Patents
Literature
278 results about "Trust third party" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
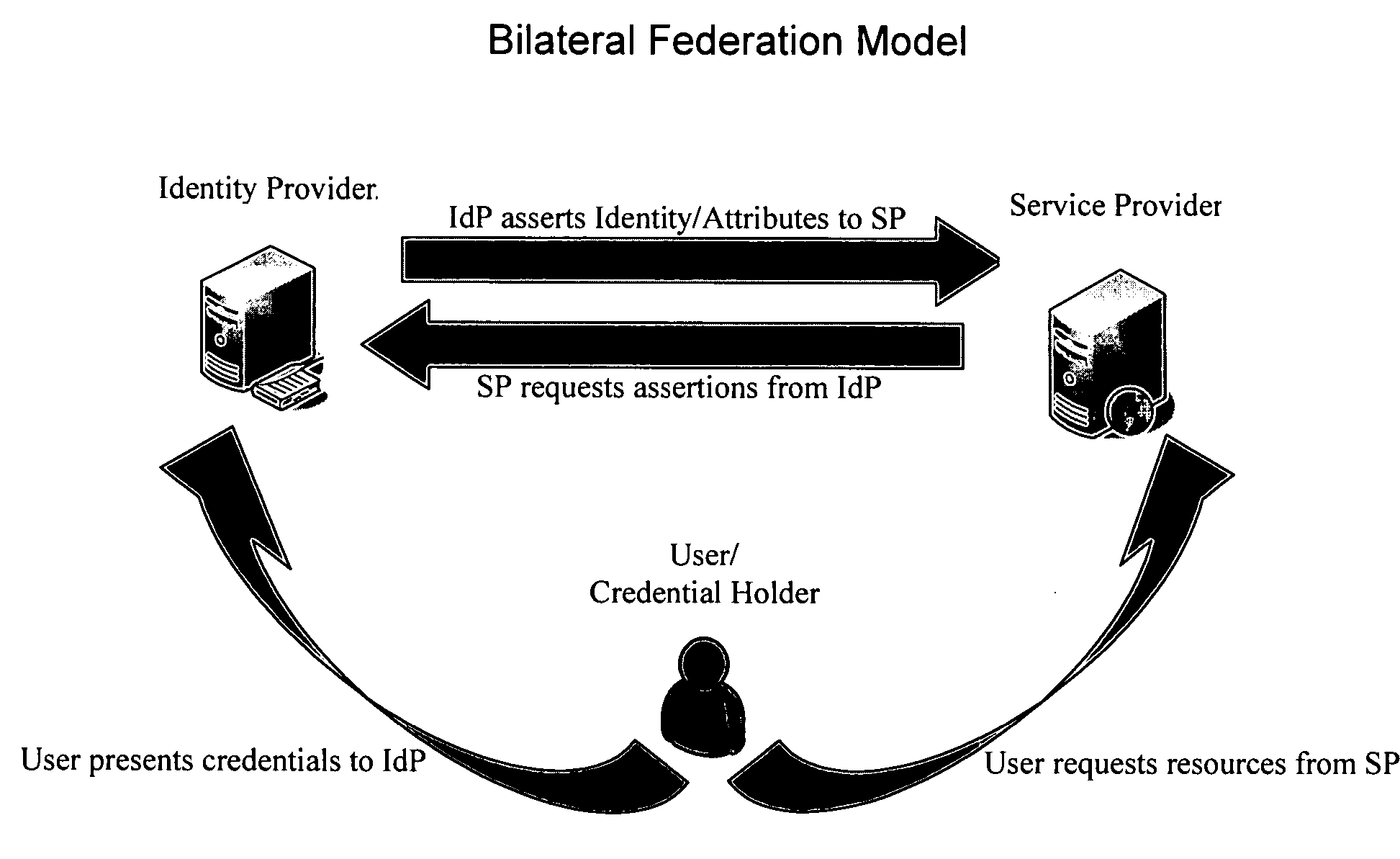
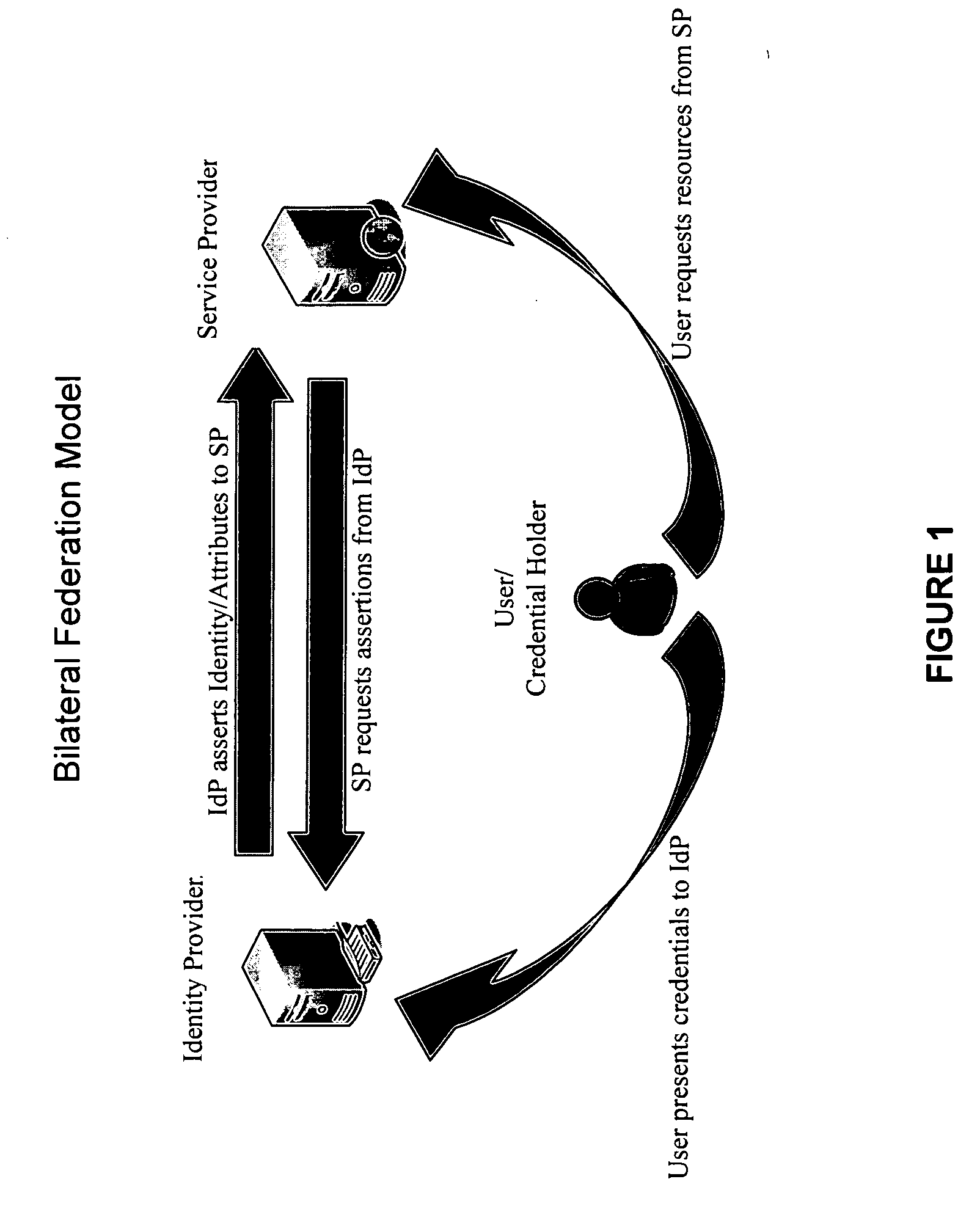
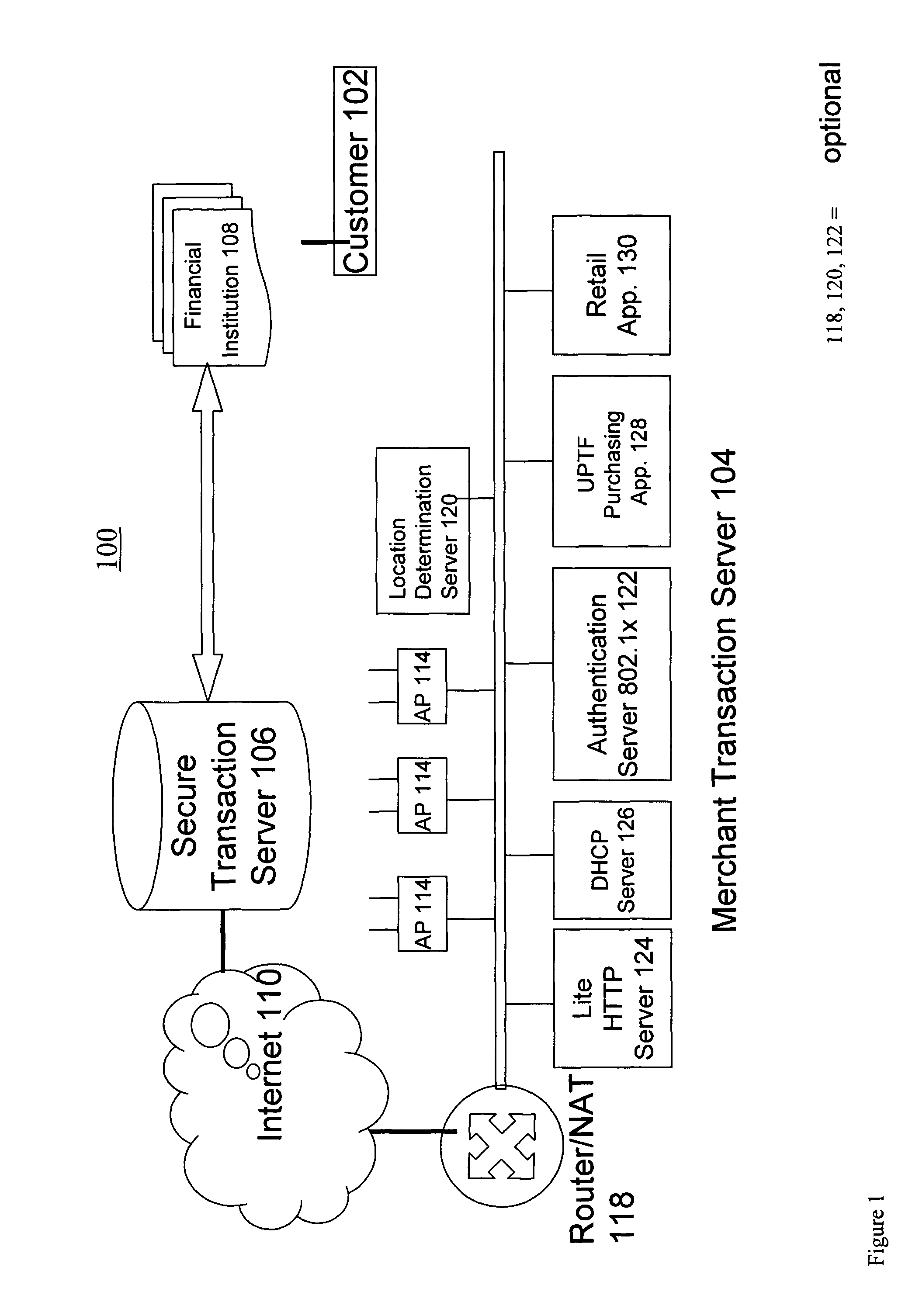
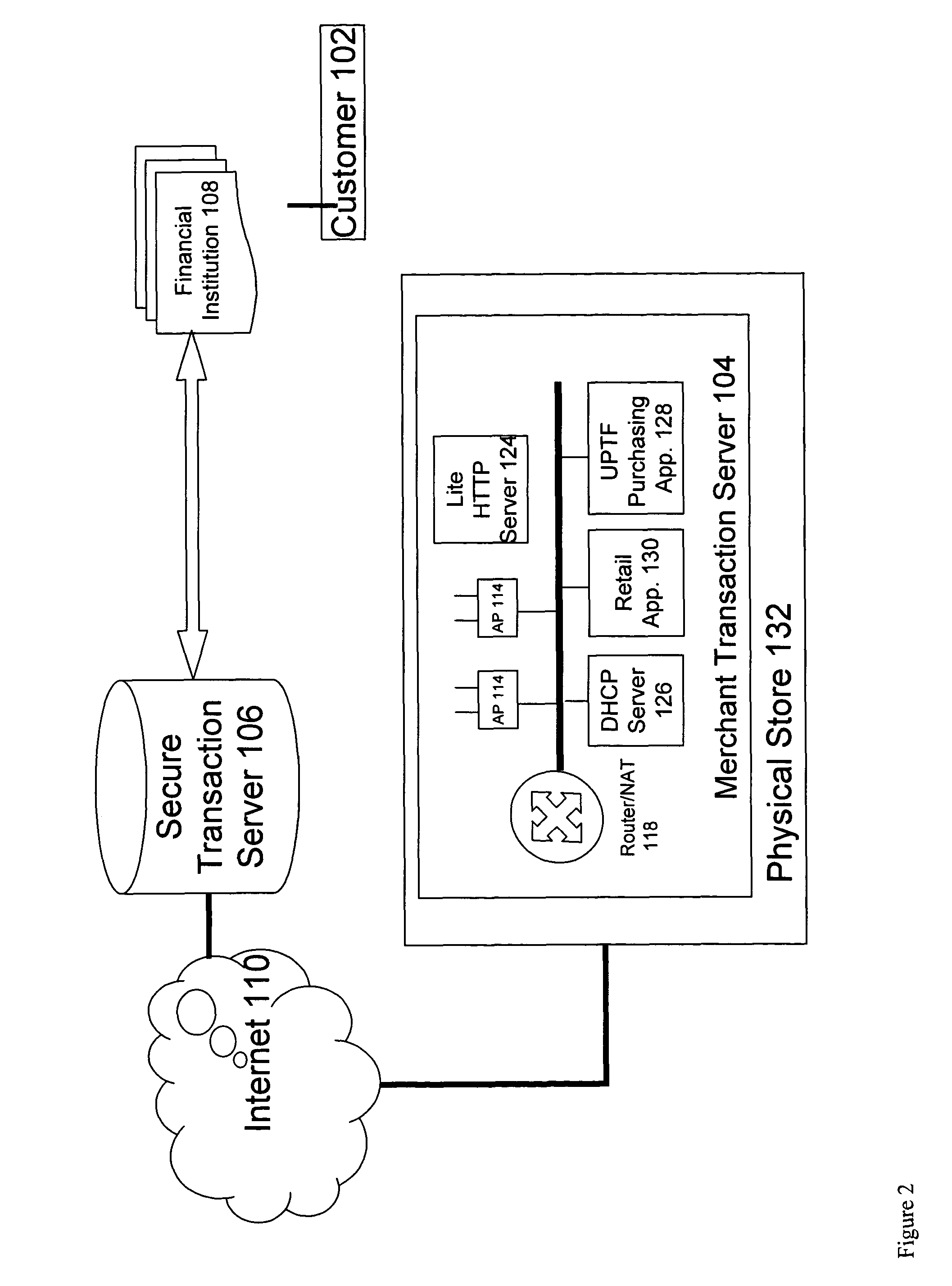
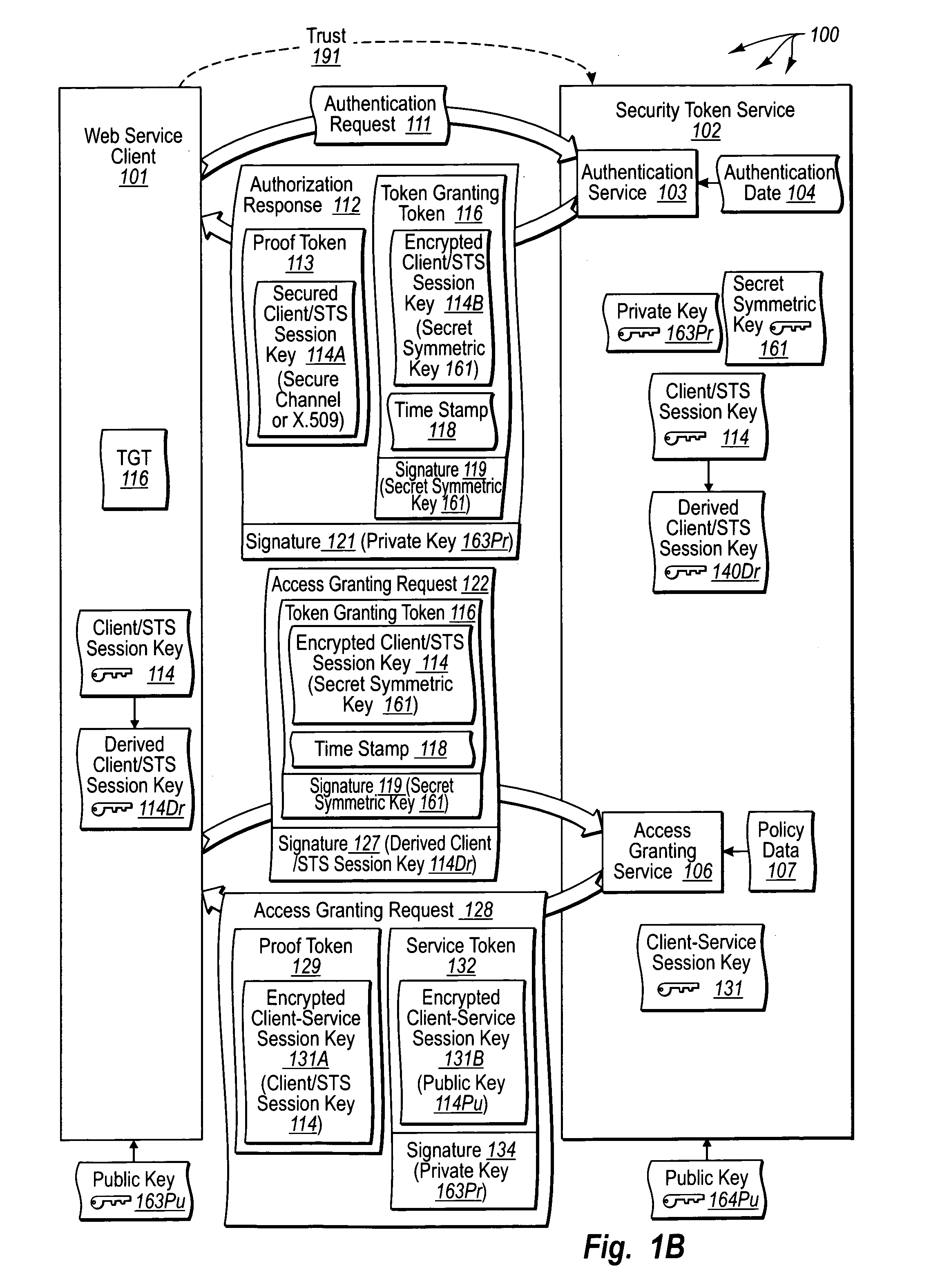
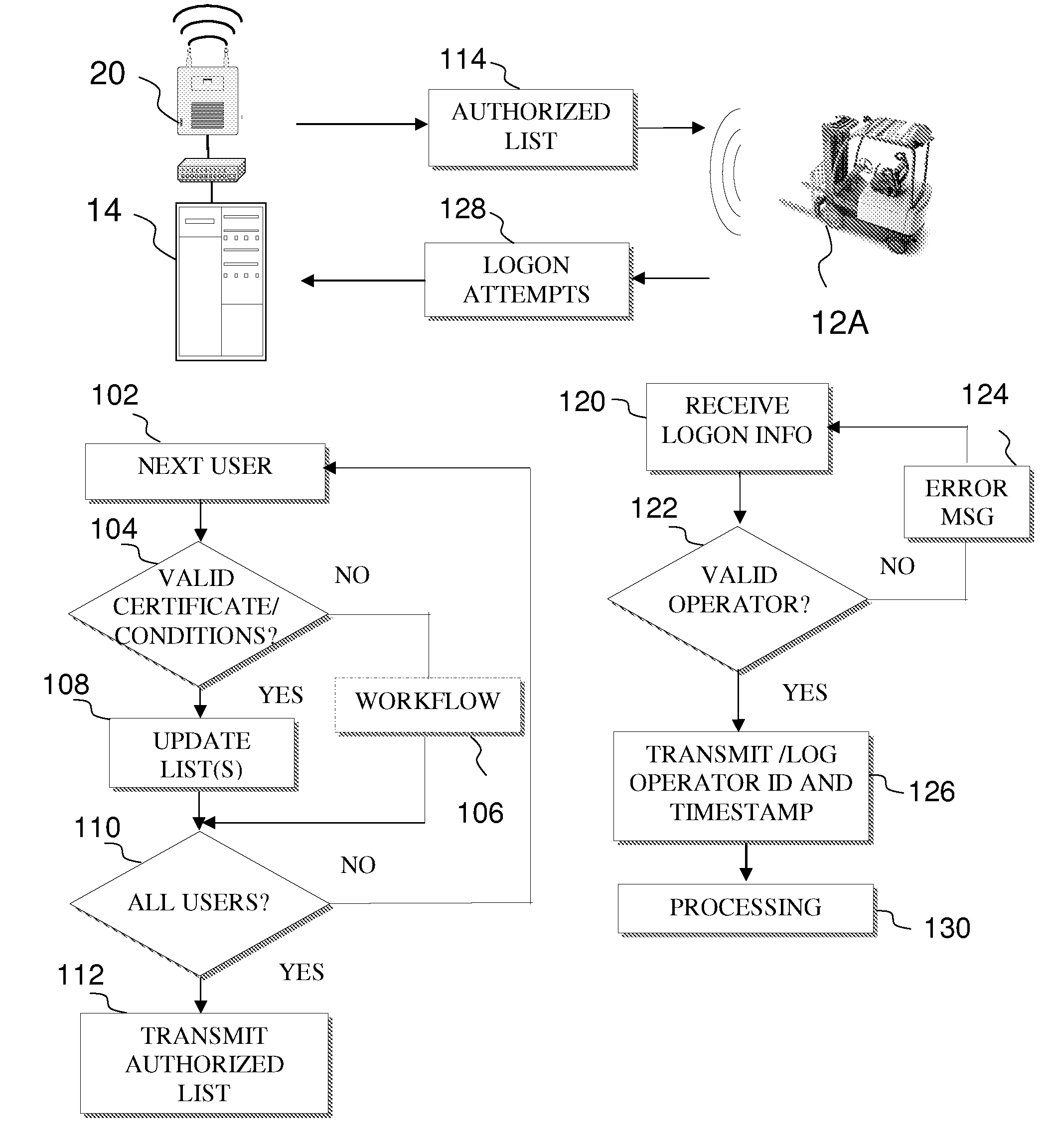
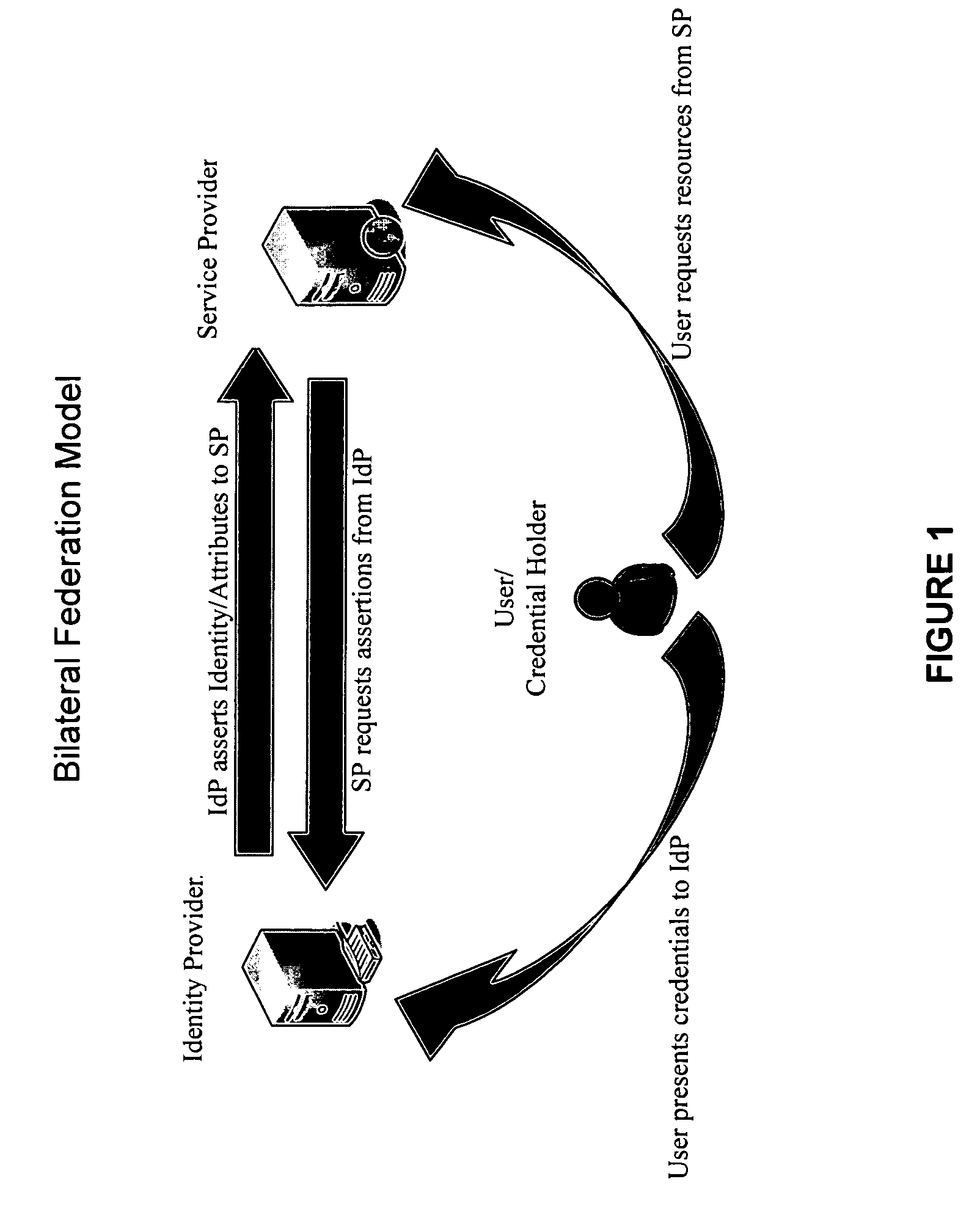
Systems and methods for enabling trust in a federated collaboration
ActiveUS20060129817A1Ensure complianceDigital data processing detailsUser identity/authority verificationThird partySuccessful completion
Systems and methods consistent with the present invention enable explicit and multilateral trust across a community of federated servers via a network. A trusted third party establishes a framework of policies and procedures governing a federation. Organizations joining the federation submit to an audit process of internal policies and procedures to ensure compliance with the policies and procedures of the federation. Upon successful completion of an audit, an organization may receive a digital certificate containing the digital public key of the organization and indicating approval of the trusted third party. The organization may then use the associated digital private key for signing security assertions associated with a request for resources from another federation service provider. The service provider may trust the assertion from the organization based on trust placed in trusted third party by the service provider and the trust placed in the organization by the trusted third party.
Owner:EXOSTAR CORP
Framework and system for purchasing of goods and services
InactiveUS7801826B2Risk minimizationReducing credit card fraudComputer security arrangementsPayment protocolsThird partyPurchasing
A system for conducting an agreement between two parties relying on a trusted a third party includes a first party generating a first view of the agreement and transmitting the first view of the agreement to the third party, a second party independently generating a second view of the agreement and transmitting the second view of the agreement to the third party, a wireless network connecting the first party and the second party, and a wired or wireless network connecting the second party to the third party. The trusted third party, receives the first view of the agreement and the second view of the agreement, verifies conditions including that the identities of the parties that transmitted the agreements and that the independent views of the agreement are consistent with each other, and takes action to execute the agreement if the conditions are satisfied.
Owner:PCMS HOLDINGS INC
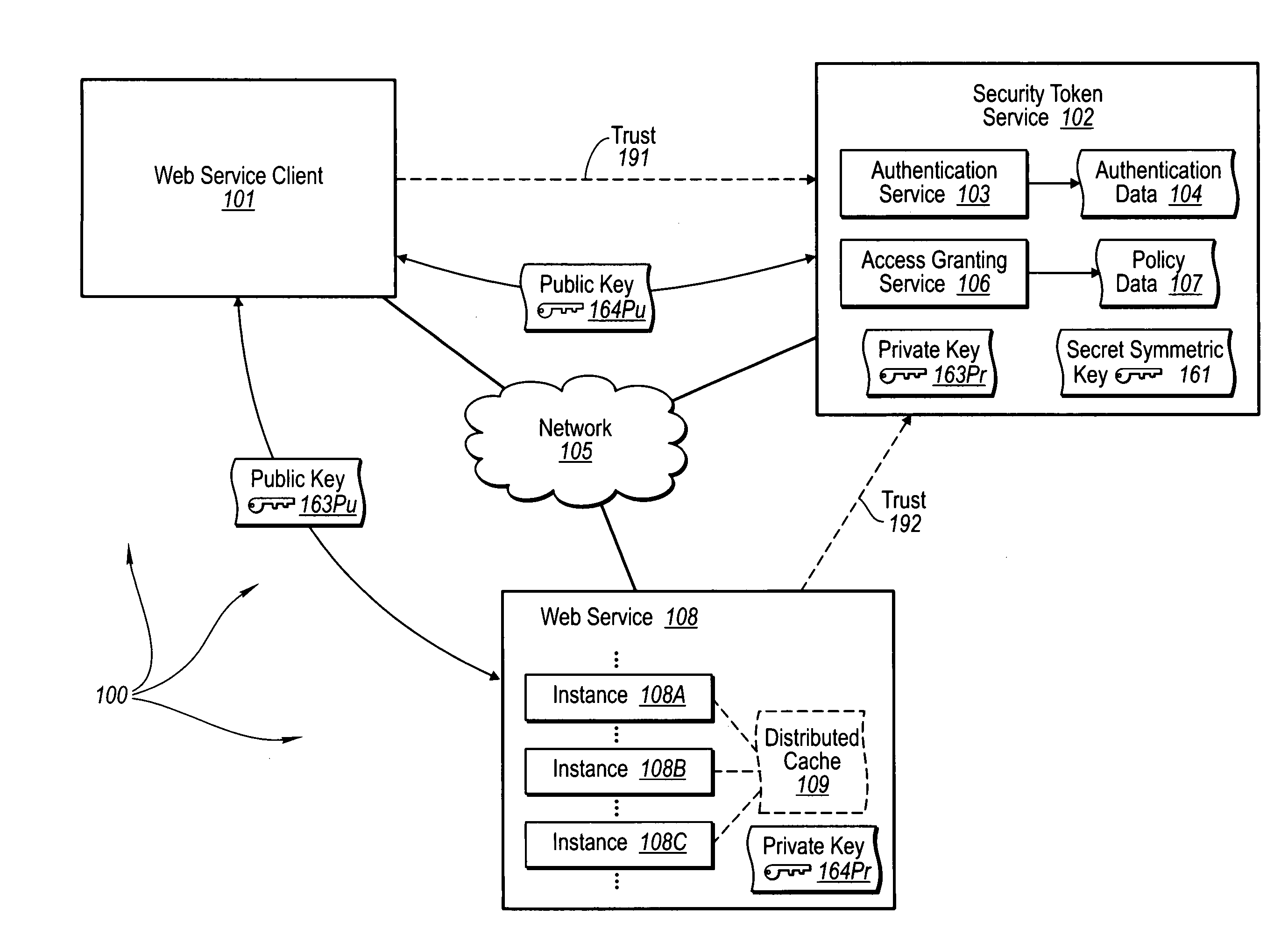
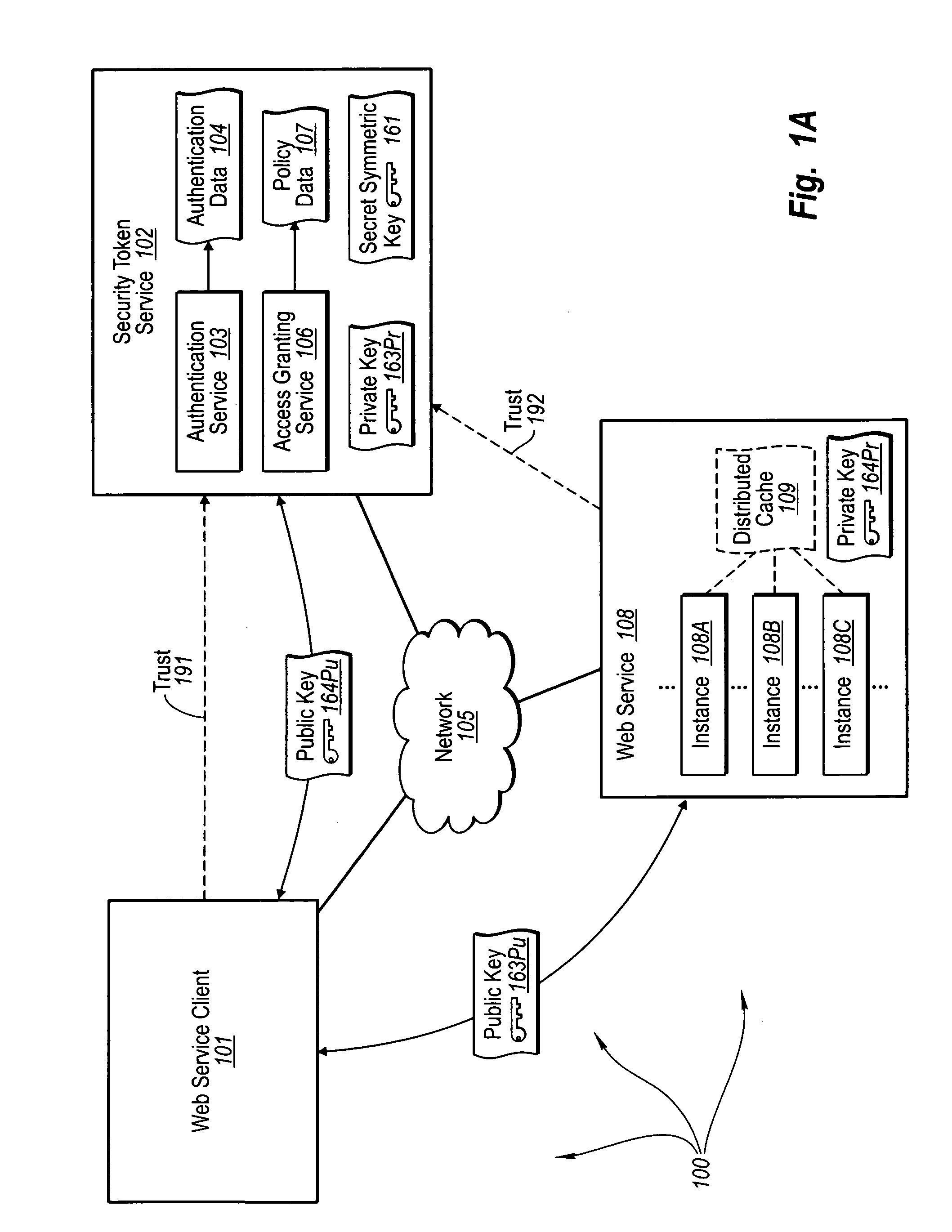
Trusted third party authentication for web services
InactiveUS20060206932A1Communication securityDigital data processing detailsUser identity/authority verificationWeb serviceInternet privacy
The present invention extends to trusted third party authentication for Web services. Web services trust and delegate user authentication responsibility to a trusted third party that acts as an identity provider for the trusting Web services. The trusted third party authenticates users through common authentication mechanisms, such as, for example, username / password and X.509 certificates and uses initial user authentication to bootstrap subsequent secure sessions with Web services. Web services construct user identity context using a service session token issued by the trusted third party and reconstruct security states without having to use a service-side distributed cache.
