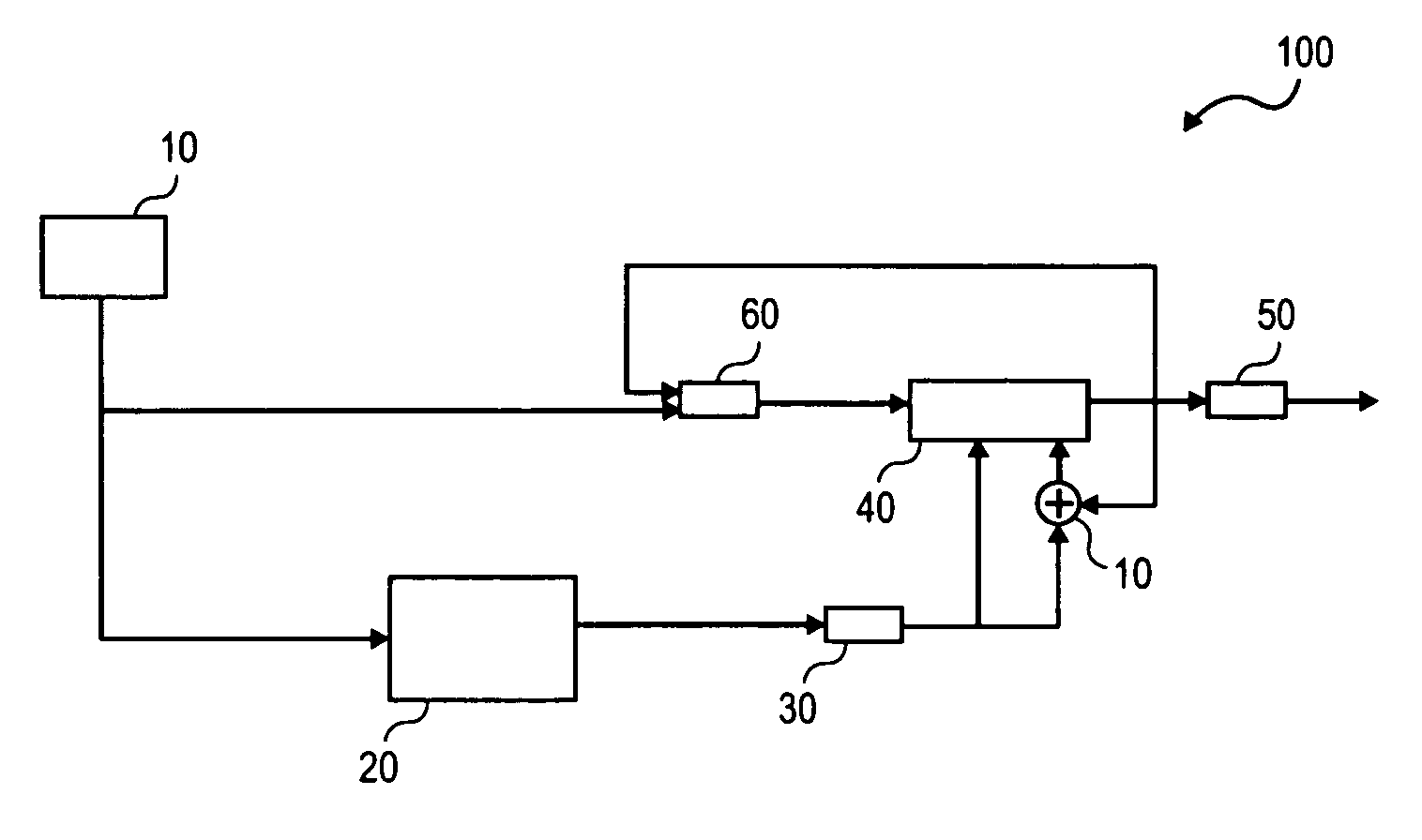
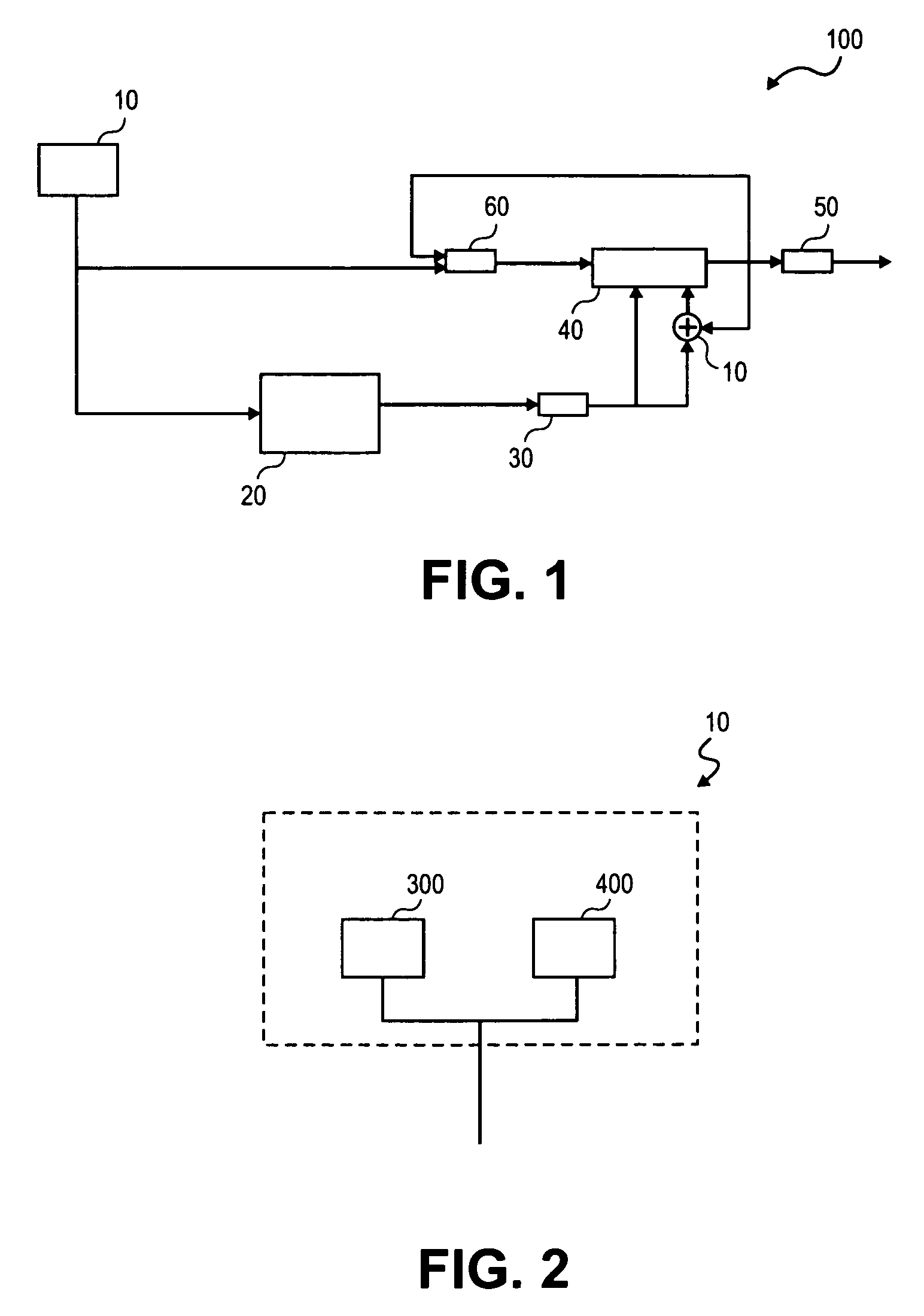
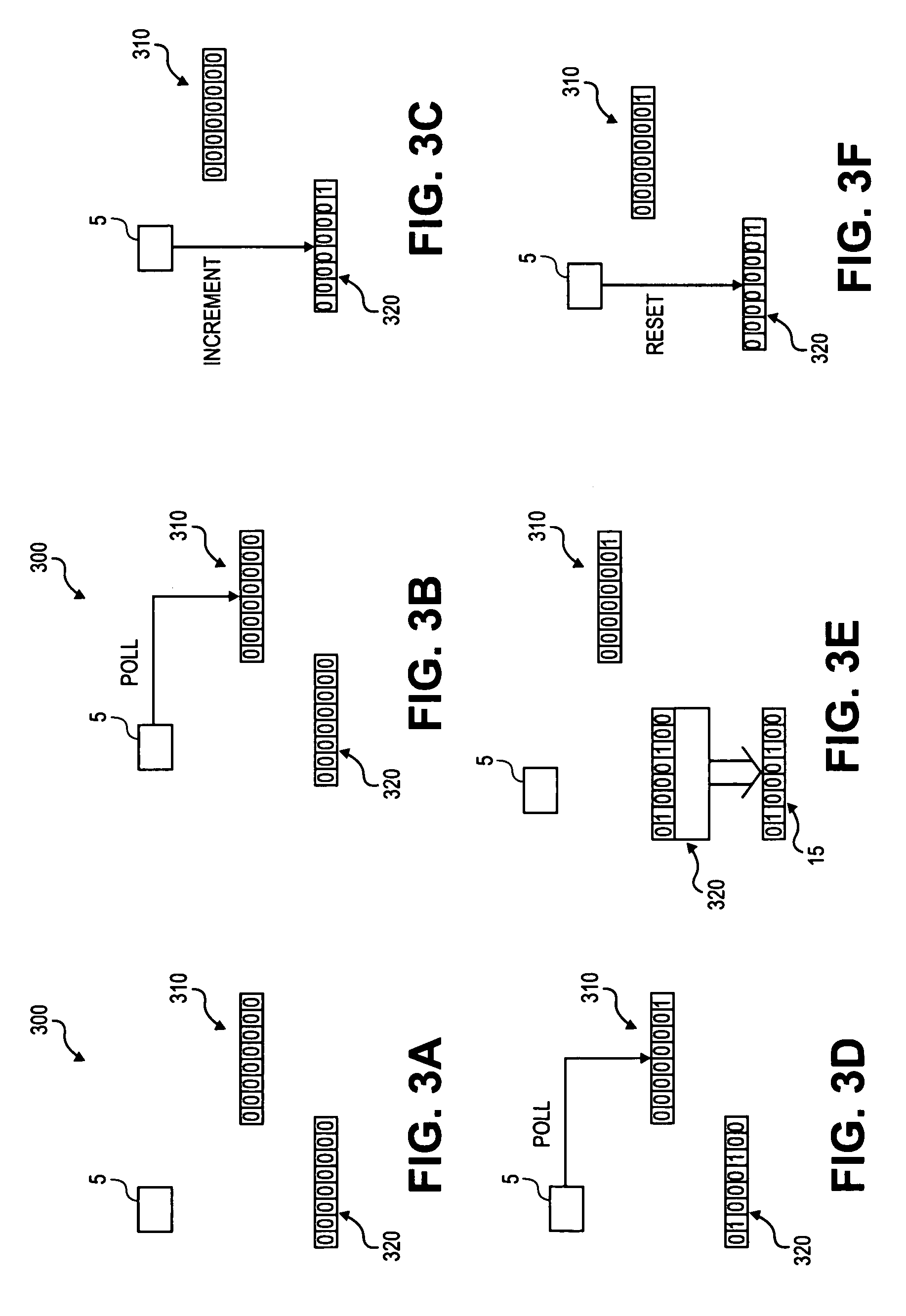
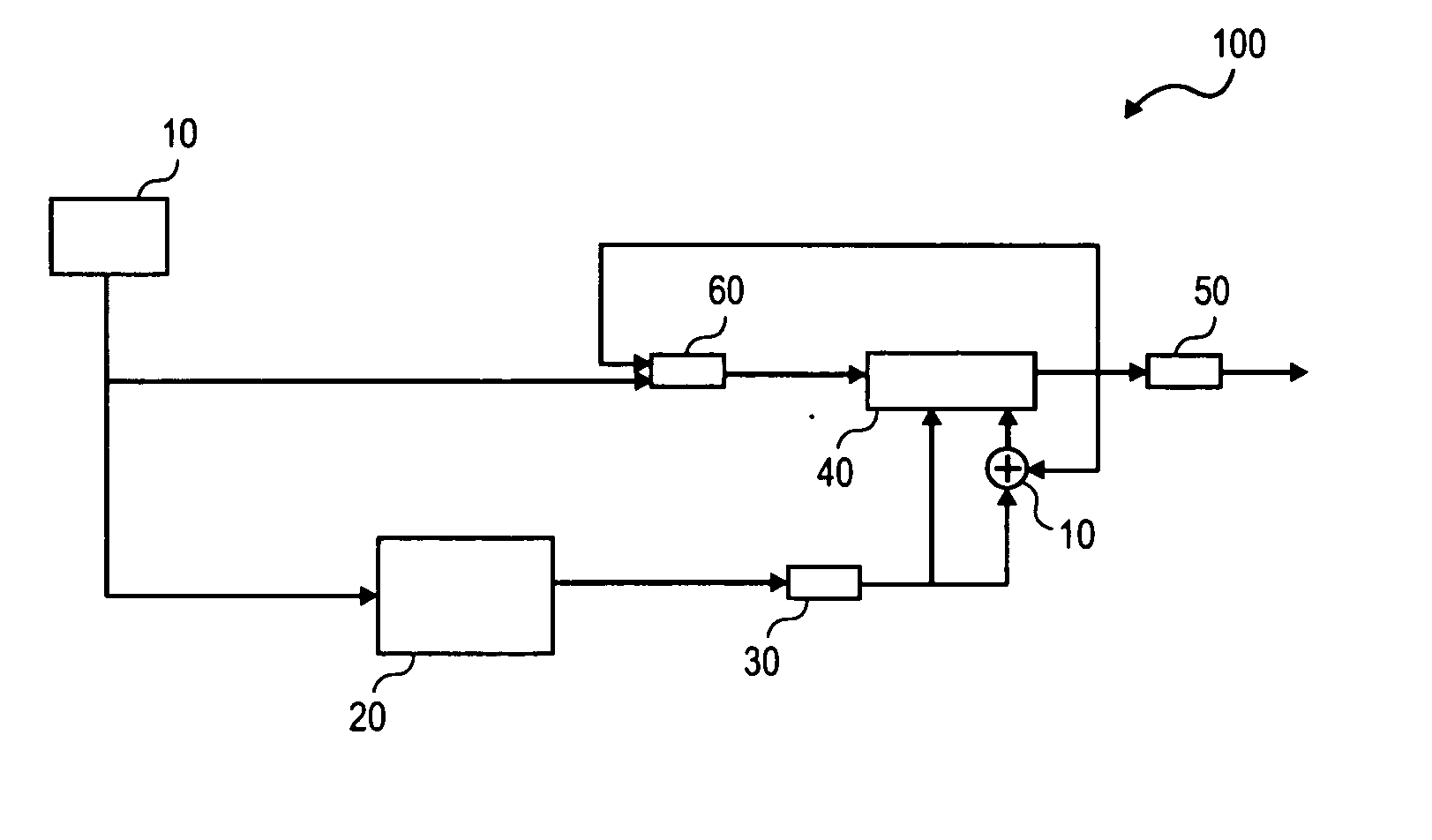
Patents
Literature
117 results about "Cryptographic hash function" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
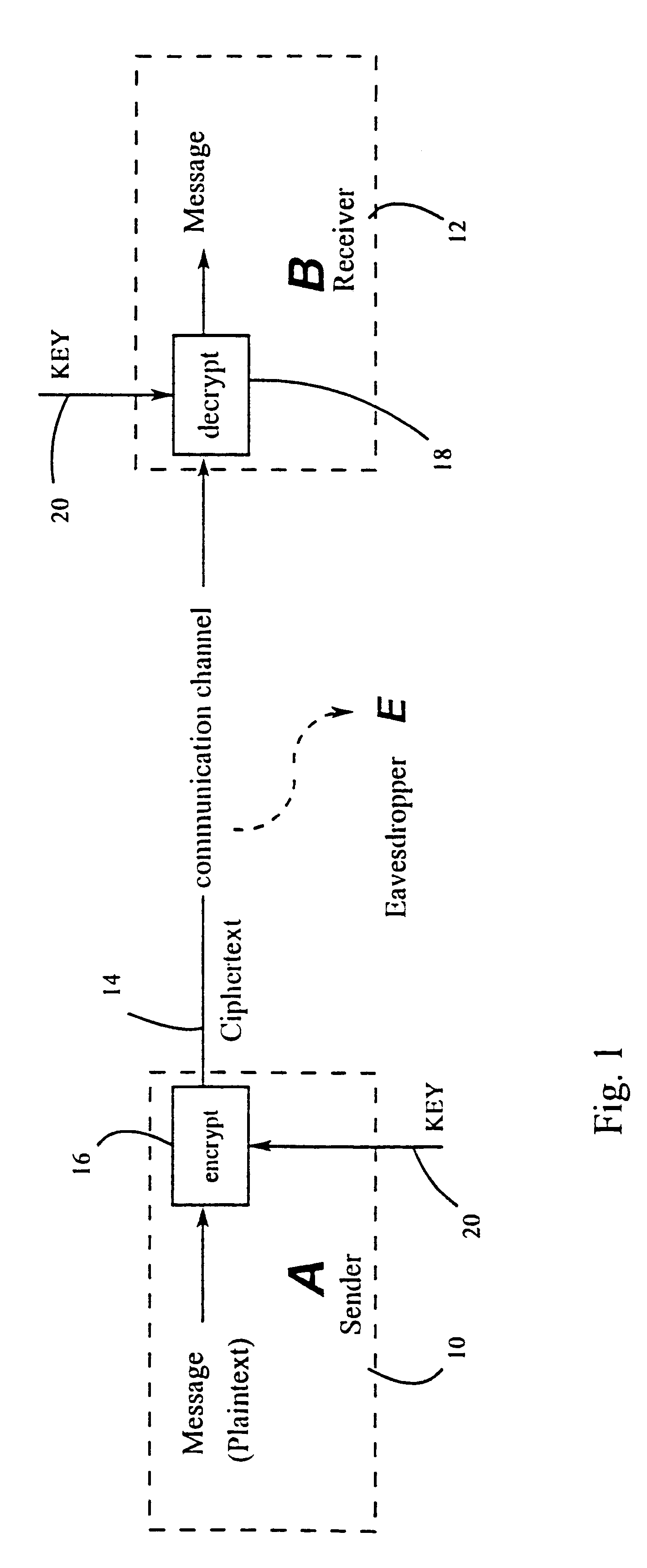
A cryptographic hash function (CHF) is a hash function that is suitable for use in cryptography. It is a mathematical algorithm that maps data of arbitrary size (often called the "message") to a bit string of a fixed size (the "hash value", "hash", or "message digest") and is a one-way function, that is, a function which is practically infeasible to invert. Ideally, the only way to find a message that produces a given hash is to attempt a brute-force search of possible inputs to see if they produce a match, or use a rainbow table of matched hashes. Cryptographic hash functions are a basic tool of modern cryptography.
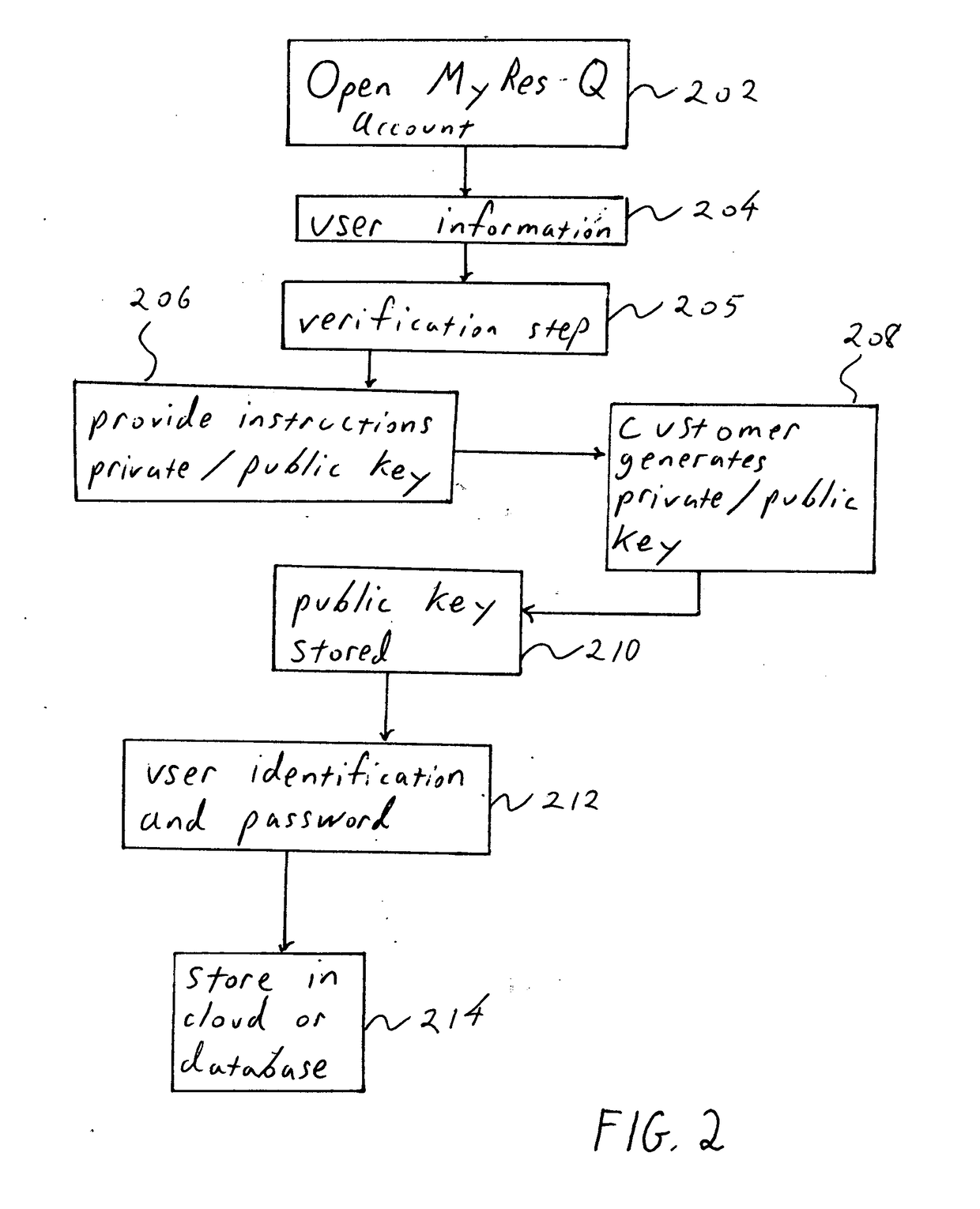
Decentralized identity verification systems and methods
InactiveUS20150356523A1Cryptography processingUser identity/authority verificationRegulatory authorityFinancial transaction
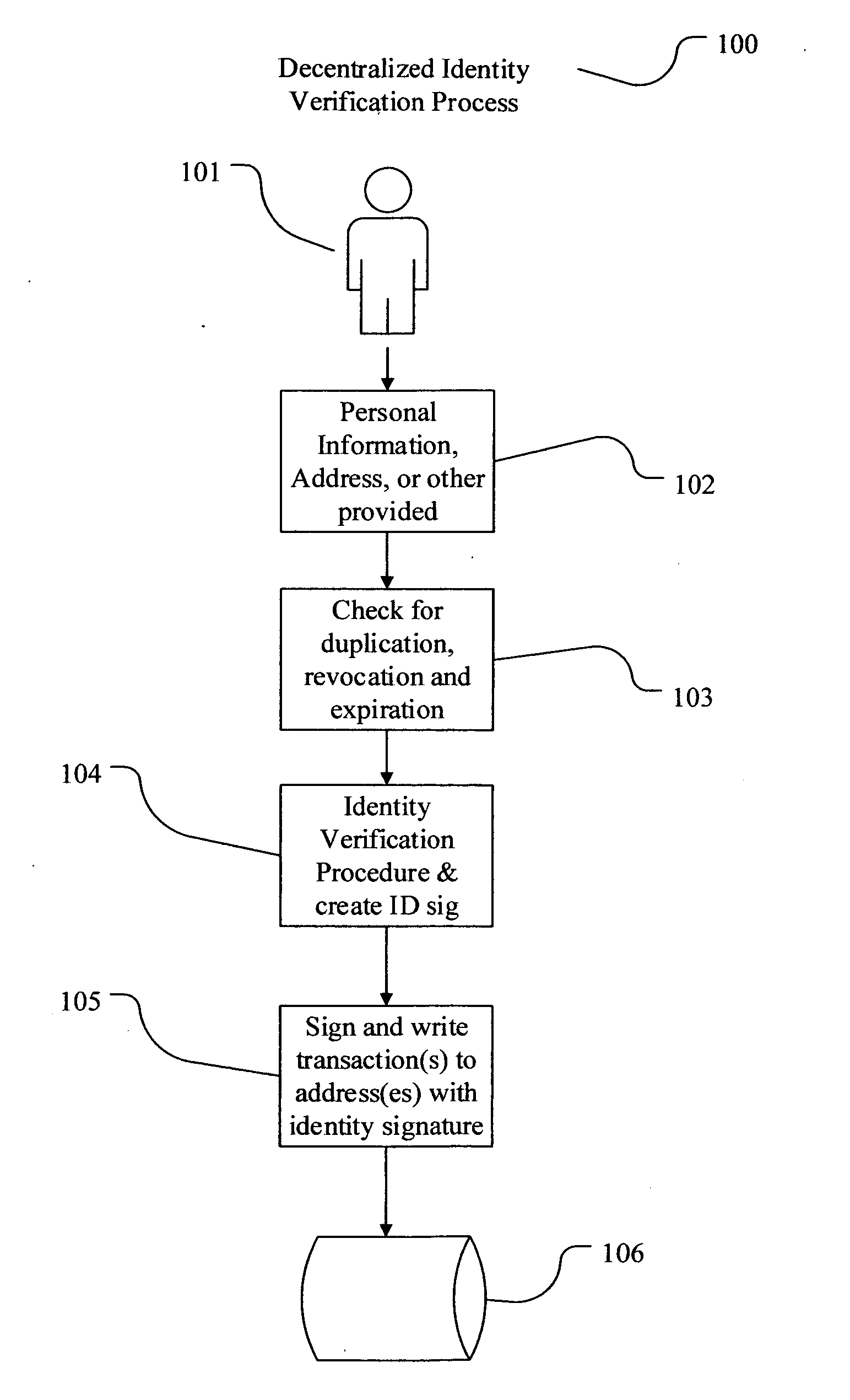
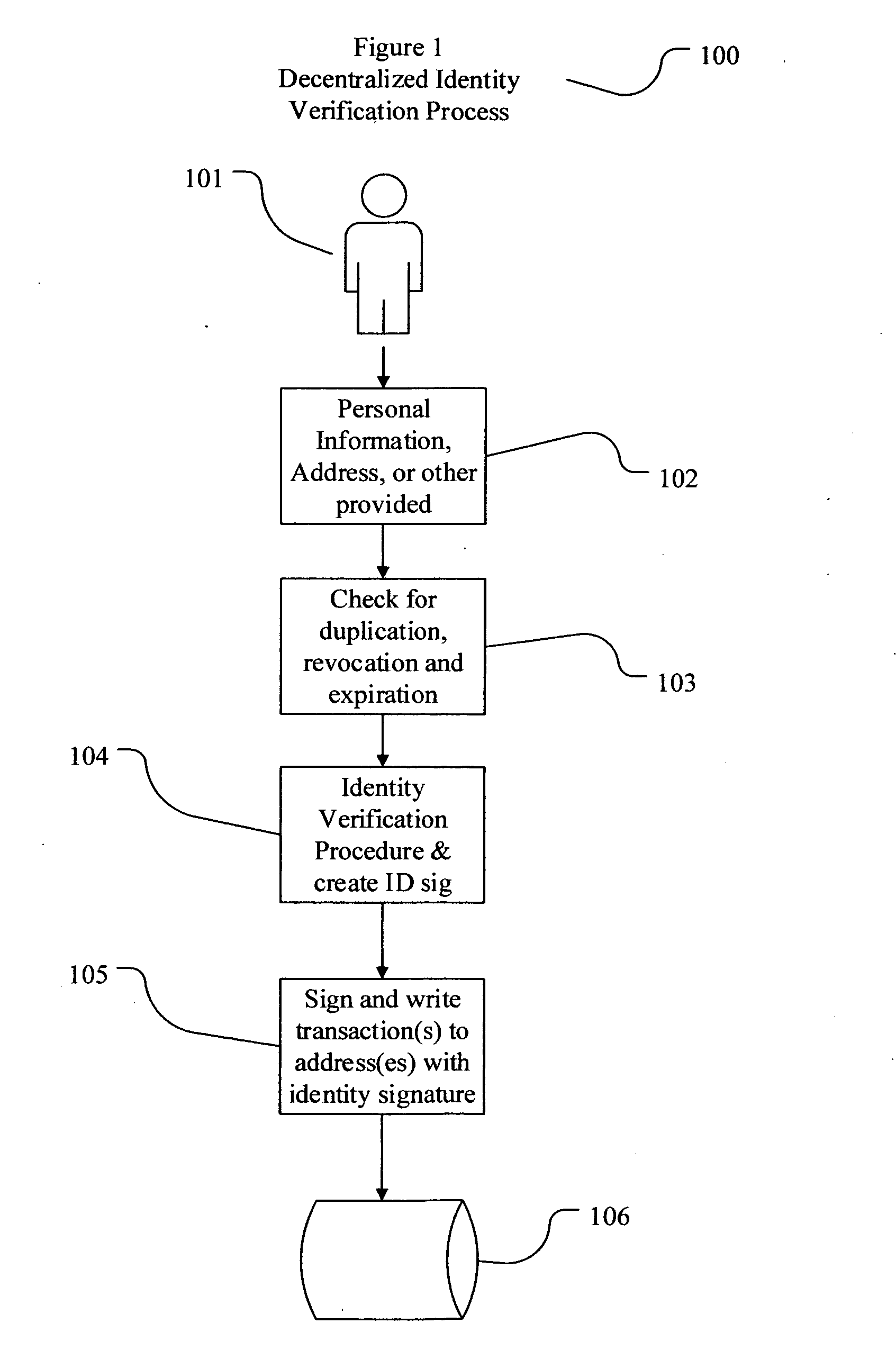
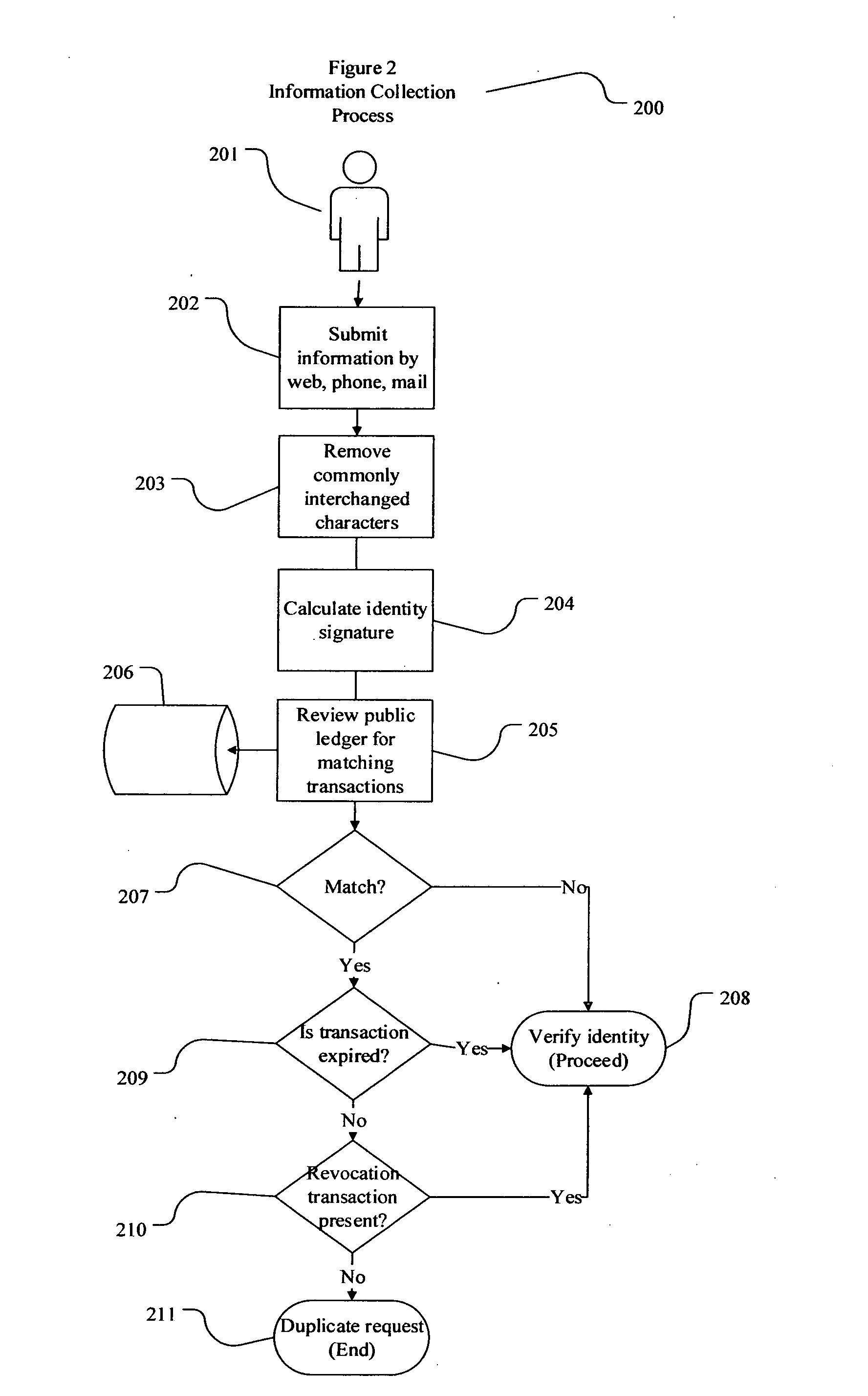
The present invention involves systems and methods that allow participants in cryptocurrency networks to exchange cryptocurrency for traditional currency legally and safely without requiring the use of a traditional exchange or online brokerage as a fiduciary. The invention accomplishes this through the use of a decentralized identity verification protocol that allows a service provider to verify the identity of a participant and then publish an identity signature on the participant's cryptocurrency address or addresses. The invention enables full compliance with Country specific customer identification program and anti-money laundering requirements, and maintains the ability to independently satisfy requests for information or data retention requirements if requested by legally authorized parties, but does not require that the participant store the private keys or access controls to their cryptocurrency on an exchange or brokerage service.The invention serves to verify a participant's identity in full compliance with US Bank Secrecy and Patriot Act provisions or similar regulations where identification may be achieved through non-documentary or documentary identity verification procedures. After passing the applicable verification procedure, the service provider stamps the participant's cryptocurrency address with a transaction containing an identity signature. This identity signature within the transaction consists of a public indicator of the participant's Country and subdivision, a compliance level code, an ID type indicator, and an identity hash. The identity hash is created from the digests of cryptographic hash functions where the participant's personal information is used as an input. The service provider signs the transaction with their authorized private key that corresponds to their publicly accessible public key. This serves as a publicly verifiable confirmation that the identity associated with the address in question was validated by the service provider authorized to act on behalf of the regulatory authority.The participant may then purchase and sell cryptographic currency from and to a third party exchange or brokerage service legally and safely when using their verified cryptocurrency address. This is because the third party is able to confirm compliance by openly referencing and verifying the identity verification transaction present on the address. Subsequent transactions where the third party sells or purchases cryptocurrency for the verified participant are similarly stamped with a transaction conforming to the identity verification protocol. This allows the third party interacting with the verified participant's address to observe any regulations limiting the amount or frequency of transactions over a variable period of time. It follows that this address could be used with any third party or participant in the cryptocurrency network that observes the decentralized identity verification protocol, all without requiring the third party or participant to collect and verify personal information redundantly. The ability to verify an identity remotely also eliminates the need for the third party to act as a fiduciary holding the private keys or access controls to the verified address. Lawful requests for information by authorized authorities are served to the service provider as digitally signed transactions that may then be linked to the participant's identity and transactions, allowing the protocol to observe subpoenas or similar lawful requests for information. The encrypted personal information may be held in escrow by the service provider indexed to the verified cryptocurrency address for such purposes. An alternate embodiment would store the encrypted personal information in a decentralized network of other participants, with the information accessible for retrieval using the public key of the verified cryptocurrency address and decryption using the corresponding private key, decentralizing the process entirely except for the identity verification step.
