Patents
Literature
58 results about "Cipher suite" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
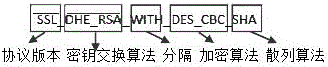
A cipher suite is a set of algorithms that help secure a network connection that uses Transport Layer Security (TLS) or its now-deprecated predecessor Secure Socket Layer (SSL). The set of algorithms that cipher suites usually contain include: a key exchange algorithm, a bulk encryption algorithm, and a message authentication code (MAC) algorithm.
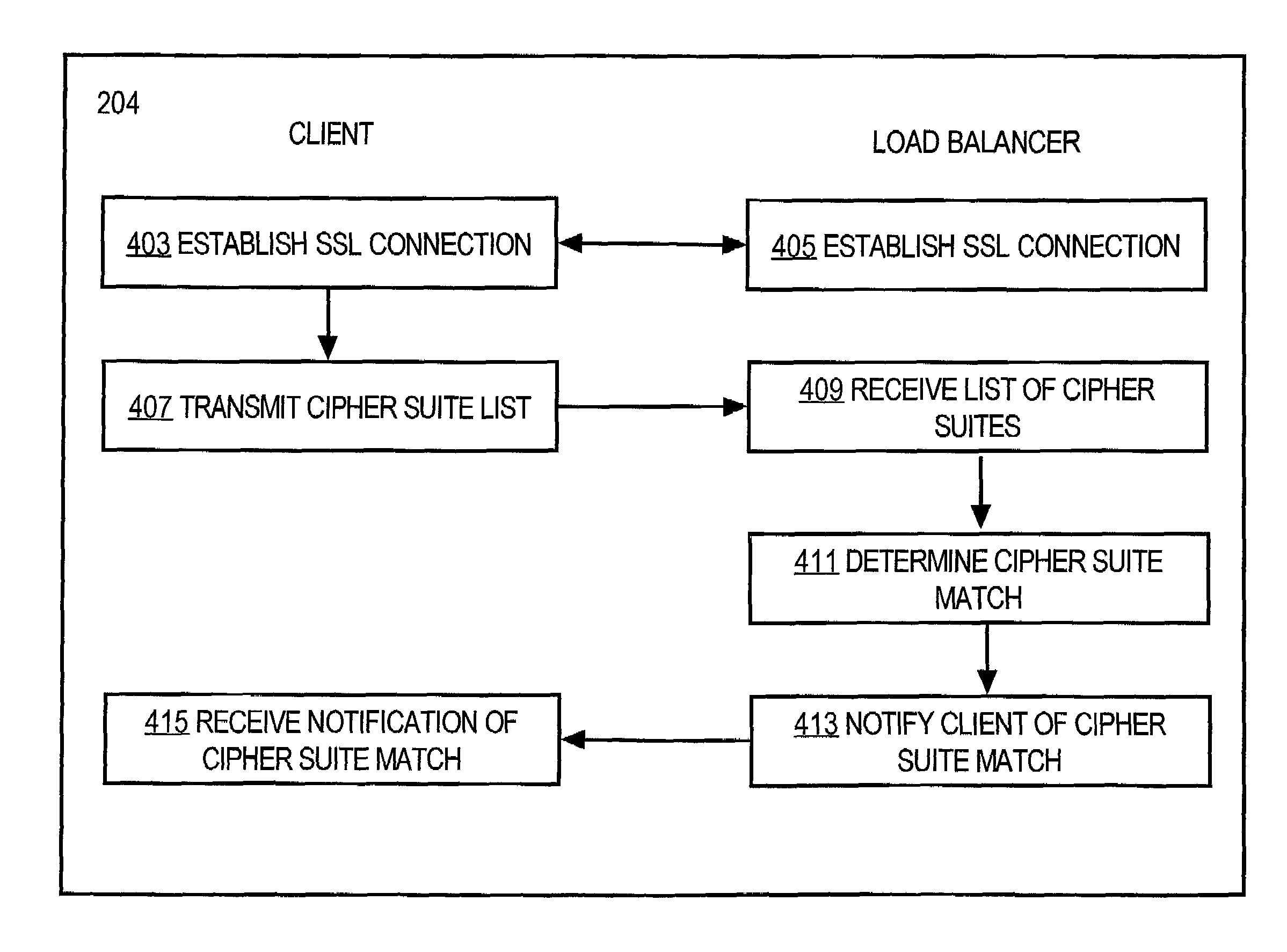
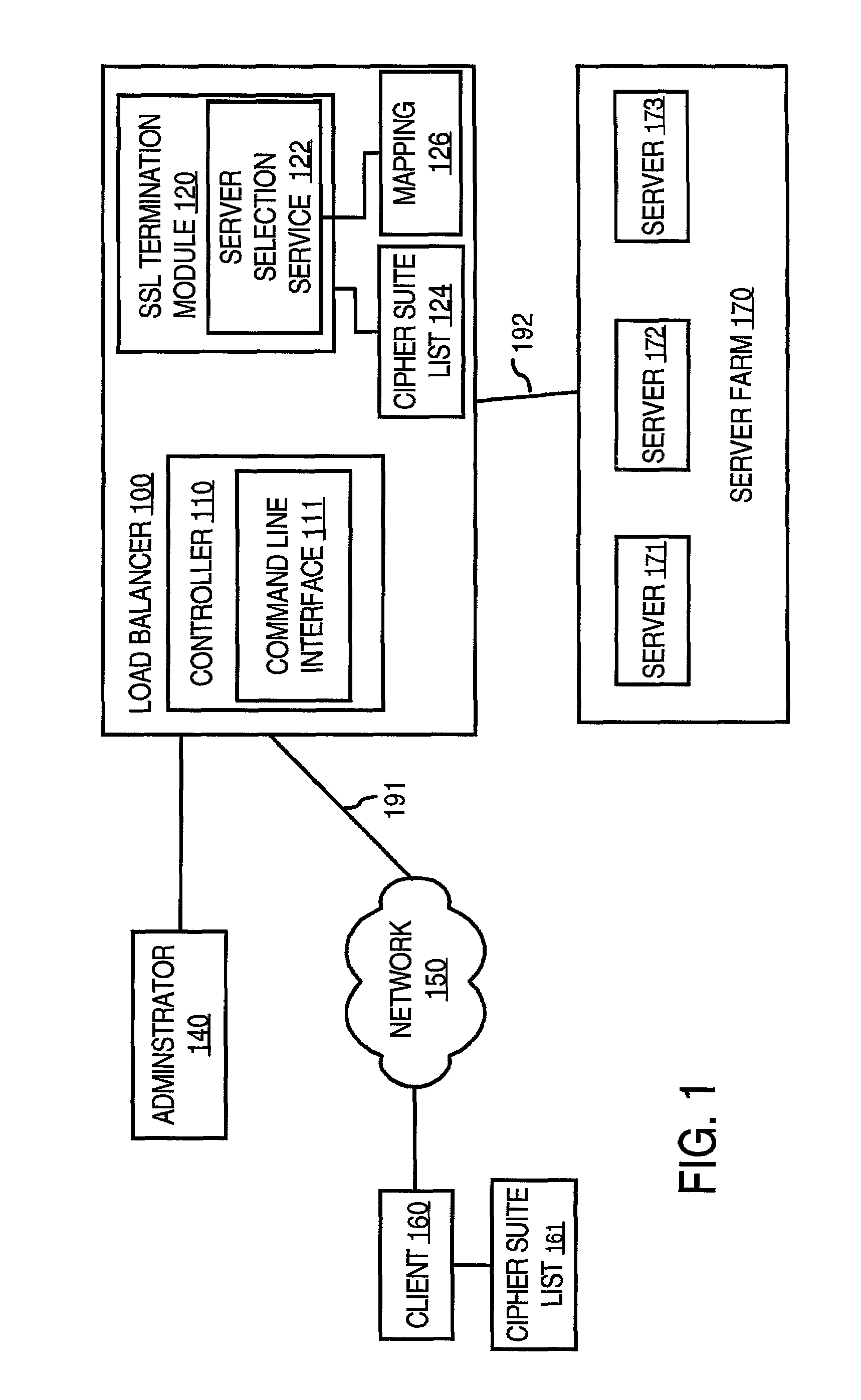
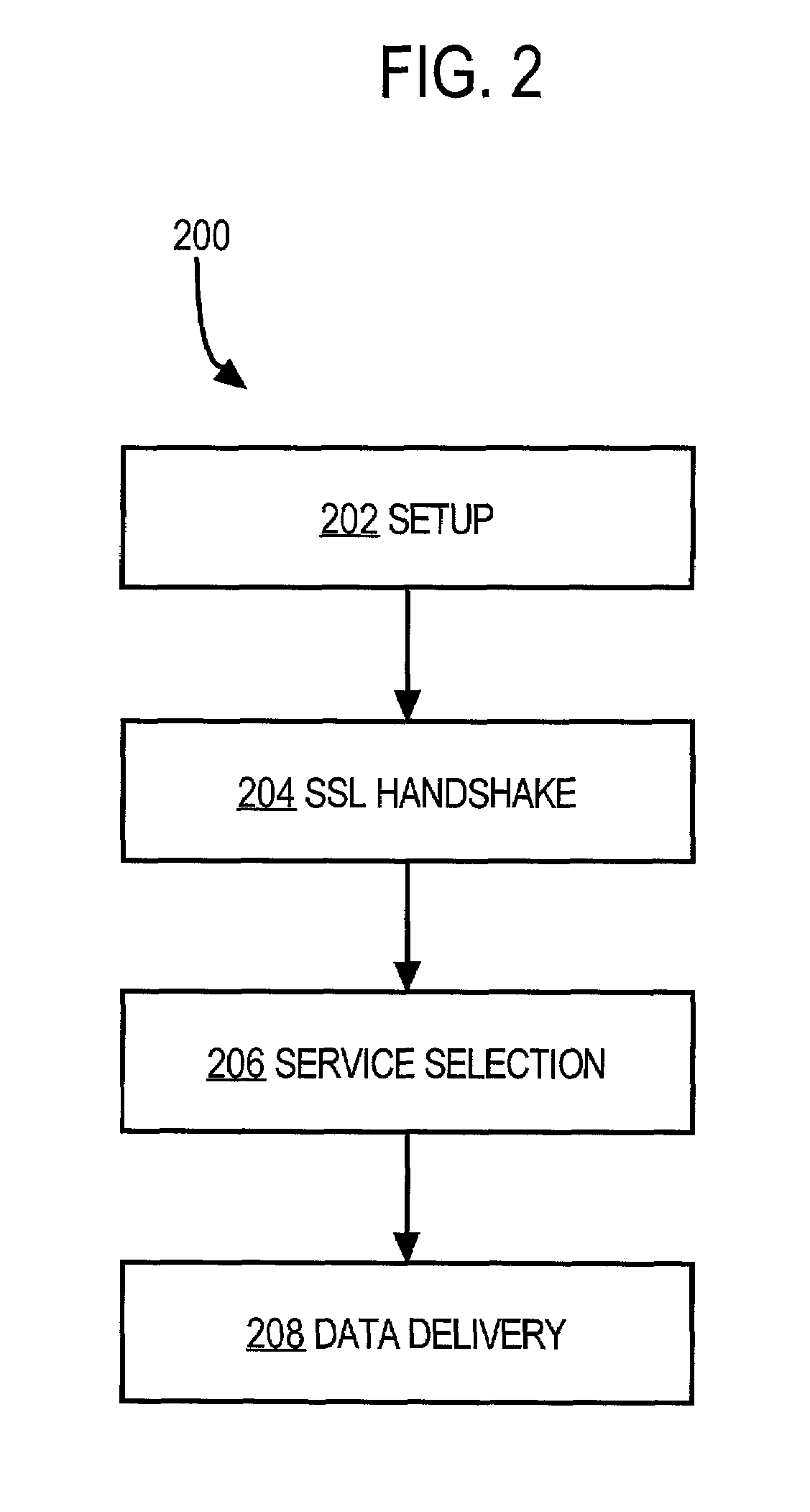
Method and apparatus for providing data from a service to a client based on encryption capabilities of the client
A method and apparatus are disclosed for providing data from a service to a client based on the encryption capabilities of the client. Cipher suite lists are exchanged between a client and an endpoint. On the endpoint, the cipher suite list incorporates a mapping of cipher suite names to services. The endpoint uses the client's list of cipher suites in conjunction with the mapping of cipher suite names to services to determine a cipher suite match. A service is selected based on the cipher suite match. A server farm is selected based on the service. The client is informed of this cipher suite match and the endpoint retains knowledge of the cipher suite match throughout the session. Therefore, the encrypted connection between the client and the endpoint can be disconnected and later reestablished to provide data from the particular server.
Owner:CISCO TECH INC
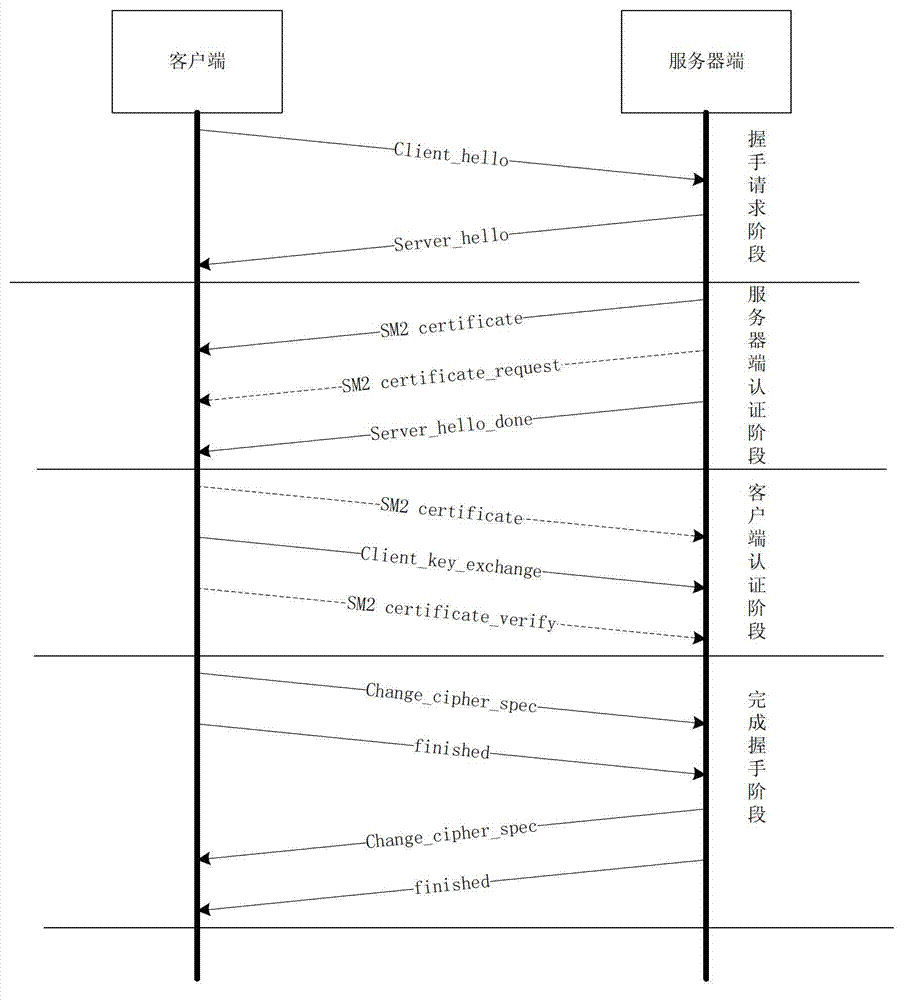
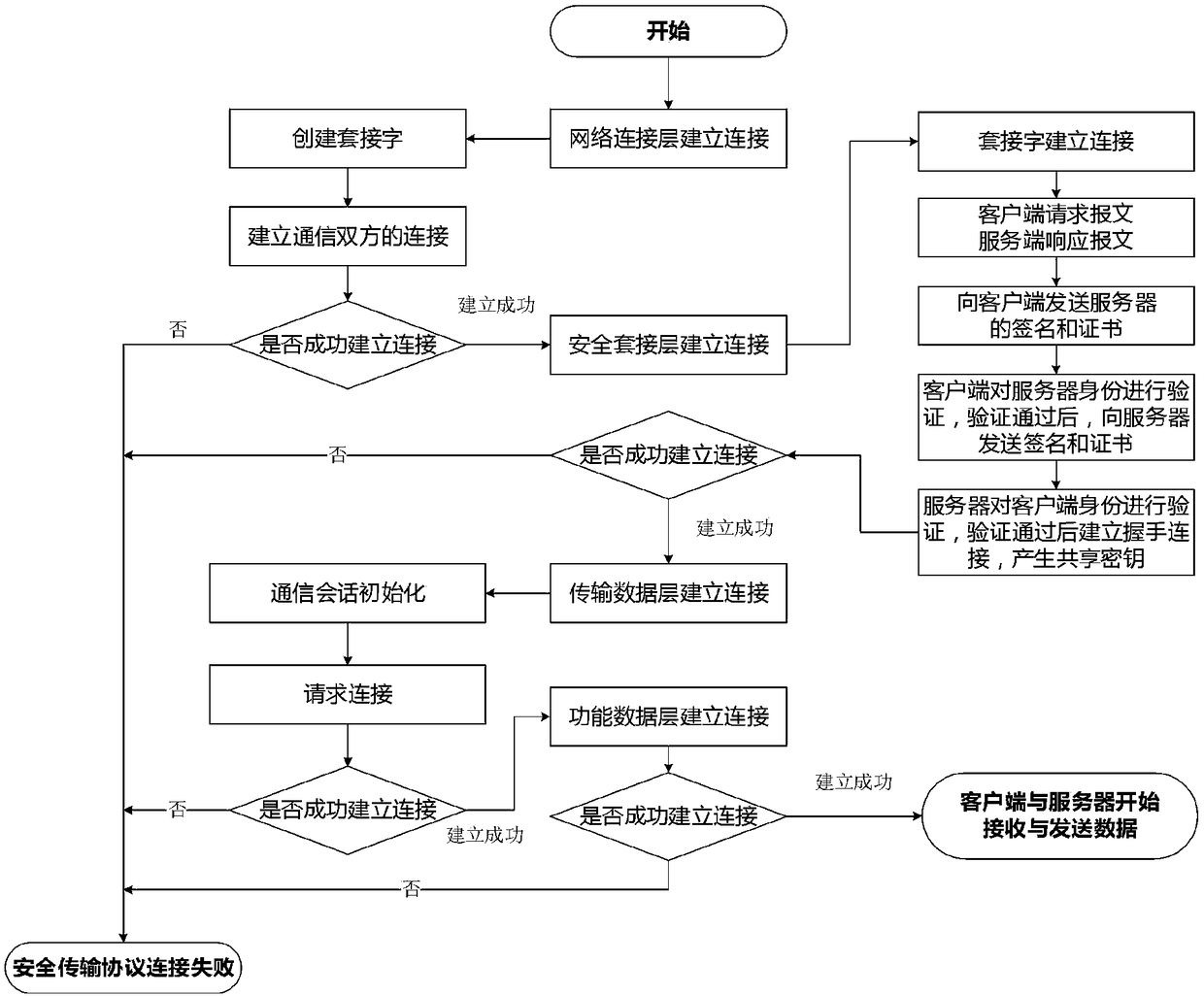
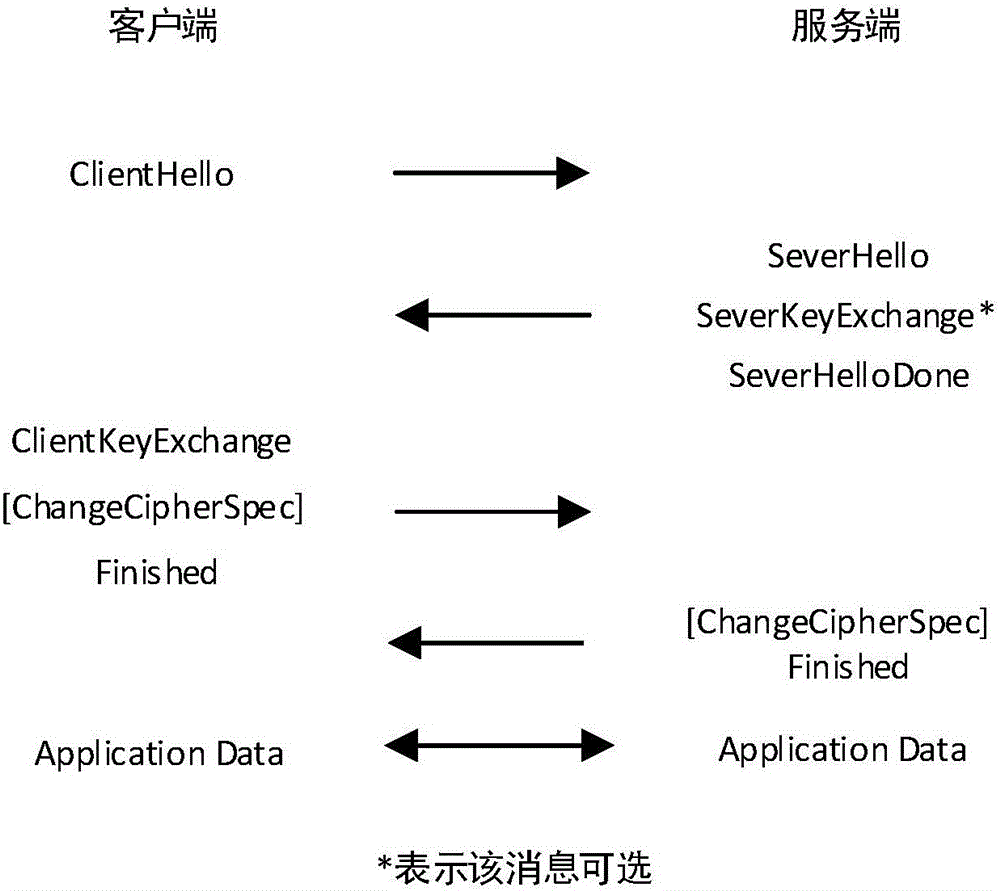
Transport layer security (TLS) channel constructing method based on cryptographic algorithm
The invention relates to the technical field of network safety and provides a transport layer security (TLS) channel constructing method based on a cryptographic algorithm. The TLS channel constructing method includes steps that: a server side launches a request and a client side respond to a hello message, or the client side launches the hello message; the server side responds to the hello message of the server side; the server side transmits an SM2 certificate to the server side and then transmits a hello completing message; the client side receives the hello completing message and then transmits a secret key exchange message; the client side transmits a cipher suite change message and a finishing message, and the server side transmits the cipher suite change message and the finishing message after receiving the finishing message of the client side; and the server side and the client side perform data safe transmission according to the agreed safety parameters after receiving the finishing messages of each other and passing verification. According to the TLS channel constructing method, the cryptographic algorithm is blended into a TLS protocol to perform safety communication, the signature speed is obviously superior to that of a remote signaling alarm (RSA) algorithm by aid of short secret key length, and the TLS channel constructing method is a data safety method with the 2048-bit safety level of the RSA algorithm.
Owner:CHINA FINANCIAL CERTIFICATION AUTHORITY
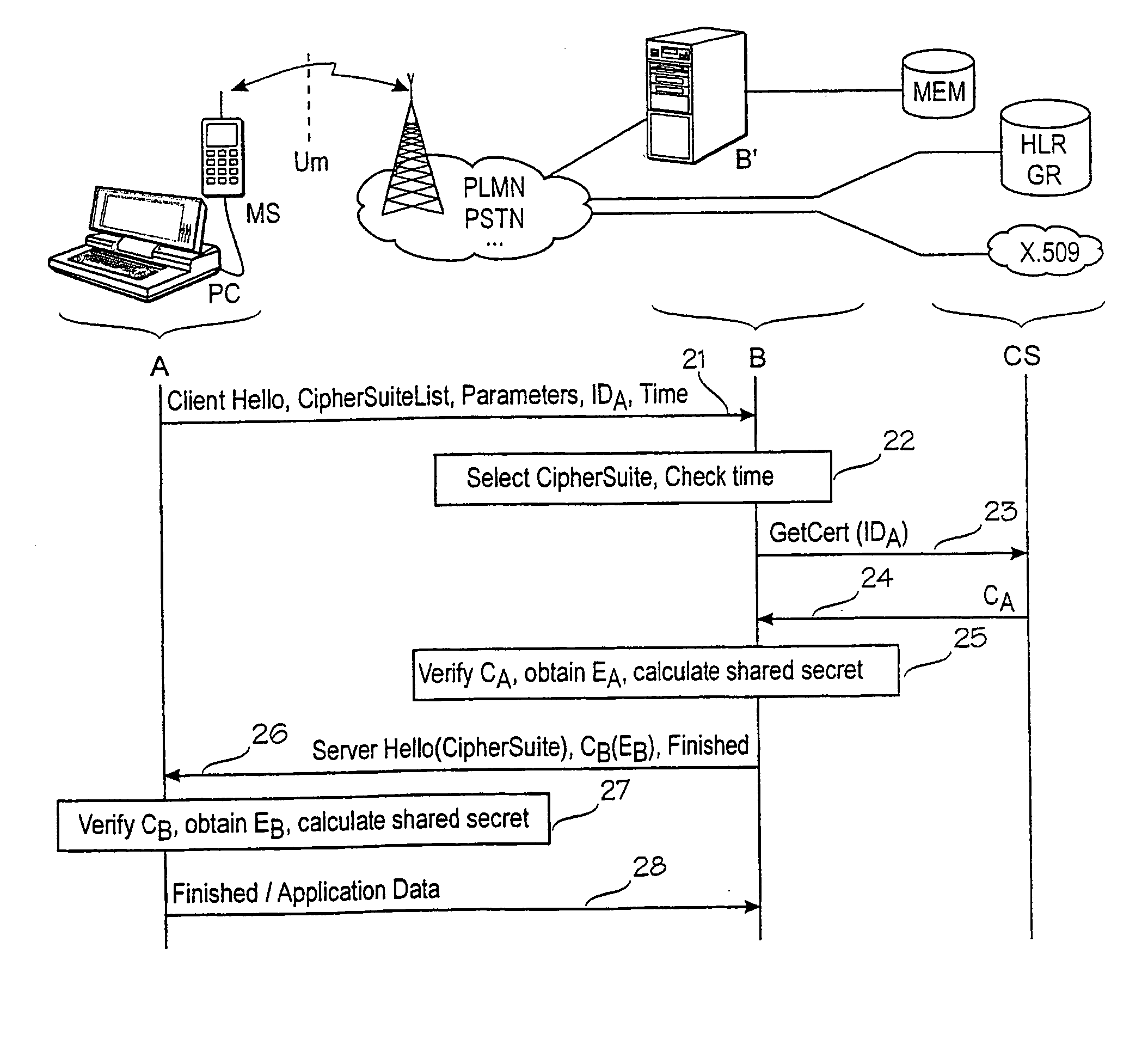
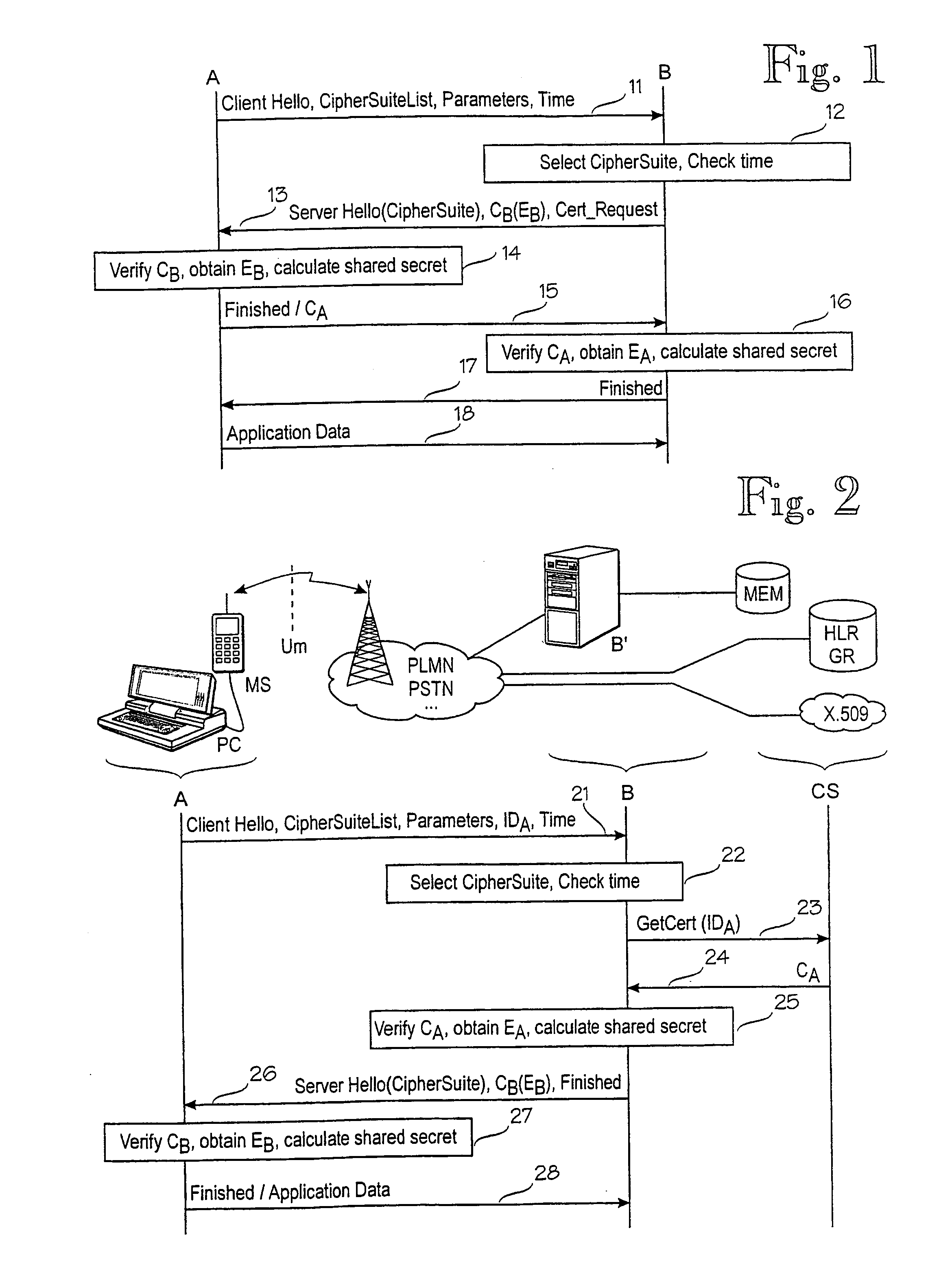
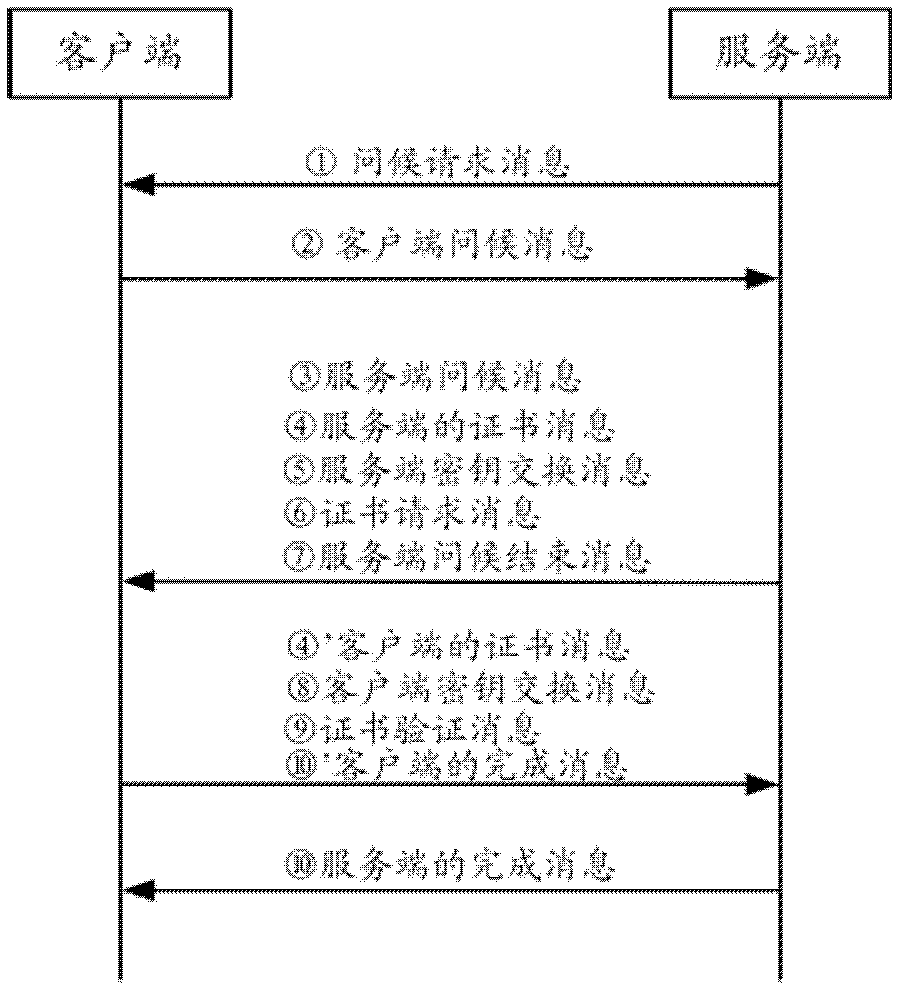
Secure handshake protocol
InactiveUS6931528B1Air interface can be eliminatedMinimize overheadKey distribution for secure communicationDigital data processing detailsProtocol for Carrying Authentication for Network AccessCipher suite
A method for a secure handshake protocol between A and B, connected by a slow channel is provided in which A sends a first message indicating a set of cipher suites with parameters, and its identifier and B selects a cipher suite, obtains A's certificate over a fast connection, verifies A's certificate and obtains A's public key. Next B sends a second message comprising B's certificate, and an indication that B has verified A's certificate, and an indication about the selected cipher suite. A begins to use the selected cipher suite, verifies B's certificate and obtains B's public key. Next A sends a third message indicating that A has verified B's certificate.
