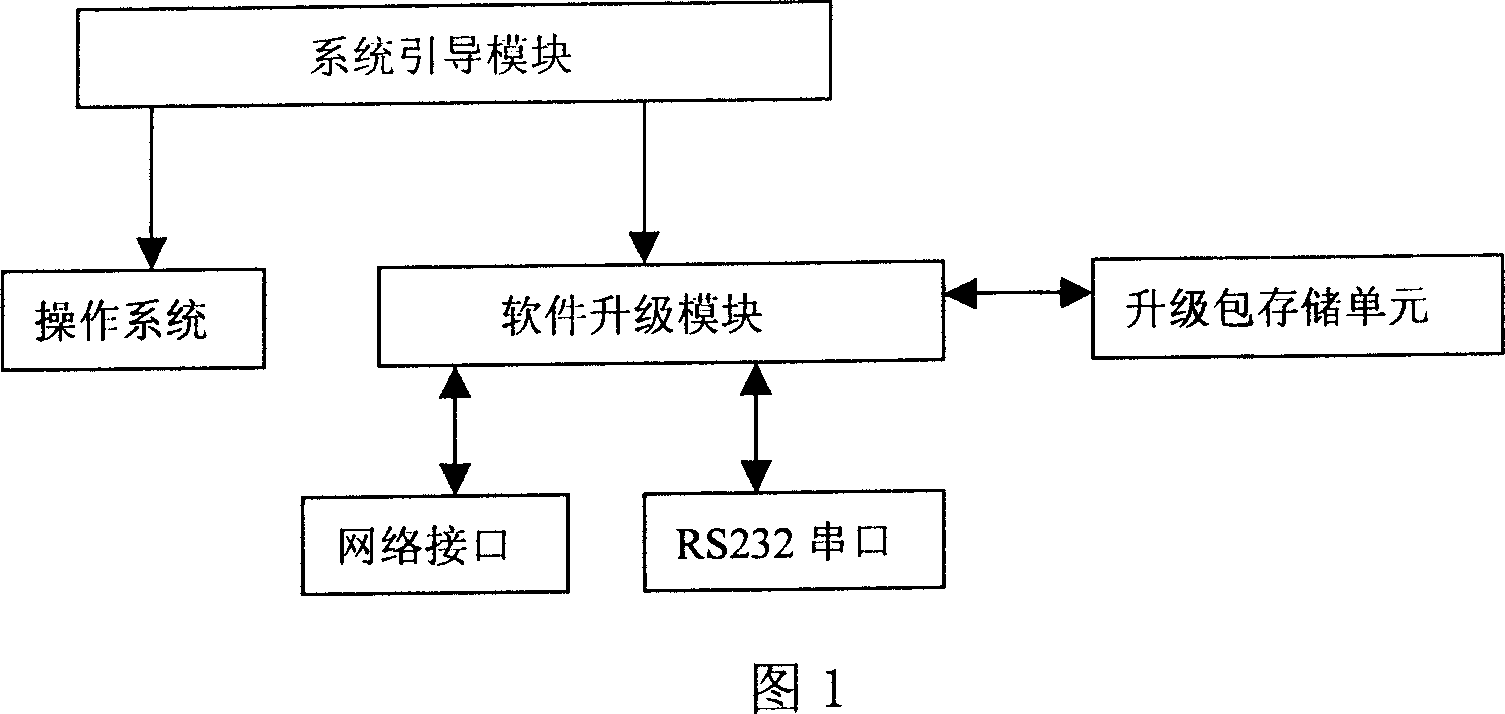
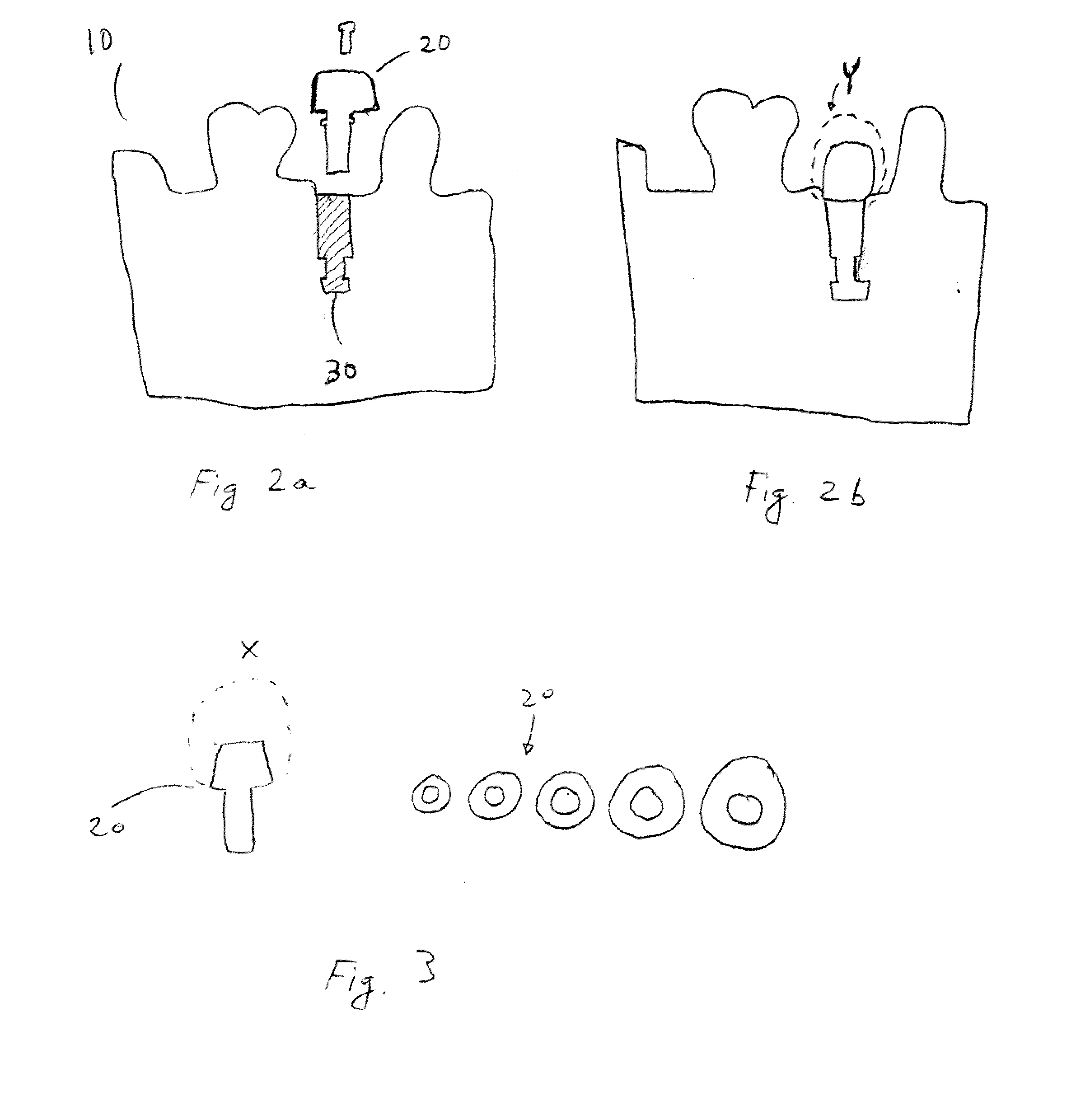Patents
Literature
235 results about "Master file" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
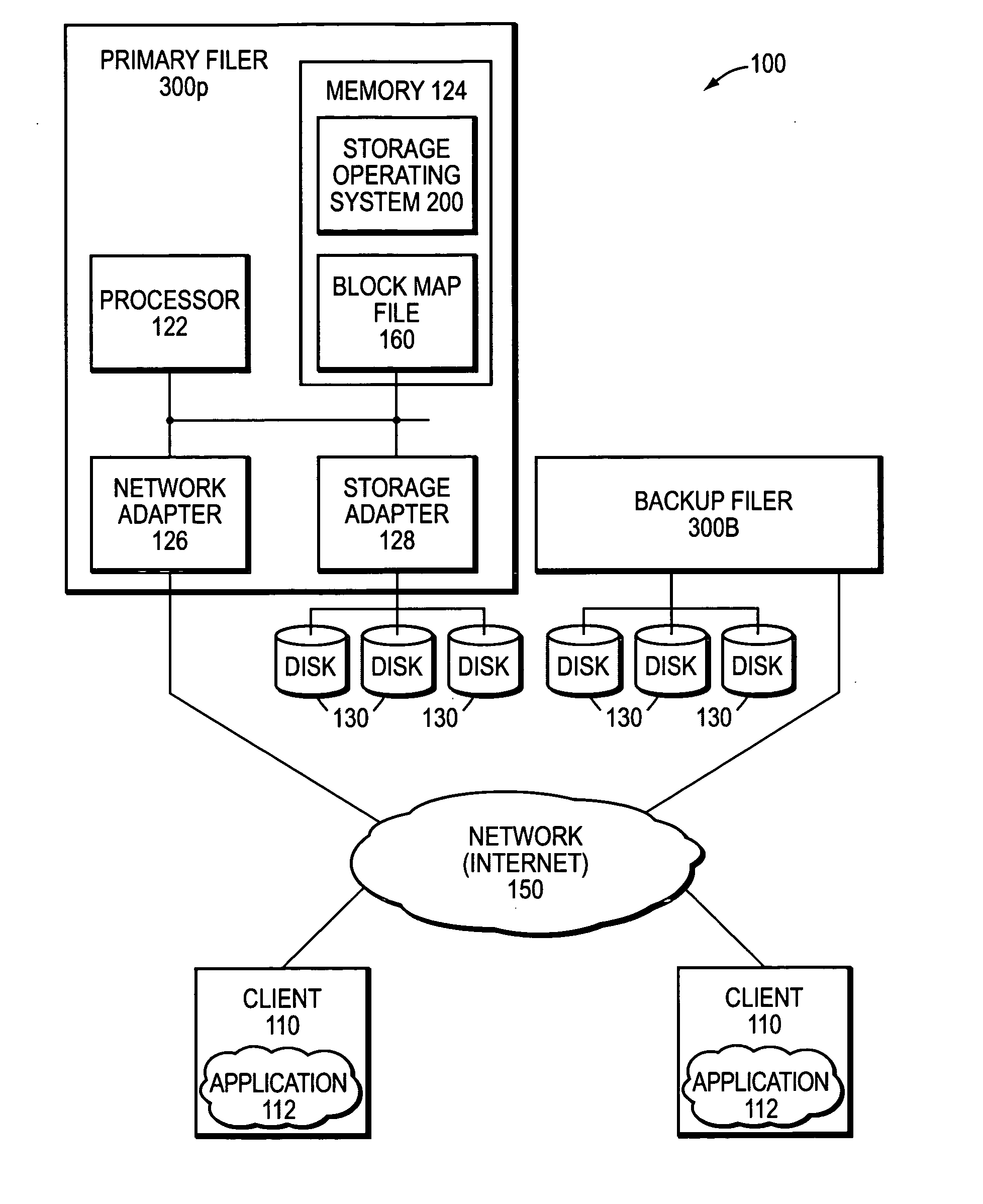
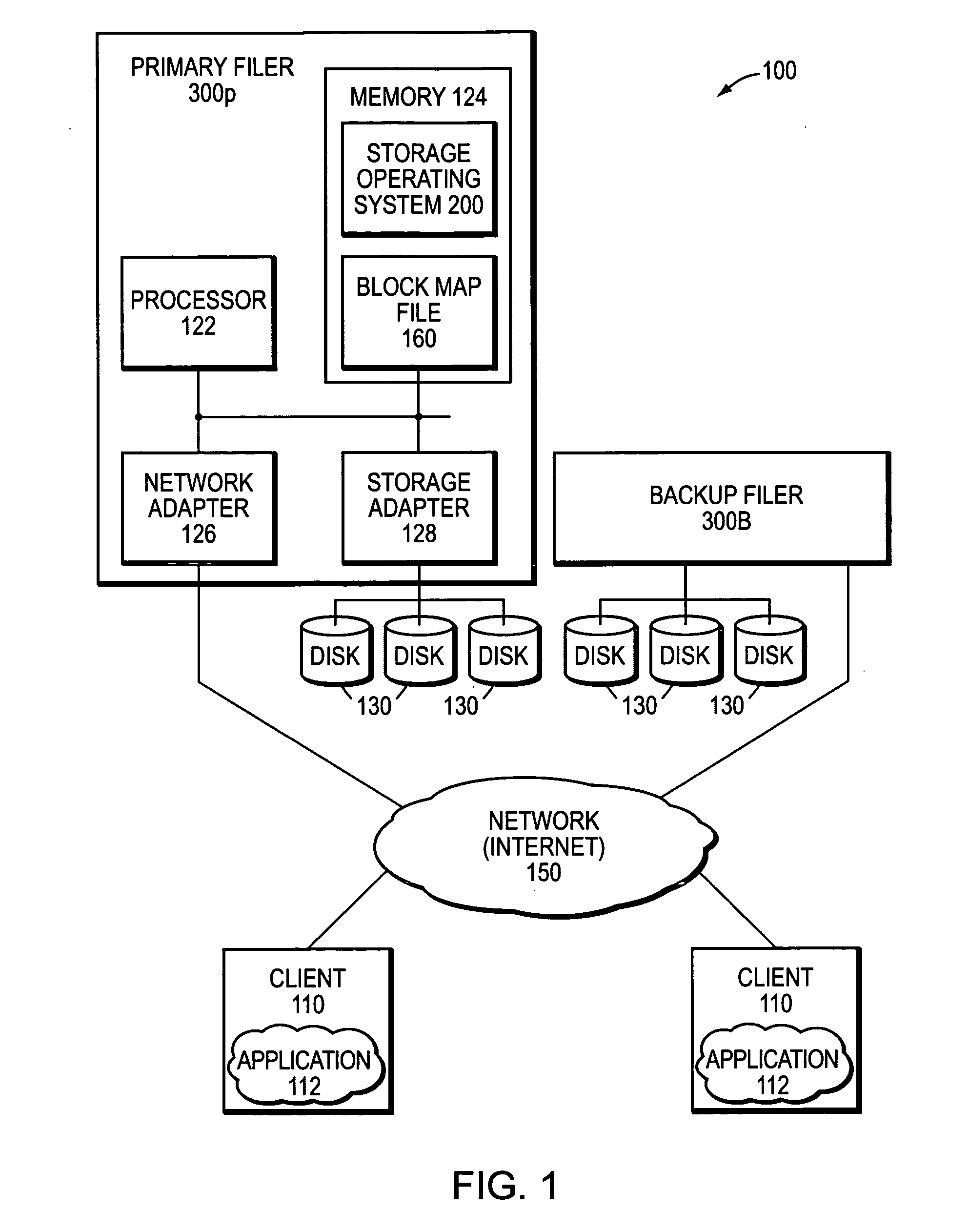
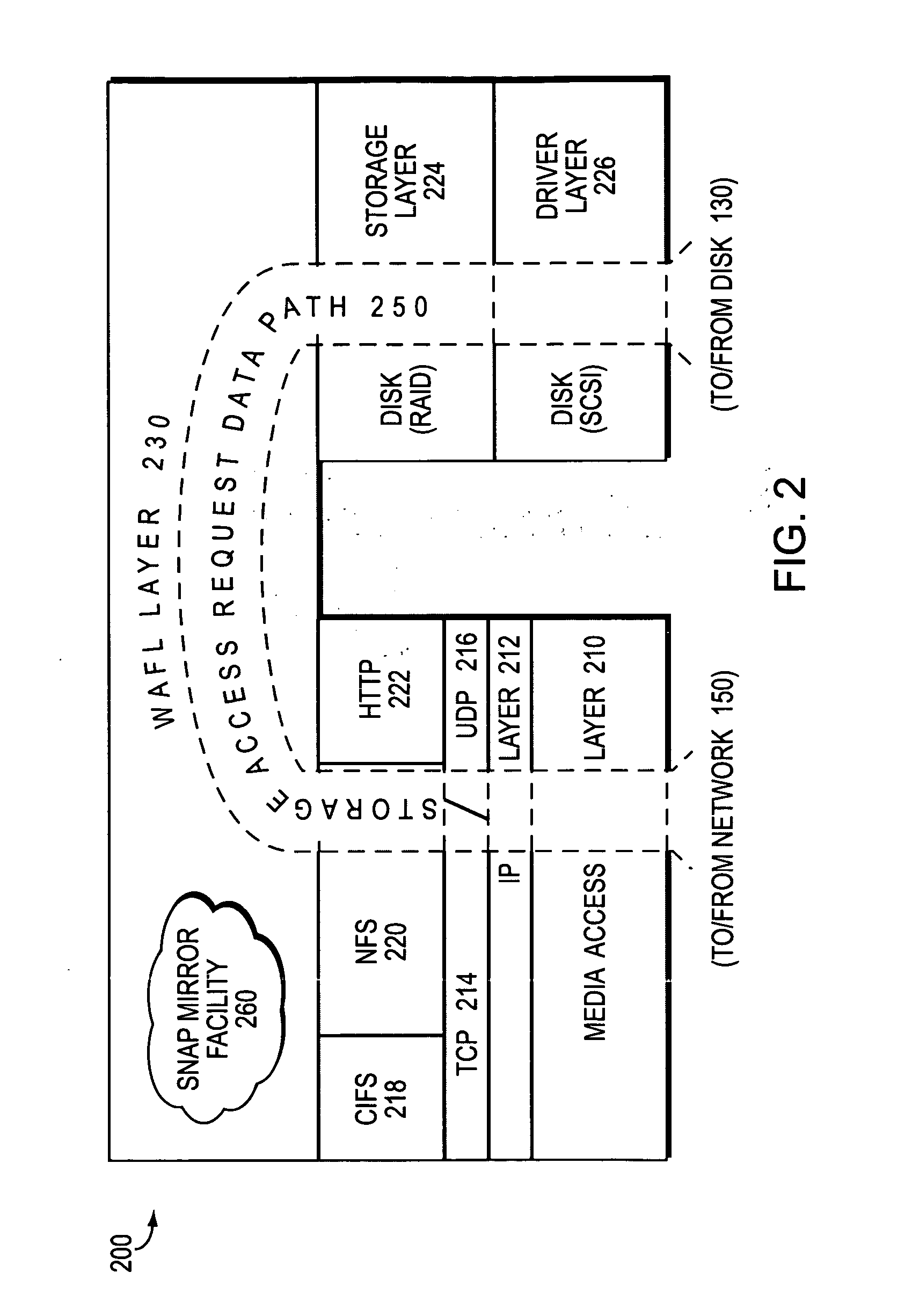
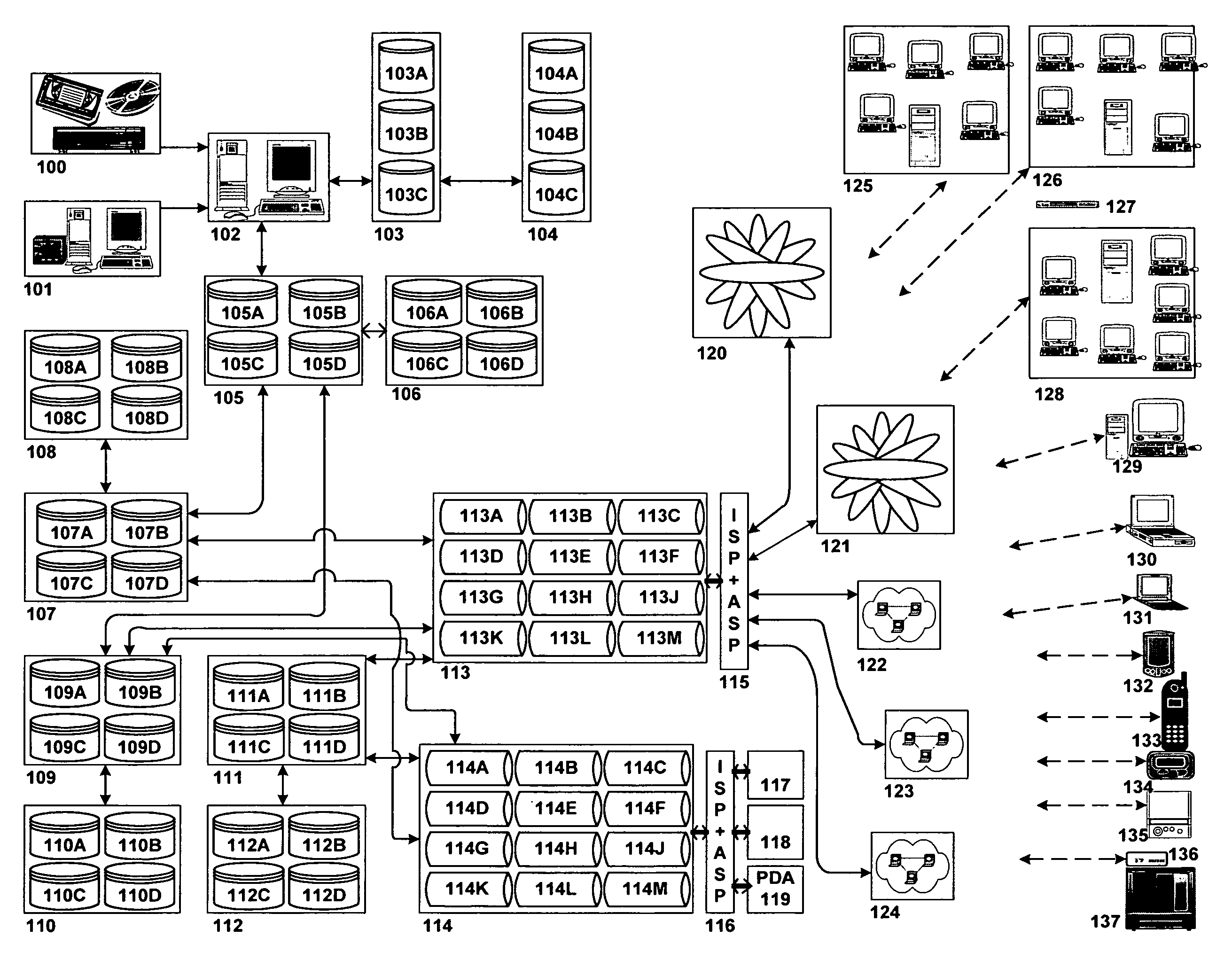
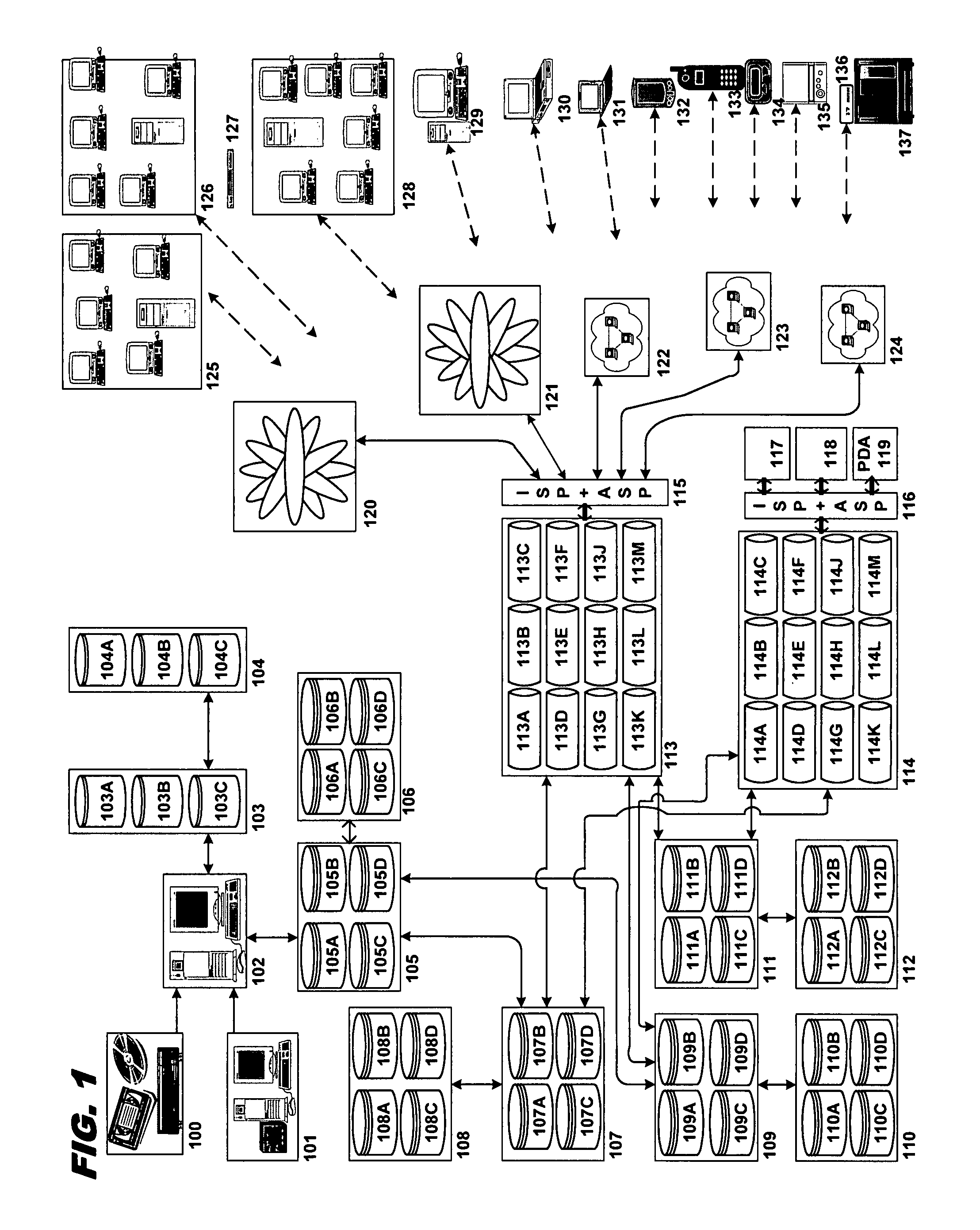
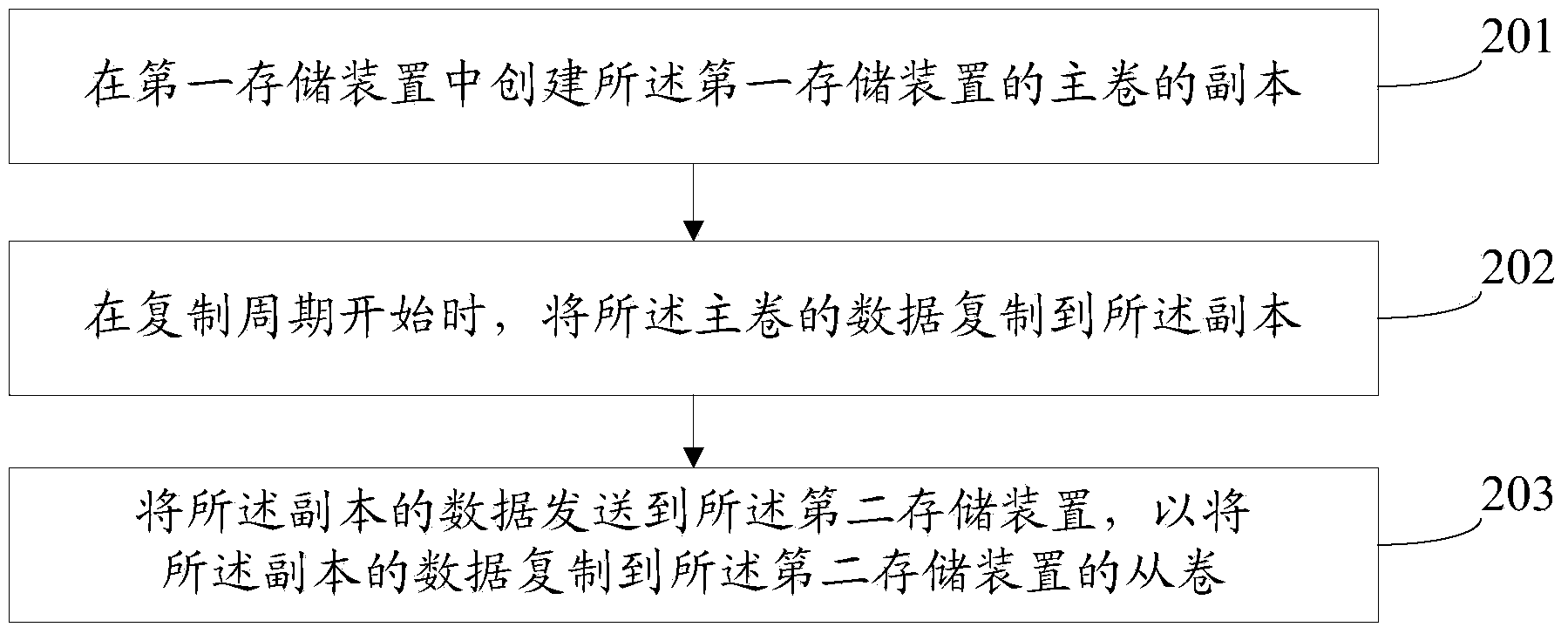
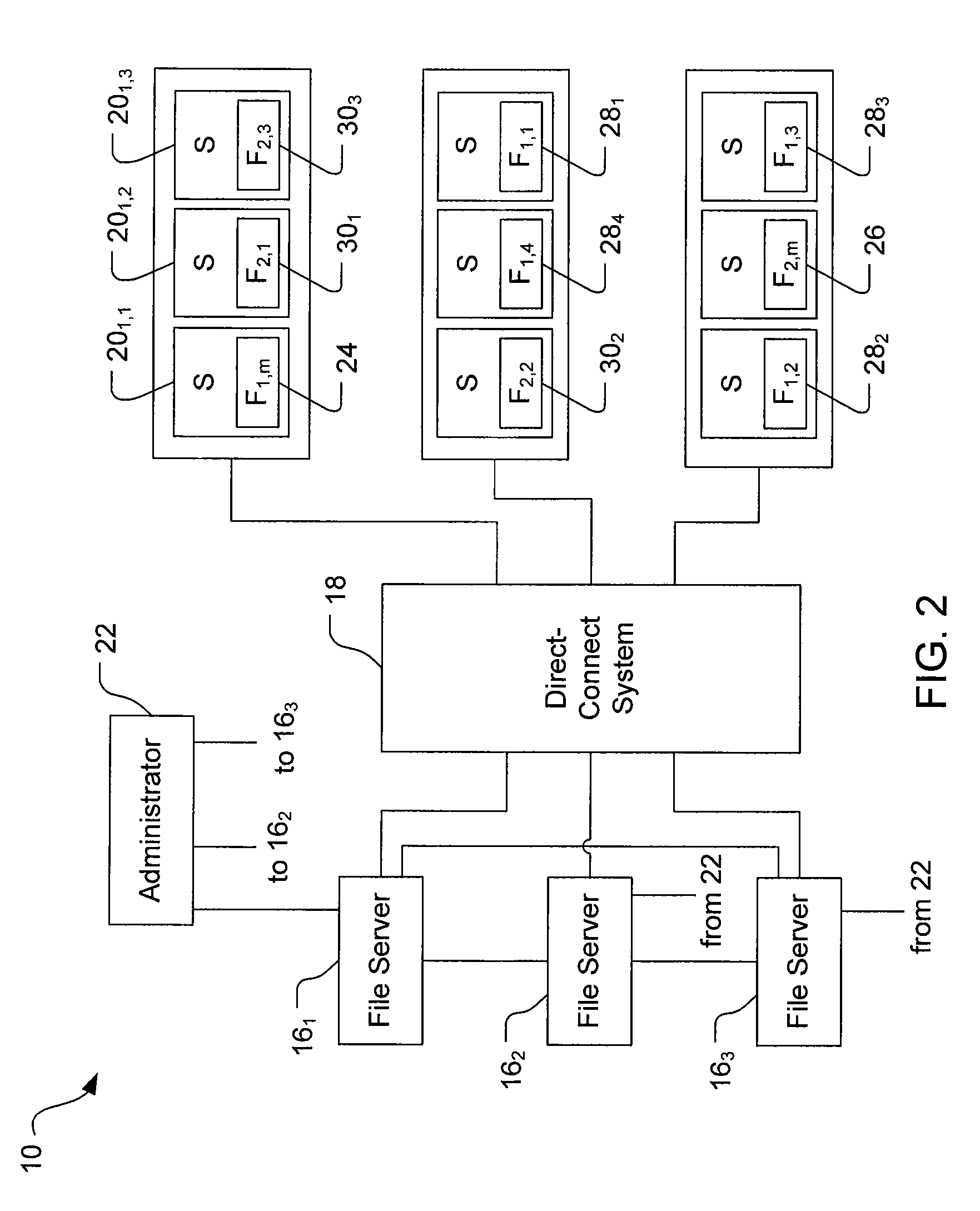
Data recovery with internet protocol replication with or without full resync
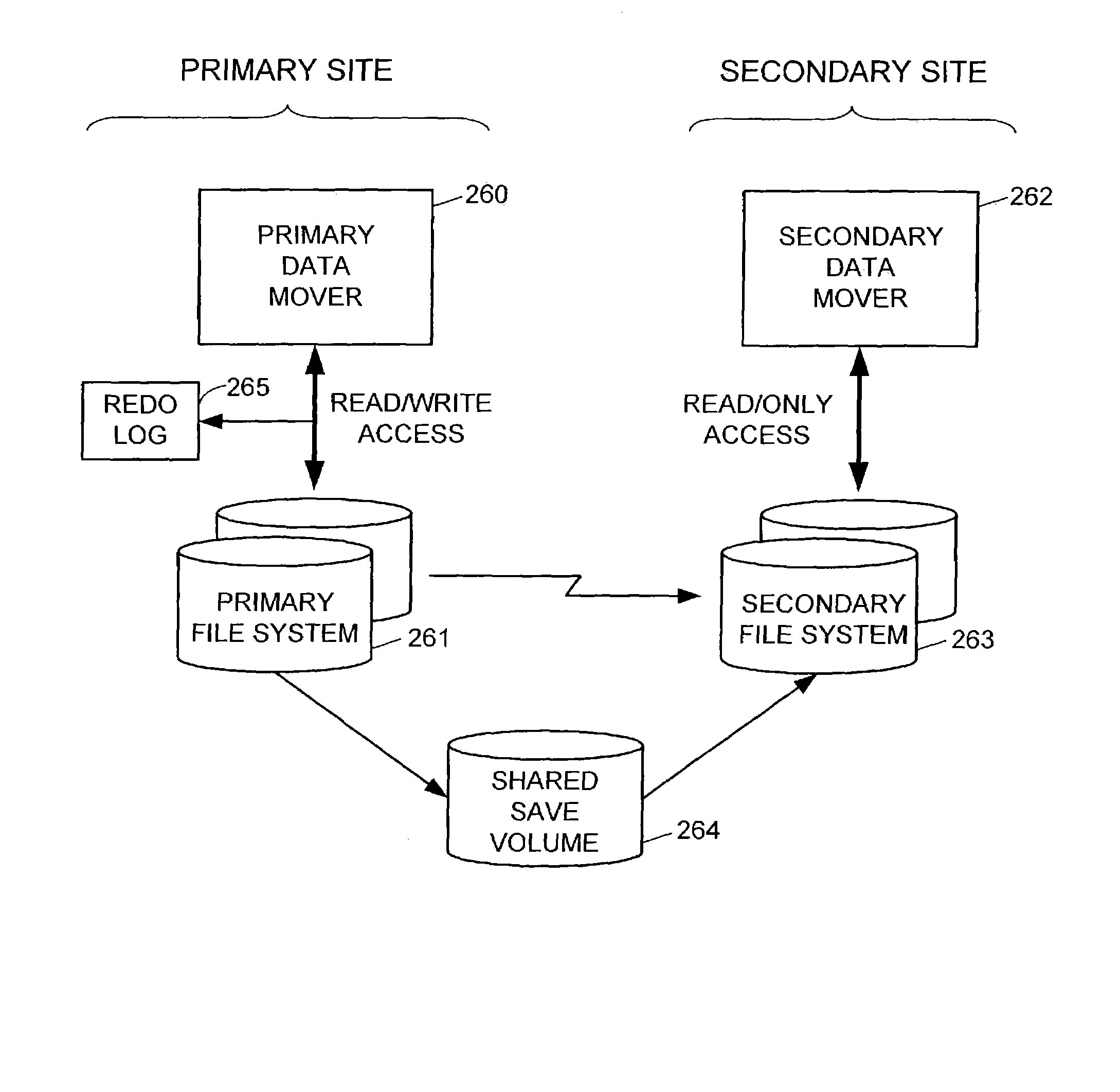
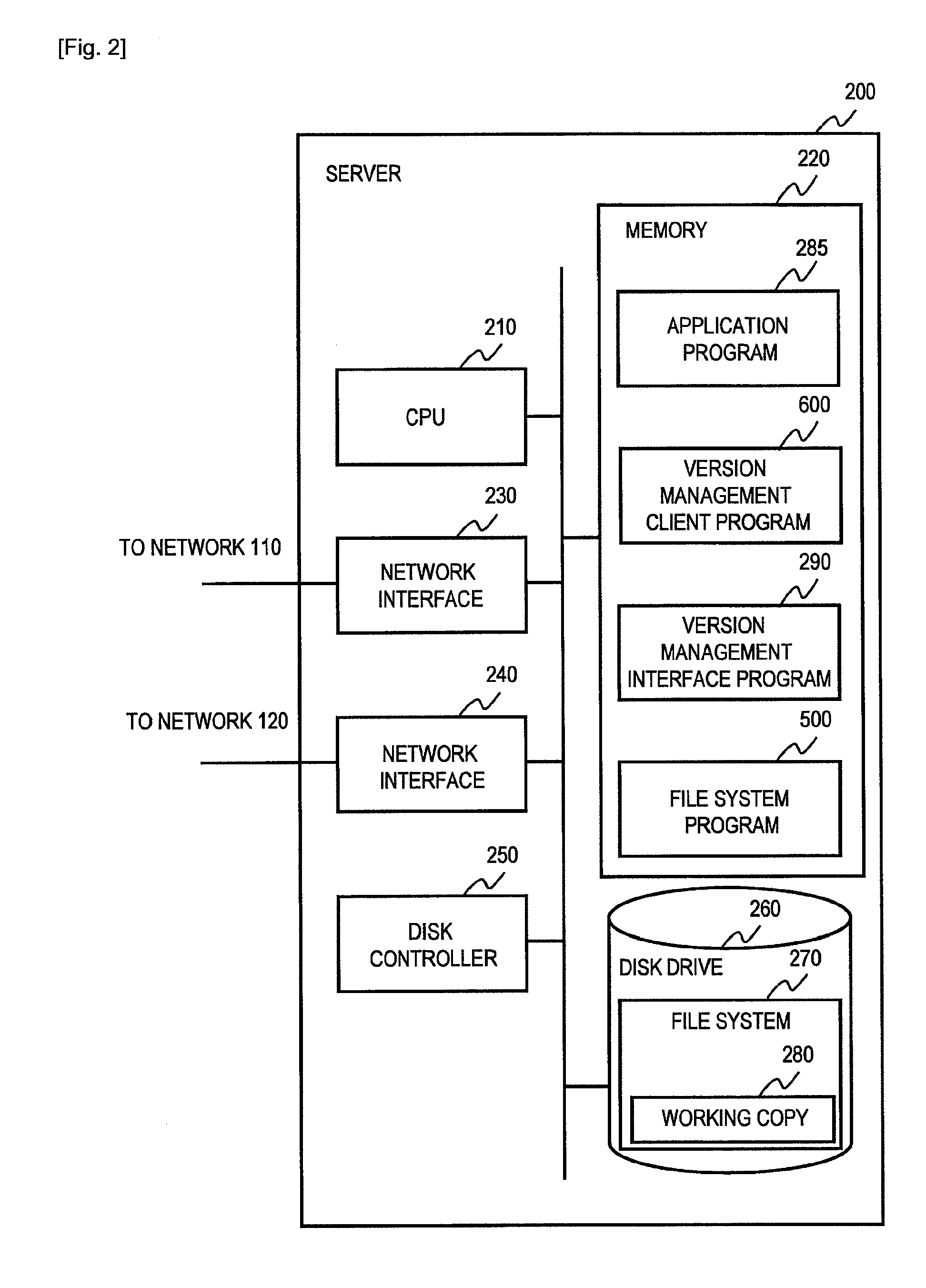
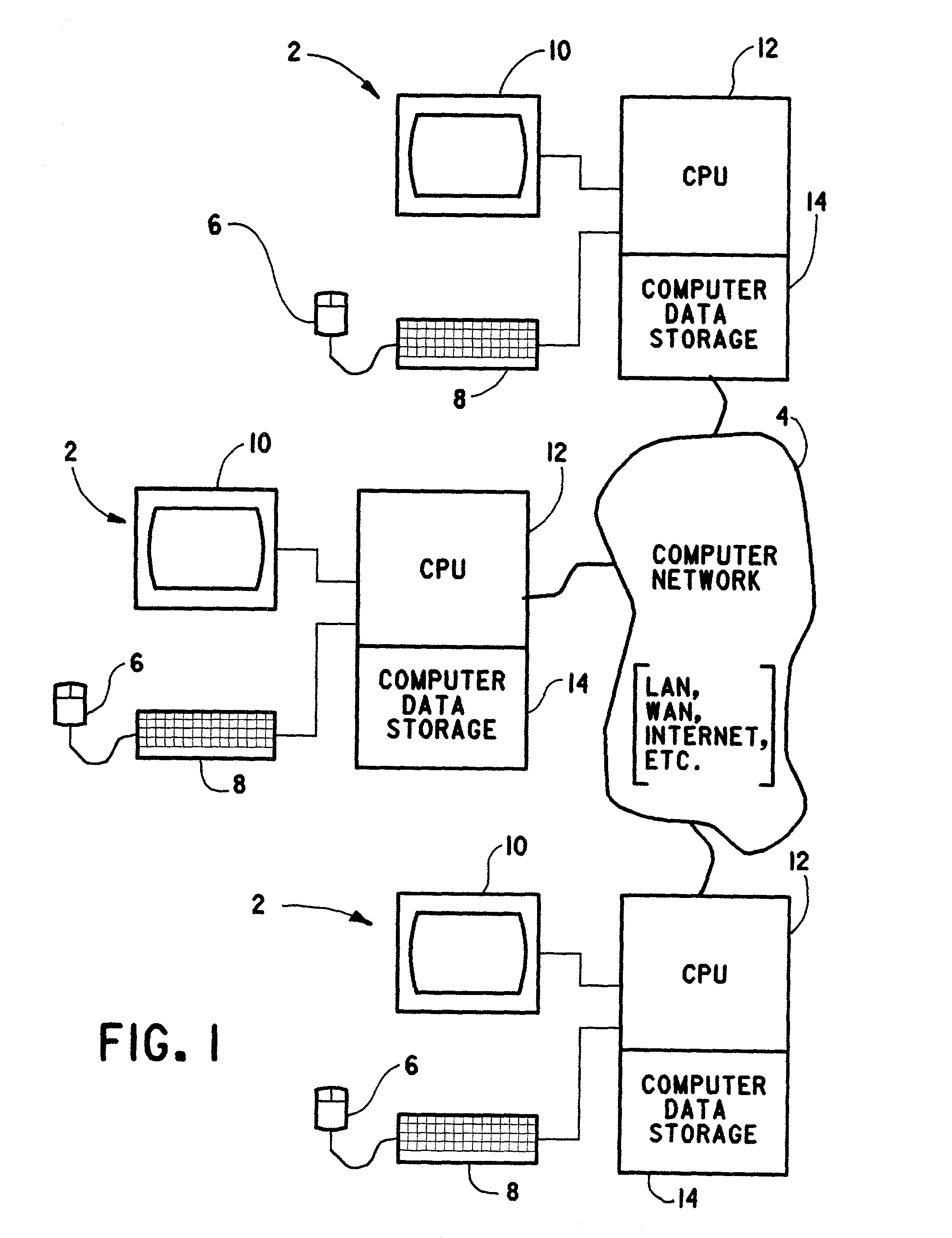
ActiveUS7275177B2Data processing applicationsEmergency protective arrangements for automatic disconnectionPrimary sitesFile system
In an asynchronous remote copy system, a primary site keeps a list of data blocks for which changes have been made to a primary file system and transmitted to a secondary file system at a secondary site. When the primary site becomes inoperative, the secondary site begins read / write access to the secondary file system and keeps a snapshot copy of the restart point. Once the primary site becomes operative, the primary file system is restored to the state of the secondary file system at the restart point by using the list of data blocks for obtaining from the snapshot copy the data of the blocks for which changes had been made to the primary file system after the restart point. Then the primary file system is synchronized to the secondary file system, and read / write access is switched back from the secondary file system to the primary file system.
Owner:EMC IP HLDG CO LLC
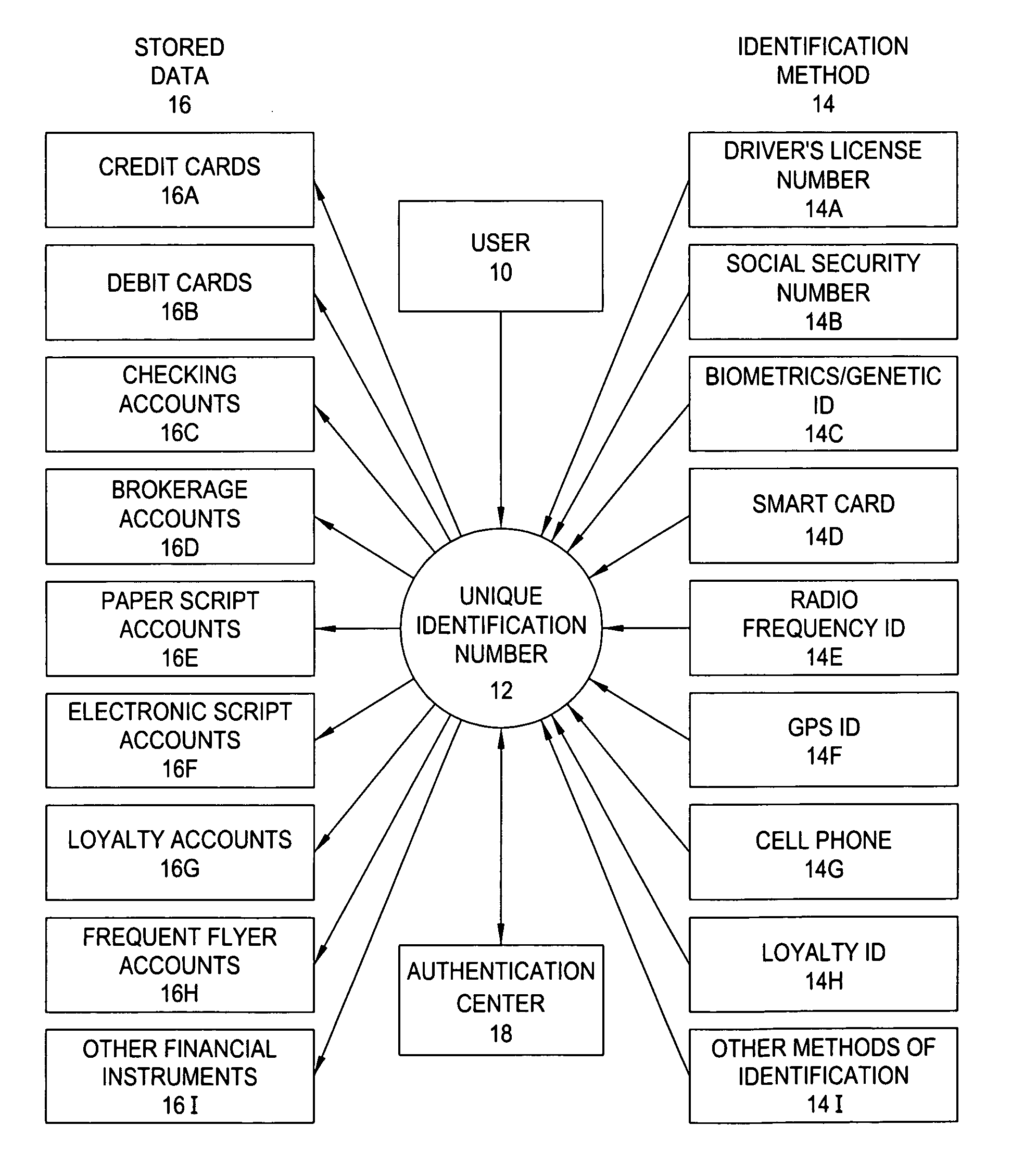
Secure transaction system
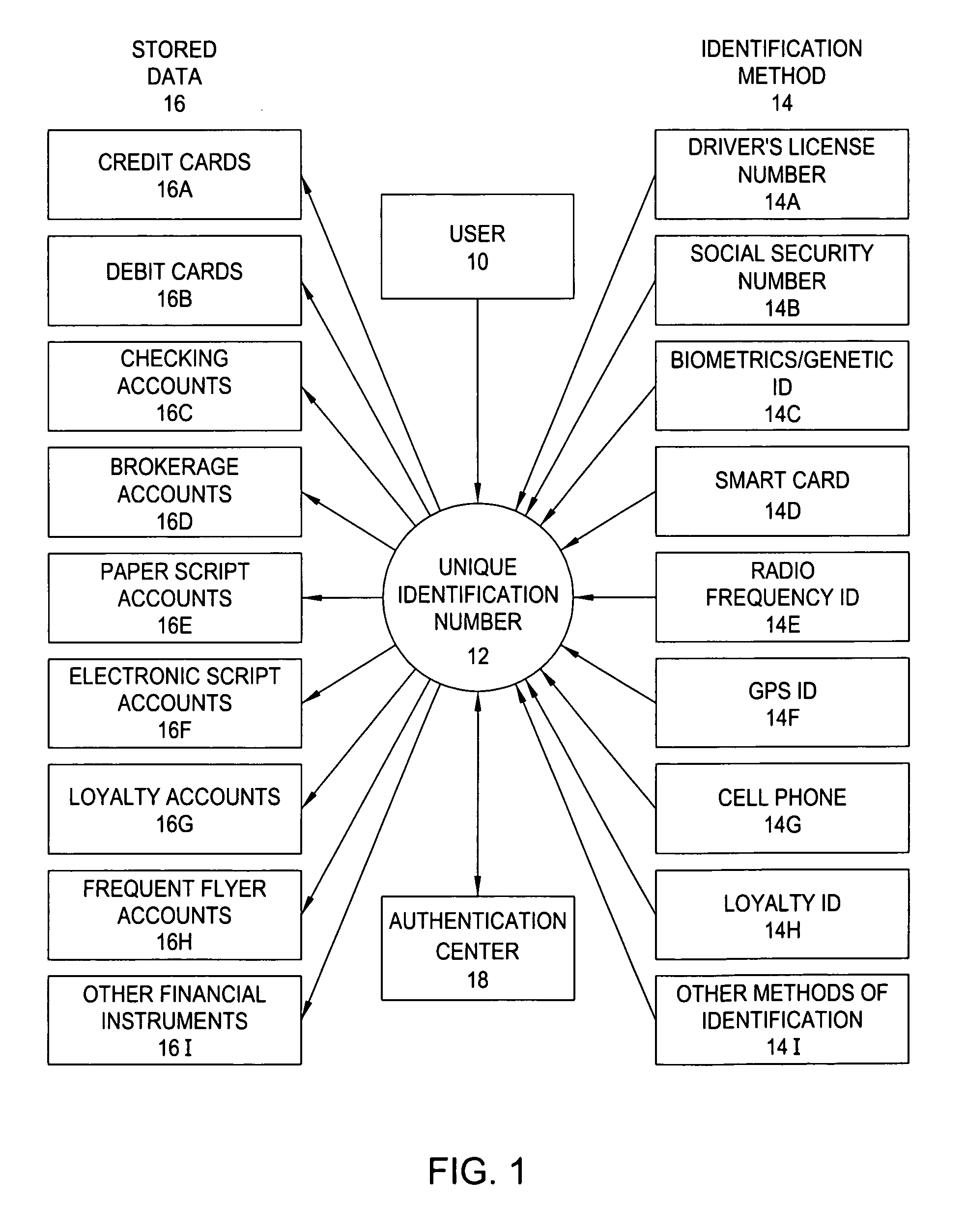
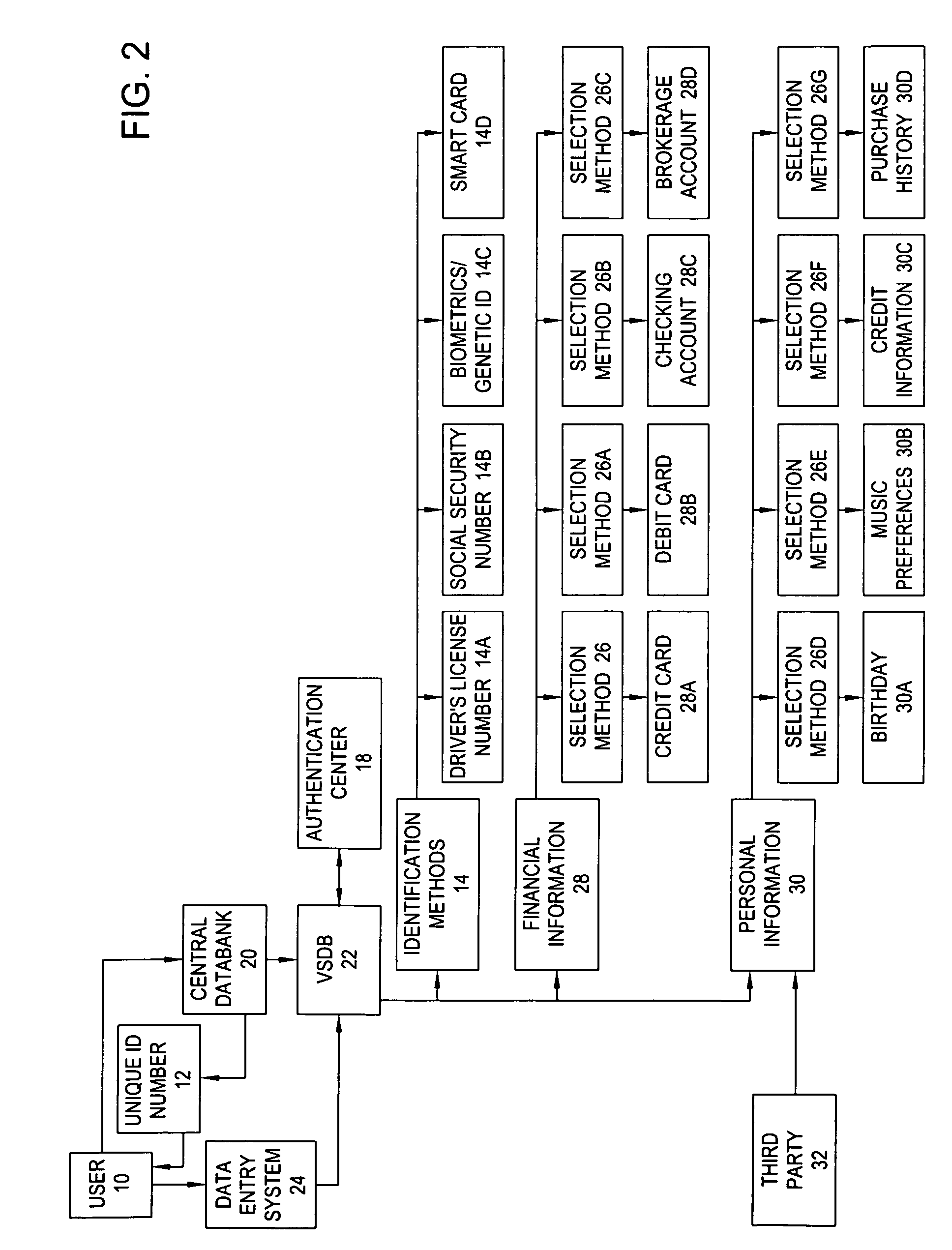
InactiveUS20060191995A1Improve management efficiencyComplete banking machinesFinanceData fieldCentral database
The system of the present invention comprises a personal Virtual Safety Deposit Box where users are able to enroll their identification methods, financial accounts and personal information. Once authenticated, this information is transferred to a master file within a central databank. Enrollment enables the user to link each item (collectively referred to as the “stored data”) to any one of the plurality of identification methods they enter. Thereafter, the user may employ their enrolled identification methods to select a desired one of the stored data fields. A secure intermediary uses the identification method and a selection method to determine which of the stored data fields the user desires to employ by accessing a database containing each of the stored data fields and the corresponding selection method. The selected field is activated and any relevant outside agencies are notified of the transaction and the transaction is concluded.
Owner:SOURCE
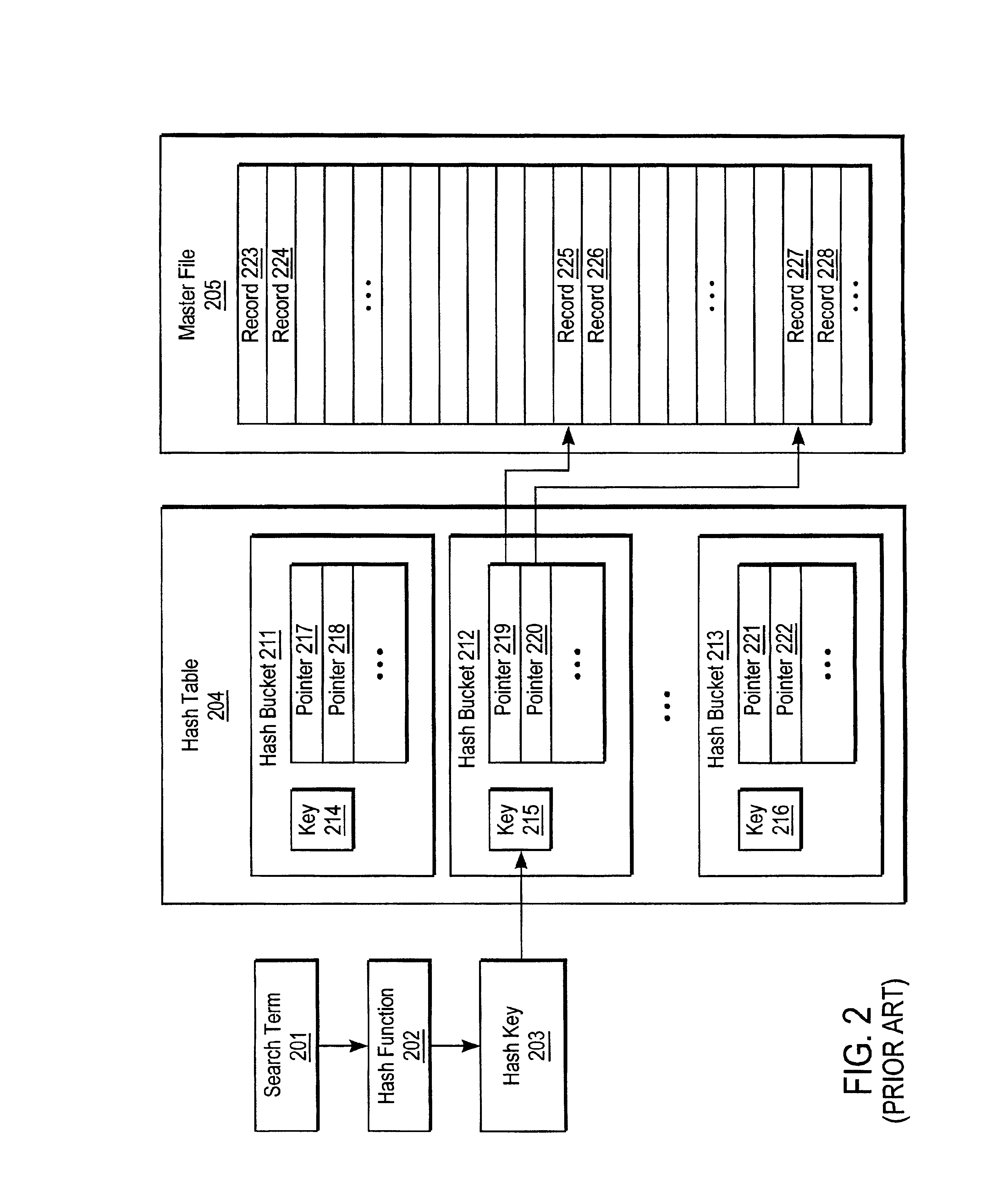
System and method for rapidly identifying the existence and location of an item in a file
InactiveUS6862602B2Rapid and efficient mannerMinimizes numberData processing applicationsDigital data information retrievalTheoretical computer scienceHash table
