Patents
Literature
34results about How to "Secure data communication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
System and method for interaction object reconciliation in a blockchain environment
ActiveUS10192073B2Secure data communicationEncryption apparatus with shift registers/memoriesUser identity/authority verificationObject basedNetwork connection
Owner:ROCK INNOVATION LLC
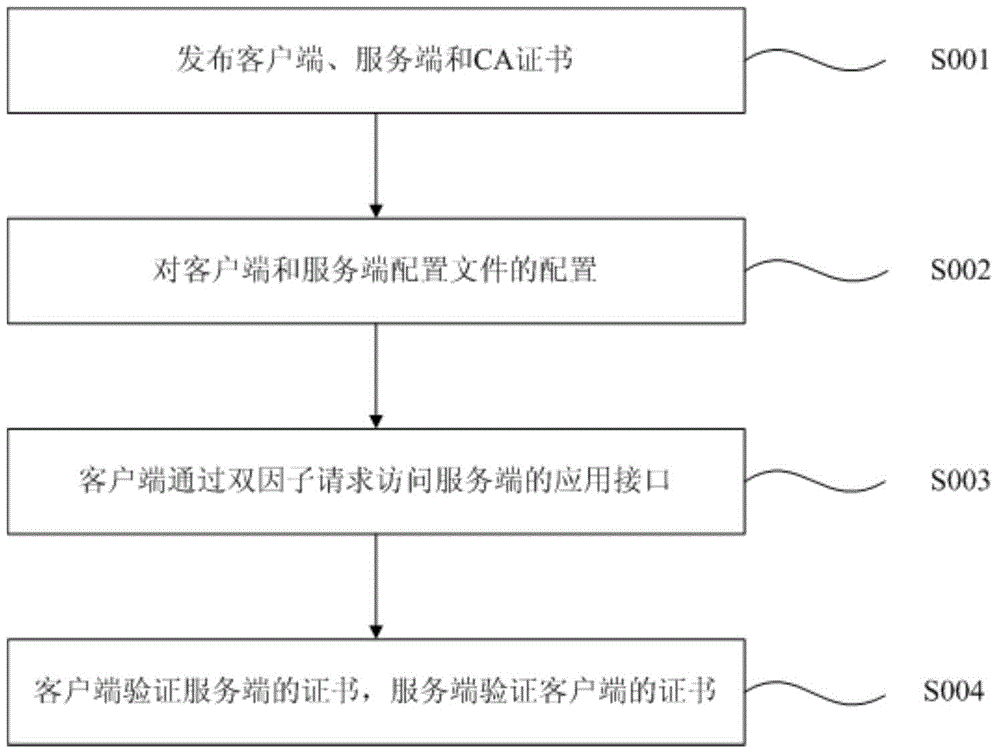
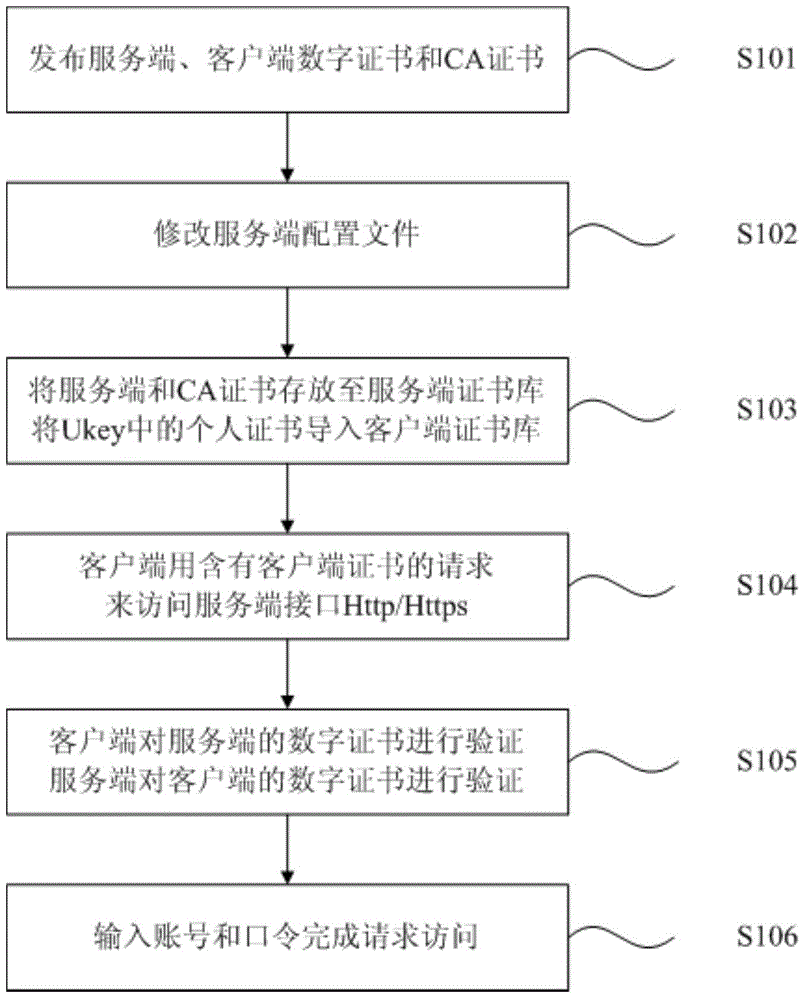
Method and system for double-factor bidirectional authentication
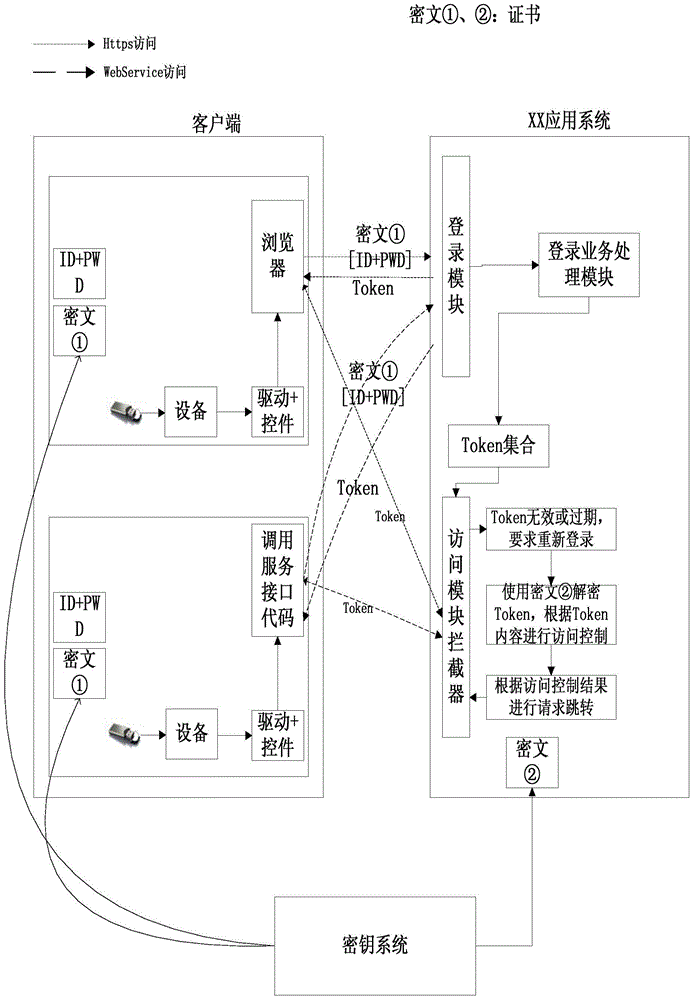
ActiveCN104486343AImprove compatibilitySimple designUser identity/authority verificationClient-sideClient certificate
The invention discloses a method for double-factor bidirectional authentication. The method comprises the following steps: releasing a digital certificate and a CA certificate used for signature during the making of the digital certificate by a secret key system; configuring the configuration files of a client and a server-side so as to support the access of the client to an application interface of the server-side; accessing the application interface of the server-side by the client in a double-factor authentication mode; carrying out first verification on a server-side certificate by the client, carrying out second verification on a client certificate by the server-side, and after passing through of both the first verification and the second verification, allowing the client to access the application interface of the server-side. Besides, the invention discloses a system for double-factor bidirectional authentication, corresponding to the method. The method and the system for double-factor bidirectional authentication have the advantages of higher compatibility, wider application range, simpler design, more efficiency in use, and higher safety in data communication.
Owner:GUANGDONG RAILWAY TECH
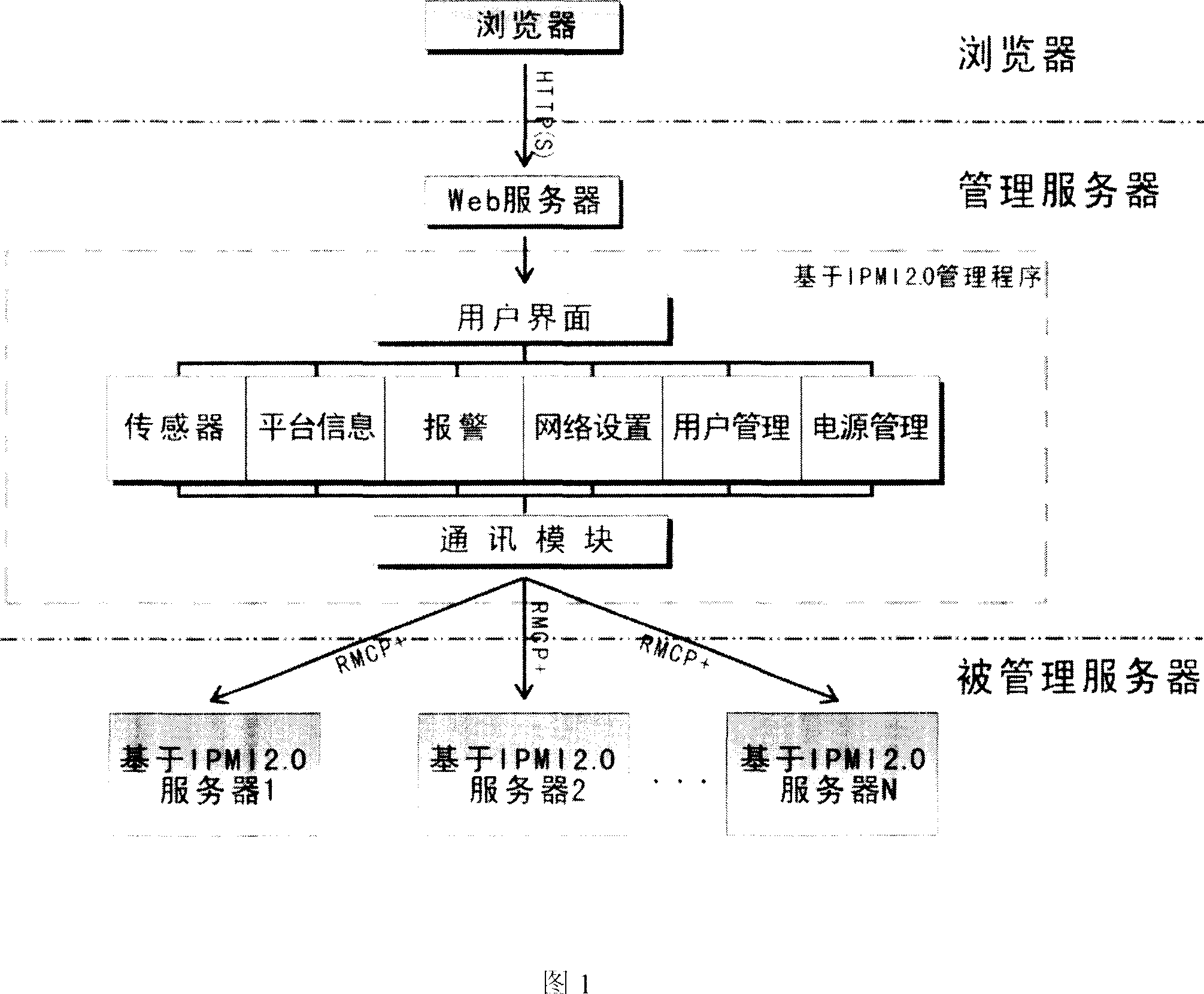
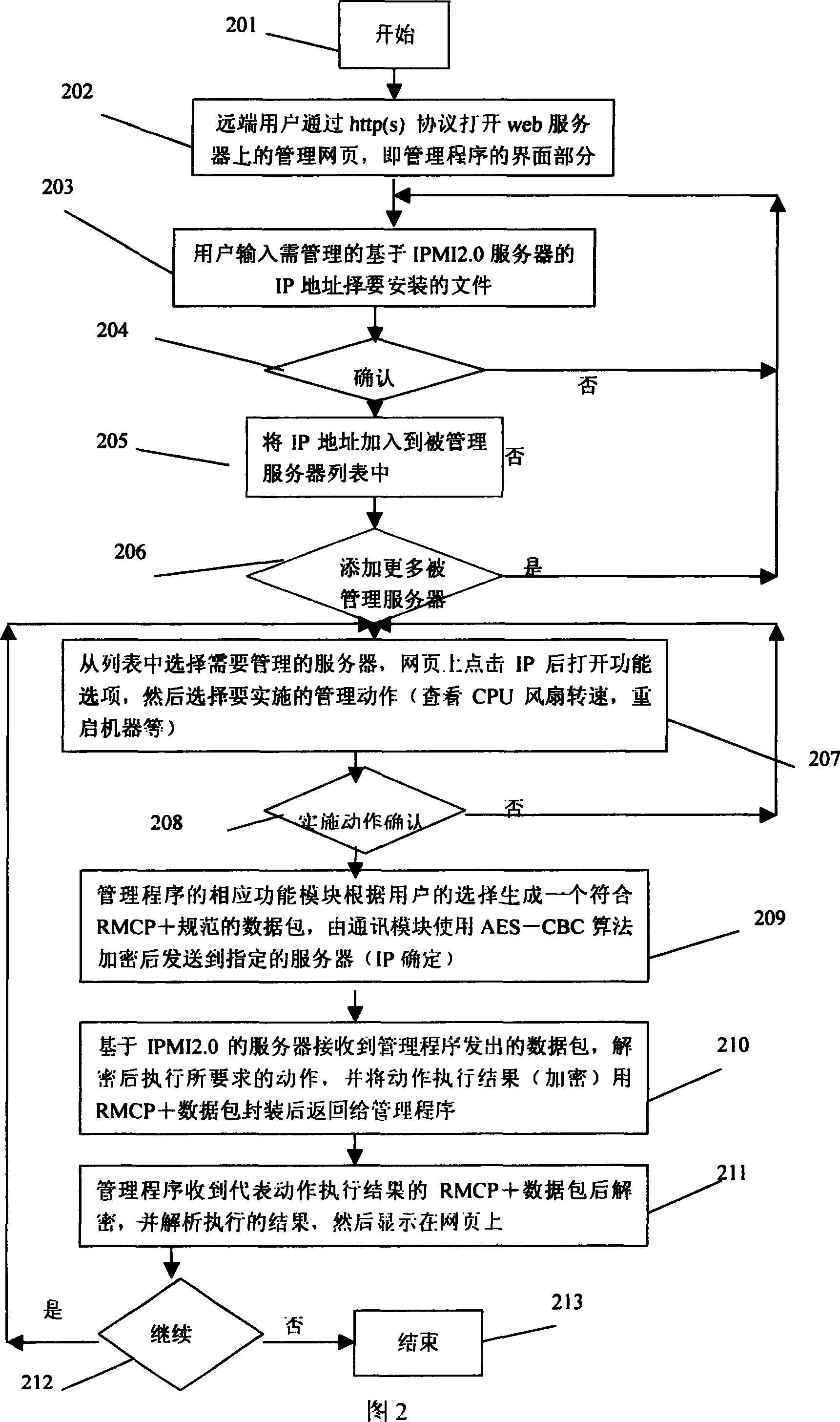
Multi-server management system and method
InactiveCN101030880ASafety managementEfficient managementData switching networksComputer hardwareWeb service
The system comprises a management server comprising a WEB server module, a user interface module, a sensor module, an information platform module, an alarm module, a network setting module, a users' management module, a power management module and a communication module. Each module in the management server uses IPMI2.0 management technology; the communication module uses RMCP+ protocol to respectively connect with multi IPMI 2.0-based servers. The invention also uses encryption algorithms HMAC-MD5, HMAC-SHAl, AES-CBC to encrypt and decrypt communication data packets.
