Patents
Literature
57 results about "Trusted timestamping" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
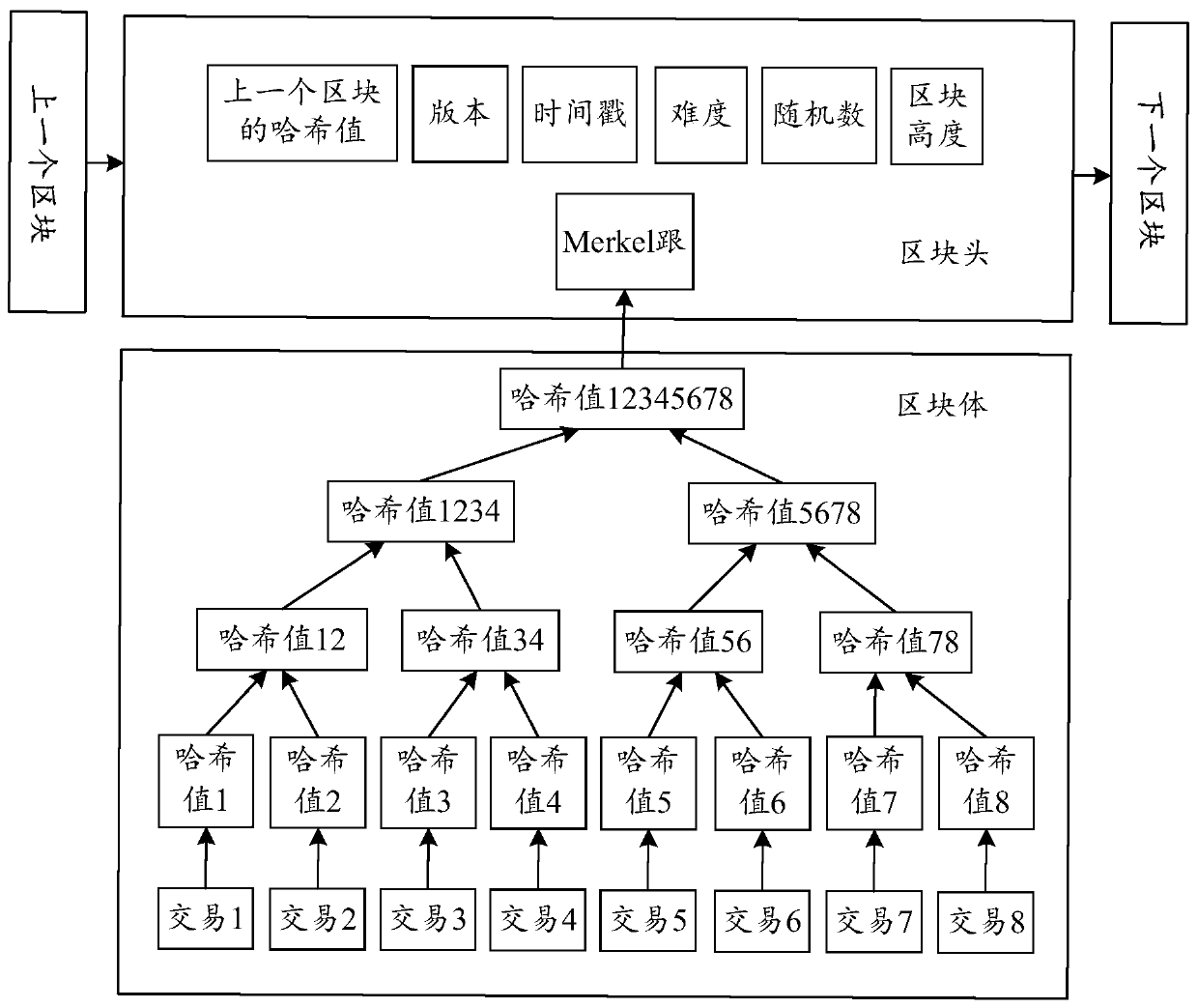
Trusted timestamping is the process of securely keeping track of the creation and modification time of a document. Security here means that no one—not even the owner of the document—should be able to change it once it has been recorded provided that the timestamper's integrity is never compromised.
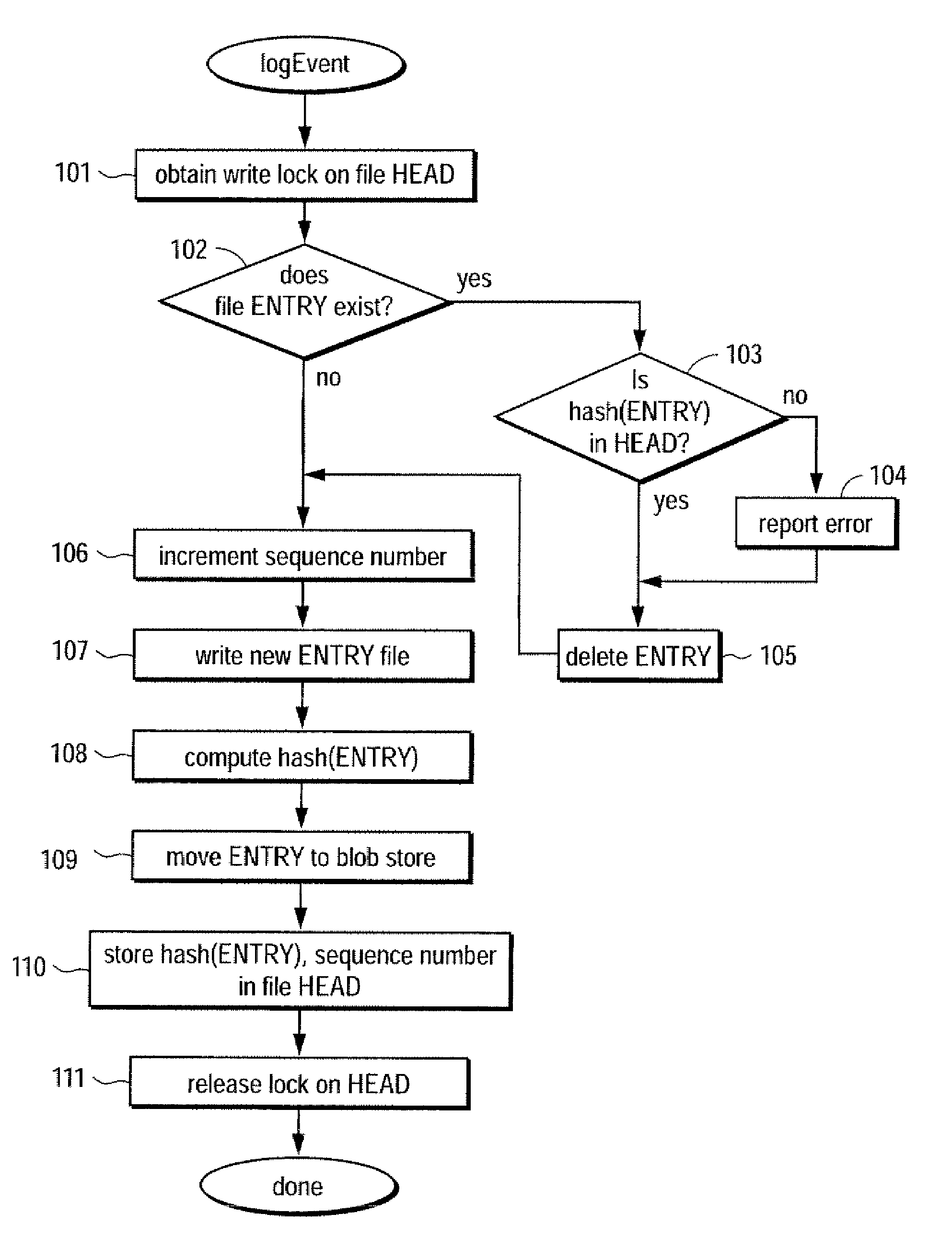
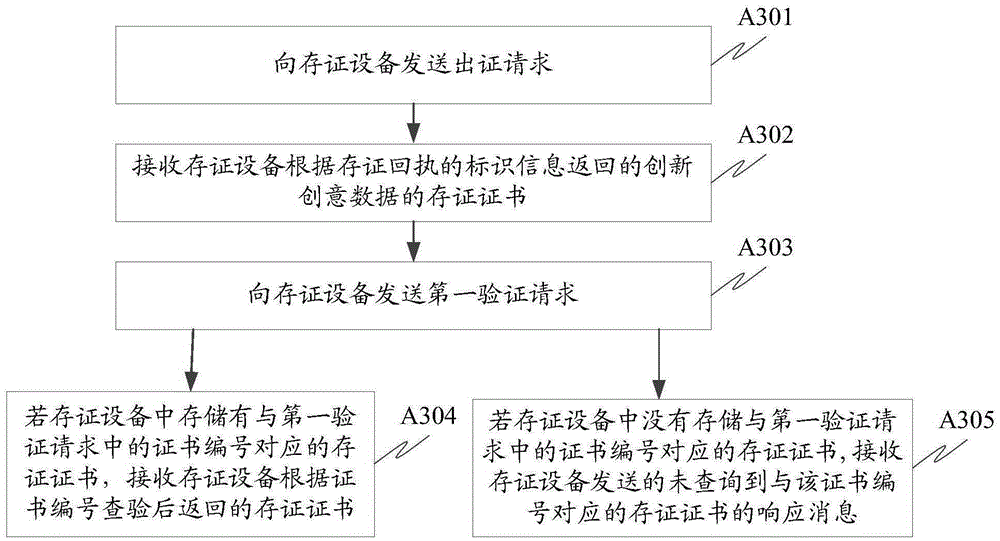
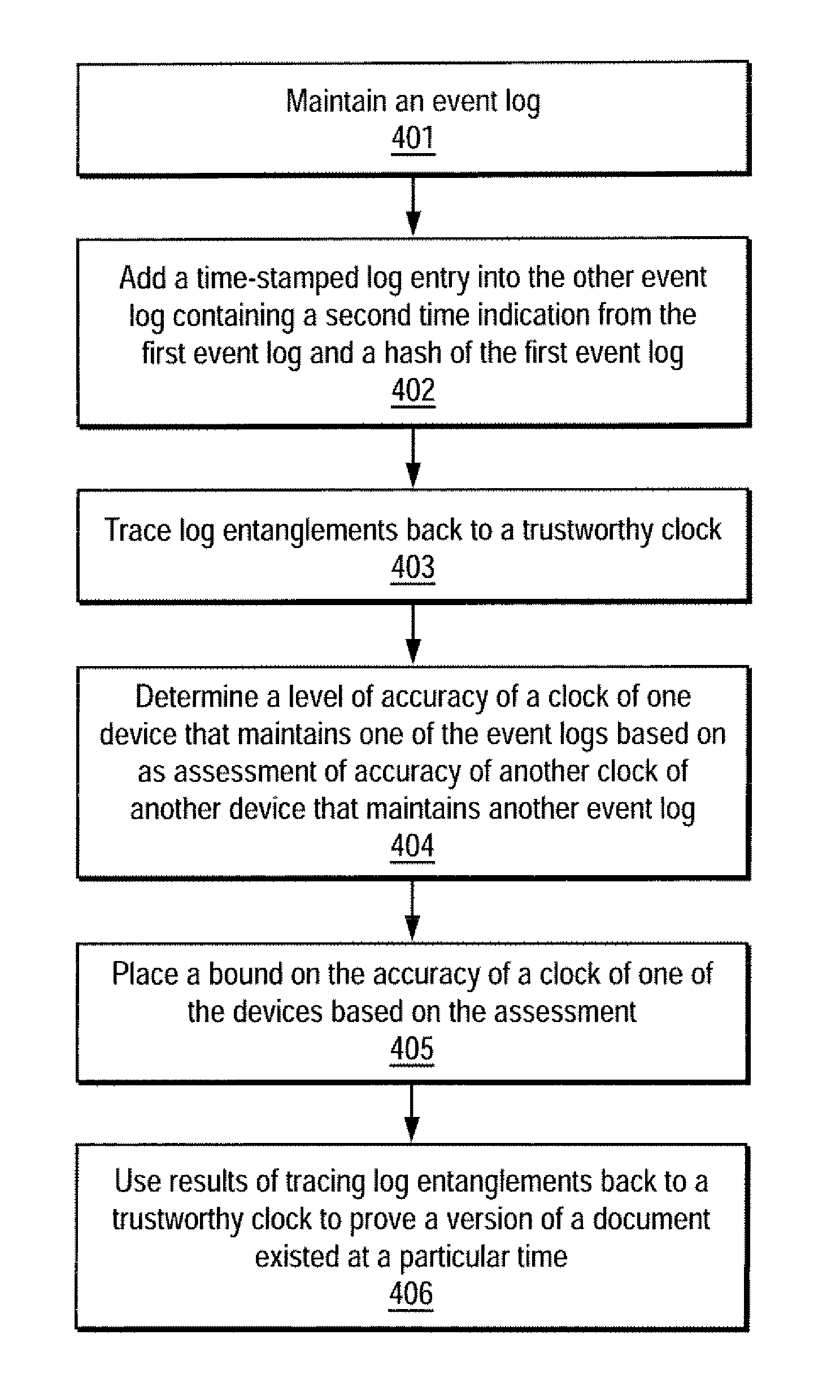
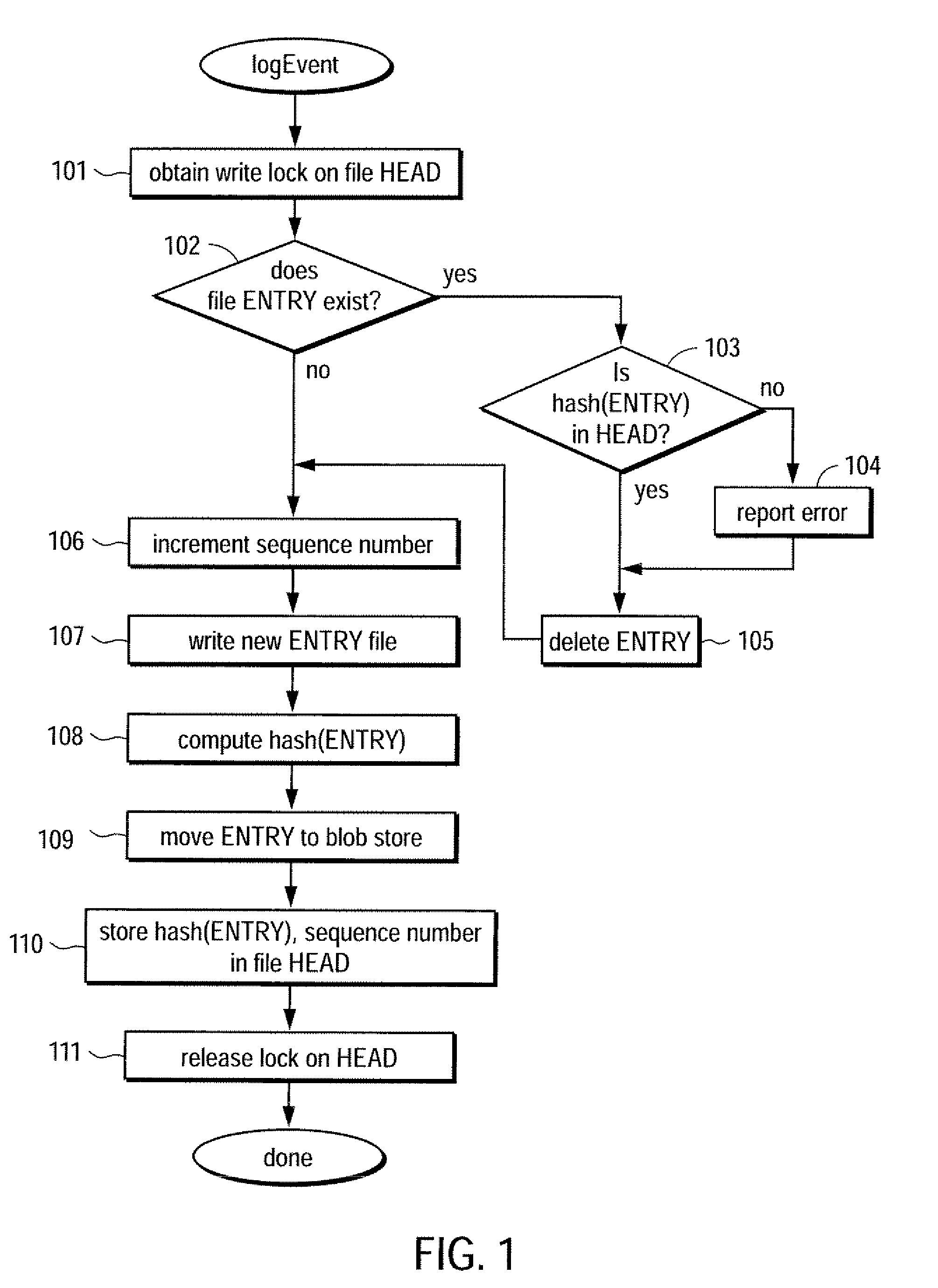
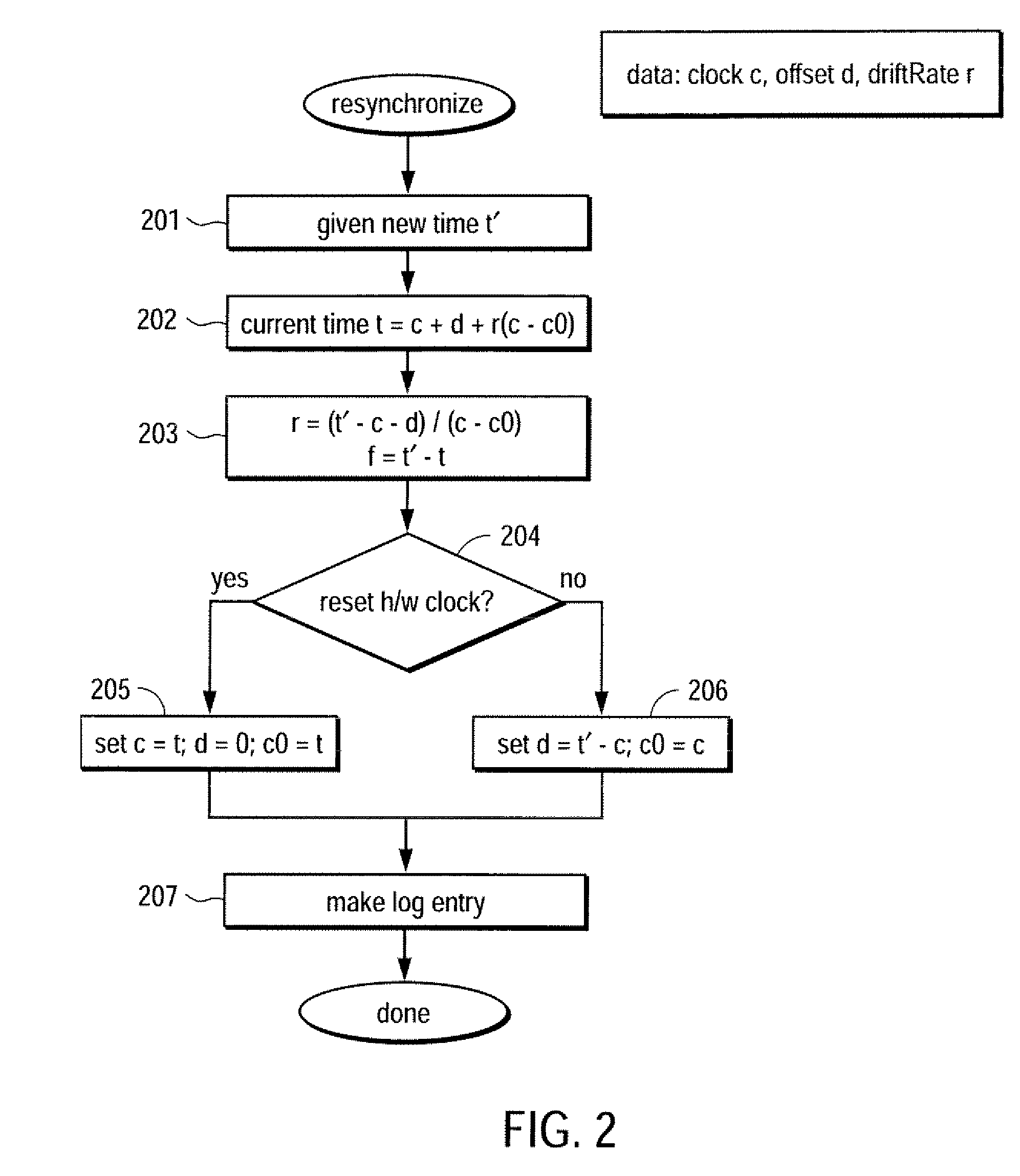
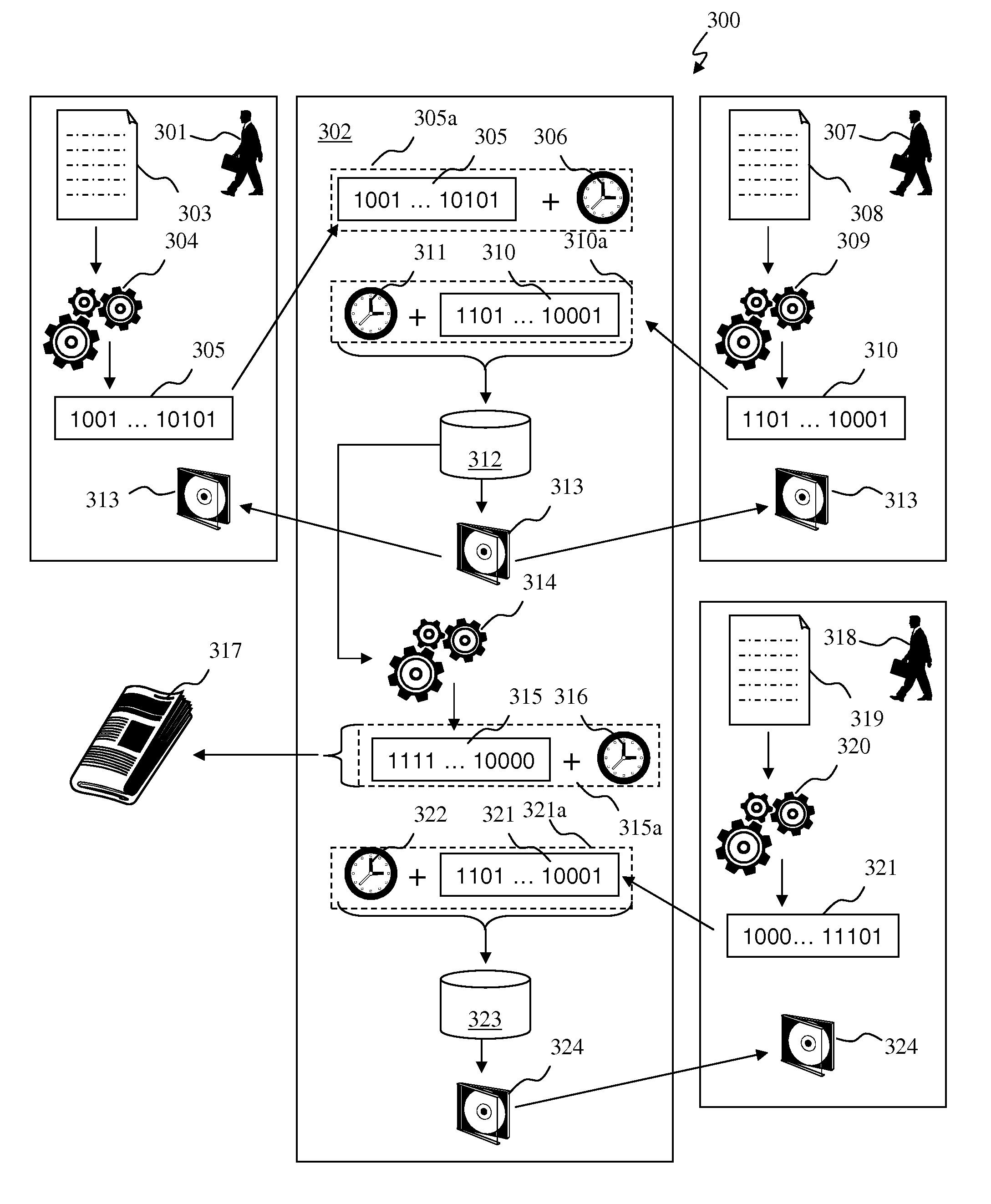
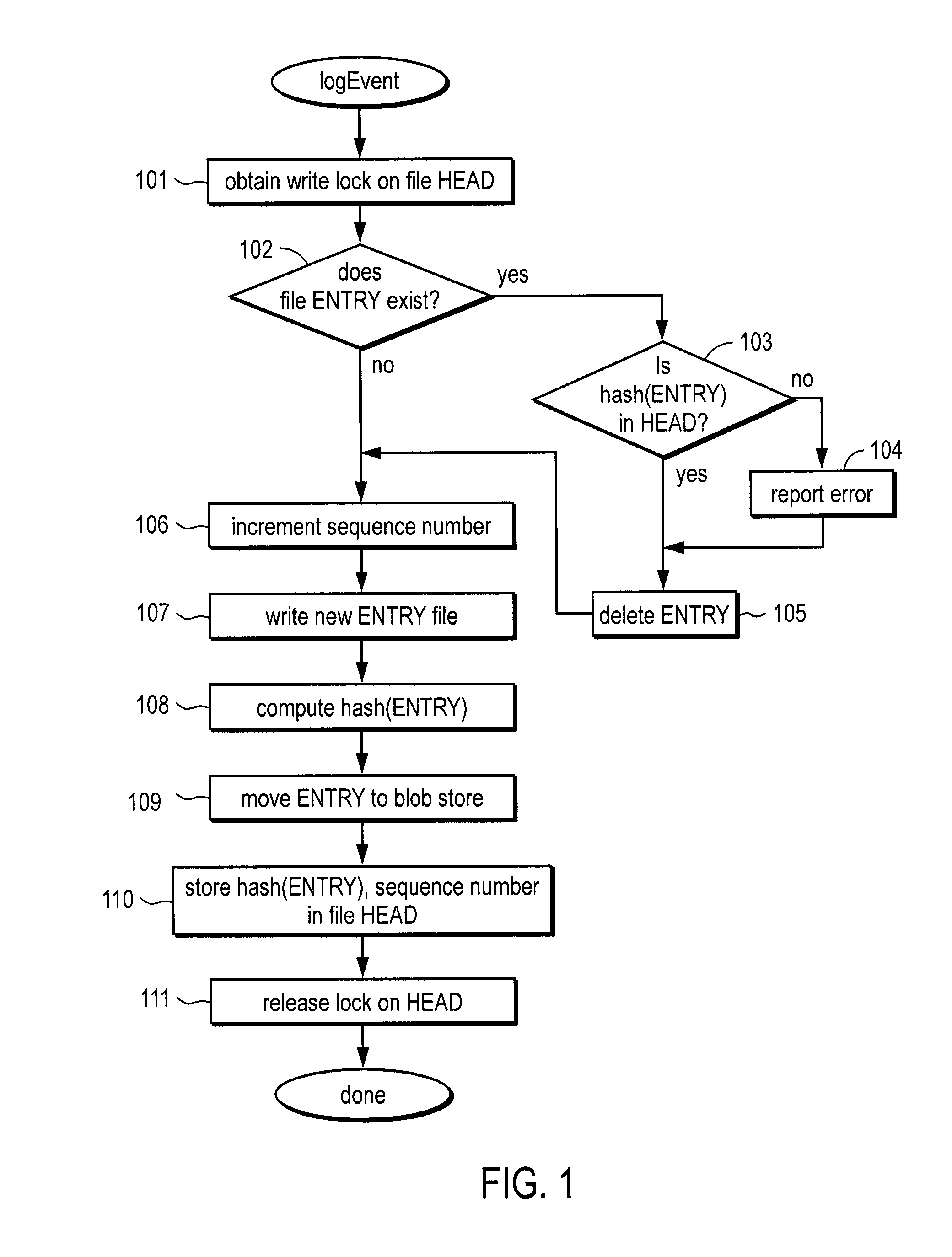
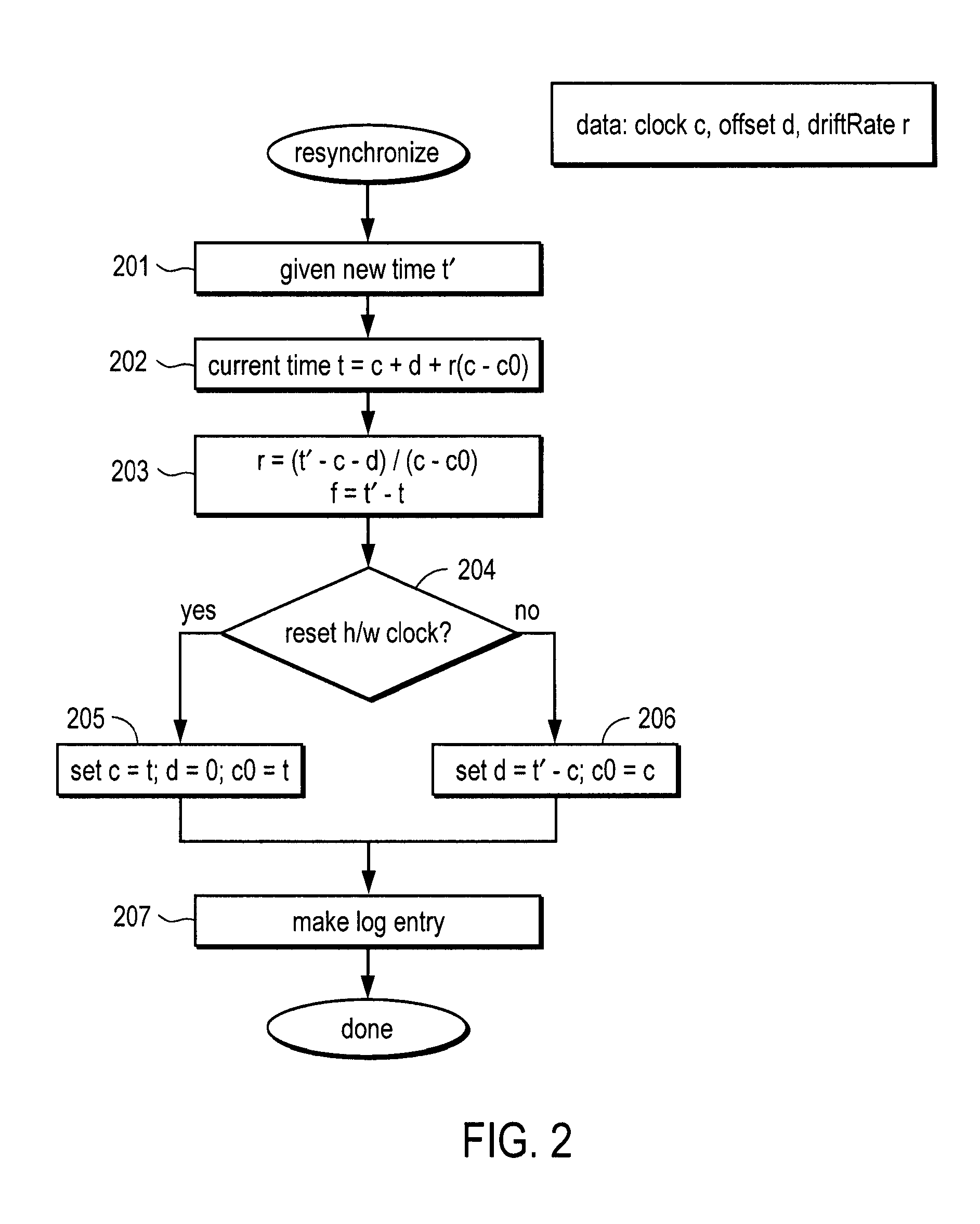
Trustworthy timestamps and certifiable clocks using logs linked by cryptographic hashes
ActiveUS20080201580A1User identity/authority verificationUnauthorized memory use protectionCryptographic hash functionTrusted timestamping
A method and apparatus for creating and / or using trustworthy timestamps and certifiable clocks using logs linked by cryptographic hashes. In one embodiment, the method comprises maintaining a first, chained-hash log; associating a first clock with the chained-hash log, and entangling the first log; with a second by adding a time-stamped synchronization entry to the chained-hash log, where the synchronization entry has a second time indication associated with the second log and a hash of one or more entries in the first log.