Owner:MICROSOFT TECH LICENSING LLC
Fleet management system
ActiveUS20080154712A1Ticket-issuing apparatusRegistering/indicating working of vehiclesFleet managementSoftware system
Systems of hardware and software are provided for enabling mobile assets to communicate across a wireless network environment. Systems, computer-implemented methods and computer program products are also provided for leveraging wireless communication and / or processing capabilities of mobile assets against a robust software solution to implement enterprise wide asset management functions, to integrate mobile asset data into existing enterprise workflows and / or to enable trusted third party integration into the enterprise for enhanced asset and / or workflow management.
Owner:CROWN EQUIP CORP
Fleet management system
ActiveUS20080154691A1Registering/indicating working of vehiclesElectric testing/monitoringFleet managementSoftware system
Systems of hardware and software are provided for enabling mobile assets to communicate across a wireless network environment. Systems, computer-implemented methods and computer program products are also provided for leveraging wireless communication and / or processing capabilities of mobile assets against a robust software solution to implement enterprise wide asset management functions, to integrate mobile asset data into existing enterprise workflows and / or to enable trusted third party integration into the enterprise for enhanced asset and / or workflow management.
Owner:CROWN EQUIP CORP
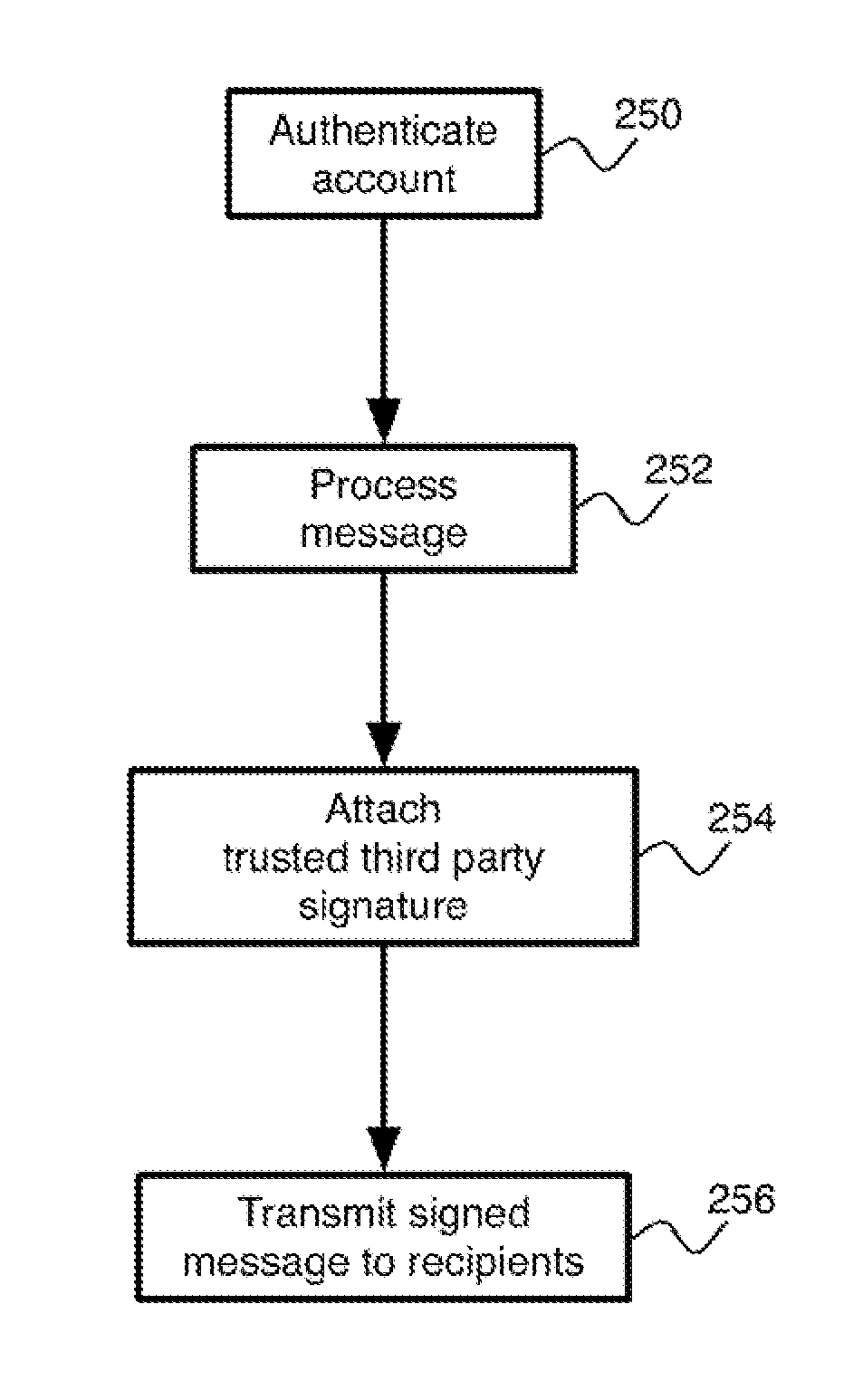
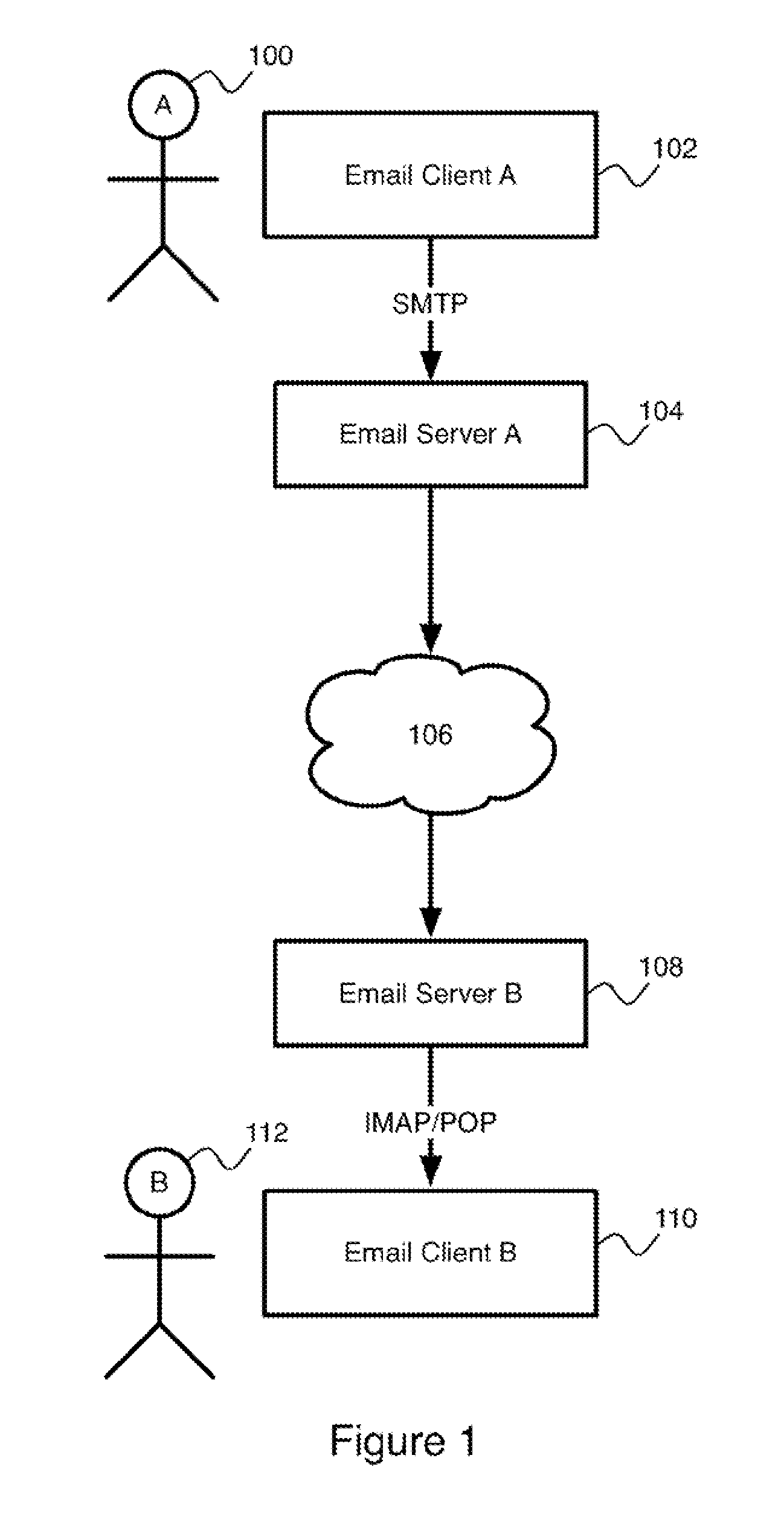
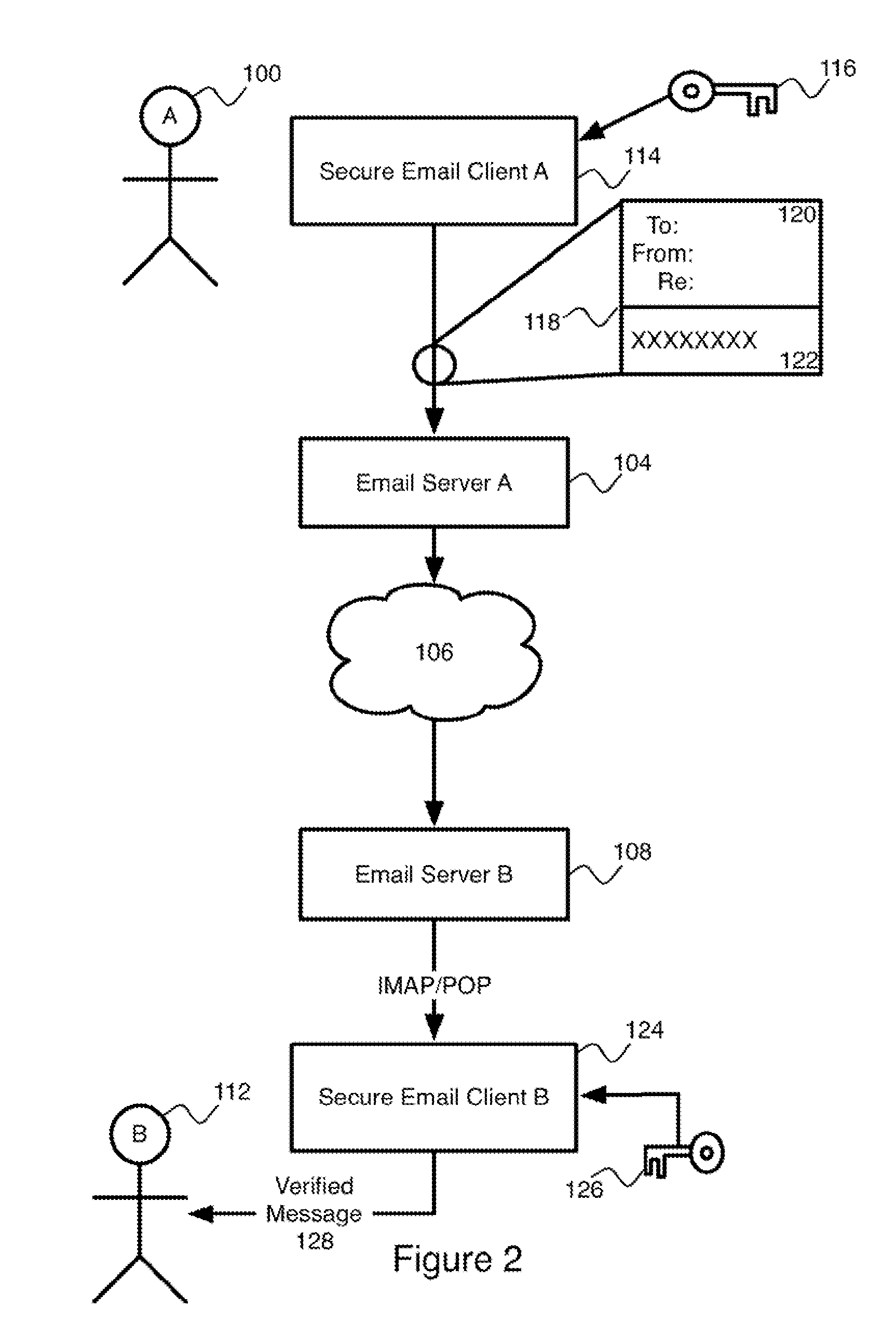
Trusted third party authentication and notarization for email
A system and method for providing trustworthy processing of electronic messages applies the digital signature of a trusted third party to a message en route from the sender to a recipient. The signature is preferably applied, so that it is compliant with the S / MIME standard. The use of a trusted third party applying the digital signature allows for simplified timestamping of the message and reduces the complexity of verification of the authenticity of an archived message.
Owner:INNOVAPOST
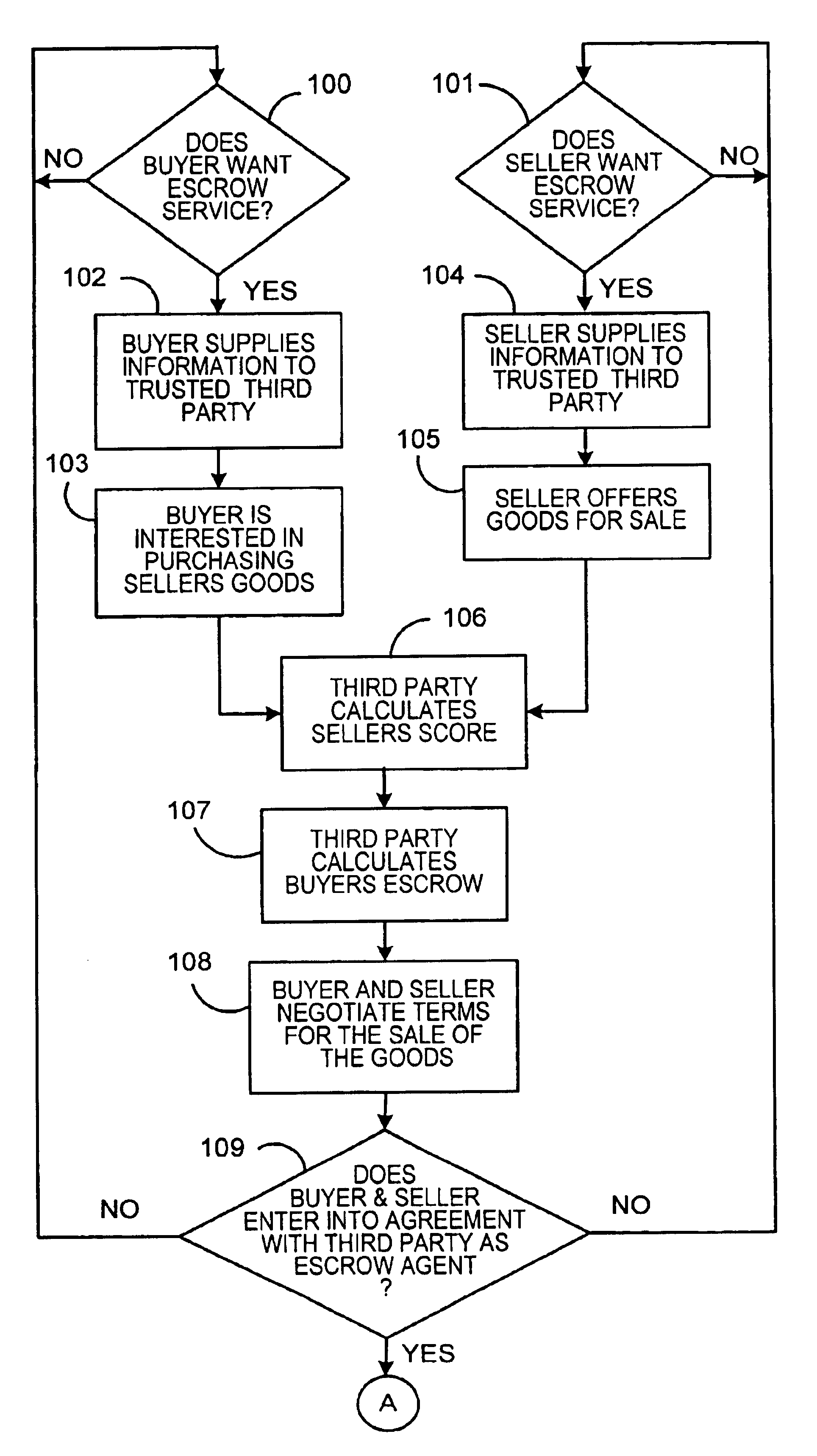
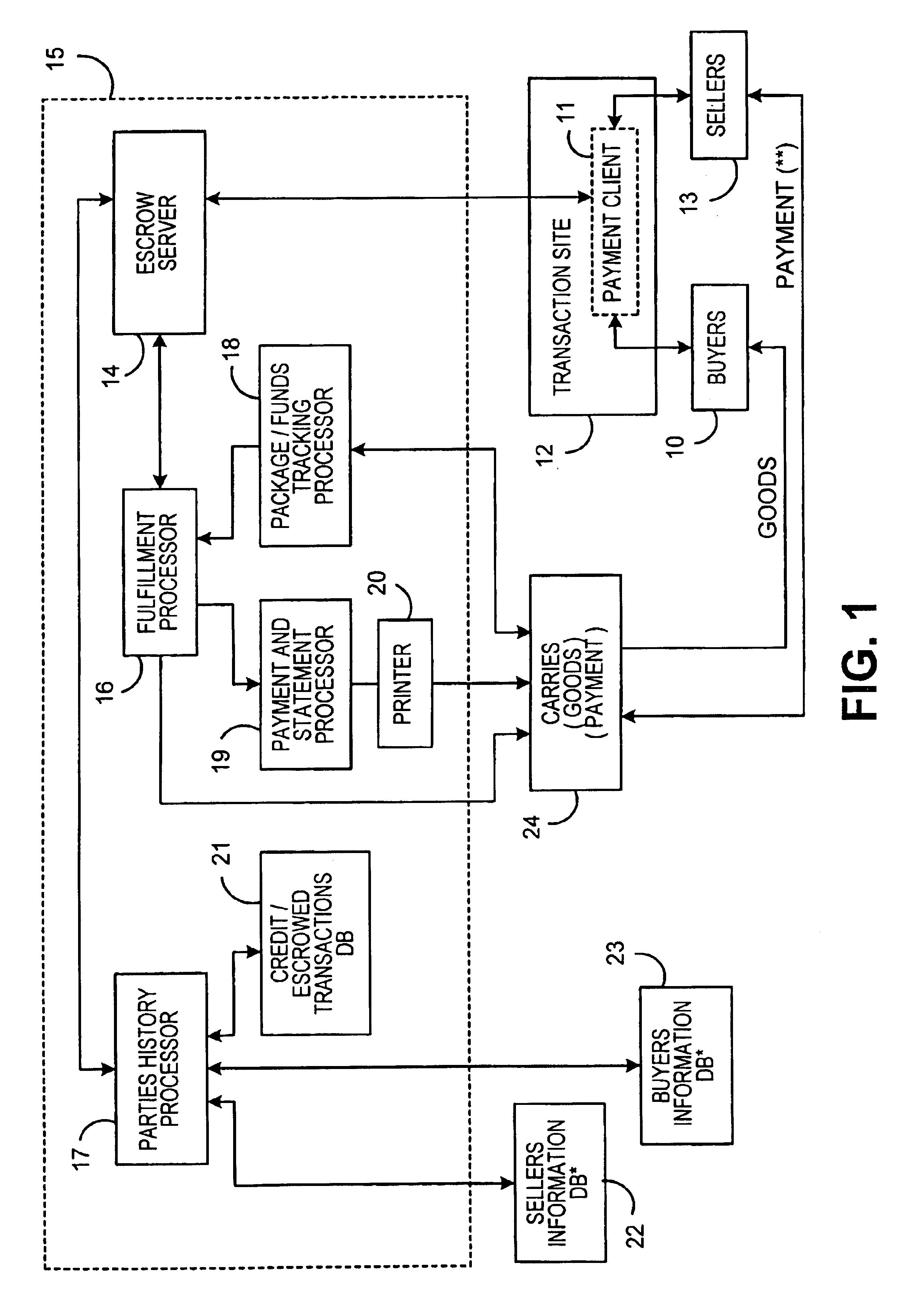
System for conducting business over the internet
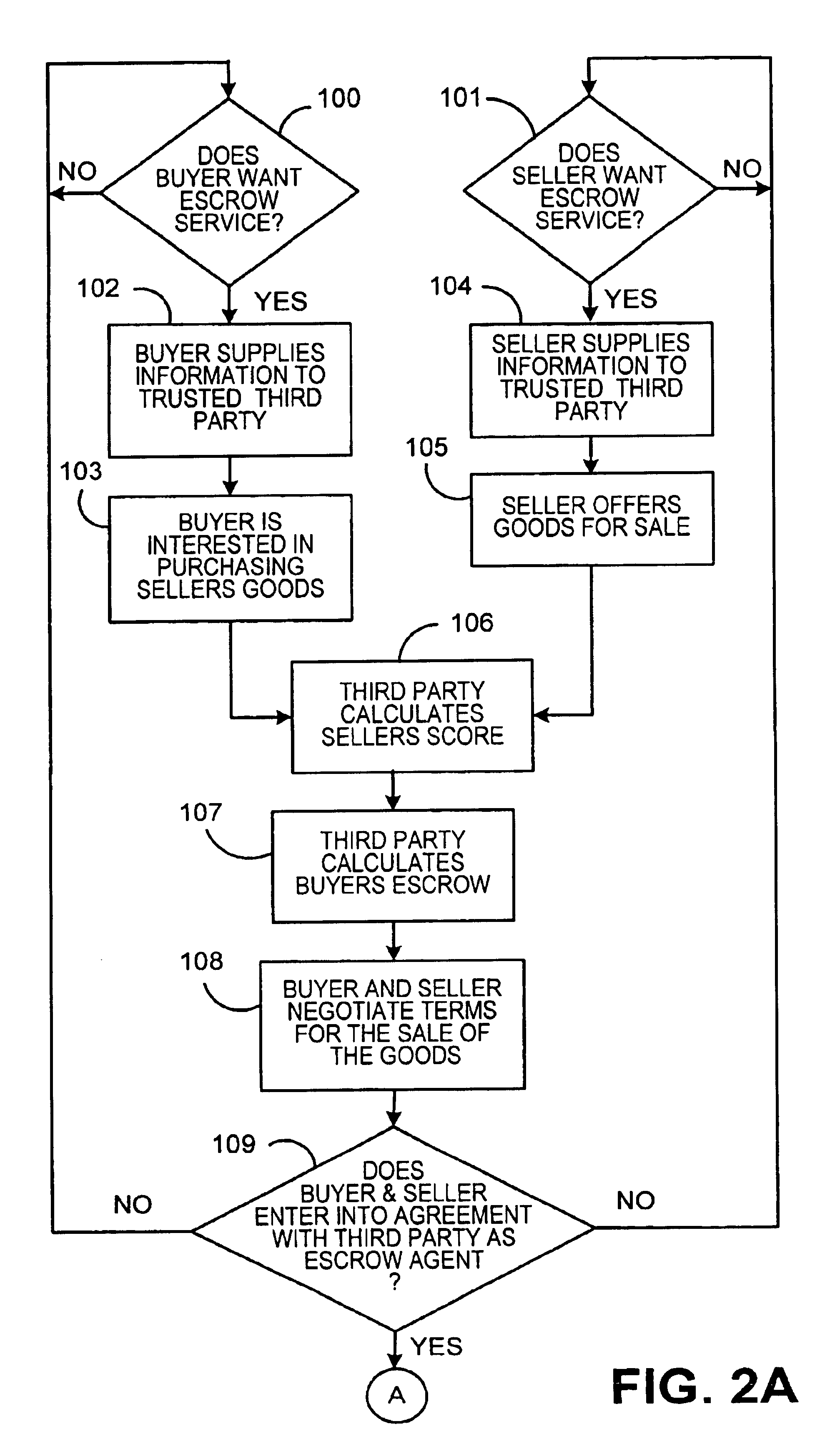
An Internet-based system that allows a buyer and a seller to obtain information about each other while remaining somewhat anonymous. The system provides historic information to buyer and seller by having a trusted third party give the buyer and seller the other party's trading history information without revealing the actual identity of the parties. A buyer registers with the trusted third party by submitting an online application. The trusted third party establishes a credit score for the buyer. A seller registers with the trusted third party by submitting an online application. The trusted third party establishes a score for the seller based upon the seller's trading history, reputation and financial standing. When the buyer chooses to purchase a product from a seller over the Internet, certain parameters i.e., dollar value of transaction, type of purchase, level of current outstanding credit available, credit score, etc. are substituted into an algorithm to determine the maximum purchase amount that may be financed at what terms and how much money the buyer will have to place in escrow. The buyers escrow may be furnished to the trusted third party by credit cards, ACH, wire transfer, etc. If the trusted third party is not satisfied with the seller's score, the trusted third party may require the seller to post a bond for some or all of the seller's transactions.
Owner:PITNEY BOWES INC
Fleet management system
ActiveUS8060400B2Ticket-issuing apparatusRegistering/indicating working of vehiclesFleet managementSoftware system
Owner:CROWN EQUIP CORP
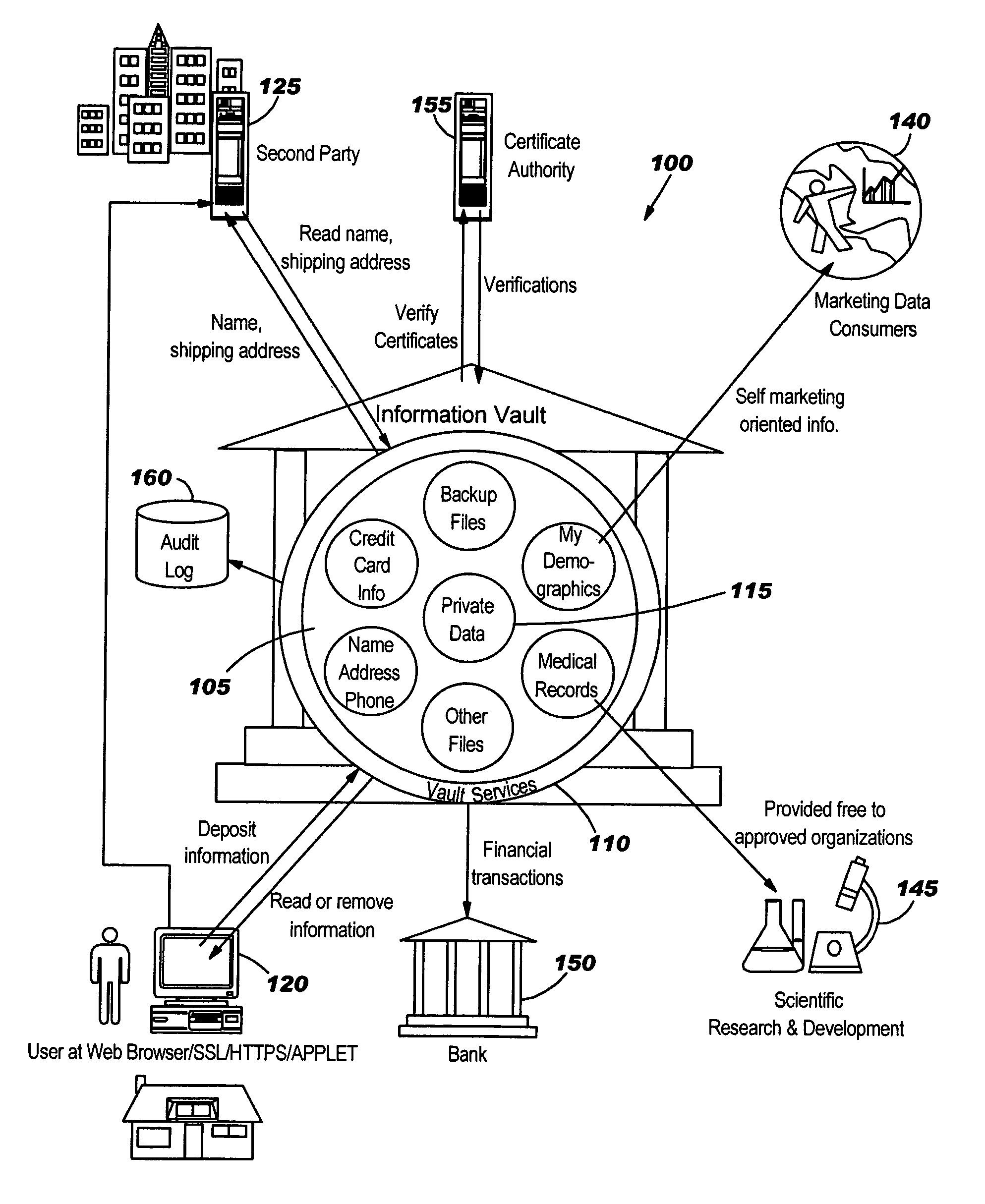
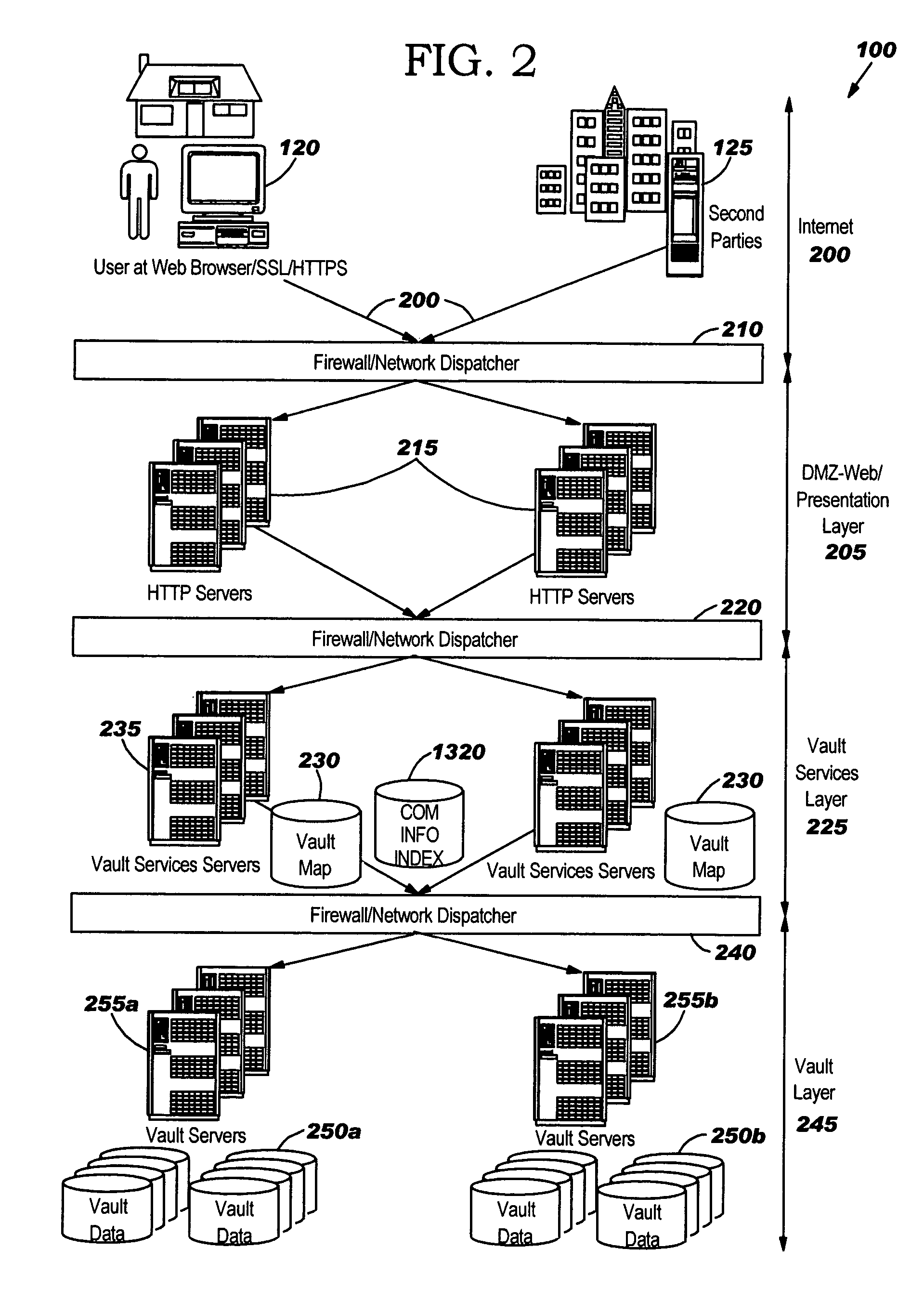
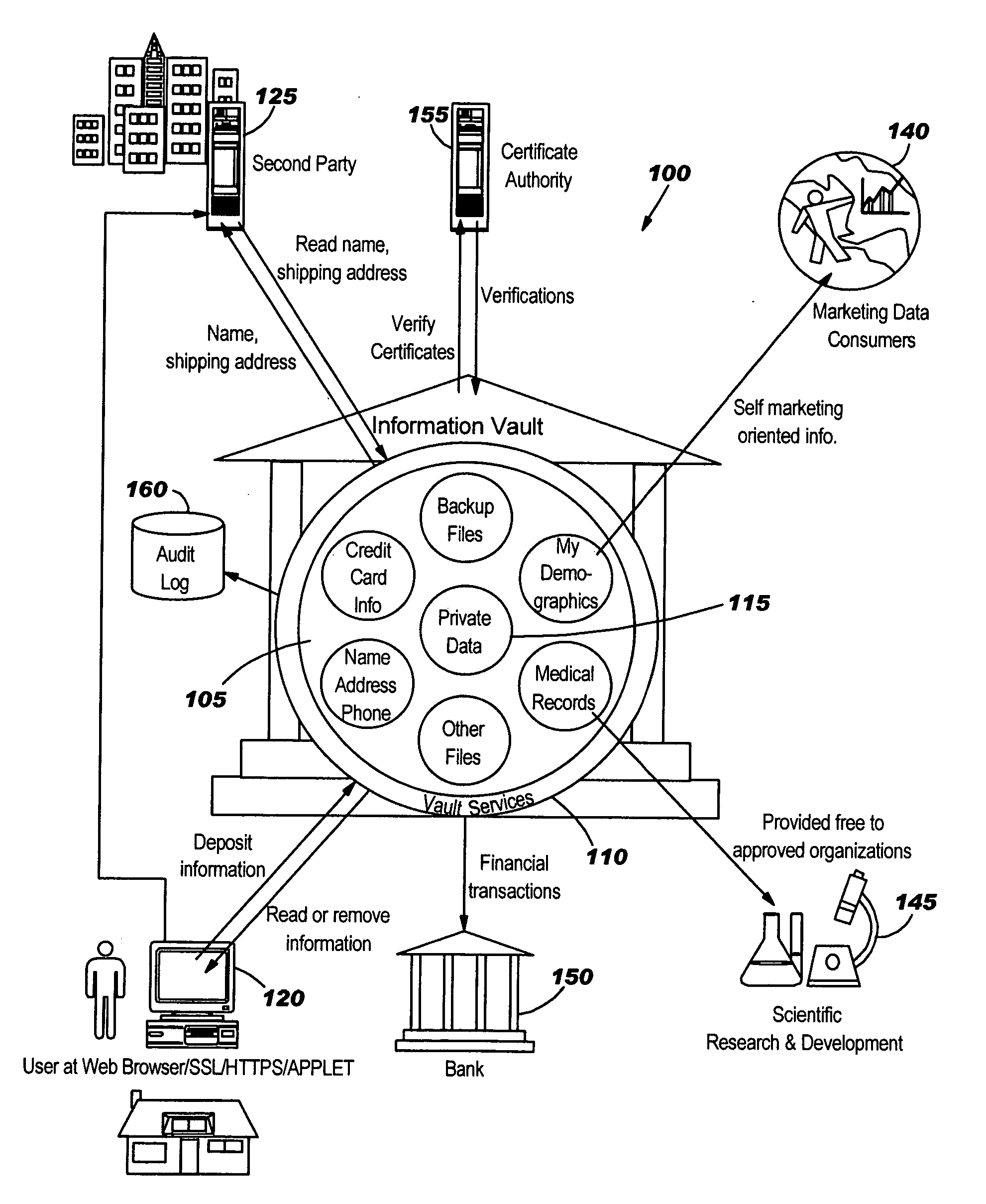
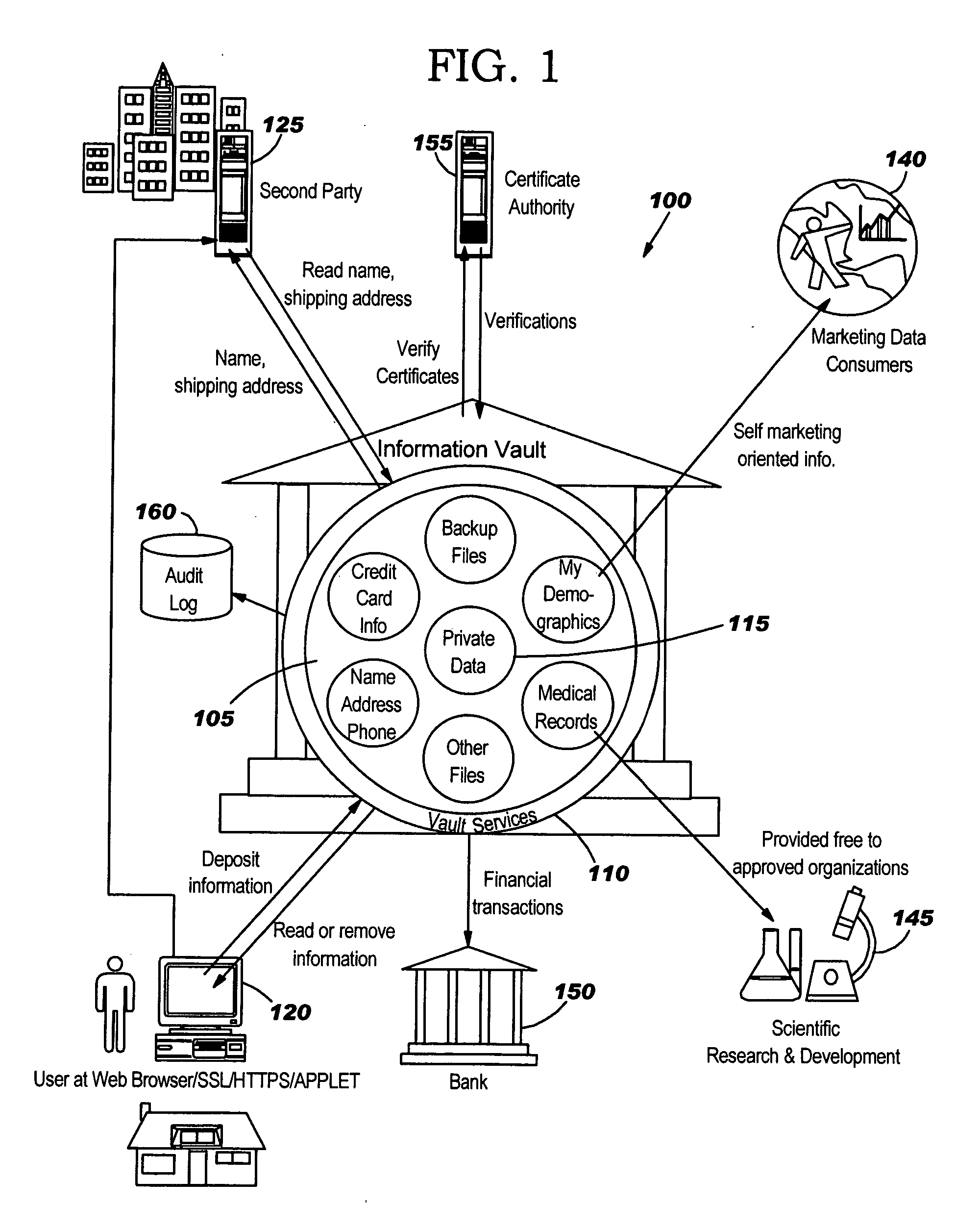
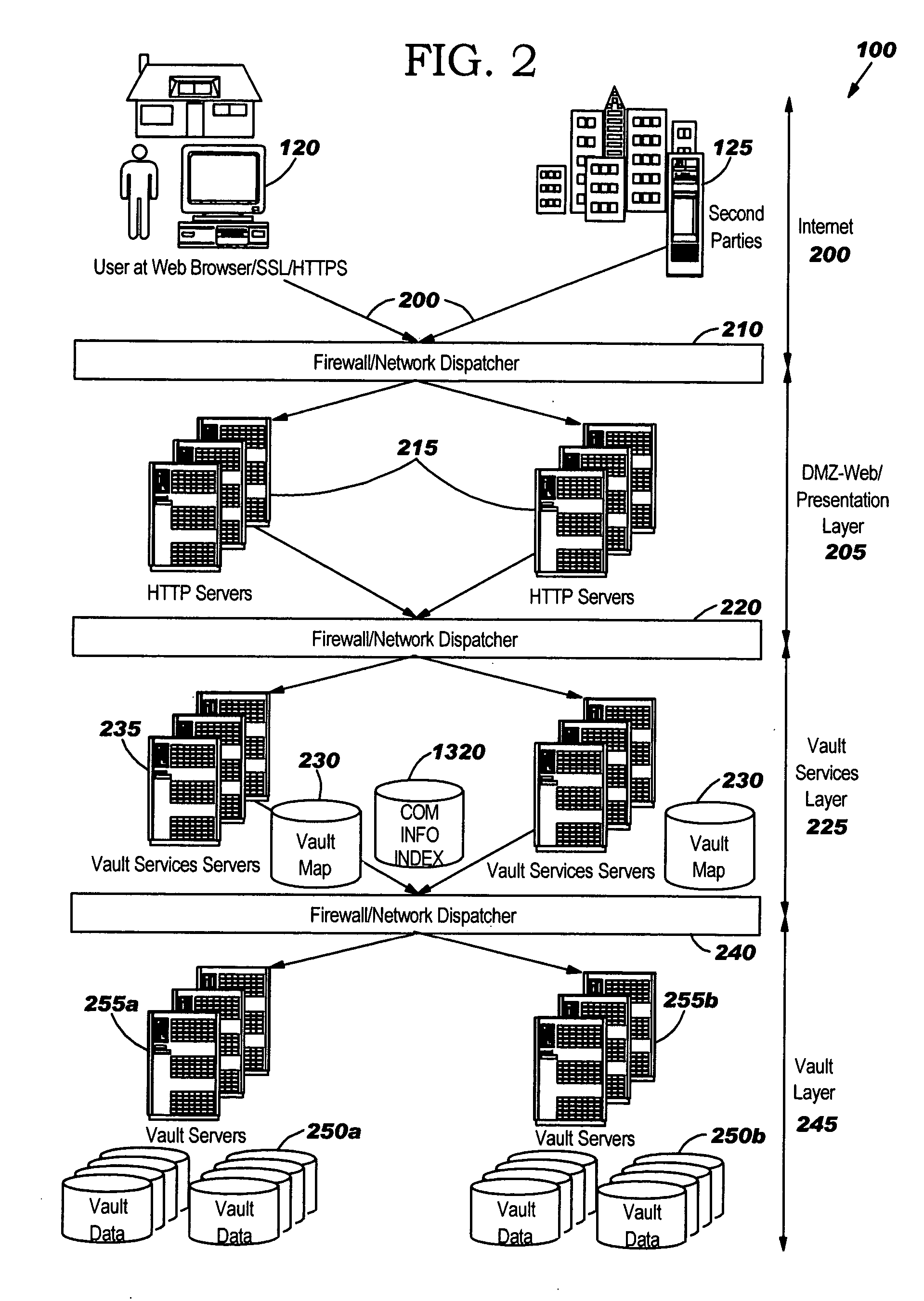
Secure information vault, exchange and processing system and method
A system and method for providing an information vault so that individual owners of personal data may control and manage the access and dissemination of the personal data and provides for the owner of the personal data to receive compensation for the use of the personal data, thus, in effect, the personal data becomes a valuable commodity analogous to money. A business model is provided that allows competitive, unbiased trusted third parties whose business is protecting the information analogous to how a commercial bank protects money. Centralized protected storage of personal data is provided, thereby minimizing the number of copies that may be in existence. Second party access to the centralized storage of personal data may be made on-demand, as required for commerce, with a provision for assessing fees for accesses.