A system and method for rapidly identifying the existence and location of an item in a file using an improved hash table architecture. A hash table is constructed having a plurality of hash buckets, each identified by a primary hash key. Each hash entry in each hash bucket contains a pointer to a record in a master file, as well as a secondary hash key independent of the primary hash key. A search for a particular item is performed by identifying the appropriate hash bucket by obtaining a primary hash key for the search term. Individual hash entries within the hash bucket are checked for matches by comparing the stored secondary keys with the secondary key for the search term. Potentially matching records can be identified or ruled out without necessitating repeated reads of the master file. The improved hash table system and method is employed in a contextual text searching application for determining the intersection of a text search with a hierarchical categorization scheme.
Owner:APPLE INC
Remote disaster recovery and data migration using virtual appliance migration
InactiveUS20070038887A1Create efficientlyEfficiently servingError detection/correctionData setClient-side
A technique efficiently creates and serves a backup data set on a backup filer located at a remote site from a primary filer by essentially moving an entire operating environment of a primary data set to the backup filer. The primary filer is organized into one or more virtual filers (vfilers), one of which (the primary vfiler) is configured to serve data, such as the primary data set, for a client. In the event that the primary filer or primary vfiler becomes unavailable, the technique may be implemented as a disaster recovery or data migration sequence to enable efficient instantiation of a backup vfiler to serve the backup data set for the client.
Owner:NETWORK APPLIANCE INC
Video-on-demand system
InactiveUS7254622B2Increase speedFast dataMultiple digital computer combinationsTwo-way working systemsVideo playerPager
A video-on-demand system provides efficient commercial distribution for renting and / or selling movies, video programs, video games and electronic data. Data input stations upload original video data from videotapes, videocassettes, videodisks or film, or from electronic data format on transferable storage media or over a telecommunications line. A video data capture computer converts the original video data into a preferred video data storage format and stores the video data files in a first generation video data storage unit. The video data files are sorted by categories and classified in indexed master files stored on a second generation video data storage unit. NTSC, PAL and / or HDTV versions of the video data files are created and stored in separate data storage units for serving different markets. Customers access the system through computer servers connected to the Internet. The computer servers access the video data file in the data storage units and create a temporary video data file, which is downloaded to the customer via the Internet. The video data file is downloaded at high speed and stored on the customer's video player device for viewing at a later time. The video data files can be downloaded, stored and viewed on a desktop computer, a laptop computer, palmtop computer, a set-top data storage device connected to a television set, video game device, or a personal digital assistant, cellular telephone or pager with video capabilities. The system includes back-up mirror storage files at all levels of the system for security against data loss.