Owner:NOKIA TECHNOLOGLES OY
Application virtualization security communication method in autonomous and controllable environment
ActiveCN109347809AKey distribution for secure communicationUser identity/authority verificationVirtualizationNetwork connection
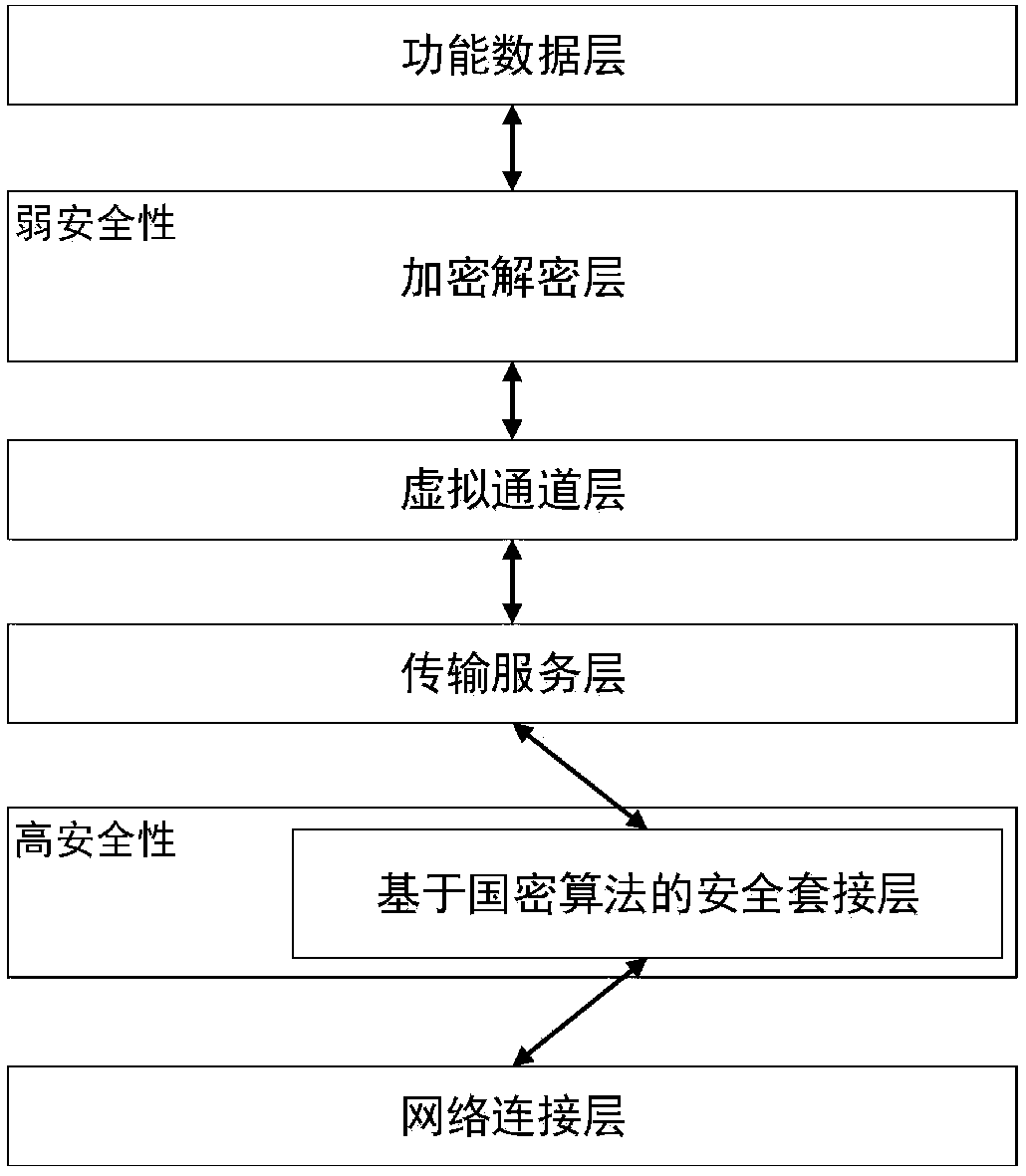
The invention relates to an application virtualization security communication method in an autonomous and controllable environment, and relates to the technical field of network security. The invention expands a security socket layer based on the domestic commercial cipher suite based on the RDP protocol by reconstructing the original RDP protocol stack, and adds the security socket layer to the network connection layer of the protocol stack, which can provide a secure transmission service for the client to the server, thereby realizing the dual identity authentication between the client and the server, and completing the identity verification of the client to the server.
Owner:BEIJING INST OF COMP TECH & APPL
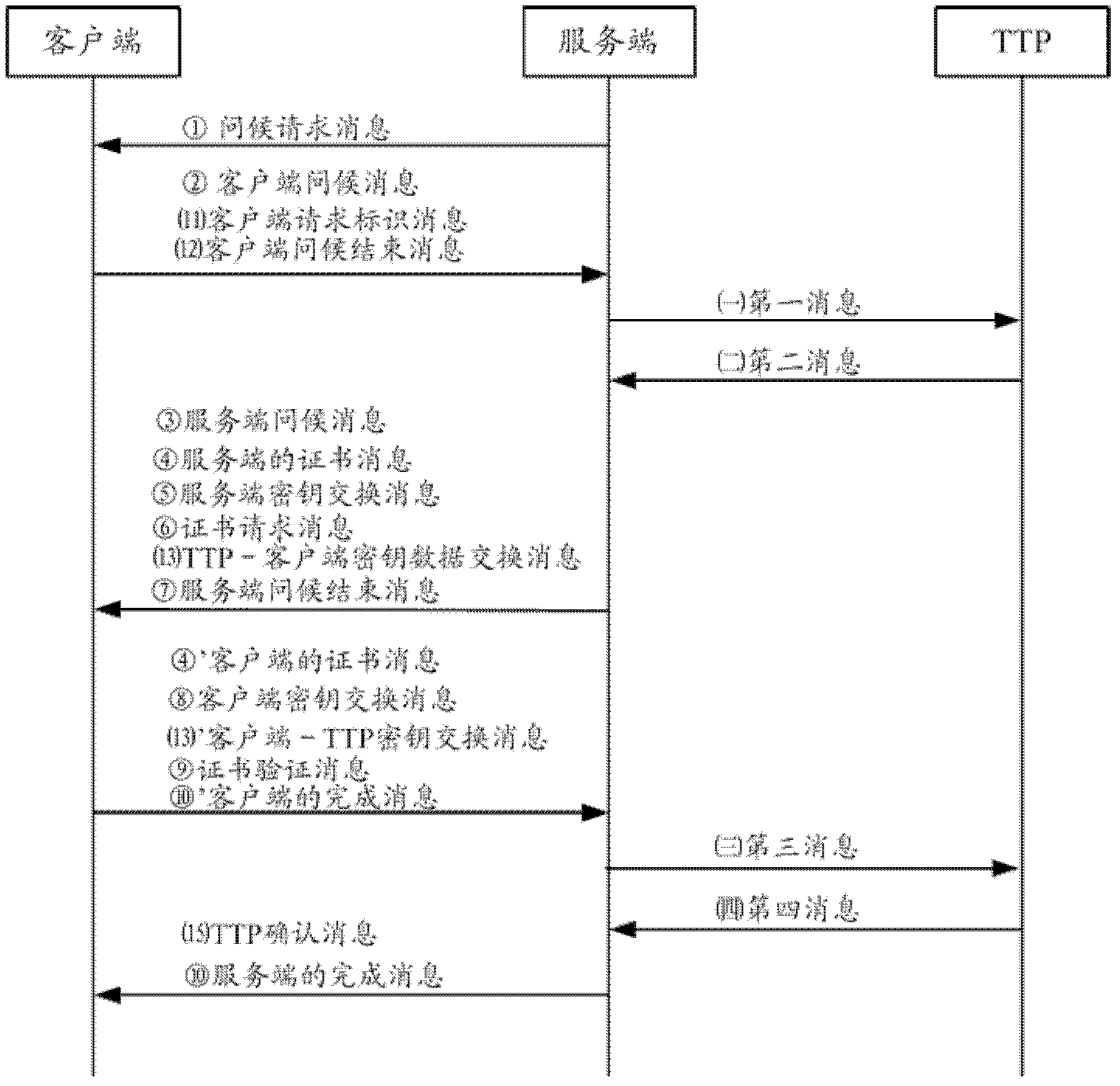
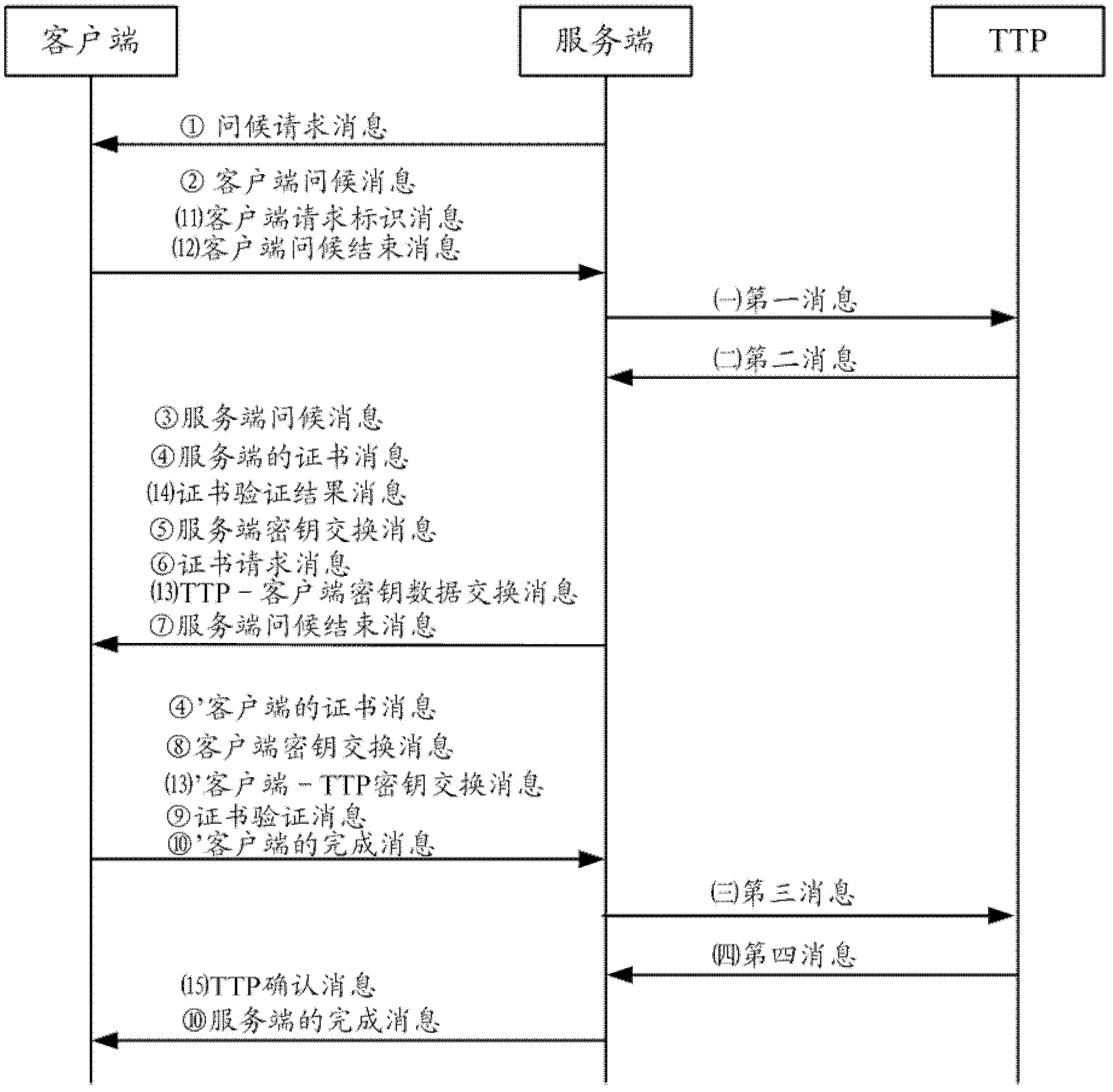
Transport layer security (TLS) handshaking method and device, and trusted third party (TTP)
ActiveCN102510387AImprove securityAchieve backward compatibilityTransmissionSecure transmissionMessage authentication code
The invention discloses a transport layer security (TLS) handshaking method, a TLS handshaking device and a trusted third party (TTP). The method comprises the following steps that: on the basis of the TLS handshaking process of two parties, a first party sends a question of the first party and a cipher suite list which is supported by the first party to the TTP; the TTP informs the first party of the question of the TTP, a temporary public key of the TTP and a TTP-first-party cipher suite; the first party informs the TTP of a first-party-TTP message authentication code by using a session key which is generated between the first party and the TTP; the TTP identifies the first-party-TTP message authentication code by using the session key which is generated between the first party and the TTP; after the first-party-TTP message authentication code passes identification, the TTP sends a TTP-first-party message authentication code to the first party; the first party identifies the TTP-first-party message authentication code; and if the TTP-first-party message authentication code passes identification, a secure tunnel between the first party and the TTP is established. The invention has the advantages that: on the basis of the TLS handshaking method of the two parties, the secure tunnel is established between the first party and the TTP, the security is improved, and high downward compatibility is realized.
Owner:CHINA IWNCOMM
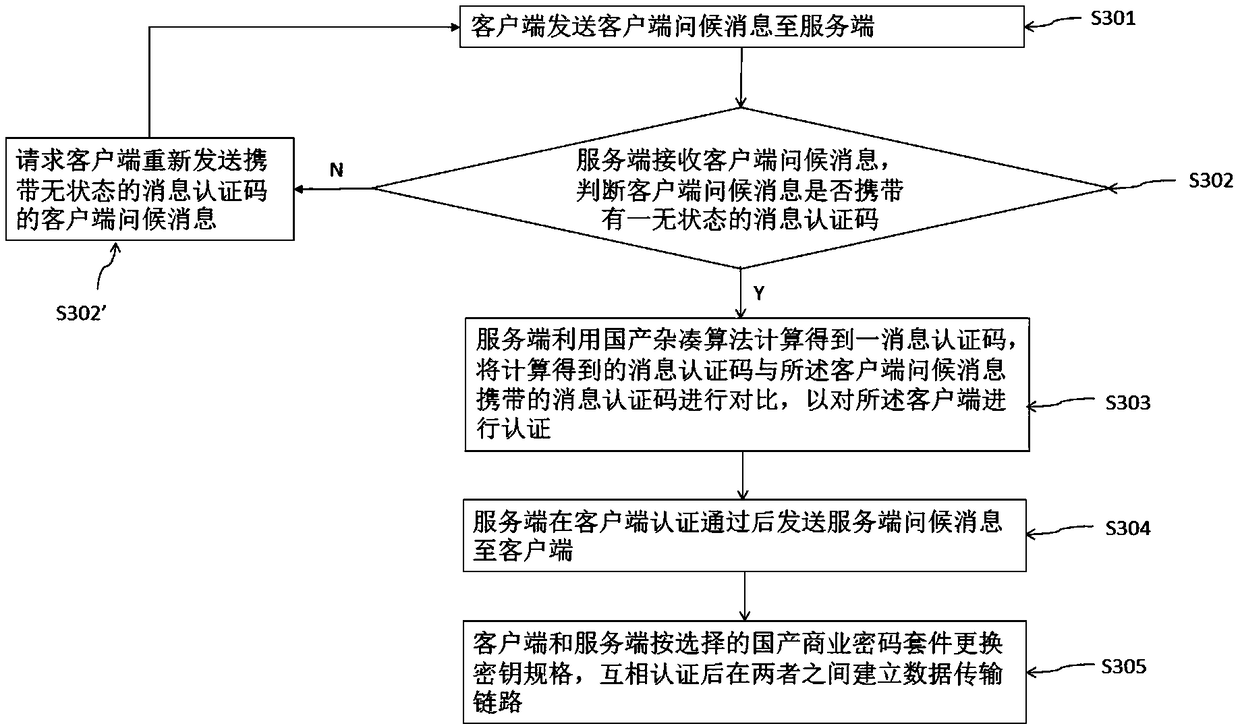
Handshake method and system based on datagram secure transmission protocol
ActiveCN108650227ASatisfy the needs of safety, autonomy and controllabilityTake advantage ofKey distribution for secure communicationTransmission protocolComputer hardware
The invention refers to a handshake method and a handshake system based on a datagram secure transmission protocol. The handshake method comprises: sending a client greeting message to the server by the client, wherein the client greeting message contains a list of all domestic commercial cipher suites supported by the client; receiving and determining whether the client greeting message carries astateless message authentication code by the server: if so, calculating to obtain a message authentication code by using a domestic hash algorithm, and comparing with the message authentication codecarried by the client greeting message to authenticate the client; sending a server greeting message to the client after the authentication, and informing the client of the domestic commercial ciphersuite selected by the client; and replacing the key specification according to the selected domestic commercial cipher suite by the client and the server, thereby establishing a data transmission link. The invention is capable of meeting the requirement of self-controllable information security in China and fully utilizing the unique advantages of the domestic encryption algorithm, and is compatible with the original DTLS protocol, and convenient for horizontal expansion.
Owner:SUZHOU KEDA TECH
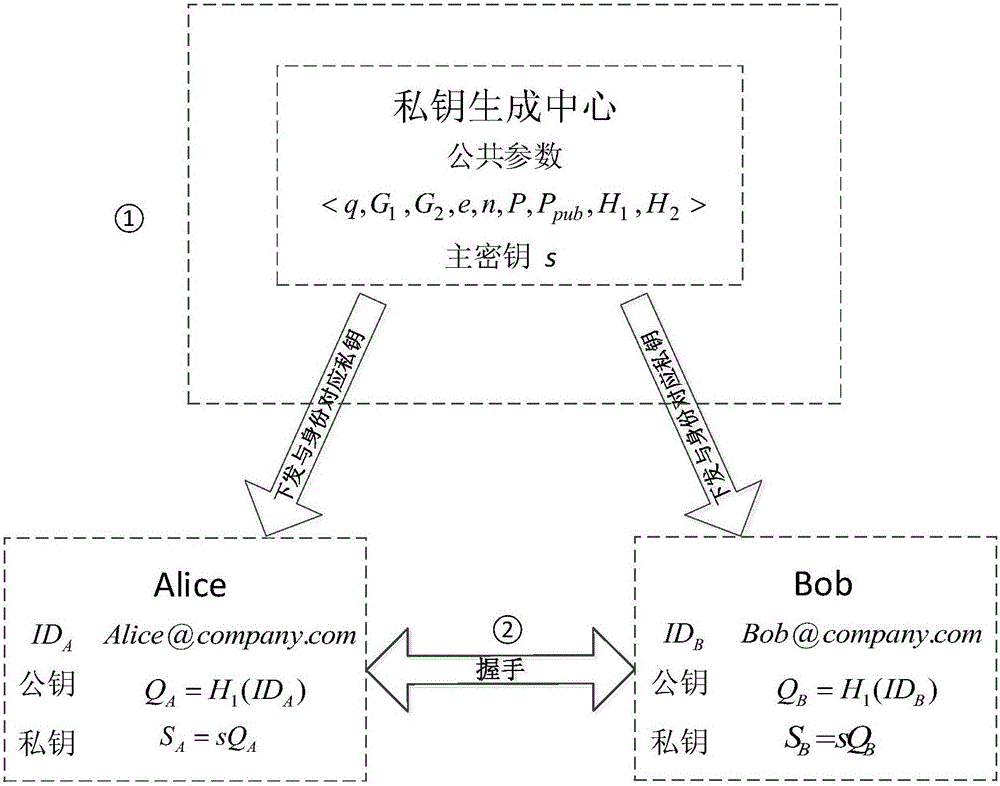
TLS handshake protocol for identity-based cryptosystem
The invention discloses a TLS handshake protocol for an identity-based cryptosystem, and in particular relates to the field of basic communication of trusted security networks. The problems of high delay, high calculation amount and the like due to finding, transferring, verifying and the like of a certificate in a TLS handshake process in the traditional PKI system can be solved by defining a new ciphersuite; and the handshake protocol performance is improved while the security is ensured. The handshake protocol comprises the following steps of: (1), establishing the identity-based cryptosystem, and distributing secret keys; and (2), handshaking to negotiate a security parameter. The TLS handshake protocol disclosed by the invention has the advantages that: the certificate is unnecessary to send and verify, such that the network flow and the memory are saved; authentication and secret key negotiation are completed simultaneously; the number of messages is reduced; the network delay is reduced while the high security is ensured; and the TLS handshake protocol is perfectly compatible with a TLS by newly increasing a selective ciphersuite and an expansion option.
