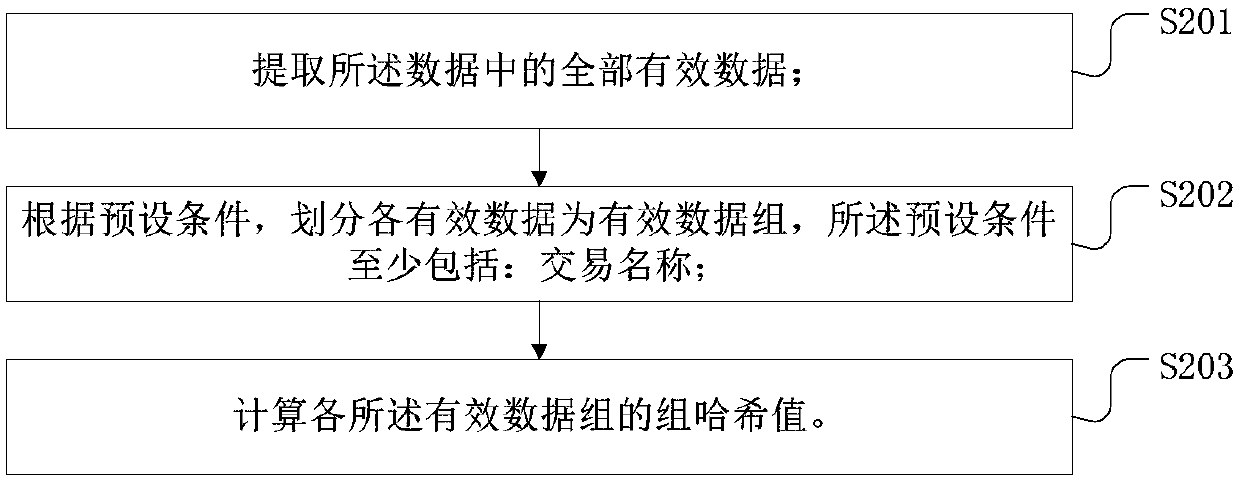
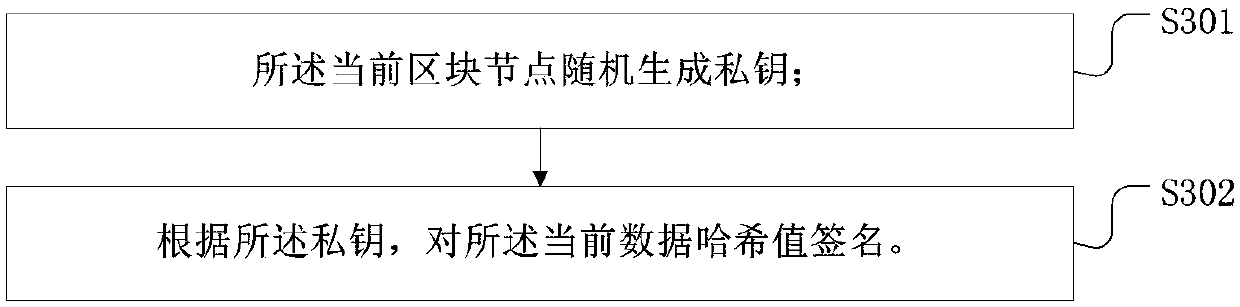
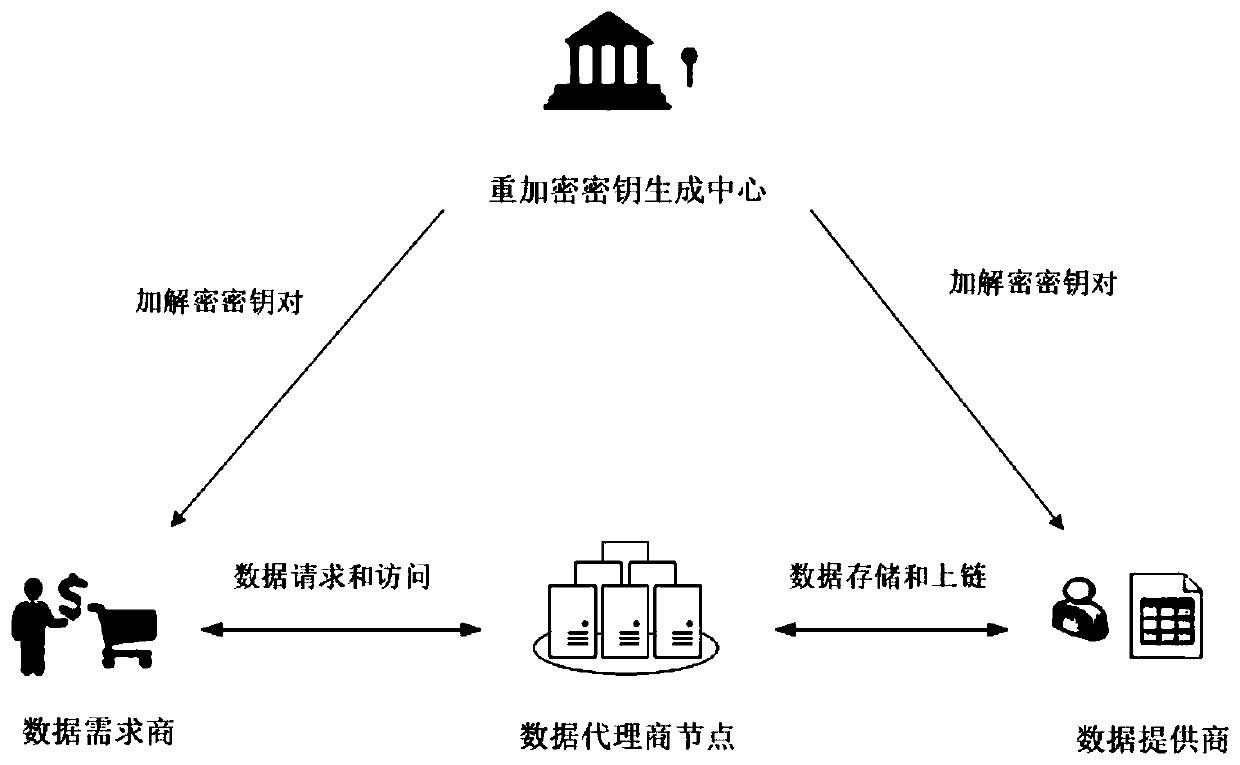
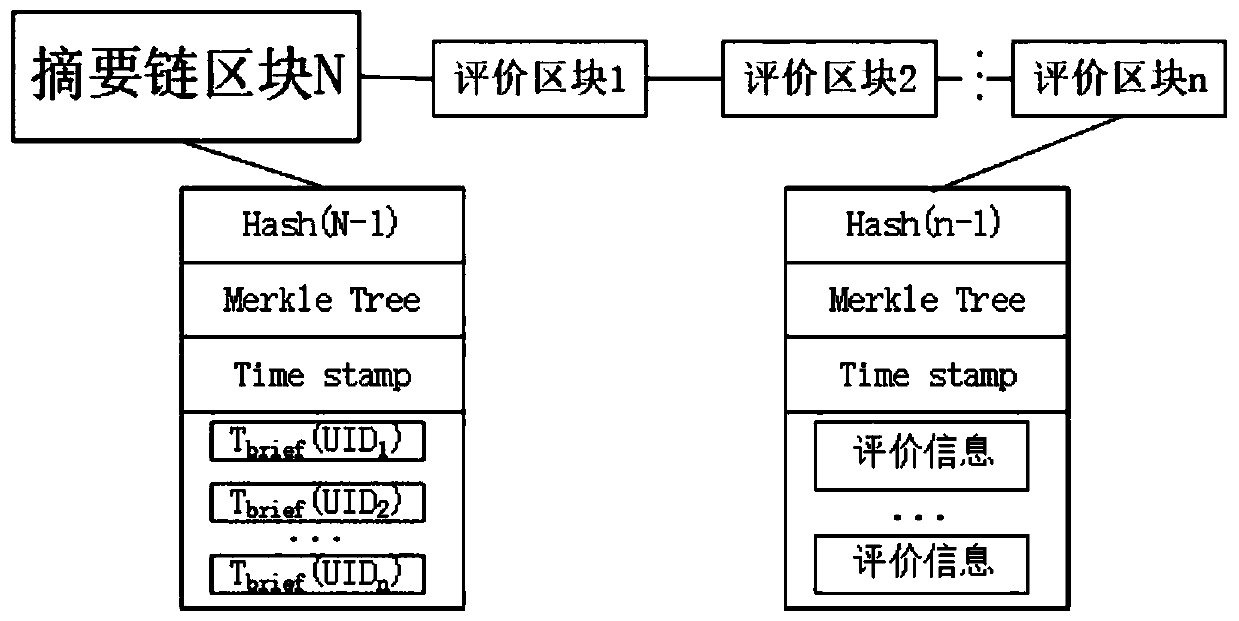
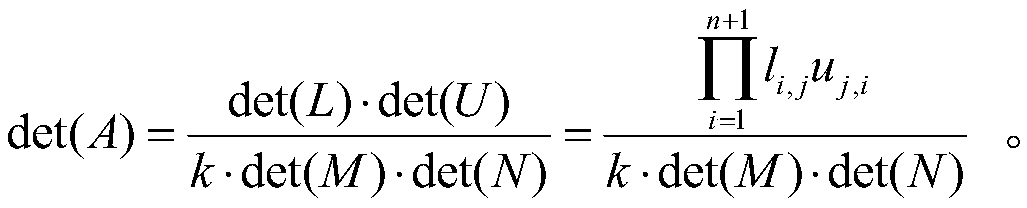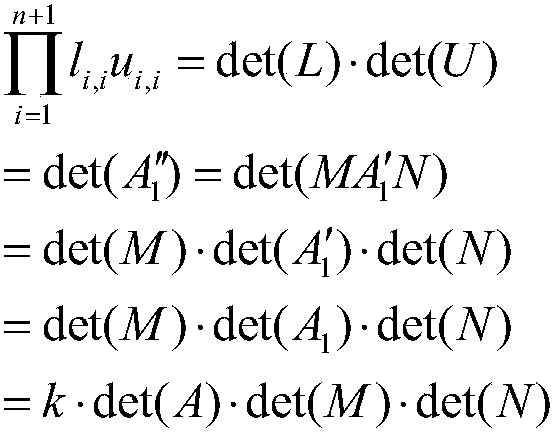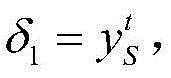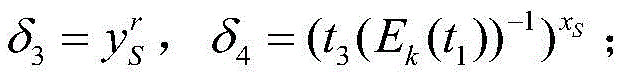Patents
Literature
47results about How to "Guaranteed verifiability" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
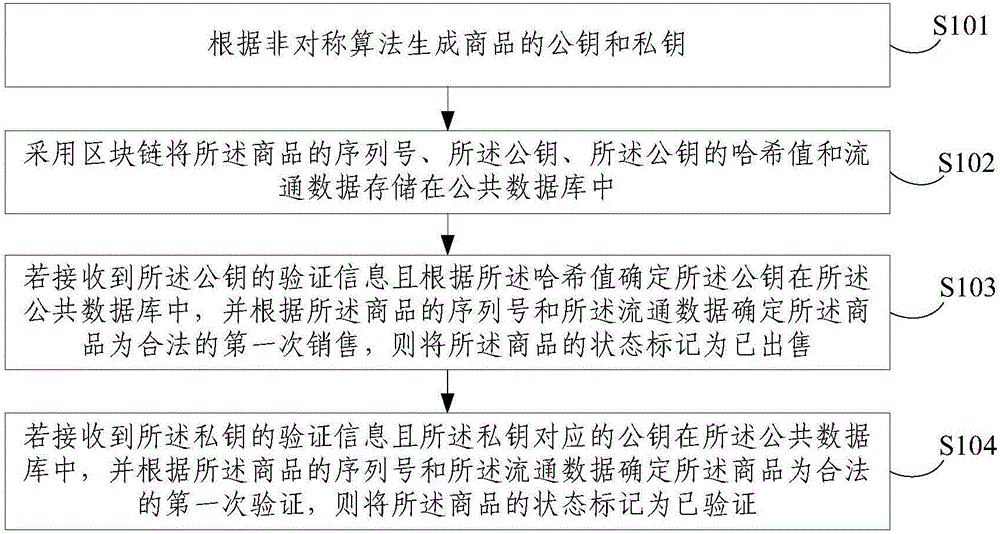
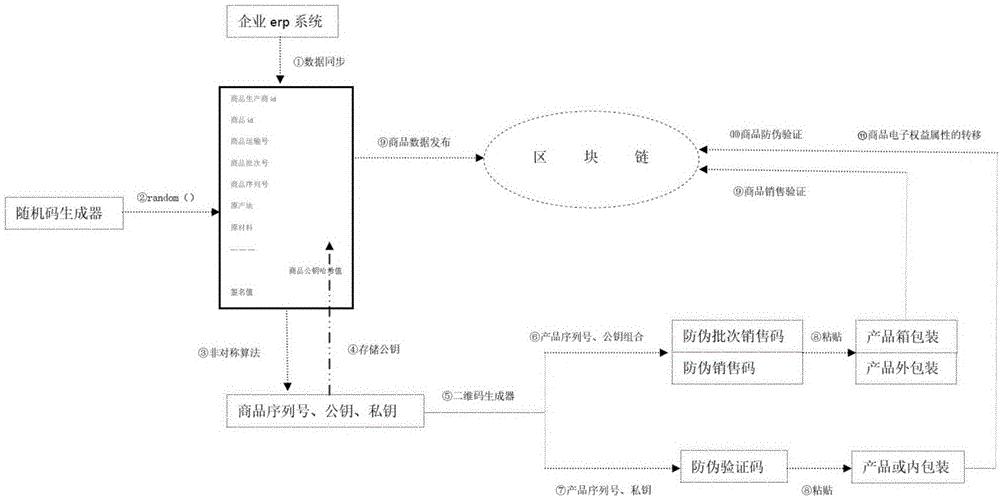
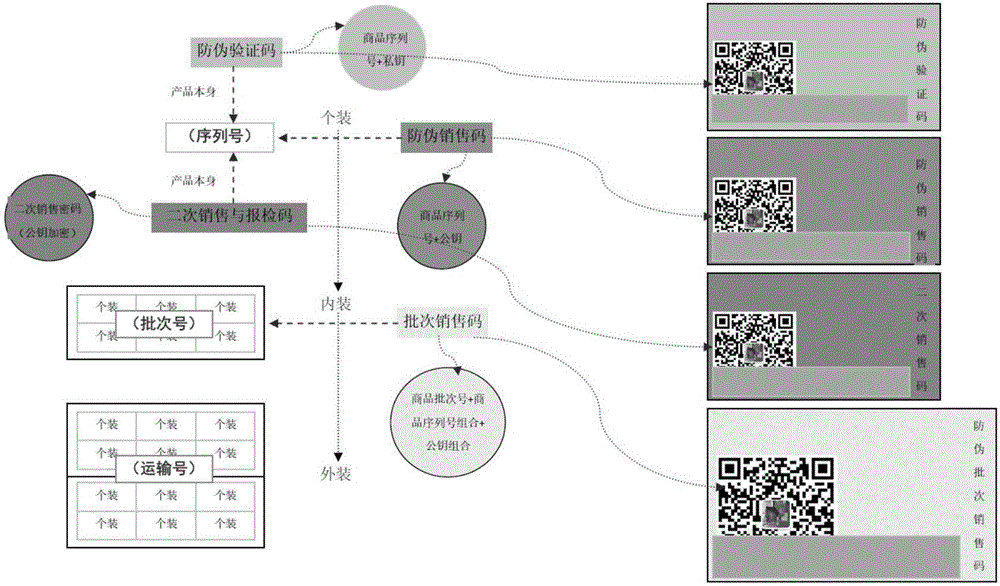
Commodity anti-counterfeiting method and device
InactiveCN106570710AGuaranteed readabilityGuaranteed verifiabilityCommerceRecord carriers used with machinesSerial codeReadability
The embodiment of the invention discloses a commodity anti-counterfeiting method and a device. The method comprises the following steps of generating the public key and the private key of a commodity; storing the hash values of the serial number, the public key and the private key of the commodity and the circulation data of the commodity in a common database by using a block chain; upon receiving the verification information of the public key of the commodity and determining the stored state of the public key in the common database, determining the first legal sales state of the commodity according to the serial number and the circulation data of the commodity, and marking the state of the commodity to be sold out; upon receiving the verification information of the secret key of the commodity and determining the stored state of the public key corresponding to the secret key in the common database, determining the first legal verification state of the commodity according to the serial number and the circulation data of the commodity, and marking the state of the commodity to be verified. Through preparing the public key and the private key of the commodity into special two-dimension codes and pasting the special two-dimension codes onto the outer package and the surface of the commodity, the readability, the verifiability and the binding performance of anti-counterfeiting marks are ensured. Meanwhile, by means of the block chain, the commodity circulation traceability and the commodity source uniqueness are ensured. At the same time, the cost is reduced.
