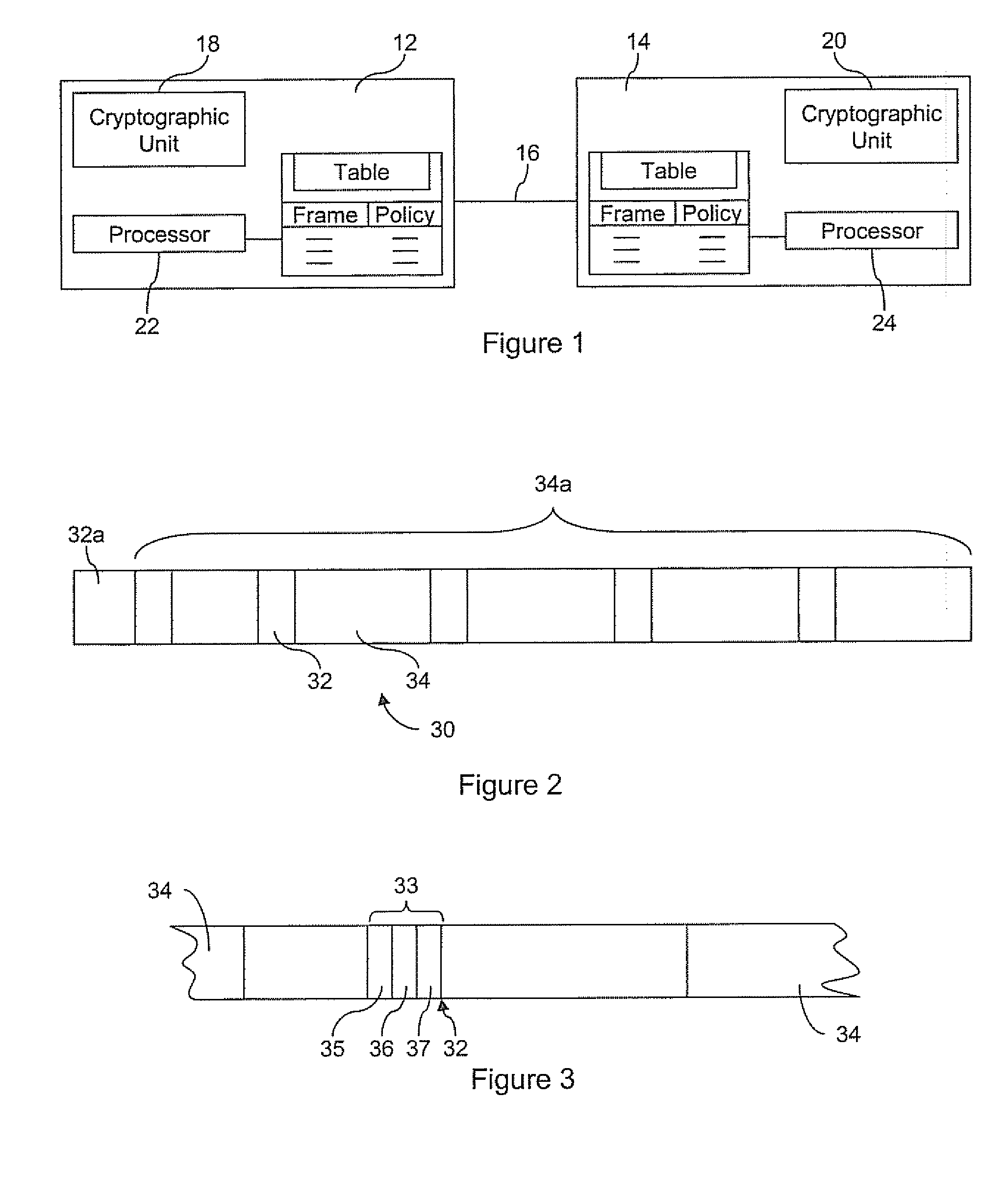
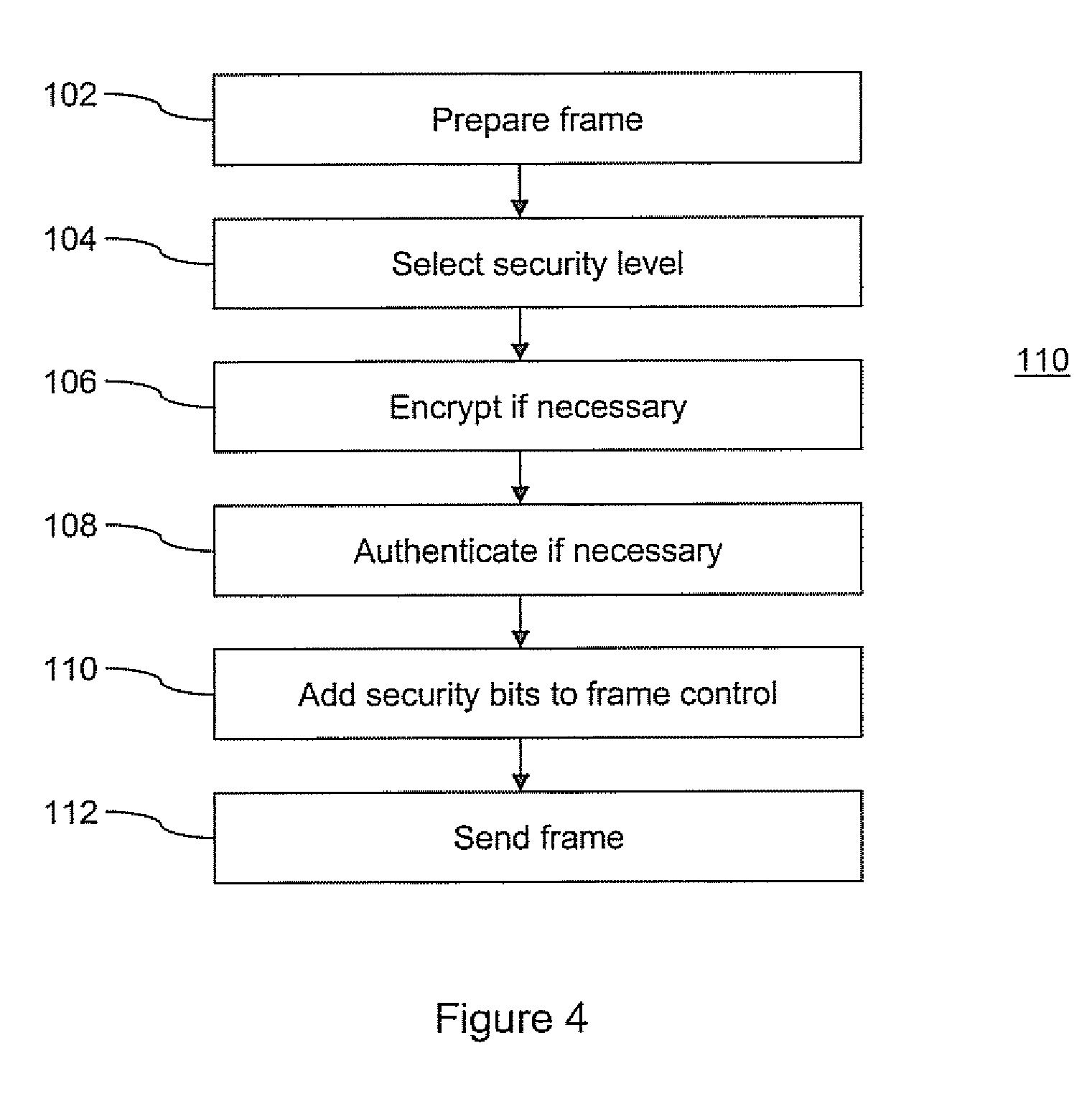
Method and apparatus for providing an adaptable security level in an electronic communication
ActiveUS20050076197A1Security arrangementSecuring communicationComputer hardwareElectronic communication
A method of communicating in a secure communication system, comprises the steps of assembling a message at a sender, then determining a security level, and including an indication of the security level in a header of the message. The message is then sent to a recipient.
Owner:BLACKBERRY LTD
Method and apparatus for providing an adaptable security level in an electronic communication
ActiveUS20070255954A1Public key for secure communicationUser identity/authority verificationComputer hardwareElectronic communication
Owner:BLACKBERRY LTD
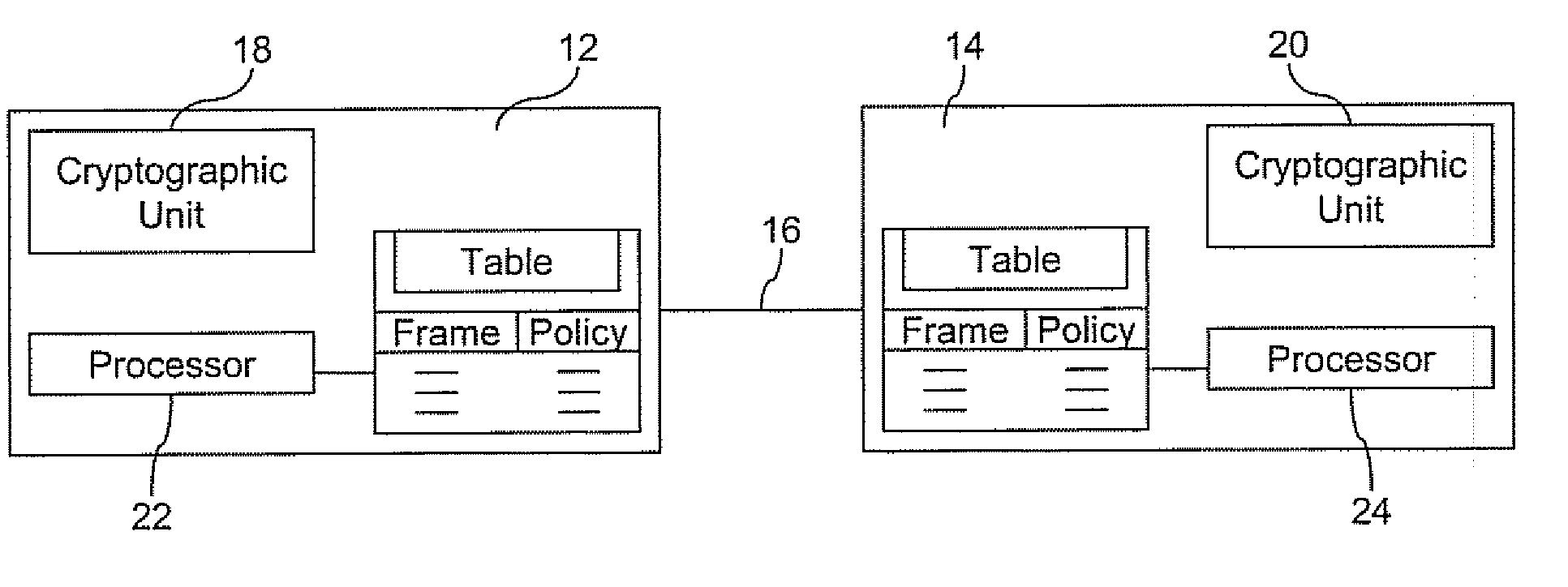
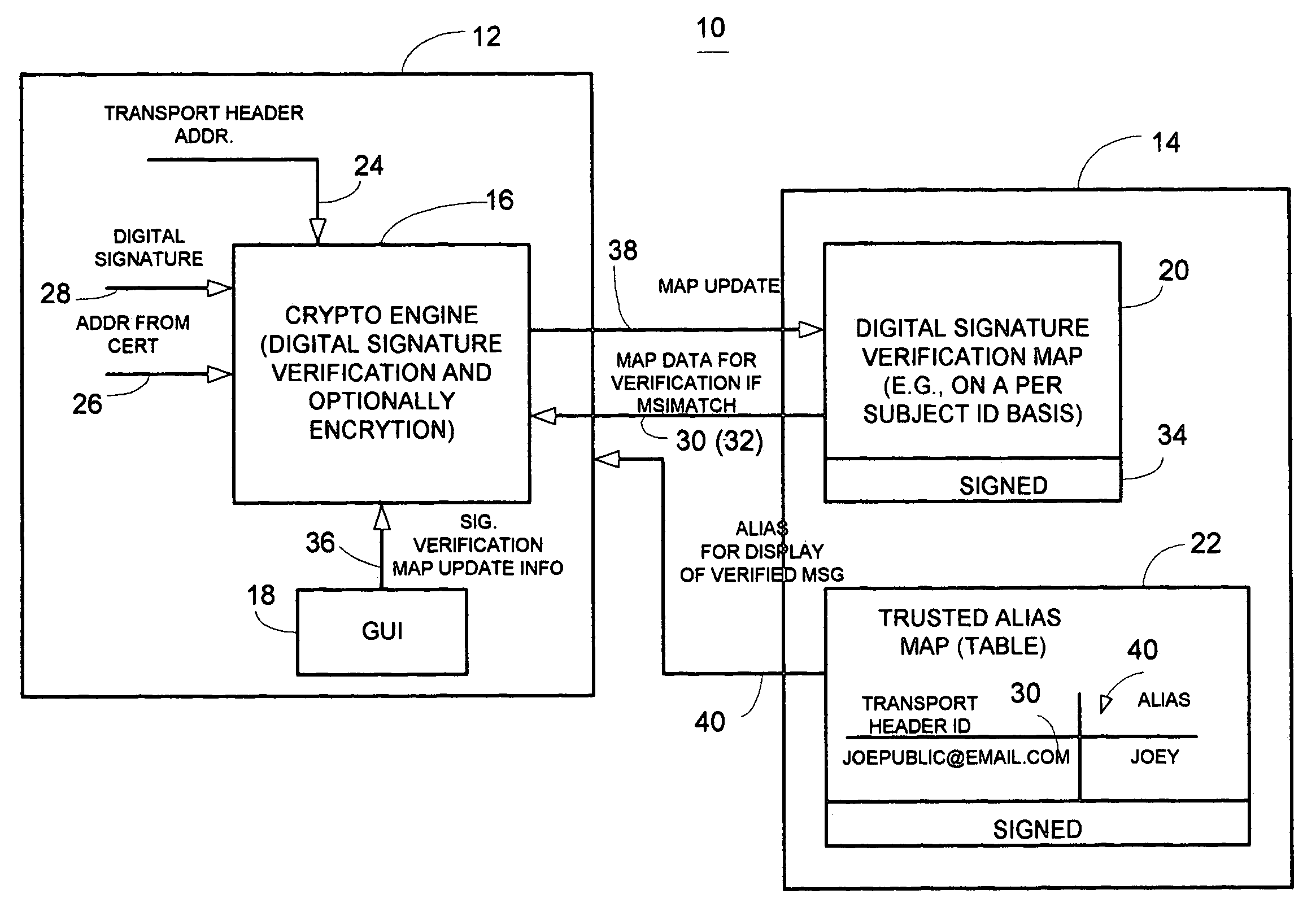
Method and apparatus for providing information security to prevent digital signature forgery
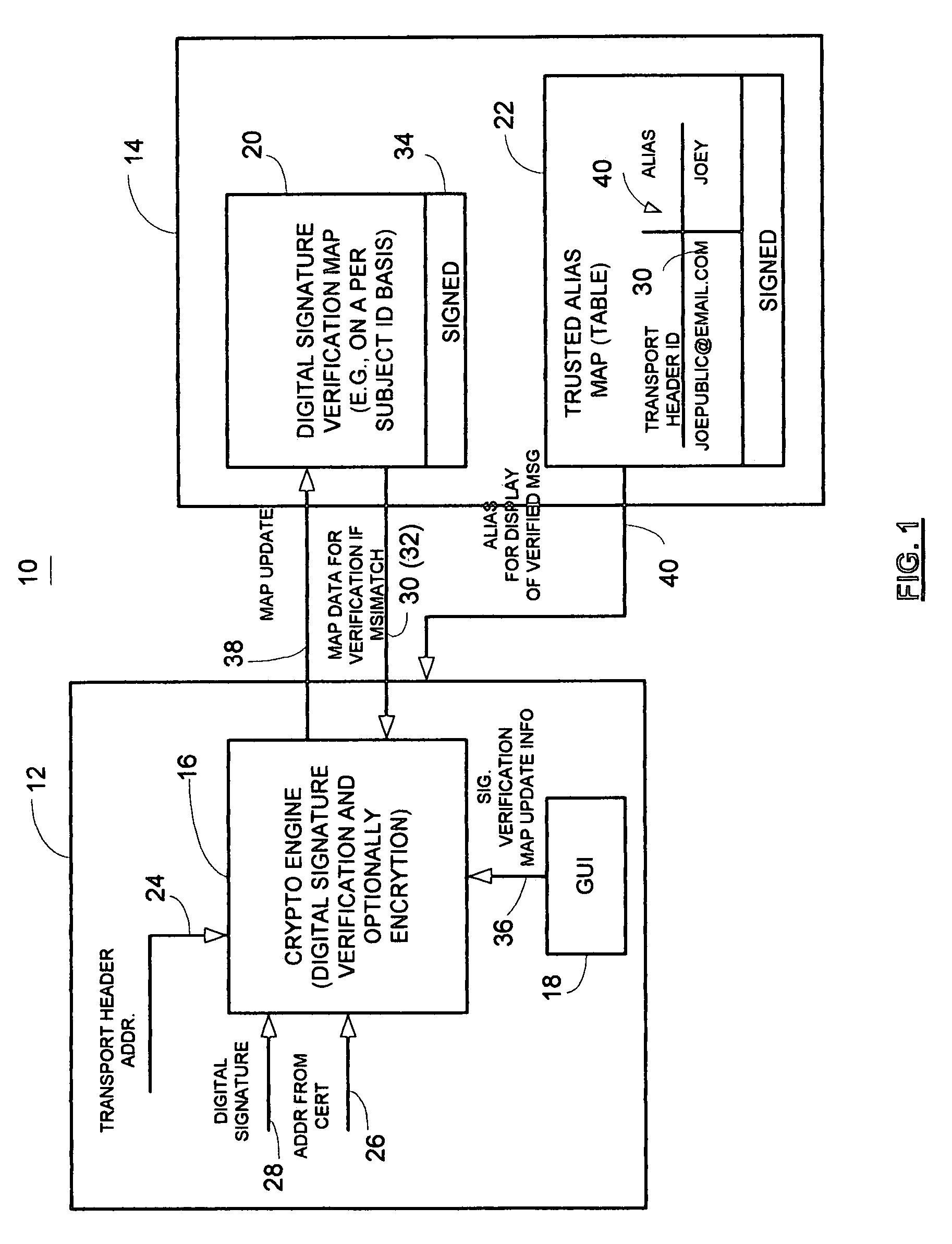
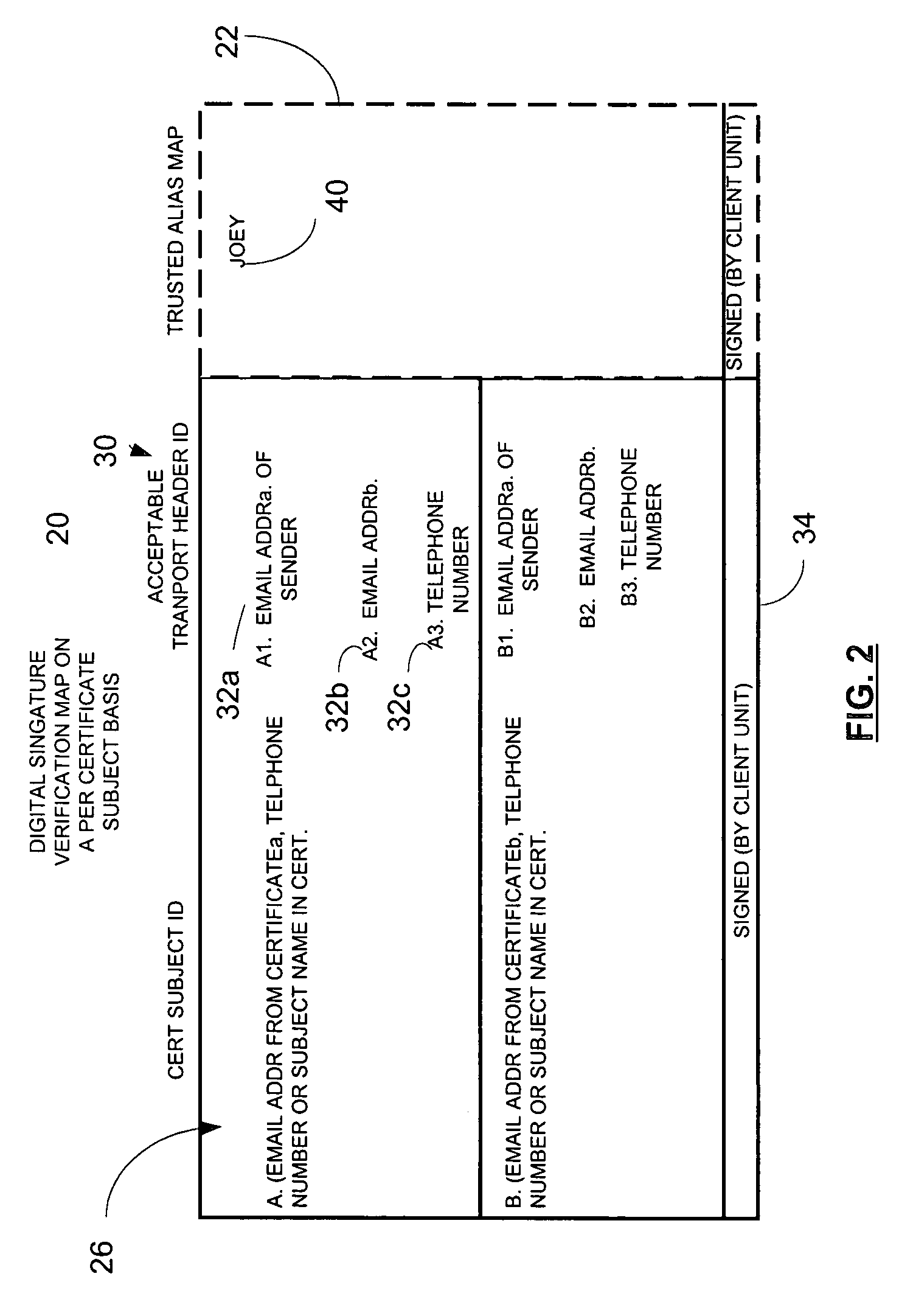
A method and apparatus utilizes a digital signature verification map containing a plurality of acceptable message header identifiers associated with a public key certificate identifier. In one embodiment, a method includes determining a digital signature verification error based on a received message header, such as transport header identifier associated with a public key certificate identifier, such as the subject field of the certificate. The method includes generating a signature verification map or updating a signature verification map containing a plurality of acceptable message header identifiers associated with the common public key certificate identifier in response to determining the digital signature verification error. Accordingly, a link is provided between a transport header and a digitally signed message. A digital signature verification map is continually updated to accommodate aliases to a common subject associated with the certificate. The digital signature verification map is preferably digitally signed to maintain a trusted verification map to operate as part of a secure communication system. If desired, a trusted alias map may also be used.
