Patents
Literature
312 results about "System identifier" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
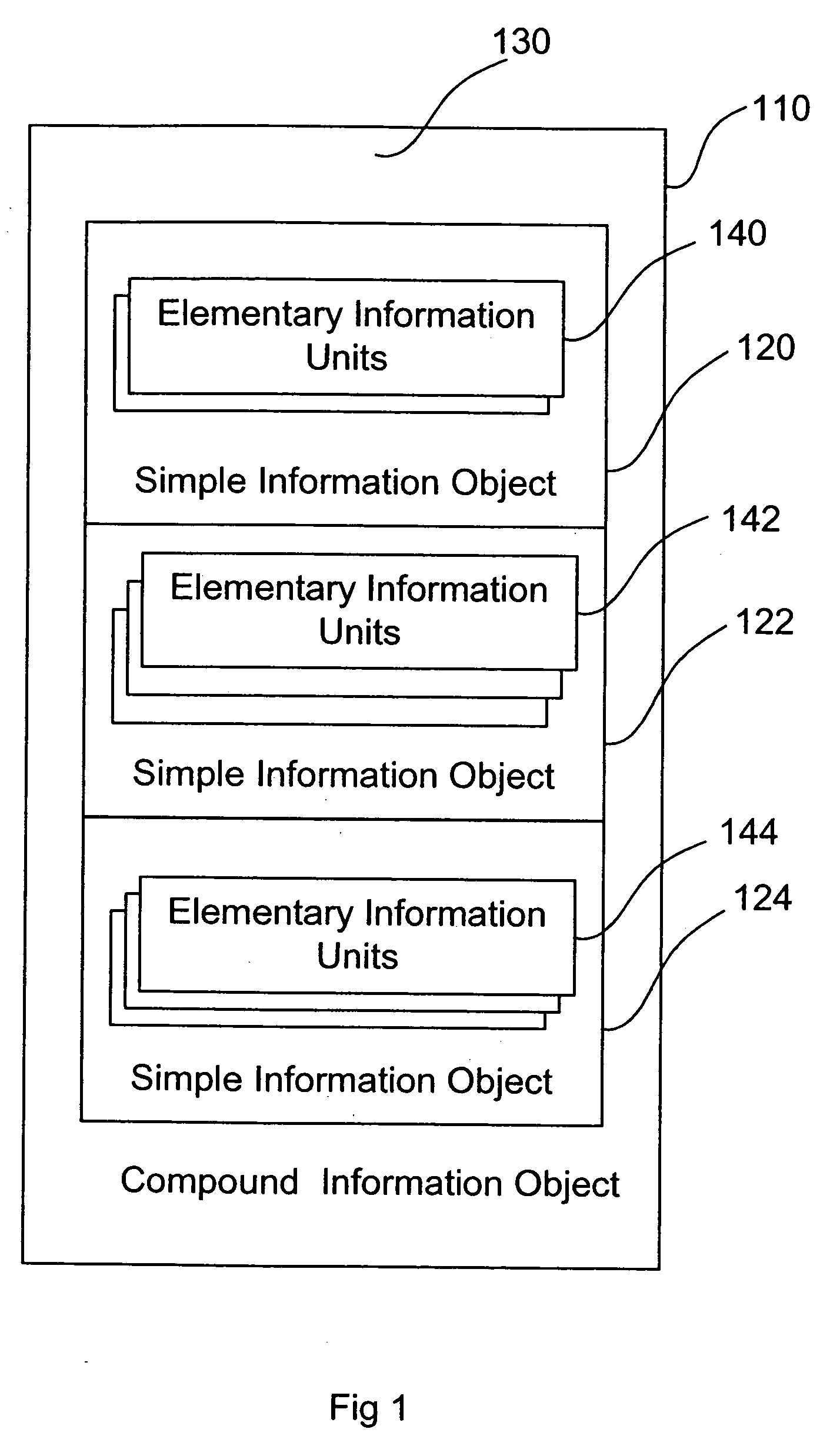
A system identifier is a document-processing construct introduced in the HyTime markup language as a supplement to SGML. It was subsequently incorporated into the HTML and XML markup languages. In HyTime, there are two kinds of system identifier: formal system identifier (FSI) and simple system identifier.
System and method for user access to a distributed network communication system using persistent identification of subscribers
InactiveUS20030233332A1Market predictionsMetering/charging/biilling arrangementsDevice registerCommunications system
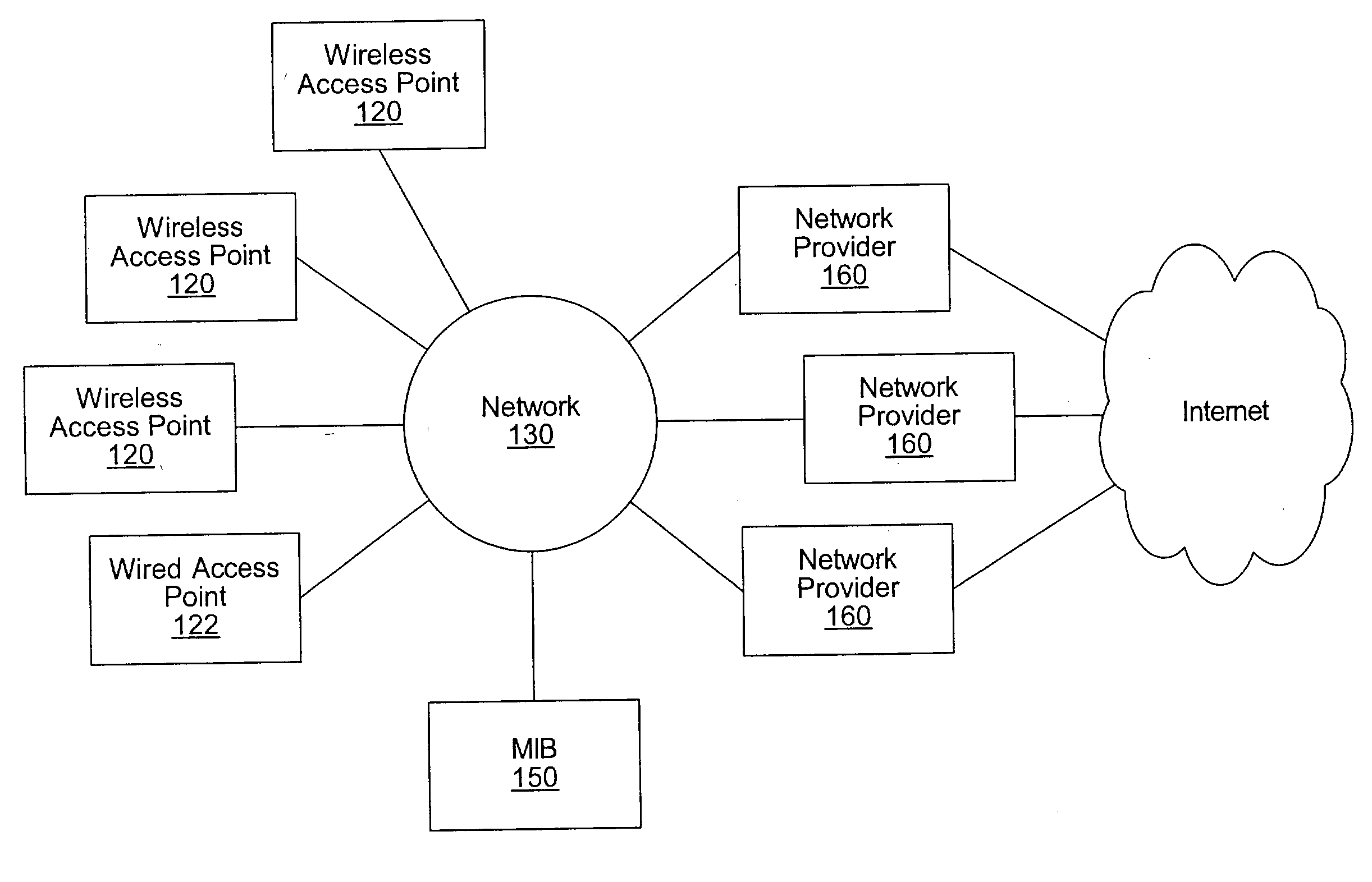
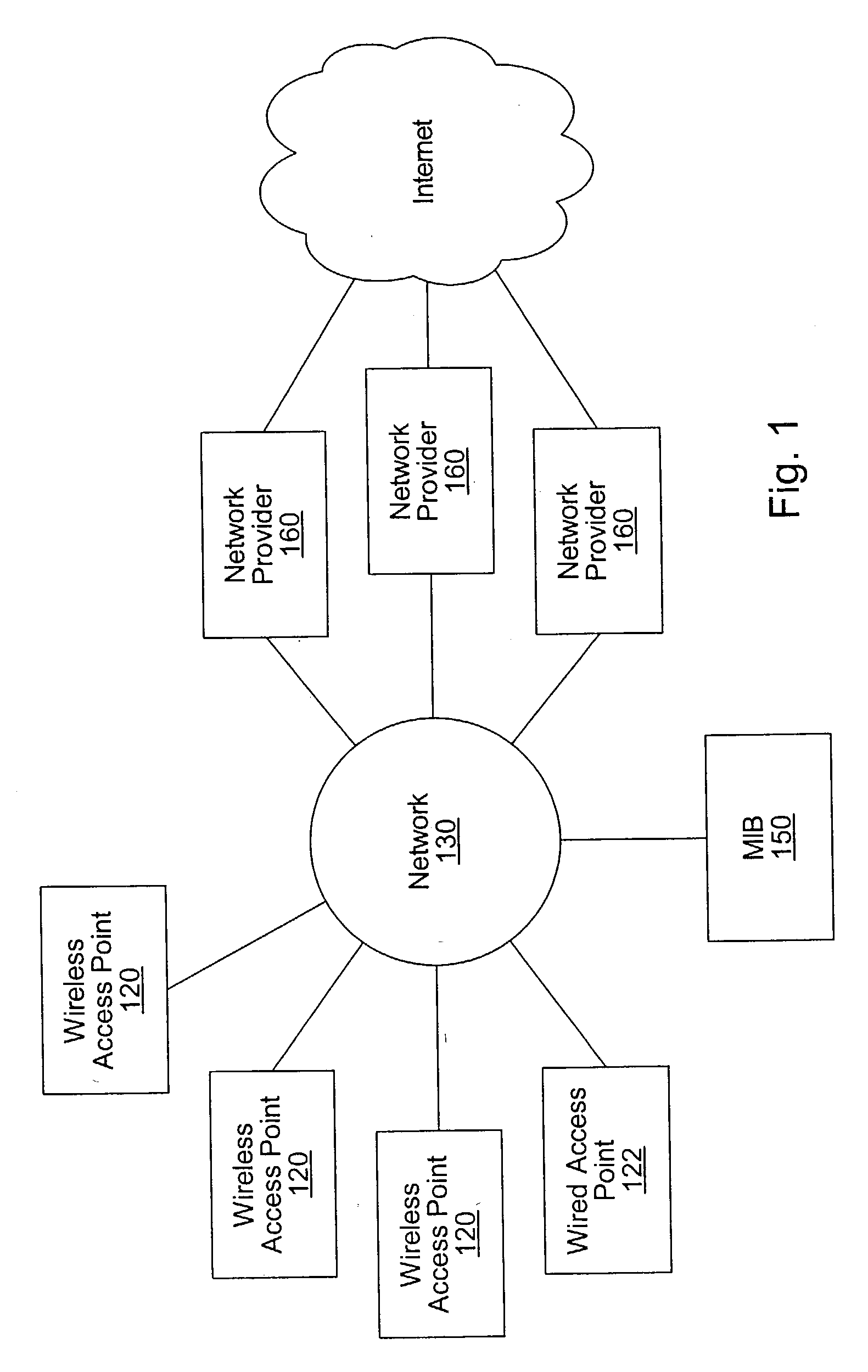
A system and method for providing network access are disclosed. After connecting to a network at an access point, a user of a computing device registers for network access with a network provider. In response to the registration, the network provider sends a completion page to the computing device. The completion page includes a link to an embedded file such as a small, transparent GIF image. When the computing device retrieves the embedded file, the embedded file is associated with a header than includes an instruction to generate a network system identifier (e.g., a cookie). The network system identifier may be stored by the computing device and later used to identify the computing device as a registrant for network access with the network provider. The embedded file may also be sent at other times, such as after authentication of the user for network access.
Owner:WAYPORT
Method and system for managing confidential information
ActiveUS20050288939A1Flexible and efficient policy managementFlexible and efficient and enforcementDigital data protectionMultiple digital computer combinationsDigital dataElectronic form
A method and a system for information management and control is presented, based on modular and abstract description of the information. Identifiers are used to identify features of interest in the information and information use policies are assigned directly or indirectly on the basis of the identifiers, allowing for flexible and efficient policy management and enforcement, in that a policy can be defined with a direct relationship to the actual information content of digital data items. The information content can be of various kinds: e.g., textual documents, numerical spreadsheets, audio and video files, pictures and images, drawings etc. The system can provide protection against information policy breaches such as information misuse, unauthorized distribution and leakage, and for information tracking.
Owner:FORCEPOINT LLC
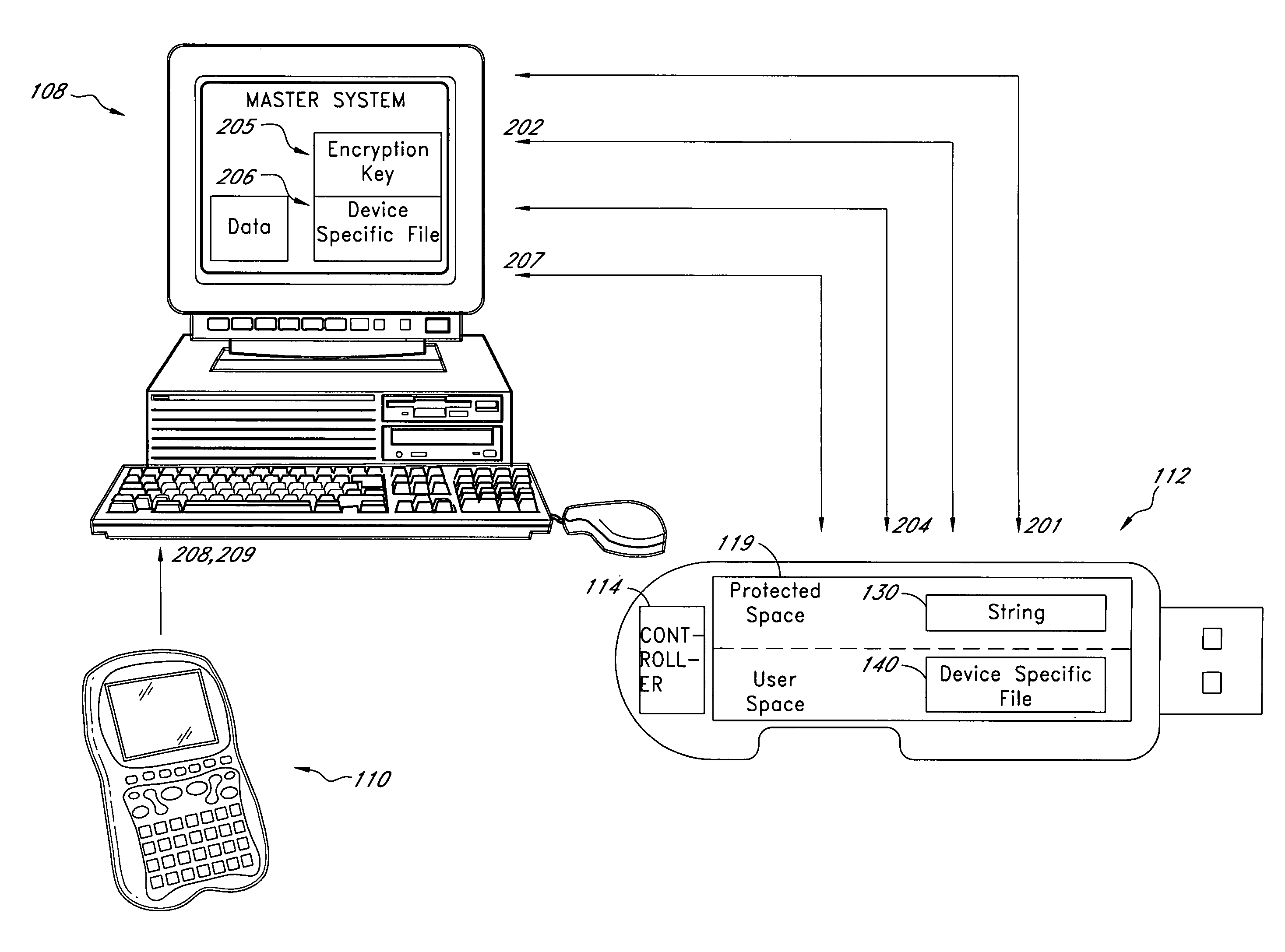
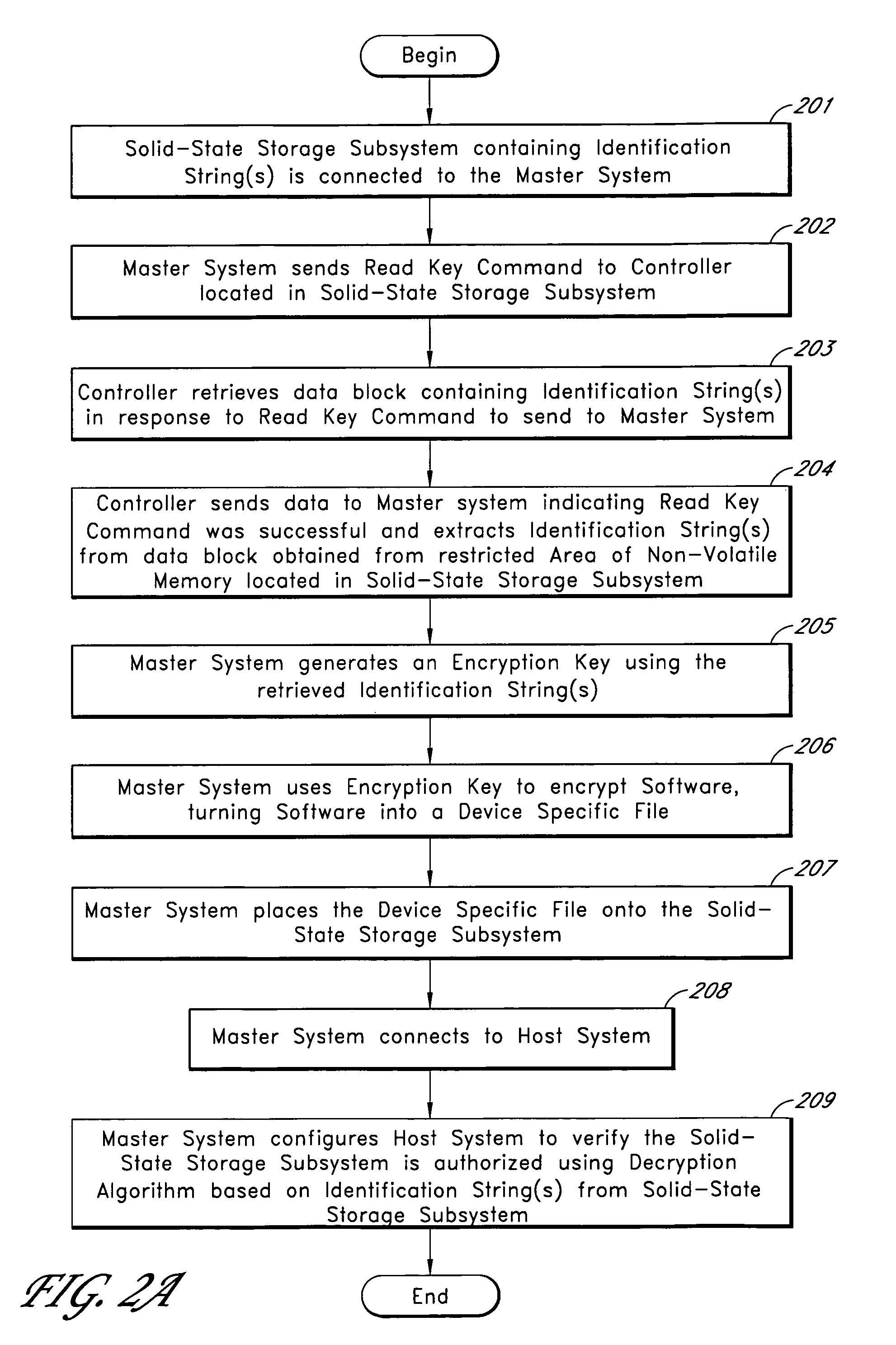
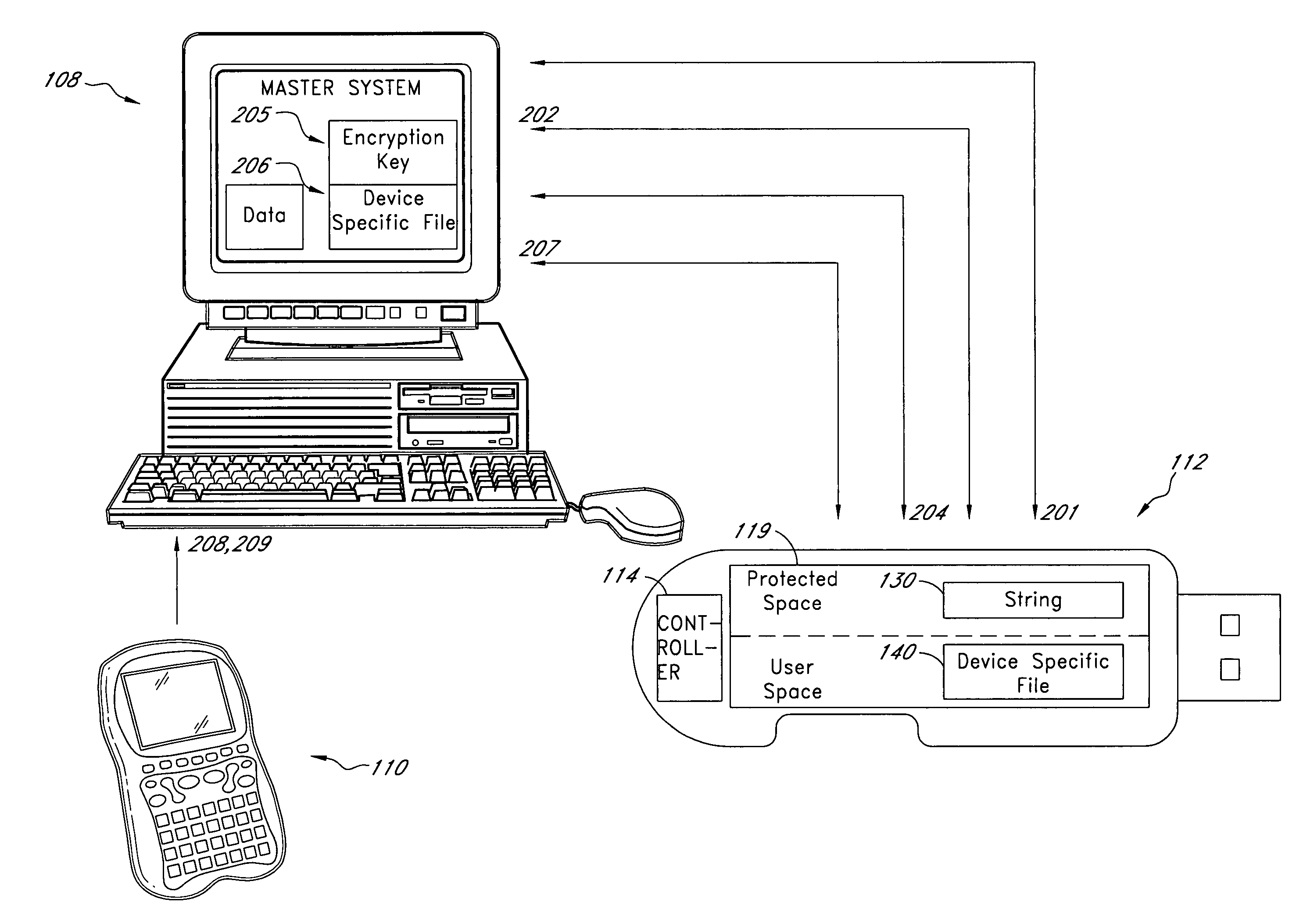
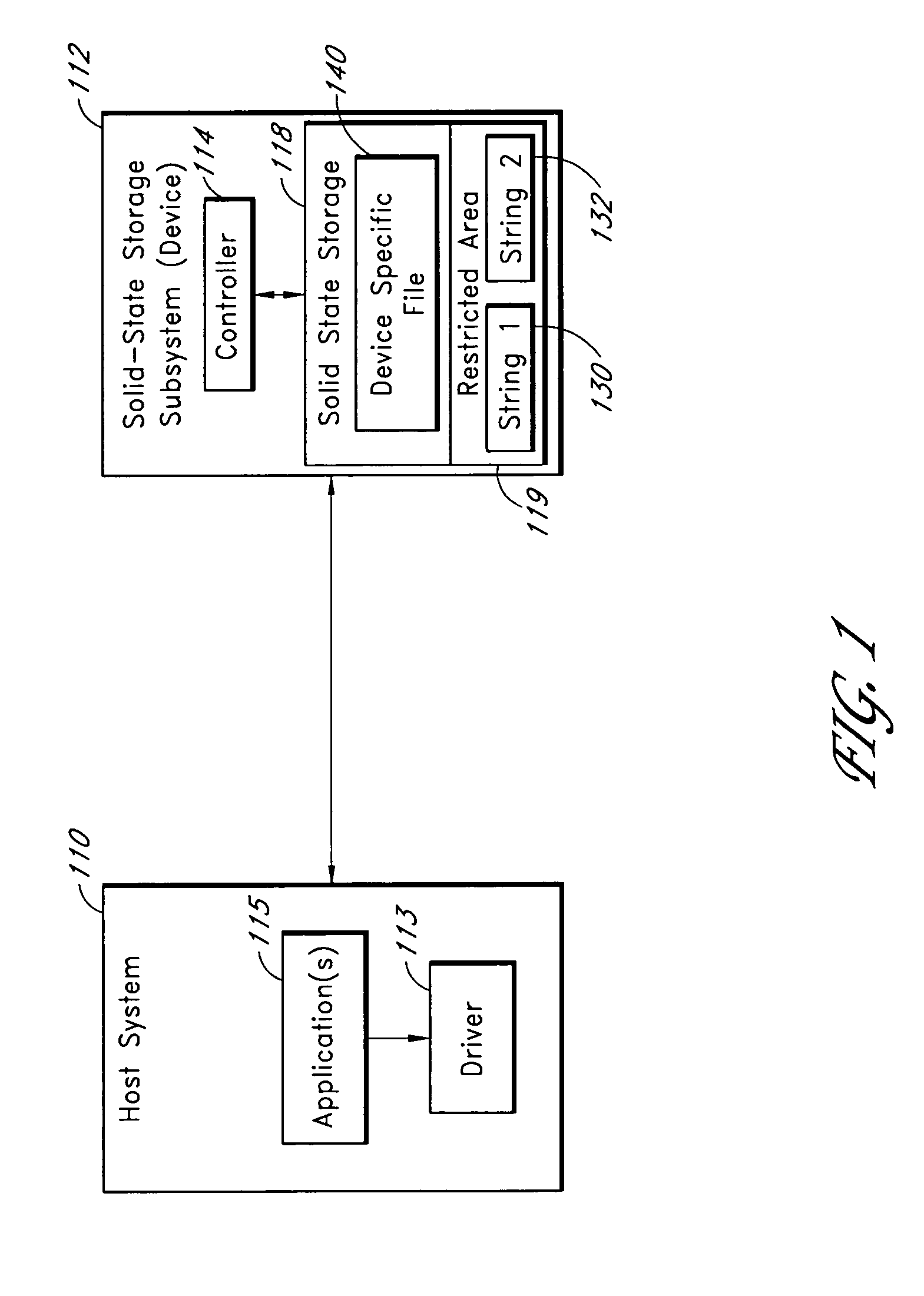
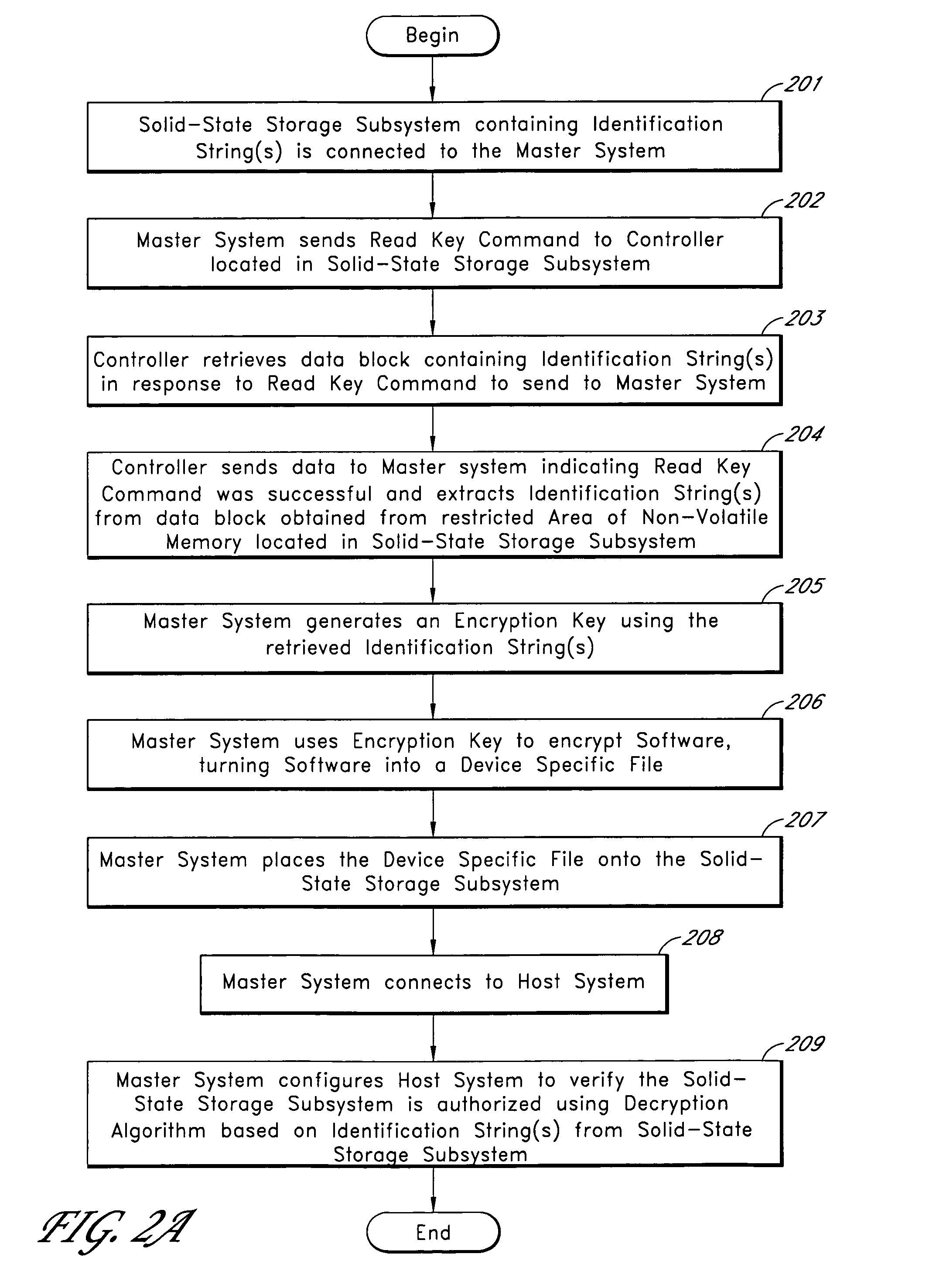
System for controlling use of a solid-state storage subsystem
ActiveUS7765373B1Digital data processing detailsUnauthorized memory use protectionSolid-state storageData file
A solid-state storage subsystem, such as a non-volatile memory card or drive, includes a main memory area that is accessible via standard memory access commands (such as ATA commands), and a restricted memory area that is accessible only via one or more non-standard commands. The restricted memory area stores information used to control access to, and / or use of, information stored in the main memory area. As one example, the restricted area may store one or more identifiers, such as a unique subsystem identifier, needed to decrypt an executable or data file stored in the main memory area. A host software component is configured to retrieve the information from the subsystem's restricted memory area, and to use the information to control access to and / or use of the information in the main memory area.
