Transport layer security (TLS) handshaking method and device, and trusted third party (TTP)
A secure transport layer, TTP-technology, applied in the field of network security, can solve problems such as the inability to enhance the security of the TLS handshake process, and achieve the effect of enhanced security and good backward compatibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0050] In this embodiment, the first party is the client, and the second party is the server. The TLS handshake method provided in this embodiment can establish a secure tunnel between the client and the TTP during the existing two-party TLS handshake process.
[0051] Such as Figure 2a As shown, the TLS handshake method in this embodiment specifically includes the following steps:
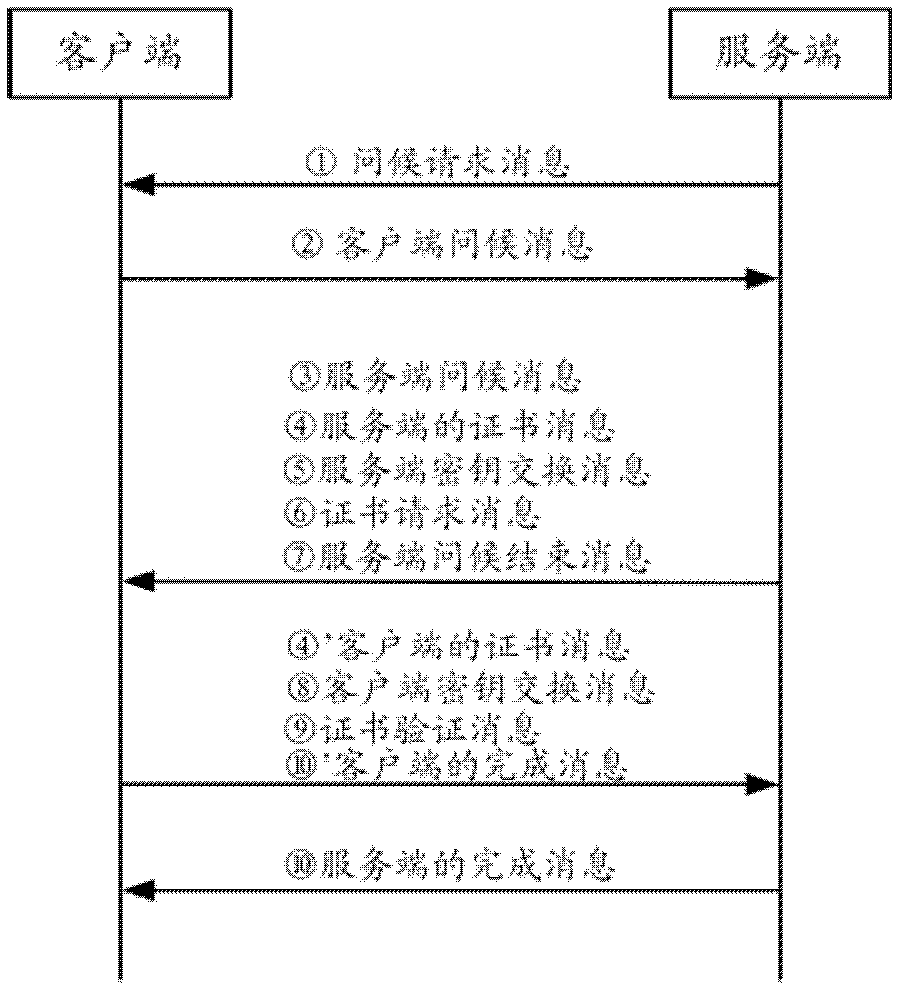
[0052] Step 1) When the server actively initiates the TLS handshake process between the two parties, the server sends to the client: ①Hello request message.
[0053] Step 2) When the client receives the hello request message or actively initiates both parties' TLS handshake process, it sends to the server: 2. the client hello message, the client hello message includes the inquiry of the client, the list of cipher suites supported by the client, The client's query is a random number generated by the client;
[0054] Preferably, in order to realize whether the identification client needs to estab...