Owner:CHAINID
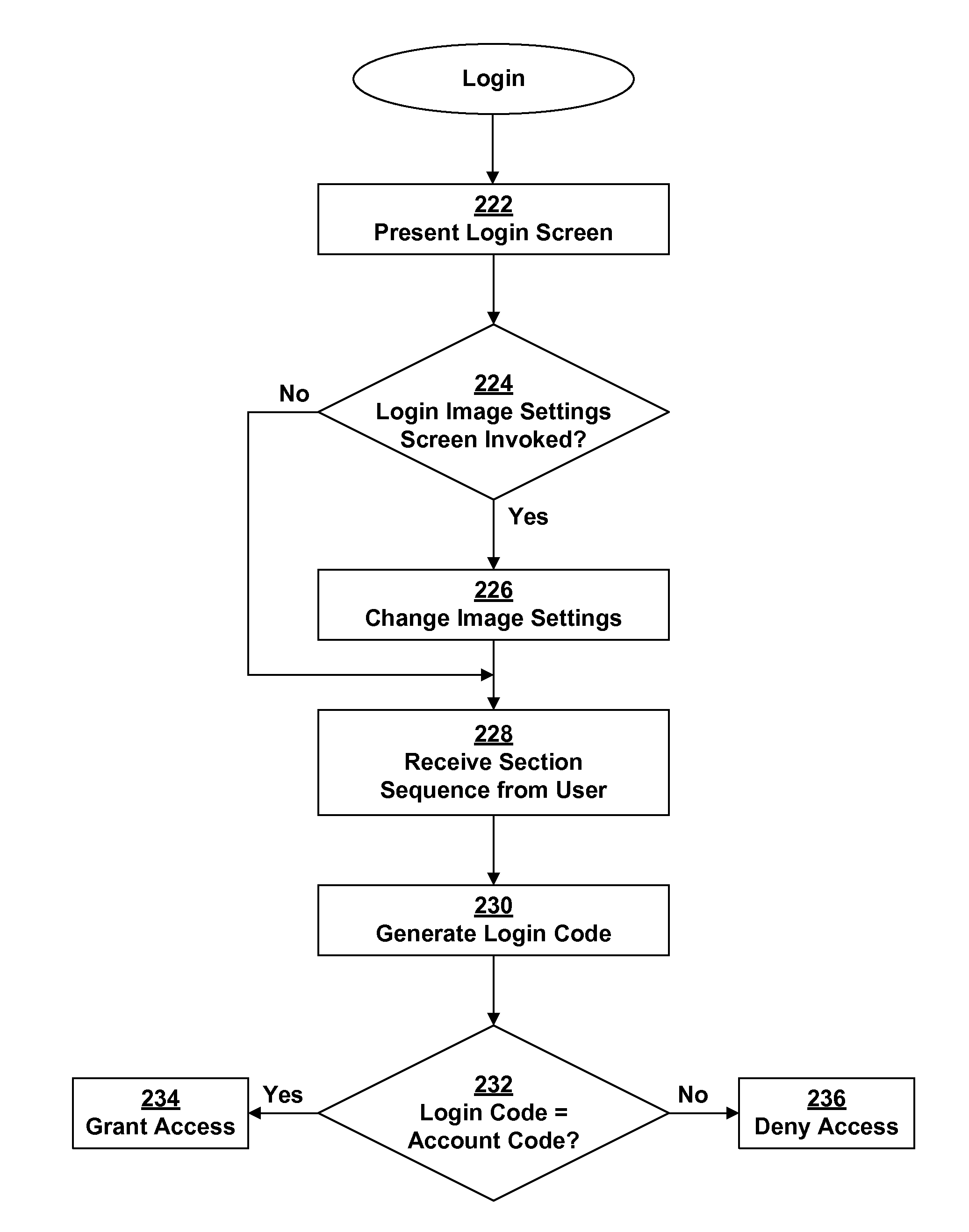
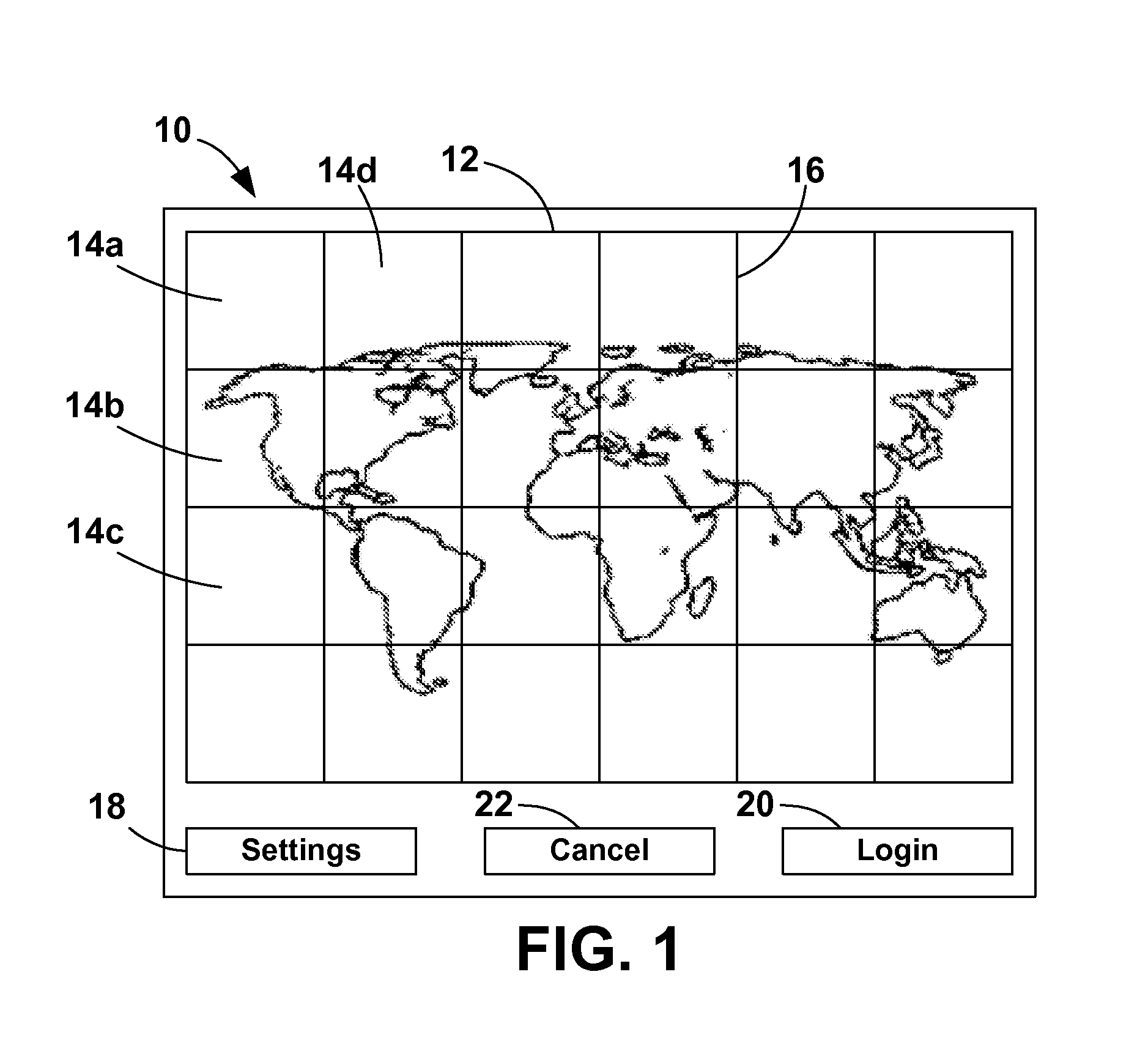
Method for Image-Based Authentication
InactiveUS20120005483A1Digital data processing detailsDigital data authenticationCryptographic hash functionAuthentication
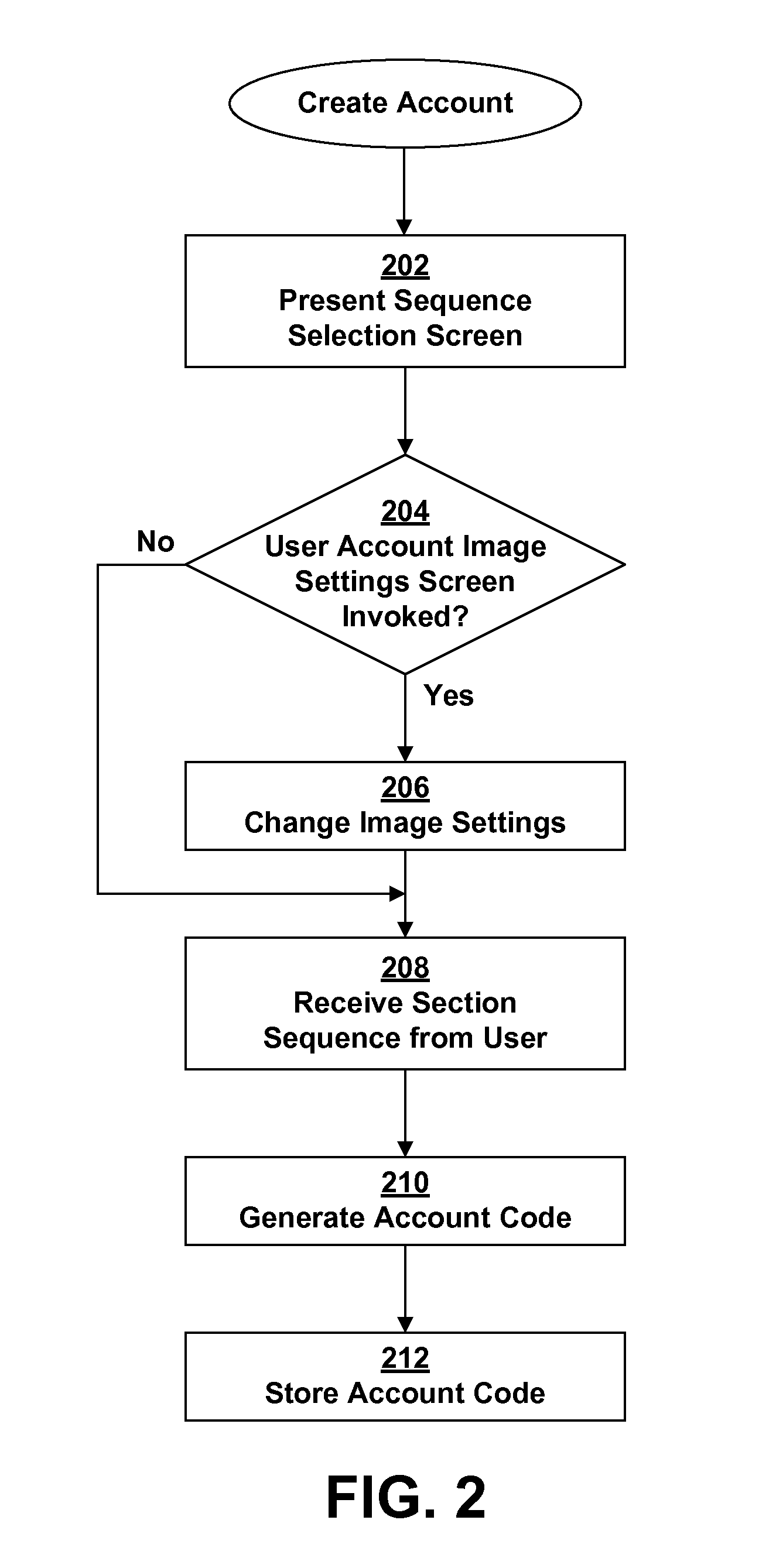
A method for authenticating user access to a restricted resource that presents a login screen with an image separated into sections. To login, the user triggers sections in a preset sequence that is set up at account creation. At account creation, a cryptographic hash function is applied to a chosen sequence of sections to generate the user's account code. Optionally, elements of the image and / or the user name are included. The user invokes the login screen when access to a restricted resource is desired. The user must change login settings if any parameters, such as a particular image, are elements of the account code. The user triggers the sections in the appropriate order. The cryptographic hash function is applied to the section sequence and any optional elements to generate the login code, which is compared to the stored account codes to either grant or deny access to the restricted resource.
Owner:HYDRABYTE
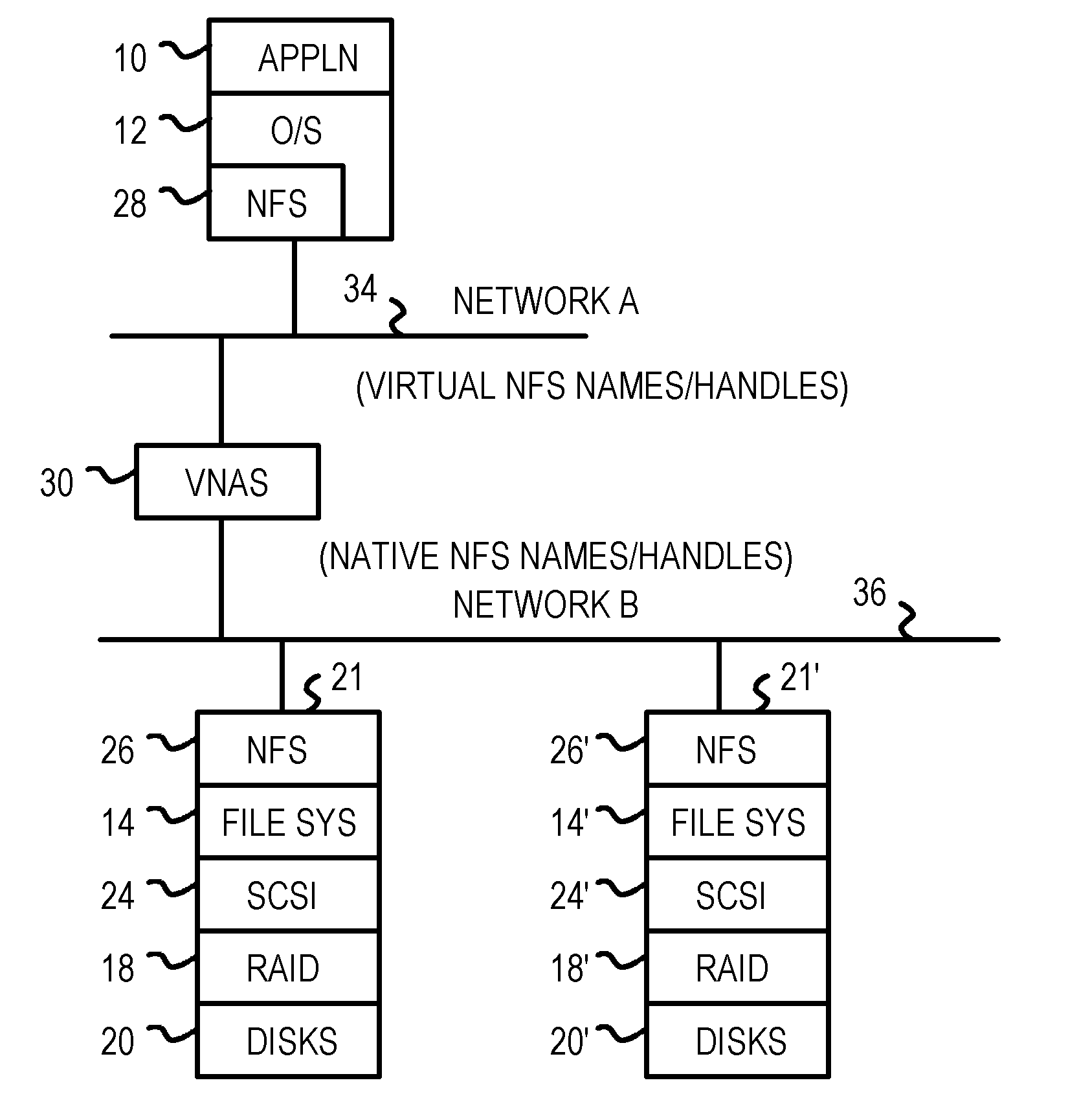
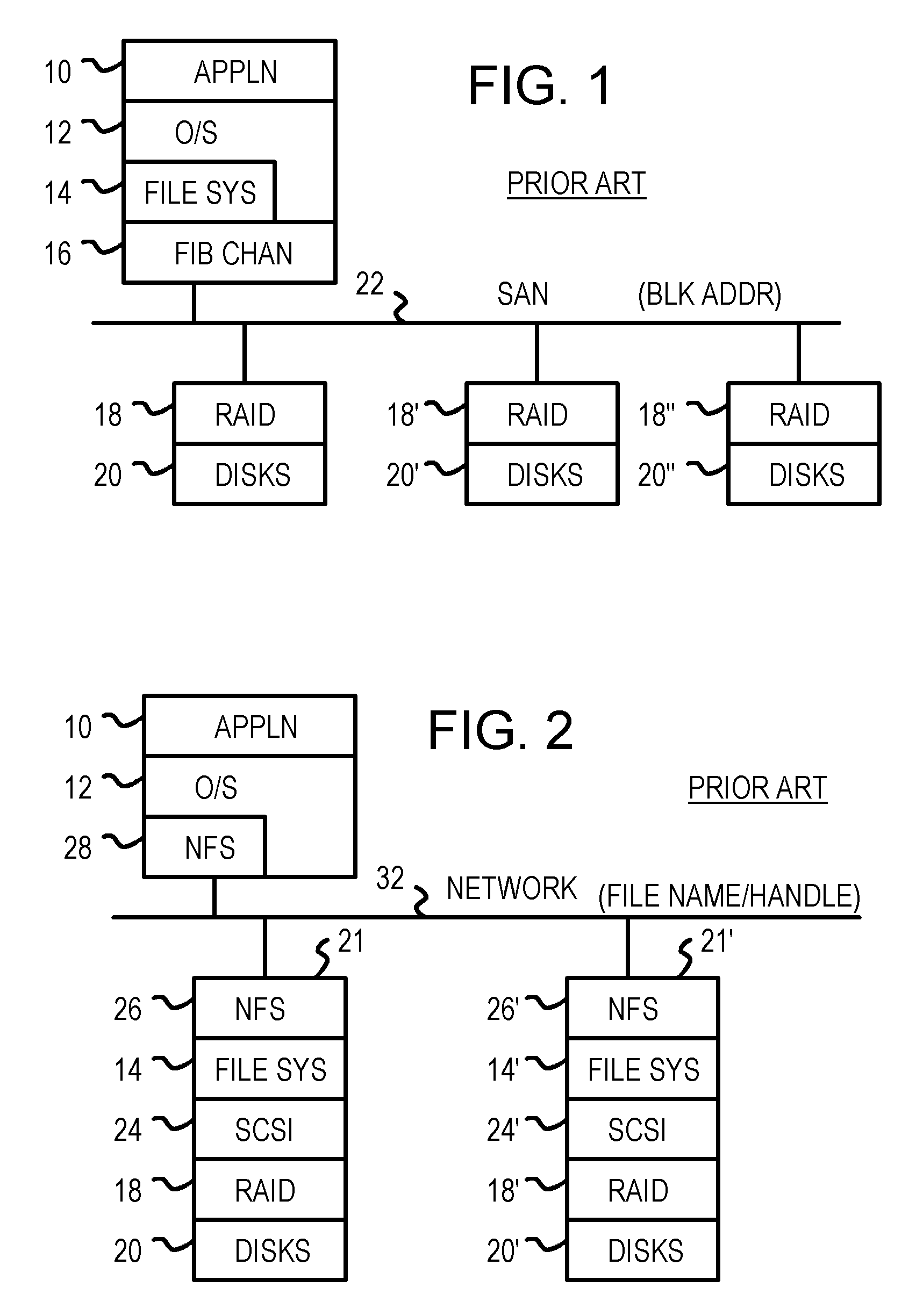
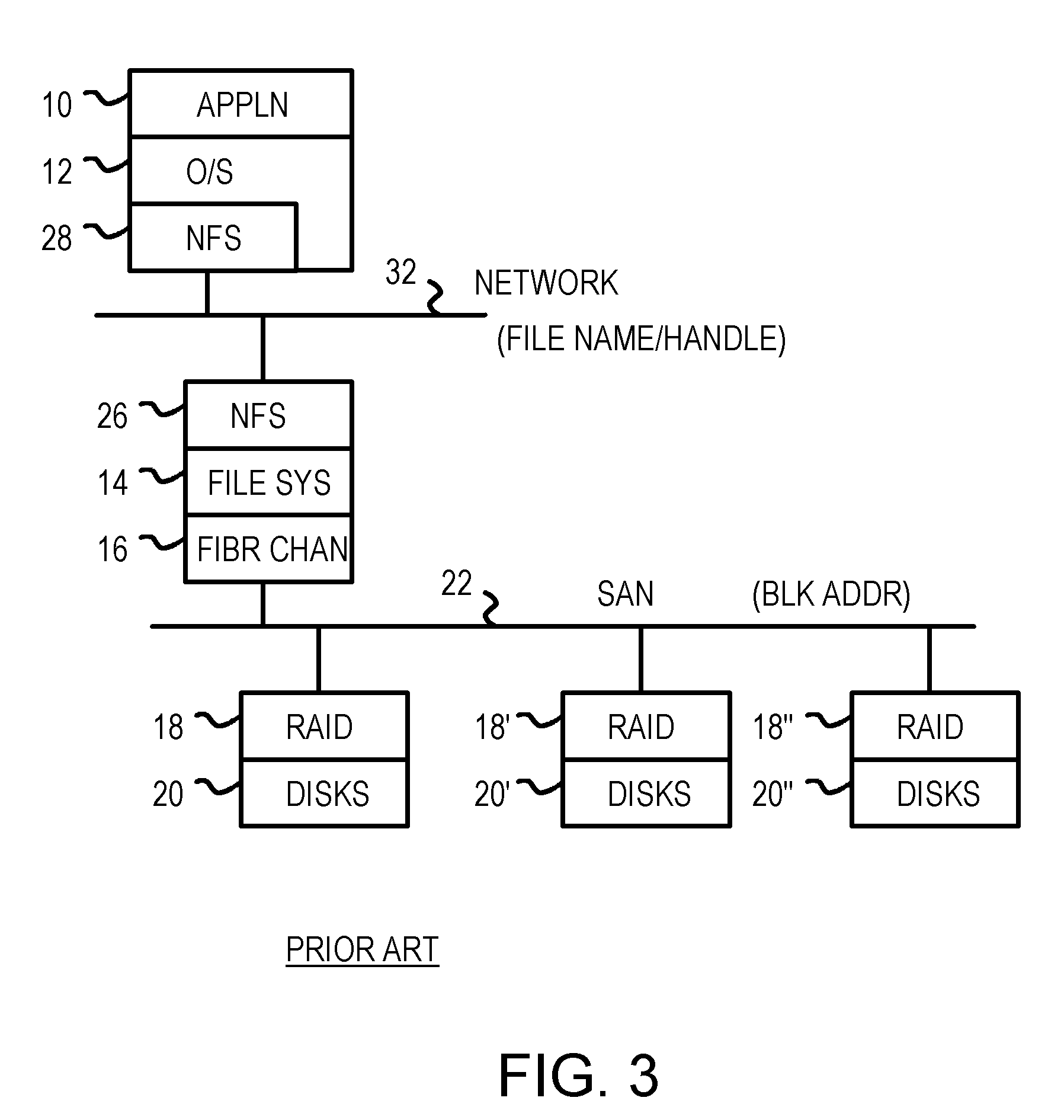
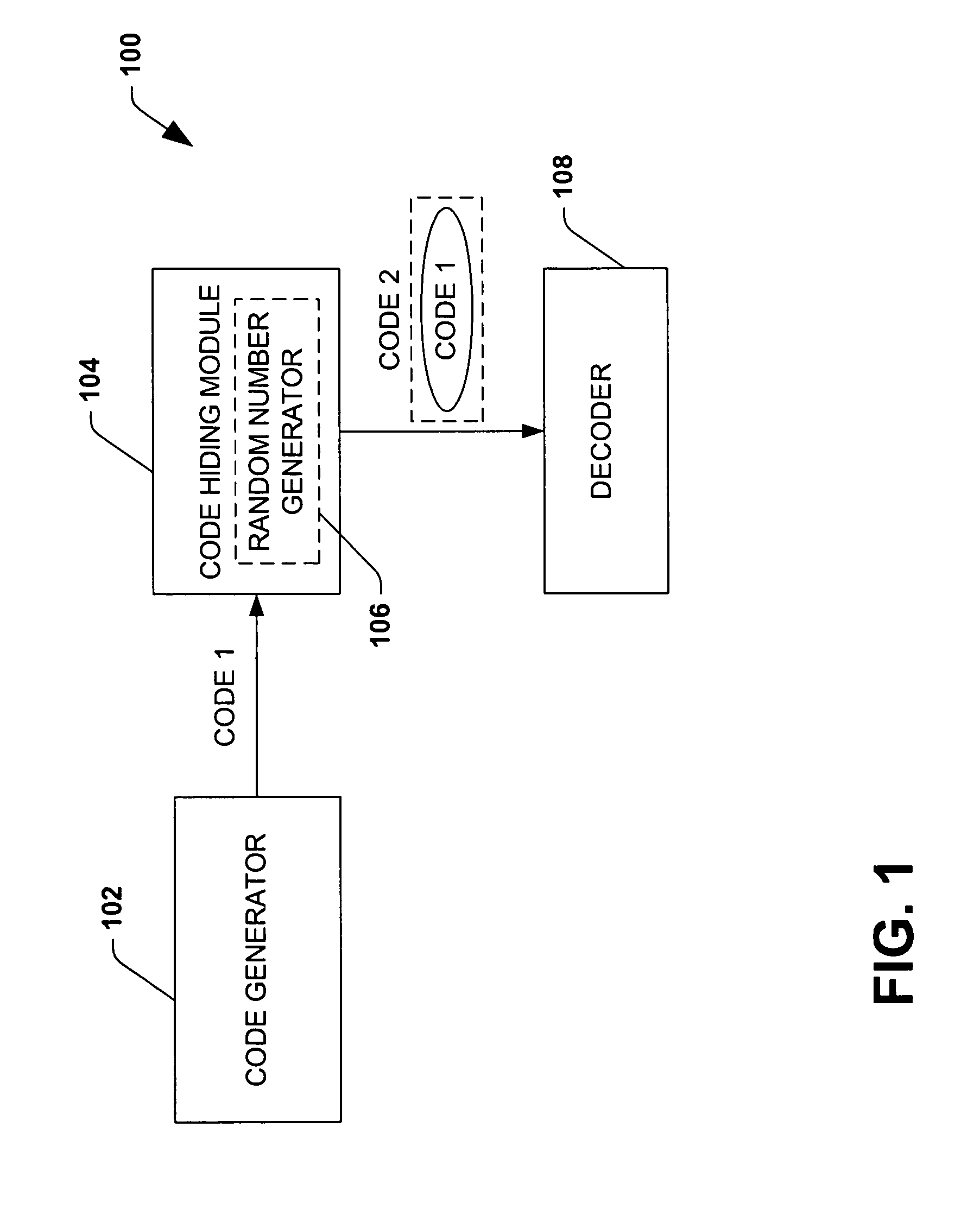
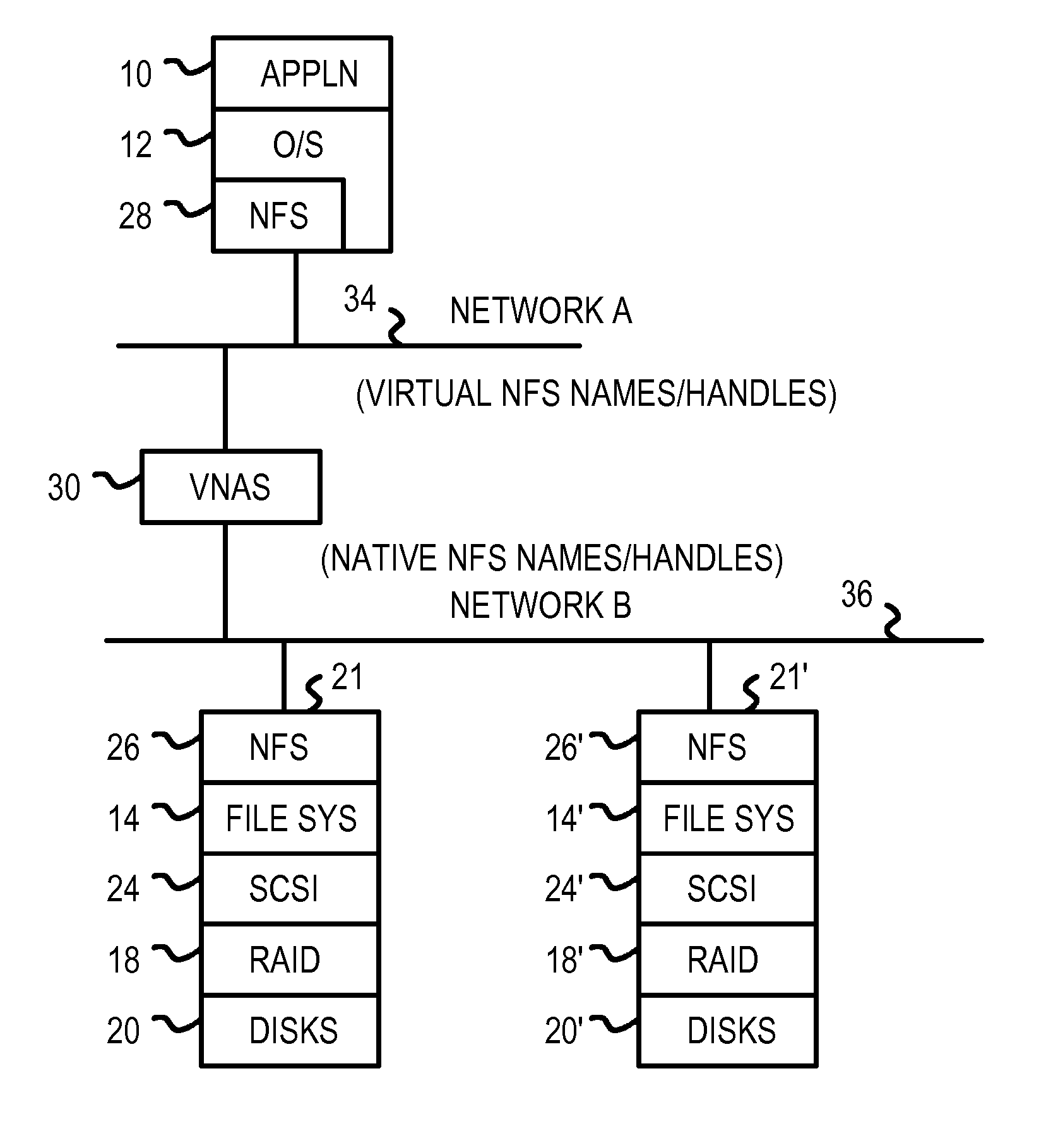
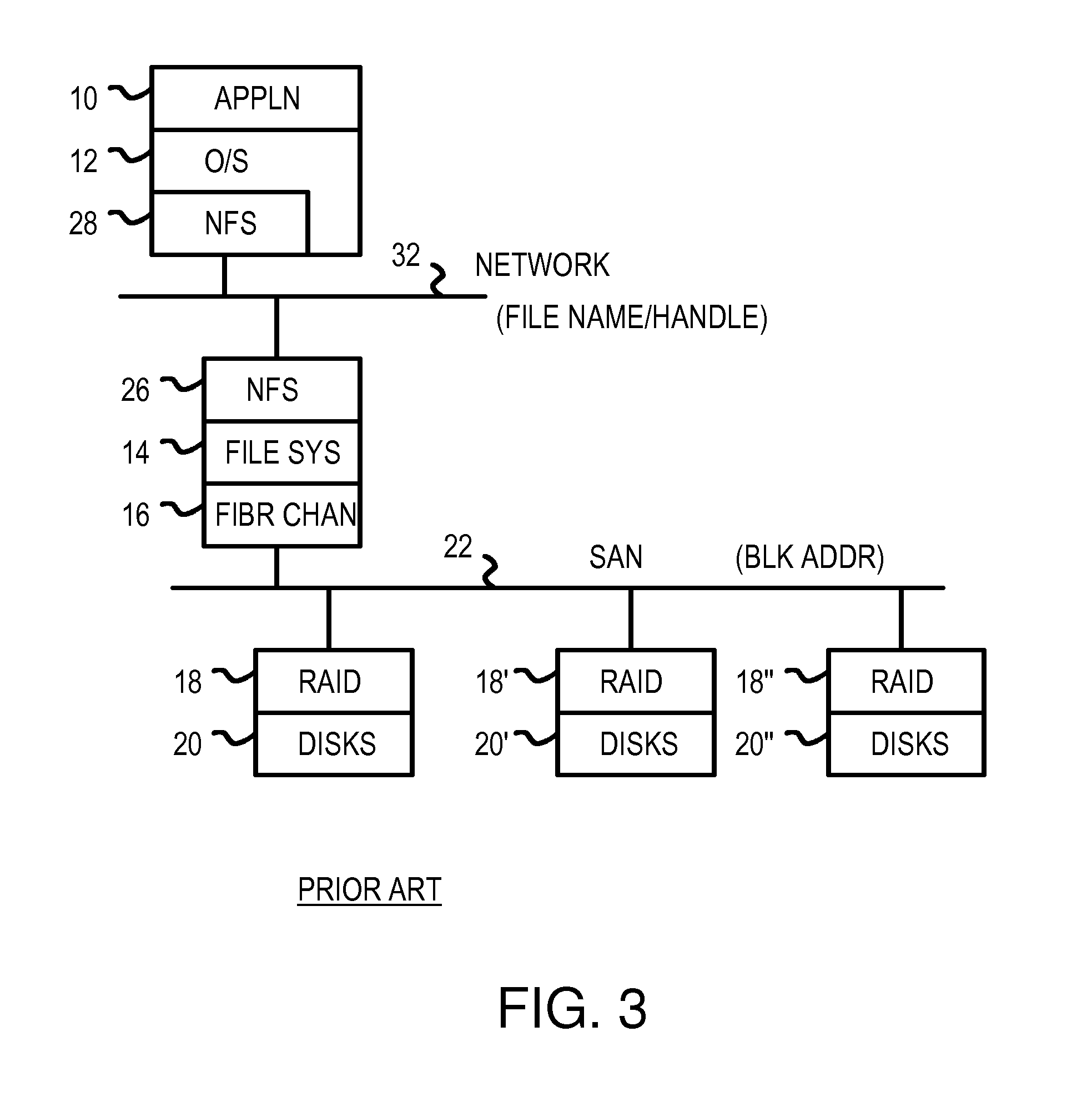
Virtualizing network-attached-storage (NAS) with a compact table that stores lossy hashes of file names and parent handles rather than full names
ActiveUS7272654B1Multiple digital computer combinationsFile access structuresVirtualizationCommon name
Multiple Network Attached Storage (NAS) appliances are pooled together by a virtual NAS translator, forming one common name space visible to clients. Clients send messages to the virtual NAS translator with a file name and a virtual handle of the parent directory that are concatenated to a full file-path name and compressed by a cryptographic hash function to generate a hashed-name key. The hashed-name key is matched to a storage key in a table. The full file-path name is not stored, reducing the table size. A unique entry number is returned to the client as the virtual file handle that is also stored in another table with one or more native file handles, allowing virtual handles to be translated to native handles that the NAS appliance servers use to retrieve files. File movement among NAS servers alters native file handles but not virtual handles, hiding NAS details from clients.