Owner:WESTERN DIGITAL TECH INC
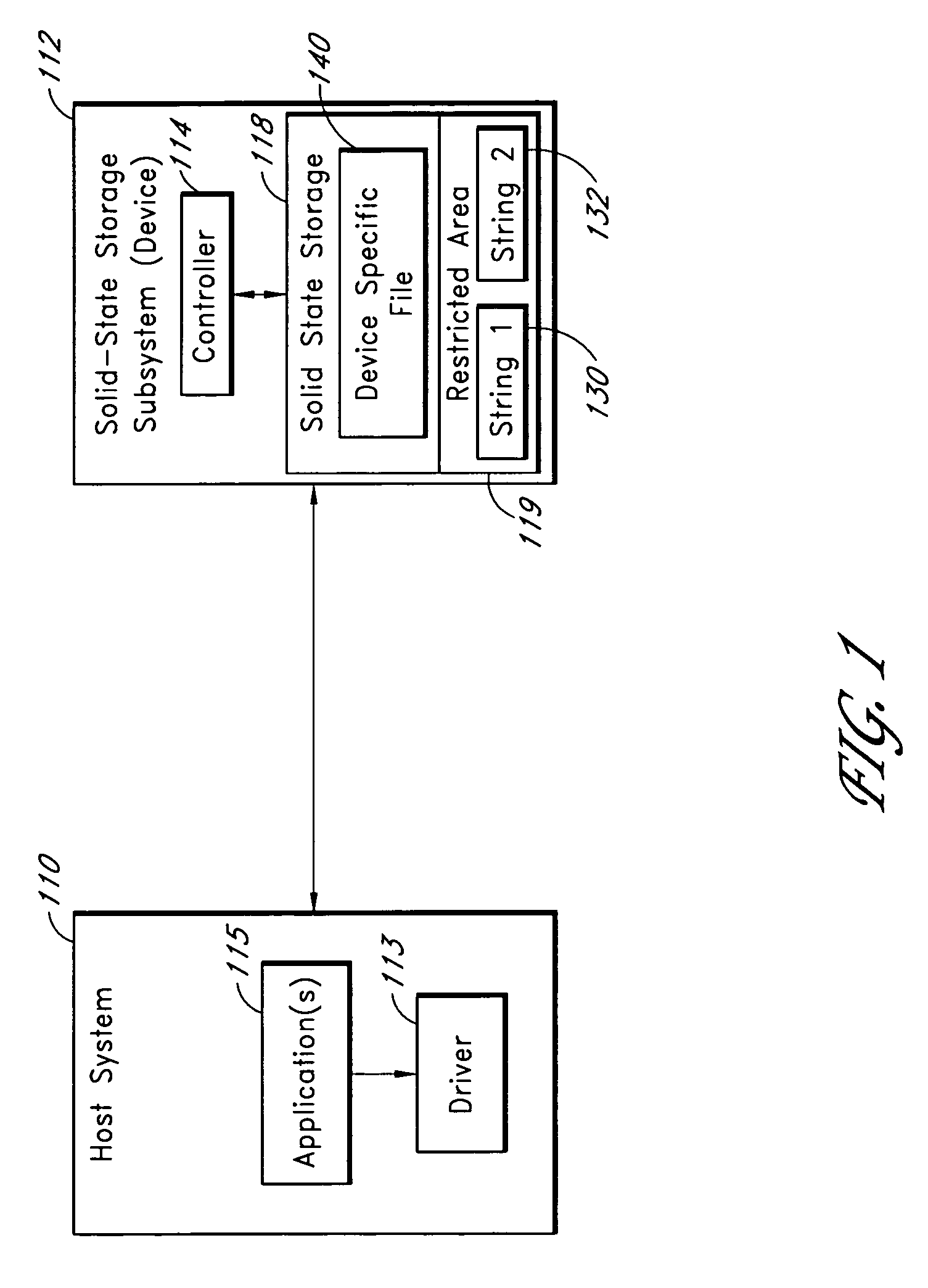
Solid-state storage subsystem security solution
ActiveUS8108692B1Unauthorized memory use protectionHardware monitoringSolid-state storageSecurity solution
A solid-state storage subsystem, such as a non-volatile memory card or drive, includes a main memory area that is accessible via standard memory access commands (such as ATA commands), and a restricted memory area that is accessible only via one or more non-standard commands. The restricted memory area stores information used to control access to, and / or use of, information stored in the main memory area. As one example, the restricted area may store one or more identifiers, such as a unique subsystem identifier, needed to decrypt an executable or data file stored in the main memory area. A host software component is configured to retrieve the information from the subsystem's restricted memory area, and to use the information to control access to and / or use of the information in the main memory area.
Owner:WESTERN DIGITAL TECH INC
System and method for concurrently utilizing multiple system identifiers
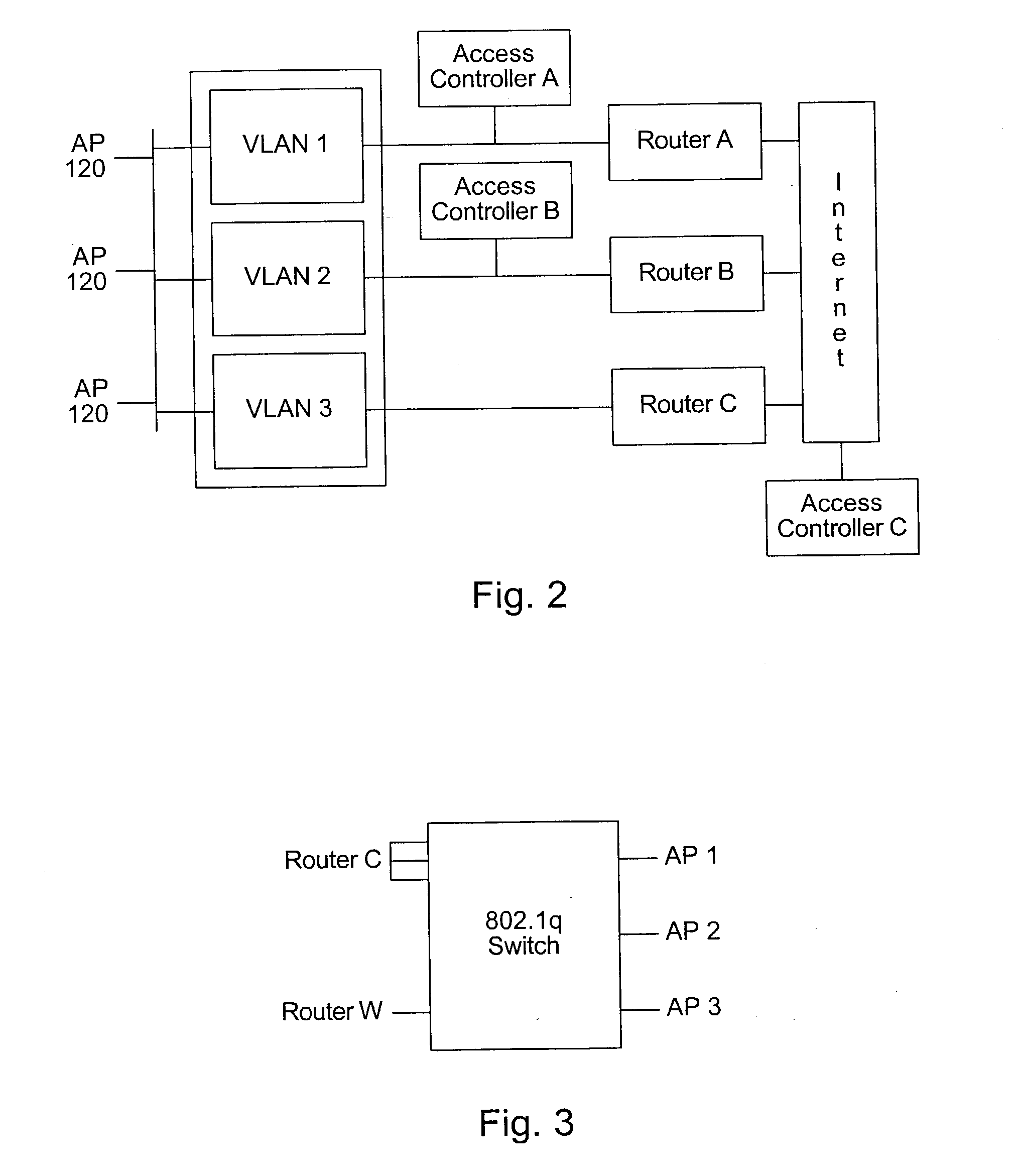
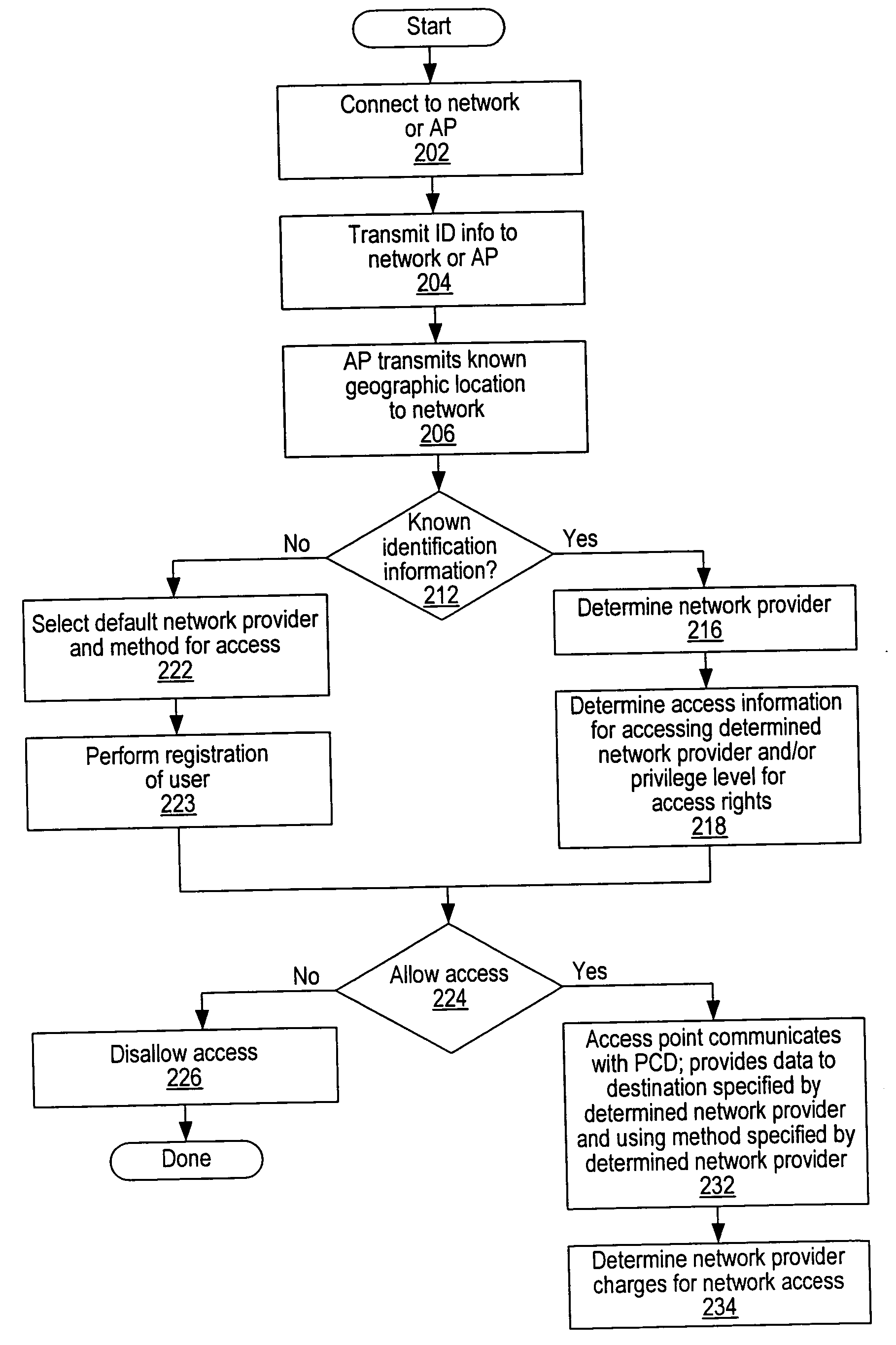
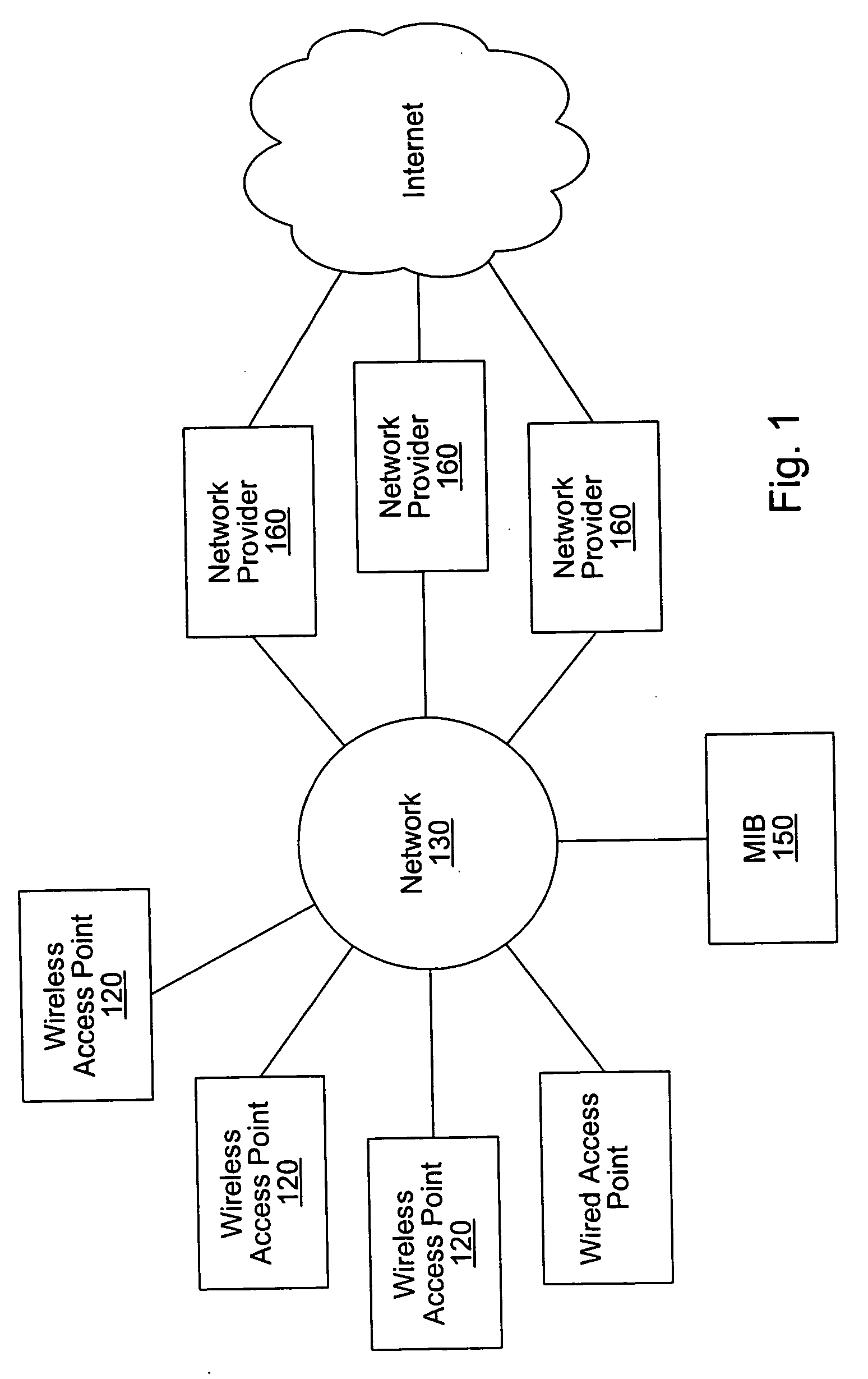
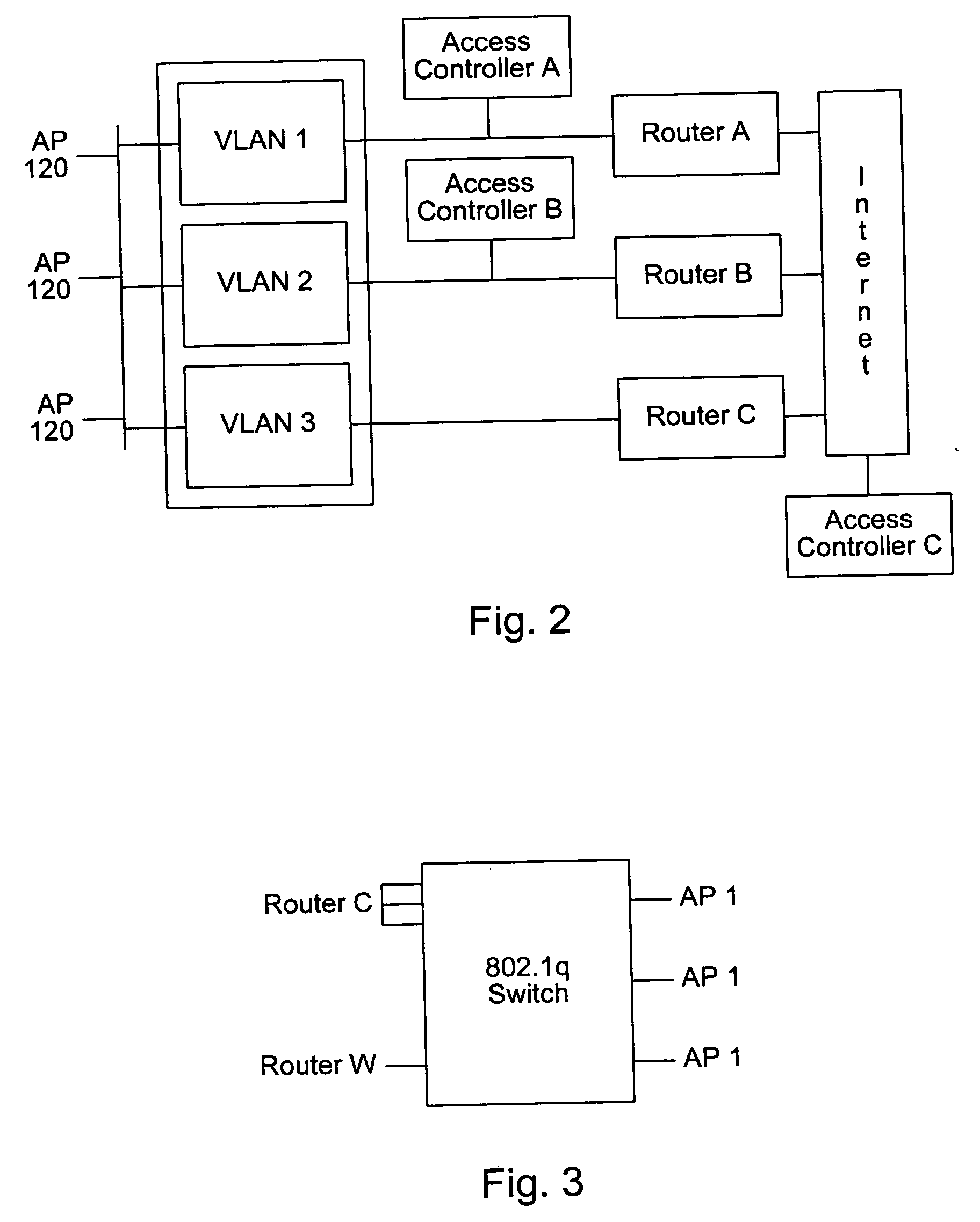
System and method for providing access to multiple wireless service providers (WSPs) on a shared network infrastructure. The system includes a plurality of access points (APs) coupled to a network which may be distributed in airports, mass-transit stations, businesses, etc. The network may couple to a wide area network, such as the Internet. Each AP may include a plurality of virtual APs (VAPs), each corresponding to a WSP. A portable computing device (PCD) of a user stores identification information indicating a WSP of a plurality of possible WSPs, and which may include an access level of the user. Each AP "listens for" or detects identification information associated with numerous WSPs. When the AP receives the identification information from the PCD, it determines the VAP / WSP for the PCD using the identification information. Network access is then provided to the PCD through the determined WSP at the determined access level.
Owner:CISCO TECH INC
Method and device for system information monitoring
ActiveCN105721193AAchieve positioningRealize information traceabilityData switching networksSource tracingComputer science
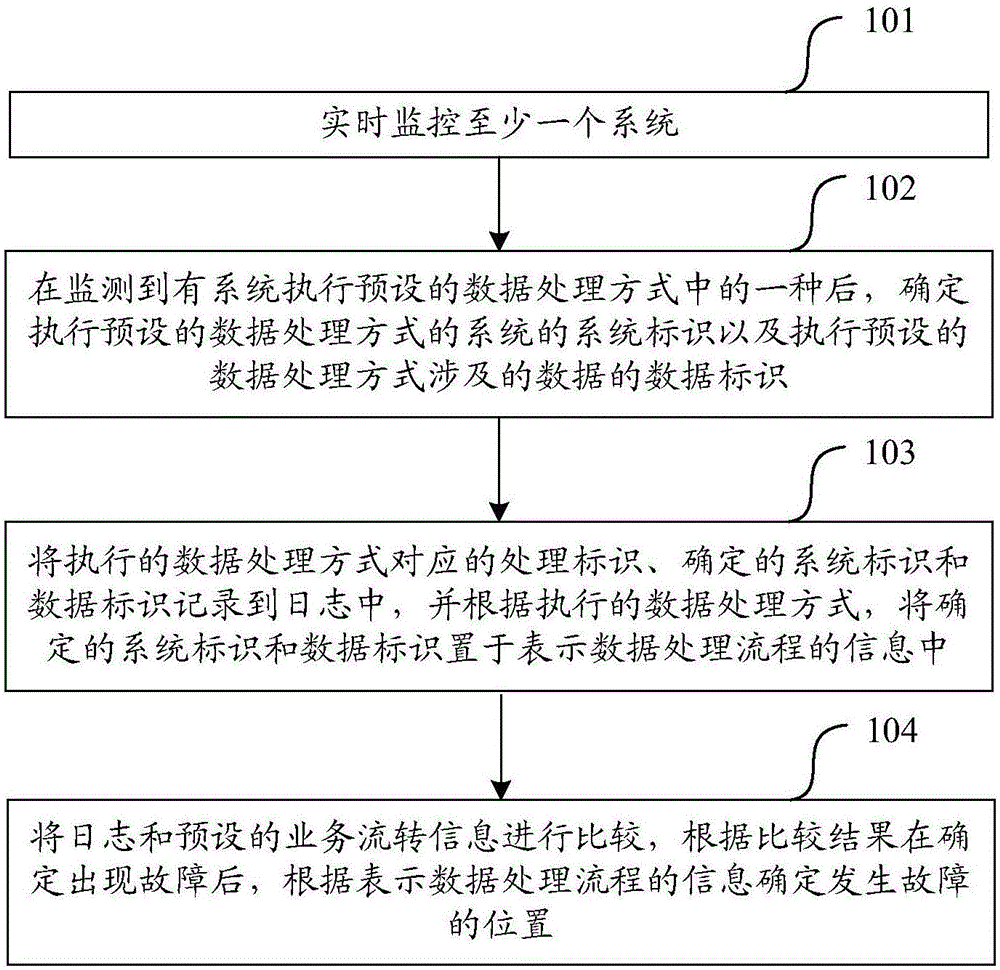
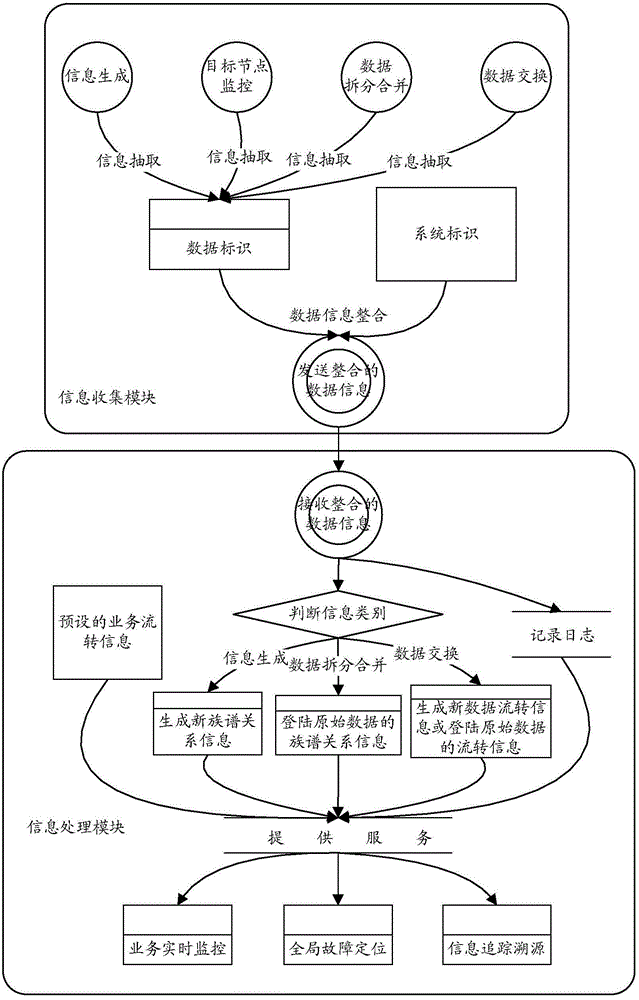
The invention relates to the technical field of information, and specifically relates to a method and device for system information monitoring. The method includes the steps: monitoring at least one system in real time; determining the system identifier of a system for executing the preset data processing mode, and the data identifier of the data related with the executed preset data processing mode; recording the processing identifier corresponding to the executed data processing mode, and the determined system identifier and data identifier in a log, and according to the executed data processing mode, placing the determined system identifier and data identifier in the information expressing the data processing flow; and comparing the log with the preset business flow information, and determining the position where a fault occurs according to the information of the data processing flow after determining occurrence of the fault according to the comparative result. The method for system information monitoring increases the information for expressing the data processing flow; and if the interface data has problems, global fault positioning and information tracking and source tracing for multi systems can be realized according to the information of the processing flow.
Owner:方正国际软件(北京)有限公司 +1
Using an enhanced preferred roaming list in a terminal device
ActiveUS20060079224A1Assess restrictionRadio/inductive link selection arrangementsTerminal equipmentComputer science
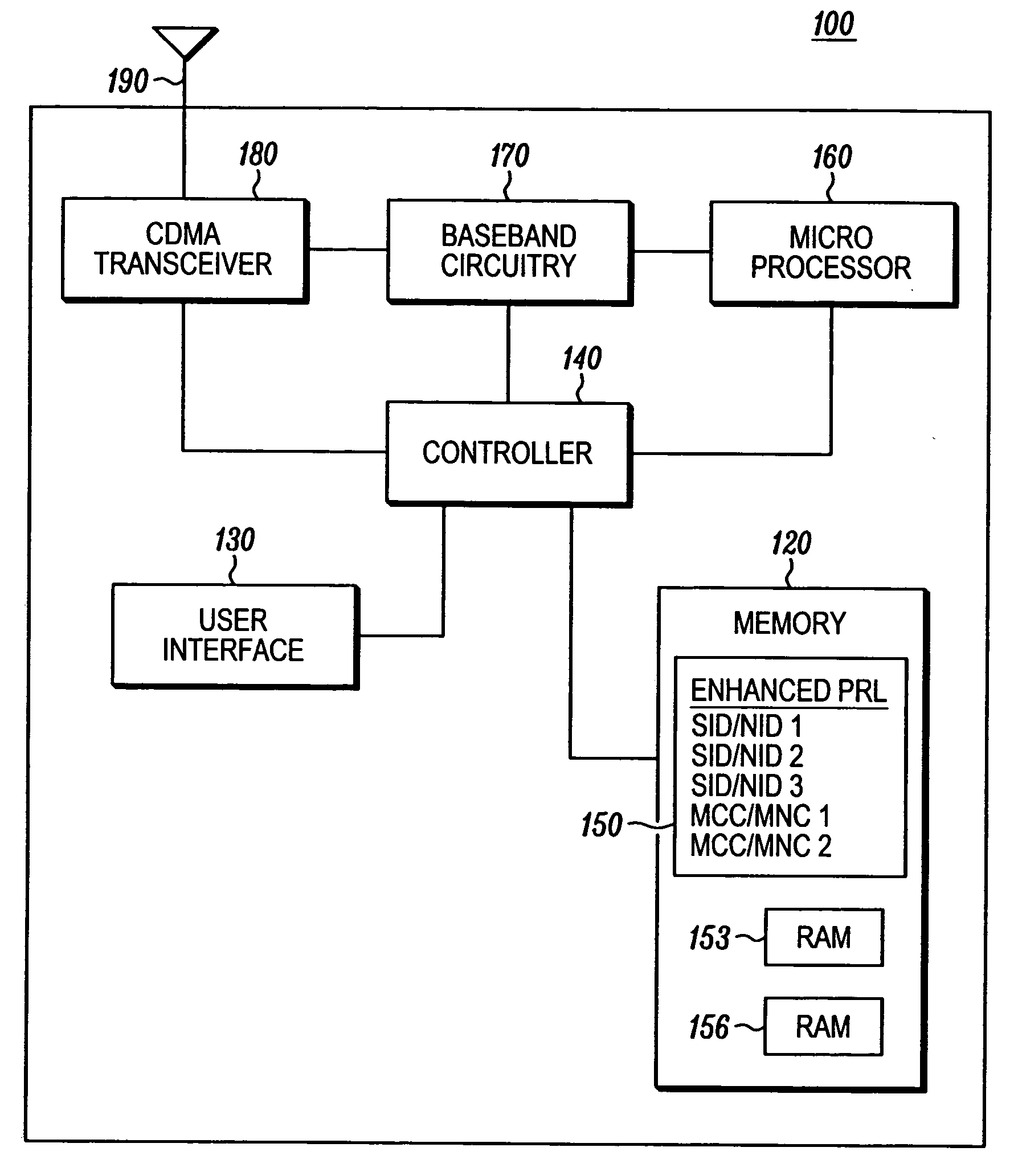
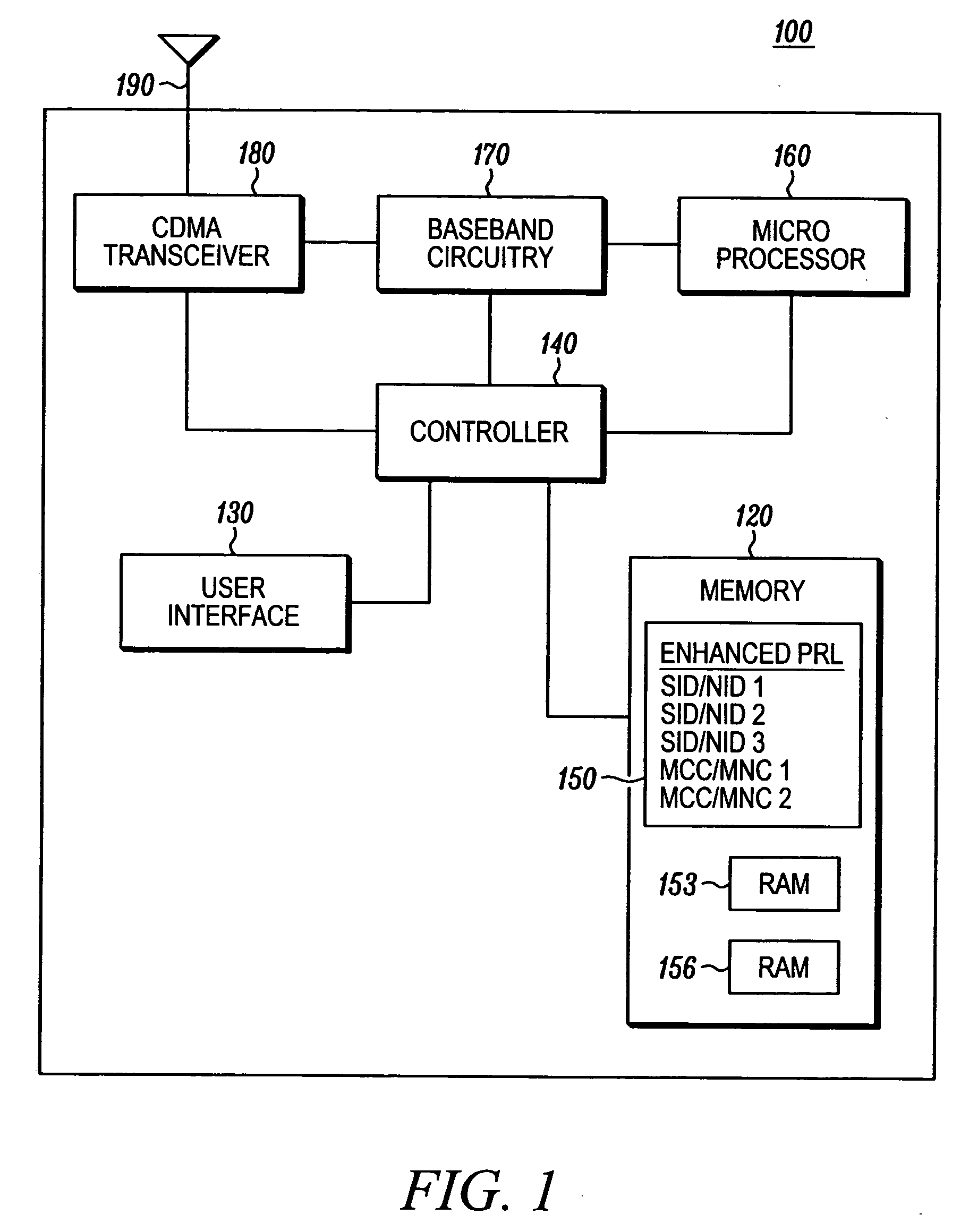
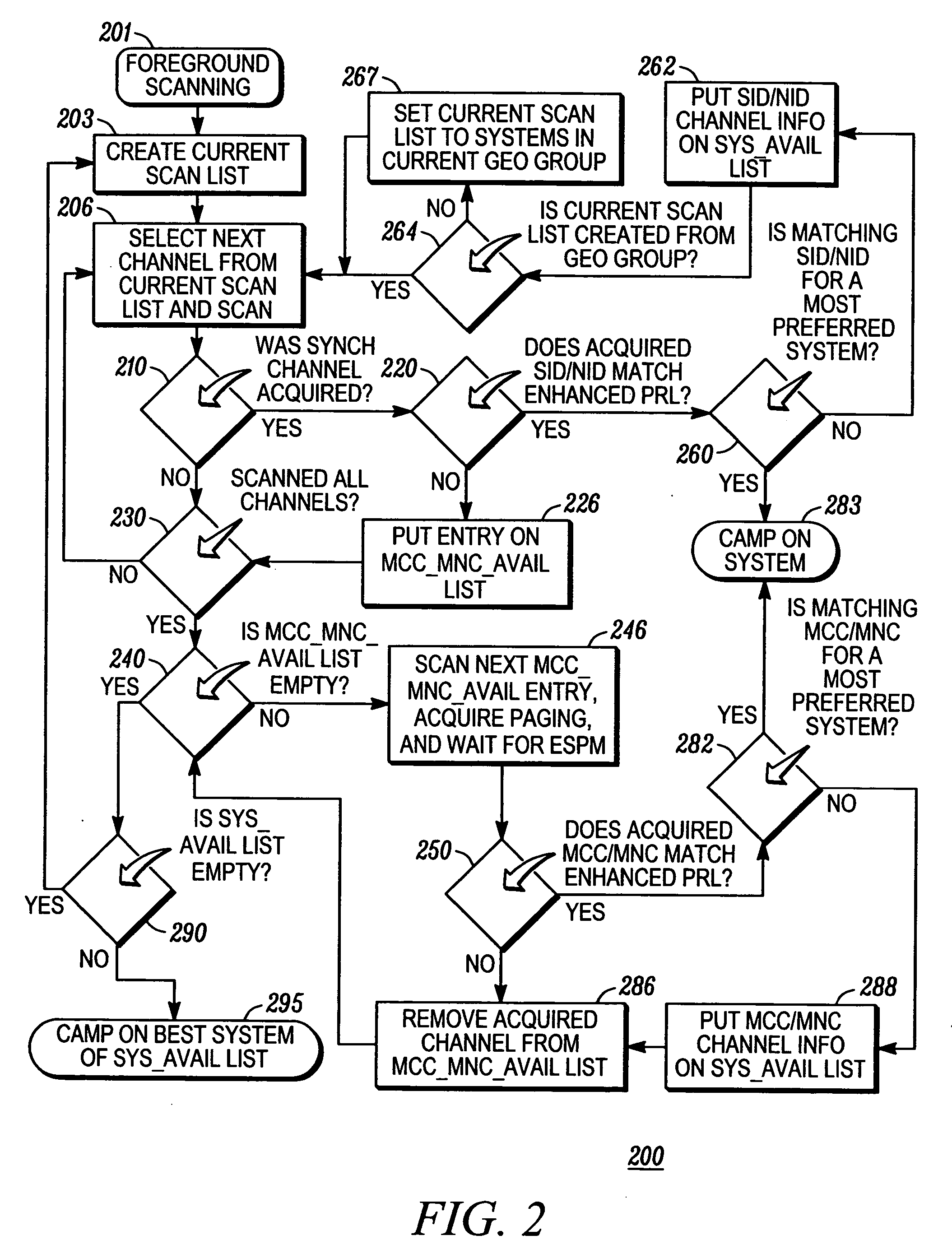
A method (200) in a CDMA terminal device for acquiring a system identified in an enhanced preferred roaming list (enhanced PRL), with at least one entry containing a mobile country code, includes the steps of obtaining (210) system identifiers from SYNCH channels on a scan list, determining (220) if the system identifiers match entries on the enhanced PRL, and inserting (226) channel information items on a first list if the system identifiers do not match entries on the enhanced PRL. If all channels on the scan list have been scanned without any system identifiers matching entries on the enhanced PRL, the method obtains (246) mobile country codes using channel information items from the first list, determines (250) if the mobile country codes match entries on the enhanced PRL, and camps (283) on a system if its mobile country code matches an entry on the enhanced PRL.