Owner:NAT UNIV OF DEFENSE TECH
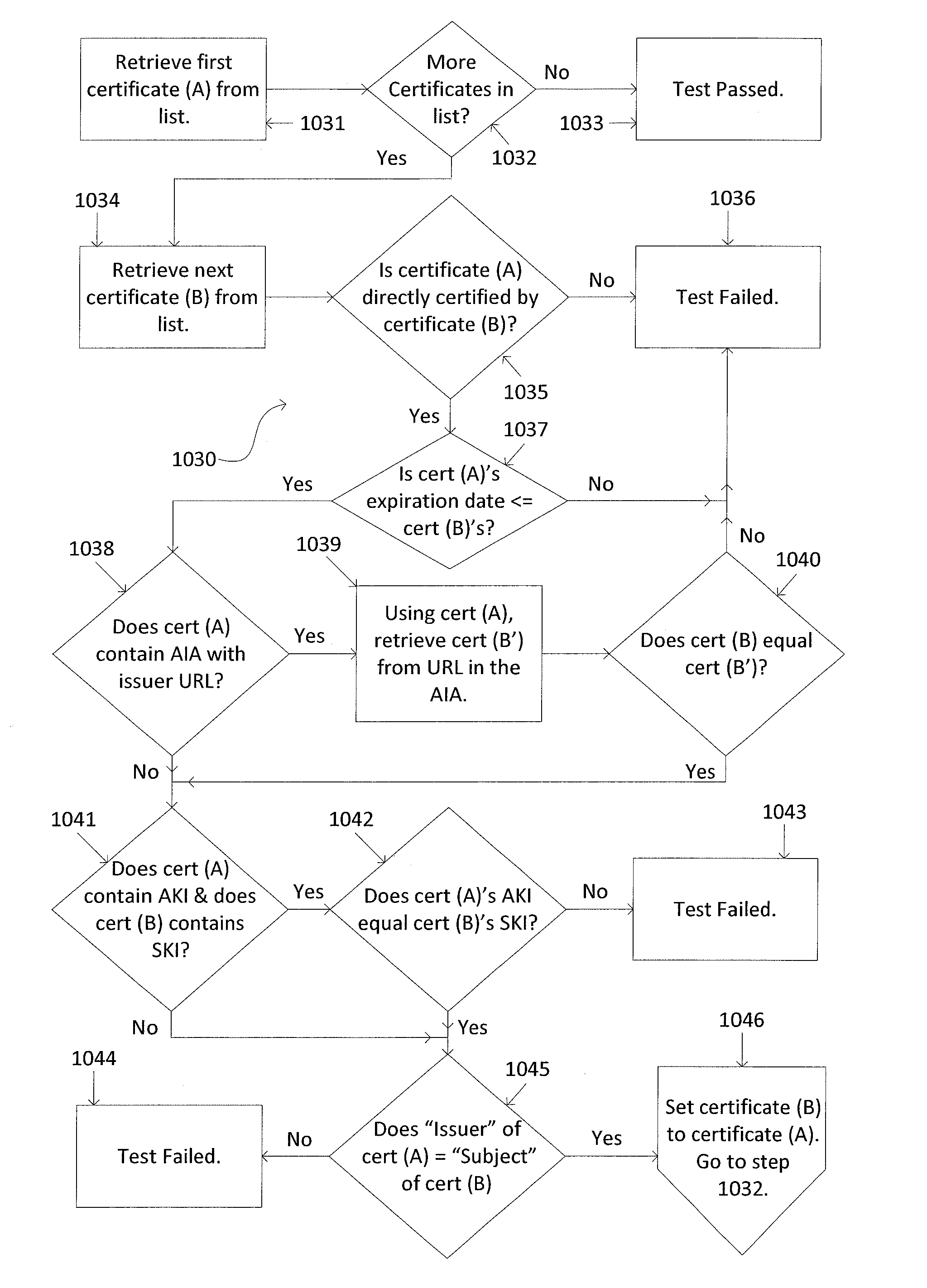
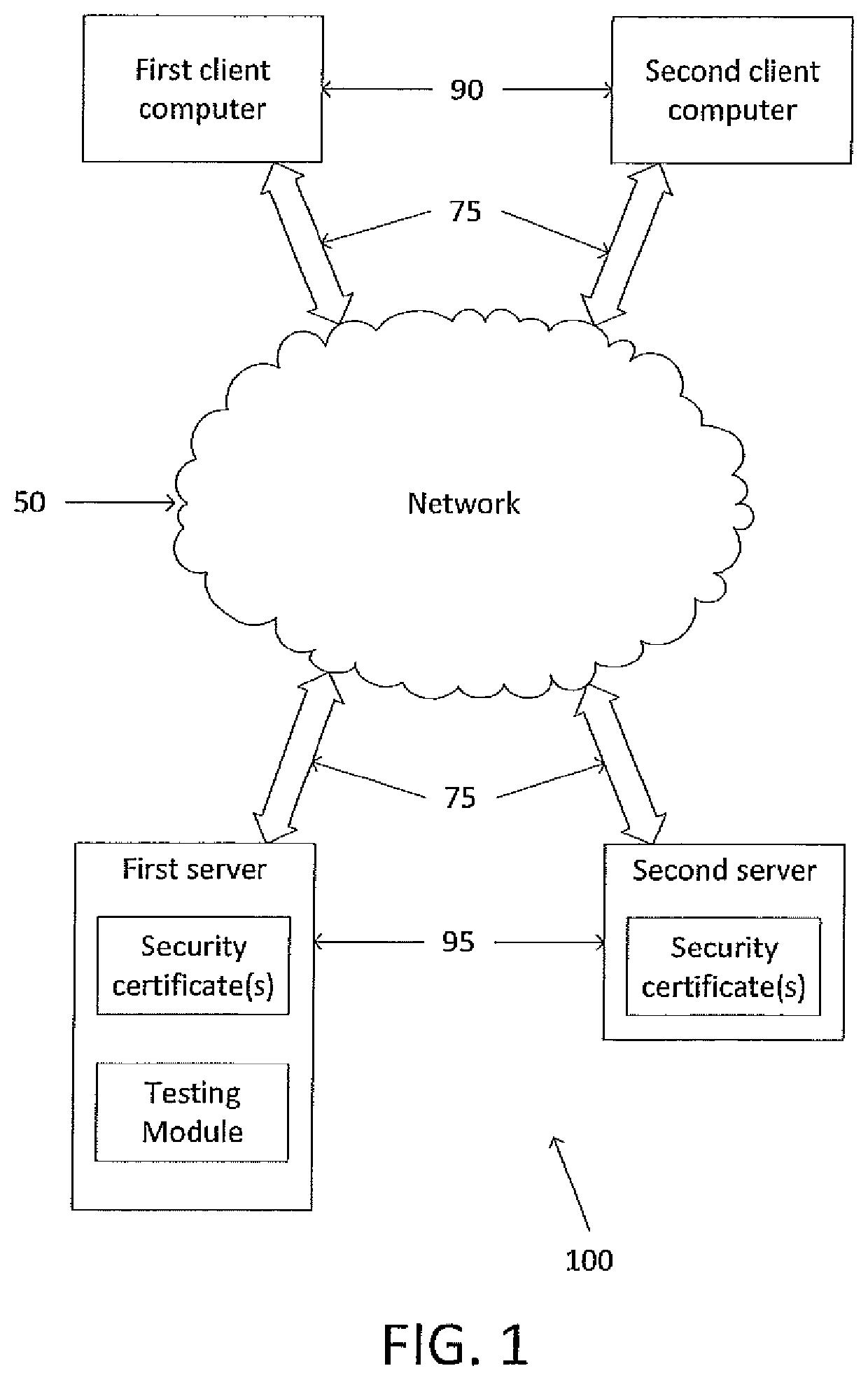
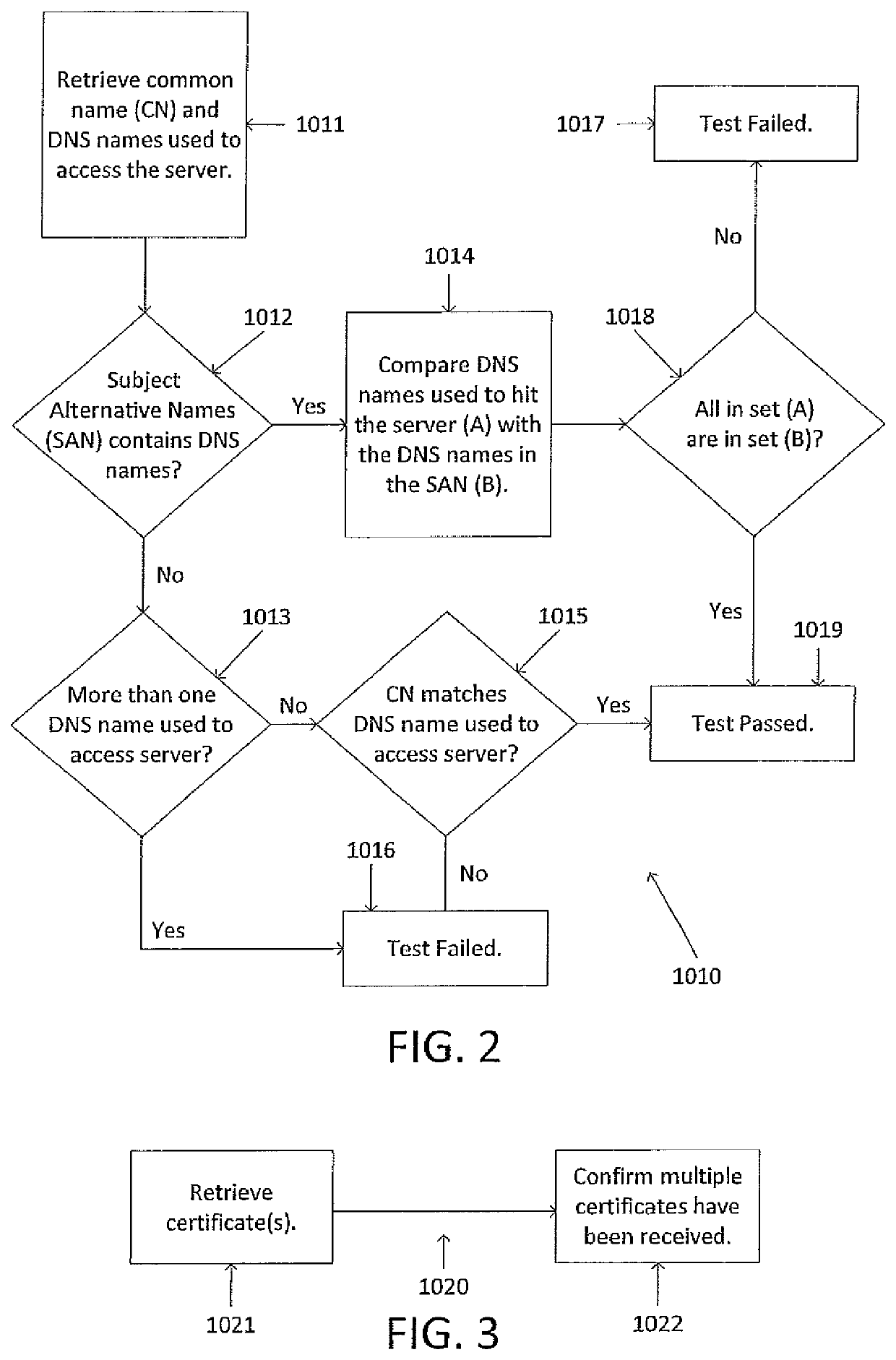
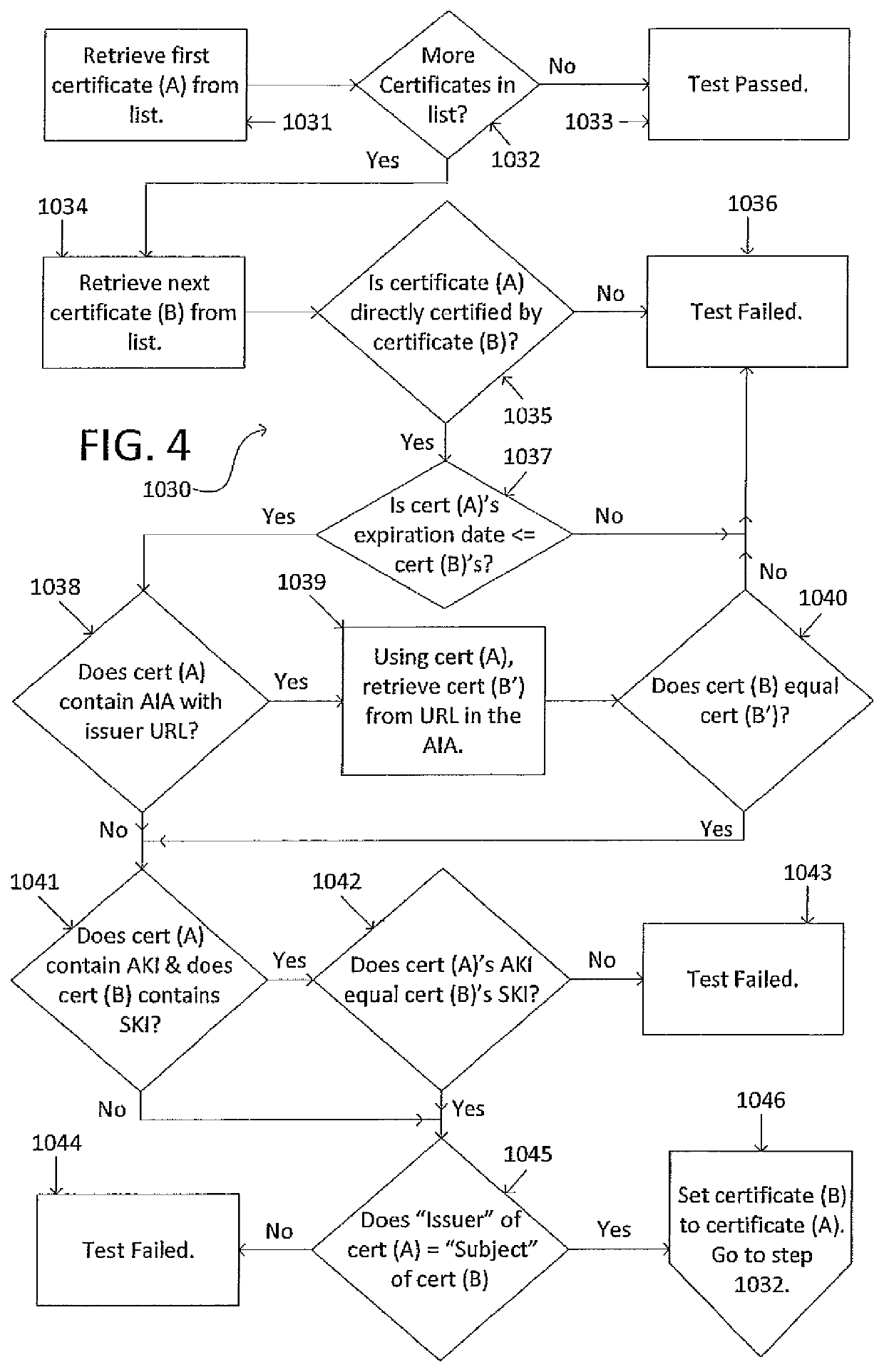
Systems and methods for computer digital certificate management and analysis
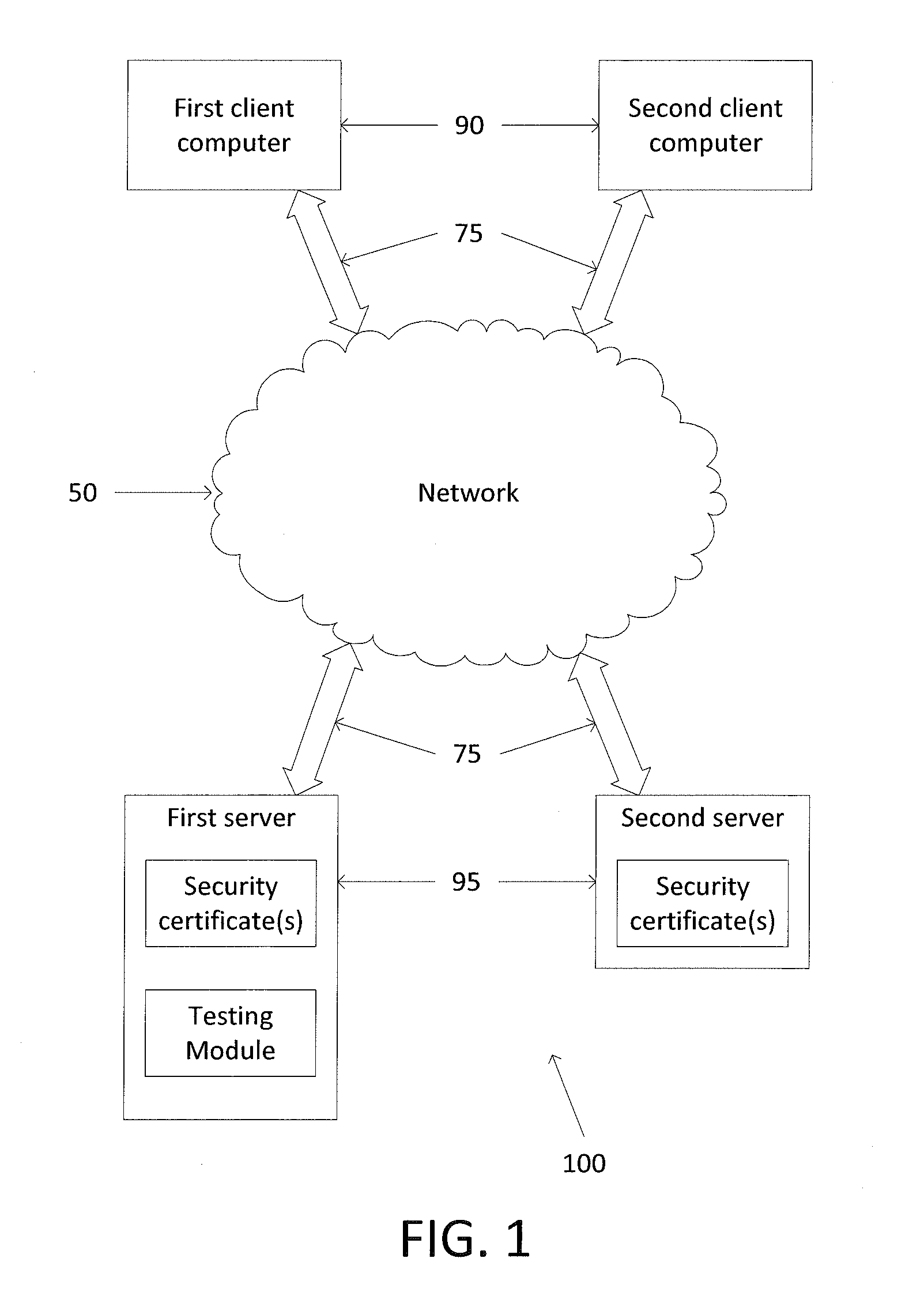
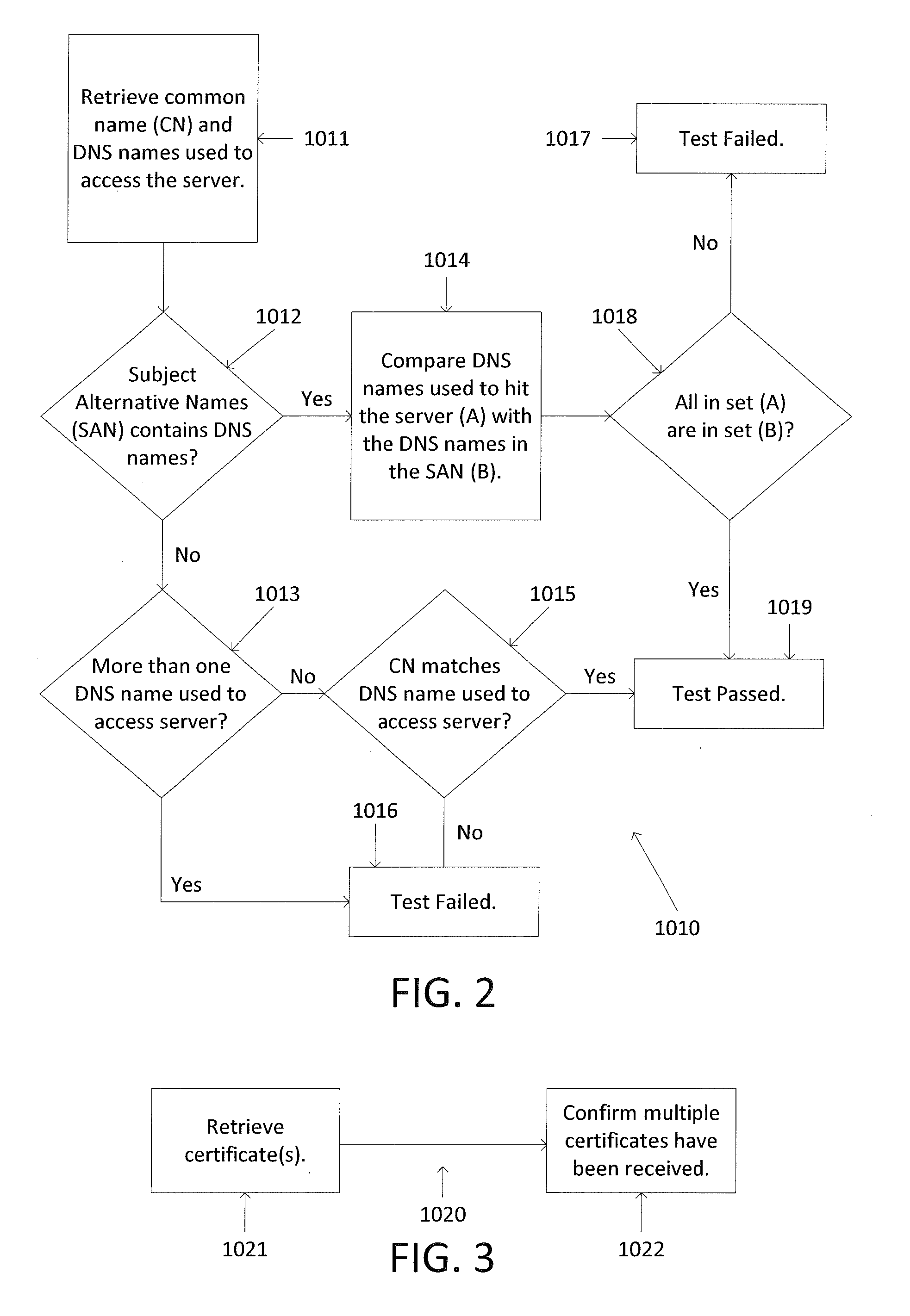
Described herein are methods and systems for updating digital certificates on a computer and testing to confirm that the update was performed correctly. The testing may involve confirming that a server's common name (CN) and / or a server's subject alternative name (SAN) matches the domain name server (DNS) name utilized to access the server, confirming that, for all the certificates sent in chain, each certificate's expiration date is less than or equal to the expiration date of that certificate's parent certificate, confirming that the certificates' authority key identifier (AKI), subject key identifier (SKI), and / or authority information access (AIA) are in compliance, and comparing available cipher suites to a list of pre-approved cipher suites.
Owner:USAA
Facilitating Communications Using Hybrid Cryptography
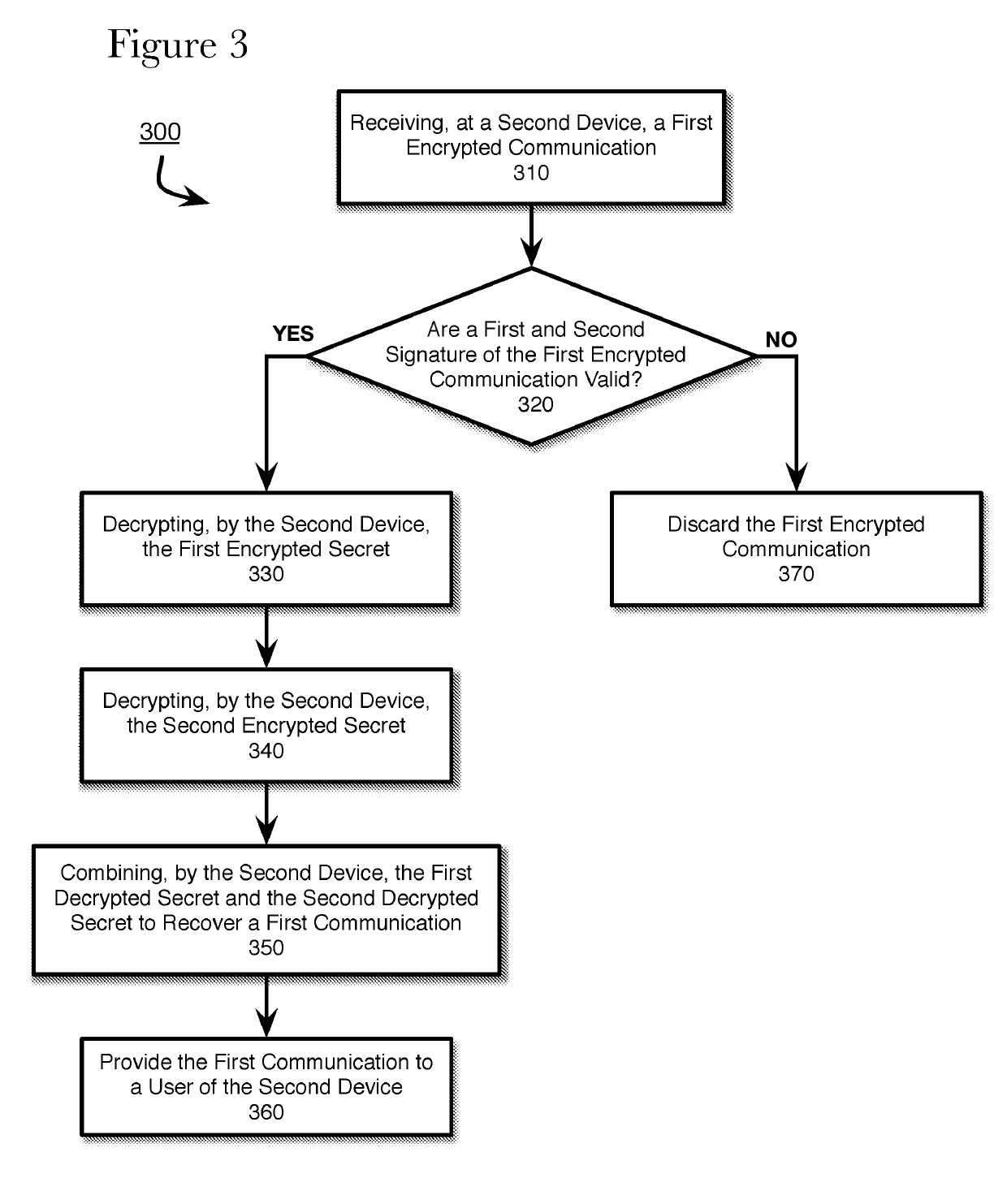
ActiveUS20190245681A1Key distribution for secure communicationMultiple keys/algorithms usageCryptography protocolsCipher suite
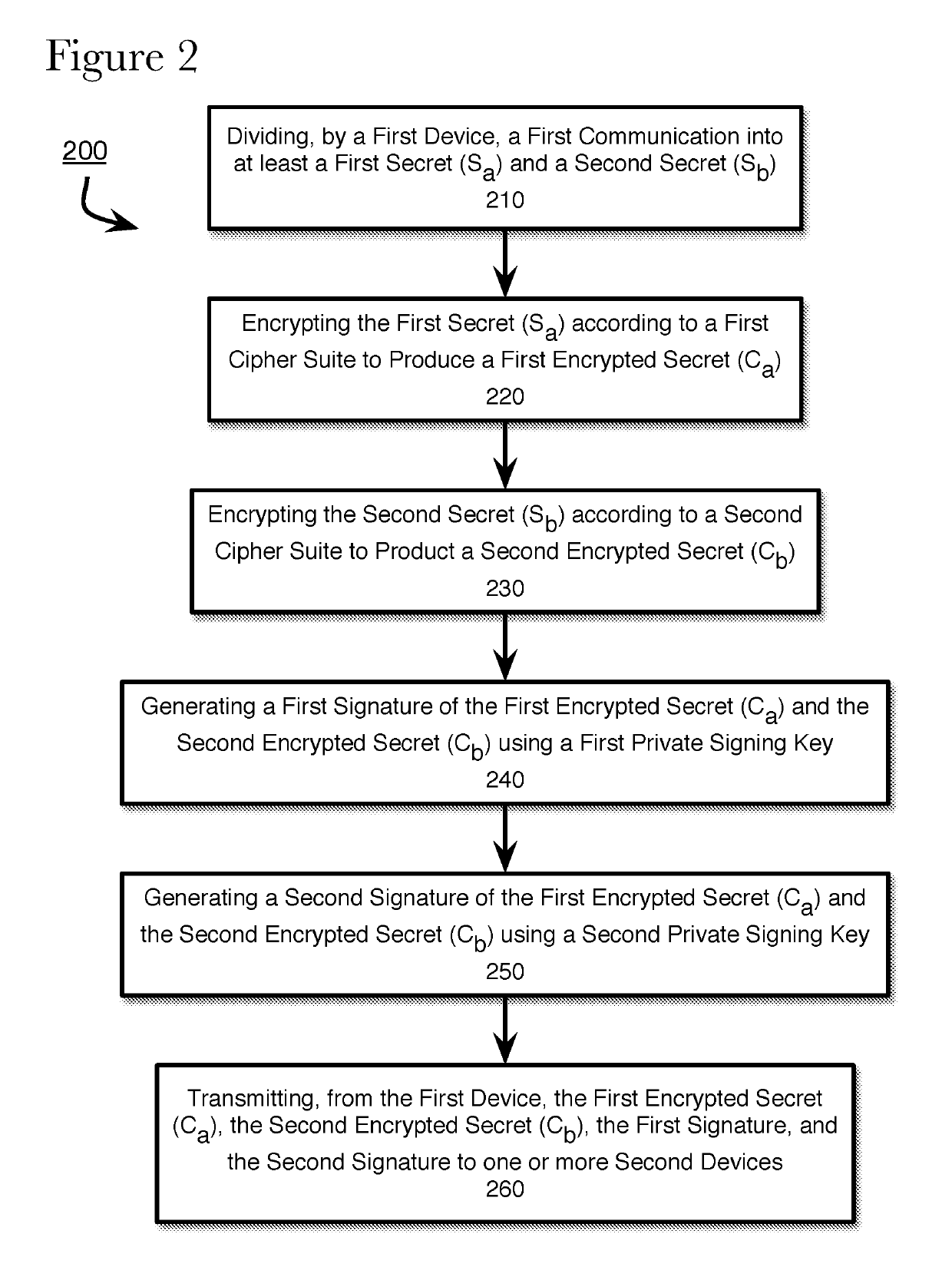
The present application describes a method, system, and non-transitory computer-readable medium for exchanging encrypted communications using hybrid cryptography protocol. According to the present disclosure, a first device divides a first communication into at least a first secret and a second secret. The first device encrypts the first secret using a first cipher suite and the second secret using a second cipher suite. The first device generates a first signature of the first encrypted secret and the second encrypted secret according to a first signature generation algorithm associated with the first cipher suite and a second signature of the first encrypted secret and the second encrypted secret according to a second signature generation algorithm associated with the second cipher suite. The first device transmits the first encrypted secret and the second encrypted secret, the first signature, and the second signature to the second device.