Owner:CUFER ASSET LTD LLC
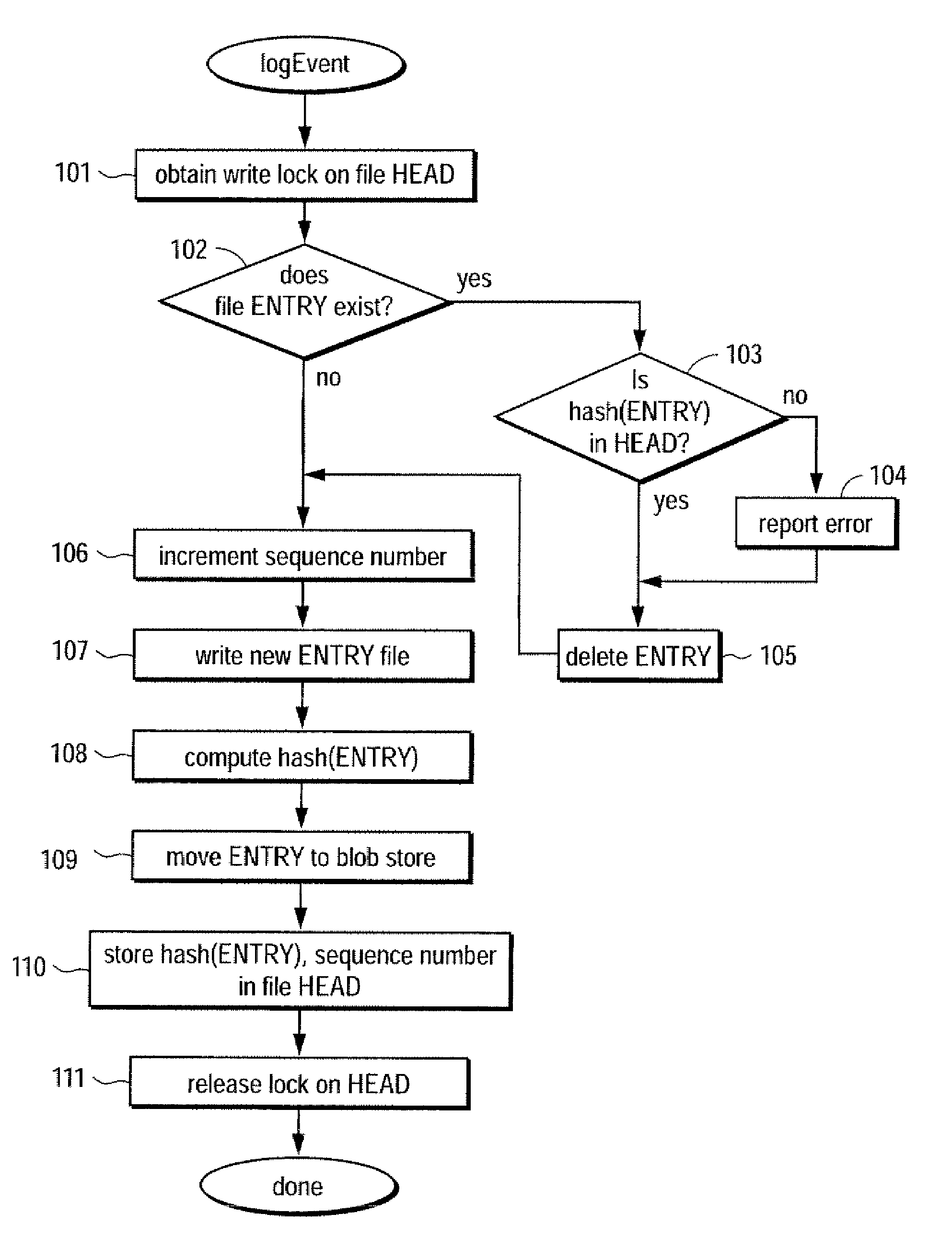
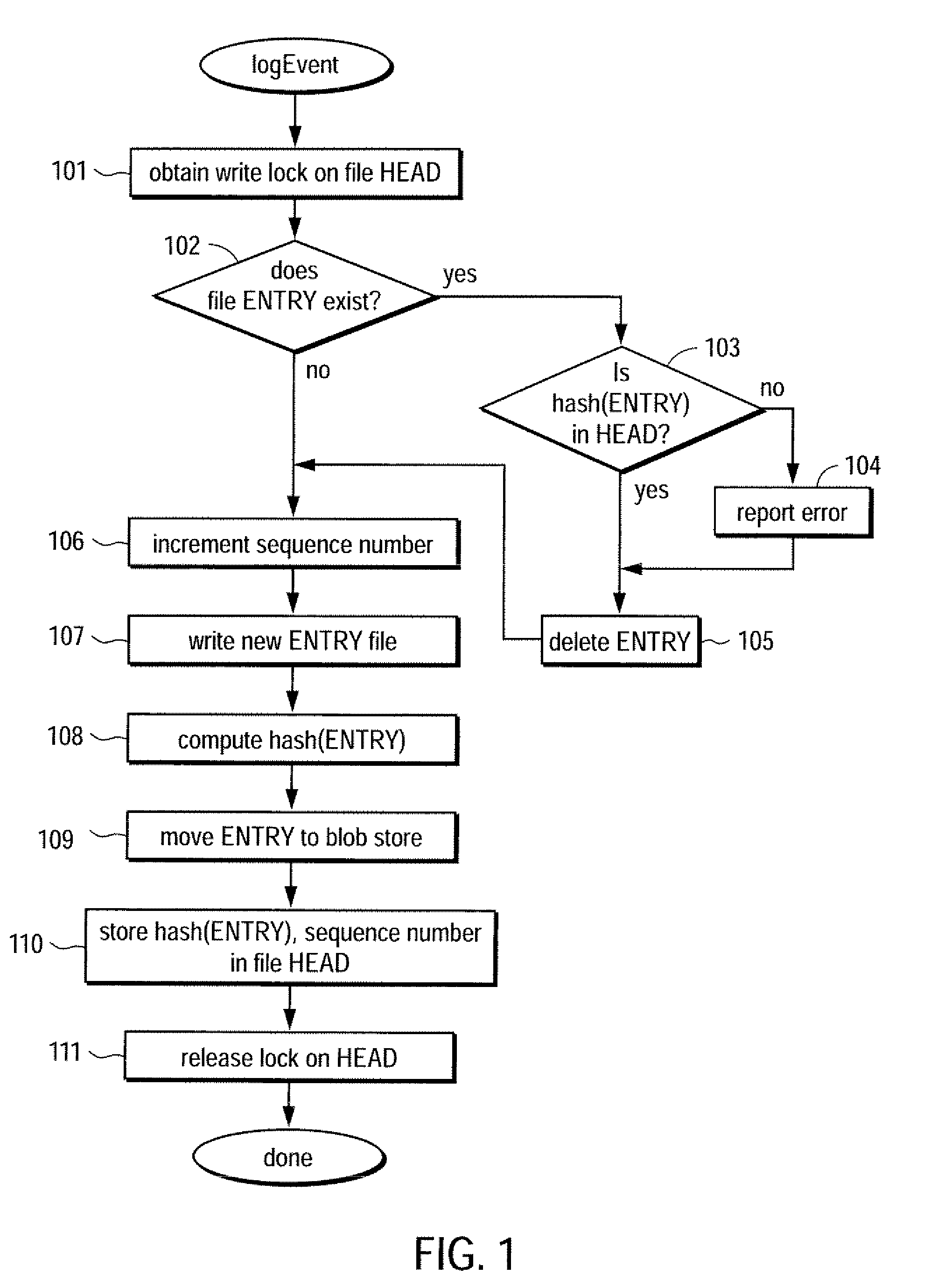
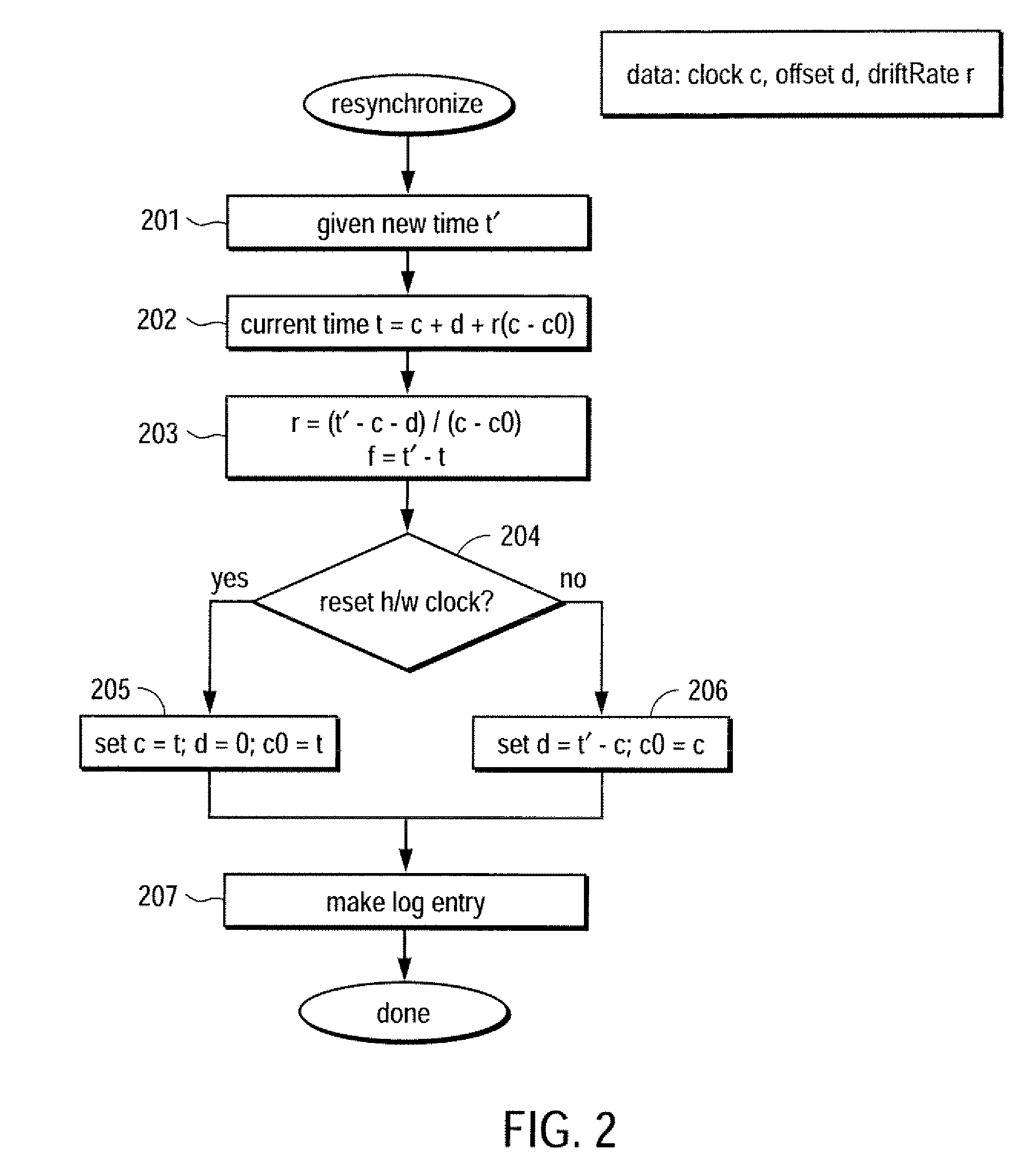
Trustworthy timestamps and certifiable clocks using logs linked by cryptographic hashes
ActiveUS20080201580A1User identity/authority verificationUnauthorized memory use protectionCryptographic hash functionTrusted timestamping
A method and apparatus for creating and / or using trustworthy timestamps and certifiable clocks using logs linked by cryptographic hashes. In one embodiment, the method comprises maintaining a first, chained-hash log; associating a first clock with the chained-hash log, and entangling the first log; with a second by adding a time-stamped synchronization entry to the chained-hash log, where the synchronization entry has a second time indication associated with the second log and a hash of one or more entries in the first log.
Owner:RICOH KK
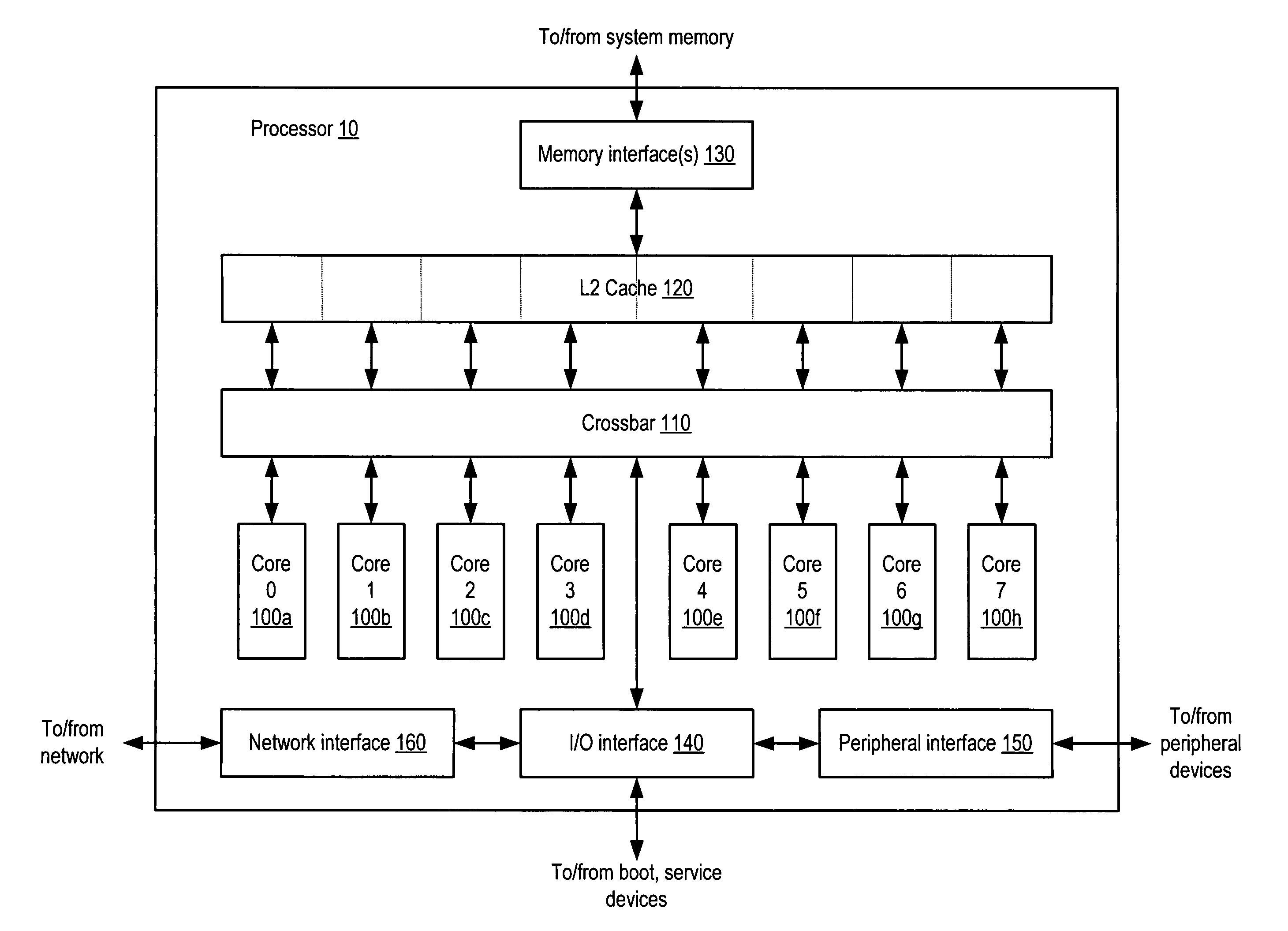
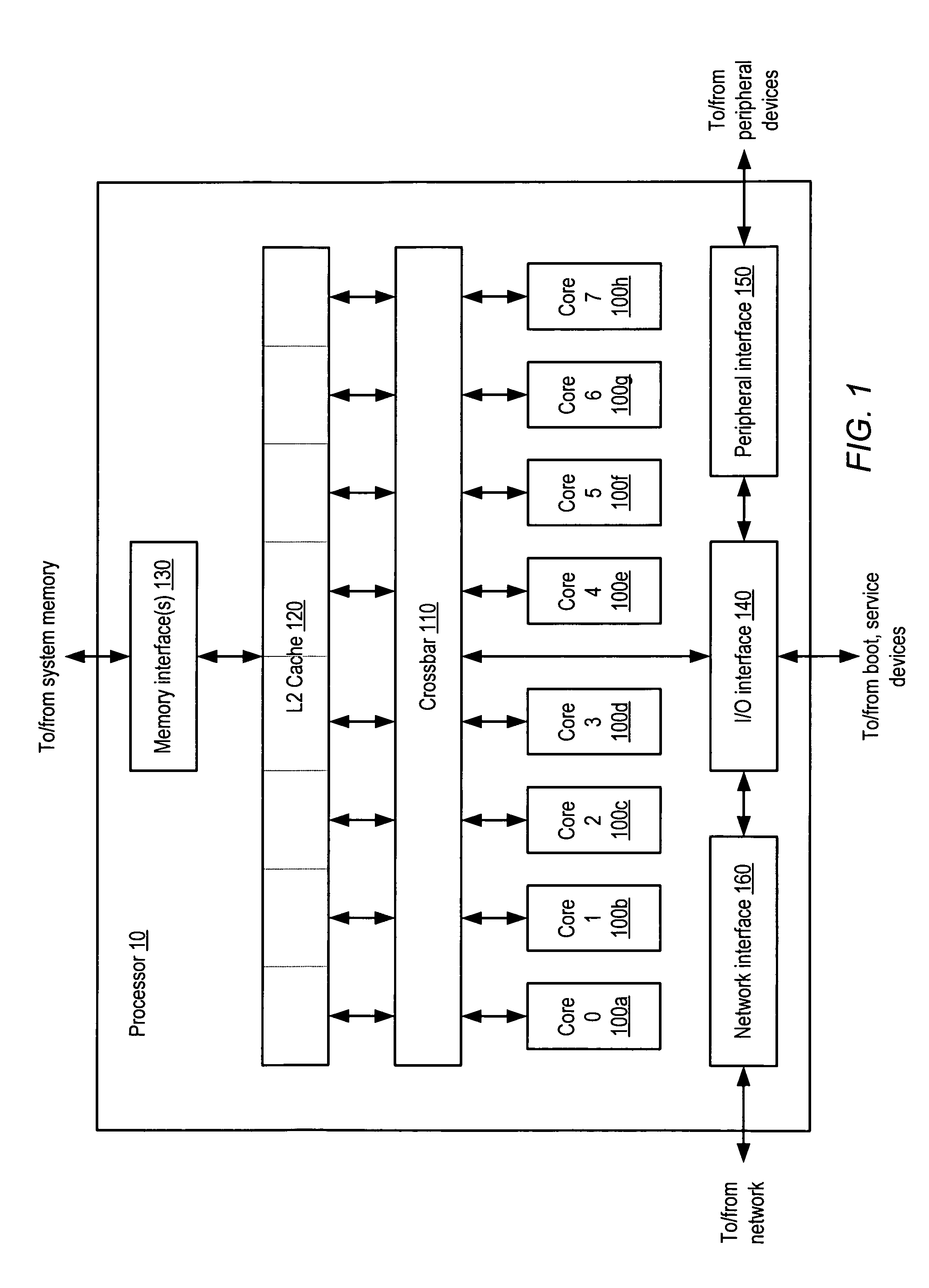
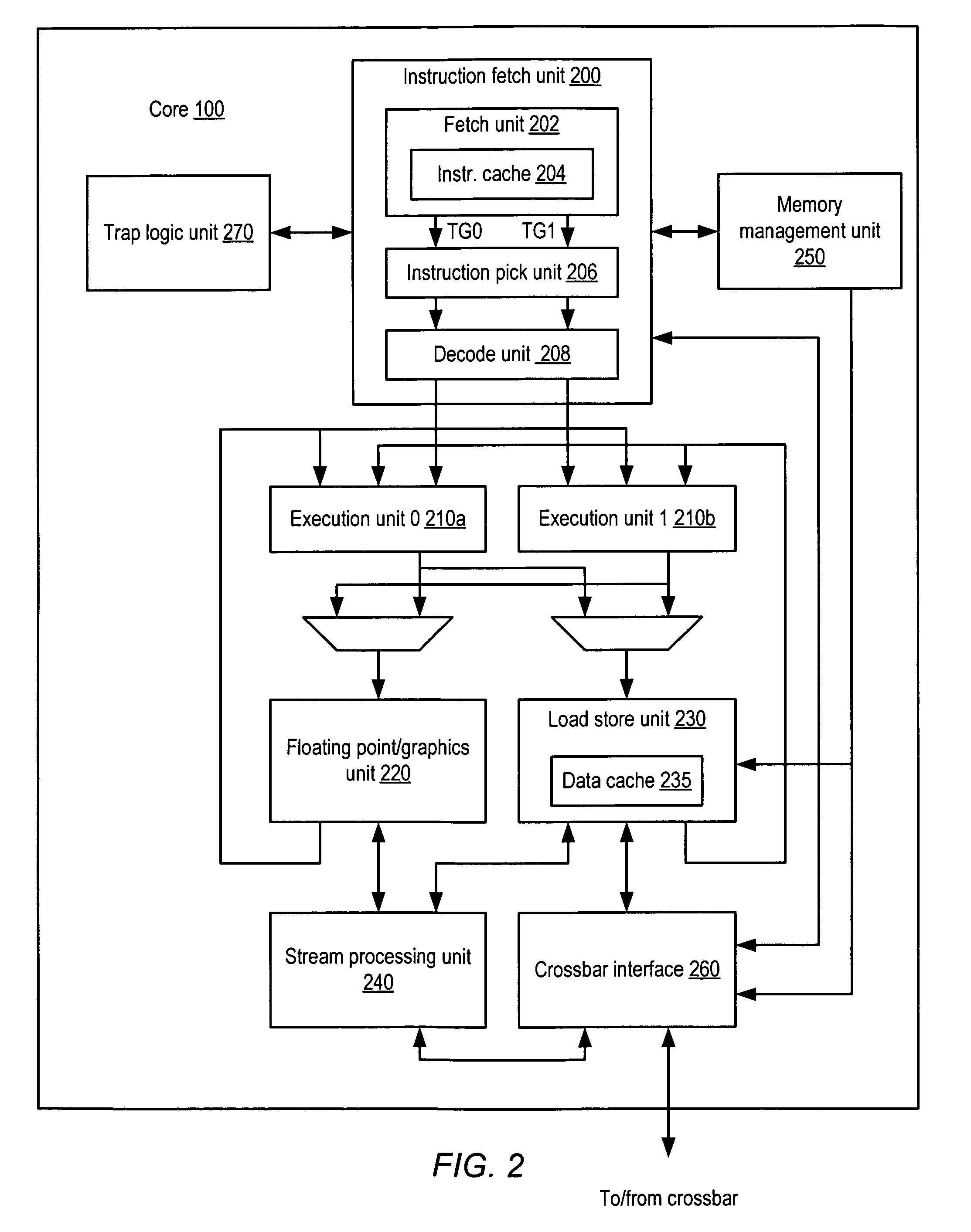
Processor including general-purpose and cryptographic functionality in which cryptographic operations are visible to user-specified software
ActiveUS7620821B1Memory loss protectionDigital data processing detailsGeneral purposeComputer hardware
A processor including general-purpose and cryptographic functionality, in which cryptographic operations are visible to user-specified software. According to one embodiment, a processor may include instruction execution logic configured to execute instructions specified by a user of the processor, where the instructions are compliant with a general-purpose instruction set architecture. The processor may further include a cryptographic functional unit configured to implement a plurality of cryptographic operations, and further configured to process the cryptographic operations independently of the instruction execution logic. A subset of the instructions may be executable to cause individual ones of the cryptographic operations to be processed by the cryptographic functional unit.
Owner:ORACLE INT CORP
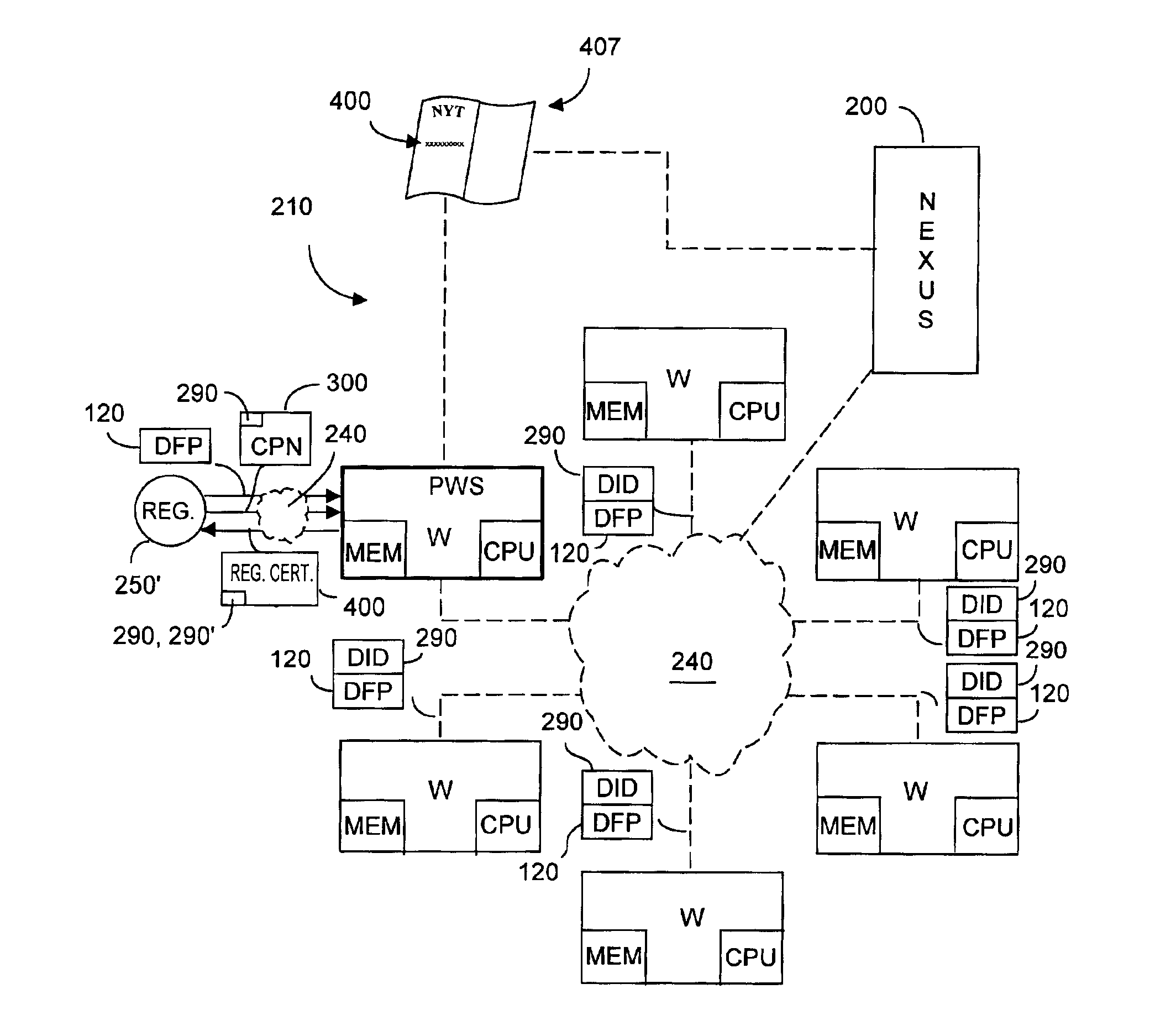
Distributed information system and protocol for affixing electronic signatures and authenticating documents
InactiveUS6938157B2System overhead associated with couponsImprove effectivenessUser identity/authority verificationUnauthorized memory use protectionCryptographic hash functionCryptogram
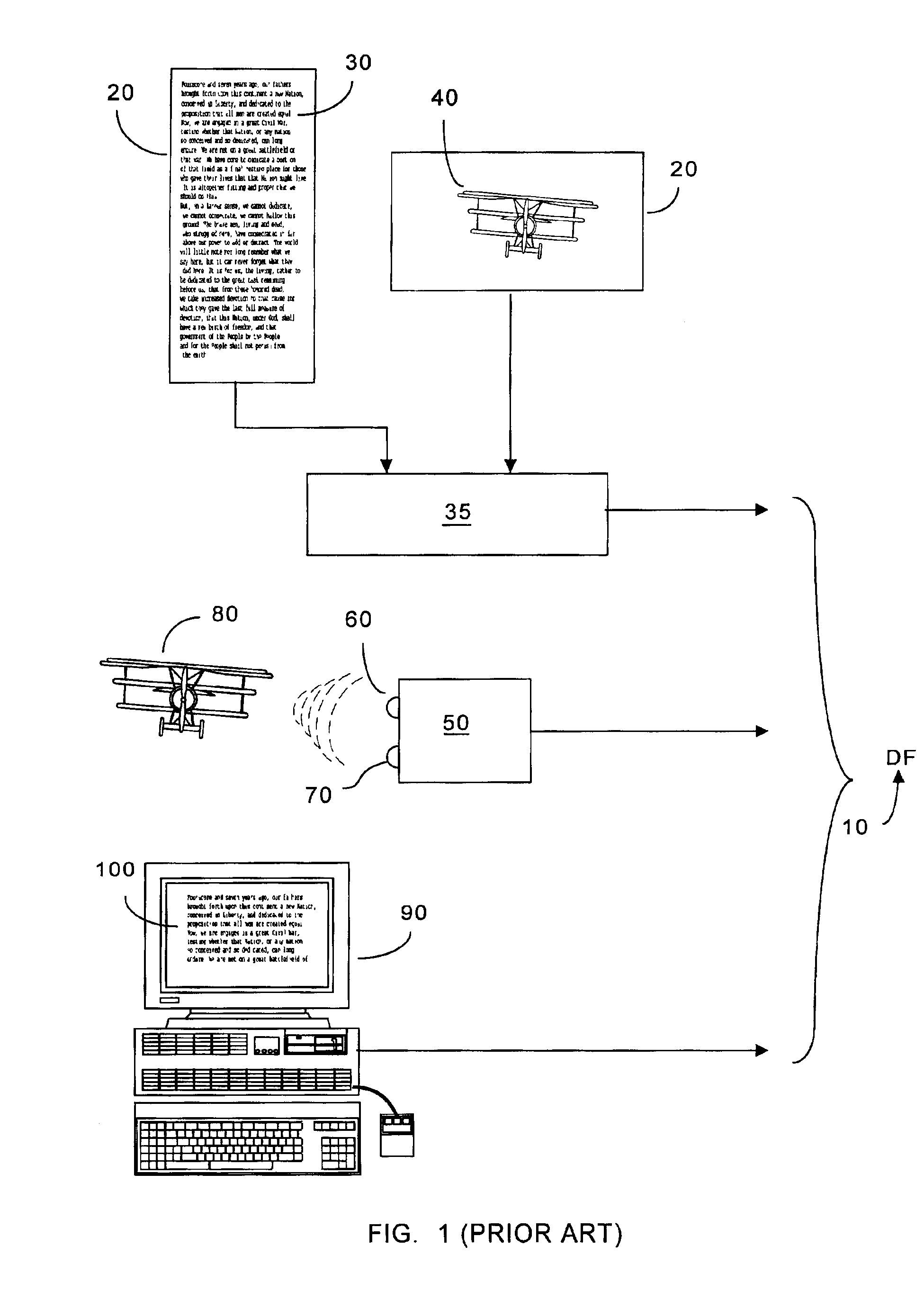
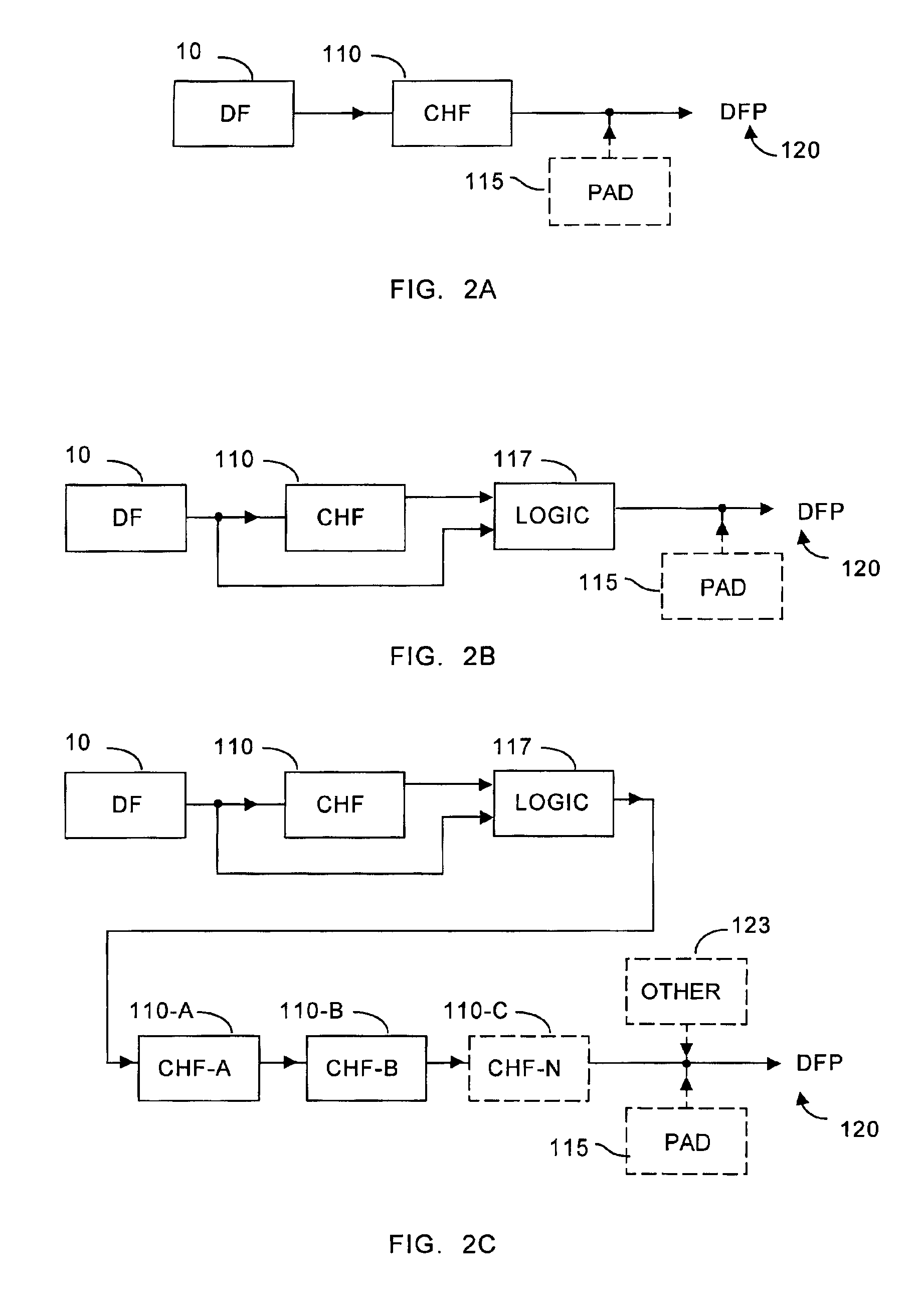
A system can process a digital representation (DF) of a document with a one-way cryptographic hash function (CHF) to yield a digital fingerprint (DFP) value that is associated with the DF. A document identification number (DID) is created, uniquely associated with the DFP, and with DID and DFP are associated optional credential information (C). A registration certificate DFC that represents an optional electronic signature associated with the document and that includes the DID and DFP is promulgated and archived at a plurality of storage locations. The system can authenticate whether a putative document is the original document by generating a digital fingerprint value for the putative document and comparing it to DFP retrieved from various of the storage locations. Authentication can confirm that the electronic signature is unaltered.