Owner:HUANDA COMPUTER (SHANGHAI) CO LTD
System and method for secure communication of electronic documents
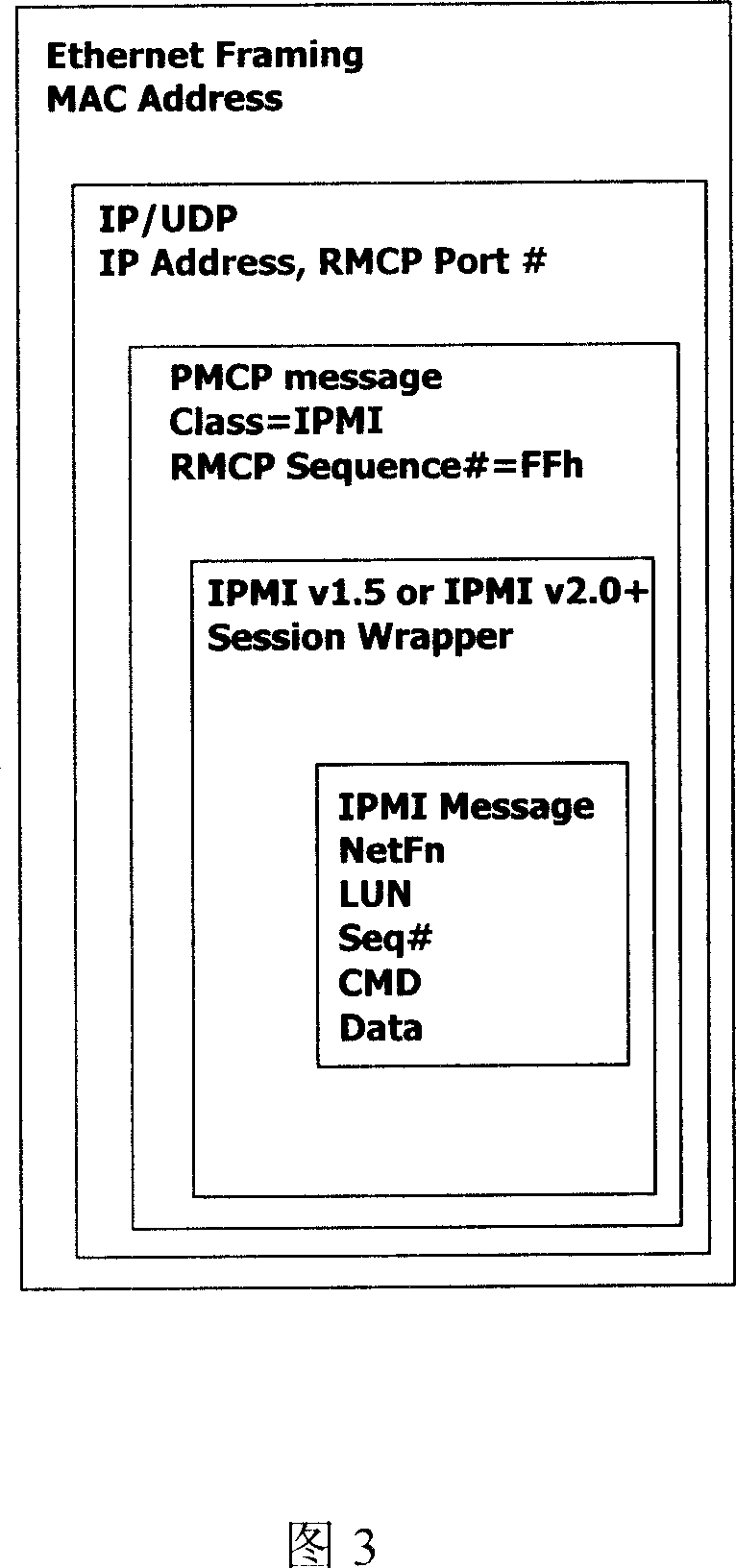
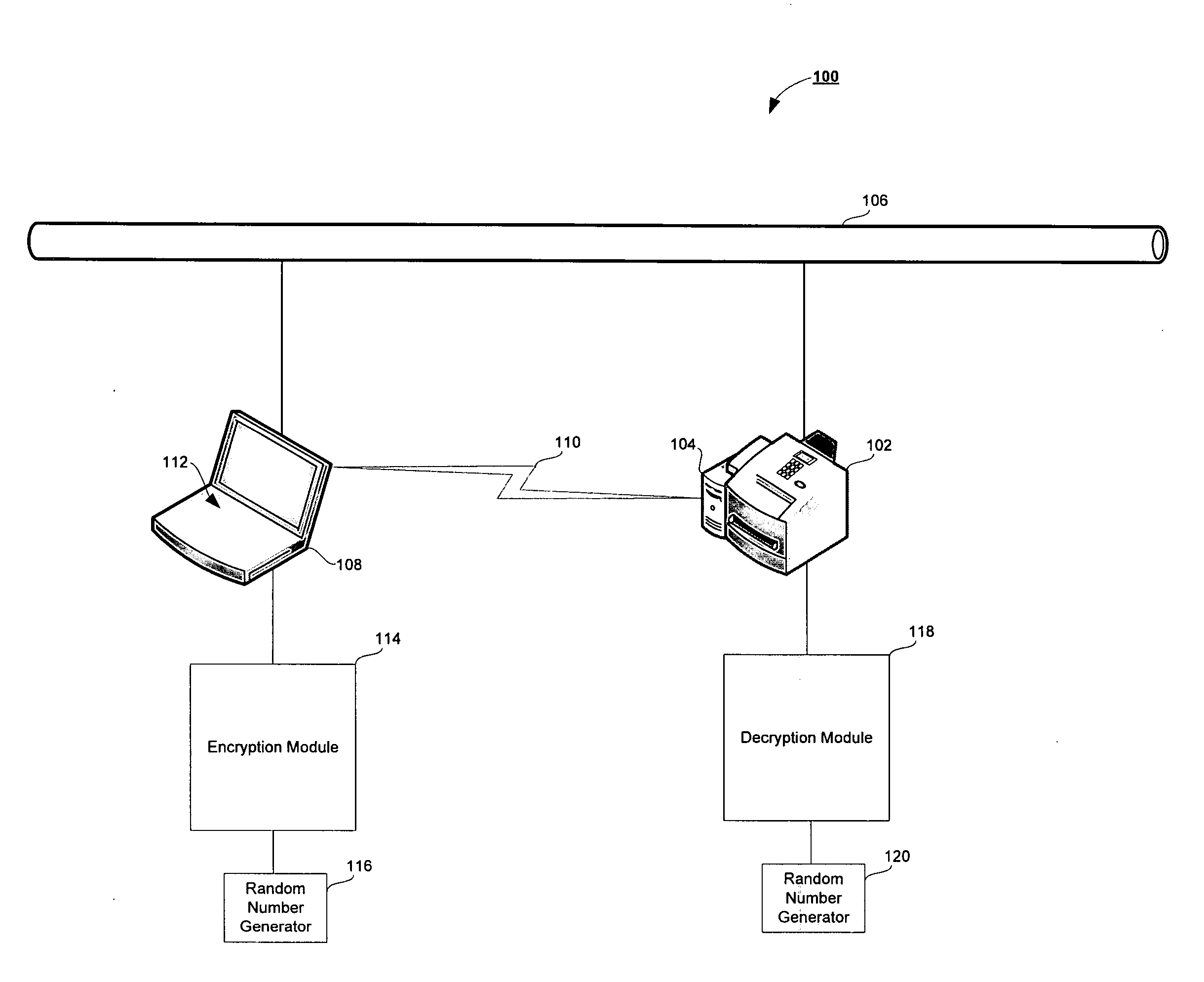
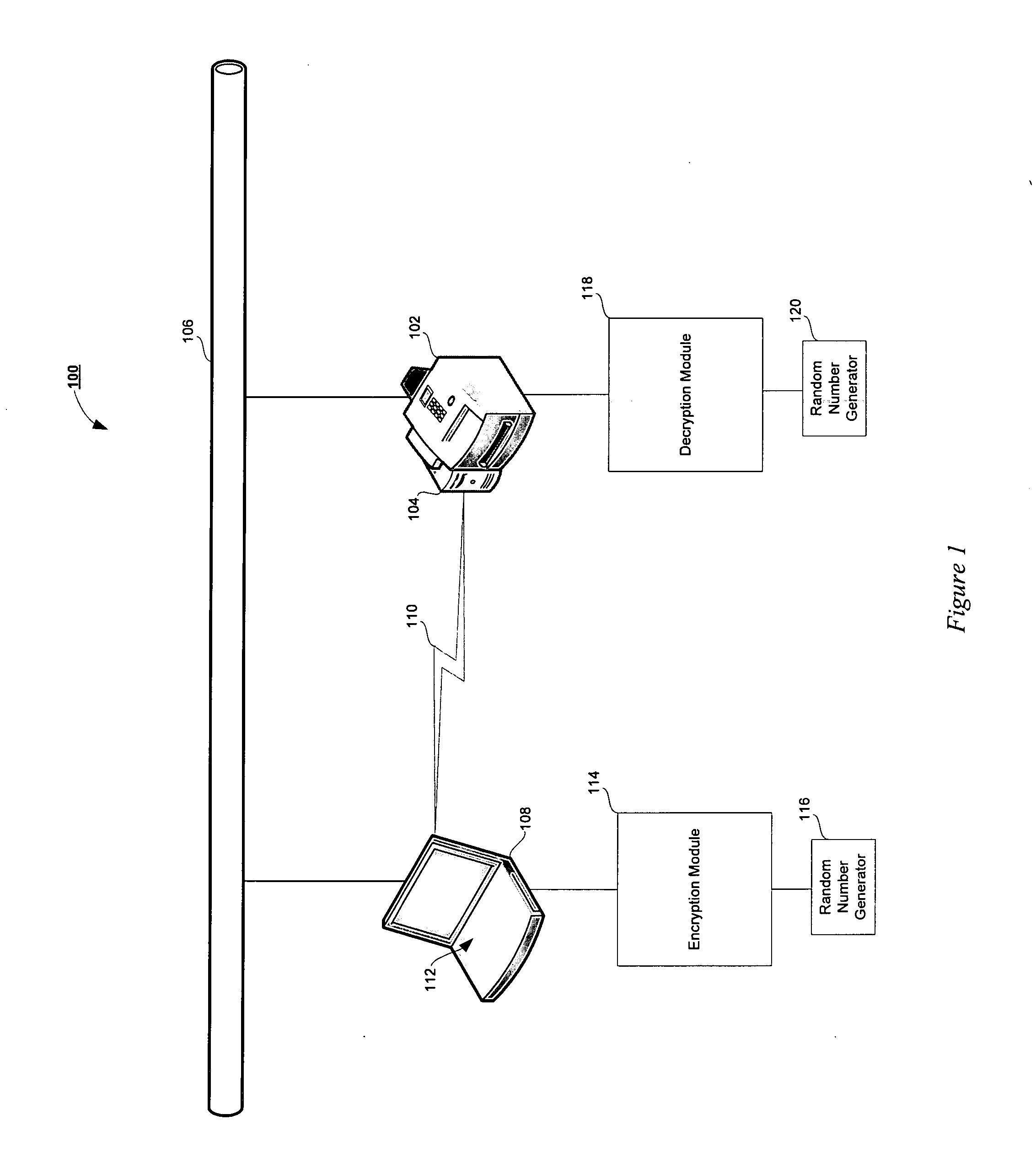
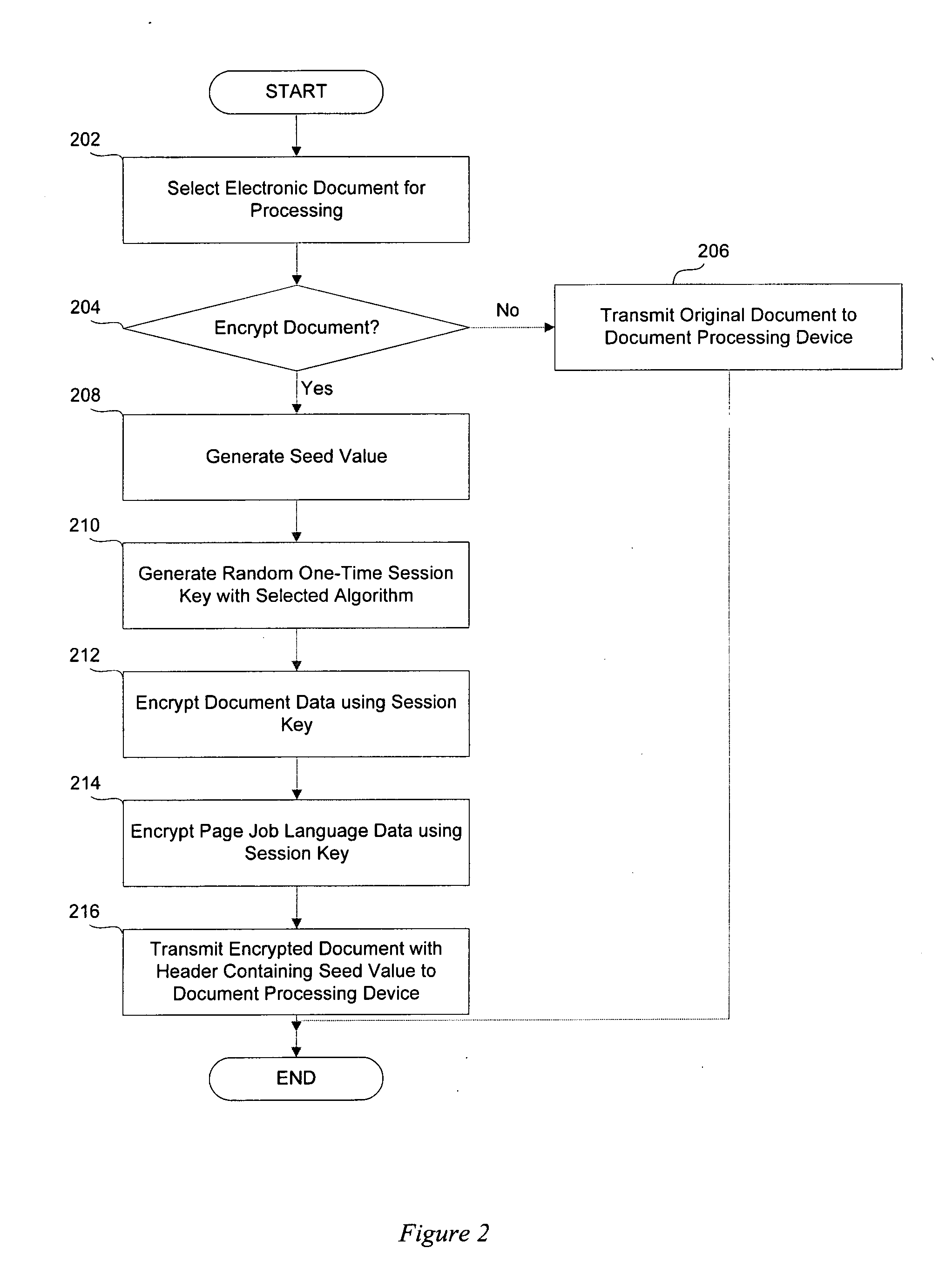
InactiveUS20060153374A1Secure data communicationCommunication securitySecret communicationTelevision systemsSecure communicationPaper document
The present invention is directed to a system and method for secure communication of electronic documents to a document processing device. A document processing request containing electronic document data is received containing document data in an unencrypted form. A seed value is then received and used to generate a random number. The random number is used to encrypt the electronic document. The seed value, in a header, is transmitted, along with the encrypted electronic document, to a document processing device. The document processing device extracts the seed value from the header and uses the seed value to generate a random number. The encrypted document is then decrypted using the random number generated from the seed value. The document processing device subsequently performs the selected document processing operation on the decrypted electronic document.
Owner:KK TOSHIBA +1
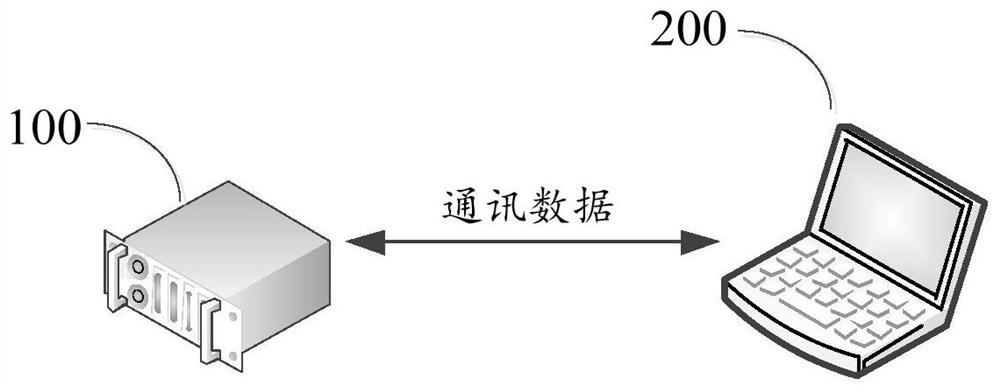
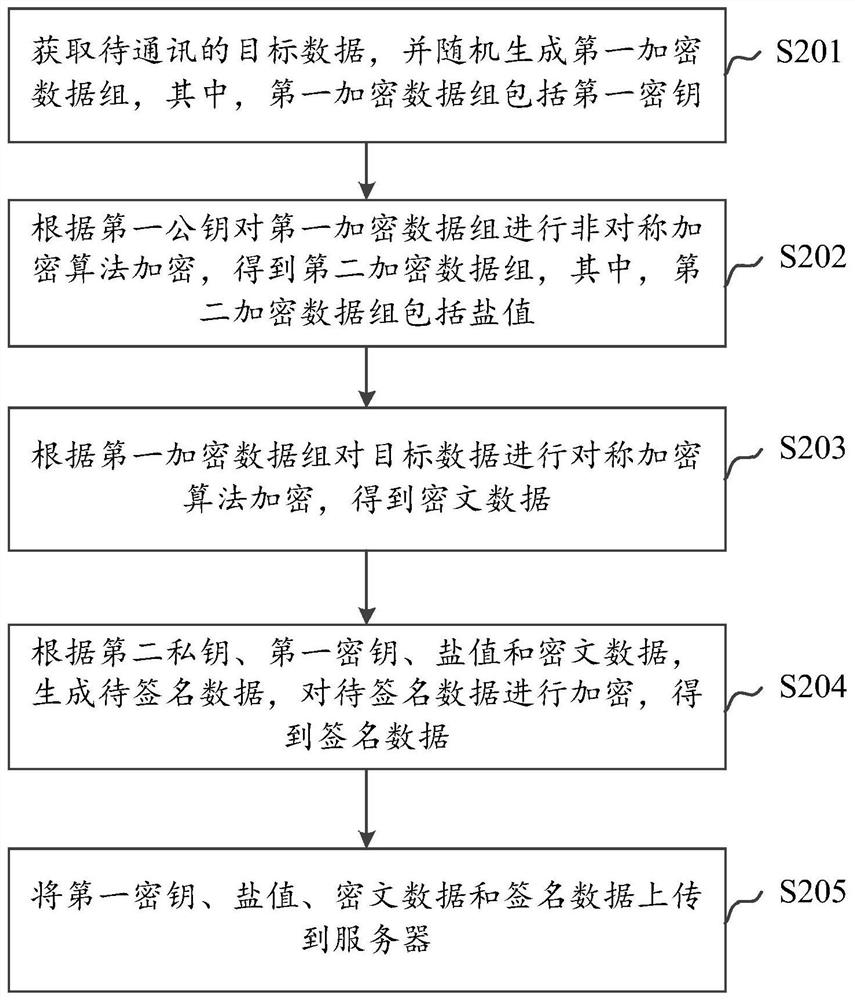
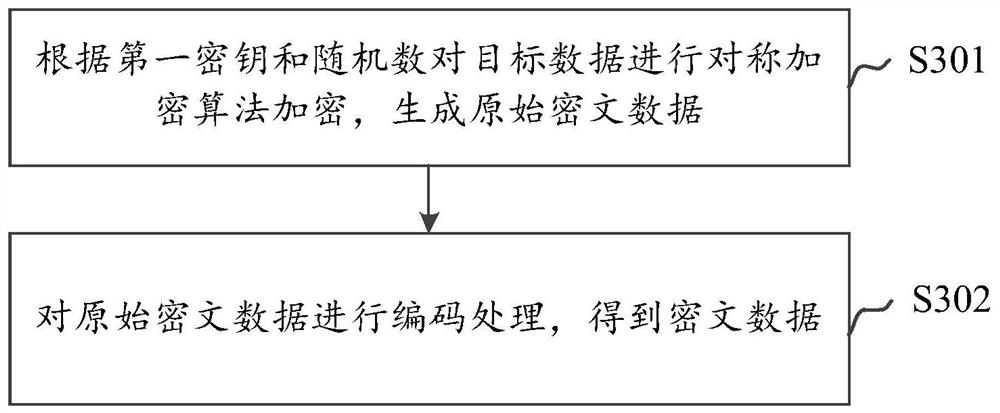
Data communication method and device, equipment and storage medium
ActiveCN112866237AGuaranteed non-repudiationGuaranteed legalityUser identity/authority verificationData setCiphertext
The invention discloses a data communication method and device, equipment and a storage medium, and the method comprises the steps: obtaining to-be-communicated target data, and randomly generating a first encrypted data group comprising a first secret key; performing asymmetric encryption algorithm encryption on the first encrypted data set according to the first public key to obtain a second encrypted data set, the second encrypted data set comprising a salt value; performing symmetric encryption algorithm encryption on the target data according to the first encrypted data group to obtain ciphertext data; according to the second private key, the first secret key, the salt value and the ciphertext data, generating to-be-signed data, and encrypting the to-be-signed data to obtain signature data; and uploading the first key, the salt value, the ciphertext data and the signature data to a server. According to the method and the device, the non-repudiation of the data sender is ensured through the signature data, so that the legality of both communication parties is ensured, the data is prevented from being tampered, the replay attack is prevented, and the data communication can be performed more safely and efficiently on the basis of not reducing the encryption performance.
Owner:广州TCL互联网小额贷款有限公司
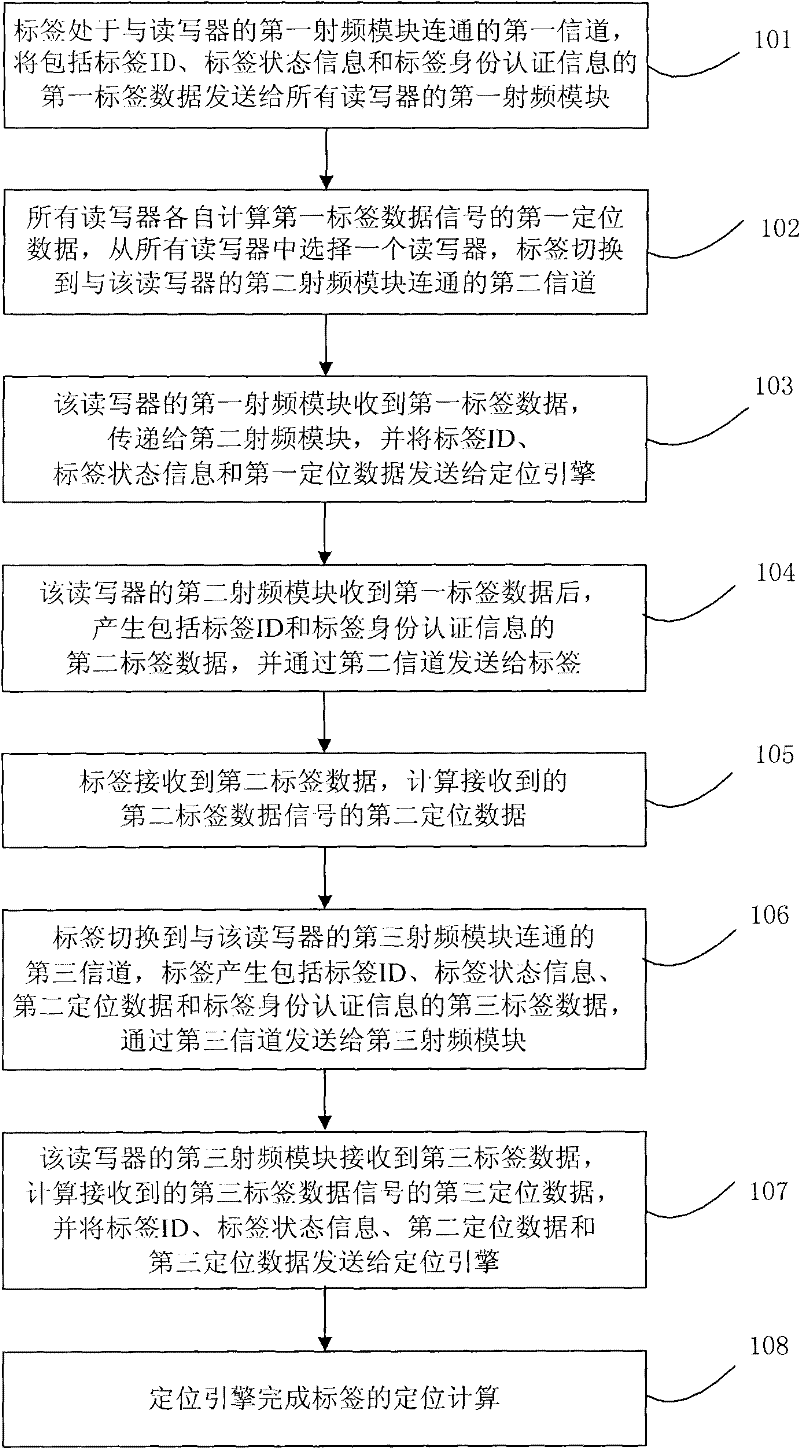
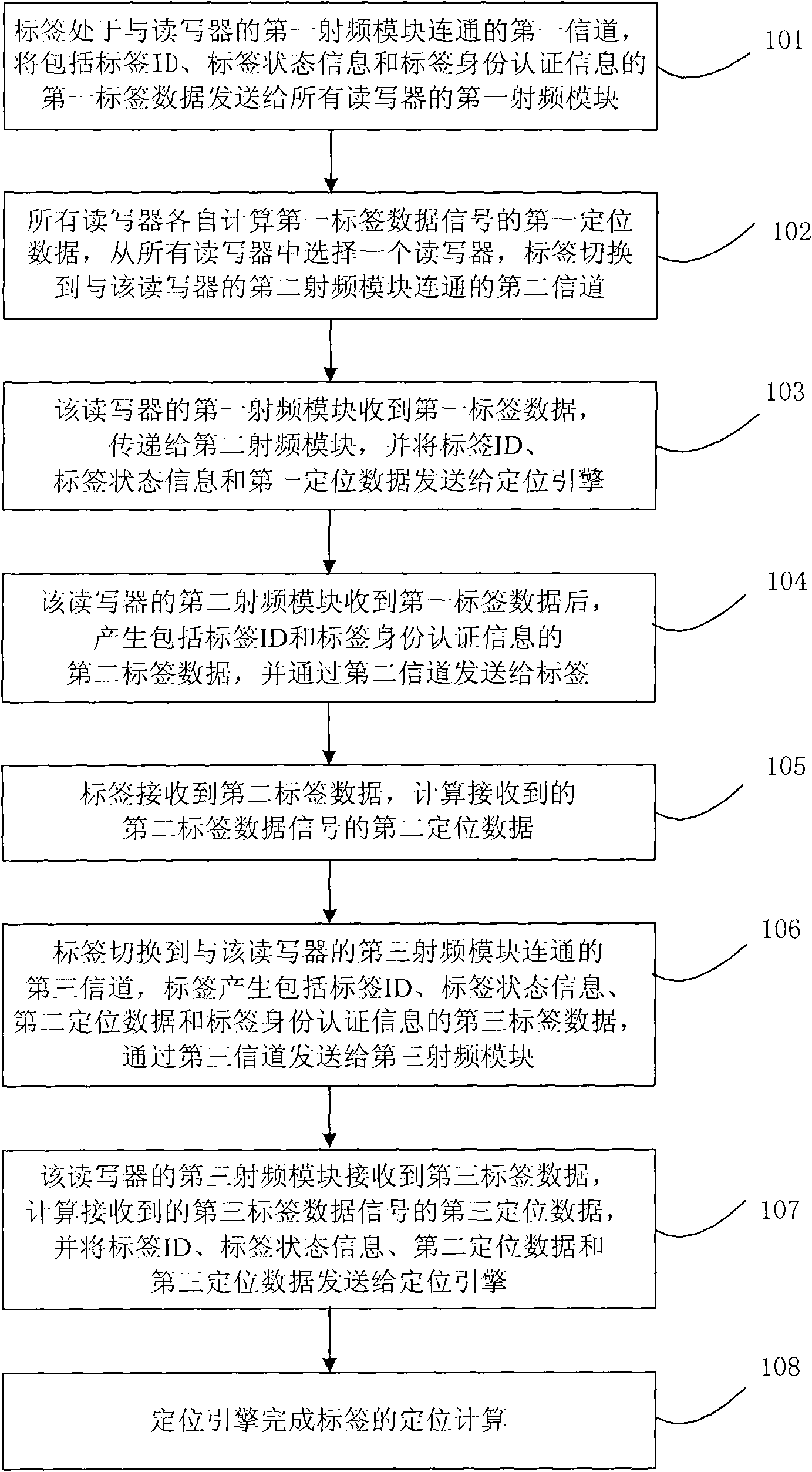
Wireless real time location system and method
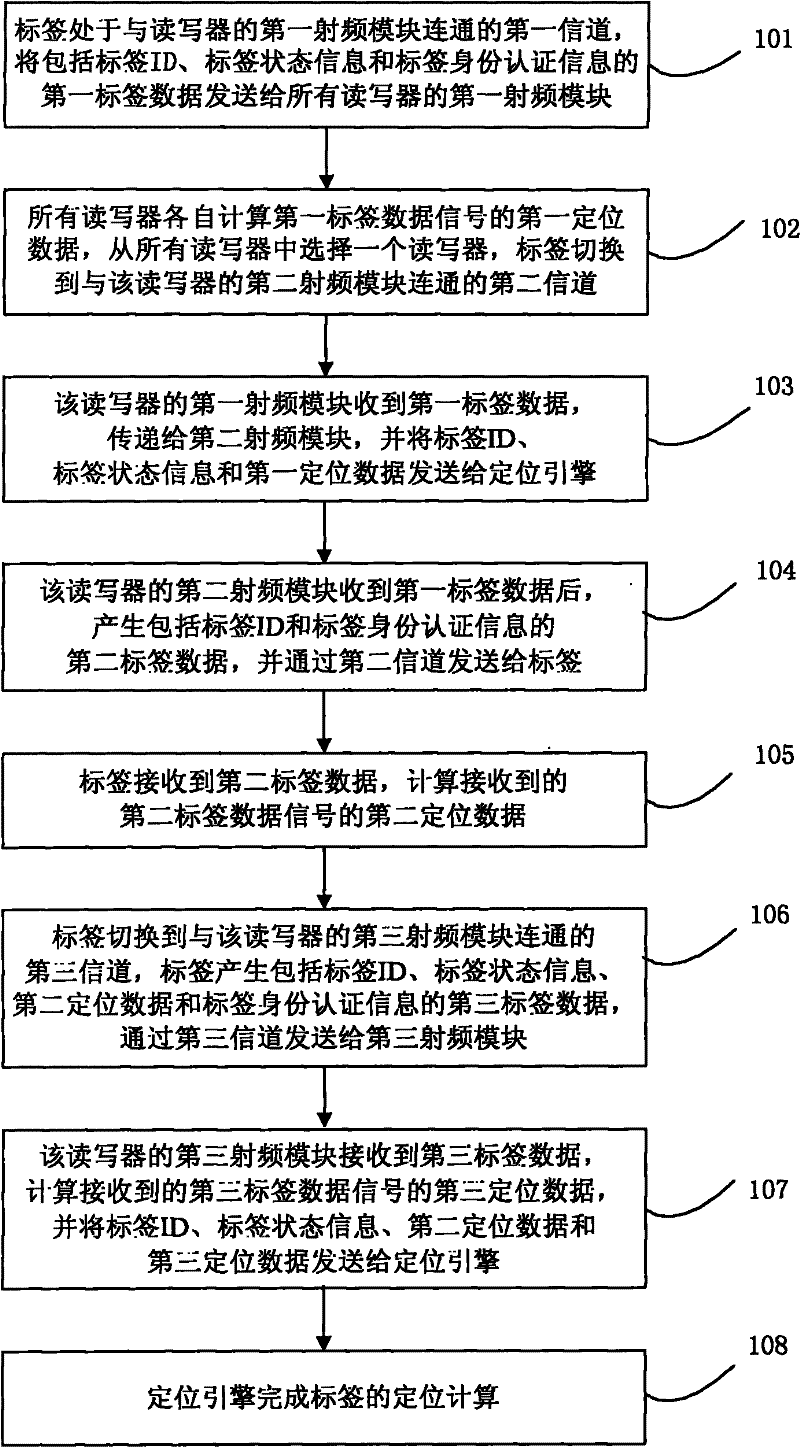
InactiveCN102238536ASecure data communicationHigh positioning accuracySecurity arrangementCommunications securityEngineering
The invention discloses a wireless real time location system and a wireless real time location method. The wireless real time location system comprises a label, a reader-writer and a location engine. The reader-writer comprises three radio frequency modules and three antennae. The label establishes three channels with the reader-writer by the three radio frequency modules and the three antennae. The reader-writer is connected with the location engine. The label and the reader-writer achieve data security and finish location computation by triple authentication. By the technical scheme provided by the invention, the security of data communication between the label and the reader-writer can be achieved, the capacity of the label can be increased and the location accuracy can be improved.
