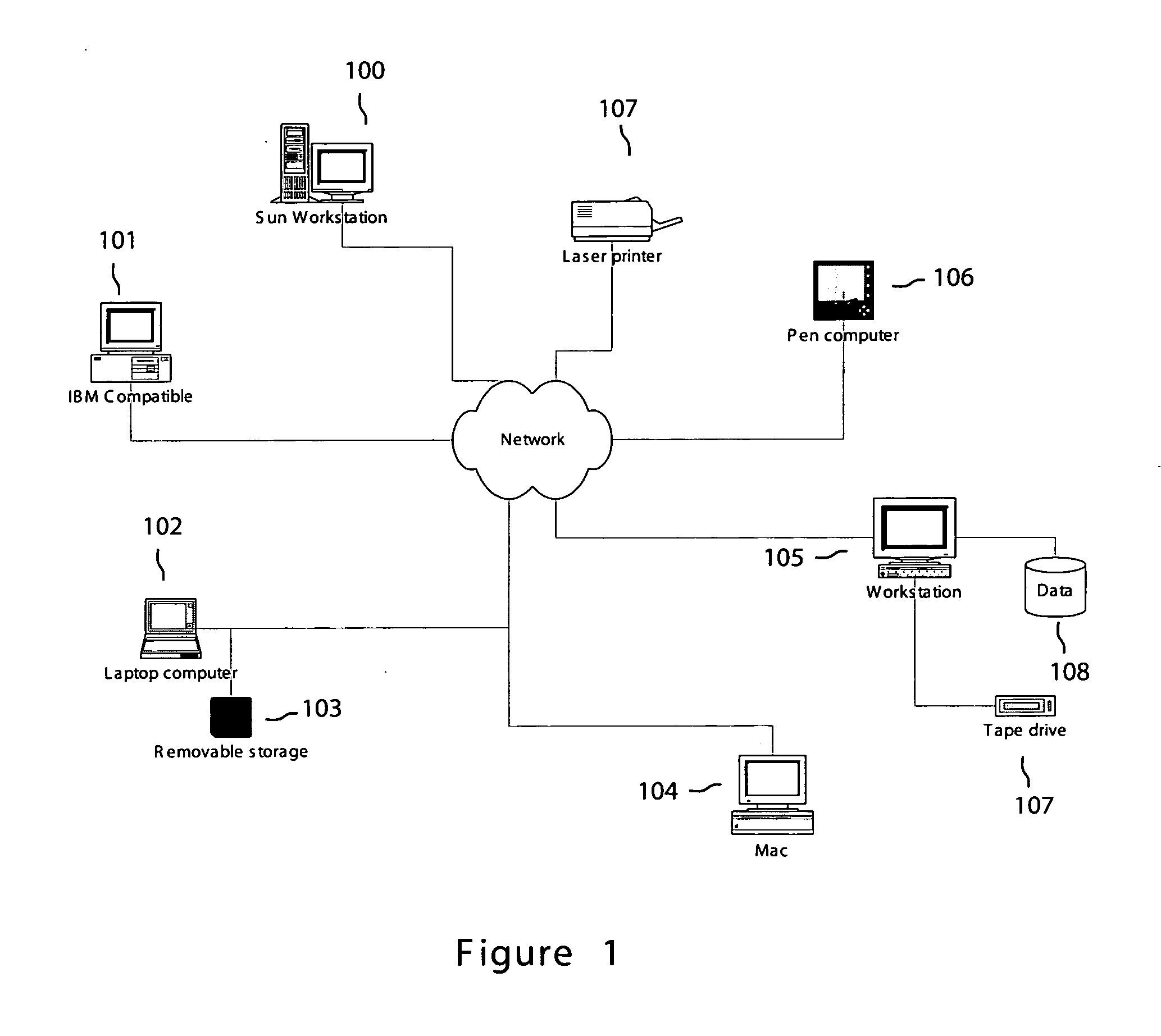
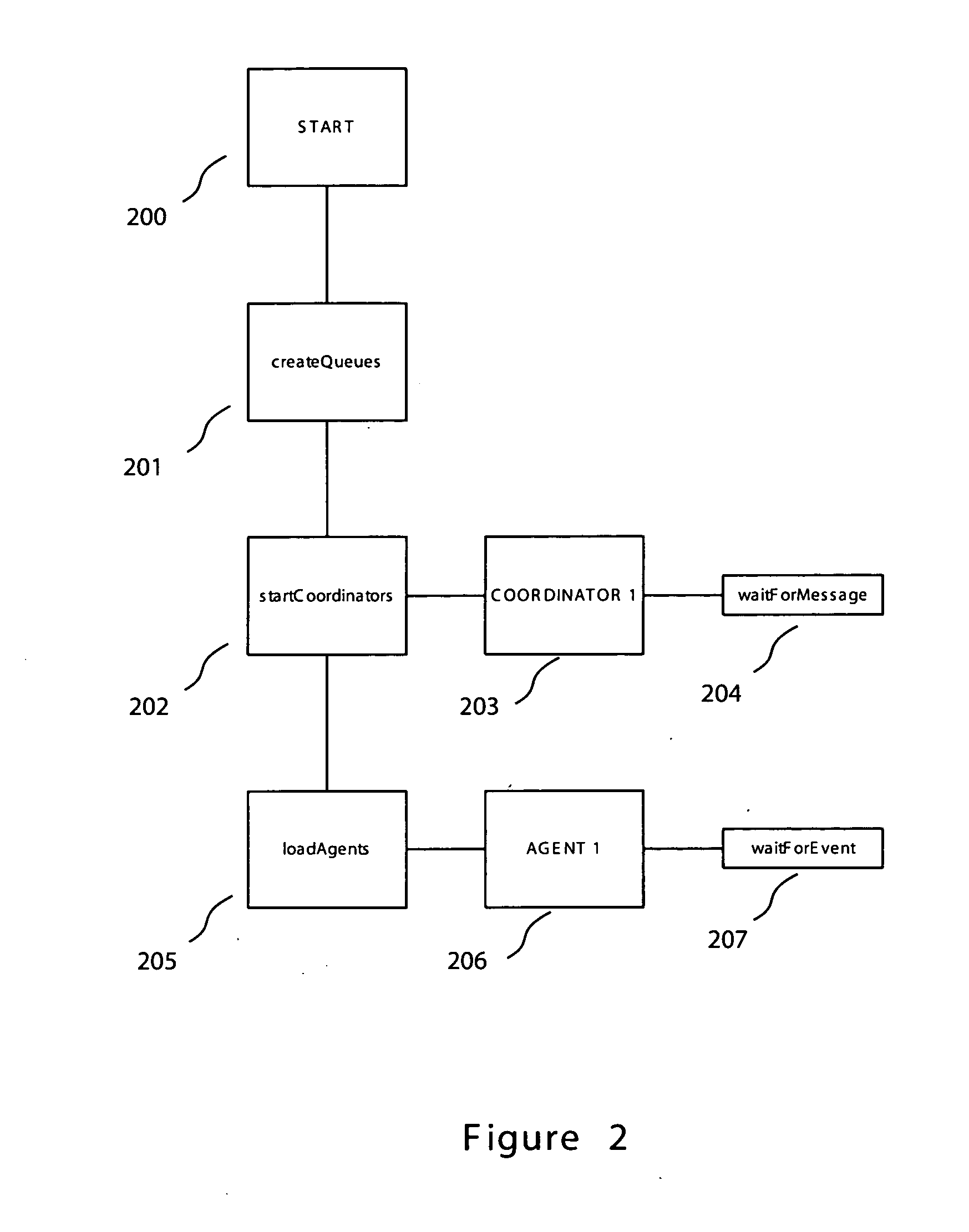
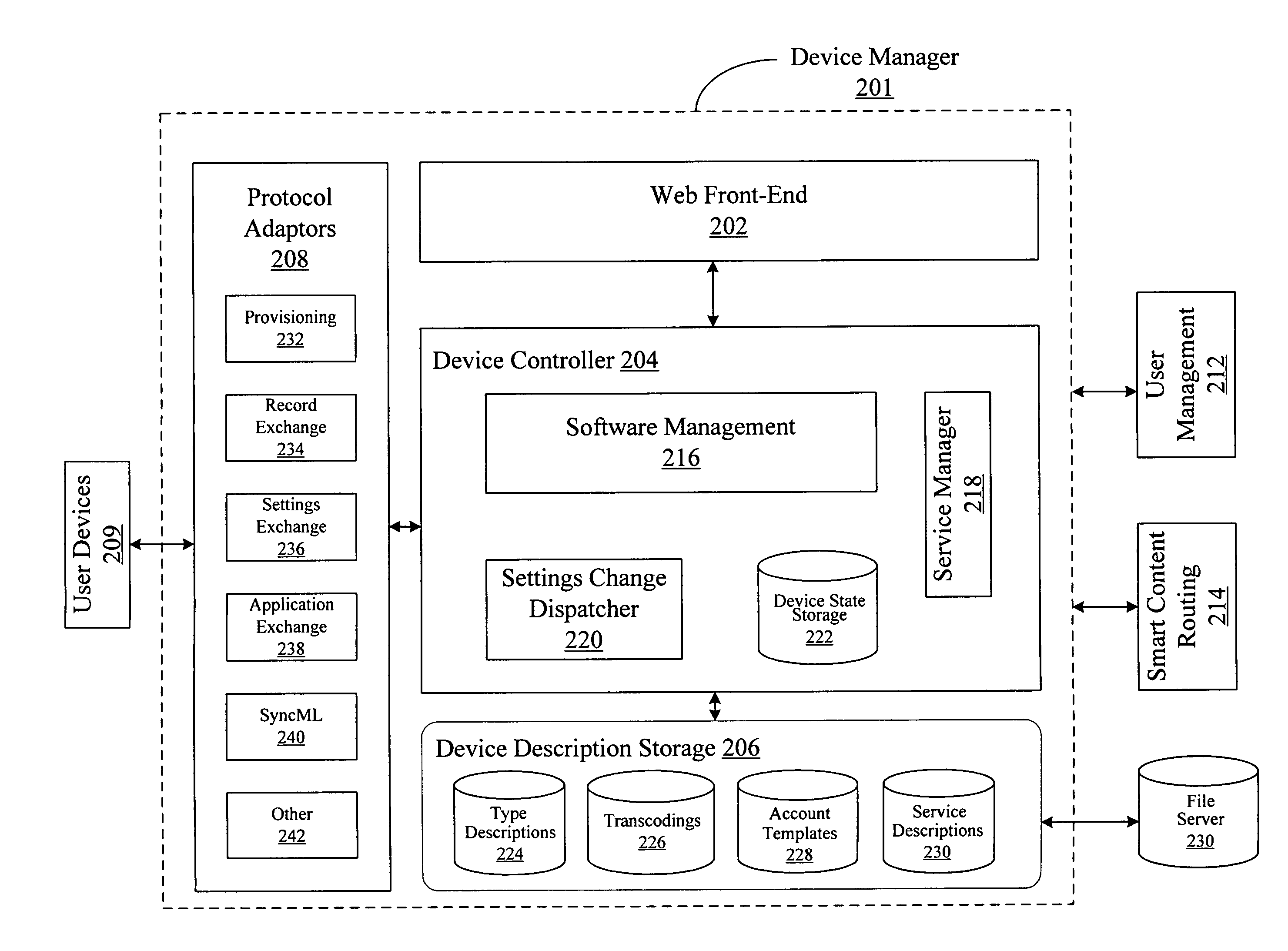
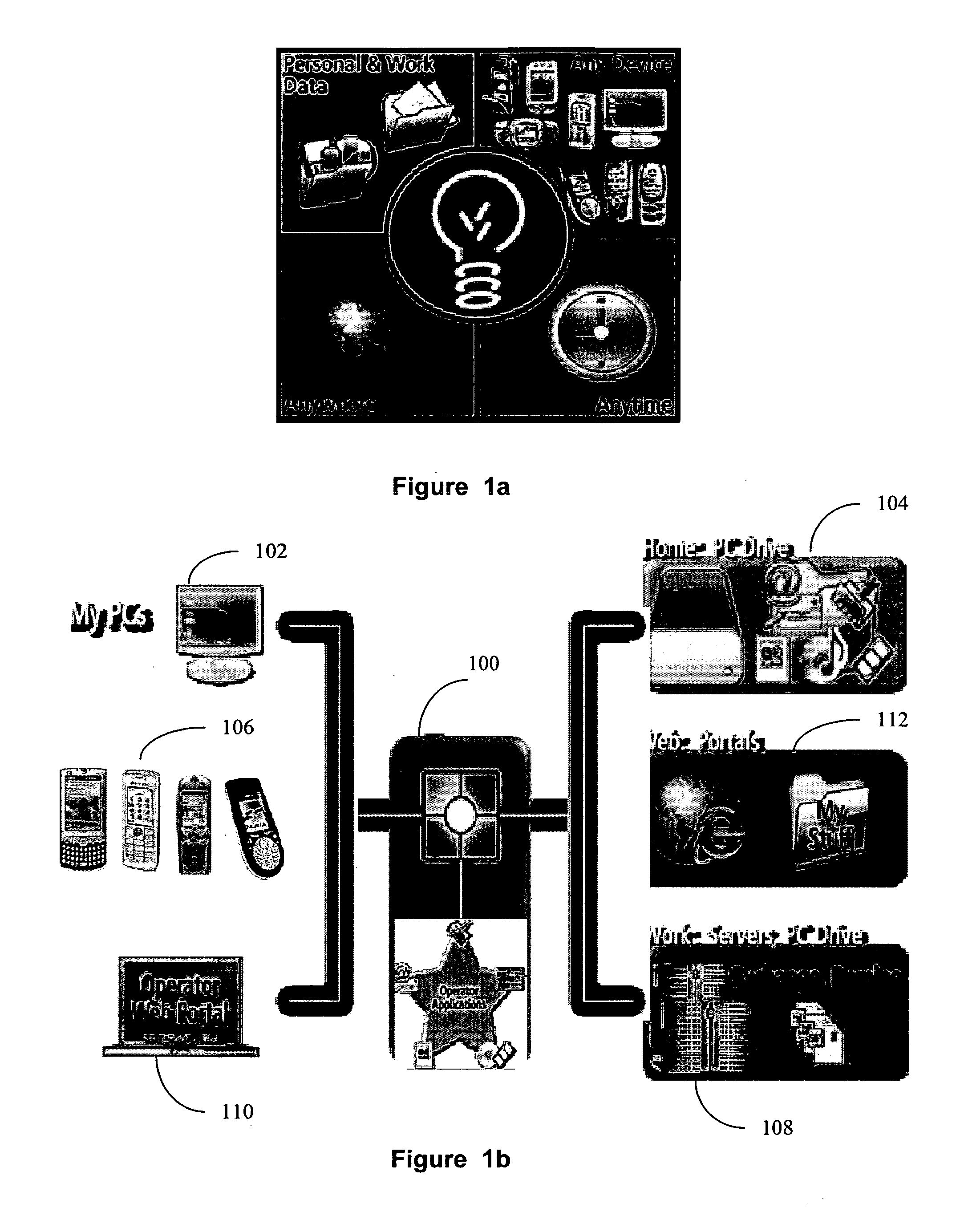
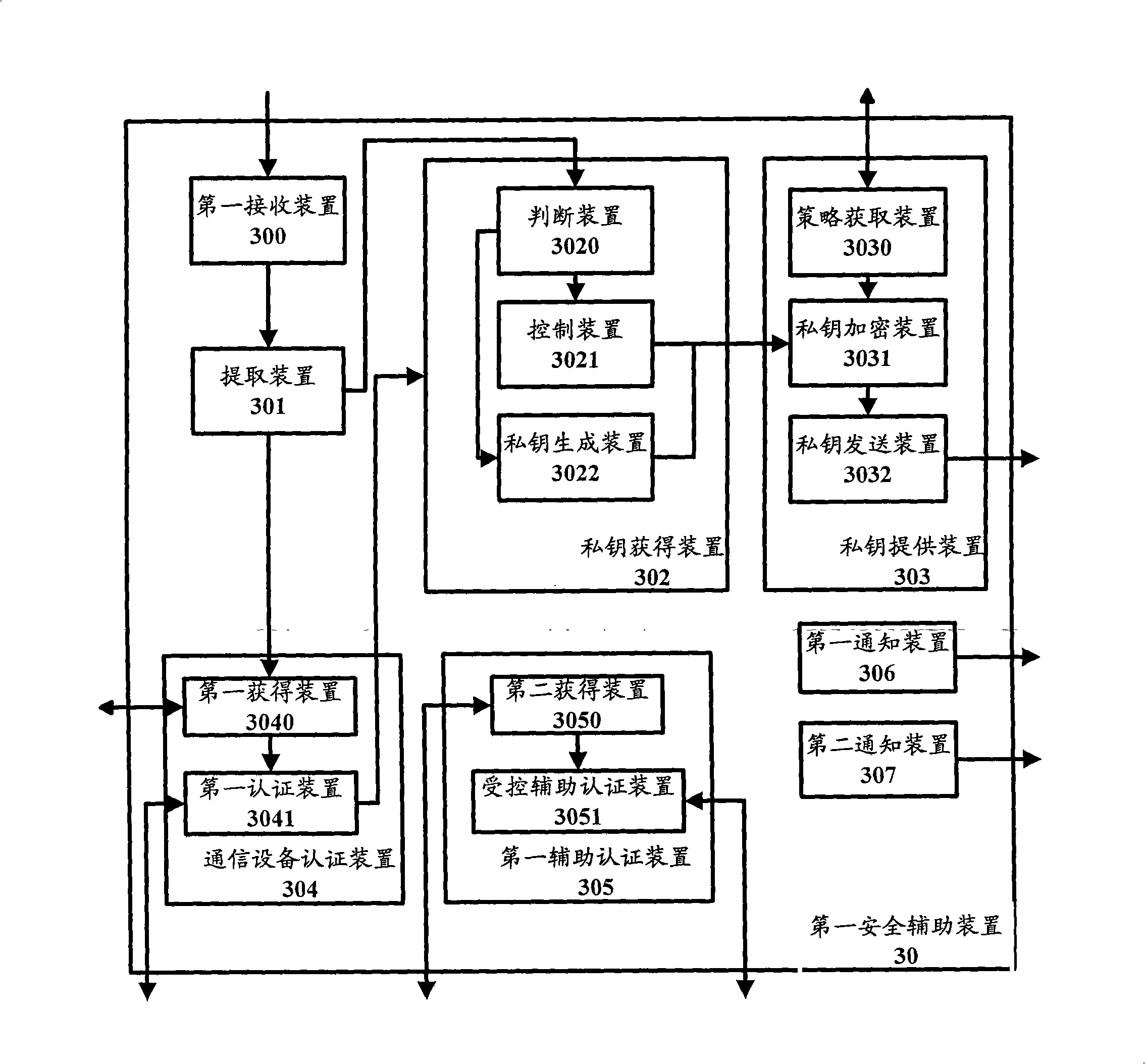
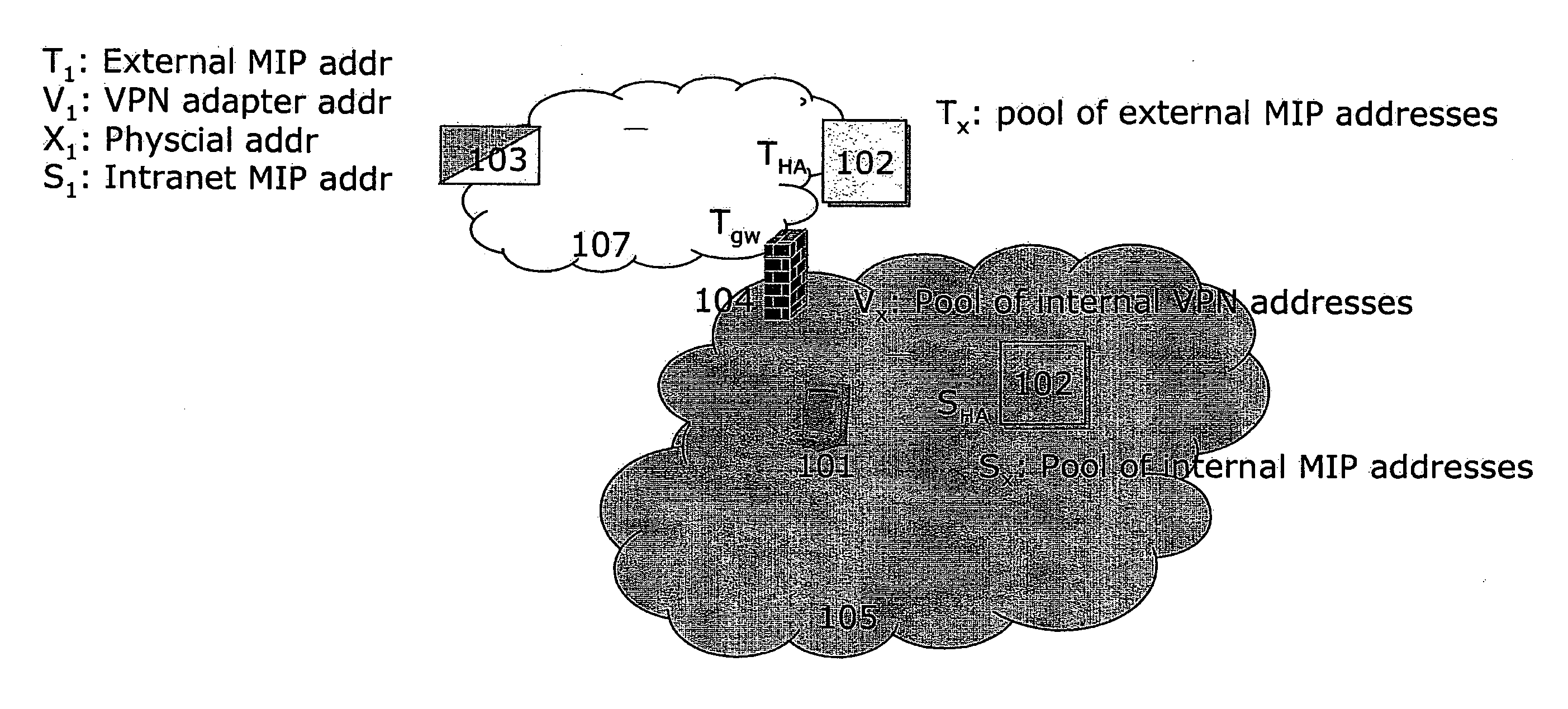
Patents
Literature
143 results about "Security solution" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
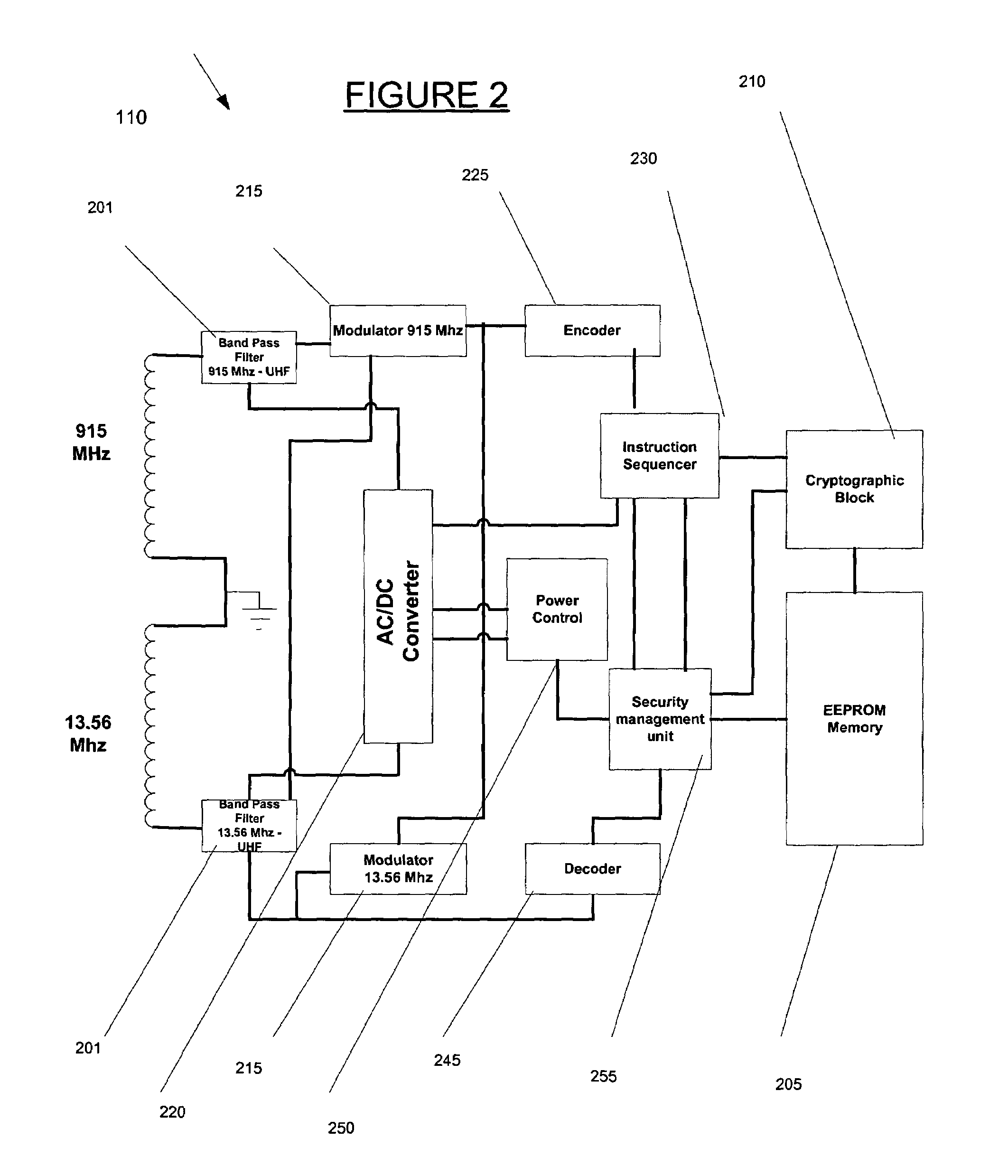
Modular approach for smart and customizable security solutions and other applications for a smart city
ActiveUS20170301220A1Inhibition of attachmentMechanical apparatusCharacter and pattern recognitionSecurity solutionUrban infrastructure
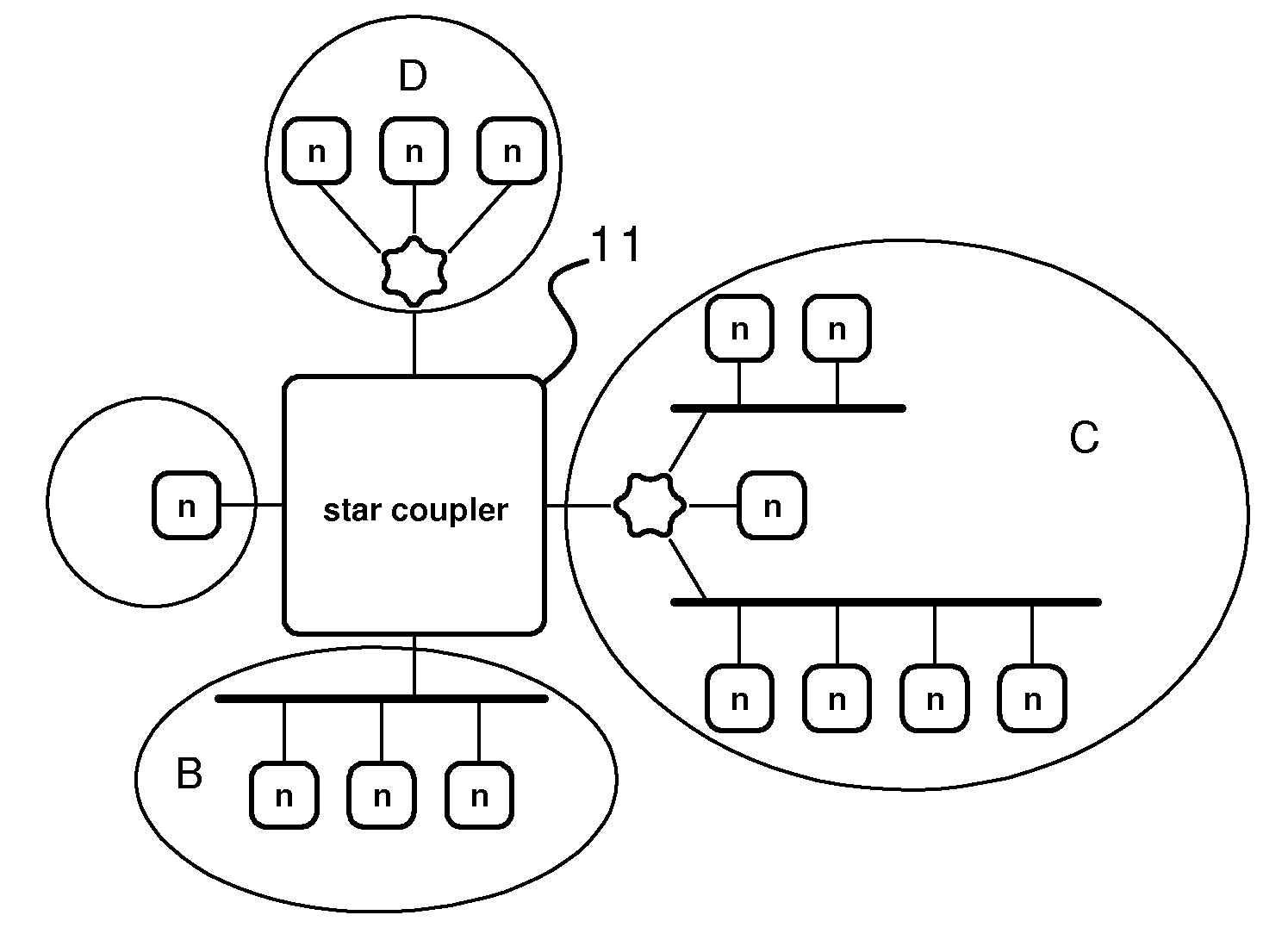
A modular approach is provided for sensing and responding to detected activity or an event in a region that can be implemented quickly and easily using existing city infrastructure to establish a grid of sensors and detectors to provide localized or wide area coverage. The approach provides a turnkey solution or smart city in a box that can be adapted to different situations and needs to provide communications functionality and / or a desired or customized functionality for a wide range of different applications.