Owner:纸飞机(北京)科技有限公司
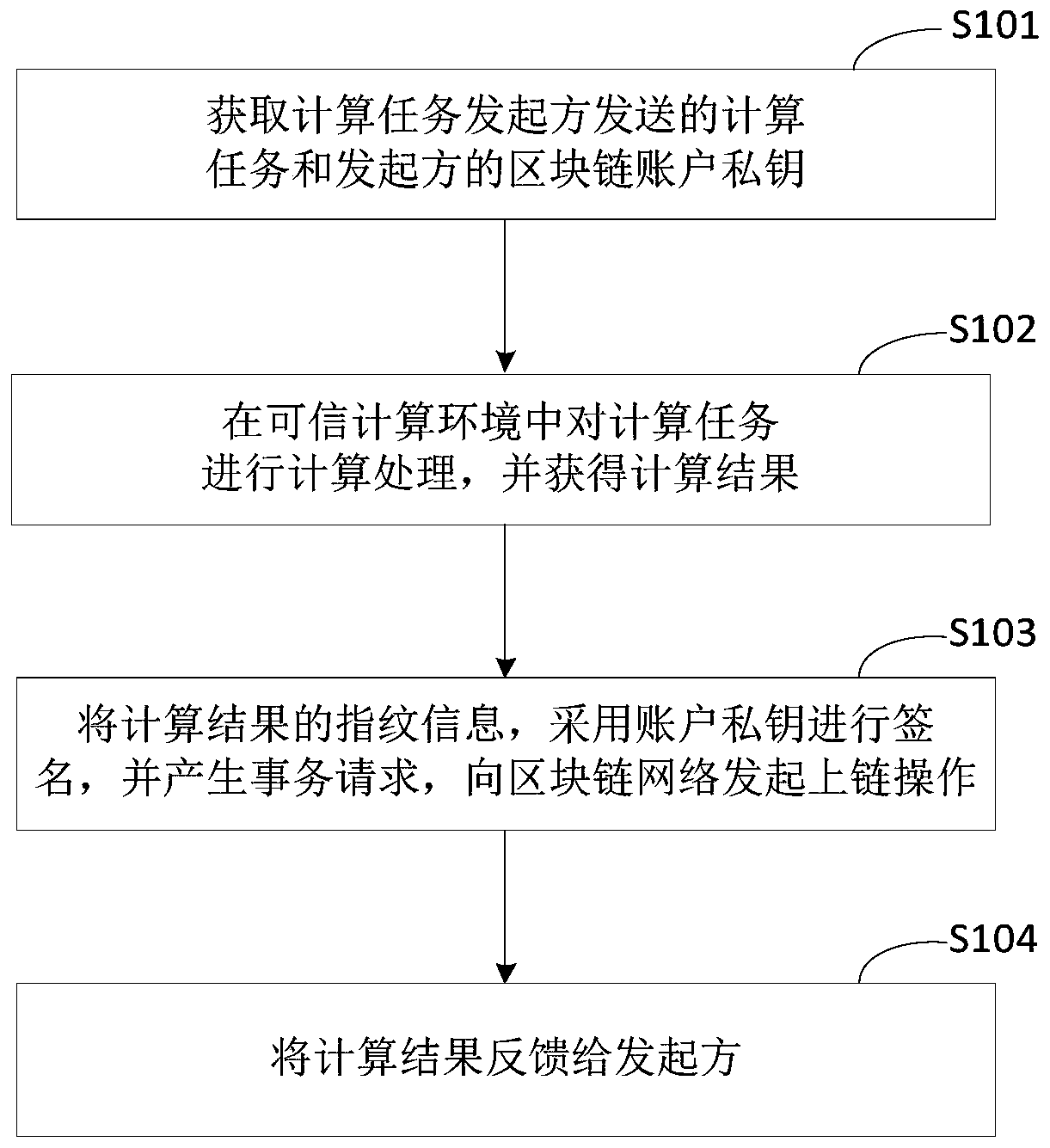
Calculation processing method and device based on block chain, equipment and medium
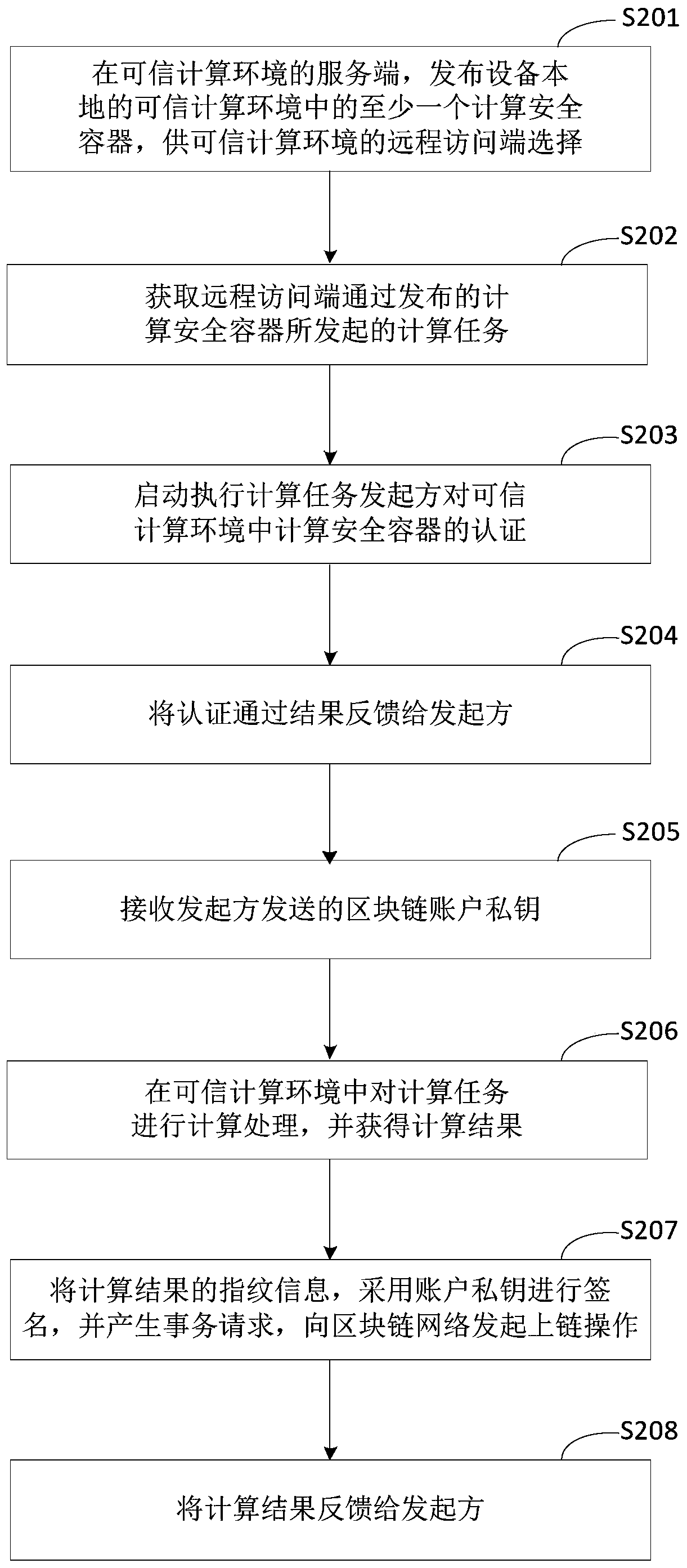
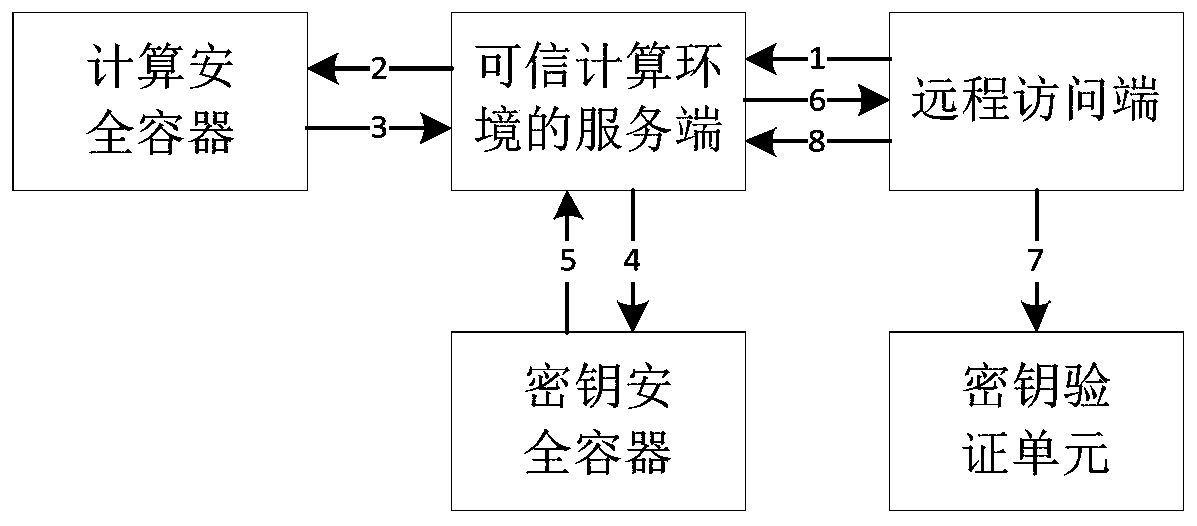
ActiveCN111143890AAvoid disclosureGuaranteed privacyDatabase distribution/replicationDigital data protectionComputer networkTrusted Computing
The invention discloses a computing processing method and device based on a block chain, equipment and a medium, and relates to the technical field of block chains. When the method is executed by trusted computing equipment configured with a trusted computing environment, the specific implementation scheme is as follows: obtaining a computing task sent by a computing task initiator and a blockchain account private key of the initiator; performing calculation processing on the calculation task in a trusted computing environment, and obtaining a calculation result; signing the fingerprint information of the calculation result by adopting the account private key, generating a transaction request, and initiating an uplink operation to a blockchain network; and feeding back the calculation result to the initiator. The problem of computational verifiability of private data is solved.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
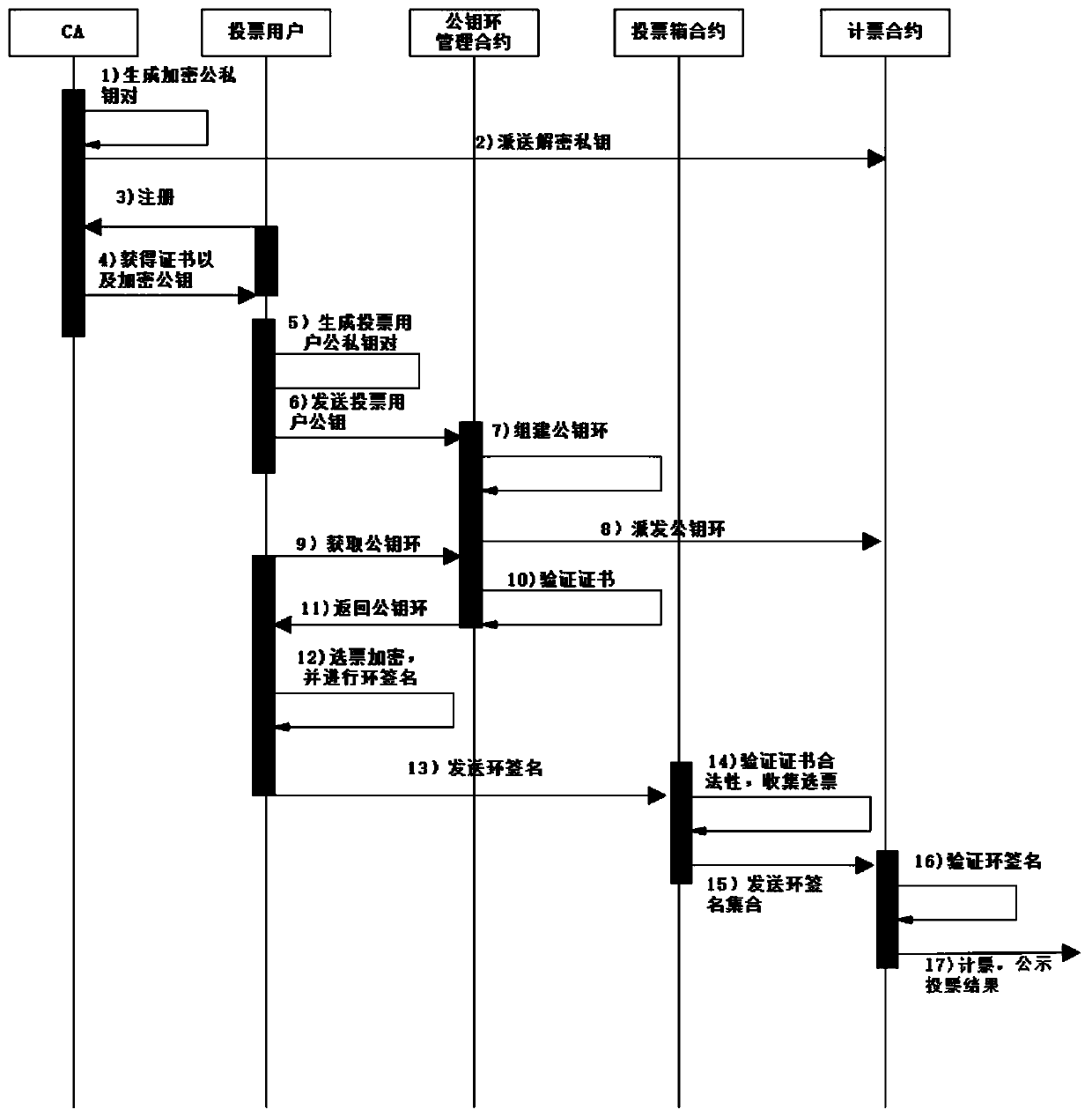
Anonymous electronic voting method based on alliance block chain
ActiveCN110572267AEnsure safetyGuaranteed reliabilityVoting apparatusUser identity/authority verificationRing signatureSmart contract
The invention discloses an anonymous electronic voting method based on an alliance block chain technology. A new anonymous voting method is designed by combining an alliance block chain technology andan existing ring signature algorithm. Based on the alliance block chain, the system has an admission mechanism, and only voters who are authenticated by the CA mechanism and acquire certificates havevoting qualification, so that the legality of the voters is ensured; the ring signature algorithm is adopted to ensure the anonymity of the votes, the votes subjected to ring signature are collectedthrough an intelligent contract and then sent to the vote counting contract, and the relevance of voter information and the votes is isolated. According to the method provided by the invention, the anonymity of voting is ensured, voters and voting information are thoroughly isolated through the vote collection contract, the whole voting process and the voting result are recorded in the block chain, the voting information is public, transparent and verifiable, and the anonymous voting function of the alliance block chain is realized.
Owner:BEIJING UNIV OF TECH
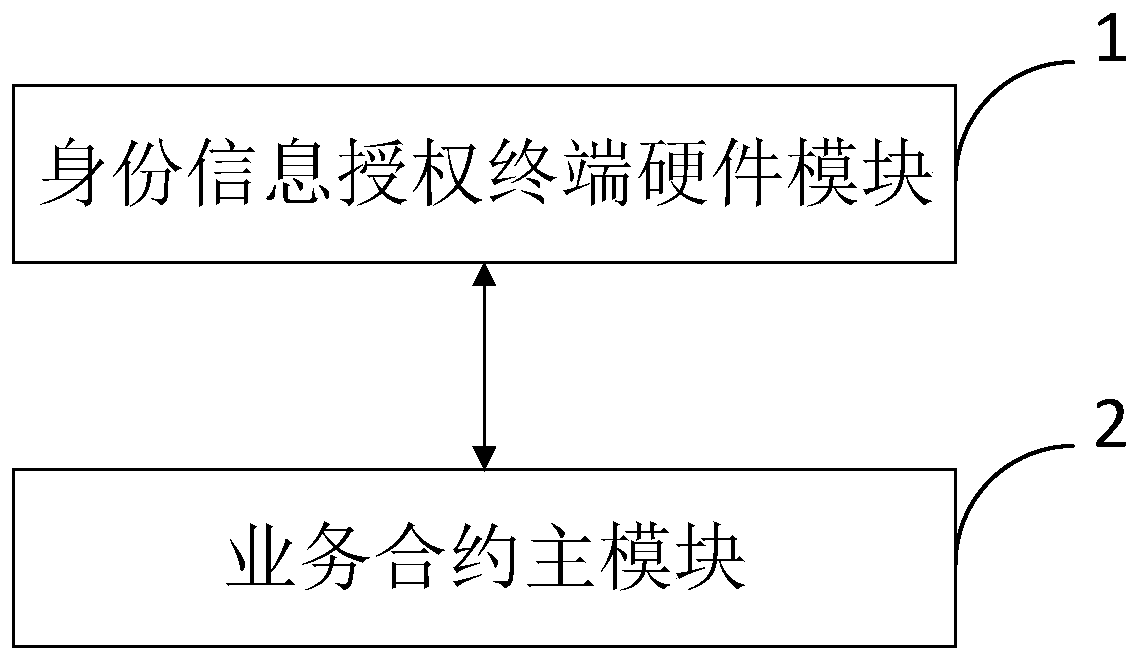
Identity information safety authorization system and method based on block chain
ActiveCN111046352AProtection securityEnsure consistencyDigital data authenticationInternet privacyEngineering
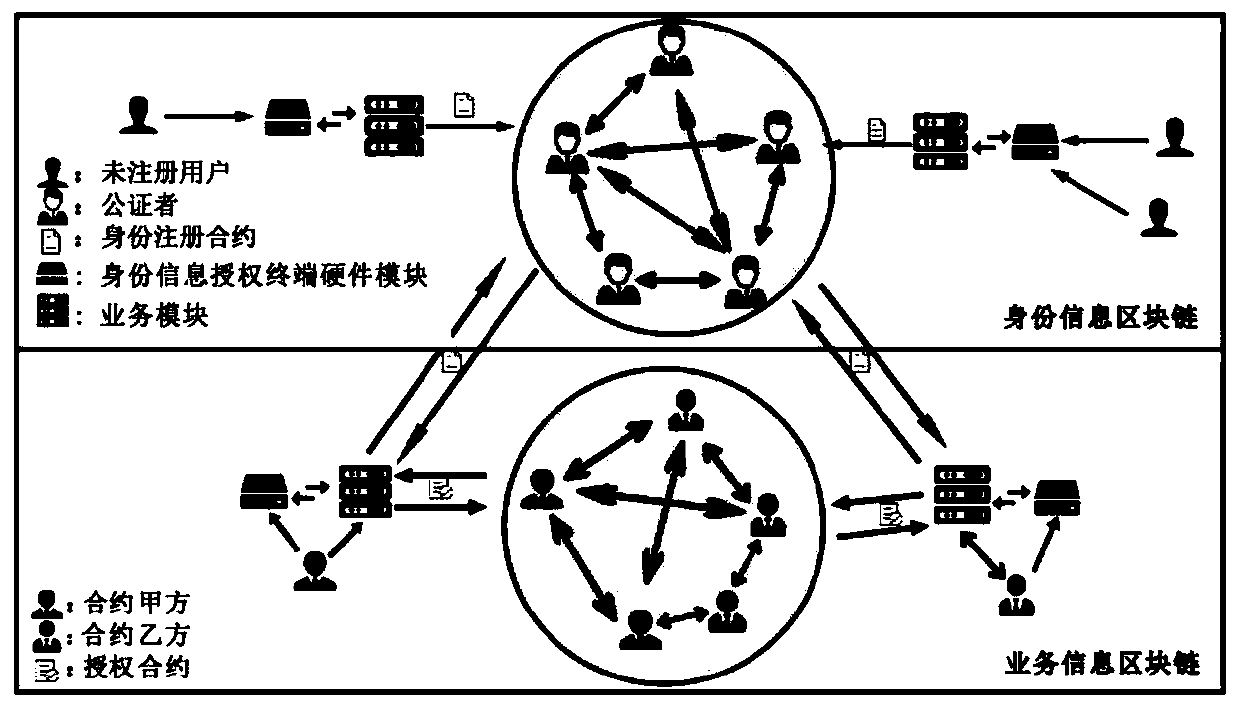
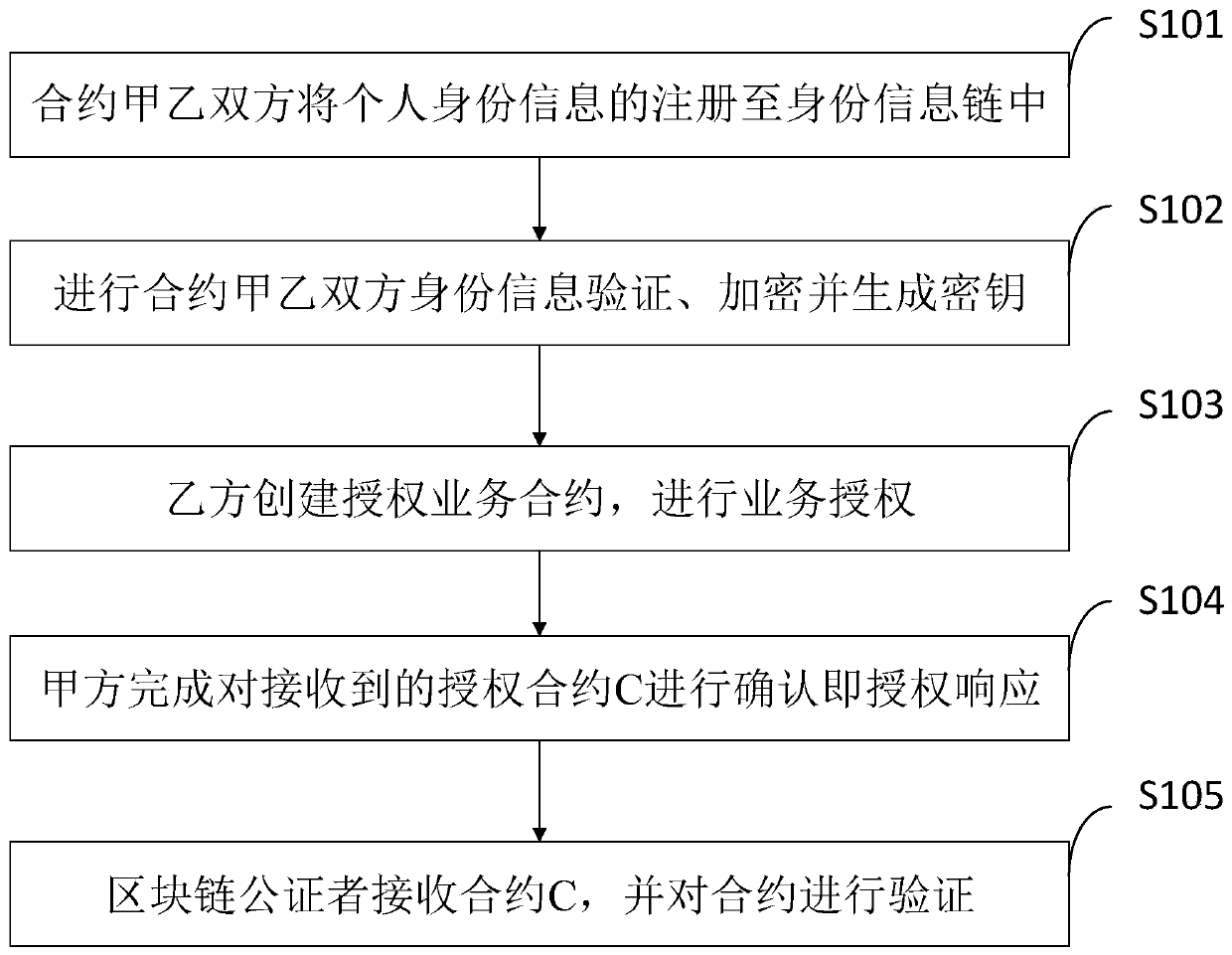
The invention belongs to the technical field of information safety technologies, and discloses an identity information safety authorization system and method based on a blockchain. The system comprises an identity information authorization terminal hardware module which is used for recognizing an identity IC card of a user, and is connected with an identity information chain through a service contract main module to carry out the verification of the identity information of the user; the encryption module is also used for encrypting identity information, generating a secret key for each user passing identity information verification and completing encryption and decryption operations on authorized contracts created by both parties of the contracts; the service contract main module is used for a contract B to carry out identity information authorization contract, identity information registration contract creation and contract sending, receiving and verification; Meanwhile, the contractparty A decides whether to accept the received authorization information. The identity information authorization record evidence is formed through the block chain technology, and it is guaranteed thatidentity information authorization cannot be falsely used, tampered and repudiated, and traceable verification is achieved.
