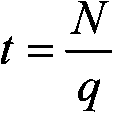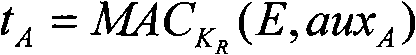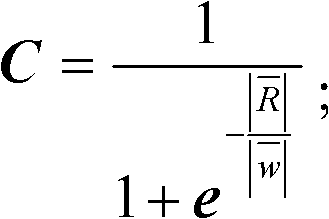Patents
Literature
123 results about "Cryptography protocols" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A cryptographic protocol is a protocol executed by several distant agents through a network where the messages or part of the messages are produced using cryptographic functions (encryption, hashing, etc.).
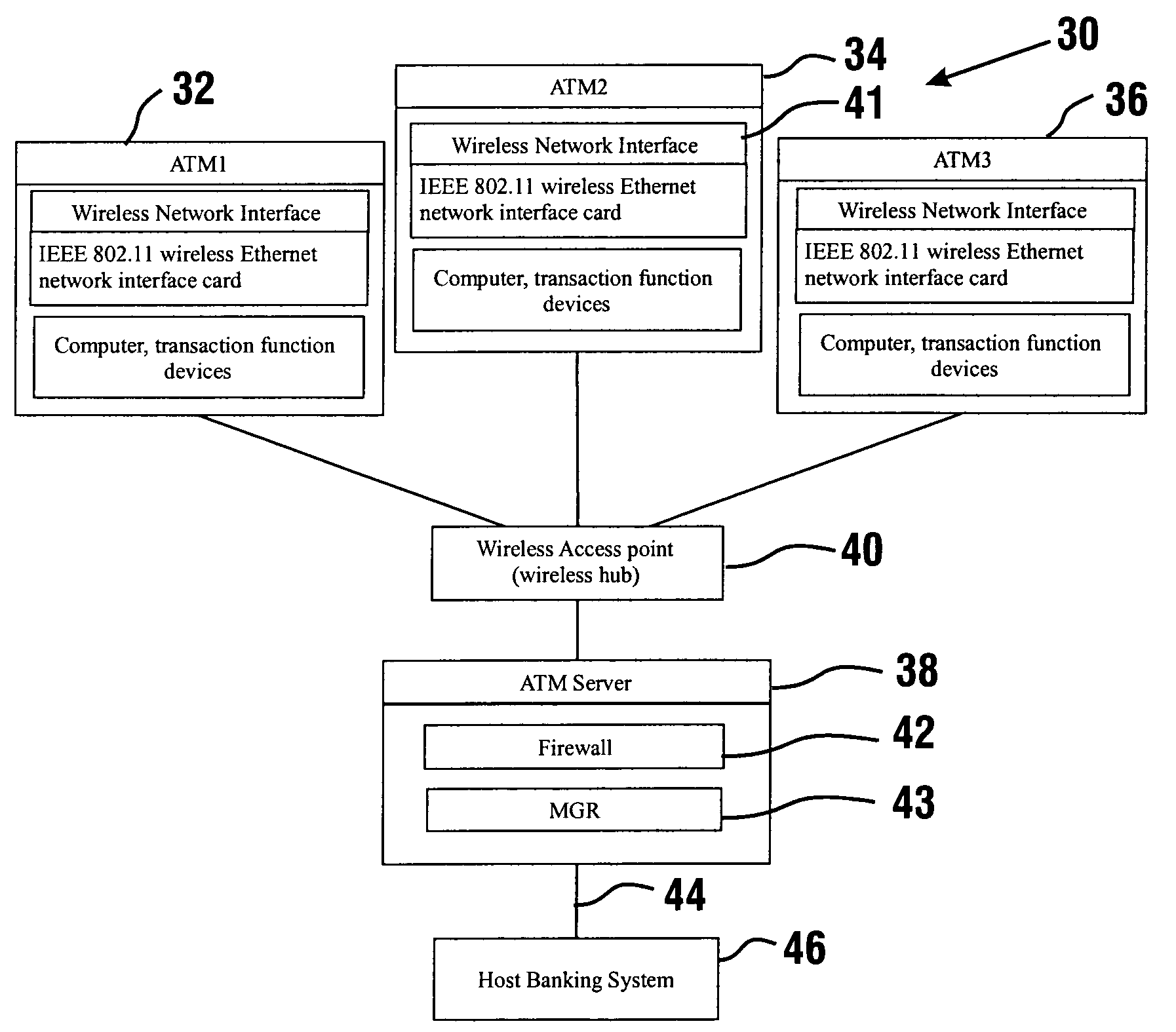
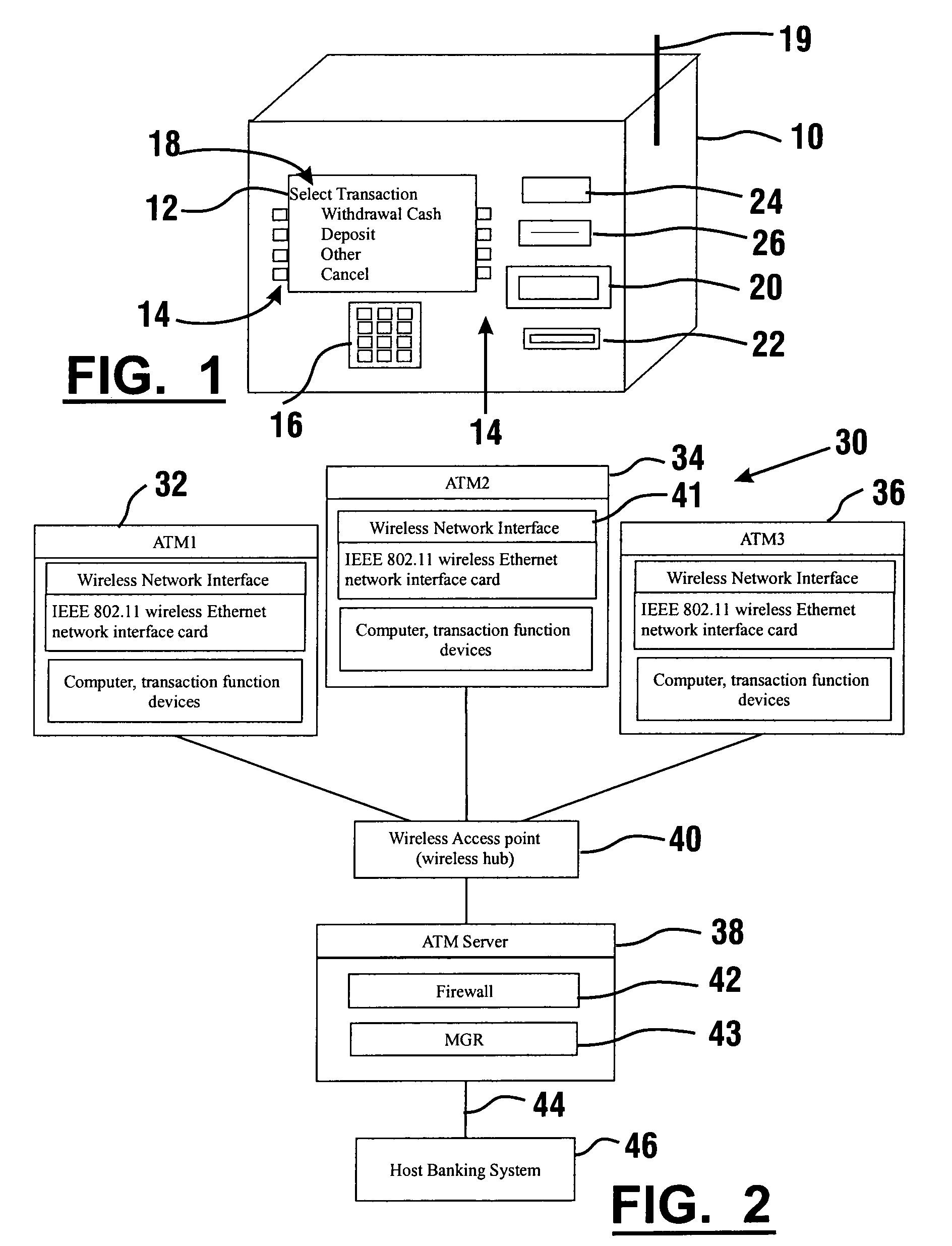
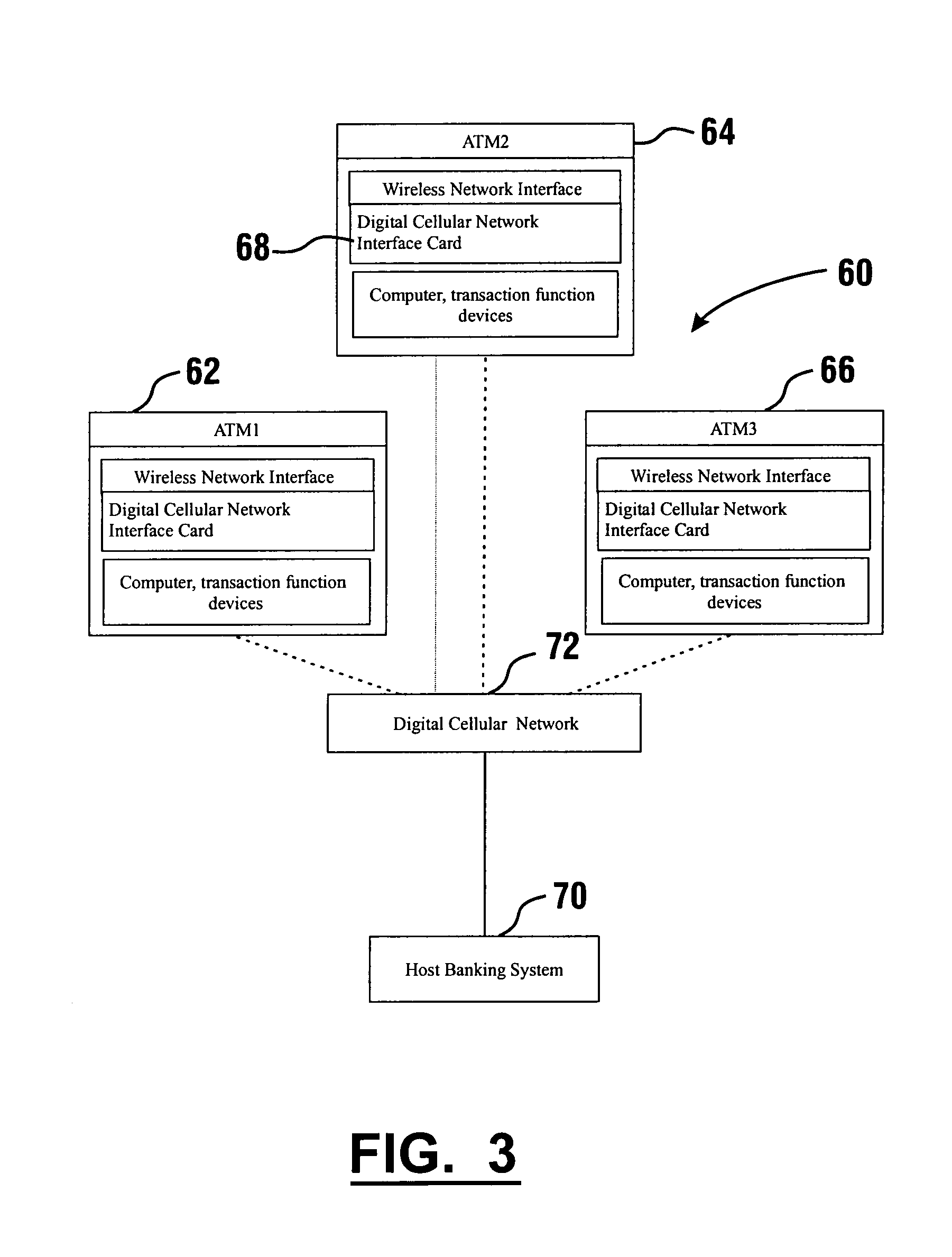
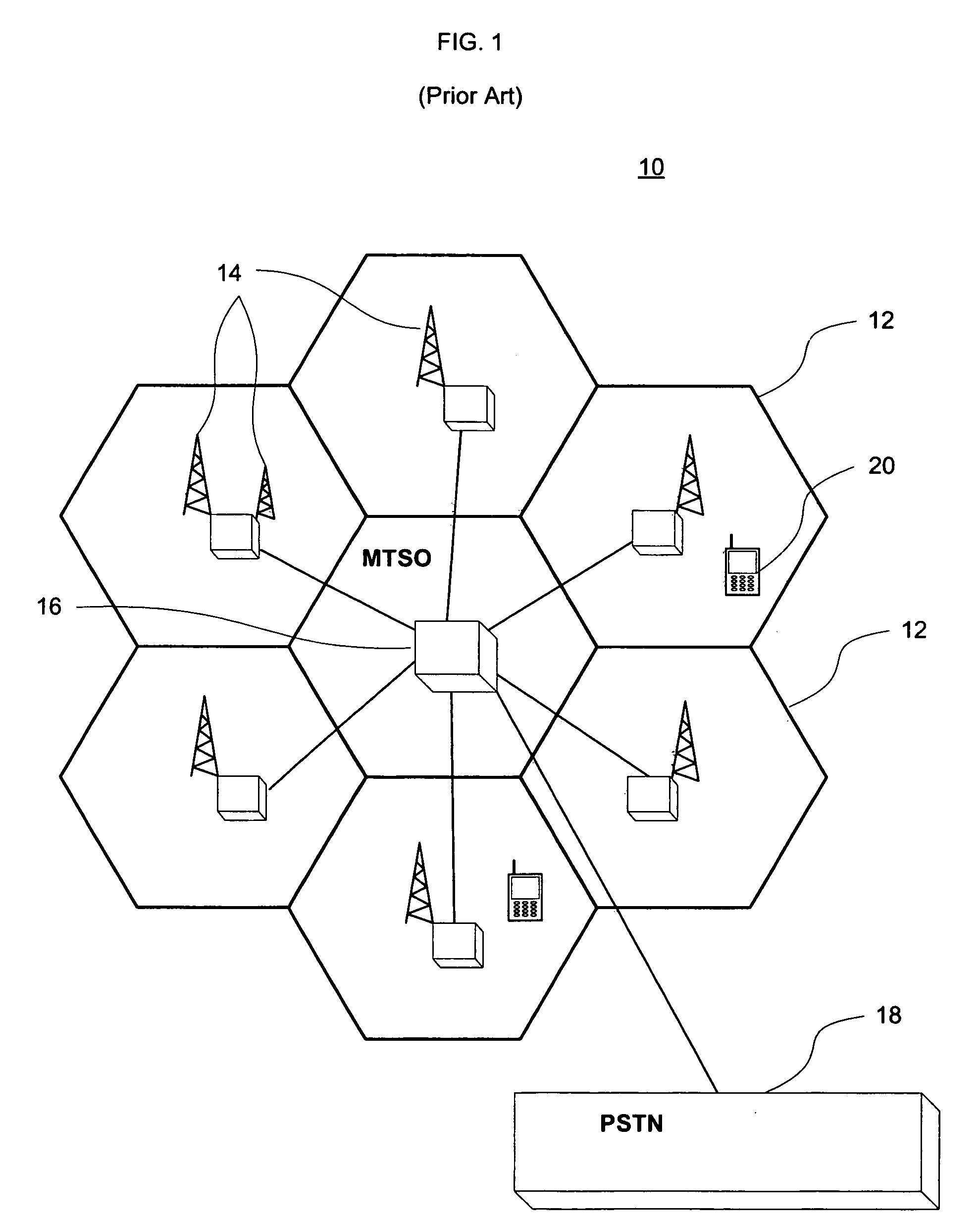
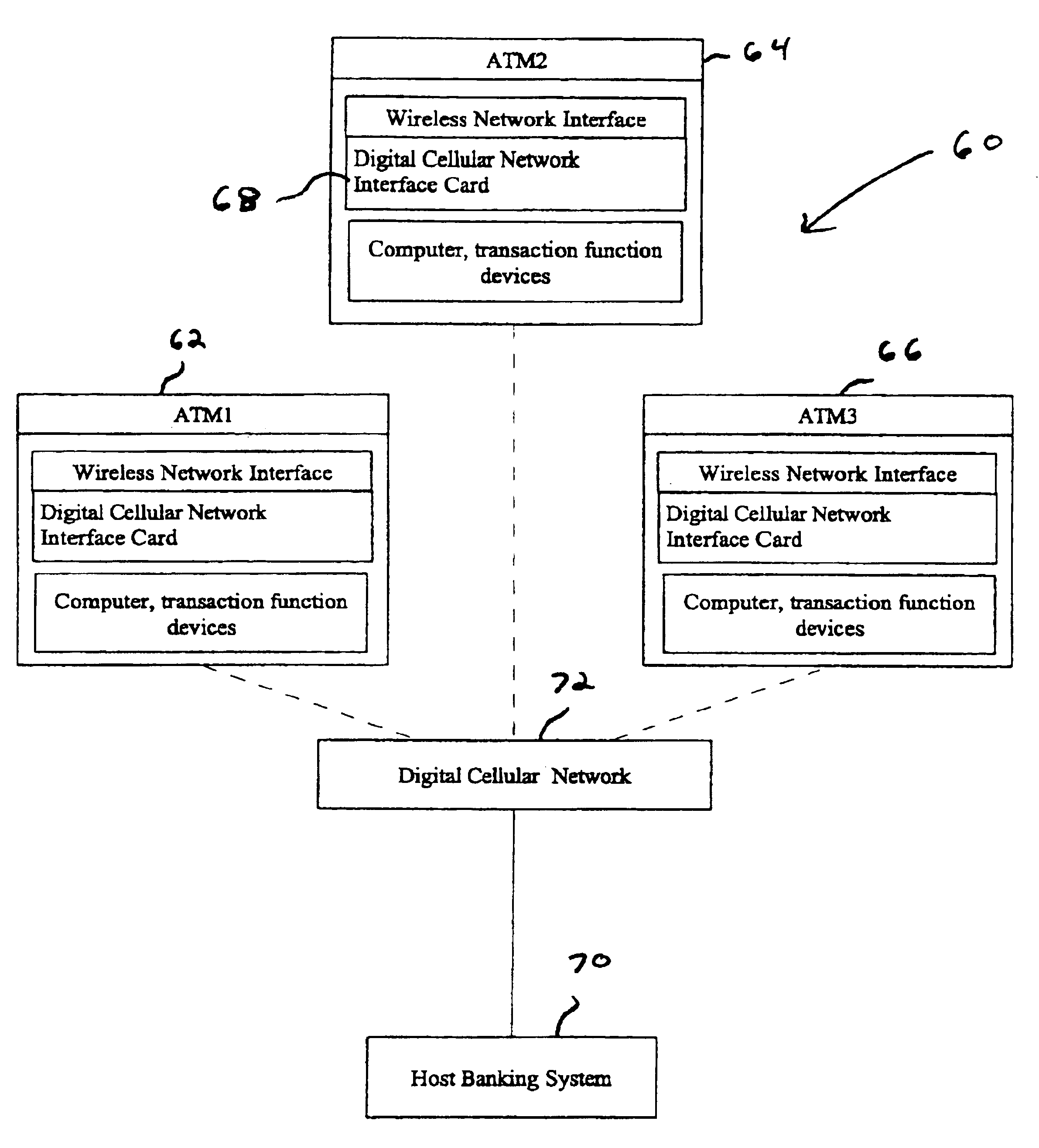
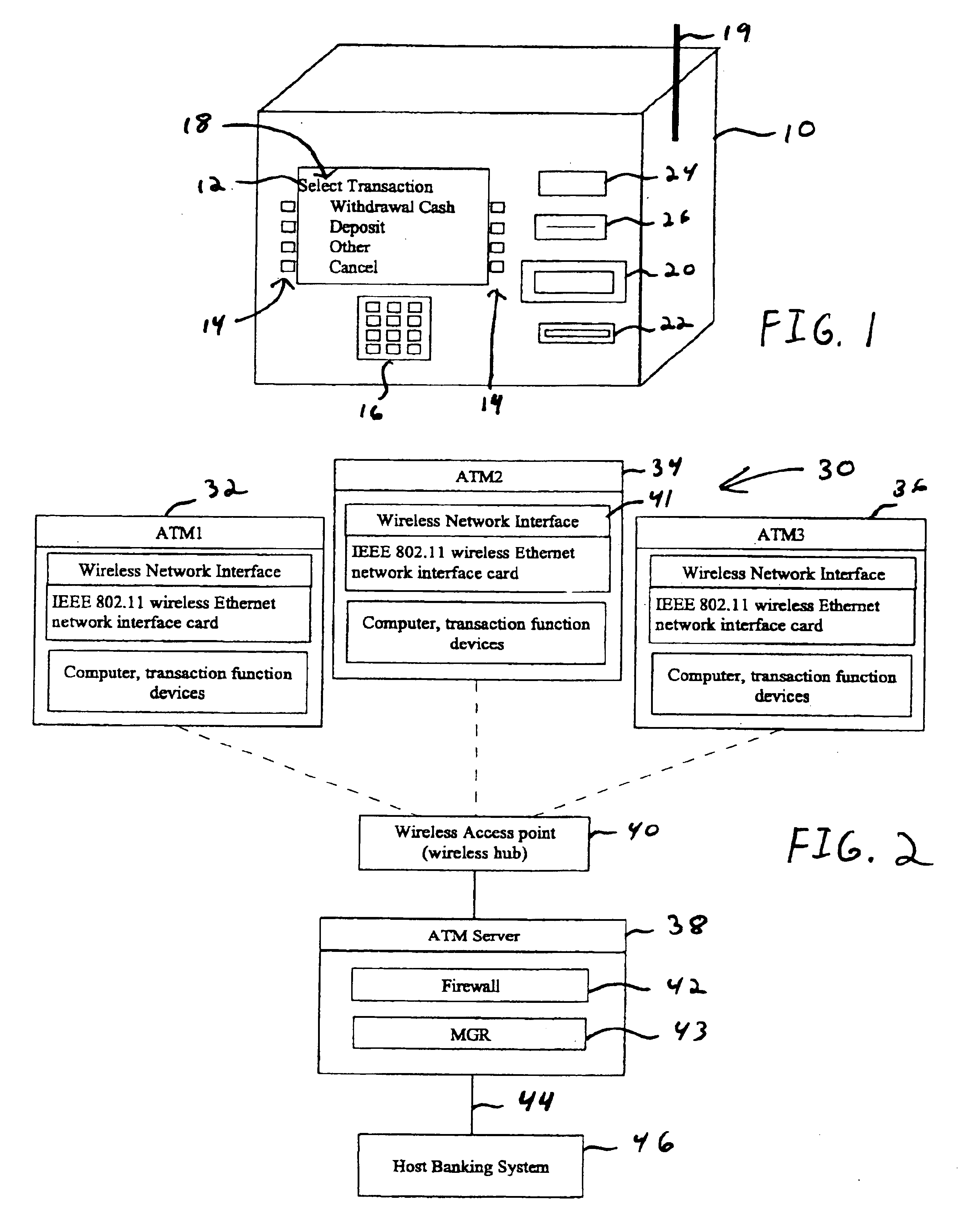
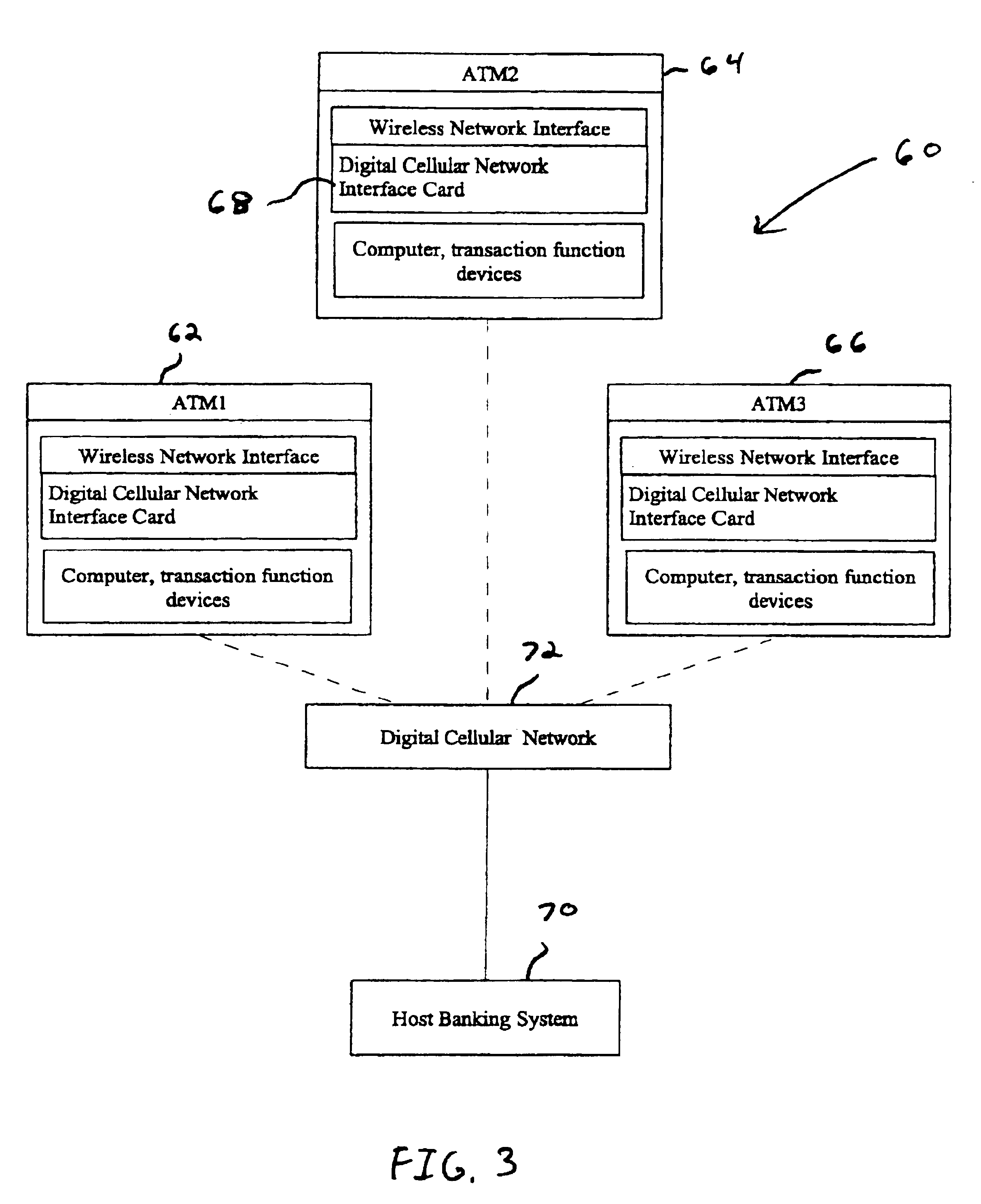
Automated banking machine system and method
InactiveUS7025256B1Reduce interceptionComplete banking machinesFinanceWireless transmissionPrivate network
A wireless ATM system (30) comprises one or more wireless ATMs (32, 34, 36) that are operative to wirelessly communicate with a wireless ATM server (38). The wireless ATMs each include a wireless network interface (41). The wireless ATM server includes a corresponding wireless access point or wireless hub (40). Wireless transmission between the wireless ATMs and wireless ATM server is secured with a wireless encryption protocol. The wireless ATM server is operative to communicate with at least one host banking system (46) through at least one public or private network (44). The wireless ATM server is operative to route transaction and event messages between the host banking system and each of the wireless ATMs using a message gateway router (43). The wireless ATM server further includes a firewall (42).
