Method, device and system for encrypting transmission data, controlling and detecting encrypted protocol
An encryption protocol and encrypted transmission technology, applied in the field of Internet data transmission, can solve the problems of lack of control ability on the business server and affect user experience, and achieve the effect of improving experience and improving control ability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0089] In the following description, numerous specific details are set forth in order to provide a thorough understanding of the present invention. However, the present invention can be implemented in many other ways different from those described here, and those skilled in the art can make similar extensions without violating the connotation of the present invention, so the present invention is not limited by the specific implementations disclosed below.
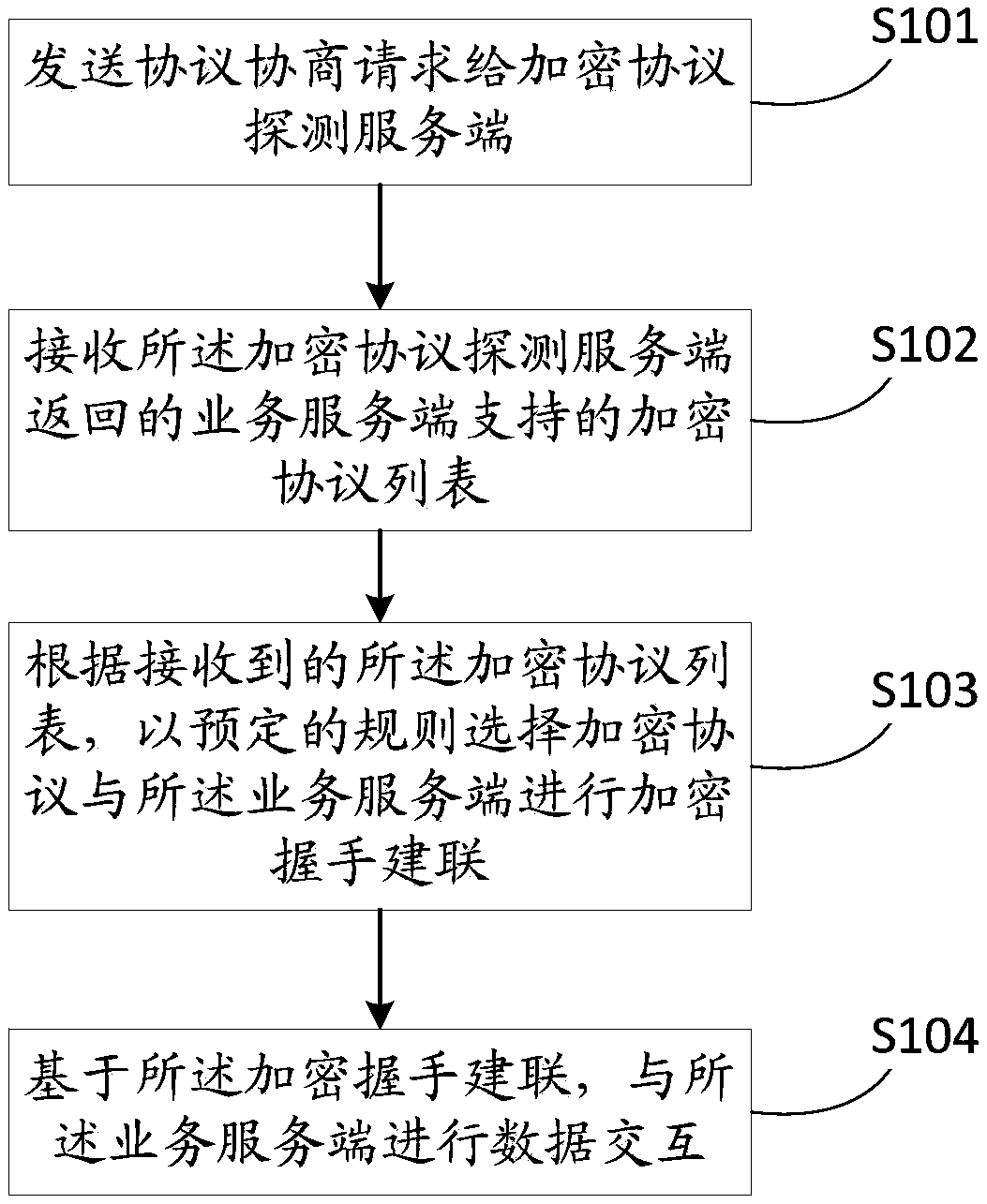
[0090] The first embodiment of the present application provides a method for encrypting transmission data. Please refer to figure 1 , which shows a flowchart of a method for encrypting transmission data provided according to an embodiment of the present application. The following combination figure 1 Describe in detail. This embodiment is a method for encrypting data transmission provided from the perspective of a client; that is, it is the client that executes the method provided by this embodiment.
[0091] Step S101,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com