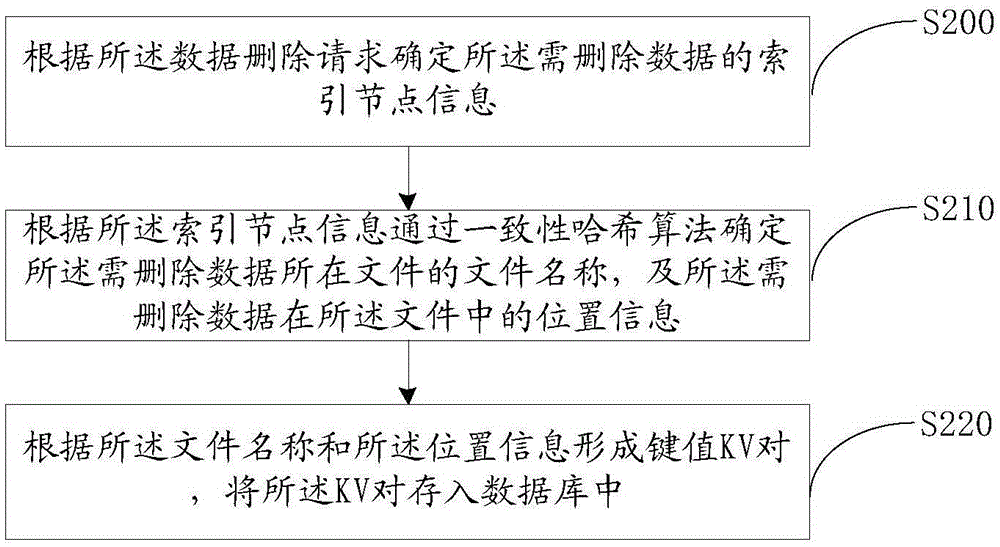
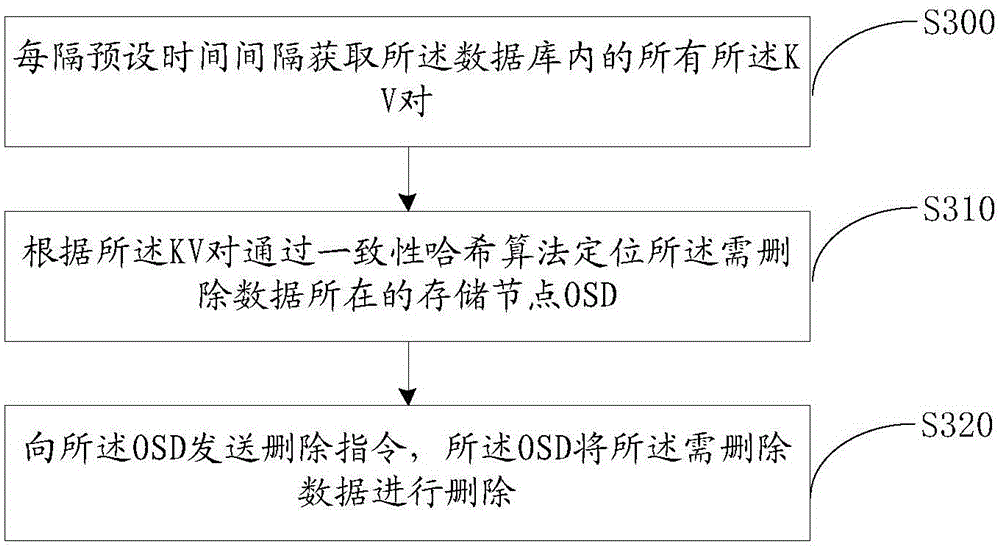
Patents
Literature
337 results about "File deletion" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
File deletion is a way of removing a file from a computer's file system.
Changed file identification, software conflict resolution and unwanted file removal
InactiveUS20050155031A1Memory loss protectionUnauthorized memory use protectionData miningProcess information
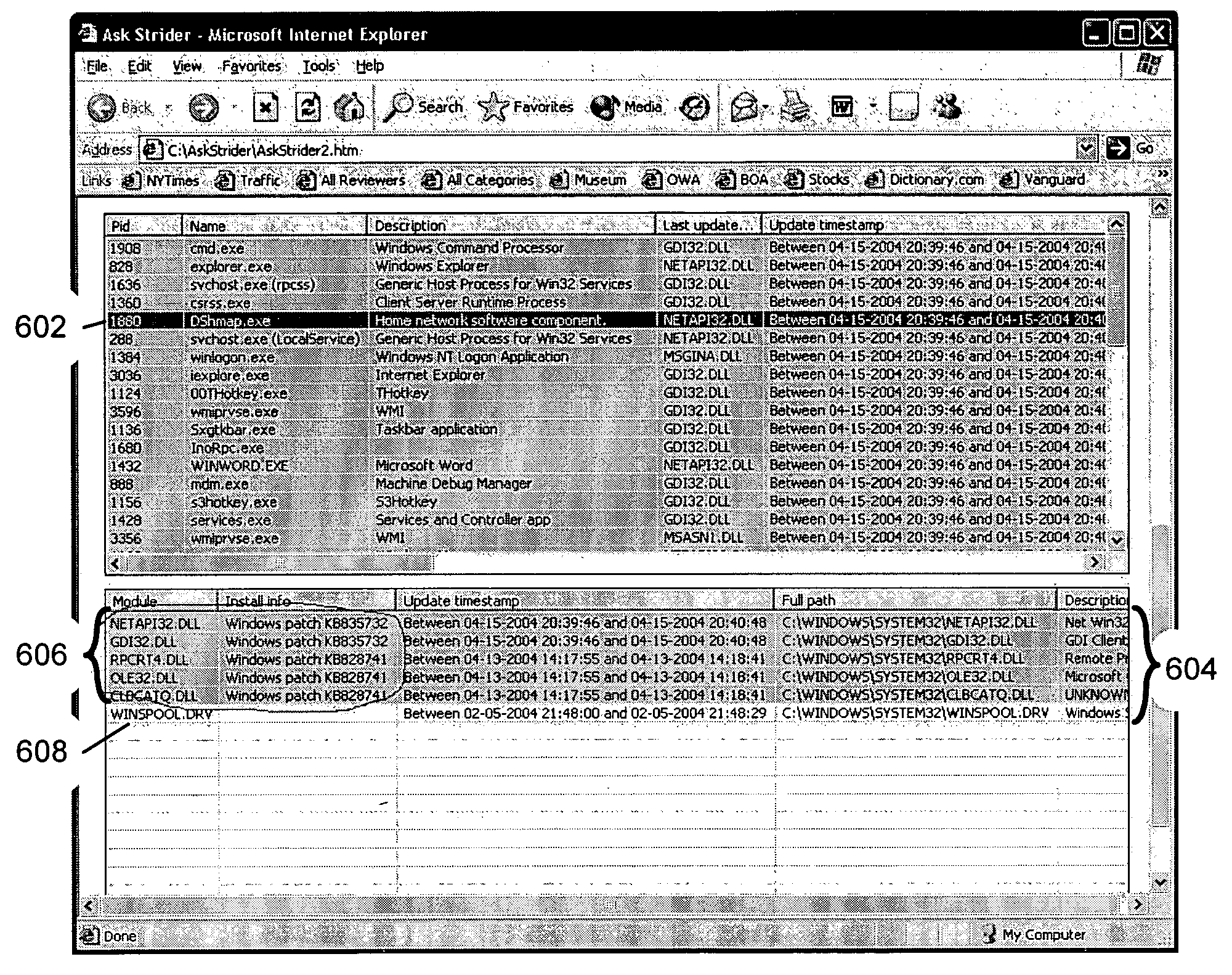
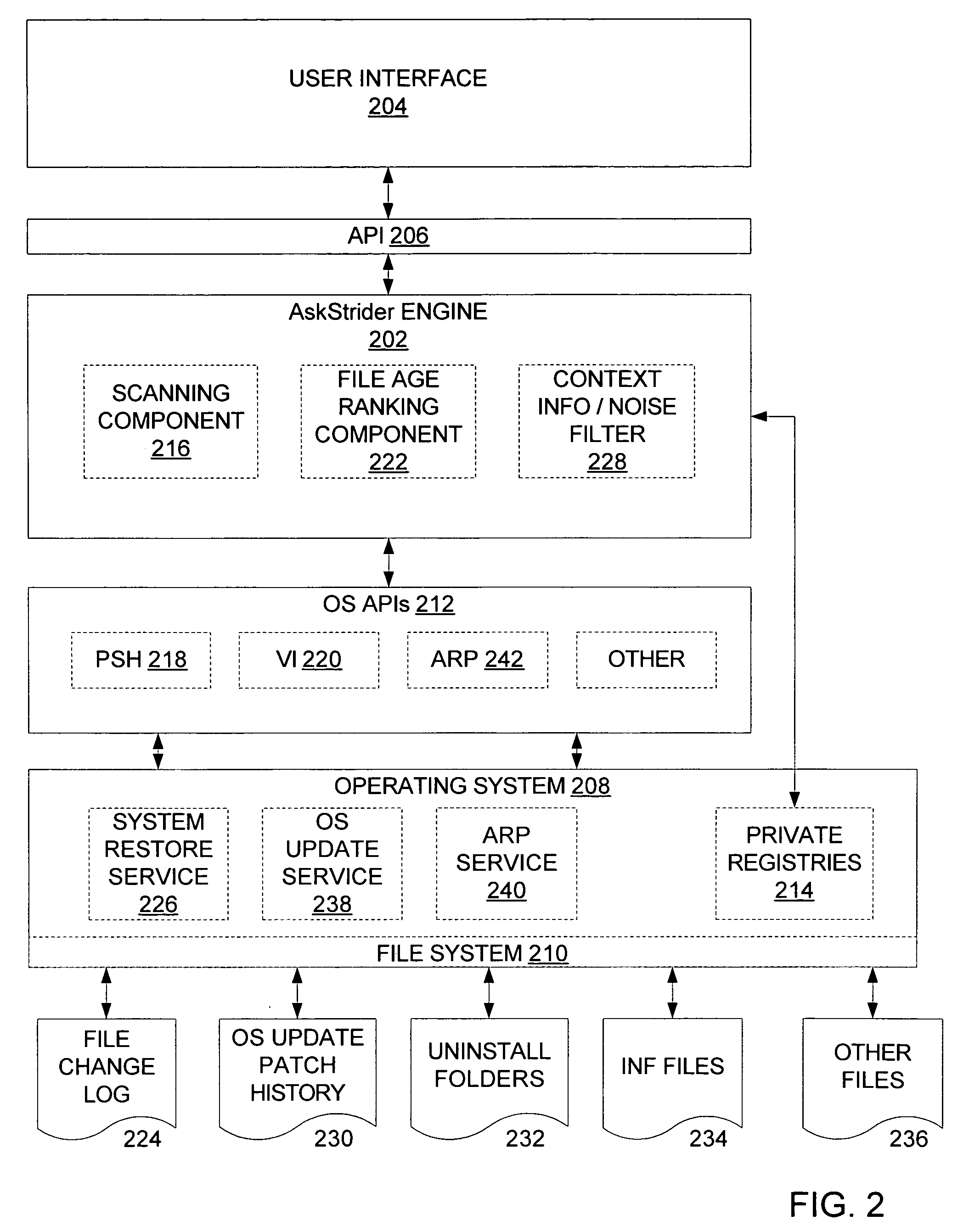
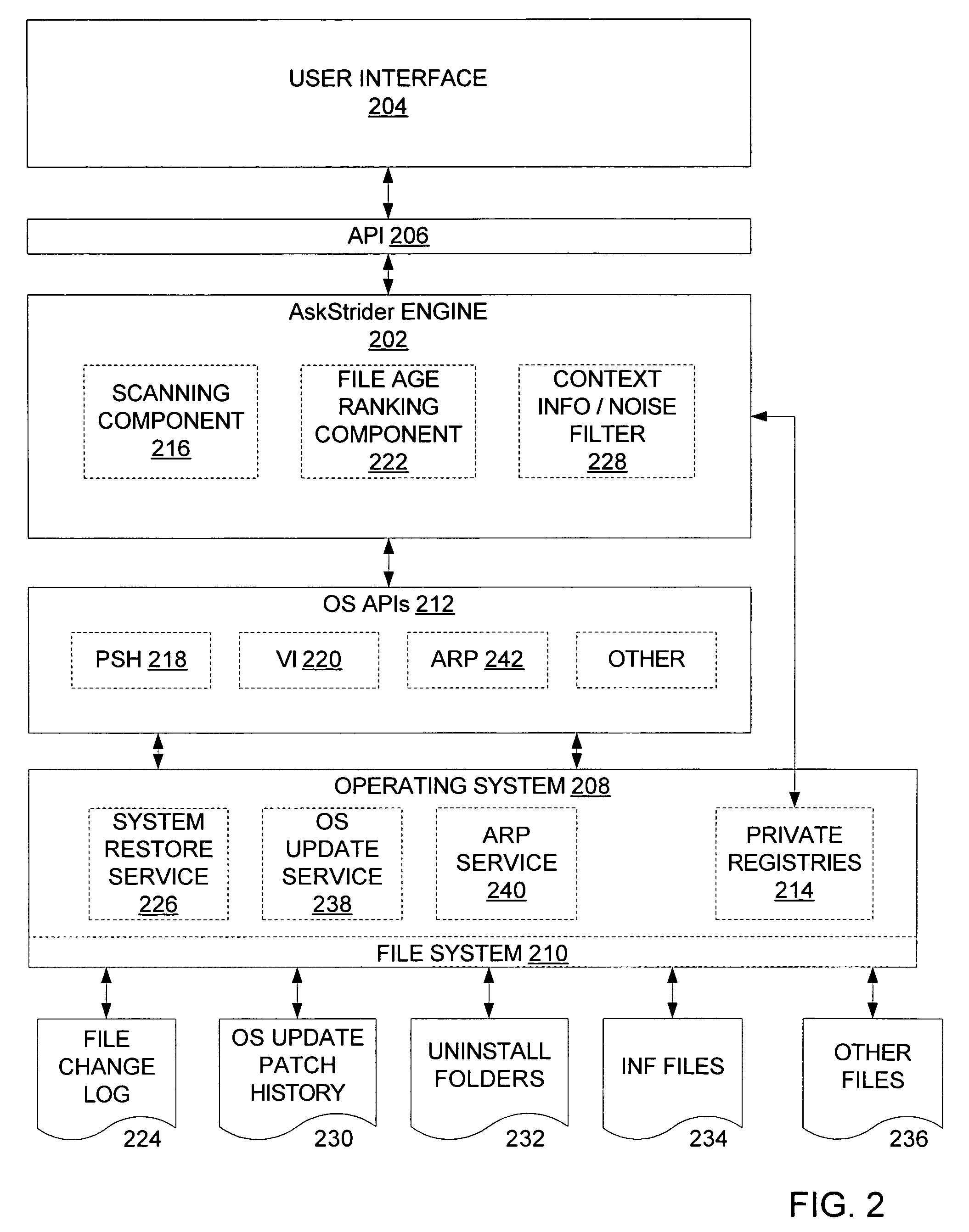
As computer programs grow more complex, extensible, and connected, it becomes increasingly difficult for users to understand what has changed on their machines and what impact those changes have. An embodiment of the invention is described via a software tool, called AskStrider, that answers those questions by correlating volatile process information with persistent-state context information and change history. AskStrider scans a system for active components, matches them against a change log to identify recently updated and hence more interesting state, and searches for context information to help users understand the changes. Several real-world cases are provided to demonstrate the effectiveness of using AskStrider to quickly identify the presence of unwanted software, to determine if a software patch is potentially breaking an application, and to detect lingering components left over from an unclean uninstallation.
Owner:MICROSOFT TECH LICENSING LLC
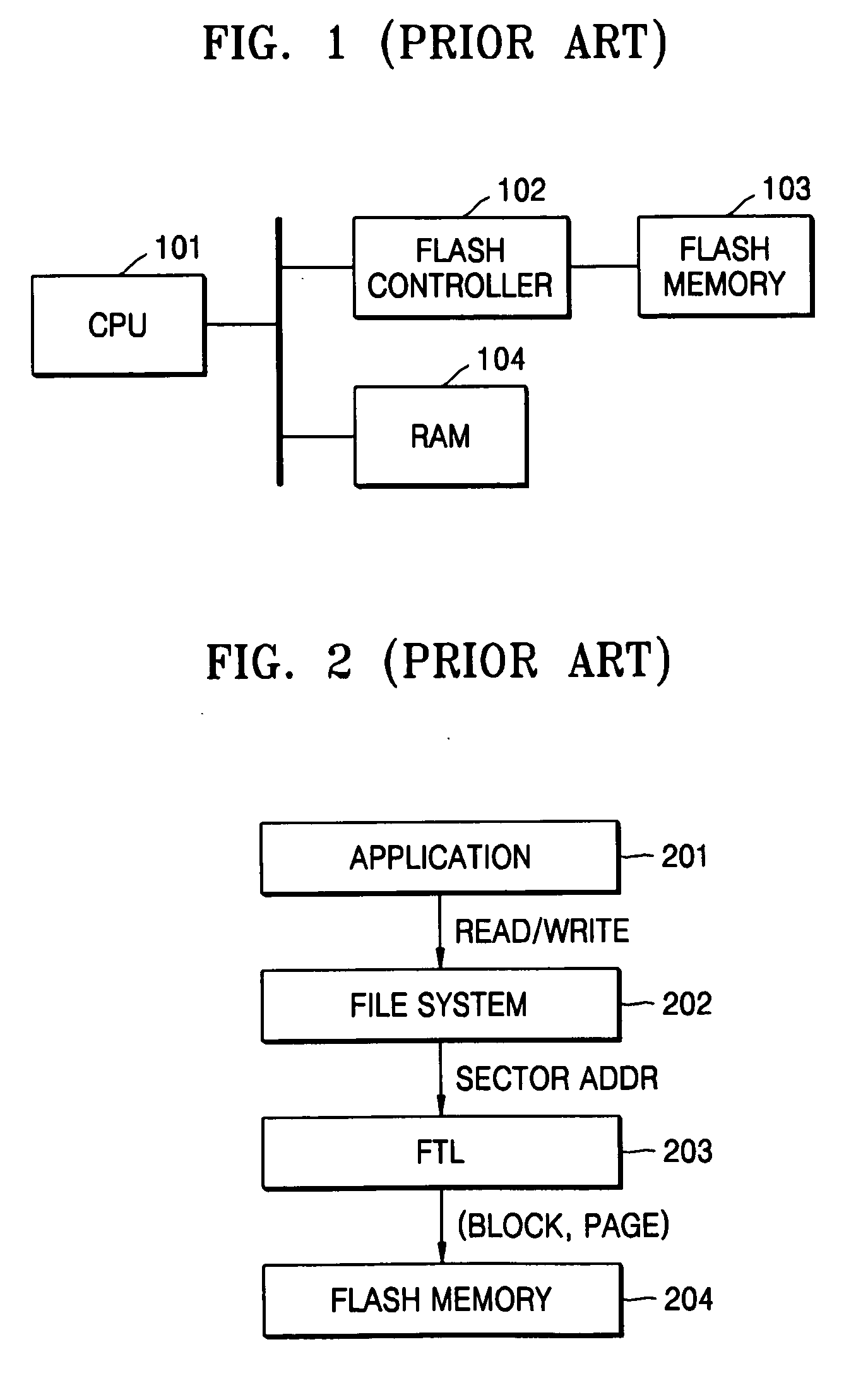
Flash memory management method and flash memory system
InactiveUS20070043900A1Reduce loadMemory systemsInput/output processes for data processingFile systemInterface layer
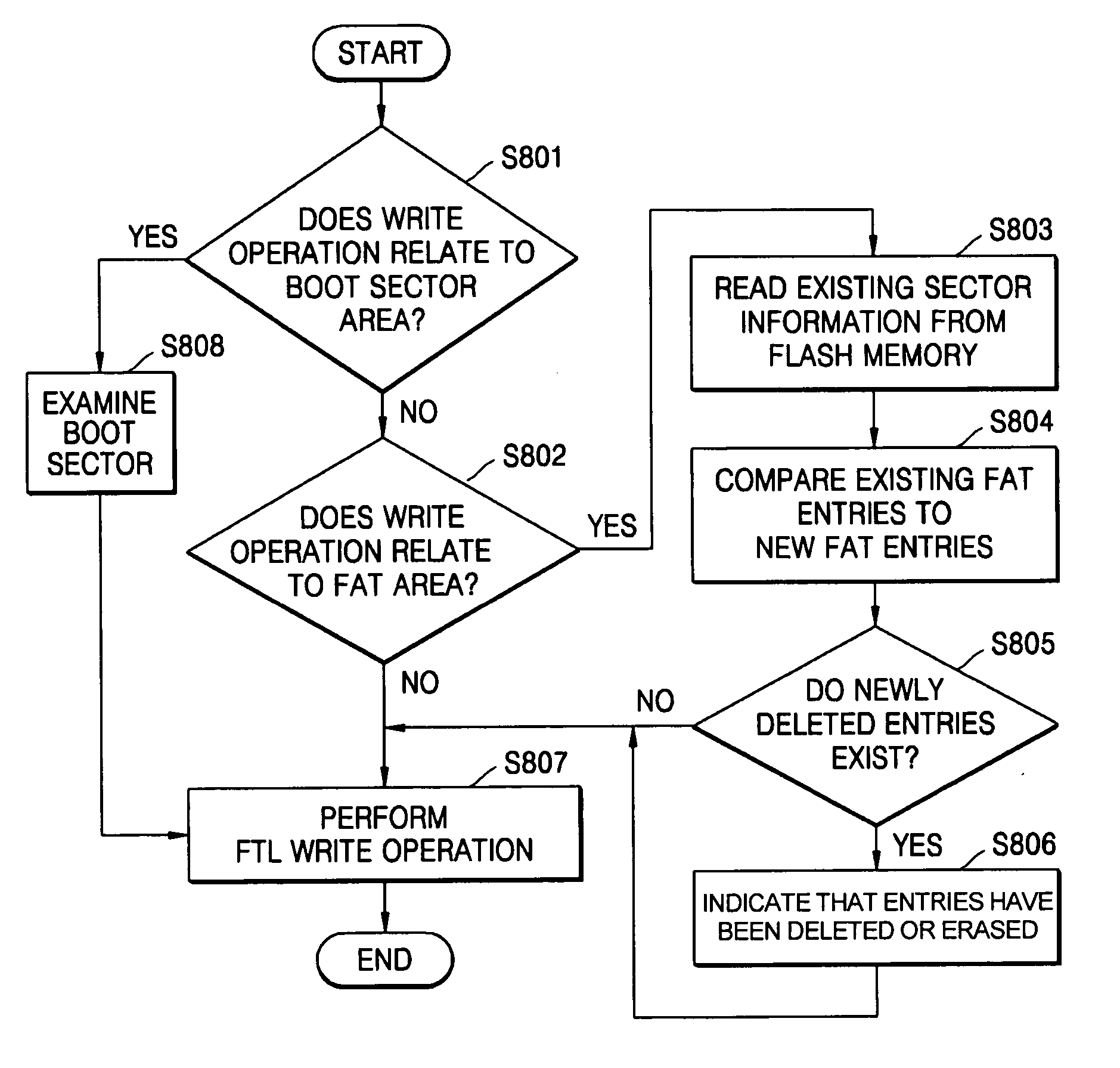
A flash memory management method for effectively deleting a file and a flash memory system, the flash memory system including: a flash memory; and an interface determining whether a sensed sector write operation instructs a file system to delete a file by examining metadata of the file system and deleting data in the flash memory corresponding to the file if the sensed sector write operation instructs deletion of the file. Accordingly, an interface layer between the flash memory and the file system can prevent unnecessary data from being copied in a future garbage collection process by recognizing a delete operation of the file system and quickly performing a future rewrite operation since actual data blocks are erased in file deletion.