Owner:GOOGLE LLC
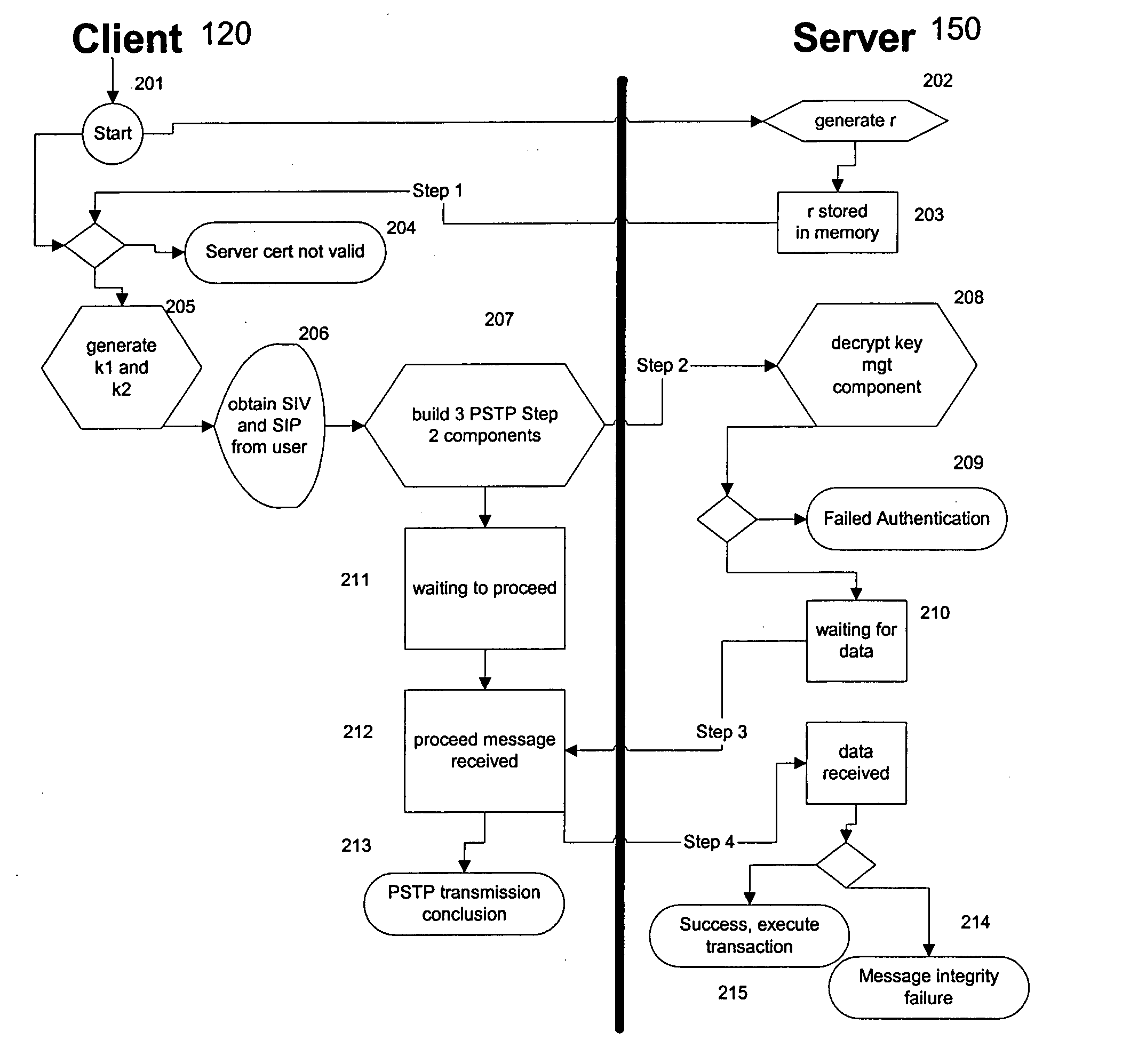
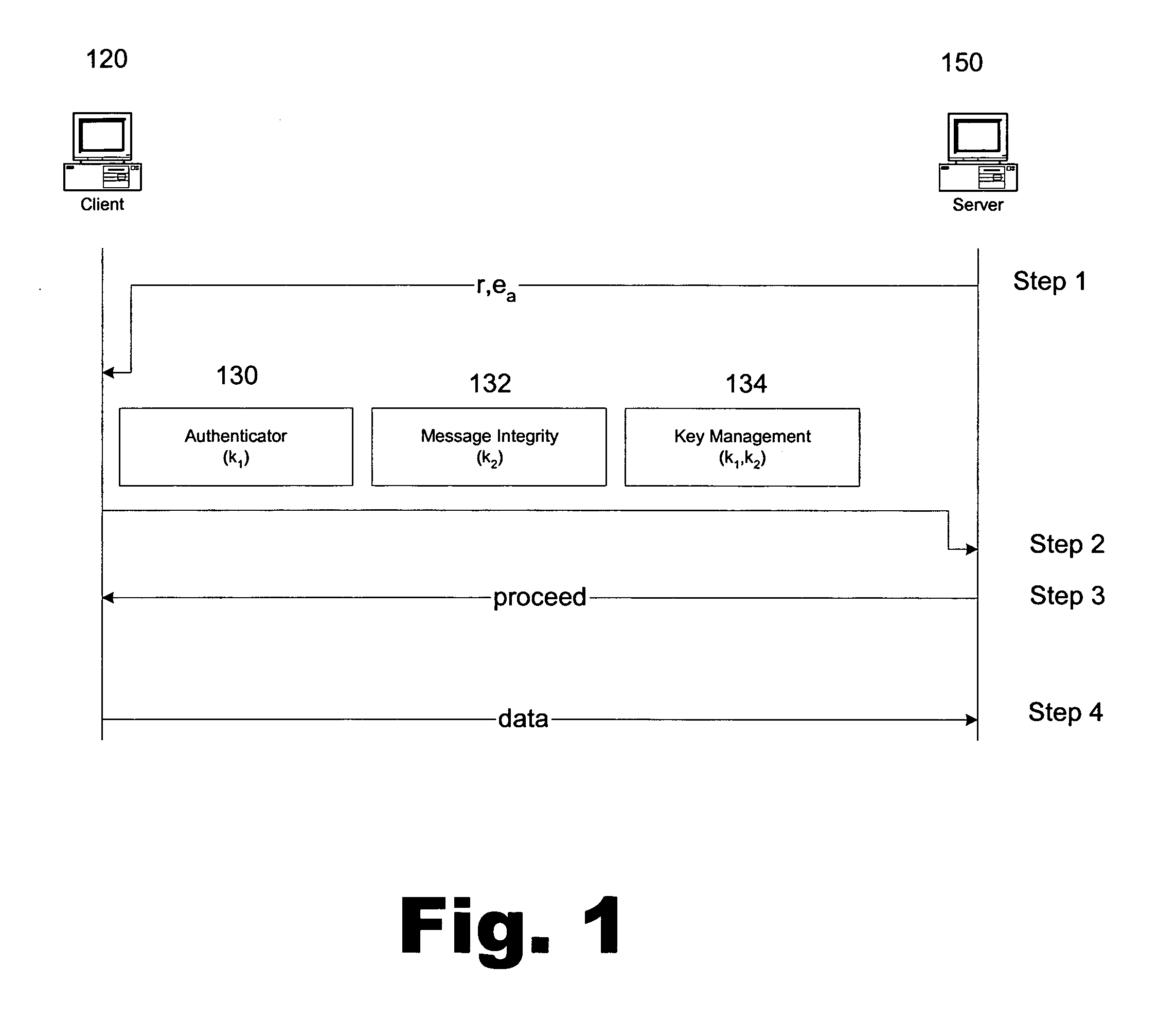
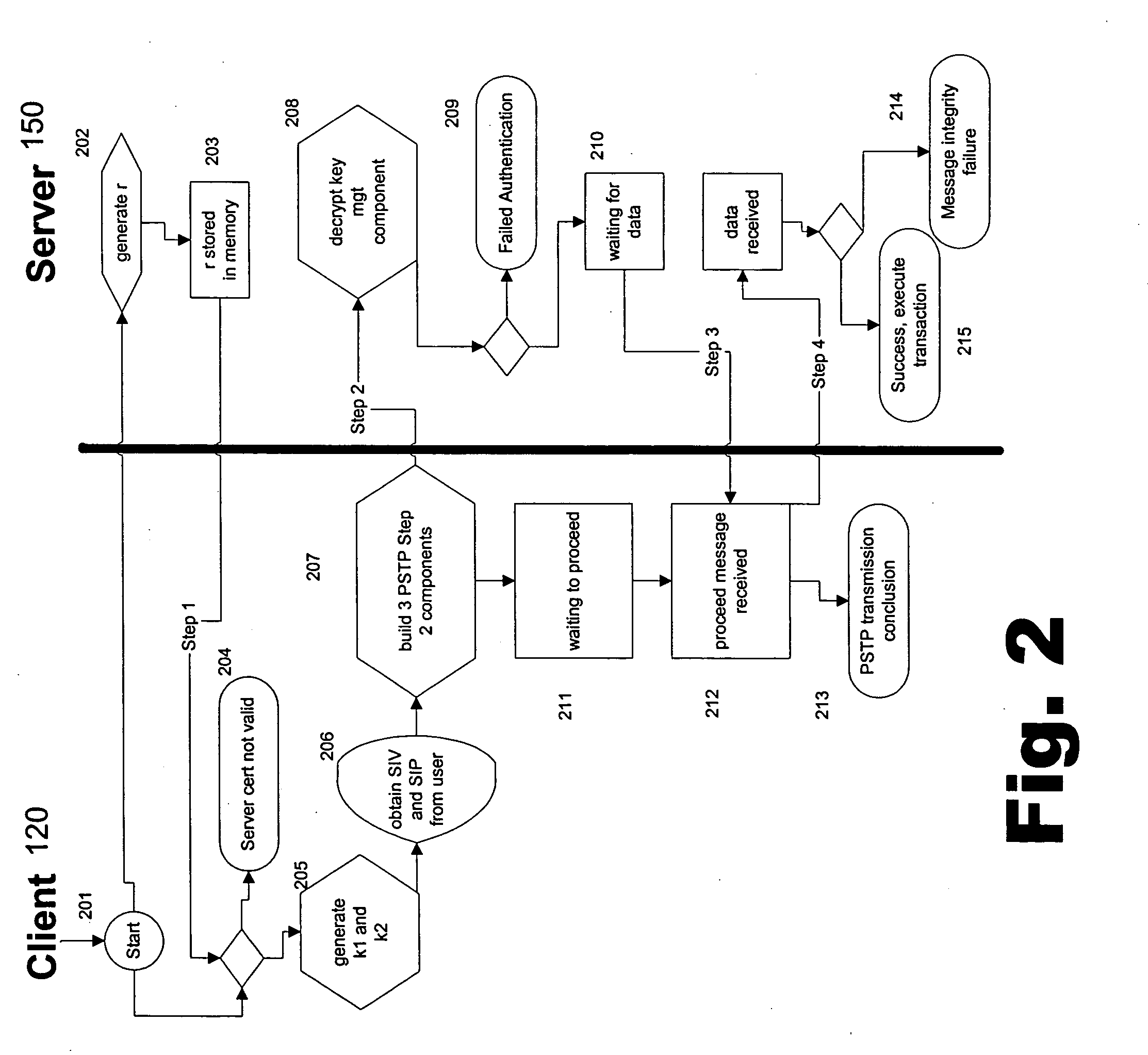
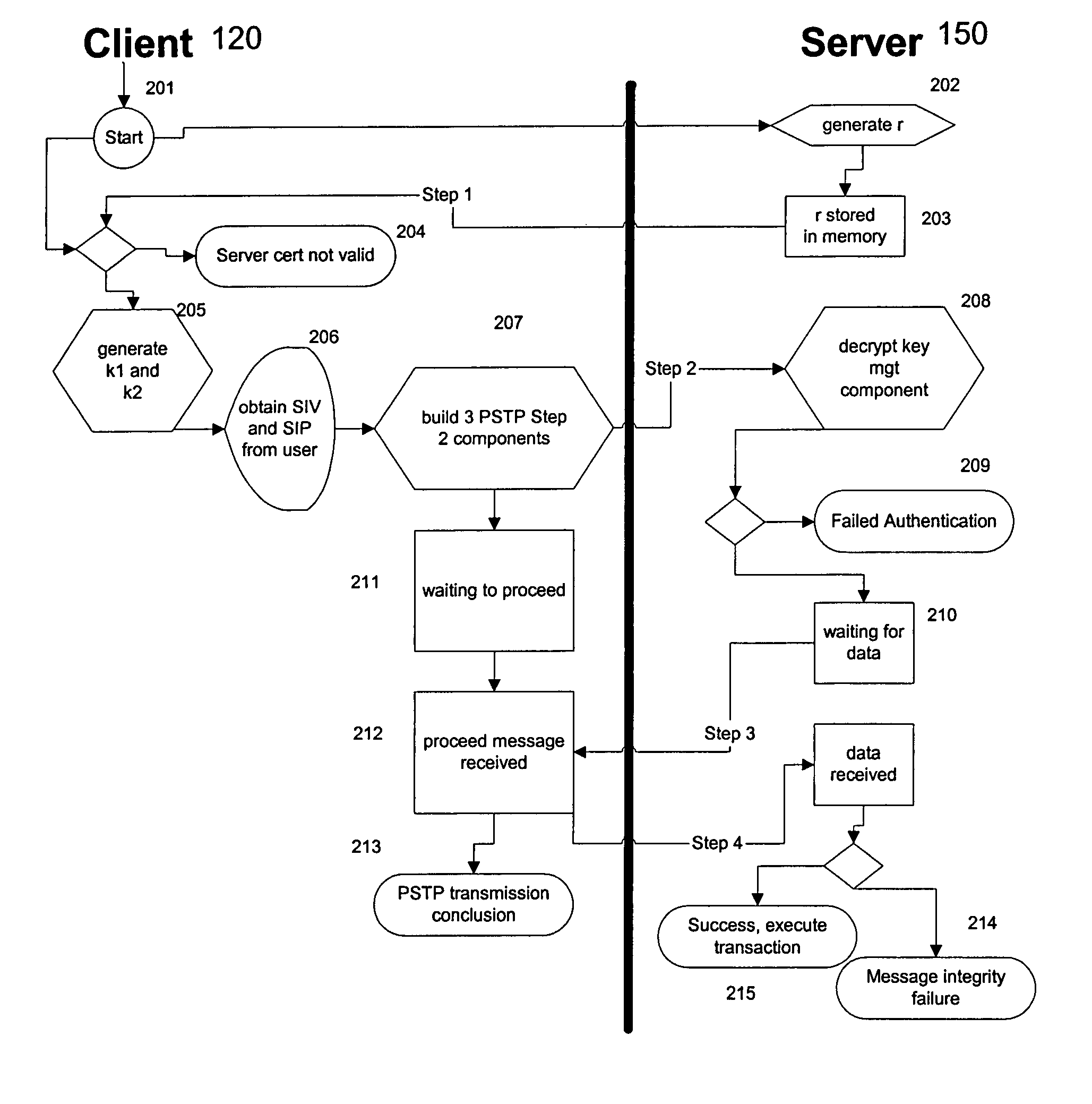
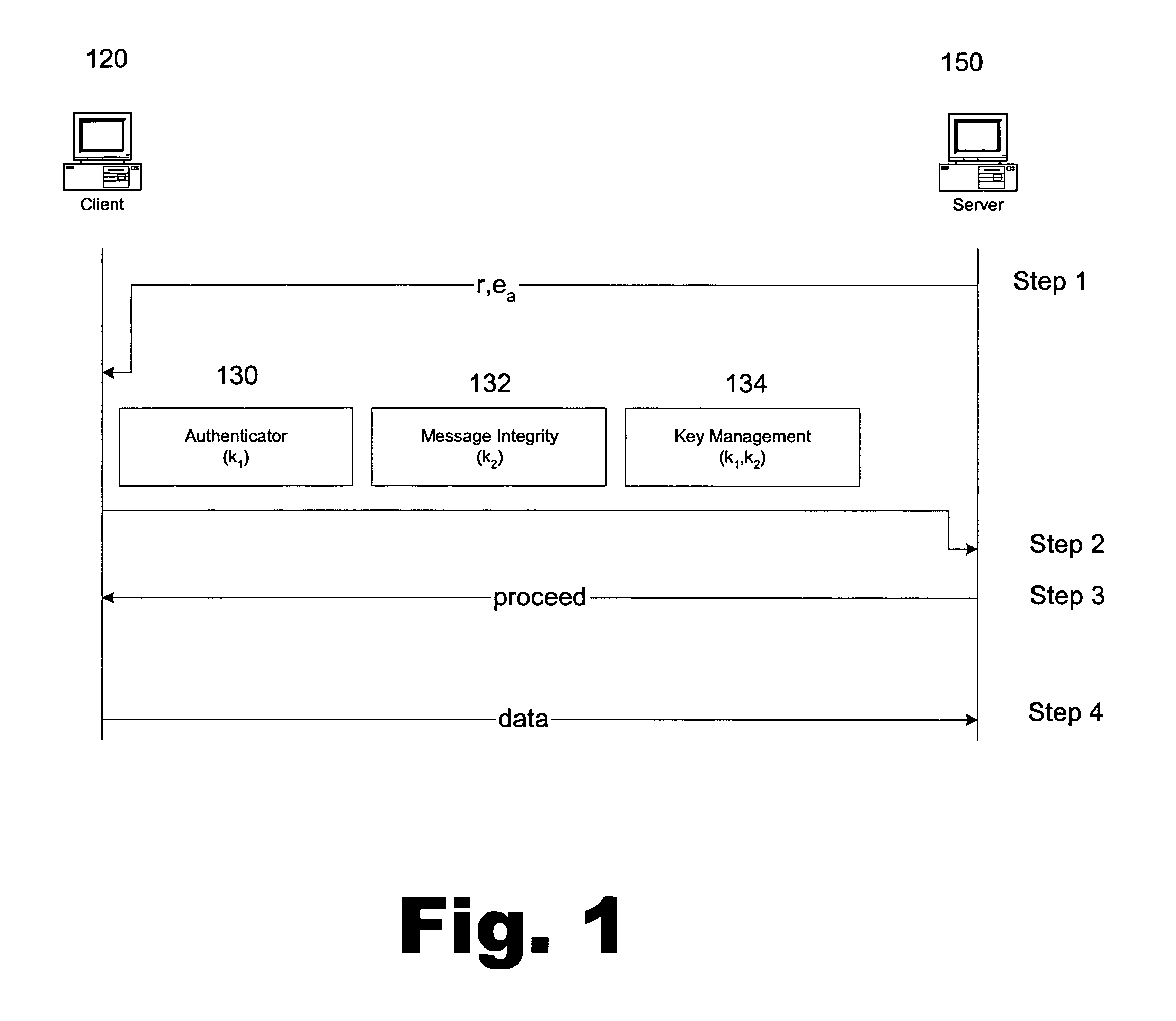
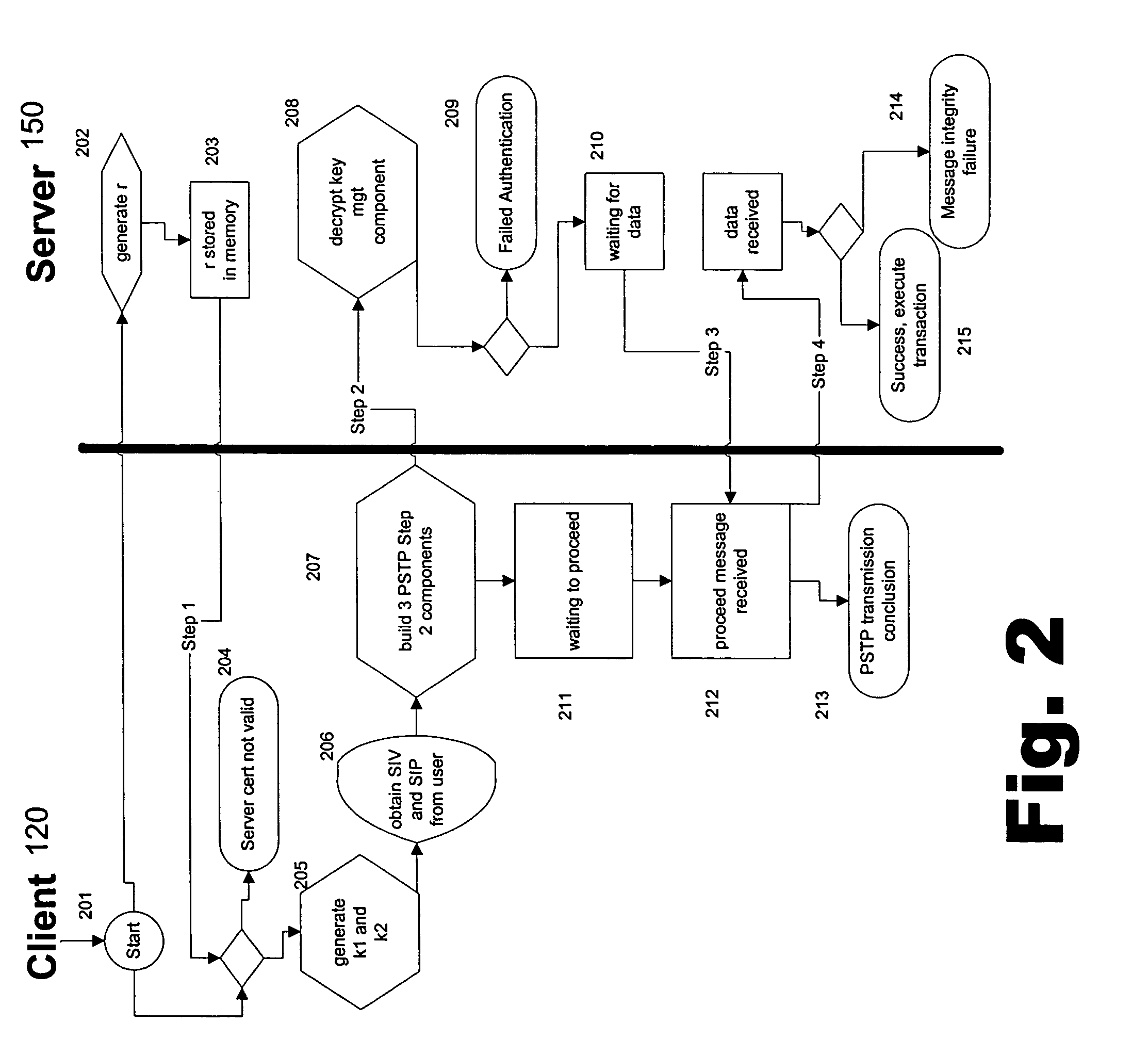
Portable security transaction protocol
ActiveUS20050091492A1Provide authenticityUser identity/authority verificationPayment circuitsThird partyCredit card
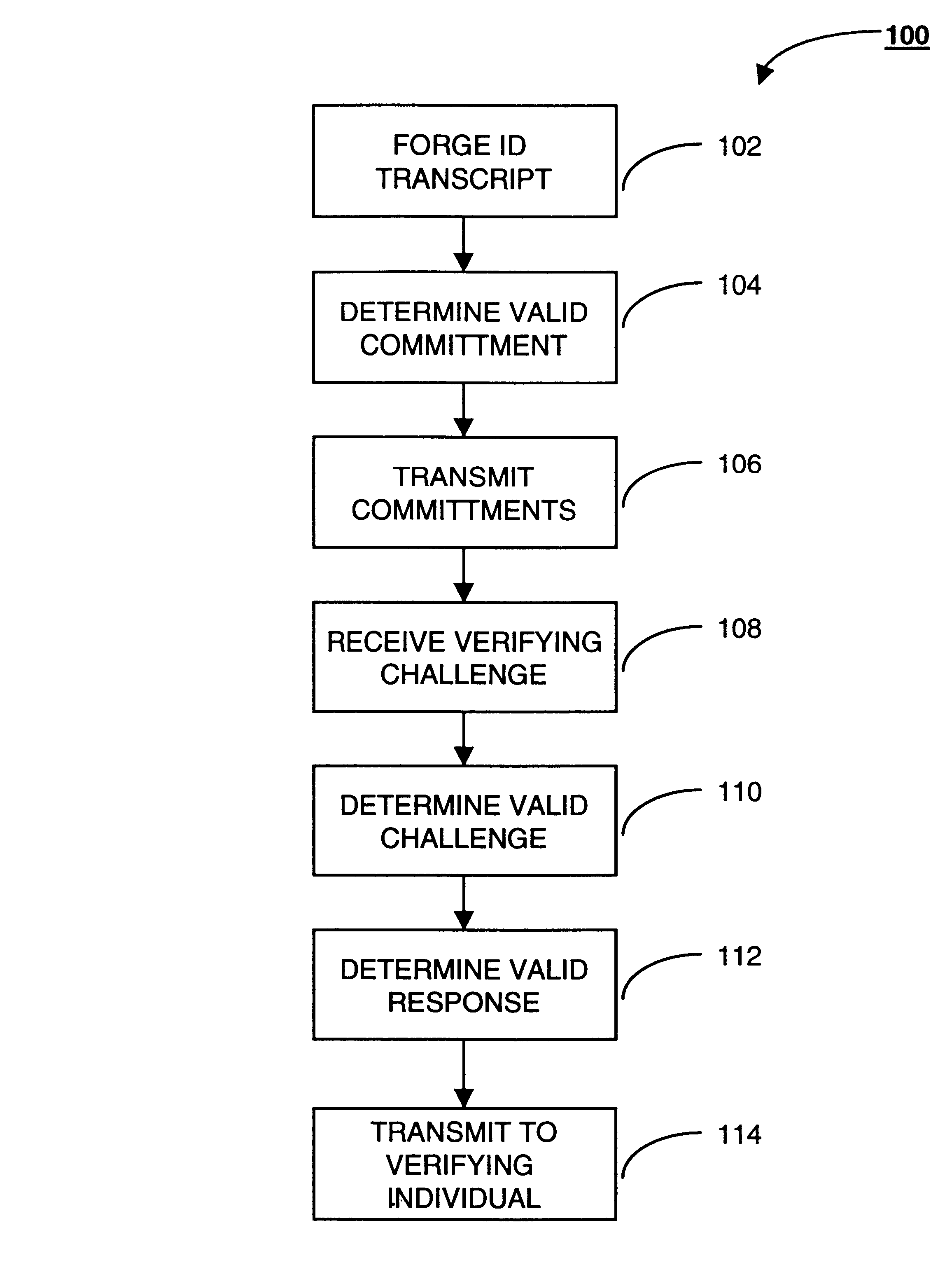
A technique for providing message authenticity includes accepting transaction information, accepting a first data item used for authenticating an originating user, cryptographically processing the transaction information using only a second data item, wherein the entropy of the first data item is less than the entropy of the second data item, and authenticating the originating user using the first data item. The first data item can be a sequence of digits corresponding to those displayed on an external device, such as, for example, an RSA authorization token, credit card, etc. In general, the first data item will be a short alphanumeric string and the second data item will generally be much larger, e.g., a 128 bit sequence to be used principally for data authentication. According to another aspect of the present invention, consequential evidence of the transaction may be secured to provide after-the-fact evidence of the transaction. This evidence can include a message written to a tamper-resistant log record, the message including the transaction information, the first data item, the second item, and an identifier for the originating user, as well as other information. At a subsequent point, the transaction can be shown to have been sent by the originating user and received by the intended recipient, by consulting the log record. Preferably, the validity of the transaction would be ascertained by an independent, mutually trusted third party.