Owner:DISTRIBUTED TRUST MANAGEMENT
Method for establishing, securing and transferring computer readable information using peer-to-peer public and private key cryptography
InactiveUS20170324711A1Protected contentMinimal costPublic key for secure communicationCryptographic hash functionStructure of Management Information
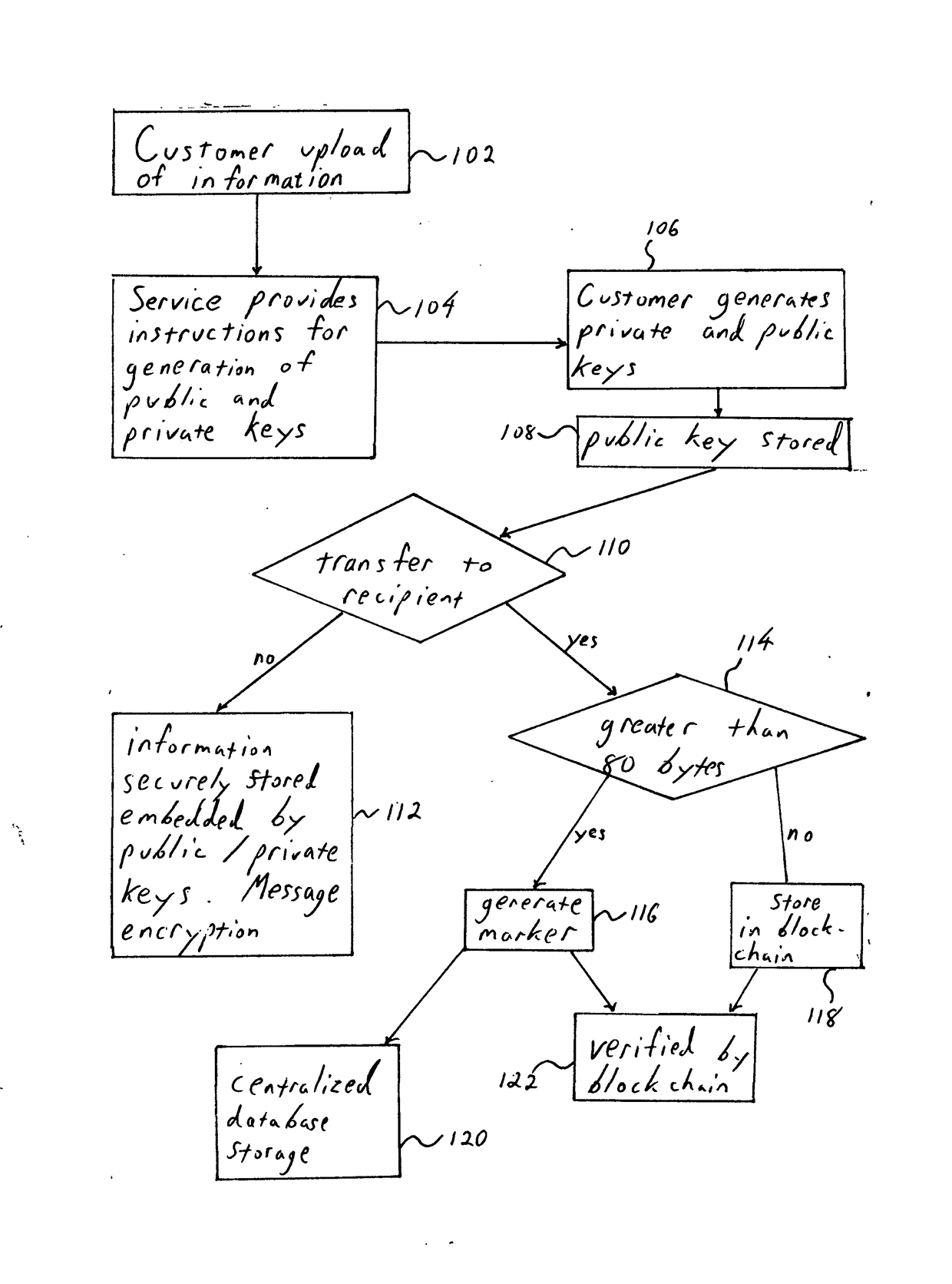
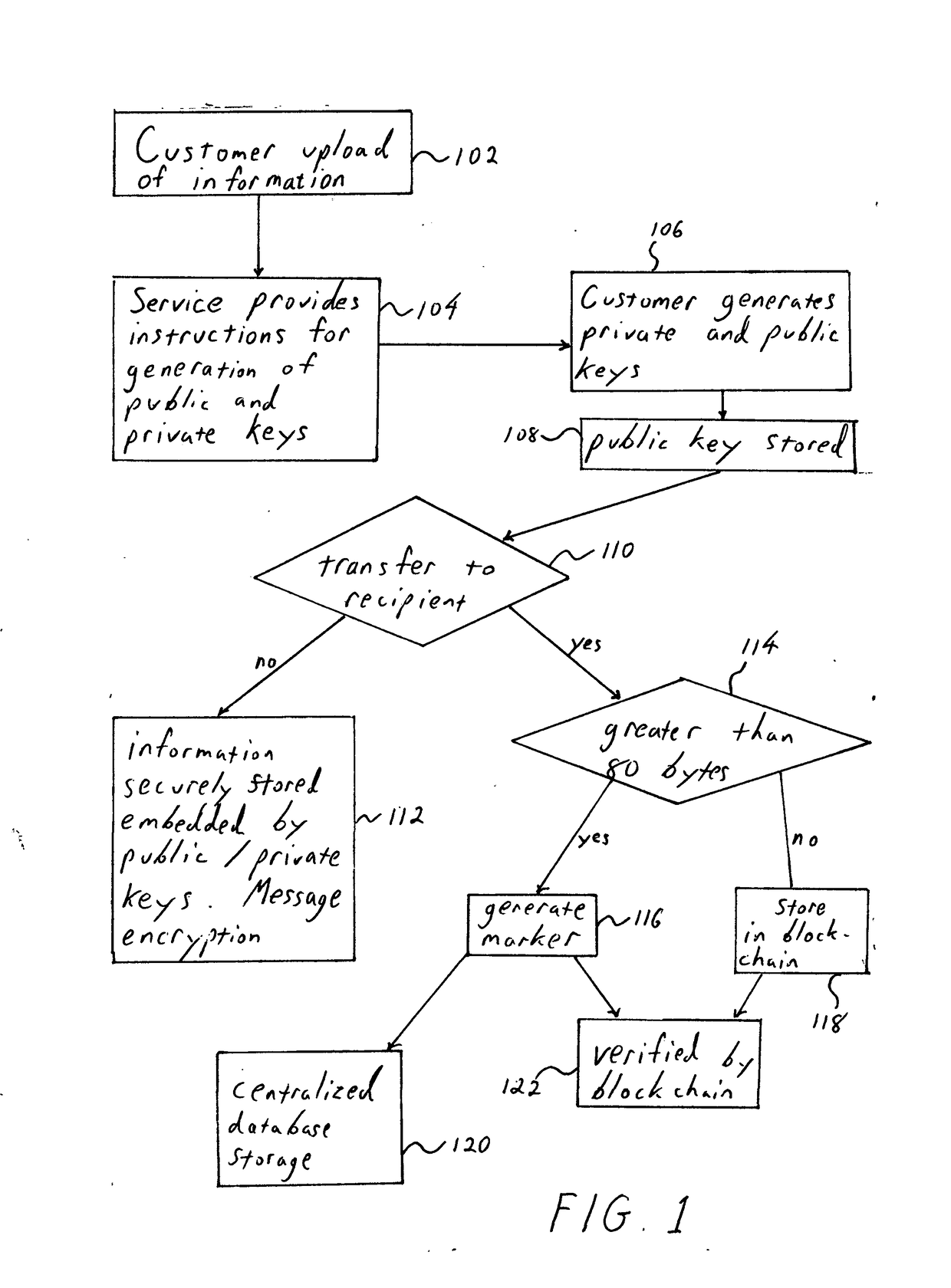
System and method for confirming and transferring information from one party to another via block chain escort, using central and decentralized databases acting as online storage providers. Files are linked to cryptographic currency structures comprised of a public and private key identification processes. Locking, unlocking, retrieving, storing, confirming and transferring files requires linked association to block chain protocol measures of crypto-currency processes.Establishing file space requires that the owner links it to a centralized or decentralized peer-to-peer cryptographic block chain protocol. This secures and locks files for subsequent confirmation and transfer. Confirmation and transfer of the file is processed with a cryptographic hash function of crypto currency block chain process. The system and method requires that the transferee obtain the file using crypto currency transfer protocol. The system and method associates a piece of information with a public key and private keys, which are accessed only by the owner.
Owner:THE REAL MCCOY LLC INC
Systems and methods for generating a DNS query to improve resistance against a DNS attack
ActiveUS20100269174A1Accelerating transactionMore resistant to being compromisedMemory loss protectionEncryption apparatus with shift registers/memoriesDomain nameCryptographic hash function
Owner:CITRIX SYST INC
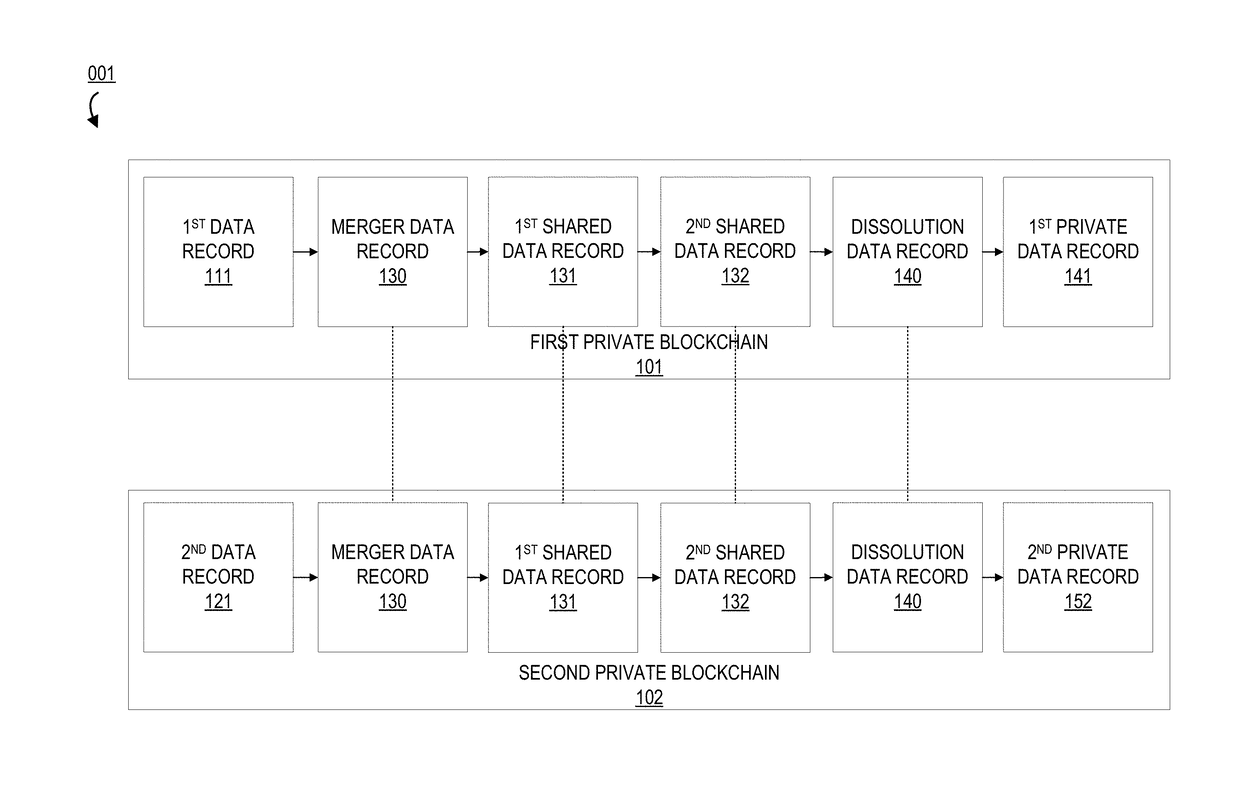
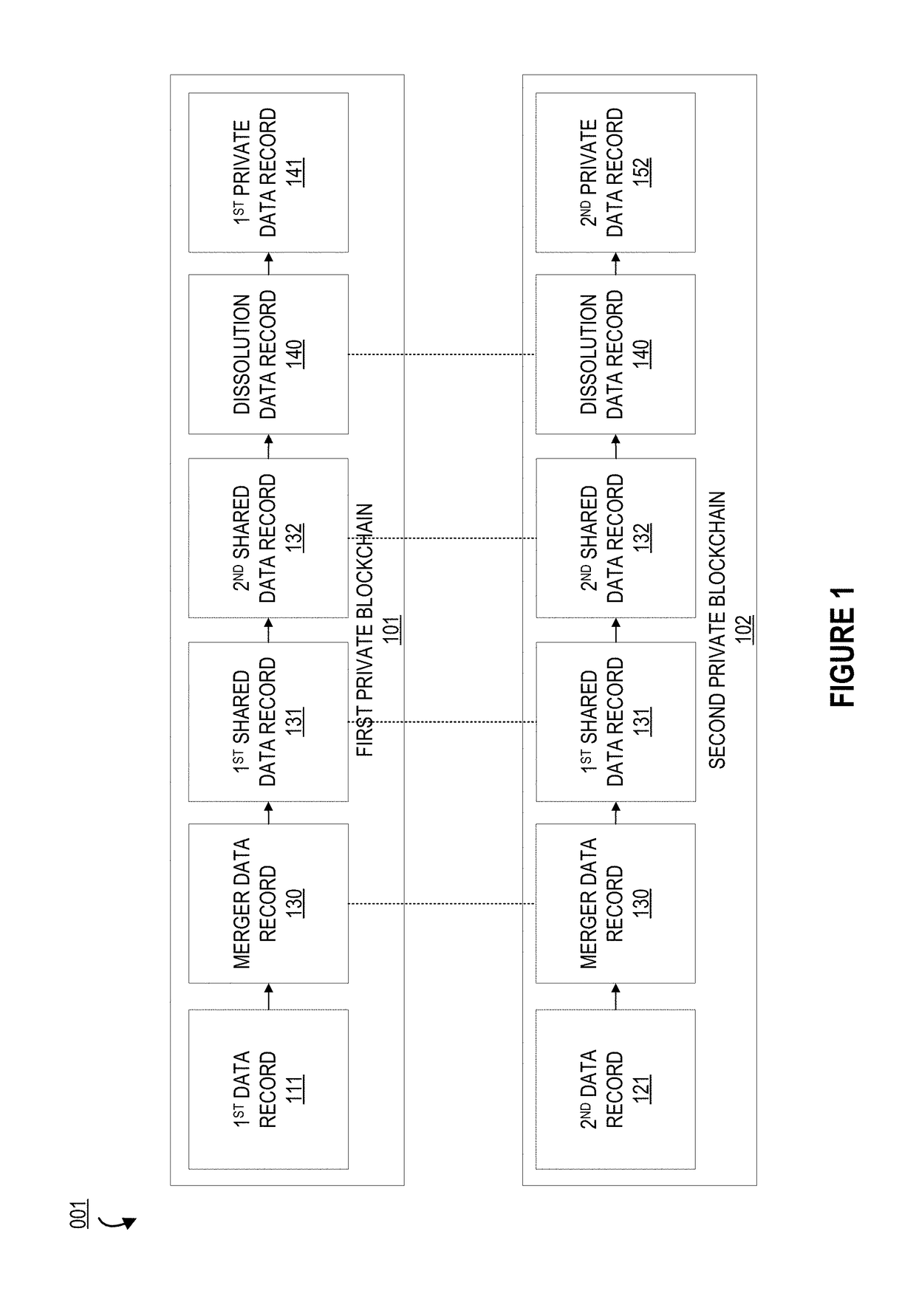
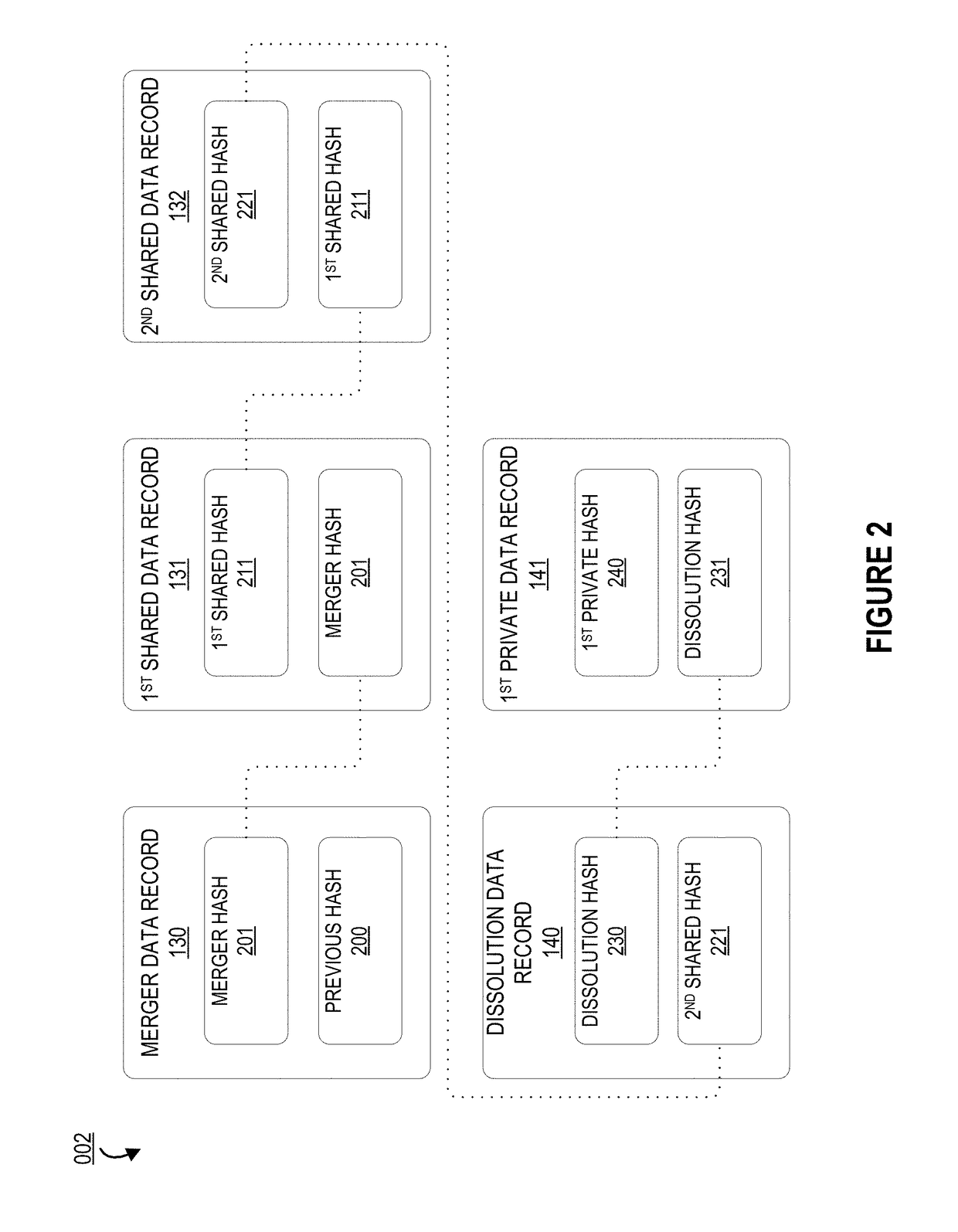
System for multiplexing and demultiplexing blockchain ledgers via a cryptographic hash
ActiveUS20180139186A1Well formedKey distribution for secure communicationUser identity/authority verificationMultiplexingCryptographic hash function
Embodiments of the present invention provide a system for multiplexing and demultiplexing blockchain ledgers via a cryptographic hash. In particular, the invention uses cryptographic keys and hashes to combine and dissociate blockchain records from the private blockchains two or more entities. The system provides a mechanism by which blockchains owned by distinct entities may be multiplexed upon formation of a union between the entities, in order to securely share data records and establish an authentic, tamper-resistant timeline for said data records. Furthermore, the system provides a mechanism by which the blockchains may be demultiplexed upon dissolution of said union.
Owner:BANK OF AMERICA CORP
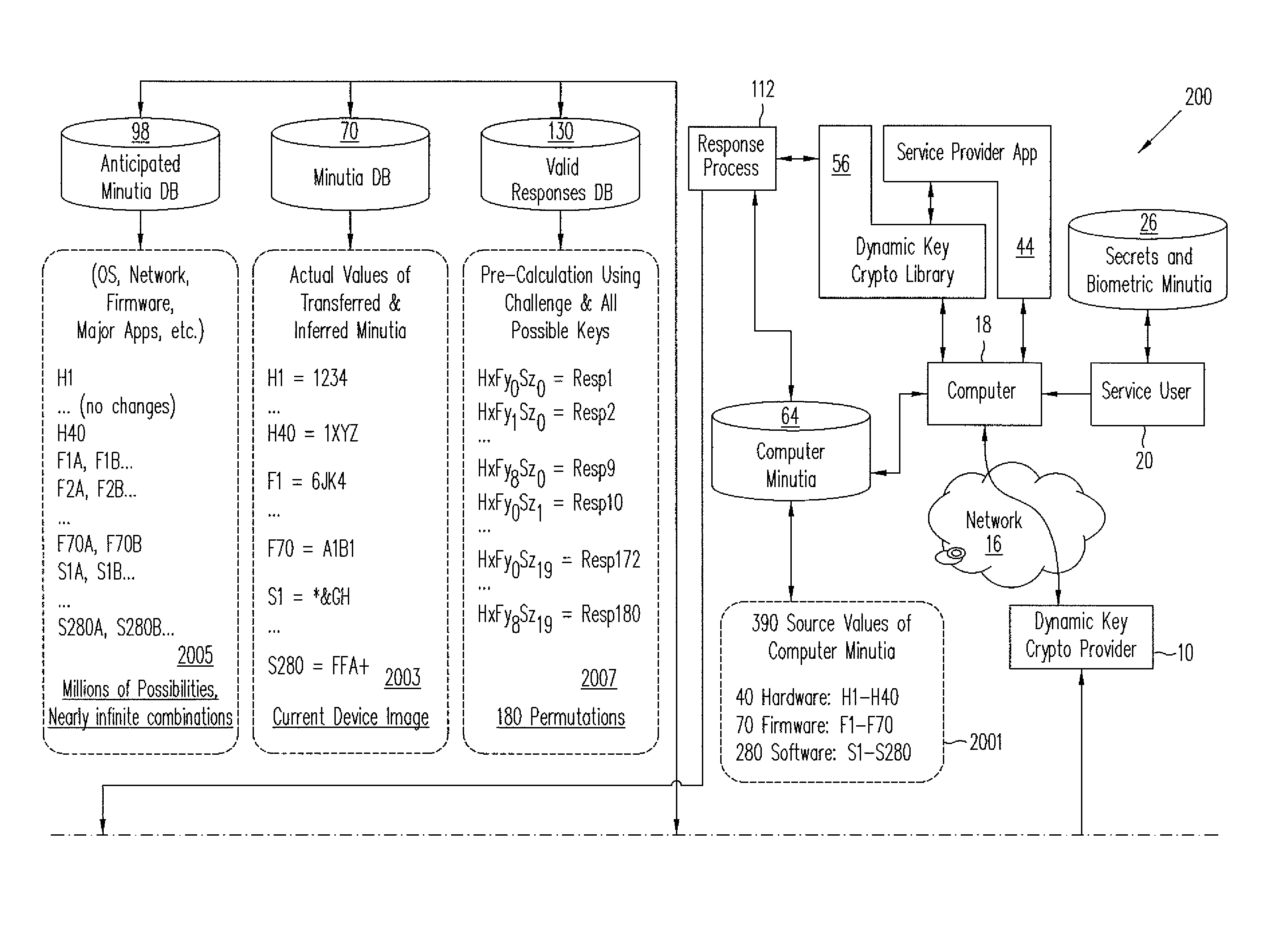
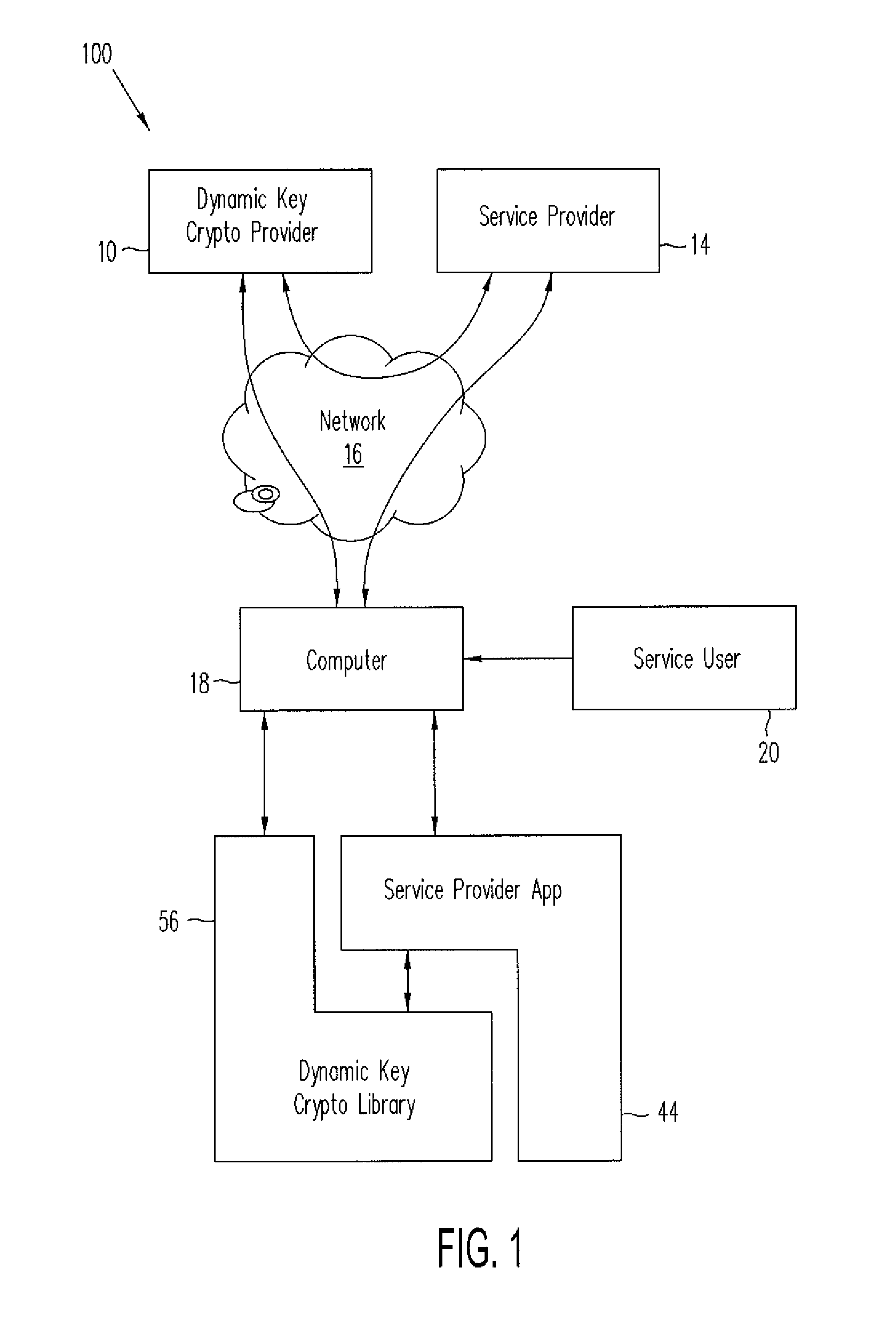
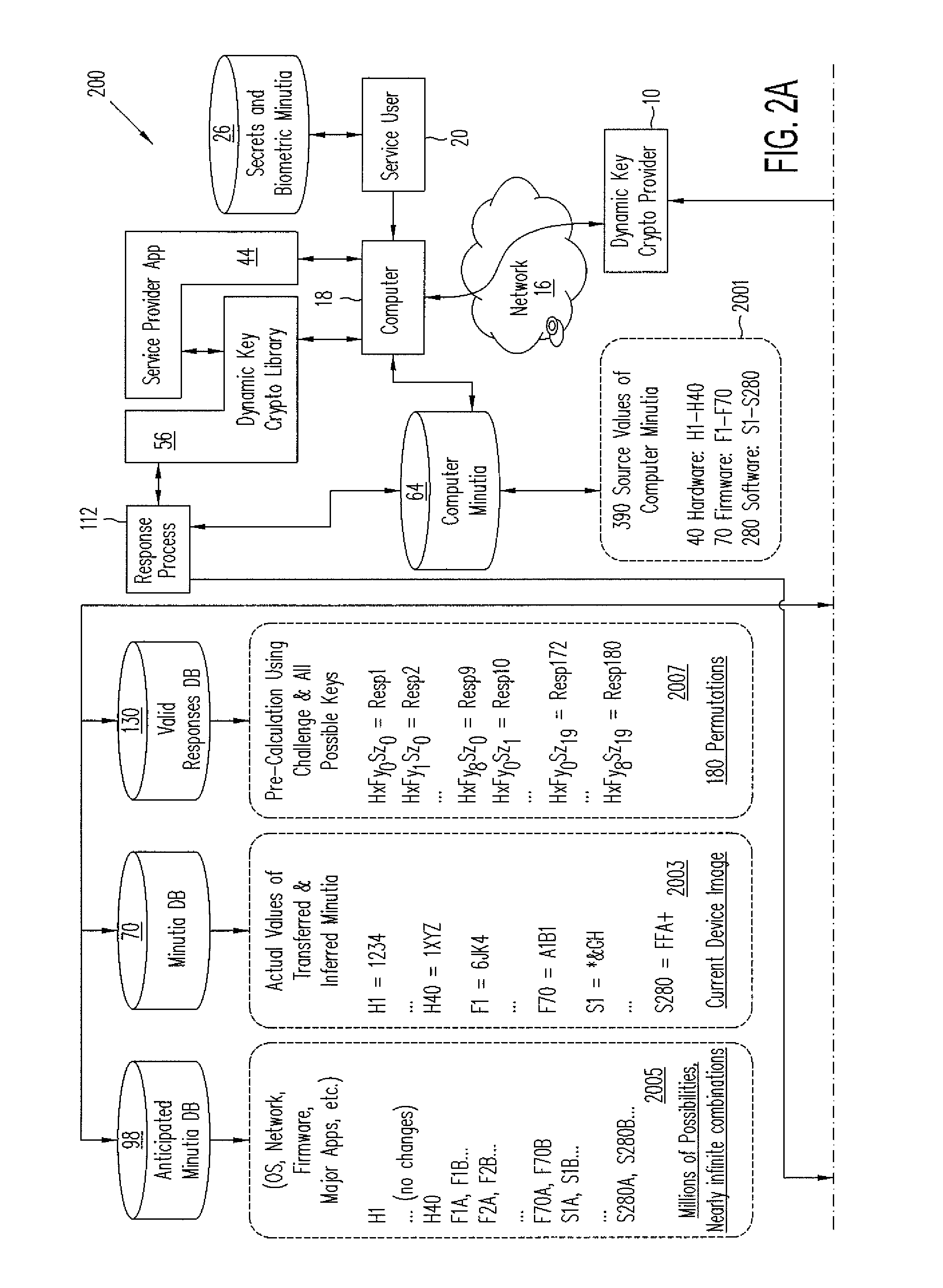
Cryptographic security functions based on anticipated changes in dynamic minutiae
InactiveUS8817984B2Multiple keys/algorithms usageSecret communicationUser deviceCryptographic hash function
Dynamic key cryptography validates mobile device users to cloud services by uniquely identifying the user's electronic device using a very wide range of hardware, firmware, and software minutiae, user secrets, and user biometric values found in or collected by the device. Processes for uniquely identifying and validating the device include: selecting a subset of minutia from a plurality of minutia types; computing a challenge from which the user device can form a response based on the selected combination of minutia; computing a set of pre-processed responses that covers a range of all actual responses possible to be received from the device if the combination of the particular device with the device's collected actual values of minutia is valid; receiving an actual response to the challenge from the device; determining whether the actual response matches any of the pre-processed responses; and providing validation, enabling authentication, data protection, and digital signatures.
