Password verification method and device based on zero knowledge proof and electronic equipment
A zero-knowledge proof and password verification technology, applied in the field of password verification methods, devices and electronic equipment based on zero-knowledge proof, can solve the problems of server keys being removed from the database, user information leakage, poor security and other problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
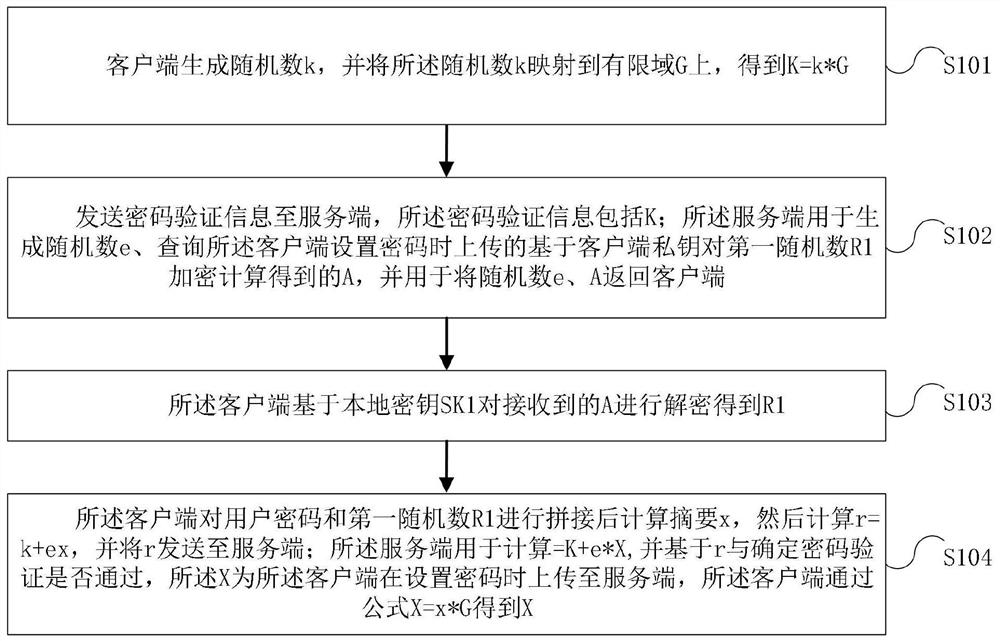
[0065] The embodiment of this application provides a password verification method based on zero-knowledge proof, which is applied to the client, such as figure 1 As shown, the method may include the following steps:
[0066] Step S101, the client generates a random number k, and maps the random number k to a finite field G to obtain K=k*G;
[0067] Step S102, sending password verification information to the server, the password verification information includes K; the server is used to generate a random number e, and query the first random number based on the client private key pair uploaded when the client sets the password R1 encrypts and calculates A, and uses it to return random numbers e and A to the client;
[0068] Step S103, the client decrypts the received A based on the local key SK1 to obtain R1;
[0069] Step S104, the client concatenates the user password and the first random number R1 to calculate the digest x, then calculates r=k+ex, and sends r to the server;...
Embodiment 2
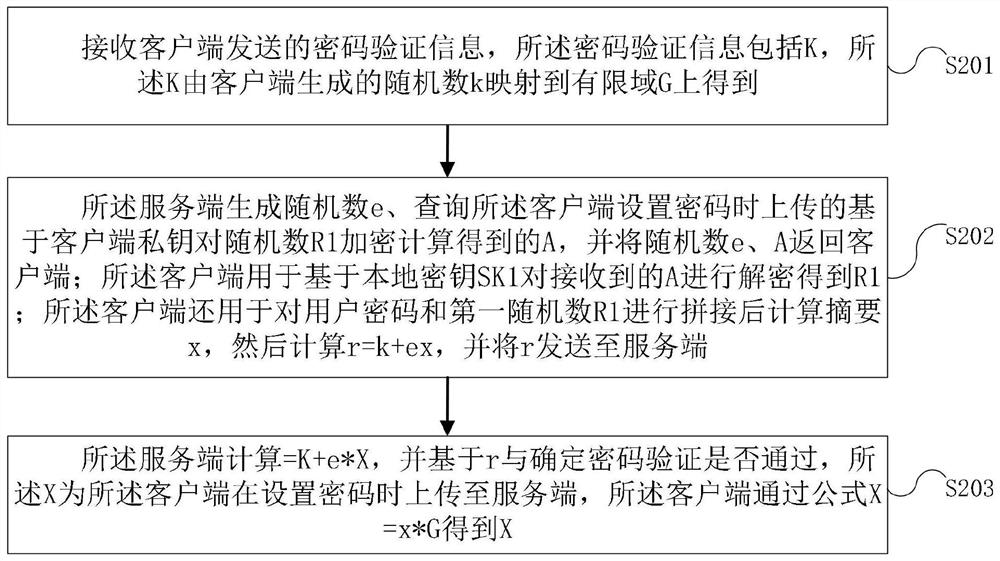
[0092] The embodiment of this application provides a password verification method based on zero-knowledge proof, which is applied to the server, such as figure 1 As shown, the method may include the following steps:
[0093] Step S201, receiving password verification information sent by the client, the password verification information includes K, and the K is obtained by mapping a random number k generated by the client to a finite field G;
[0094] Step S202, the server generates a random number e, queries the A obtained by encrypting and calculating the random number R1 based on the client private key uploaded when the client sets a password, and returns the random numbers e and A to the client; The client is used to decrypt the received A based on the local key SK1 to obtain R1; the client is also used to concatenate the user password and the first random number R1 to calculate the digest x, and then calculate r=k+ex, and send r to the server;
[0095] Step S203, the ser...
