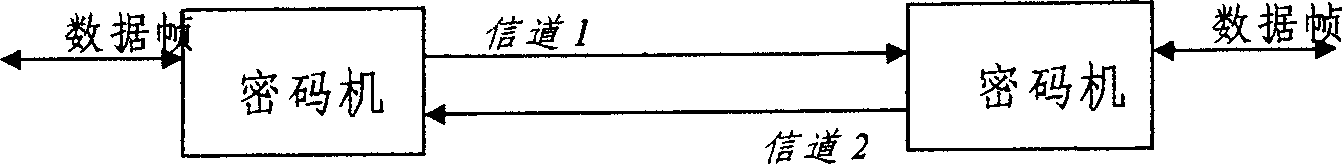Patents
Literature
127 results about "Keystore" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
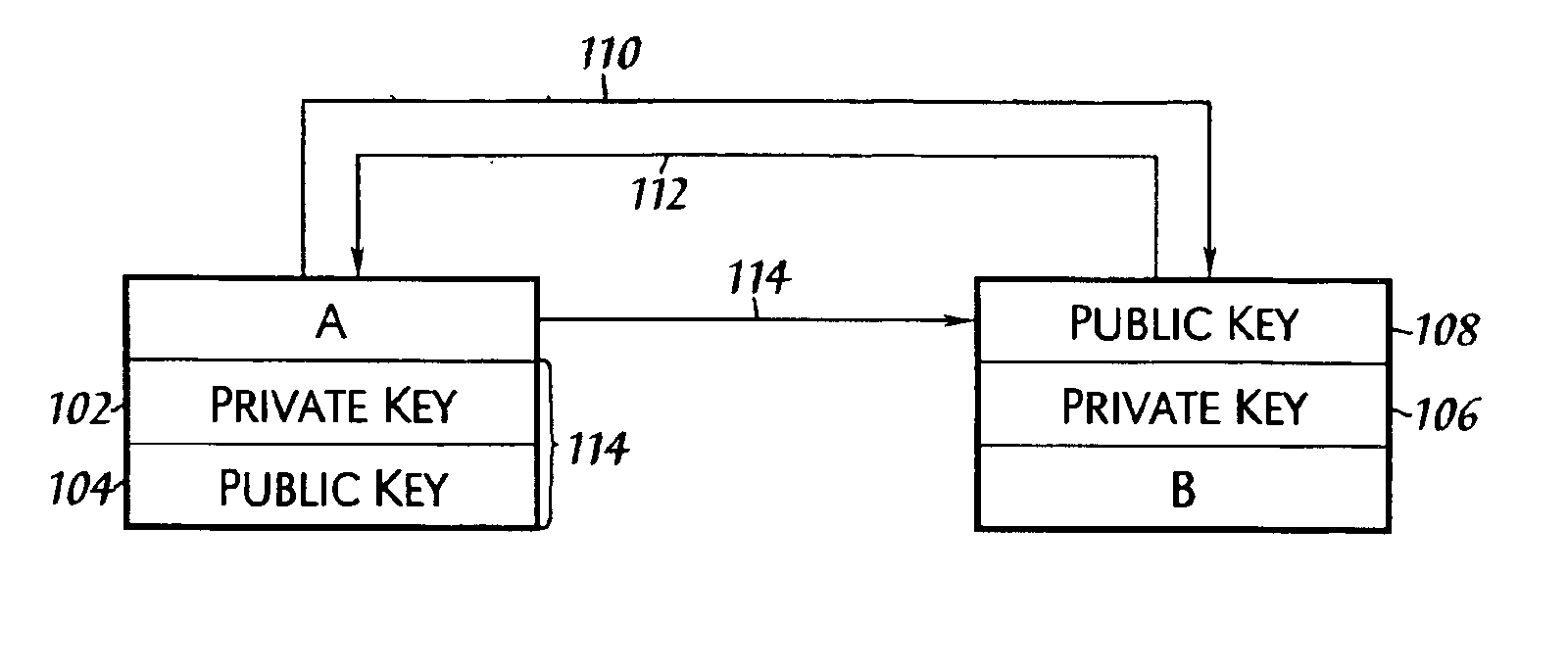
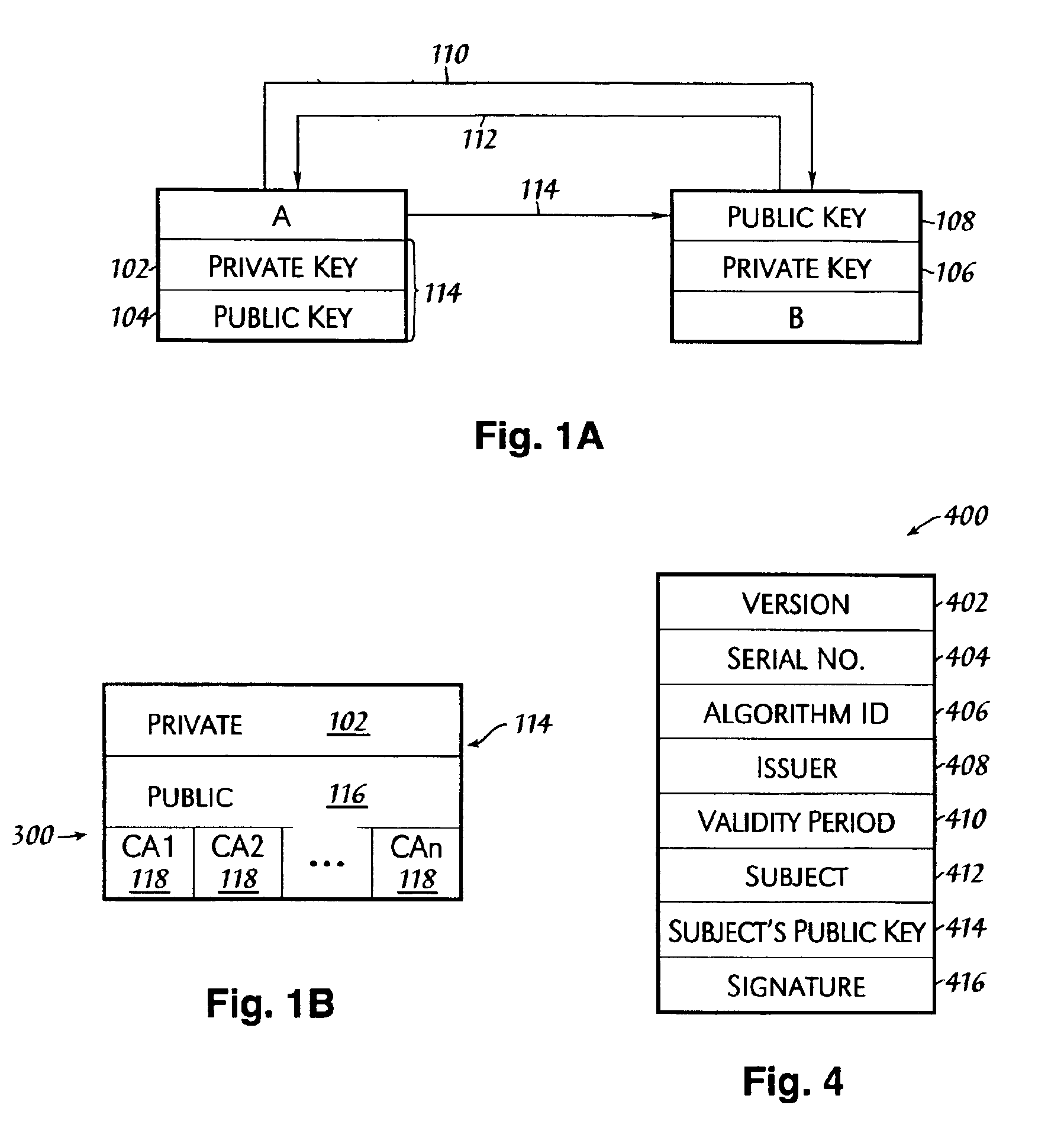
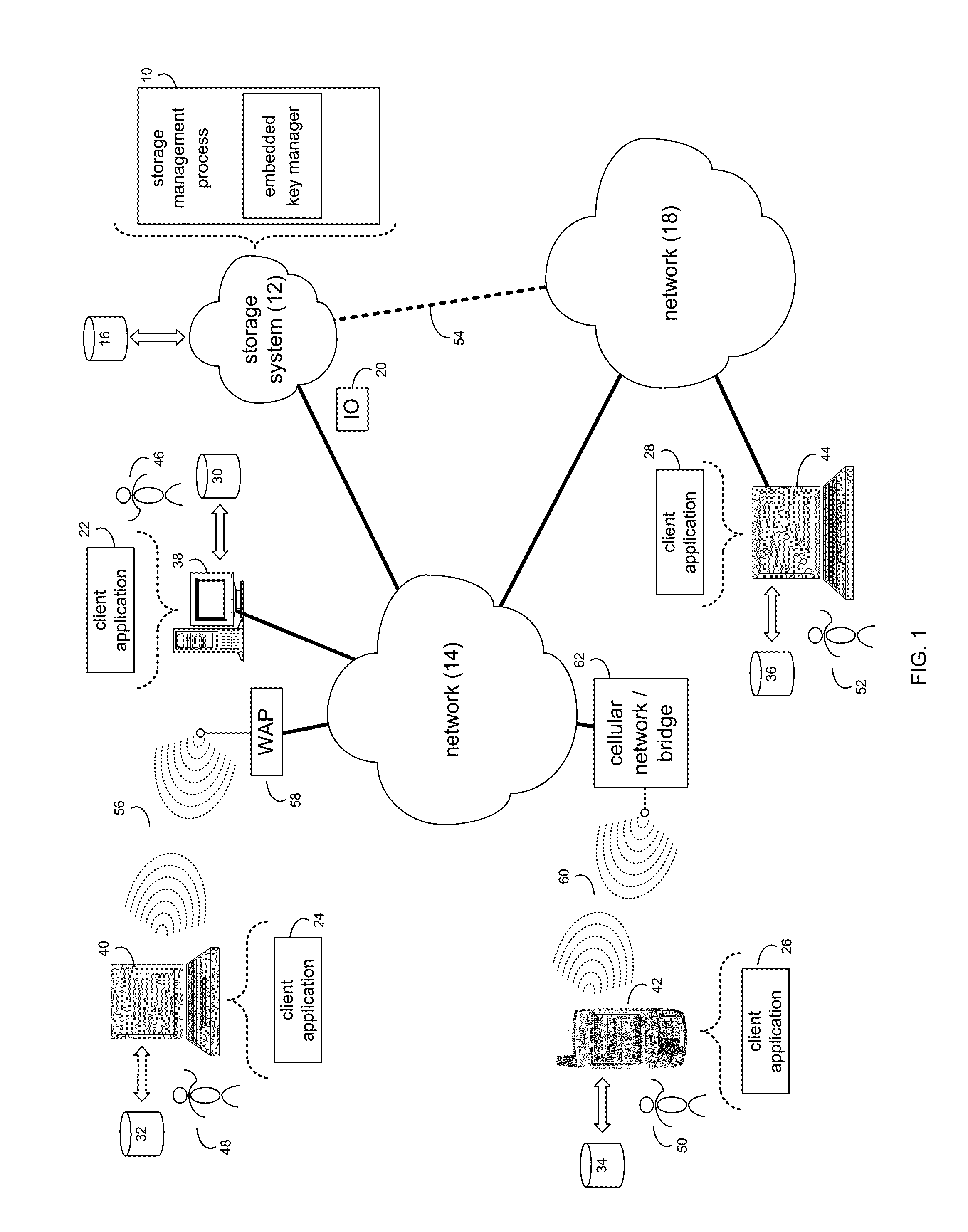
A Java KeyStore (JKS) is a repository of security certificates – either authorization certificates or public key certificates – plus corresponding private keys, used for instance in SSL encryption. In IBM WebSphere Application Server and Oracle WebLogic Server, a file with extension jks serves as a keystore.
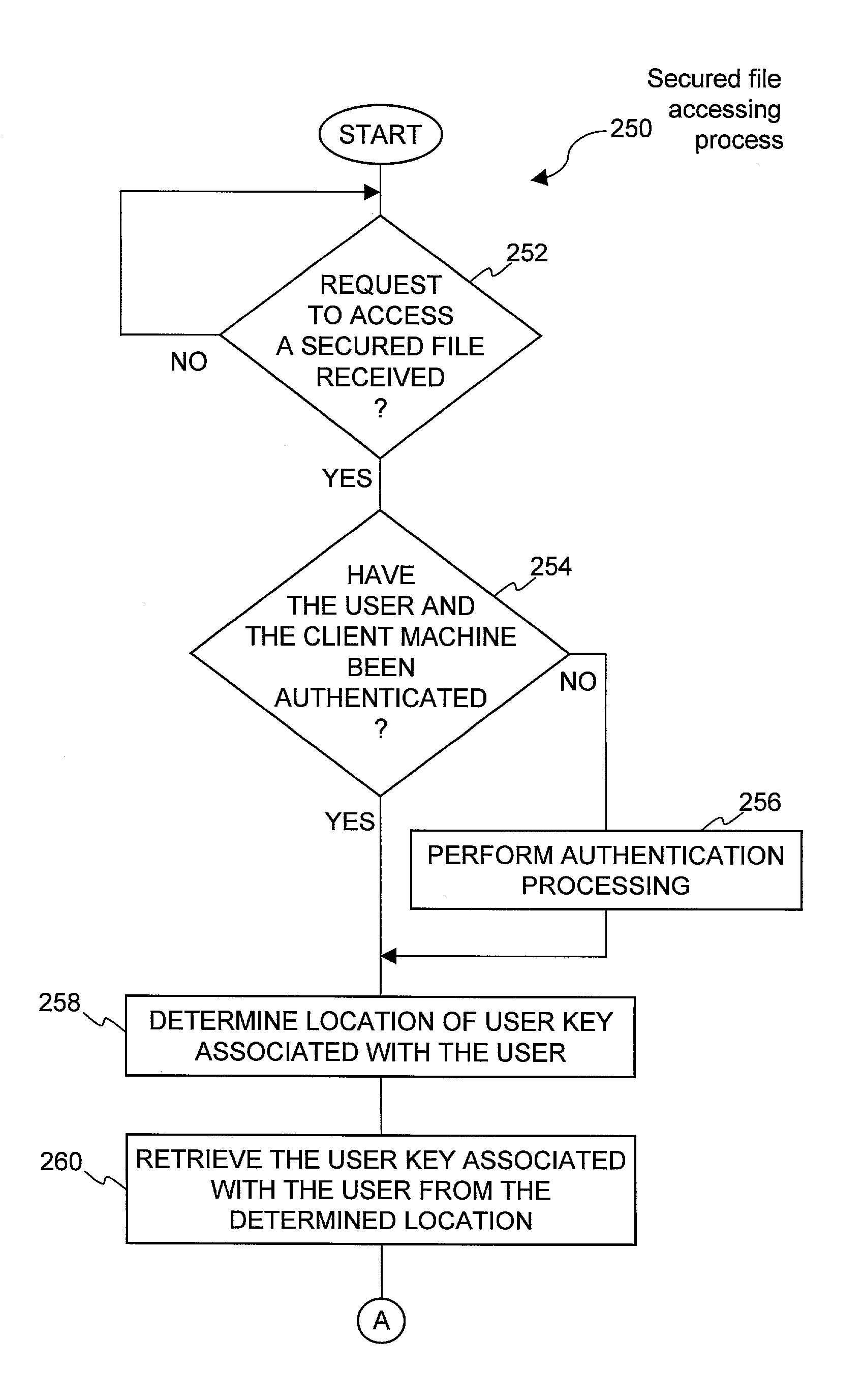
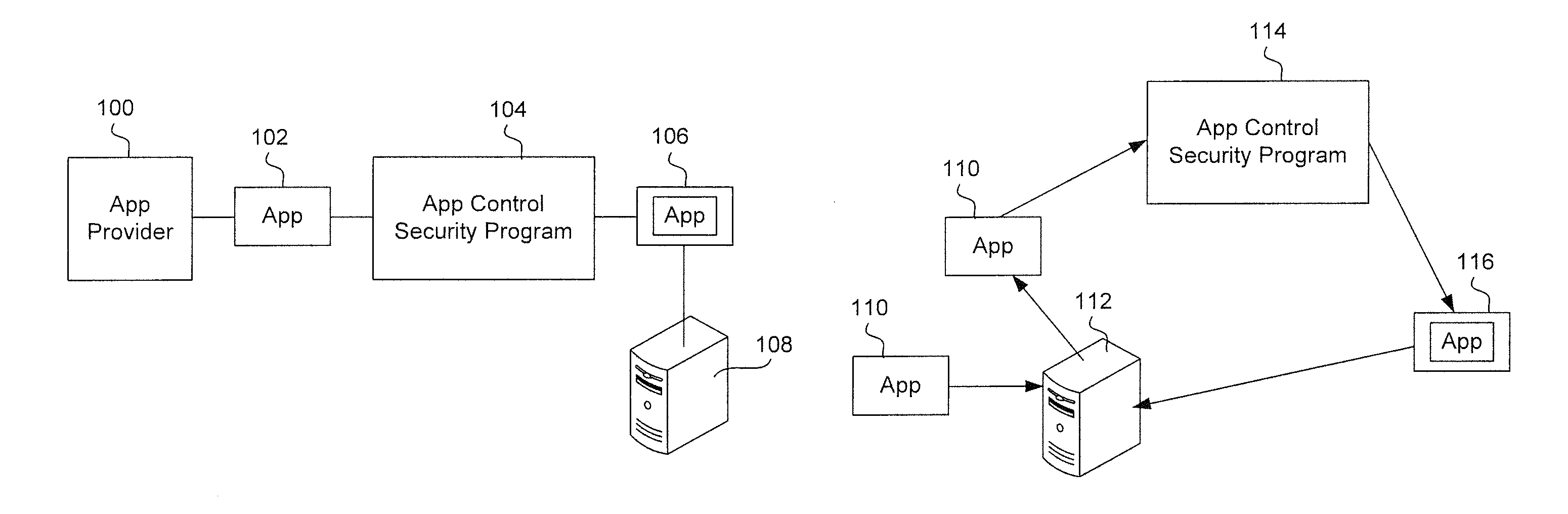
System and method for providing different levels of key security for controlling access to secured items
With files secured by encryption techniques, keys are often required to gain access to the secured files. Techniques for providing and using multiple levels of keystores for securing the keys are disclosed. The keystores store keys that are needed by users in order to access secured files. The different levels of keystores offer compromises between security and flexibility / ease of use.
Owner:INTELLECTUAL VENTURES I LLC
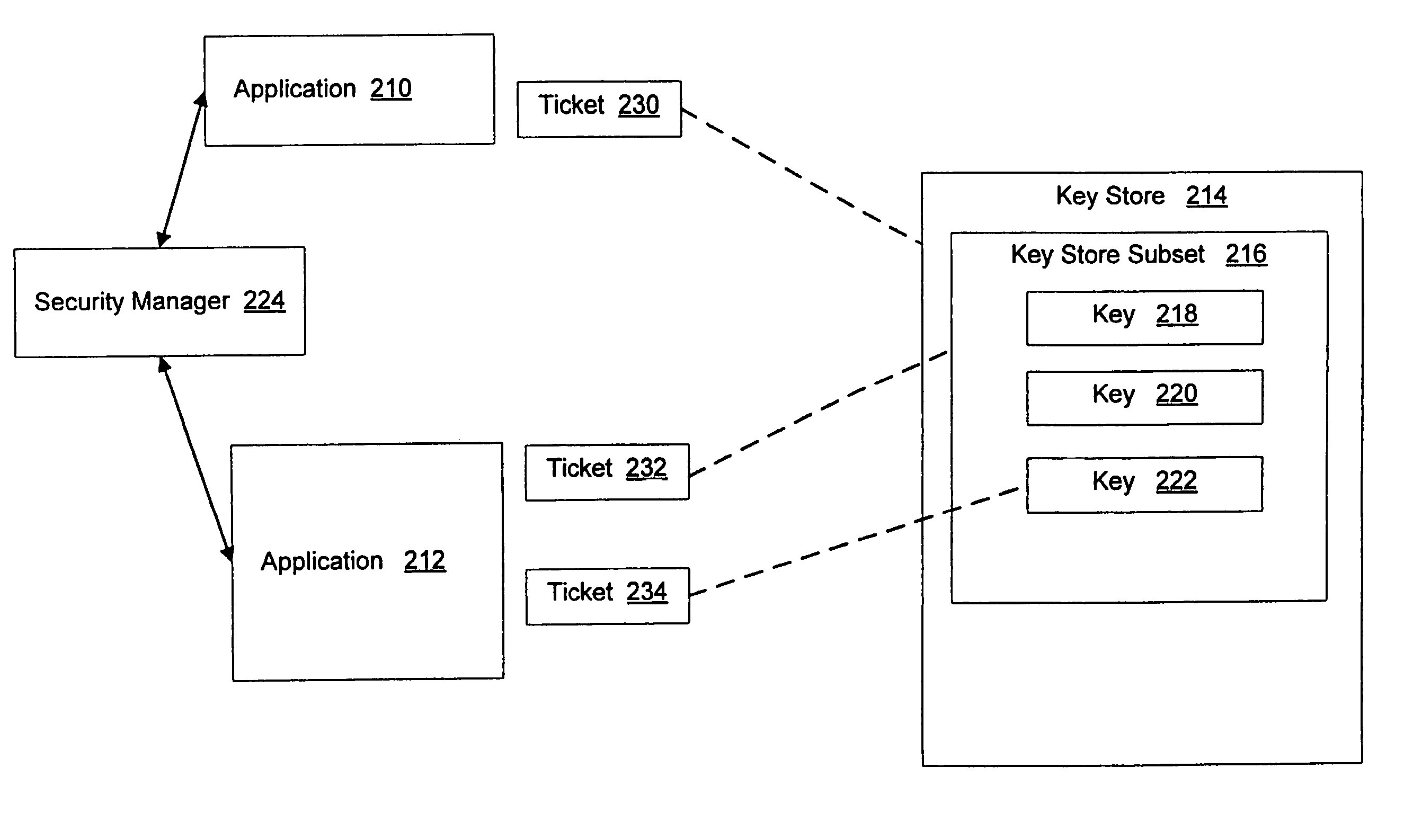
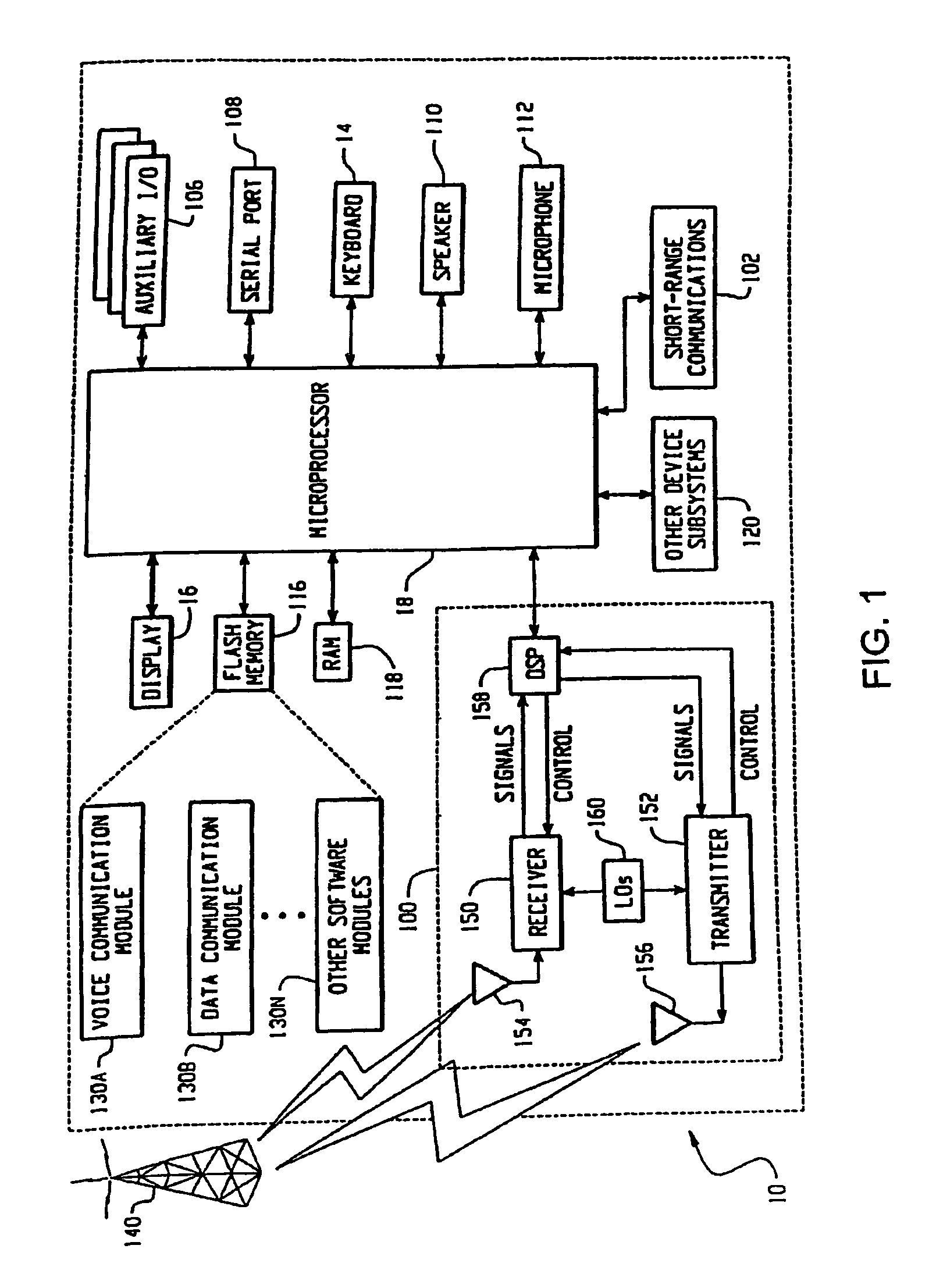
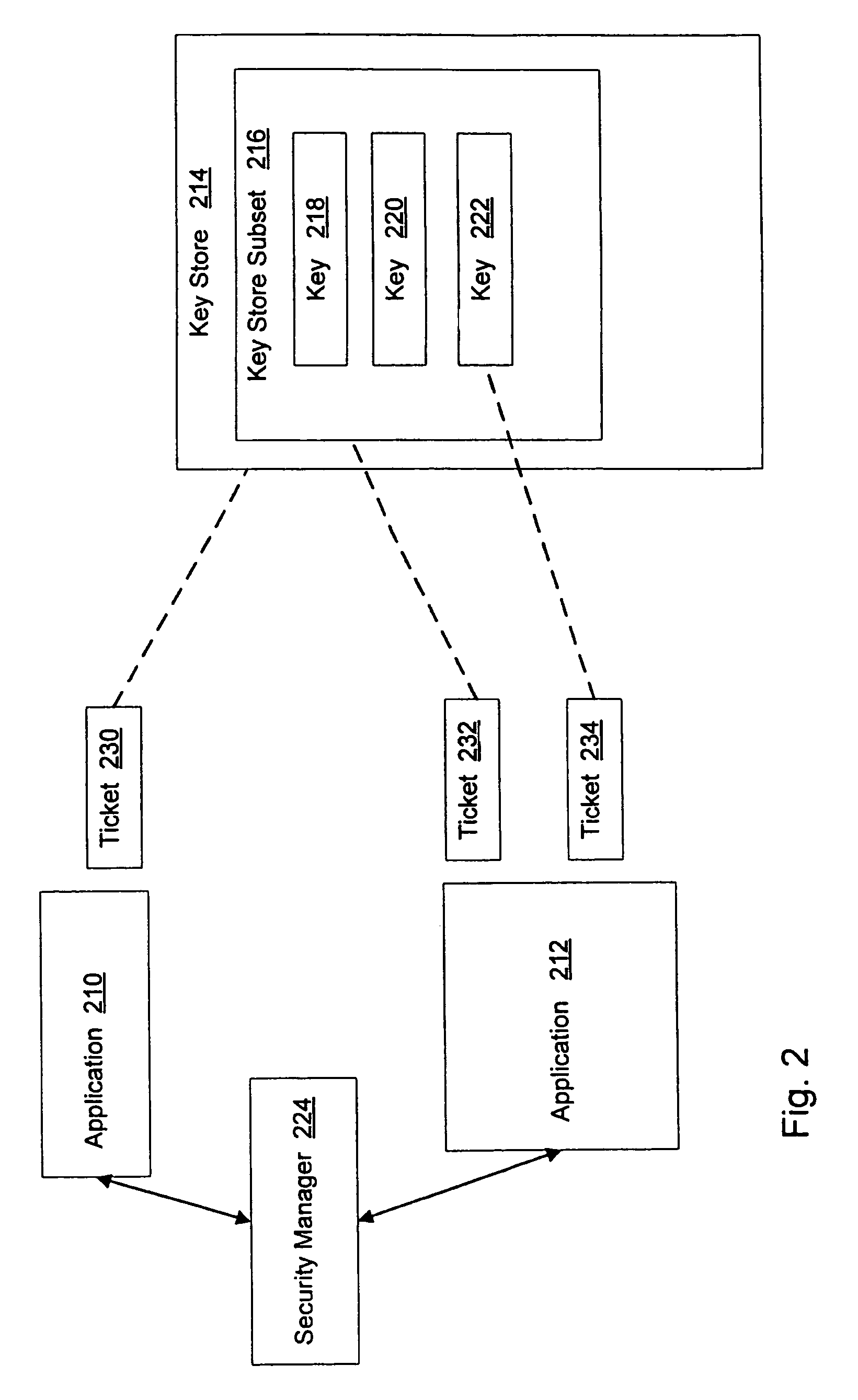
System and method for application authorization
ActiveUS7805755B2Reduced promptingDigital data processing detailsUnauthorized memory use protectionPasswordApplication software
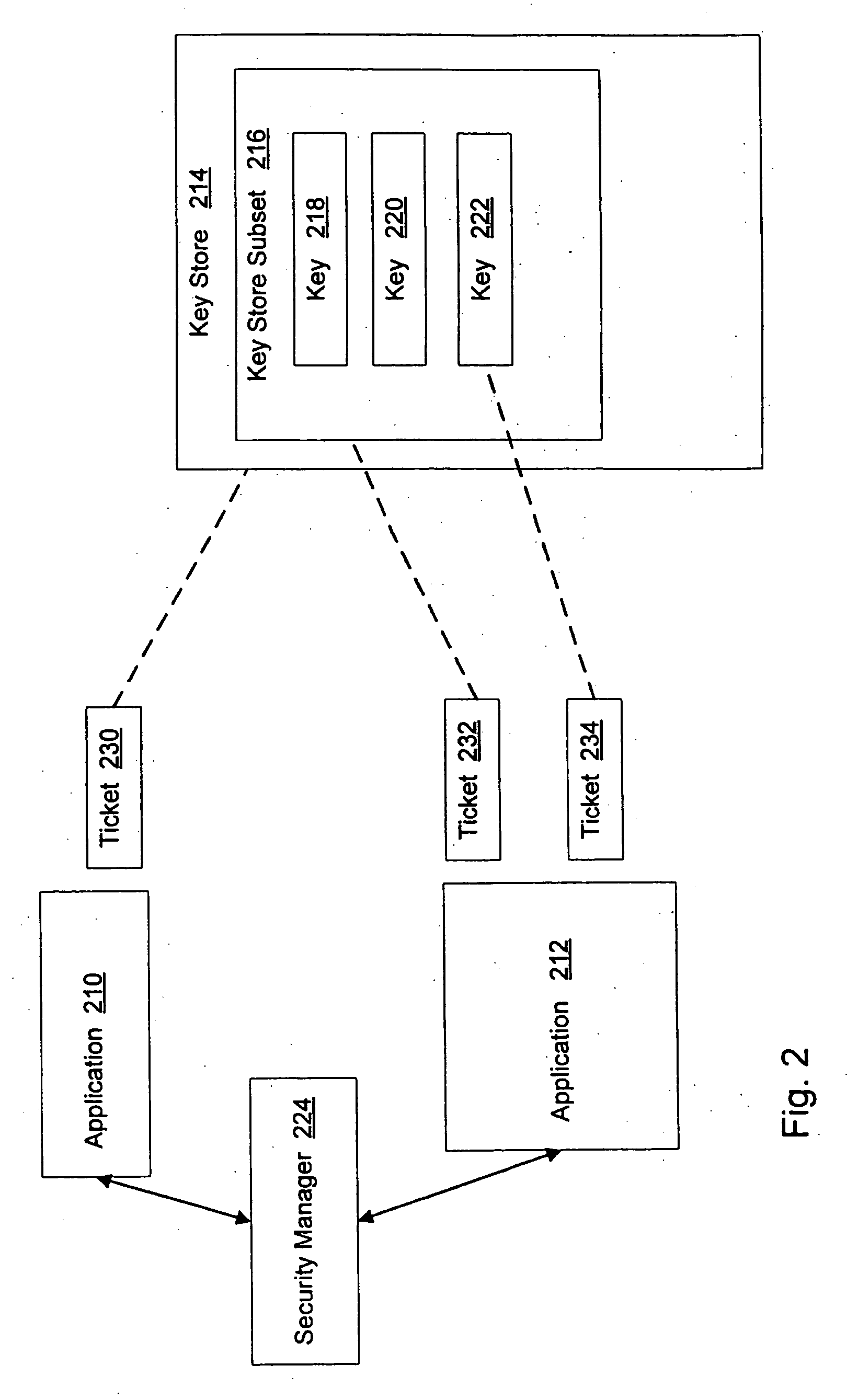
A method and system for authorization of applications executing on a device having a key store. Applications obtain an application-level ticket to permit access to one or more key values located in the key store. Each ticket is securely associated with an application and being generated on the determination that the application is a trusted application. Tickets are potentially associated with one key value in the key store, with a subset of key values in the key store, or with all key values in the key store. Access to key values by an application is possible independently of a user providing a password for each such access.