Owner:MSIGNIA
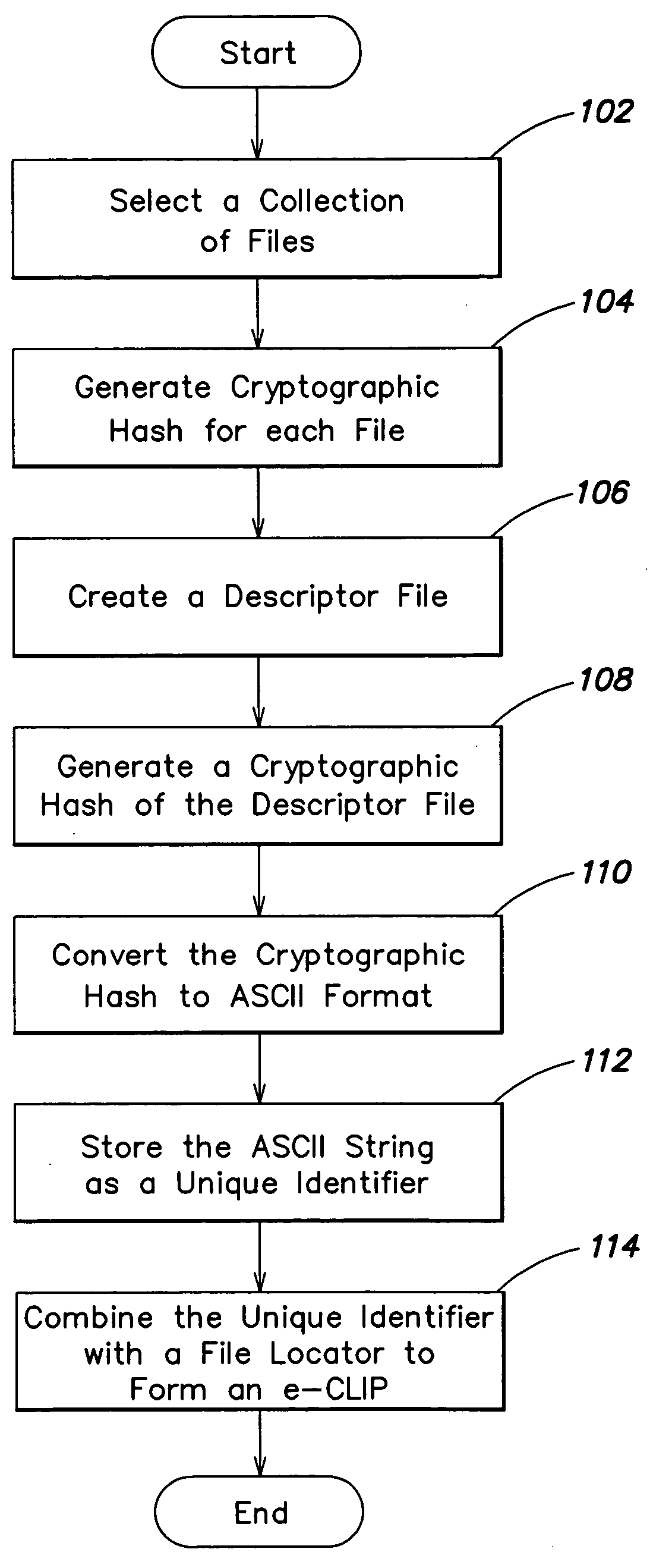
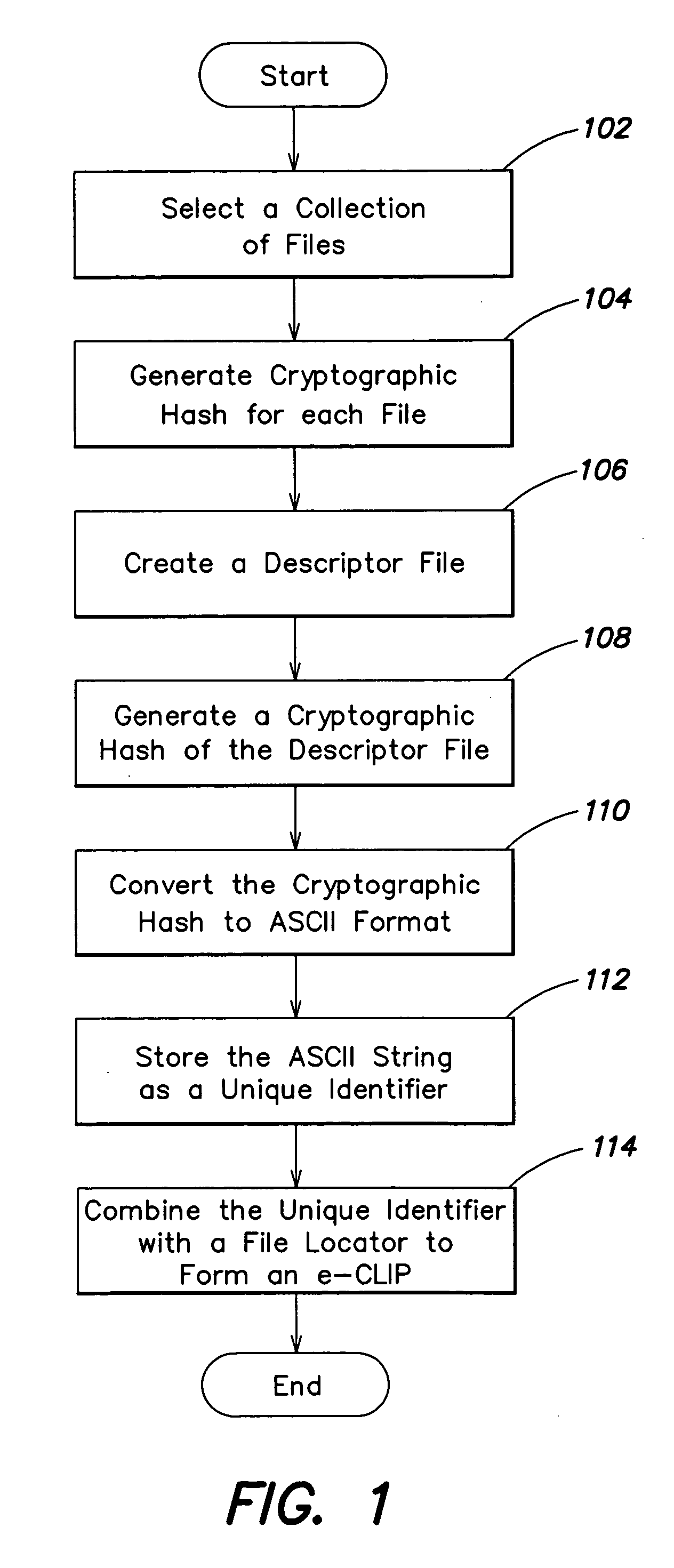
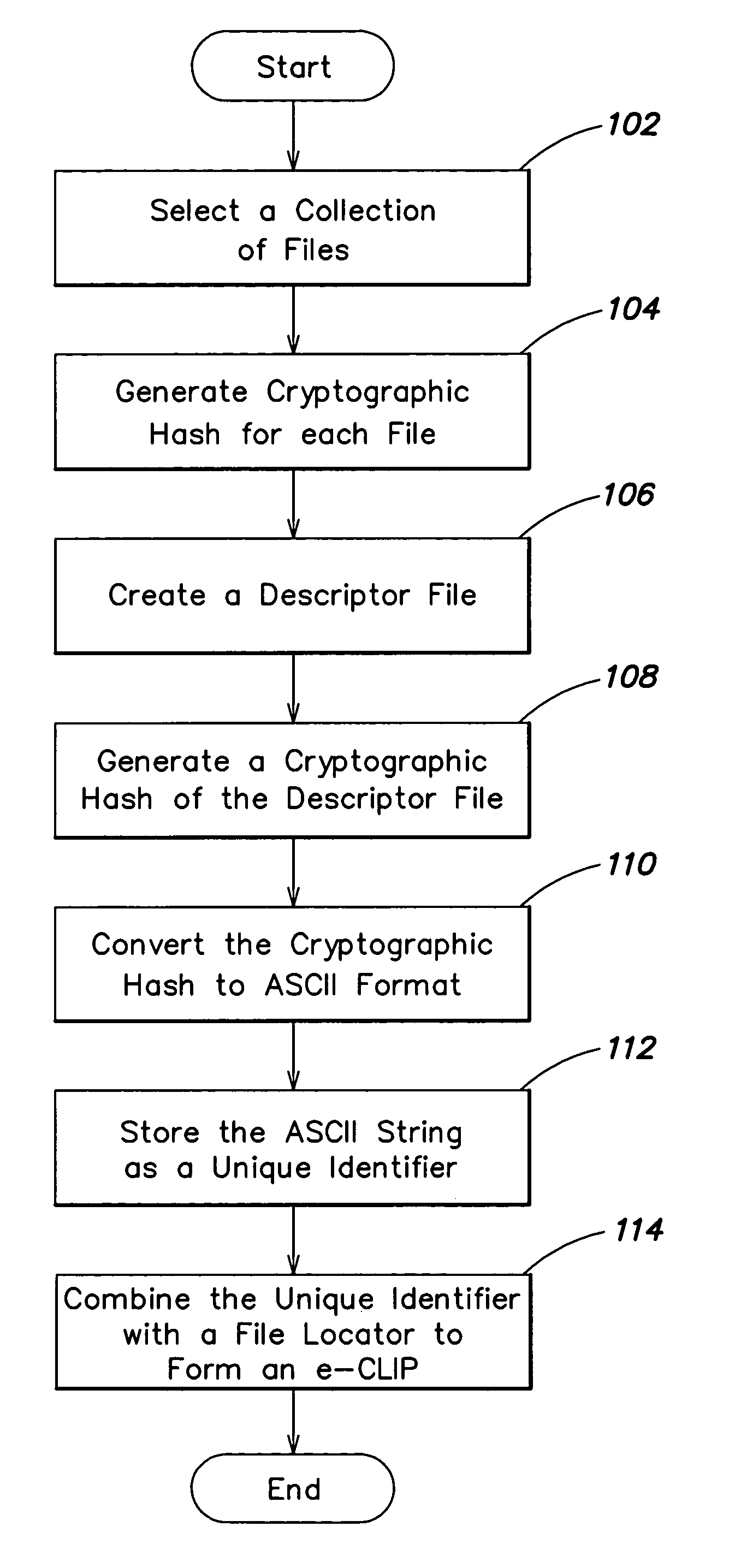
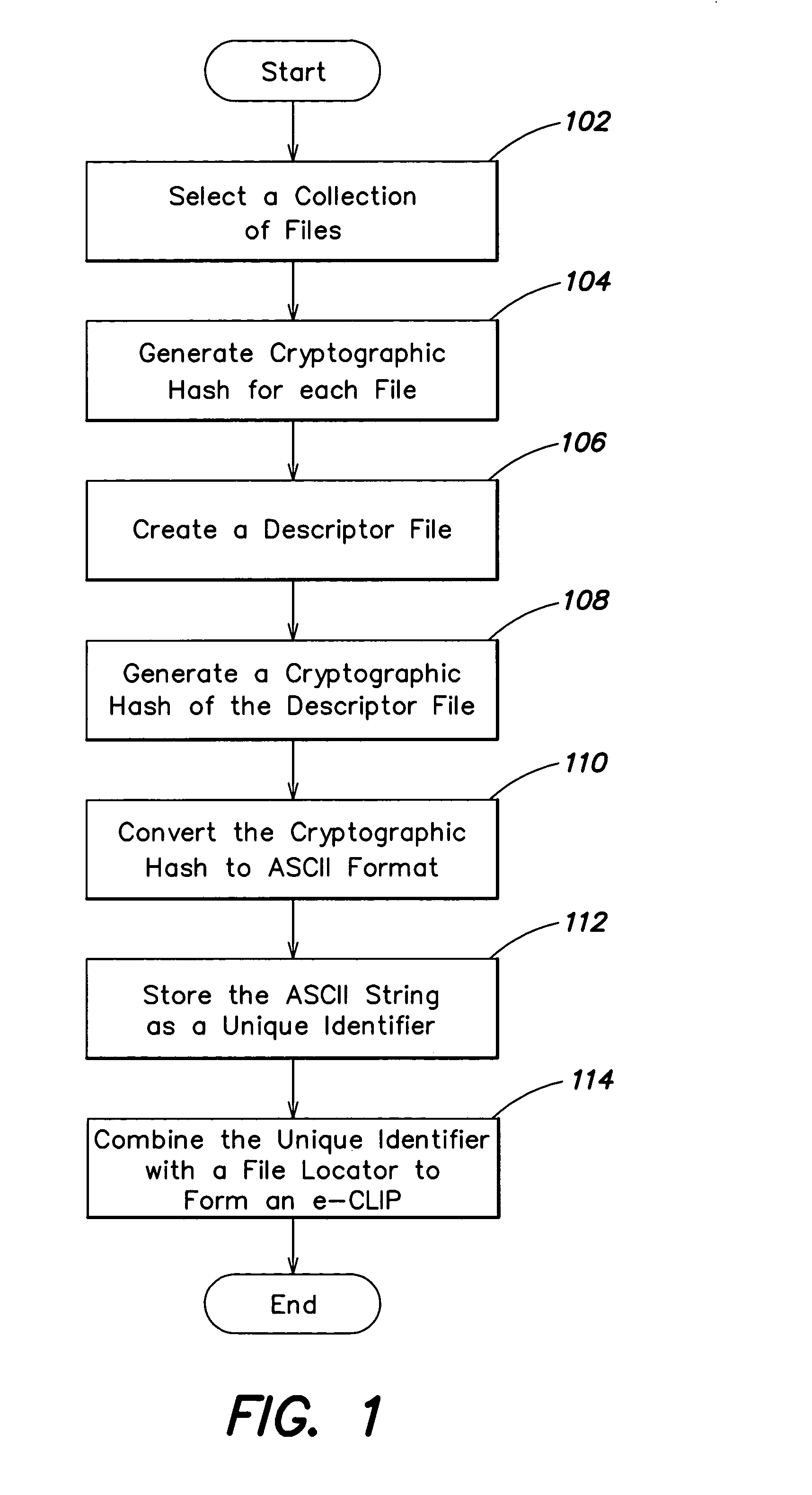
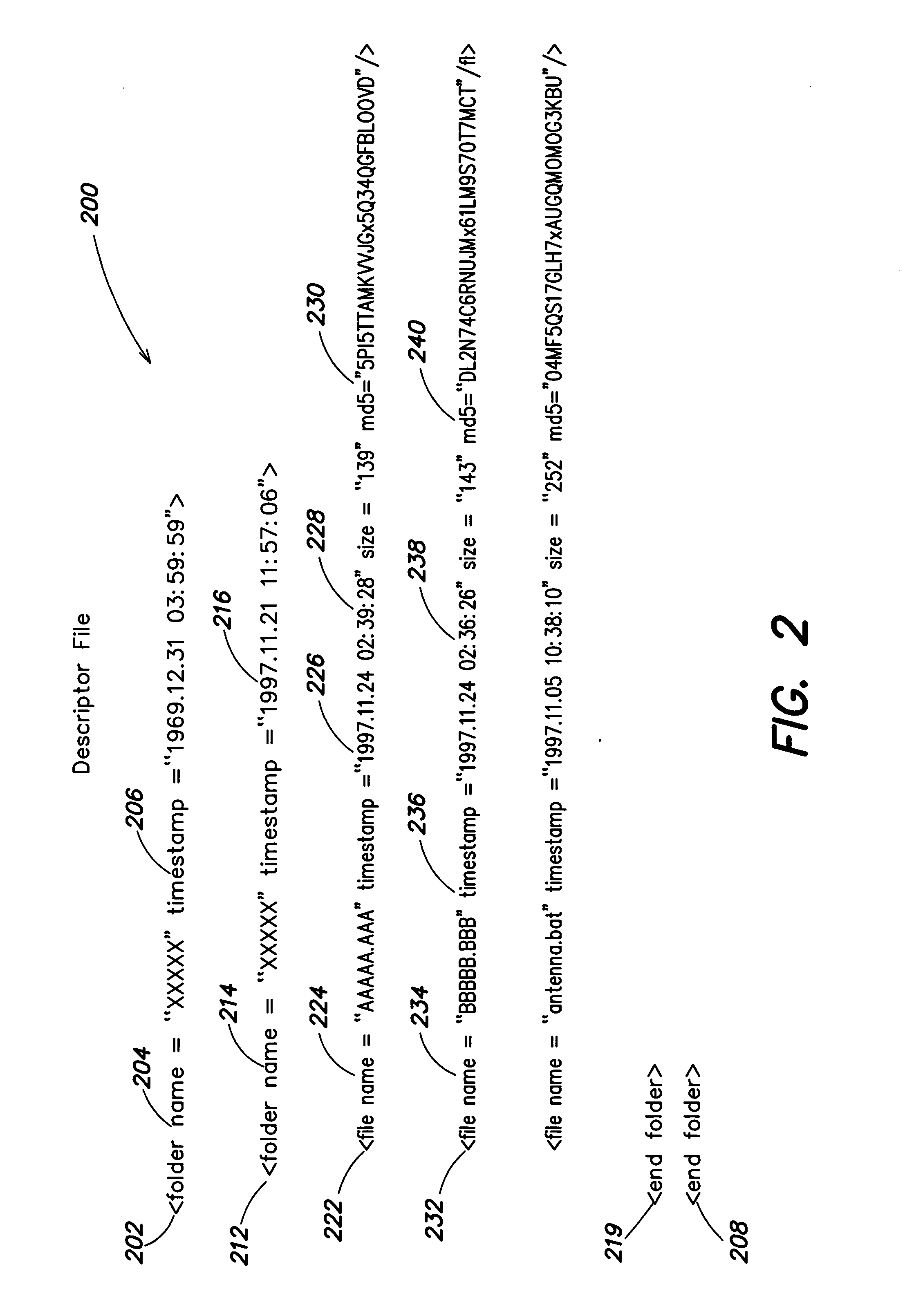
Content addressable information encapsulation, representation, and transfer
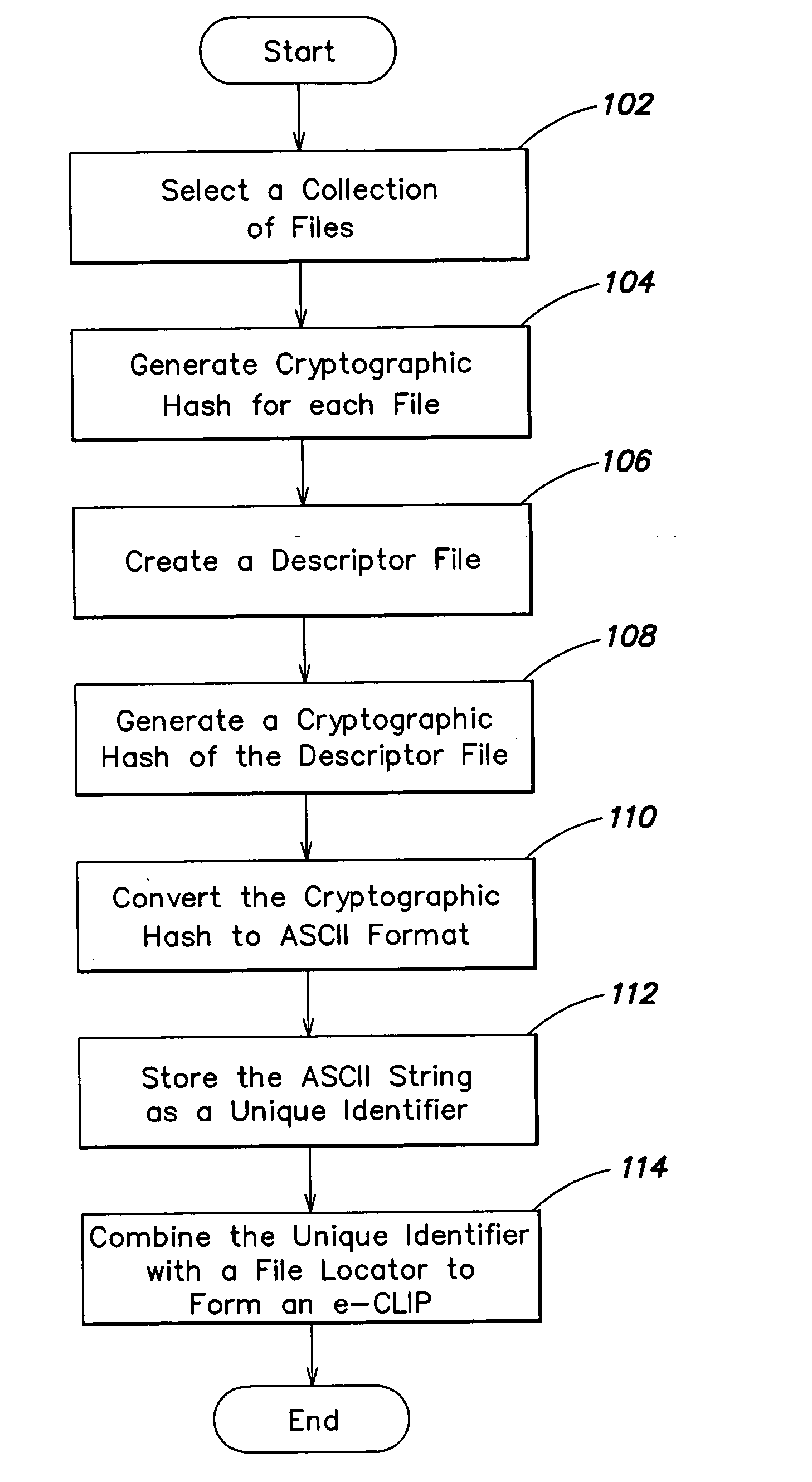
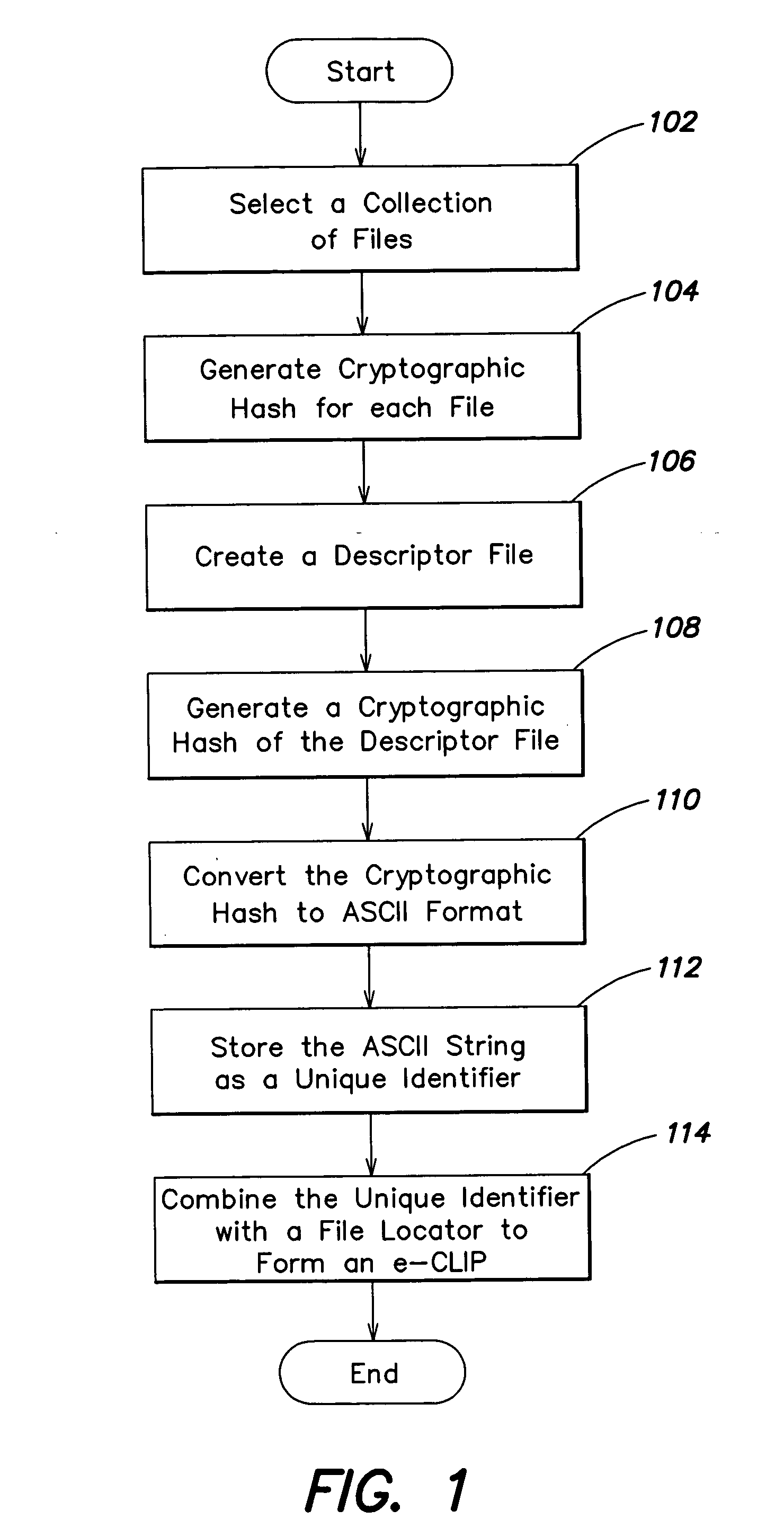
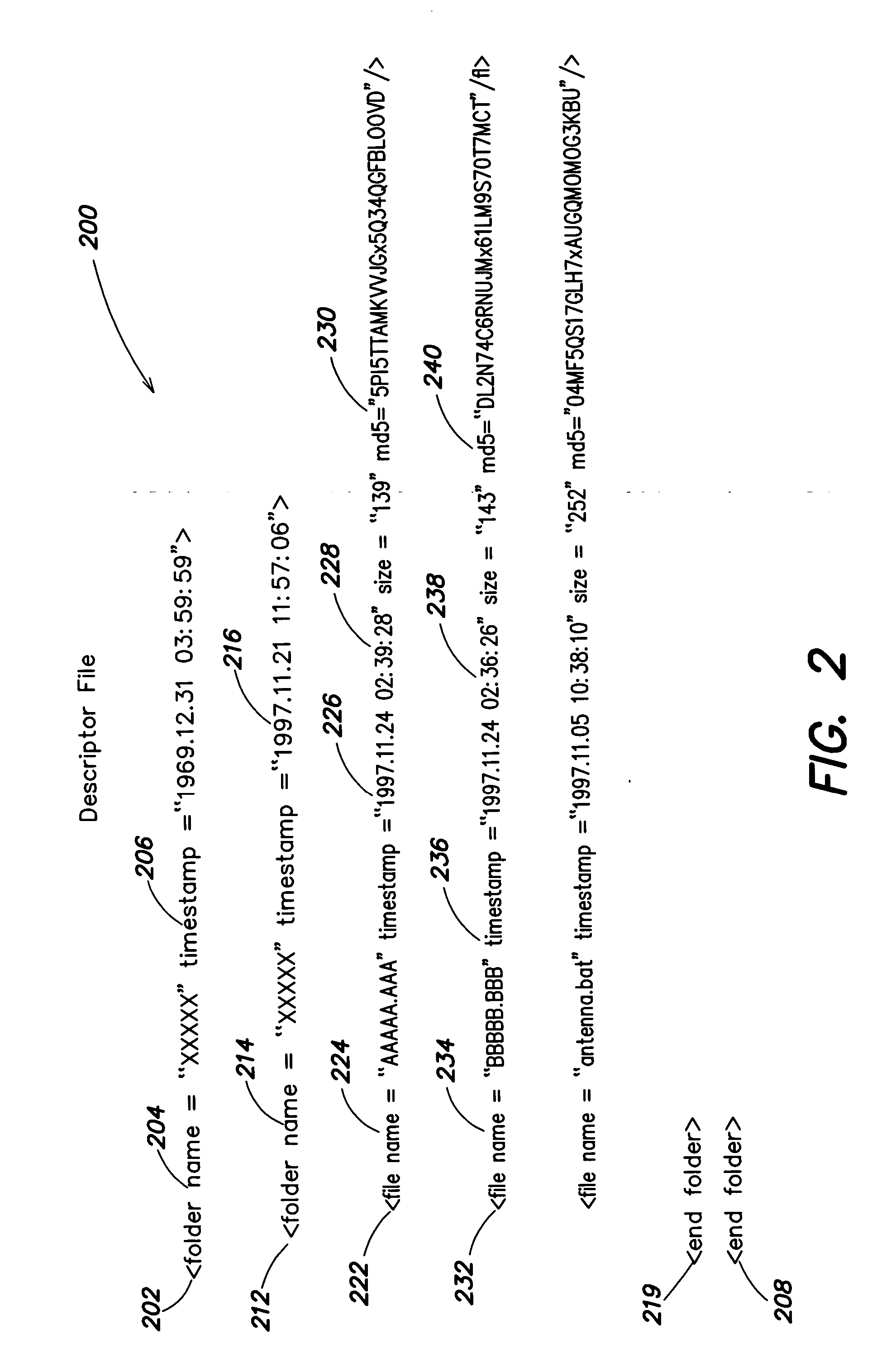
InactiveUS20050044417A1Simple structureSpecial service provision for substationDigital data processing detailsCryptographic hash functionMD5
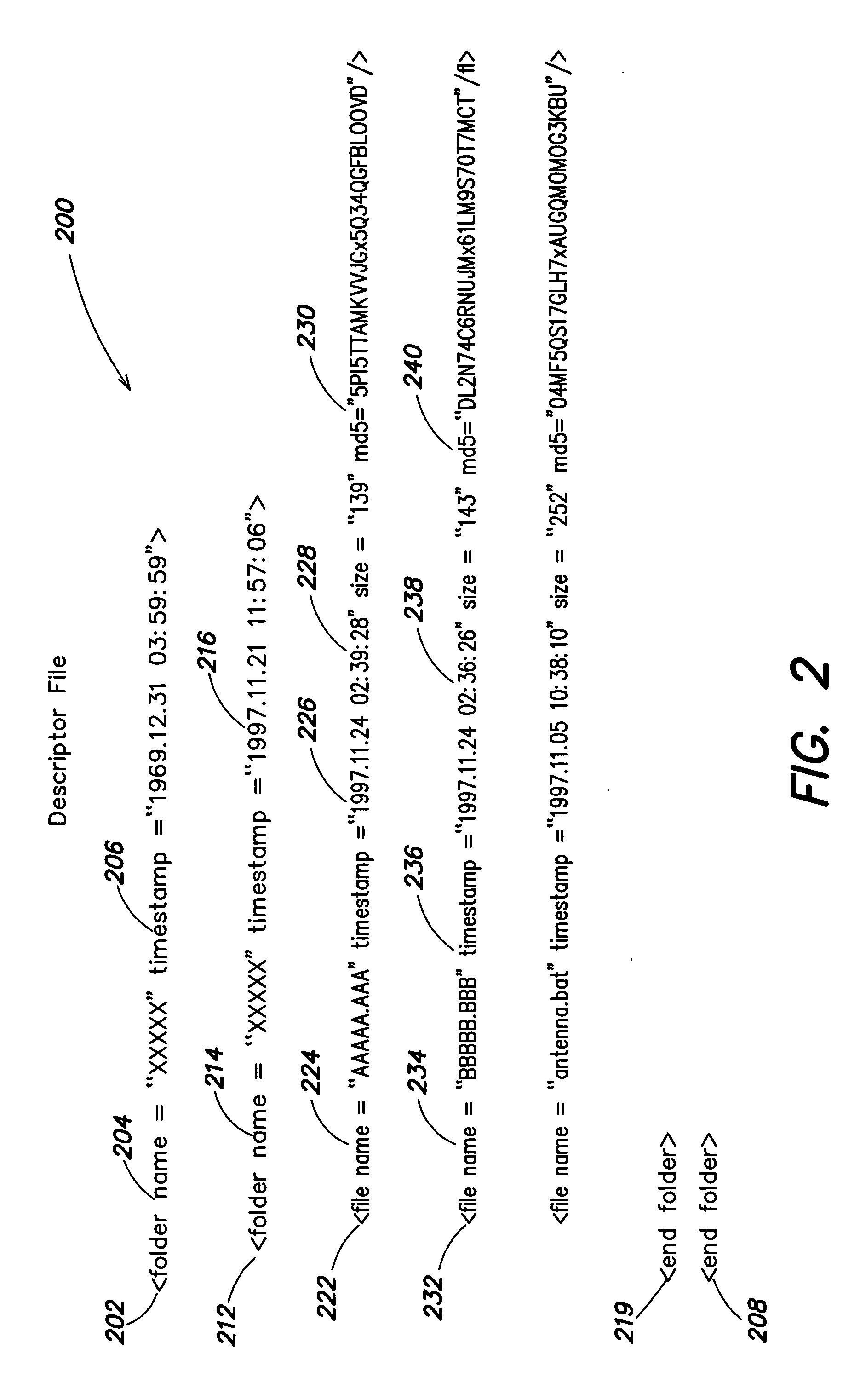
Representing a number of assets on an originating computer begins with selecting the assets to be represented. Cryptographic hash asset identifiers are generated; each of the asset identifiers is computed using the contents of a particular asset. The asset identifier is a content-based or content-addressable asset name for the asset and is location independent. An asset list is generated that includes the asset identifiers computed from the assets. A cryptographic hash asset list identifier is generated that is computed from the asset list. The asset list identifier is stored for later retrieval. The assets selected are also stored for safekeeping either locally or on a computer network. In the event of loss of the files from the originating computer, the asset list identifier is retrieved. Using the asset list identifier, the original asset list is found and retrieved from its safe location. The asset identifiers from the retrieved asset list are used to find and retrieve the individual assets from their backup locations. The assets are verified by recomputing the cryptographic hash asset identifier for each asset retrieved and comparing it to the asset identifier from the asset list. The MD5 algorithm is used for the cryptographic hash function. Assets are retrieved using a multicast protocol. A series of importer programs searches for assets to retrieve in progressively more remote locations. Assets are retrieved whole or in segments.