Owner:RICOH KK
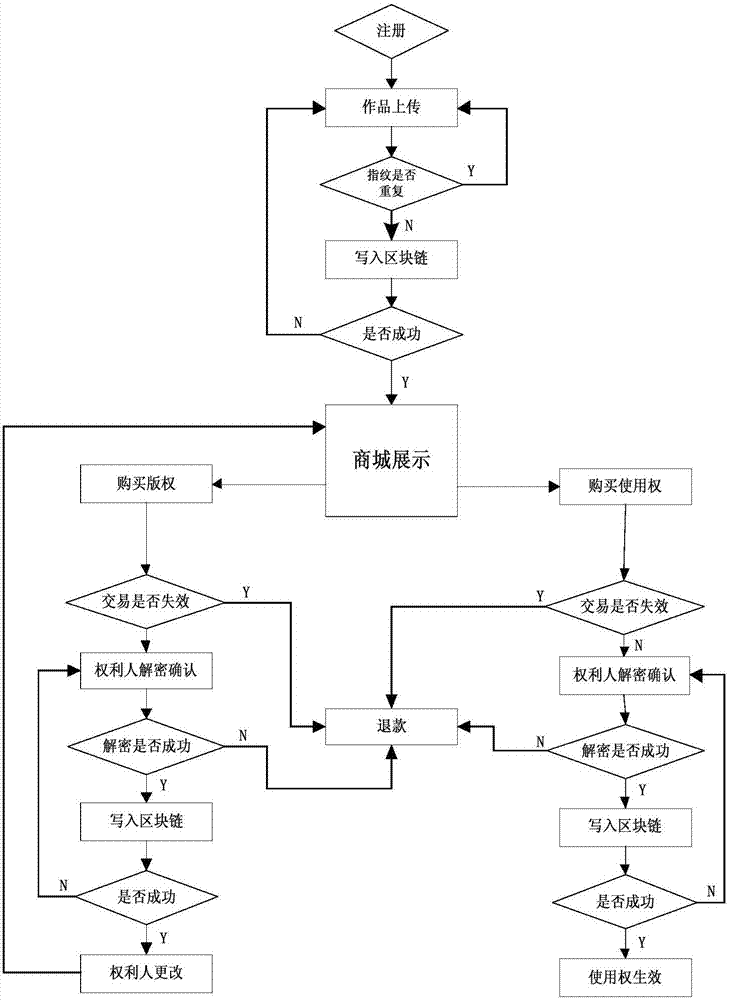
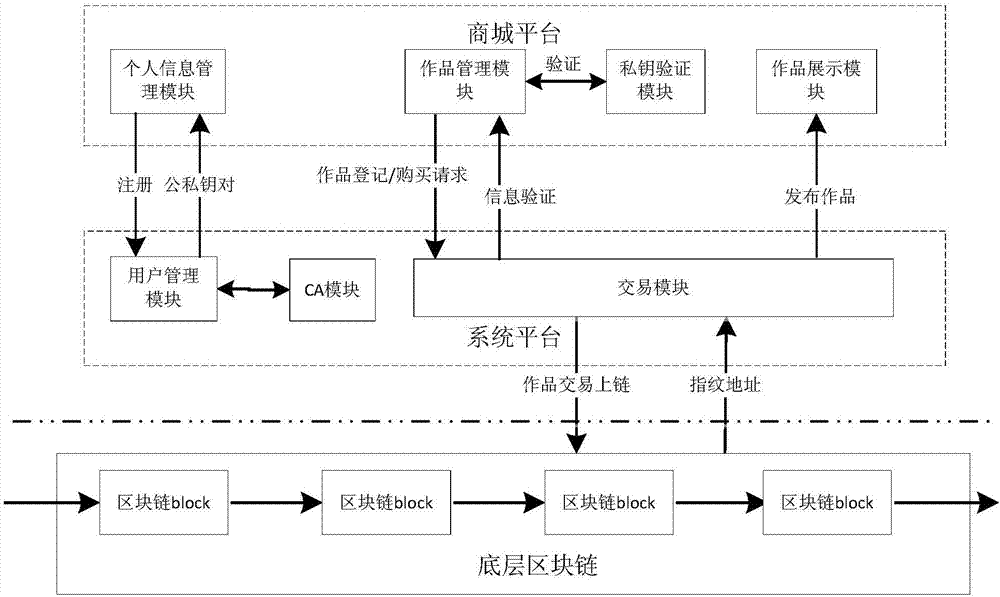
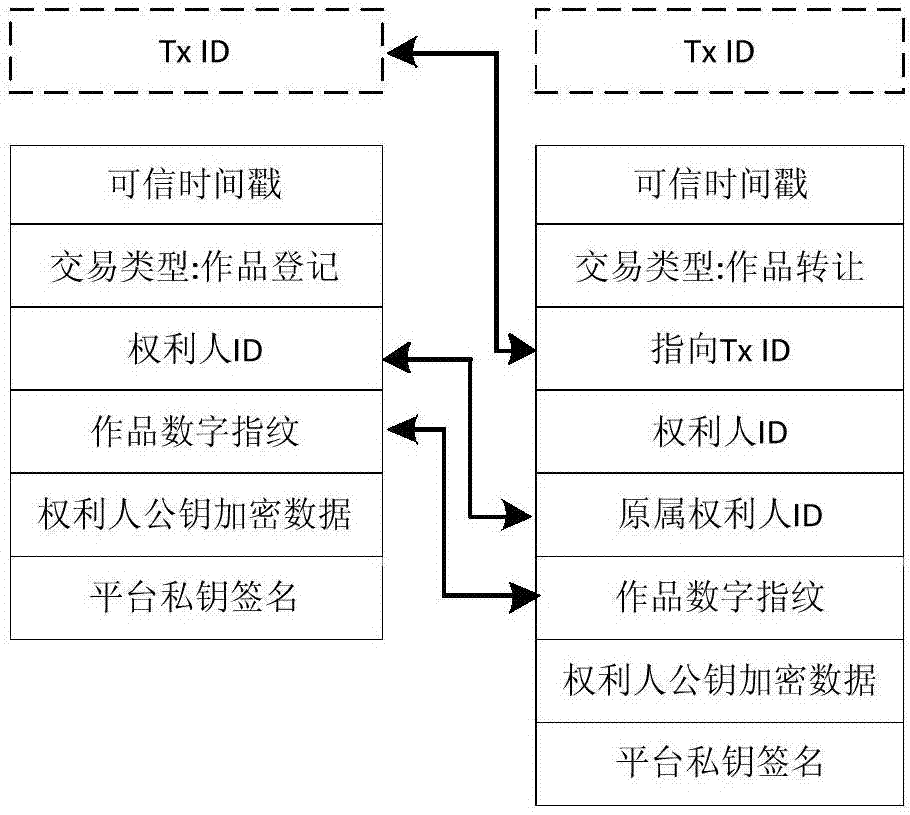
Blockchain-based copyright trading system and trading method
InactiveCN107330694AEliminate secondary transactionsCopyright transactions are open and transparentProtocol authorisationTimestampTransaction data
The invention discloses a blockchain-based copyright trading system and a trading method. The blockchain-based copyright trading method comprises creating the copyright trading system, and the trading system comprises a system platform, a shopping mall platform and bottom blockchains. The method is characterized in that a user is registered as a platform user through the system platform, and the system platform issues a unique public-private key pair and a unique user ID for the platform user; a copyright owner uploads a work to the shopping tall platform, and adds signatures of public and private keys to the work; the shopping mall platform verifies signature information of the copyright owner through the private key, and generates fingerprint information uniquely corresponding to the signature information for the work; and the system platform creates a blockchain transaction, and perform cochain on fingerprint information, copyright owner public key encrypted data, the copyright owner ID, a transaction type, a credible timestamp and the platform private key signature, which are taken as transaction data, at the same time. All transaction details are recorded by utilizing the blockchains, and then copyright trading is very secure.
Owner:重庆小犀智能科技有限公司
Method and system for secure transmission of biometric data
InactiveUS20060112280A1Improve quality scoreSecure transmissionDigital data authenticationSecret communicationBiometric dataSecure transmission
Embodiments of the invention provide methods and systems for securely transmitting a biometric identifier template across a network using a transport unit formed by appending a trusted time-stamp to the biometric template, and for authenticating such templates based on the time stamp. The method is applicable to fingerprint and other biometric identifier based identification and authentication systems.
Owner:TRIAD BIOMETRICS LLC
Trusted and verifiable data storage system, method, apparatus and device
A data set is stored in a data storage medium by determining a checksum value of the data set. The checksum value is substantially unique to the data set. Trusted time stamp data forming a receipt data are obtained by applying an encryption to the checksum value and the trusted time stamp data, such that the receipt data form an encrypted data packet. The data set and receipt data are stored on the data storage medium.
Owner:HEWLETT PACKARD DEV CO LP
A credible timestamp system based on a block chain
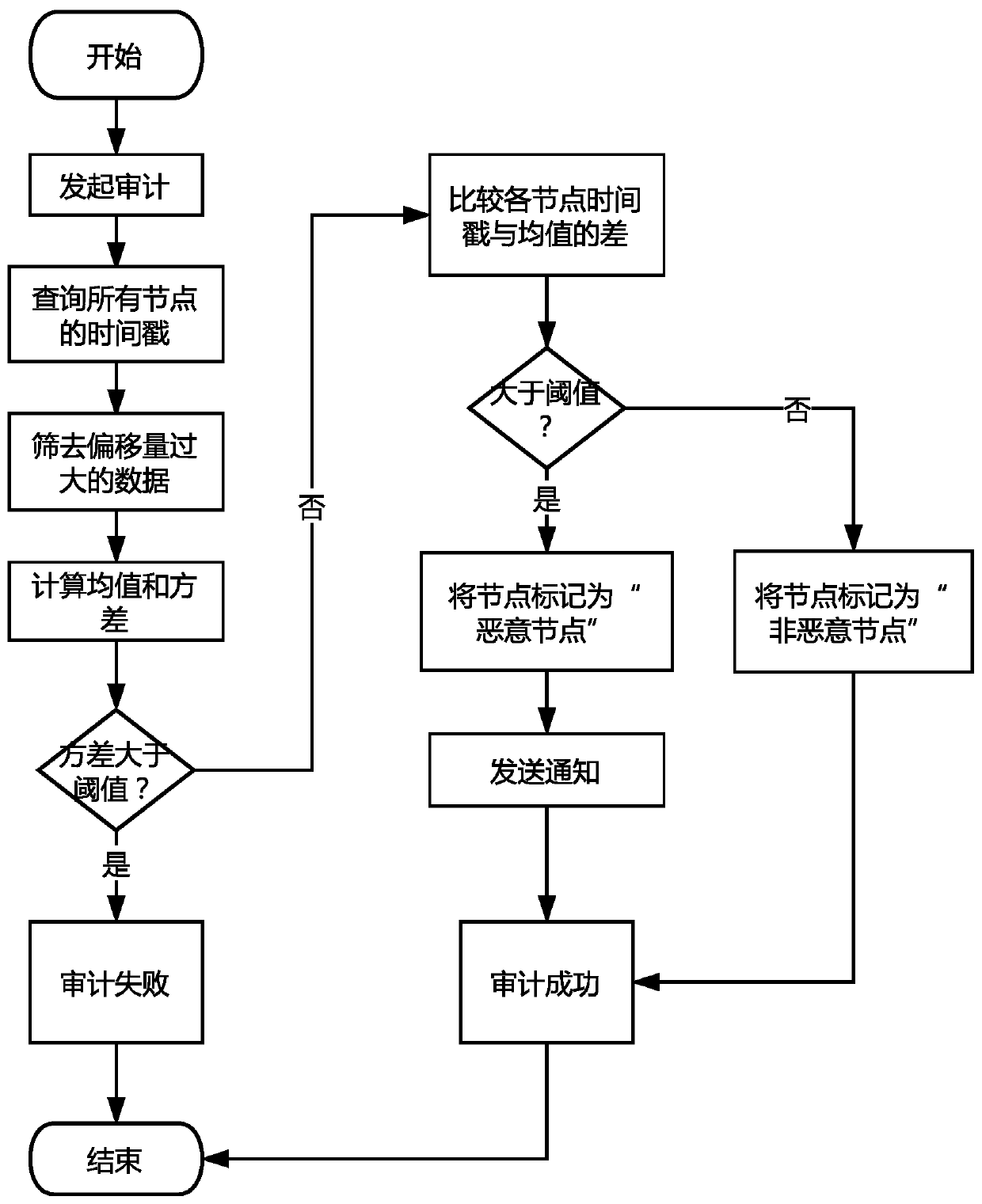
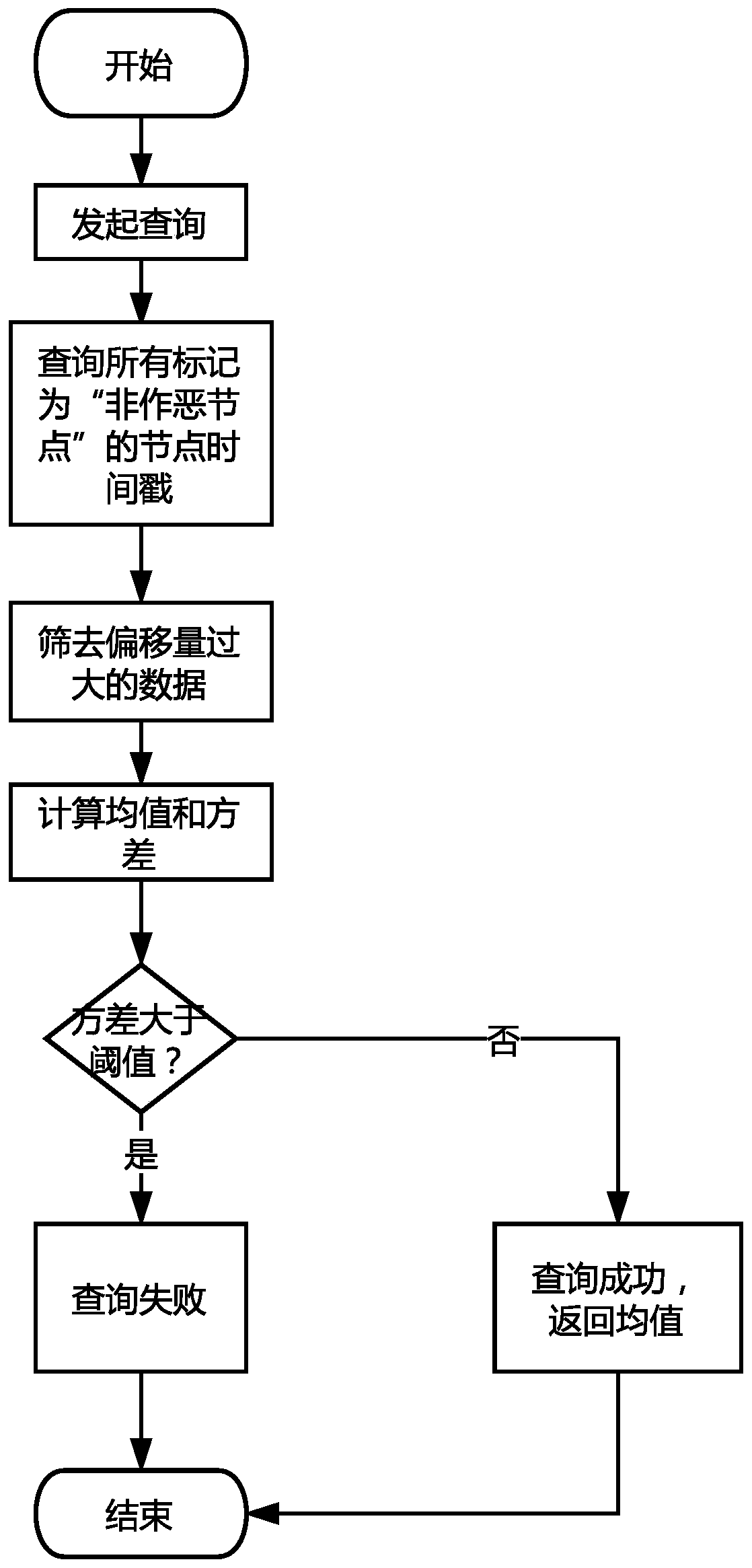
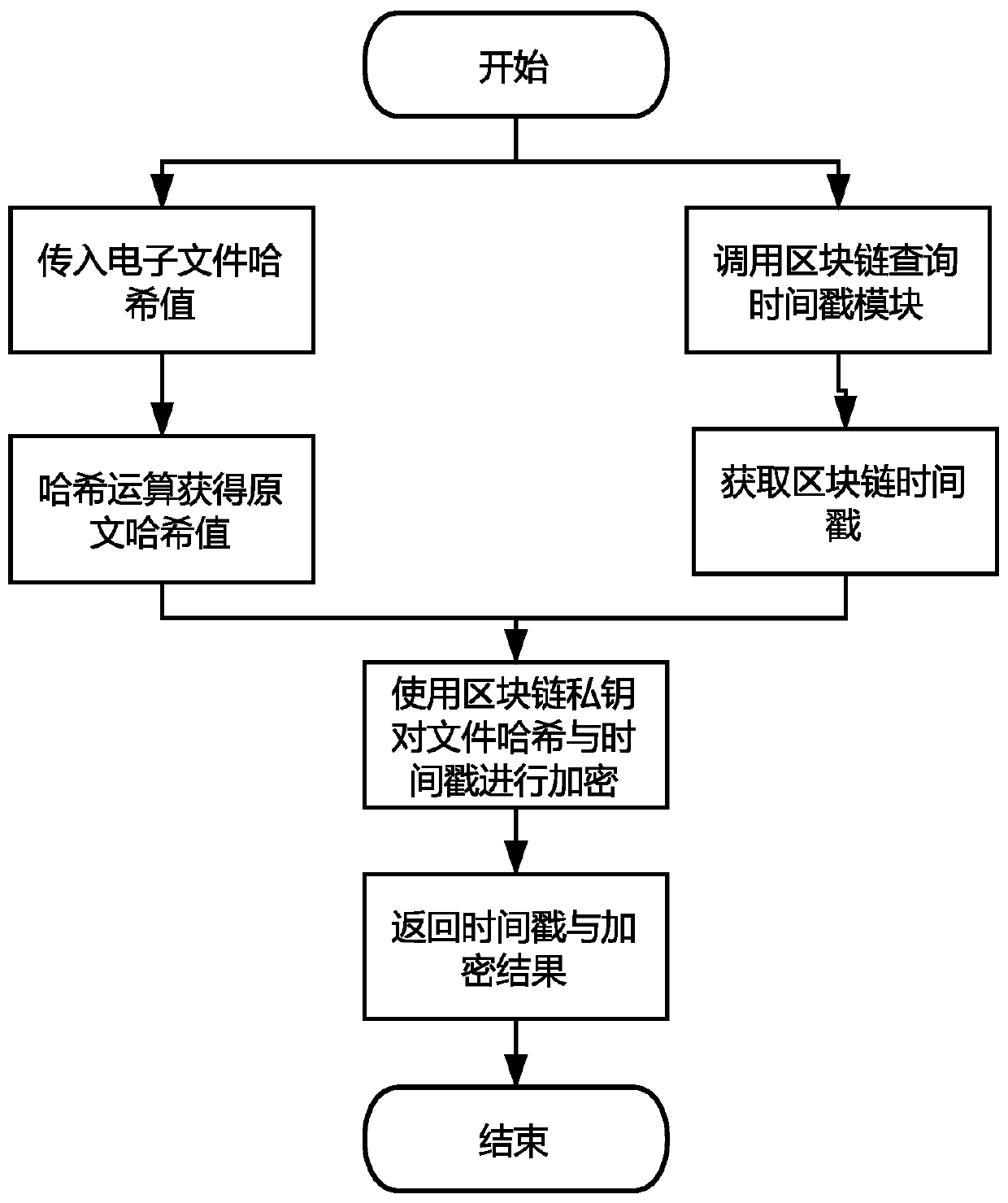
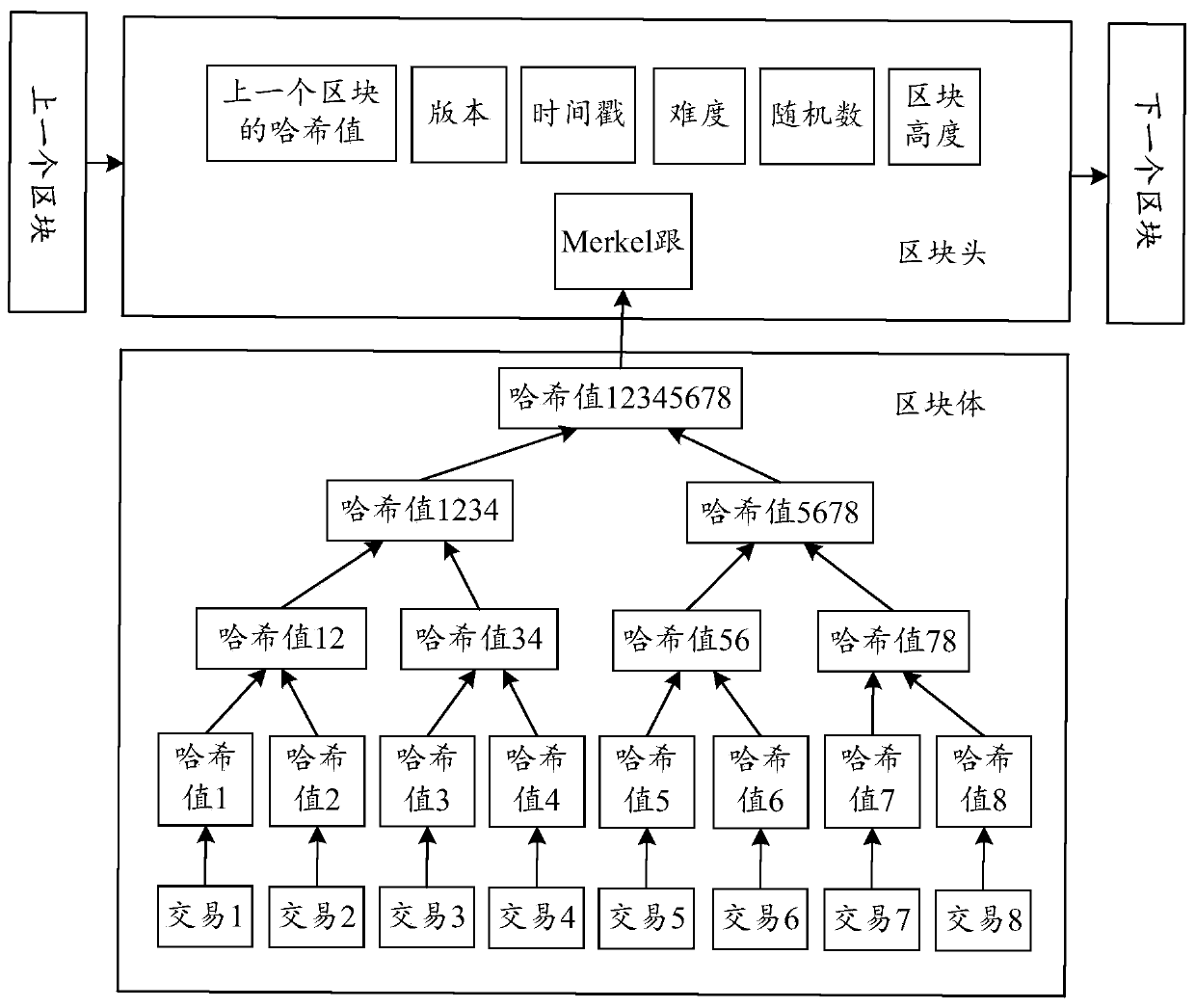
The invention discloses a credible timestamp system realized by utilizing a block chain, and relates to the technical field of blockchain technology, smart contracts and electronic signatures. The system comprises a timestamp initialization module, a timestamp auditing module, a timestamp acquisition module and an electronic file signature module. According to the method, the authenticity and tamper resistance of the timestamps are ensured by virtue of the block chain technology, the timestamps requested to each block chain node at the same time are credible and the same, and meanwhile, the timestamps consented by the block chain are added into the electronic file, so that the effectiveness of the timestamps of the electronic file is ensured.
