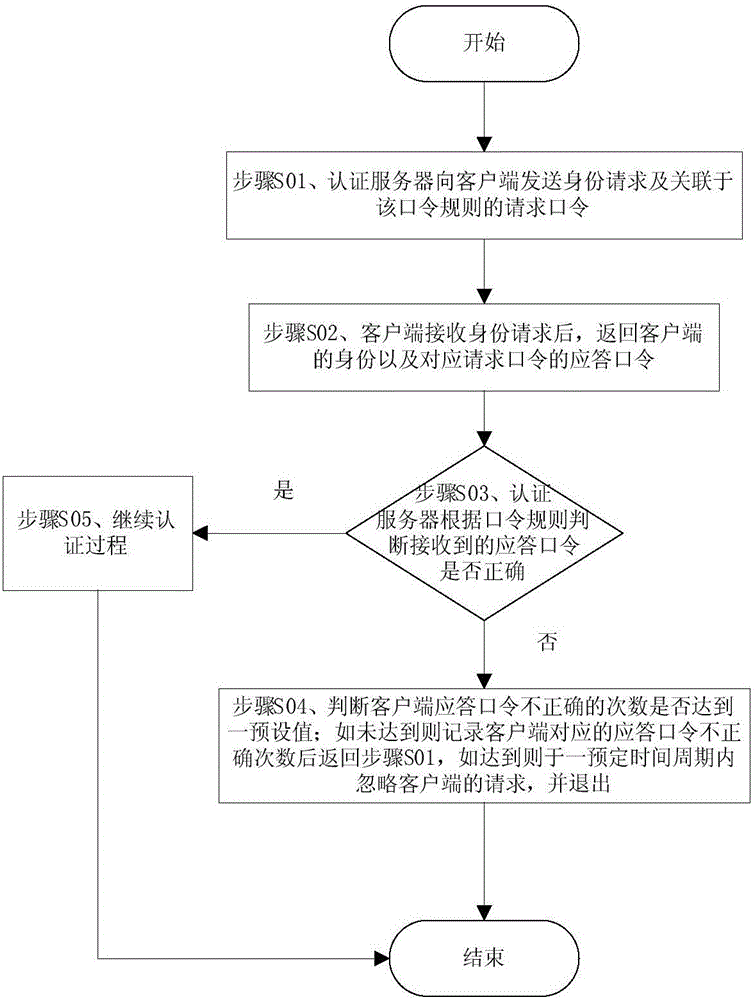
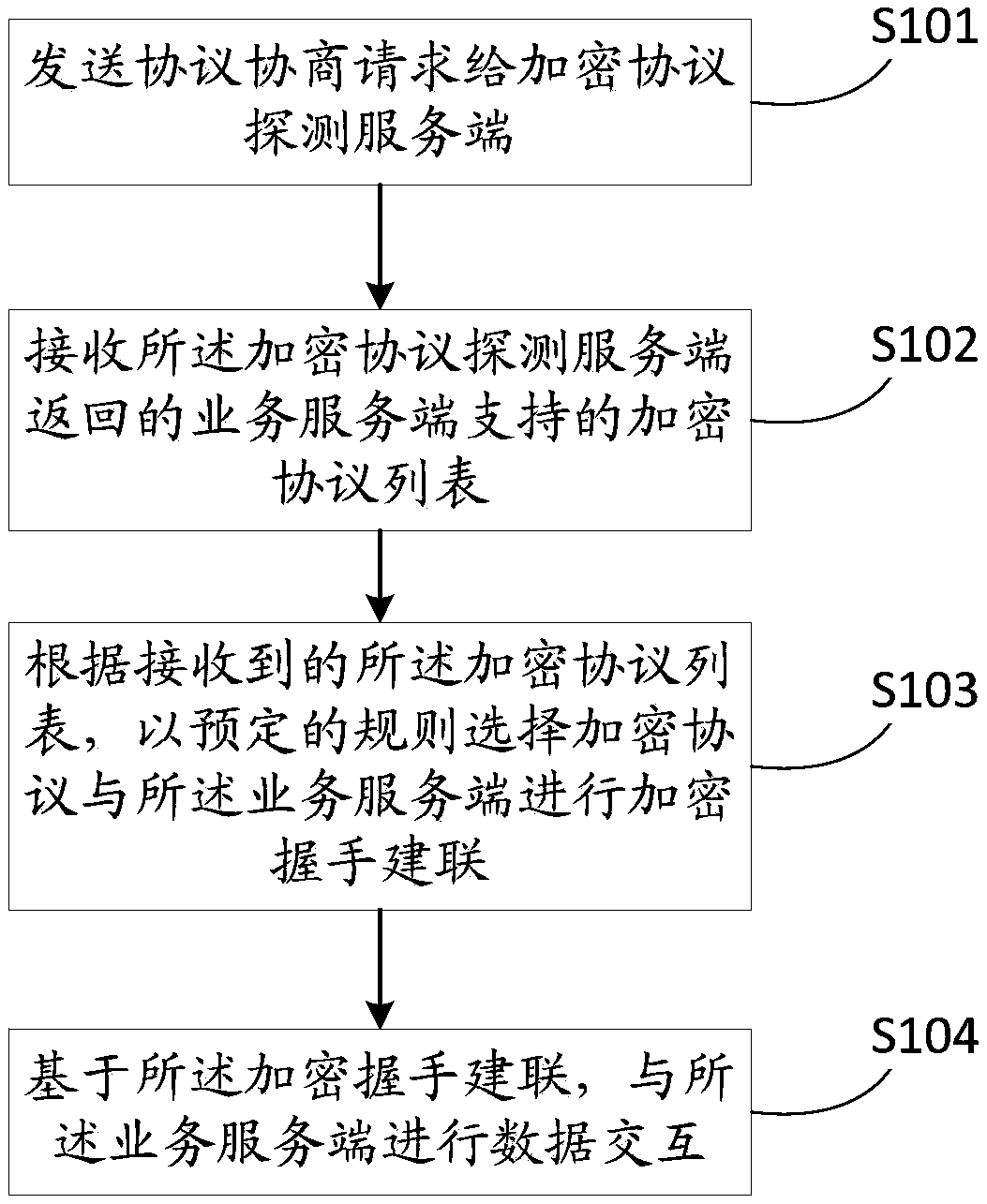
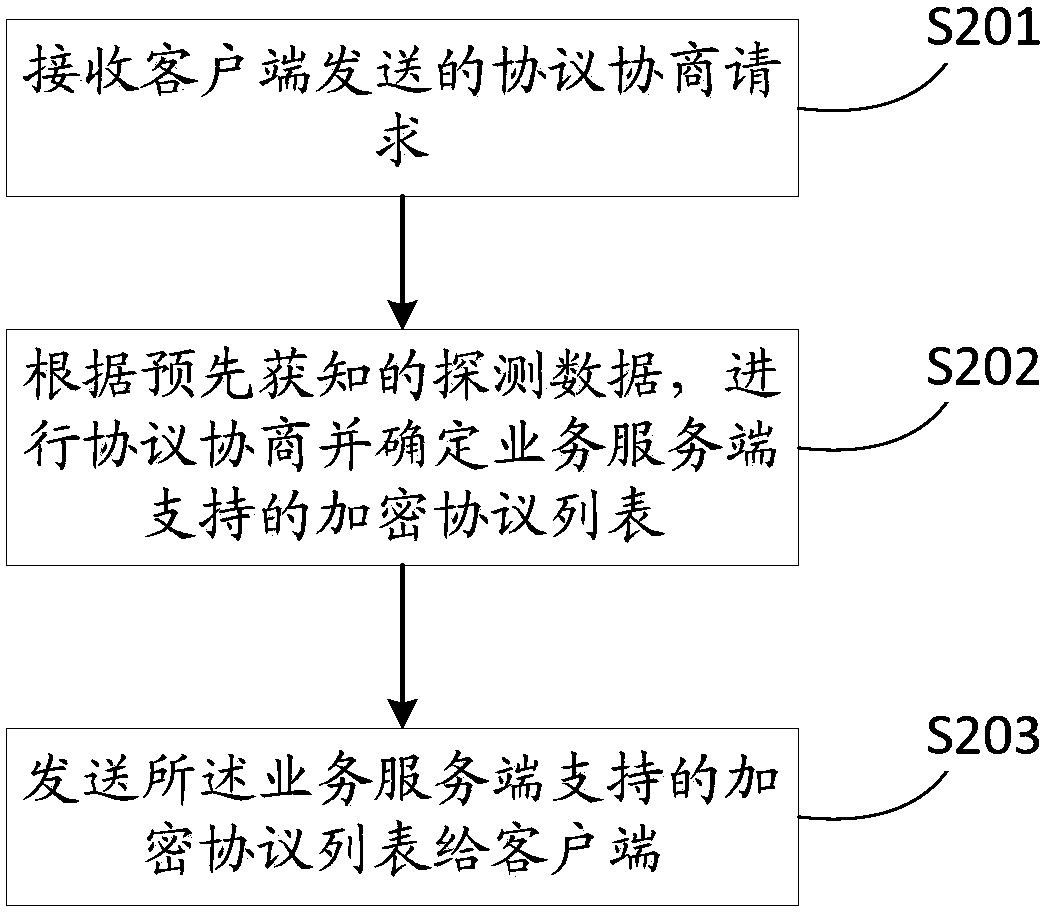
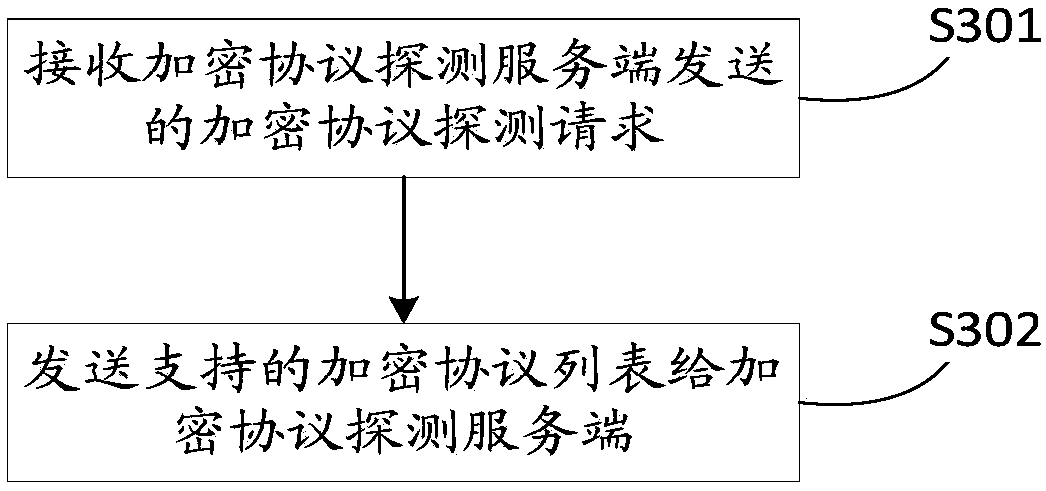
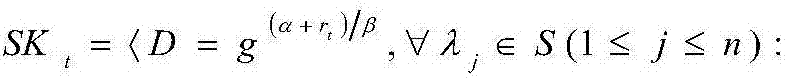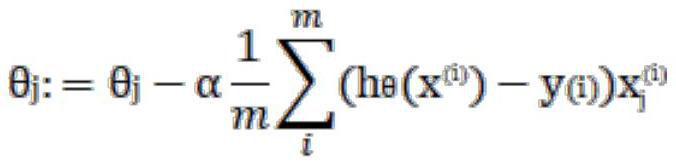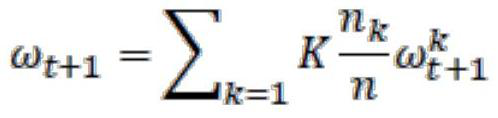Patents
Literature
85 results about "Client-side encryption" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Client-side encryption is the cryptographic technique of encrypting data on the sender's side, before it is transmitted to a server such as a cloud storage service. Client-side encryption features an encryption key that is not available to the service provider, making it difficult or impossible for service providers to decrypt hosted data. Client-side encryption allows for the creation of applications whose providers cannot access the data its users have stored, thus offering a high level of privacy. Those applications are sometimes marketed under the misleading term "zero-knowledge".
Method and system for data backup
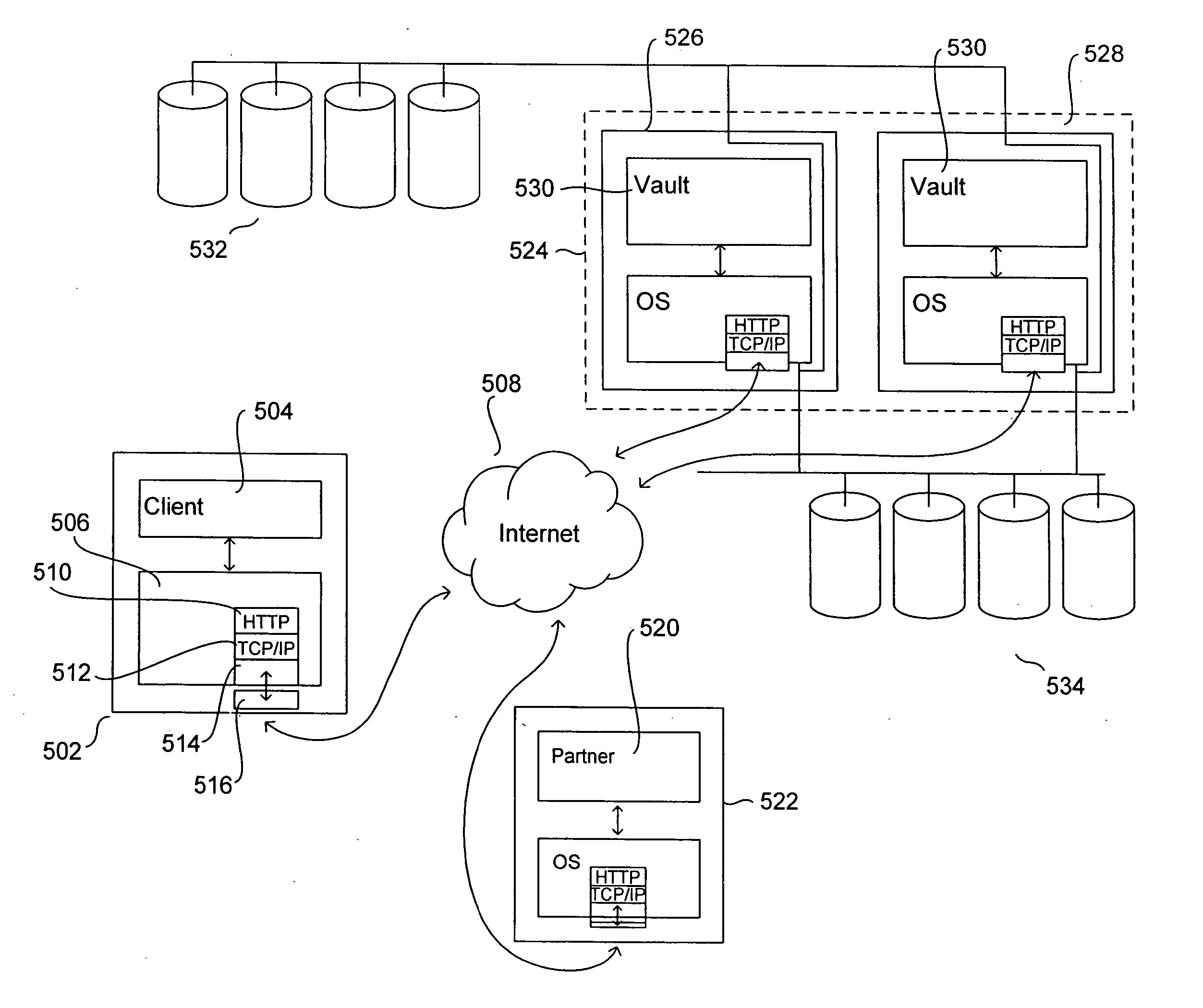
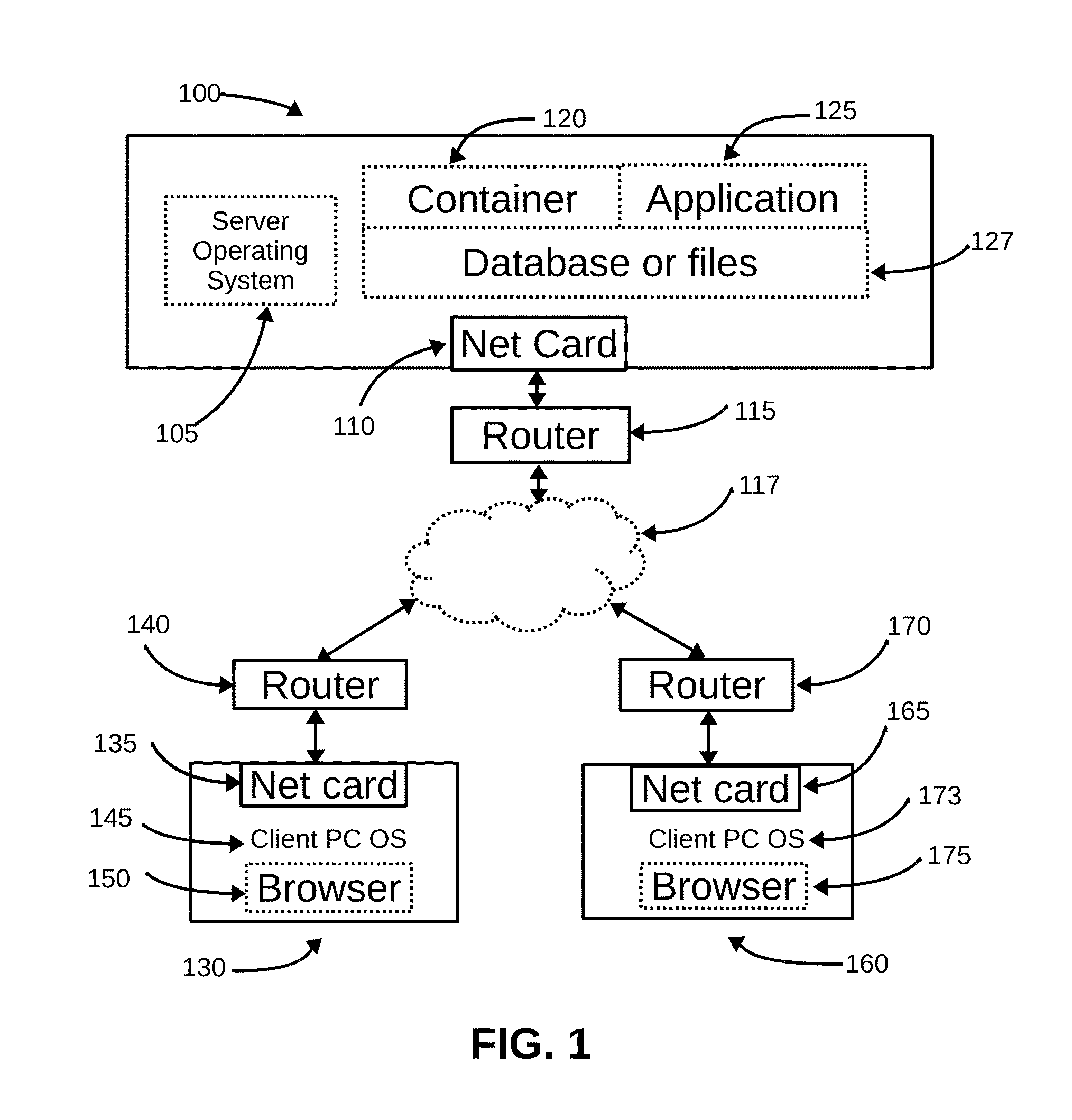
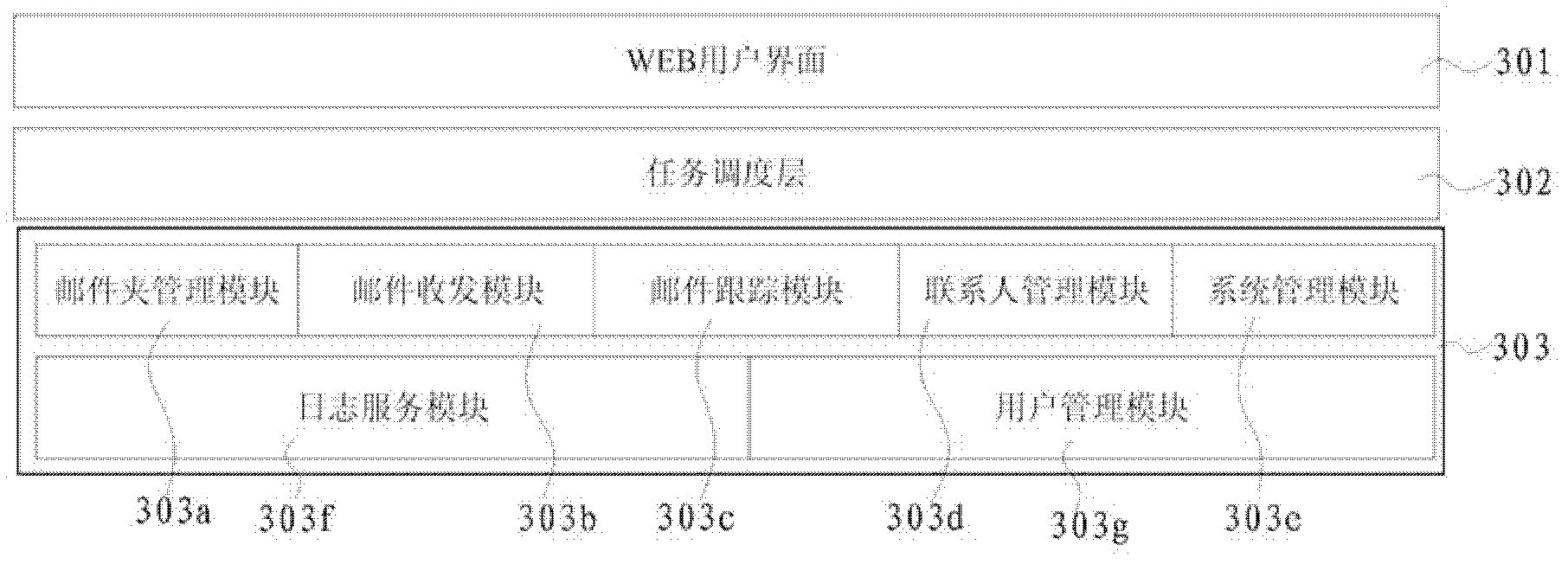
ActiveUS20070100913A1Cost-effectiveAvoid accessMemory loss protectionError detection/correctionWeb serviceApplication software
Embodiments of the present invention are directed to Web-Services-based data backup and data-archiving applications that provide remote data backup and data archiving to private individuals, small businesses, and other organizations that need reliable, secure, geographically remote, and cost-effective data backup, data archiving, and backed-up and archived-data retrieval. In one embodiment of the present invention, a private or small-business client contracts with a service provider for data-backup and data-archiving services. The service provider, in turn, contracts with a remote data-storage facility to provide secure, reliable data backup and data archiving to the personal or small-business client. A client-side application is downloaded to the client computer and configured to allow the client to store locally encrypted data at the remote, data-storage facilities. Neither the service provider nor the data-storage facility can decrypt or otherwise access the information stored by the client. In addition, the encryption key or encryption keys used by the client to encrypt the data for remote storage are securely stored at the remote, data-storage facility for subsequent recovery by the client, should the client suffer damage or loss to a local computer system. However, the client encryption key is stored in a doubly encrypted fashion, preventing access to the client's encryption key by either the service provider or the data-storage facility. Certain embodiments of the present invention also provide local indexing for remotely stored, encrypted data and efficient storage of updates to already remotely stored data.
Owner:CARBONITE GMBH
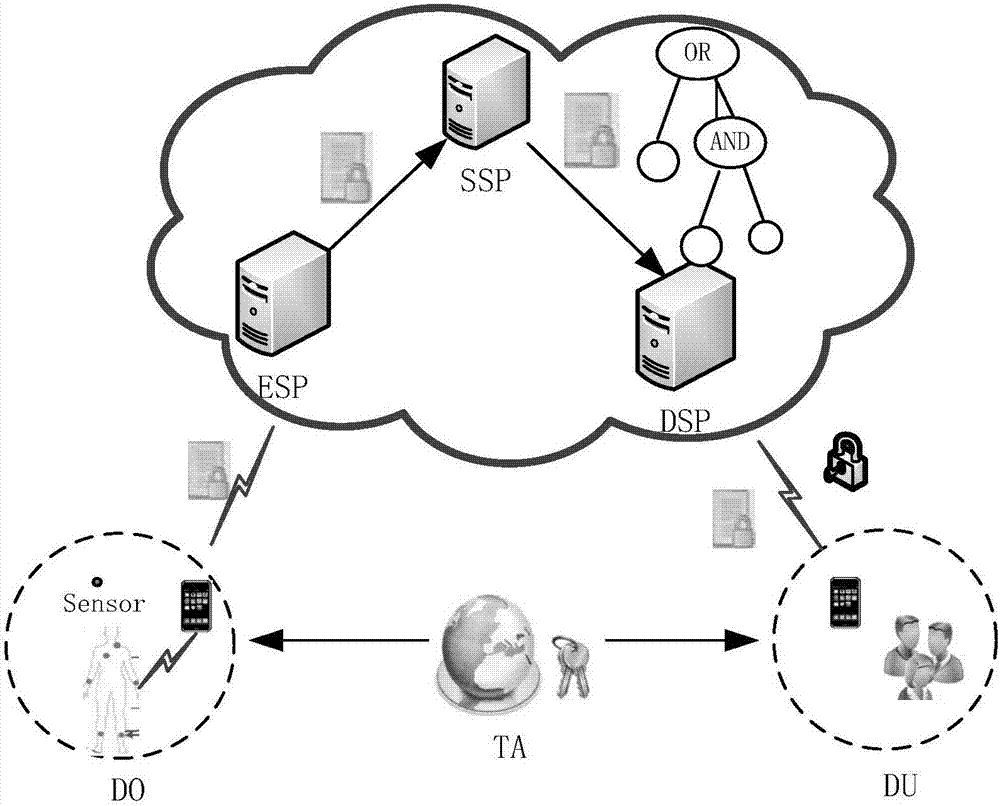
Secure and zero knowledge data sharing for cloud applications
ActiveUS10608817B2Key distribution for secure communicationMultiple keys/algorithms usageData setInternet privacy
Disclosed is a zero-knowledge distributed application configured to securely share information among groups of users having various roles, such as doctors and patients. Confidential information may be encrypted client-side, with private keys that reside solely client side. Encrypted collections of data may be uploaded to, and hosted by, a server that does not have access to keys suitable to decrypt the data. Other users may retrieve encrypted data from the server and decrypt some or all of the data with keys suitable to gain access to at least part of the encrypted data. The system includes a key hierarchy with multiple entry points to a top layer by which access is selectively granted to various users and keys may be recovered.