Owner:PATHWAYS TO RIGHT-OF-WAYS INC
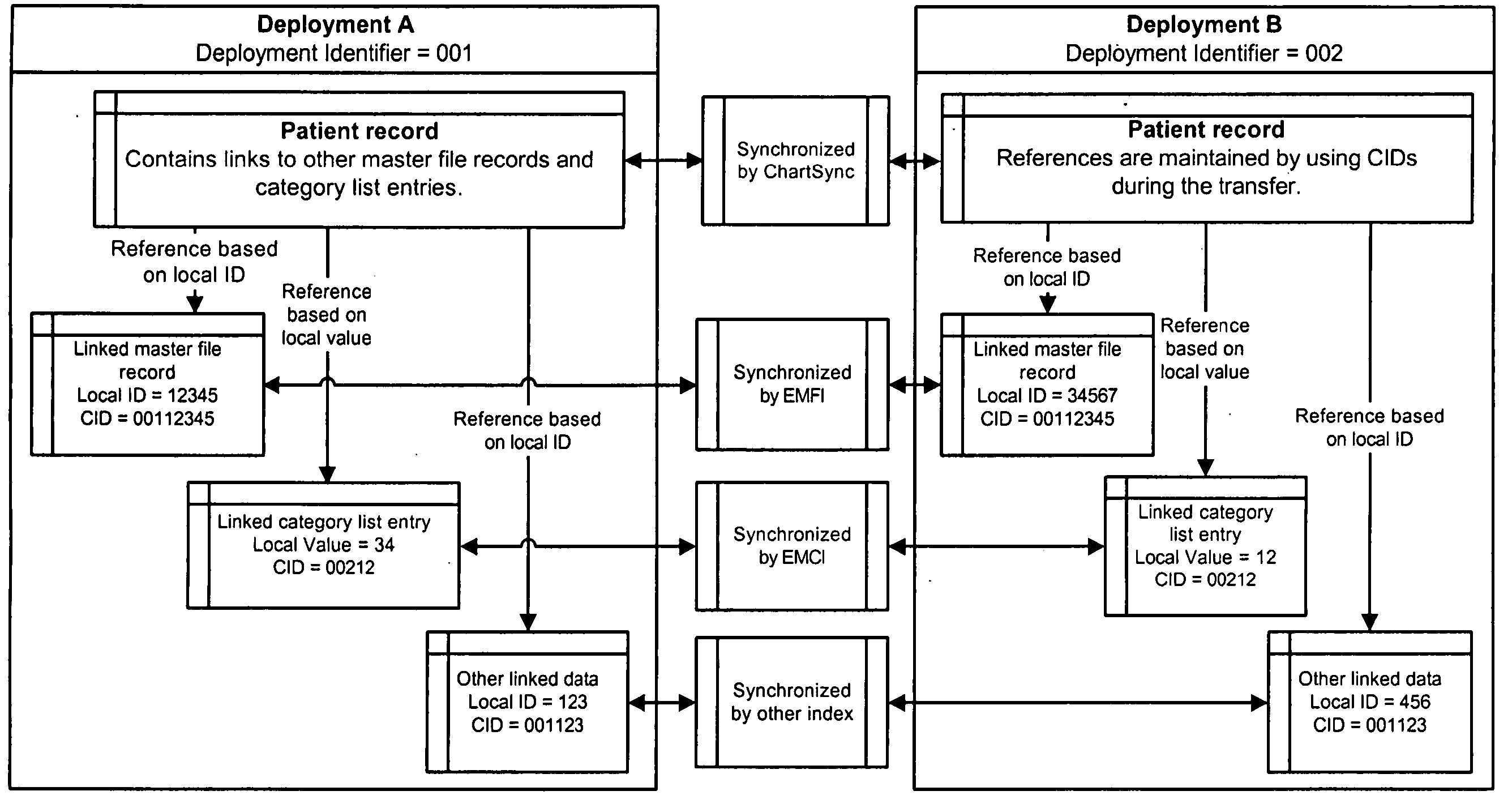
System and method of synchronizing data sets across distributed systems
InactiveUS20050071195A1Digital data information retrievalPatient personal data managementData setUnique identifier
A system and method is provided for synchronizing a data set across a distributed, electronic, health record system which includes creating and storing the data set at a first deployment, assigning a unique identifier to the data set, designating the first deployment as a home deployment for the data set, and transmitting a copy of the data set, the unique identifier, and the home deployment designation to a master index server. The method also includes causing the master file index server to transmit the copy of the data set, the unique identifier, and the home deployment designation to the second deployment if it is determined that the data set should be transmitted to the second deployment, and causing the master file index server to synchronize the data set between the first deployment and the second deployment.
Owner:EPIC SYST CORP (US)
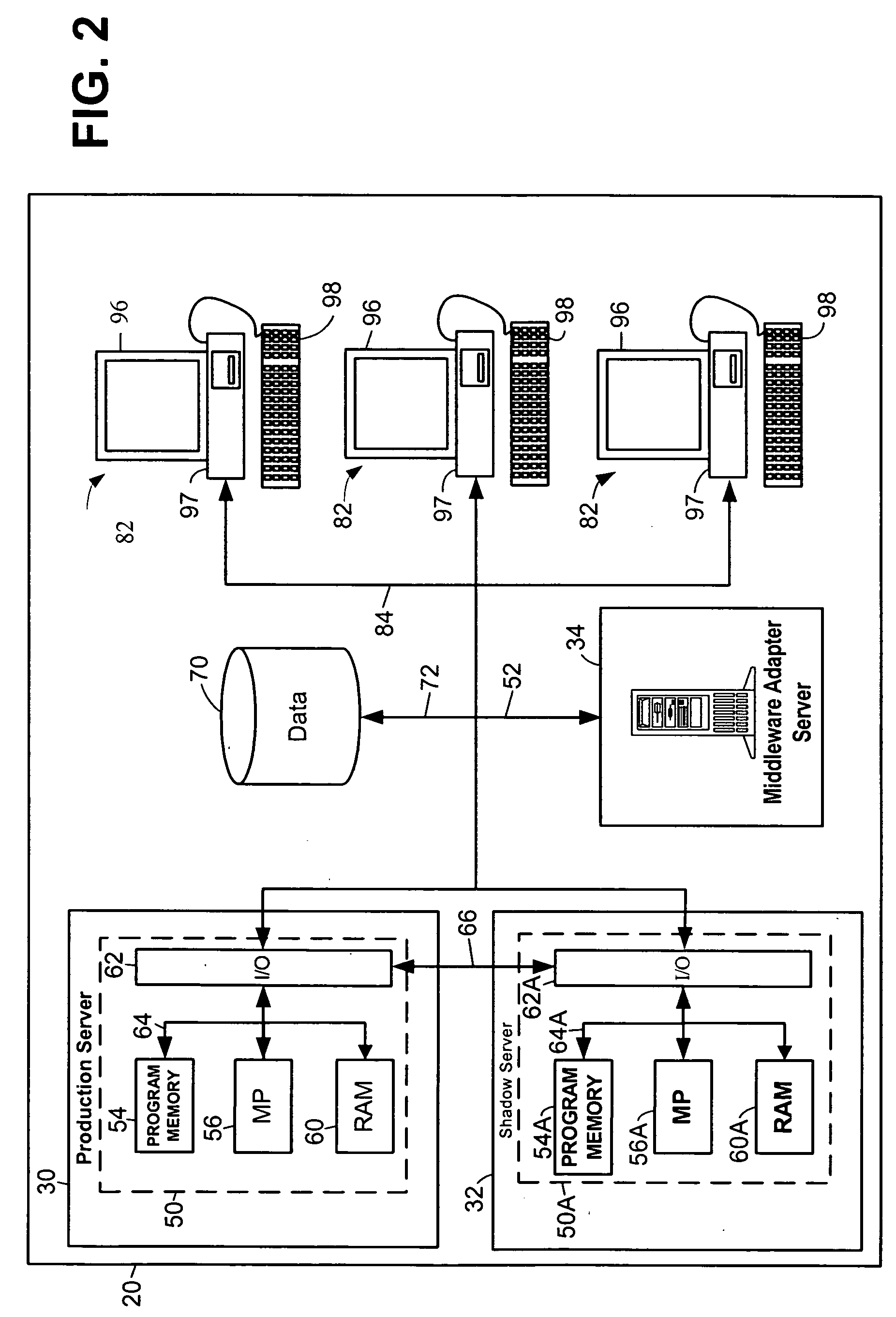
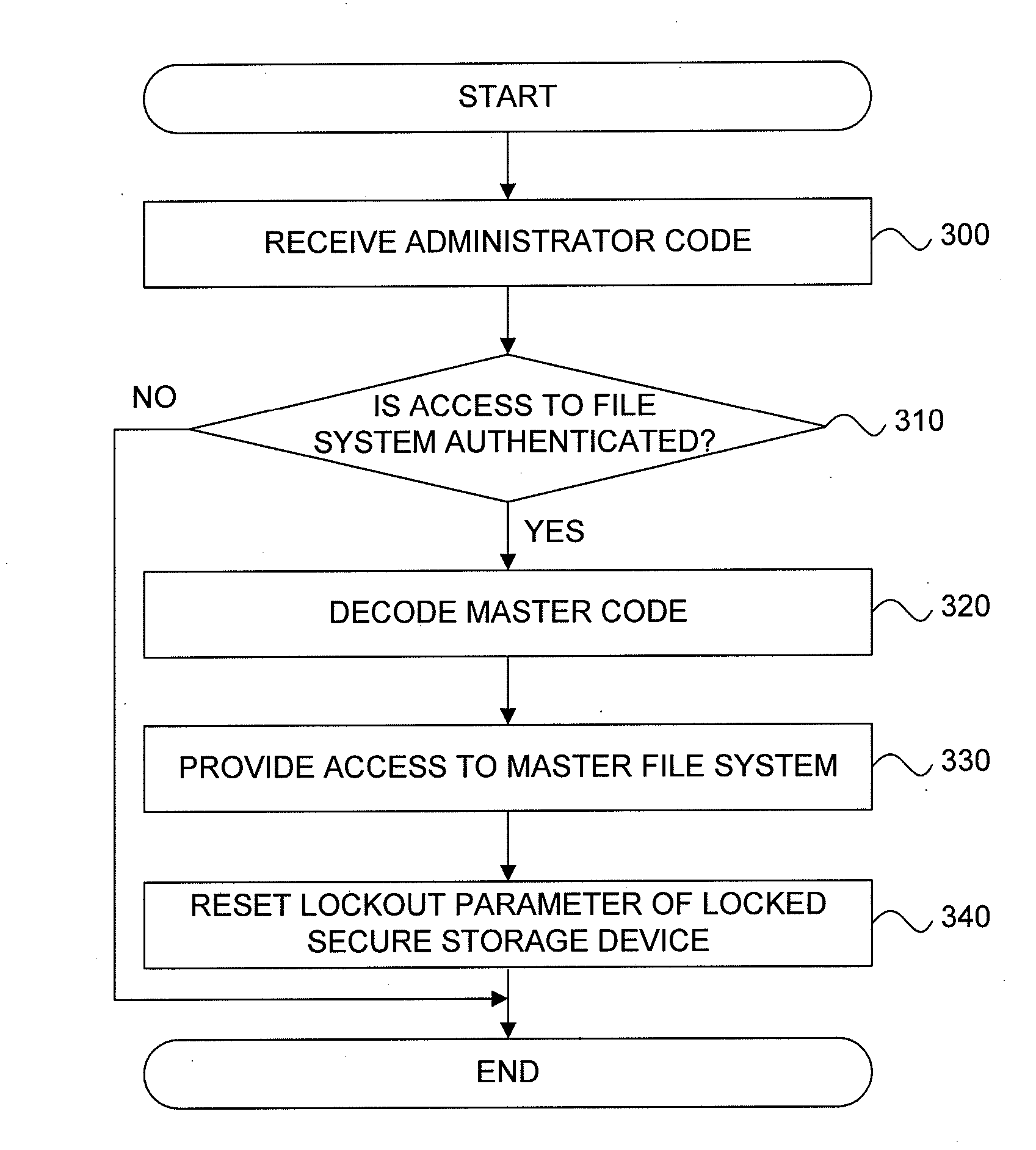
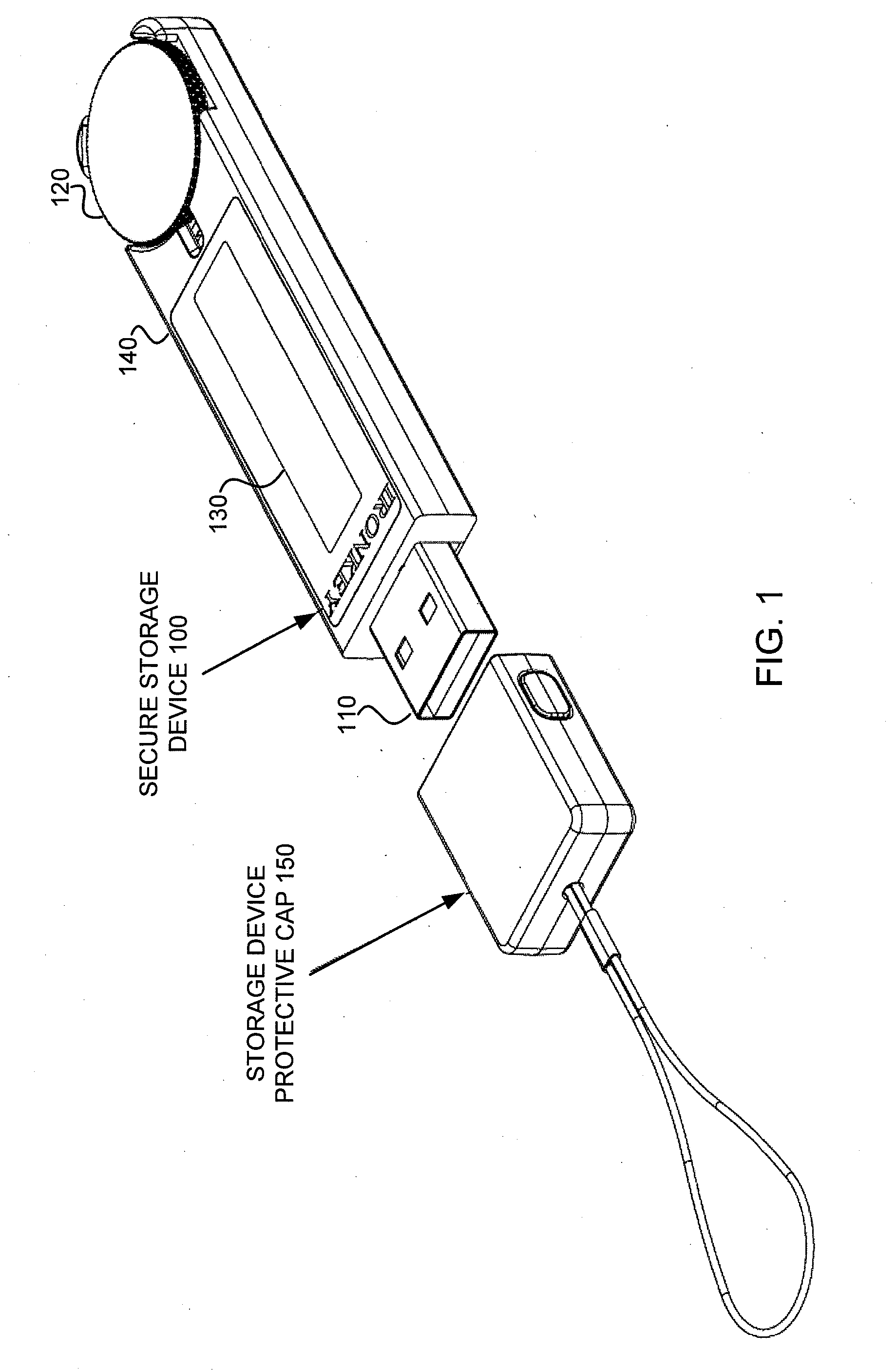
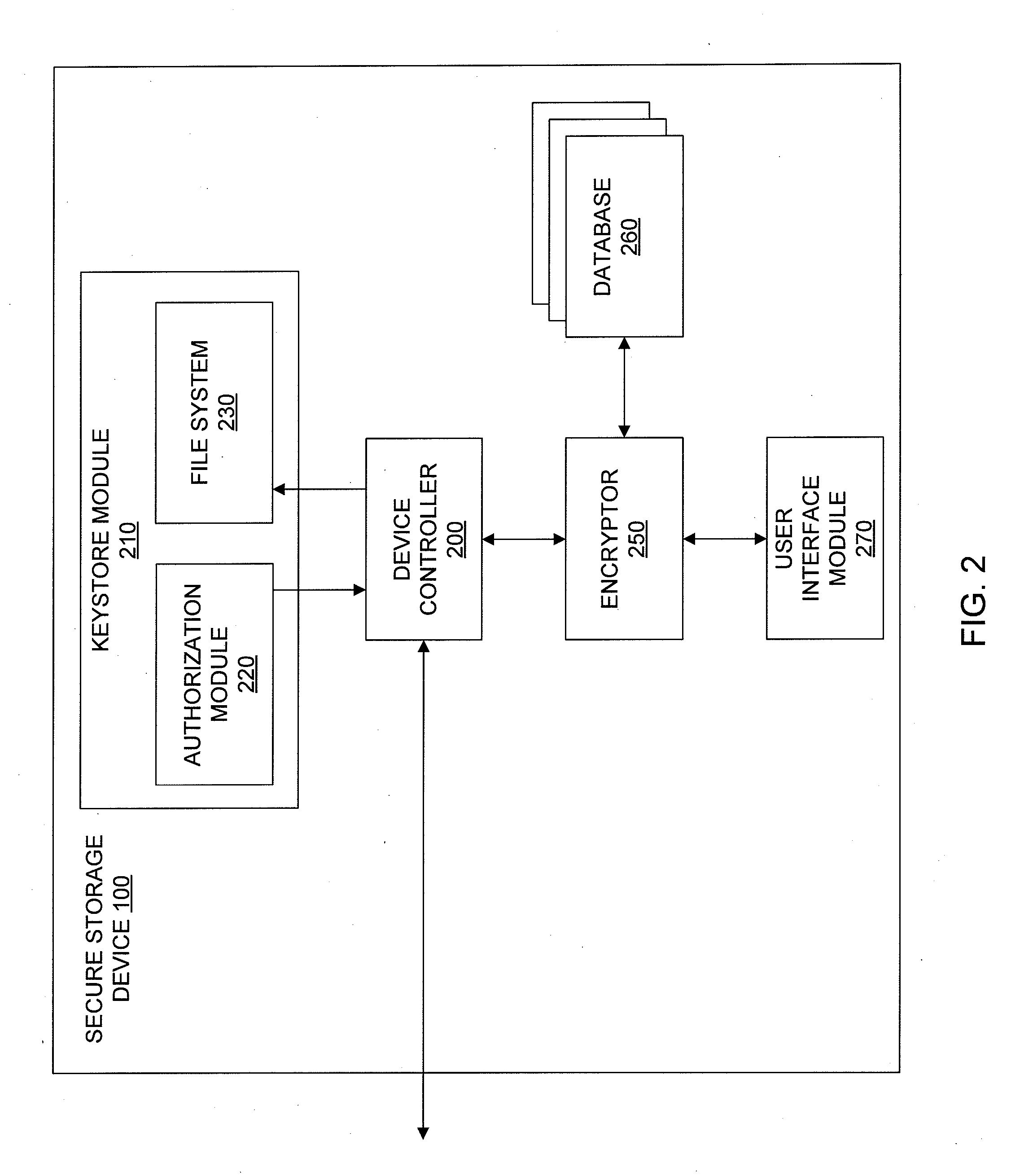
Recovery of Data Access for a Locked Secure Storage Device
A system for recovery of data access of a locked secure storage device can comprise a keystore module and an authorization module. The keystore module may be configured to allow access to a master file system comprising a user encryption key for data stored within the locked secure storage device based on a master code. The authorization module may be configured to receive the administrator code, authenticate the administrator code, decode the master code, and reset a lockout parameter of the locked secure storage device.
Owner:DATA LOCKER INC
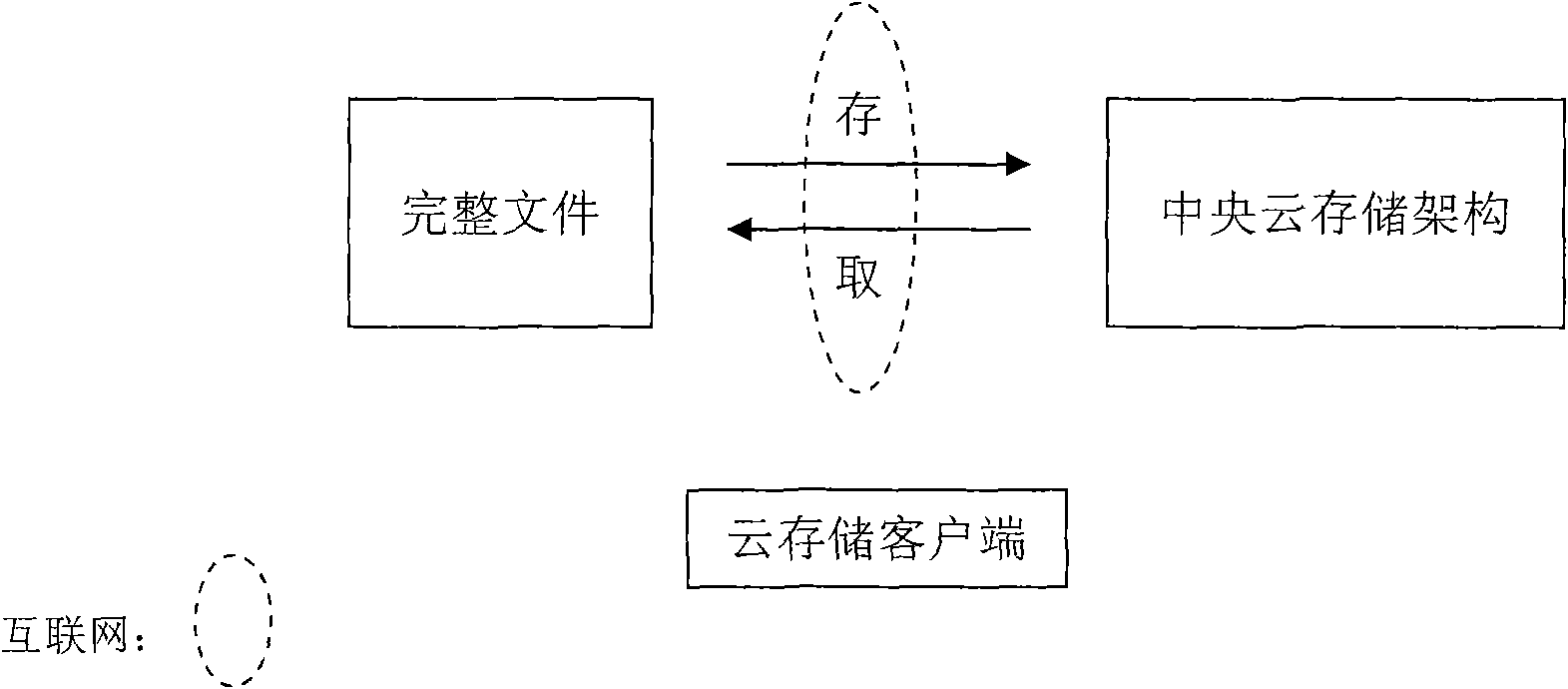
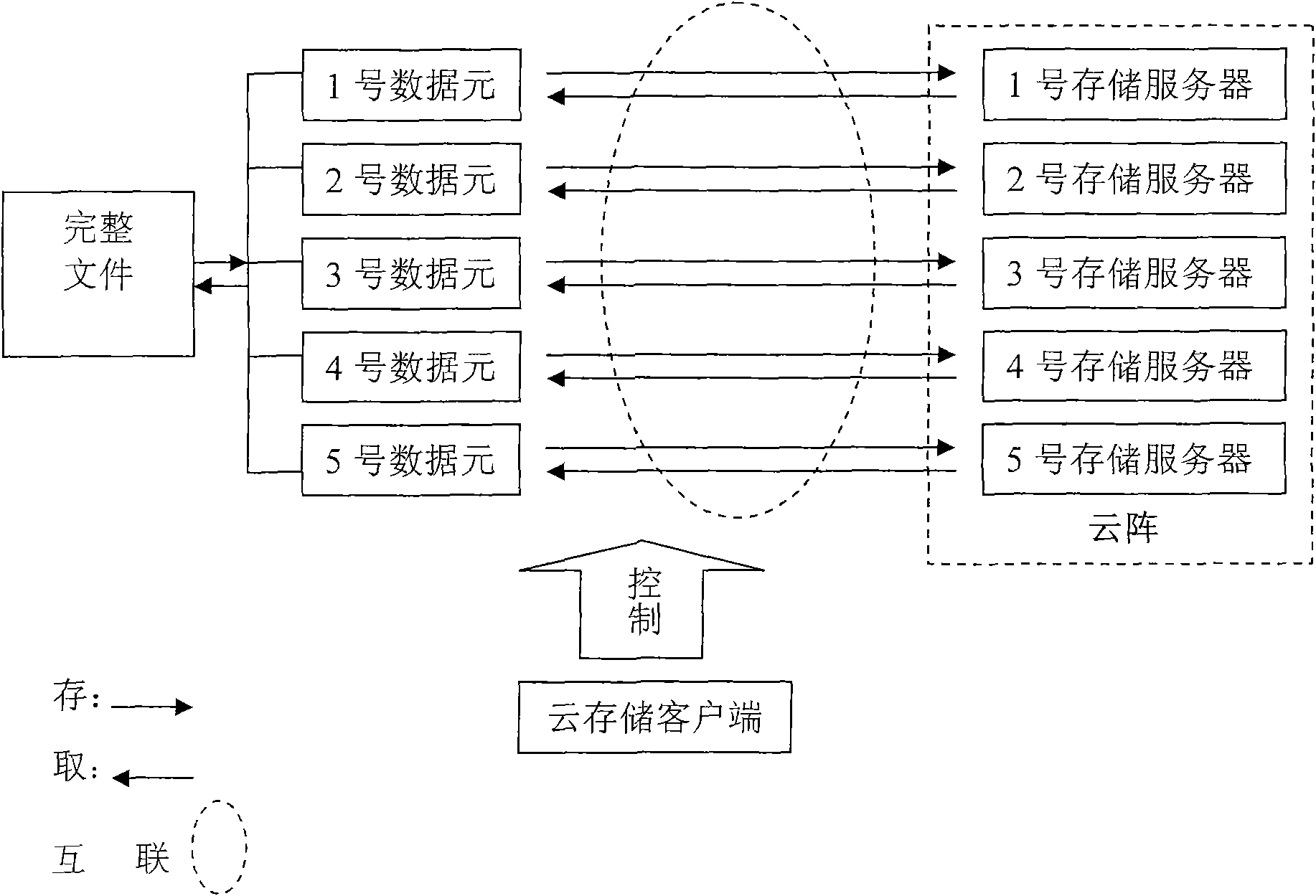
Method for structuring parallel system for cloud storage
The invention is mainly characterized in that: (1) a novel technical proposal for decentralizing network central storage is established, namely before being stored, a master file is broken into a plurality of sub-files known as data elements, as the smallest units for storage, by a program; (2) a prior network central storage method is replaced by cloud array storage technology, wherein a cloud array consists of a plurality of servers set by special serial numbers; an access relation of the data elements corresponding to the servers is established according to the serial numbers; and an original file is broken into the data elements respectively stored in the cloud arrays; (3) the storage of the data elements adopts a multi-process parallel mode, namely one process executes the storage of one data element, and N processes execute the storage of N data elements; and due to the parallel processes, the storage speed can be improved; (4) the data elements are encrypted and compressed, and an original password is not allowed to save; and (5) an operating system of the servers is Unix. The method for structuring a parallel system for the cloud storage can effectively solve the problem of the security of cloud storage data, and has important value for cloud storage structuring and application development.
Owner:何吴迪
File sharing system and file sharing method
InactiveUS20120265836A1Alleviate network delayMultiple digital computer combinationsFile metadata searchingComputerized systemSystem identifier
In a computer system according to an embodiment of the present invention, a first slave server includes copy management information associating a master file system identifier with an identifier of a slave server including a copy of the master file system identified by the master file system identifier. The first slave server acquires a copy of a part of a master file system. The copy includes a stub-state object (file or directory). The first slave server searches the copy management information for a slave server to be queried regarding information for materializing the stub-state object. If the slave server to be queried includes the information for materialization, the first slave server materializes the stub-state object using the information for materialization acquired from the queried slave server.