Owner:GOOGLE TECH HLDG LLC
Network abstraction and isolation layer for masquerading machine identity of a computer
ActiveUS20050108407A1Data switching by path configurationMultiple digital computer combinationsIdentity transformIp address
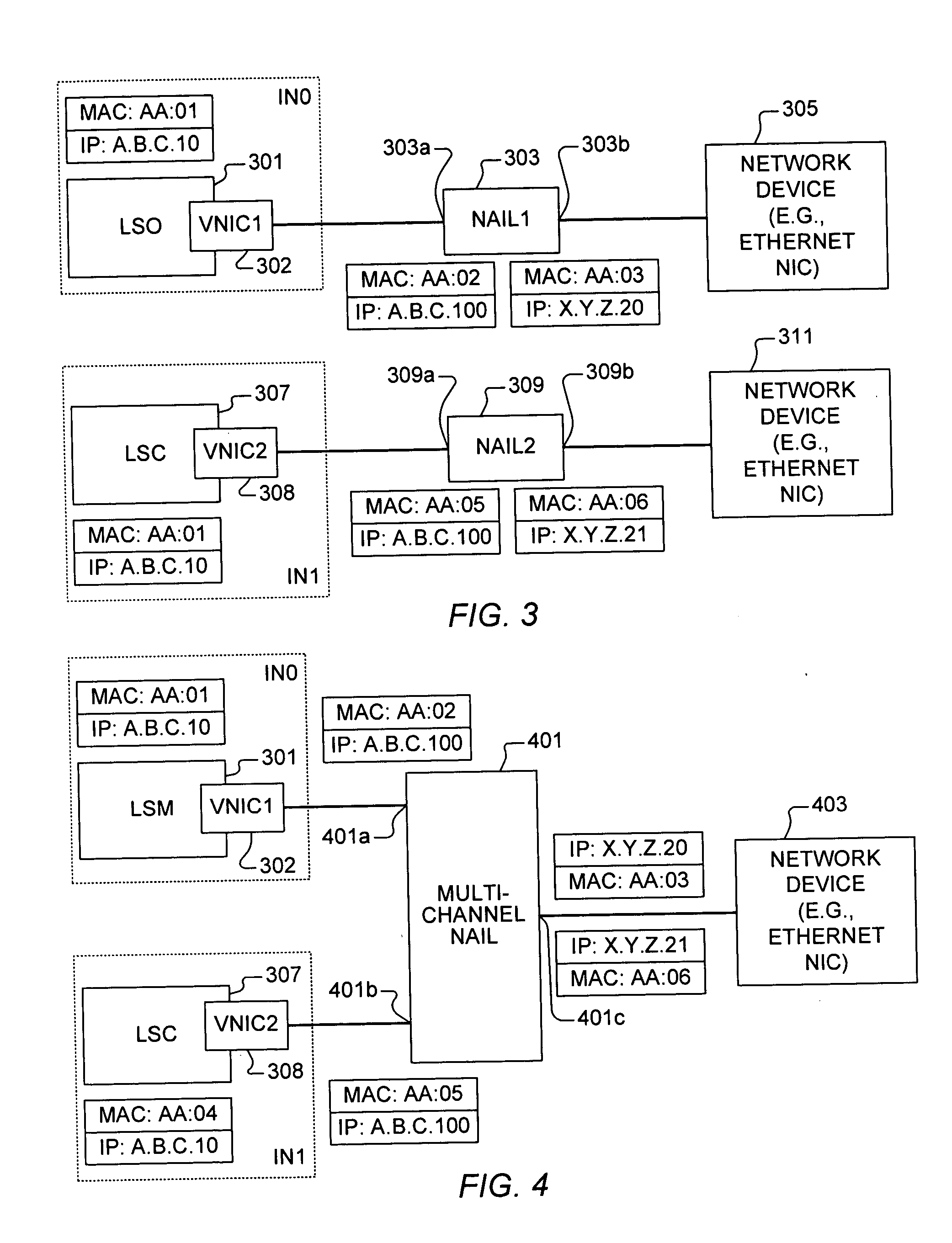
A network abstraction and isolation layer (NAIL) for masquerading the machine identity of a computer in a network to enable the computer to communicate in the network with a different machine identity including an isolated network interface for communicating with the computer, an abstraction network interface for communicating with a network device coupled to the network, and control logic. The control logic is coupled to the isolated and abstraction network interfaces and performs machine identity translation to masquerade machine identity of the computer relative to the network. Machine identity masquerading includes selectively translating any one or more of an IP address, a MAC address, a machine name, a system identifier, and a DNS Name in the header or payload of communication packets.
Owner:QUEST SOFTWARE INC
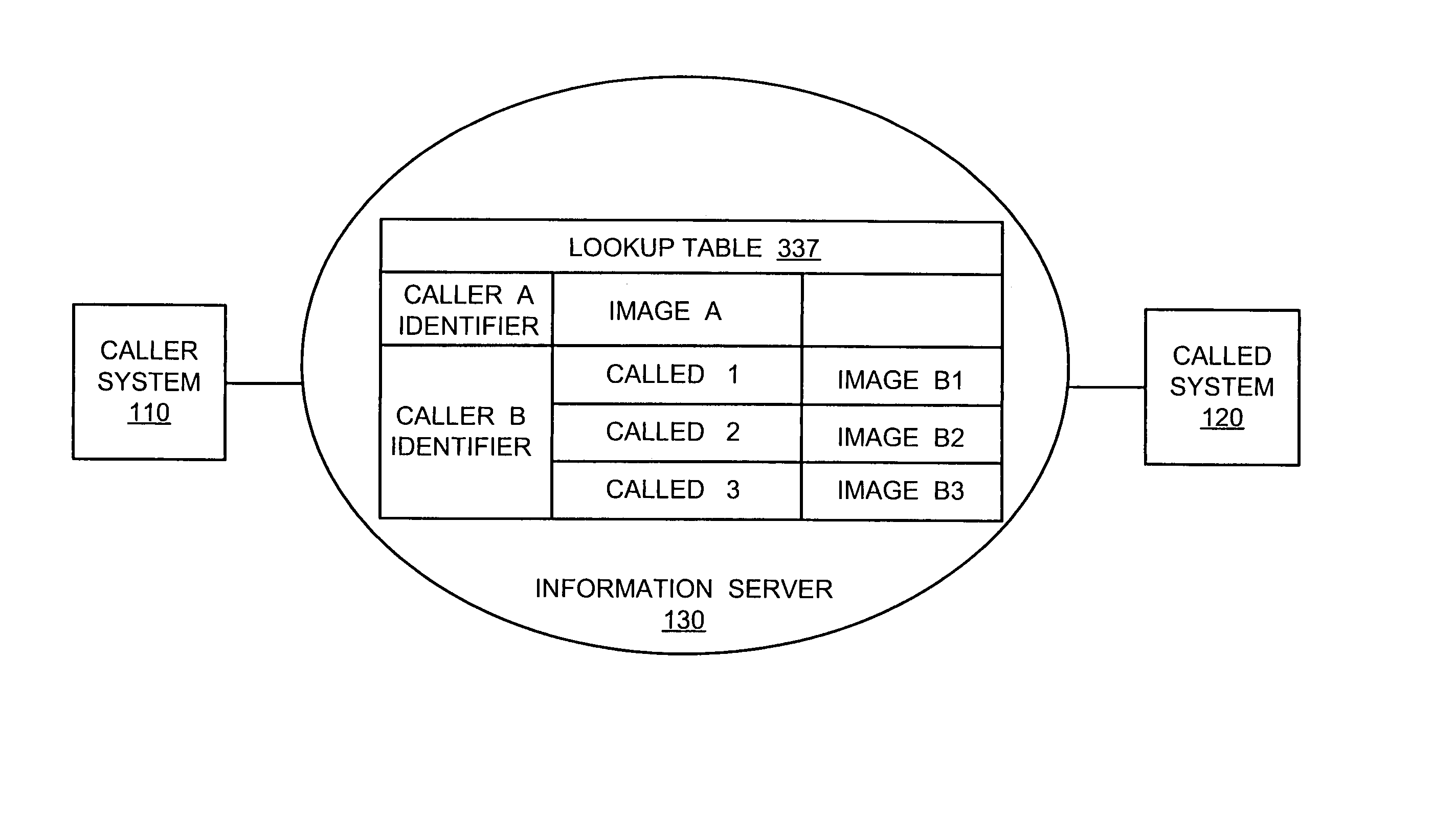
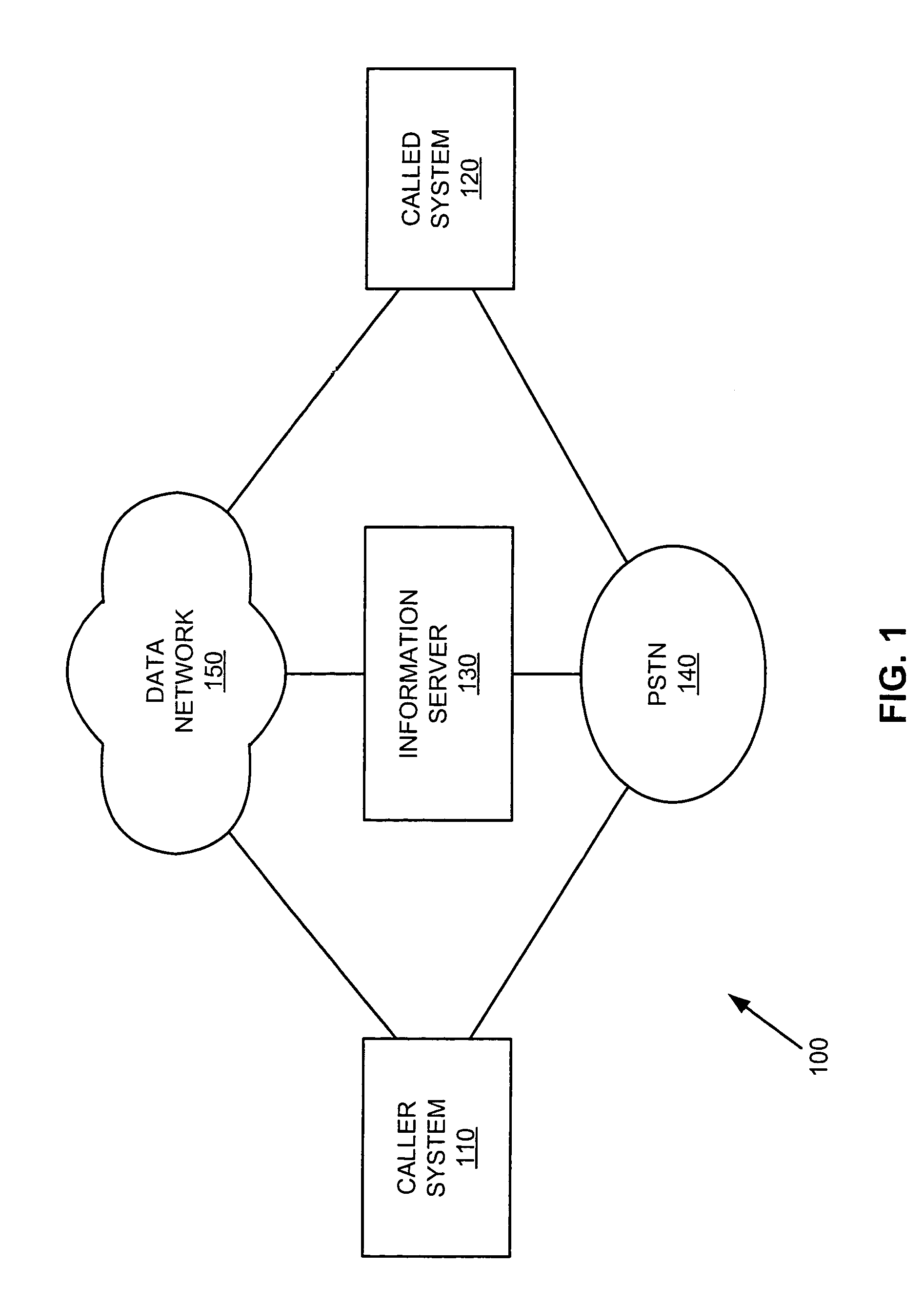
Caller identification employing a digital content set
ActiveUS20050084084A1Telephone data network interconnectionsCalling susbscriber number recording/indicationCommunication interfaceComputer network
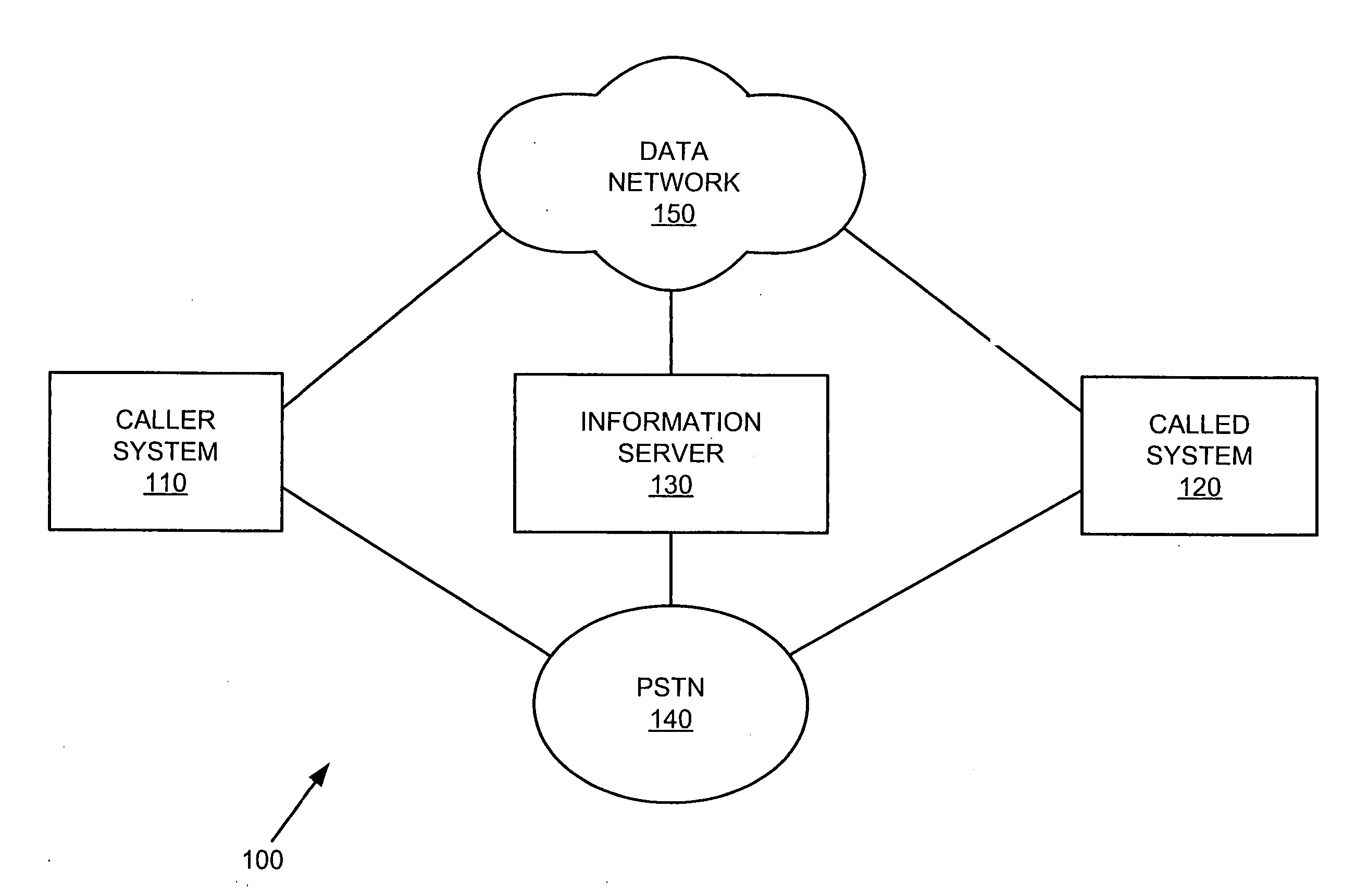
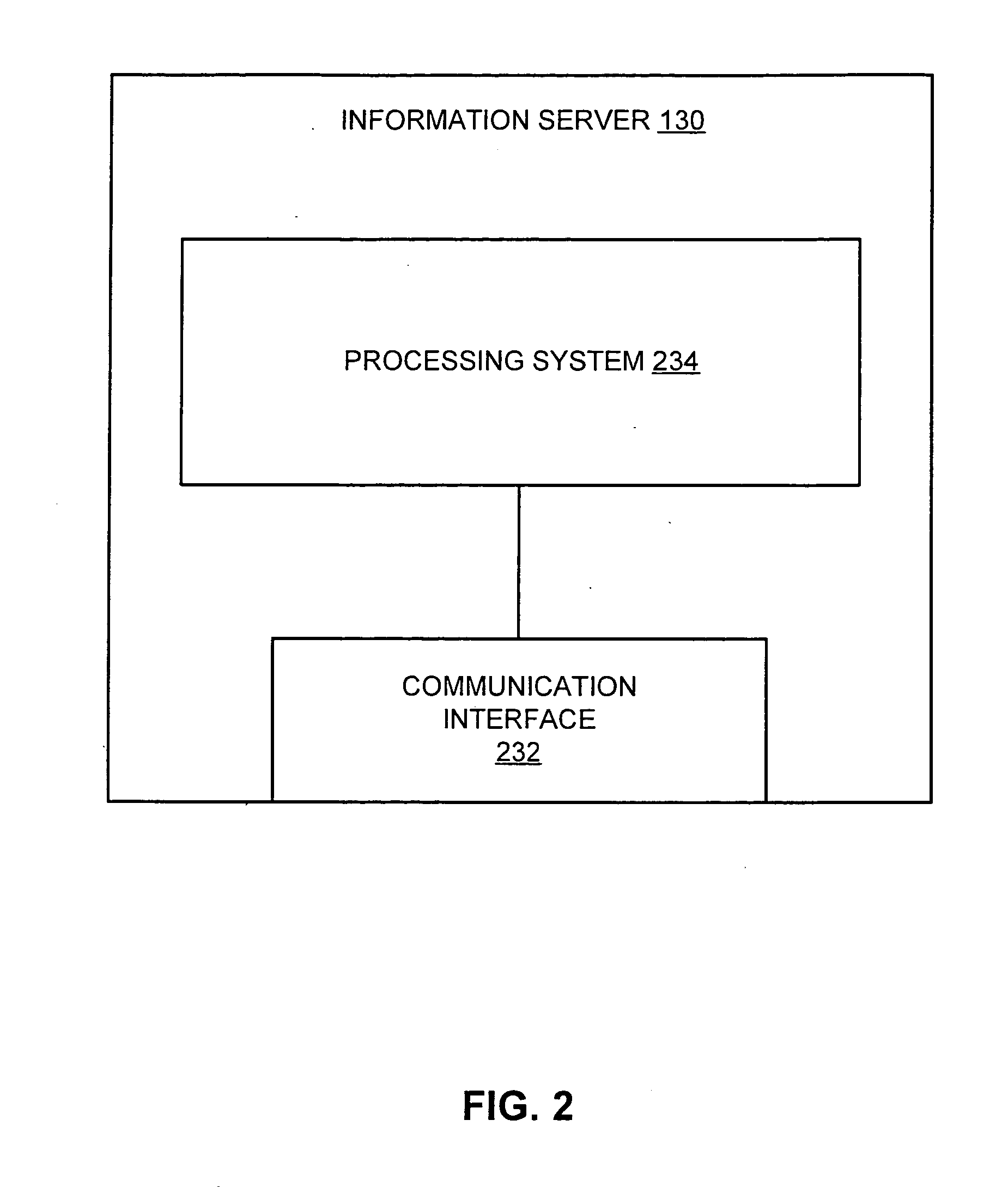
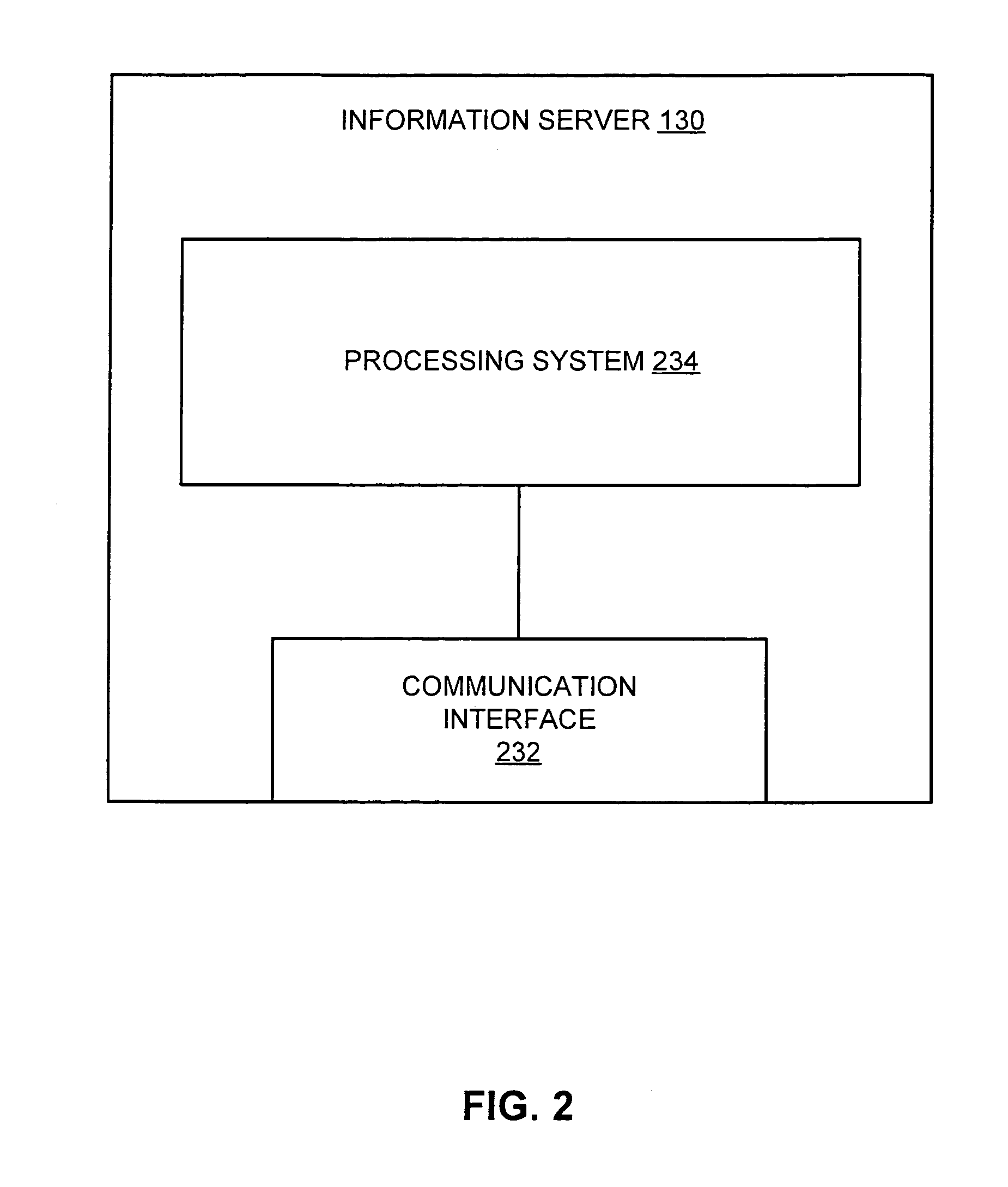
An information server according to one embodiment of the invention includes a communication interface configured to communicate over a communication network and a processing system connected to the communication interface. The processing system is configured to receive one or more digital content sets, receive a caller system identifier and a called system identifier from the caller system, select a digital content set from among the one or more digital content sets using the caller system identifier and the called system identifier, and provide the selected digital content set to a called system corresponding to the called system identifier prior to the caller system establishing a communication channel to the called system.