Owner:NAVIO INT INC
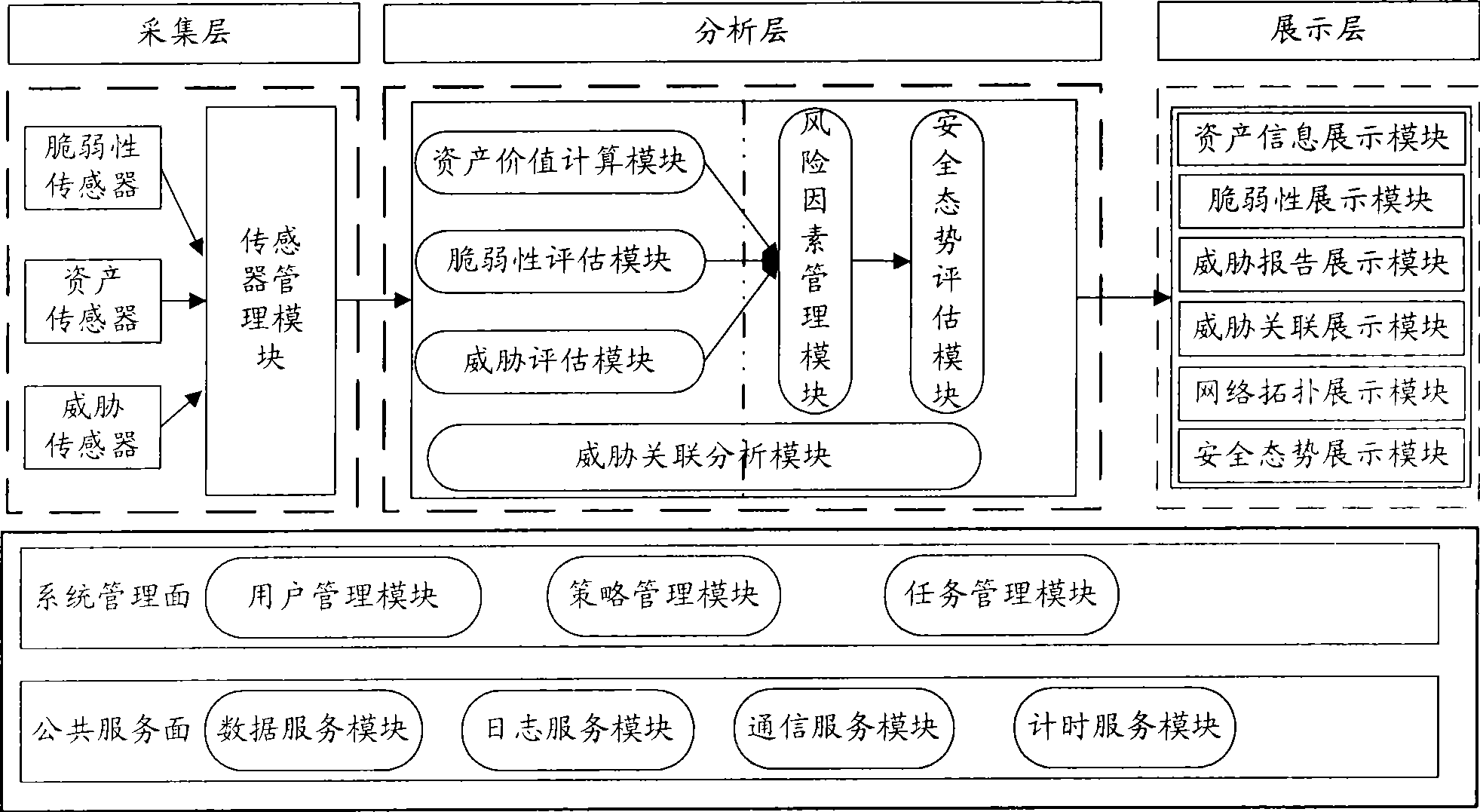
Method and system for evaluating network safety situation
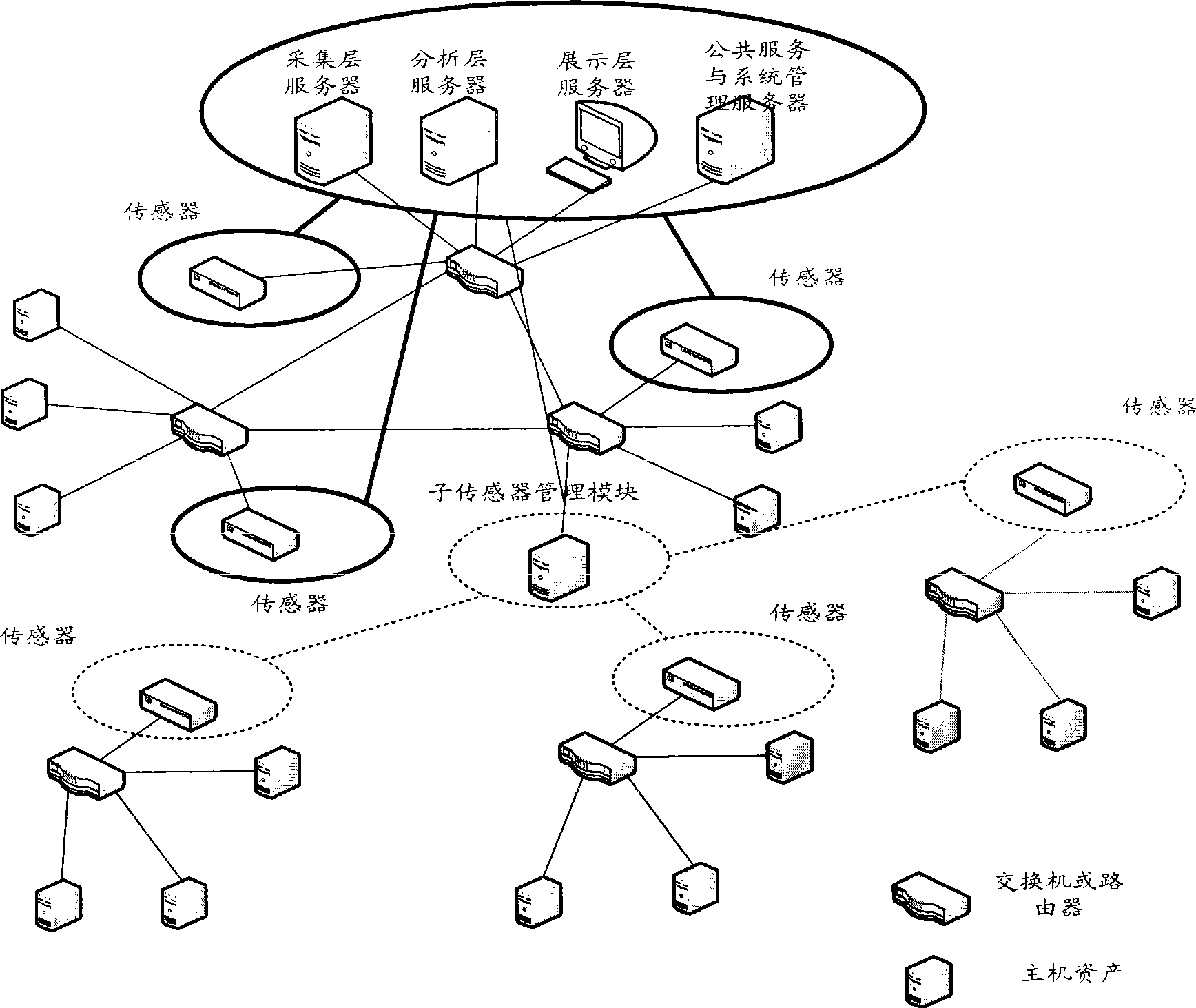
InactiveCN101436967AEasy to operateImprove securityData switching networksThree levelSecurity solution
The invention relates to a method for evaluating the security situation of a network and a system thereof. The system has a two-surface three-level framework and is provided with a public service surface and a service management surface for executing uniform coordinated management on each functional module of the system; according to a service logic processing flow, the system is divided into three levels: an acquisition level, an analysis level and an exhibition level for completing four evaluating operations of assets, frangibility, threat and security situation; the invention is based on the characteristic of service operation in the network, combines the prior risk evaluation method, the prior flow and the prior security detection tool and provides a set of a novel dynamic real-time evaluation method. The system can analyze the assets and service of the network and the risk of the whole network and carries out the evaluation of the security situation. The system can provide the security state of the whole network in macroscopy, can deepen to specific service and assets and know the specific security problem, thereby effectively helping network security personnel to analyze the root of the security problem and assisting to provide a security solution proposal and implement a defense measure.
Owner:BEIJING UNIV OF POSTS & TELECOMM
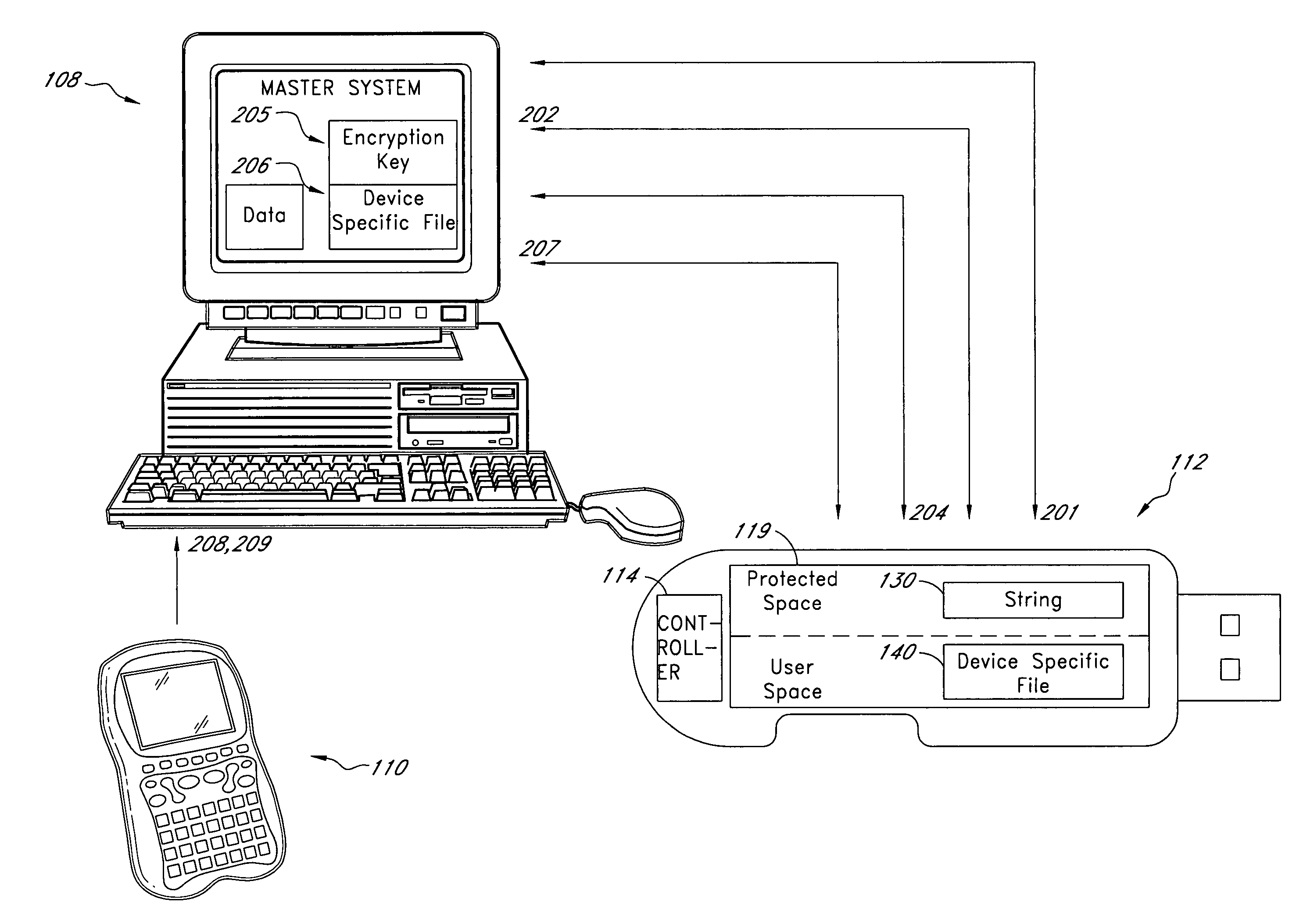
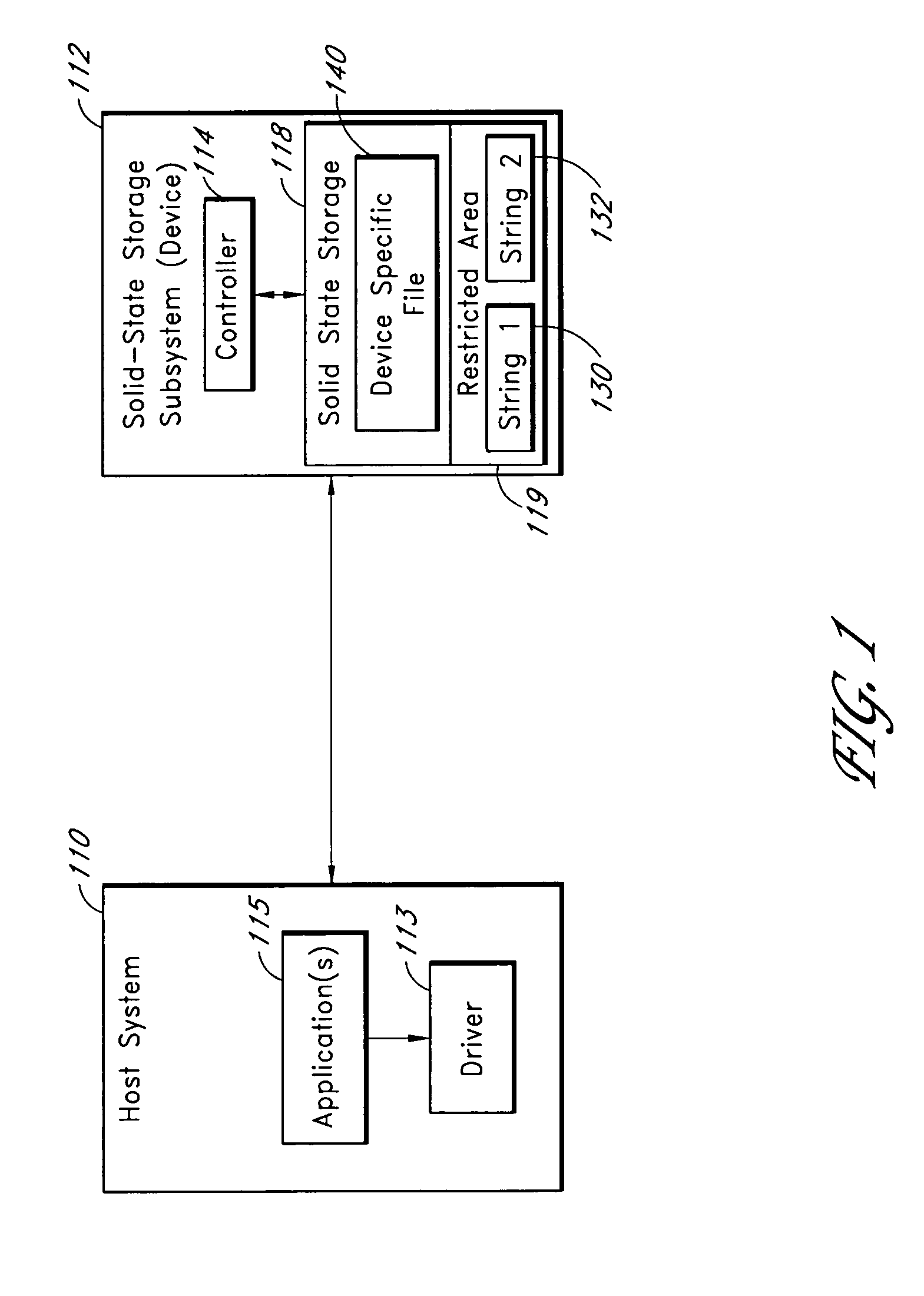
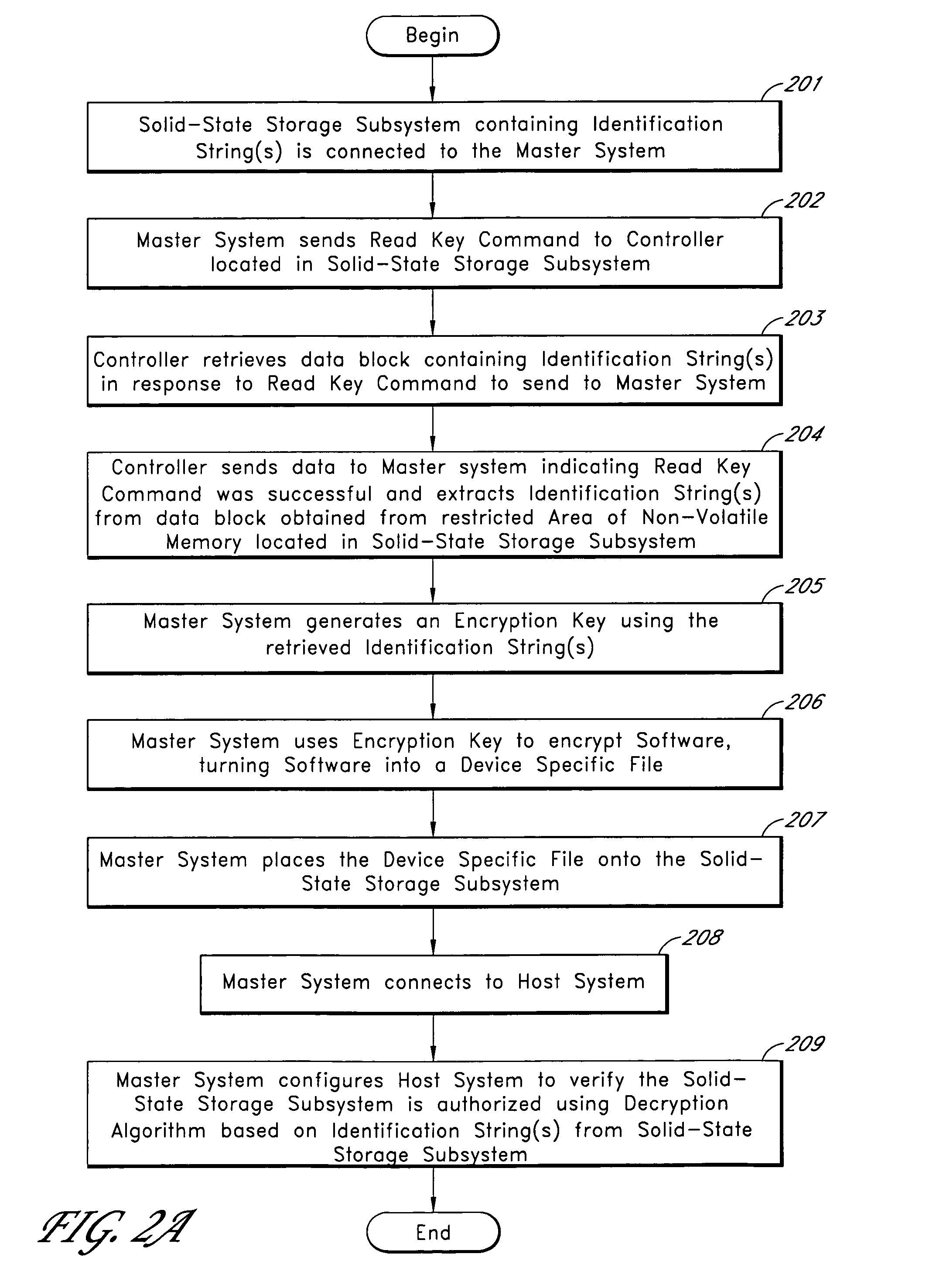
Solid-state storage subsystem security solution
ActiveUS8108692B1Unauthorized memory use protectionHardware monitoringSolid-state storageSecurity solution
A solid-state storage subsystem, such as a non-volatile memory card or drive, includes a main memory area that is accessible via standard memory access commands (such as ATA commands), and a restricted memory area that is accessible only via one or more non-standard commands. The restricted memory area stores information used to control access to, and / or use of, information stored in the main memory area. As one example, the restricted area may store one or more identifiers, such as a unique subsystem identifier, needed to decrypt an executable or data file stored in the main memory area. A host software component is configured to retrieve the information from the subsystem's restricted memory area, and to use the information to control access to and / or use of the information in the main memory area.
Owner:WESTERN DIGITAL TECH INC
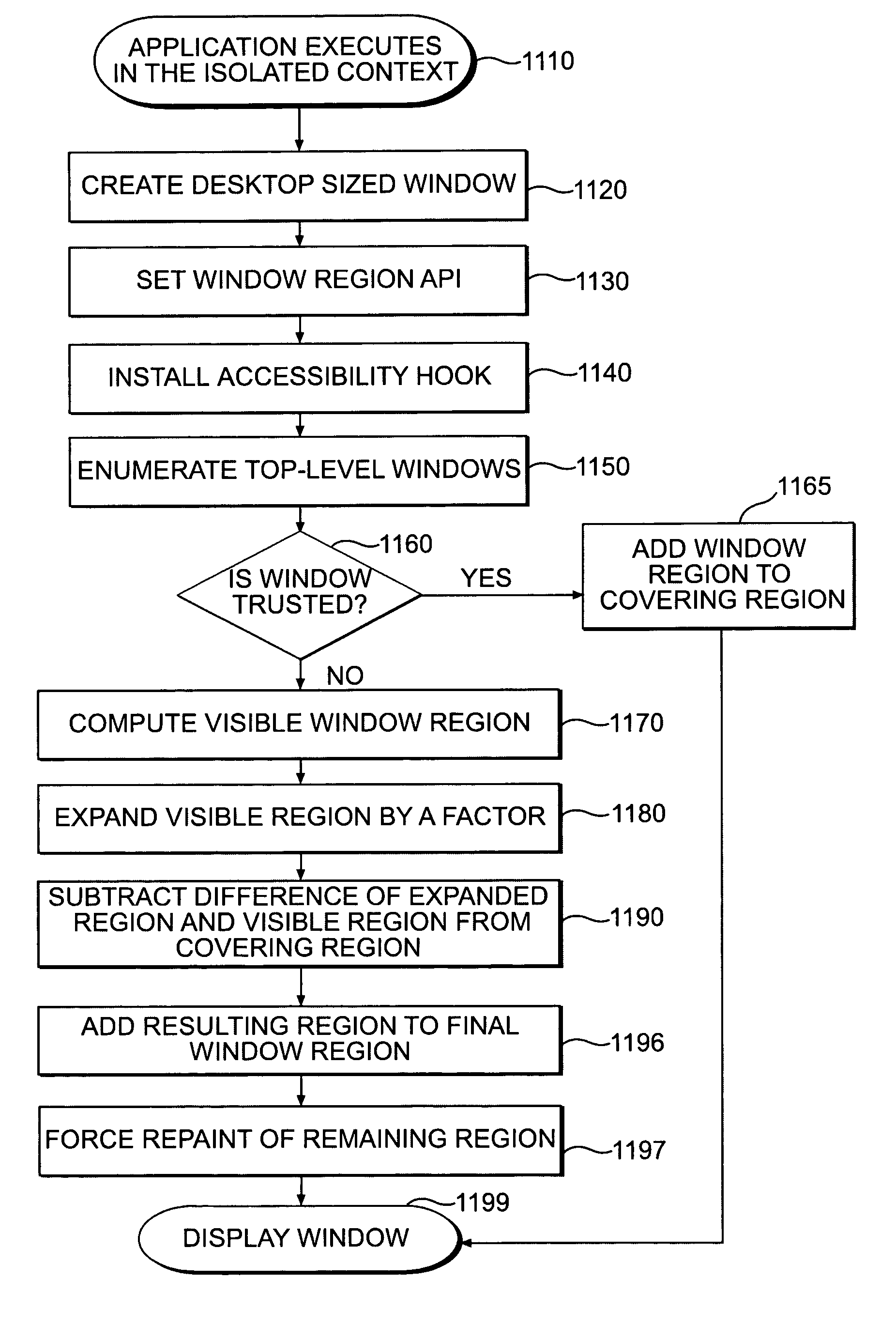
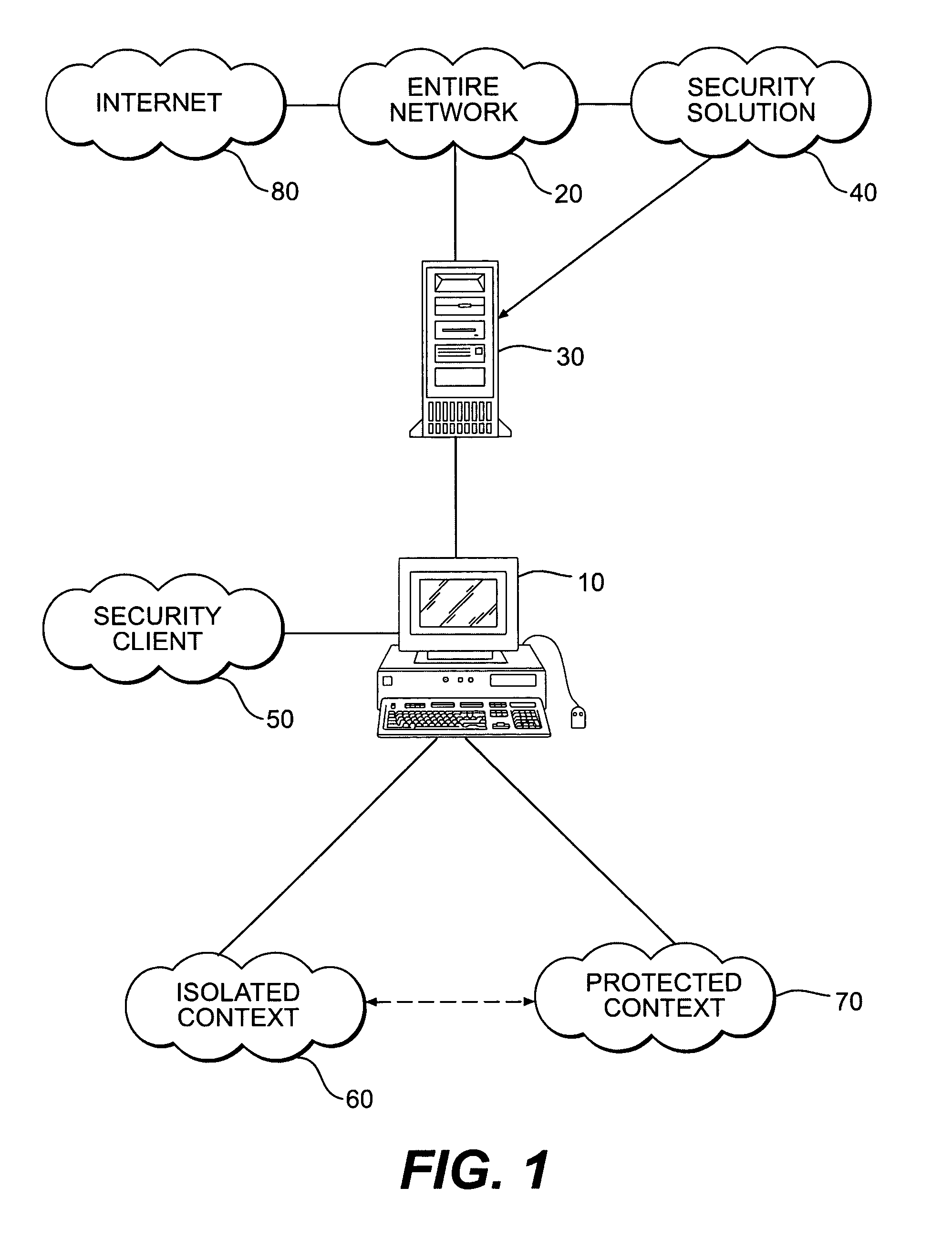
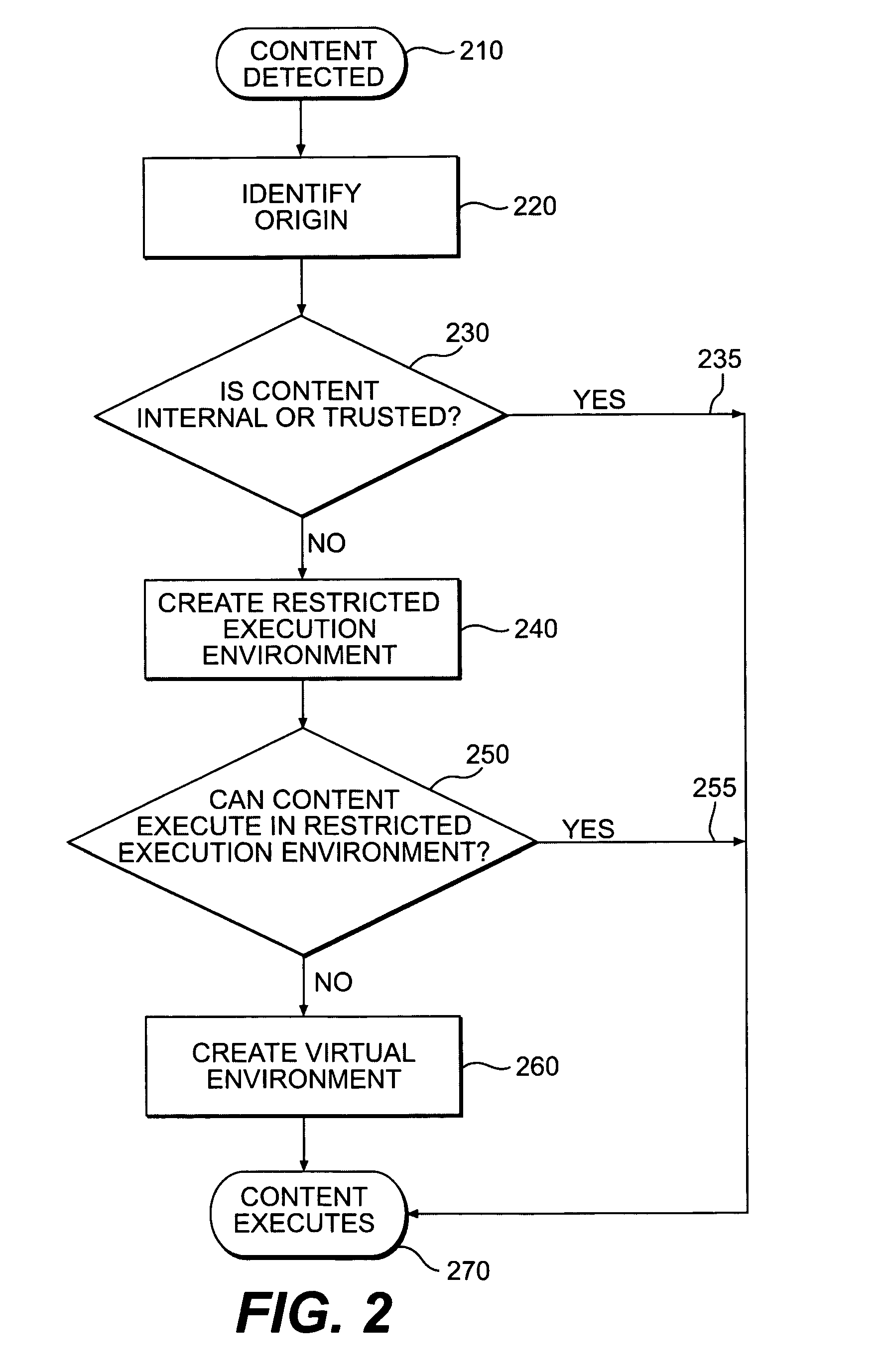
Systems and methods for secure client applications
ActiveUS7694328B2Minimize impactMinimal impactDigital data processing detailsUser identity/authority verificationSecurity solutionVirtualization
An innovative security solution which separates a client into a Protected Context, which is the real files and resources of the client, and an Isolated Context, which is a restricted execution environment which makes use of virtualized resources to execute applications and modify content in the Isolated Context, without allowing explicit access to the resources in the Protected Context. The solution further consolidates user interfaces to allow users to seamlessly work with content in both contexts, and provide a visual indication of which display windows are rendered from content executed in the Isolated Context.
Owner:GOOGLE LLC
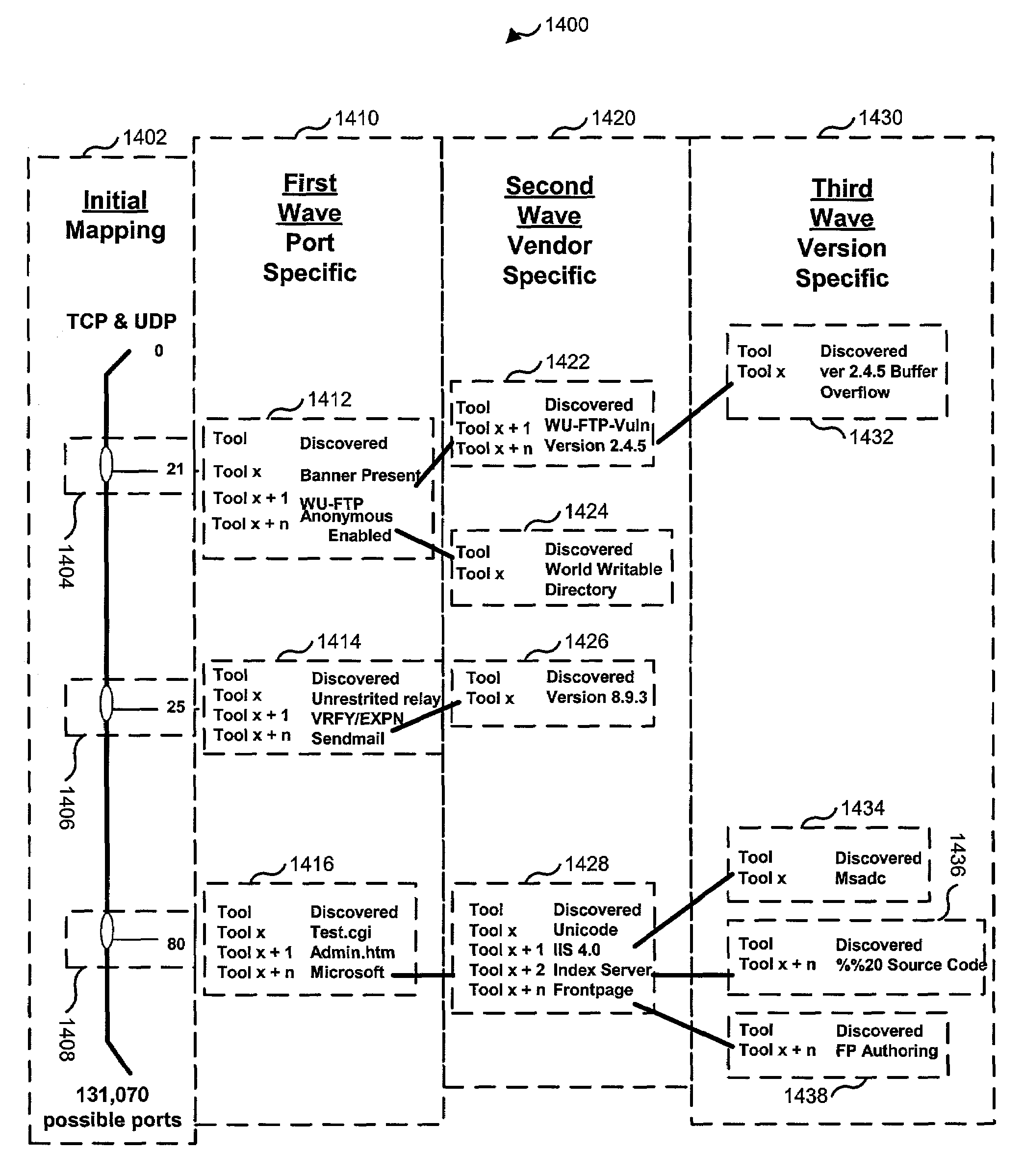
Network security testing
ActiveUS7325252B2Improve viewing effectShort working hoursMemory loss protectionError detection/correctionSecurity solutionWork period
To answer the security needs of the market, a preferred embodiment was developed. A preferred embodiment provides real-time network security vulnerability assessment tests, possibly complete with recommended security solutions. External vulnerability assessment tests can emulate hacker methodology in a safe way and enable study of a network for security openings, thereby gaining a true view of risk level without affecting customer operations. Because this assessment can be performed over the Internet, both domestic and worldwide corporations benefit. A preferred embodiment's physical subsystems combine to form a scalable holistic system that can be able to conduct tests for thousands of customers any place in the world. The security skills of experts can be embedded into a preferred embodiment systems and automated the test process to enable the security vulnerability test to be conducted on a continuous basis for multiple customers at the same time. A preferred embodiment can reduce the work time required for security practices of companies from three weeks to less than a day, as well as significantly increase their capacity. Component subsystems typically include a Database, Command Engine, Gateway, multiple Testers, Report Generator, and an RMCT.