Owner:HANGZHOU QULIAN TECH CO LTD
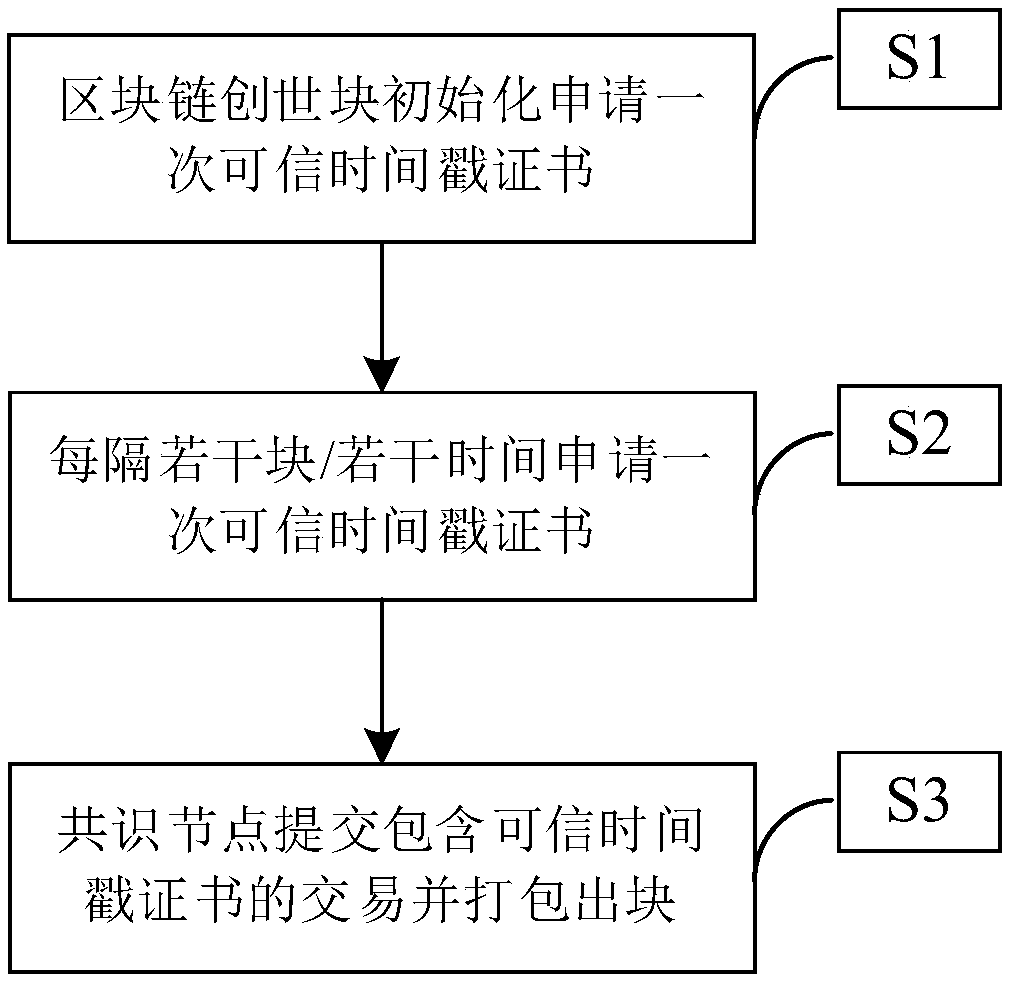
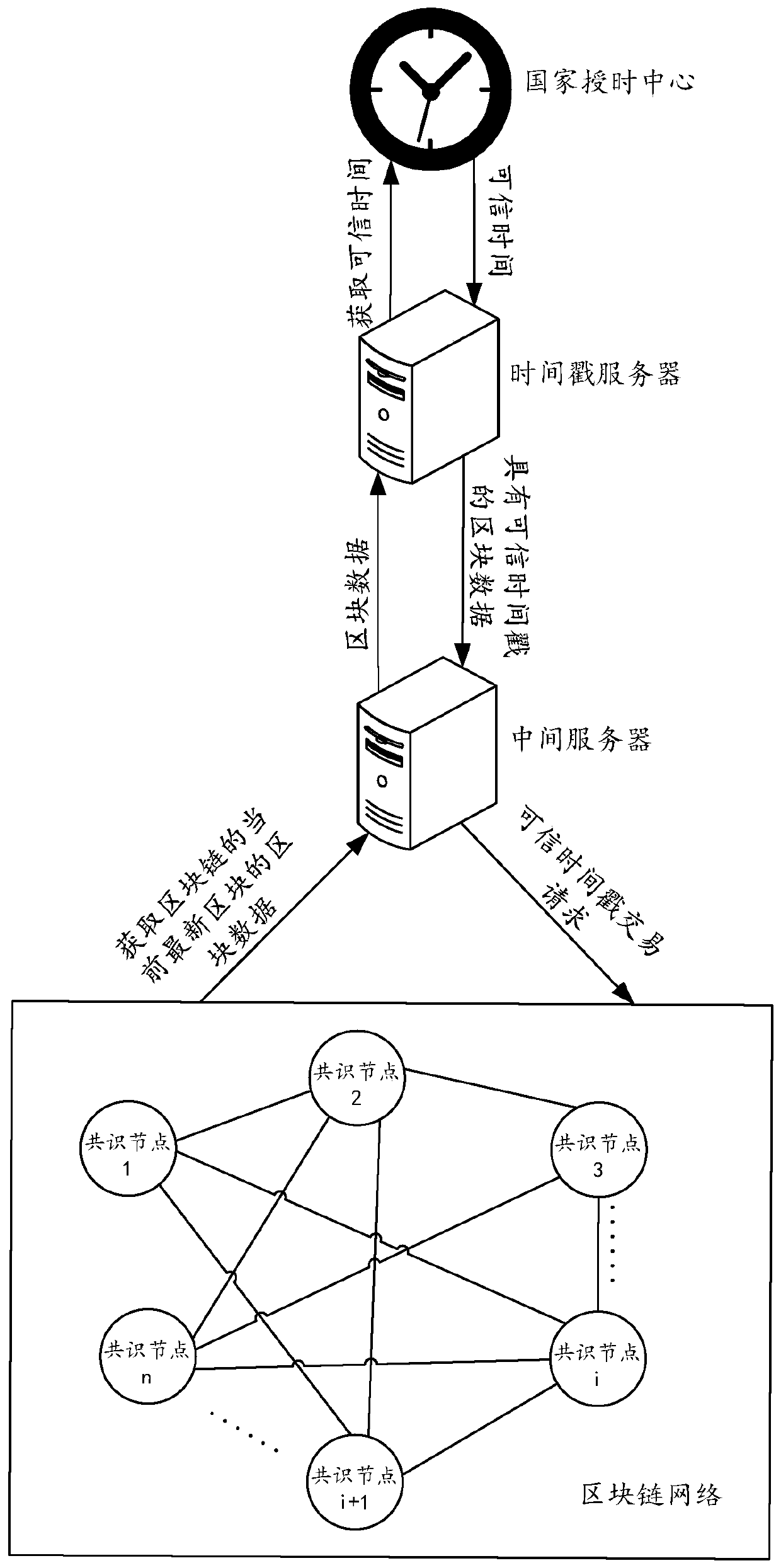
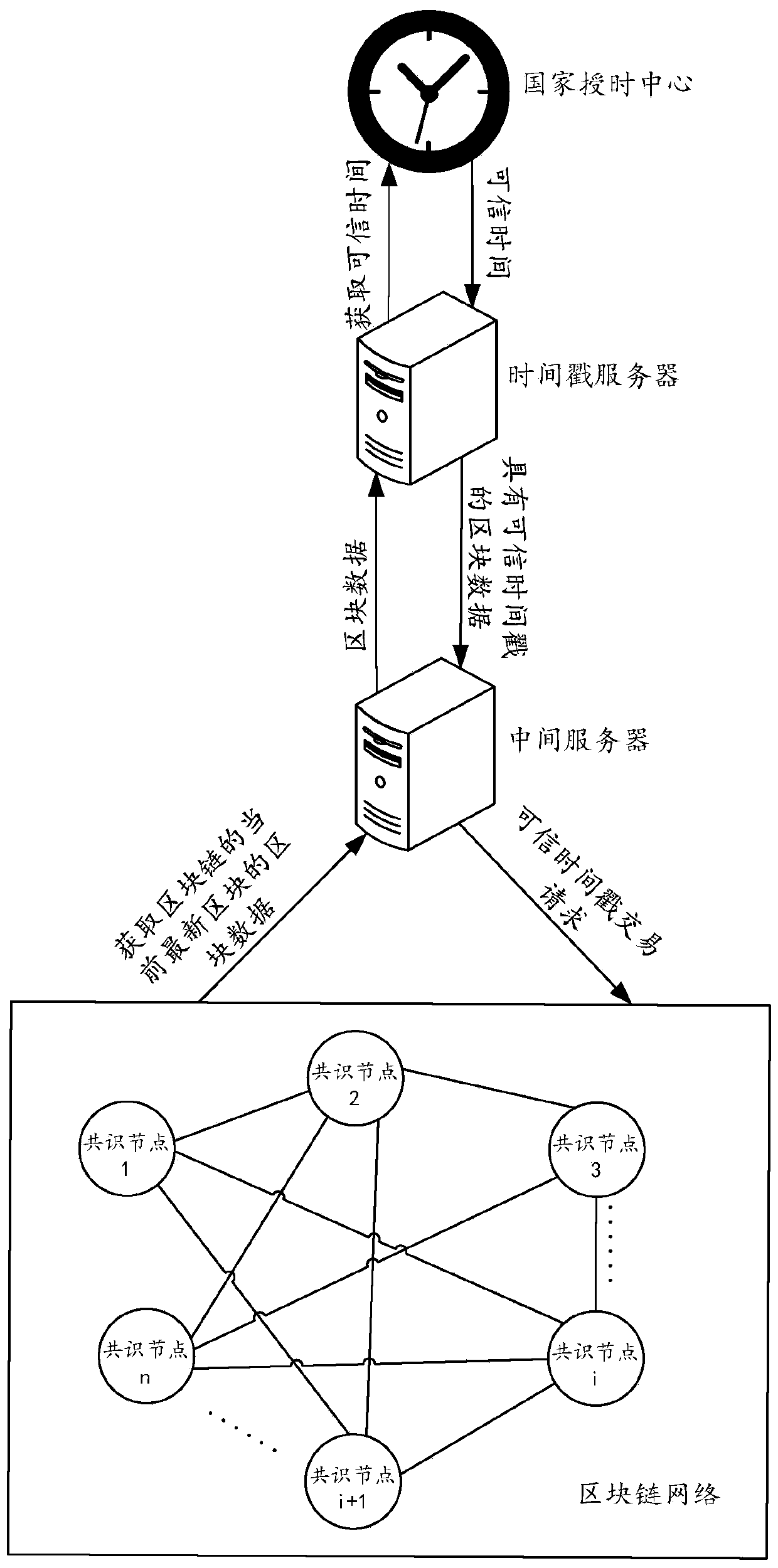
A block chain electronic storage method based on deterministic consensus and trusted timestamp
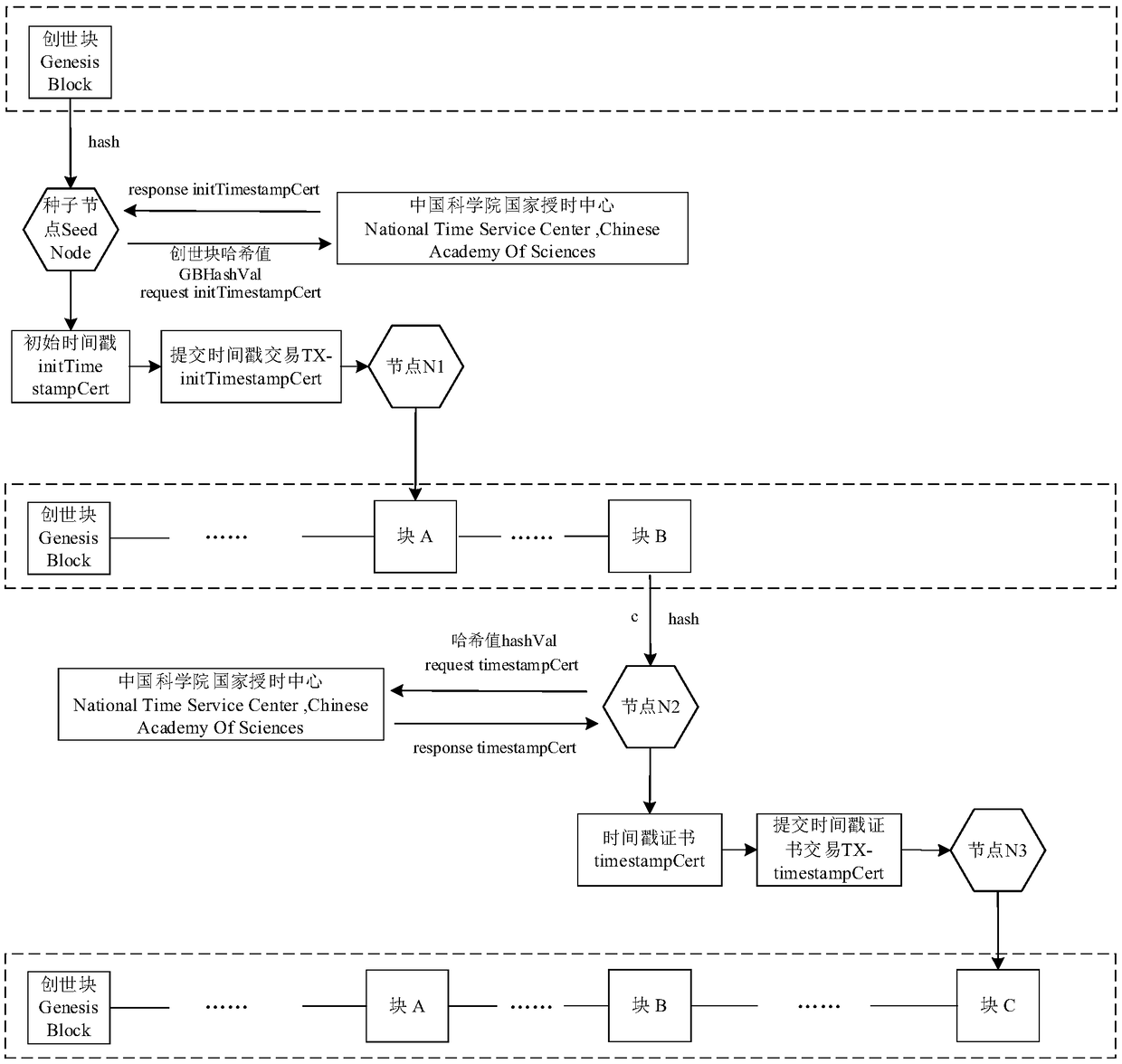
The invention provides a block chain electronic storage method based on deterministic consensus and trusted timestamp, the invention relates to the field of electronic storage of block chains, By applying for trusted timestamp certification to the National Time Service Center of the Chinese Academy of Sciences at regular intervals / number of blocks, A chunk node in a chunk chain system constructs atransaction using a trusted timestamp returned by a national time service center and broadcasts the transaction, Finally, packaging the transaction nto a new block together with other certificates inthe system, which not only improves the cost performance, but also effectively enhances the accuracy of time data and the reliability of electronic evidence in the block chain.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
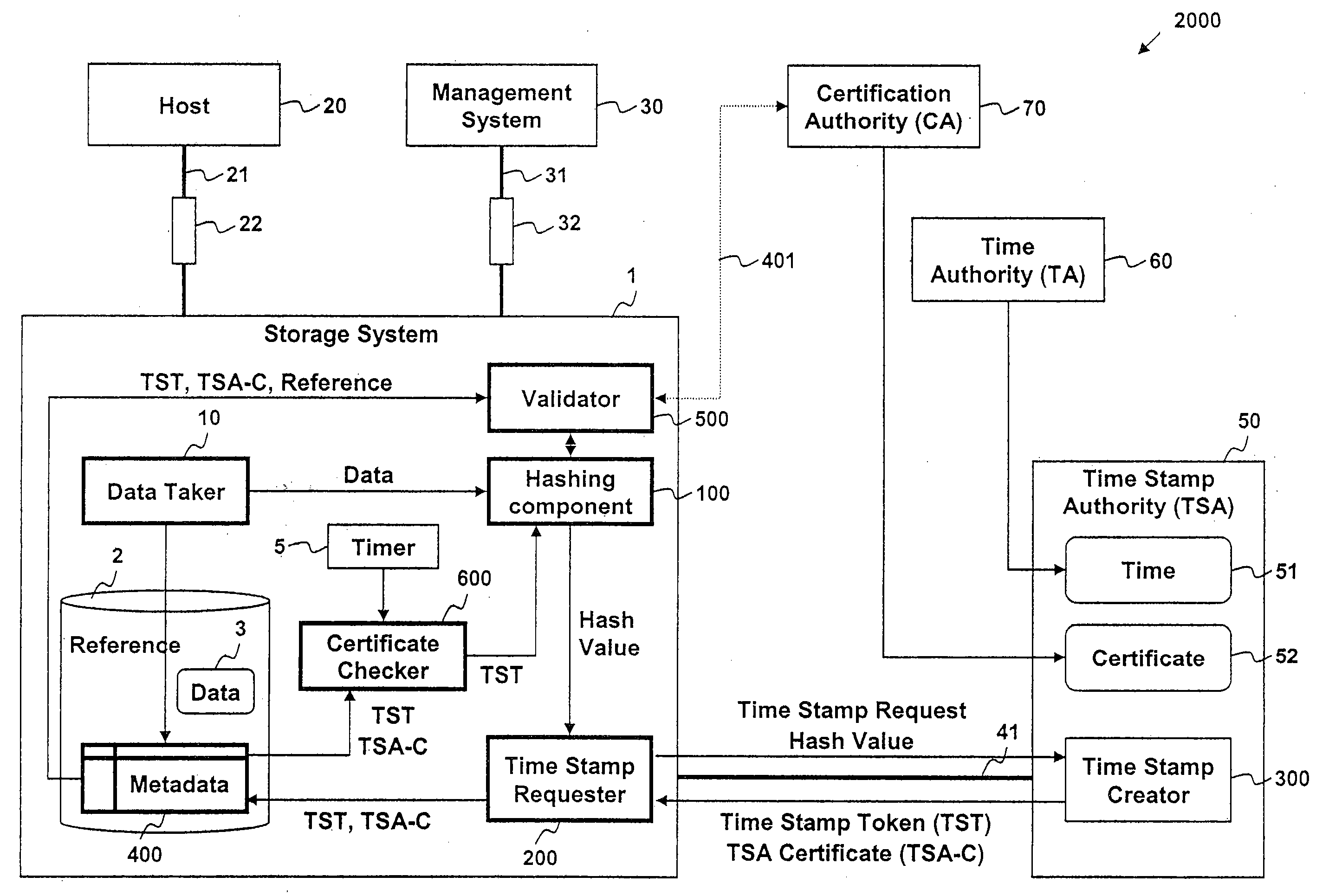
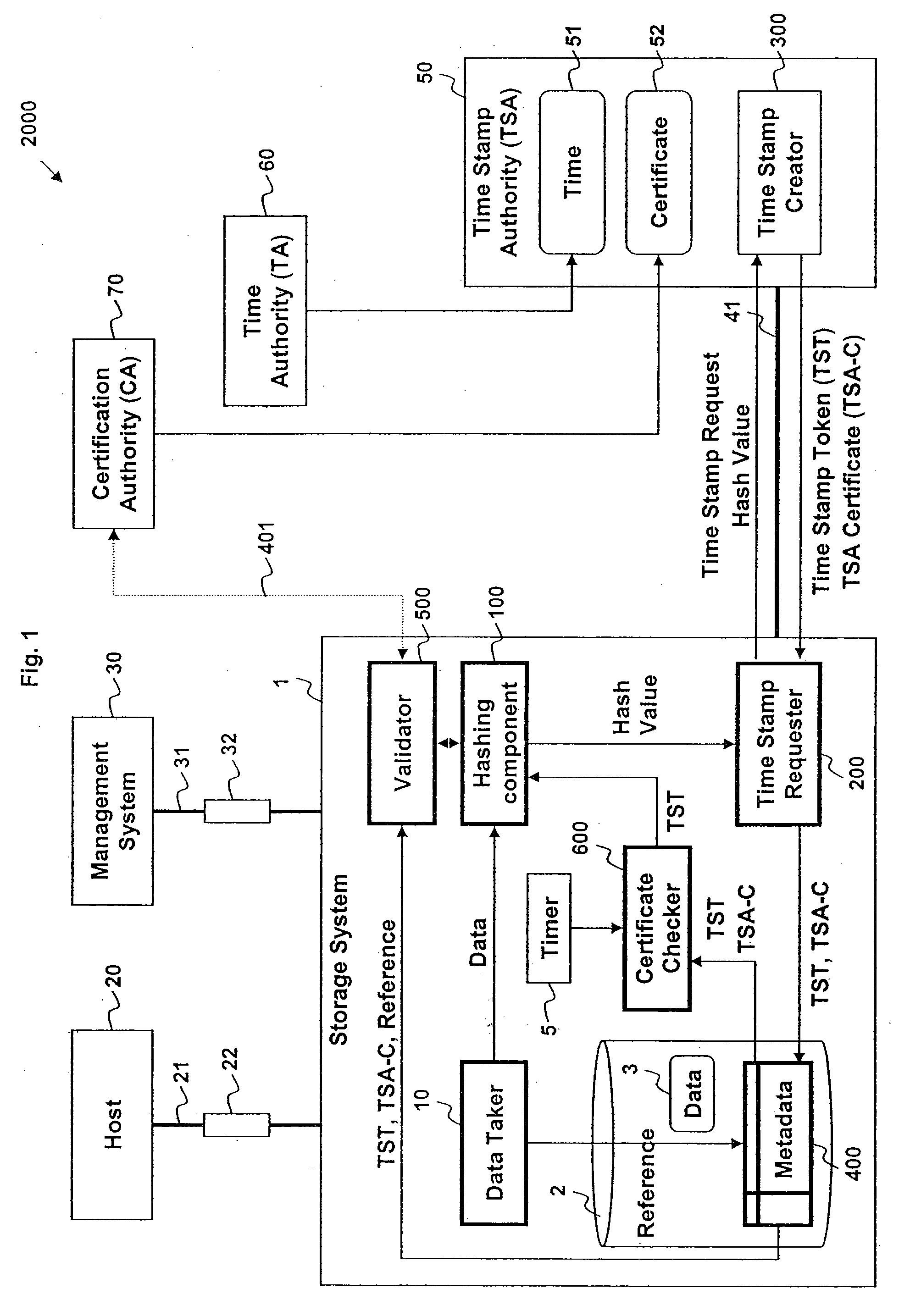
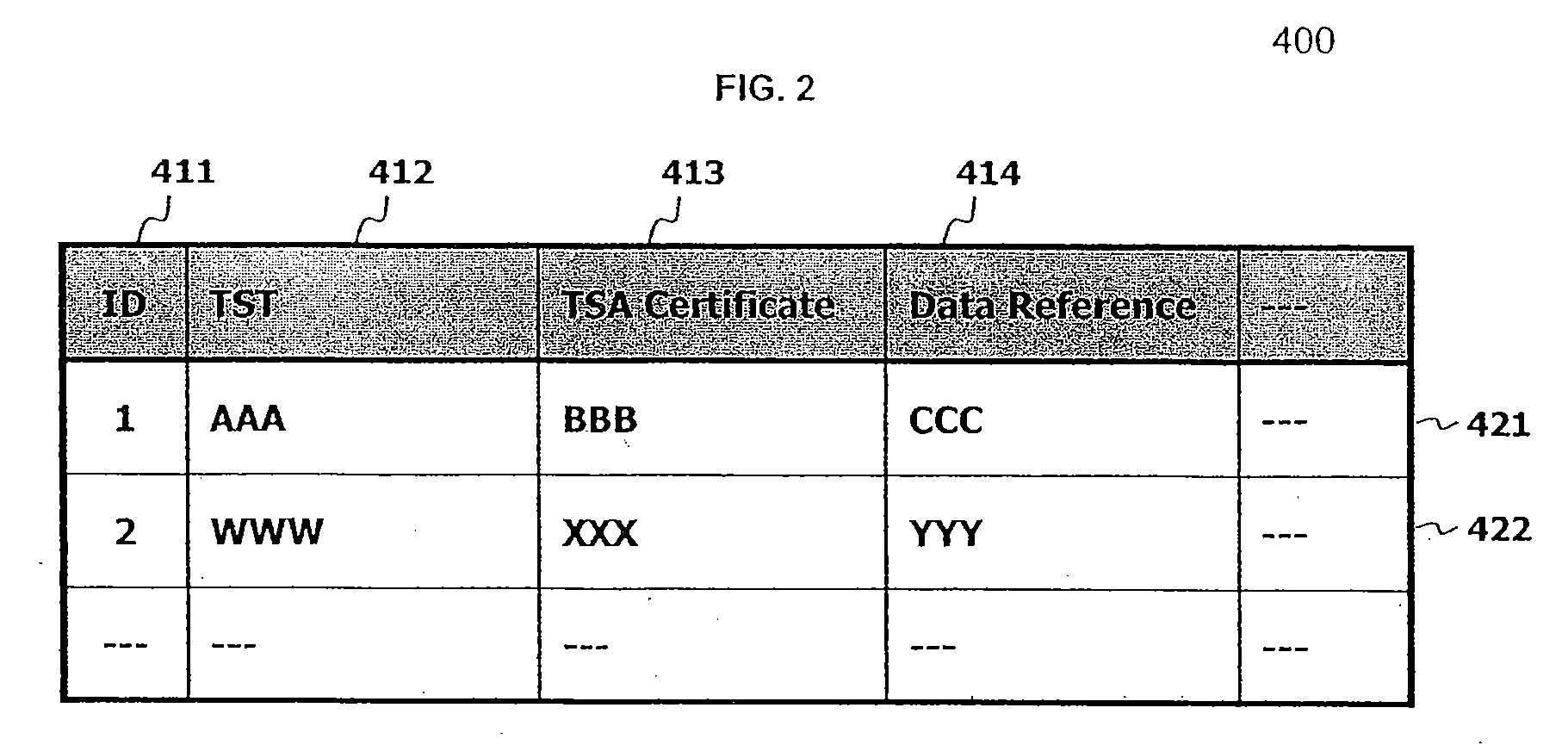
Trusted time stamping storage system
InactiveUS7340610B1User identity/authority verificationDigital data protectionComputer networkTrusted timestamping
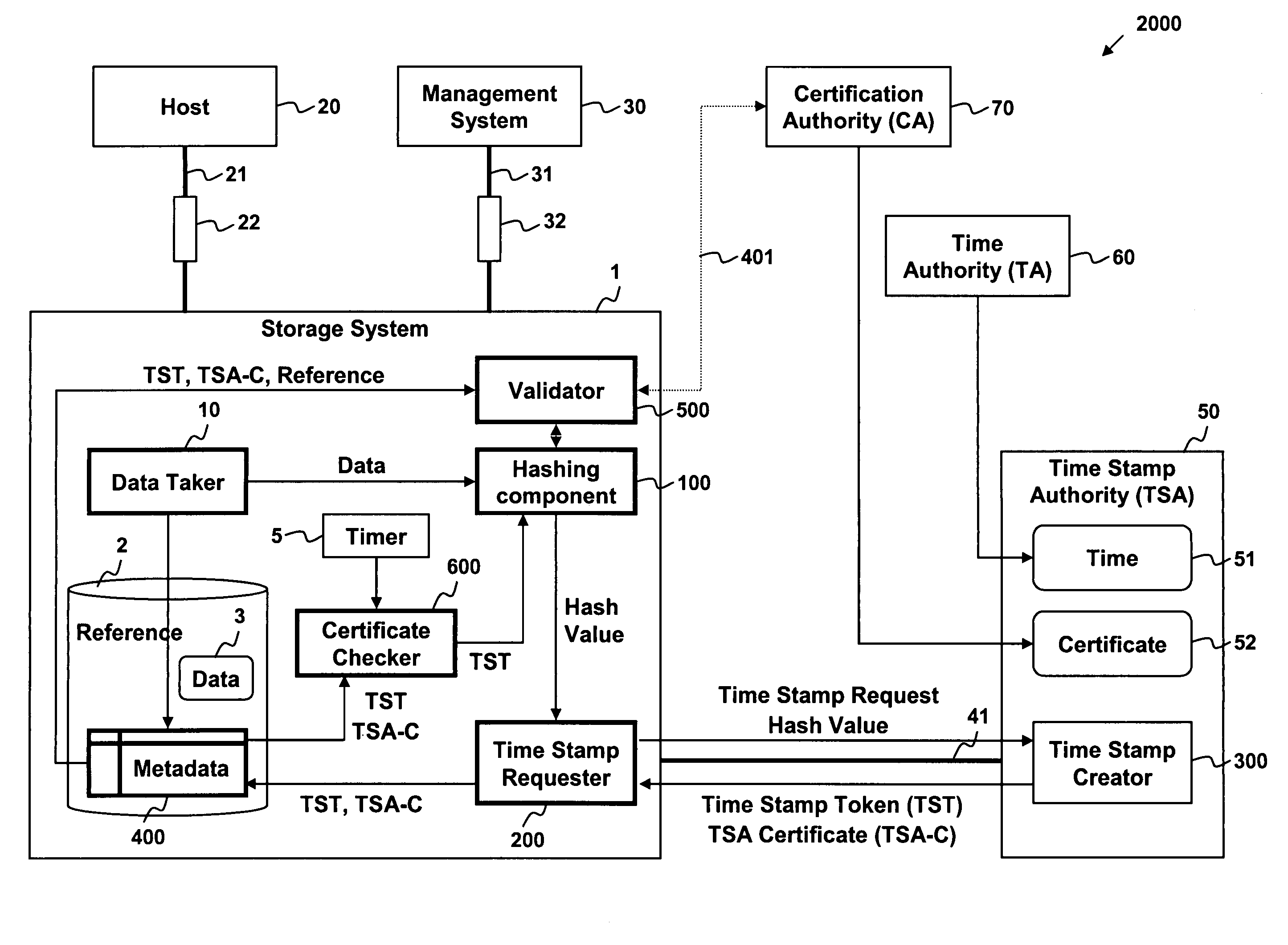
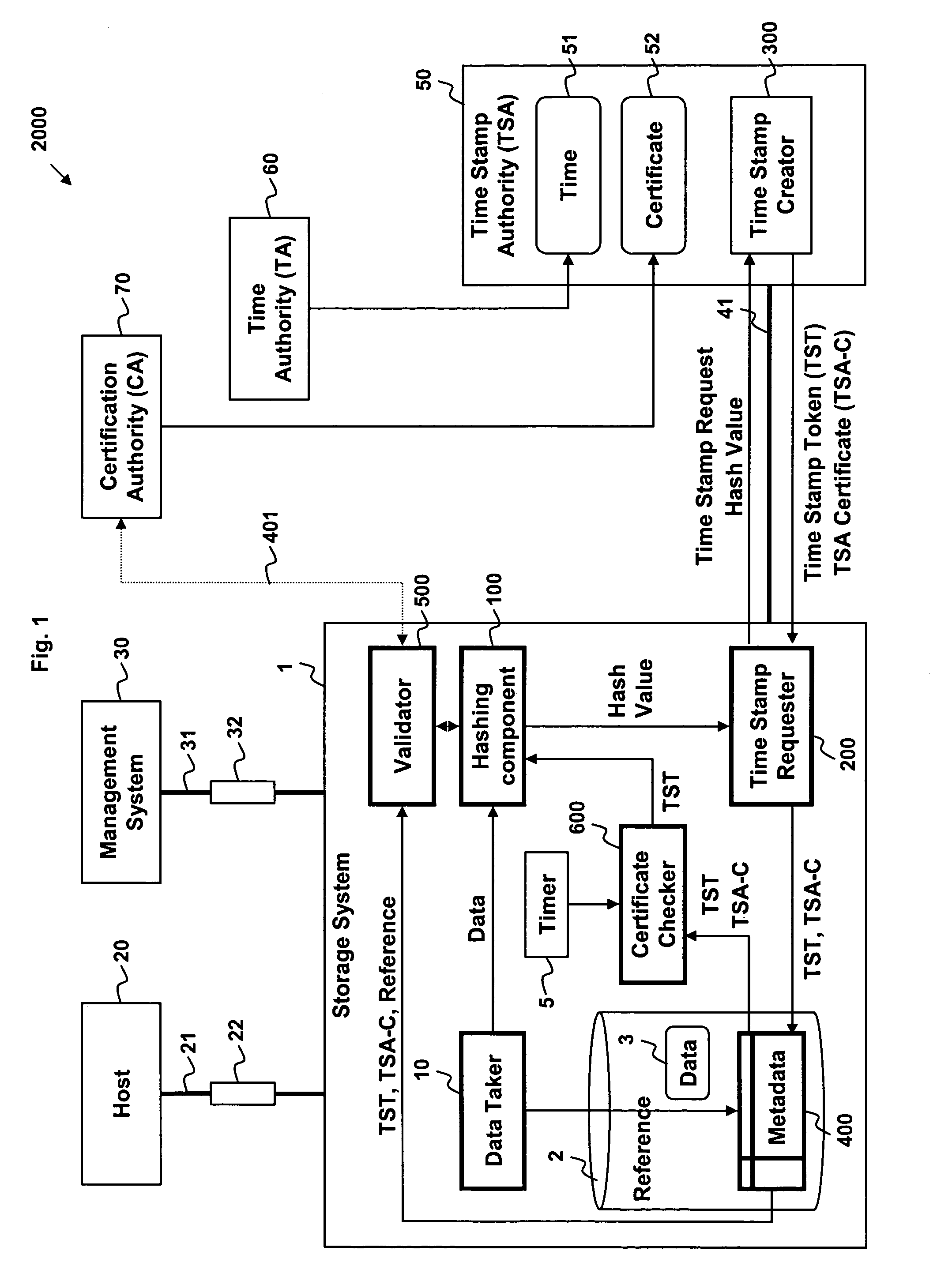
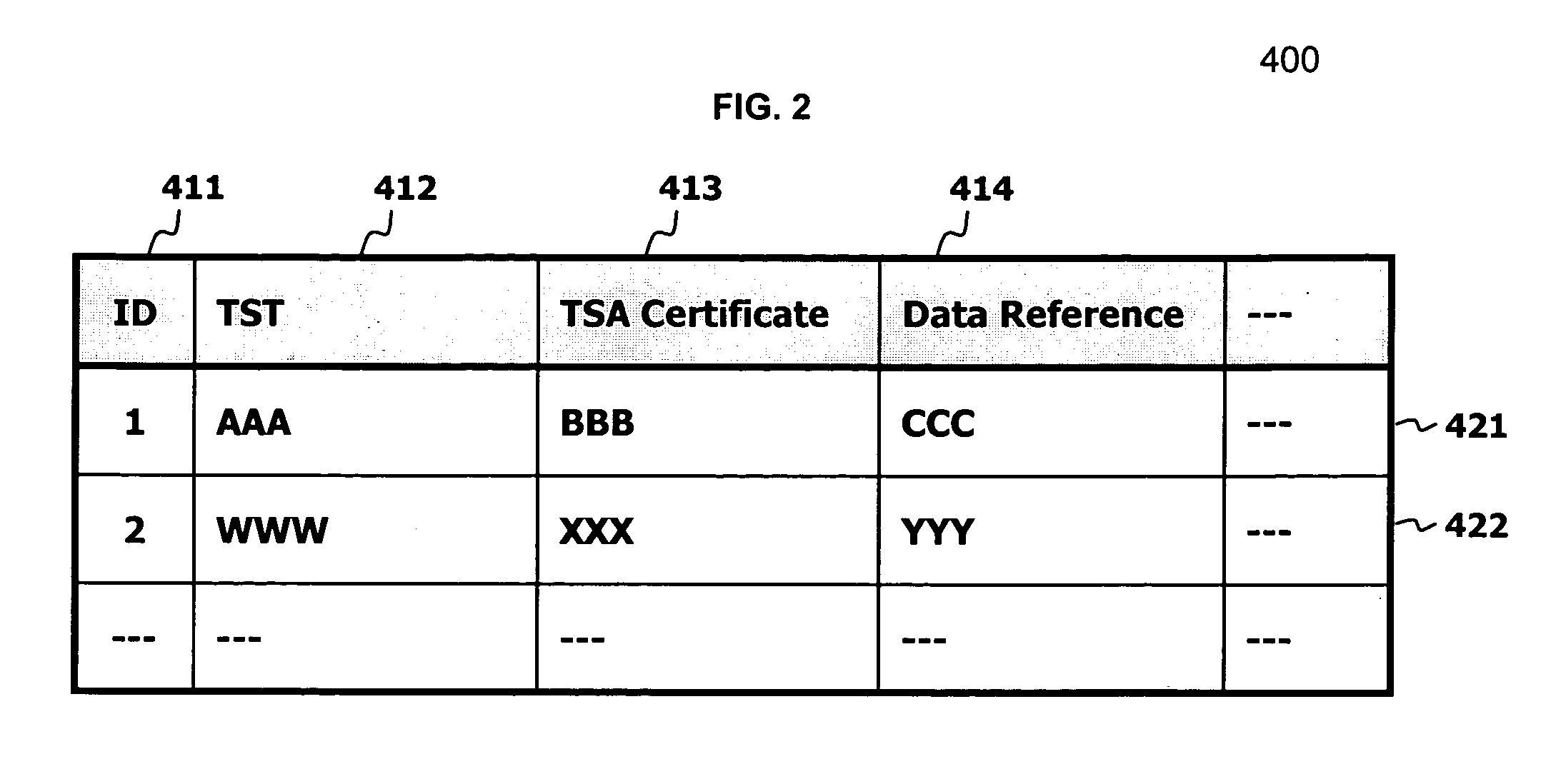
Data stored in a data storage system is hashed to generate a hash value. The hash value and a request for a time stamp are then sent to a time stamping authority. A time stamp token and / or a time stamp certificate is received from the time stamping authority. The time stamp token includes a time stamp and the hash value, and may be encrypted using a private key of the time stamping authority. The time stamp token and / or time stamp certificate is then stored with, for example, a reference to the data being stored in the data storage system. The time stamp token and / or time stamp certificate may then be used to validate the data being stored and the time stamp.
Owner:HITACHI LTD
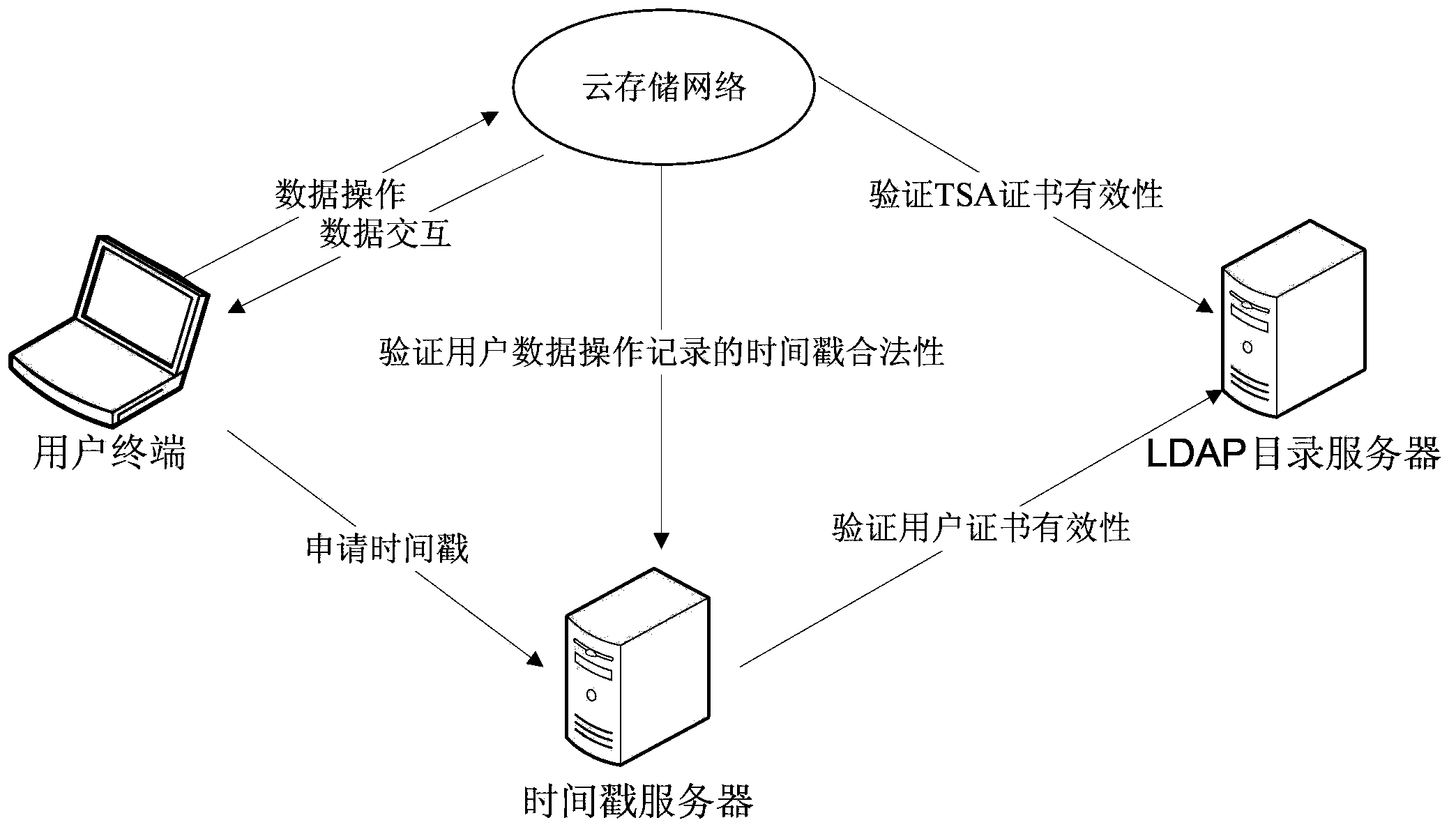
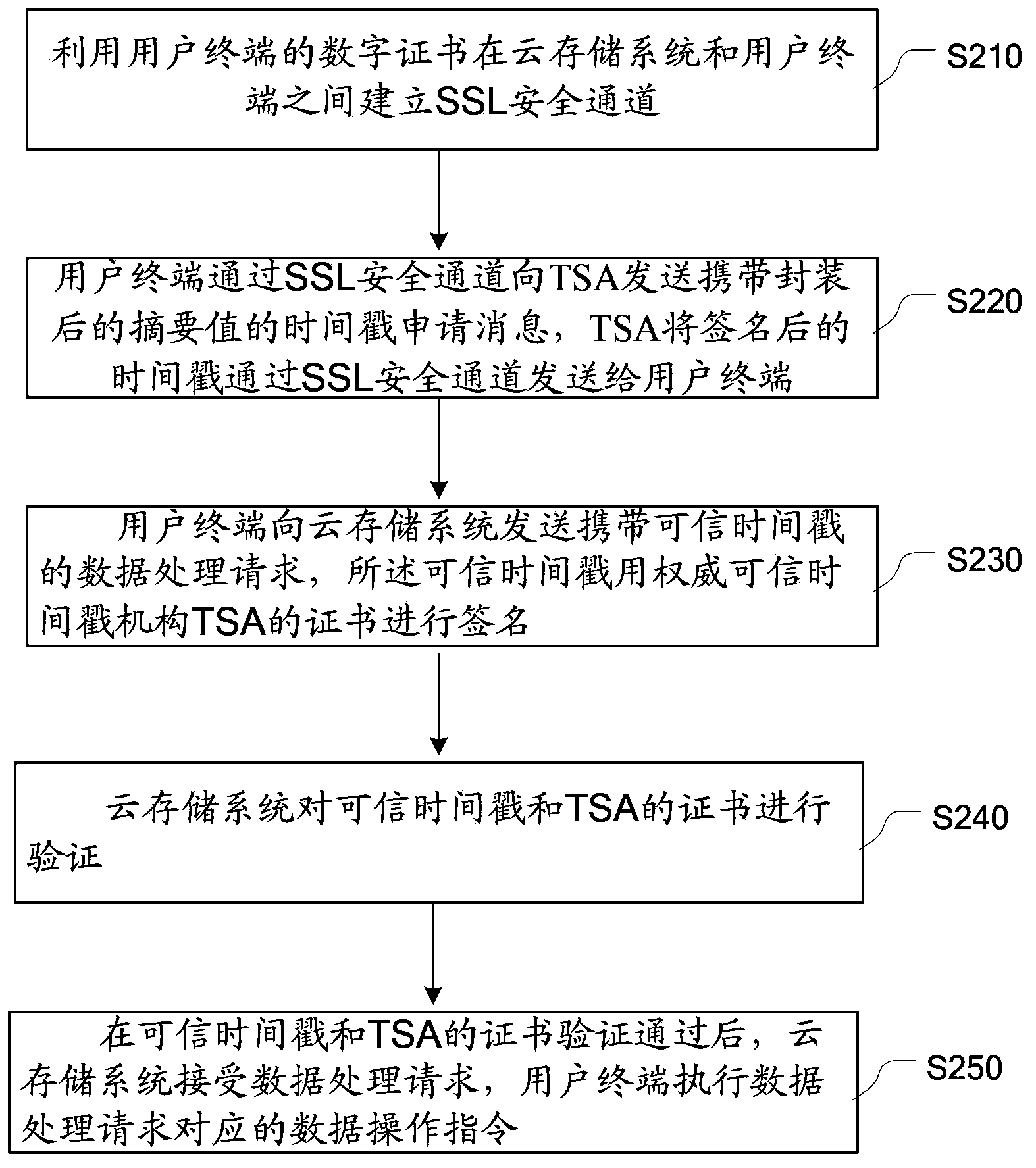
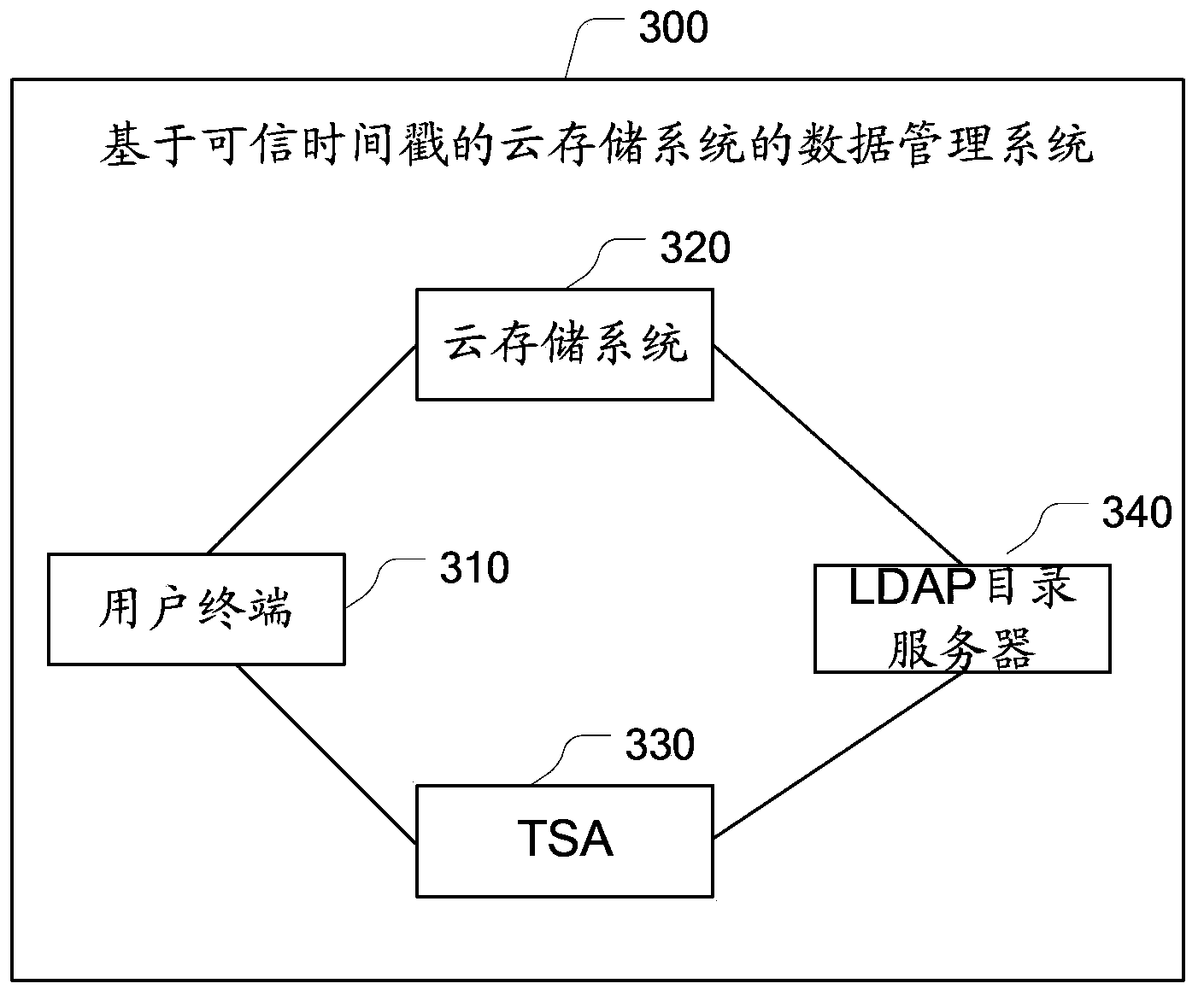
Data management method and system of cloud storage system based on trusted timestamp
InactiveCN104348870ADoes not increase the complexity of the service processGuarantee data securityUser identity/authority verificationThird partyTimestamp
The embodiment of the invention provides a data management method and system of a cloud storage system based on a trusted timestamp. The method mainly includes the following steps: the cloud storage system receives a data processing request which is sent by a user client and carries the trusted timestamp signed through use of a TSA certificate; and the cloud storage system verifies the trusted timestamp and the TSA certificate and after the trusted timestamp and the TSA certificate pass the verification, the cloud storage system receives the data processing request and the