Owner:EMC CORP
Efficient authenticated dictionaries with skip lists and commutative hashing
ActiveUS20040107346A1Data processing applicationsUser identity/authority verificationSkip listCryptographic hash function
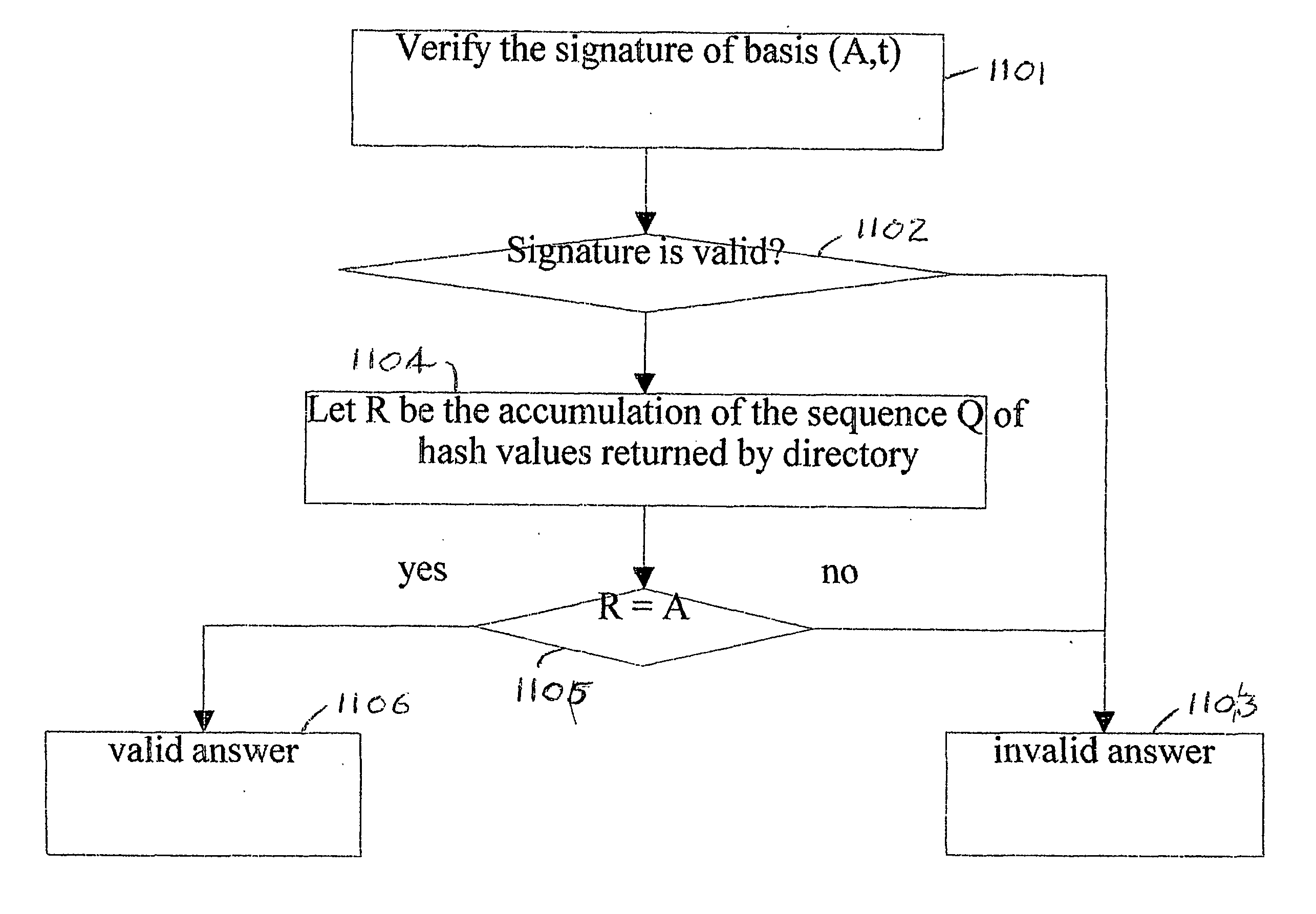
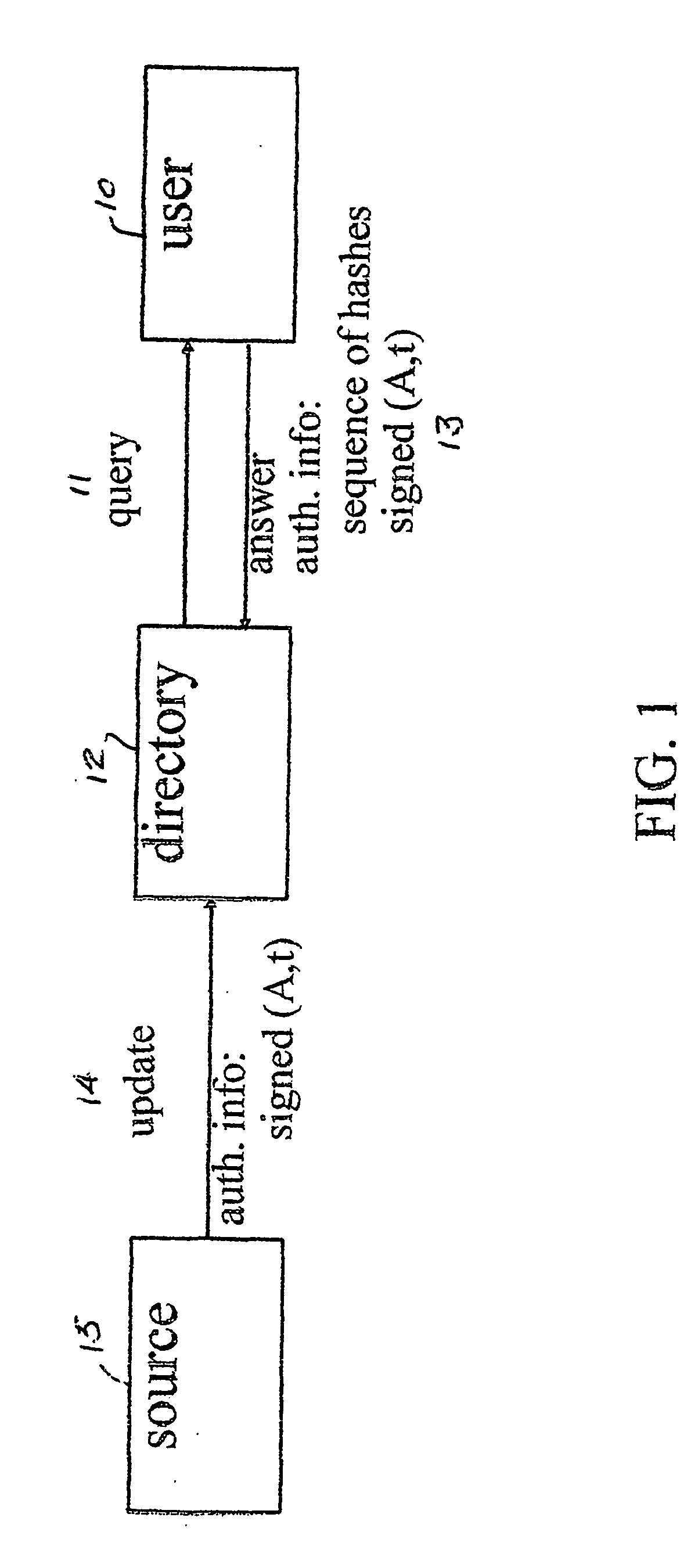
An efficient and practical method for dynamically maintaining an authenticated dictionary uses a skip list data structure and communicative hash functions to provide a dictionary database (201) that stores information objects so that any individual object can be authenticated as belonging or not belonging to the dictionary. The authentication consists of a short sequence of vales that begin with an element and a sequence of values that, when hashed in order using a cryptographic associative hash function, create the same value as the hashed digest of the entire dictionary. Rather than hashing up a dynamic 2-3 tree, hashes are created in a skip list. Validation of the result of the authenticating step is provided if the hash of the short sequence matches a signed hash of the entire skip list.
Owner:BROWN UNIVERSITY +1
System and method for generating pseudo-random numbers
ActiveUS7894602B2Random number generatorsSecuring communicationCryptographic hash functionNumber generator
A process and system for generating a pseudo-random number is presented. Input data having entropy is gathered in an Entropy Pool and transformed once by a cryptographic hash function. The transformed data forms the internal state of the pseudo-random number generator. The generator forms the output by applying a second cryptographic hash function to this internal state. Finally, the generator updates the internal state by inputting the current internal state and data from the Entropy Pool into a third cryptographic hash function. The output of the third hash function forms the new internal state of the pseudo-random number generator.
Owner:SAP AG
System and method for generating pseudo-random numbers
ActiveUS20070230693A1Random number generatorsSecuring communicationCryptographic hash functionNumber generator
A process and system for generating a pseudo-random number is presented. Input data having entropy is gathered in an Entropy Pool and transformed once by a cryptographic hash function. The transformed data forms the internal state of the pseudo-random number generator. The generator forms the output by applying a second cryptographic hash function to this internal state. Finally, the generator updates the internal state by inputting the current internal state and data from the Entropy Pool into a third cryptographic hash function. The output of the third hash function forms the new internal state of the pseudo-random number generator.
Owner:SAP AG
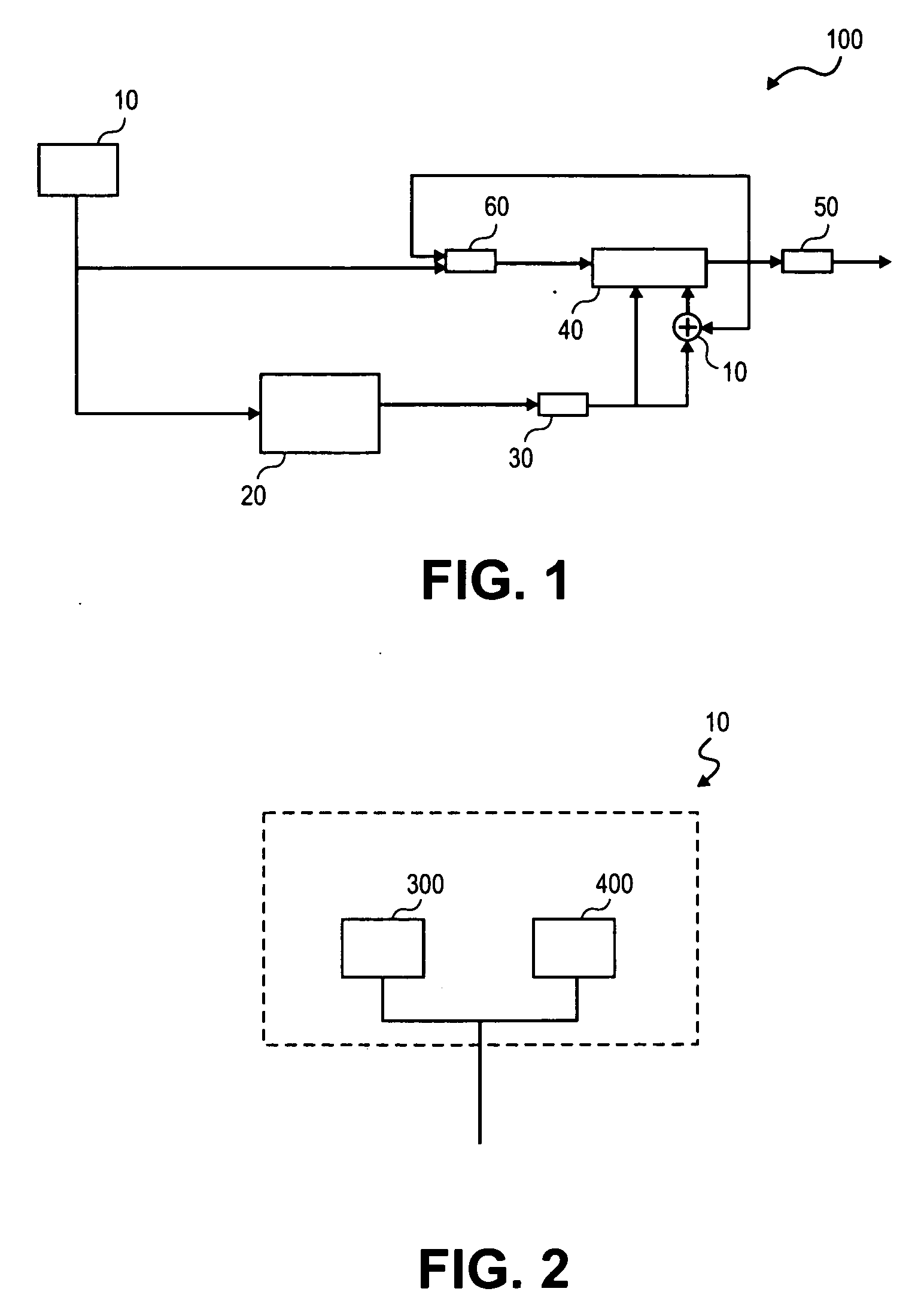
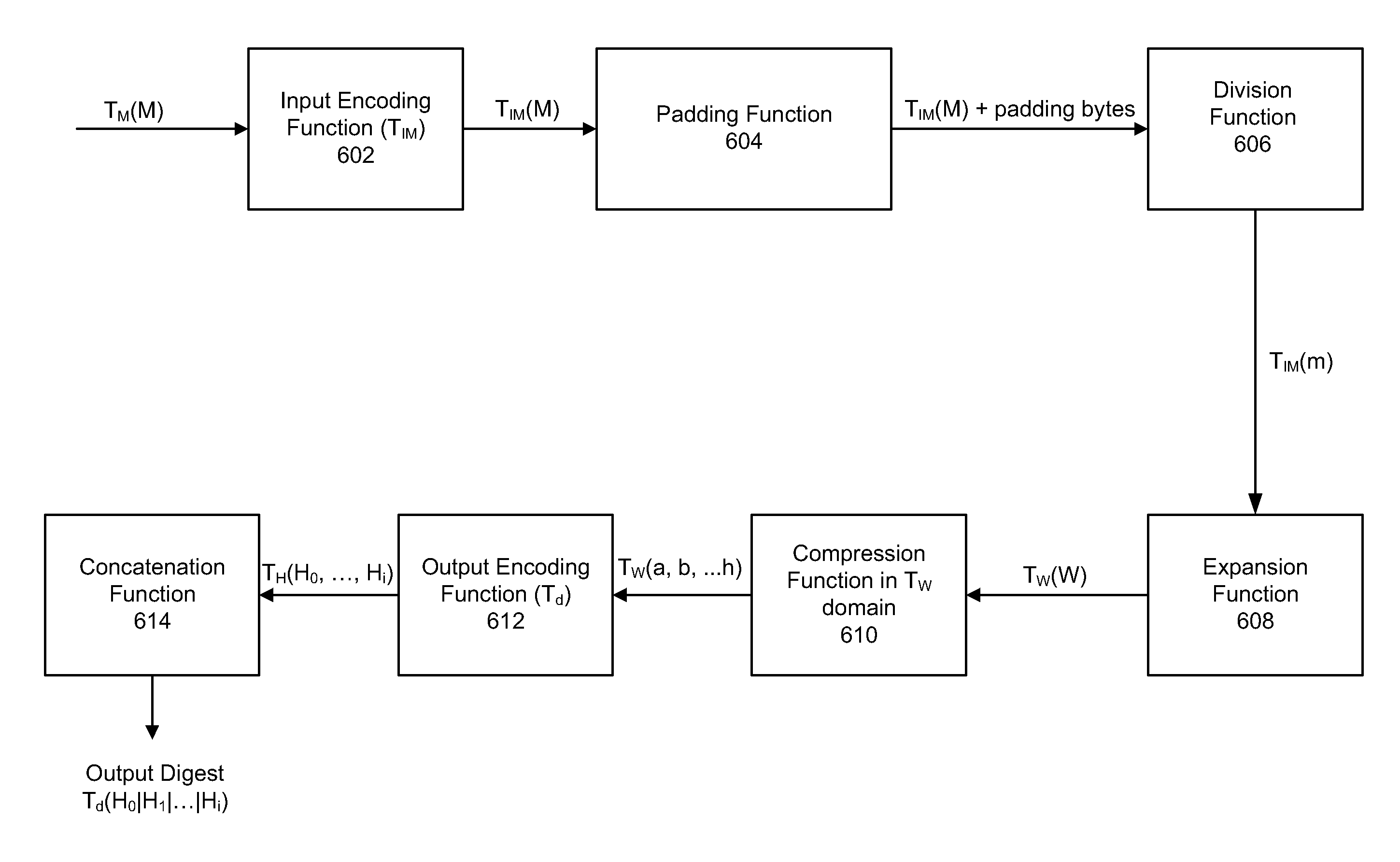
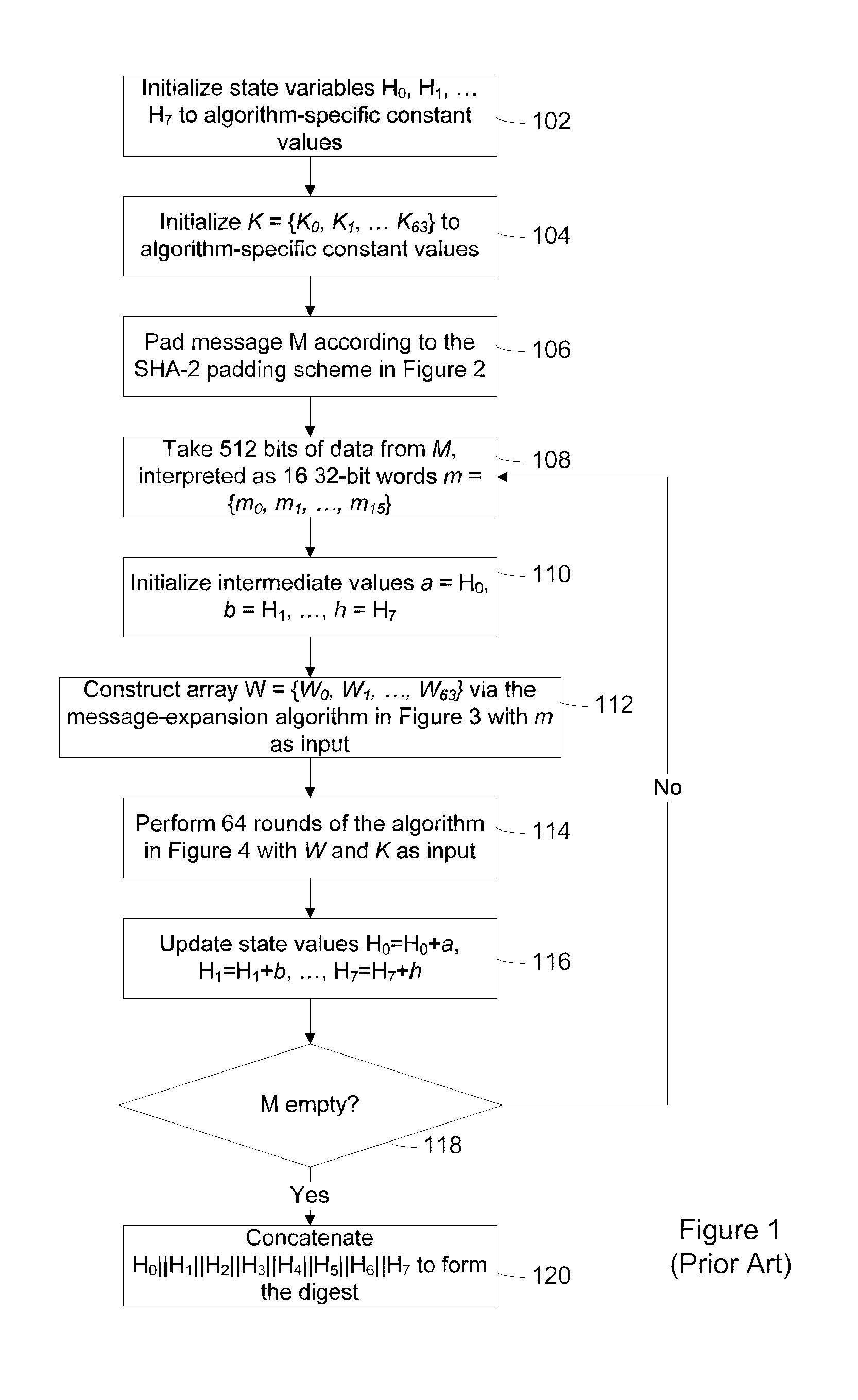
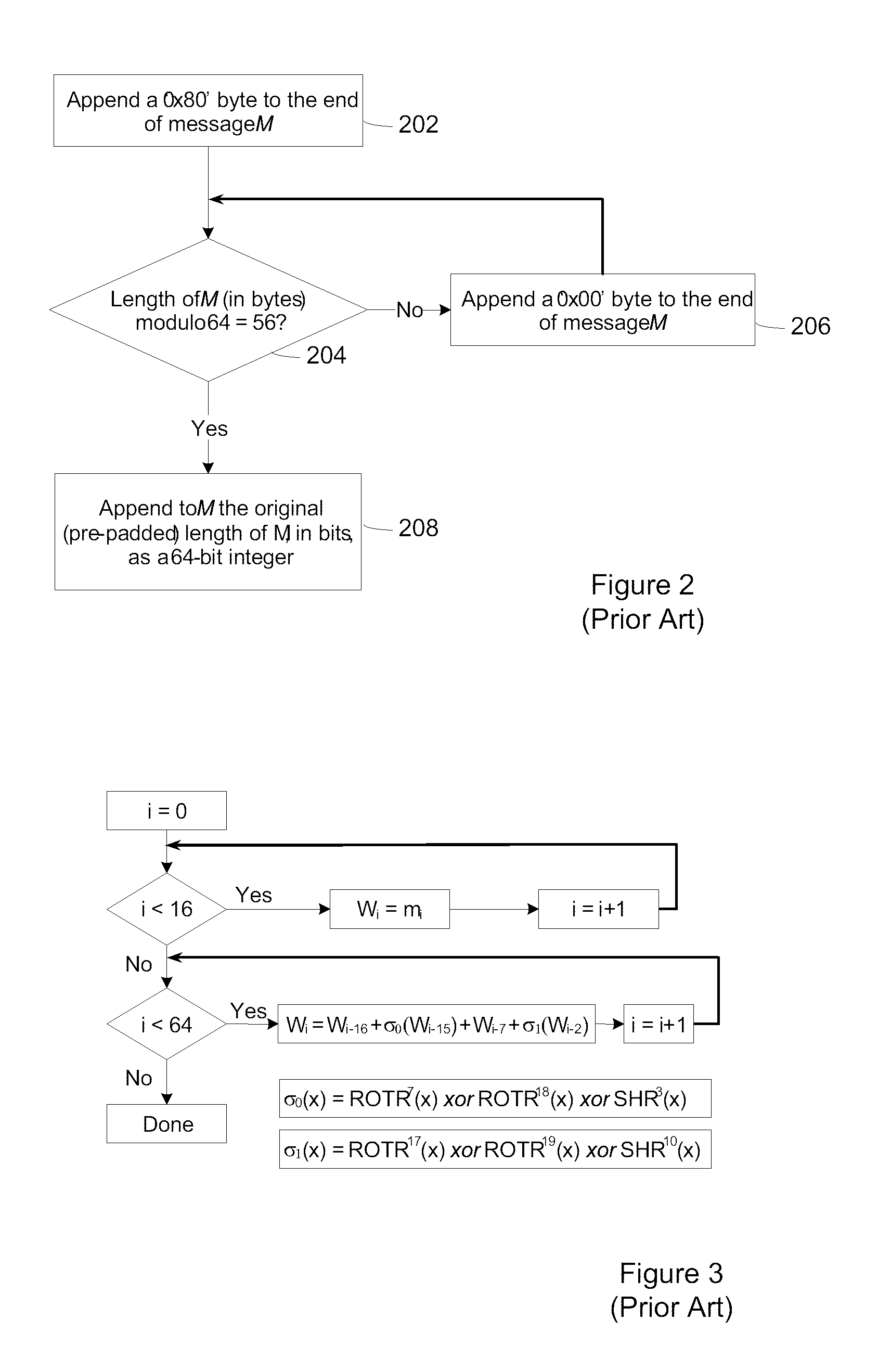
Method and System for Protecting Execution of Cryptographic Hash Functions
ActiveUS20140019771A1Digital data processing detailsUnauthorized memory use protectionComputer hardwareCryptographic hash function
A method of protecting the execution of a cryptographic hash function, such as SHA-256, in a computing environment where inputs, outputs and intermediate values can be observed. The method consists of encoding input messages so that hash function inputs are placed in a transformed domain, and then applying a transformed cryptographic hash function to produce an encoded output digest; the transformed cryptographic hash function implements the cryptographic hash function in the transformed domain.
Owner:IRDETO ACCESS
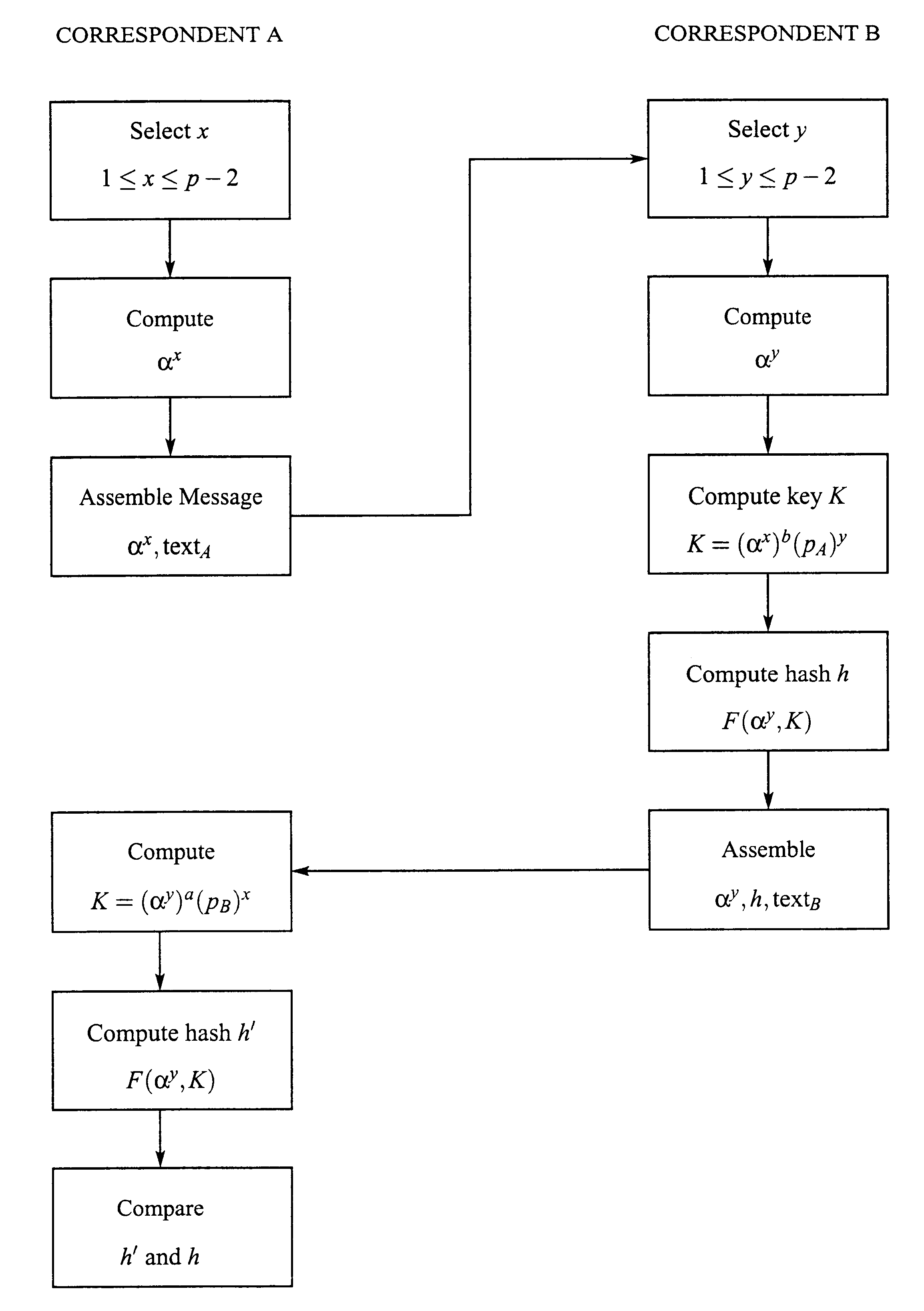
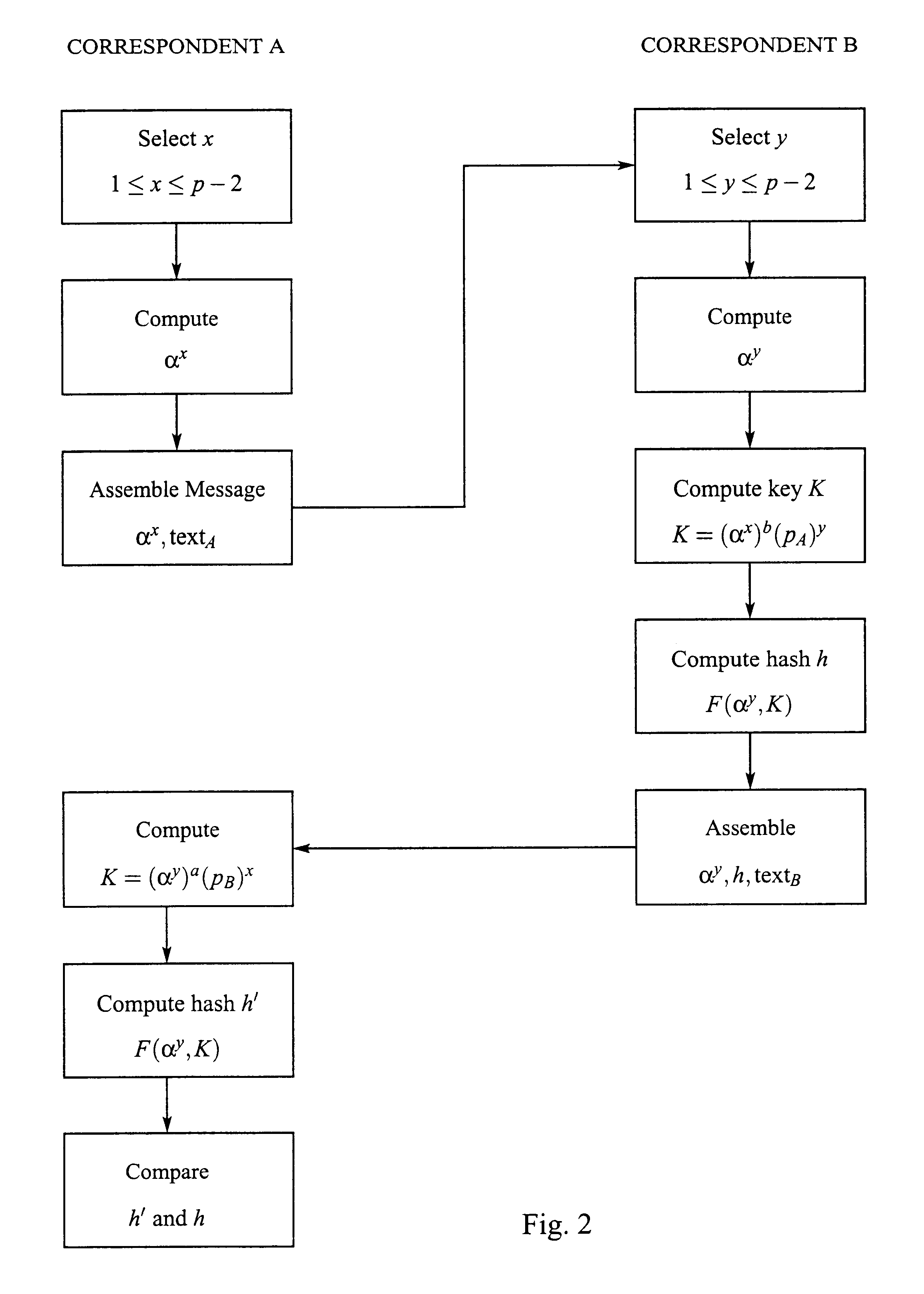
Key agreement and transport protocol
InactiveUS6487661B2Key distribution for secure communicationPublic key for secure communicationTransmission protocolCryptographic hash function
A key establishment protocol includes the generation of a value of cryptographic function, typically a hash, of a session key and public information. This value is transferred between correspondents together with the information necessary to generate the session key. Provided the session key has not been compromised, the value of the cryptographic function will be the same at each of the correspondents. The value of the cryptographic function cannot be compromised or modified without access to the session key.
Owner:MALIKIE INNOVATIONS LTD +1
Methods and systems for automatic object recognition and authentication
ActiveUS10193695B1Effectively authenticatingEffectively recognizingEncryption apparatus with shift registers/memoriesUser identity/authority verificationLearning basedPattern recognition
A system and a method of receiving object data representing one or more discriminating characteristics of a physical object or group of physical objects is described herein. The method includes: processing the object data by means of a machine-learning-based object recognition process to obtain discriminating data representing one or more collision resistant virtual representations of the physical object or group of physical objects; comparing at least one of the discriminating data and an original hash value derived therefrom by application of a pre-determined cryptographic hash function thereto with corresponding reference data stored in one or more data repositories with restricted access; and, if said comparison with the reference data results in a match, outputting digitally signed identification data comprising said hash value.