Owner:MASIMO CORP
Secure and zero knowledge data sharing for cloud applications
Disclosed is a zero-knowledge distributed application configured to securely share information among groups of users having various roles, such as doctors and patients. Confidential information may be encrypted client-side, with private keys that reside solely client side. Encrypted collections of data may be uploaded to, and hosted by, a server that does not have access to keys suitable to decrypt the data. Other users may retrieve encrypted data from the server and decrypt some or all of the data with keys suitable to gain access to at least part of the encrypted data. The system includes a key hierarchy with multiple entry points to a top layer by which access is selectively granted to various users and keys may be recovered.
Owner:MASIMO CORP
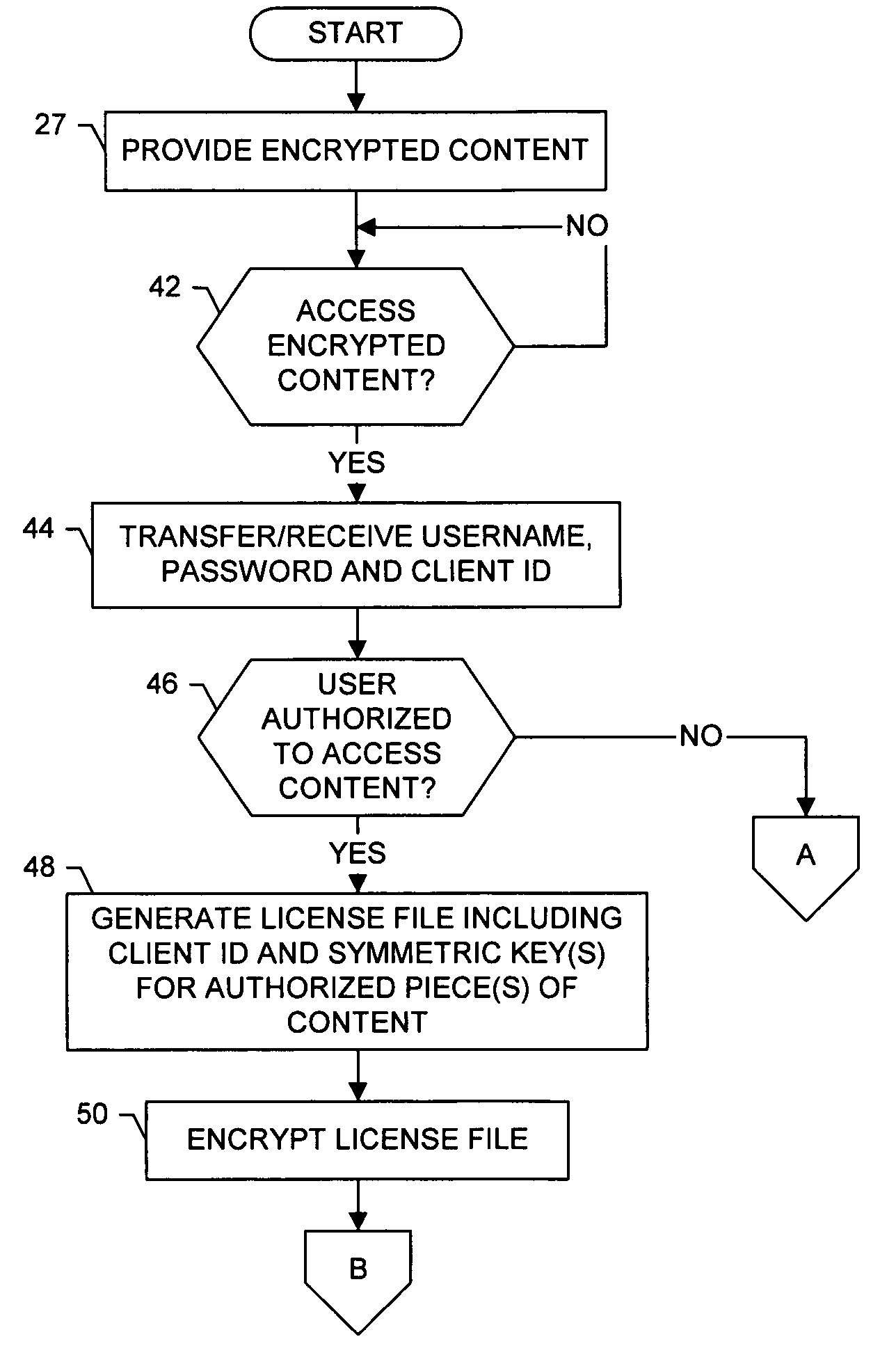
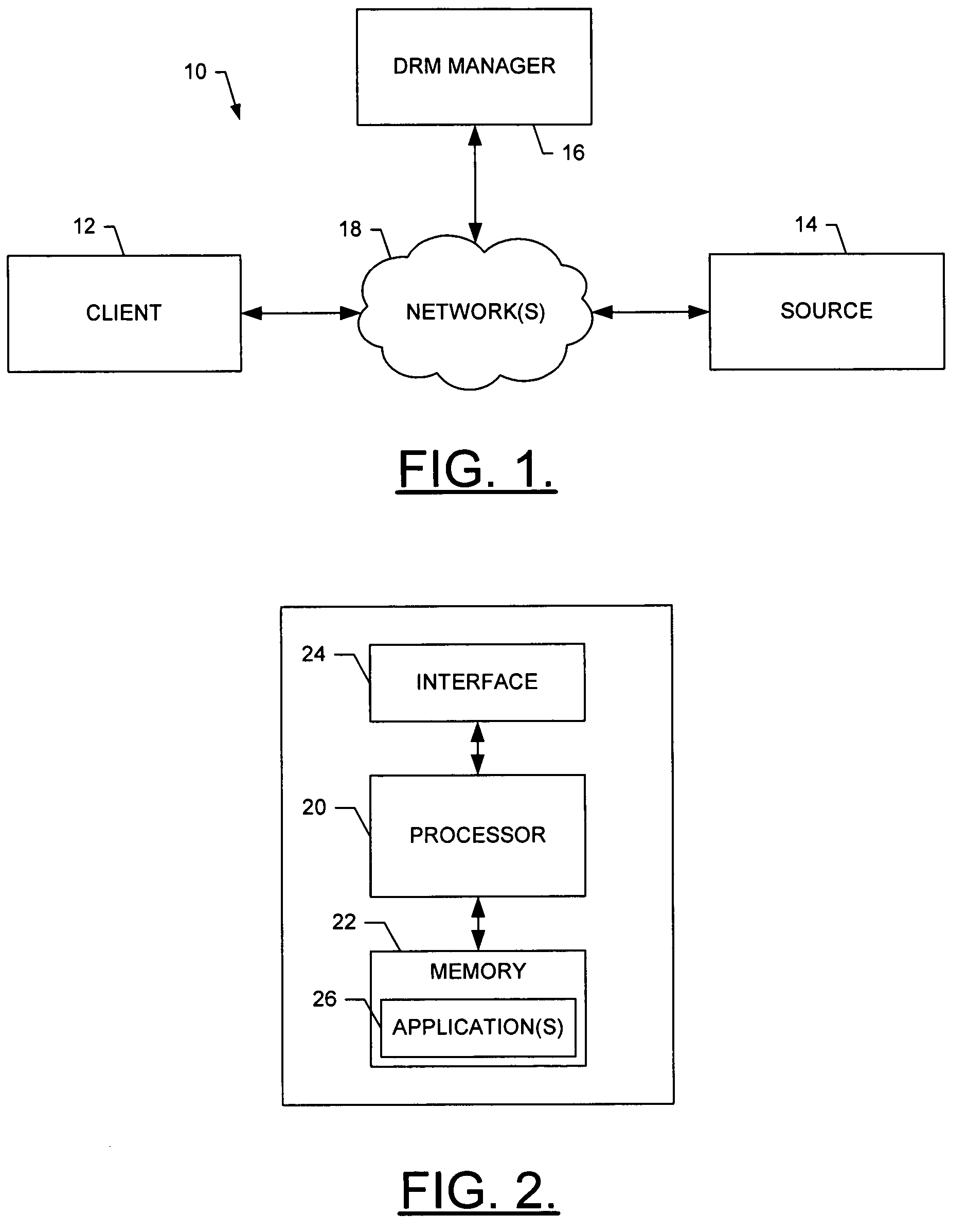
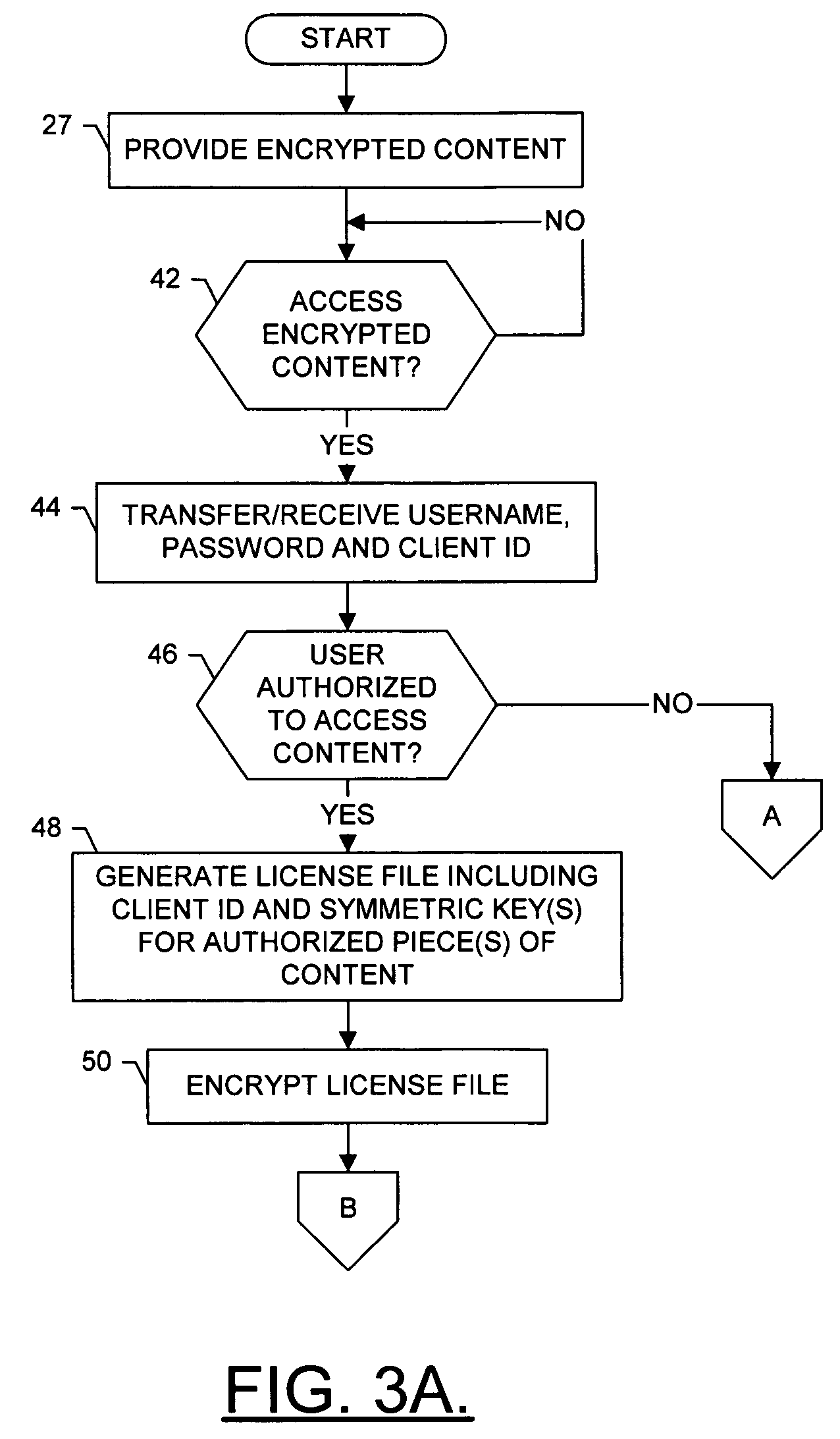
System, method and computer program product for providing digital rights management of protected content
InactiveUS20050273629A1Shorten the timePrecise managementUser identity/authority verificationUnauthorized memory use protectionRights managementDigital rights management
A system for providing digial rights management of protected content includes a client and a DRM manager. The client is capable of receiving at least one piece of content, the piece(s) of content being encrypted with at least one encryption key regardless of client user(s) authorized to access the piece(s) of encrypted content. To facilitate the client accessing one or more of the piece(s) of content, the DRM manager is capable of transferring the encryption key(s) to the client, the encryption key(s) being encrypted with a private key of a public key / private key pair unique to a client user associated with the client. The client can thereafter decrypt the encryption key(s) using the public key of the public key / private key pair unique to the client user. Then, the client can decrypt the piece(s) of content using the decrypted encryption key(s), and access the decrypted piece(s) of content.
Owner:VITALSOURCE TECH INC
Secure File Drawer and Safe
ActiveUS20130198521A1Improve securityReduce riskMultiple keys/algorithms usagePublic key for secure communicationClient-sideOnline document
An online file storage system having secure file drawer and safe is disclosed for securely storing and sharing confidential files. The system comprises a web-based user interface, tools for setting up server-side encryption method and client-side encryption method, tools for synchronizing encryption between different computers, tools for uploading files, tools for tracking files, tools for granting the right of access to files to the owner of other safes, and tools for generating authenticity certificate for proving the upload time and the substance of the files in a future time.
Owner:WU JIANQING
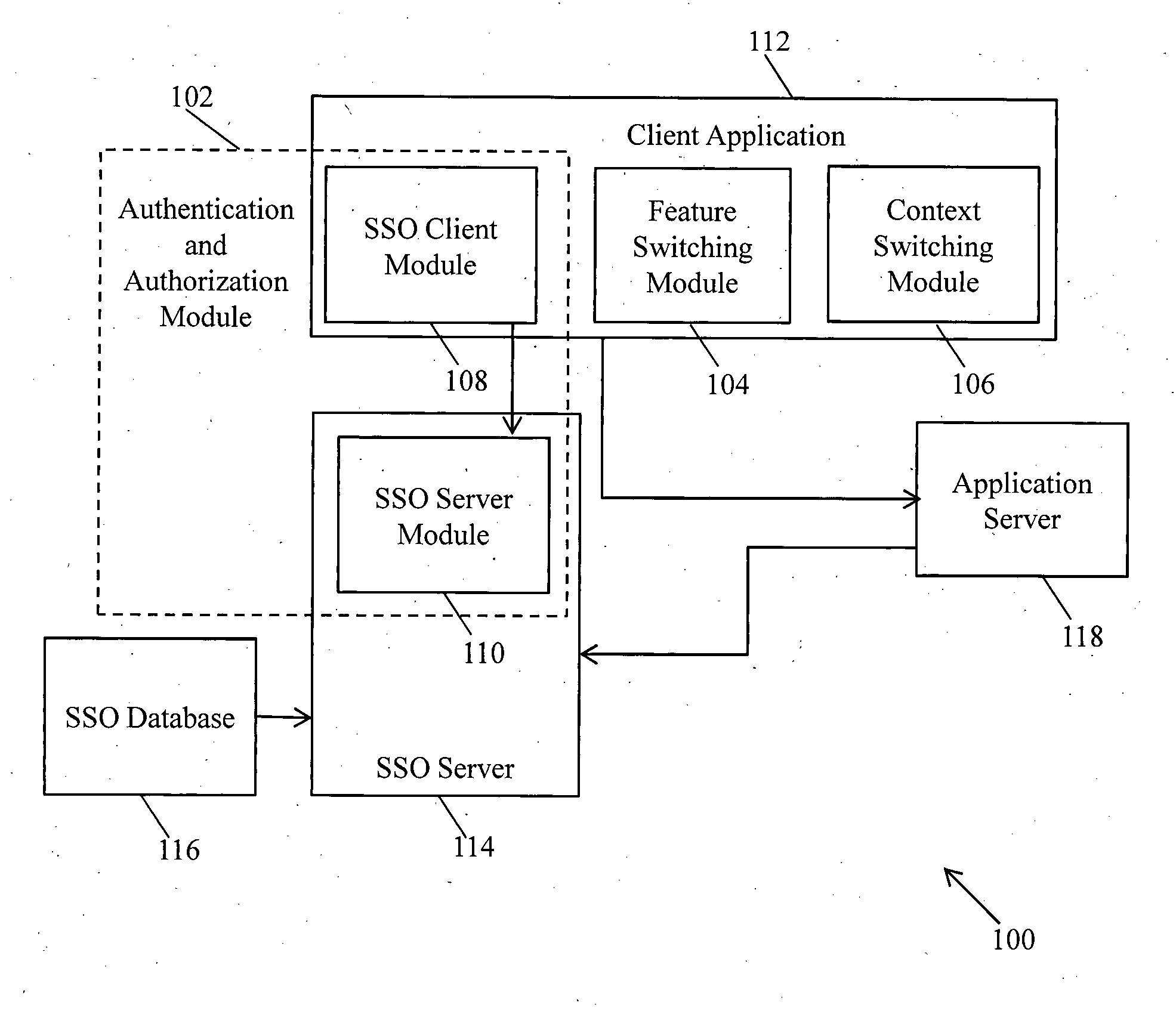
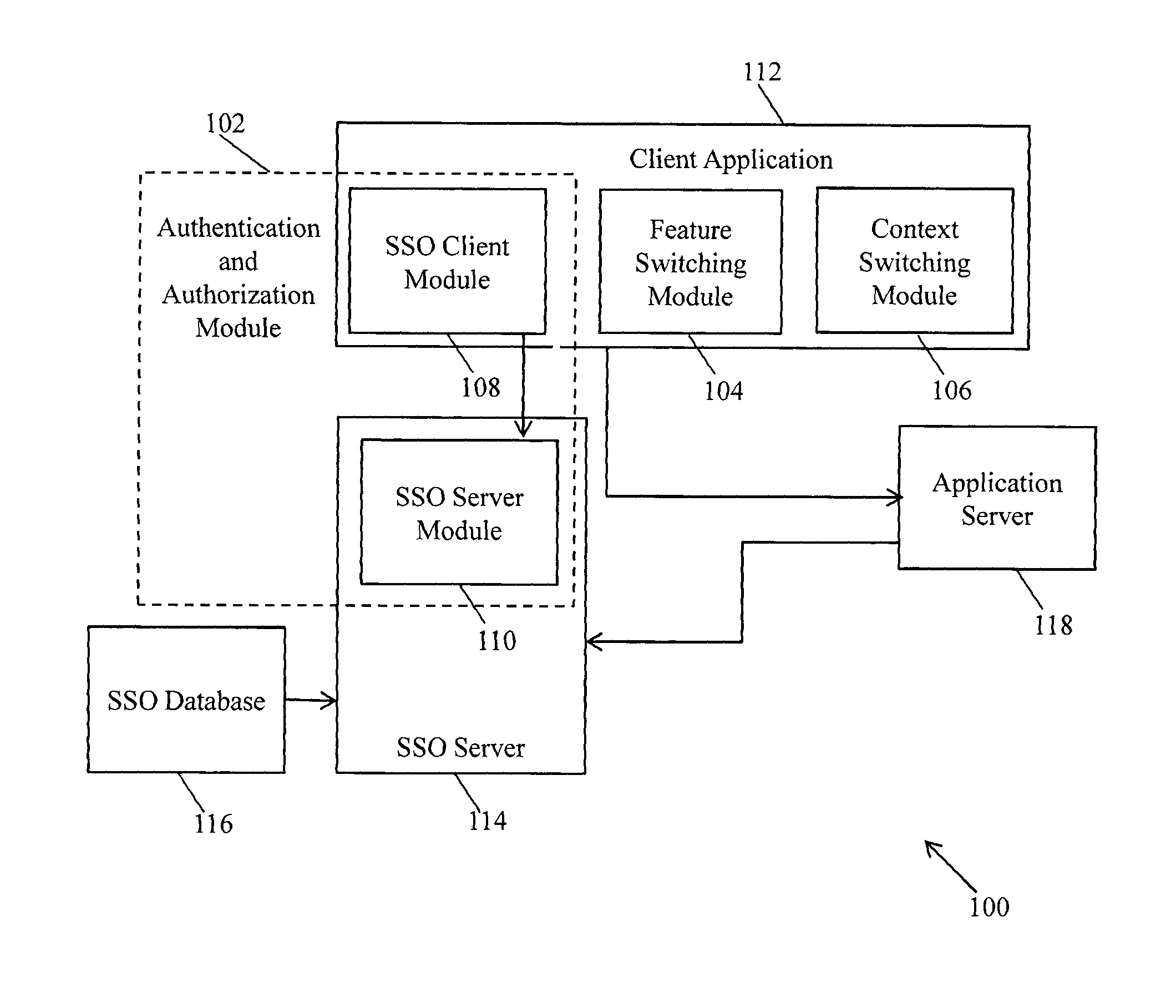
System and method for accessing integrated applications in a single sign-on enabled enterprise solution
ActiveUS20130290719A1Facilitates user accessUser identity/authority verificationDigital data authenticationClient-sideAccess management
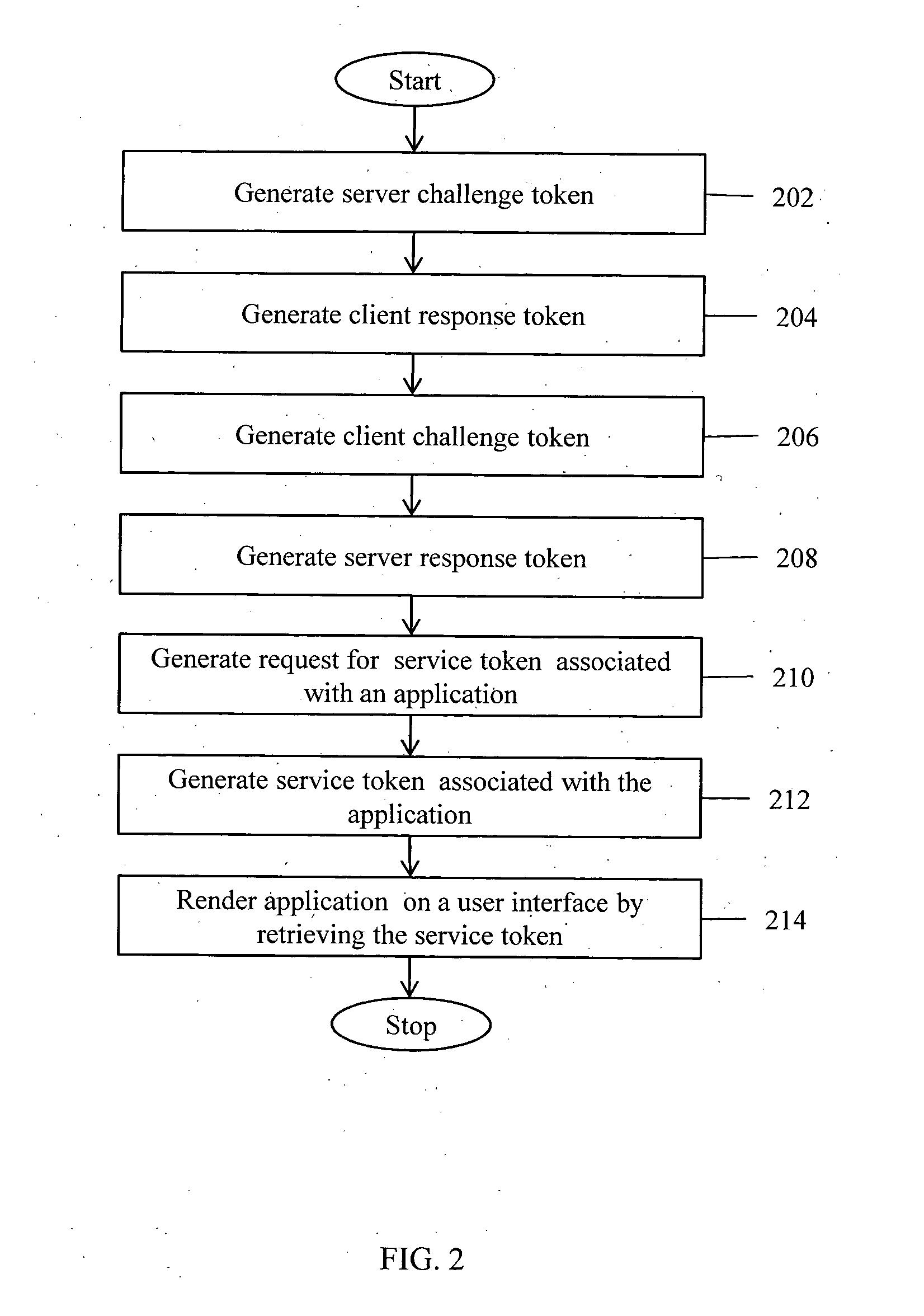
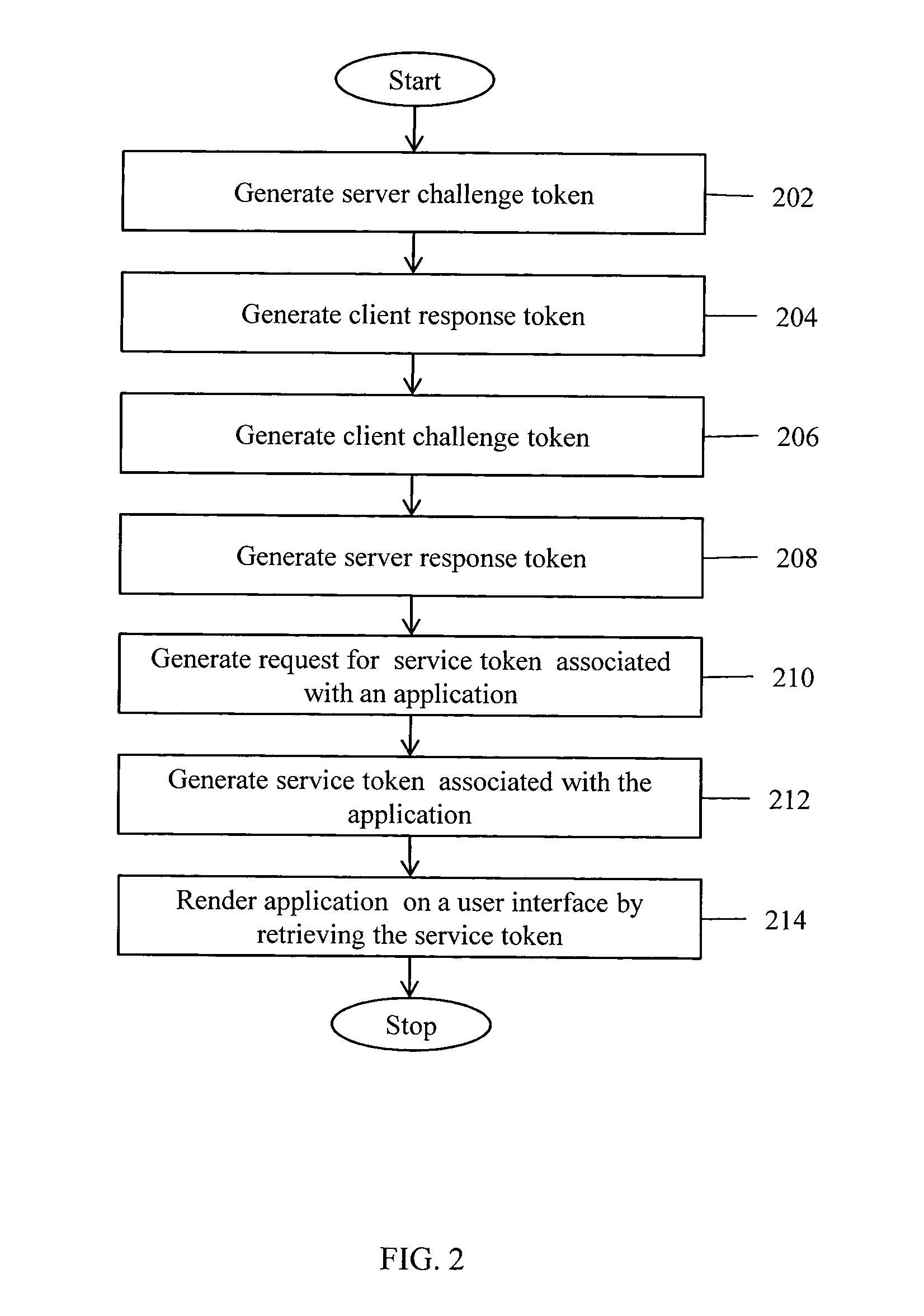
A method for performing access management to facilitate a user to access applications in a single sign-on enabled enterprise solution is provided. A challenge token and a response token are transmitted between a server and a client. The challenge token and response token comprises one-way hashed data. The response token is verified at the server and the client to authenticate the user. Further, a request for service token is transmitted between the server and the client. The request for service token is encrypted at the client and decrypted at the server using a unique session key negotiated between the server and client. A service token is generated and transmitted between the server and the client. The service token is encrypted and decrypted at the server using a secret key to verify the service token. Based on the verification, the requested applications are rendered on client based user interface.