Owner:HITACHI LTD
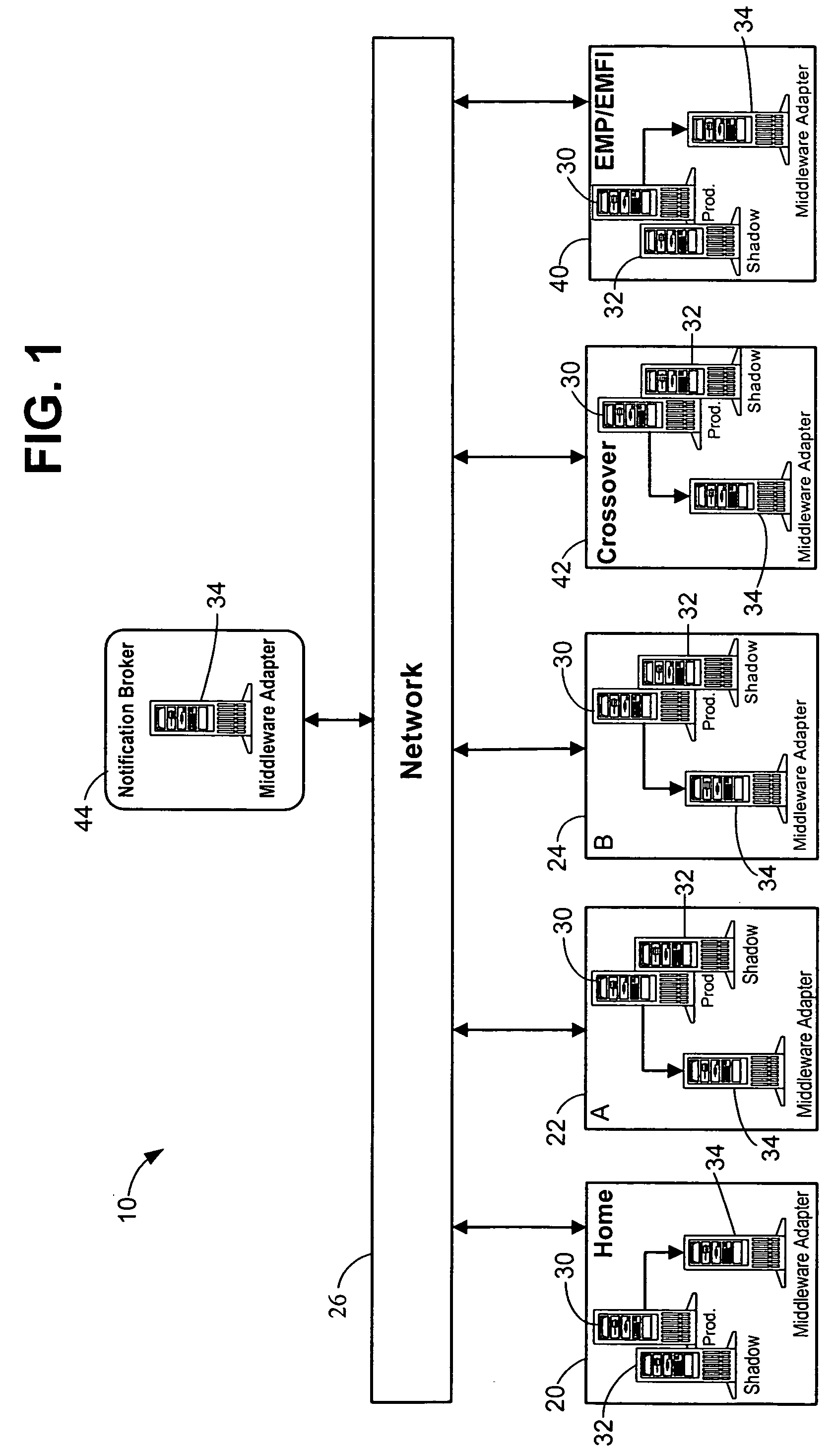
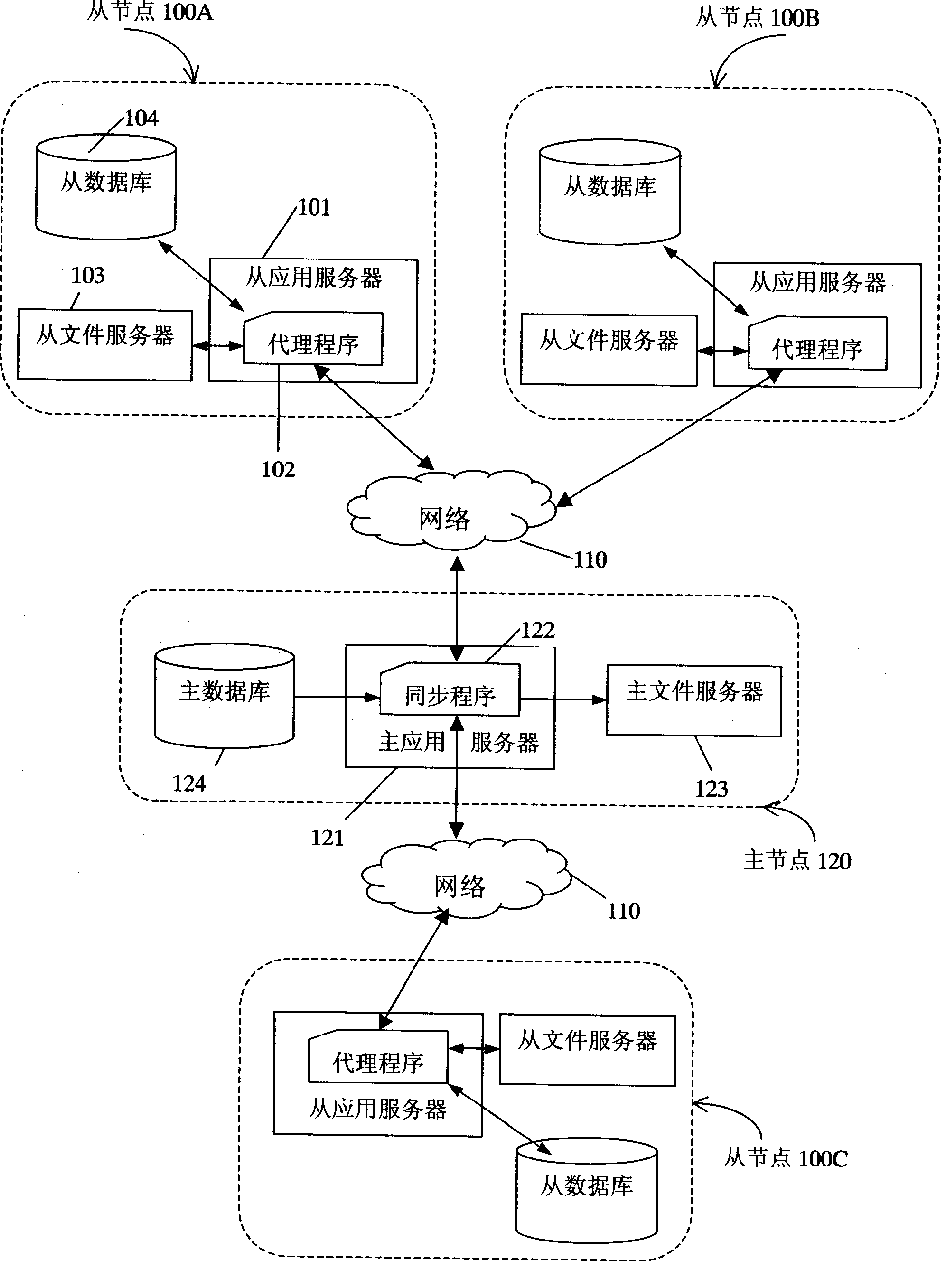
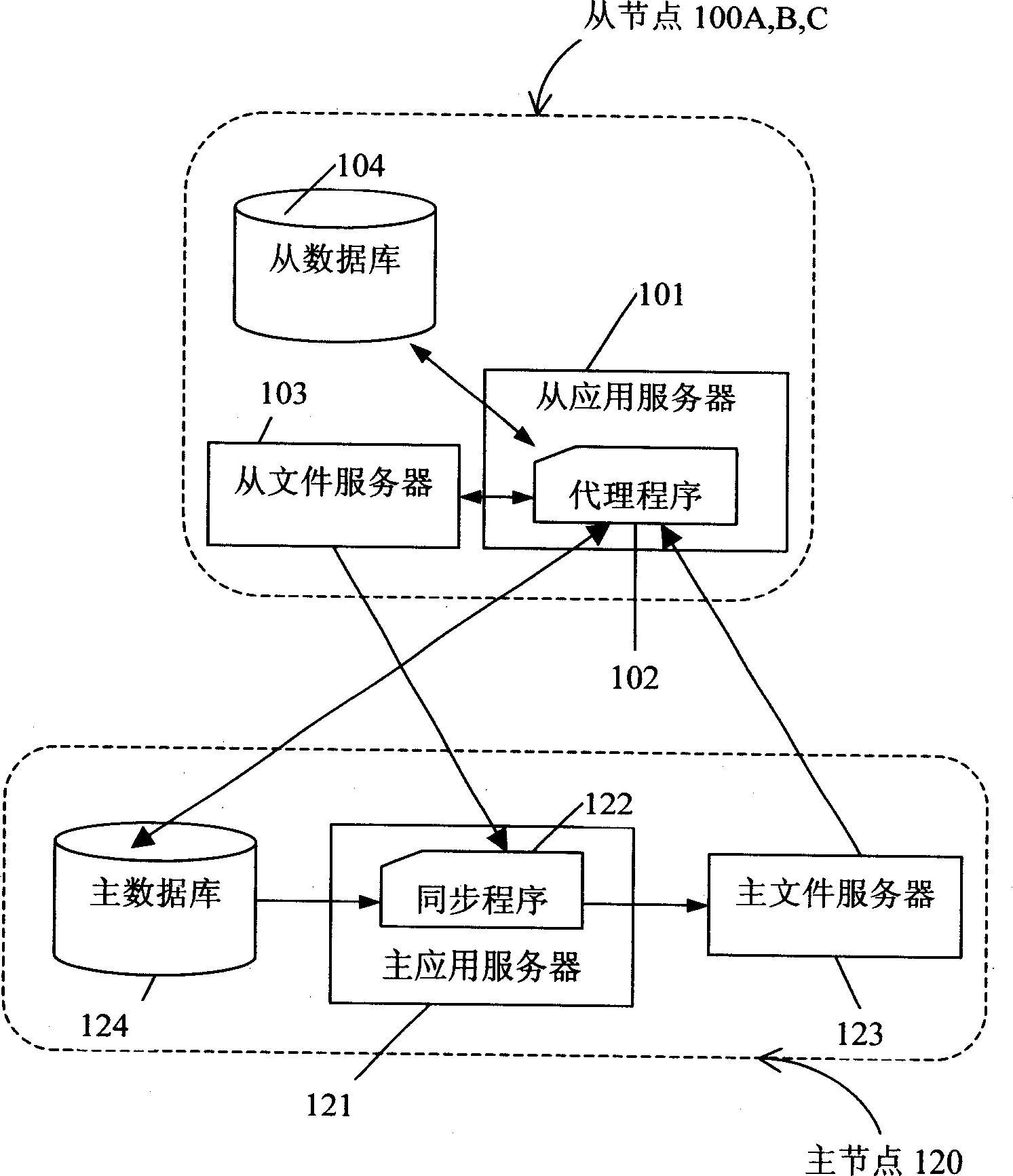
Multi-node file syn chronizing system and method
InactiveCN1489052AAvoid heavy traffic situationsReduce synchronization operationsMemory systemsFile synchronizationApplication server
The system comprises a master node, multiple slave nodes, and network connecting the master node to these slave nodes. The slave node comprises a slave application server, a slave file server and a slave database. The master node comprises a master application server, a master file server and a master database. Based on file updated record in the master database, running an agent program on a slave application server and running a synchronous program on the master application server complete synchronization between files in the master file server and files in slave file server. The system and method realizes synchronization of files shared between master node and slave nodes on network, as well as reduces unnecessary file synchronization operation and prevents the condition of too large networked traffic needed by some synchronization operations.
Owner:扭矩资本解决方案有限责任公司
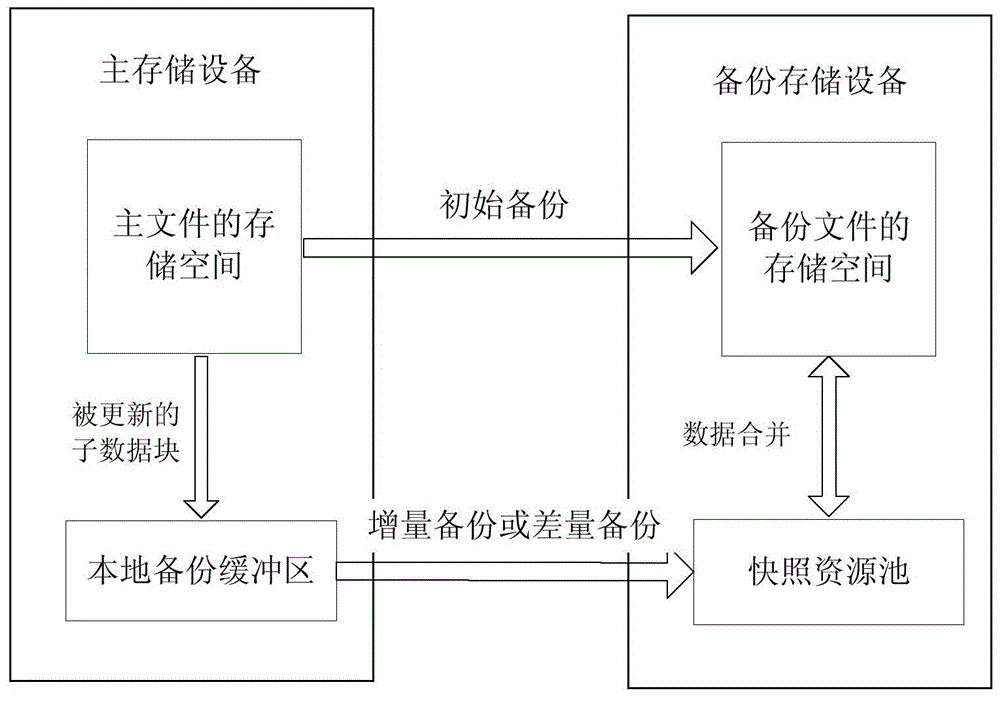
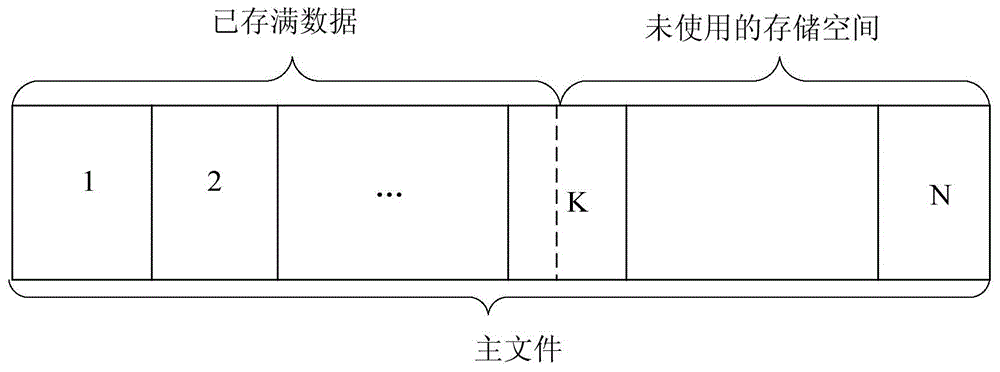
File backup method and main storage device
ActiveCN104166606AImprove backup efficiencyReduce data volumeRedundant operation error correctionSpecial data processing applicationsIncremental backupBackup
The embodiment of the invention provides a file backup method and a main storage device. According to the file backup method, the storage space of a main file in the main storage device is divided into N secondary data blocks, at every backup moment of incremental backup, data in the updated secondary data blocks from the previous backup moment to the current backup moment are copied to a local backup buffer area, and at every backup moment of differential backup, data in the updated secondary data blocks from the initial backup moment to the current backup moment are copied to the local backup buffer area. Because the main storage device only needs to synchronize the data in the updated secondary data blocks stored in the local backup buffer area and the data in the secondary data blocks which are not updated do not need to be synchronized, the data size of file backup can be reduced, file backup efficiency is improved, and the storage space of the backup data is saved.
Owner:HUAWEI TECH CO LTD
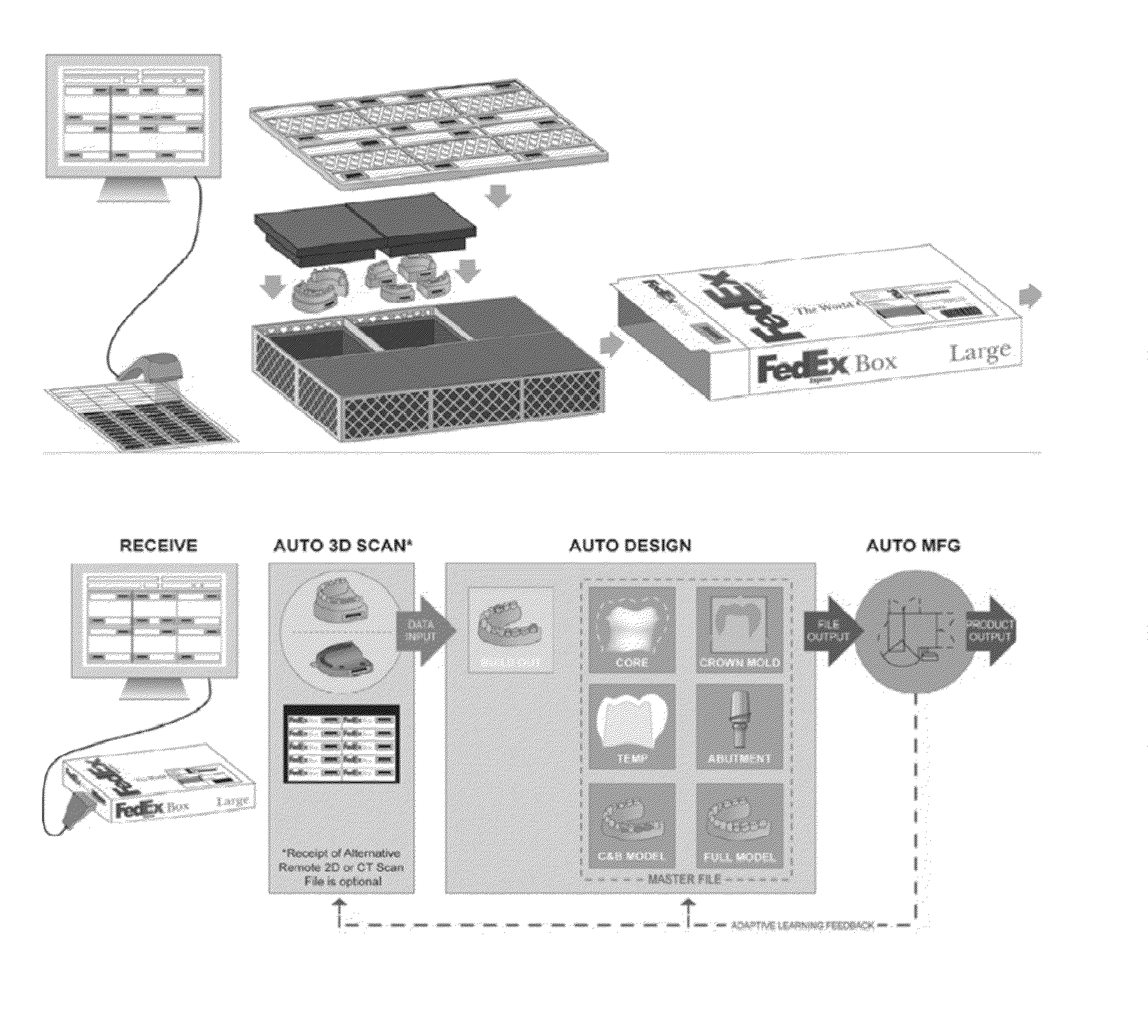
System and method for mass custom manufacturing of dental crowns and crown components
InactiveUS20090319068A1Reduce the amount requiredReduce materialMedical simulationProgramme controlMass customizationDesign phase
A Mass Custom Manufacturing System and methods are provided. A single master file is created for a restoration (or multiple restorations for a single patient) from a scan. Copings / cores, abutments and other companion pieces are designed using the master file through a deconstruction method allowing for simultaneous CAM of those pieces. A centralized system controls design and manufacturing, allowing the system to “learn” from feedback from the CAM operations of prior pieces and incorporate such feedback into the design phase.
Owner:ZIRCORE
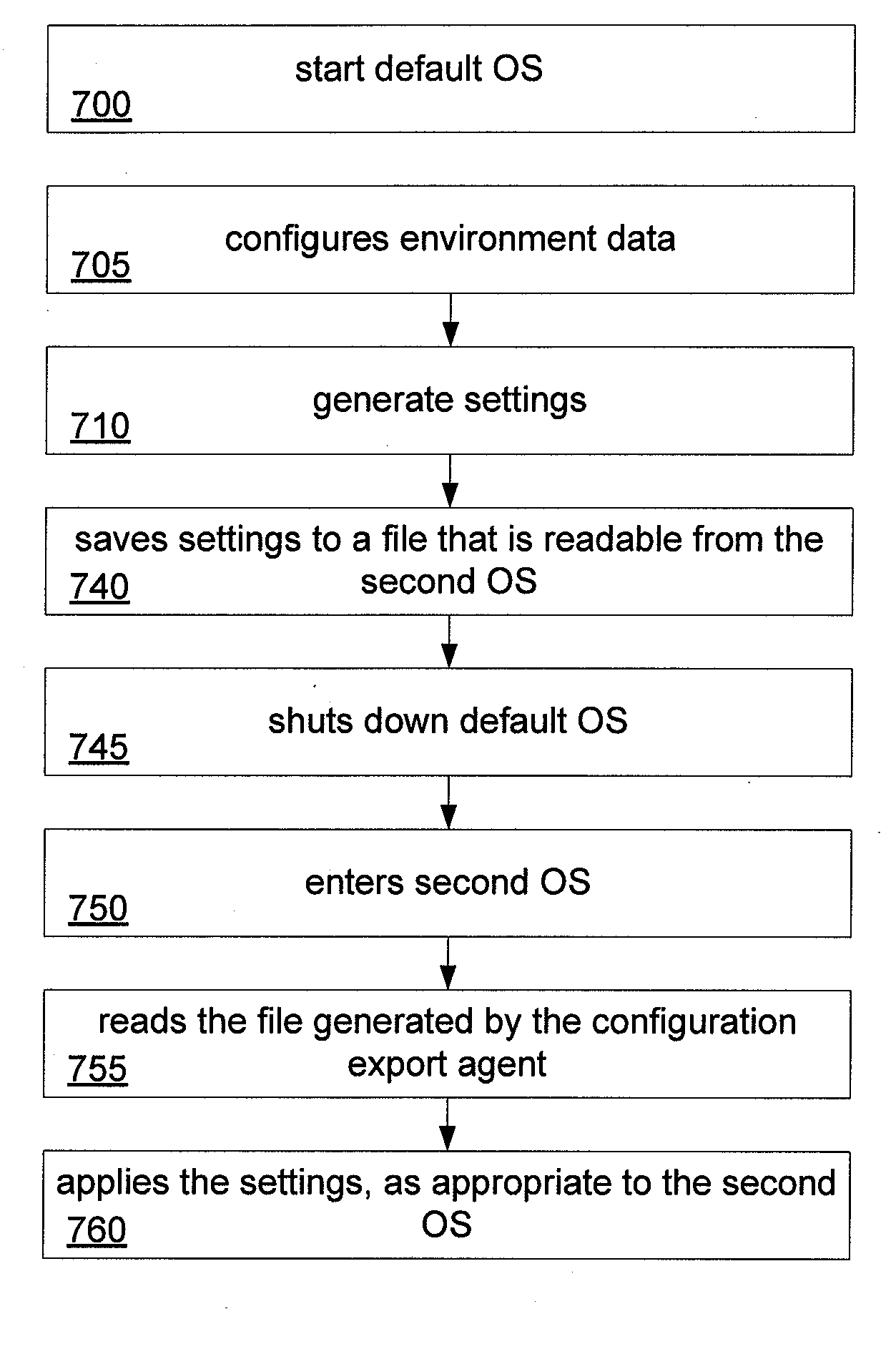
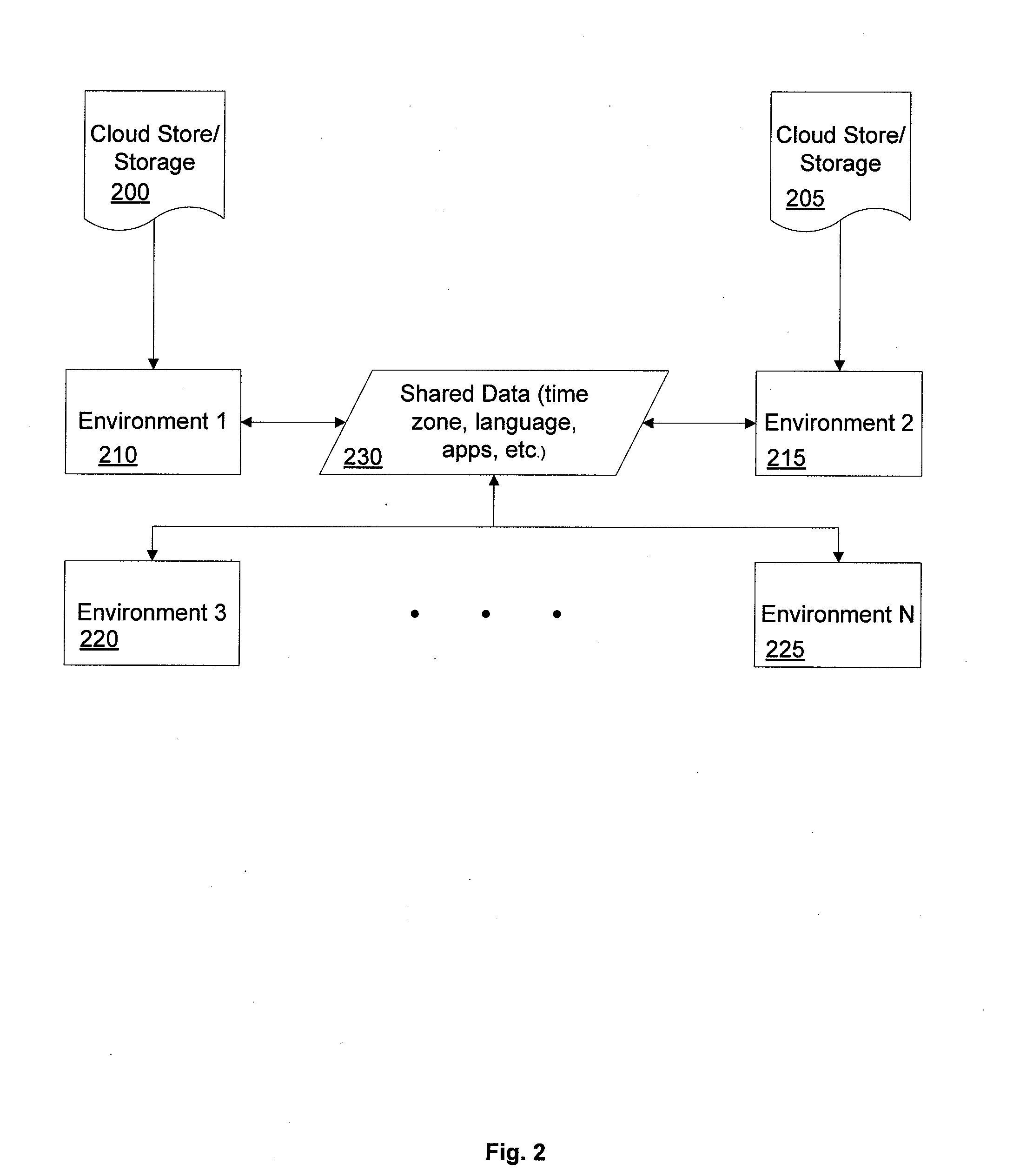
Synchronization in Multiple Environments
InactiveUS20100115254A1Digital data processing detailsDigital computer detailsData synchronizationWeb application
A method and apparatus for synchronizing different environments in response to a change in one of the environments. The term environment encompasses operating systems, virtual machines, and states. The synchronization functions when one environment controls a master file or the environments access a shared folder. The synchronization is one-way or two-ways. The synchronization applies to digital photos, personal information management data, shared maps and directions, documents, configuration data, network settings, browser data sync, account information for accessing the client, and local and web applications.
Owner:SPLASHTOP INC
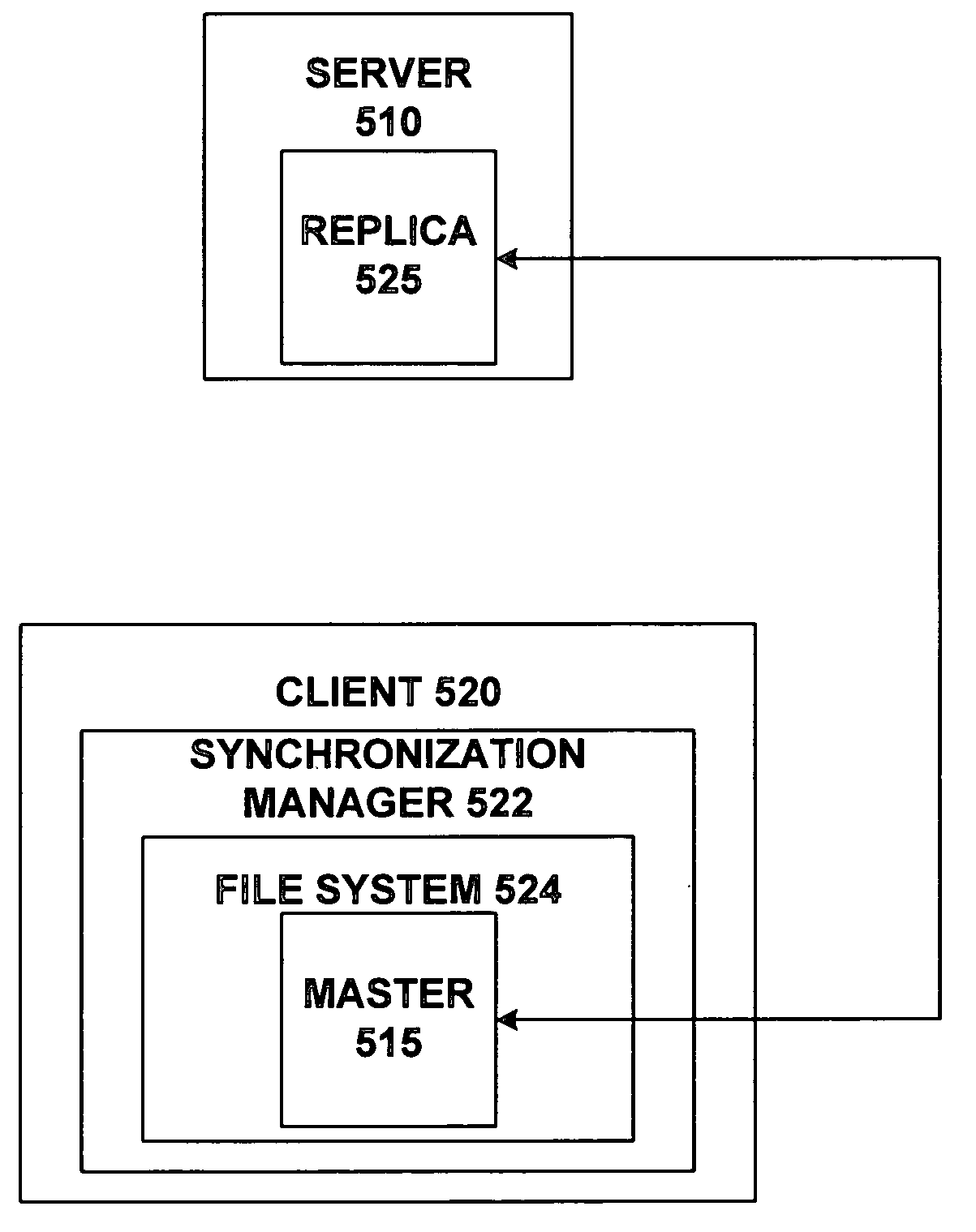
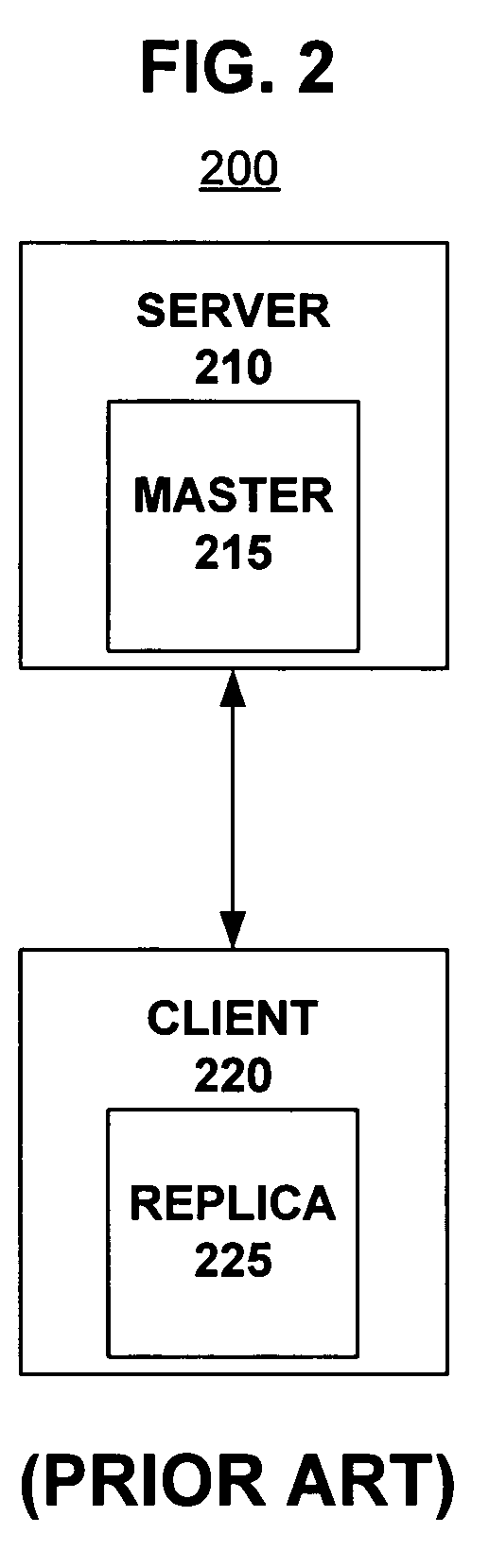
System and method for client mastered replication of local files
ActiveUS20050114412A1Data processing applicationsDigital data information retrievalClient-sideFile copying
A master file may be created and stored on a client computing device. Changes to the master file may be made locally at the client computing device. The master file may be selected for replication using an associated replication property. Changes to the master file may be replicated to a connected computing device such as a server. Changes to a replica of the master file may be made at the connected computing device. If they do not conflict with local changes the to master file, changes to the replica may be replicated back to the master file.
