Patents
Literature
203 results about "Software analytics" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Software analytics is the analytics specific to the domain of software systems taking into account source code, static and dynamic characteristics (e.g., software metrics) as well as related processes of their development and evolution. It aims at describing, monitoring, predicting, and improving efficiency and effectivity of software engineering throughout the software lifecycle, in particular during software development and software maintenance. The data collection is typically done by mining software repositories, but can also be achieved by collecting user actions or production data. One avenue for using the collected data is to augment the integrated development environments (IDEs) with data-driven features.
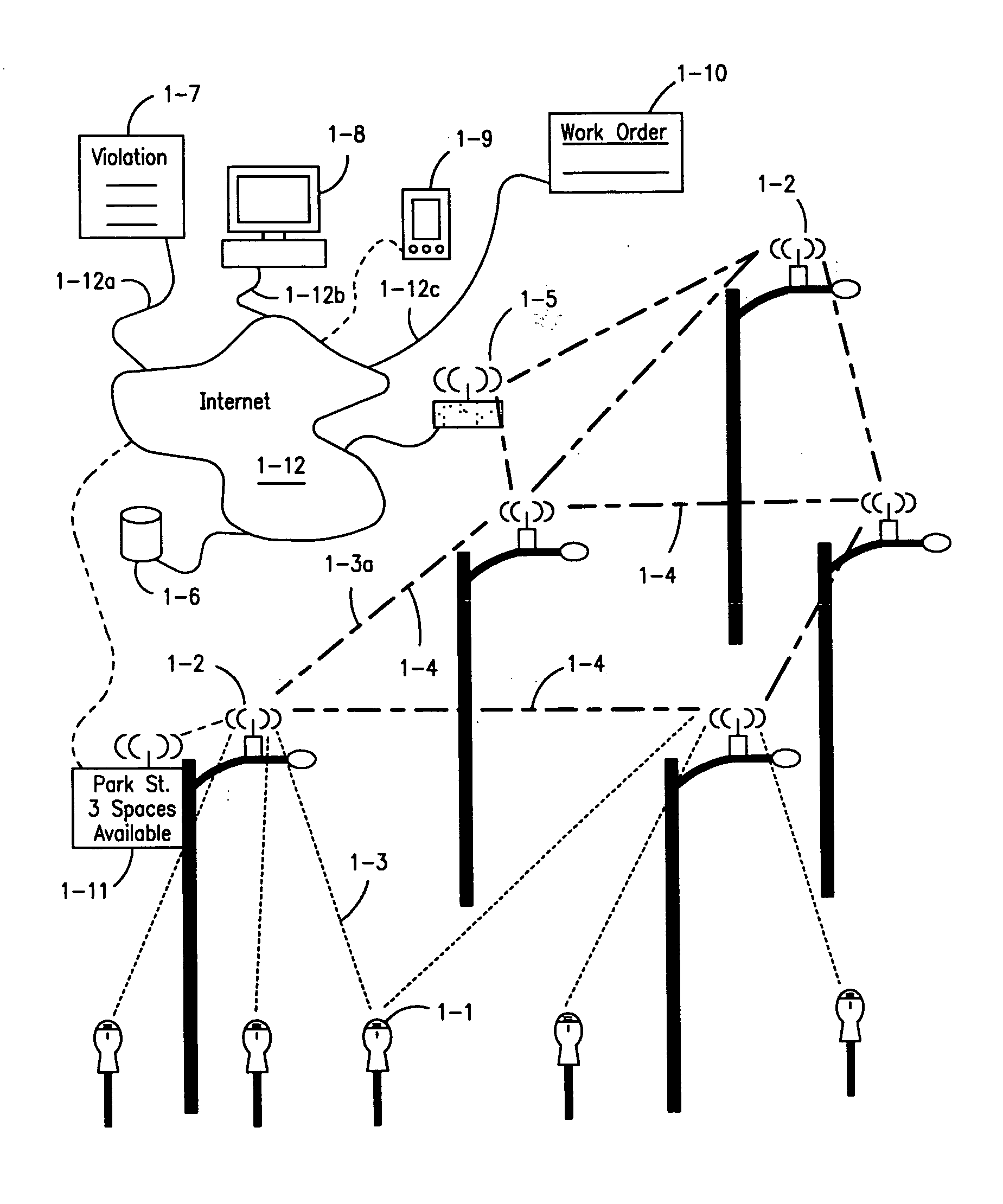
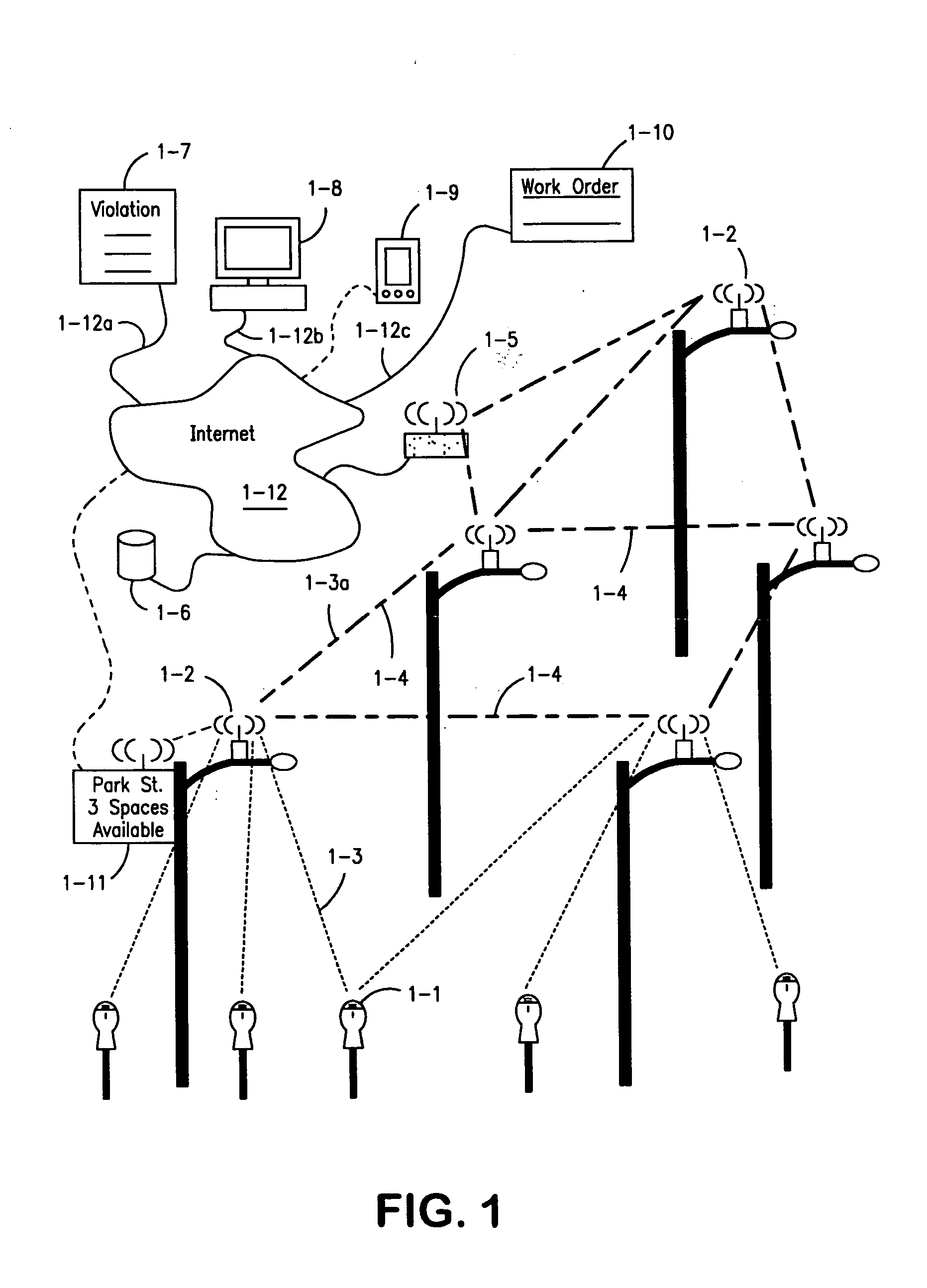
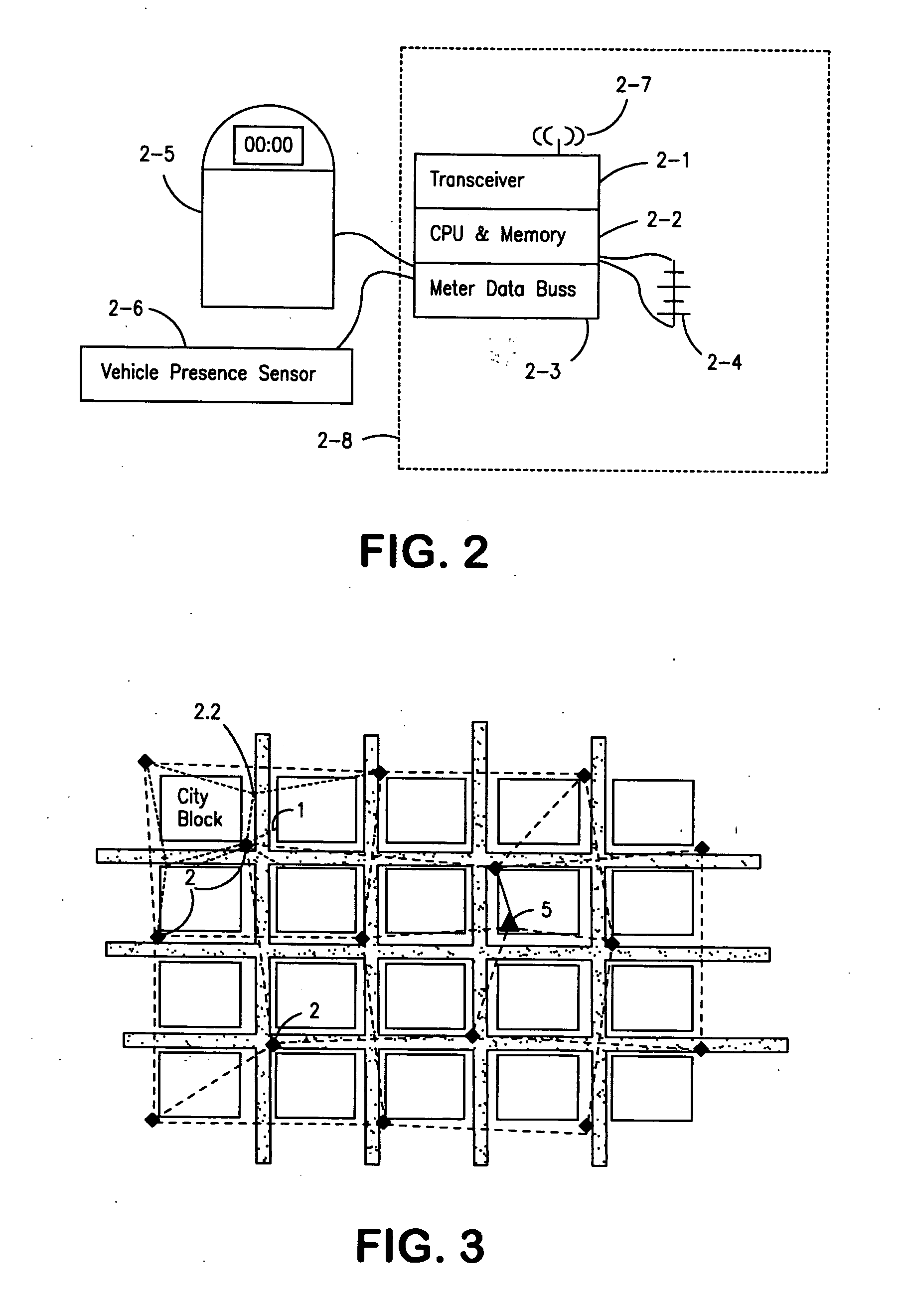
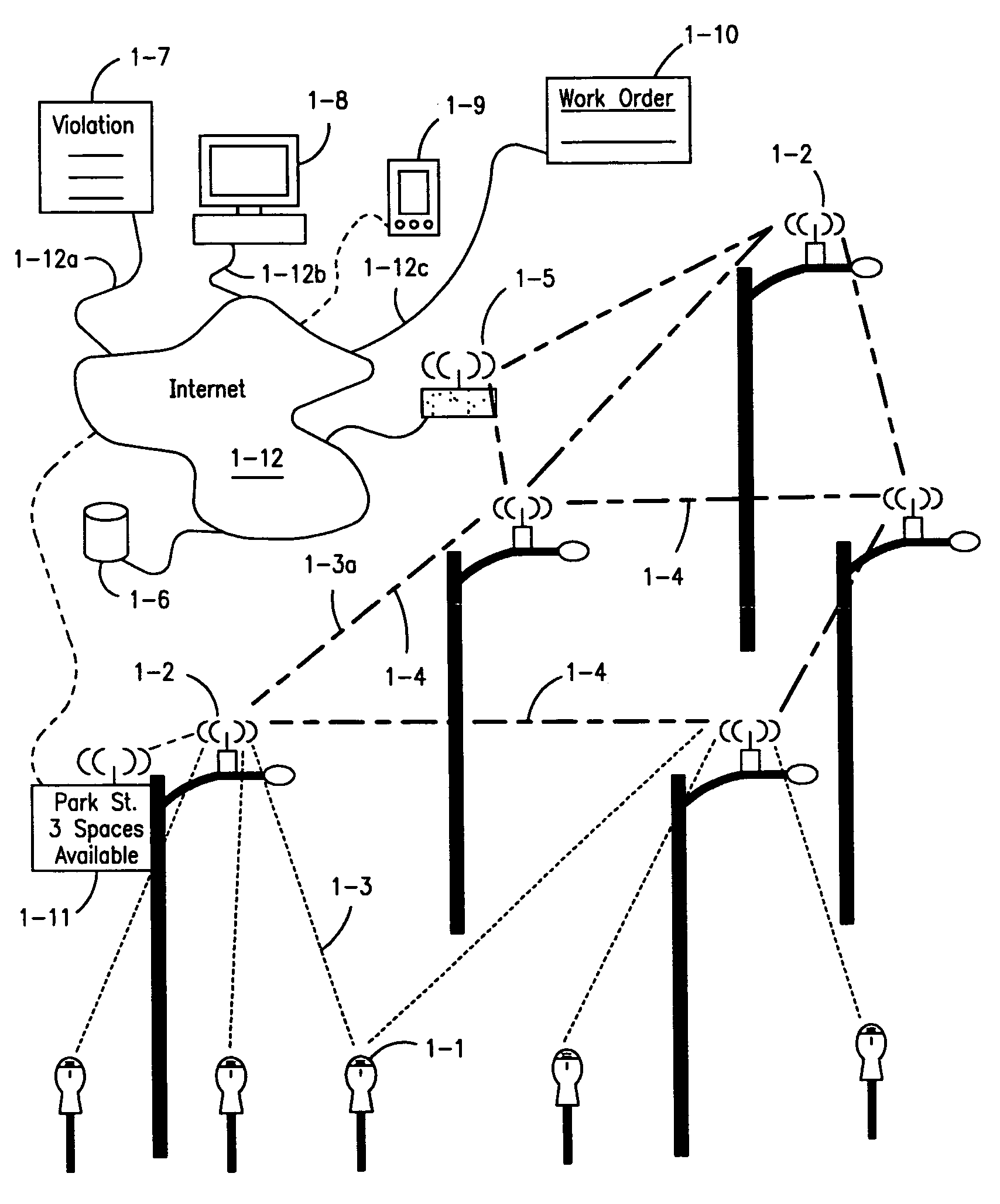
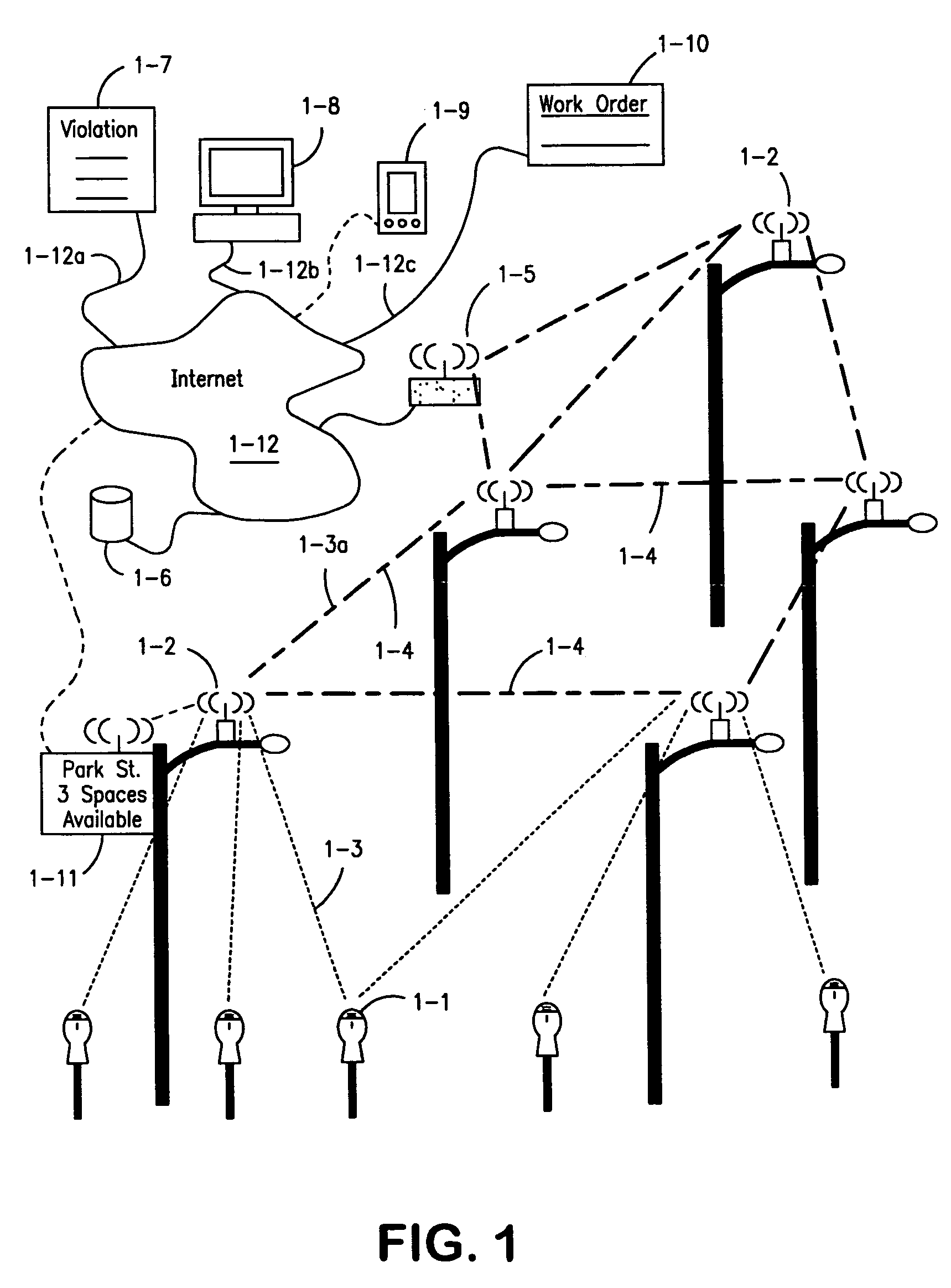
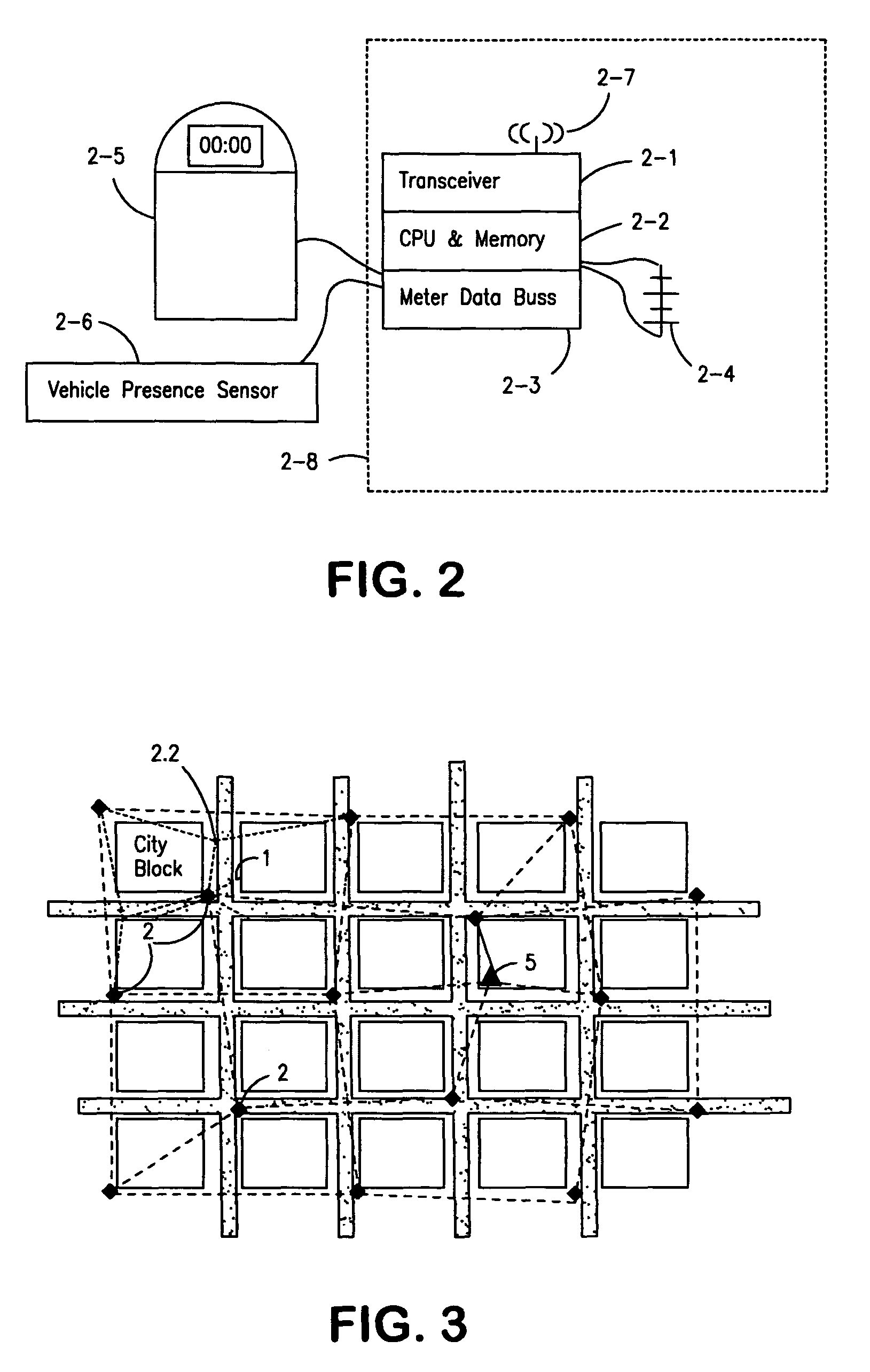
Parking system employing rem techniques
ActiveUS20080291054A1Low efficiencyAllocation is accurateTicket-issuing apparatusTransmission systemsVehicle detectorSoftware analytics
The system described is an integrated parking management system which makes use of patented vehicle detectors to collect and transmit data, essentially in near real time, as to all events happening as to single or multiple parking spaces (e.g. current and historic use, length of time of occupancy of current occupant) to a central clearing device for which patent application has been made which serves as a logic core and repository, making use of proprietary software, analyzing, displaying and distributing the data so developed as to a parking plant and all of its components to allow all parties (including prospective users) who are concerned with the various aspects of a parking plant and its components (e.g. determination as to availability of spaces, maintenance and repair of meters, collection of revenues and enforcement of parking regulations) not only to access and make passive use of the information developed, in near real time, to permit them to identify what's happening to the plant and its components as to their own particular interest in such plant and so maximize the efficient use both of the resources of the plant and their own resources directed to the particular aspect of their interface with the plant and its components but also to access and make active use of such information for whatever purpose and in whatever fashion using whatever means of access they may wish. While others have made claim to certain of the individual functions described, e.g. vehicle detection, nobody has identified or patented
Owner:INNOVAPARK
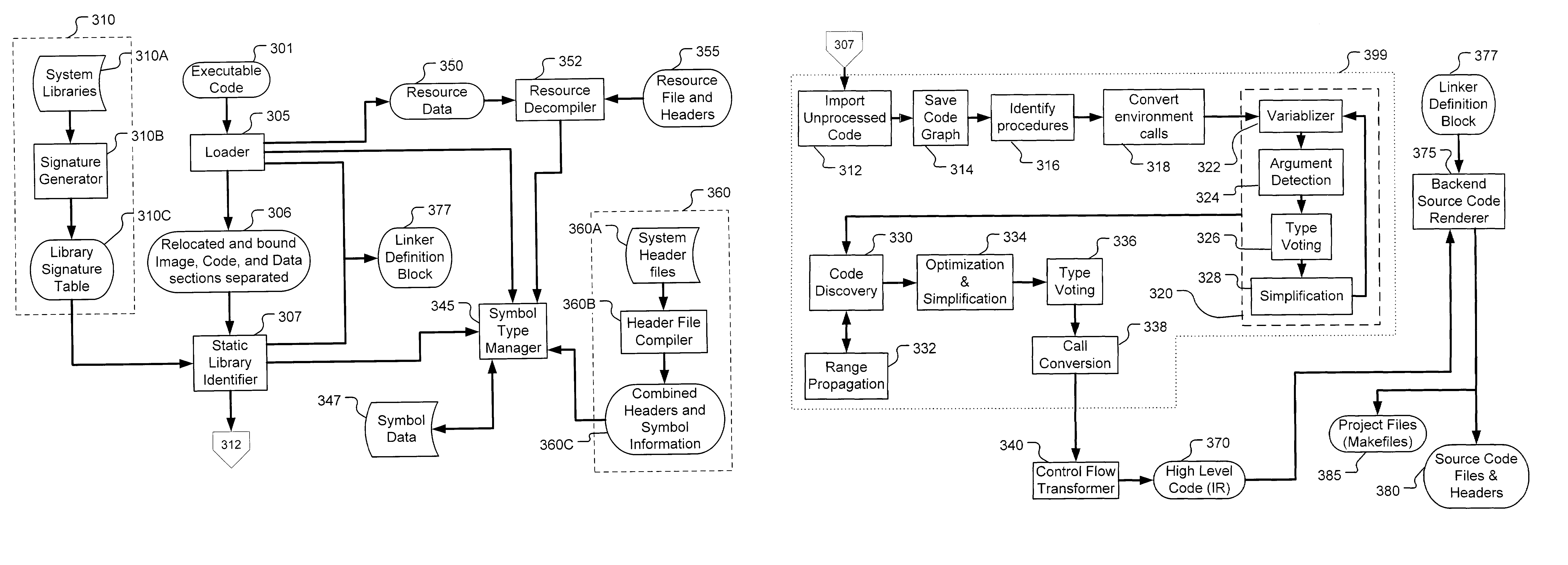
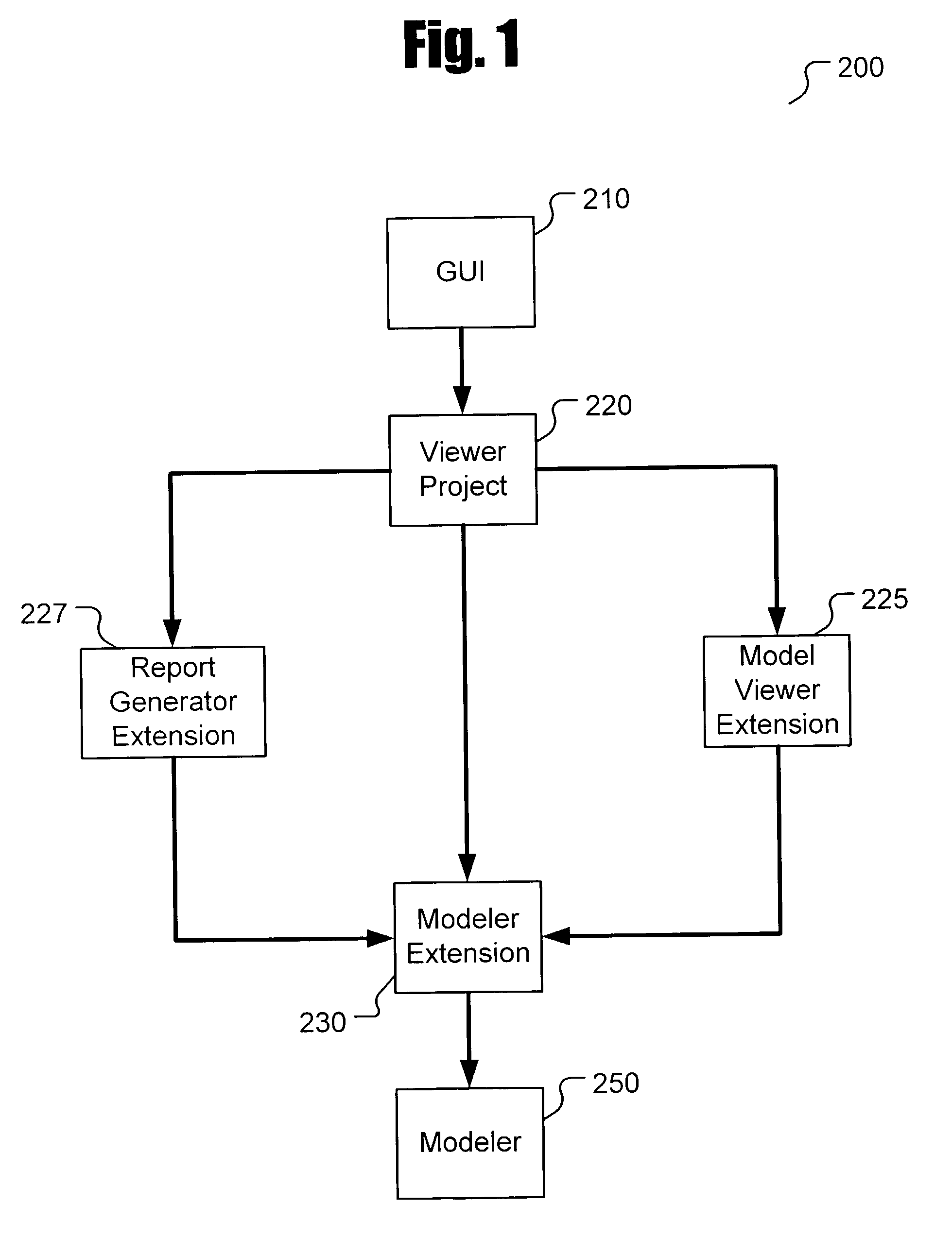
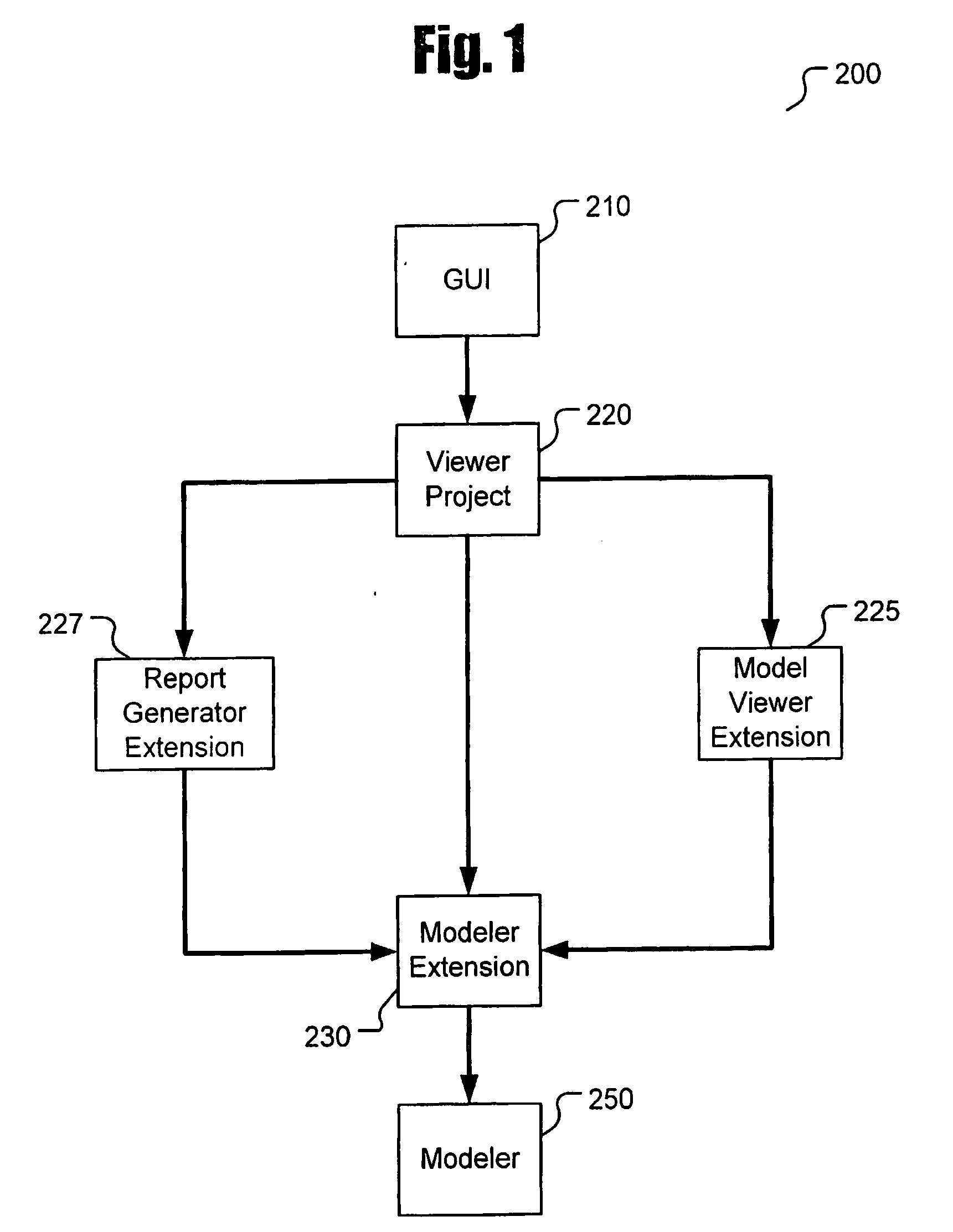
Software analysis framework
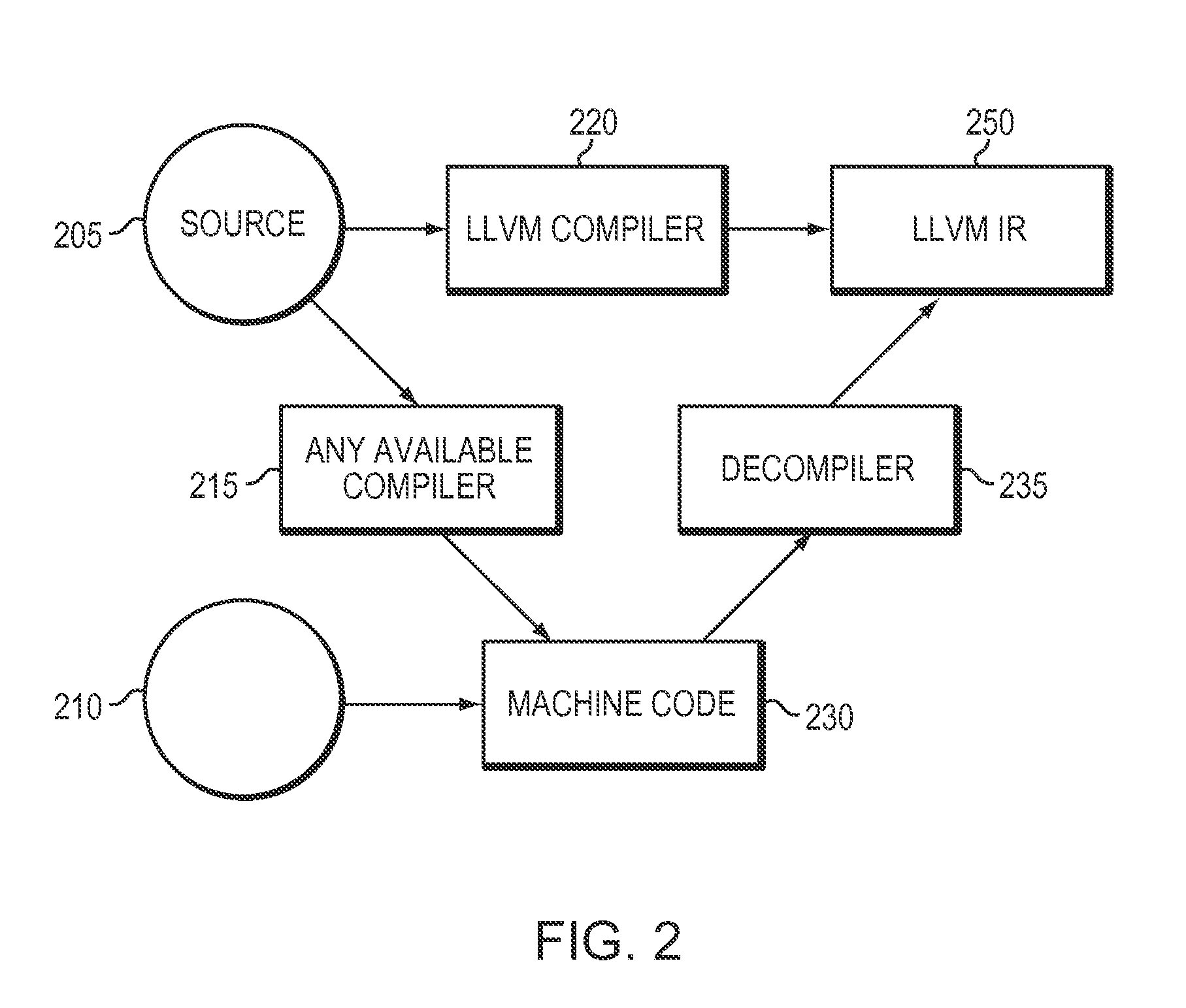
InactiveUS7051322B2Decompilation/disassemblySpecific program execution arrangementsSoftware analyticsScript analysis
Presently described is a decompilation method of operation and system for parsing executable code, identifying and recursively modeling data flows, identifying and recursively modeling control flow, and iteratively refining these models to provide a complete model at the nanocode level. The nanocode decompiler may be used to determine if flaws, security vulnerabilities, or general quality issues exist in the code. The nanocode decompiler outputs in a standardized, human-readable intermediate representation (IR) designed for automated or scripted analysis and reporting. Reports may take the form of a computer annotated and / or partially human annotated nanocode listing in the above-described IR. Annotations may include plain English statements regarding flaws and pointers to badly constructed data structures, unchecked buffers, malicious embedded code or “trap doors,” and the like. Annotations may be generated through a scripted analysis process or by means of an expert-enhanced, quasi-autonomous system.