Owner:WICKR +1
Cipher device using RC4 algorithm and method thereof
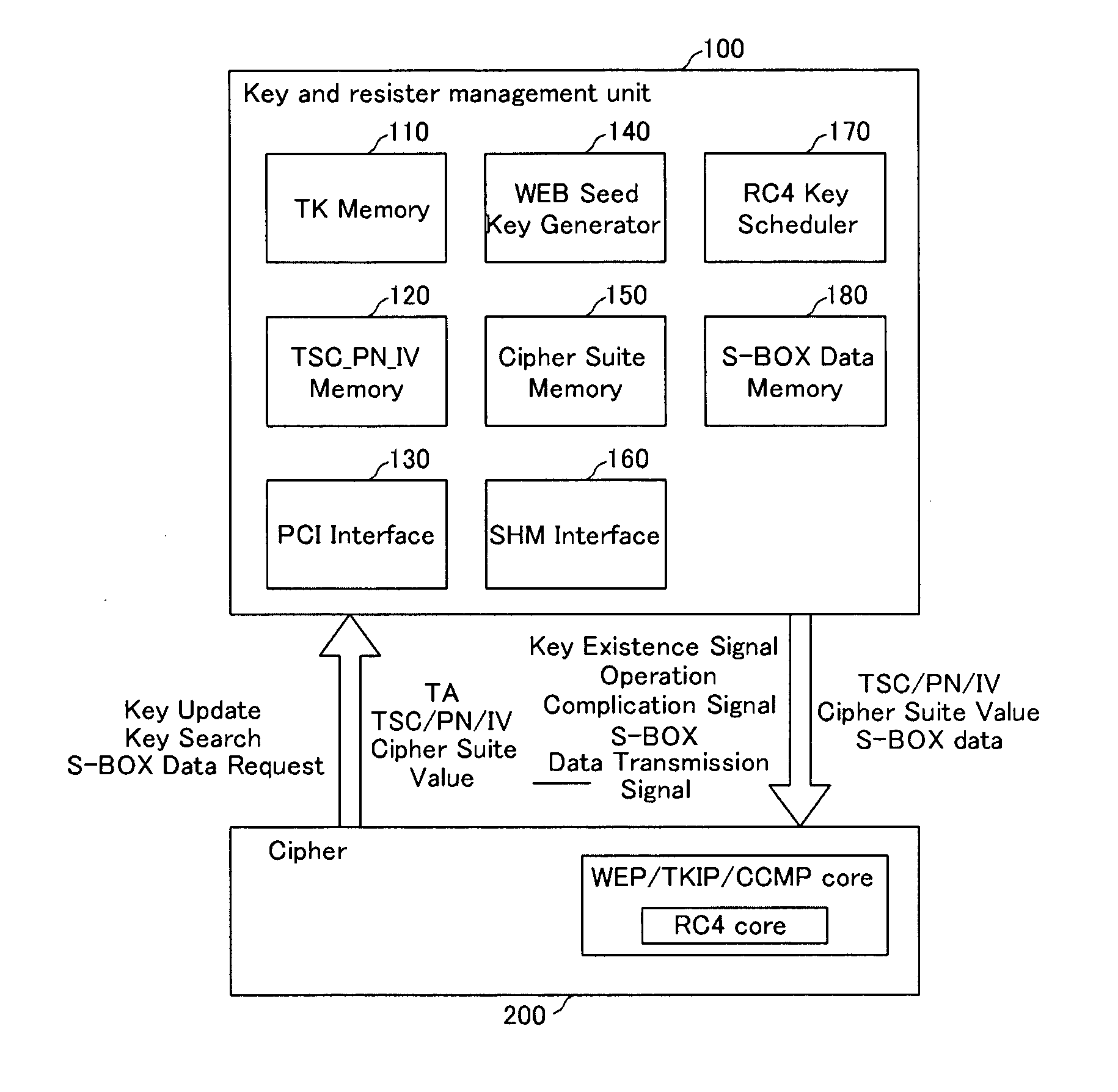
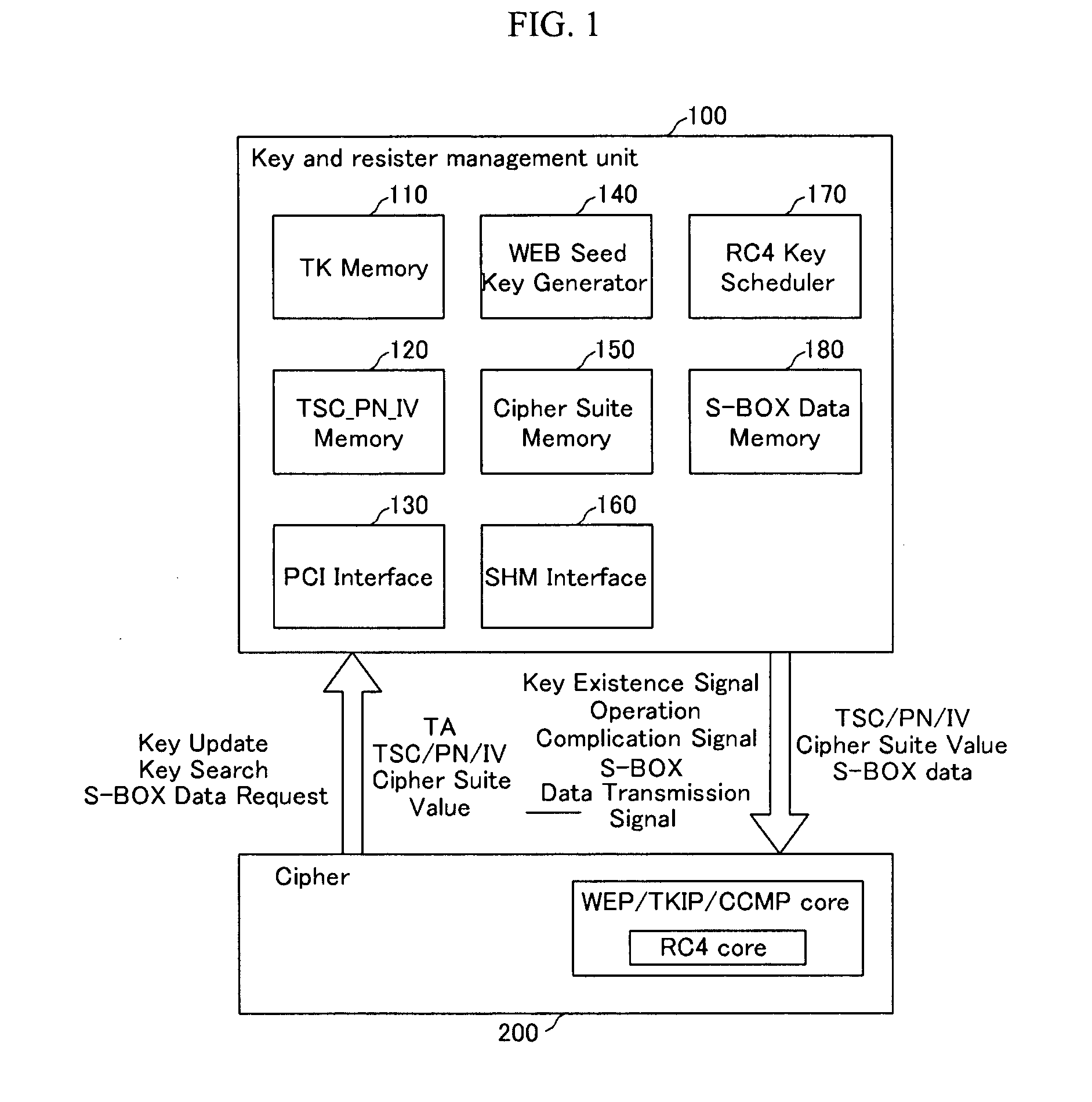
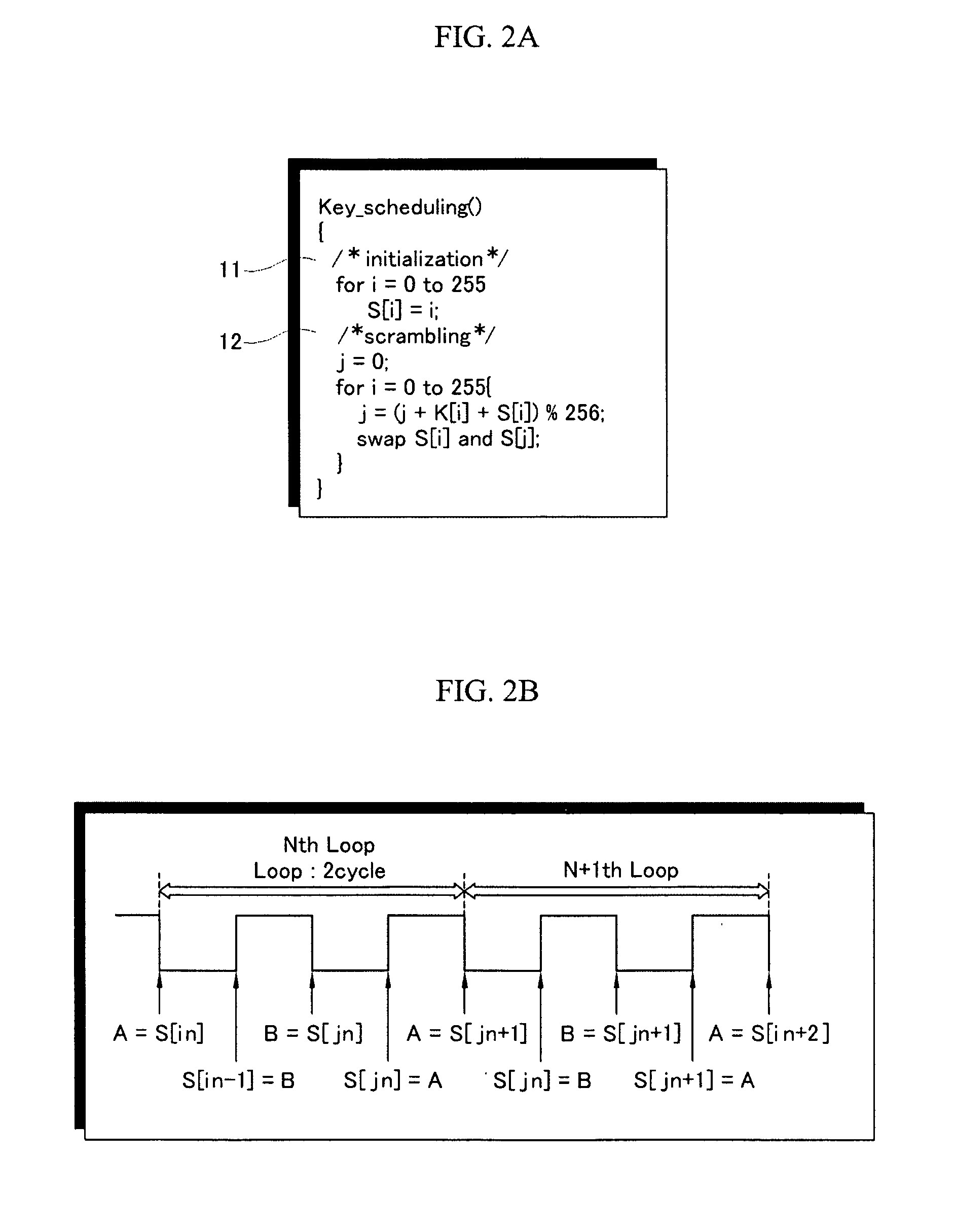
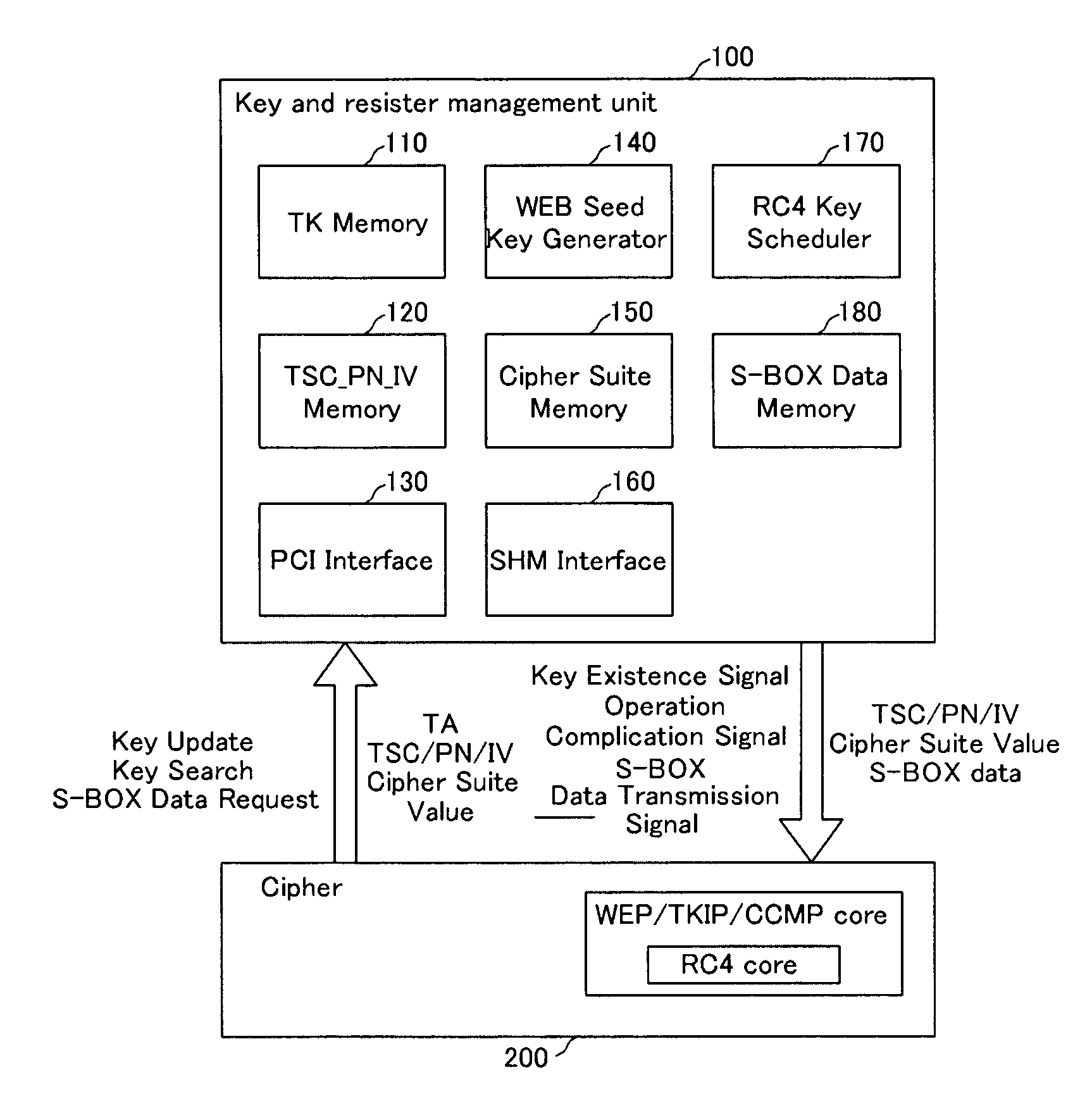
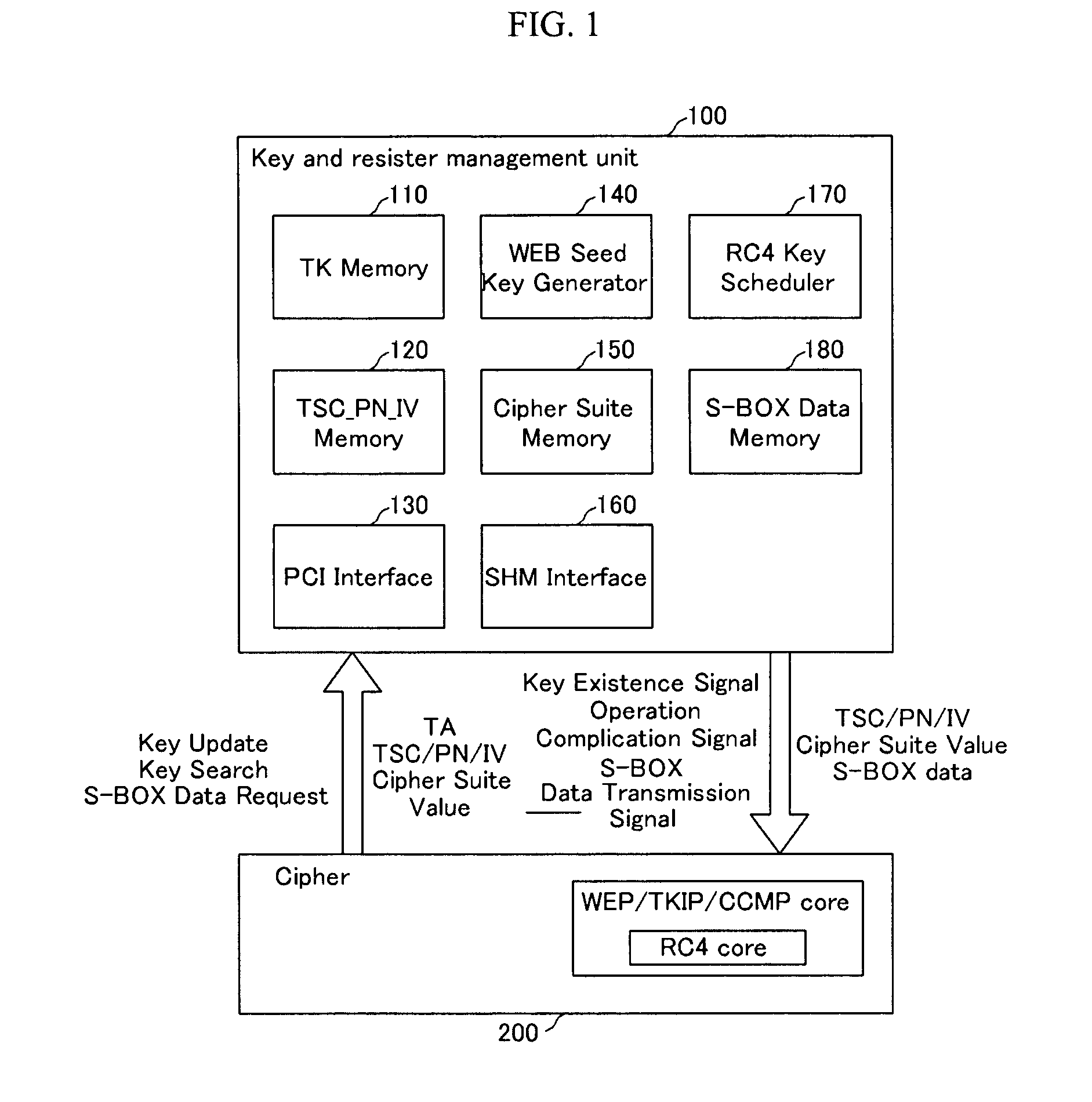
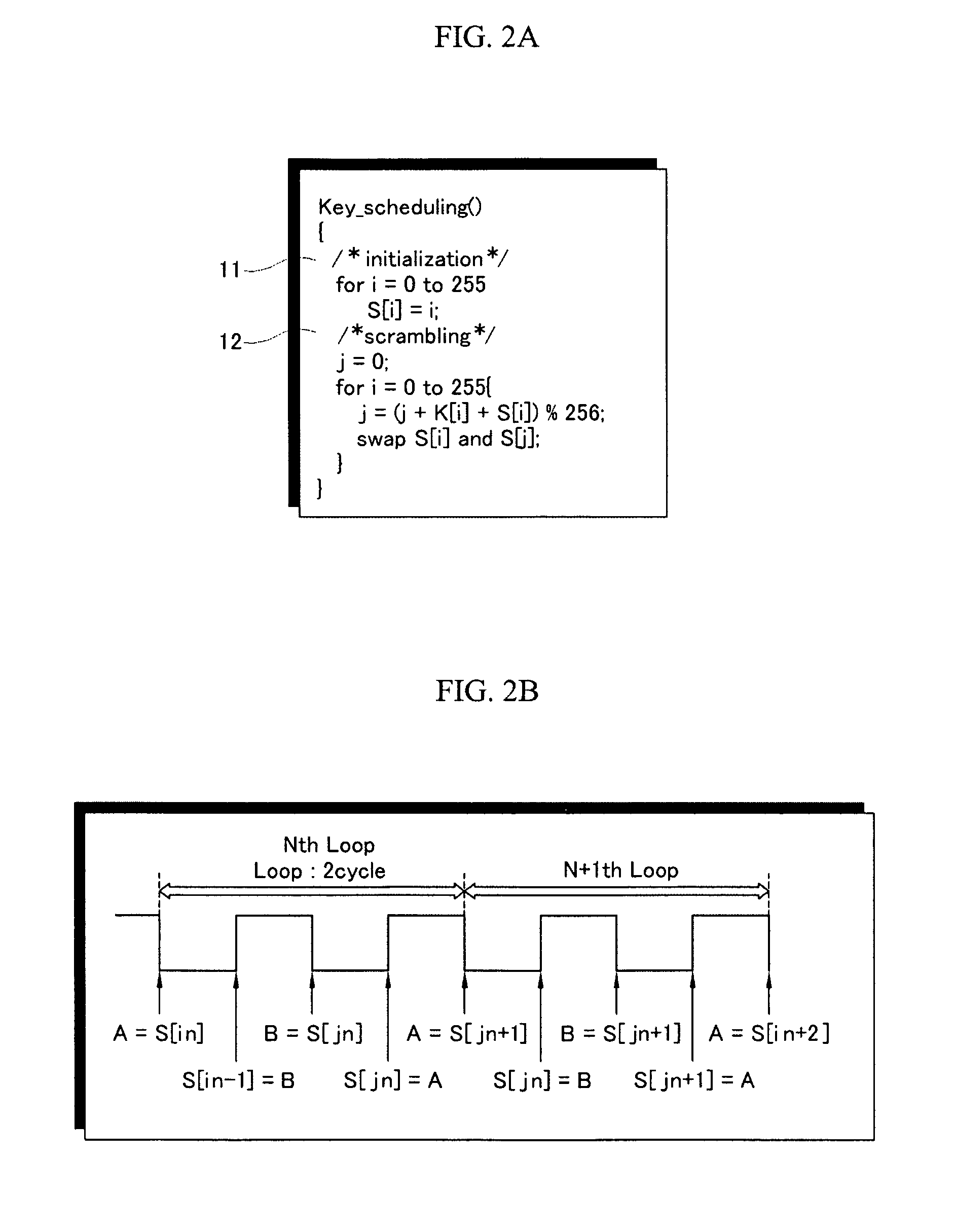
InactiveUS20060133616A1Avoid delayAddressing slow performanceData stream serial/continuous modificationSecret communicationS-boxControl signal
An encryption / decryption device and a method thereof use an RC4 algorithm to reduce a waiting time for encryption / decryption thereby avoiding data process delay. The encryption / decryption device includes a management unit, an encryption / decryption unit, and a first interface. The management unit includes a WEP seed key generator for generating a WEP seed key based on a transmitter address of first data and a cipher suite value representing a cipher protocol type for the transmitter address, an RC4 key scheduler for generating S-Box data using the WEP seed key, and an S-Box data memory storing the S-Box data generated from the RC4 key scheduler for the transmitter addresses. The encryption / decryption unit has a core for performing the RC4 algorithm-corresponding to the cipher suite, encrypting / decrypting the first data using the S-Box data transmitted from the management unit, and transmitting a signal for generating the S-Box data of second data to the management unit. The first interface transmits a control signal and a data signal between the management unit and the encryption / decryption unit.
Owner:ELECTRONICS & TELECOMM RES INST
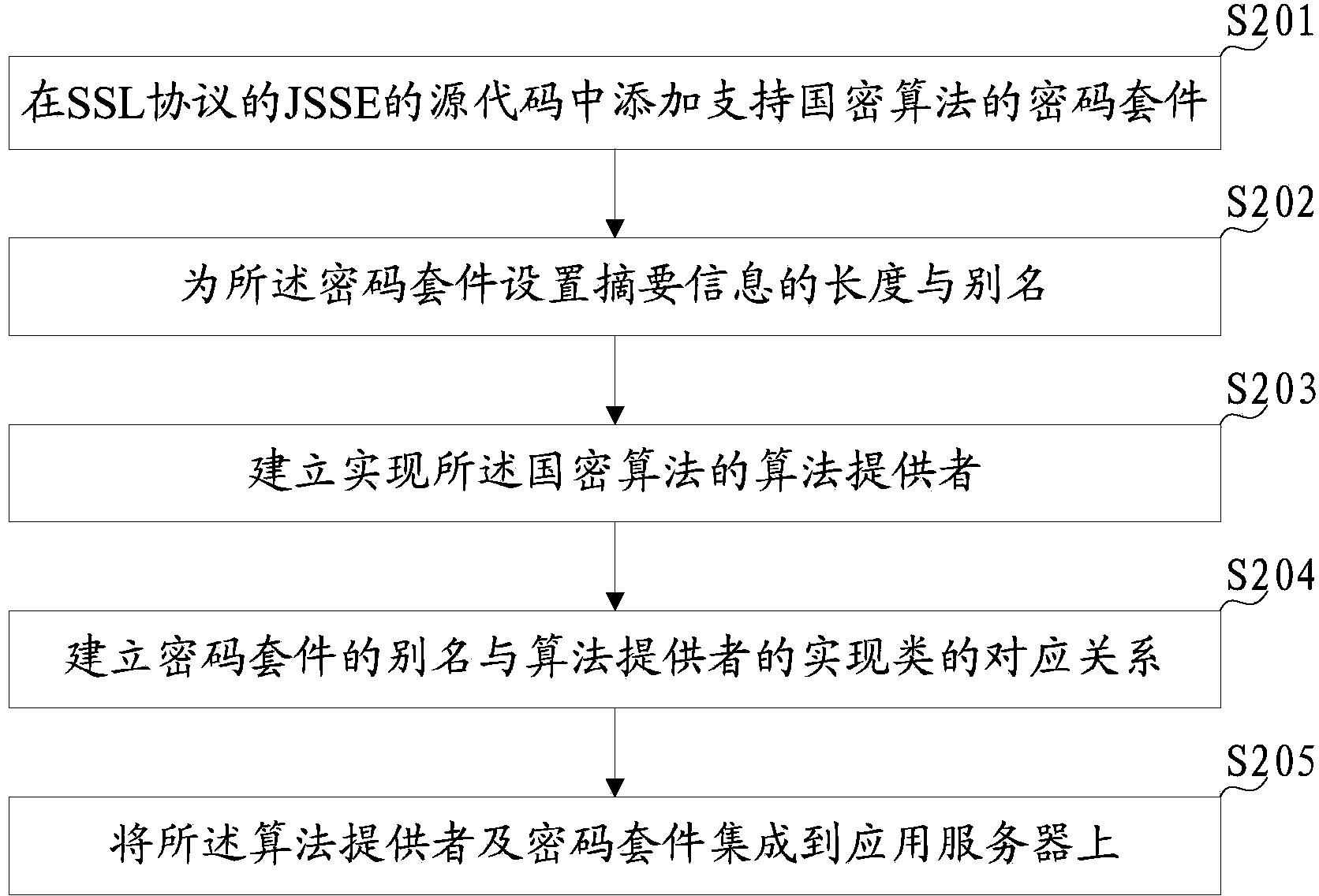
Secure socket layer protocol extension method supporting domestic cipher algorithm
ActiveCN104394179ADoes not change the operating mechanismImprove securityPublic key for secure communicationUser identity/authority verificationSource codeCipher suite
The invention discloses a secure socket layer protocol extension method supporting a domestic cipher algorithm. The secure socket layer protocol extension method comprises the following steps: adding a cipher suite supporting the domestic cipher algorithm into a secure socket layer extended source code of the secure socket layer protocol; setting corresponding parameters and alias for the cipher suite; establishing an algorithm provider for implementing the domestic cipher algorithm; establishing a corresponding relationship between the alias of the cipher suite and an implementation class of the algorithm provider. According to the secure socket layer protocol extension method provided by the invention, an operating mechanism of the SSL (secure socket layer) protocol is not changed and extra security problems are not caused; after adoption of the cipher suite supporting the domestic cipher algorithm, the domestic cipher algorithm can be used during handshake and interaction of the SSL, so that the safety performance of online banking is enhanced, and thus the secure socket layer protocol extension method has an important significance in autonomy and the product security of an online banking application system and the security of a whole system.