Owner:MALIKIE INNOVATIONS LTD
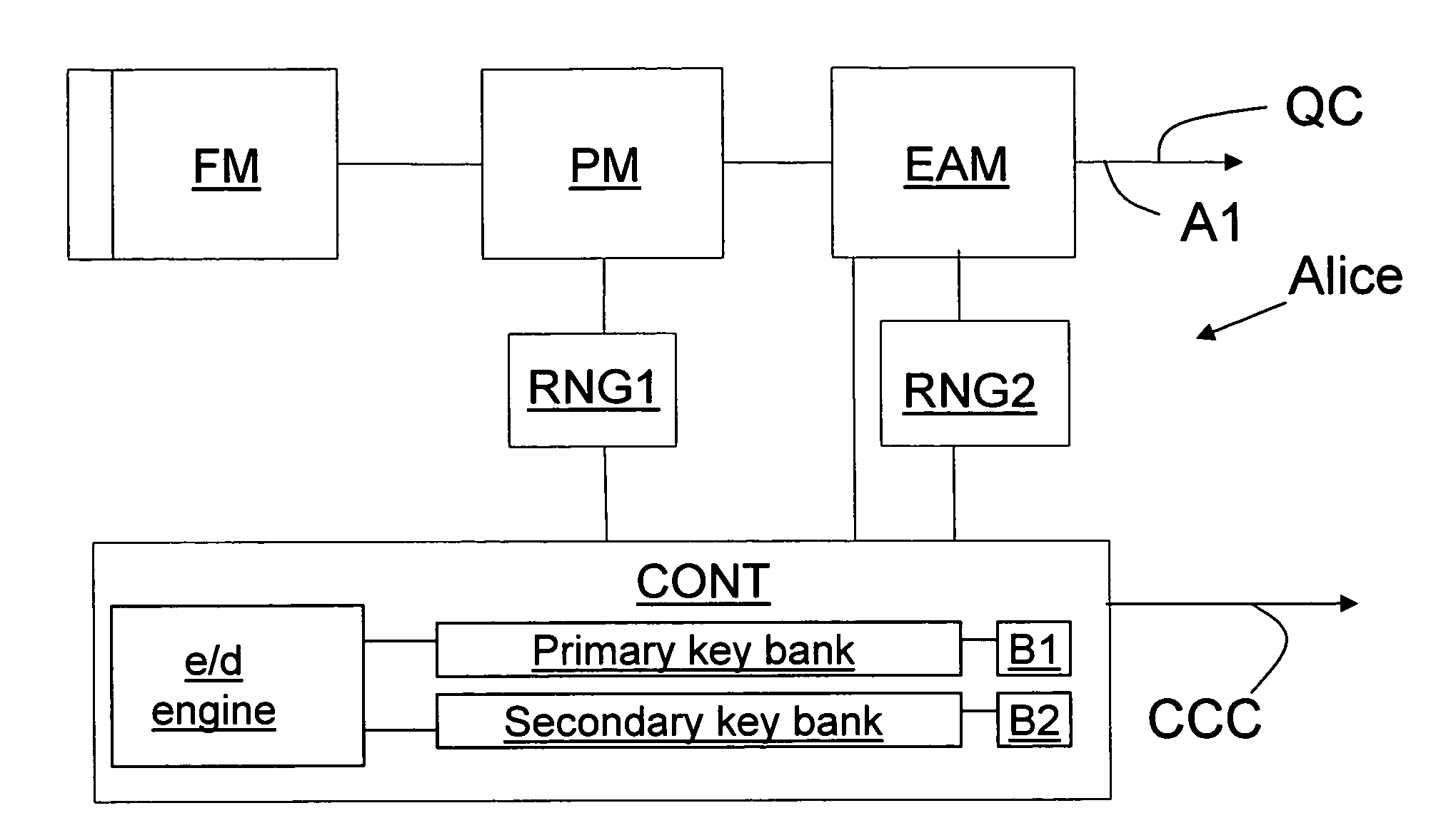
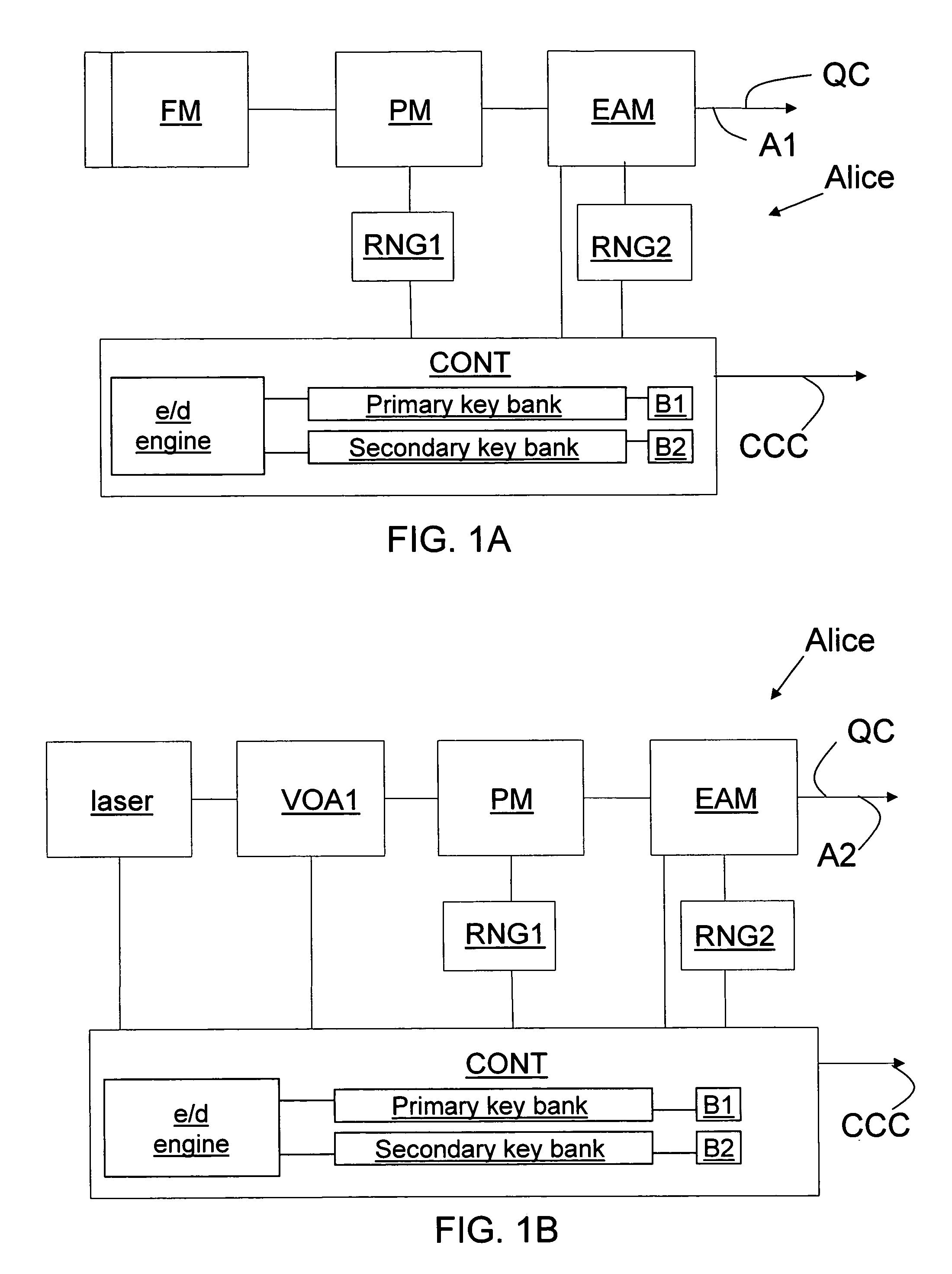
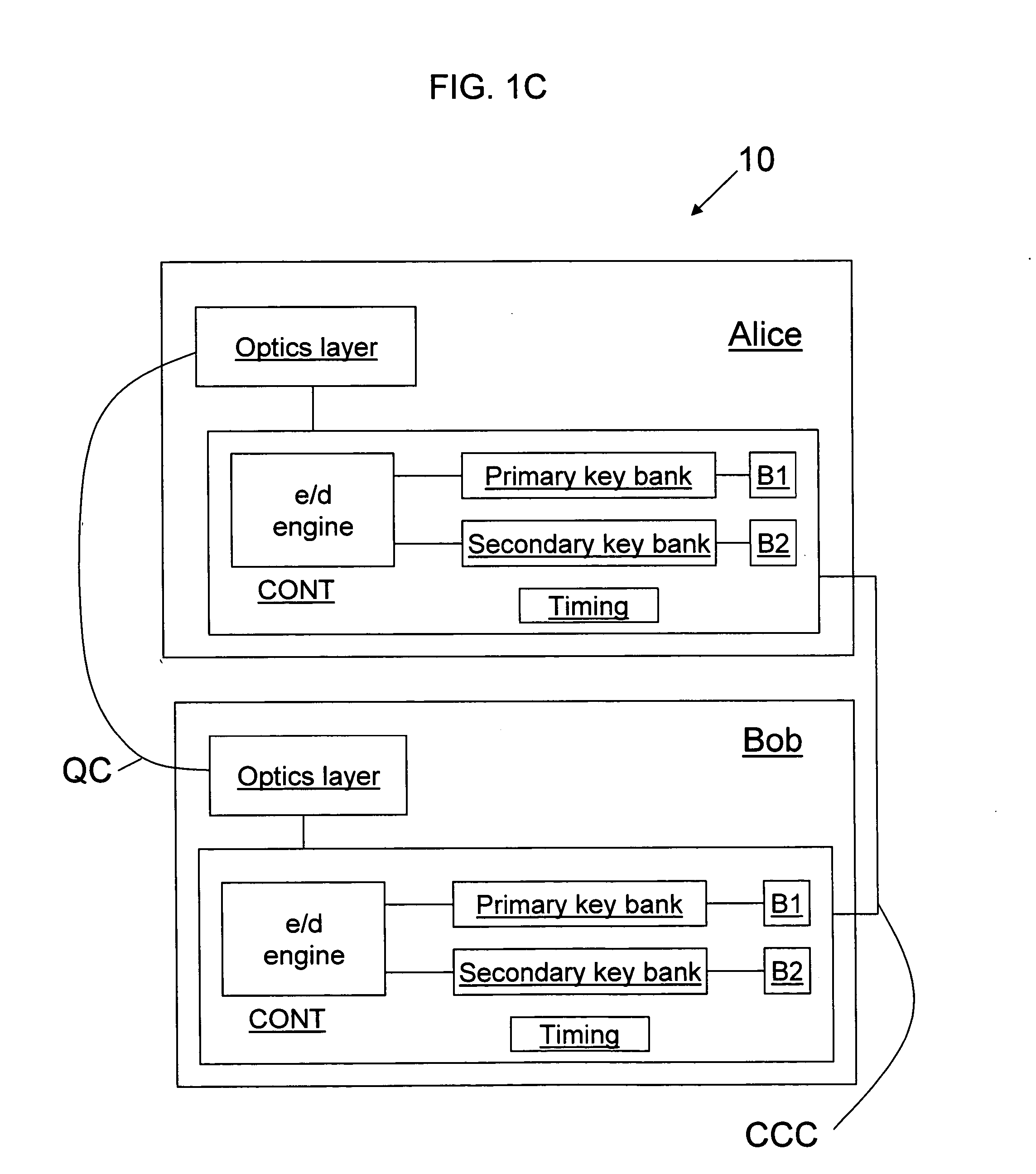
Key bank systems and methods for QKD
ActiveUS20050259825A1Increase distanceIncrease in key generation rateKey distribution for secure communicationSecret communicationAuthenticationQuantum key distribution
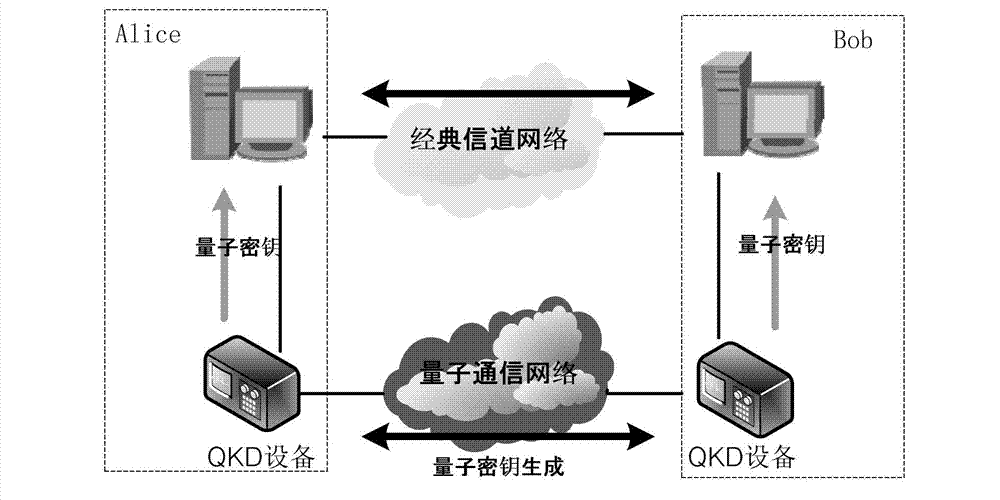
Key banking methods and systems for quantum key distribution (QKD) are disclosed. A method of the invention includes establishing a primary key bank that stores perfectly secure keys associated with exchanging true quantum pulses between two QKD stations Bob and Alice. The method also includes establishing a secondary key bank that stores less-than-perfectly secure keys associated with exchanging relatively strong quantum pulses between Bob and Alice. The primary keys are used for select applications such as authentication that are deemed to require the highest security, while the secondary keys are used for applications, such as encrypted bit sifting, that are deemed to require less-than-perfect security. A benefit of the two-key-bank architecture is that exchanging primary and secondary keys actually allows for an increase in the distance over which the primary keys can be securely distributed
Owner:MAGIQ TECH INC
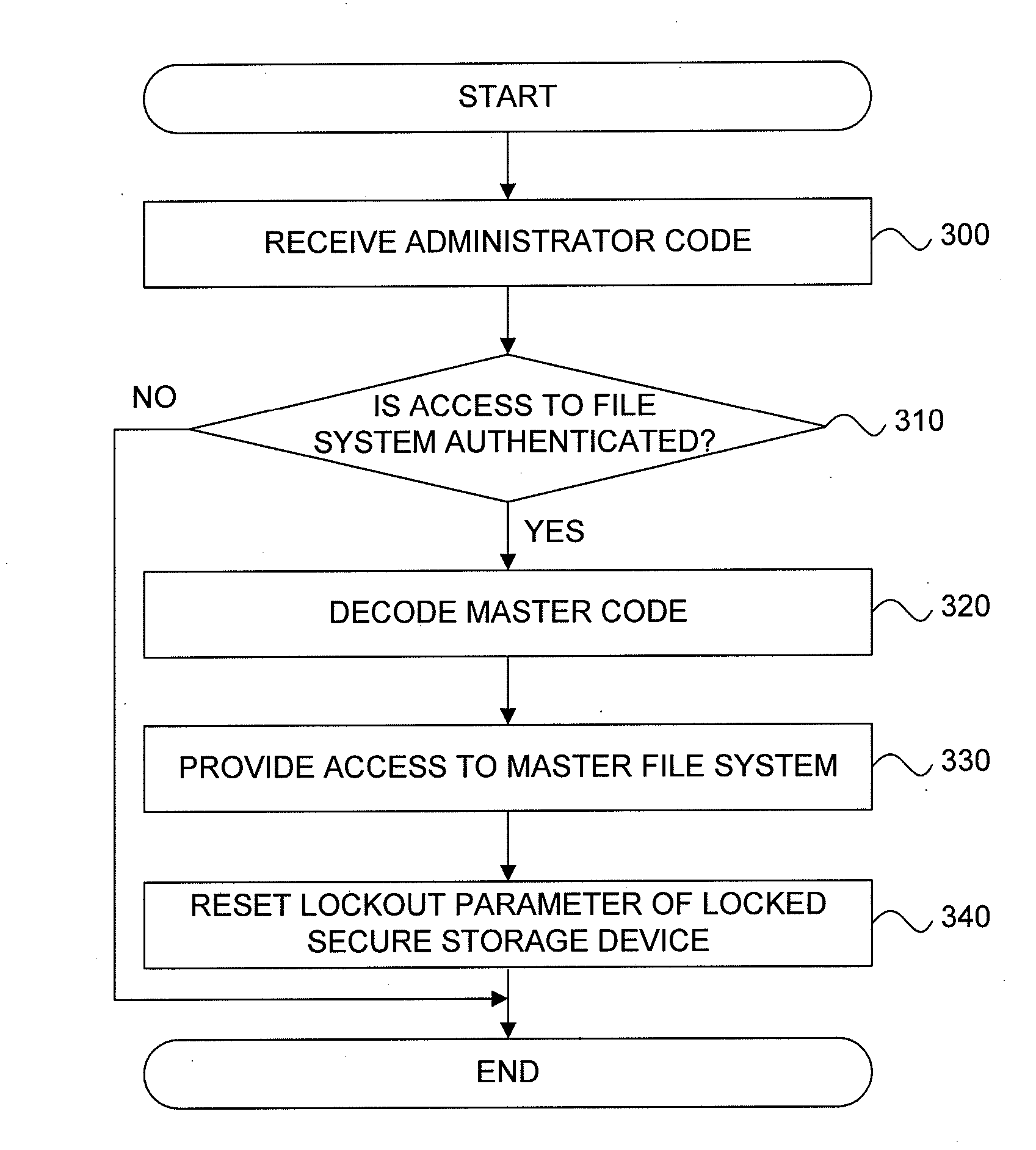
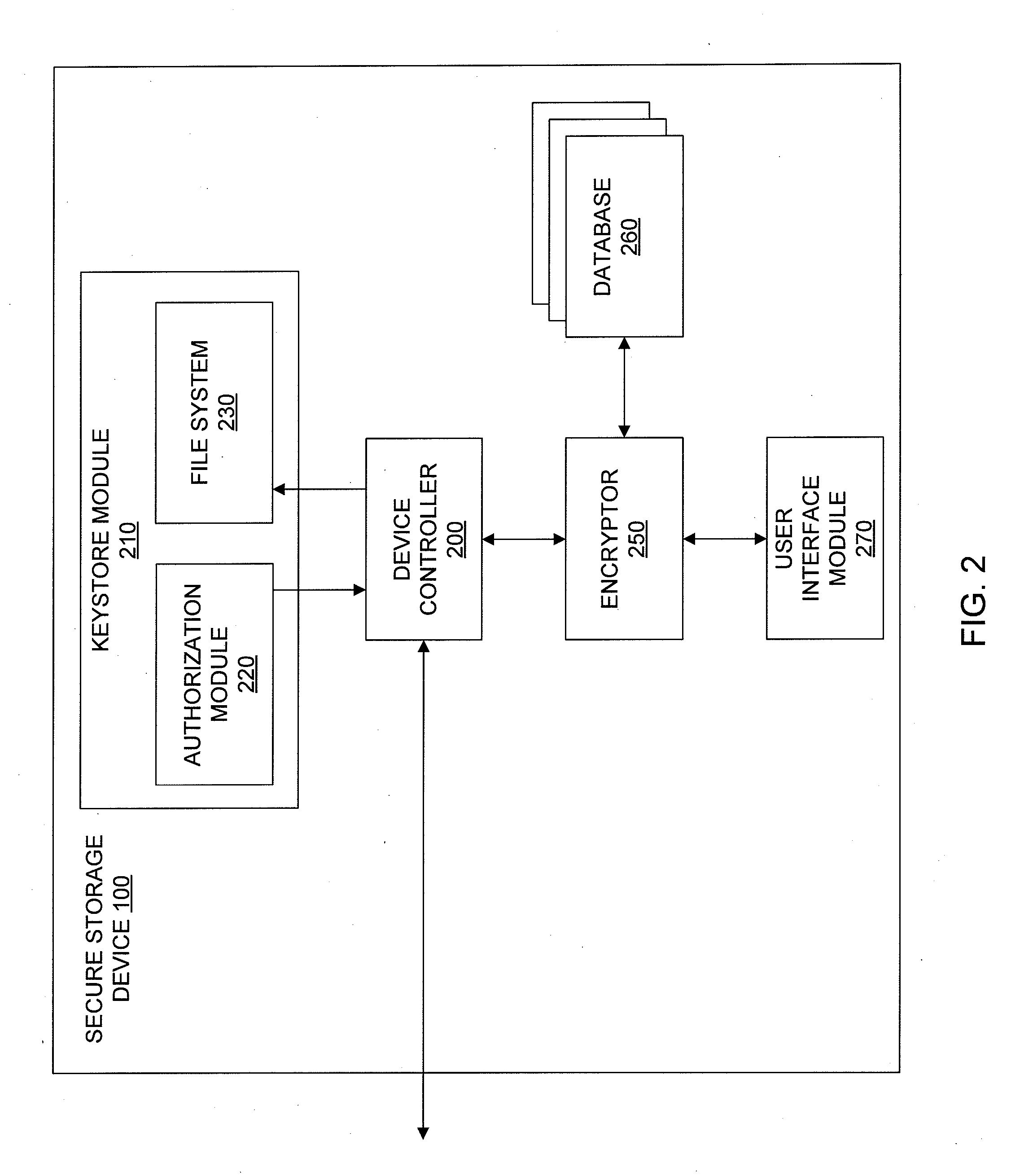
Recovery of Data Access for a Locked Secure Storage Device
A system for recovery of data access of a locked secure storage device can comprise a keystore module and an authorization module. The keystore module may be configured to allow access to a master file system comprising a user encryption key for data stored within the locked secure storage device based on a master code. The authorization module may be configured to receive the administrator code, authenticate the administrator code, decode the master code, and reset a lockout parameter of the locked secure storage device.
Owner:DATA LOCKER INC
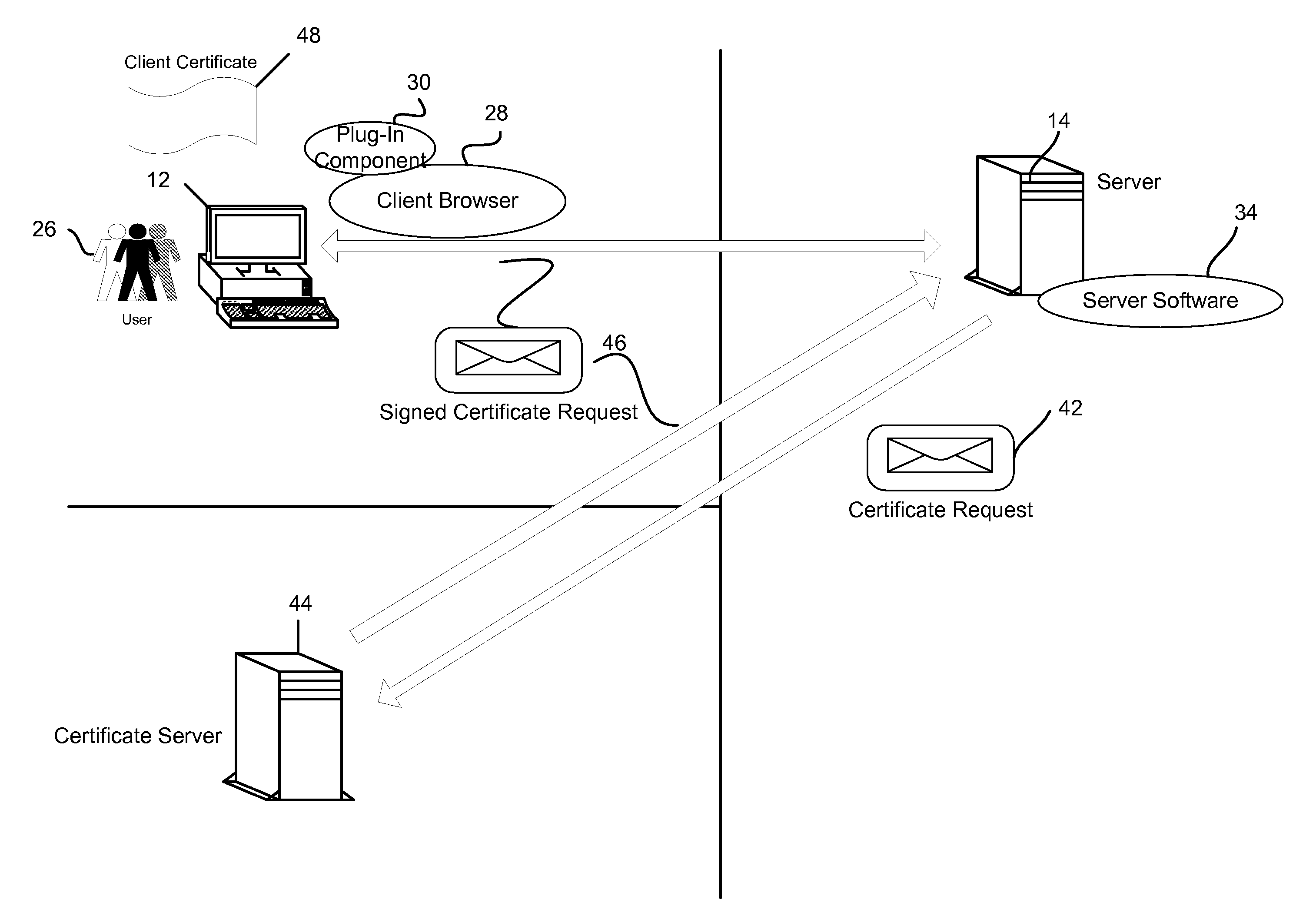
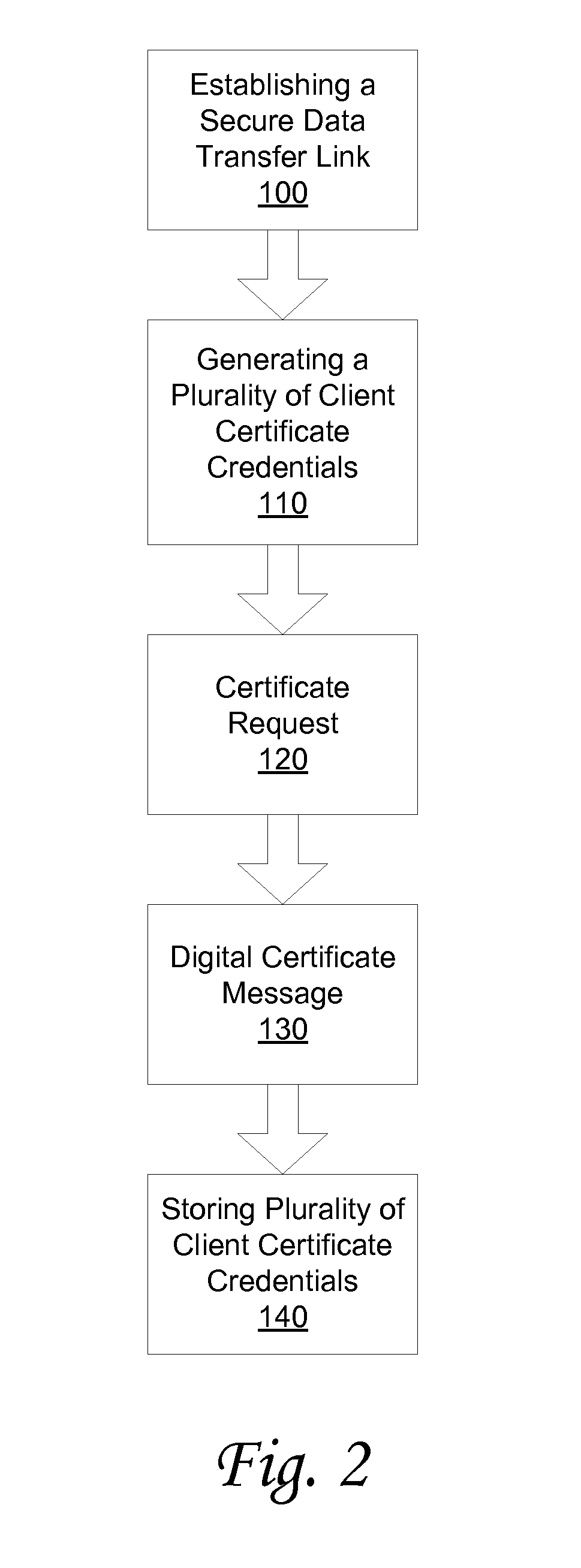
System and method for storing client-side certificate credentials
InactiveUS20090240936A1Digital data authenticationSecuring communicationWeb browserDigital signature
A method and system is provided for storing a plurality of client certificate credentials via a client web browser into one or more keystore file(s). The client web browser is used to establish the secure data transfer link between the client and the server. The client web browser includes a plug-in software component. The plug-in software component is configured to generate the keystore file and a key pair. The method may continue with generating a certificate request on the client. The certificate request generated is then transmitted to a certificate server. The certificate server is configured to digitally sign the certificate request generated. The method continues with the client receiving a signed certificate request. The signed certificate request is received by the client via the client web browser. The method may conclude by storing the plurality of client certificate credentials associated with the signed certificate request in one or more keystore file(s).