Owner:北京烽火联拓科技有限公司
Unified identity management system of distributed public certificate service network
ActiveCN111049835AManagement is automatically effectiveAuthentication is convenientUser identity/authority verificationComputer securityEngineering
The invention discloses a unified identity management system of a distributed public certificate service network. A root public certificate service center and a regional public certificate service center are accessed to a backbone network; the user terminal accesses the backbone network through the backbone network access point; the regional public certificate service center is provided with a regional public certificate server and a regional administrator; the backbone network is a data communication network based on a UID address; wherein different devices and terminal users in the backbonenetwork have unique and different UID addresses; wherein the UID address format is C _ R _ X, C represents the country, R represents the region, and X represents the equipment or the terminal user; the terminal user applies to the regional public certificate service center to obtain a user UID address and a user public certificate; wherein the user UID address of the terminal user and the equipment UID address of the public certificate service center of the area to which the terminal user belongs have the same C and R; unified identities of network users can be automatically and effectively managed.
Owner:朱亚农
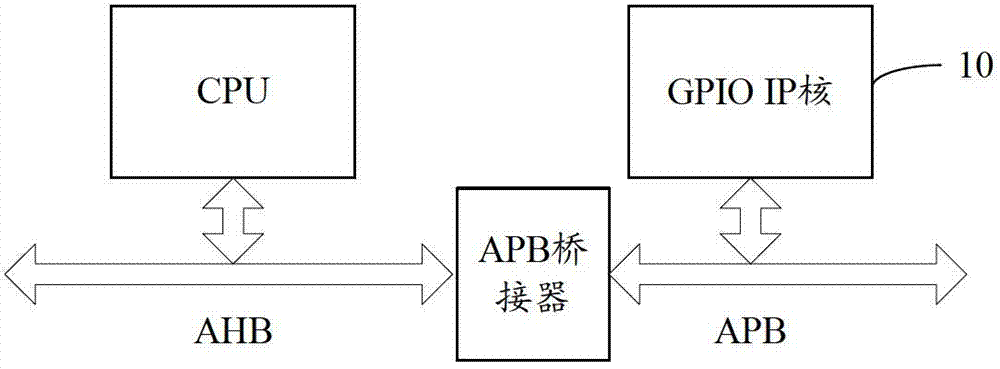
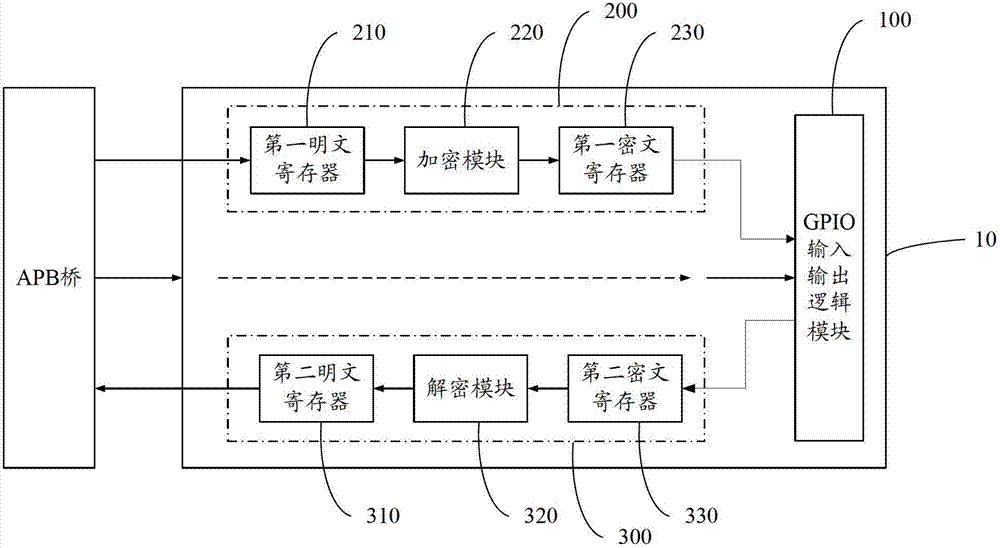
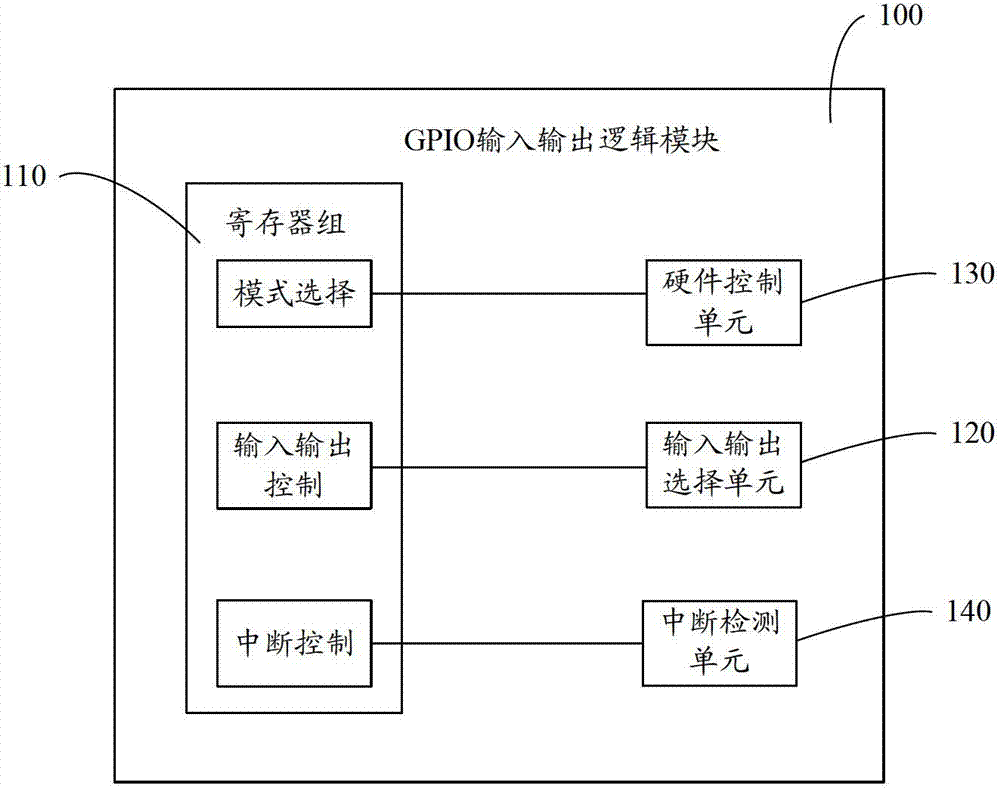
GPIO (general purpose input/output) IP (internet protocol) core with security mechanism
ActiveCN103077362ASecure data communicationInternal/peripheral component protectionCommunications securityCiphertext
The invention discloses a GPIO (general purpose input / output) IP (internet protocol) core with a security mechanism. The GPIO IP core with the security mechanism comprises a GPIO logic module, an encryption module and a decryption module, wherein the GPIO logic module is connected with an APB (advanced peripheral bus) bridge to receive configuration information from the APB bridge; after configuration is finished, a function of inputting and outputting data is at least finished; the encryption module receives clear data from the APB bridge; after the clear data is encrypted, the clear data is transmitted to the GPIO logic module; the decryption module receives ciphertext data from the GPIO logic module; and the ciphertext data is output to the APB bridge after being decrypted. The GPIO IP core is used for encrypting and decrypting data subjected to GPIO so as to guarantee the data communication security of a GPIO interface.
Owner:SUZHOU ZHONGKE ADVANCED TECH RES INST CO LTD
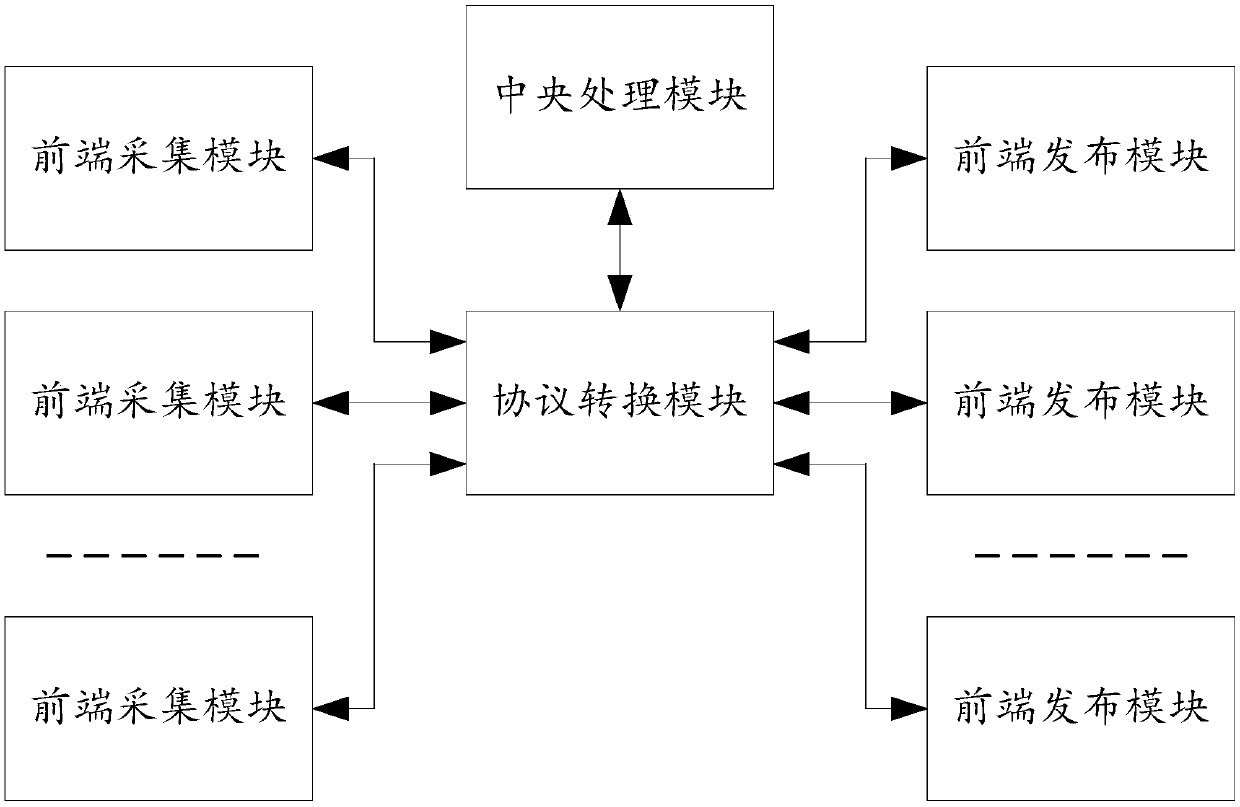
Multi-protocol multi-manufacturer internet of things equipment integration management and meteorological information release system
The invention discloses a multi-protocol multi-manufacturer Internet of Things equipment integration management and meteorological information releasing system, comprising a plurality of front-end acquisition modules, a plurality of front-end issuing modules, a protocol conversion module, a central processing module and a front-end acquisition module, wherein meteorological information is collected and transmitted to a protocol conversion module. The protocol conversion module receives the meteorological information and processes the meteorological information into a unified format for data transmission to the central processing module. The central processing module receives the data of uniform format for content supplementary processing and transmits the data of content supplementary processing back to the protocol conversion module. The conversion protocol moduleis used for receiving the data processed by the content supplement and reading the attributes of the data and matching theattributes of each front-end publishing module, and converting the data processed by the content supplement into a corresponding format and transmitting the data to the corresponding front-end publishing module. The front-end publishing module receives the data supplemented by the content and performs actions according to the data; Only one logical encoding of the data is required to match different network protocols.
Owner:河南知天科技有限公司
Data communication method and device, electronic equipment, upper computer and storage medium
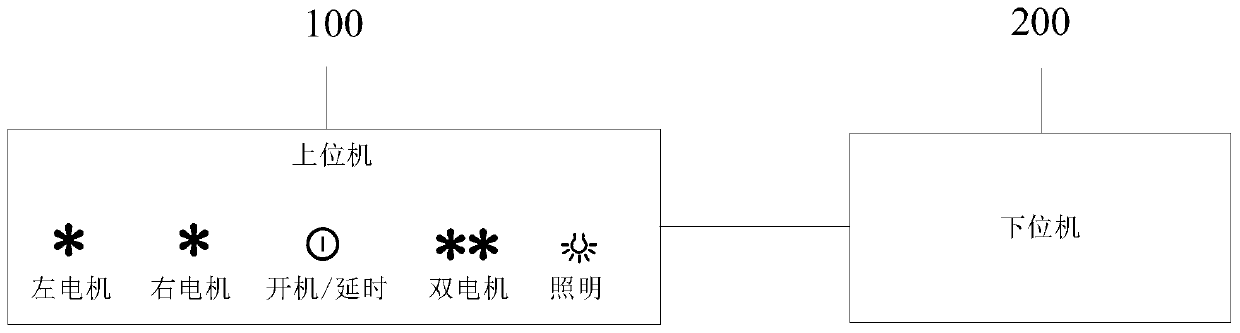
InactiveCN110933059ALow costSecure data communicationTransmissionCommunications systemEmbedded system
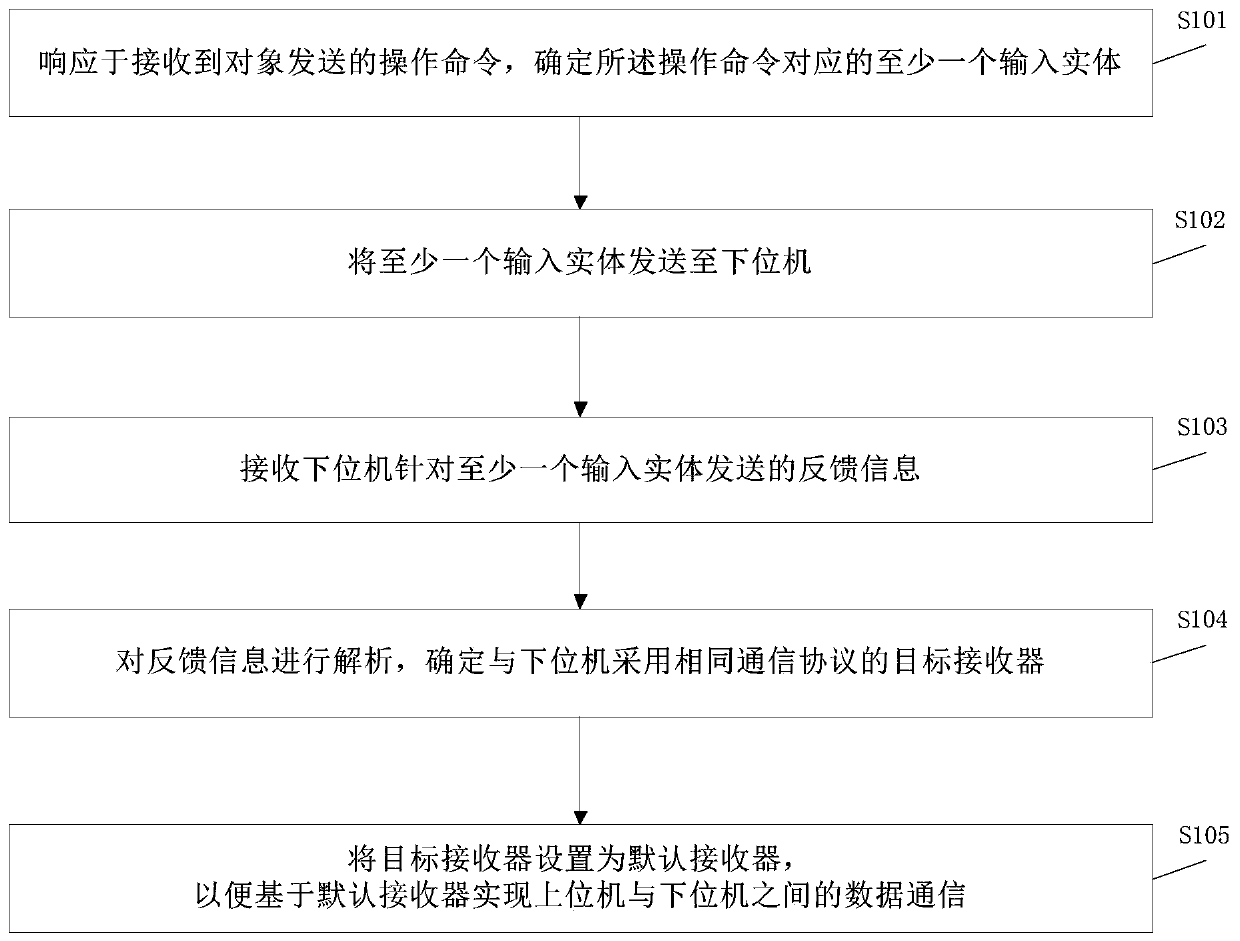
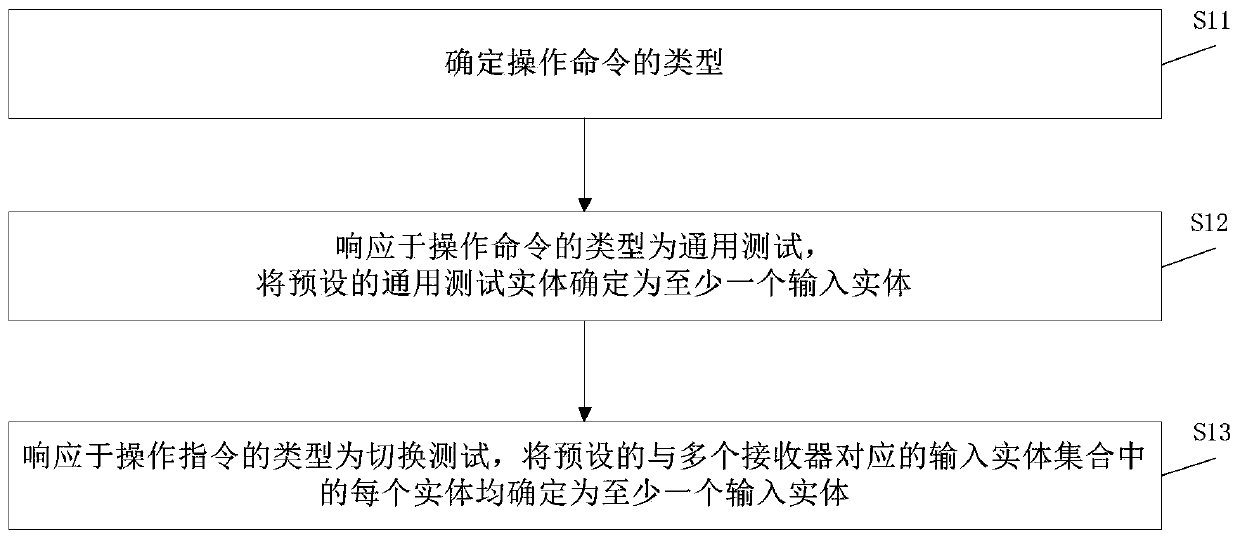
The invention provides a data communication method and device, electronic equipment, an upper computer and a storage medium. The method comprises the steps of responding to a received operation command sent by an object, determining at least one input entity corresponding to the operation command, sending the at least one input entity to a lower computer, receiving feedback information sent by thelower computer for the at least one input entity, analyzing feedback information, and determining a target receiver adopting the same communication protocol as the lower computer; setting the targetreceiver as a default receiver; and achieving data communication between the upper computer and the lower computer by using the default receiver. The feedback information is analyzed; a target receiver with the same communication protocol is determined as the lower computer according to the feedback information, the target receiver is determined as the default receiver, so that data communicationbetween the upper computer and the lower computer is realized, a serial port communication system does not need to be reset, the cost is saved, and the technical effect of safe and reliable data communication between the upper computer and the lower computer is ensured.