Owner:SAMSUNG ELECTRONICS CO LTD
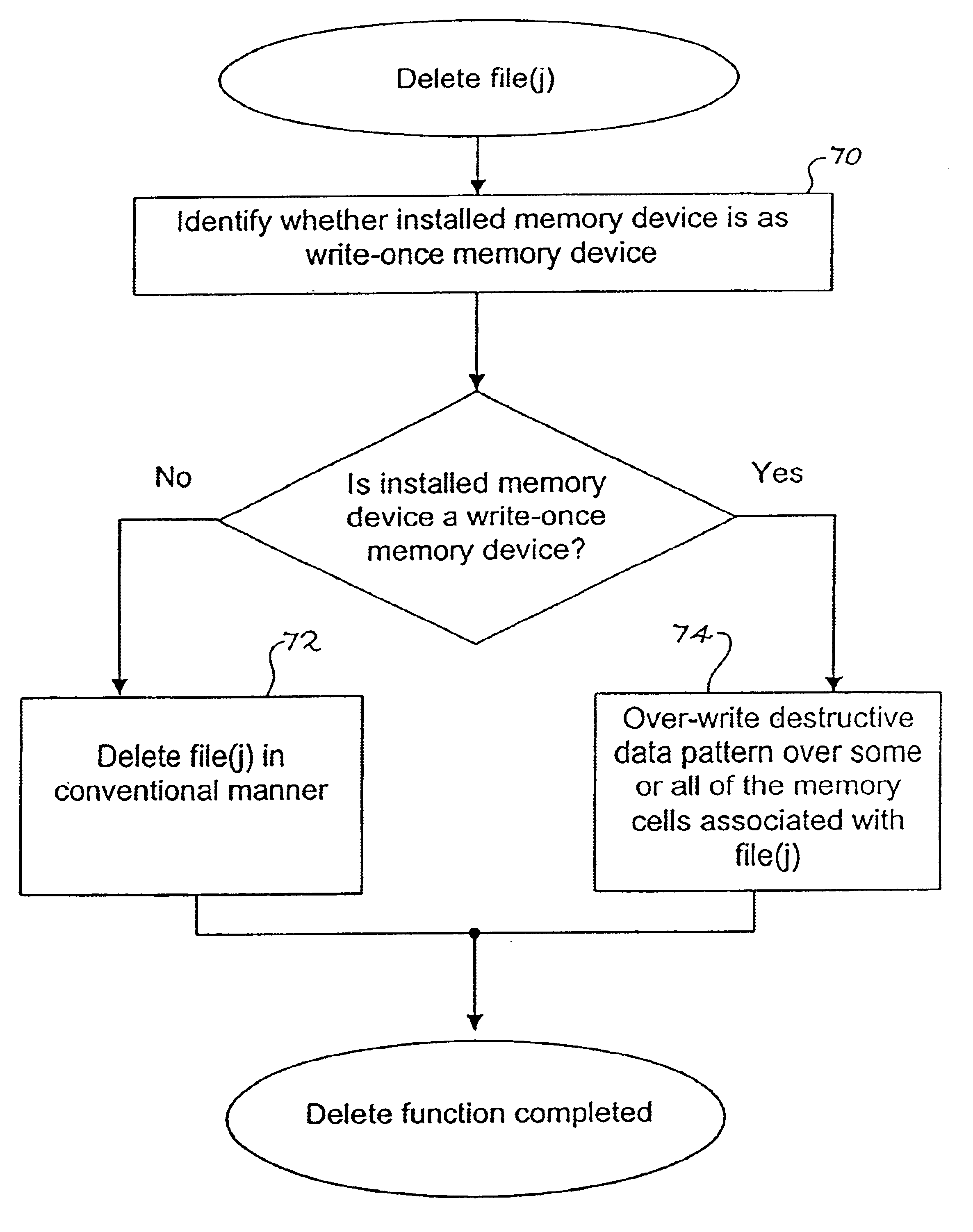
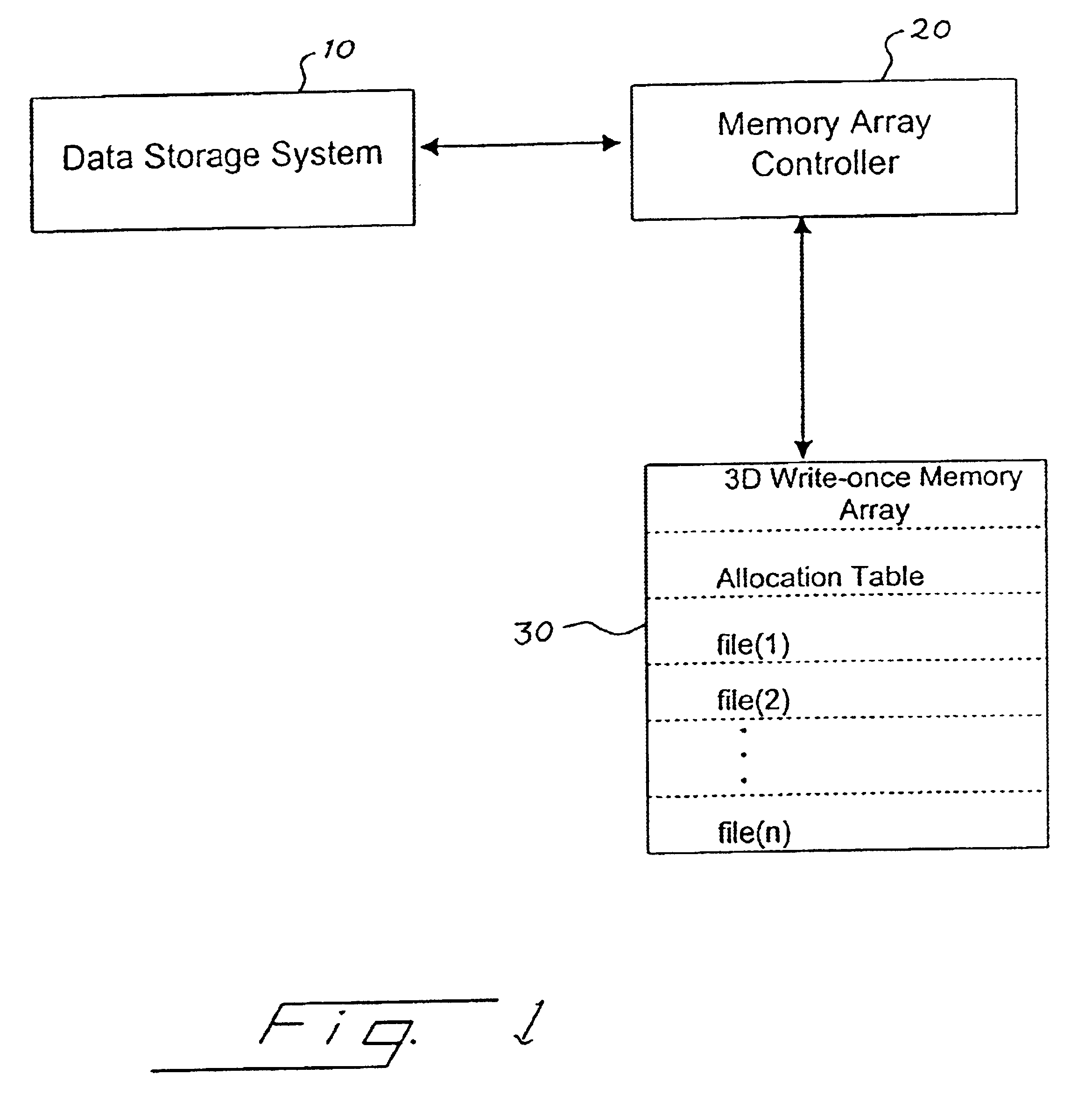
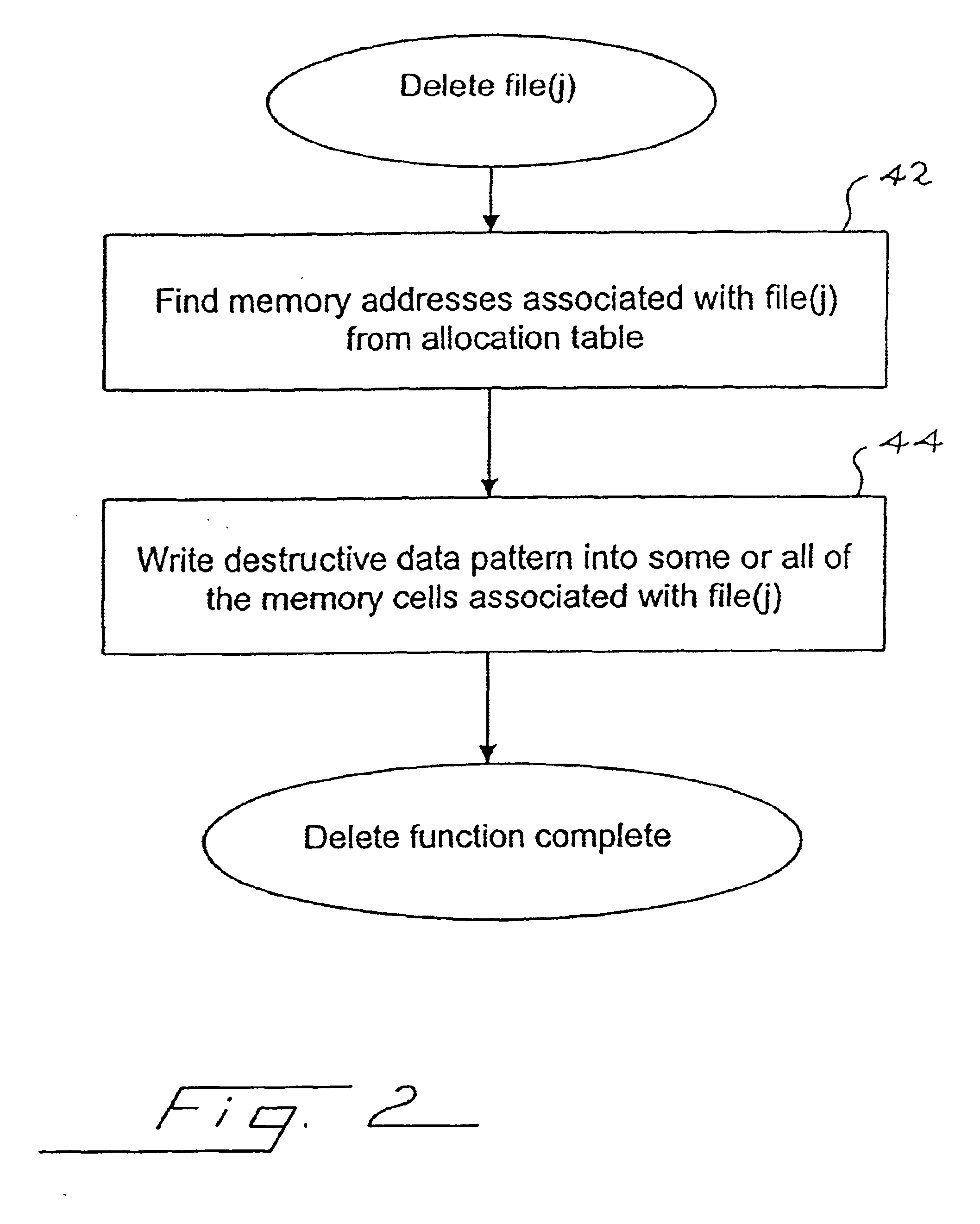
Method for deleting stored digital data from write-once memory device
InactiveUS6658438B1Data processing applicationsDigital data information retrievalDigital dataDigital storage
A digital storage system is coupled to a write-once memory array. File delete commands are implemented by over-writing a destructive digital pattern to at least a portion of the memory cells associated with the file to be deleted. One disclosed system alters the manner in which a file delete command is implemented, depending upon whether the file is stored in a write-once memory or in a re-writable memory.
Owner:SANDISK TECH LLC
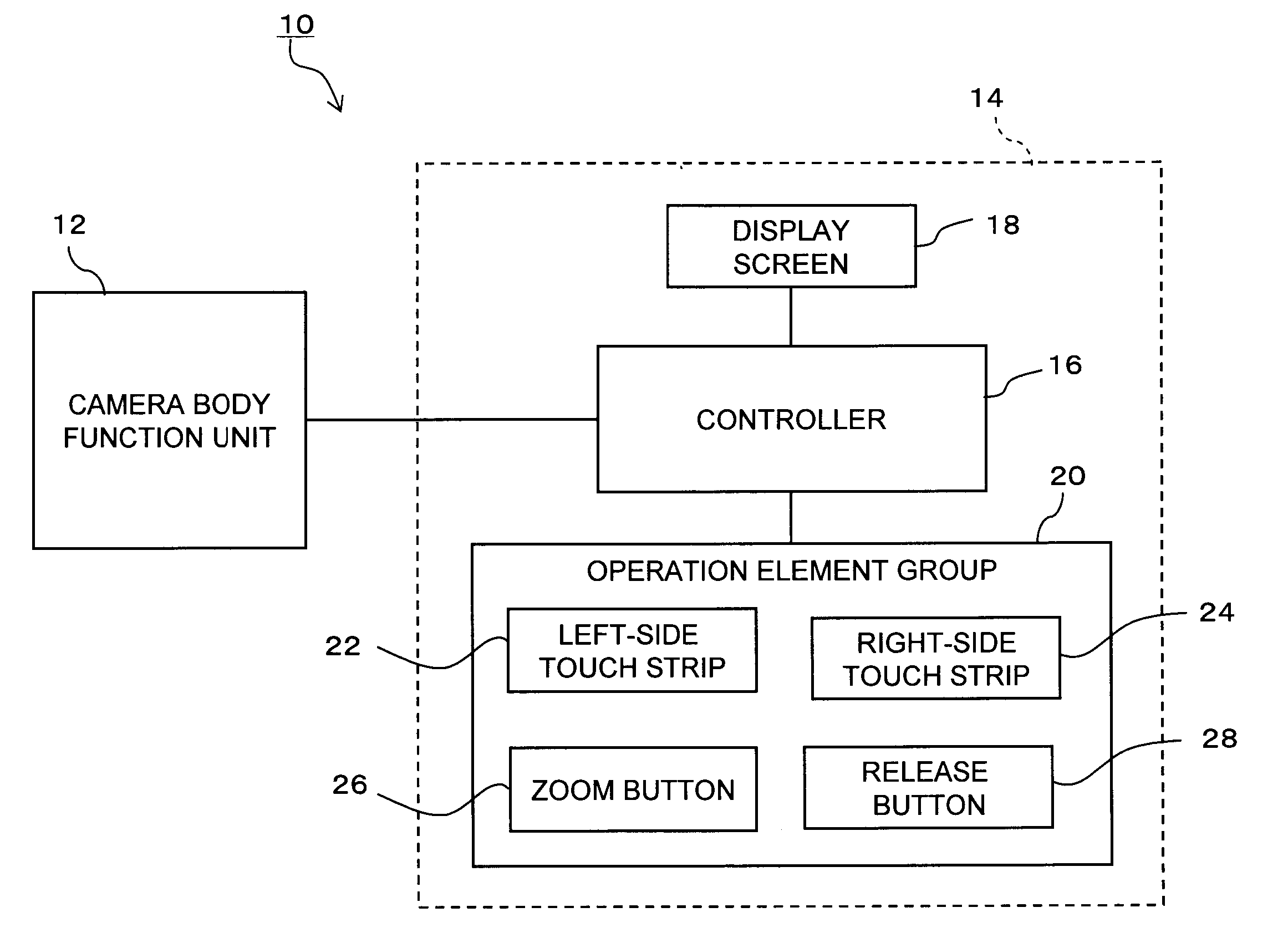
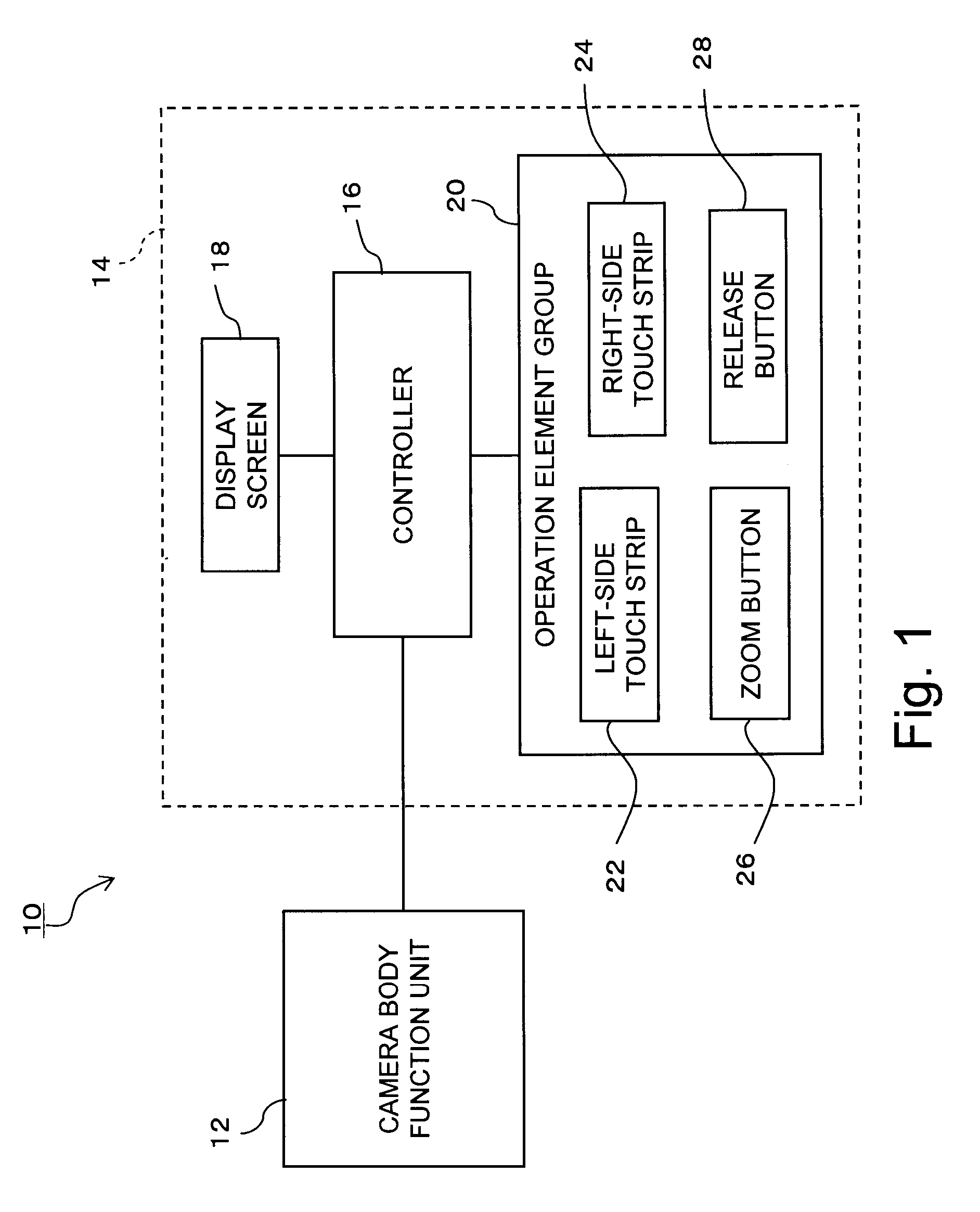
User interface device
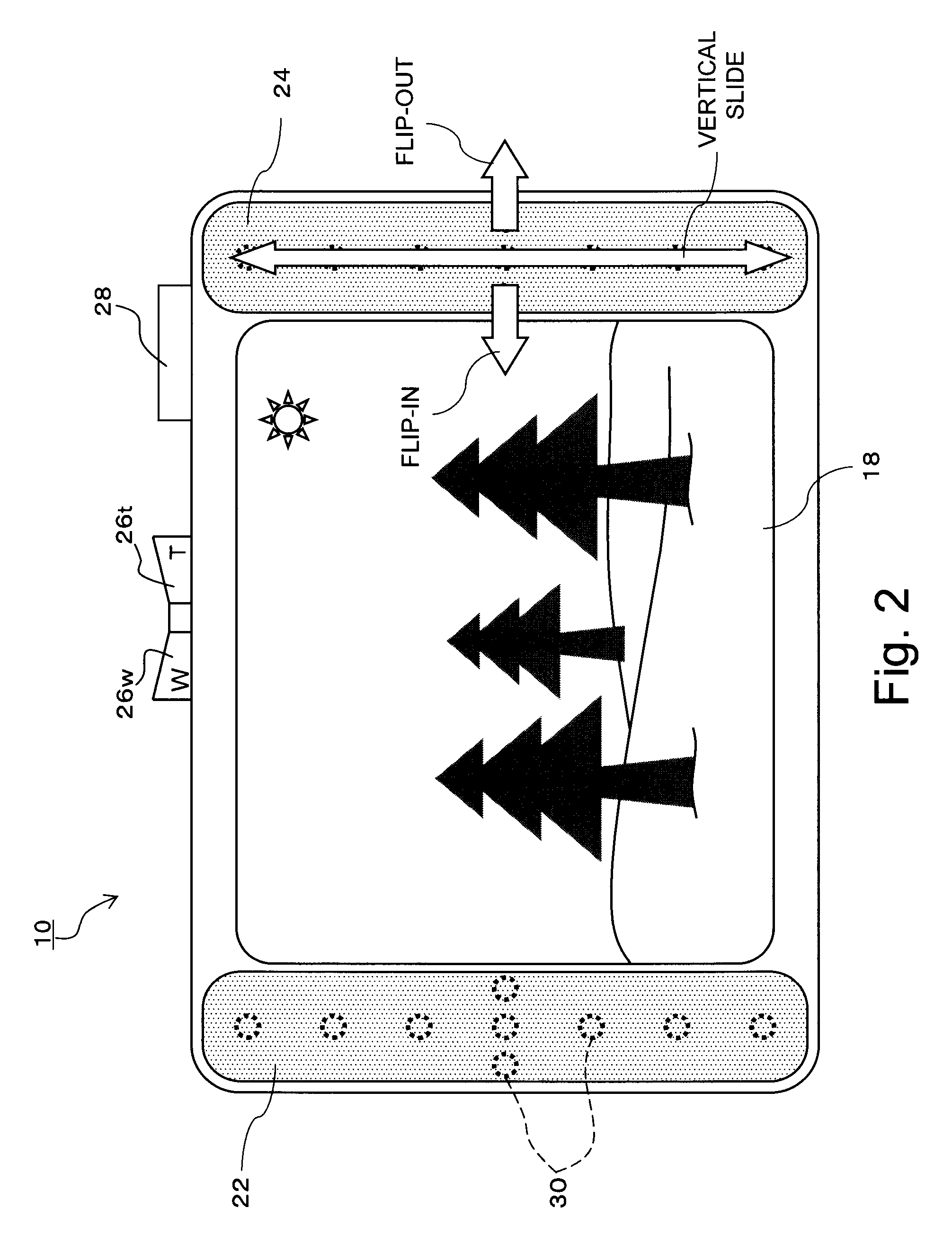
InactiveUS20080204402A1Easy to operateSmall sizeTelevision system detailsCathode-ray tube indicatorsScrollingHuman–computer interaction
A UI device of a digital camera has a display screen, a left-side touch strip provided outside of and on a left side of the display screen and a right-side touch strip provided outside of and on a right side of the display screen. The touch strips 22 and 24 can distinguishably detect a slide operation in a vertical direction by the user and a slide operation in a horizontal direction by the user. When a slide operation in the vertical direction is detected, a controller of the UI device recognizes the operation as a manipulative instruction in which the amount of movement is considered important, such as an operation for selection of items or scrolling of a screen. When a slide operation in the horizontal direction is detected, the controller recognizes the slide operation as a triggering manipulative instruction in which the amount of movement is not as important, such as a file deletion instruction or display or non-display of a new hierarchical item.
Owner:EASTMAN KODAK CO
Method and system for providing restricted access to a storage medium
InactiveUS20090271586A1Digital data processing detailsUnauthorized memory use protectionFile systemData storing
A method of restricting file access is disclosed wherein a set of file write access commands are determined from data stored within a storage medium. The set of file write access commands are for the entire storage medium. Any matching file write access command provided to the file system for that storage medium results in an error message. Other file write access commands are, however, passed onto a device driver for the storage medium and are implemented. In this way commands such as file delete and file overwrite can be disabled for an entire storage medium.
Owner:KOM
Distributed, secure digital file storage and retrieval
InactiveUS20070067332A1Digital data information retrievalDigital data processing detailsDistributed File SystemEncryption
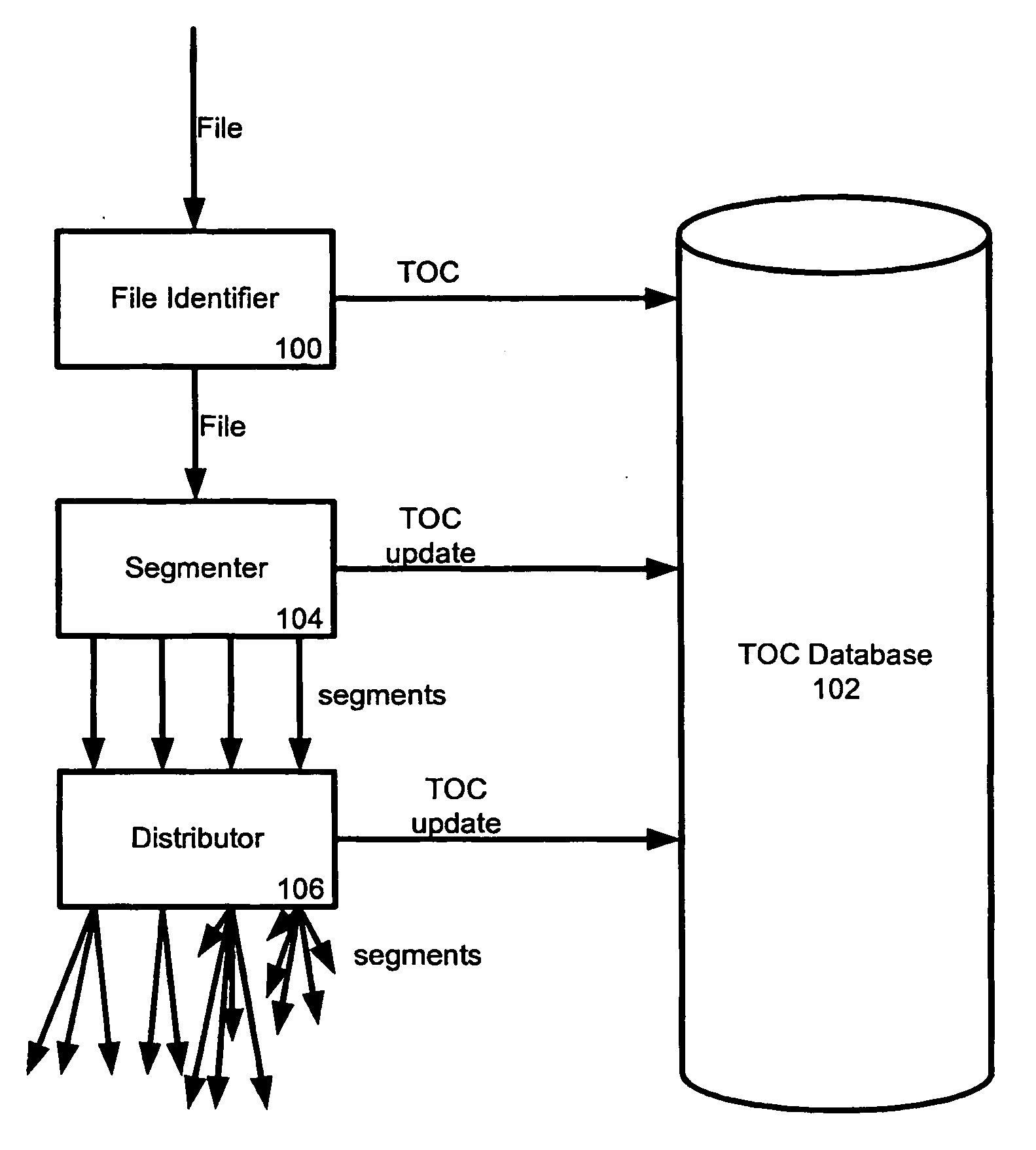
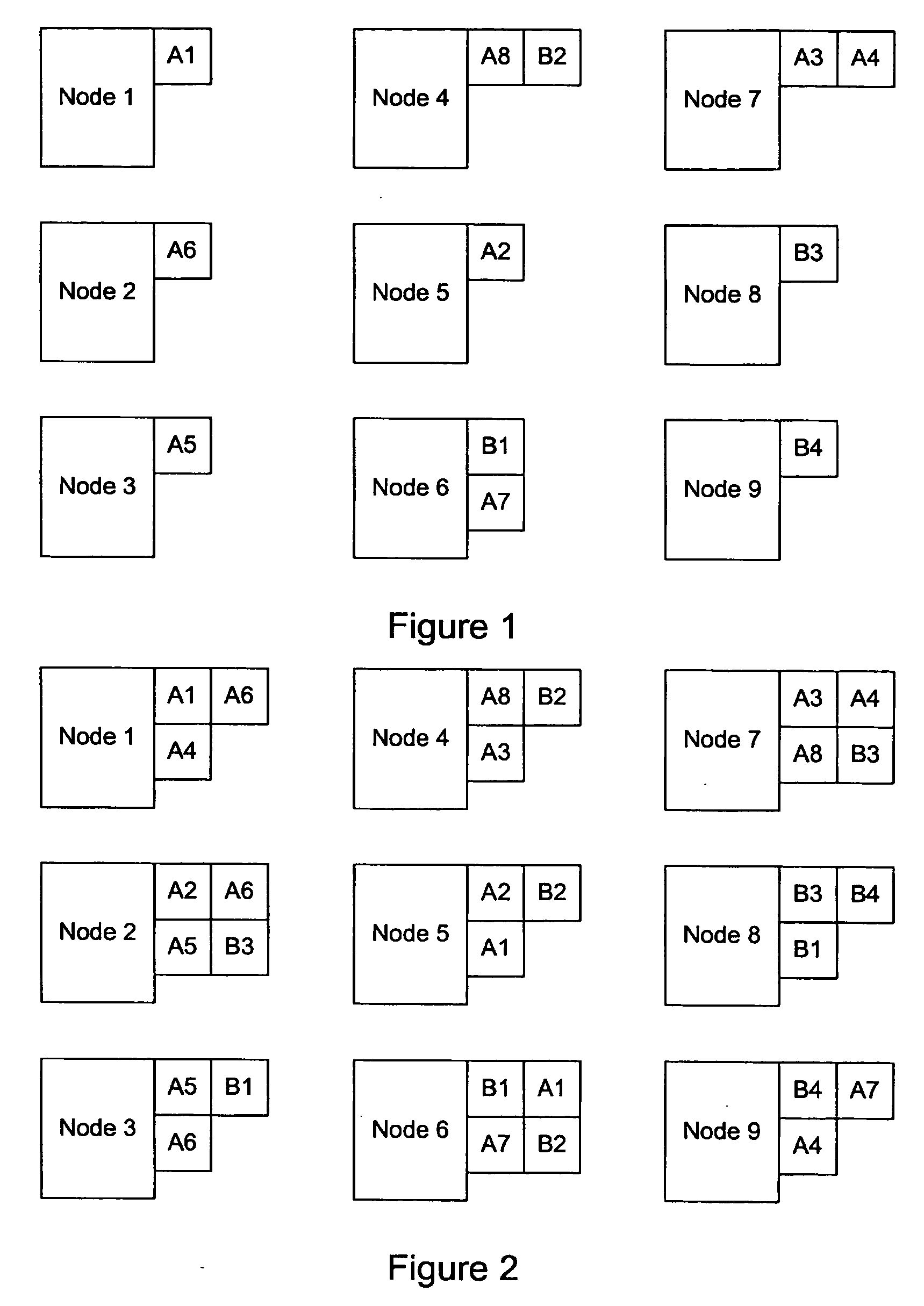
A distributed file system makes use of peer resources to store file segments that can be later re-assembled to reconstitute the original file. Encryption using public keys can be employed to provide access control to a select set of users, and file deletion can be accomplished by removing the file listing, including the location of the various segments, from a table of contents. Storing each file segment on a plurality of nodes allows for redundant file storage in the event of a node being unavailable when a file is retrieved.