Owner:INFOSYS LTD
Establishment method, device and system for connection of secure sockets layers
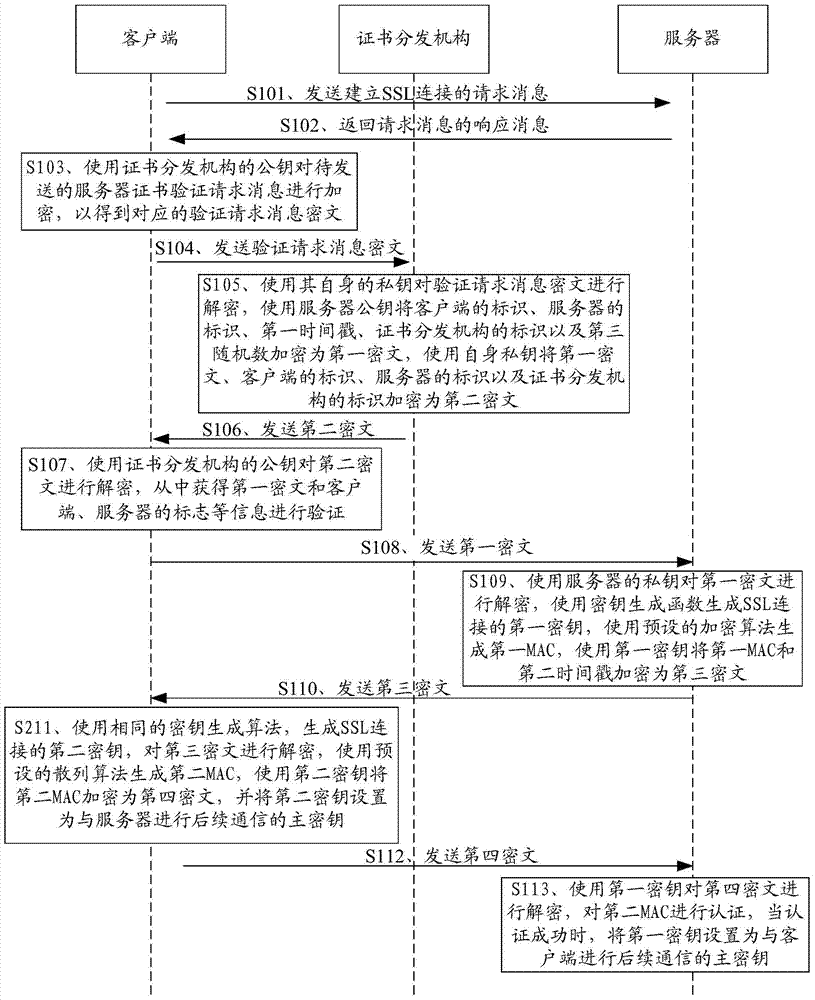
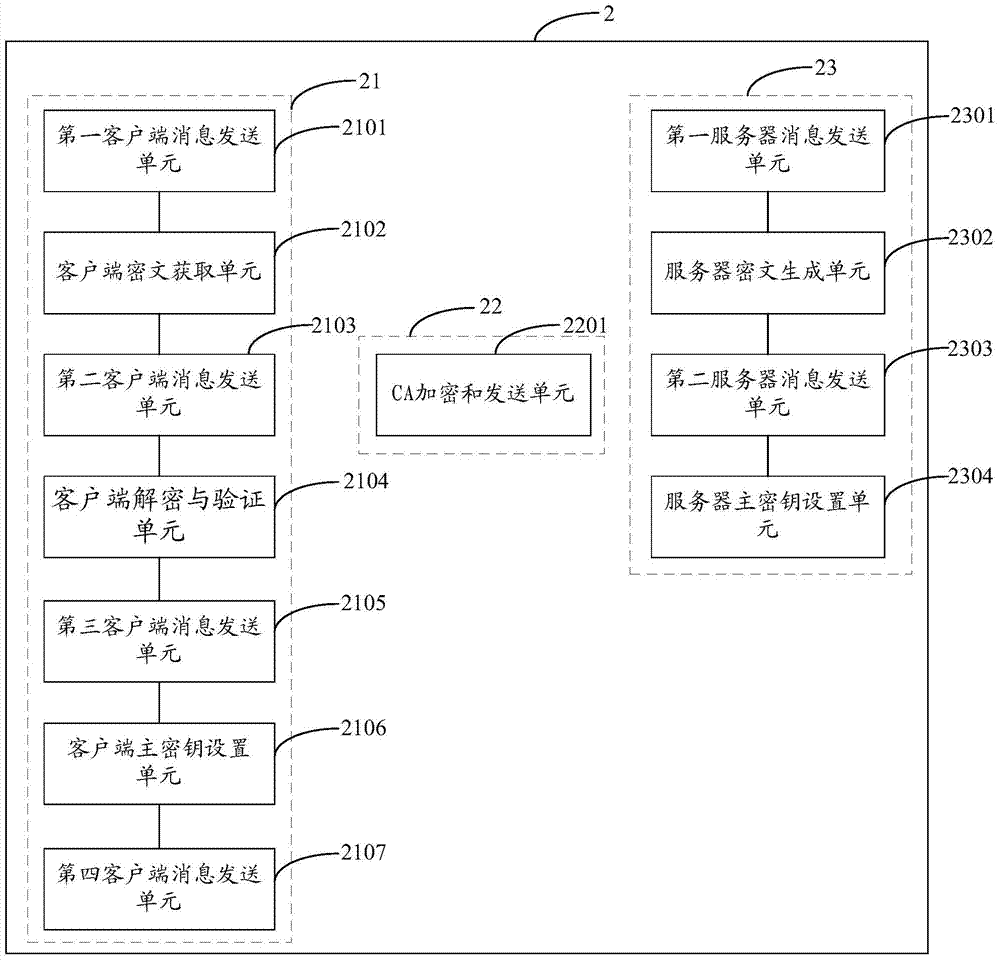
The invention is applicable to the field of communication security and provides an establishment method, device and system for connection of secure sockets layers. The method includes the steps that a client side sends a request message to establish SSL connection; a server returns a response message to the client side; the client side encrypts and verifies a request message ciphertext and sends the request message ciphertext to an CA, the CA decrypts the request message ciphertext to obtain a second ciphertext and sends the second ciphertext to the client side; the client side receives a first ciphertext and sends the first ciphertext to the server; the server decrypts the first ciphertext to generate a first secret key of the SSL connection, uses the first secret key to encrypt a generated first MAC and sends the first MAC to the client side; the client side generates a second secret key of the SSL connection, decrypts the received ciphertext, sets the second secret key as a master key for subsequent communication after succeeding in verifying the first MAC, and generates a second MAC; the server uses the first secret key to decrypt a received fourth ciphertext and sets the first secret key as a master key for subsequent communication after succeeding in verifying the second MAC, so that the SSL connection is established.
Owner:SHENZHEN UNIV
Data processing method and system based on neural network and federated learning
PendingCN110874484AEasy to handleReduce computing loadDigital data protectionNeural architecturesNetwork outputEngineering
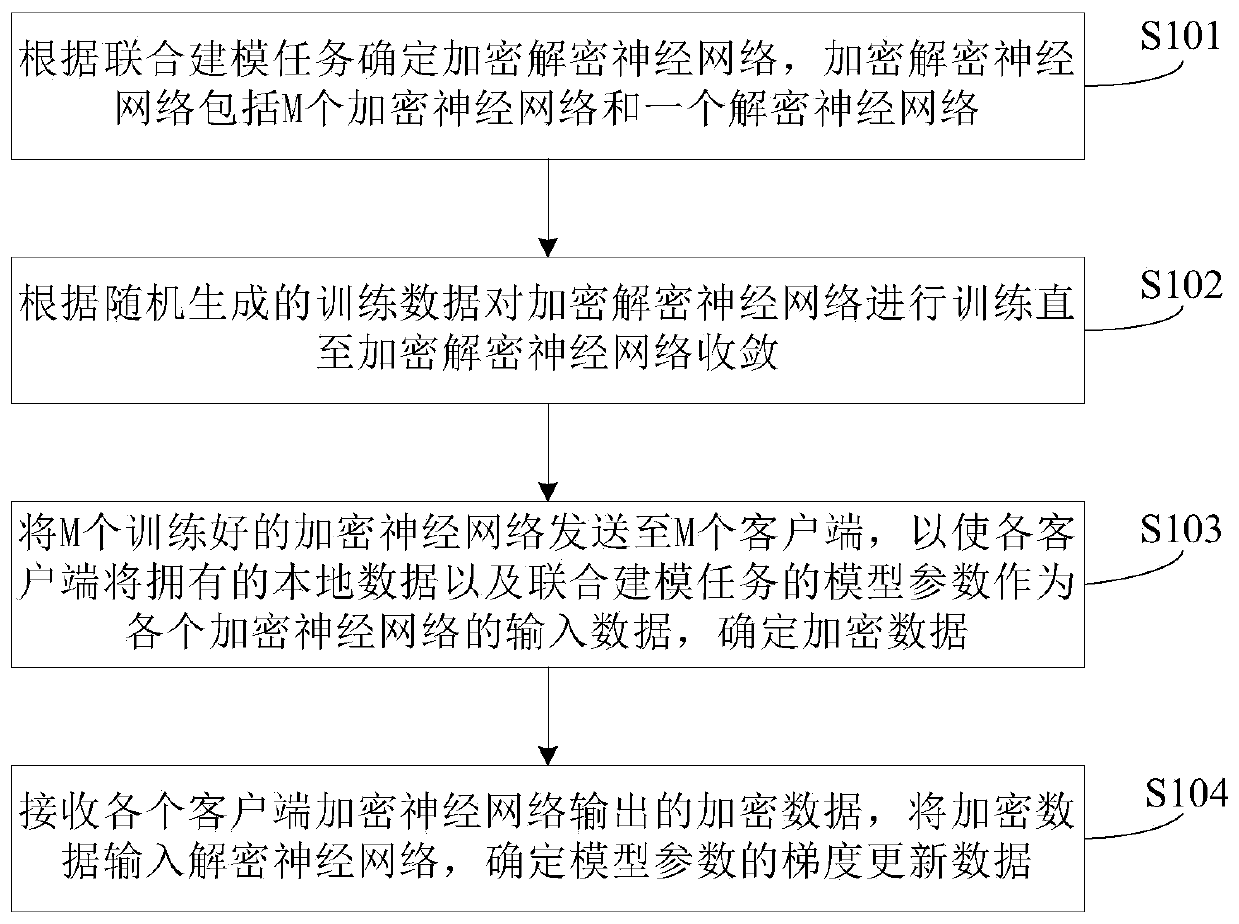
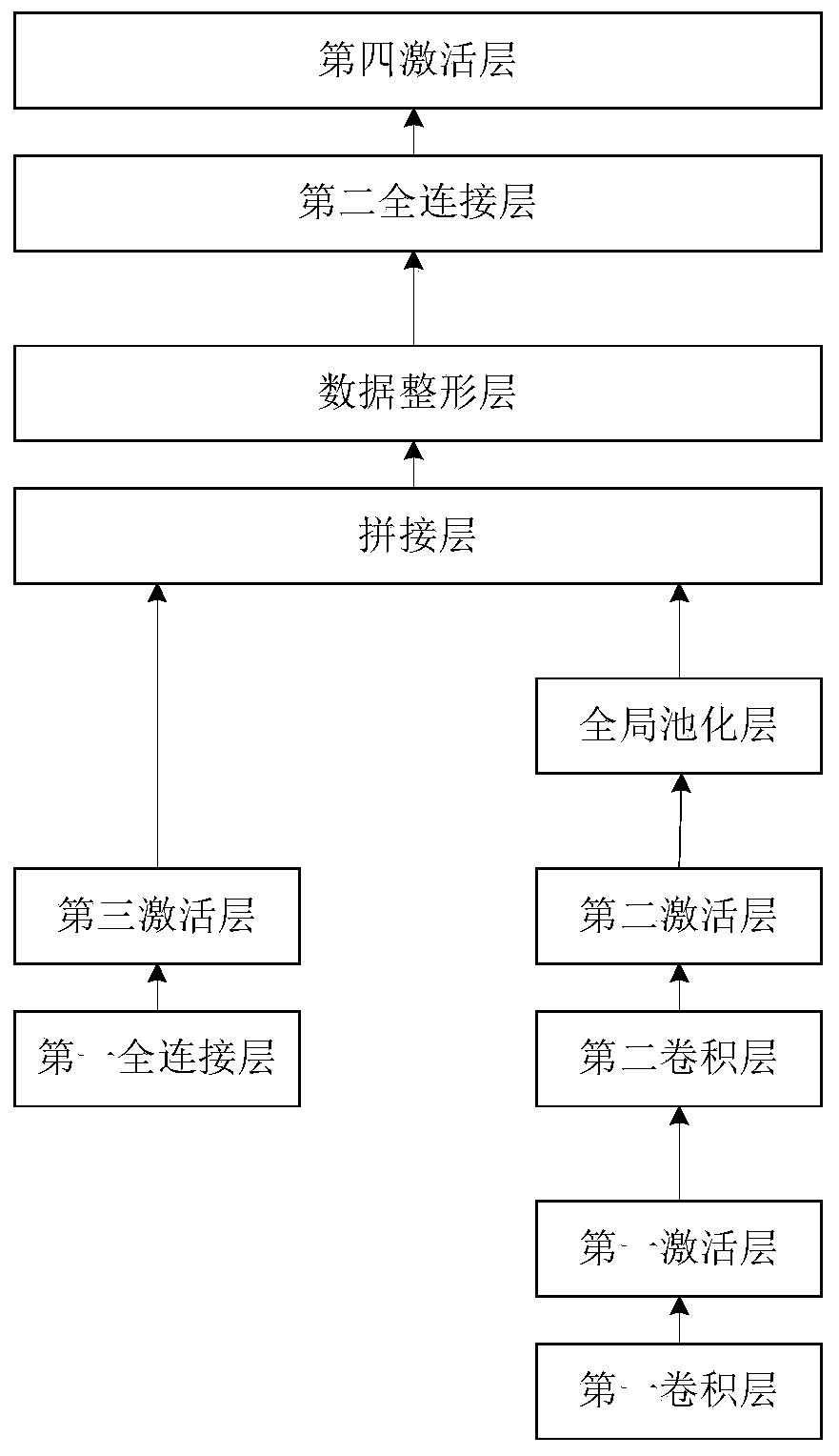
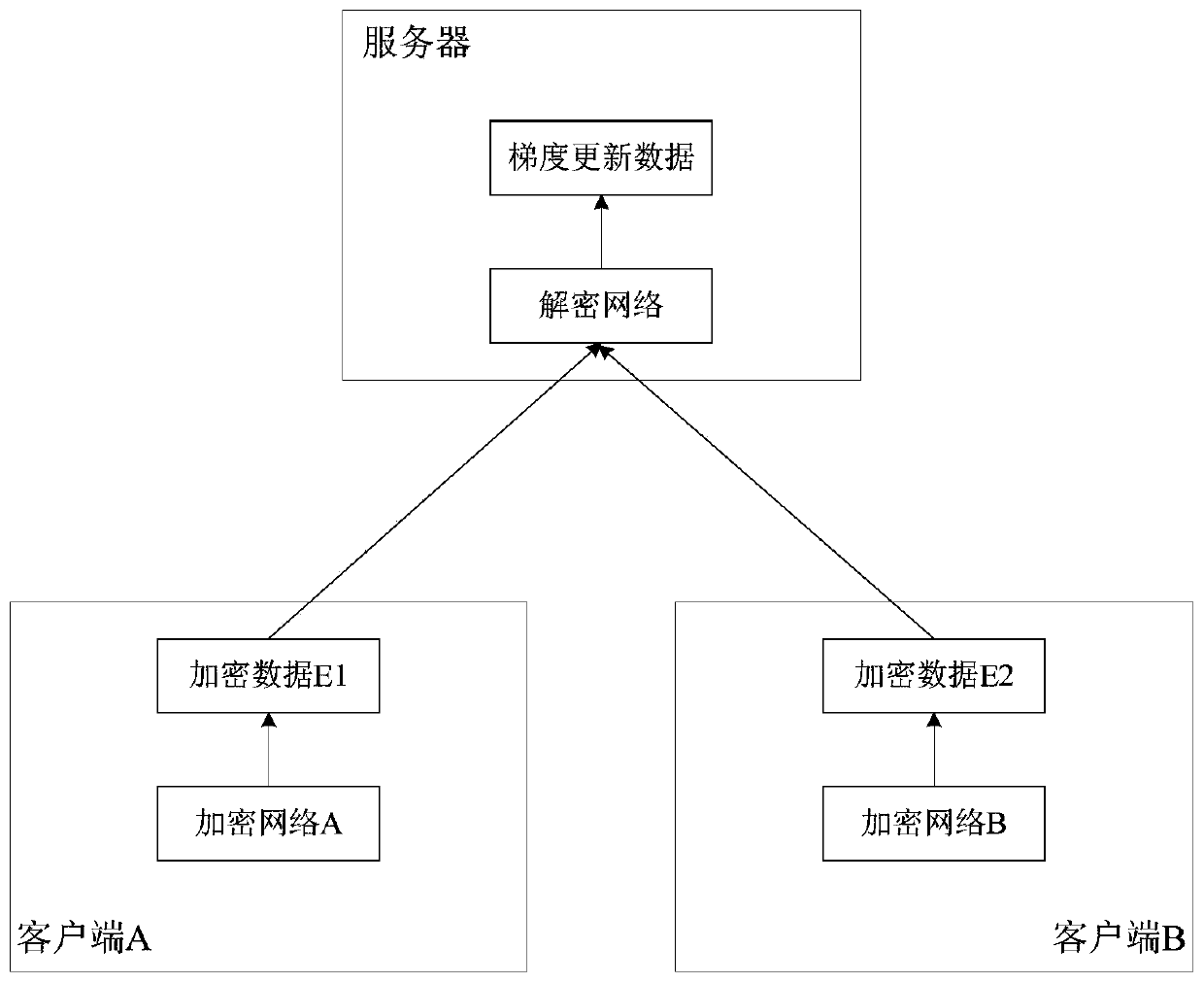
The embodiment of the invention provides a data processing method and system based on a neural network and federated learning. The method comprises the following steps: determining an encryption and decryption neural network according to a joint modeling task, wherein the encryption and decryption neural network comprises M encryption neural networks and a decryption neural network; training the encryption and decryption neural network according to randomly generated training data until the encryption and decryption neural network converges; sending the M trained encrypted neural networks to Mclients, so that each client determines encrypted data by taking owned local data and model parameters of the joint modeling task as input data of each encrypted neural network; and receiving encrypted data output by the encrypted neural network of each client, inputting the encrypted data into the decrypted neural network, and determining gradient update data of the model parameters. According to the method provided by the embodiment of the invention, the joint modeling is realized while the data privacy is ensured, the operation is simple and convenient, and the data processing efficiency is improved.
Owner:ZHONGAN INFORMATION TECH SERVICES CO LTD
Data processing method
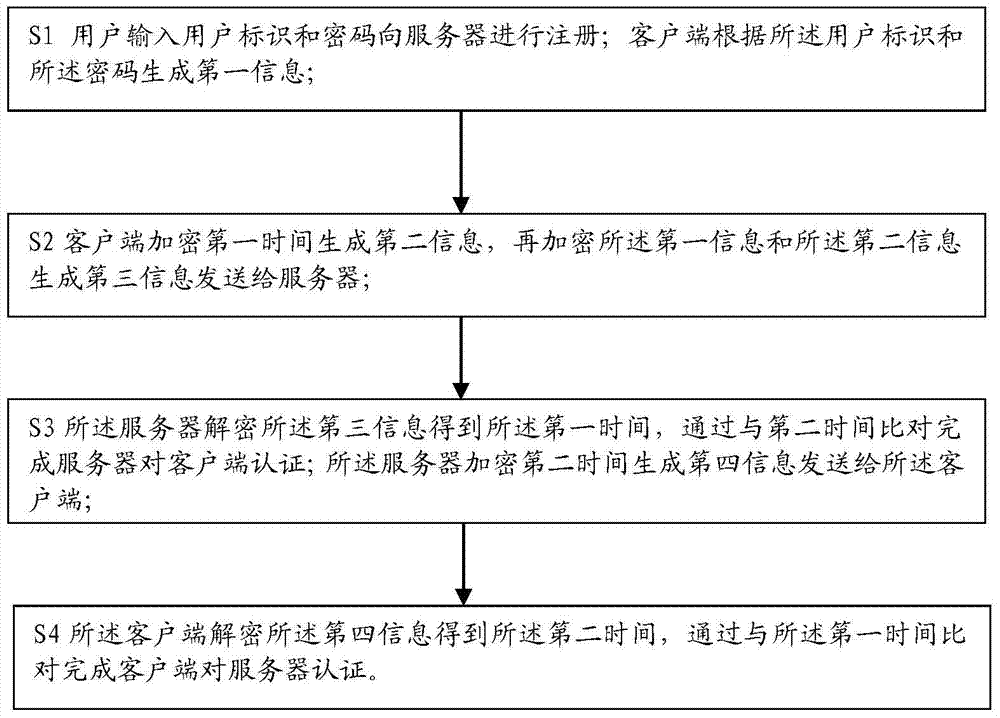
ActiveCN104243494AGood technical effectPrevent impersonation attacksMultiple keys/algorithms usageUser identity/authority verificationData integrityUser input
The invention discloses a data processing method. The data processing method includes that a user inputs a user identity and a password to register in a server; a client side generates first information according to the user identity and the password; the client side encrypts first time to generate second information, encrypts the second information and the first information to generate third information and sends the third information to the server; the server decrypts the third information to acquire the first time and completes authentication of the client side by the server by comparing the first time with second time; the server encrypts the second time to generate fourth information and sends the fourth information to the client side. The data processing method realizes network identity authentication, data encrypting transmission and data completeness checking and has better technical background.
Owner:SHANGHAI PEOPLENET SECURITY TECH
Safe E-mail system
ActiveCN103188246APublic key for secure communicationUser identity/authority verificationKey exchangeConfidentiality
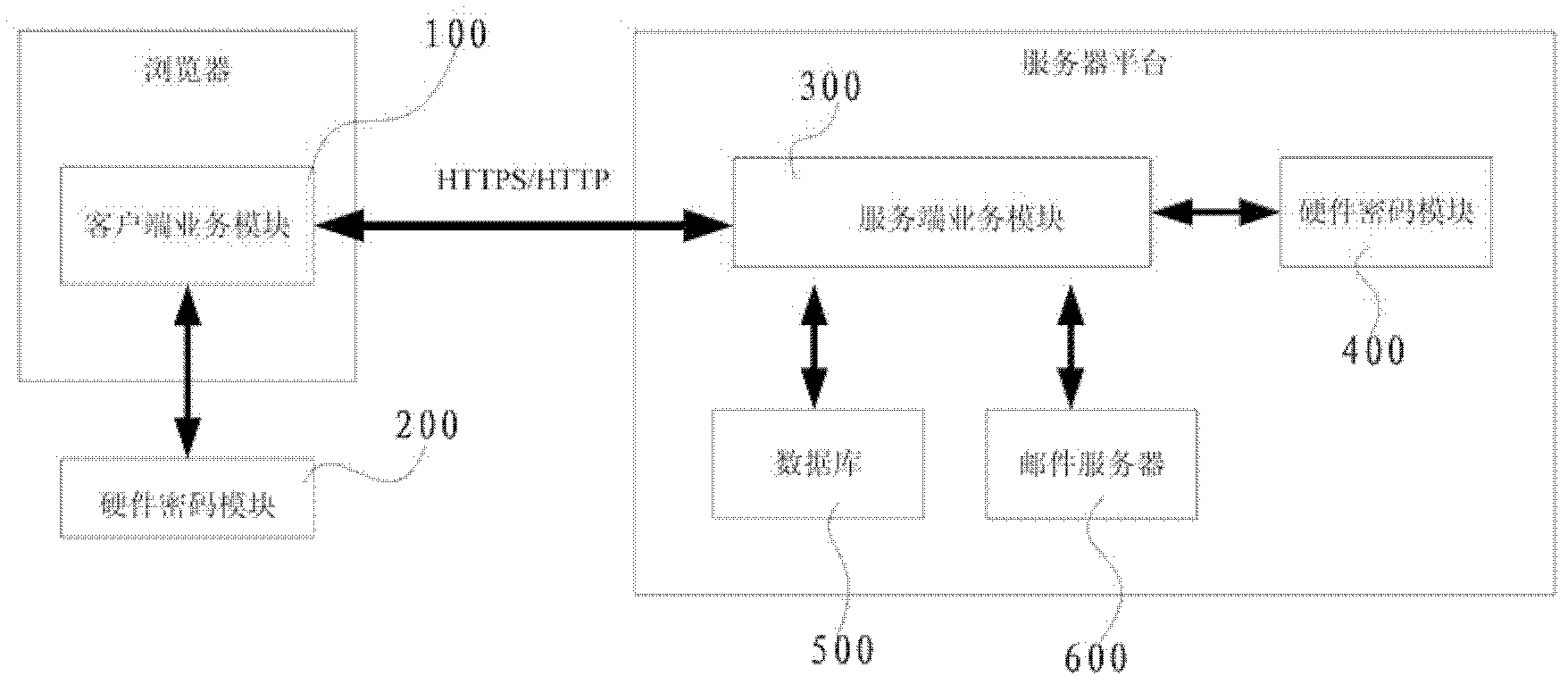
The invention discloses a safe E-mail system. The safe E-mail system is characterized in that a client side service module is used for client side encryption and decryption of mail contents and mail attachments, mail signature and communication with a server service module; a client side hardware crypto module is called by the client side service module to complete corresponding code computation; a server side service module is used for receiving connection with the client side service module to complete identity authentication and service processing requests; a server side hardware crypto module is called by the server side service module to complete key exchange and user management; a mail server is called by the server side service module to complete mail transmission and mail storage; and a database is called by the server side service module to achieve storage of system information and data. The safe E-mail system achieves confidentiality, integrity and non-repudiation of mail information in the process of mail transmission by utilizing data encryption technique, and the confidentiality of the mail information is guaranteed due to the fact that a symmetrical encryption structure is used in the safe E-mail system for encryption processing of the mail information.