Owner:T MOBILE INNOVATIONS LLC
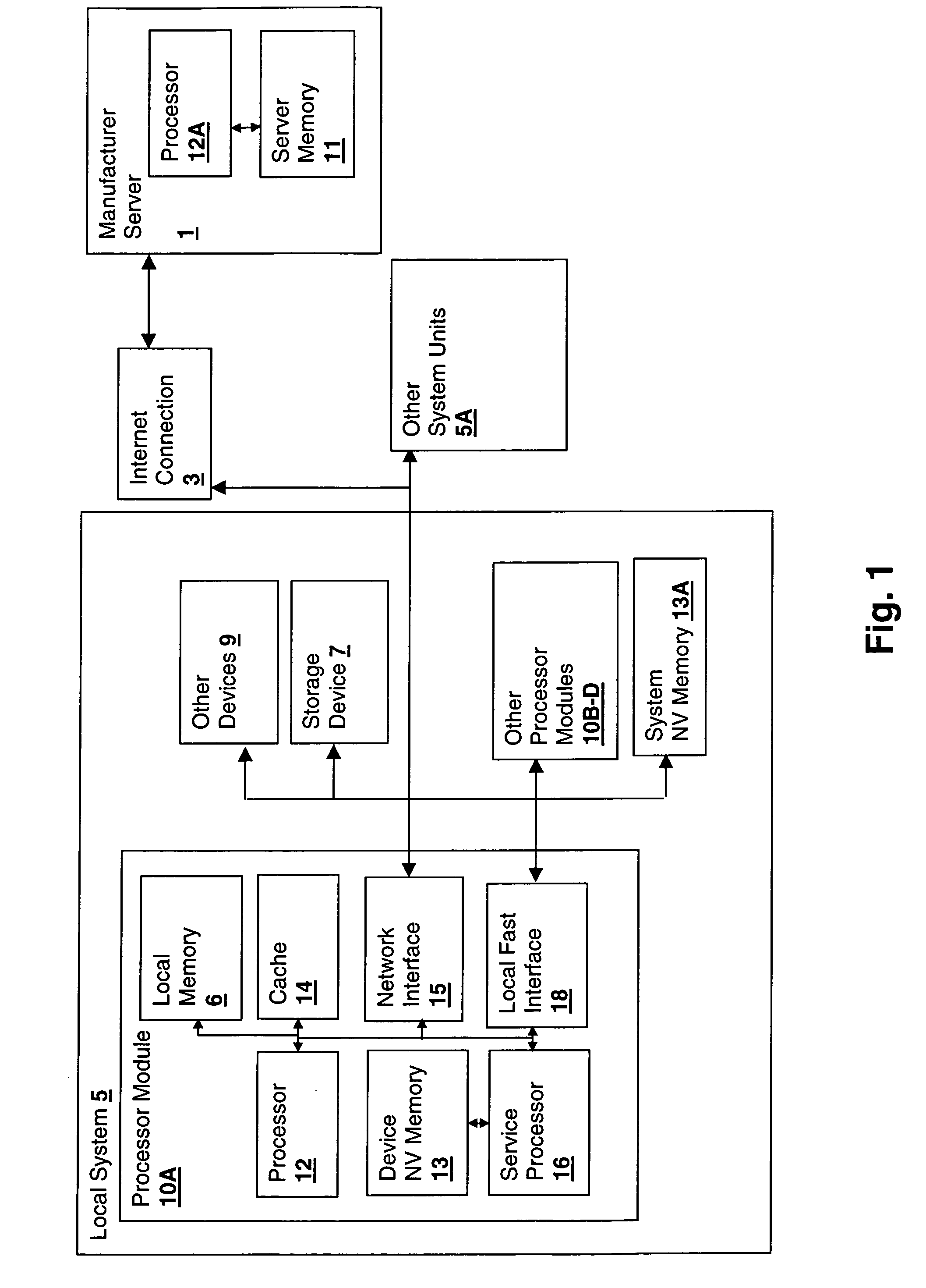
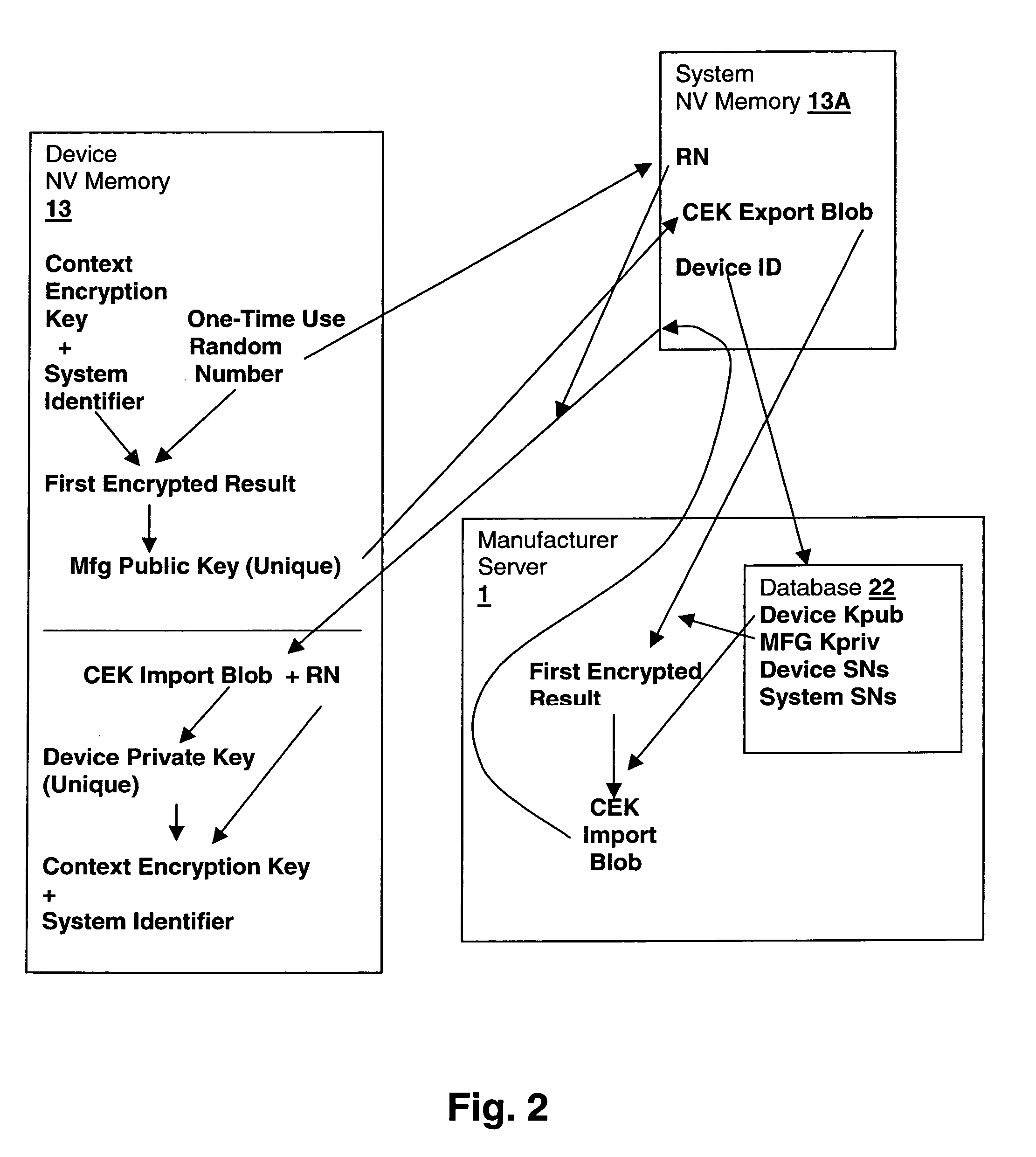
Method and system for backup and restore of a context encryption key for a trusted device within a secured processing system
ActiveUS20060088167A1Key distribution for secure communicationPublic key for secure communicationVirtualizationSystem maintenance
A method and system for backup and restore of a context encryption key (CEK) for a trusted device within a secured processing system maintains security of virtualized trusted device contexts, providing for replacement of a trusted device in the field. The CEK is encrypted along with a system identifier by a random number to yield a first result. The first result is again encrypted with a manufacturer public key. The resulting blob is stored along with the random number. To restore, the system sends the blob and the device ID to a server. The server obtains the first result by decrypting with the manufacturer private key, re-encrypts with the device public key and sends the new result back. The system sends the new result to the device along with the associated random number. The device decrypts the new result using its private key and decrypts the CEK using the random number.
Owner:LENOVO GLOBAL TECH INT LTD
File sharing system and file sharing method
InactiveUS20120265836A1Alleviate network delayMultiple digital computer combinationsFile metadata searchingComputerized systemSystem identifier
In a computer system according to an embodiment of the present invention, a first slave server includes copy management information associating a master file system identifier with an identifier of a slave server including a copy of the master file system identified by the master file system identifier. The first slave server acquires a copy of a part of a master file system. The copy includes a stub-state object (file or directory). The first slave server searches the copy management information for a slave server to be queried regarding information for materializing the stub-state object. If the slave server to be queried includes the information for materialization, the first slave server materializes the stub-state object using the information for materialization acquired from the queried slave server.
Owner:HITACHI LTD
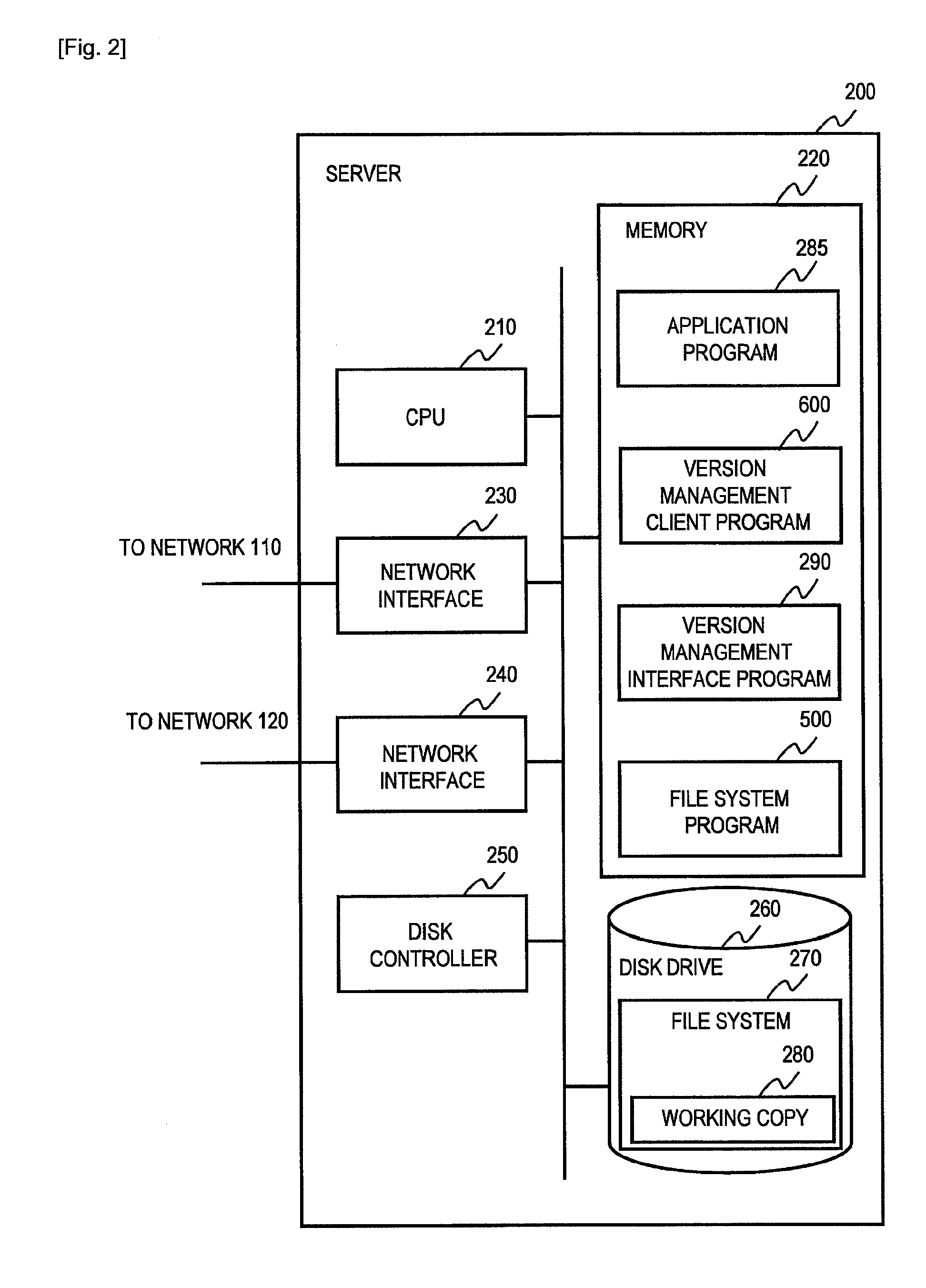
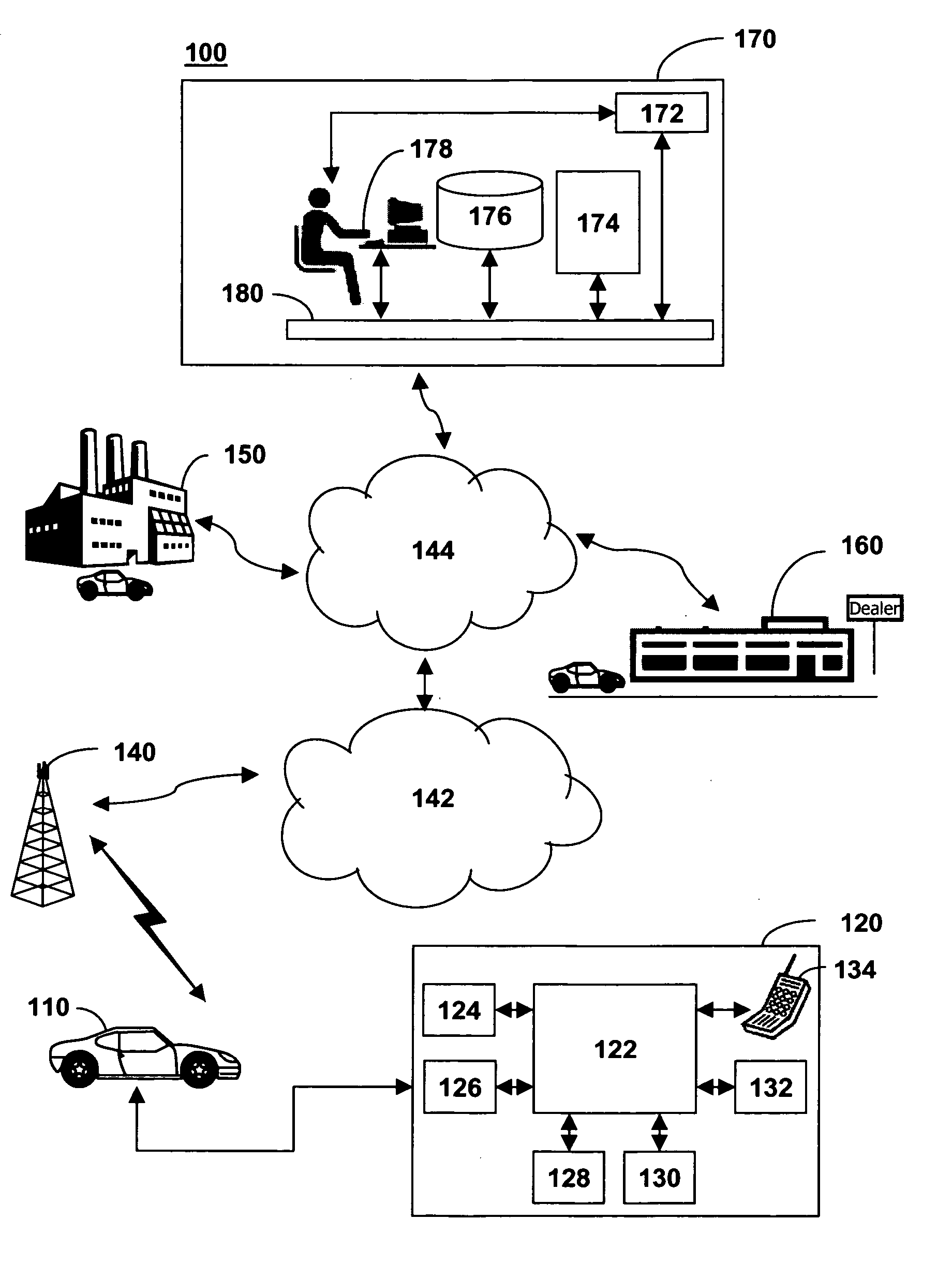
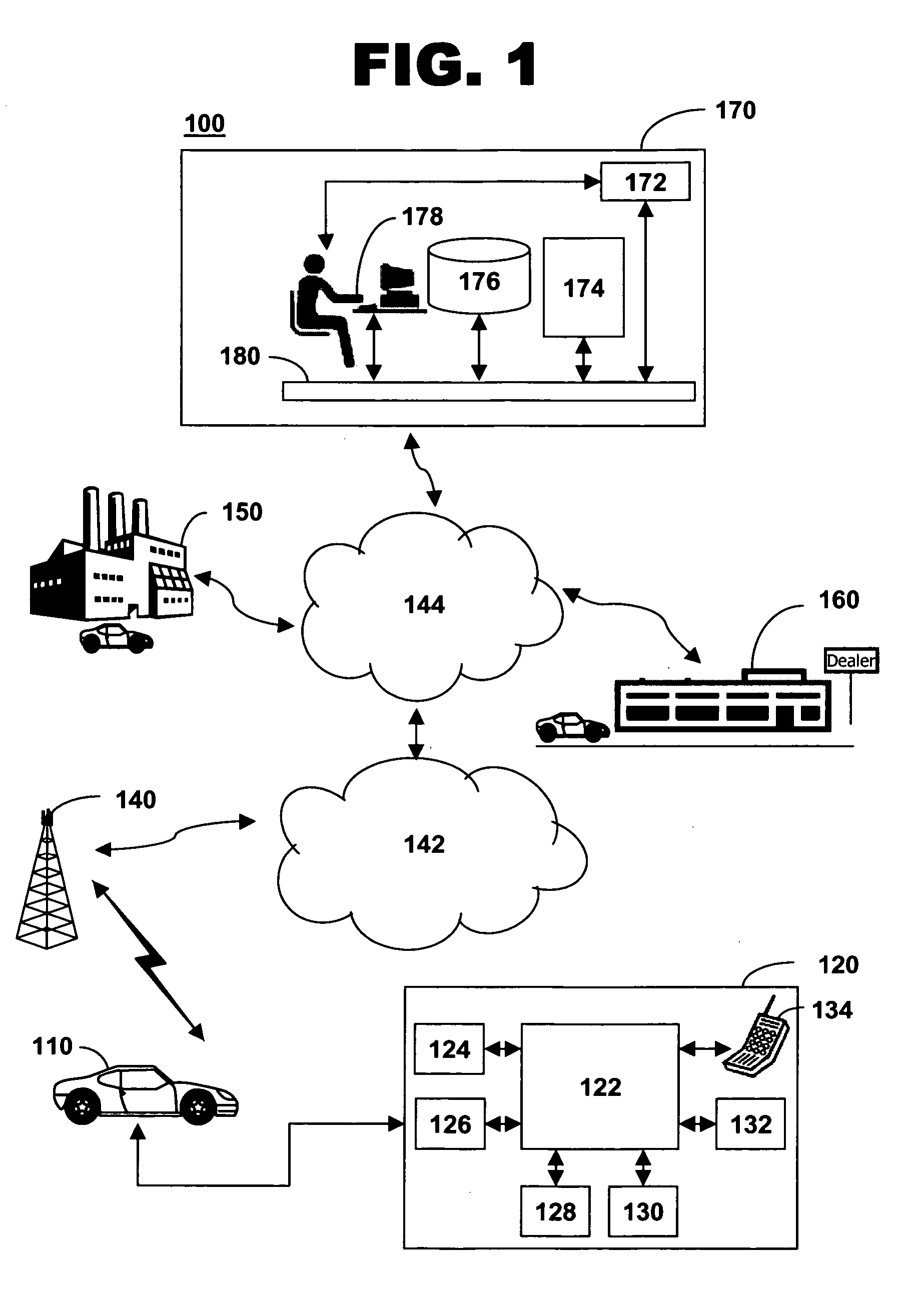
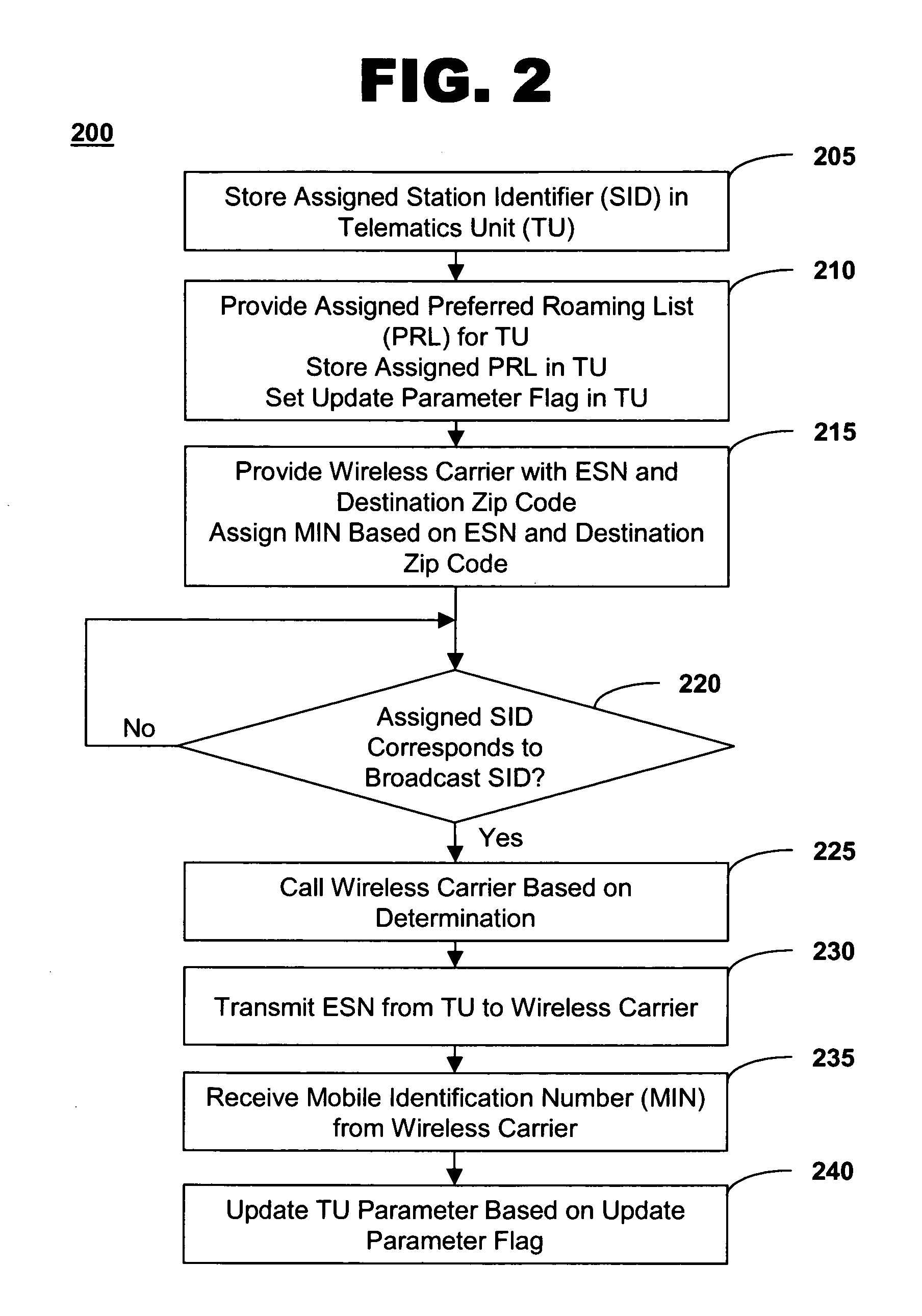
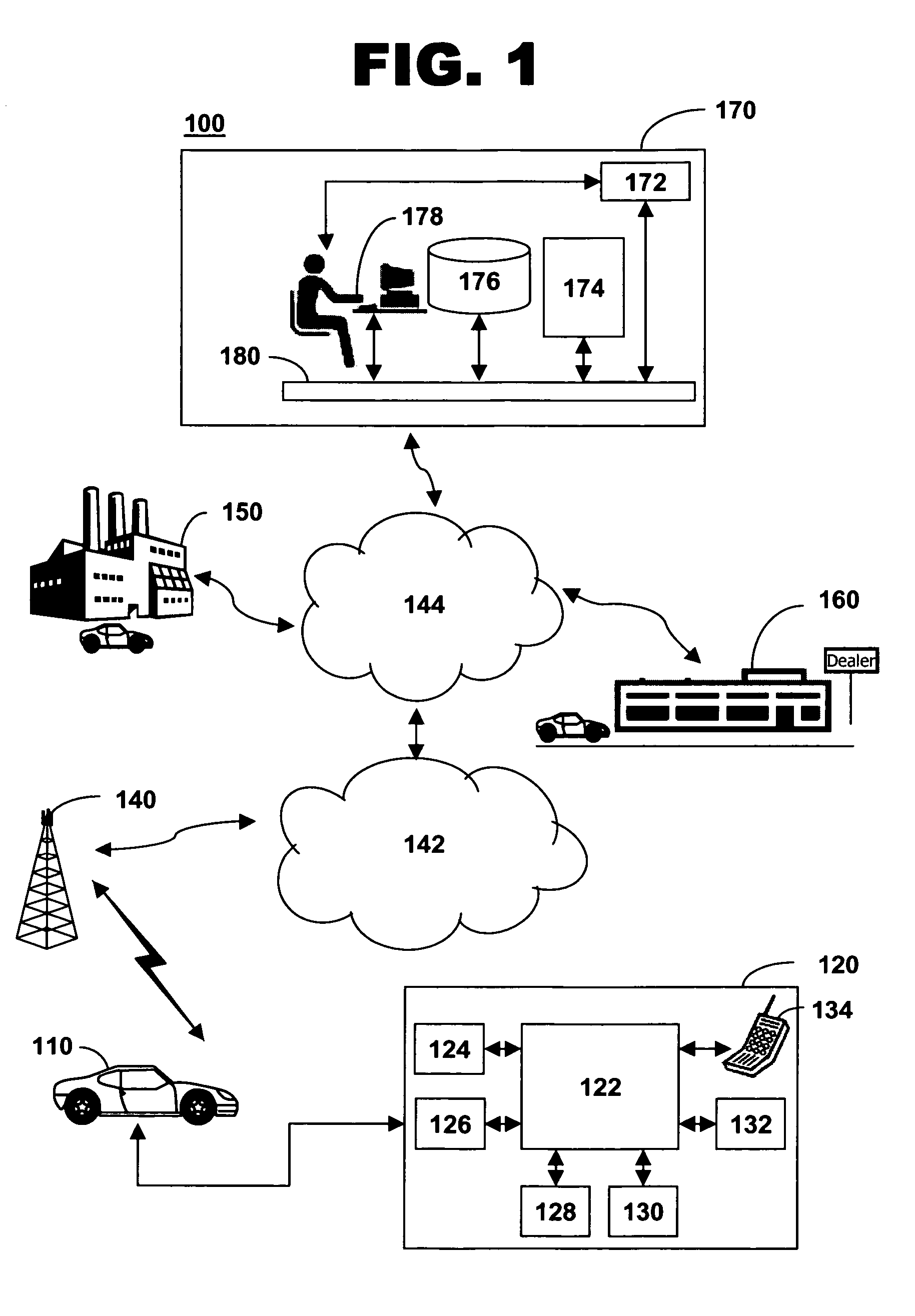
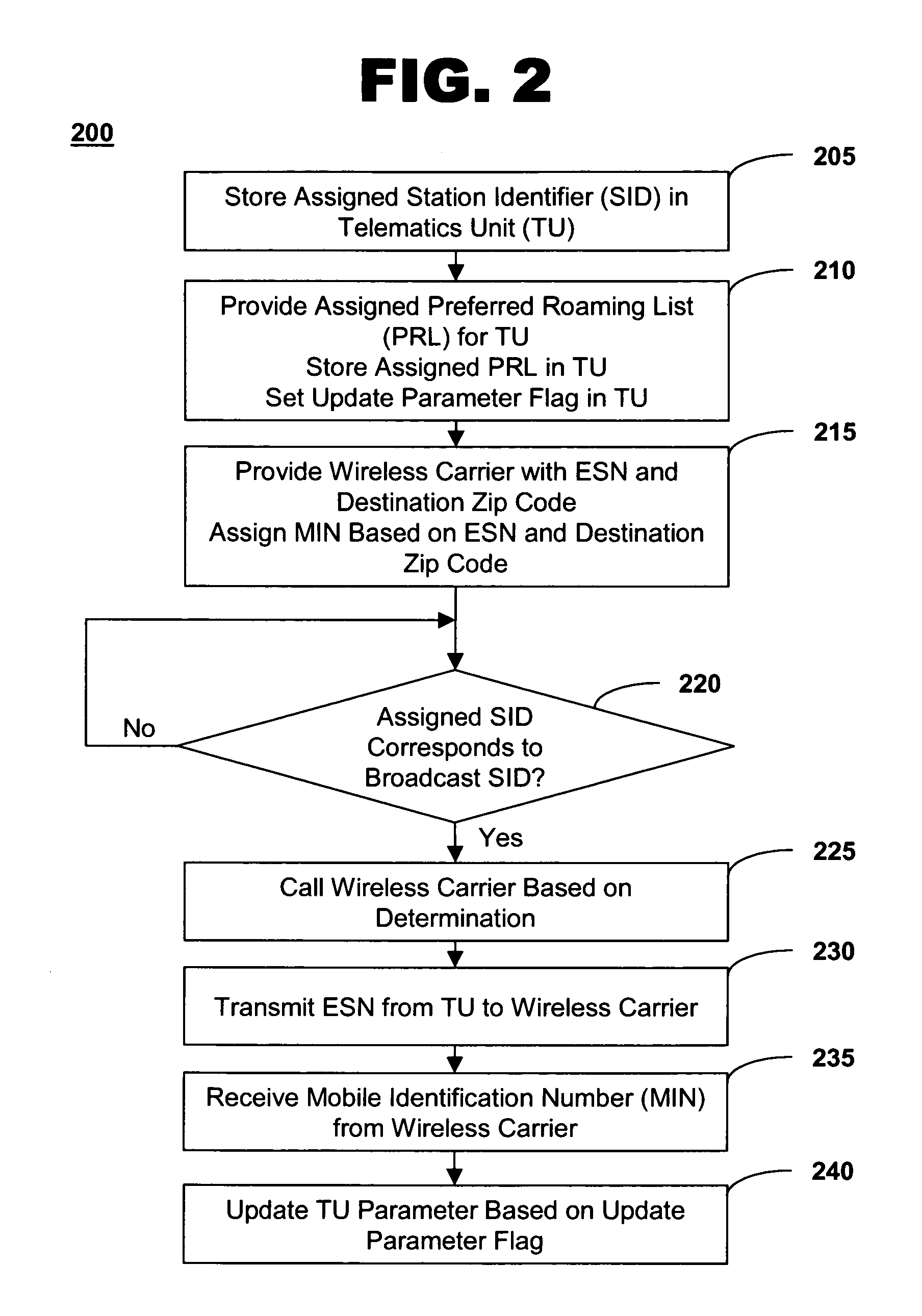
Method of configuring an in-vehicle telematics unit
InactiveUS20060052092A1Registering/indicating working of vehiclesActive radio relay systemsMobile identification numberInformation processing
The present invention present invention provides a method and system for configuring a telematics unit in a mobile vehicle. An assigned system identifier is stored in the telematics unit, and a determination is made as to whether the assigned system identifier corresponds to a broadcast system identifier. A wireless carrier is called based on the determination, and a mobile identification number is received from the wireless carrier.