Embodiment 2
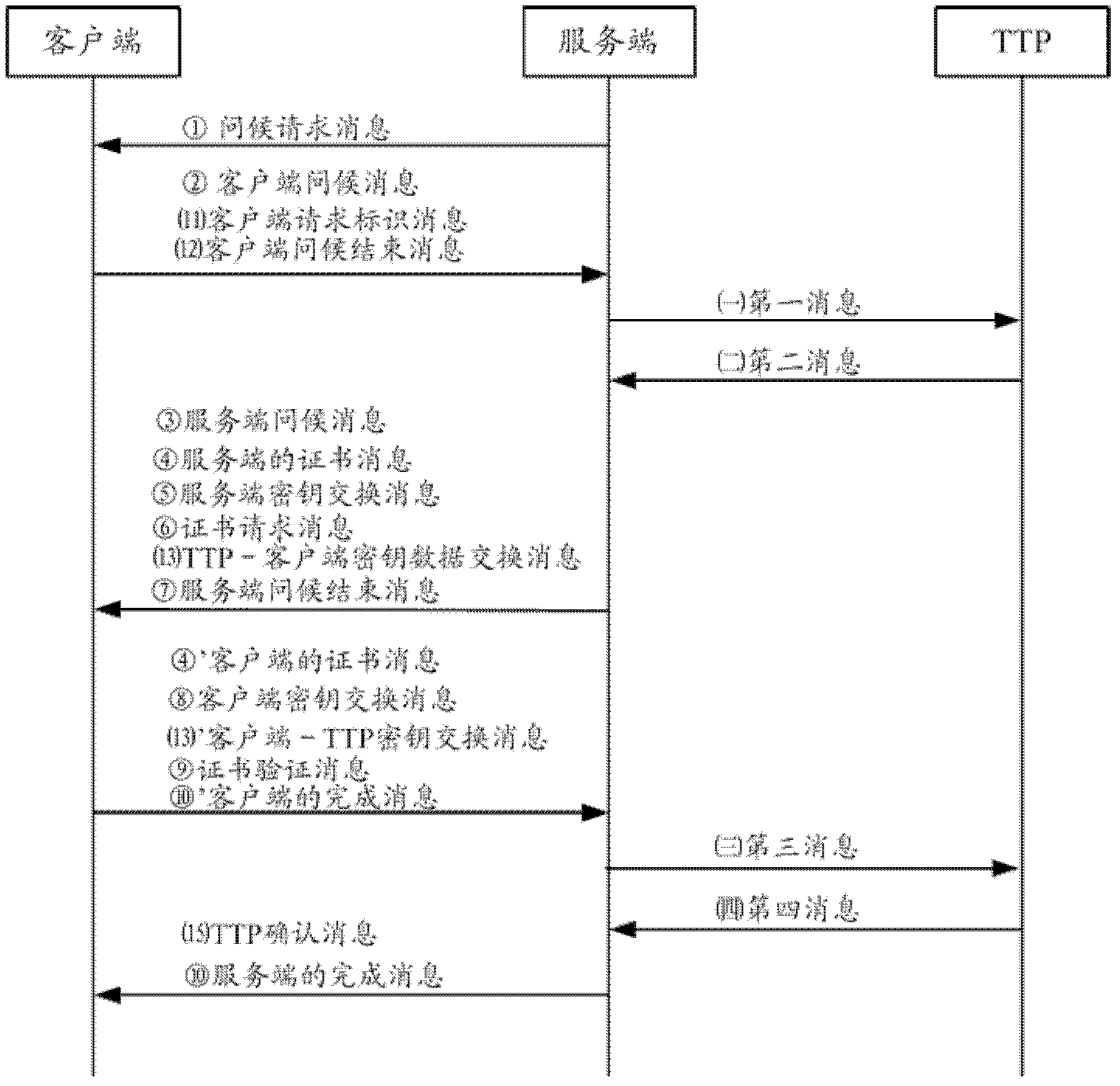
[0105] In this embodiment, the first party is the client, and the second party is the server. The TLS handshake method provided in this embodiment, on the basis of implementing the establishment of a secure tunnel between the client and the TTP in Embodiment 1, further establishes the connection between the server and the TTP. A secure tunnel between TTPs.
[0106] The TLS handshake method in this embodiment specifically includes the following steps:
[0107] Step 1) When the server actively initiates the TLS handshake process between the two parties, the server sends to the client: ①Hello request message.
[0108] Step 2) When the client receives the hello request message or actively initiates both parties' TLS handshake process, it sends to the server: 2. the client hello message, the client hello message includes the inquiry of the client, the list of cipher suites supported by the client, The client's query is a random number generated by the client;
[0109] Preferably,...