Owner:JPMORGAN CHASE BANK NA
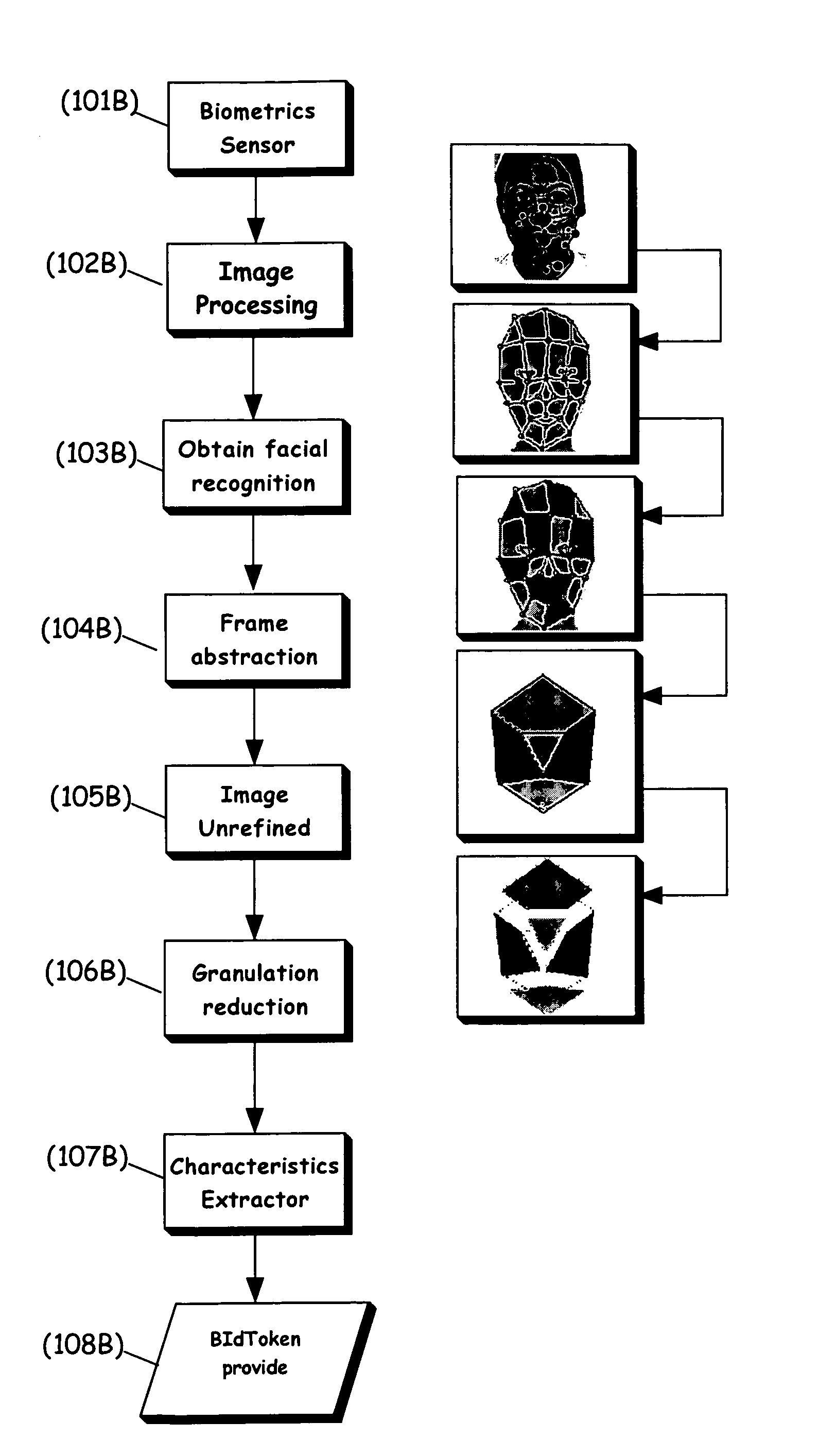
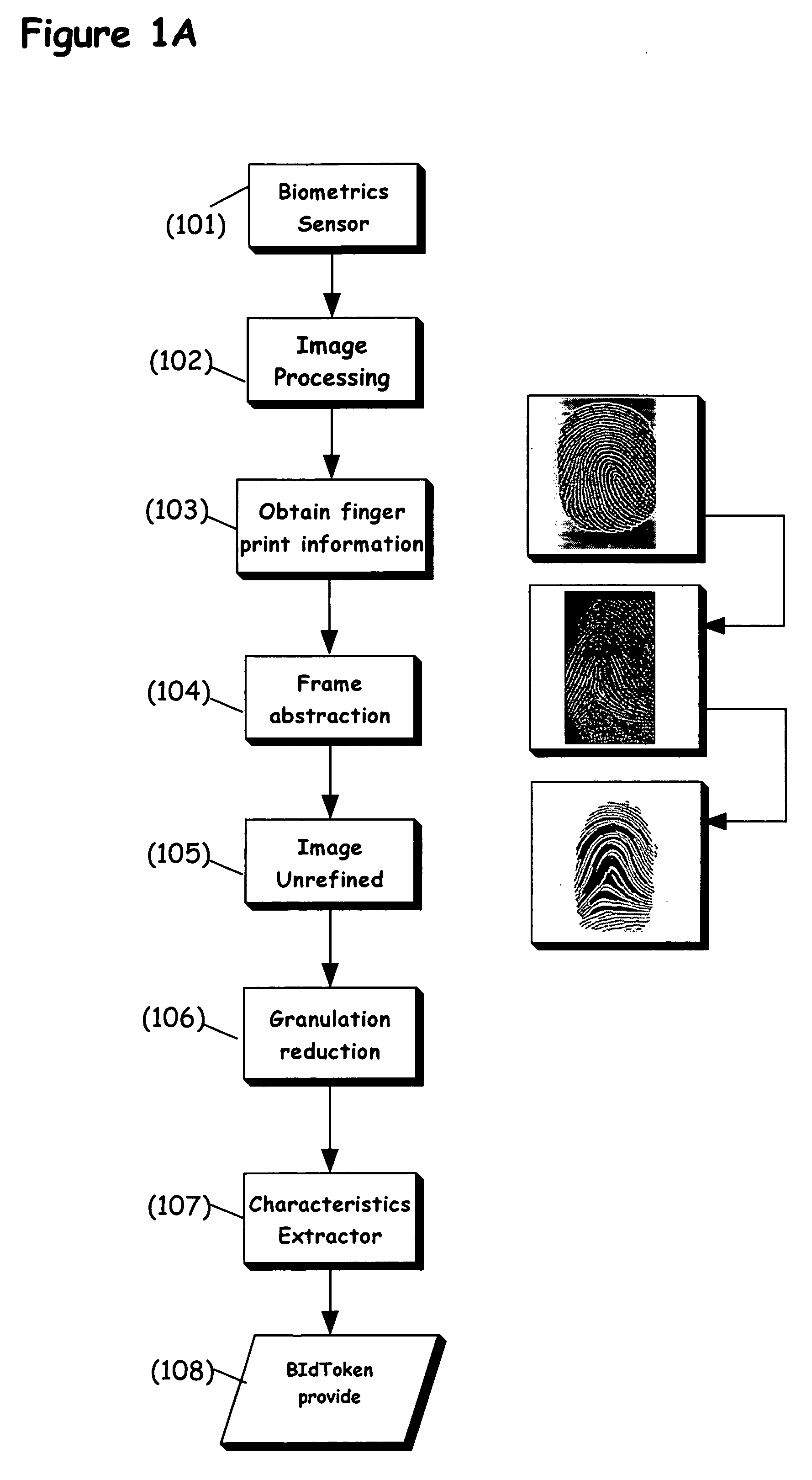
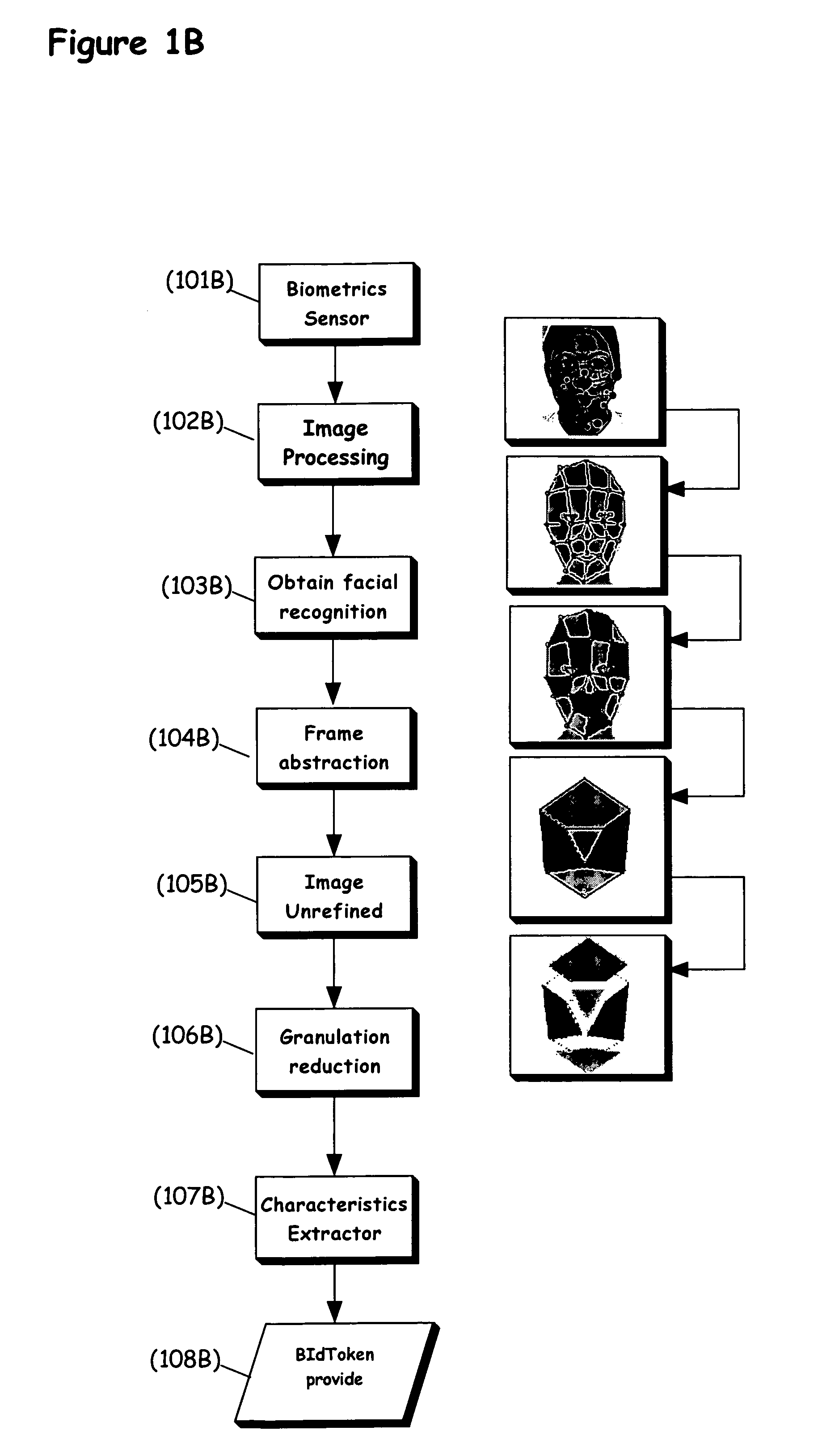
System and method for traceless biometric identification
InactiveUS20080005578A1Easy to replaceIncrease opportunitiesDigital data authenticationSecret communicationThird partyInternet privacy
A device, system and method for identifying an individual with a biometric identifier that is designed to be non-unique, such that at least one other individual in a given population has the identical biometric identifier. The biometric identifier according to the present invention, also referred to herein as a “BIdToken”, is implemented to be biometrically traceless, such that an exact image or copy of the biometric information is preferably not maintained by the present invention. Instead, the BIdToken refers to an incomplete identifier obtained from the biometric information, which is non-unique. Preferably the invention operates so as to obviate the obligation to trust a third party.
Owner:INNOVYA RES & DEV
Portable security transaction protocol
ActiveUS8190893B2Digital data processing detailsUser identity/authority verificationCredit cardThird party
A technique for providing message authenticity includes accepting transaction information, accepting a first data item used for authenticating an originating user, cryptographically processing the transaction information using only a second data item, wherein the entropy of the first data item is less than the entropy of the second data item, and authenticating the originating user using the first data item. The first data item can be a sequence of digits corresponding to those displayed on an external device, such as, for example, an RSA authorization token, credit card, etc. In general, the first data item will be a short alphanumeric string and the second data item will generally be much larger, e.g., a 128 bit sequence to be used principally for data authentication. According to another aspect of the present invention, consequential evidence of the transaction may be secured to provide after-the-fact evidence of the transaction. This evidence can include a message written to a tamper-resistant log record, the message including the transaction information, the first data item, the second item, and an identifier for the originating user, as well as other information. At a subsequent point, the transaction can be shown to have been sent by the originating user and received by the intended recipient, by consulting the log record. Preferably, the validity of the transaction would be ascertained by an independent, mutually trusted third party.
Owner:JPMORGAN CHASE BANK NA
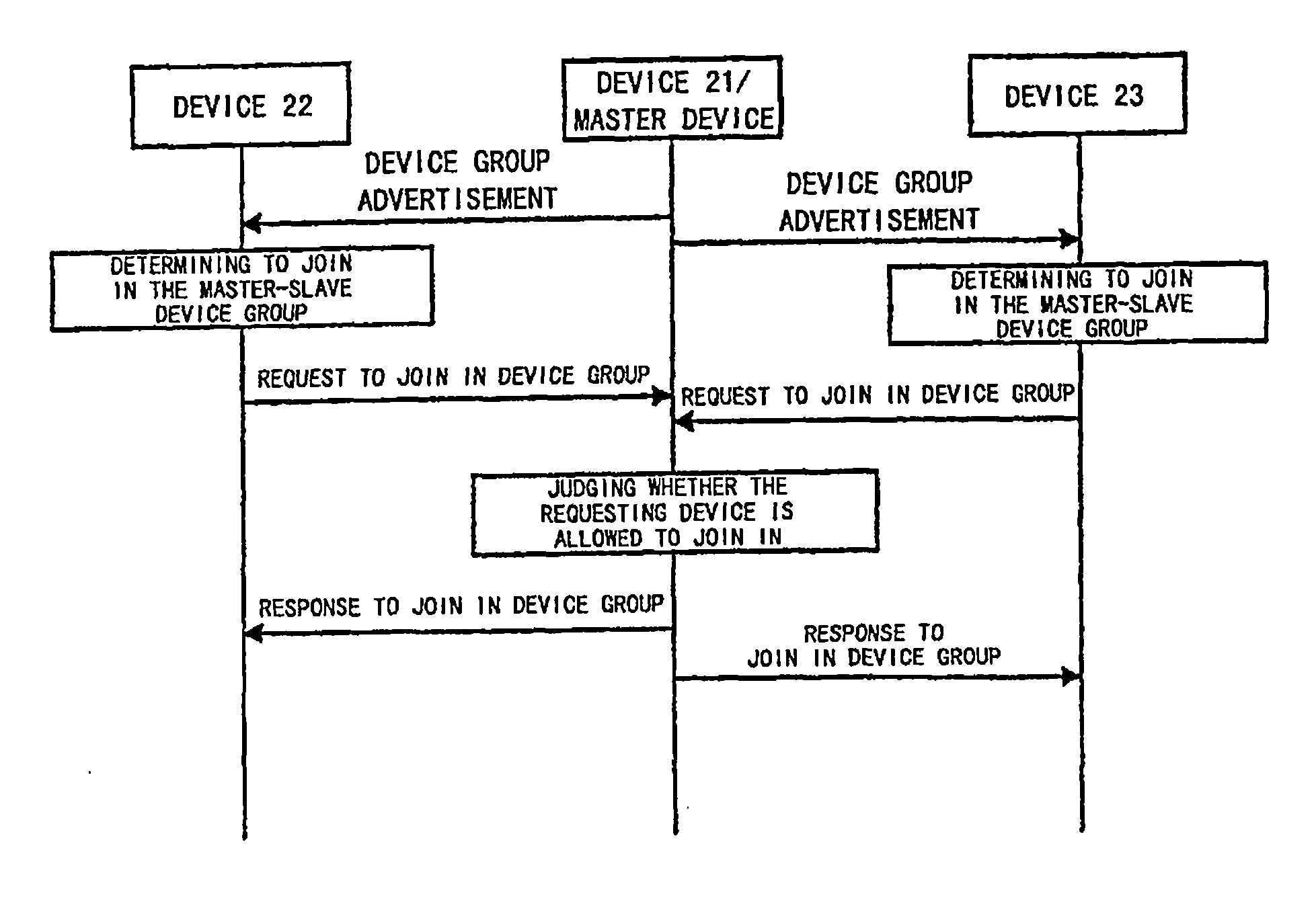
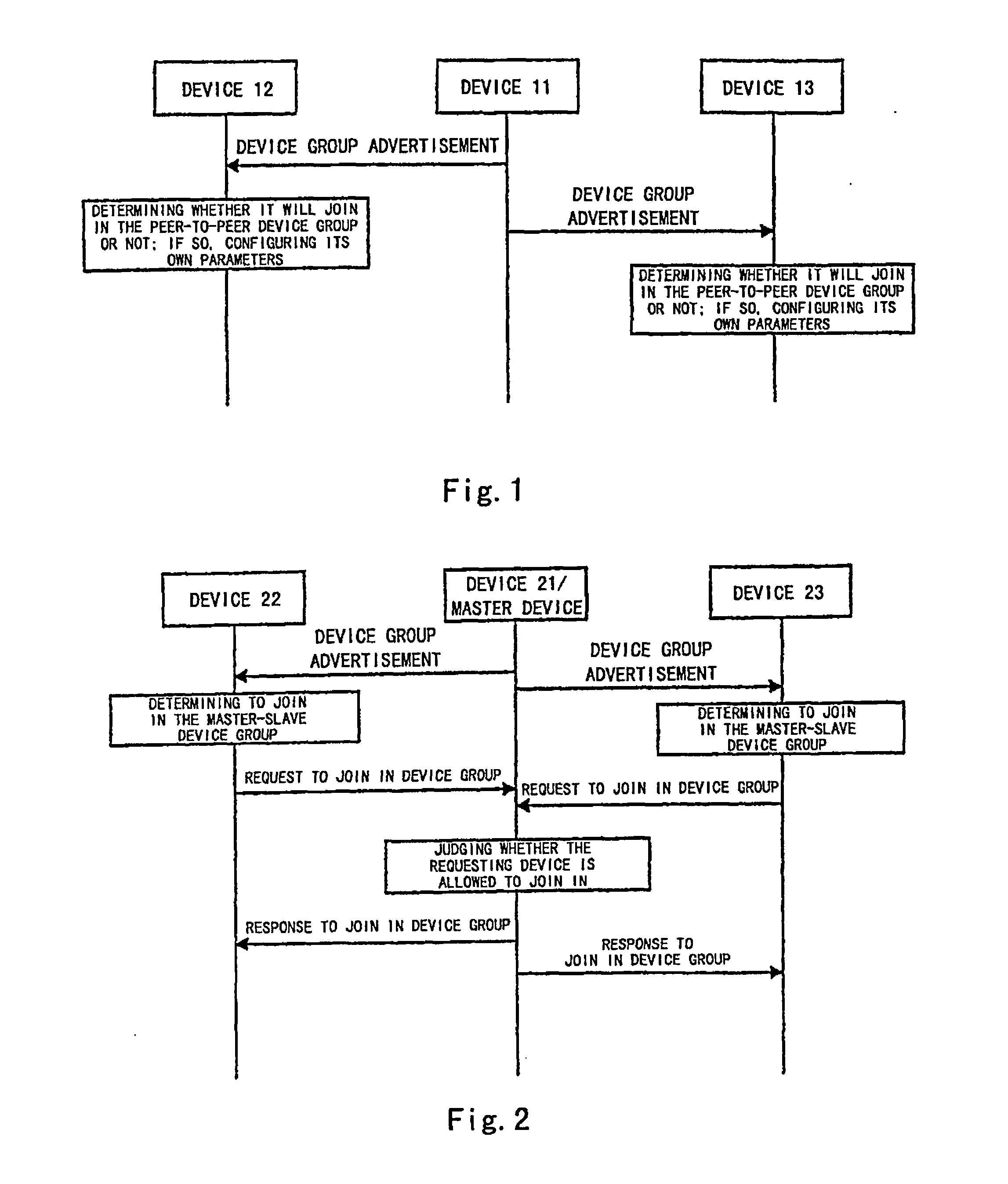
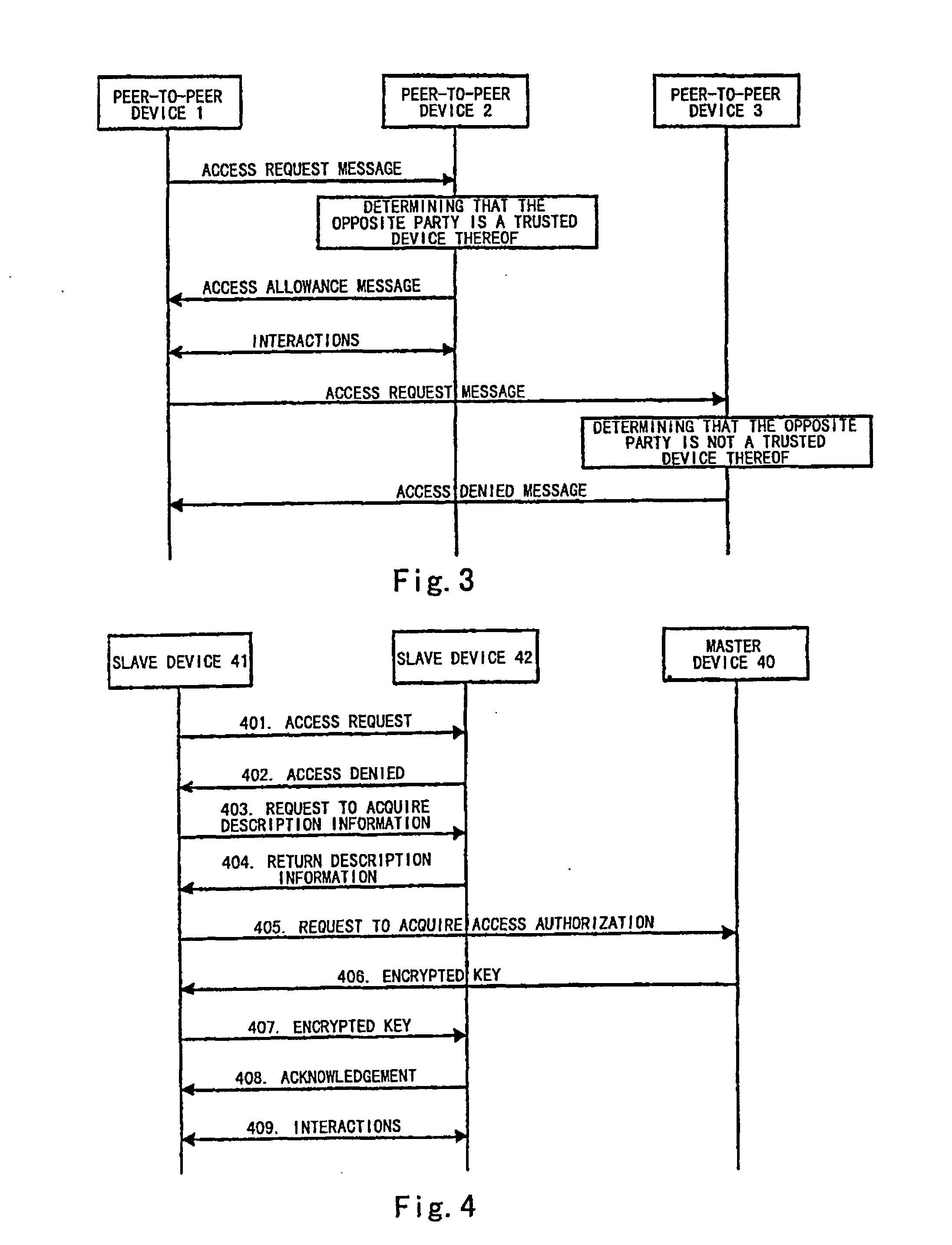
Method for Implementing Grouping Devices and Interacting Among Grouped Devices
ActiveUS20070223398A1User identity/authority verificationNetwork topologiesSecure authenticationTrust third party
The present invention discloses a method for implementing device grouping and interactions between grouped devices. In a network, a device creating a device group sends an advertisement message carrying identification information of a device group to which it belongs, to the network. After receiving the advertisement message, a network device which wants to join in the corresponding device group joins in the device group identified by the corresponding advertisement message. When two network devices interact with each other, the method further comprises: sending by an initiating device, an access request to an accessed device; judging by the device receiving the access request, whether the device sending the request is a trusted device thereof or not, if so, interacting by both parties with each other; otherwise, denying the access request, or determining a common trusted third party together with the initiating device; acquiring by the initiating device, key information of the accessed device from the common trusted third party, and interacting with the accessed device by using the acquired key information. The method can support one and the same device to join in deferent groups while facilitating the device management, and can achieve secure authentication based communication interactions between any devices.
Owner:LENOVO (BEIJING) CO LTD
Systems and methods for enabling trust in a federated collaboration
ActiveUS7953979B2Digital data processing detailsUser identity/authority verificationSuccessful completionTrust third party
Systems and methods consistent with the present invention enable explicit and multilateral trust across a community of federated servers via a network. A trusted third party establishes a framework of policies and procedures governing a federation. Organizations joining the federation submit to an audit process of internal policies and procedures to ensure compliance with the policies and procedures of the federation. Upon successful completion of an audit, an organization may receive a digital certificate containing the digital public key of the organization and indicating approval of the trusted third party. The organization may then use the associated digital private key for signing security assertions associated with a request for resources from another federation service provider. The service provider may trust the assertion from the organization based on trust placed in trusted third party by the service provider and the trust placed in the organization by the trusted third party.
Owner:EXOSTAR CORP
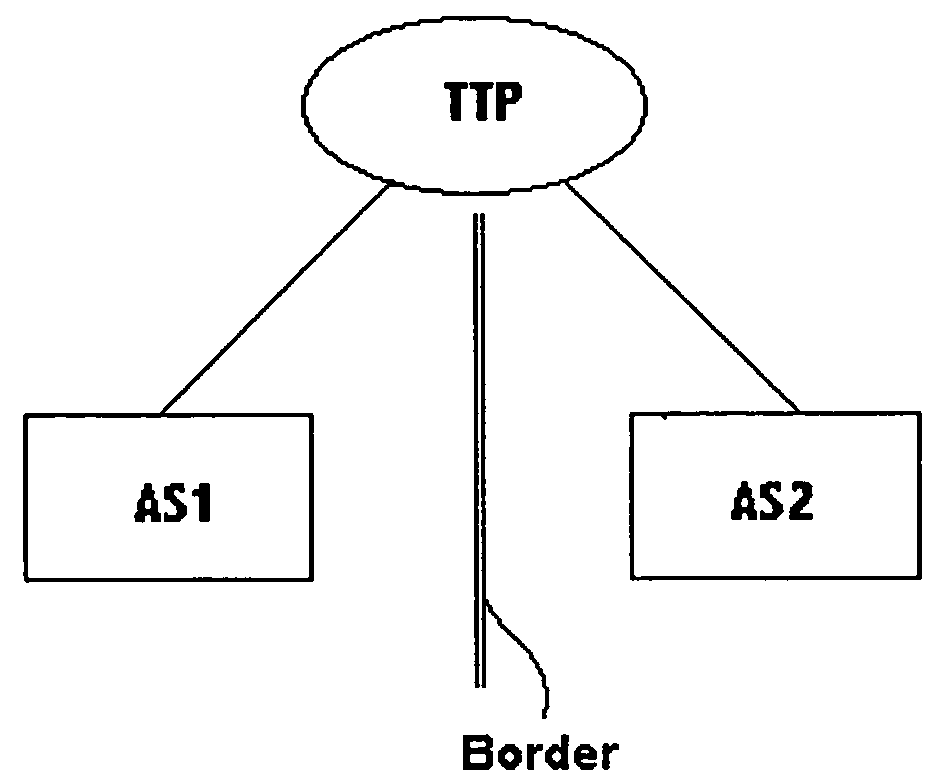
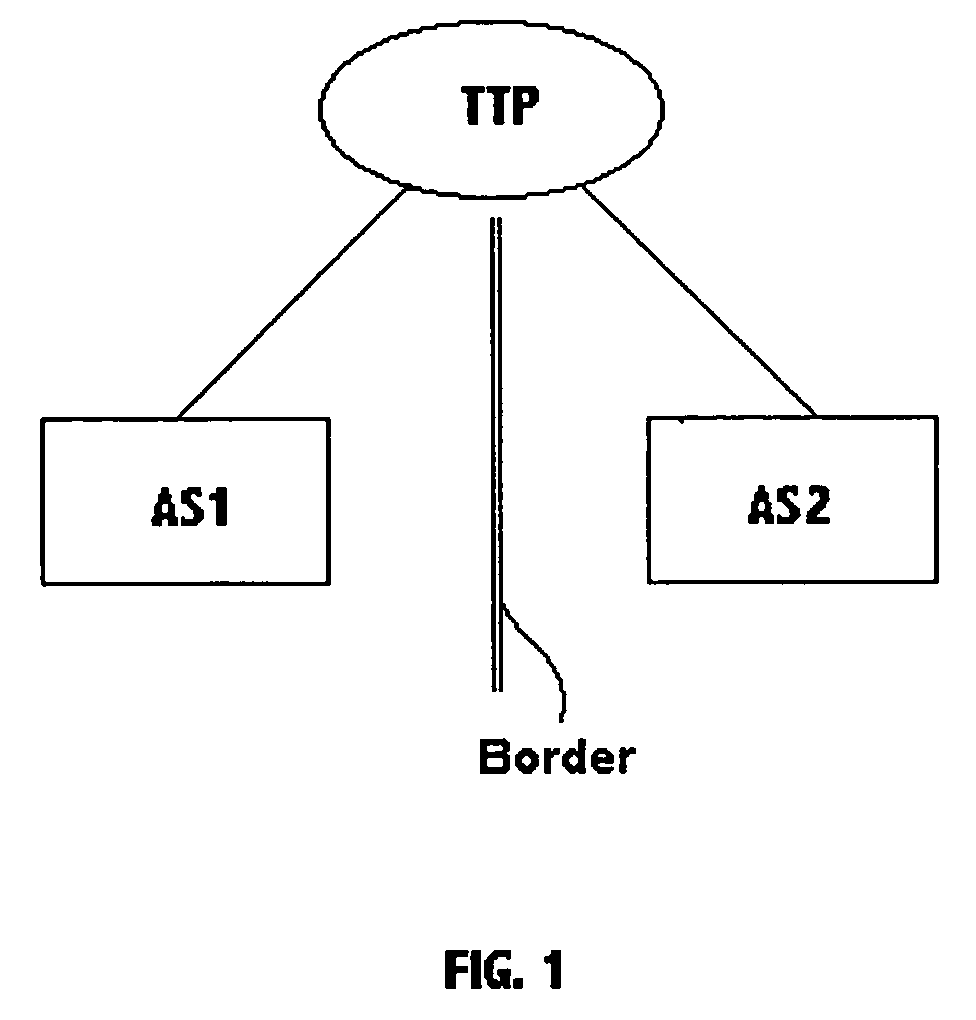
Multicast peering
InactiveUS20050108419A1Reduce the amount of informationSpecial service provision for substationMultiple digital computer combinationsThird partyPeering
Multicast peering in commercial Internets is performed by a trusted third party which has a connection into two or more Autonomous Systems. Multicast streams pass from the trusted third party into the Autonomous Systems independently. There is thus no need for any sharing of information between the Autonomous Systems, with any information sharing taking place only between each Autonomous System and the trusted third party.