Owner:GENERA MOTORS LLC
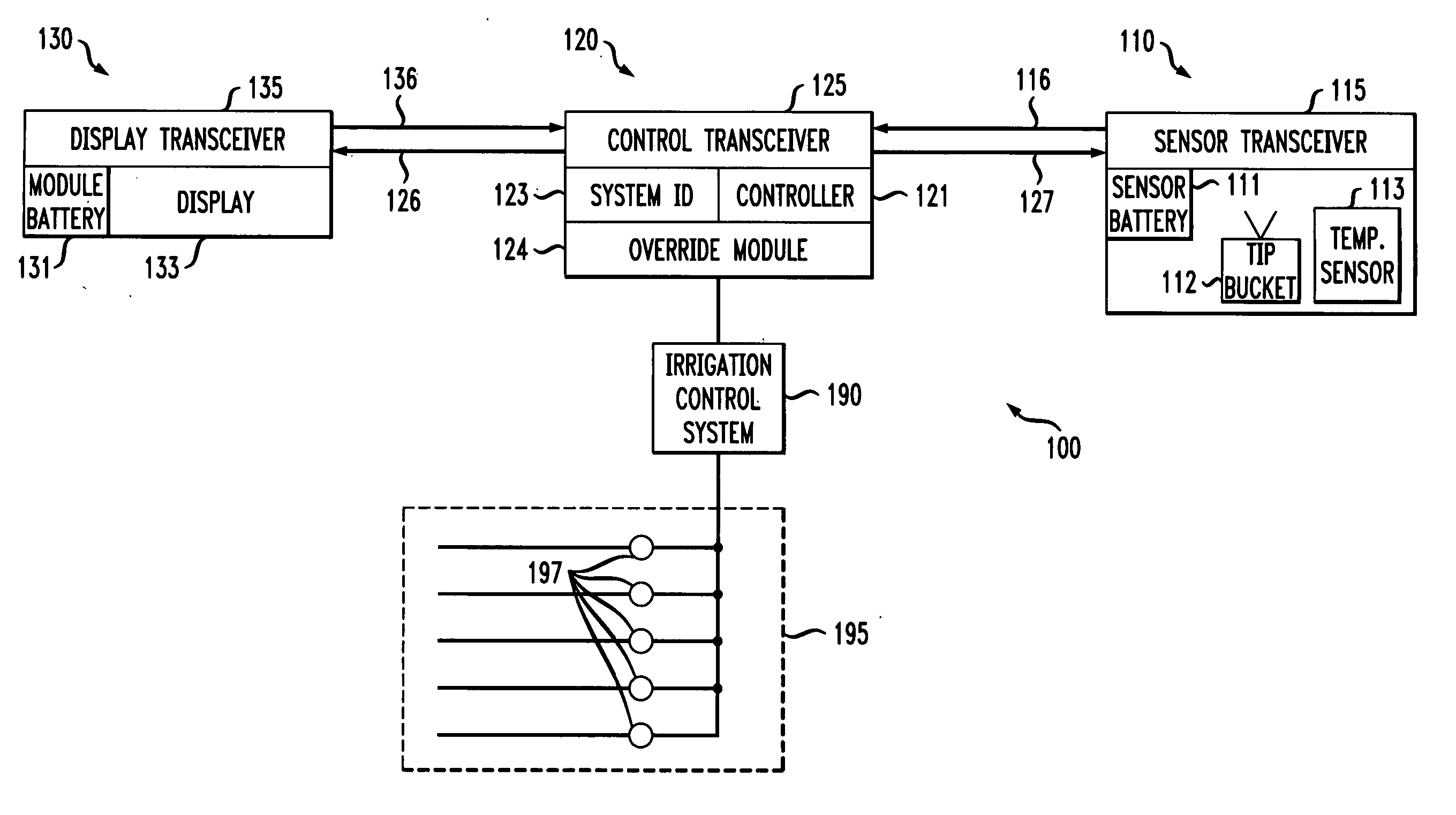
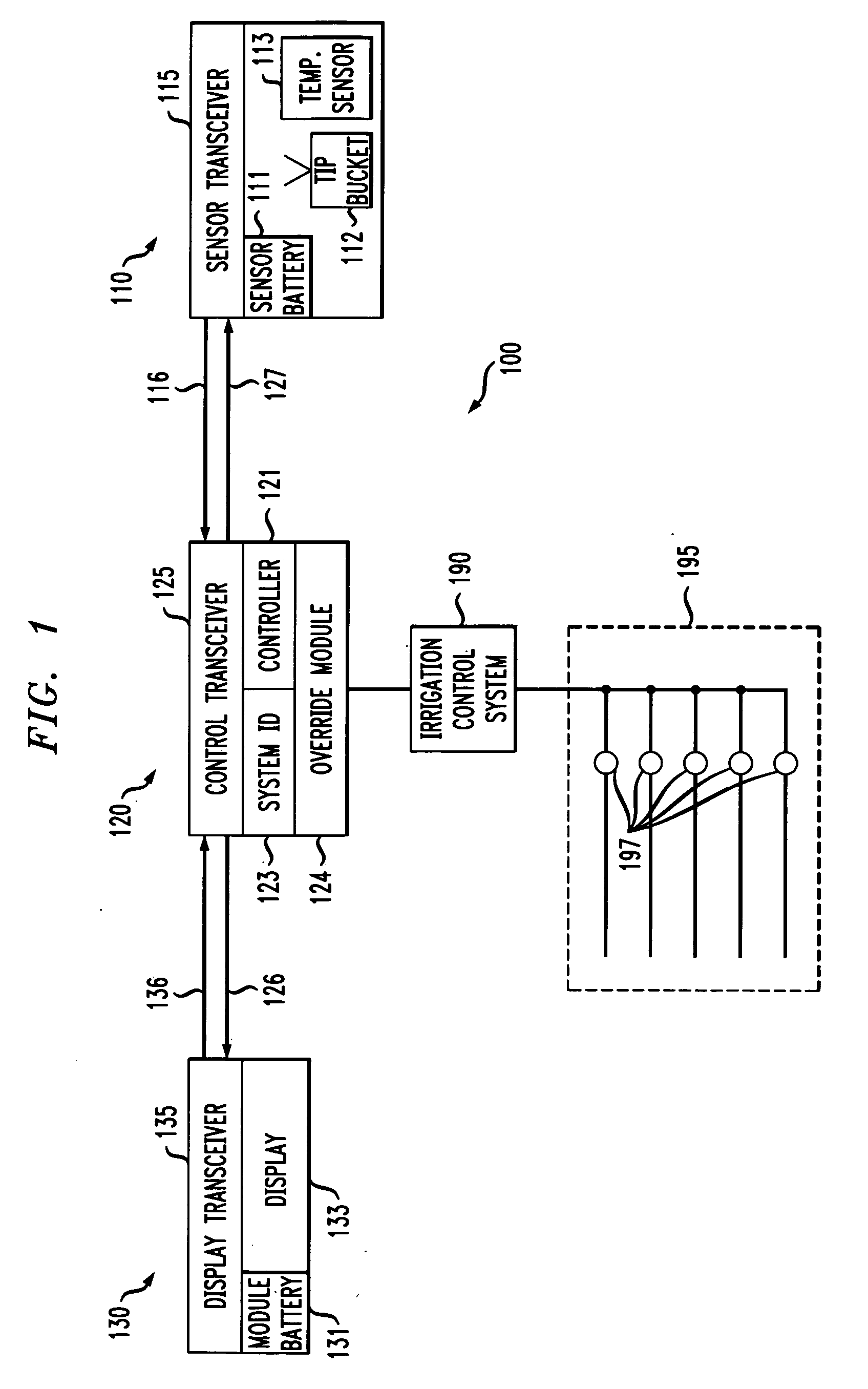
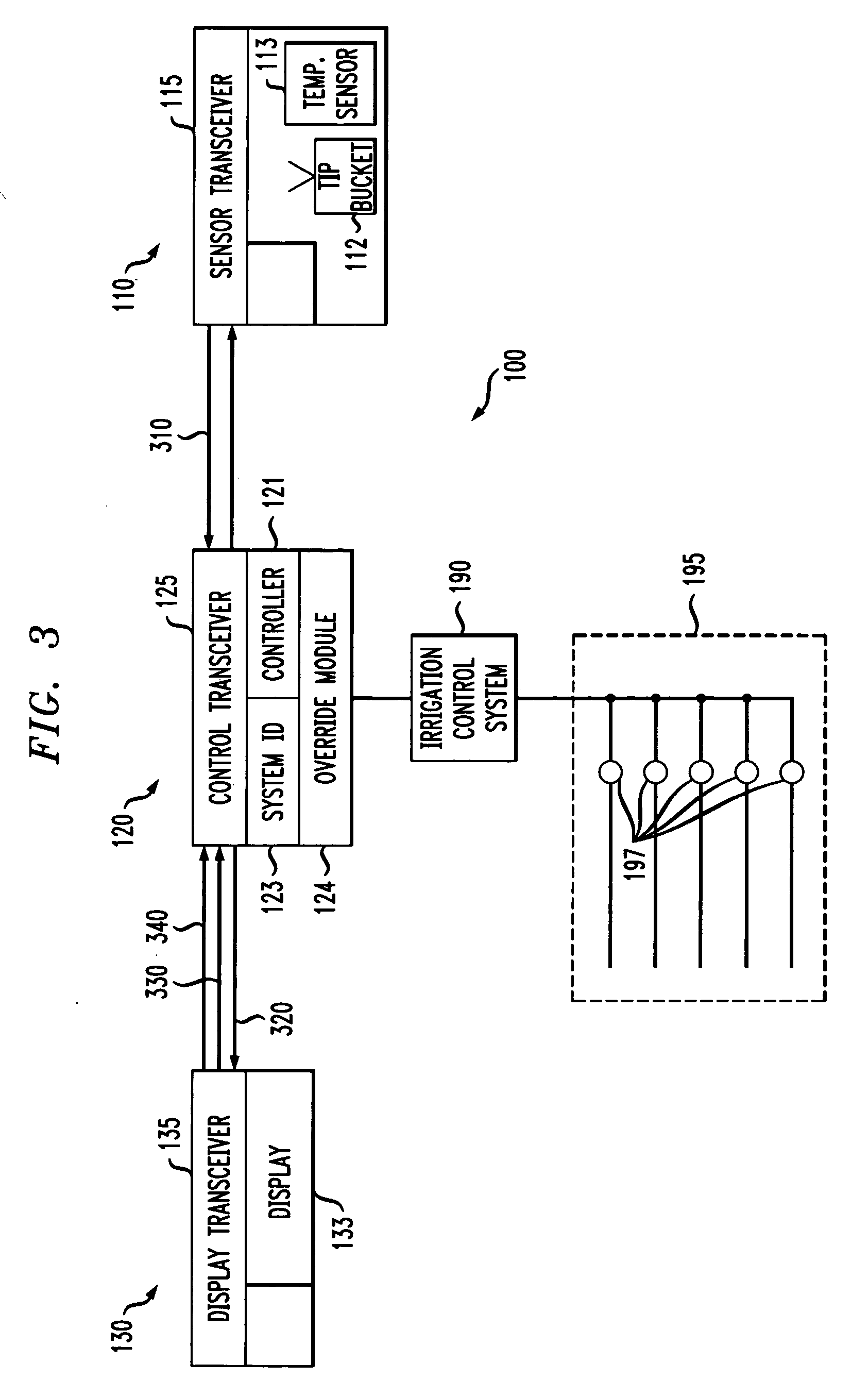
Weather monitor and irrigation overrride system with unique system identifier
InactiveUS20070010915A1Self-acting watering devicesClimate change adaptationTransceiverWireless transmission
A weather monitor and irrigation override system for use with an irrigation control system. In a preferred embodiment, the weather monitor and irrigation override system comprises a controller transceiver couplable to an irrigation control system, an environmental sensor, a sensor transceiver coupled to the environmental sensor and configured to wirelessly and bi-directionally communicate with the controller transceiver, and a system identifier module coupled to the controller transceiver having a communications identifier unique to the sensor transceiver and the controller transceiver whereby the controller transceiver accepts wireless transmissions only from the sensor transceiver. A method of manufacturing the weather monitor and irrigation override system is also provided.
Owner:PIONEER SALES
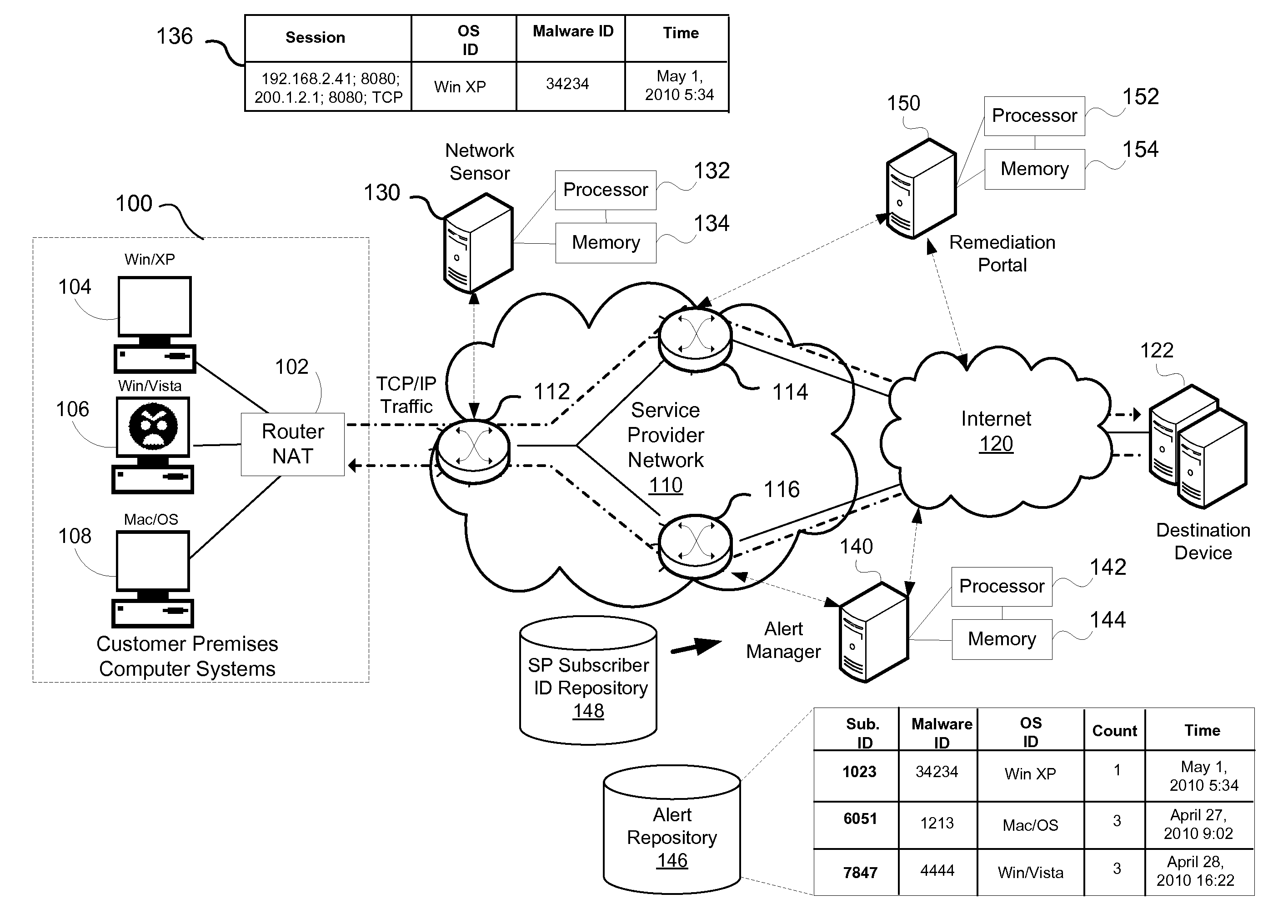
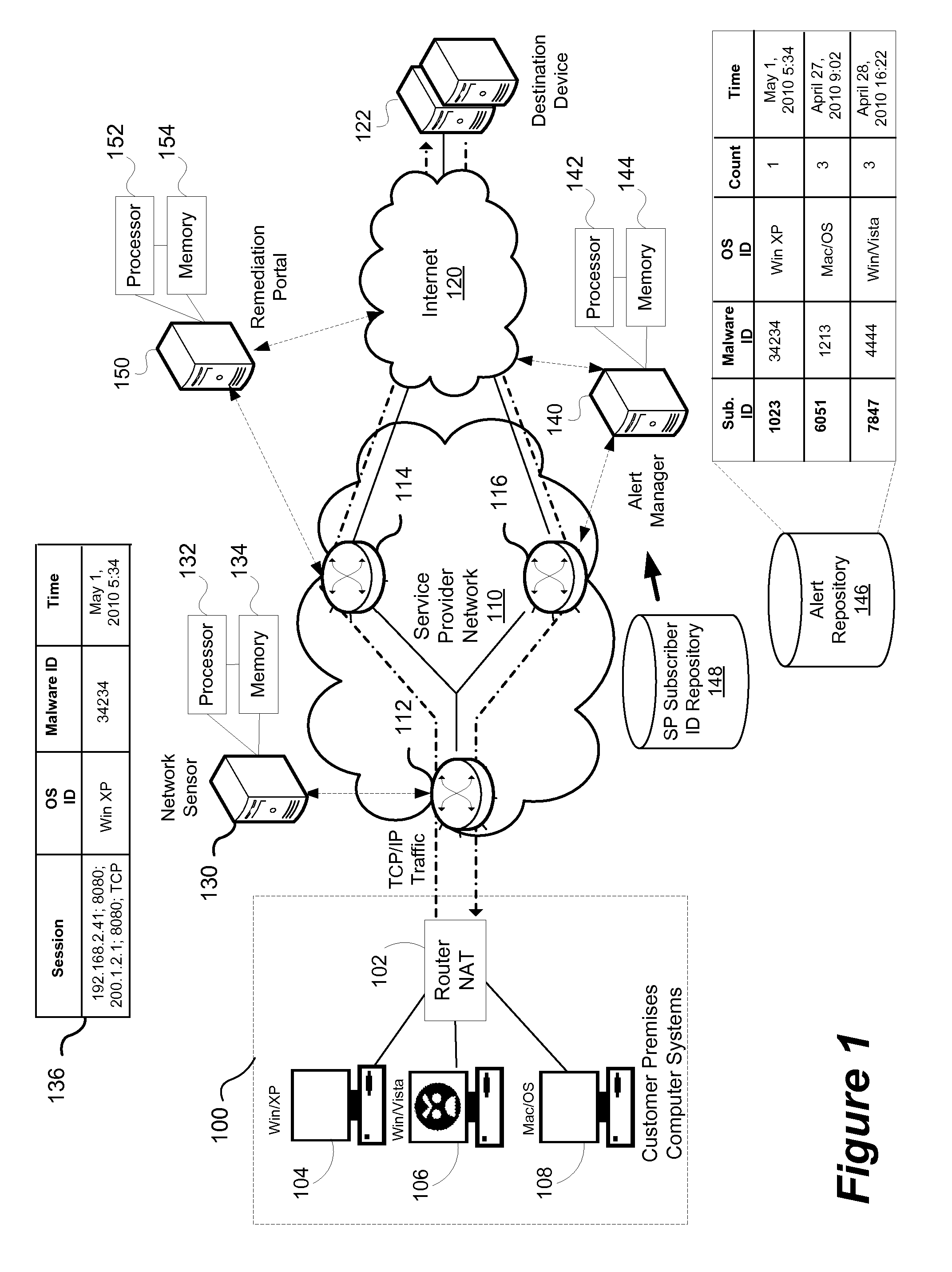
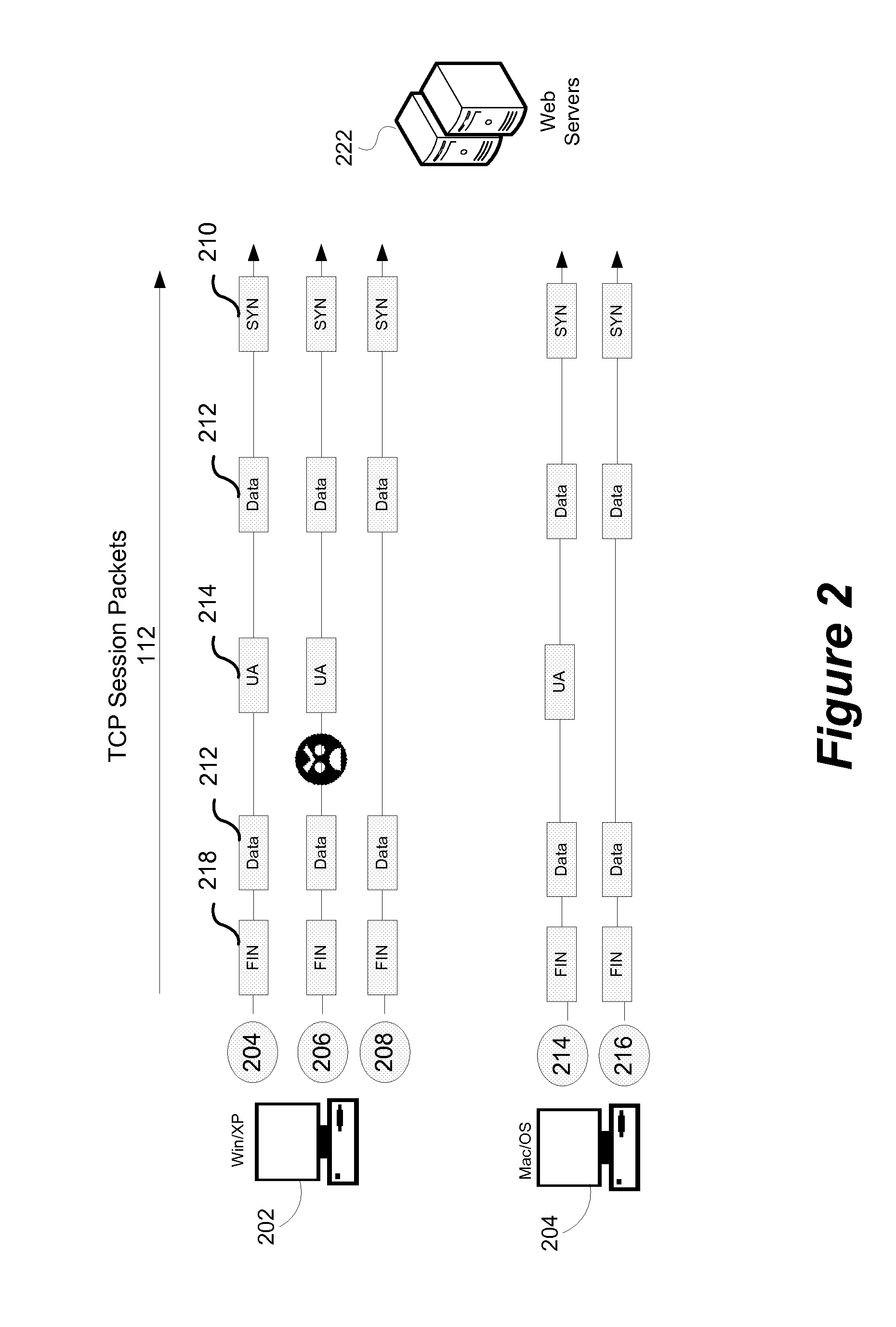
Method and system for operating system identification in a network based security monitoring solution
ActiveUS20120255019A1Memory loss protectionError detection/correctionService provisionNetwork addressing
A method and system for providing network based malware detection in a service provider network is disclosed. Transmission control protocol (TCP) packets defining originating from an access device coupled to the service provider network defining a TCP session between a computing device coupled to the access device, and a destination coupled to the service provider network are received. An operating system identifier (OS ID) associated with the TCP session and the computing device is determined. If malware is present in the TCP session and an associated malware ID is determined by comparing a malware signature to the one or more TCP packets. An alert identifying a network address associated with the access device, the malware ID and the OS ID associated with TCP session that generated the alert can then be generated.
Owner:RPX CORP
Caller identification employing a digital content set
ActiveUS7113577B2Telephone data network interconnectionsCalling susbscriber number recording/indicationCommunication interfaceComputer network
An information server according to one embodiment of the invention includes a communication interface configured to communicate over a communication network and a processing system connected to the communication interface. The processing system is configured to receive one or more digital content sets, receive a caller system identifier and a called system identifier from the caller system, select a digital content set from among the one or more digital content sets using the caller system identifier and the called system identifier, and provide the selected digital content set to a called system corresponding to the called system identifier prior to the caller system establishing a communication channel to the called system.
Owner:T MOBILE INNOVATIONS LLC
Virtual machine computer system for running guest operating system on a central processing means virtualized by a host system using region ID virtual memory option
InactiveUS20060112212A1Improve performanceComputer security arrangementsProgram controlVirtual memoryVirtualization
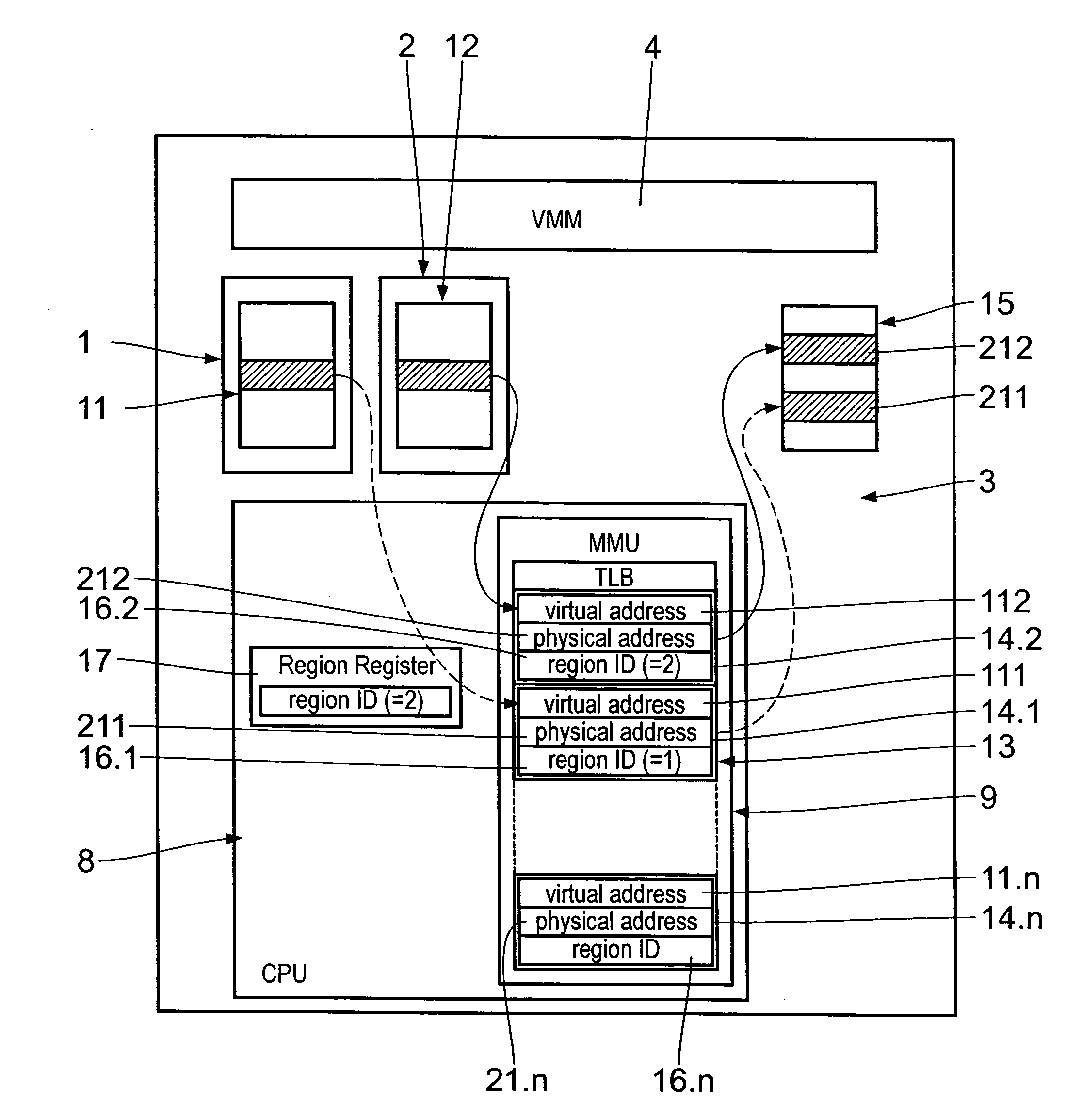
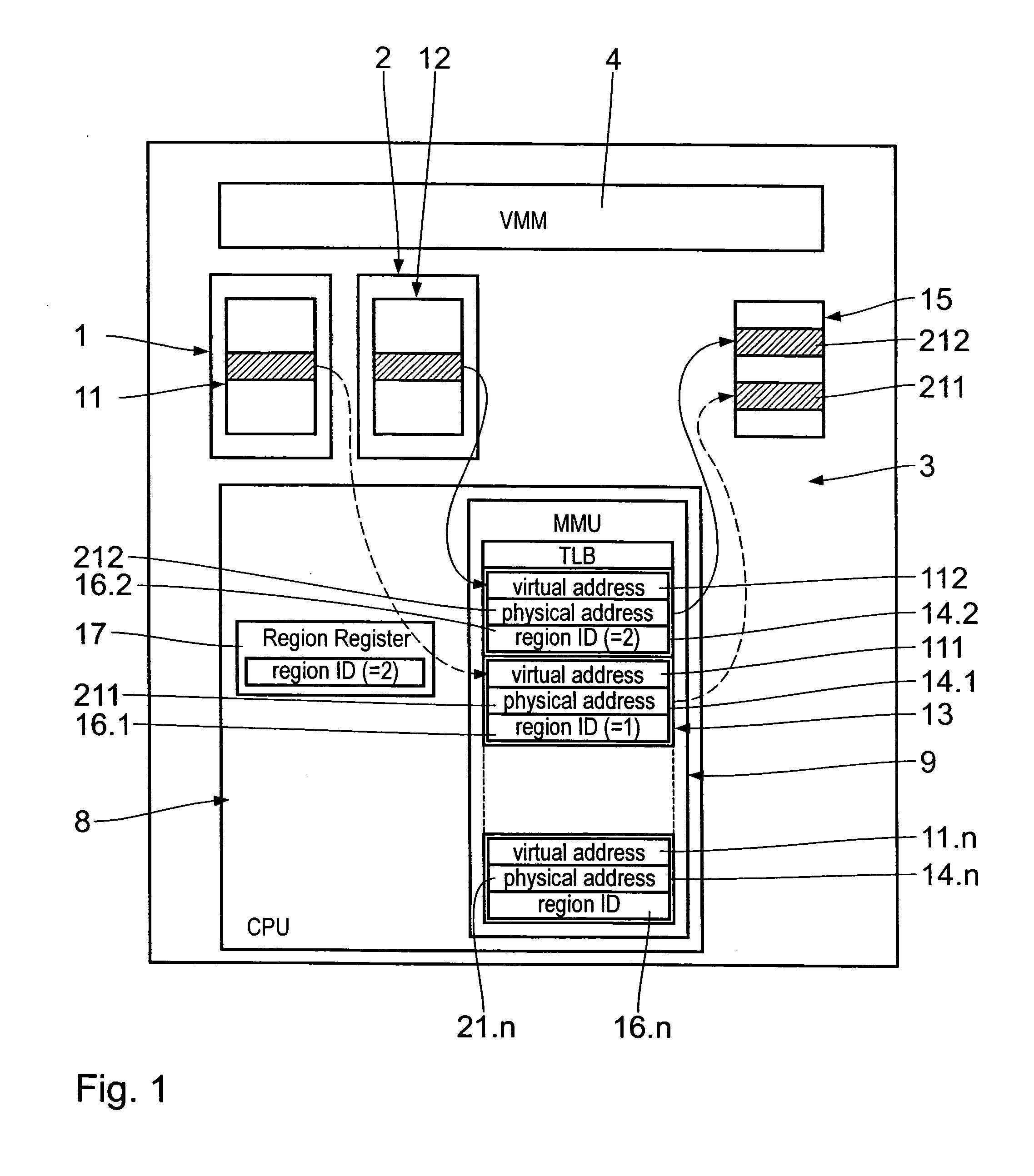
The virtual machine system for running computer guest processes on a central processing means 8 virtualized by the virtual machine monitor (VMM) includes a host central processing unit 8 on which a host memory management unit 9 is implemented. The latter has a translation look-aside buffer 13 with a plurality of entries 14 each of which consists of a virtual address value 111, a physical address value 211 and a region identification value 16. The region register 17 in the host CPU 8 contains the region ID 16 of the currently running guest process. The region ID 16 is composed of a guest allocated bit field 18, in which a region sub ID is entered, and a guest system identifier bit field 19, in which an identification value uniquely identifying an associated guest system is entered.
Owner:HOB GMBH & CO KG
Method and system to grant indefinite use of software options resident on a device
InactiveUS6983375B2Data processing applicationsError detection/correctionBiological activationUser identifier
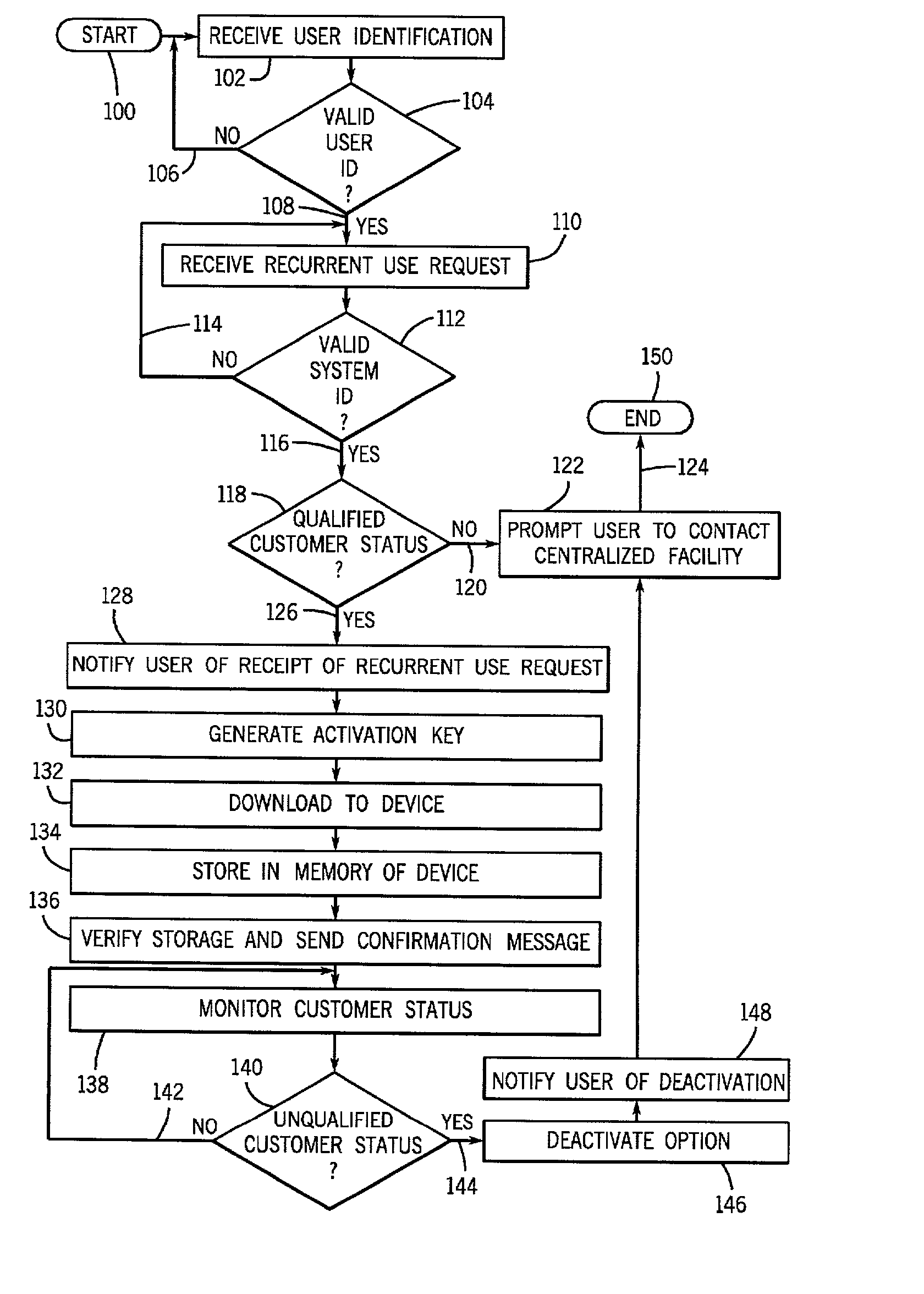
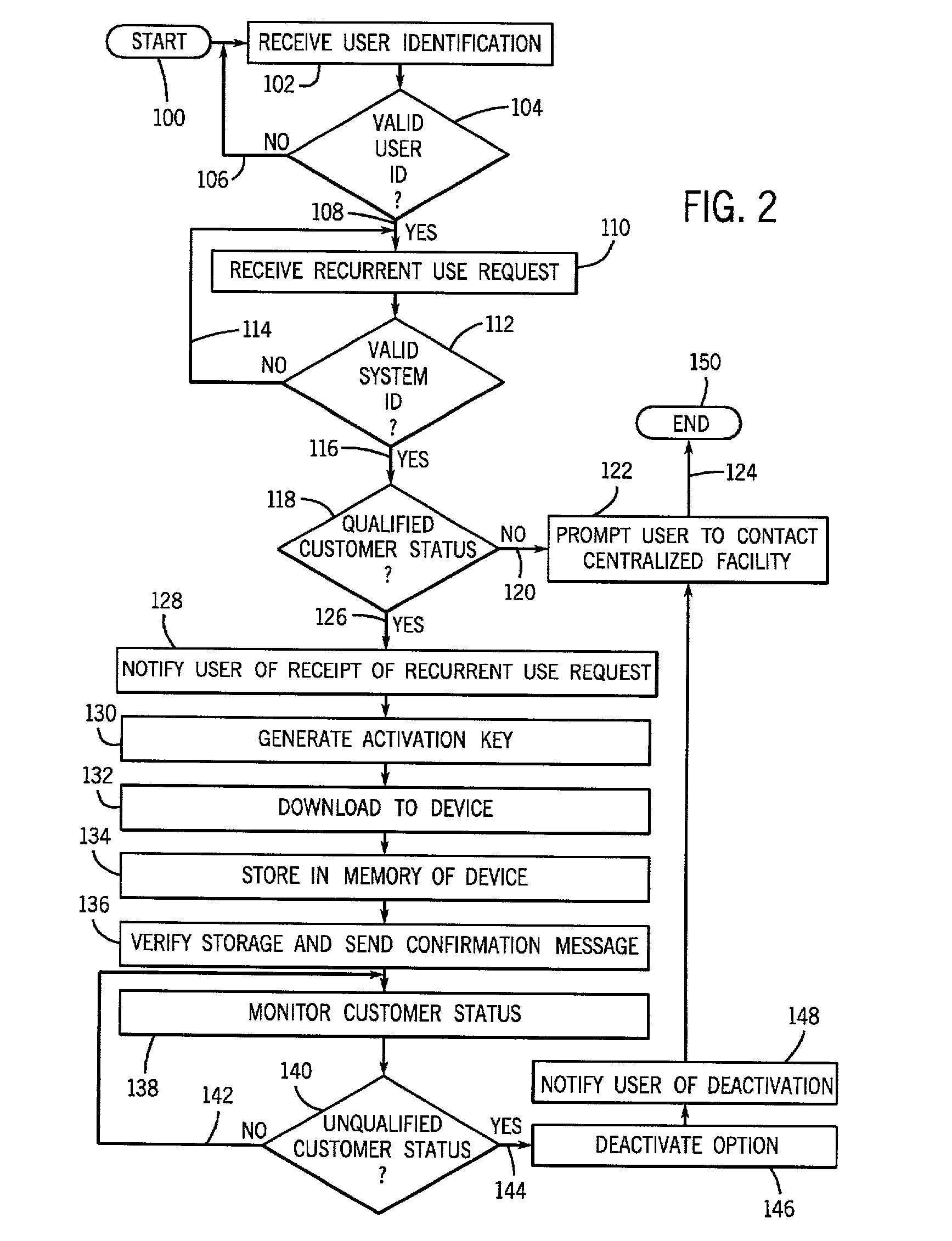
A system for granting indefinite use of inactivated software options pre-installed on a device is provided. The system includes receiving, at a remote processing facility, a recurrent use request from a user requesting access to an inactivated software option resident on the device. The system is further configured to validate the request and generate an activation key. The activation key is transmitted from the processing facility to the device automatically activating the option and granting recurrent access. The activation key or code is generated at the processing facility using data from at least one of a user identifier, a system identifier, a recurrent use identifier, and the selected option. A method to permit recurrent use of resident, yet, inactivated software of a device is also provided.