Owner:GRIDIRON SOFTWARE
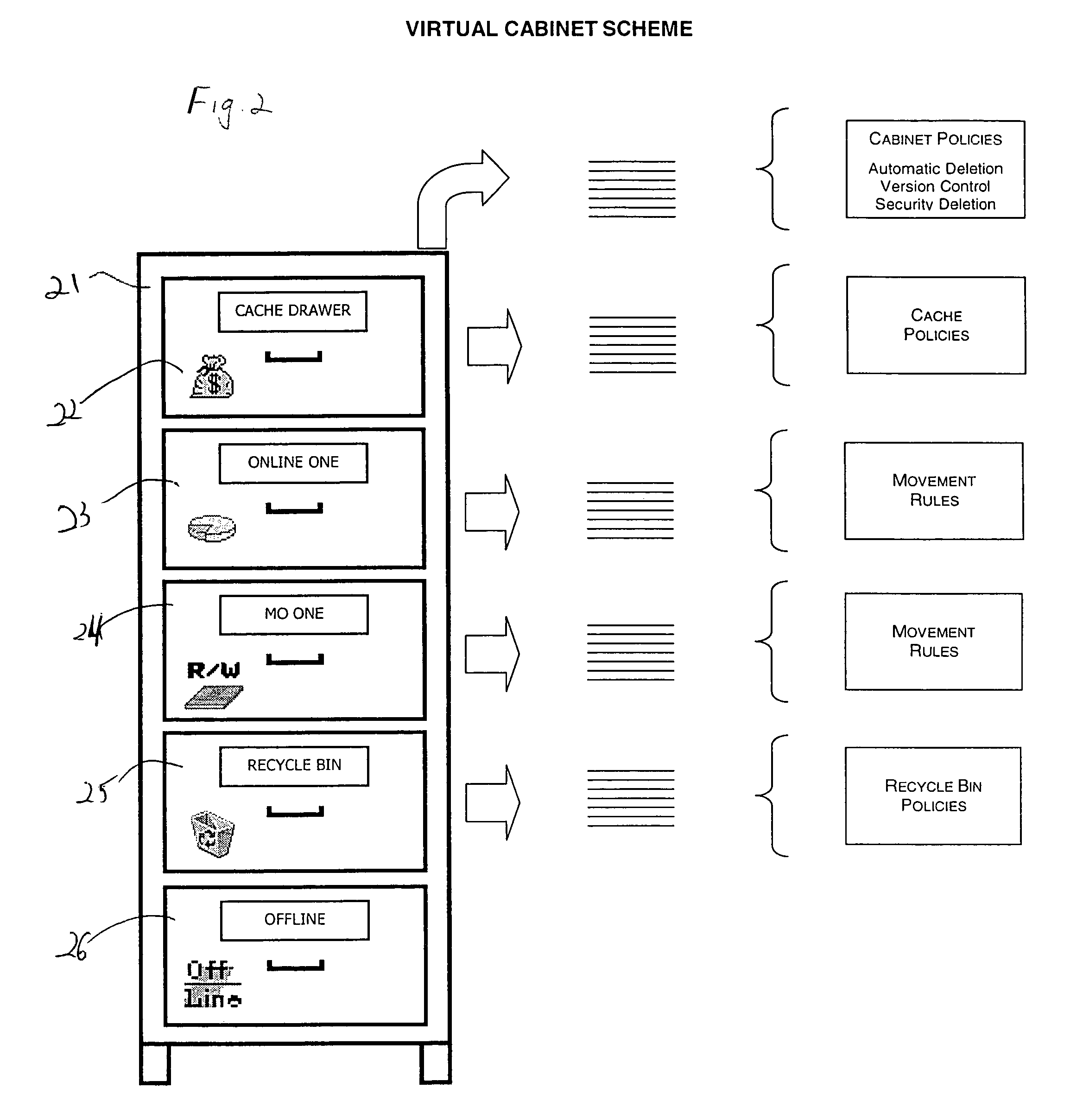
Method and system for electronic file lifecycle management
InactiveUS7392234B2Existing technologyData processing applicationsDigital data information retrievalElectronic systemsDatabase
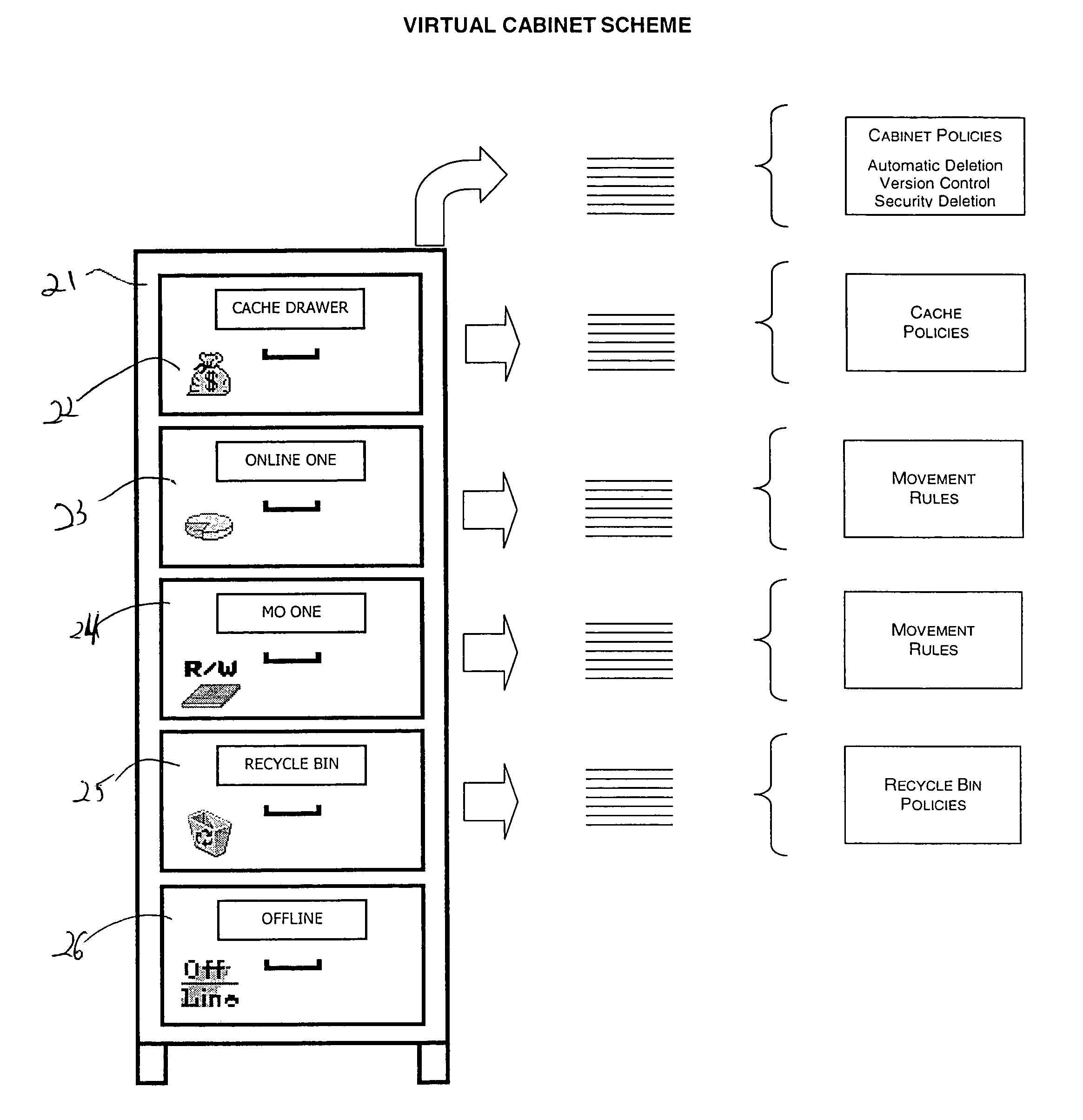
A method and system for managing a file lifecycle is disclosed. The method incorporates a virtual file cabinet having virtual drawers. Files are moved from drawer to drawer throughout their lifecycle in accordance with policies associated with each drawer. The files are moved automatically and as such, a file's lifecycle is managed from file creation to file deletion in an automated fashion. By using an archiving device such as magneto optical storage media, the files are automatically moved to their final archived location in an archiving drawer once certain policies of their present drawer are met. The system is an electronic system employing the inventive method.
Owner:KOM
Method and system for providing restricted access to a storage medium
InactiveUS20130198474A1Unauthorized memory use protectionComputer security arrangementsFile systemData storing
A system, apparatus, method, or computer program product of restricting file access is disclosed wherein a set of file write access commands are determined from data stored within a storage medium. The set of file write access commands are for the entire storage medium. Any matching file write access command provided to the file system for that storage medium results in an error message. Other file write access commands are, however, passed onto a device driver for the storage medium and are implemented. In this way commands such as file delete and file overwrite can be disabled for an entire storage medium.
Owner:KOM
Computer machine and access control method
ActiveUS20100275205A1Digital data protectionMultiple digital computer combinationsClient-sideFile server
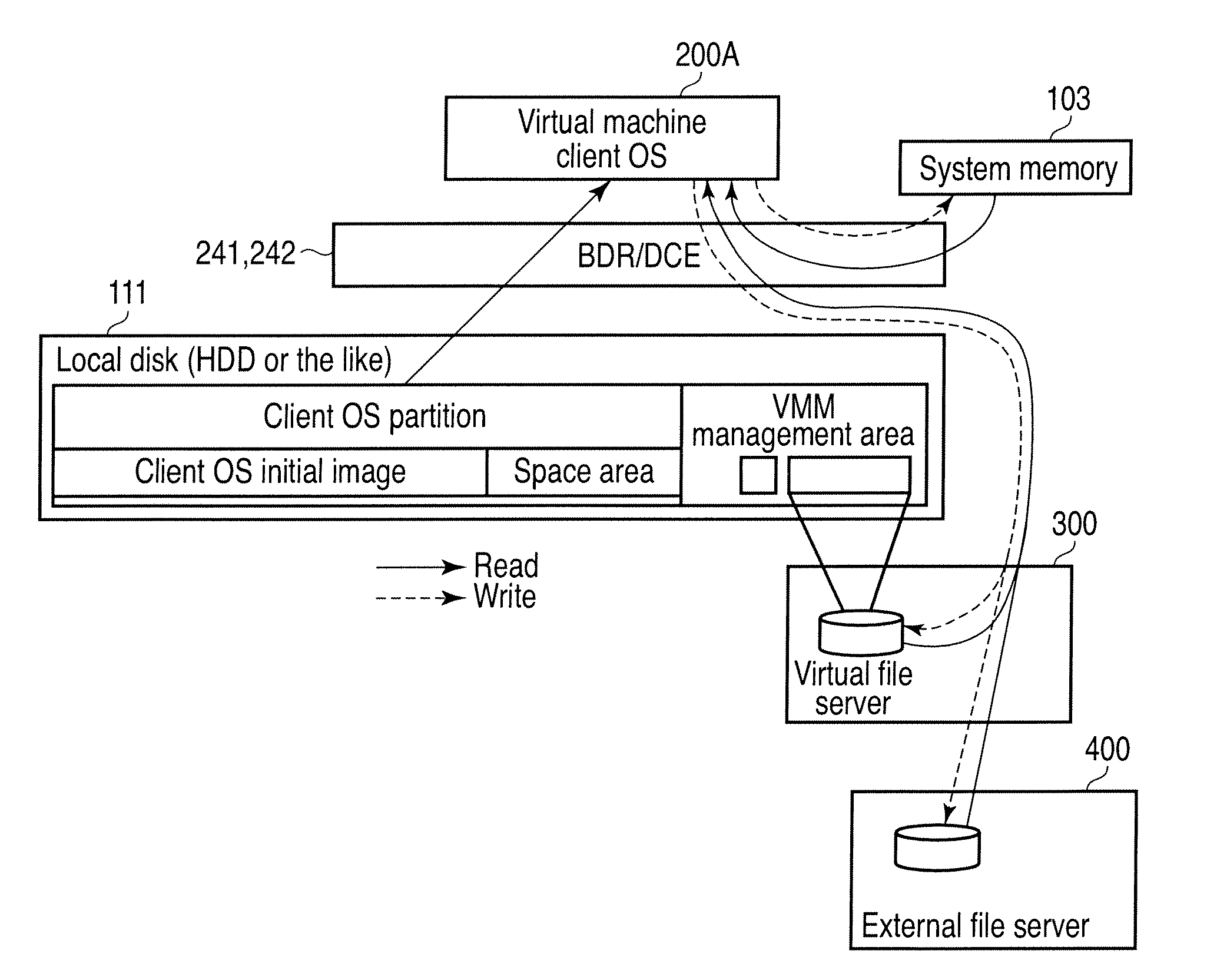
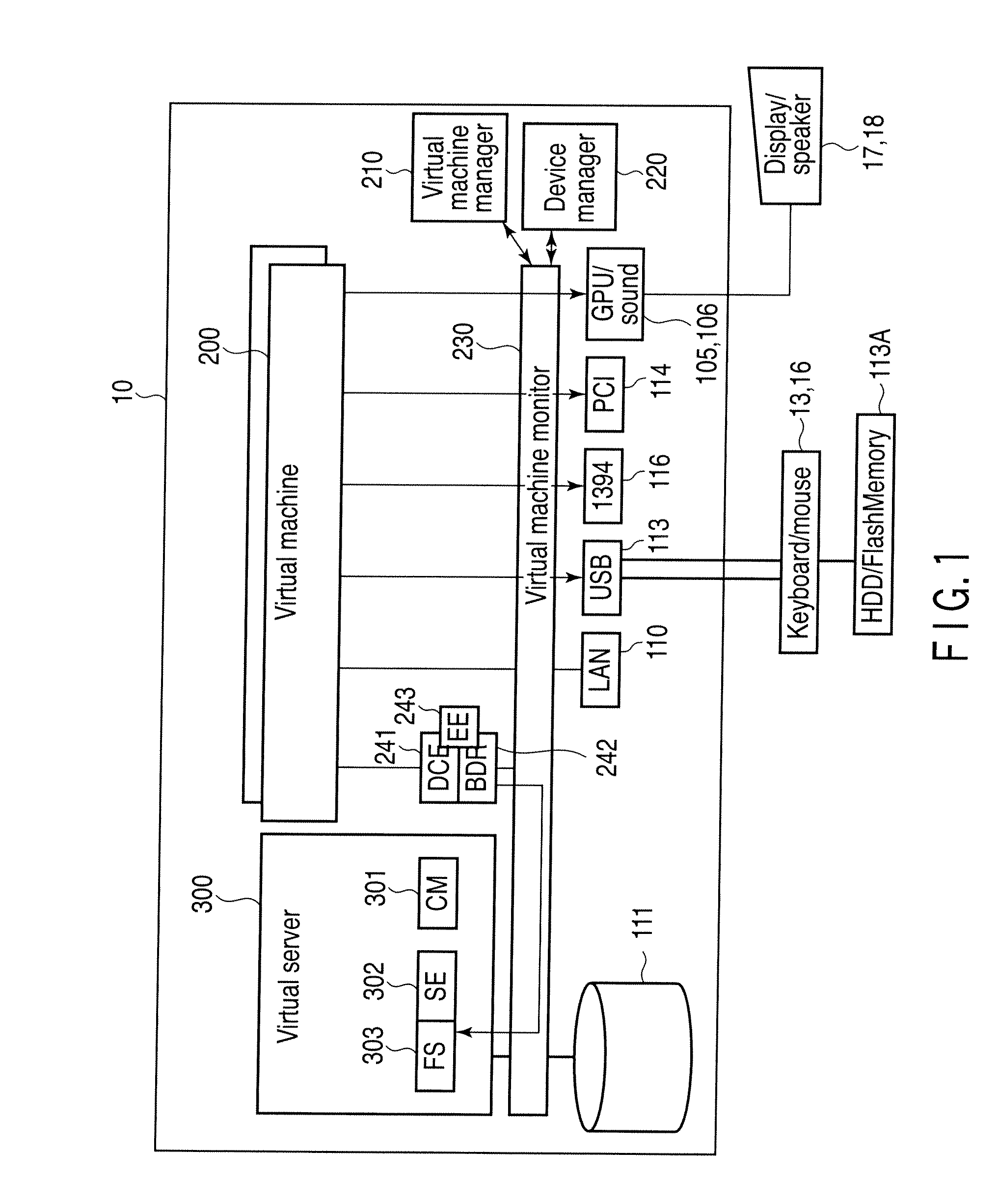
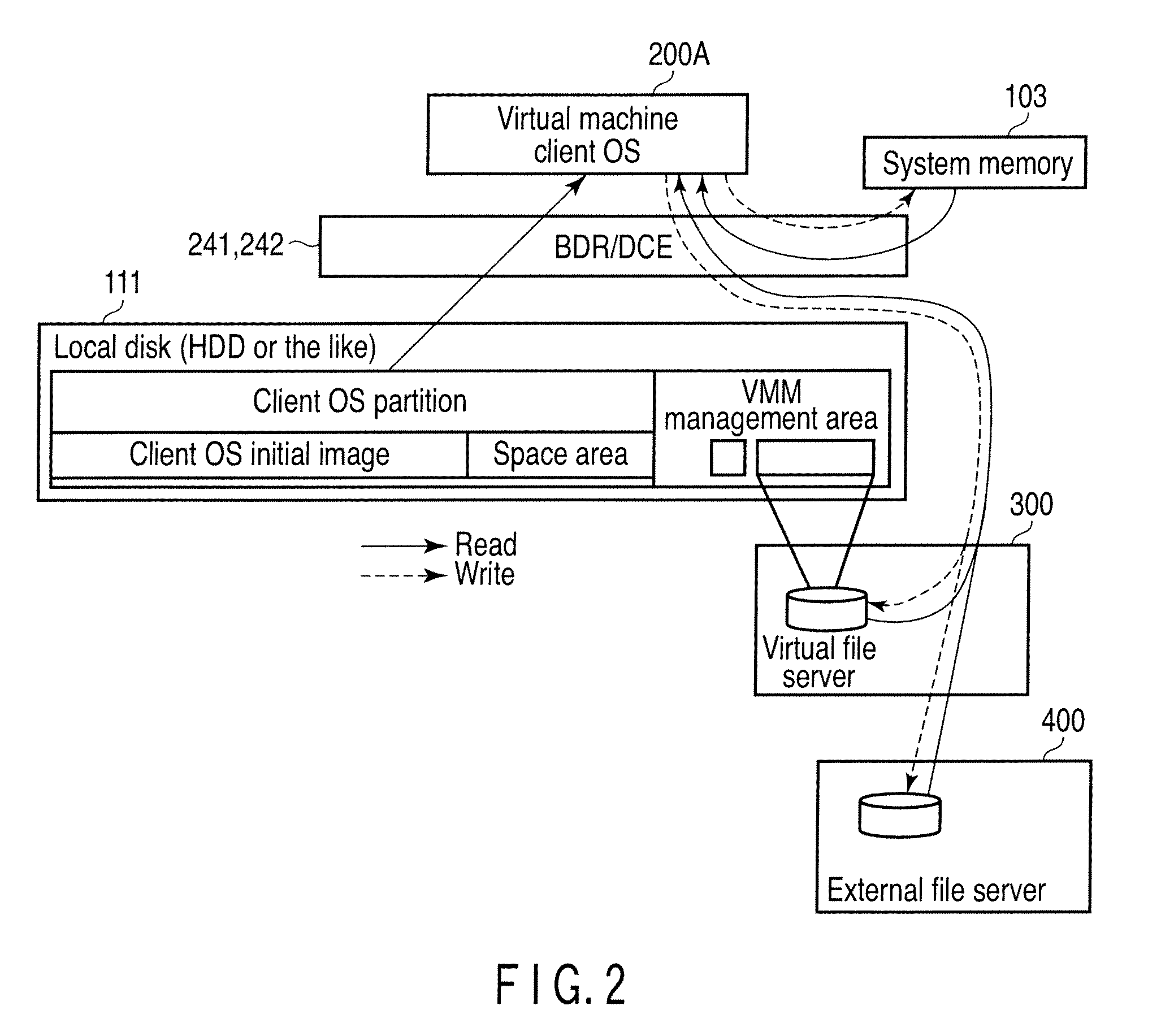
According to one embodiment, a computer machine includes a client virtual machine and a file server virtual machine configured to simultaneously run, a virtual machine manager configured to control booting of the client and file server virtual machines, a monitoring module configured to monitor whether a communication with an external file server is possible, an access control module configured to access to a duplicate file which is a duplicate of the file and is stored in a part of a local disk or a part of a memory which are managed by the monitoring module when the monitoring module determines that the communication is impossible after determining that the communication is possible, and a file deletion module configured to delete the duplicate file when the monitoring module detects the communication is impossible in a preset time.
Owner:TOSHIBA DIGITAL SOLUTIONS CORP
Method and apparatus for a parallel data storage and processing server
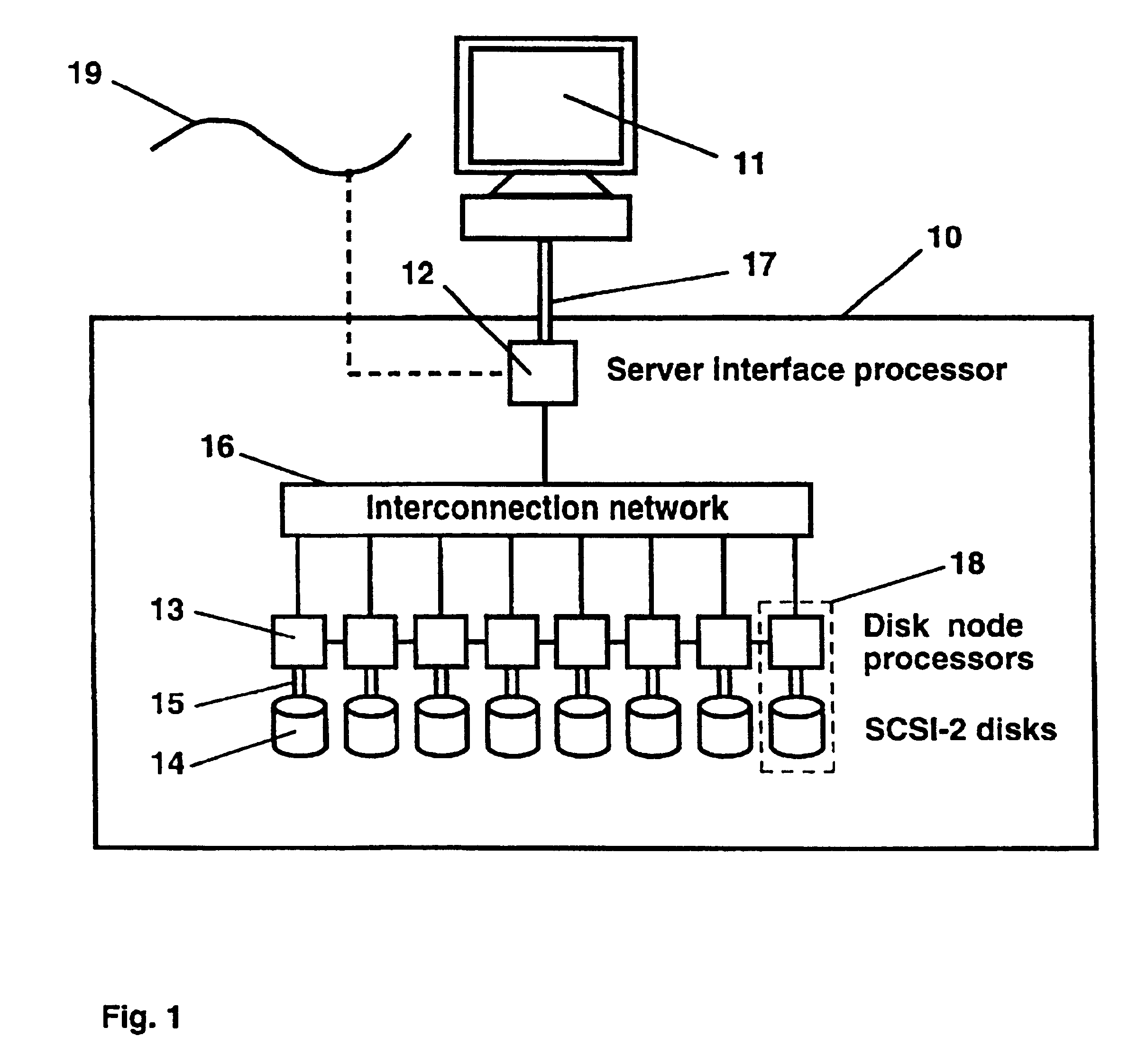
InactiveUSRE38410E1Lower latencyImprove throughputImage memory managementMultiple digital computer combinationsConcurrent computationComputer architecture
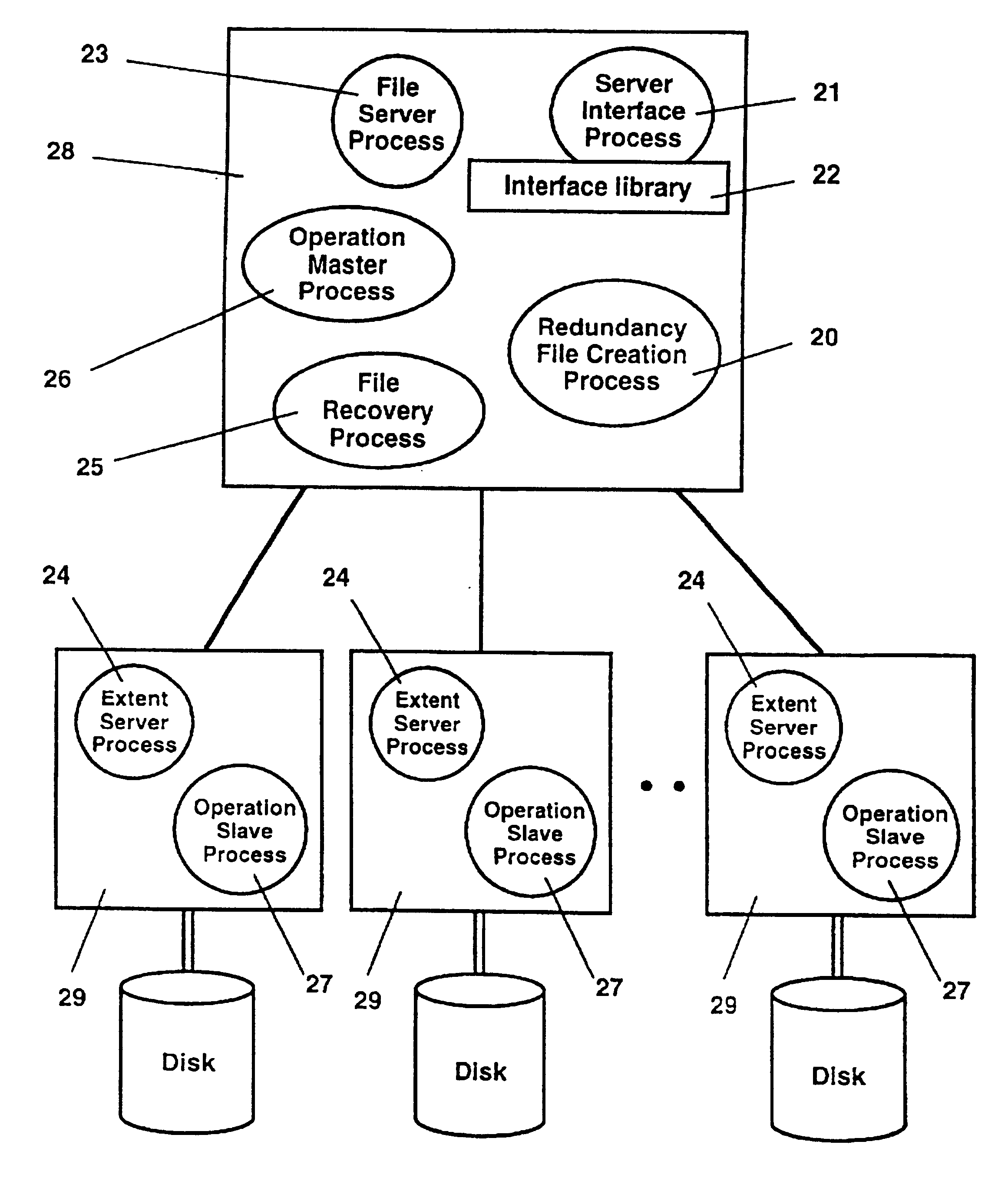
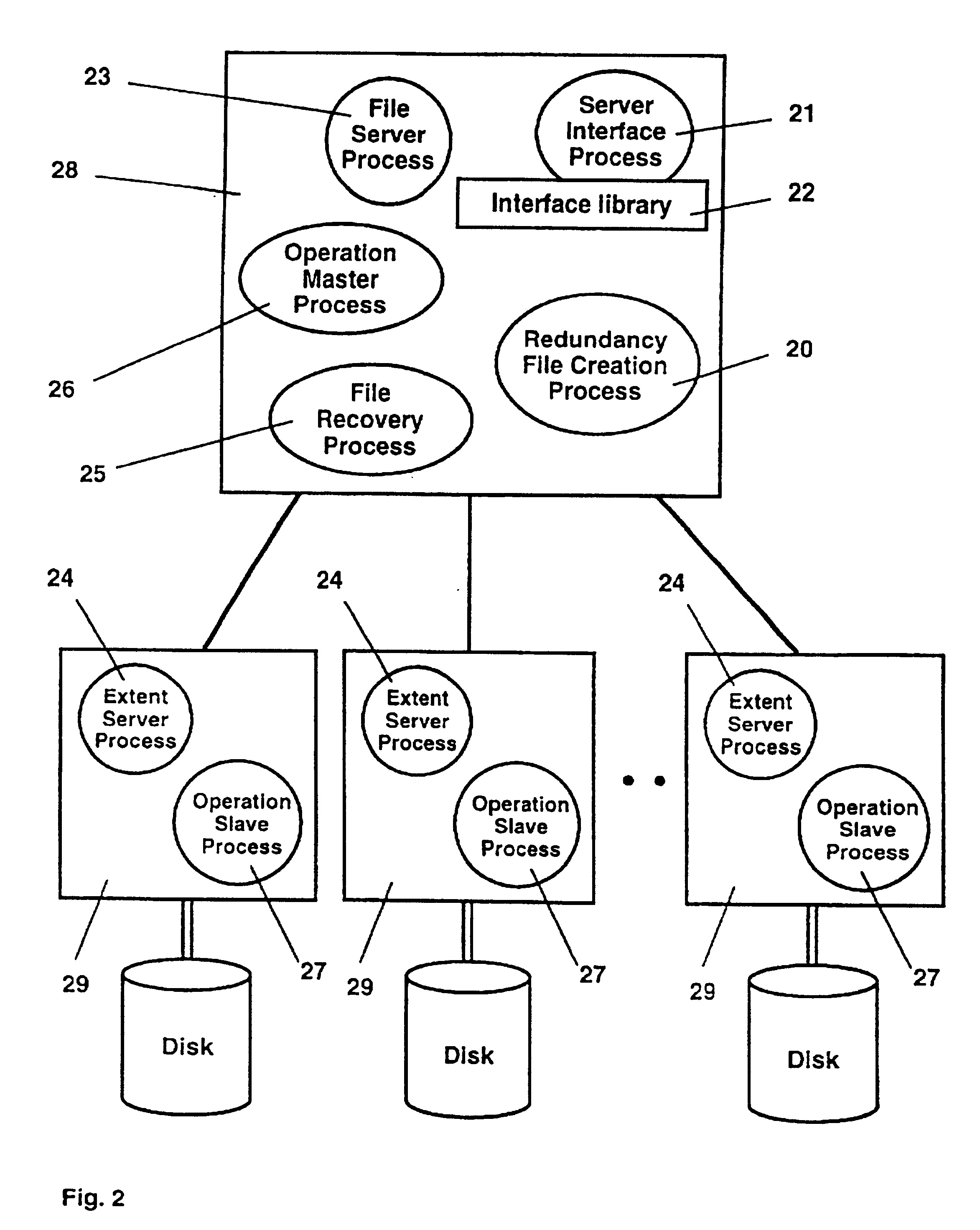
The present invention concerns a parallel multiprocessor-multidisk storage server which offers low delays and high throughputs when accessing and processing one-dimensional and multi-dimensional file data such as pixmap images, text, sound or graphics. The invented parallel multiprocessor-multidisk storage server may be used as a server offering its services to computer, to client stations residing on a network or to a parallel host system to which it is connected. The parallel storage server comprises (a) a server interface processor interfacing the storage system with a host computer, with a network or with a parallel computing system; (b) an array of disk nodes, each disk node being composed by one processor electrically connected to at least one disk and (c) an interconnection network for connecting the server interface processor with the array of disk nodes. Multi-dimensional data files such as 3-d images (for example tomographic images), respectively 2-d images (for example scanned aerial photographs) are segmented into 3-d, respectively 2-d file extents, extents being striped onto different disks. One-dimensional files are segmented into 1-d file extents. File extents of a given file may have a fixed or a variable size. The storage server is based on a parallel image and multiple media file storage system. This file storage system includes a file server process which receives from the high level storage server process file creation, file opening, file closing and file deleting commands. It further includes extent serving processes running on disk node processors, which receive from the file server process commands to update directory entries and to open existing files and from the storage interface server process commands to read data from a file or to write data into a file. It also includes operation processes responsible for applying in parallel geometric transformations and image processing operations to data read from the disks and a redundancy file creation process responsible for creating redundant parity extent files for selected data files.