Owner:VERACODE
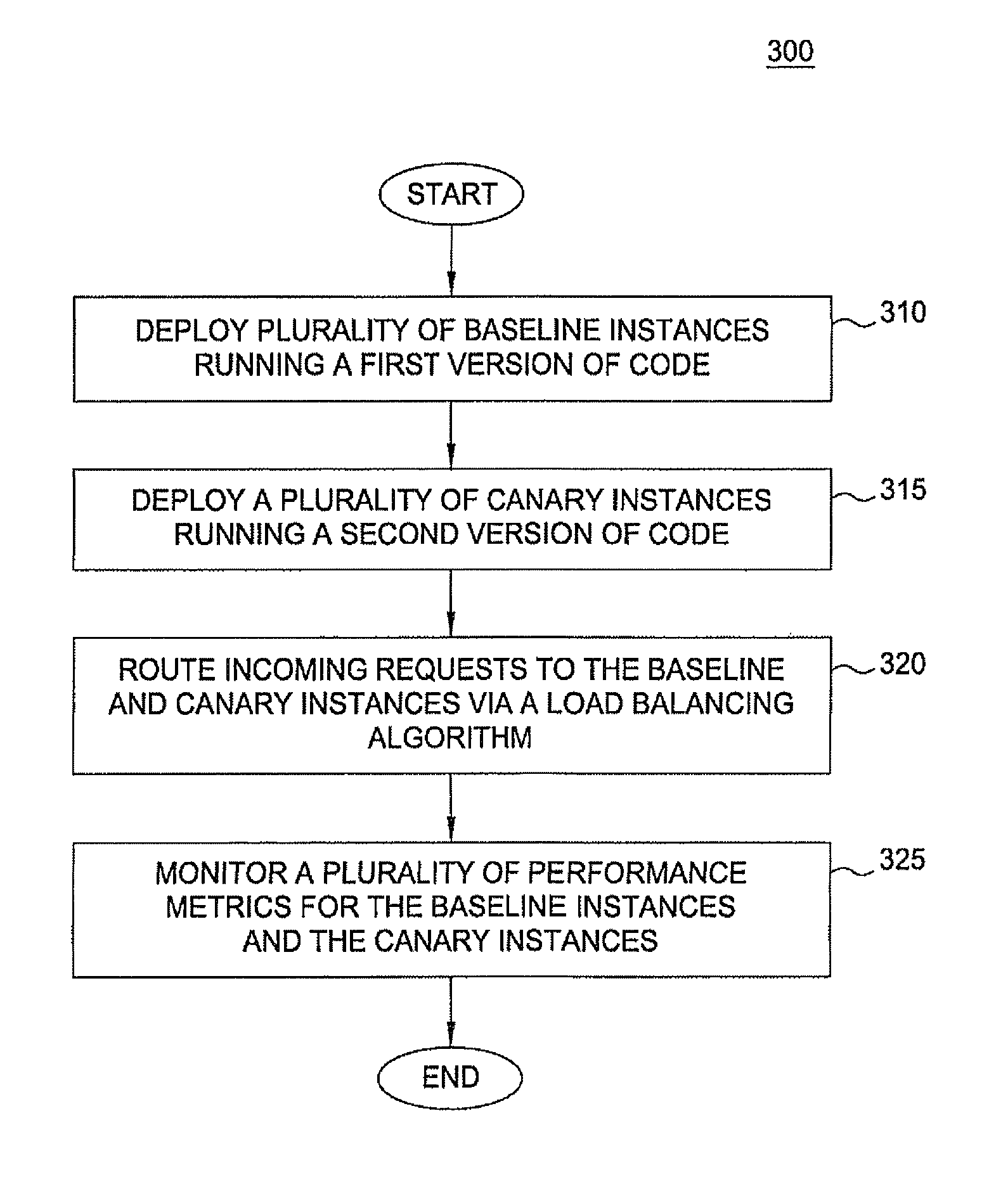
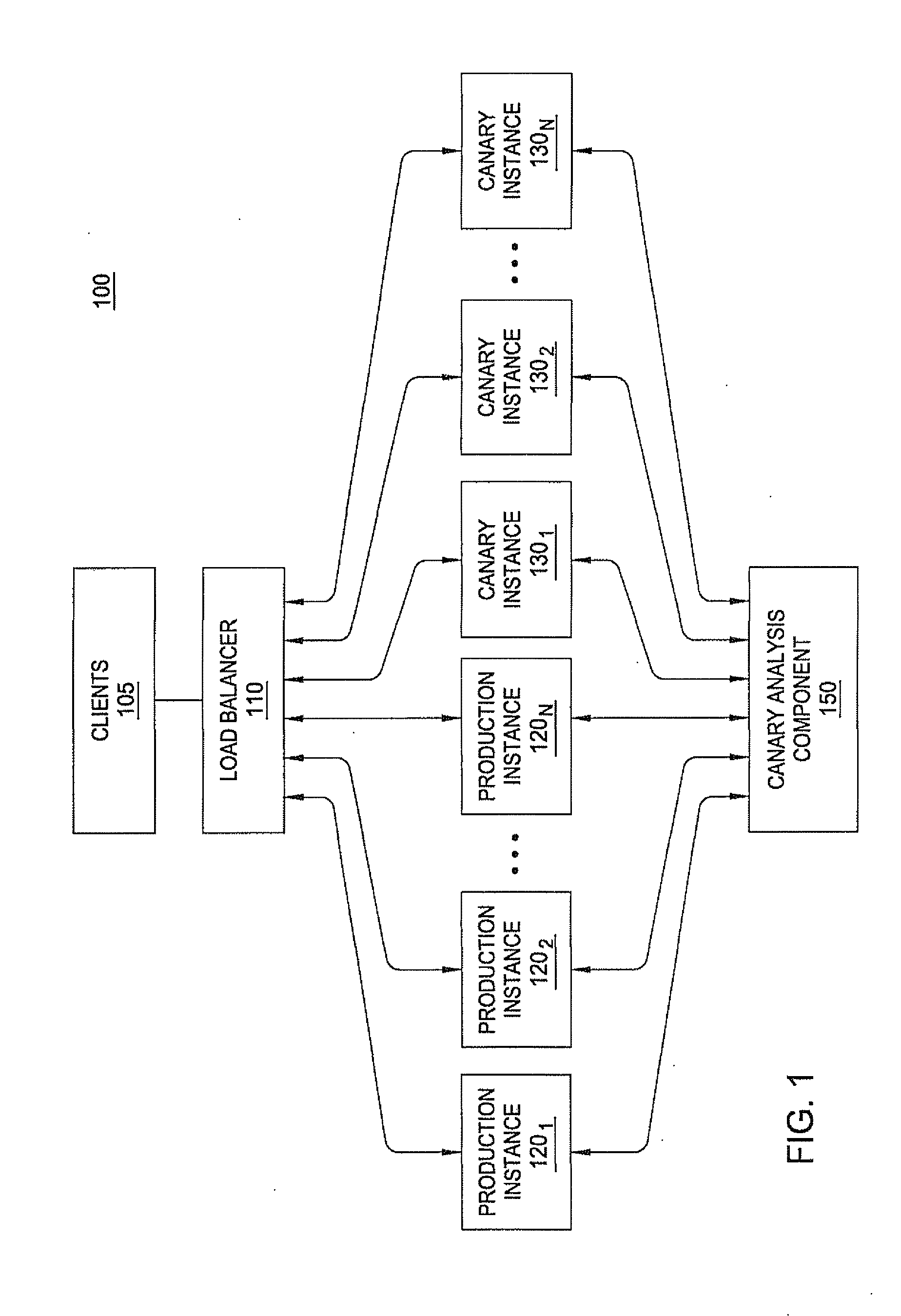
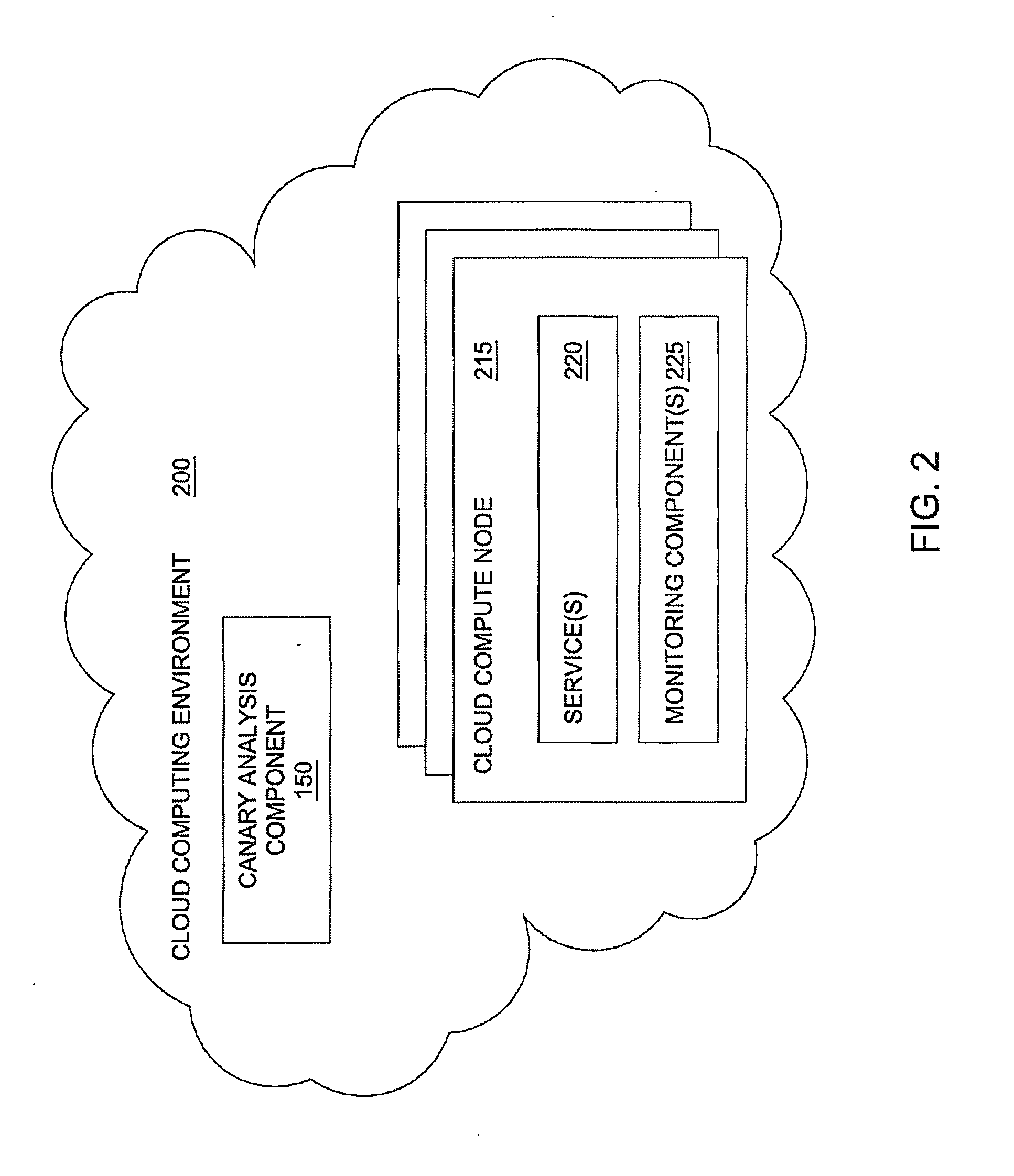
Progressive deployment and termination of canary instances for software analysis
ActiveUS20140379901A1Error detection/correctionDigital computer detailsSoftware analyticsEngineering
A data processing method, comprising: using computing apparatus, causing instantiating a plurality of baseline application instances that are running a first version of software, and one or more canary application instances that are running a second version of the software; using computing apparatus including a load balancer, causing selectively routing a first proportion of incoming requests to the baseline instances, and routing a second proportion of the incoming requests to the canary instances; monitoring the plurality of canary instances to collect performance data for performance metrics; determining that the performance data indicates a negative performance issue, and in response thereto: using computing apparatus, automatically updating the first proportion to be larger and updating the second proportion to be smaller, and then reconfiguring the load balancer based upon the first proportion and the second proportion; terminating one or more of the canary application instances.
Owner:NETFLIX
System and method for providing simulated images through cosmetic monitoring
InactiveUS20080219528A1Accurate storageImprove accuracyTypewritersCharacter and pattern recognitionAnimationSoftware analytics
An automated cosmetic applicator uses wide-angle cameras, a high-resolution camera, and a differential lighting process to capture images of a body. Software analyzes these images to identify large and small features of the subject and to use these features as landmarks to create in computer memory a corresponding map that is highly accurate and data rich with pixel-level data about the subject's color, light value and texture characteristics. The rich images may be used for tracking the device on the skin, for making accurate corrections to skin, for simulating possible cosmetic enhancements and selecting a desired correction, and for use in other applications such as video games and animations.
Owner:TCMS TRANSPARENT BEAUTY LLC
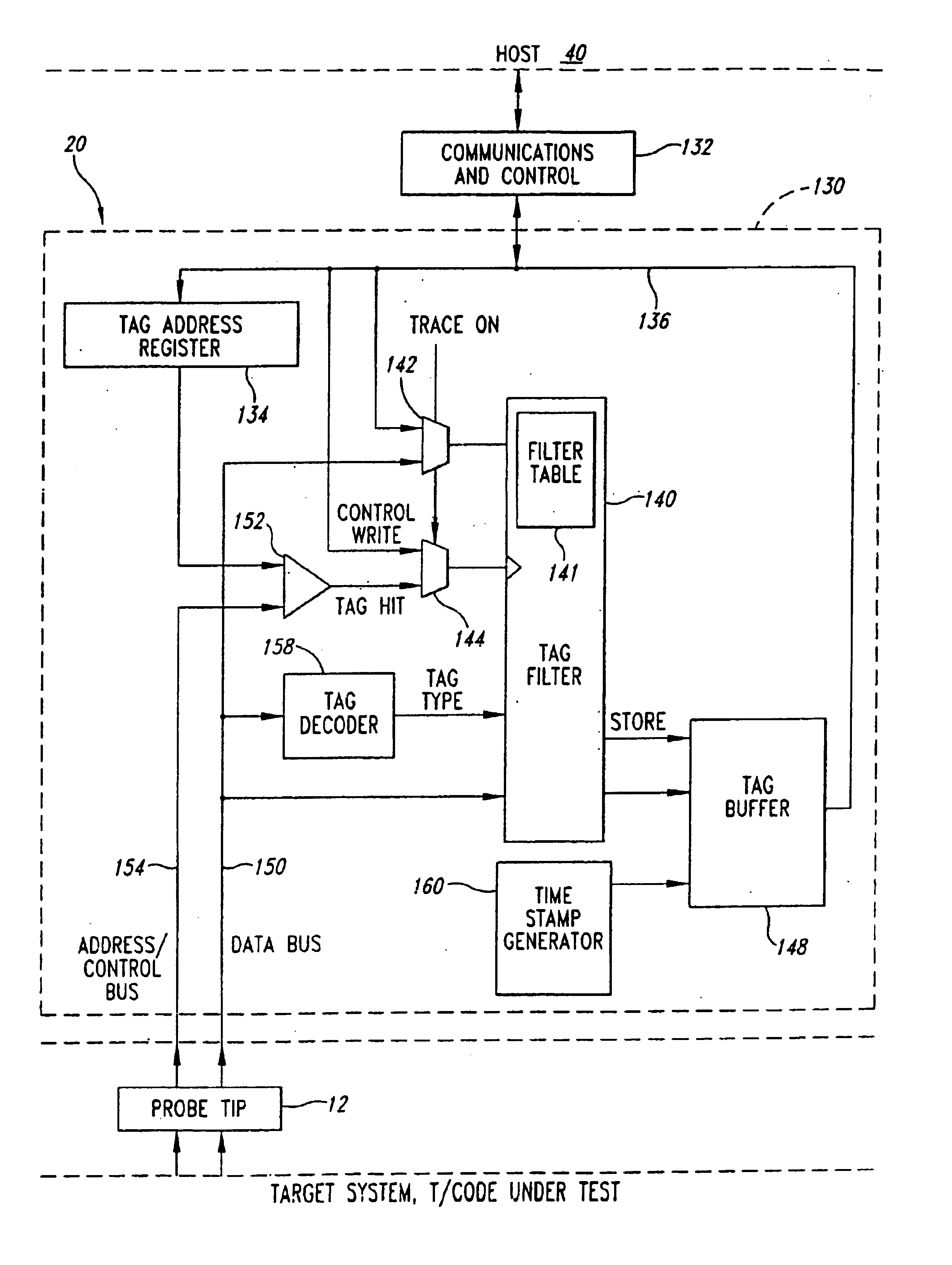
Software analysis system having an apparatus for selectively collecting analysis data from a target system executing software instrumented with tag statements and method for use thereof
A software analysis system having a filter for selectively collecting tags generated by a target system during execution of a software program under analysis in accordance to a programmable filtering criteria. The system includes a decoder for decoding the tag type of the tags captured from the data bus of the target system, and a comparator for comparing the tag types to the programmable filtering criteria to determine whether the tag should be collected. The programmable filtering criteria may be programmed by collecting filter tags from the target system, or directly programmed by a software developer using a filtering user interface. The programmable filtering criteria is implemented by a filter table that stores a flag associated with each tag type. The flag is indicative of whether tag data of a respective tag type should be collected. Tag data of the tag types meeting the programmable filtering criteria have timestamp information appended to the tag data and are collected in a tag buffer.
Owner:NXP USA INC
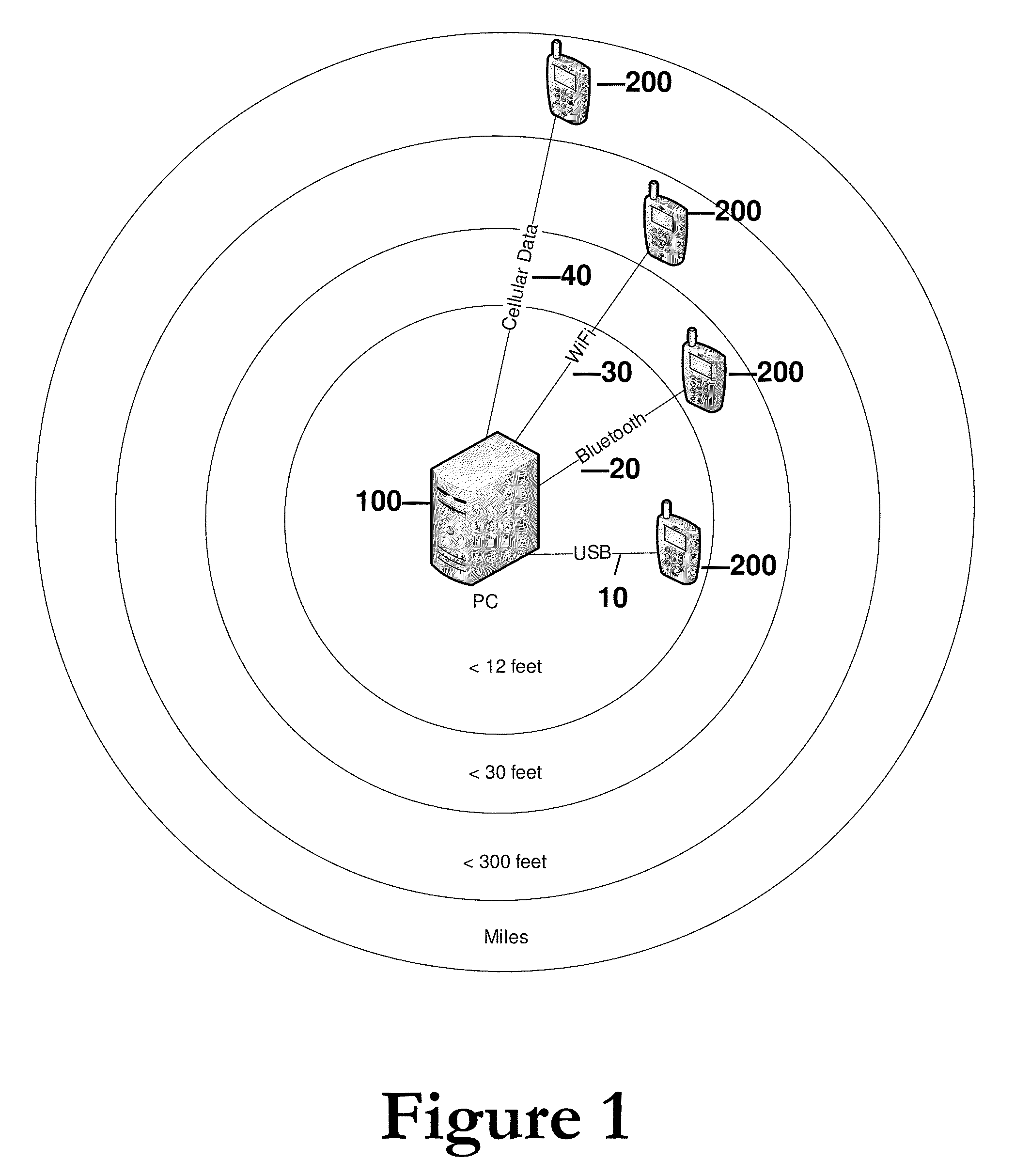
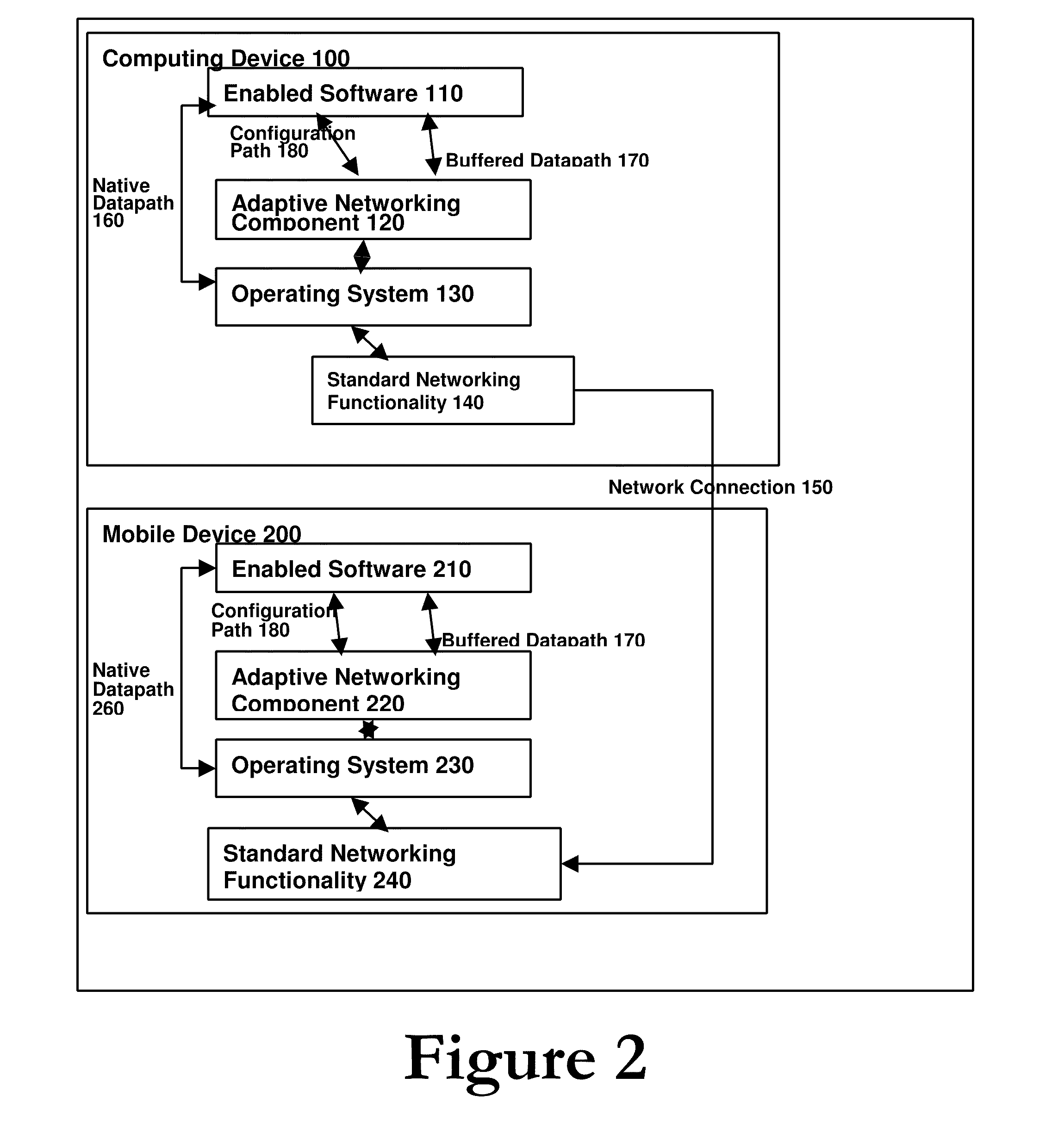
Adaptive Networking For Power Savings
InactiveUS20100159948A1Improve and maintain network connectivityMinimize power consumptionEnergy efficient ICTAssess restrictionNetwork connectionSoftware analytics
An adaptive networking system for power savings which applies to distributed computing systems includes a computing device which runs Adaptive Networking Component software which analyzes, obtains and maintains reliable network connection(s) to one or more mobile device(s) containing cooperating similar software. An Adaptive Networking Component provides power optimized, reliable network connection between a Computing device and a Mobile device. Enabled Software (for example, a communications application) uses the Adaptive Networking Component to reduce system power consumption while maintaining reliable network connections and best available user experience, compared to the power consumption, reliability and user experience when no Adaptive Networking Component(s) are available. The Adaptive Networking Component chooses between different communications transport mechanisms and communicates between connected devices to provide this service.