Owner:GE MEDICAL TECH SERVICES
Method of configuring an in-vehicle telematics unit
InactiveUS7398082B2Registering/indicating working of vehiclesActive radio relay systemsMobile identification numberMobile vehicle
Owner:GENERA MOTORS LLC
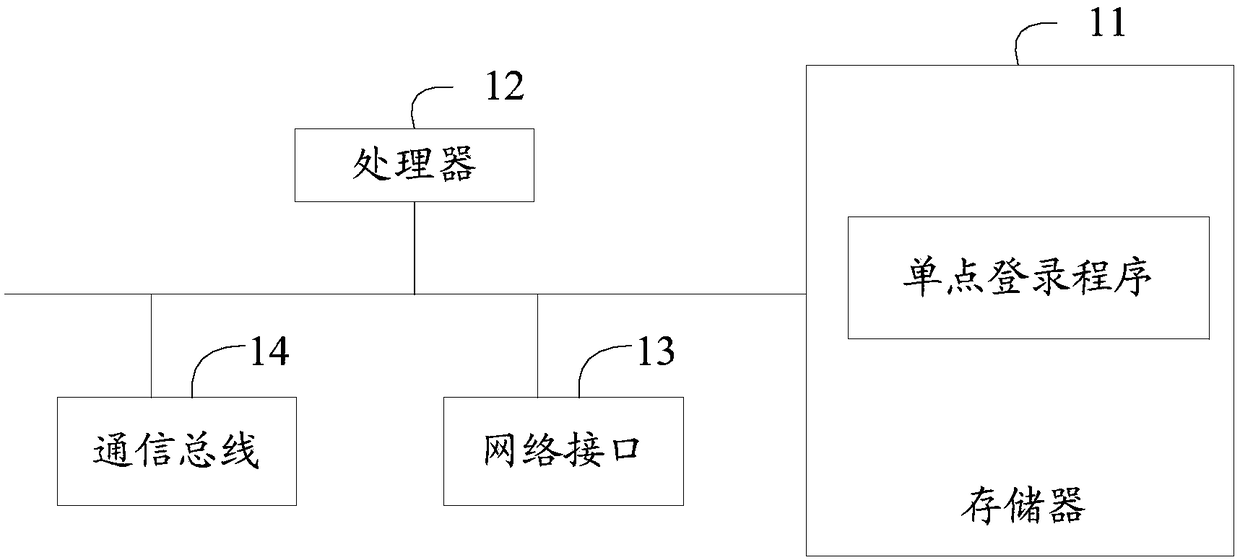
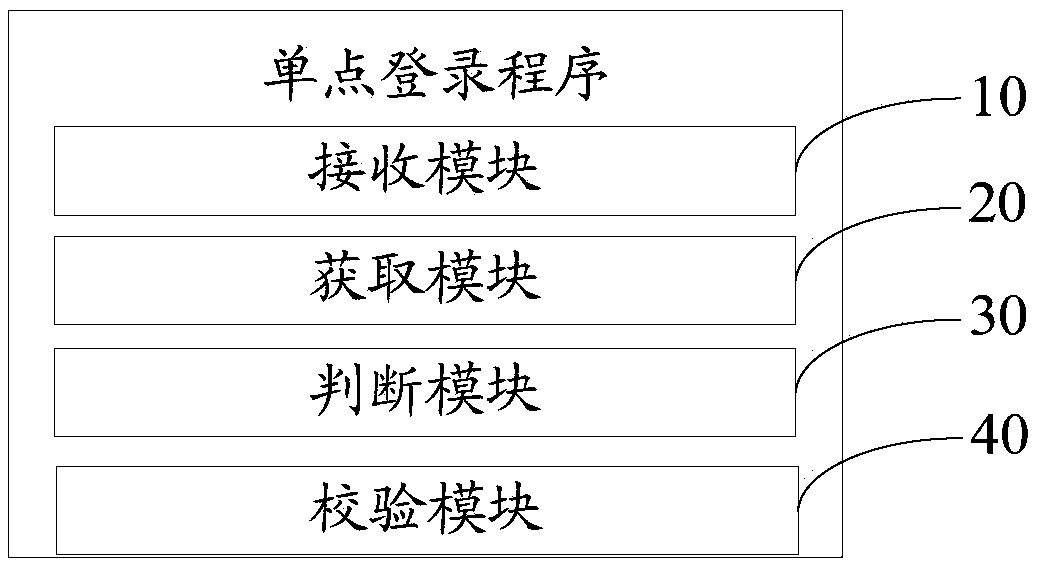
Single sign-on server, single sign-on method and computer readable storage medium
The invention discloses a single sign-on server. The single sign-on server comprises a memory and a processor; a single sign-on program which can be run in the processor is stored in the memory. Whenthe program is carried out by the processor, steps below are realized: obtaining a sign-on request sent from a client to the server based on a reorientation information sent by a service system; obtaining account information from the sign-on request, obtaining a system identifier of the service system and an associated white list from the reorientation information and judging whether account information exists in the white list; if so, verifying the account information and a password in the sign-on request; if the verification passes, returning token information to the client for storage and storing the token information after the token information is associated with the account information of the client. The invention also provides a single sign-on method and a computer readable storage medium. According to the single sign-on server, the single sign-on method and the computer readable storage medium, a system code amount is reduced, the system reusability is improved, and centralizedmanagement of each service system authority in the single sign-on system is realized.
Owner:重庆金融资产交易所有限责任公司
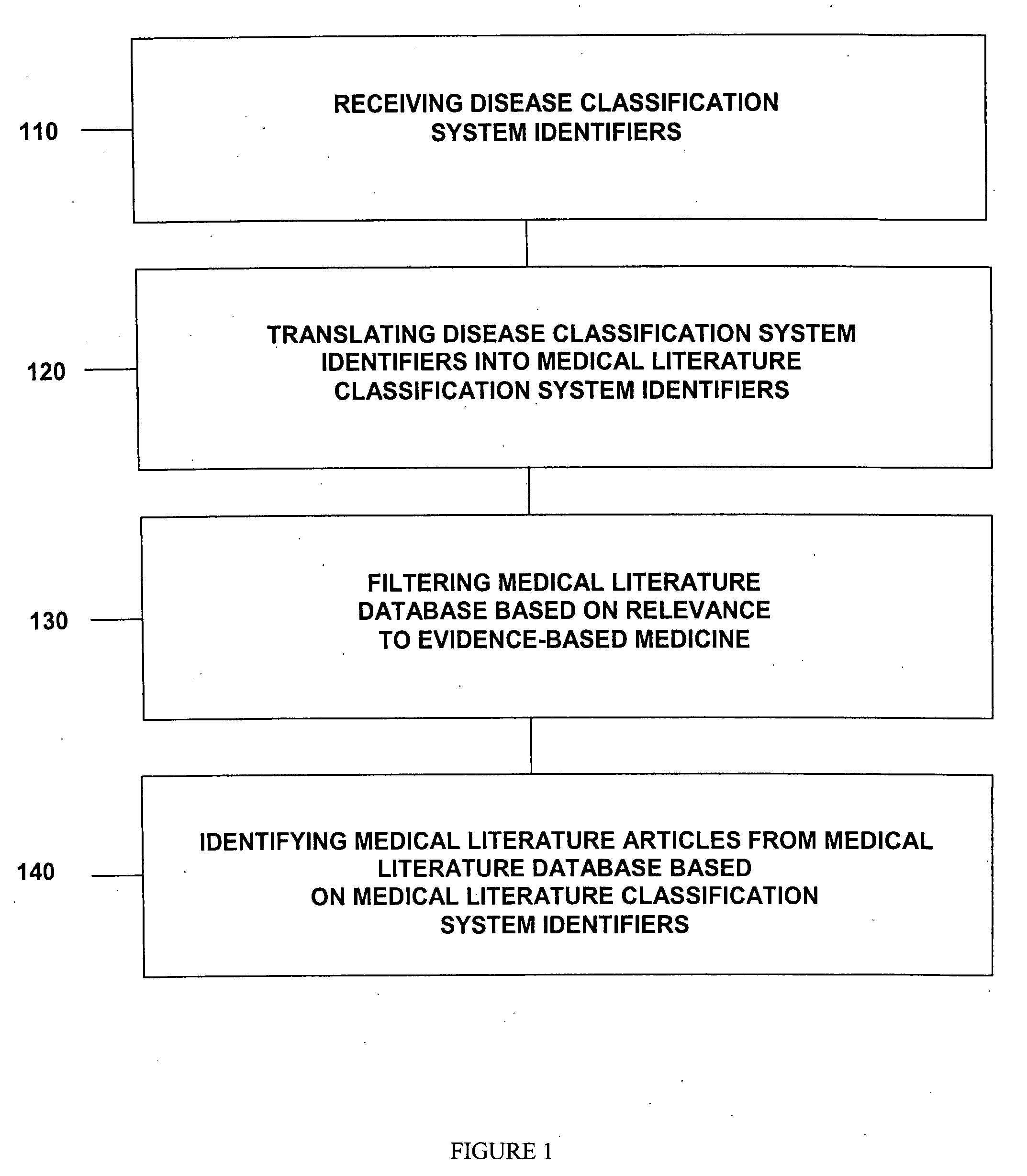
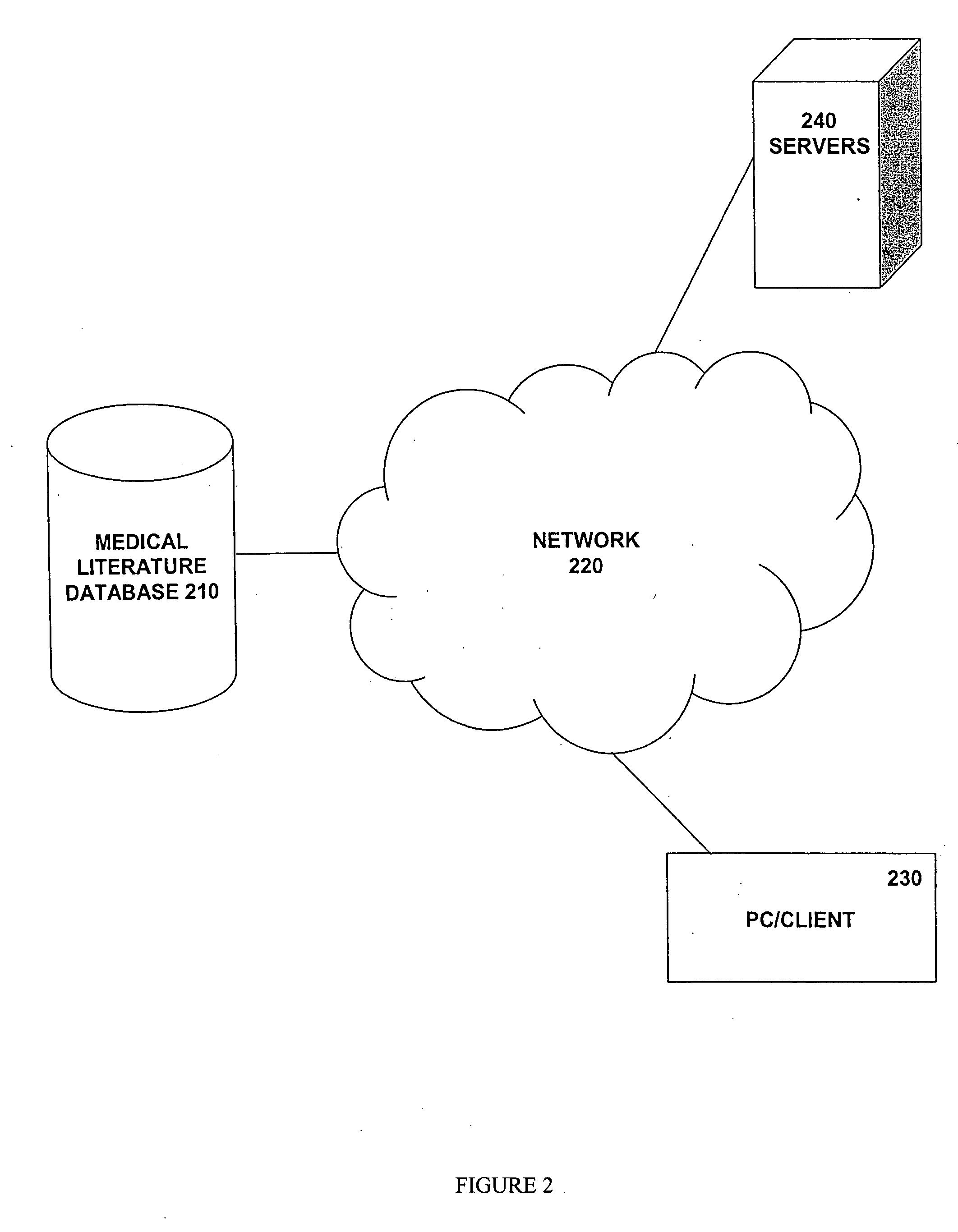
Medical literature database search tool
InactiveUS20050086078A1Data processing applicationsMedical equipmentDisease classificationLibrary science
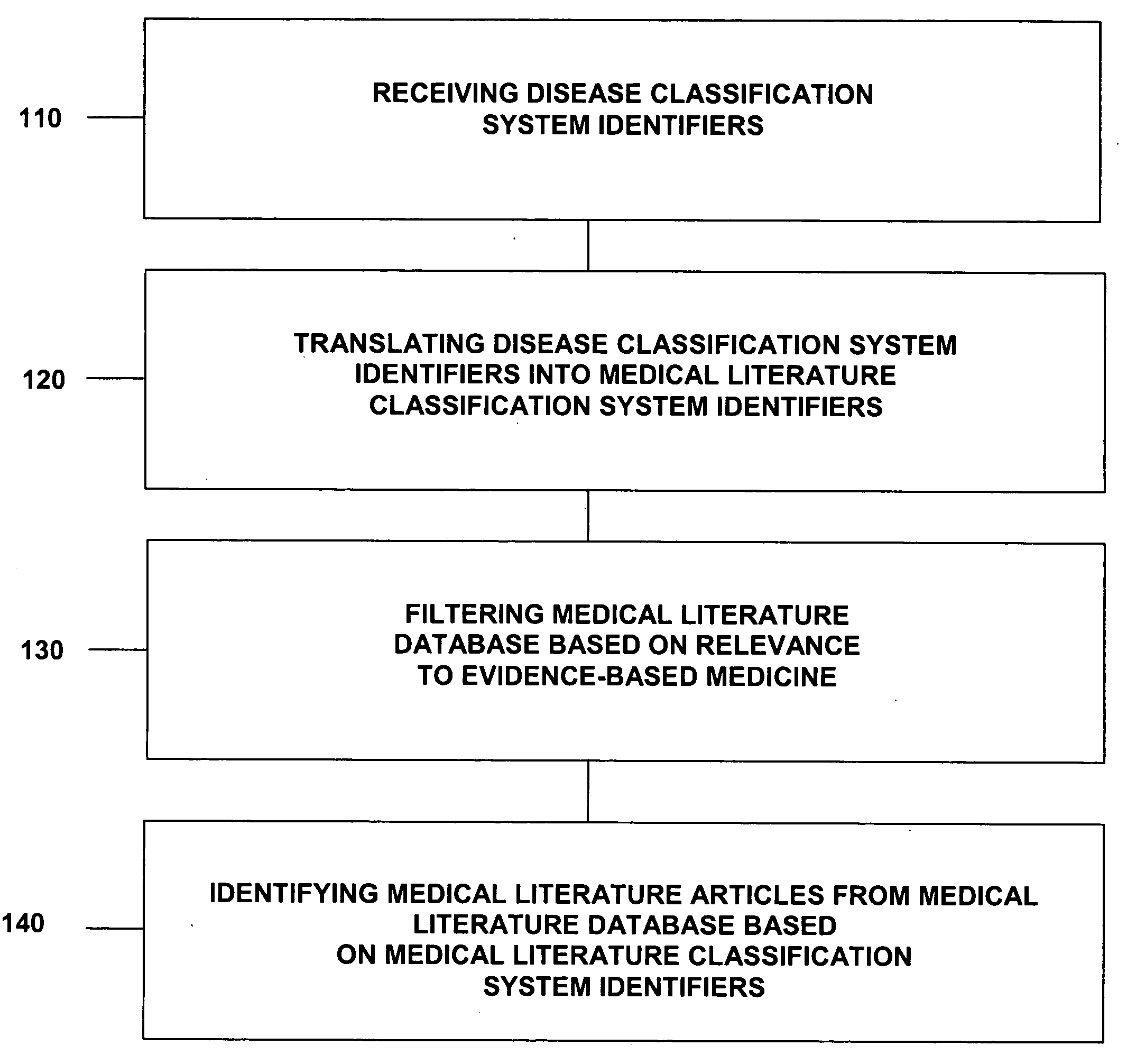
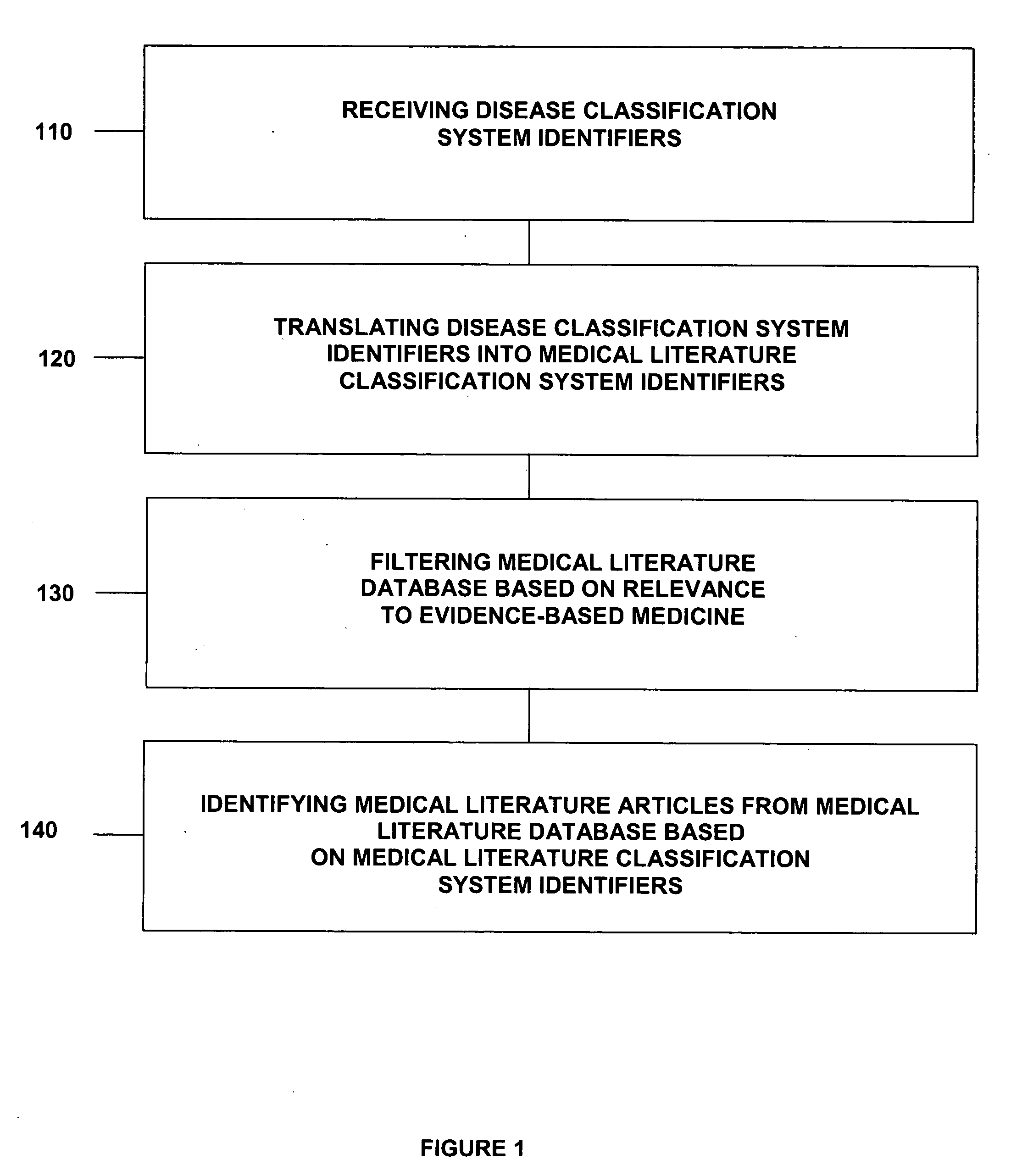
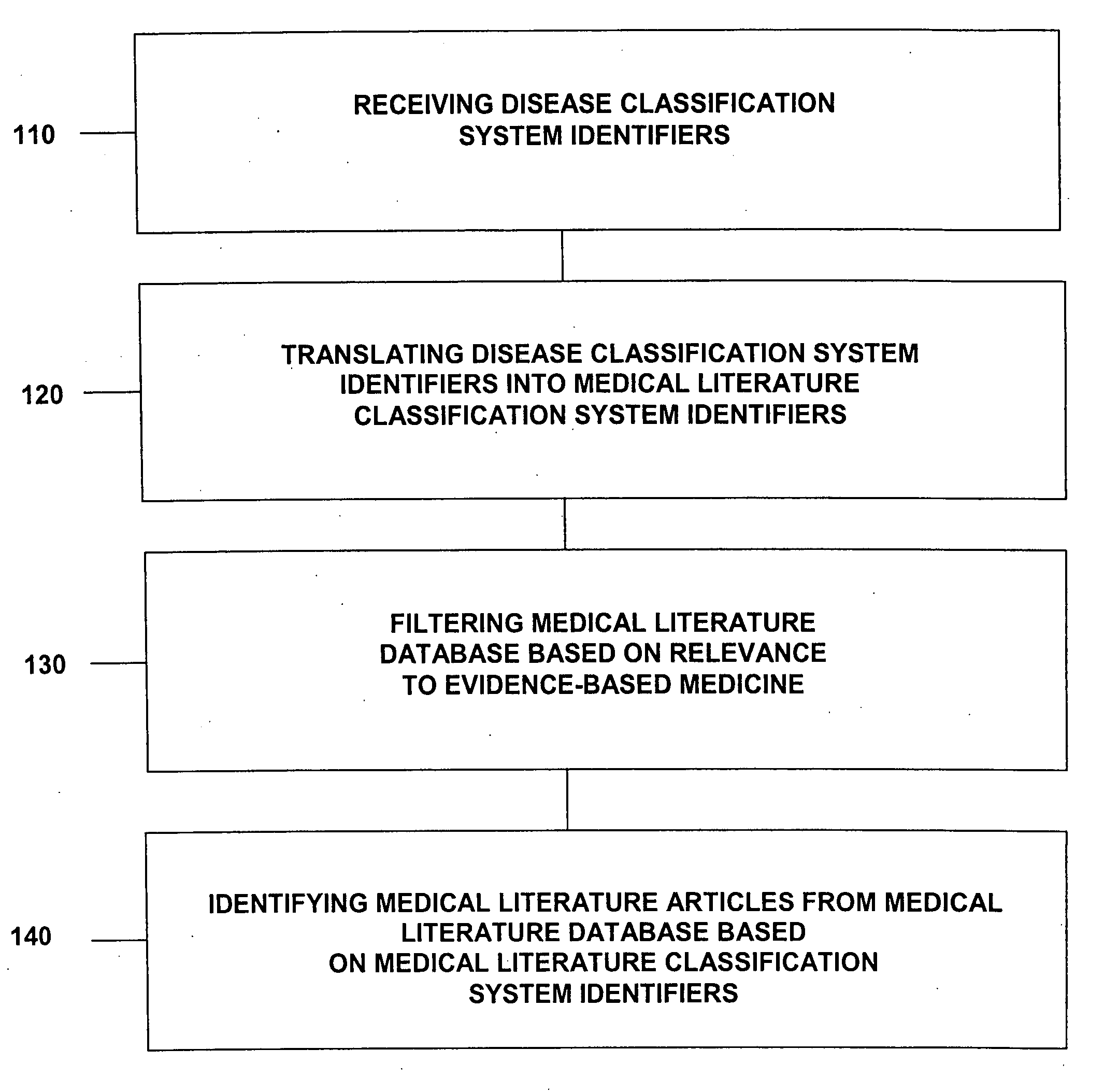
In some embodiments, disease classification system identifiers are received; disease classification system identifiers are translated into medical literature classification system identifiers; a medical literature database is filtered based on relevance to evidence-based medicine; and medical literature articles are identified from a medical literature database based on medical literature classification system identifiers. Various embodiments add, delete, and modify portions of the claimed methods and apparatuses. In other embodiments, genetic profiles of patients are received; genetic profiles are translated into medical literature classification system identifiers; a medical literature database is filtered based on relevance to evidence-based medicine; and medical literature articles are identified from a medical literature database based on medical literature classification system identifiers. Various embodiments add, delete, and modify portions of the claimed methods and apparatuses. Some embodiments include code on a computer readable medium.
Owner:COGENT MEDICINE
Medical literature database search tool
This invention provides a method of identifying clinically relevant, evidence based medical literature on diseases and their treatment to physicians, nurses and other healthcare personnel. This method accesses a medical literature database that is then searched using a medical literature classification system identifier for a disease integrated with an evidence based medicine search filter. In conjunction with identifying the evidence based medical literature, a database of articles selected and reviewed by experts that concern the disease is also searched. The results of both searches are then displayed to the user. This invention can be implemented through the use of an encoded computer readable medium.