Owner:ALERT LOGIC
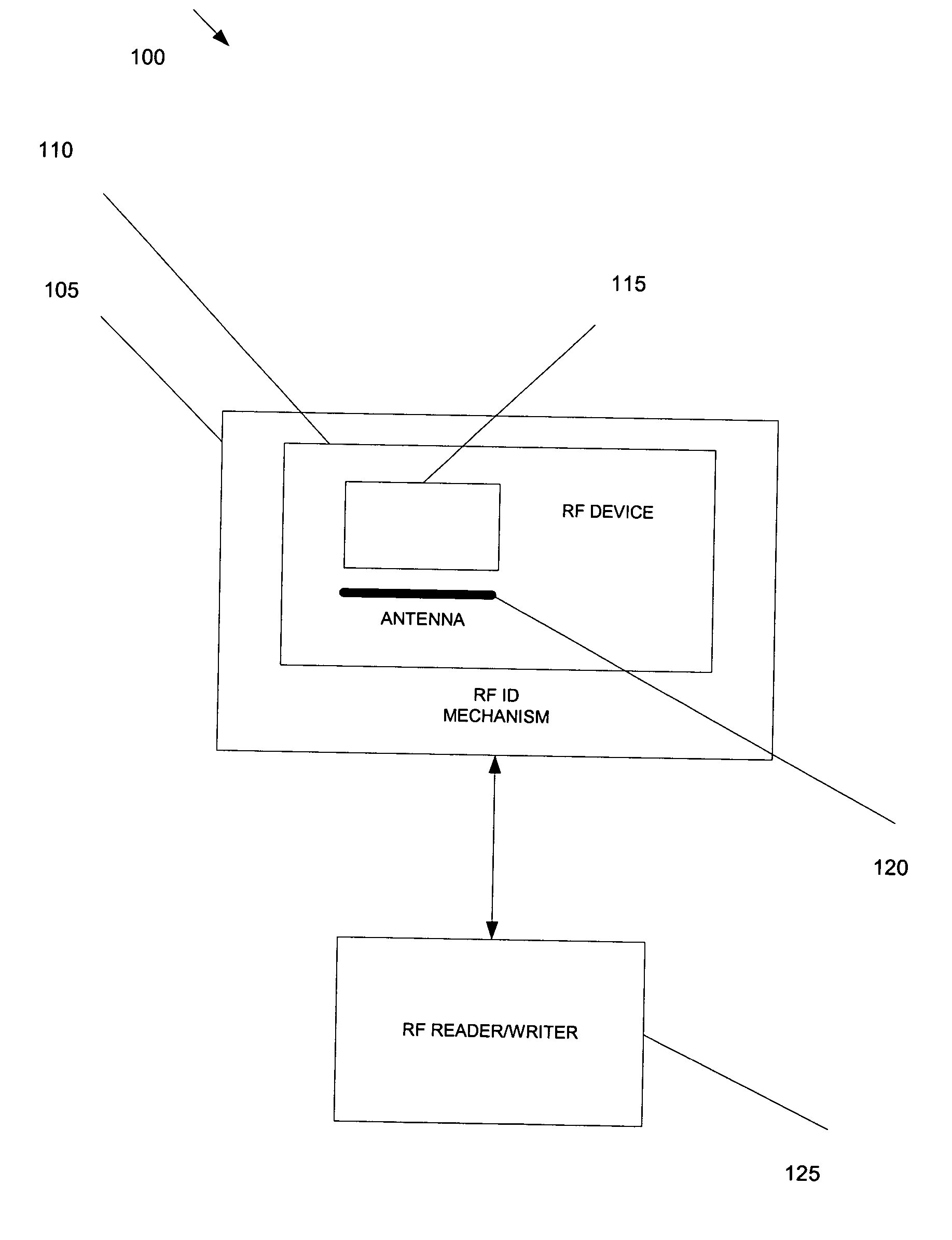
System and method for providing secure identification solutions
InactiveUS20040066273A1Electric signal transmission systemsConveying record carriersSecurity solutionIdentification device
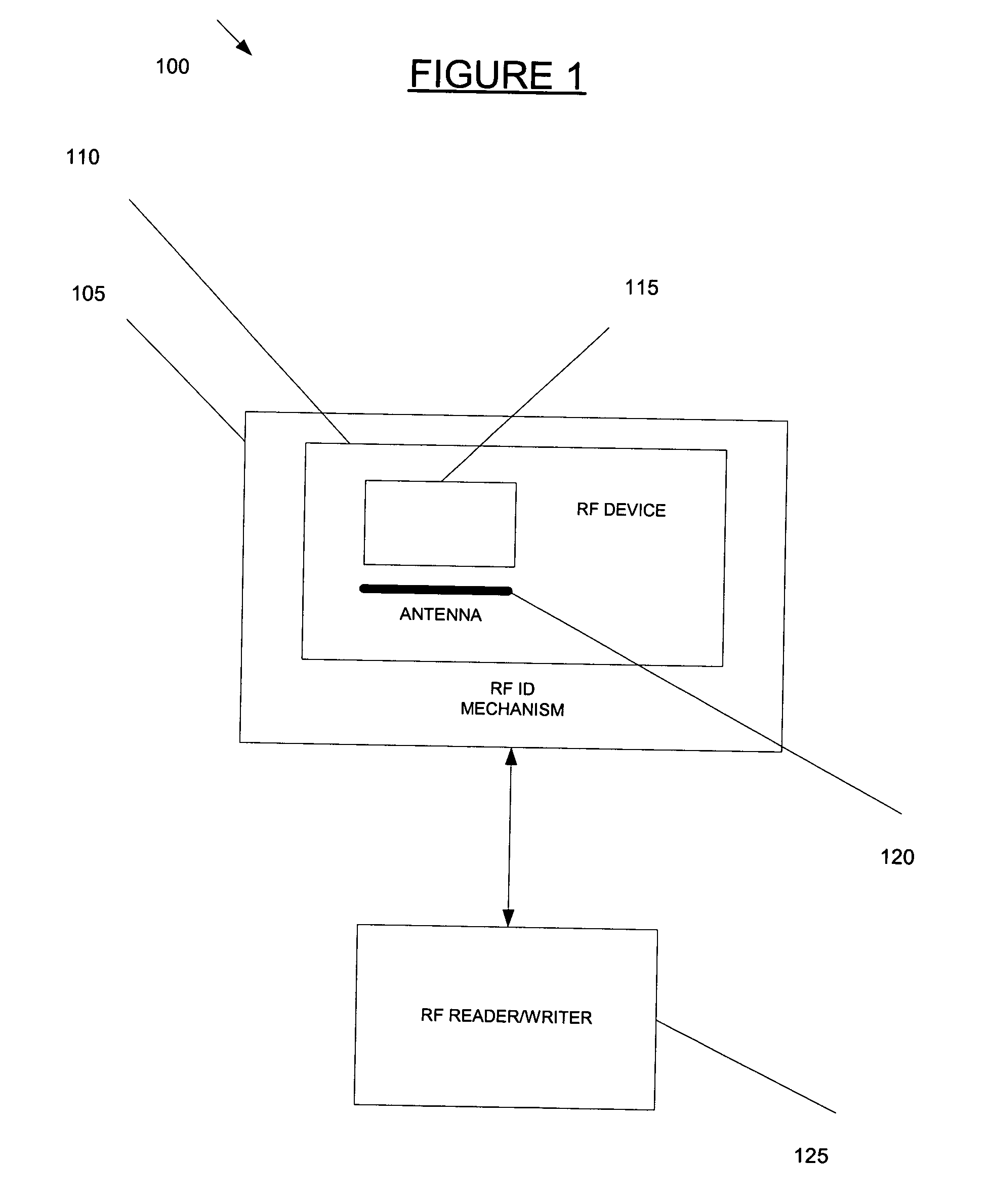
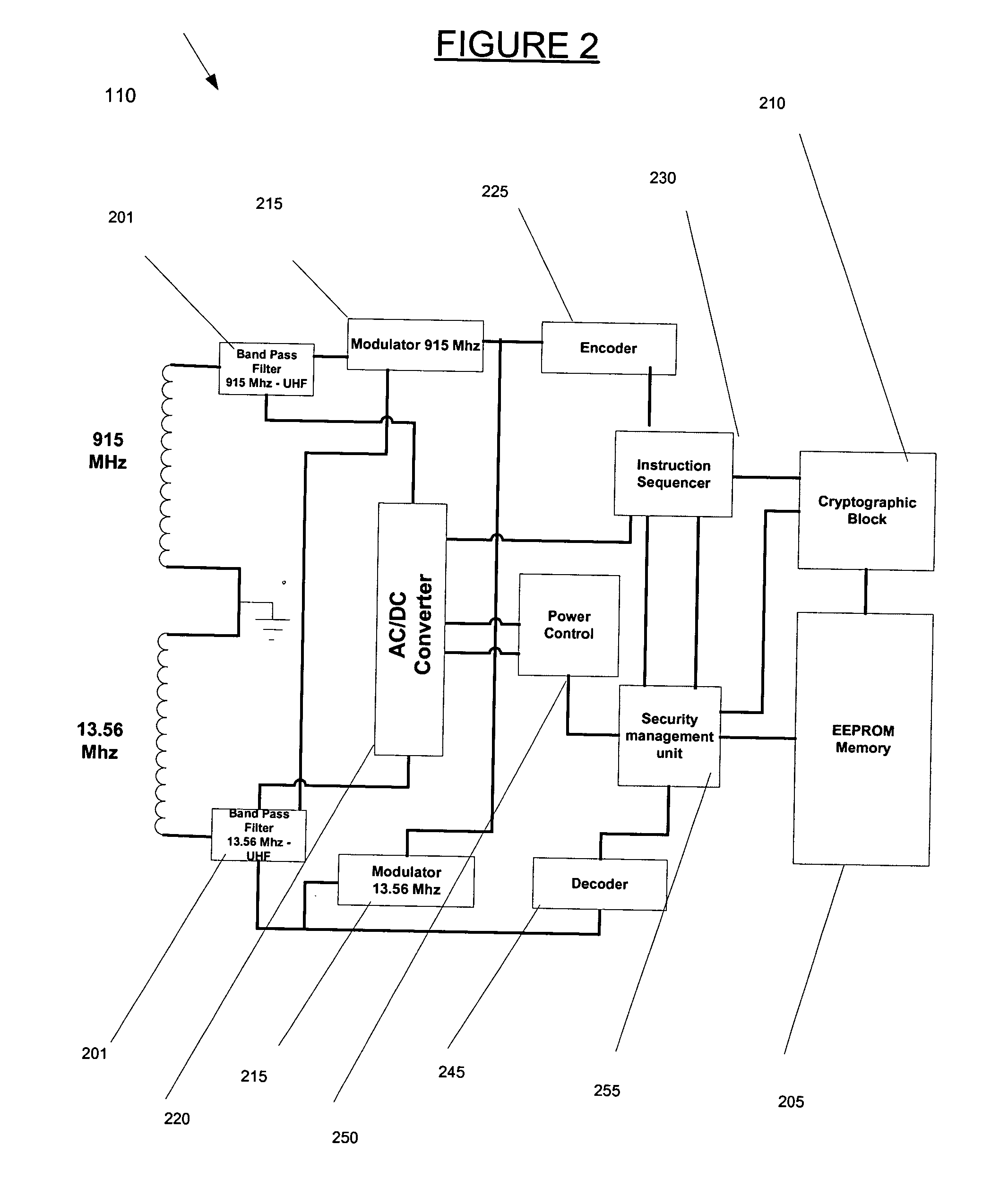
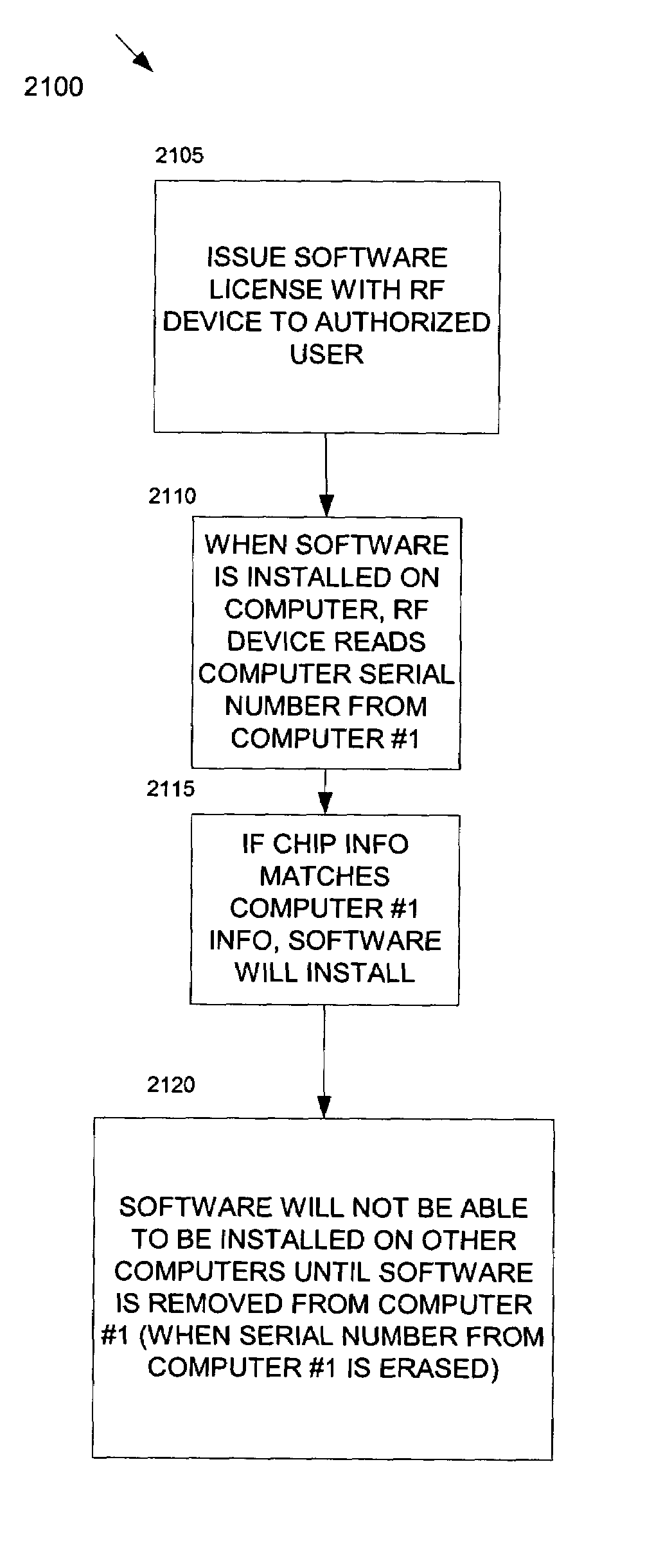
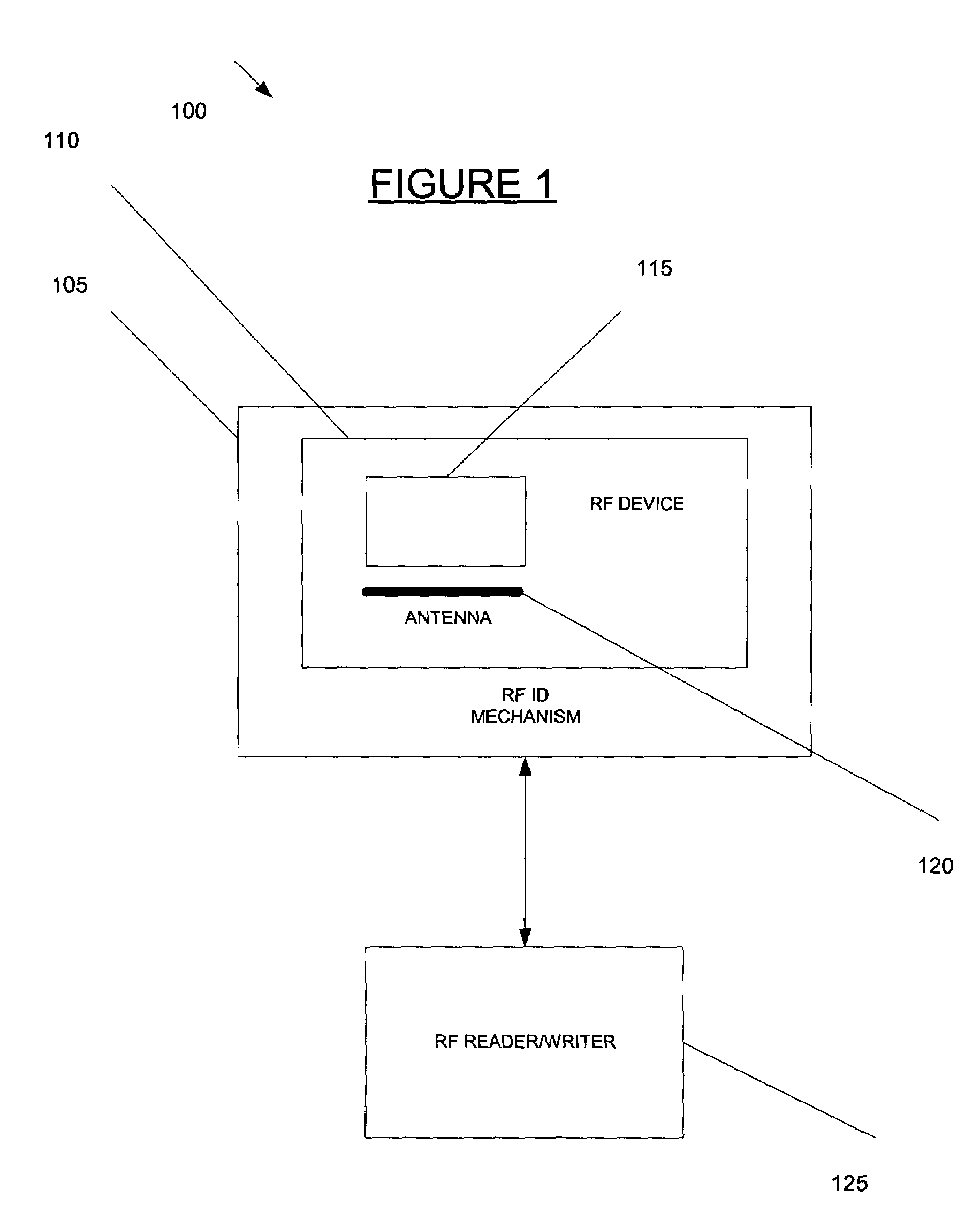
The present invention provides a method and system for verifying and tracking identification information. In an embodiment of the invention, a system for delivering security solutions is provided that includes at least one of the following: a radio frequency (RF) identification device, an identification mechanism (e.g., a card, sticker), and an RF reader.
Owner:NEOLOGY INC
System and method for providing secure identification solutions
InactiveUS7081819B2Cryptography processingMemory record carrier reading problemsSecurity solutionIdentification device
The present invention provides a method and system for verifying and tracking identification information. In an embodiment of the invention, a system for delivering security solutions is provided that includes at least one of the following: a radio frequency (RF) identification device, an identification mechanism (e.g., a card, sticker), and an RF reader.
Owner:NEOLOGY INC
Deriving security and privacy solutions to mitigate risk
InactiveUS20050080720A1Reduce security risksFinanceSpecial data processing applicationsSecurity solutionDecision maker
Techniques are disclosed for systematically assessing an enterprise's security risks in view of a set of security patterns. Each pattern that is applicable to the enterprise's operation is then considered against the backdrop of a set of common attributes that are used, in turn, to further distinguish each pattern from a risk and security solution perspective. Using the disclosed techniques, specific security risks can be identified and appropriate security products can be selected to address those risks in a systematic manner, thereby assisting information technology decision makers across a wide variety of enterprises in deriving security solutions. These security solutions will typically be more effective and efficient from a functional perspective, as well as being more cost-effective, than security solutions created using prior art ad hoc approaches. The disclosed techniques may also be leveraged to create a requirements list for function to be included in a security product.
Owner:IBM CORP
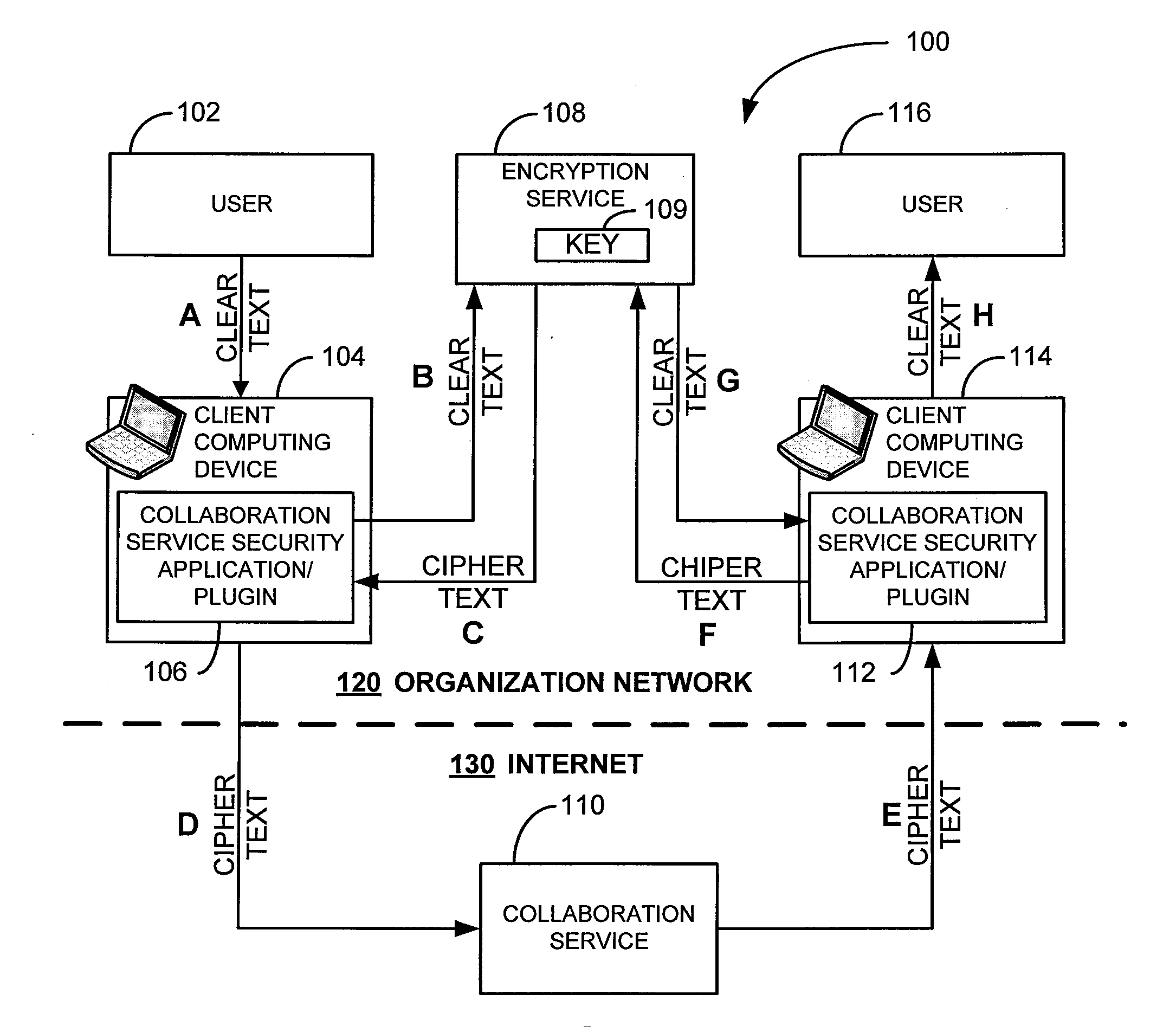
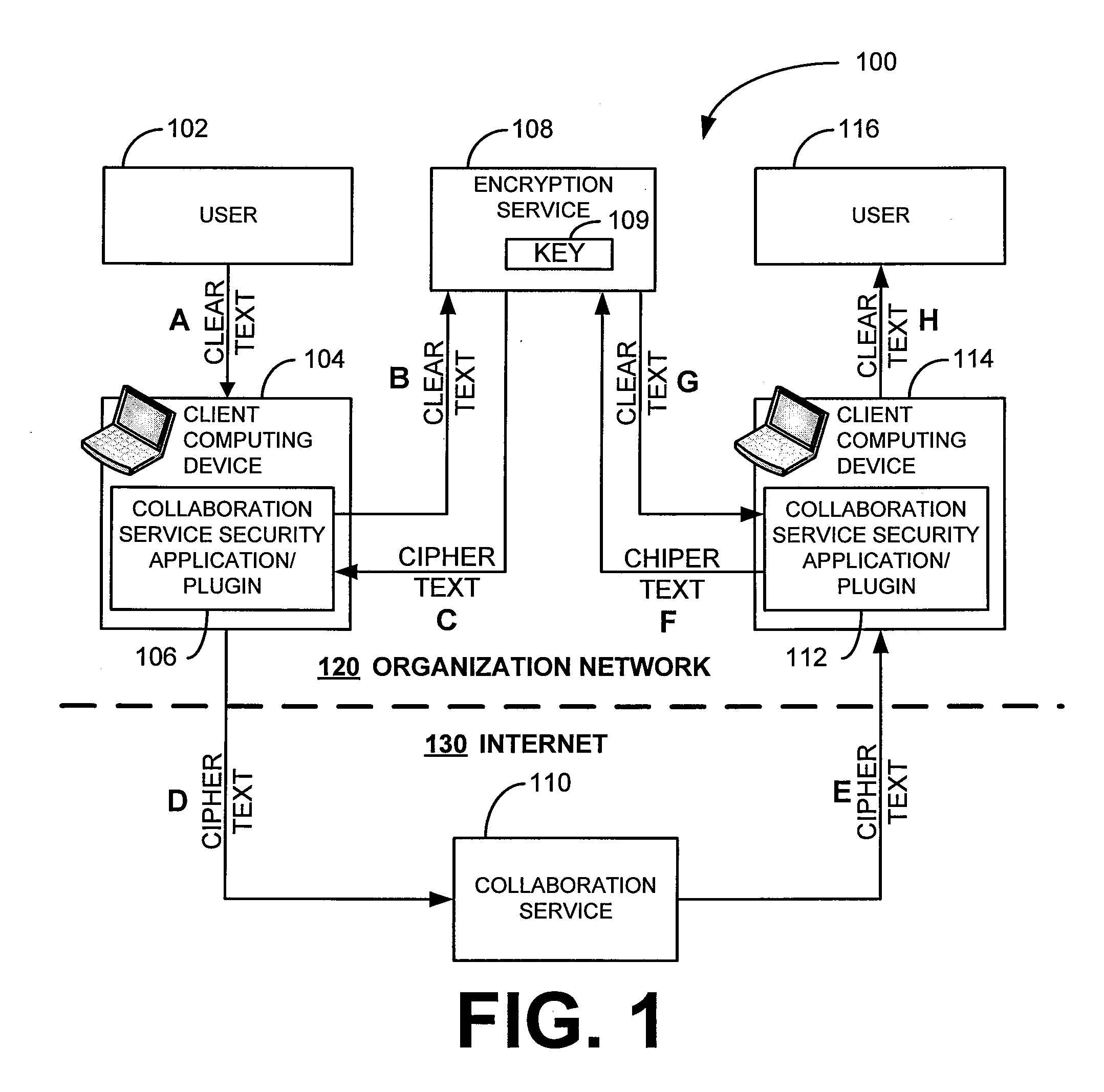
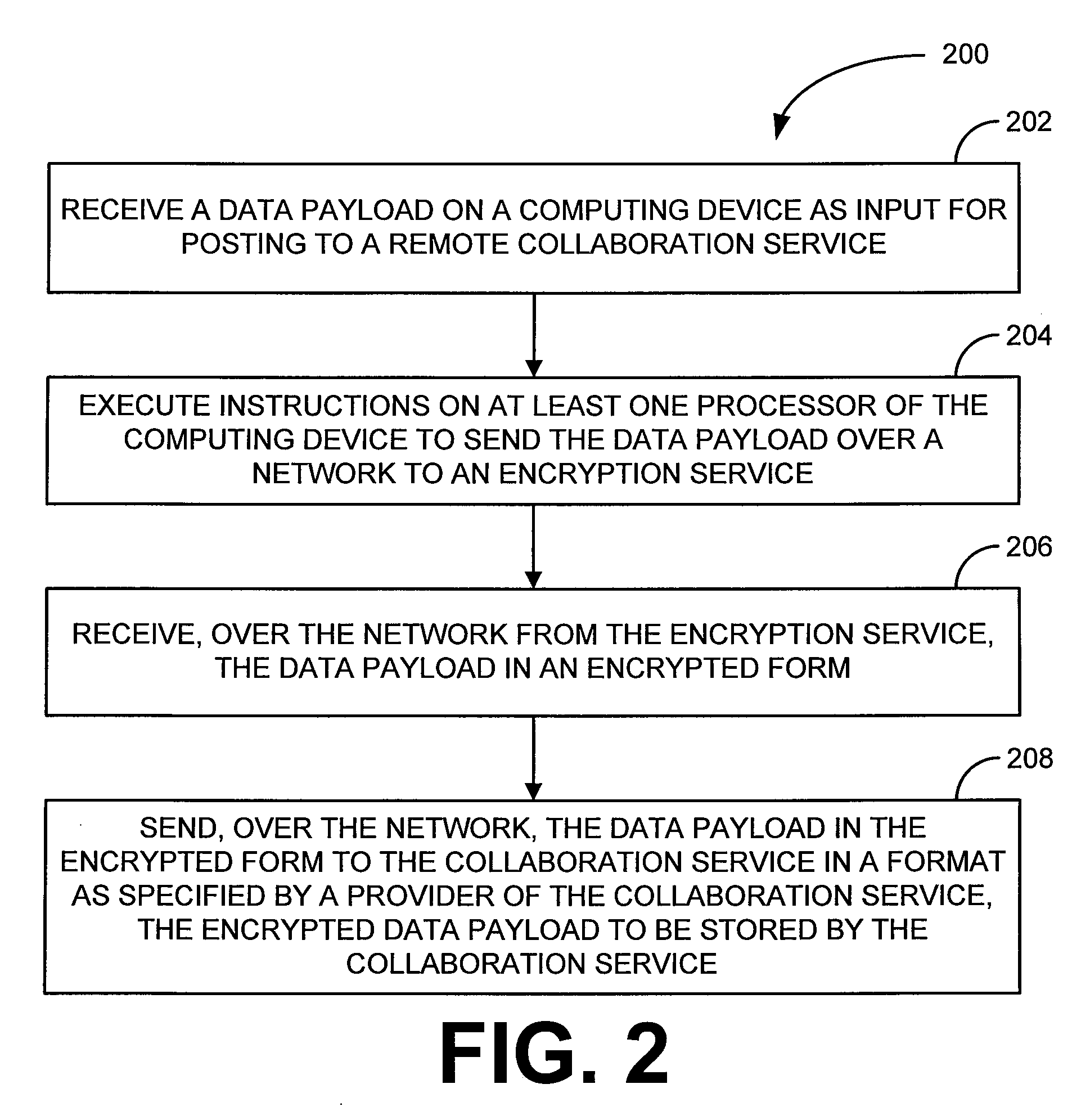
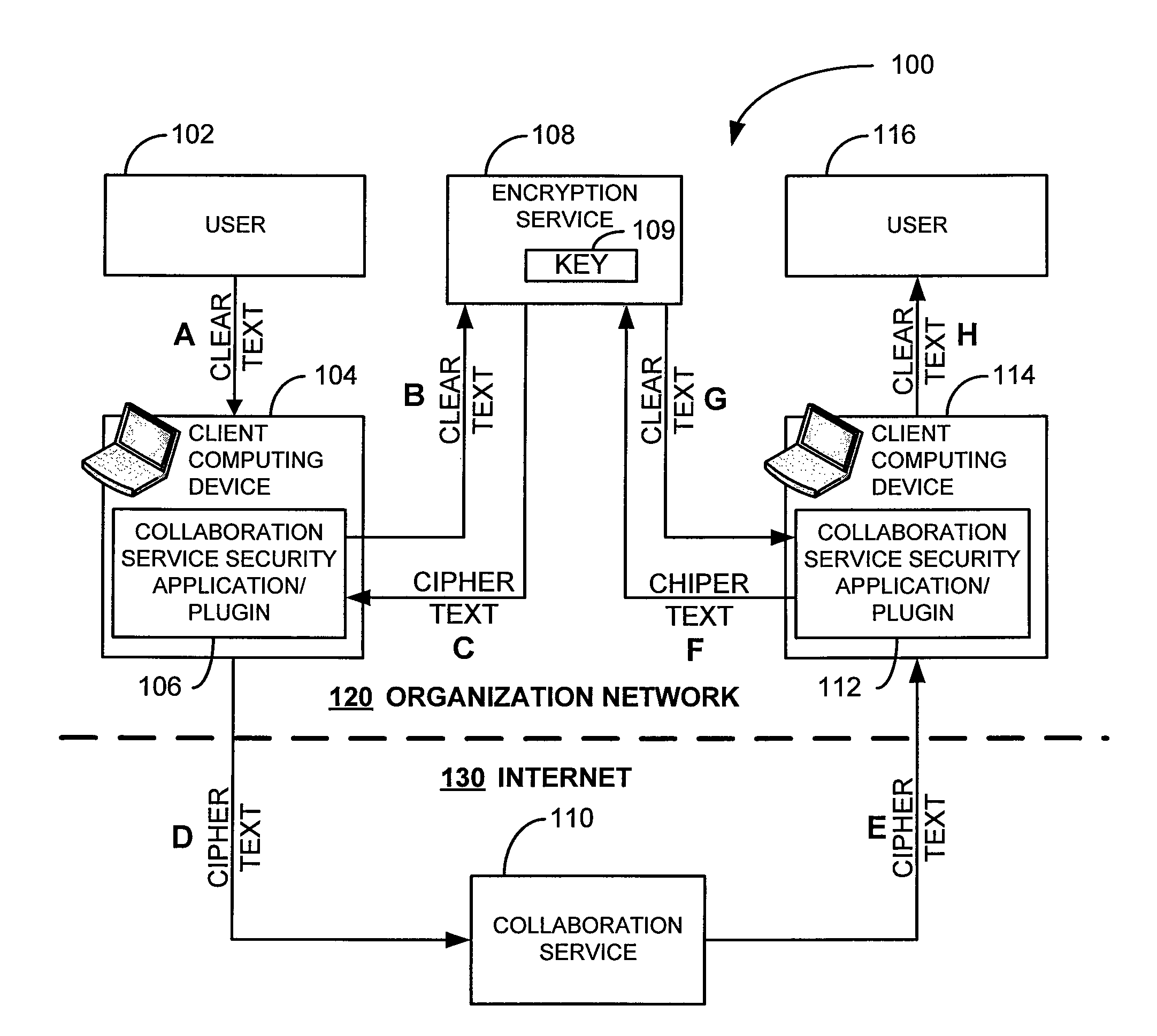
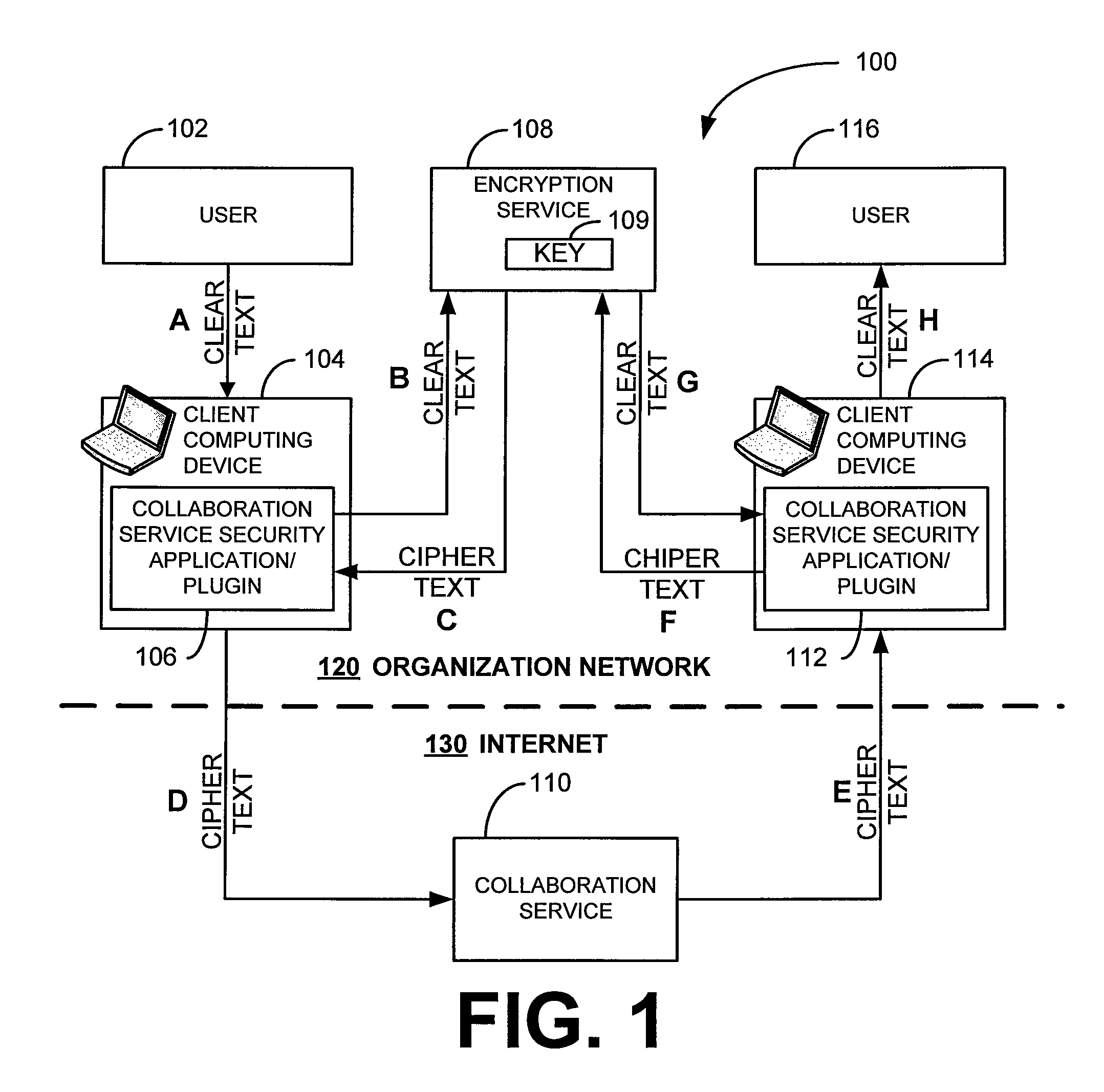
Security for collaboration services
ActiveUS20110145571A1Key distribution for secure communicationUser identity/authority verificationSecurity solutionApplication software
Owner:SAP AG
Security for collaboration services
ActiveUS8572369B2Key distribution for secure communicationUser identity/authority verificationSecurity solutionApplication software
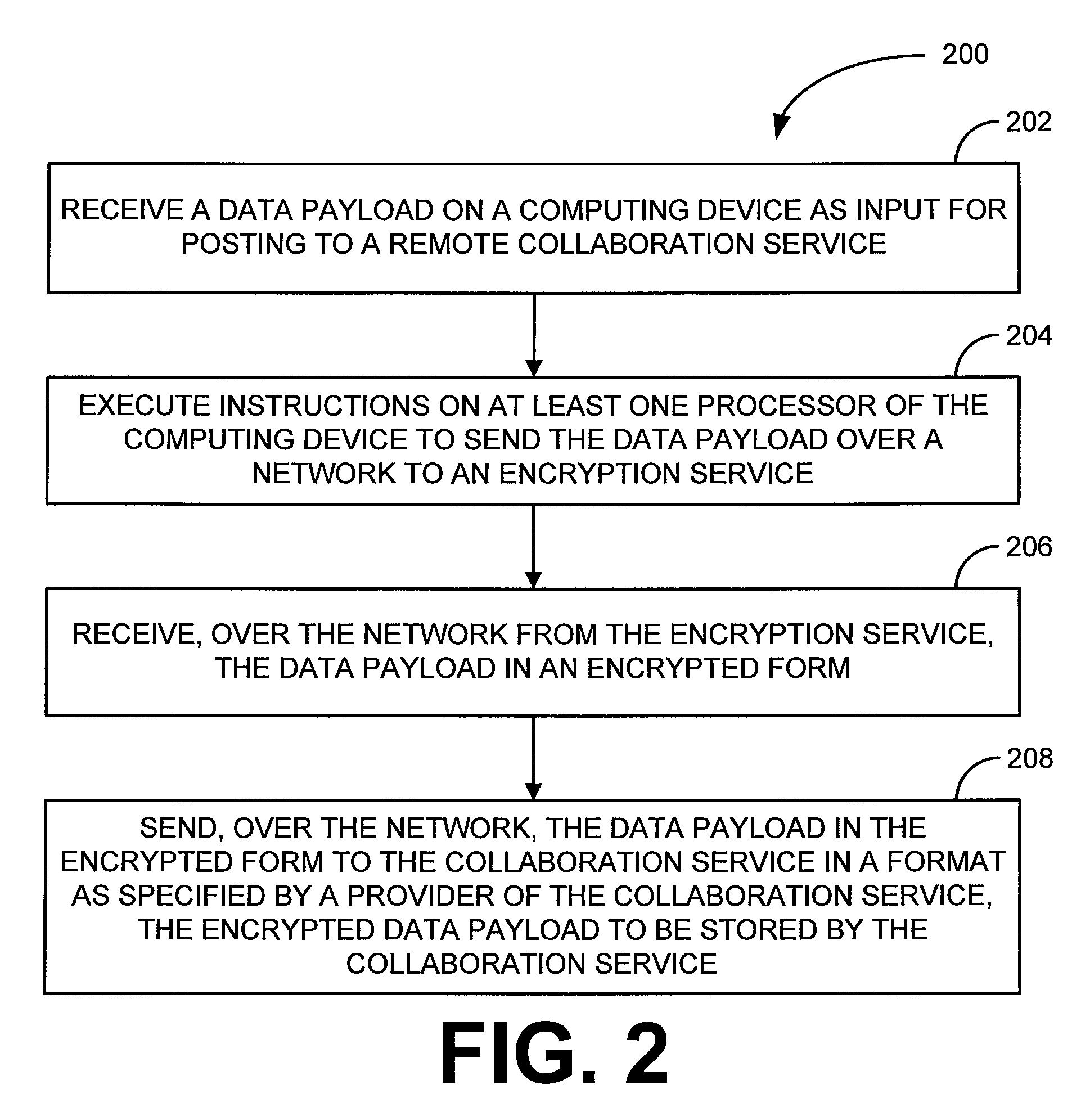
Various embodiments, in the form of at least one of systems, methods, and software, are provided that include security solutions for use of collaboration services. Some embodiments include encrypting data to be sent to and stored by a collaboration service. These and other embodiments include capturing, within a computer application used to post data to a collaboration service, data to be sent to the collaboration service, encrypting the captured data, and returning the data in an encrypted form to the computer application for posting to the collaboration service.
Owner:SAP AG
Process for securing digital transactions
Due to the inability of merchants to secure their data, the credit card / debit card / bank number information must be hidden in a way that the merchant receives only what is needed to process the order. For the system to be immune to hackers, it must be hardware and software based. The invention is a process in which consumer's information is put into a hardware device and encrypted into a package with two sections, the first which can be decrypted by merchants, the second which can be decrypted by credit card offices only. If the data is accurate, the transaction proceeds normally. This secures the credit card data 1) before a transaction occurs, 2) during a transaction, and 3) after a transaction occurs. This method of global protection is revolutionary and protects the credit card data in all possible ways, a solution that no other existing security solution even tries.
Owner:LLOYD JOSEPH ALEXANDER +2
Seamless IP mobility across security boundaries
InactiveUS20040078600A1Digital data processing detailsUnauthorized memory use protectionSecurity solutionUser device