Owner:TAPROOT SYST
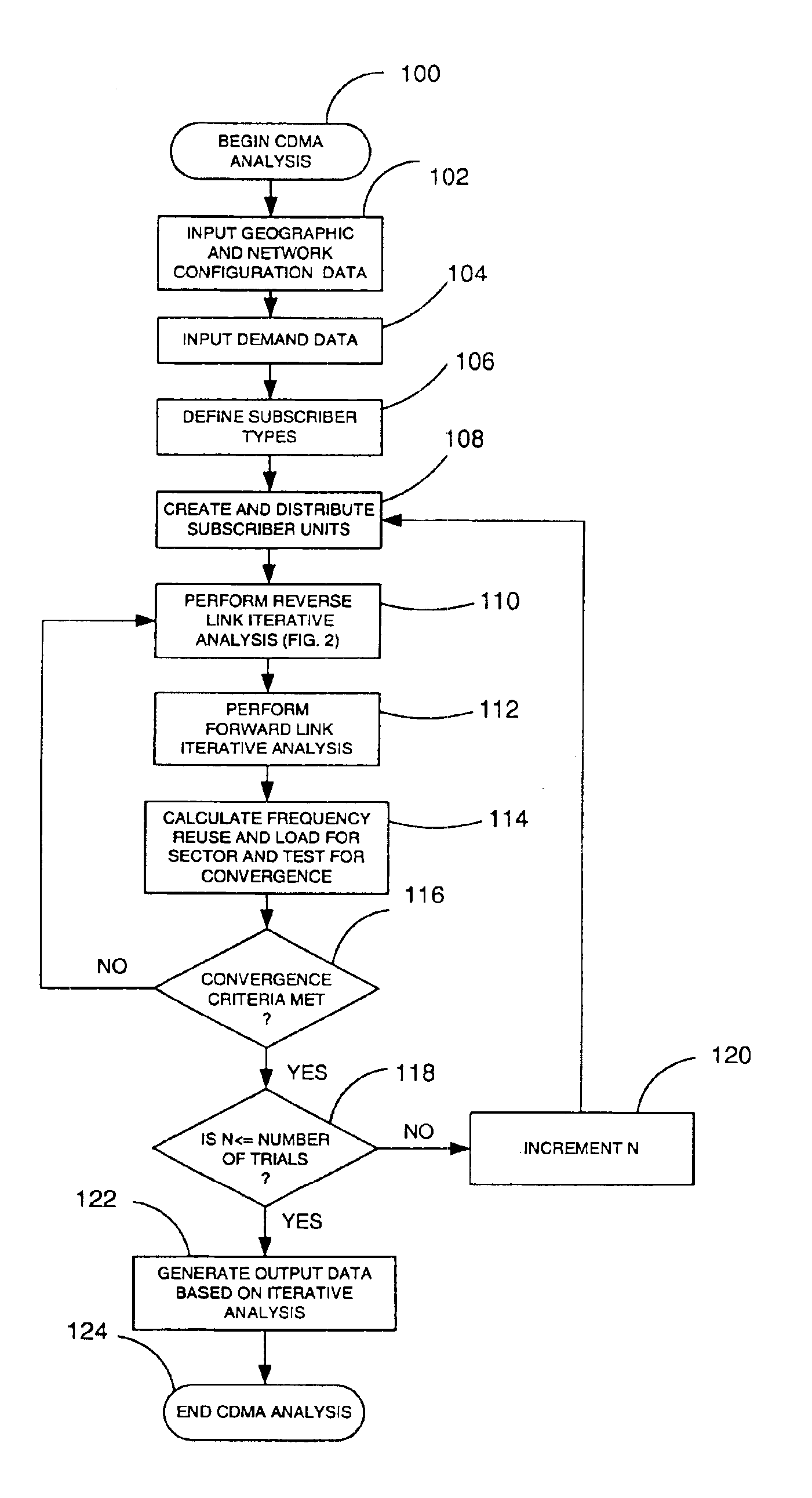
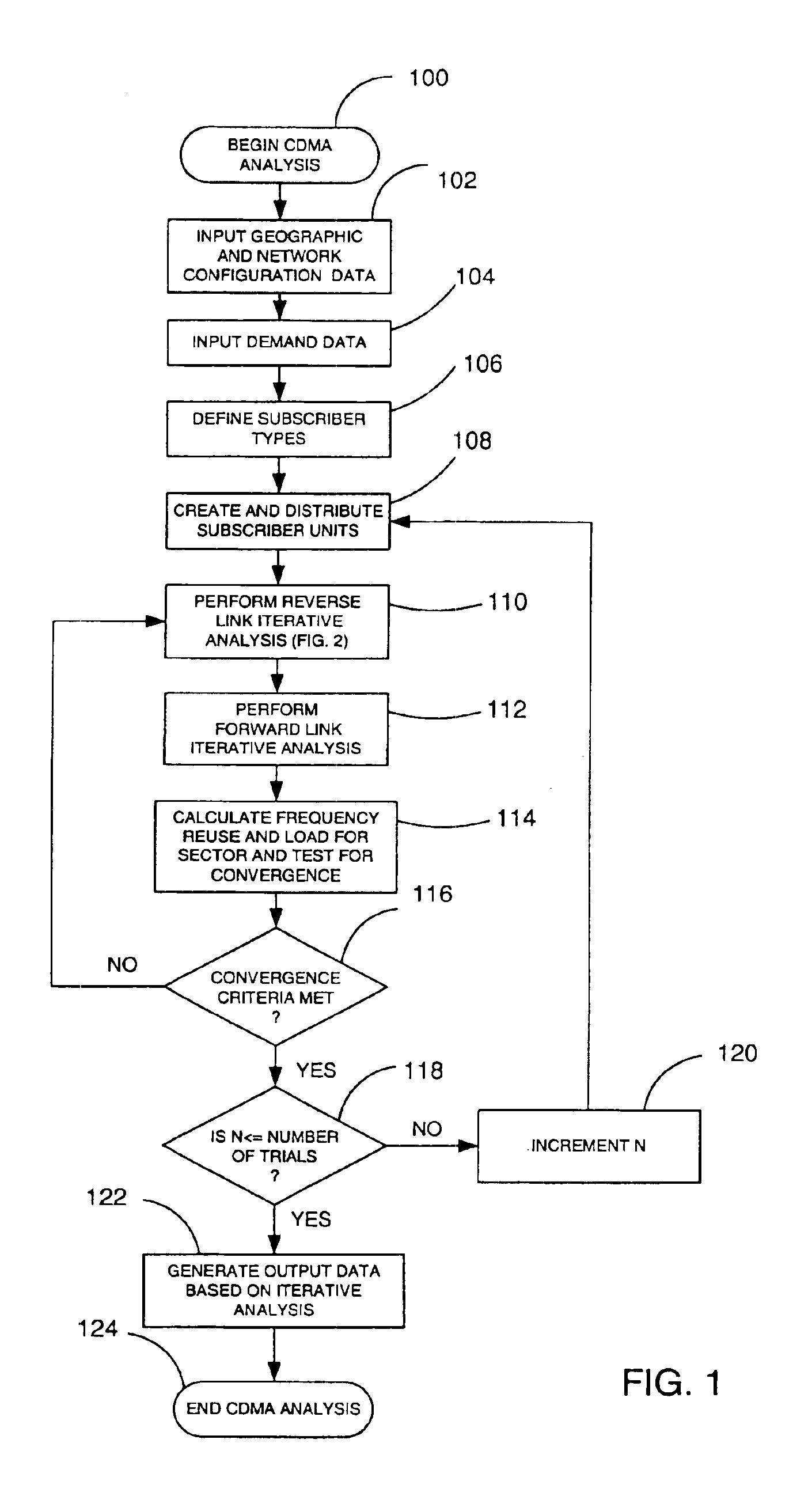
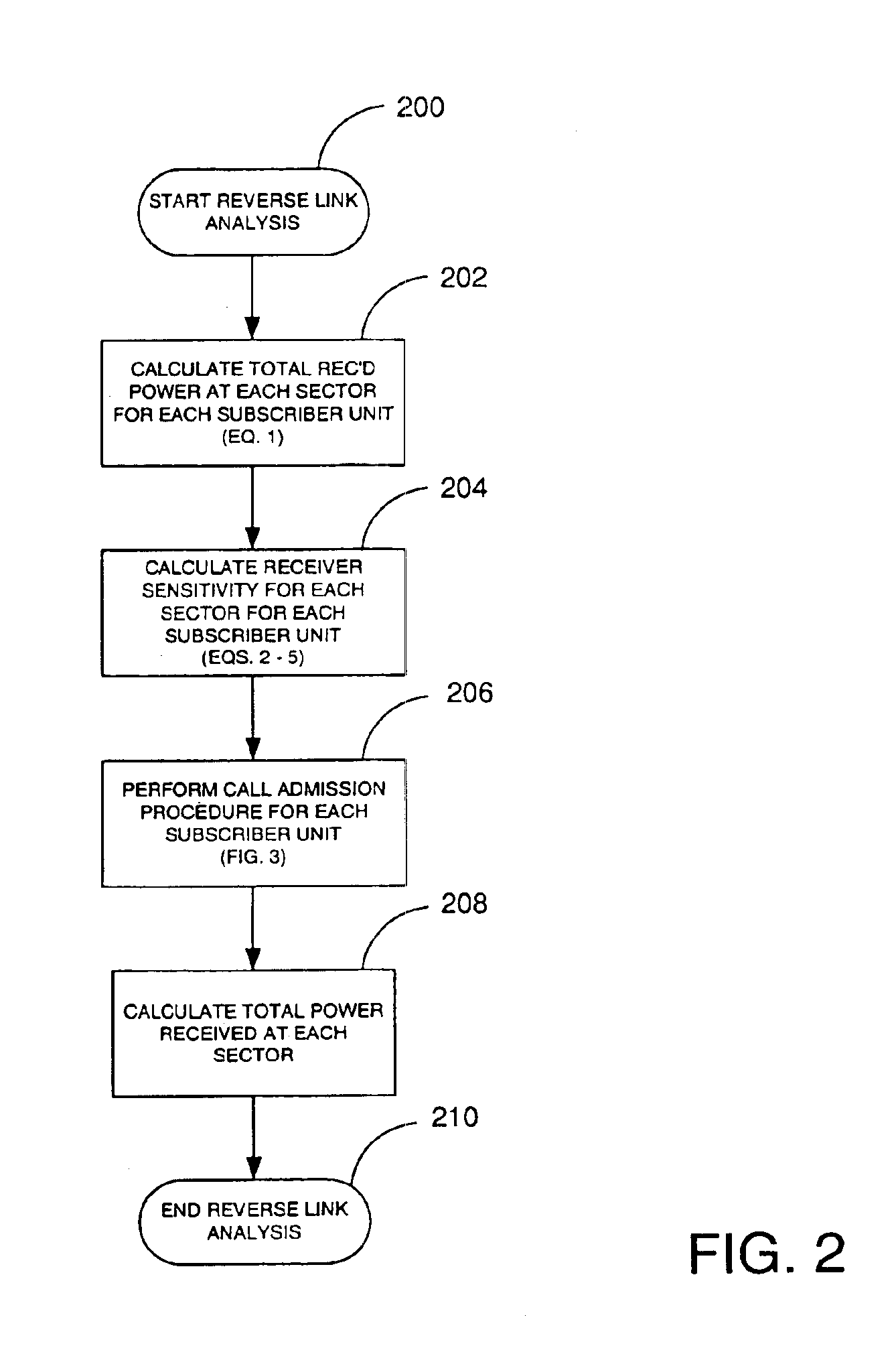
Software analysis tool for CDMA system
InactiveUS6934555B2Power managementNetwork traffic/resource managementSoftware analyticsAnalysis tools
A wireless network planning tool simulates wireless network operation, including subscriber admission processing based resource reservation procedures. Simulated subscribers are associated with an application type. Application types are broadly categorized as either voice type or data type applications. Subscribers of both types are simultaneously simulated. During subscriber admission processing, the CDMA planner attempts to admit simulated subscribers to individual sectors or base stations. At each sector, a percentage of the total forward power capacity is reserved for voice users, and a second or remaining percentage may be reserved for data users. When admitting a voice user to a sector with insufficient remaining power in its voice bucket, the CDMA planner may borrow from the power bucket reserved for data users. Setting aside a power bucket for voice users at each sector insures that one or a few high data rate users do not consume all available resources in a sector.
Owner:INFOVISTA
Parking system employing rem techniques
The system described is an integrated parking management system which makes use of patented vehicle detectors to collect and transmit data, essentially in near real time, as to all events happening as to single or multiple parking spaces (e.g. current and historic use, length of time of occupancy of current occupant) to a central clearing device for which patent application has been made which serves as a logic core and repository, making use of proprietary software, analyzing, displaying and distributing the data so developed as to a parking plant and all of its components to allow all parties (including prospective users) who are concerned with the various aspects of a parking plant and its components (e.g. determination as to availability of spaces, maintenance and repair of meters, collection of revenues and enforcement of parking regulations) not only to access and make passive use of the information developed, in near real time, to permit them to identify what's happening to the plant and its components as to their own particular interest in such plant and so maximize the efficient use both of the resources of the plant and their own resources directed to the particular aspect of their interface with the plant and its components but also to access and make active use of such information for whatever purpose and in whatever fashion using whatever means of access they may wish. While others have made claim to certain of the individual functions described, e.g. vehicle detection, nobody has identified or patented.
Owner:INNOVAPARK
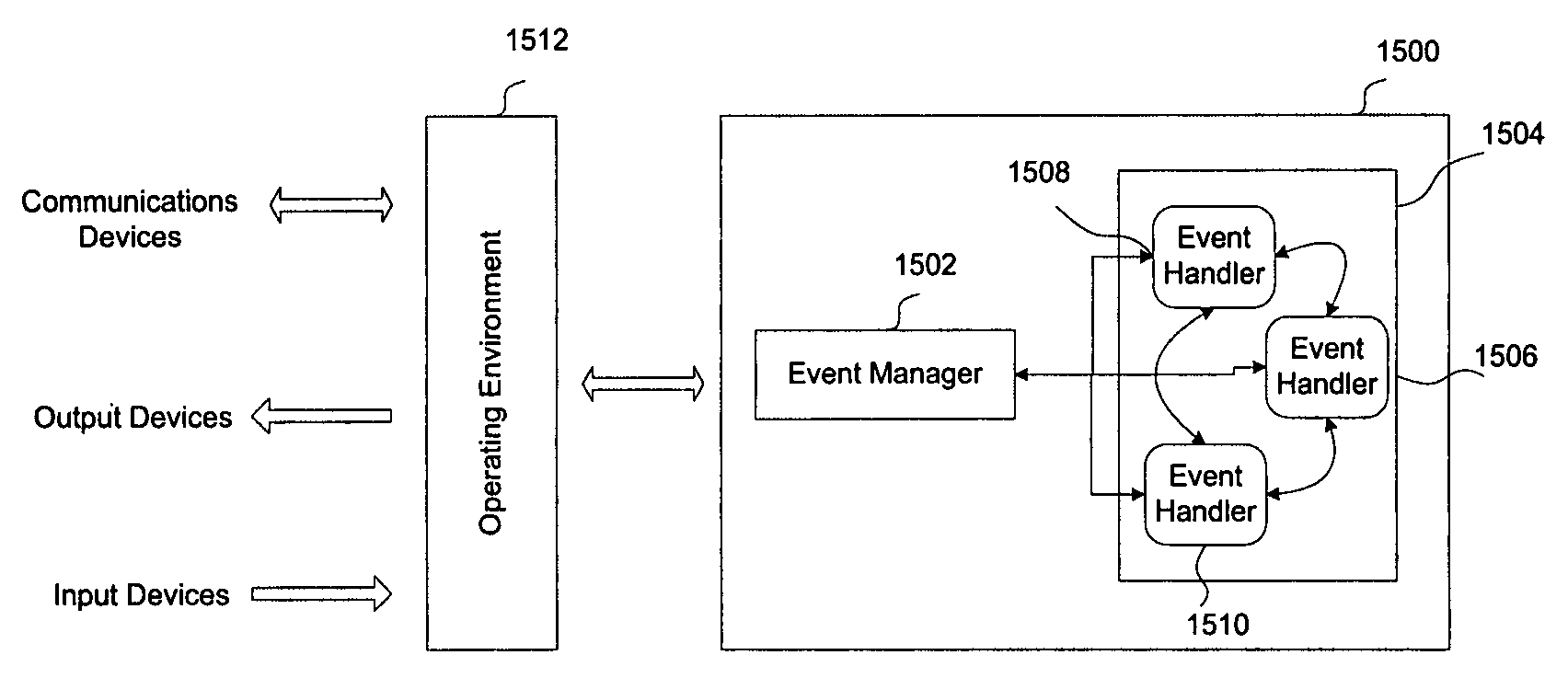
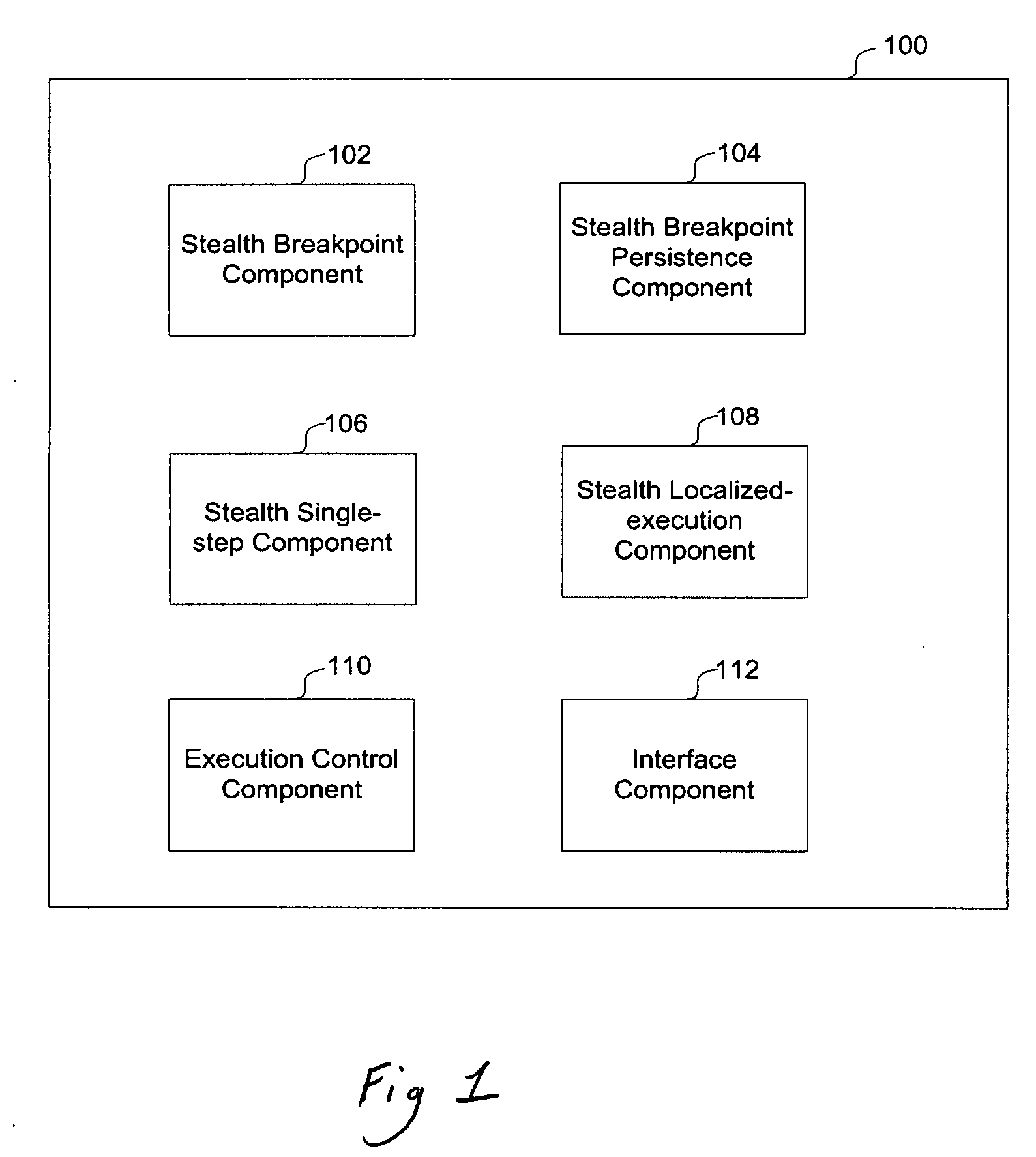
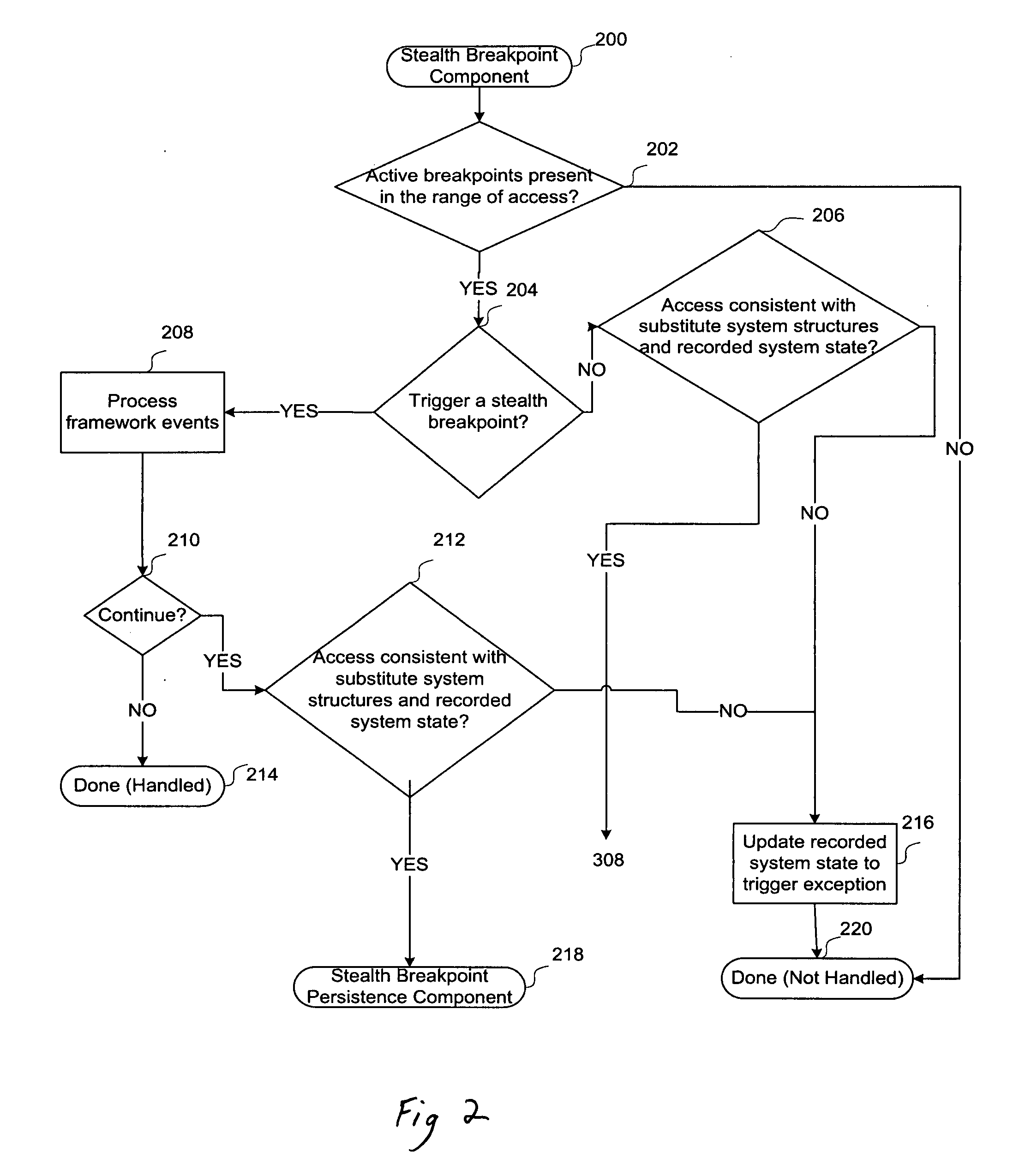
Framework for stealth dynamic coarse and fine-grained malware analysis
InactiveUS20080127114A1Computer security arrangementsSpecific program execution arrangementsMalware analysisGranularity
A framework and method for creating malware analysis tools for dynamic and stealth coarse- and fine-grained malware analysis is provided. In one embodiment a method stalls the execution of a desired code on any form of access to memory or other devices. This can be used to monitor the behavior of the malware with respect to the system at a high level. Upon identification of a high level access, another method can be employed in order to decompose a desired range of code into its individual instructions as they execute thereby revealing the inner structure of the malware as it executes. Since the framework does not employ any processor debugging features, and its methods are self-resilient and completely invisible to the executing code, malware that employ any form of anti-debugging and / or anti-analysis strategy including using framework methods can be easily and effectively analyzed.