Owner:GUANGZHOU SHIYUAN ELECTRONICS CO LTD +1
Removable data storage medium, medical device and method for operating a removable data storage medium
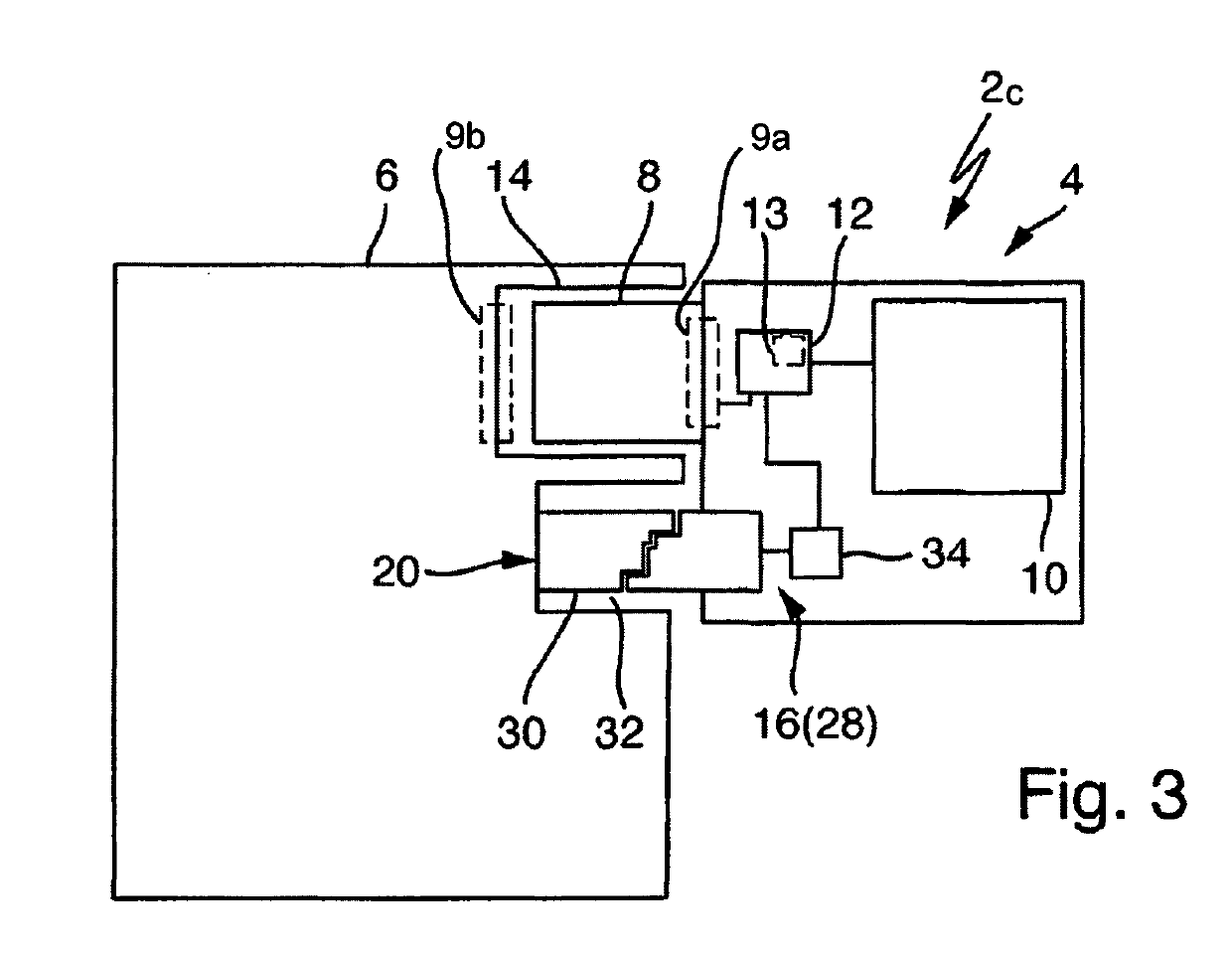
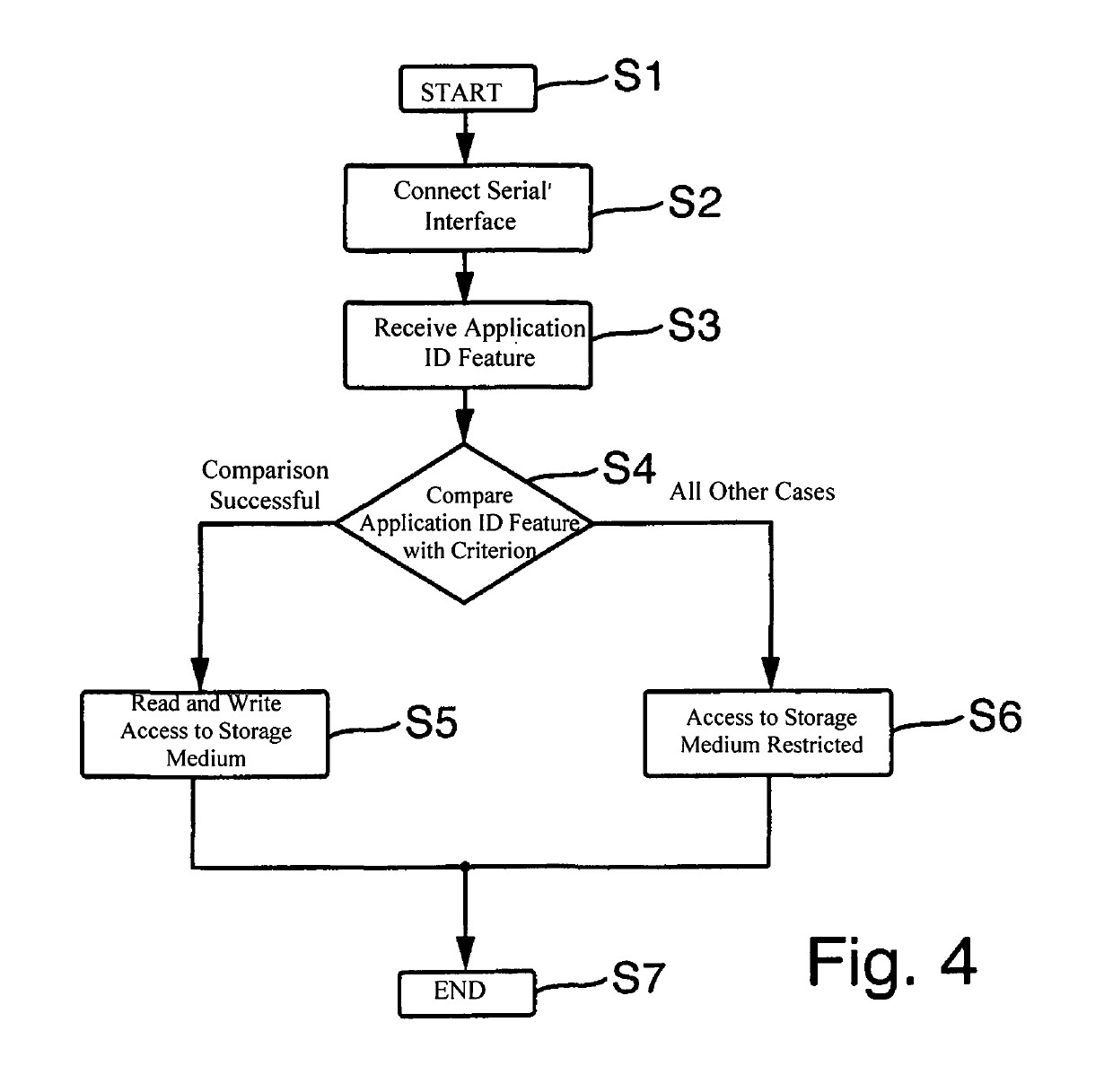
ActiveUS20160321467A1Data transmission is limitedReduce restrictionsDigital data protectionInternal/peripheral component protectionWrite protectionMemory controller
A removable data storage medium including a serial interface; a non-volatile storage medium; a memory controller controlling data transmission between the serial interface and the non-volatile storage medium, a receiving unit; and a write protection unit; wherein the receiving unit is configured to receive a device identification feature from a medical device that can be connected to the removable data storage medium; and the write protection unit is configured to compare the device identification feature with a predetermined internal criterion, and, if the device identification feature complies with the predetermined internal criterion, permits read and write access from the medical device to the non-volatile storage medium and, if the device identification feature does not comply with the predetermined internal criterion, limits access of the medical device to the non-volatile storage medium to read access.
Owner:OLYMPUS WINTER & IBE
Secure Communication System Based on Wireless Channel Characteristics
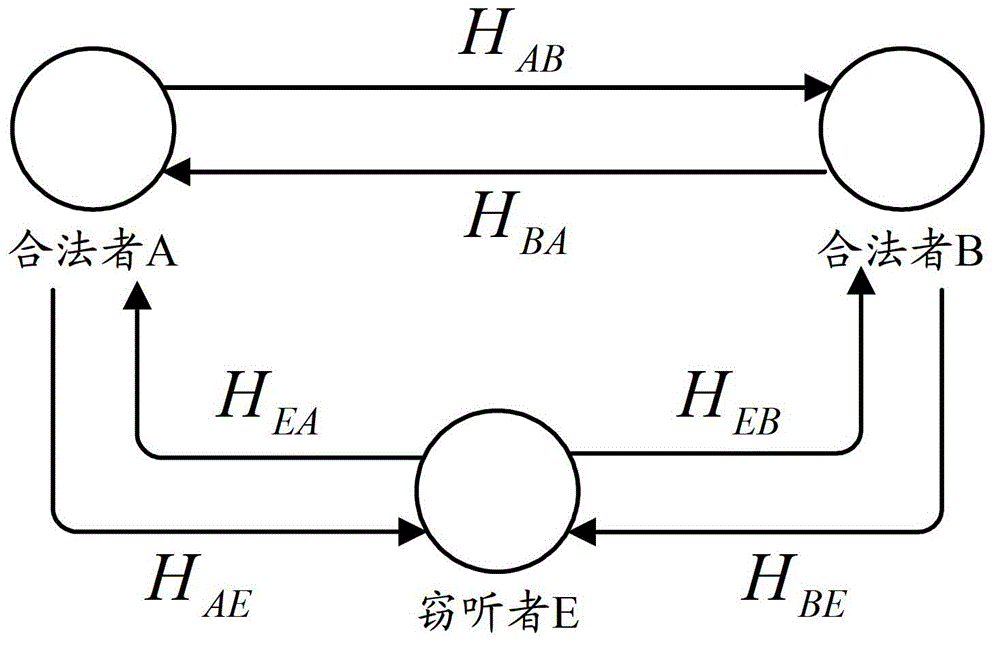
ActiveCN102869013BAvoid hidden dangersSecure data communicationKey distribution for secure communicationSecurity arrangementTelecommunicationsRadio channel
The invention discloses a secure communication system based on a wireless channel characteristic. The system comprises a first communication terminal and a second communication terminal which communicate with each other, wherein the first communication terminal and the second communication terminal transmit data which comprise a pilot frequency sequence to each other; and the first communication terminal comprises a first channel estimation module, a first quantization module, a first negotiation module, a first confidential amplification module, a first phase rotation secret key mapping module and a first phase rotation encryption module. By the system, secure data communication is realized.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Data encryption method for remote communication of energy hosting platform system
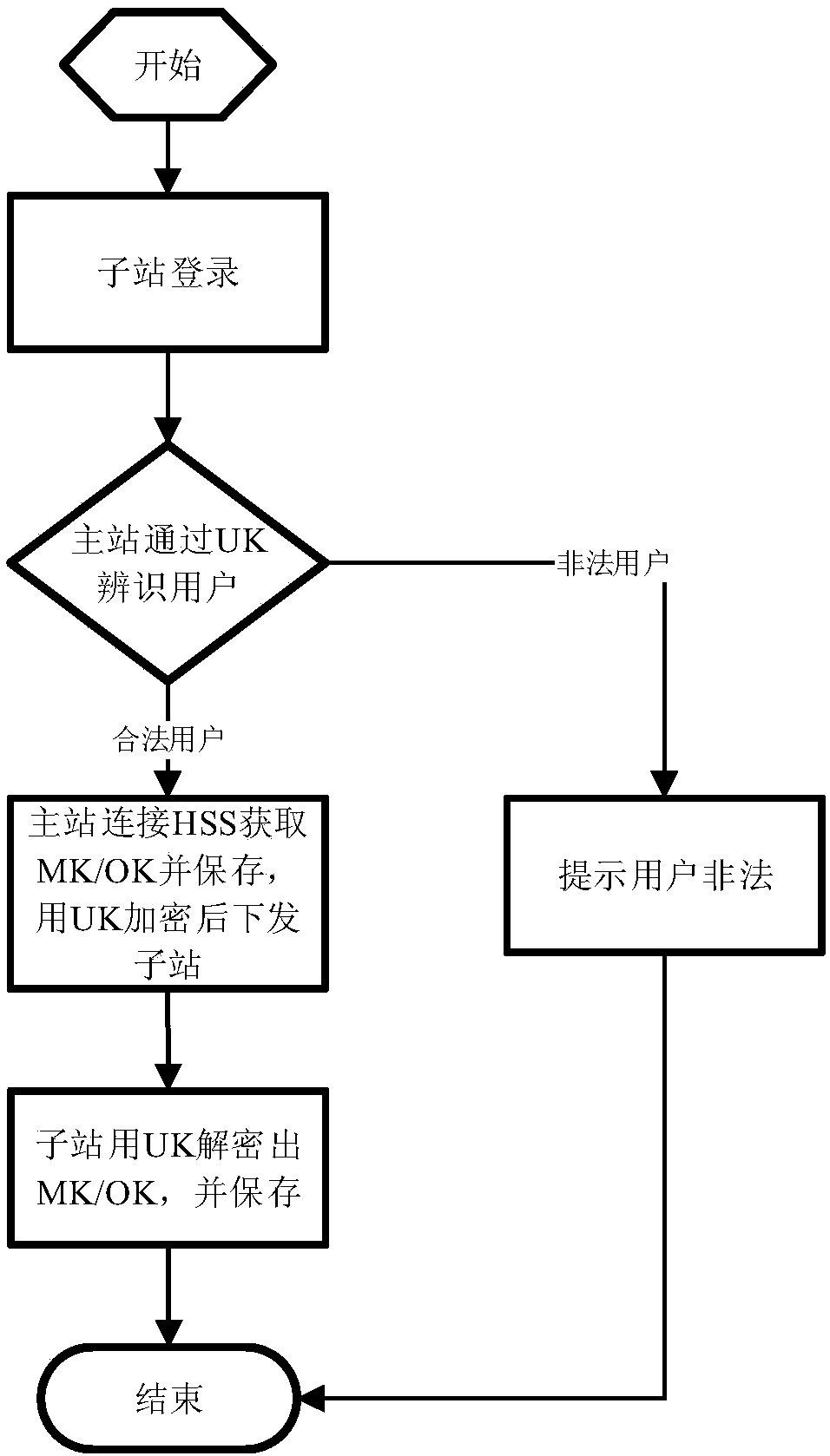
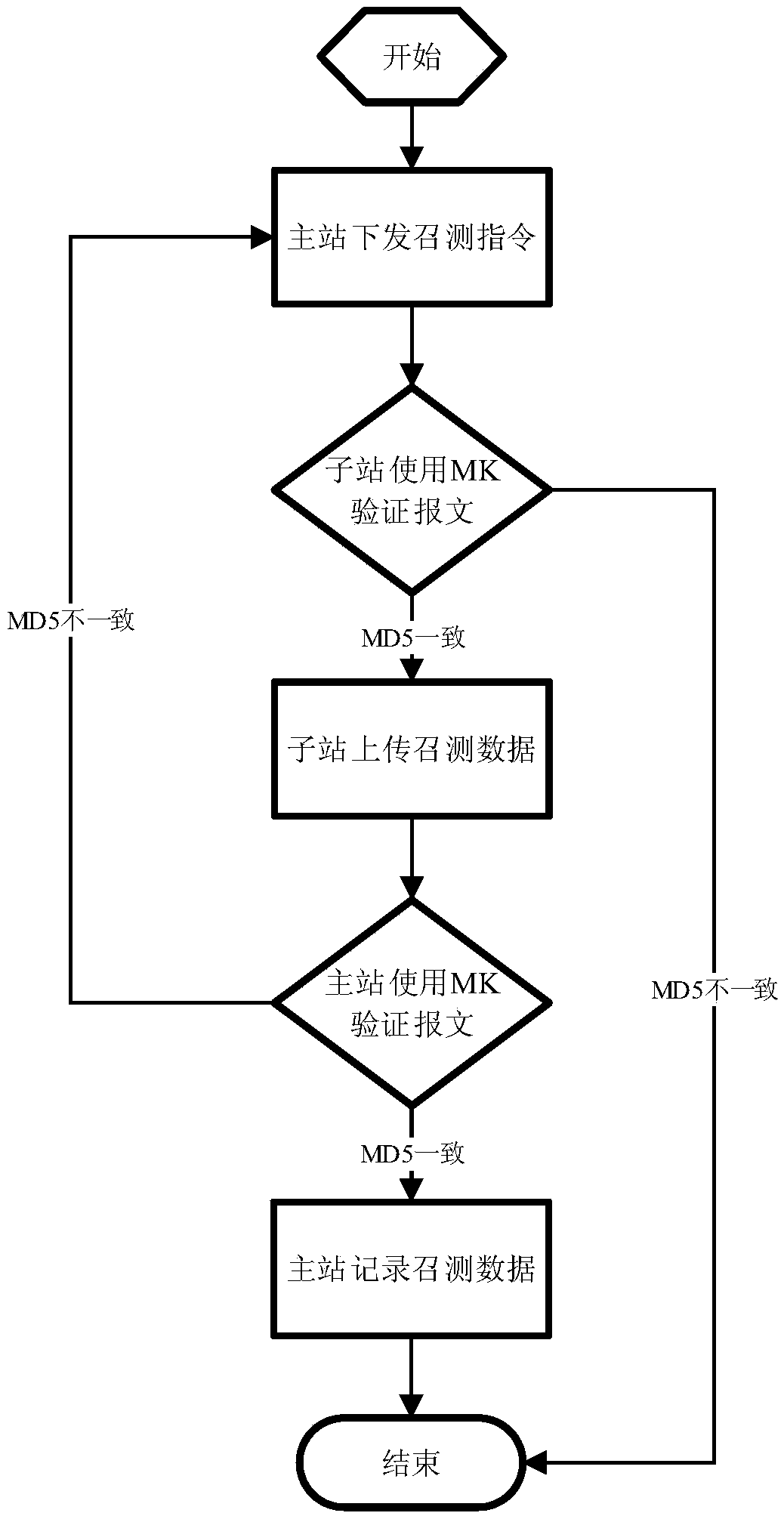
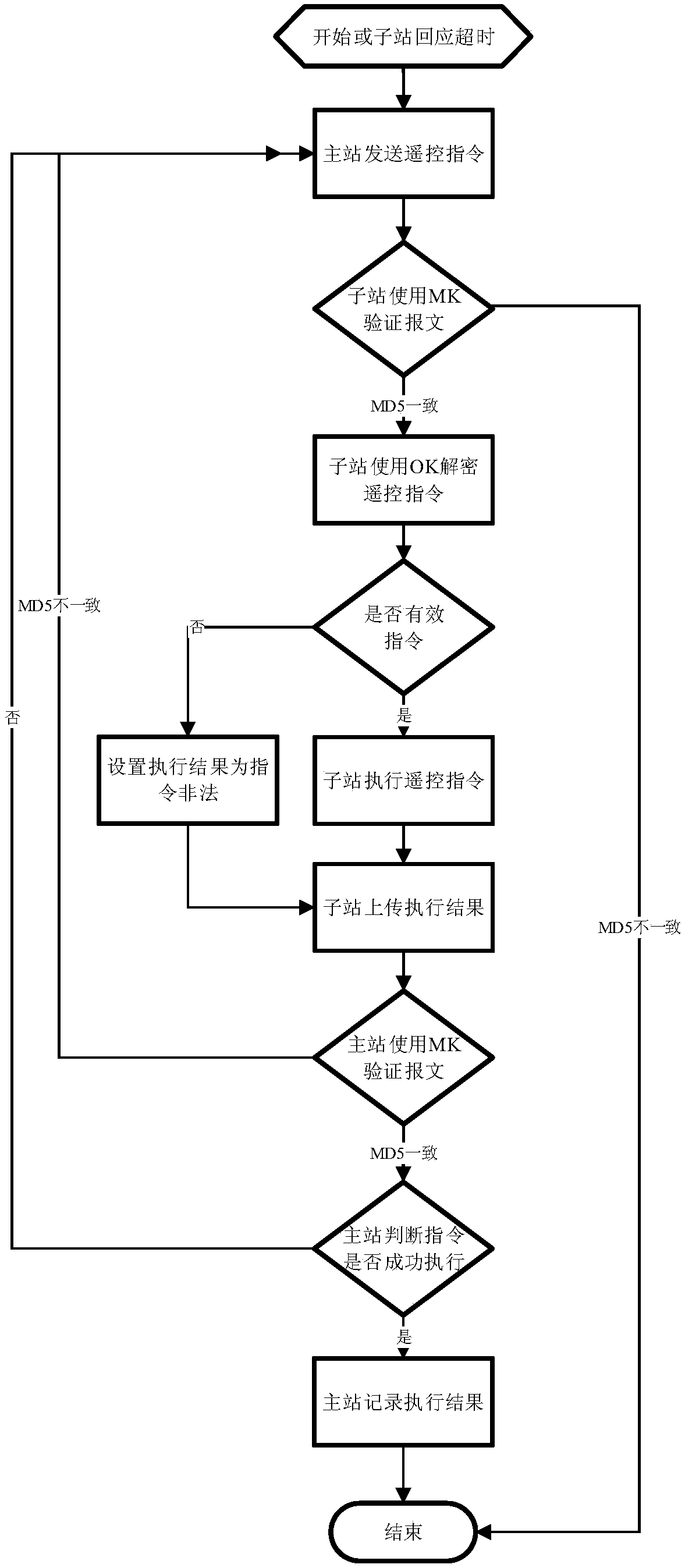
ActiveCN107896231AMonitor energy consumption dataMonitor securityTransmissionRemote controlMaster station
The invention discloses a data encryption method for remote communication of an energy hosting platform system. The method comprises the steps of generation and management of a secret key, applicationand distribution of the secret key, and encryption and decryption processing of a communication message between a master station and a son station, wherein the secret key in the step of generation and management of the secret key is generated and managed by a master station encryption server, the way that one client has one secret key is used, and the step comprises generation and management of UK and generation and management of MK and OK; the application and distribution of the secret key comprises application of the UK and application of the MK and OK; and the encryption and decryption processing of the communication message between the master station and the son station comprises interrogation of the master station and remote control of the master station. By using the method providedby the invention, the condition that the communication packet between the master station and the son station is prevented from being illegally eavesdropped and tampered can be ensured, and thus the stable operation of the energy system of each son station in the hosting system is ensured.