Owner:COGENT MEDICINE
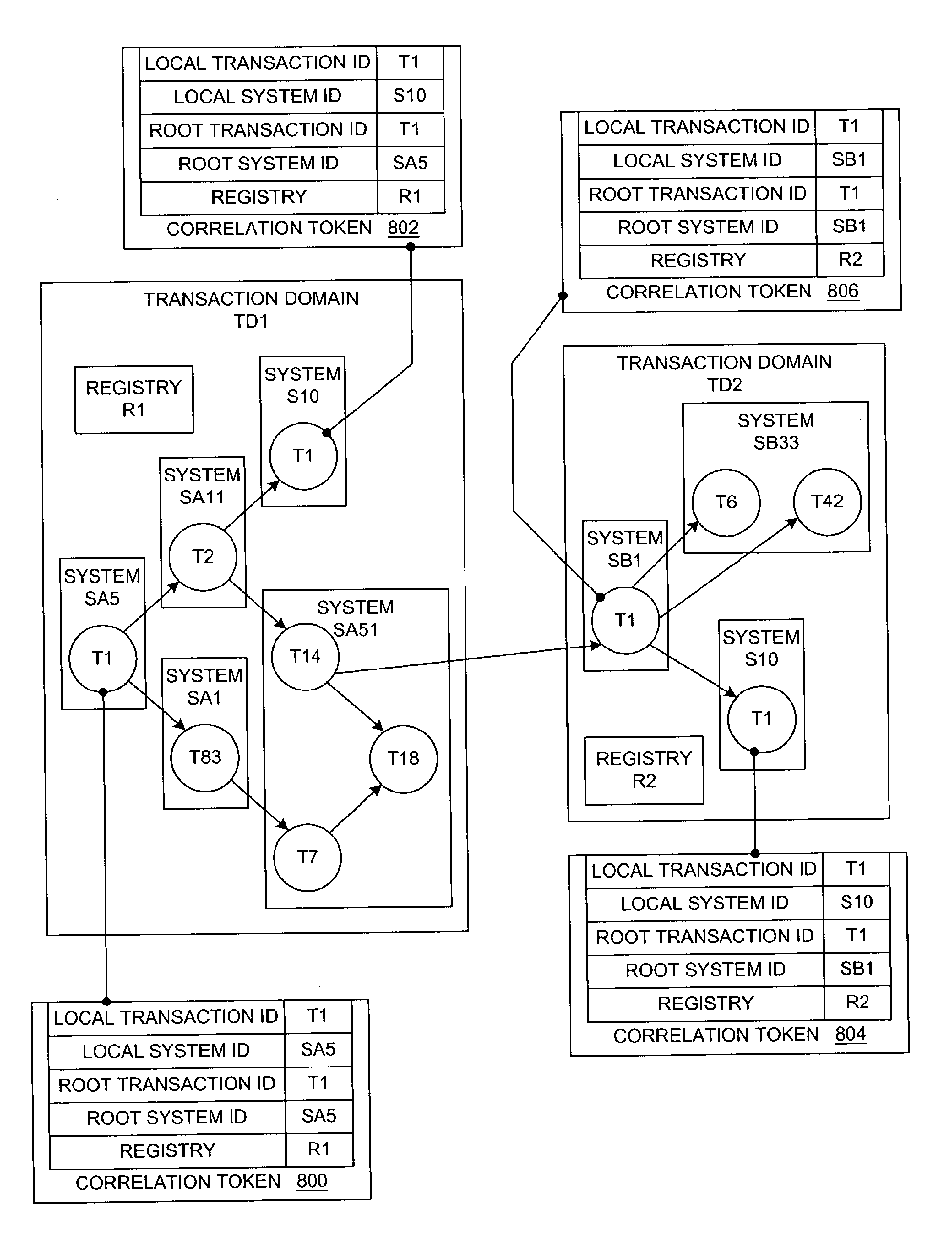
Method and System for Correlating Transactions and Messages
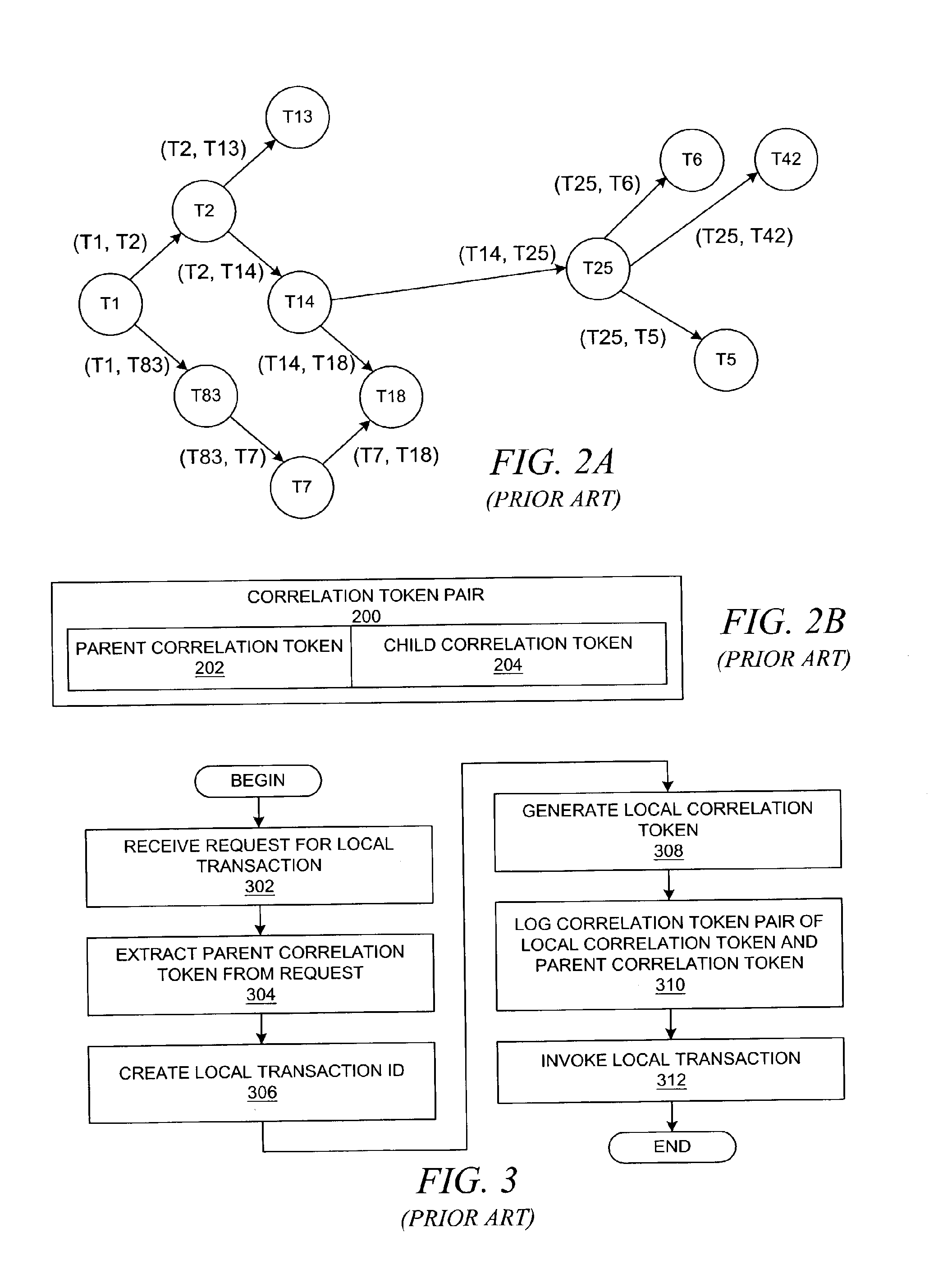
InactiveUS20080288608A1Digital computer detailsTransaction processingData processing systemRegistry Identifier
A method is presented for correlating related transactions, such as a parent transaction that invokes a child transaction within a distributed data processing system, using a particular format for the correlation tokens. Each transaction is associated with a correlation token containing a hierarchical, three-layer identifier that includes a local transaction identifier and a local system identifier, which are associated with the local system of the child transaction, along with a root transaction identifier, a root system identifier, and a registry identifier. The local transaction identifier is unique within the local system, and the local system identifier is unique within a registry that contains a set of system identifiers. The registry is associated with a domain in which the local systems operate, and multiple domains exist within a transaction space of entities that use these correlation tokens. Correlation token pairs are analyzed to construct a call graph of related transactions.
Owner:IBM CORP
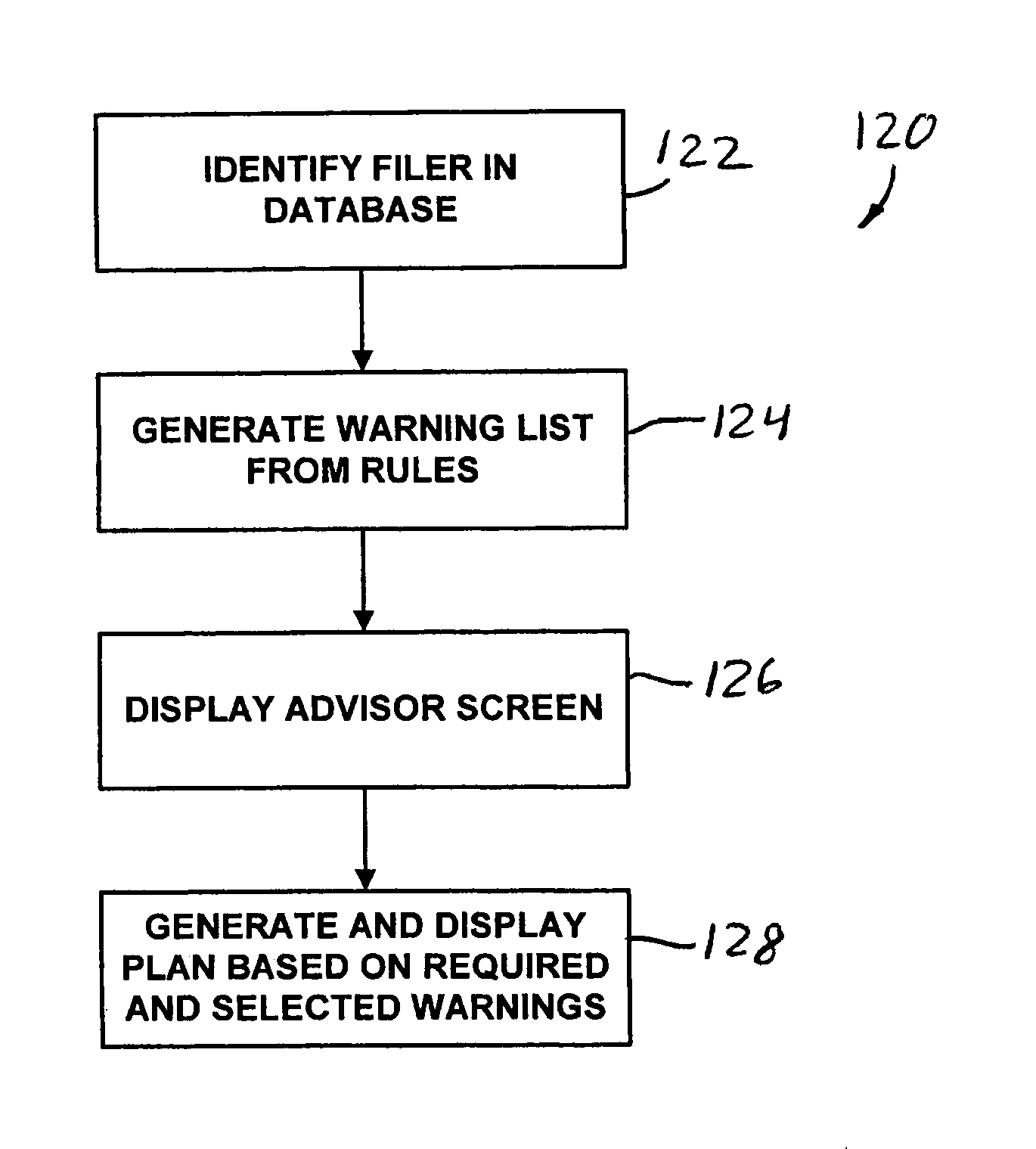
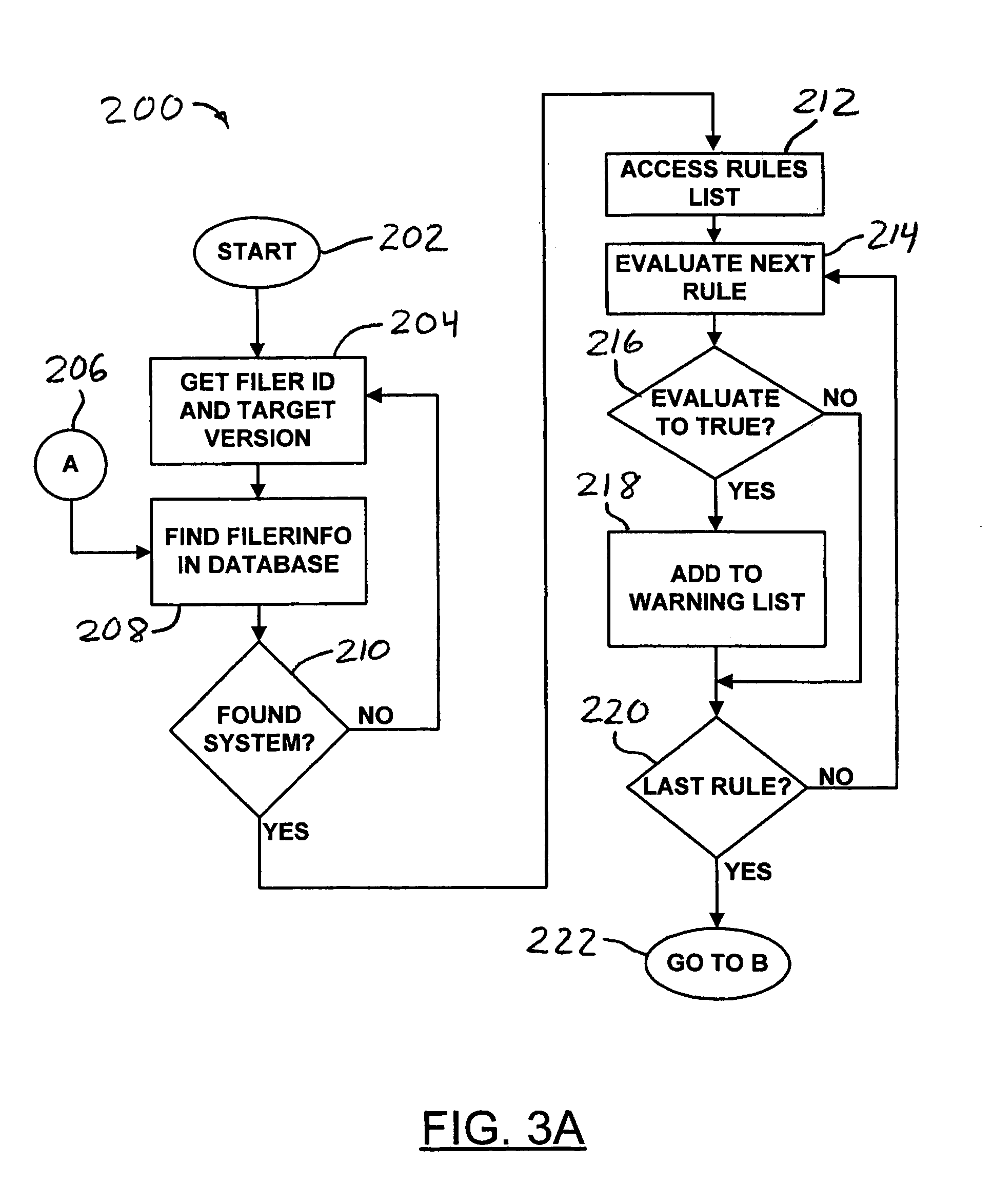
Automated compatibility and upgrade/downgrade knowledge base
An automated knowledge base includes a system identifier and a target version. The system identifier identifies a particular computer system and the target version identifies a target computer program to be installed on the computer system. Configuration information of the particular computer system is retrieved using the system identifier and a warning statement that describes a conflict between the configuration information and the target computer program is identified. A warning document that includes the identified warning statement is generated.
Owner:NETWORK APPLIANCE INC
Log processing method and device, electronic equipment and storage medium
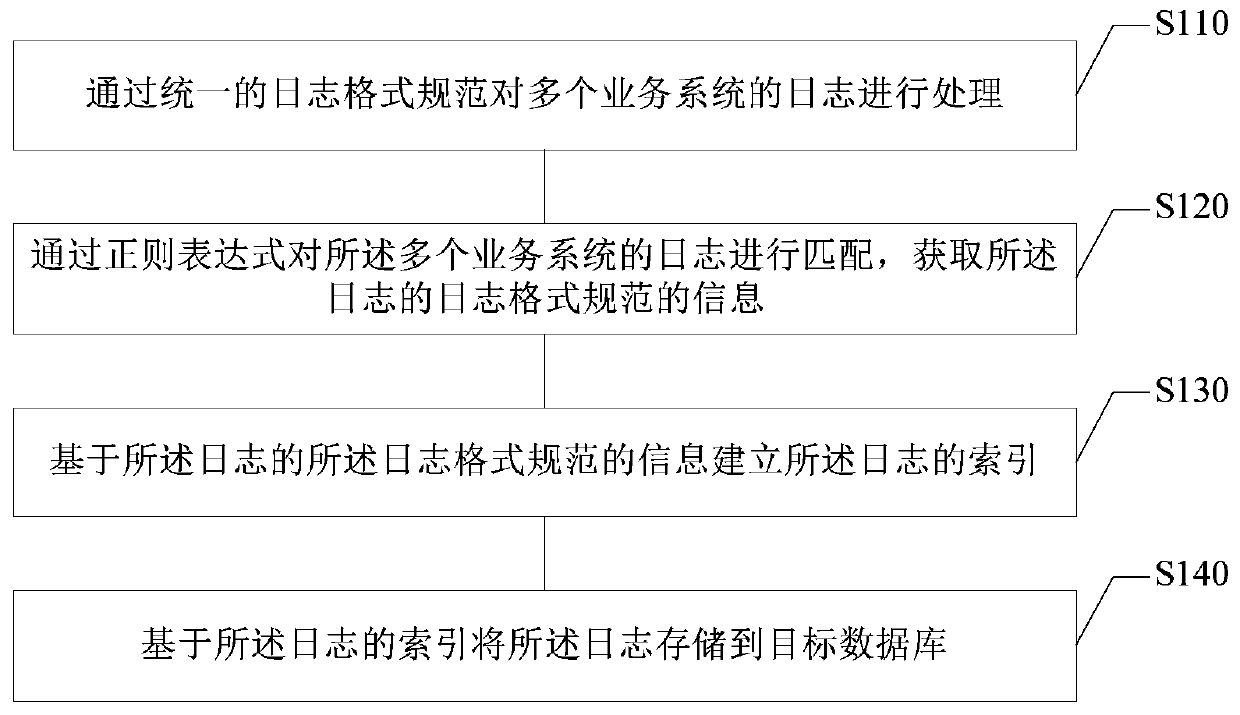
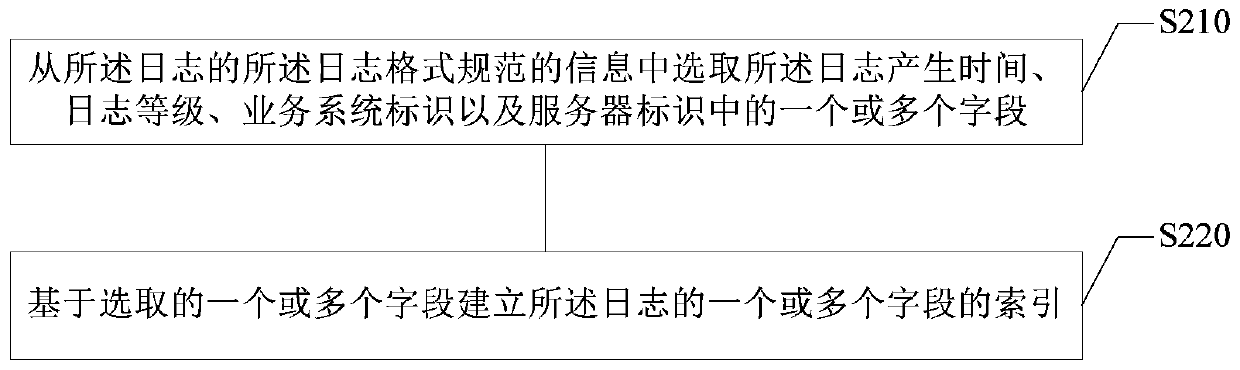
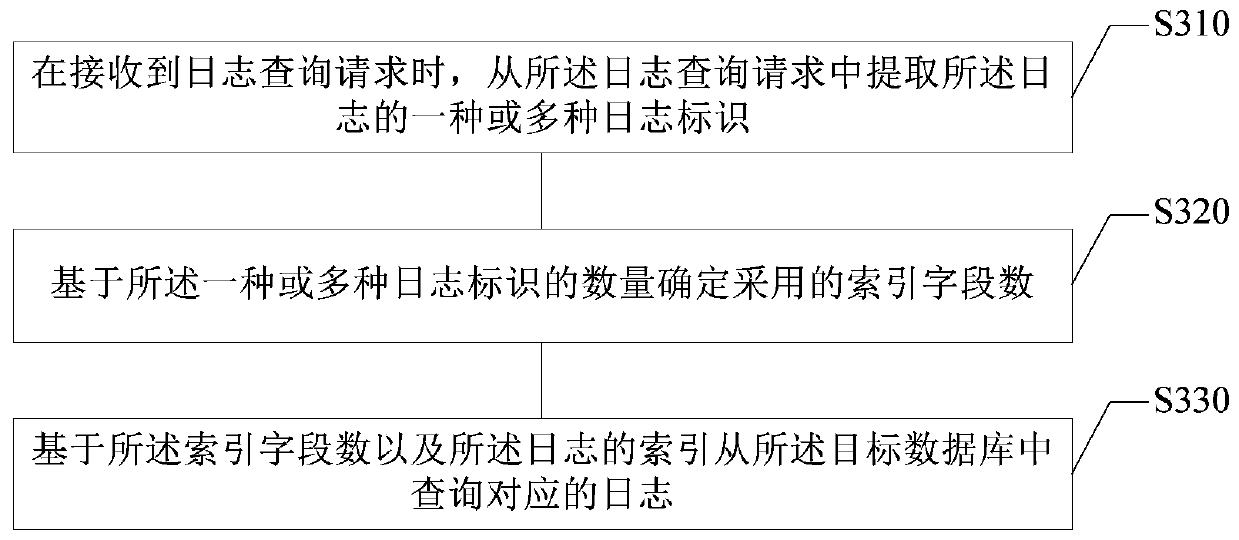
PendingCN109800223AEase of batch processingImprove query efficiencySpecial data processing applicationsDatabase indexingBatch processingRegular expression
The embodiment of the invention provides a log processing method and device, electronic equipment and a storage medium, and relates to the technical field of computers. The method comprises the following steps: processing logs of a plurality of business systems through a unified log format standard; matching the logs of the plurality of business systems through a regular expression to obtain log format specification information of the logs with the log format specification information comprising log generation time, log levels, business system identifiers and server identifiers; establishing an index of the log based on the information of the log format specification of the log; and storing the log into a target database based on the index of the log. According to the technical scheme provided by the embodiment of the invention, logs of various business systems can be unified, batch processing of the logs is facilitated, and the log query efficiency can be improved.
Owner:PING AN TECH (SHENZHEN) CO LTD
Method, device and network equipment for generating multilink transparent transmission interconnection forwarding table
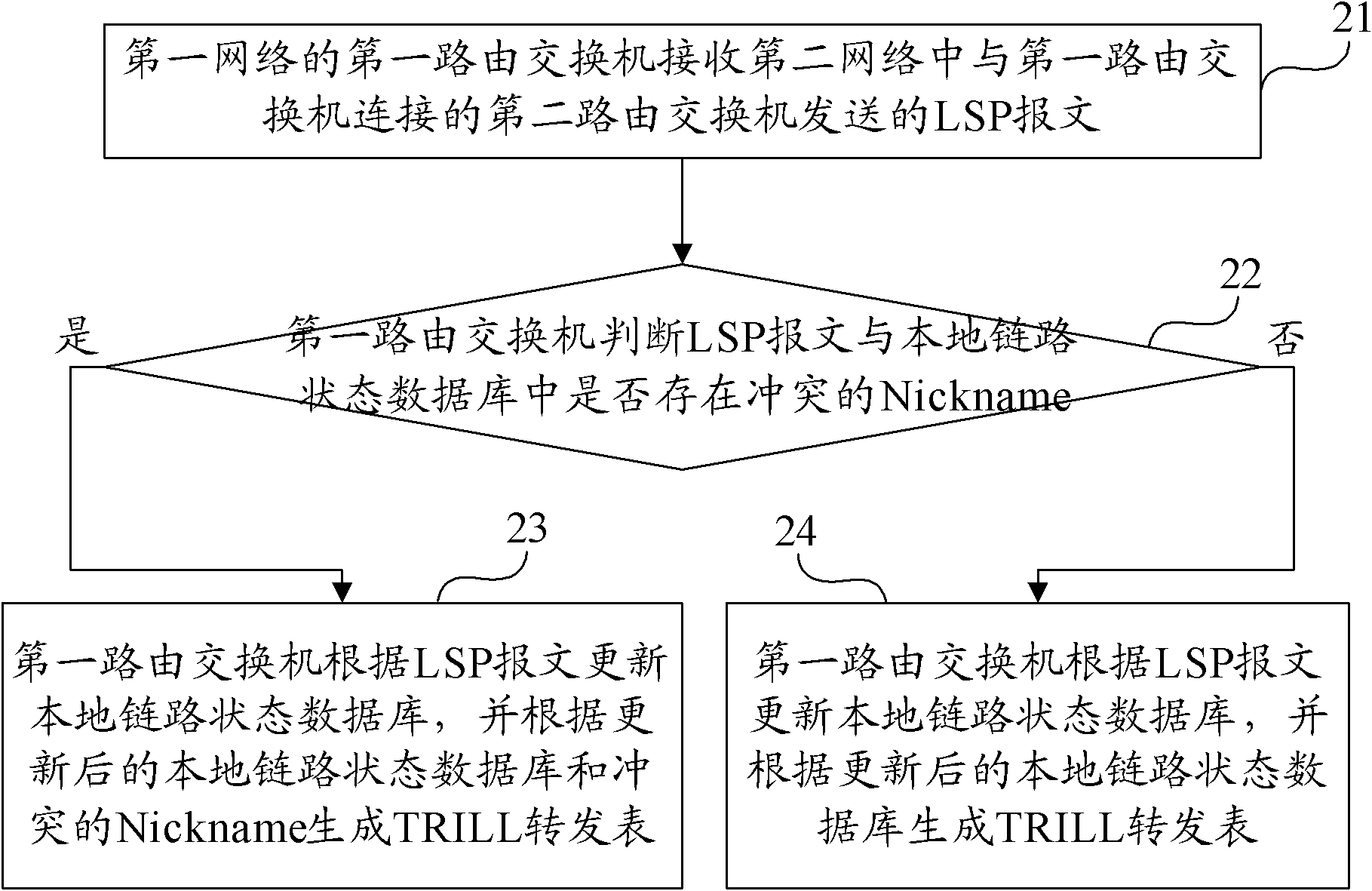
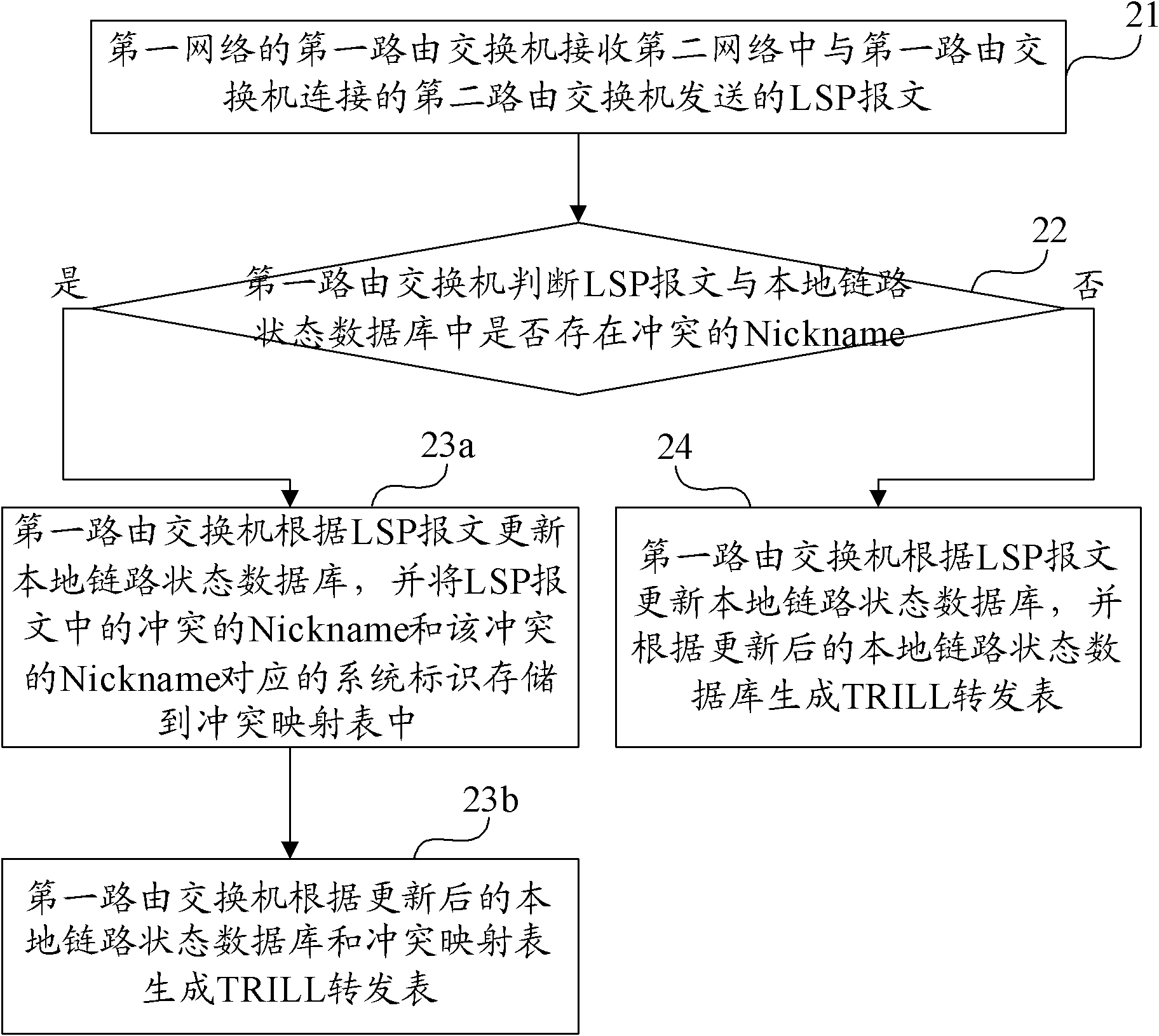
ActiveCN102123091ASolve the lossIncrease success rateData switching networksData streamInterconnection
The invention provides a method, device and network equipment for generating a multilink transparent transmission interconnection forwarding table. The method comprises the following steps of: receiving, by a first routing switch in a first network, an LSP (Label Switching Path) message sent by a second routing switch connected with the first routing switch in the second network; respectively comparing Nicknames and system identifiers corresponding to the Nicknames in the LSP message with that in a local link state database so as to judge whether conflicting Nicknames exist; and updating the local link state database according to the LSP message when the judging result shows that the conflicting Nicknames exist, and generating a TRILL (Transparent Interconnection of Lots of Links) forwarding table according to the updated local link state database and the conflicting Nicknames. When the technical scheme provided by the invention is adopted, the problem of data stream losses caused by the wrong forwarding of the data stream due to the conflict of the Nicknames is solved, and the success rate of the forwarding of the data stream is improved.