Owner:VASUDEVAN AMIT
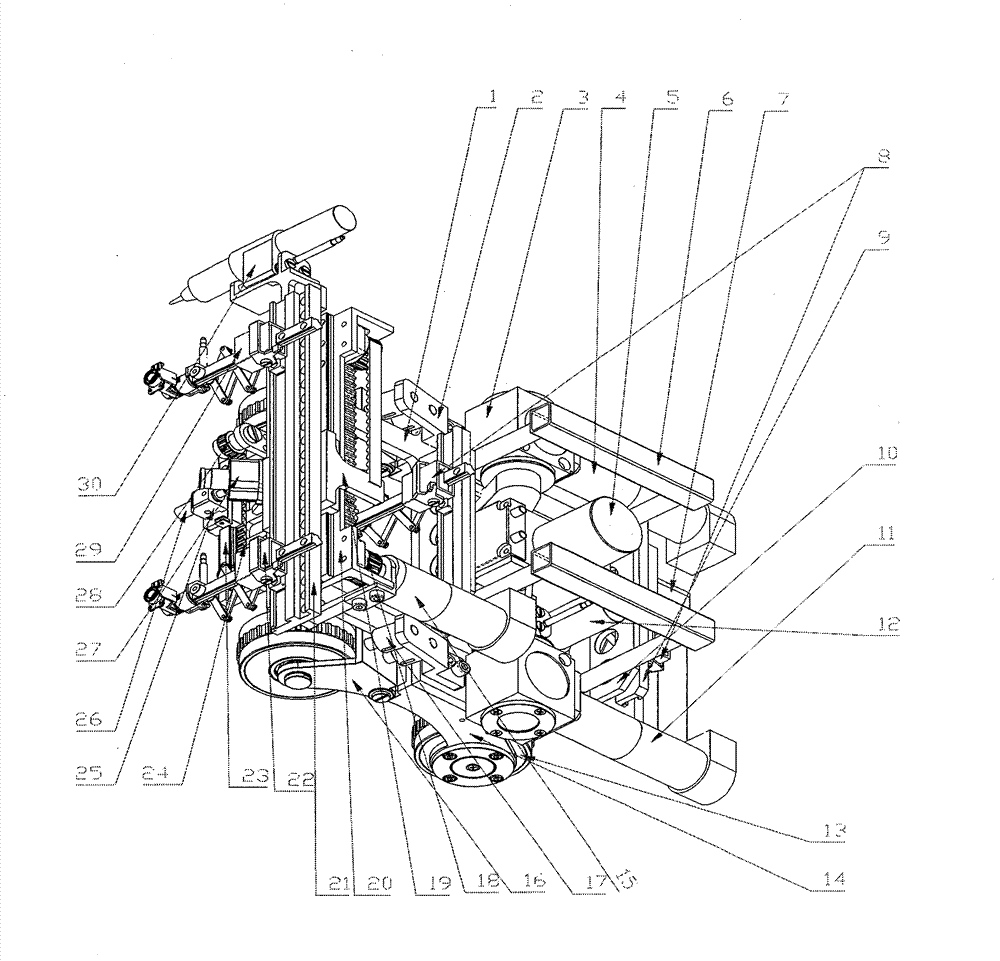
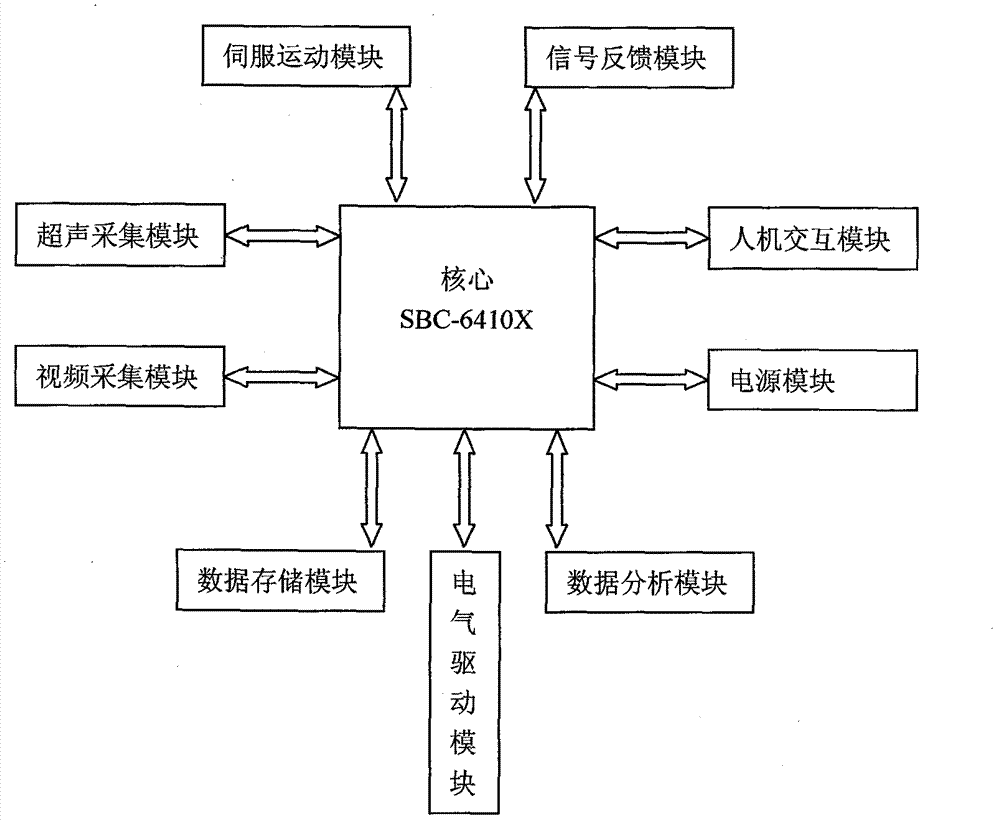
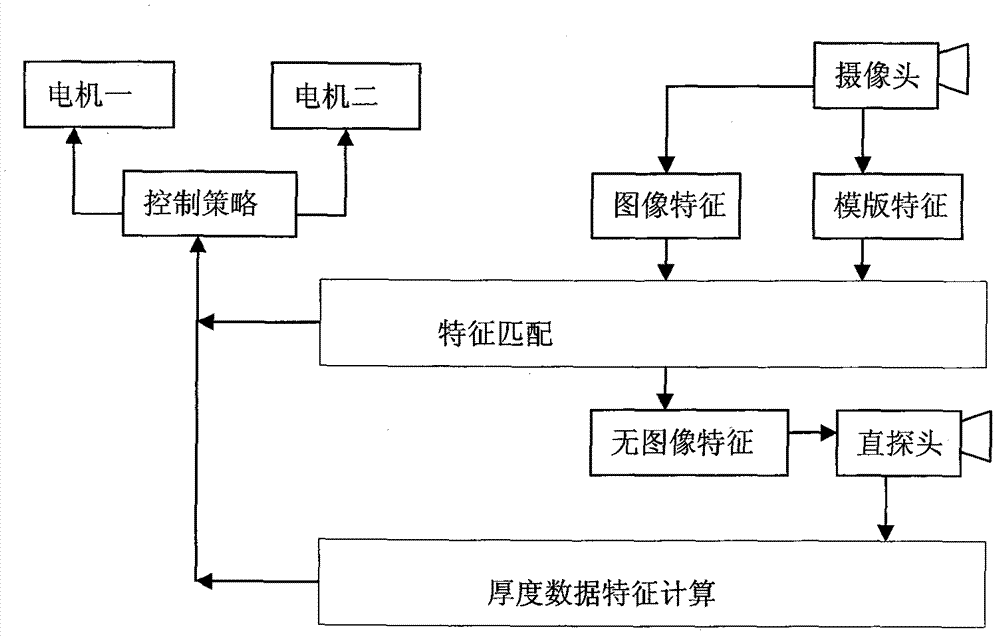
Robot for intelligent tracking ultrasonic detection of welding line, and software analysis system therefor
InactiveCN102901772AAvoid influenceReduce dependenceAnalysing solids using sonic/ultrasonic/infrasonic wavesVehiclesSonificationSimulation
The invention discloses a robot for intelligent tracking ultrasonic detection of a welding line, and a software analysis system therefor. The robot is a crawling robot for intelligent identification and real-time tracking of a welding line. The software analysis system is a system which is used for ultrasonic detection acquisition and software analysis and is loaded into the robot. The robot can be used in the field of ship body welding line ultrasonic detection in ship maintenance and building. In use, the robot can completely store detection data, provide a basis for inquiry of traceability of a detection report, and reduce detection result controversy. In use, the robot can reduce the dependence on an operating personnel technical level, avoid the influence produced by human factors on a detection result, change a simple display reading mode of data analysis into a storage reading mode, realize software-based automatic analysis according to a set judgment standard, and reduce a misreading rate of a large amount of data analyzed artificially. The robot can automatically adapt to surface and inner welding line structures, can simplify multi-step multi-way manual detection into single-step one-way detection, and carries an array-type ultrasonic probe unit which can be replaced freely so that detection requirements of different ultrasonic detection methods are satisfied.
Owner:江西华核天宇检测技术发展有限公司
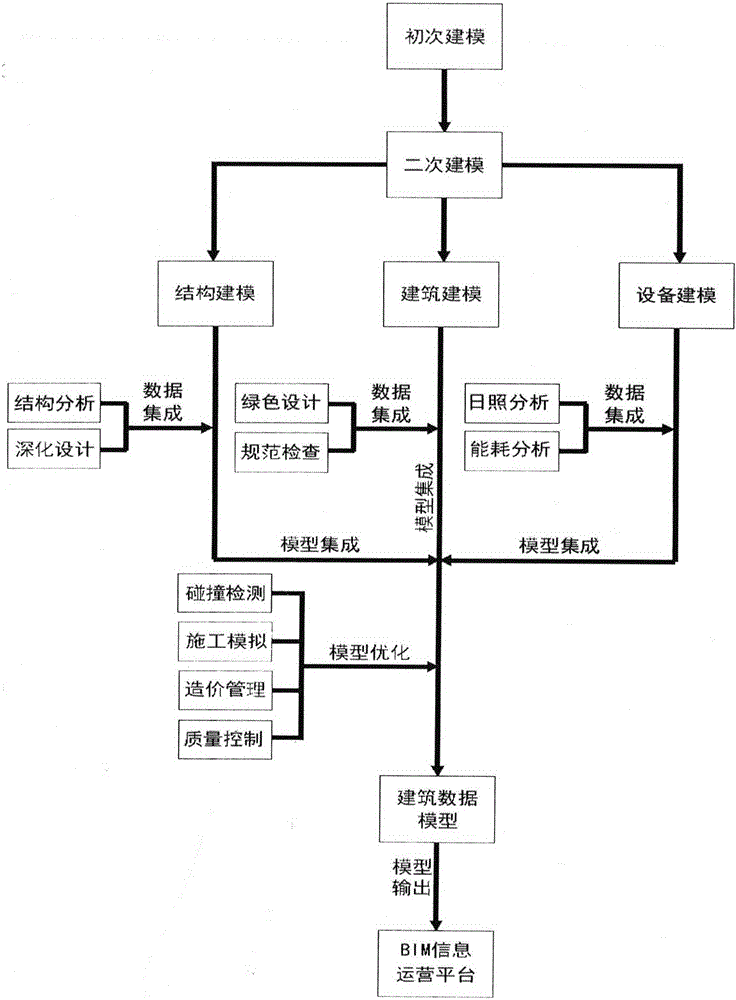
Construction engineering data modeling method based on BIM (Building Information Modeling) technology
InactiveCN105868440AImprove build qualityGood interaction abilityGeometric CADSpecial data processing applicationsInformatizationData modeling
The invention relates to a construction engineering data modeling method based on the BIM (Building Information Modeling) technology. The technical scheme of the construction engineering data modeling method comprises the steps of: primary modeling: carrying out visual geometric modeling design on a project through Rhino software, and determining a building shape scheme; secondary modeling: finishing the informatization definition of a three-dimensional primitive in Revit software, wherein the informatization definition of the three-dimensional primitive includes building modeling, structure modeling and equipment modeling, and the building modeling, the structure modeling and the equipment modeling are simultaneously carried out and are mutually associated; model optimization: on the basis of a software analysis platform, carrying out analogue simulation on the model finished in the second step, and finally finishing the further optimization of the model; and integrating a building data model into a BIM information operation platform. The construction engineering data modeling method overcomes the problems that traditional AutoCAD (Computer Aided Design) software information transmission has the defects of losses or distortion, poor cooperativity, lack of equipment data information and the like and the defect that a simulation test can not be carried out. Data on a traditional drawing and text is imported into a three-dimensional model, resources are integrated through the integrated data model, an interactive cooperative capability is good, engineering quality is improved, construction cost is lowered, a construction period is shortened, and safety is improved.
Owner:YANGZHOU UNIV
Build optimization with applied static analysis
InactiveUS20100042974A1Version controlSpecific program execution arrangementsAnti-patternSoftware analytics
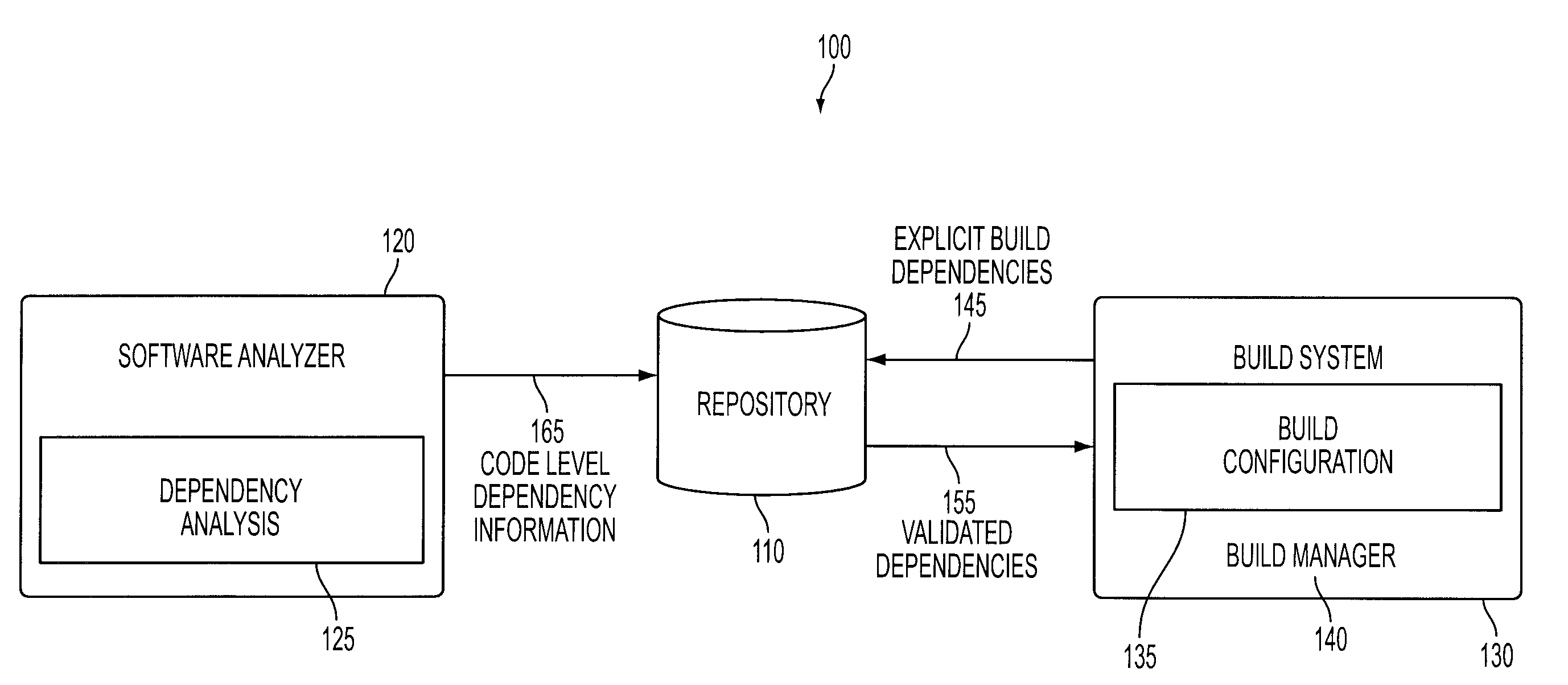
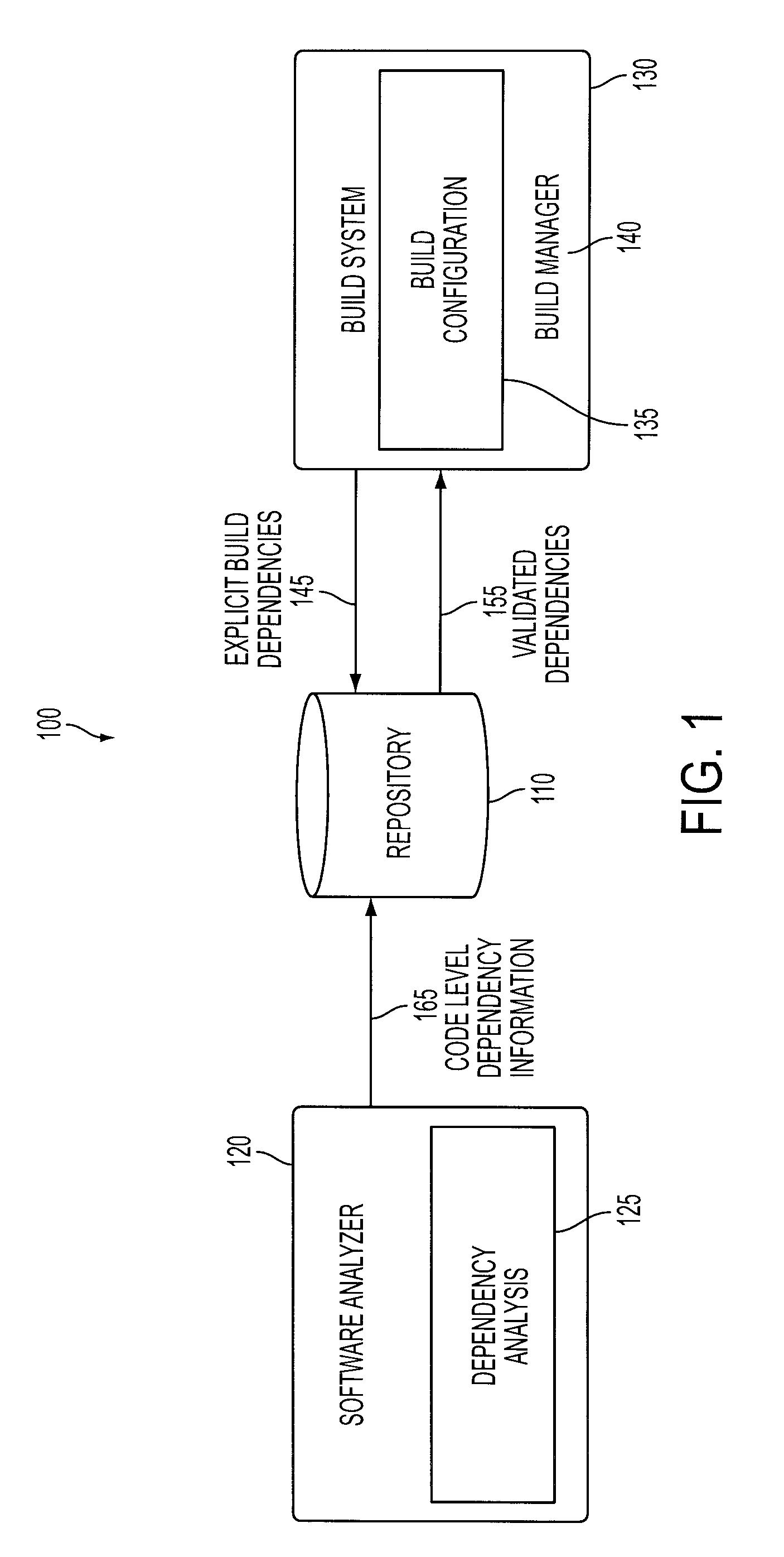
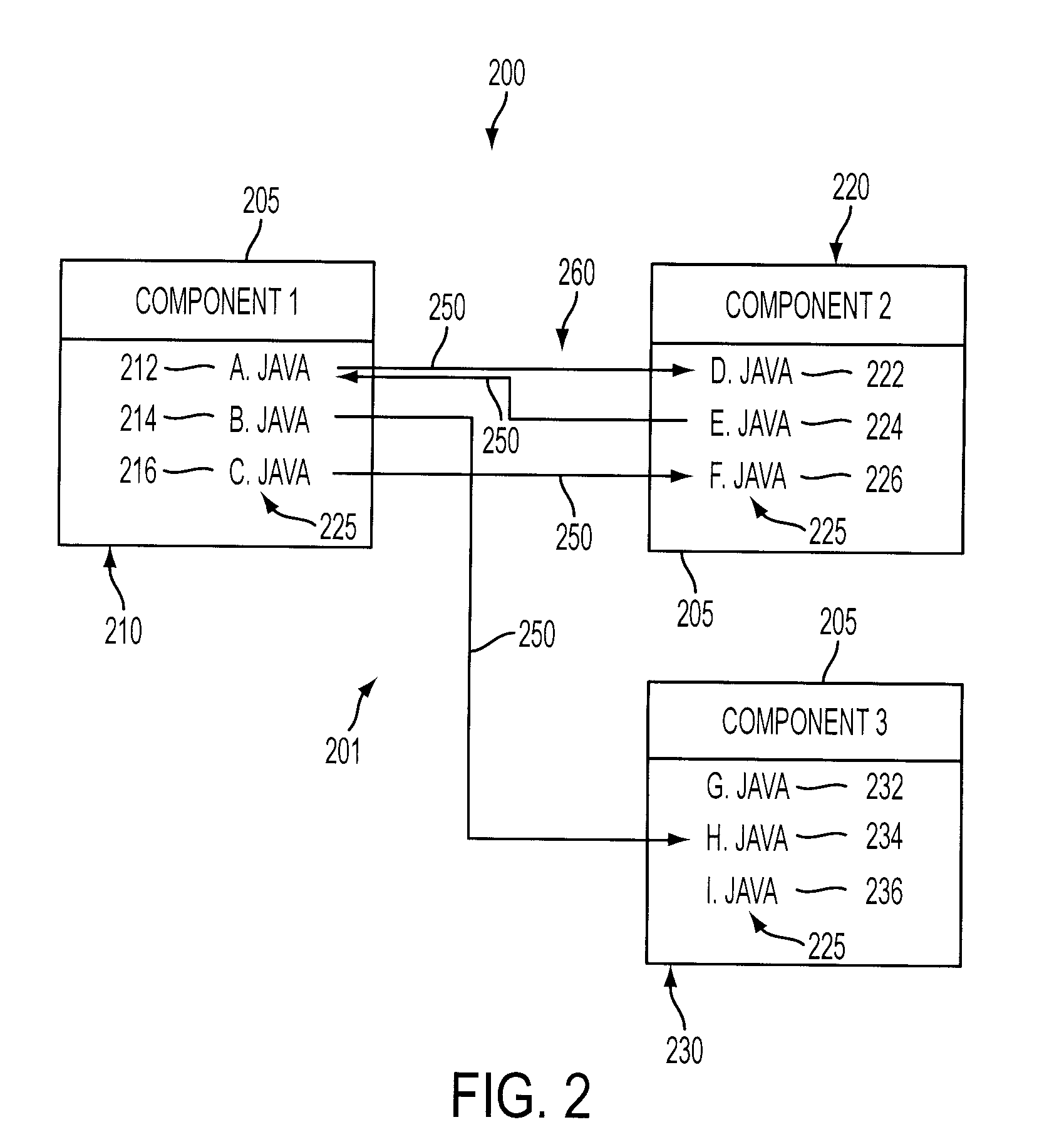
A method of constructing a software build using a static structural analysis system is disclosed. A software build configuration may be run and analyzed by a software analyzer to detect dependencies among code classes and components. A code dependency map is constructed identifying code level dependencies. The code dependency map may be referenced for code classes and components selected for modification. Identified dependency relationships with the selected code classes and components enable a builder to rebuild those code classes and components affected by the modification. Additionally, the software analyzer may identify undesirable dependencies and anti-patterns in potential need of deletion or modification.
Owner:IBM CORP
Automatic application bug mining system and method under Android platform
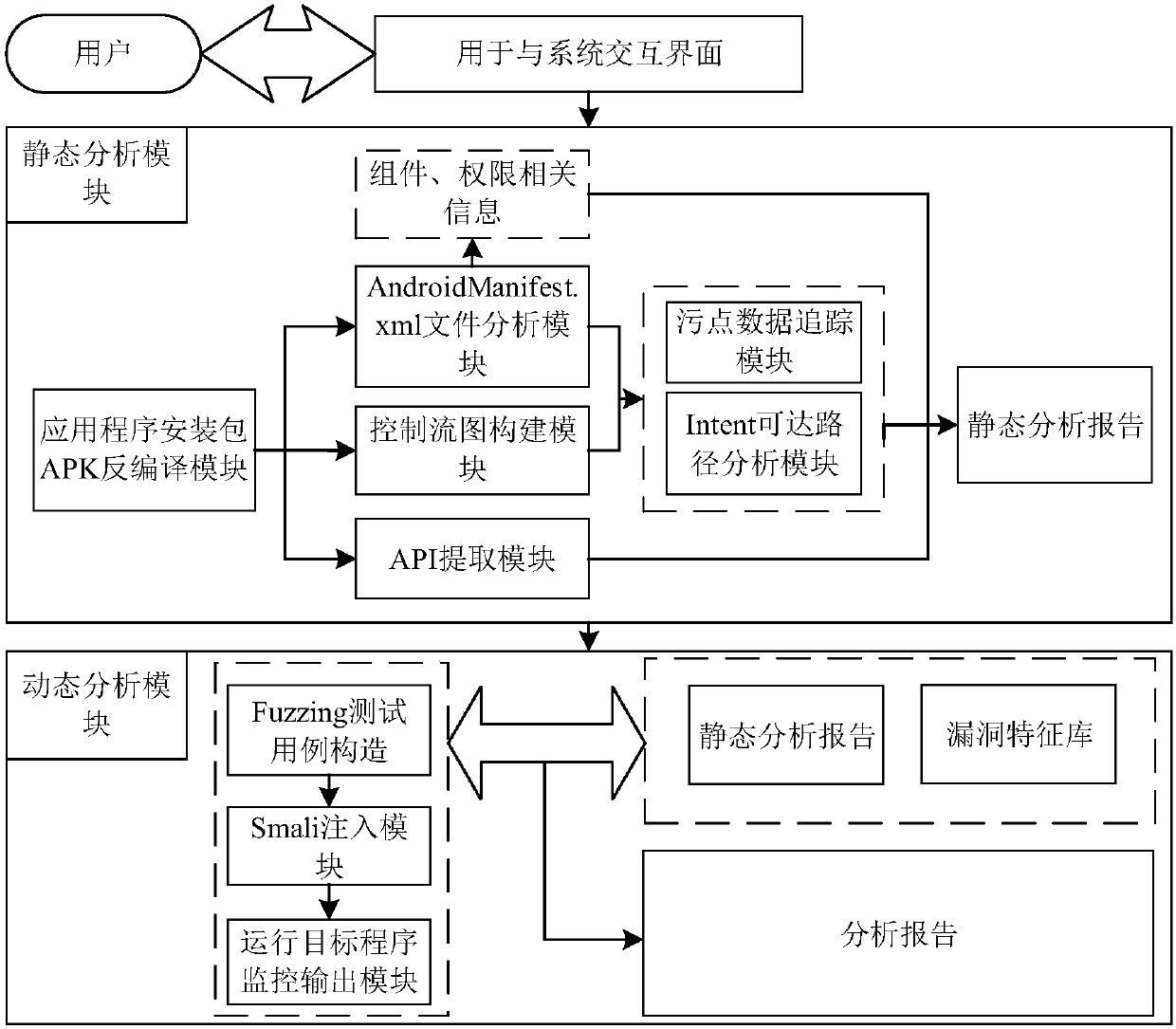
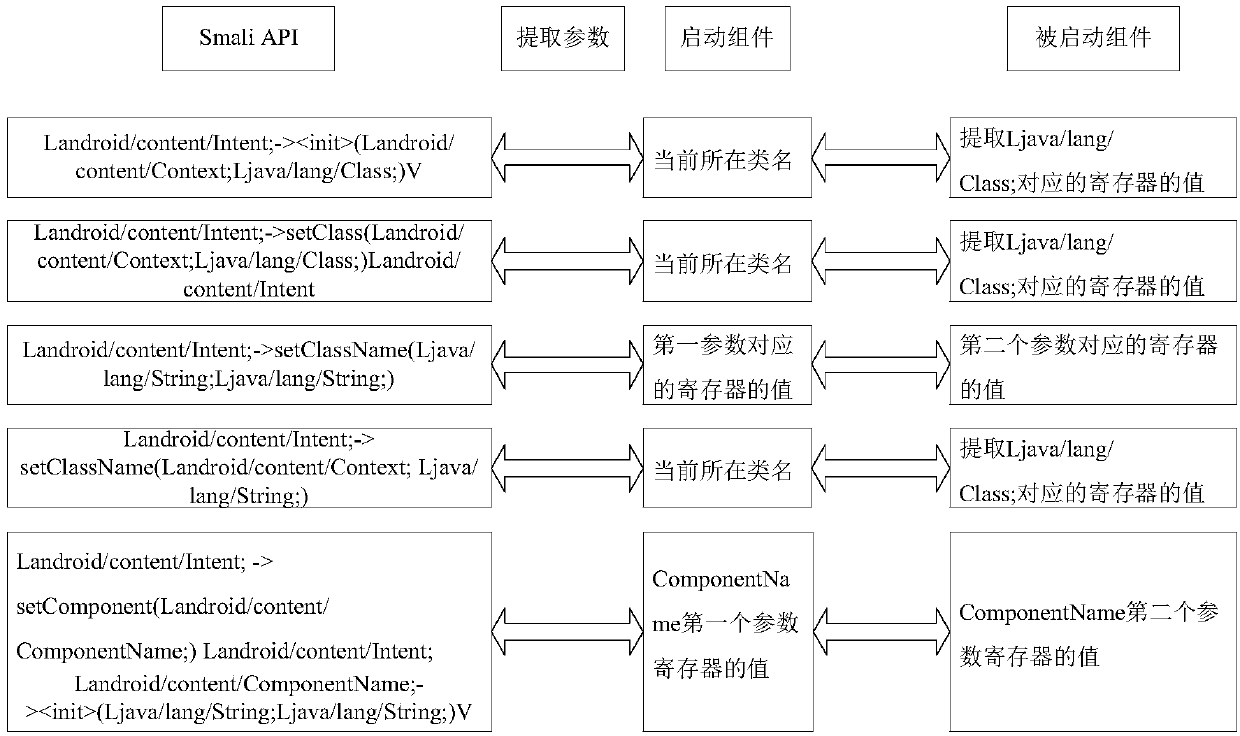
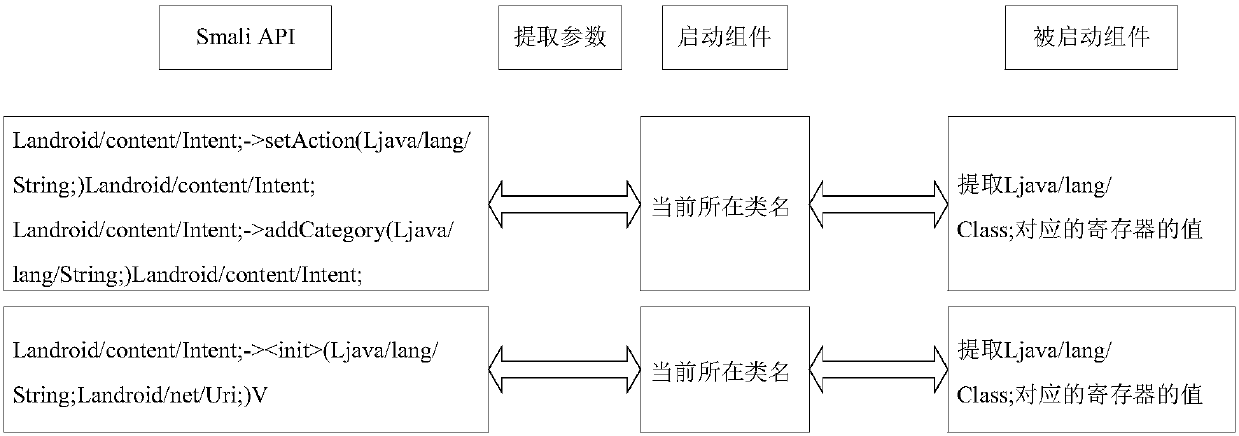
ActiveCN107832619AAvoid false positivesAvoid problems such as poor performanceSoftware testing/debuggingPlatform integrity maintainanceControl flowSoftware analytics
The invention discloses an automatic application bug mining system and method under an Android platform, and belongs to the technical field of software analysis. The system is mainly divided into an application static analysis module and an application dynamic analysis module; the static analysis module mainly aims at carrying out analysis of control flow and dataflow on android package files (apk), extracting module permission and other property information, and carrying out reachable path analysis on communication problems among the modules in an application; during the dynamic analysis, a Fuzzing test case data is constructed on the basis of a static analysis result at first, Smali code instrumentation is conducted on decompiled Smali files, the application is enabled to run to obtain output information, and under the combination of the static analysis result, bugs existing in the application can be obtained finally. By adopting the automatic application bug mining system and methodunder the Android platform, the bugs possibly existing in the application can be automatically mined, the system and method have certain flexibility and solve the problem that a manual mining mode consumes a lot of time, and meanwhile, by combining the static analysis with the dynamic analysis, the accuracy can be greatly improved.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Software fault analysis method based on multi-sample difference comparison
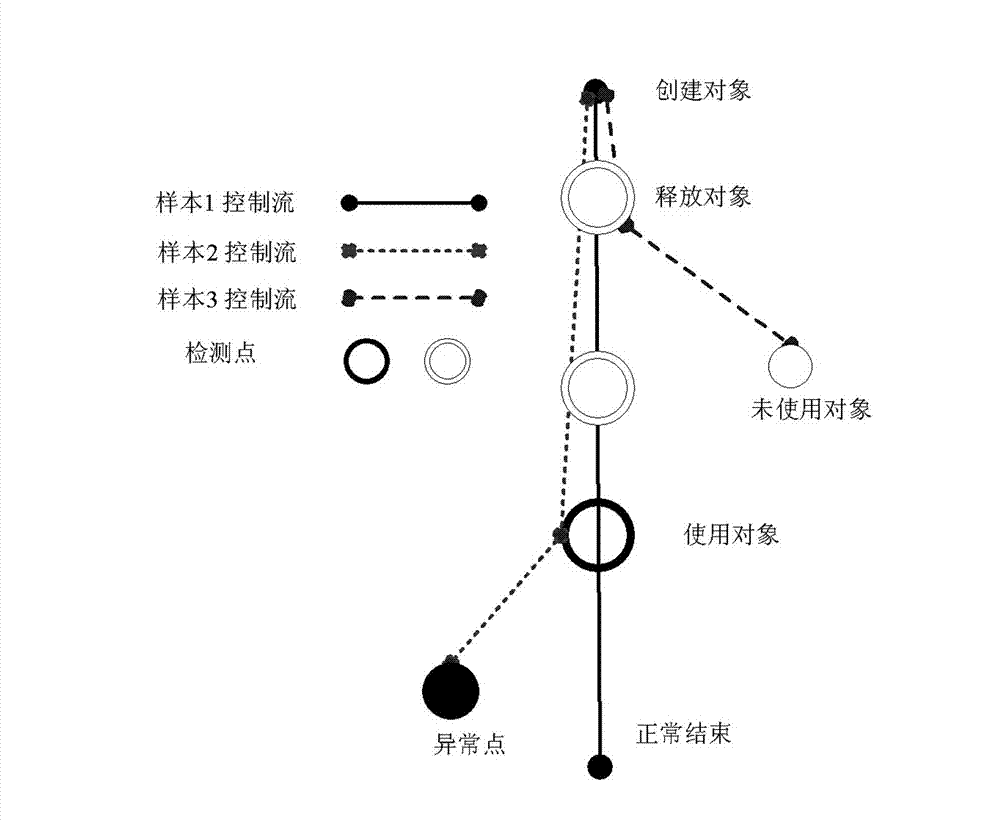
InactiveCN102789419AFailure Analysis Work Efficiency ImprovementUnable to locateSoftware testing/debuggingControl flowDynamic instrumentation
The invention relates to a software analysis method belonging to the technical field of computers, and particularly relates to a software fault analysis method based on multi-sample difference comparison. The method comprises the steps as follows: (1) executing disassemble and dynamic instrumentation of an analyzed program; (2) tracking and recording an execution instruction flow of a program to be analyzed and constructing control flow graphs of the program, which take a basic block as the minimum unit; and (3) selecting a data processing access point as a comparison basic point, constructing a multi-sample difference tree model, executing comparison of control flow graphs of multiple samples which are divided into several groups, wherein each group consists of two samples, finding out a key instruction flow branch point, and acquiring a key path from a false data input point to each difference point. The software fault analysis method, provided by the invention, effectively solves the problem that a dual-sample difference comparison method cannot achieve positioning of complex faults, thereby remarkably improving analysis efficiency of software faults.