Owner:EUBANKS THOMAS MARSHALL
Fine-grained access control method for data in cloud storage
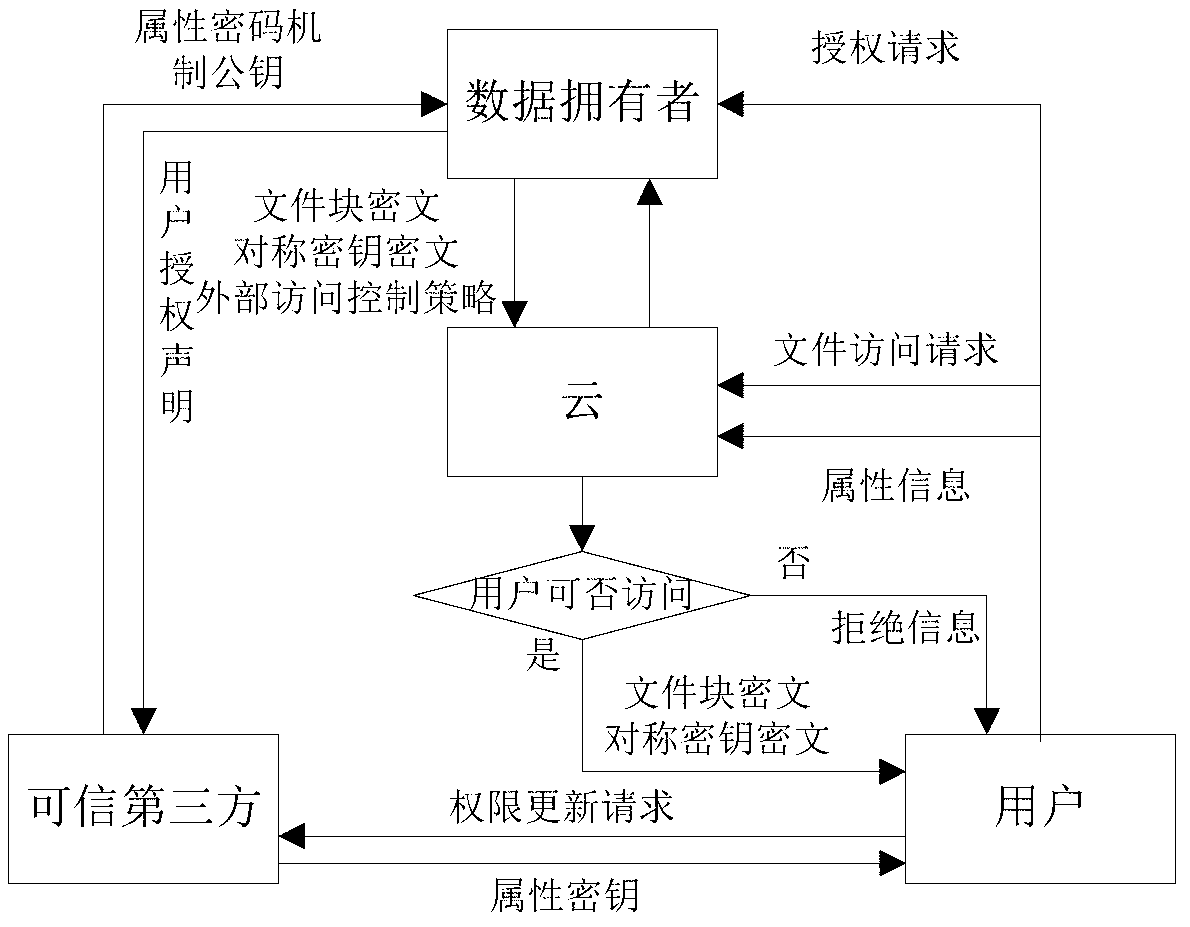
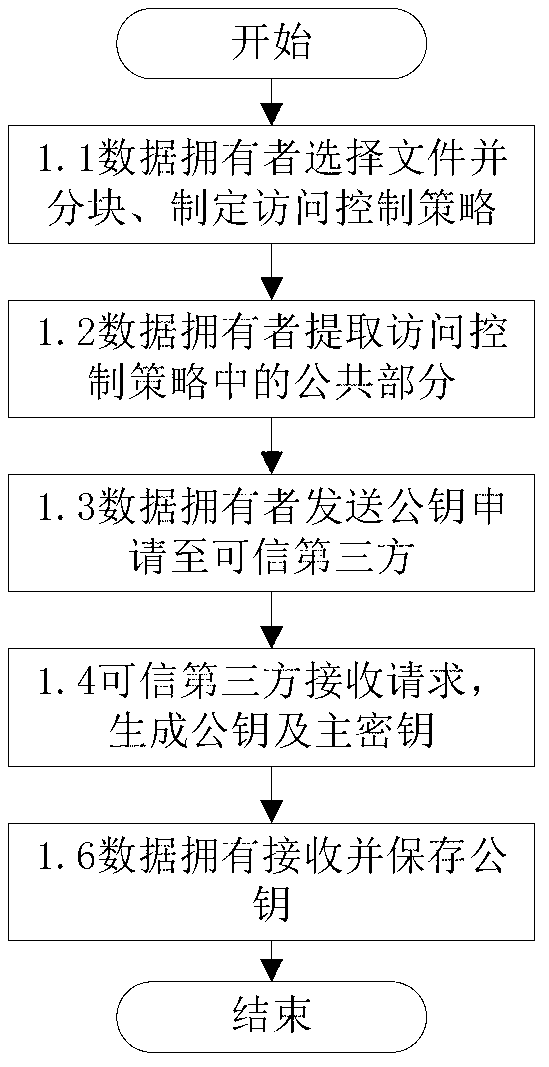
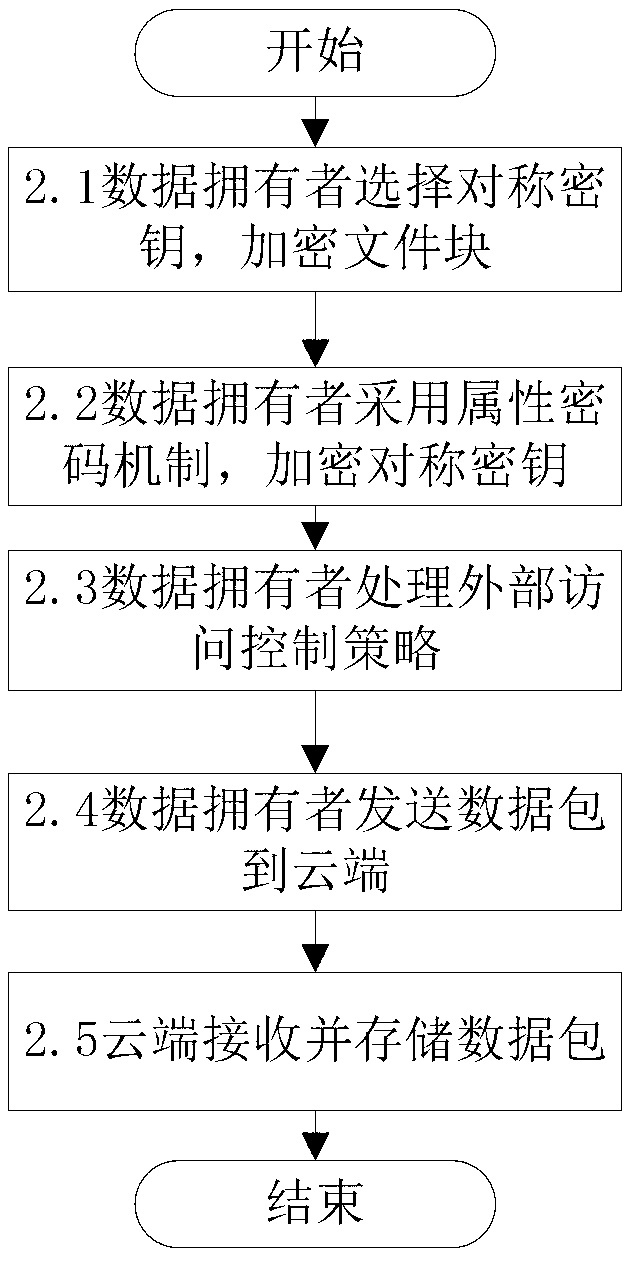
ActiveCN103179114AImplement access controlReduce overheadTransmissionUser PrivilegeAccess control matrix
The invention discloses a fine-grained access control method for data in cloud storage. The method includes the steps: firstly, a data owner blocking files and formulating an external access strategy of file blocks and an internal access strategy of the file blocks according an access control policy, and a trusted third party generating a public key and a master key according to an attribute password mechanism; the data owner utilizing a symmetric password mechanism to encipher the file blocks, utilizing the attribute password mechanism to encipher a symmetric key, and sending a cypher text of the file blocks and a cypher text of a secret key to the cloud; the data owner and the trusted third party utilizing the attribute password mechanism to authorize a user, and generating an attribute key and an attribute processed by an attribute encryption function for each attribute of the user; the data owner sending an user permission change statement to the trusted third party; and the trusted third party judging whether adding or deleting the user permission or not for the user according to the user permission change statement. Compared with the prior art, the method for the fine-grained data access control in the cloud storage has the access control with more fine-grained data under the condition of not increasing additional costs.
Owner:HUAZHONG UNIV OF SCI & TECH
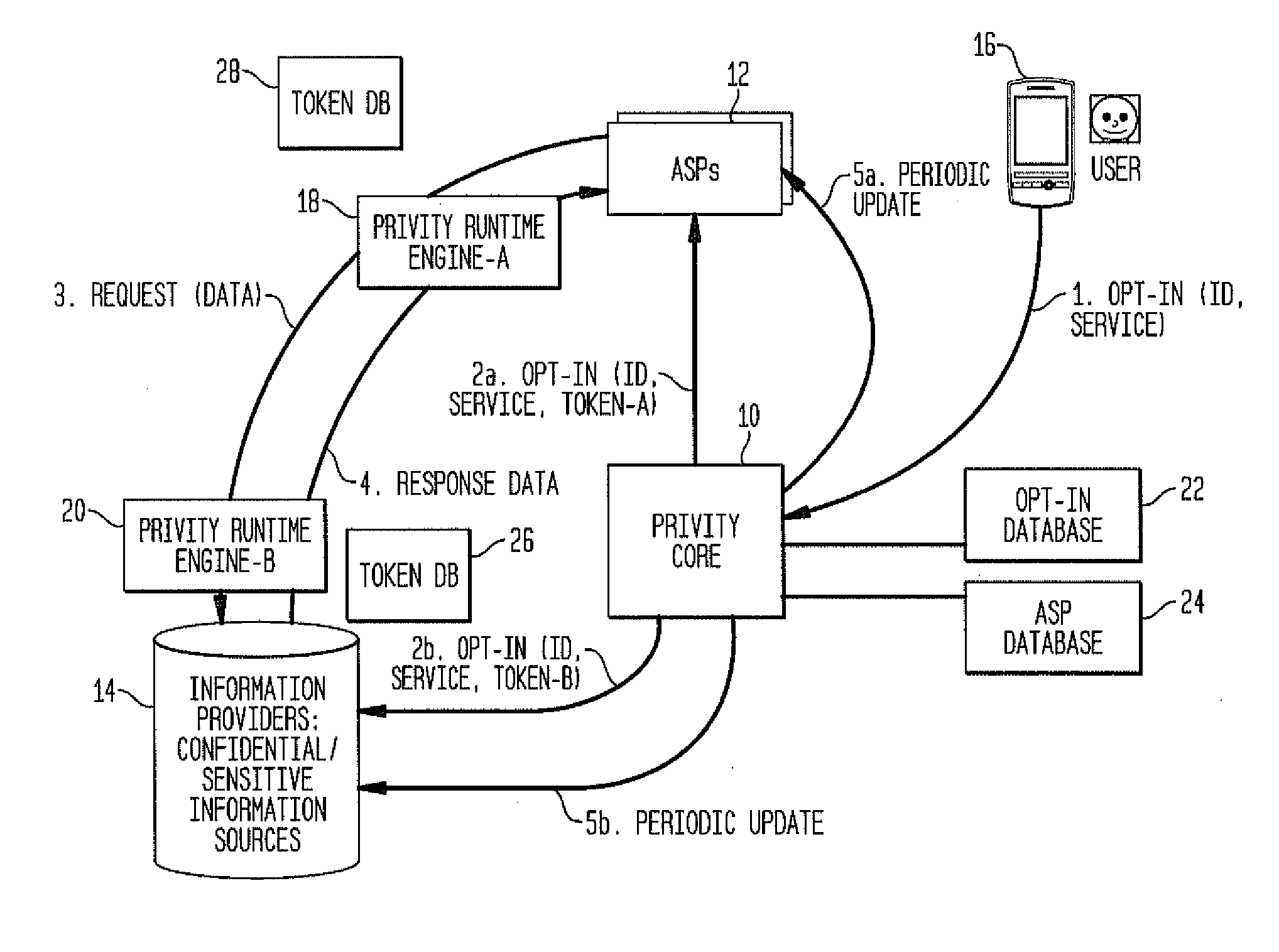
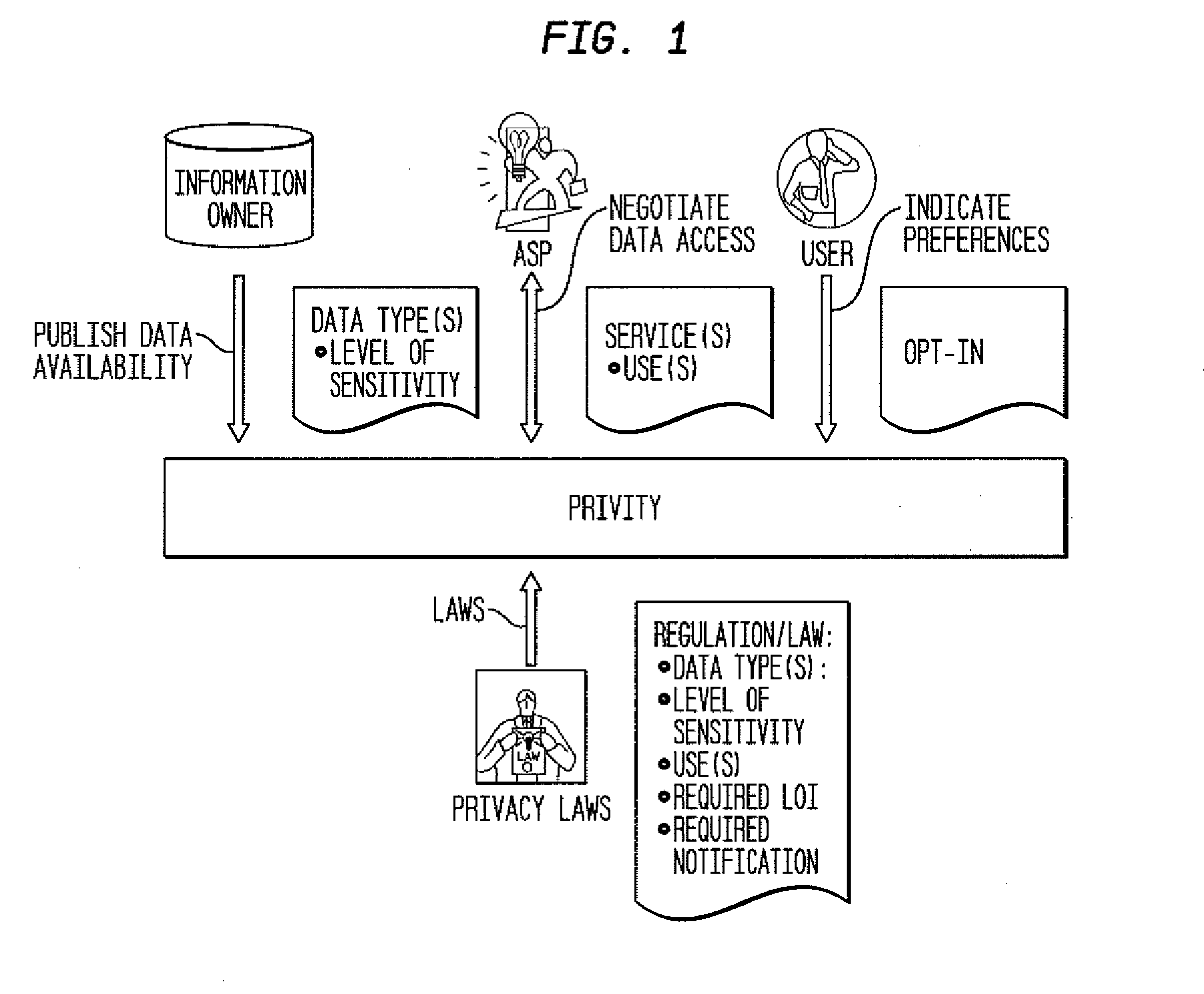
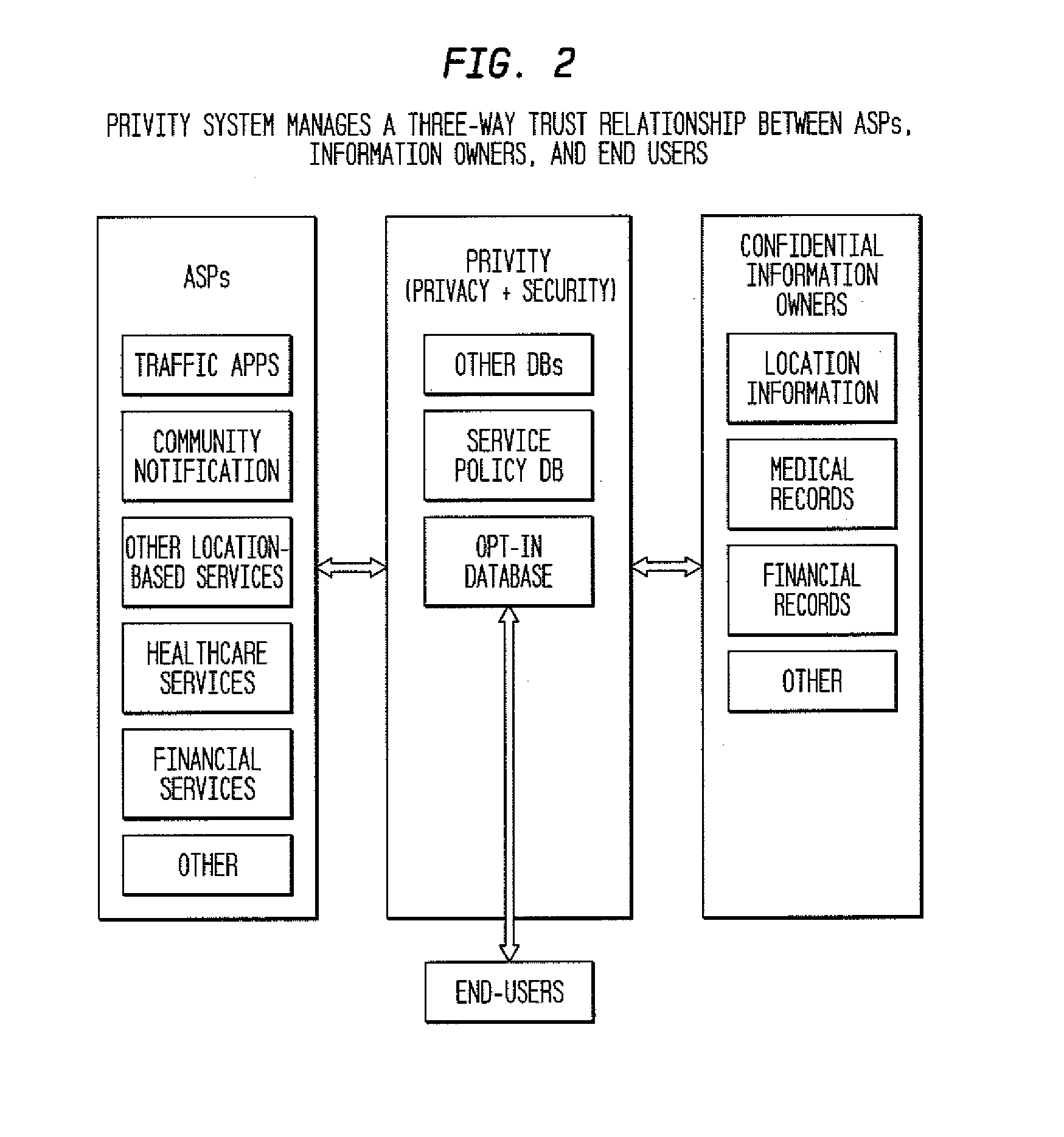
System and method establishing trusted relationships to enable secure exchange of private information
ActiveUS20120036360A1Digital data processing detailsUser identity/authority verificationPersonalizationInformation repository
The invention disclosed here is aimed at enabling a trusted third party to manage user opt-ins which would enable growth of personalized information services, that is, enabling trusted business relationships between three types of entities—an end-user, an information source / provider, and an application service provider / developer—so that they can have a controlled, secure and private exchange of sensitive and / or confidential information. The inventive system has modes of operation recommended based on various conditions, enabling a secure exchange of private information between personal information repository owners and application services providers to enable deliver of personalized services. One mode is Durable Subscription Management, which is used when per transaction approval is not needed, that is, when an end-user has given permission to access data for a given or predefined period of time. A second mode is Per-Transaction Subscription Management Without Logs and a third mode is Per-Transaction Subscription Management With Logs.
Owner:TELCORDIA TECHNOLOGIES INC
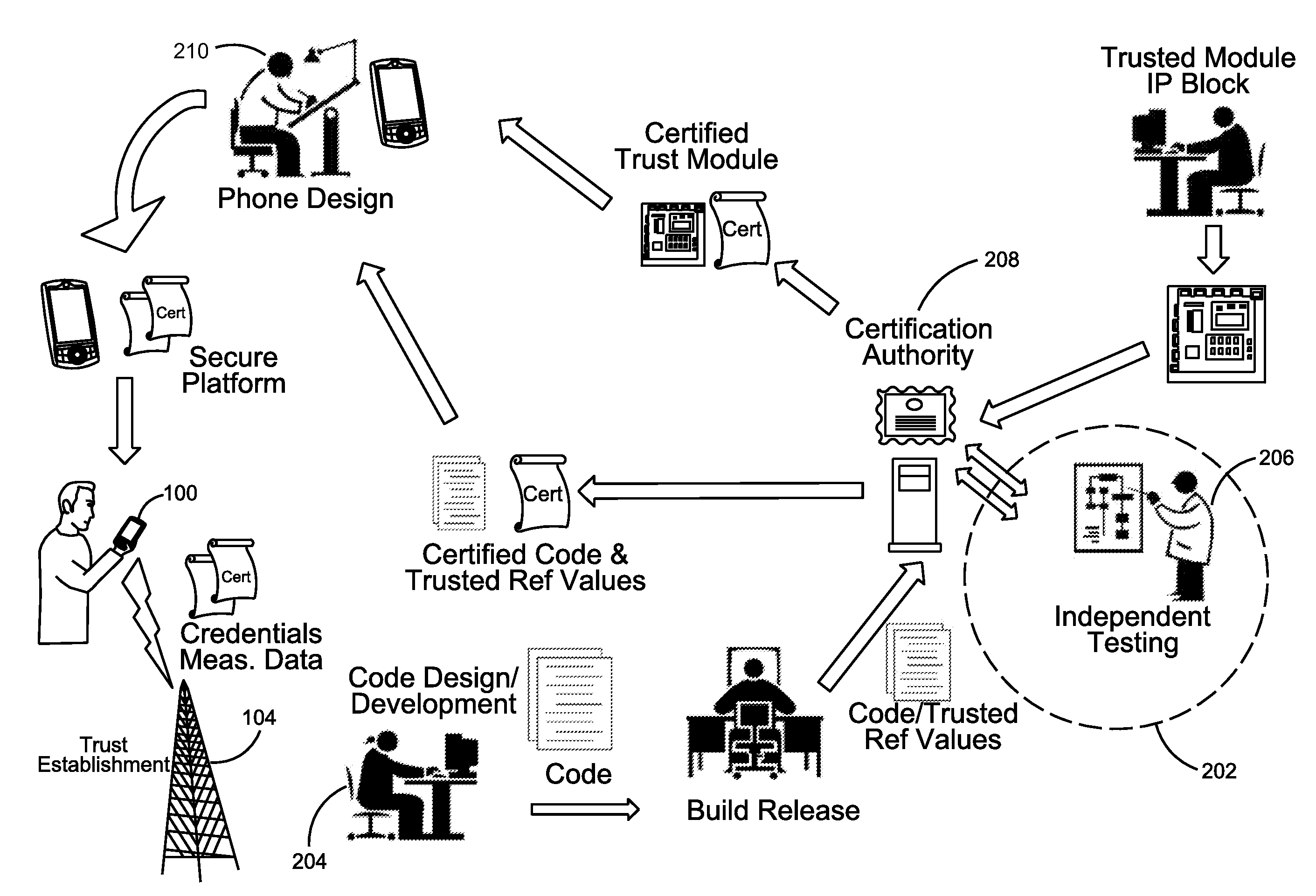
Validation And/Or Authentication Of A Device For Communication With Network
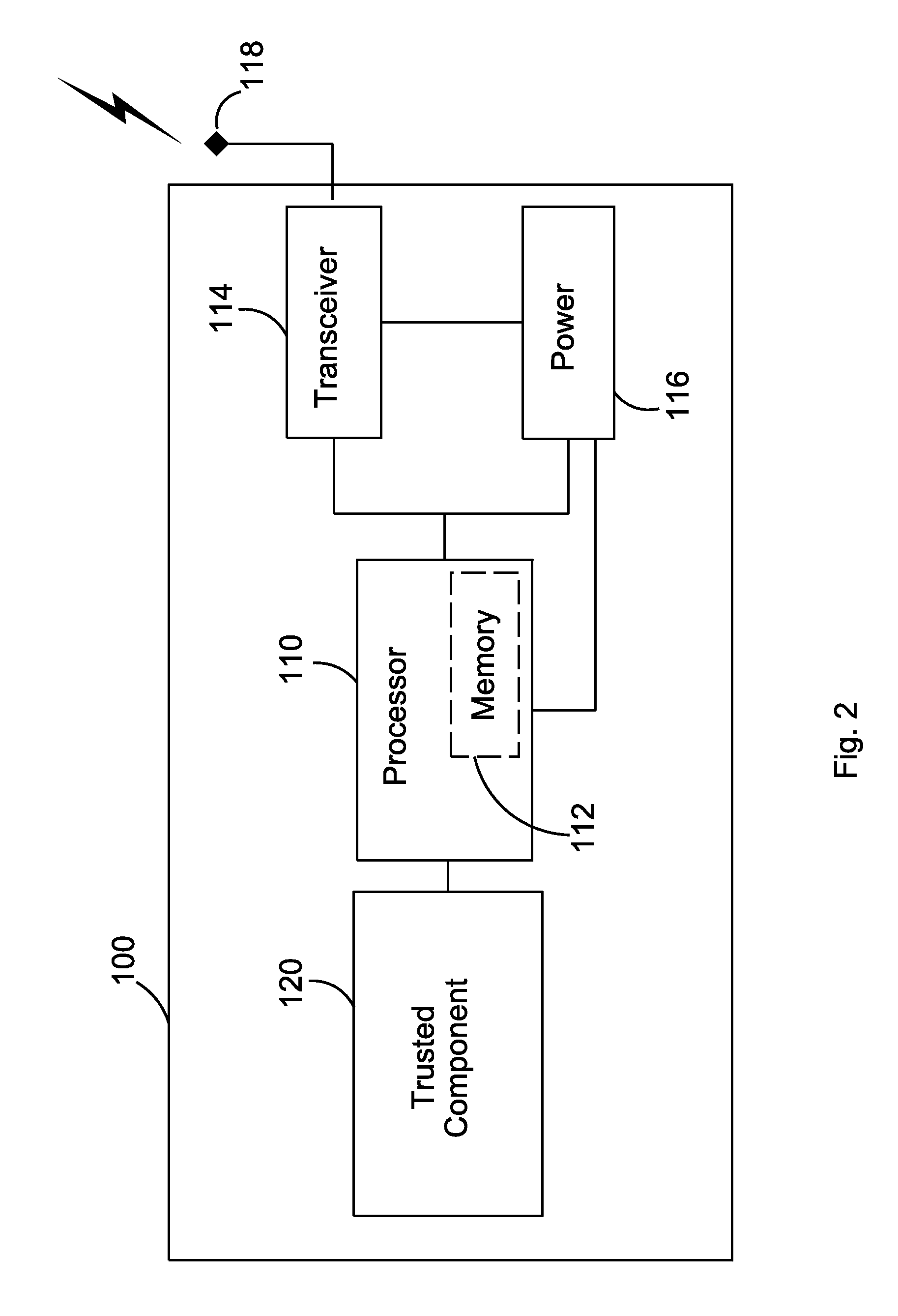
InactiveUS20110099361A1Data taking preventionError detection/correctionThird partyTrusted components
A device may include a trusted component. The trusted component may be verified by a trusted third party and may have a certificate of verification stored therein based on the verification by the trusted third party. The trusted component may include a root of trust that may provide secure code and data storage and secure application execution. The root of trust may also be configured to verify an integrity of the trusted component via a secure boot and to prevent access to the certain information in the device if the integrity of the trusted component may not be verified.
Owner:INTERDIGITAL PATENT HLDG INC
Security process for private data storage and sharing
InactiveUS20090083544A1Without riskEffectively transparentUser identity/authority verificationInternal/peripheral component protectionSecure Electronic TransactionPrivate network
A method and system for supplementing and / or replacing current security protocols and / or mechanisms used to store, manage and / or disseminate information for use on private data management devices and / or a private network and / or public network access provider's network. The system includes processing hardware, proprietary software, and firmware. The system protects private data without the need to trust the security or veracity of third parties and / or intermediate computers and / or networks. When a “user” stores data it is immediately protected from active and passive compromise attempts. Once protected and stored, data is never released and / or transferred unprotected. Only the authorized “receiver” of the data is capable of accessing the protected data. Encryption is used to enhance authentication of the participants and / or protection of the data. This method can be used in conjunction with other secure data transfer applications such as, but not limited to, Secure Socket Layer (SSL) encryption and / or the Secure Electronic Transaction (SET) protocol, etc. This method can also be used in conjunction with any data transfer mechanism such as, but not limited to, Ethernet, WiFi, Bluetooth, RFID transponders, etc.