user client executes a data operation instruction corresponding to the data processing request. Through the third-party trusted timestamp, the cloud storage system is capable of carrying out effective management and audit on user data and carrying out verification and recording and filing on data operation records of a user so that the security of user operations and the authenticity of cloud storage data are guaranteed and it is achieved that the data security of the user is guaranteed while the complexity of the service procedure of the cloud storage system is not increased.
Owner:AEROSPACE INFORMATION
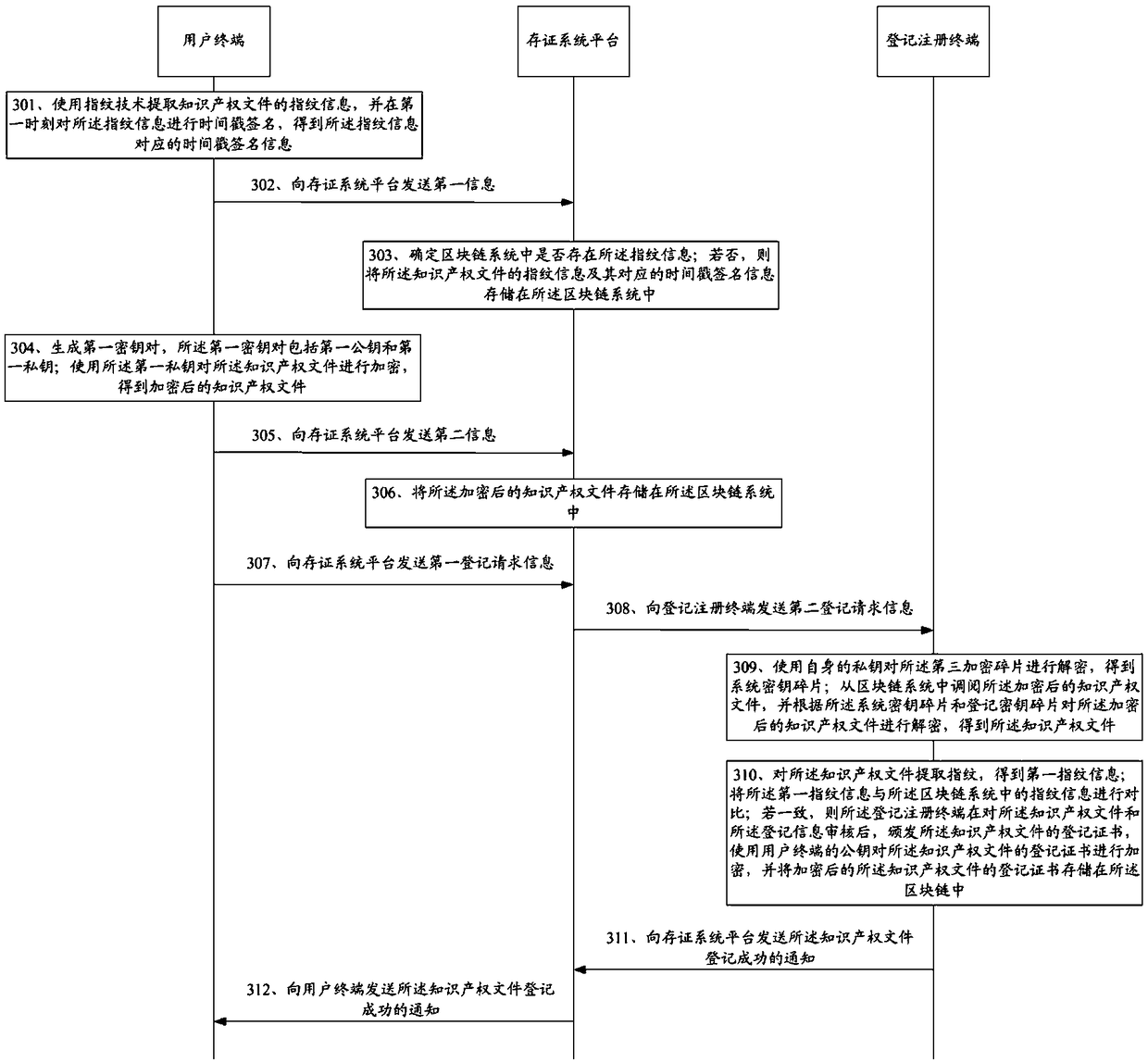
Method and a device for storing intellectual property documents based on a block chain
The invention discloses a method and a device for storing intellectual property documents based on a block chain;through the block chain system on the certificate depositing system platform, combinedwith multi-signature technology and trusted timestamp signature technology, a user terminalencrypts and stores the intellectual property documents in the process of storage and registration, which ensures that the intellectual property documents will not leak out during the storage and registration, and provides proof of rights for users by taking advantage of the untamperable characteristics of the block chain system.
Owner:深圳市乘法信息技术有限公司
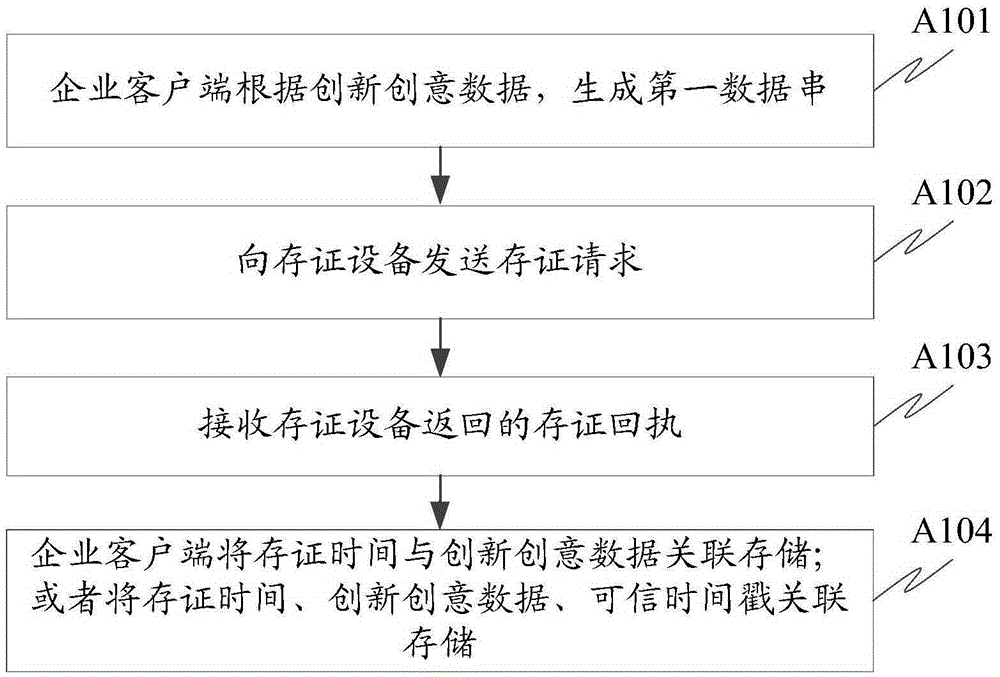
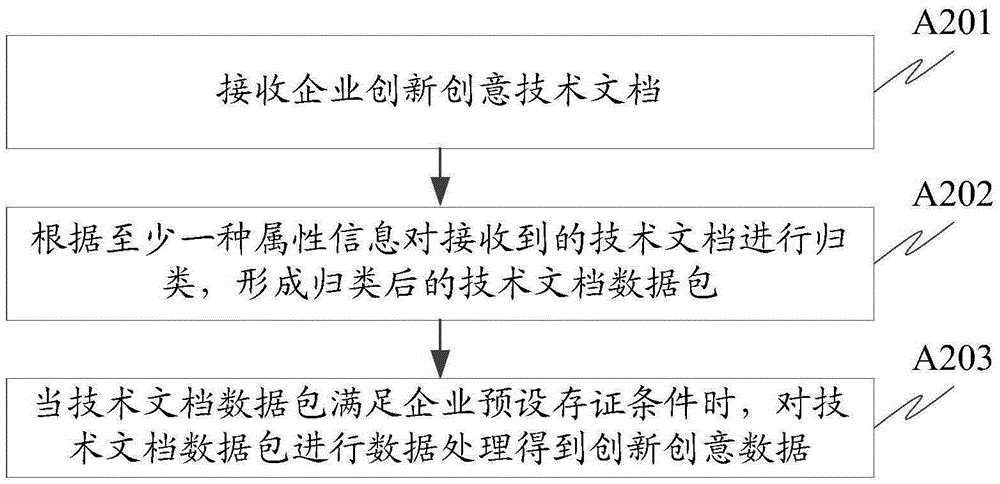
Innovation and creativity data processing method, device and system and certificate storing equipment
ActiveCN105335667AEvidence time solidificationGuaranteed confidentialityDigital data protectionThird partyTimestamp
The invention provides an innovation and creativity data processing method, device and system and certificate storing equipment. An enterprise client generates a unique corresponding first data string on the basis of innovation and creativity data; in addition, the first data string is sent to the certificate storing equipment for certificate storage; the certificate storing equipment returns return receipts such as certificate storing time and credible timestamp, wherein the certificate storing time is credible time issued by credible time issuing equipment; the credible timestamp is obtained by performing digital signature on a second data string generated by the certificate storing equipment through a private key on the basis of the first data string and the certificate storing time, so that the authenticity and the credibility of the certificate storing equipment are ensured; the certificate storing time of innovation and creativity data is cured through the credible time issued by the credible time issuing equipment; in addition, the certificate storing process is based on the first data string but not non-innovation and creativity data contents per se; the security of enterprise client data contents is effectively ensured; meanwhile, the certificate storing process is realized by a third party without the benefit relationship with a user; the credibility of enterprise innovation and creativity data original creativity authentication is improved.