Owner:RUIJIE NETWORKS CO LTD
Method for enabling a program written in untrusted code to interact with a security subsystem of a hosting operating system
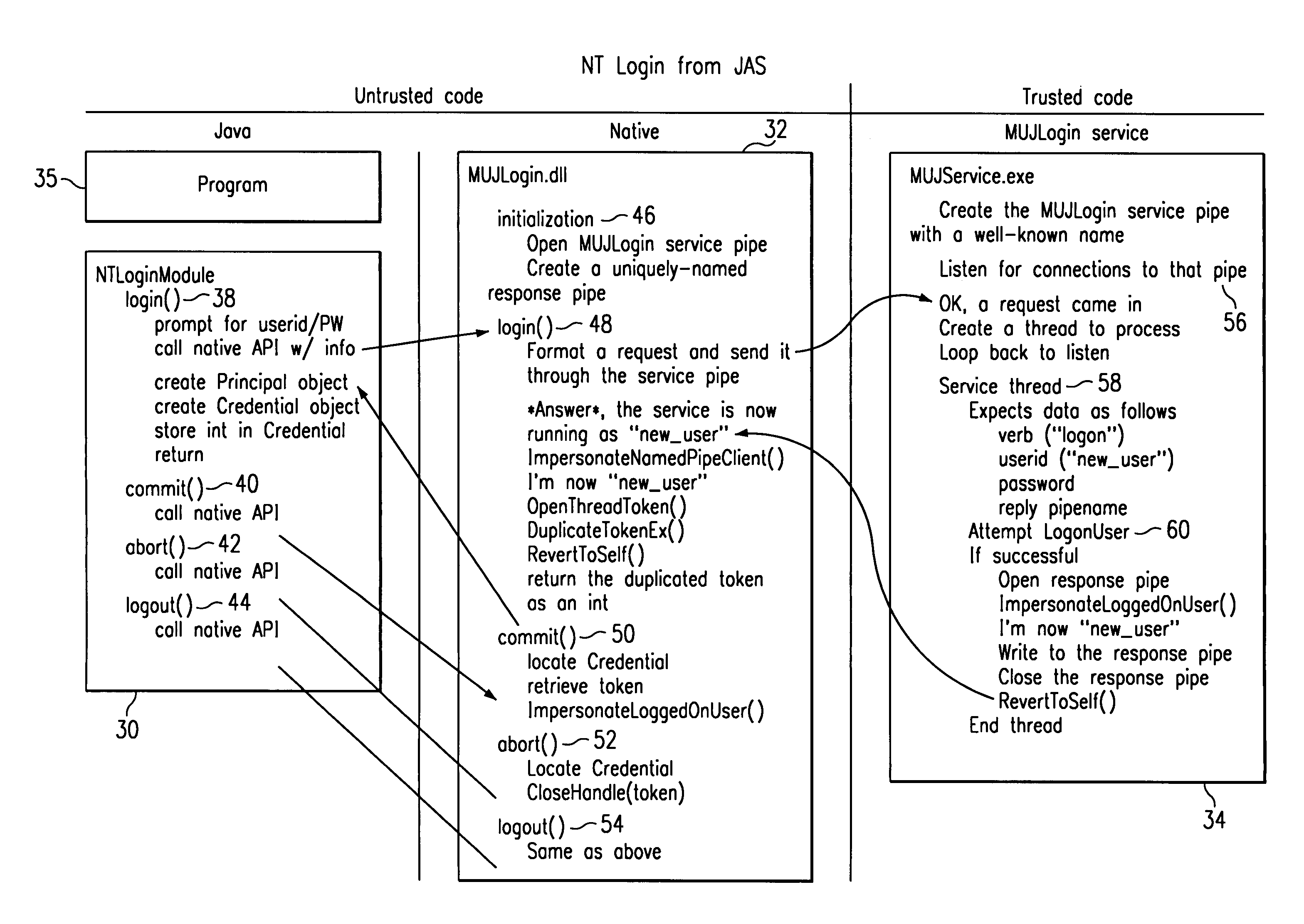
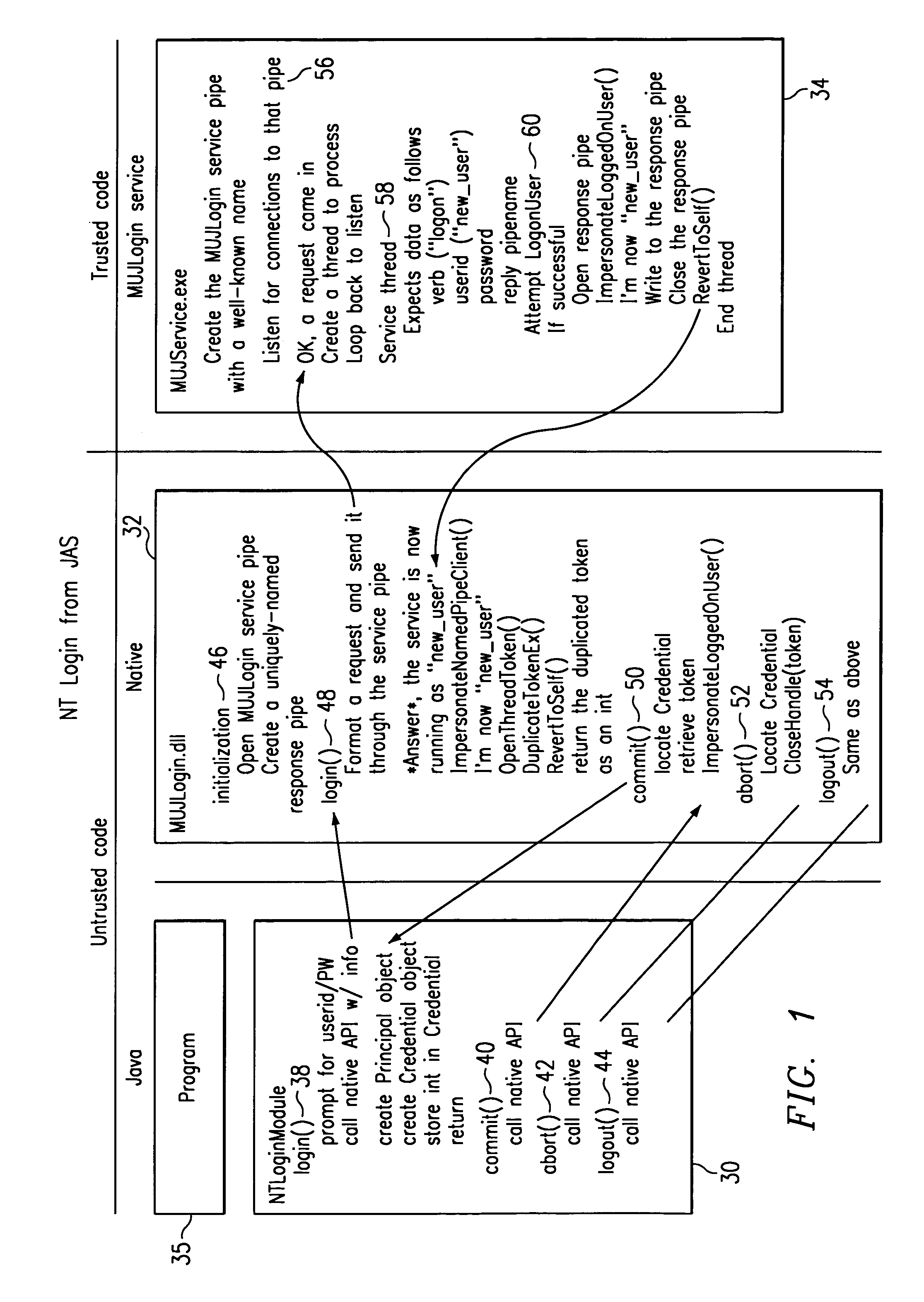
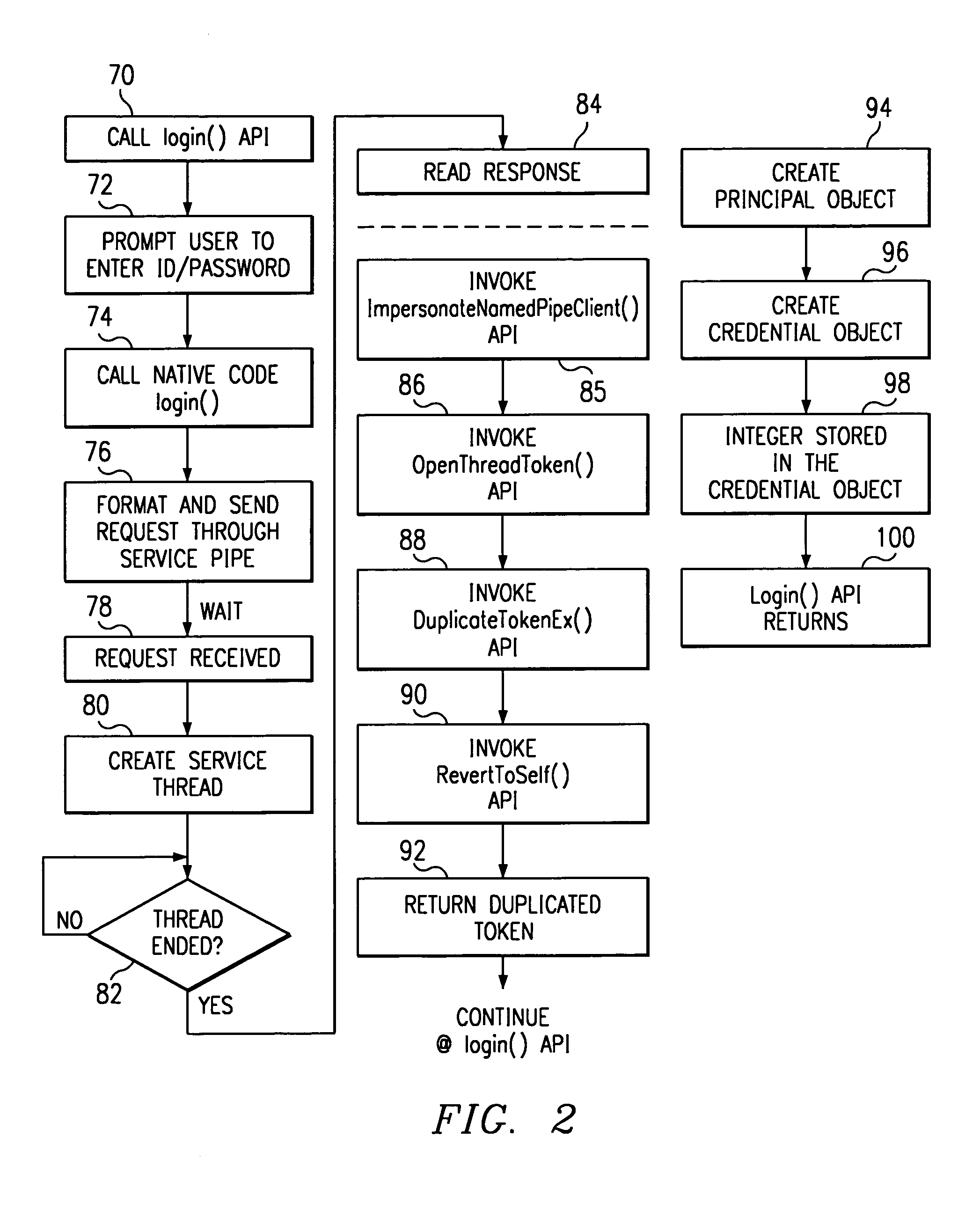
InactiveUS7451484B1Digital data processing detailsUnauthorized memory use protectionOperational systemSystem identifier
A program written in untrusted code (e.g., JAVA) is enabled to access a native operating system resource (e.g., supported in WINDOWS NT) through a staged login protocol. In operation, a trusted login service listens, e.g., on a named pipe, for requests for login credentials. In response to a login request, the trusted login service requests a native operating system identifier. The native operating system identifier is then sent to the program. Using this identifier, a credential object is then created within an authentication framework. The credential object is then used to login to the native operating system to enable the program to access the resource. This technique enables a JAVA program to access a WINDOWS NT operating system resource under the identity of the user running the JAVA program.
Owner:IBM CORP
Client-side boot domains and boot rules
InactiveUS6978365B2Digital data processing detailsUser identity/authority verificationComponent LoadEngineering
Each software component loaded for a verified operating system on a client computer must satisfy a set of boot rules for a boot certificate. A verified operating system identifier is created from the boot certificate. The boot certificate is published and signed by a boot authority that attests to the validity of the operating system booted under the boot certificate. Each software component for the operating system is associated with a component certificate published and signed by the same boot authority that signed the boot certificate. The boot rules determine the validity of the software component based on the contents of the component and boot certificates. The client computer can transmit the verified operating system identity and the boot certificate to a server computer, such as a content provider, and the content provider can determine whether to trust the verified operating system with its content.
Owner:MICROSOFT TECH LICENSING LLC
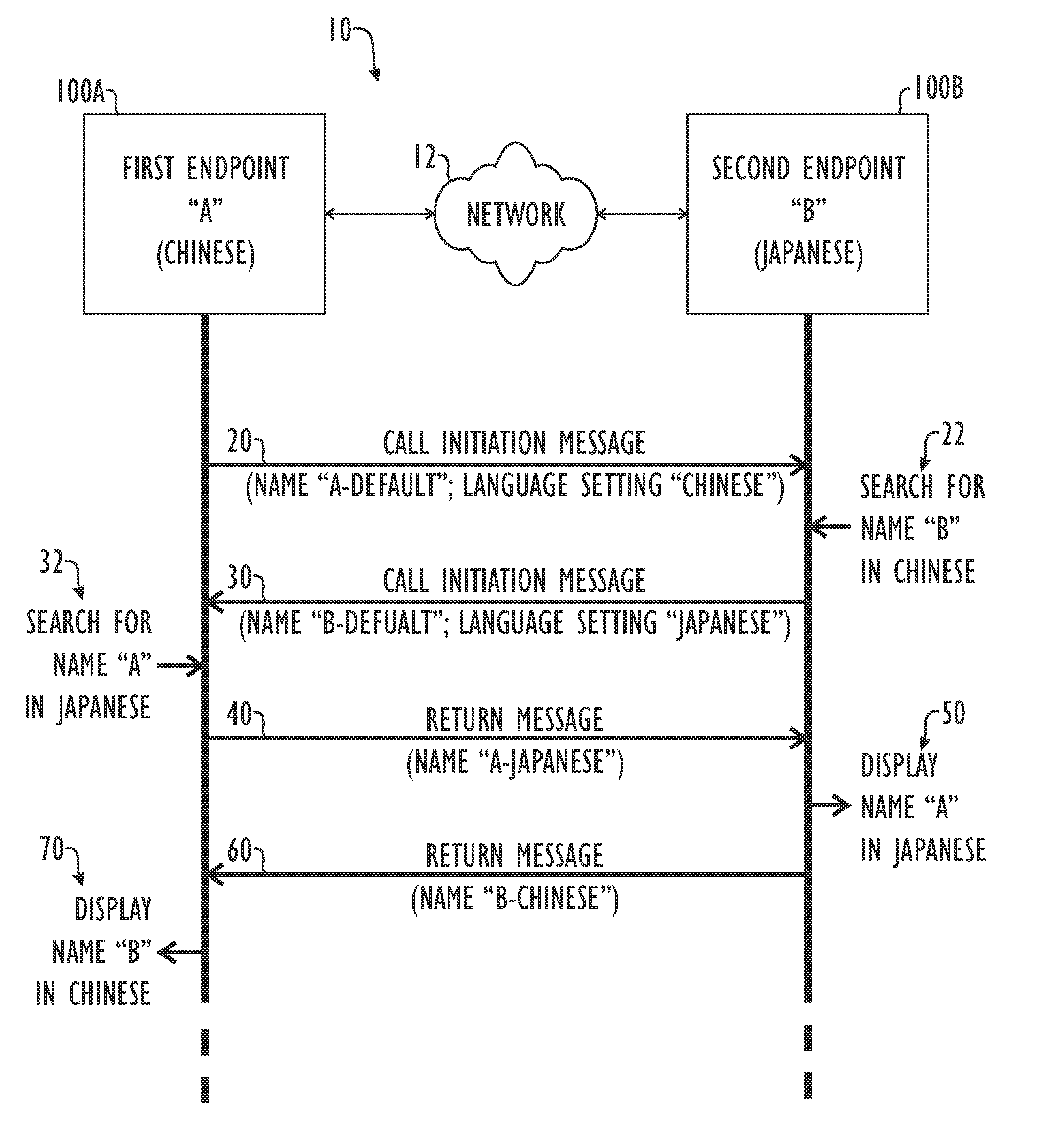
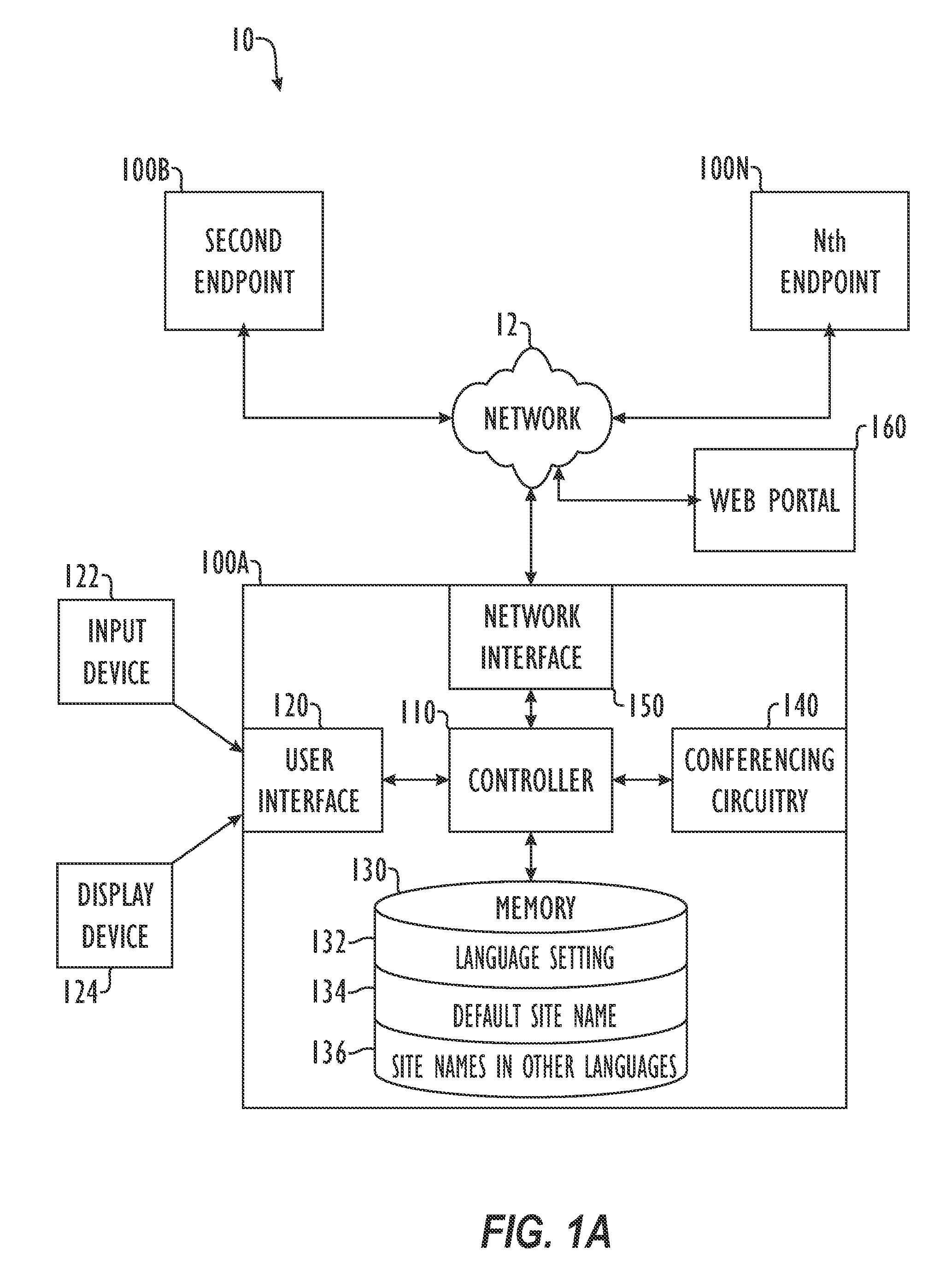
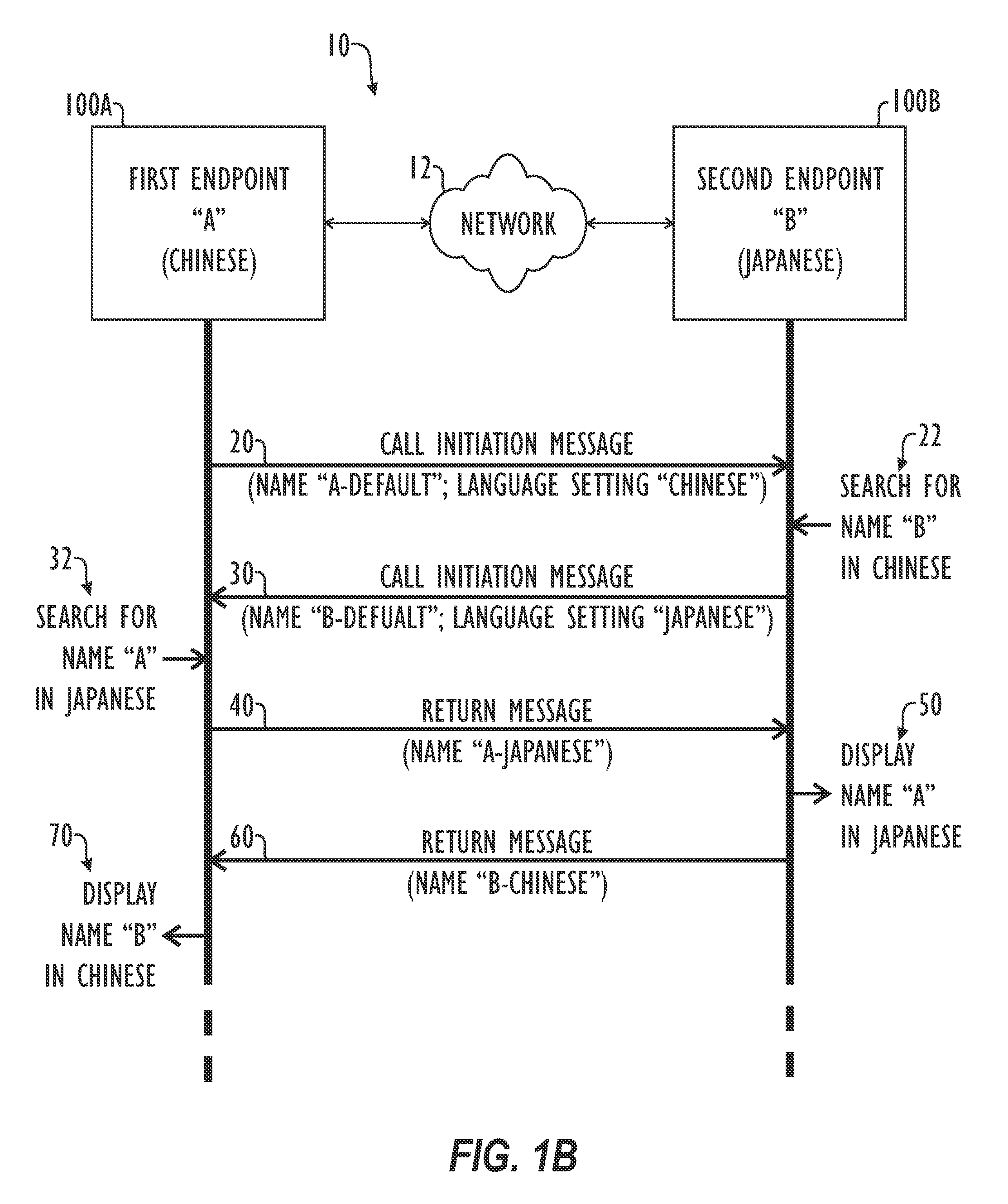
Conferencing System and Method for Exchanging Site Names (Caller ID) in Languages Based on Double or Multiple Byte Character Sets
ActiveUS20070041540A1Television conference systemsSpecial service for subscribersComputer compatibilityByte
Disclosed herein is a system and method for storing and transmitting a videoconference system name (identifier) in the languages of double byte character sets. Although described in terms of a videoconferencing system, the techniques described herein have applicability to various other systems that rely upon inter-language compatibility, including telephonic communication such as cell phones or IP phones, as well as various computer network applications in which computers having different default languages are in communication. In a preferred embodiment, the system identifier is stored in a text or ASCII format rather than native (binary) format. Additionally, a system employing a preferred embodiment of the teachings described herein allows a particular system to have multiple site names in multiple different languages. This allows such a system to interface and exchange identifier data with other systems having different language settings during a caller ID exchange.
Owner:HEWLETT PACKARD DEV CO LP
Method, device and system for acquiring application programs
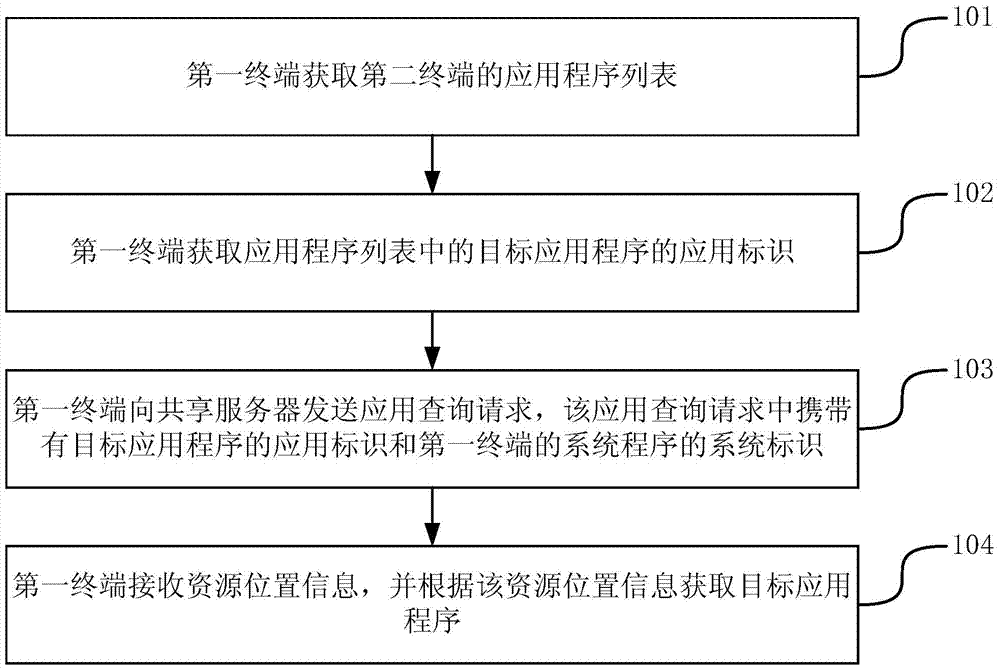
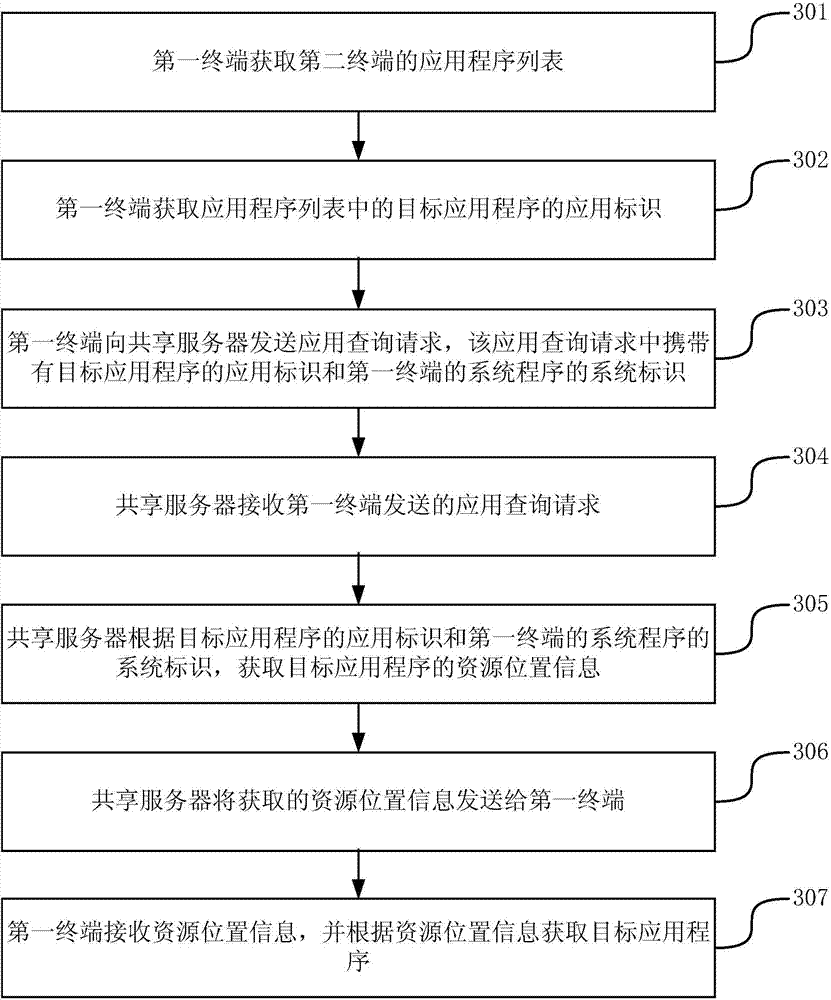
ActiveCN103294515AIncrease flexibilityProgram loading/initiatingTransmissionComputer terminalApplication Identifier
The invention discloses a method, a device and a system for acquiring application programs, and belongs to the technical field of computers. The method includes the steps: acquiring an application program list of a second terminal by a first terminal; acquiring an application identifier of a target application program in the application program list by the first terminal; transmitting an application query request to a shared server by the first terminal; acquiring resource position information of the target application program according to the application identifier of the target application program and a system identifier by the shared server and transmitting the resource position information to the first terminal by the shared server; and receiving the resource position information and acquiring the target application program according to the resource position information by the first terminal. The application query request carries the application identifier of the target application program and the system identifier of a system program of the first terminal. Flexibility of the application program acquisition process can be improved.
Owner:XIAOMI INC
Method capable of reducing the information exchange redundancy in the WLAN 802.11
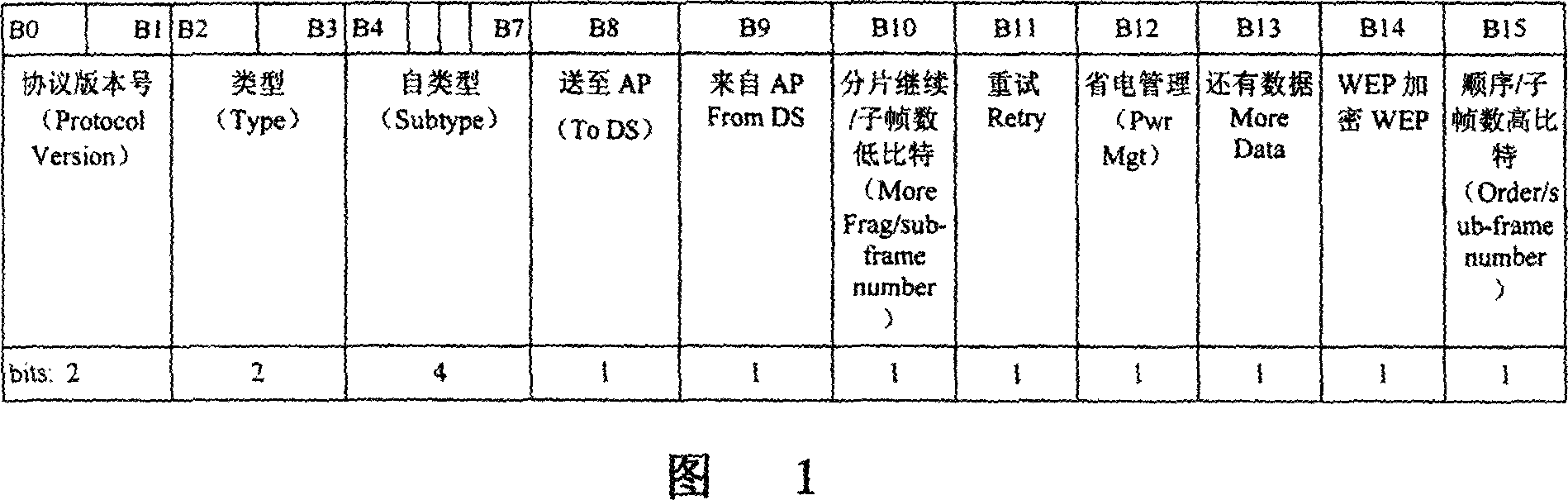
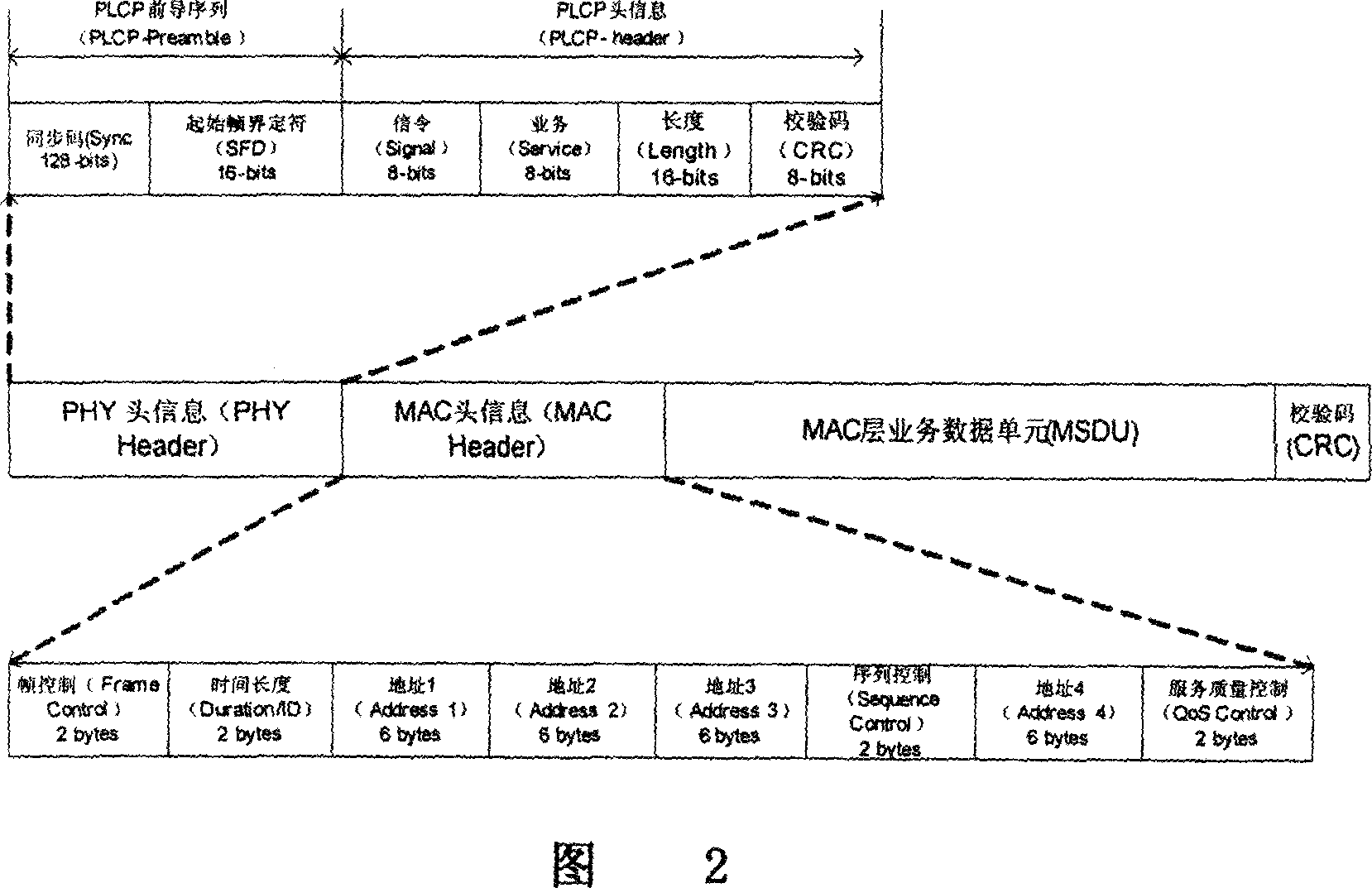
InactiveCN101056258AGuaranteed normal transmissionImprove transmission efficiencyNetwork traffic/resource managementData switching by path configurationStart timeNetwork packet
A method for reducing the information exchange redundancy in the radio LAN 802.11, the steps are as follows: a) construct the small packets to different user terminals as one sub-frame body at the AP end and then concentrate them to one super MAC down link frame; one sub-frame will include the start time and length of the TXOP of the corresponding user terminal and one link identifier; all sub-frames share one PHY information header; b) set CRC check code for every sub-frame; c) the link of every AP and non-AP user terminal will replace the MAC source and destination address with one link identifier; d) set the duration of the whole super MAC down link frame in the Duration / ID of the super MAC down link frame and the duration of total uplink of the corresponding terminal user; e) the uplink MAC frame includes the link identifier and the size of the user terminal queue; the queue size is defined as total size of all packets which are sent by the user terminal; f) the and or result between the uplink MAC frame and BSSID, or one system identifier is used to differentiate the different basic service set BSS.
Owner:ZTE CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com