Owner:DIEBOLD SELF SERVICE SYST DIV OF DIEBOLD NIXDORF INC
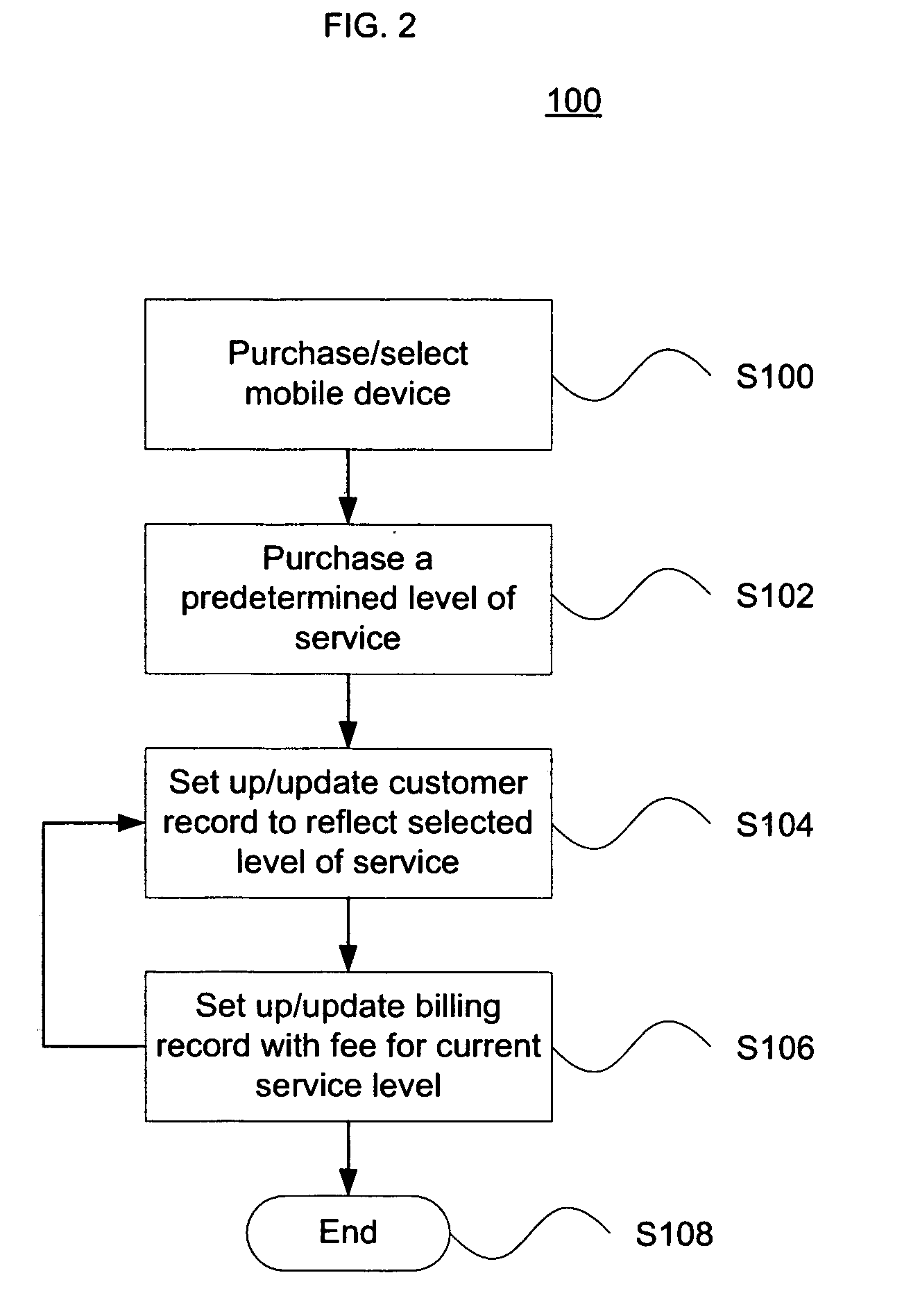
Multi-tier and secure service wireless communications networks
ActiveUS20100279653A1Power managementAccounting/billing servicesCommunications securitySecure communication
The present invention pertains to improved communication quality and security of transmission in cellular communication networks. A customer has the option to pay different fees for different tiers of service relating to voice quality, bandwidth access, and different tiers of service relating to communications security. Higher tiers may guarantee a specific vocoder or bit rate is used, or guarantee a specific encryption protocol is use to ensure secure communications. Different tiers may be associated with customers' records for billing purposes. The network may afford high end devices higher voice quality and / or security via a lookup table indicating what level of service is associated with a given device. Calling or receiving devices may negotiate with each other to change to a more robust vocoder or bit rate to ensure a higher quality and / or security. Furthermore, the user may opt to change the quality and / or security level before or during a call.
Owner:PRIVILEGE WIRELESS
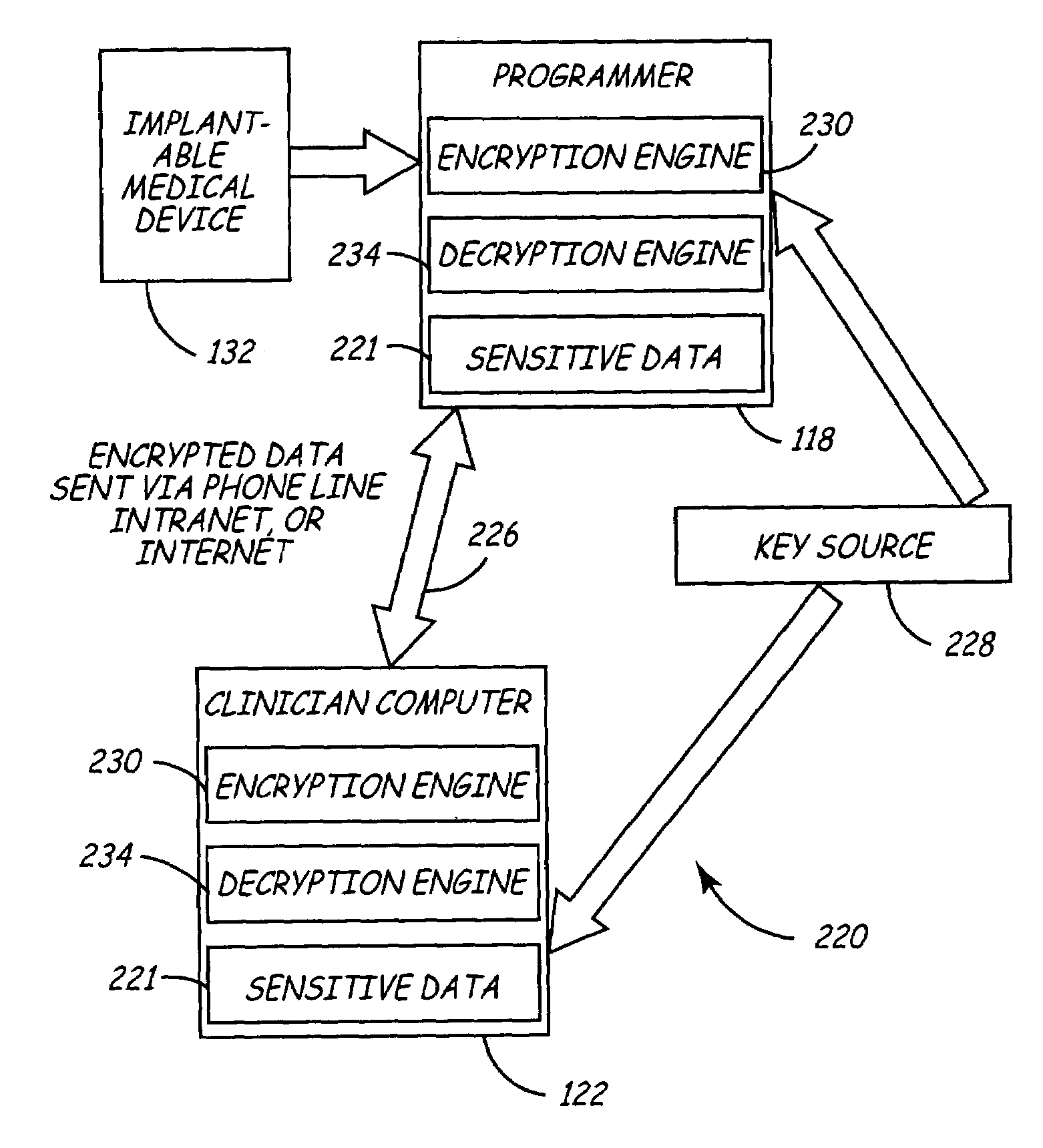
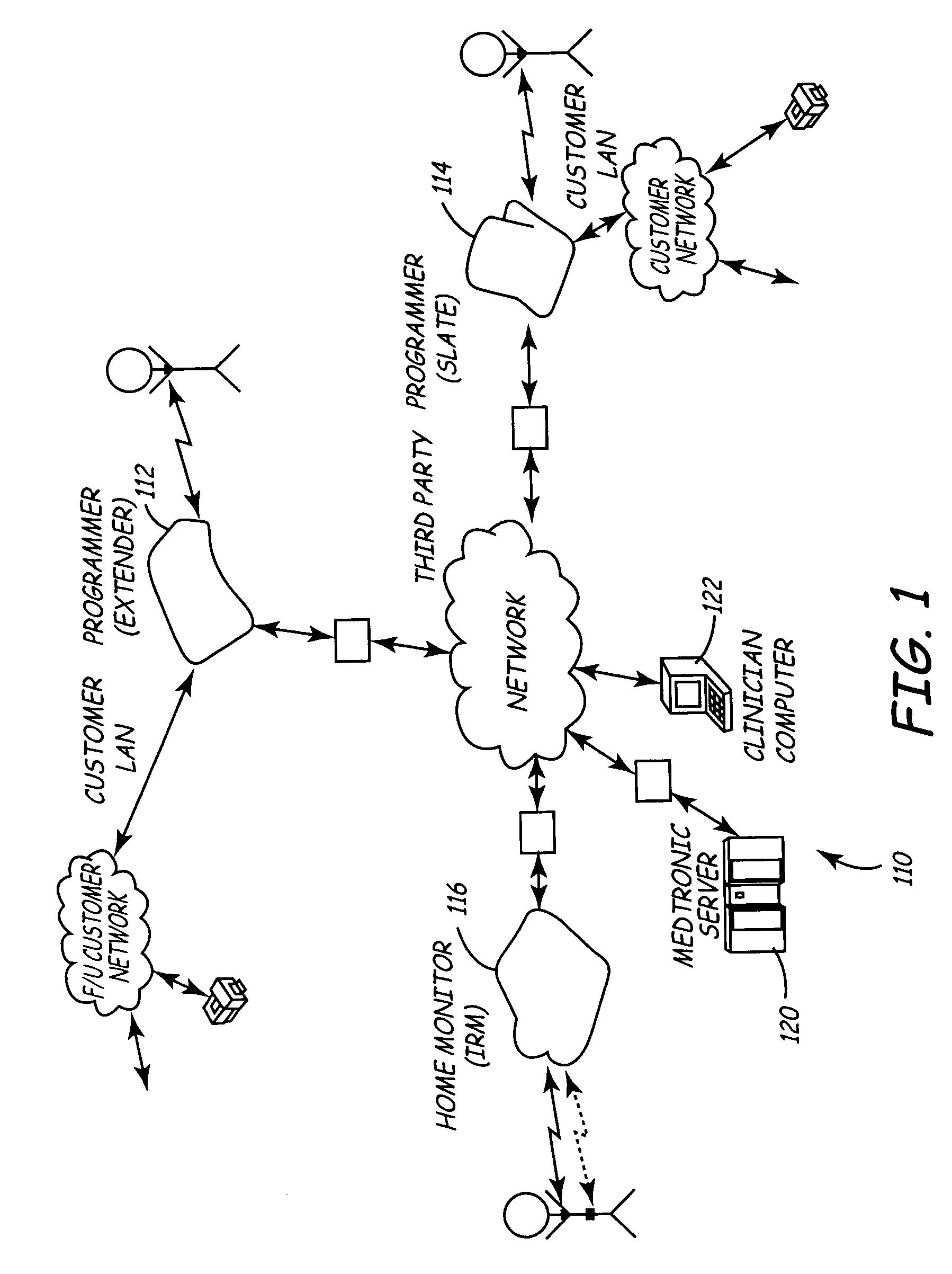
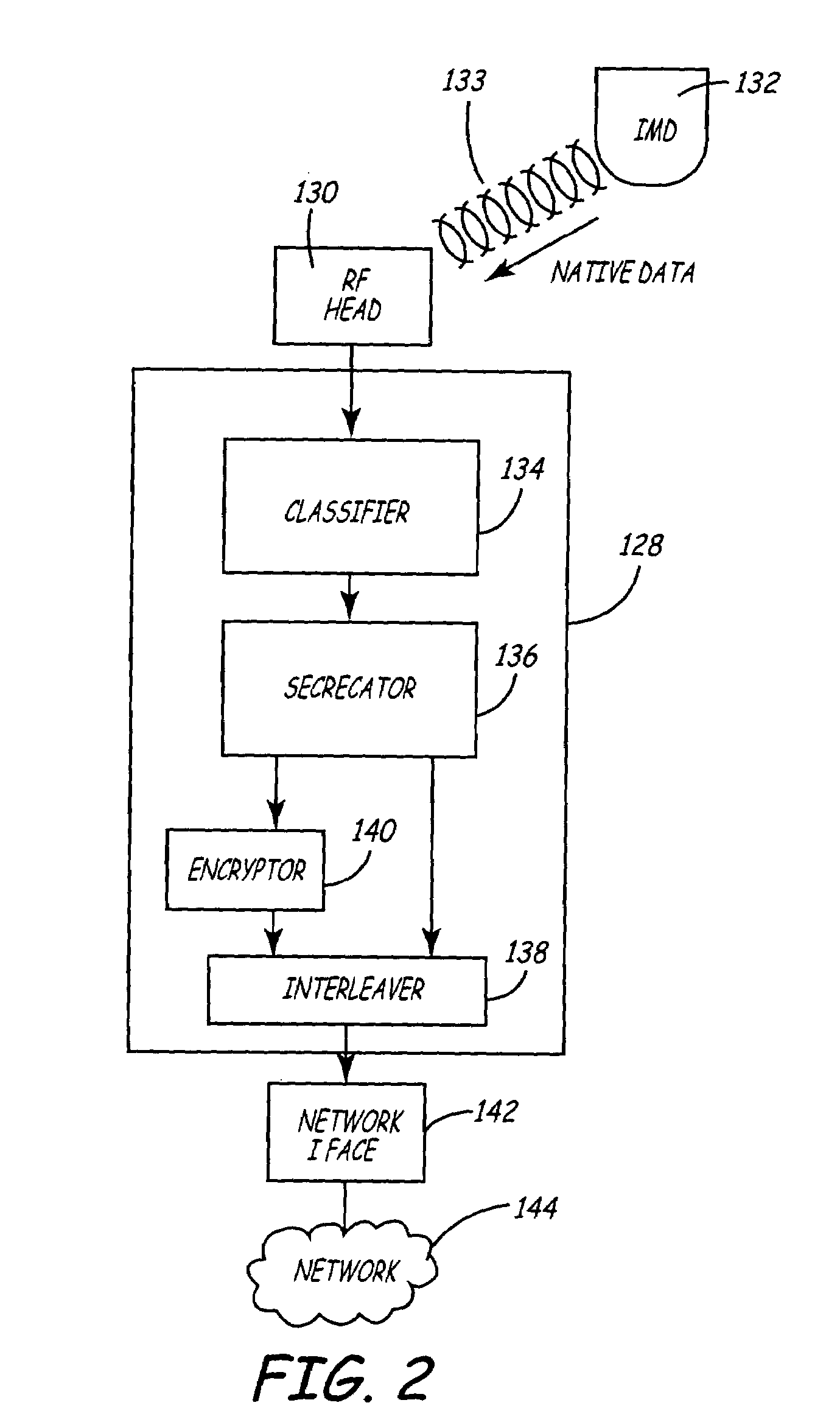
Variable encryption scheme for data transfer between medical devices and related data management systems
InactiveUS7027872B2Ensure authenticityEnsure integrityElectrotherapyData processing applicationsData centerData management
Owner:MEDTRONIC INC
Automated banking machine system and method
InactiveUS6796490B1Reduce interceptionComplete banking machinesFinanceWireless transmissionPrivate network
A wireless ATM system (30) comprises one or more wireless ATMs (32, 34, 36) that are operative to wirelessly communicate with a wireless ATM server (38). The wireless ATMs each include a wireless network interface (41). The wireless ATM server includes a corresponding wireless access point or wireless hub (40). Wireless transmission between the wireless ATMs and wireless ATM server is secured with a wireless encryption protocol. The wireless ATM server is operative to communicate with at least one host banking system (46) through at least one public or private network (44). The wireless ATM server is operative to route transaction and event messages between the host banking system and each of the wireless ATMs using a message gateway router (43). The wireless ATM server further includes a firewall (42).
Owner:DIEBOLD SELF SERVICE SYST DIV OF DIEBOLD NIXDORF INC
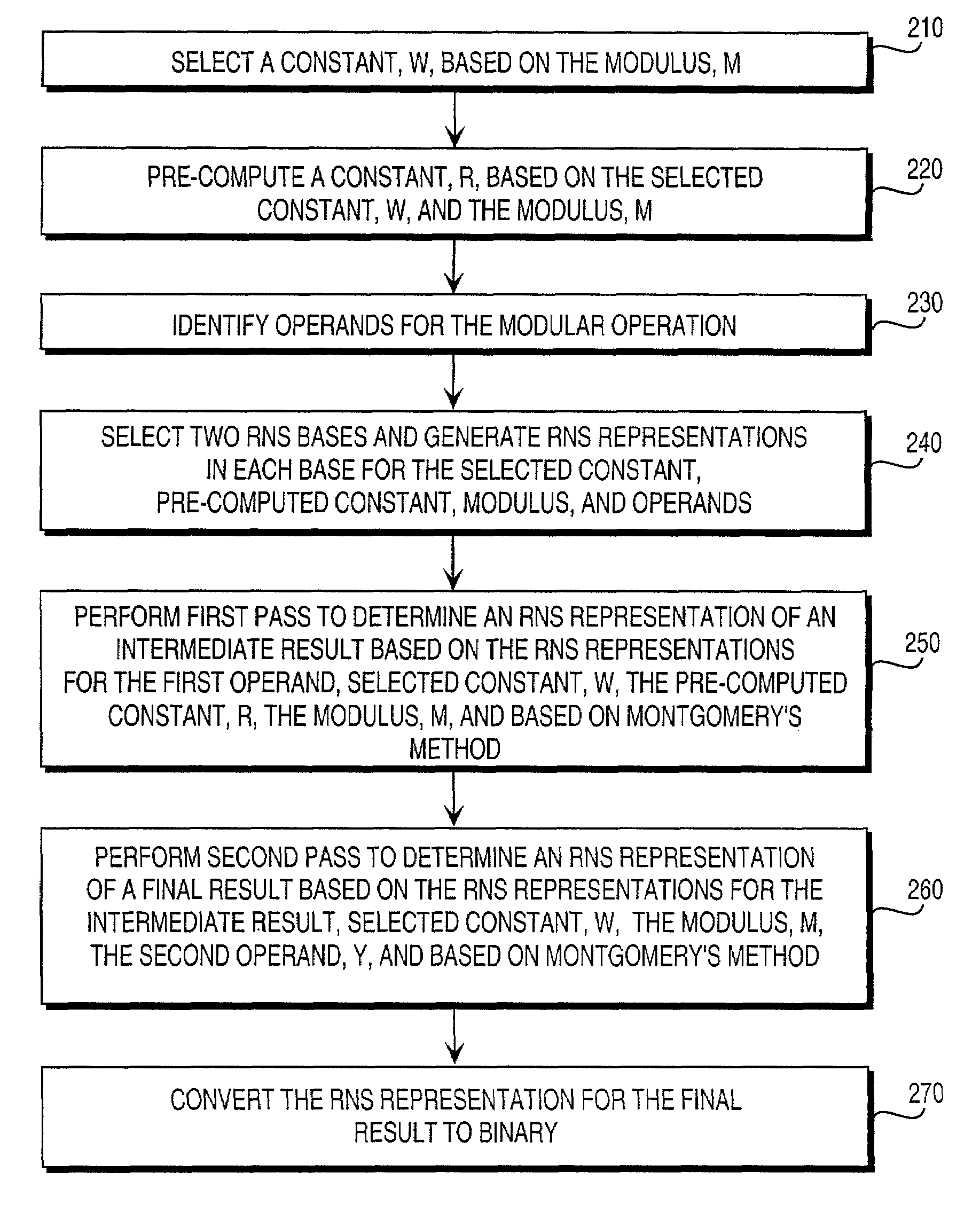
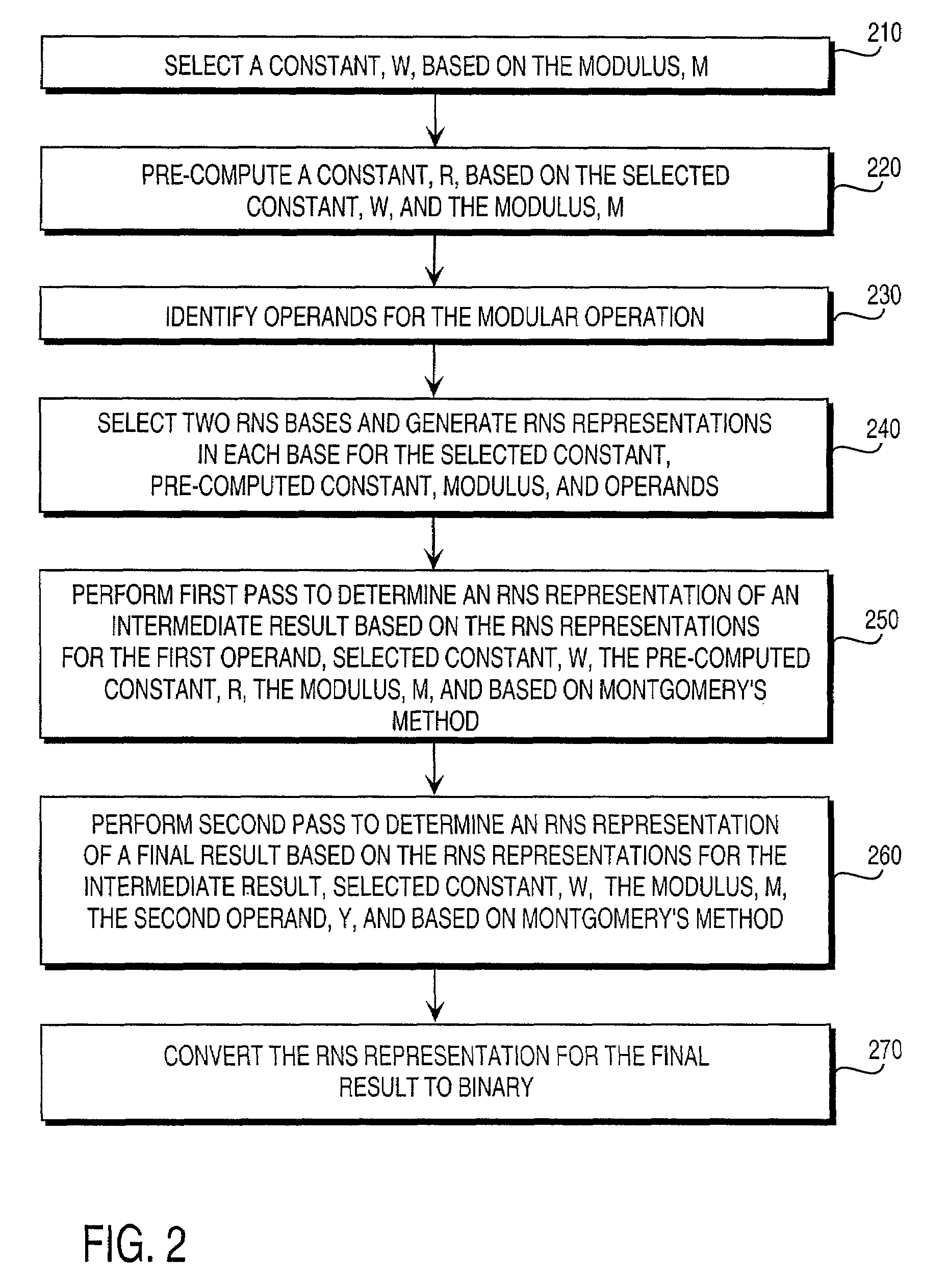
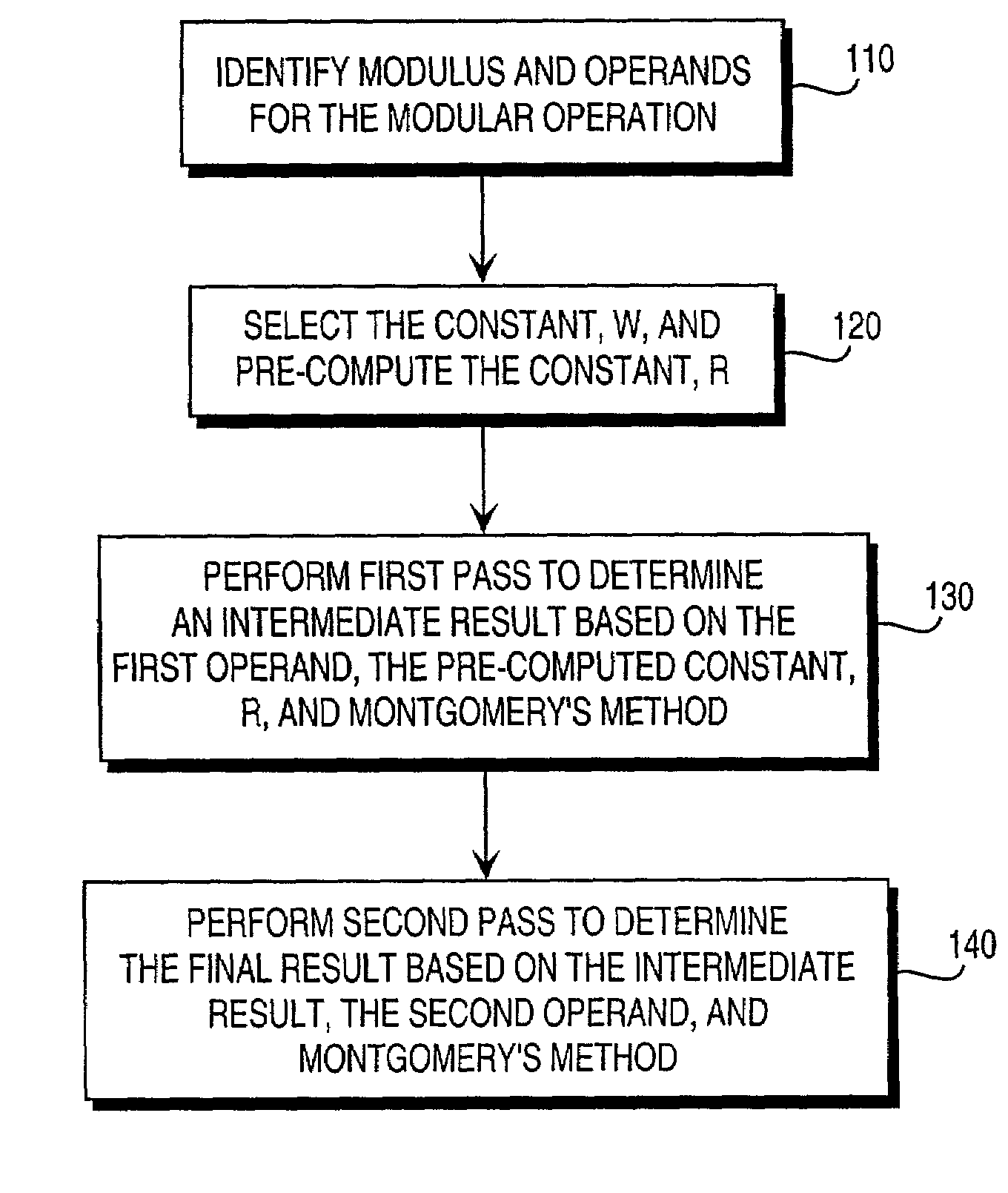
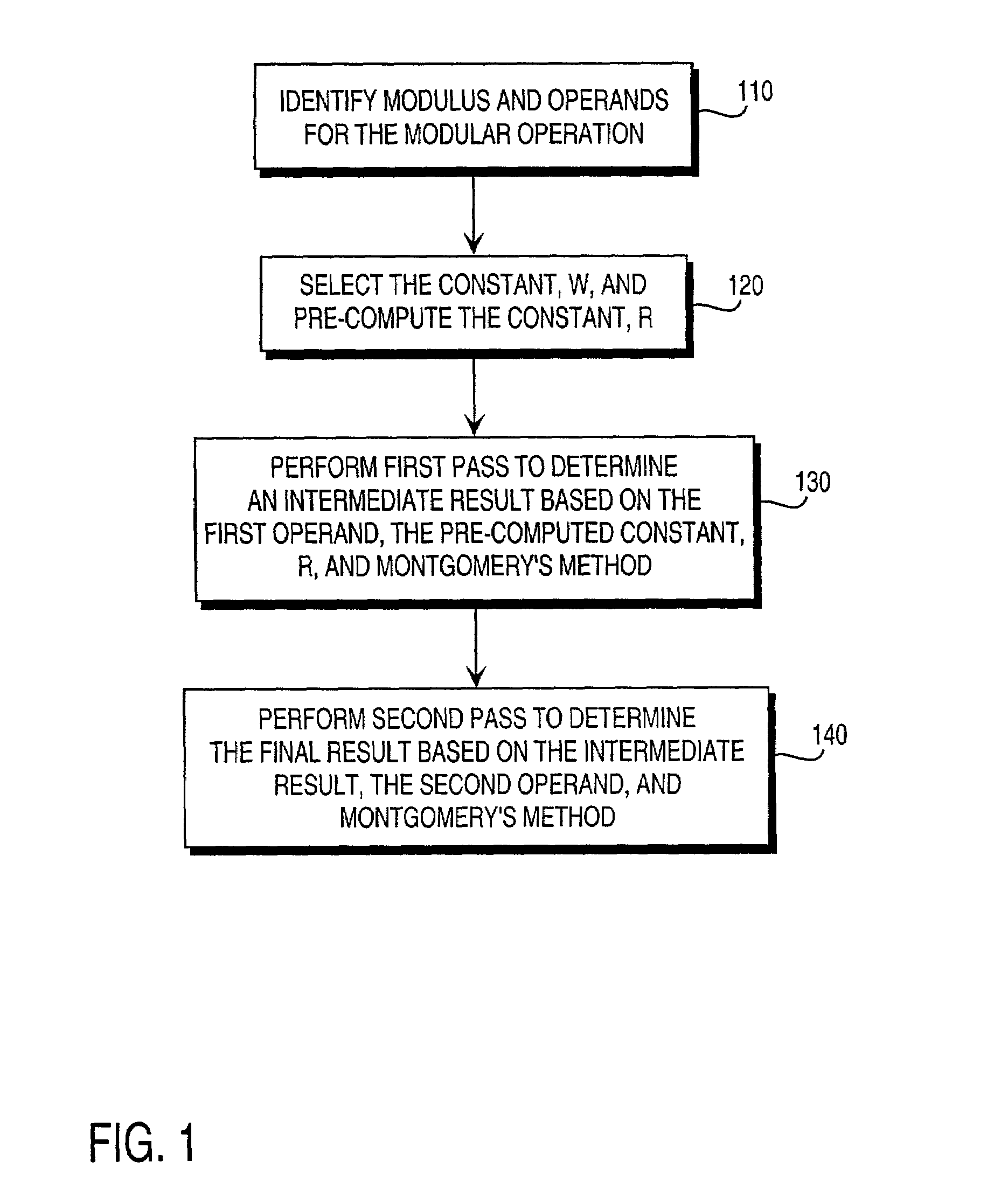
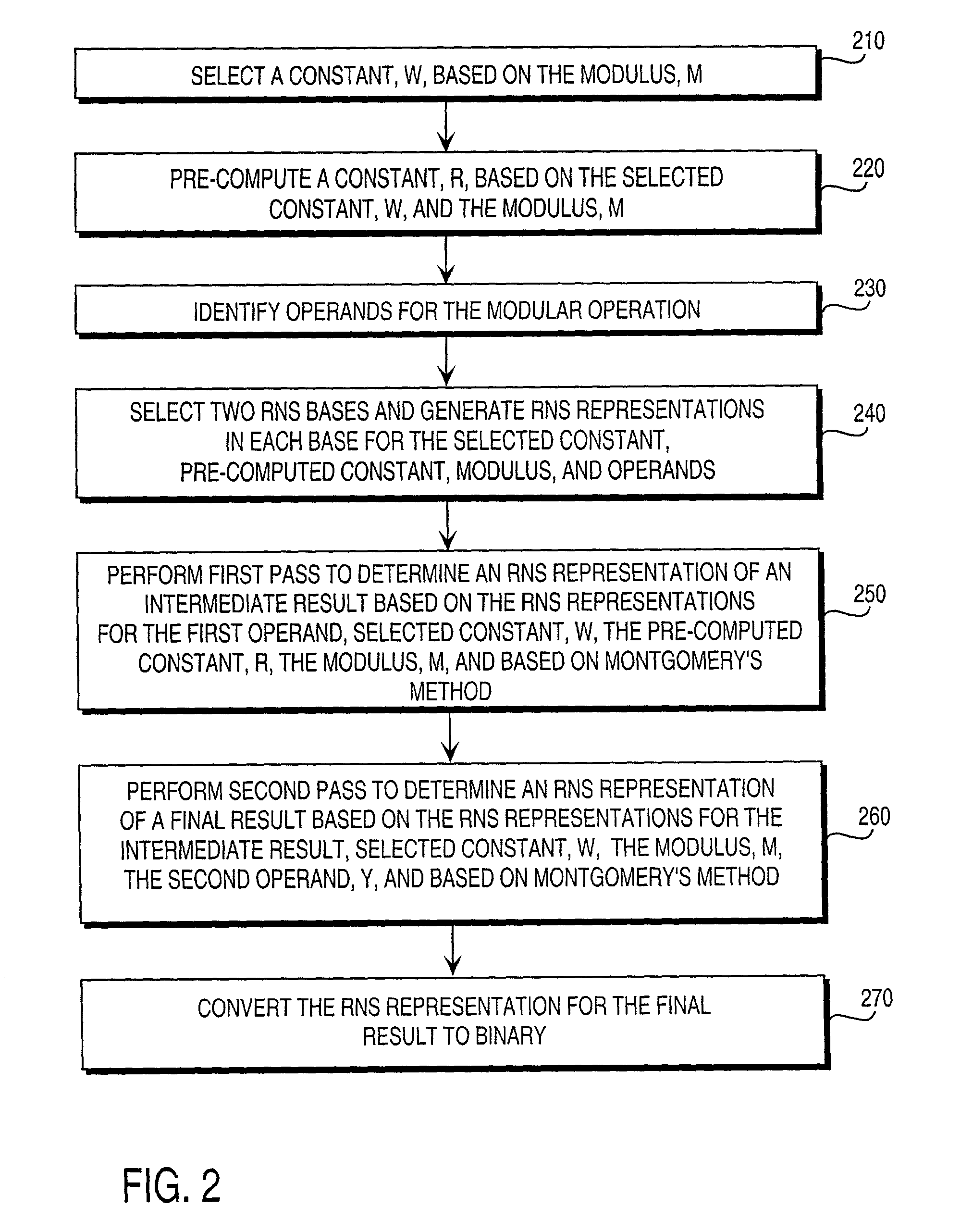
Residue number system based pre-computation and dual-pass arithmetic modular operation approach to implement encryption protocols efficiently in electronic integrated circuits
InactiveUS7027598B1Computations using contact-making devicesComputation using non-contact making devicesProcessor registerModularity
A pre-computation and dual-pass modular operation approach to implement encryption protocols efficiently in electronic integrated circuits is disclosed. An encrypted electronic message is received and another electronic message generated based on the encryption protocol. Two passes of Montgomery's method are used for a modular operation that is associated with the encryption protocol along with pre-computation of a constant based on a modulus. The modular operation may be a modular multiplication or a modular exponentiation. Modular arithmetic may be performed using the residue number system (RNS) and two RNS bases with conversions between the two RNS bases. A minimal number of register files are used for the computations along with an array of multiplier circuits and an array of modular reduction circuits. The approach described allows for high throughput for large encryption keys with a relatively small number of logical gates.