A method, an arrangement and a computer program product, for providing seamless IP mobility across a security boundary between two domains is described. The invention comprises a novel architecture of known network infrastructure components along with enabling client software on the user device. The specific client software as well as the novel architecture represents the invention. Unlike state-of-art today, the method is based on the combined use of independent IP mobility systems in each of the two domains. The key to the invention is client software being able to operate with both mobility systems simultaneously. Moreover, communication takes place in such a way that the ordinary remote access security solution is in control of all access to the secure home domain of the user. The resulting method provides secure and seamless IP mobility in any domain with independent choice of mobility and security technologies. The invention does not require any significant changes (adaptations nor extensions) to any IP mobility or security technology beyond existing or upcoming standards. Nor does it require any significant changes to existing infrastructure components. The mobility client software is the only component that is affected, thus making the method client-centric, as opposed to a network-centric approach that is otherwise the alternative. The invention applies both for the current IPv4 family of standards as well as the forthcoming IPv6 family of standards. The invention applies in particular for the Mobile IP and IPSec VPN standards but is not restricted to these technologies. The invention is applicable for any IP mobility and IP security protocols as long as they are based on the same set of underlying principles.
Owner:BIRDSTEP TECHNOLOGY AS
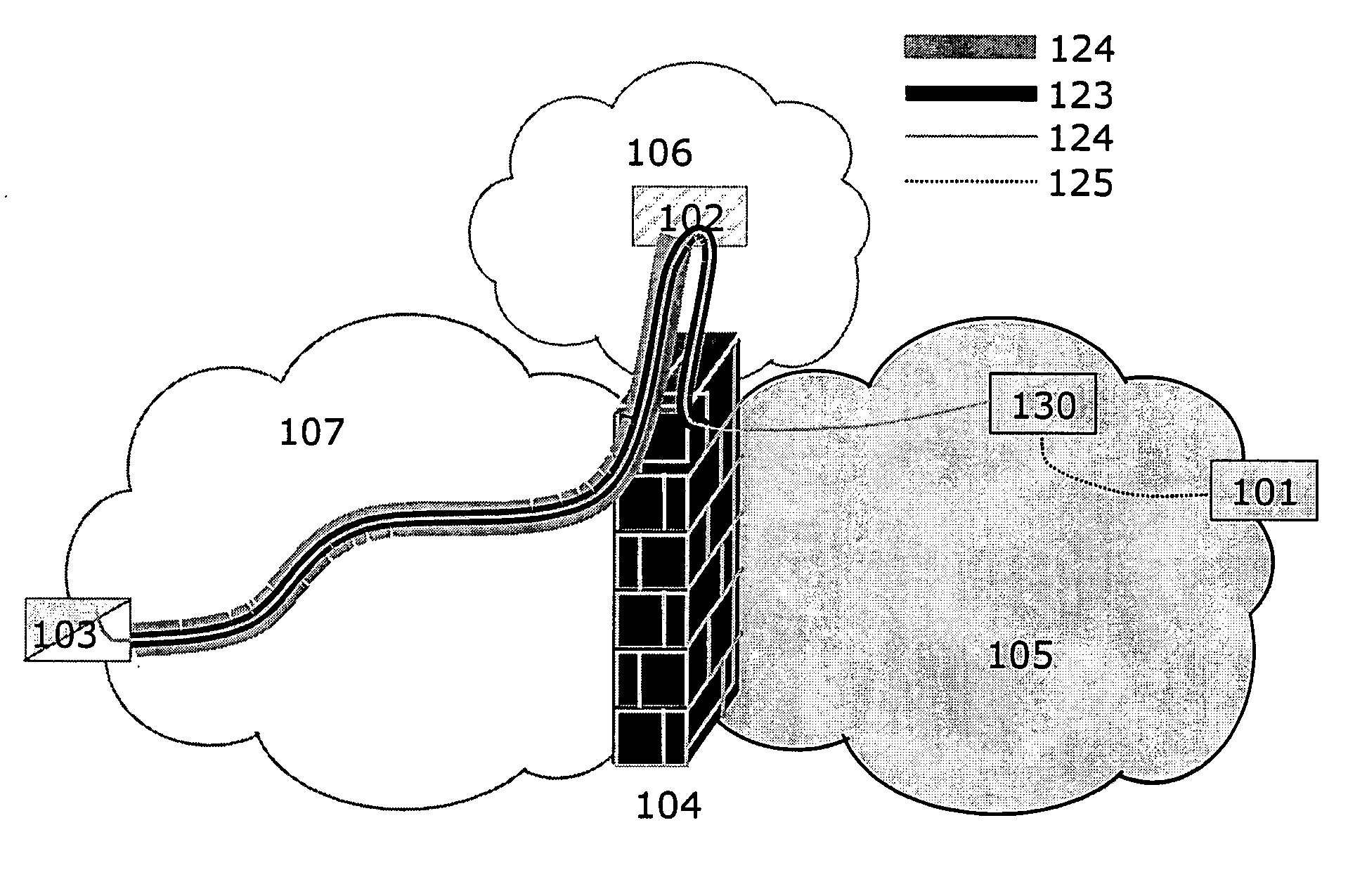
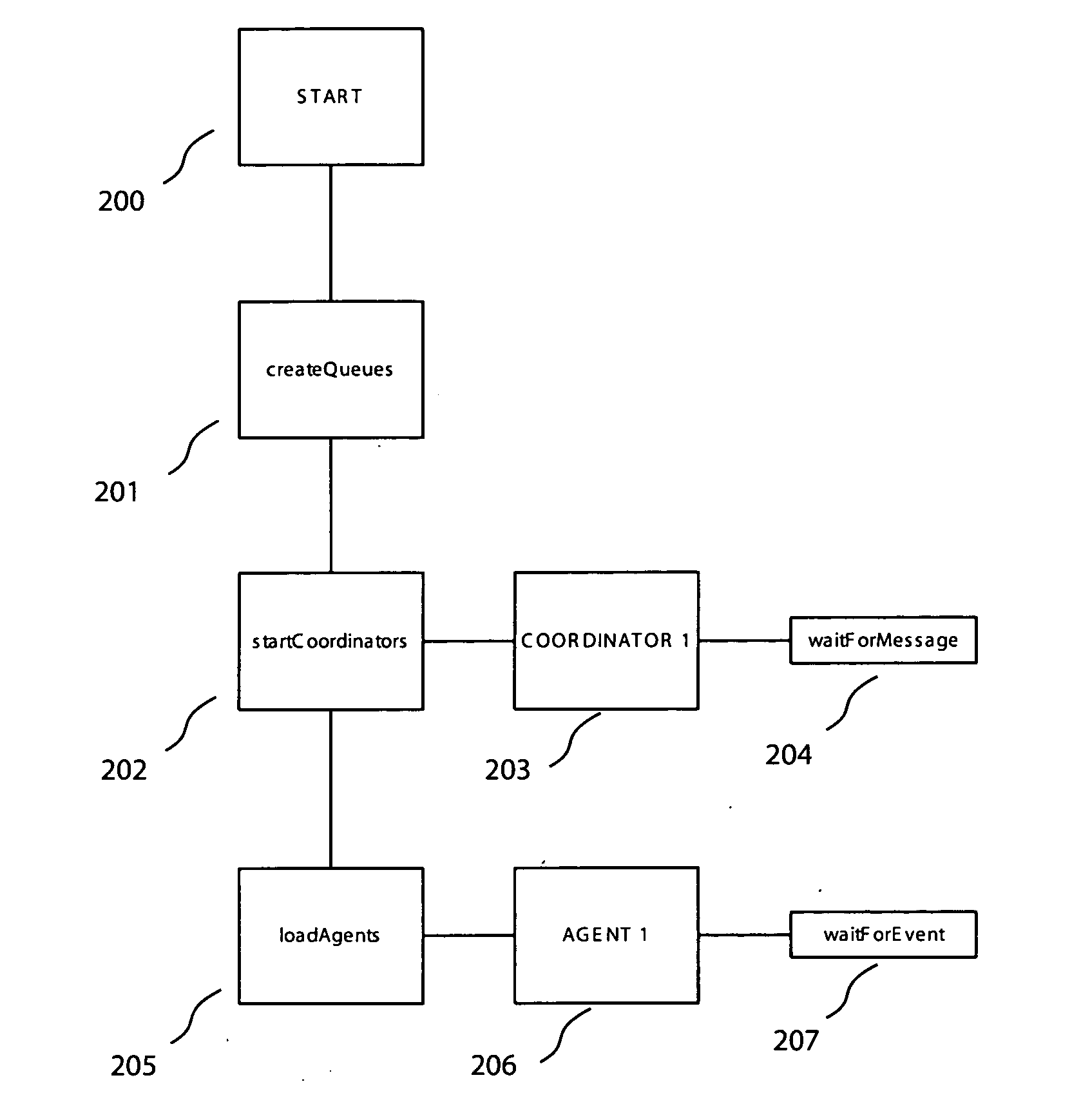
Enterprise security monitoring system and method
InactiveUS20060136986A1Memory loss protectionDetecting faulty computer hardwarePush technologySecurity solution
Embodiments of the invention provide an enterprise security solution wherein each network node itself enforces a predetermined security policy. In these embodiments, platform independent agents and coordinators run on any type of network node and require no central server to implement policy are utilized. With no requirement for access to a server, the security policy of a network node may be enforced without an operable network connection. Agents are responsible for monitoring, recording and reporting attempted violations of predetermined security policies of an enterprise. Agents may be general agents and may be written in a platform independent language or may be special agents that may comprise platform specific code whether written in a platform independent language or not. Coordinators are responsible for configuring, controlling and providing support services such as routing to the agents. Agent and coordinator functionality may be combined into one component if desired. Agents and coordinators are capable of terminating processes on network nodes that they are monitoring. A policy may be specific to a device, user, group or enterprise or any combination thereof. Agents and coordinators may be deployed via disks, via the network via push technologies, or via download from the network. After agents and coordinators have been installed on a network node the security policy is enforced and may not be terminated without administrator privilege. Embodiments of the invention may be controlled and administered remotely without technical support at each network node site from any location hosting an administrator. This allows for flexible administration that is not dependent on the location of the administrator. In addition, since network connections may become inactive, it is possible for an administrator to change locations while administering a network node.
Owner:ERGOMD +1
Low code-footprint security solution
InactiveUS20070101412A1Digital data processing detailsUser identity/authority verificationSecure communicationSecurity solution
Apparatus and method for conducting secured communications with a client device in a network are disclosed. The method includes receiving at the server a request message from the client device, wherein the request message comprises a nonce, a nonce count and an encrypted request, determining whether the client device has permission to access the server using the nonce and the nonce count, forming an encrypted server response message in response to the encrypted request and the client device has permission to access the server, and issuing the encrypted server response message from the server to the client device.
Owner:R2 SOLUTIONS
Monitoring system using multiple pick-up cameras
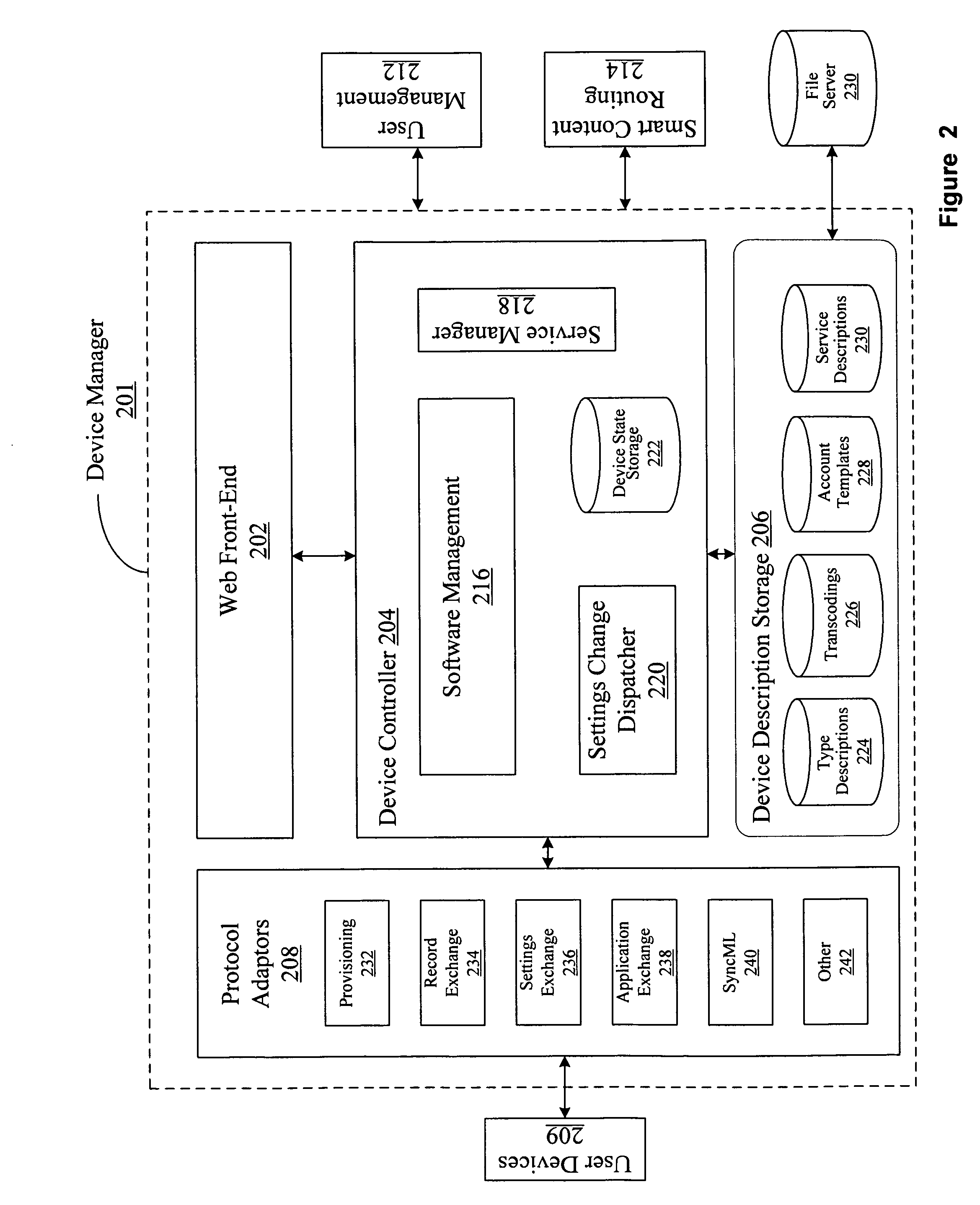
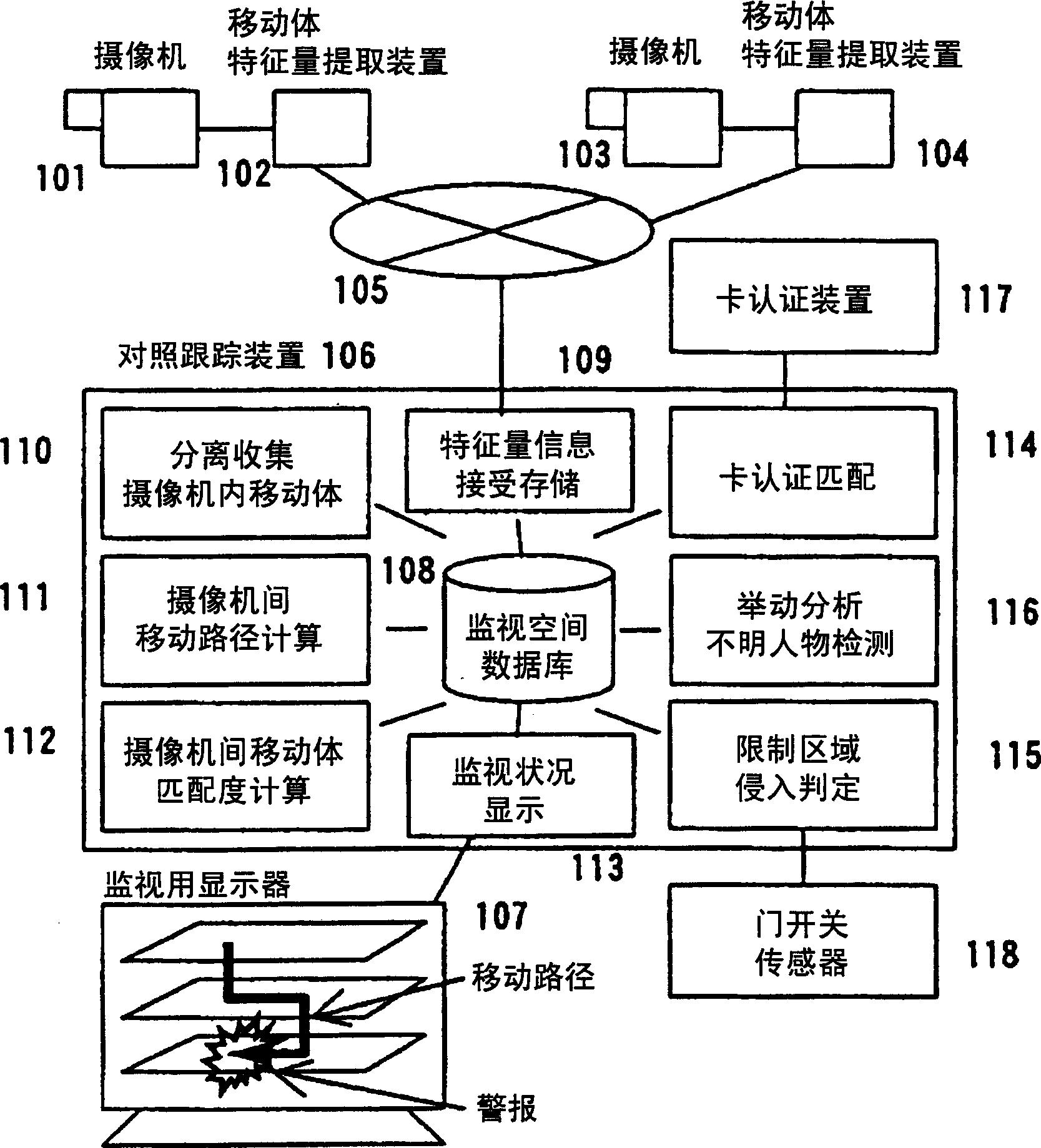
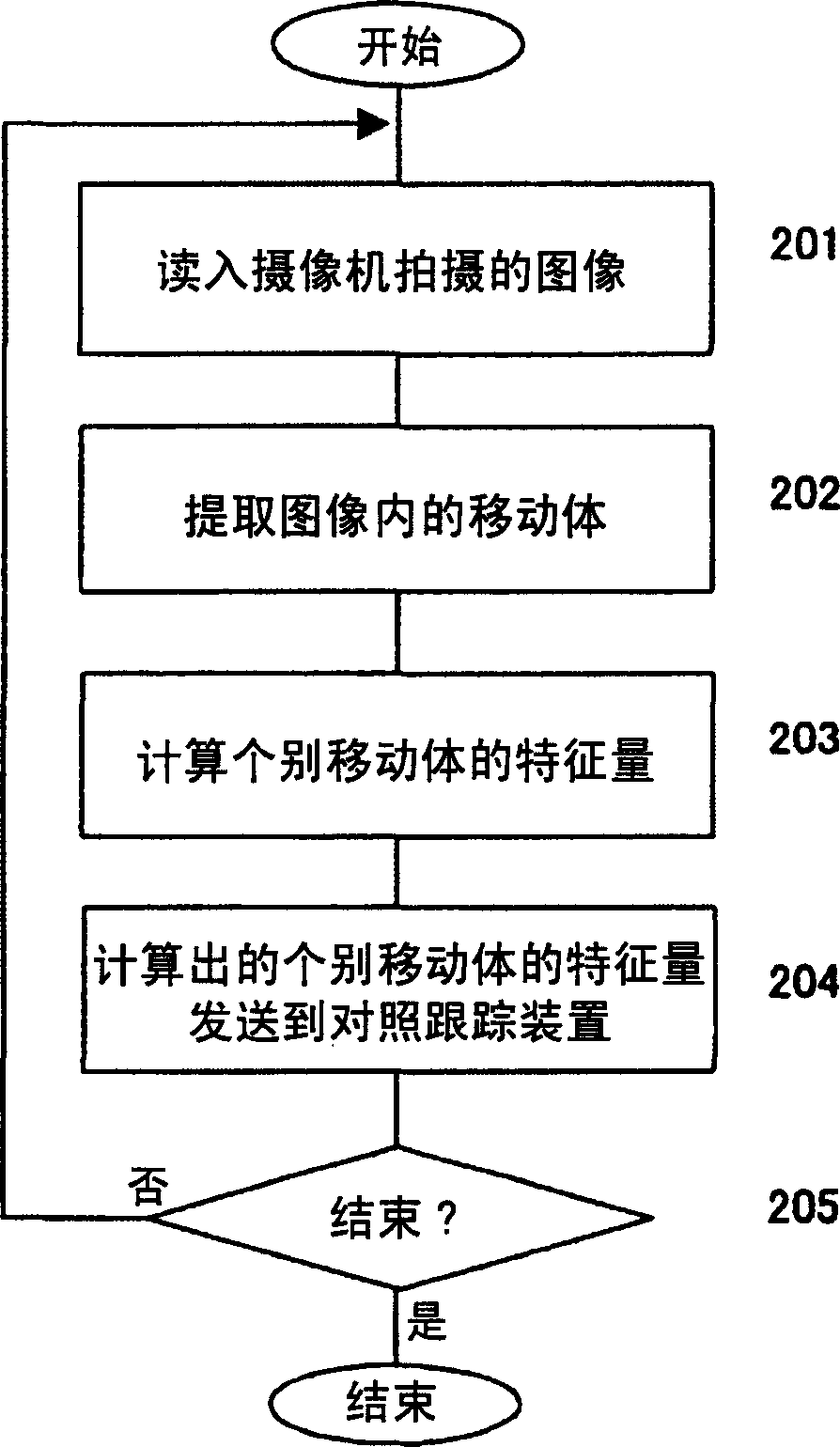
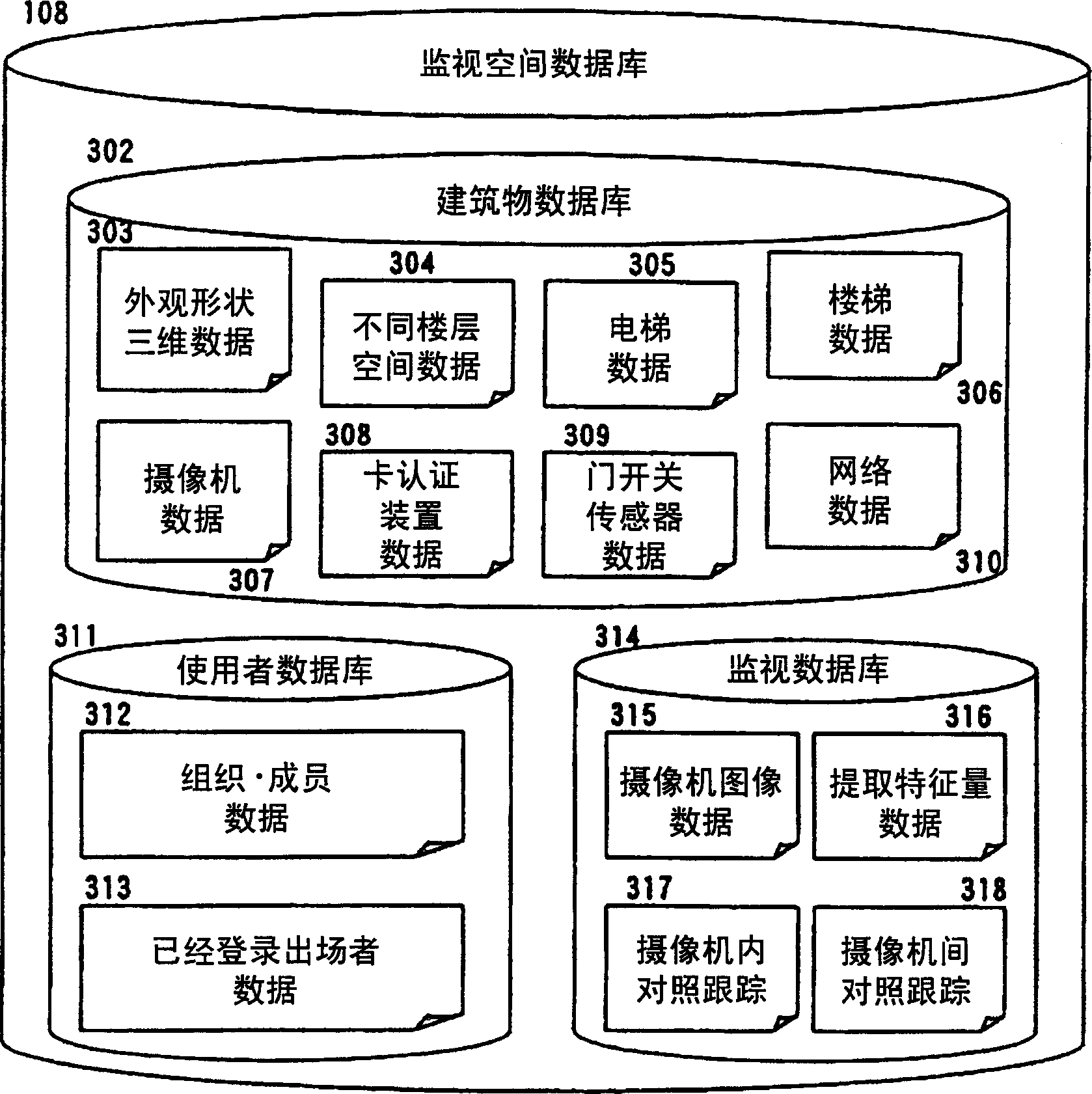
InactiveCN1777281AImprove tracking performanceReduce the burden onClosed circuit television systemsImage extractionSecurity solution
Provides a security solution that reduces the burden on surveillance personnel and is not troublesome for users in a system that monitors a target space with multiple cameras. Use image recognition technology to extract moving objects from images captured by each camera, and compare them between cameras. Then, the moving path of the moving body is obtained, and whether or not the restricted area is entered is judged, and an alarm is displayed to the supervisor. Whether you have permission to enter restricted areas is judged by individual-specific institutions such as combination card authentication and camera monitoring and tracking. In addition, by analyzing the moving track and path to determine whether it is an unknown person, an alarm warning is also issued. As a basis for the above-mentioned processing, a monitoring space database is built, and the processing is carried out in transit.