Owner:ENTRUST
Secure communication system and method of operation for conducting electronic commerce using remote vault agents interacting with a vault controller
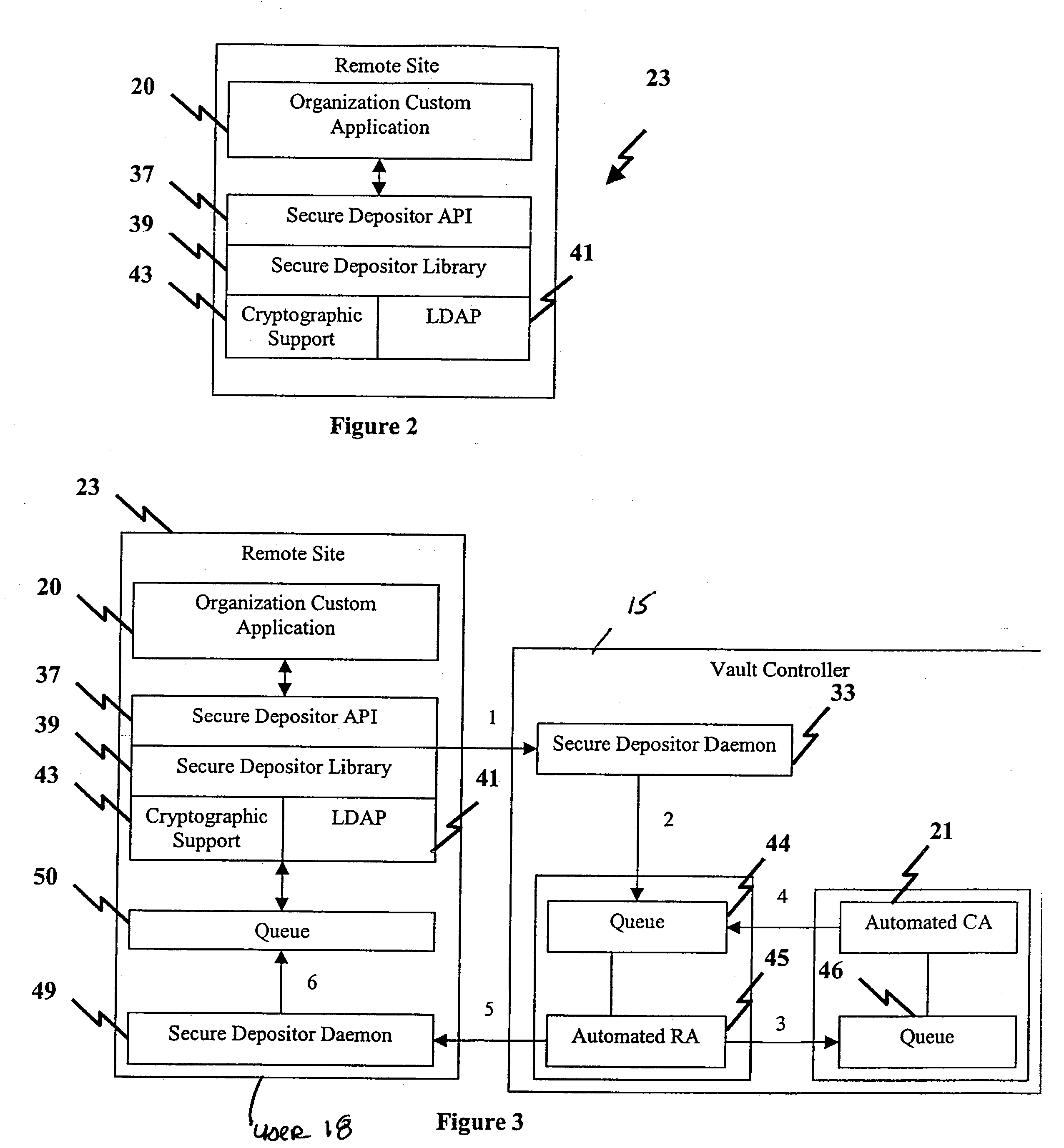
InactiveUS20030105955A1Digital data processing detailsUser identity/authority verificationCommunications systemApplication programming interface
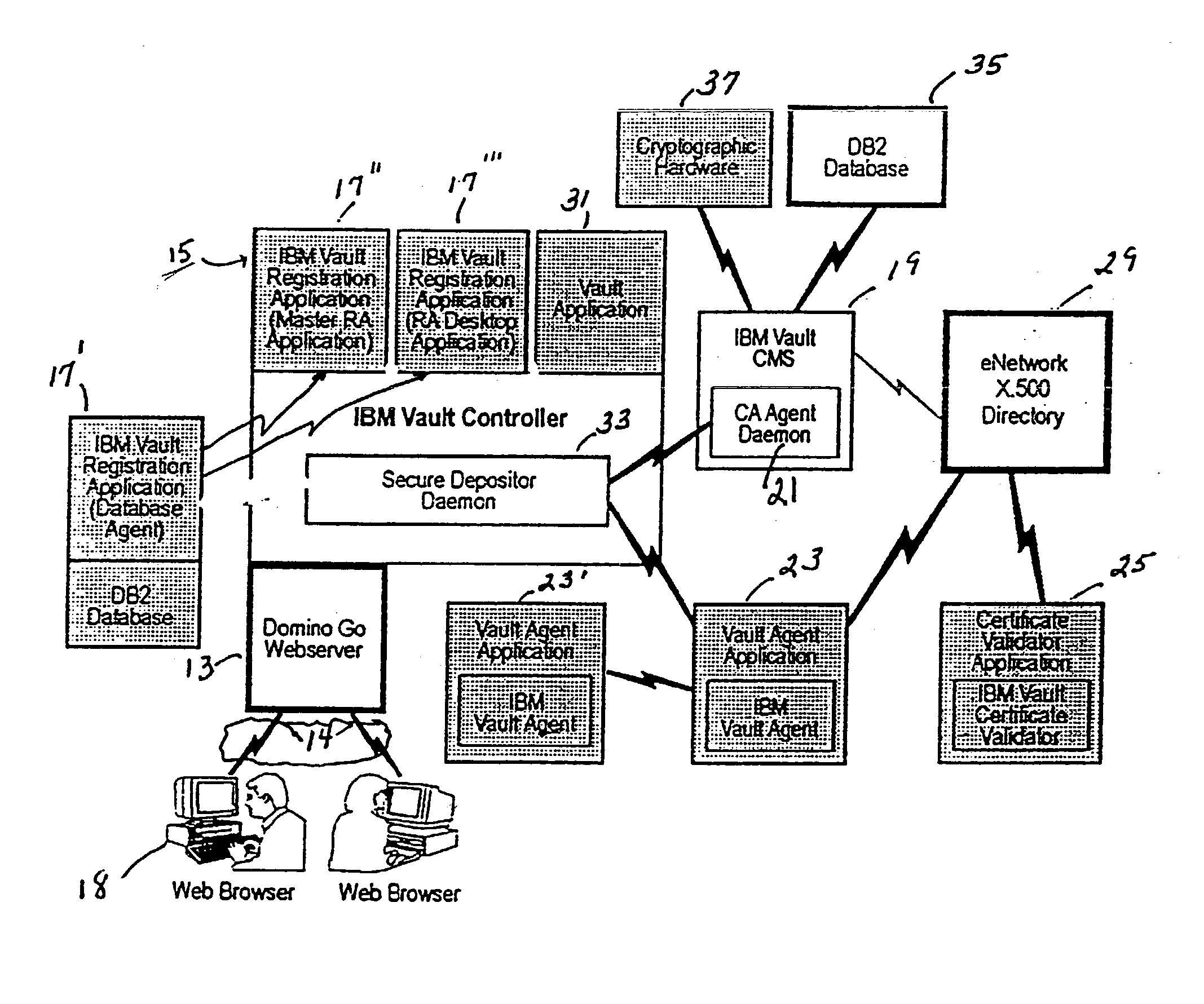
A secure end-to-end communications system provides end users access to vault-based custom applications of an organization for purposes of conducting electronic commerce. The system includes a web-based vault controller running an application, e.g. a registrations application in a vault cryptographically linked to a database and a Certificate Management System (CMS) for generating digital certificates, and at least one remote vault agent coupled to the vault controller for providing vault-based custom applications to end users. An X.500 directory is coupled to the CMS and cryptographically linked to the remote vault agents for storing end user data. The remote vault agent is an application which comprises a collection of Application Programming Interfaces (APIs) which provide a secure interface to the vault controller; a Lightweight Data Access Protocol (LDAP) used to access the X.500 directory; a secure depositor coupled to vault-based custom applications of an organization. The secure depositor includes APIs to perform cryptographic functions in passing communications between vaults used by the vault agent and vaults used by the vault controller or vaults used by other vault agent applications and a secure depositor library which uses functions in the LDAP to access the X.500 directory. The remote vault agent accesses the web based vault controller on a non-web basis to enable remote custom applications to communicate securely with vault-based applications, such as a registration application that administers digital certificates.