Owner:BEIJING YUANCHUANGYUN NETWORK TECH CO LTD
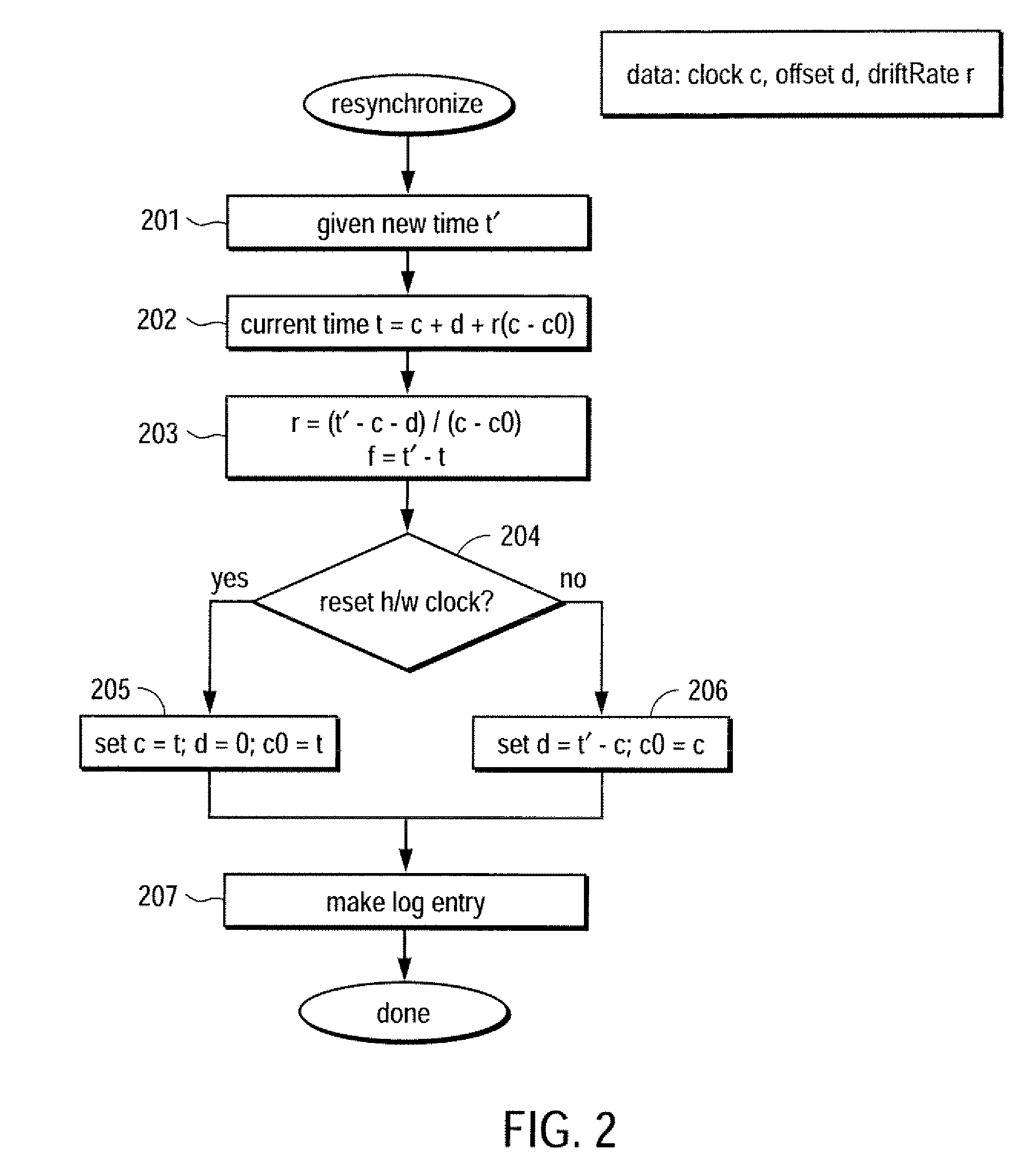
Trustworthy timestamps and certifiable clocks using logs linked by cryptographic hashes
ActiveUS8006094B2User identity/authority verificationUnauthorized memory use protectionCryptographic hash functionTrusted timestamping
A method and apparatus for creating and / or using trustworthy timestamps and certifiable clocks using logs linked by cryptographic hashes. In one embodiment, the method comprises maintaining a first, chained-hash log; associating a first clock with the chained-hash log, and entangling the first log; with a second by adding a time-stamped synchronization entry to the chained-hash log, where the synchronization entry has a second time indication associated with the second log and a hash of one or more entries in the first log.
Owner:RICOH KK
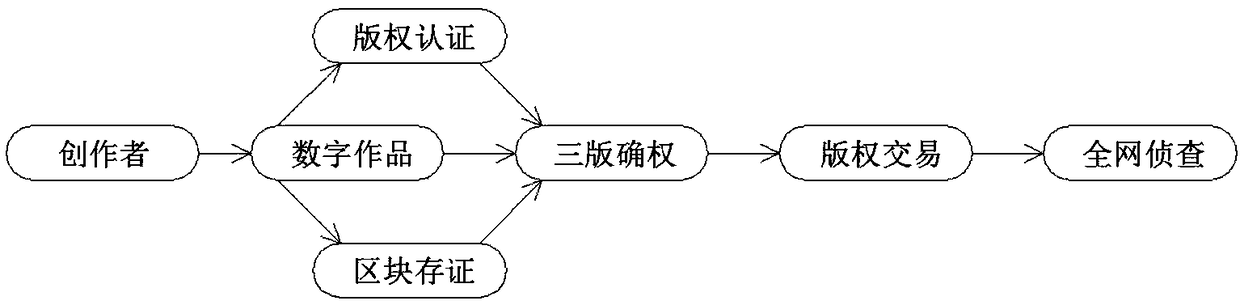
Method for constructing a three-dimensional digital block chain weight determination system
InactiveCN109064152ARealize traceabilityProtection of legitimate rights and interestsPayment architectureProgram/content distribution protectionTimestampTrusted timestamping
The invention provides a method for constructing a three-dimensional digital block chain confirmation system. The method comprises the following steps of: uploading a work; Copyright Certification; Block Depository; The third edition confirms the right; Copyright trading; Net-wide investigation. The invention adopts a self-developed block chain copyright registration network, Match trusted timestamp, chain stamp double authentication, Generating copyright DNA for each original model can really realize the traceability of three-dimensional model, and the copyright guardian based on the block chain model certification system and the whole network copyright monitoring tool can monitor the network infringement of original works, reconstruct the industry order, make the sovereignty belong to three-dimensional designers, and ensure the legitimate rights and interests of three-dimensional designers.
Owner:十一维度(厦门)网络科技有限公司
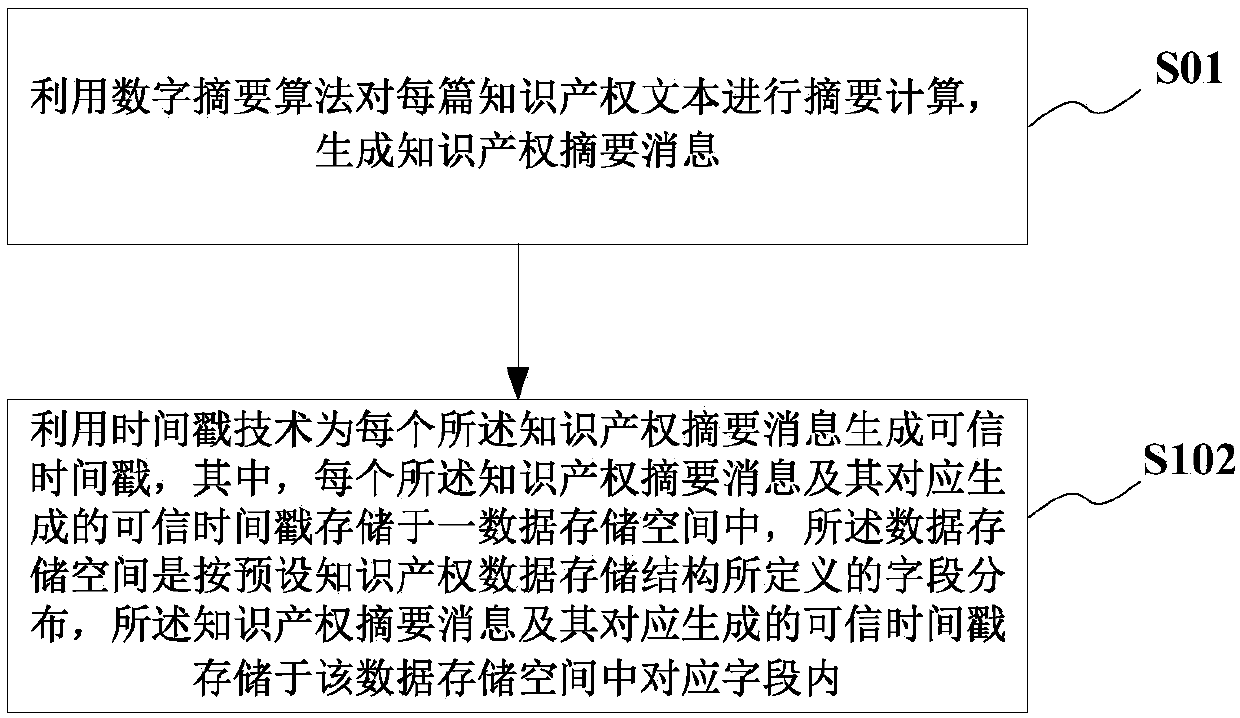
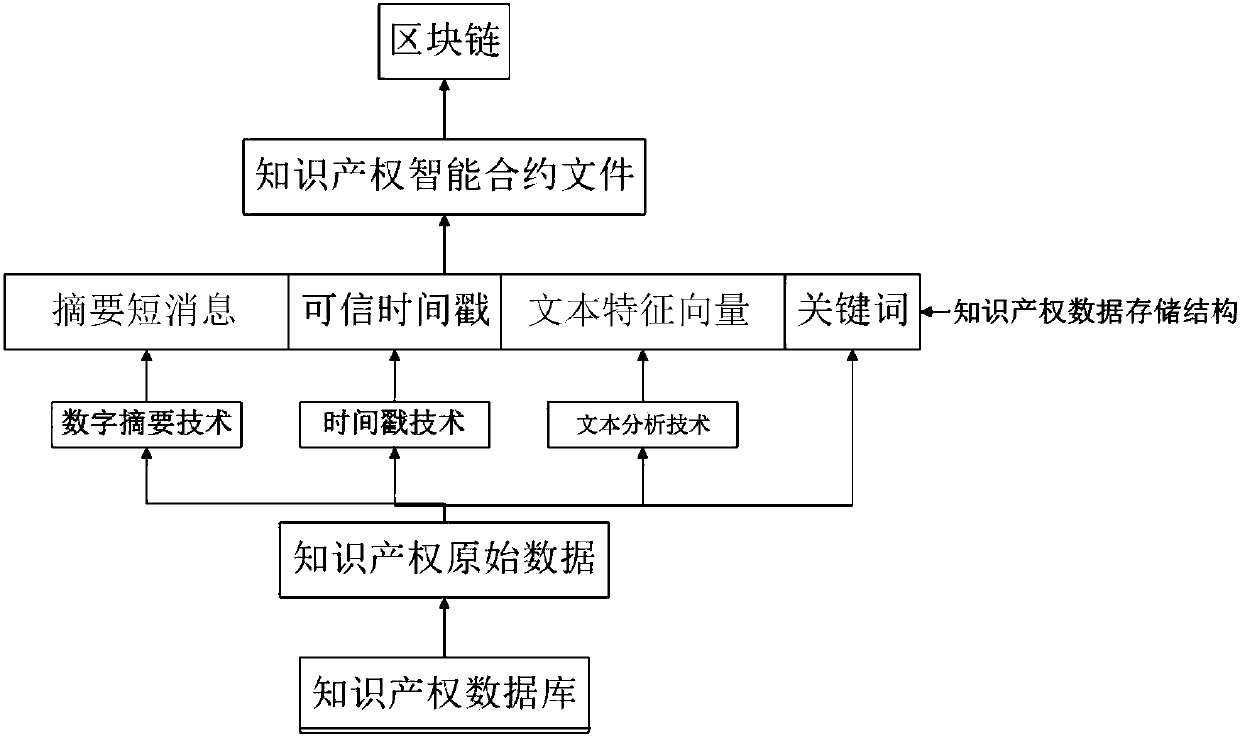
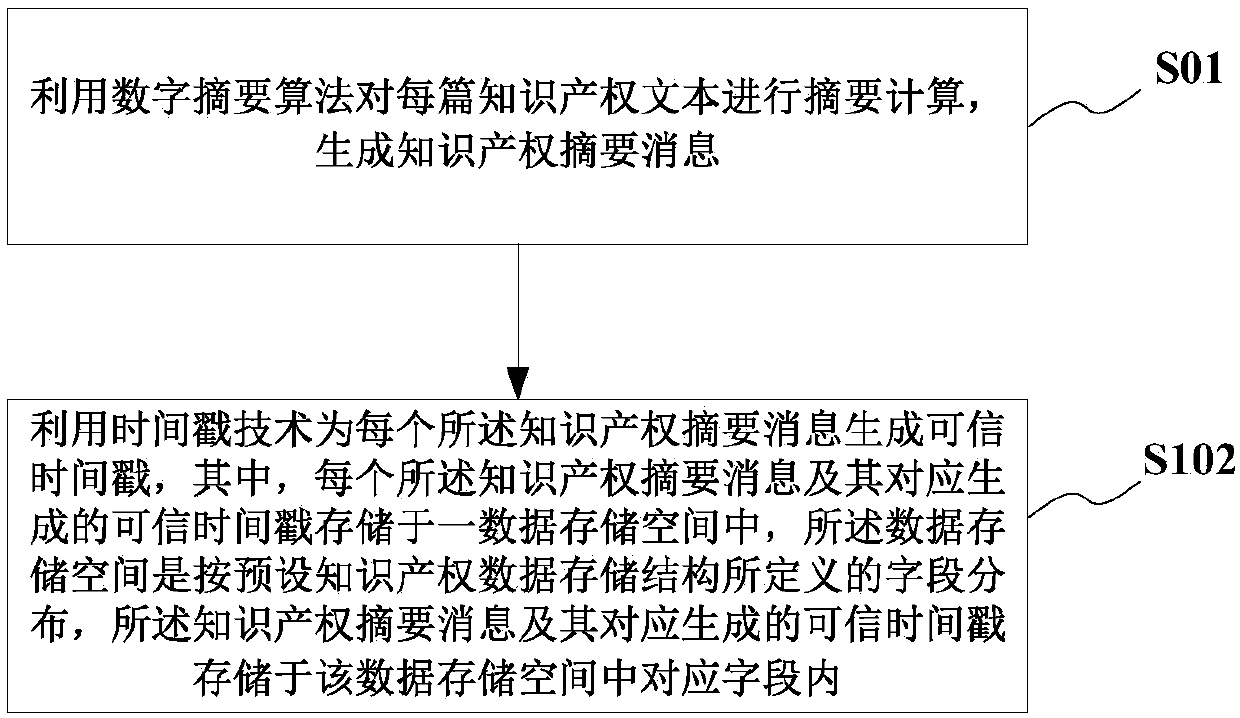
Intellectual property data storage method based on block chain, medium and computer equipment
ActiveCN110019216AImprove securityImprove integrityData processing applicationsSpecial data processing applicationsFeature vectorTimestamp
According to the intellectual property data storage method based on the block chain, the medium and the computer equipment. The method includes: carrying out summary calculation on each intellectual property text through a digital summary algorithm, and generating intellectual property summary information; generating a credible timestamp for each intellectual property abstract message by utilizinga timestamp technology, wherein each intellectual property abstract message and the credible timestamp correspondingly generated by the intellectual property abstract message are stored in a data storage space, the data storage space is stored according to a preset intellectual property data storage structure, and the intellectual property abstract message and the credible timestamp correspondingly generated by the intellectual property abstract message are stored in corresponding fields; the intellectual property data storage structure can also define a text feature vector field for storingintellectual property texts, keywords can be added into intellectual property abstract information for query and retrieval, and data of the whole intellectual property data storage structure can forman intelligent agreement file through an intelligent agreement technology and is stored in a block chain; and intellectual property data protection is enhanced.
Owner:SHANGHAI ADVANCED RES INST CHINESE ACADEMY OF SCI
Public electronic document dating list
InactiveUS7904450B2Eliminate needWithout expenseDatabase queryingWeb data indexingElectronic documentTimestamp
Systems and methods are disclosed which enable the establishment of file dates and the absence of tampering, even for documents held in secrecy and those stored in uncontrolled environments, but which does not require trusting a timestamping authority or document archival service. A trusted timestamping authority (TTSA) may be used, but even if the TTSA loses credibility or a challenger refuses to acknowledge the validity of a timestamp, a date for an electronic document may still be established. Systems and methods are disclosed which enable detection of file duplication in large collections of documents, which can improve searching for documents within the large collection.
Owner:WILSON KELCE S
Trustworthy timestamps and certifiable clocks using logs linked by cryptographic hashes
ActiveUS20120017093A1User identity/authority verificationComputer security arrangementsCryptographic hash functionTrusted timestamping
Owner:RICOH KK
Trusted timestamp adding method and device and storage medium
ActiveCN110601849AImprove performanceEasy to shareFinanceUser identity/authority verificationTimestampTrusted timestamping
The embodiment of the invention provides a trusted timestamp adding method and device and a storage medium, and relates to the technical field of block chains. The method comprises the steps that a first node in a block chain receives a timestamp transaction request, and the timestamp transaction request carries block data with a trusted timestamp; when the first node is a target node capable of generating a block, the block is generated, and the block comprises block data with a credible timestamp; a verification request of the block is broadcast to a second node in the block chain, the second node being a node other than the first node in the block chain; a verification result returned by the second node based on the verification request is received; and the block is added to the block chain based on a verification result returned by the second node. According to the embodiment of the invention, the timestamp transaction request is received, and the block data with the credible timestamp is added to the block chain according to the timestamp transaction request, so that the credible timestamp is added to the block data of the block chain, and the performance of the block chain isimproved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
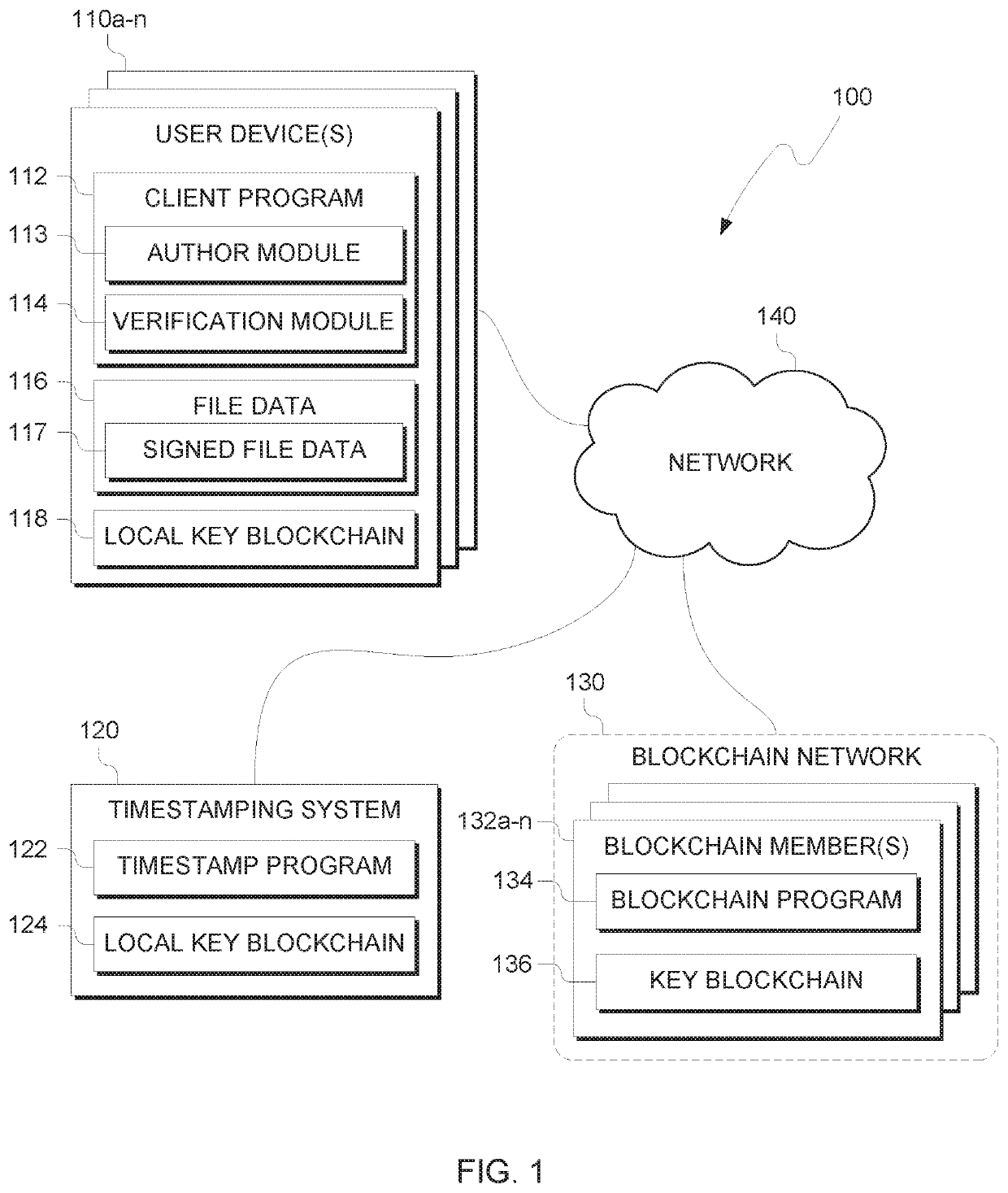
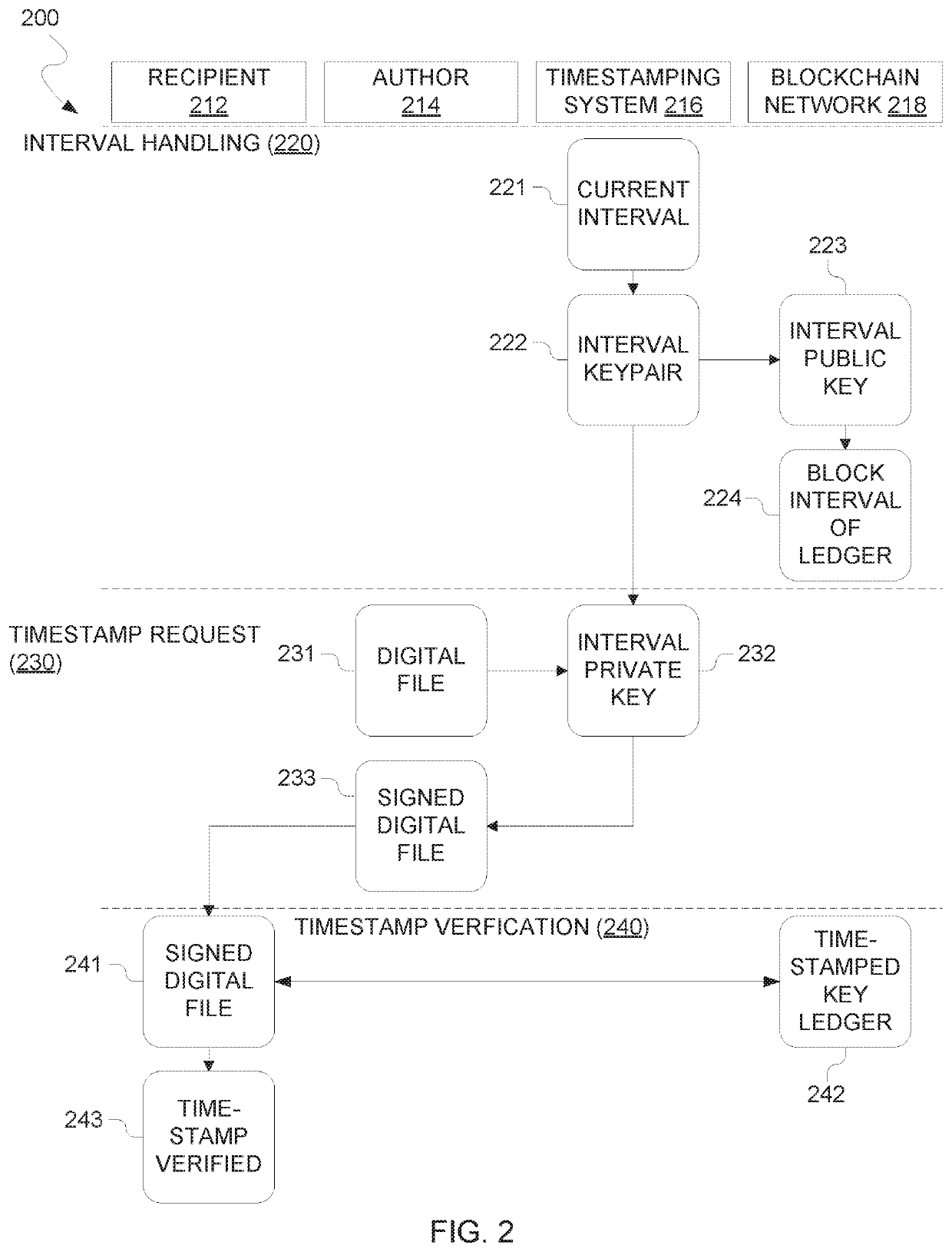
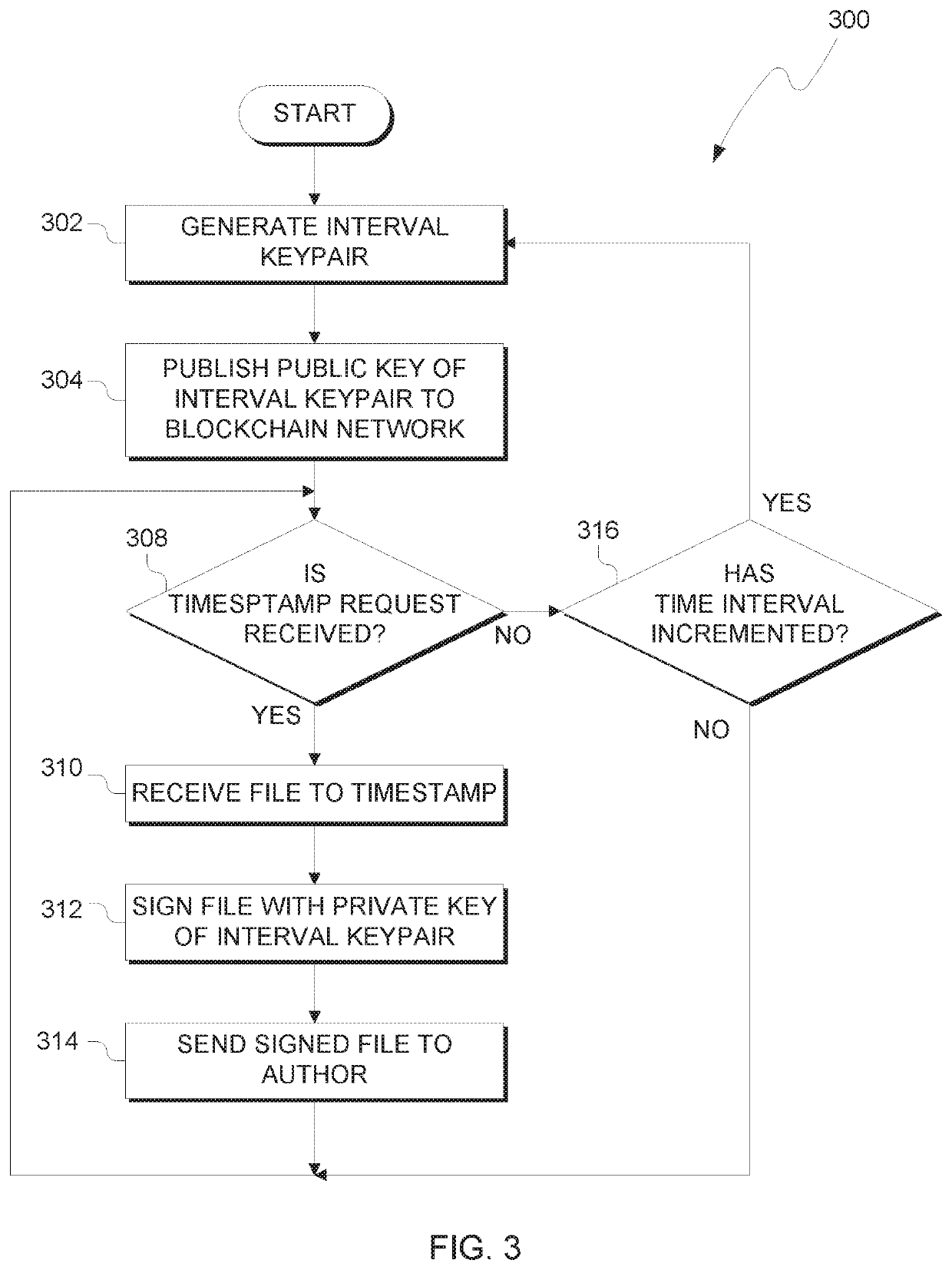
Trusted timestamping
PendingUS20200169425A1Key distribution for secure communicationEncryption apparatus with shift registers/memoriesSoftware engineeringTrusted timestamping
A method, computer program product and computer system for trusted timestamping is provided. A processor generates a first key pair, where the key pair includes a public key and a private key. A processor publishes the public key of the first key pair to an immutable data structure. A processor receives a first digital file for timestamping. A processor signs the first digital file with the private key of the first key pair.