Owner:浙江万里共链科技发展有限公司
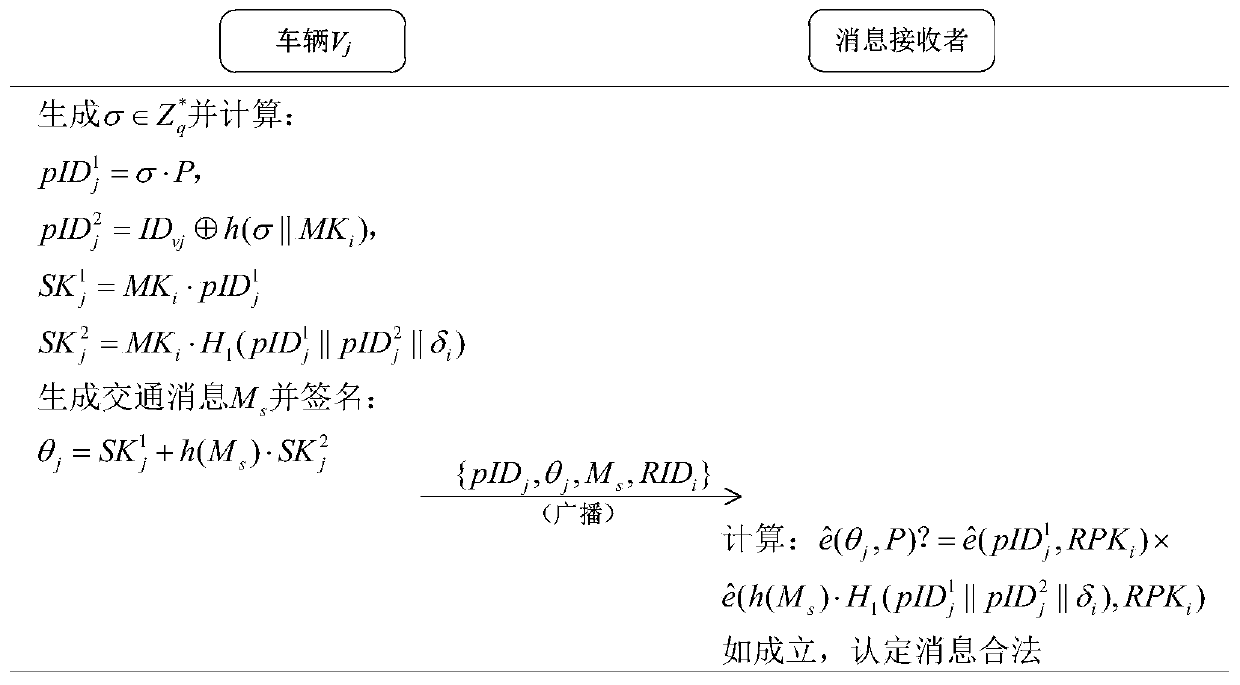
A vehicle authentication and message verification method in a vehicle-mounted network environment
ActiveCN109922475AGuaranteed privacyPrivacy protectionPublic key for secure communicationParticular environment based servicesDigital signatureValidation methods
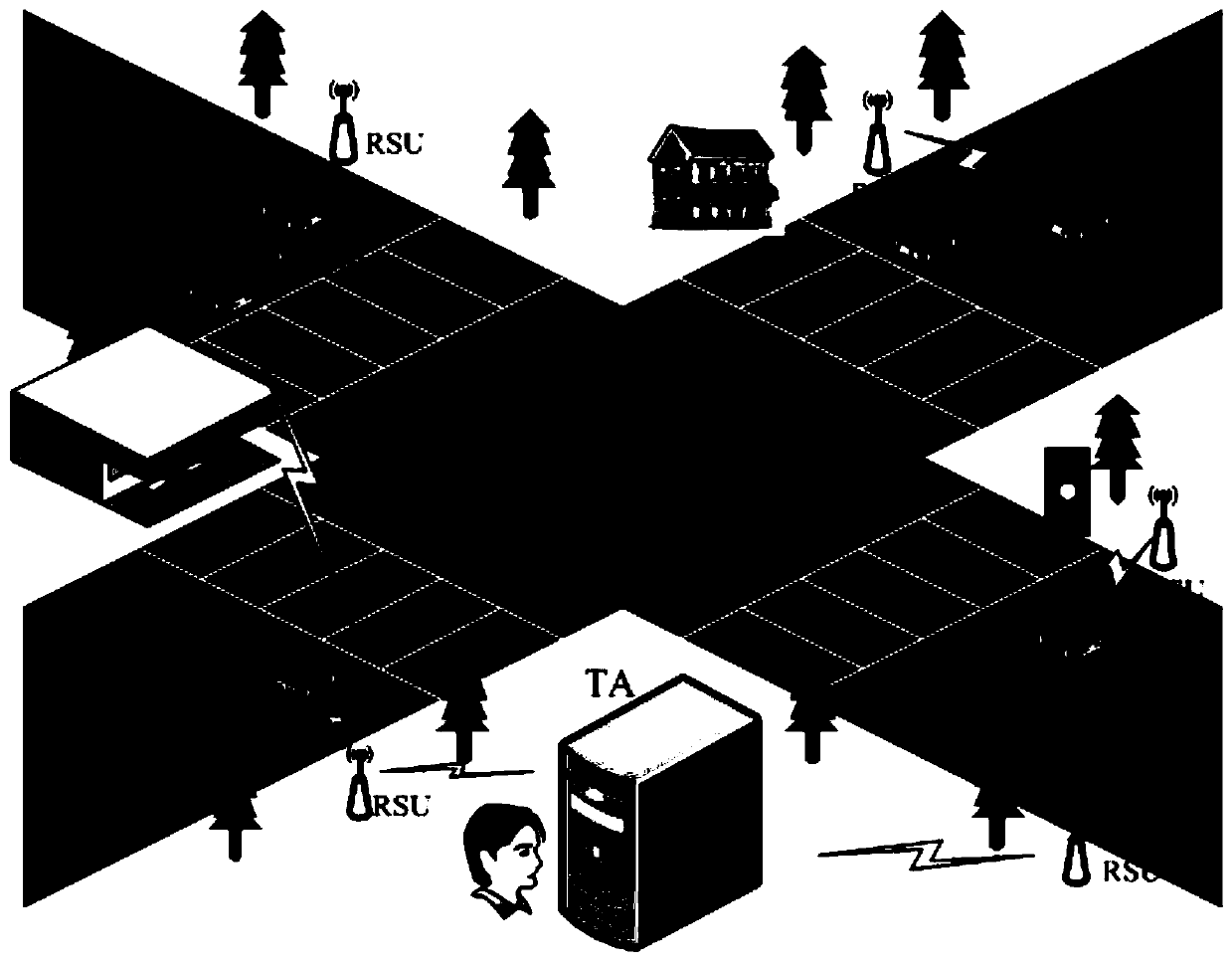
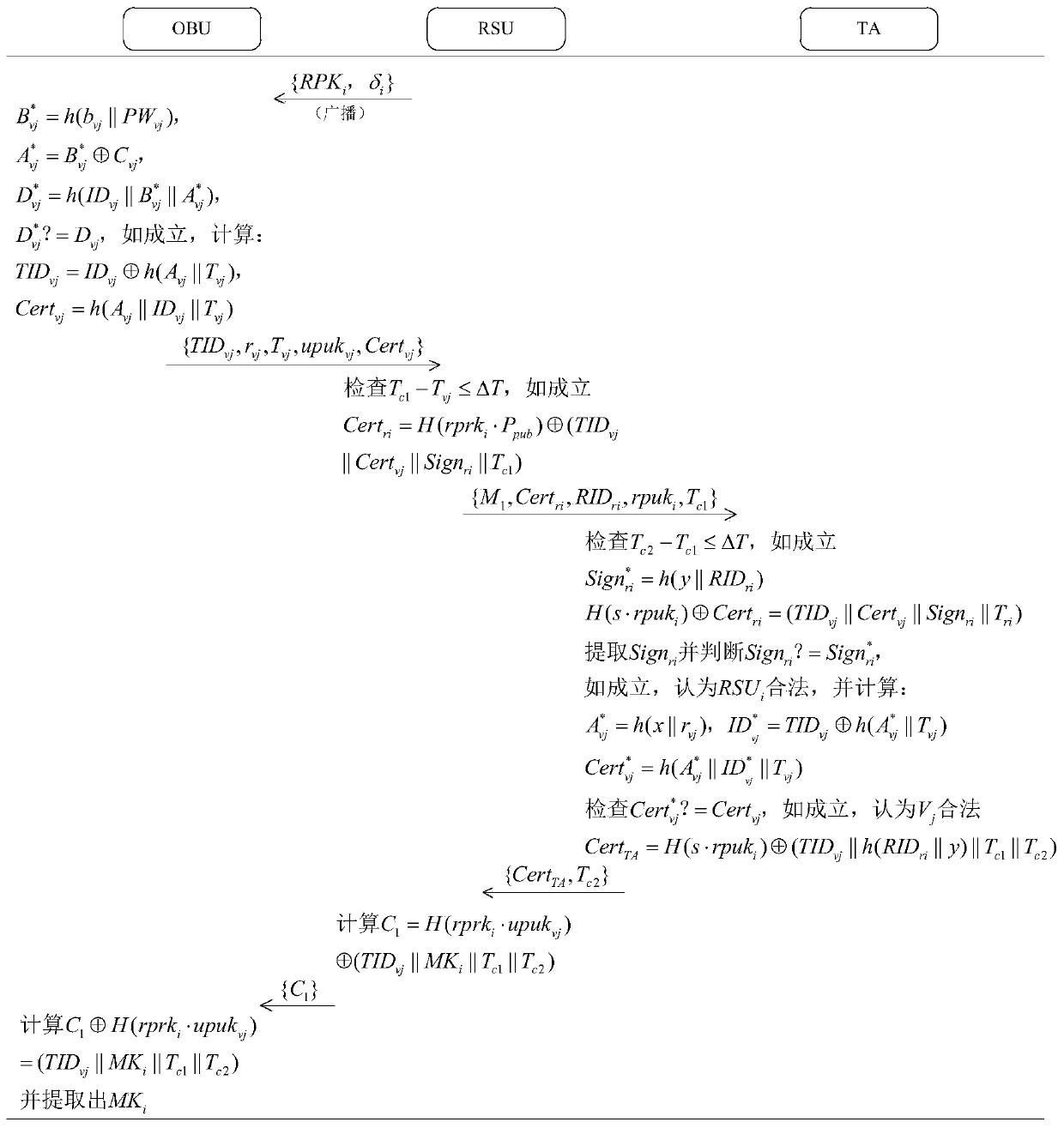
The invention provides a vehicle authentication and message verification method in a vehicle-mounted network environment. The vehicle authentication and message verification method comprises the stepsthat a trust mechanism initializes a system; the vehicle-mounted unit is registered, and the roadside unit is registered; a temporary key of the roadside unit is released; a vehicle authentication stage; the trust mechanism verifies the legality of the roadside unit through the digital signature, extracts the message and verifies the legality of the automobile, the trust mechanism sends the identity identifier of the automobile to the roadside unit, the roadside unit sends the private key and the temporary main key to the automobile, and the automobile extracts the temporary main key; the automobile calculates a temporary identifier and a temporary private key, generates a traffic message and signs and broadcasts the traffic message; and when other automobiles receive the automobile broadcast message, verifying the effectiveness of the broadcast message through bilinear mapping. According to the method, the vehicle access safety in the Internet of Vehicles environment can be ensured,the safety of traffic information sent by legal vehicles is also ensured, and the method has a relatively high application value in an application environment in the mobile vehicular network environment.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
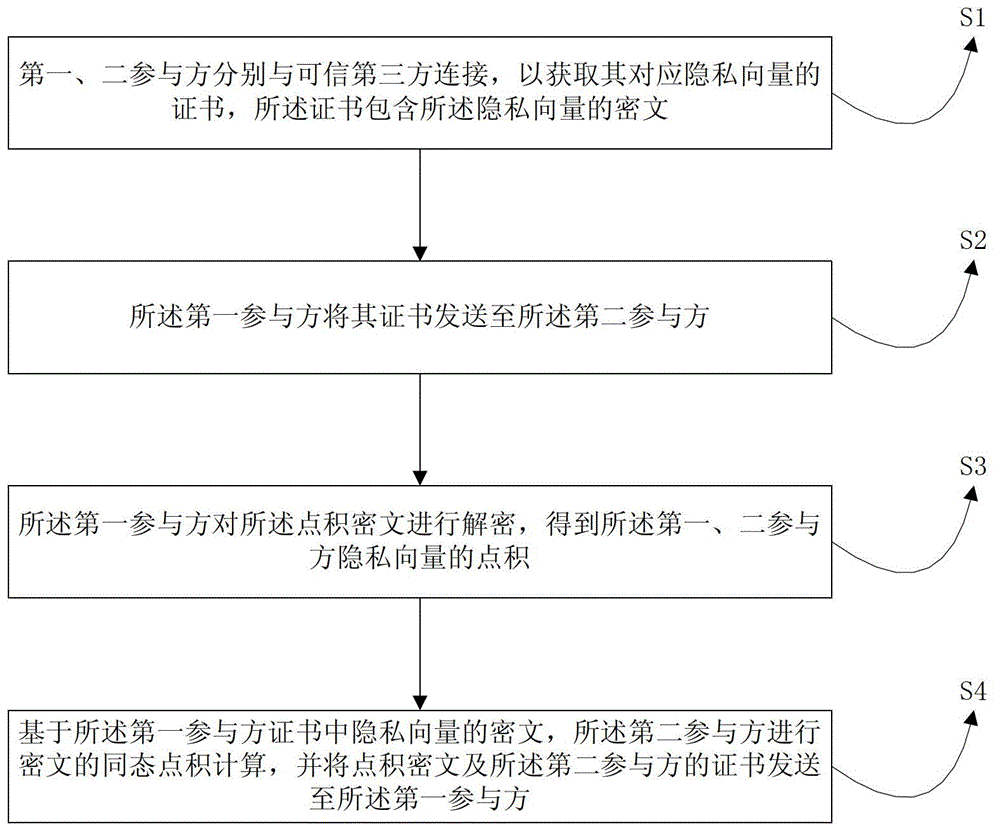
Non-center dot product computing method achieving privacy protection
InactiveCN104156671AGuaranteed legalityReduce computational complexityUser identity/authority verificationDigital data protectionThird partyIndividual data
The invention provides a non-center dot product computing method achieving privacy protection. The non-center dot product computing method achieving privacy protection includes the following steps that 1, a first participant and a second participant are connected with a trusted third party, so that corresponding privacy vector certificates of the first participant and the second participant are obtained, wherein the certificates comprise privacy vector ciphertext; 2, the first participant sends the certificate of the first participant to the second participant; 3, the second participant carries out ciphertext homomorphic dot product computation on the basis of the privacy vector ciphertext in the certificate of the first participant, and sends the dot product ciphertext and the certificate of the second participant to the first participant; 4, the first participant decodes the dot product ciphertext to obtain the privacy vector dot product of the first participant and the privacy vector dot product of the second participant. Safety multi-party dot product computation is achieved without participation of a center server, input and output verifiability is ensured for users, and the requirements of the users for personal data privacy protection and the reliability of dot product computing results in a not credible environment are met.
Owner:TSINGHUA UNIV
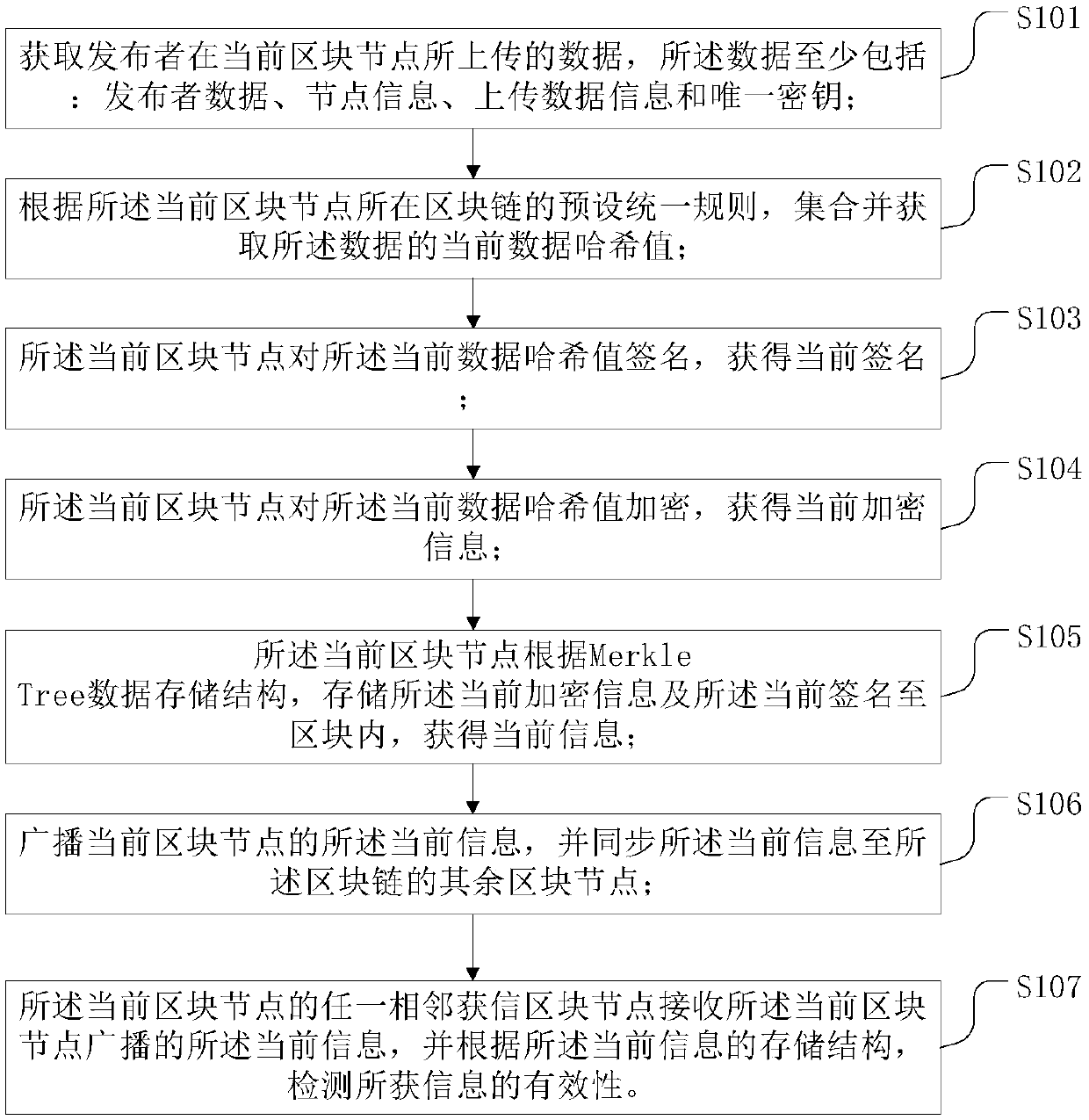
An information validity detection method and device based on a block chain
ActiveCN109558742ATest effectivenessGuaranteed reliabilityDigital data protectionBroadcastingMerkle tree
The invention provides an information validity detection method and device based on a block chain, and the method comprises the steps of obtaining the data uploaded by a publisher at a current block node, carrying out the division of a preset unified rule of the block chain, and carrying out the collection and obtaining the Hash value of the current data; using the current block node to sign the current data hash value to obtain a current signature; using the current block node to encrypt the current data hash value to obtain current encrypted information; using the current block node to storethe current encrypted information and the current signature into the block according to the Merkle Tree data storage structure, and obtain the current information; broadcasting the current information, and synchronizing the current information to other block nodes; and using any adjacent trusted block node of the current block node to receive the current information broadcast by the current blocknode, and detecting the validity of the information according to the storage structure of the current information. According to the detection method and device provided by the invention, the problemsthat the existing data is easily tampered and the effectiveness cannot be ensured, can be effectively solved.
Owner:北京庚金科技有限公司
Decentralized data transaction method based on block chain
ActiveCN111402055ASolve untrustworthySolve the central single point of failure problemFinanceDigital data protectionTransaction serviceData provider
The invention discloses a decentralized data transaction method based on blockchain. The method is applied to a big data transaction environment composed of a secret key generation center, a blockchain and an intelligent contract; data summary information collection of a data transaction market is achieved through the blockchain, evaluation information of data use conditions is recorded, and transaction records in data transaction are recorded; data requirements can be issued through the intelligent contract, data required by a data demander is matched and screened, and distribution of data rewards is automatically completed. The problem that a data transaction center is not credible can be solved, ownership and informed rights of a data provider to personal data in transaction are guaranteed, intelligence and high efficiency of the data transaction process are improved, and therefore safe and reliable big data transaction service can be provided for two transaction parties.
Owner:HEFEI UNIV OF TECH
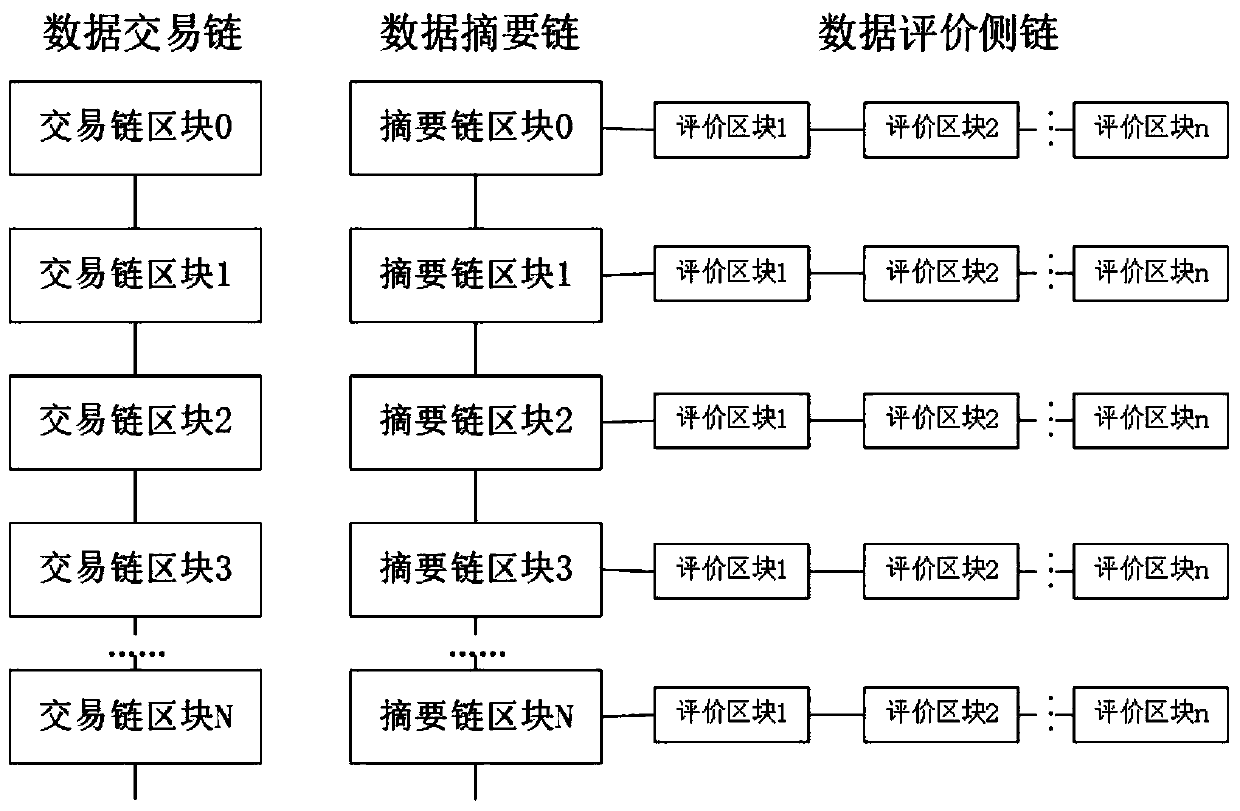
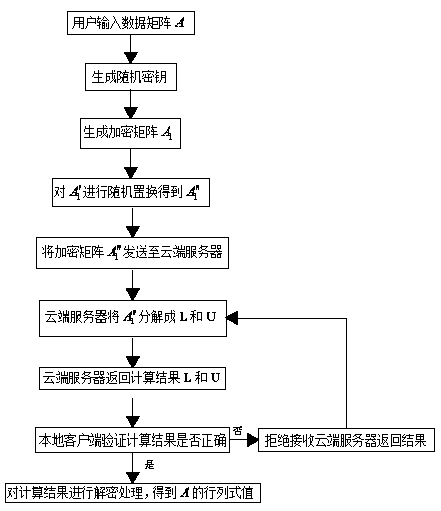
Cloud computing matrix determinant secure outsourcing computation encryption method
PendingCN108768622AEnsure safetyGuaranteed verifiabilityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesClient-sideCloud computing
The invention discloses a cloud computing matrix determinant secure outsourcing computation encryption method. A brand-new matrix determinant outsourcing computation encryption method is put forward by using matrix determinant identical transformation and the relevant properties of the partition matrix so that the security of each data element in the matrix and the verifiability of the operation result can be guaranteed. The system according to the method is composed of a key module, an encryption module, a computing module, a verification module and a decryption module. The key module, the encryption module, the verification module and the decryption module are arranged on the user local client side. The computing module is arranged on the cloud side server. Complex computation is performed on the cloud side server so that the time complexity of the algorithm can be reduced and the efficiency of the algorithm can be greatly enhanced.
Owner:XINXIANG POWER SUPPLY COMPANY STATE GRID HENAN ELECTRIC POWER +1
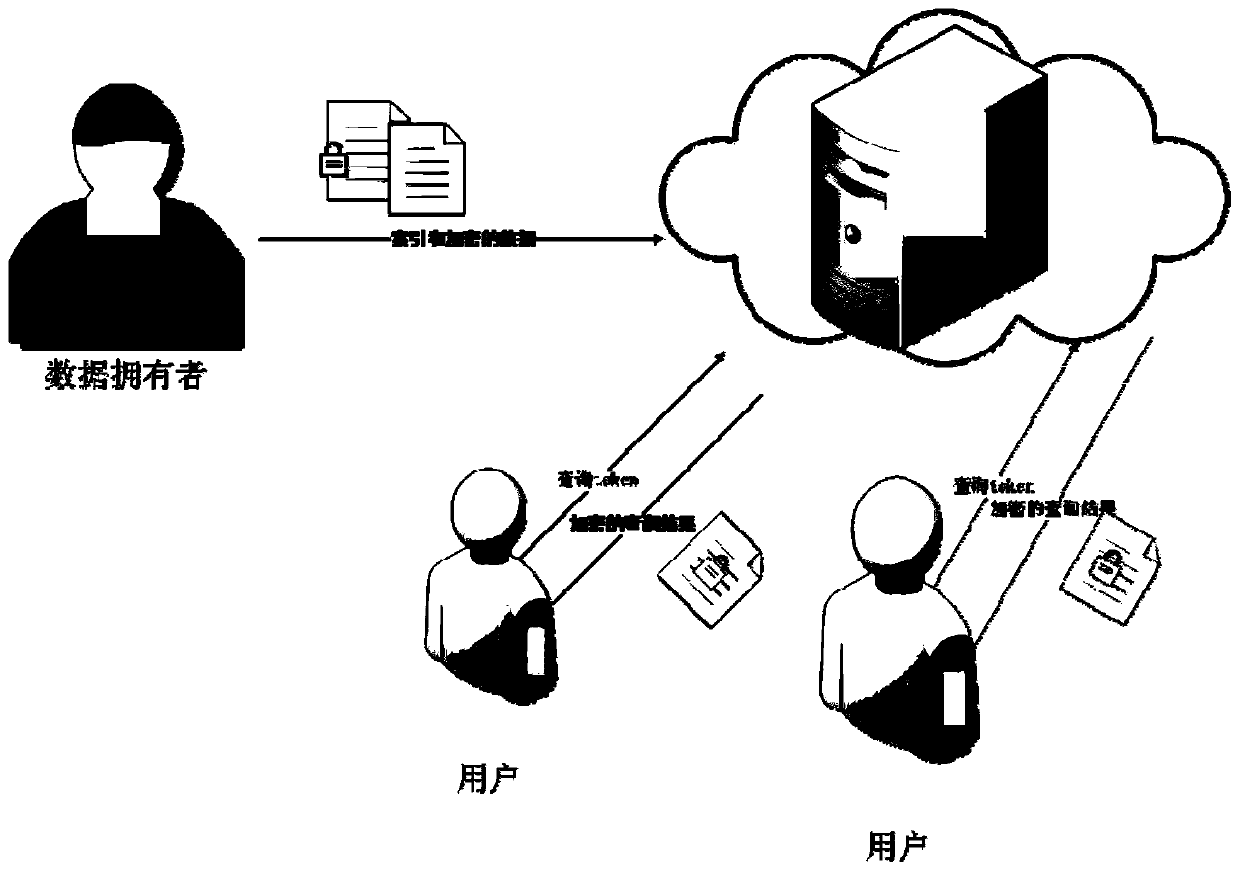
Privacy protection method based on verifiable symmetric searchable encryption
ActiveCN110602099APrevent replay attacksGuaranteed freshnessKey distribution for secure communicationUser identity/authority verificationUser needsPrivacy protection
The invention discloses a privacy protection method based on verifiable symmetric searchable encryption. The privacy protection method is mainly composed of a data owner, a plurality of authorized users and a cloud server. The data owner encrypts the data by using symmetric encryption and stores the data in the cloud; an authorized user authorized by the data owner can initiate a query operation to the cloud server to query the data stored in the cloud; and the cloud server feeds back query results to the user, the user needs to verify the integrity and freshness of the results, the integrityis that the check results do not contain all results which should be contained in all queries, and the freshness is that the detection server does not send data results of historical versions to the user. The method is a universal, verifiable, safe and symmetric searchable technical scheme under a three-party model, and can ensure the integrity and freshness of the search query result returned tothe user by the server, namely prevent the server from initiating a replay attack.