Owner:IBM CORP
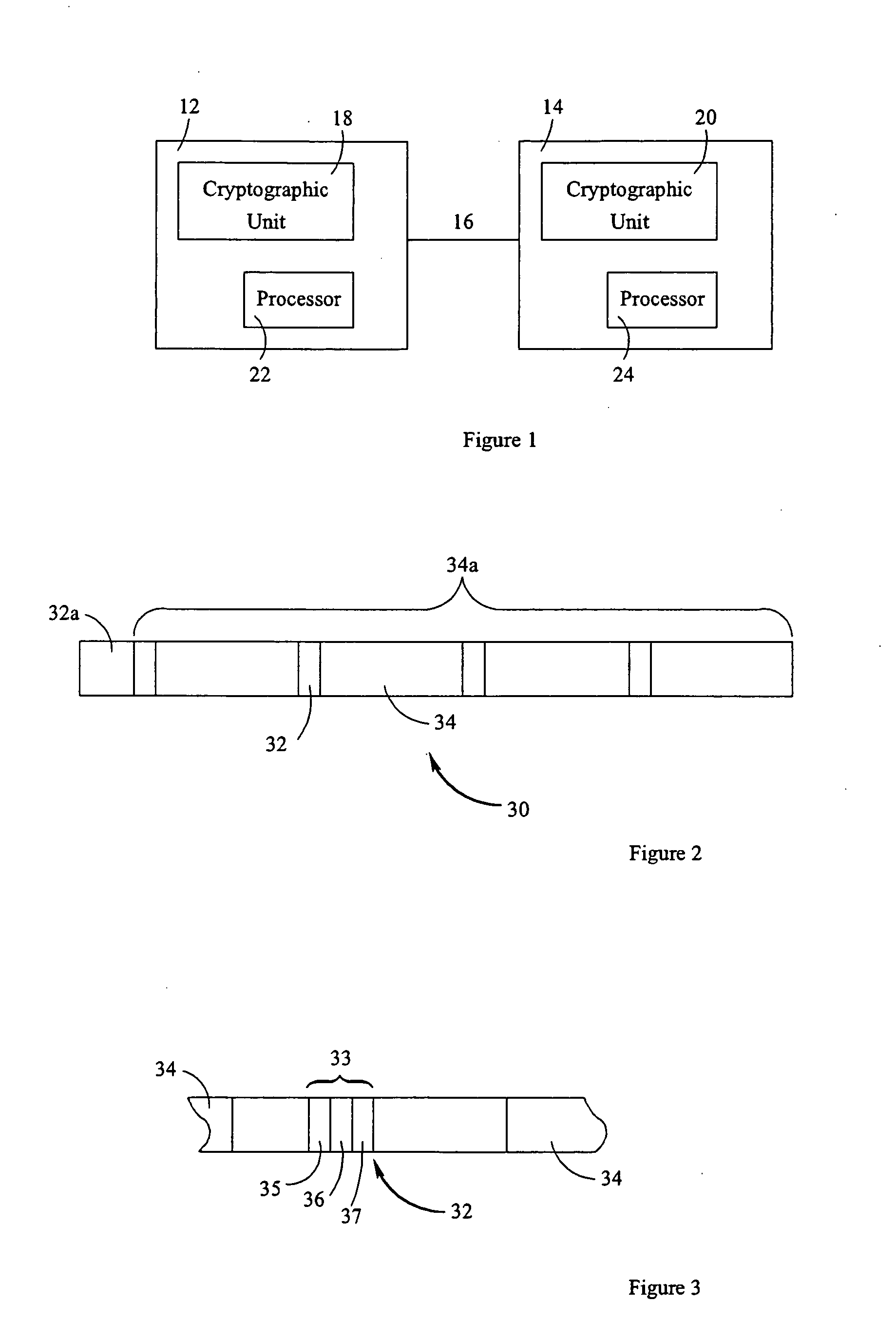
Secure communication system
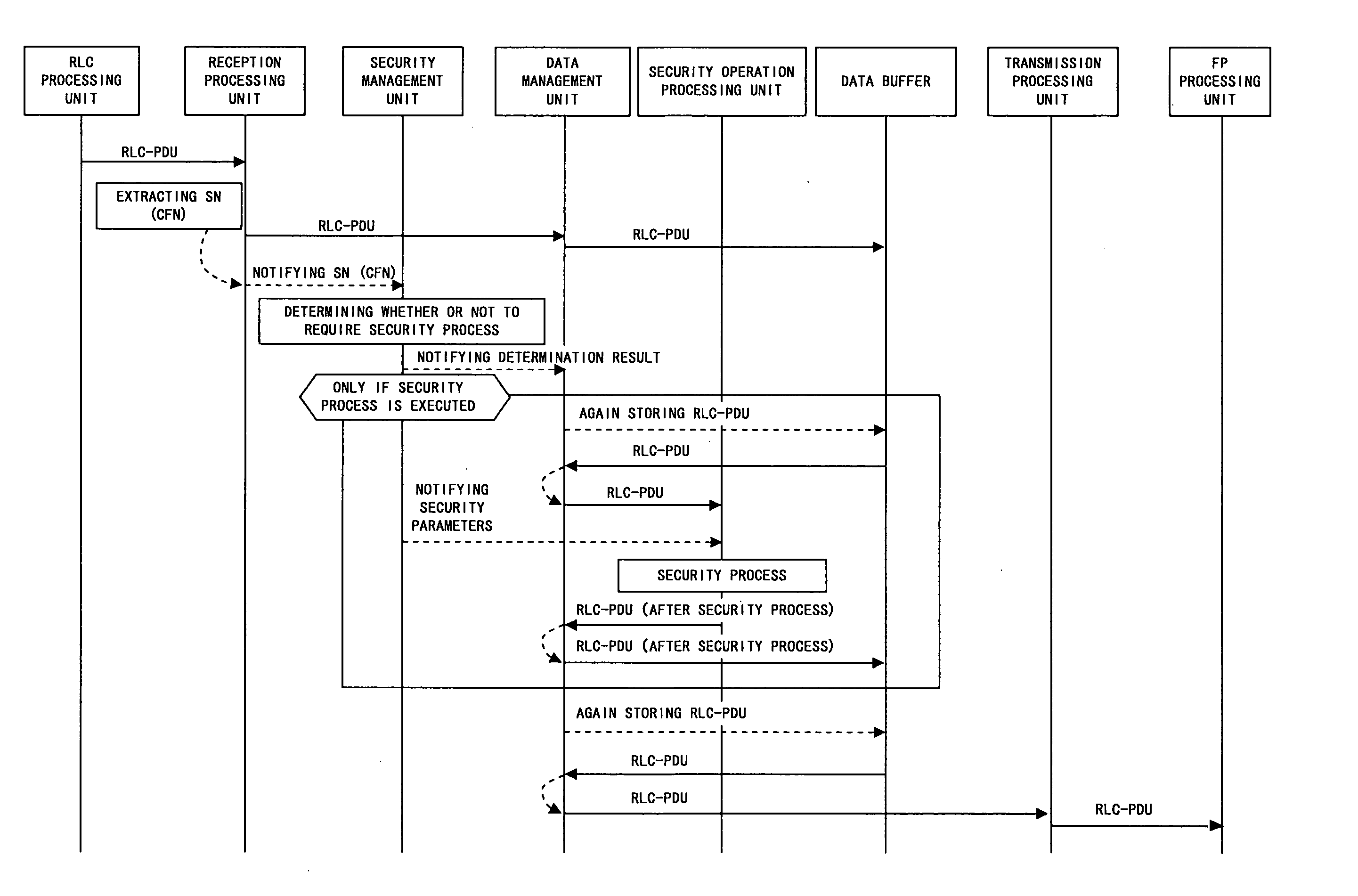
InactiveUS20070201424A1Low costImprove data throughputTime-division multiplexSecurity arrangementCommunications systemData management
A reception part receives RLC-PDU from an RLC processing part to extract information to be used for determining whether security is required. This information is sent to a security management part, which determines whether security is required. Data outputted from the reception part is stored into a data buffer via a data management part. The data, which is regarded by the security management part as requiring security, is read by the data management part from the data buffer, then encrypted by a security calculation part, and then stored back into the data buffer again. Concealed or non-concealed data is read from the data buffer and sent to an FP processing part via a transmission part.