Owner:SECUREAUTH CORP
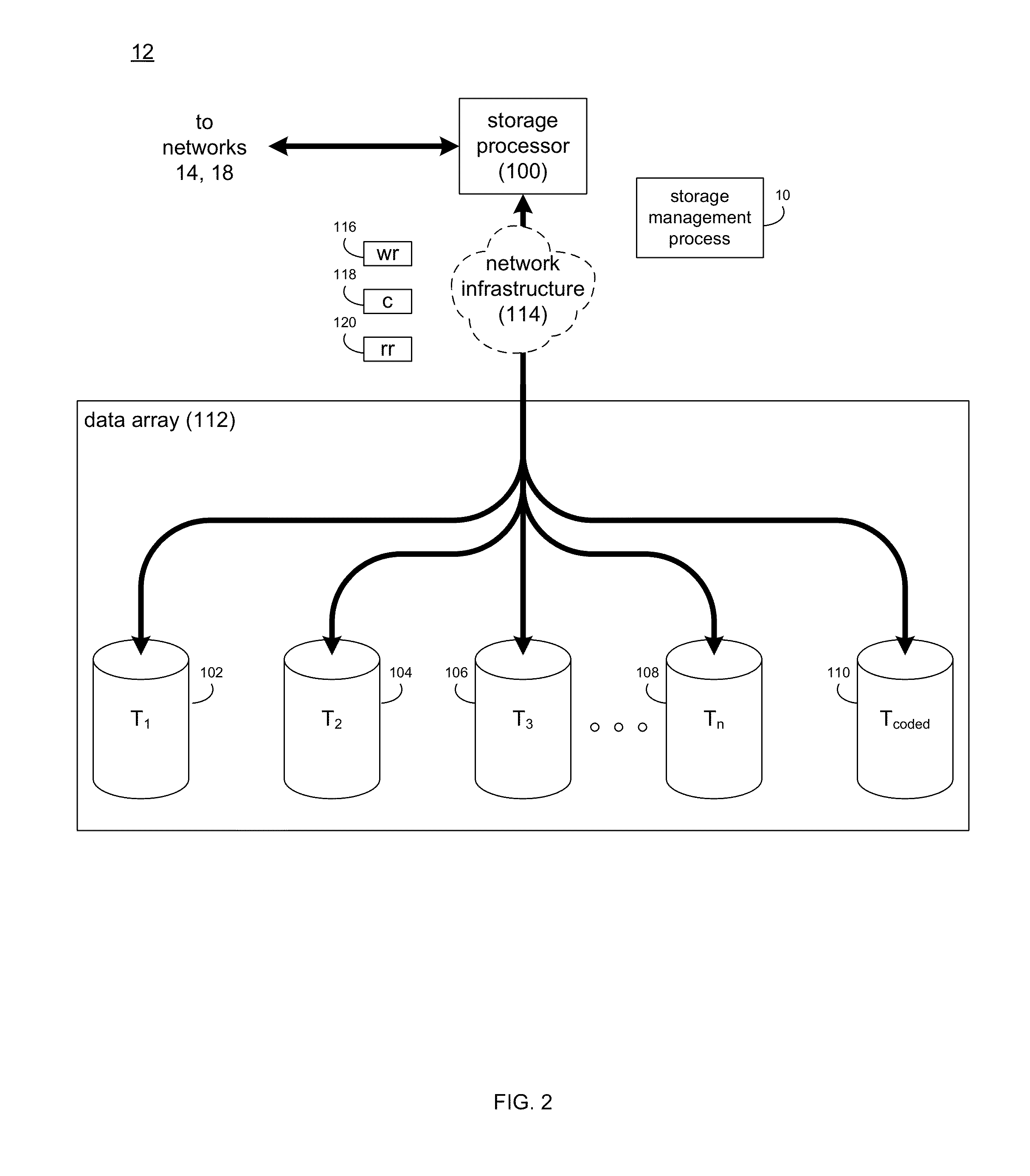
Encryption key recovery in the event of storage management failure
ActiveUS8588425B1Key distribution for secure communicationUser identity/authority verificationData processing systemOccurrence data
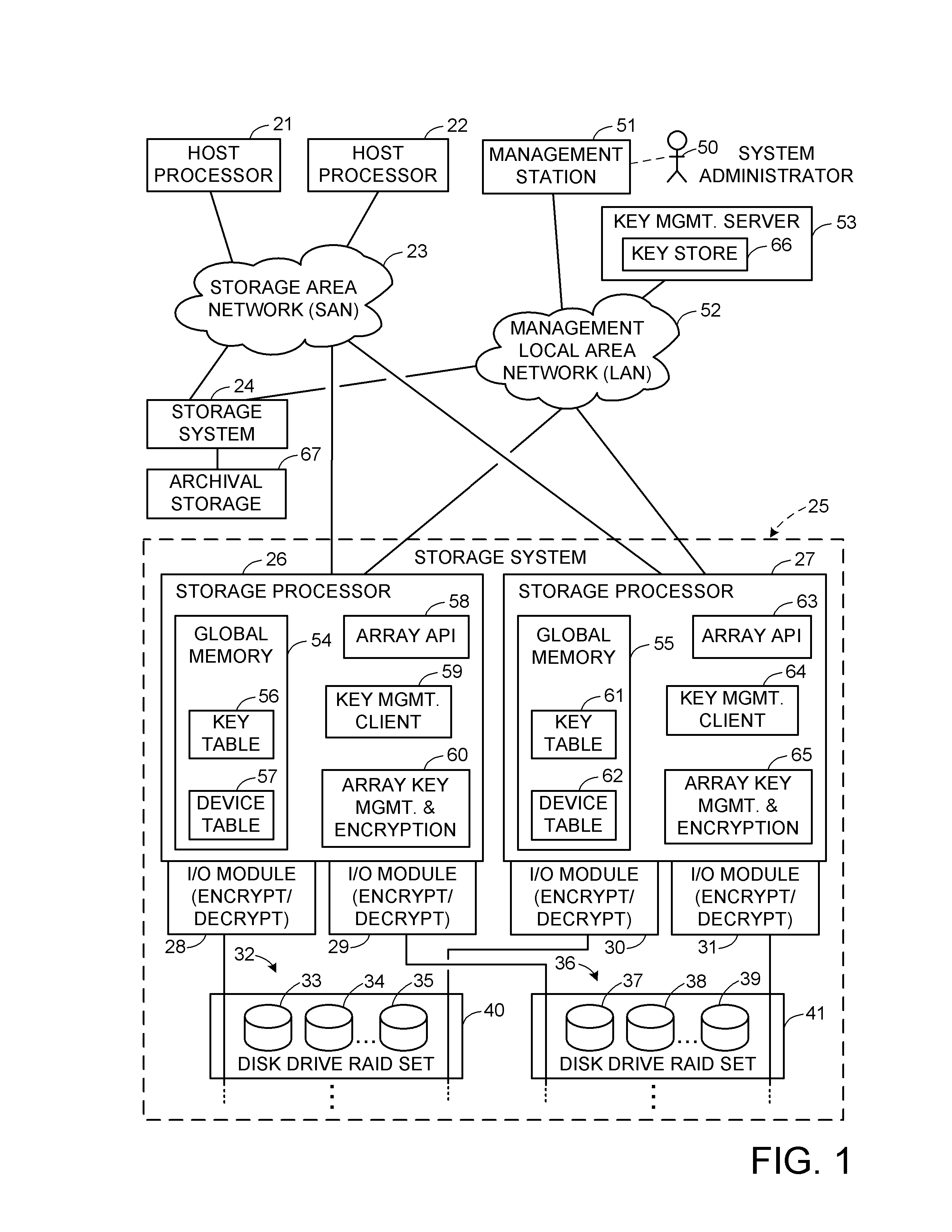
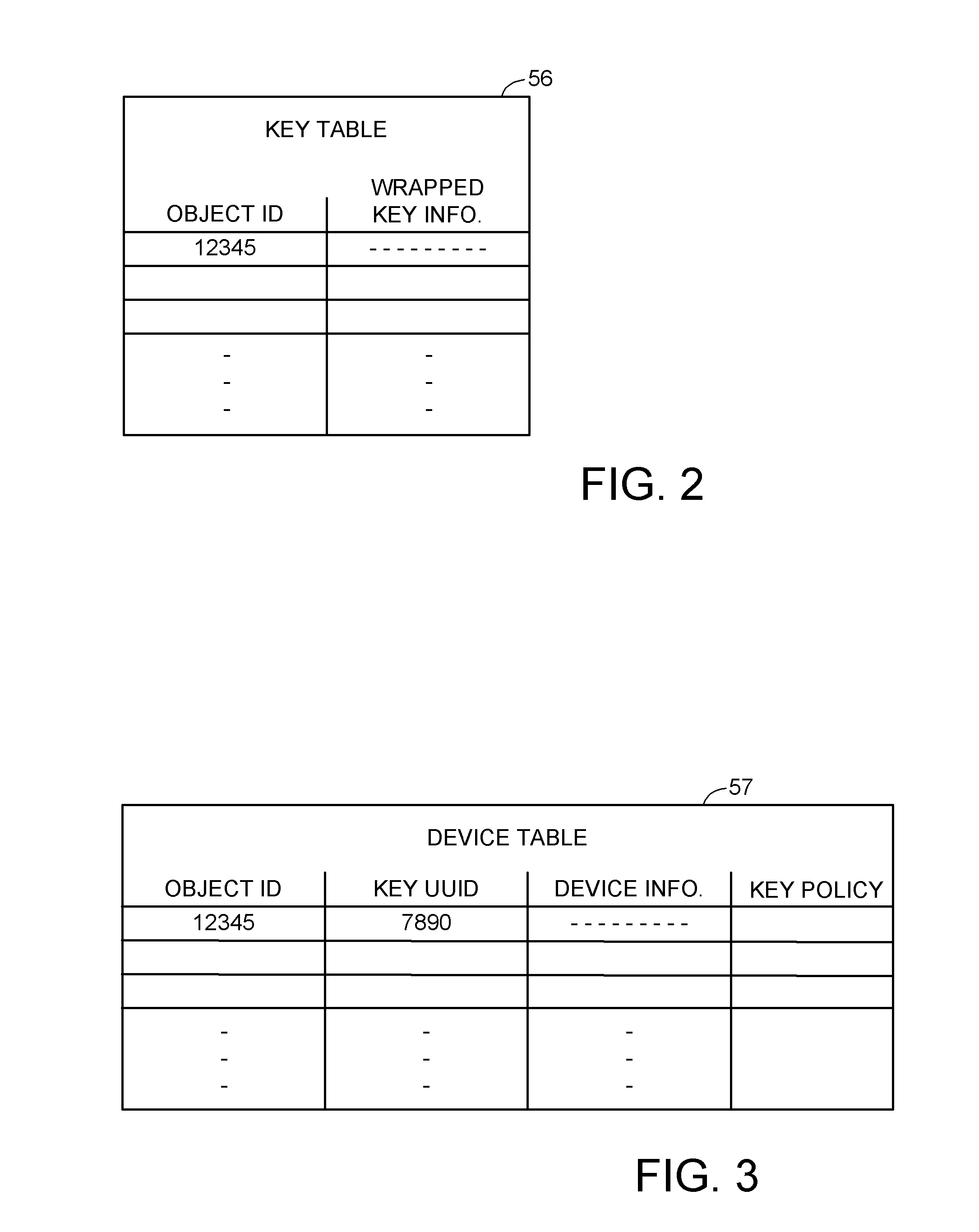
A data processing system stores encrypted data. Object identifiers are assigned to storage objects, and data encryption keys are assigned to the storage objects. When performing an operation upon a storage object, data encryption key failure may occur due to a corrupt or incorrect key. In this case, a copy of the data encryption key is fetched from a key server. It is possible for the association of the object identifiers with the data encryption keys to become lost or confused, so that the key server may fail to provide the correct key for a specified object identifier. Therefore, an absolute key identifier that is unique across the key server namespace also is stored in association with the object identifier in the storage system and in the key store of the key server, and the absolute key identifier is used as a failsafe for recovery of encrypted data.
Owner:EMC IP HLDG CO LLC
Secure unlocking and recovery of a locked wrapped app on a mobile device
InactiveUS20140040622A1Key distribution for secure communicationUnauthorised/fraudulent call preventionPassphraseApplication software
A security-wrapped app that is locked and inaccessible is unlocked and recovered using a secure and user-friendly protocol. Apps that are security wrapped are passphrase protected. The app security keystore on the device becomes locked. The keystore is encrypted with a recovery key which is only in an encrypted form on the device and cannot be decrypted or otherwise accessed by the user. As such, the user cannot unlock the keystore on the device and therefore is not able to unlock the app. The app can be unlocked using a recovery mechanism that is highly secure in all communications between the mobile device and the service provider server. At the same time the recovery mechanism is easy for the end user to carry out.
Owner:BLUE CEDAR NETWORKS INC
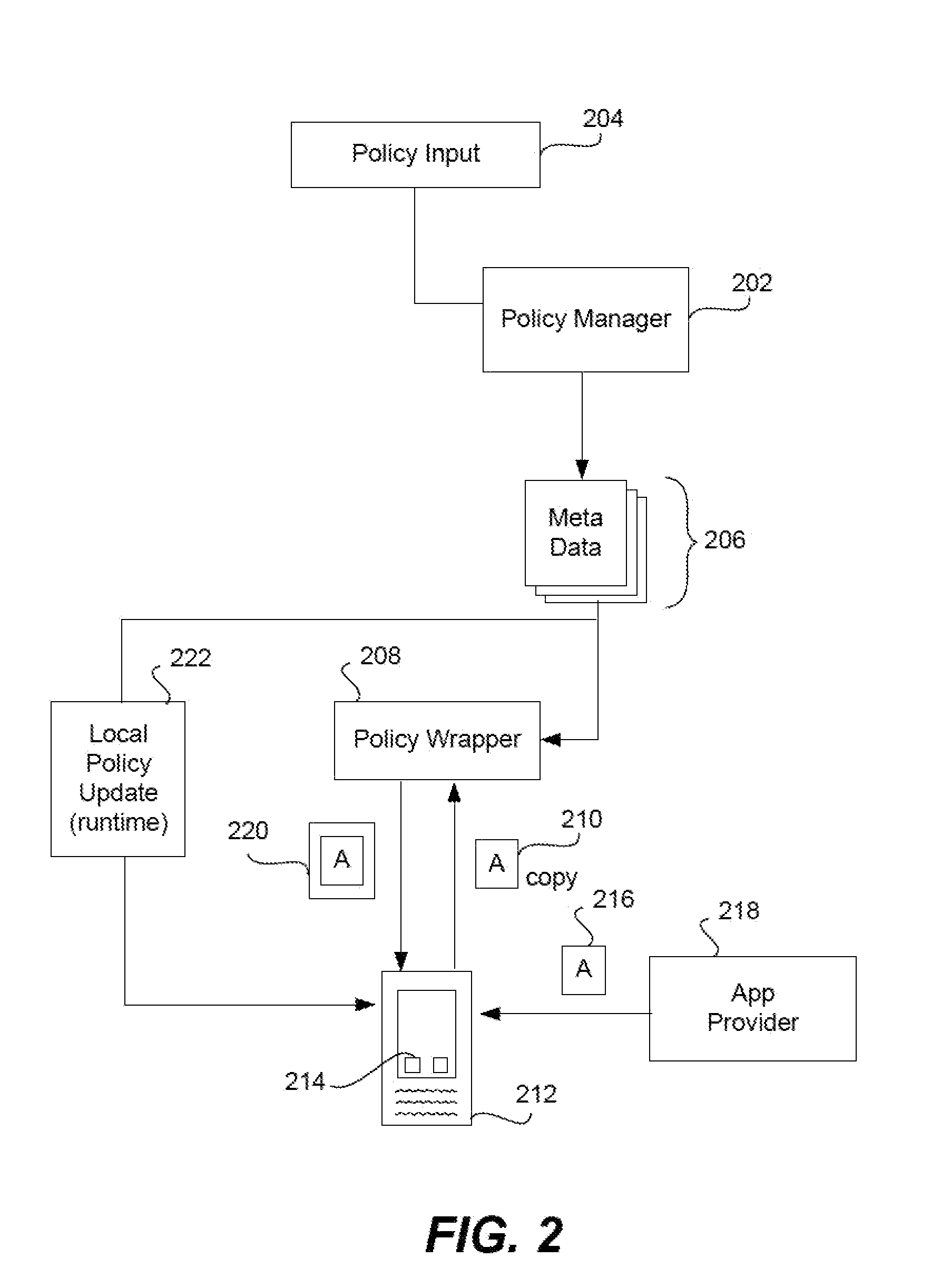
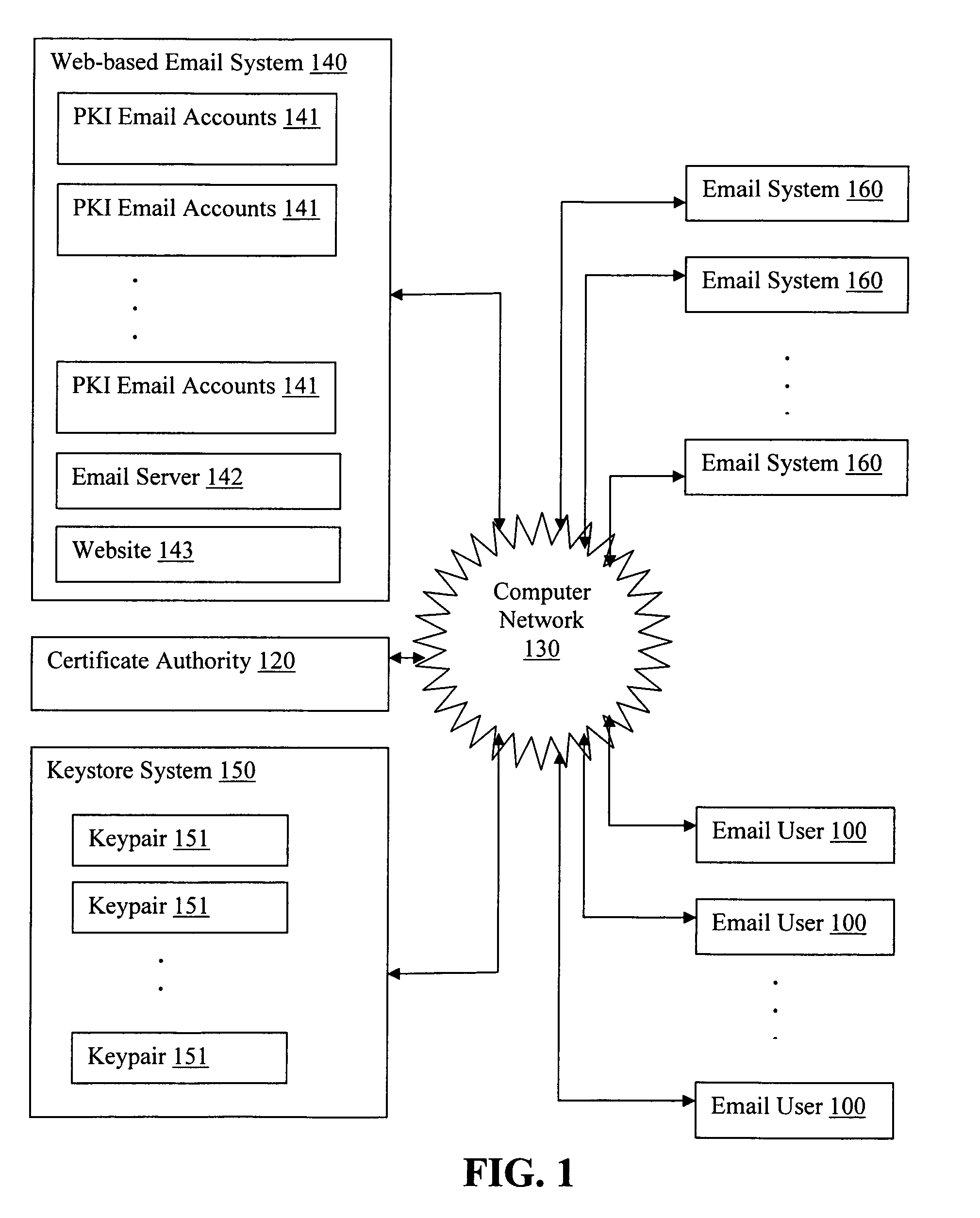
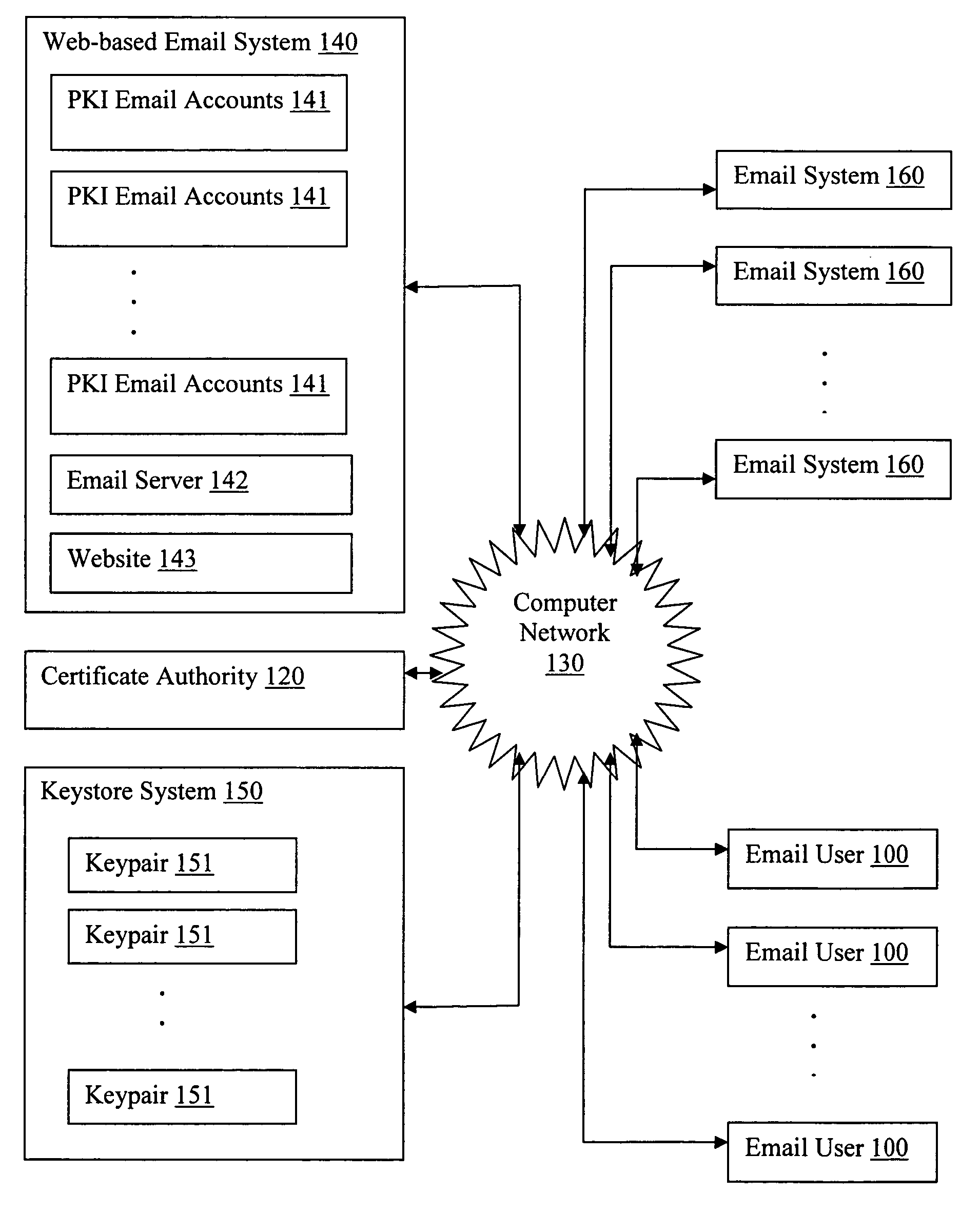
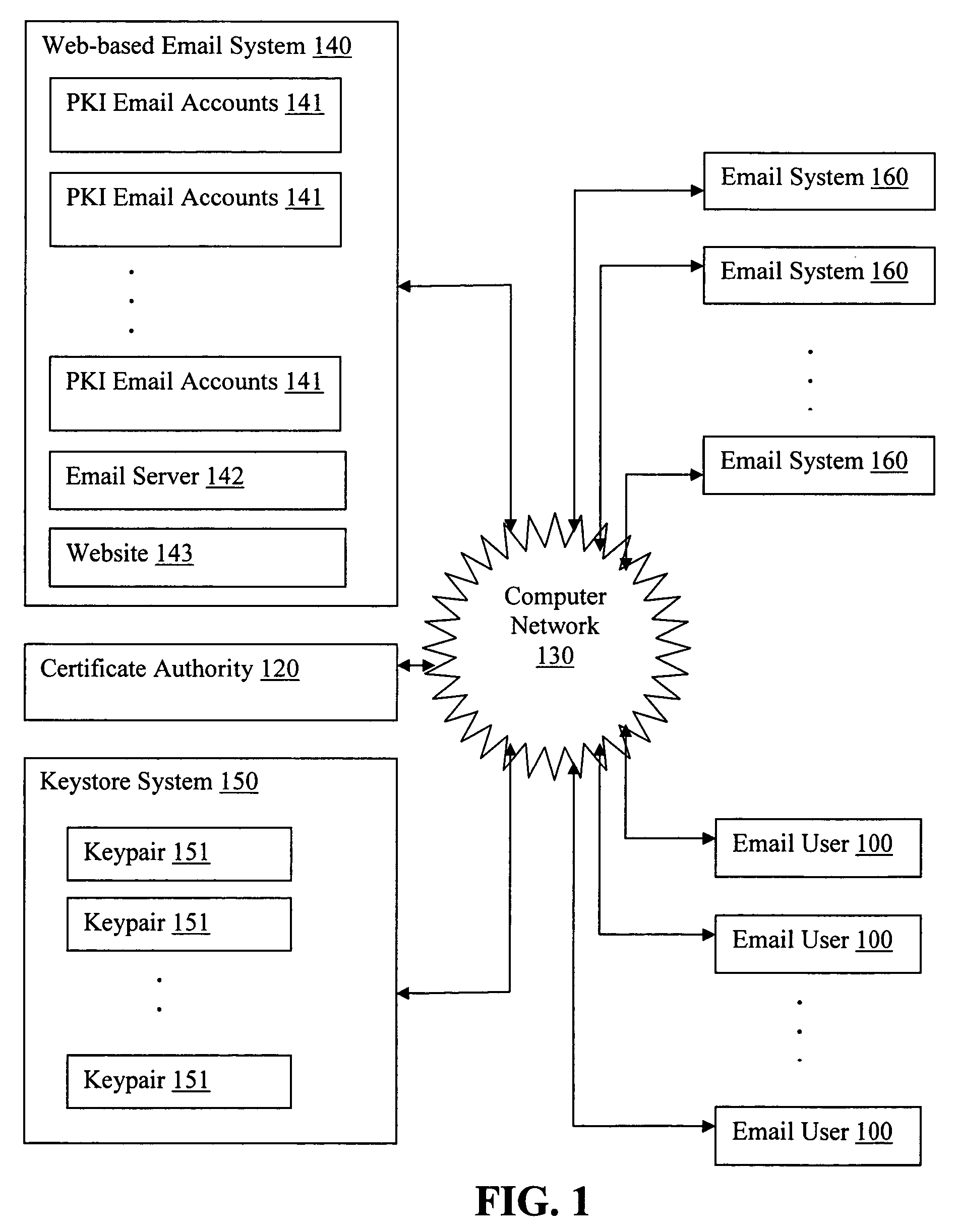
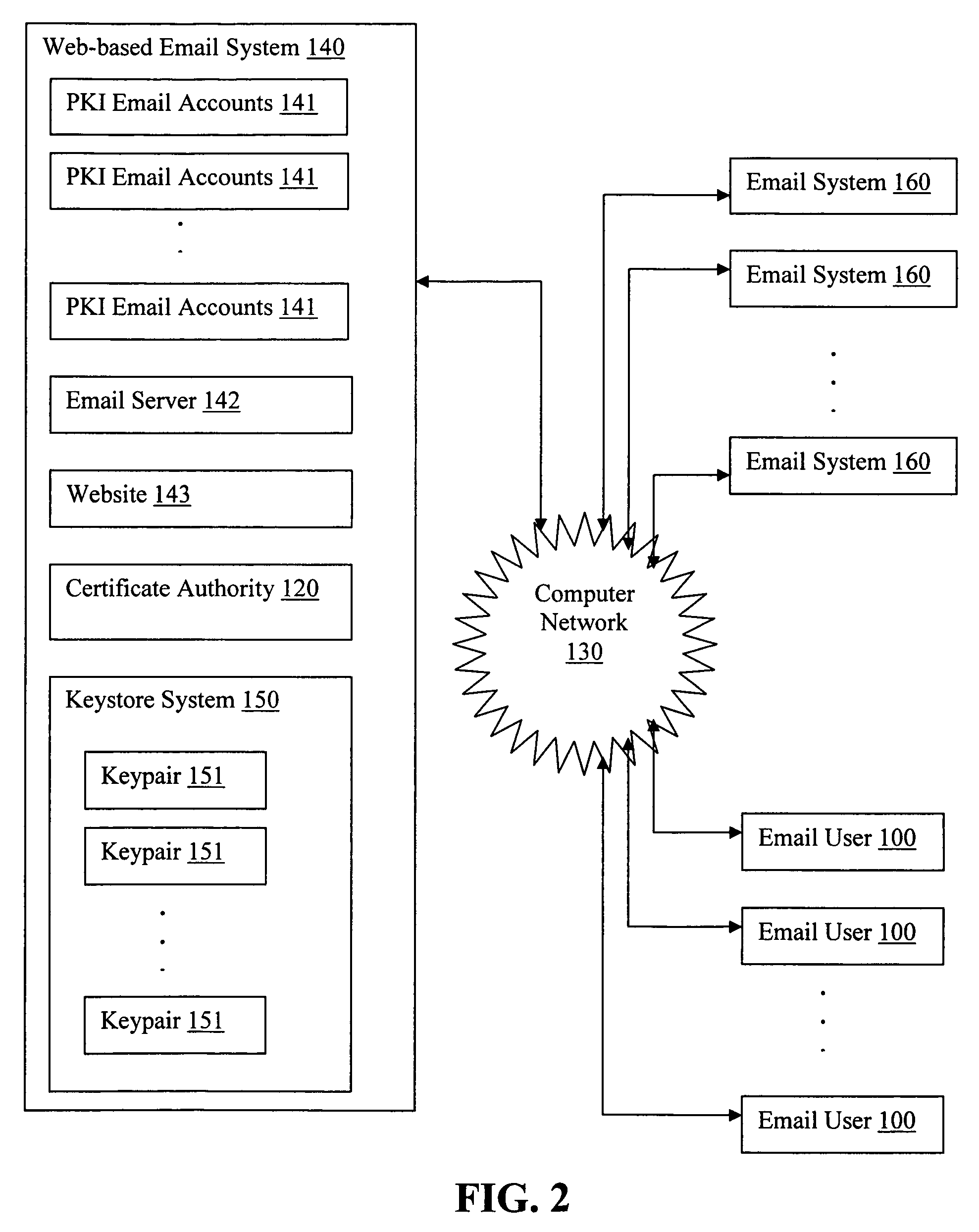
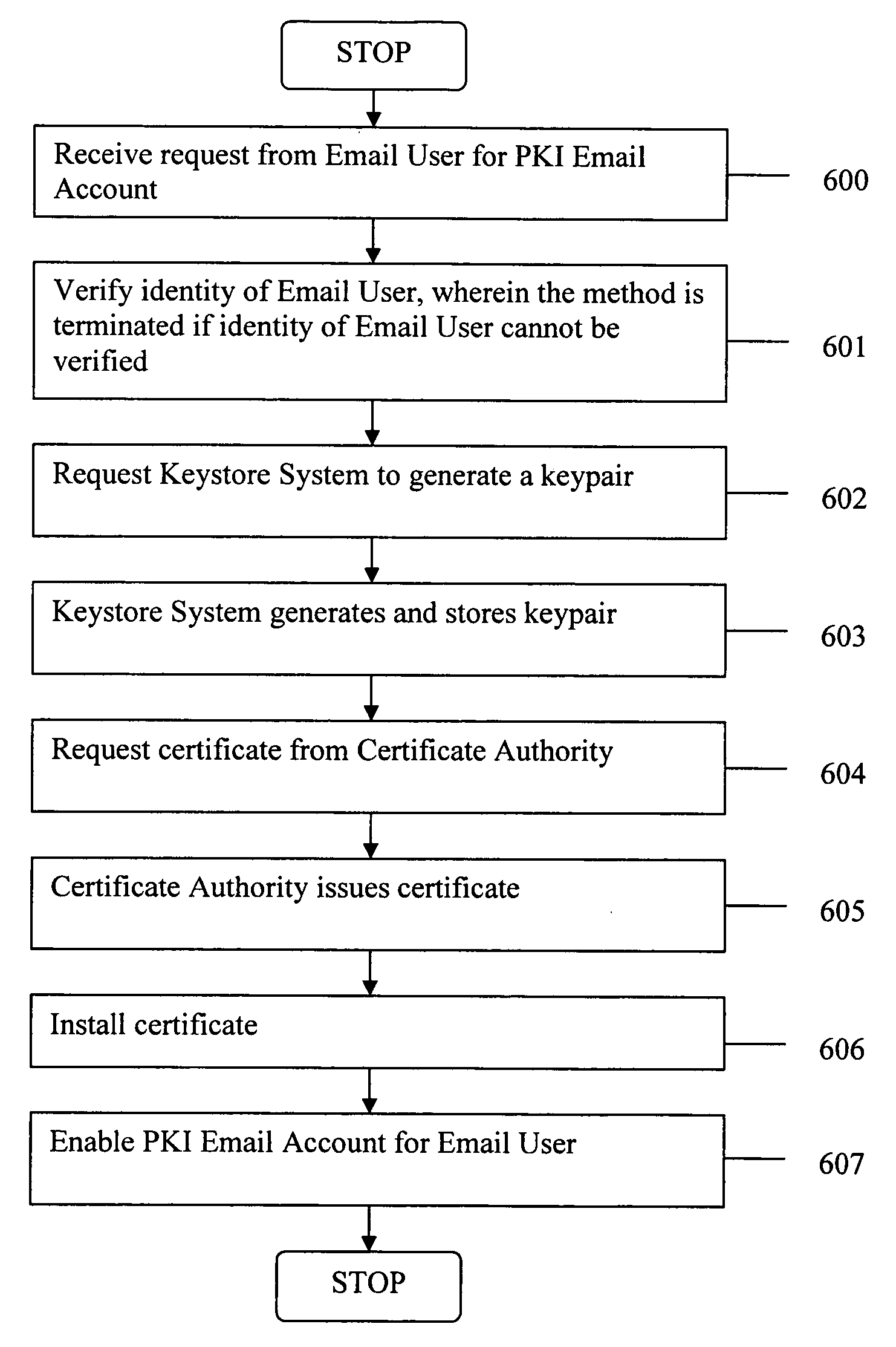
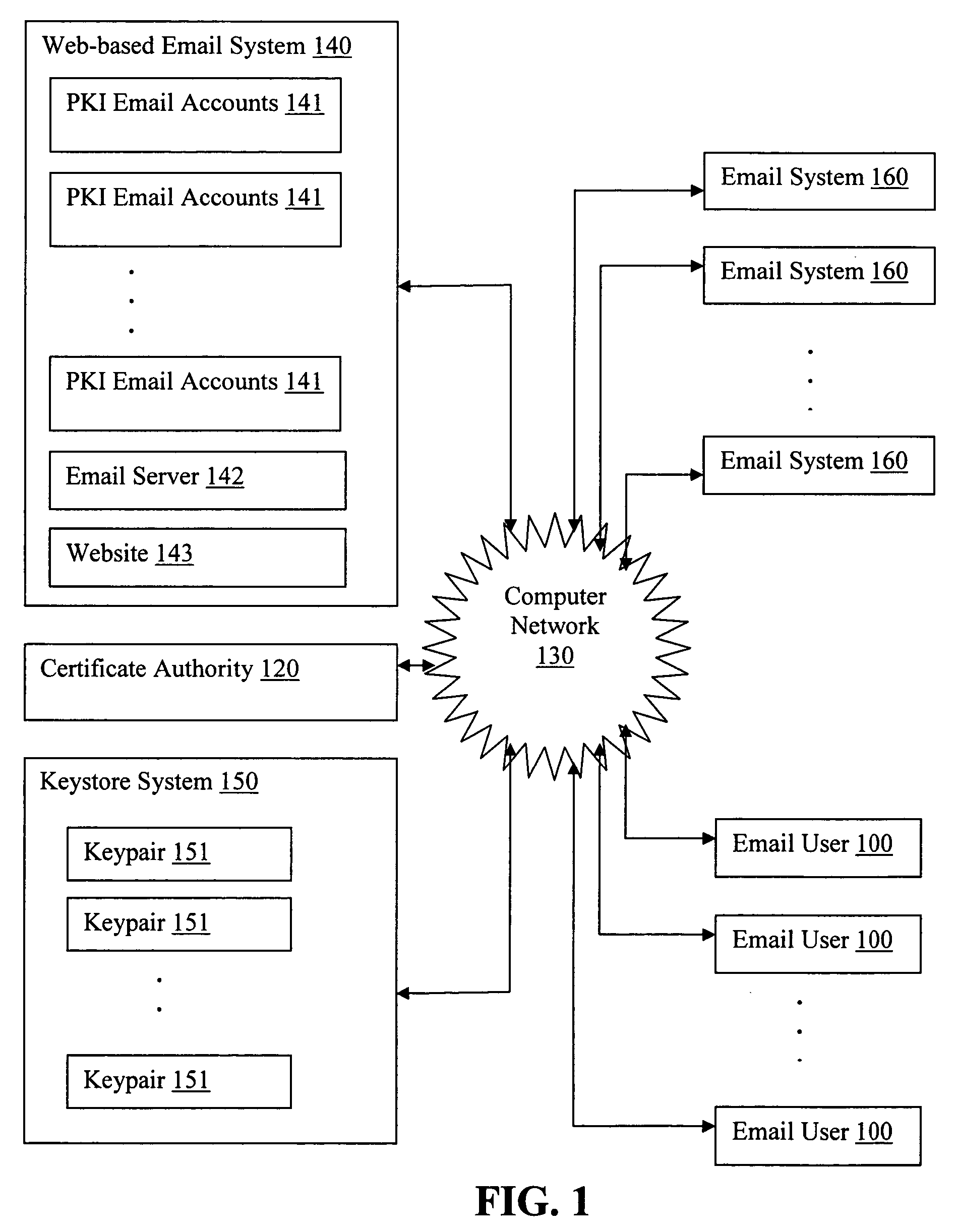
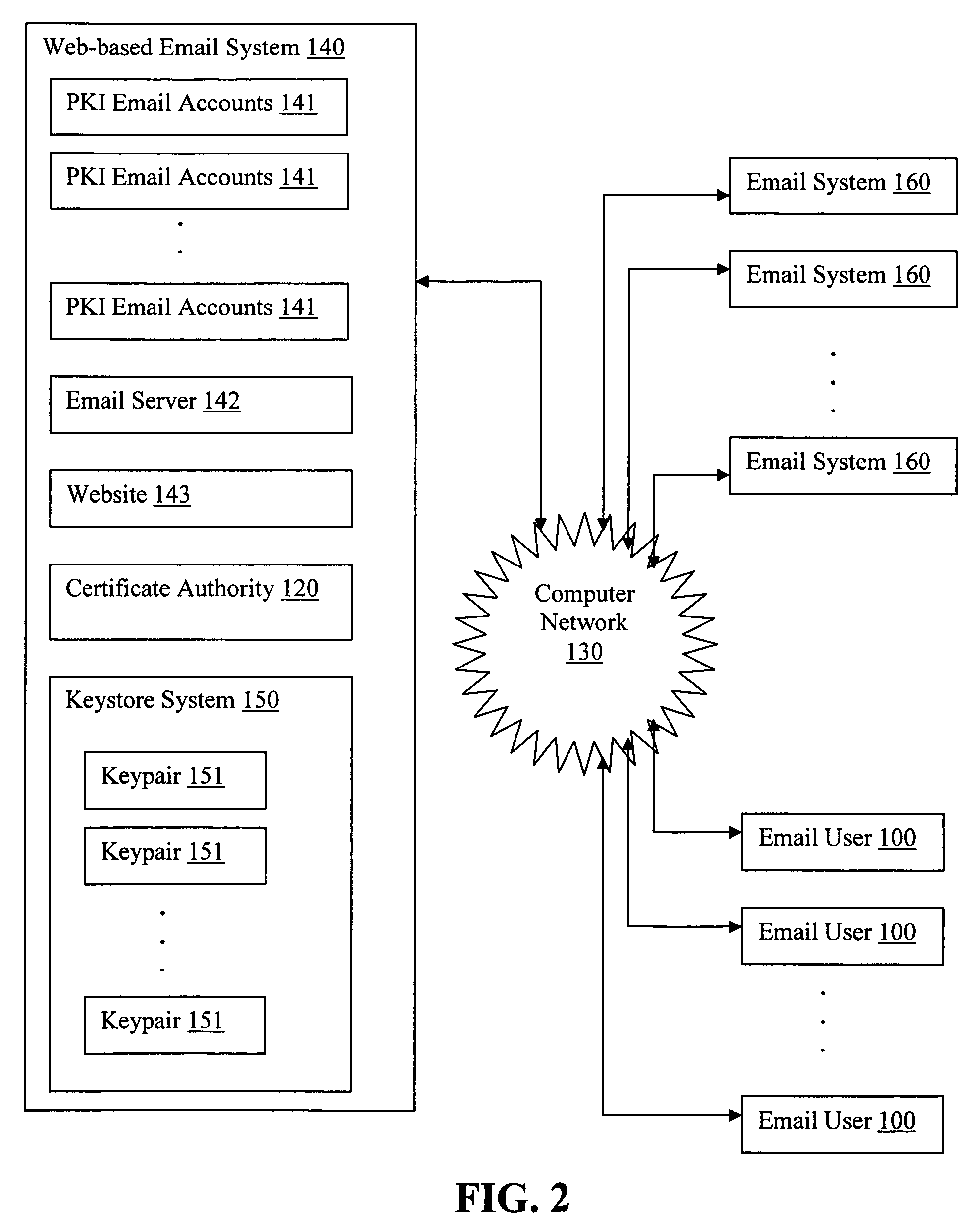
Generating PKI email accounts on a web-based email system
ActiveUS20070022162A1Simple processImprove securityMultiple digital computer combinationsData switching networksInternet privacyDigital signature
The present invention provides systems and methods for allowing an Email User to create a Public Key Infrastructure (PKI) Email Account and thereafter to digitally sign, send, verify and receive PKI encrypted emails over a computer network, such as the Internet. The systems and methods preferably include a Web-based Email System and a Certificate Authority that coordinate their actions to make the process of creating, maintaining and using the PKI Account as easy as possible for the Email User. In a preferred embodiment, a Keystore System may also be used to enhance the management and use of digital keypairs.