Owner:SCHOLNICK ANDREW +1
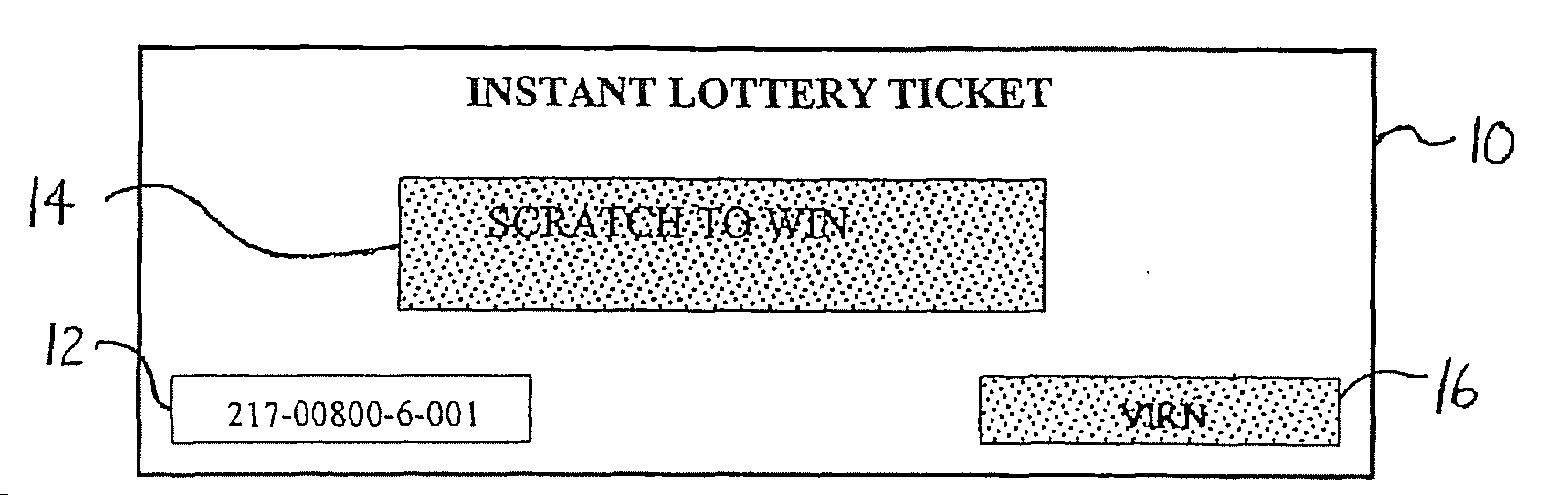
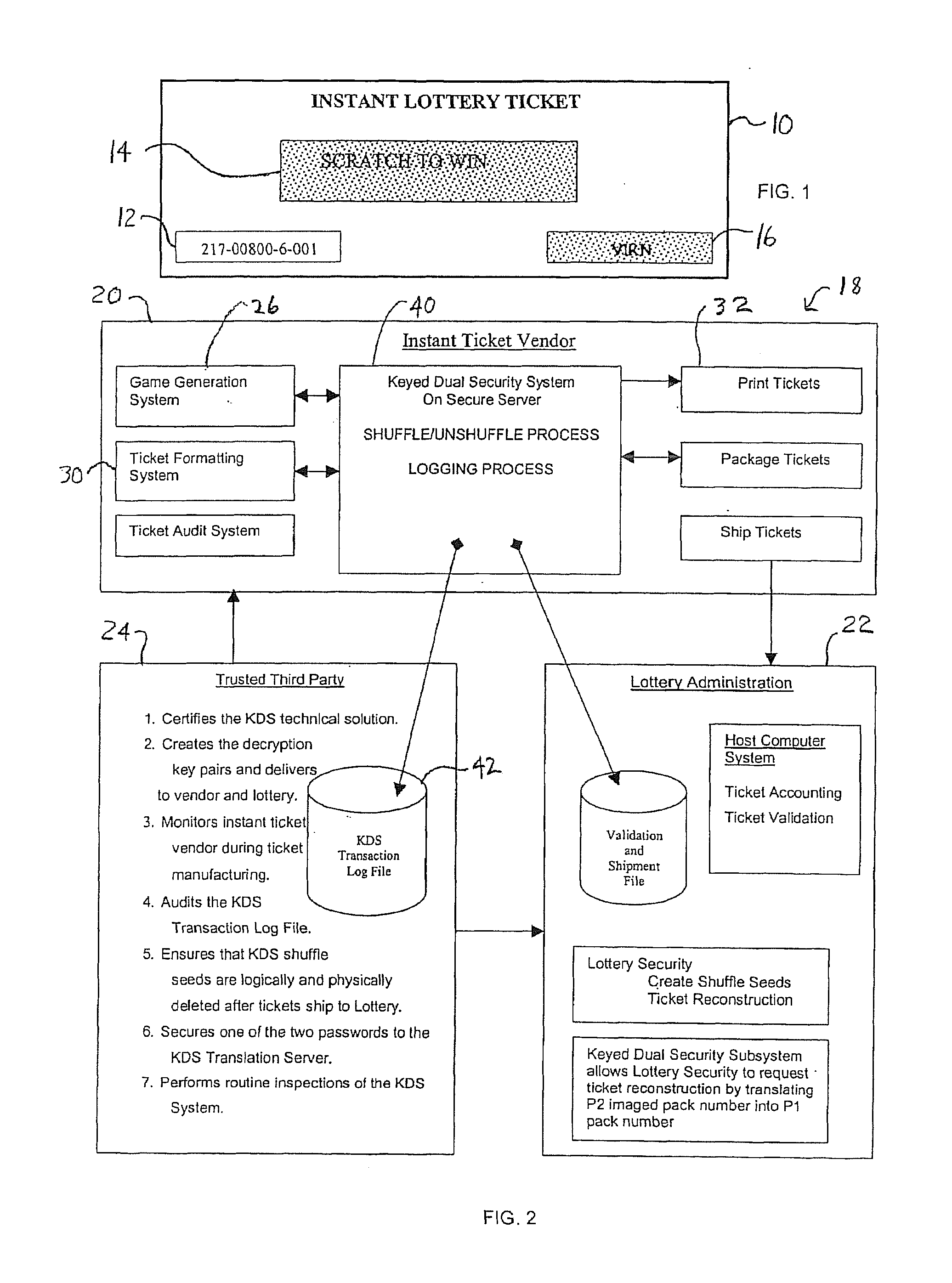
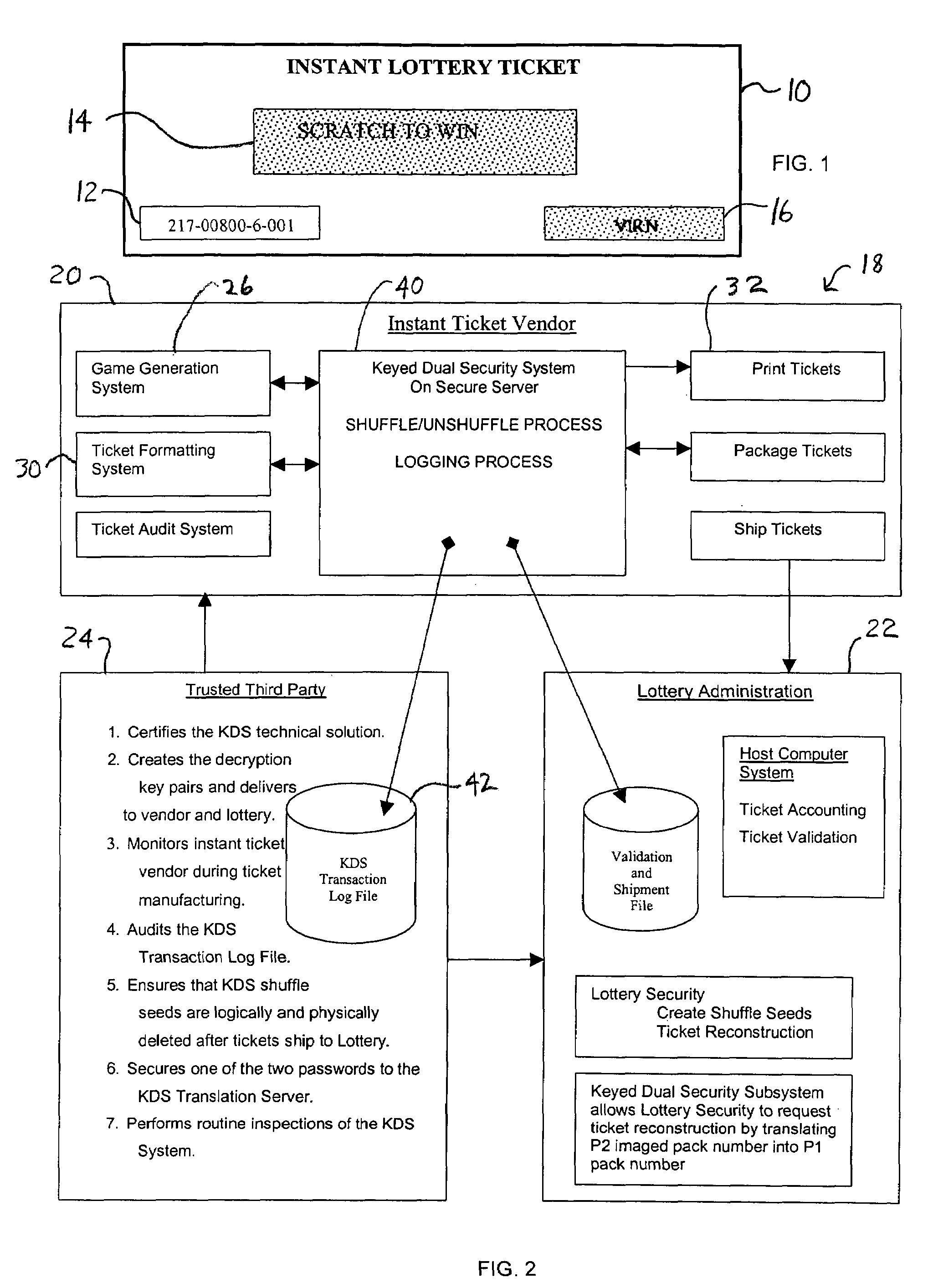
Lottery Ticket Security Method
ActiveUS20080287176A1Process safetyProvide capabilityLottery apparatusVideo gamesThird partyValidation rule
Owner:SCI GAMES LLC
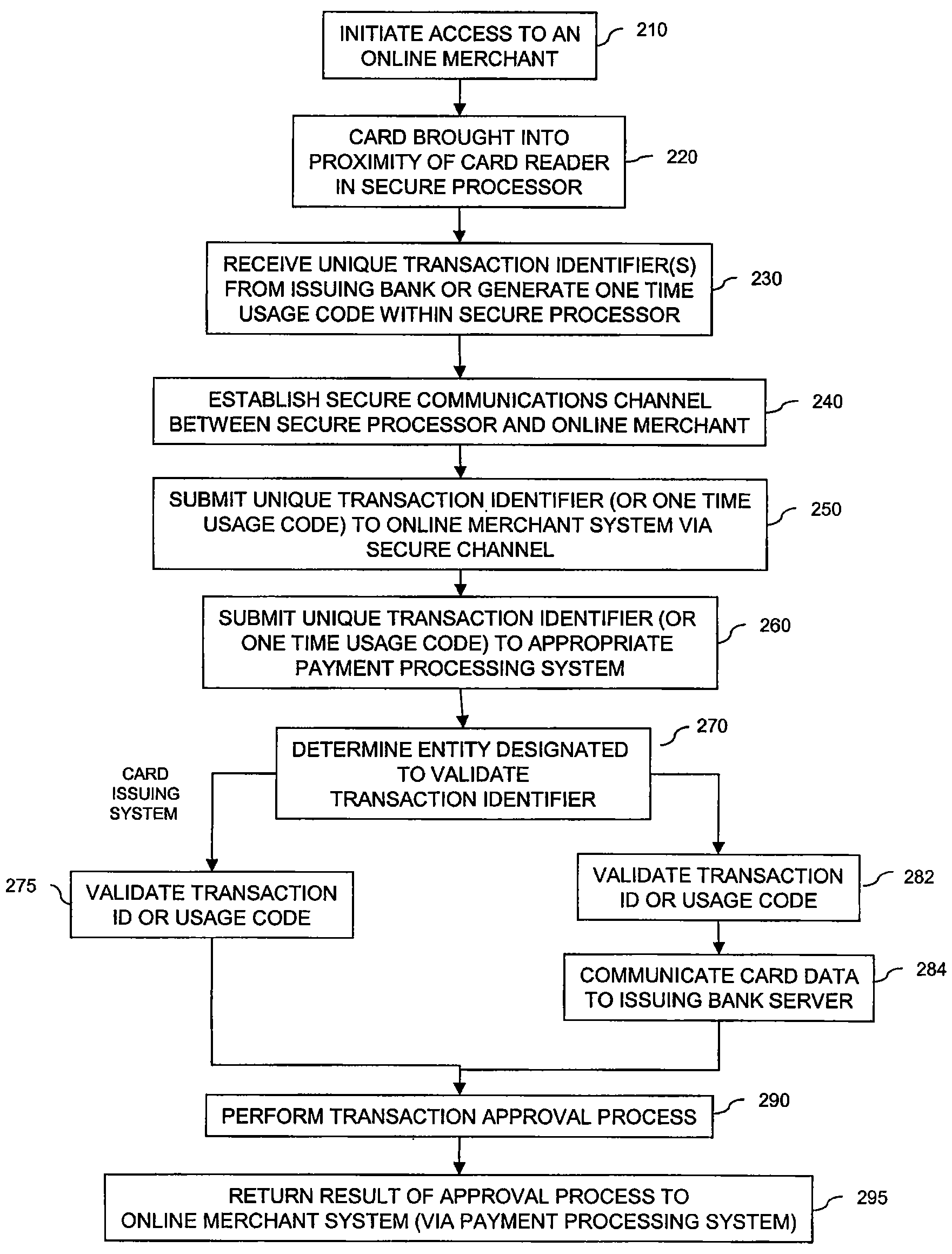
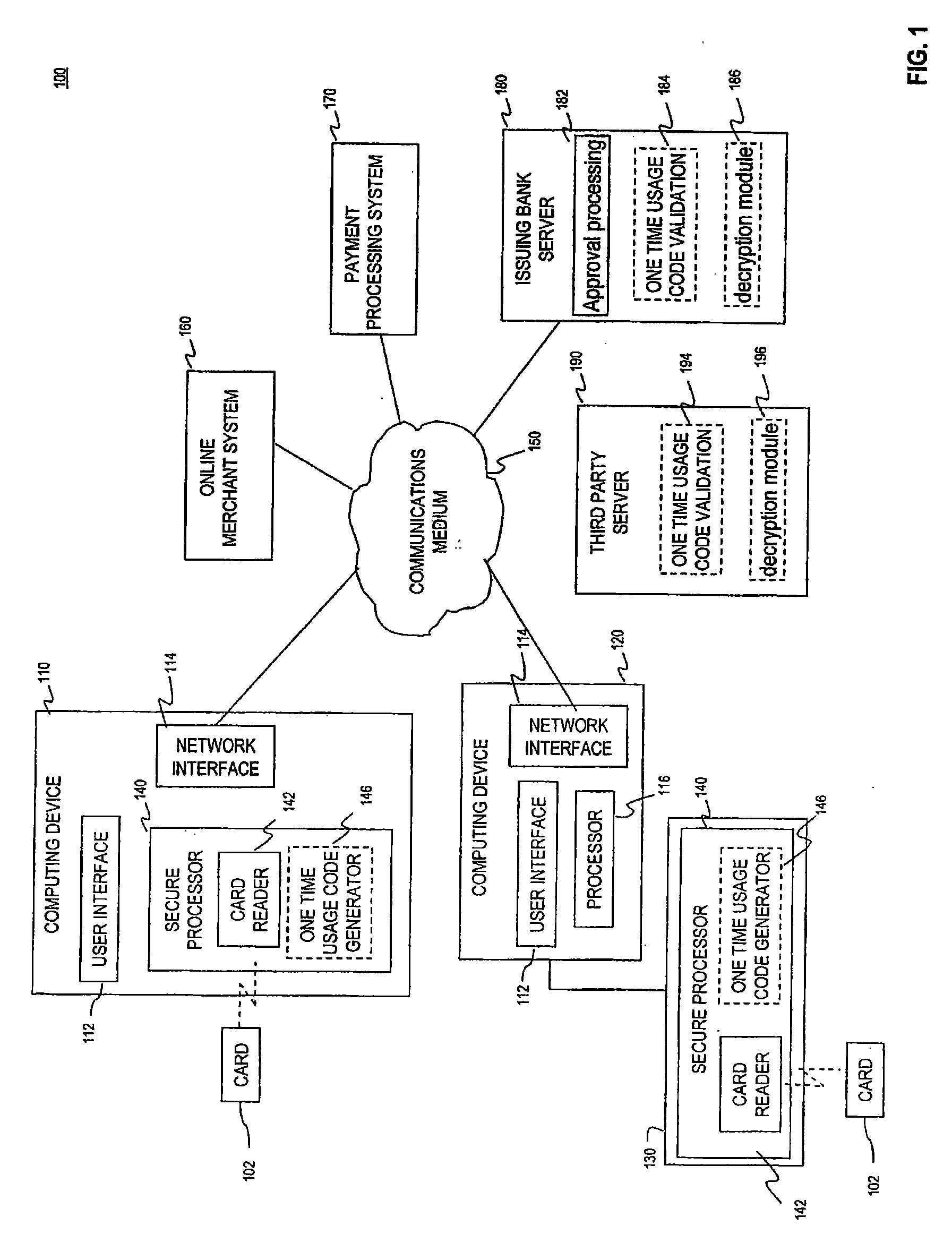
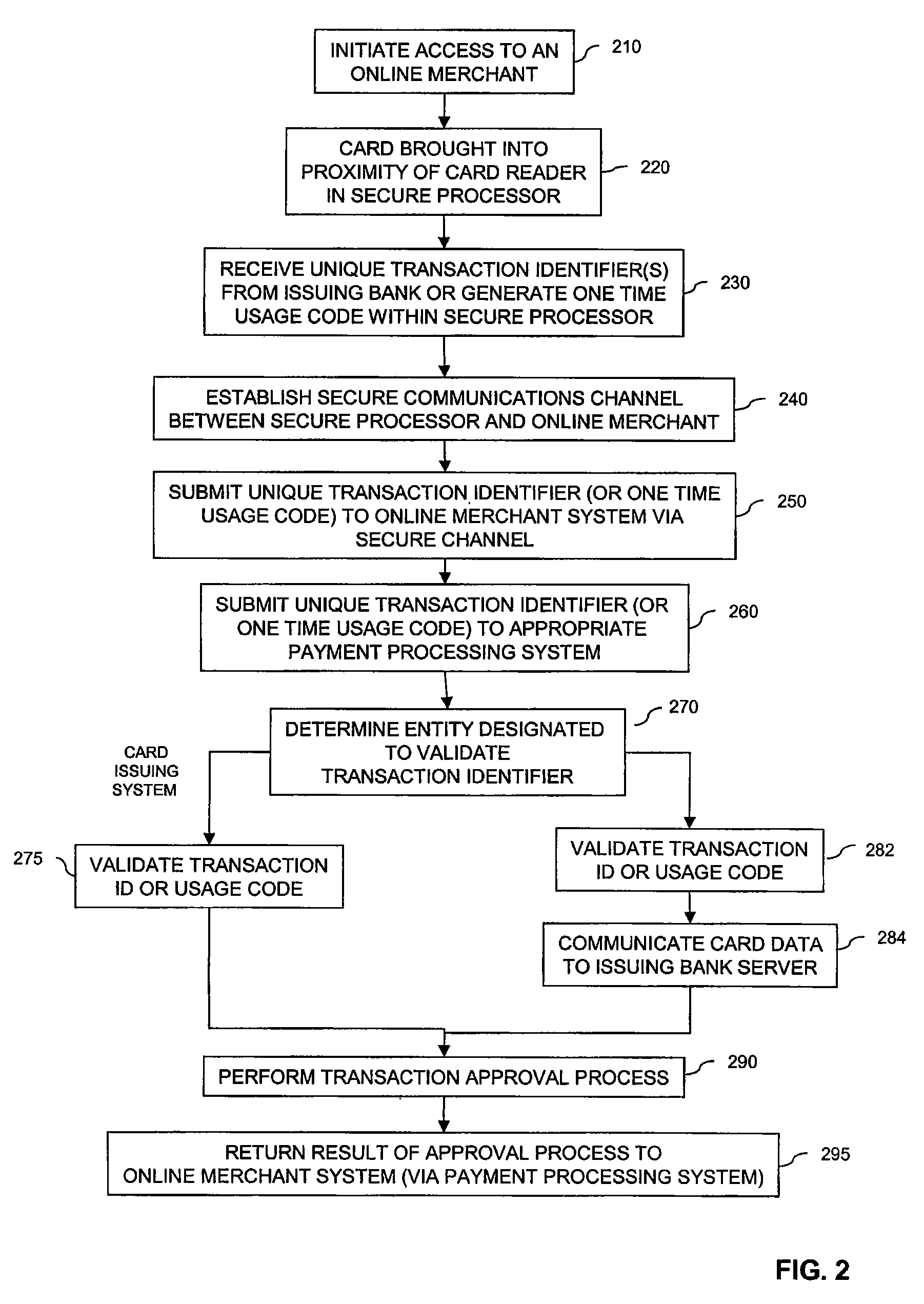
Secure Financial Reader Architecture
Methods and systems are provided for secure transaction processing. A secure processor may include an integrated wireless card reader and optionally a secure memory. When a request for payment information associated with an on-line transaction is received, the integrated wireless card reader reads data from the payment card. The secure processor may retrieve a set of transaction identifiers from the payment card issuer or optionally a trusted third party. The secure processor transmits one of the retrieve transaction identifiers to the on-line merchant instead of payment card data. The on-line merchant communicates the transaction identifier to the payment card issuer or the trusted third party for validation. Alternatively, the secure processor may encrypt the read payment card data utilizing the payment card number as the shared secret required by the cryptographic algorithm. The secure processor then forwards the encrypted payment card data to the on-line merchant.
Owner:NXP BV
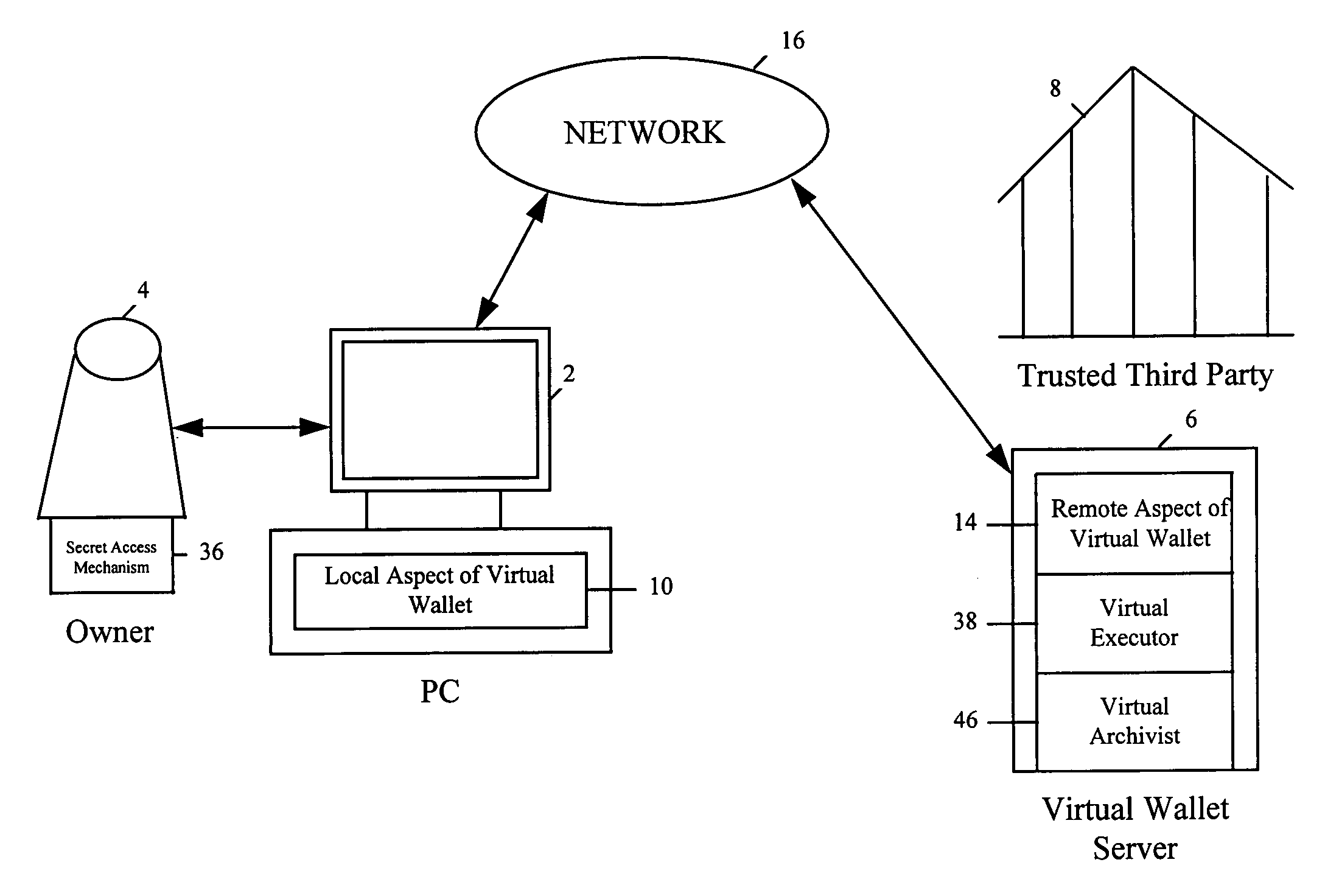
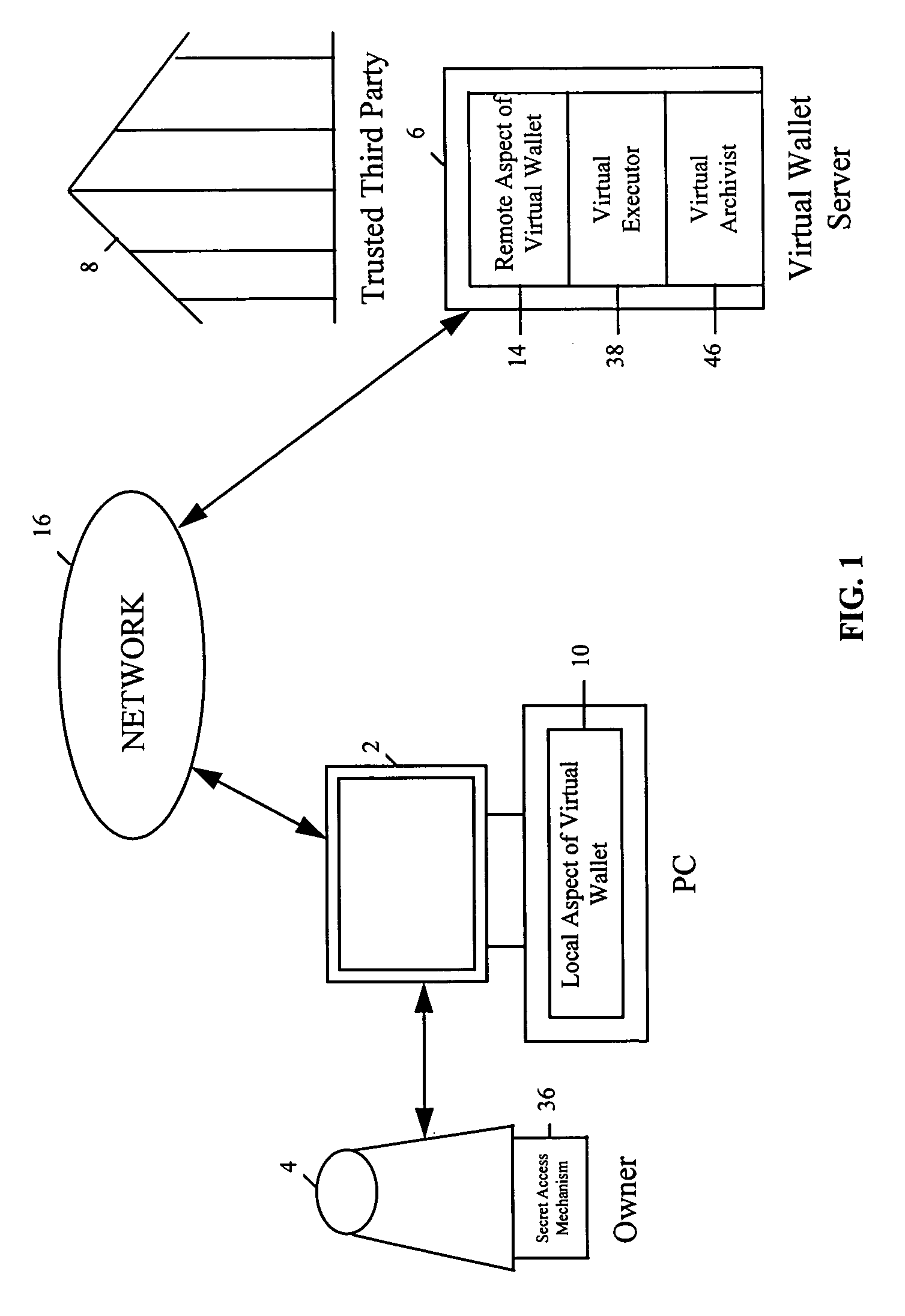
System and method for securely storing electronic data
InactiveUS6970836B1Key distribution for secure communicationComputer security arrangementsThird partyApplication software
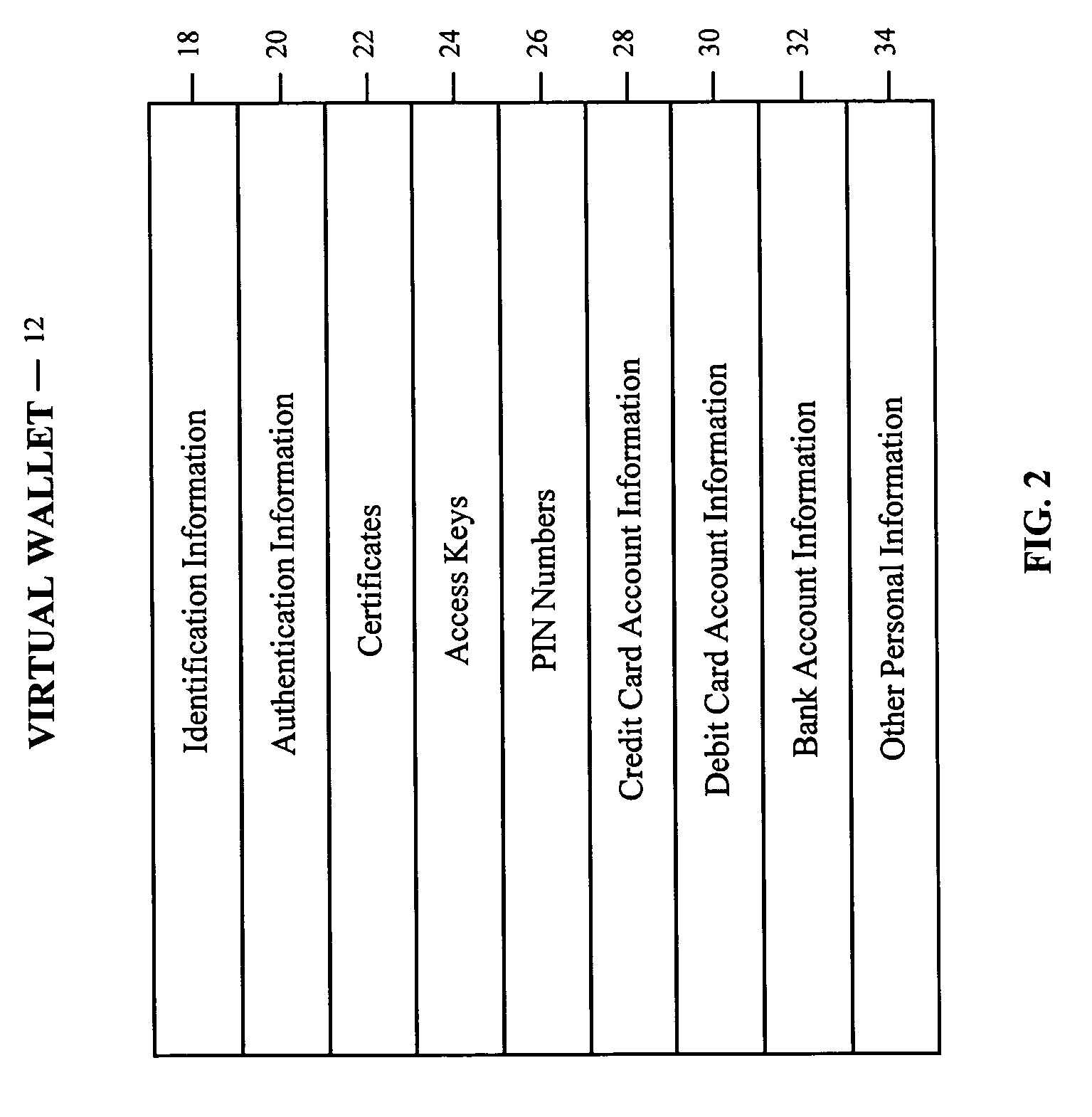
A system and method for securely storing data provides for storing, managing, and updating an owner's secret data and for accessing the stored data by a trusted third party upon the occurrence of an event, such as the death of the owner. The system and method makes use of application software, such as a virtual wallet running at least in part on the server of a trusted third party and with a virtual executor function and a virtual archivist function. The virtual executor function automatically escrows a trusted third party's access aspect of the owner's secret device for accessing the stored data. Upon verification of the occurrence of the event, the virtual executor provides access to the stored data using the trusted third party's access aspect. The virtual archivist function automatically updates technologies related to the stored data.