Owner:FUJITSU LTD
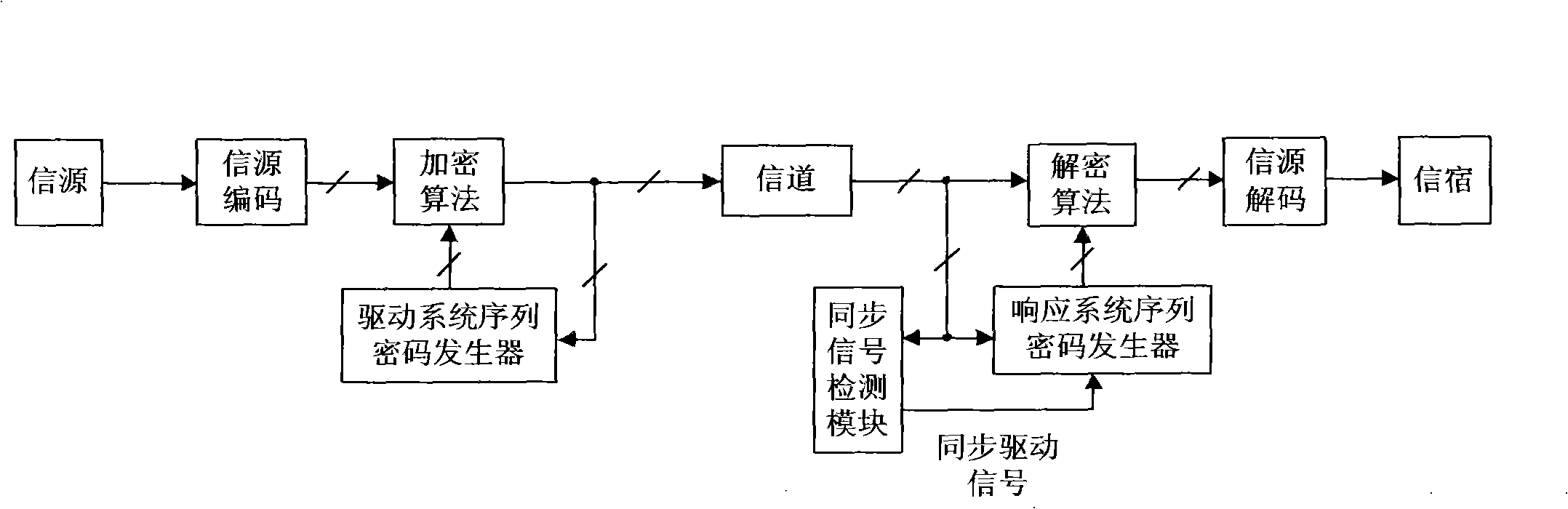
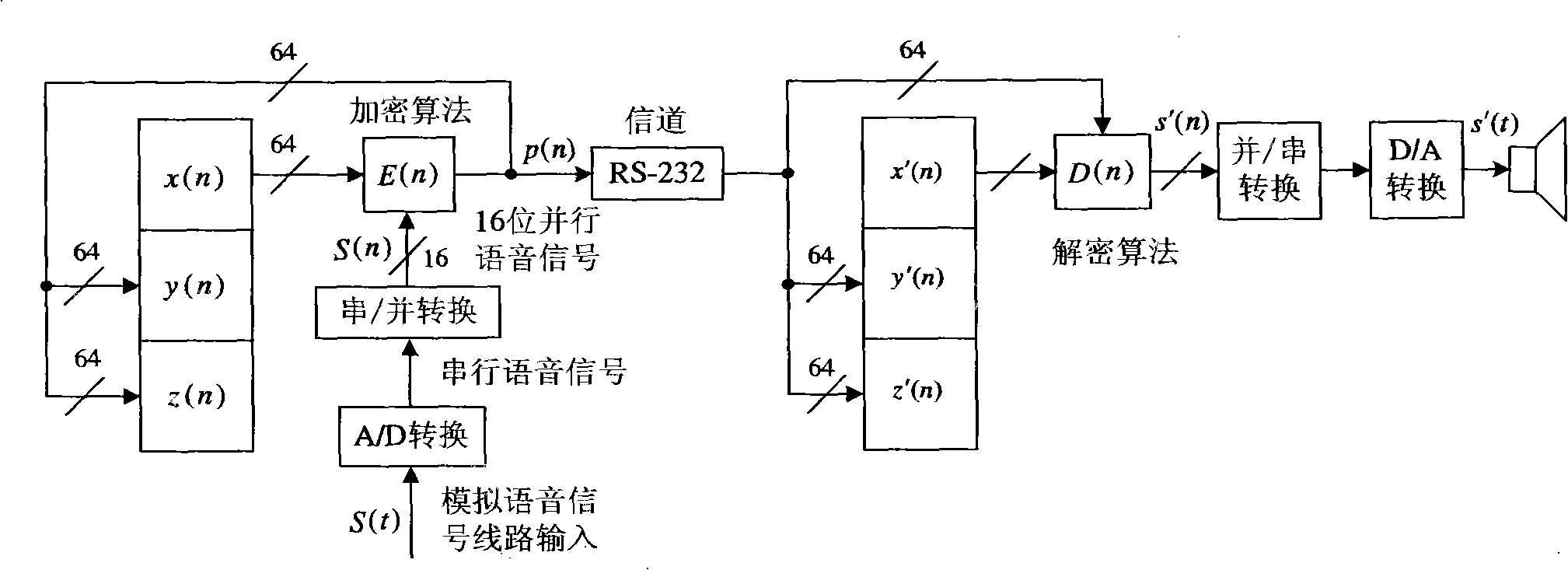
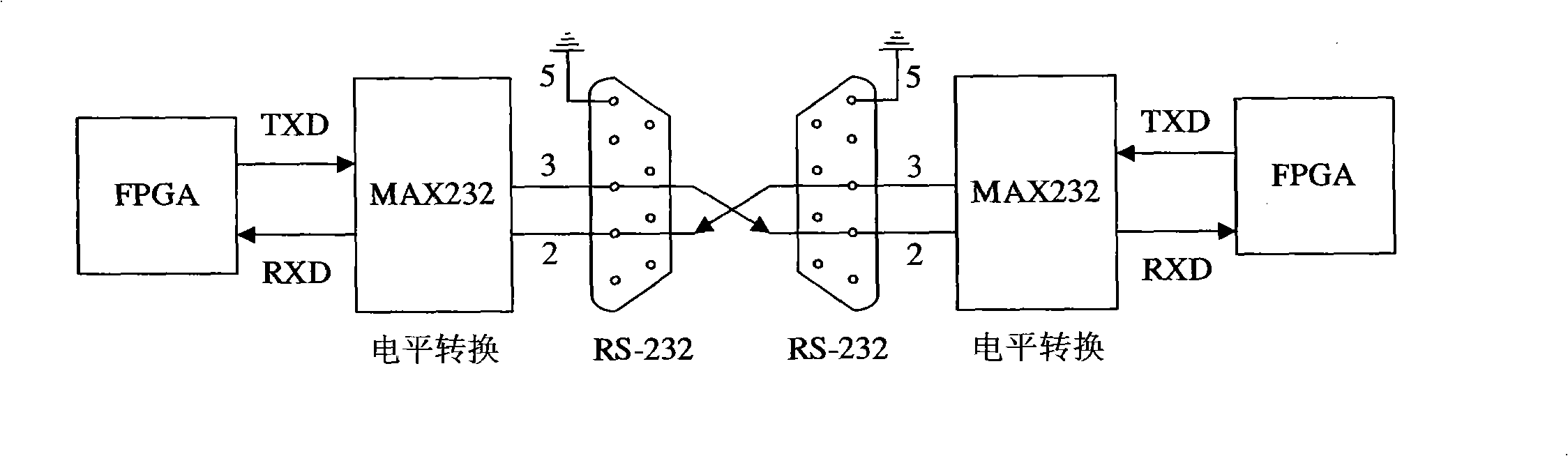
Design method for chaos digital secret communication system based on FPGA
InactiveCN101345615AIncreased complexityImprove real-time performanceSecuring communicationComputer architectureCommunications system
The invention relates to design method for FPGA based chaos digital secure communication system comprising following steps: executing discrete process for continuous chaos system by FPGA hardware, designing chaos discrete system by FPGA hardware and make it produce digital chaos sequence in a certain accuracy, adopting the digital chaos sequence as key, designing drive response type synchronous secure communication system based on choas discrete system, constructing a closed loop with interior signal, accomplishing two block FPGA development board finite digital voice communication using lattice type Cai chaos and real time voice secure communication system design based on lattice type Cai chaos. The invention is highly secure and accomplishes combination of chaos encryption system and traditional cipher system. The inventive secure communication system not only serve voice secure communication, but transmit confidential binary file. As long as data can be represented as binary data, it can execute secure communication. The inventive system can employ graph encryption / decryption and transmit over Ethernet.
Owner:GUANGDONG UNIV OF TECH
Method and system for transporting configuration protocol messages across a distribution system (DS) in a wireless local area network (WLAN)
ActiveUS20060039340A1Multiple digital computer combinationsRadio/inductive link selection arrangementsDistribution systemWireless lan
Aspects of a method and system for transporting configuration messages across a DS in a WLAN are presented. Aspects of a method for enabling communication of information in a secure communication system may comprise configuring a wireless client station located in a client network based on configuration information received from a configurator. The configurator is located in a configurator network that is located external to and communicatively coupled to the client network. Aspects of a system for enabling communication of information in a secure communication system may comprise a configurator located in a configurator network that is located external to and communicatively coupled to a client network. The configurator configures a wireless client station located in the client network based on configuration information transmitted by the configurator to the wireless client station.
Owner:AVAGO TECH INT SALES PTE LTD
Secure communication system based on wireless channel characteristic
ActiveCN102869013AAvoid hidden dangersSecure data communicationKey distribution for secure communicationSecurity arrangementTelecommunicationsComputer terminal
The invention discloses a secure communication system based on a wireless channel characteristic. The system comprises a first communication terminal and a second communication terminal which communicate with each other, wherein the first communication terminal and the second communication terminal transmit data which comprise a pilot frequency sequence to each other; and the first communication terminal comprises a first channel estimation module, a first quantization module, a first negotiation module, a first confidential amplification module, a first phase rotation secret key mapping module and a first phase rotation encryption module. By the system, secure data communication is realized.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Vehicular electronic secure communication system and communication method
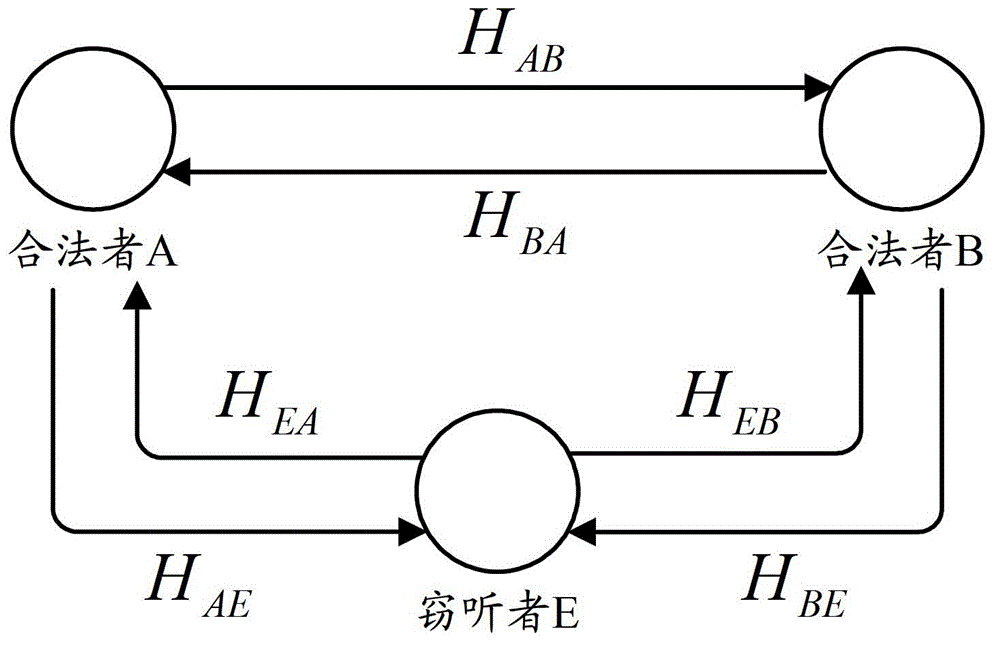
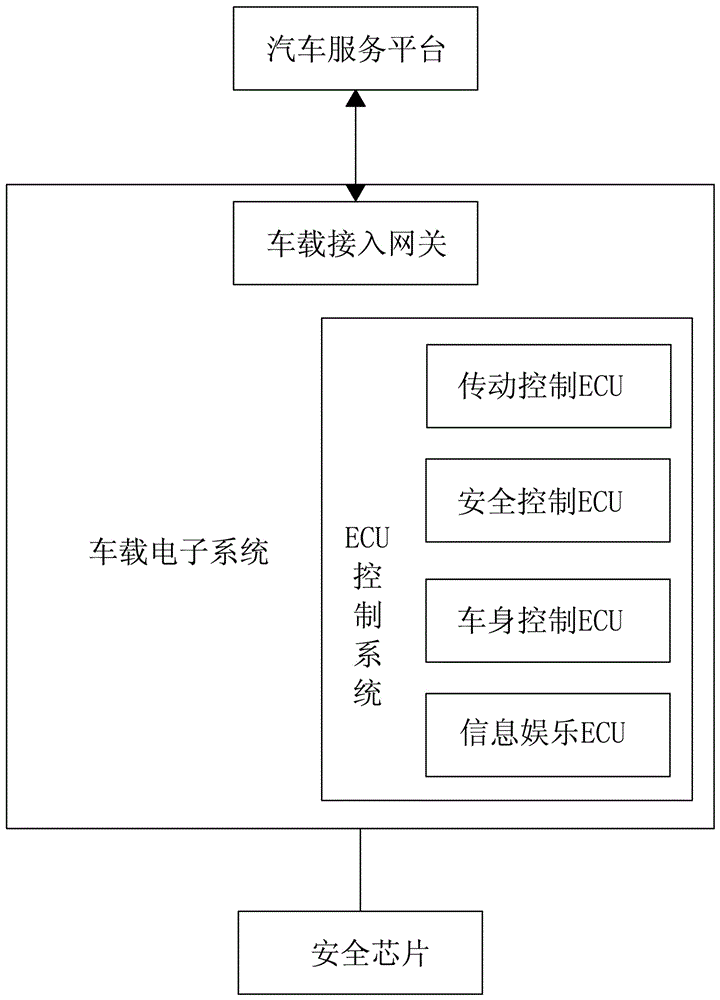
ActiveCN106101111AImprove securityImplement security authenticationTransmissionSecure communication systemEngineering
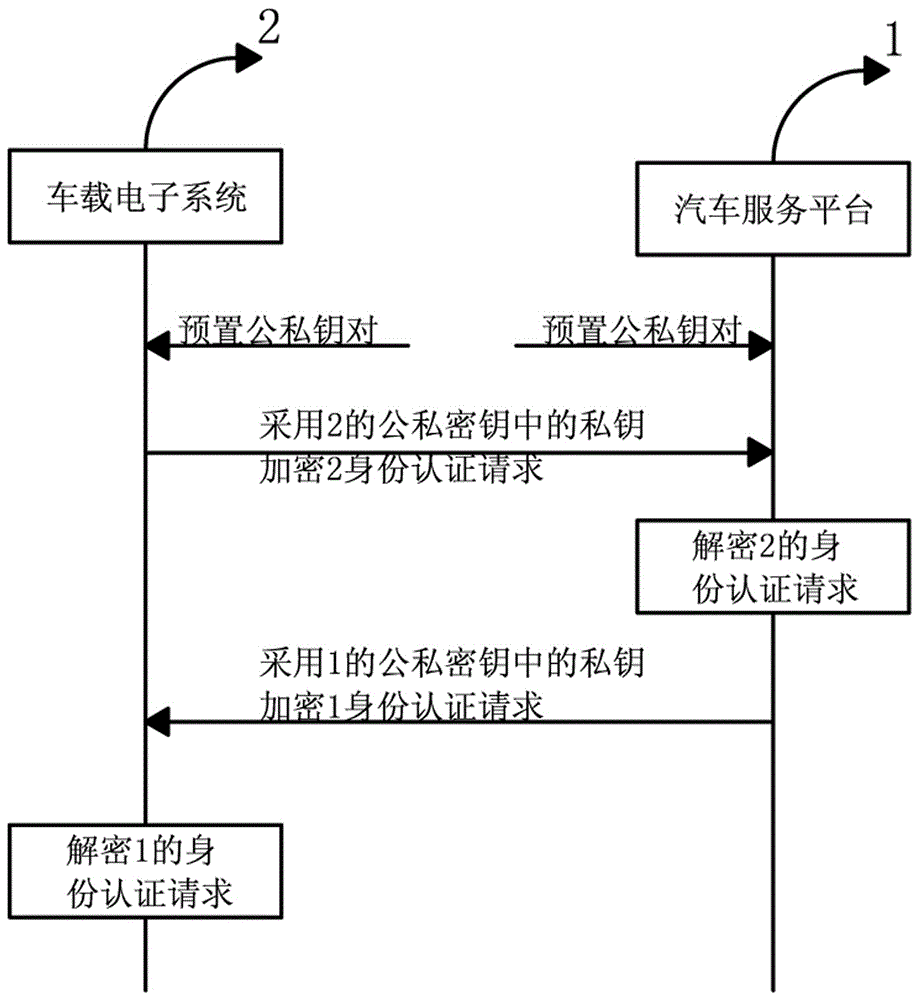
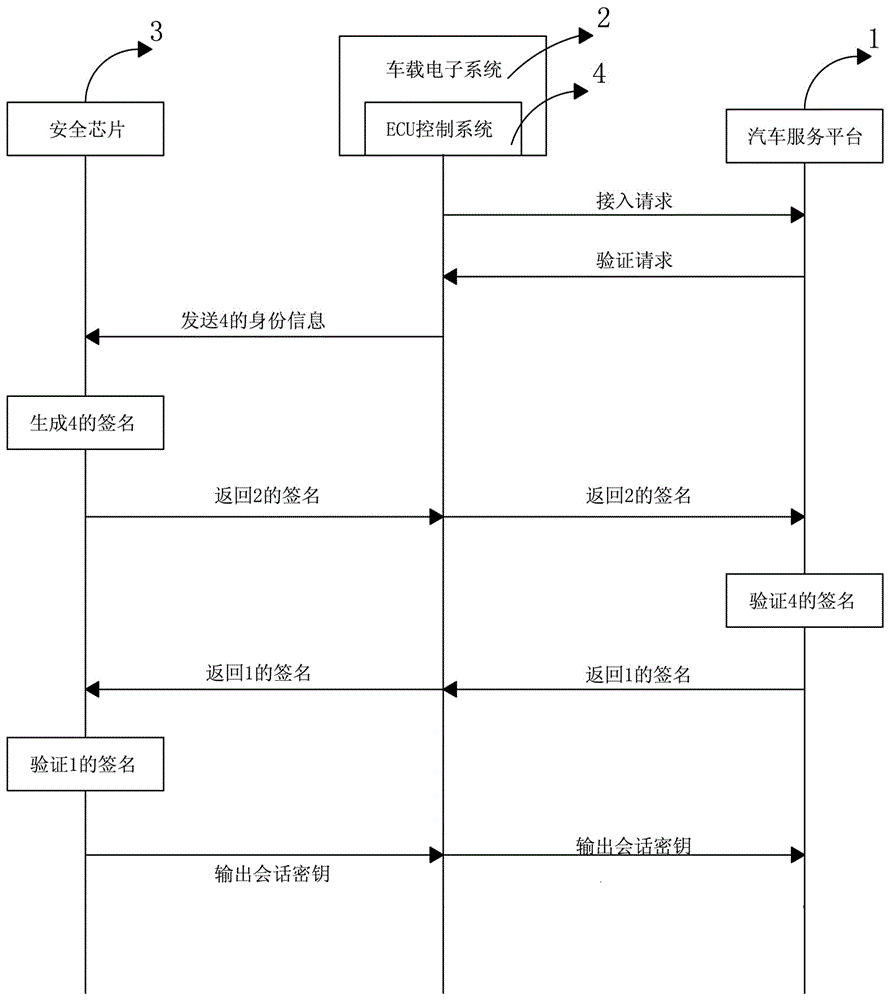
The invention provides a vehicular electronic secure communication system. The vehicular electronic secure communication system comprises a secure chip, a vehicular electronic system and an automobile service platform; the vehicular electronic system and the automobile service platform perform bidirectional identity authentication; the vehicular electronic system comprises an ECU control system; the ECU control system and the automobile service platform perform bidirectional signature authentication through the secure chip; and, after bidirectional signature is successfully verified, the automobile service platform and the ECU control system are in encrypted communication. The invention further provides a communication method of the vehicular electronic secure communication system. The communication method comprises the following steps that: (1), the vehicular electronic system and the automobile service platform perform bidirectional identity authentication; (2), after verification is successful, the ECU control system of the vehicular electronic system and the automobile service platform perform bidirectional signature authentication through the secure chip; and (3), after verification is successful, the automobile service platform and the ECU control system are in encrypted communication through a session key output by the secure chip.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
