Mobile phone scrambler and its privacy communication method
A mobile phone, secure communication technology, applied in secure communication, secure communication devices, electrical components, etc., can solve problems such as the inability to meet security and confidentiality levels, and achieve the effects of reducing costs and maintenance overhead, easy to use, and clear voice
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
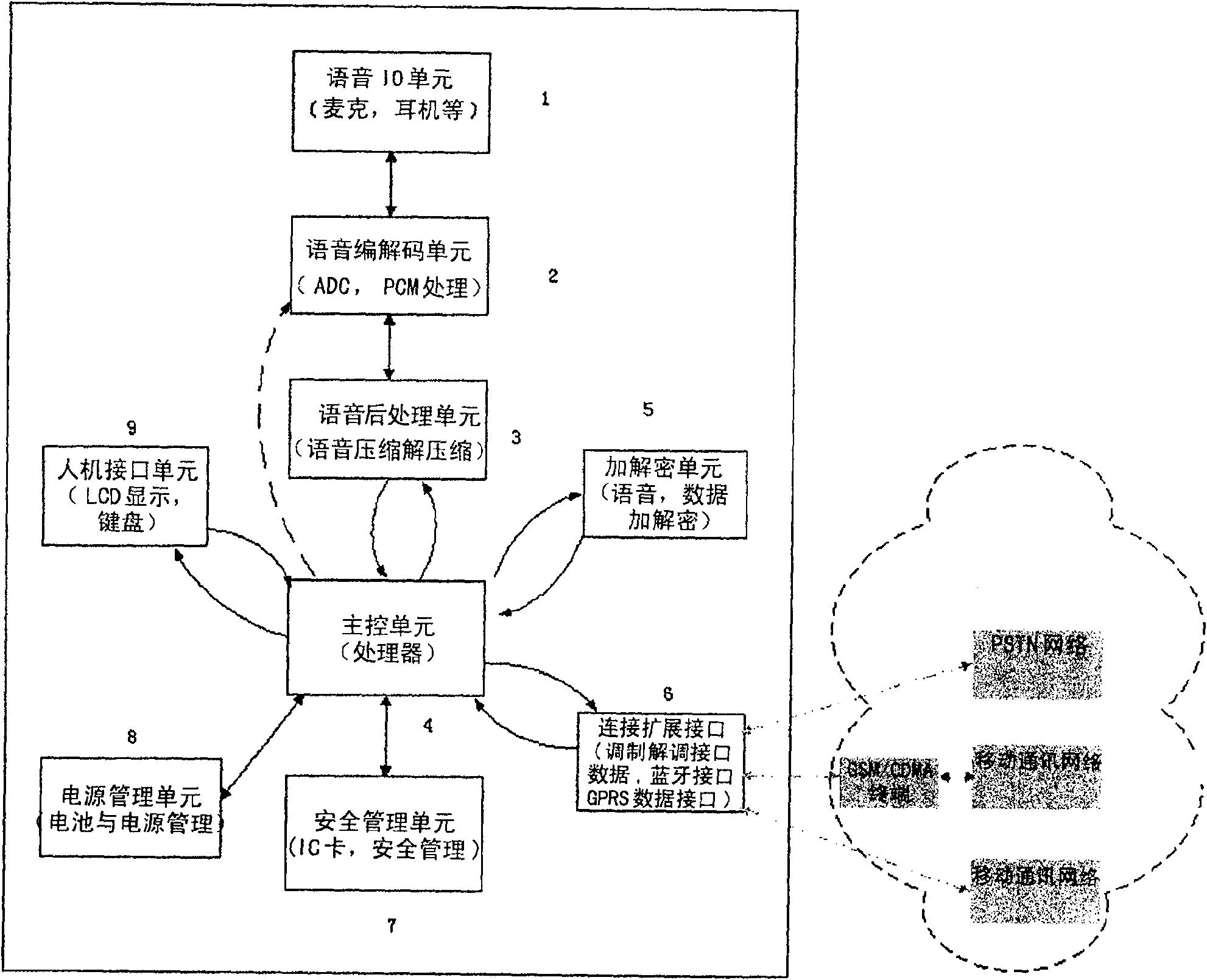
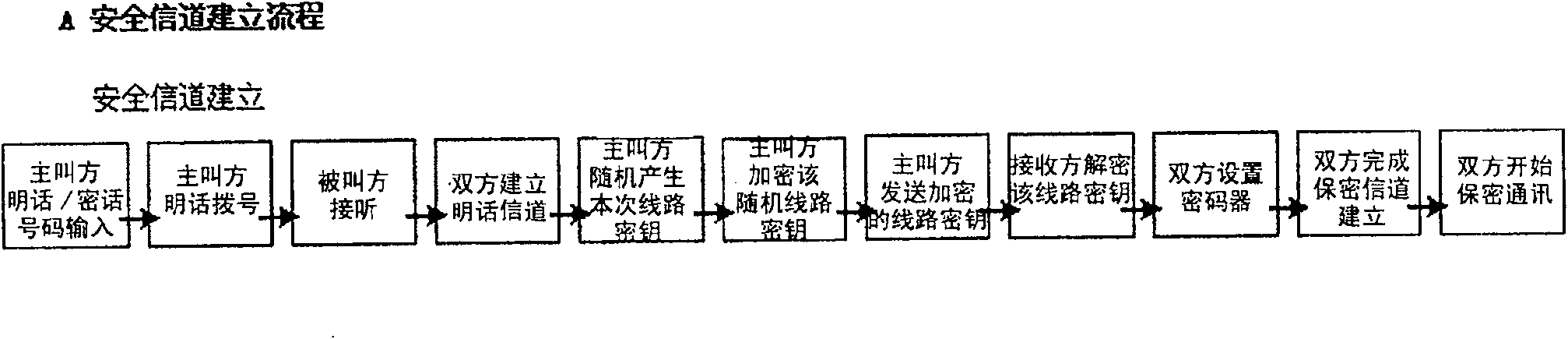
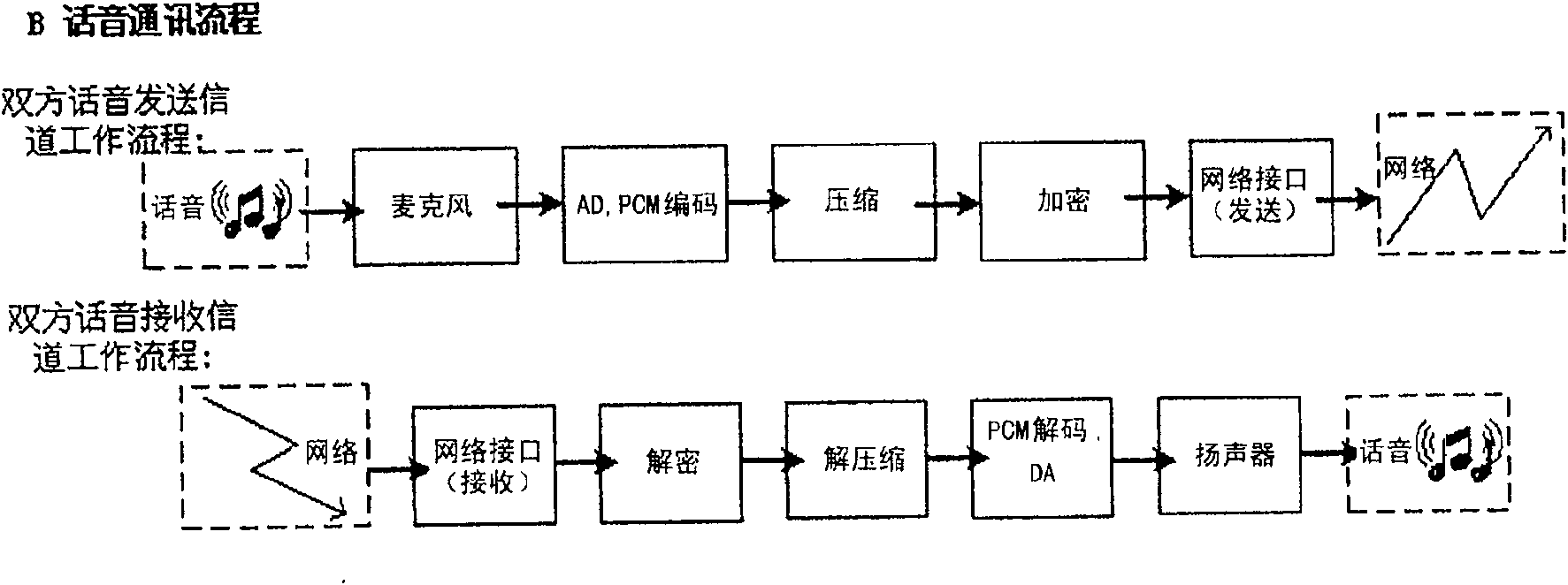
[0035] The present invention provides a mobile phone cipher machine that supports mobile communication network and public switching network at the same time, relies on the communication channel provided by the existing network, and uses the user key IC card built in the cipher machine to realize user identity verification and one-time pad Communication password, and rely on the voice processing, encryption and decryption inside the device and the connection of the expansion interface unit to realize high-security and confidential communication that is not related to the network structure.
[0036] According to the method for realizing end-to-end confidential communication in the mobile communication network and the public switching network and the mobile phone cipher device of the present invention, relying on its built-in functional interface, realize end-to-end confidential communication that is independent of the communication network and satisfies high security , the call q...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com