Owner:GUANGXI NORMAL UNIV
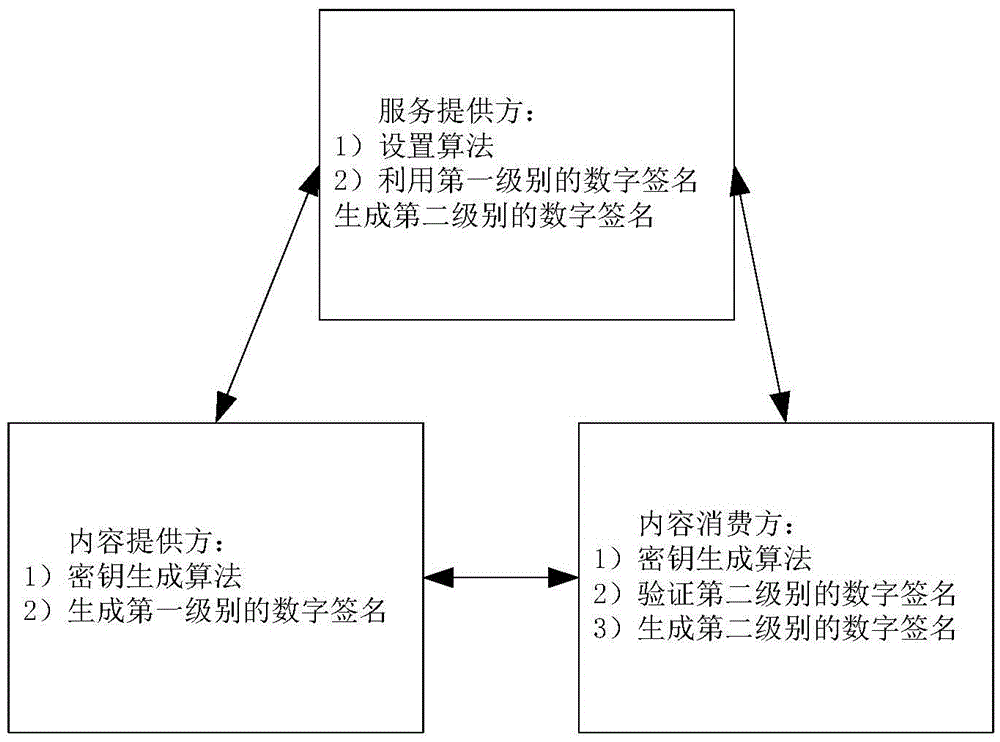
Agent re-assignment verifier signature method
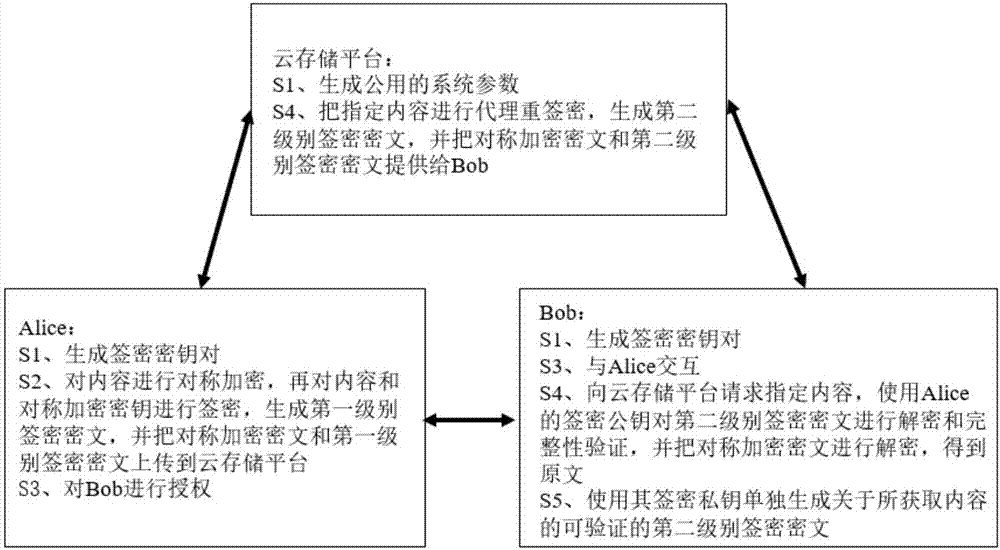
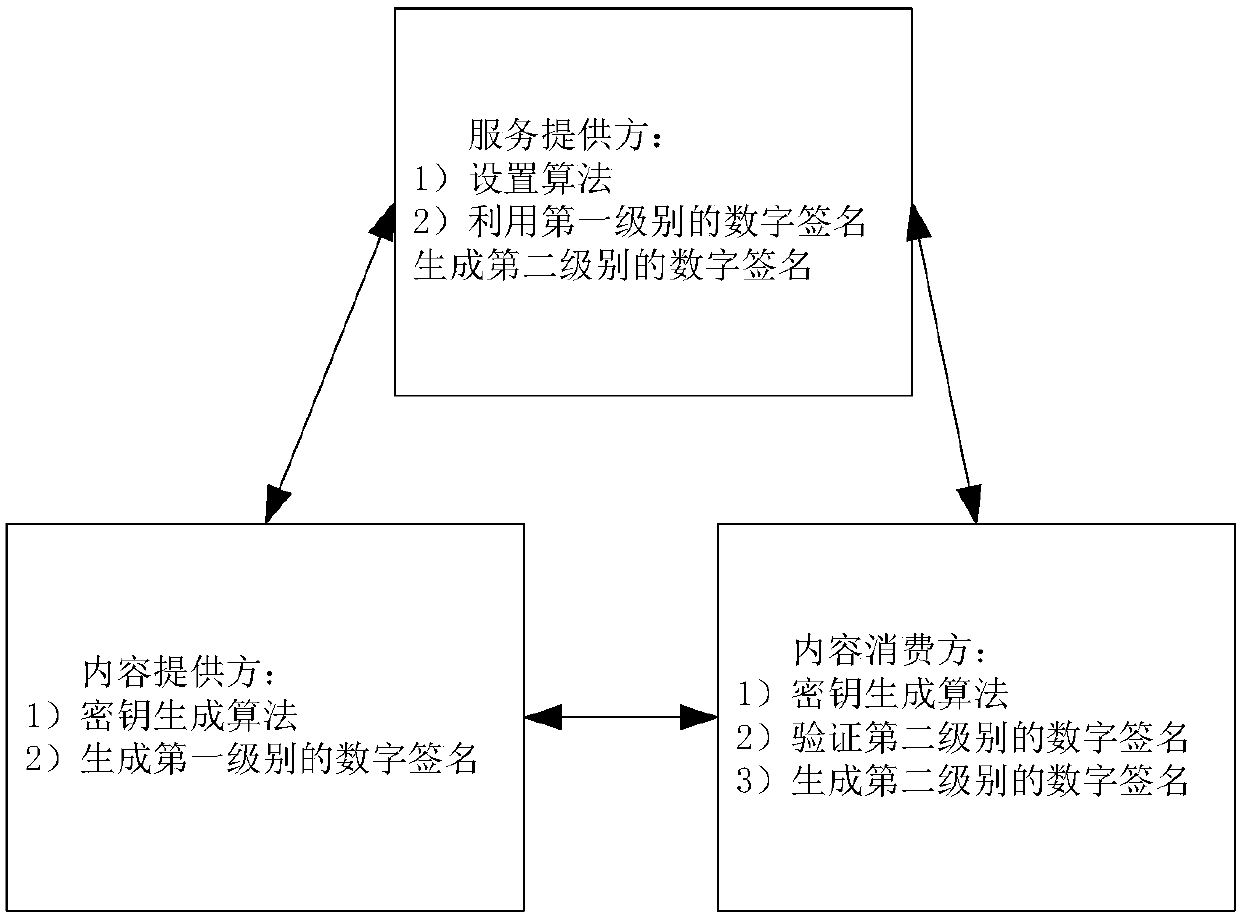
InactiveCN105471918AOne more chance to verify content consumersIncreased opportunity for fine-grained controlTransmissionDigital signatureService provision
The invention relates to an agent re-assignment verifier signature method, comprising the steps of: a service provider operating a setting algorithm to generate public system parameters for all sides; a content provider and a content consumption side operating a key generation algorithm to generate a self key pair; the content provider using a self private key to perform a first level digital signature on contents, and uploading first level digital signature values and contents to the service provider; the content consumption side exchanging contents with the content provider, and the content provider generating a resign key and uploading key information to the service provider; the content consumption side requiring the service provider to provide assigned contents, the service provider generating a second level digital signature, and providing the assigned contents and the second level digital signature for the content consumption side; the content consumption side using the public key provided by the content provider to verify the second level digital signature; and the content consumption side using a self key to independently generate a verifiable second level digit signature about the obtained contents.
Owner:SUN YAT SEN UNIV
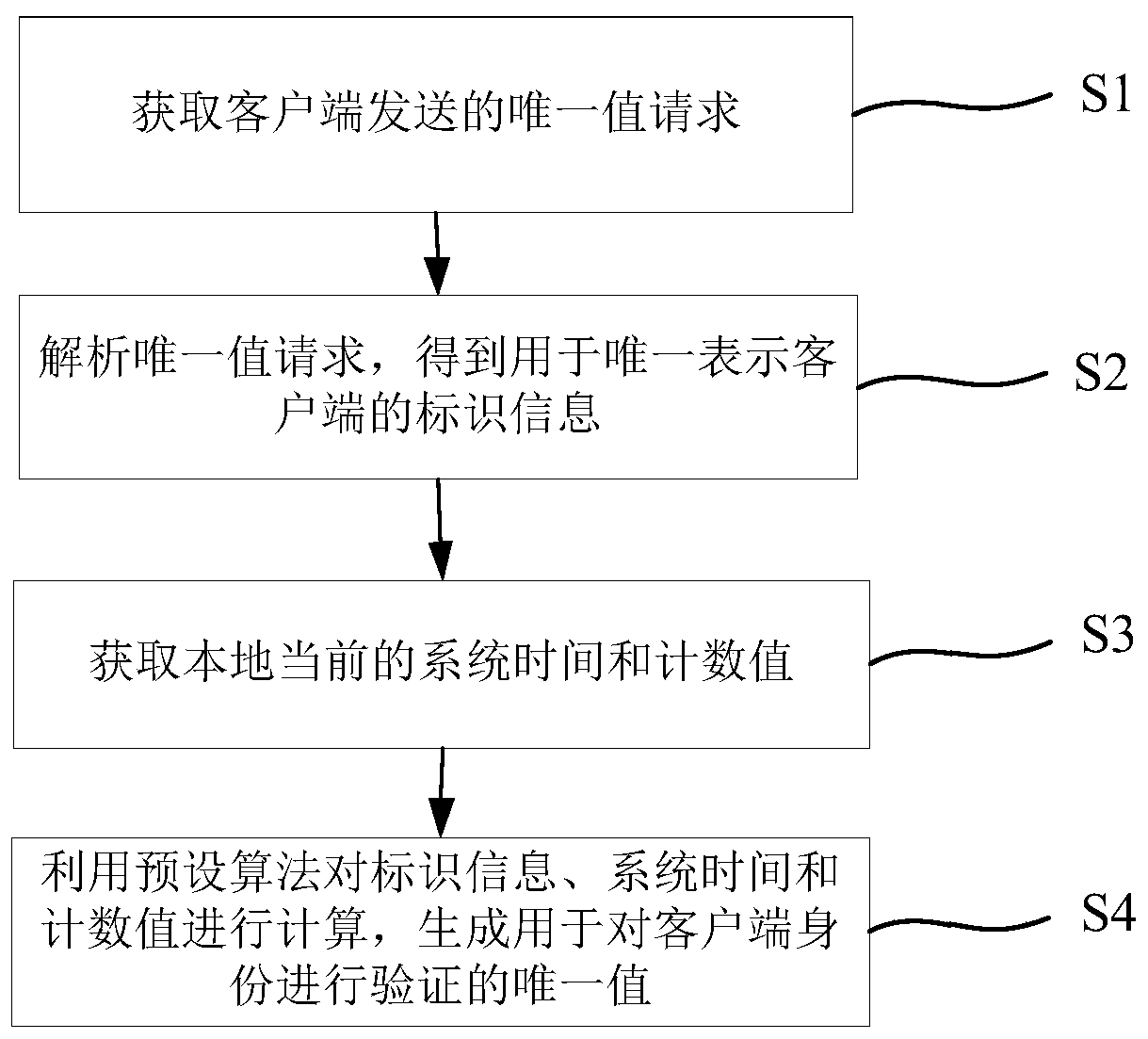
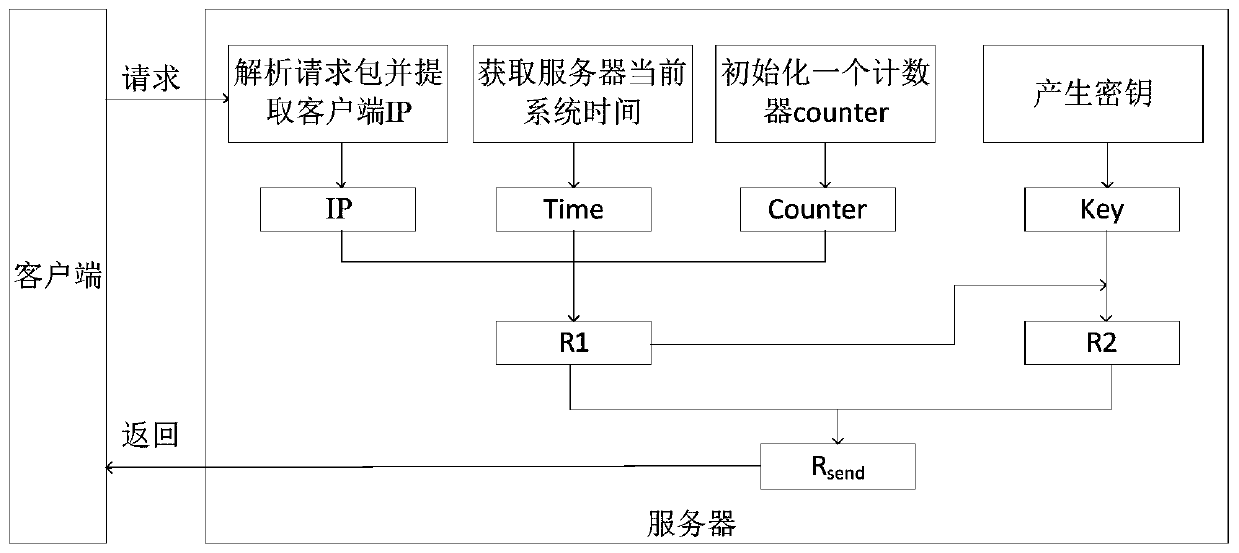
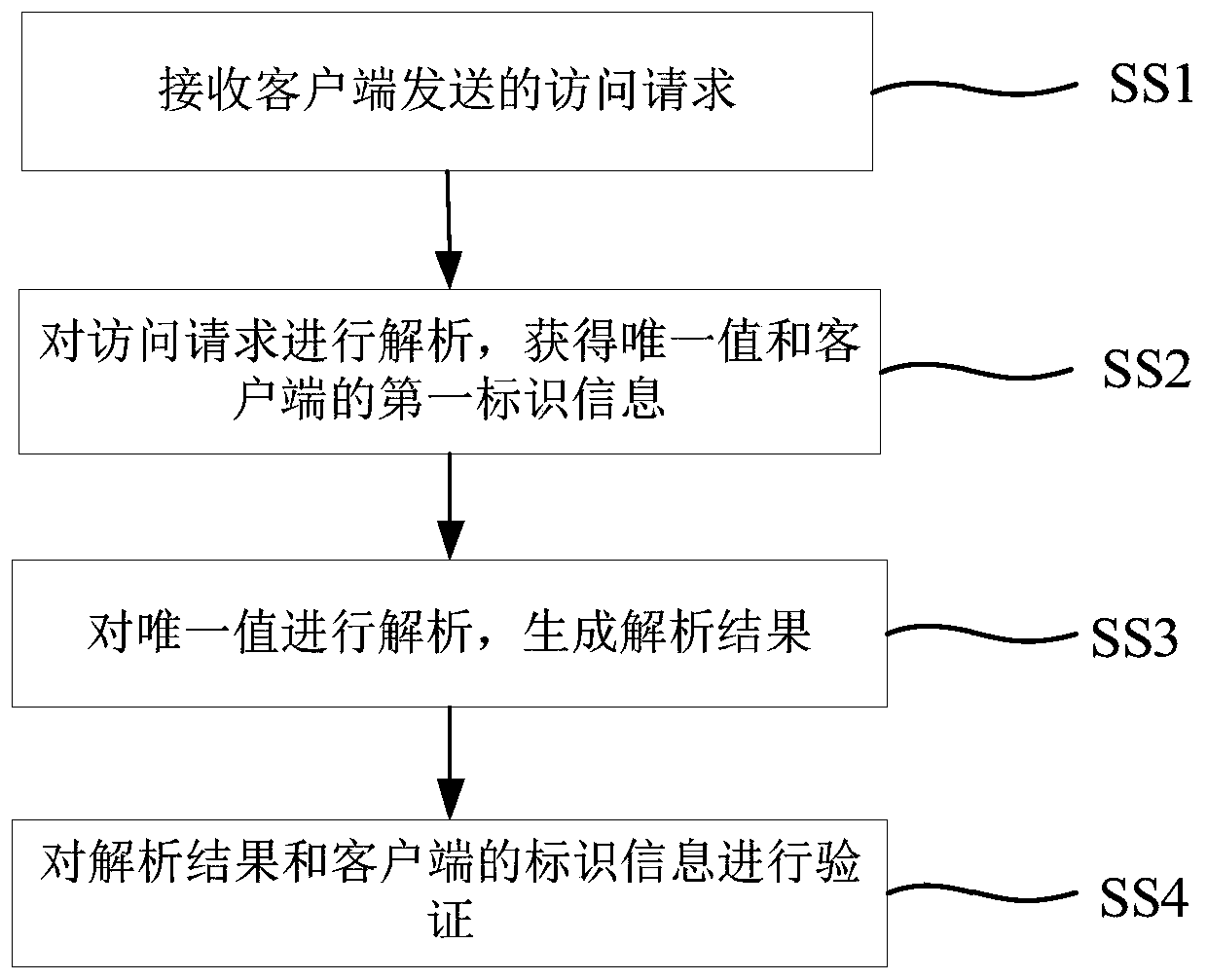
Unique value generation and verification method and system
PendingCN110912689AImprove securityAvoid safety hazardsKey distribution for secure communicationInformation resourceInformation security
The invention provides a unique value generation and verification method and system, and the method comprises the steps: obtaining a unique value request transmitted by a client, the unique value request being used for requesting a unique value; analyzing the unique value request to obtain identification information used for uniquely representing the client; obtaining local current system time anda count value, the count value being an accumulated count value after the local receives the access request each time; and calculating the identification information, the system time and the count value by using a preset algorithm to generate a unique value for verifying the identity of the client. The generated unique value is ensured to have higher security, so that the security and reliabilityof the unique value of the application are ensured, a basis is provided for subsequent security verification of the server on the access request, potential safety hazards caused by illegal access toinformation resources of the server are avoided, and the application range of the unique value in the field of information security is expanded.