Owner:AXS TECH
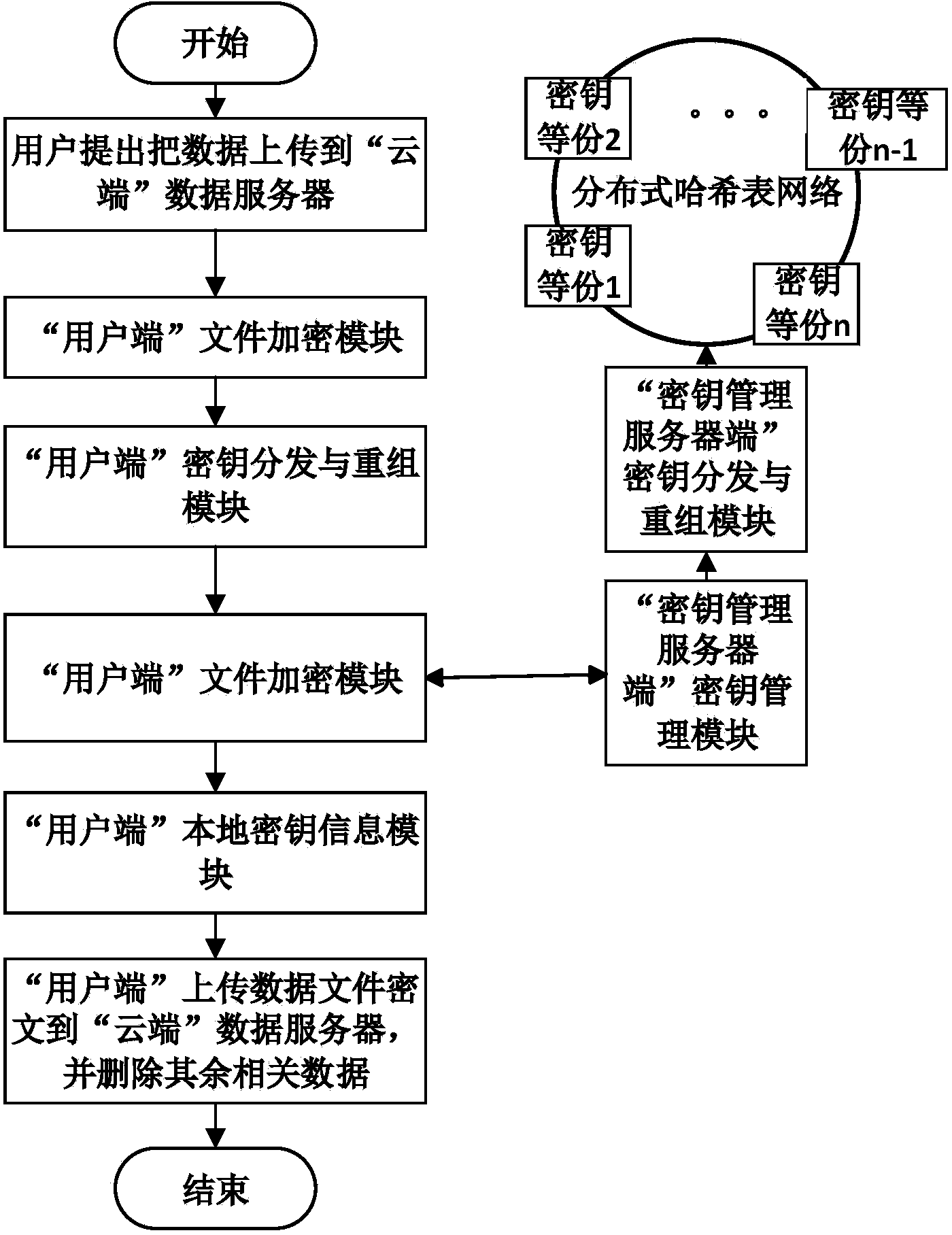
Cloud data safe deleting system and method without support of trusted third party
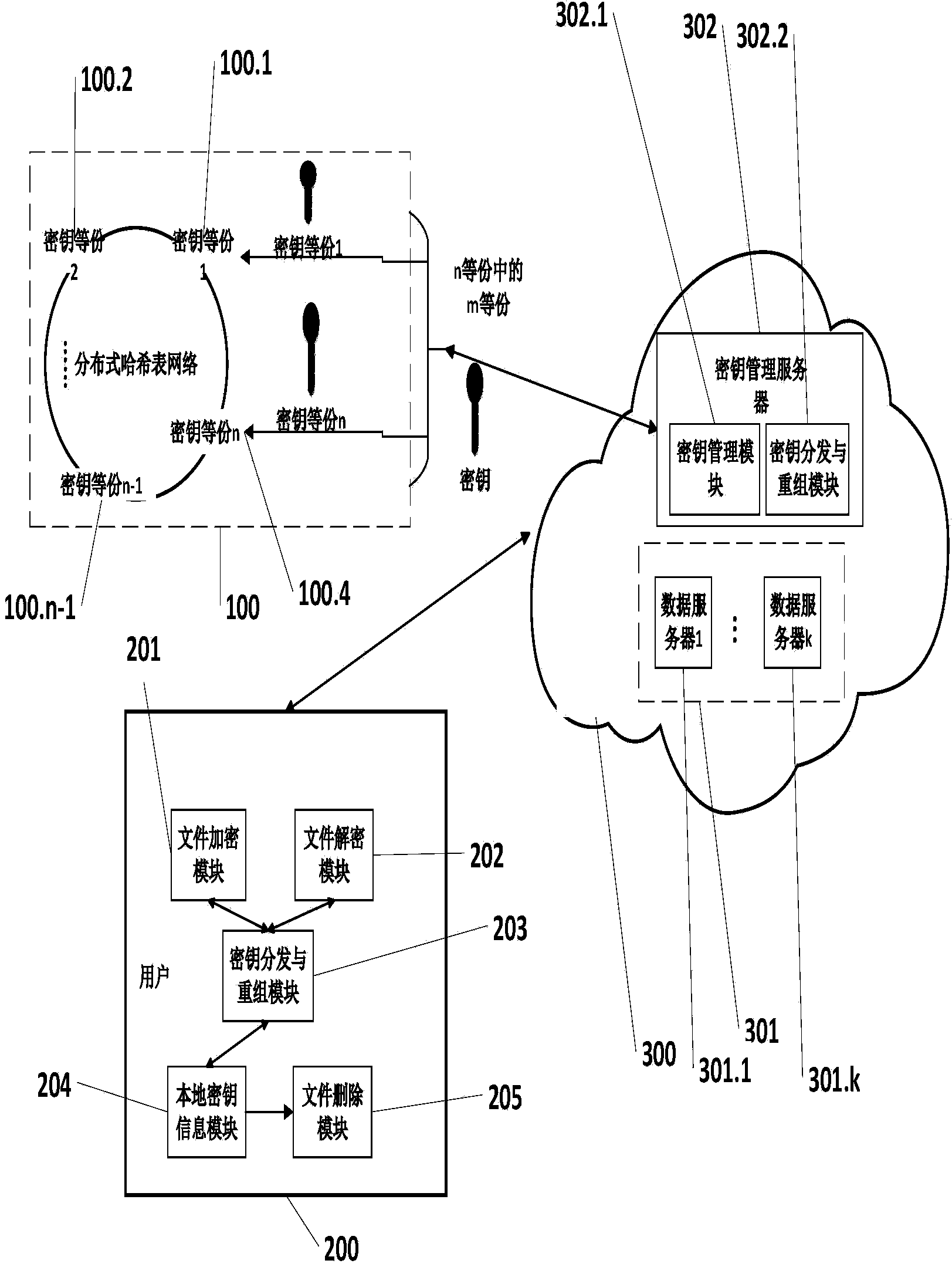
The invention discloses a cloud data safe deleting system and method without the support of a trusted third part. The system comprises a distributed hash table network, a user side and a cloud. The distributed hash table network is used for storing decryption key fragments. The user side is used for encrypting and decrypting files and deleting key information and comprises a file encryption module, a file decryption module, a key distribution and reorganization module, a local key information module and a file deletion module. The file encryption module and the file decryption module are used for encrypting and decrypting the files respectively; the key distribution and reorganization module is used for fragmenting and reorganizing keys; the local key information module is used for storing relevant key information; the file deletion module is used for deleting the key information. The cloud is provided with a data server and a key management server and used for storing data ciphertext information and key information and comprises the data server and the key management server, wherein the data server is used for storing file ciphertexts, and the key management server is used for managing key relevant information. The cloud data safe deleting system and method can be used for a cloud storage environment to protect data privacy of the user side.
Owner:HUAZHONG UNIV OF SCI & TECH
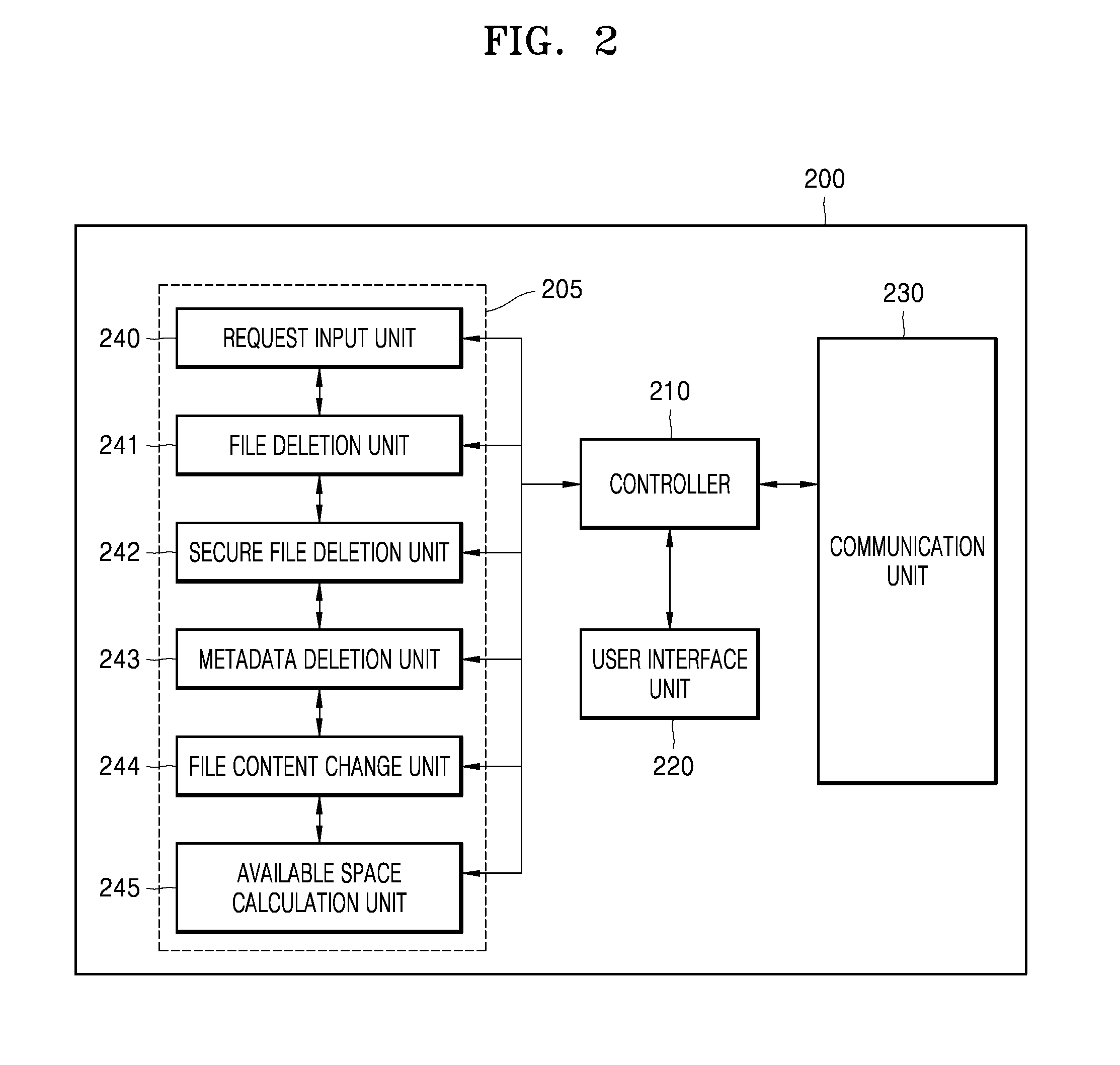
Apparatuses, systems, methods, and computer readable media for providing secure file-deletion functionality
A secure file-deletion function providing apparatus includes a request input unit configured to receive a file deletion request to delete a file stored in an apparatus from a user; a file deletion unit for deleting the file included in the file deletion request, and a secure file-deletion unit for overwriting a region including a region that stores the file with a dummy value in order to make it more difficult and / or impossible to recover the file deleted by the file deletion unit.
Owner:NAVER CLOUD CORP
Information management method
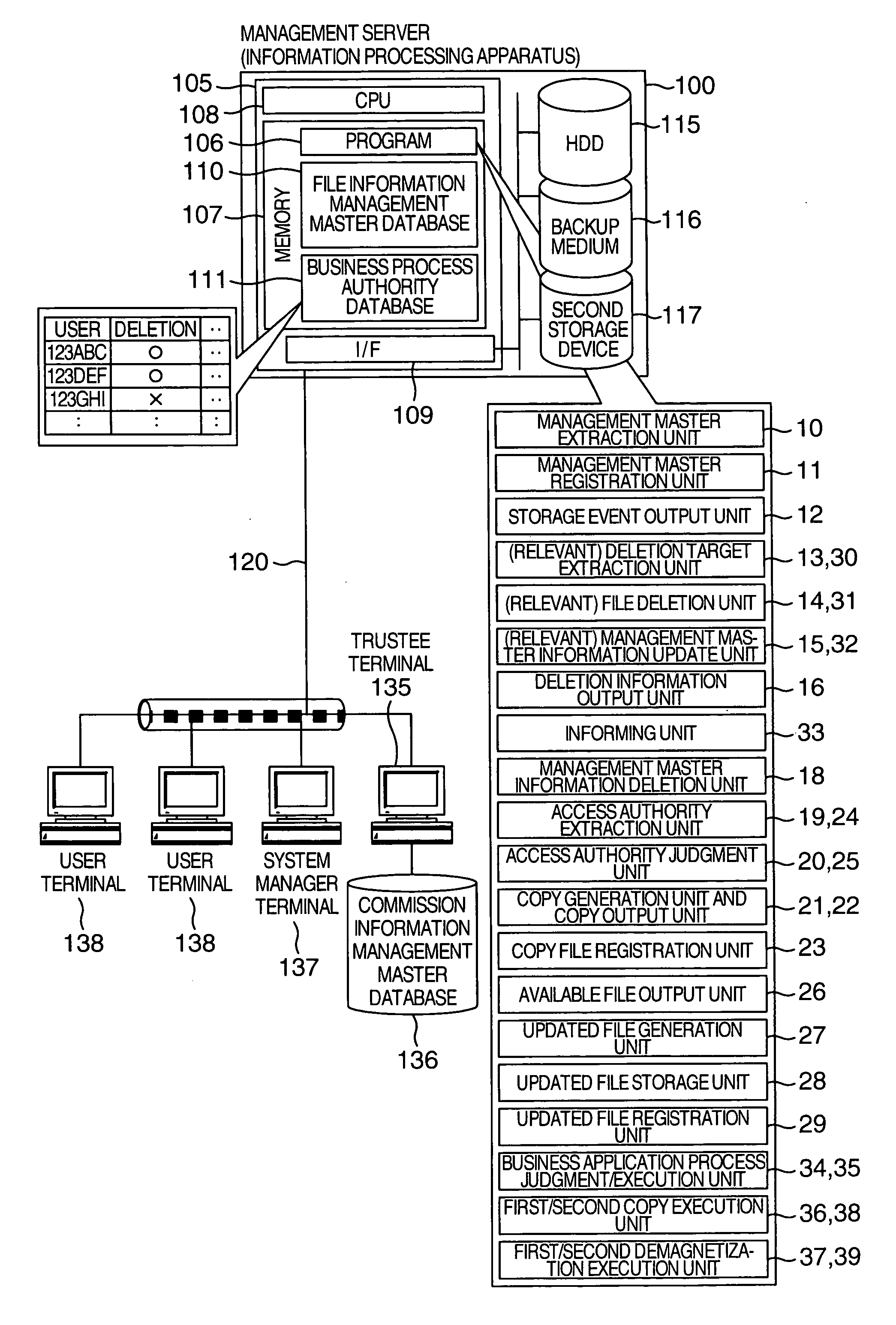
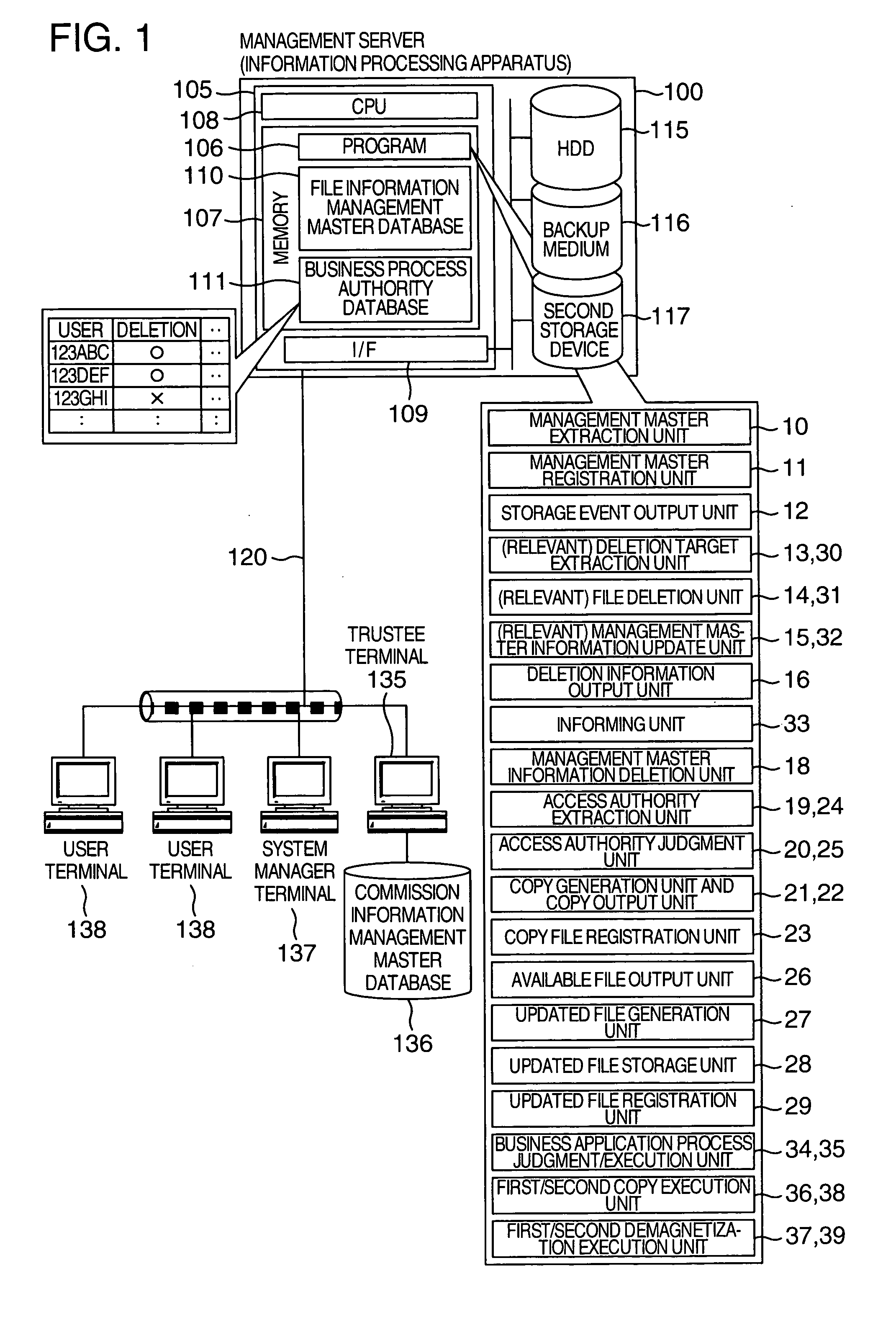
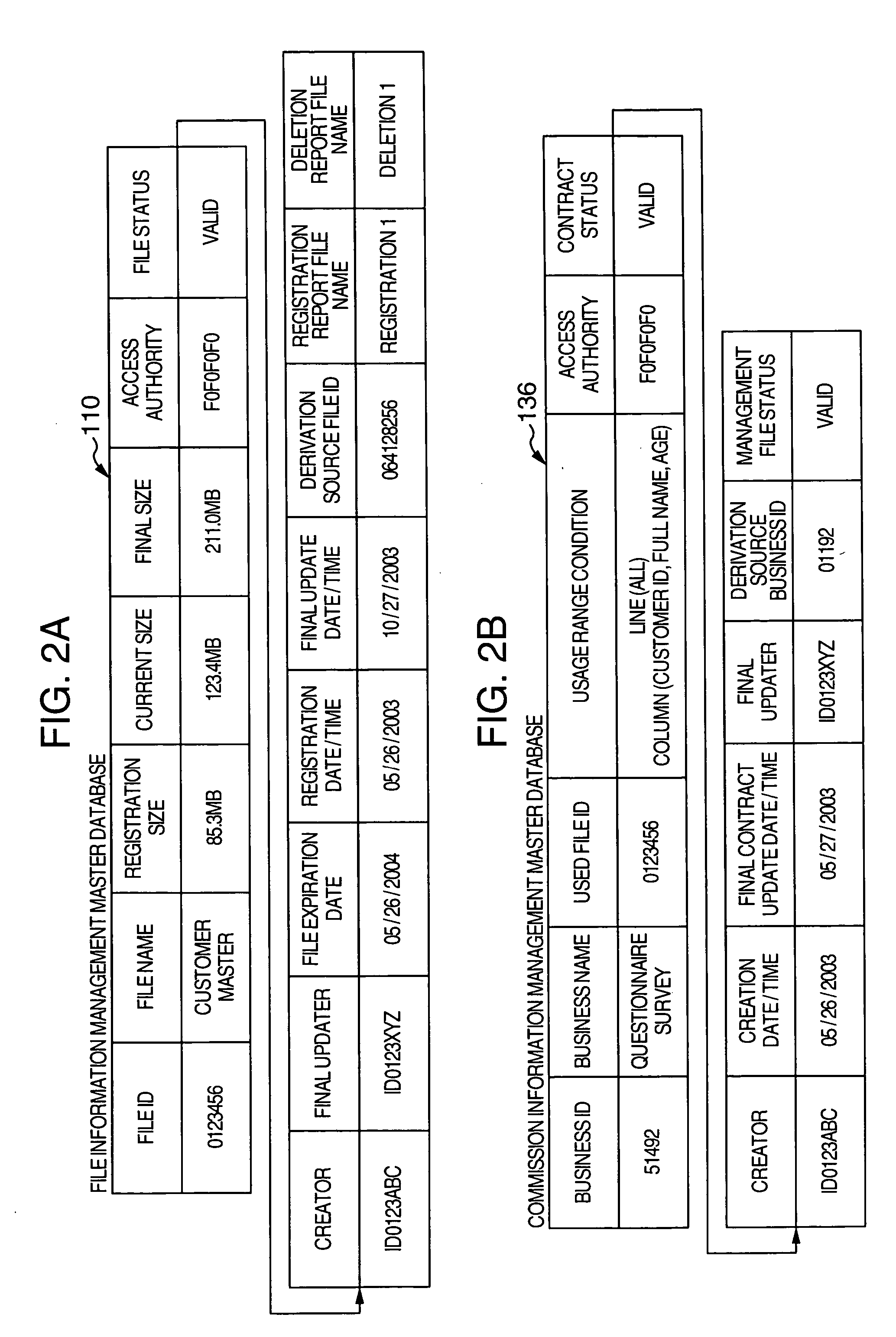
InactiveUS20050102312A1Promote recoveryEfficient managementData processing applicationsUnauthorized memory use protectionInformation processingManagement object
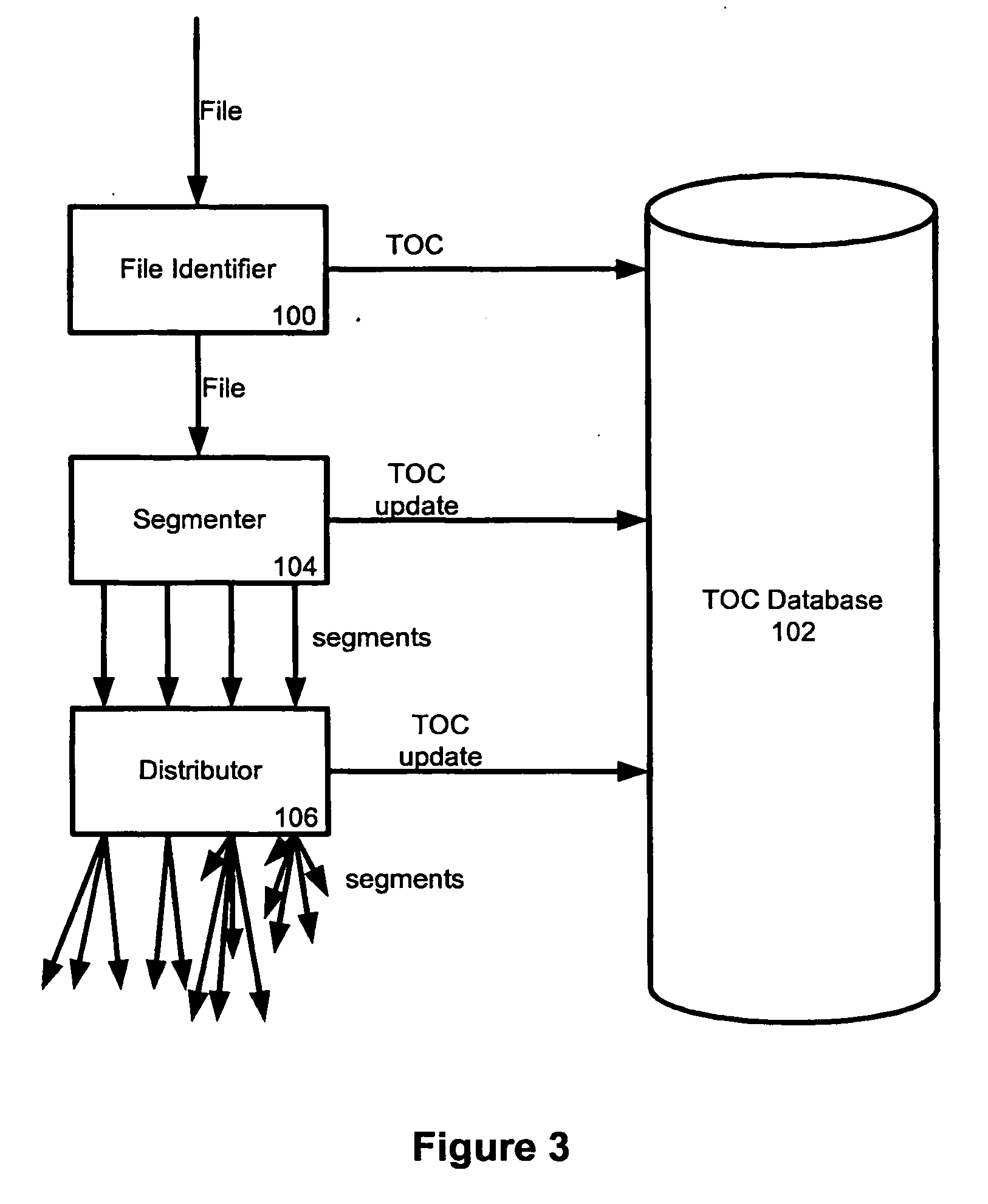
An information processing apparatus includes a management master extraction unit which extracts management master information from a management target file; a storage device which stores a file management database in which the management master information on each management target file is registered; a storage event output unit which outputs a signal indicating a storage event of the file; a deletion target extraction unit which extracts information on a management target file corresponding to a deletion request from the file management database; a file deletion unit which deletes the management target file from the storage device based on the information; a management master information update unit which updates validity information on the deleted file in the management master information in the file management database into invalid; and a deletion information output unit which outputs a signal indicating the deletion of the management target file.