Owner:GO DADDY OPERATING
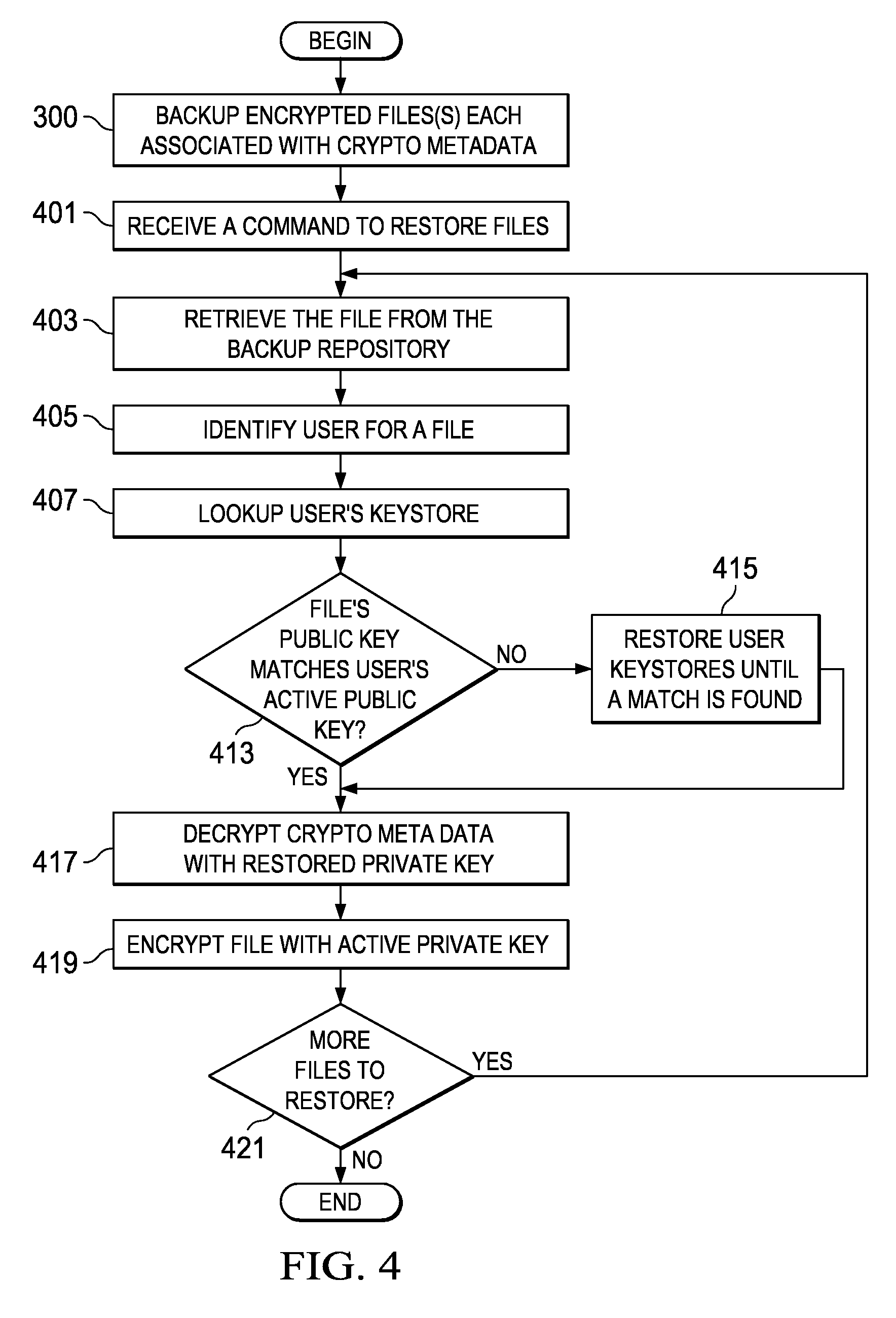
Method and apparatus for restoring encrypted files to an encrypting file system based on deprecated keystores
InactiveUS20090110198A1Error detection/correctionVolume/mass flow measurementData processing systemEncrypting file system
The present invention provides a computer implemented method, data processing system, and computer program product to restore an encrypted file. A computer receives a command to restore an encrypted file, wherein the encrypted file was previously backed up. The computer identifies a user associated with the encrypted file. The computer looks up a first keystore of the user based on the user, the first keystore having an active private key. The computer determines that a public key of the encrypted file fails to match an active public key of the first keystore. The computer restores a second keystore of the user to form a restored private key, wherein the second keystore was previously backed up. The computer responsive to a determination that the public key of the encrypted file fails to match the active public key of the first keystore, decrypts the encrypted file encryption key based on the restored private key to form a file encryption key. The computer encrypts the file encryption key with the active private key of the first keystore.
Owner:IBM CORP
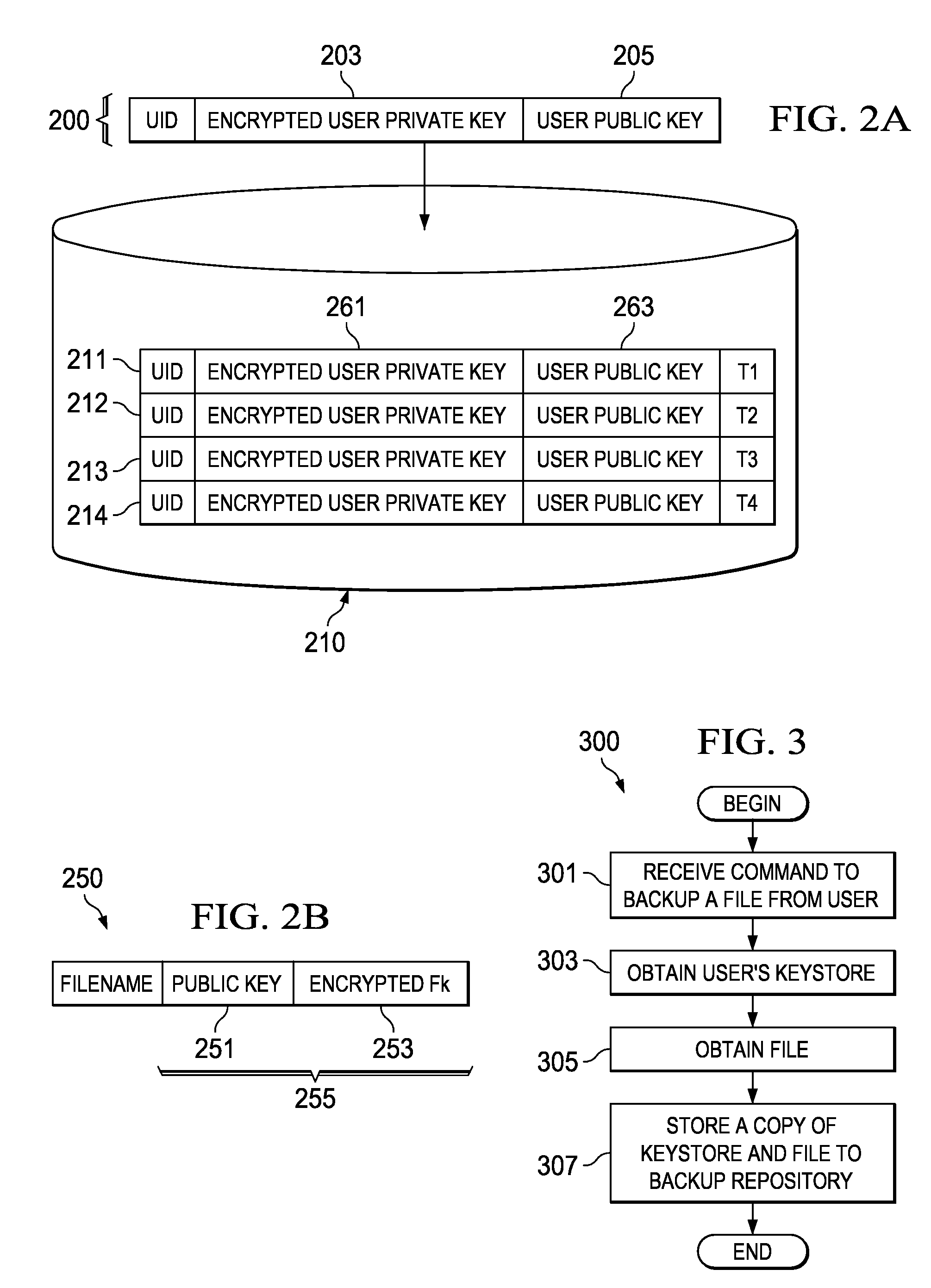
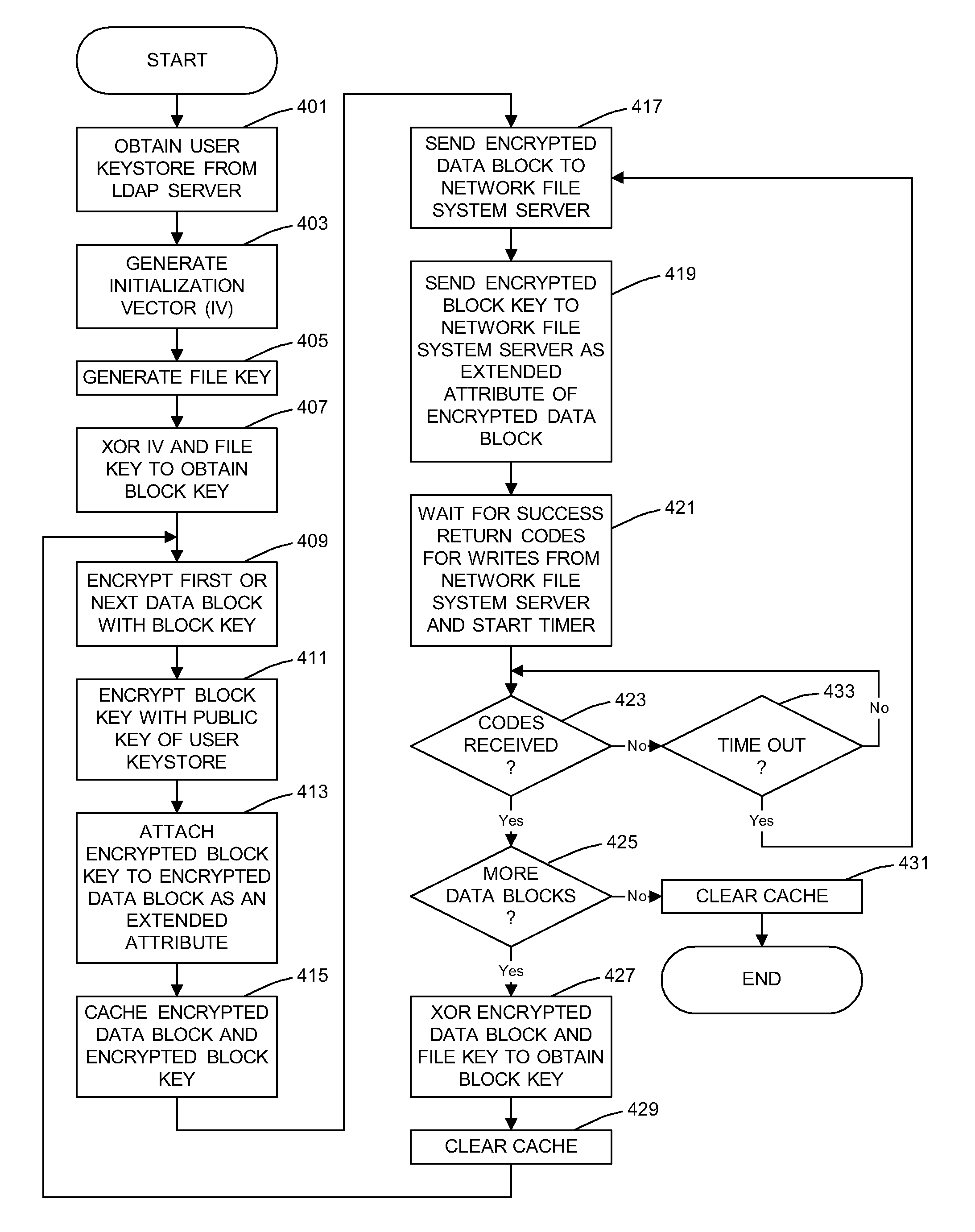
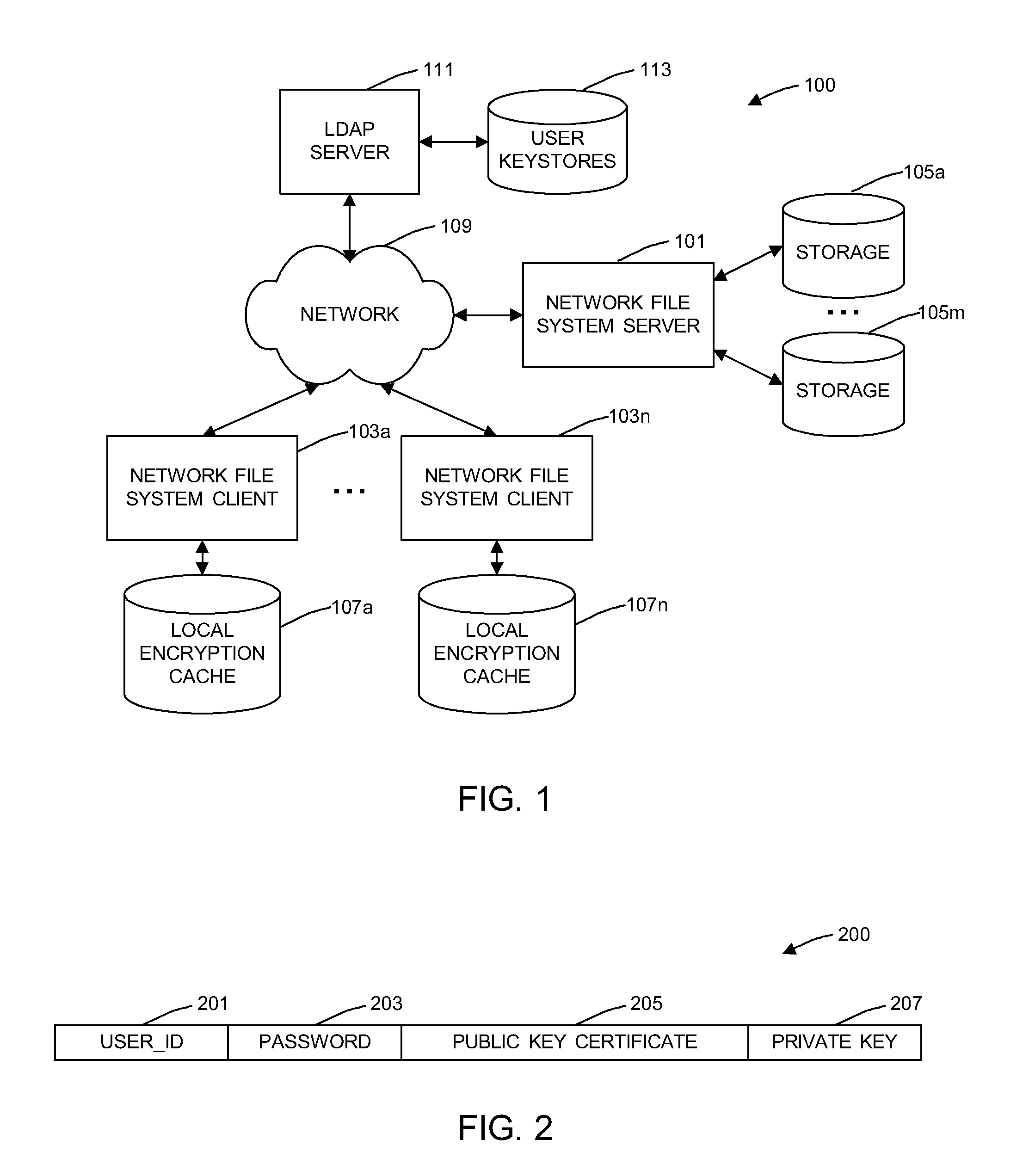
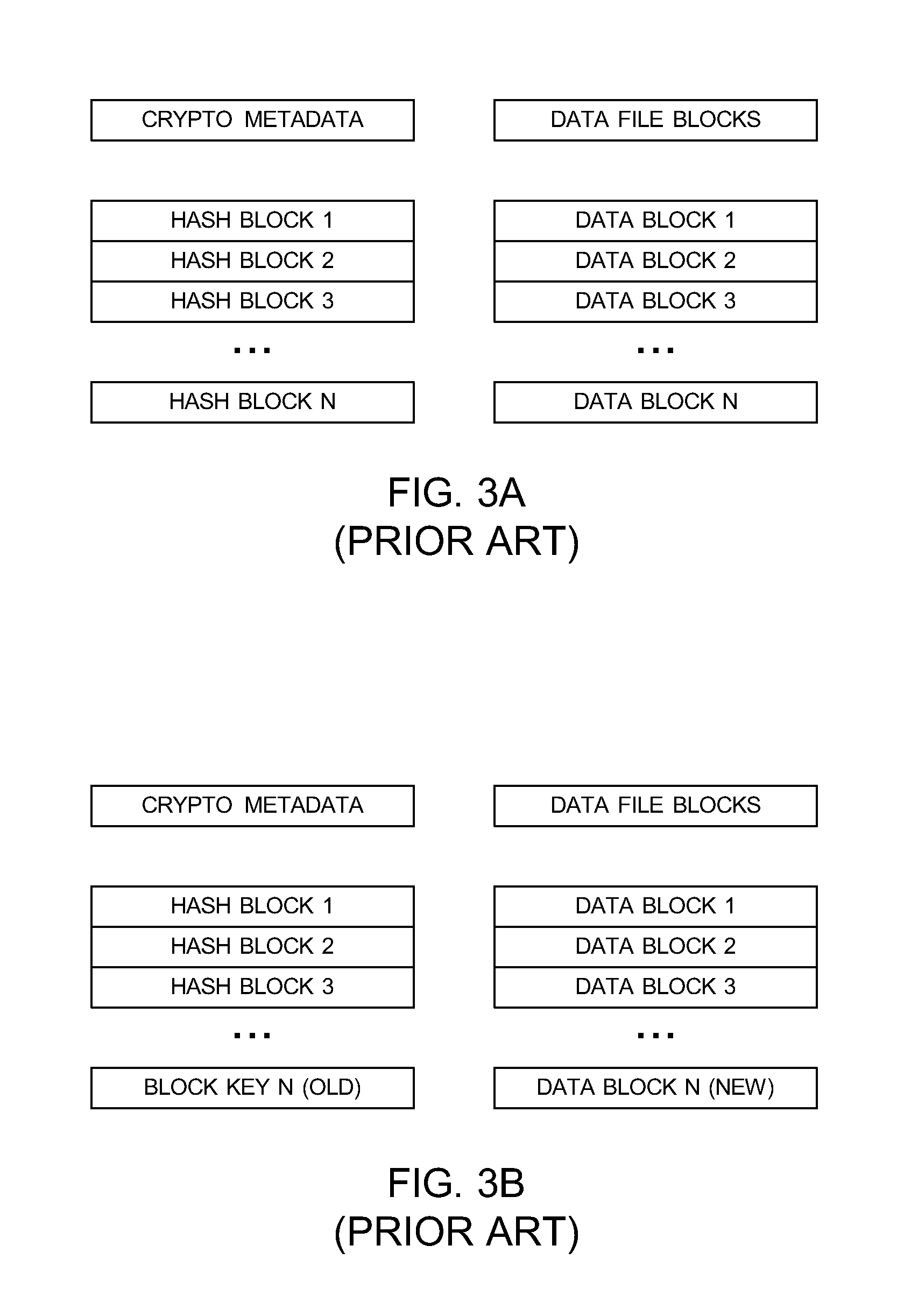
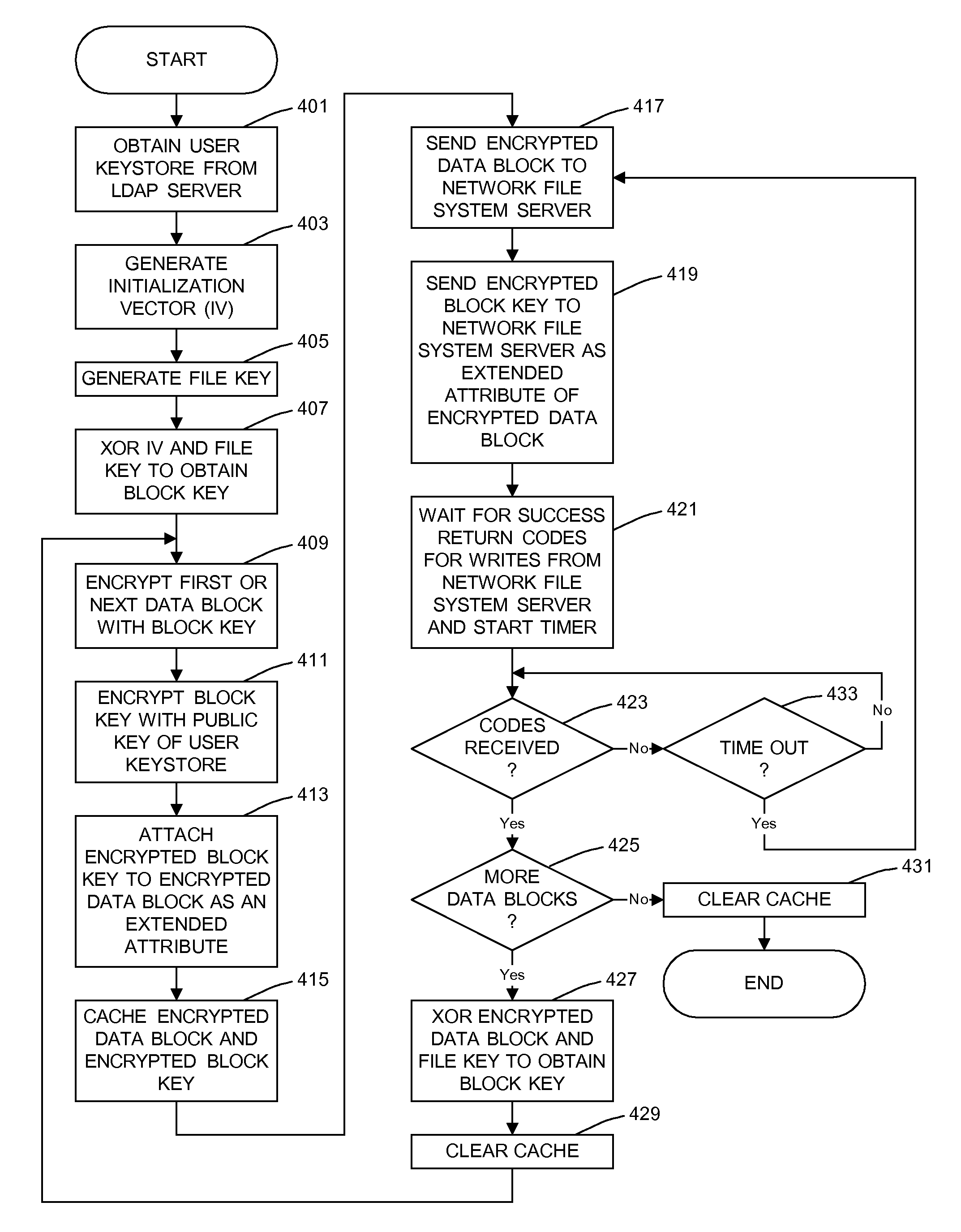
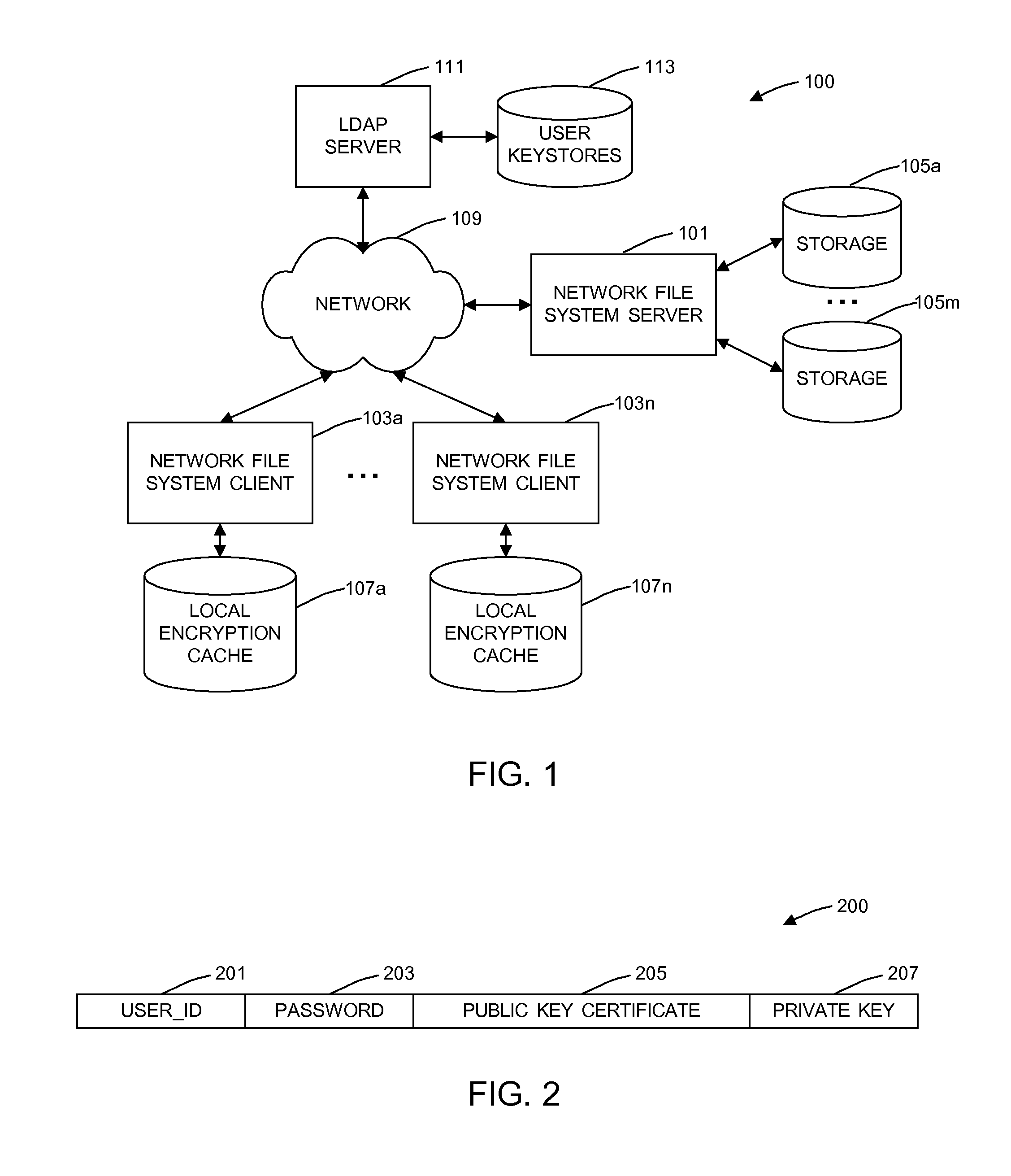
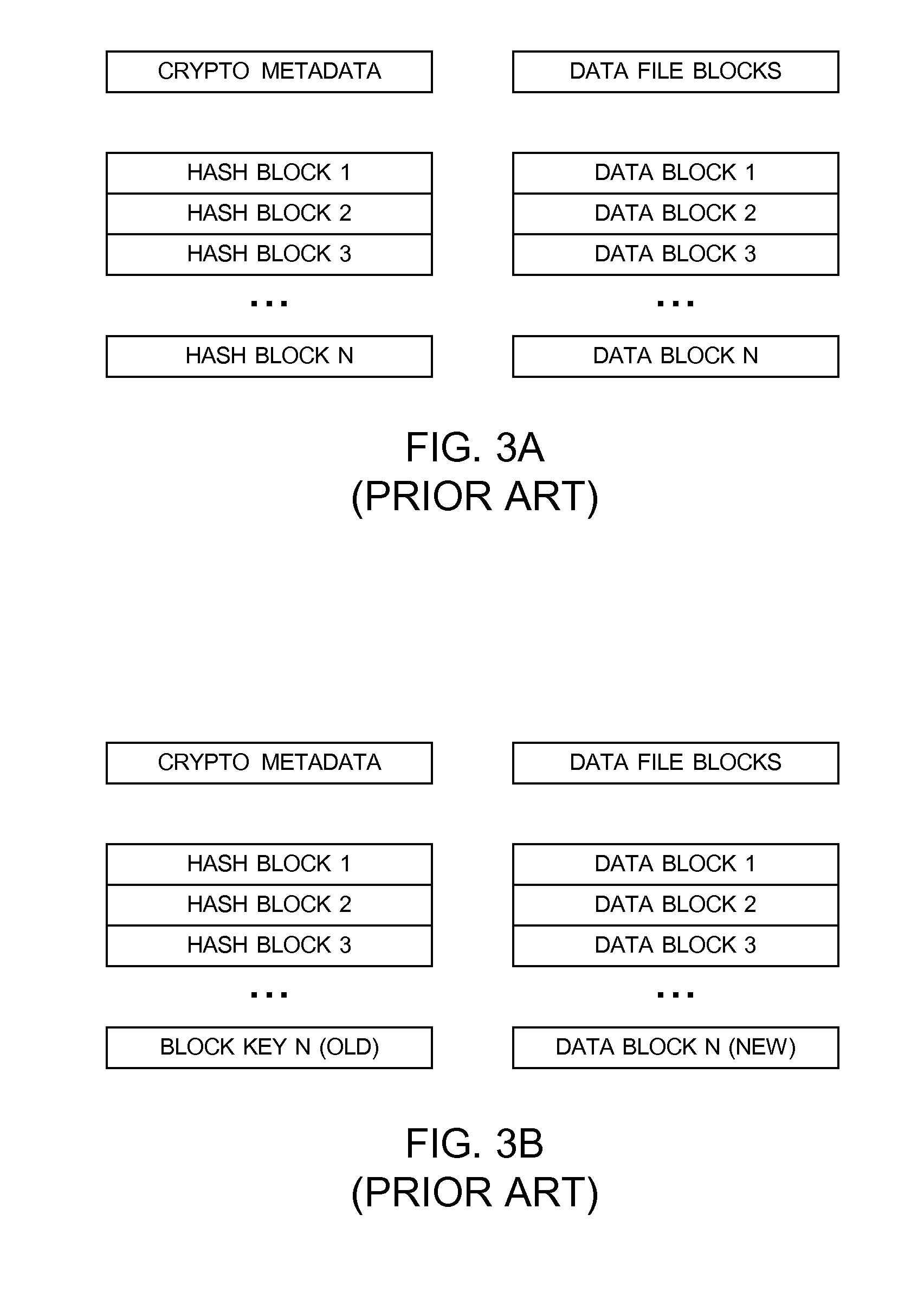
General Purpose Distributed Encrypted File System
A general purpose distributed encrypted file system generates a block key on a client machine. The client machine encrypts a file using the block key. Then, the client encrypts the block key on the first client machine with a public key of a keystore associated with a user and associates the encrypted block key with the encrypted data block as crypto metadata. The client machine caches the encrypted data block and the crypto metadata and sends the encrypted data block and the crypto metadata to a network file system server. When the client machine receives a return code from the network file system server indicating successful writes of the encrypted data block and the crypto metadata, the client machine clears the cached encrypted data block and the crypto metadata.