Owner:MERCK PATENT GMBH
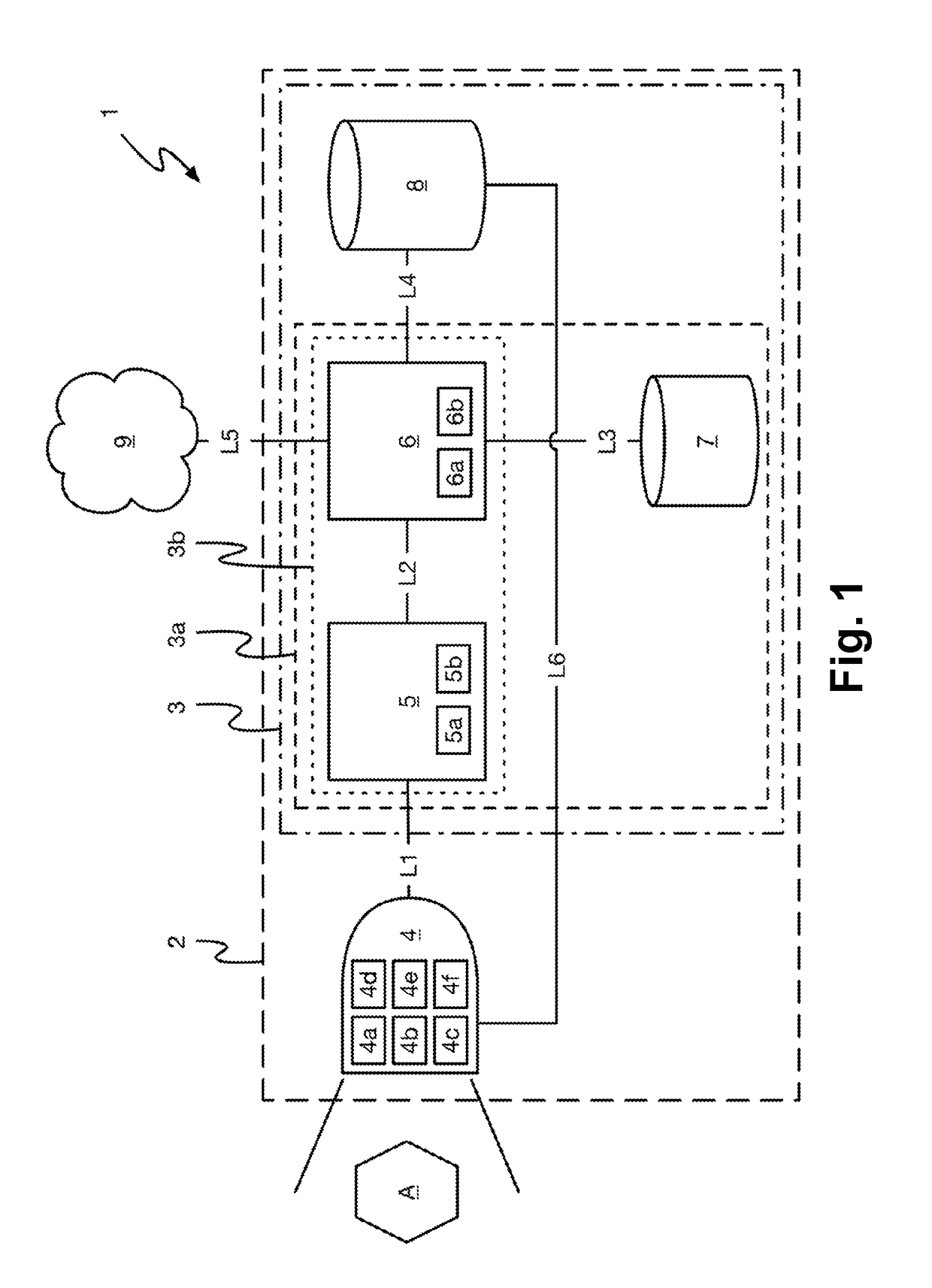
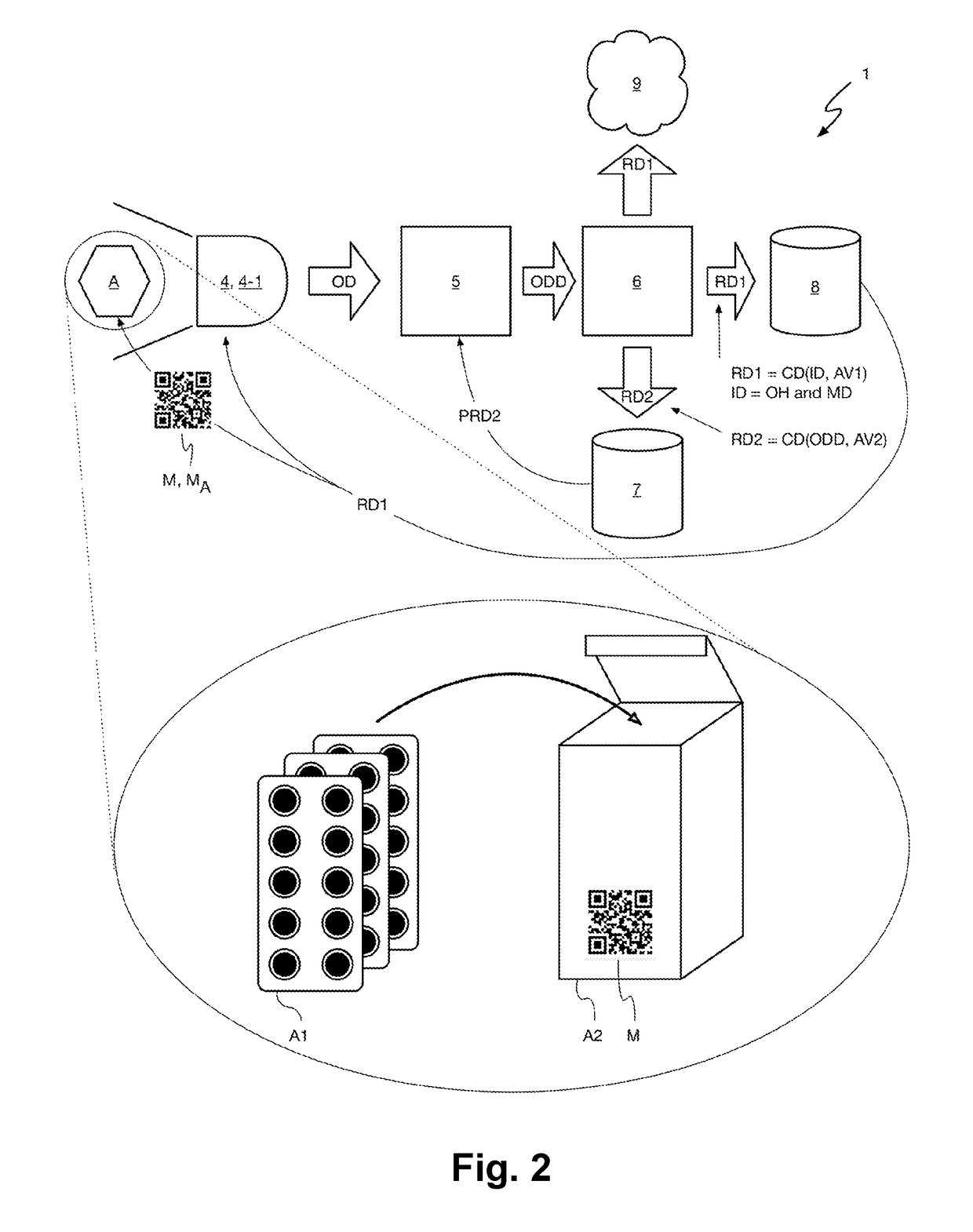
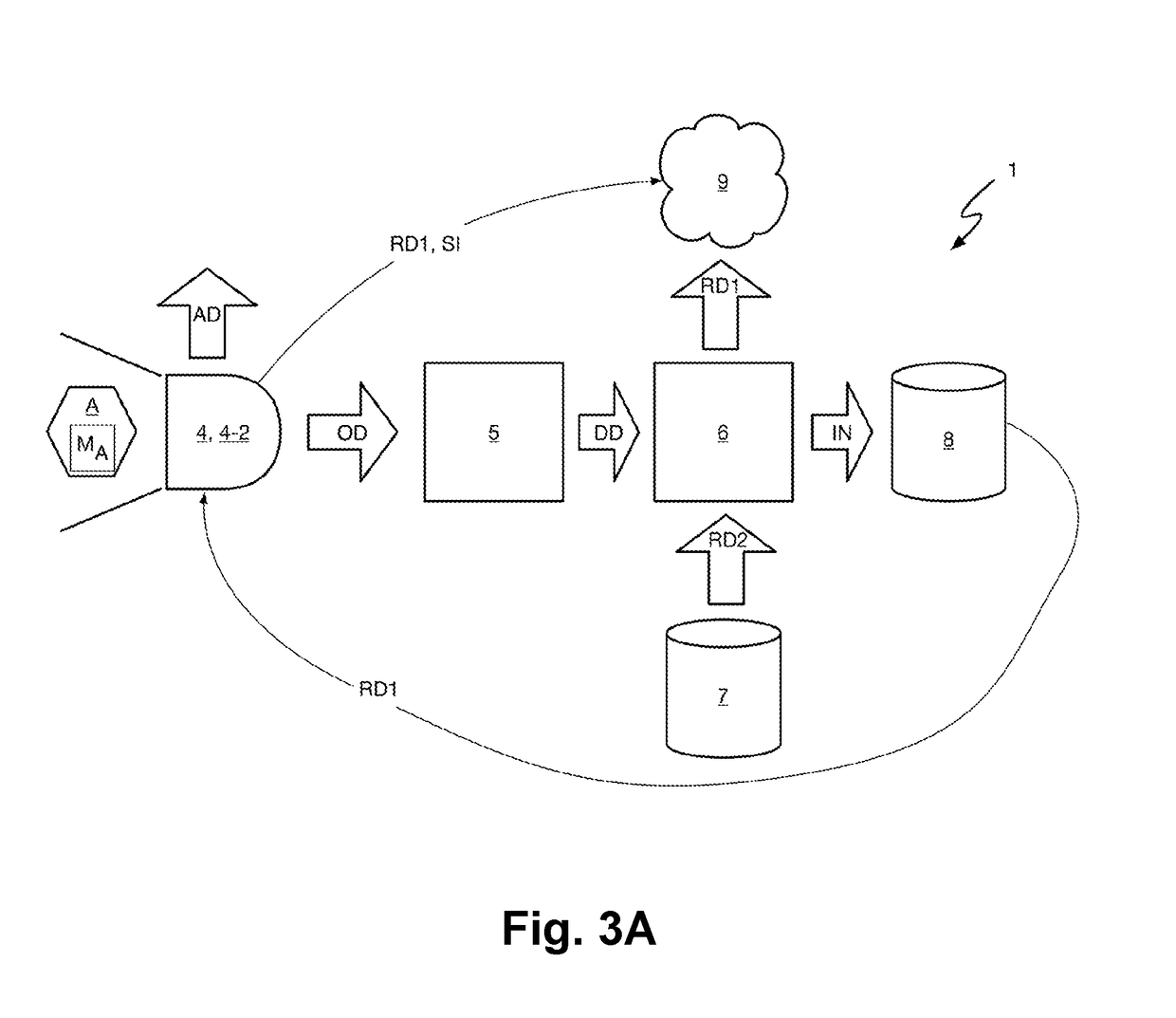
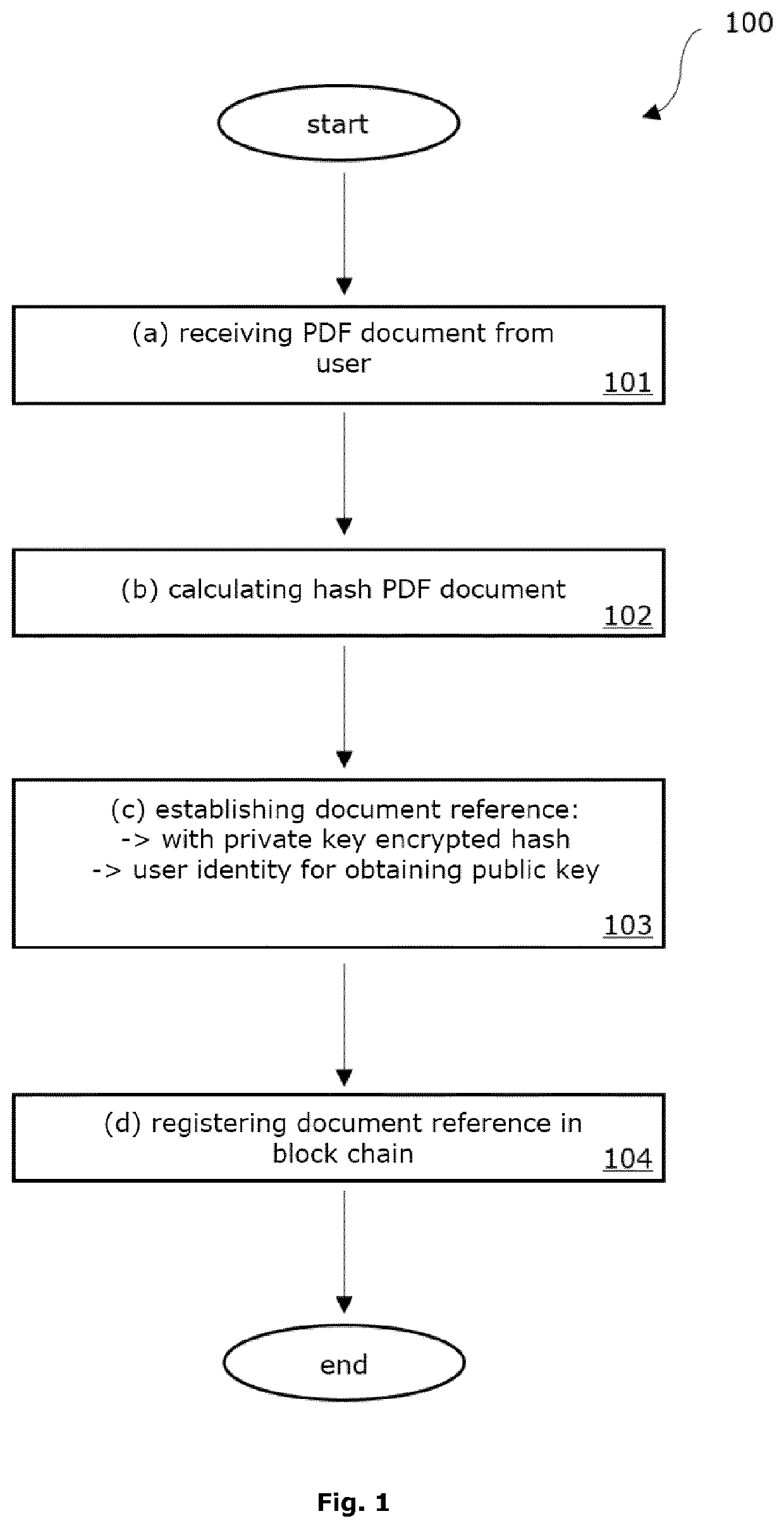
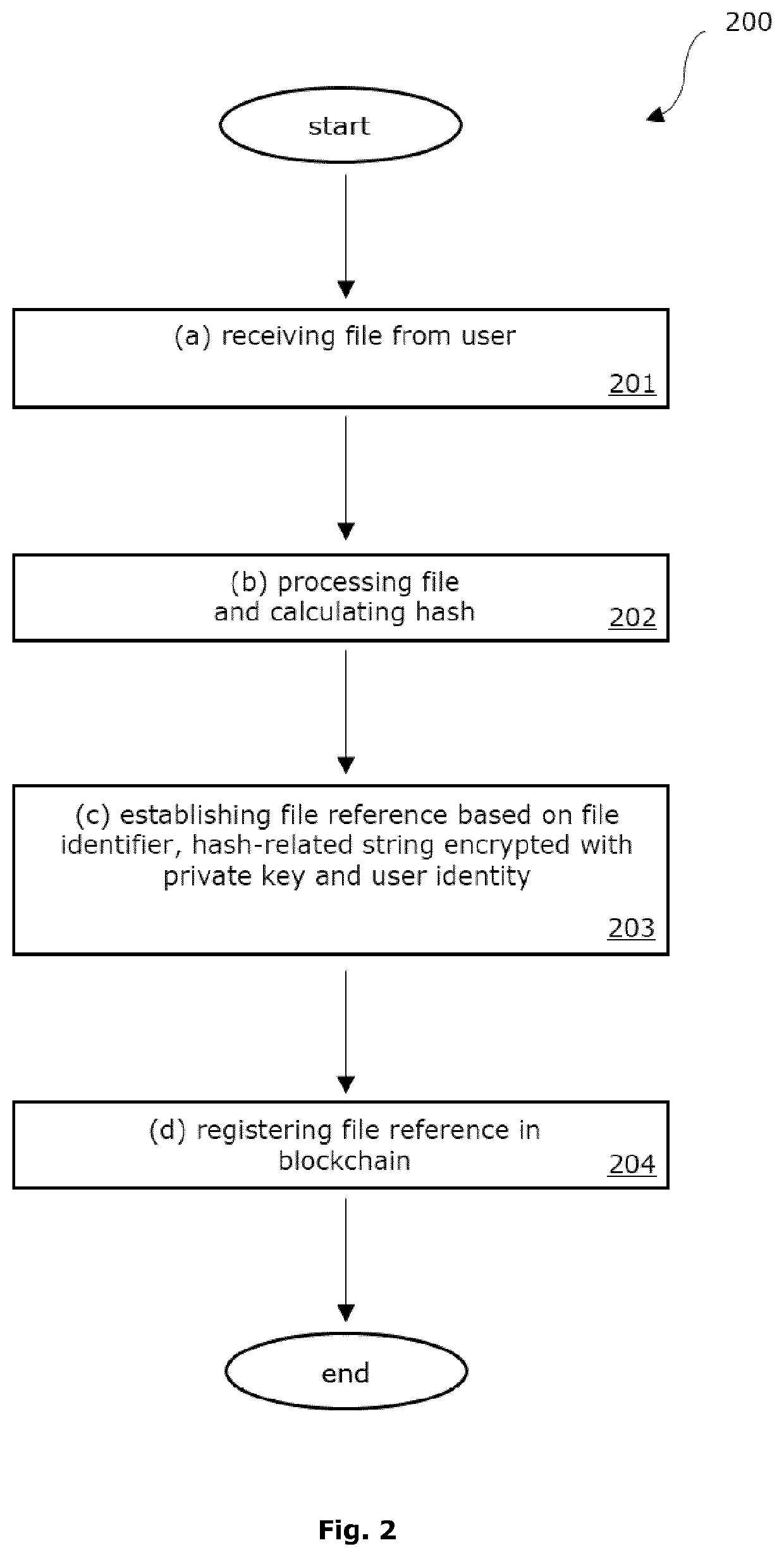
Improved Blockchain-Based Method for Registration and Verification of a File
ActiveUS20200099534A1Avoid registrationImprove securityEncryption apparatus with shift registers/memoriesUser identity/authority verificationCryptographic hash functionSoftware engineering
Owner:ITEXT GRP
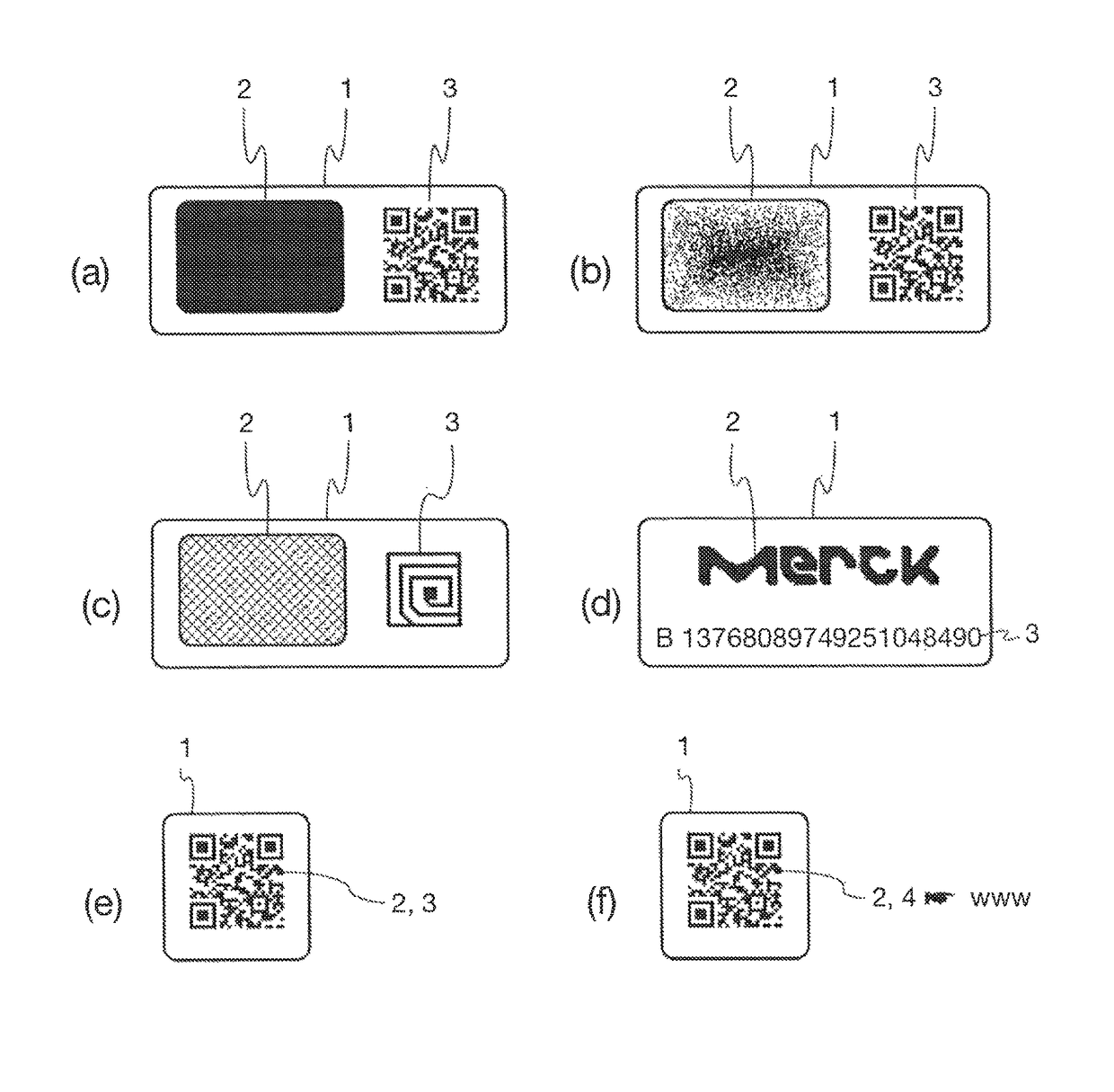
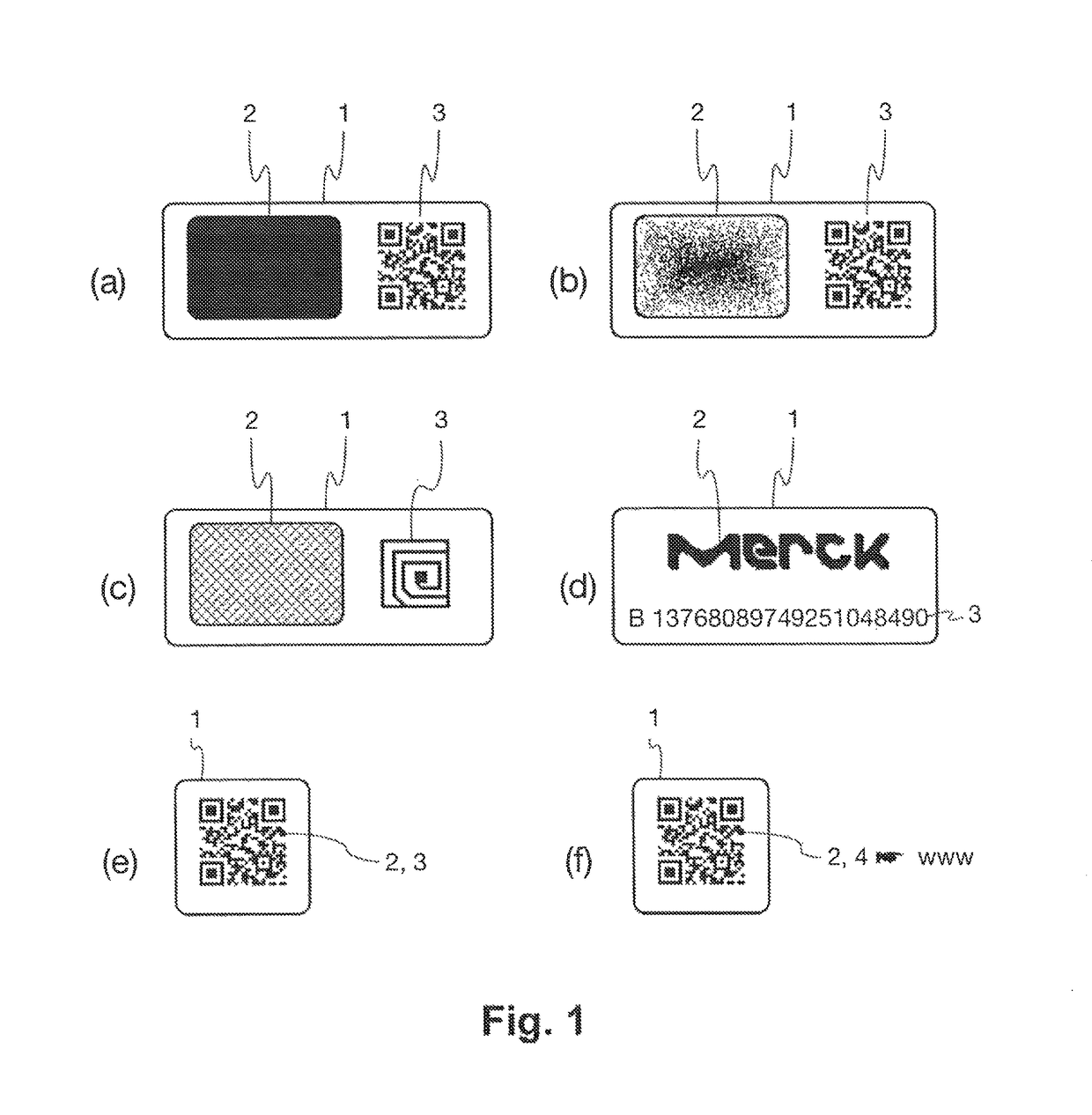
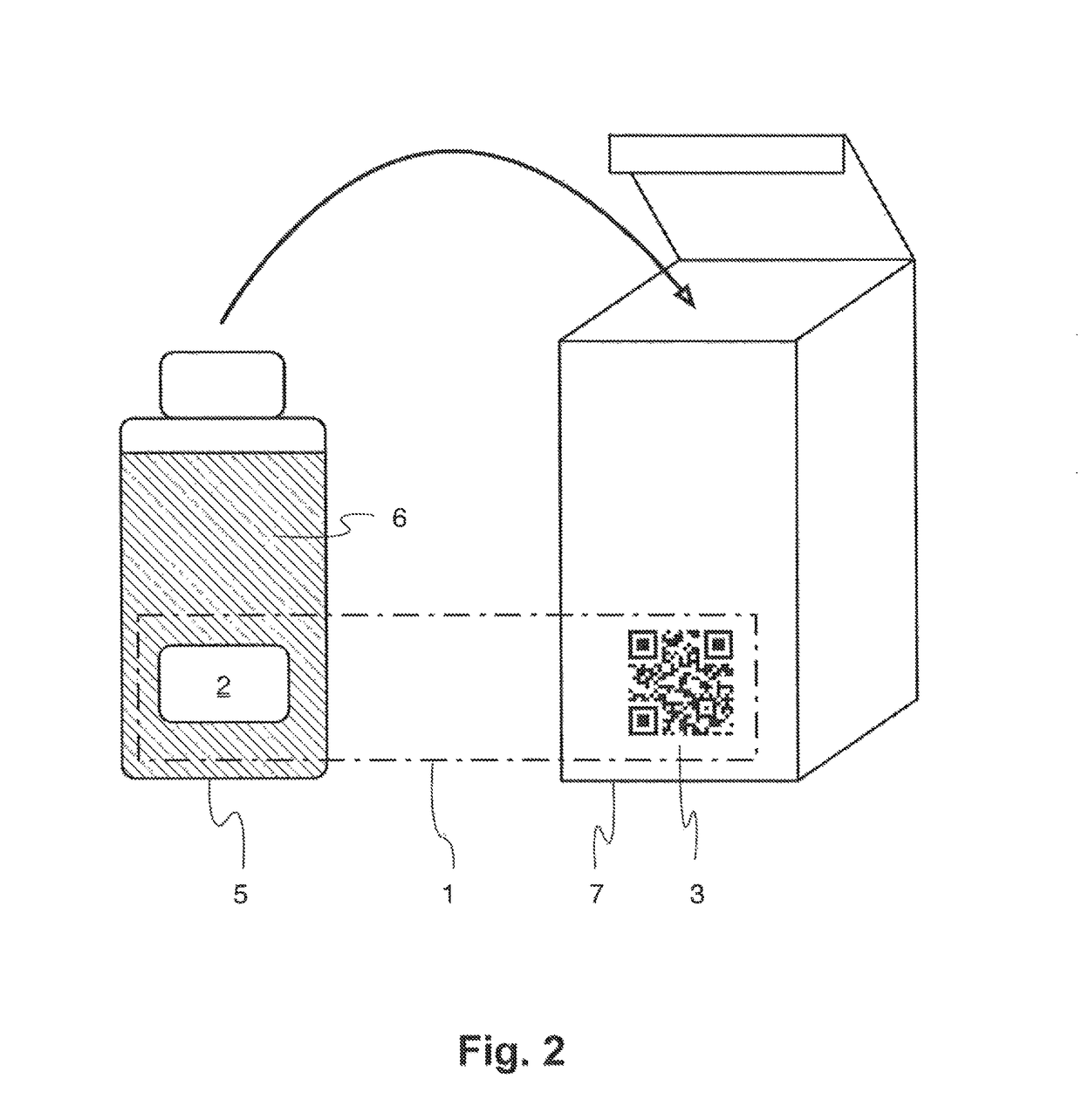
Reader device for reading a marking comprising a physical unclonable function
ActiveUS10002277B1Efficient readingVerify authenticityEncryption apparatus with shift registers/memoriesCoding/ciphering apparatusSecurity solutionCryptographic hash function
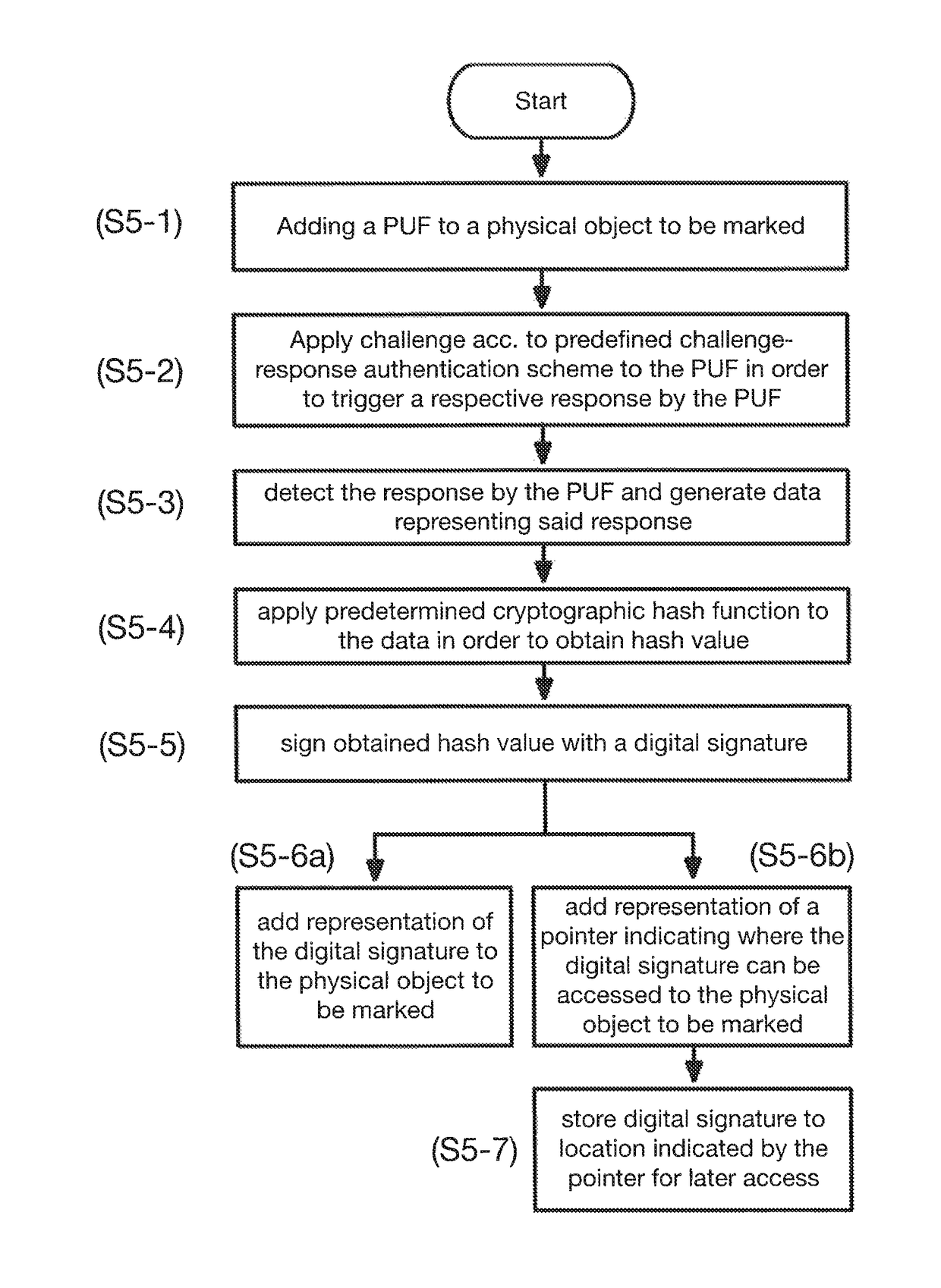
The present invention relates to the field of anti-counterfeit protection of products. Specifically, the invention is directed to a method of reading with a reader device a marking comprising a physical unclonable function, PUF, and a corresponding reader device. In particular, such reader device marking can be used in connection with or can form a component of a multi-component security system, in particular of an anti-counterfeit protection system, which is also disclosed herein as part of an overall security solution for anti-counterfeit protection. The method comprises a stimulation step, wherein a physical challenge according to a predetermined challenge-response authentication scheme corresponding to the PUF is created and applied to a PUF; a detection step, wherein a response generated by the PUF in accordance with the challenge-response authentication scheme in reaction to the challenge is detected and a digital signal representing the response is generated; a processing step, wherein the digital signal is processed in order to generate a hash value of the response by application of a predetermined cryptographic hash function to the digital signal; and an output step, wherein data representing the generated hash value as a first reading result is output.
Owner:MERCK PATENT GMBH
Content addressable information encapsulation, representation, and transfer
InactiveUS20050010794A1Simple structureCompact formSpecial service provision for substationData processing applicationsCryptographic hash functionMD5
Representing a number of assets on an originating computer begins with selecting the assets to be represented. Cryptographic hash asset identifiers are generated; each of the asset identifiers is computed using the contents of a particular asset. The asset identifier is a content-based or content-addressable asset name for the asset and is location independent. An asset list is generated that includes the asset identifiers computed from the assets. A cryptographic hash asset list identifier is generated that is computed from the asset list. The asset list identifier is stored for later retrieval. The assets selected are also stored for safekeeping either locally or on a computer network. In the event of loss of the files from the originating computer, the asset list identifier is retrieved. Using the asset list identifier, the original asset list is found and retrieved from its safe location. The asset identifiers from the retrieved asset list are used to find and retrieve the individual assets from their backup locations. The assets are verified by recomputing the cryptographic hash asset identifier for each asset retrieved and comparing it to the asset identifier from the asset list. The MD5 algorithm is used for the cryptographic hash function. Assets are retrieved using a multicast protocol. A series of importer programs searches for assets to retrieve in progressively more remote locations. Assets are retrieved whole or in segments.
Owner:EMC IP HLDG CO LLC
Apparatus and method for providing configurable cryptographic key size
ActiveCN1655496AKey distribution for secure communicationSynchronising transmission/receiving encryption devicesComputer hardwareKey size
The present invention provides an apparatus and method for performing cryptographic operations. In one embodiment, an apparatus is provided for performing cryptographic operations. The apparatus includes a cryptographic instruction, keygen logic, and execution logic. The cryptographic instruction is received by a computing device as part of an instruction flow executing on the computing device. The cryptographic instruction prescribes one of the cryptographic operations, and also prescribes that a provided cryptographic key be expanded into a corresponding key schedule for employment during execution of the one of the cryptographic operations. The keygen logic is operatively coupled to the cryptographic instruction. The keygen logic directs the computing device to expand the provided cryptographic key into the corresponding key schedule. The execution logic is coupled to the keygen logic. The execution logic expands the provided cryptographic key into the corresponding key schedule.