Owner:HITACHI LTD
Apparatus and method of securing network
ActiveUS20080163356A1Error detection/correctionMultiple digital computer combinationsSecurity solutionPattern matching
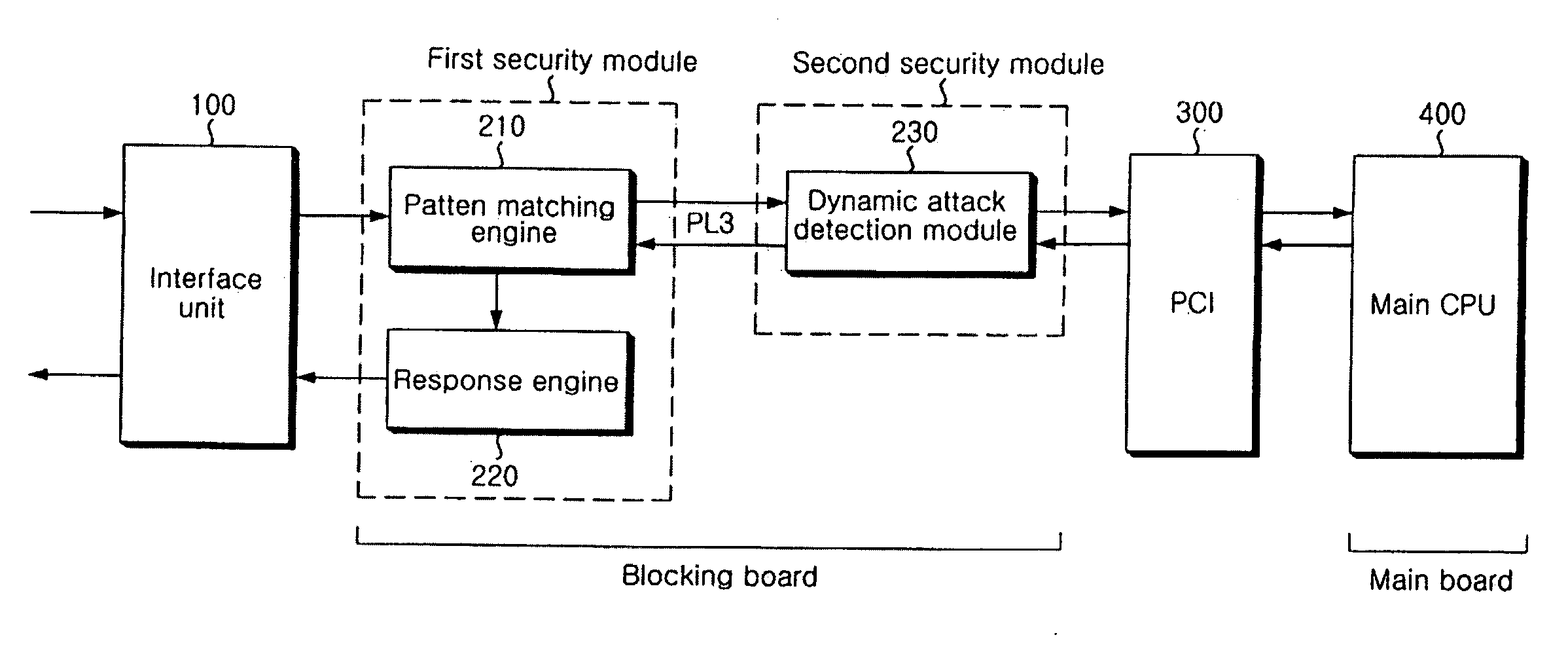
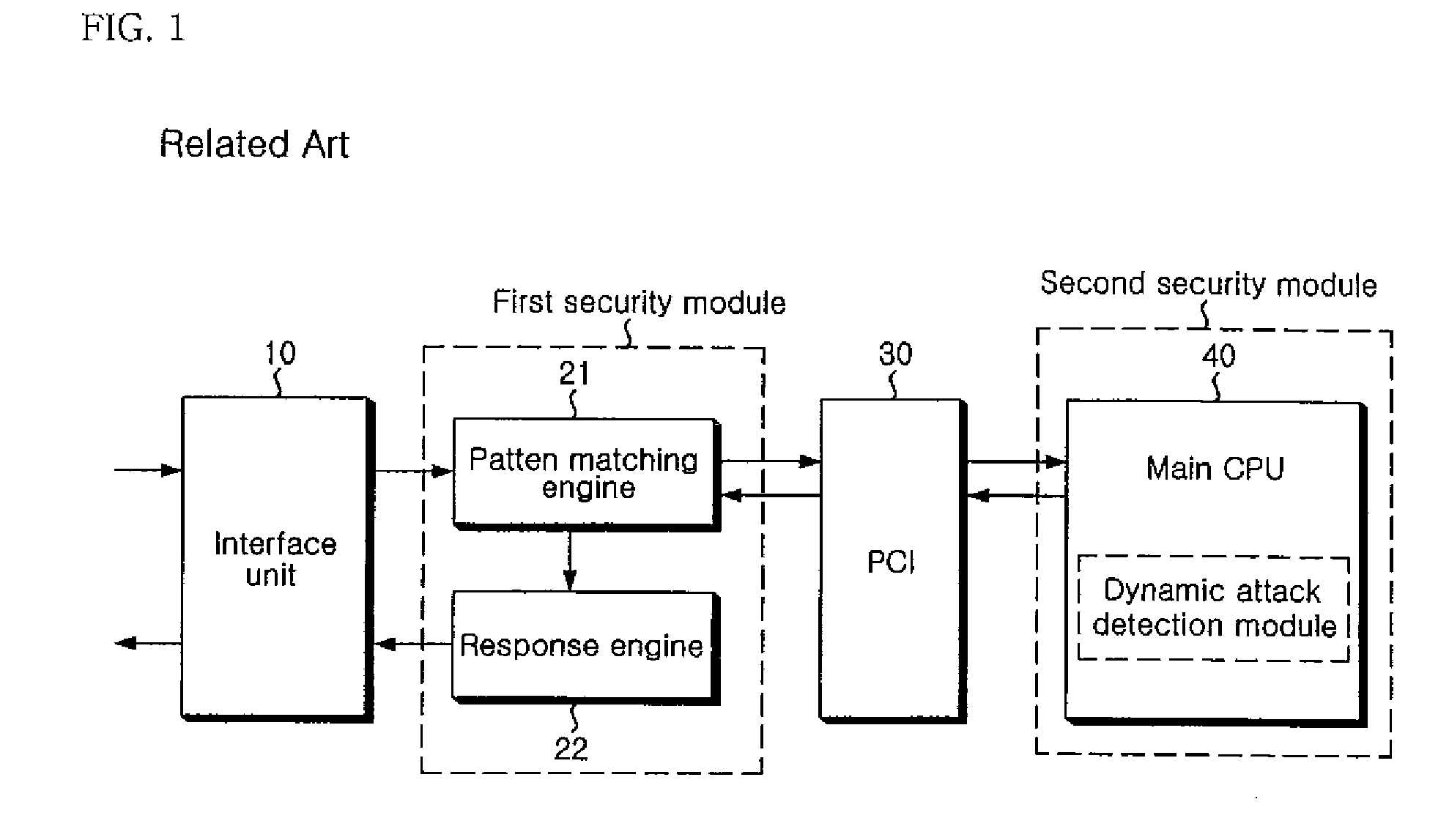
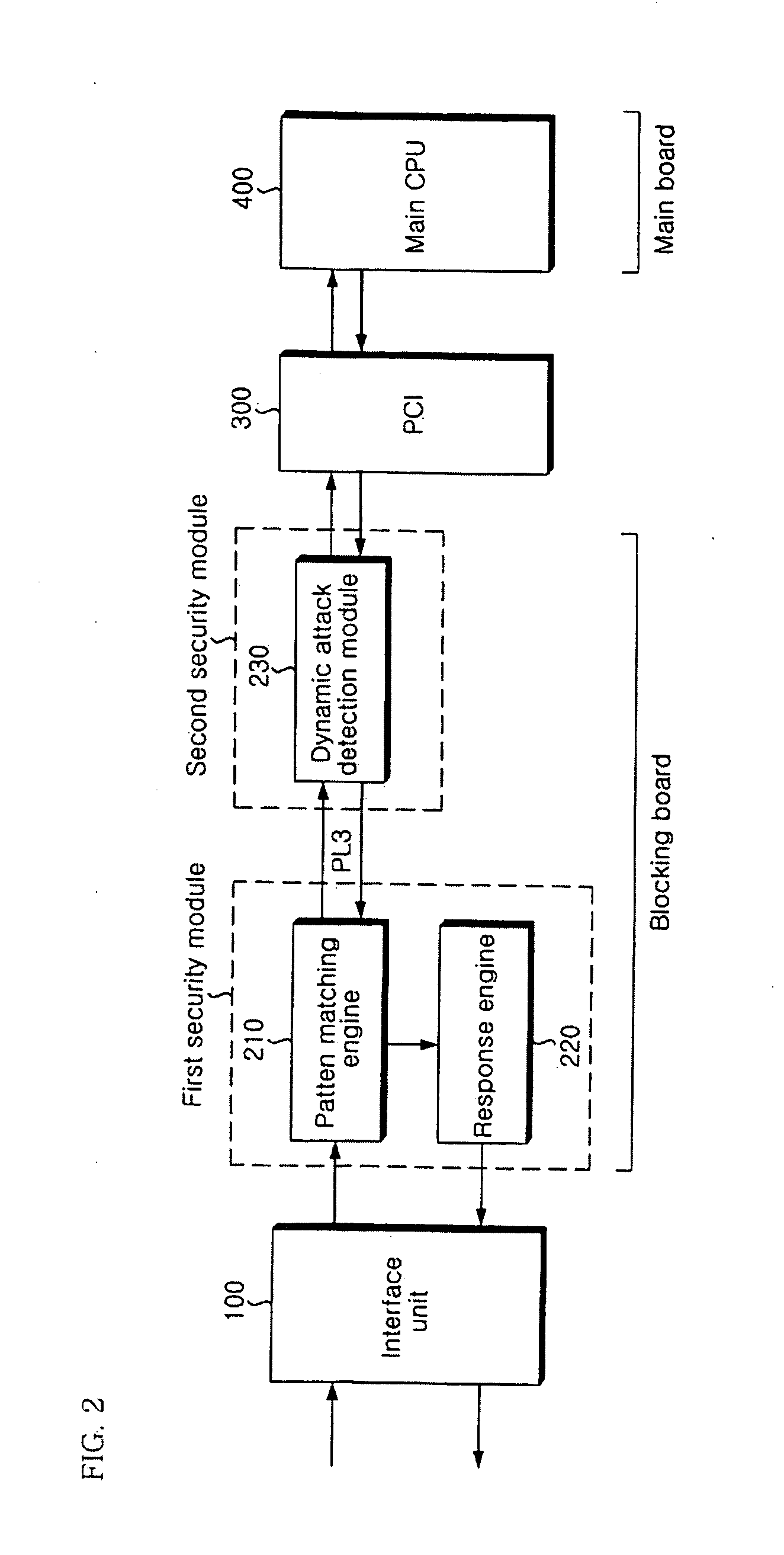
The present invention relates to an apparatus and method of securing a network. In the present invention, a pattern matching engine 210 corresponding to a first security module initially performs a hardware-based filtering process for a static attack of an input network packet and transmits a normal packet determined to be normal as a result of the filtering to a dynamic attack detection module 230 corresponding to a second security module through a PL3 interface. The dynamic attack detection module230 performs a hardware-based filtering process for a dynamic attack of the normal packet transmitted from the pattern matching engine 210. The dynamic attack detection module 230 transmits the filtering result to a main CPU 400 through a PCI 300 if filtering the dynamic attack is completed. Then, a main CPU 400 transmits a response policy based on the transmitted filtering result to a response engine 220 through the PCI 300 and the dynamic attack detection module 230 to block an abnormal packet. Therefore, the present invention is very effective in that accuracy of detection is enhanced, and weakness in processing speed and performance of a network security solution can be compensated to meet requirements on real-time.
Owner:LG CNS
Reader device for reading a marking comprising a physical unclonable function
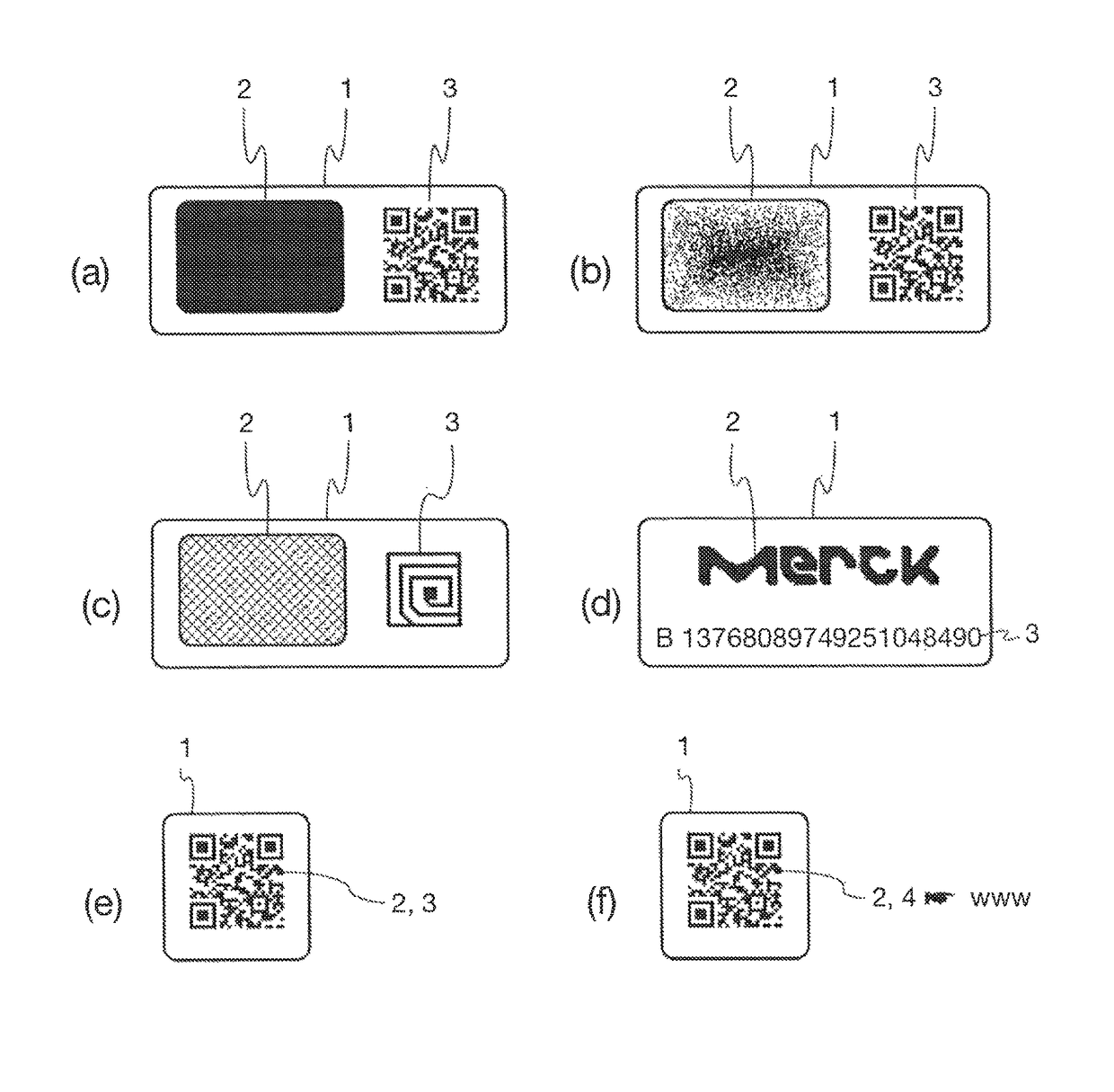
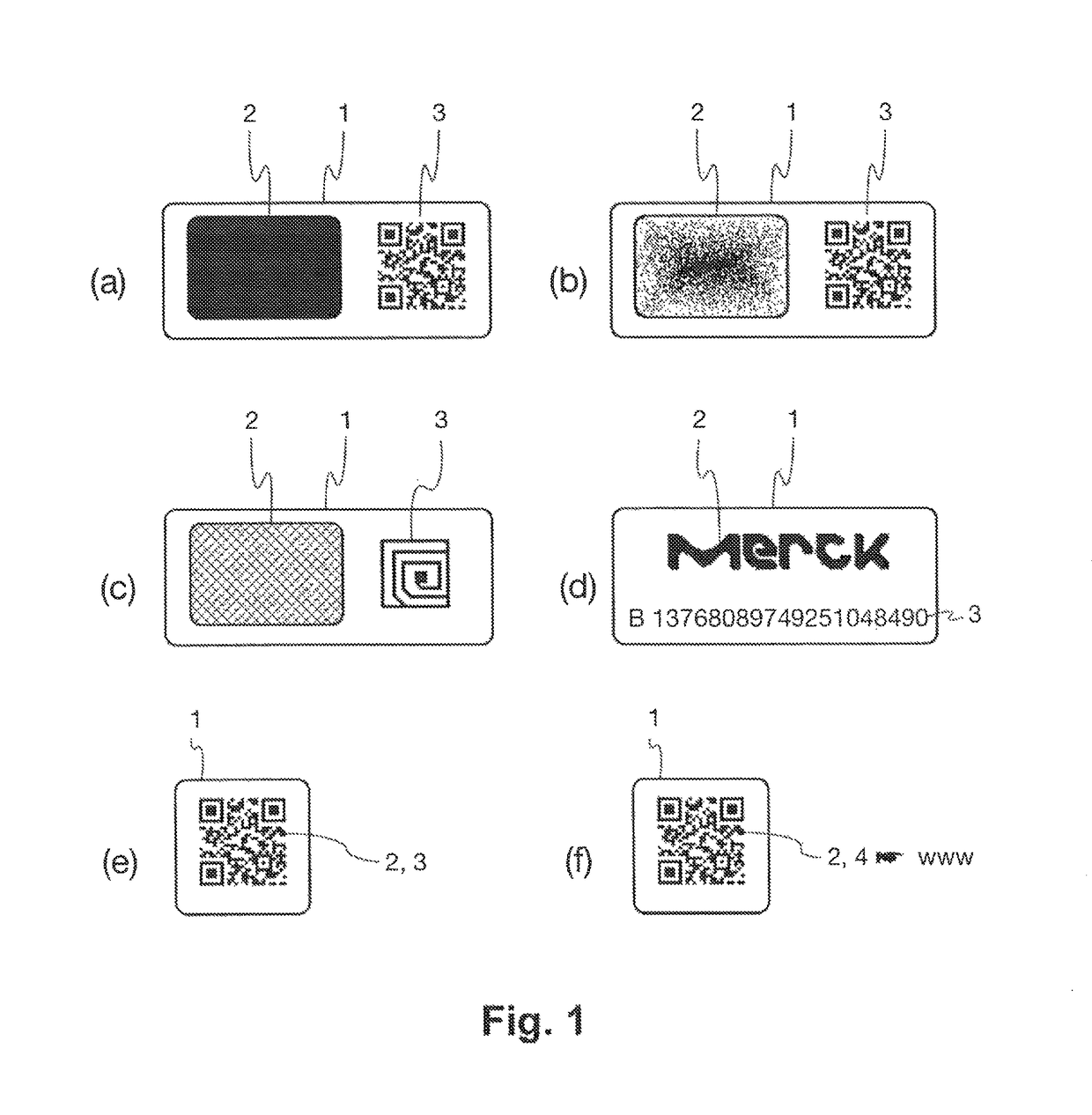
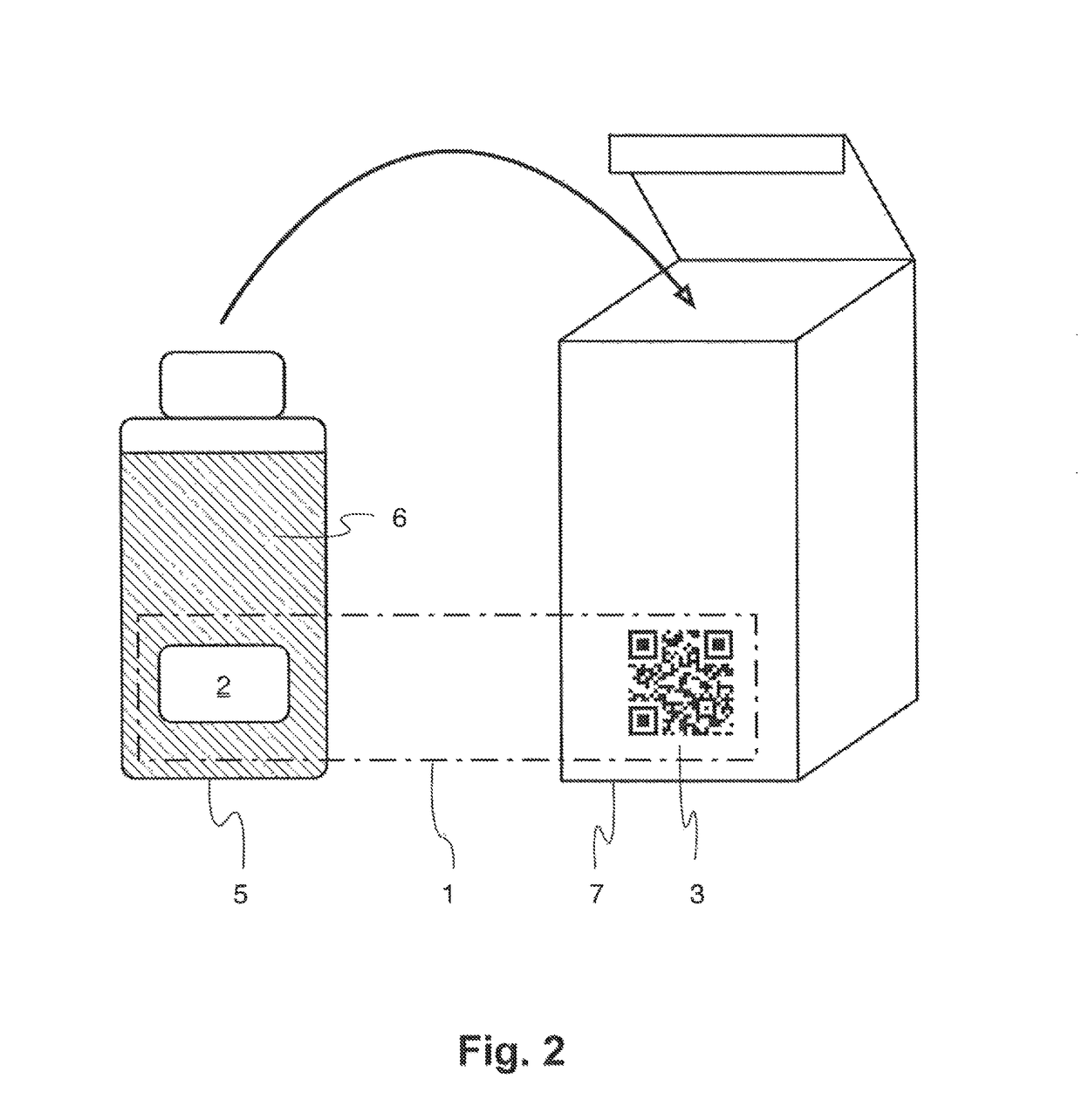
ActiveUS10002277B1Efficient readingVerify authenticityEncryption apparatus with shift registers/memoriesCoding/ciphering apparatusSecurity solutionCryptographic hash function
The present invention relates to the field of anti-counterfeit protection of products. Specifically, the invention is directed to a method of reading with a reader device a marking comprising a physical unclonable function, PUF, and a corresponding reader device. In particular, such reader device marking can be used in connection with or can form a component of a multi-component security system, in particular of an anti-counterfeit protection system, which is also disclosed herein as part of an overall security solution for anti-counterfeit protection. The method comprises a stimulation step, wherein a physical challenge according to a predetermined challenge-response authentication scheme corresponding to the PUF is created and applied to a PUF; a detection step, wherein a response generated by the PUF in accordance with the challenge-response authentication scheme in reaction to the challenge is detected and a digital signal representing the response is generated; a processing step, wherein the digital signal is processed in order to generate a hash value of the response by application of a predetermined cryptographic hash function to the digital signal; and an output step, wherein data representing the generated hash value as a first reading result is output.