Owner:IBM CORP
Trusted Time Stamping Storage System
InactiveUS20080229113A1Unauthorized memory use protectionHardware monitoringComputer networkTrusted timestamping
Data stored in a data storage system is hashed to generate a hash value. The hash value and a request for a time stamp are then sent to a time stamping authority. A time stamp token and / or a time stamp certificate is received from the time stamping authority. The time stamp token includes a time stamp and the hash value, and may be encrypted using a private key of the time stamping authority. The time stamp token and / or time stamp certificate is then stored with, for example, a reference to the data being stored in the data storage system. The time stamp token and / or time stamp certificate may then be used to validate the data being stored and the time stamp.
Owner:HITACHI LTD
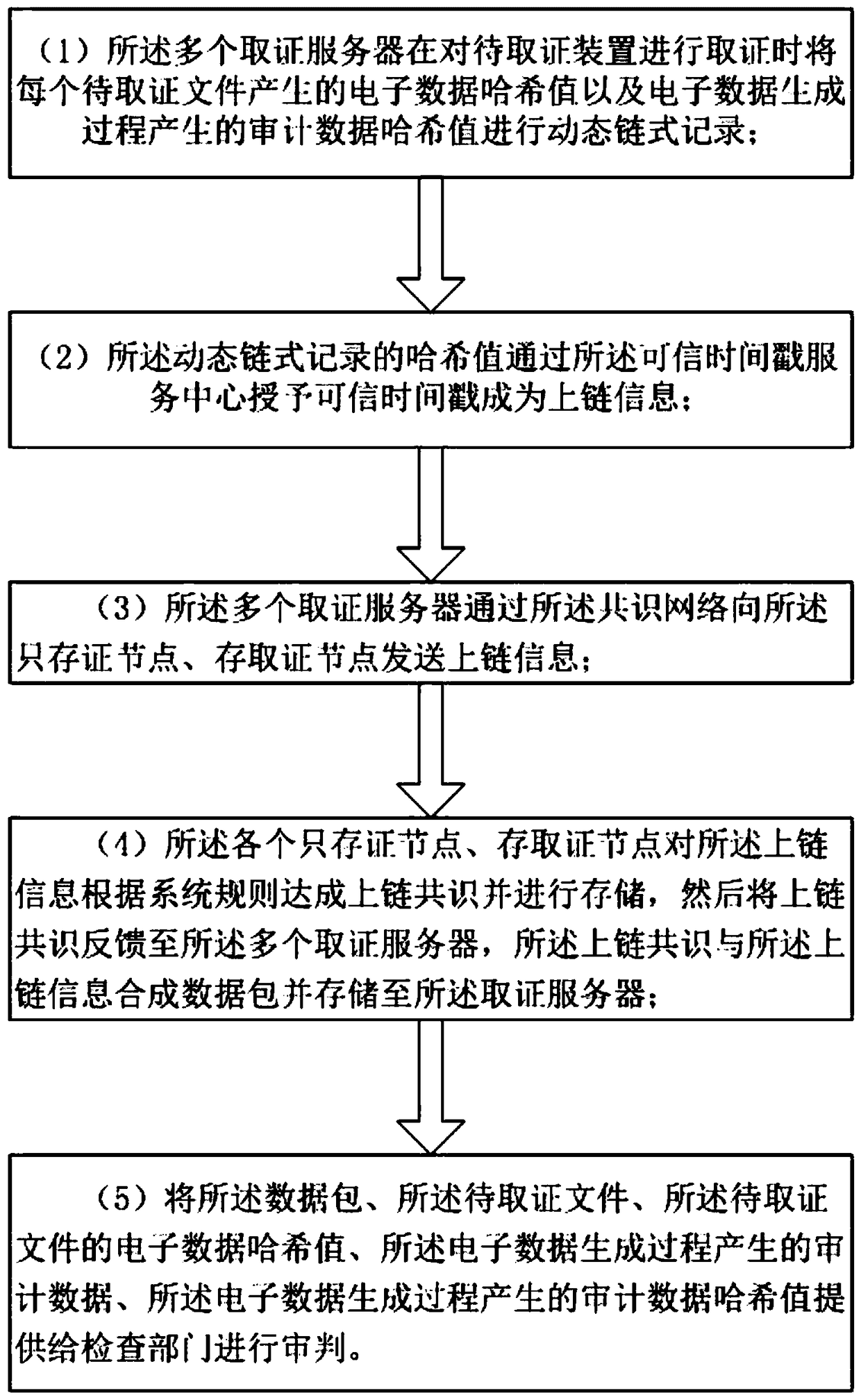
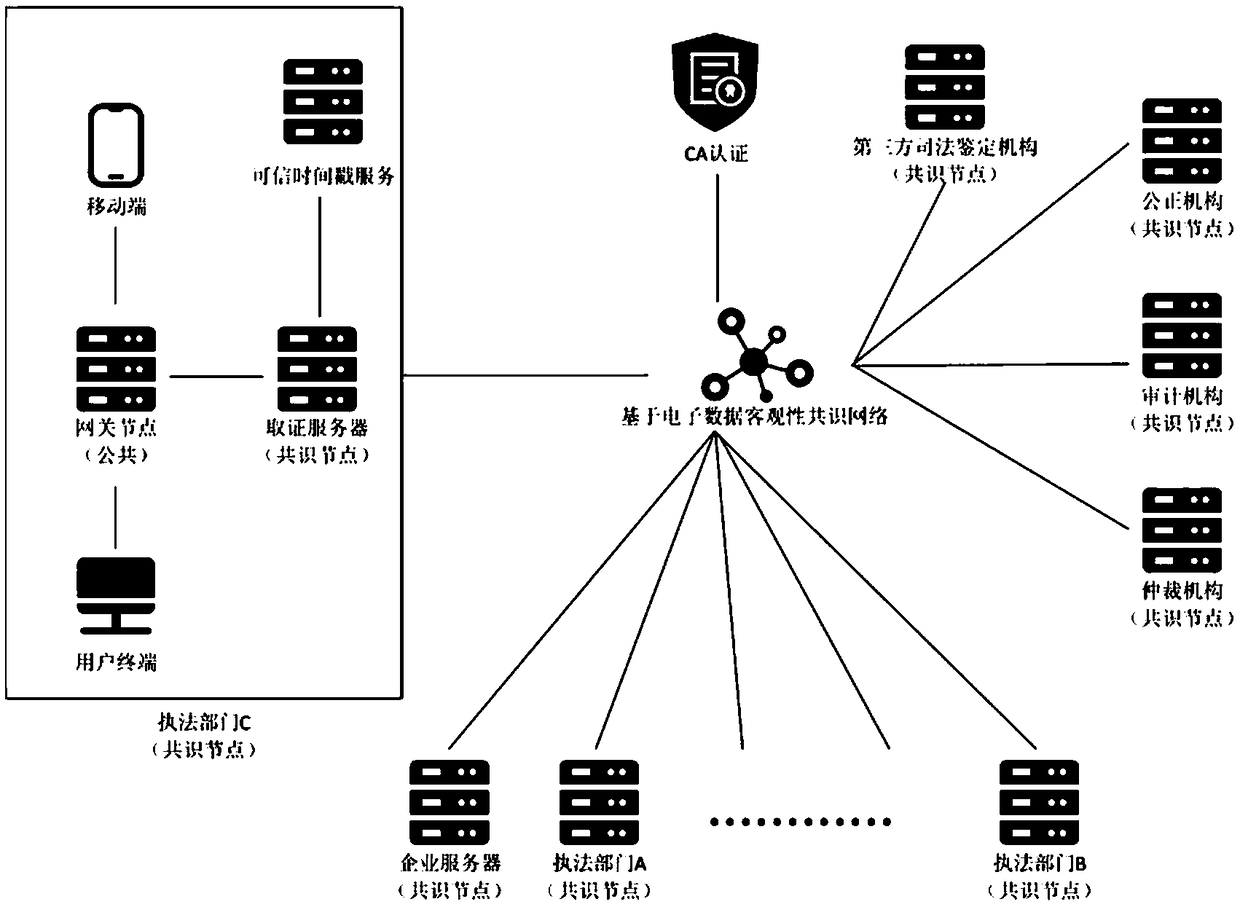
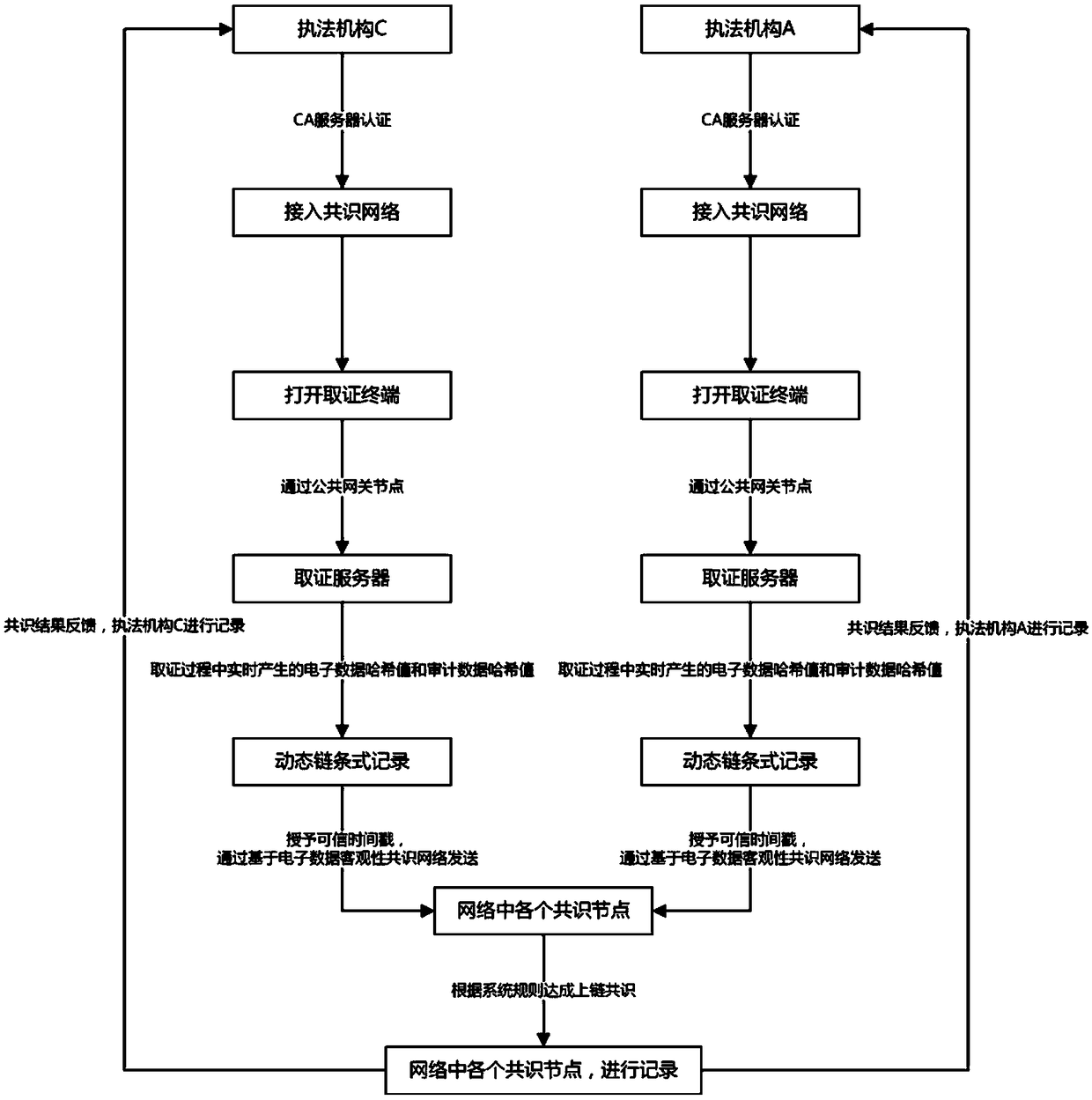
An electronic data dynamic hash chain consensus storage system and method thereof
InactiveCN109150550AGuarantee authenticityIntegrity guaranteedUser identity/authority verificationDigital data protectionTimestampNetwork packet
The invention discloses an electronic data dynamic hash chain consensus storage system and a method thereof. The system comprises a plurality of consensus nodes and a consensus network. The pluralityof forensics servers dynamically record the electronic data hash value and the audit data hash value generated by each forensics document when the forensics device is forensics. The hash value of thedynamic chain record is granted with a trusted timestamp by the trusted timestamp service center to become uplink information. The plurality of forensics servers send uplink information to the only forensics node and the forensics node through the consensus network. Each of the certificate-only nodes, wherein the certificate-storing node reaches an uplink consensus on the uplink information according to the system rules and stores the uplink consensus and the uplink information into a data packet and stores the data packet and the uplink information to the plurality of forensic servers. The authenticity, integrity and legitimacy of the electronic data are ensured through the dynamic hash chain certification method.
Owner:爱思科技(重庆)集团有限公司
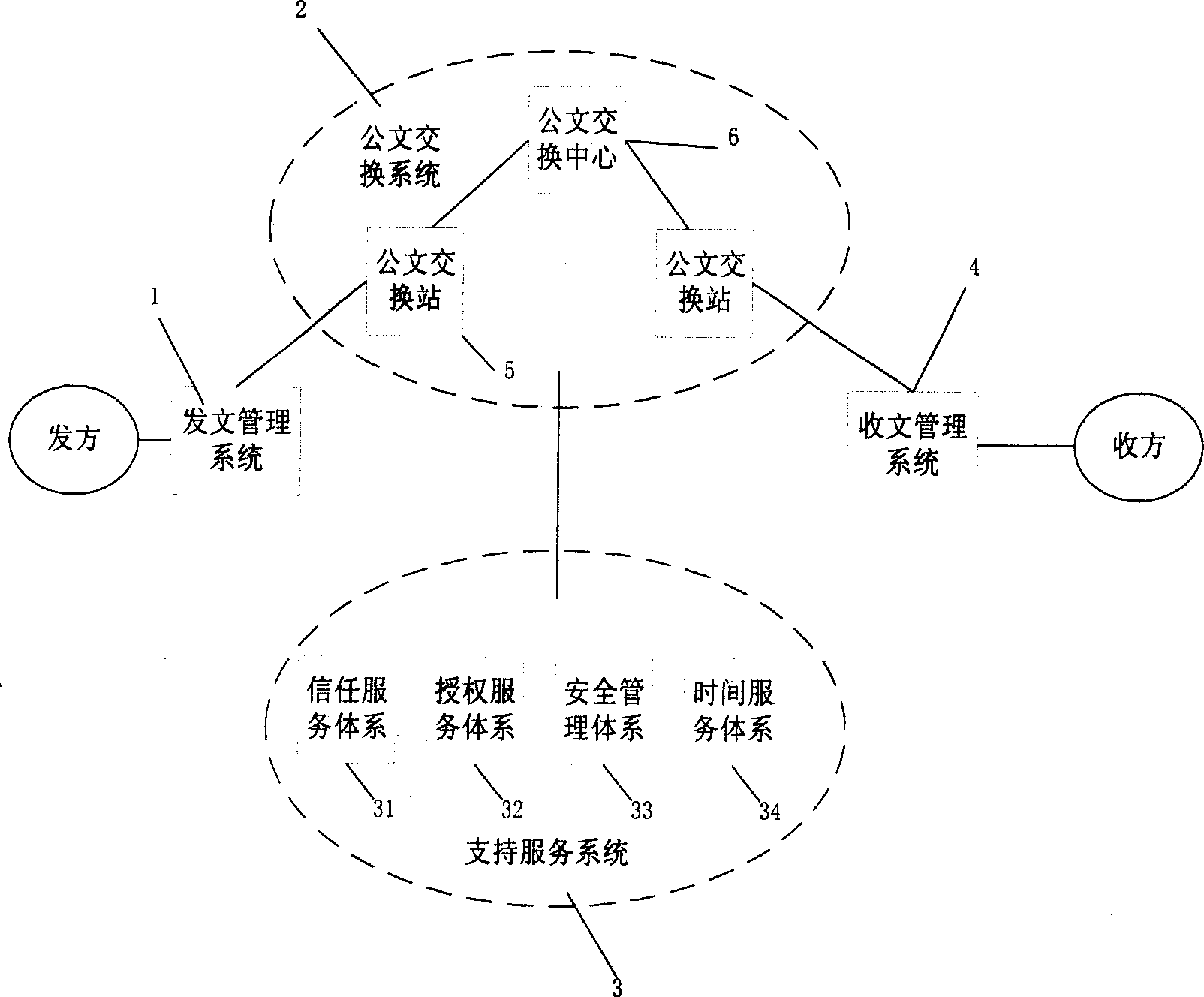
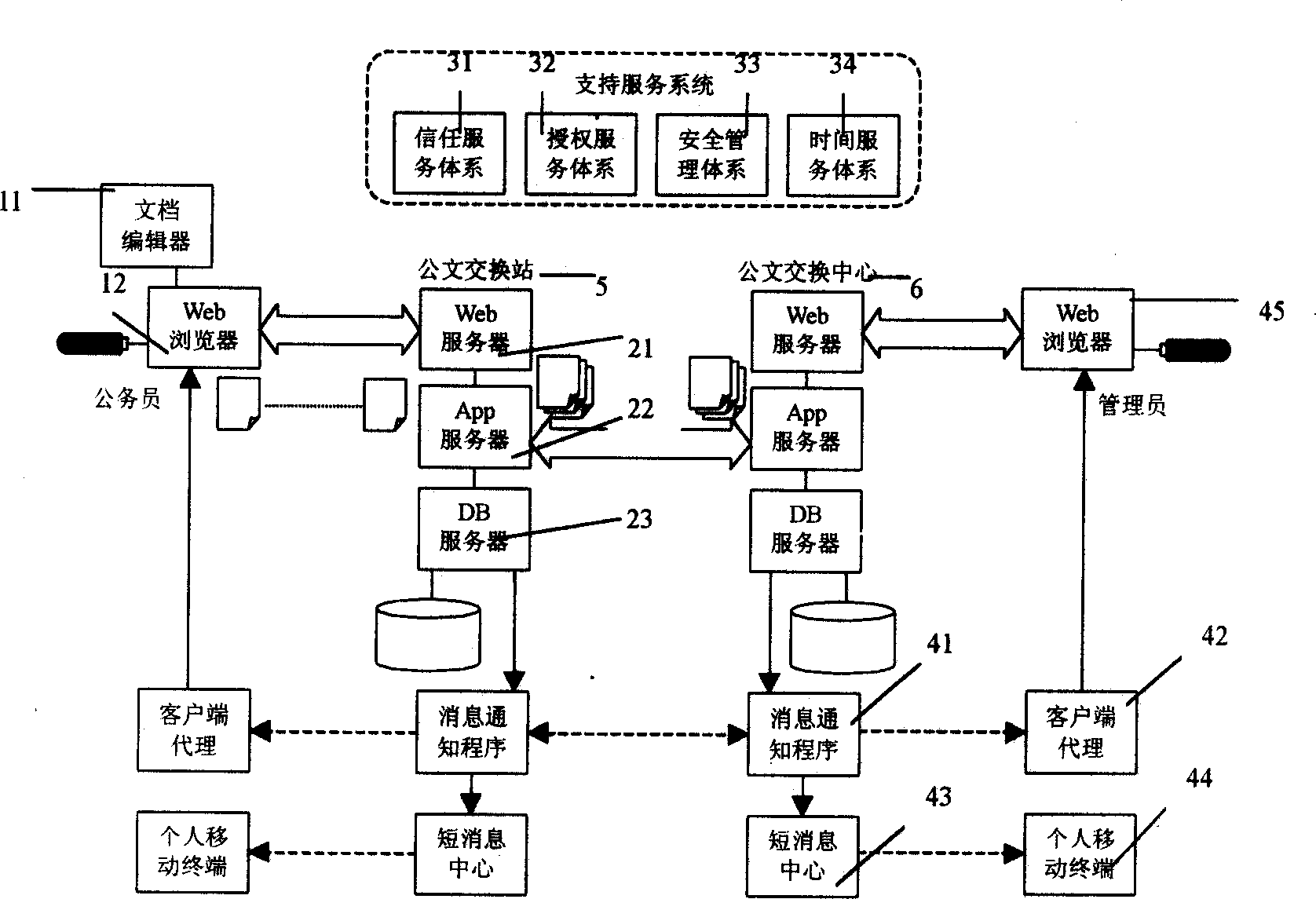
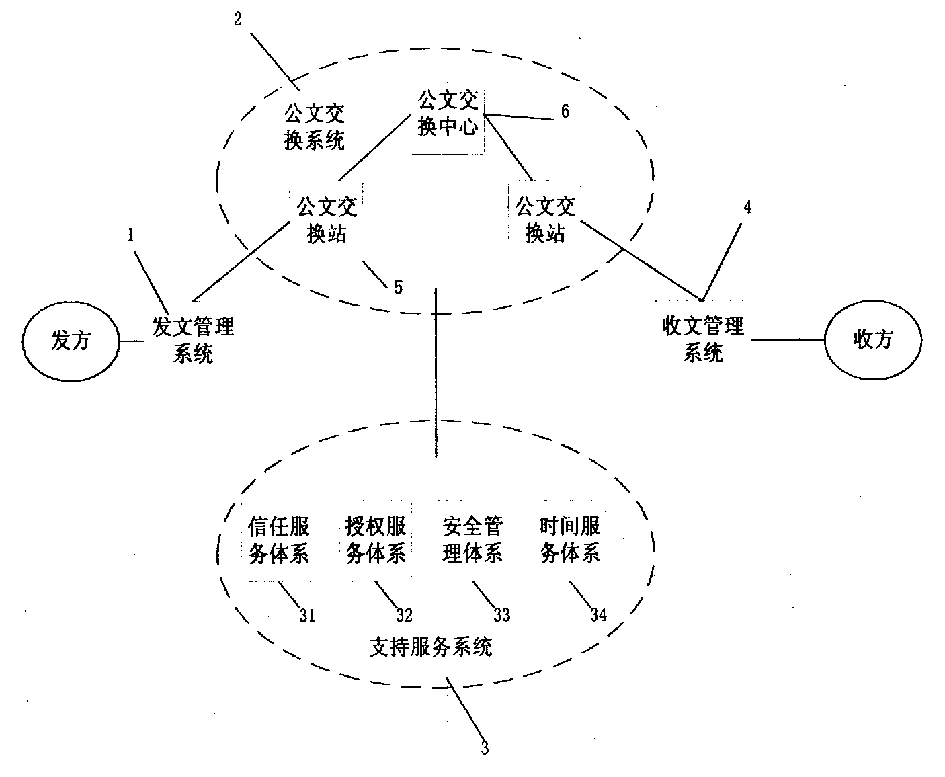
Official document circulating system based on goverment affairs trust and authorized service
InactiveCN1350255AImprove reliabilityImprove securityProgram controlSpecial data processing applicationsXMLHuman language
The present invention discloses an official document exchange system based on government confidence and authorization service, which is characterized by that that said system utilizes the government confidence system based on public key basic facility PKI technique and government authorized management system based on authorization management basic facility PMI technique as operating platform, andadopts public key cipher technique based digital signature and operation mark in the fiducial time stamp service retantion transmissino process to make official document exchange process become into the process which can be monitored. Said invention adopts XML marking language technique as official document data expression and exchange format to provide cross-platform shared power of official document data.