Embodiment 3
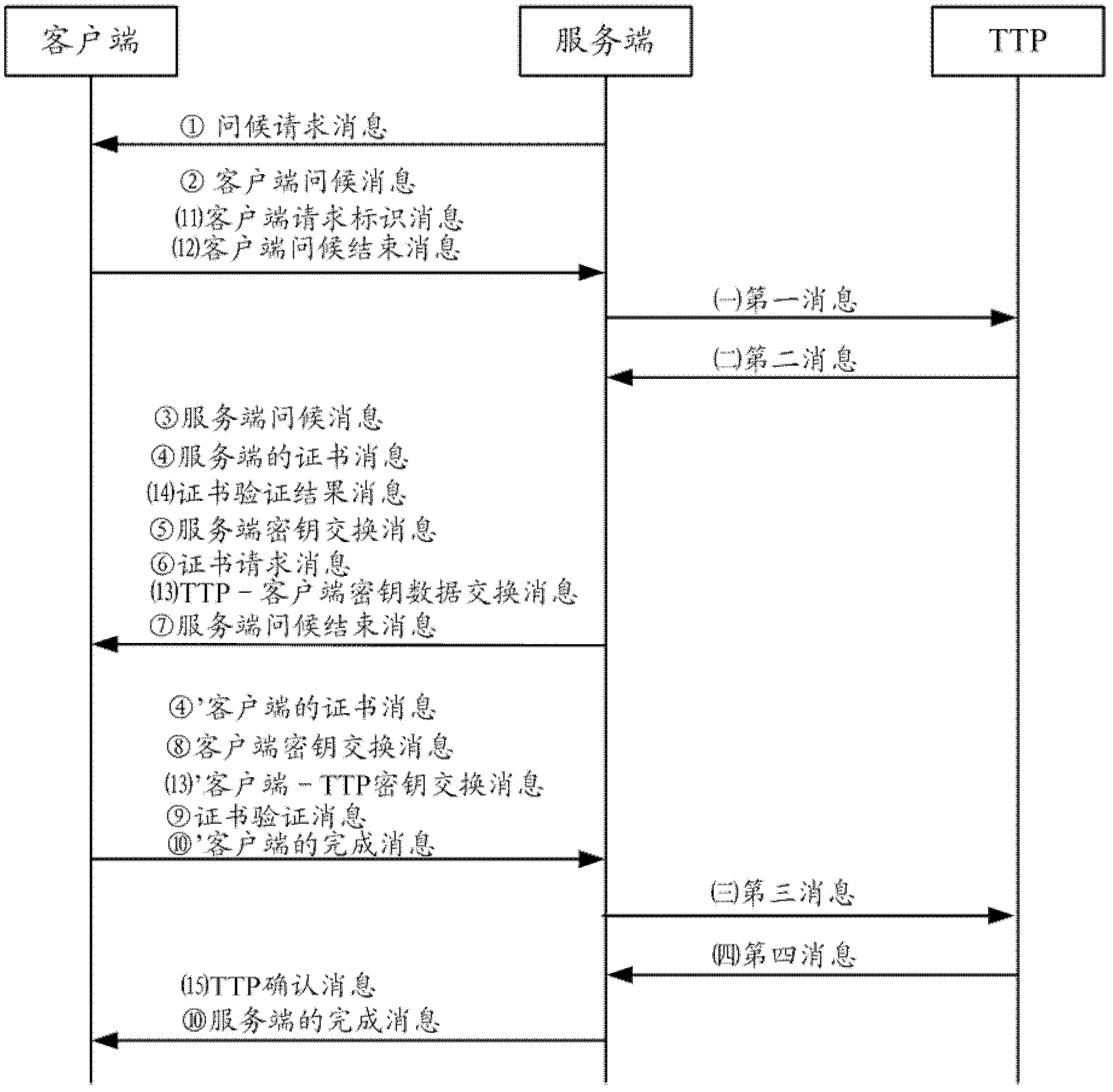
[0159] In this embodiment, the first party is the server, and the second party is the client. The TLS handshake method provided in this embodiment can establish a secure tunnel between the server and TTP during the existing two-party TLS handshake process.
[0160] Such as Figure 3a As shown, the TLS handshake method in this embodiment specifically includes the following steps:
[0161] Step 1) When the server actively initiates the TLS handshake process between the two parties, the server sends to the client: ①Hello request message.
[0162] Step 2) When the client receives the hello request message or actively initiates both parties' TLS handshake process, it sends to the server: 2. the client hello message, the client hello message includes the inquiry of the client, the list of cipher suites supported by the client, The client's query is a random number generated by the client;
[0163] Preferably, in order to realize whether the identification client needs to establish...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com