Owner:HITACHI LTD
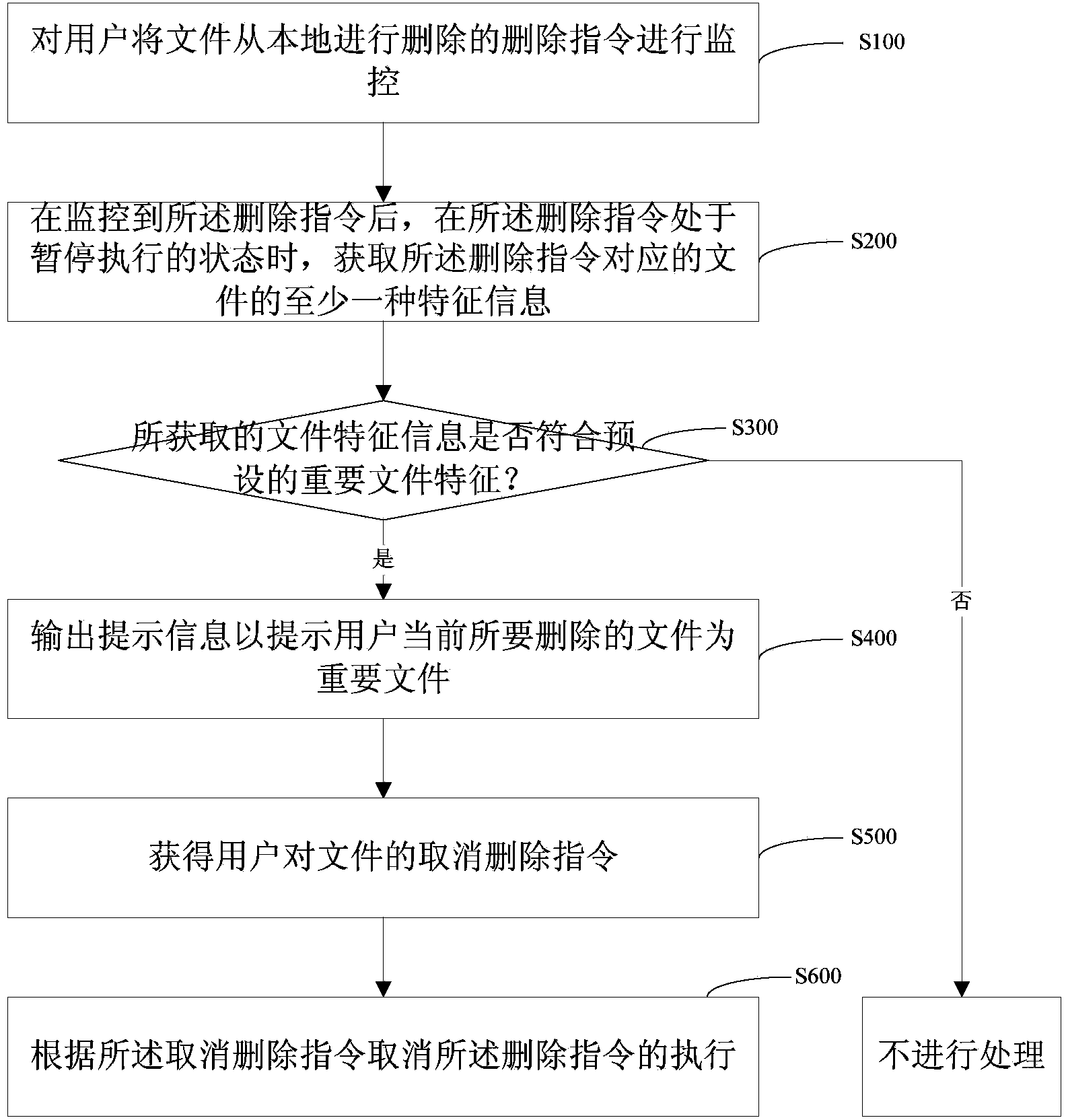
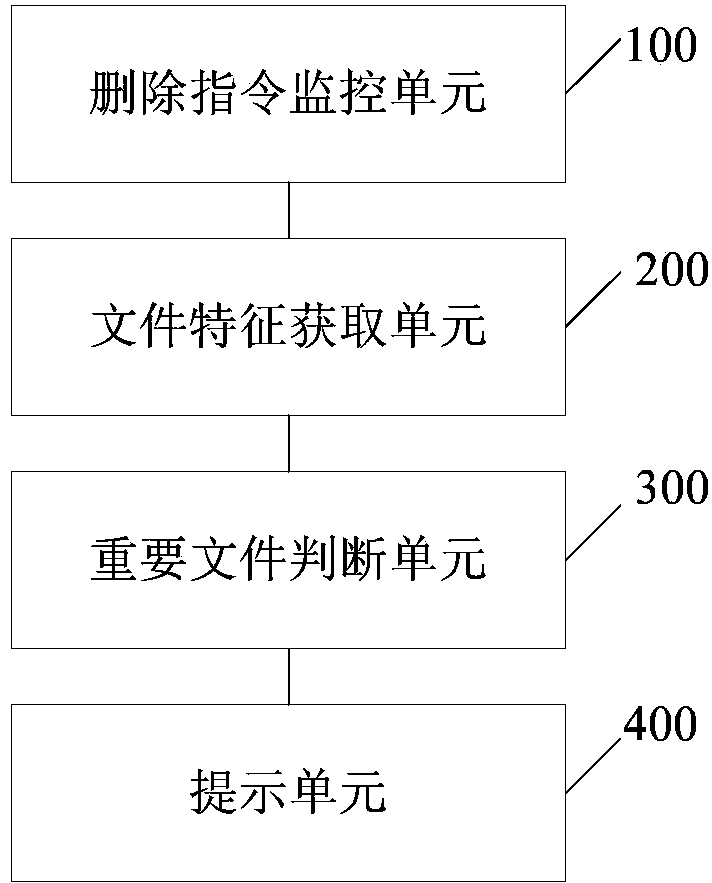
Method and system for file deletion
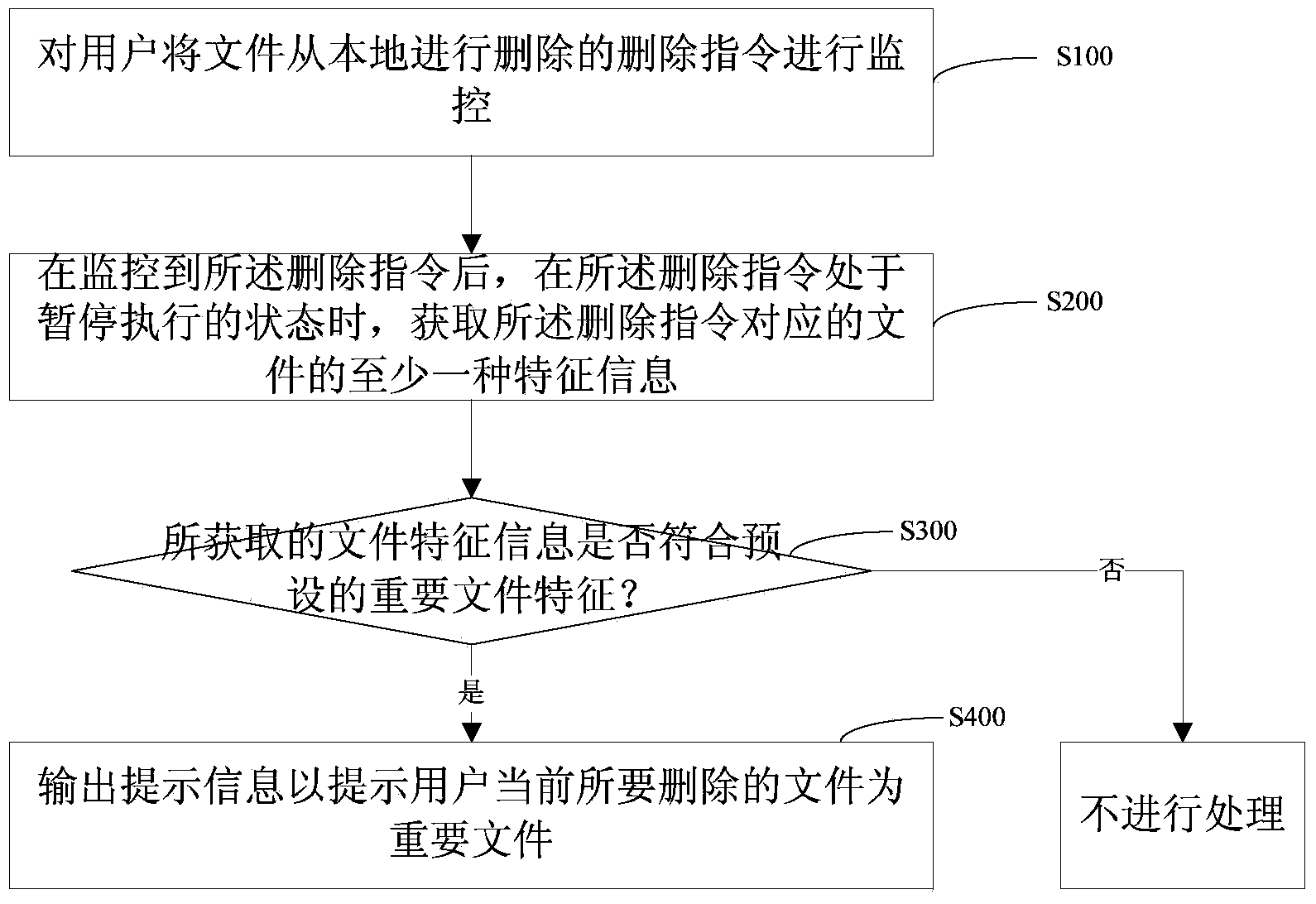
The embodiment of the invention provides a method and system for file deletion. The technical scheme is as follows: when a deletion order is in the state of pause execution, the feature information of files corresponding to the deletion order can be obtained and the obtained feature information of the files are judged whether accords with preset vital file features or not; if the obtained feature information of the files accords with the preset vital file features, prompt message is output and users are prompted that the files to be deleted currently are important files. According to the invention, the files can be confirmed whether the files are important or not before the deletion order is executed, which can prevent the users from deleting important files by accident.
Owner:ZHUHAI JUNTIAN ELECTRONICS TECH
Security erase of a delete file and of sectors not currently assigned to a file
InactiveUS20100211541A1Optimal overwrite patternDigital data information retrievalDigital data processing detailsFile systemFile deletion
Secure erase of files and unallocated sectors on storage media such that any previous data is non-recoverable. The database contains sets of data patterns used to overwrite the data on different physical media. The software programs manage the overwriting process automatically when a file has been deleted. When de-allocated sectors in the file system are pruned from a file or escaped the file deletion process also finds them. Data will never be found on deleted sectors or on pruned sectors is overwritten.
Owner:CMS INTPROP
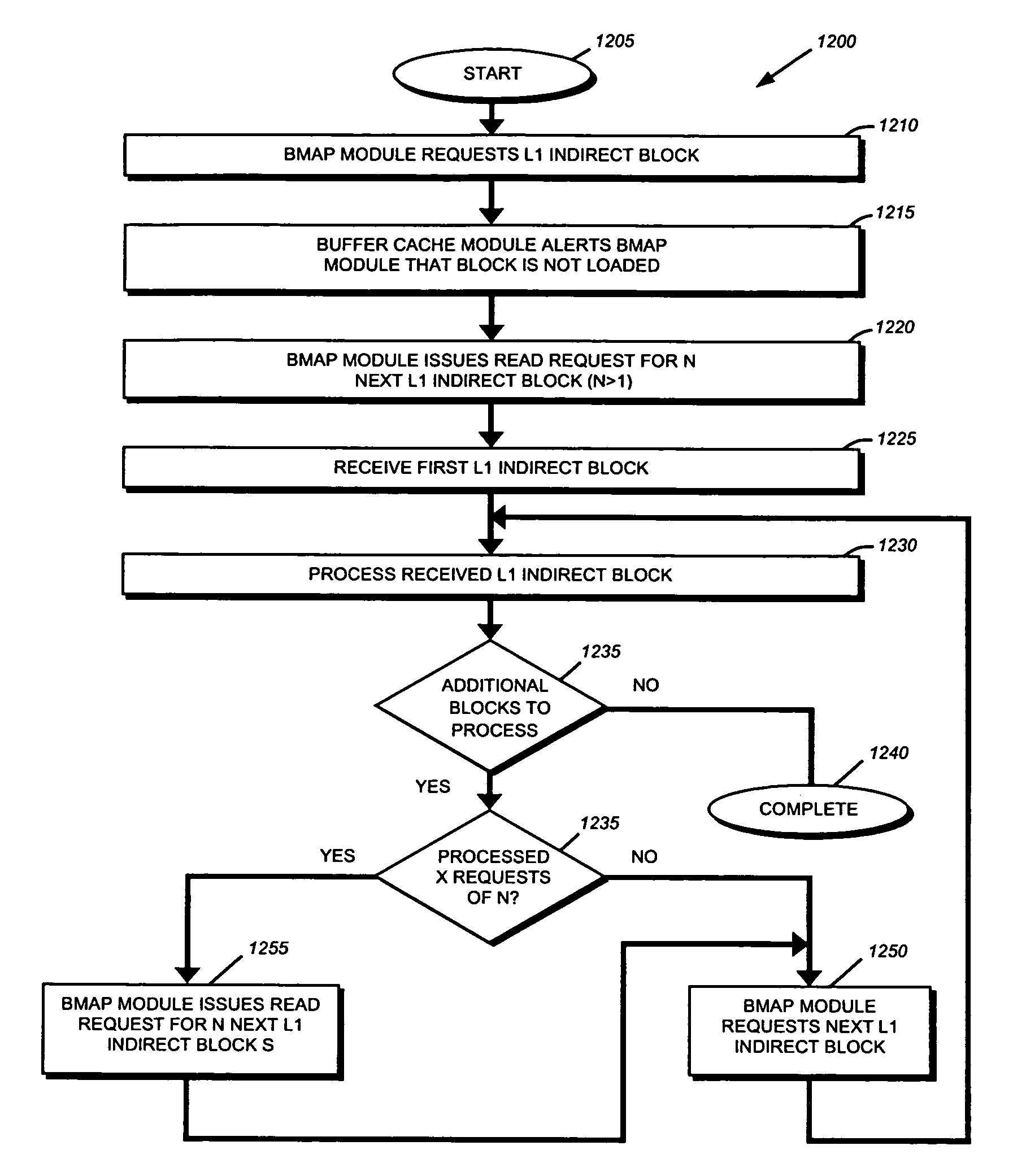
Technique for accelerating file deletion by preloading indirect blocks
ActiveUS7509329B1Improves file deletion performanceEasy to traverseDigital computer detailsSpecific program execution arrangementsParallel processingFile server
A system and method for accelerating file deletion by preloading indirect blocks. When processing level 1 (L1) indirect blocks, the file server issues a read request for the next N indirect blocks to be loaded into a buffer cache. The file server processes the indirect blocks from the buffer cache without requiring multiple single block disk accesses. Once the N indirect blocks have been processed, a read request for the next N L1 indirect blocks is then sent. The technique permits parallel processing by loading indirect blocks to be processed while previously cached indirect blocks are being processed.