Owner:上海维豪信息安全技术有限公司
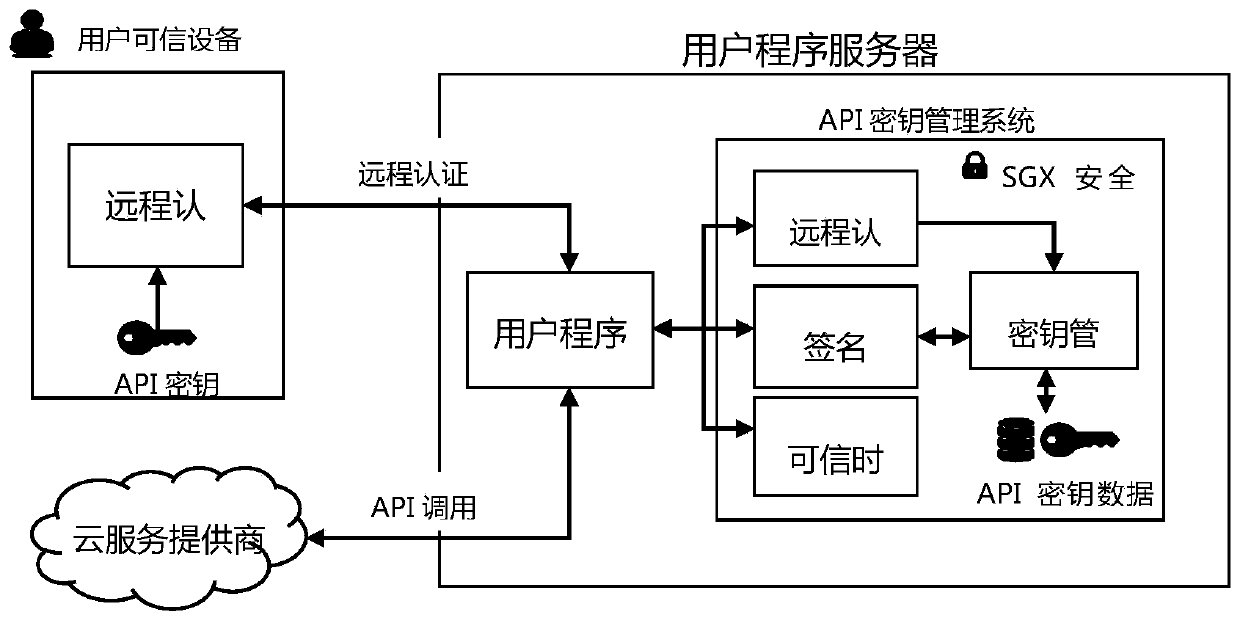
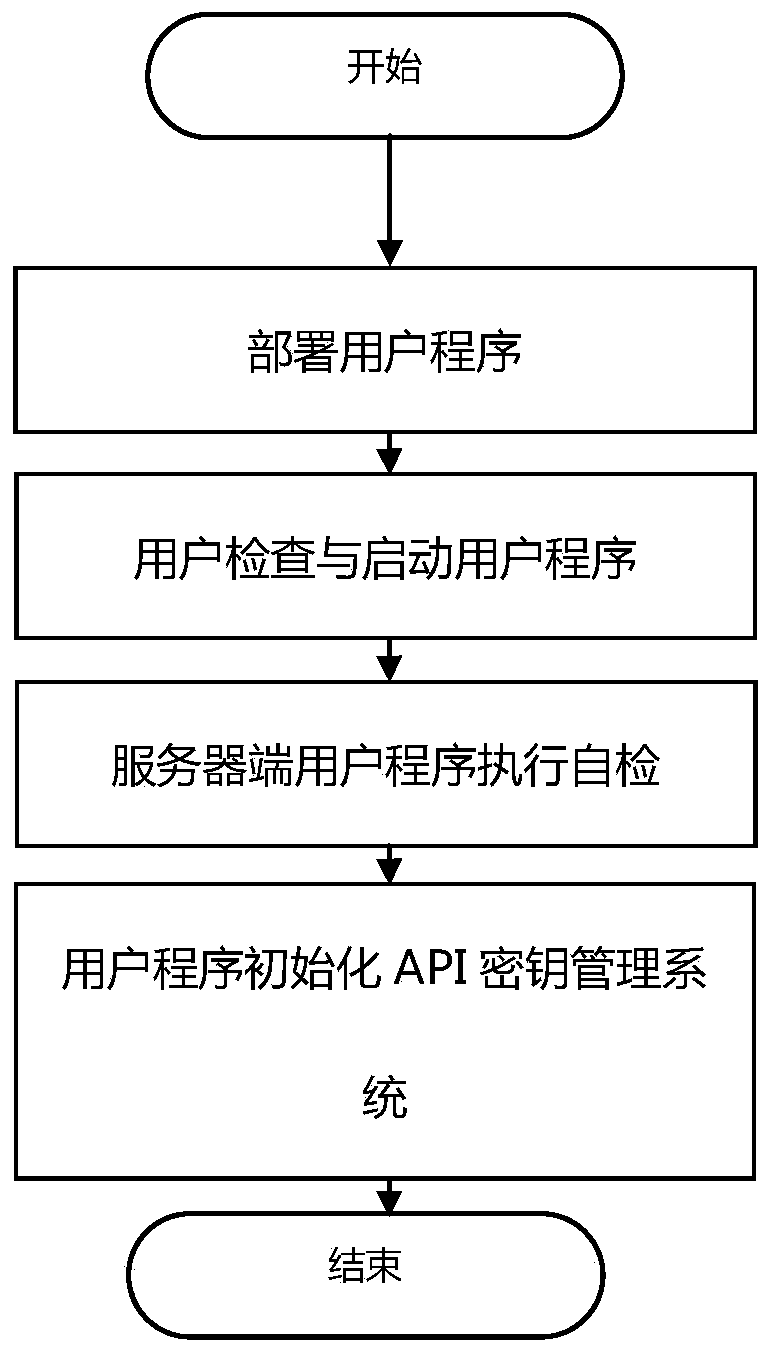
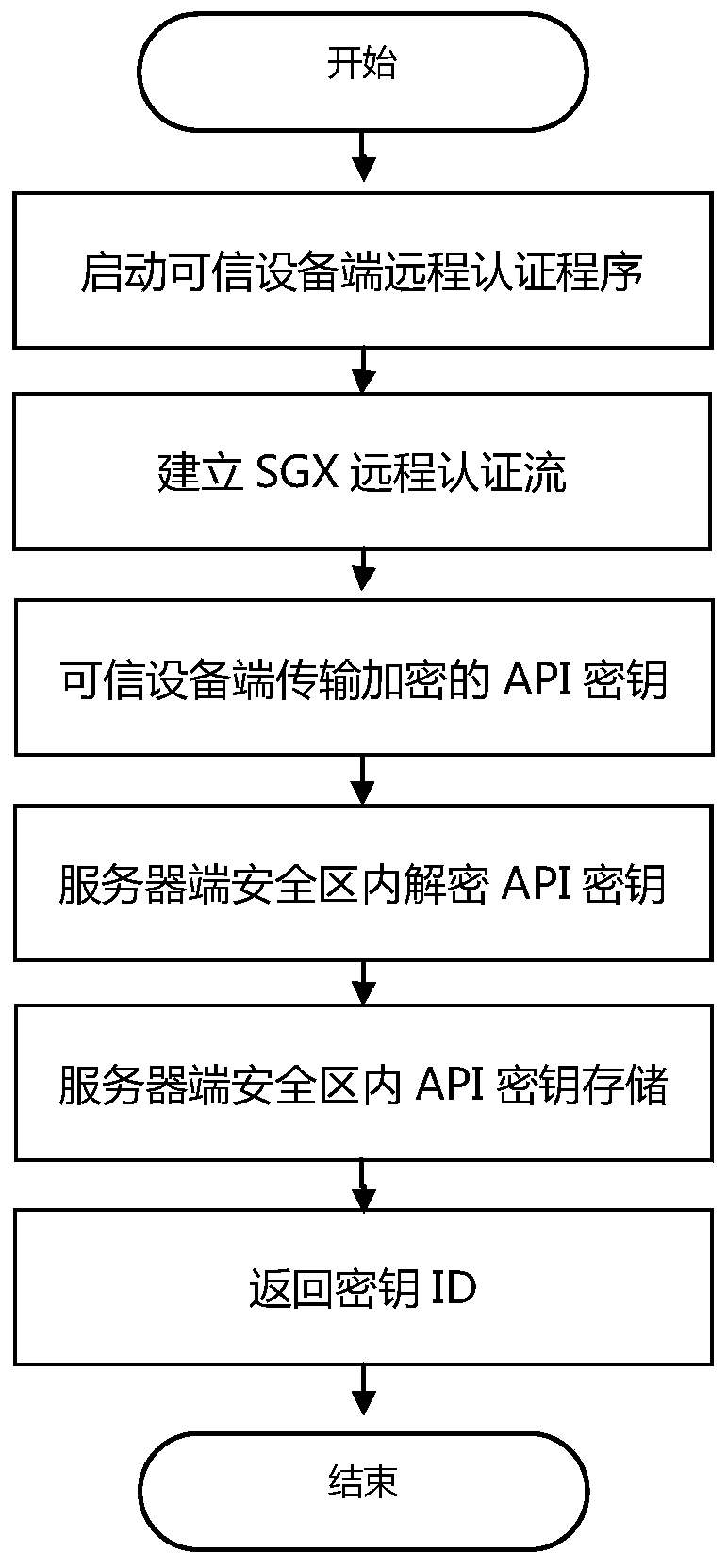
API key protection method and system based on SGX software extension instruction
ActiveCN111475782AEnsure safetyImprove migration abilityDigital data protectionDigital data authenticationTimestampSoftware engineering
The invention discloses an API key protection method based on an SGX software extension instruction. The API key protection method comprises the following steps: (1) API key protection system initialization; (2) remote authentication and API key import; (3) API request signature and signature information export. According to the method, a secure API key storage and use environment is constructed by introducing Intel SGX hardware and a trusted space mechanism of the SGX, and protection is provided for a user API key; the invention further discloses an API secret key protection system based on the SGX software extension instruction. The API secret key protection system comprises a remote authentication module used for cooperating with user trusted equipment to complete SGX remote authentication. The key management module is used for storing and managing the acquired API key in the SGX security area; the trusted time module is used for providing a trusted timestamp for a user program; andthe signature module is used for generating an effective signature according to the request of the user program and the API key.
Owner:ZHEJIANG UNIV
Trusted digital signature method and device based on blockchain
ActiveCN112202558AGuaranteed traceabilityGuaranteed verifiabilityKey distribution for secure communicationPublic key for secure communicationData packSignature file
The invention discloses a trusted digital signature method and device based on a blockchain. The method comprises the steps of generating a digital certificate request; acquiring a digital certificate, and respectively storing the digital certificate and the digital certificate application record into a blockchain and a database; calculating a hash value of local to-be-signed data; generating a timestamp request according to the hash value of the to-be-signed data; obtaining an authoritative timestamp; storing the timestamp application record in the blockchain; generating a signature file according to the digital certificate, the hash value of the to-be-signed data and an authoritative timestamp; generating a signature data packet and uploading the signature data packet to the blockchain;and obtaining a verification result of a verification party on the signature data packet. According to the application, the blockchain technology is adopted, the application and issuing records of thecredible timestamp and the authoritative digital certificate are backed up in the blockchain respectively, the traceability and verifiability of user behaviors are ensured, and thus the credibility of authoritative CA service and authoritative TSA service is ensured.
Owner:南京通付盾区块链科技有限公司
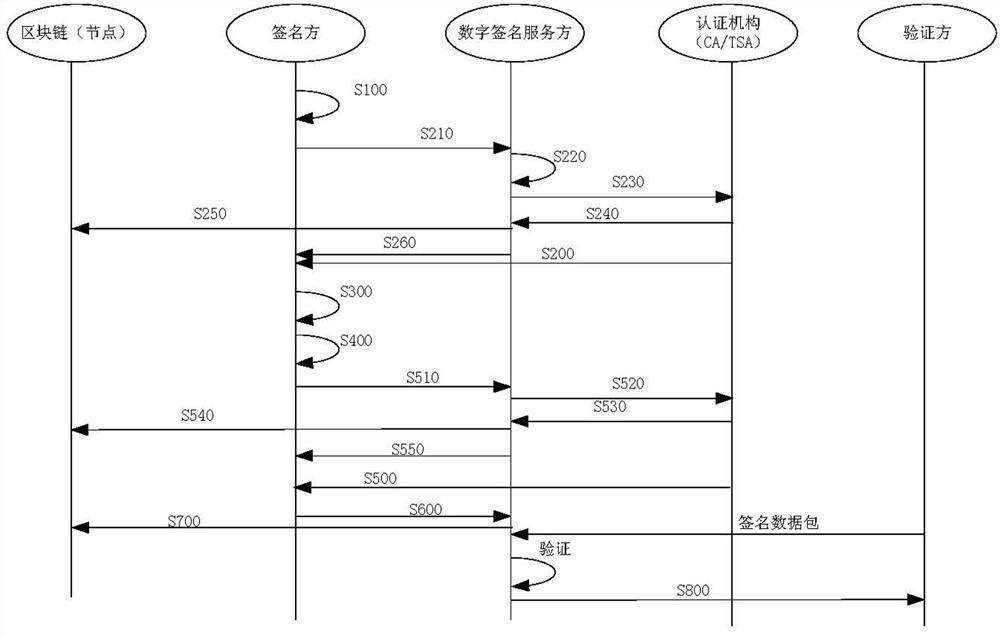
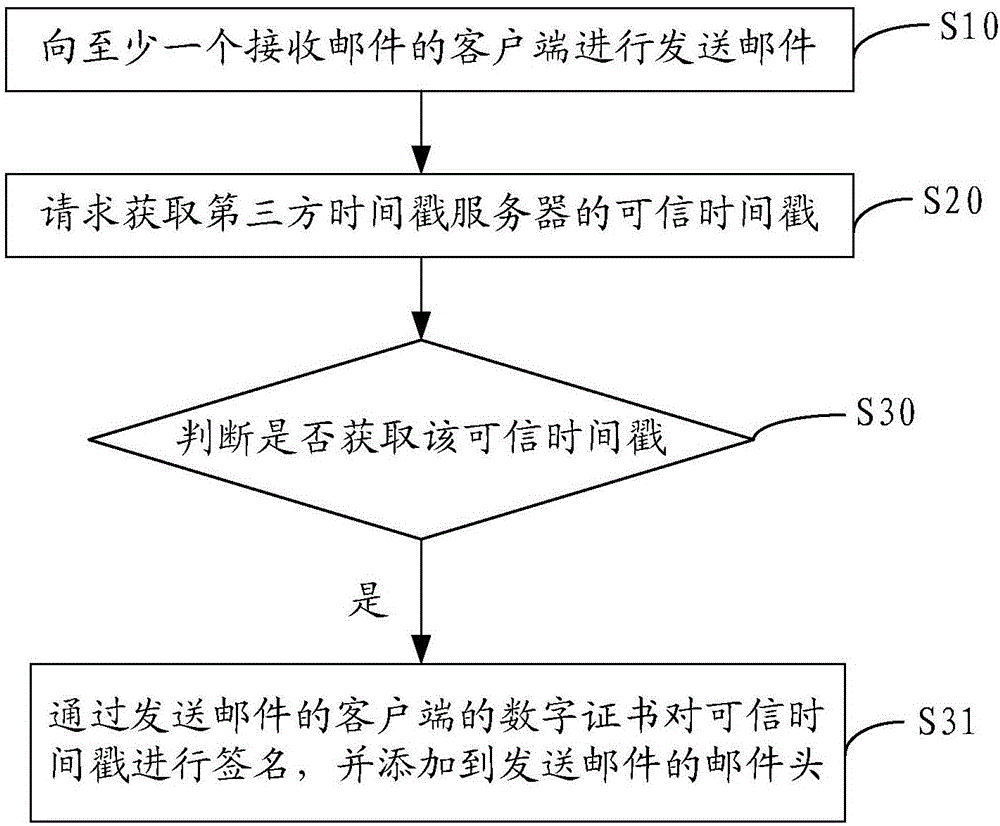
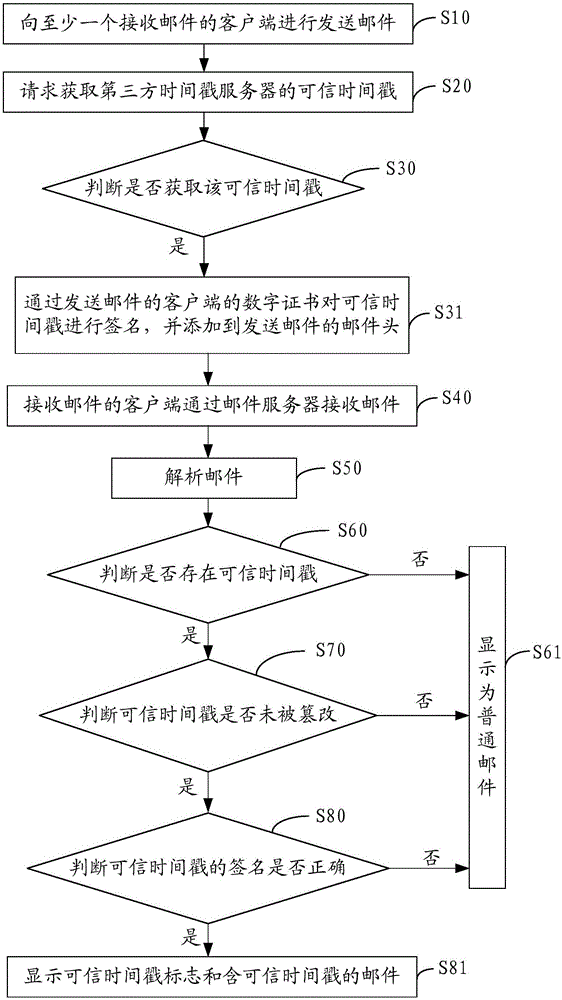
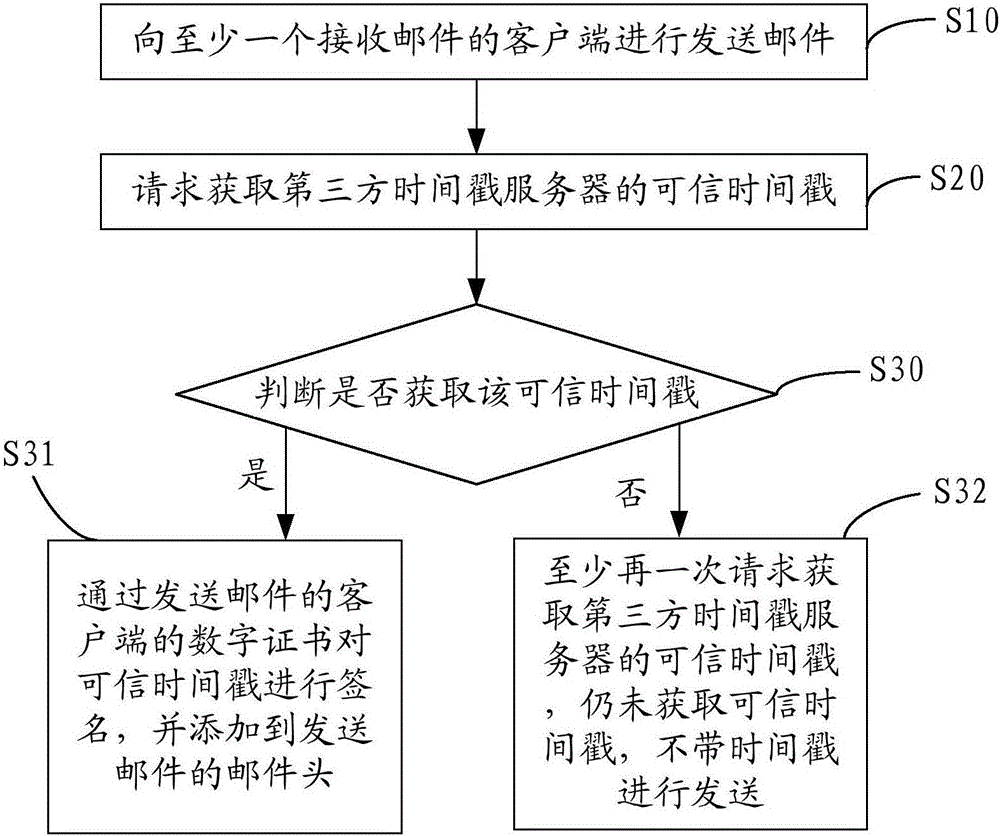
Method and device capable of verifying e-mail sending time
InactiveCN106789585AGuaranteed accuracy and reliabilityConvenient verificationData switching networksTimestampTrusted timestamping
The invention discloses a method and a device capable of verifying e-mail sending time. The method capable of verifying e-mail sending time comprises the following steps: sending an e-mail to at least one e-mail receiving client, requesting to acquire trusted timestamp of a third timestamp server, judging whether the trusted timestamp is acquired, if yes, signing the trusted timestamp through a digital certificate of an e-mail sending client and adding the signed trusted timestamp to a header of the sent e-mail. With adoption of the method, accuracy and reliability of the e-mail sending time are guaranteed, and verification is facilitated.
Owner:WOSIGN CA LTD
Inter cut prevention method for terrestrial digital television
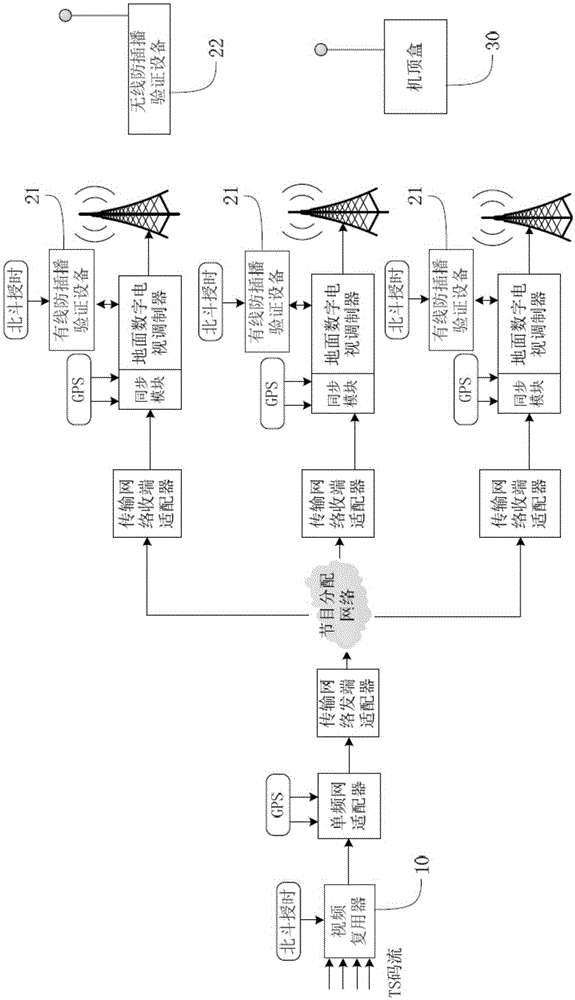
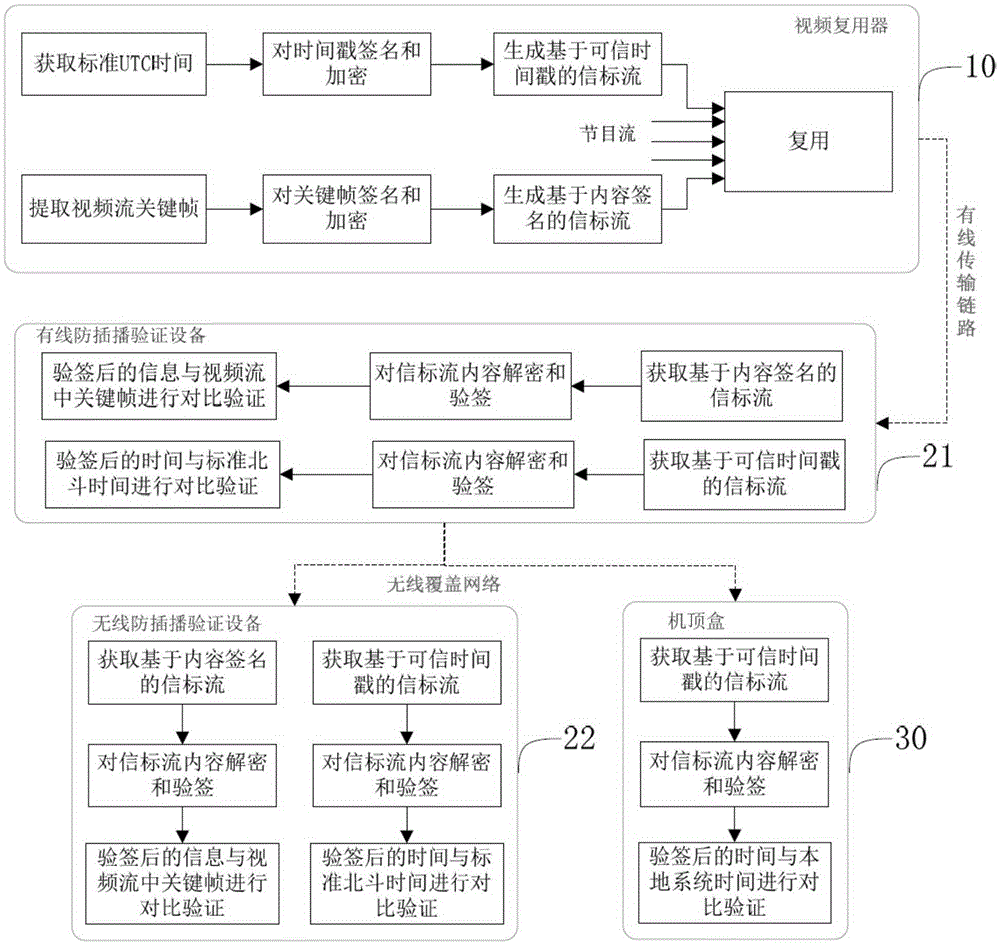
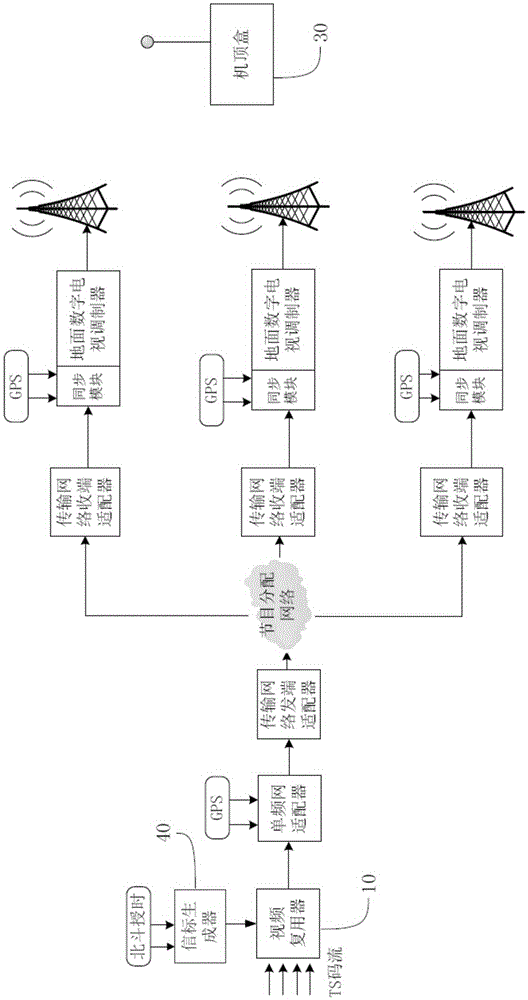
InactiveCN105307054ARapid deploymentSimple configurationSelective content distributionTimestampTime delays
The invention discloses an inter cut prevention method for a terrestrial digital television. The inter cut prevention method comprises the following steps: a first step, a beacon flow generator in a transmitting terminal device obtains a standard UTC time through a built-in Beidou time service module at first, and then carries out signature and encryption processing on a timestamp to generate an inter cut prevention beacon flow based on a credible timestamp; a second step, a video multiplexer in the transmitting terminal device integrates the inter cut prevention beacon flow with other program beacon flows and then transmits the same to a receiving end terminal through a transmission link; and a third step, a set-top box in the receiving end terminal obtains the inter cut prevention beacon flow based on the credible timestamp, decrypts and verifies the inter cut prevention beacon flow based on the credible timestamp, compares a local system time with a decrypted and verified timestamp, if the time delay exceeds a preset threshold, the set-top box has an inter cut attack and stops playing; and otherwise, the set-top box normally plays the program. The inter cut prevention method for the terrestrial digital television disclosed by the invention is used for protecting the security of a communication network of the digital television and preventing inter cut of illegal signals.
Owner:CHENGDU SANLING KAITIAN COMM IND
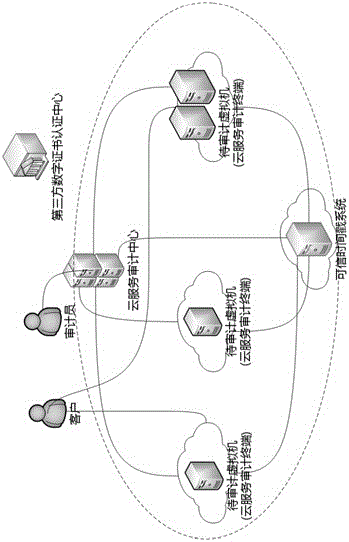
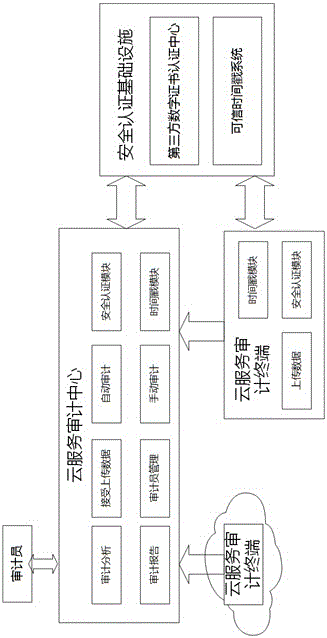
Cloud service auditing system and method based on digital signature and time stamp
InactiveCN106169954AResolve integritySolve authentication problemsUser identity/authority verificationThird partyDigital signature
The invention belongs to the technical field of server safety, and specifically relates to a cloud service auditing system and method based on a digital signature and a time stamp. The auditing system comprises a cloud service auditing center, a cloud service auditing terminal, a third party digital certificate authentication center and a credible time stamp system. Based on the system, auditing management can be carried out on a cloud virtual machine to be audited and a cloud application installed in the virtual machine by the auditing method. Compared with the prior art, the auditing validity authentication problem of each virtual machine and the application system in the cloud calculation environment can be solved, the reality and integrality of the auditing information and process is ensured, forged or falsified auditing data is prevented, and the responsibility of each party of the auditing process and result is clearly identified.