Owner:江苏联宏智慧能源股份有限公司
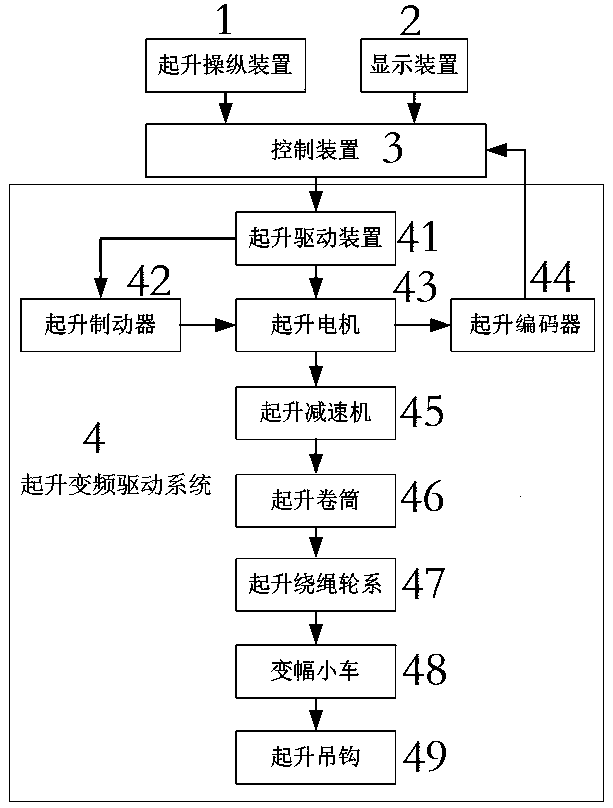
Tower crane lifting dead-slow control system and method
InactiveCN109132870AImprove performanceSecure data communicationLoad-engaging elementsControl systemDisplay device
The invention discloses a tower crane lifting dead-slow control system and a tower crane lifting dead-slow control method. The tower crane lifting dead-slow control system comprises a control device;the control device is connected with a display device for providing a human-machine interaction interface and displaying information such as a tower crane working mode, an operation parameter, parameter setting and alarm; a lifting variable-frequency driving system for executing a control device lifting command is connected; dead-slow control and millimeter precision can be achieved through the steps of mode selection, lifting signal generation and lifting execution; the working condition of high-precision lifting requirement can be met; itching control is not limited by the level of an operator, so that misoperation is effectively avoided and safety and reliability are achieved; various dead-slow control distances can be selected, so that different lifting precision requirements can be met; and the human-machine interaction interface is convenient and dead-slow control selection can be realized through one key.
Owner:XUZHOU CONSTR MACHINERY
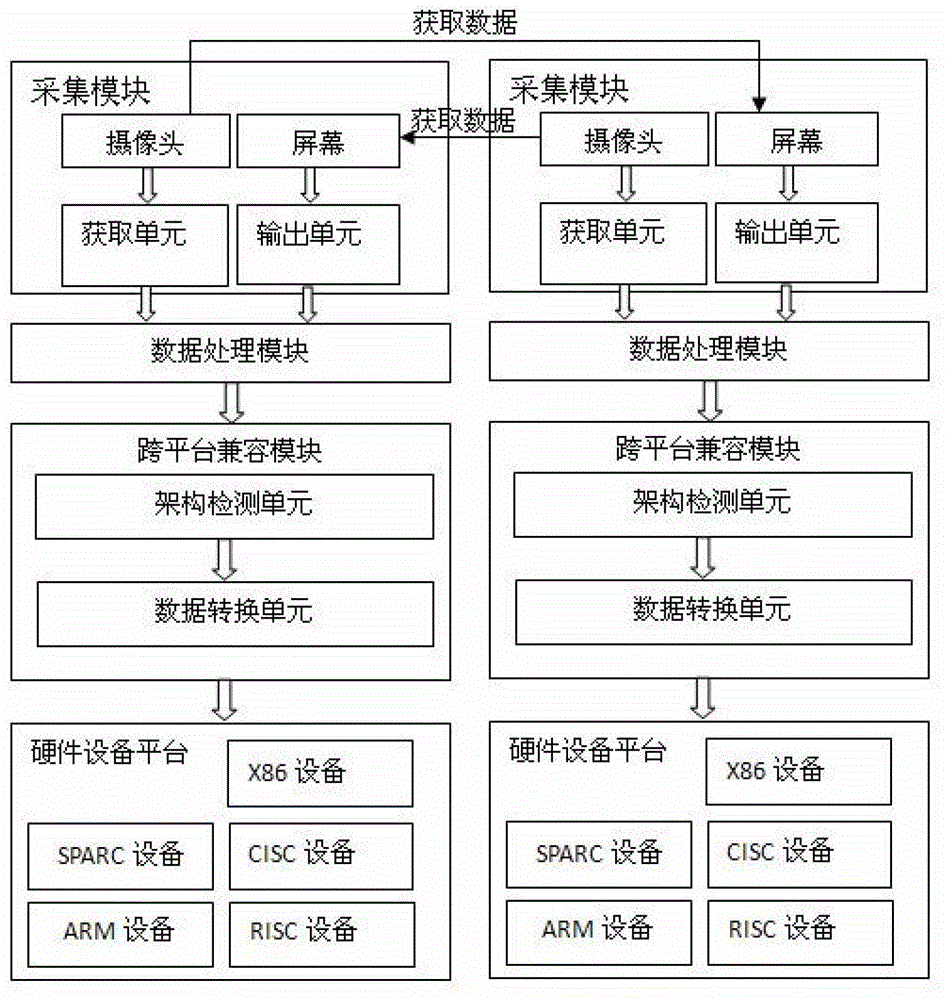
Cross-platform device based on visual data transmission
InactiveCN102984502AComplete data communicationSecure data communicationClosed circuit television systemsComputer moduleData transmission
The invention provides a cross-platform data transmission device based on visual data transmission and capable of achieving mutual data transmission among various types of devices. The transmission device comprises a collecting module, a data processing module, a cross-platform compatible module and a hardware platform, wherein the collecting module is used for collecting, receiving and feed backing the transmitted visual data; the data processing module is used for processing the received visual data; the cross-platform compatible module is used for detecting and identifying the types of a hardware device which requires for receiving the visual data, and mutually converting the visual data and data used by the hardware device which requires for receiving the visual data; and the hardware platform is sued for receiving the data converted by the cross-platform compatible module and sending data to the cross-platform compatible module. The device has the advantages that accurate, complete and safe data communication of various hardware devices can be achieved under various complicated conditions, the cost is low, the implementation is easy, and the like.
Owner:天津爱迪尔软件开发有限公司
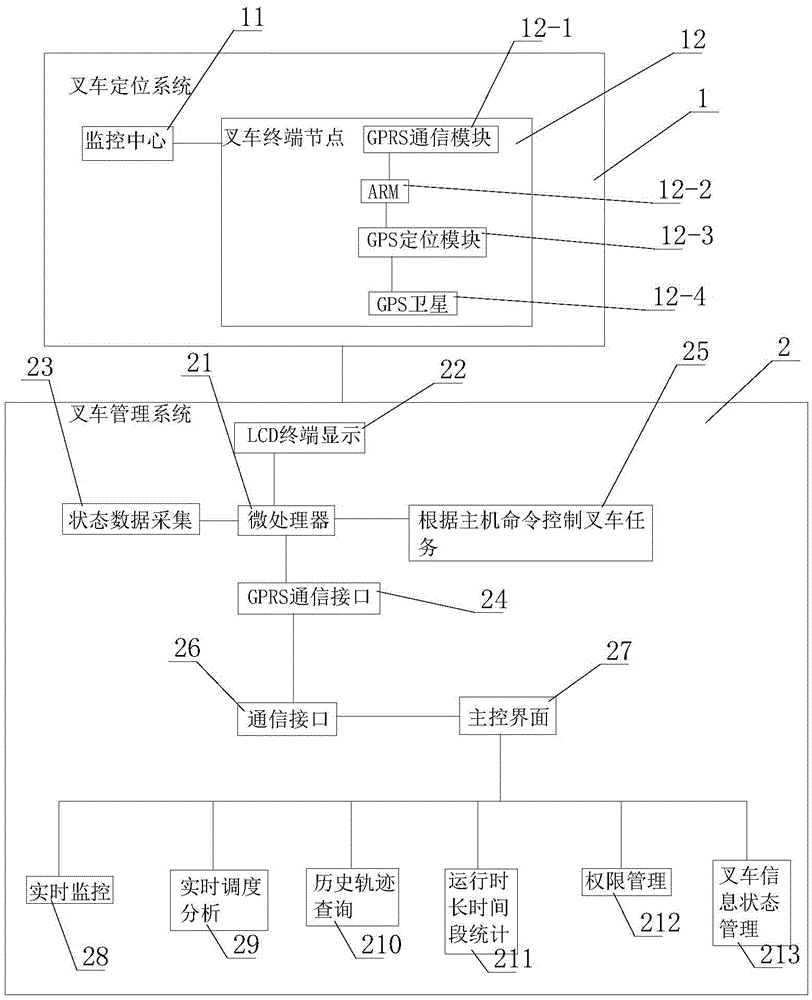
GPS based intelligent positioning and managing system for fork trucks in harbor
InactiveCN105487504ASecure data communicationHumanizedTotal factory controlProgramme total factory controlSoftware designEngineering
The invention relates to a GPS based intelligent positioning and managing system for fork trucks in a harbor. The intelligent positioning and managing system comprises a fork truck positioning system and a fork truck managing system connected to the fork truck positioning system, and the fork truck positioning system comprises a monitoring center and fork truck terminal nodes connected with the monitoring center. According to the intelligent positioning and managing system, data communication relies on the strong GPRS communication network and is thus safe and reliable, a digital type screen is used to be more human-based, and software design based on host interface of PC provides convenience for expansion and improvement.
Owner:GUANGXI PROVINCE NANNING CITY ZHIJIANZHIFAN TECH CONSULTING
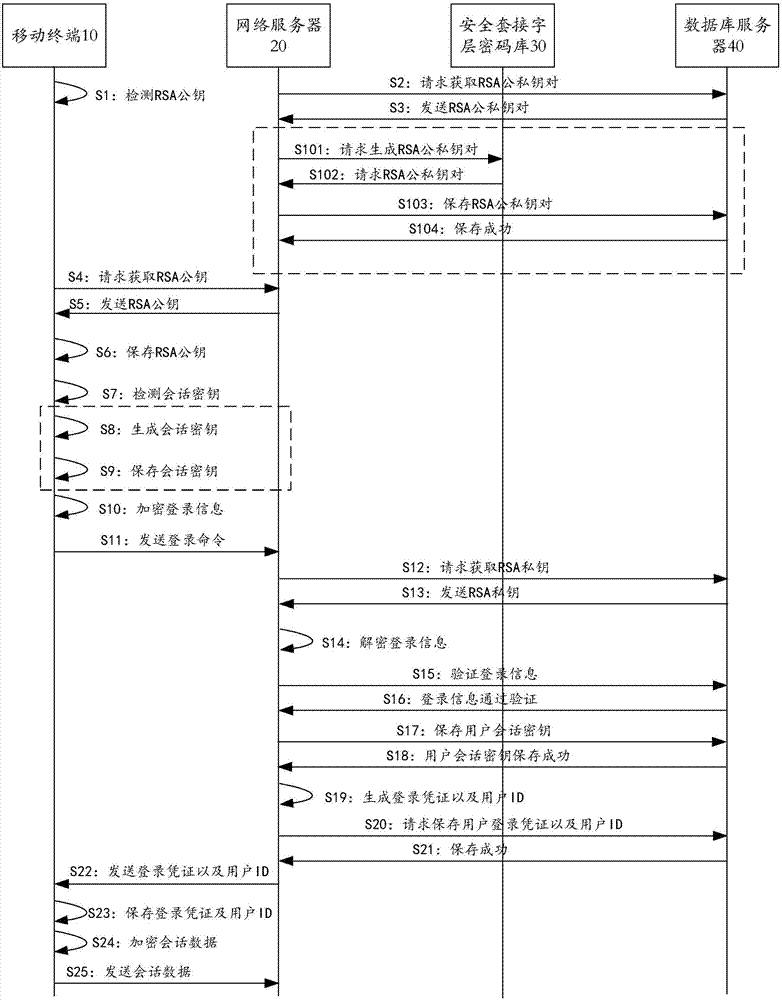
Emergency command scheduling method and system for sudden environmental event
ActiveCN107171784AImproving the Ability to Respond to Sudden Environmental Pollution AccidentsReduce casualtiesEncryption apparatus with shift registers/memoriesPublic key for secure communicationCommunications securityPassword
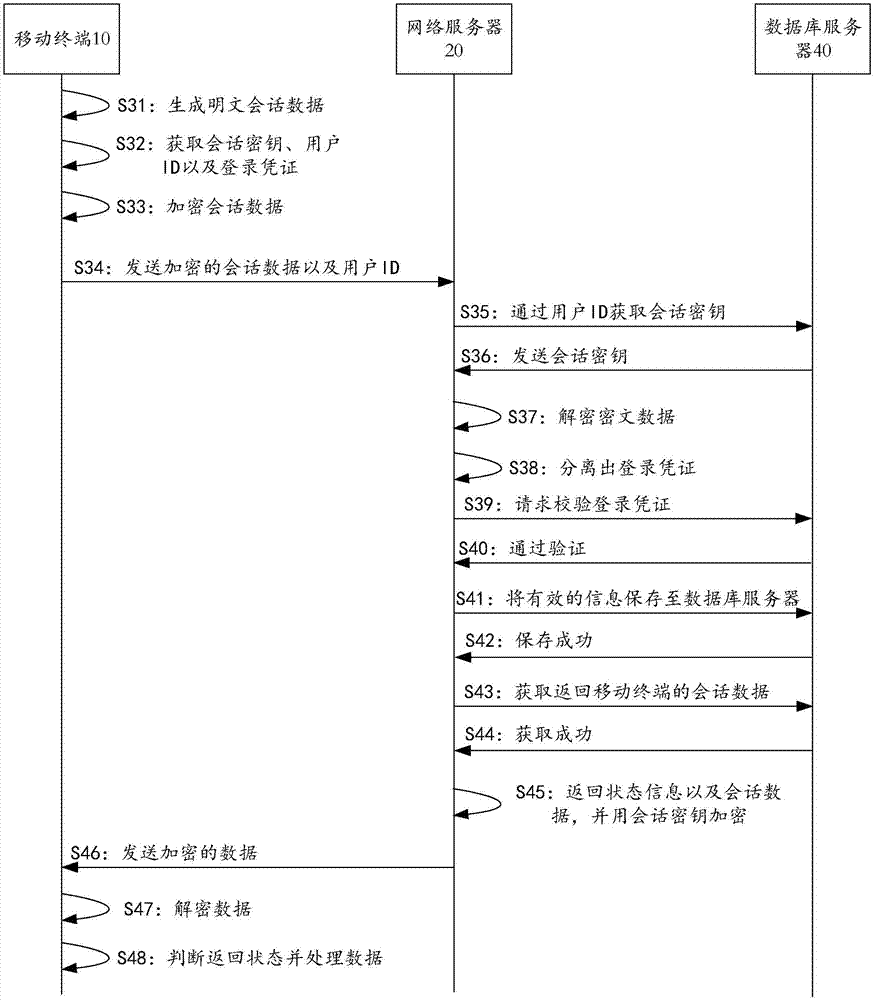
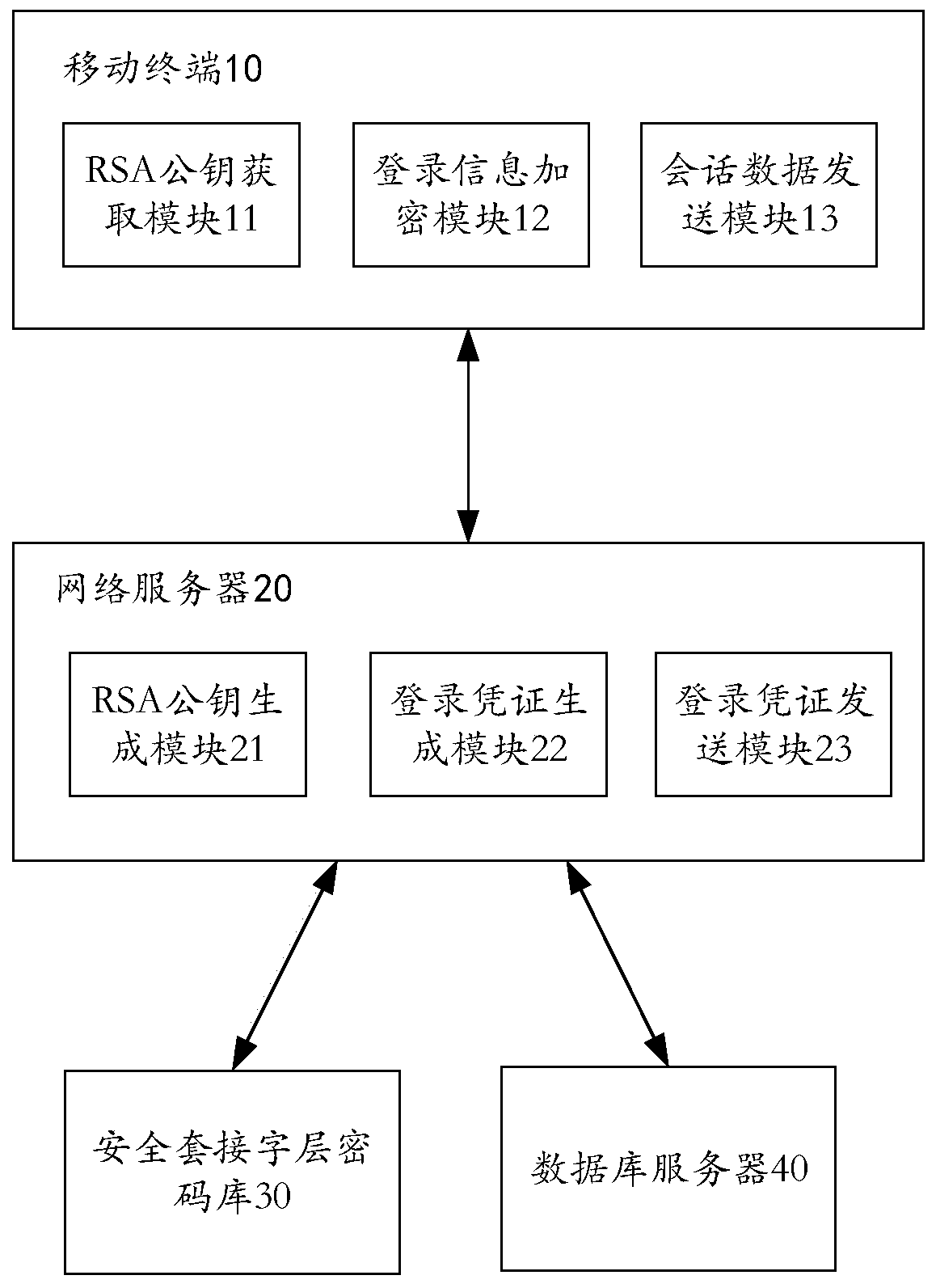
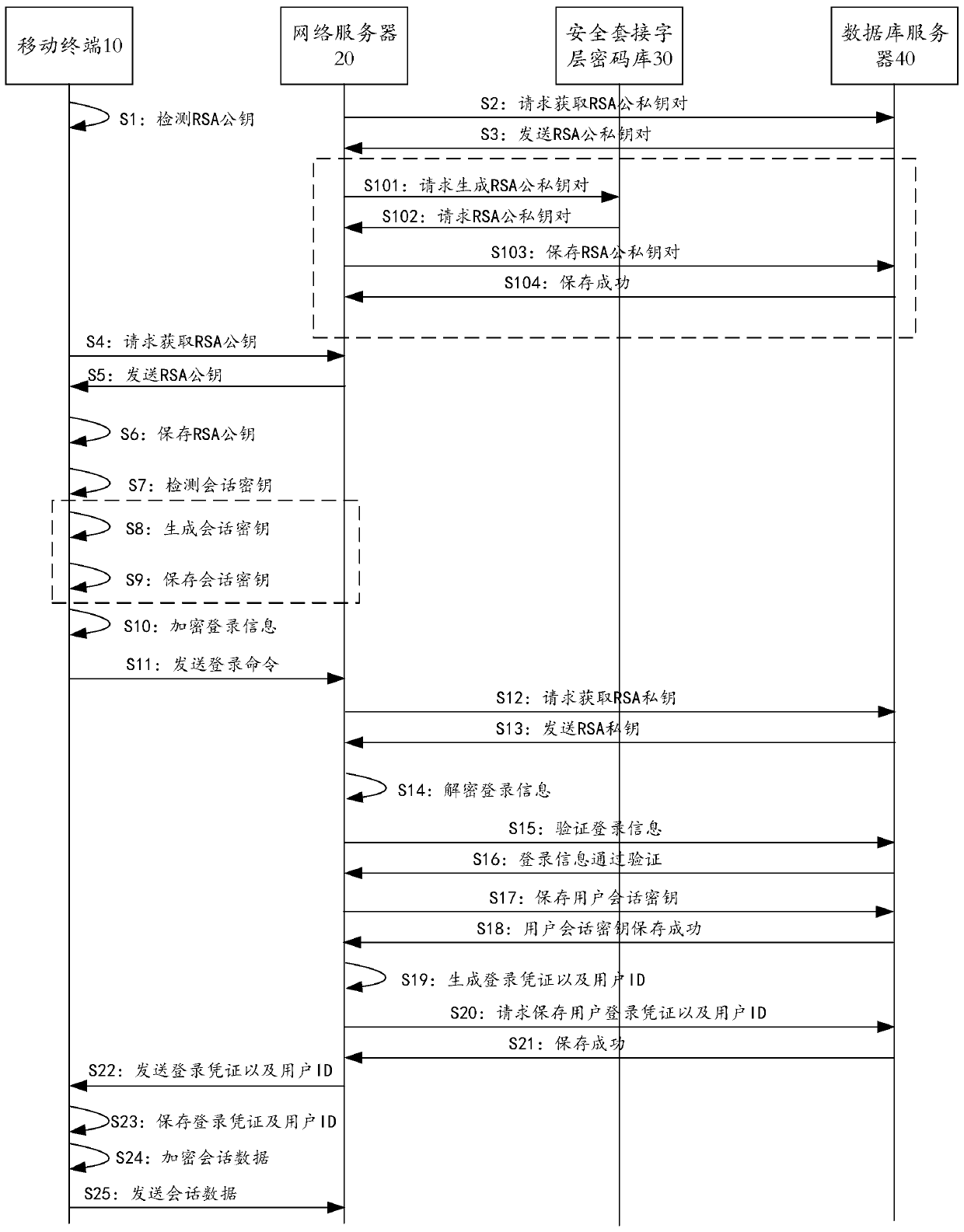
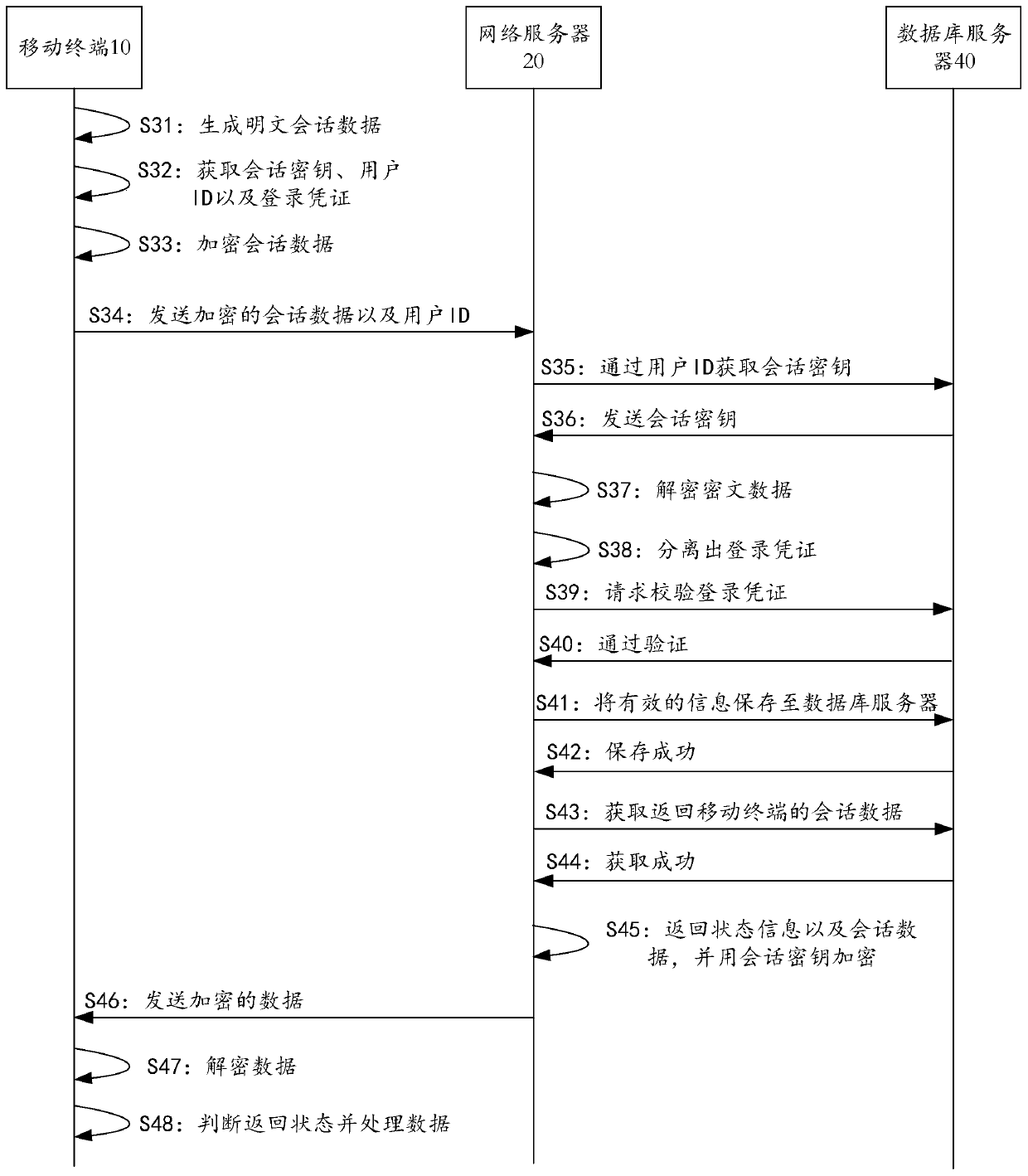
The invention provides an emergency command scheduling method and an emergency command scheduling system for a sudden environmental event. The method comprises the steps as follows: a mobile terminal acquires a RAS public key from a network server, and stores the RSA public key in a local memory; the mobile terminal encrypts login information by using the RAS public key, and sends the encrypted login information to a network server, wherein the login information comprises a session key, an account name, a login password and hardware equipment information of the mobile terminal; after verifying authenticity of the login information, the network server generates the login information into a login certificate and a user ID, and stores the user certificate and the user ID into a database server; the network server encrypts the user certificate and the user ID by using the session key and then sends the encrypted user certificate and user ID to the mobile terminal; and session data and the user certificate are encrypted by using the session key and then sent to perform communication between the mobile terminal and the network server. The system is used for implementing the above method. According to the method and the system provided by the invention, data communication security between the mobile terminal and the server can be ensured.