Owner:SHANDONG CVIC SOFTWARE ENG
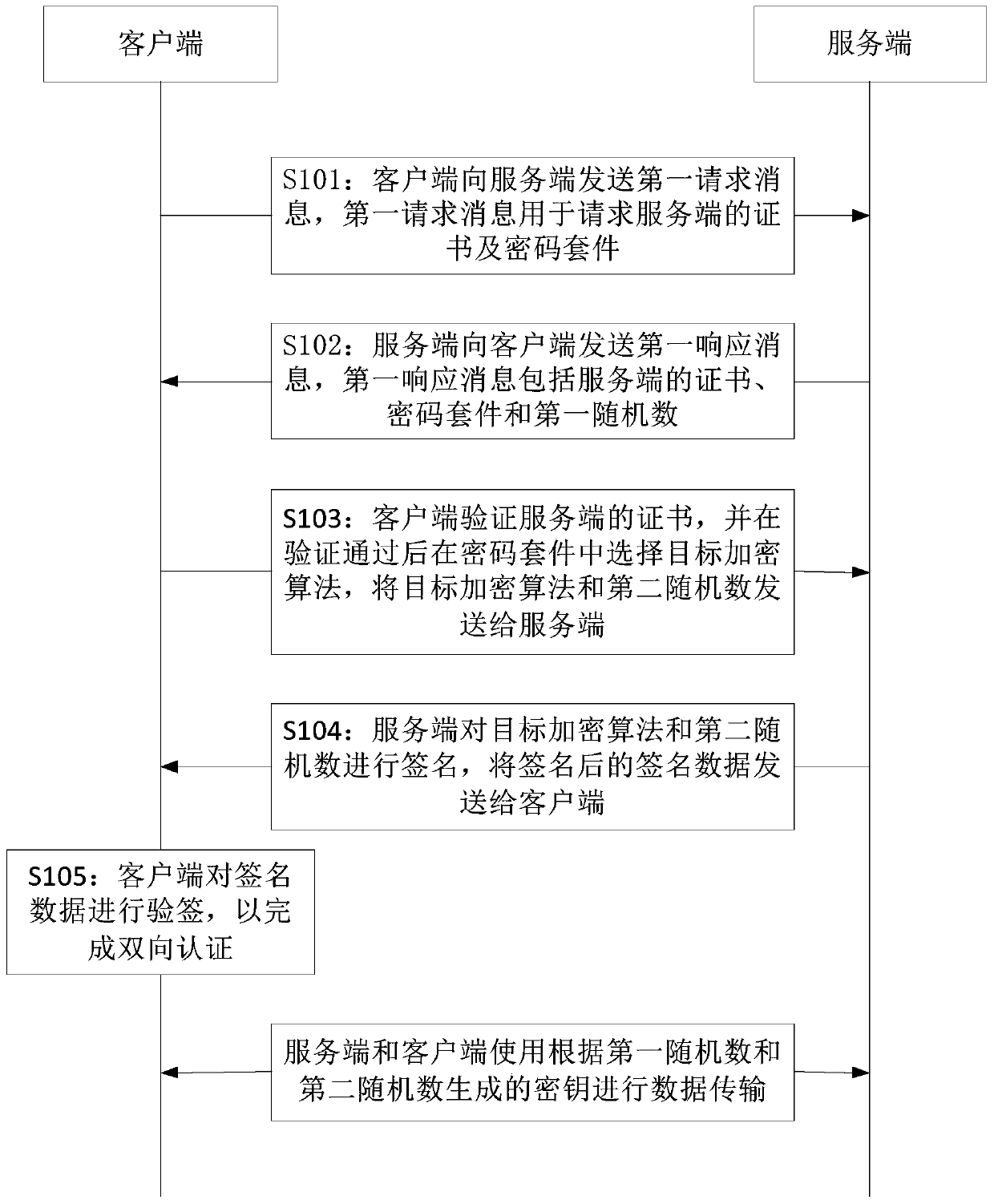
Bidirectional authentication method and communication system
ActiveCN110380852AReduce the number of interactionsShorten communication timeKey distribution for secure communicationUser identity/authority verificationCommunications systemPassword
The invention provides a bidirectional authentication method and a communication system. The bidirectional authentication method comprises the following steps: a client sending a first request messageto a server; wherein the first request message is used for requesting a certificate and a password suite of the server; the server sending a first response message to the client; wherein the first response message comprises a certificate, a password suite and a first random number of the server; the client verifying the certificate of the server, selecting a target encryption algorithm in the password suite after the certificate passes the verification, and sending the target encryption algorithm and a second random number to the server; the server signing the target encryption algorithm andthe second random number, and sending signed signature data to the client; the client performing signature verification on the signature data to complete bidirectional authentication; wherein the first random number and the second random number are used for generating a key. The communication efficiency is improved.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
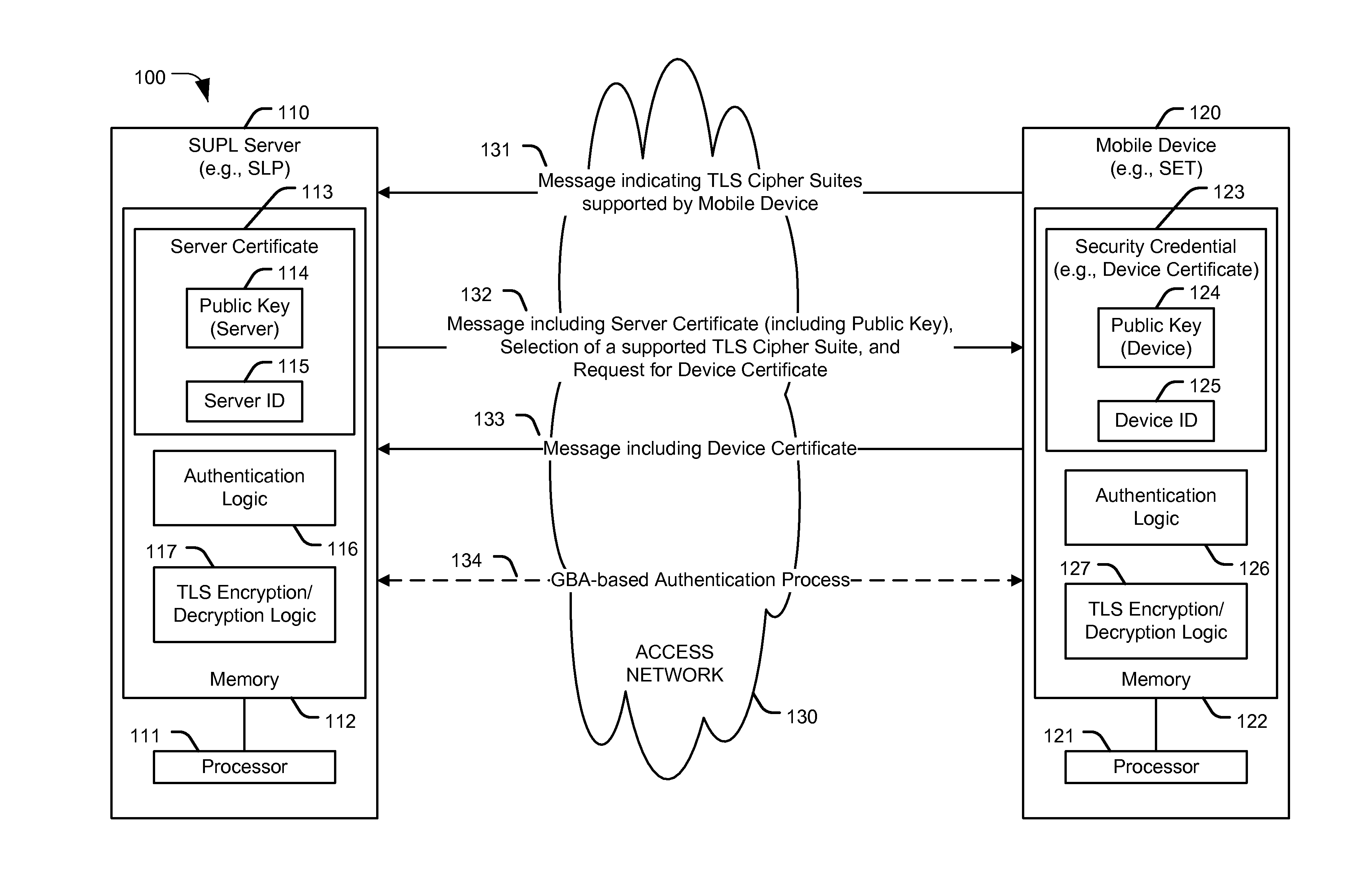
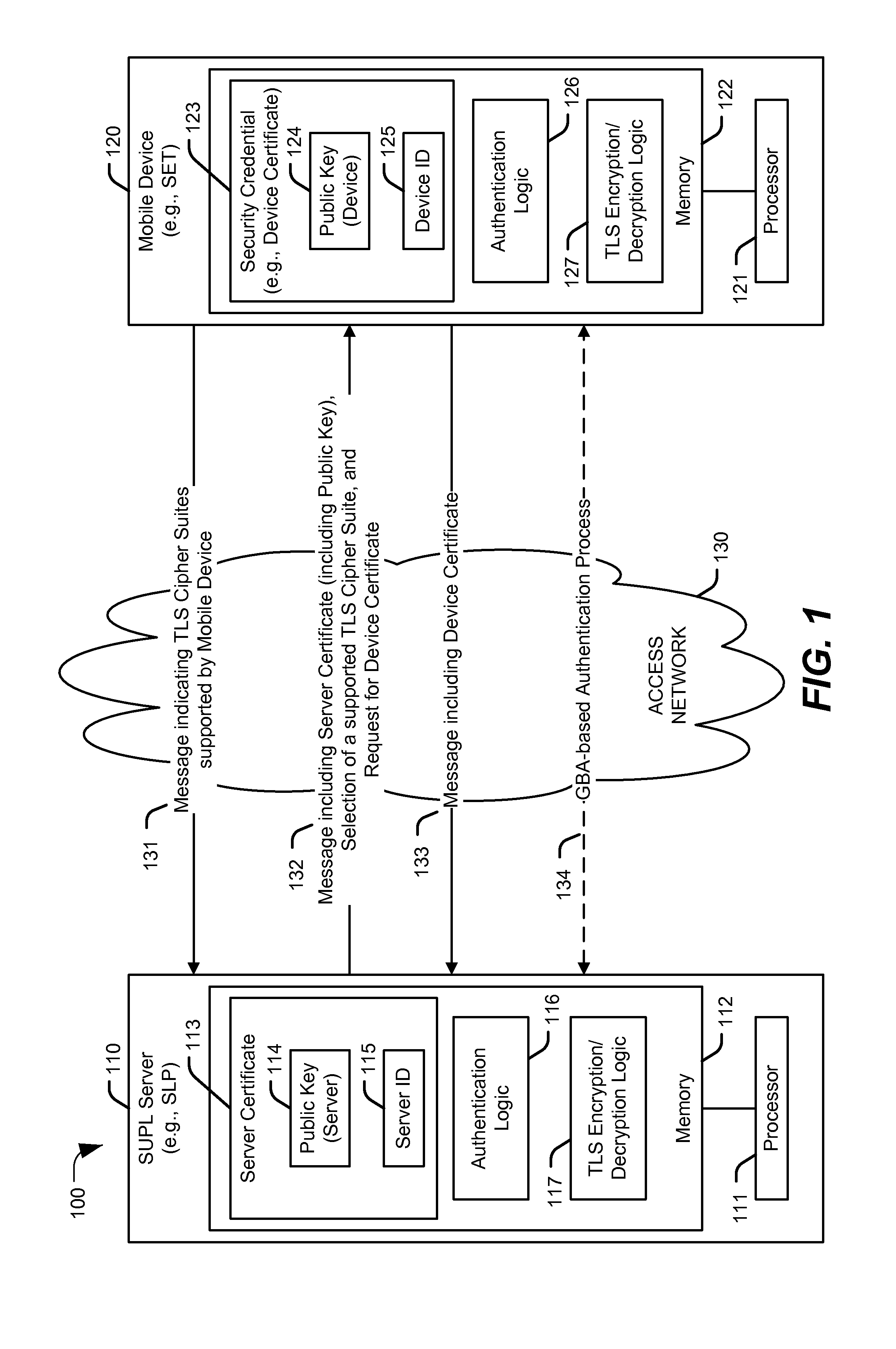
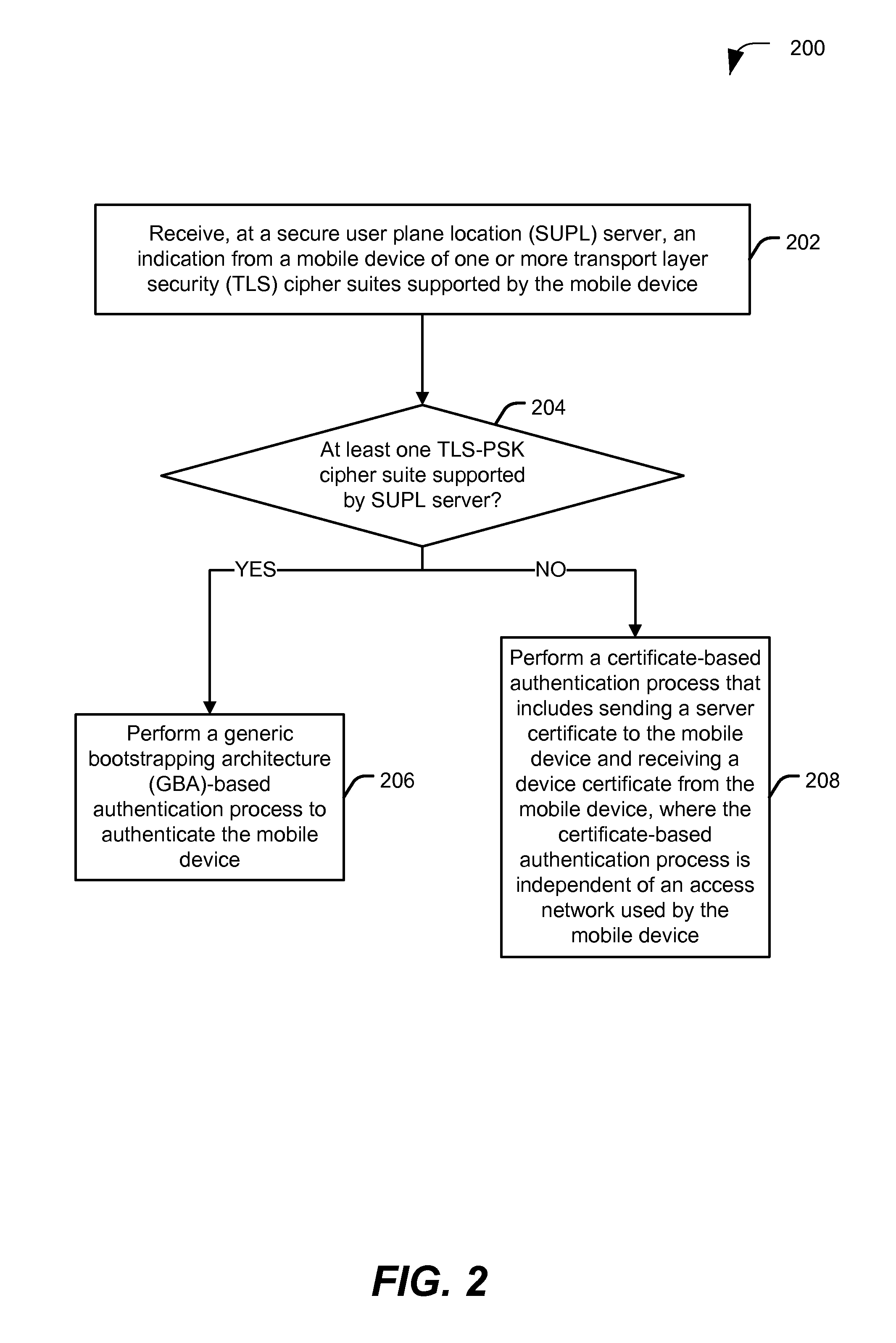
Authentication in secure user plane location (SUPL) systems
A particular method includes receiving, at a secure user plane location (SUPL) server, an indication from a mobile device of one or more transport layer security (TLS) cipher suites supported by the mobile device; determining whether the one or more TLS cipher suites include a TLS pre-shared key (TLS-PSK) cipher suite that is supported by the SUPL server; in response to determining whether the one or more TLS cipher suites include the TLS-PSK cipher suite that is supported by the SUPL server, performing a generic bootstrapping architecture (GBA)-based authentication process to authenticate the mobile device, or determining whether the SUPL server supports a certificate-based authentication method; and in response to determining that the SUPL server supports the certificate-based authentication method, performing the certificate-based authentication method that includes sending a server certificate to the mobile device and receiving a device certificate from the mobile device.
Owner:QUALCOMM INC
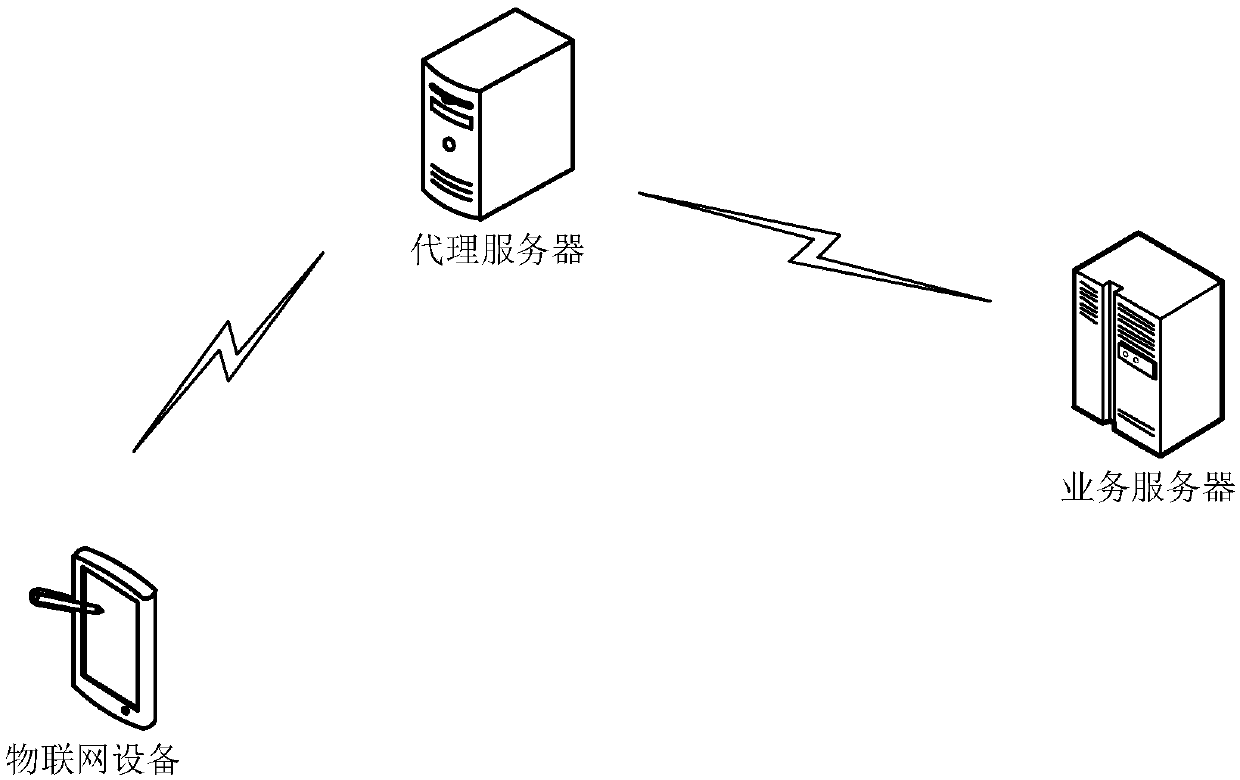
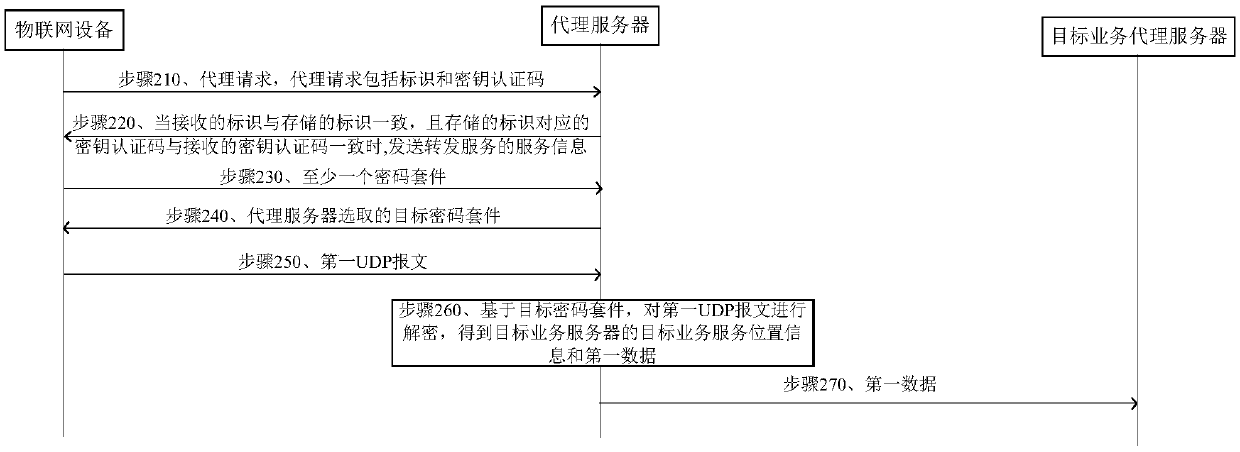
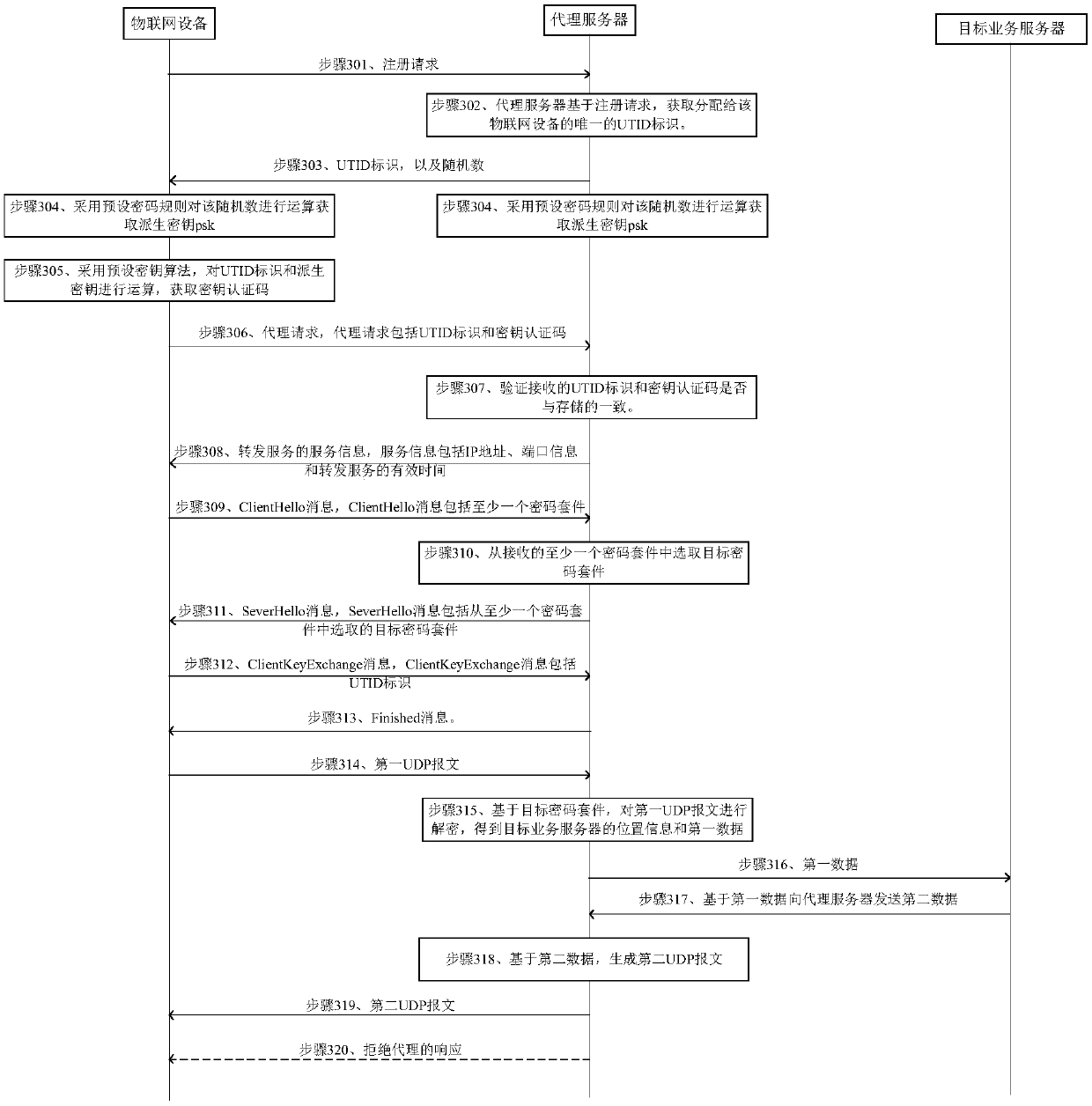
Method and device for forwarding user datagram protocol message
The embodiment of the invention discloses a method and a device for forwarding a user datagram protocol message. After a proxy server receives the identifier and the secret key authentication code sent by the Internet of Things equipment, when the identifier is consistent with the stored identifier and the secret key authentication code corresponding to the stored identifier is consistent with thesecret key authentication code. The service information of forwarding service is sent to the Internet of Things equipment. Based on the at least one password suite sent by the Internet of Things device, a target password suite is sent to the Internet of Things device. Then, a first UDP message sent by the Internet of Things device is received. After the first UDP message comprises the position information and the first data of the target service server, the first UDP message is decrypted based on the target password suite to obtain the position information and the first data of the target server. Finally, the first data is sent to the target service server corresponding to the position information, thereby realizing forwarding of the UDP message completely based on the UDP protocol, and improving the safety of the UDP message.
Owner:CHINA MOBILEHANGZHOUINFORMATION TECH CO LTD +1
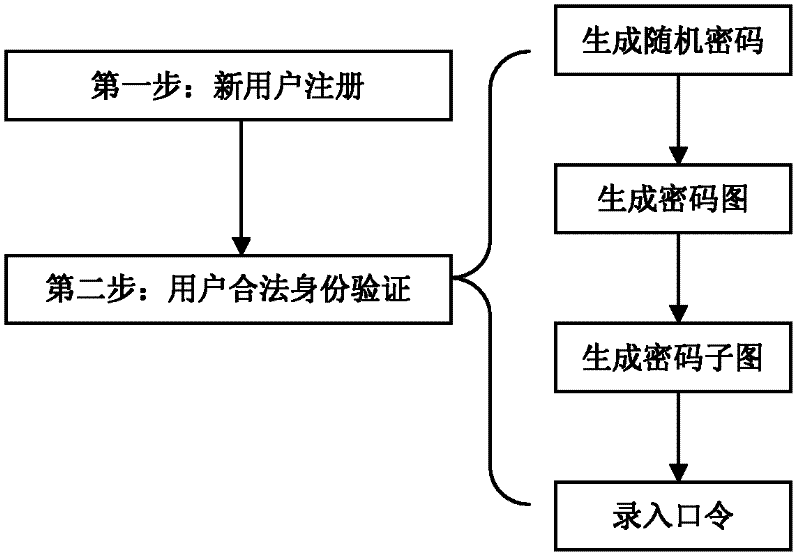
Identity authentication method based on visual cryptography
InactiveCN102340402ARealize dynamic passwordUncertainUser identity/authority verificationImage data processing detailsUser needsPassword
The invention provides an identity authentication method realizing a dynamic password encryption mode. The technical scheme comprises the following steps of: I, registering a new user, generating a mask picture M of the new user, and storing the other information and the mask picture M of the new user in a database as the registration information of the new user; II, authenticating the legal identity of the user; if the identity of any user needs authentication, executing the following steps: (1) generating a random cipher; (2) generating a cipher picture; (3) generating a cipher sub-picture;and (4) entering passwords to prove whether the user to be authenticated is a registered user. The invention has the beneficial effects that dynamic passwords can be realized, the decryption mode is simple, and the security is high. In spite of dynamic passwords, cipher transfer is not involved in the authentication process, thus the security is further improved.