Owner:SUZHOU KEDA TECH
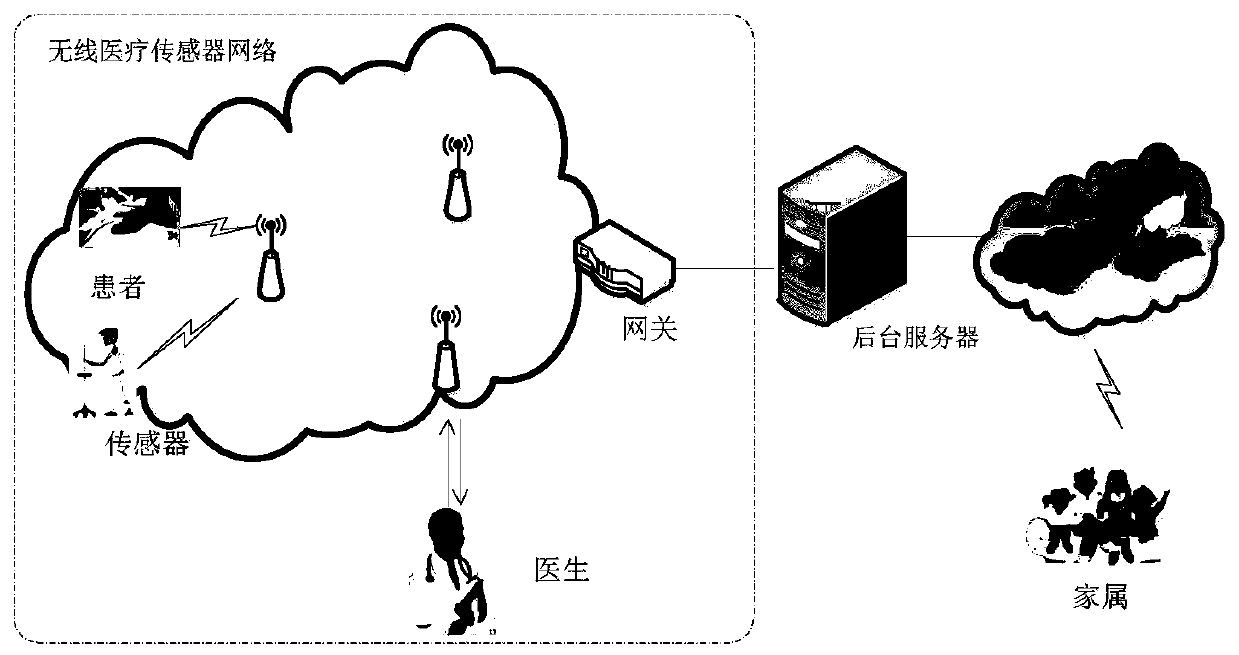
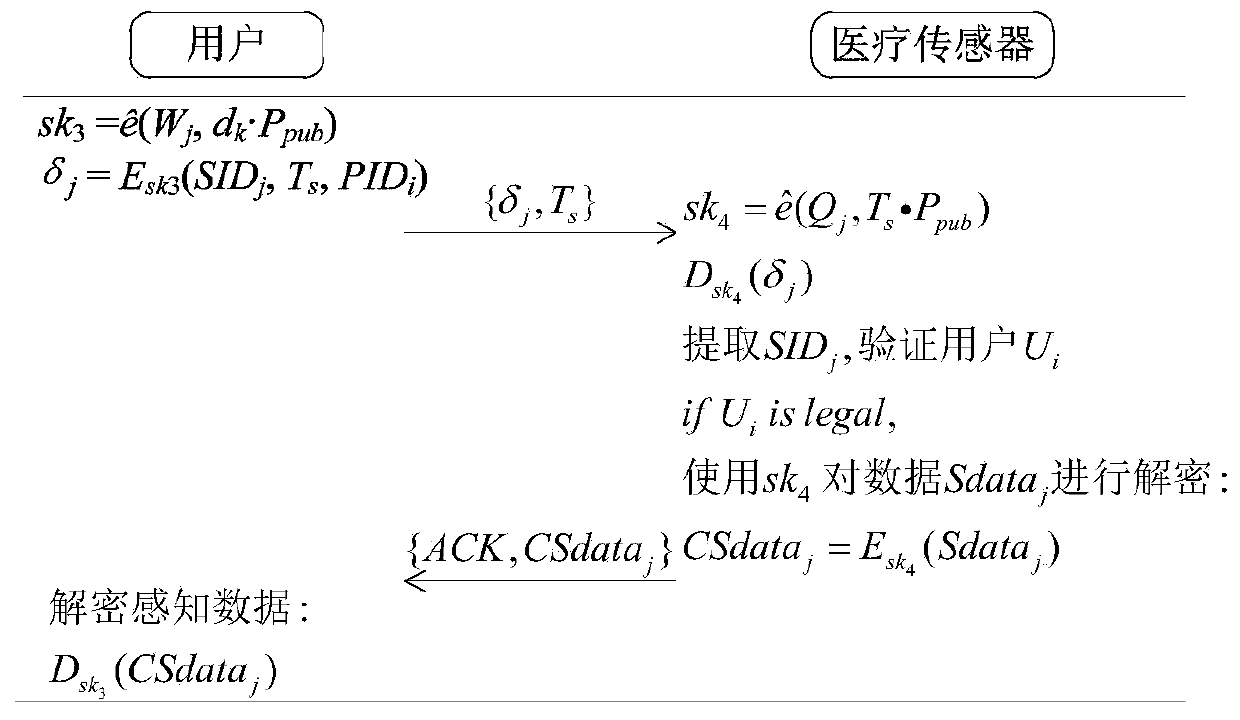
Identity authentication and data security transmission method in medical sensor network environment
InactiveCN111083150AHigh application valueIntegrity guaranteedKey distribution for secure communicationEncryption apparatus with shift registers/memoriesMedical emergencyData security
The invention provides an identity authentication and data security transmission method in a medical sensor network environment. The method comprises the following steps: initialization: enabling a background server to initialize a medical sensor network; a registration stage: registering the medical sensor nodes and medical workers in a background server; a login stage of a user: identity verification and key negotiation: after an authentication request sent by the user is received, enabling the background server to verify the legality of the user and negotiate with the user to generate a communication key after successful verification; and secure transmission of the data: enabling the user to obtain the medical data of the patient from the background server, or directly communicate withthe medical sensor node to obtain the stored medical data of the patient. According to the invention, it is ensured that medical data of a patient can be safely transmitted to the background server, and it is also ensured that the data is only read by legal medical workers, so private data of the patient is not leaked; identity verification based on the temporary value can ensure the integrity andverifiability of the identity of the authenticated user.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
Card game anti-cheating method and system based on block chain intelligent contract
ActiveCN109985389AGuaranteed verifiabilityGuaranteed to be tamper-proofUser identity/authority verificationVideo gamesComputer hardwareEncryption
The invention provides a card game anti-cheating method and system based on a block chain intelligent contract. The method comprises the following steps of: storing card drawing information and card issuing information of a player on the block chain by using a coding method and an encryption method; comparing a Hash value A and a Hash value B of a winner in the block chain; if the two values are the same, that cheating behavior occurs is determined, if the two values are not the same, that cheating behavior does not occur is determined. According to the invention, the defect of the existing combination of the block chain and the game is considered, the application scene is changed, and the cheating behavior is effectively found out by utilizing a unique mechanism of the block chain for de-trust and de-centralization. Meanwhile, the chess and card game data is not complex, too much burden is not caused during operation, the cost is low, the effect is obvious, and the serious situation of cheating of the current card game can be effectively improved.
Owner:NANJING UNIV OF POSTS & TELECOMM
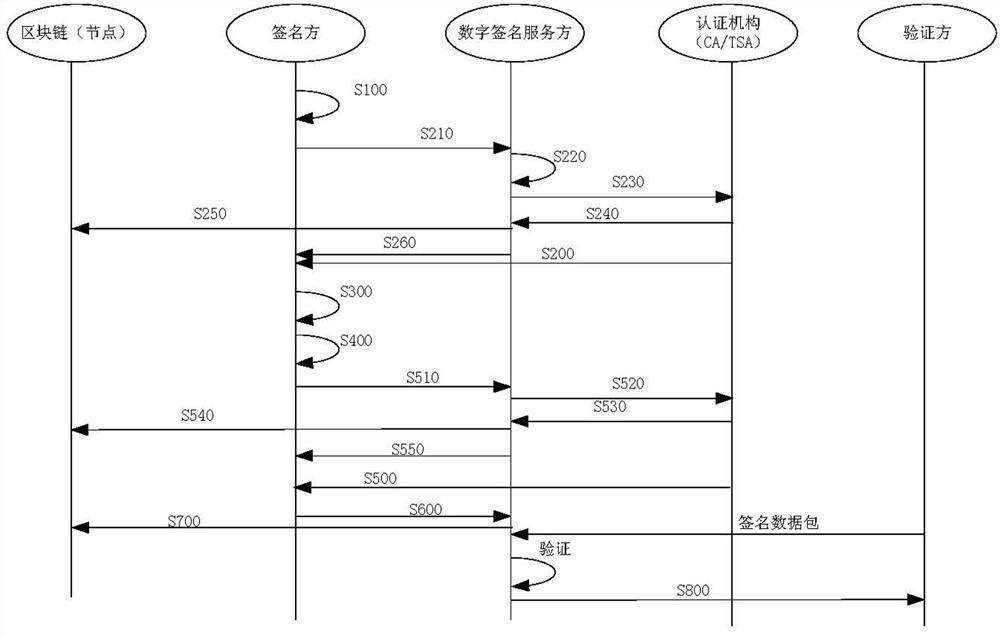
Trusted digital signature method and device based on blockchain
ActiveCN112202558AGuaranteed traceabilityGuaranteed verifiabilityKey distribution for secure communicationPublic key for secure communicationData packSignature file
The invention discloses a trusted digital signature method and device based on a blockchain. The method comprises the steps of generating a digital certificate request; acquiring a digital certificate, and respectively storing the digital certificate and the digital certificate application record into a blockchain and a database; calculating a hash value of local to-be-signed data; generating a timestamp request according to the hash value of the to-be-signed data; obtaining an authoritative timestamp; storing the timestamp application record in the blockchain; generating a signature file according to the digital certificate, the hash value of the to-be-signed data and an authoritative timestamp; generating a signature data packet and uploading the signature data packet to the blockchain;and obtaining a verification result of a verification party on the signature data packet. According to the application, the blockchain technology is adopted, the application and issuing records of thecredible timestamp and the authoritative digital certificate are backed up in the blockchain respectively, the traceability and verifiability of user behaviors are ensured, and thus the credibility of authoritative CA service and authoritative TSA service is ensured.
Owner:南京通付盾区块链科技有限公司
User verification method of shared vehicle
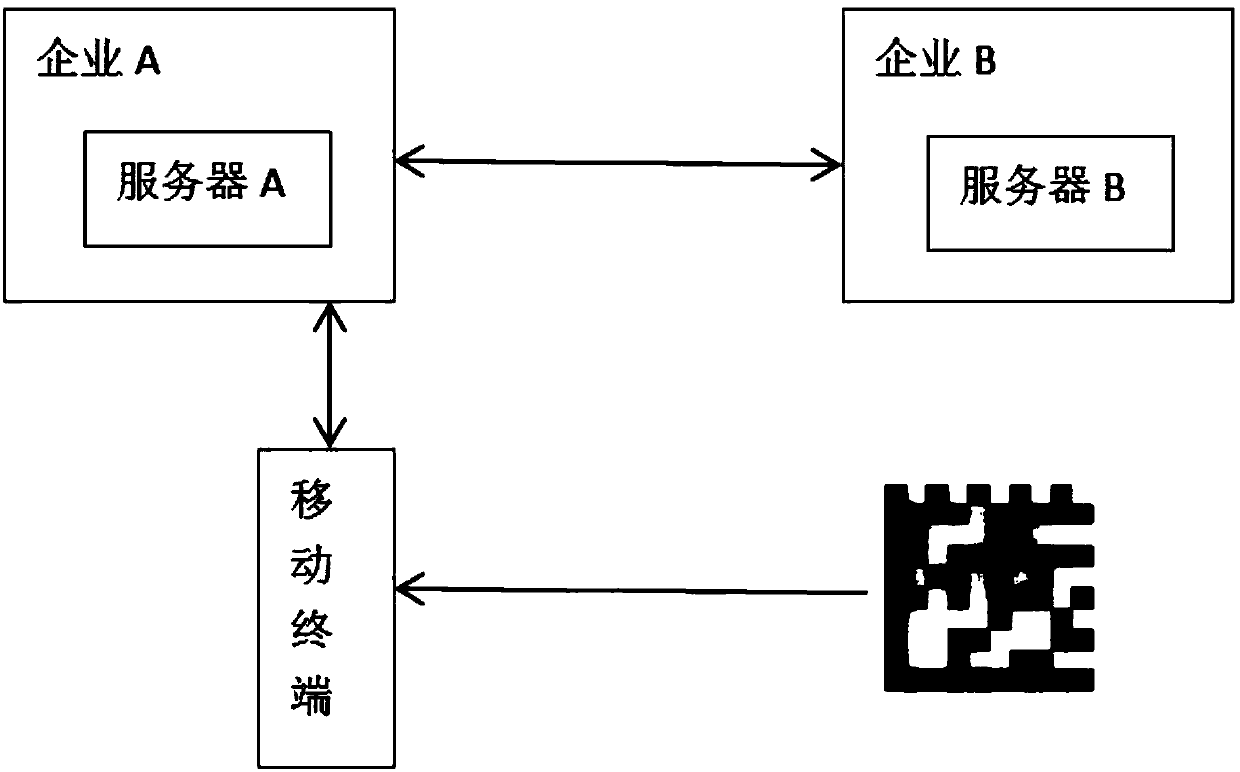
InactiveCN108055240AGuaranteed verifiabilityTransmissionProtocol authorisationUser verificationMobile enterprise
The invention relates to a user verification method of a shared vehicle. The method comprises the following steps: a user of a shared vehicle enterprise A scans a shared vehicle two-dimensional code of another enterprise B through a client, the enterprise A creates a temporary identity for the user and provides the same for the enterprise B, so that the user can use the shared vehicle without revealing user information to the enterprise B, and after the vehicle is used, integrity and verifiability of a transaction record are guaranteed through three-party signature of the transaction record.
Owner:SHANGHAI INT AUTOMOBILE CITY GRP CO LTD
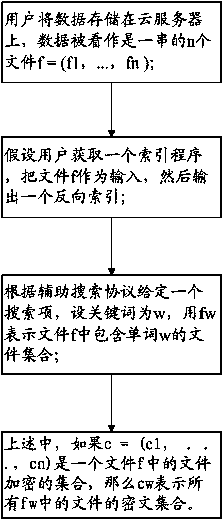
Dynamically retrievable cloud computing data encryption method
The invention discloses a dynamically retrievable cloud computing data encryption method. The method comprises the following steps: storing data on a cloud server by a user, wherein the data are considered as a string of n files, and f is equal to (f1, ellipsis, fn); supposing that the user acquires an index program, taking the file f as input and outputting a reverse index; giving a search item according to an auxiliary search protocol, setting a keyword as w, and representing a file set containing the word w in the file f by using fw, wherein if c which is equal to (c1, ellipsis, cn) is a set of encrypted files in the file f, cw represents a cipher text set of all the files in fw. By such a mode, the retrieval of encrypted data is realized, so that the privacy, the integrality and the verifiability can be guaranteed, the user can efficiently retrieve data through a search interface, and the data can also be safely added and deleted.
Owner:SUZHOU UNIV
Reconnaissance data management system based on block chain and working method thereof
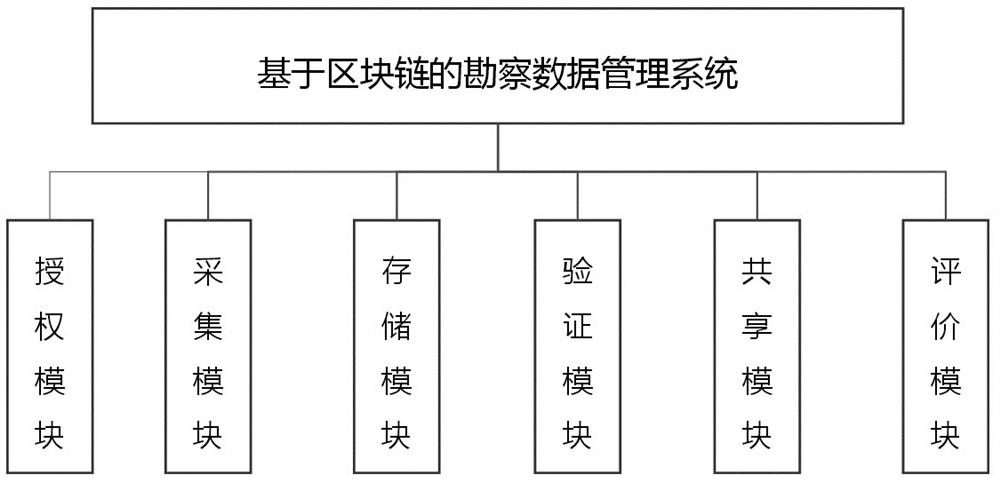
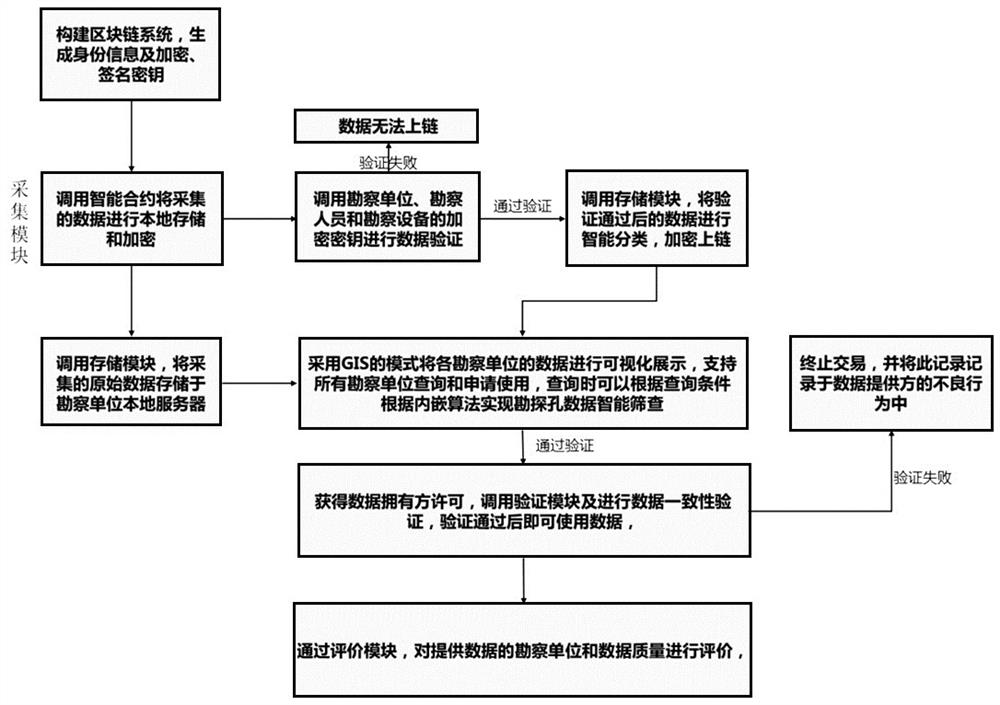
PendingCN112016132ASecure private custodyShared supportDigital data protectionData OriginEngineering
The invention discloses a reconnaissance data management system based on a block chain and a working method thereof. The reconnaissance data management system comprises an authorization module, an acquisition module, a storage module, a verification module, a sharing module and an evaluation module, the storage module comprises a local storage unit and a block chain storage unit; and the sharing module comprises a data query and display unit and a data exchange unit. The system has the advantages that the whole system comprises authorization, collection, storage, verification, sharing and evaluation, private storage of survey data is guaranteed, data sharing among different survey units is supported, and the efficiency and reliability of the data are improved; with the help of a block chain technology, information of an investigation unit, investigation personnel, investigation equipment, investigation data and a data exchange process is encrypted and uploaded to a chain, so that the non-modifiability and the verifiability of the uploaded data are ensured; each investigation unit, the investigation personnel and the equipment are endowed with unique identities, and the identities cannot be modified, so that the uniqueness of a data source is ensured.