Owner:MERCK PATENT GMBH
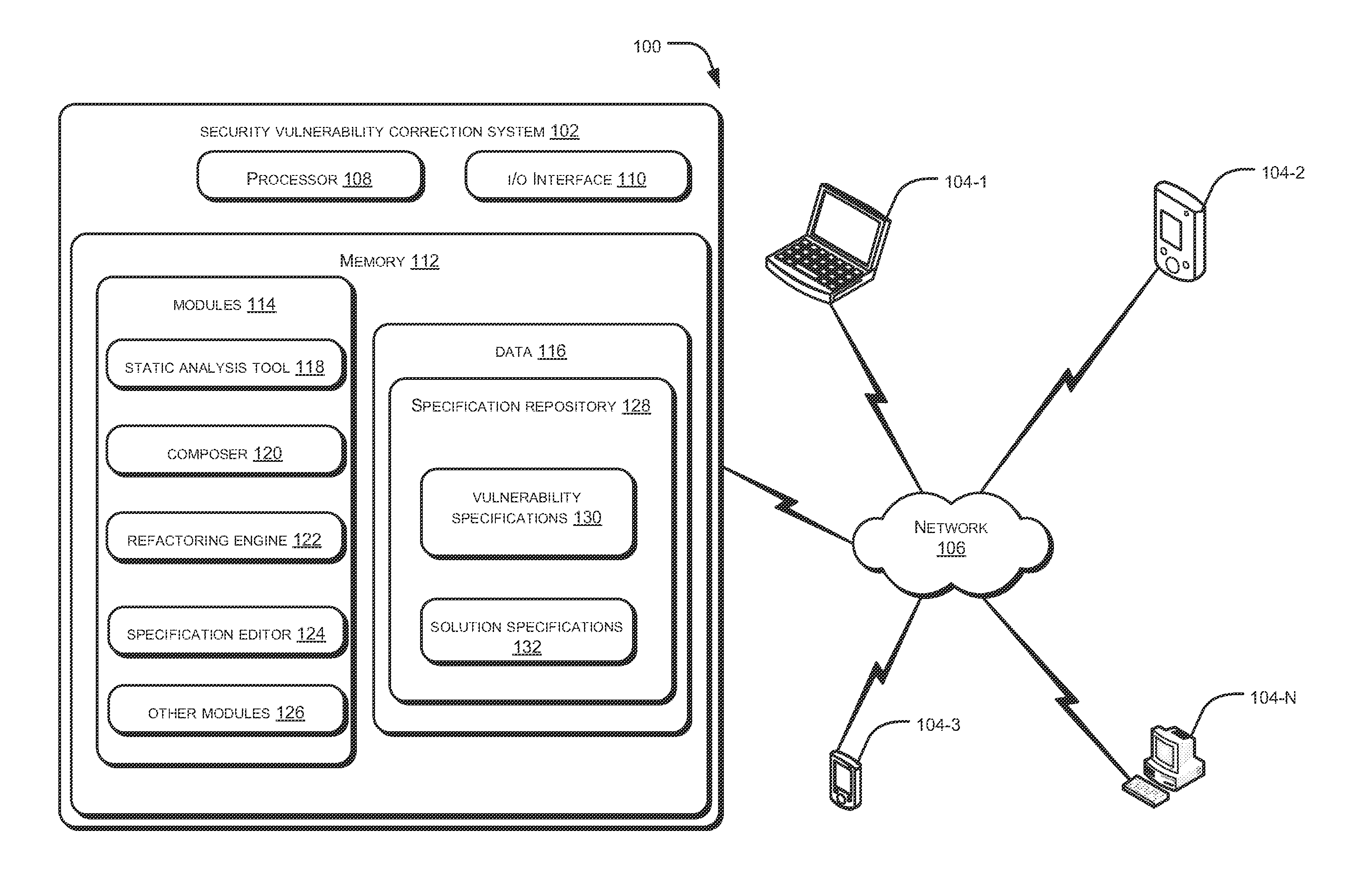
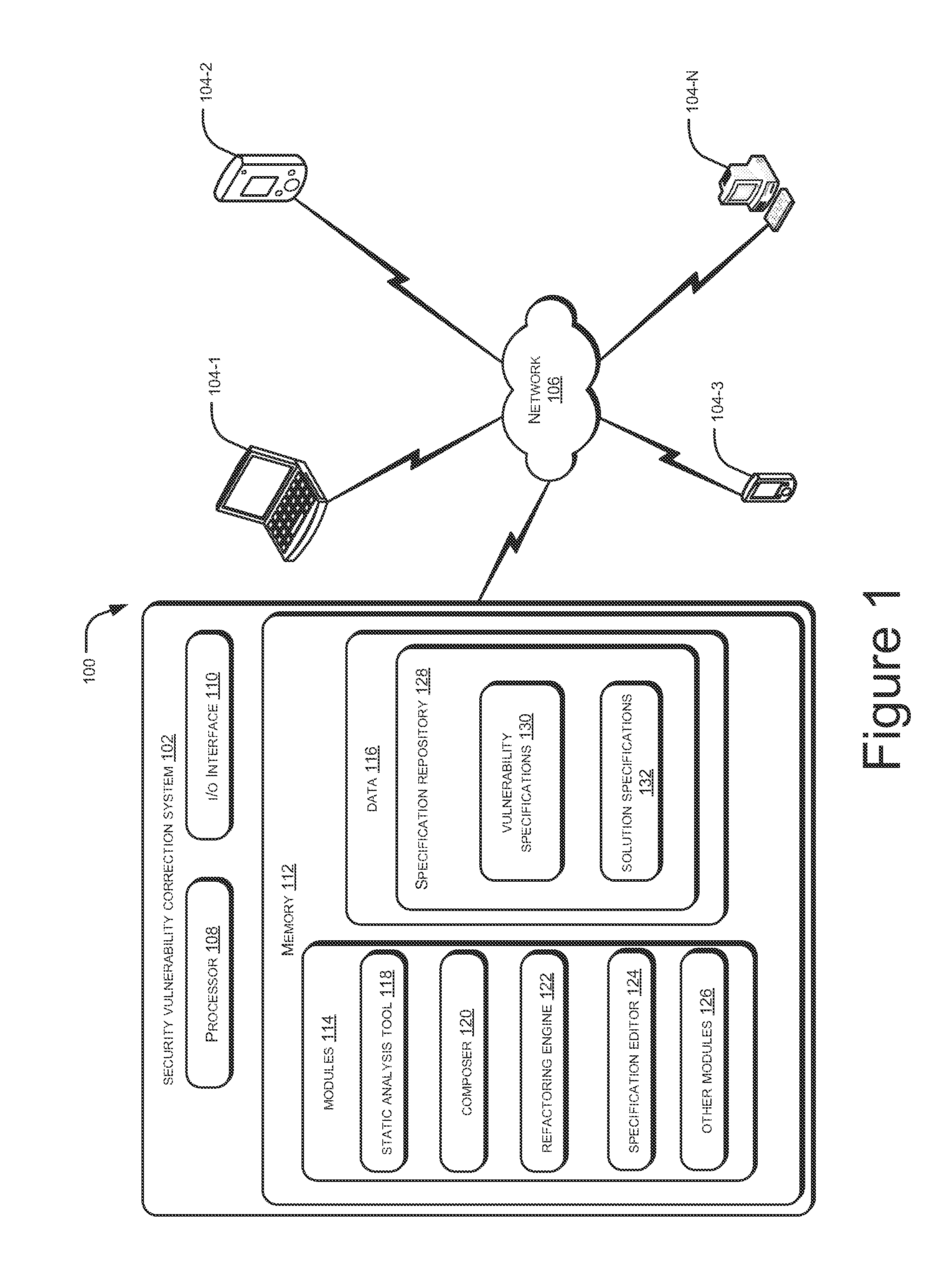
Security vulnerability correction
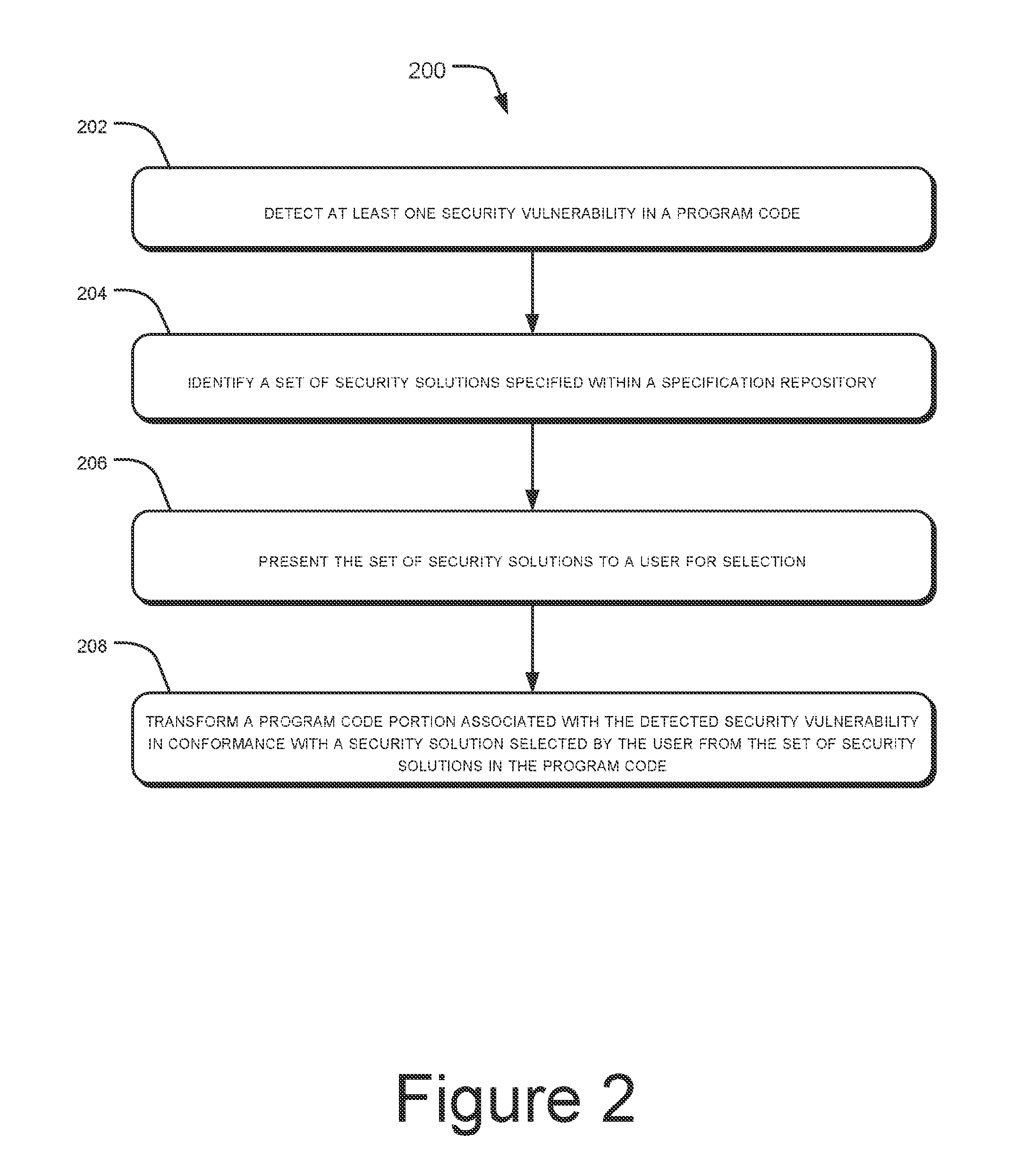
ActiveUS20130086689A1Limit scopeMemory loss protectionError detection/correctionSecurity solutionProgram code
Systems and methods for addressing security vulnerability in a program code are described. The method comprises detecting a security vulnerability. The method further comprises identifying a set of security solutions specified within a specification repository, wherein each security solution is associated with the detected security vulnerability. The method further comprises presenting the set of security solutions to a user for selection. The method further comprises transforming a program code portion associated with the detected security vulnerability in conformance with a security solution selected by the user from the set of security solutions.
Owner:TATA CONSULTANCY SERVICES LTD
Method and system for realizing network identity authentication based on two pieces of isolation equipment
The invention relates to a method and system for realizing network identity authentication based on two pieces of isolation equipment. One piece of network computing equipment used in the network identity authentication process is increased to two pieces of physically-isolated network computing equipment, and each piece of network computing equipment does not process all identity authentication information, so that the Internet log-on and transaction activity security of a user is promoted. In a typical application of the method and the system, on the basis of the characteristic that a mobile phone is highly bound with the user, the same function of a special hardware key device is realized by using the mobile phone, the mobile phone becomes a general digital signature terminal, and the user can safely complete log-on and transaction activities by using a public computer, so that user experience is enhanced greatly, a PKI (Public Key Infrastructure) certificate system is easier to implement, and a general safe resolution is provided for network identity authentication based on a PKI / CA (Public Key Infrastructure / Certification Authority) structure.
Owner:BEIJING SOFTLUMOS TECH
Method and apparatus for controlling transportation, storage and sale of fluids such as petrochemicals
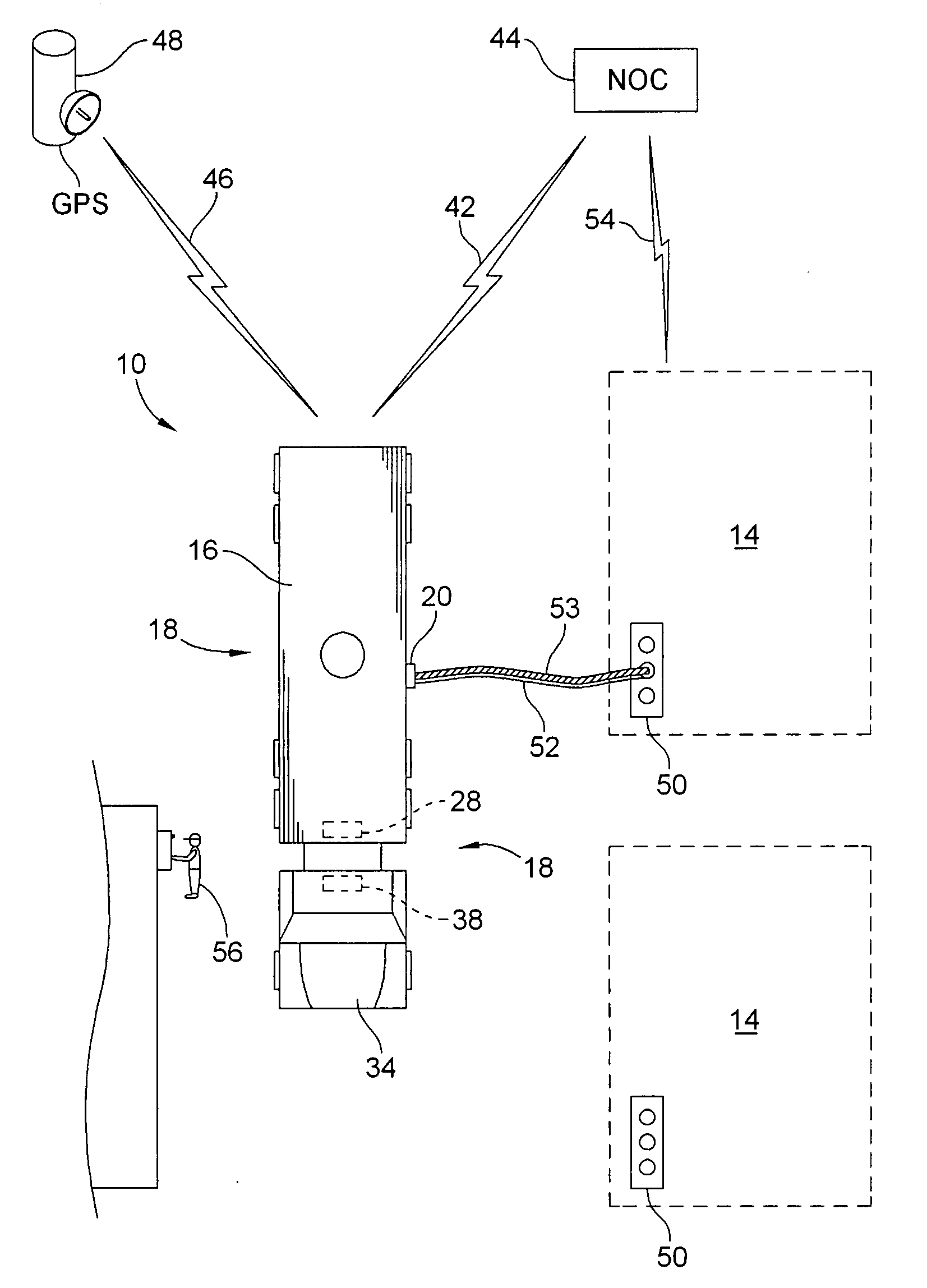
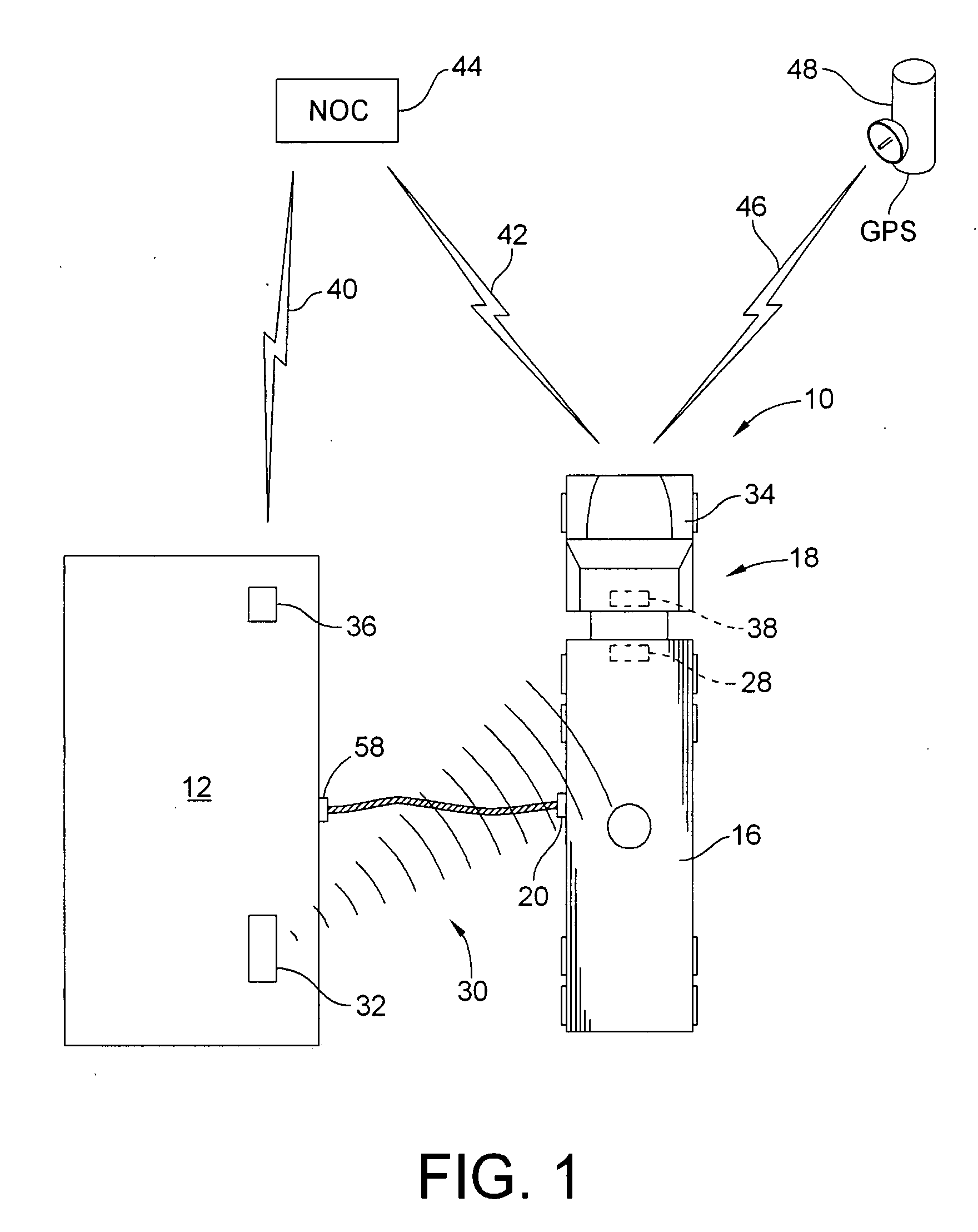
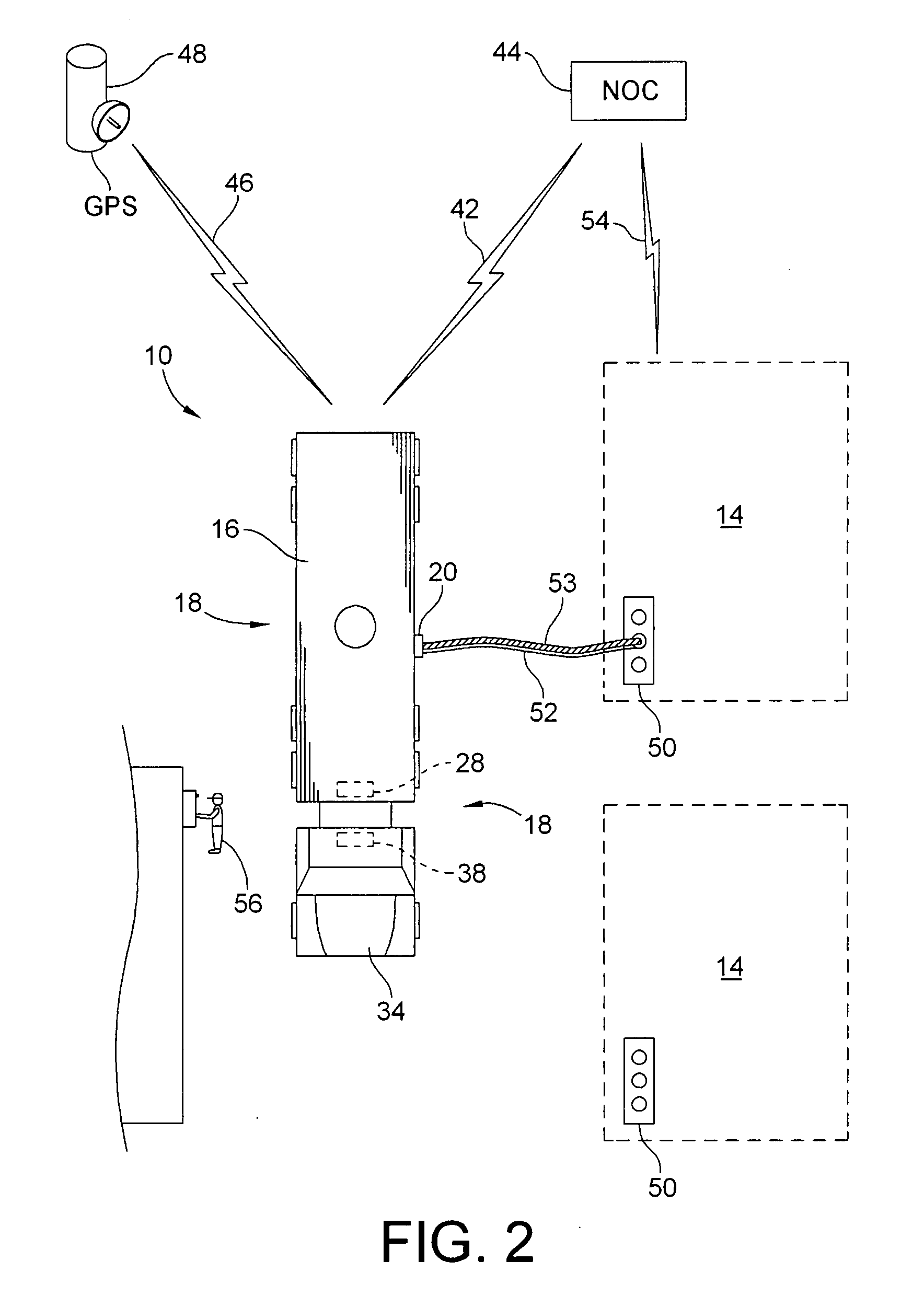
Methods and apparatuses are provided, for use singlely, or as part of a comprehensive security solution, for ensuring the integrity of a supply chain involving transportation, storage and / or sale of fluids such as petrochemicals. Passage of a fluid through an opening in an otherwise closed fluid tank is controlled by locking the opening against passage of fluid therethrough until a signal derived from a GPS is received, indicating that the tank is positioned at a pre-determined location whereat the opening in the tank is to be unlocked for allowing passage therethrough of the fluid. The tank may be, inter alia, a mobile tank, a stationary tank at a bulk station, or a stationary tank at a service station.
Owner:TRANZILIENT
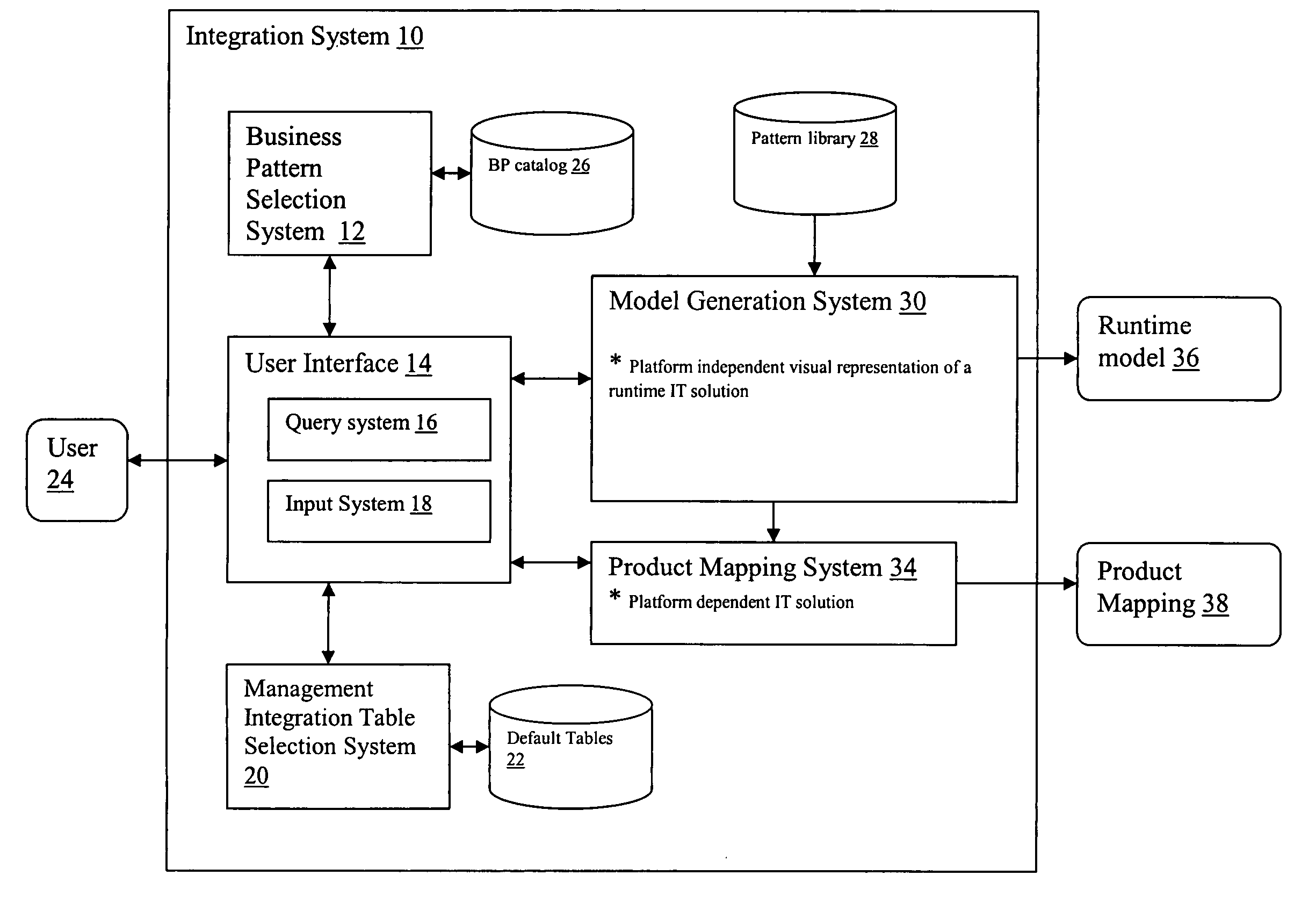
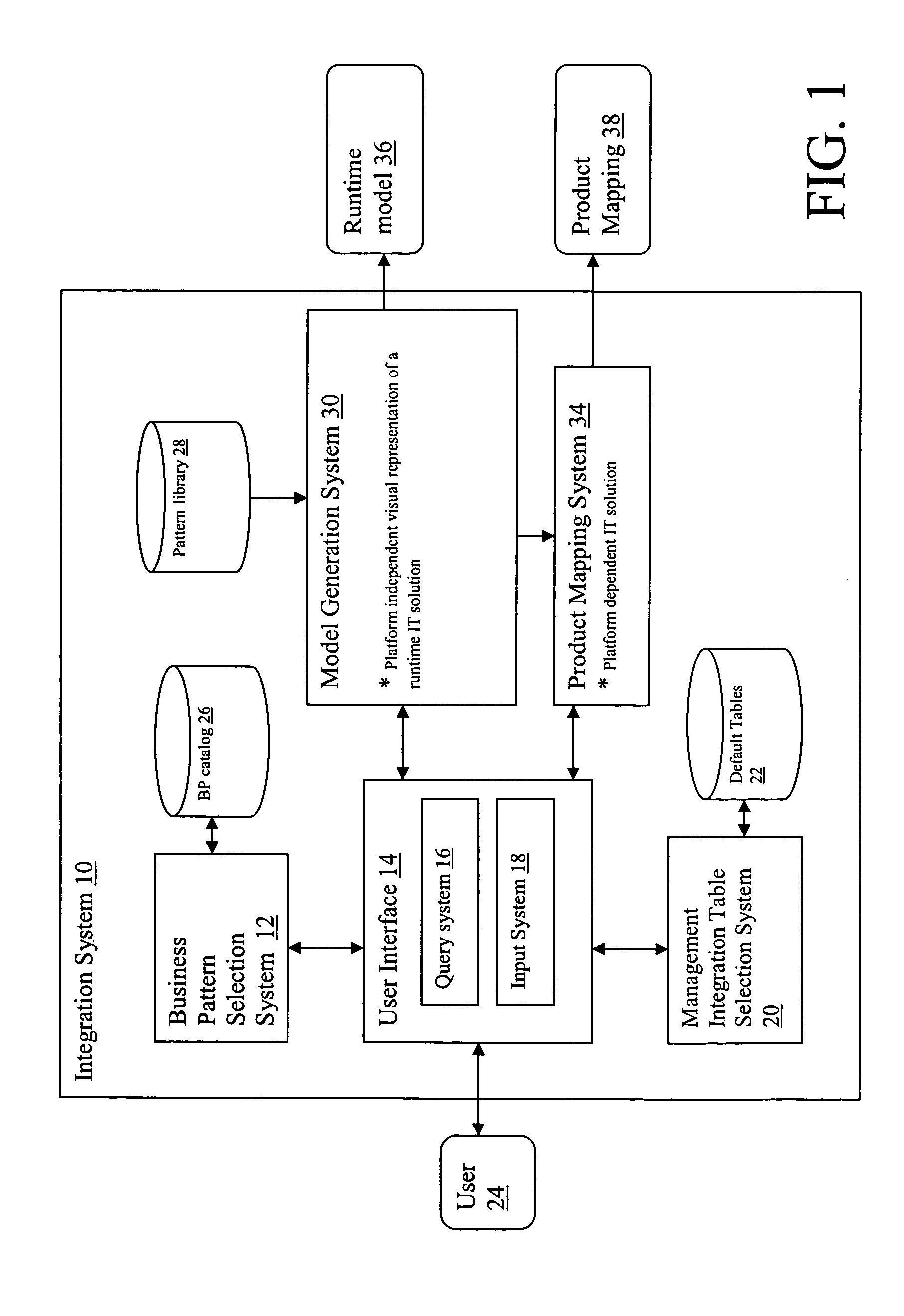
System and method for designing secure solutions using patterns
A system and method for generating an information technology solution. A system for generating a runtime model is provided, comprising: a system for selecting a business pattern; a system for providing a management integration table, wherein the management integration table includes a plurality of cells, each representing at least one management application pattern; and a system for generating a runtime model from the selected business pattern and management integration table, wherein the generating system supplements the business pattern with additive patterns, bridge patterns, and management application patterns in order to generate the runtime model.
Owner:IBM CORP
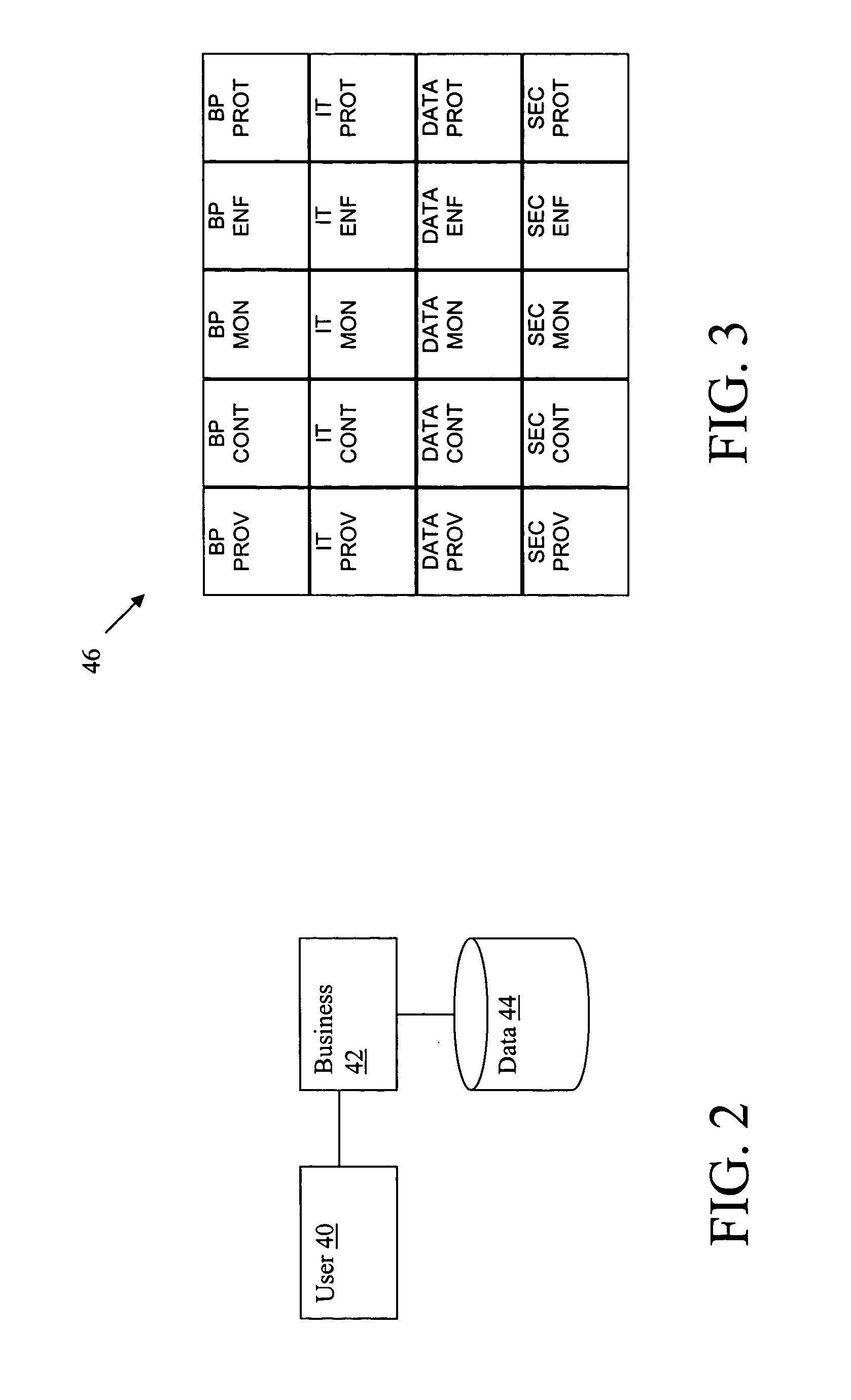
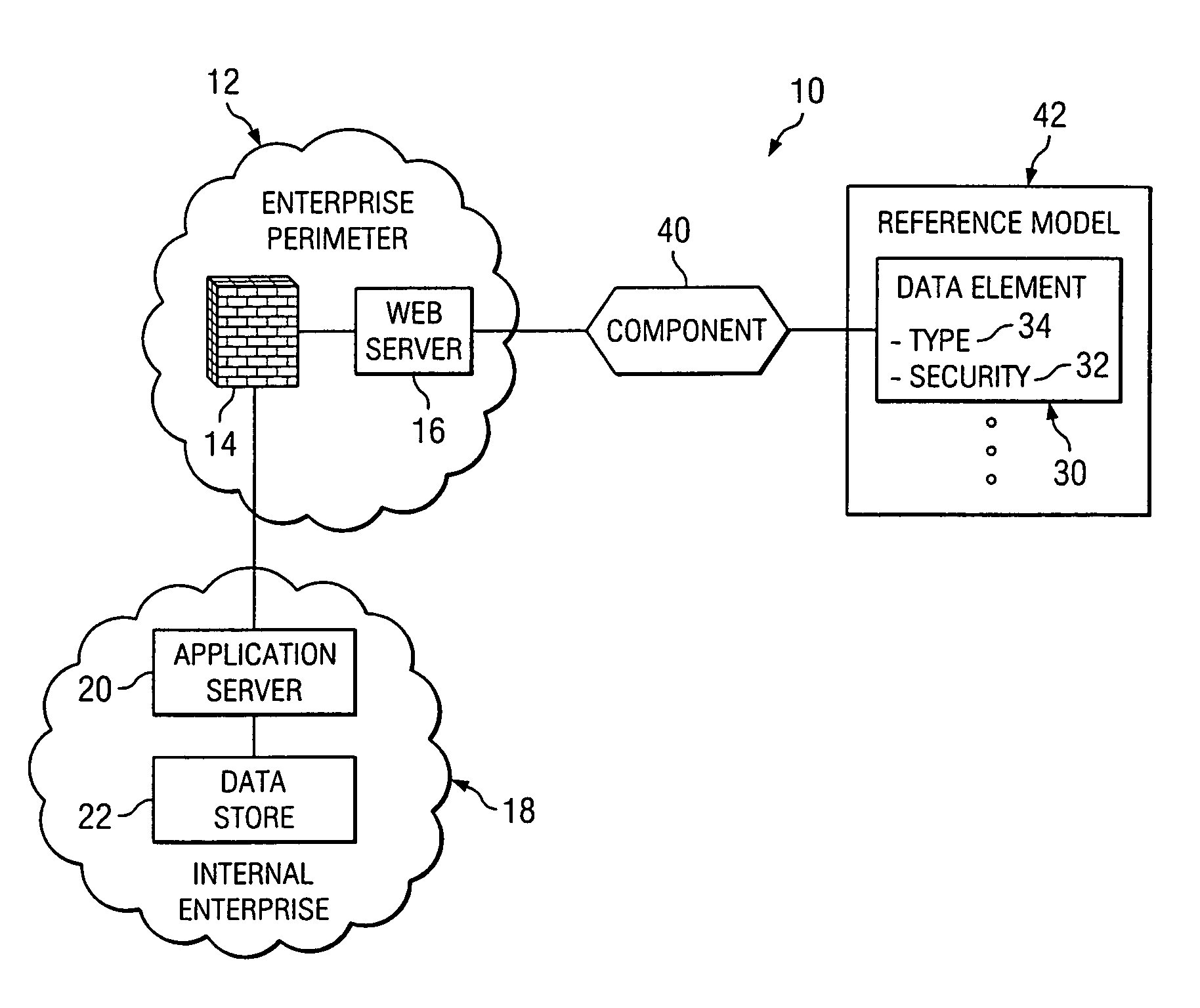
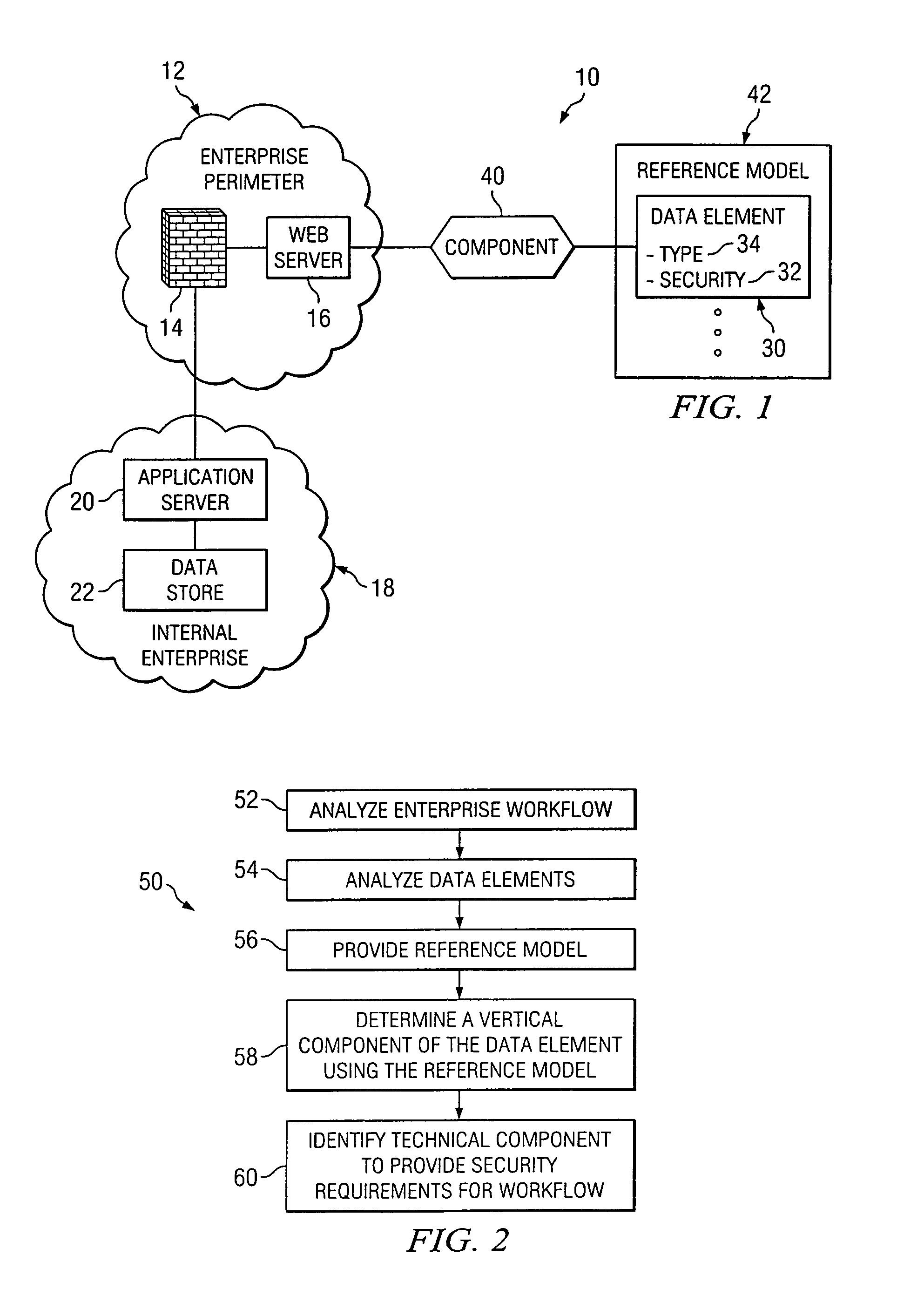
Method and system for architecting enterprise data security
A method for architecting enterprise data security solutions for an enterprise having multiple levels is provided. The method includes analyzing the enterprise levels and a workflow related to the plurality of levels and analyzing a data element having a security requirement. The method includes providing a reference model including the data element. The reference model associates the data element and the security requirement with the workflow. The method includes determining a vertical component of the data element using the reference model. The vertical component identifies the security requirement for the data element based on the workflow for each of the plurality of levels of the enterprise. The method includes identifying a technical component using the reference model and the vertical component. The technical component is operable to provide the security requirement of the data element for the workflow across each of the plurality of levels of the enterprise.