Owner:NAT UNIV OF DEFENSE TECH
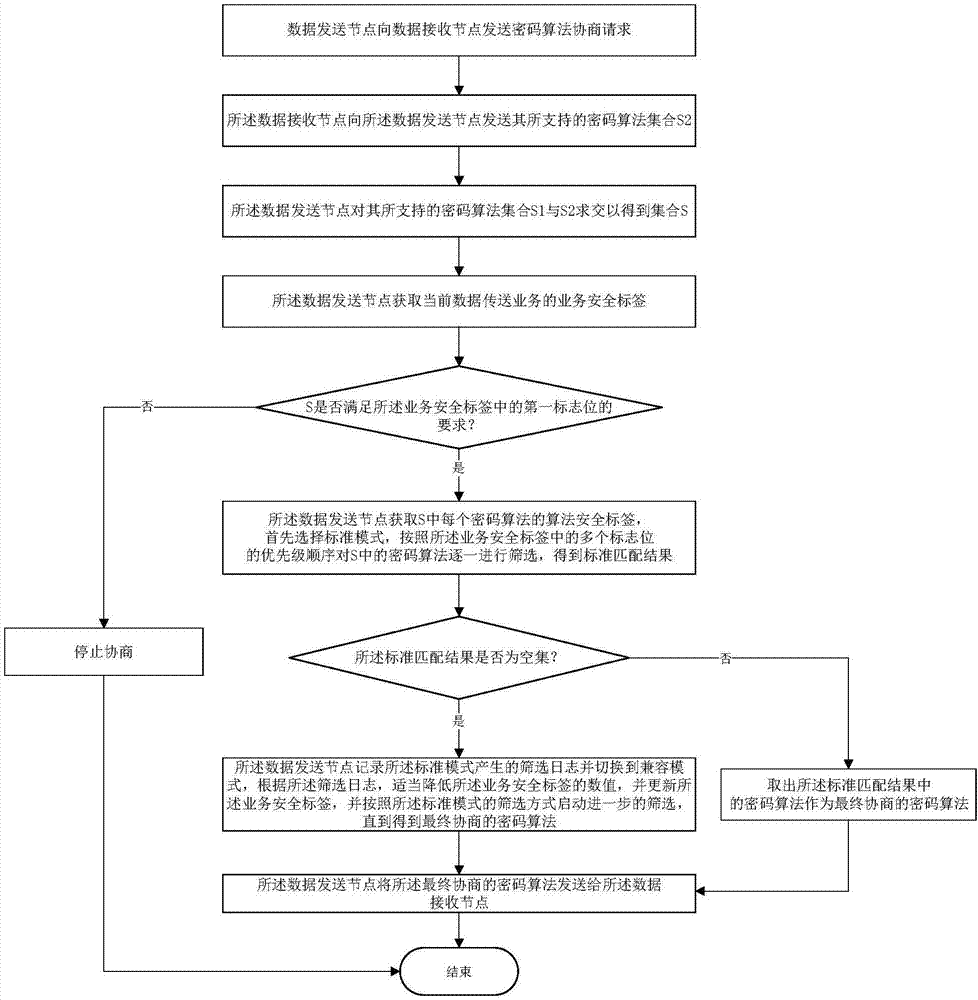
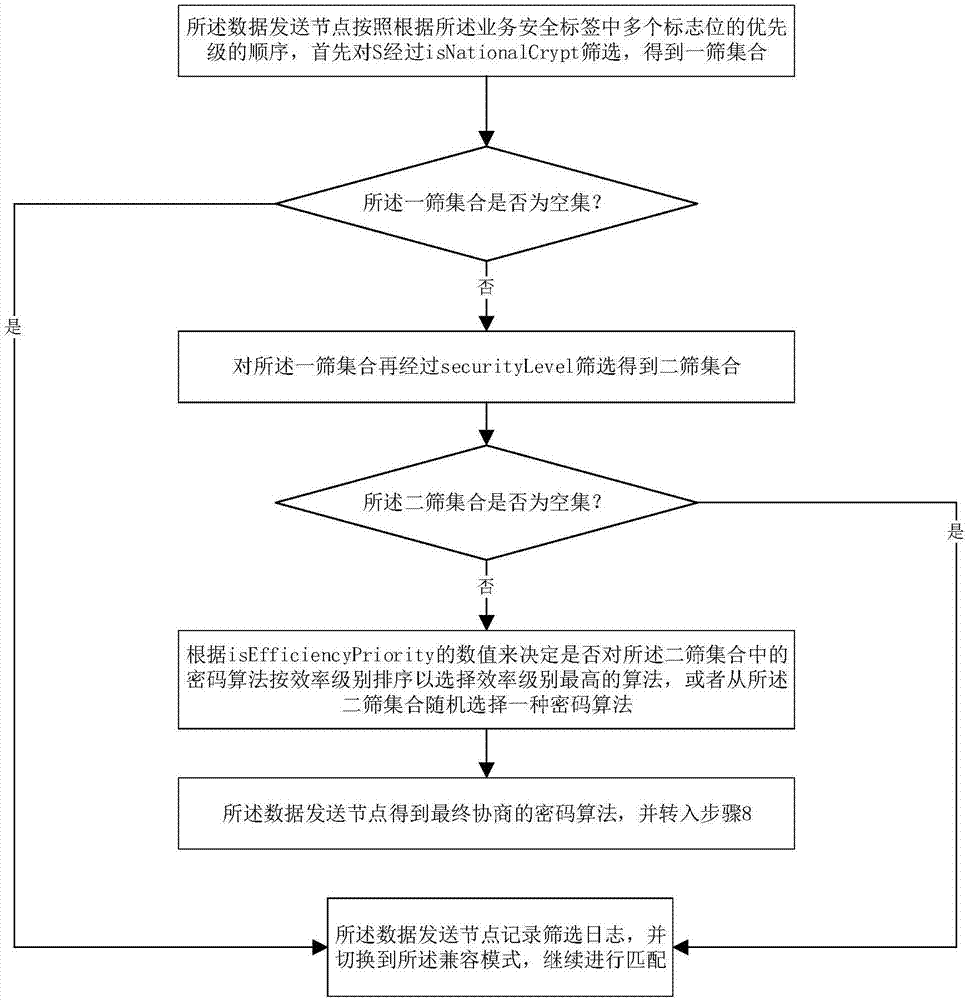
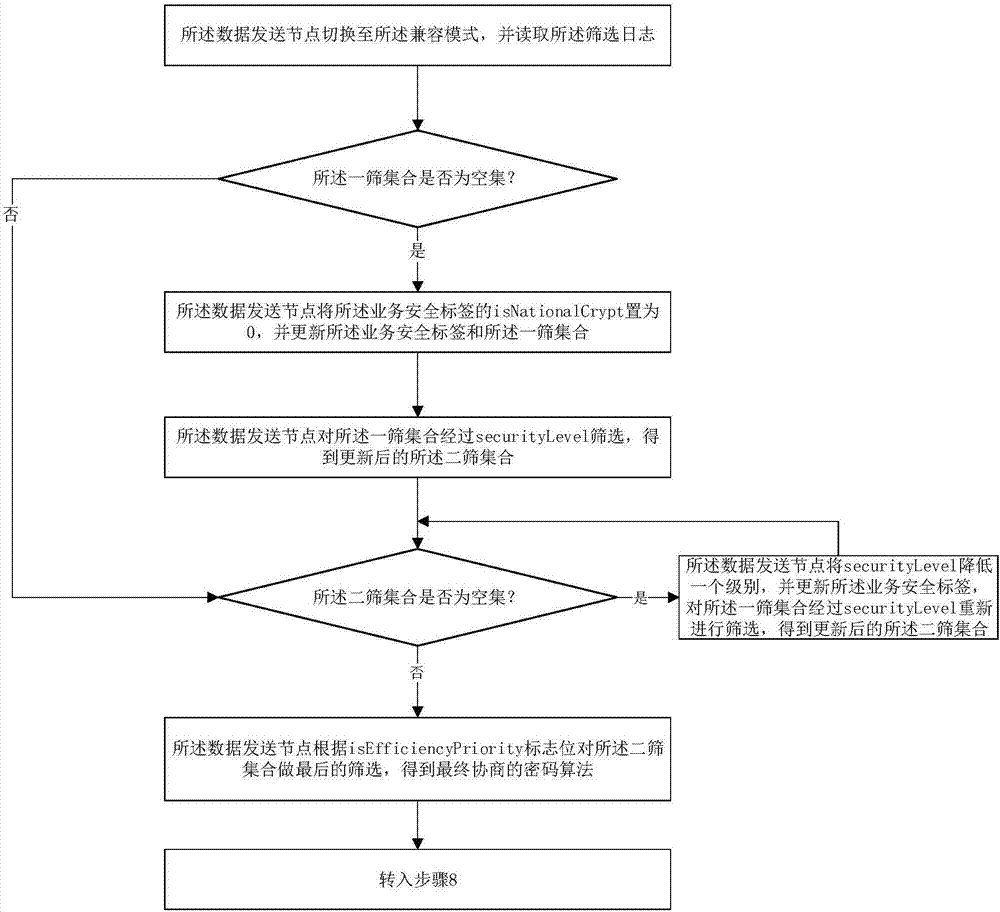
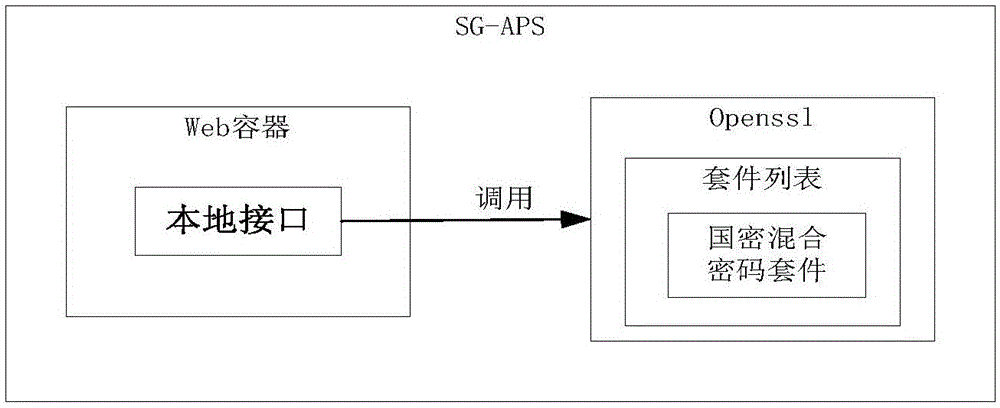
Negotiation method for cryptographic algorithm of data transport services in distribution network
ActiveCN107302428AAvoid attackEnsure fast matching of needsKey distribution for secure communicationData transportData shipping
The invention provides a negotiation method for a cryptographic algorithm of data transport services in a distribution network. The negotiation method is characterized by comprising a service security label, an algorithm security label and two matching modes, wherein the negotiation process of the cryptographic algorithm between network nodes in the distribution network completely refers to the service security label of the current data transport service. The negotiation method avoids the problem of weak cipher suite matching security caused by the client cryptographic algorithm priority in the traditional network security protocol. The two matching modes not only consider the quick matching requirement of novel distribution equipment, but also consider the compatibility matching requirement of old equipment, thereby effectively solving the problem of transition from the cryptographic algorithm to national cryptographic algorithm standards in the distribution network.
Owner:BEIJING CHINA POWER INFORMATION TECH +5
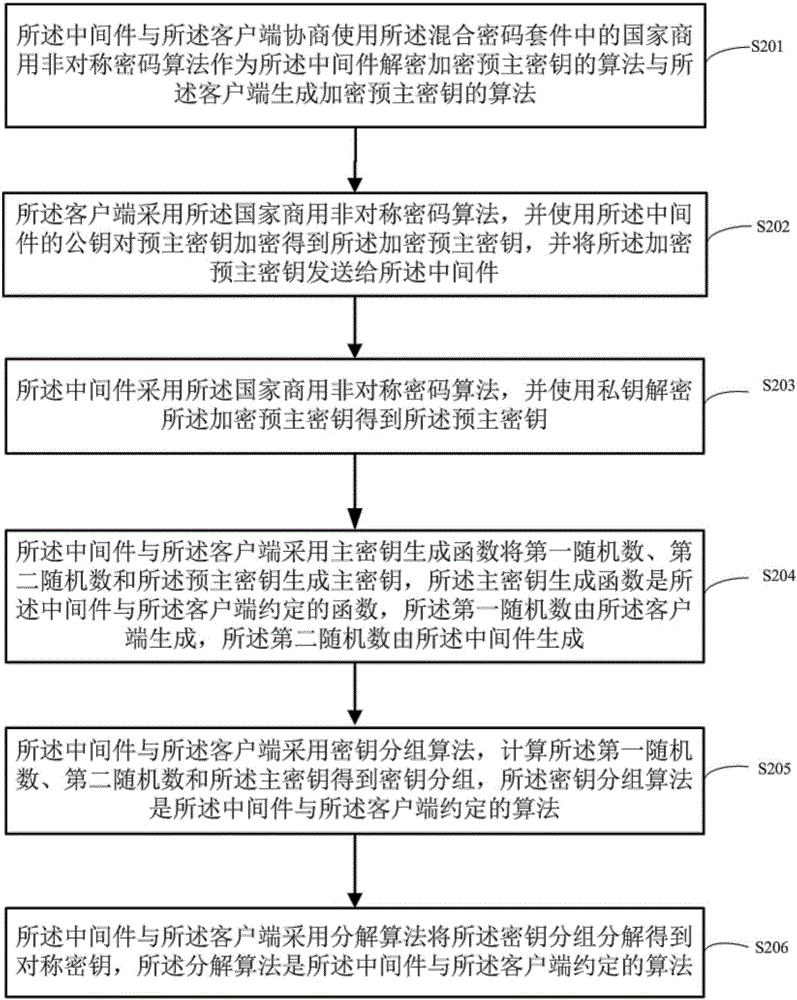
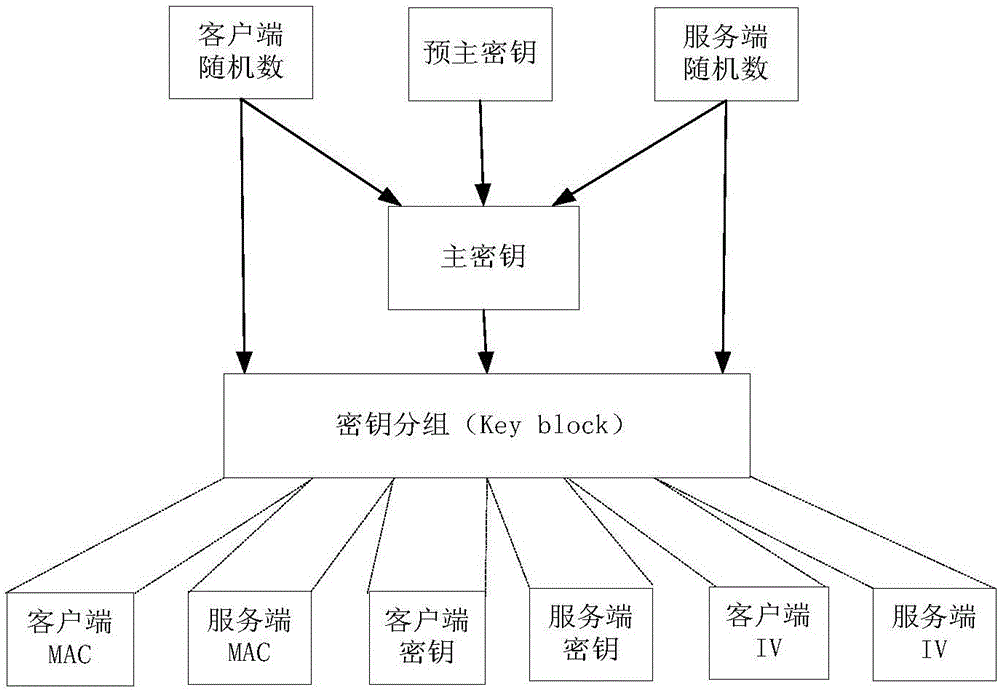
Secure data transmission method and device of middleware based on hybrid cipher suite
The invention discloses a secure data transmission method and device of middleware based on a hybrid cipher suite. The secure data transmission method is used by a client to obtain necessary data from a server securely. According to the secure data transmission method provided by the invention, the hybrid cipher suite is adopted during the secure data transmission between the middleware and the client, and the hybrid cipher suite comprises a national commercial asymmetric cryptography algorithm, a digest algorithm and a foreign standard symmetric cryptography algorithm. The secure data transmission between the middleware and the client comprises the following steps: firstly, in a secure connection establishment process of the middleware and the client, generating a symmetric key by using the hybrid cipher suite, and establishing a secure connection by the middleware and the client by comparing the digest values of both parties; and finally, encrypting the data necessary for the client by the middleware on the basis of the secure connection established by the both parties to obtain encrypted data, sending the encrypted data to the client, and decrypting the encrypted data by the client by using a negotiated key to obtain the necessary data.
Owner:BEIJING CHINA POWER INFORMATION TECH +3
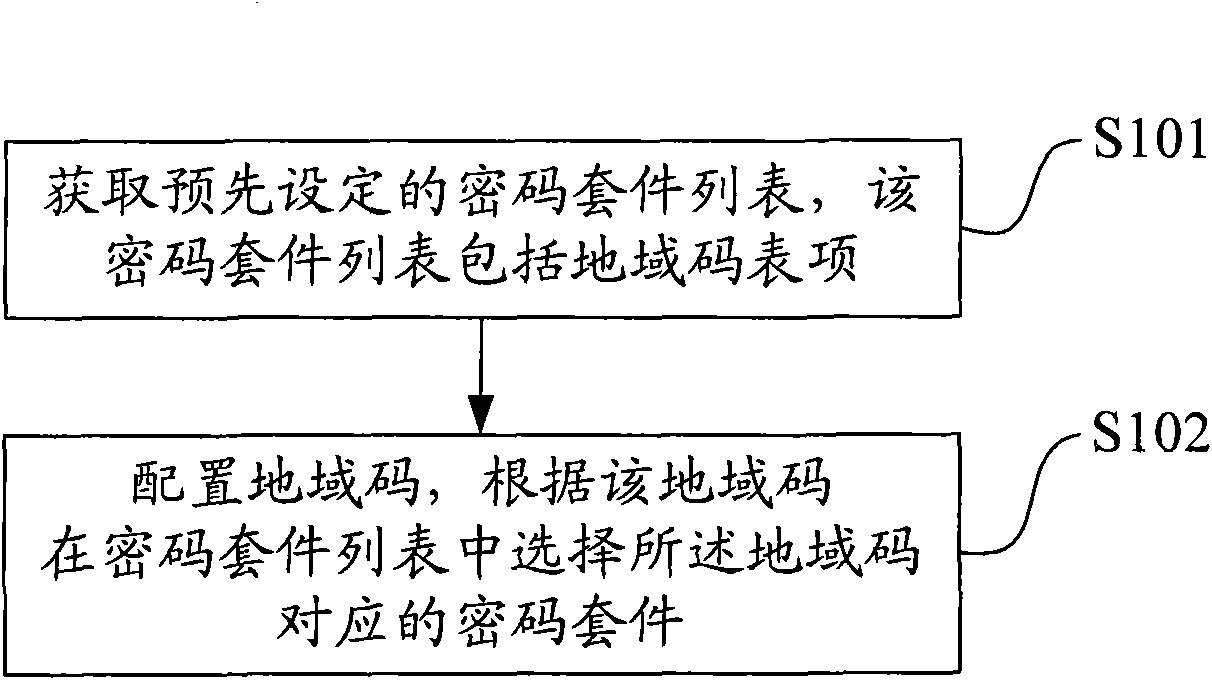
Configuration method and device of cipher suite
InactiveCN101562527ASolve conflictsIncrease flexibilityUser identity/authority verificationSerial codeCipher suite
The embodiment of the invention discloses a configuration method and a device of a cipher suite. The configuration method of a cipher suite comprises the steps: obtaining a preset cipher suite list, wherein the cipher suite list comprises a region code list item, and one cipher suite is uniquely determined by a suite serial number and a region code together; configuring the region code, and selecting the cipher suite corresponding to the region code according to the region code in the cipher suite list. The embodiment selects the cipher suite corresponding to the region code according to the configured region code in the obtained cipher suite list so as to realize the selection of the cipher suite according to the region code, solves the problem that the cipher suite of equipment in different regions can conflict with each other, and increases the flexibility of the equipment.
Owner:HUAWEI DIGITAL TECH (CHENGDU) CO LTD
Identity authentication method, device and system
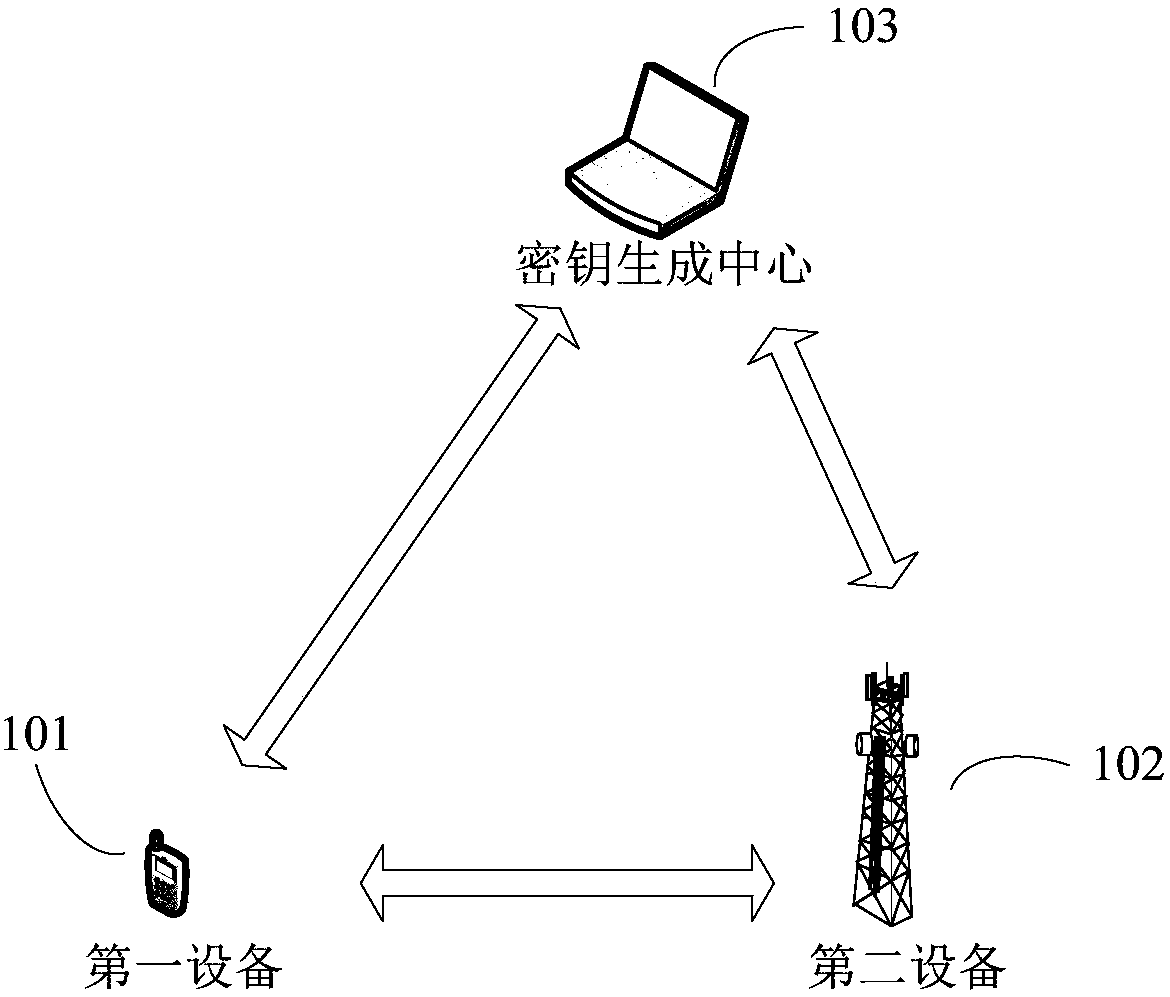
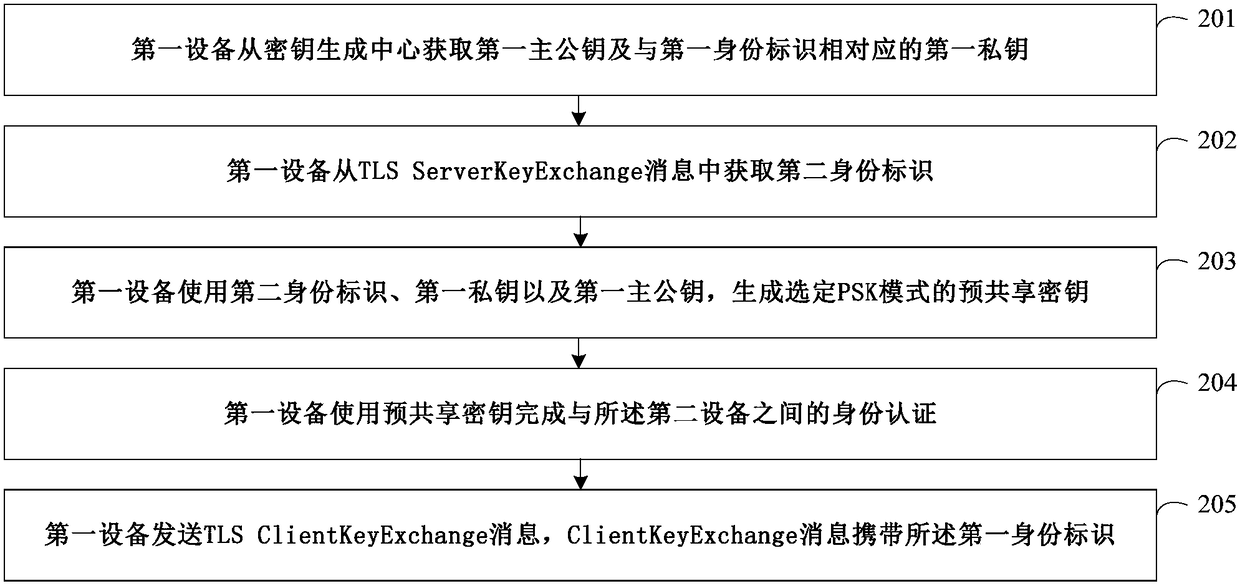
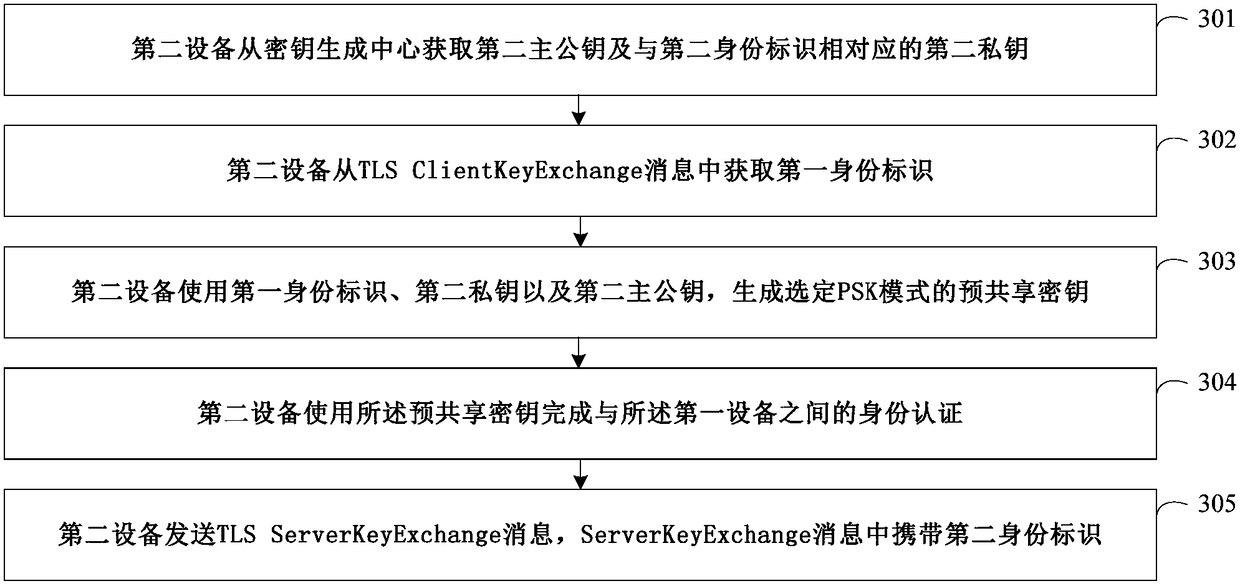
ActiveCN108111467AFix compatibility issuesSecurity arrangementSecuring communicationKey exchangeComputer compatibility
The invention discloses an identity authentication method, a device and a system. The method comprises the steps that a first device obtains a first main public key and a first private key from a keygeneration center; the first device sends a client hello message, wherein the client hello message carries cipher suites of pre-shared key cipher suites (PSK) modes; the first device obtains a secondidentity from a server key exchange message; the first device generates a pre-shared key of the selected PSK mode through utilization of the second identity, the first private key and the first main public key; and the first device finishes identity authentication with a second device through utilization of the pre-shared key. Through adoption of the method, the device and the system provided by the embodiment of the invention, the identity can be transmitted through utilization of information in a TLS (Transport Layer Security) protocol, so the TLS protocol does not need to be expanded, and the compatibility problem resulting from expanding the TLS protocol can be avoided.