Owner:THE PLA INFORMATION ENG UNIV
Method for dynamically setting parameters of coordinated control system on basis of preliminary coal supply control model
ActiveCN102914966AShorten fetch timeComprehensive historical dataSpecial data processing applicationsInformation technology support systemSoftware analyticsPerformance index
The invention belongs to the field of boiler-turbine coordinated control for thermal generator sets, and particularly relates to a method for dynamically setting parameters of a coordinated control system on the basis of a preliminary coal supply control model. The method is applied to optimizing the dynamic parameters of the coordinated control system when a thermal power generating unit runs in an AGC (automatic gain control) mode, performance indexes of main controlled variables of the unit are improved, and load of the unit meets requirements of a power grid on technical indexes. Computer software assists in solving parameters of a control algorithm, a debugging process is simplified, and dynamic parameter solving time is shortened. In addition, characteristics of comprehensiveness of historical data, high precision, long time span and the like of a current DCS (data communication system) are sufficiently played, the historical running data of the unit are analyzed by the software, and the method is combined with field load change tests for the unit, and realizes an effect of yielding twice the result with half the effort by using the computer software to assist in solving the parameters of the control algorithm.
Owner:LIAONING ELECTRIC POWER COMPANY LIMITED POWER SCI RES INSTION +2
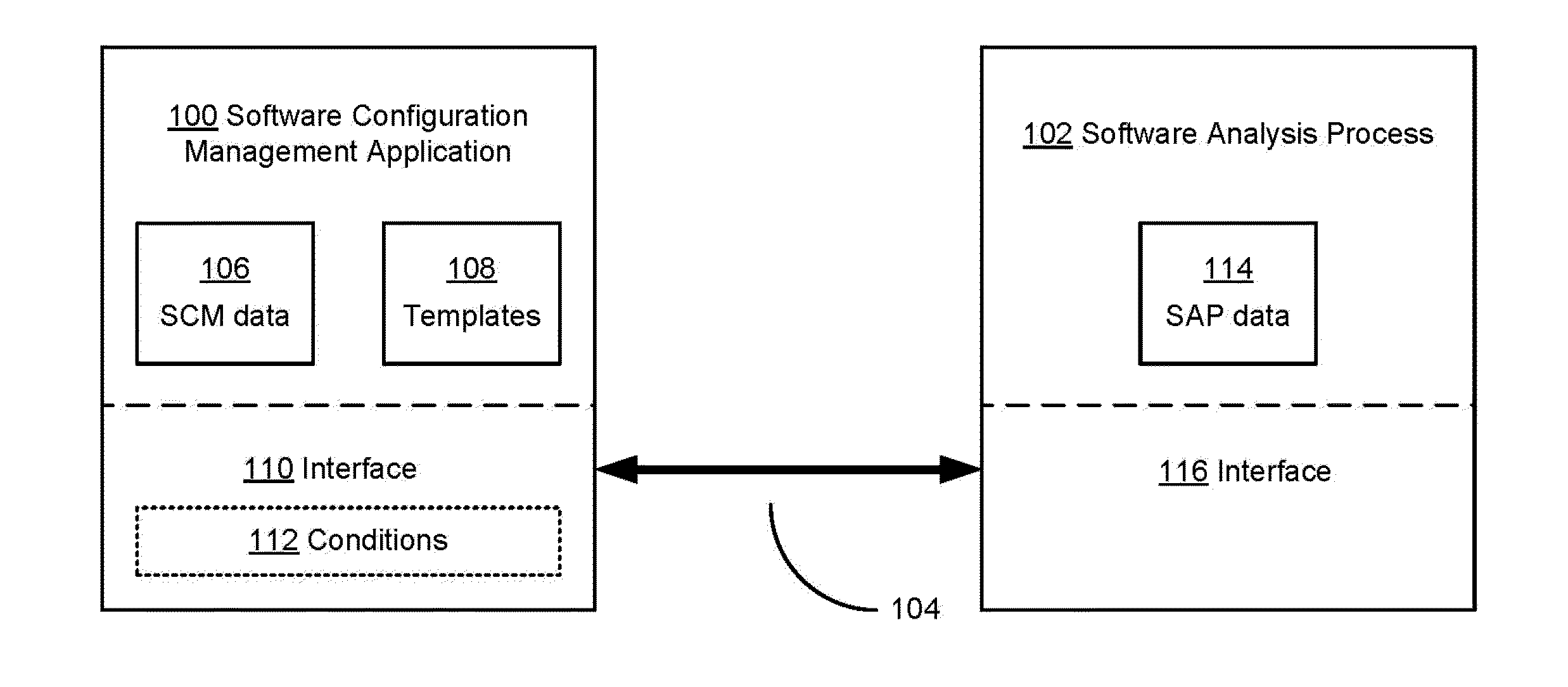
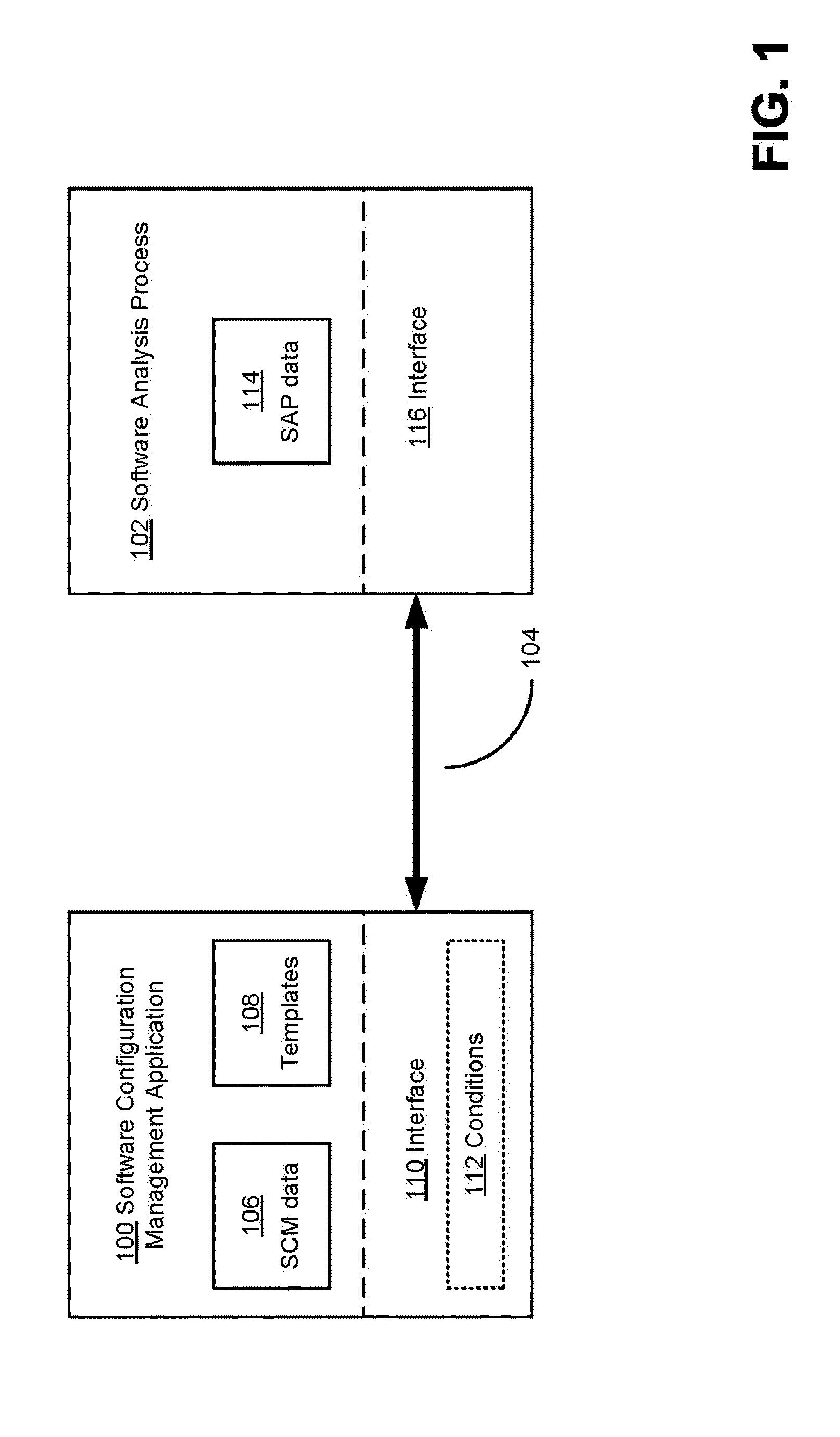
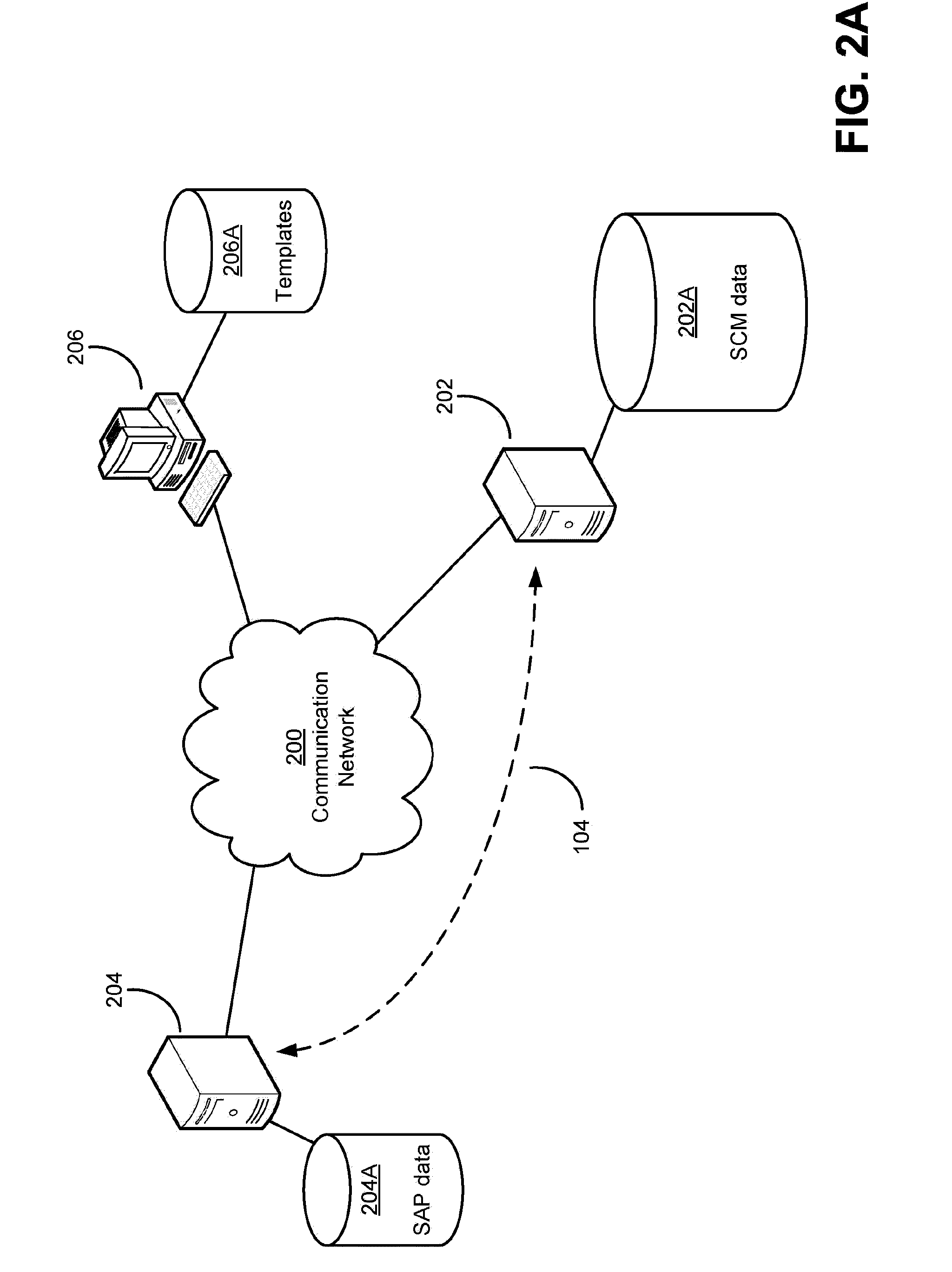
Integration of external software analysis processes with software configuration management applications
ActiveUS20100083211A1Easily and efficiently performance of taskEasy to buildVersion controlReverse engineeringSoftware engineeringSoftware analytics
A platform is provided for enabling developers to customize easily and efficiently the performance of tasks on versions of a software project. An interface may be established in a software configuration management (SCM) application for communicating with software analysis processes, and information about a manner in which the software analysis process is triggered or stores data may be input as parameters to the interface. Additionally, generic parameters for a task to be performed by the software analysis process may be provided in a template. The template may then be provided to developers to populate with specific parameters regarding the particular task that developer would like performed, such as to identifying information for a version and a condition upon which the task is to be performed. Each developer of a team may make use of the template and the interface to customize the automation of tasks that he / she would like performed.
Owner:ACCUREV
Software analysis framework
InactiveUS20060253841A1Decompilation/disassemblySpecific program execution arrangementsSoftware analyticsScript analysis
Presently described is a decompilation method of operation and system for parsing executable code, identifying and recursively modeling data flows, identifying and recursively modeling control flow, and iteratively refining these models to provide a complete model at the nanocode level. The nanocode decompiler may be used to determine if flaws, security vulnerabilities, or general quality issues exist in the code. The nanocode decompiler outputs in a standardized, human-readable intermediate representation (IR) designed for automated or scripted analysis and reporting. Reports may take the form of a computer annotated and / or partially human annotated nanocode listing in the above-described IR. Annotations may include plain English statements regarding flaws and pointers to badly constructed data structures, unchecked buffers, malicious embedded code or “trap doors,” and the like. Annotations may be generated through a scripted analysis process or by means of an expert-enhanced, quasi-autonomous system.
Owner:VERACODE
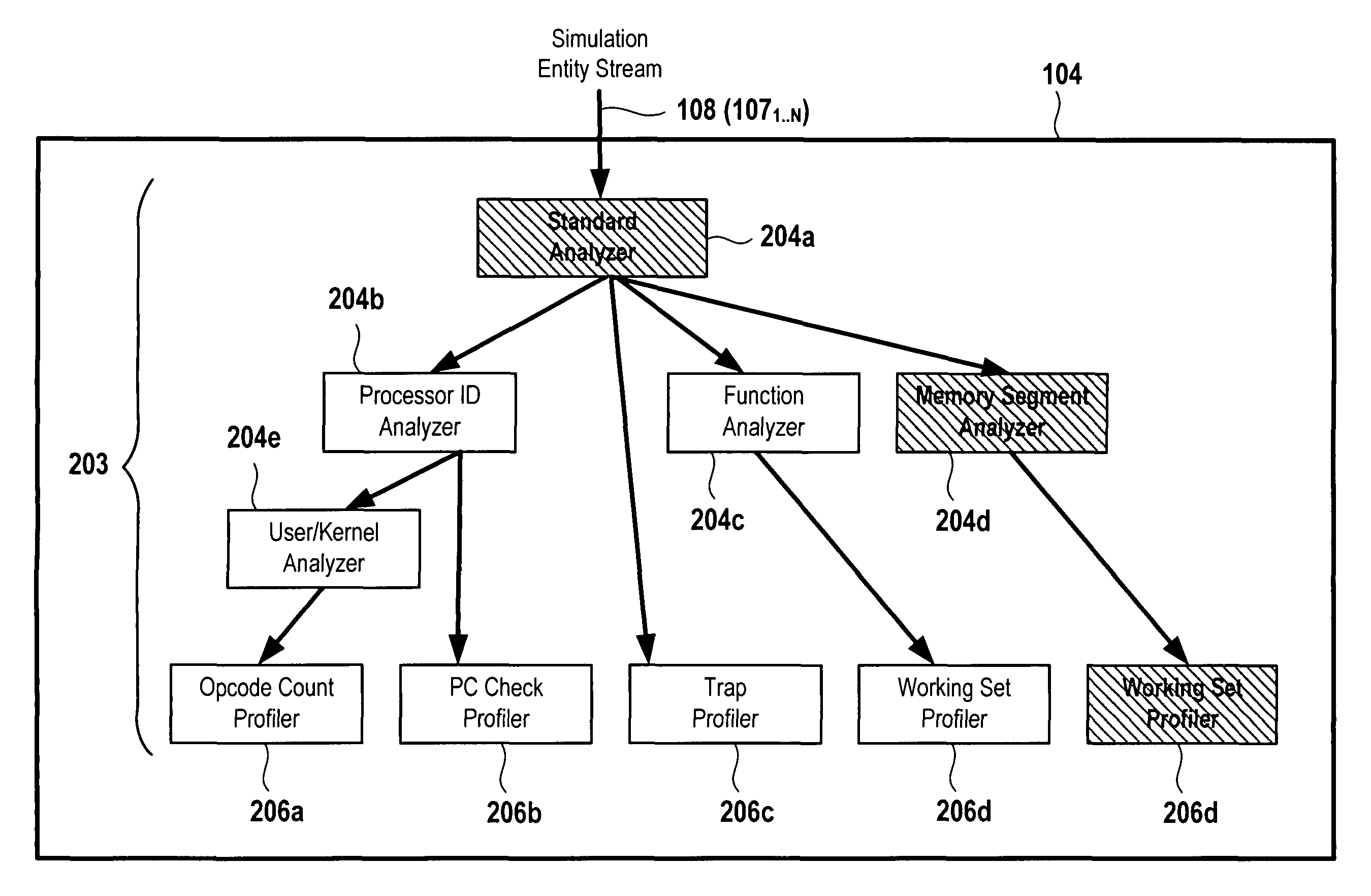
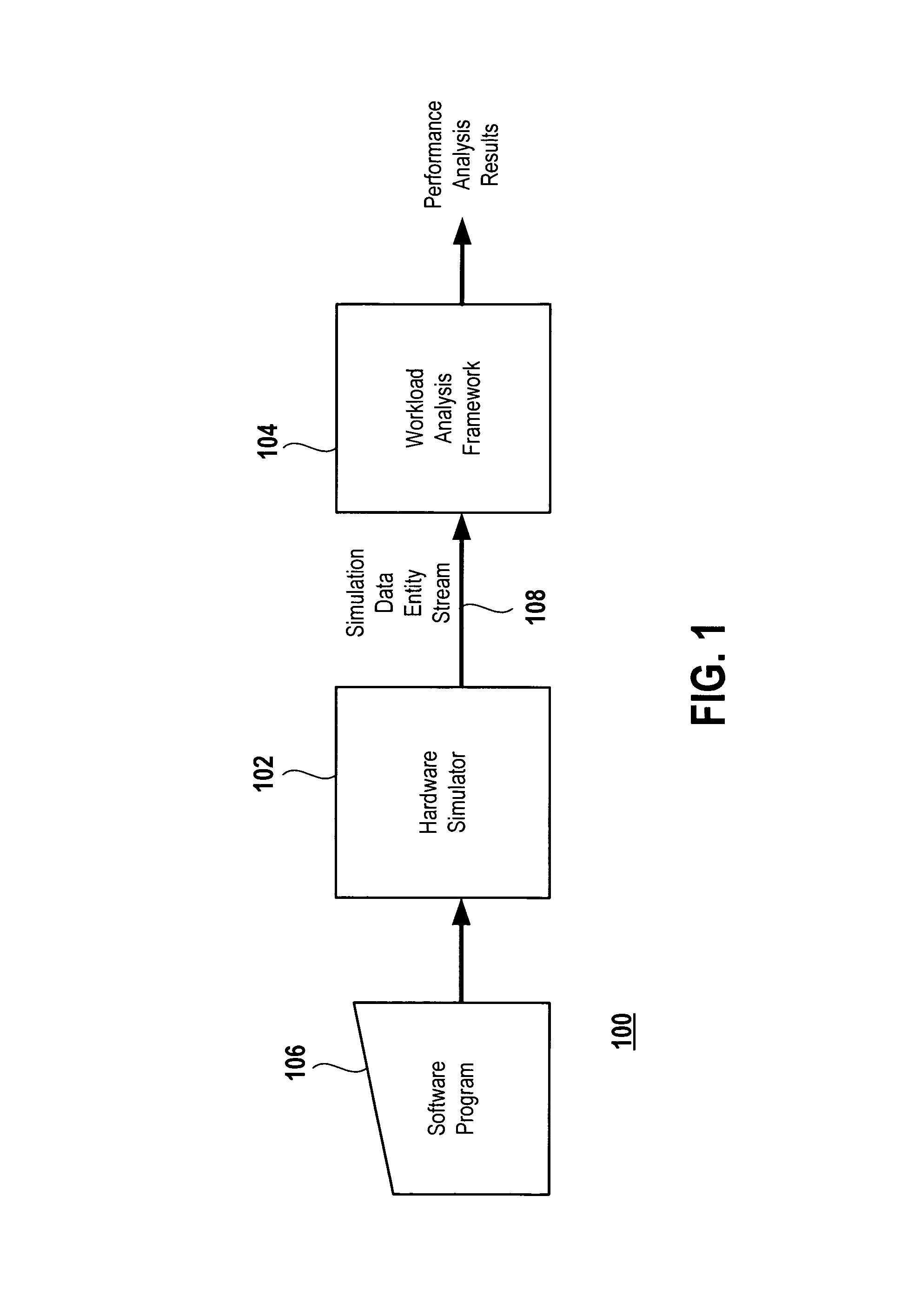
System for application level analysis of hardware simulations
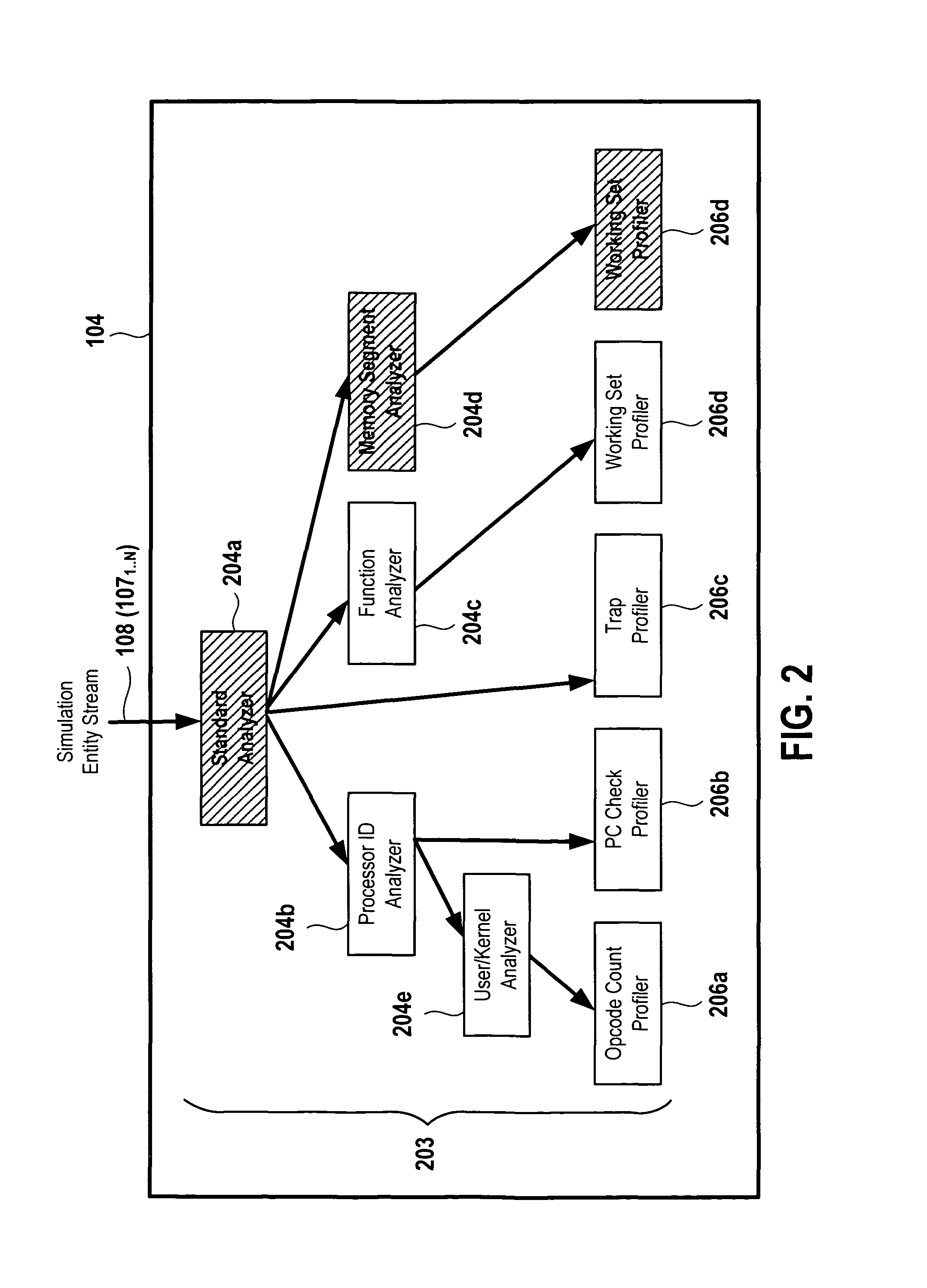
ActiveUS8229726B1CAD circuit designSoftware simulation/interpretation/emulationProcessor registerSoftware analytics
An object-oriented software analysis framework is provided for enabling software engineers and hardware engineers to gain insight into the behavior of software applications on emerging hardware platforms even before the hardware is fabricated. In this analysis framework, simulation data containing instruction, address and / or hardware register information is sent to interchangeable and parameterizable analyzer and profiler modules that decode the data and perform analysis of the data according to each module's respective analysis function. This detailed analysis is performed by constructing a tree of such modules through which the data travels and is classified and analyzed or filtered at each level of the tree. Each node of the tree is represented by an analyzer or a profiler module that performs sub-analysis based on the analysis performed by its parent such that at the end of a hardware simulation, each node, starting at the root, recursively calls on its children to dump their analysis, resulting in a categorized performance report.