Secure communication system and communication route selecting device
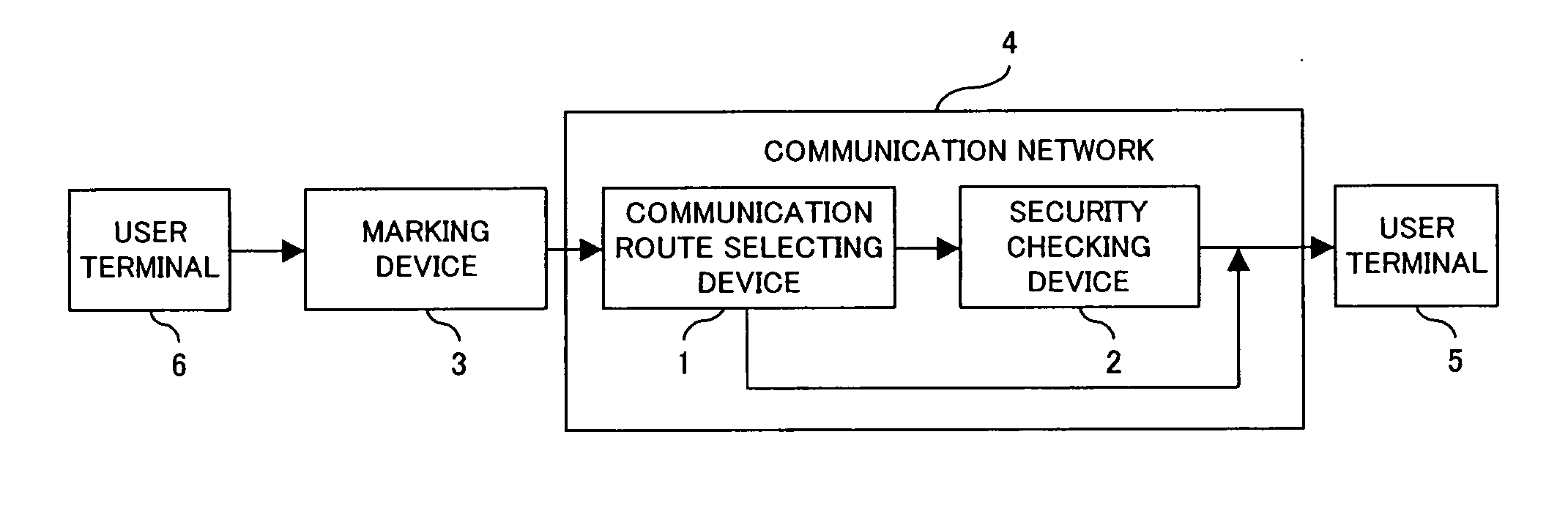
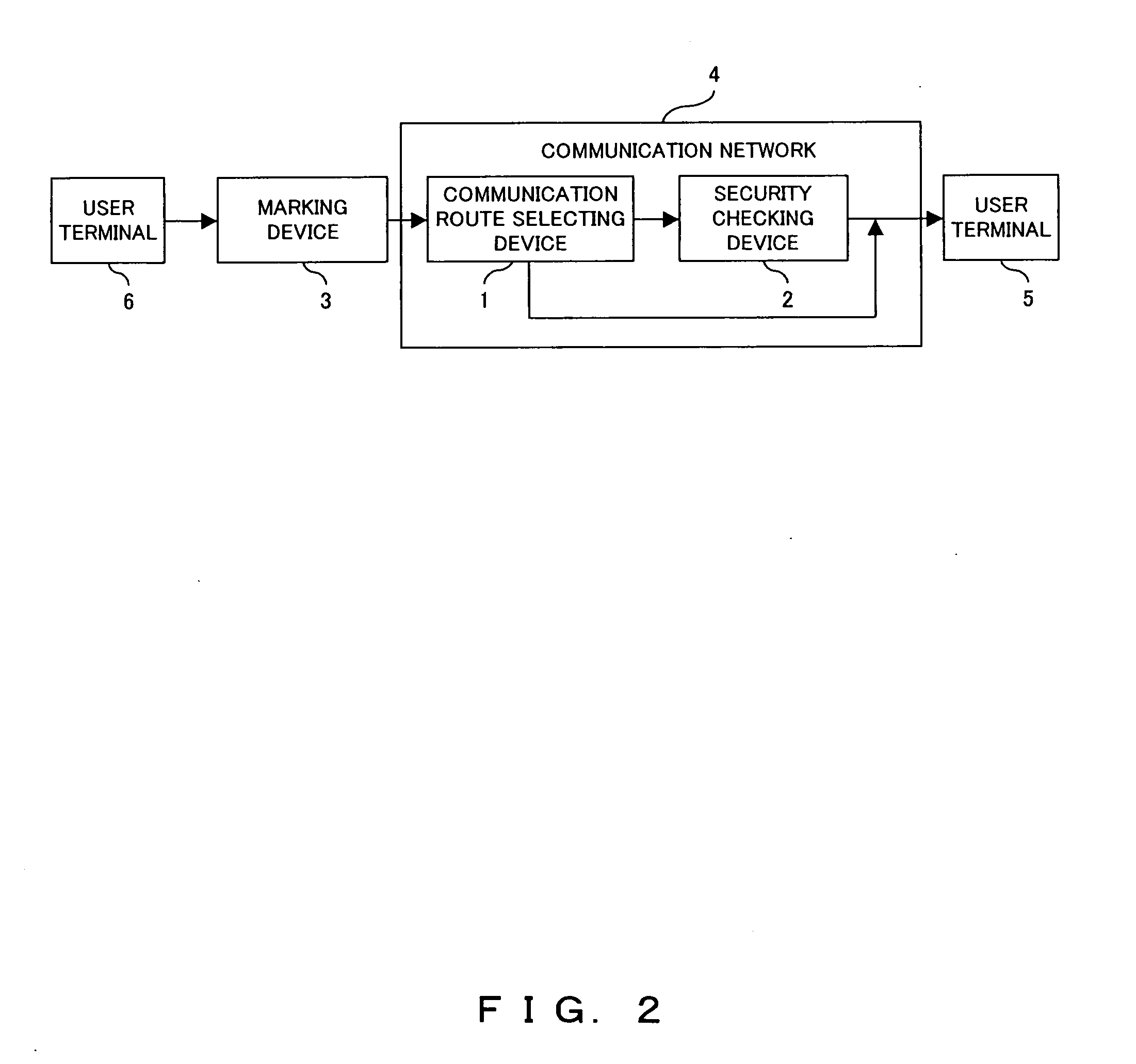
InactiveUS20060136722A1Reduce loadReduce throughputMemory loss protectionUser identity/authority verificationCommunications systemSecurity check
A communication system for realizing a secure communication comprises a selecting device for making a selection between a communication route for a direct communication with a communication partner side and a communication route via a security checking device for checking security of communication, in accordance with a communication partner or an application corresponding to the communication. Also, the communication system comprises a device for marking a communication packet for route selection in order that the selecting device conducts a route selection in accordance with contents of the marking.
Owner:FUJITSU LTD
Method and database system for secure storage and communication of information
InactiveUS20140372752A1Key distribution for secure communicationMultiple keys/algorithms usageCommunications systemInternet privacy
A secure communications system for the secure storage and communication of authenticated user identity and personal information. The system includes a database of anonymised, individually encrypted user records. Access to the records is only permissible using a user key which is stored in a user keychain on a client device. The keychain itself is password protected and cryptographically tied to the client device.
Owner:QREDO
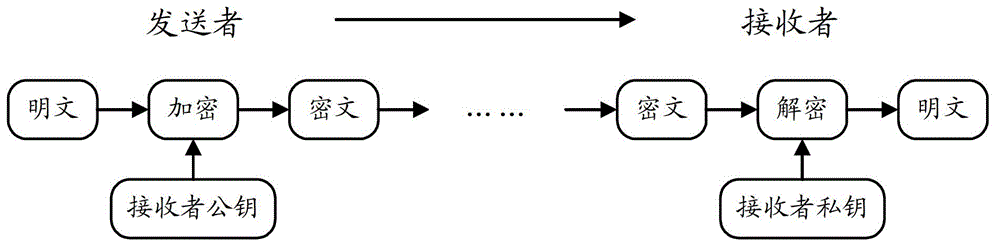
Methods, devices and systems for generating anonymous public keys in a secure communication system
InactiveUS20060098819A1Communication securityReducing individual managing costKey distribution for secure communicationMultiple keys/algorithms usageSecurity levelSecure communication system
Methods, devices and systems for generating a plurality of public keys from one private key with the same generator of a group are described. A public key cryptosystem is also disclosed for generating a plurality of anonymous public keys all of which relate to the same party used for secure communications. Those anonymous public keys are generated using the same generator from one single private key. With the invention, computation is reduced, memory can be saved and security level can be improved.
Owner:NEC (CHINA) CO LTD
Secure communication system and method using shared random source for key changing
ActiveUS20060067533A1Overcome difficultiesKey distribution for secure communicationSynchronising transmission/receiving encryption devicesTelecommunications linkCommunication link
Apparatus for use by a first party for key management for secure communication with a second party, said key management being to provide at each party, simultaneously remotely, identical keys for said secure communication without transferring said keys over any communication link, the apparatus comprising: a datastream extractor, for obtaining from data exchanged between said parties a bitstream, a random selector for selecting, from said bitstream, a series of bits in accordance with a randomization seeded by said data exchanged between said parties, a key generator for generating a key for encryption / decryption based on said series of bits, thereby to manage key generation in a manner repeatable at said parties.
Owner:KING GREEN
Secure communications system for collaborative computing
InactiveUS20050198141A1Improve scalabilityEliminate single point of failure limitationSpecial service provision for substationMultiple digital computer combinationsCommunications systemHigh-speed link
A distributed collaborative computer system is provided that comprises a plurality of server computers interconnected via a high-speed link. Client computers can connect to any available server computer and start or join a conference hosted on either the server computer to which the client computer is connected or any other server in the system. As a result, the system and method of the present invention is easily scalable to support an arbitrary number of participants to a conference by merely adding the appropriate number of server computers to the system. In addition, by replicating the conference information on more than one server computer, the single point of failure limitation is eliminated. In fact, if a server hosting or participating in a conference malfunctions, the failure is detected by other server computers and the client computer is able to reconnect to the conference through a new server computer.
Owner:CISCO TECH INC
Communication method with encryption key escrow and recovery
InactiveUS20030012387A1Key distribution for secure communicationMultiple keys/algorithms usageInternet privacySecret code
Communication process with key encryption escrow and recovery systems. The entity participating in a communication session generates a session key (SK) through a pseudorandom generator that is initiated by the entity's secret key and an initial value (IV). The session key codes the message. The escrow authority that files the secret code may recover the message and the initial value (IV). Application to secure communication systems.