Owner:珠海富鸿科技有限公司
Remote control for air conditioner and air conditioner provided with same
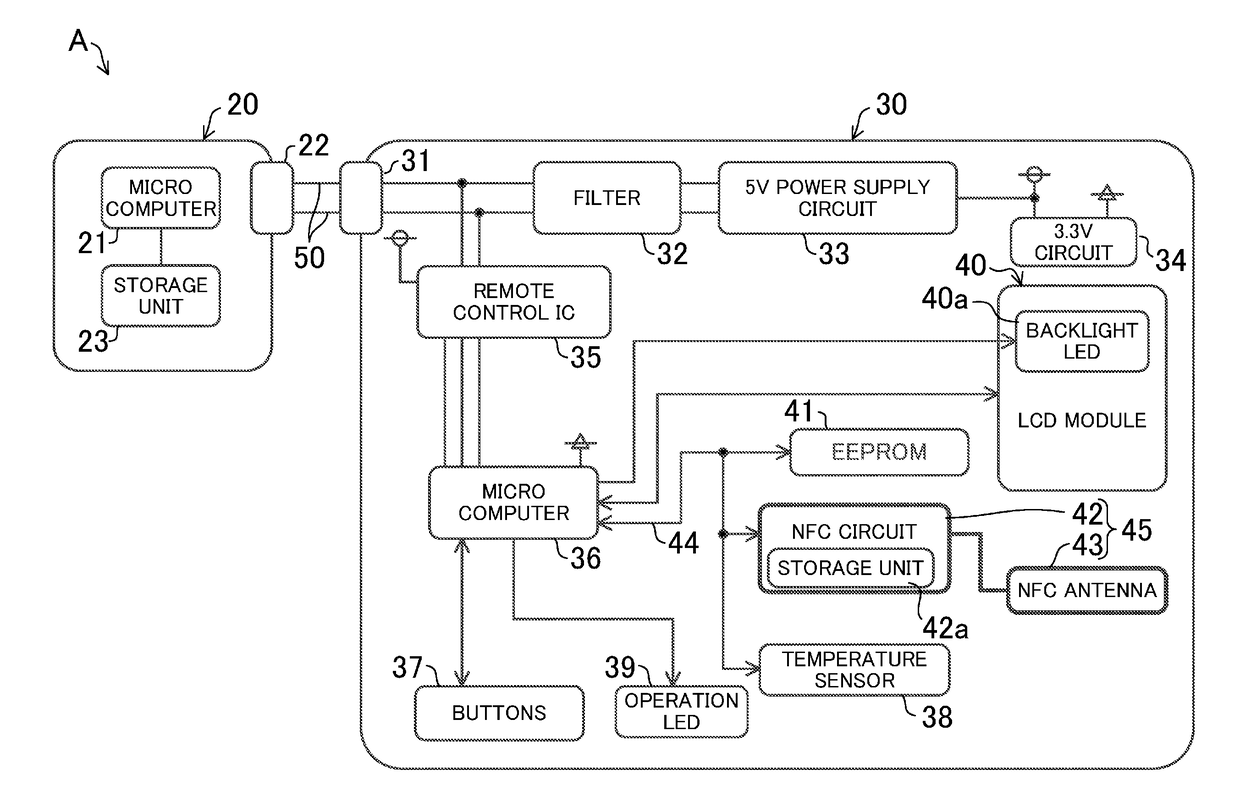
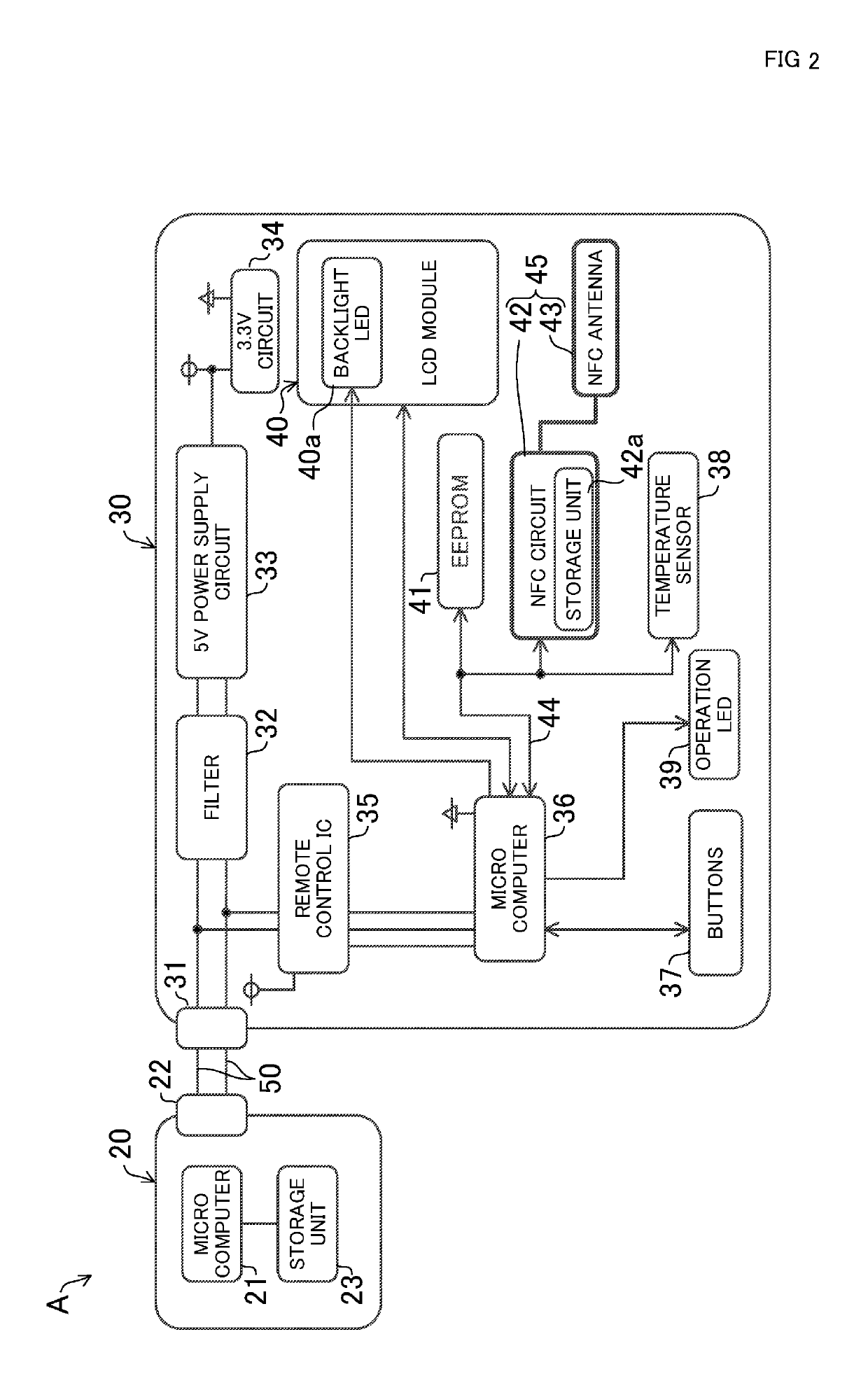
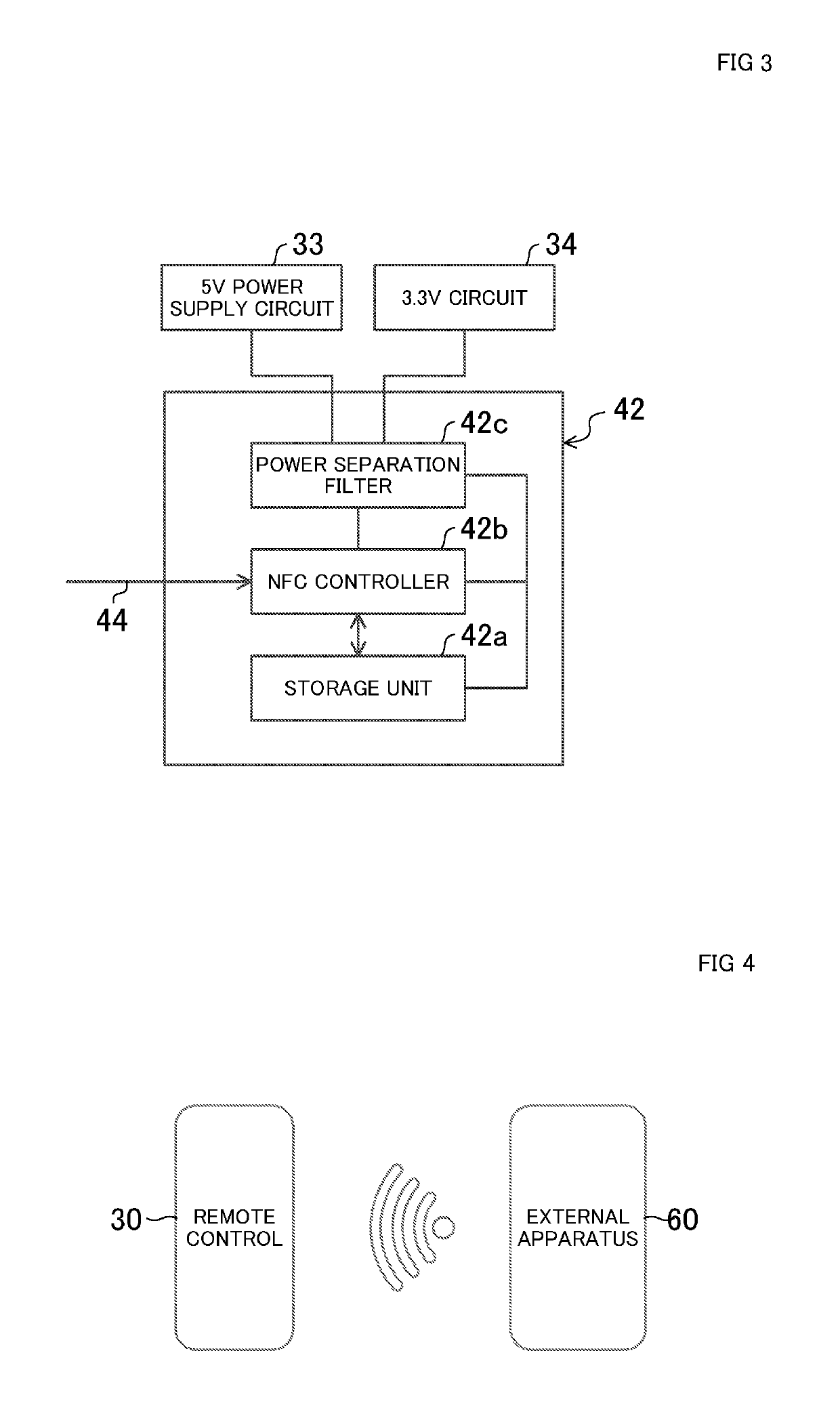
ActiveUS20180080672A1Secure data communicationMechanical apparatusSpace heating and ventilation safety systemsEngineeringMicrocomputer
A remote control for an air conditioner facilitates setting of various kinds of data without operation of a button. A remote control (30) includes an external communication unit (45) having an NFC circuit (42) and an NFC antenna (43). The external communication unit (45) is capable of wirelessly communicating with an external apparatus even when a microcomputer (36) in the remote control (30) is not supplied with power (i.e., in a non-operating state). Hence, through the wireless communication between the external communication unit (45) of the remote control (30) and the external apparatus, the various kinds of data is forwarded from the external device to the remote control (30), and stored in the remote control (30).