Owner:KOAL SOFTWARE CO LTD
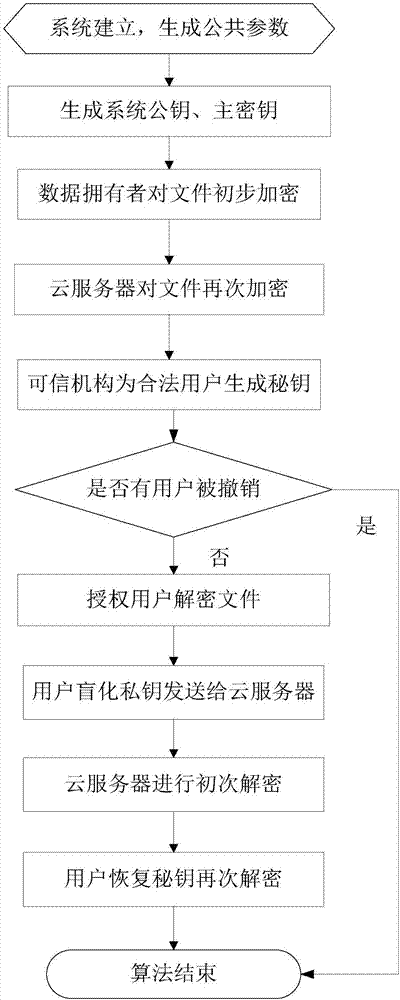
Outsourcing encryption and decryption CP-ABE method capable of achieving user revocation
InactiveCN107359986AFunction increasePerfect rights management functionKey distribution for secure communicationPlaintextMobile cloud
The invention discloses an outsourcing encryption and decryption CP-ABE method capable of achieving user revocation, and relates to the technical field of data encryption and decryption in a mobile cloud environment. The method further achieves the outsourcing encryption operation on the basis of conventional outsourcing attribute encryption, and reduces the encryption calculation cost of a local client. The method achieves the access control of fine granularity of a file on a cloud server, simplifies the secret key management operation for a user, and achieves the revocation of the access authority of an unauthorized user. When the user is revoked, a legal user does not need to update a secret key, and alleviates the burden of an authorization mechanism. The local user just needs to carry out the simple XOR operation to update a cryptograph. The security proof indicates that the method provided by the invention has the non-adaptive selection plaintext safety under a common dual linear group model. The performance analysis indicates that the method reduces the encryption calculation cost of mobile equipment more effectively, can achieve the revocation of an illegal user efficiently, and achieves the control of the access authority of the user effectively.
Owner:JINAN UNIVERSITY
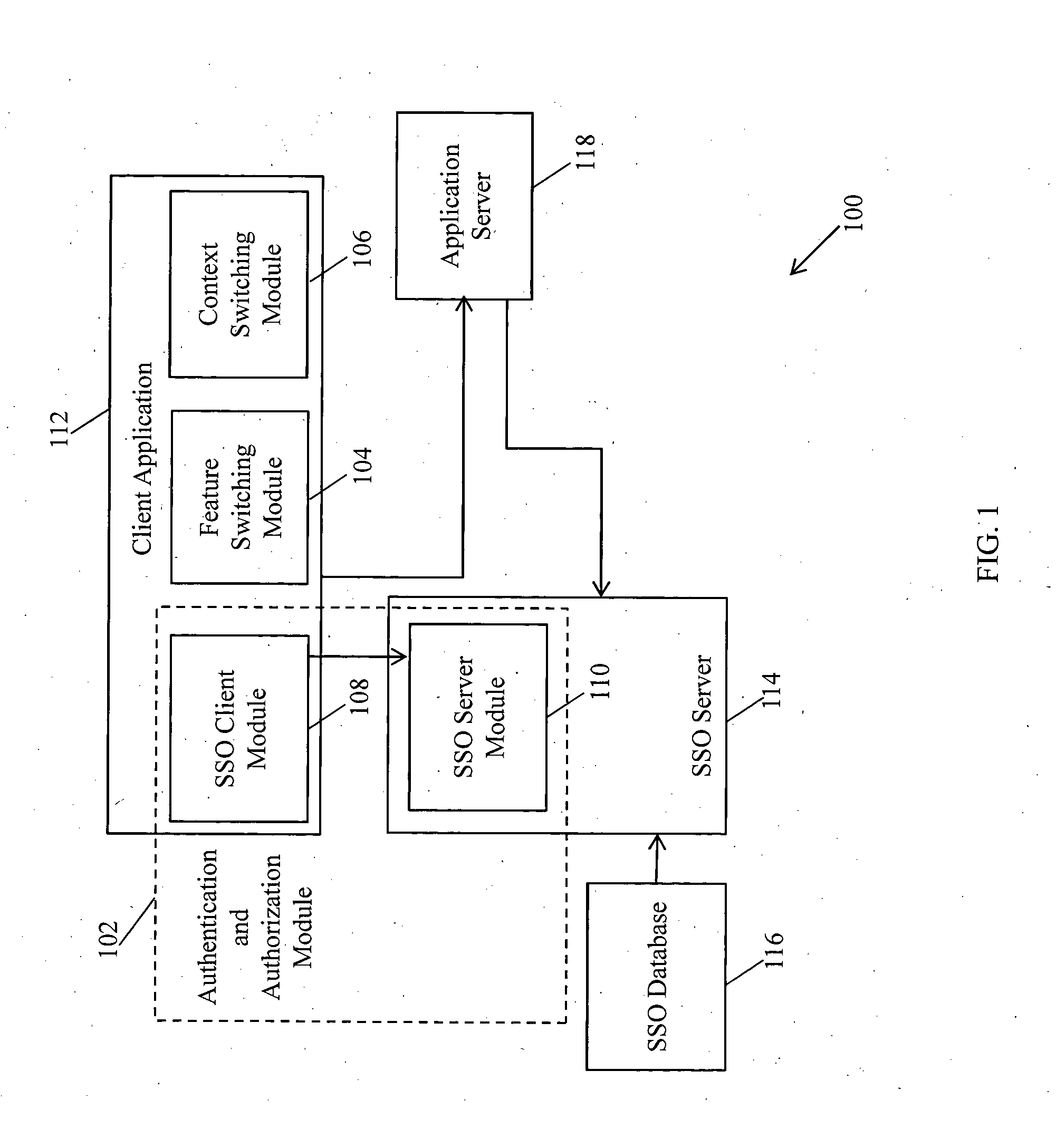
System and method for accessing integrated applications in a single sign-on enabled enterprise solution
ActiveUS9191375B2User identity/authority verificationDigital data authenticationClient-sideApplication software
Owner:INFOSYS LTD
Electronic official document safety transmission method based on Web service
InactiveCN101321057AEnsure safety featuresSolve security issues such as confidentialityPublic key for secure communicationUser identity/authority verificationWeb serviceSOAP
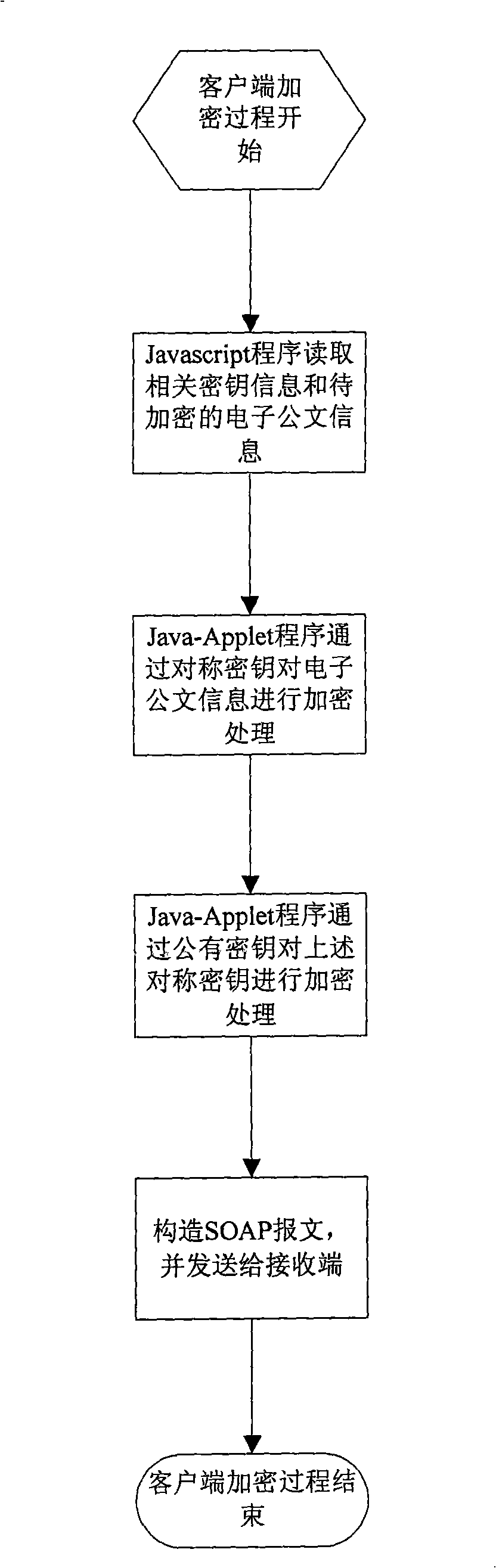
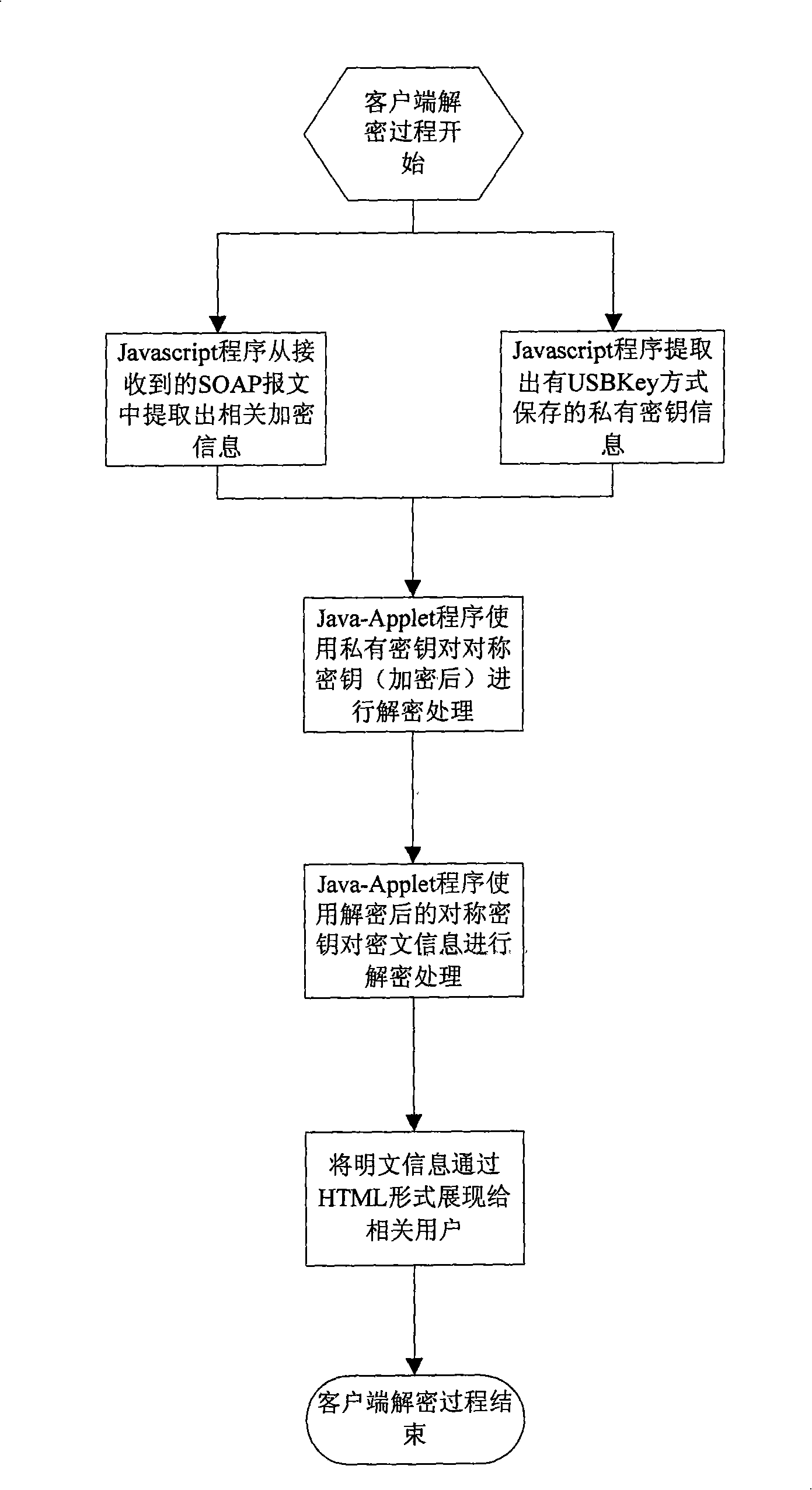
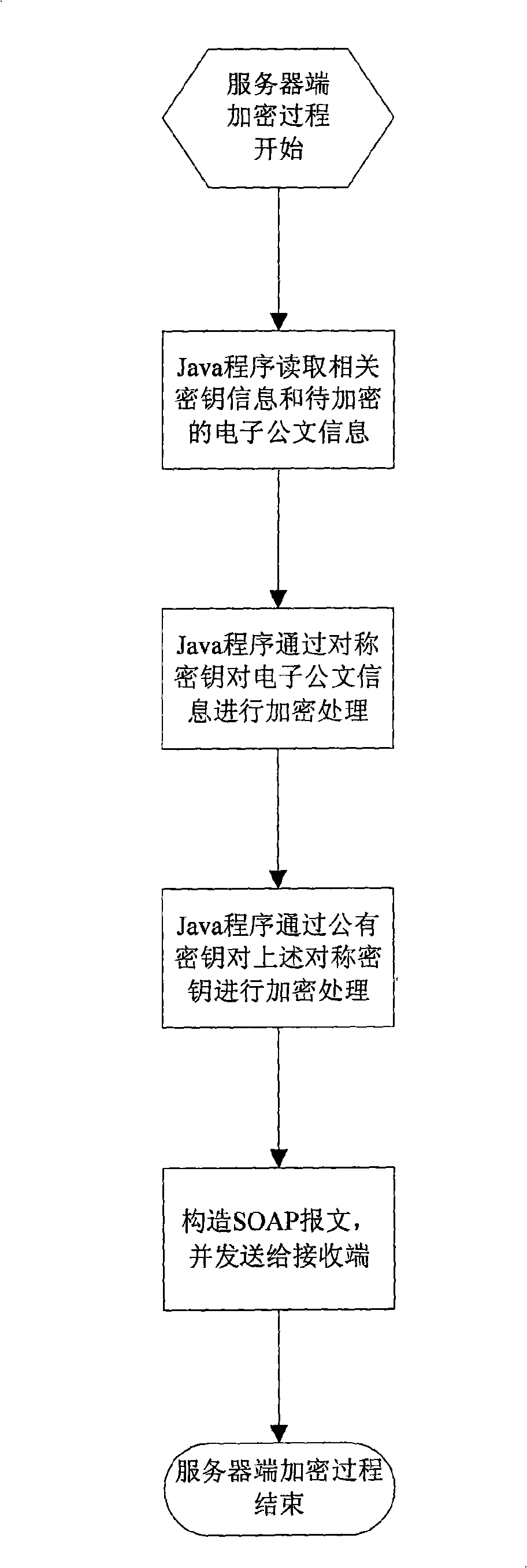
An electronic document secure transmission method based on the Web service is disclosed, comprising: encrypting by the client-end and reading the electronic document information and the related cipher key by the Javascript, performing the encryption by the Java-Applet program; finally constructing the SOAP information, transmitting to the receiver; decrypting the by the client-end, receiving the SOAP information by the Javascript and extracting the electronic document information and the encrypted information, then performing the decrypting process by the Java-Applet program, exhibiting to the user through the HTML form. The encryption of the server end is the same to that of the client-end, with the difference in that, the JAVA program is used in the encrypting process on the electronic document information, rather than the Java-Applet program; the server directly uses the Java program on the server to search the private cipher key information, rather than on the USBKey, and in the decrypting process, the server end uses the Java program to perform the decrypting process rather than the Java-Applet program. According to the invention, the transmission safety between the end to end transmission and the multipoint is ensured.
Owner:BEIHANG UNIV
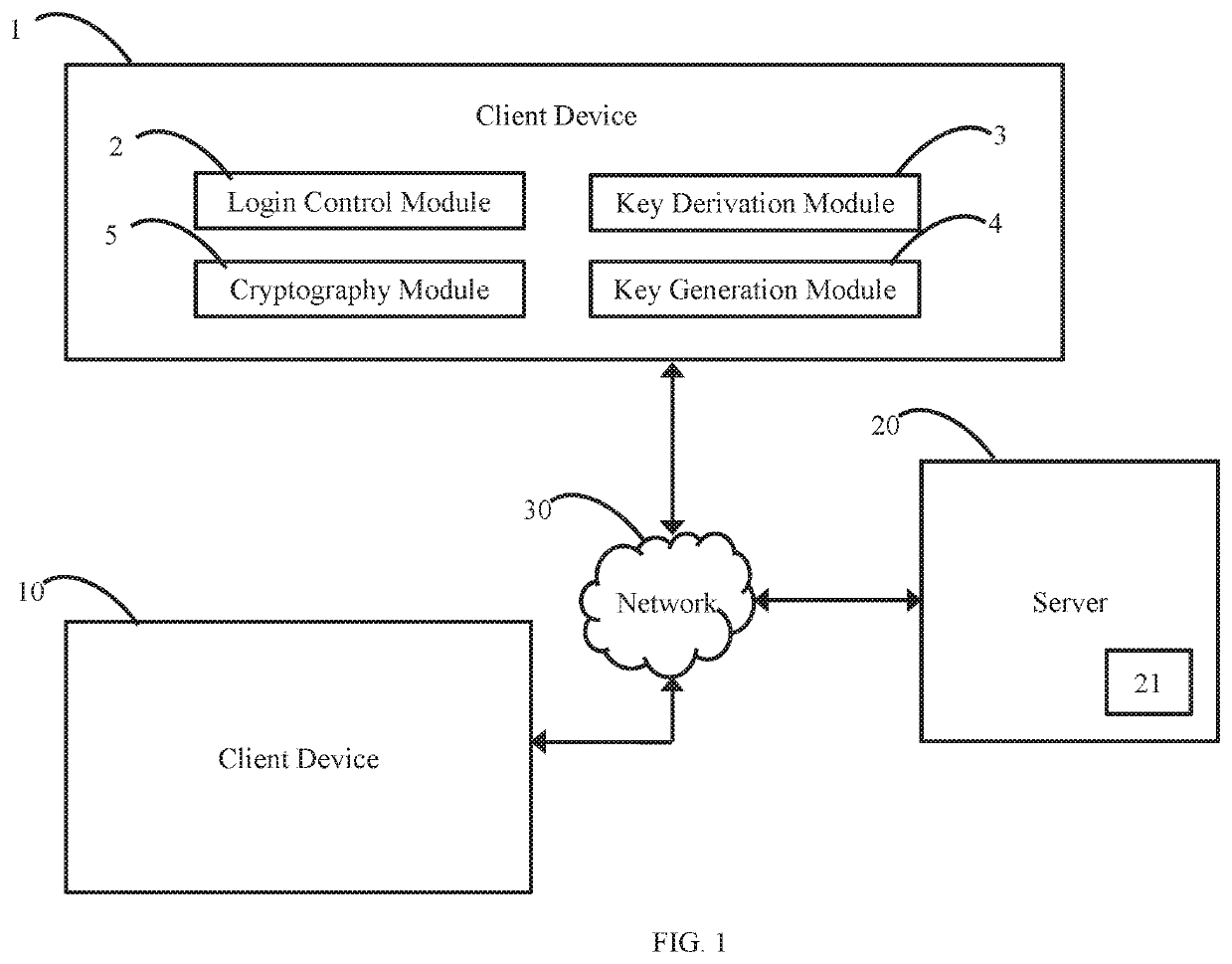
Method, system, and program product for asymmetric key generation
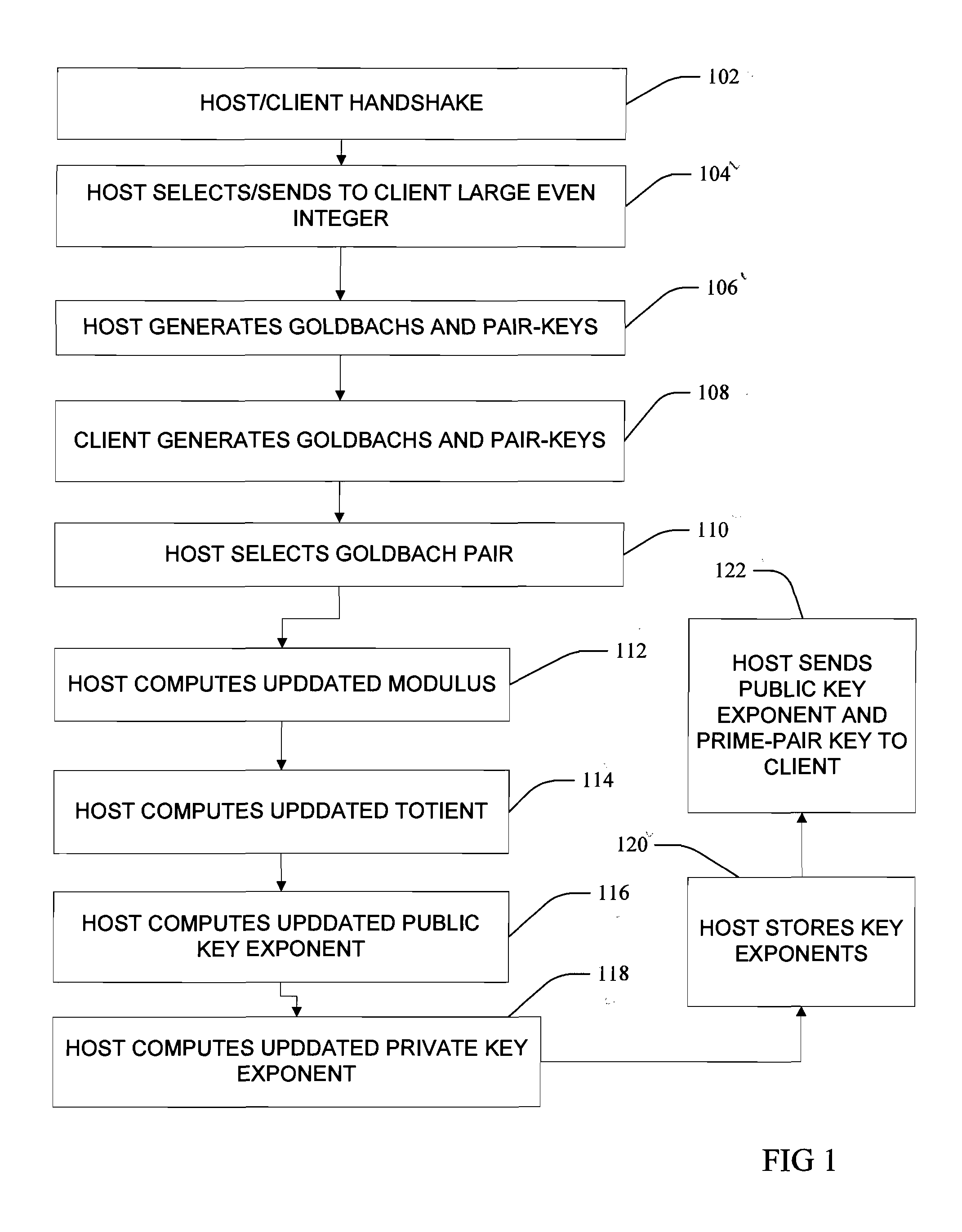
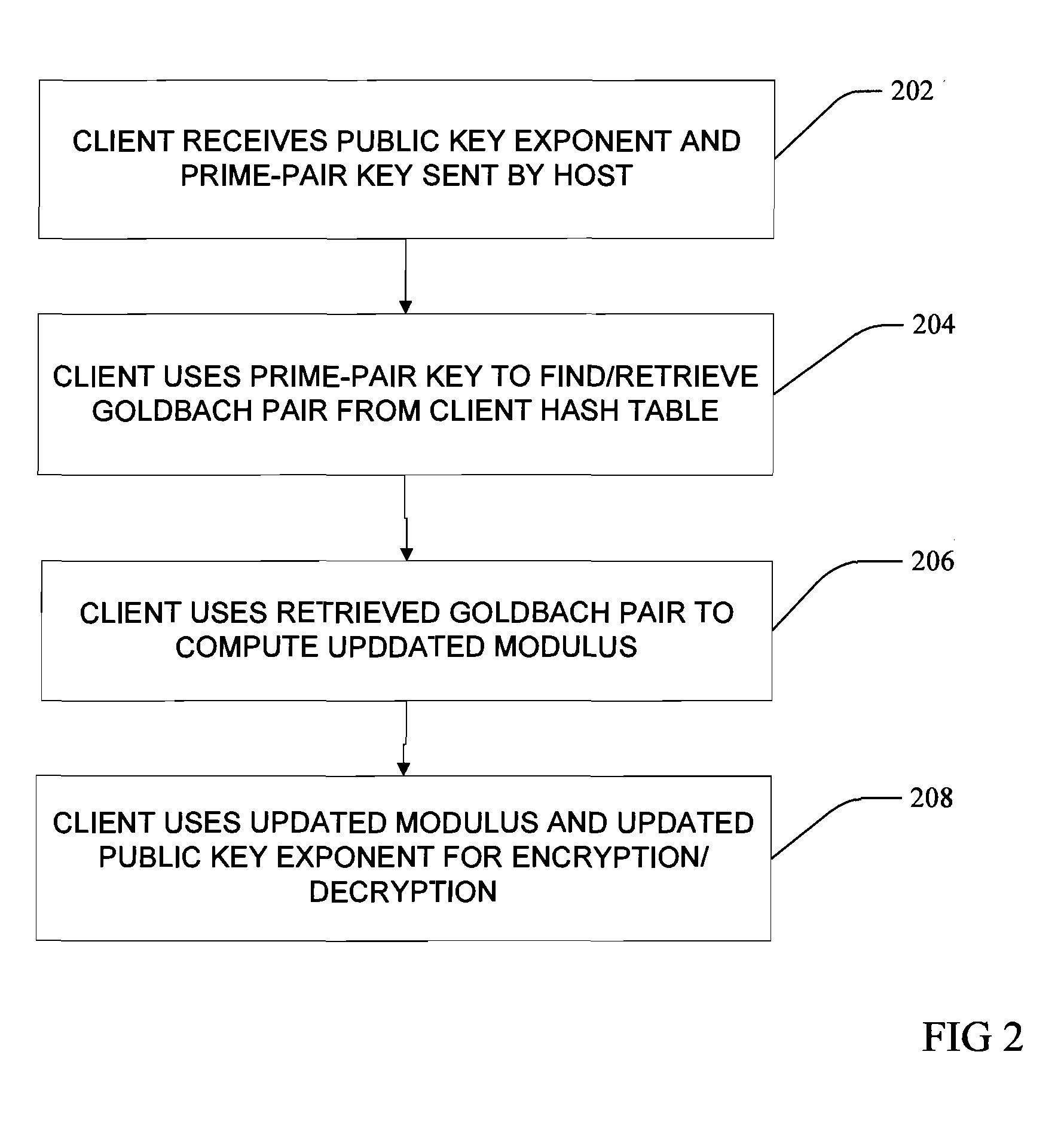
InactiveUS20090245515A1Key distribution for secure communicationPublic key for secure communicationKey generationClient-side encryption
In asymmetric cryptography, initially-set public key and private keys are updated as a function of the chosen prime number pair, a host sending an updated public key exponent and a unique prime-pair key associated with the chosen prime number pair to the client, the client using the unique prime-pair key to look-up and retrieve the chosen prime number pair and determine the updated public key and the updated private key as a function of the retrieved chosen prime number pair, the host and the client encrypting and decrypting exchanged messages with the updated public key and the updated private key without executing another handshake. In one aspect, a large even integer is used by host and client to generate a plurality of prime number pairs, and the unique prime-pair key may be a distance between each prime number of an associated prime number pair.