Owner:CISCO TECH INC
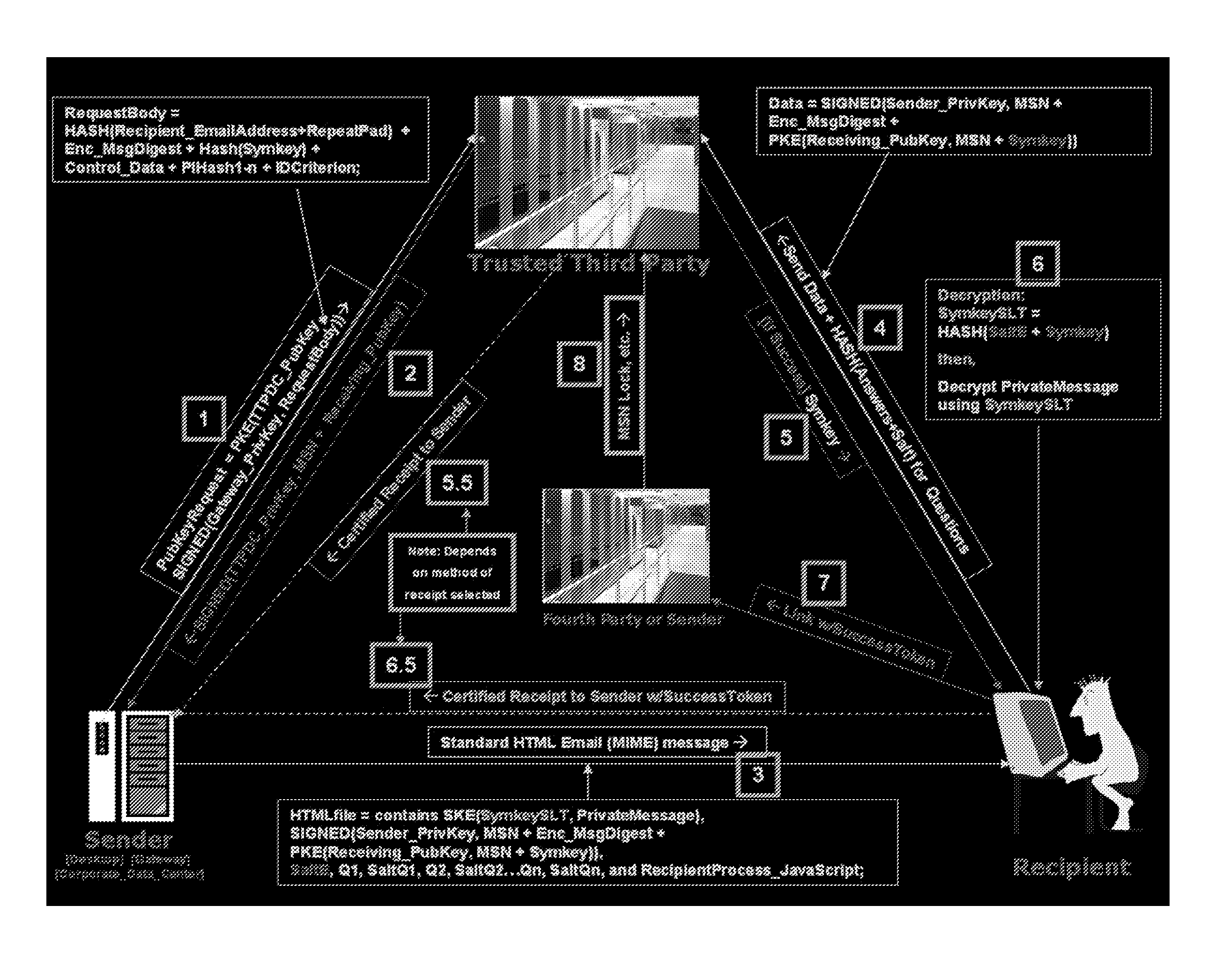
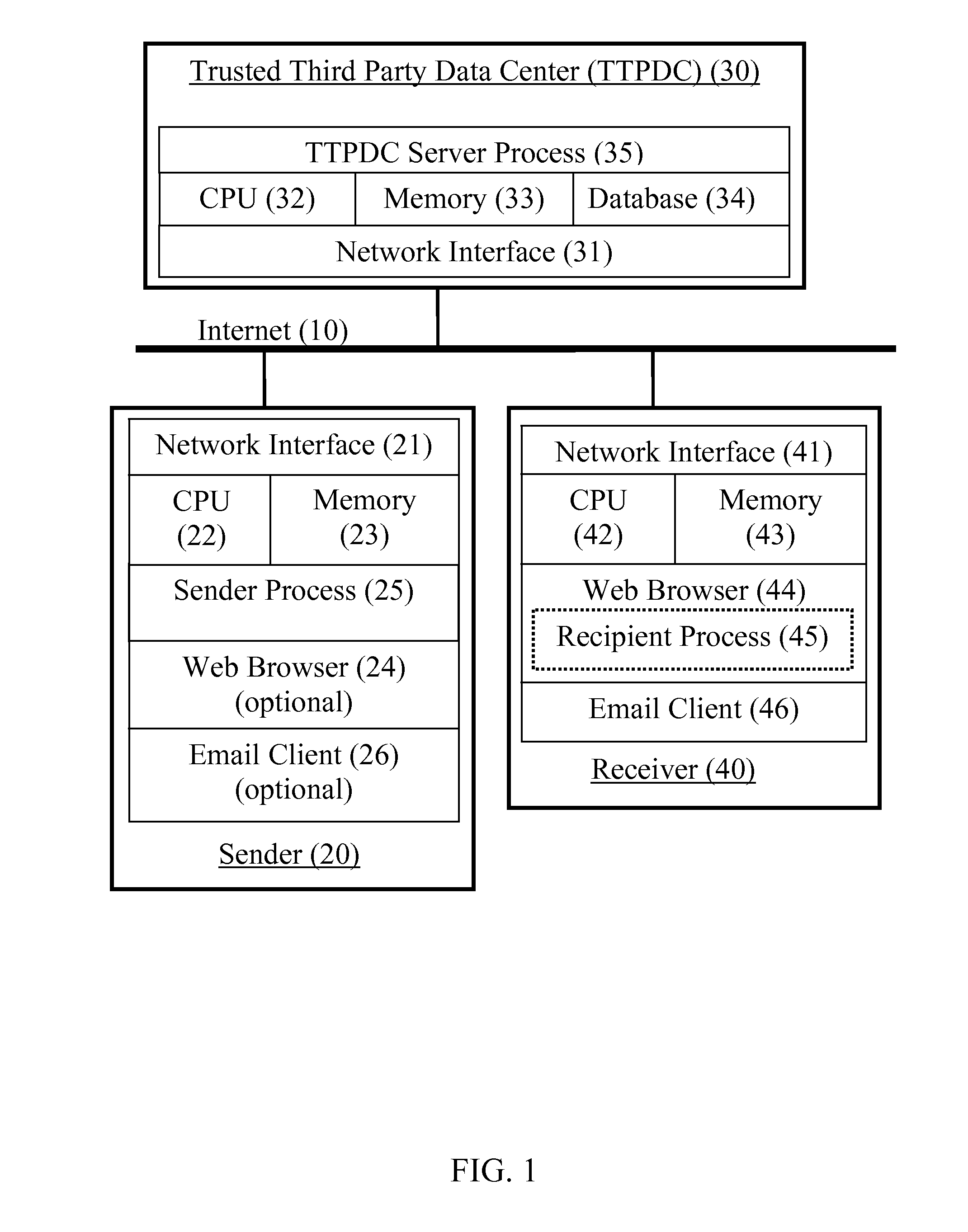
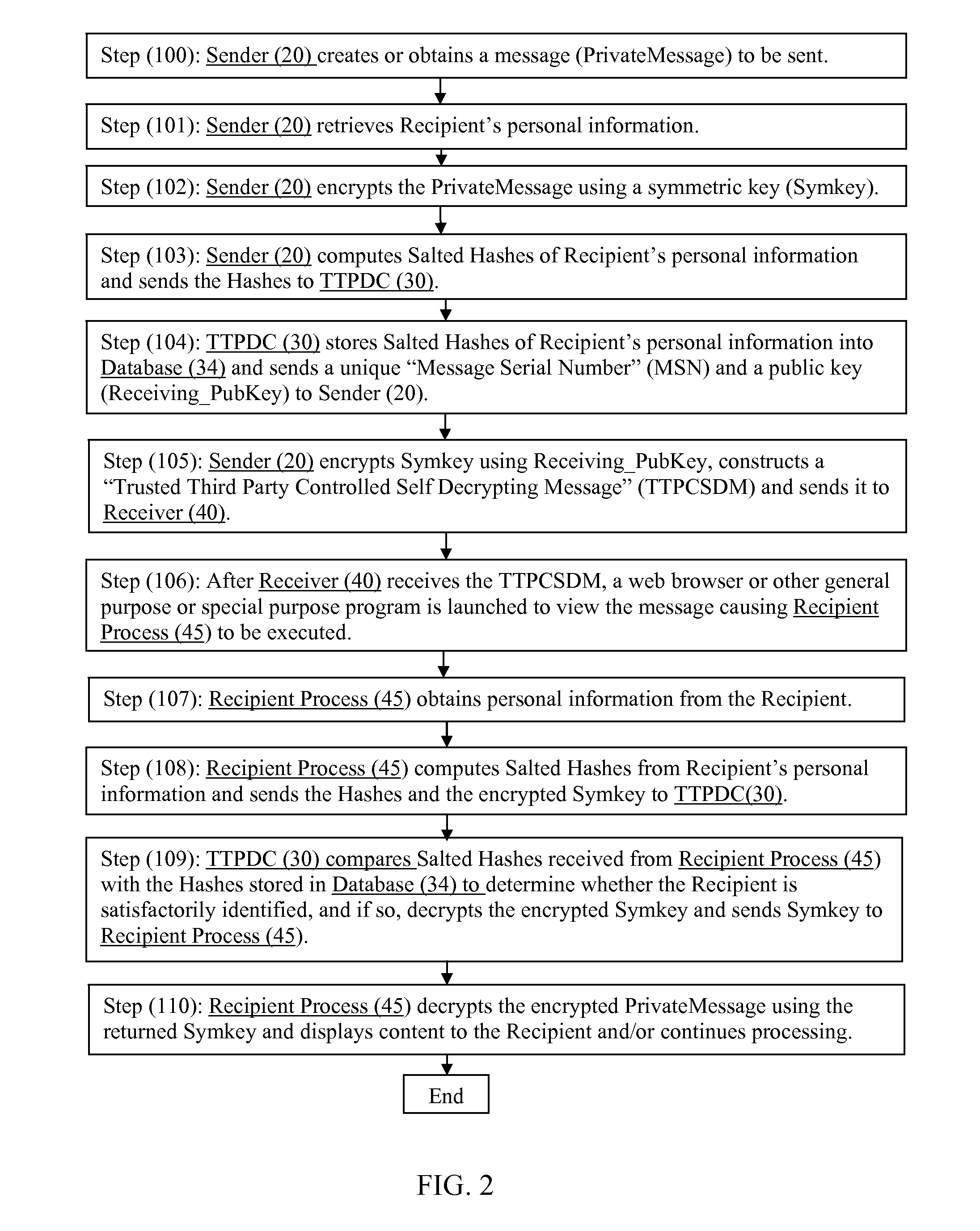
Secure messaging using a trusted third party
A system and method to send a secure message from a sender to a recipient using strong encryption protocols without the need for the recipient to create a public / private key pair and by using a third party to appropriately identify the recipient without revealing actual identification information to the third party. Upon successful identification, the third party is able to provide a recipient with information that enables recipient to create and use the actual decryption key without revealing the actual decryption key to the third party.
Owner:COOK DAVID P +1
Quality of service methods and systems for mobile printing
InactiveUS20080084578A1Preventing the media from fallingDigital output to print unitsSecure communicationQuality of service
Systems and methods for secure, remote printing includes a mobile device (e.g., cell phone or PDA) establishing a secure communication connection with a mobile printer and a server, such a connection using one or more encryption protocols (e.g., SSL, TLS, etc.). The server encrypts the requested data and transmits it to the printer via the secure connection, whereon the printer decrypts and prints the data. The mobile device can, according to other aspects of the invention, logs operational performance characteristic of the printer, the server, and / or the communication connections therebetween. A media cartridge can be provided includes an enclosure having a substantially planar shape, wherein each of its length and width dimensions are greater than its height. An opening is disposed along a width-wise edge (e.g., a “front” of the enclosure), and one or more regions are also disposed on opposing length-wise edges (e.g., a “left side” and a “right side” of the enclosure). The regions permit a user to see and / or exert a force on sheet media (e.g., paper) contained within the enclosure.
Owner:AIRPRINT NETWORKS
System and method for secure mobile commerce
ActiveUS7512236B1Synchronising transmission/receiving encryption devicesPayment architectureSecure communicationNetwork Communication Protocols
A method and system for secure communications in a mobile commerce system having a pre-defined communications protocol. The method and system are backward compatible, providing reader configured to distinguish between a first type of transponder using an unencrypted protocol and a second type of transponder using an encrypted protocol. The reader determines the type of transponder and alters its communications protocol accordingly. The encrypted protocol provides for encrypted communications within the constraints of the existing pre-defined communications protocol.
Owner:MARK IV INDS
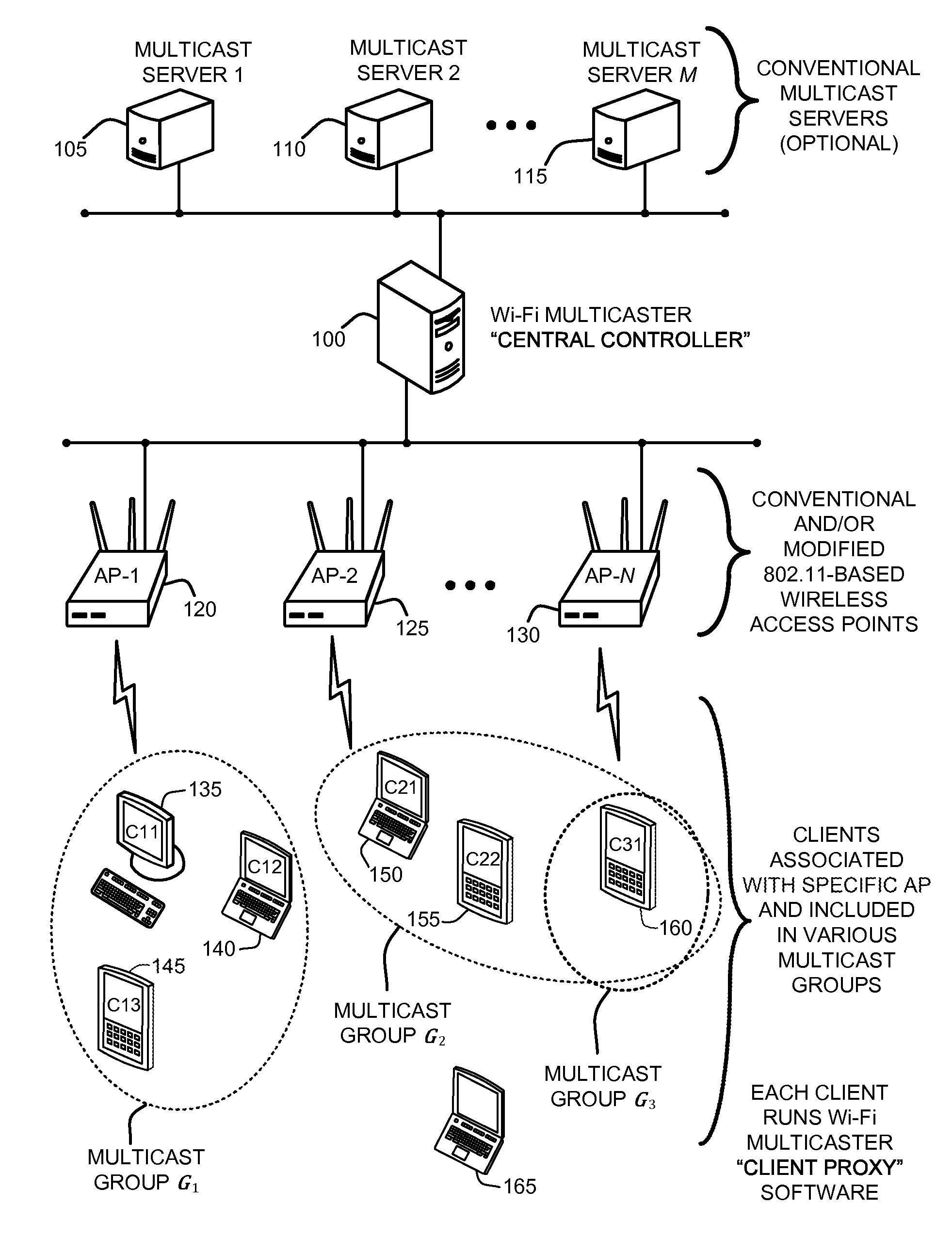
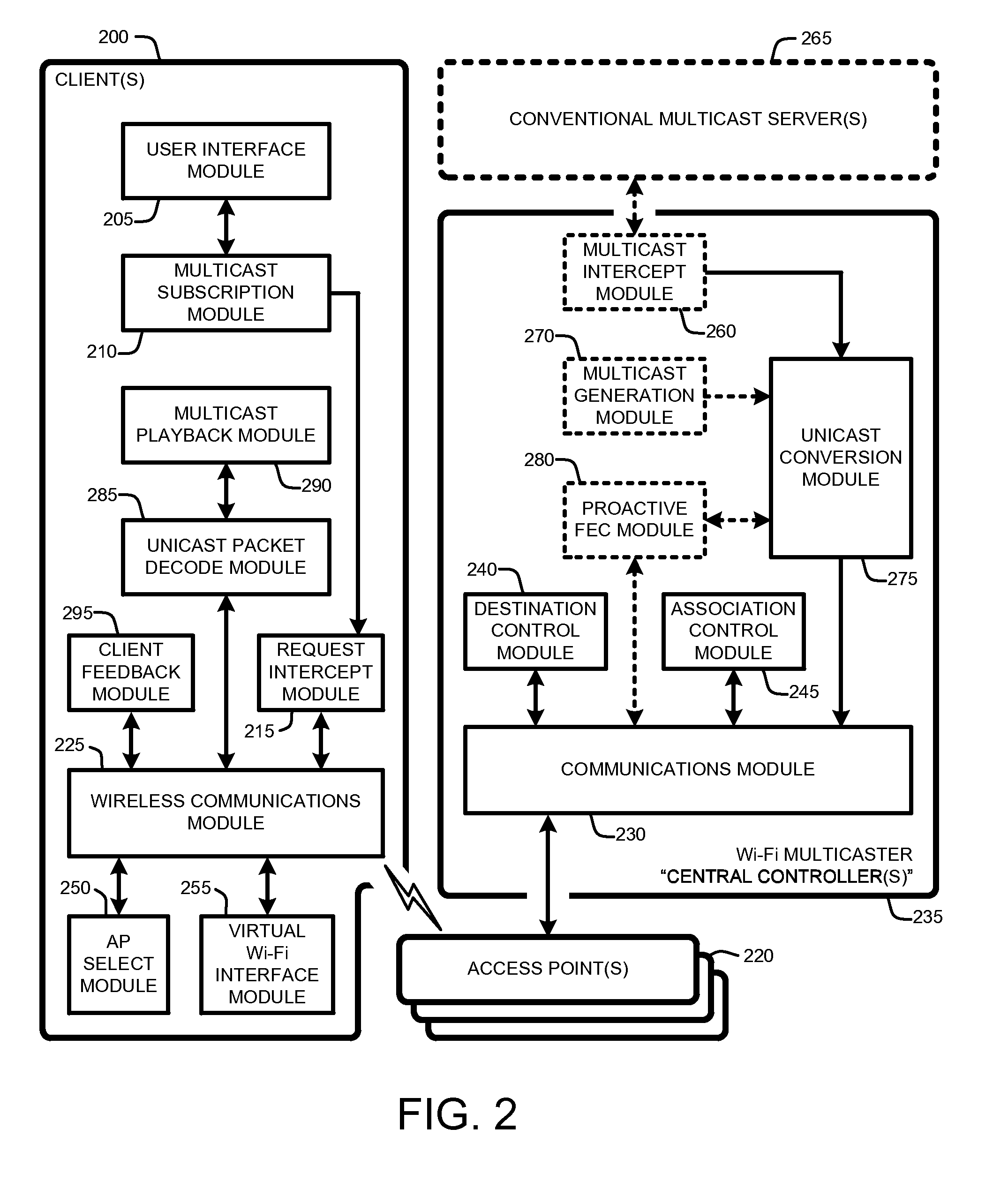
EFFICIENT AND RELIABLE MULTICAST OVER A Wi-Fi NETWORK
ActiveUS20110211517A1Reduce lossesLittle overheadError prevention/detection by using return channelBroadcast specific applicationsWi-FiPacket loss
A “Wi-Fi Multicaster” provides a practical and efficient Wi-Fi multicast system for environments having potentially large numbers of Wi-Fi clients. Significantly, the Wi-Fi Multicaster does not require any changes to the 802.11 protocol, or to the underlying Wi-Fi infrastructure. In various embodiments, the Wi-Fi Multicaster uses pseudo-broadcast, and augments it with destination control, association control and optional proactive FEC (forward error correction) to improve multicast performance. More specifically, the Wi-Fi Multicaster system converts multicast packets to targeted unicast transmissions. To minimize the amount of airtime consumed, the Wi-Fi Multicaster uses destination control in combination with various algorithms for association control. Further, in various embodiments, the Wi-Fi Multicaster includes an adaptive, proactive FEC scheme to reduce overall packet losses. Finally, to overcome the challenges posed by encryption protocols such as 802.1x, the Wi-Fi Multicaster uses a “virtual multicast interface” that allows clients to “share” a common key for each multicast.