Owner:MICROSOFT TECH LICENSING LLC
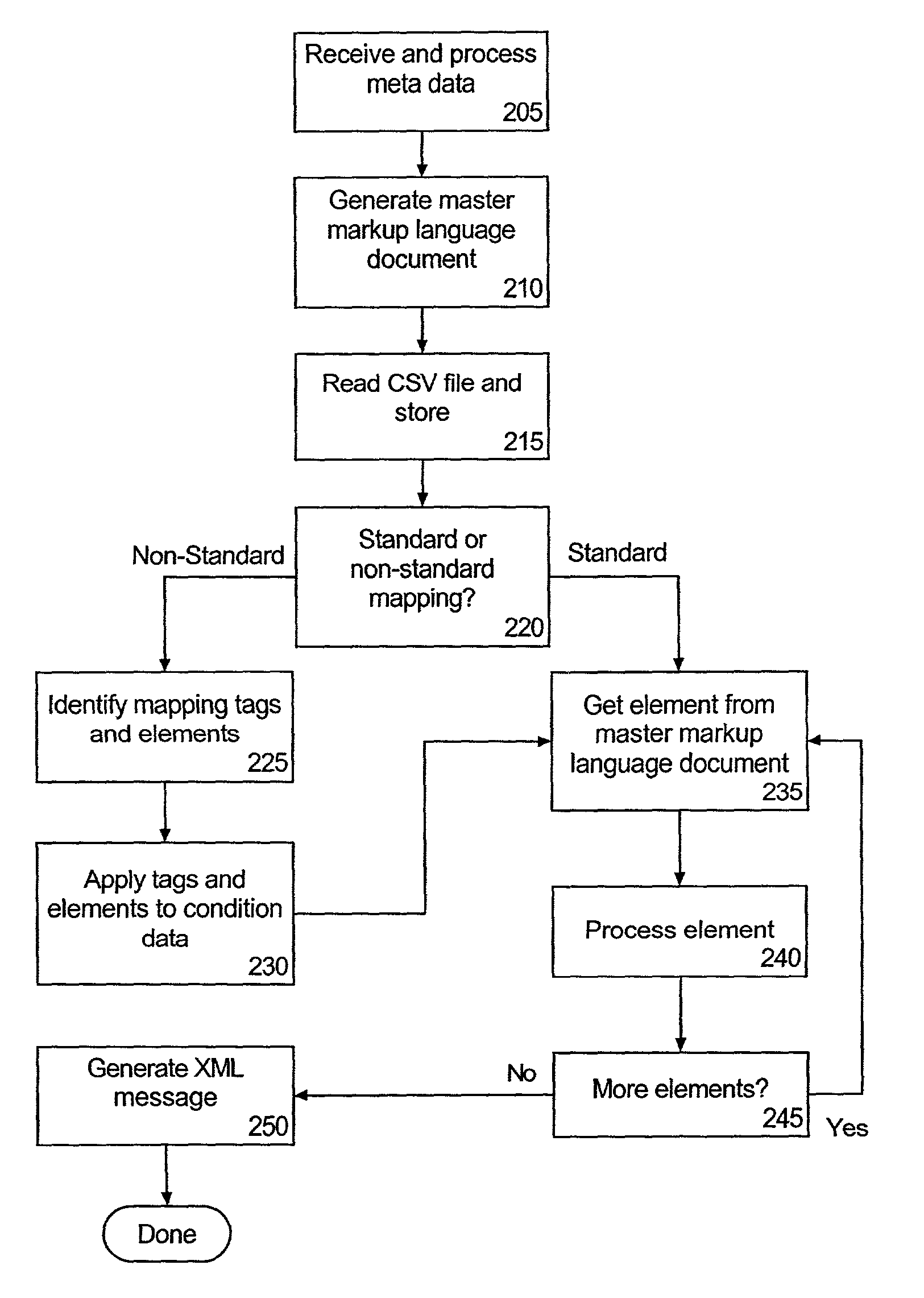
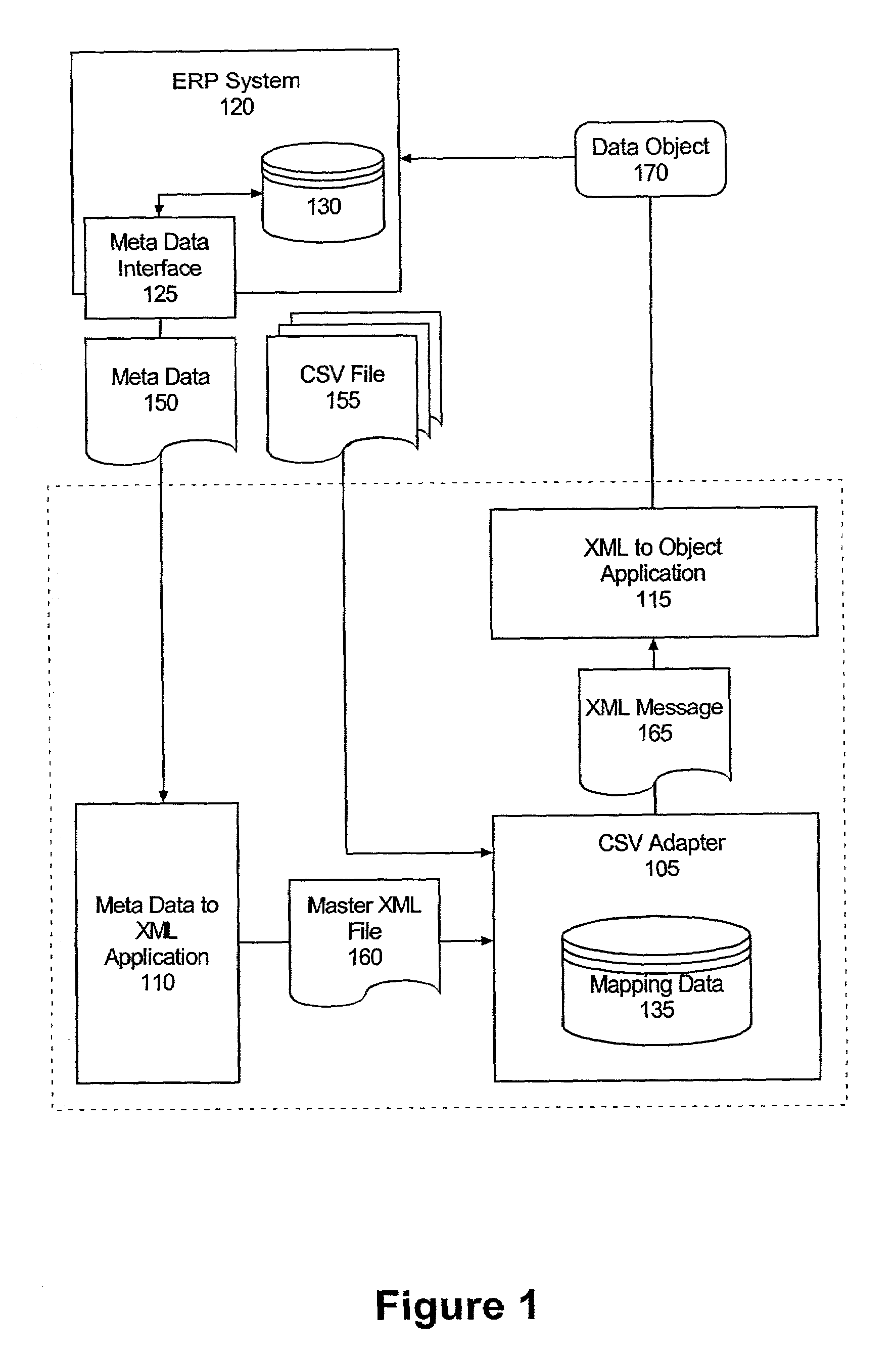
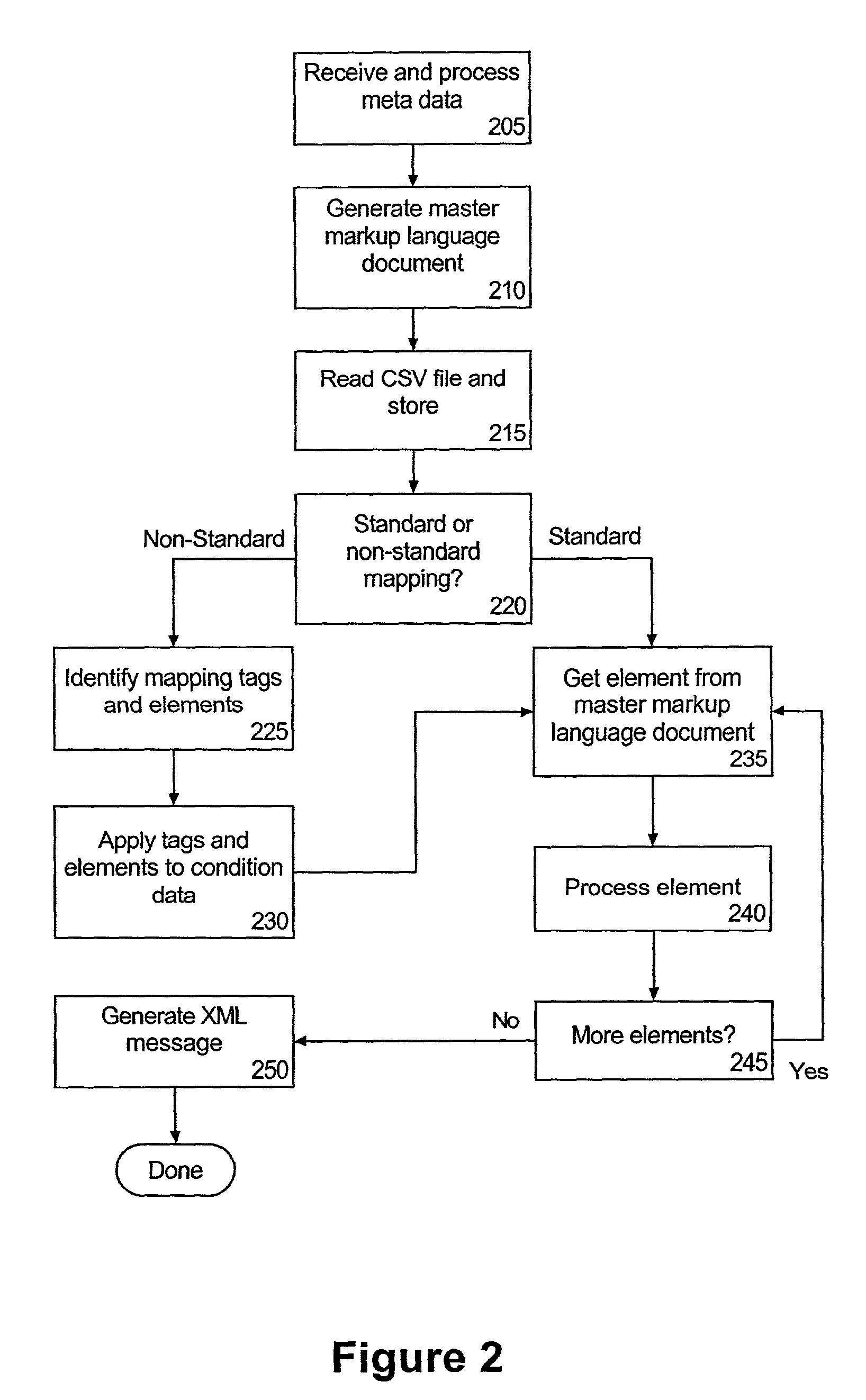
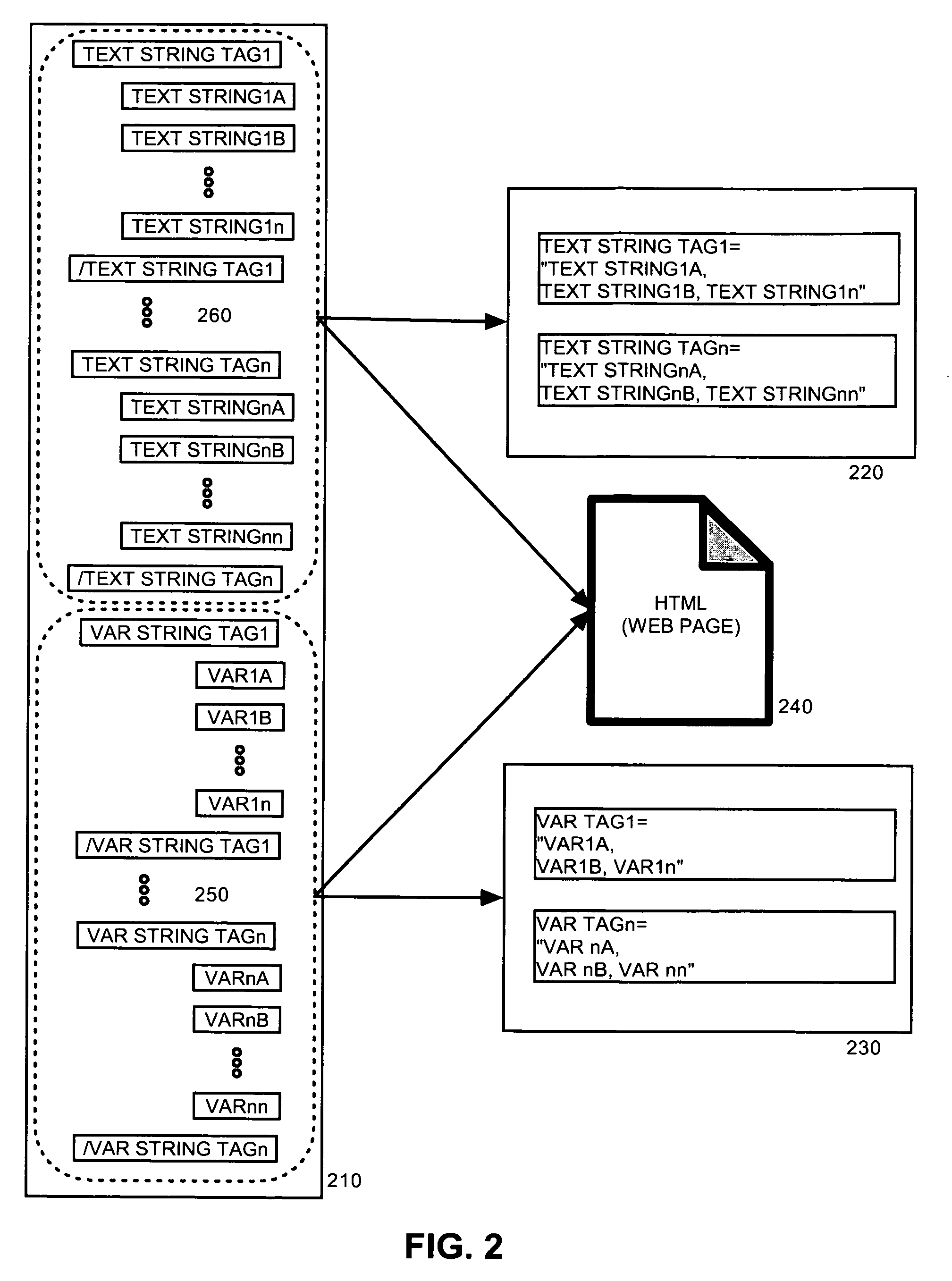
Standards-based formatting of flat files into markup language representations
InactiveUS7093195B2Facilitate of dataFacilitate populationData processing applicationsDigital data processing detailsMapping techniquesDocument preparation
A method of building an application response message can include receiving a master file specifying a message format for populating a particular data object of an application. The master document can specify element names which correspond to fields of the data object. A technique for mapping particular data items specified by at least one flat file to the element names specified in the master file can be determined; and a markup language representation of the data object can be generated according to the determined mapping technique and the specified message format.
Owner:IBM CORP
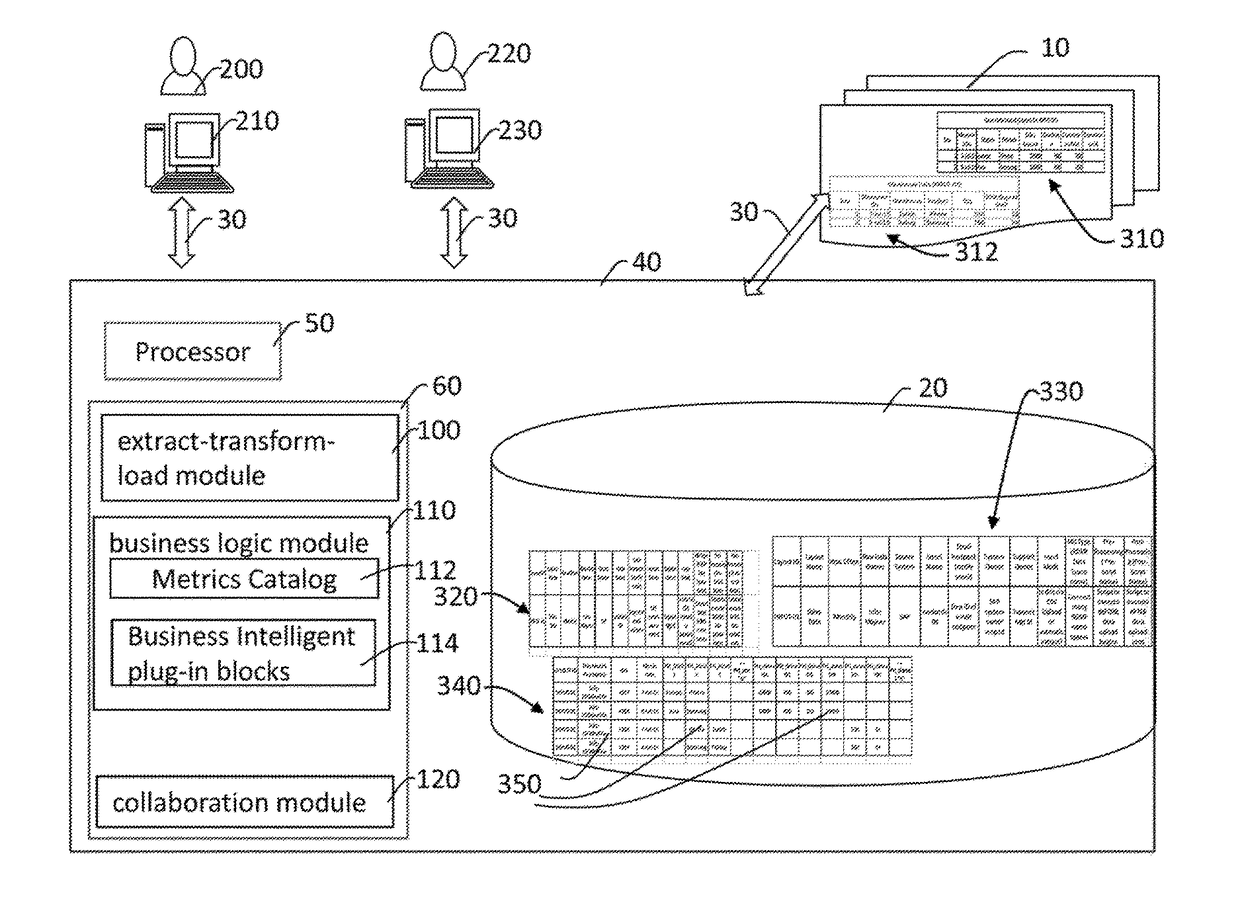
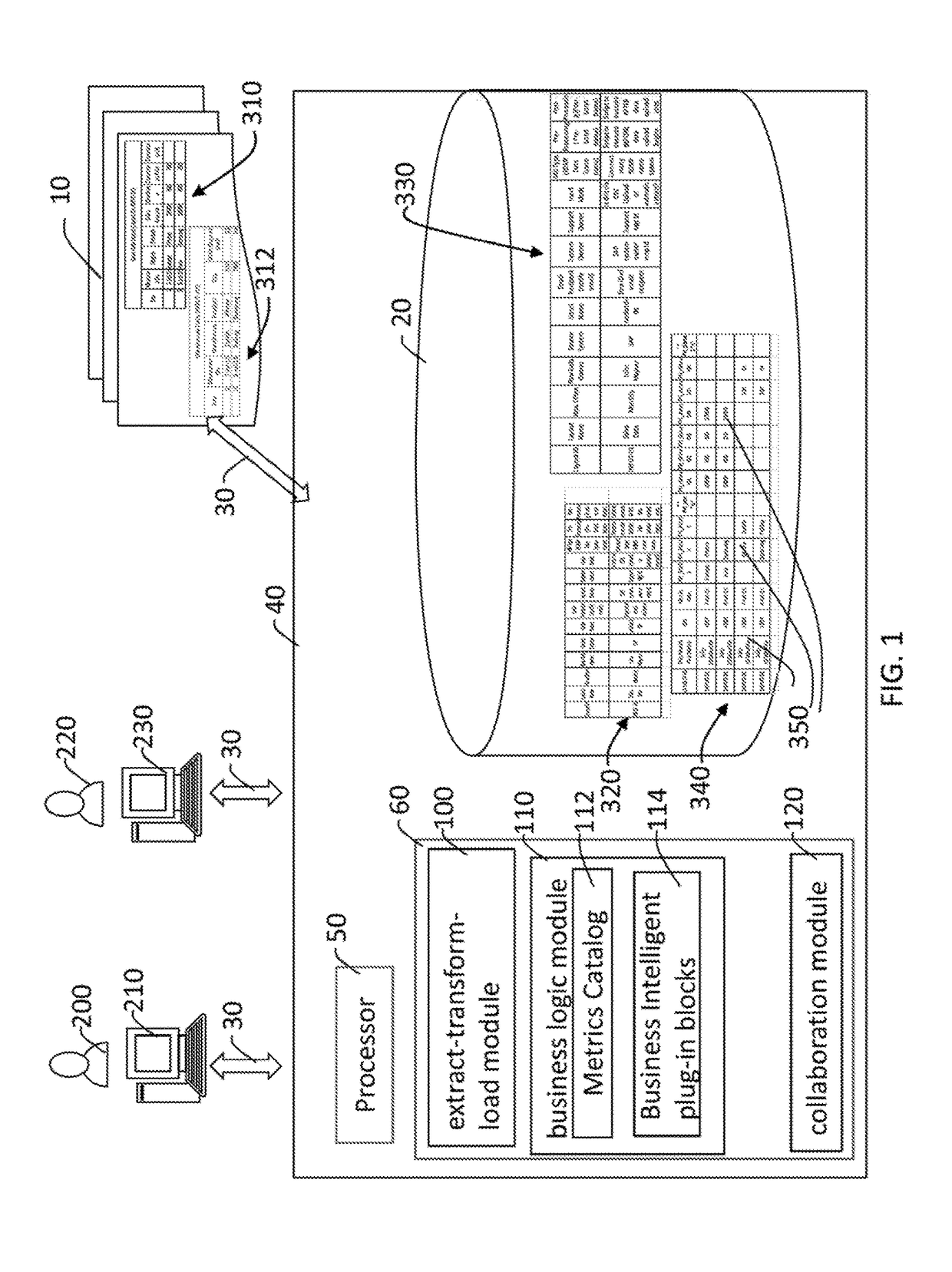
System and methods for integrated performance measurement environment
ActiveUS20170132300A1Overcome problemsVisual data miningStructured data browsingDrill downDistributed File System
A system for integrated performance measurement environment comprises a plurality of distributed file systems; a database, wherein the database further comprises a layout details table, a layout definition table, and at least one raw data master file; at least one network; an extract-transform-load module in a memory; and a business logic module in the memory, wherein the business logic module further comprises metrics catalog and business intelligent plug-in blocks; and a collaboration module in the memory; and methods performing the same including extracting, transforming, and loading data into the system, retrieving data in accordance with rules in metrics catalog and business intelligent plug-in blocks, drilling down the metrics catalog and business intelligent plug-in blocks, and collaborating over the system.
Owner:OPENMETRIK INC
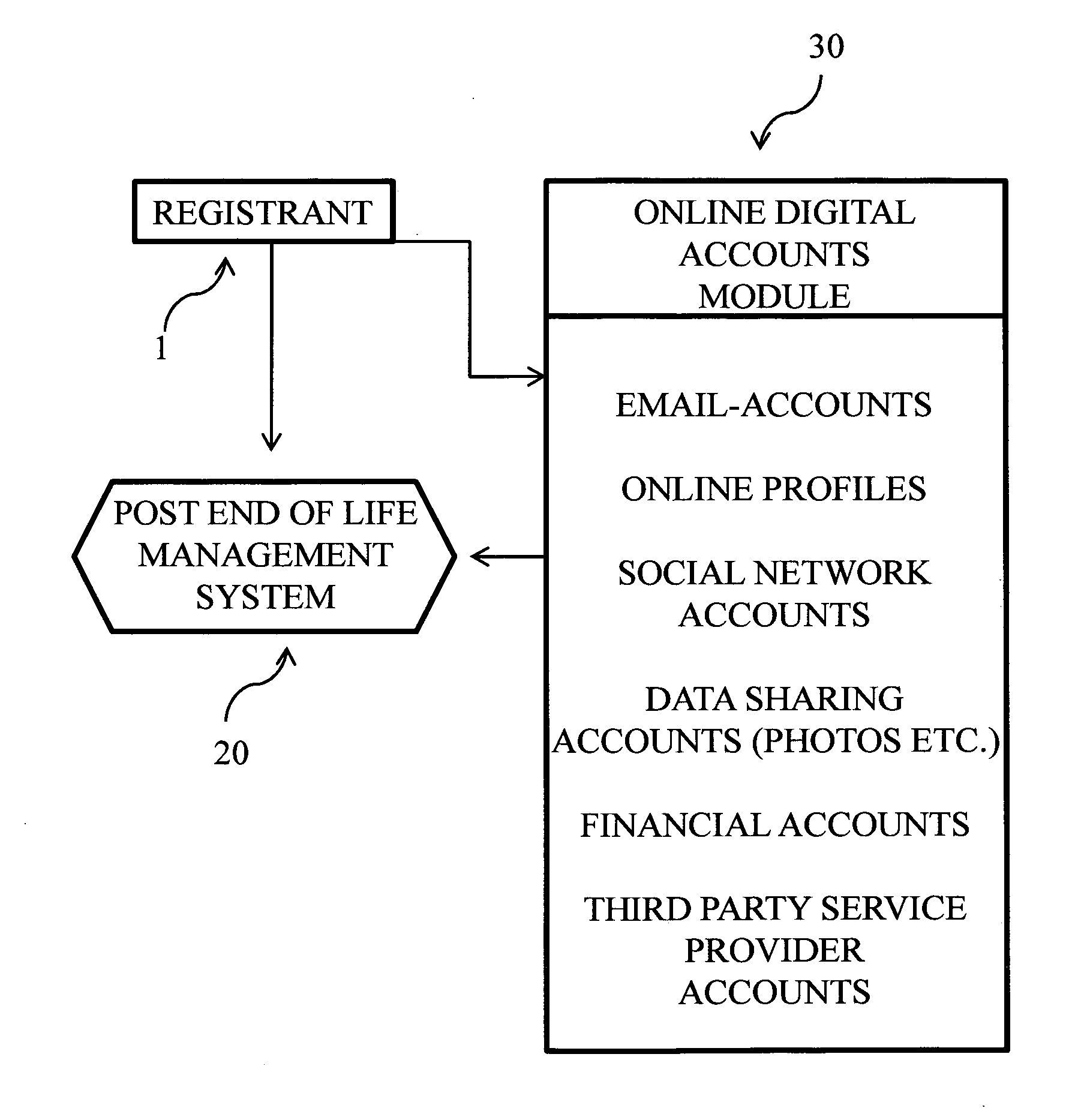
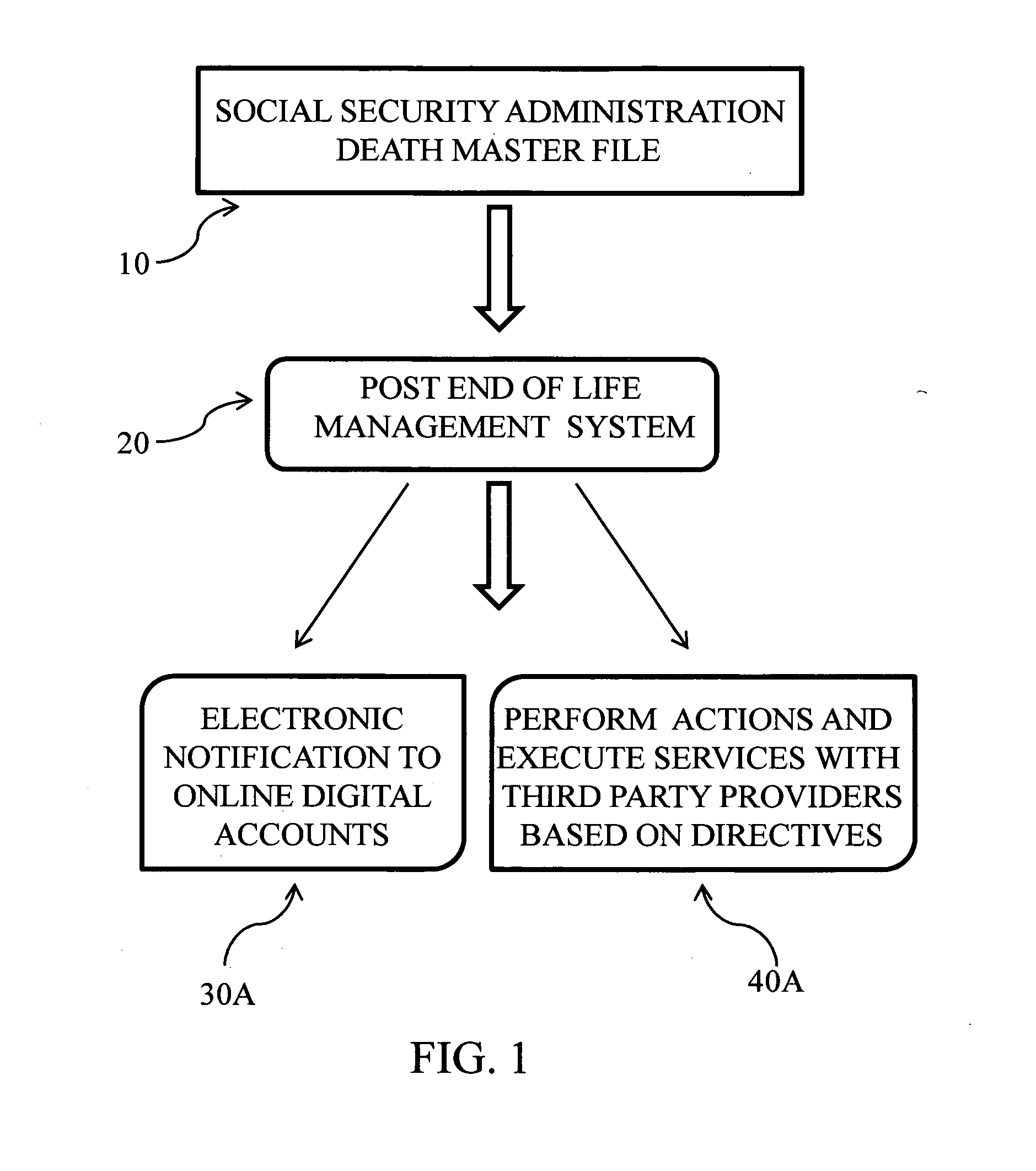
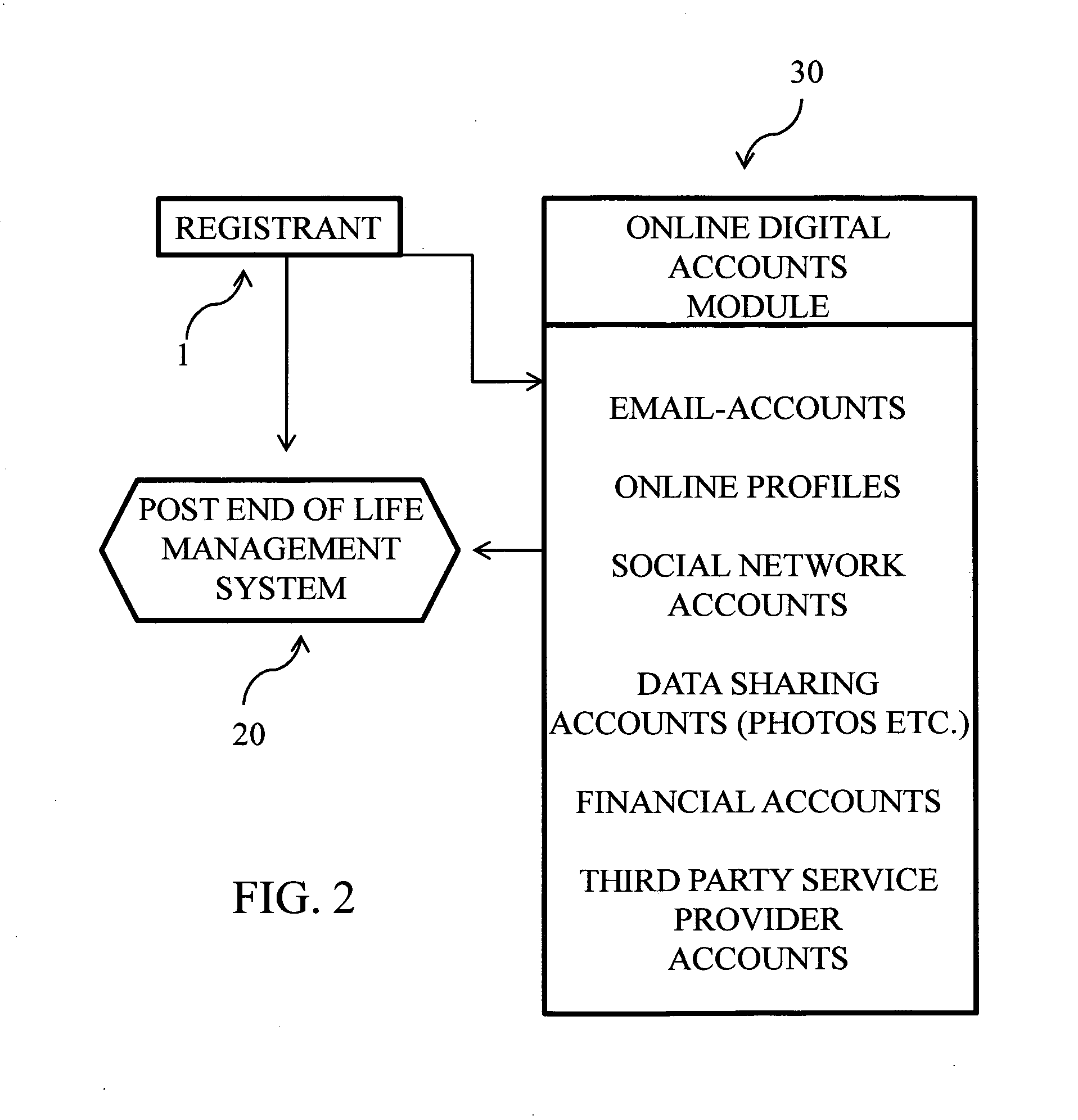
Post end of life management system and method
A post end of life management system and method comprising, registering and setting up directives to manage online accounts, digital data, and perform other functions by providers after the death of the registrant. The system is integrated with the social security administration to receive death notifications from the death master file as well as with the deceased individual registry counterparts of other countries. Registrant accounts are encrypted and stored in the system and triggered to decrypt in order to carry out directives left by the deceased after notification of death is received from the social security administration or the deceased individual registry counterpart of another country.