Owner:IBM CORP
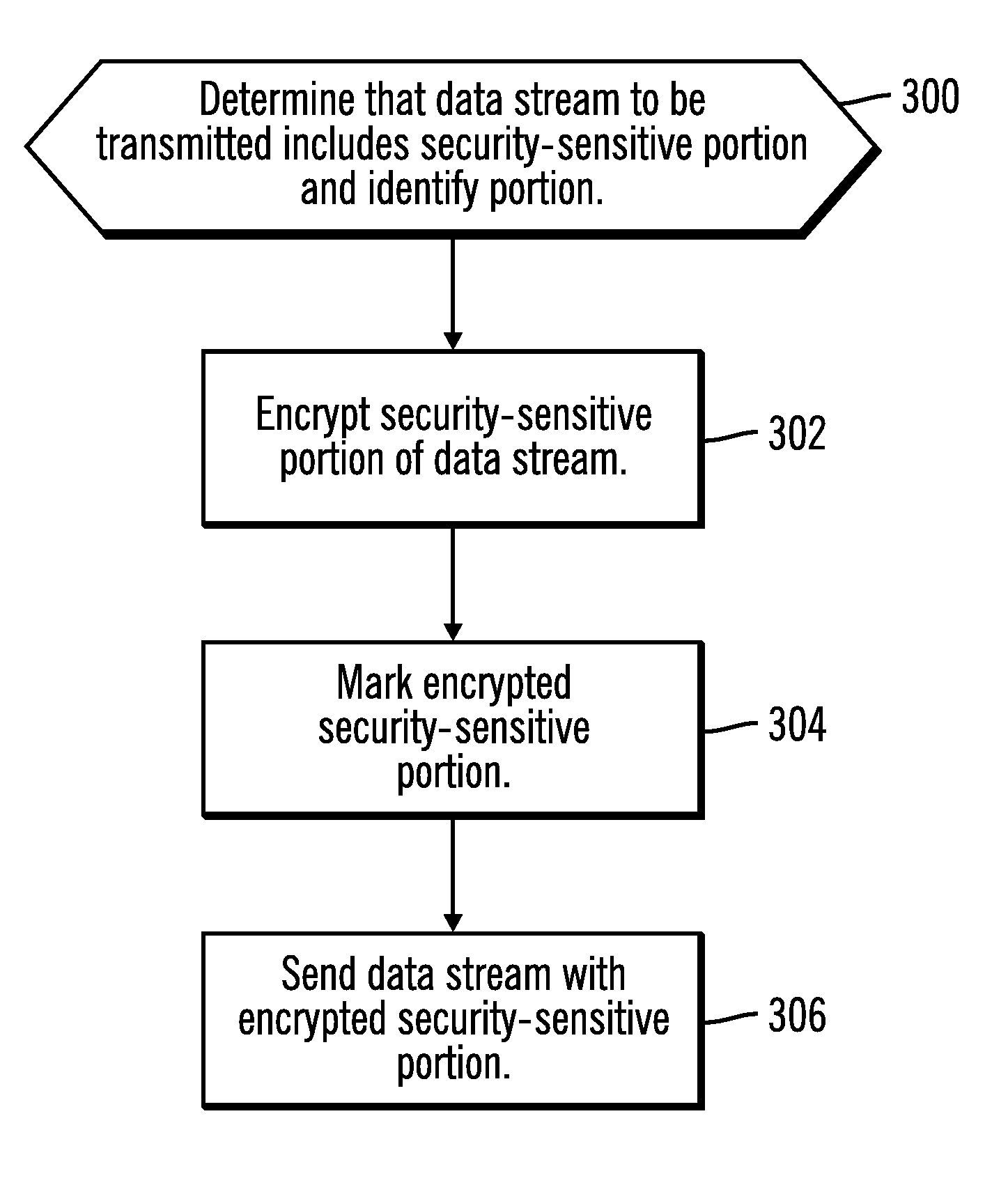
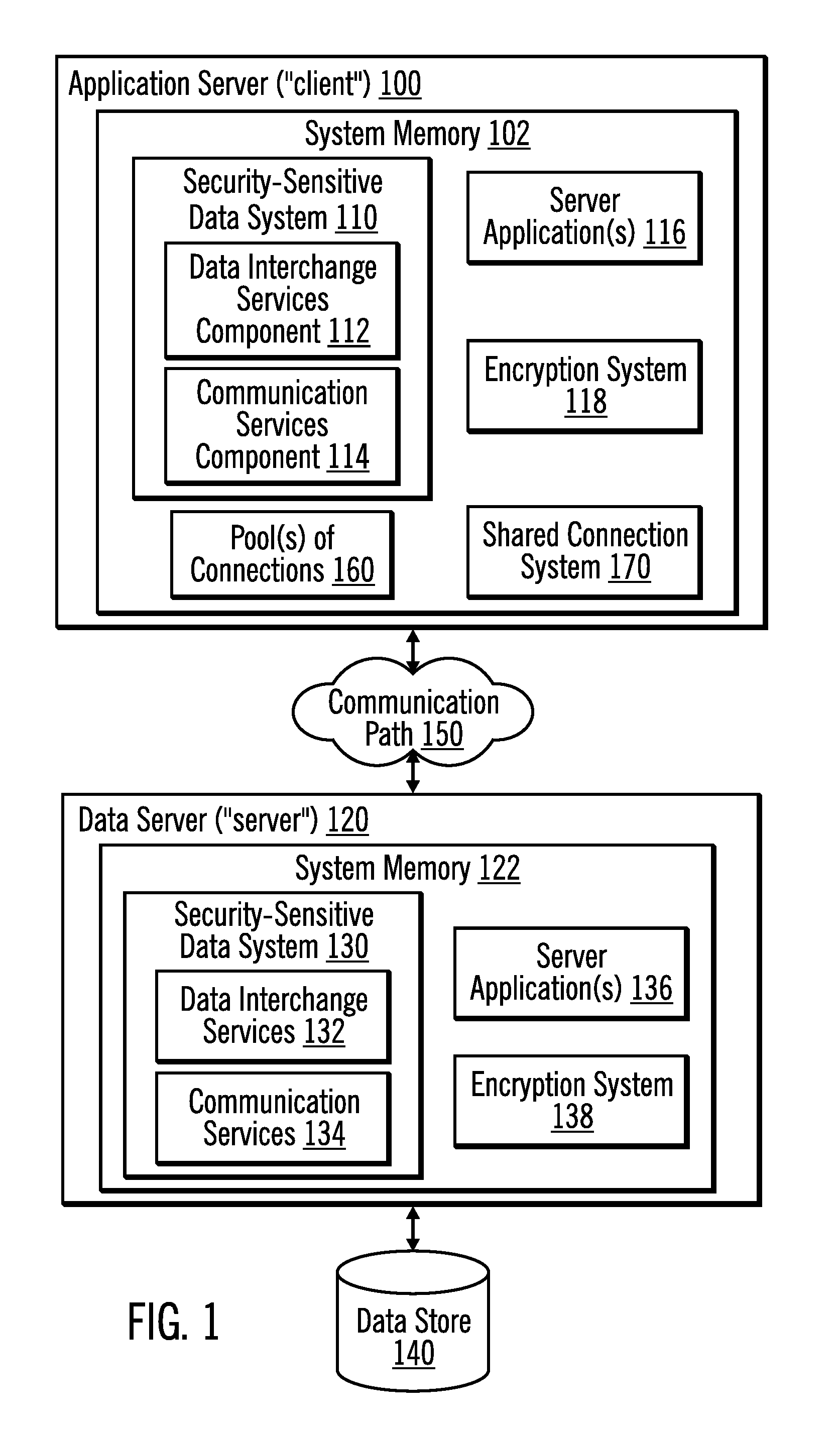
Encryption of security-sensitive data by re-using a connection
InactiveUS20110055563A1Digital data processing detailsUser identity/authority verificationData sourceSecurity properties
Techniques are provided for processing data. Connections having different security properties are stored, wherein each of the connections allows applications at the client computer to access data sources at a server computer. A request is received from an application to access a data source, wherein the request has associated security properties. In response to the client computer requesting establishment of a connection on behalf of the application, it is determined whether there is a stored connection that used a same set of security properties as are associated with the request from the application and that connected to the data source that the application requests access to. In response to determining that there is a stored connection that used the same set of security properties and that connected to the data source, the connection and an associated client encryption seed, client encryption token, server encryption seed, and server encryption token are re-used. In response to determining that there is not a connection that used the same set of security properties and that connected to the data source, a new client connection key, client encryption seed, client encryption token, sever connection key, server encryption seed, and server encryption token are generated.
Owner:IBM CORP
Data processing method based on homomorphic encryption and device thereof
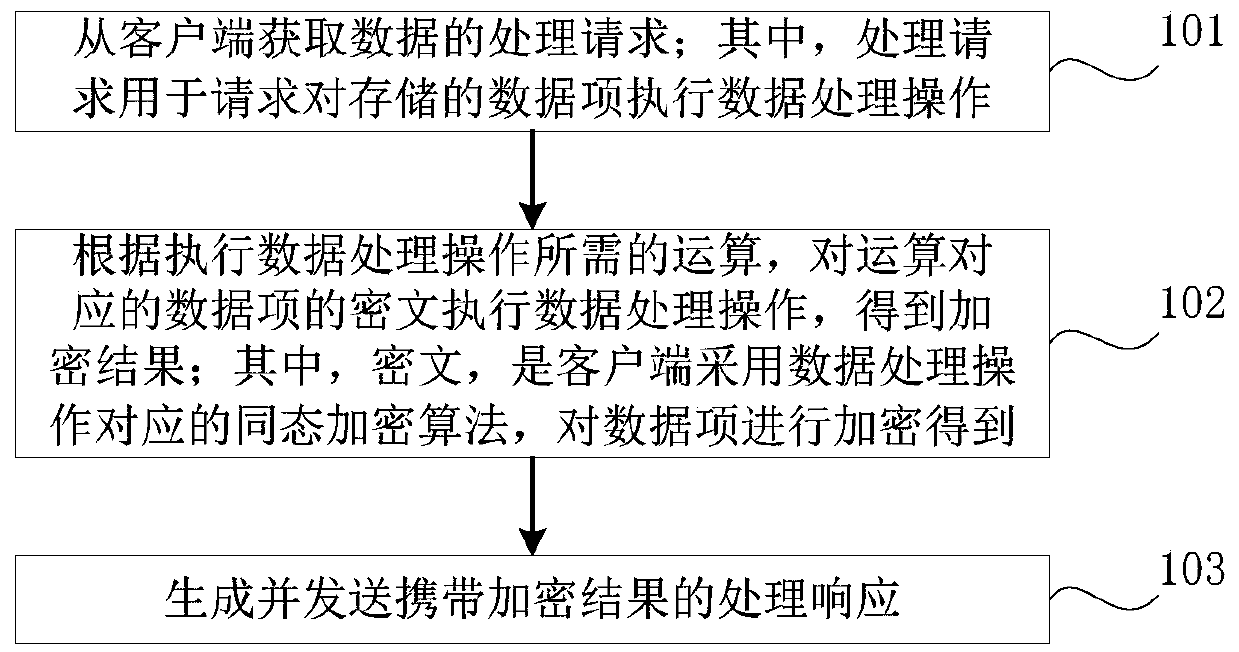
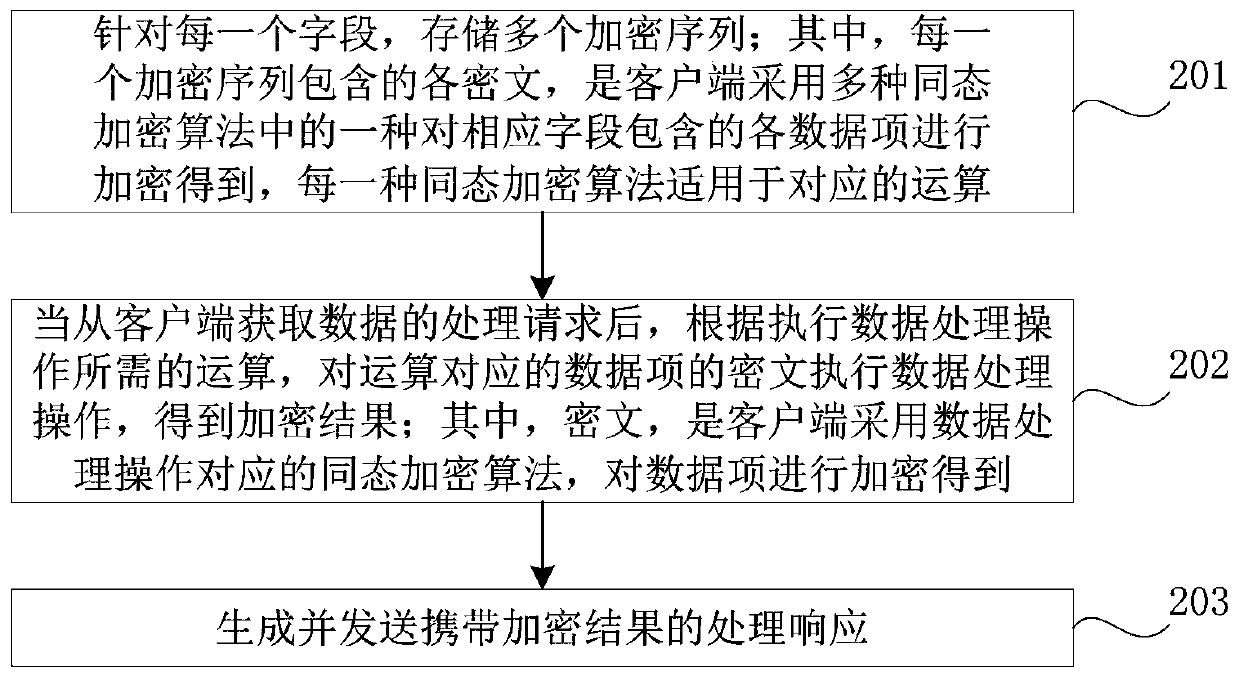
PendingCN111464282APrevent leakageImprove reliabilityCommunication with homomorphic encryptionAlgorithmCiphertext
The invention provides a data processing method based on homomorphic encryption and a device thereof, and the method comprises the steps: obtaining a processing request of data from a client; whereinthe processing request is used for requesting to execute a data processing operation on a stored data item; executing the data processing operation on a ciphertext of the data item corresponding to the operation according to the operation required for executing the data processing operation to obtain an encryption result; wherein the ciphertext is obtained by encrypting the data item by the clientthrough adoption of a homomorphic encryption algorithm corresponding to the data processing operation; and generating and sending a processing response carrying the encryption result. According to the method, the processing functions of query, analysis and the like of the encrypted data can be provided on the server side, and since the ciphertext is obtained after encryption processing of the client, the server cannot view the private data of the user, and the private data of the user can be prevented from being leaked.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
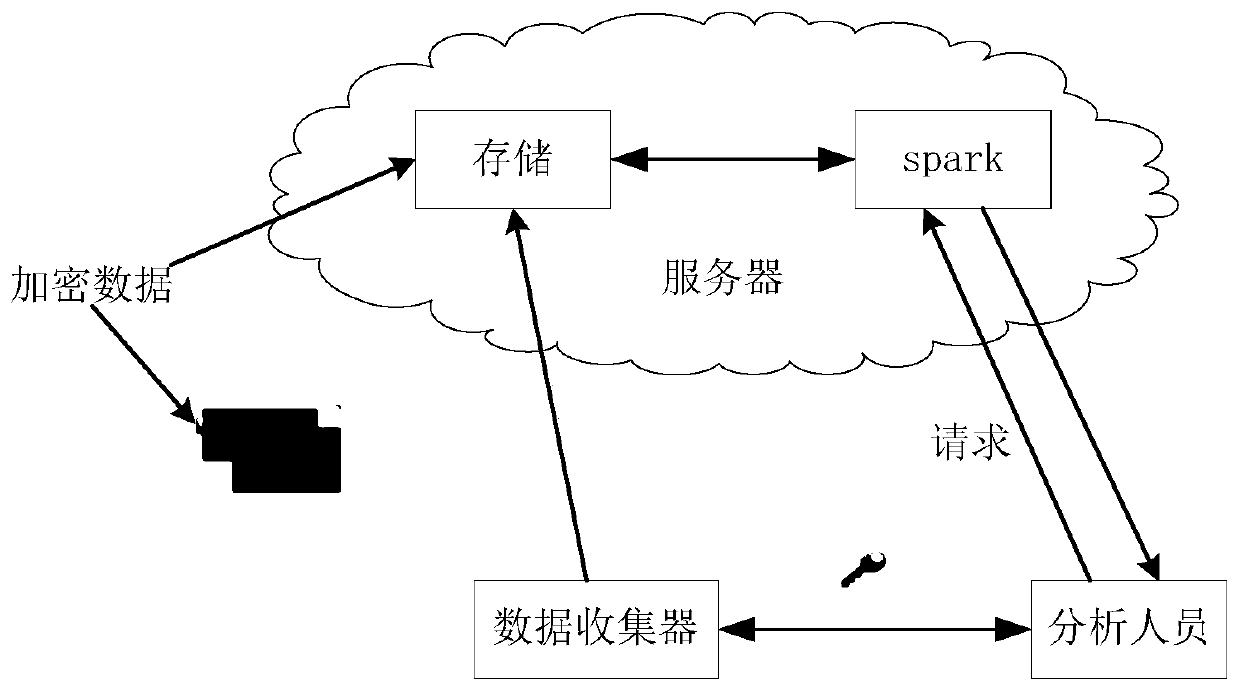
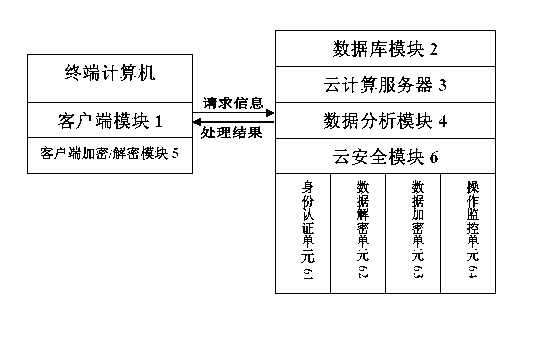
Cloud computing processing system with security architecture
A cloud computing processing system with a security architecture includes a client module, a database module, a cloud computing server and a data analysis module. The client module sends a request to the data analysis module, the database module is used for storing data, the cloud computing server is used for setting computing rules and providing the special computing rules to the data analysis module according to different situations, the data analysis module is used for receiving the request and acquiring the corresponding computing rules according to the requested parameters, combining with the data in the database to carry out the cloud computing process according to the computing rules and returning processed results to the client module. The cloud computing processing system further includes a client encryption / decryption module and a cloud security module, the client encryption / decryption module is used for encrypting the request and sending the encrypted request to the data analysis module and for decrypting the results returned by the data analysis module. The cloud security module is used for authenticating the identities of users, decrypting the request, encrypting the results returned by the data analysis module and monitoring the operation of the users. The cloud computing processing system with the security architecture can improve the safety of the cloud computing processing system.