Owner:ORACLE INT CORP
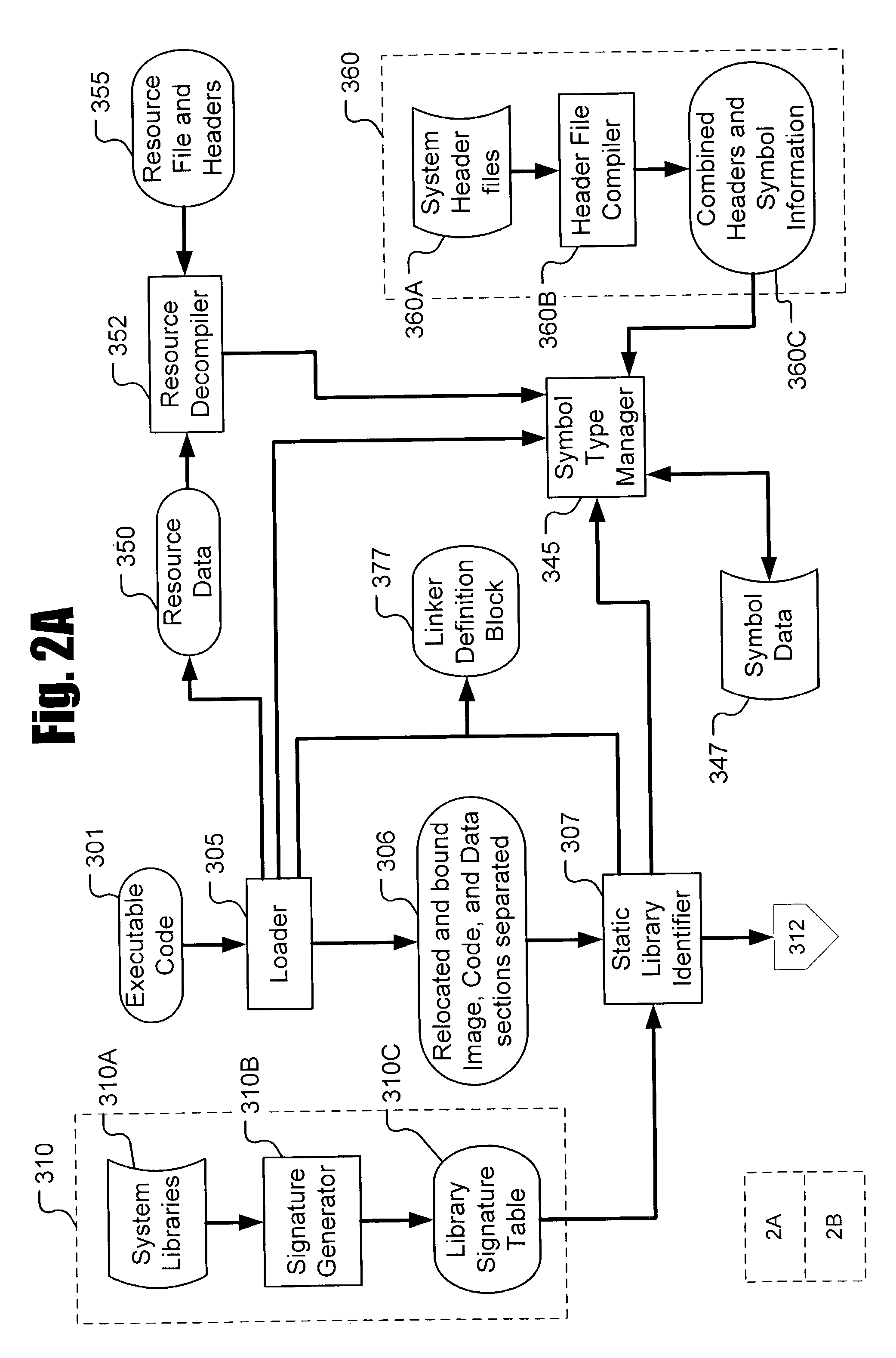
Extracting system for internal curing data of windows application program
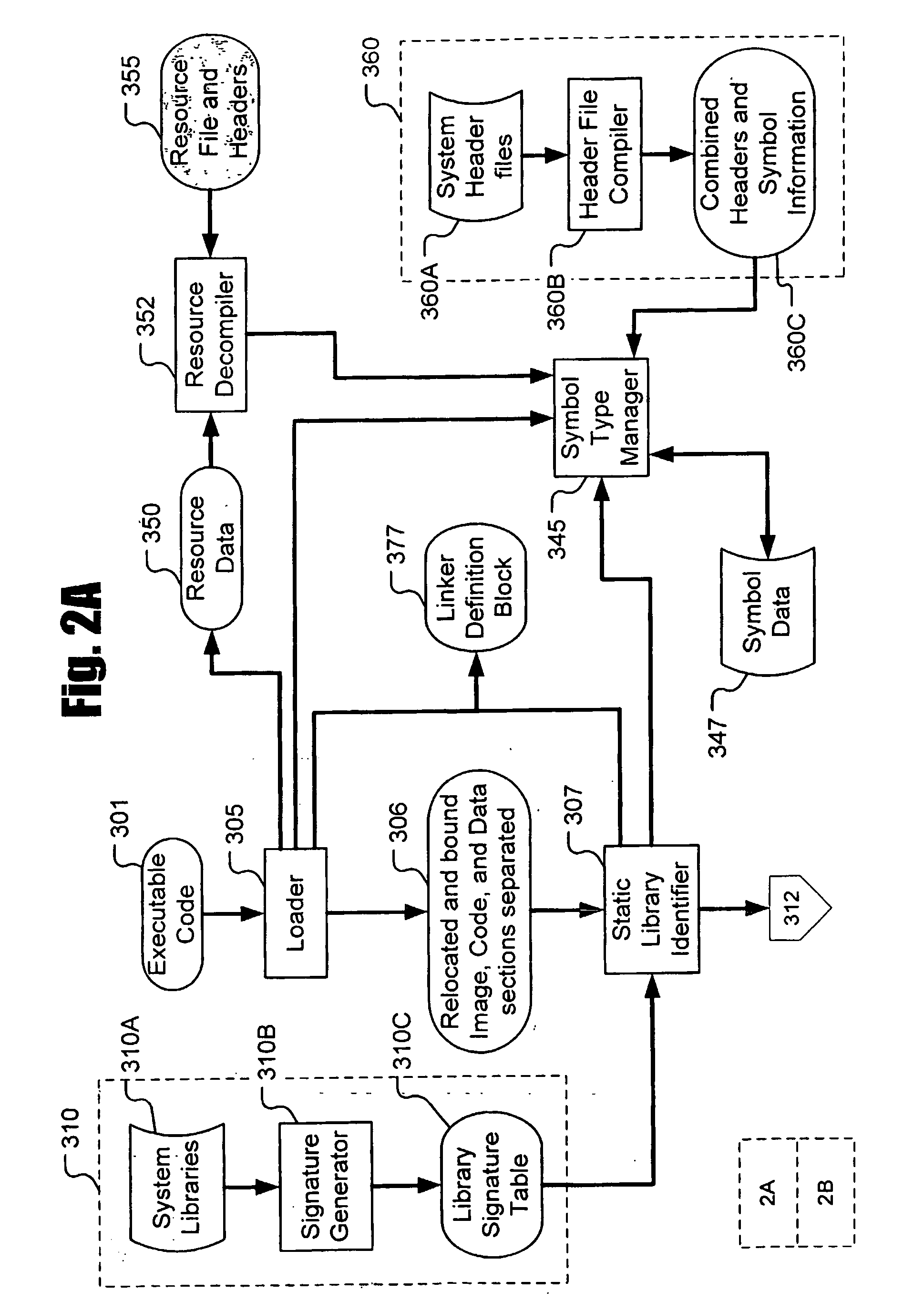
ActiveCN101393521AEfficient determinationInformativeSpecific program execution arrangementsData informationSoftware analytics
The invention provides a system for extracting data solidified in a Window application program, which belongs to the technical field of software analysis and information safety, wherein an executable file type information identification module identifies the format, development language type and protection type of an executable file; an executable file counter-protection module is responsible for the counter-protection of the executable file needing the covering protection of a protection code; an executable file code analysis module disassembles and decompiles the executable file to obtain compilation and high level language codes and give the structural and logical information; a cryptography analysis module is responsible for the identification of the cryptography algorithm adopted in the executable file when the solidified data information stored by encryption appears in the executable file; and an executable file debugging and information extraction module checks the internal state of the running program in the running process so as to extract the information. The system can effectively extract and analyze the data information solidified in the program and give a generation method and original information of the data information.
Owner:SHANGHAI JIAO TONG UNIV
Systems And Methods For Software Analytics
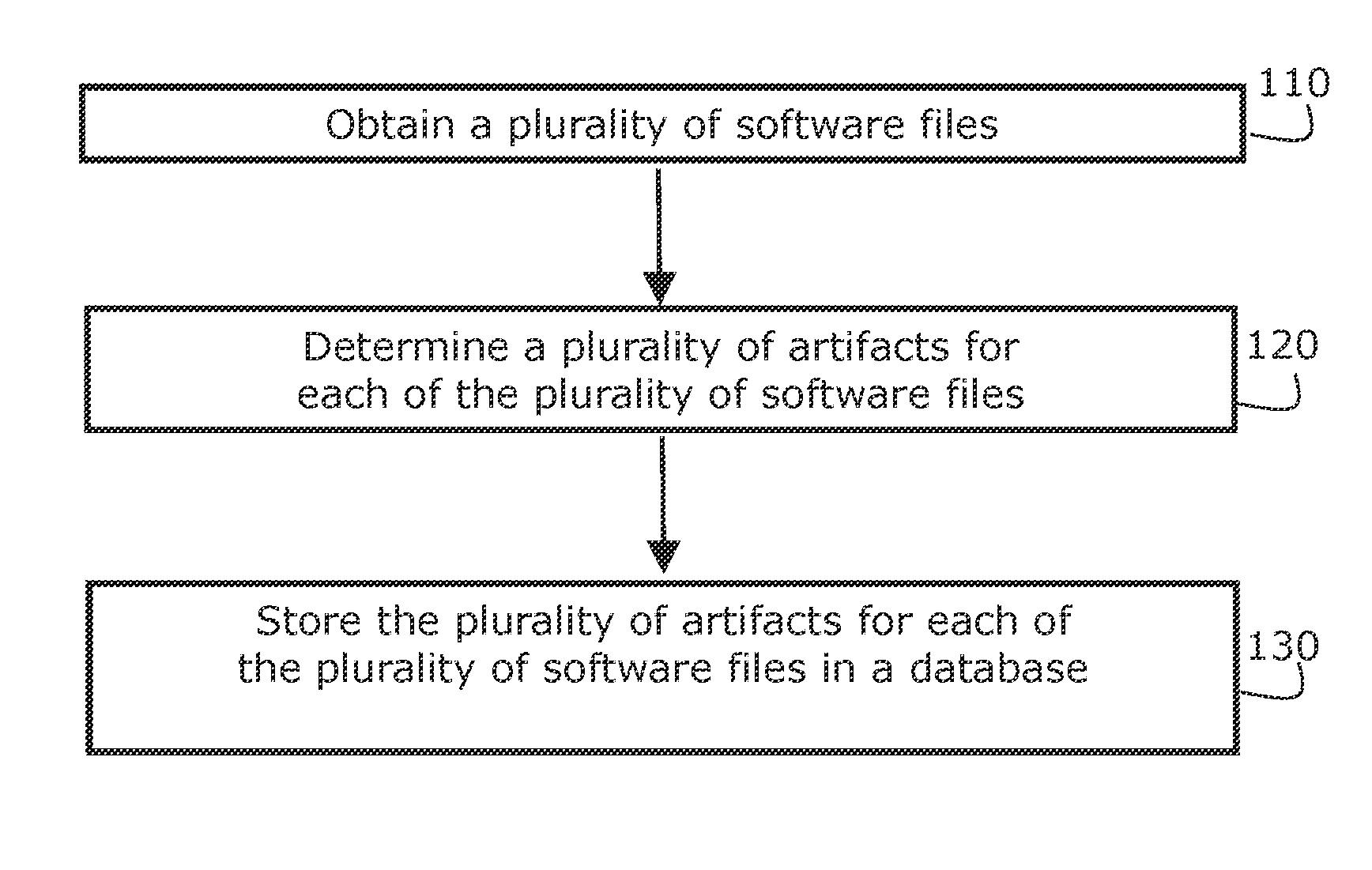
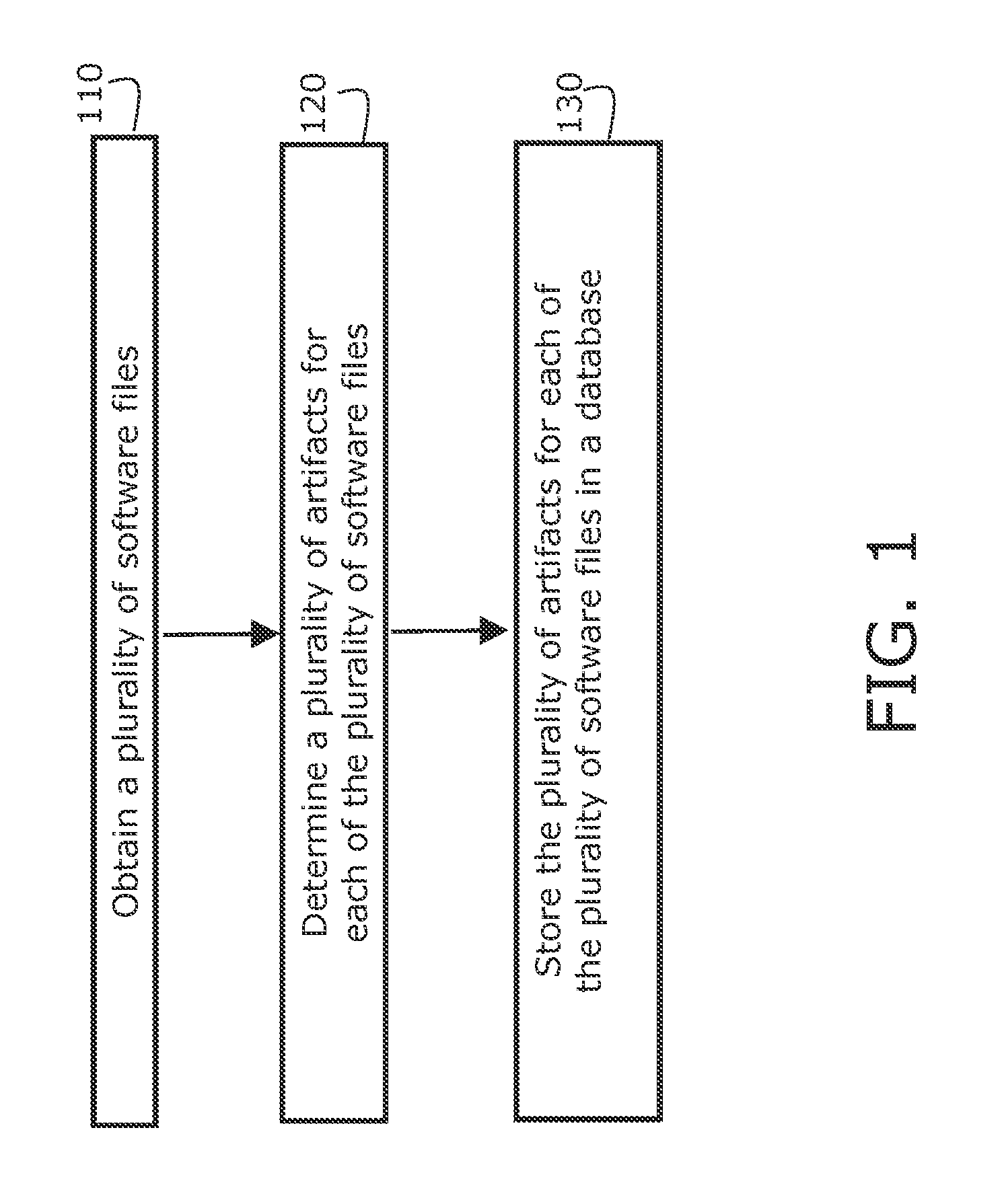
InactiveUS20150363197A1Error detection/correctionProgram documentationProgram fragmentSoftware analytics
Systems, methods, and computer program products are provided for locating design patterns in software. An example method includes accessing a database having multiple artifacts corresponding to multiple software, and identifying a design pattern for at least one of the software files by automatically analyzing at least one of the artifacts associated with the software. Additional embodiments also provide for storing an identifier for the design pattern for the software in the database. For certain example embodiments, the artifacts include developmental, which may be searched for a string that denotes a design pattern, such as flaw, feature, or repair. Additional example embodiments also include finding in the software file a program fragment that implements the design pattern.
Owner:CHARLES STARK DRAPER LABORATORY
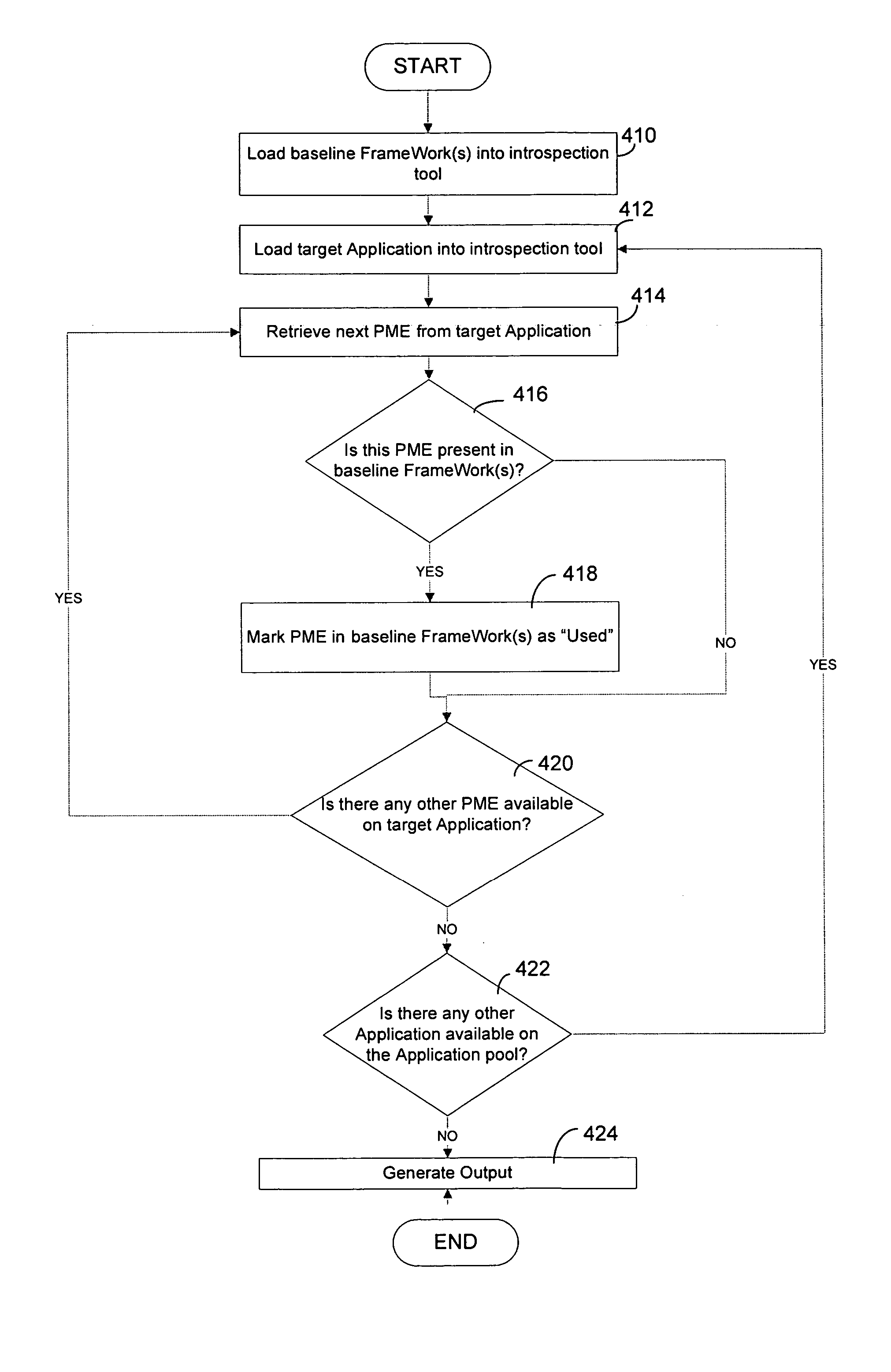
Software analysis tool
InactiveUS20070038974A1Error detection/correctionSpecific program execution arrangementsSoftware analyticsAnalysis tools
A tool for analyzing software. The tool identifies calls to framework components made from within one or more application programs. The information may be processed to indicate usage of framework components. This usage information may be aggregated over a pool of application programs to derive statistical usage information for each component in the framework, allowing components to be selected for inclusion in a compact framework. Usage information may also be used for scheduling development tasks so that the most widely used framework components are developed first or to estimate the amount of development required to modify an application program for execution against a target framework.
Owner:MICROSOFT TECH LICENSING LLC
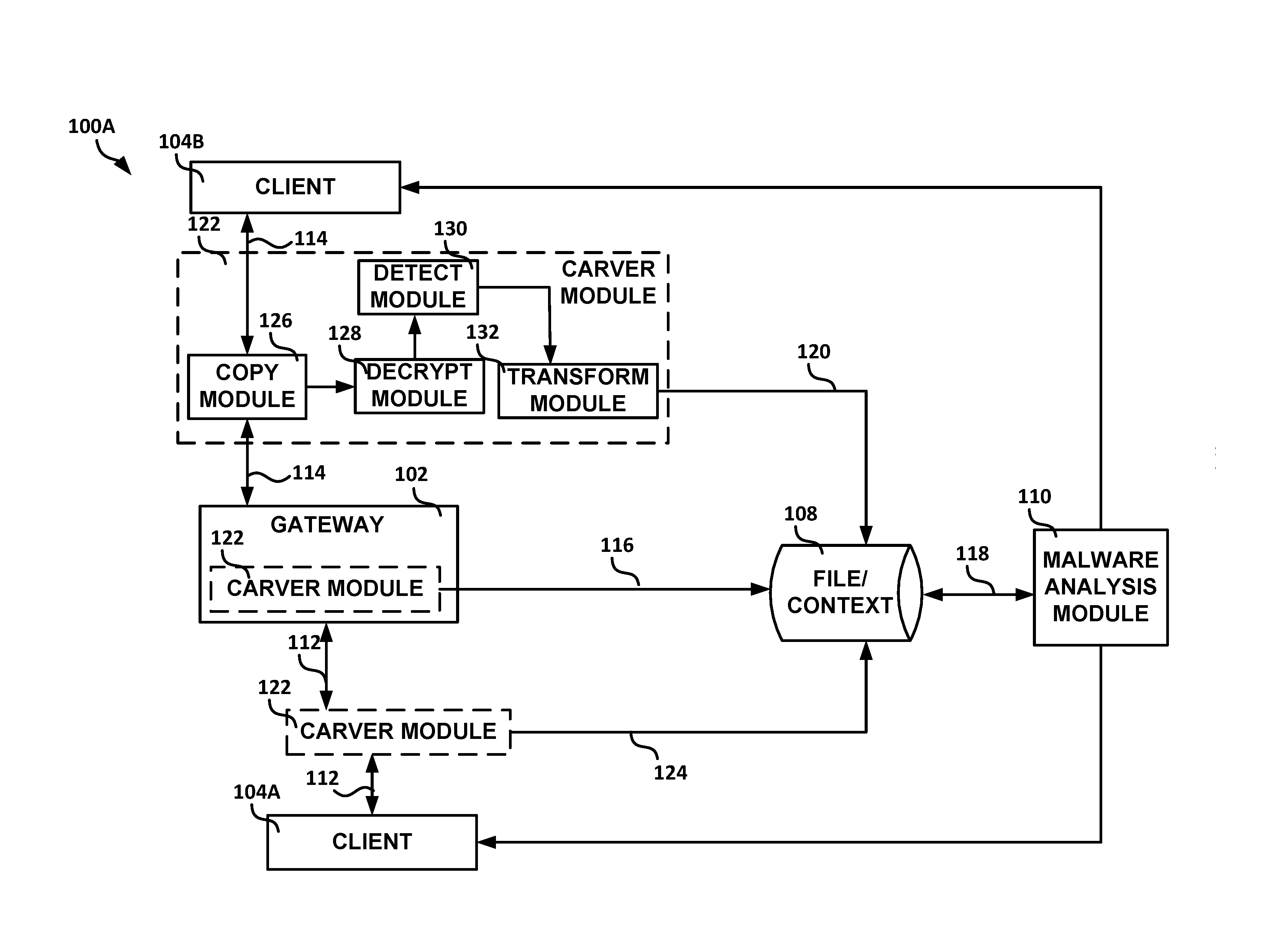
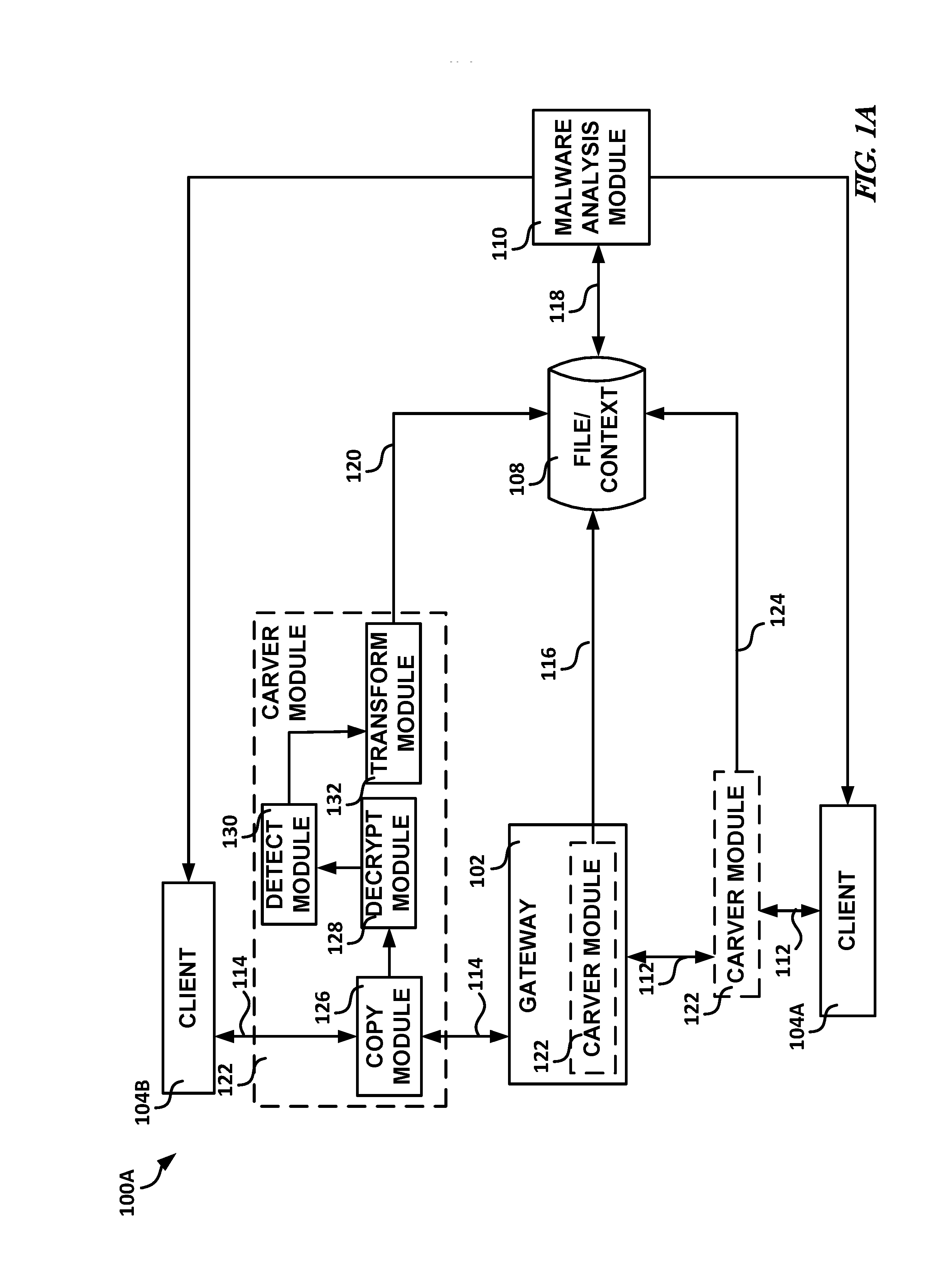
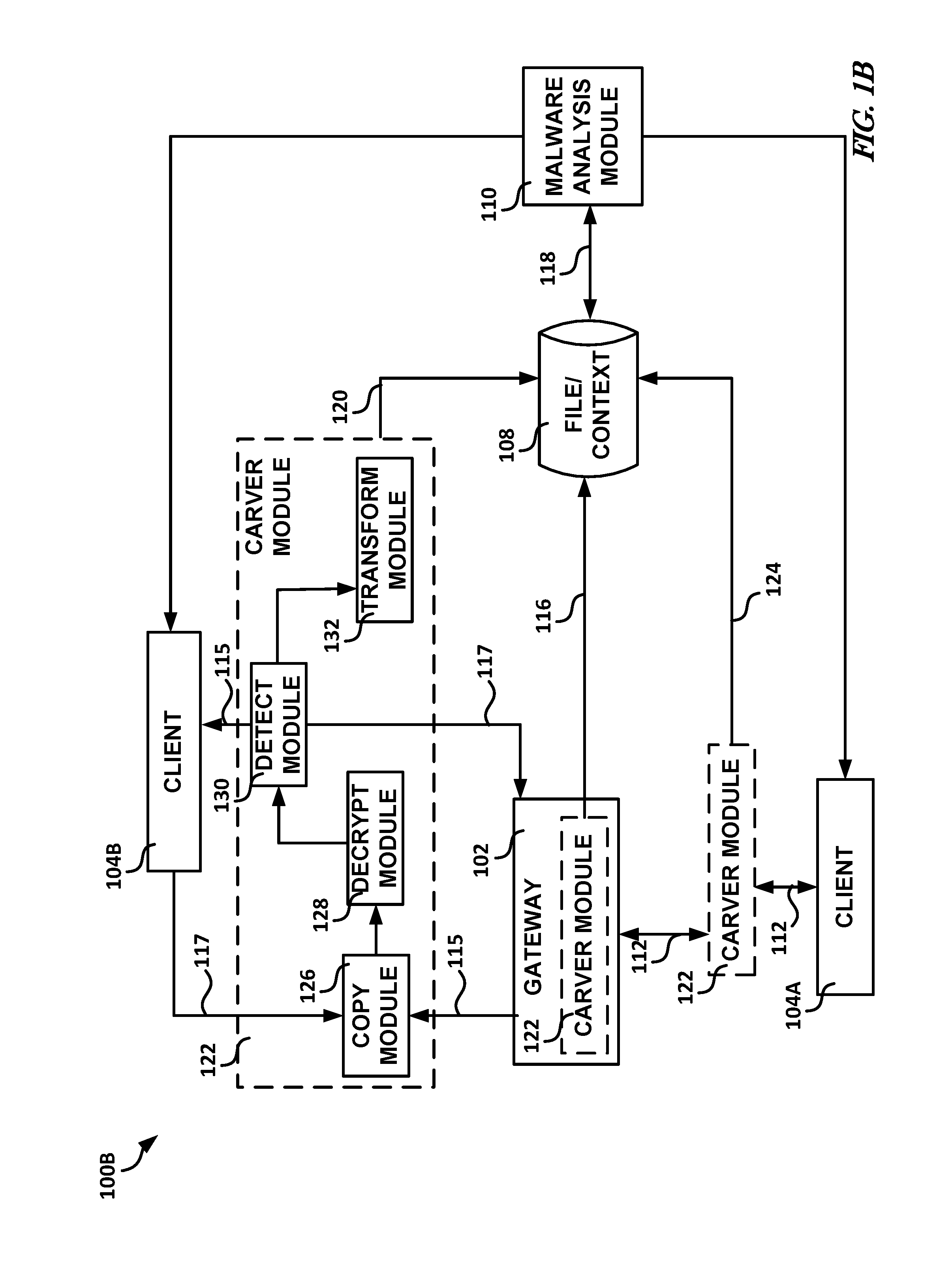
Systems and methods for malware analysis of network traffic
Generally discussed herein are systems, devices, and methods for malware analysis. In one or more embodiments, a method can include copying application layer data traffic to create copied application layer data traffic, forwarding at least a portion of the application layer data traffic to a destination client prior to a malware analysis of corresponding copied application layer data traffic, determining whether the copied application layer data traffic includes a specified property, and in response to a determination that the copied application layer data traffic includes the specified property, storing the copied application layer data traffic determined to include the specified property for subsequent malware analysis, the stored copied application layer data traffic including context data of the copied application layer data traffic.