Owner:DAIKIN IND LTD
Method for sending data and first control host
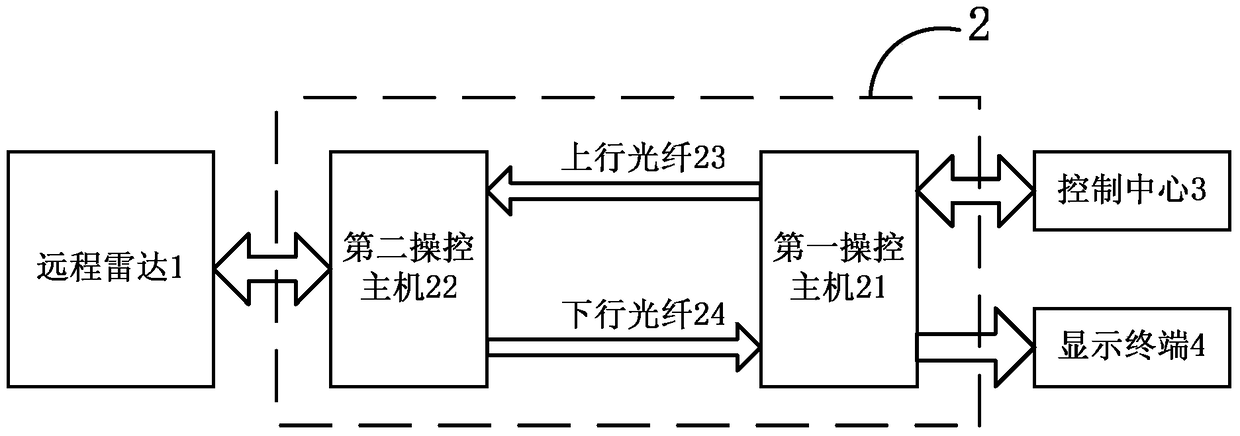
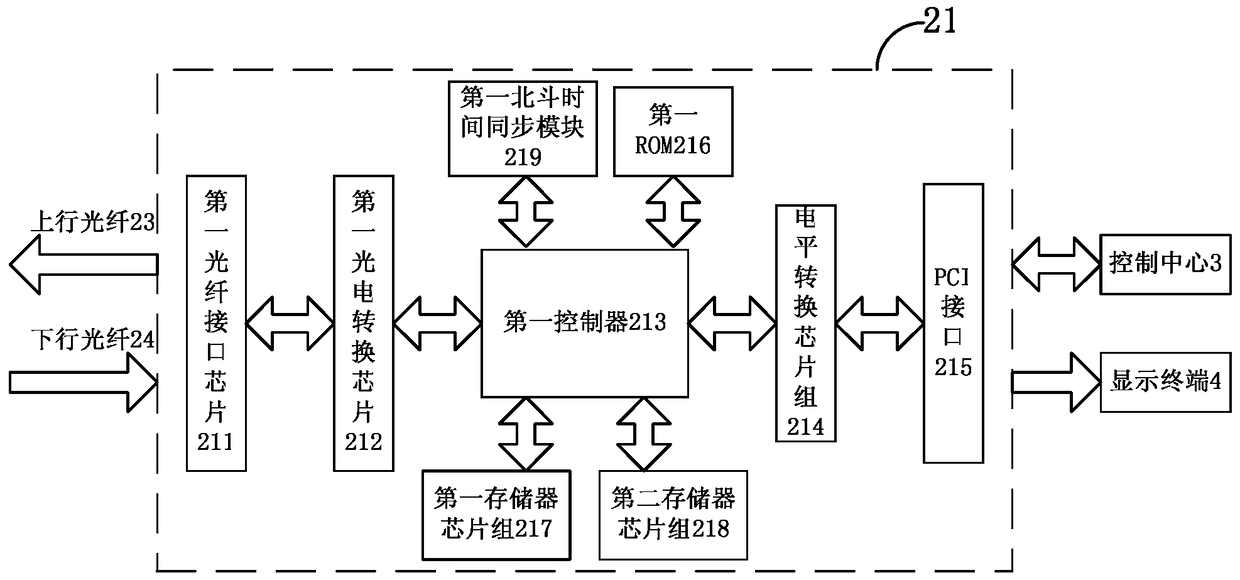
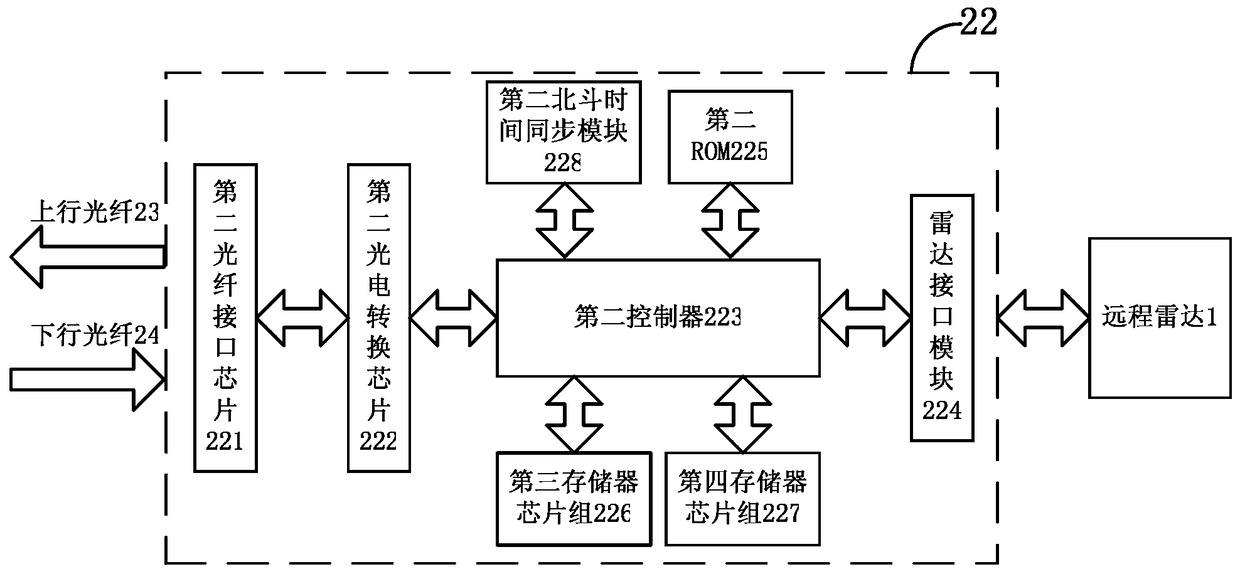
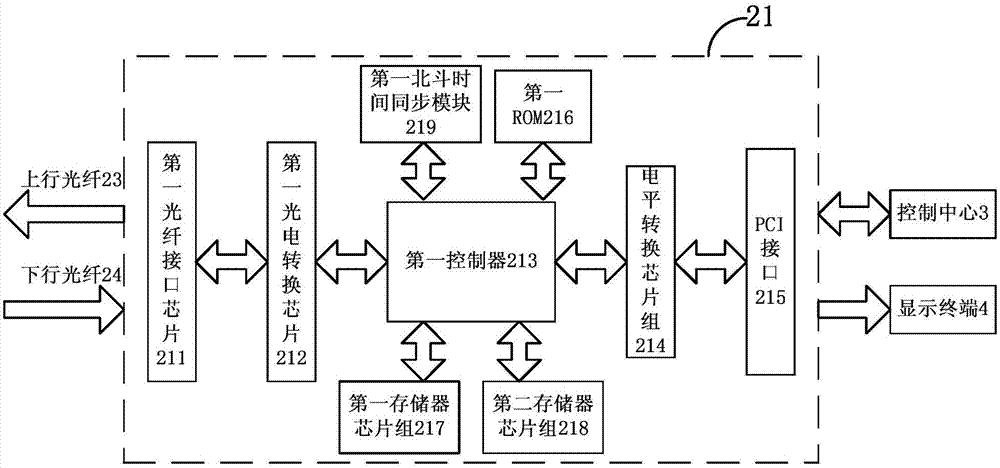
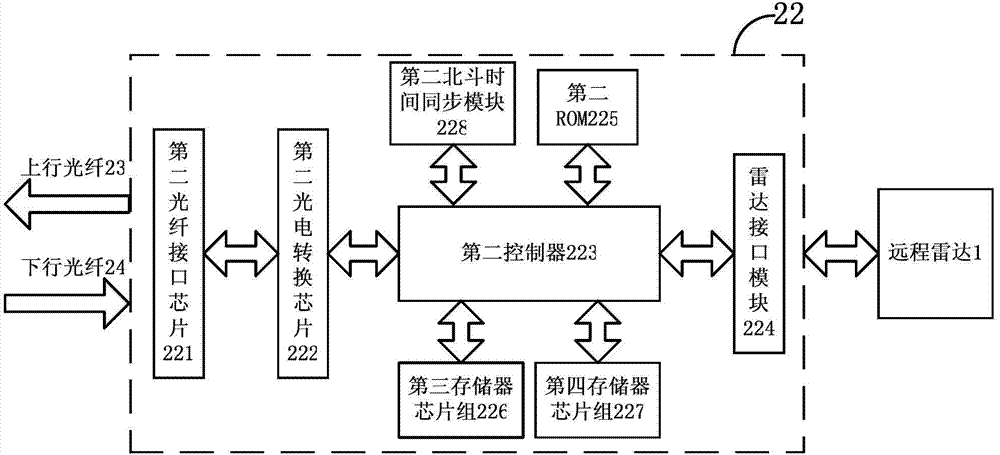
ActiveCN104506577BSecure data communicationIncrease the level of automationFibre transmissionRadarCommunication control
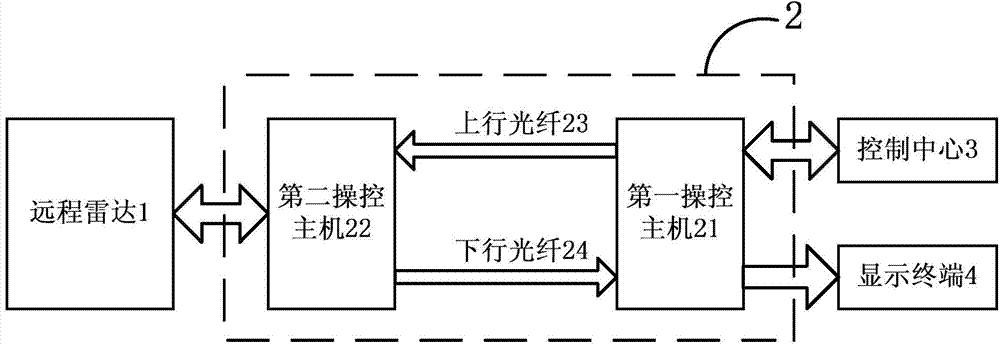
The invention relates to a data transmitting method and a first manipulation host. The method comprises the steps that a first Beidou time synchronization module is utilized to synchronize the first clock of the first manipulation host so that the determined time after completion of synchronization is obtained; the determined seed data uniquely corresponding to the determined time are obtained according to the stored agreed rules; data to be transmitted are encrypted by utilizing the determined seed data so that the determined non-feature code source is obtained; electro-optic conversion is performed on the determined non-feature code source so that the determined optical signal is obtained; and the determined optical signal is transmitted to a second manipulation host by utilizing optical fibers. Secure and high-efficiency data communication and command control between a far-end unattended radar station and a near-end control center can be effectively realized so that the method has the communication control means which is high in anti-interception capability, long in transmission distance, great in real-time performance, low in cost and easy to realize. Besides, practicality, reliability and stability are quite high so that the method has important social, economic and military meaning in enhancing automation level of national defense equipment of China.
Owner:SICHUAN JIUZHOU ELECTRIC GROUP
Radio transmission between aircraft and its environment, through the window of the aircraft
InactiveCN107534483ASimple retrofit installationSecure data communicationAntenna adaptation in movable bodiesRadio transmissionAerospace engineeringLarge capacity
Owner:汉莎航空系统公司
Physical Layer Key Extraction Method Based on Channel Gain Compensation and Subcarrier Correlation
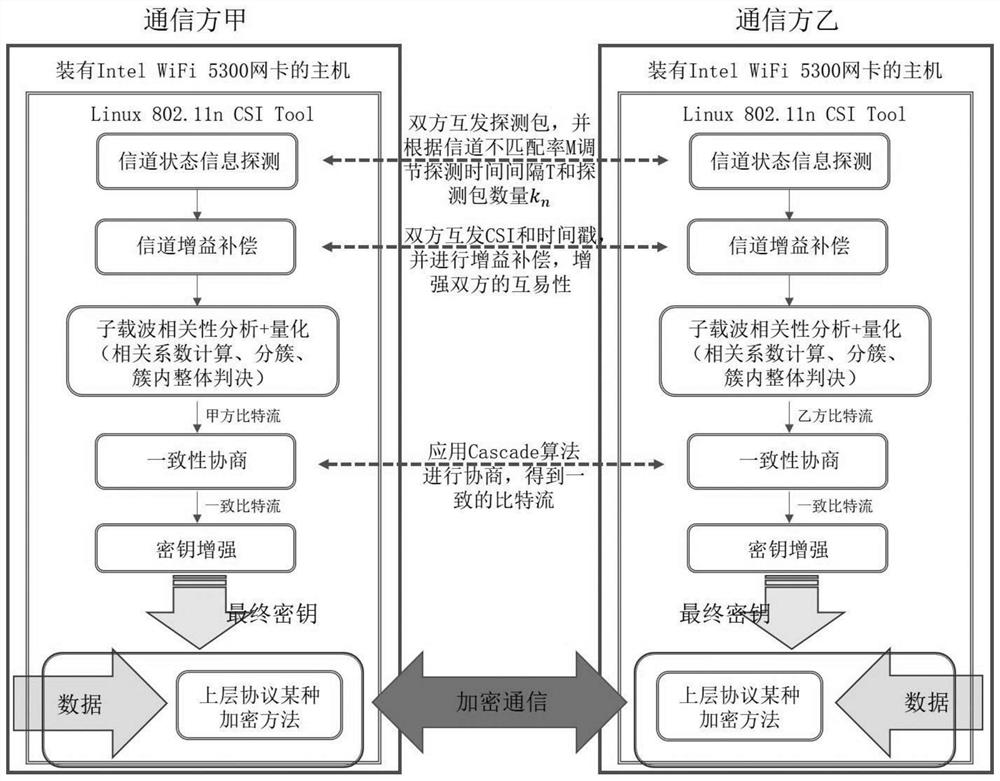
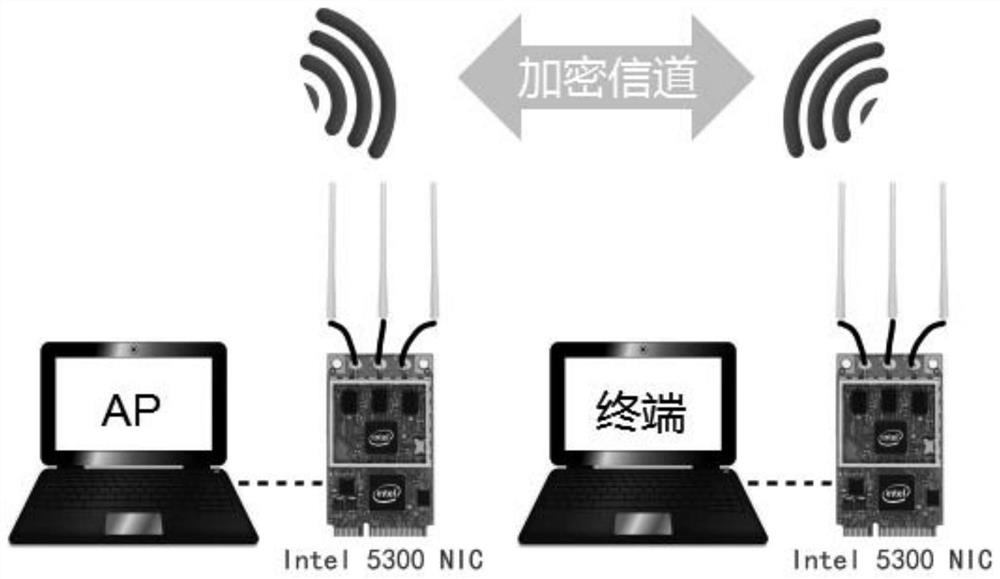
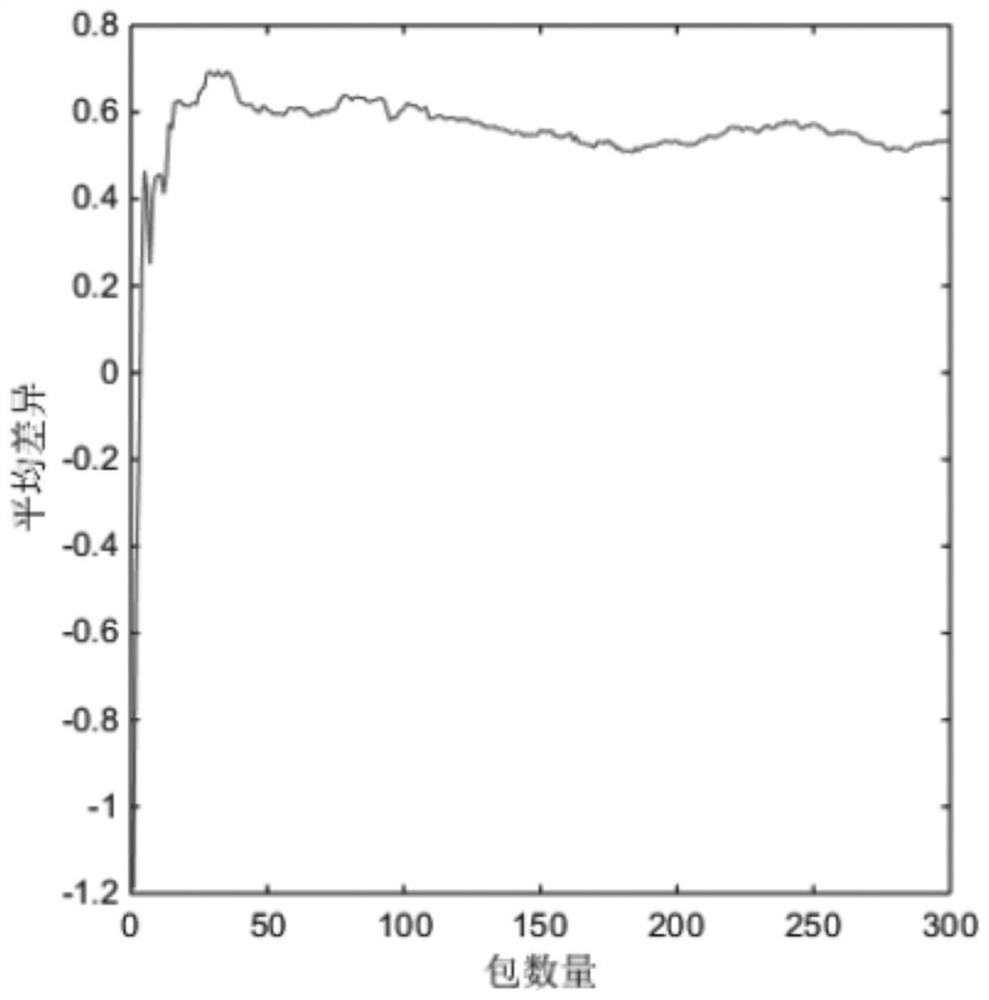
ActiveCN110213767BStrong reciprocityImprove reciprocityKey distribution for secure communicationData stream serial/continuous modificationChannel state informationCommunications system
Owner:NORTHWESTERN POLYTECHNICAL UNIV
Removable data storage medium, medical device and method for operating a removable data storage medium
ActiveUS10354087B2Improve data securityFacilitate data communicationDigital data protectionInternal/peripheral component protectionWrite protectionMemory controller
Owner:OLYMPUS WINTER & IBE
Mobile phone scrambler and its privacy communication method
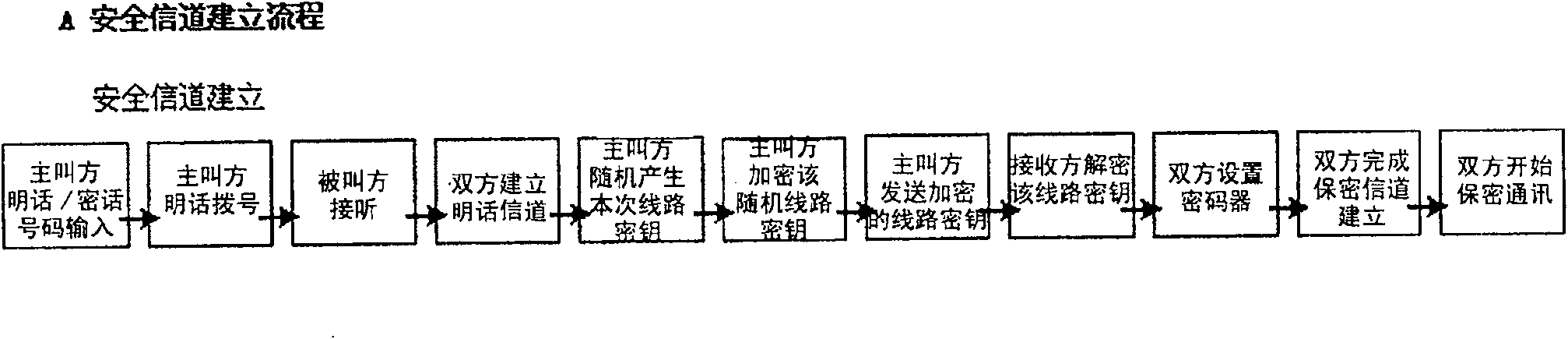
InactiveCN100576856CShort connection timeCall reliableEavesdropping prevention circuitsSecret communicationComputer hardwareSupply management
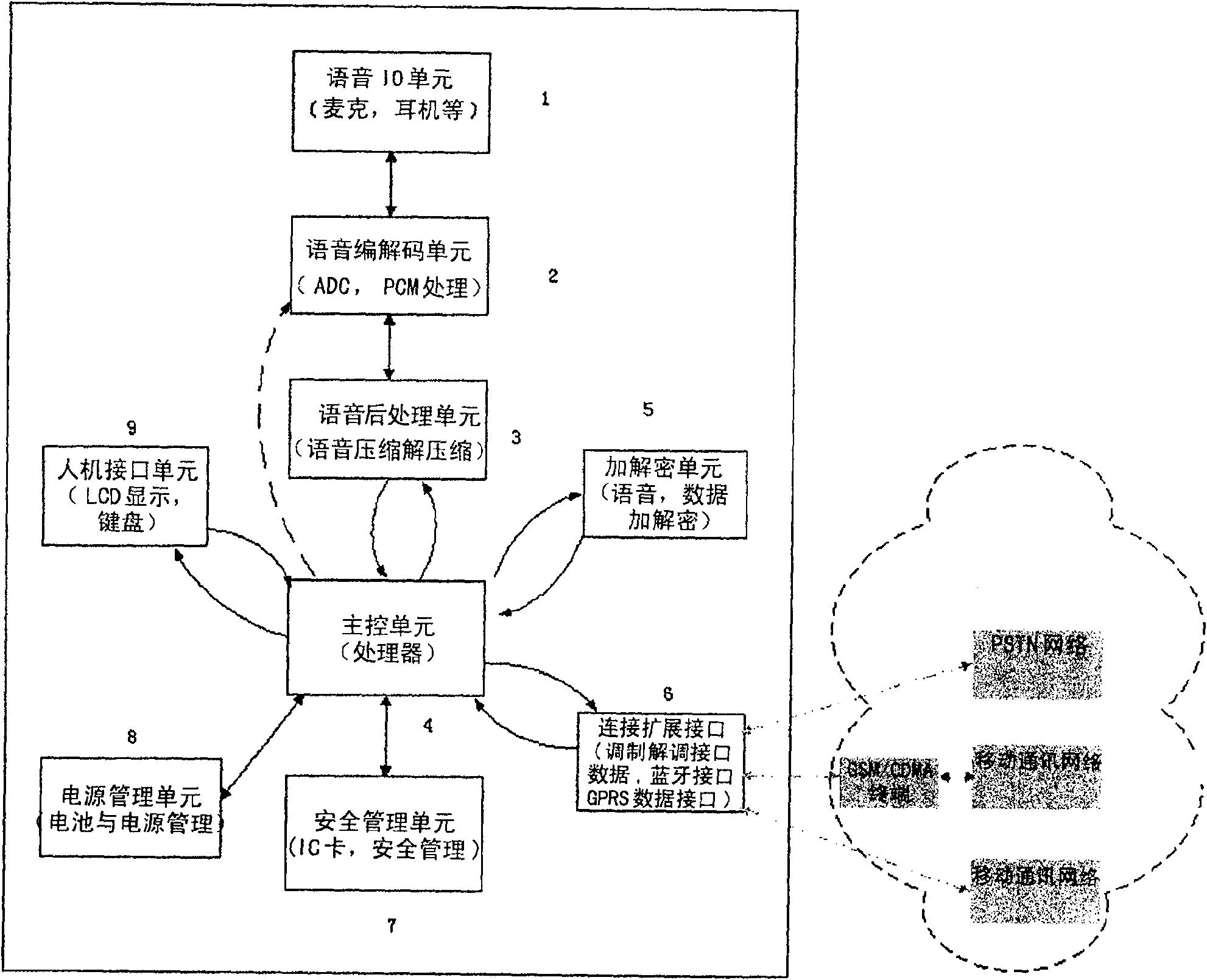
This invention relates to a mobile phone crypto suitable for realizing security voice and data communication of mobile communication network and PSTN including a handheld terminal set integrating a voice IO unit, a voice code and decode unit, a voice post process unit, a primary control unit, a supply management unit, a man-machine interface unit, a connection-expansion unit, a ciphere / de-ciphere unit and a security management unit, a special connection cable and special interface fittings. When a security communication is needed, the crypto of said mobile phone can cut in the mobile communication net or the PSTN quickly in the way of wire or wireless to ensure the security voice session or data communication by end to end and ciphering every time under the internal control of the crypto.