Owner:JIANGSU LEMAIDAO NETWORK TECH
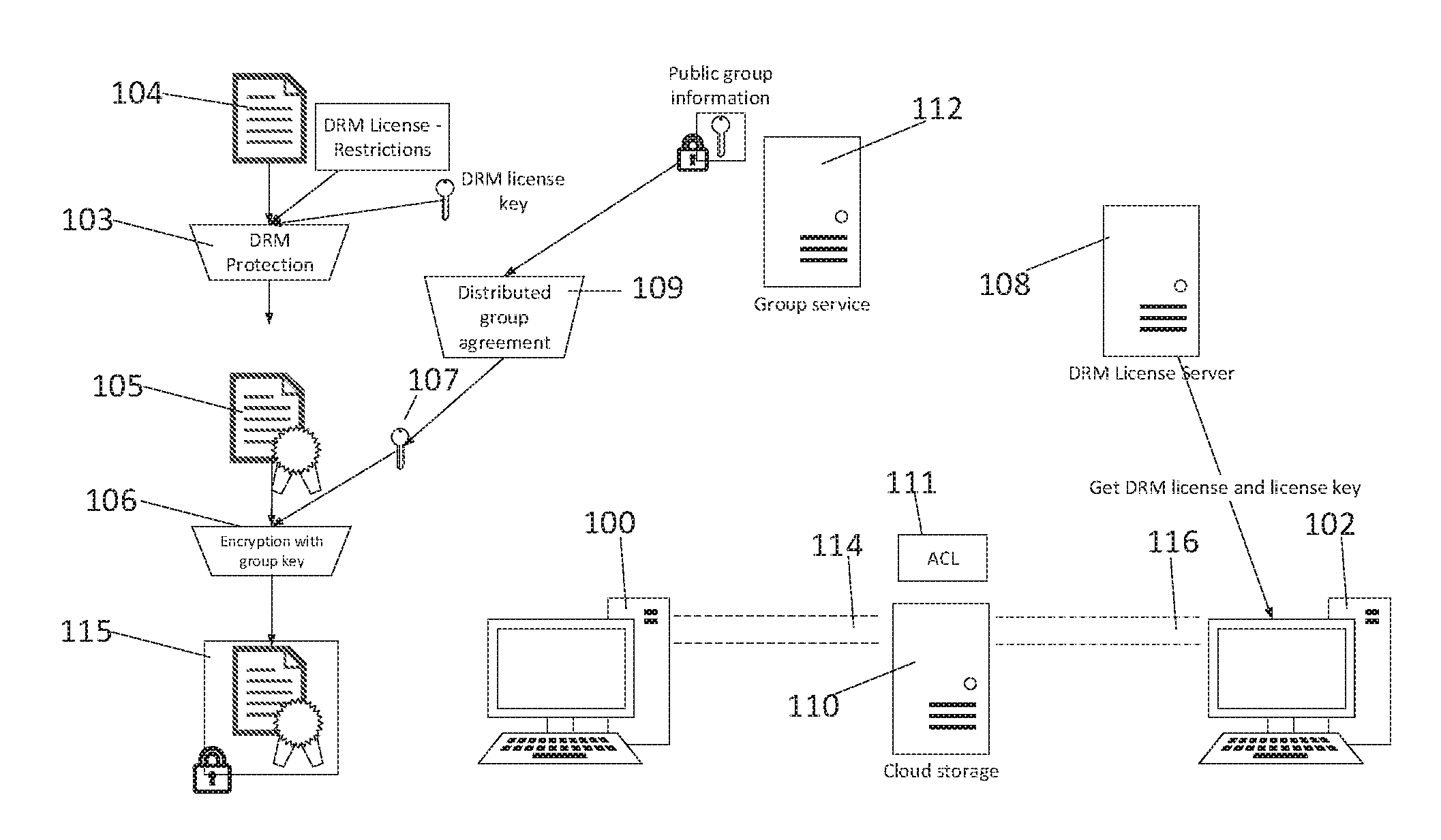
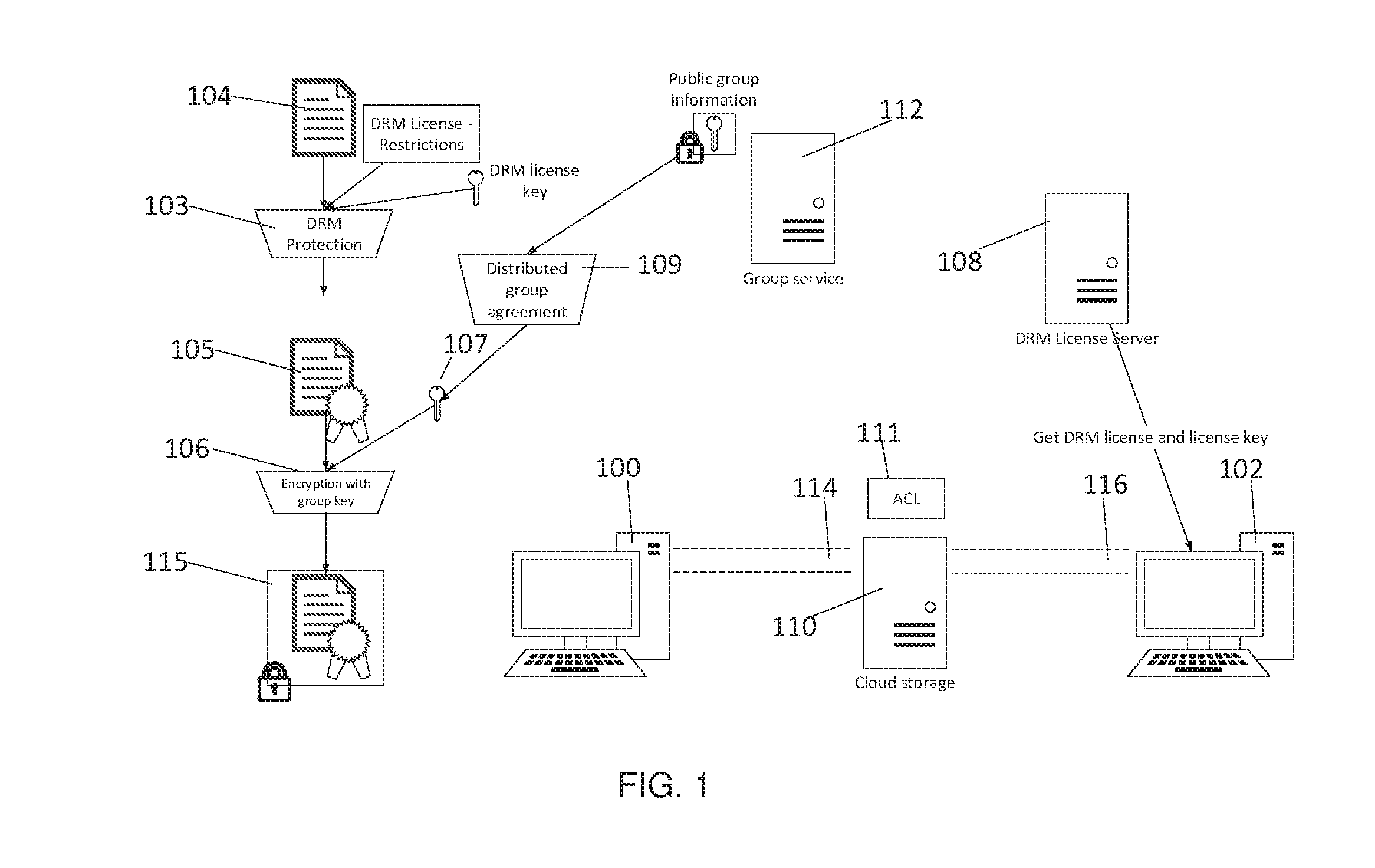
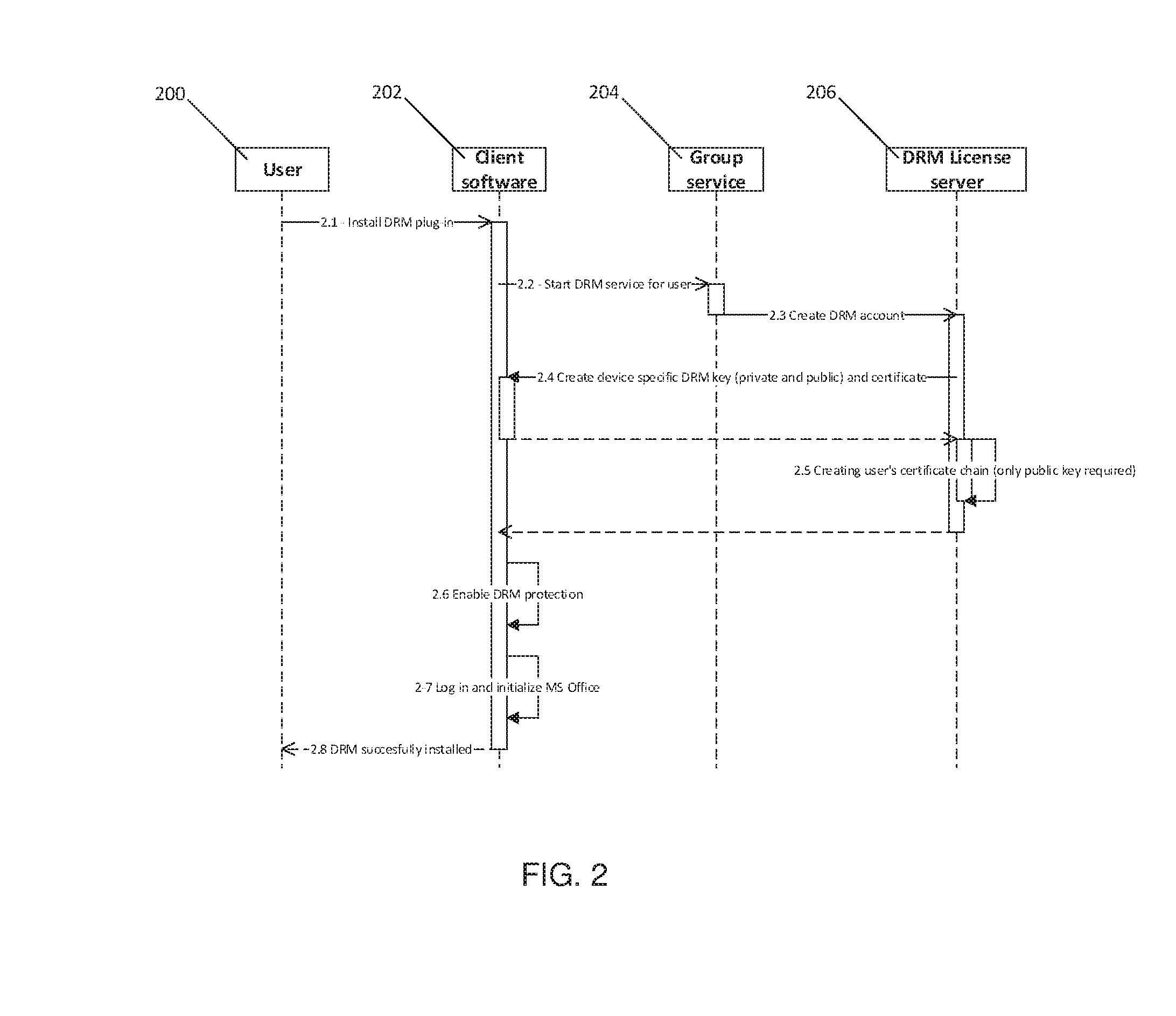
Client-side encryption with DRM
ActiveUS20160182465A1User identity/authority verificationDigital data protectionDocumentation procedureDigital rights management
A technique for extending security to a data object (e.g., a document, a file, a message, etc.) once it has been shared and during collaboration with others who have access rights to that data object. The approach advantageously combines group key-based client-side encryption to secure the data object as it travels from a user's computer, to the cloud, and to a chosen collaborator's computer, together with a digital rights management (DRM) layer that provides permission management that associates a set of permission rights that travel with the data object.
Owner:TRESORIT KFT
Customer Call Logging Data Privacy in Cloud Infrastructure
ActiveUS20170244693A1Safe storageKey distribution for secure communicationMultiple keys/algorithms usageComputer hardwareService provision
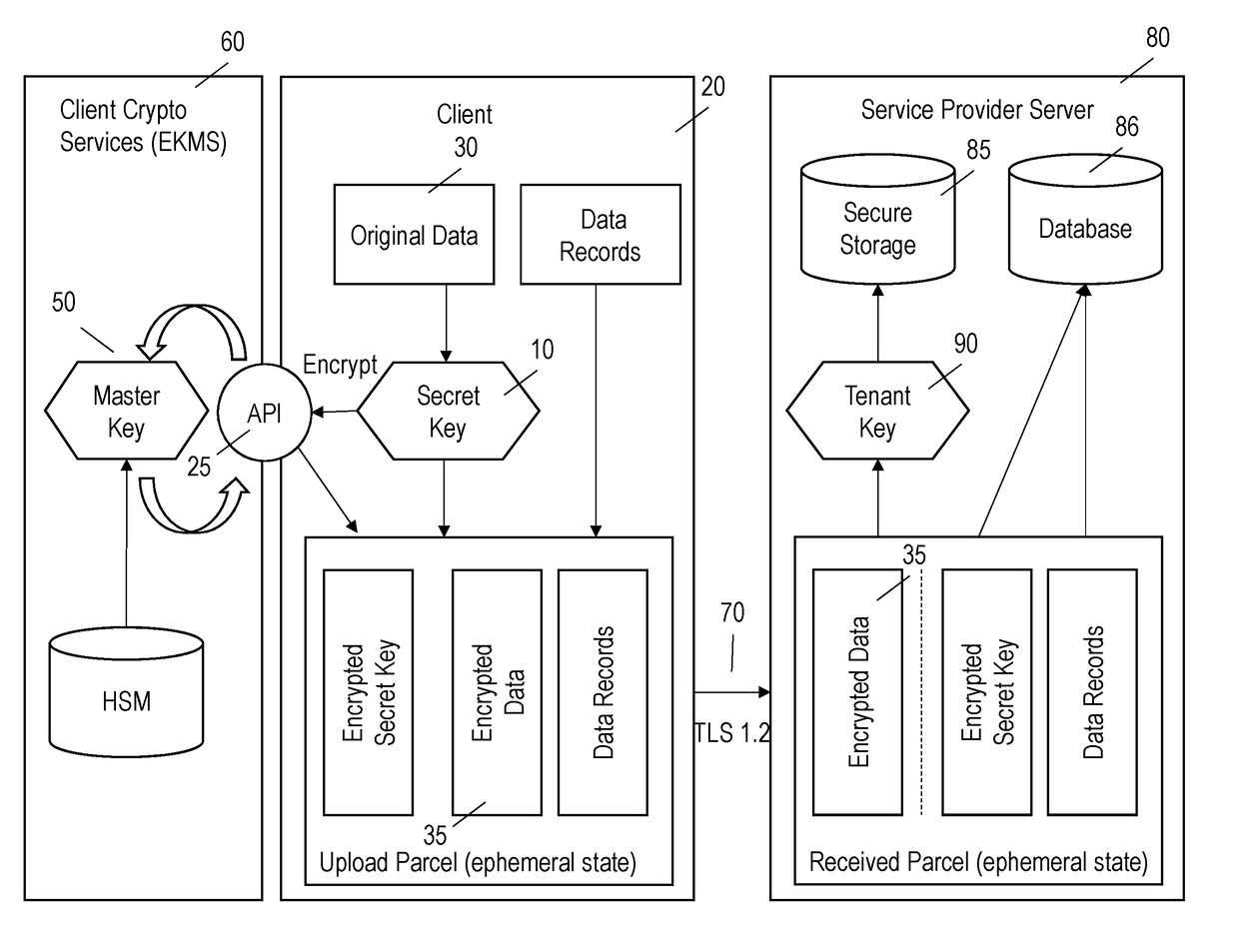
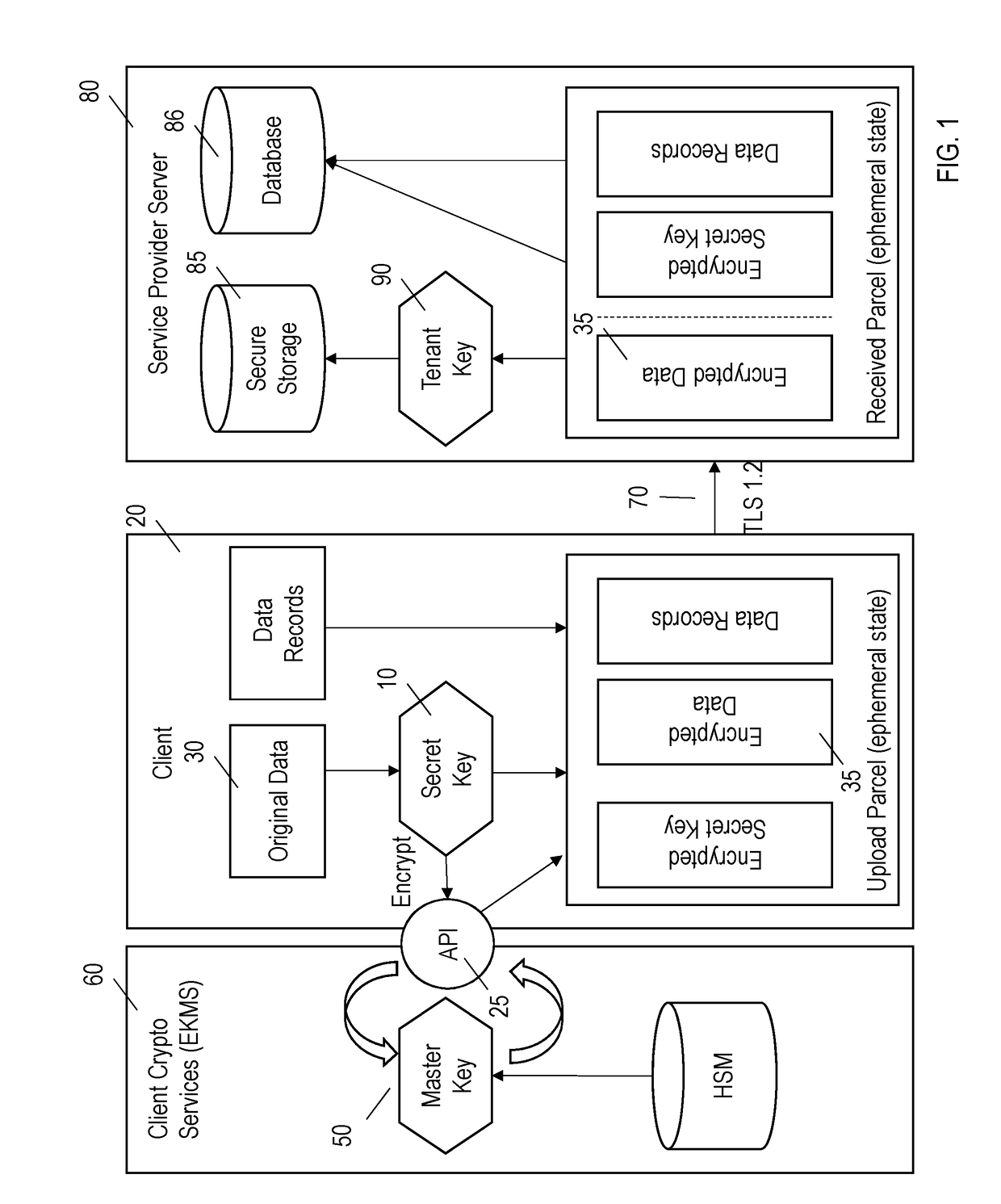
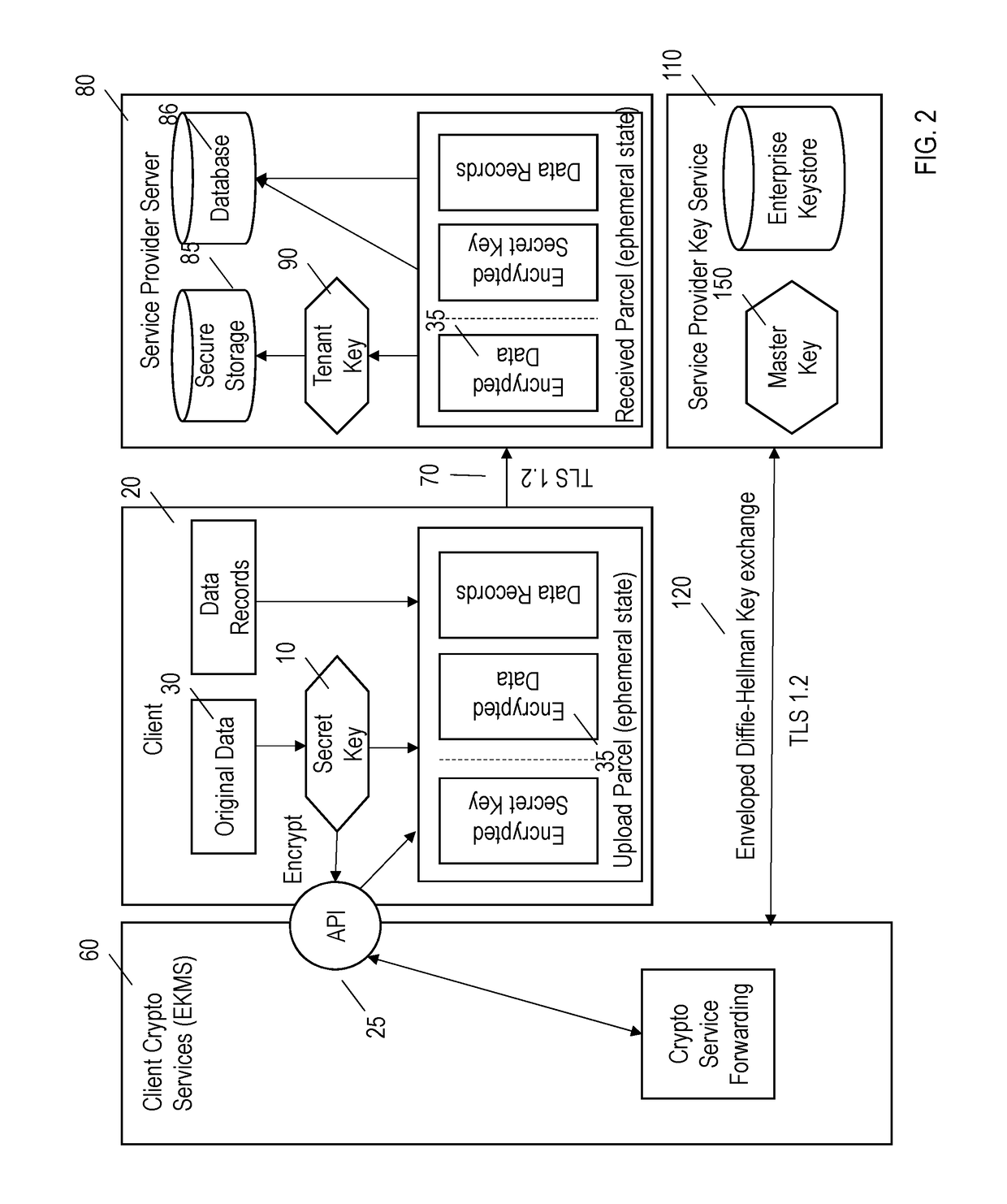
Systems and methods are provided for encrypting data at a customer for storage at a hosted service provider. In addition to the data being encrypted by the client, the secret encryption key used to encrypt the data is also encrypted. Both the encrypted data and the encrypted secret encryption key are transmitted to the service provider who may further encrypt the data with another encryption key and who stores the further encrypted data, the encrypted secret encryption key and the another encryption key.
Owner:CLOUD9 TECH LLC
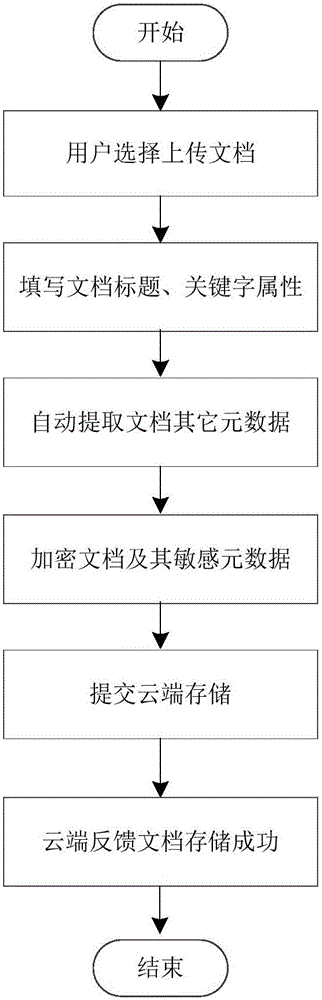
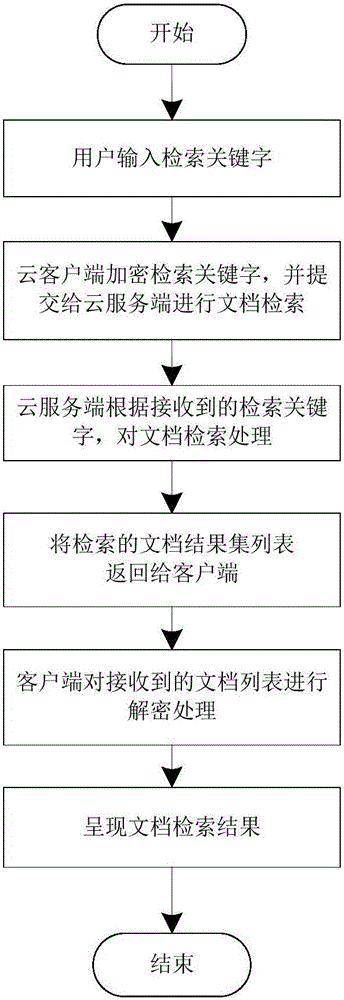
Document safety access method for cloud storage environment
InactiveCN104992124AImprove securityImprove storage securityDigital data protectionAccess methodDigital signature
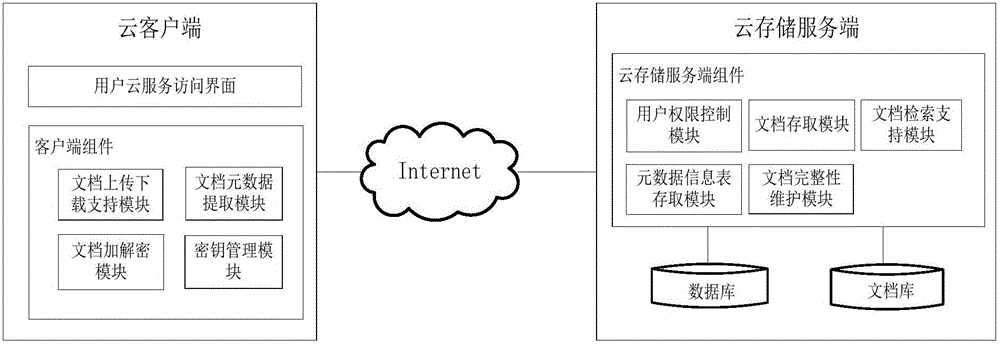
The invention belongs to the cloud technical field, and relates to a document safety access method for a cloud storage environment; the method uses client document encryption / decryption process and cloud cryptograph storage technology to ensure document safety access, and realizes cloud retrieval process through document meta-data information. The method can encrypt data content of uploaded documents, and can encrypt sensitive meta-data of the uploaded documents; a user can retrieval the documents through document keyword meta-data, and can determine document integrity according to a digital signature. The beneficial effects are that the cloud client can encrypt the document data, so the documents can be transmitted and stored in the cloud environment in an encryption mode, thus enhancing data safety level of the documents in the cloud environment. In addition, the document condition retrieval process can enable the user to realize fast retrieval access of the cloud documents; the method is especially suitable for user document safety storage application under a public cloud environment.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
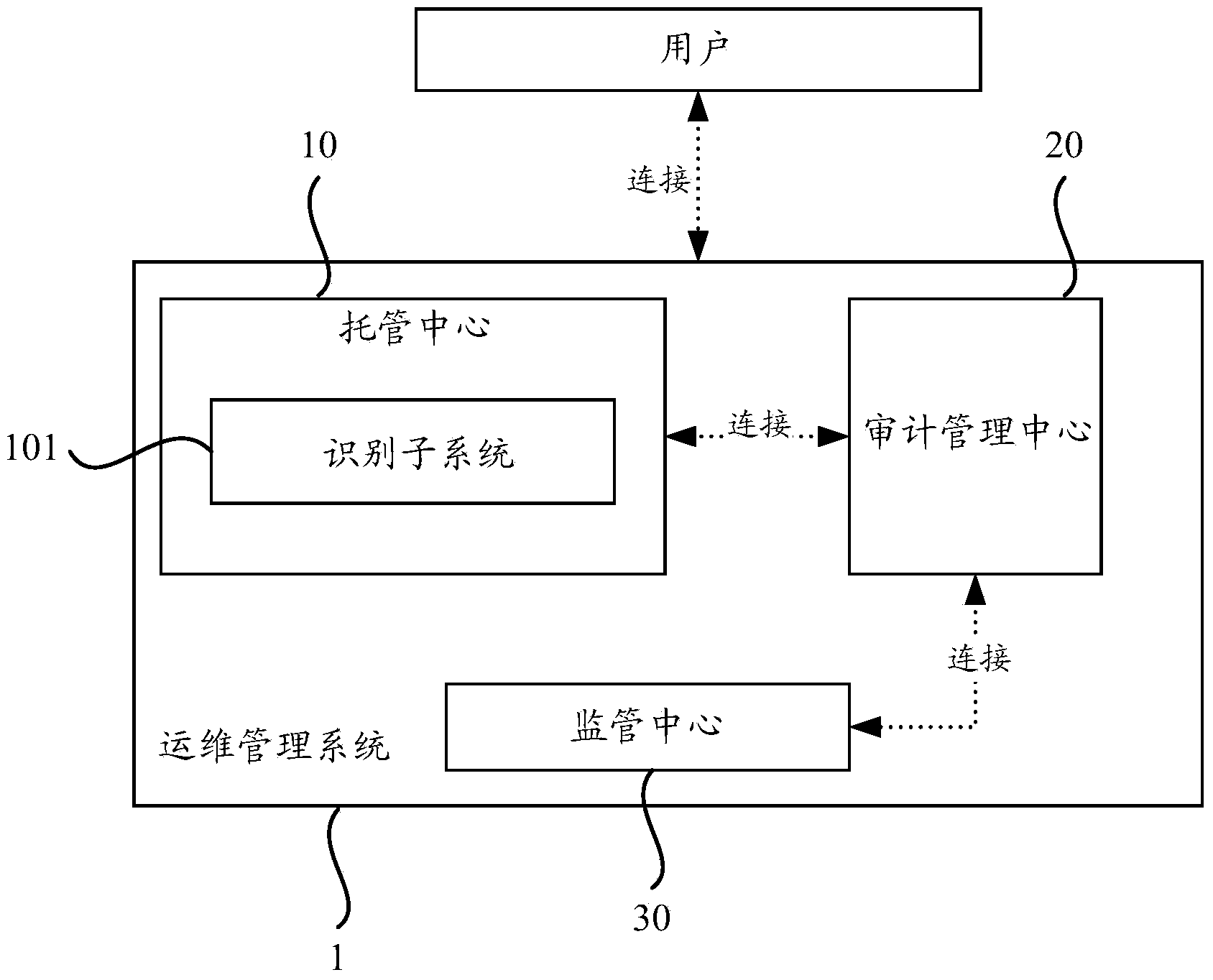
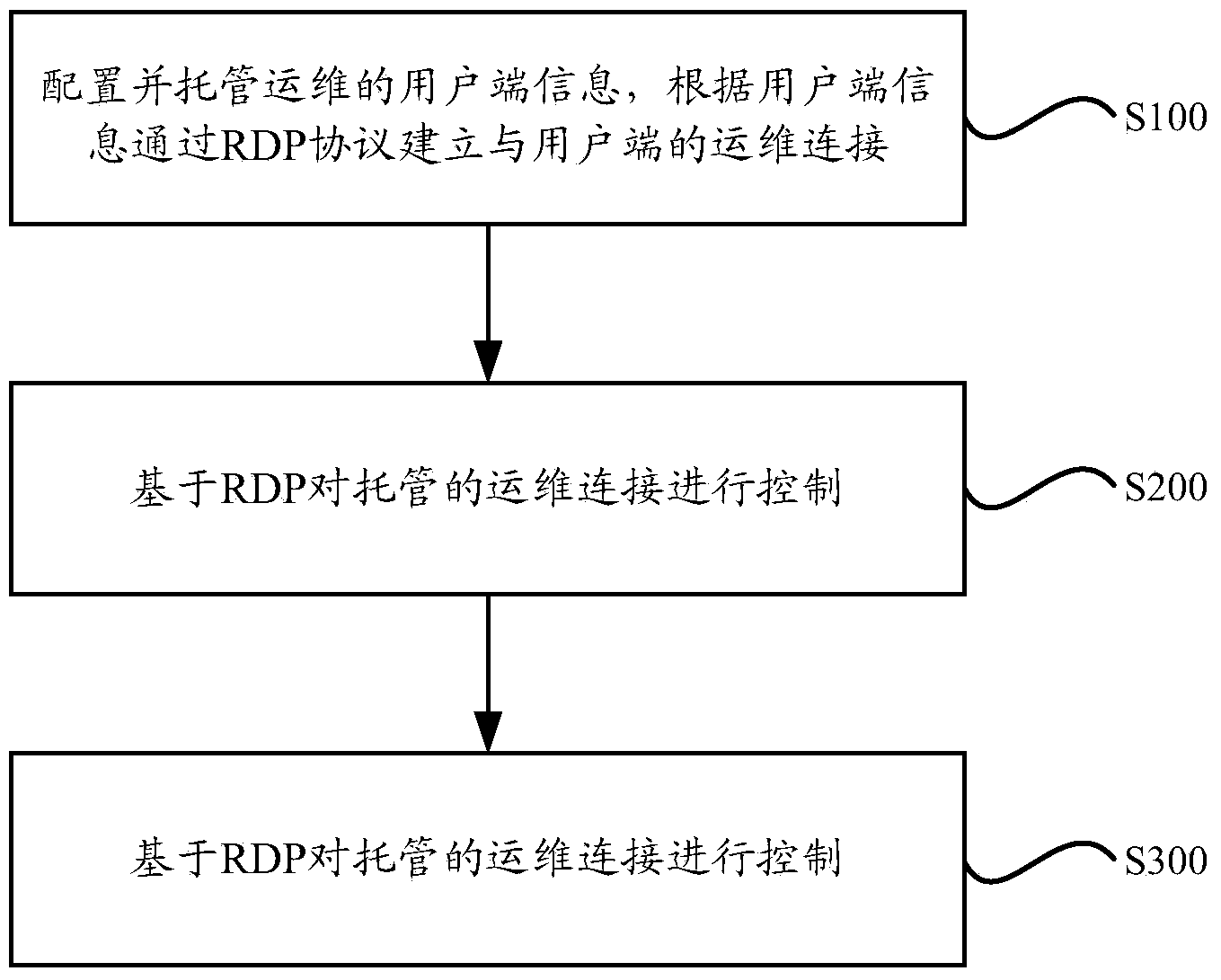
Operation and maintenance management system and method based on RDP protocol
ActiveCN103973488AImprove securityImprove timelinessData switching networksMaintenance managementClient-side
The invention provides an operation and maintenance management system and method based on an RDP protocol. The operation and maintenance management system comprises a hosting center, the hosting center is used for configuring and hosting client side information, and operation and maintenance connection is established between the hosting center and a client side through the RDP protocol according to the hosted client side information. The invention further provides the operation and maintenance management method based on the RDP protocol. Compared with the prior art, the operation and maintenance connection with the client side is established based on the RDP protocol according to the operation and maintenance management system and method, and operation and maintenance of various client sides can be hosted, monitored and managed in real time, so that security and timeliness of the operation and maintenance management system are improved.