Owner:FRANCE TELECOM SA
Private and secure communication systems and methods
InactiveUS20160142374A1Doubling levelHigh transparencyMultiple digital computer combinationsProgram controlSession Initiation ProtocolCommunications system
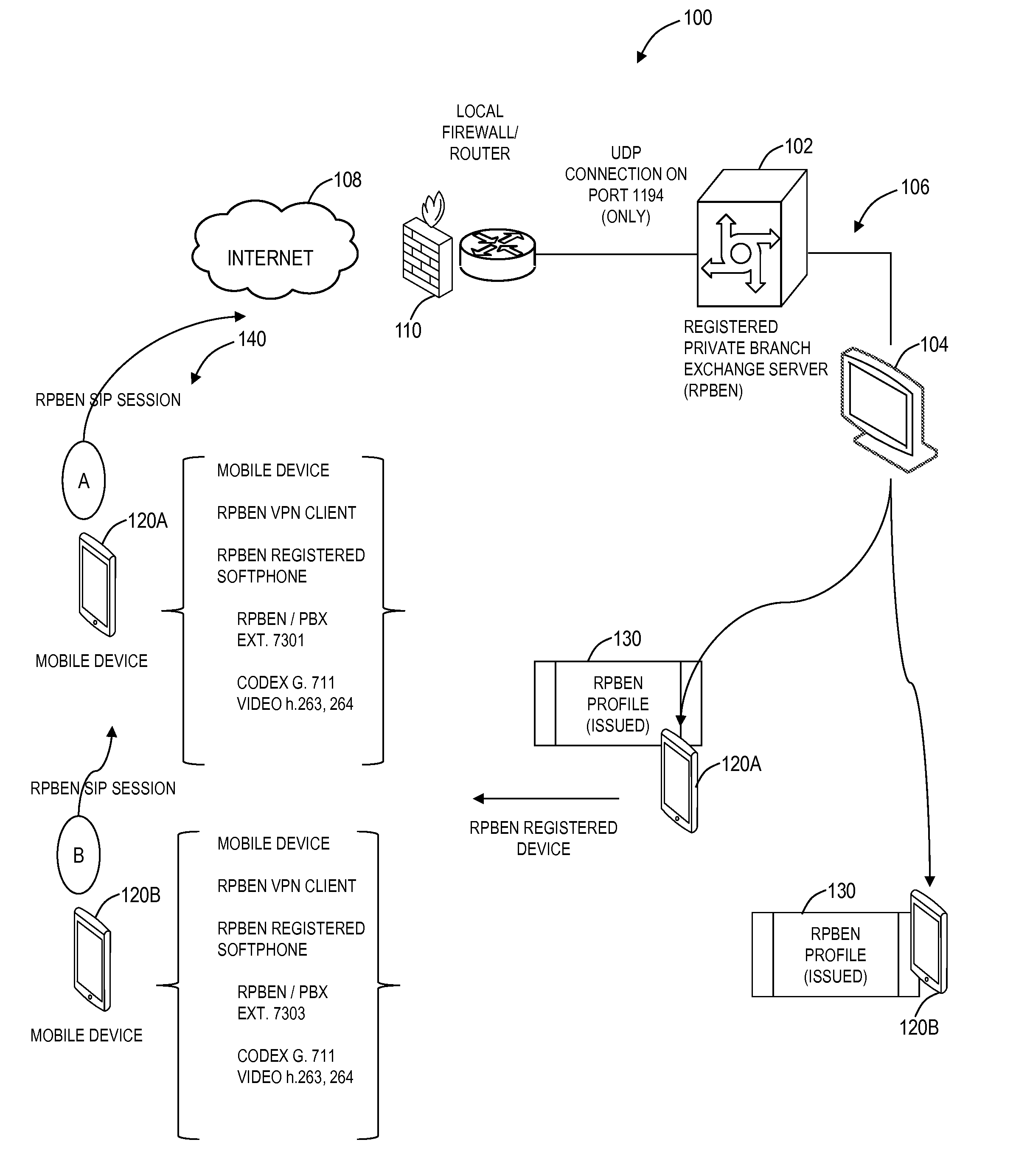
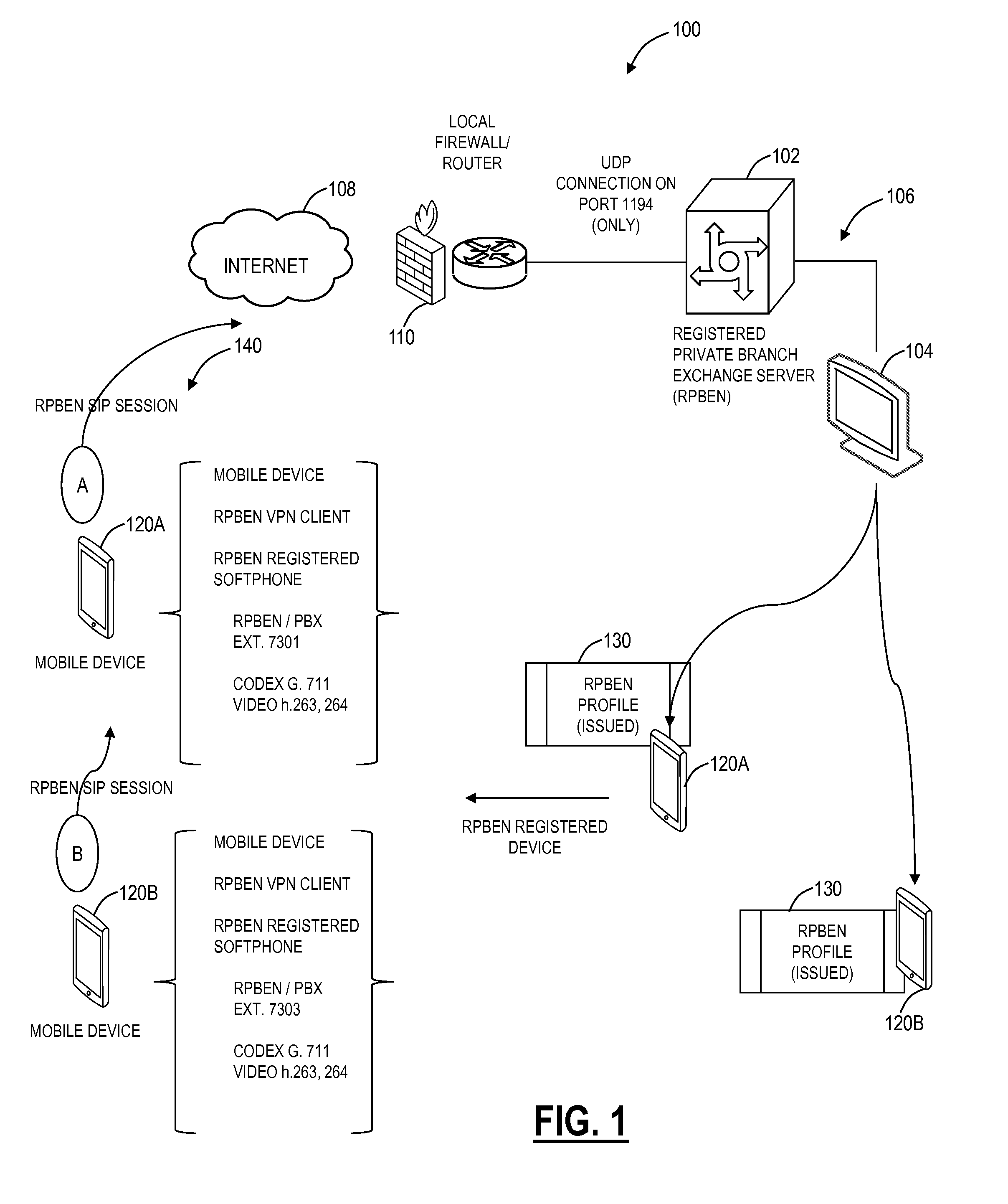
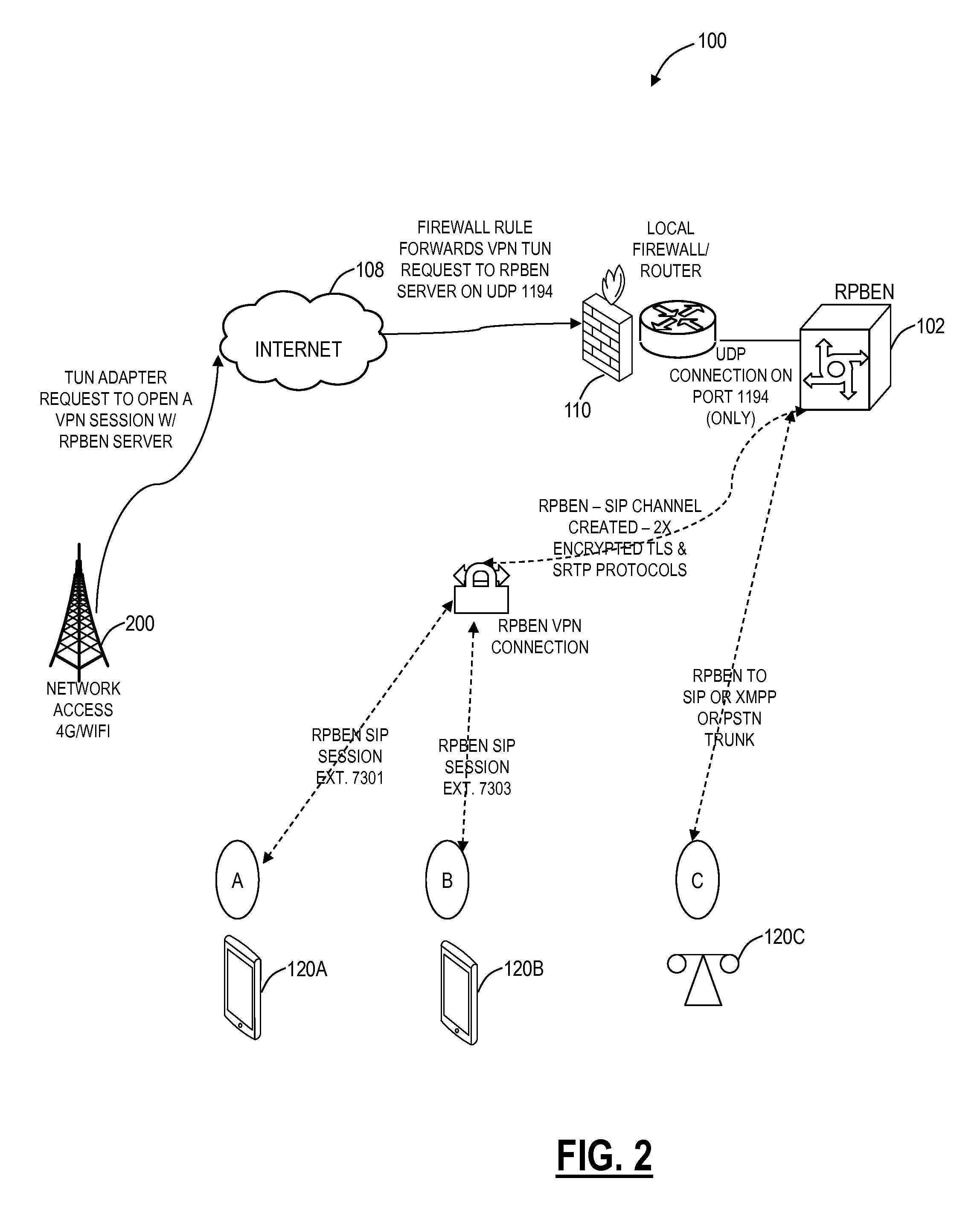
Private and secure communication systems and methods implemented by a server in a local network behind a local router / firewall include authenticating a client device based on a request from the client device, wherein the request is for a tunnel from the server to the client device through the local router / firewall for a communication session with another client device; configuring and establishing a Virtual Private Network (VPN) tunnel over the Internet with the client device; and establishing the communication session with the another client device utilizing Session Initiation Protocol (SIP) for both signaling and media, wherein the server operates both as a VPN server and a Private Branch Exchange (PBX) for communication sessions utilizing SIP, and wherein the communication session is logged at a local level of the server.