Owner:LIFEENSURED
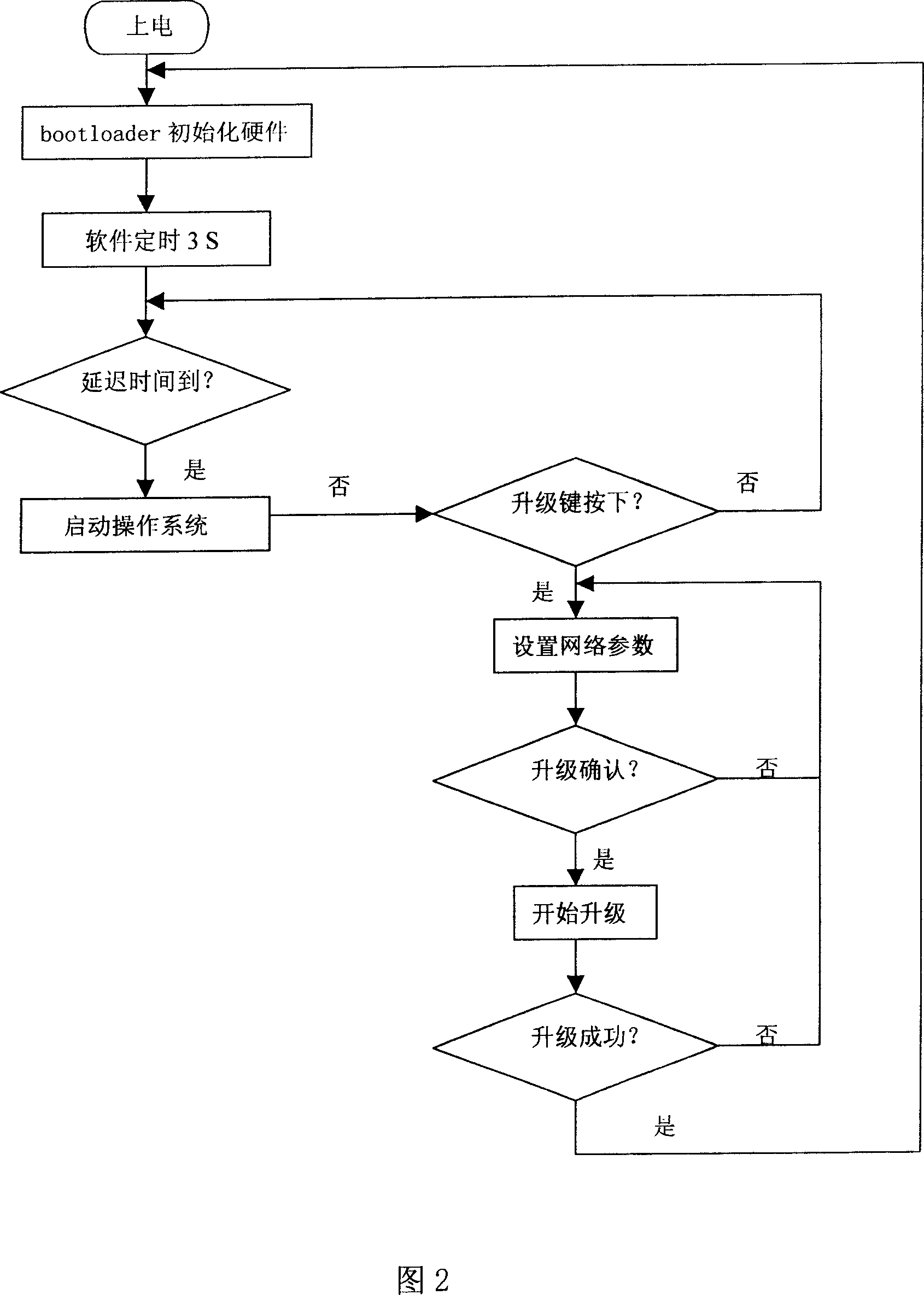
Embedded system and its upgrading method
InactiveCN1928820AEasy maintenanceReduce workloadProgram loading/initiatingTransmissionOperational systemSystem recovery
The related embedded system update method comprises: without writing driver or network protocol to expand the bootloader, adding a reduced software update module in the FLASH to download the update software. This invention can update system during the bootstrap stage without added cost, and can provide system recovery function to improve security and maintenance, and has great social and economic benefits.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
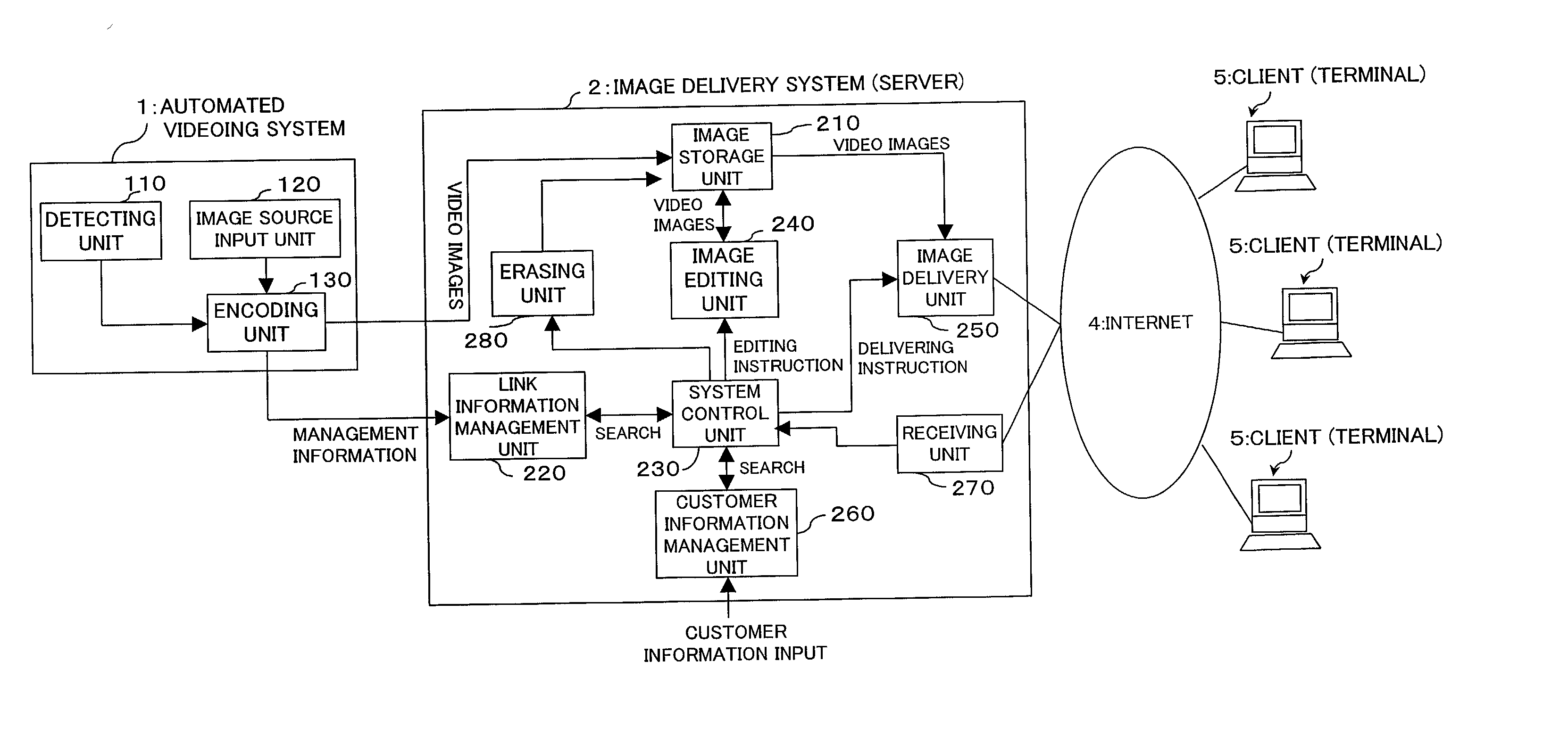
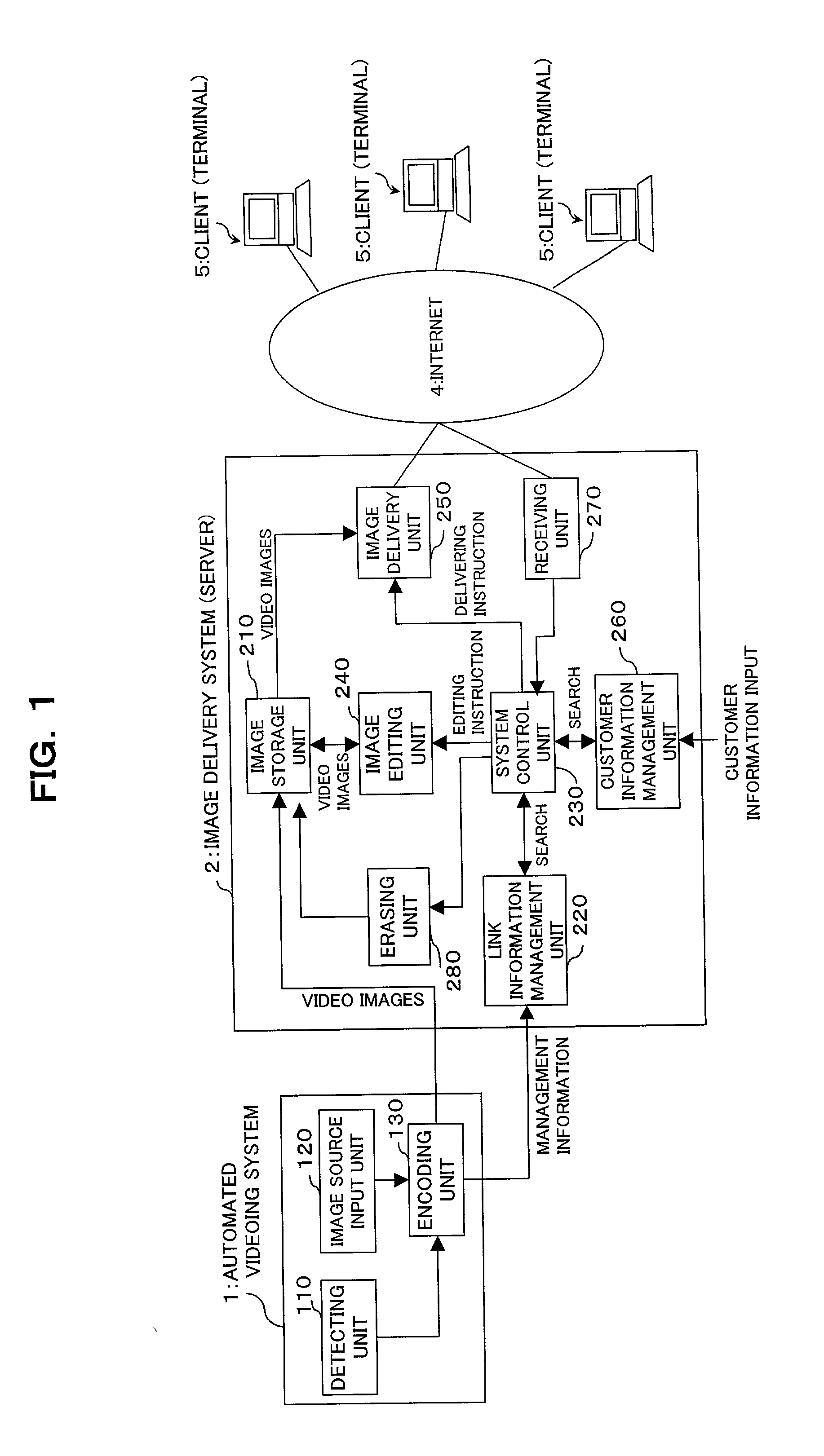
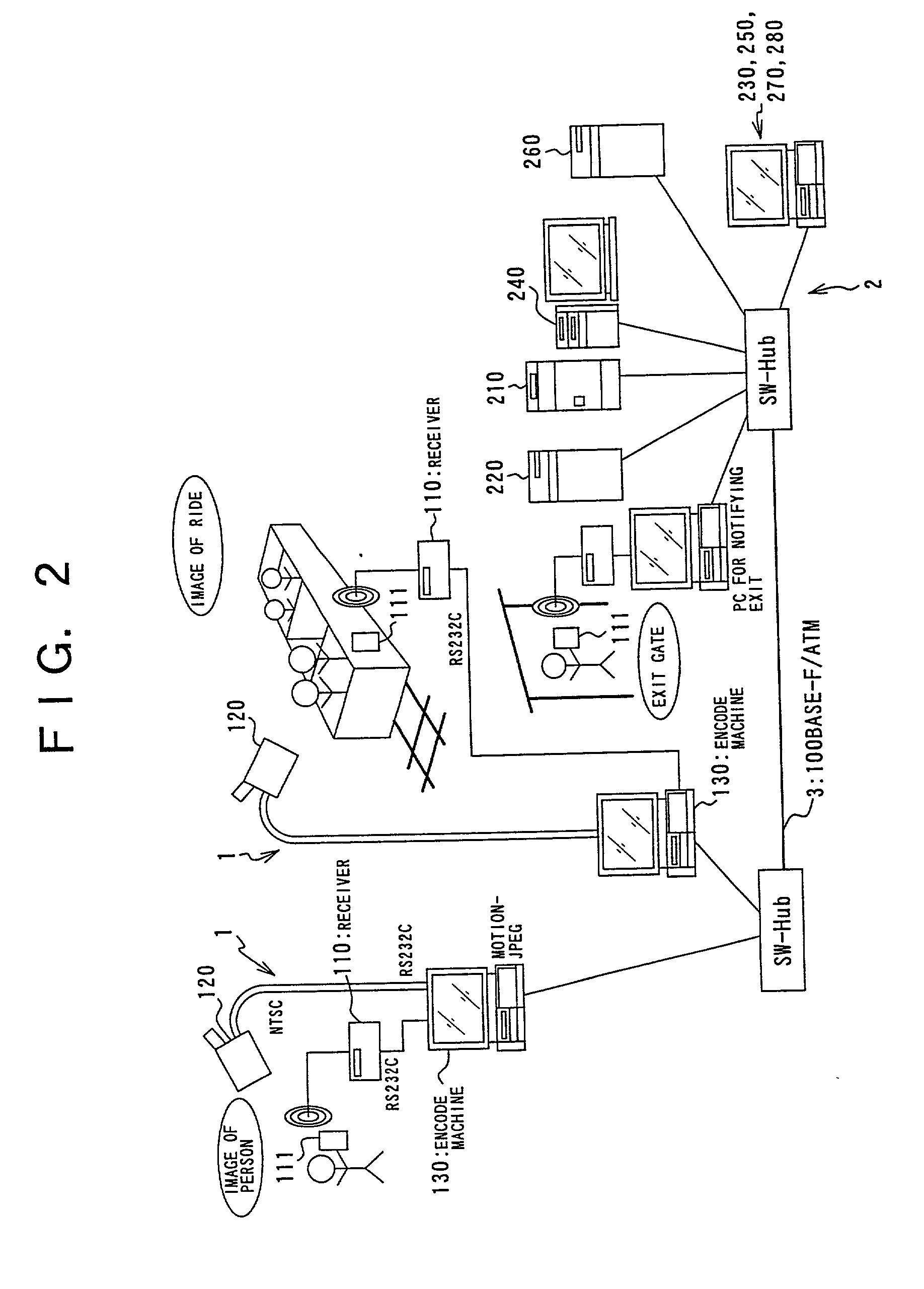
Image delivery system, image delivery method, and recording medium in which image delivery program is recorded
InactiveUS20030018974A1Improve the level ofReduce data volumeTelevision system detailsColor television detailsComputer terminalVideo image
To provide an image delivery system which allows users to previously check their video images that have been obtained at leisure facilities, such as theme parks and aquariums, and megastores, and which also allows the users to edit the images so as to comply with their preferences. The system, being interconnected with a user terminal via an communications network, includes: means for storing a master file that records video images of plural users substantially continuously; means for storing link information linking a plurality of parts of the master file with the respective users; and means, responsive to the receipt of an file delivery request of a user from a user terminal, for reading out a corresponding one of the plural parts of the master file, in which part the user appears, and delivering the read-out part to the terminal through the communications network.
Owner:FUJITSU LTD
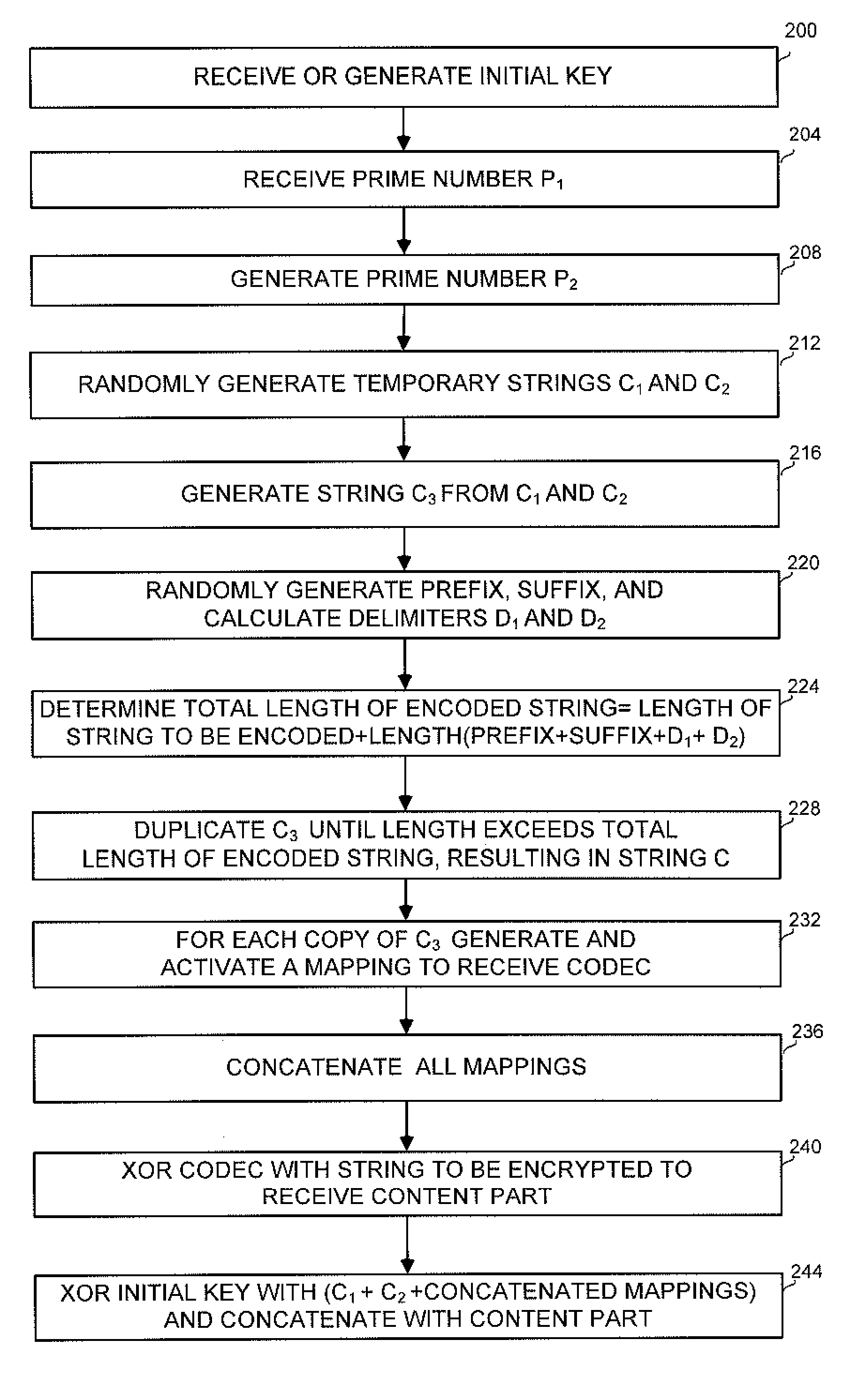
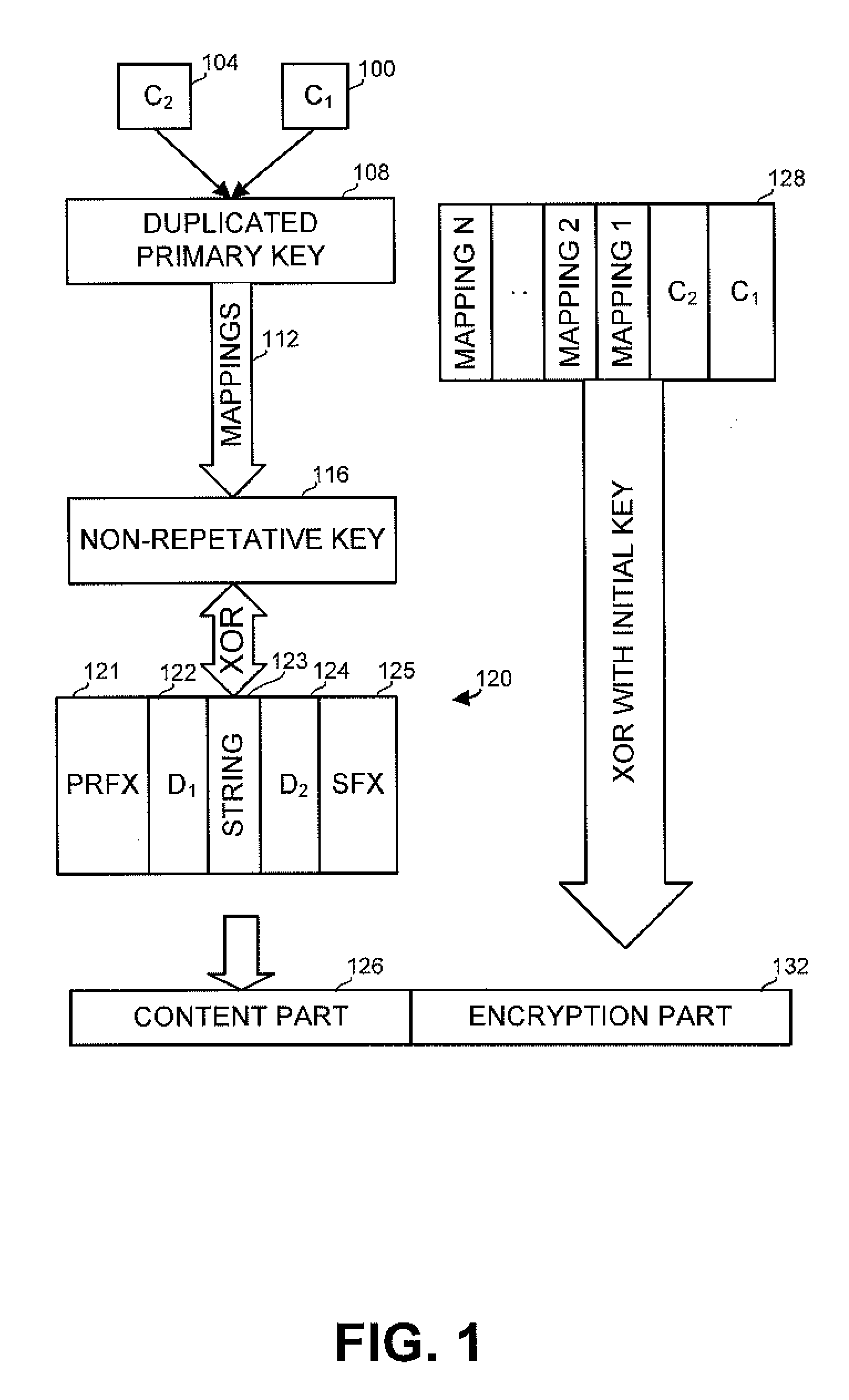
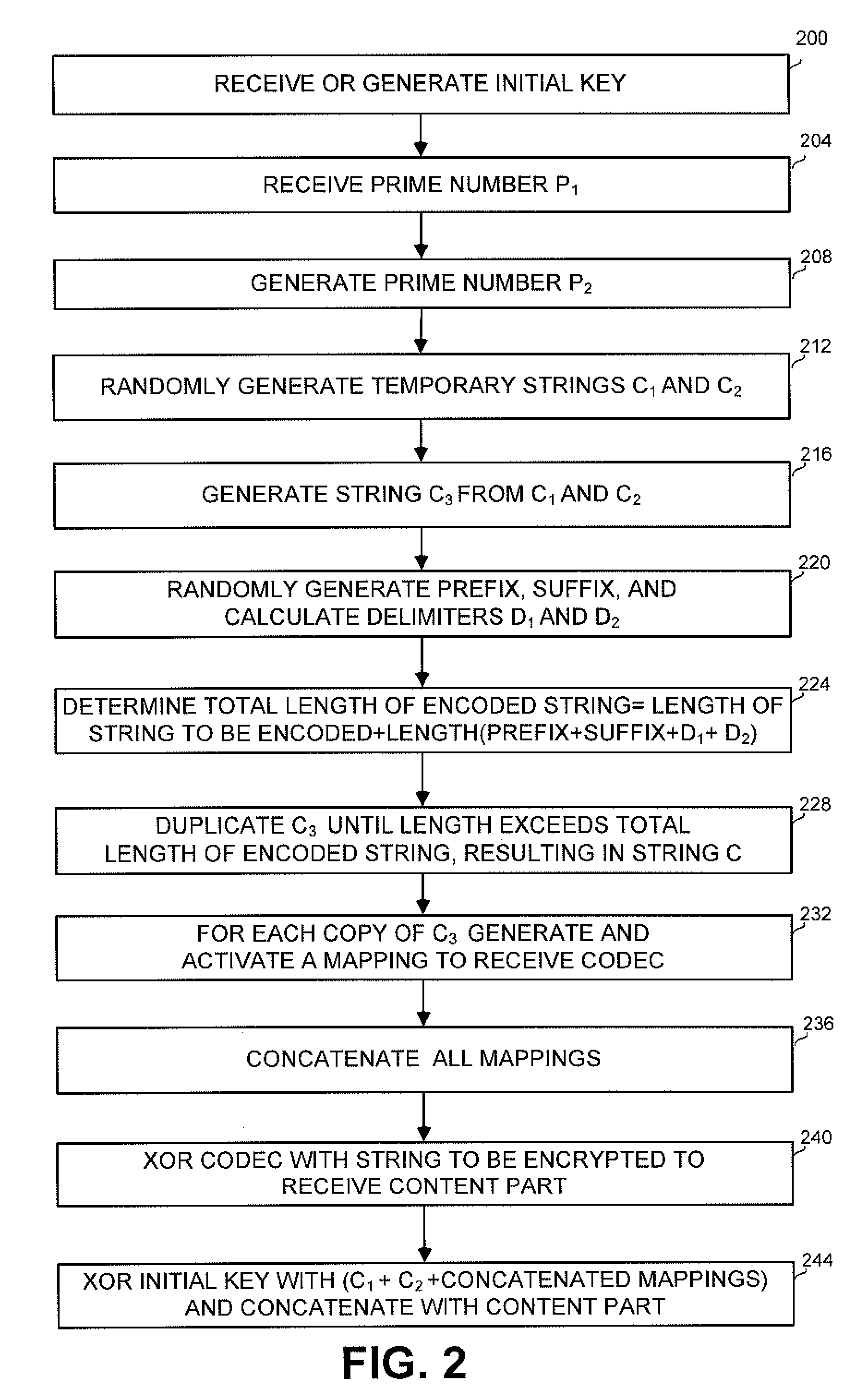
Method and apparatus for securing data and communication
A method and apparatus for securing digital data, and applications for securing multiple data items such as multiple files or messages exchanged between two communicating parties. The methods use a randomly created non-repetitive codec, with which the information to be encrypted is XORed. The codec is XORed with a user initial key, and the two results are concatenated. For securing multiple items, a master file is created comprising a number of keys, while the master file itself is encrypted with the initial key. A communication application enables a login-free communication between a client and a server, thus blocking intrusion attempts on the client side, and pishing attempts on the server side.