Owner:MICROSOFT TECH LICENSING LLC
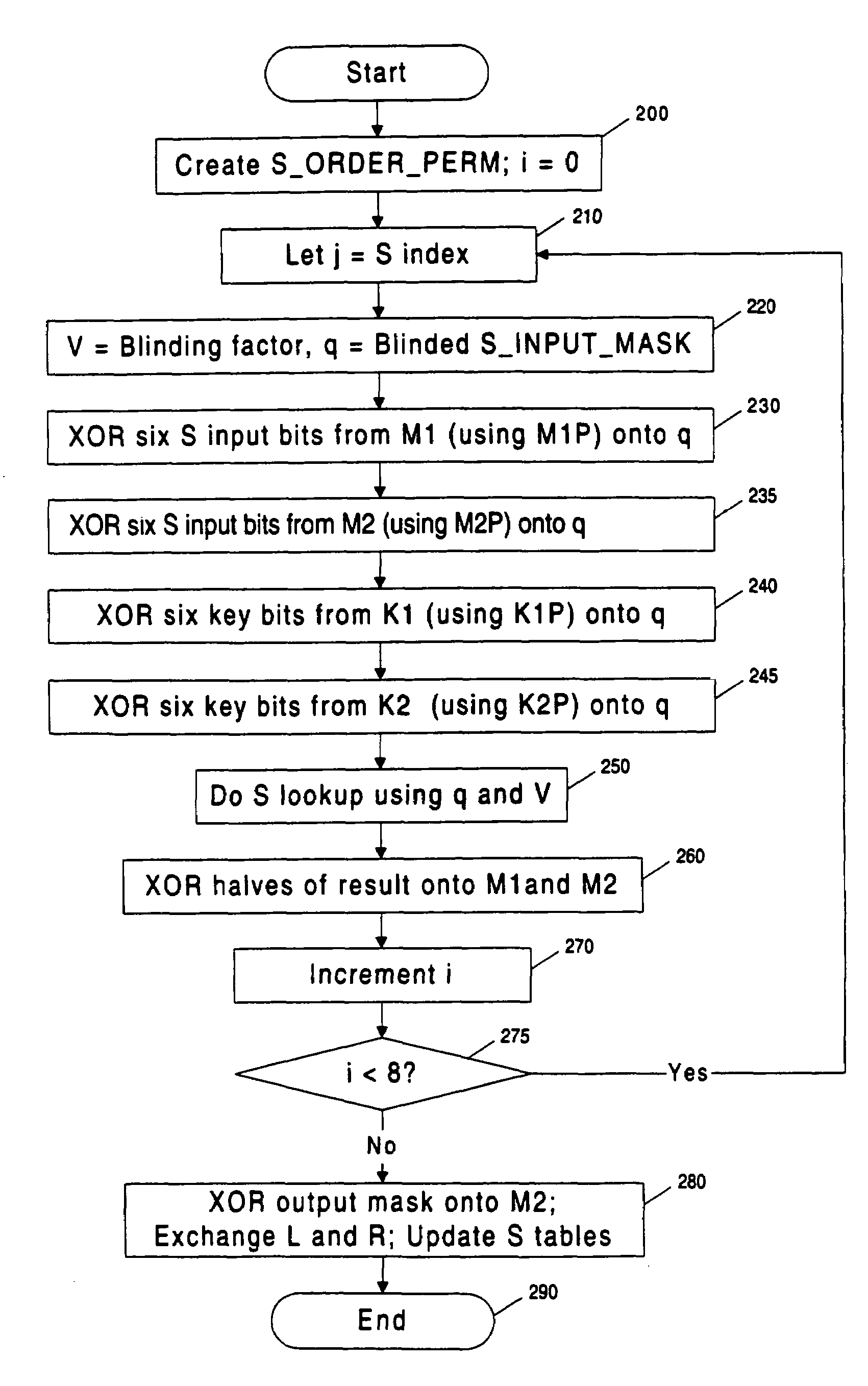
Cryptographic computation using masking to prevent differential power analysis and other attacks
InactiveUS7668310B2Easy to convertInhibition of informationEncryption apparatus with shift registers/memoriesComputer security arrangementsPlaintextPower analysis
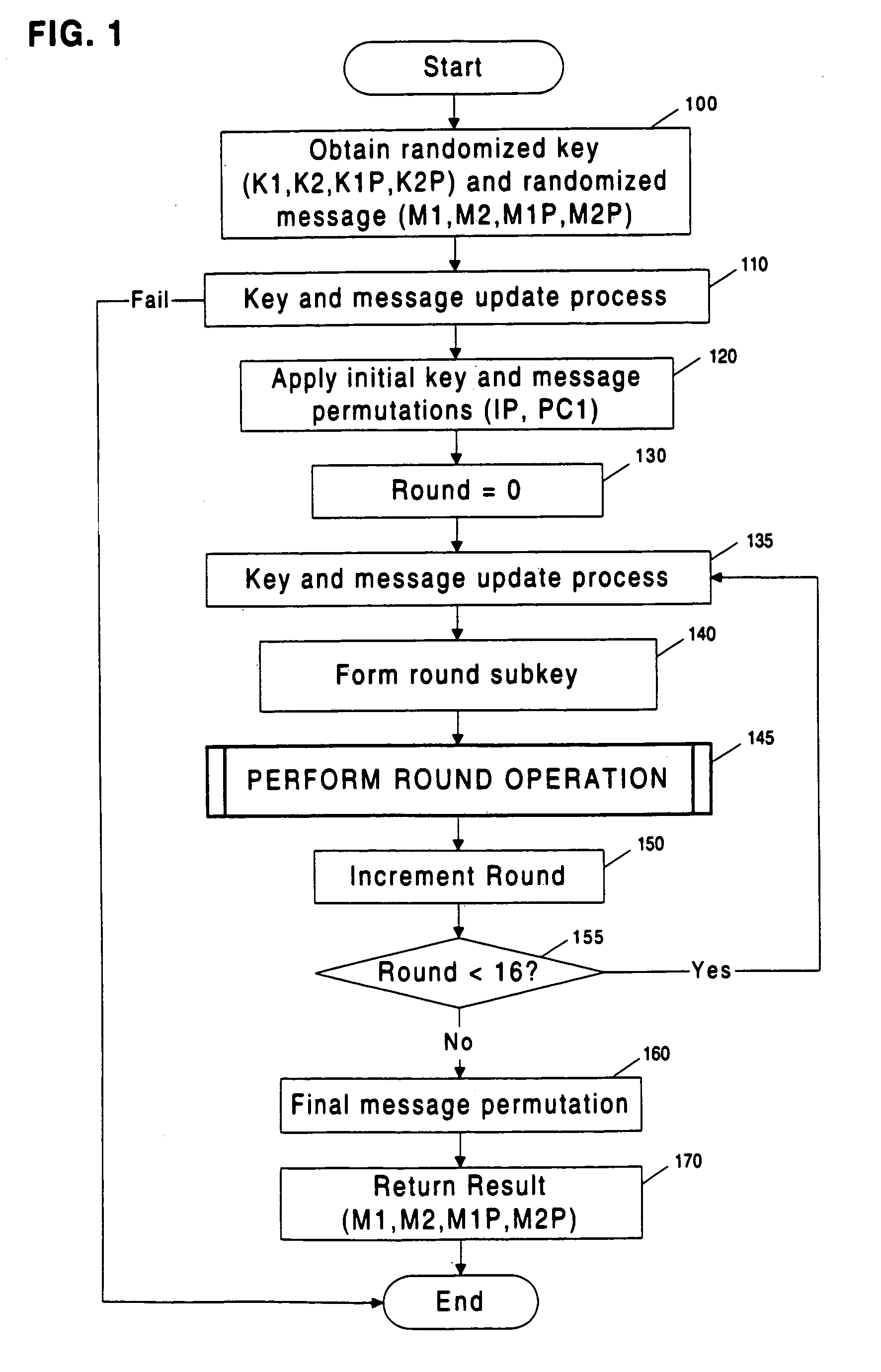
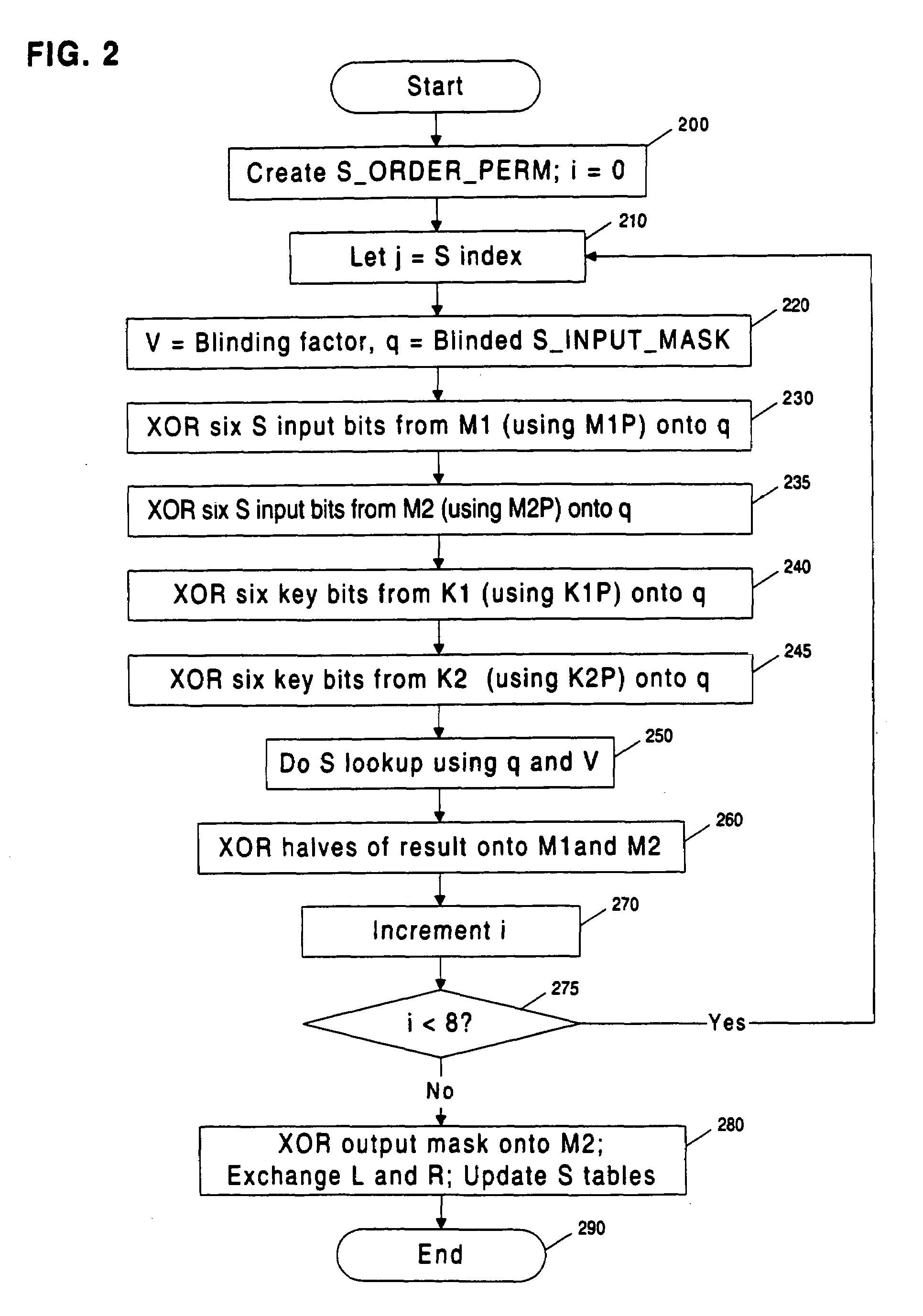
Methods and apparatuses are disclosed for improving DES and other cryptographic protocols against external monitoring attacks by reducing the amount (and signal-to-noise ratio) of useful information leaked during processing. An improved DES implementation of the invention instead uses two 56-bit keys (K1 and K2) and two 64-bit plaintext messages (M1 and M2), each associated with a permutation (i.e., K1P, K2P and M1P, M2P) such that K1P{K1} XOR K2P {K2} equals the “standard” DES key K, and M1P{M1} XOR M2P{M2} equals the “standard” message. During operation of the device, the tables are preferably periodically updated, by introducing fresh entropy into the tables faster than information leaks out, so that attackers will not be able to obtain the table contents by analysis of measurements. The technique is implementable in cryptographic smartcards, tamper resistant chips, and secure processing systems of all kinds.
Owner:CRYPTOGRAPHY RESEARCH
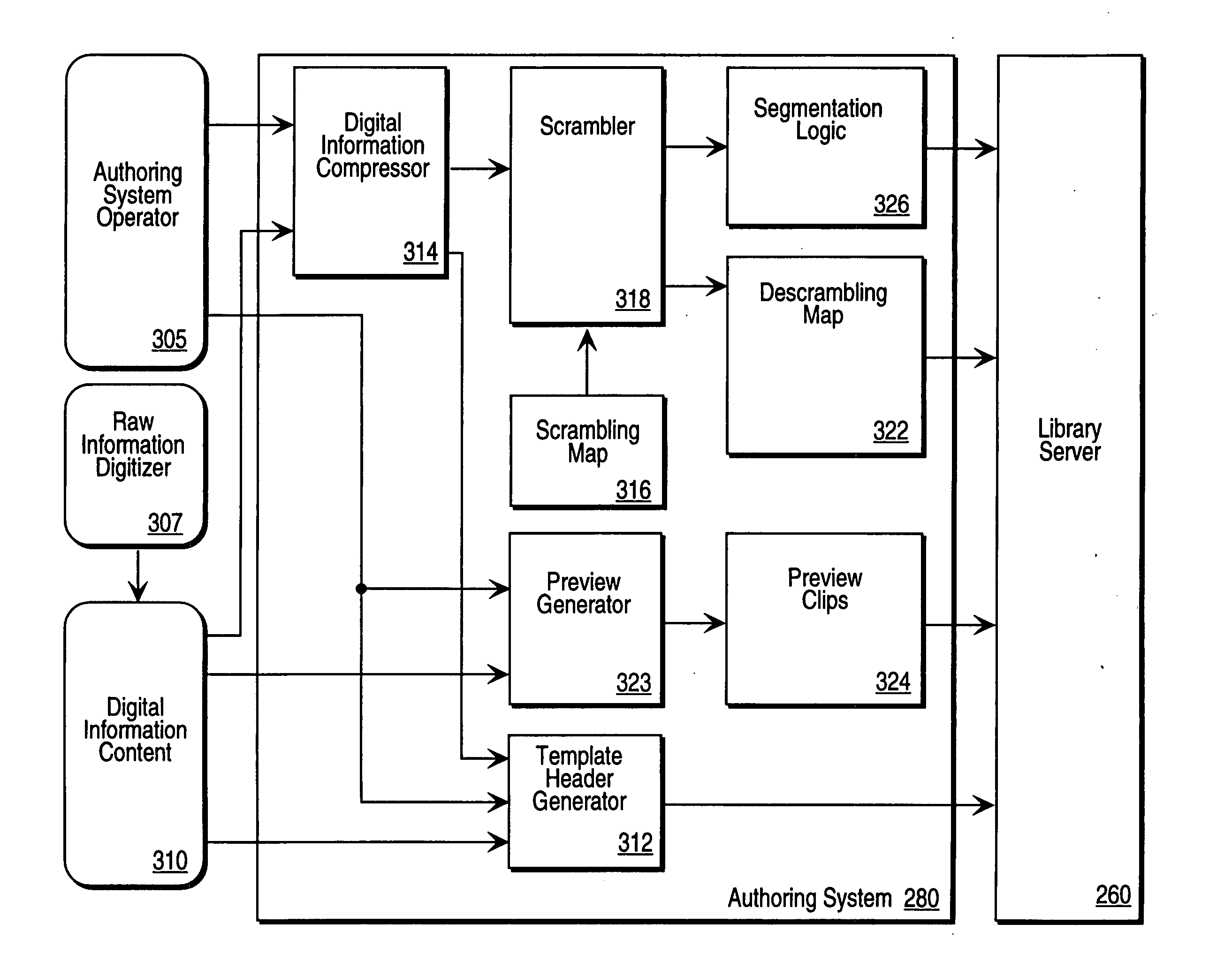
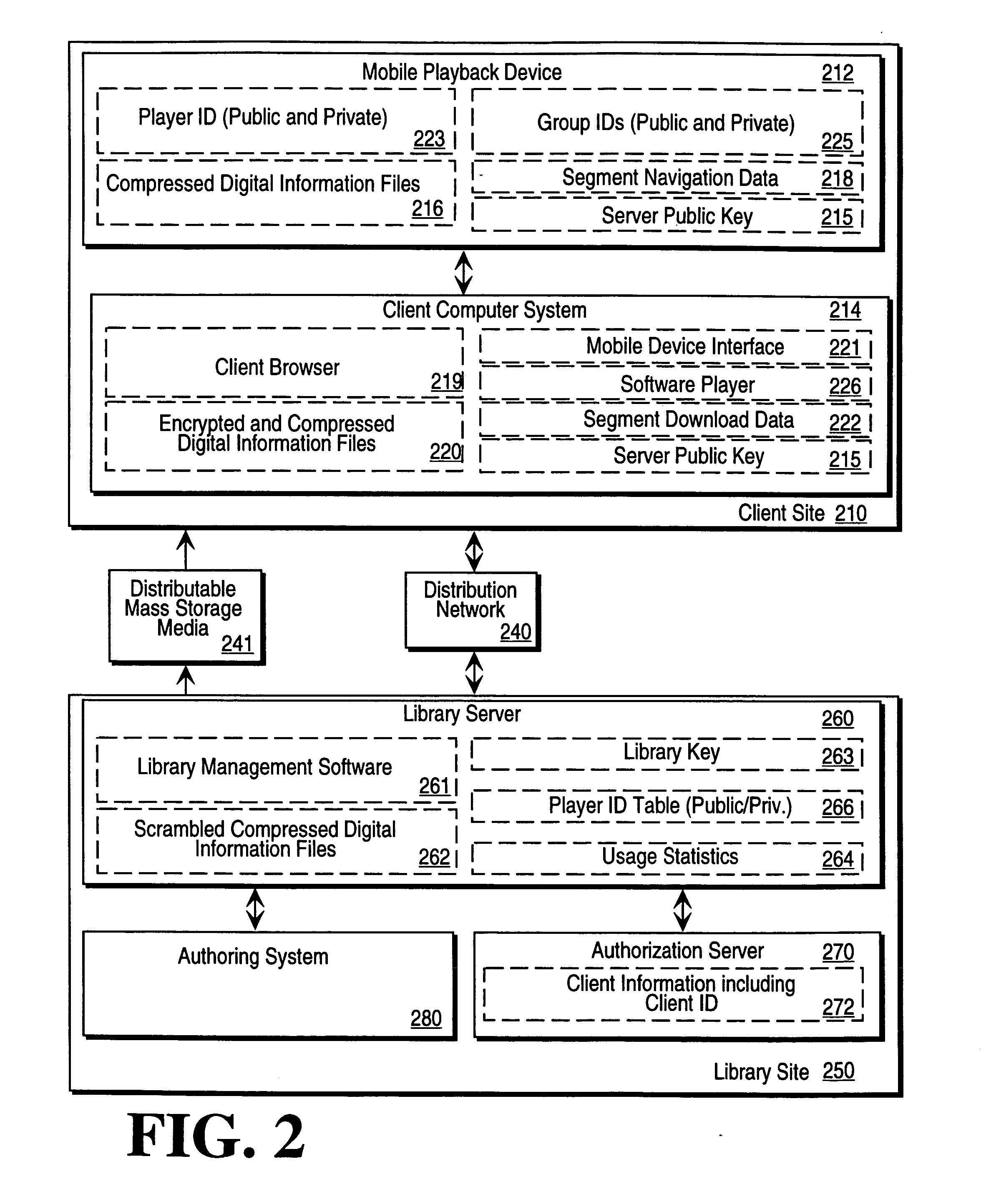
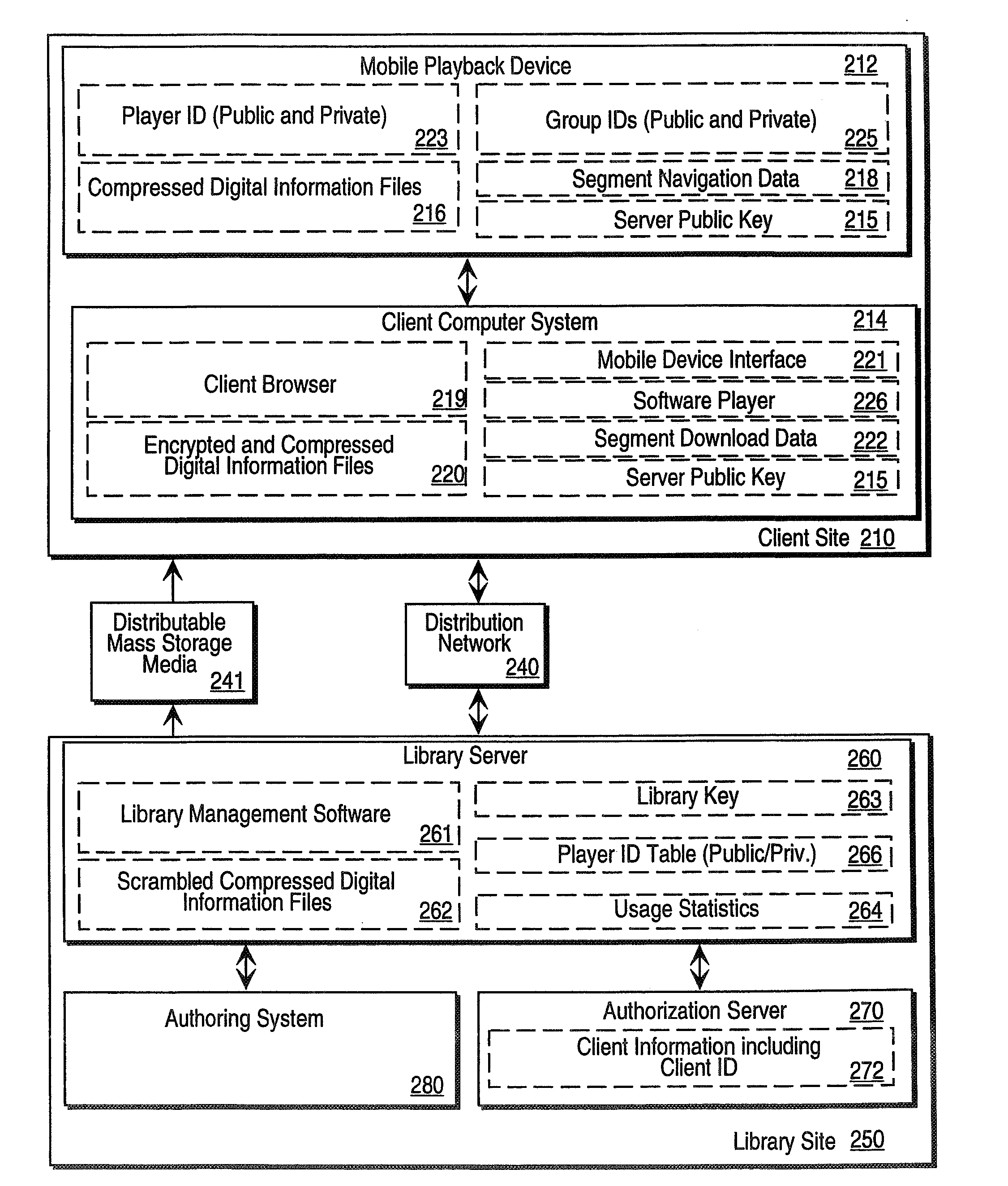
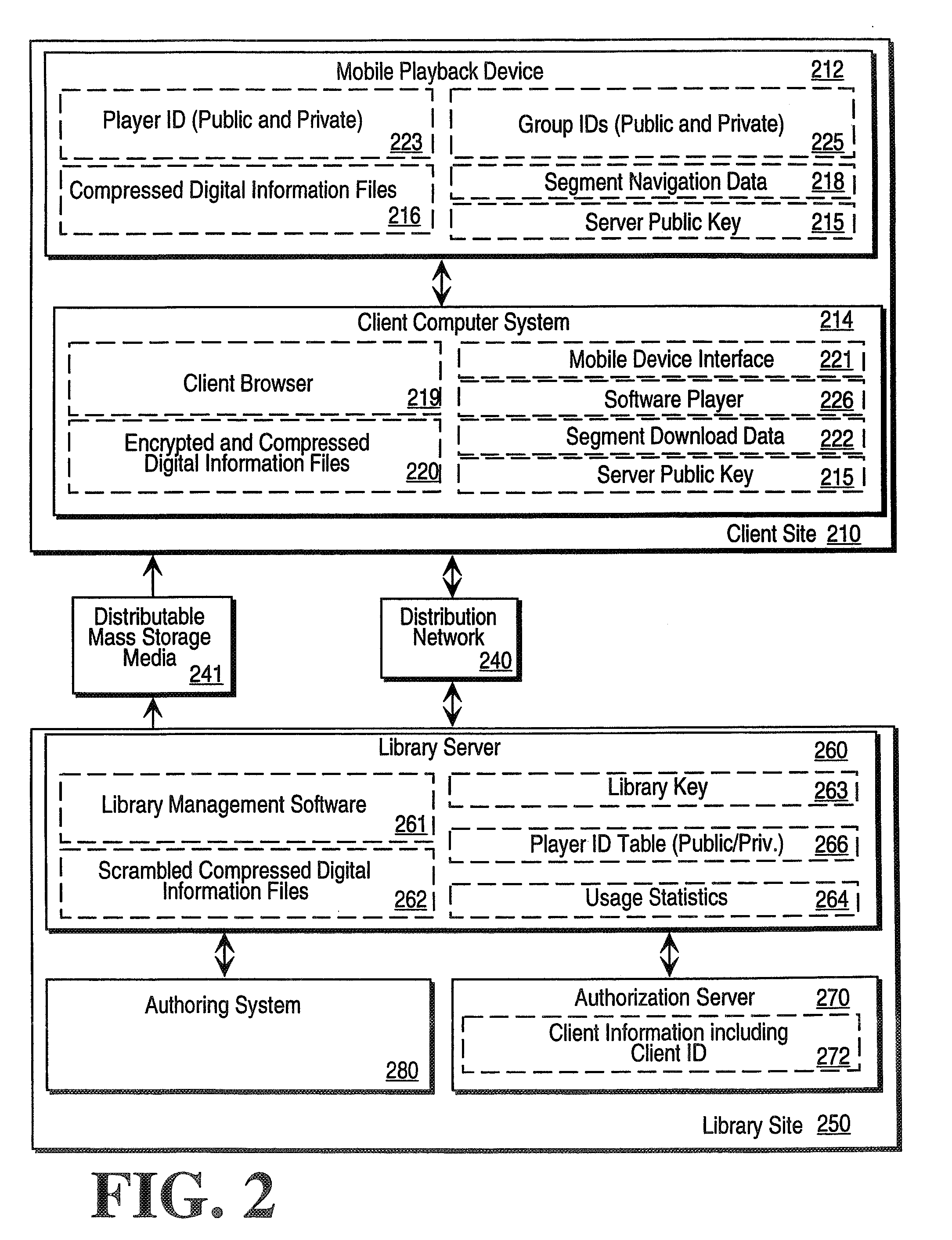
Digital information library and delivery system
InactiveUS20060074985A1Digital data protectionPayment architectureInformation repositoryComputerized system
A computer network based digital information library system employing authentication and encryption protocols for the secure transfer of digital information library programs to a client computer system and a mobile digital information playback device removably connectable to the client computer system. The present invention is a computer network based library and information delivery system for accessing and obtaining selected digital information files. The library and information delivery system comprises: 1) a library server having a plurality of digital information files; 2) a client computer system coupled to the library server over a network; and 3) a mobile device removably connectable to the client computer system, the client computer system including logic for requesting a download of a selected one or more of the digital information files from the library server, the client computer system further including logic for downloading the selected one or more of the digital information files to the mobile device.
Owner:AUDIBLE
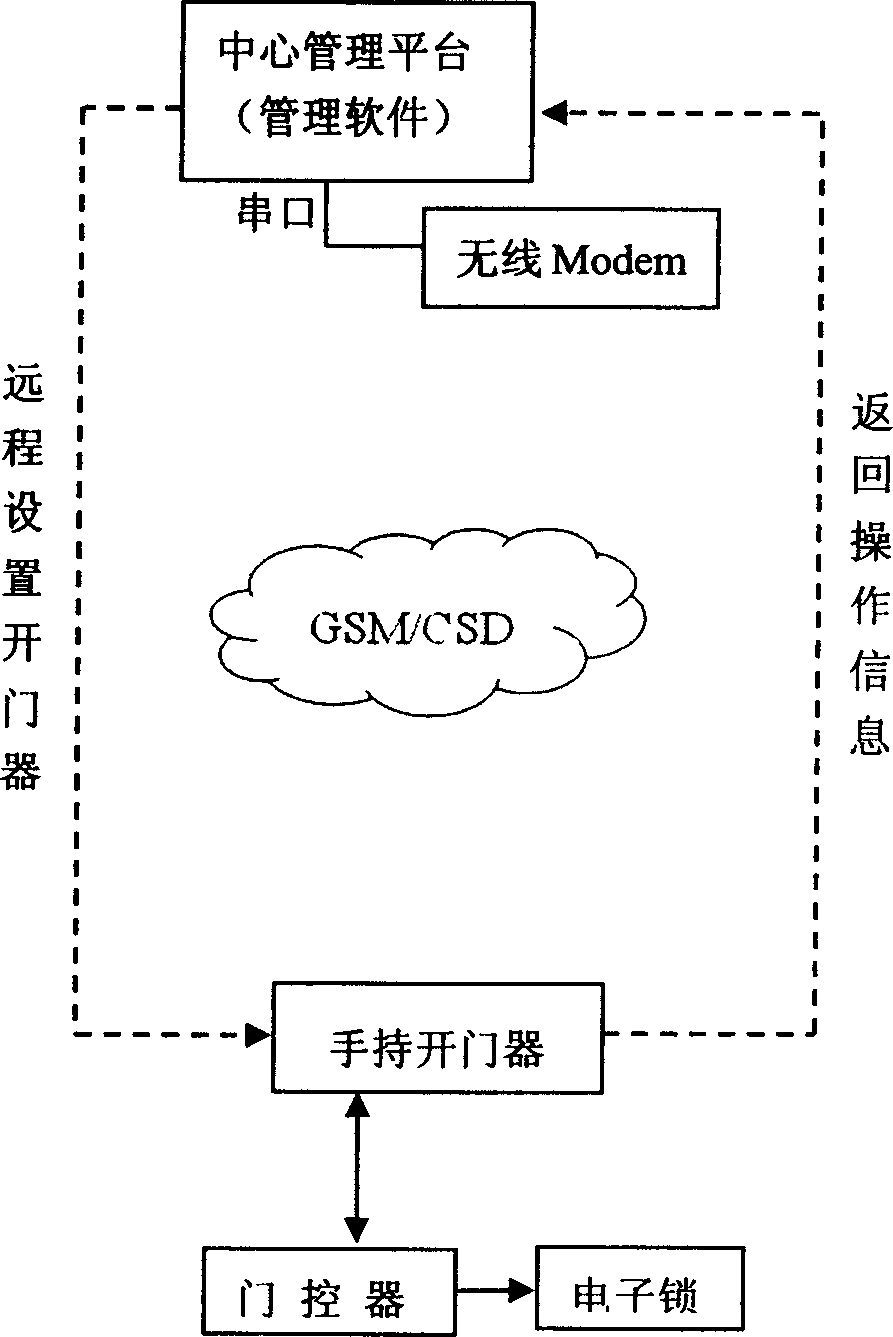
Radio communication Long-distance gate management system and apparatus
InactiveCN1741555AGet job location in real timeGet operation time in real timeTelephonic communicationIndividual entry/exit registersEngineeringCryptography protocols
A management system of radio communication gate inhibition comprises central managing platform including computer , radio remote management software and radio MODEN being connected to network through GSM net ; hand door opener including mobile phone SIM card to carry out communication with center in GSM mode ; gate controller including unique status code for executing command issued by hand door opener ; electronic lock being connected with gate controller by power for realizing unlock .