Owner:IBM CORP
System, method and device for dynamically encrypting data based on key library
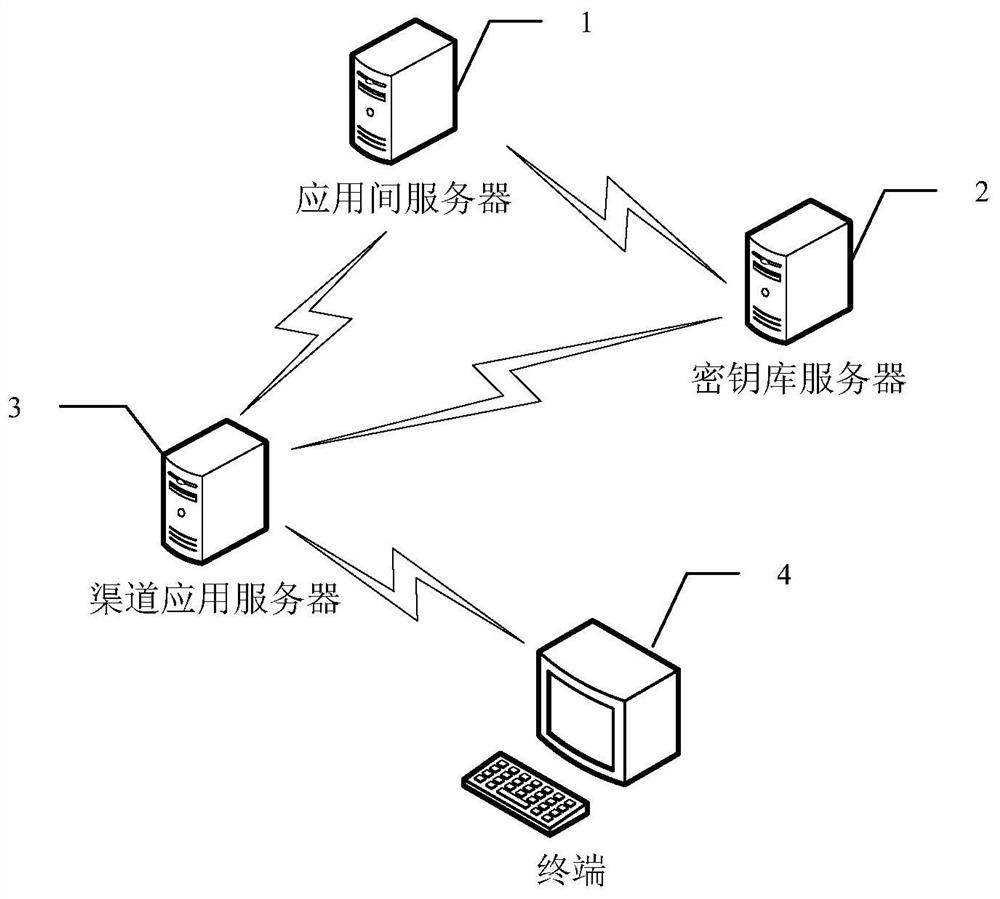
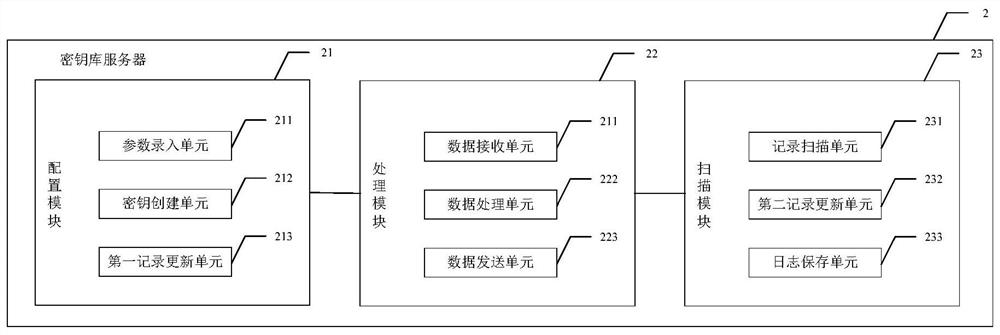
ActiveCN112929172AImprove securityReduce operation and maintenance costsKey distribution for secure communicationMultiple keys/algorithms usageApplication serverEngineering
The invention discloses a system, method and device for dynamically encrypting data based on a key library, which can be used in the field of information security, and the system comprises an inter-application server, a key library server, a plurality of channel application servers and terminals interacting with respective channel application servers, wherein the key library server is used for configuring a data encryption rule for data interacting among different channel application servers and data interacting in the same channel application server, and generating a corresponding encryption program and a key file according to the data encryption rule; the inter-application server is used for downloading a corresponding encryption program and the key file from the key library server according to a data processing request of each channel application server, and encrypting or decrypting application data; and the channel application servers are used for downloading the corresponding encryption program and the key file from the key library server according to the data processing request of the terminal, and encrypting or decrypting the application data. According to the invention, the system safety can be improved.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
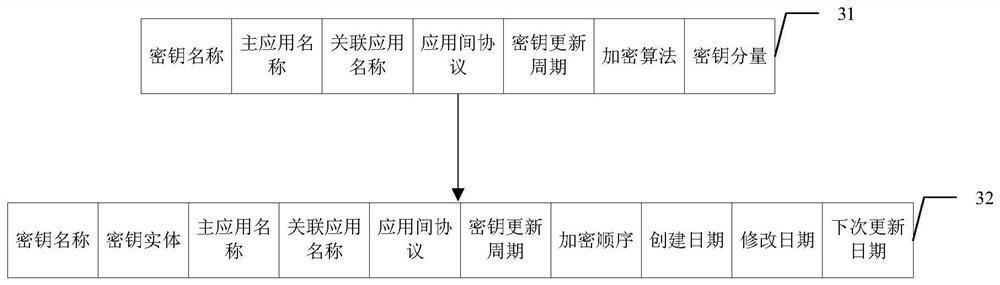
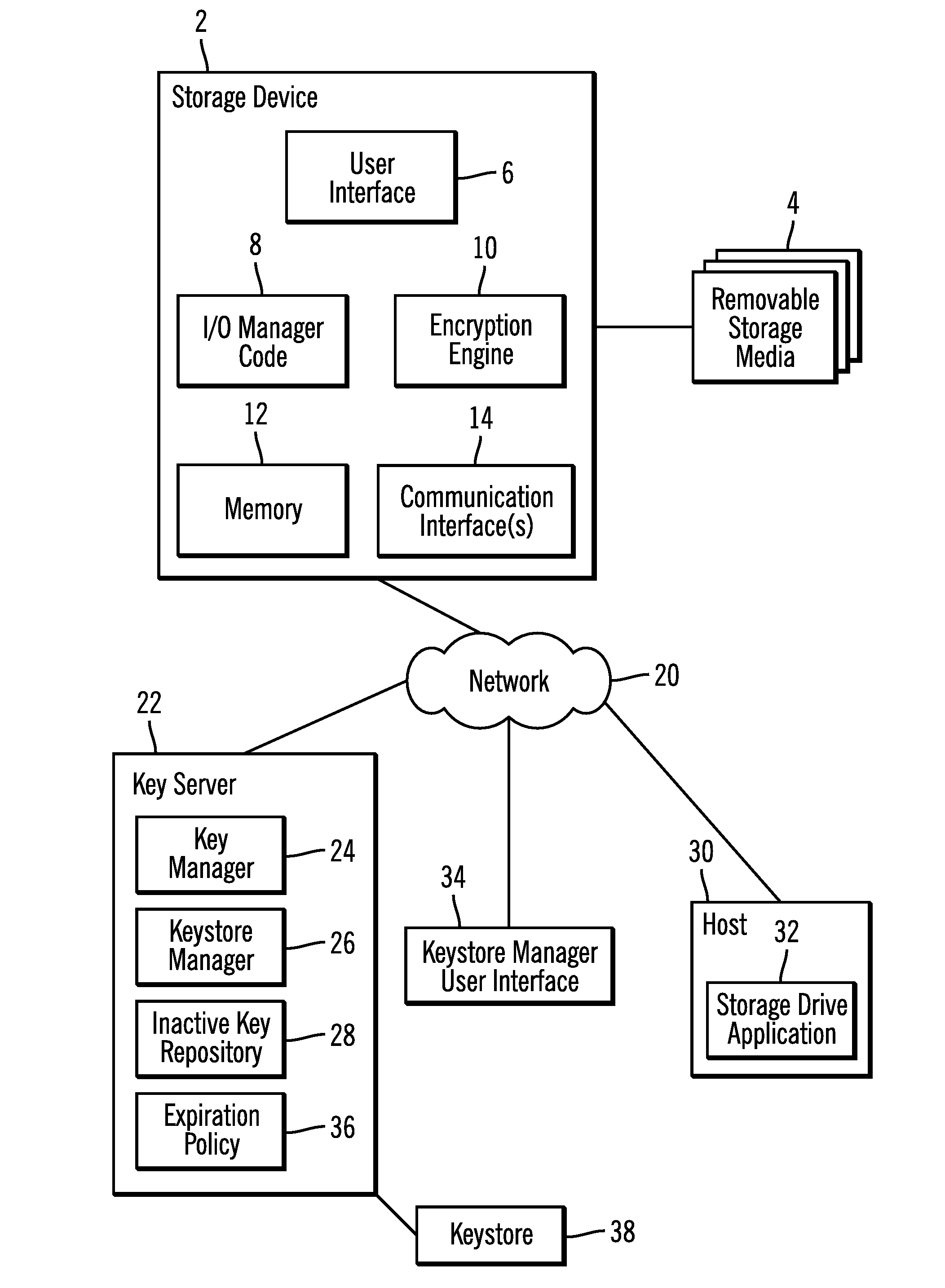
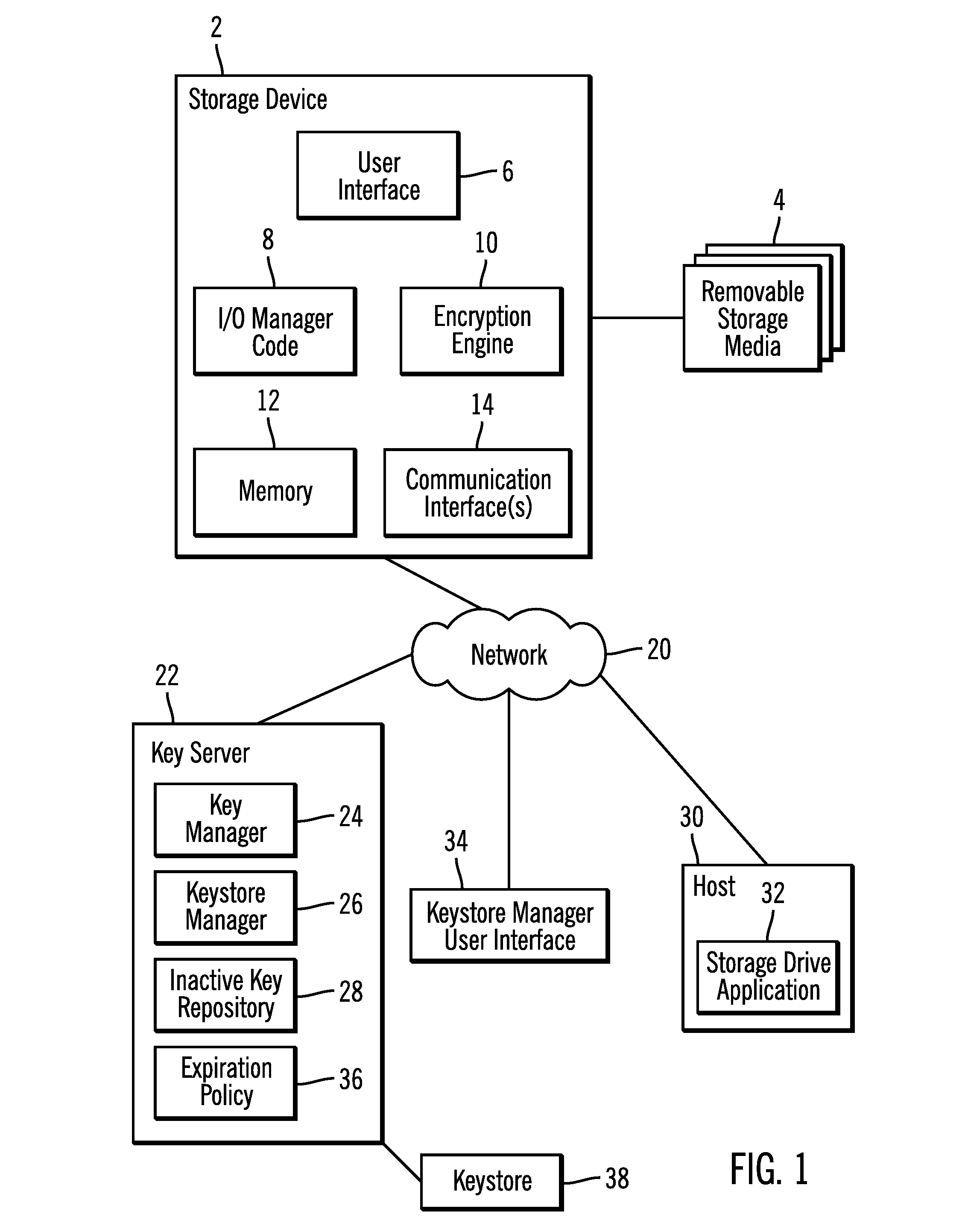
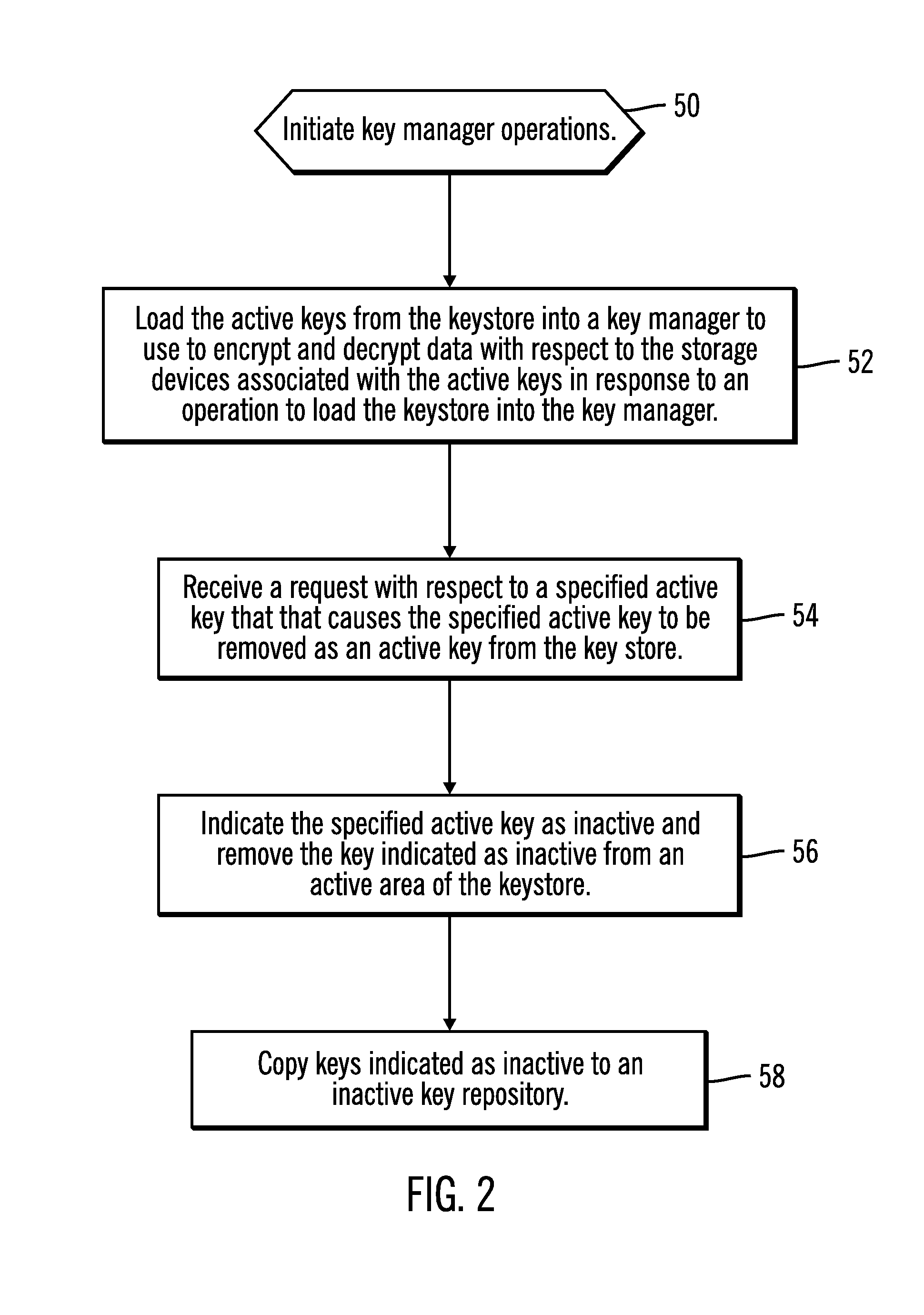
Maintaining keys removed from a keystore in an inactive key repository
Provided are a method, system, and article of manufacture for maintaining keys removed from a keystore in an inactive key repository. A keystore includes active keys, wherein at least one active key in the keystore is associated with at least one storage device and available for encrypting and decrypting data with respect to the associated storage device. A request is received for an operation with respect to a specified active key that causes the specified active key to be removed as an active key from the keystore. The specified active key is indicated as inactive, wherein keys indicated as inactive are not available for use to encrypt and decrypt data. A request is received to restore one of the inactive keys to make available to decrypt and encrypt data for the at least one associated storage device associated with the requested inactive key. The requested inactive key to restore is indicated as active in the keystore, wherein the restored key and any other active key in the keystore associated with the at least one storage device with which the restored key is associated are available to be provided to use to encrypt and decrypt data with respect to the at least one storage device with which they are associated.
Owner:IBM CORP
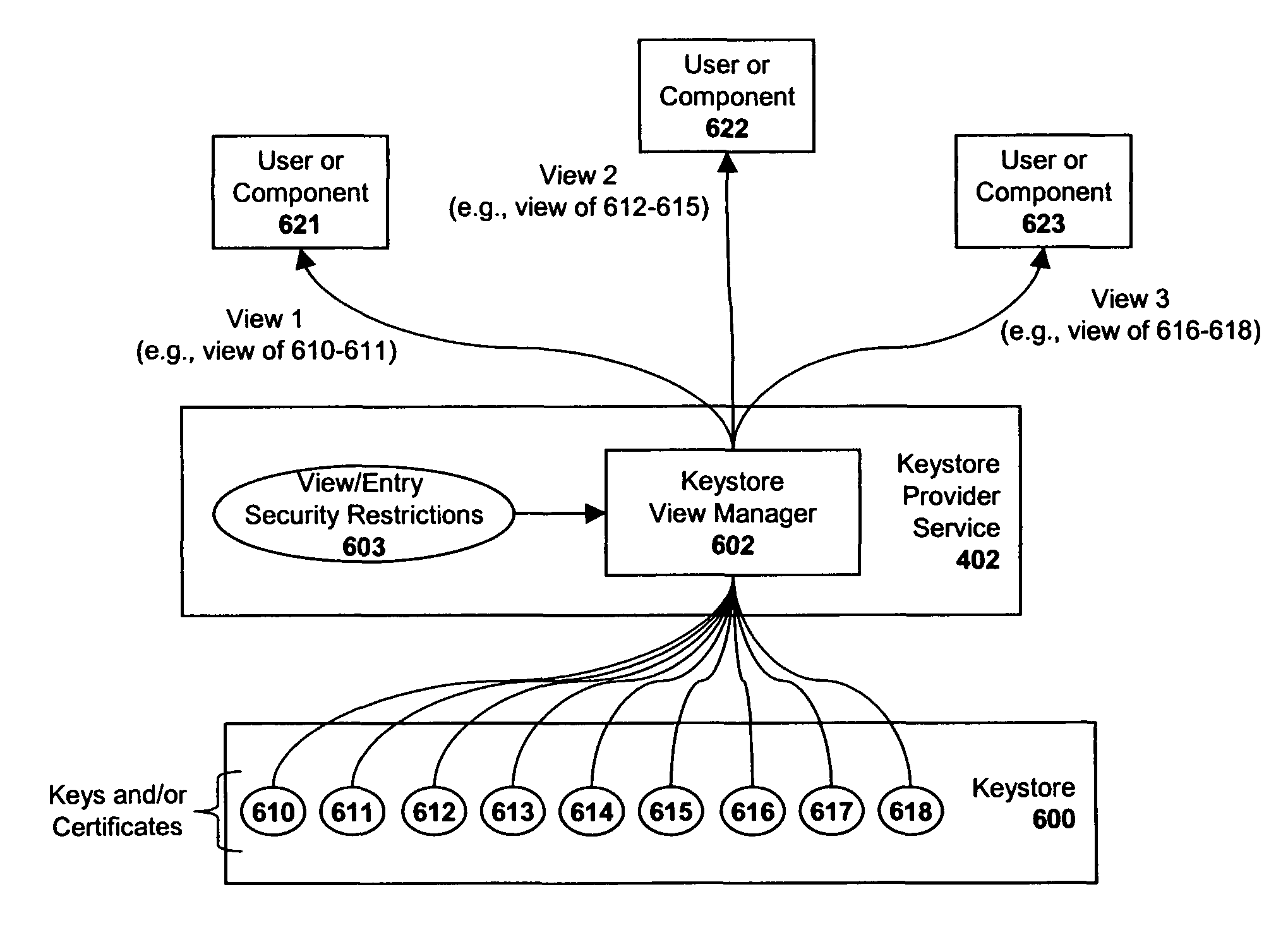
System and method for implementing a distributed keystore within an enterprise network
ActiveUS7823190B1Key distribution for secure communicationDigital data processing detailsNetsniff-ngComputer security
A keystore is described which provides unique views of certificates and keys to particular application components and / or users. Upon receiving a request from a user and / or an application component to view keystore data, the keystore system implements a first set of security restrictions associated with the request and provides a limited view of the keystore data to the requesting user and / or application component based on the results of the first set of security restrictions. Then, upon detecting an attempt by the user and / or application component to access specified portions of the keystore data provided in the view, the keystore system implements a second set of security restrictions associated with the attempt to access the specified portions of the keystore data, and provides access to the keystore data to the user and / or application component based on the results of the second set of security restrictions.