Owner:SHAHAF MARK +1
Mobile transcoding architecture
InactiveUS20050197108A1Speech analysisRadio/inductive link selection arrangementsComputer hardwareDigital rights management
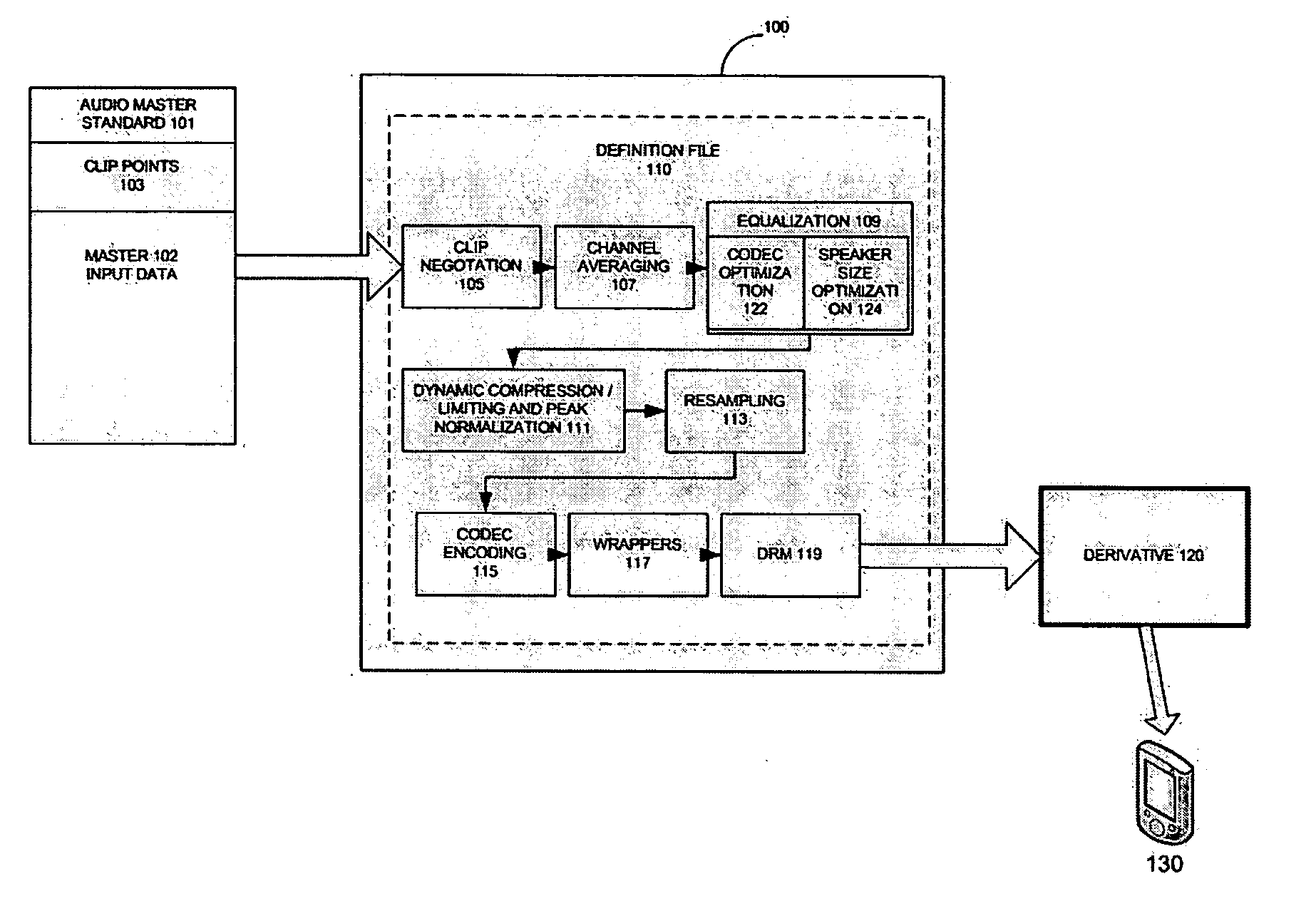
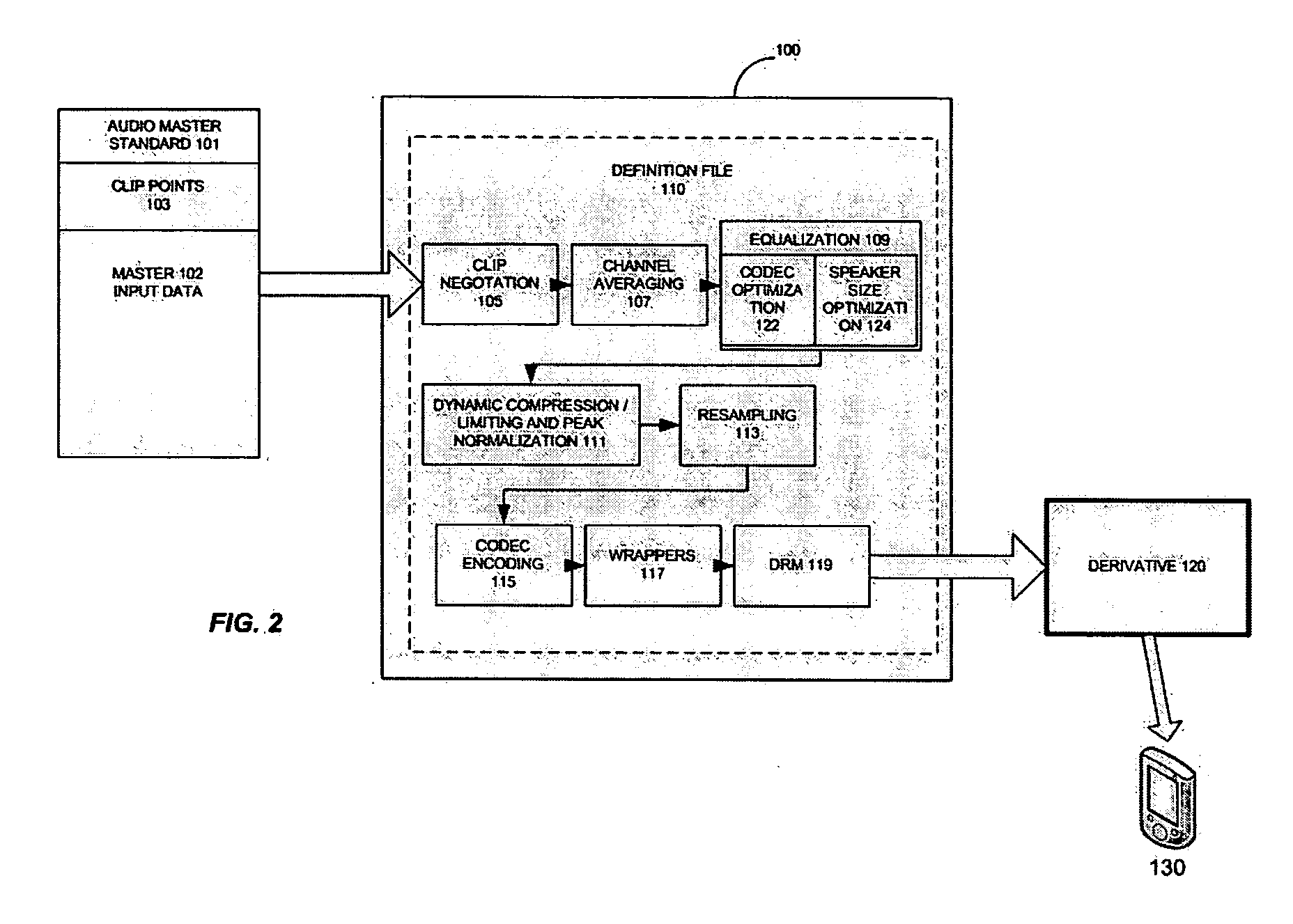
A method and system for transcoding for a mobile device. The method includes accepting a master file, processing the master file with steps laid out in a definition file, the definition file providing instructions for converting the master file to a derivative file appropriate for playback on a pre-specified mobile handset, and outputting the results of the processing step into the derivative file. The system includes a definition file, the definition file providing instructions for converting a master file to a derivative file appropriate for playback on a pre-specified mobile handset. A plurality of modules is employed that are controlled by the definition file and which perform a corresponding plurality of functions on the master file or derivatives thereof. The function or processing steps may include one or more or all of the following: channel averaging, equalization, dynamic compression, limiting and peak normalization, resampling, CODEC encoding, applying a wrapper, or applying digital rights management.
Owner:SONY CORP +1
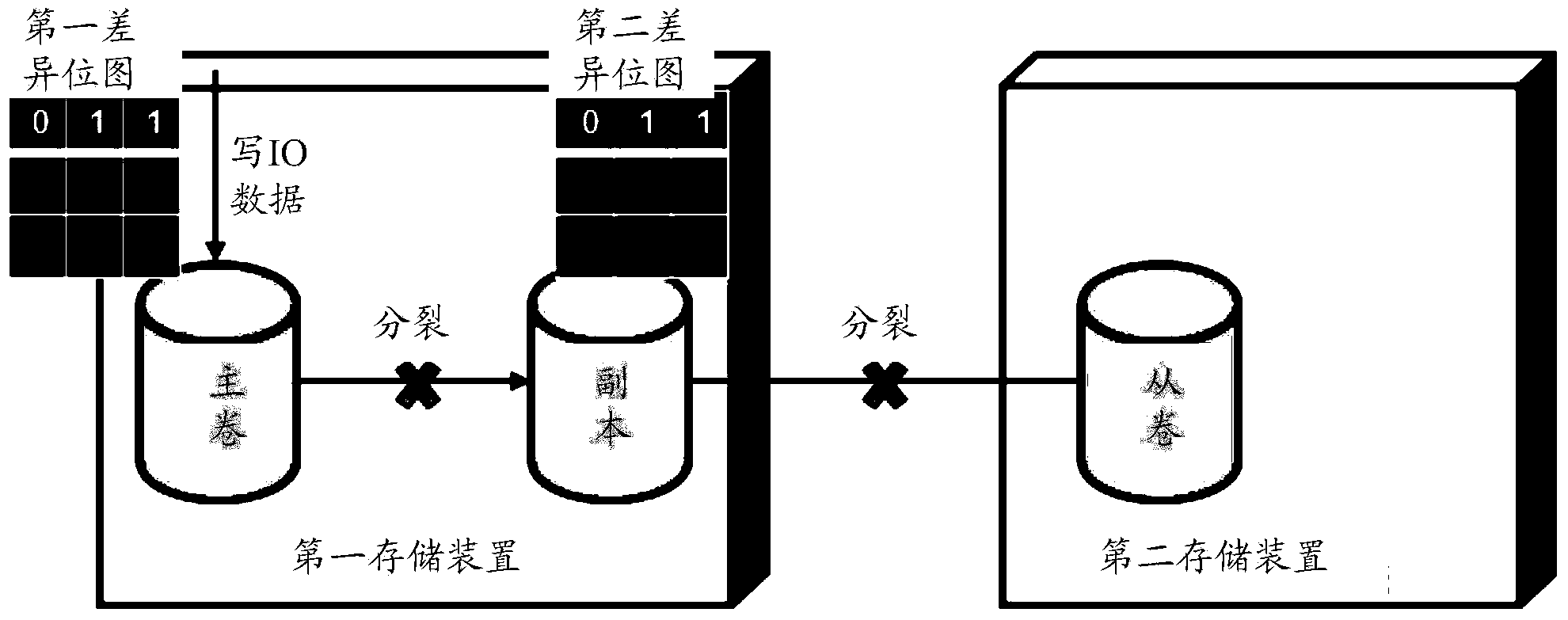
Storage data copying method, equipment and system
InactiveCN103617096AAvoid processing delaysImprove performanceRedundant operation error correctionComputer hardwareReplication method
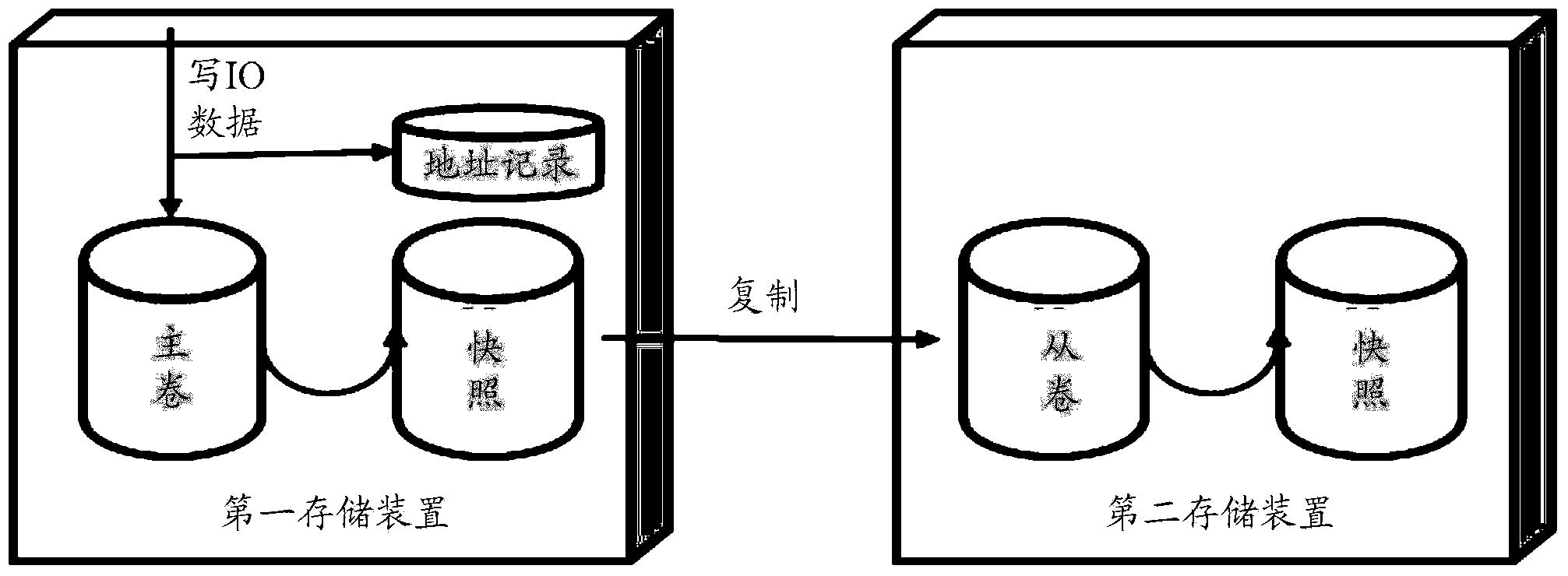
The invention discloses a storage data copying method, equipment and system, and belongs to the field of data storage. The method includes the steps that a copy of a master file of a first storage device is created in the first storage device; when a copying cycle begins, data of the master file are copied to the copy; data of the copy are sent to a second storage device so that the data of the copy can be copied to a secondary file of the second storage device. The copy of the master file is created in the first storage device, the data of the master file are copied to the copy when the copying cycle starts each time, and the data of the copy are copied to the second storage device, so that a snapshoot of the master file does not need to be created in the copying process, COW or ROW processing on write IO data received by the master file is not needed, delay of write IO data processing is avoided, and performance of a copying system of storage data is improved.
Owner:HUAWEI TECH CO LTD
File replication in a distributed segmented file system
InactiveUS7836017B1Expand accessDigital data information retrievalDigital data processing detailsFile replicationFile system
A system includes storage configured to store file system entities, including directories and files, residing in segments of a distributed, segmented single file system, file servers configured to implement the single file system with separate ones of the file servers controlling metadata of separate ones of the segments, and a controller configured to control storage of files in the file system such that for a master file stored in a first segment, a first replica of the master file will be stored in a second segment that is physically separate from the first segment, the controller being further configured to control storage of directories in the file system such that a single directory will include identifiers for the master file and the first replica.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
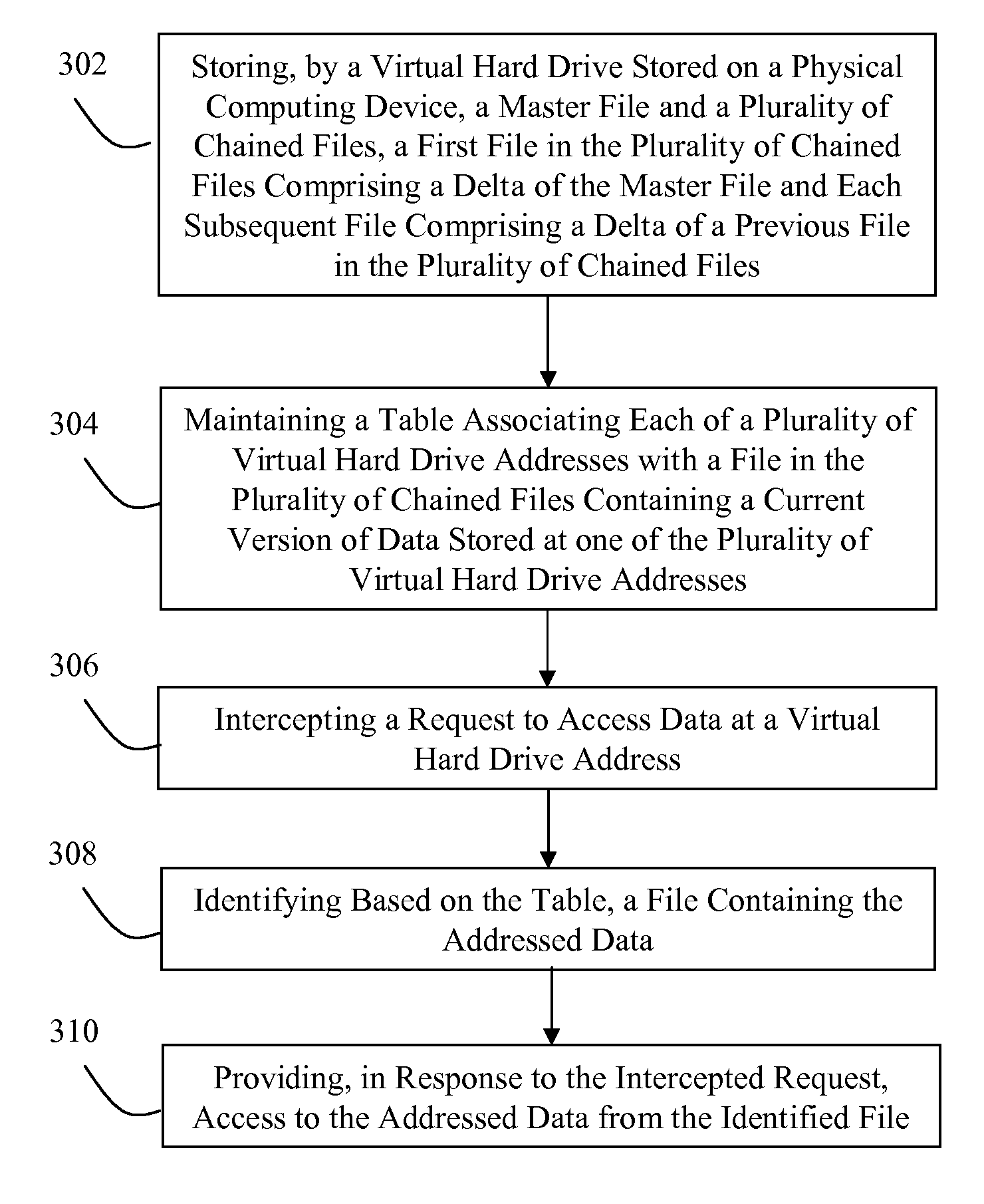
Systems and Methods for Optimizing a Process of Determining a Location of Data Identified by a Virtual Hard Drive Address
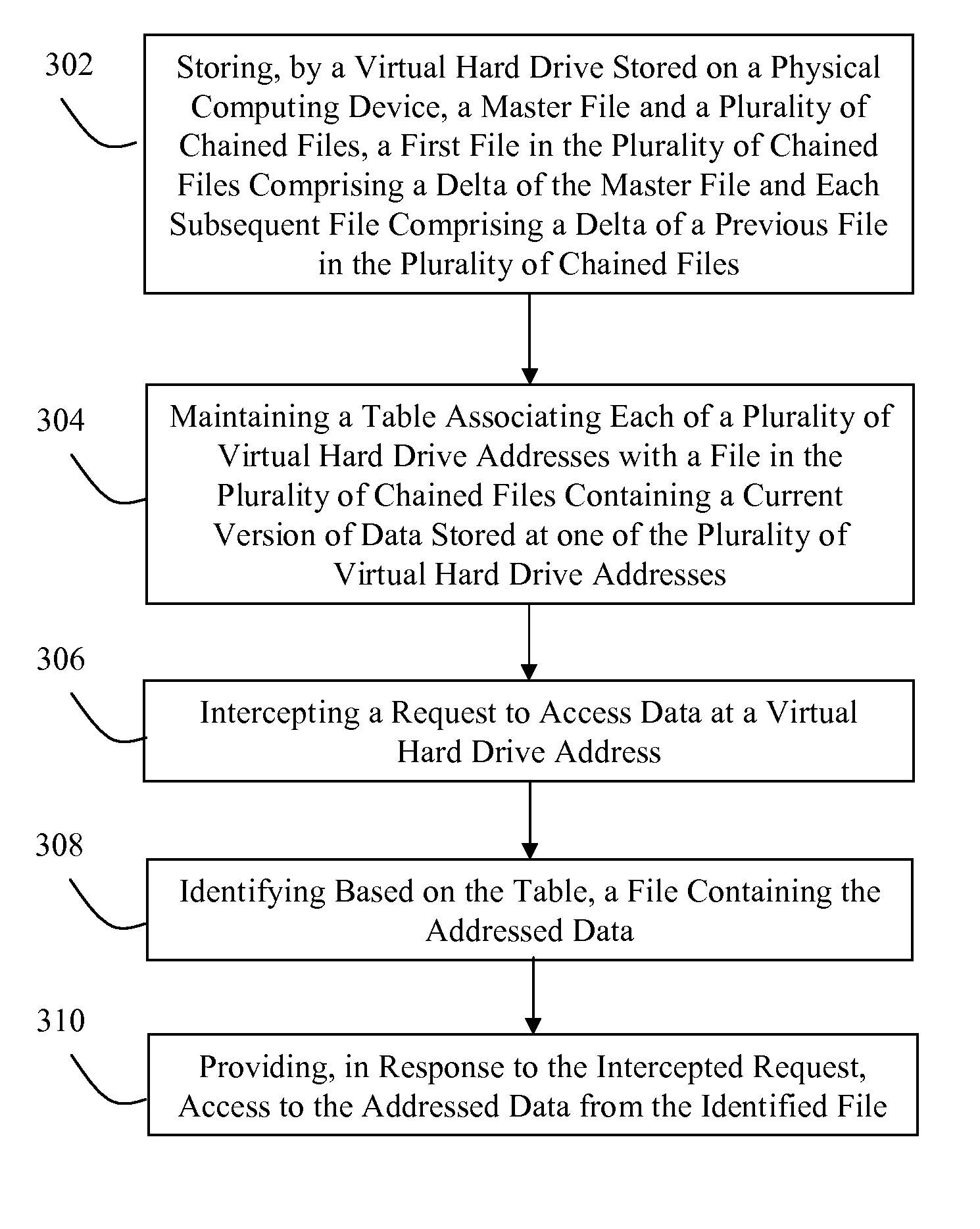
ActiveUS20100162239A1Digital data processing detailsSoftware simulation/interpretation/emulationHard disc driveComputer science
A system for optimizing a process of determining a location of data identified by a virtual hard drive address includes a virtual hard drive, a hypervisor, a plurality of chained files and a table. The plurality of chained files includes a first file comprising a delta of a master file and each subsequent file comprising a delta of a previous file in the plurality of chained files. The table enumerates associations between each of a plurality of virtual hard drive addresses with one of the master file and a file in the plurality of chained files. The virtual hard drive stores the master file, the plurality of chained files, and the table. The hypervisor intercepts a request to access data at a virtual hard drive address and identifies, based on the table, a file containing the requested data and responds to the request with access to the requested data.
Owner:CITRIX SYST INC
Systems and methods for optimizing a process of determining a location of data identified by a virtual hard drive address
ActiveUS8132168B2Digital data processing detailsSoftware simulation/interpretation/emulationHard disc driveOperating system
A system for optimizing a process of determining a location of data identified by a virtual hard drive address includes a virtual hard drive, a hypervisor, a plurality of chained files and a table. The plurality of chained files includes a first file comprising a delta of a master file and each subsequent file comprising a delta of a previous file in the plurality of chained files. The table enumerates associations between each of a plurality of virtual hard drive addresses with one of the master file and a file in the plurality of chained files. The virtual hard drive stores the master file, the plurality of chained files, and the table. The hypervisor intercepts a request to access data at a virtual hard drive address and identifies, based on the table, a file containing the requested data and responds to the request with access to the requested data.
Owner:CITRIX SYST INC
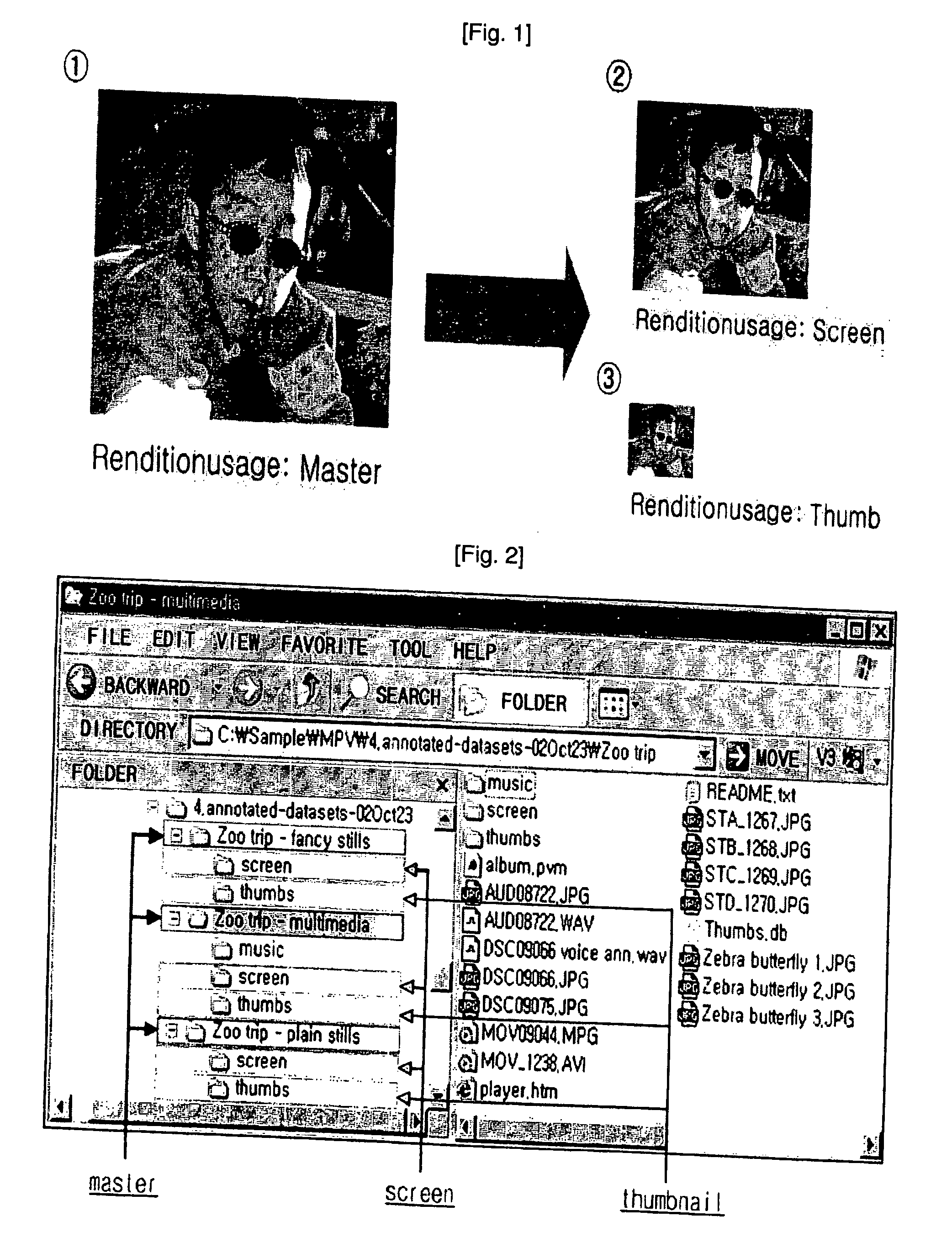
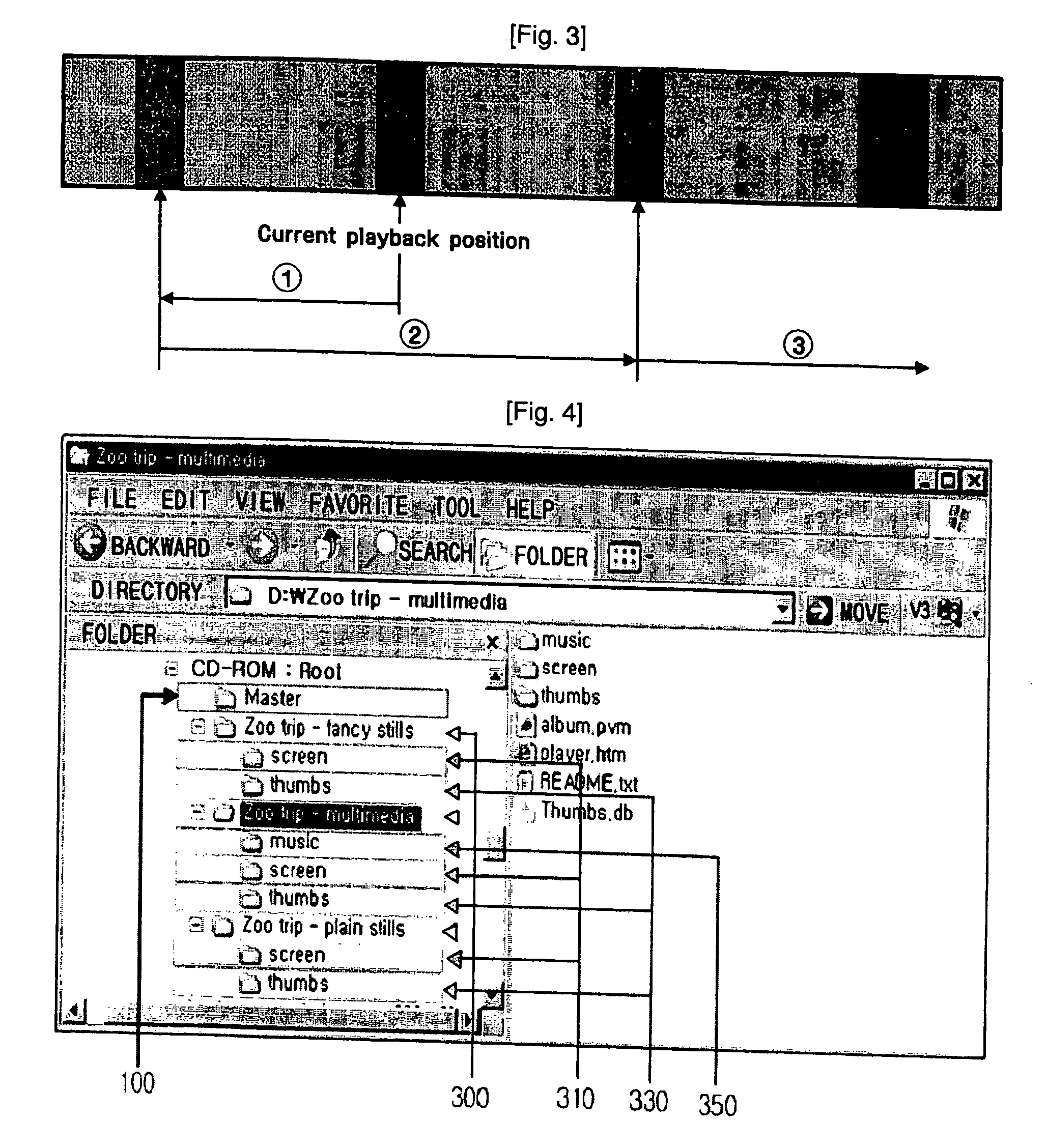
Method of efficiently managing multimedia content and storage medium storing therein multimedia content using the same
InactiveUS20070094231A1Efficient managementAvoid wasting storage spaceRecording carrier detailsMultimedia data indexingMetadataMaster file
Disclosed is a method of efficiently managing multimedia content and a storage medium using the same. A primary object of the present invention is to provide a method for arranging the multimedia content to efficiently manage multimedia content according to MPV standards and a method of improving the speed of search of multimedia content. To this end, a method of efficiently managing multimedia content according to the present invention comprises the steps of reading out a metadata file from a storage medium for the reproduction of specific multimedia content; when the multimedia content is reproduced using the read metadata file, reading out, from the metadata file, a path name and an actual address on the storage medium, which correspond to each of the multimedia content files; and directly accessing the relevant multimedia content file using information on the read path name and actual address. Therefore, there is an advantage in that the waste of storage space due to the storage of redundant master files can be prevented.