Owner:深圳市颂雅科技有限公司
A device using power line communication
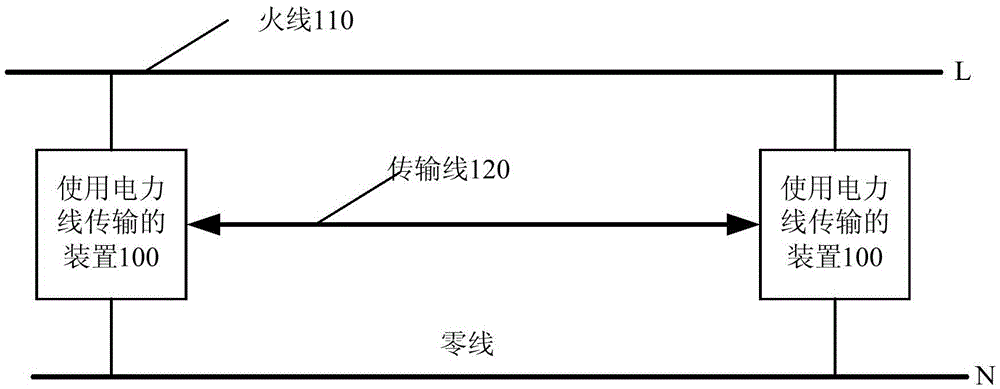
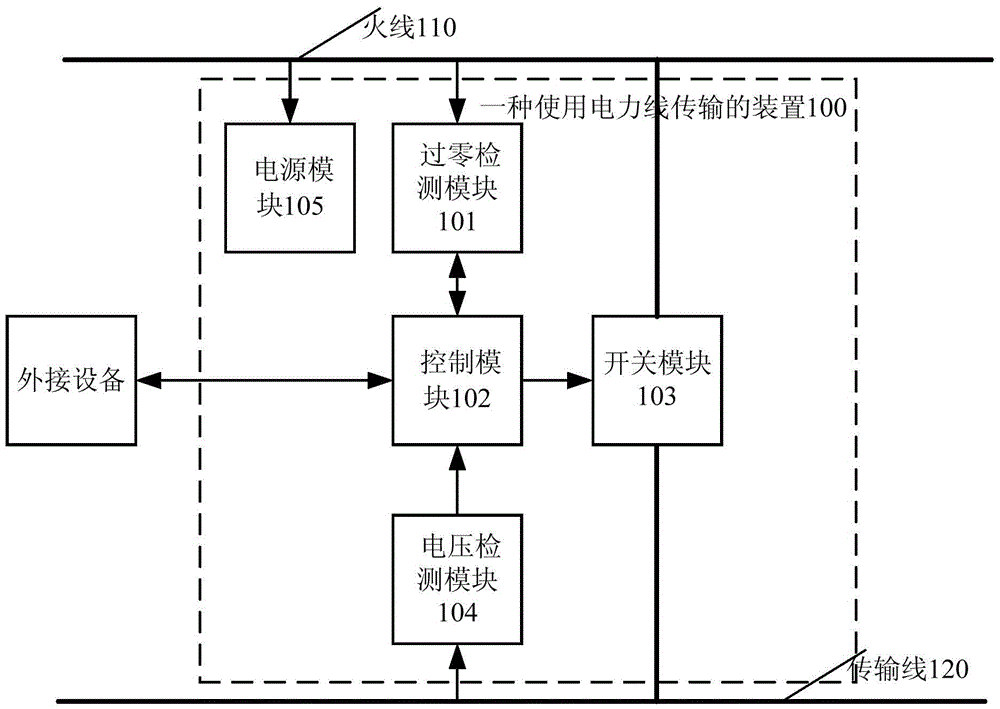
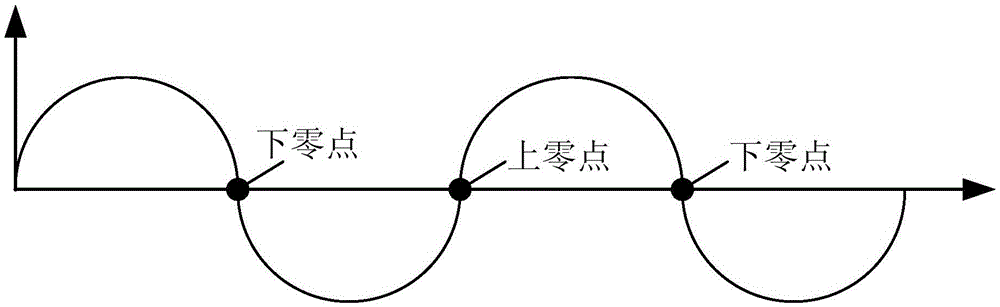
ActiveCN104270173BSimple structureLow costPower distribution line transmissionInformation controlVoltage variation
The present invention provides a device using power line communication. The fire wire is connected to the device using power line communication as a power supply input, and communicates cascaded with other devices using power line communication through a transmission line, which includes: a zero-crossing detection module, a voltage A detection module, a power module, a switch module and a control module, the control module is connected to the zero-crossing detection module, the voltage detection module and the switch module, and is used to control the switch module to adjust the signal voltage change in the transmission line according to the information to be sent; And it is used to obtain information according to the voltage variation of the voltage detection module. By adopting the technical scheme of the present invention, data communication through AC signals can be realized only by adding one transmission line, and the transmission line and the live wire can be arranged together during wiring, so as to realize safe and reliable long-distance data communication with a low-cost and simple circuit structure .
Owner:HANGZHOU DIANZI UNIV
Emergency command and dispatch method and system for environmental emergencies
ActiveCN107171784BImproving the Ability to Respond to Sudden Environmental Pollution AccidentsReduce casualtiesEncryption apparatus with shift registers/memoriesPublic key for secure communicationCommunications securityDatabase server
The invention provides an emergency command scheduling method and an emergency command scheduling system for a sudden environmental event. The method comprises the steps as follows: a mobile terminal acquires a RAS public key from a network server, and stores the RSA public key in a local memory; the mobile terminal encrypts login information by using the RAS public key, and sends the encrypted login information to a network server, wherein the login information comprises a session key, an account name, a login password and hardware equipment information of the mobile terminal; after verifying authenticity of the login information, the network server generates the login information into a login certificate and a user ID, and stores the user certificate and the user ID into a database server; the network server encrypts the user certificate and the user ID by using the session key and then sends the encrypted user certificate and user ID to the mobile terminal; and session data and the user certificate are encrypted by using the session key and then sent to perform communication between the mobile terminal and the network server. The system is used for implementing the above method. According to the method and the system provided by the invention, data communication security between the mobile terminal and the server can be ensured.
Owner:珠海富鸿科技有限公司
Data transmitting method and first manipulation host
ActiveCN104506577ASecure data communicationIncrease the level of automationFibre transmissionRadarComputer module
The invention relates to a data transmitting method and a first manipulation host. The method comprises the steps that a first Beidou time synchronization module is utilized to synchronize the first clock of the first manipulation host so that the determined time after completion of synchronization is obtained; the determined seed data uniquely corresponding to the determined time are obtained according to the stored agreed rules; data to be transmitted are encrypted by utilizing the determined seed data so that the determined non-feature code source is obtained; electro-optic conversion is performed on the determined non-feature code source so that the determined optical signal is obtained; and the determined optical signal is transmitted to a second manipulation host by utilizing optical fibers. Secure and high-efficiency data communication and command control between a far-end unattended radar station and a near-end control center can be effectively realized so that the method has the communication control means which is high in anti-interception capability, long in transmission distance, great in real-time performance, low in cost and easy to realize. Besides, practicality, reliability and stability are quite high so that the method has important social, economic and military meaning in enhancing automation level of national defense equipment of China.
Owner:SICHUAN JIUZHOU ELECTRIC GROUP
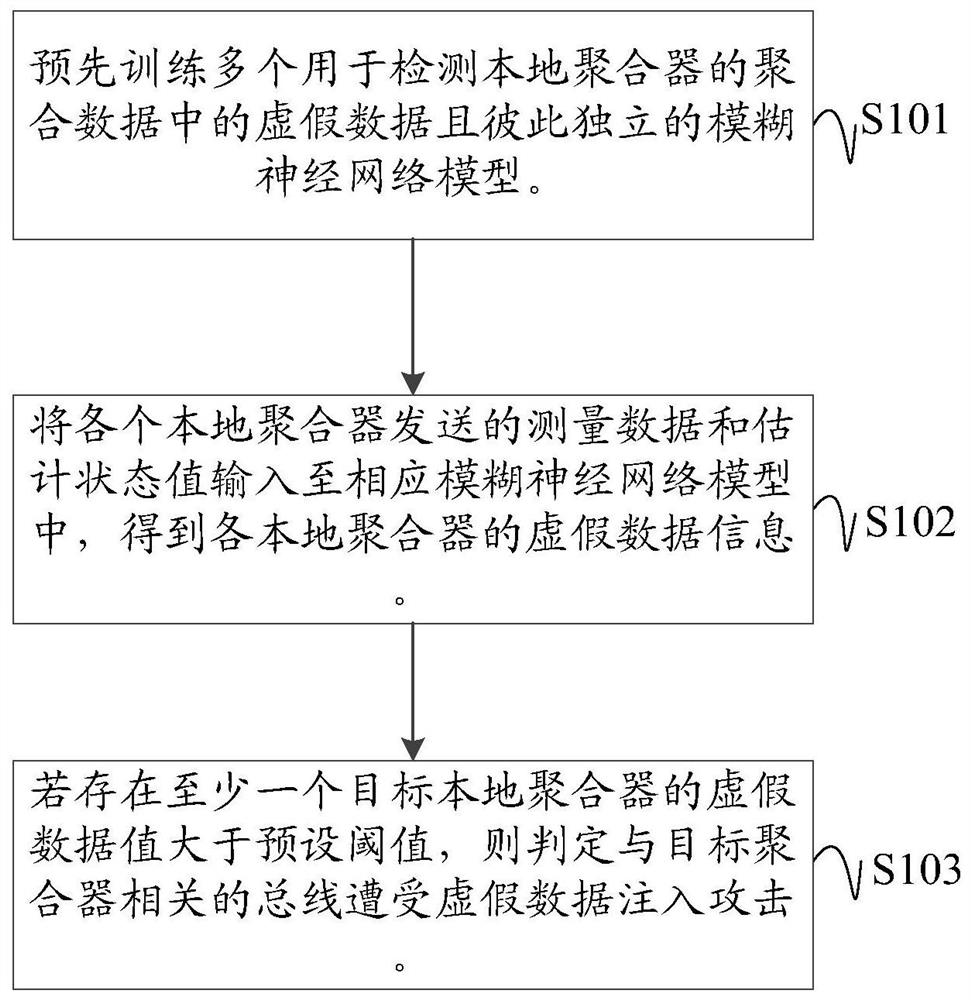
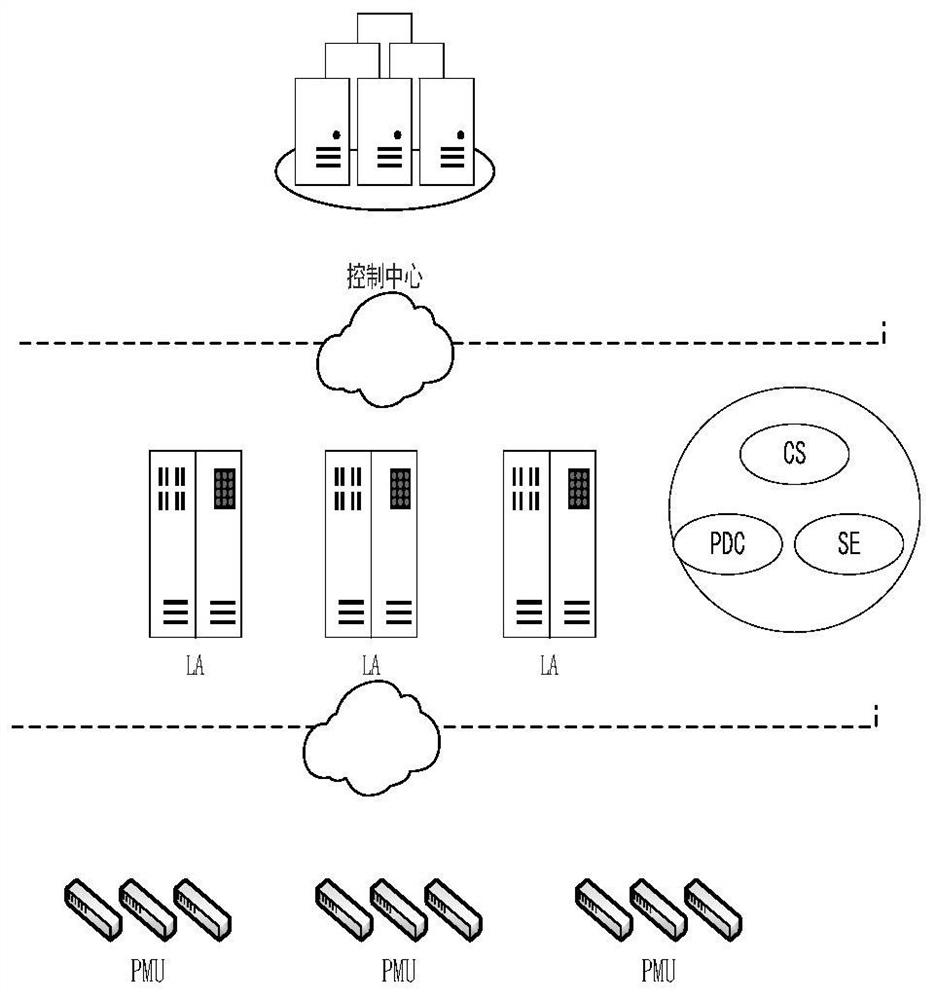
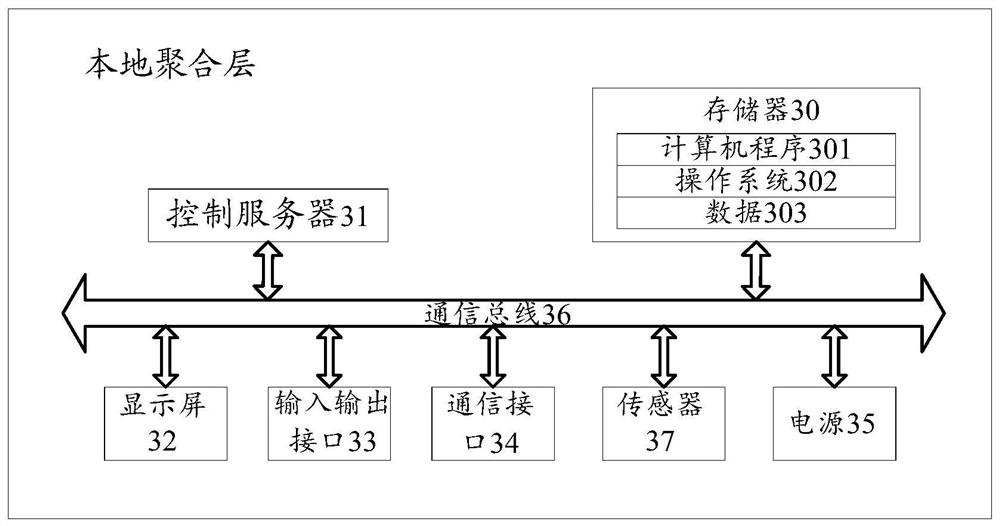
Method, device and readable storage medium for detecting false data injection attack
ActiveCN110995761BEnsure safetyInjection attacks are efficientTransmissionAc network circuit arrangementsCommunications securityData information
The present application discloses a method, device and computer-readable storage medium for detecting false data injection attacks. Applied to a three-layer smart grid framework consisting of PMU layer, local aggregation layer, and control layer, the local aggregation layer pre-trains multiple fuzzy neural network models that are independent of each other and are used to detect false data in the aggregated data of the local aggregator; Receive the measurement data and estimated state values sent by each local aggregator and input them into the corresponding fuzzy neural network model to obtain the false data information of each local aggregator; if there is at least one target local aggregator whose false data value is greater than the threshold, then determine the bus Suffering from false data injection attacks; the local aggregator aggregates the measurement data collected by the PMUs in the corresponding area and performs state estimation to obtain the estimated state value, and sends the data to the control layer after the identity legality verification request is passed. This application can effectively resist false data injection to attack the grid and ensure the security of grid communication.
Owner:CHANGSHA UNIVERSITY OF SCIENCE AND TECHNOLOGY
A wireless real-time positioning system and method
InactiveCN102238536BSecure data communicationHigh positioning accuracySecurity arrangementCommunications securityEngineering
The invention discloses a wireless real time location system and a wireless real time location method. The wireless real time location system comprises a label, a reader-writer and a location engine. The reader-writer comprises three radio frequency modules and three antennae. The label establishes three channels with the reader-writer by the three radio frequency modules and the three antennae. The reader-writer is connected with the location engine. The label and the reader-writer achieve data security and finish location computation by triple authentication. By the technical scheme provided by the invention, the security of data communication between the label and the reader-writer can be achieved, the capacity of the label can be increased and the location accuracy can be improved.
Owner:北京烽火联拓科技有限公司
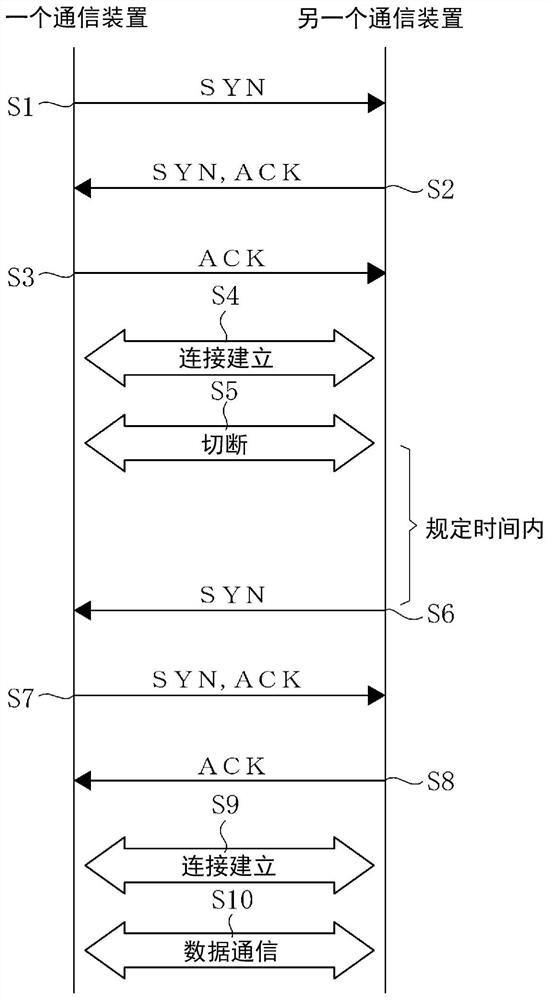
data communication method
ActiveCN110178339BSimple and reliable judgmentSecure data communicationSynchronisation information channelsUser identity/authority verificationTelecommunicationsCommunication device
Connect a plurality of communication devices to the IP network through a communication line assigned a unique identification number, register the identification numbers of other communication devices that are allowed to communicate in each communication device, and connect the communication line to the IP network through a three-way handshake based on the identification number. Uniquely connect for data communication. When a connection is established between these communication lines by starting another communication line, the connection is temporarily cut off. Afterwards, in the communication line on the activated side, it is judged whether the signal of response from the communication line on the activation side to the call-back signal sent to the communication line on the activation side arrives at a predetermined timing. , to determine whether a call-back signal is sent from the activated side communication line at a predetermined timing, and data communication is performed only when the legitimacy of the communication lines of both the activation side and the activated side is confirmed.
Owner:KOGA ELECTRONICS
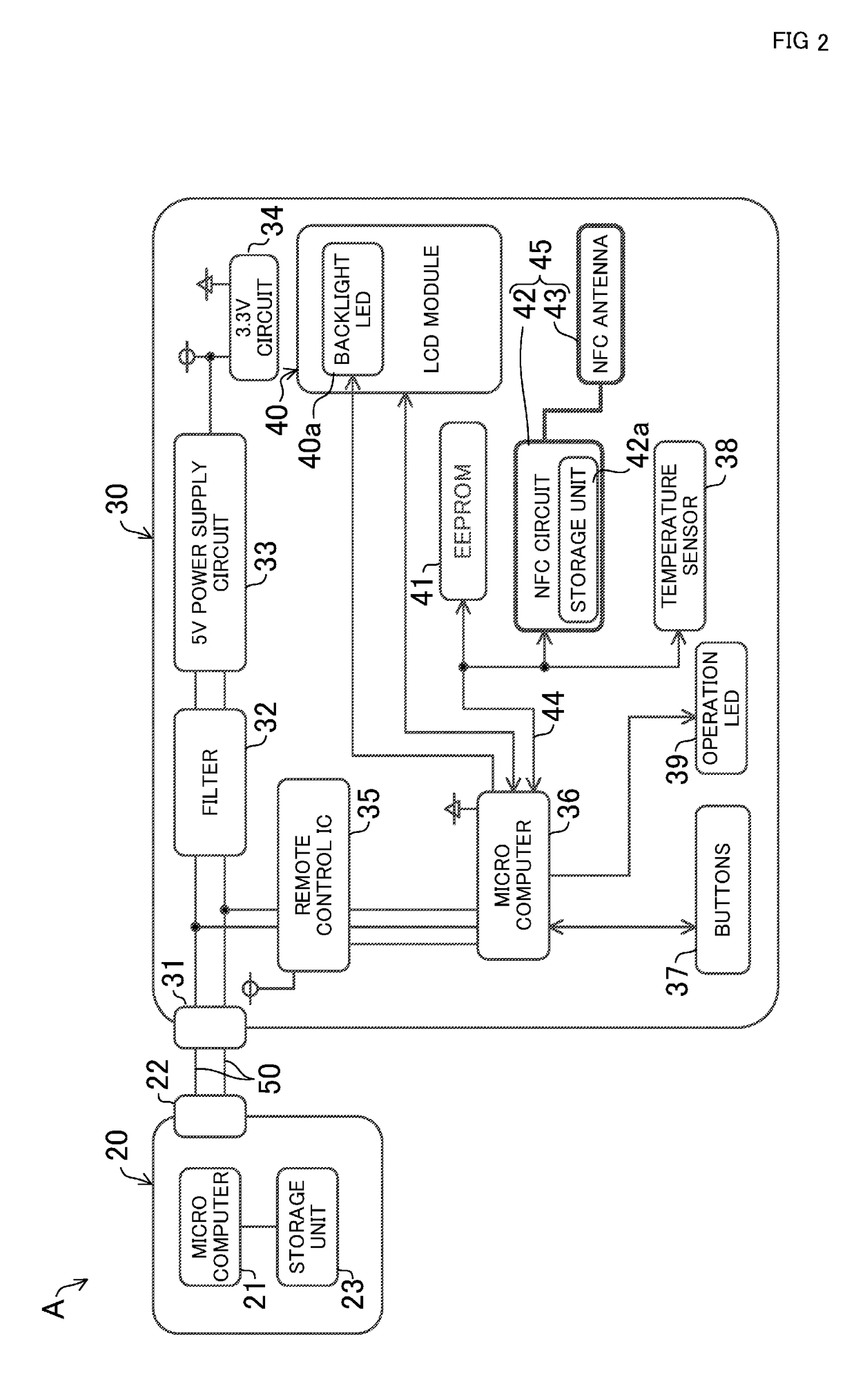
Remote control for air conditioner and air conditioner provided with same
ActiveUS10373036B2Secure data communicationMechanical apparatusSpace heating and ventilation safety systemsMicrocomputerRemote control
A remote control for an air conditioner facilitates setting of various kinds of data without operation of a button. A remote control (30) includes an external communication unit (45) having an NFC circuit (42) and an NFC antenna (43). The external communication unit (45) is capable of wirelessly communicating with an external apparatus even when a microcomputer (36) in the remote control (30) is not supplied with power (i.e., in a non-operating state). Hence, through the wireless communication between the external communication unit (45) of the remote control (30) and the external apparatus, the various kinds of data is forwarded from the external device to the remote control (30), and stored in the remote control (30).
Owner:DAIKIN IND LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com