Owner:SAP AG
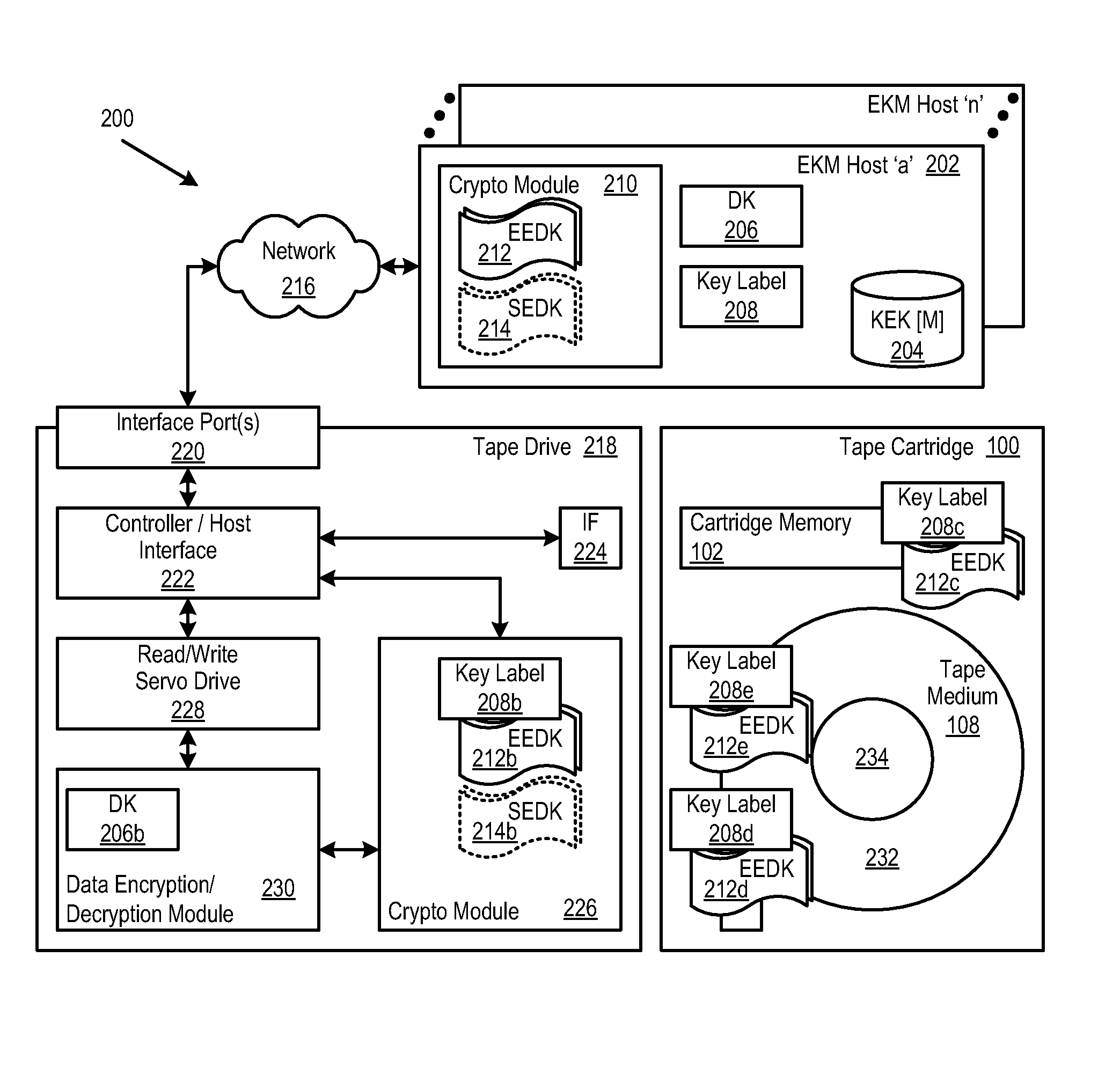
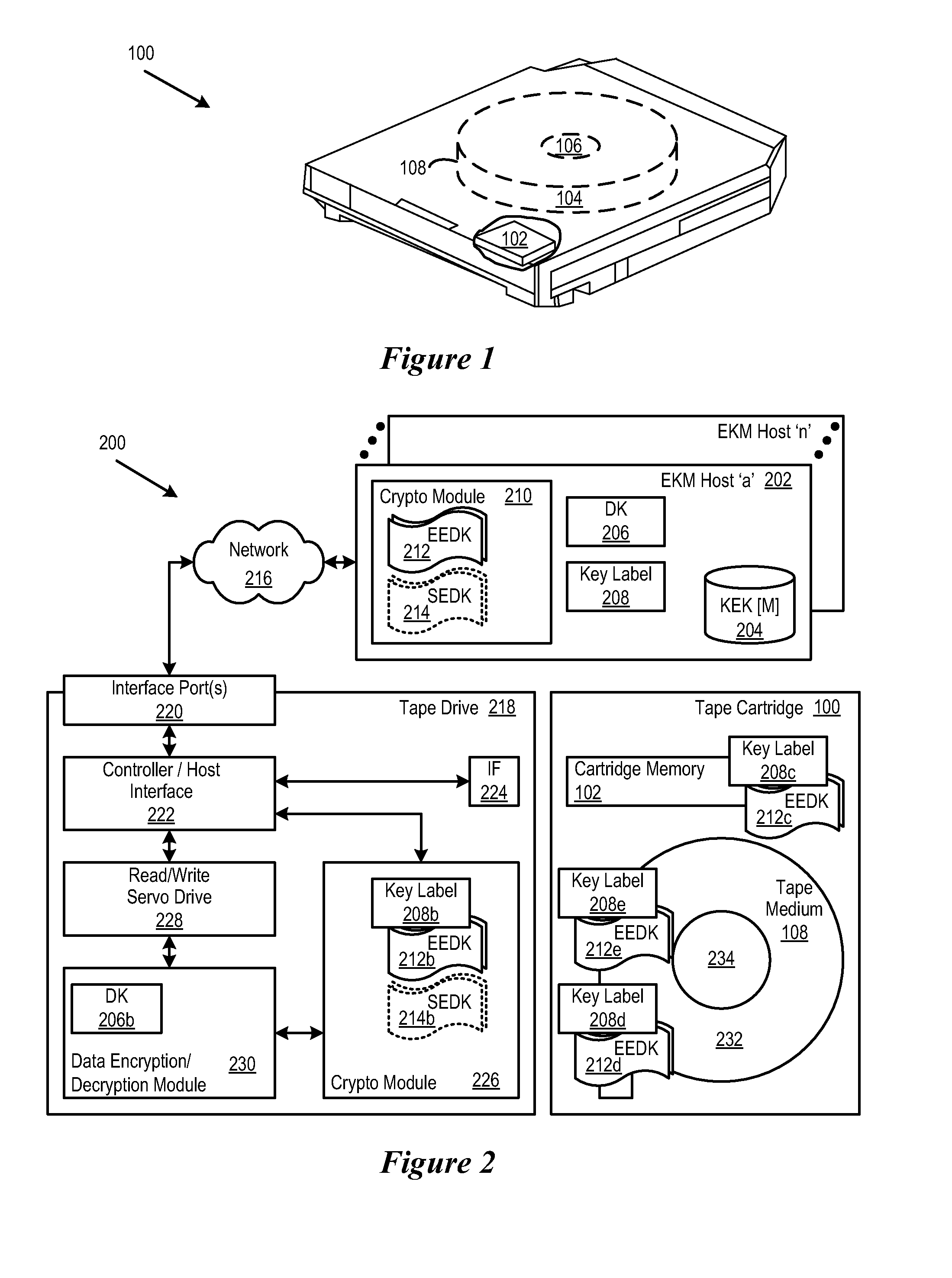
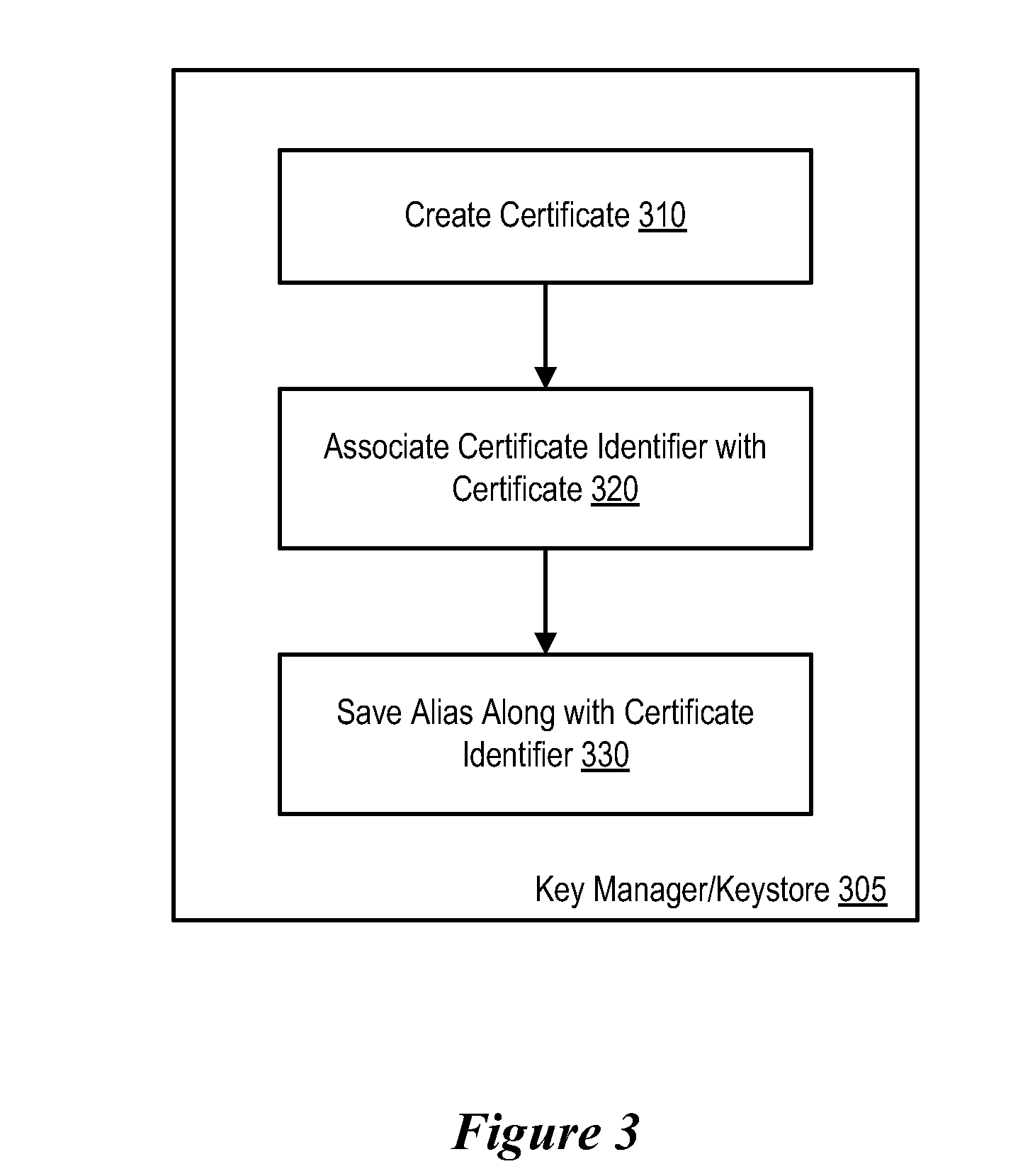
Retrieval and Display of Encryption Labels From an Encryption Key Manager Certificate ID Attached to Key Certificate
InactiveUS20080294906A1Easy accessEasy retrievalUser identity/authority verificationComputer security arrangementsComputer hardwareMagnetic tape
A method, system and program in which a certificate identifier (ID) is associated with an encryption certificate. In certain embodiments, the certificate ID is stored in a cartridge memory (CM). Thus, keystore or key manager administrators can trace keystore locations, versions of keystores, etc. when a cart cannot locate a correct key. This certificate ID, as it is stored on the cartridge memory, is viewable by all.
Owner:IBM CORP
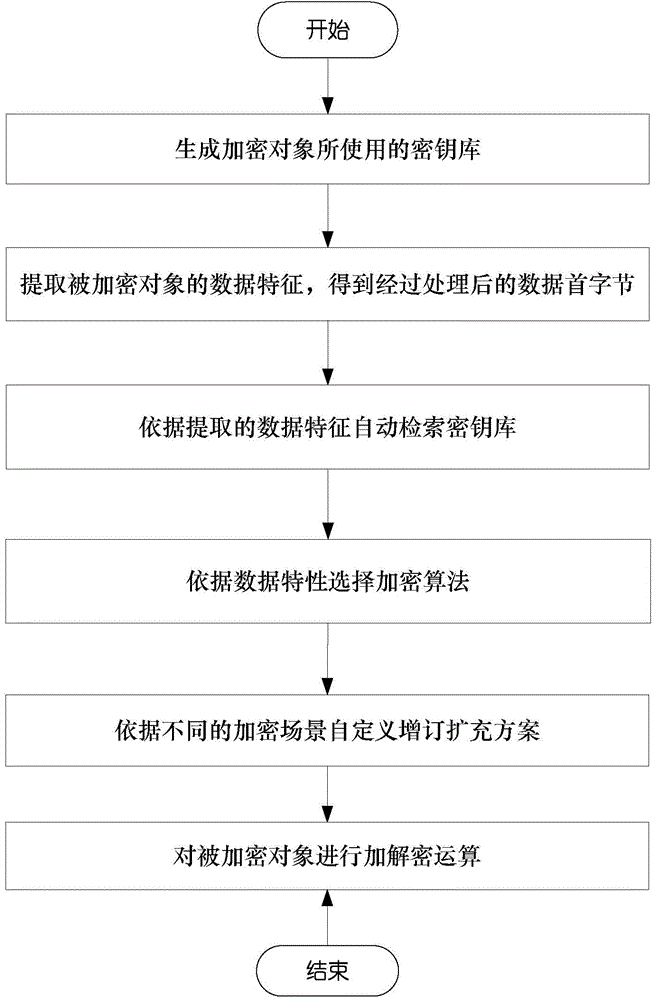
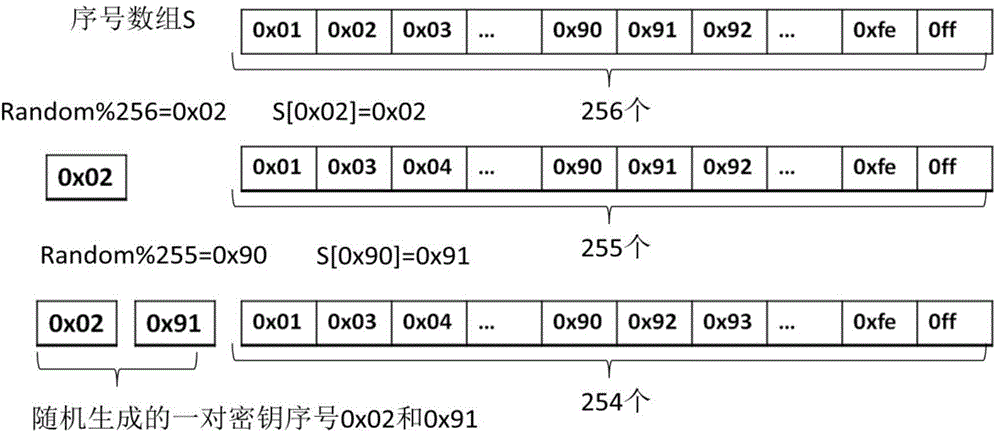
Encryption and decryption method capable of automatically retrieving keys and selecting algorithms
ActiveCN104363091AImprove securityImprove scalabilityPublic key for secure communicationByteDisk encryption
The invention discloses an encryption and decryption method capable of automatically retrieving keys and selecting algorithms, which comprises the following steps: generating a keystore used by a cryptographic object; extracting the data characteristic of an encrypted object, thereby obtaining the processed data first byte; according to the extracted data characteristic, automatically retrieving the keystore; according to the data feature, selecting an encryption algorithm; according to different encryption scenes, carrying out user-defining on an additional expansion scheme; and performing an encryption and decryption algorithm on the encrypted object. Based on the existing encryption algorithm, the keystore is used for replacing the traditional single key, so that the safety of key management is enhanced, the key is selected according to the data characteristic, an appropriate encryption algorithm is selected to play the best encryption performance, and the additional expansion scheme can be supported to meet the specific encryption scene, therefore, the method has very high practicality and adaptability, and has very wide application scenarios.
Owner:NAT COMP NETWORK & INFORMATION SECURITY MANAGEMENT CENT +1
Authentication method for network signaling between quantum safety network equipment
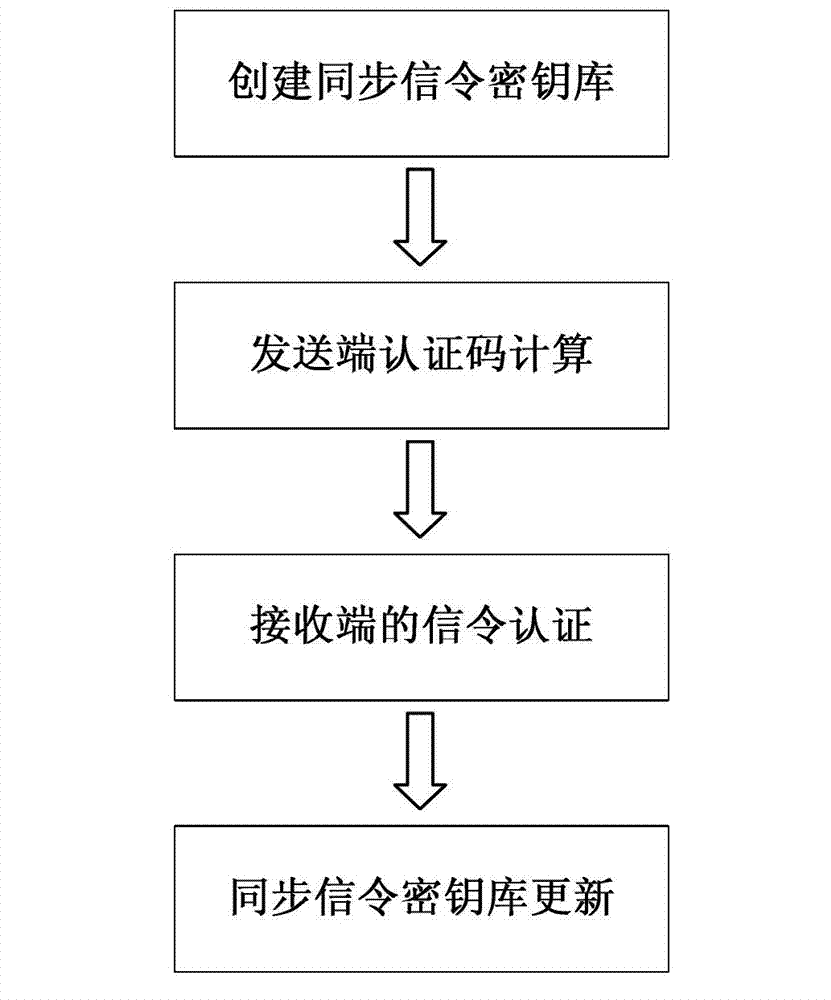
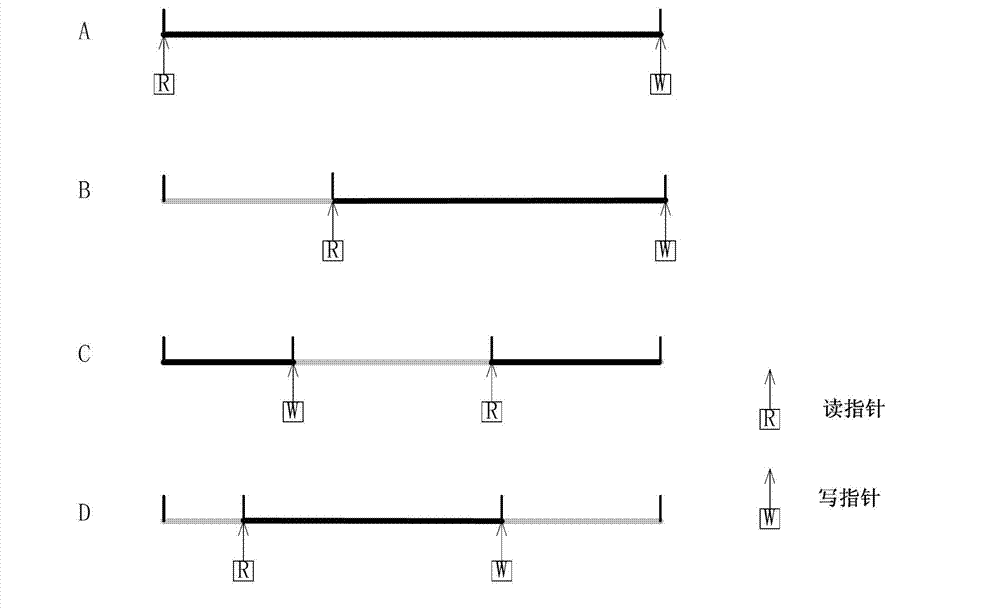
ActiveCN103095461AFast operationWith absolute securityKey distribution for secure communicationError preventionNetwork packetMessage authentication code
The invention discloses an authentication method for network signaling between quantum safety network equipment. The authentication method includes the following steps: creating synchronous signaling key stores used for signaling authentication for both sides between the communicated network equipment, wherein the synchronous signaling key stores are divided into an encrypting signaling key store and a decrypting signaling key store, and setting a read indicator and a write indicator for each signaling key store; a sending end calculating related hash operation message authentication codes H of keys based on key data and a read indicator offset address of the encrypting signaling key store of the sending end, and sending a corresponding signaling data packet to a receiving end; the receiving end receiving the signaling data packet, acquiring a read indicator offset address in the signaling data packet, and judging whether the key data of the read indicator offset address of the decrypting signaling key store of the receiving end is already used or not; and if the key data is not used, calculating H and verifying the content of the signaling data packet. The authentication method for the network signaling between the quantum safety network equipment has the advantages that the authentication is fast, and the method has a certain preventive effect on distributed denial of service (DDoS) attacks, can achieve true one-time-one-key encrypting authentication and is absolutely safe theoretically.
Owner:SHANDONG INST OF QUANTUM SCI & TECH +2
System and Method for Providing Different Levels of Key Security for Controlling Access to Secured Items
InactiveUS20110258438A1Efficient accessEnsure protectionKey distribution for secure communicationUnauthorized memory use protectionEase of AccessEncryption
With files secured by encryption techniques, keys are often required to gain access to the secured files. Techniques for providing and using multiple levels of keystores for securing the keys are disclosed. The keystores store keys that are needed by users in order to access secured files. The different levels of keystores offer compromises between security and flexibility / ease of use.
Owner:INTELLECTUAL VENTURES I LLC
Searching data
InactiveUS20110131419A1Digital data information retrievalDigital data processing detailsEngineeringLabeled data
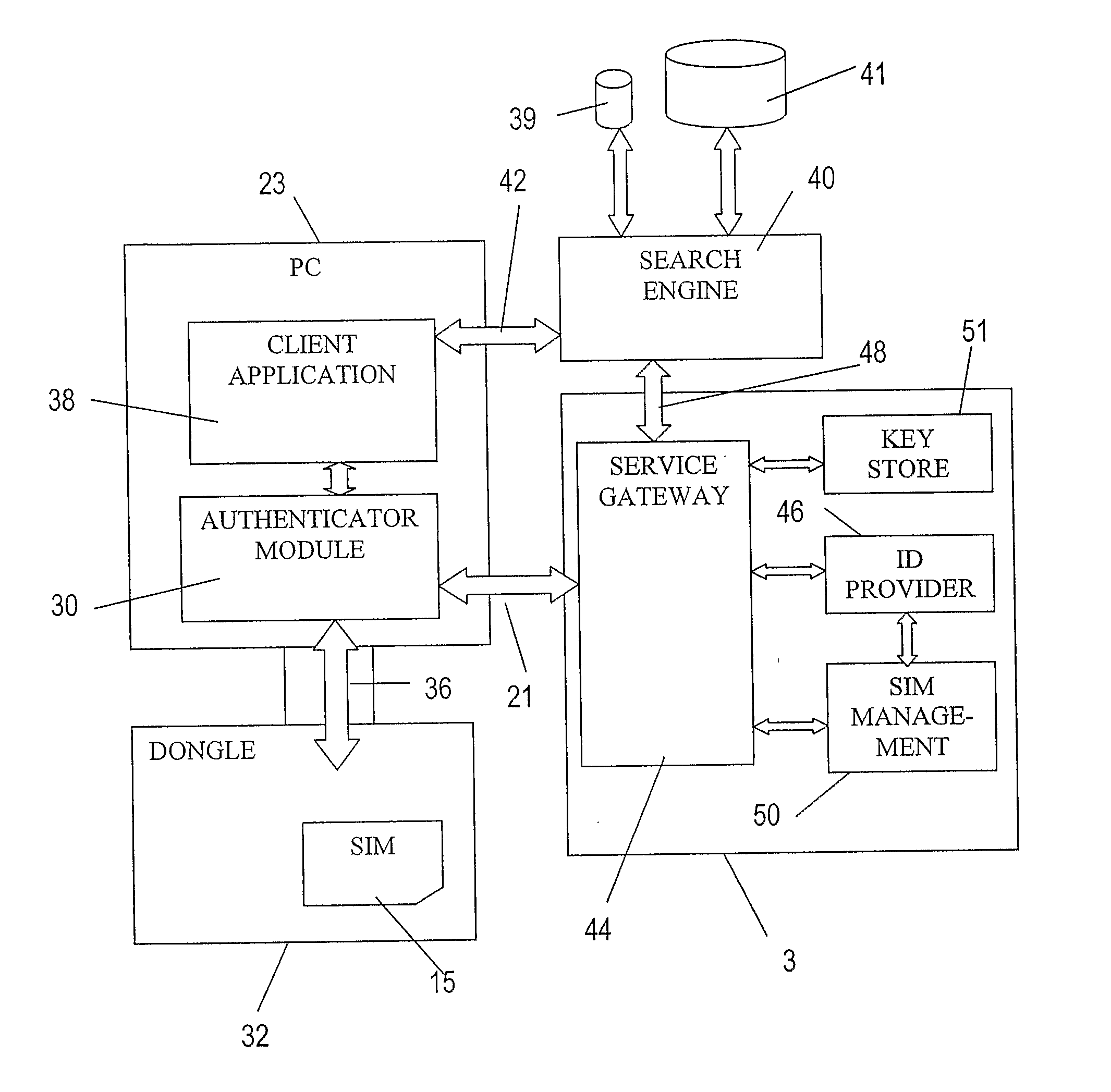
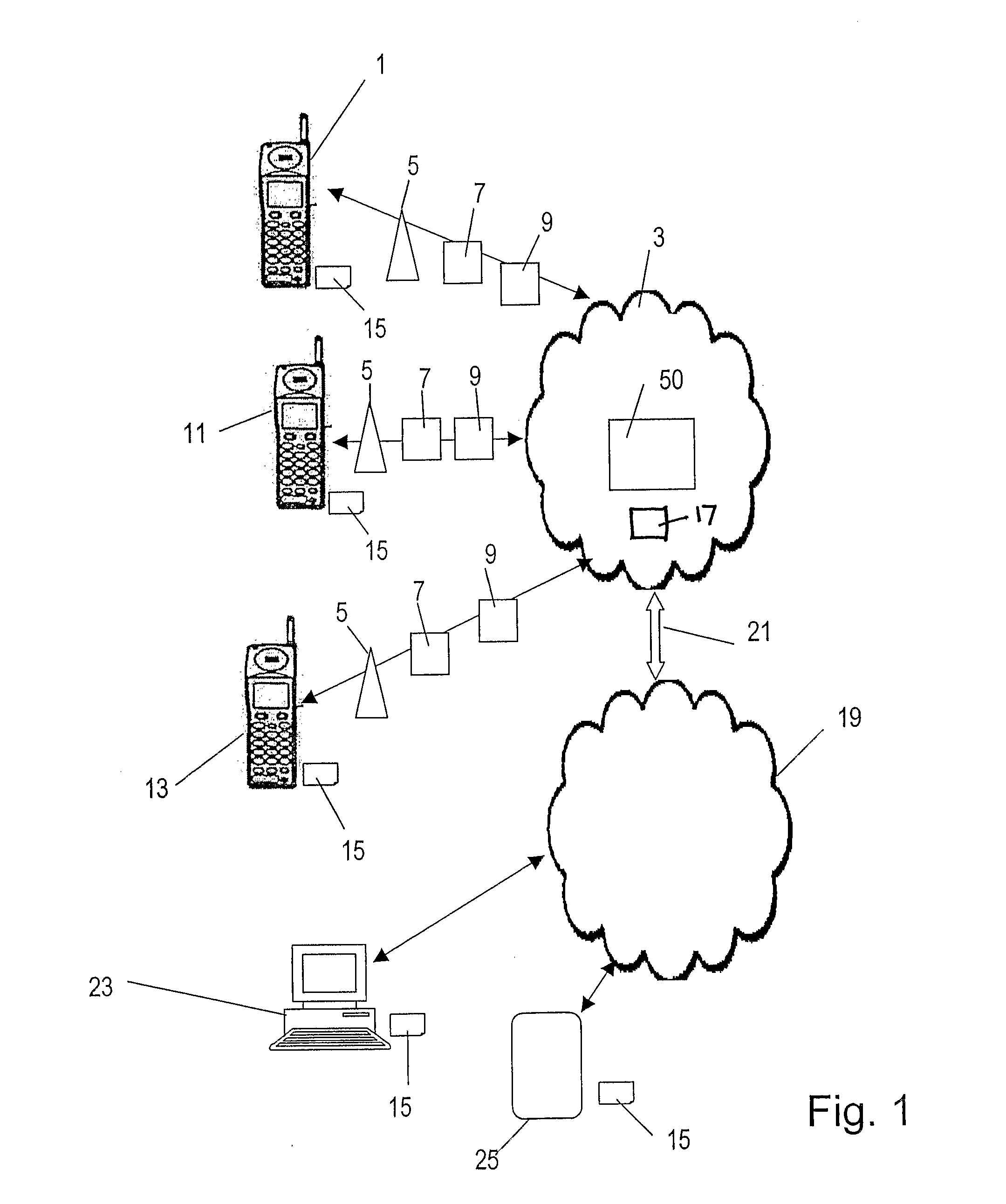
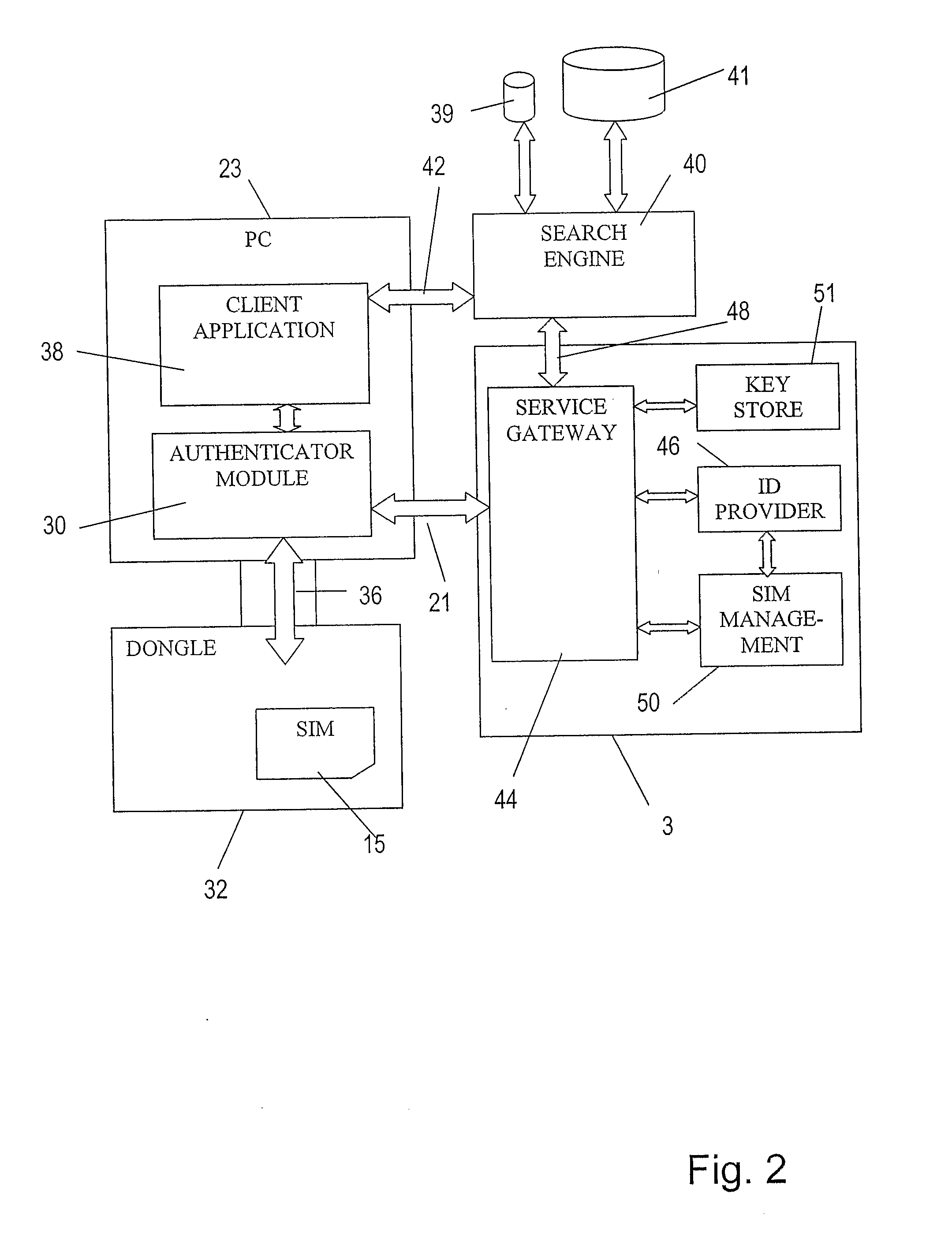
A device or “dongle” (32) is provided for coupling to a Windows-based PC (23). The dongle (32) includes a subscriber identity module (SIM) (15), such as the type used in GSM or UMTS cellular or mobile telecommunications networks. A search engine (40) is accessed by the PC (23) by means of a client application (38) on the PC. The search engine (40) generates a list of search results in response to search criteria in a known manner. Further, the search engine is able to return search results relating to data for which there is restricted access (for example, encrypted data). Such data is identified with a tag which may, for example indicated which users or entities are able to access that data. A user's dongle (32) authenticates that user with the network (3) using a authentication arrangement similar to that employed for authenticating users of a GSM or UMTS mobile telecommunications network. The authenticated identity of the user is communicated to the search engine. The search engine then includes in the search results tagged data items for which the tag indicates that the authenticated user has permission to view. Tagged data items that the authenticated user does not have permission to view are not returned in the search results. Therefore, the user not entitled to view data is not distracted by search results corresponding to data that the user is unable to access. The network (3) may include a key store (51) which stores keys that allow encrypted data items identified by the search engine (40) to be decrypted.