Owner:SUNINFO INFORMATION TECH
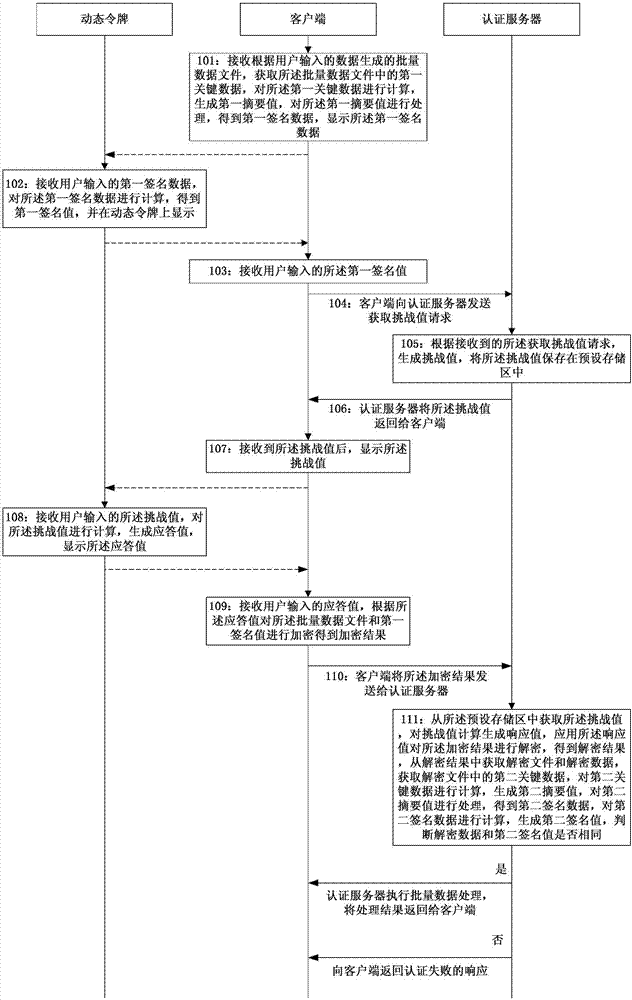
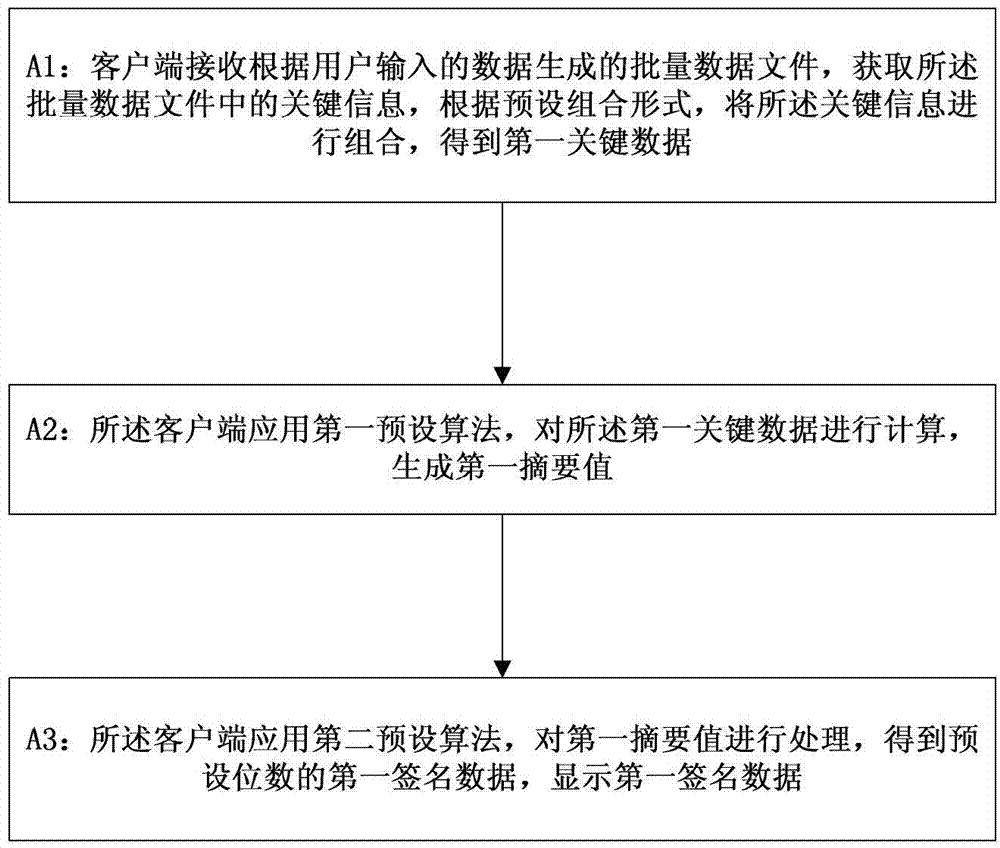
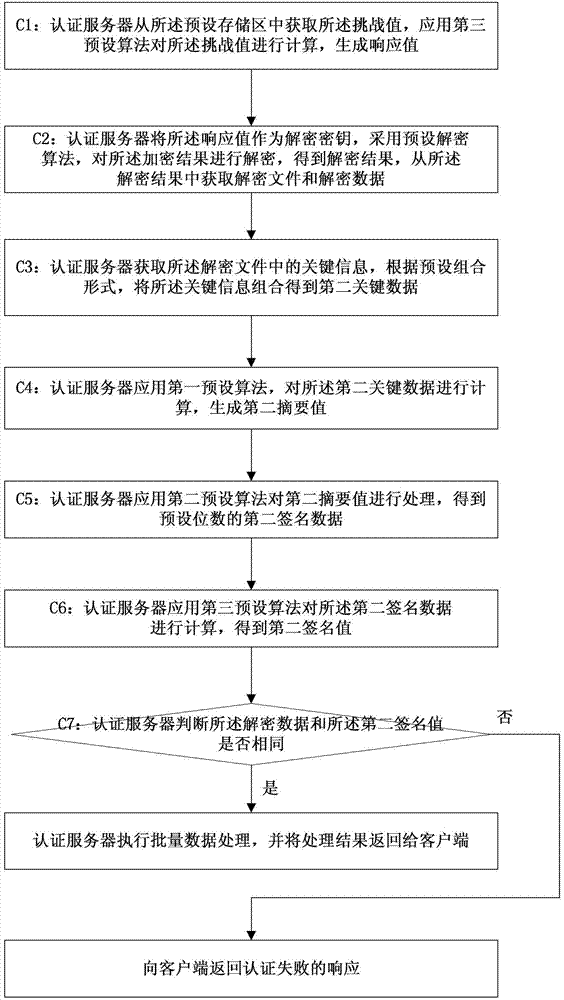
Method and system for safe transmission of batch of data
The invention discloses a method and a system for safe transmission of a batch of data and belongs to the field of information safety. The method comprises the following steps: a client receives a batch of data files and calculates to generate first signature data; a dynamic token calculates to generate a first signature value; the client encrypts the batch of the data files and the first signature value; an encryption result is sent to an authentication server and the authentication server decrypts the encryption result to obtain a decrypted file and decrypted data; the decrypted file is calculated to generate a second signature value; when the second signature and the decrypted data are the same, a batch of data processing is carried out. With the adoption of the technical scheme disclosed by the invention, a lot of data do not need to be manually input when a batch of target data are operated by applying the dynamic token; the usability is greatly improved and the target data can be operated so as to prevent the data from being tampered or stolen and guarantee the safety of the transmission of the batch of the data.
Owner:FEITIAN TECHNOLOGIES
Federal learning incentive method and system based on license chain
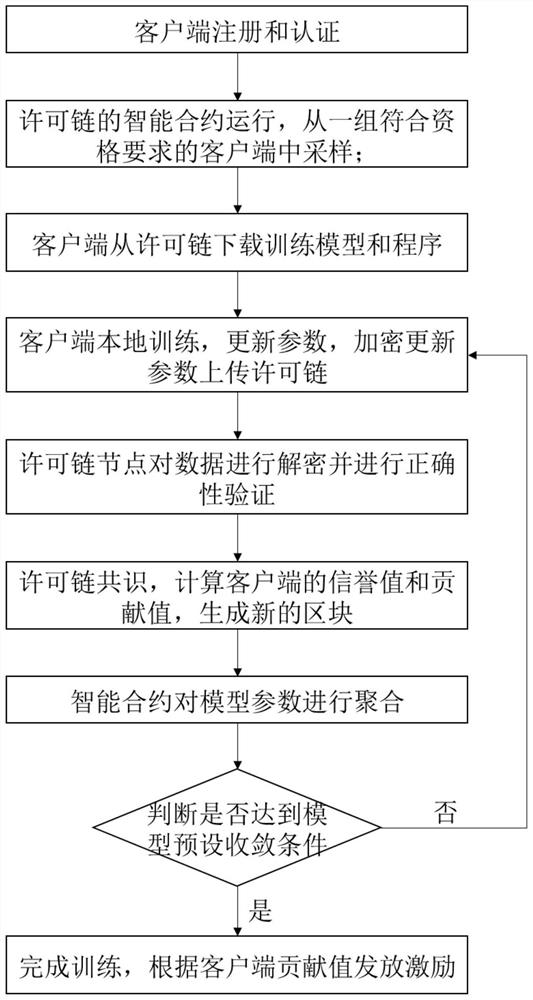
The invention discloses a federal learning incentive method and system based on a license chain, and relates to the technical field of blockchains, and the method comprises the steps that the registration and authentication of clients is carried out, the registration of each client is carried out to the license chain, and the authentication and certificate issuing of each client is carried out through the license chain; the smart contract of the license chain runs, and sampling is carried out from a group of clients meeting qualification requirements; the client downloads the training model and the program from the license chain; the client updates parameters of the model by executing a training program in local calculation, encrypts the updated parameters and uploads the encrypted parameters to the license chain; the license chain node receives the data encrypted by the client, decrypts the data and verifies the correctness of the data; the license chain node carries out consensus, after the consensus is passed, the reputation value and the contribution value of the client are calculated, and a new block is generated; the intelligent contract aggregates the model parameters and updates the parameters; and the smart contract judges whether a preset convergence condition of the model is met, if not, the next round of training is carried out, if yes, training is terminated, and excitation is issued according to the contribution value of the client. According to the method and system, the license block chain and the intelligent contract technology are applied, the problem that a federal learning malicious client or participants damage the correctness of training by utilizing wrong gradient collection and parameter updating is solved, an incentive mechanism is provided, the enthusiasm of providing data and updating network model parameters among the participants is increased, and meanwhile, the security of private data is improved.
Owner:BEIHANG UNIV
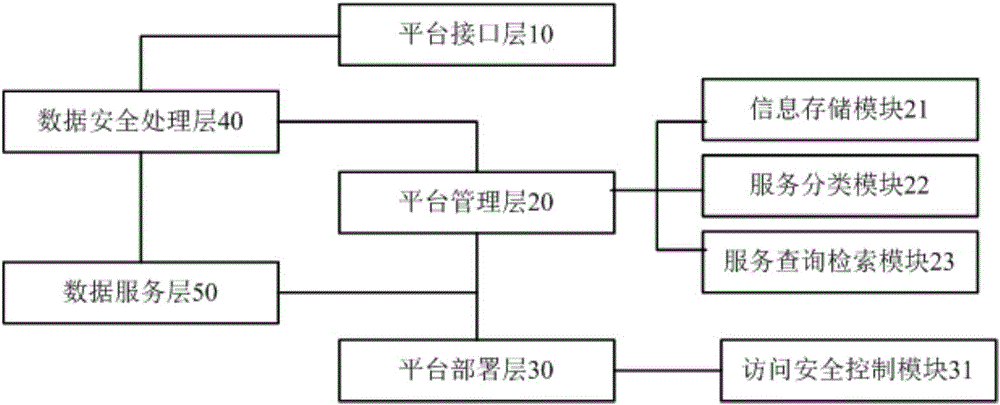
Method for constructing information service platform based on cloud computing
InactiveCN106230790ASolve problems such as concentrated pressure and difficult management of a large number of servicesSave time and costUser identity/authority verificationDigital data protectionDigital signatureSmart card
The invention provides a method for constructing an information service platform based on cloud computing. The method is characterized by comprising realization of cloud computing safety and platform construction, wherein the cloud computing safety is realized in the following steps: a chip hardware device, a symmetric cipher algorithm and the combined key technology are adopted; in a non-cloud computing environment, a smart card is used as the hardware device of a client encryption system; in a chip of the smart card, the symmetric cipher algorithm is adopted to establish the client encryption system; and the client encryption system, a digest algorithm, a combined key generation algorithm, a key 'base', a client identity authentication protocol, a digital signature protocol, a signature verification protocol and an encryption / decryption protocol are written in.
Owner:蔡雄
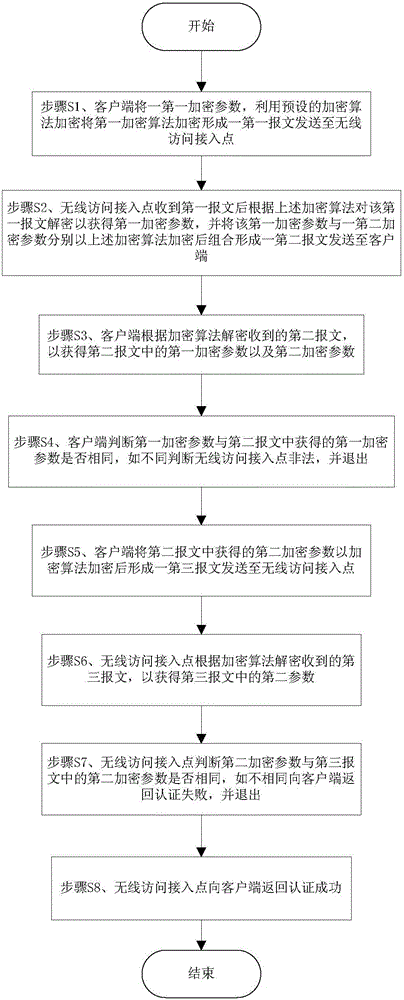
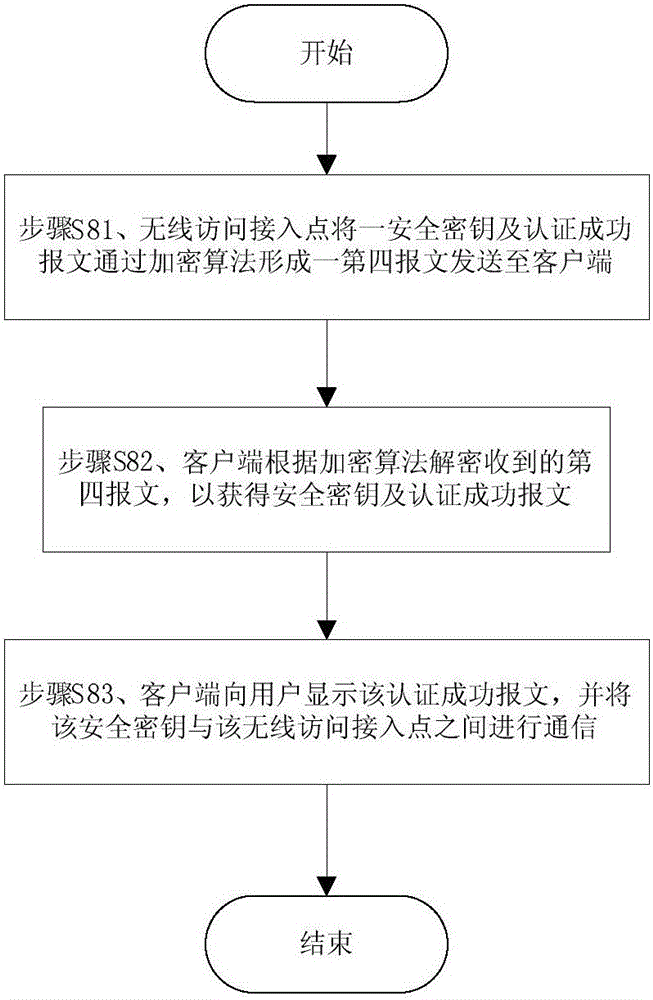
Method of improving wireless local area authentication mechanism
ActiveCN105828332APreventing "man-in-the-middle" attacksAvoid "communication hijacking" attacksKey distribution for secure communicationMultiple keys/algorithms usageMan-in-the-middle attackWireless access point
The invention provides a method of improving a wireless local area authentication mechanism. After a wireless access point sends a message that the authentication is successful in a plain text to a client in a bidirectional authentication process, the method comprises the steps of providing a first encryption parameter, if the first encryption parameter remains unchanged after being encrypted by the client, decrypted by the wireless access point, encrypted by the wireless access point and decrypted by the client, judging that the wireless access point is legal; providing a second encryption parameter, if the second encryption parameter remains unchanged after being encrypted by the wireless access point, decrypted by the client, re-encrypted by the client and re-decrypted by the wireless access point, judging that the entire authentication process is completed. The method of improving the wireless local area authentication mechanism provided by the invention can effectively prevent the "man-in-the-middle attack", i.e., the illegal user is unable to access the network through the port of the legal user, so as to avoid the "communication hijack" attack.
Owner:湖州帷幄知识产权运营有限公司
Method, device and system for encrypting transmission data, controlling and detecting encrypted protocol
Owner:ALIBABA GRP HLDG LTD
A system and method for providing integration via a dial-up interface
InactiveUS20030236984A2User identity/authority verificationMultiple digital computer combinationsComputer hardwareNetworked system
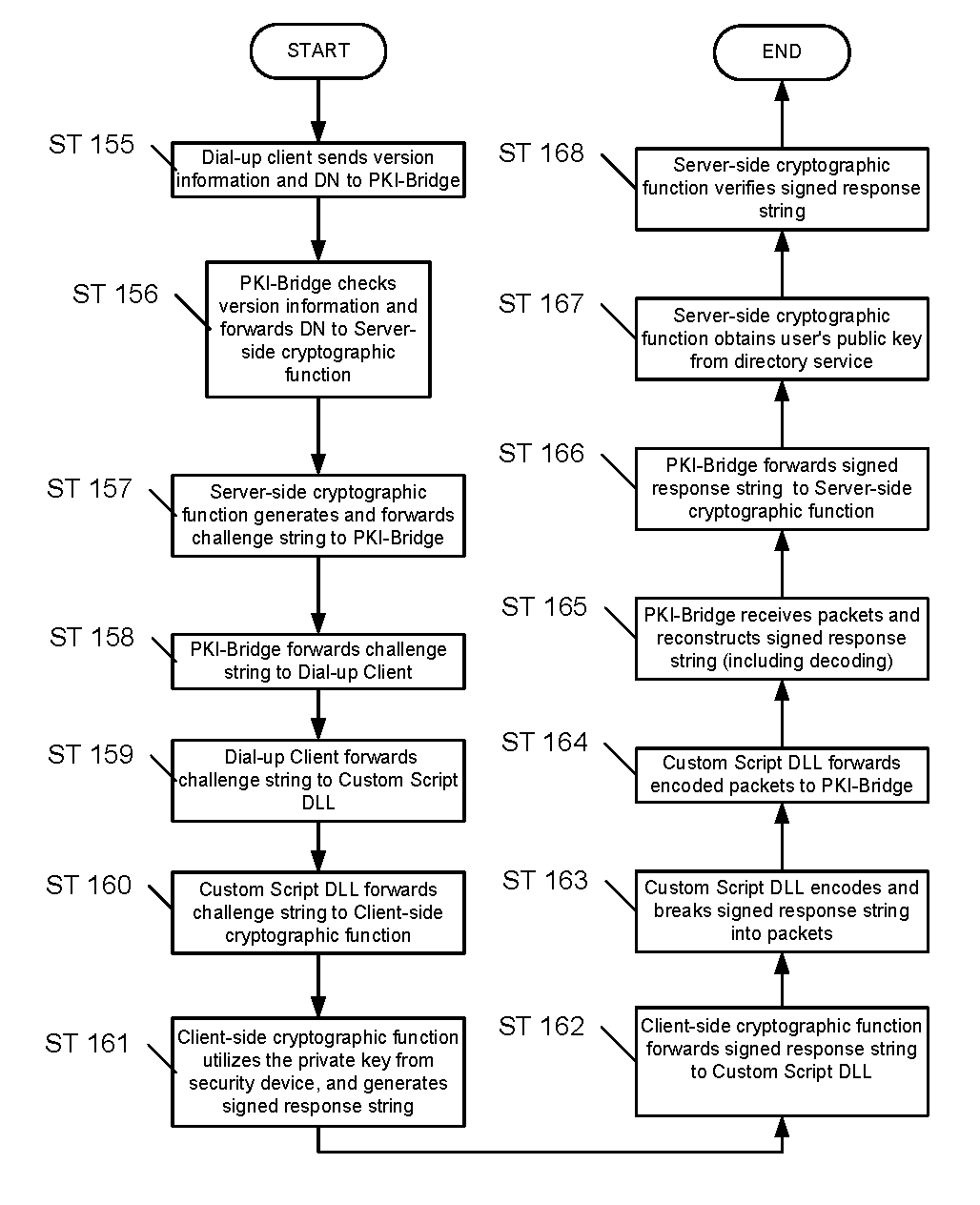
Abstract of the Disclosure A network system providing integration. The network system includes a client computer, a server, a server-side cryptographic function, a PKI-Bridge, a remote access switch, a client-side cryptographic function, a dial-up client, and a custom script dynamically linked library. The server-side cryptographic function is located on the server and provides cryptographic services. The PKI-Bridge provides an interface between the server and the server-side cryptographic function. The remote access switch provides an interface between the client computer and the server. The client-side cryptographic function is located on the client computer and provides cryptographic services. The dial-up client provides dial-up services to access the remote access switch. The custom script dynamically linked library provides an interface between the dial-up client and the client-side cryptographic function.