Owner:CITICORP CREDIT SERVICES INC (USA)
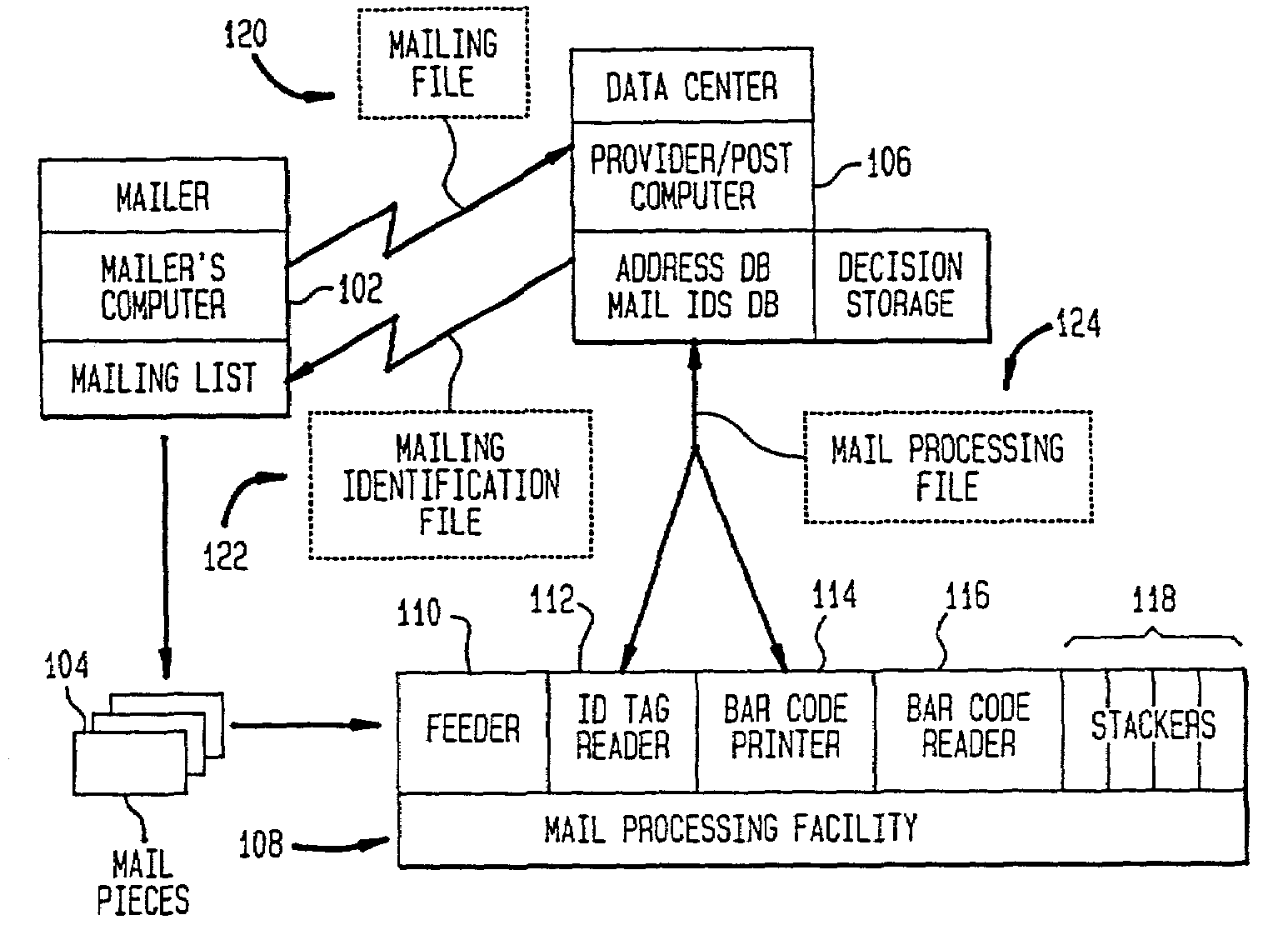
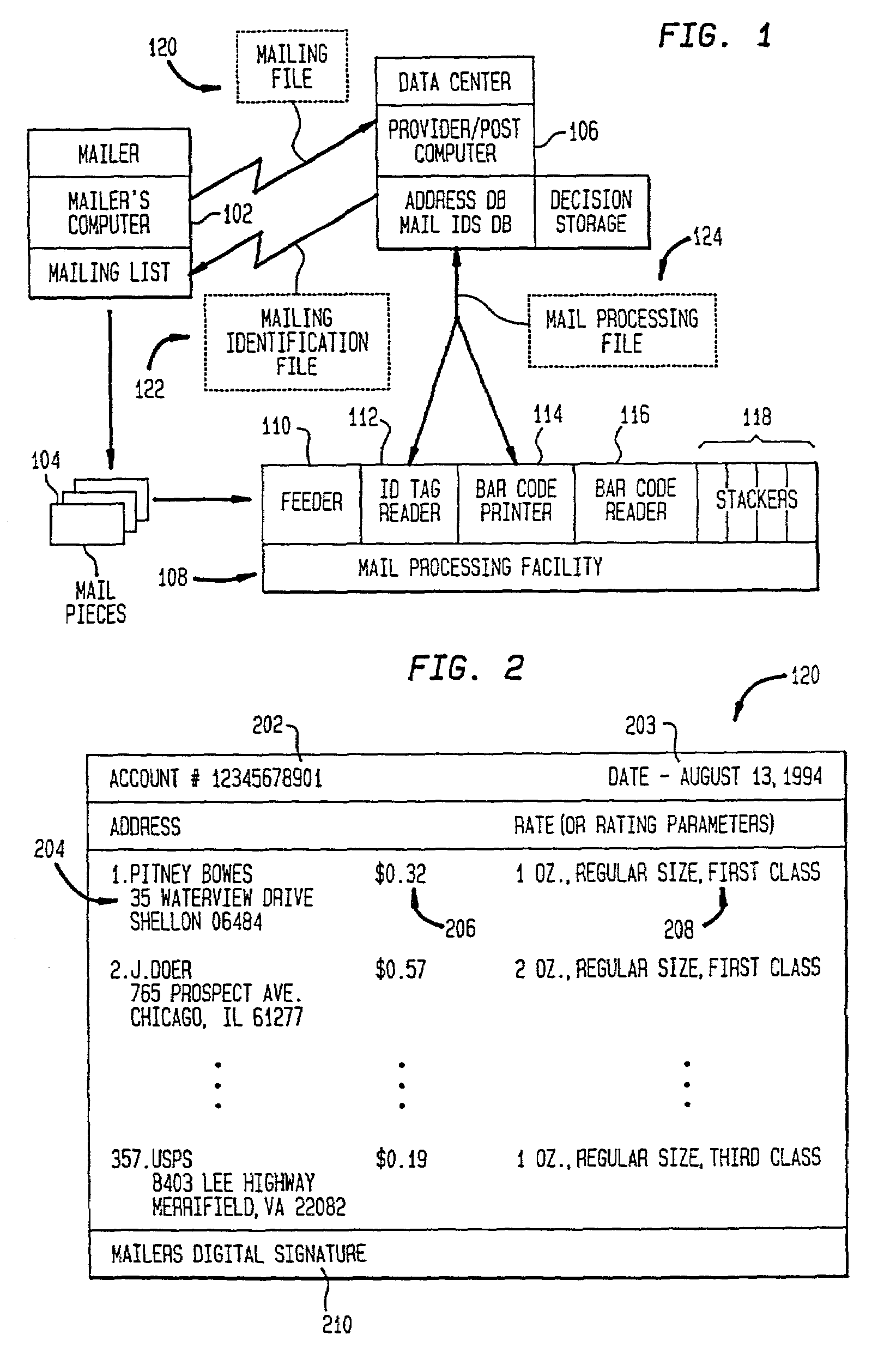
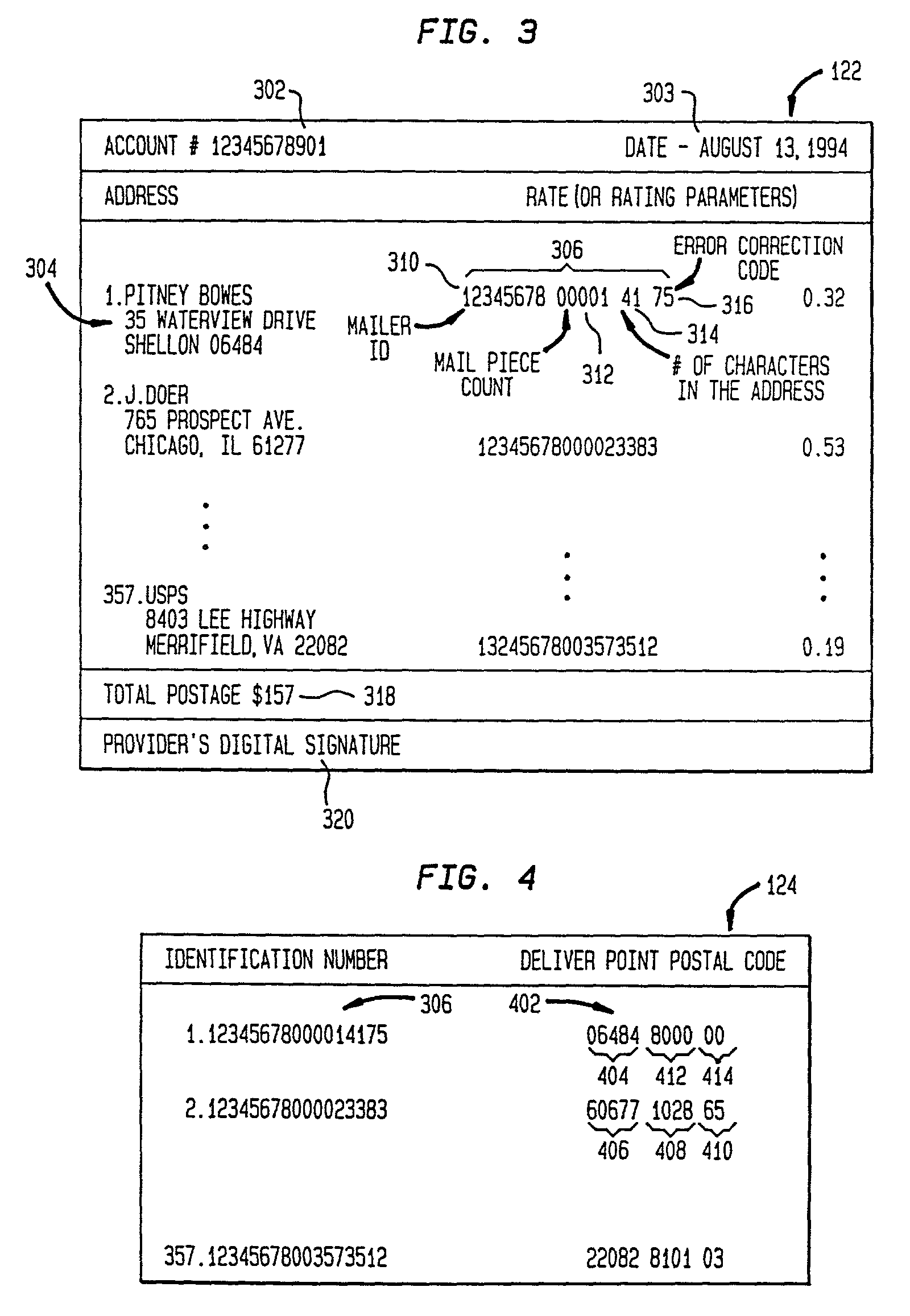
Mail processing system with unique mailpiece authorization assigned in advance of mailpieces entering carrier service mail processing stream
InactiveUS7266531B2Improve the level ofDigital data processing detailsCharacter and pattern recognitionMailing listPayment
Owner:PITNEY BOWES INC
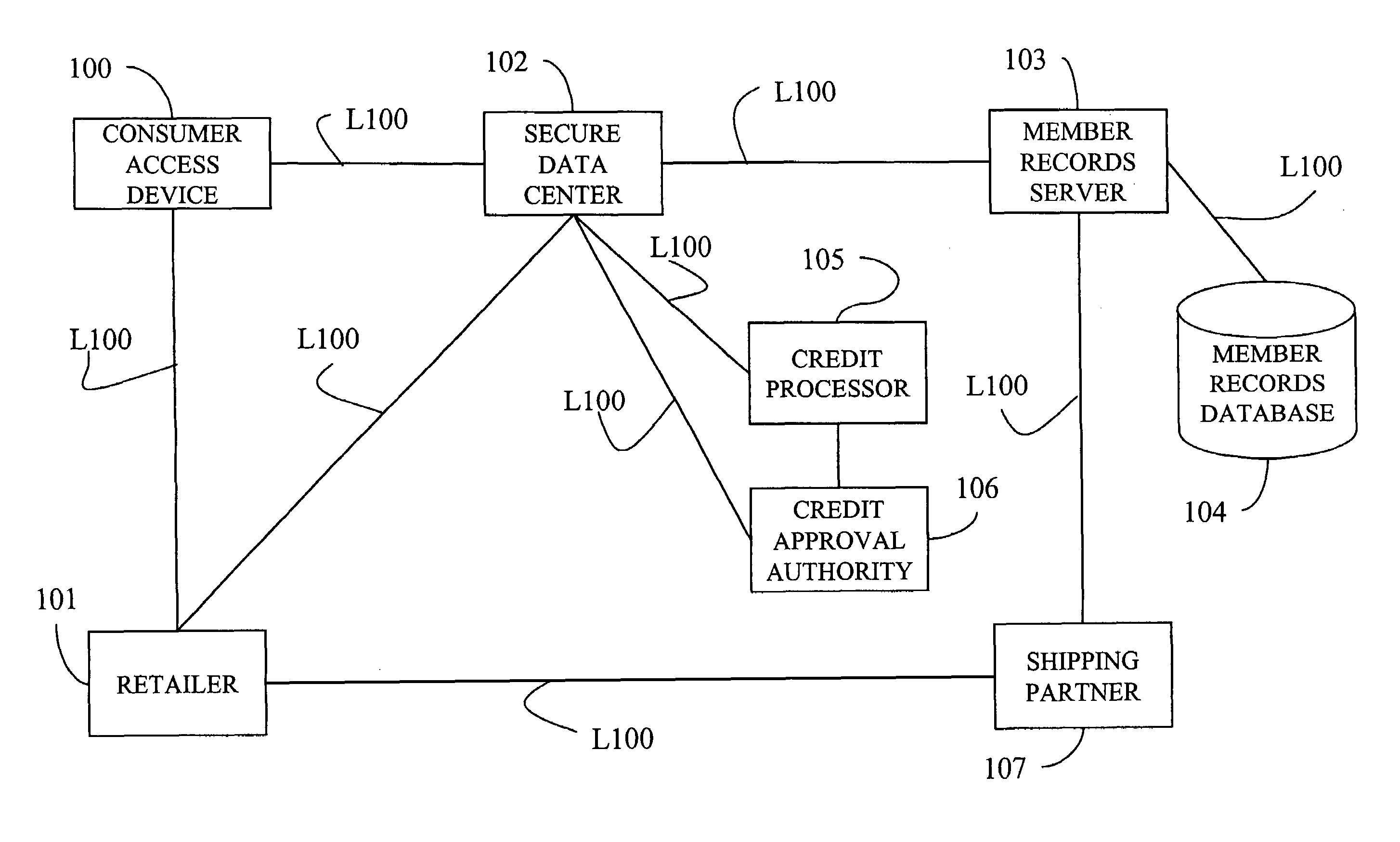
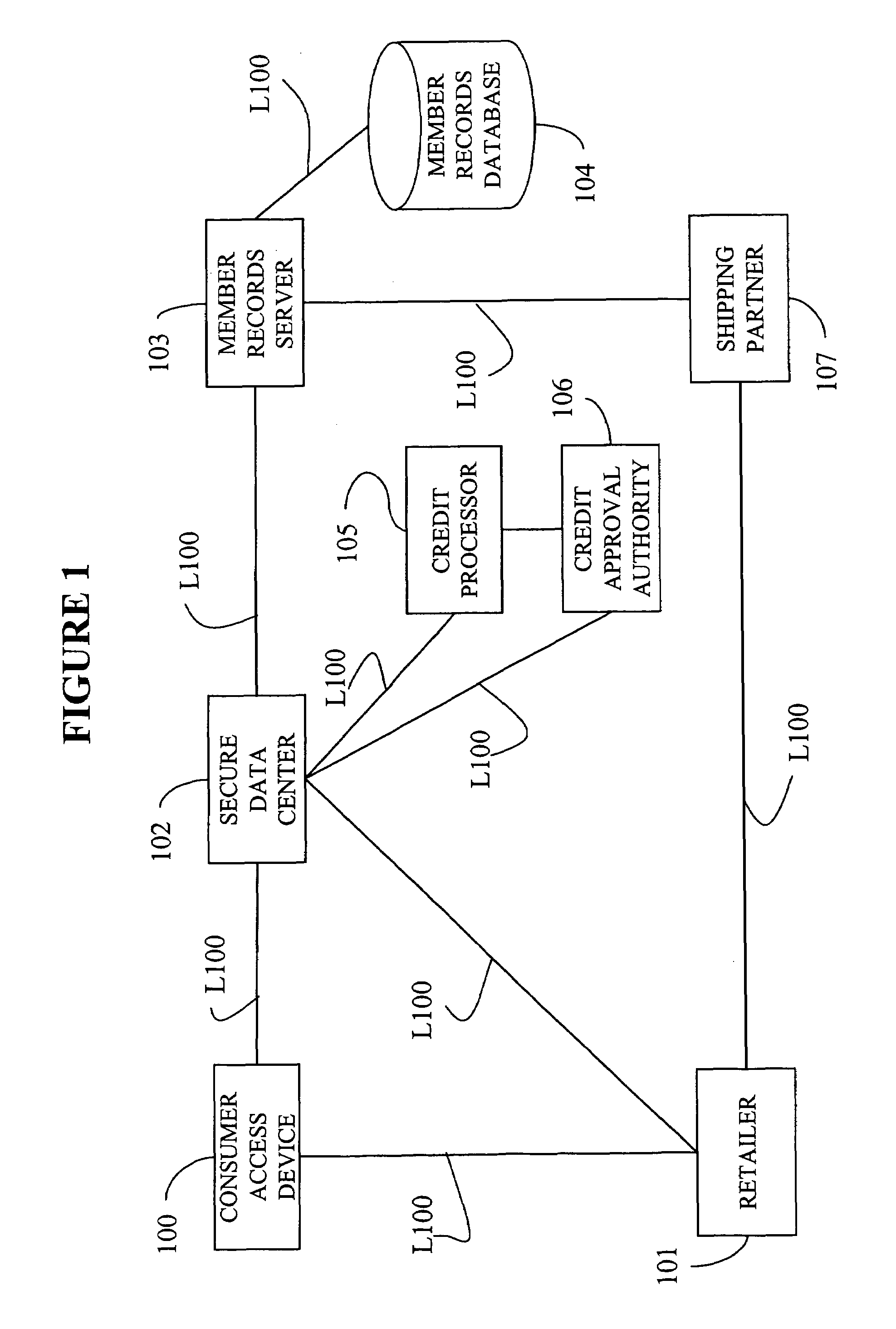
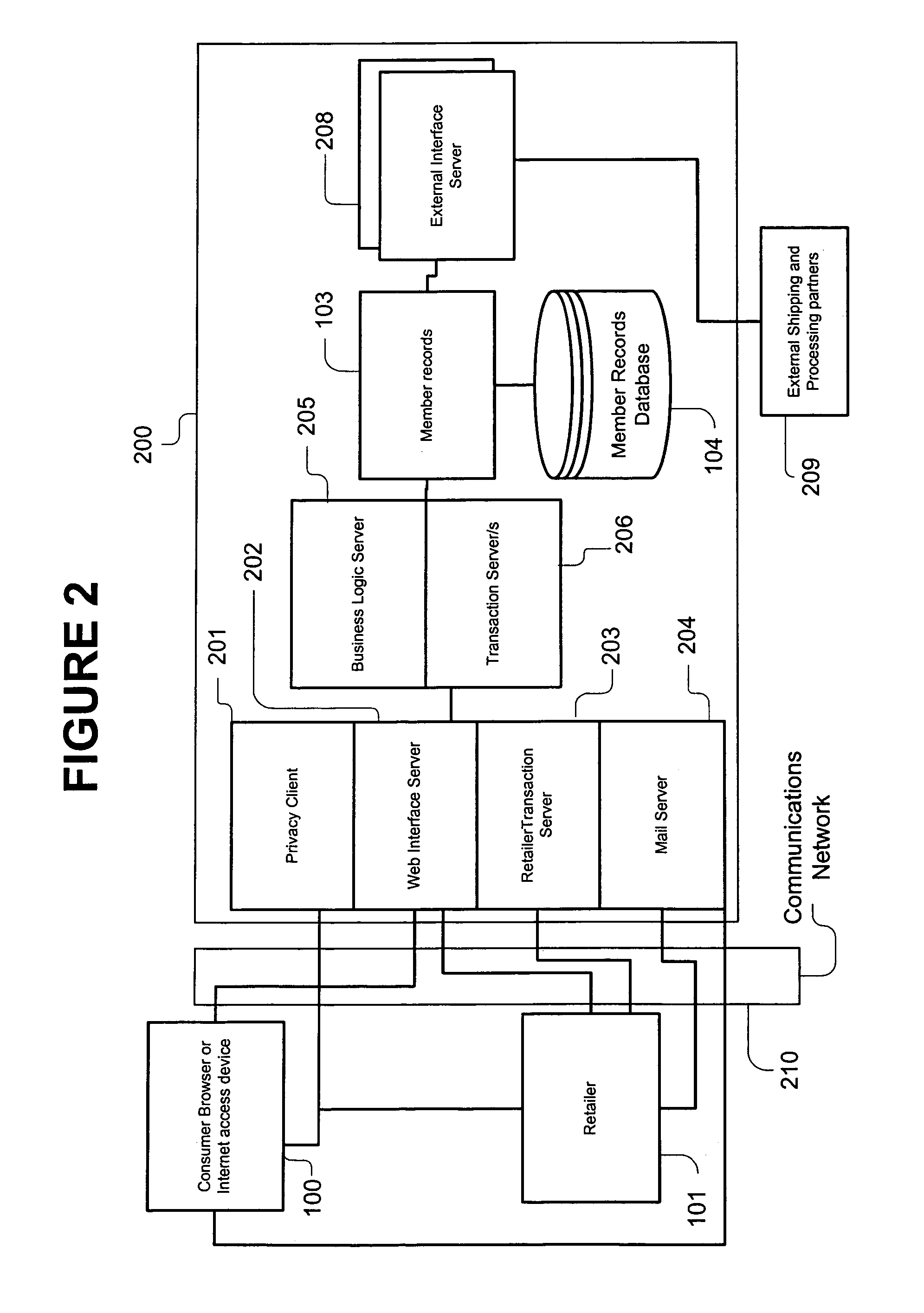
System, method, and computer program product for maintaining consumer privacy and security in electronic commerce transactions
InactiveUS7636696B1Keep it privateDisclosure is limitedComputer security arrangementsBuying/selling/leasing transactionsPaymentInternet privacy
A system, method, and computer program product for maintaining the anonymity of a consumer in a transaction with a retailer. The consumer provides payment method information and ship-to address information to a trusted third party. The consumer purchases products from a retailer by providing the trusted third party anonymous identifiers (e.g., nicknames, unique codes, or one time use codes either supplied by the consumer or by the trusted third party) corresponding to the selected payment methods and ship-to addresses. The retailer requests payment approval from the trusted third party. The trusted third party receives payment approval from a payment partner using the payment method information determined from the anonymous identifier received from the consumer. The trusted third party provides payment approval to the retailer along a transaction unique shipment identifier to place on the parcel. The trusted third party sends the same transaction unique shipment identifier and the actual shipping address determined from the anonymous identifier received from the consumer to a shipping partner who re-labels the package and delivers it to the consumer. The trusted third party acts as an e-mail conduit for messages sent to member consumers.
Owner:MEGASOFT
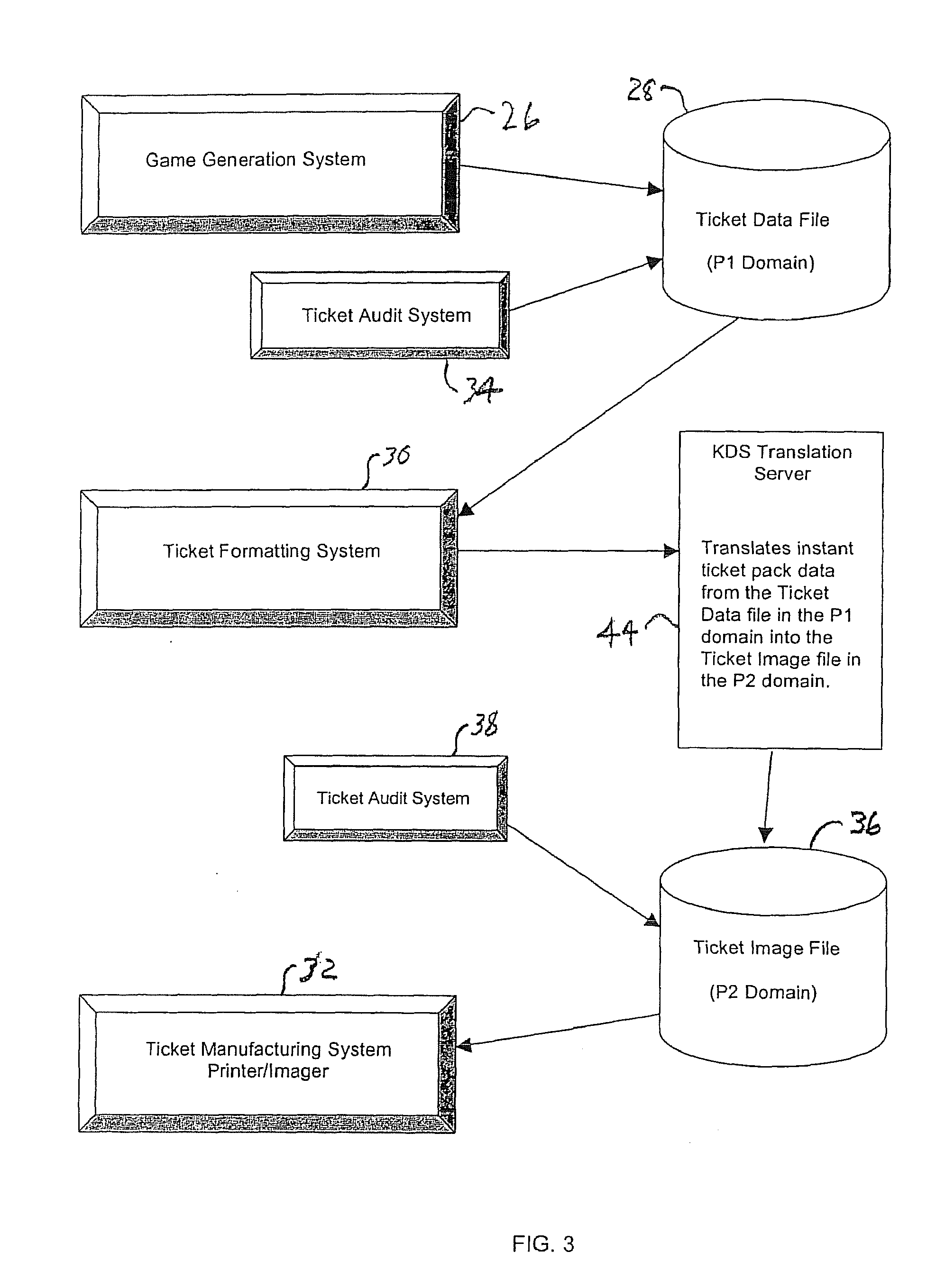
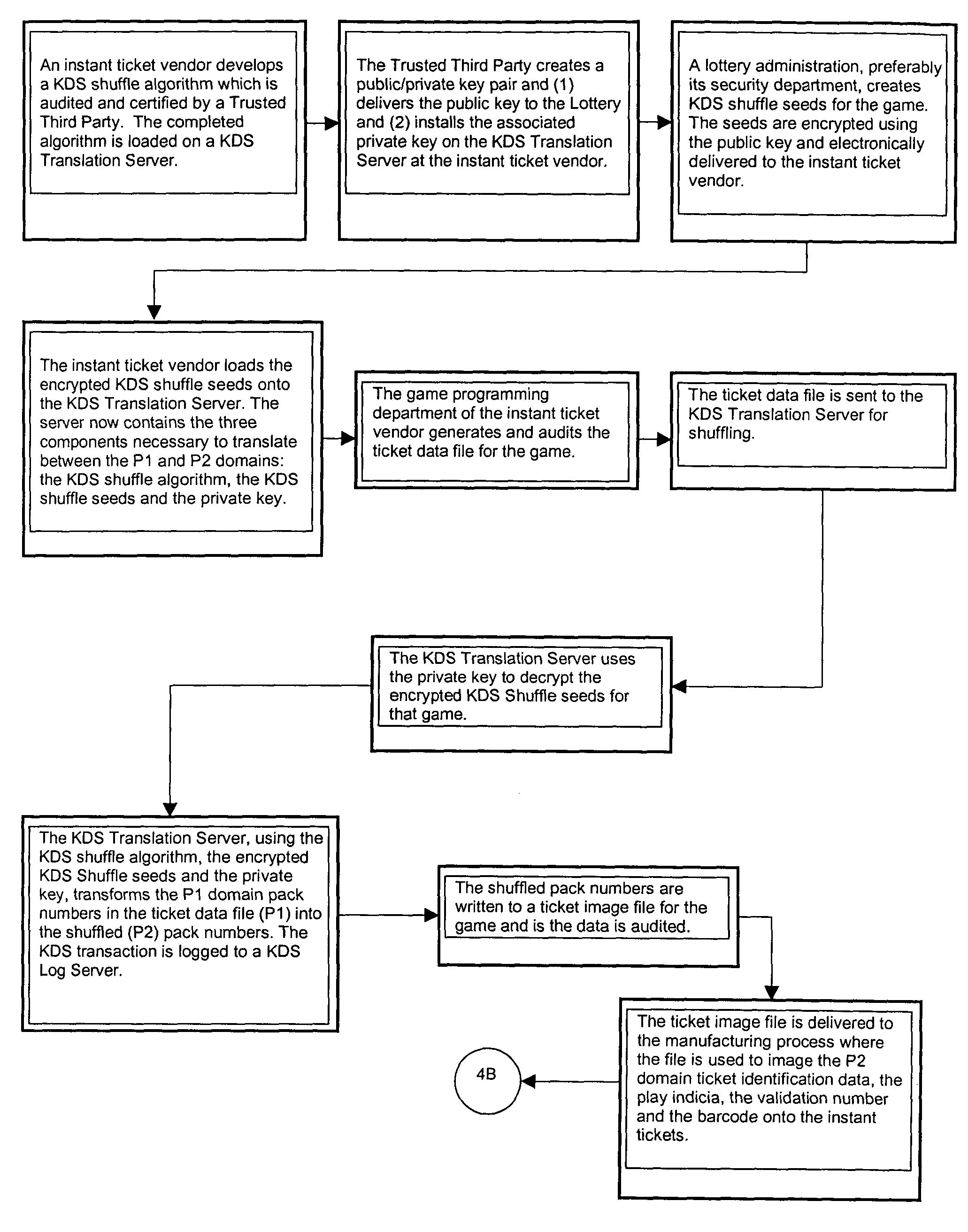
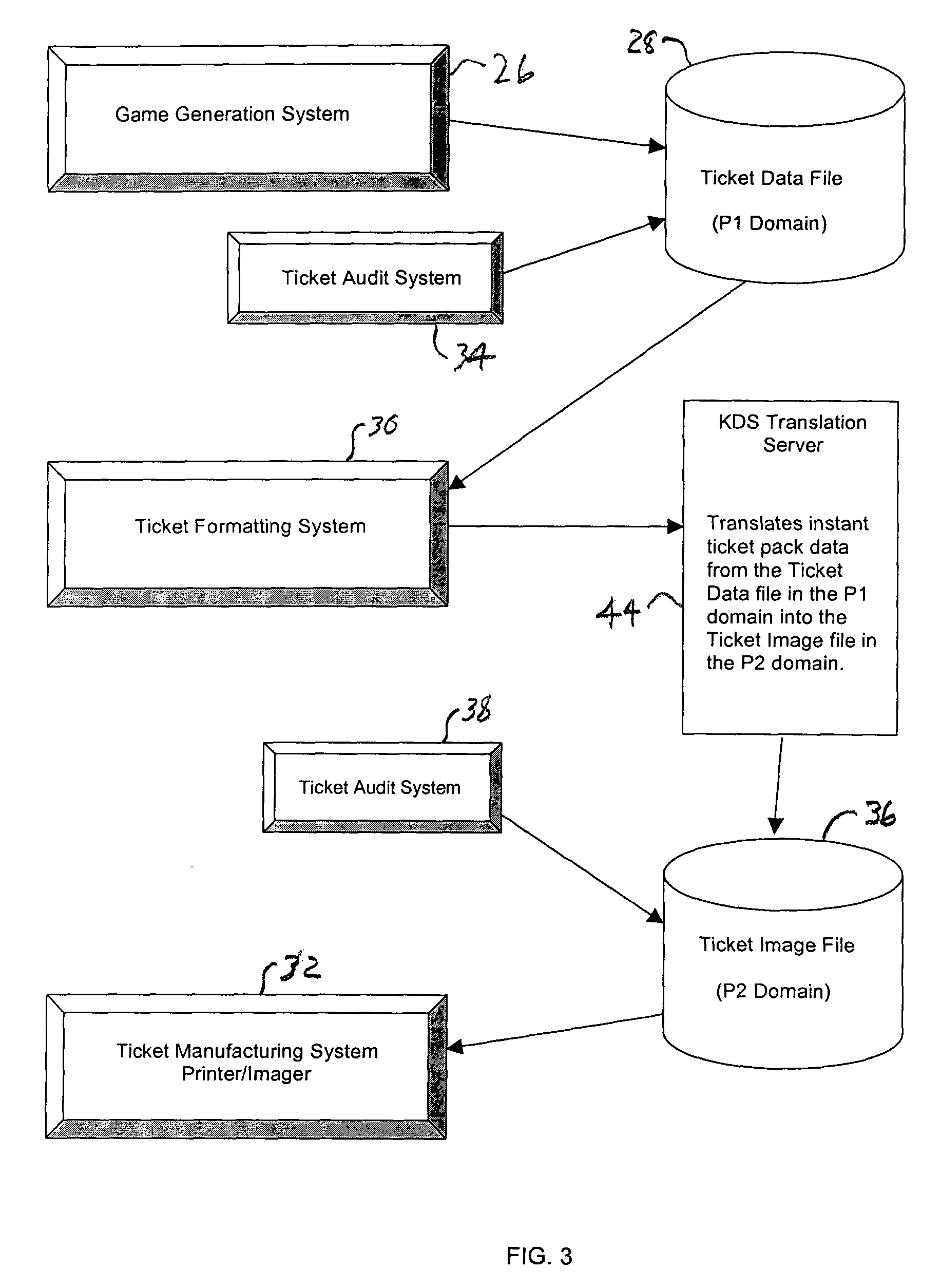
Lottery ticket security method
ActiveUS7374484B2Process safetyProvide capabilityOther printing matterLottery apparatusThird partyValidation rule
In a method for manufacturing instant lottery tickets where book numbers and ticket numbers are printed on the tickets utilizing a dual security process such that the book numbers are shuffled in each pool before the tickets are printed to break the link between the book numbers the ticket numbers or validation numbers, a reversing process can be used under certain predefined conditions to relate the original book numbers to the ticket numbers or validation numbers. In one example, where a shuffling algorithm utilizing seeds is used to shuffle the book numbers, the seeds used in the algorithm are maintained in an encrypted file. A decryption key for the encrypted seed file can be used by a lottery administration or trusted third party to reconstruct game play indicia for game adjustment purposes and manufacturing adjustments. To enhance security, the independent third party can also be used to administer the encryption and decryption keys during the ticket manufacturing process and during life of the instant ticket game.
Owner:SCI GAMES LLC
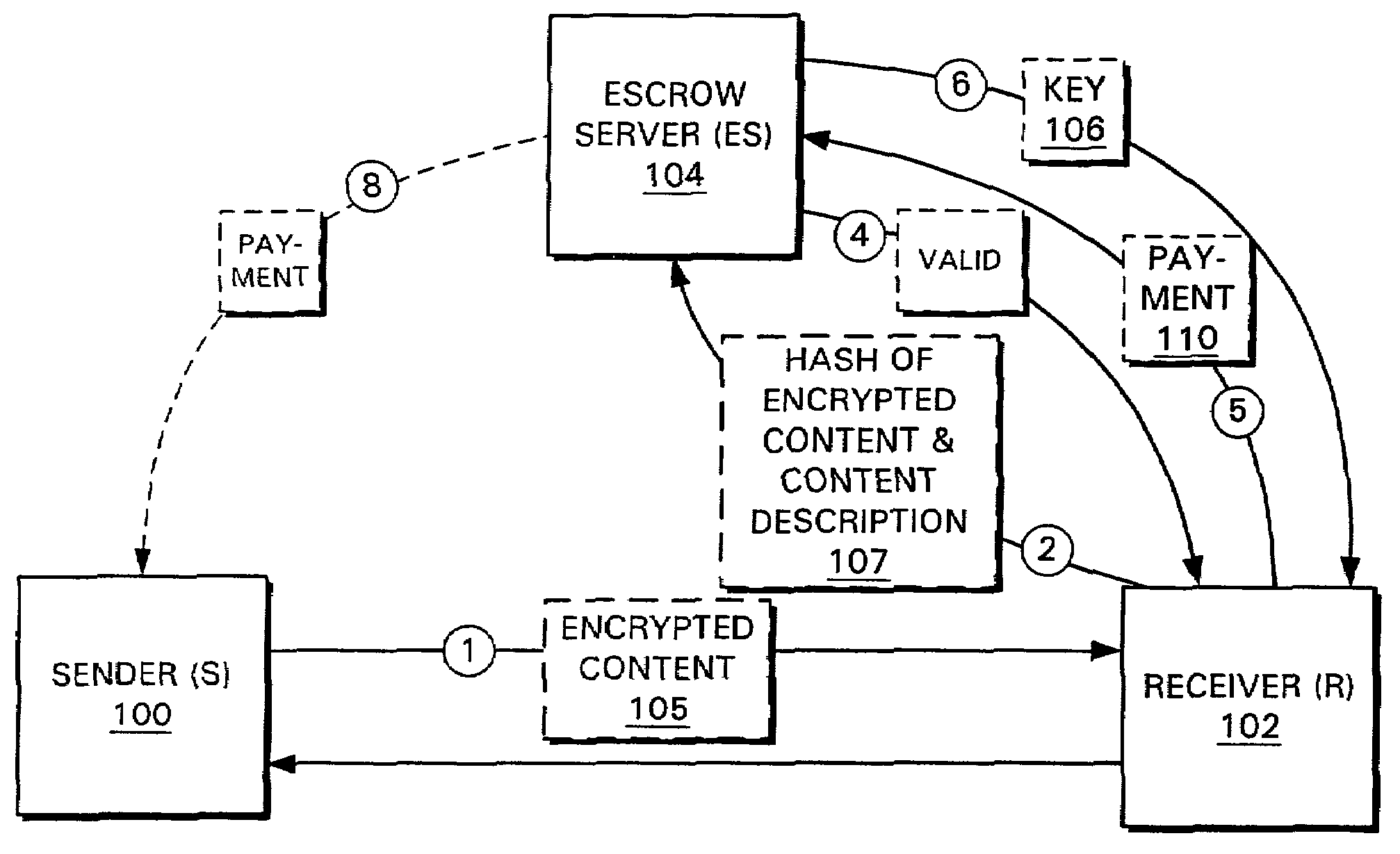
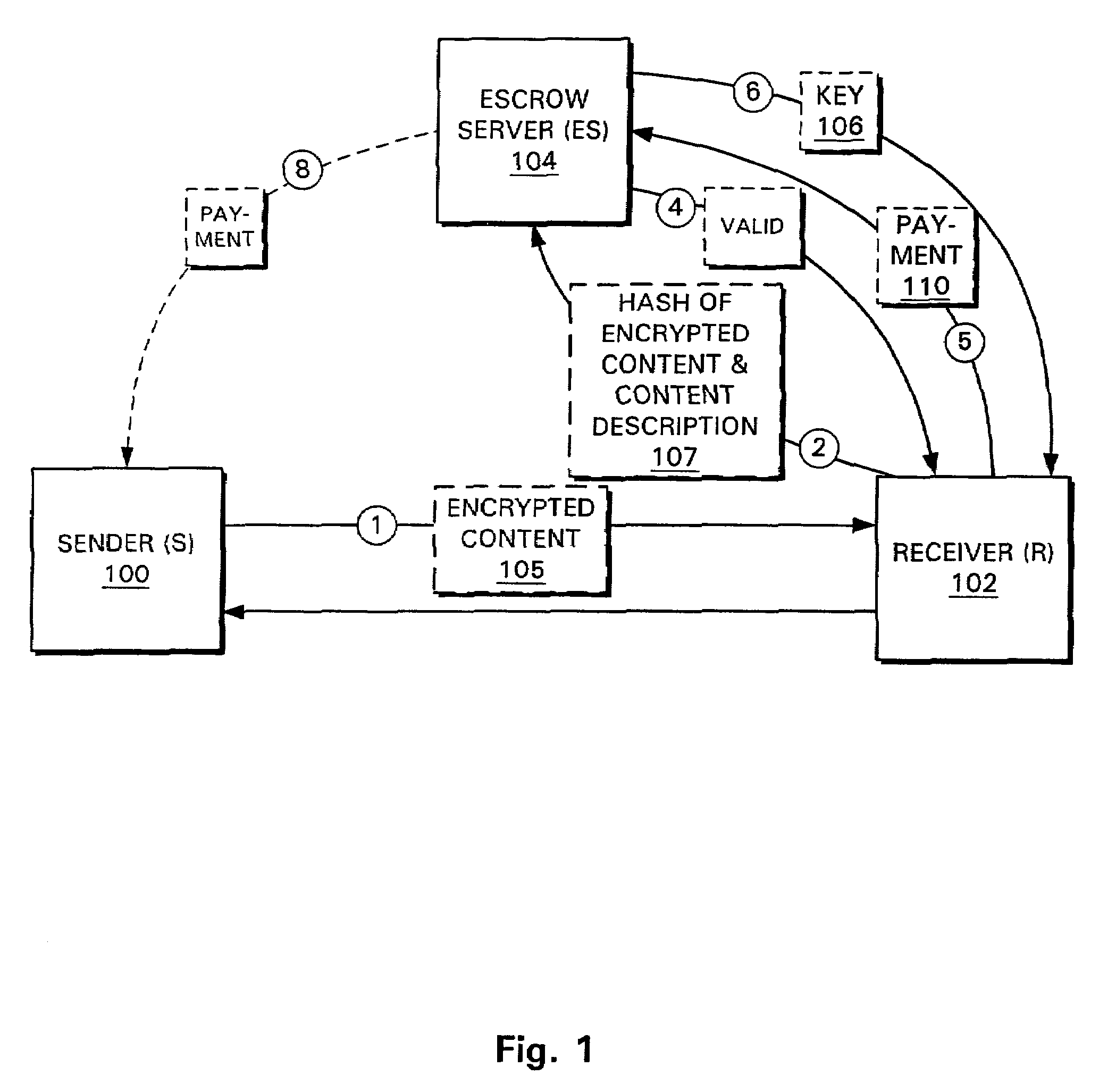
Systems and methods for conducting transactions and communications using a trusted third party
InactiveUS7136840B2Small overheadCryptography processingUser identity/authority verificationThird partyFile transmission
Systems and methods are provided for managing the transfer of electronic files. In one embodiment, a sender transfers an encrypted version of a file (such as a digitally encoded audio track, movie, document, or the like) to someone who wishes to receive it. The receiver computes a hash of the encrypted file, and sends it to a trusted third party. The trusted third party compares the hash that was computed by the receiver with another hash computed by the sender. If the two hashes match, the third party sends the file decryption key to the receiver. In some embodiments, the receiver may also send the third party payment information so that the sender, the content owner, and / or the third party can be paid for their role in the transaction. In a preferred embodiment, the payment information is only sent to, and / or used by, the third party once the third party has confirmed to the satisfaction of the receiver that the encrypted file in the receiver's possession will decrypt correctly. In some embodiments, the sender computes a hash of the encrypted version of the file and sends it directly to the third party. In other embodiments, the sender encrypts this hash using a key associated with the third party and sends the encrypted hash to the receiver, who then forwards it to the third party.