Owner:SAMSUNG ELECTRONICS CO LTD
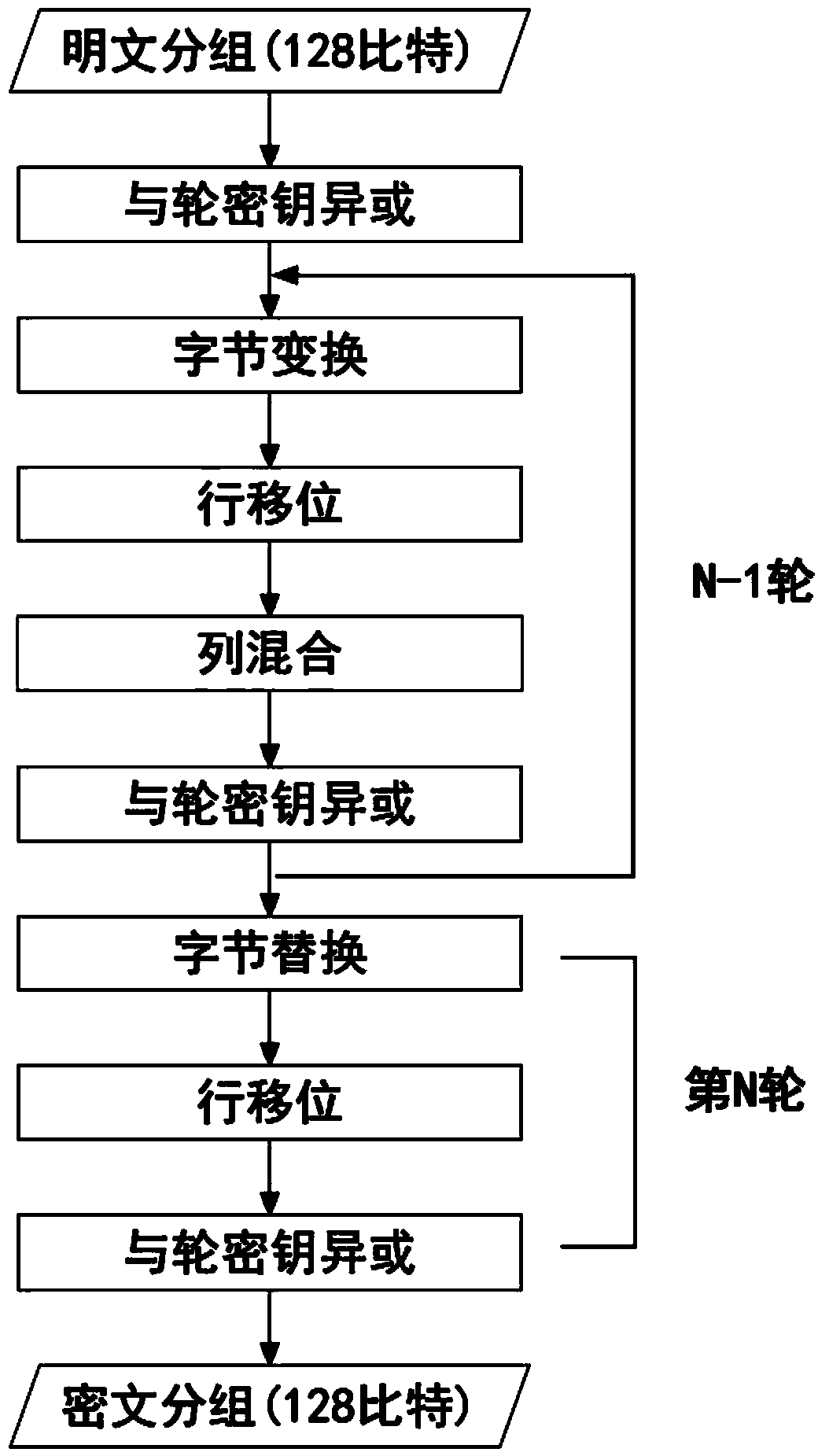
AES parallel implementation method based on OpenCL
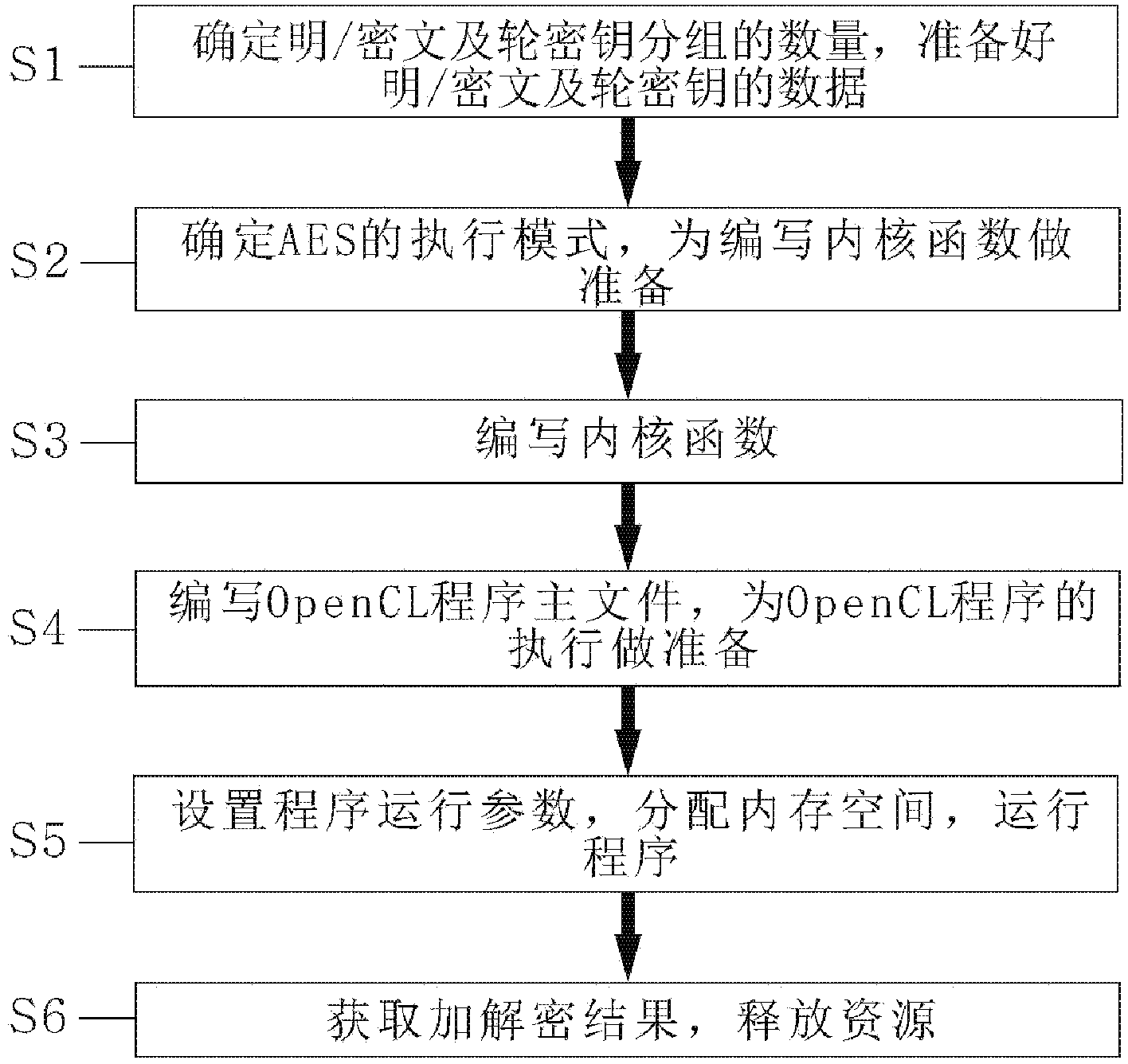
ActiveCN103973431AHigh-speed programmingImprove matchEncryption apparatus with shift registers/memoriesConcurrent instruction executionPassword crackingComputer hardware
The invention discloses an AES parallel implementation method based on OpenCL. According to the scheme, when an AES performs parallel running on an AMD GPU based on OpenCL, optimum performance can be achieved. The method includes the following steps that first, the number of plaintext / ciphertext and the number of round key groups are determined, and plaintext / ciphertext and round key data are prepared; second, an executing mode of the AES is determined, and preparation is made for writing of a KiReadyThread; third, the KiReadyThread is written; fourth, a master OpenCL program file is written, and preparation is made for execution of an OpenCL program; fifth, program running parameters are set, memory space is allocated, and the program runs; sixth, the encryption and decryption result is acquired, and resources are released. According to the method, in parallel running process of the AES, data are reasonably allocated in a memory and parallel granularity is reasonably selected so that running performance can be improved, and the method can be used for fast encryption and decryption or password cracking machines.
Owner:SOUTH CHINA NORMAL UNIVERSITY
Generating storage reports using volume snapshots
InactiveUS20060235892A1Preventing I/O loadAvoid loadData processing applicationsError detection/correctionLiving systemsFile system
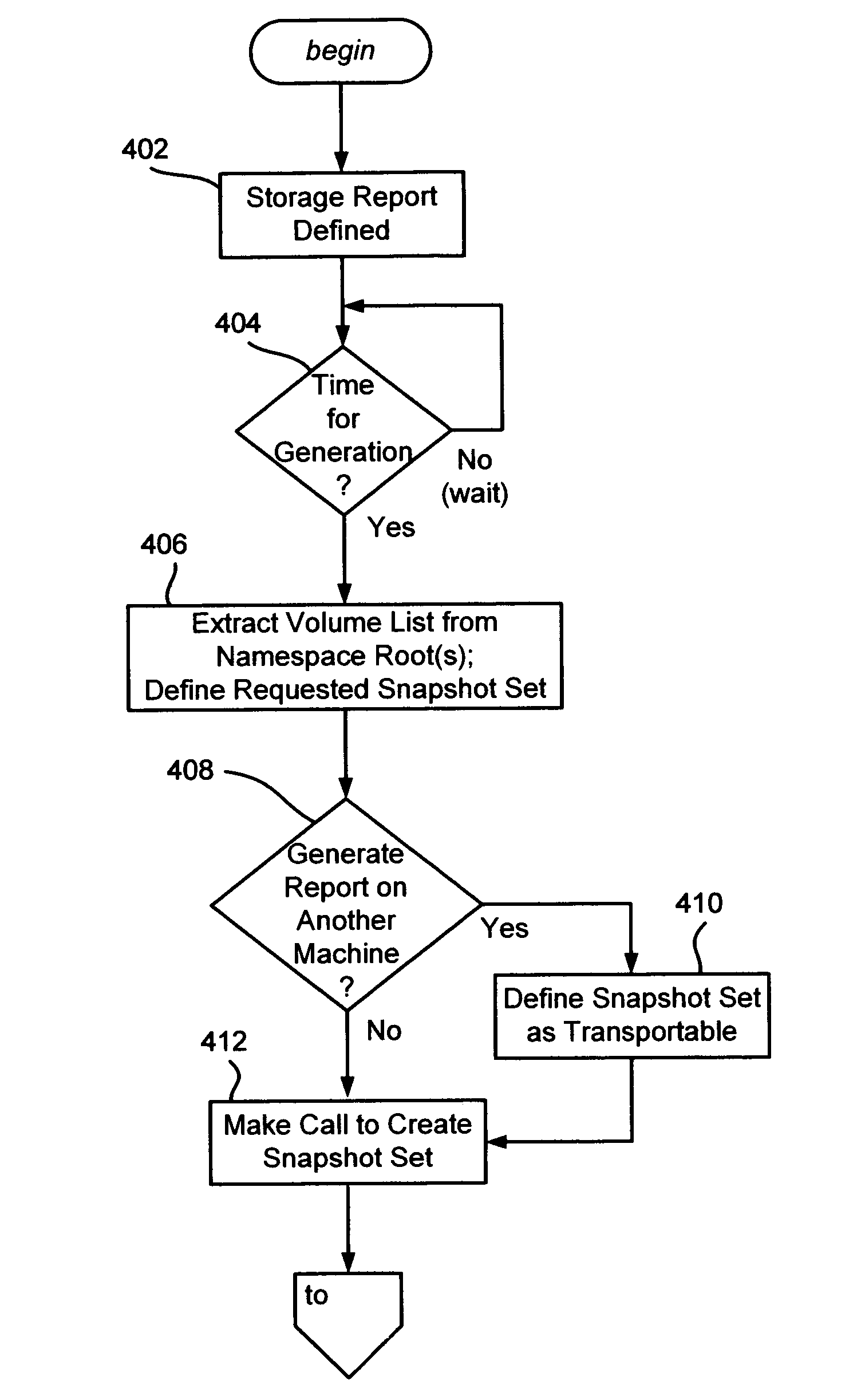
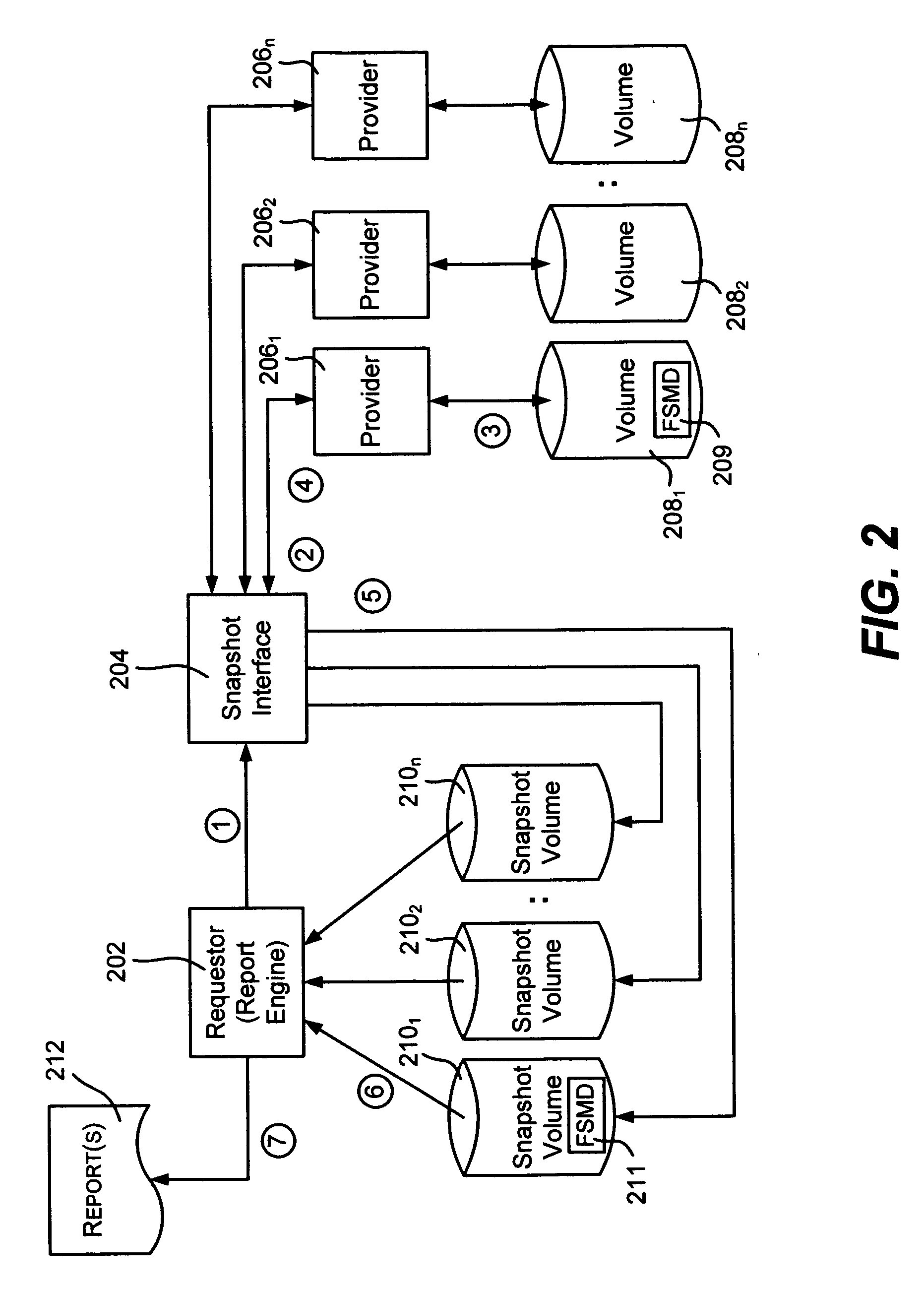
Described is a method and system by which storage reports are generated from a volume snapshot set rather than the live volume or volumes, wherein a volume snapshot set comprises a representation or copy of one or more volume at a single point-in-time. By scanning the snapshot, a consistent file system image is obtained. Scanning may take place by enumerating a volume's directories of files, or, when available, by accessing a file system metadata of file information (e.g., a master file table) separately maintained on the volume. With some (e.g., hardware-based) snapshot technologies, the snapshot can be transported to another computing system for scanning by that other computing system, thereby avoiding burdening a live system's resources when scanning. Accurate and consistent storage reports are thus obtained at a single point in time, independent of the number of volumes being scanned.
Owner:MICROSOFT TECH LICENSING LLC
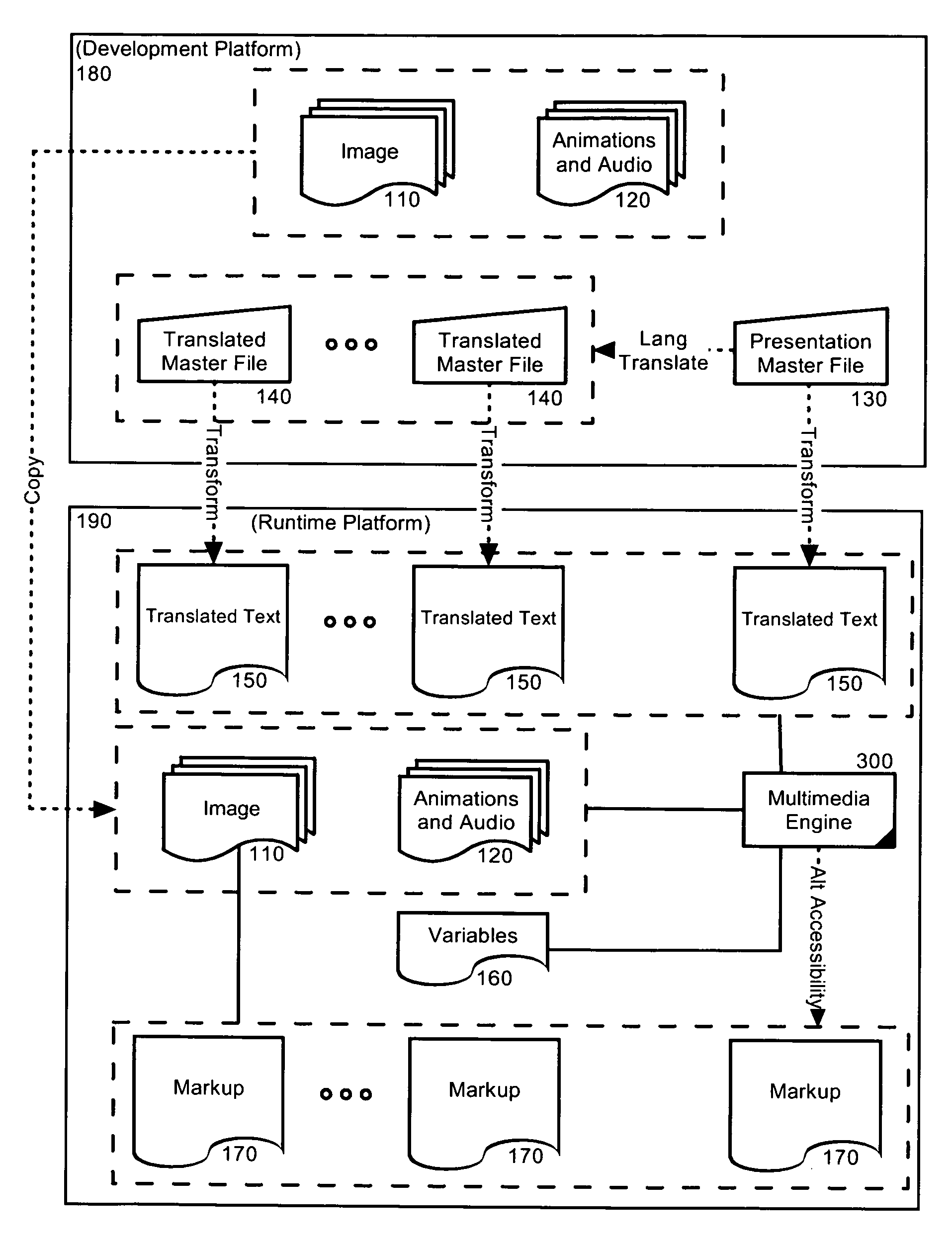
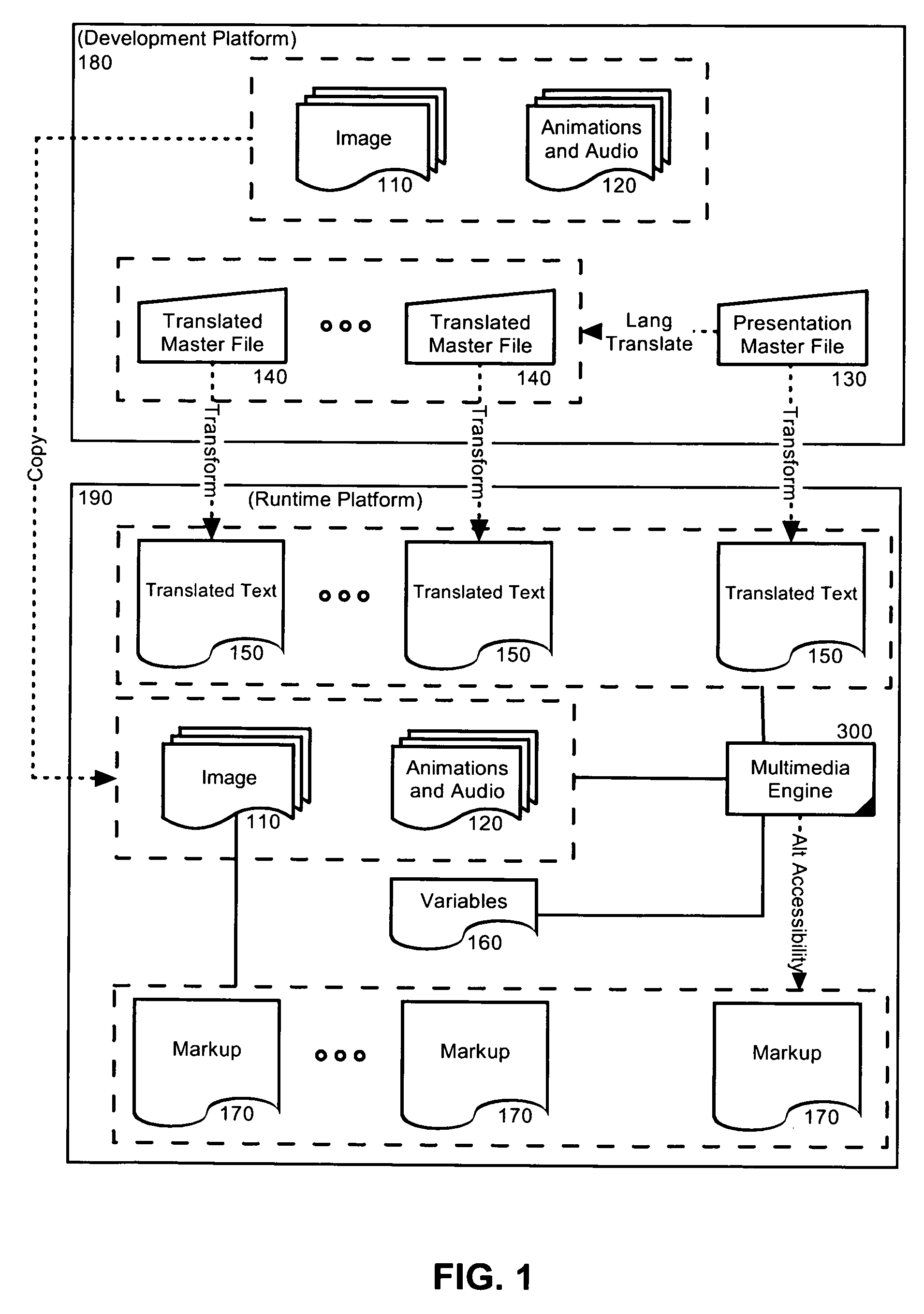
Creating accessible, translatable multimedia presentations
InactiveUS20070106927A1Natural language translationSpecial data processing applicationsAssistive technologyPaper document
The present invention provides a computer implemented method for generating translatable and accessible multimedia presentations. The method can include transforming a presentation master file defining a multimedia presentation into each of a text file and a variables file, generating a plurality of slides for a slide show with text strings from the text file and imagery and audiovisual elements from the variables file, and launching the slide show. Transforming a presentation master file into each of a text file and a variables file can include additionally transforming the presentation master file into a visual markup language document emulating the multimedia presentation. As such, in an aspect of the embodiment, the method further can include detecting an assistive technology, and rendering the visual markup language document in lieu of the slide show.
Owner:IBM CORP
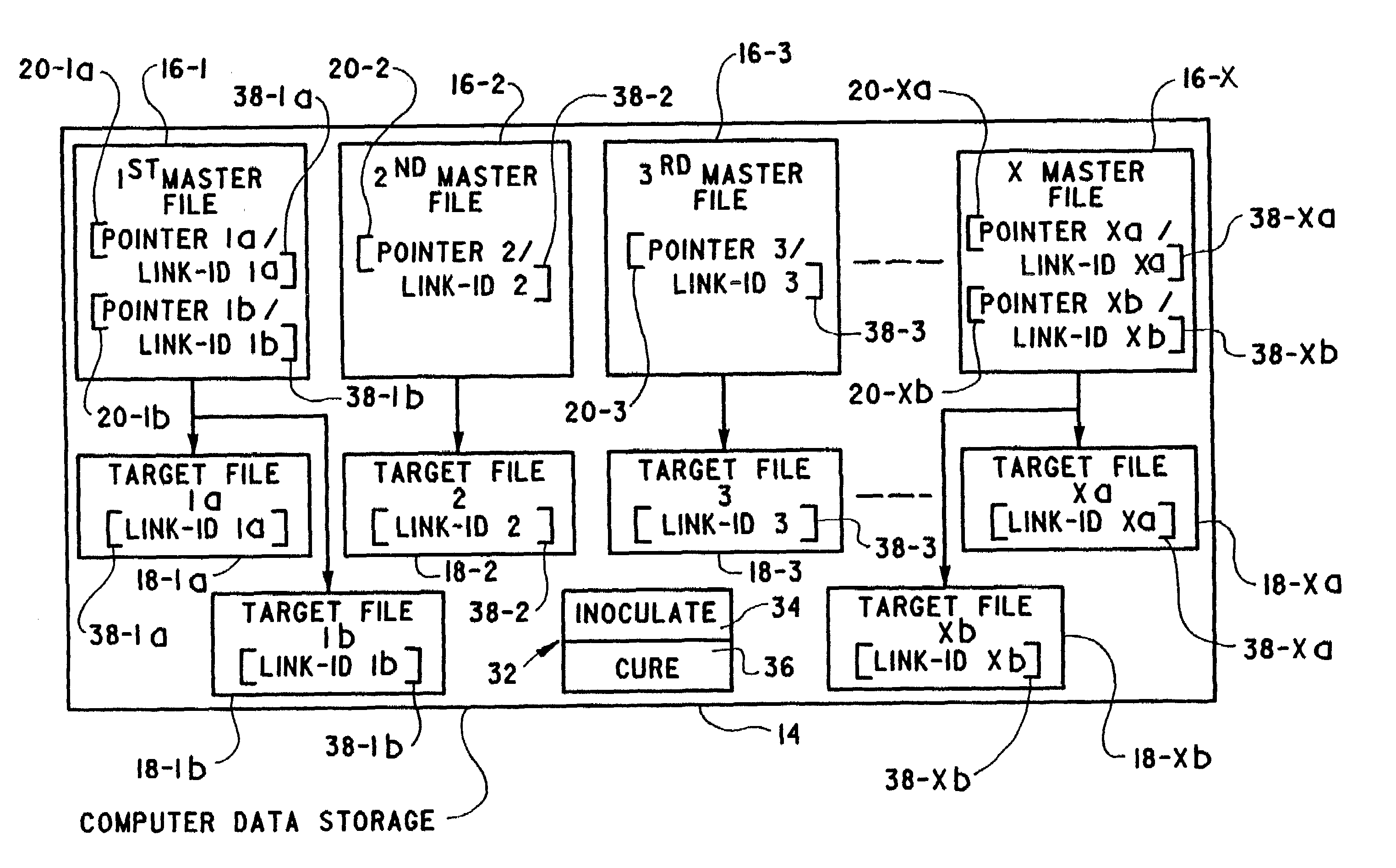
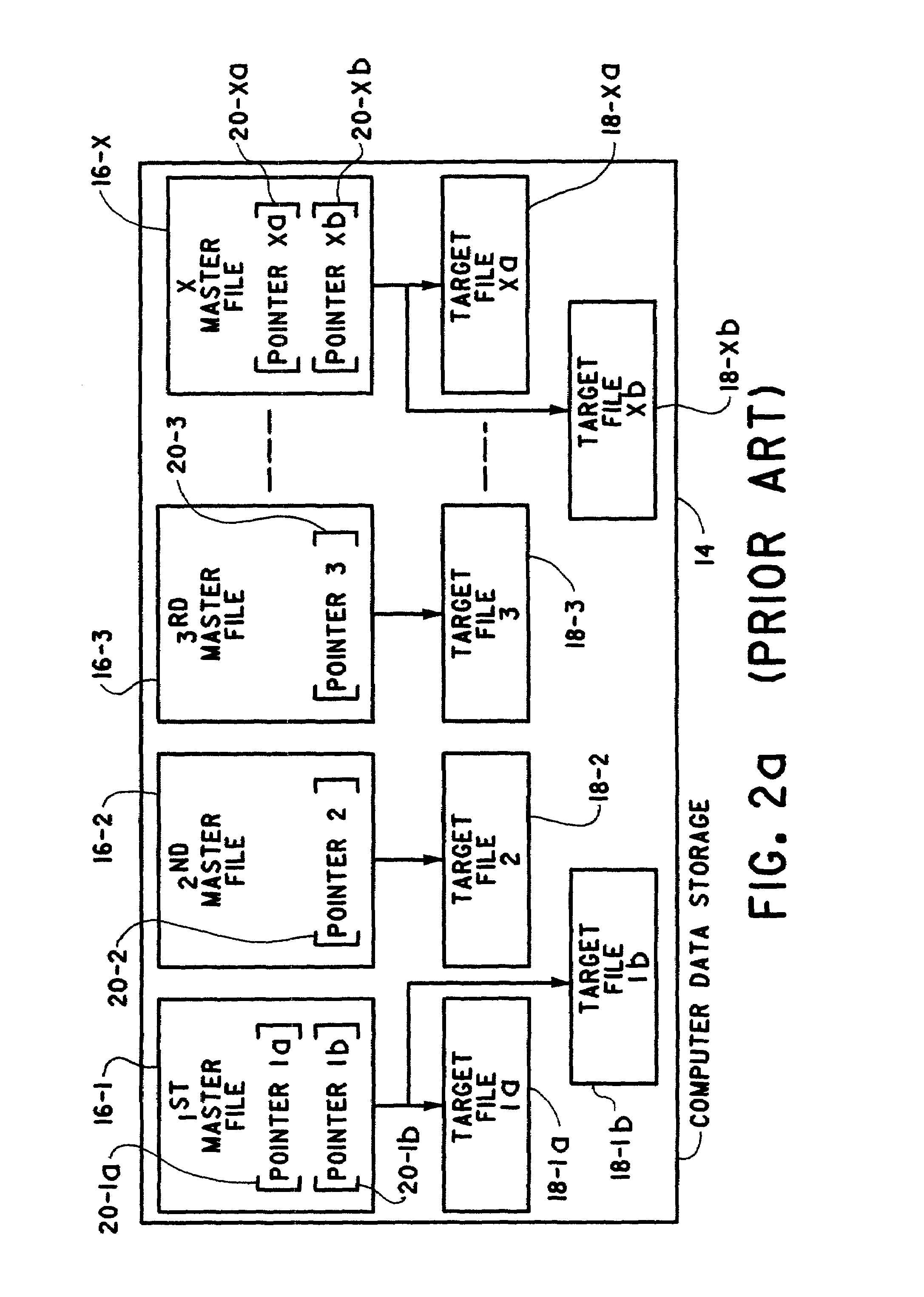
Method of automatically correcting broken links to files stored on a computer
InactiveUS7032124B2Data processing applicationsError detection/correctionComputer data storageData memory
A method of correcting broken software links includes providing a computer data storage having target files and master files. Each master file includes a pointer to a storage location where at least one target file called by the master file resides. A link-id is determined for each target file and is stored in each master file configured to call the target file. The target file is then either renamed or moved so that each master file configured to call the target file cannot locate it from the pointer data. The target file is then located on the computer data storage based on a match between the link-id for the target file and the link-id stored in the calling master file. The data comprising the pointer of the master file is then updated whereupon it can locate the target file on the computer data storage.
Owner:AXIOM SERVICES
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com