Owner:FORCEPOINT FEDERAL
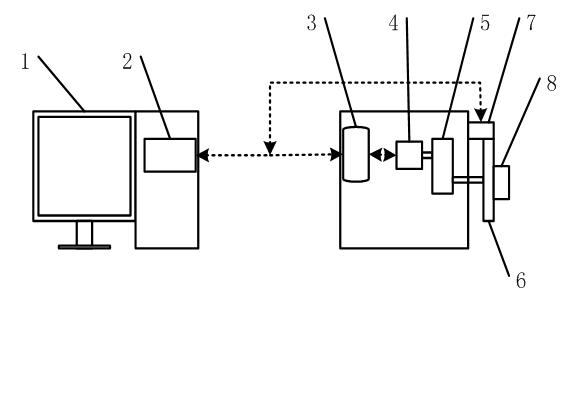
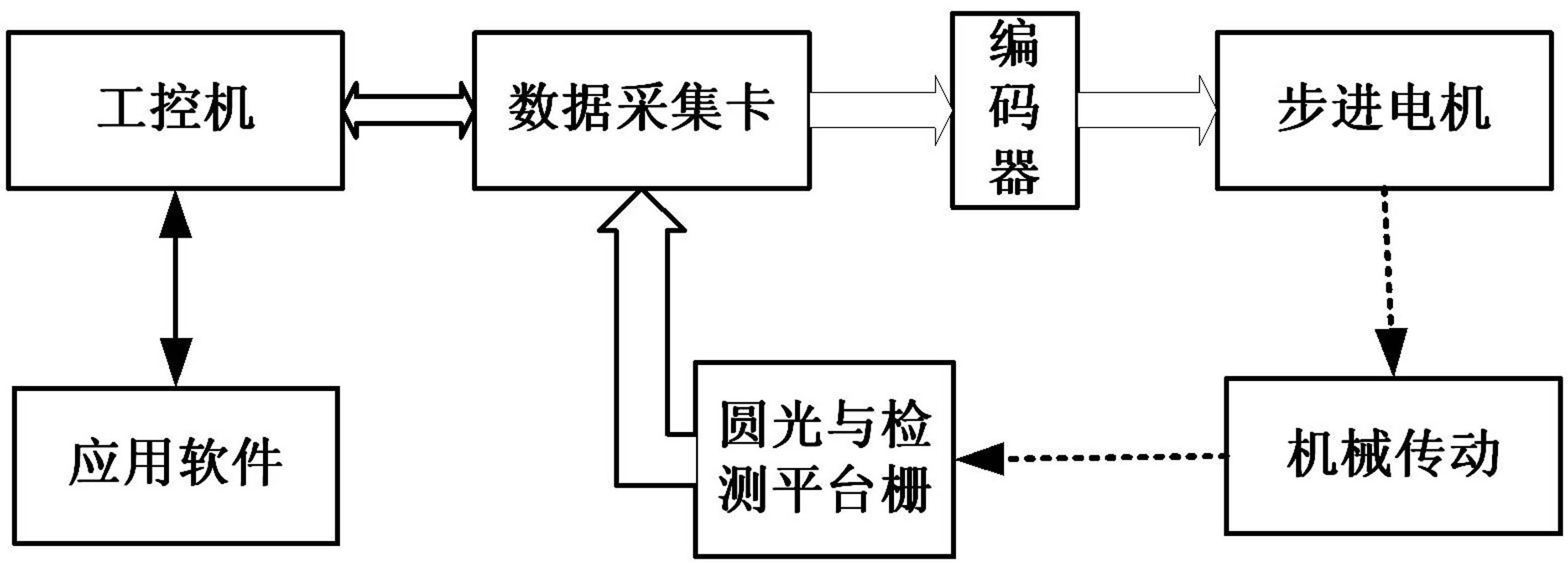
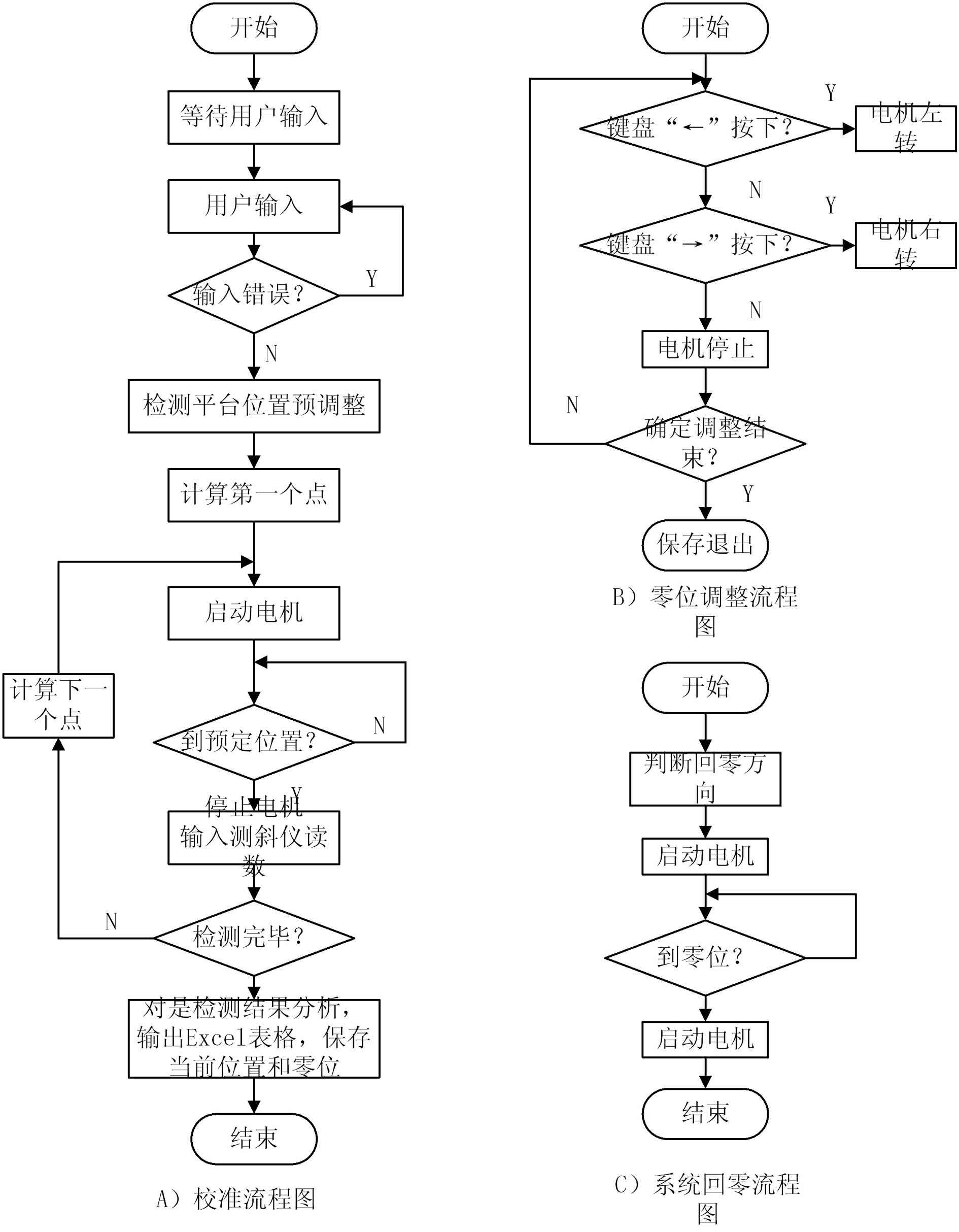
Automatic calibration method for inclinometer
InactiveCN102032921AImprove calibration accuracyEasy CalibrationUsing optical meansControl engineeringData acquisition
The invention discloses an automatic calibration method for an inclinometer, which comprises the following steps of: firstly, reading a set series of numerical values through industrial personal computer software, and calculating to obtain the number of pulses for controlling a step motor; secondly, outputting a control pulse to a step motor controller through a data collecting card by an industrial personal computer, and further controlling the step motor to rotate a corresponding angle, and driving a detection platform and a round grating sensor to rotate through a mechanical transmission mechanism; then, sending the detected rotation angle to the industrial personal computer through the data collecting card in the form of pulse by the round grating sensor, comparing the rotation angle with a set angle, sending a stopping command by the industrial personal computer so that the motor stop rotating when the set value is reached, and inputting the reading of the inclinometer by a subscriber; and finally, analyzing by the software to obtain a calibrated equation and error. In the invention, the continuous high precision calibration of a distance-measuring range at multiple angles without limitation is realized, wherein the calibration precision can reach 3'', and the inclinometer is particularly suitable for the calibration of the inclinometer in inclinometer manufacturing enterprises, using units and metering technological organizations, and the like.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
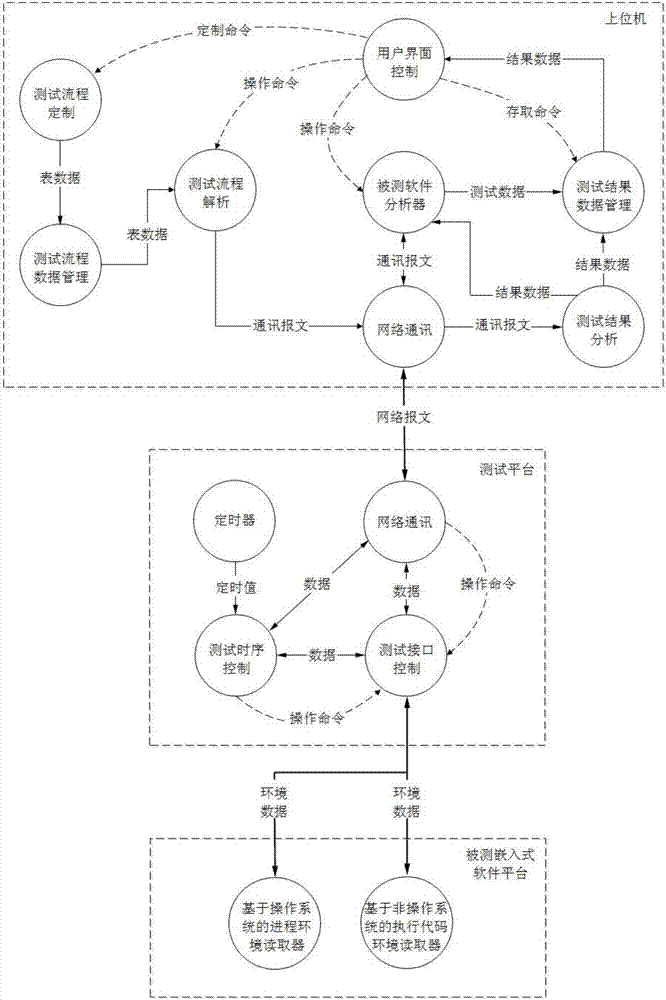
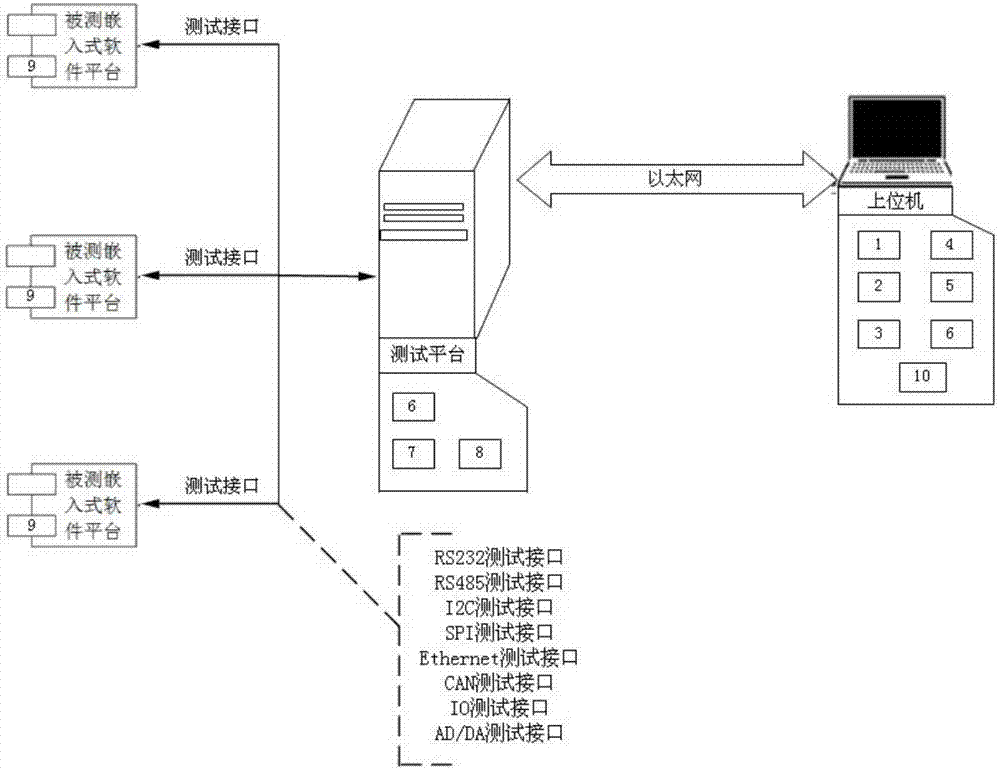
Automatic confirmation testing method and system for embedded software
InactiveCN107315679AExact expansion rateReduce expansionSoftware testing/debuggingSoftware analyticsNetwork communication
The invention discloses an automatic confirmation testing method and system for embedded software. The testing method comprises the following steps that: customizing a testing process, managing testing data, parsing the testing process, analyzing tested software, analyzing a testing result, carrying out network communication, controlling a testing interface, controlling a testing time sequence and reading tested platform software environment. The testing system comprises a testing process customization module, a testing data management module, a testing process parsing module, a tested software analyzer, a testing result analysis module, a network communication module, a testing interface control module, a testing time sequence control module and a tested platform software environment reader. By use of the method, the problems of the accurate input of a test case and the real-time collection of the output of tested software in an embedded software testing process are solved, the operation situation of the tested software is tracked under a situation that the code bloat rate of the tested software is almost not changed, and a full-automatic and visual corresponding relational graph of the test case and the operation situation of the tested software can be provided for testing personnel.
Owner:昆明奥多智能科技有限公司
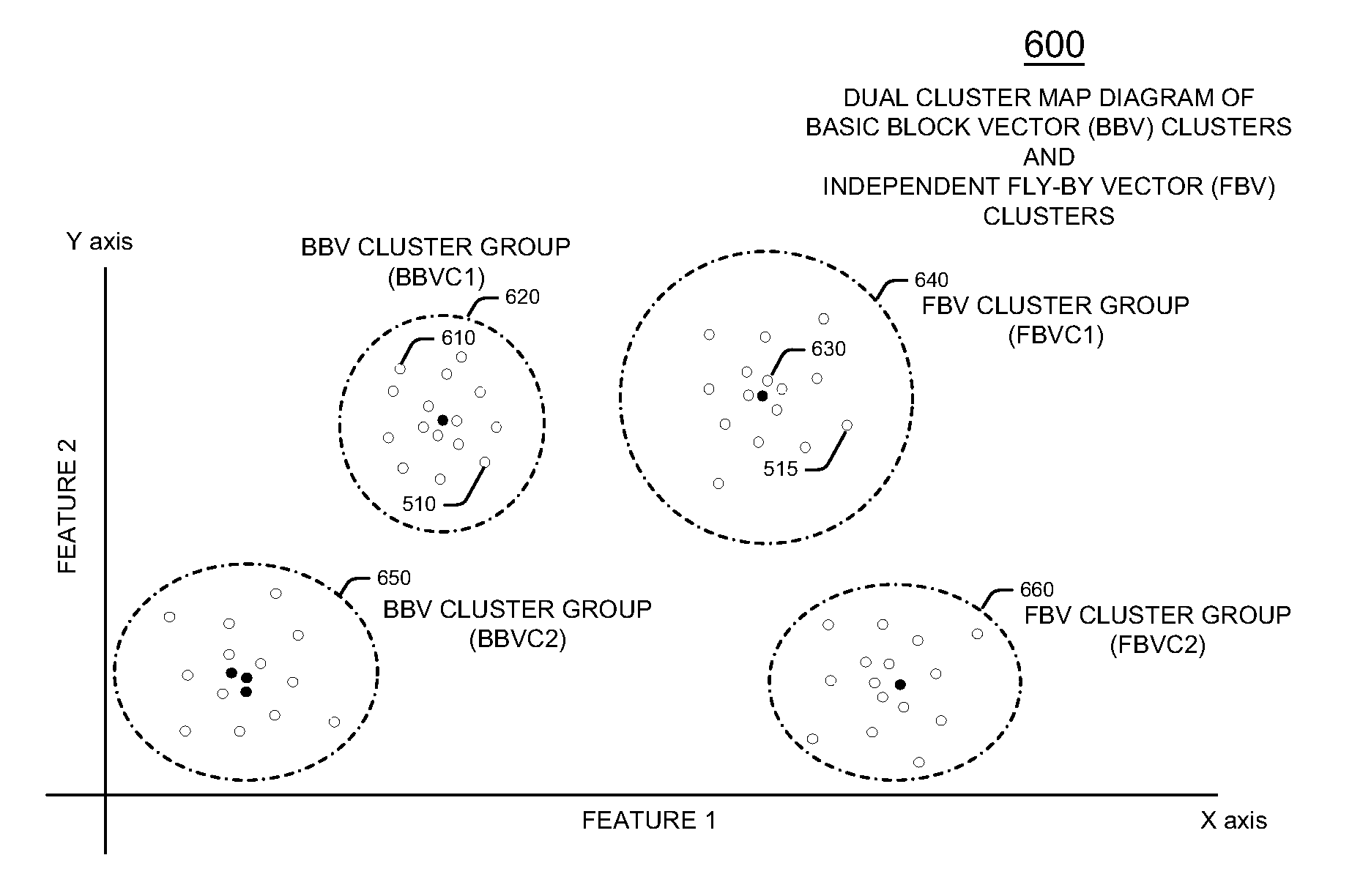
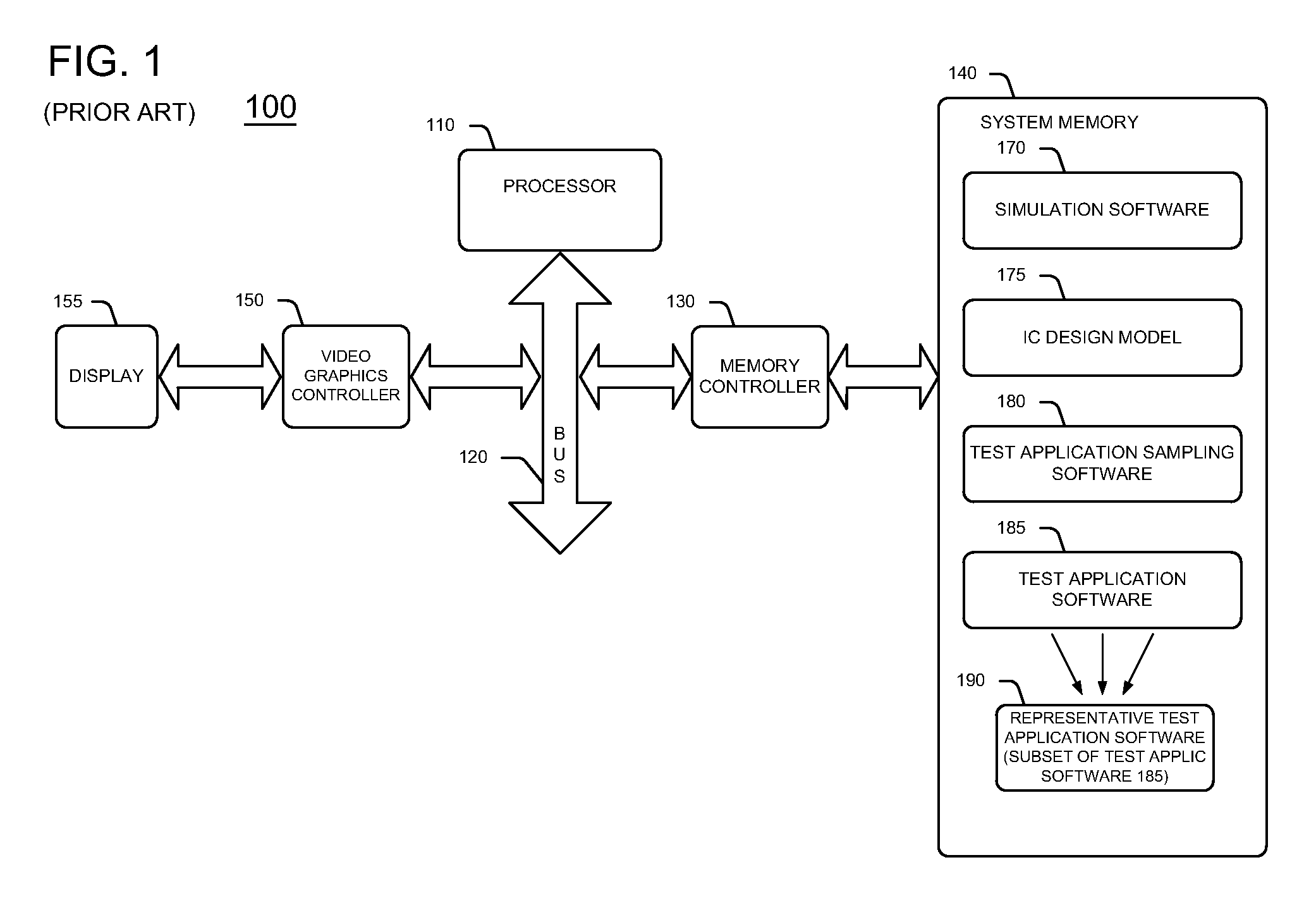
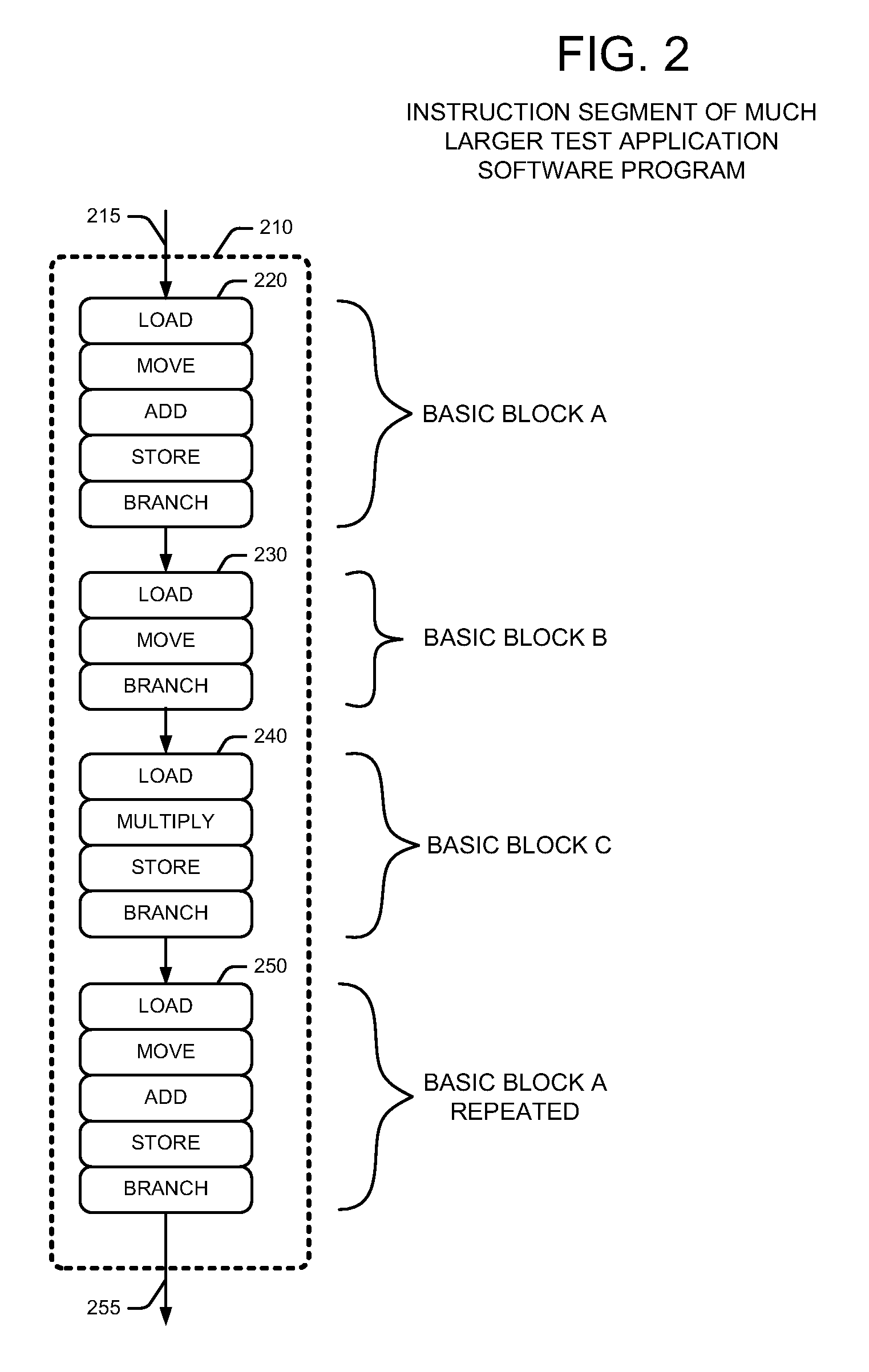
Method and apparatus for evaluating integrated circuit design model performance using basic block vectors and fly-by vectors including microarchitecture dependent information
ActiveUS7770140B2Detecting faulty computer hardwareSoftware simulation/interpretation/emulationSoftware analyticsApplication software
A test system or simulator includes an IC test application sampling software program that executes test application software on a semiconductor die IC design model. The test application sampling software includes trace, simulation point, CPI error, clustering and other programs. IC designers utilize the test application sampling software to evaluate the performance characteristics of IC designs with test software applications. The test application sampling software generates basic block vectors (BBVs) and fly-by vectors (FBVs) from instruction trace analysis of test application software. The test application sampling software analyzes microarchitecture dependent information that it uses to generate the FBVs. Test application sampling software generates a reduced representative test application software program from the BBV and FBV data utilizing an instruction budgeting method. Designers use the test system with test application sampling software to evaluate IC design models by using the representative test application software program.