Owner:美迪特科技(沈阳)有限公司
Digital Information Library and Delivery System
InactiveUS20090150487A1Program control using stored programsRecord information storageInformation repositoryComputerized system
A computer network based digital information library system employing authentication and encryption protocols for the secure transfer of digital information library programs to a client computer system and a mobile digital information playback device removably connectable to the client computer system. The present invention is a computer network based library and information delivery system for accessing and obtaining selected digital information files. The library and information delivery system comprises: 1) a library server having a plurality of digital information files; 2) a client computer system coupled to the library server over a network; and 3) a mobile device removably connectable to the client computer system, the client computer system including logic for requesting a download of a selected one or more of the digital information files from the library server, the client computer system further including logic for downloading the selected one or more of the digital information files to the mobile device.
Owner:WOLFISH HOWARD +4
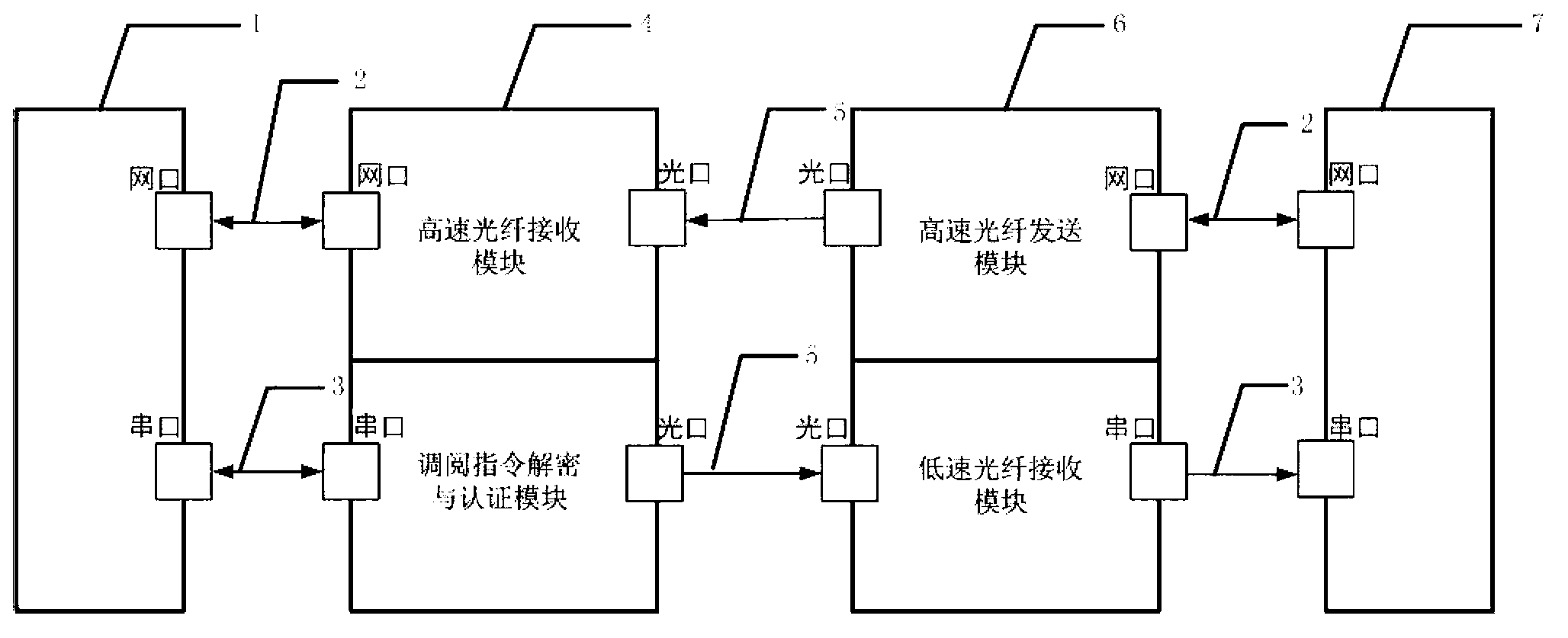
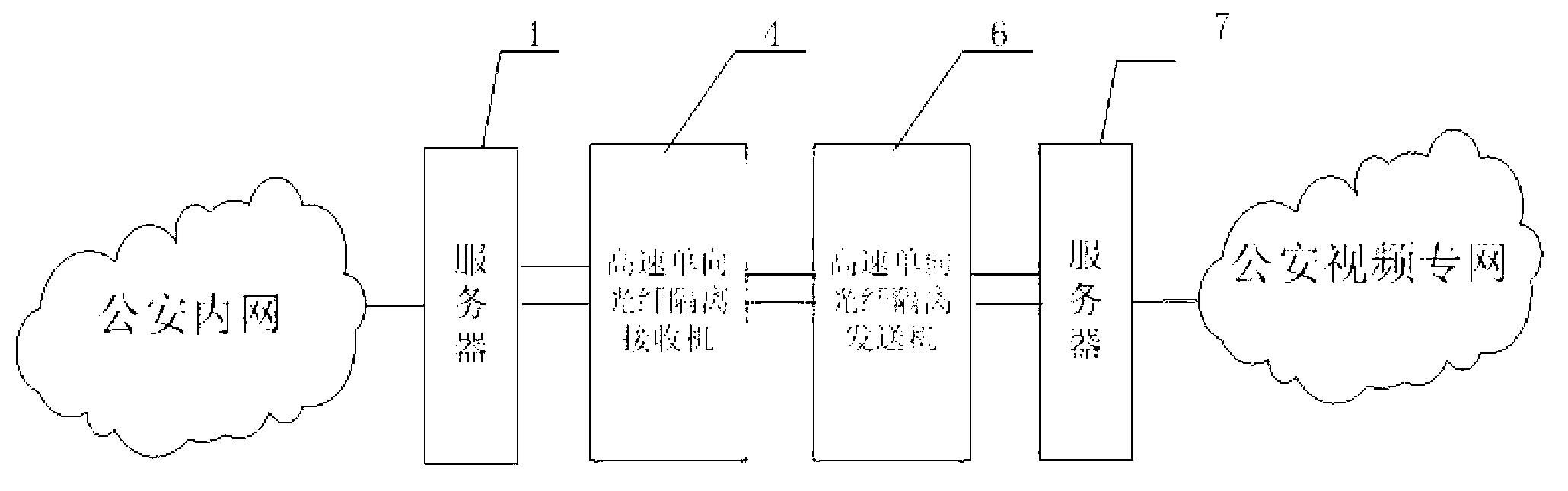
Public-security inner network and special video network isolation system and method
ActiveCN103200201AIntranet protectionClosed circuit television systemsTransmissionNetwork packetNetwork isolation
The invention discloses a public-security inner network and special video network isolation system and method. A limited unidirectional serial channel and a high-speed unidirectional network channel are creatively selected for connection; according to the method, a user-defined encryption protocol and a packet format are used for carrying out unidirectional video access instruction transmission; and an attacker cannot obtain decryption methods, so that even in the most extreme case that an internal network video server is manipulated by the attacker and data are sent out through a serial port, the data can be intercepted by a high-speed unidirectional optical-fiber isolating receiver and cannot be transmitted to special video networks, and then, an inner network is effectively protected.
Owner:OB TELECOM ELECTRONICS
Method of generating a password protocol using elliptic polynomial cryptography
InactiveUS20110202773A1Unauthorized memory use protectionHardware monitoringPasswordTheoretical computer science
The method of generating password protocols based upon elliptic polynomial cryptography provides for the generation of password protocols based on the elliptic polynomial discrete logarithm problem. It is well known that an elliptic polynomial discrete logarithm problem is a computationally “difficult” or “hard” problem.
Owner:KING FAHD UNIVERSITY OF PETROLEUM AND MINERALS
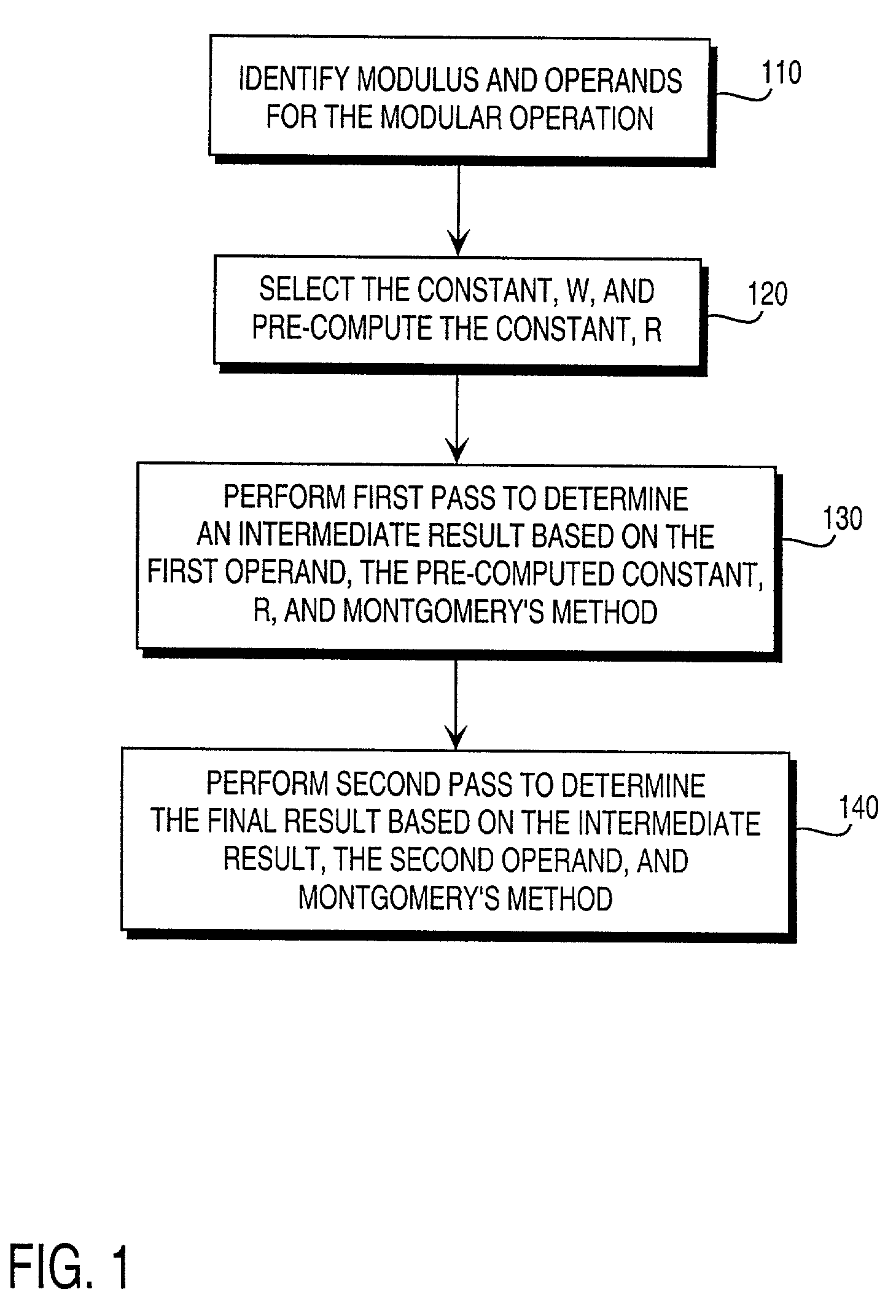
Pre-computation and dual-pass modular arithmetic operation approach to implement encryption protocols efficiently in electronic integrated circuits
InactiveUS7027597B1Effective encryptionEfficient implementationComputations using contact-making devicesComputation using non-contact making devicesProcessor registerModularity
A pre-computation and dual-pass modular operation approach to implement encryption protocols efficiently in electronic integrated circuits is disclosed. An encrypted electronic message is received and another electronic message generated based on the encryption protocol. Two passes of Montgomery's method are used for a modular operation that is associated with the encryption protocol along with pre-computation of a constant based on a modulus. The modular operation may be a modular multiplication or a modular exponentiation. Modular arithmetic may be performed using the residue number system (RNS) and two RNS bases with conversions between the two RNS bases. A minimal number of register files are used for the computations along with an array of multiplier circuits and an array of modular reduction circuits. The approach described allows for high throughput for large encryption keys with a relatively small number of logical gates.
Owner:CISCO TECH INC
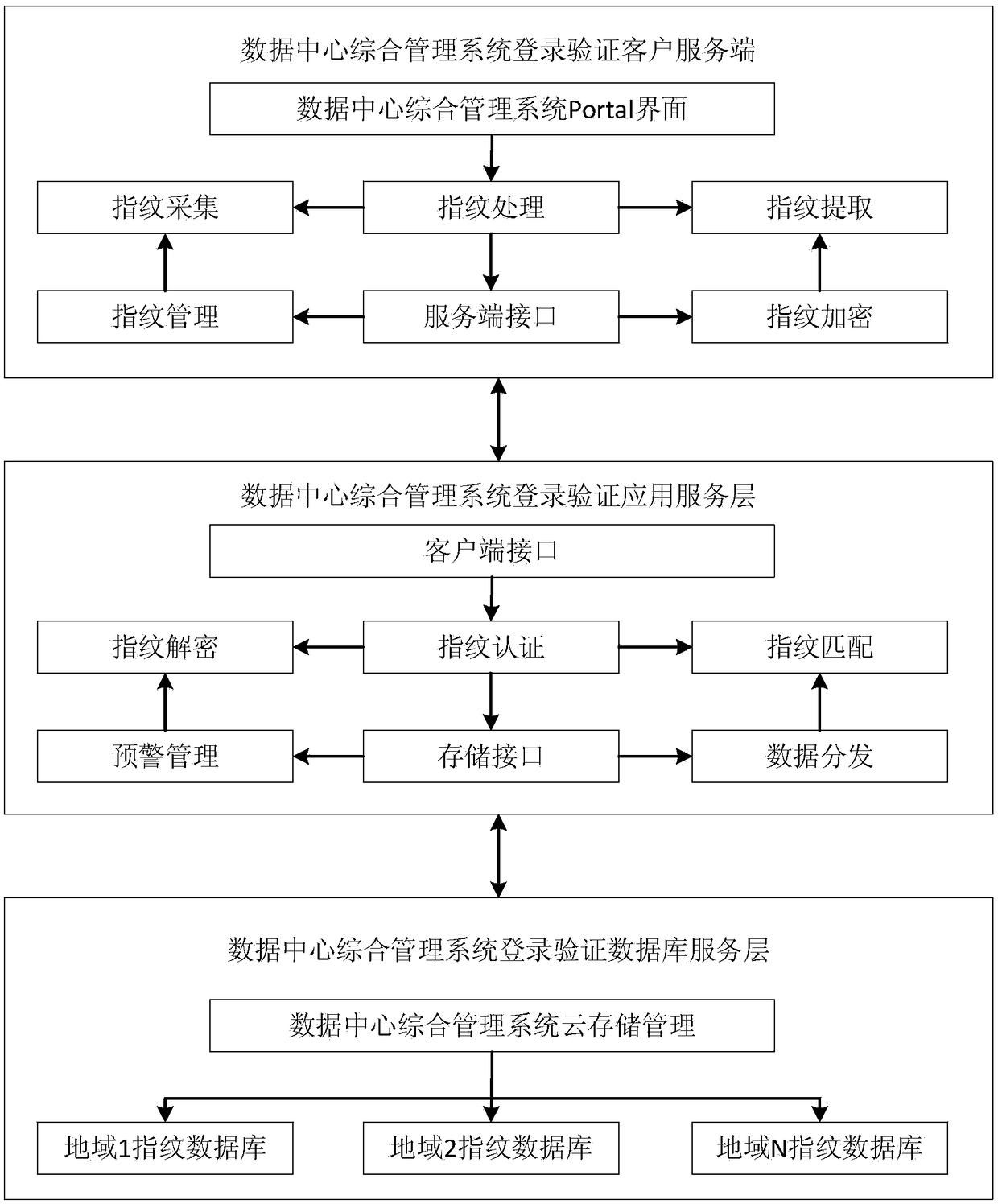
Login verification method for data centre integrated management system
InactiveCN108134791AImprove operation and maintenance security levelImprove operational management efficiencyUser identity/authority verificationData switching networksData centerValidation methods
The invention relates to a login verification method for a data centre integrated management system. A bidirectional authentication mechanism is adopted in the method, so that the security of the system is improved; when fingerprint identification and identity authentication are carried out, an encryption protocol is adopted at first, so that shaking between a client side and a cloud side is successful; after bidirectional verification of respective validities is carried out, a secure link is established; furthermore, a shared key is obtained; then, according to user service requirements, userfingerprint registration and fingerprint login authentication are carried out; high-security-level requirements of the data centre integrated management system are satisfied; to improve the securitylevel of an authentication system, an authentication threshold value can be set in an authentication process; and thus, the service support capability of the data centre integrated management system is improved.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
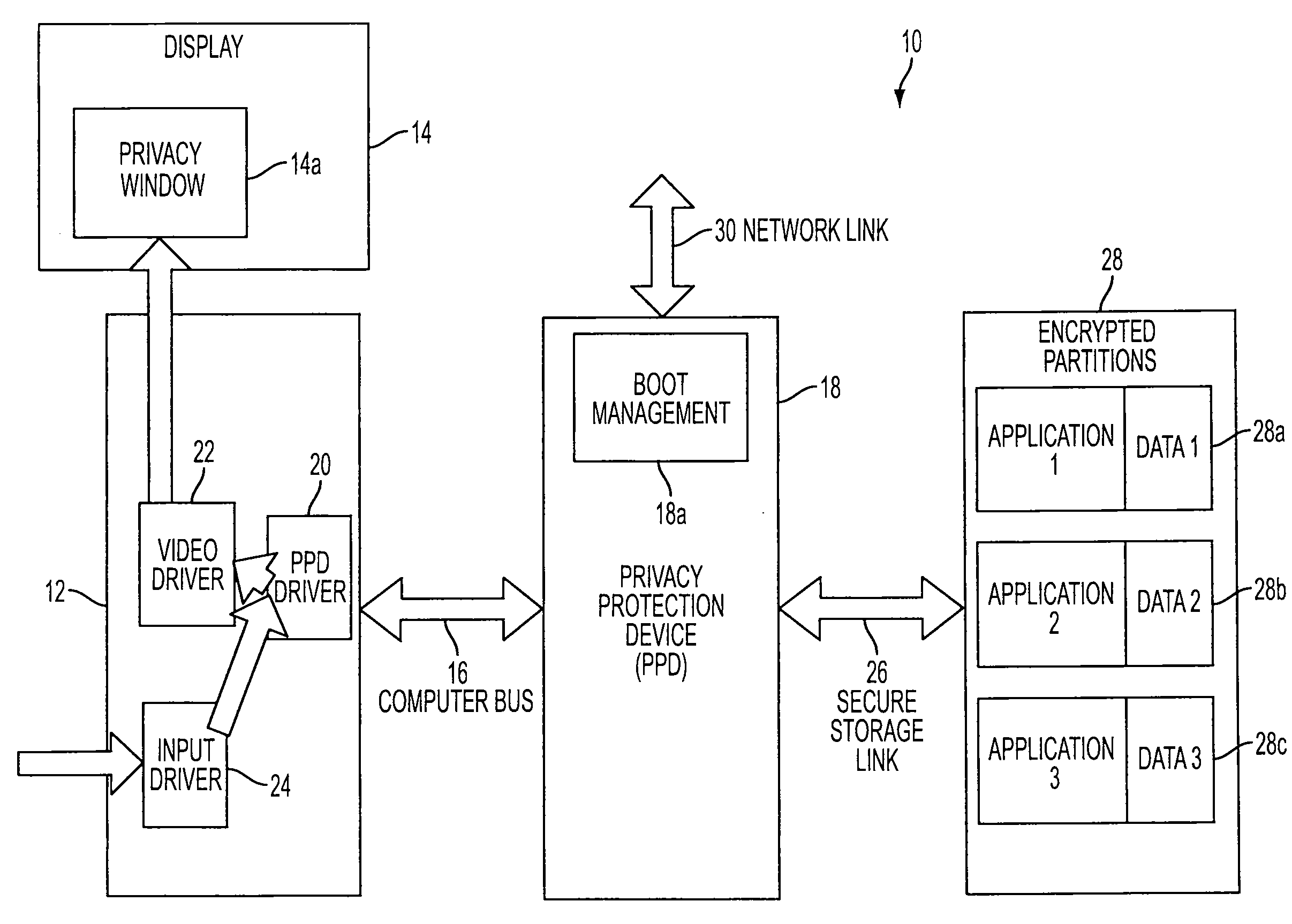
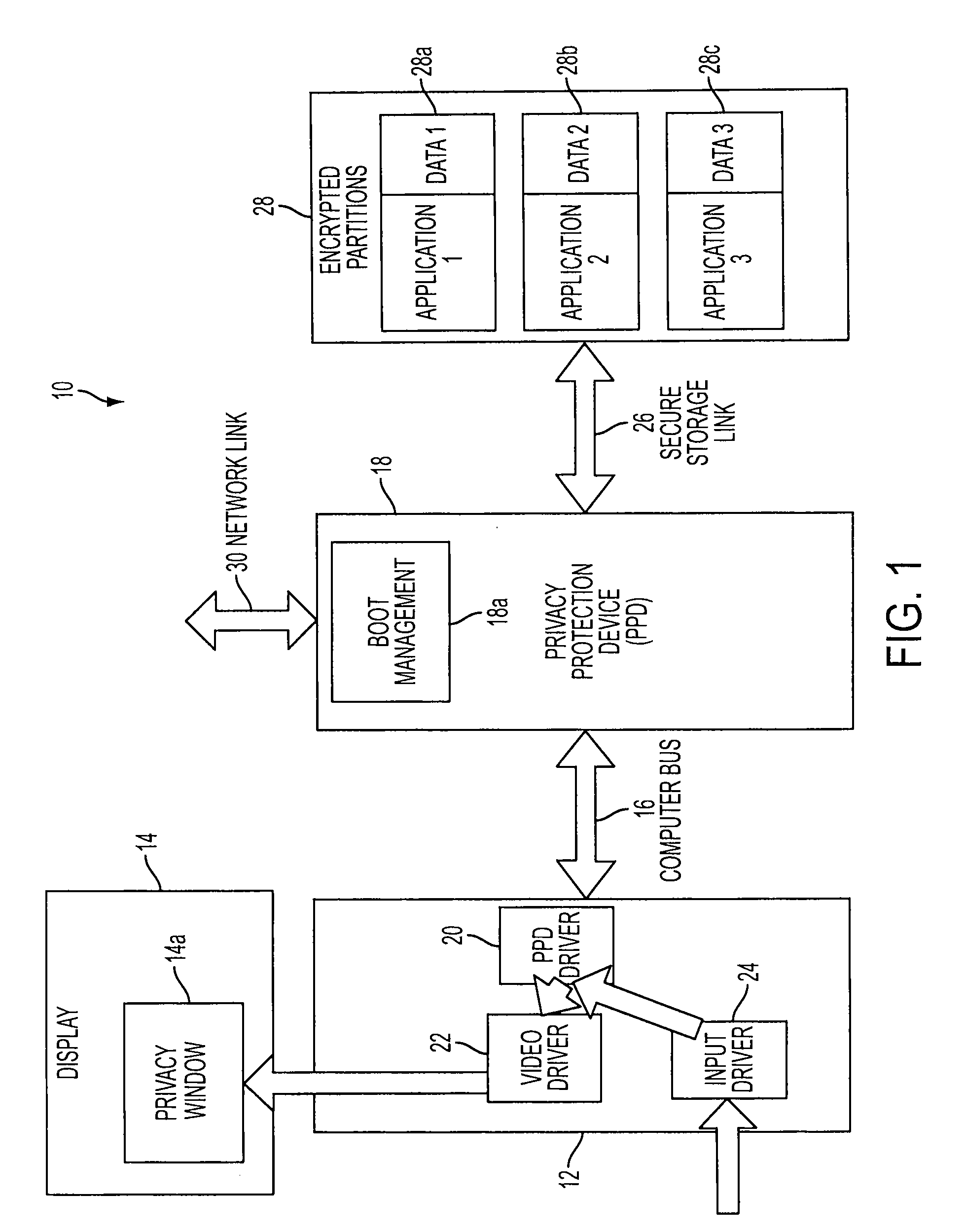
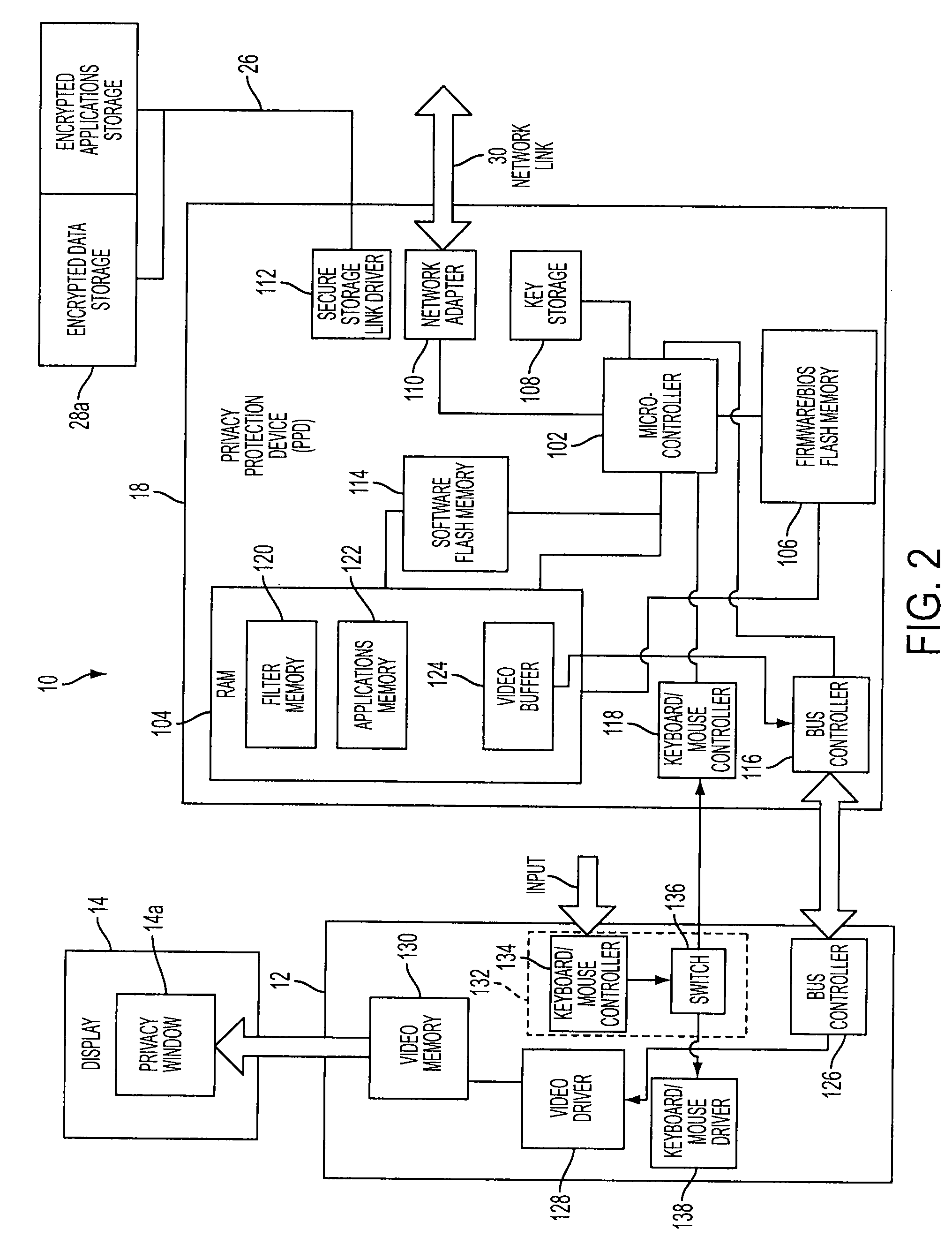
Privacy protection system
ActiveUS20100146301A1Encryption apparatus with shift registers/memoriesDigital data processing detailsPrivacy protectionUser privacy
Novel system and methodology for protecting privacy of a computer device's user. A privacy protection device interacts with the computer device to enable the user to operate in multiple private modes. The system involves a data storage coupled to the privacy protection device, via a secure link, such as a Secure Sockets Layer (SSL) tunnel that provides an encryption protocol. The data storage is divided into multiple storage sections corresponding to the multiple private modes. Each section is configured for storing encrypted data supporting a particular private mode. The privacy protection device enables the user to set a selected private mode and runs software applications that use the data from the storage section corresponding to the selected mode.
Owner:GBS LAB
Method for authentication for resisting secrete data disclosure and key exchange based on passwords
InactiveCN101626364AImprove computing efficiencyPrevention analysisPublic key for secure communicationUser identity/authority verificationKey exchangeCryptographic protocol
The invention belongs to a cryptographic protocol, and in particular relates to a method for authentication for resisting secrete data disclosure and key exchange based on passwords. The method is superior to correlative American or international current standard in the aspects of user password protection, secrete data disclosure resistance, better user privacy protection, better online efficiency calculation, less communication bandwidth and higher security. The method for the authentication and the key exchange comprises sub-methods of an innovative method for public key encryption and signcryption based on passwords, a method for knowledge binding certification, a method for resisting temporary secrete data disclosure, a method for awarding a public key certificate. The method has the advantages of good systematicness, adaptability and compatibility.