Embodiment 3
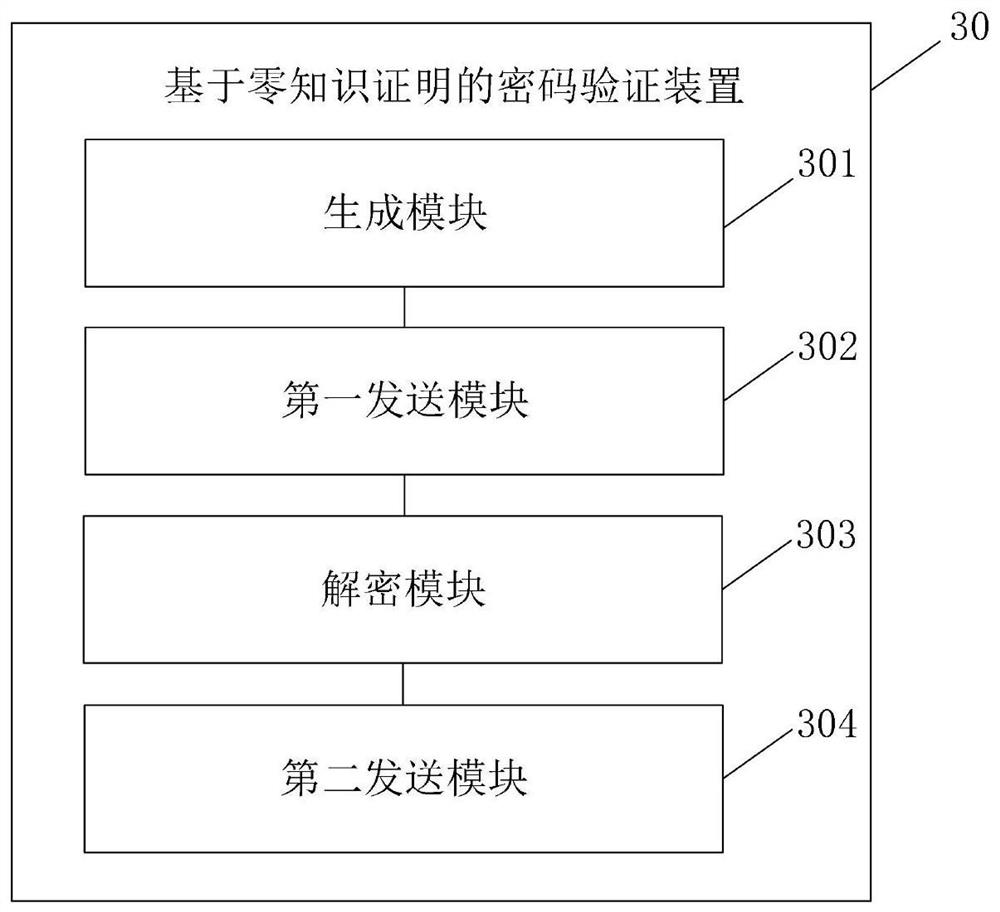
[0106] image 3 The password verification device based on zero-knowledge proof provided for the embodiment of this application is applied to the client, wherein the device 30 includes:
[0107] A generating module 301, configured to generate a random number k, and map the random number k onto a finite field G to obtain K=k*G;
[0108] The first sending module 302 is used to send password verification information to the server, and the password verification information includes K; the server is used to generate a random number e, query the client private key uploaded when the client sets the password A obtained by encrypting and calculating the first random number R1 is used to return the random numbers e and A to the client;
[0109] A decryption module 303, configured to decrypt the received A based on the local key SK1 to obtain R1;
[0110] The second sending module 304 is used to concatenate the user password and the first random number R1 to calculate the digest x, then...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com