Owner:SIEMENS PROD LIFECYCLE MANAGEMENT SOFTWARE INC
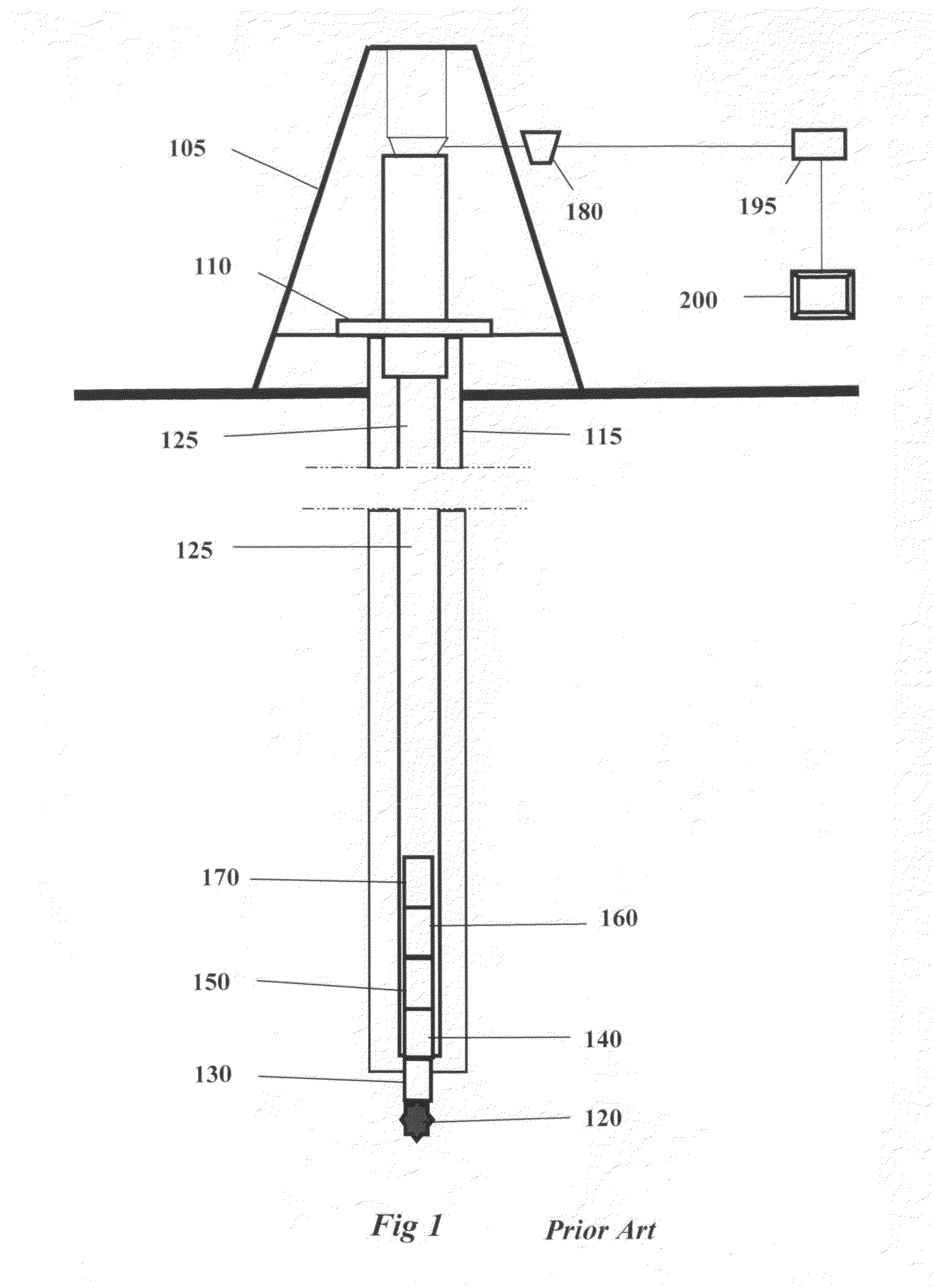
Method and apparatus for recording and using down hole sensor and diagnostic events in measurement while drilling
ActiveUS20100161227A1Electric/magnetic detection for well-loggingConstructionsData transmissionSoftware
A method and apparatus for providing a downhole measurement-while-drilling (MWD) tool with diagnostic capability by including one or more printed circuit boards to the tool with firmware processors that internally record significant system diagnostic events that can be time correlated with known tool operational problems. The concept includes firmware protocol to enable transfer all of the recorded data to an external software analysis program after the MWD tool is removed from a drilling run.
Owner:TOLTEQ GROUP
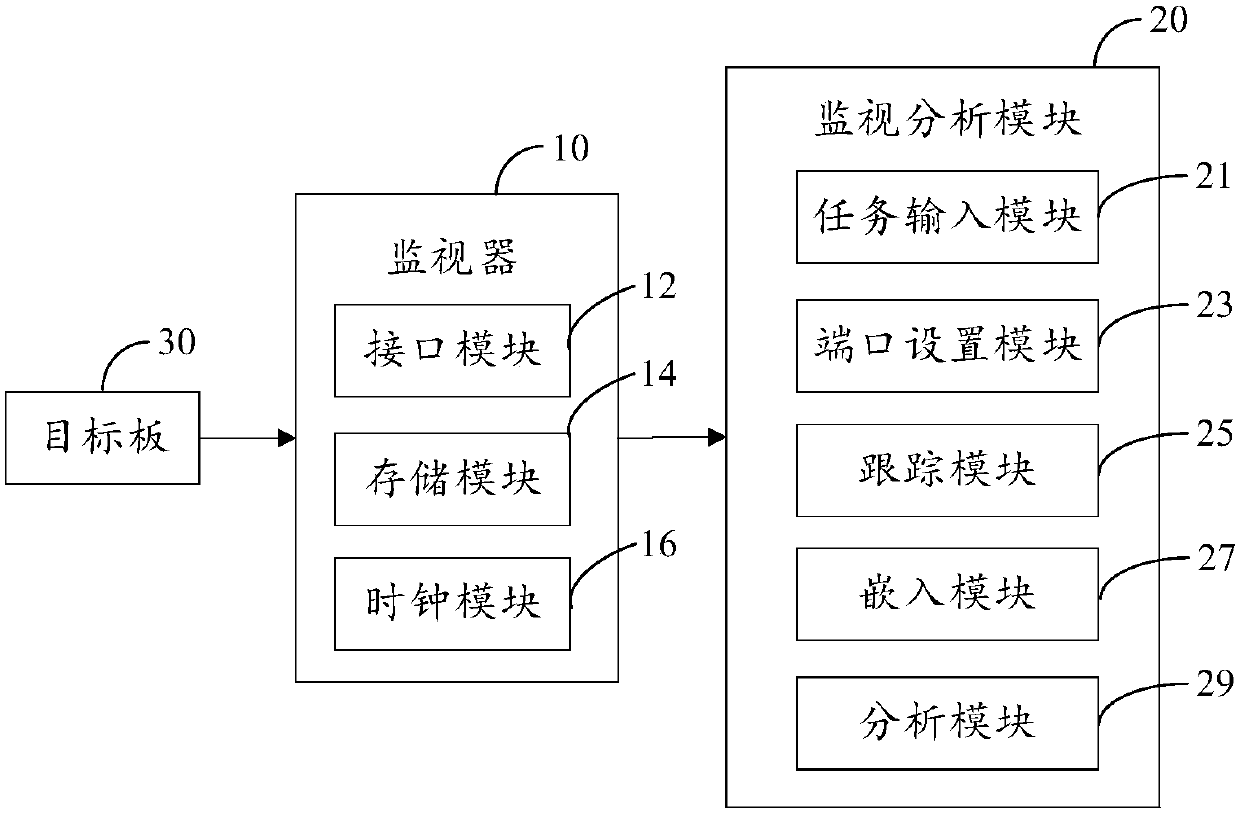
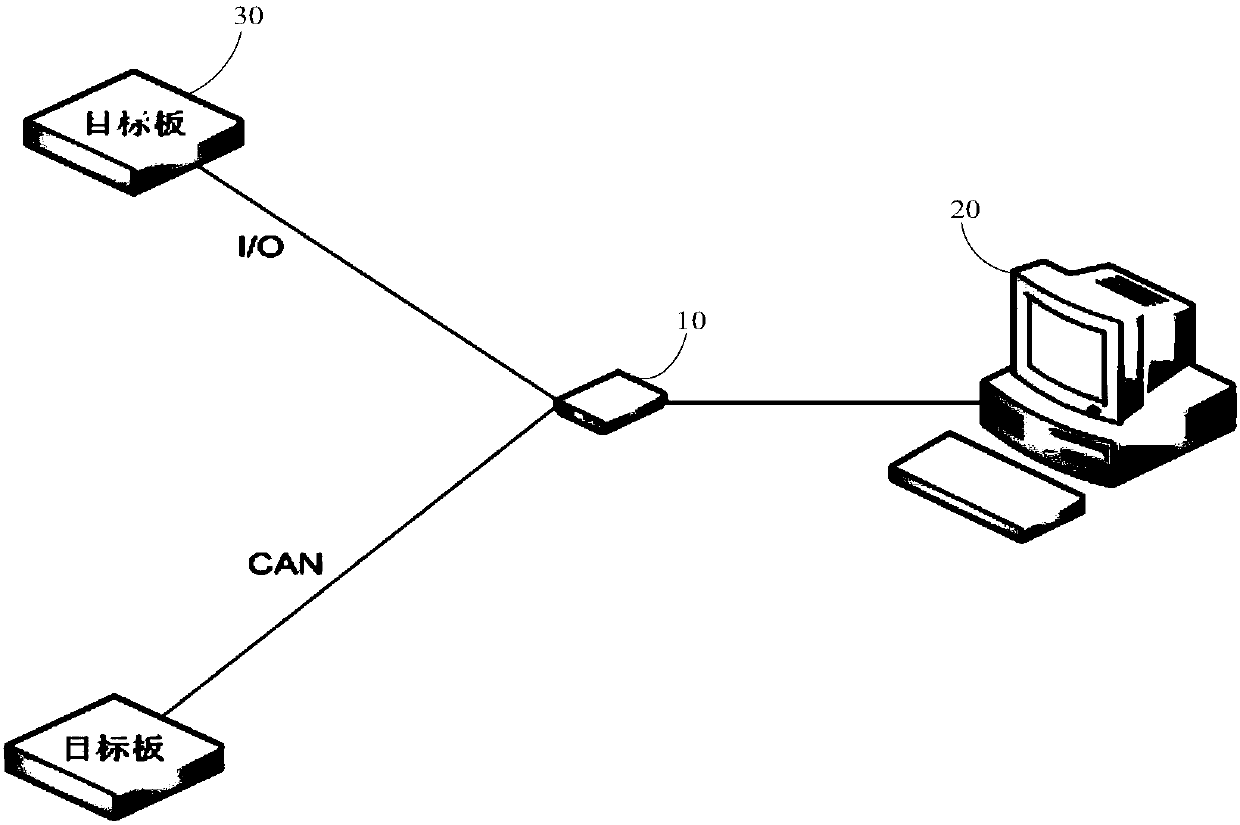
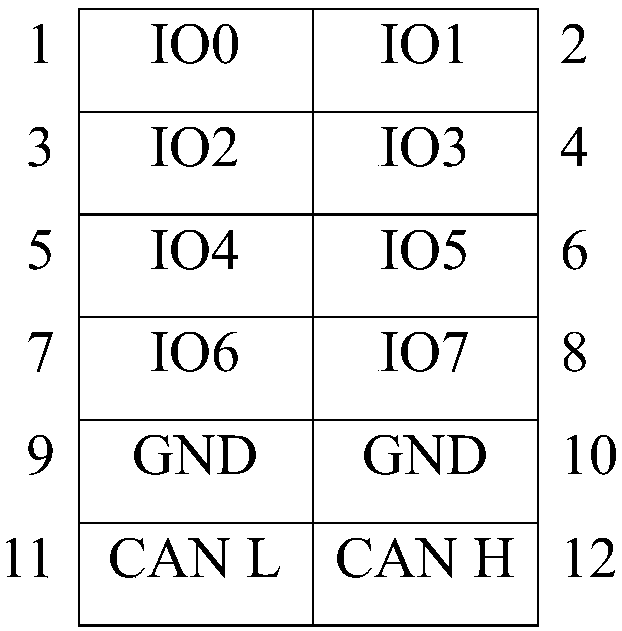
Software analysis system and method of real-time system
InactiveCN107797913AAvoid only fitting the same modelAvoid problems with products from the same manufacturerSoftware testing/debuggingLoad timeSoftware analytics
The invention discloses a software analysis system and method of a real-time system, and aims at carrying out task monitoring and performance analysis on a target board which comprises a processor. The software analysis system comprises a monitor and a monitoring analysis module, wherein the monitor and the monitoring analysis module are electrically connected; an output port of the target board is connected with a port of the monitor; the port of the monitor comprises an I / O interface and / or a CAN interface; the port type of the monitor can be set to be matched with the output port of the target board by the monitoring analysis module; the monitor is used for loading a time stamp, storing tracking data of the target board and periodically uploading the tracking data to the monitoring analysis module; and the monitoring analysis module is used for inputting a software task list of the target board, setting the port of the monitor, generating and embedding a tracking module which is capable of tracking tasks of the target board to target board software, and analyzing the tracking data of the target board to obtain task execution sequence and / or execution time of the target board.
Owner:CONTINENTAL AUTOMOTIVE CORP LIANYUNGANG CO LTD
Analysis method, recommendation method, analysis apparatus and recommendation apparatus for software
ActiveCN102693229AMultiple install rateRaise attentionSpecial data processing applicationsCluster algorithmData set
The embodiment of the invention discloses a software analysis method, comprising: acquiring the software installation information of each currently-online client; constructing a user vector data set of specific software with a predetermined number according to the software installation information of each client; calculating the user vector data set based on a clustering algorithm to acquire at least one user category; and calculating an installation ranking list of the specific software with a predetermined number of each user category. The embodiment of the invention further discloses a software recommendation method, a software analysis apparatus and a software recommendation apparatus. The analysis method, recommendation method, analysis apparatus and recommendation apparatus for software can analyze the software and sort the software list according to the client characteristics, and improve the installation efficiency of the software.
Owner:SHENZHEN TENCENT COMP SYST CO LTD
Safe operating and fault remote-positioning system for ring network cabinet
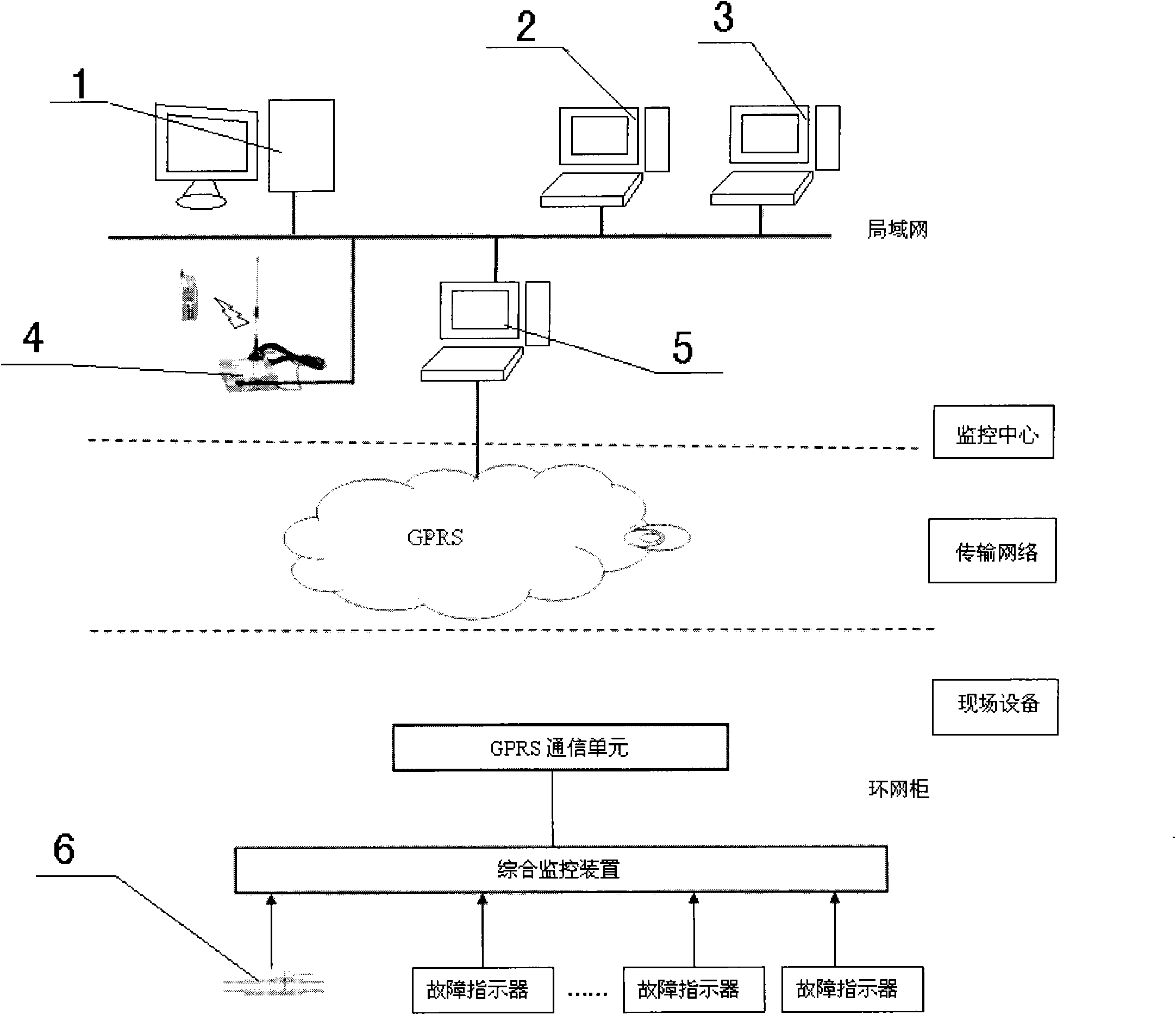
InactiveCN102088482AEasy constructionGuaranteed uptimeCircuit arrangementsMessaging/mailboxes/announcementsFault indicatorSoftware analytics
The invention relates to a remote automatic monitoring device, especially to a safe operating and fault remote-positioning system for a ring network cabinet. The technical scheme comprises three parts: a monitoring center, transmission networks and on-site equipment. The monitoring center is provided with a data server, a browsing terminal, an operation terminal, a network short message server and a preposition work station, which are used for receiving the data of each monitoring point, realizing the functions of data storage, analysis, determination and alarming, etc, and reminding relevant work staff of the on-site operation condition in different ways. The system of the invention can timely detect the cases of the ring network cabinet such as the rising of a cable temperature, the alarming of a fault indicator, etc, and when the temperature rises to a certain limit value, the system can immediately give an alarm and prompt users to take measures to prevent accidents, thereby greatly raising the operation security of distribution networks. Besides, when a line has a fault, the system can automatically report fault information, and through the analysis of software, automatically determine a fault position, rapidly search for the fault and timely recover power supply, thereby raising the reliability of power supply.
Owner:STATE GRID CORP OF CHINA +1
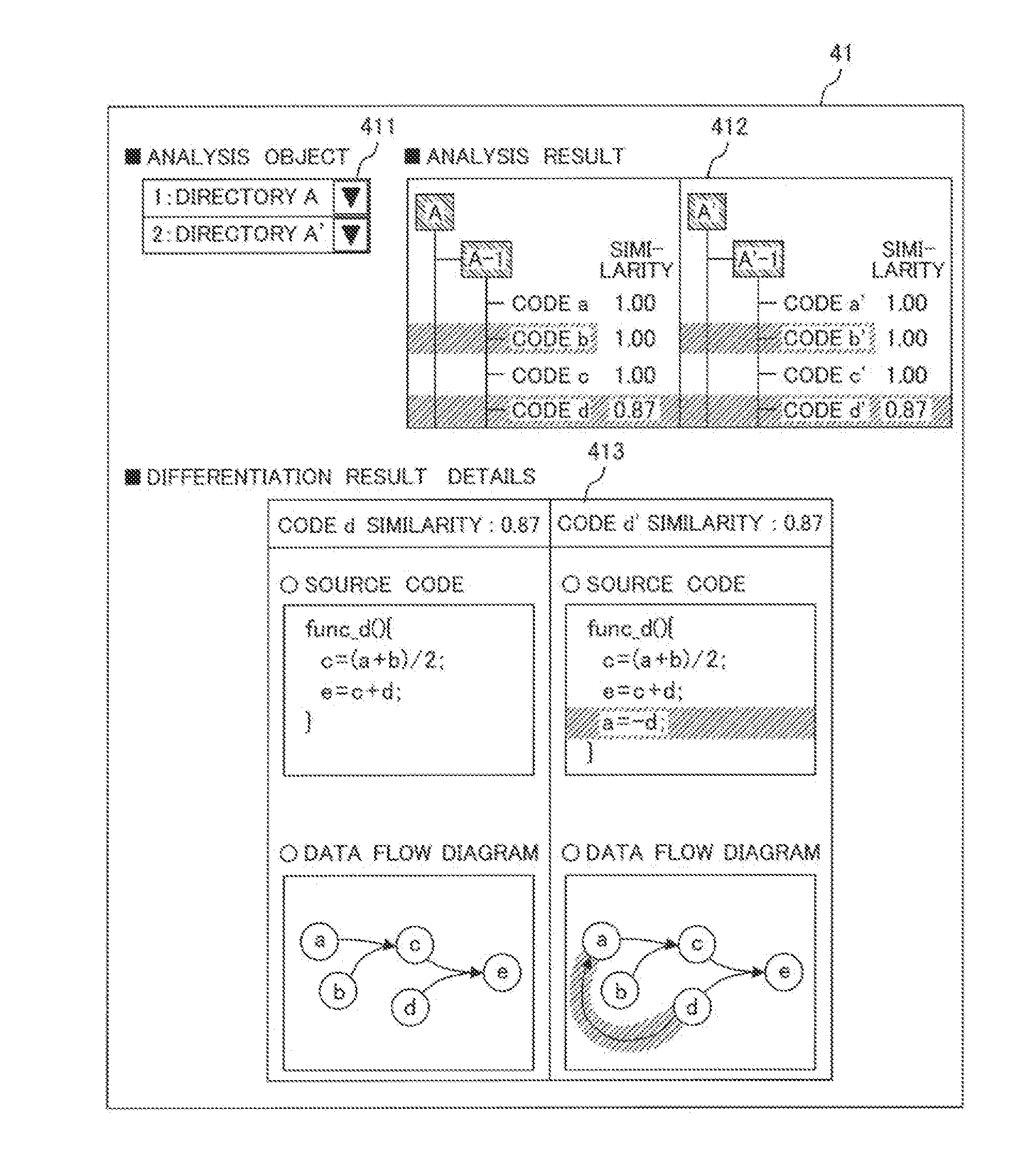
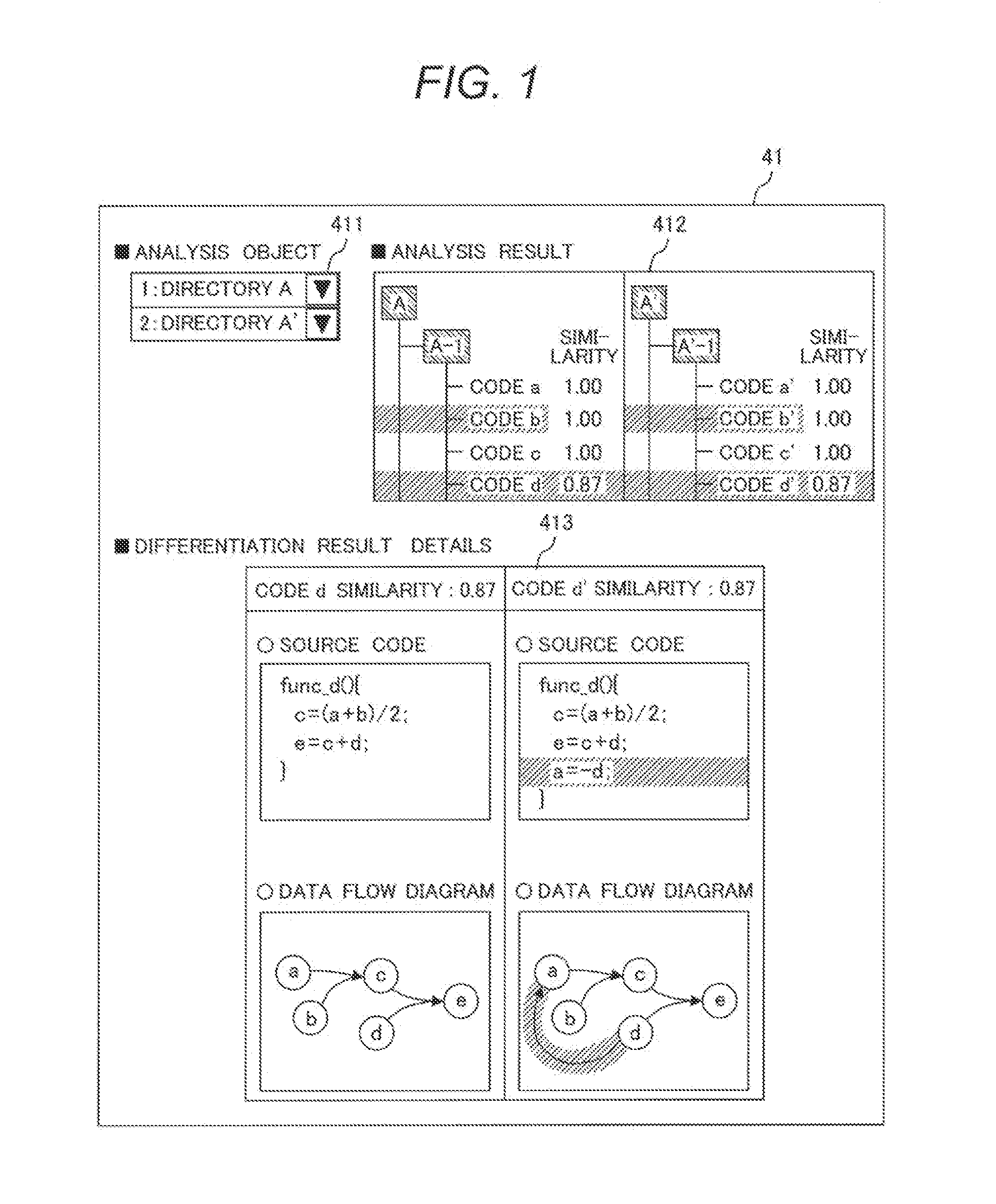
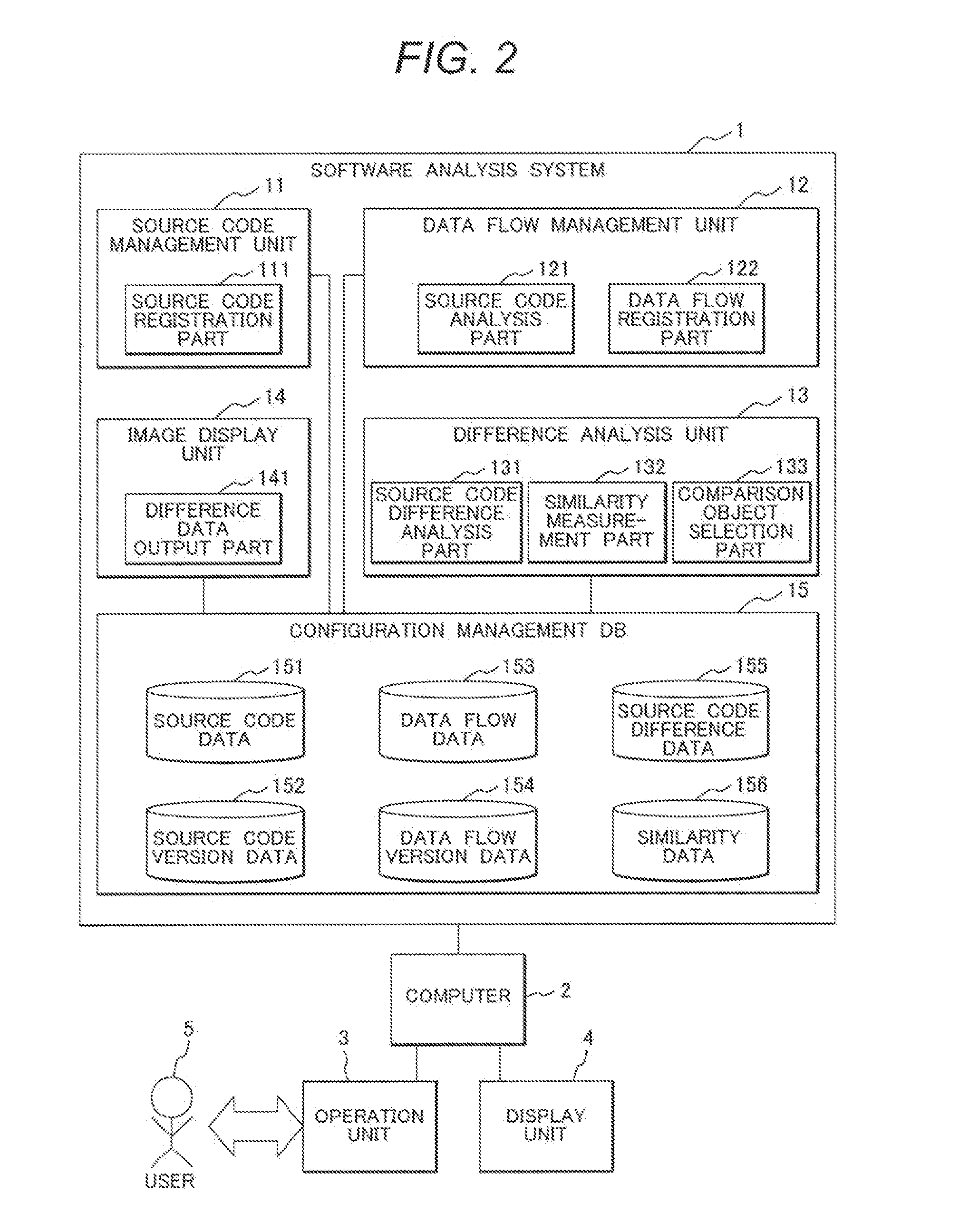
Software Analysis Program and Software Analysis System
InactiveUS20140331202A1Easy to specifyEasily areaReverse engineeringSpecific program execution arrangementsGraphicsSoftware analytics
To easily specify a difference part among multiple source codes even in the case of software that is relatively large scaled and complicated as an embedded system, and to make it possible for an area of influence that the difference part has to be easily understood. In a software analysis system of an embedded system into which a computer system is embedded, the software analysis system has a similarity measurement part that treats a dependence relationship in the source code controlling the embedded system as a graphical structure and measures a similarity of one or more source codes, and an image display unit for displaying the similarity.
Owner:HITACHI LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com