Owner:VIA TECH INC
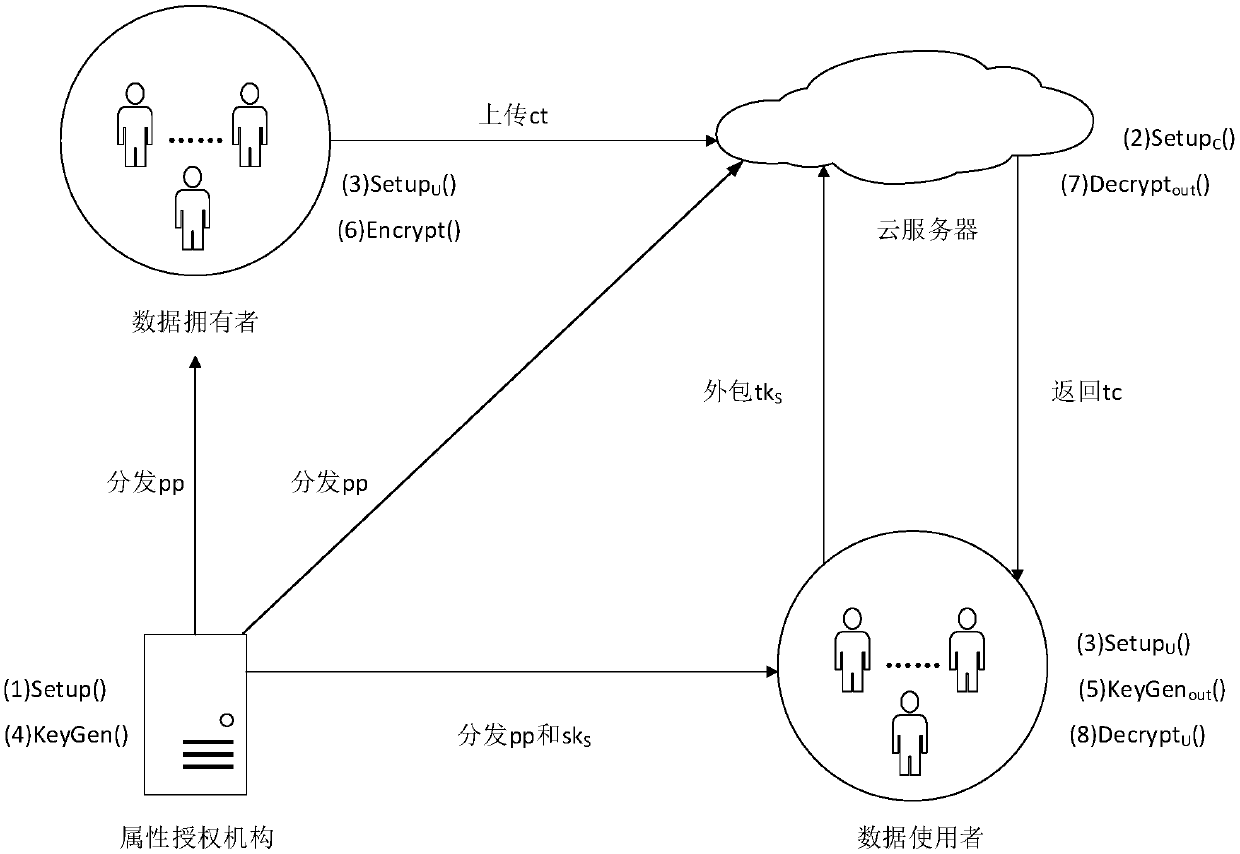
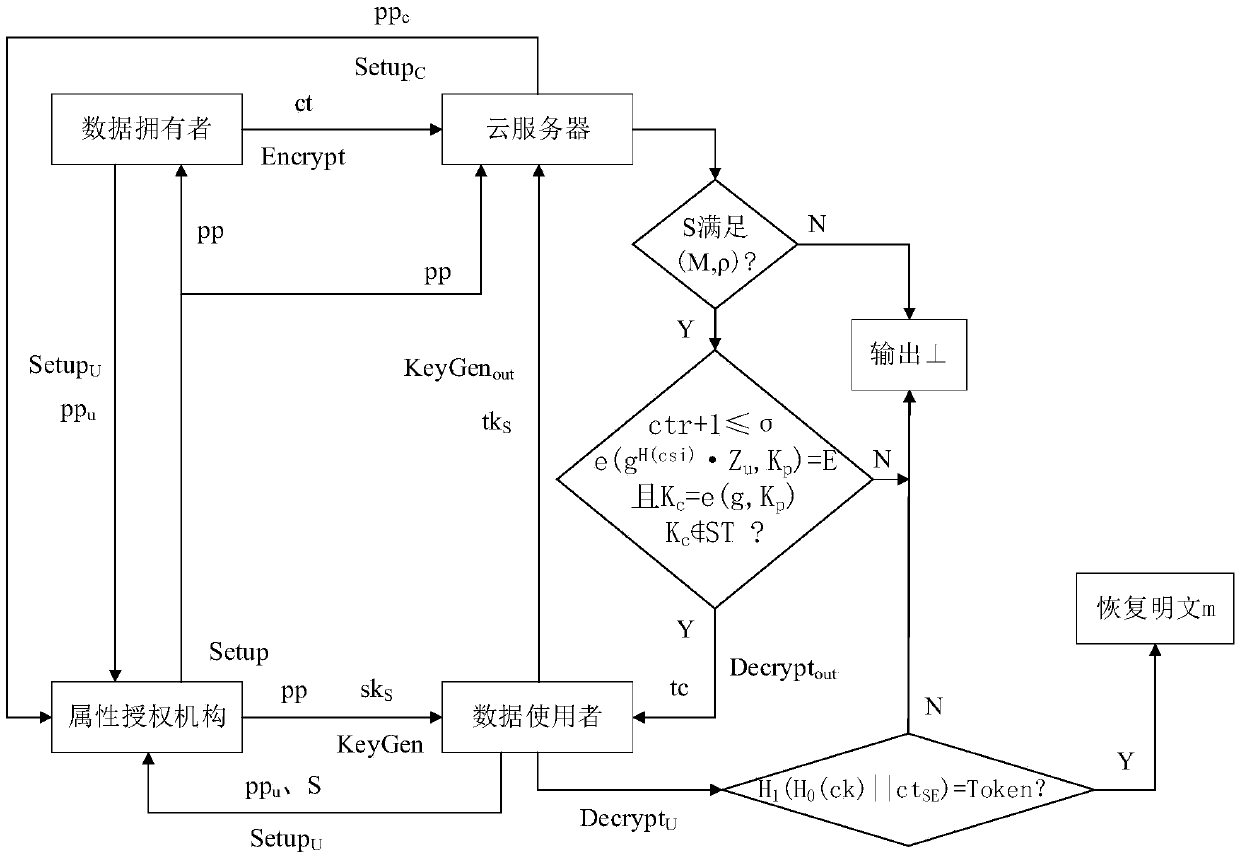
Cloud storage outsourced decryption attribute-based encryption method capable of limiting access times
ActiveCN109639677ASecure outsourcing decryption serviceKey distribution for secure communicationUser identity/authority verificationAccess structureCryptographic hash function
The invention discloses a cloud storage outsourced decryption attribute-based encryption method capable of limiting access times, wherein a data user generates a corresponding conversion key accordingto a decryption key distributed by an attribute authority mechanism; the conversion key is outsourced to a cloud server when a decryption service needs to be outsourced; and a conversion ciphertext returned by the cloud server is subjected to outsourced decryption verification. In the method, an access structure of LSSS is adopted, a verifiable random function (VRF) is used to limit the access times of the user, a decryption operation of the client is outsourced to the cloud by using an outsourcing computing technology, a secure decryption outsourcing service is realized by using a key blinding technology, and the correctness of the outsourced decryption is verified through a verification token generated by using a cryptographic hash function. The fine-grained access control mode capableof limiting the access times of the users in a fixed time realizes public verification of the correctness of outsourced decryption in the attribute-based encryption.
Owner:GUANGDONG UNIV OF TECH +1
Composite security marking
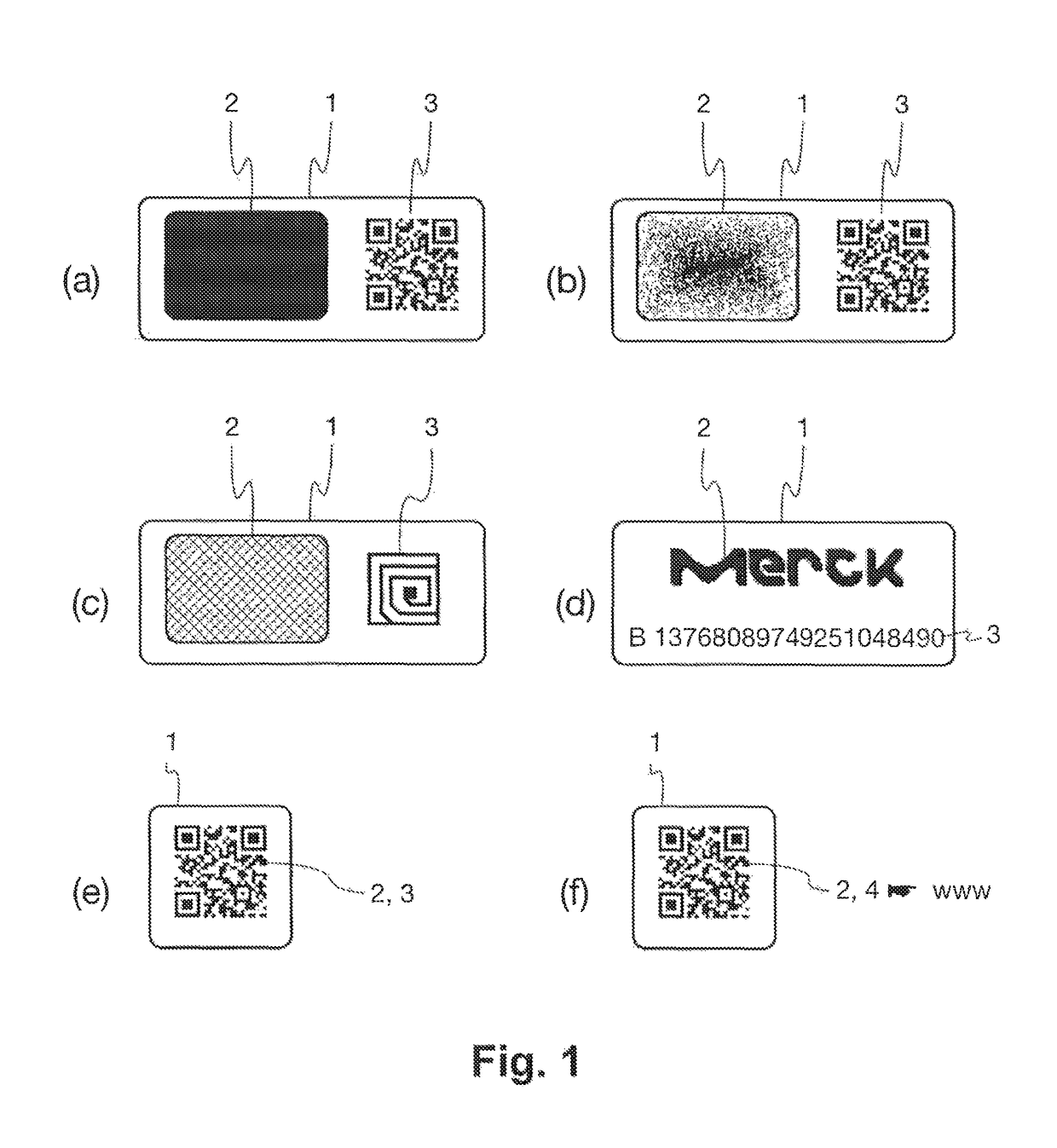
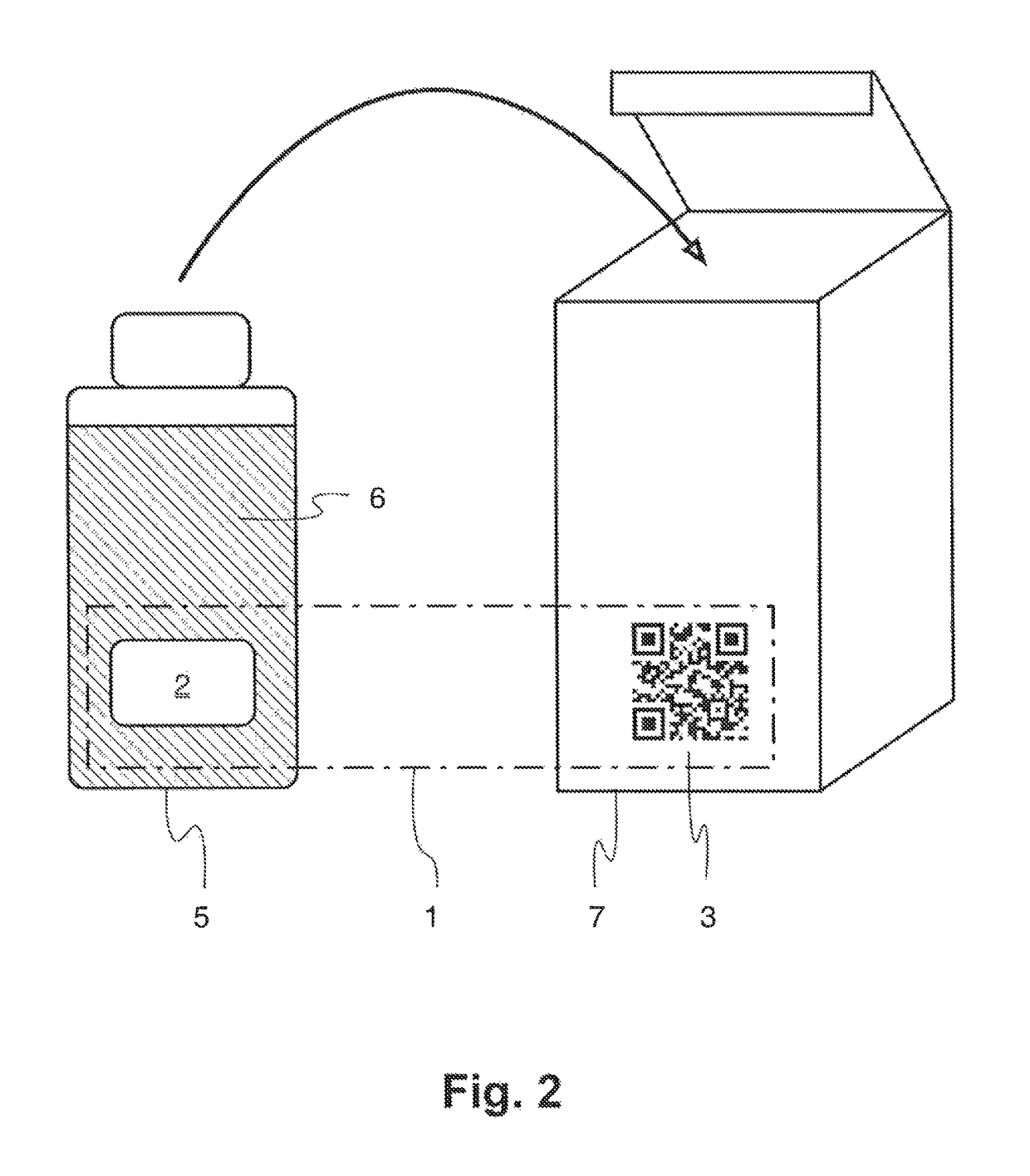
ActiveUS10002362B1User identity/authority verificationCharacter and pattern recognitionCryptographic hash functionDigital signature
Owner:MERCK PATENT GMBH
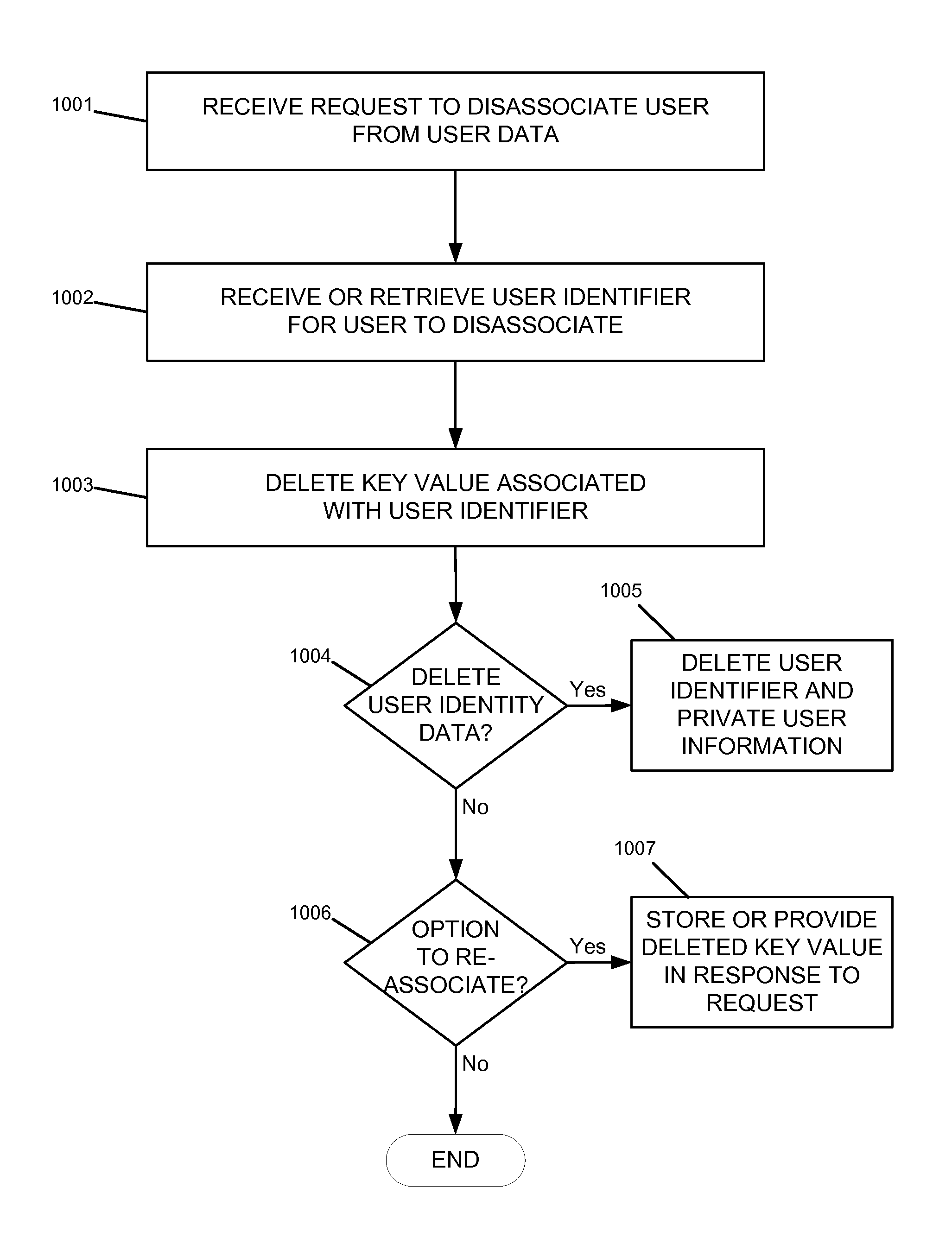
Data access and anonymity management
Techniques described herein provide data access and data anonymity management within various implementations of content distribution networks. In some embodiments, a data anonymity management system may include multiple different data stores configured to store identity data, user data, and / or linking data, as well as a data anonymity server configured to support data anonymity features such as active user data anonymity, one-way linking and permanently breakable links between user identity data and associated user data. In some embodiments, storage systems and techniques may be used for storing identity data, user data, and link data in multiple different data stores, with different data storage requirements and different processes and policies for data availability, data backup, online disaster recovery, offline storage archiving, and the like. Additionally, cryptographic hash functions may be used to implement one-way encryption between identity data and user data.
Owner:PEARSON EDUCATION
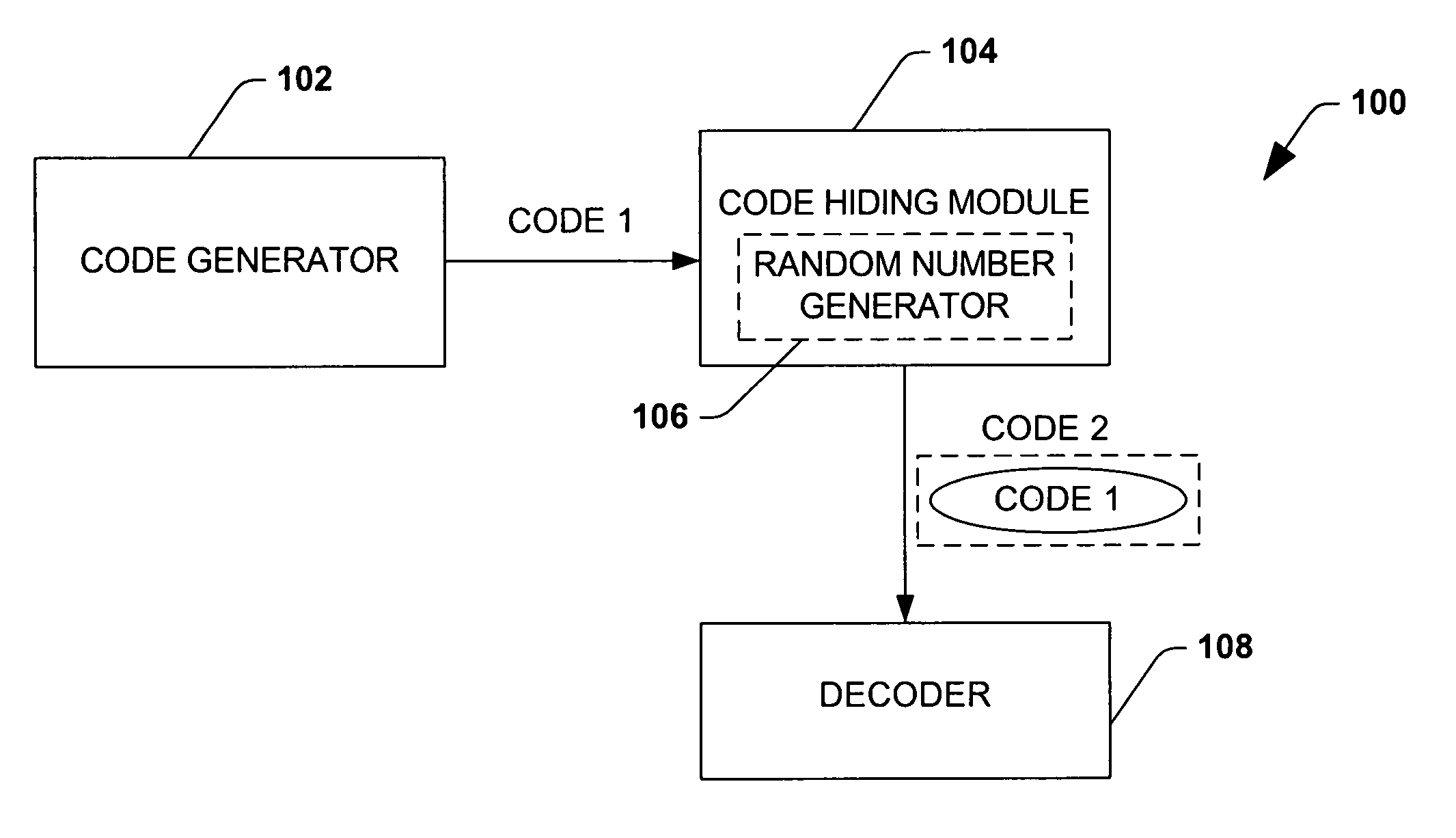
Efficient code constructions via cryptographic assumptions
InactiveUS20050175180A1High level of performanceEffectively randomizesReed-muller codesSynchronising transmission/receiving encryption devicesCryptographic hash functionTheoretical computer science
A system that facilitates efficient code construction comprises a component that receives a first code and a transformation component that transforms the first code to a new code. The new code has essentially same length parameters as the first code but is hidden to a computationally bounded adversary. The first code can be designed in the noise model and appear random to a computationally bounded adversary upon transformation.
Owner:MICROSOFT TECH LICENSING LLC
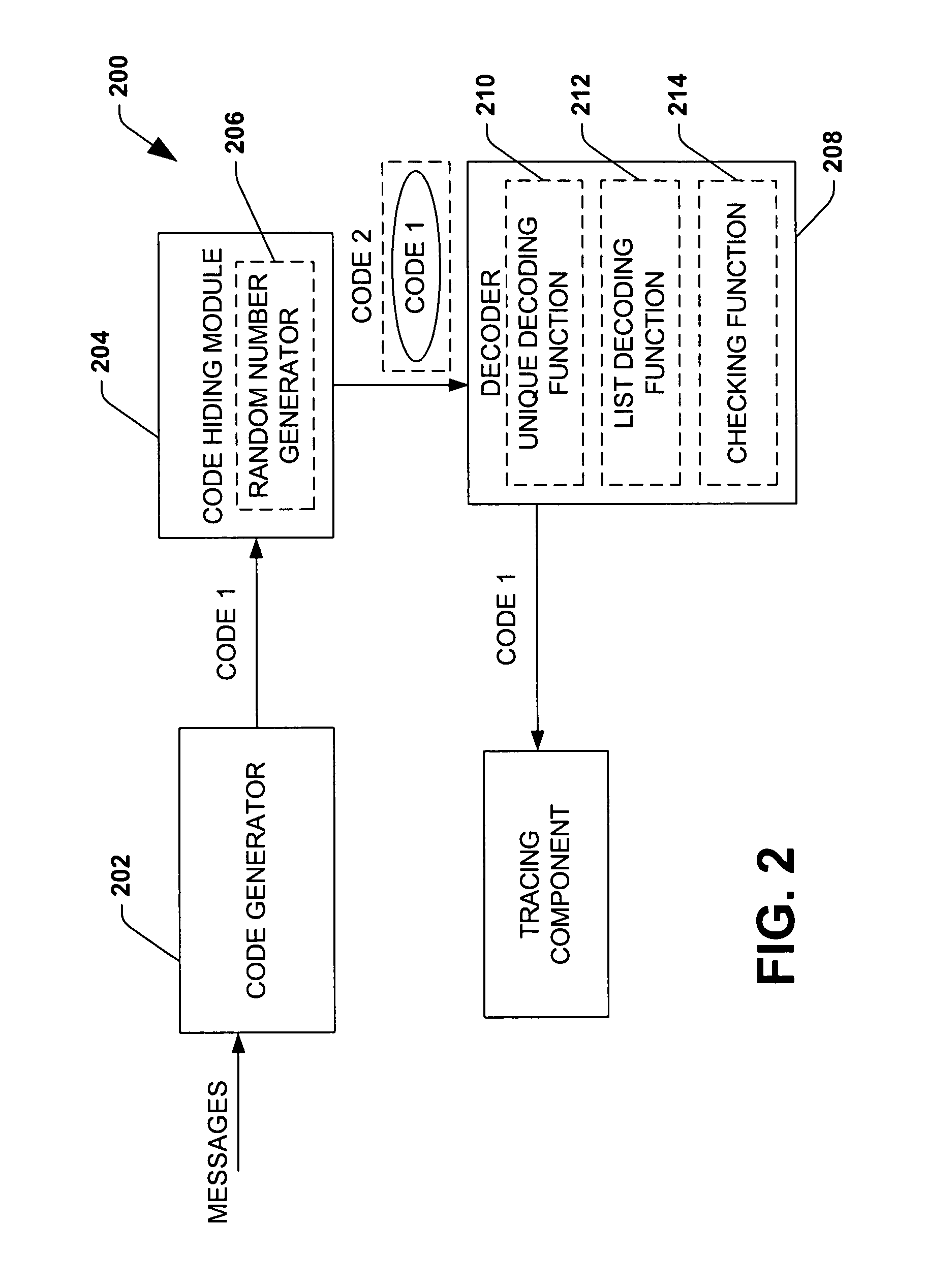
Probabilistic key distribution in vehicular networks with infrastructure support
ActiveUS20150139421A1High RSU densityConnection securityMultiple keys/algorithms usagePublic key for secure communicationCryptographic hash functionUser identifier
Method and system of key distribution by trusted nodes for a vehicular ad hoc network, the nodes of said network having at least one pair of public-private keys and the corresponding certificates, issued by a CA, said method comprising each vehicle node, on entering said network region, requesting a set of keys from an RSU node that is within range and within that region, said RSU node sending said vehicle node a set of private keys, selected from a pool of private keys, and a list with the key identifiers of the private keys shared by said vehicle node and the other vehicle nodes that have most recently contacted said RSU for a predetermined period of time; such that two nodes are able to establish a secure connection without further interaction by deriving a shared secret which is a cryptographic hash function of the keys shared by said two nodes.
Owner:UNIV DO PORTO
Content distribution with renewable content protection
PendingUS20160171186A1Key distribution for secure communicationUnauthorized memory use protectionContent distributionCryptographic hash function
A method and apparatus for playing back a media content instance is disclosed. The method permits the use of downloadable variants to upgrade or change cryptographic functions performed by the playback device, thus permitting content protection schemes to be renewed.
Owner:WARNER BROS ENTERTAINMENT INC
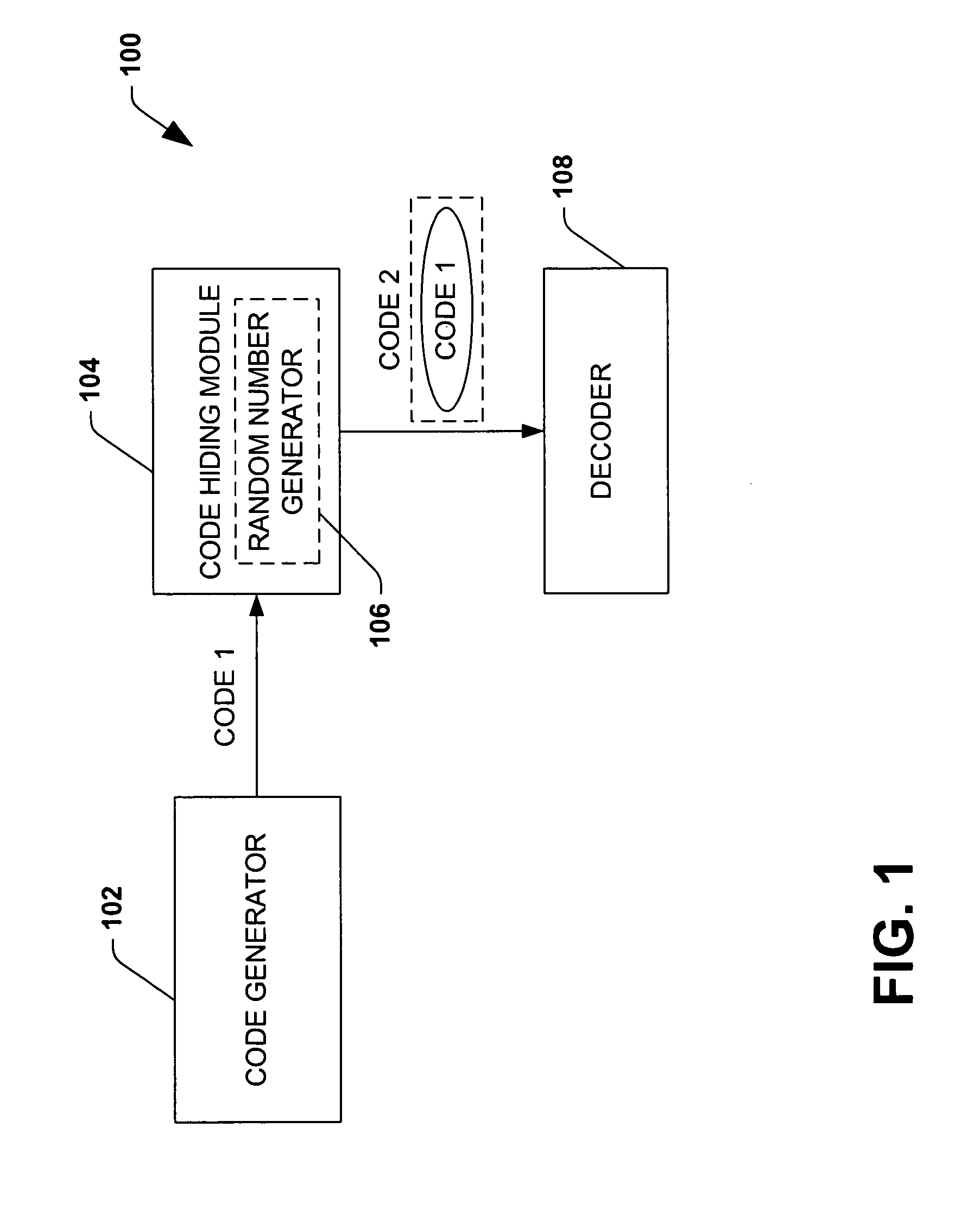
Efficient code constructions via cryptographic assumptions
InactiveUS7643637B2High levelSynchronising transmission/receiving encryption devicesReed-muller codesCryptographic hash functionTheoretical computer science
A system that facilitates efficient code construction comprises a component that receives a first code and a transformation component that transforms the first code to a new code. The new code has essentially same length parameters as the first code but is hidden to a computationally bounded adversary. The first code can be designed in the noise model and appear random to a computationally bounded adversary upon transformation.
Owner:MICROSOFT TECH LICENSING LLC
Storing Lossy Hashes of File Names and Parent Handles Rather than Full Names Using a Compact Table for Network-Attached-Storage (NAS)
ActiveUS20070277227A1Digital data processing detailsMultiple digital computer combinationsCommon nameCryptographic hash function
Multiple Network Attached Storage (NAS) appliances are pooled together by a virtual NAS translator, forming one common name space visible to clients. Clients send messages to the virtual NAS translator with a file name and a virtual handle of the parent directory that are concatenated to a full file-path name and compressed by a cryptographic hash function to generate a hashed-name key. The hashed-name key is matched to a storage key in a table. The full file-path name is not stored, reducing the table size. A unique entry number is returned to the client as the virtual file handle that is also stored in another table with one or more native file handles, allowing virtual handles to be translated to native handles that the NAS appliance servers use to retrieve files. File movement among NAS servers alters native file handles but not virtual handles, hiding NAS details from clients.
Owner:CUFER ASSET LTD LLC
Content addressable information encapsulation, representation, and transfer
InactiveUS20050187902A1Simple structureSpecial service provision for substationDigital data information retrievalCryptographic hash functionMD5
Representing a number of assets on an originating computer begins with selecting the assets to be represented. Cryptographic hash asset identifiers are generated; each of the asset identifiers is computed using the contents of a particular asset. The asset identifier is a content-based or content-addressable asset name for the asset and is location independent. An asset list is generated that includes the asset identifiers computed from the assets. A cryptographic hash asset list identifier is generated that is computed from the asset list. The asset list identifier is stored for later retrieval. The assets selected are also stored for safekeeping either locally or on a computer network. In the event of loss of the files from the originating computer, the asset list identifier is retrieved. Using the asset list identifier, the original asset list is found and retrieved from its safe location. The asset identifiers from the retrieved asset list are used to find and retrieve the individual assets from their backup locations. The assets are verified by recomputing the cryptographic hash asset identifier for each asset retrieved and comparing it to the asset identifier from the asset list. The MD5 algorithm is used for the cryptographic hash function. Assets are retrieved using a multicast protocol. A series of importer programs searches for assets to retrieve in progressively more remote locations. Assets are retrieved whole or in segments.
Owner:CARPENTIER PAUL R +2
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com