Owner:T MOBILE INNOVATIONS LLC
Terminal and method for improving system safety
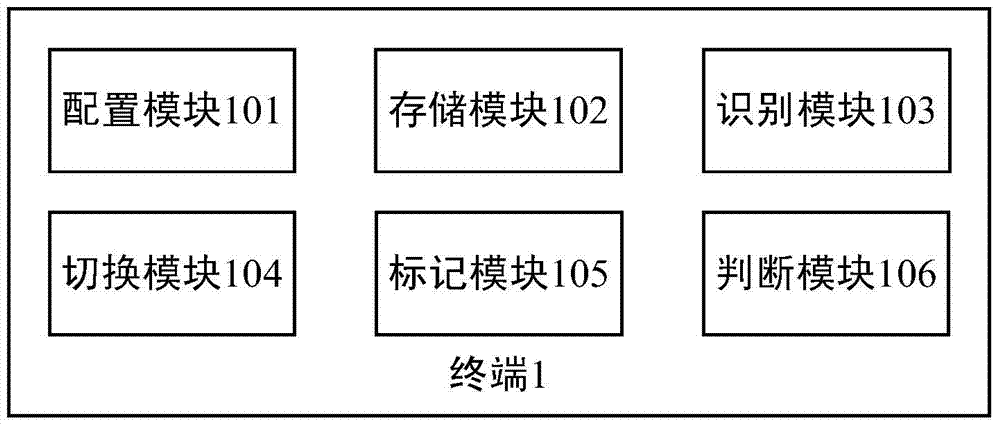
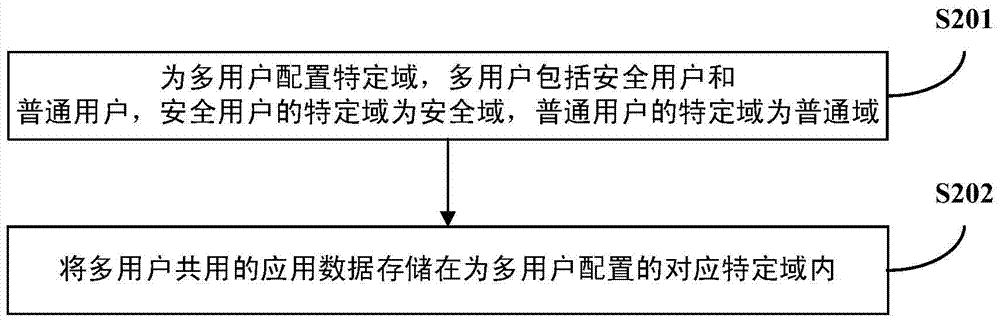
InactiveCN103886270AEnable secure accessImprove securityInternal/peripheral component protectionSecurity solutionComputer terminal
The invention discloses a terminal and a method for improving system safety. The terminal comprises a configuration module and a storage module, wherein the configuration module is used for configuring specific domains to a plurality of users, the users comprise the safe users and the common users, the specific domain of each safe user is a safe domain, and the specific domain of each common user is a common domain; the storage module is used for storing application data commonly used by the users in the specific domains corresponding to the users. By means of the technical scheme, the terminal and the method for improving the system safety solve the problem that an existing safe system cannot relate to multi-user safety solution schemes. By combining a multi-user mechanism and a Seandroid mechanism, a safety solution scheme is provided for the system, application can process the data in the specific domains of the users, and therefore the effect of improving the system safety is achieved, and the single terminal can have safe access to the data in the specific domains.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Identity authentication and secret key negotiation method and device in communication network
InactiveCN101267301AAvoid dependencePublic key for secure communicationUser identity/authority verificationSecure communicationSecurity solution
In the prior art, PKI which is taken as a safety settling plan is widely applied in the internet (IT network) field. But PKI has the disadvantages of high requirement to the capability of the communication equipment and consuming considerable system resource for managing and maintaining the digital certificate and can not adapted for the requirement of the communication network which is fusing. The aim of the invention is to provide a technical scheme which specially actualizes the cryptographic technique based on identity to the communication network. In particular, a management device is leaded into for generating and managing a private key based on the characteristic information of the communication equipment. The communication equipment uses the public key which is generated based on the corresponding characteristic information, the private key that is obtained based on the corresponding characteristic information and preferably the conversation key that is obtained based on the keys for the safety communication between other communication equipments.
Owner:ALCATEL LUCENT SHANGHAI BELL CO LTD
Seamless IP mobility across security boundaries
InactiveUS20080040793A1Connection managementMultiple digital computer combinationsSecurity solutionUser device
Owner:BIRDSTEP TECHNOLOGY AS
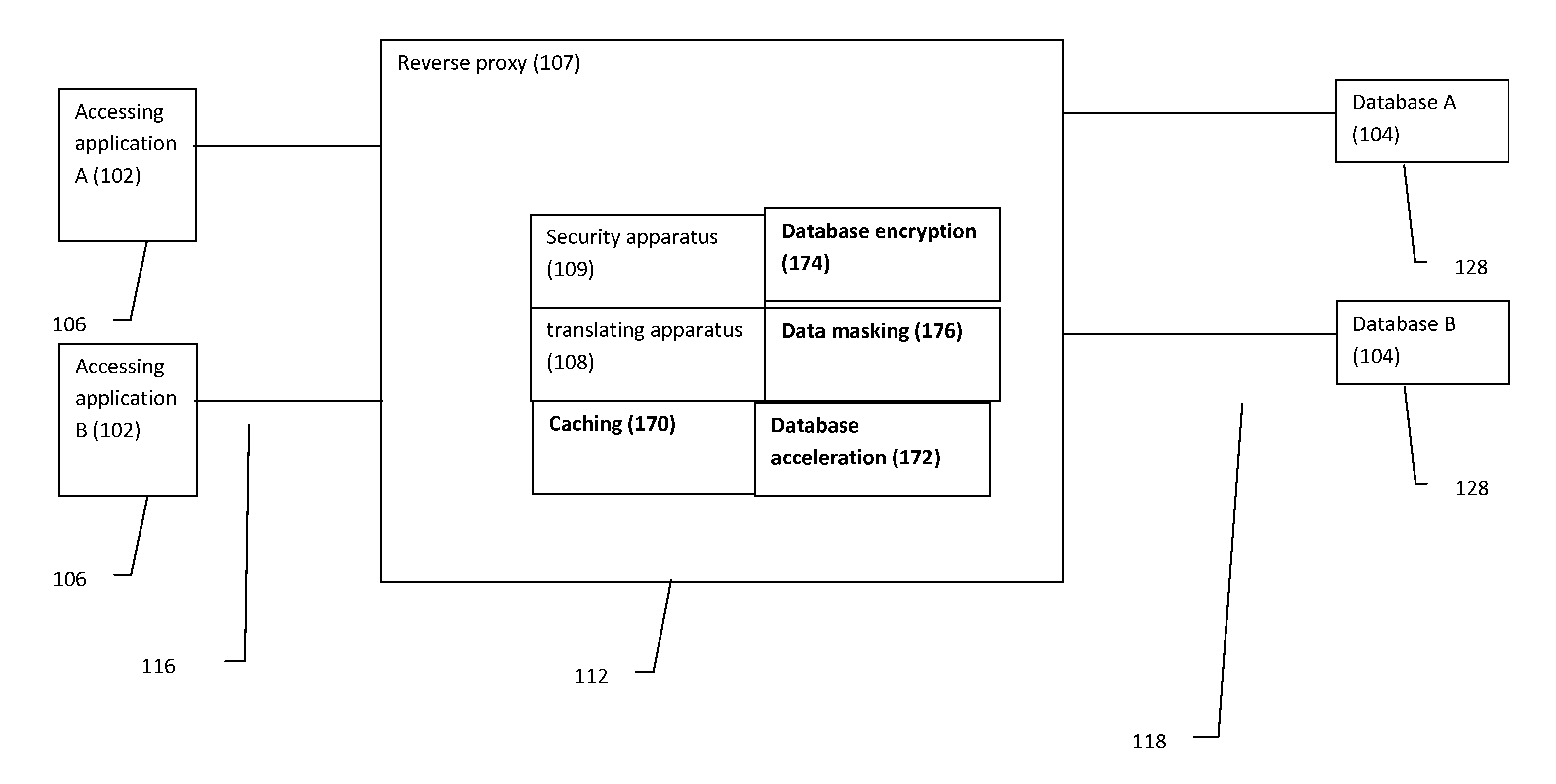
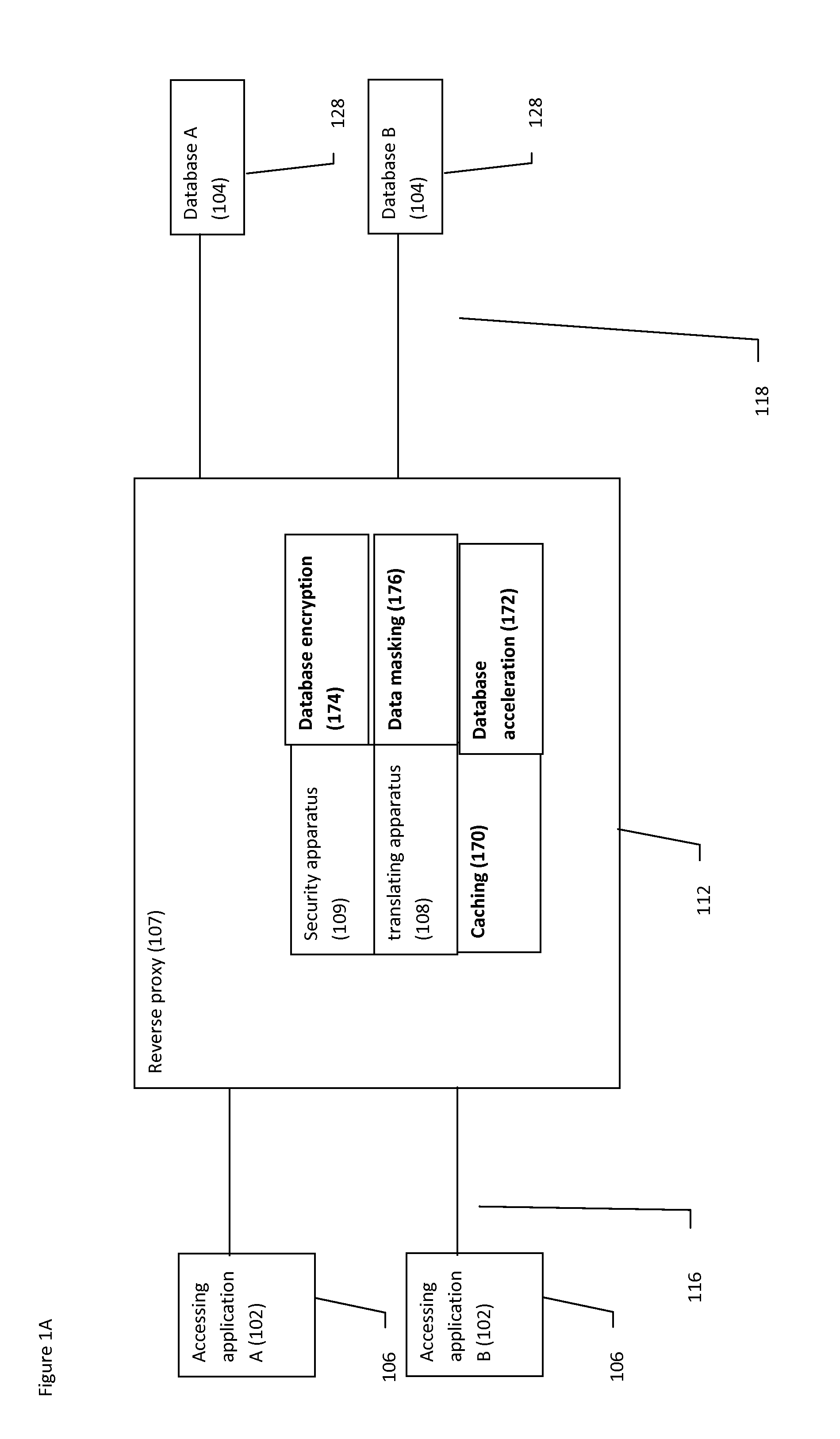
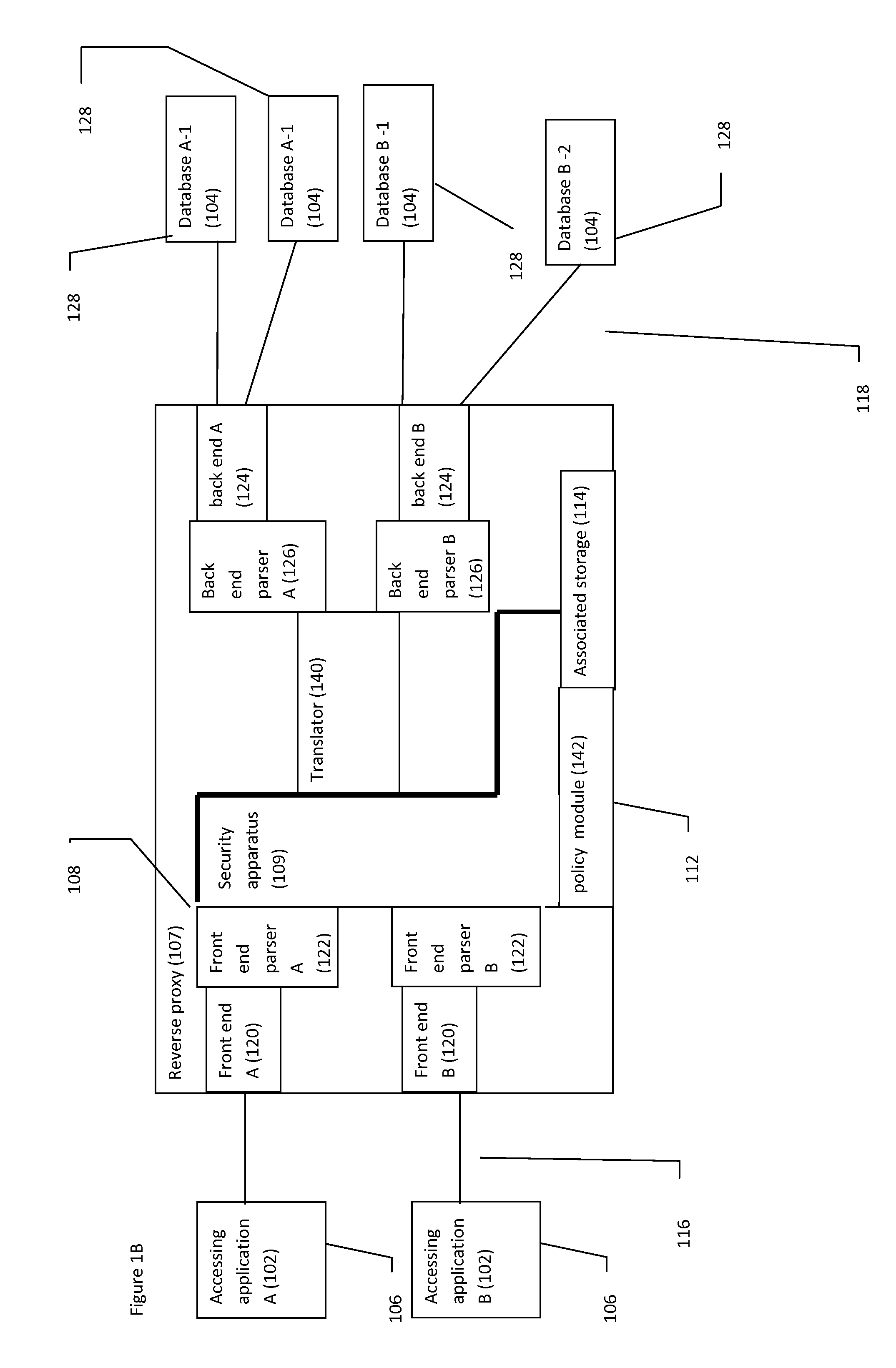
Reverse proxy database system and method
InactiveUS20130133059A1Multiple digital computer combinationsProgram controlSecurity solutionReverse proxy
A system and method for providing a comprehensive security solution for databases through a reverse proxy, optionally featuring translating database queries across a plurality of different database platforms.
Owner:GREEN SQL
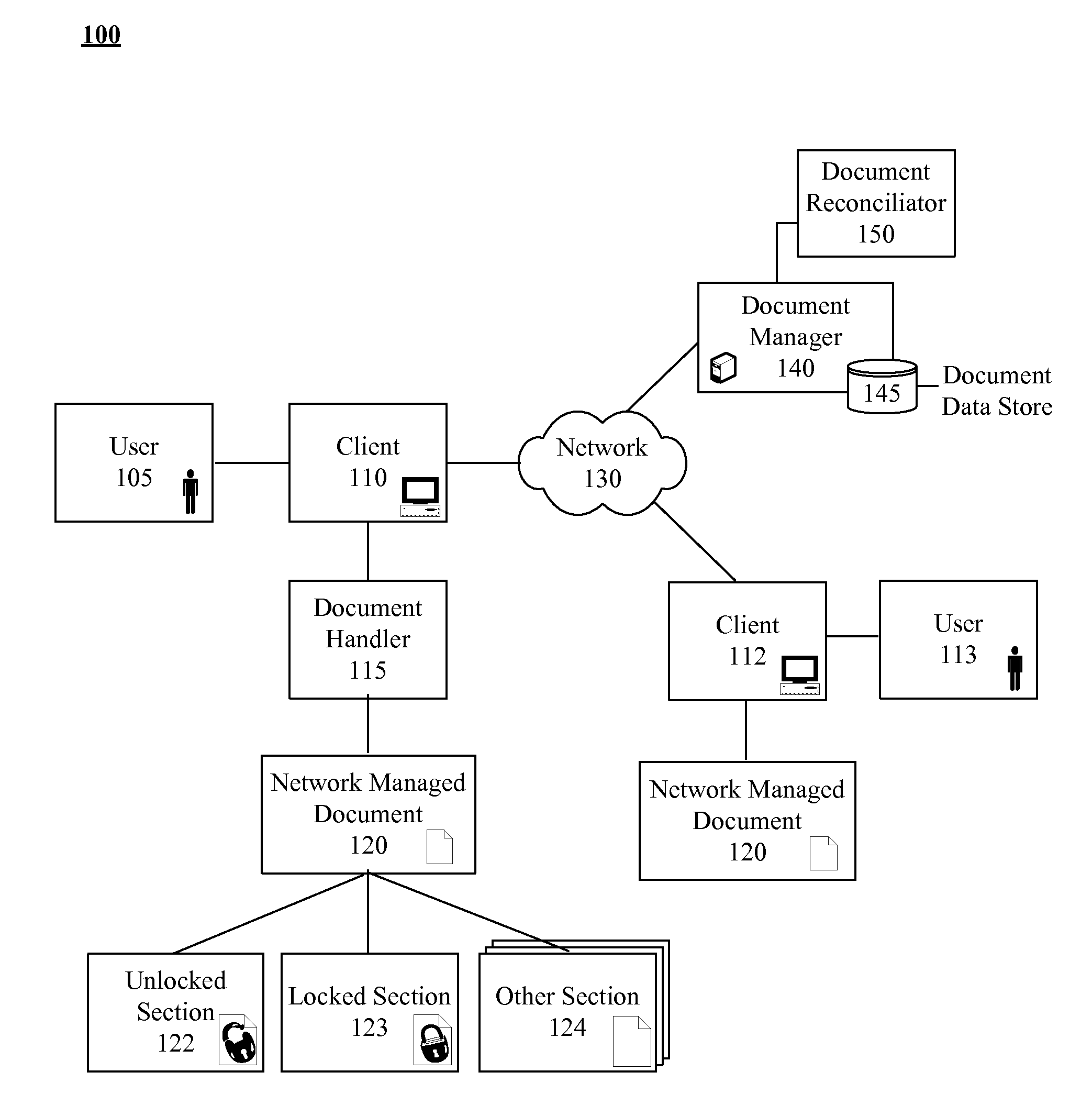
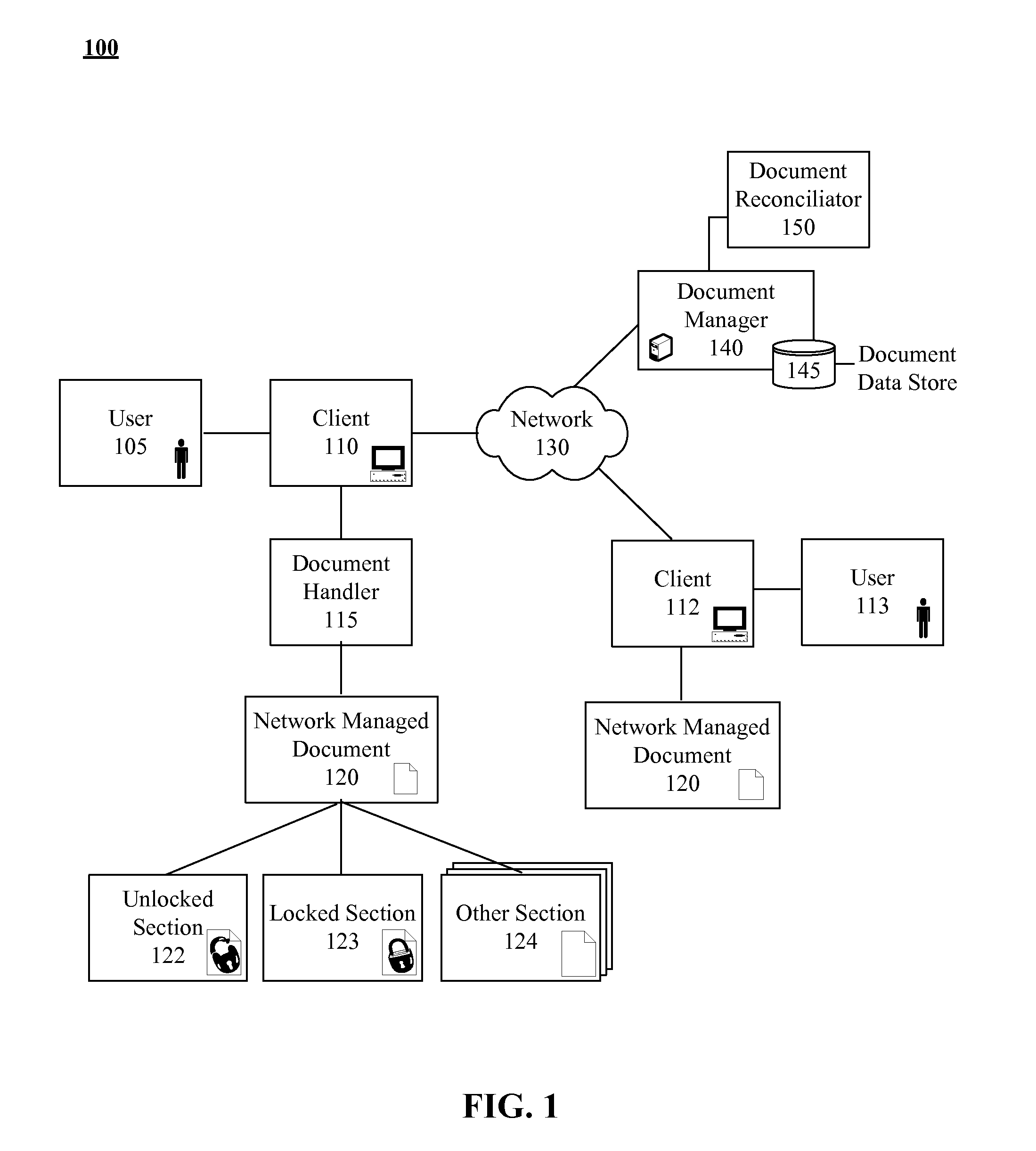
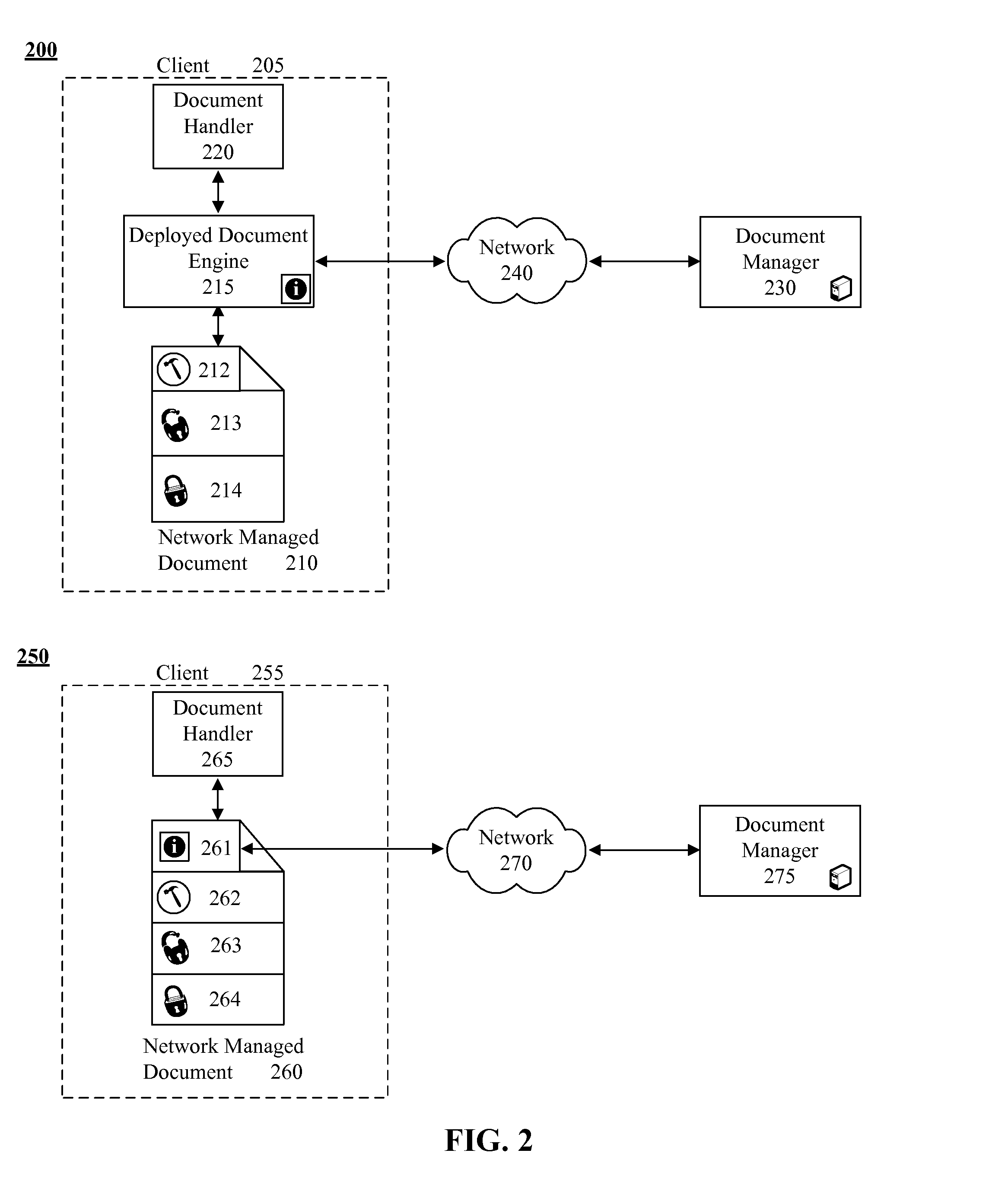
Post deployment electronic document management and security solution
InactiveUS20080018926A1Computer security arrangementsVisual presentationSecurity solutionElectronic document
A method for managing deployed electronic documents that can begin when the deployed electronic document is accessed. A data probe can be automatically conveyed to a remotely located document manager responsive to the access attempt. The data probe can include data specific to the deployed electronic document. A management command can be received from the document manager. At least one management action can be locally and automatically performed for the deployed electronic document in accordance with the received management command. The management action can alter the content of the deployed electronic document and / or access rights to existing content of the deployed electronic document.