Owner:赵运磊 +3
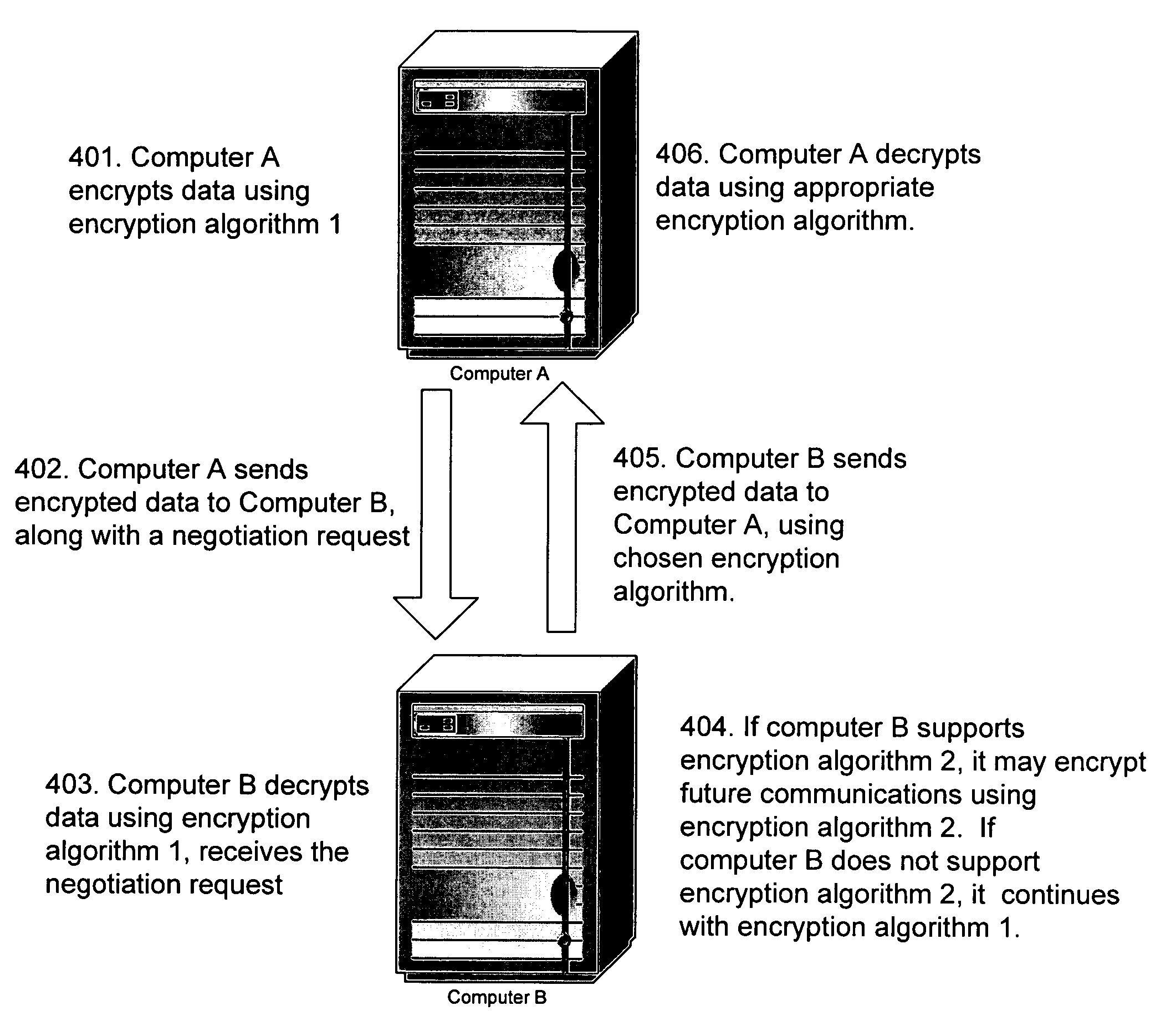
Dynamic negotiation of encryption protocols
ActiveUS7591012B2Key distribution for secure communicationEncryption apparatus with shift registers/memoriesDynamic equationClient-side
Systems and methods for negotiating an encryption algorithm may be implemented in the context of encryption-based authentication protocols. The invention has the added benefit of providing a system an method that need not interfere with the standard operation of authentication protocols. A first computer, or client computer, can send a negotiation request to a second computer, or server computer. The negotiation request can specify that the client computer supports a selected encryption algorithm. In response, the server computer can return a subsession key for encryption using the selected encryption algorithm. Both client and server may then switch to encryption in the selected encryption algorithm, using the subsession key to encrypt future communications.
Owner:MICROSOFT TECH LICENSING LLC
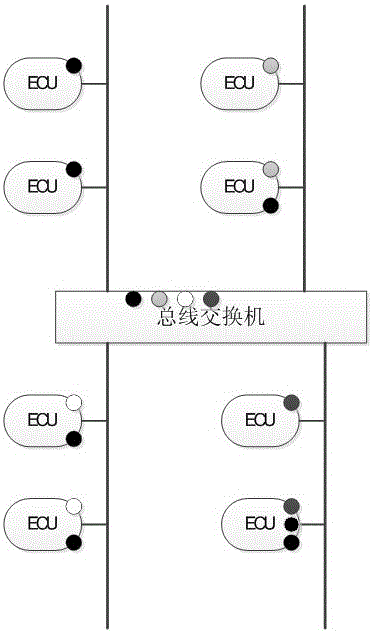
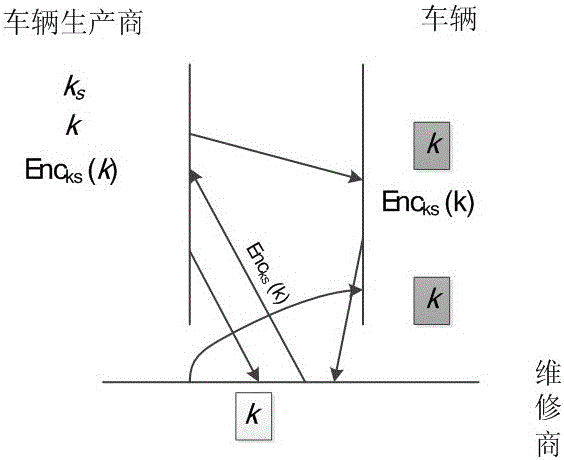
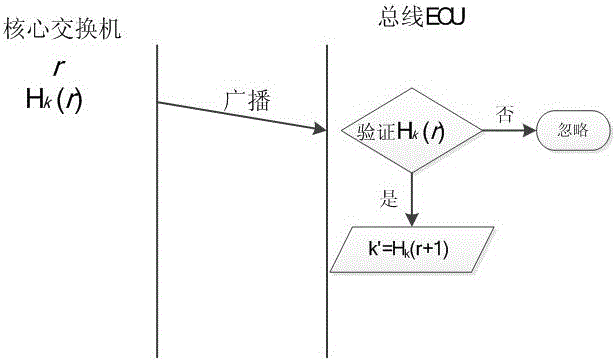
Authentication and access control method for CAN (Controller Area Network) bus
ActiveCN106453326AAchieve authenticationAchieve protectionBus networksArea networkCryptography protocols
The invention relates to an authentication and access control method for a CAN (Controller Area Network) bus, which is characterized by particularly comprising the following steps of: (1) completing functional partitioning of a vehicle system, and defining each function as a logic functional region; (2) based on functional partitioning of the vehicle system in the step (1), partitioning nodes of the vehicle system into each logic functional region according to functions to which the nodes belong; (3) based on partitioning of each node logic functional region in the step (2), allocating a secret key to each logic functional region; (4) based on each secret key in the step (3), generating a session secret key of the corresponding logic functional region after a vehicle is started up every time; (5) based on each session secret key in the step (4), completing authentication and encryption of CAN data, and based on each secret key in the step (3), implementing secret key resetting on updated nodes. According to the authentication and access control method disclosed by the invention, based on a cryptography technology, a node authentication and encryption protocol of the CAN bus is constructed by utilizing a cryptographic algorithm, and resource access control on the integral CAN bus is implemented.
Owner:CHINA FIRST AUTOMOBILE
Method and system for securing data utilizing reconfigurable logic
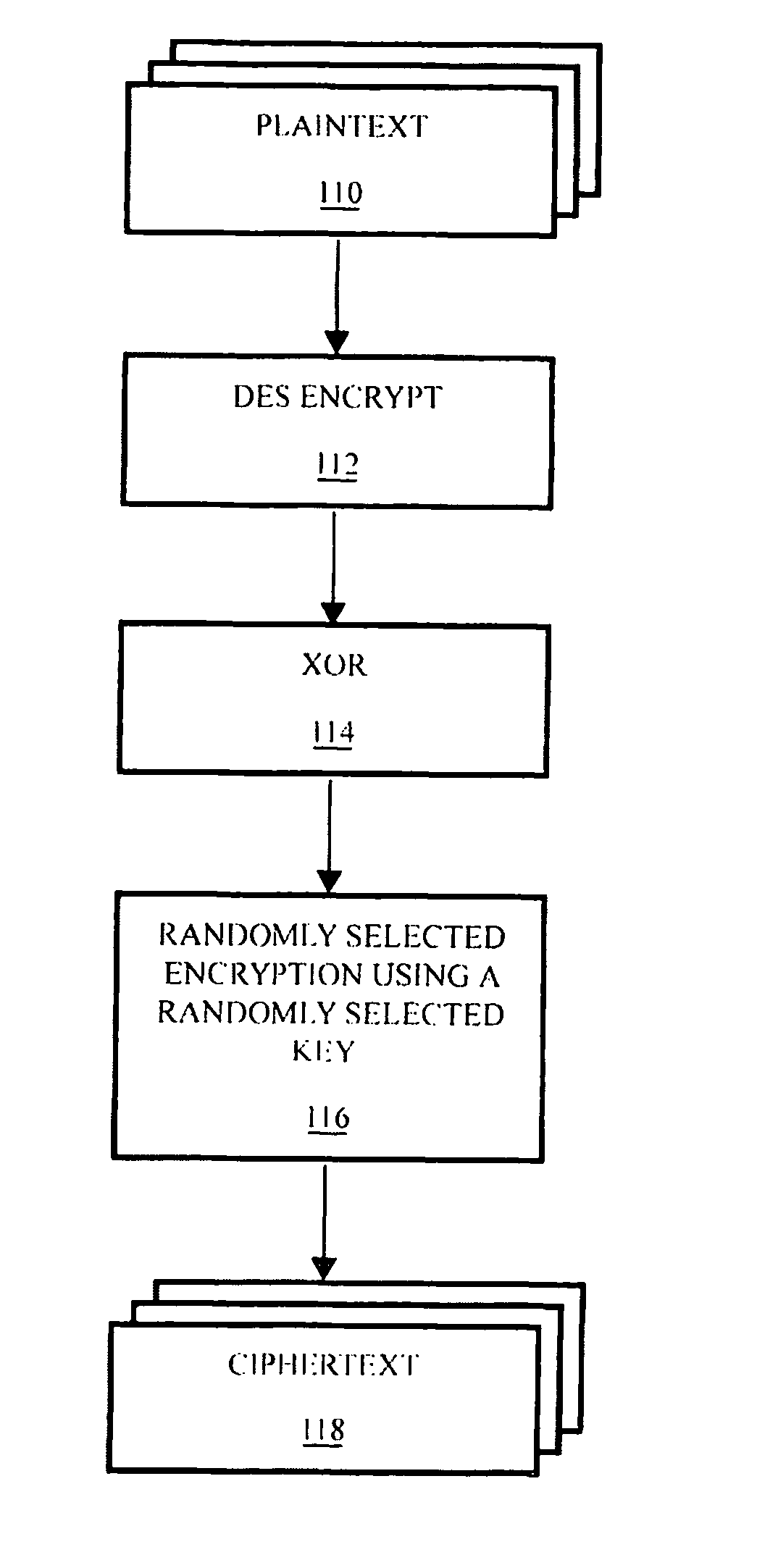
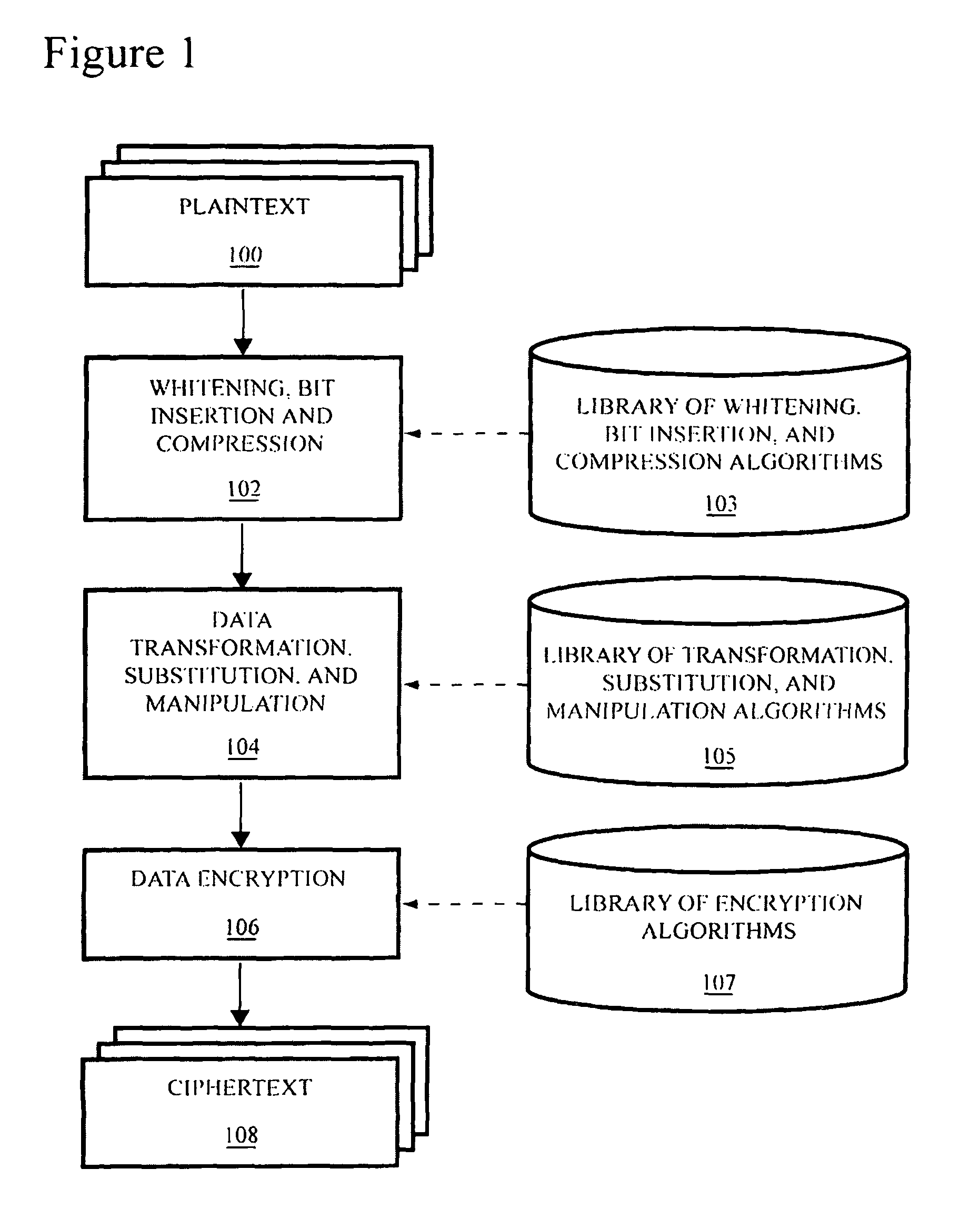
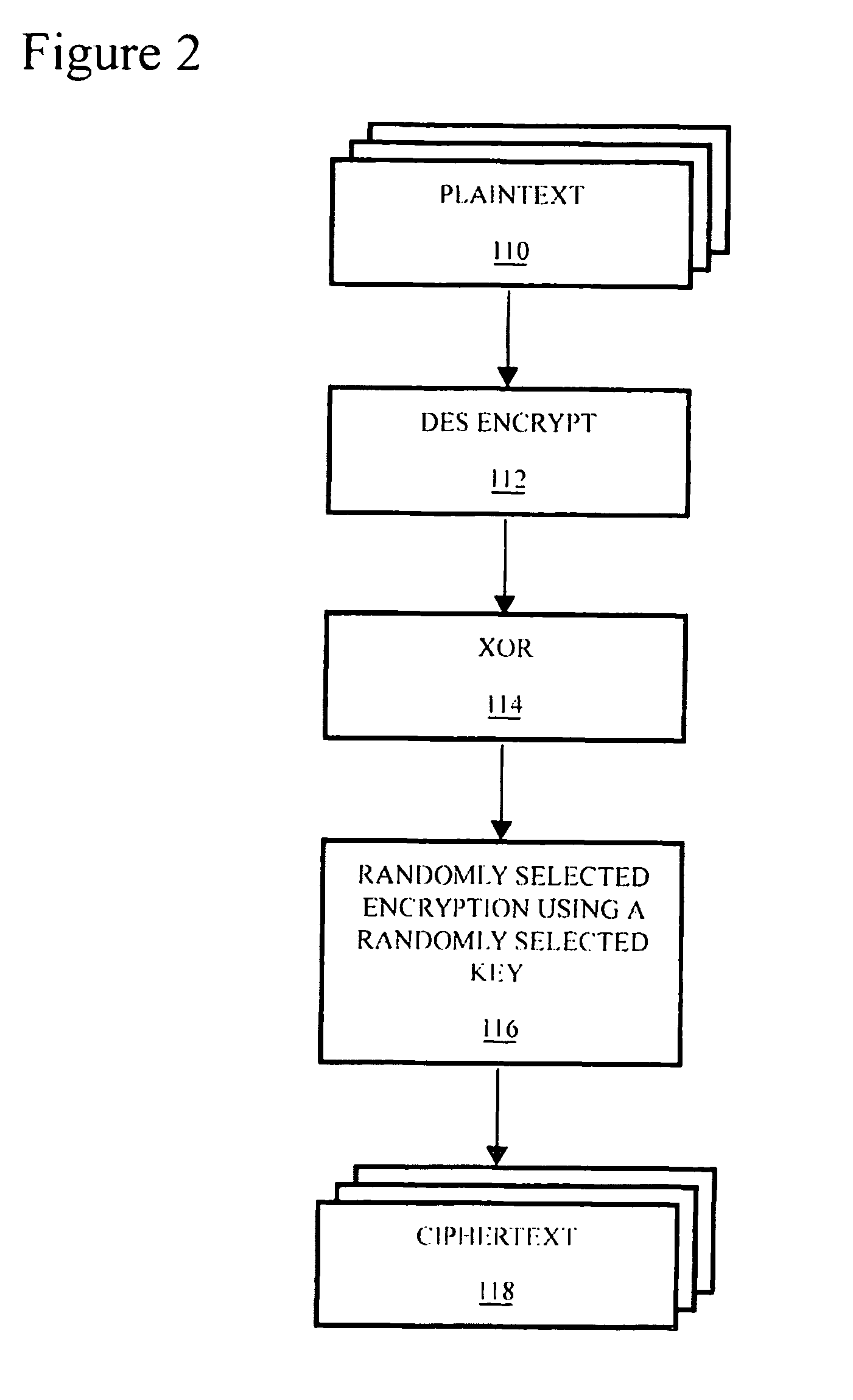
A method is provided for securing data sets by dynamically hopping amongst a variety of data encryption and / or manipulation protocols. Such dynamic protocol hopping can be implemented in reconfigurable logic, or some combination of reconfigurable logic and fixed circuitry or software. The encryption and / or manipulation protocol applied to the data set is selected from among a plurality of encryption protocols in an, optionally upgradeable, library of protocols. Preferably, the selection can be driven by a random number generator. More preferably, the number of encryption protocols available can be extended using a logic-stretching engine. An apparatus is also provided for securing data, including a memory that contains data describing encryption protocols, a communications interface that is configured to receive data, and a processor that reads from the memory one of the encryption protocols and encrypts the received data based on the encryption protocol. Preferably, the apparatus also includes a random number generator, and the processor selects the encryption protocol to read, and encryption parameters to use, based on the output of the random number generator.
Owner:ADVANCED COMM CONCEPTS
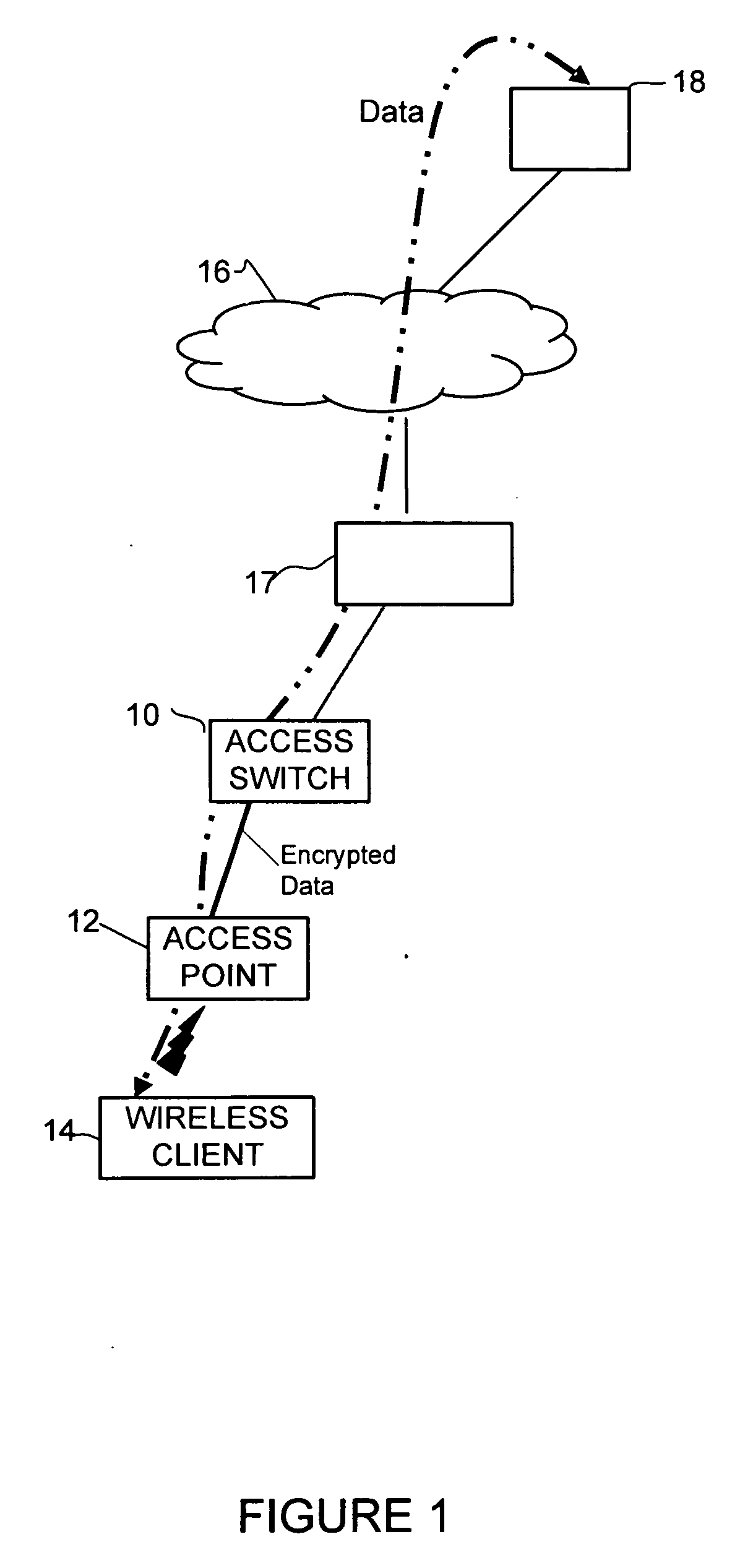
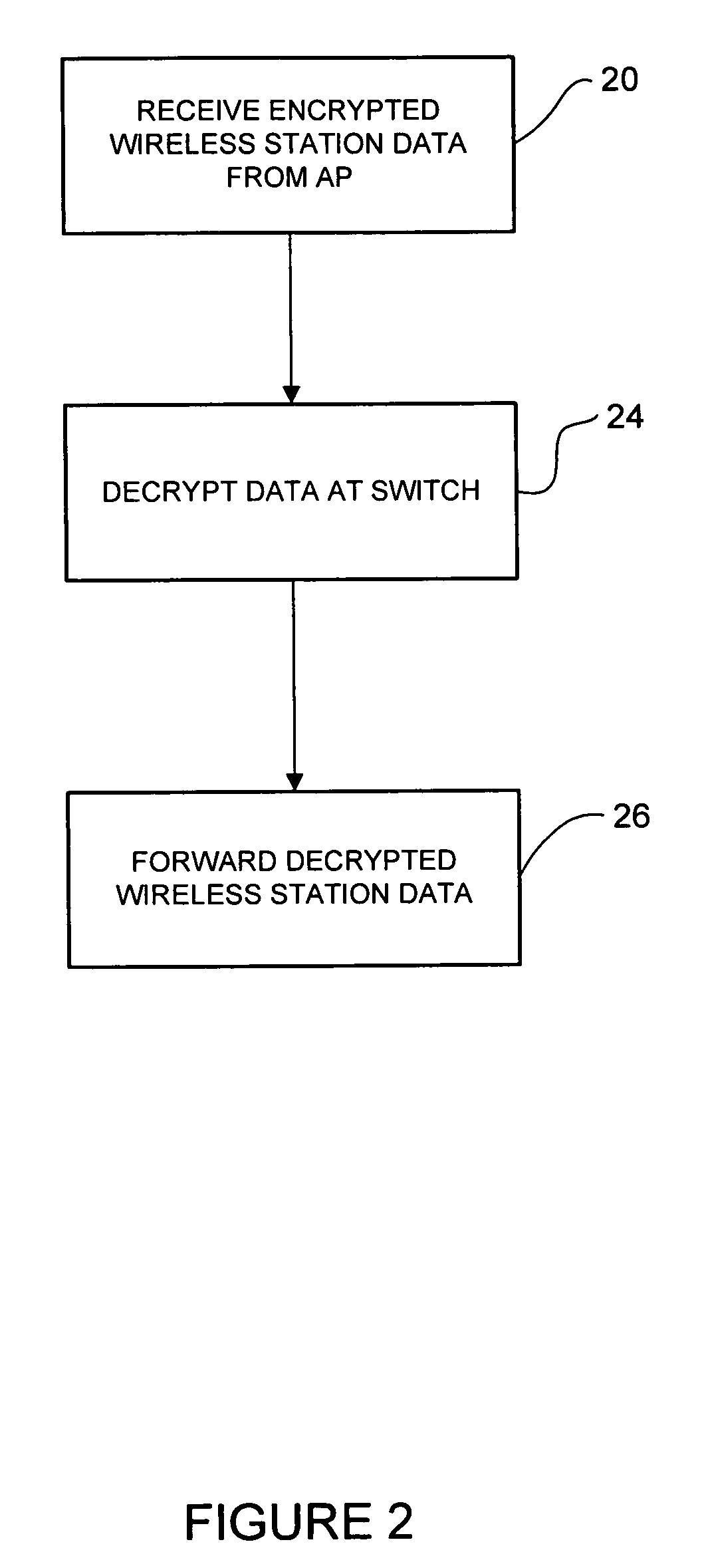
Efficient data path encapsulation between access point and access switch
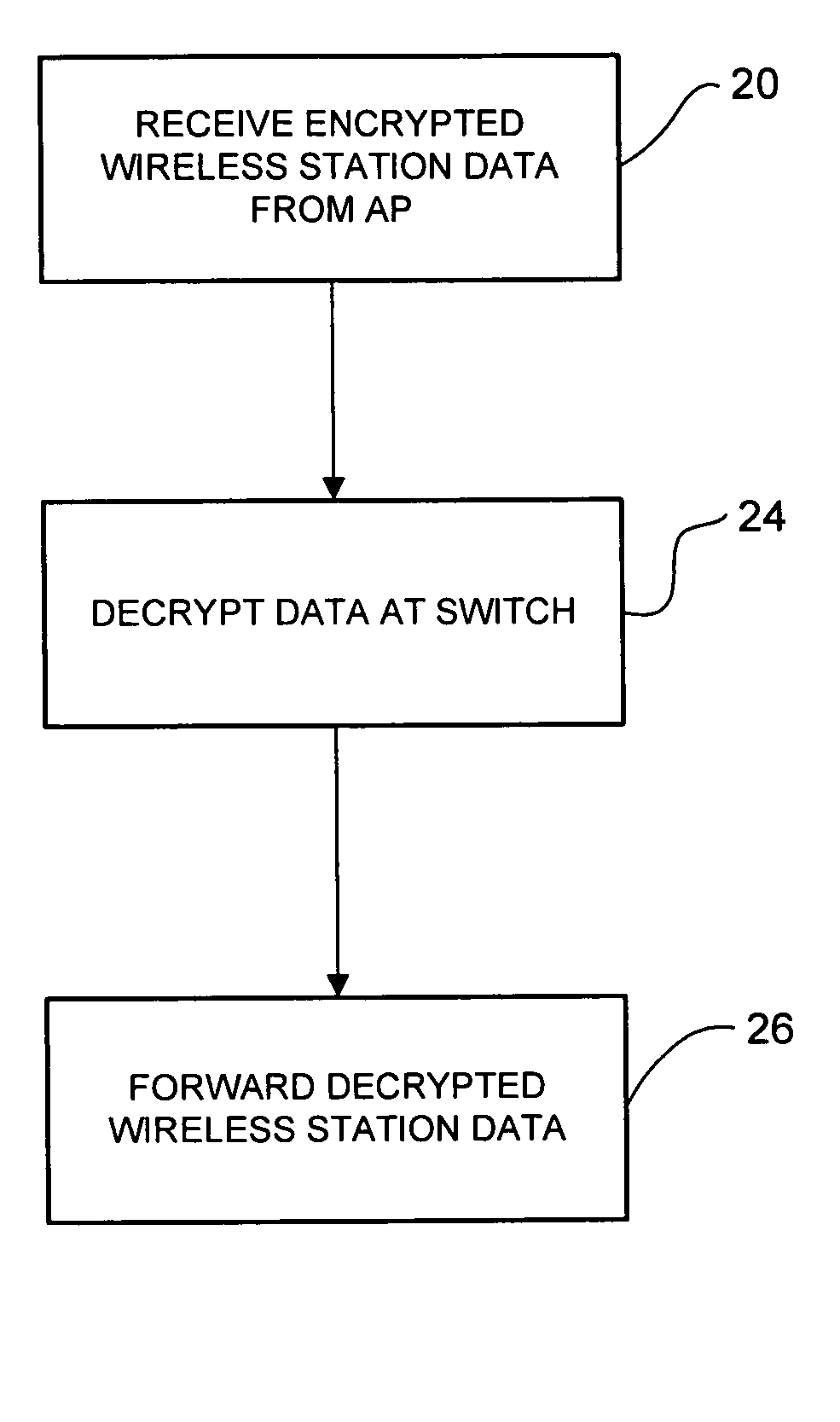
In one embodiment, a method for processing encrypted wireless station data at a network device includes receiving from an access point, one or more frames comprising wireless station data fragmented into a plurality of encrypted protocol data units. The frames are configured to identify the encrypted protocol units associated with the wireless station data. The method further includes decrypting the encrypted protocol data units and forwarding the wireless station data. An apparatus for processing encrypted wireless station data, a method for transmitting encrypted multicast data for a wireless client, and a method for processing encrypted wireless station data at an access point are also disclosed.