Owner:SHANGHAI GEOTECHN INVESTIGATIONS & DESIGN INST
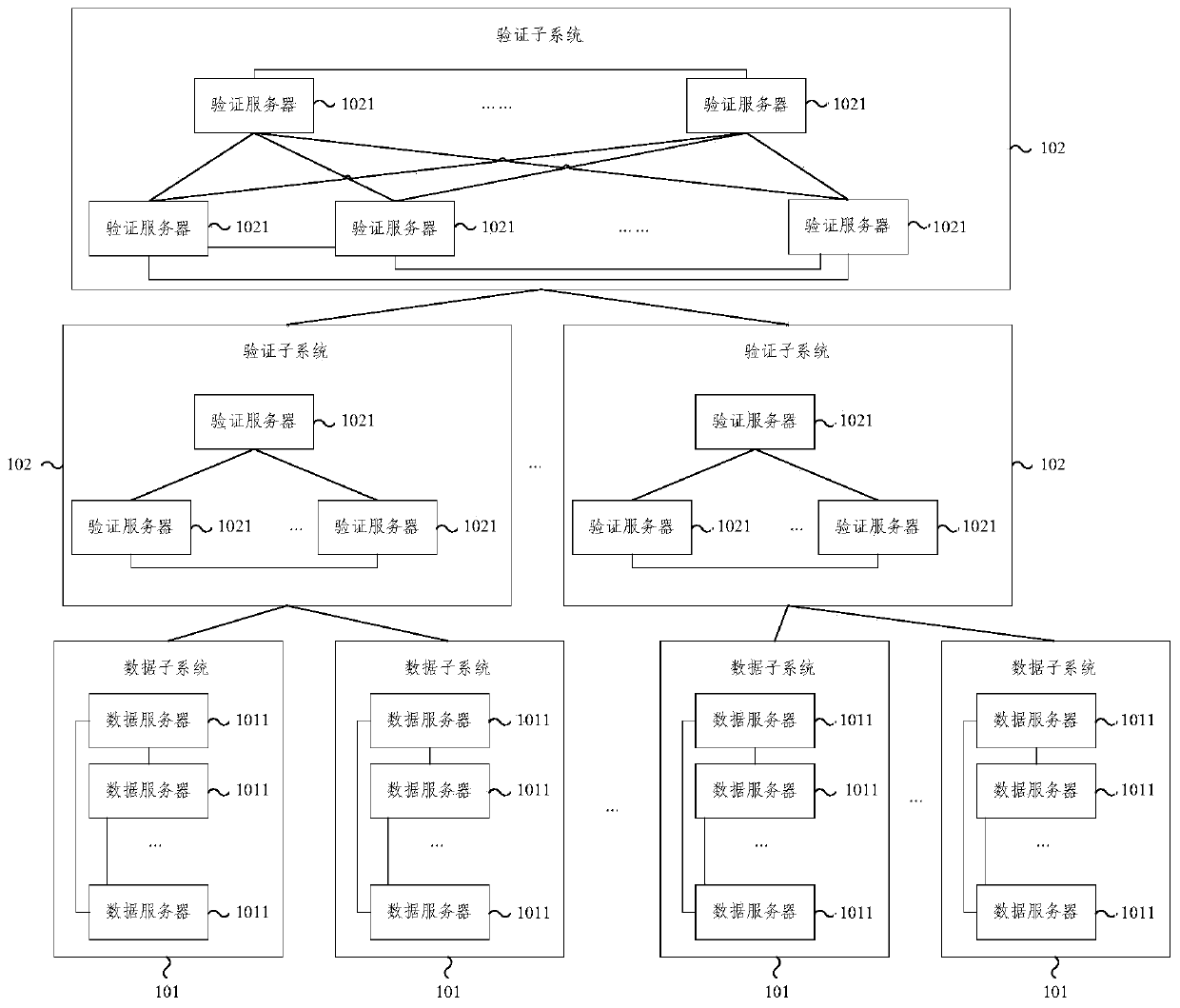
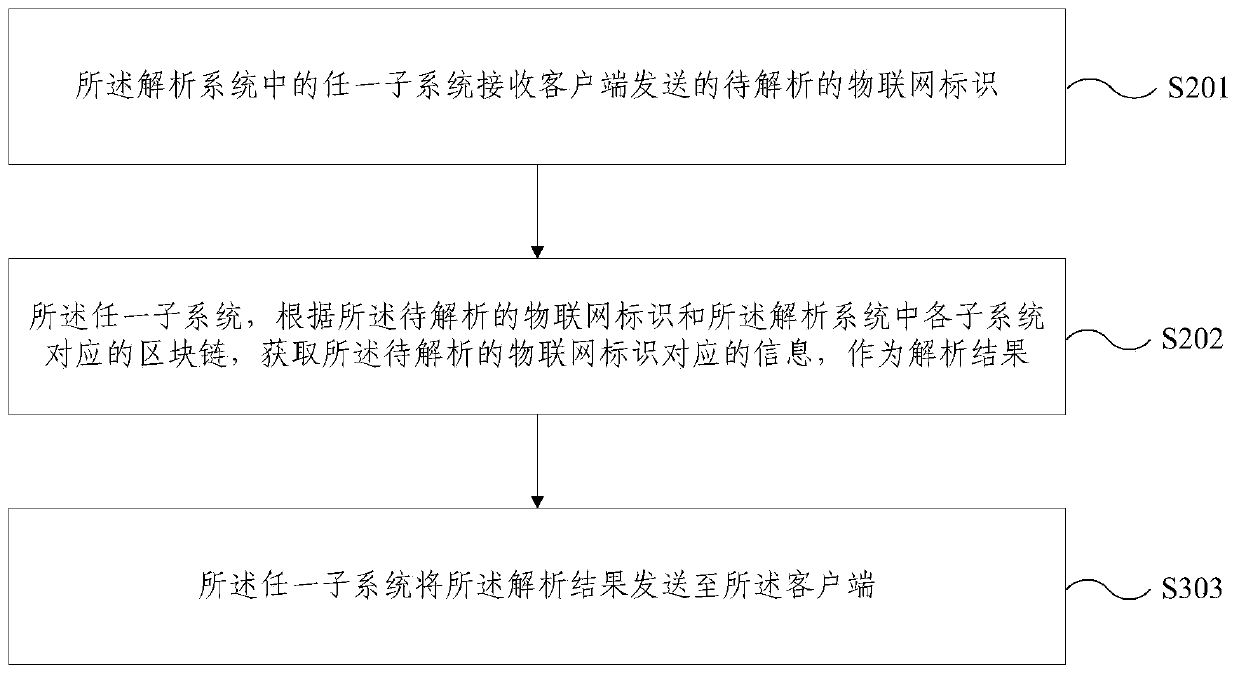
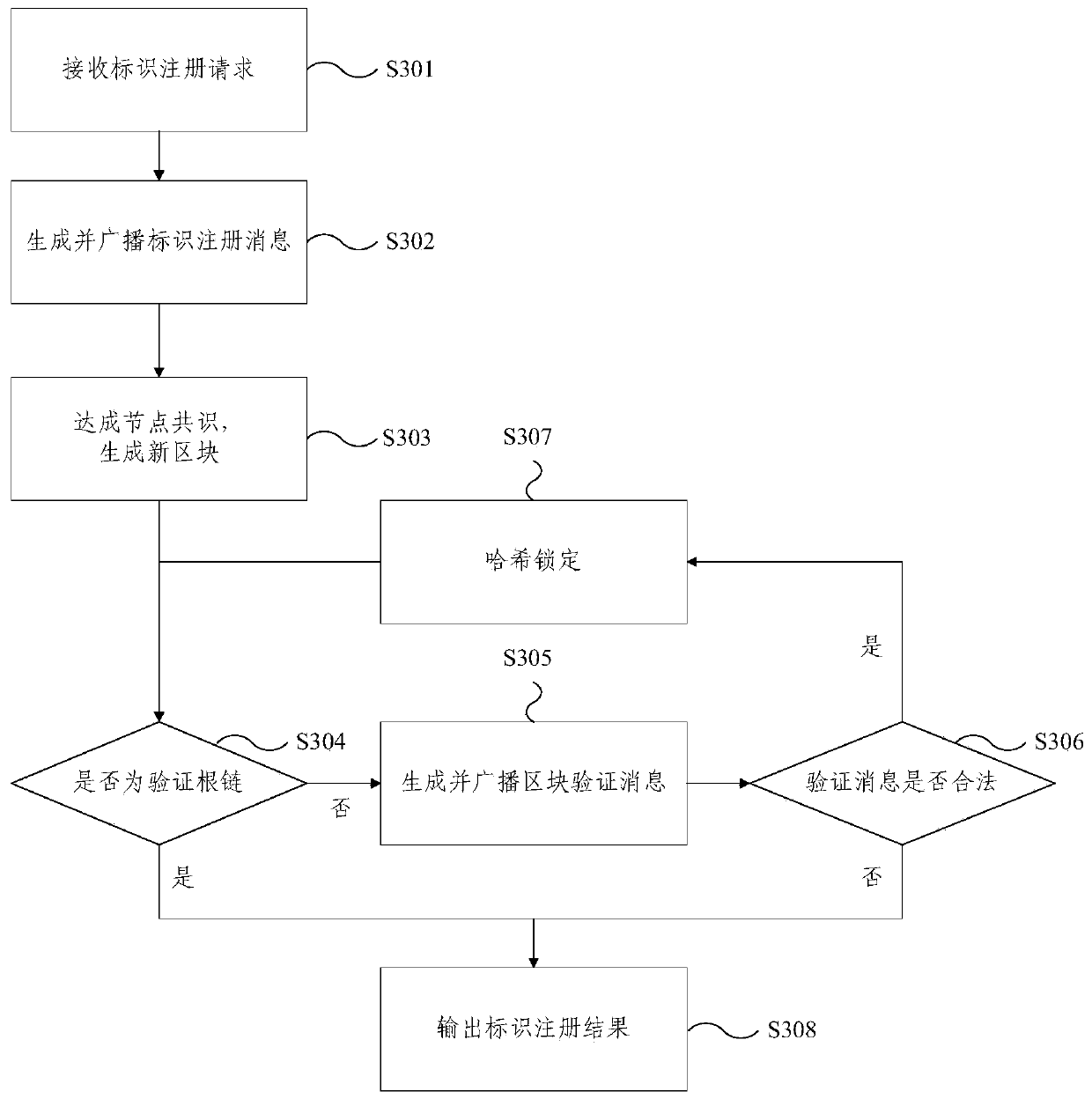
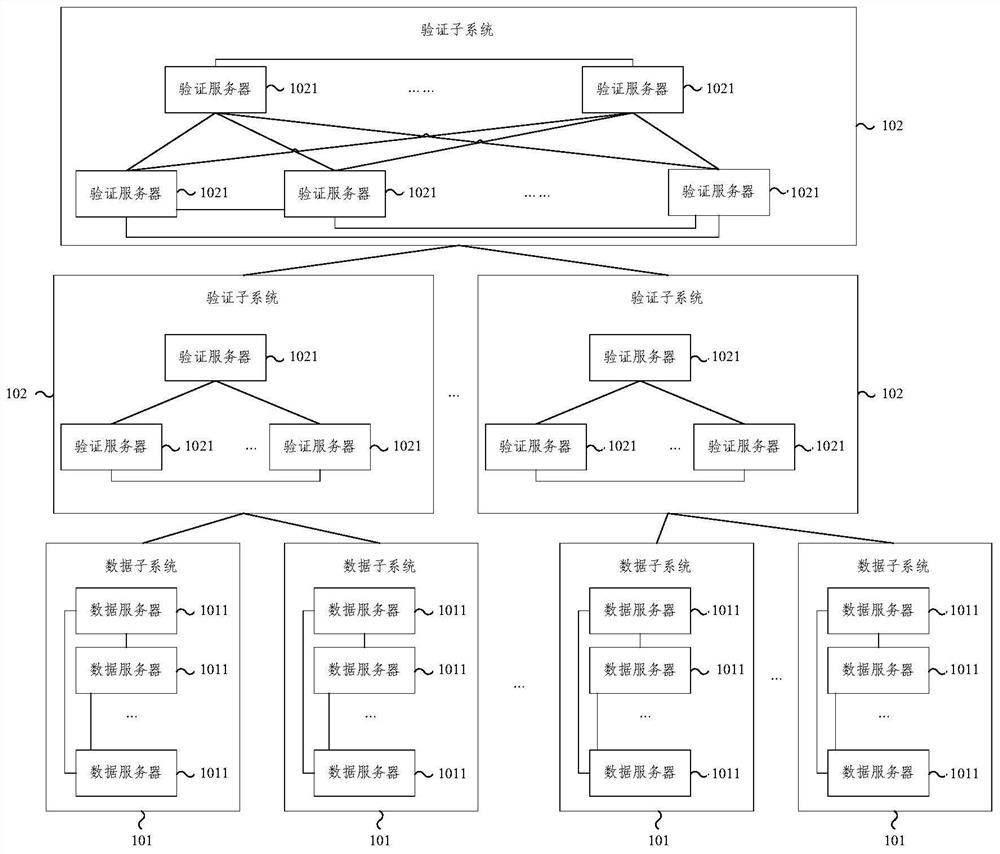
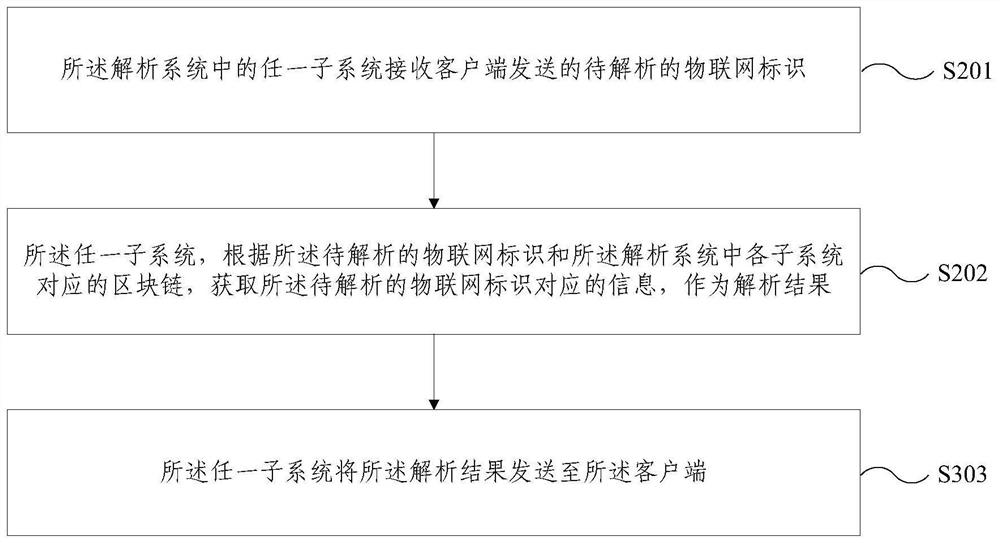
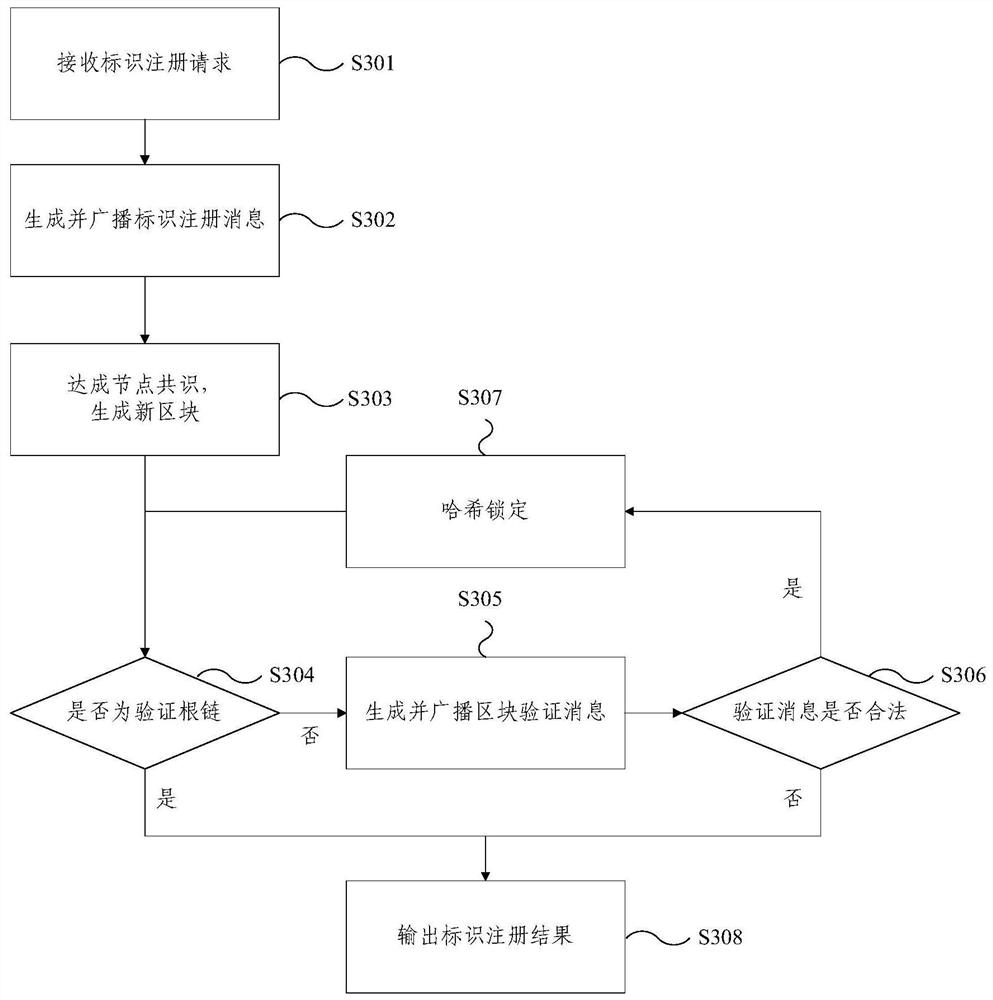
Internet of Things heterogeneous identifier analysis system and method based on block chain
The embodiment of the invention provides an Internet of Things heterogeneous identifier analysis system and method based on a block chain. The system comprises a plurality of subsystems forming a treestructure; the top layer is a verification subsystem; the bottom layer comprises a plurality of data subsystems; the middle layer comprises a plurality of verification subsystems; the subsystems which are located on the middle layer or the bottom layer are in communication connection with one subsystem on the upper layer; each data subsystem corresponds to one coding standard; the data subsystemsare used for storing the Internet of Things identifiers conforming to the corresponding coding standards and the information corresponding to the Internet of Things identifiers on the corresponding block chains; and the verification subsystems are used for storing the verification information of each block on the block chain corresponding to the next layer of subsystem in communication connectionon the corresponding block chain. According to the Internet of Things heterogeneous identifier analysis system and method based on the block chain provided by the embodiment of the invention, the Internet of Things heterogeneous identifiers are classified, stored and managed through different data chains, and more efficient analysis of the Internet of Things heterogeneous identifiers can be realized.
Owner:STATE GRID HENAN INFORMATION & TELECOMM CO +2
Proxy re-designated verifier signcryption method
InactiveCN107276749AImprove securityImprove computing efficiencyKey distribution for secure communicationCiphertextService provision
The invention relates to a proxy re-designated verifier signcryption method. The method comprises the following steps: generating system parameters and a signcryption key pair; performing symmetric encryption on contents by a content provider, performing signcryption on the contents and a symmetric encryption key to generate a first level signcryption ciphertext, and uploading the signcryption ciphertext and a symmetric encryption ciphertext to a service provider; interacting with the content provider by a content consumer, and authorizing the content consumer by the content provider; providing contents designated by the service provider by the content consumer, performing proxy re-signcryption on the designated contents by the service provider to generate a second level signcryption ciphertext, providing the symmetric encryption ciphertext and the second level signcryption ciphertext for the content consumer, decrypting and performing integrity version on the second level signcryption ciphertext by the content consumer, and decrypting the symmetric encryption ciphertext to obtain an original text; and singly generating the second level signcryption ciphertext of the obtained contents by the content consumer by using a signcryption private key.
Owner:SUN YAT SEN UNIV
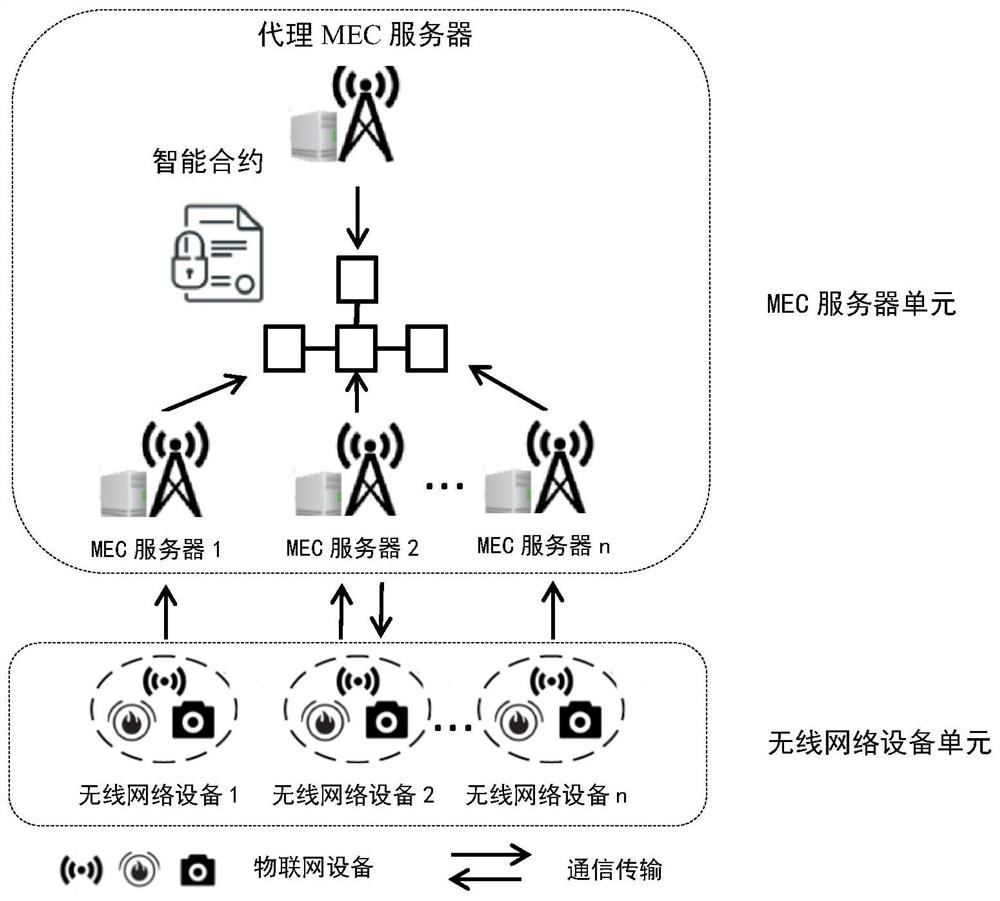
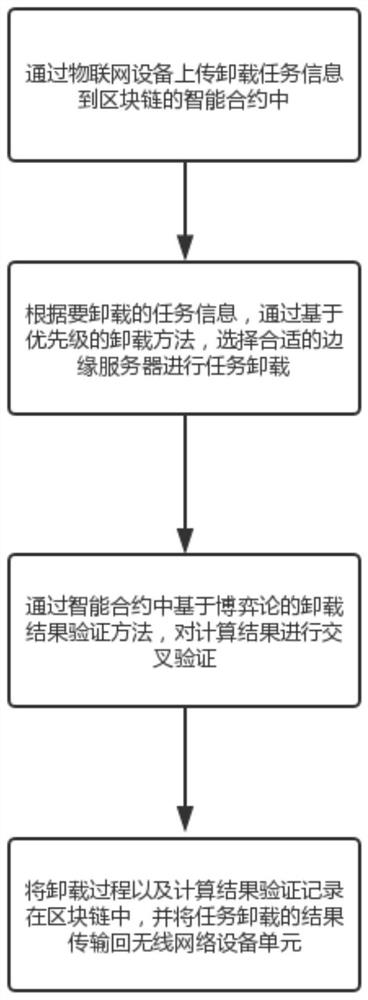
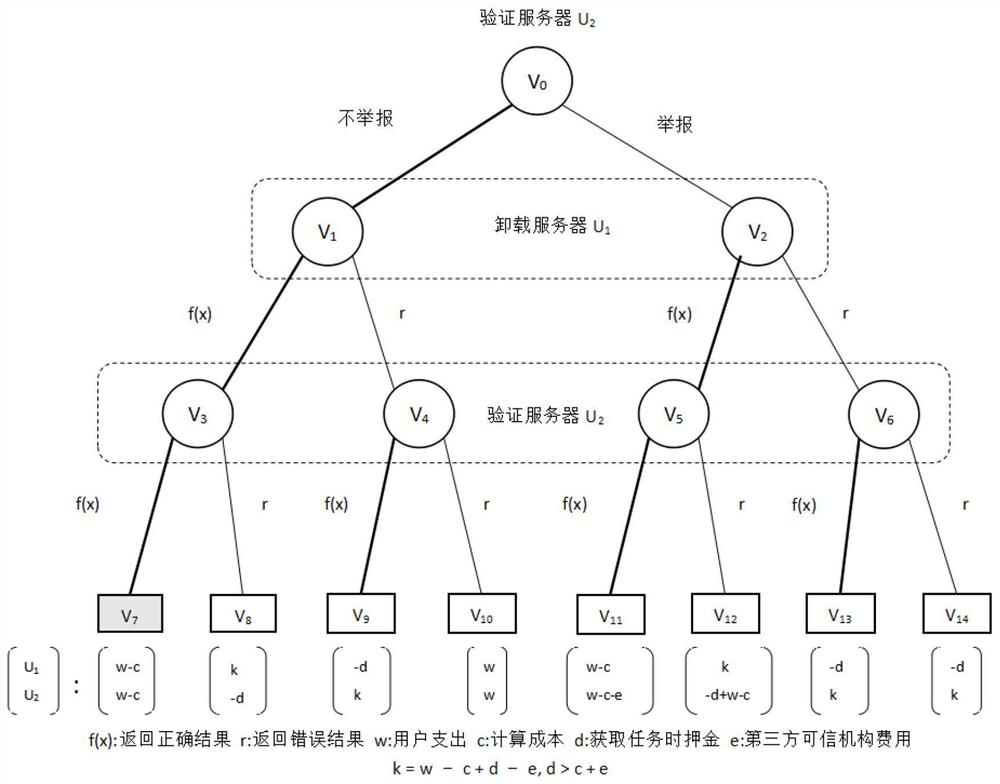
Blockchain-based edge computing task unloading system and method
ActiveCN113282348AGuaranteed correctnessGuaranteed verifiabilityProgram loading/initiatingData informationEdge computing
The invention discloses a blockchain-based edge computing task unloading system and method, and the system comprises a wireless network device unit which comprises a plurality of Internet-of-things devices which are connected through a network, and the Internet-of-things devices collect data information of Internet-of-things application programs from a physical environment, and forwards the information to the MEC server unit to execute task calculation; and an MEC server unit which comprises a plurality of MEC servers and is used for realizing a consensus mechanism of the blockchain and realizing signing registration and task unloading of the wireless network equipment according to the intelligent contract deployed in the blockchain network on the MEC servers. According to the method, by using the blockchain technology, the traceability and visibility of the edge computing task unloading process are ensured; through the task unloading method based on the priority, the requirements of users with different time delay requirements on the current unloading task can be more reasonably met; through an unloading result verification method based on the game theory, the correctness and verifiability of a calculation result are ensured, so that the task unloading quality is improved.