Owner:HUAWEI TECH CO LTD
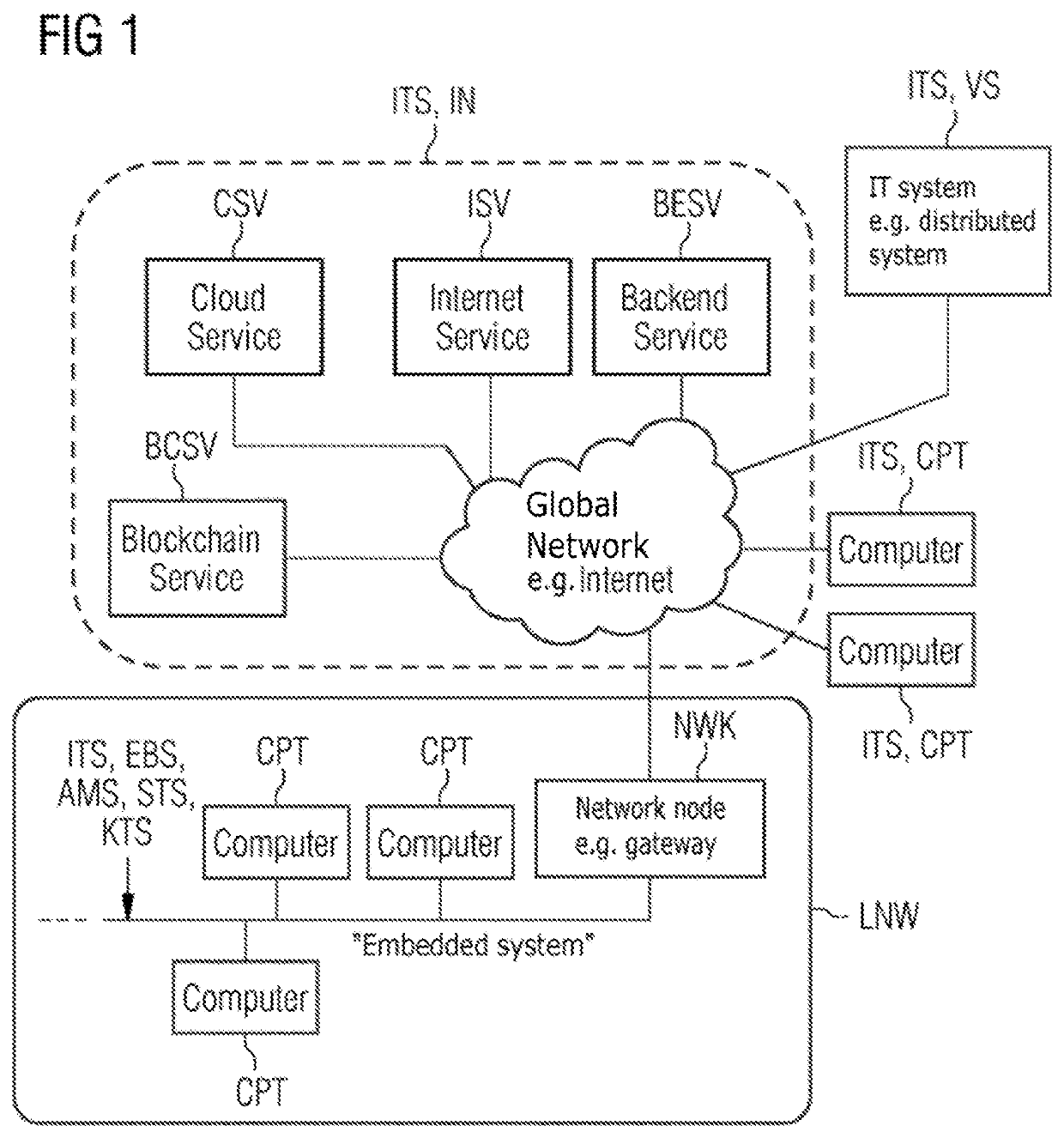
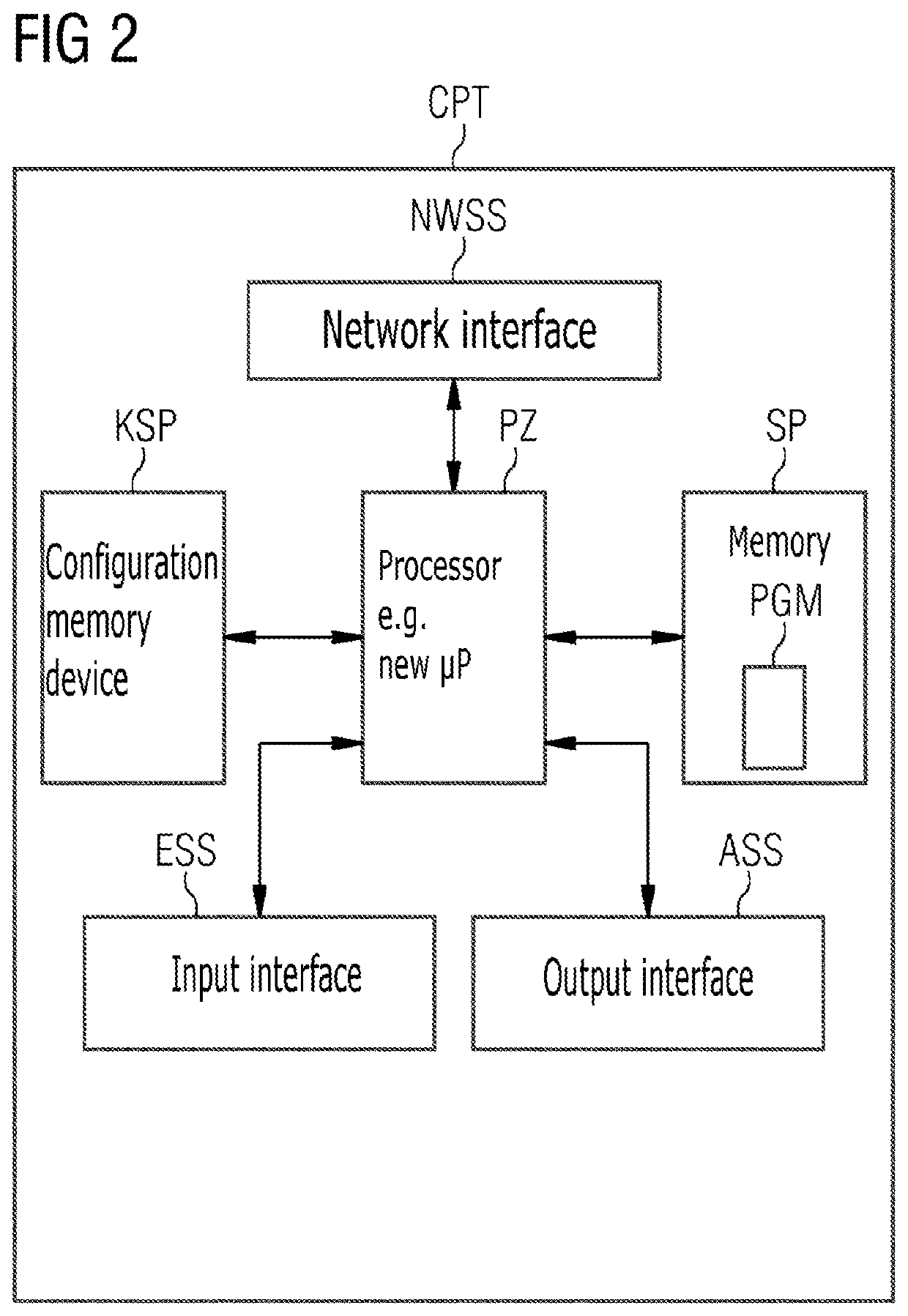
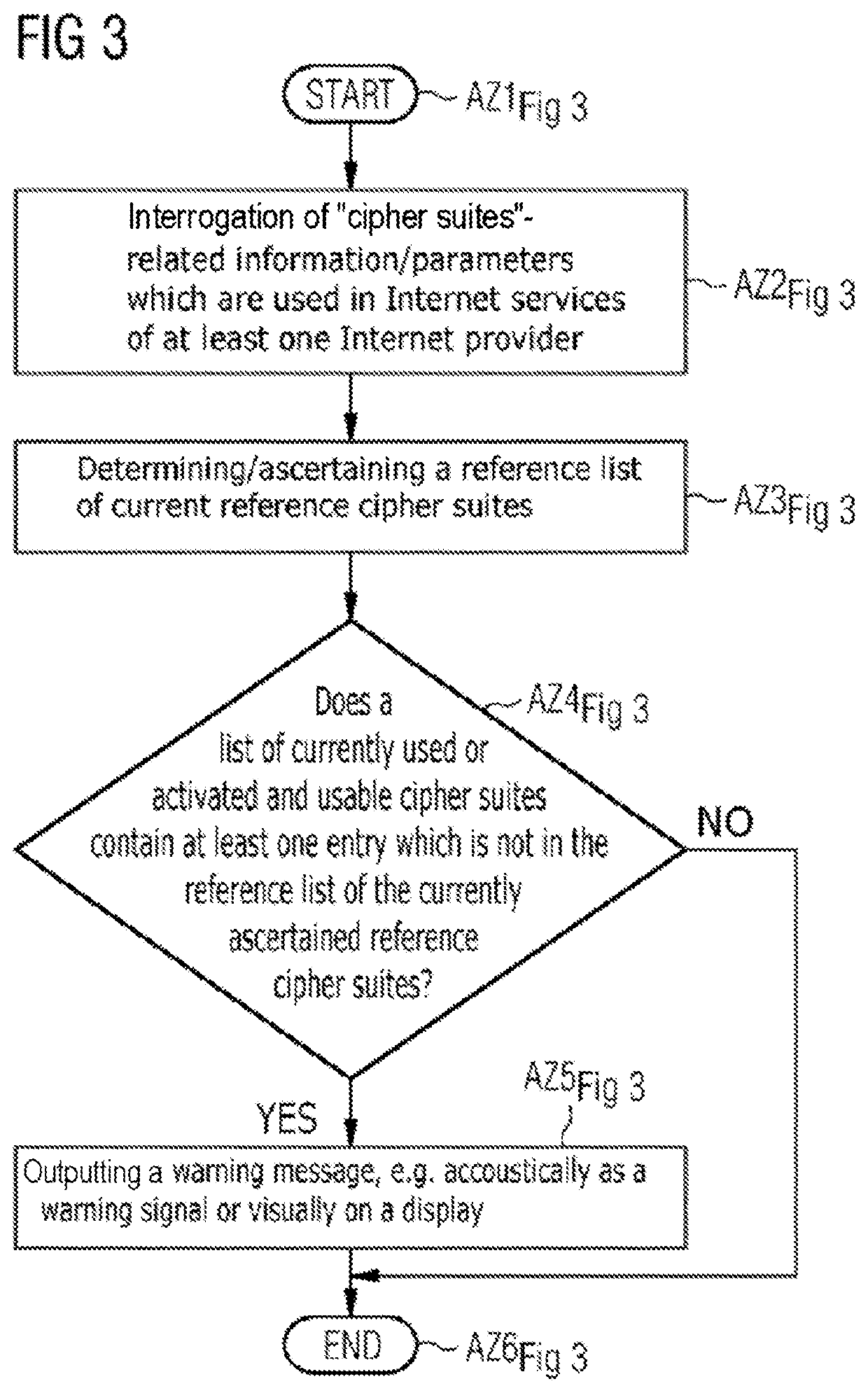
Method and computer for cryptographically protecting control communication in and/or service access to it systems, in particular in connection with the diagnosis and configuration in an automation, control or supervisory system
ActiveUS20190394027A1Improve robustnessControl of accessKey distribution for secure communicationEncryption apparatus with shift registers/memoriesKey sizeControl communications
Automatically and dynamically ascertain by means of autoconfiguration whether used or activated and usable cipher suites and / or key lengths are sufficiently strong for current cryptographic protection of the control communication and / or other service access by virtue of 1) “cipher-suite”-based / -specific information available in the network / system being called up to ascertain reference cipher suites and / or 2) block chain information available in the network / system, containing data records referred to as “proof of work” for solving complex computation tasks, being called up or ascertained, with the ascertainment of block chain difficulty parameters as key length estimation parameters to ascertain appropriate reference key lengths, in particular reference minimum key lengths required for cryptoalgorithms, and 3) the ascertained reference cipher suites and / or the reference key lengths ascertained by the key length estimation parameters being compared with the used or activated and usable cipher suites and / or key lengths.
Owner:SIEMENS AG
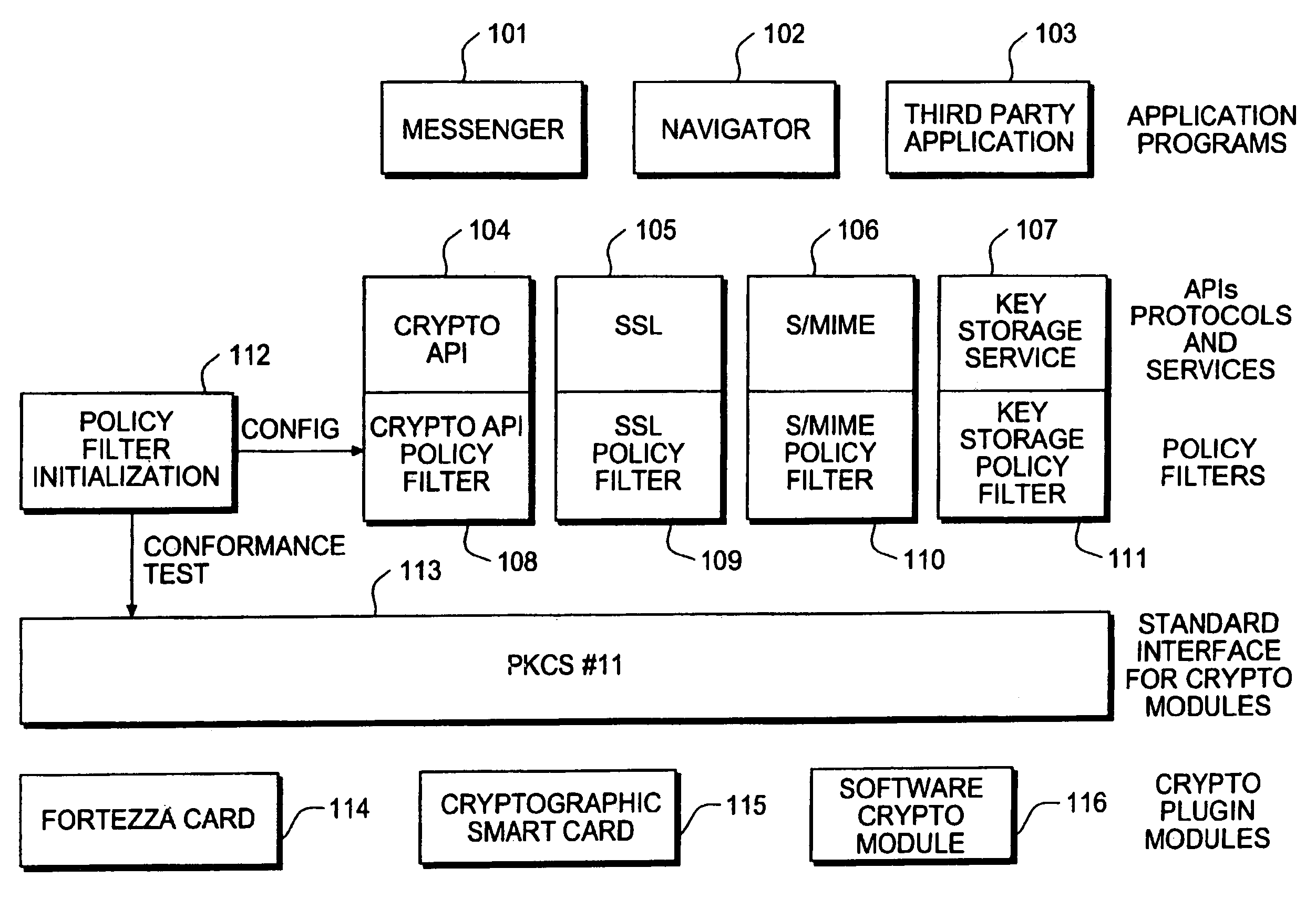
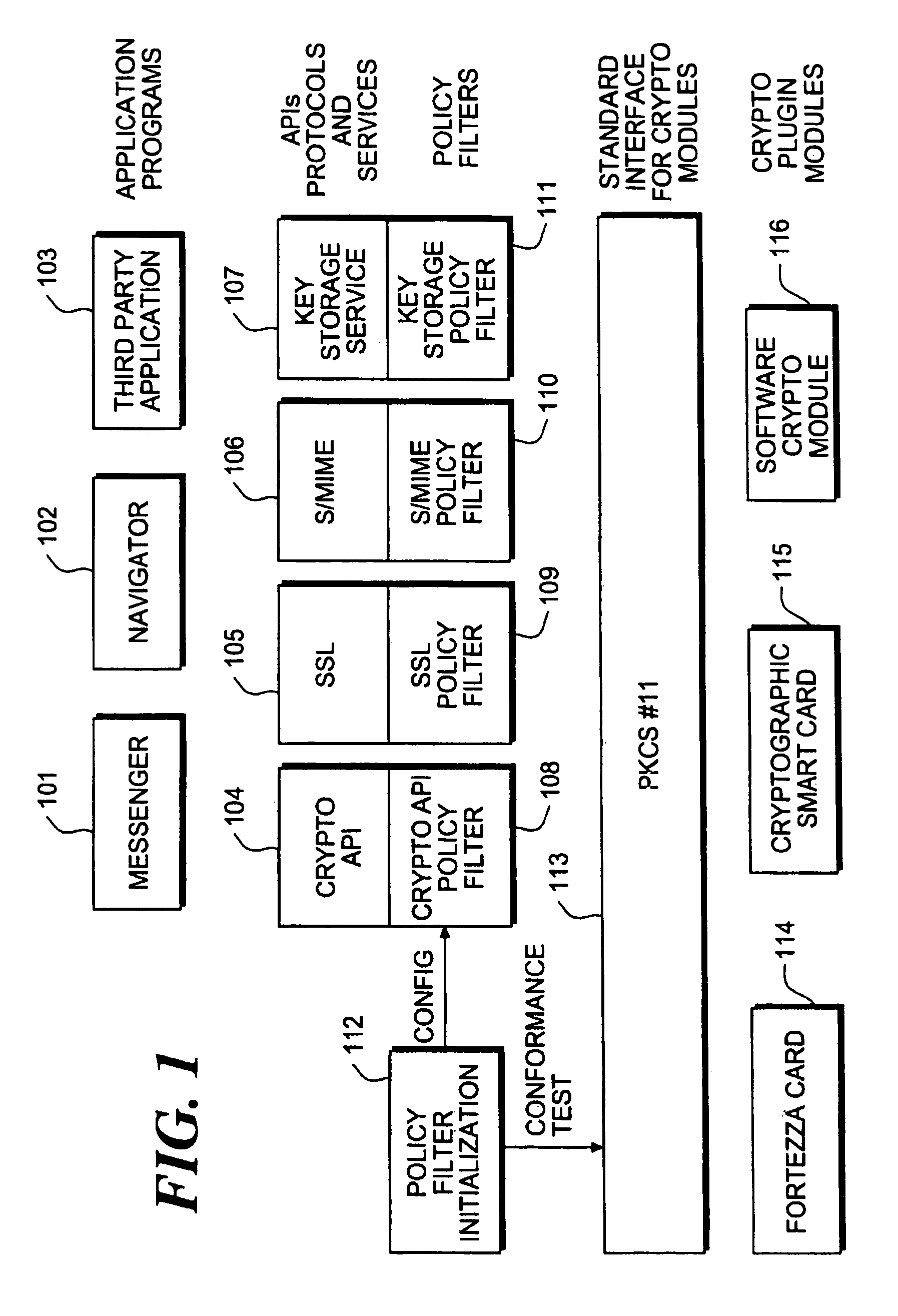
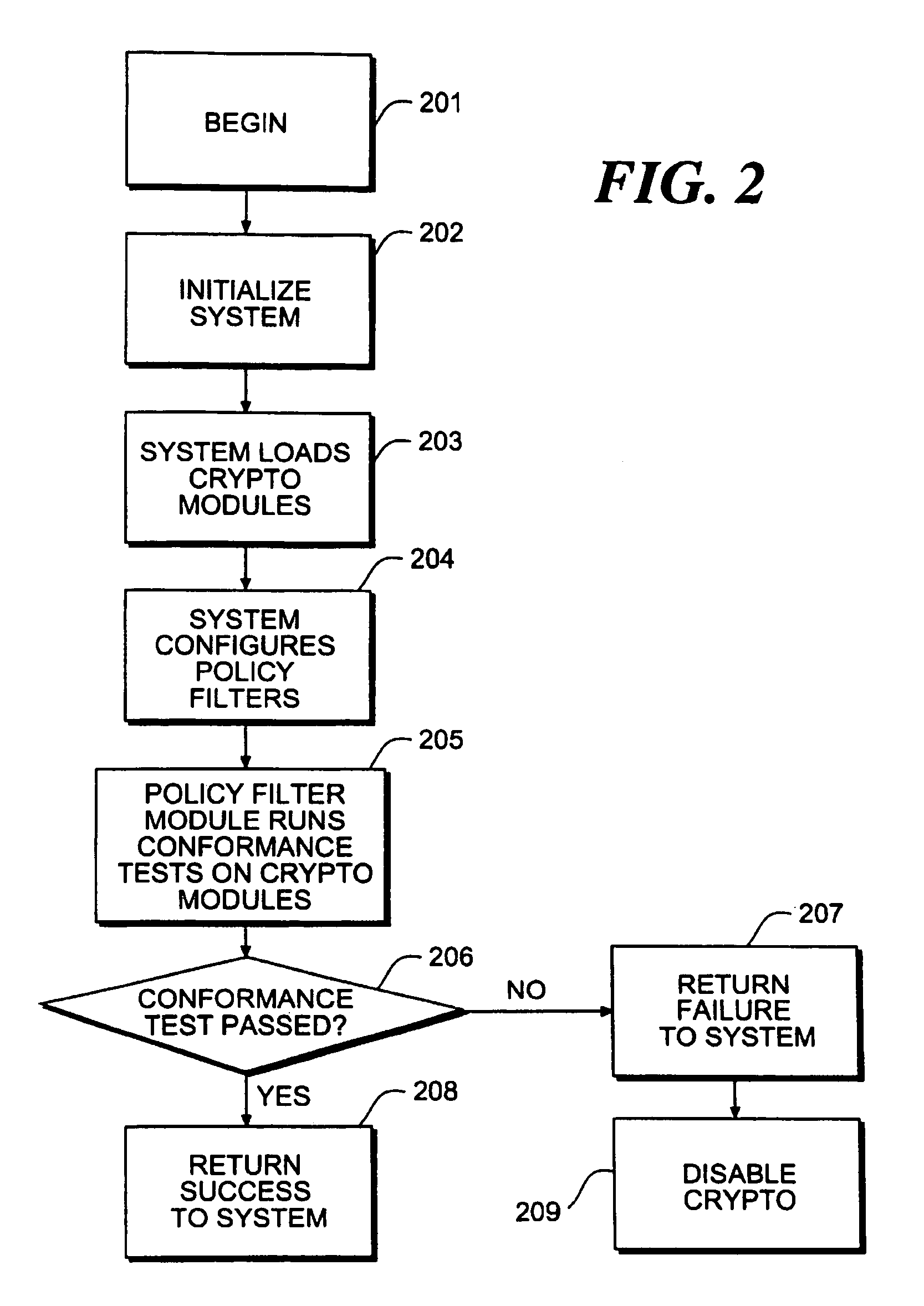
Cryptographic policy filters and policy control method and apparatus
InactiveUS7013390B1Unauthorized memory use protectionHardware monitoringDigital signatureService module
An apparatus for an integrated dynamic encryption and / or decryption for use in an application includes a policy filter, a policy filter module coupled to said policy filter, a service module coupled to said policy filter, and a cryptographic module, where the apparatus retrieves the cryptographic module and configures the policy filter in accordance with the cryptographic module and the policy filter module performs a plurality of verification upon the cryptographic module, and further where the service module is configured to generate a plurality of cipher suites and the policy filter is configured to filter the plurality of cipher suites in accordance with a predetermined policy filter parameters to generate a plurality of filtered cipher suites.Moreover, an apparatus for an integrated dynamic encryption and / or decryption for use in an application includes storage means for storing a plurality of predetermined attributes and corresponding values, and a digital signature, a controller for controlling selective retrieval of said plurality of attributes and values, and said digital signature from said storage means, processing means for selectively processing said plurality of predetermined attributes and values, and said digital signature and in accordance thereto, providing a supportable encryption and / or decryption level to said application, compression means for compressing said plurality of attributes and values and in accordance thereto generating a compressed plurality of attributes and values for storing in said storage means, and decompressing means for decompressing said compressed plurality of attributes and values in accordance to said controller retrieving said compressed plurality of attributes and values.
Owner:META PLATFORMS INC
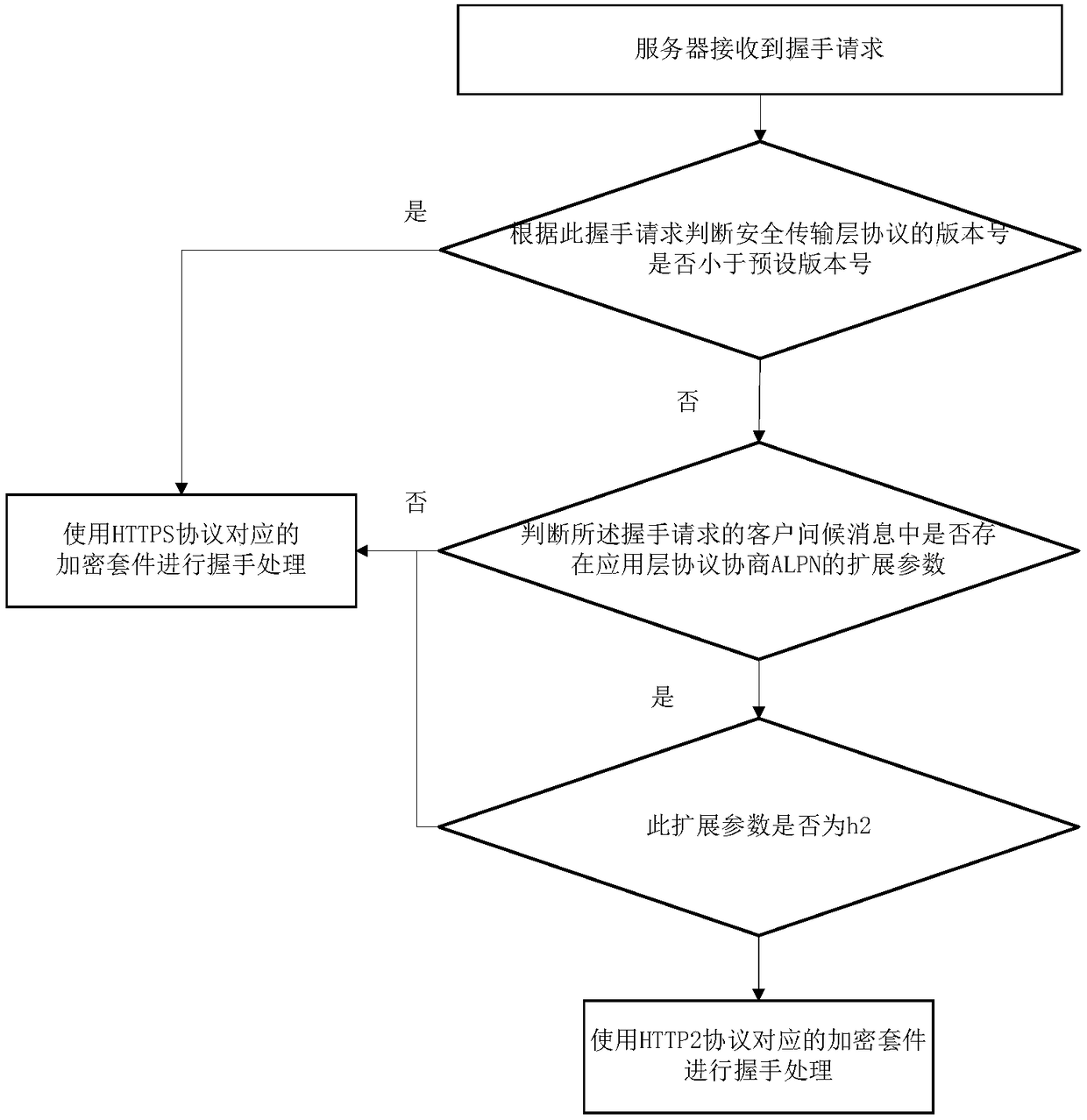
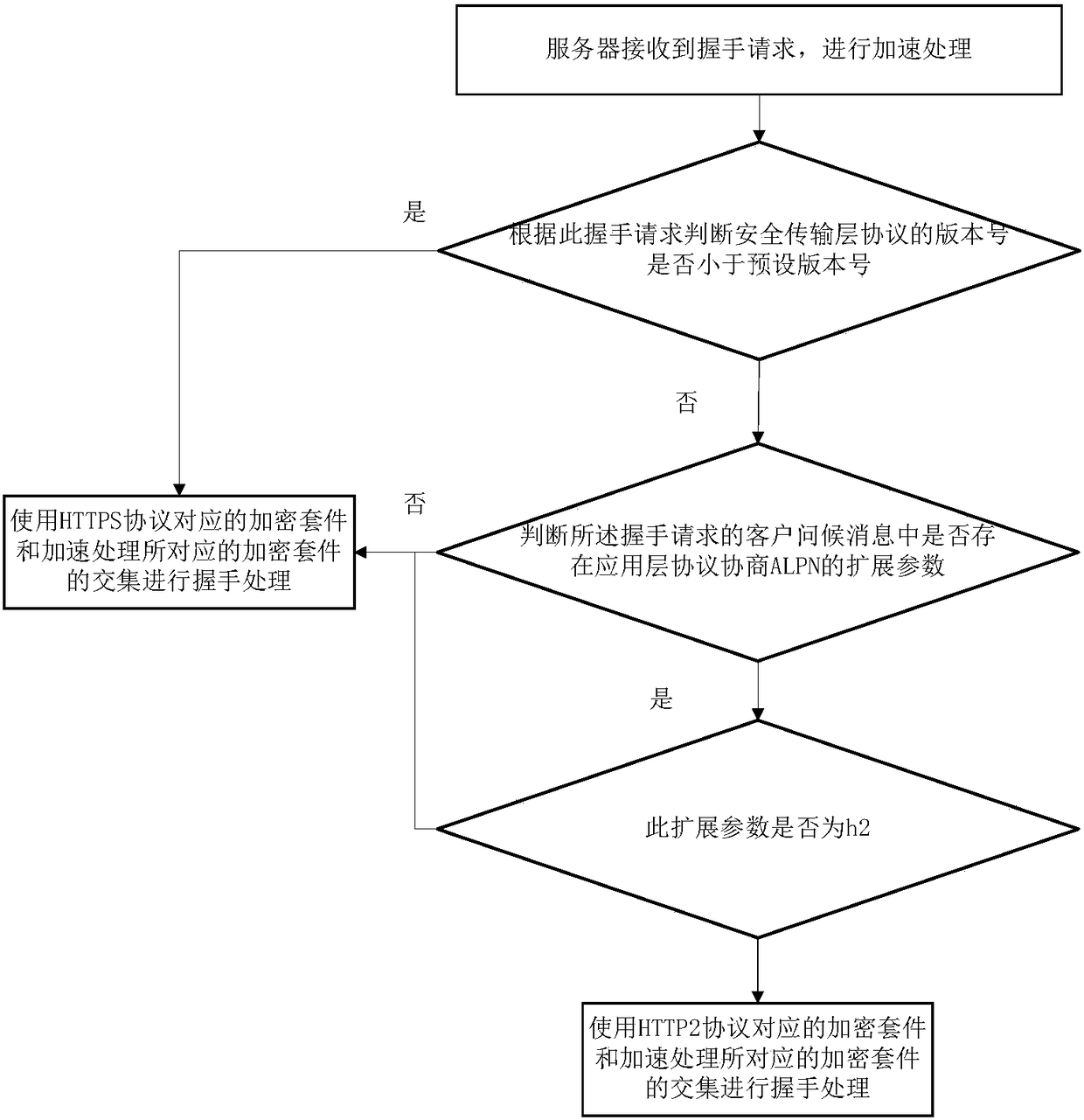
Cipher suite selection method and cipher suite selection device used for handshake processing process
ActiveCN108429724AImprove performanceImprove intelligenceTransmissionSecure transmissionHigh intensity
The invention discloses a cipher suite selection method and a cipher suite selection device used for a handshake processing process. The cipher suite selection method comprises steps that a handshakerequest is received by a server, and when a version number of a safety transmission later protocol is smaller than a preset version number according to the handshake processing process, a cipher suitecorresponding to a HTTPS protocol is used for the handshake processing. Compatibility of selection of a cipher suite list is realized during the handshake processing under an old version of HTTPS anda new version of HTTPS, and on the basis of the old version of HTTPS, the cipher suite having low safety strength and high performance is realized, and the HTTP2 handshake adopting the high-strengthcipher suite is also fully supported, and therefore the intelligent performance of the handshake processing process can be improved, and the successful handshake during the use of different versions of protocols is guaranteed, and costs can be saved.