Owner:CISCO TECH INC
Realization method for reasonable construction and correct parse of communication data package based on alarm system
InactiveCN103095835ASolve the problem that it is difficult to distinguish correctly, and some even cannot be parsed correctlyAccurate analysisError preventionNetwork packetStream data
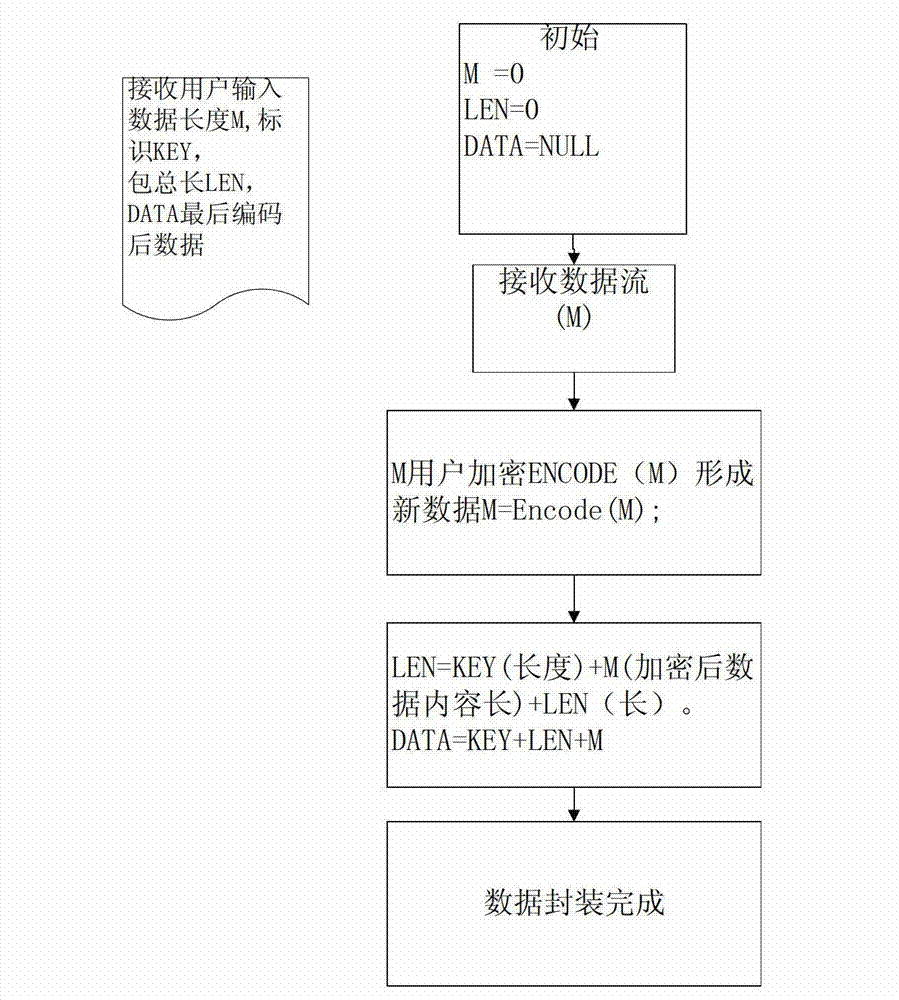
The invention relates to the technical field of security of computer networks, in particular to a realization method for reasonable construction and correct parse of a communication data package based on an alarm system. Fixed-length data package header identification is used as data package feature identification, the length of a fixed-length data package is set at the rear of the data package header identification, the system can parse the finial size of the package according to the length of the data package after receiving data and then parse out the whole data package, and the size of the whole package can be known without traversing to the end of the package. A coding scheme of abstract syntax markup is used for coding to divide the data into the operation type of Cmd and the operation content of Value, wherein Key corresponds to the header of data package, Length corresponds to the data length, Cmd and Value both correspond to the data, Key, Length, Cmd and Value are coded through the coding and the decoding rule to form a bit stream data package, and the data content is encrypted and decrypted through a special encryption protocol. The security and the transmission speed are obviously promoted.
Owner:成都理想科技开发有限公司
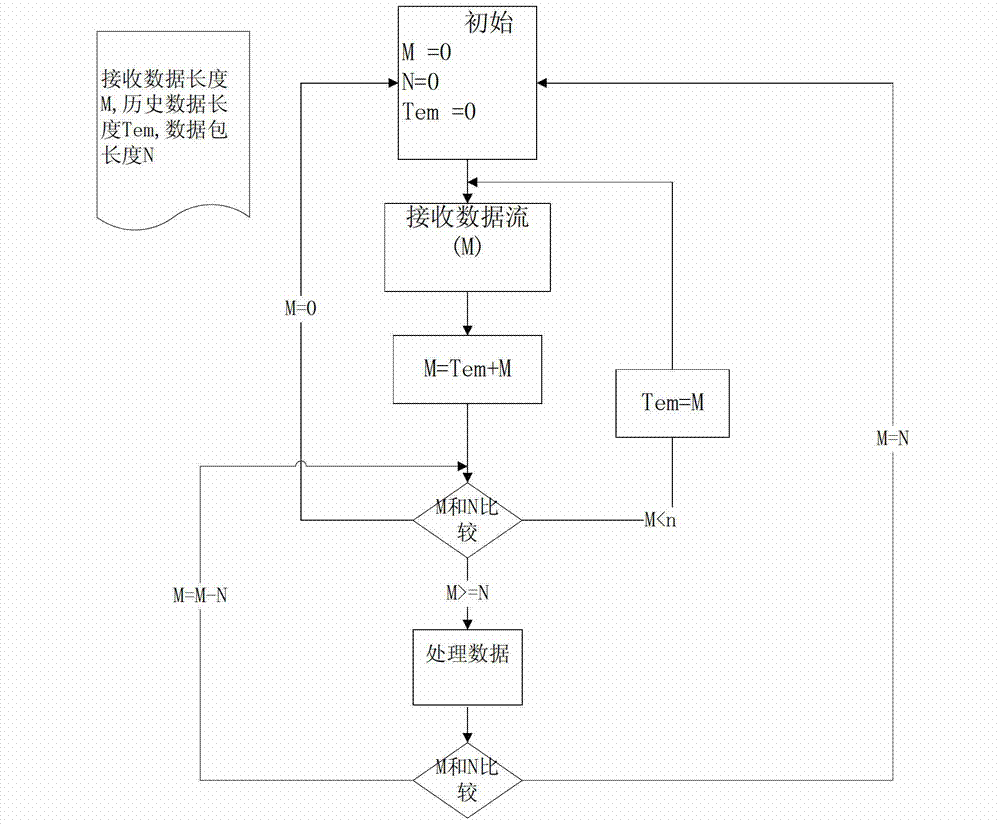
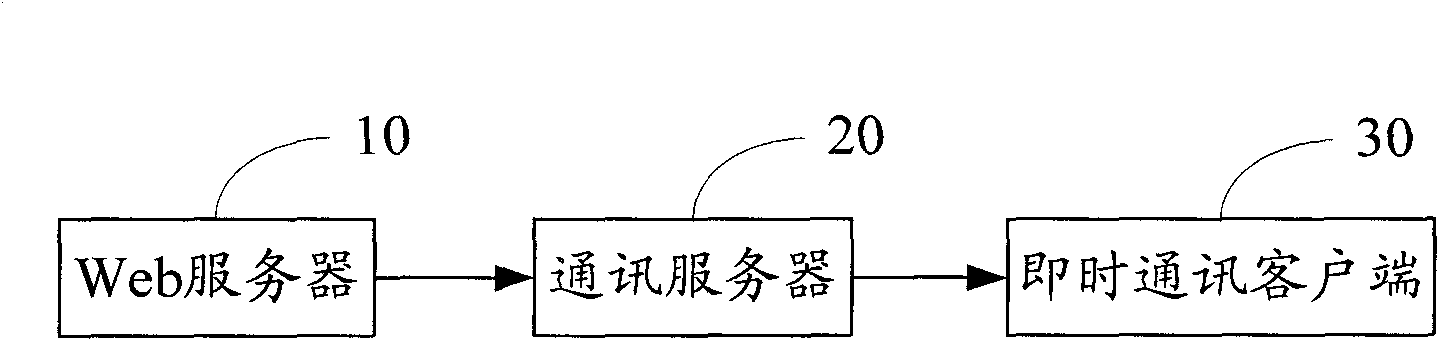
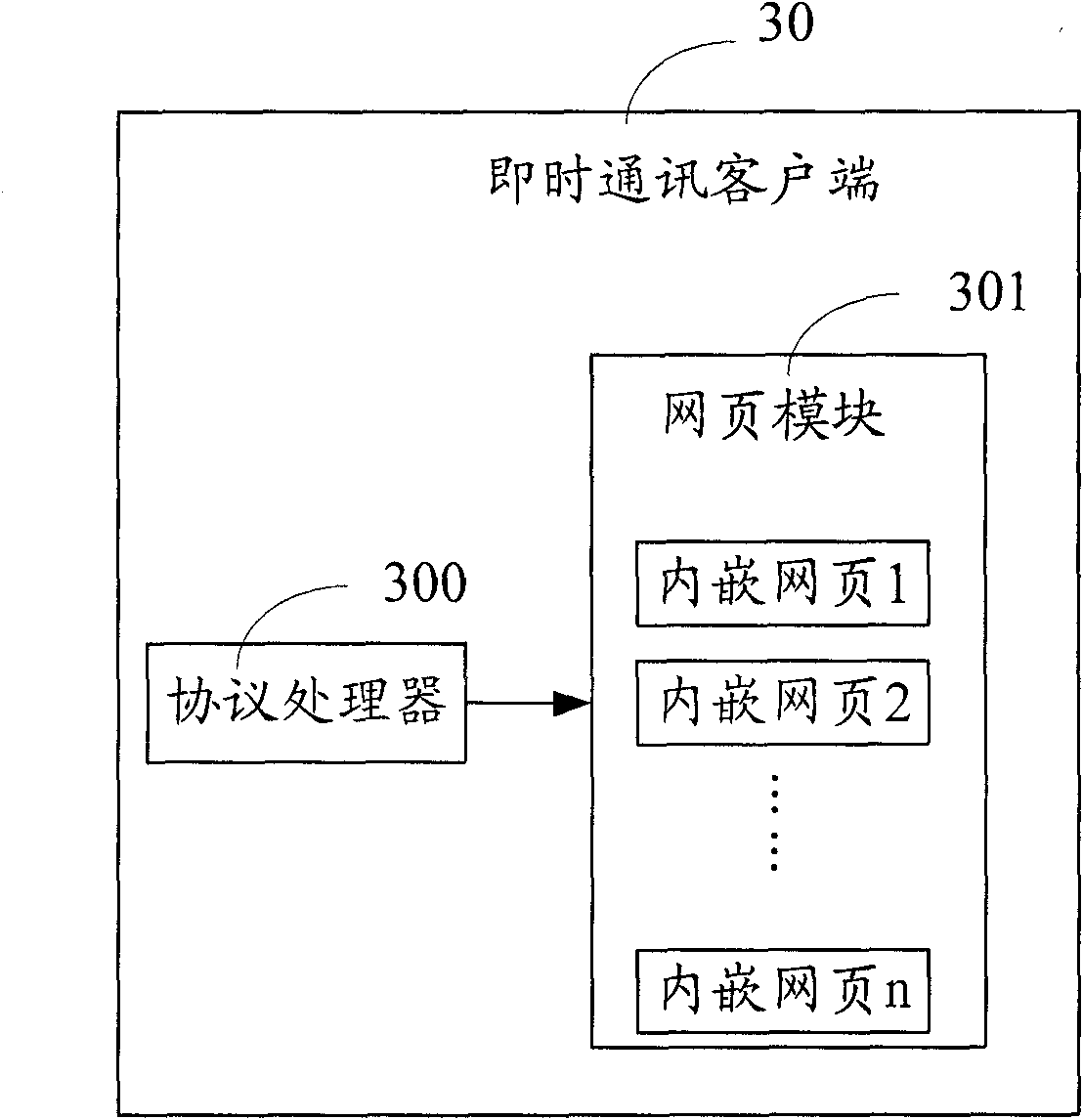
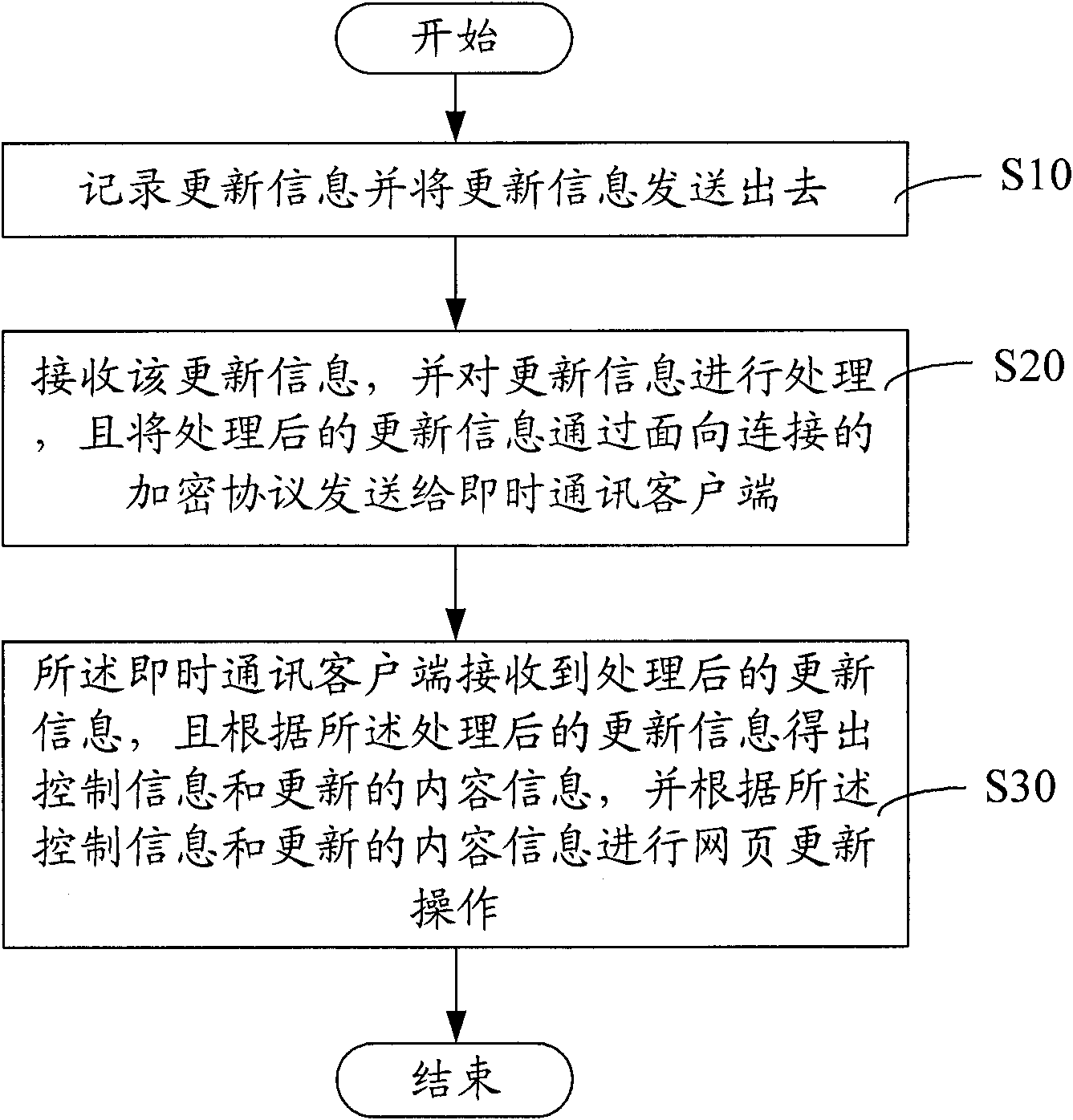
System and method for updating web data
The invention relates to a system for updating web data which comprises a web server, a communication server and an instant messaging client side, wherein the web server is used for recording update information and transmits the update information to the communication server; the communication server receives and processes the update information, and transmits processed update information to the instant messaging client side through an encryption protocol connected with the communication server; and the instant messaging client side receives the processed update information, obtains control information and updated content information according to the processed update information, and conducts web update operation according to the control information and the updated content information. In addition, the invention relates to a method for updating the web data. By the system and the method, the pressure on a server and network bandwidth is reduced, the updating response of web at the instant massaging client side is fast, the operation is simple, a complicated webpage is avoided, and the property is good.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Multiple encrypting method and system for encrypting a file and/or a protocol
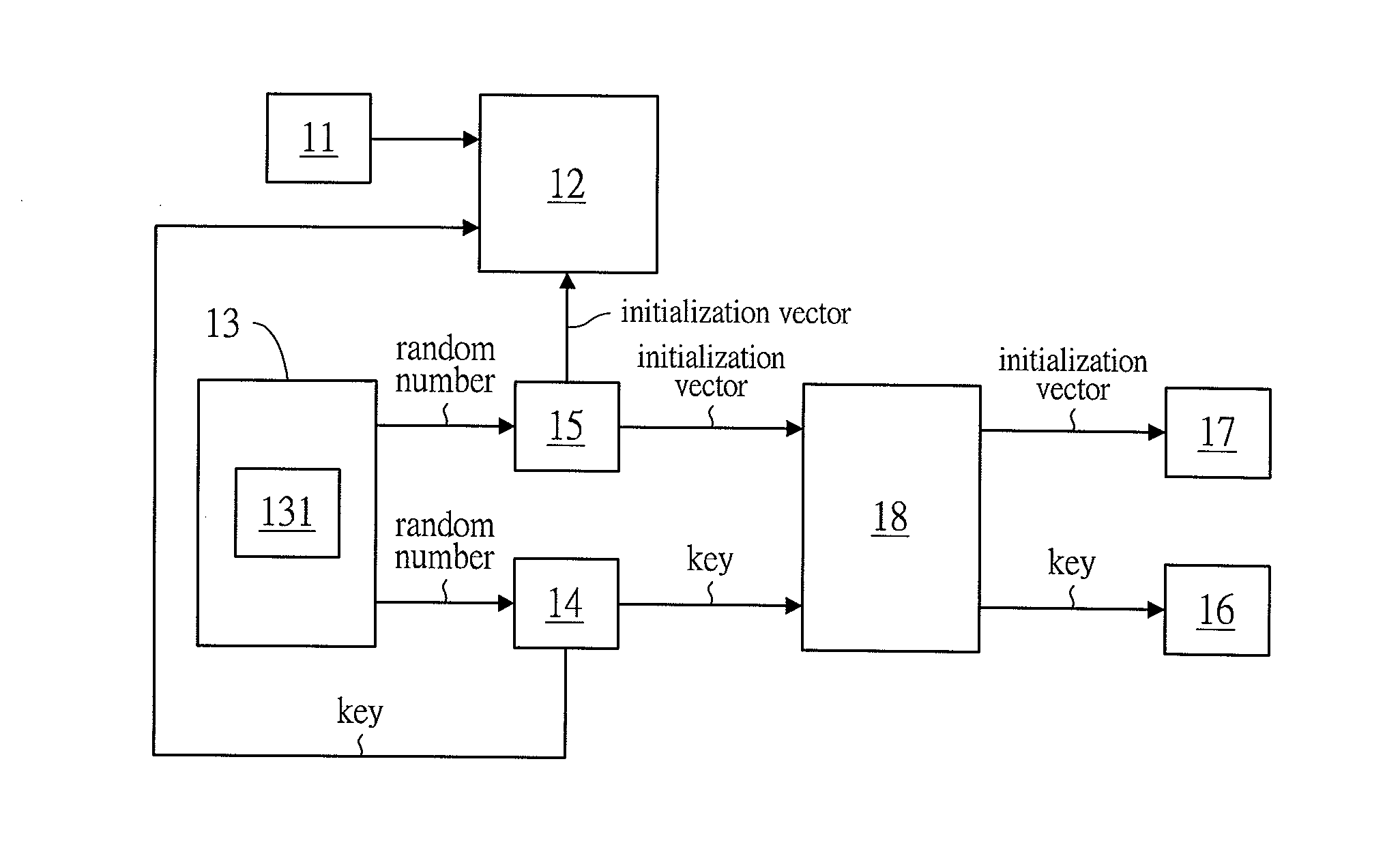
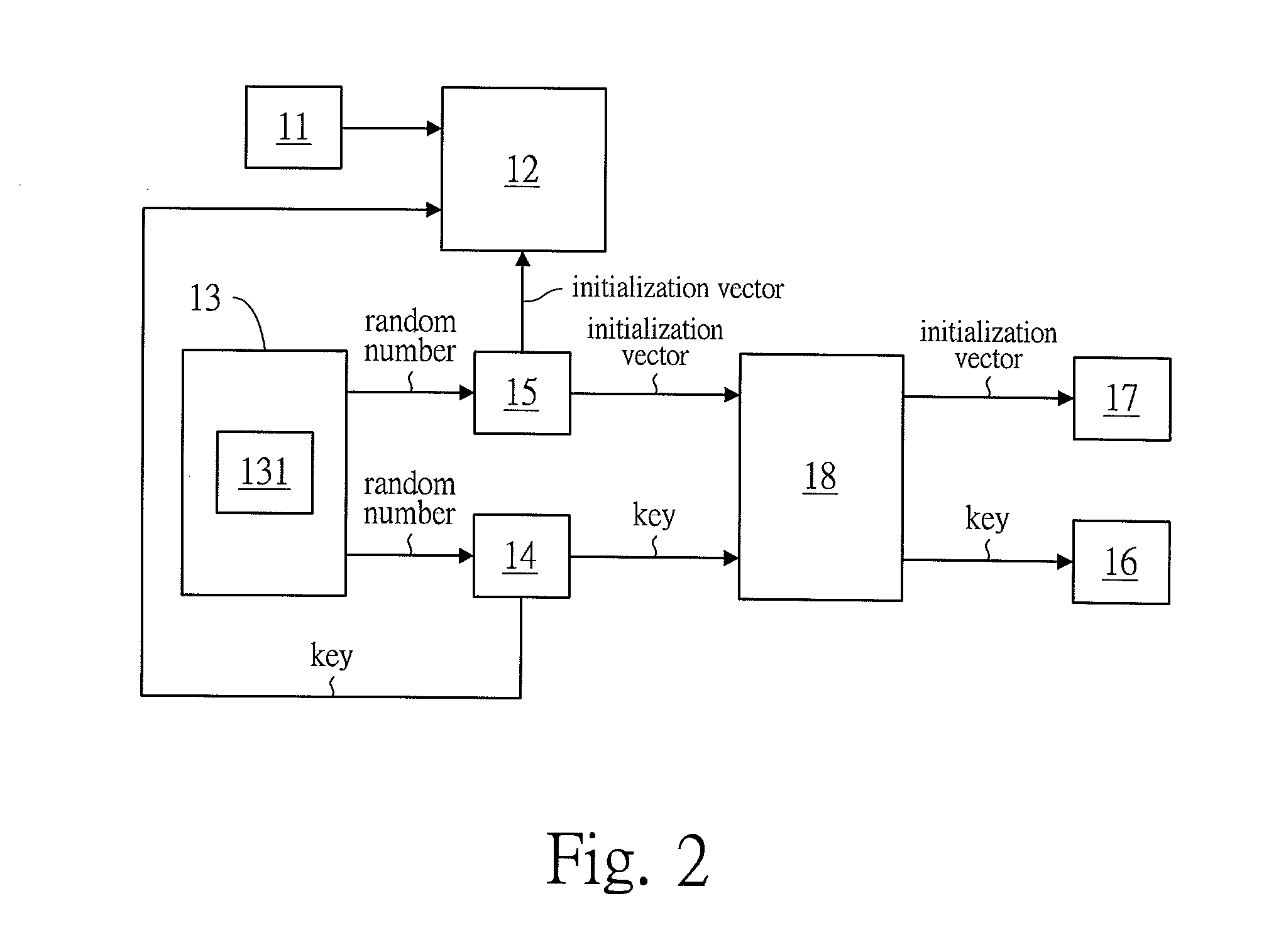
InactiveUS20160028540A1Key distribution for secure communicationMultiple keys/algorithms usageMultiple encryptionInitialization vector
The present invention relates to a multiple encrypting method, for encrypting a file and / or a protocol and generating encryption keys. Comprising the steps of: uploading at least one of a file and a protocol by a file uploading unit; generating random numbers by a random number generation unit; arranging the random numbers to form at least one key and at least one initialization vector respectively by a key generation unit and an initialization vector generation unit; encrypting the file and / or the protocol from the file uploading unit via using AES encryption by an encryption unit, so as to generate an encrypted file and / or an encrypted protocol; saving the key and the initialization vector respectively in a first storage unit and a second storage unit; Repeating the above steps at least one time.
