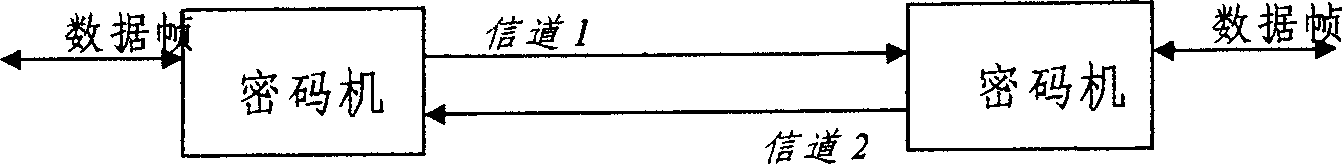Seamless key exchanging technology based on secret communication
A technology of secure communication and seamless key change, which is applied in the field of seamless key change technology, can solve problems such as communication interruption, meet the needs of operation, overcome cumbersome operations, and improve cost performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041]In the process of full-duplex communication, each cipher machine mainly has two aspects of work, one is to encrypt the data received by the terminal, and then send the ciphertext to the network; the other is to encrypt the data received by the network The data is decrypted, and then the decrypted plaintext is sent to the terminal. correspond figure 1 As shown, there are two independent transmission channels, channel 1 and channel 2. For simplicity, we only discuss the data transfer processing in one channel direction.
[0042] Such as figure 1 As shown, when the data passes through the cipher machine A at the sending end, the cipher machine A encrypts the data; The channel between cipher machines is always in ciphertext state. Here, we refer to cipher machine A as an encryption cipher machine, and cipher machine B as a decryption cipher machine.
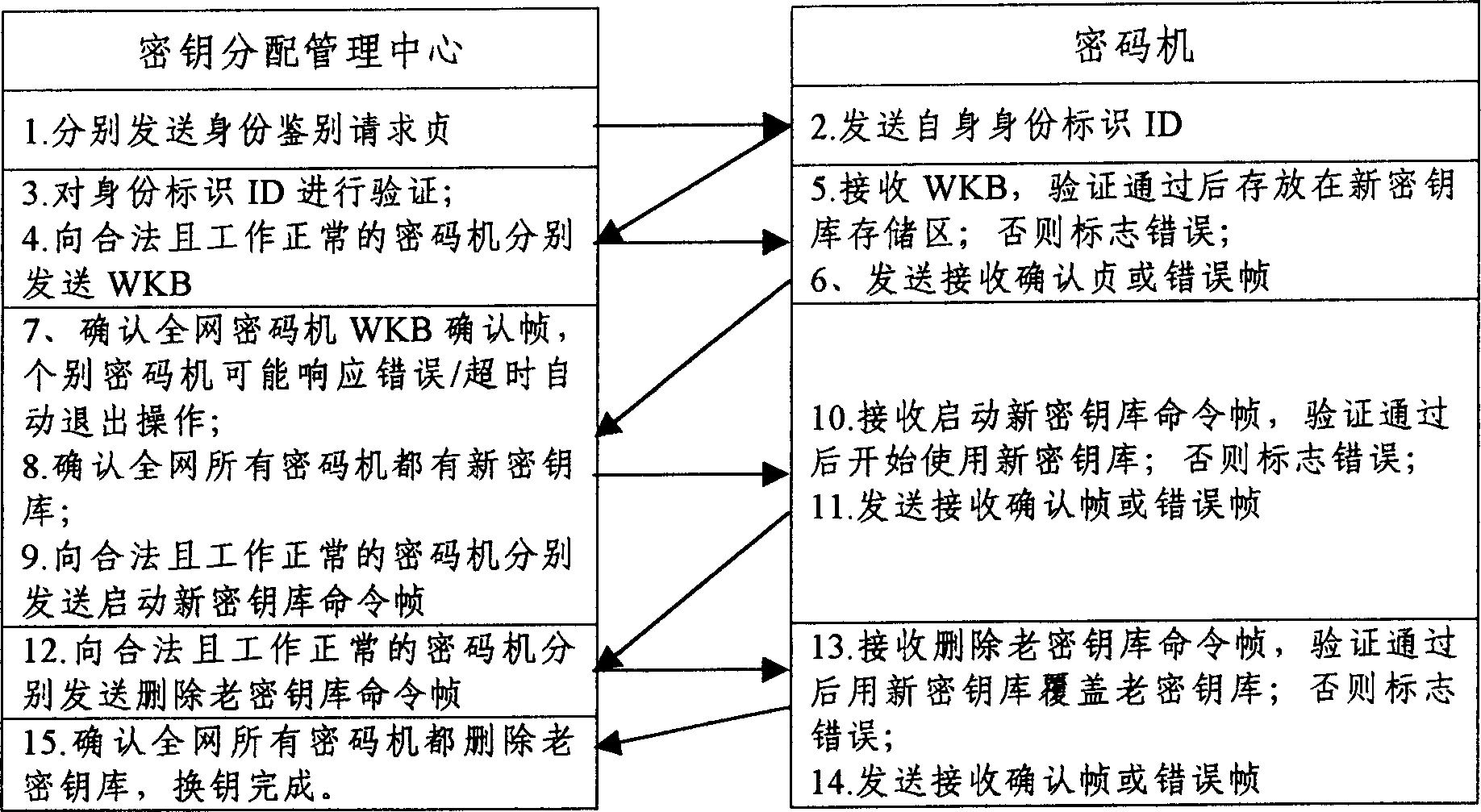
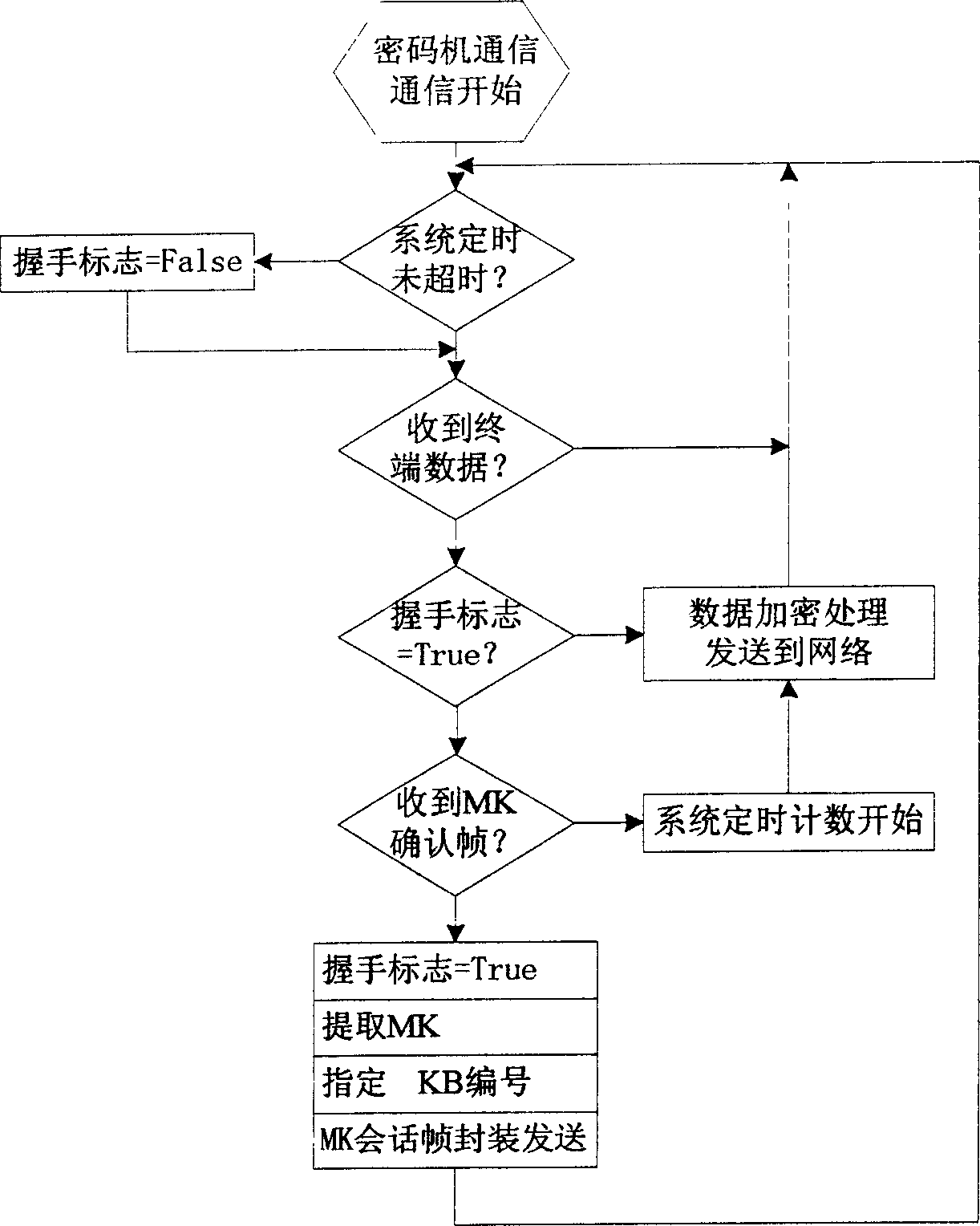
[0043] The seamless key exchange technology is mainly composed of two parts. One is the regular replacement of the netwo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com