Owner:GUIZHOU BAISHANCLOUD TECH CO LTD
Security configuration method for Nginx server cipher suite of SSR
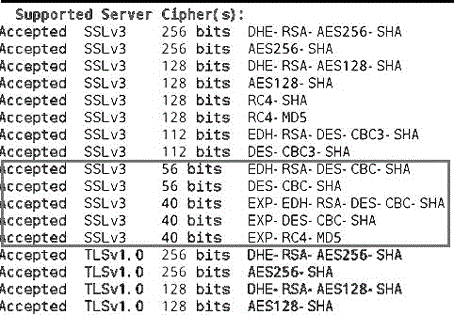
InactiveCN106209806AImprove your own securityGuaranteed uptimeTransmissionClient-sideSecurity analysis
The invention discloses a security configuration method for an Nginx server cipher suite of an SSR, and relates to the field of website security configuration. The cipher suite of an Nginx server is rationally selected, and the cipher suite of an Nginx server of the SSR is increased and decreased to realize an expected encryption accessory. The security configuration method mainly comprises the following steps: 1) checking the SSR cipher suite; 2) carrying out security analysis on the SSR cipher suite; and 3) modifying the cipher suite in an Nginx server configuration file of the SSR. According to the security configuration method disclosed by the invention, different parts of the suites are analyzed and compared; the unsecure cipher suite is selected and forbidden; a client and a server can only use the cipher suite with high security; the transmission security of transmission layer information is guaranteed; and the security of the SSR is enhanced, so that the SSR runs more safely.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Malicious software detection method and device, electronic equipment and storage medium
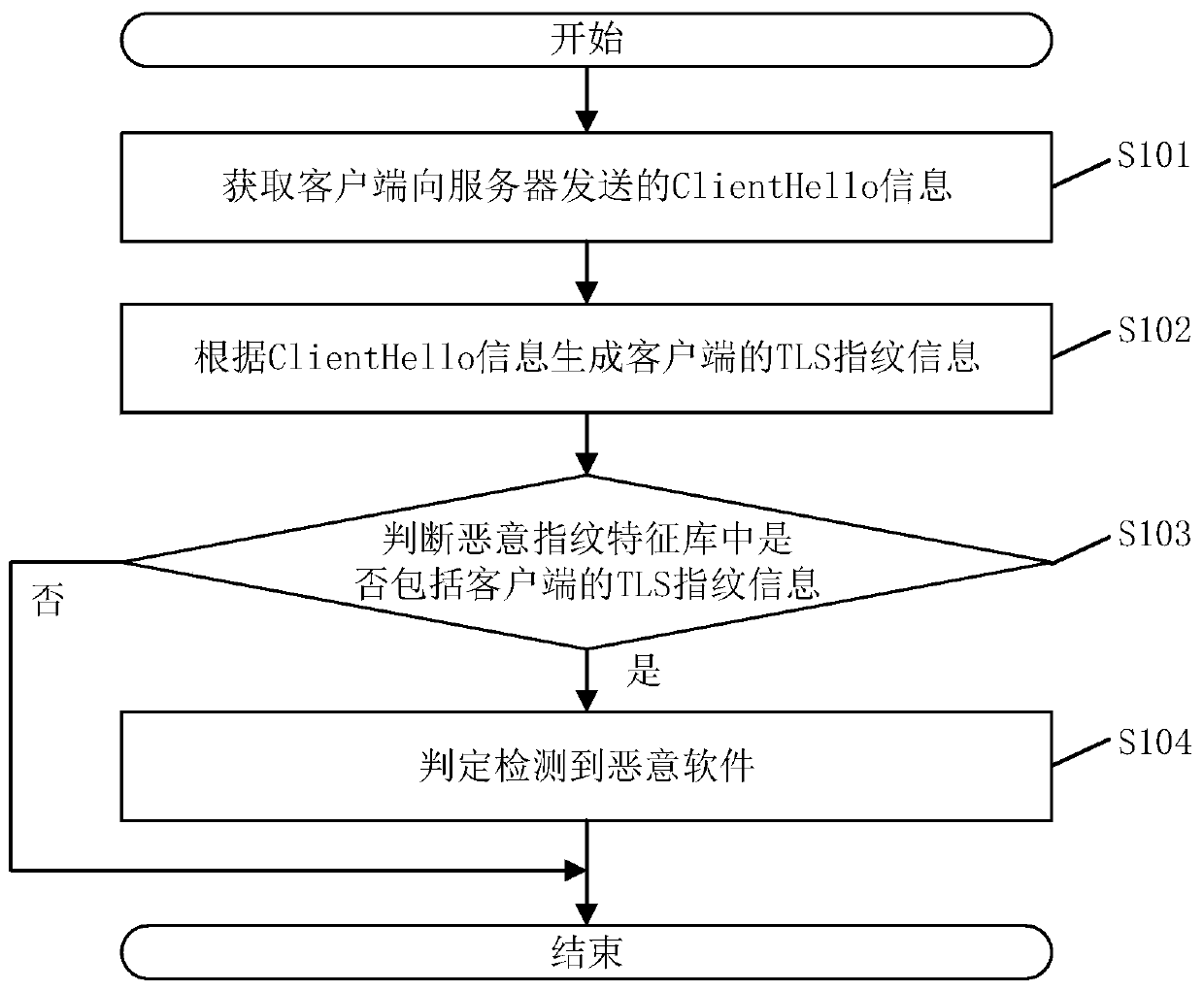
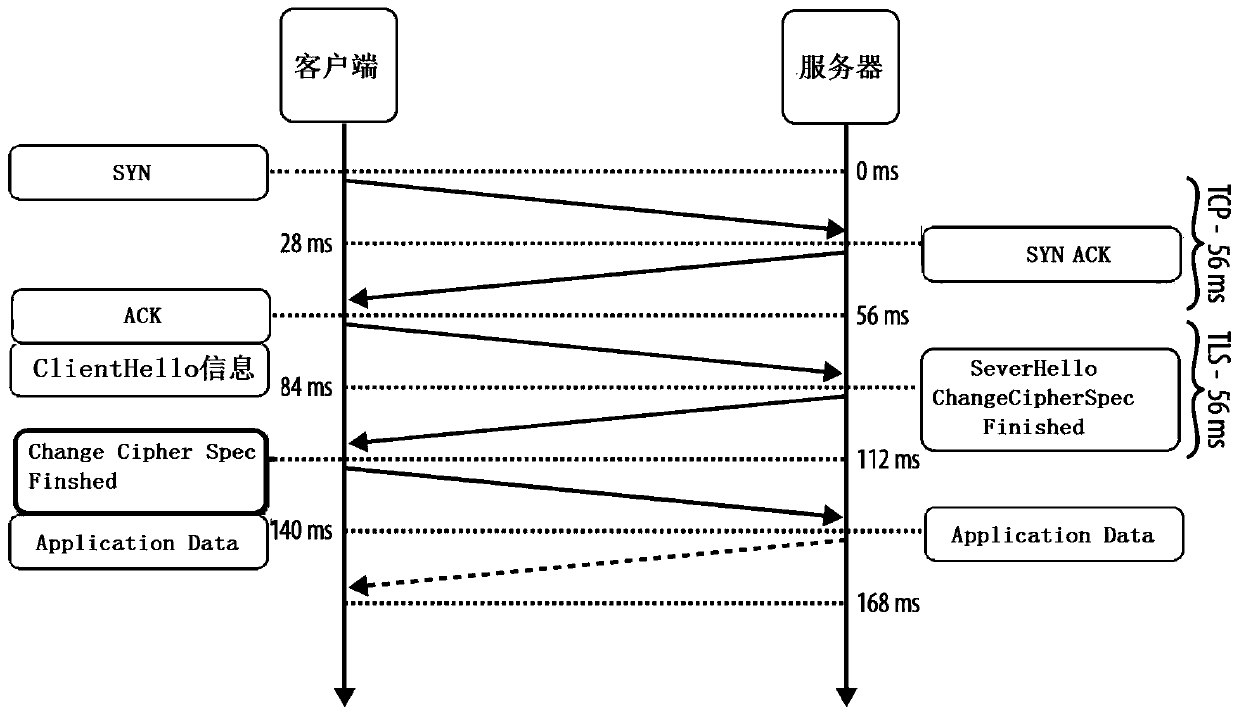
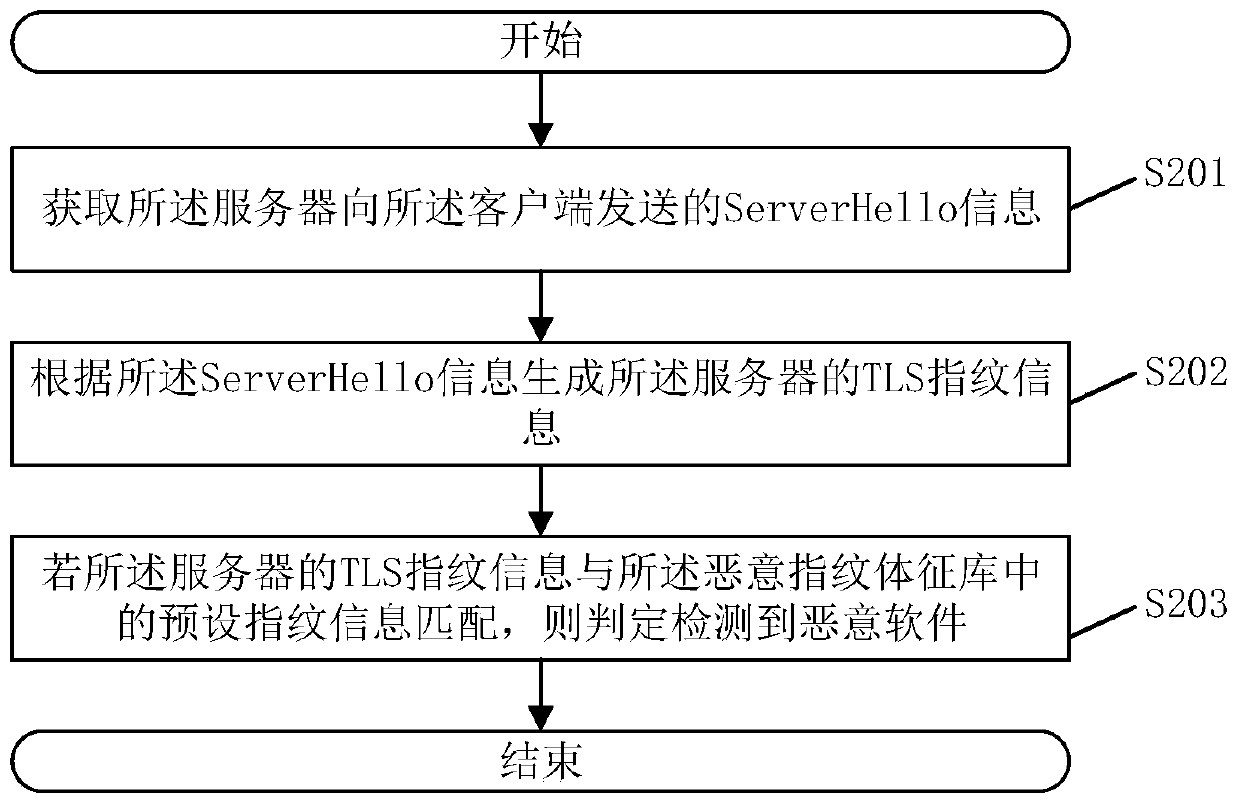
PendingCN111310187AImprove stabilityImprove recognition accuracyPlatform integrity maintainanceTransmissionPasswordEngineering
The invention discloses a malicious software detection method. The detection method comprises the steps that Client Hello information sent by a client to a server is acquired; wherein the Client Helloinformation comprises a TLS protocol version of the client, a password suite, an extension item and key encryption information; according to the Client Hello information, TLS fingerprint informationof the client side is generated; judging whether a malicious fingerprint feature library comprises TLS fingerprint information of the client or not; and if so, judging that malicious software is detected. The method can improve the identification accuracy of malicious software. The invention further discloses a malicious software detection device, a storage medium and electronic equipment, which have the above beneficial effects.
Owner:SANGFOR TECH INC
Cipher device using RC4 algorithm and method thereof
InactiveUS7634086B2Avoid delayPerformed quicklyData stream serial/continuous modificationSecret communicationS-boxRC4
An encryption / decryption device and a method thereof use an RC4 algorithm to reduce a waiting time for encryption / decryption thereby avoiding data process delay. The encryption / decryption device includes a management unit, an encryption / decryption unit, and a first interface. The management unit includes a WEP seed key generator for generating a WEP seed key based on a transmitter address of first data and a cipher suite value representing a cipher protocol type for the transmitter address, an RC4 key scheduler for generating S-Box data using the WEP seed key, and an S-Box data memory storing the S-Box data generated from the RC4 key scheduler for the transmitter addresses. The encryption / decryption unit has a core for performing the RC4 algorithm corresponding to the cipher suite, encrypting / decrypting the first data using the S-Box data transmitted from the management unit, and transmitting a signal for generating the S-Box data of second data to the management unit. The first interface transmits a control signal and a data signal between the management unit and the encryption / decryption unit.
Owner:ELECTRONICS & TELECOMM RES INST
Security configuration method of Tomact cipher suite of SSR
InactiveCN105681341AImprove securityEnsure safetyPlatform integrity maintainanceTransmissionSecurity analysisComputer science
The invention provides a security configuration method of a Tomact cipher suite of SSR, and relates to the website security configuration field. The security configuration method includes the steps of: (1) checking an SSR cipher suite; (2) performing security analysis on the SSR cipher suite; and (3) modifying the cipher suite in a Tomcat configuration file of the SSR. Through addition and deletion of the cipher suite, the cipher suite wanted to be used is realized, and the SSR self security is increased.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
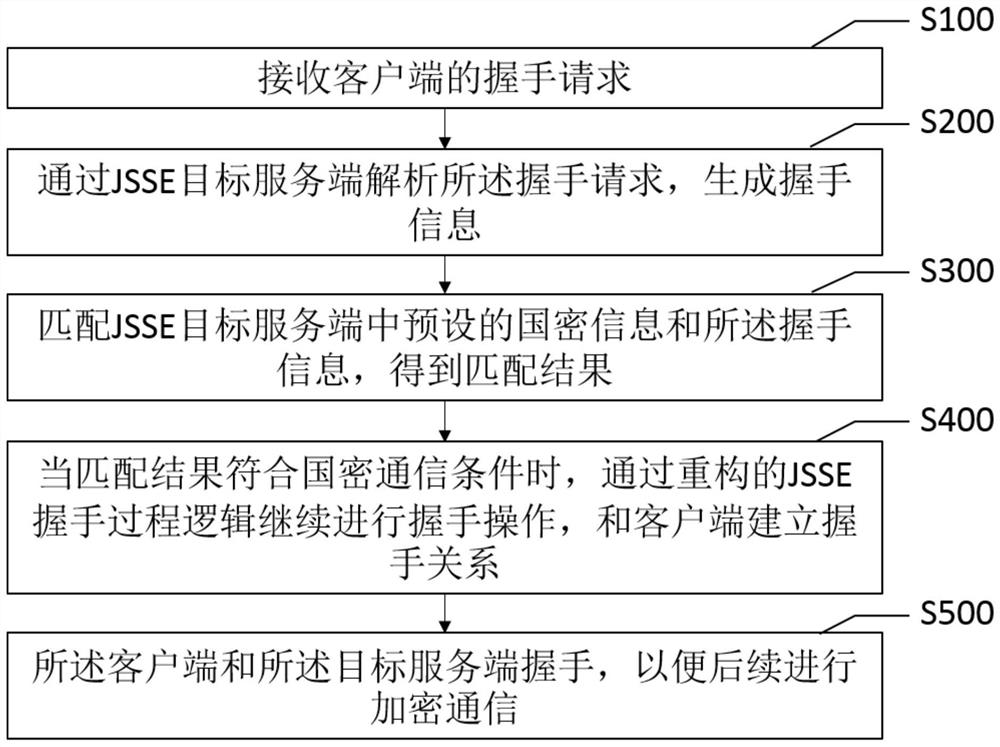
JSSE-based national secret encryption communication method and device, and storage medium
PendingCN113037480AResolve support issuesKey distribution for secure communicationPasswordEngineering
The invention discloses a JSSE-based national secret encryption communication method and device, and a storage medium. The method comprises the following steps: receiving a handshake request of a client; analyzing the handshake request through a JSSE target server, and generating handshake information; matching national secret information preset in a JSSE target server with the handshake information to obtain a matching result; when the matching result meets the national secret communication condition, enabling handshake operation to continue to be carried out through the reconstructed JSSE handshake process logic, and establishing a handshake relation with the client; and enabling the client side and the target server side to perform handshake so as to facilitate subsequent encryption communication, wherein the preset national password information comprises a national password version number which is expanded in a protocol version of the JSSE in advance and a password suite which is expanded in a JSSE password suite in advance and conforms to a national password specification. By correspondingly processing the handshake request of the client and returning the corresponding response data, national secret encryption communication based on JSSE is realized.
Owner:BEIJING THUNISOFT INFORMATION TECH
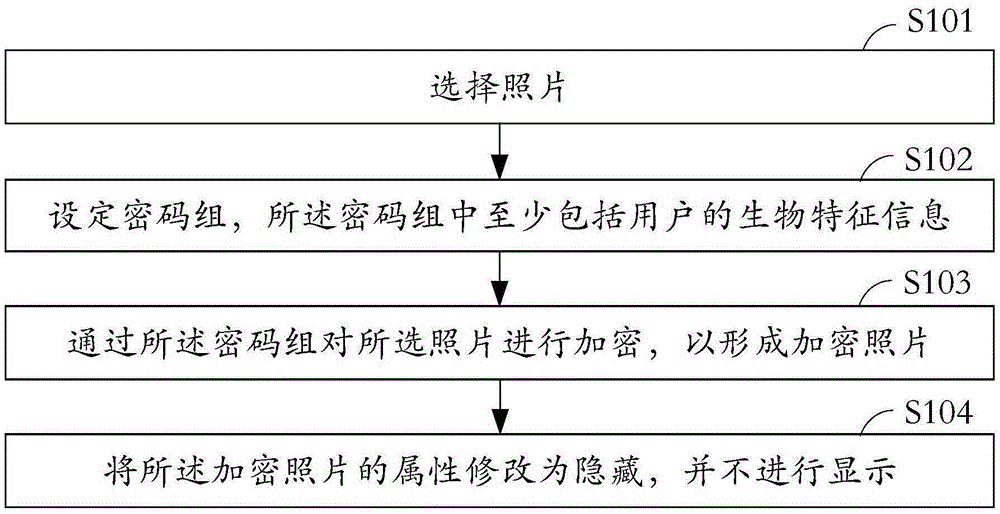
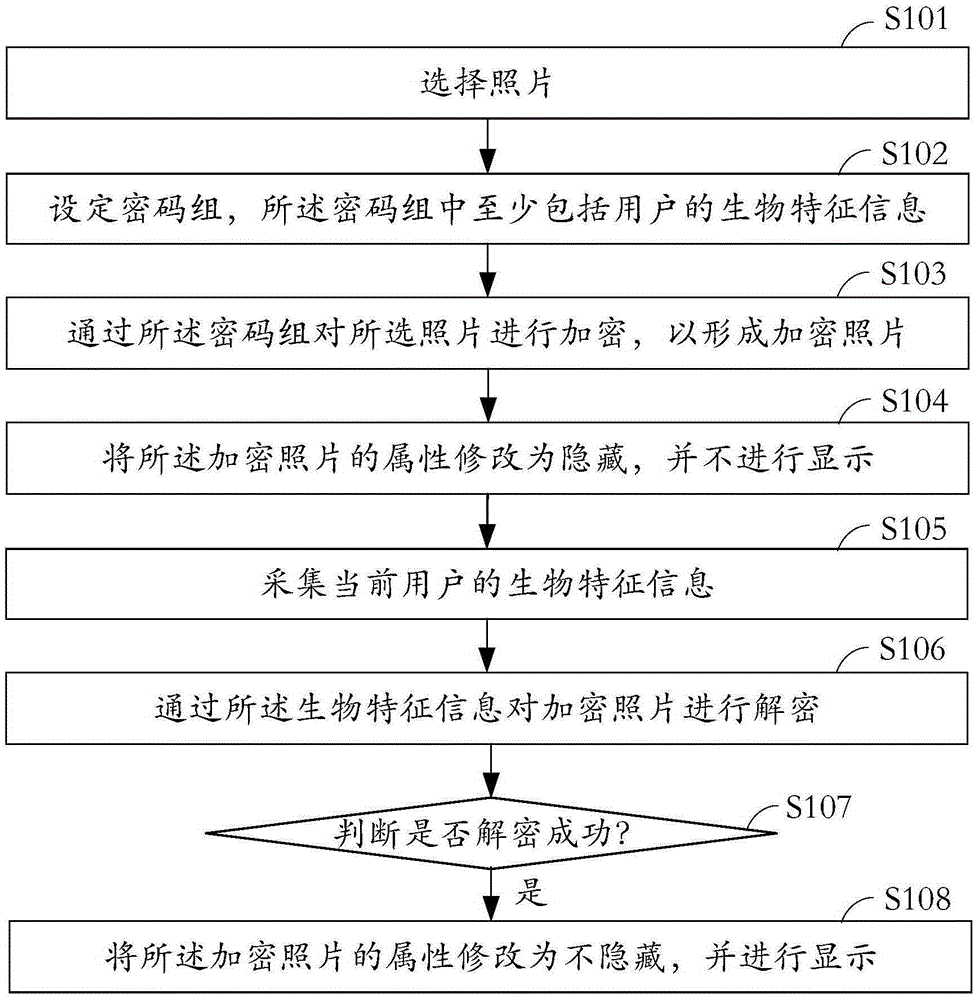
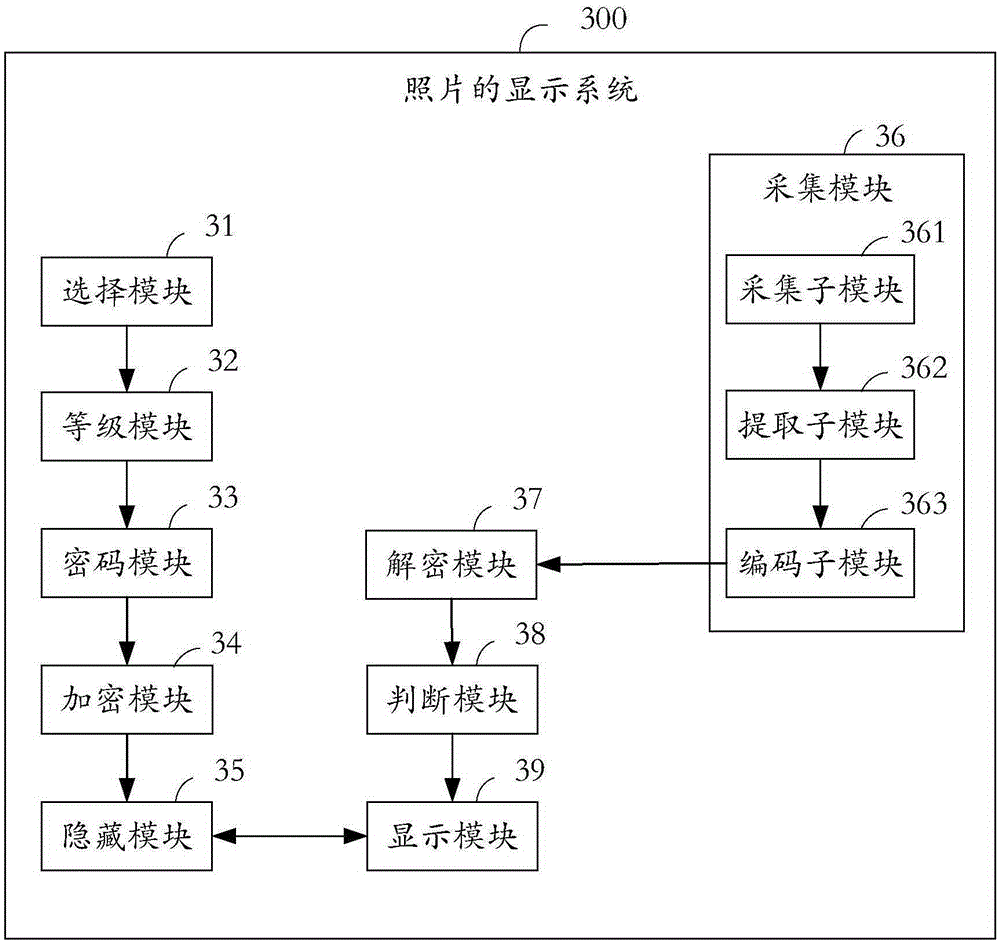
Photo display method and display system
InactiveCN105354502AImprove securityDigital data protectionDigital data authenticationCipher suiteComputer engineering
The present invention provides a photo display method and display system. The photo display method comprises: selecting photos; setting a cipher suite, wherein the cipher suite at least comprises biological feature information of a user; performing encryption on the selected photos by the cipher suite to form encrypted photos; and modifying attributes of the encrypted photos into a hidden state without carrying out displaying. According to the photo display method and display system, the cipher suite comprising the biological feature information of the user is set, and the photos encrypted by the the cipher suite are hidden. The method and the system which are provided by the present invention have the advantages of completeness for hiding, targeted selection on encrypted targets and high safety.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
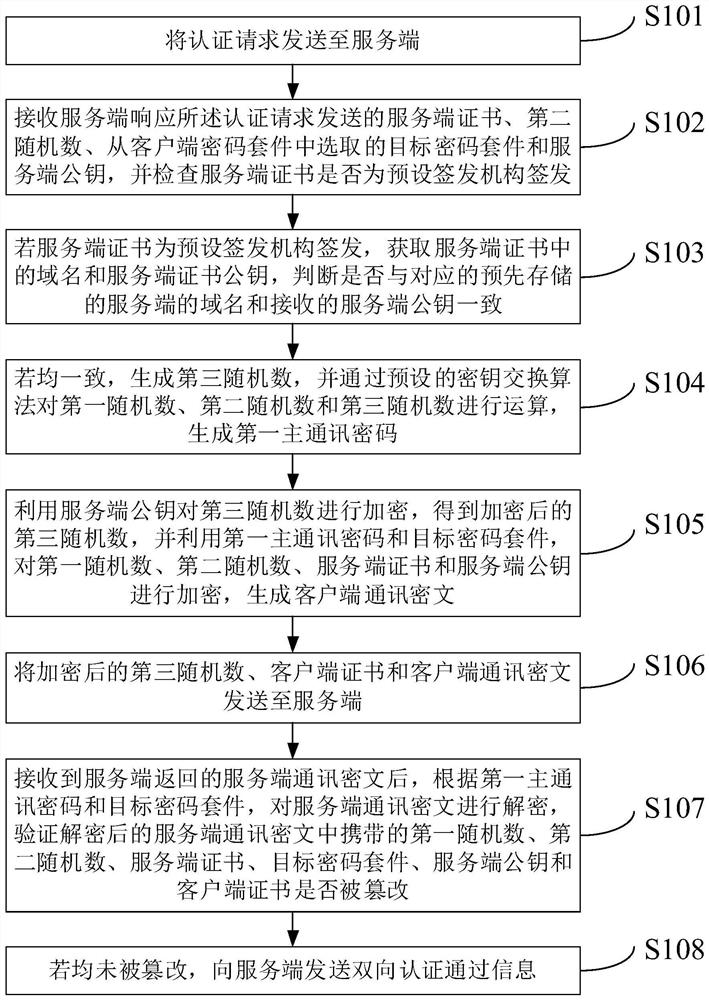
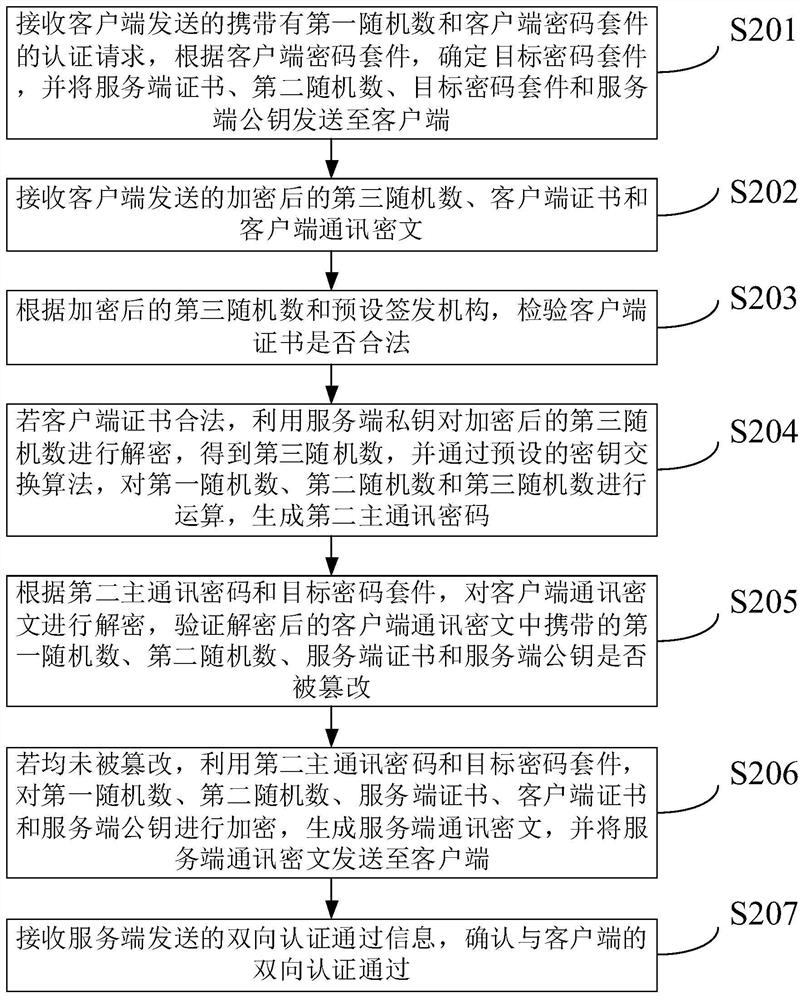
Bidirectional authentication method and device
ActiveCN113596046AImplement two-way authenticationImprove communication securityTransmissionKey exchangeCiphertext
The invention provides a bidirectional authentication method and device. The method comprises the steps: receiving a server certificate, a second random number, a target password suite and a server public key which are sent by a server in response to an authentication request, obtaining data in the server certificate if the server certificate is checked to be signed and issued by a preset signing and issuing mechanism; and if the data are consistent with the data provided by the server, generating a third random number, and generating a first main communication password through a preset key exchange algorithm; encrypting the third random number by using the server public key to obtain an encrypted third random number, and generating a client communication ciphertext by using the first main communication password and the target password suite; sending the encrypted third random number, the client certificate and the client communication ciphertext to the server; and after a server-side communication ciphertext returned by the server side is received, the server-side communication ciphertext is decrypted according to the first main communication password and the target password suite, and if data carried in the server-side communication ciphertext is not tampered, the bidirectional authentication is confirmed to pass.
Owner:中电金信软件有限公司
Systems and methods for computer digital certificate management and analysis
Described herein are methods and systems for updating digital certificates on a computer and testing to confirm that the update was performed correctly. The testing may involve confirming that a server's common name (CN) and / or a server's subject alternative name (SAN) matches the domain name server (DNS) name utilized to access the server, confirming that, for all the certificates sent in chain, each certificate's expiration date is less than or equal to the expiration date of that certificate's parent certificate, confirming that the certificates' authority key identifier (AKI), subject key identifier (SKI), and / or authority information access (AIA) are in compliance, and comparing available cipher suites to a list of pre-approved cipher suites.
Owner:USAA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com