Owner:NETWORK APPLIANCE INC
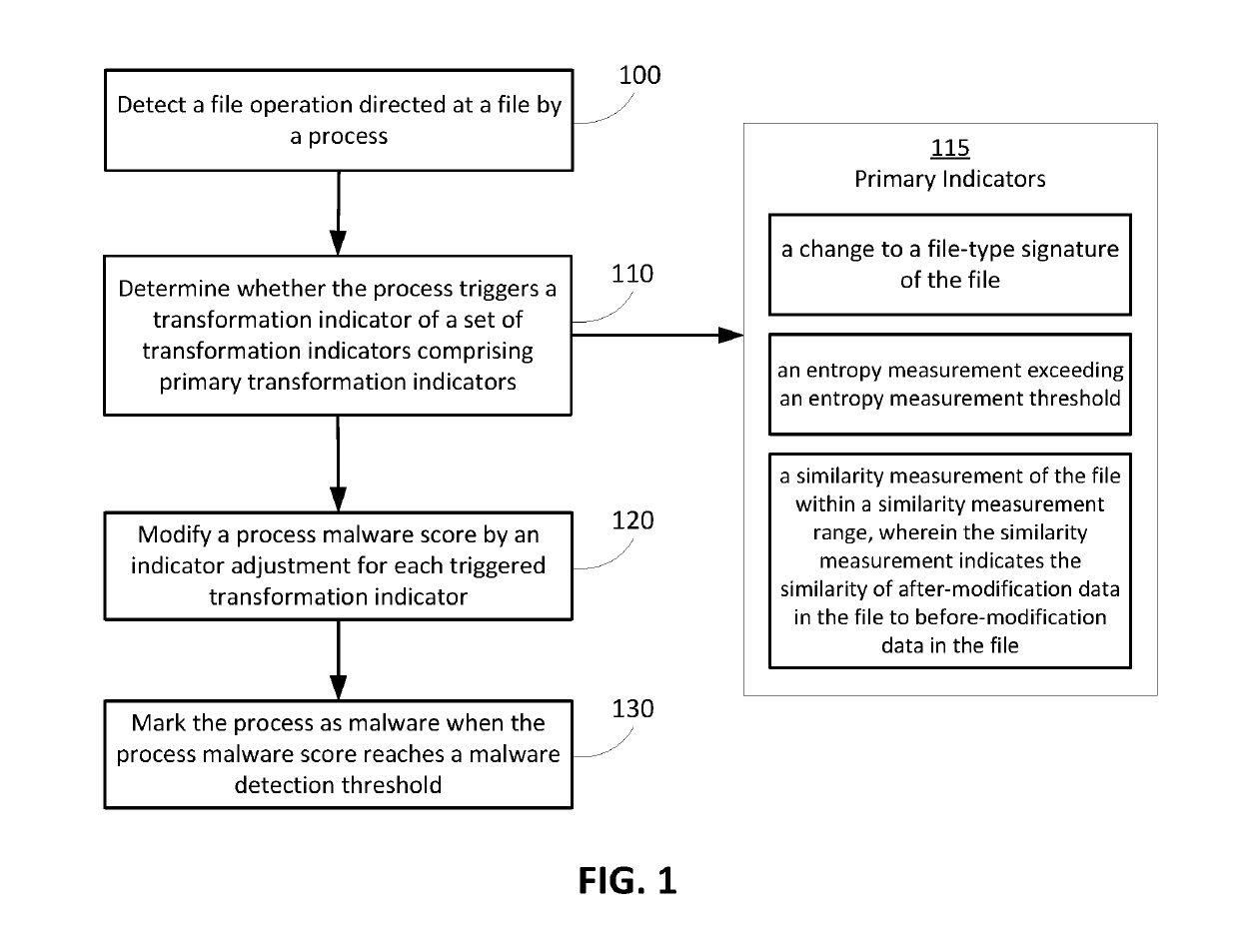
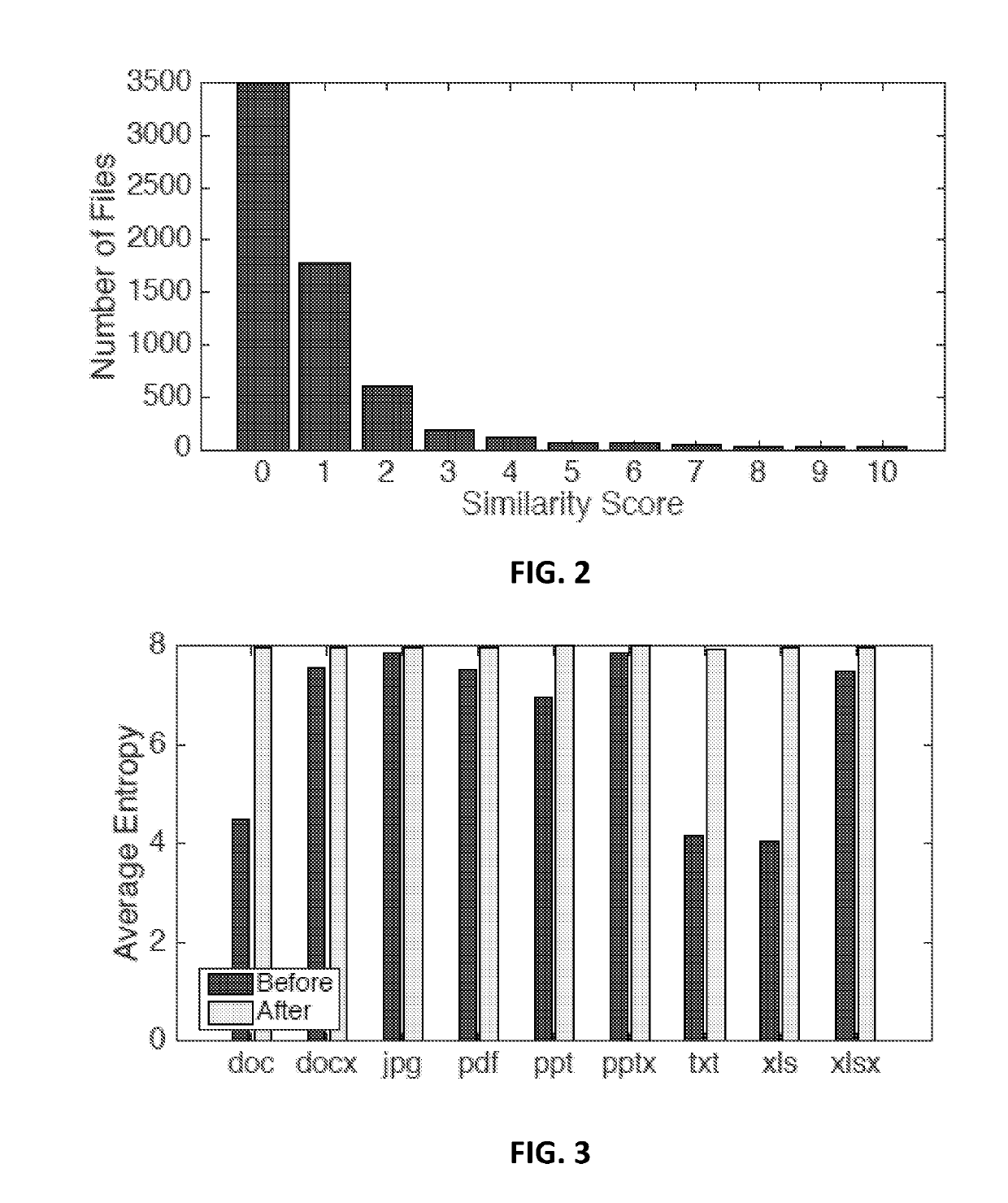
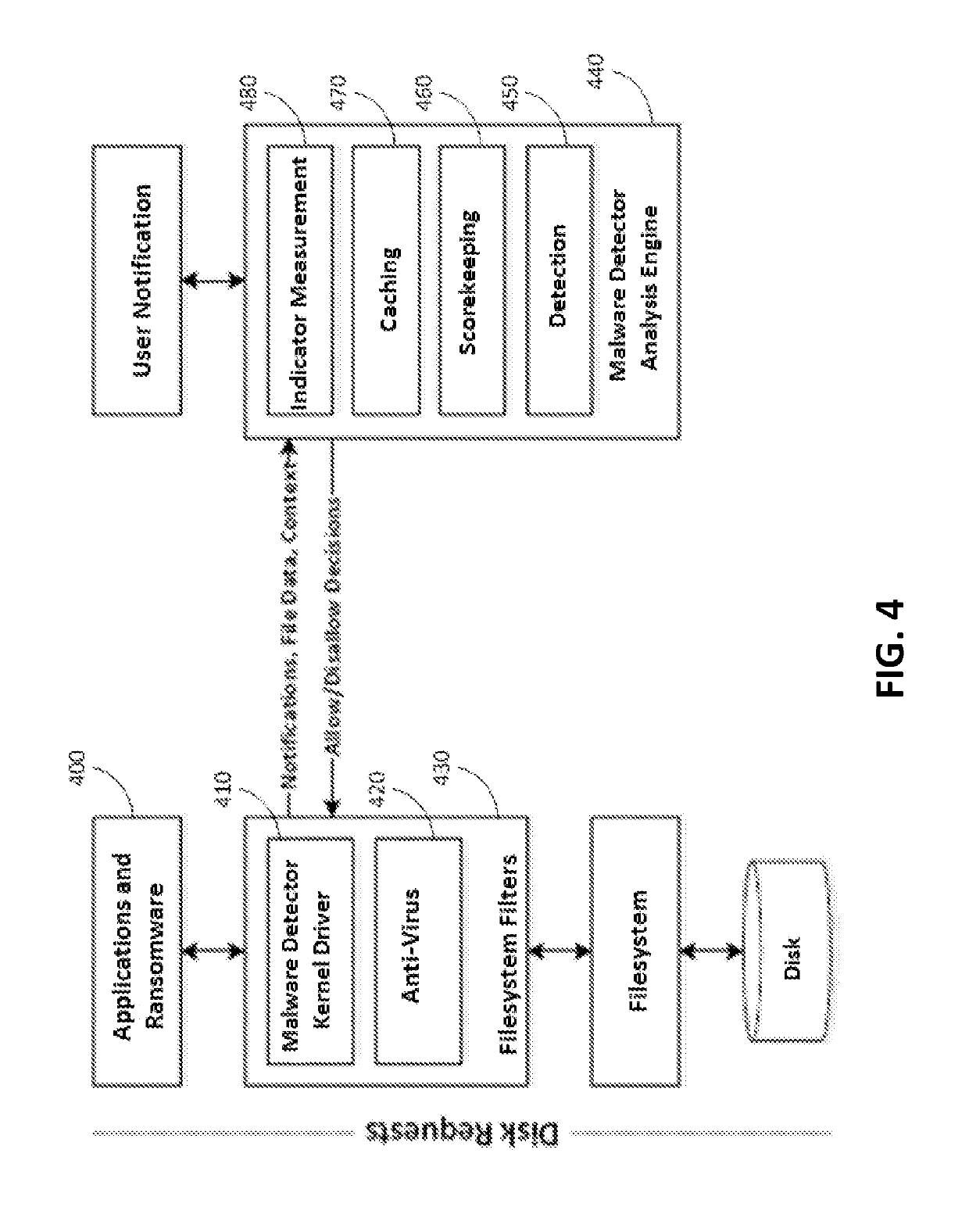
Malware detection via data transformation monitoring
ActiveUS20190228153A1Easy to detectImprove accuracyPlatform integrity maintainancePrimary IndicatorMalware
Techniques and systems are described for detecting malware's bulk transformation of a user's data before the malware is able to complete the data transformation. Included are methods and systems for enabling malware detection by monitoring the file operations of a computer application or process for particular kinds of suspicious data transformation indicators. Indicators include primary indicators, such as file-type signature changes, notable changes in file data entropy, and out-of-range similarity measurements between the read and write versions of file data, as well as secondary indicators, such as a large number of file deletions and a large reduction in the number of file-types written versus read by a process over time. When indicators are triggered by a process, an adjustment to the process' malware score is made; in the event that the process' malware score reaches a malware detection threshold, the process is marked as malware and appropriate actions are taken.
Owner:UNIV OF FLORIDA RES FOUNDATION INC
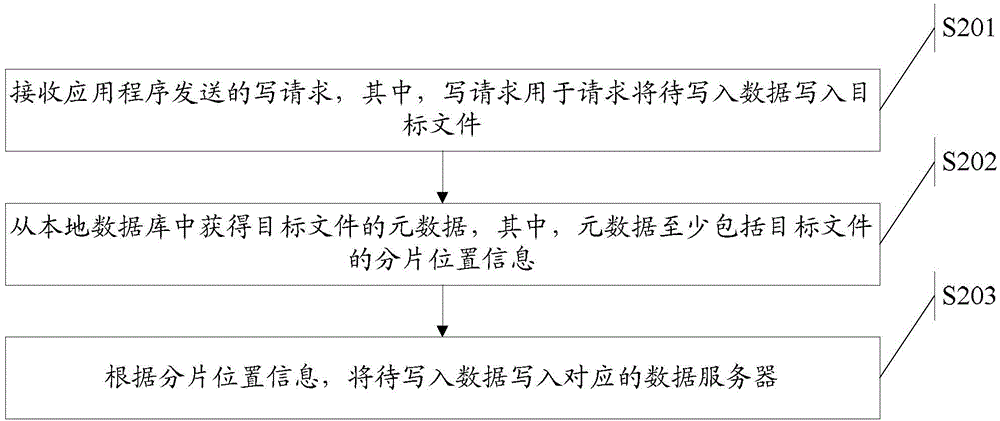
File writing method, file reading method, file deletion method, file query method and client
InactiveCN105718484ARelieve pressureReduce interaction overheadTransmissionSpecial data processing applicationsClient-sideApplication software
Embodiments of the invention disclose a file writing method which is applied to a file access client. The method comprises the following steps: receiving a write request sent by an application program, wherein the write request is used for requesting to write to-be-written data in a target file; obtaining metadata of the target file from a local database, wherein the metadata at least comprises fragment position information of the target file; and writing the to-be-written data into a corresponding data server according to the fragment position information. The embodiments of the invention furthermore provide a file reading method, a file deletion method, a file query method and corresponding equipment.
Owner:ZTE CORP
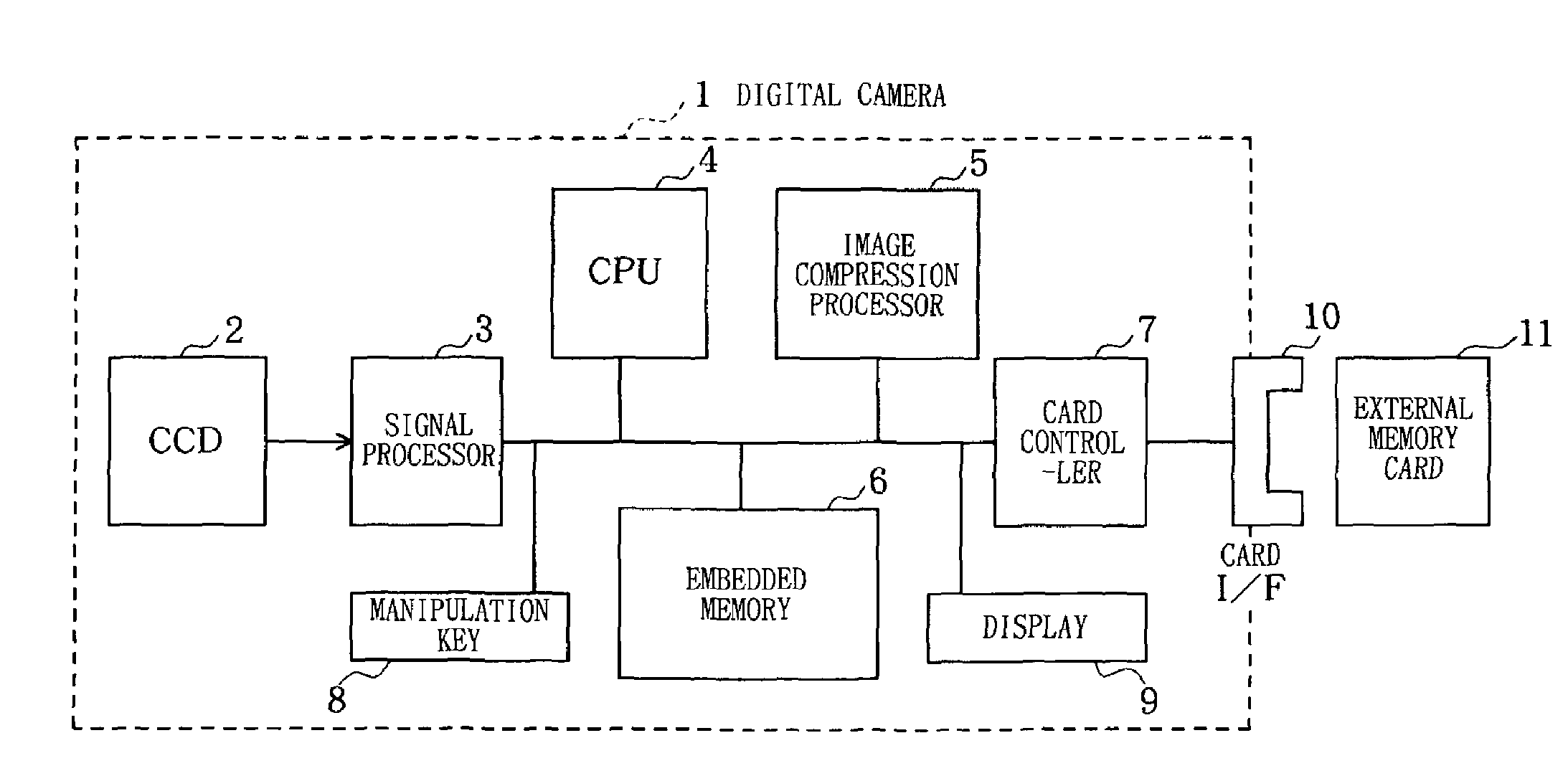
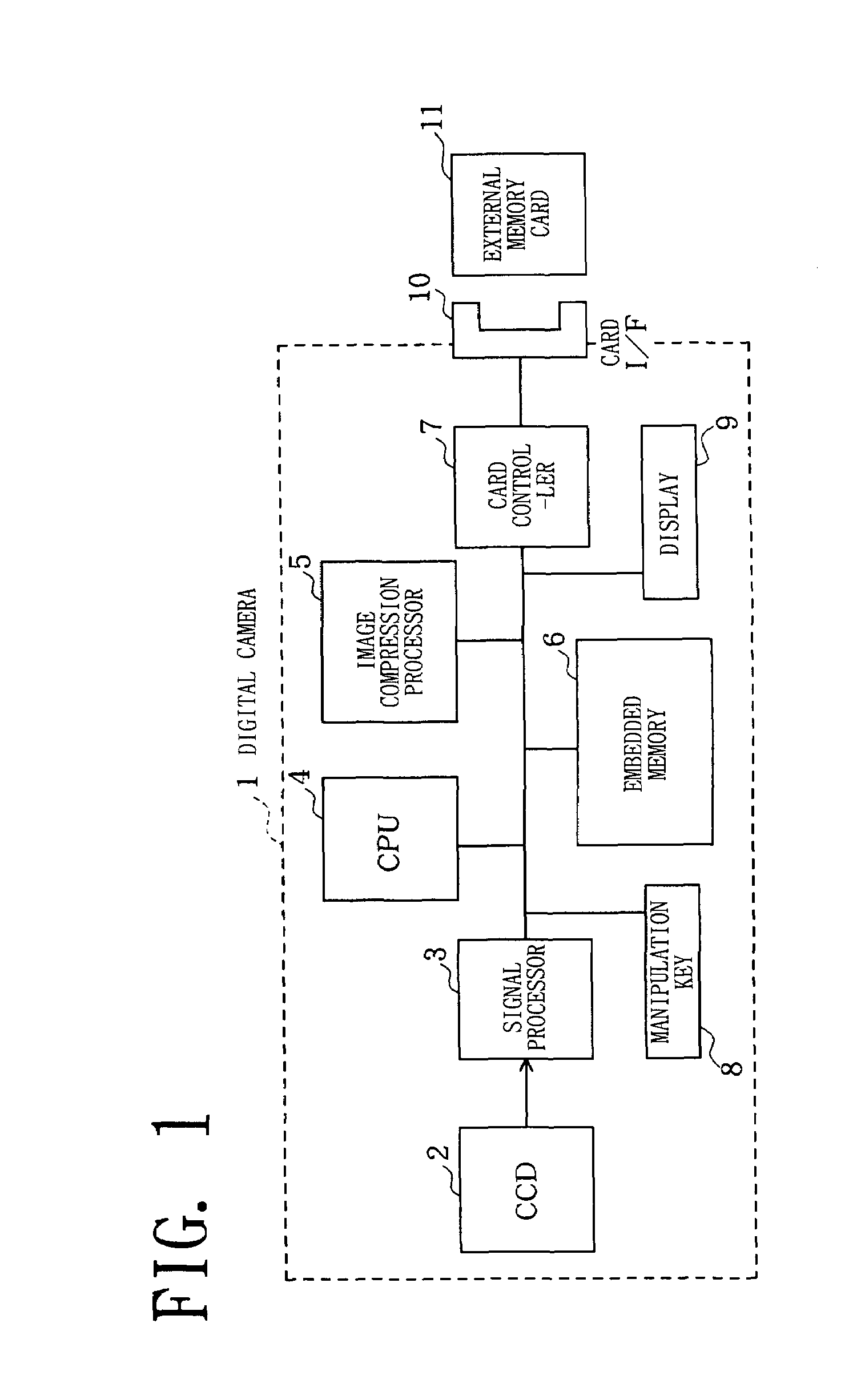
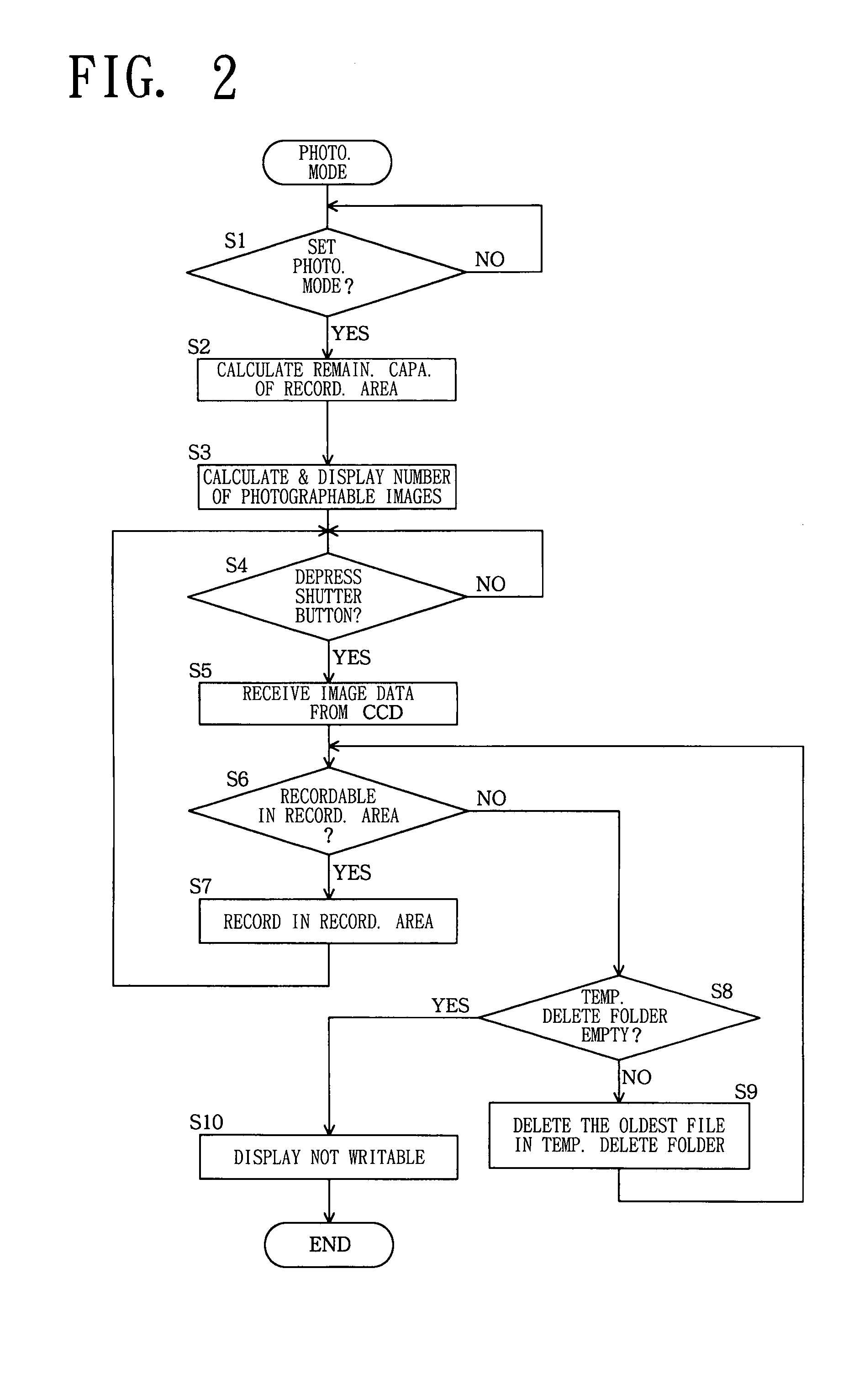
Camera with a temporary delete folder for storing images that are deleted when the memory becomes full
InactiveUS7295230B2Utilize memory capacityEfficient use ofTelevision system detailsColor television detailsData recordingFile deletion
The present invention provides a data recording device which specifies a file to be deleted from a memory card 11 in response to the user's file deleting manipulation to a manipulation key 8, and moves the specified file to a predetermined temporary delete folder. In recording data, the device calculates remaining capacity of recording area of the memory card 11, to judge whether a series of data to be recorded is recordable. When it is determined that the data is recordable, the data is recorded in the recording area. When it is not determined that the data is recordable, a file included in the temporary delete folder is deleted and the data is recorded in the recording area.
Owner:XACTI CORP
Flash memory device having secure file deletion function and method for securely deleting flash file
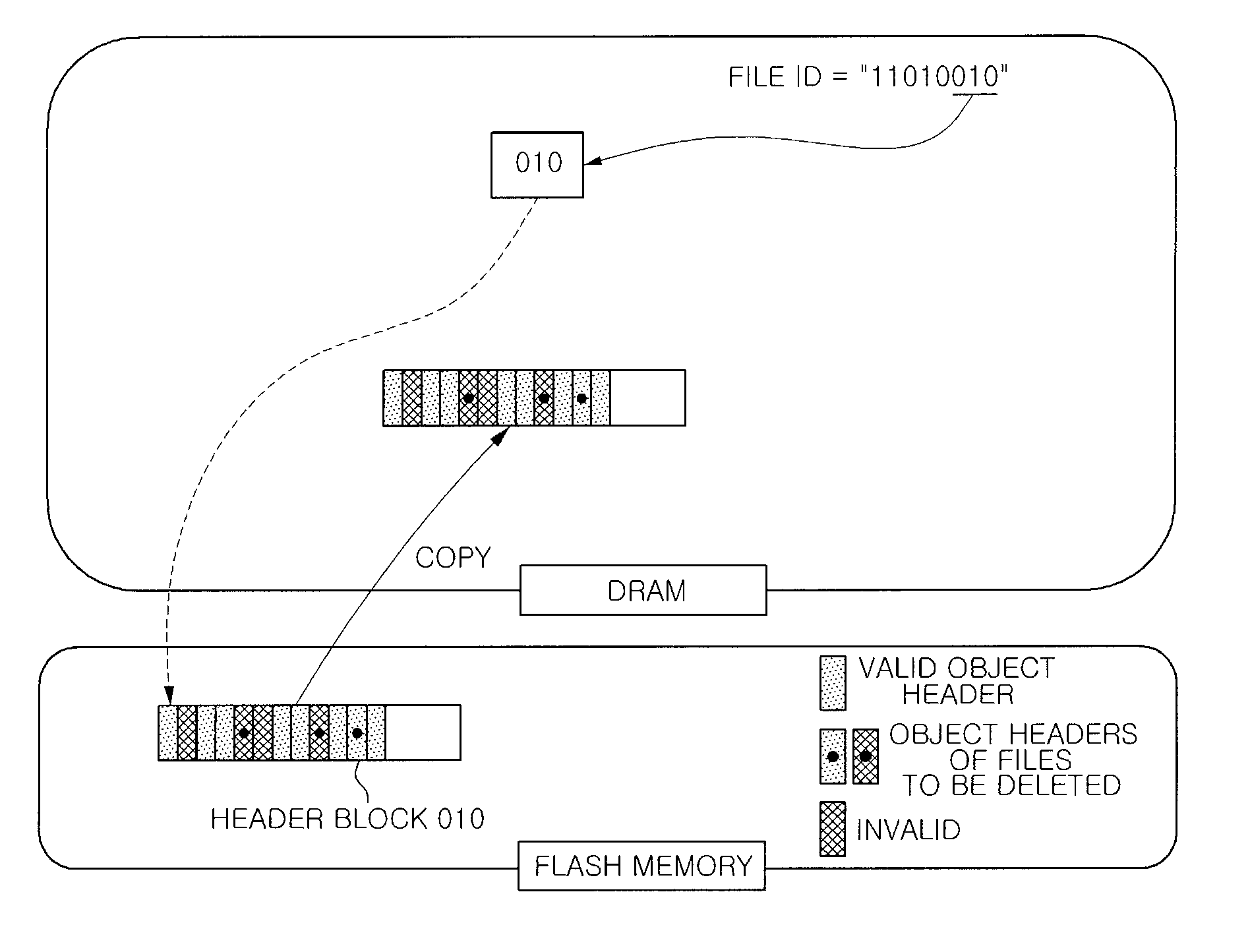
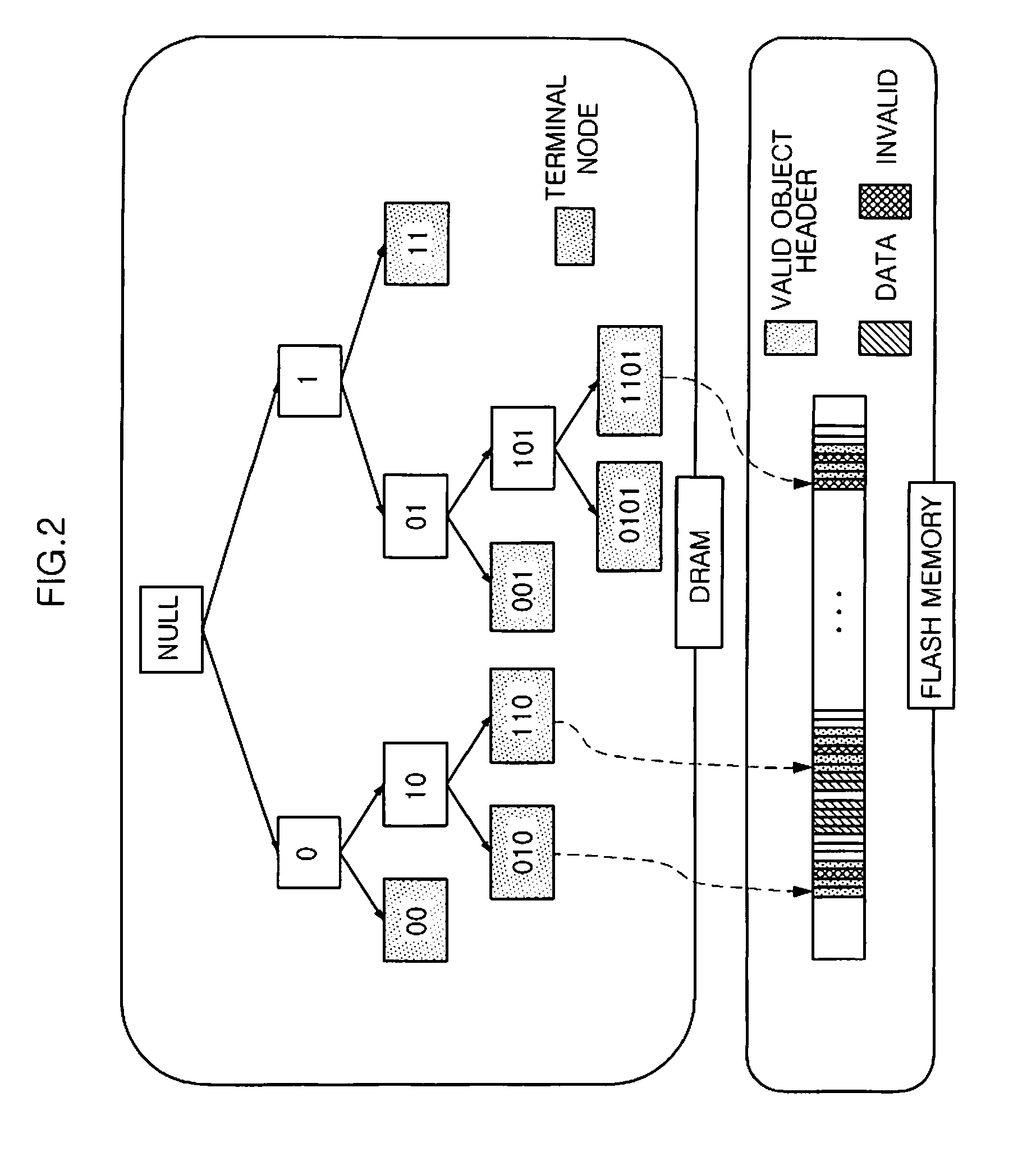
InactiveUS20090172265A1Quickly and securely deletingMemory architecture accessing/allocationDigital data information retrievalBinary treeFile deletion
Disclosed is a flash memory device having a secure flash file deletion function and a method for securely deleting a flash file. Data and object headers as actual contents of the flash file are separately stored in data blocks and header blocks. At this time, the data is encrypted and stored, and a decryption key is included in an object header and stored in a header block. When the flash file is deleted, the object header is deleted by searching the header block where the object header including the decryption key is stored. In order to search the header block, a binary tree structure is used in which a terminal node indicates an LSB of a file ID. Disclosed may be applied to an embedded system where a flash memory is used as a storage medium. In particular, disclosed is suitable for a NAND flash memory device.