Owner:VODAFONE GRP PLC
System and method for application authorization
ActiveUS20050256878A1Reduced promptingDigital data processing detailsUnauthorized memory use protectionPasswordAuthorization
A method and system for authorization of applications executing on a device having a key store. Applications obtain an application-level ticket to permit access to one or more key values located in the key store. Each ticket is securely associated with an application and being generated on the determination that the application is a trusted application. Tickets are potentially associated with one key value in the key store, with a subset of key values in the key store, or with all key values in the key store. Access to key values by an application is possible independently of a user providing a password for each such access.
Owner:BLACKBERRY LTD
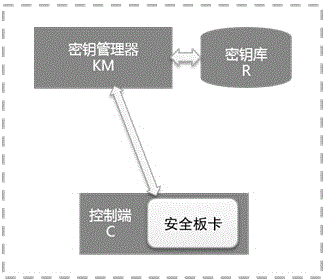
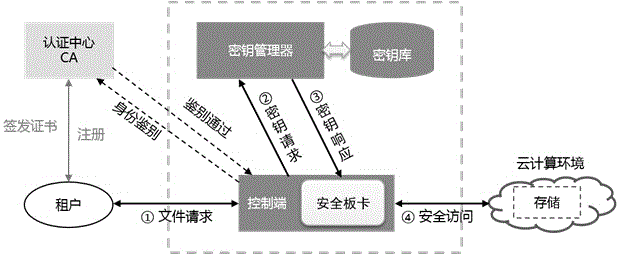
Data encryption system and method for interaction between tenants and cloud server memory
The invention discloses a data encryption system and method for interaction between tenants and a cloud server memory, and belongs to the technical field of computer data encryption. In the data encryption system, a control terminal is used for being in communication with the tenants and the cloud server memory, and receiving data file request information of the tenants; a data encryption key is obtained from a key manager, encryption and decryption are conducted on data files in safety board, and data file ciphertext is sent to the cloud server memory, or data file plaintext is transmitted to the tenants; the key manager is used for being in communication with the control terminal, generating the data encryption key, sending the data encryption key to the control terminal and sending the data file request information to a key storage; the key storage is used for safely storing the data file request information sent by the key manager. According to the data encryption system and method for interaction between the tenants and the cloud server memory, safety protection of tenant data is achieved through usage of tenant identifications and a symmetric cryptosystem encryption algorithm, intensity and complexity of key management can be reduced, and isolation of the tenant data is guaranteed.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Composite keystore facility apparatus and method therefor
InactiveUS6934840B2Key distribution for secure communicationUser identity/authority verificationLevel structureCentralized management
An apparatus and method for managing keystores is implemented. A distributed keystore is established by aggregating individual. The distributed keystore may, be organized in a multi-level structure, which may be associated with an organizational structure of an enterprise, or other predetermined partitioning. Additionally, a centralized management of certificates may be provided, whereby the expiration or revocation of the certificates may be tracked, and expired or revoked certificates may be refreshed. The keystore may be updated in response to one or more update events.
Owner:IBM CORP
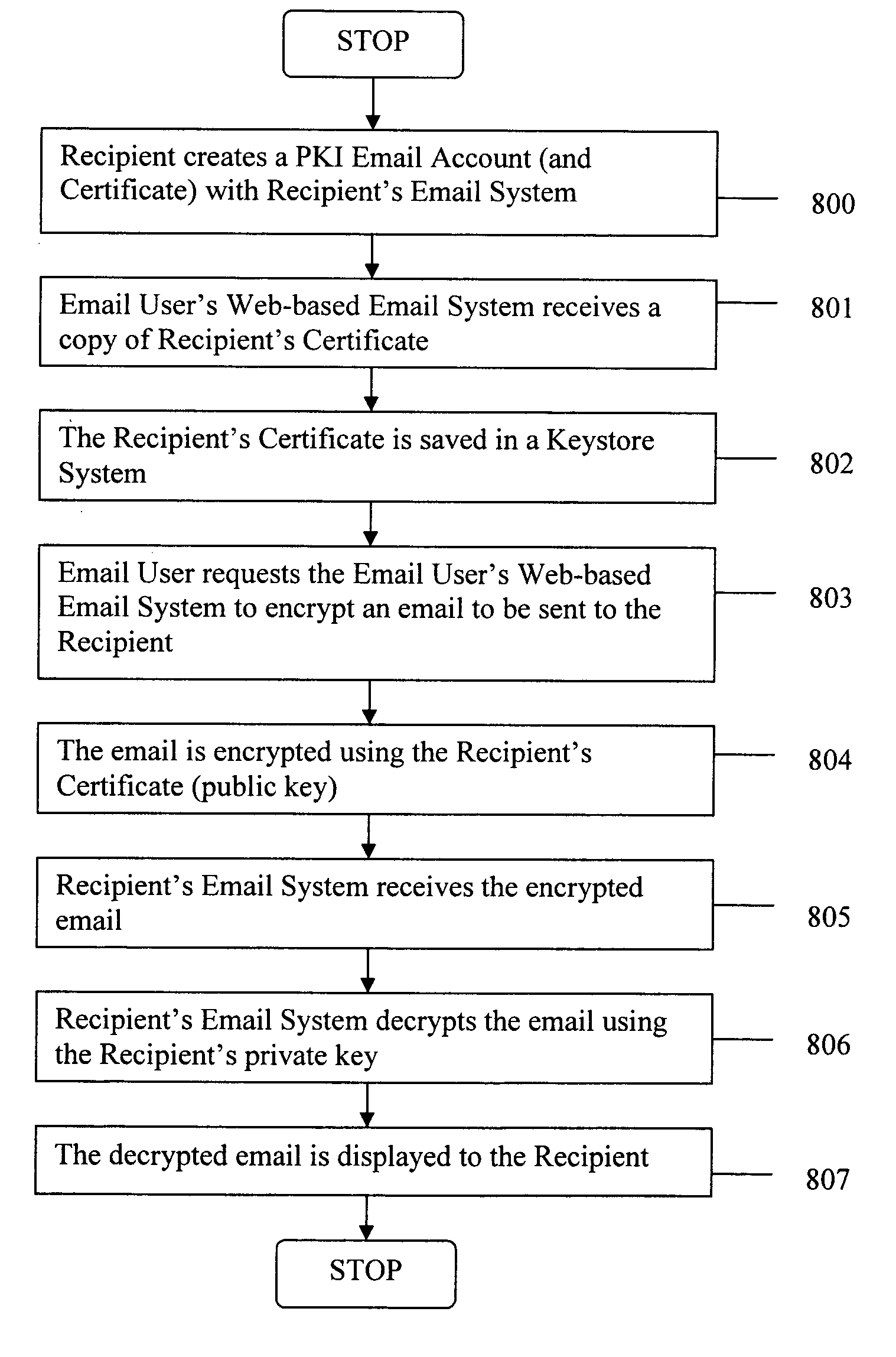
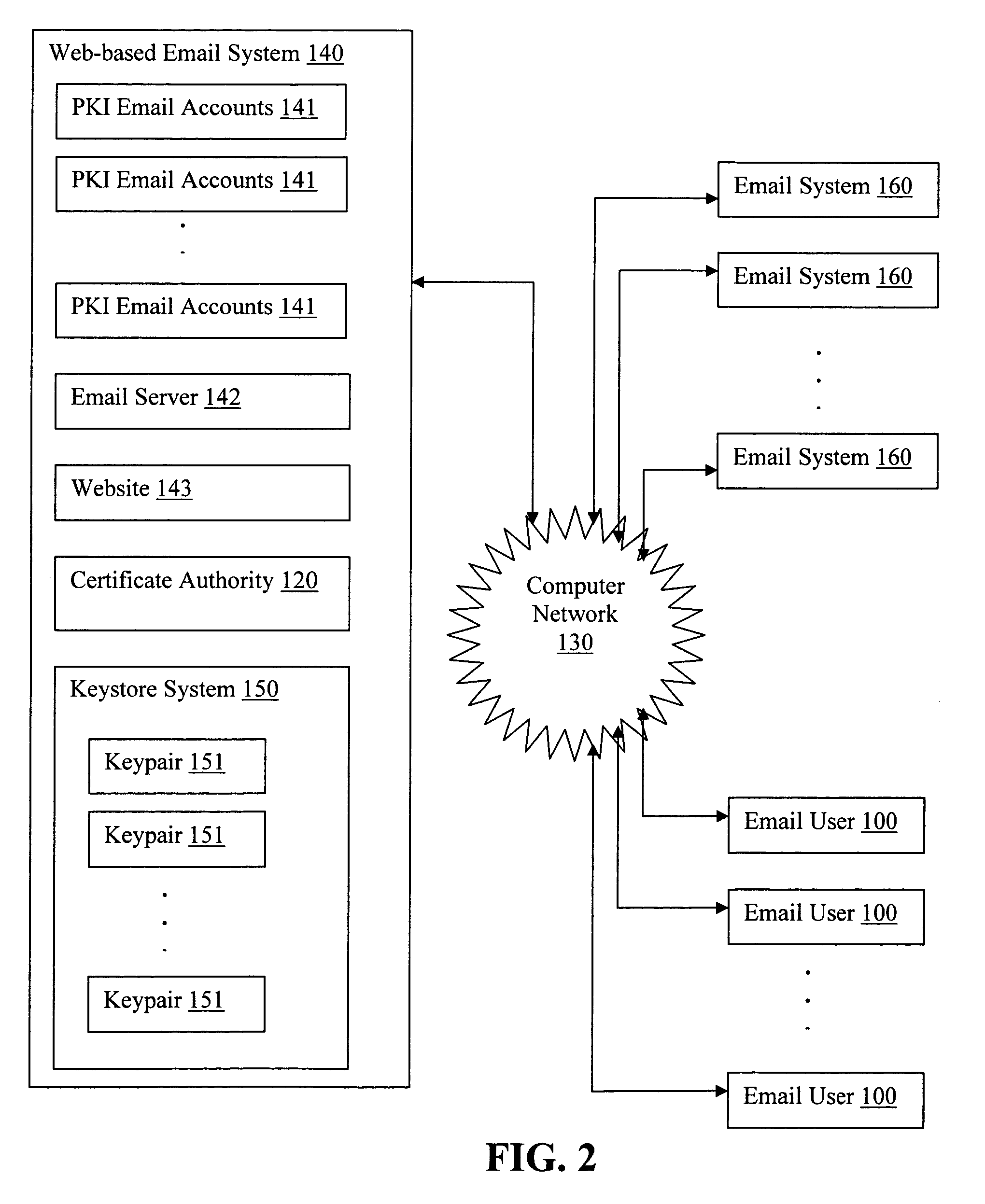
Sending digitally signed emails via a web-based email system
ActiveUS8145707B2Simple processImprove securityKey distribution for secure communicationDigital data processing detailsDigital signatureInternet privacy
Owner:GO DADDY OPERATING
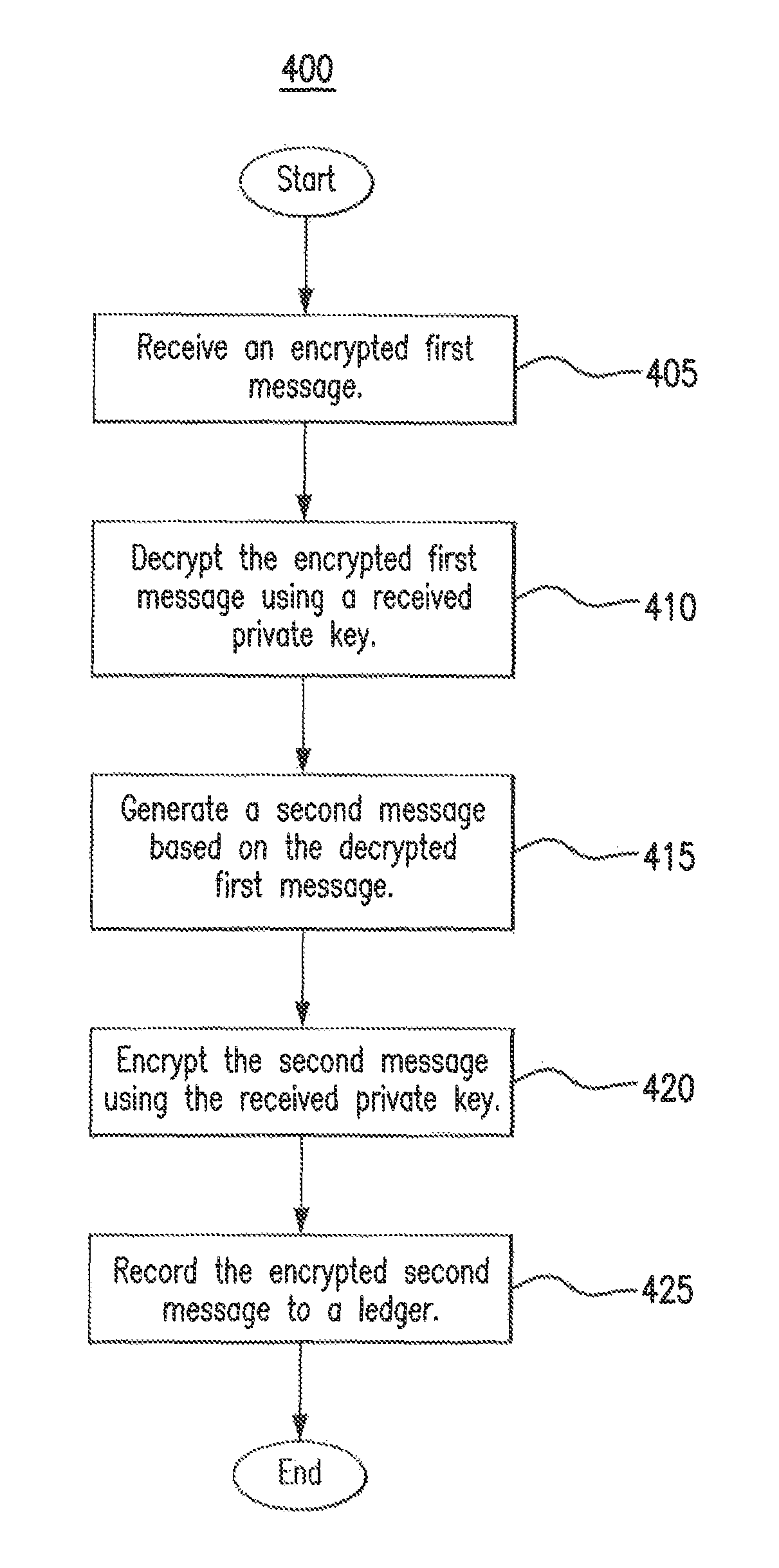
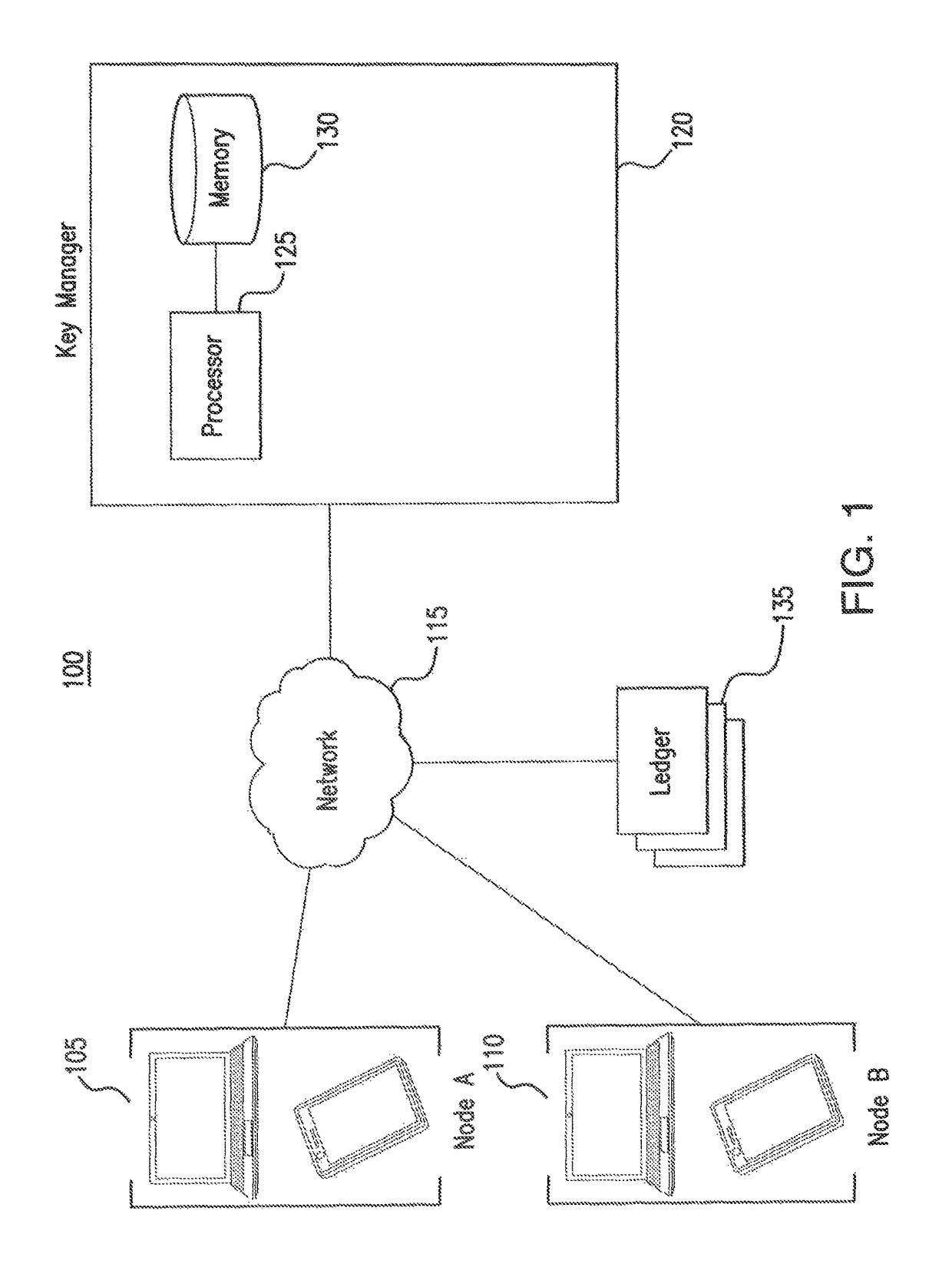
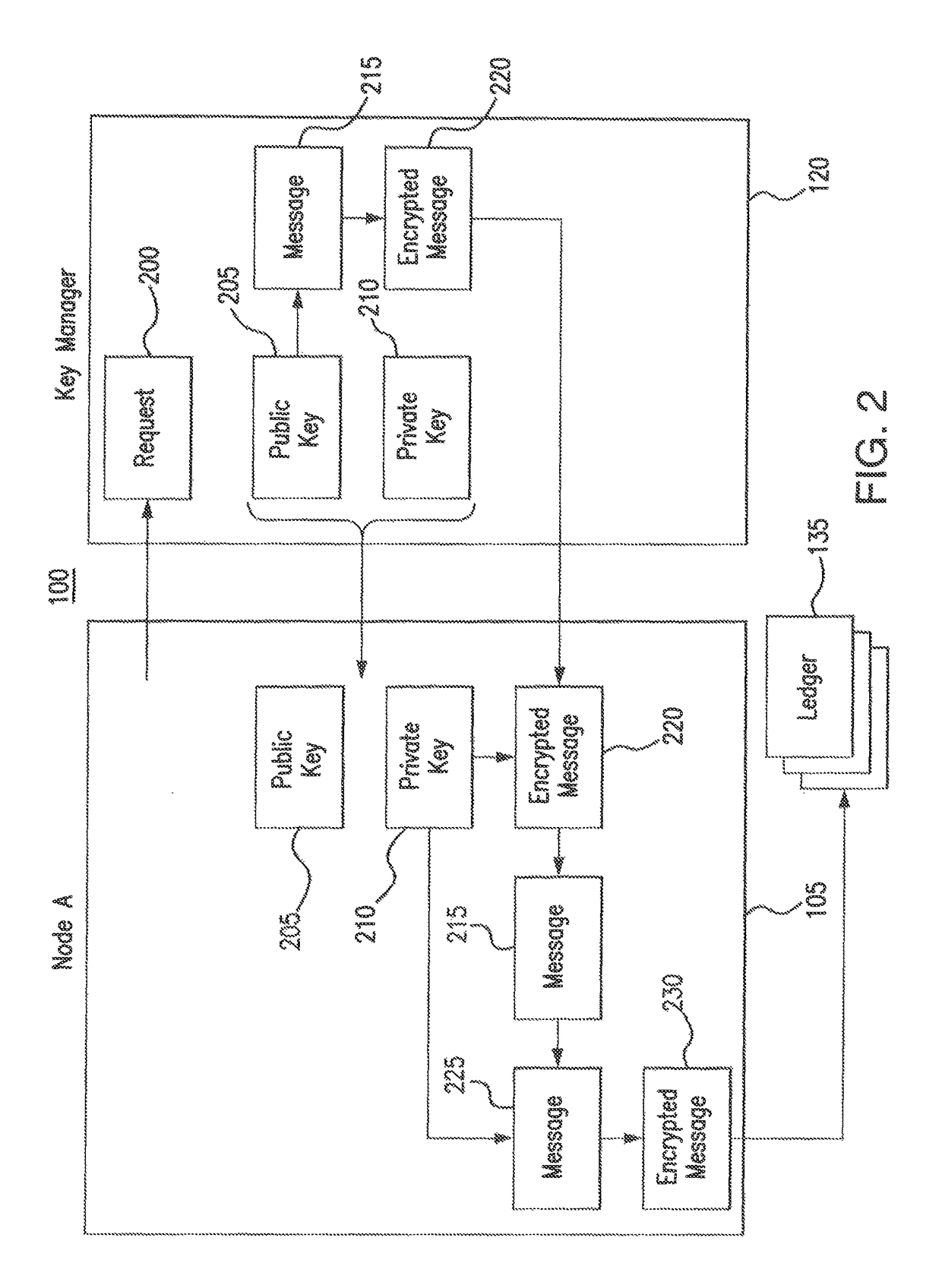
Network authorization system
ActiveUS9906513B2Improve securityReduce and prevent communicationKey distribution for secure communicationUser identity/authority verificationAuthorizationKeystore
A system includes a key repository and a network node. The key repository is configured to generate a private key and a public key of the network node, to communicate the private key and the public key to the network node, to verify whether the network node is authorized to operate on a network, to generate a first message indicating whether the network node is authorized to operate on the network, to encrypt the first message using the public key, and to communicate the encrypted first message to the network node. The network node is configured to decrypt the encrypted first message using the private key, to generate a second message based on the first message, to encrypt the second message using the private key, and to record the encrypted second message to a ledger.
Owner:BANK OF AMERICA CORP
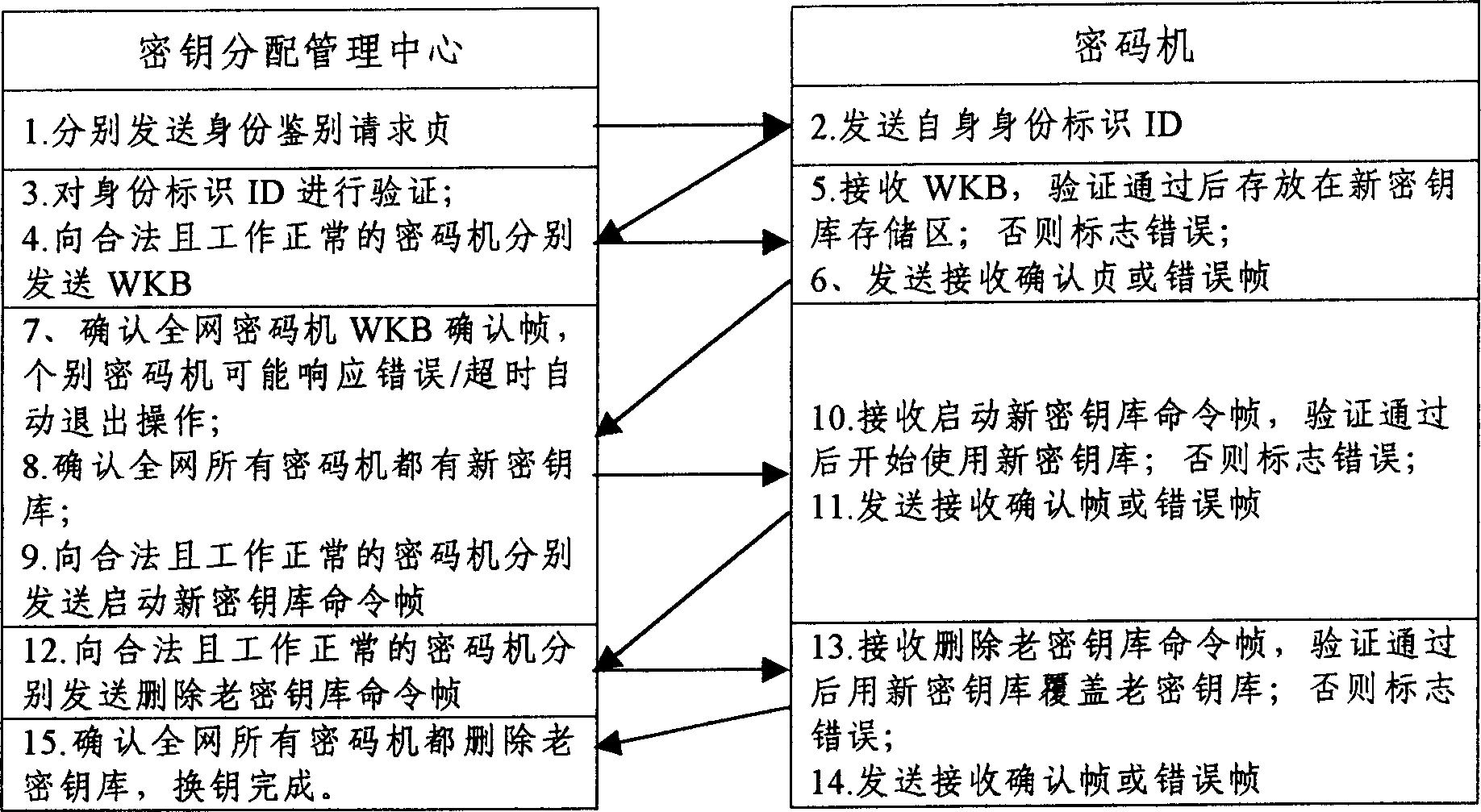
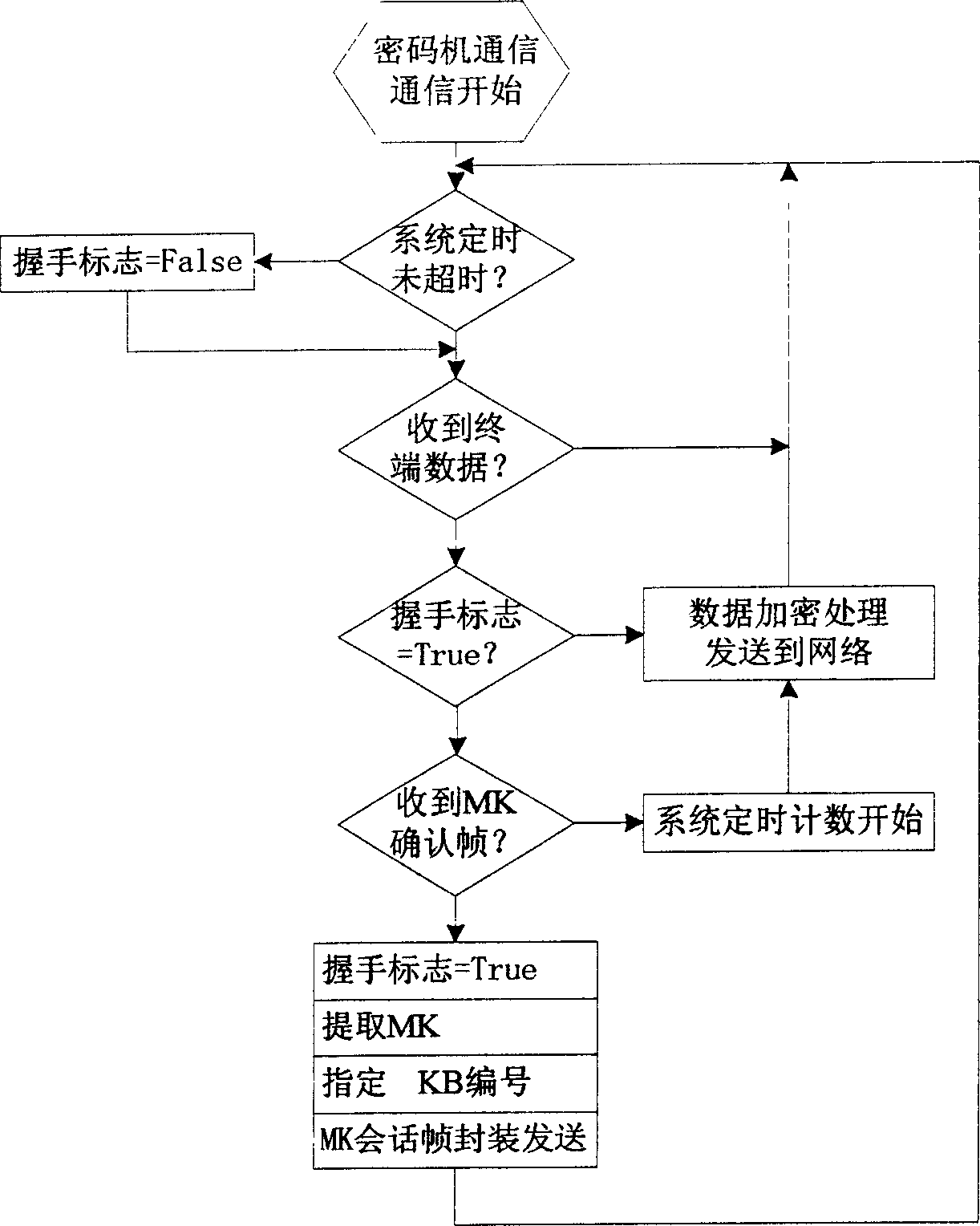
Seamless key exchanging technology based on secret communication
InactiveCN1512700ASimplify operabilitySimplify workloadSecret communicationSecuring communicationKey exchangeCommunications system
The KDMC carries out key-encrypting key base on-line replacement to related cryptces uniformly in the full-duplex secure communication system based on cryptoes. Based on the traditional way of key-encrypting key base replacement, the base buffer storage and MK handshaking switching technology are applied and improved to realize seamless key-encrypting key replacement of normal data secure communications among cryptoes continuously.
Owner:中电科网络安全科技股份有限公司
Sending digitally signed emails via a web-based email system
ActiveUS20070022291A1Simple processImprove securityUser identity/authority verificationPublic key infrastructure trust modelsInternet privacyDigital signature
The present invention provides systems and methods for allowing an Email User to create a Public Key Infrastructure (PKI) Email Account and thereafter to digitally sign, send, verify and receive PKI encrypted emails over a computer network, such as the Internet. The systems and methods preferably include a Web-based Email System and a Certificate Authority that coordinate their actions to make the process of creating, maintaining and using the PKI Account as easy as possible for the Email User. In a preferred embodiment, a Keystore System may also be used to enhance the management and use of digital keypairs.