Owner:CLARK D SCOTT
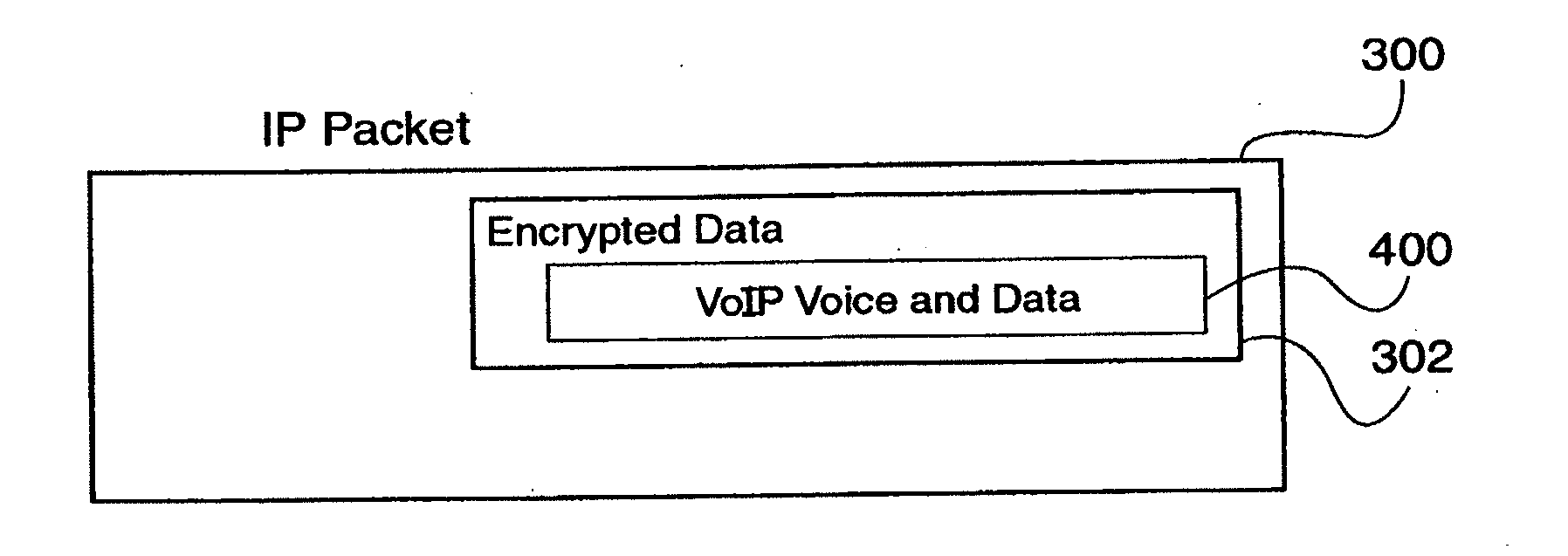
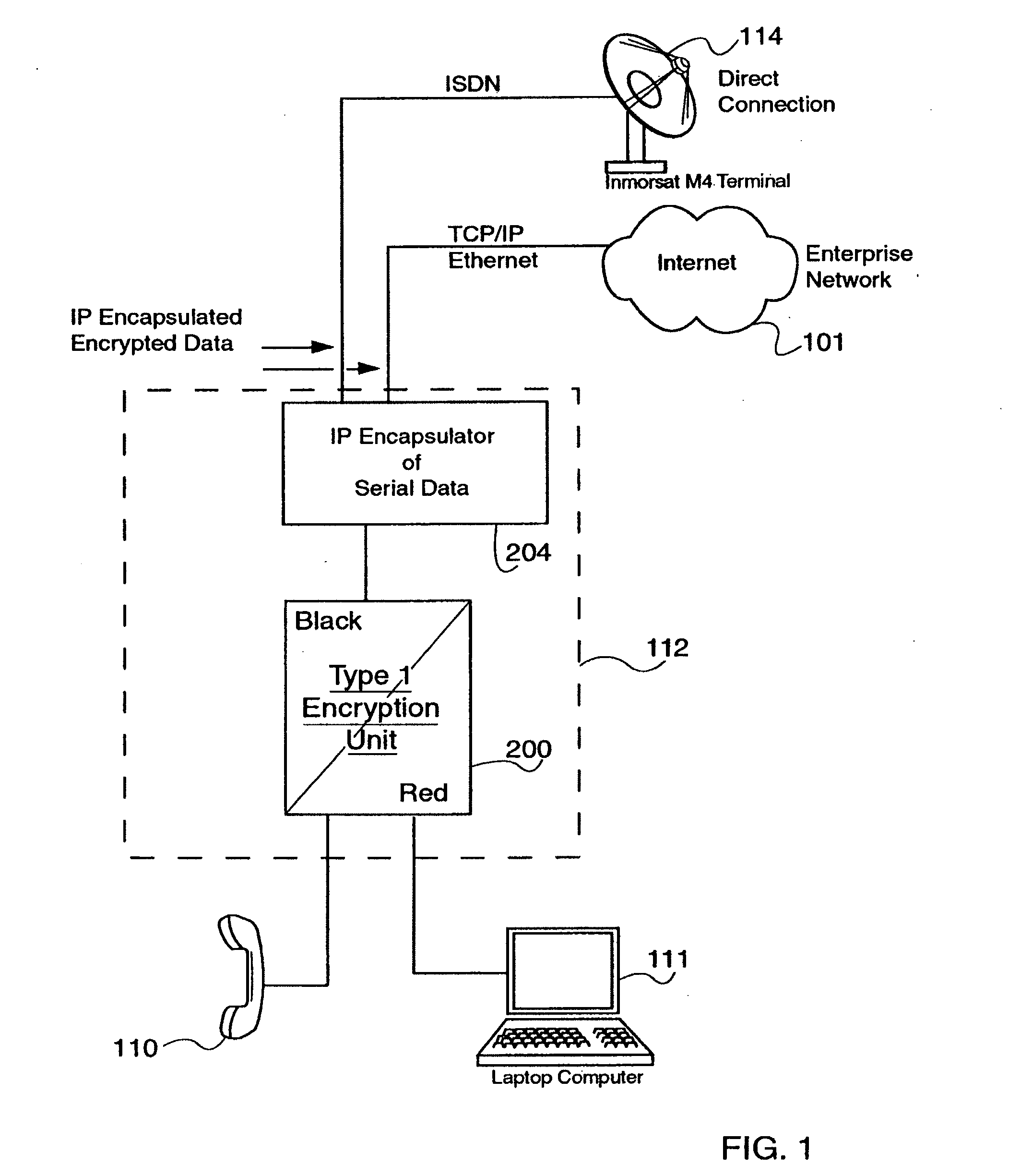
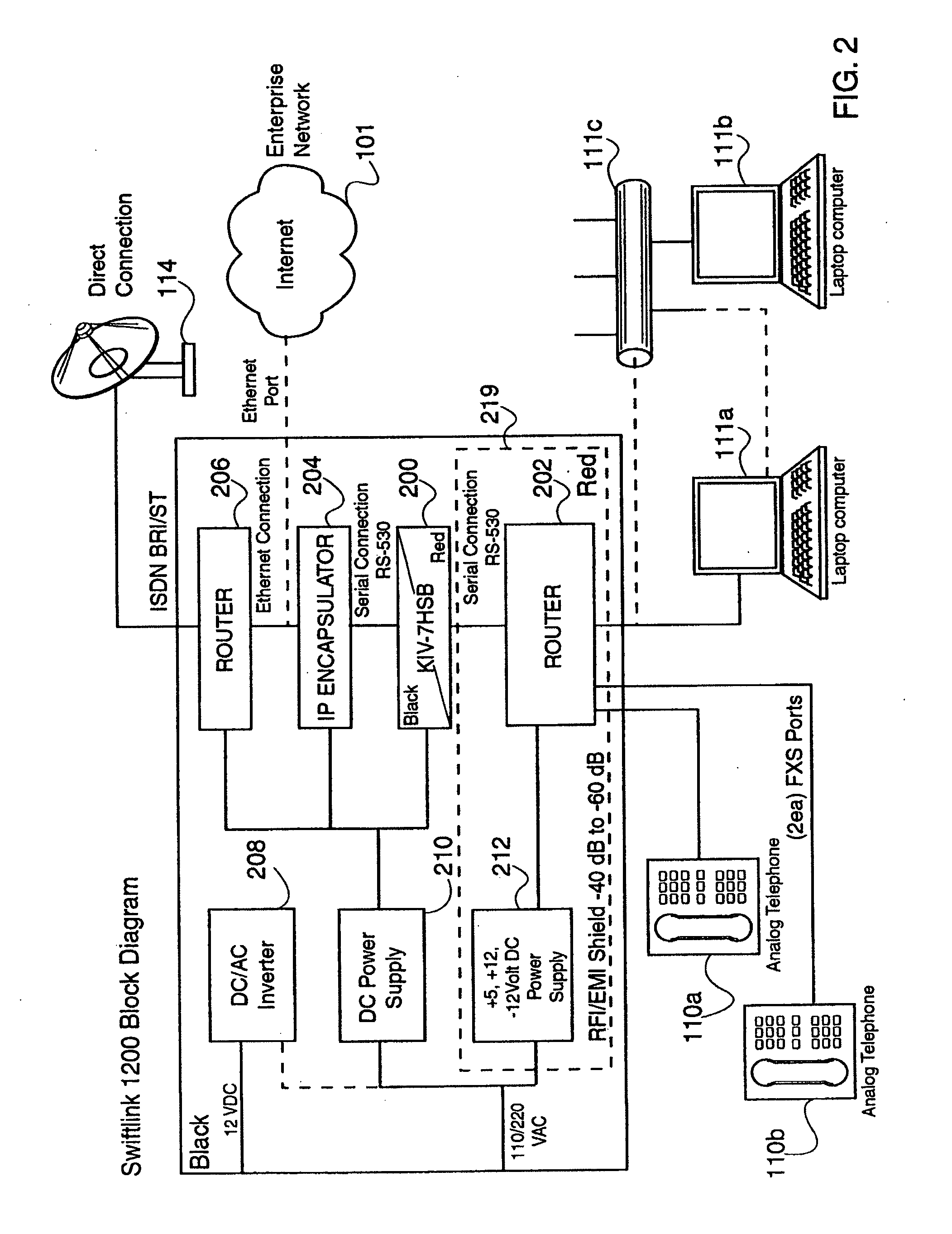
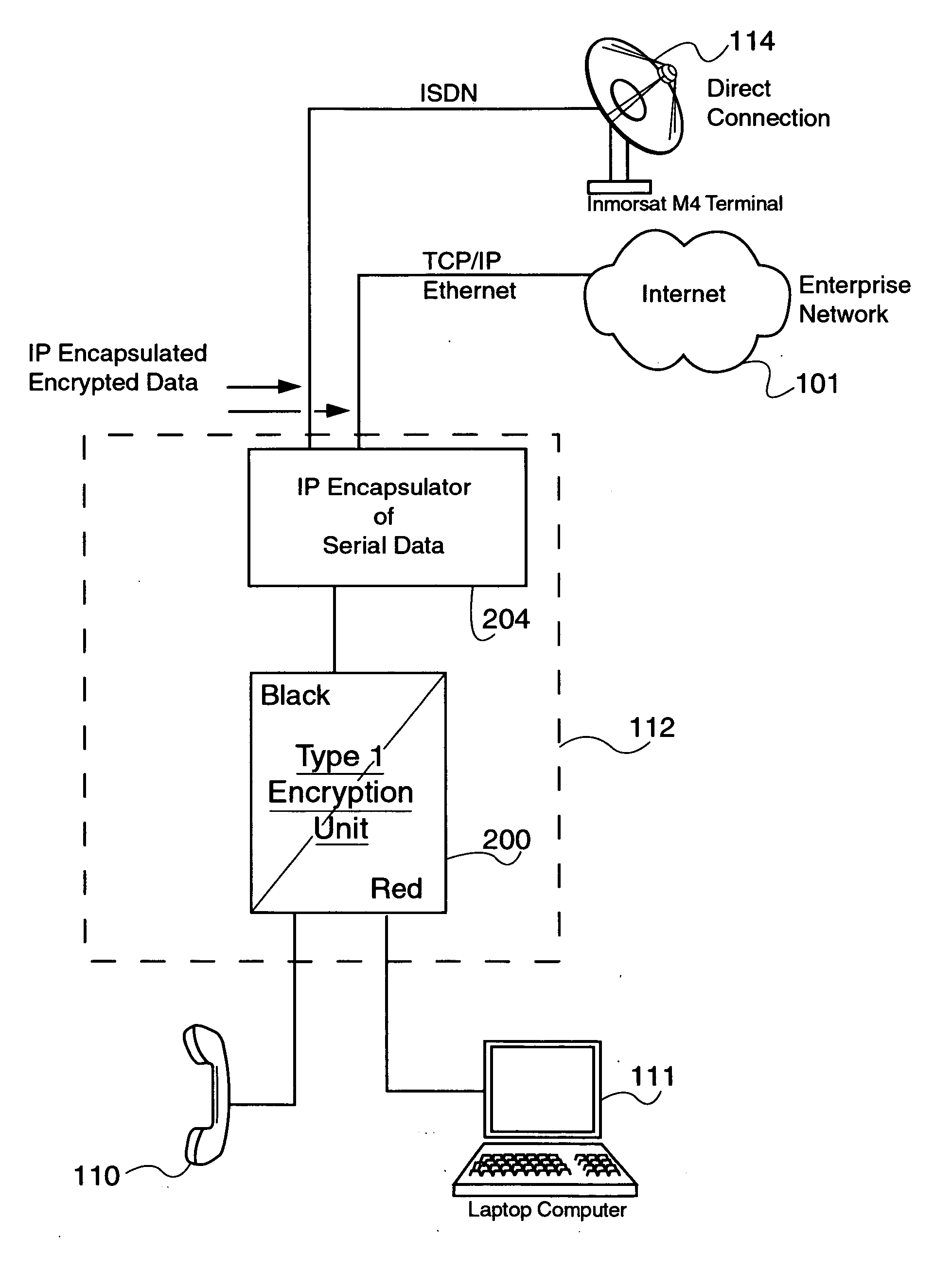
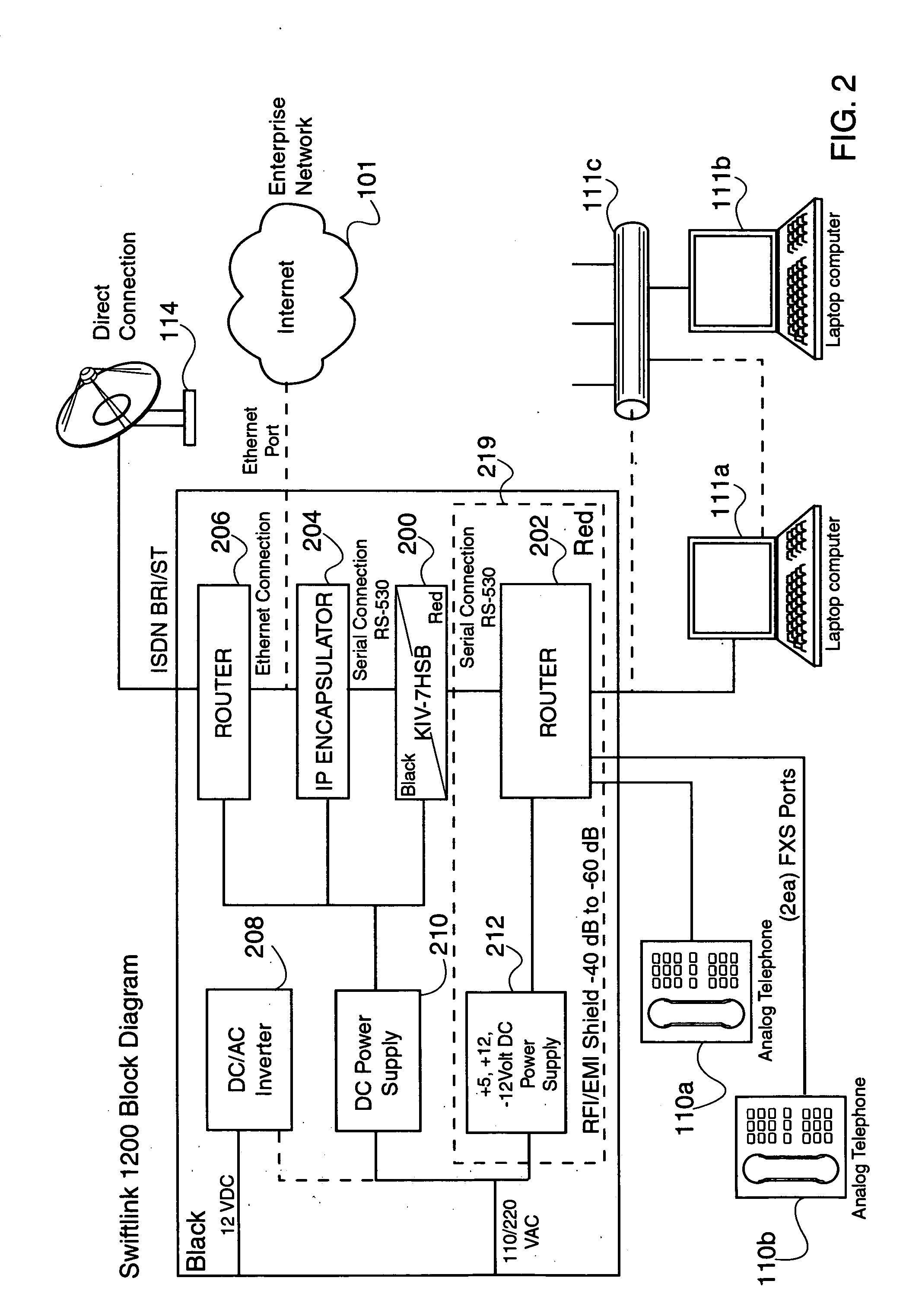
Encapsulation of Secure Encrypted Data in a Deployable, Secure Communication System Allowing Benign, Secure Commercial Transport
Sensitive, Type 1 KIV-encrypted data is encapsulated into IP packets in a remotely deployed, secure communication system. The IP packets are addressed to a matching IP encapsulator / decapsulator device over the public Internet or other IP protocol network, that then passes it to a similar Type 1 KIV device for decryption. Thus, sensitive, encrypted data is made to appear as if it were any other commercial network data, cloaking it in the vast and busy world of the Internet. The present invention is embodied in a system that provides secure Voice-Over-IP (VOIP), video and data network functionality in a single, small size deployable case, to a remote user. Most importantly, the embodiment allows for the routing of bulk encrypted (i.e., secure) data over a public network, e.g., the Internet.