Owner:KO CHENG HAN
Facilitating Communications Using Hybrid Cryptography
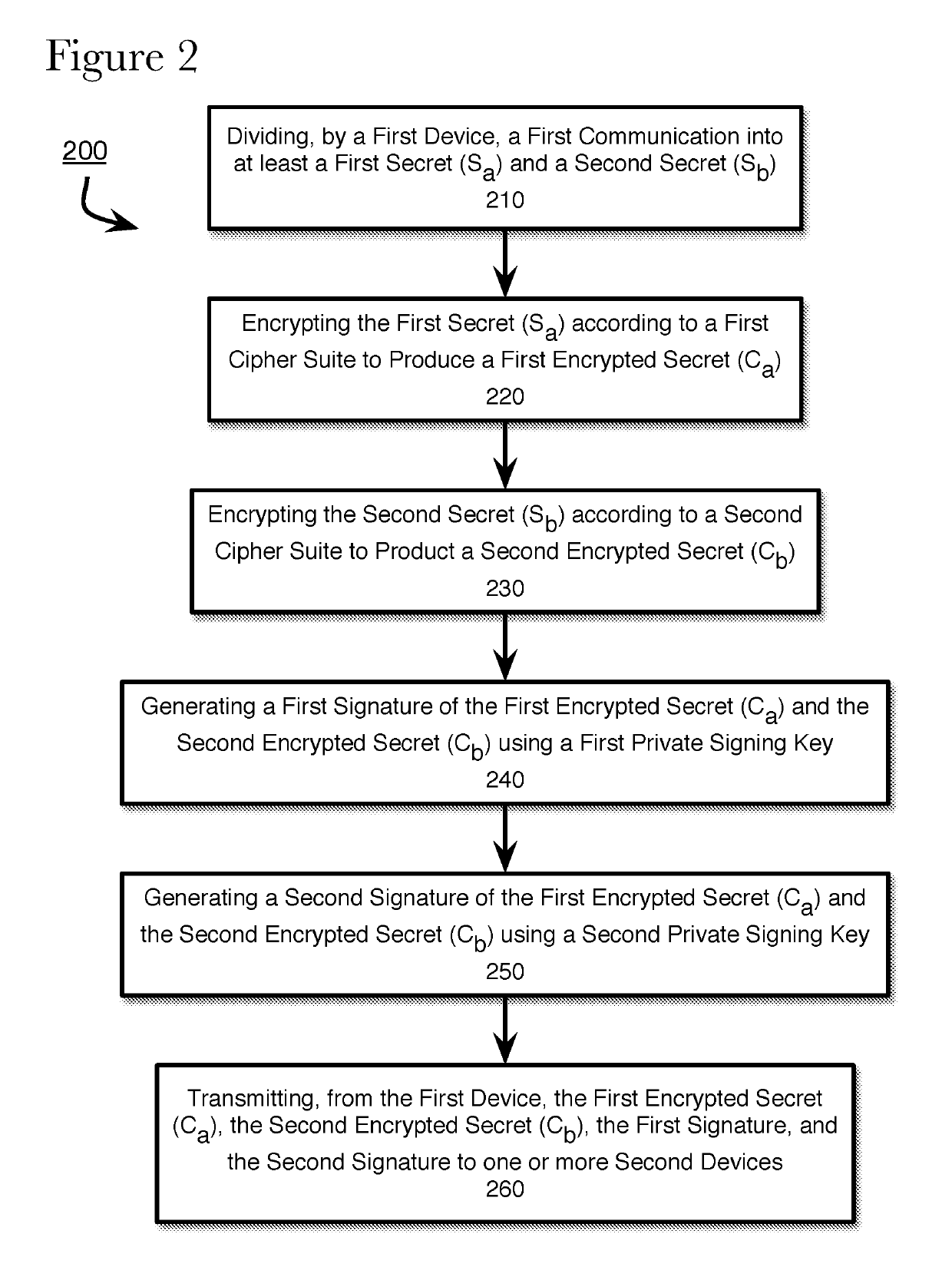
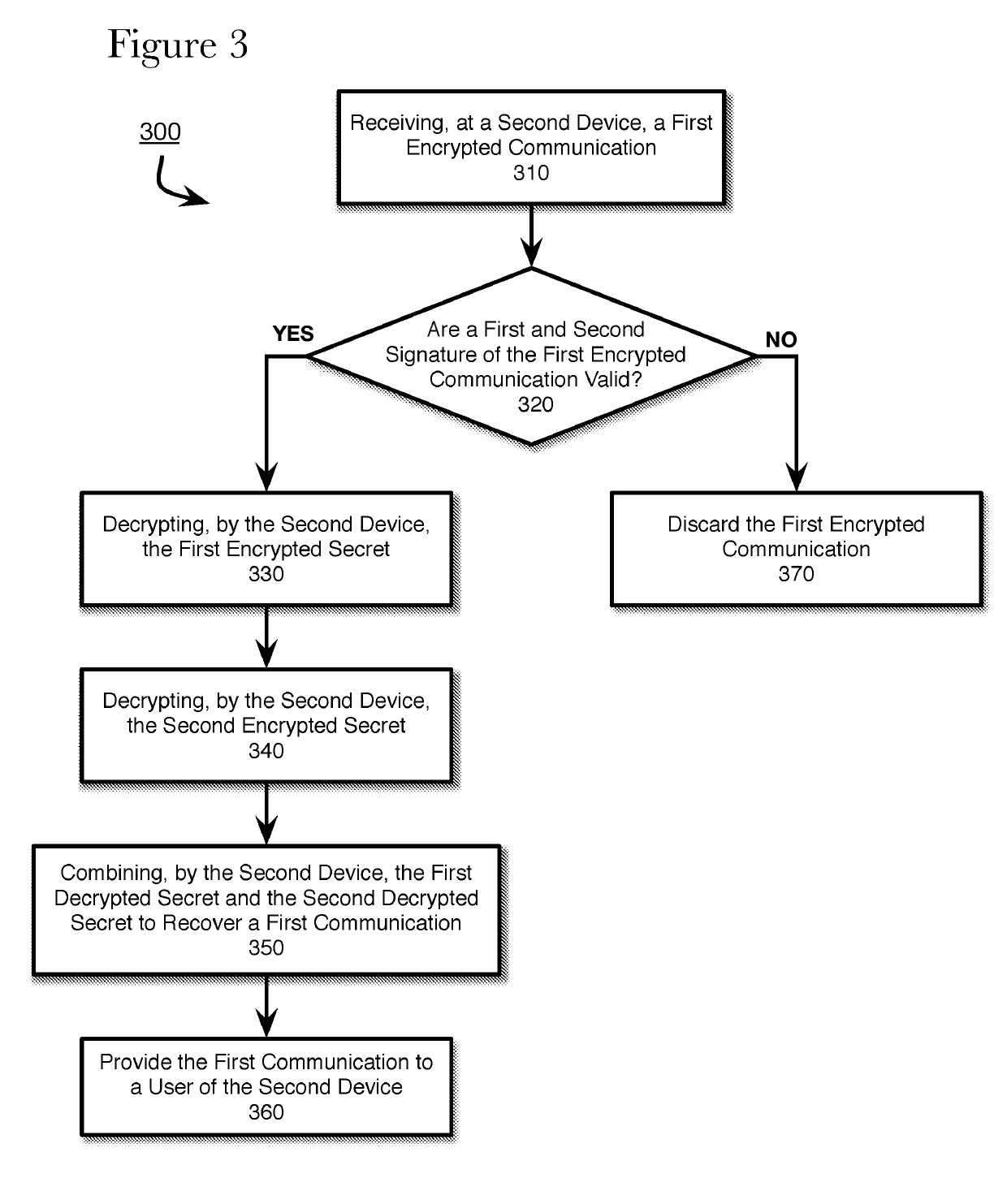
ActiveUS20190245681A1Key distribution for secure communicationMultiple keys/algorithms usageCryptography protocolsCipher suite
The present application describes a method, system, and non-transitory computer-readable medium for exchanging encrypted communications using hybrid cryptography protocol. According to the present disclosure, a first device divides a first communication into at least a first secret and a second secret. The first device encrypts the first secret using a first cipher suite and the second secret using a second cipher suite. The first device generates a first signature of the first encrypted secret and the second encrypted secret according to a first signature generation algorithm associated with the first cipher suite and a second signature of the first encrypted secret and the second encrypted secret according to a second signature generation algorithm associated with the second cipher suite. The first device transmits the first encrypted secret and the second encrypted secret, the first signature, and the second signature to the second device.
Owner:WICKR +1
Network protocol identification method and system based on semi-supervised learning
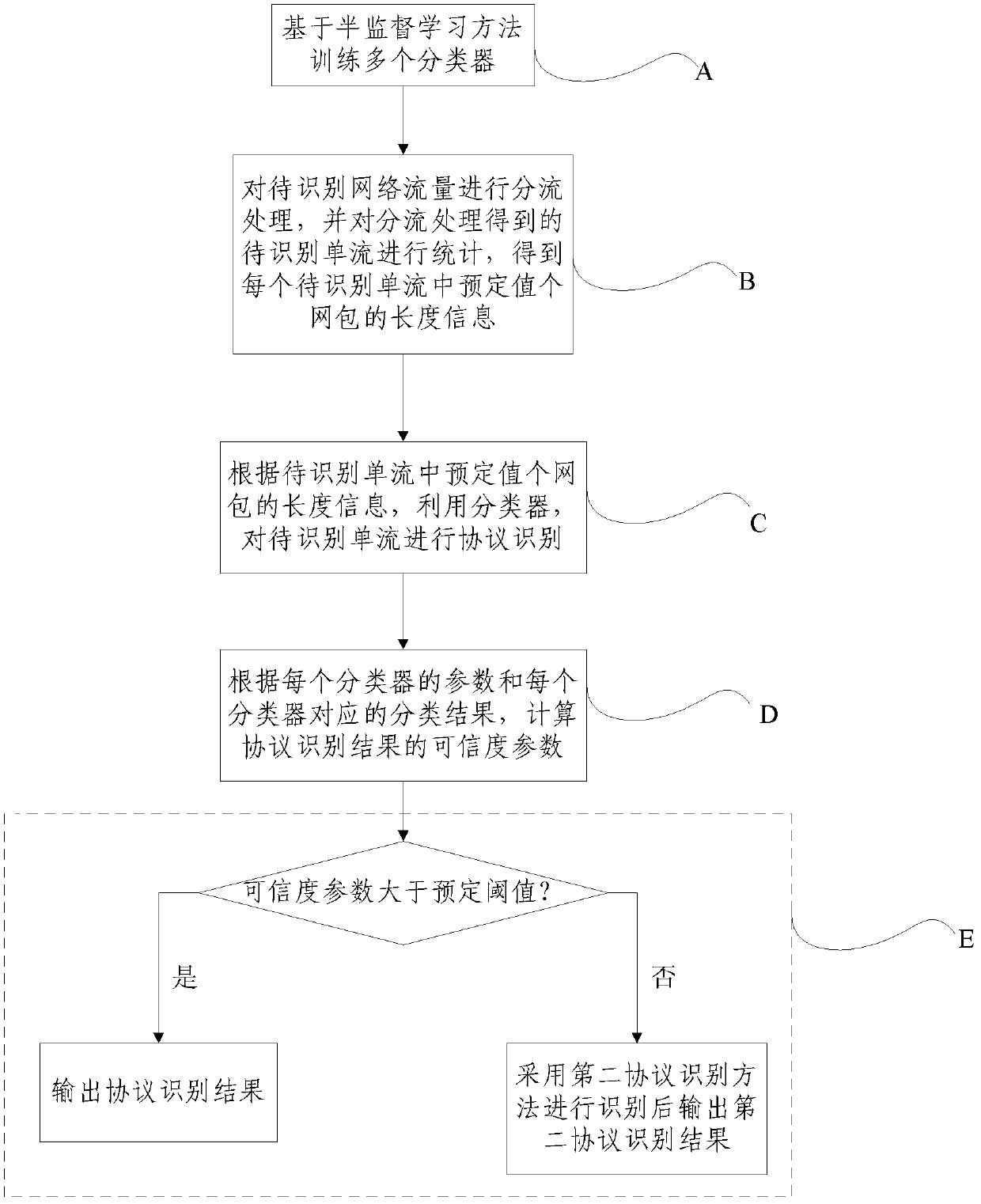
InactiveCN102611706AAchieve Classification PerformanceAchieve scalabilityData switching networksKnowledge based modelsTraffic capacityData set
The invention discloses a network protocol identification method and system based on semi-supervised learning, relating to the technical field of network safety. The method comprises the following steps of: training a plurality of classifiers based on a semi-supervised learning method; carrying out split-flow treatment on a network flow rate to be identified, and counting a single flow to be identified, which is obtained by the split-flow treatment, so as to obtain length information of a pre-set quantity of network packets in each single flow to be identified; and utilizing the classifiers to carry out protocol identification on the single flow to be identified according to the length information of the pre-set quantity of the network packets in the single flow to be identified. According to the network protocol identification method and system based on the semi-supervised learning, disclosed by the invention, a semi-supervised machine learning method is introduced into the protocol identification, namely that less calibrated sample information is used and a lot of unlabelled information is sufficiently utilized, so that the classification performance and the practical expansibility are met simultaneously; and the network protocol identification method and system have higher identification accuracy and higher identification speed, and can identify an encrypted protocol without depending on a lot of calibration data sets.
Owner:TSINGHUA UNIV
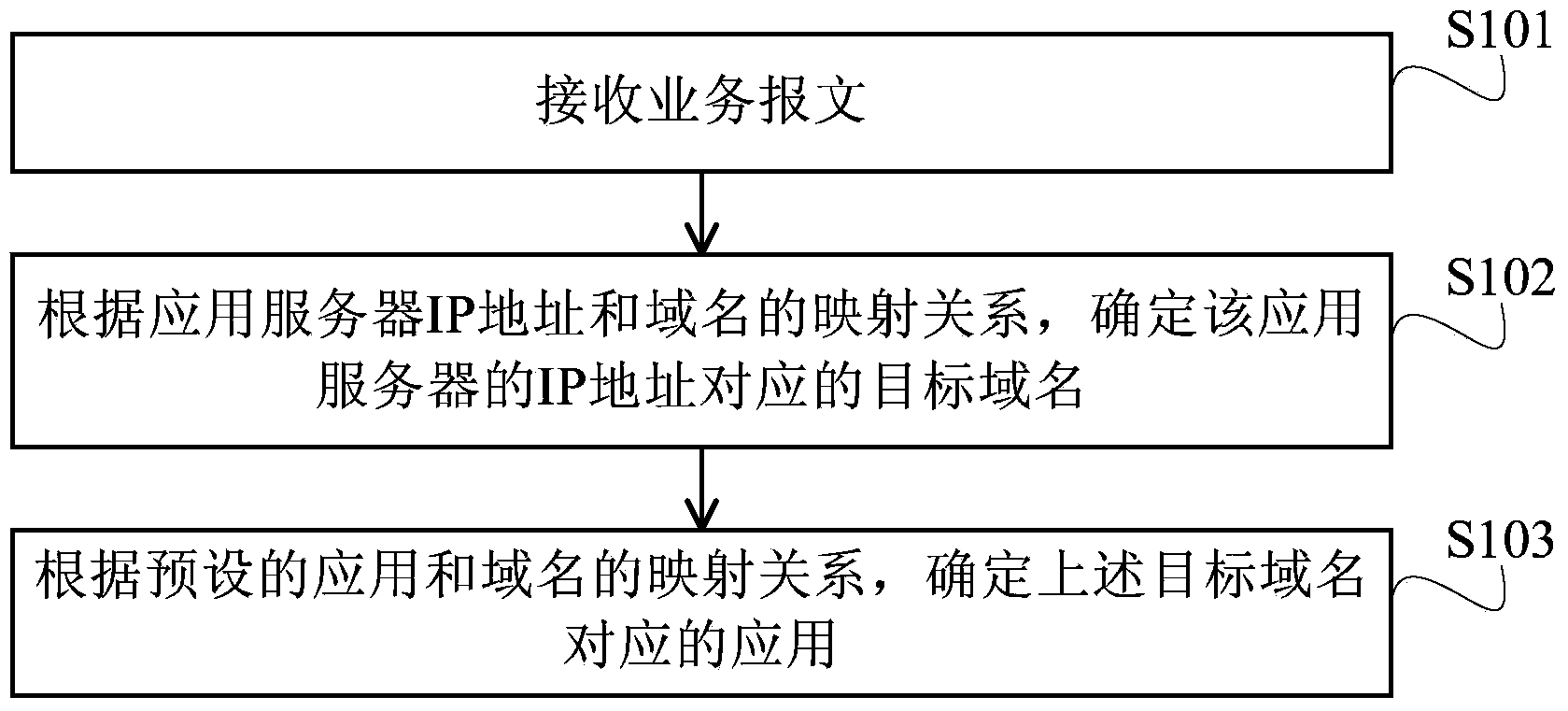
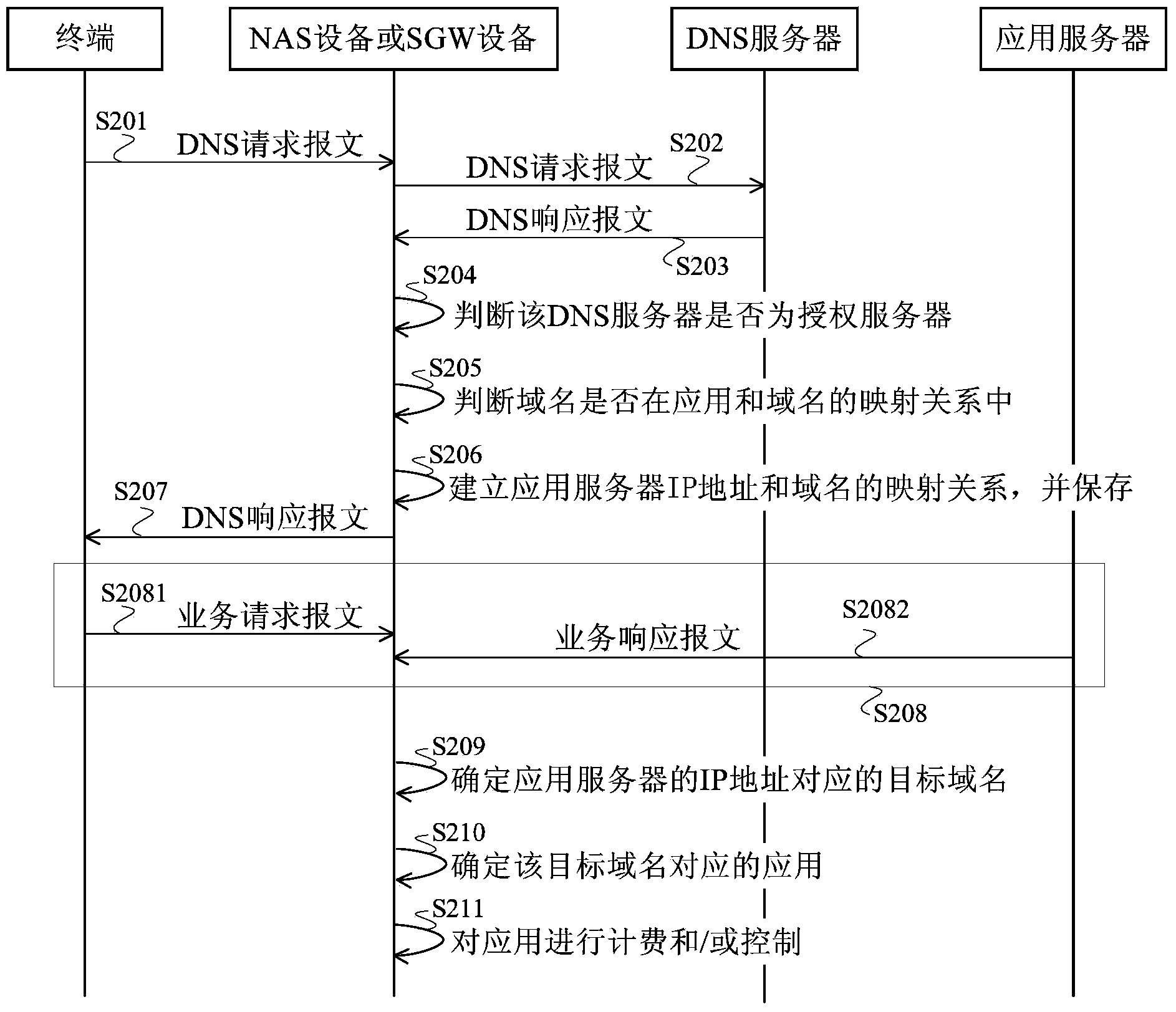
Application identification method and device
The embodiment of the invention provides an application identification method and device. The method comprises the following steps: a service message is received, wherein the service message carries a network protocol IP address of an application server; according to the mapping relation between the IP address of the application server and a domain name, a target domain name corresponding to the IP address of the application server is determined; according to the preset mapping relation between an application and the domain name, the application corresponding to the target domain name is determined. According to the IP address of the application server carried in the service message, the mapping relation between the IP address of the application server and the domain name and the mapping relation between the application and the domain name, the application corresponding to the IP address of the application server is determined, and therefore the application identification method and device realize application identification for communication adopting a proprietary protocol or an encryption protocol.
Owner:HUAWEI TECH CO LTD
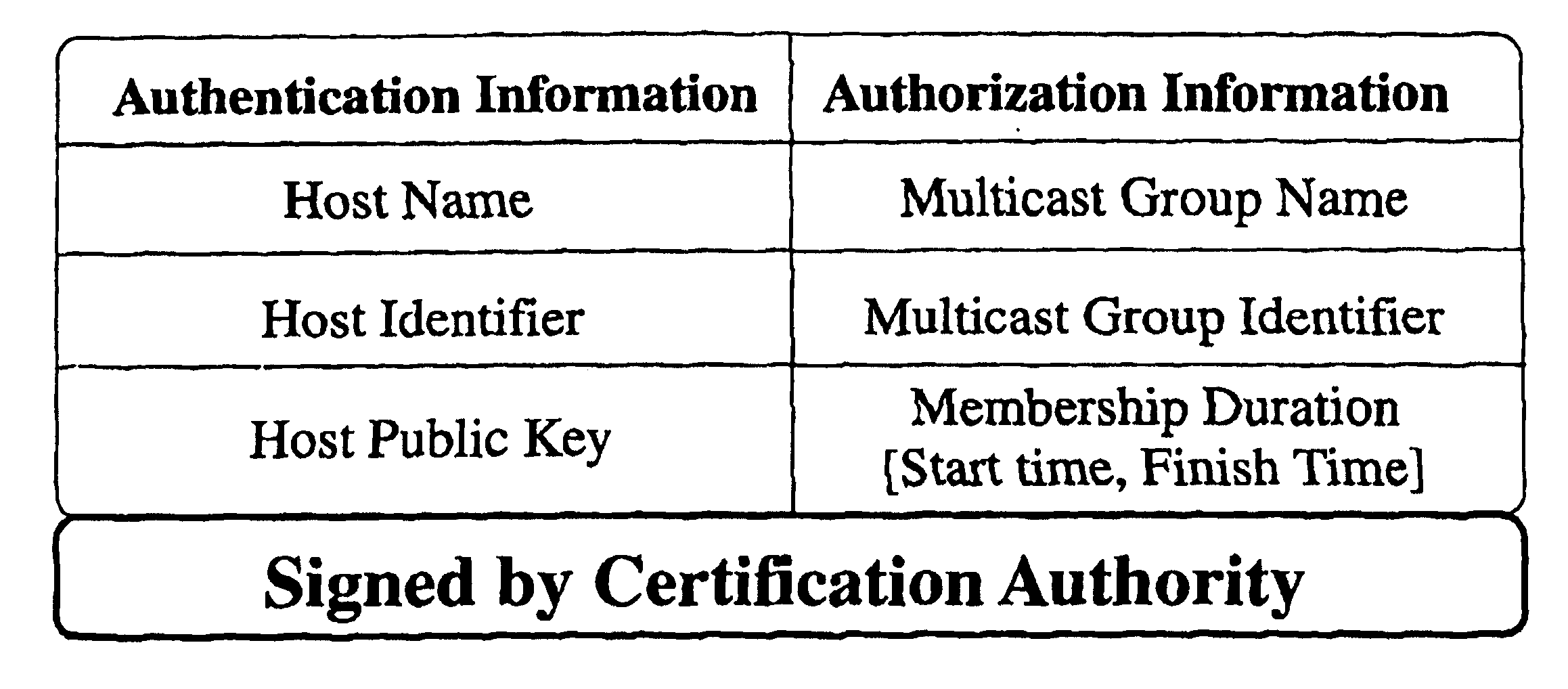
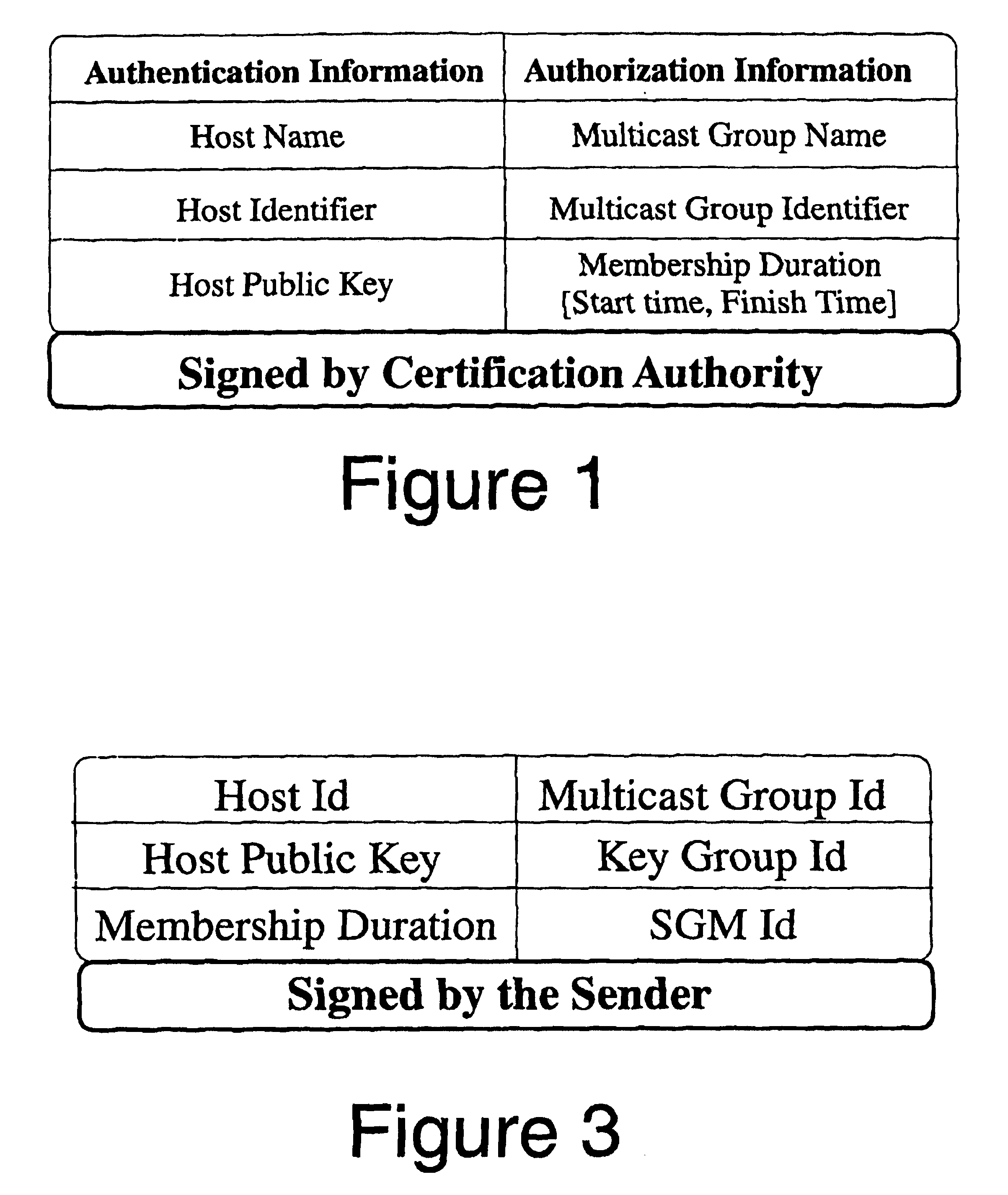
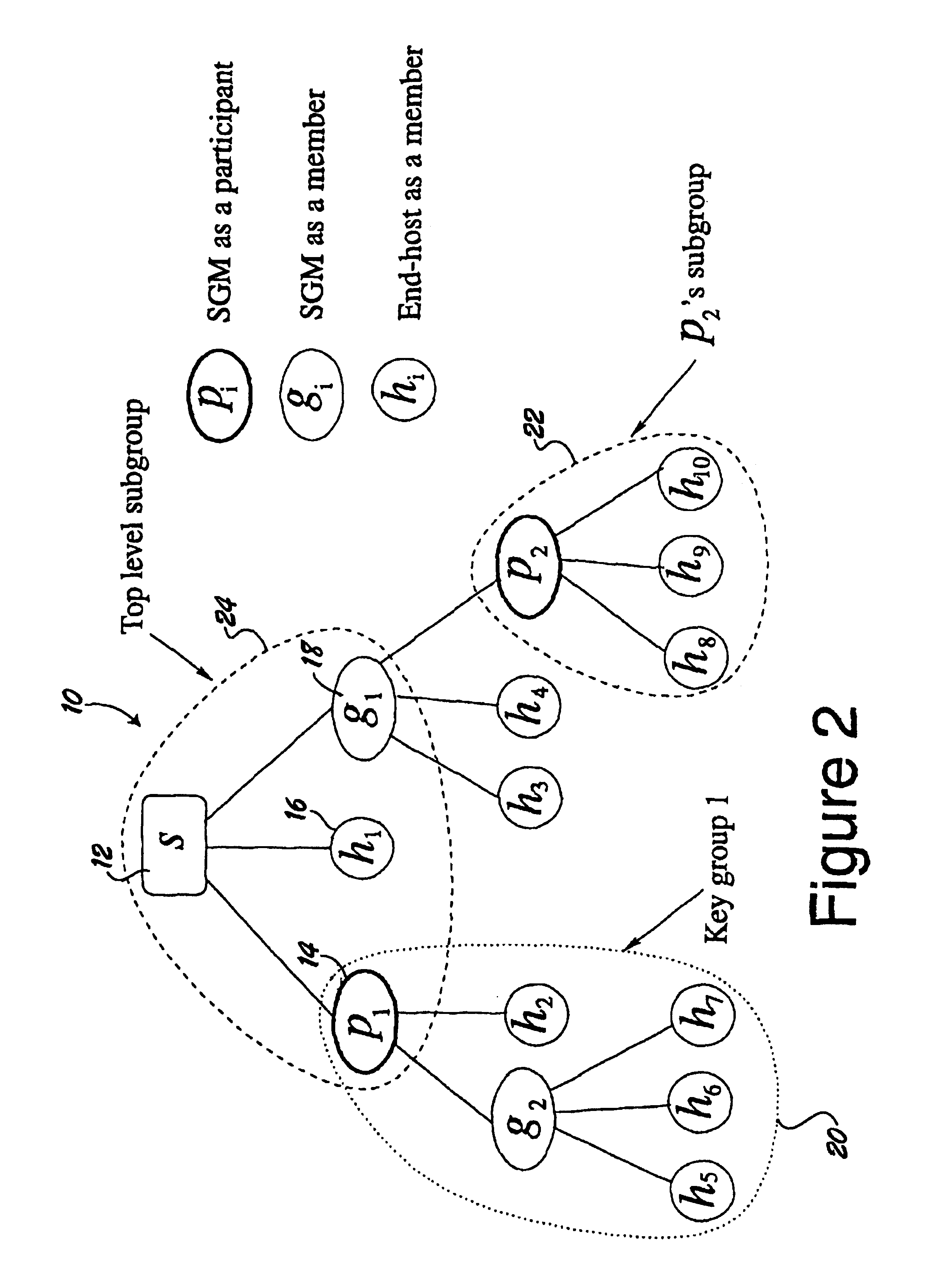
Dual encryption protocol for scalable secure group communication
InactiveUSRE40708E1Key distribution for secure communicationMultiple keys/algorithms usageExtensibilityCryptography protocols
A logical tree structure and method for managing membership in a multicast group provides scalability and security from internal attacks. The structure defines key groups and subgroups, with each subgroup having a subgroup manager. Dual encryption allows the sender of the multicast data to manage distribution of a first set of encryption keys whereas the individual subgroup managers manage the distribution of a second set of encryption keys. The two key sets allow the sender to delegate much of the group management responsibilities without compromising security because a key from each set is required to access the multicast data. Security is further maintained via a method in which subgroup managers can be either member subgroup managers or participant subgroup managers. Access to both keys is provided to member subgroup managers whereas access to only one key is provided to participant subgroup managers. Nodes can be added without the need to generate a new encryption key at the top level which provides improved scalability.
Owner:PANASONIC CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com