Owner:DEXA SYST
Private access to hash tables
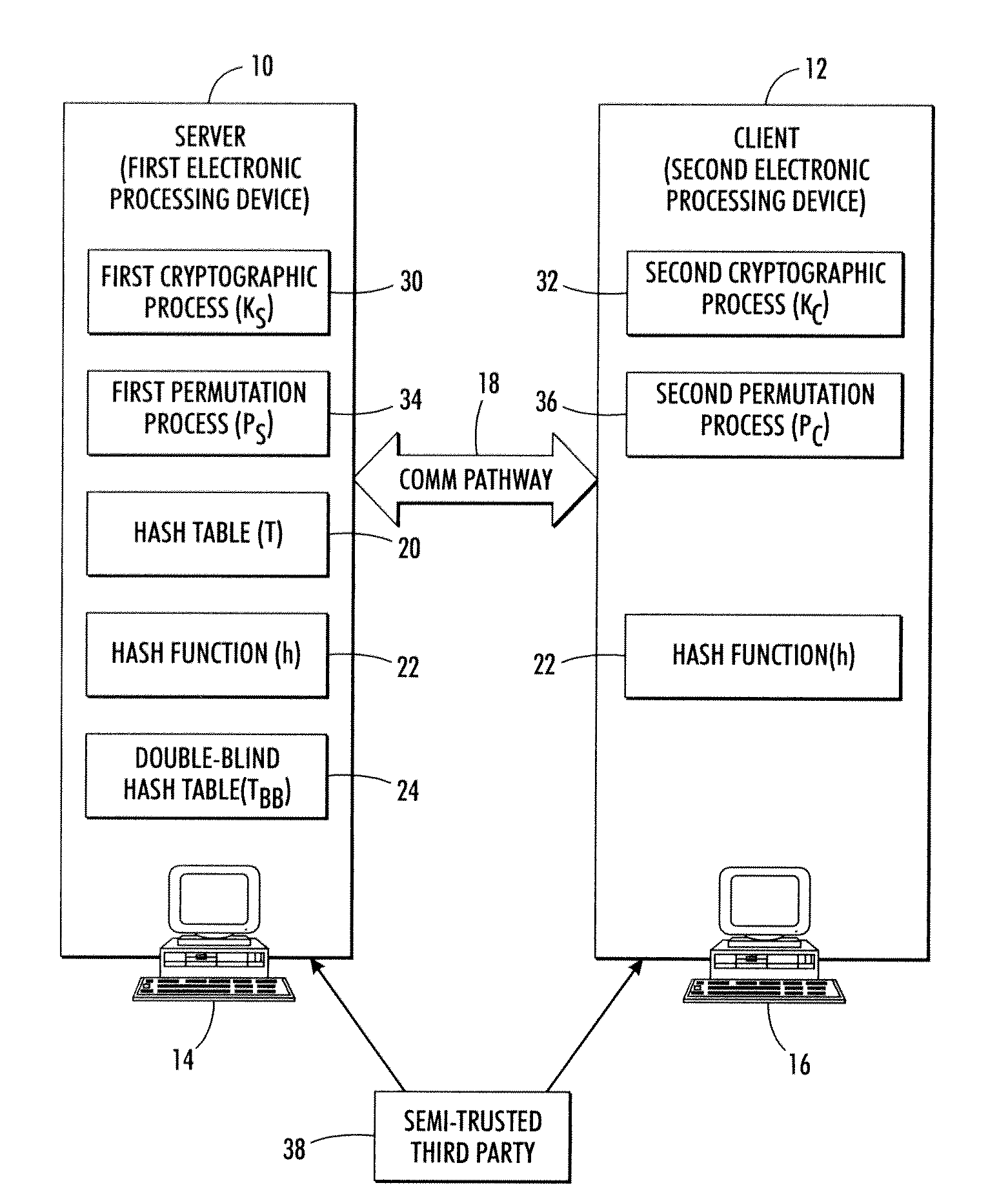
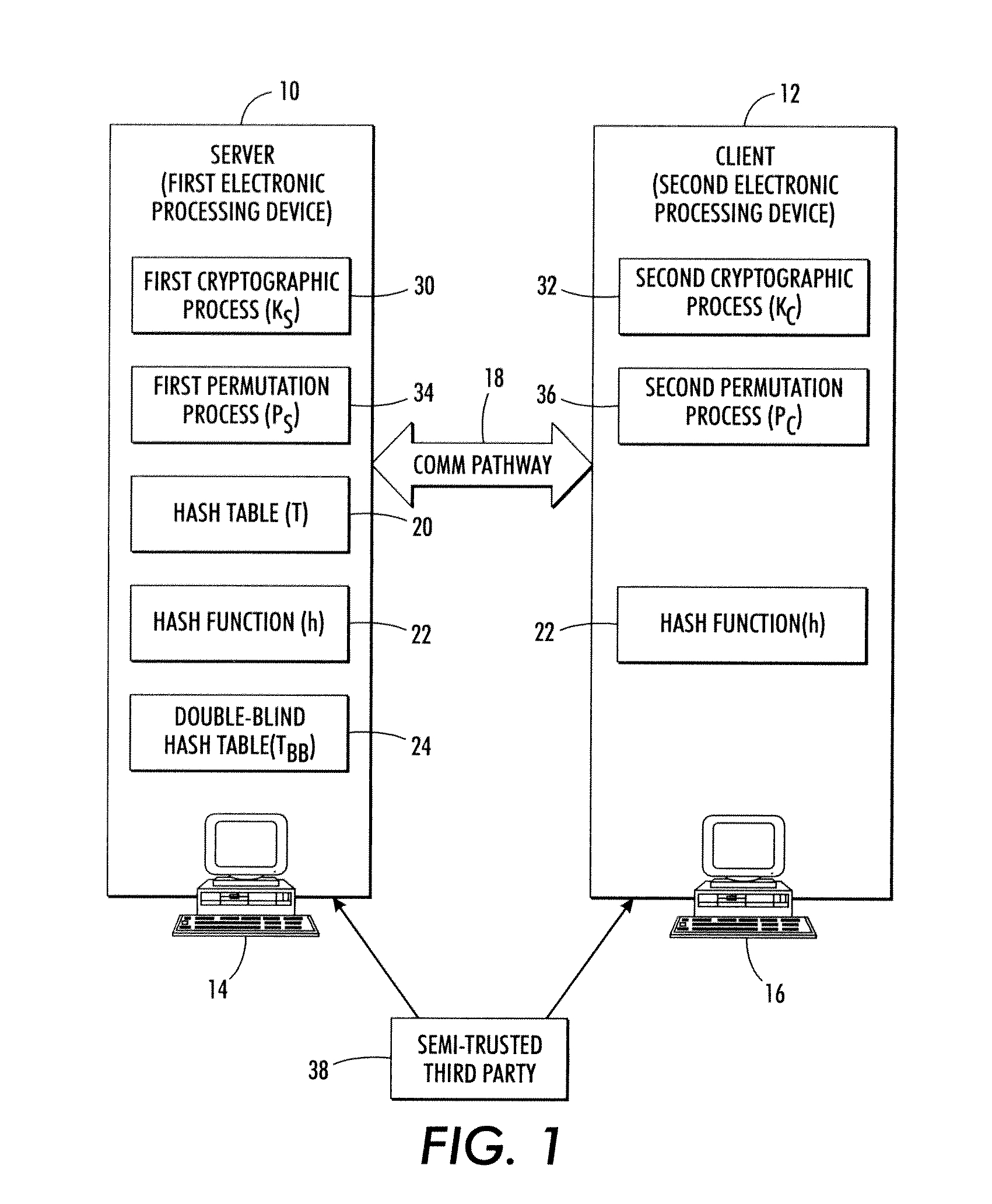
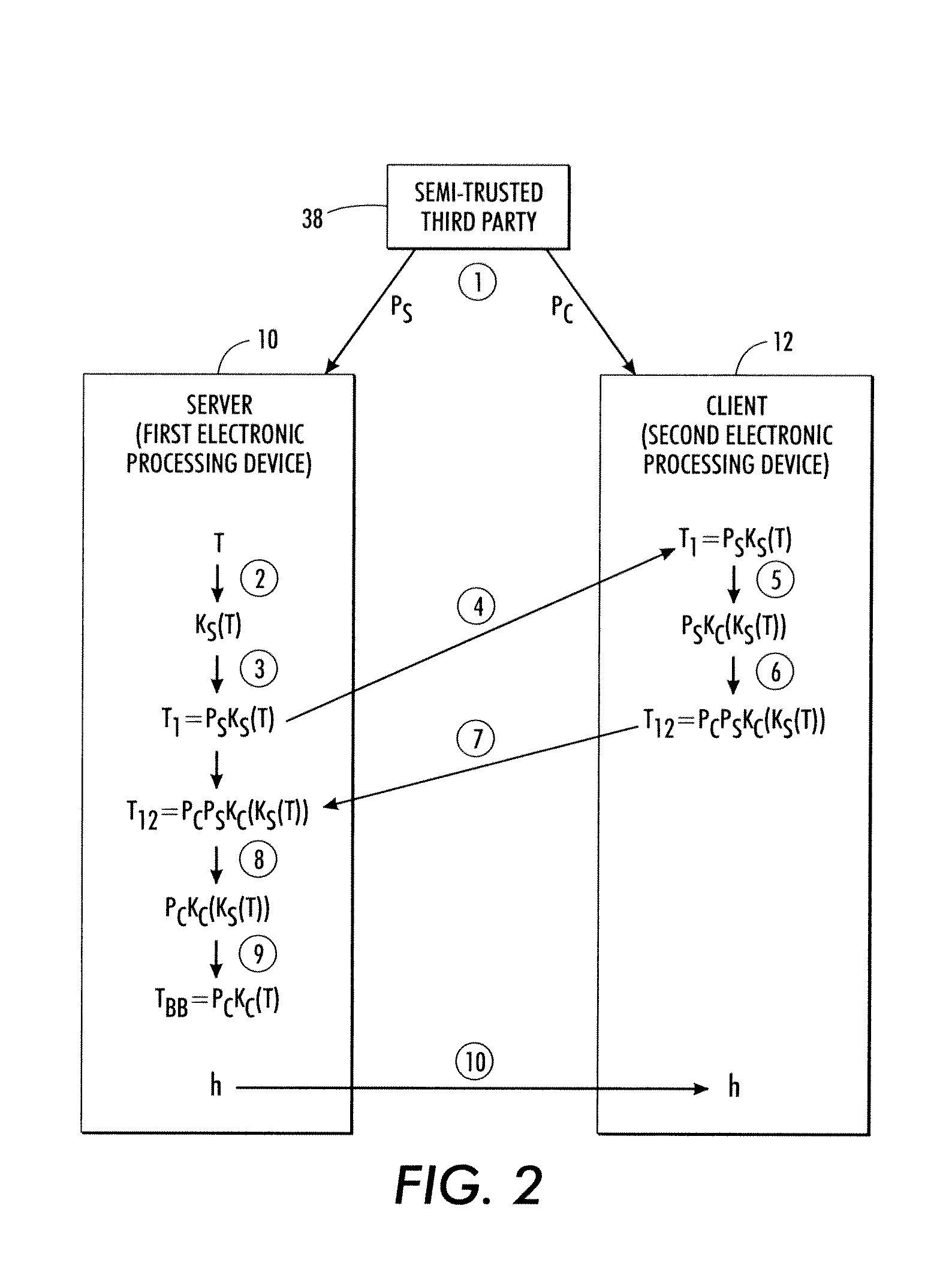
InactiveUS8572379B2User identity/authority verificationComputer security arrangementsClient-sideHash table
A server and a client mutually exclusively execute server-side and client-side commutative cryptographic processes and server-side and client-side commutative permutation processes. The server has access to a hash table, while the client does not. The server and client perform a method including: encrypting and reordering the hash table using the server; communicating the encrypted and reordered hash table to the client; further encrypting and further reordering the hash table using the client; communicating the further encrypted and further reordered hash table back to the server; and partially decrypting and partially undoing the reordering using the server to generate a double-blind hash table. To read an entry, the client hashes and permute an index key and communicates same to the server which retrieves an item from the double-blind hash table using the hashed and permuted index key and sends it back to the client which decrypts the retrieved item.
Owner:XEROX CORP
Secret information processing method, device and system
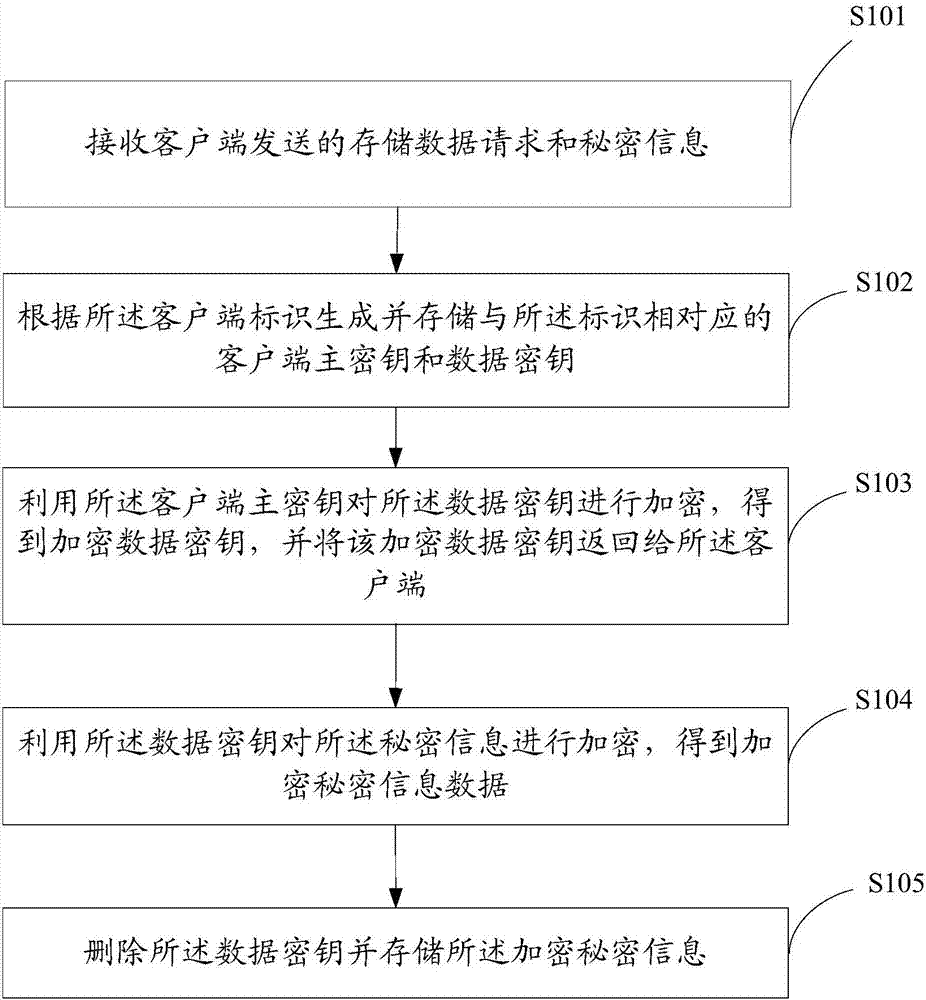
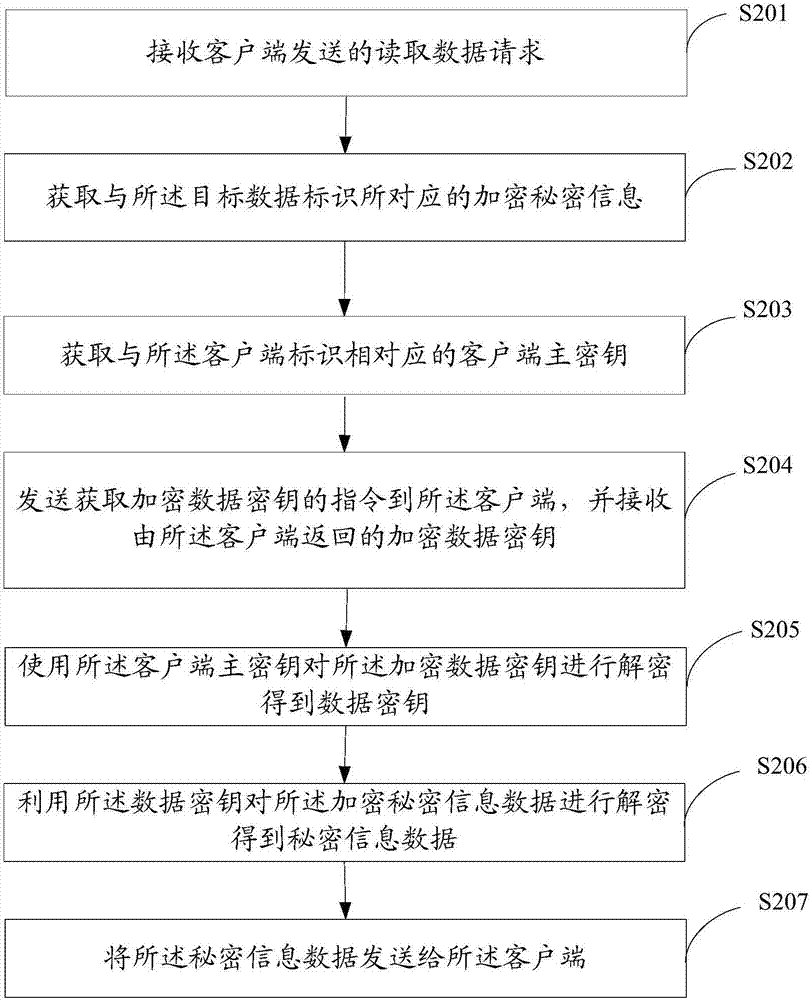
InactiveCN107359990AImprove securityKey distribution for secure communicationSecurity arrangementInformation processingMaster key
The invention provides a secret information processing method, device and system. The secret information processing method is applied to a data storage system and comprises steps of: receiving a data storage request and secret information required to be stored which are sent by a client; generating a master key and a data key of the client based on a client identifier in the data storage request, encrypting the data key by using the master key, returning the encrypted data key to the client, encrypting the secret information by using the data key, and storing the obtained encrypted secret information while deleting the data key. Thus, even if the encrypted secret information is invalidly acquired, the encrypted secret information cannot be decrypted via the data key because of the absence of the data key. Since the data key obtained from the client is encrypted by the master key of the client, the secret information cannot be decrypted even if the data key encrypted by the client is intercepted. As a result, dual protection is formed, encrypted storage of the secret information is achieved and data security is improved.
Owner:BEIJING QIYI CENTURY SCI & TECH CO LTD
Method for encrypting communication process in industrial field and data collection device
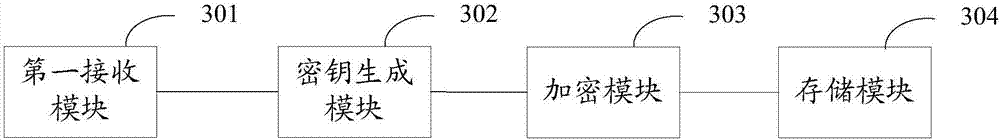
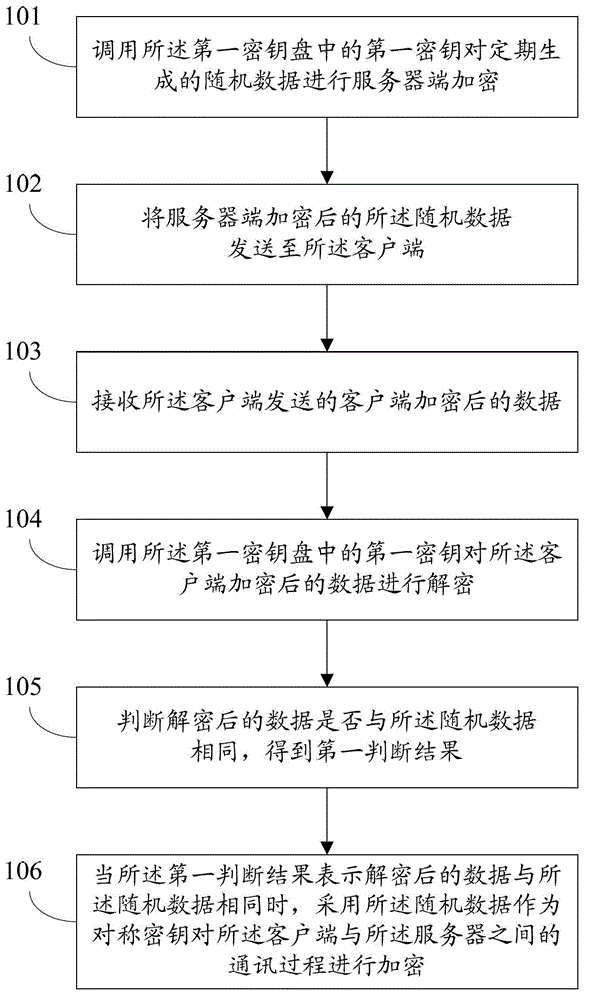
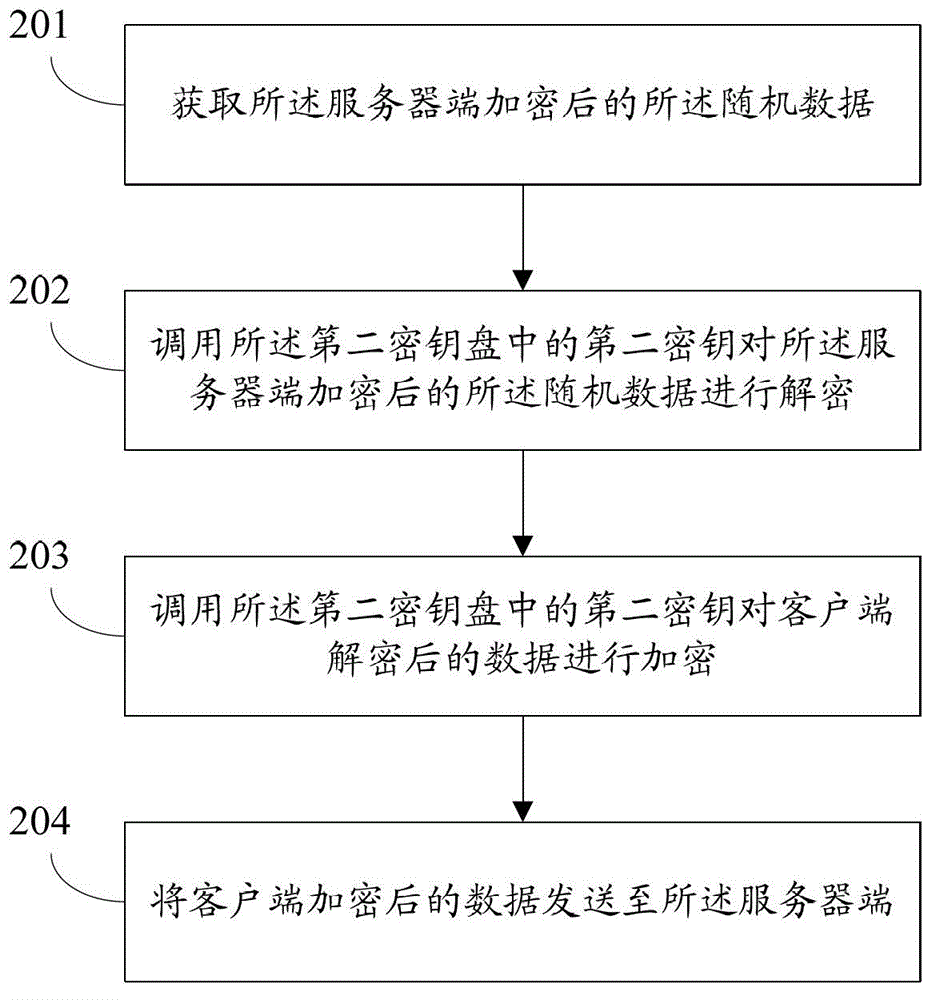
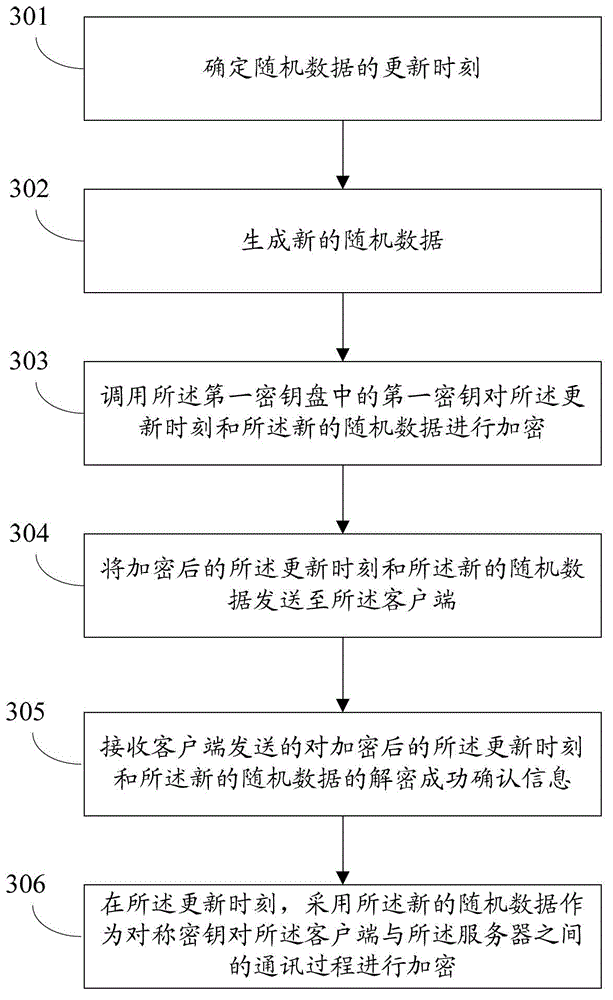
The invention discloses a method for encrypting the communication process in the industrial field and a data collection device. The method includes: invoking a first secret key in a first secret key disc to perform server side encrypting for regularly generated random data; sending the random data after server side encrypting to a client side; receiving data after client side encrypting sent by the client side; invoking the first secret key in the first secret key disc to perform decrypting for the data after client side encrypting; judging whether the decrypted data are identical to the random data to obtain a first judging result; and adopting the random data to serve as symmetrically secret keys to encrypt the communication process between the client side and the server side when the first judging result indicates that the decrypted data are identical to the random data. By adopting the method and the device, safety of the whole communication process can be improved.
Owner:ZHEJIANG SUPCON SOFTWARE +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com