Owner:INTERTRUST TECH CORP
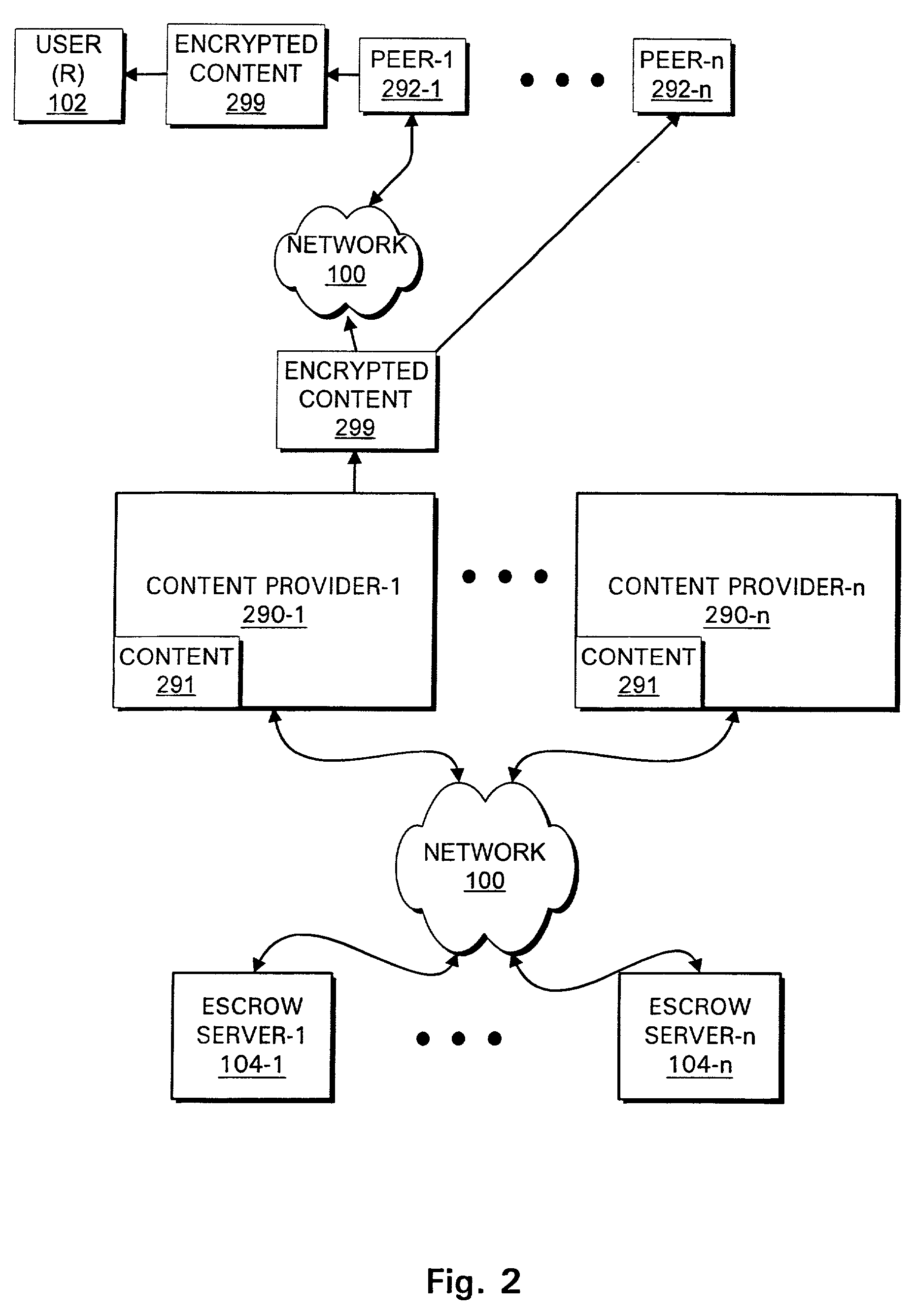
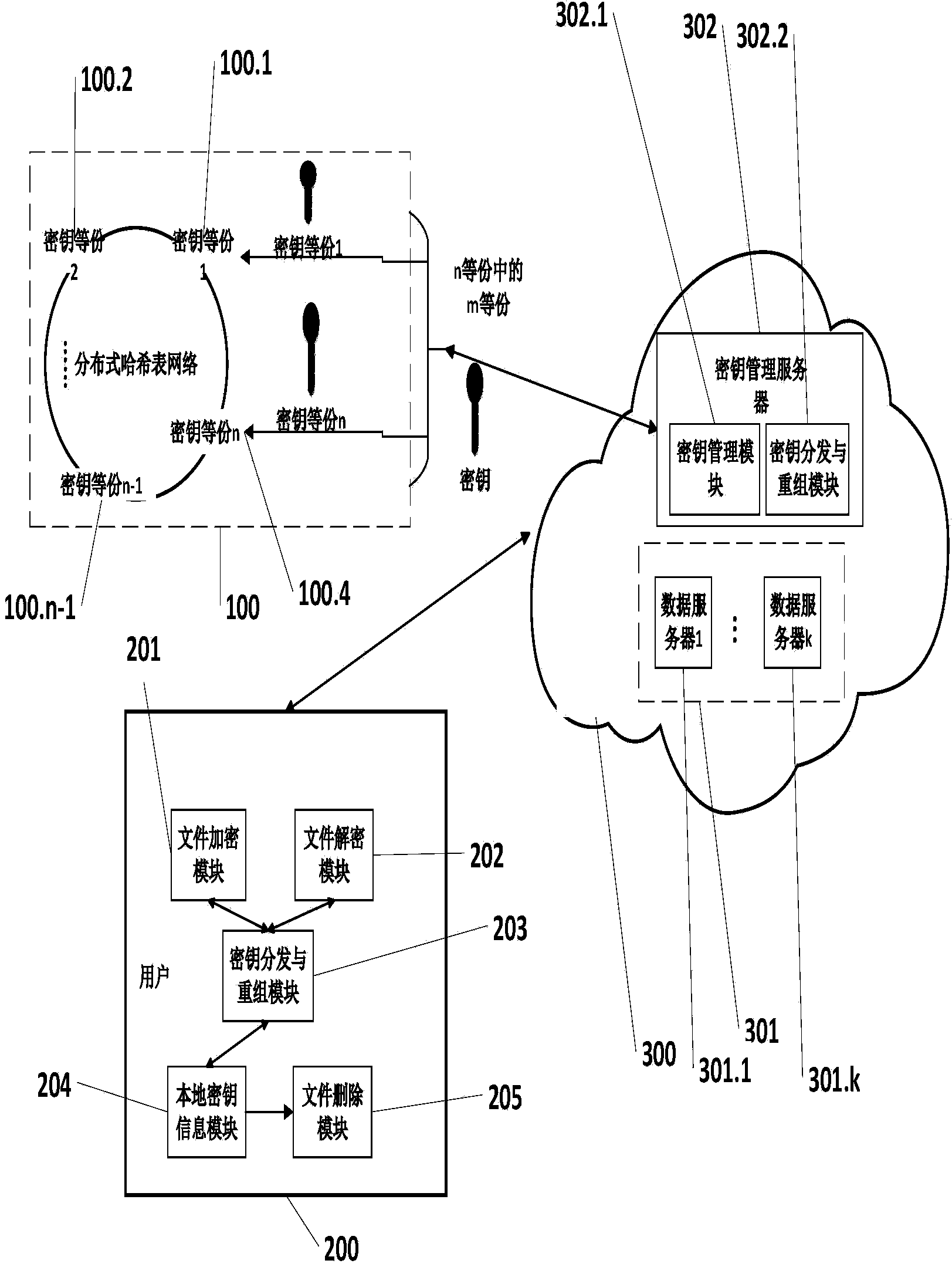
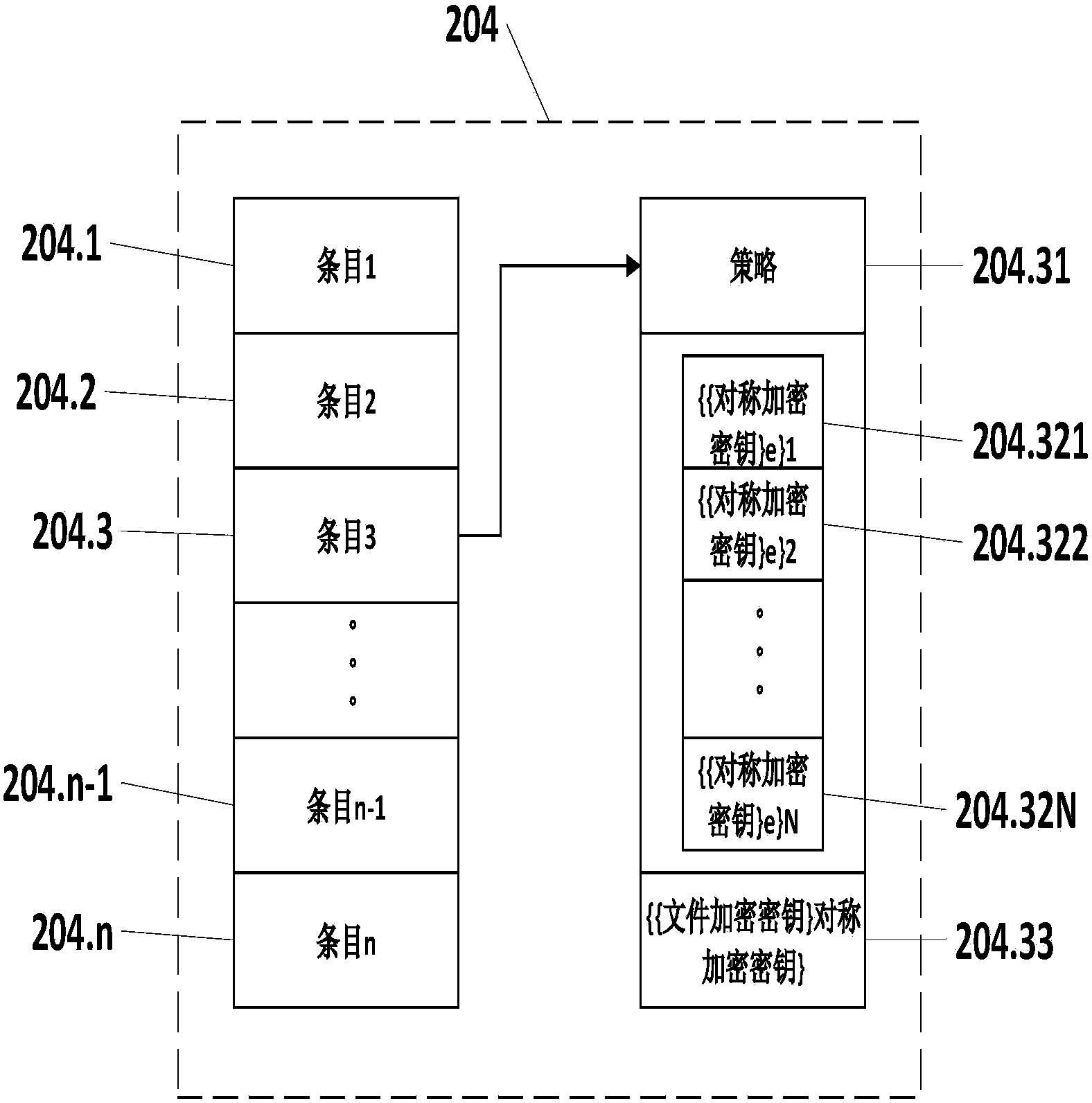
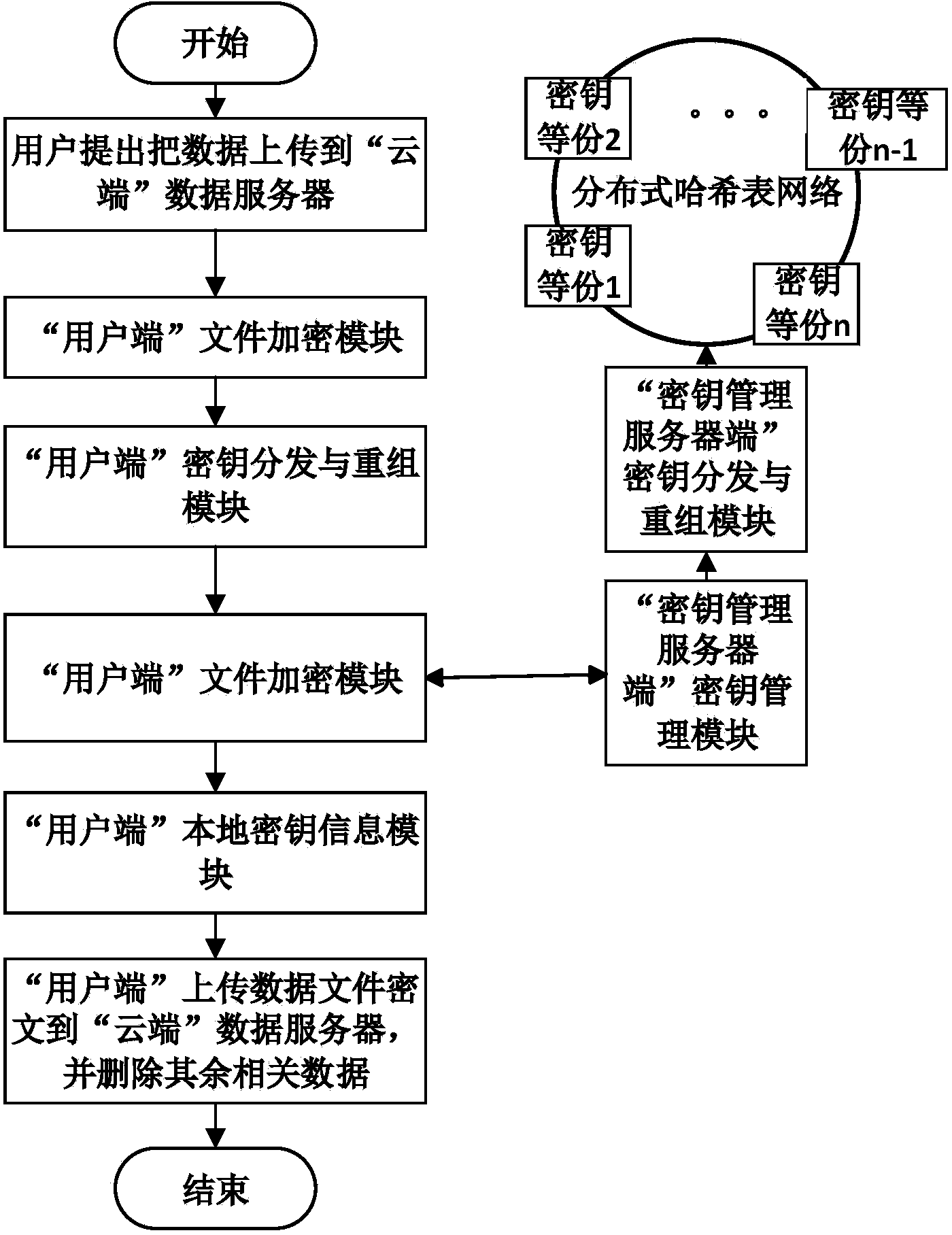
Cloud data safe deleting system and method without support of trusted third party
The invention discloses a cloud data safe deleting system and method without the support of a trusted third part. The system comprises a distributed hash table network, a user side and a cloud. The distributed hash table network is used for storing decryption key fragments. The user side is used for encrypting and decrypting files and deleting key information and comprises a file encryption module, a file decryption module, a key distribution and reorganization module, a local key information module and a file deletion module. The file encryption module and the file decryption module are used for encrypting and decrypting the files respectively; the key distribution and reorganization module is used for fragmenting and reorganizing keys; the local key information module is used for storing relevant key information; the file deletion module is used for deleting the key information. The cloud is provided with a data server and a key management server and used for storing data ciphertext information and key information and comprises the data server and the key management server, wherein the data server is used for storing file ciphertexts, and the key management server is used for managing key relevant information. The cloud data safe deleting system and method can be used for a cloud storage environment to protect data privacy of the user side.
Owner:HUAZHONG UNIV OF SCI & TECH
Secure information vault, exchange and processing system and method
A system and method for providing an information vault so that individual owners of personal data may control and manage the access and dissemination of the personal data and provides for the owner of the personal data to receive compensation for the use of the personal data, thus, in effect, the personal data becomes a valuable commodity analogous to money. A business model is provided that allows competitive, unbiased trusted third parties whose business is protecting the information analogous to how a commercial bank protects money. Centralized protected storage of personal data is provided, thereby minimizing the number of copies that may be in existence. Second party access to the centralized storage of personal data may be made on-demand, as required for commerce, with a provision for assessing fees for accesses.
Owner:GOOGLE LLC
Method for enabling privacy and trust in electronic communities
A method for enabling privacy and trust in electronic communities is disclosed. A major impediment to using recommendation systems and collective knowledge for electronic commerce is the reluctance of individuals to reveal preferences in order to find groups of people that share them. An equally important barrier to fluid electronic commerce is the lack of agreed upon trusted third parties. We propose new non-third party mechanisms to overcome these barriers. Our solutions facilitate finding shared preferences, discovering communities with shared values, removing disincentives posed by liabilities, and negotiating on behalf of a group. We adapt known techniques from the cryptographic literature to enable these new capabilities.
Owner:XEROX CORP
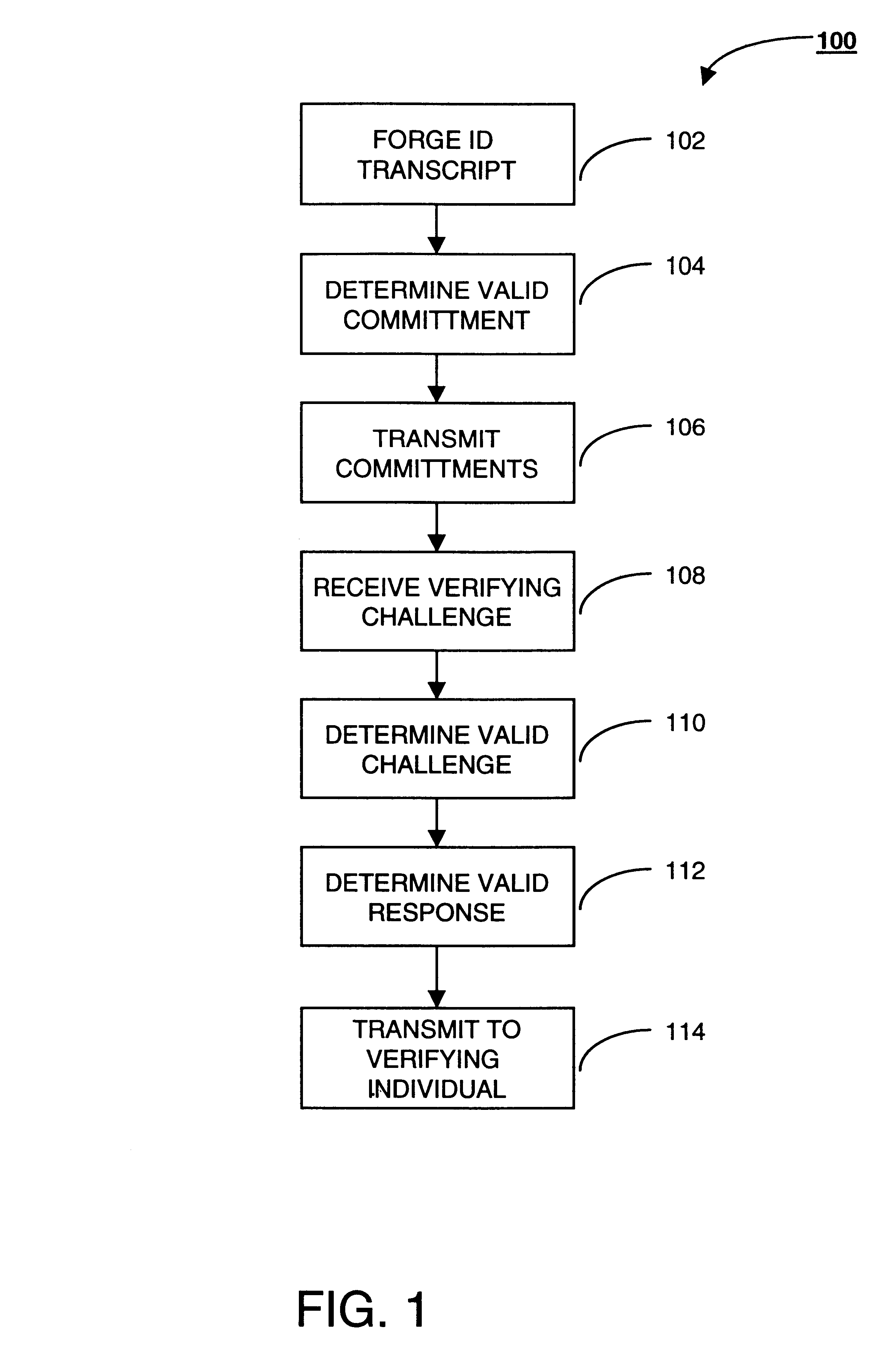
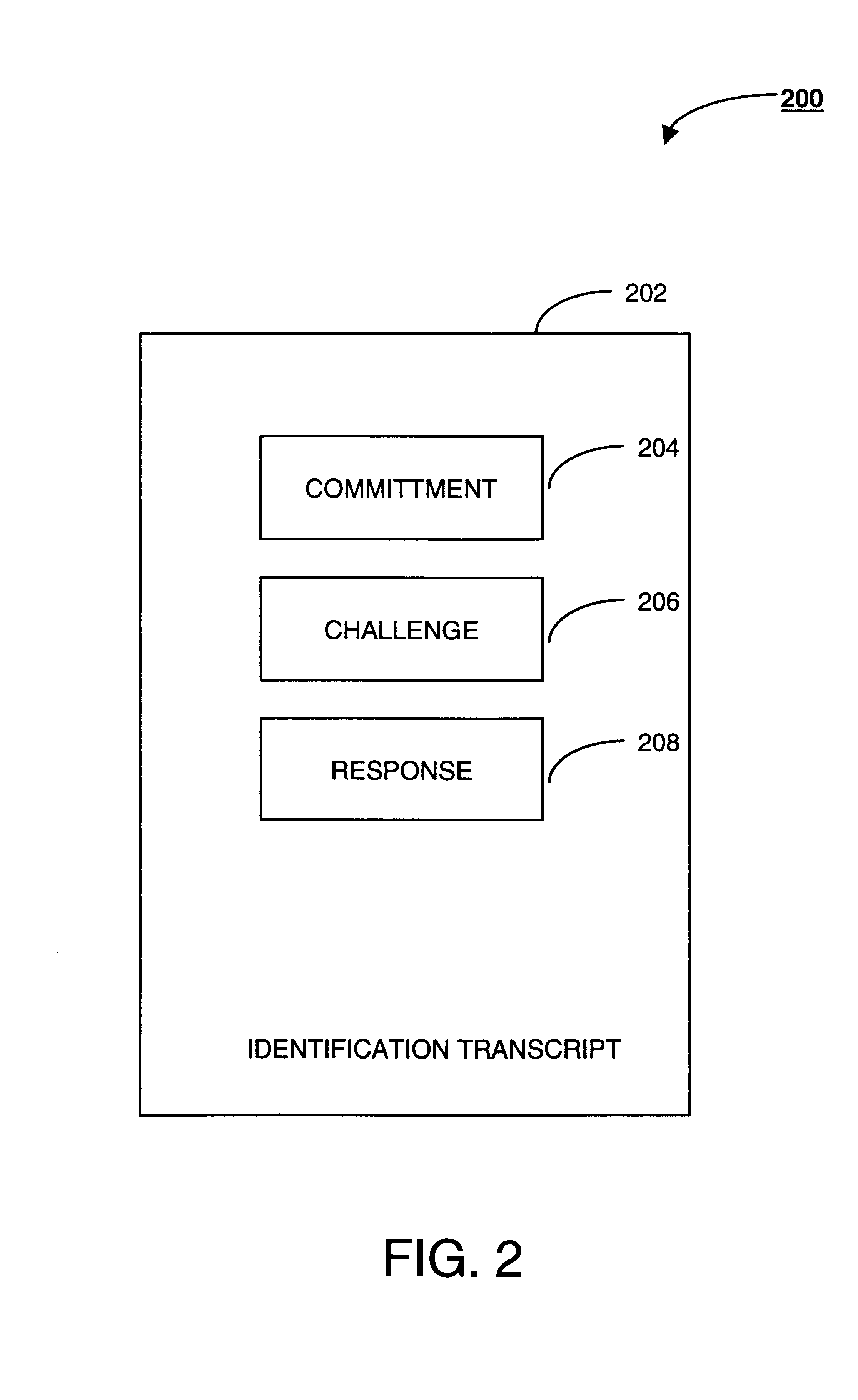
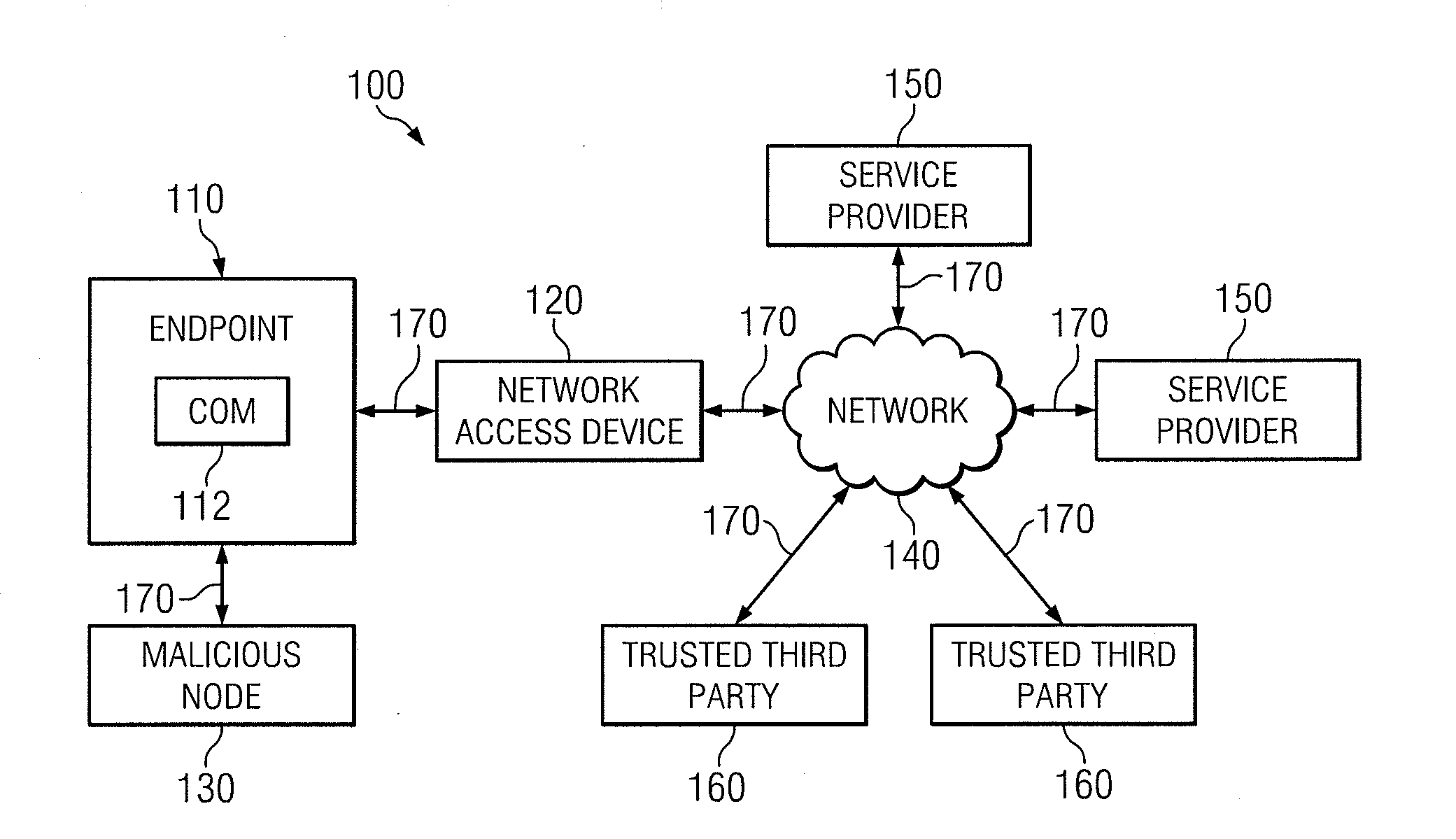
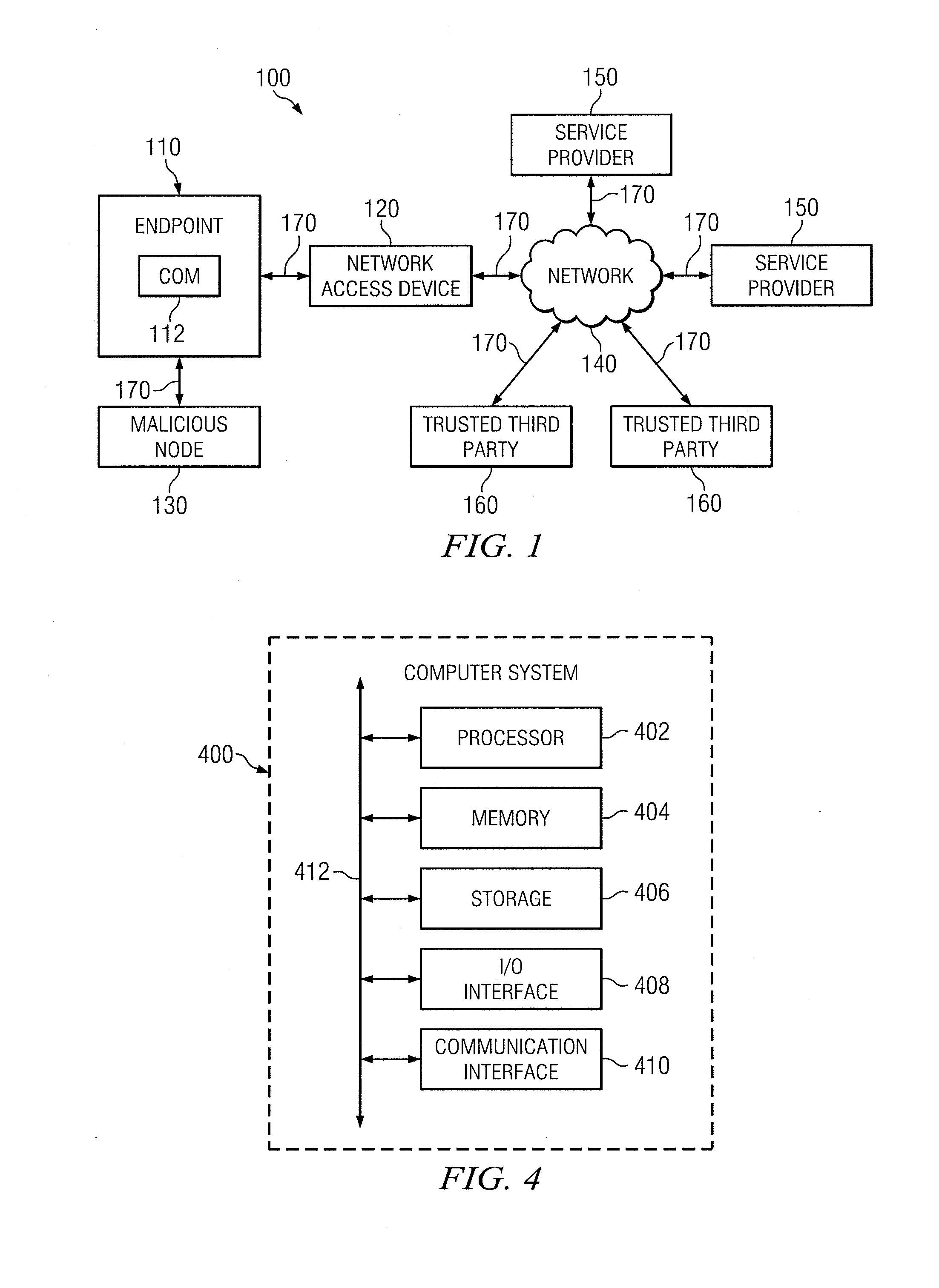
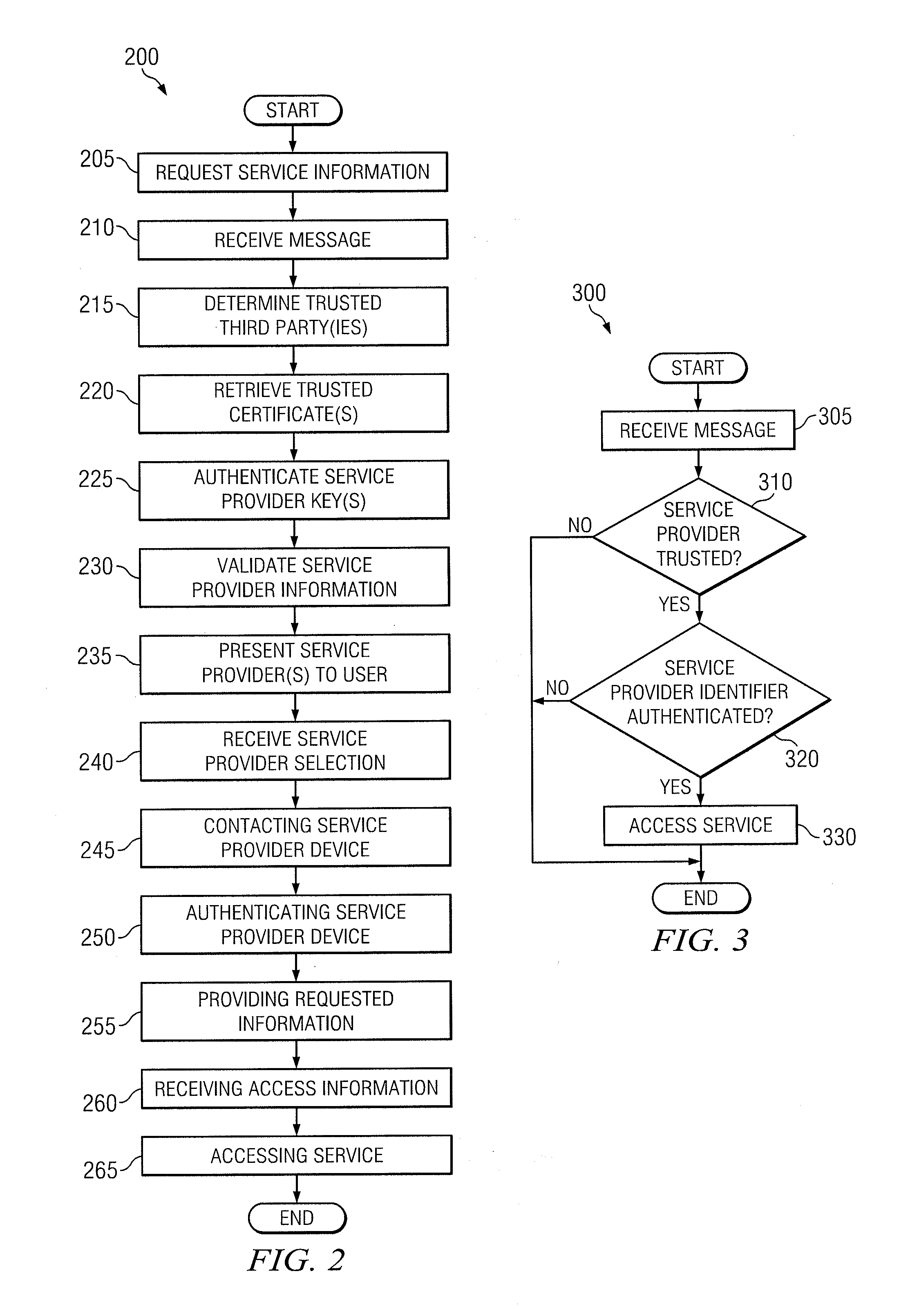
Securely Accessing An Advertised Service
In one embodiment, a method includes sending by an endpoint a request for information about available services to a network device; receiving by the endpoint a message from the network device, the message including information associated with a first service provider; determining by the endpoint whether the first address is certified by a trusted third party as being associated with the first service provider; if the first address is certified by the trusted third party, communicating by the endpoint with the first service provider using the information; and, in response to communicating with the first service provider using the information, receiving by the endpoint access to a service from the first service provider through the network device.
Owner:CISCO TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com