Owner:TELECOMM SYST INC
Seamless key exchanging technology based on secret communication
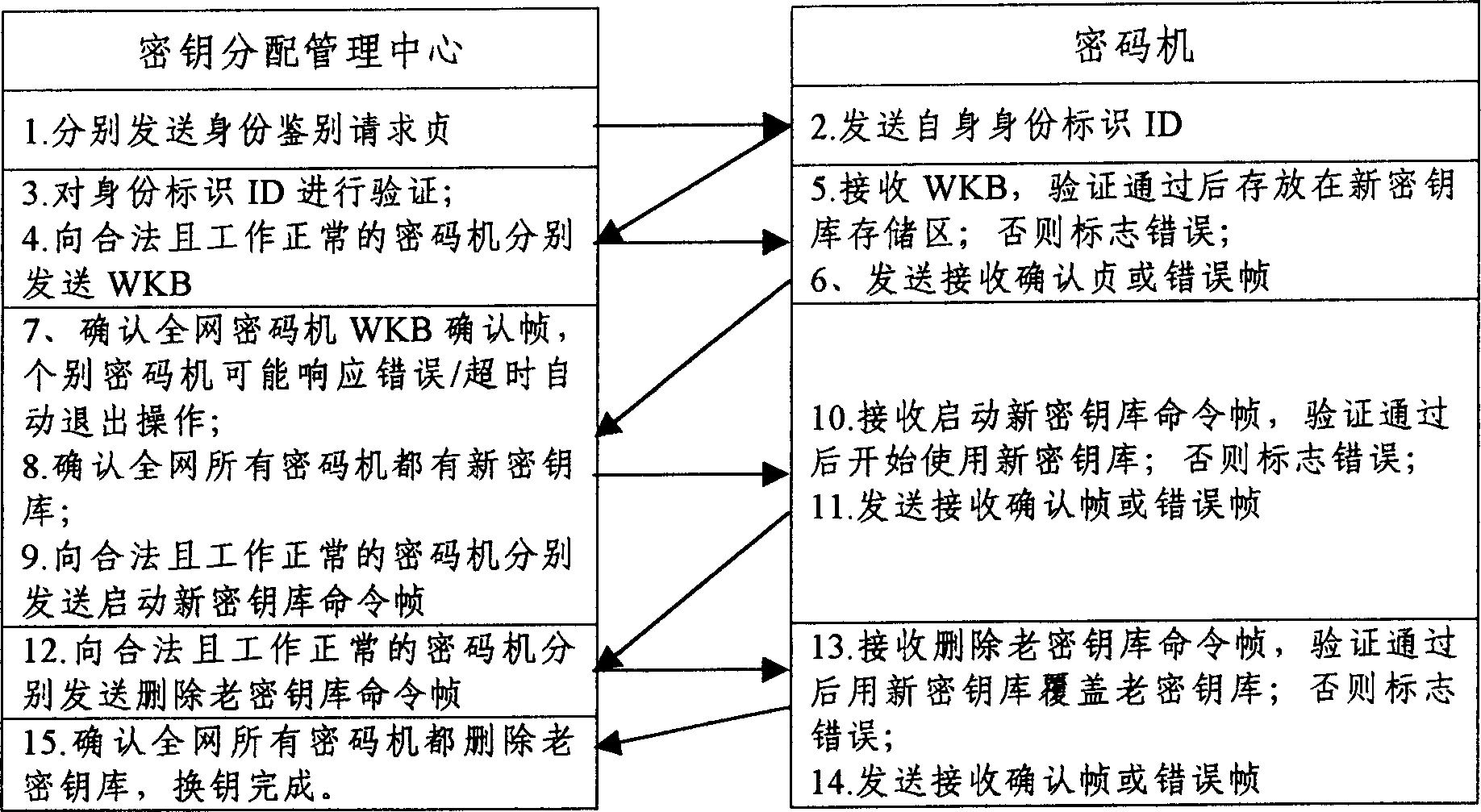
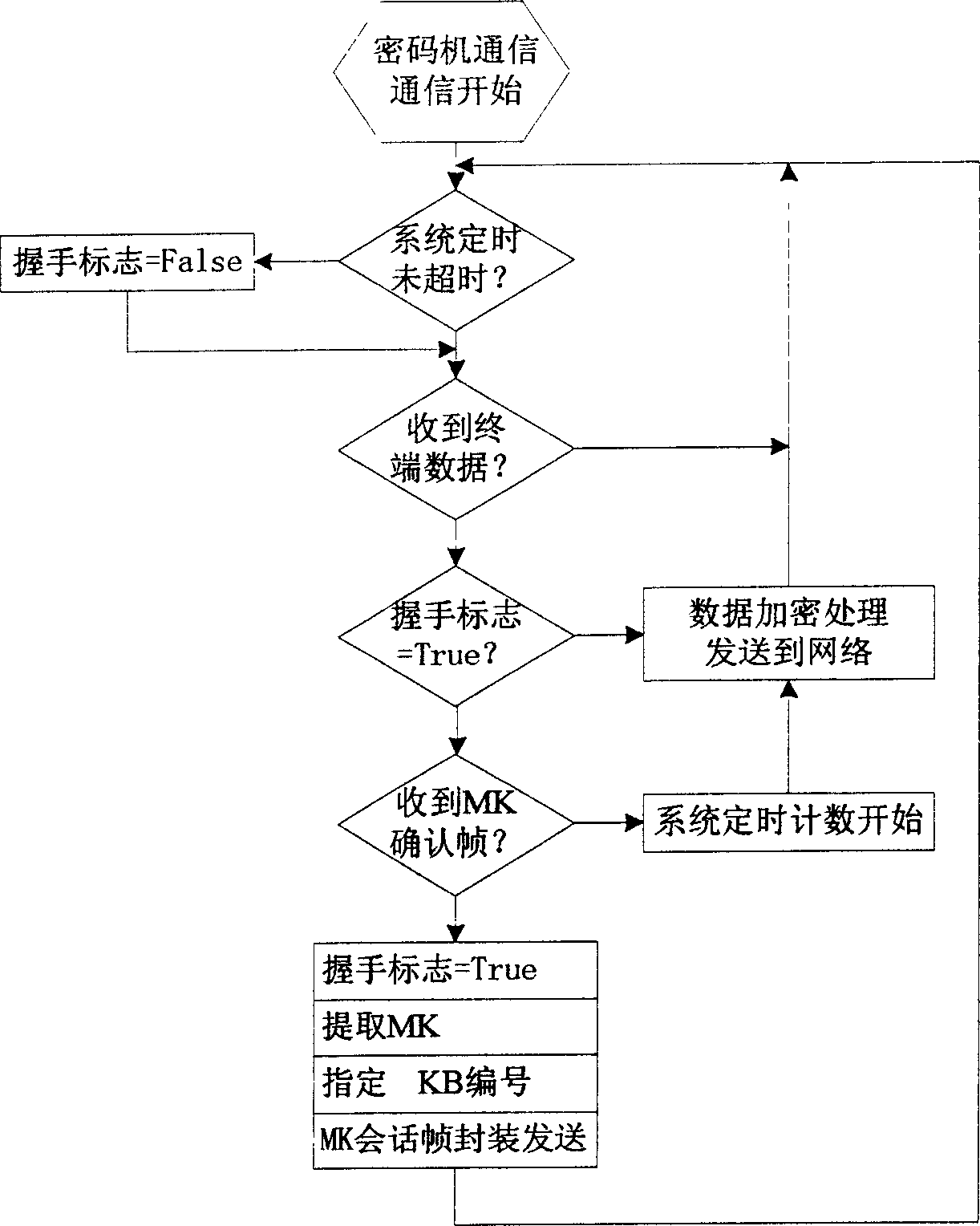
InactiveCN1512700ASimplify operabilitySimplify workloadSecret communicationSecuring communicationKey exchangeCommunications system
The KDMC carries out key-encrypting key base on-line replacement to related cryptces uniformly in the full-duplex secure communication system based on cryptoes. Based on the traditional way of key-encrypting key base replacement, the base buffer storage and MK handshaking switching technology are applied and improved to realize seamless key-encrypting key replacement of normal data secure communications among cryptoes continuously.
Owner:中电科网络安全科技股份有限公司
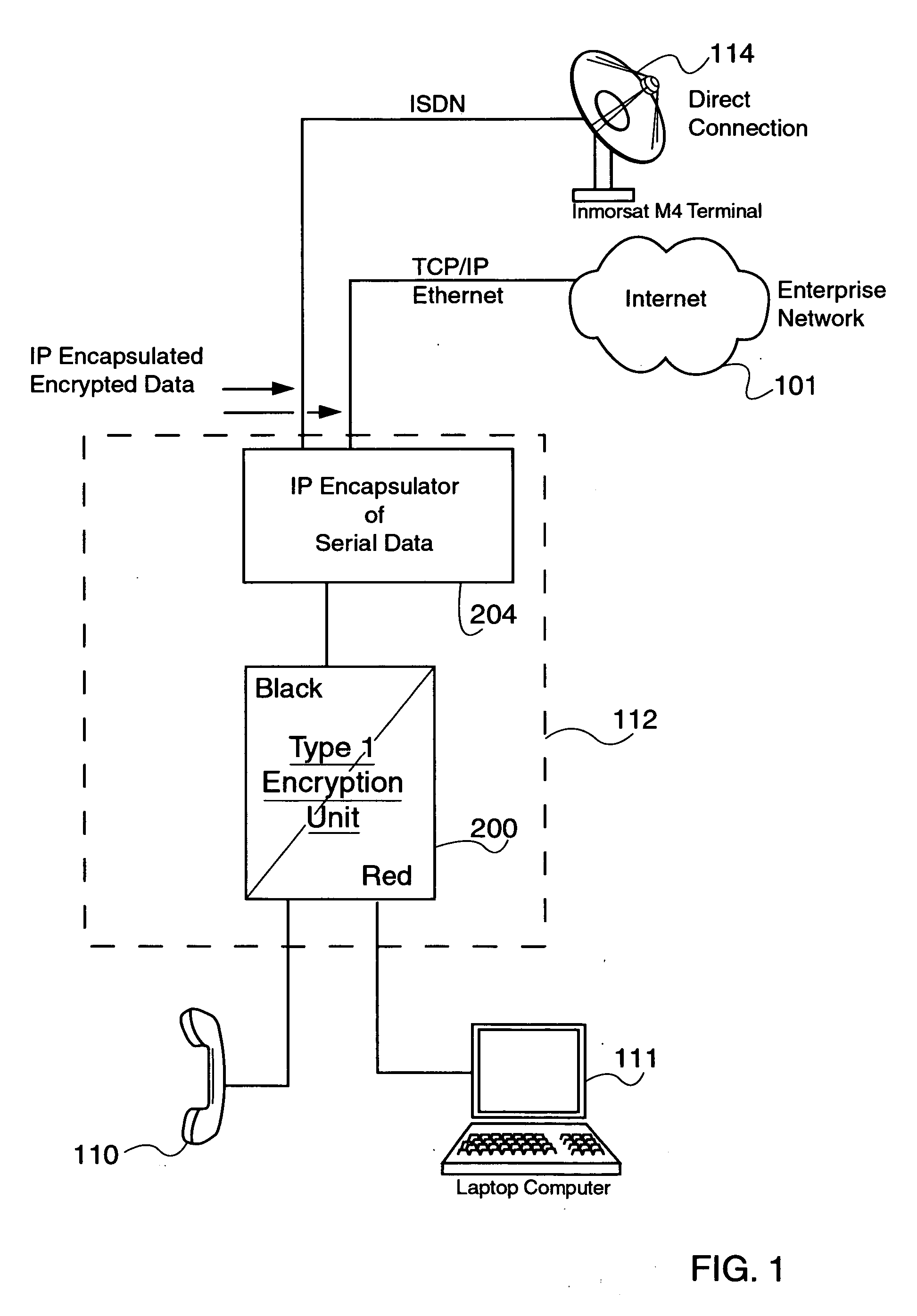
Encapsulation of secure encrypted data in a deployable, secure communication system allowing benign, secure commercial transport
Sensitive, Type 1 KIV-encrypted data is encapsulated into IP packets in a remotely deployed, secure communication system. The IP packets are addressed to a matching IP encapsulator / decapsulator device over the public Internet or other IP protocol network, that then passes it to a similar Type 1 KIV device for decryption. Thus, sensitive, encrypted data is made to appear as if it were any other commercial network data, cloaking it in the vast and busy world of the Internet. The present invention is embodied in a system that provides secure Voice-Over-IP (VOIP), video and data network functionality in a single, small size deployable case, to a remote user. Most importantly, the embodiment allows for the routing of bulk encrypted (i.e., secure) data over a public network, e.g., the Internet.
Owner:TELECOMM SYST INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com