Owner:IBM CORP
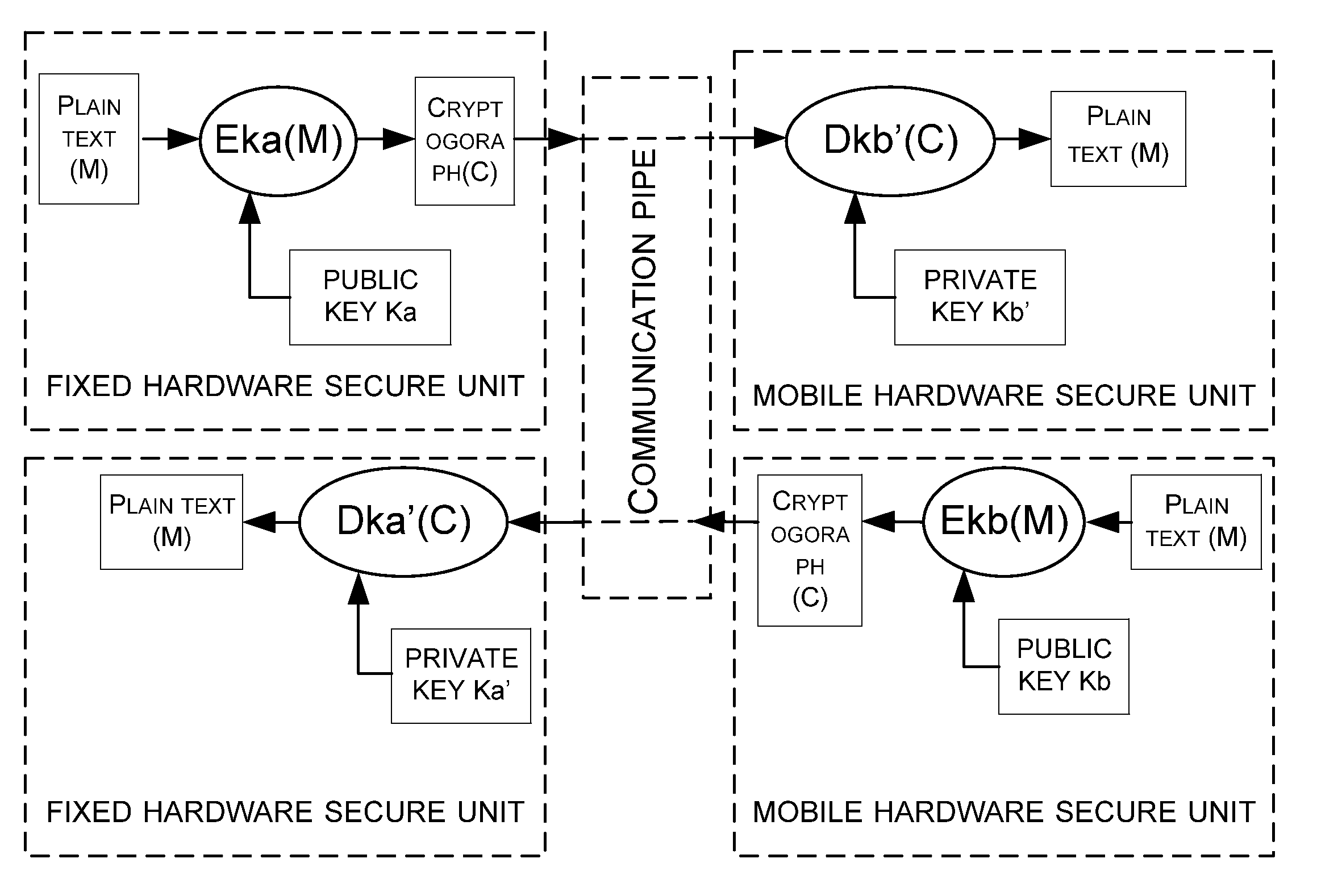
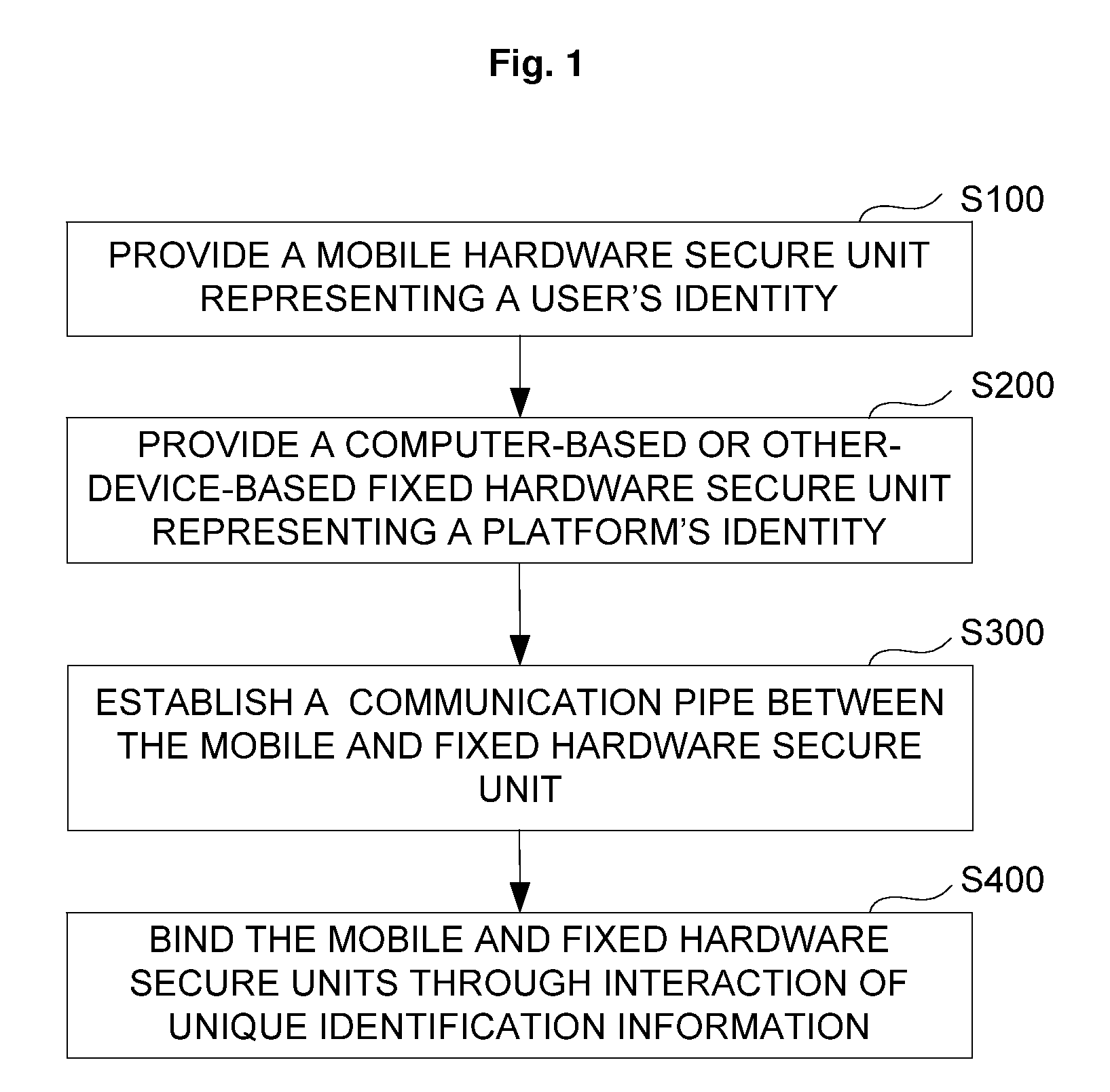
Cooperation method and system of hardware secure units, and application device
ActiveUS20090254749A1Improve securityUser identity/authority verificationDigital data authenticationSecurity solutionSecure unit
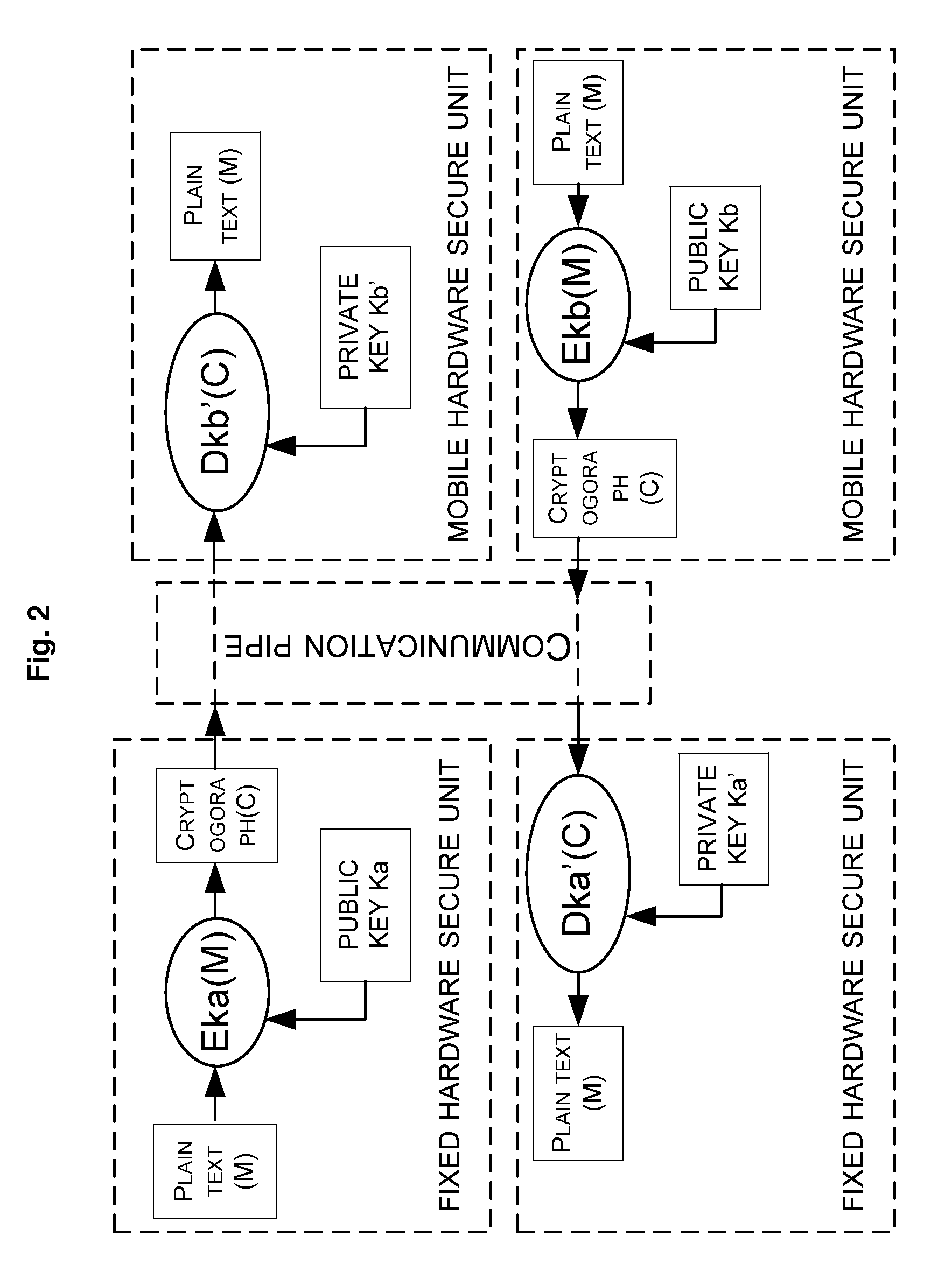
The present invention provides a cooperation method of a mobile hardware secure unit and a fixed hardware secure unit, comprising: providing user's identification information of a mobile hardware secure unit; providing platform's identification information of a computer-based or other-device-based fixed hardware secure unit; establishing a bidirectional communication pipe between the mobile and fixed hardware secure unit; and binding the mobile and fixed hardware secure units through interaction of the user's identification information and the platform's identification information. The present invention further provides a cooperation system of a mobile hardware secure unit and a fixed hardware secure unit as well as a computer device, with which the security solution based on a fixed hardware secure unit can be combined with a mobile hardware secure unit securing a user's identity.
Owner:LENOVO SOFTWARE +1
Security Method for Mobile Ad Hoc Networks with Efficient Flooding Mechanism Using Layer Independent Passive Clustering (LIPC)
ActiveUS20130145461A1Efficient mechanismEfficient flooding mechanismMemory loss protectionError detection/correctionSecurity solutionPacket forwarding
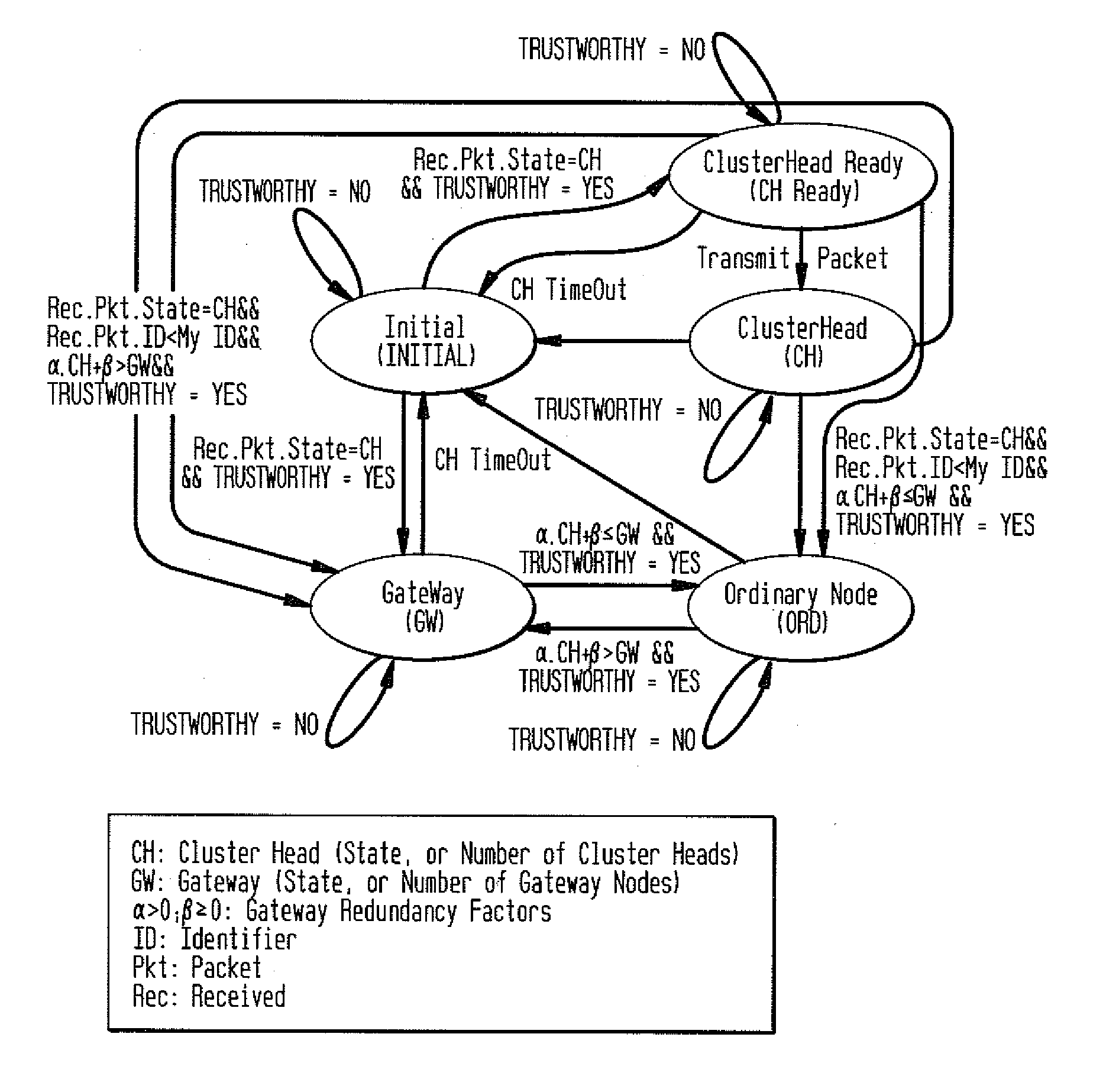
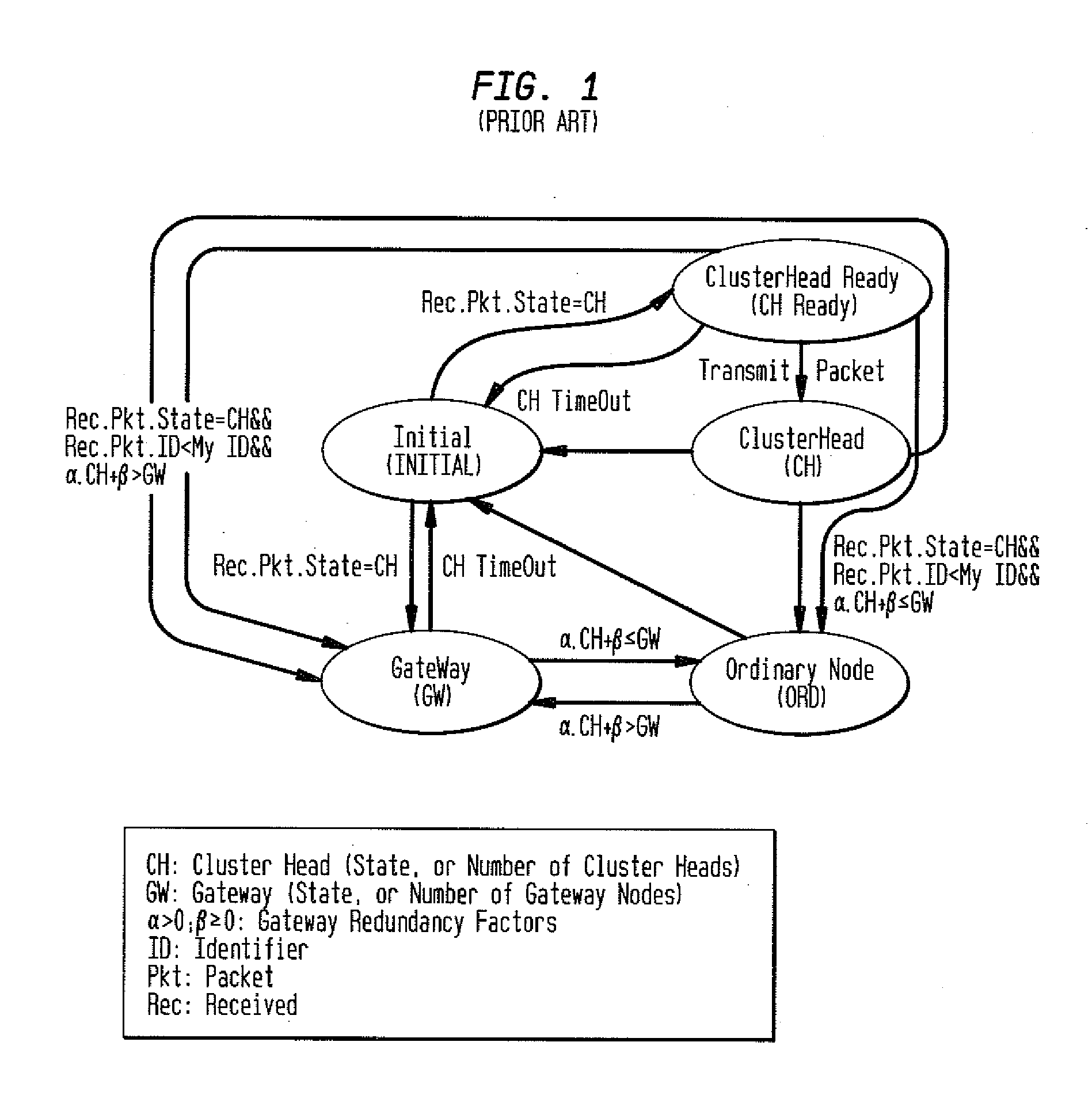
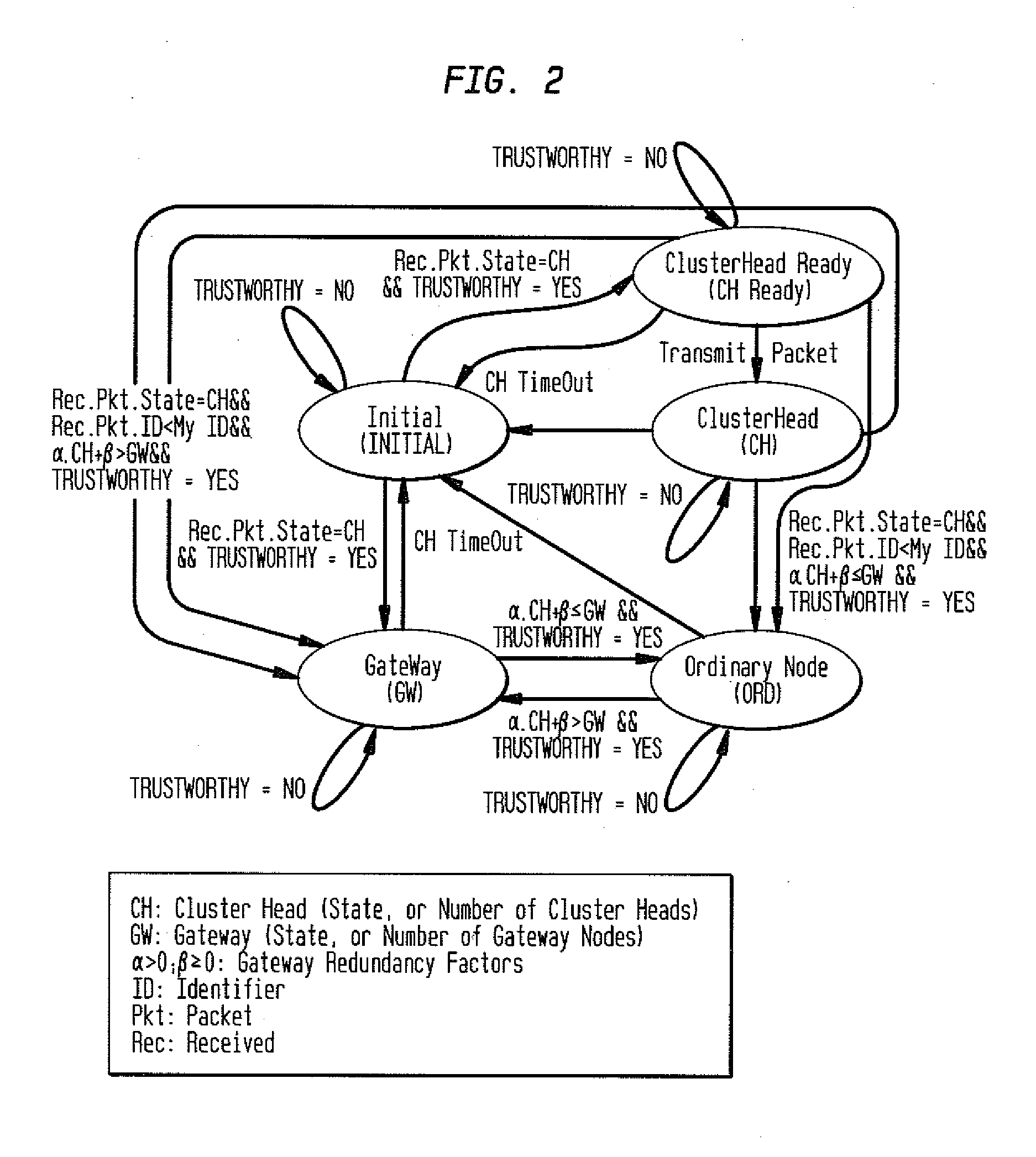
A security method and system for Layer Independent Passive Clustering (LIPC) is presented. The inventive method and system maintains the states in the LIPC cluster formation protocol while adding a ‘Trusworthy’ event to each state and provides a methodology that depends on the state of the transmitting node to quantify Trustworthy and derive a Trust Confidence Value (TCV) to represent the level of confidence in quantifying ‘Trustworthy’. The invention dynamically computes a degree of trustworthiness for each participating network node and eliminates nodes from participating in the PC cluster formation protocol and packet forwarding if they do not meet established trust metrics. The security solution can also apply to PC-based Mobile Ad hoc Networks (MANETs). The novel system and method applies a multidimensional set of security algorithms to protect the LIPC cluster formation protocol from malicious attacks that compromise cluster formation and secure routing.
Owner:TELCORDIA TECHNOLOGIES INC
Node of a distributed communication system, node and monitoring device coupled to such communication system
ActiveUS20100014439A1Improve detection errorReduce complexityError preventionFrequency-division multiplex detailsSecurity solutionCommunications system
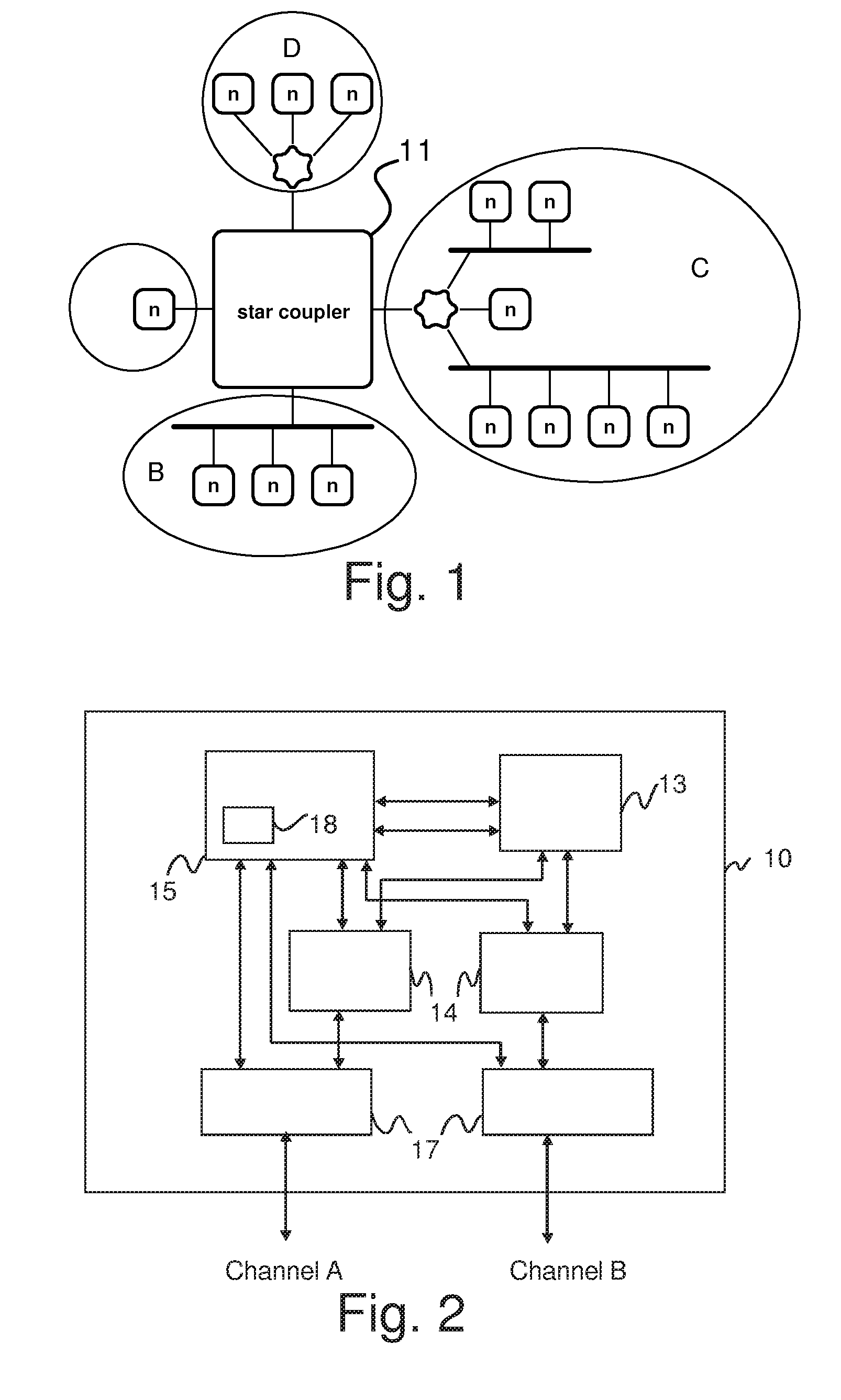
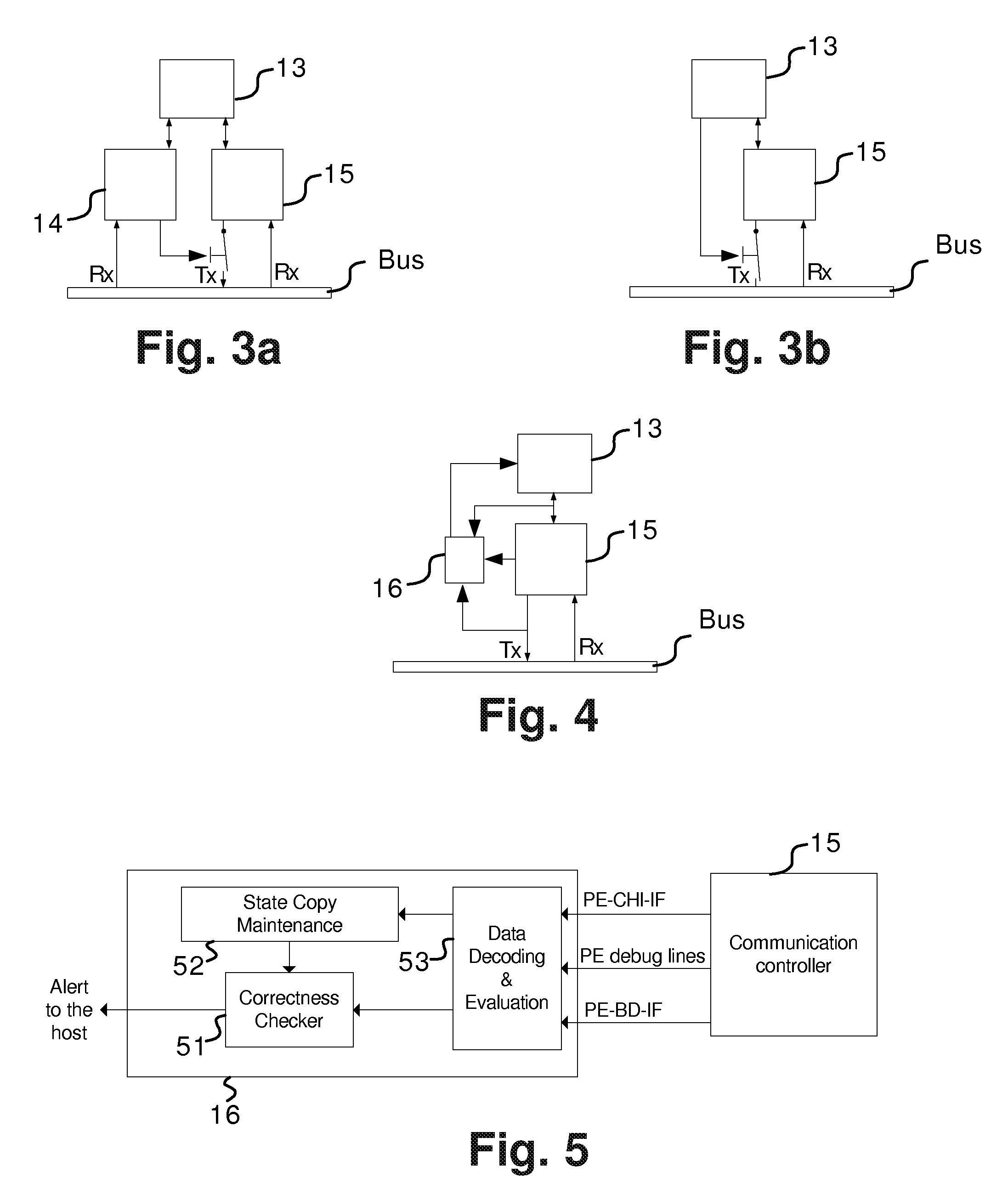
The present invention relates to a node in distributed communication system operating under a time triggered protocol, further it relates to distributed communication system and to a monitoring device coupled to such node of a communication system. To provide a node in a distributed communication system, a distributed communication system and a monitoring device increasing the error detection and reducing complexity for providing a high availability for systems which require a non 100% fail safe solution a node is proposed comprising: a communication controller (15) coupled to a receiving and a transmission path, a host (13) for performing an application, and a monitoring device (16) coupled at least to one of a transmission path of the communication controller (15), an interface (91) between communication controller (15) and the host (13), and to internal lines of the communication controller (15), wherein the monitoring device (16) is provided for evaluating information provided by the communication controller (15) to monitor at least one state of the communication controller (15), wherein in case of detecting a non-defined state the host (13) is informed for performing predetermined actions in respect to the state of the communication controller (15). Thereby, an easy cost reduced solution is provided adapted to detect a predetermined number of faults in a distributed communication system.
Owner:NXP BV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com