Owner:ELECTRONICS & TELECOMM RES INST
File Management System and Method
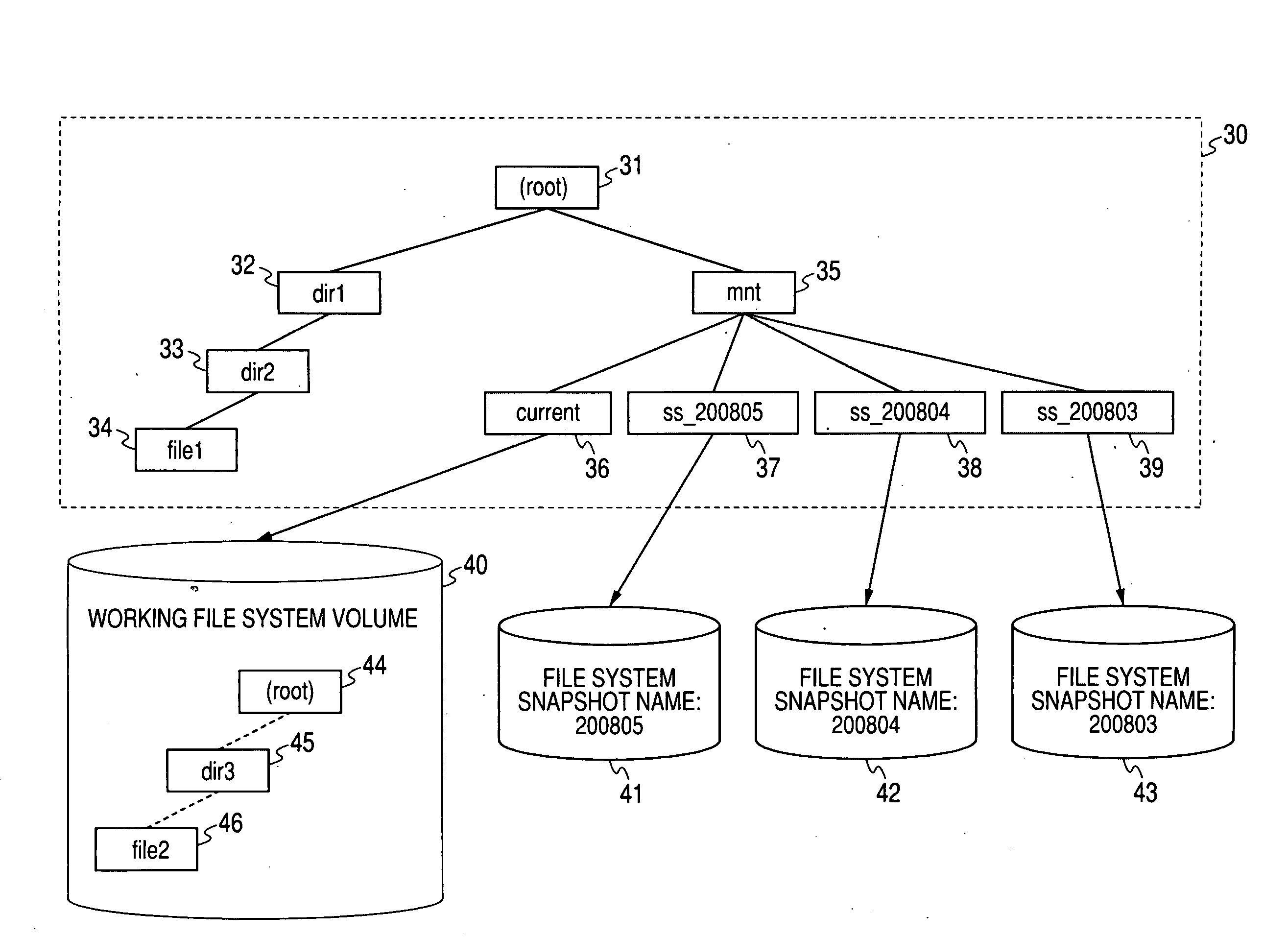
InactiveUS20100030825A1Reliable deletionDigital data information retrievalMemory loss protectionInvalid DataFile deletion
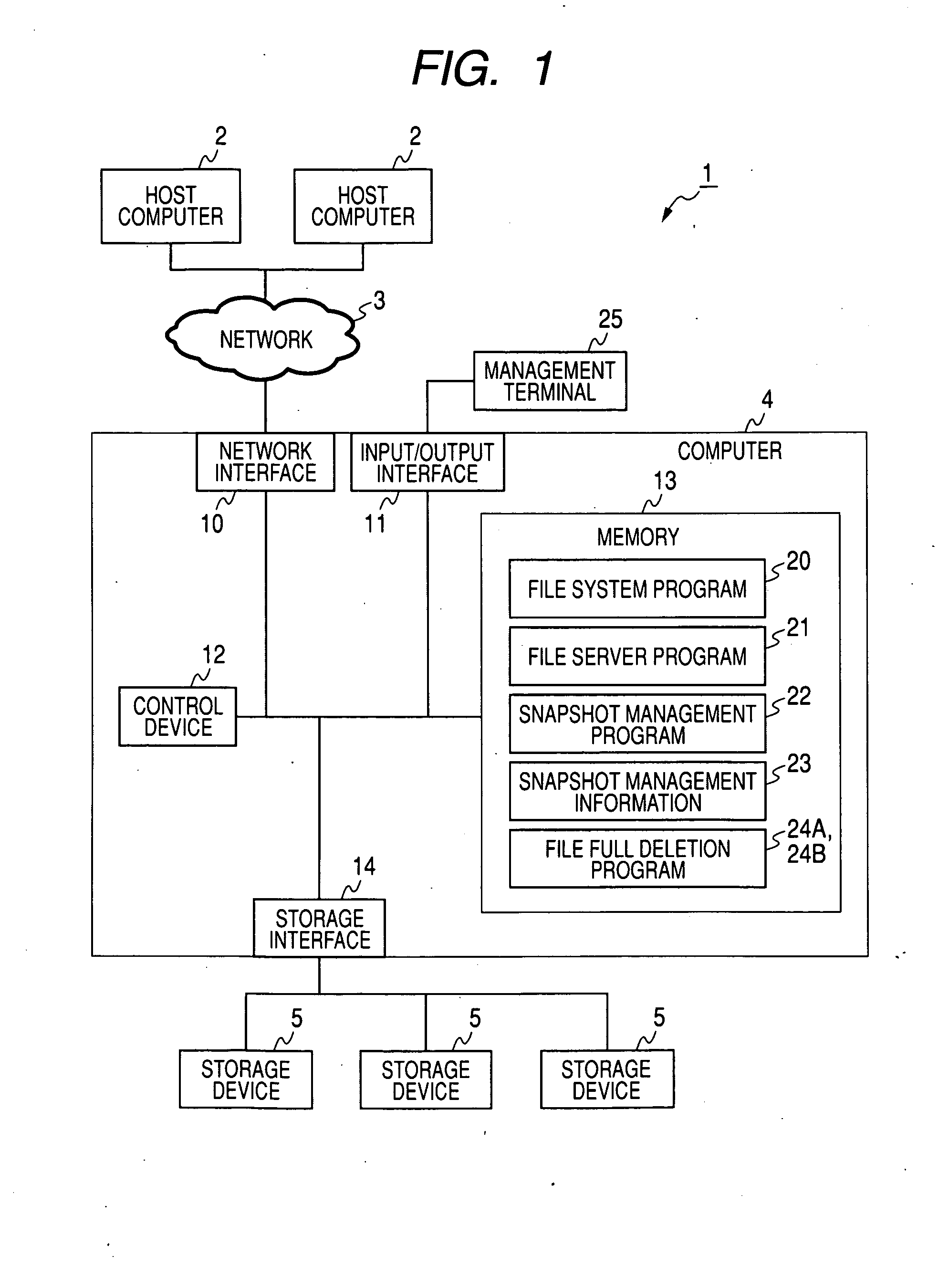
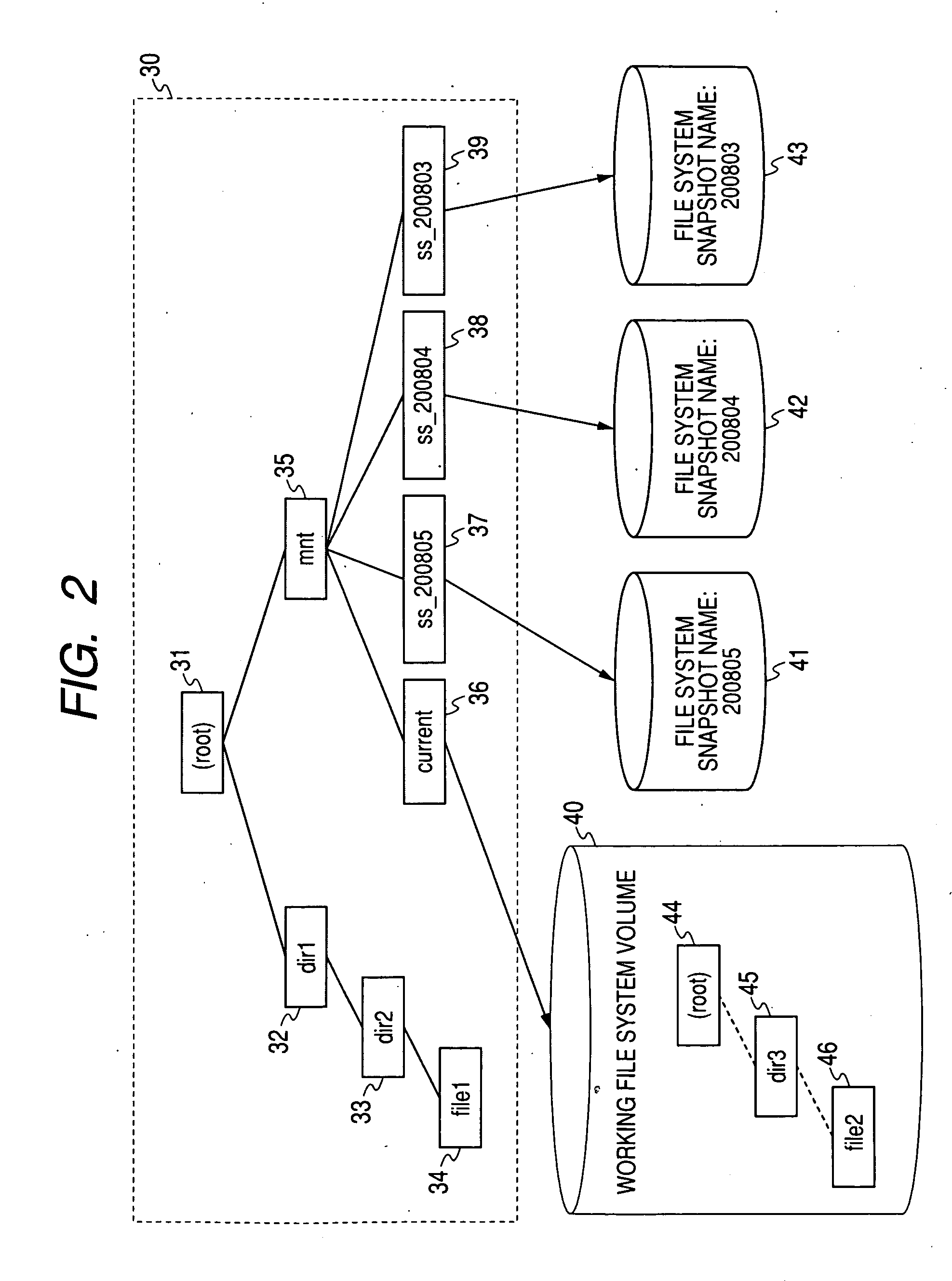
A proposal is made of a file management system and method capable of reliably deleting unnecessary data. In a file management console and method for reading or writing data of a file from or in a first volume, which is provided by a storage device, in response to a request sent from a host computer, one snapshot or multiple snapshots that relate to the first volume and can be updated are created. In response to an externally issued designated file deletion command, a designated file is deleted from all of the first volume and snapshots or part thereof specified in the deletion command. At this time, the data items of the designated file in the first volume and / or snapshots from which the designated file should be deleted are overwritten with invalid data. Moreover, pieces of management information on the designated file are changed to a reference-disabled state.
Owner:HITACHI LTD
Method and device for storing files and method and device for deleting files
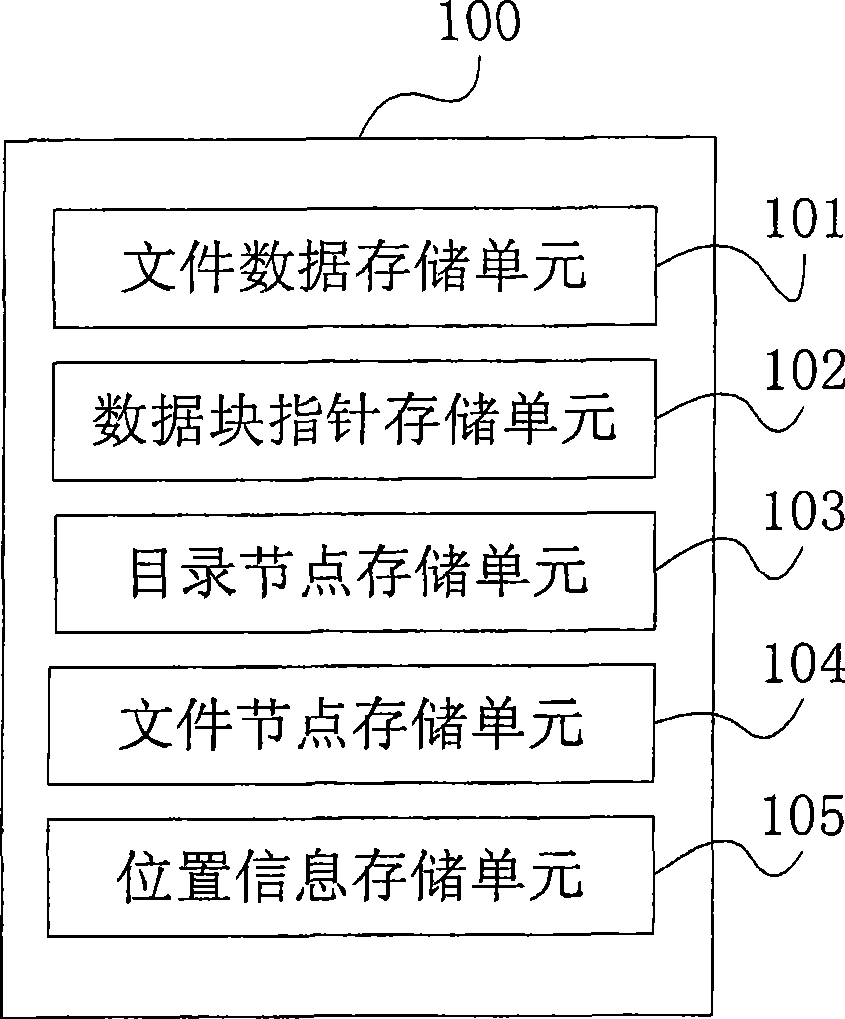
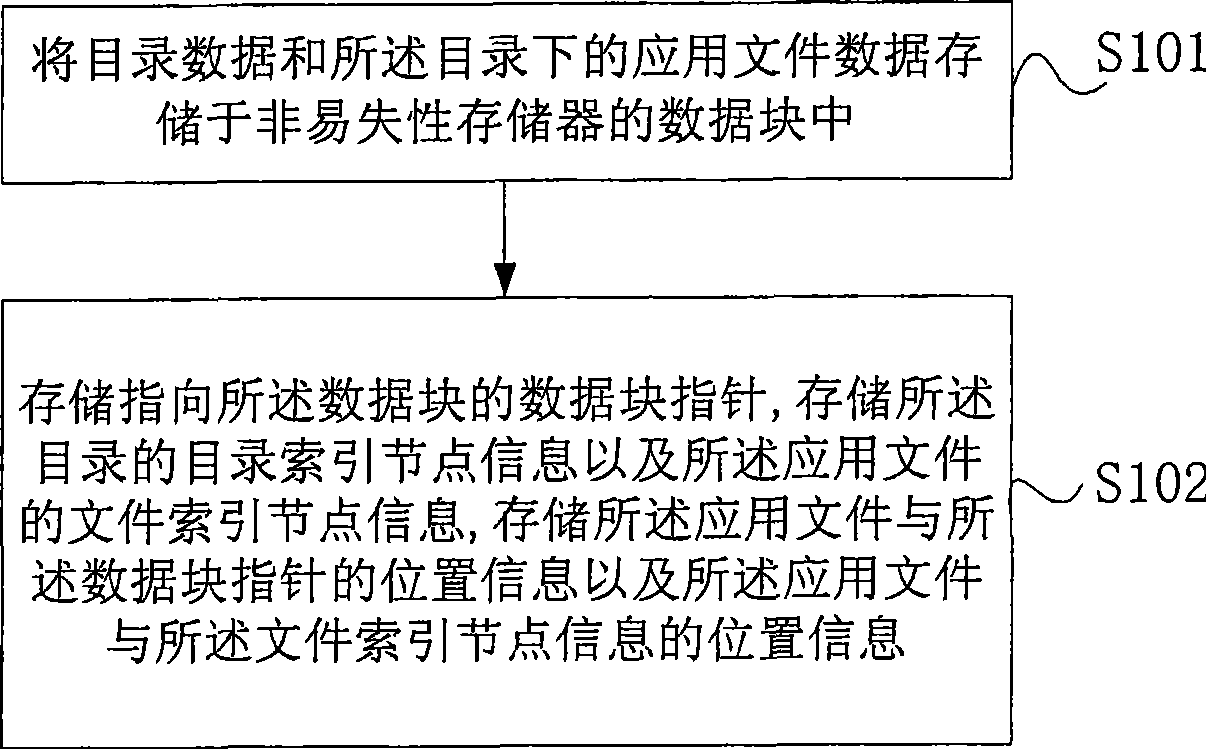
InactiveCN101446984AReduce occupancySpecial data processing applicationsFile systemsDatabaseFile deletion
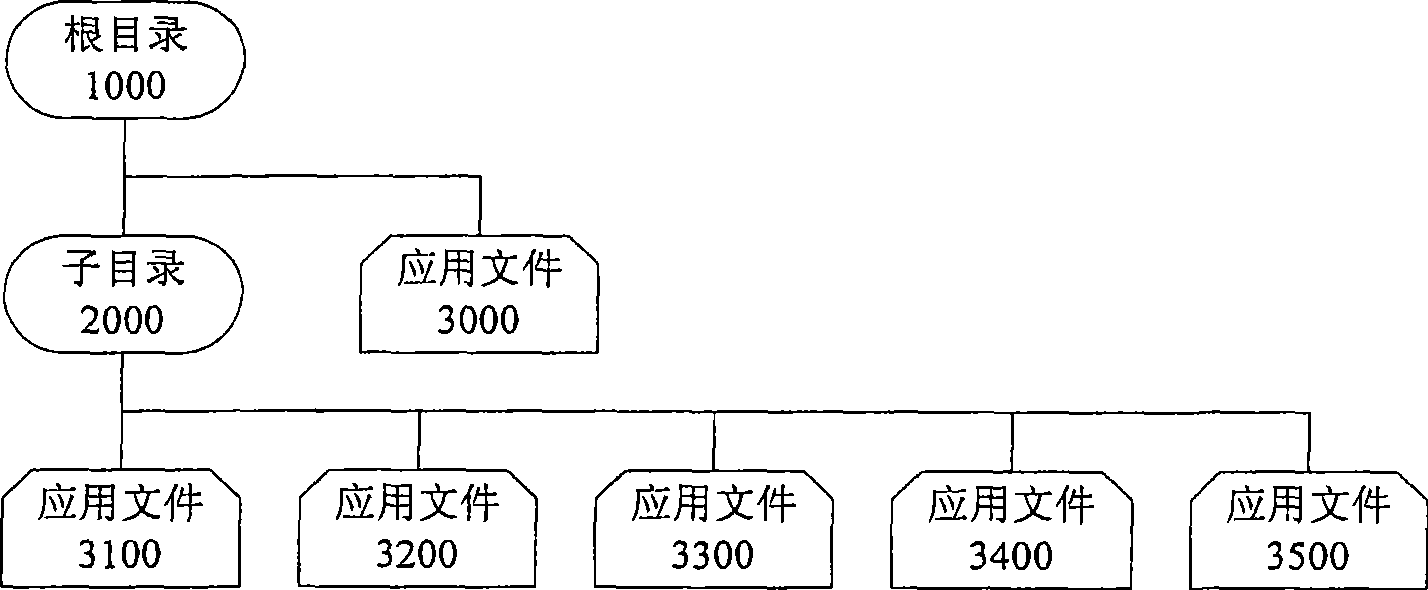
The invention provides a method and a device for storing files, and a method and a device for deleting files. The method for storing files comprises the following steps: storing a catalogue data and the application file data under the catalogue in a data block; storing the data block pointer pointing to the data block; storing the catalogue index node information of the catalogue and the file index node information of the application file; storing the position information of the application file and the data block pointer and the application file and the file index node information. In the deleting catalogue, the disk resource occupied by these files can be found without traveling the files under the catalogue and the file and the catalogue can be deleted, thereby effectively decreasing the occupied system resource during the deleting the whole catalogue process.
Owner:HUAWEI DIGITAL TECH (CHENGDU) CO LTD
Privacy protection method of distributed cloud storage system
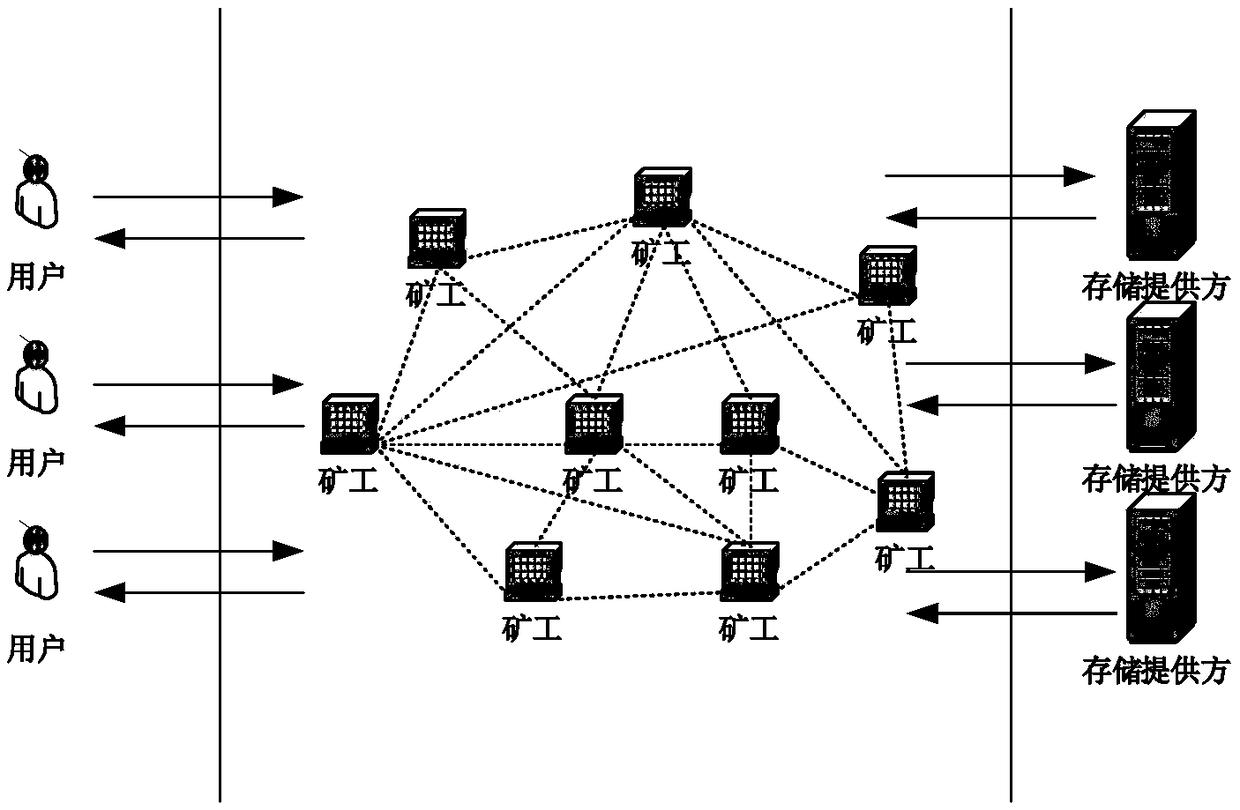
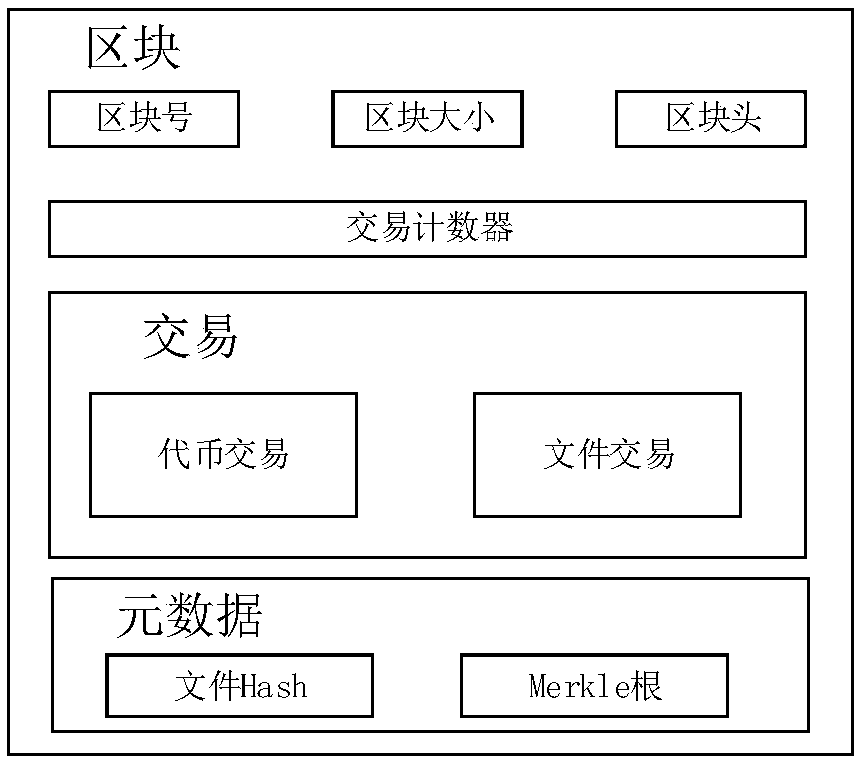
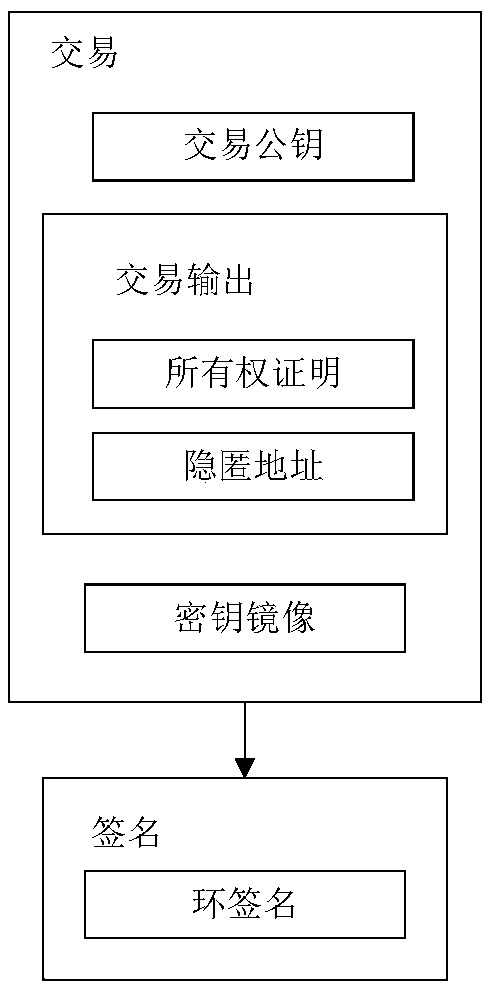
ActiveCN109508552APrecise positioningRealize privacy protectionFinanceDigital data protectionPrivacy protectionCloud storage system
The invention discloses a privacy protection method of a distributed cloud storage system, comprising a user, a miner, a storage provider, system initialization, file uploading, file sharing, file downloading, file deletion and the like. The invention combines the distributed cloud storage system with the block chain technology, and regards the file ownership processing process as the transactionprocessing, thereby realizing the privacy protection of the file ownership processing process in the distributed cloud storage system, including the hiding of the sender, the receiver and the transaction content. In addition, the invention can effectively resist the replay attack and the data forgery attack while ensuring the privacy of the user.