Owner:GO DADDY OPERATING
General purpose distributed encrypted file system
A general purpose distributed encrypted file system generates a block key on a client machine. The client machine encrypts a file using the block key. Then, the client encrypts the block key on the first client machine with a public key of a keystore associated with a user and associates the encrypted block key with the encrypted data block as crypto metadata. The client machine caches the encrypted data block and the crypto metadata and sends the encrypted data block and the crypto metadata to a network file system server. When the client machine receives a return code from the network file system server indicating successful writes of the encrypted data block and the crypto metadata, the client machine clears the cached encrypted data block and the crypto metadata.
Owner:INT BUSINESS MASCH CORP
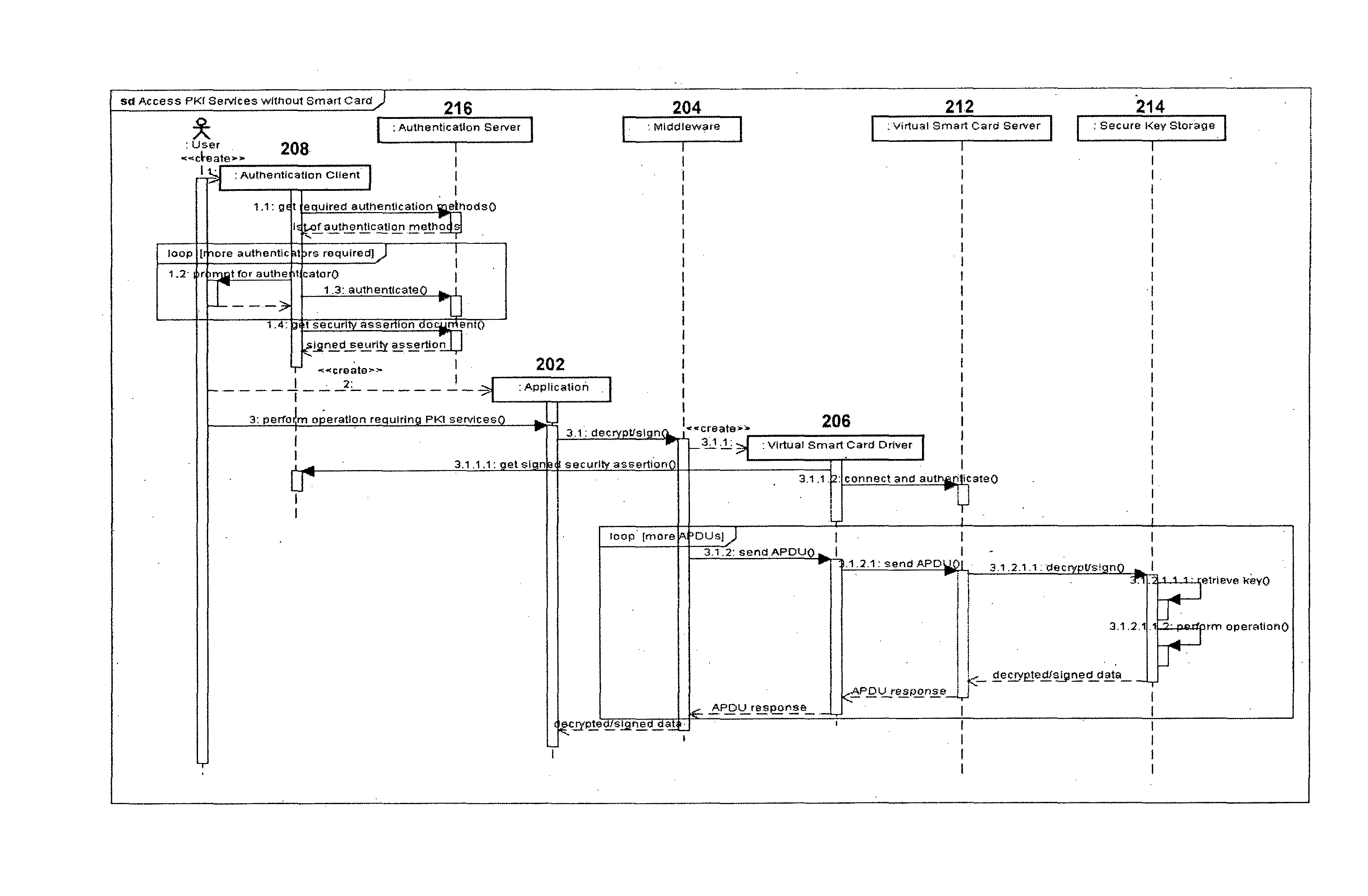
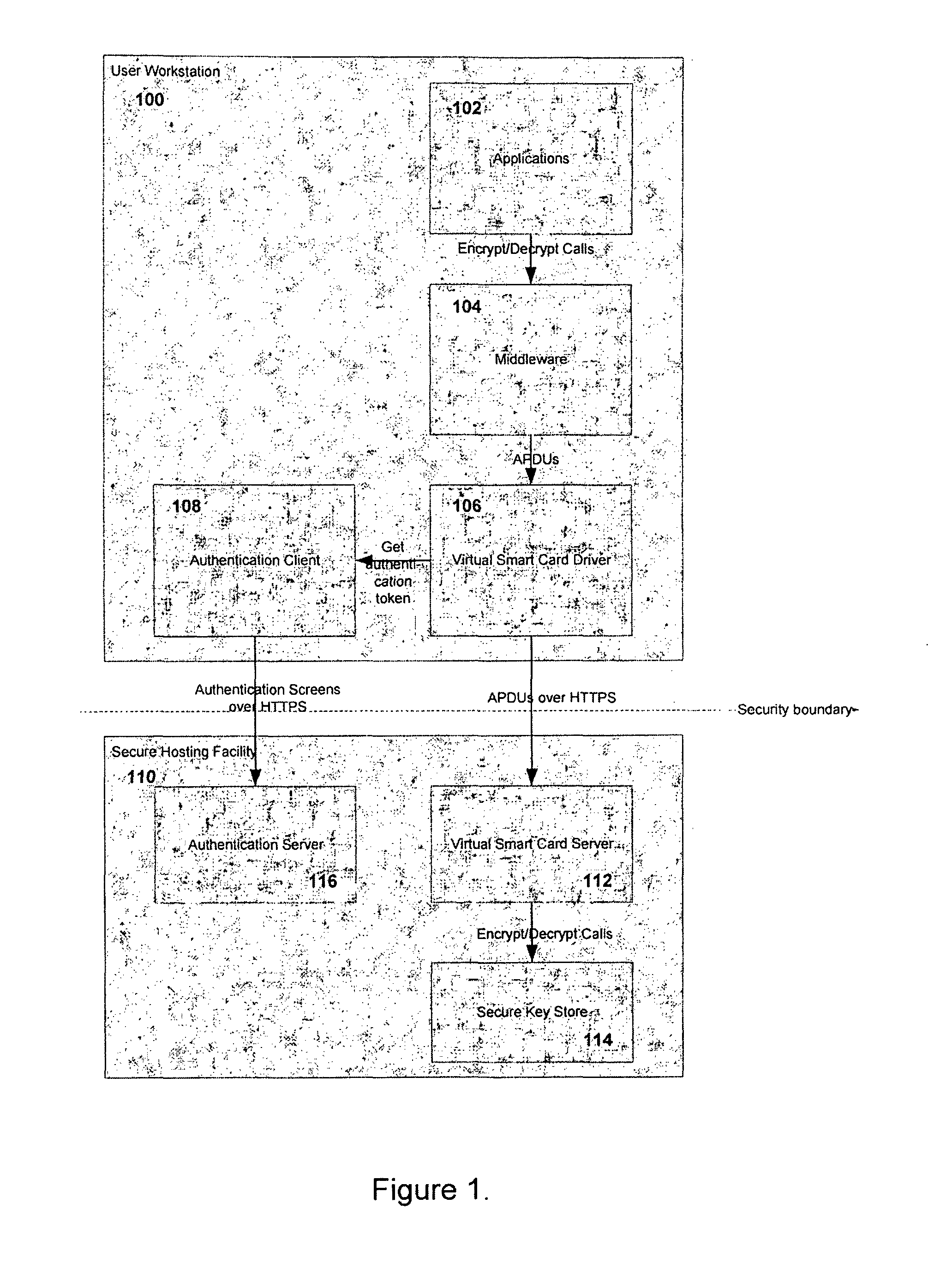
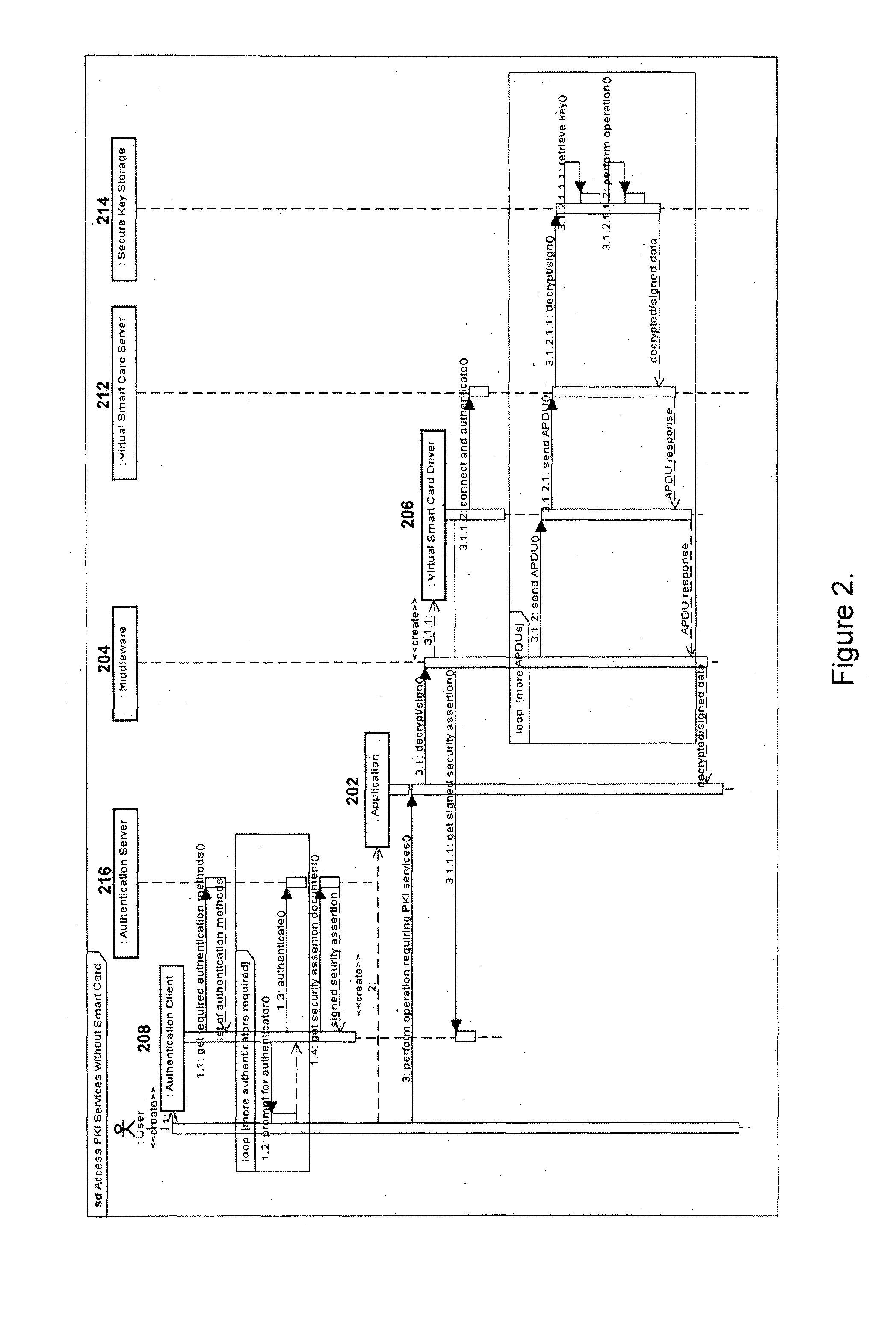
Method and system for providing continued access to authentication and encryption services
ActiveUS20130290717A1Continued accessUser identity/authority verificationDigital data protectionSmart cardClient-side
A system and method for providing continued access to authentication and encryption services that includes a secure key store communicably coupled to a virtual smart card server. A virtual smart card driver is also provided and is communicably coupled to a virtual smart card secure hardware server. The virtual smart card driver communicates with an authentication client to authenticate a user, and access the user's private key stored in the secure key store when the user's physical smart card is unavailable. Continued access is provided when the user has been authenticated.
Owner:IDONDEMAND +1
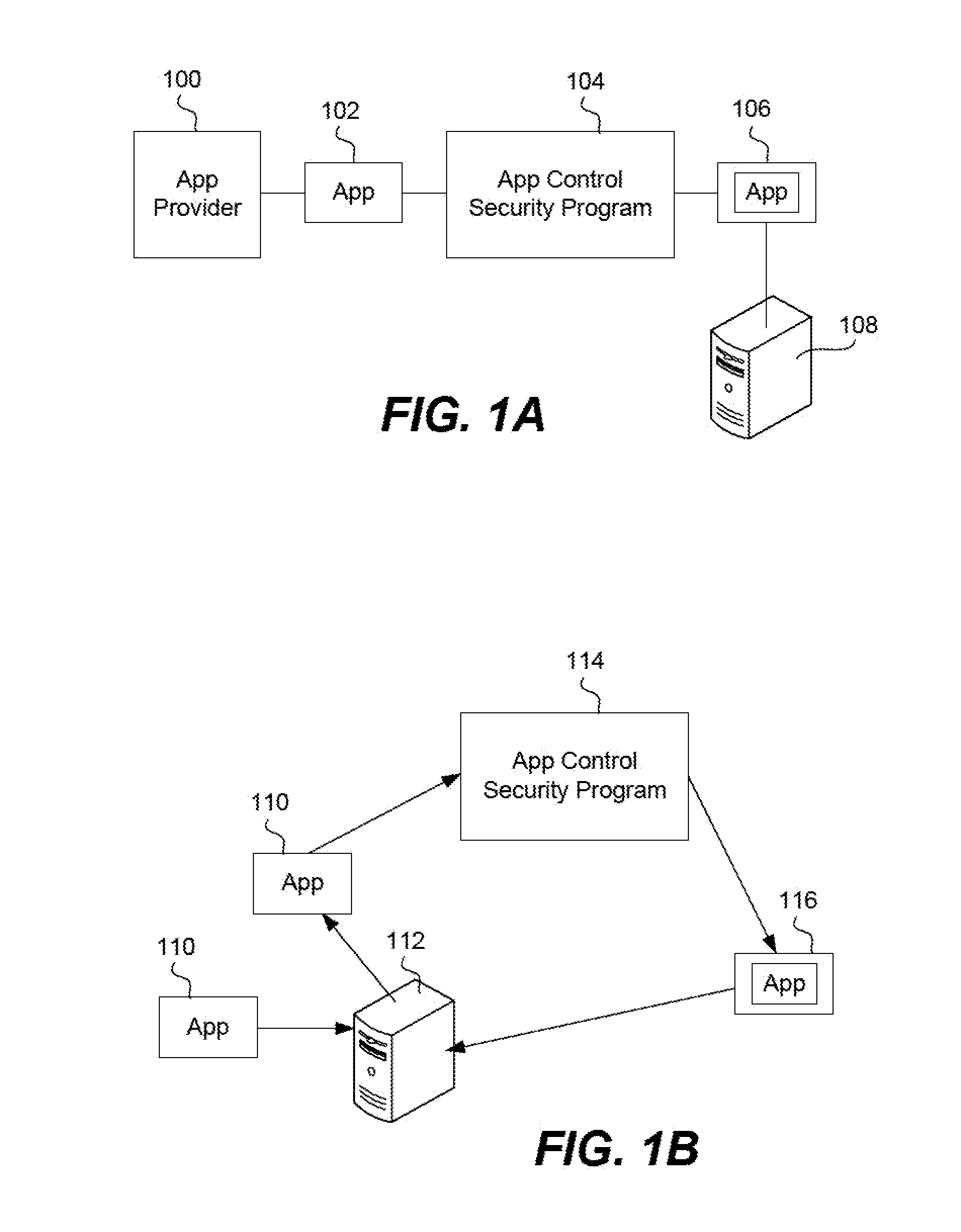
Provisioning an app on a device and implementing a keystore
ActiveUS9396325B2Key distribution for secure communicationDigital data protectionMobile appsPassphrase
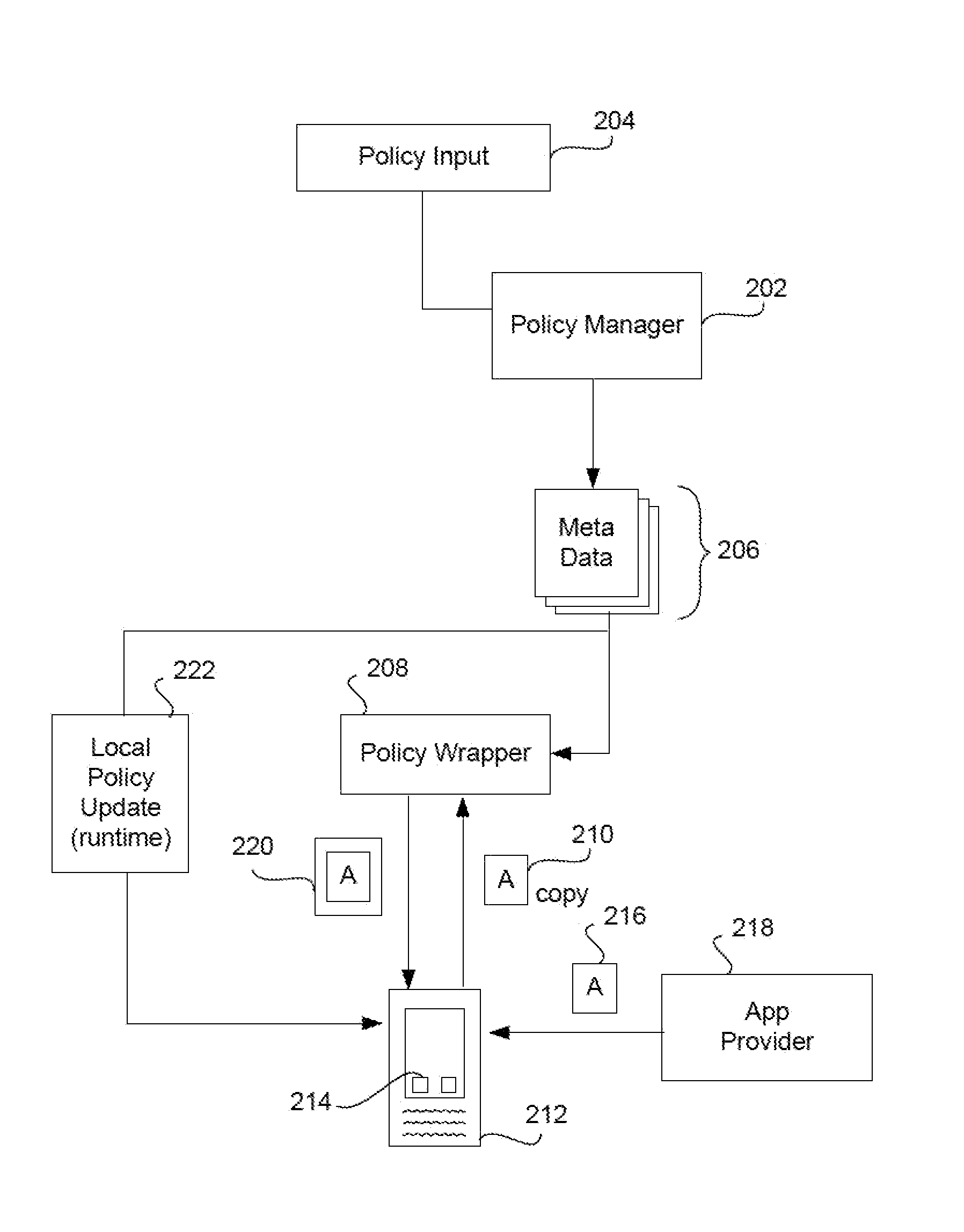
A keystore is installed on a mobile app where the keystore is created and provisioned on a server, such as an app wrapping server, under the control of an enterprise. A generic (non-provisioned) wrapped app is installed on a device. The app prompts the user to enter a passphrase. When the user does this, an app keystore is created. It has a user section and a table of contents. The keystore files are hashed, creating “first” keystore hash values. The first keystore hash values are stored in the TOC. The TOC is then hashed, creating a TOC hash value. The passphrase entered by the user is then combined with the TOC hash value. This creates a “first” master passphrase for the keystore. The keystore is then transmitted to the device where it is installed in the generic (non-provisioned) wrapped app.
Owner:BLUE CEDAR NETWORKS INC
Securely and redundantly storing encryption credentials system and method
A method, computer program product, and computing system for generating, by a computing device, a key, wherein the key includes at least one of an encryption key and an authentication key. One or more credentials may be generated to access a Secure KeyStore storing the key, wherein the one or more credentials may include one or more stable system values, and wherein the one or more stable system values may include one or more virtual values and one or more hardware values. The one or more stable system values may be provided to the Secure KeyStore to retrieve the key.
Owner:EMC IP HLDG CO LLC
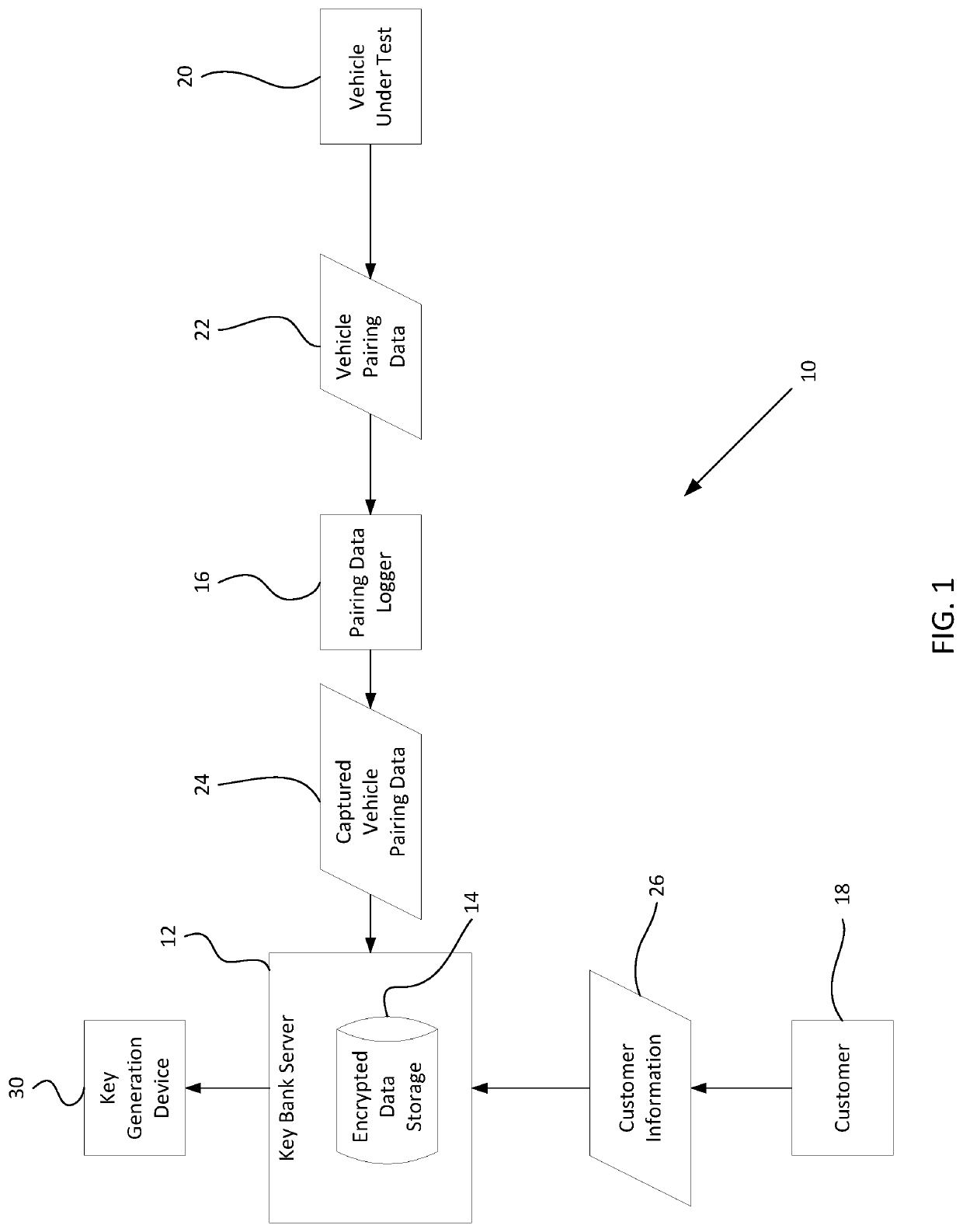
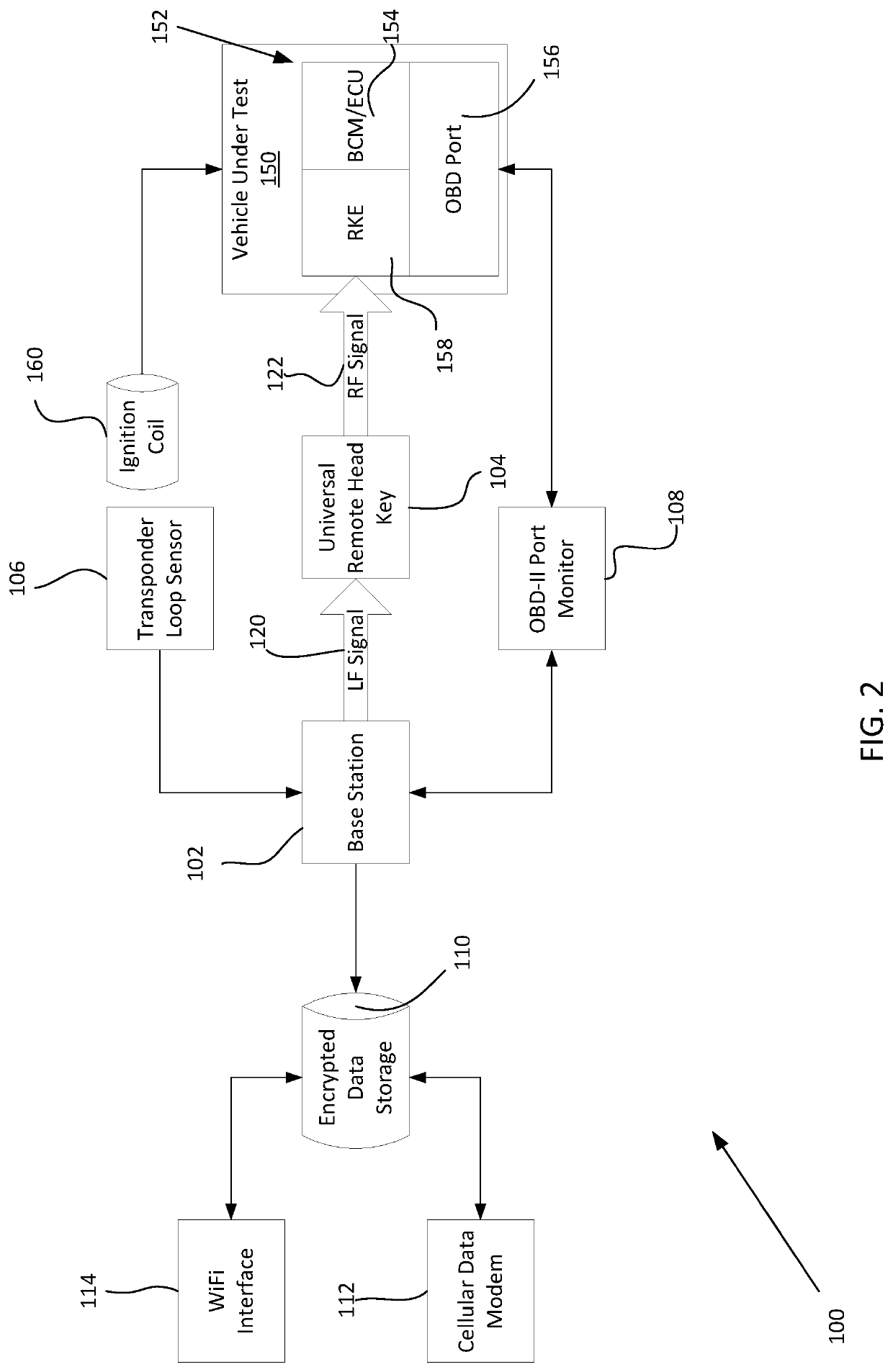
Systems and methods for creating key backups by identifying and storing unique key information and for replicating unique keys from key backups
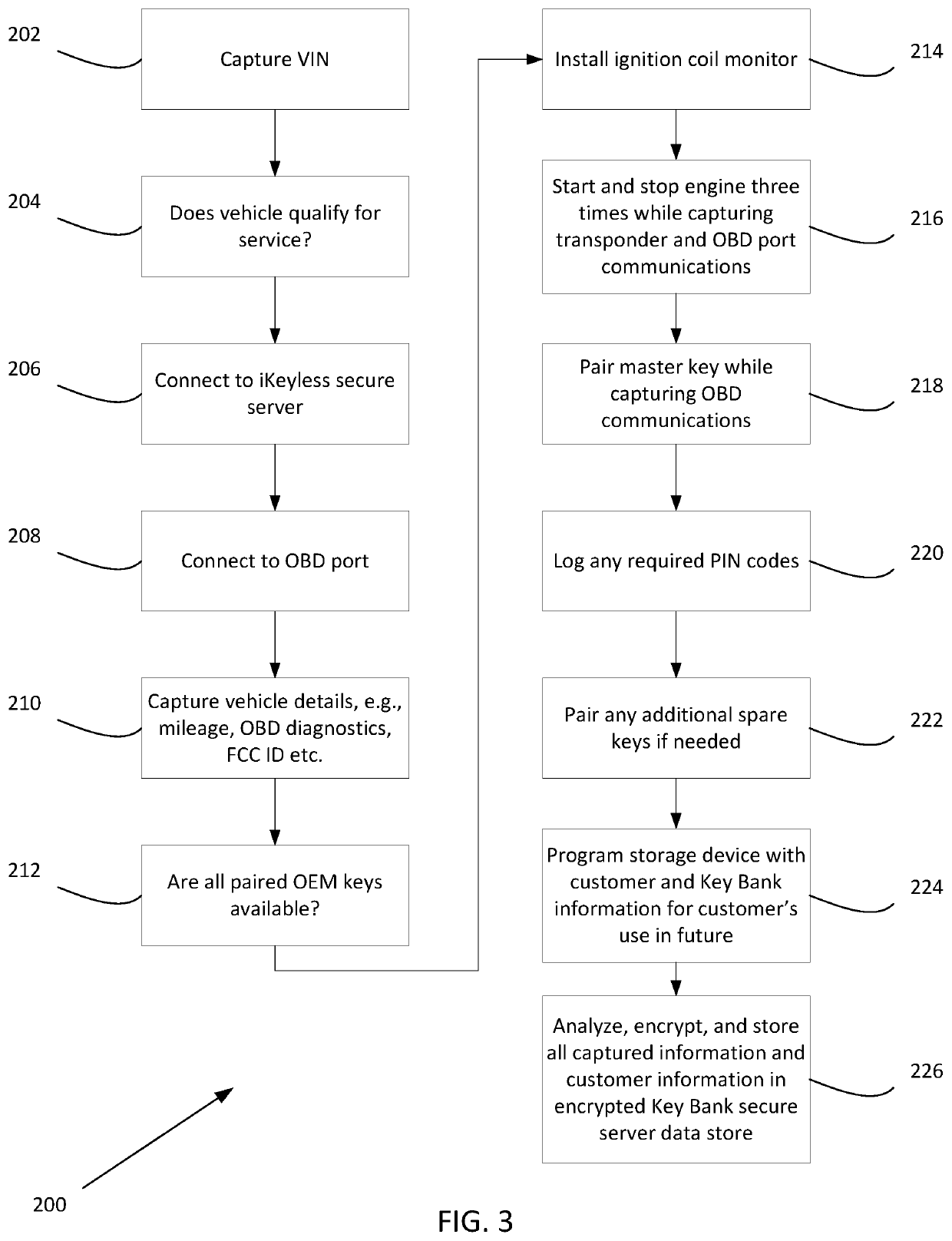
ActiveUS20200013241A1Eliminate needKey distribution for secure communicationRegistering/indicating working of vehiclesEngineeringWorld Wide Web
Owner:IKEYLESS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com