Owner:康旭科技有限公司
Ultra-high purity medium transporting integration process
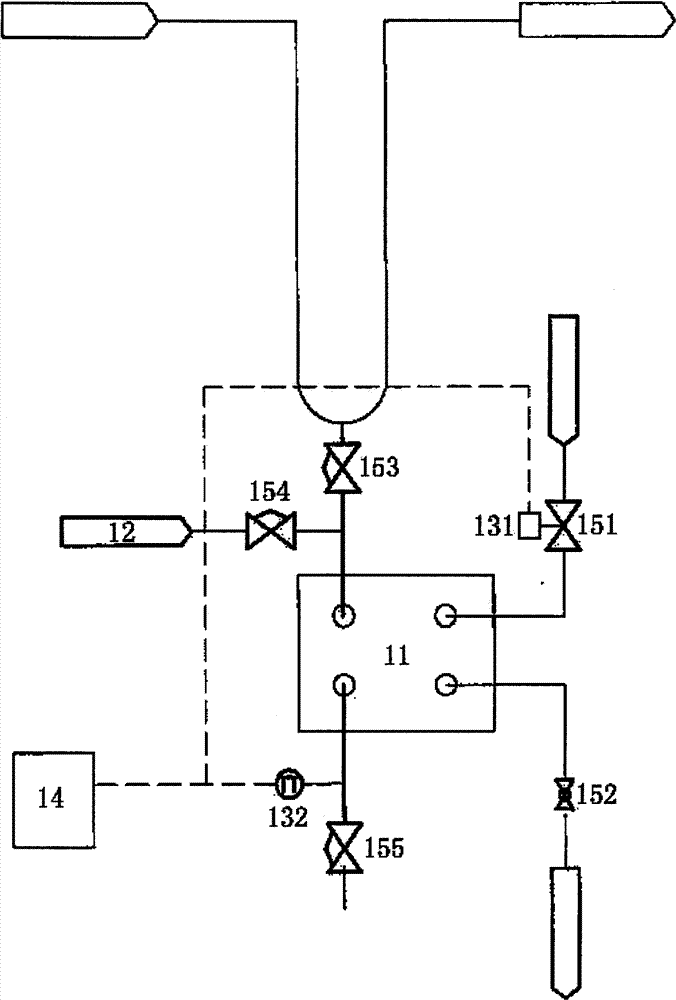
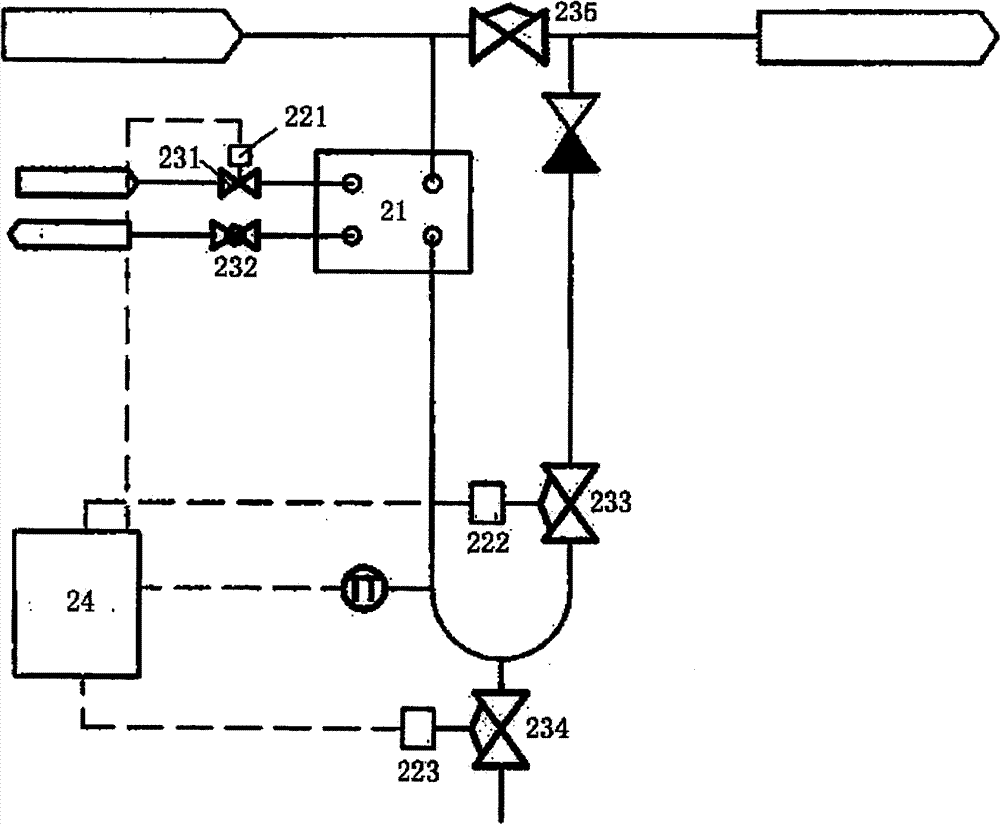
InactiveCN101482224BReduce consumptionGuaranteed verifiabilityPipeline systemsWater cyclingEngineering
The invention relates to the fluid transportation field, in particular to an ultra-pure medium transporting integrated device. The device consists of a heat interchanger, a cooling water circulating unit and an injection water circulating unit. A pure steam accessing pipe, a first temperature sensor, a second temperature sensor and a control panel are also arranged in the device. A cooling water inlet pipe is connected with the refrigerant inlet of the heat interchanger through a first valve. A cooling water outlet pipe is connected with the refrigerant outlet of the heat interchanger through a second valve. An injection water inlet pipe is connected with the injection water inlet of the heat interchanger through a third valve. The pure steam accessing pipe is connected with the outside of the injection water inlet pipe through a fourth valve. An injection water outlet pipe is connected with a fifth valve. A point of use is connected with the injection water outlet of the heat interchanger by the fifth valve. The cooling water inlet pipe and the injection water point of use are connected with the control panel respectively through first and second temperature sensors. The ultra-pure medium transporting integrated device of the invention has the advantages of high purity, convenient use and easy operation.
Owner:上海创洁科技有限公司
New energy vehicle electronic controller shell
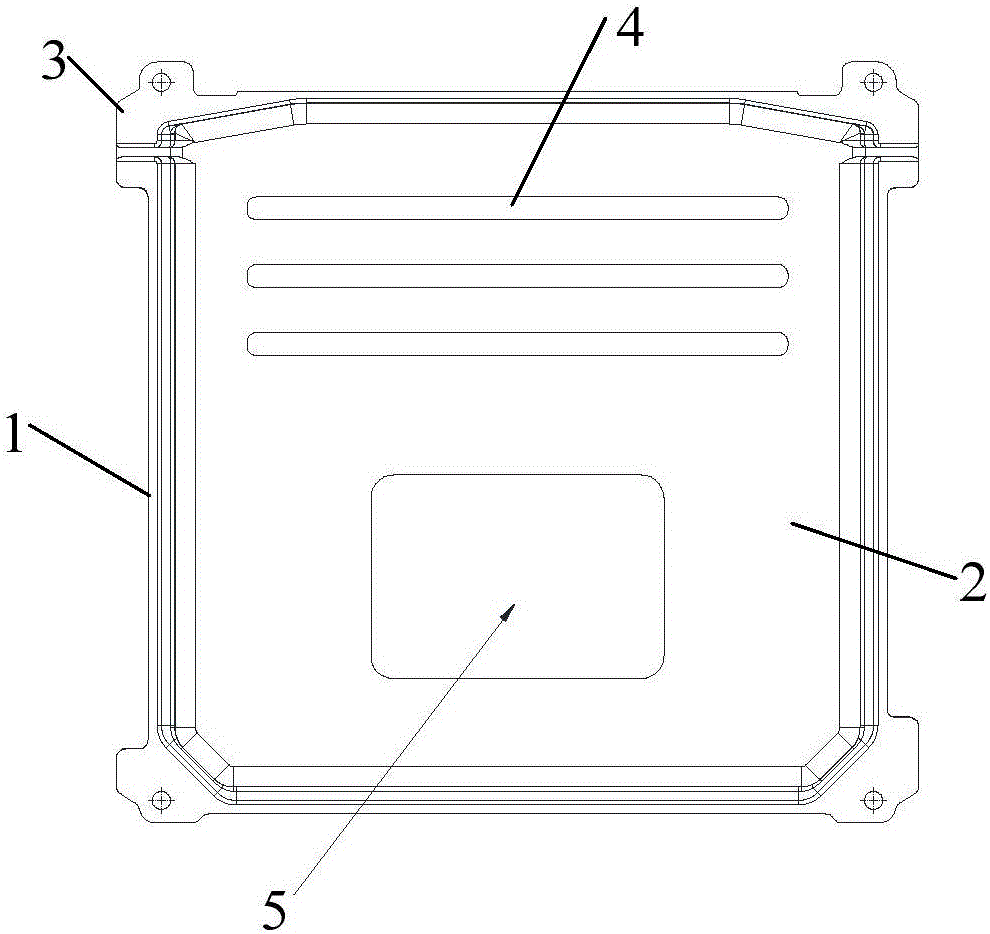
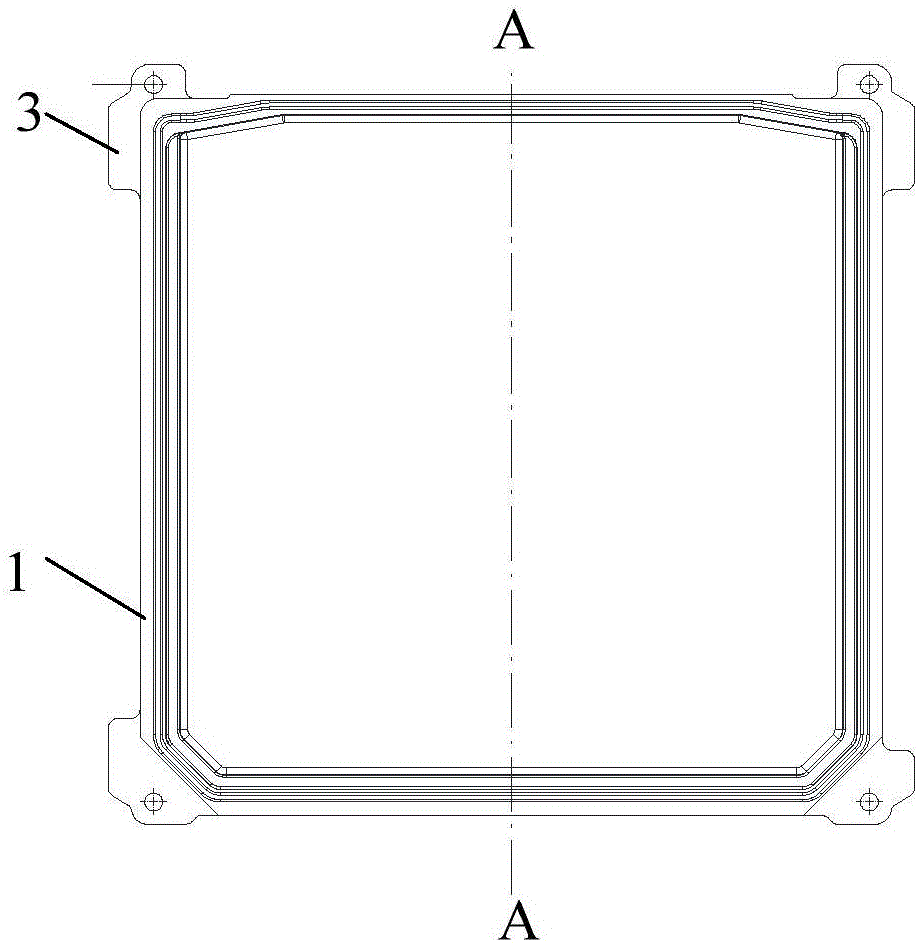
InactiveCN106170193AReasonable designEasy to produceCasings/cabinets/drawers detailsMetal casingsNon destructiveElectronic controller
The invention discloses a new energy vehicle electronic controller shell. The new energy vehicle electronic controller shell comprises a shell and an upper cover; the middle part of the upper cover is provided with a convex position; the middle part of the shell is provided with a concave position; the upper cover and the shell are connected as a whole through an edge connecting part, wherein four edges of the edge connecting part are arranged annularly; an edge connecting part of the upper cover and the shell is provided with a seal groove used for placing a seal ring; the outer sides of the four corners of the shell are provided with shell dismantling supporting edges in a protruding way; the bottom part of the shell is provided with a reinforcing rib; and one side of the reinforcing rib is provided with an elastic moveable pressing part used for fixing an electronic controller. The shell with a reasonable design is convenient for the manufacturing and maintenance, the installation is easy, the structure is solid and durable, the installation and use are convenient, and the heat dissipation effect is good; and besides, by arranging the shell dismantling supporting edges at the outer sides of the four corners of the shell in a protruding way, a shell dismantling jig can very conveniently dismantle the upper cover, thereby realizing non-destructive dismantling and improving the maintainability of products.
Owner:欧朗电子科技有限公司
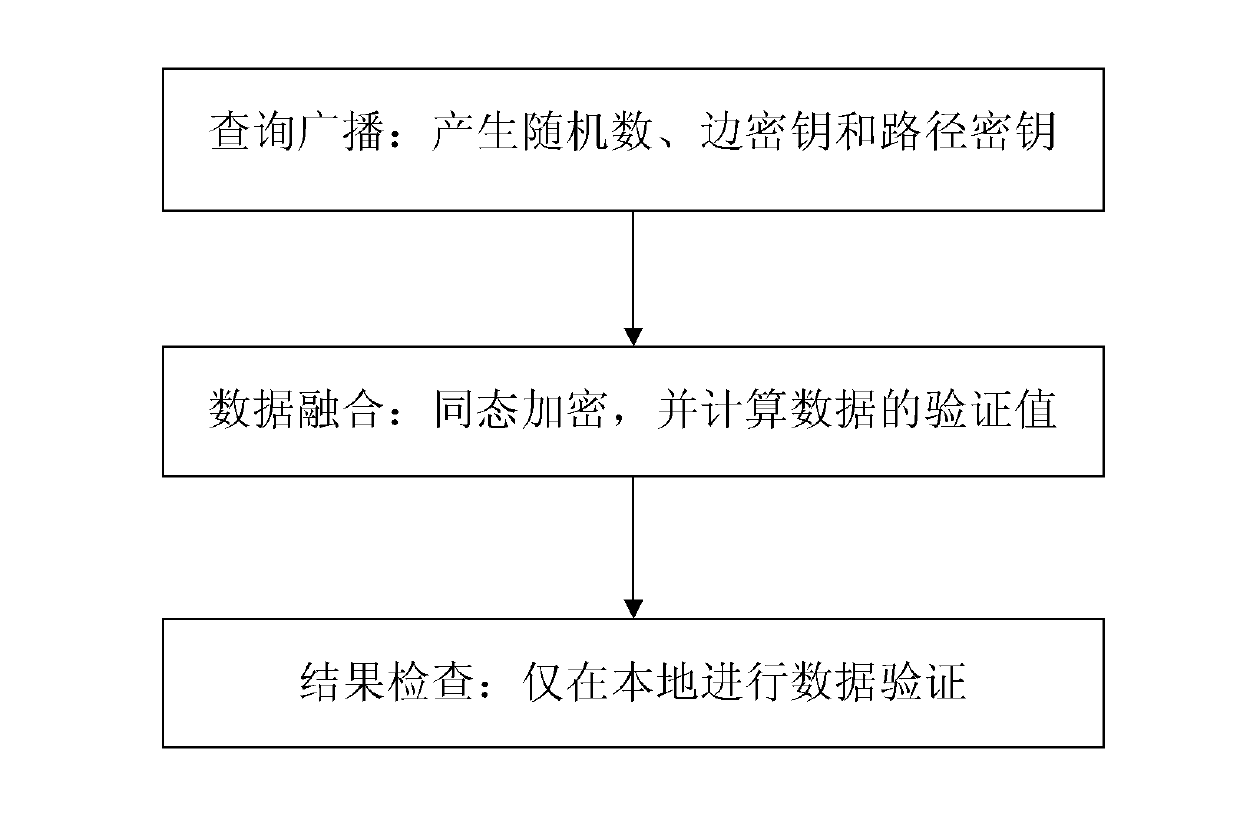
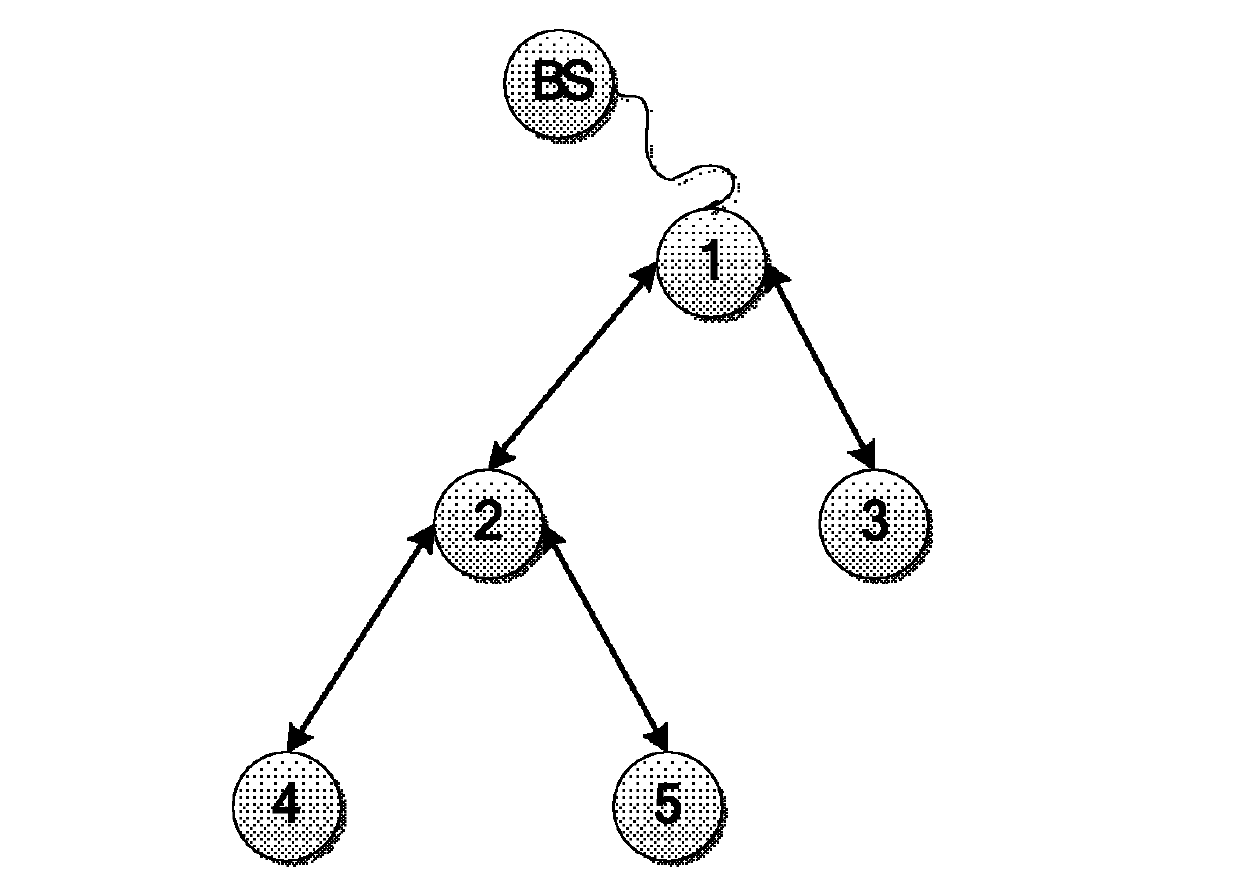
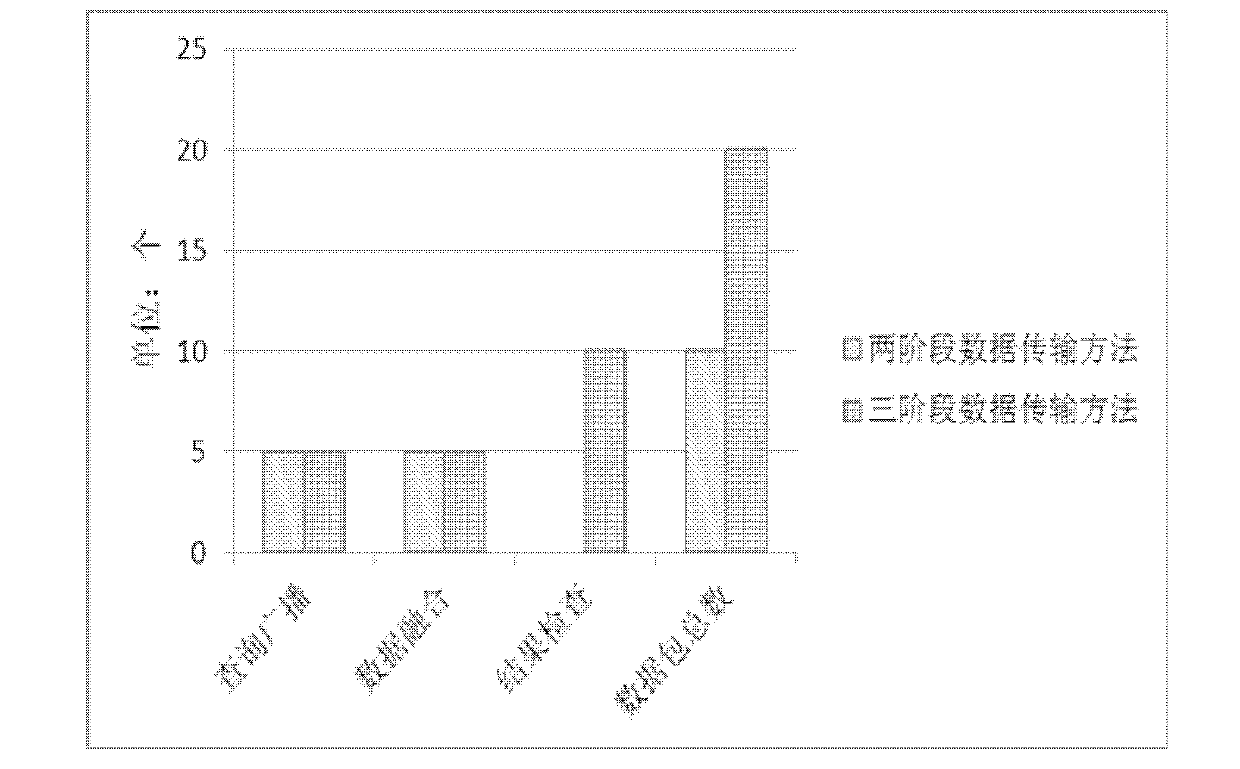
Method for safely and efficiently fusing data
InactiveCN102299792BIntegrity guaranteedGuaranteed CompatibilityKey distribution for secure communicationPublic key for secure communicationConfidentialityBroadcasting
The invention relates to a method for safely and efficiently summing and fusing data transmitted in a network, belonging to the technical field of network information safety. The method comprises the following steps of: making an inquiry base station generate a random number, and calculating and distributing every node key which participates in data fusion respectively according to a network topological structure; dynamically encrypting acquired data, transmitting to a father node from child nodes, fusing data of the father node with data of all child nodes by using the father node, and uploading continually till the data are transmitted to the inquiry base station; and decrypting by using the inquiry base station to obtain a fusion result, locally verifying the fusion result according toa verification value, accepting the fusion result if the verification is valid, otherwise, discarding the fusion result. In the method, data traffic is only required to be generated at broadcast inquiry and data fusion stages, so that the data traffic is greatly reduced. The completeness of data is ensured by performing result detection; and data are dynamically encrypted in the entire fusion process, so that the confidentiality and verifiability of data are ensured while the fusibility of data is ensured.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
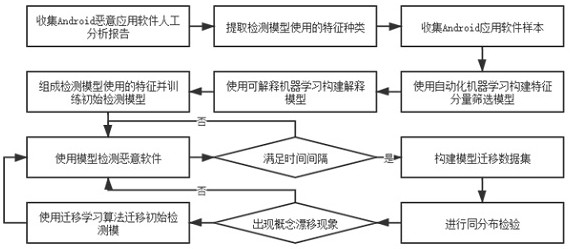
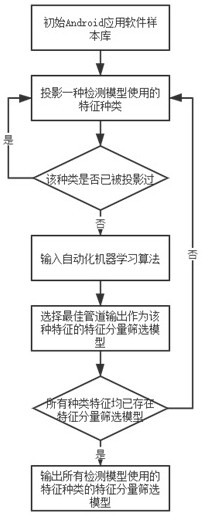
Conceptual drift-oriented interpretable Android malicious software detection method
ActiveCN113901463AImprove logicImprove rationalityEnsemble learningCharacter and pattern recognitionReverse analysisSoftware analytics
The invention discloses a concept drift-oriented interpretable Android malicious software detection method, and belongs to the technical field of information security. The method comprises the following steps: introducing detection features through an artificial Android malicious software analysis report, improving a traditional feature package based on an automatic machine learning algorithm and an interpretable algorithm, and fusing an identically distributed inspection and transfer learning algorithm. According to the method, the interpretability of the Android malicious software detection model is improved, manual verification of the detection model by reverse analysts is facilitated, the influence of the concept drift problem on the accuracy of the detection model is reduced, low-cost long-time maintenance of high accuracy of the detection model is facilitated, and the method is used for detection and analysis of Android malicious application software.