Owner:INSPUR GROUP CO LTD
Grain information management method and system
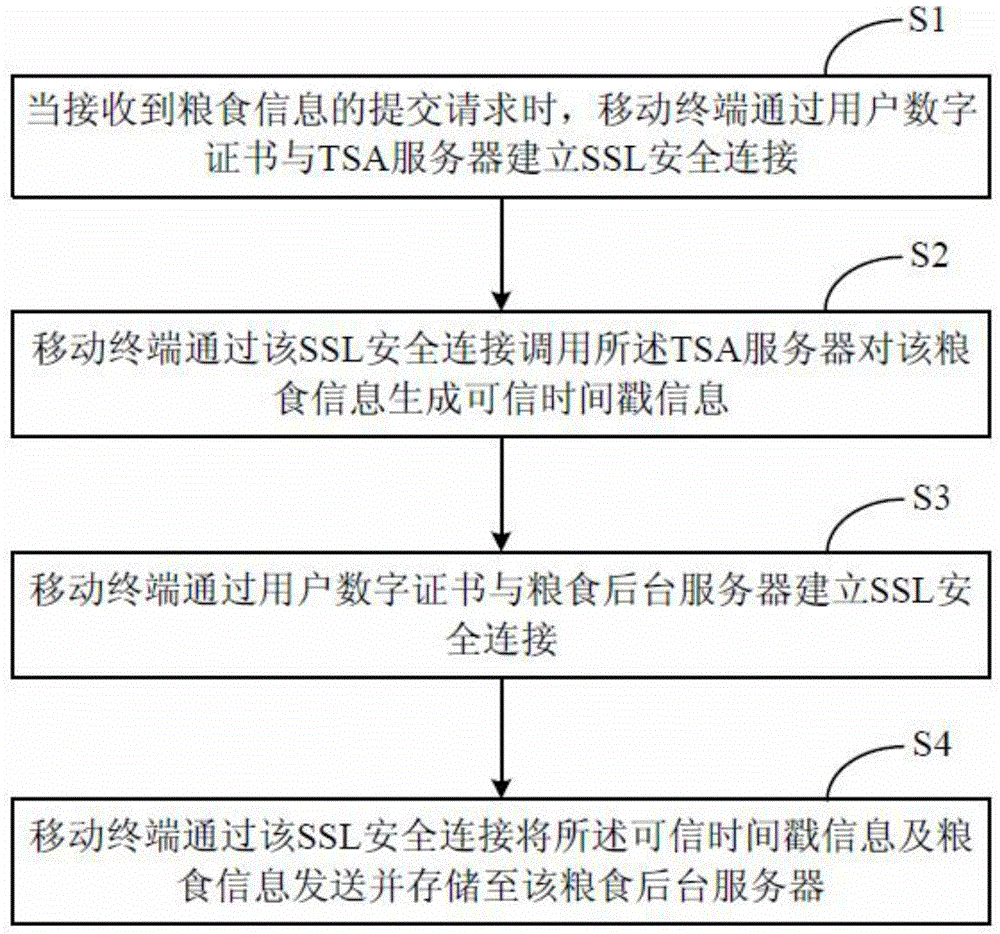
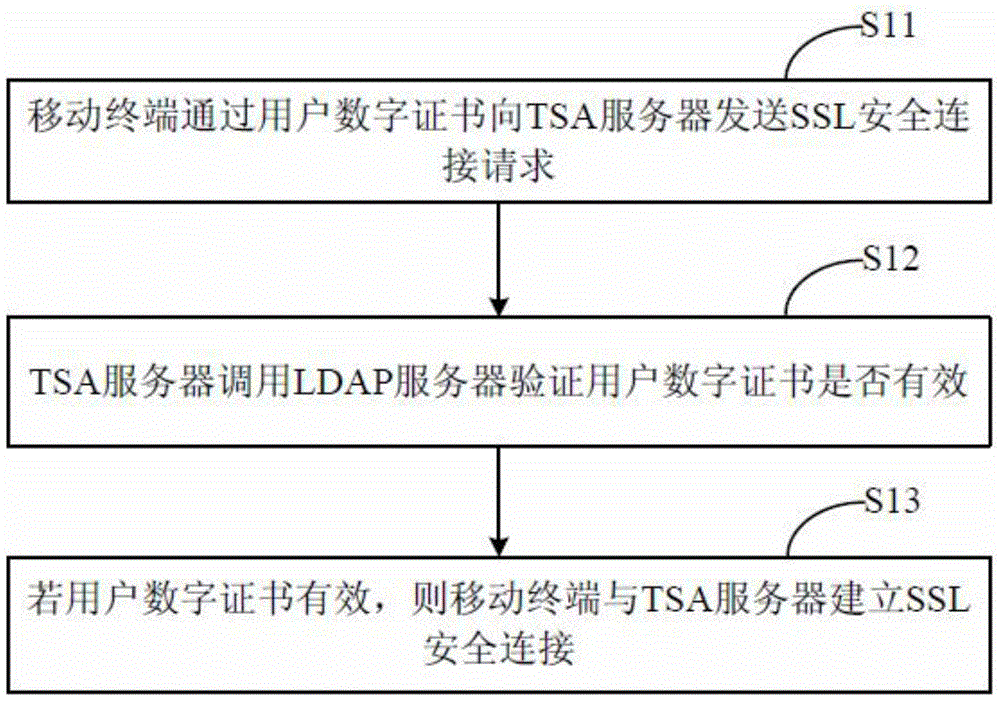
InactiveCN105763506AImprove securityNot interceptedTransmissionTelecommunicationsTrusted timestamping
The invention relates to a grain information management method, and the method comprises the steps that a mobile terminal builds safe cup-joint layer safety connection with a credible time stamp through a user digital certificate when a grain information submitting request is received; the mobile terminal carries out the call of the credible time stamp through the safe cup-joint layer safety connection, so as to generate credible time stamp information for the grain information; the mobile terminal builds safe cup-joint layer safety connection with a grain background server through the user digital certificate; and the mobile terminal enables the credible time stamp information and the grain information to be transmitted and stored in the grain background server through the safe cup-joint layer safety connection. The invention also provides a grain information management system. The method and system can provide reliable basis for the tracking of the quality safety of grains.
Owner:AEROSPACE INFORMATION
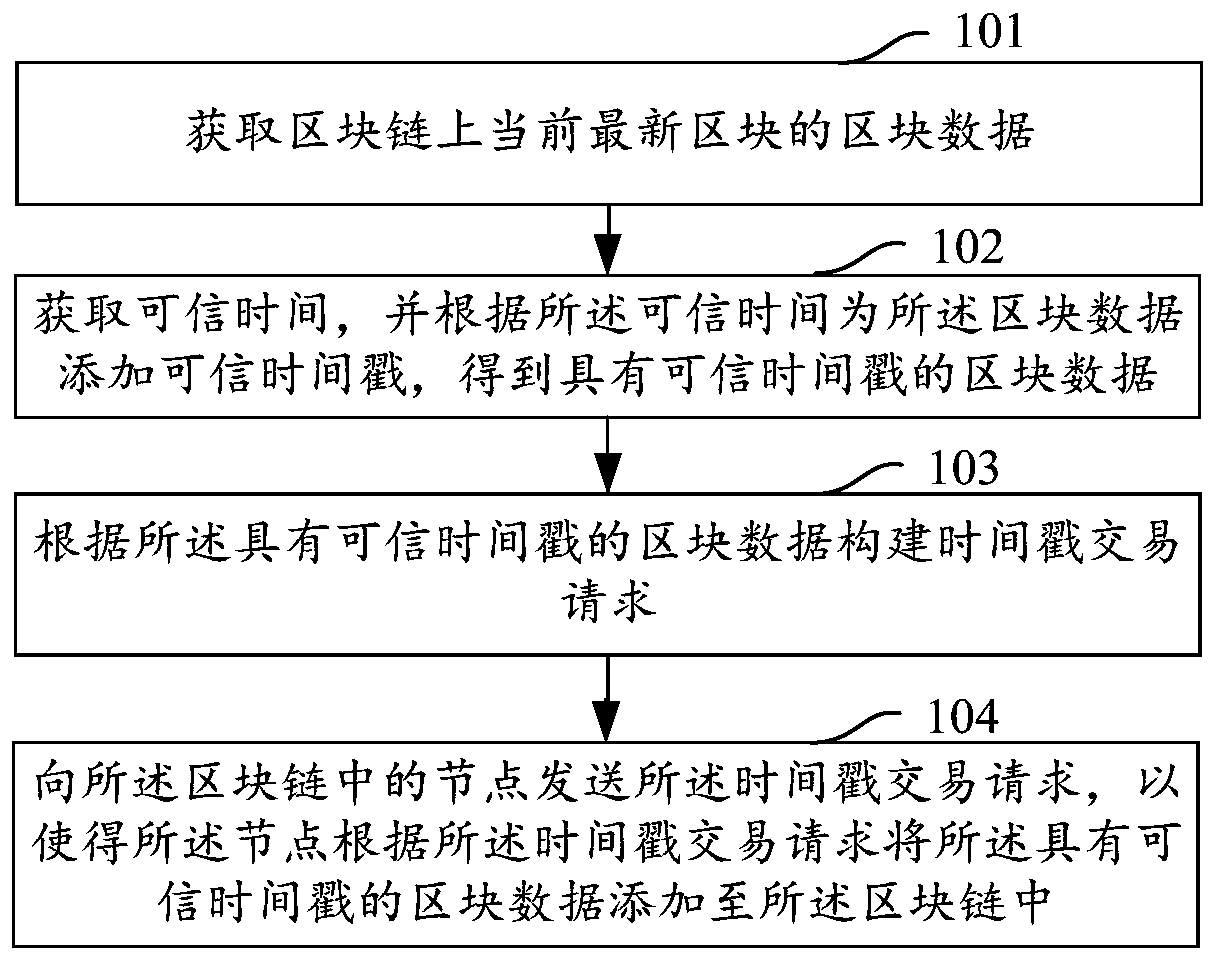
Trusted timestamp adding method and device and storage medium
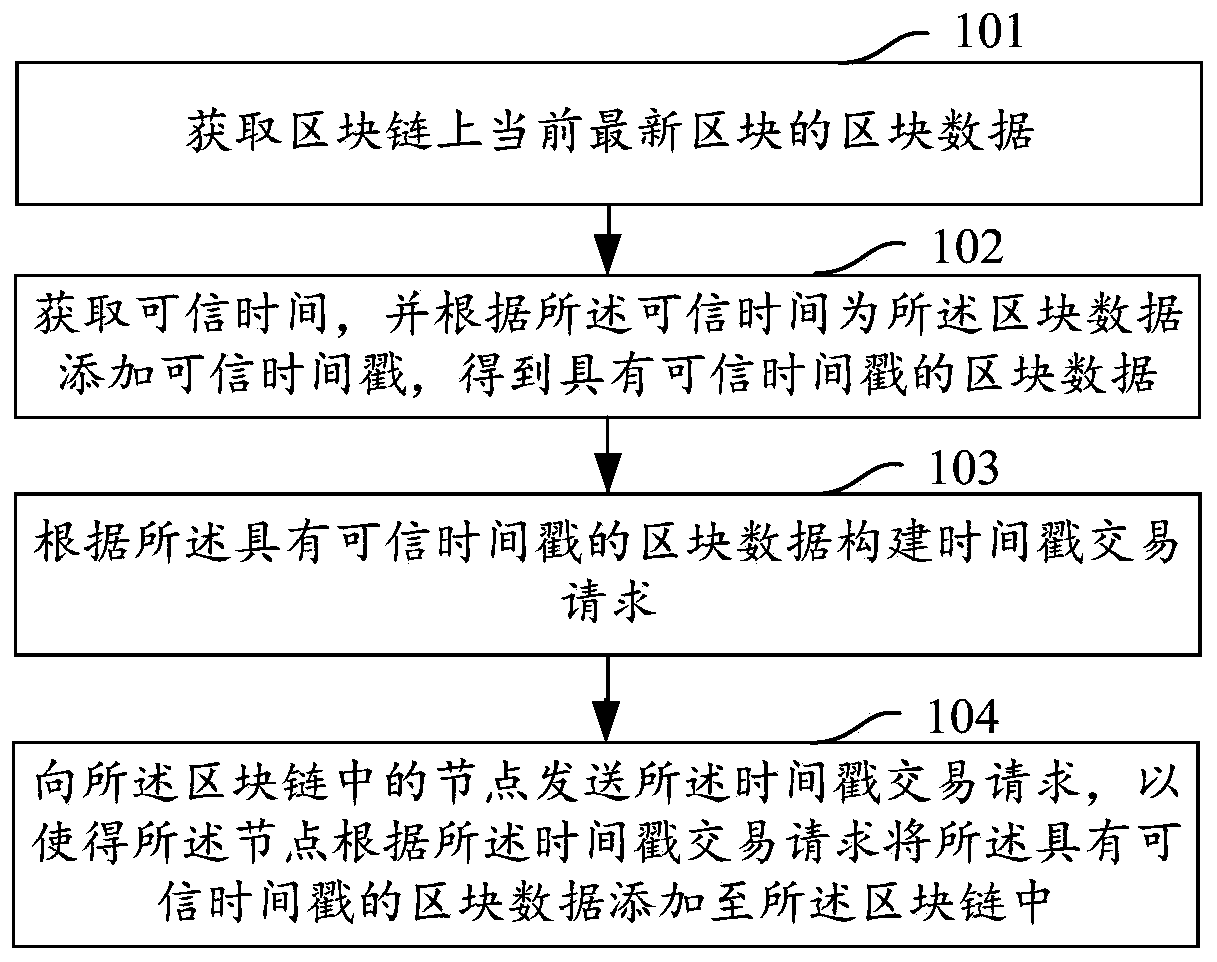
ActiveCN110505065AImprove performanceEasy to manageFinanceUser identity/authority verificationTimestampTrusted timestamping
The embodiment of the invention provides a trusted timestamp adding method and device and a storage medium, and relates to the technical field of block chains. The method comprises the steps of obtaining block data of a current latest block on a block chain; obtaining credible time, and adding a credible timestamp to the block data according to the credible time to obtain the block data with the credible timestamp; constructing a timestamp transaction request according to the block data with the credible timestamp; and sending the timestamp transaction request to a node in the block chain, soas to enable the node to add the block data with the trusted timestamp to the block chain according to the timestamp transaction request. According to the embodiment of the invention, the trusted timestamp is asynchronously added to the block data of the current latest block of the block chain, so that the performance of the block chain is improved, and the block chain is convenient to manage.
Owner:TENCENT TECH (SHENZHEN) CO LTD
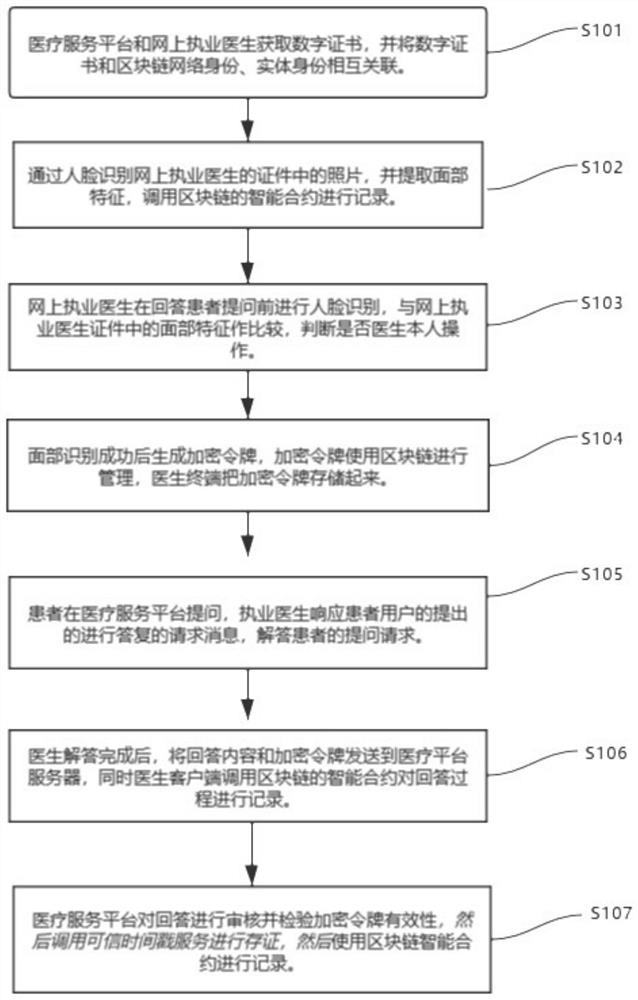
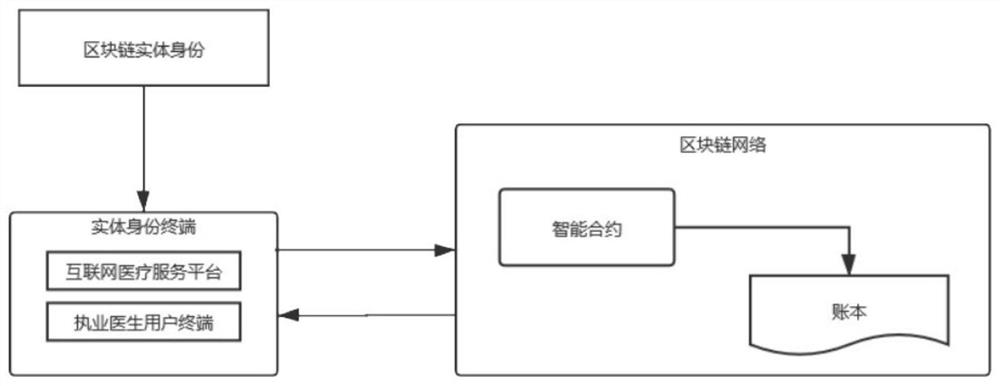
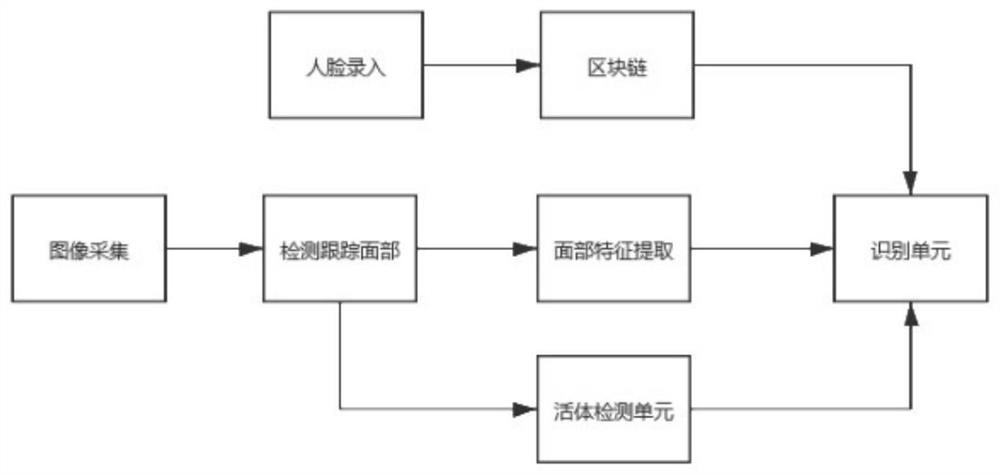
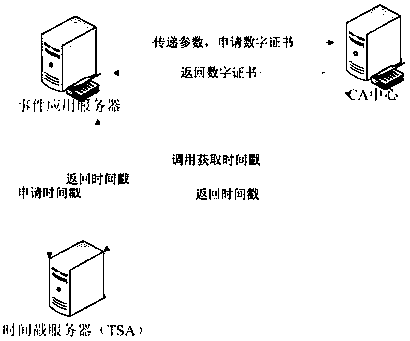
Medical question-answering method and device based on block chain and medium
PendingCN112002436AVerify authenticityImprove timelinessMedical communicationDigital data protectionTimestampInternet privacy
The invention relates to a technical scheme of a medical question-answering method and device based on a block chain and a medium. The method comprises the following steps: correlating a digital certificate with a corresponding blockchain network identity and an entity identity; calling an intelligent contract of the block chain to record facial features; comparing the face recognition result withthe facial features; generating an encryption token after the face recognition is successful, managing the encryption token through a block chain, and storing the encryption token through a doctor client; responding to, by the doctor client, a request message for answering proposed by the patient user; recording, by the intelligent contract, the answering process; and auditing the answer, checking the validity of the encryption token, calling a trusted timestamp service to obtain a trusted timestamp by the medical service platform, and further using a blockchain smart contract to record. Themethod has the beneficial effects that it is proved that the medical service generation time and content are not tampered and forged, so that the result of the medical service process has legal efficacy.
Owner:珠海健康云科技有限公司
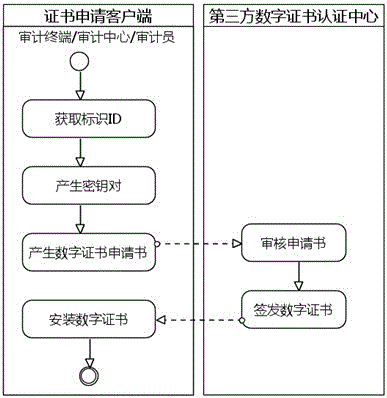
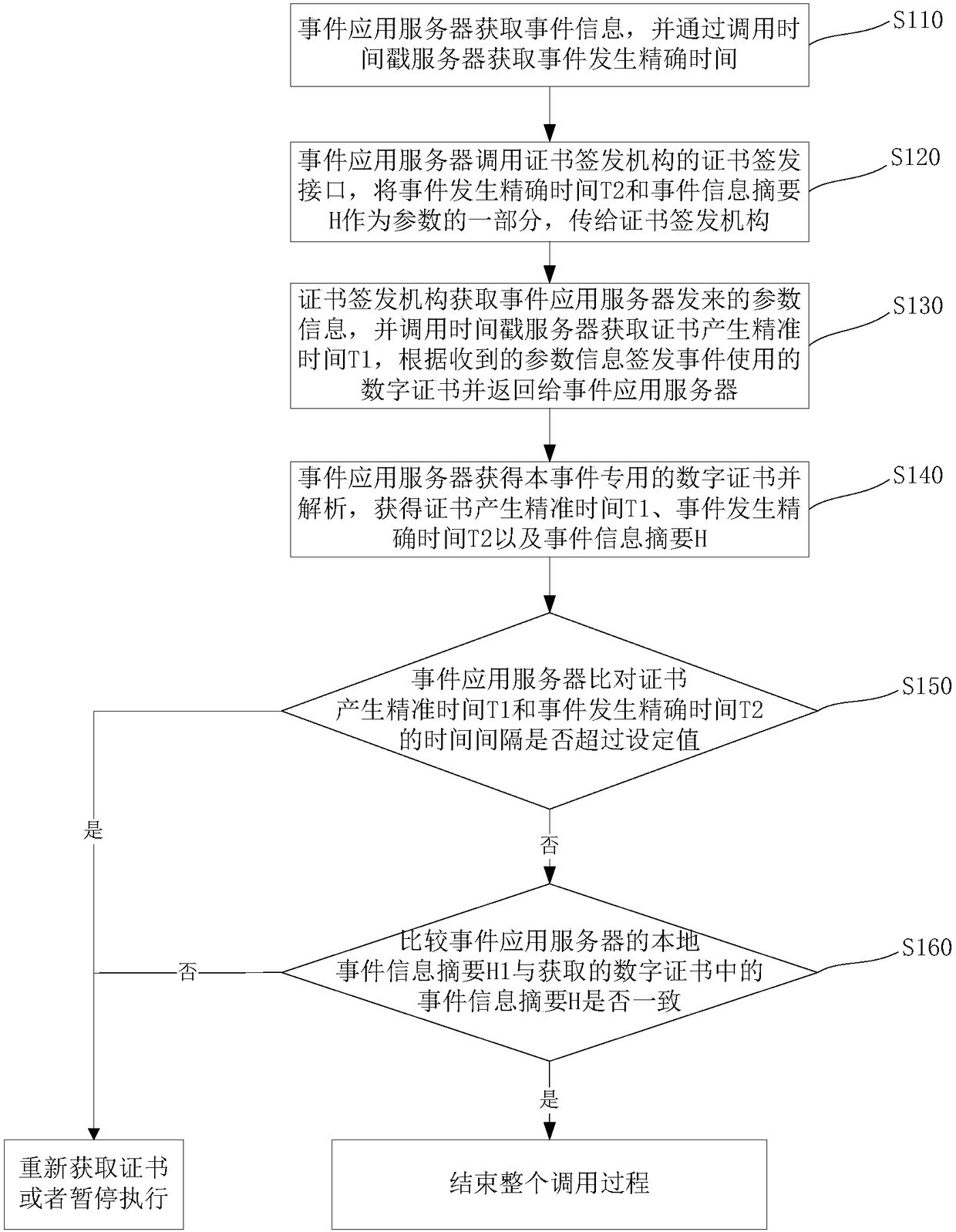
Digital certificate issuing method and system based on trusted timestamp
The invention relates to a digital certificate issuing method based on a trusted timestamp. The method includes the following steps: an event application server acquires event information, and acquires the accurate time when an event occurs by calling a timestamp server; the event application server calls a certificate issuing interface of a certificate issuing authority to transmit the accurate time when the event occurs and the summary of the event information to the certificate issuing authority as part of parameters; the certificate issuing authority calls the timestamp server to obtain the accurate time when a certificate is generated, issues a digital certificate used by the event according to the received parameter information, and returns the digital certificate to the event application server; and the event application server compares the accurate time when the certificate is generated with the accurate time when the event occurs, and compares the event information summary inthe certificate with the event information summary of the local operation to verify the digital certificate of the event. According to the scheme of the invention, time information is written into theextension of the certificate, so that the time when the certificate is generated and the time when the event occurs cannot be changed, and the validity of the certificate can be verified more effectively.
Owner:AEROSPACE INFORMATION
Implementation method and data structure of nested traceable digital twinning body
InactiveCN110730074ARealize anti-counterfeiting traceabilityUser identity/authority verificationDigital data protectionTimestampOriginal data
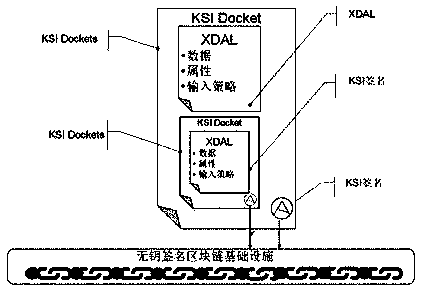
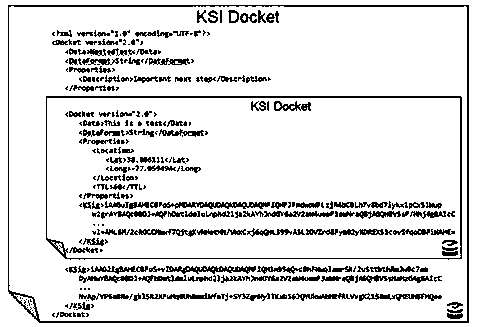
The invention discloses an implementation method and a data structure of a nested traceable digital twinning body. The implementation method includes: executing a signature step, an initial nesting step and a loop nesting step on the electronic data generated by each node; embedding the nested file of the previous node into the record file of the current node and carrying out signature verification to obtain a new nested file to obtain of a nested traceable digital twinning body, wherein the number of layers of the data structure corresponds to the number of nodes generating data, a data record file of each node comprises a data record file of a previous node and an electronic signature of the node, and the electronic signature of each node corresponds to a block structure in a block chain. The invention relates to a backtracking and source tracing technology, evolution information and evolution processing content of original data in the whole life cycle (from generation to propagationto extinction) are recorded, and after a data source is signed through a trusted timestamp and a KSI in the generation process, a nested docket data structure is used for recording the data to form aprocess of an electronic data traceable chain.
Owner:谈建
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com