Owner:YANSHAN UNIV
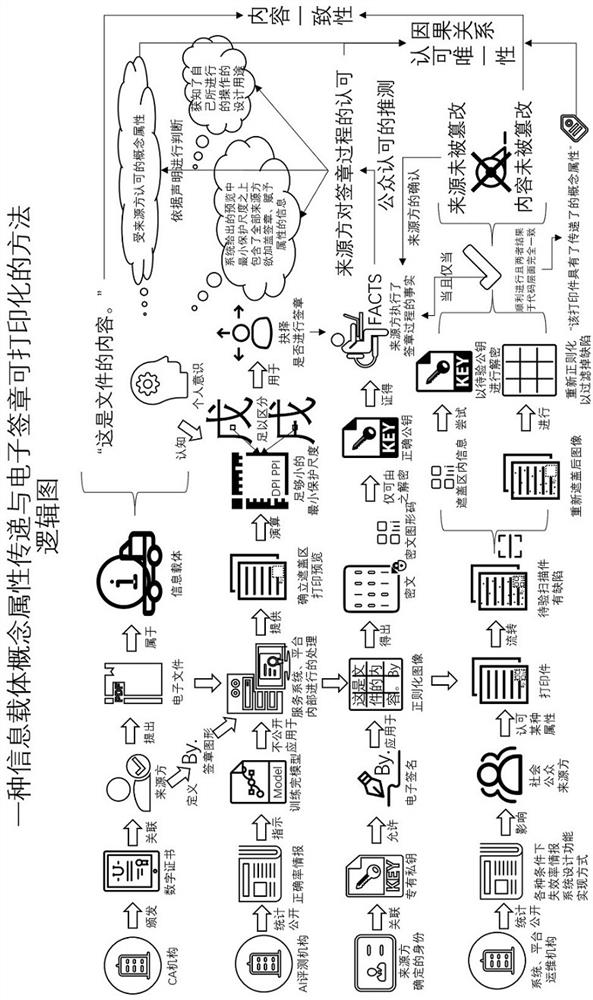
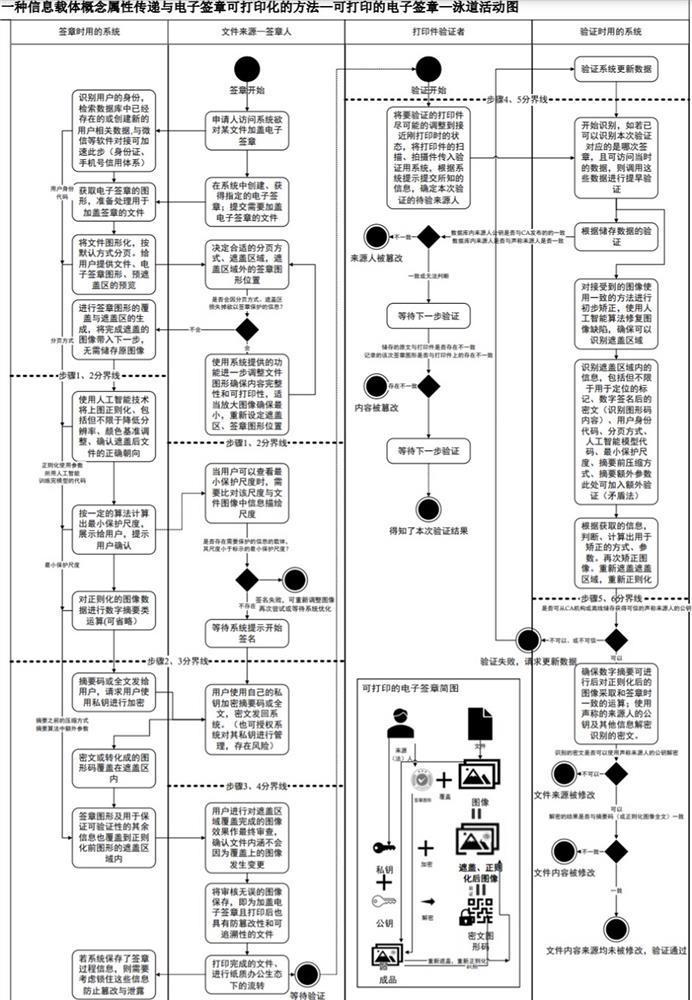
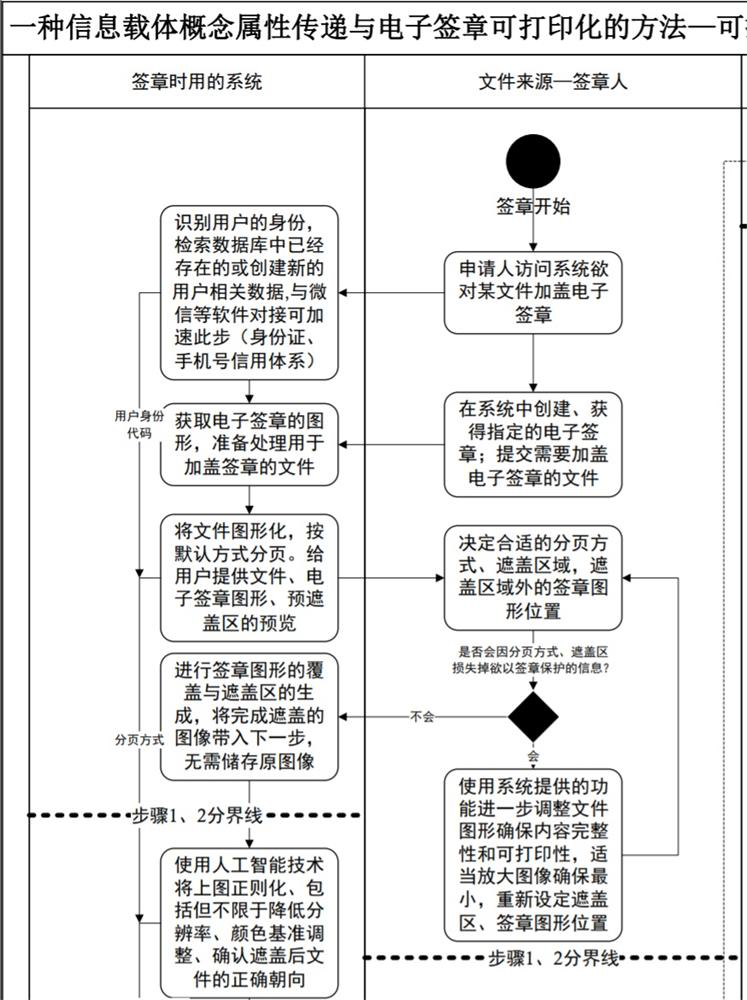
Information carrier concept attribute transmission and electronic signature printable method
PendingCN113626776AAvoid destructionGuaranteed verifiabilityDigital data protectionProgram/content distribution protectionGraphicsImaging processing
The invention discloses a method for transmitting concept attributes of an information carrier and printable an electronic signature, and provides a method for efficiently connecting electronic office ecology and paper office ecology by transmitting the concept attributes such as the effectiveness of a printable electronic file and the like which are attached to the information carrier by human beings to a printing piece of the printable electronic file through an image processing technology. The method comprises the following steps: regularizing an original file image in a predetermined mode, and filtering part of information to obtain a minimum protection scale; converting the regularized image into a code uniquely corresponding to the original file by using algorithms such as digital digest and signature, and storing the code in a covering area added on the file in the form of a graphic code; and identifying information on the printed piece, re-regularizing the obtained image, and comparing to complete verification of the specific concept attribute. The process mainly comprises six steps. The method can be applied to electronic office systems such as OA, LIMS and the like, and can be widely applied to various industries due to the fact that a universal method for transmitting specific concept attributes between information carriers is elaborated.
Owner:张雨
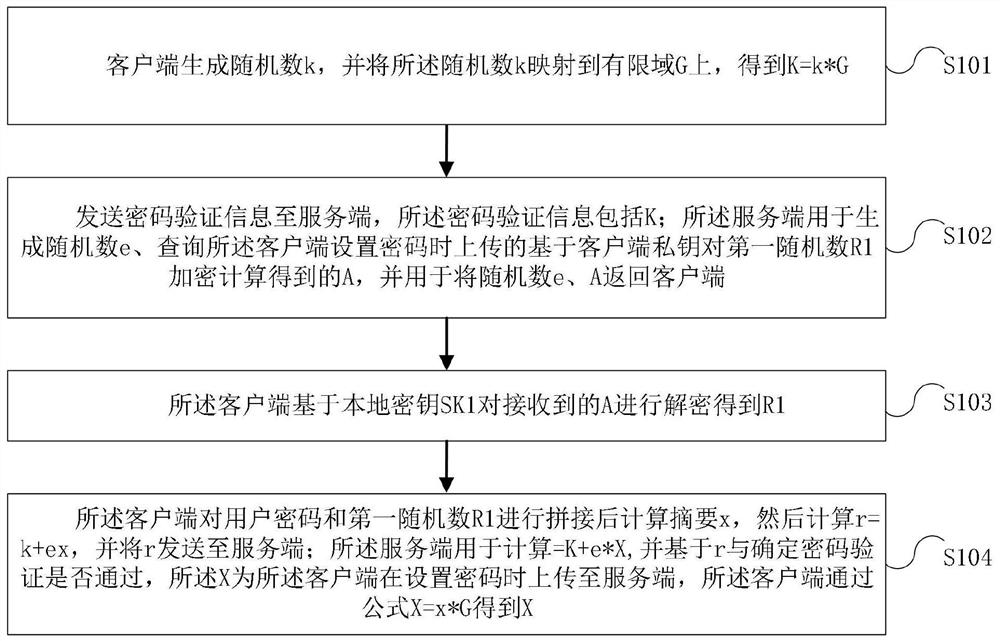
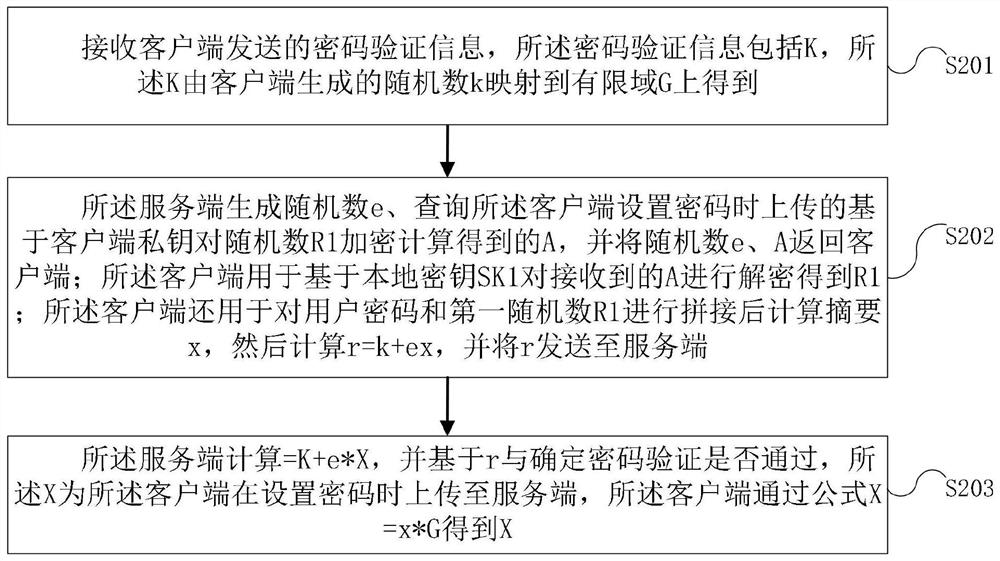
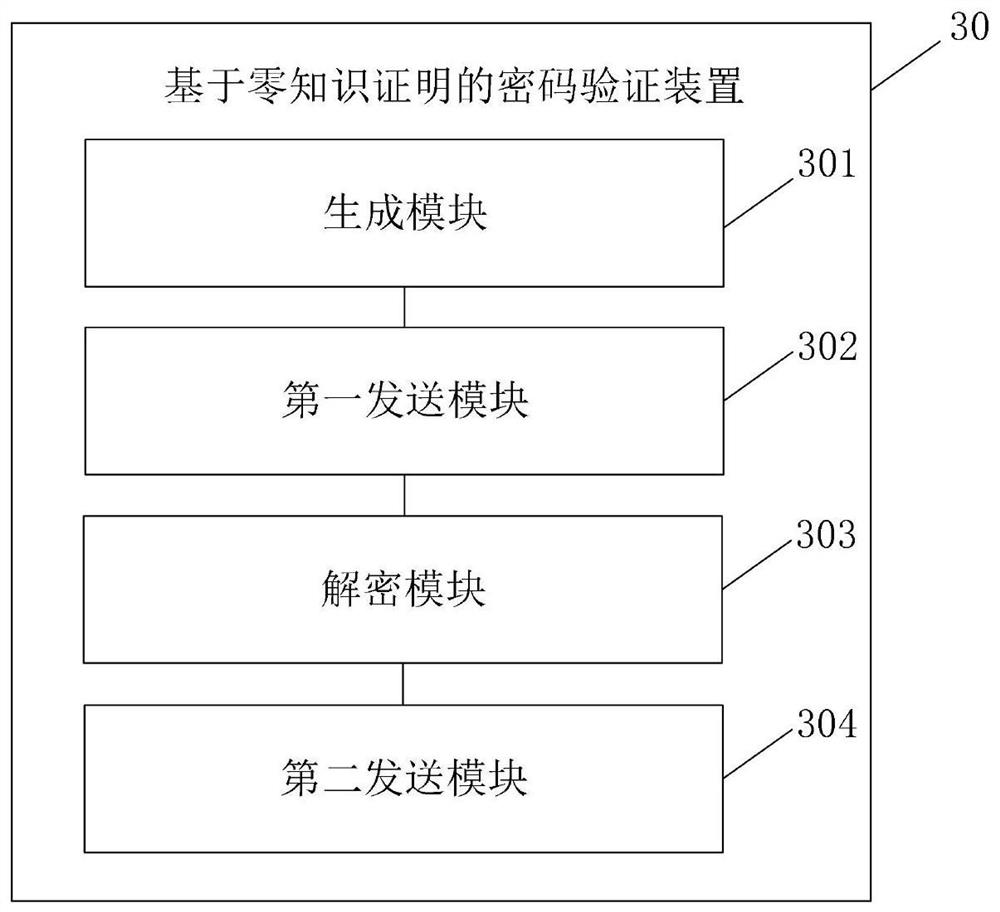
Password verification method and device based on zero knowledge proof and electronic equipment
ActiveCN112202551APrevent leakageGuaranteed verifiabilityKey distribution for secure communicationUser identity/authority verificationPasswordInformation networks
The invention provides a password verification method and device based on zero knowledge proof and electronic equipment, and is applied to the field of password verification, the method comprises thesteps that the advantages of the zero knowledge proof are exerted, information related to an account password is not transmitted in the account password verification process, and a network eavesdropper cannot obtain any information about the account password, User passwords are effectively prevented from being leaked due to network transmission. Furthermore, the replay attack is prevented, and theexistence of the two random numbers not only ensures the verifiability of the password of the mobile user, but also ensures that the password is not disturbed by the replay attack; moreover, the secret factor (mobile user password) encrypted by the client is not transmitted to the background, so that the management difficulty of the server protection key is effectively reduced, password crackingor collision cannot be carried out even if the server storage information is leaked, the server information protection requirement is small, and the password leakage risk does not exist even if the server storage information is separated from the database.
Owner:CHINA CONSTRUCTION BANK
Traceability information uplink and query method and traceability device
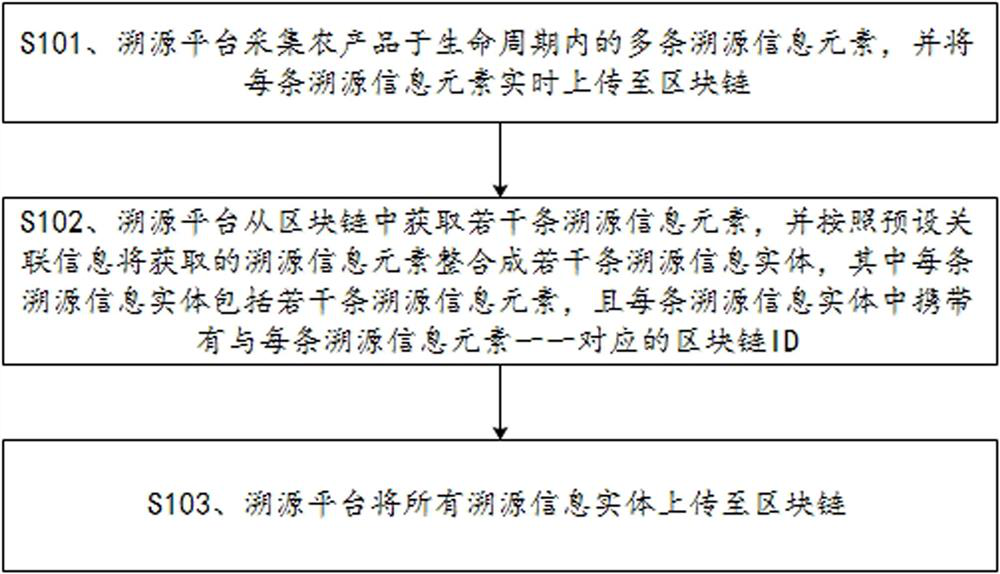
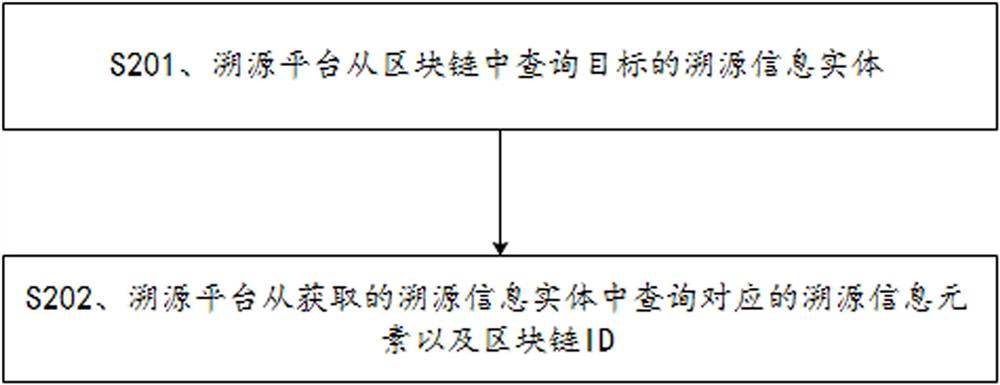
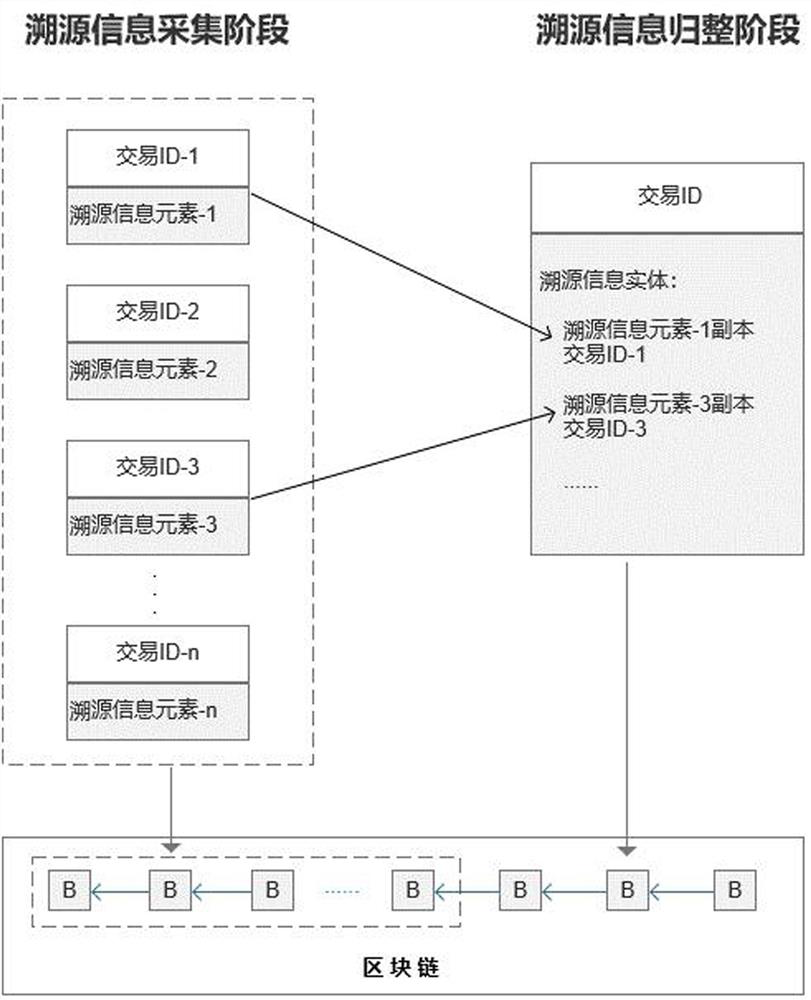
ActiveCN113127571AReduce complexityReduce the number of timesDatabase distribution/replicationCommerceDatabaseReliability engineering
The invention discloses a traceability information uplink and query method and a traceability device. The method comprises the steps of collecting multiple traceability information elements of an agricultural product, and uploading the traceability information elements to a block chain in real time; acquiring a plurality of traceability information elements from the block chain, the acquired traceability information elements being integrated into a plurality of traceability information entities according to preset associated information, and the traceability information entities carrying block chain IDs corresponding to the traceability information elements; and uploading all the traceability information entities to the block chain. According to the method, a plurality of traceability information elements are sorted into the traceability information entity, and then secondary uplink is carried out, so that repeated and redundant traceability data can be removed from the traceability query result, the authenticity of the traceability data is ensured, and due to the fact that the granularity of the uplink data is increased, the traceability information entity instead of the traceability information element is queried from the block chain, so that the traceability complexity of the user is reduced, the number of times of querying from the block chain is reduced, and the query efficiency and performance are improved.
Owner:HUAZHI RICE BIO TECH CO LTD
A Proxy Reassignment Verifier Signature Method
InactiveCN105471918BOne more chance to verify content consumersIncreased opportunity for fine-grained controlTransmissionDesignated verifier signatureDigital signature
The invention relates to an agent re-assignment verifier signature method, comprising the steps of: a service provider operating a setting algorithm to generate public system parameters for all sides; a content provider and a content consumption side operating a key generation algorithm to generate a self key pair; the content provider using a self private key to perform a first level digital signature on contents, and uploading first level digital signature values and contents to the service provider; the content consumption side exchanging contents with the content provider, and the content provider generating a resign key and uploading key information to the service provider; the content consumption side requiring the service provider to provide assigned contents, the service provider generating a second level digital signature, and providing the assigned contents and the second level digital signature for the content consumption side; the content consumption side using the public key provided by the content provider to verify the second level digital signature; and the content consumption side using a self key to independently generate a verifiable second level digit signature about the obtained contents.
Owner:SUN YAT SEN UNIV
Blockchain-based Internet of Things heterogeneous identification analysis system and method
The embodiment of the present invention provides a blockchain-based system and method for analyzing heterogeneous identifiers of the Internet of Things. The system includes: multiple subsystems forming a tree structure; the top layer is a verification subsystem; the bottom layer includes multiple data subsystems; the middle layer includes several verification subsystems; A subsystem communication connection; each data subsystem corresponds to a coding standard; the data subsystem is used to store the IoT logo and the information corresponding to the IoT logo that conform to the corresponding coding standard in the corresponding blockchain above; the verification subsystem is used to store the verification information of each block on the block chain corresponding to the communication-connected next layer subsystem on the corresponding block chain. The blockchain-based IoT heterogeneous identification analysis system and method provided by the embodiments of the present invention classify, store and manage IoT heterogeneous identifications through different data links, and can realize more efficient analysis of IoT heterogeneous identifications.
Owner:STATE GRID HENAN INFORMATION & TELECOMM CO +2
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com