Owner:JIANGSU BOZHI SOFTWARE TECH CO LTD
Distributed file deletion method, device and system
InactiveCN105095489AReduce waiting timeSpecial data processing applicationsData informationData needs
The embodiment of the invention provides a distributed file deletion method, device and system. The method comprises the steps that data deletion requests sent by a client are received and added to a processing queue, and first deletion success information is returned to the client; the data deletion requests in the processing queue are sequentially acquired, and storage capacity information of cluster nodes is updated according to the data deletion requests; data information of data needing to be deleted is determined according to the data deletion requests and stored in a database, the data information in the database is acquired every other preset time, and the data corresponding to the data information are deleted. Receiving of the data deletion request of the corresponding client and the deleted data are asynchronously processed, and therefore the waiting time of the client is effectively shortened.
Owner:INSPUR BEIJING ELECTRONICS INFORMATION IND
Method for deleting file and system
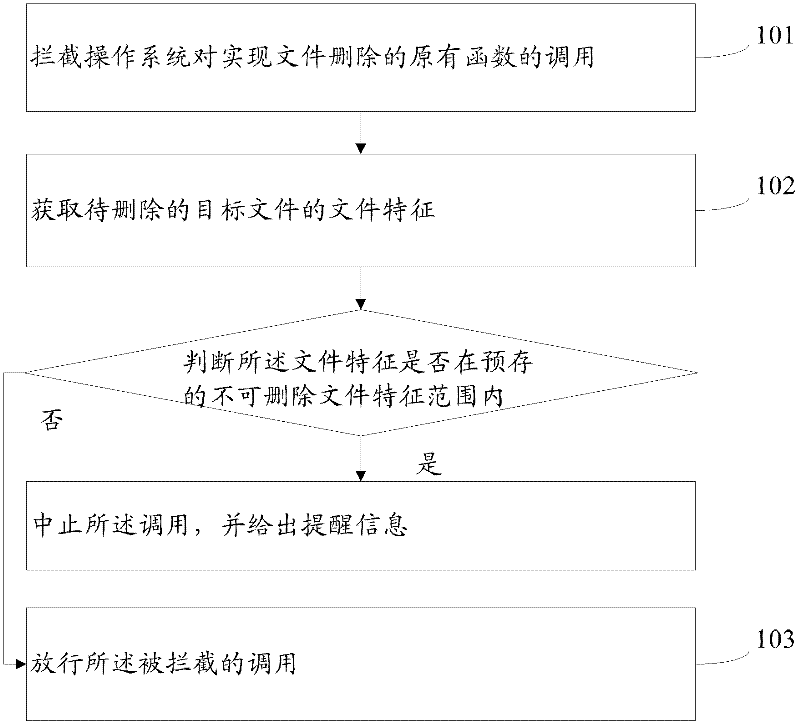
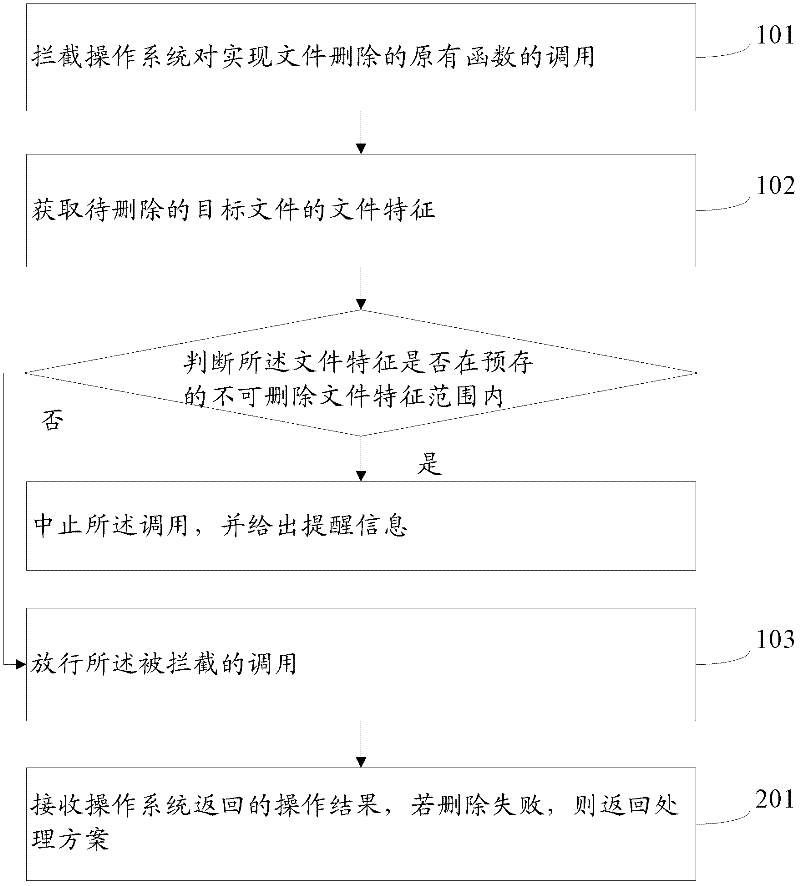
ActiveCN102609495AAvoid deletionAccurate Removal GuidanceSpecial data processing applicationsFile deletion
The invention provides a method for deleting a file. The method includes steps: intersecting calling of an original function for deleting the file from an operating system; obtaining file characteristics of the target file to be deleted from the intersected calling, judging whether the file characteristics are in a stored range of non-deletable file characteristics or not, stopping the calling and giving out reminding information of the file characteristics are in the stored range, and carrying out a next step if the file characteristics are not in the stored range; and releasing the intersected calling of the original function for deleting the file from the operating system. The invention further provides a system for deleting the file. By the aid of the method for deleting the file and the system for deleting the file, a user can be correspondingly prompted when deleting the file, and mistaken deletion of files in the operating system is avoided.
Owner:BEIJING QIHOO TECH CO LTD
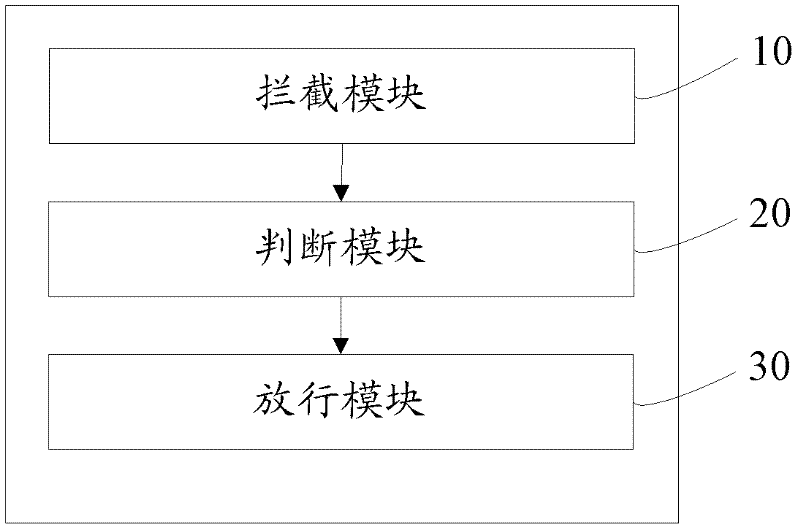
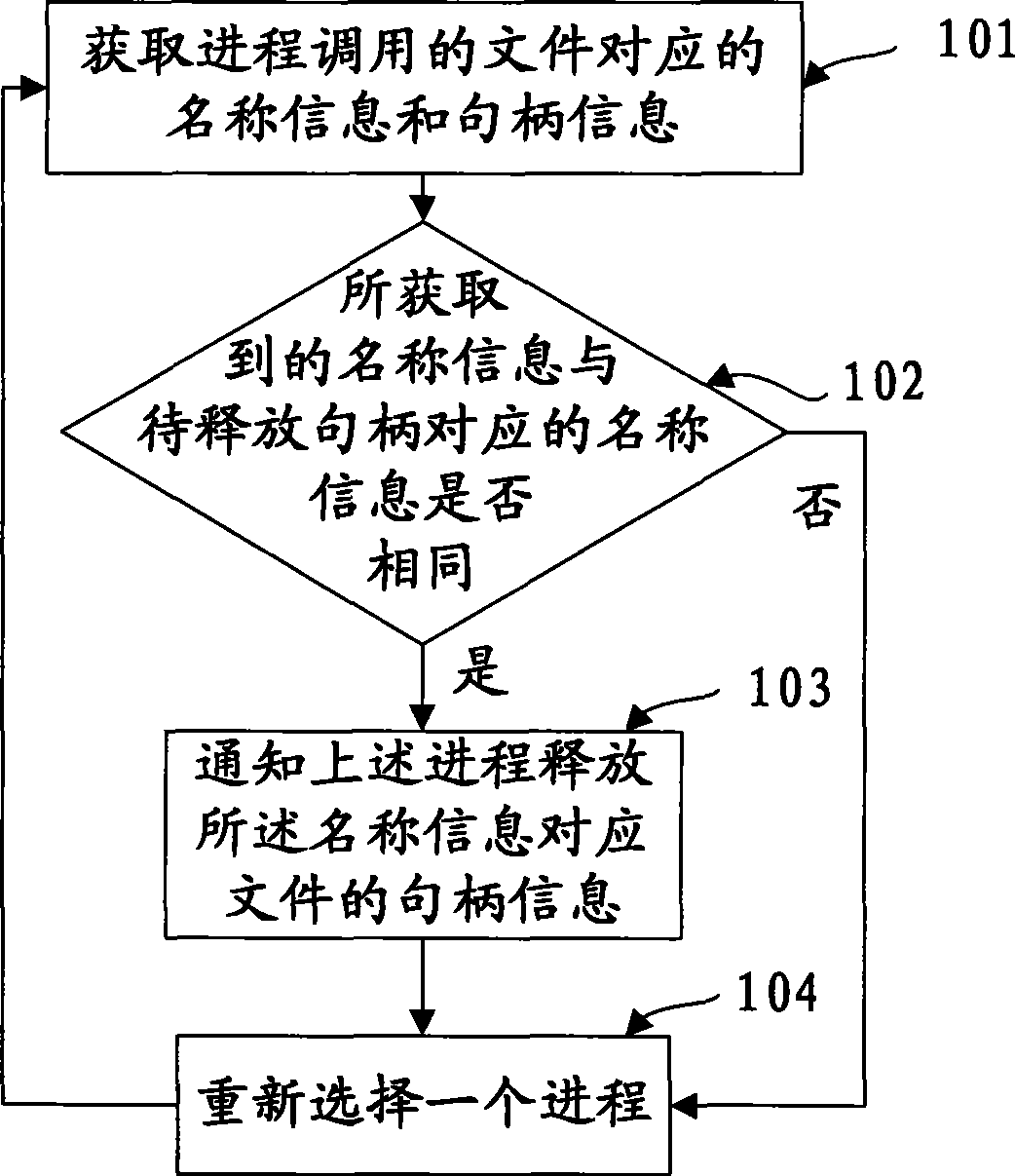
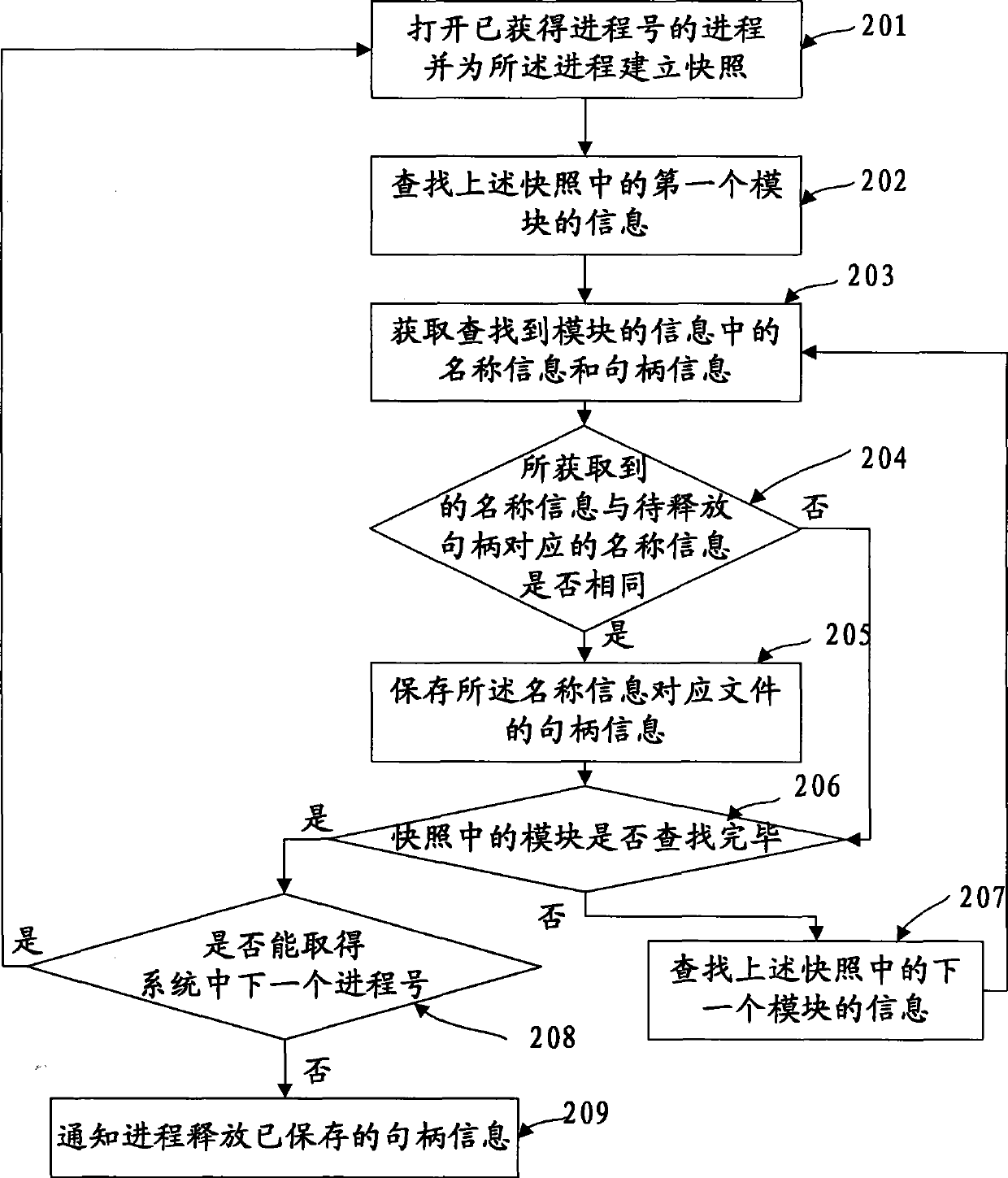
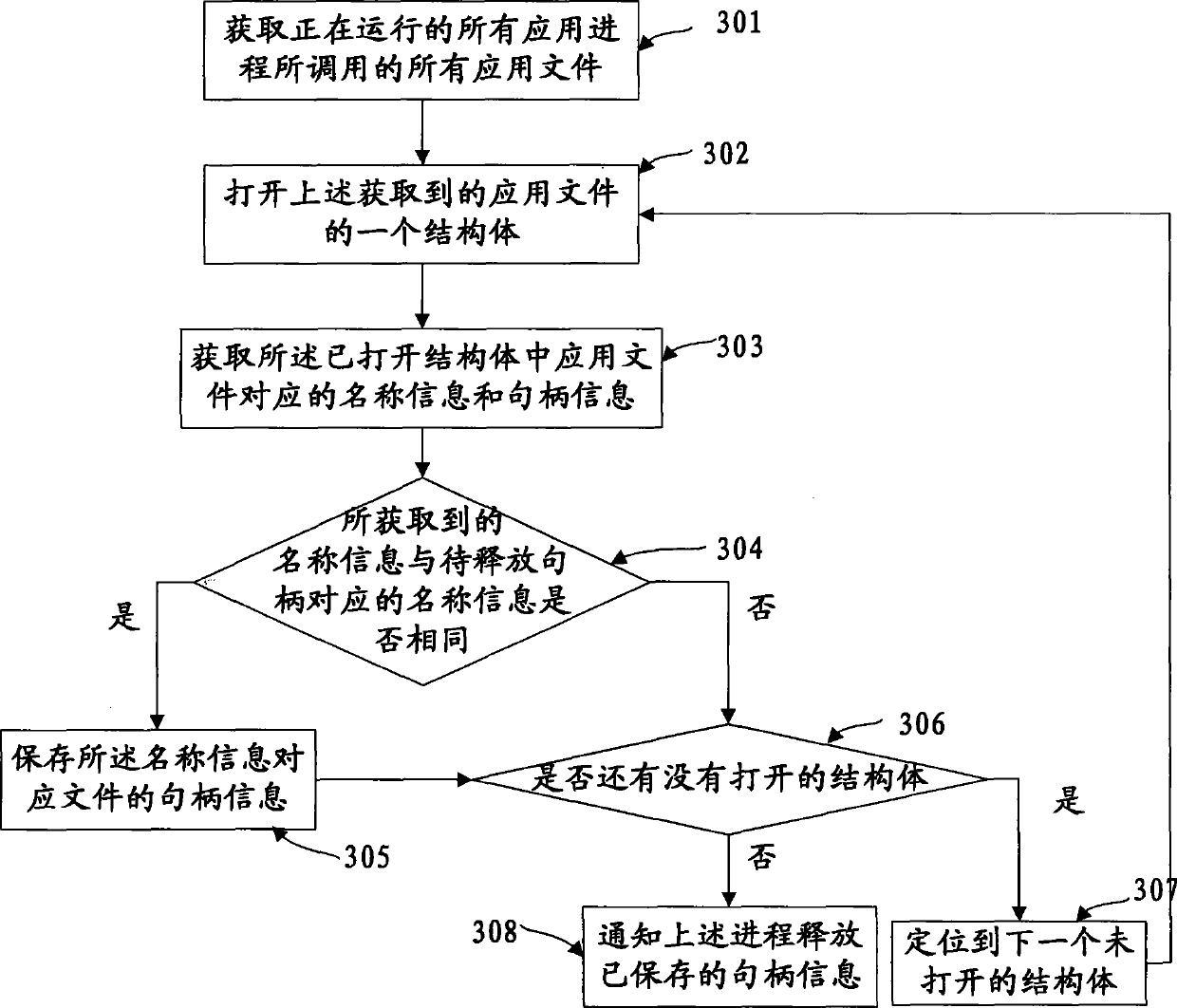
Method and apparatus for releasing handle and file deleting system
InactiveCN101373505AExit without errorAvoid searchingPlatform integrity maintainanceSoftware systemSoftware engineering
The embodiment of the invention discloses a method for releasing handles, a device and a file deletion system, relates to the technical field of releasing the handles of documents to be deleted, and solves the problem that a system needs restarting or leads error to occur to the process in the prior art of document deletion. In the embodiment, firstly, the handle information of the documents called during the process is searched for; if the handle information of the documents called during the process is the handle to be released, the process is informed of releasing the corresponding handle information, thereby completing the release of the handles. Corresponding handle information is released before documents infected with viruses are deleted in a virus-killing software system.
Owner:HUAWEI DIGITAL TECH (CHENGDU) CO LTD
Method and device for uninstalling application program
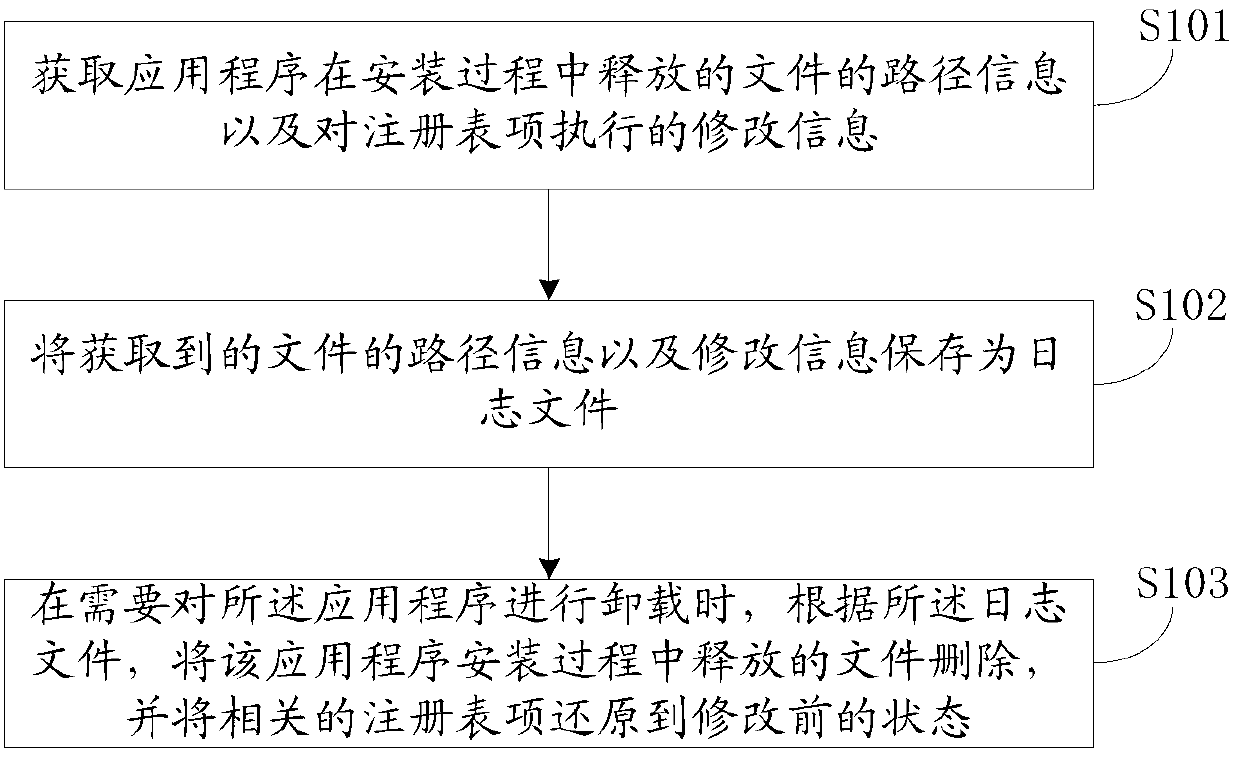
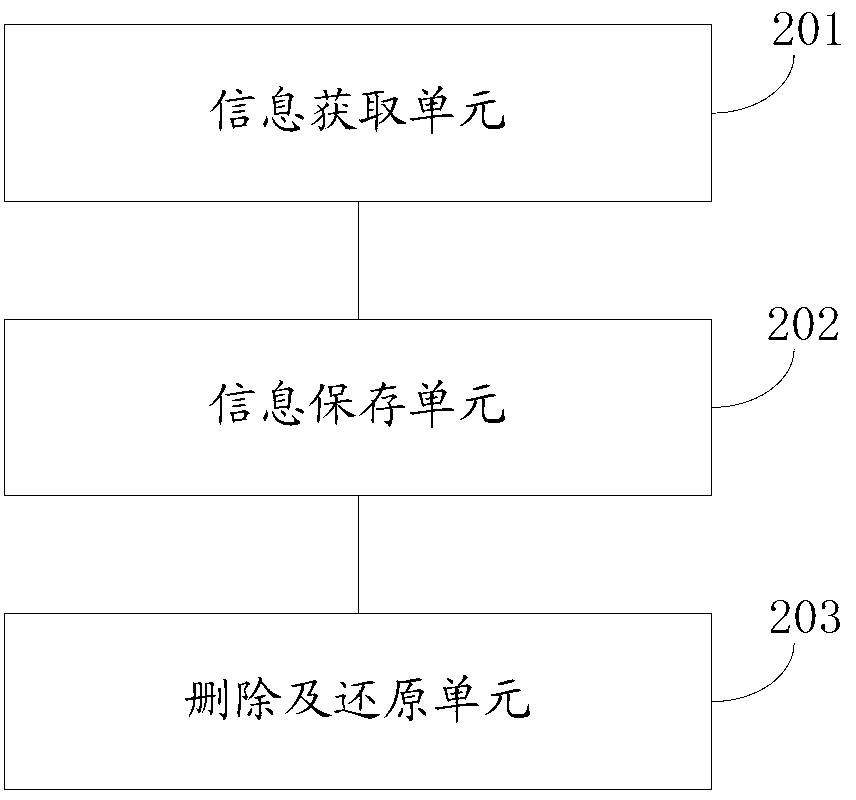
PendingCN103345411AAvoid long termImprove performanceHardware monitoringProgram loading/initiatingApplication softwareWindows Registry
The invention discloses a method and device for uninstalling an application program. The method comprises the steps of obtaining path information of a file released in the installation process of the application program and modification information executed by a registry key, storing the path information of the obtained file and the modification information as a journal file, when the application program needs to be uninstalled, deleting the file released in the installation process of the application program according to the journal file,, and restoring the related registry key into the status before modification. According to the method and device for uninstalling the application program, the complete rollback of the file released in the installation process of the application program and the modified registry information can be achieved, and waste of system resources is avoided.
Owner:BEIJING QIHOO TECH CO LTD +1
Changed file identification, software conflict resolution and unwanted file removal
InactiveUS7765592B2Memory loss protectionUnauthorized memory use protectionApplication softwareData mining
As computer programs grow more complex, extensible, and connected, it becomes increasingly difficult for users to understand what has changed on their machines and what impact those changes have. An embodiment of the invention is described via a software tool, called AskStrider, that answers those questions by correlating volatile process information with persistent-state context information and change history. AskStrider scans a system for active components, matches them against a change log to identify recently updated and hence more interesting state, and searches for context information to help users understand the changes. Several real-world cases are provided to demonstrate the effectiveness of using AskStrider to quickly identify the presence of unwanted software, to determine if a software patch is potentially breaking an application, and to detect lingering components left over from an unclean uninstallation.
Owner:MICROSOFT TECH LICENSING LLC
A log storage method and system based on a data center
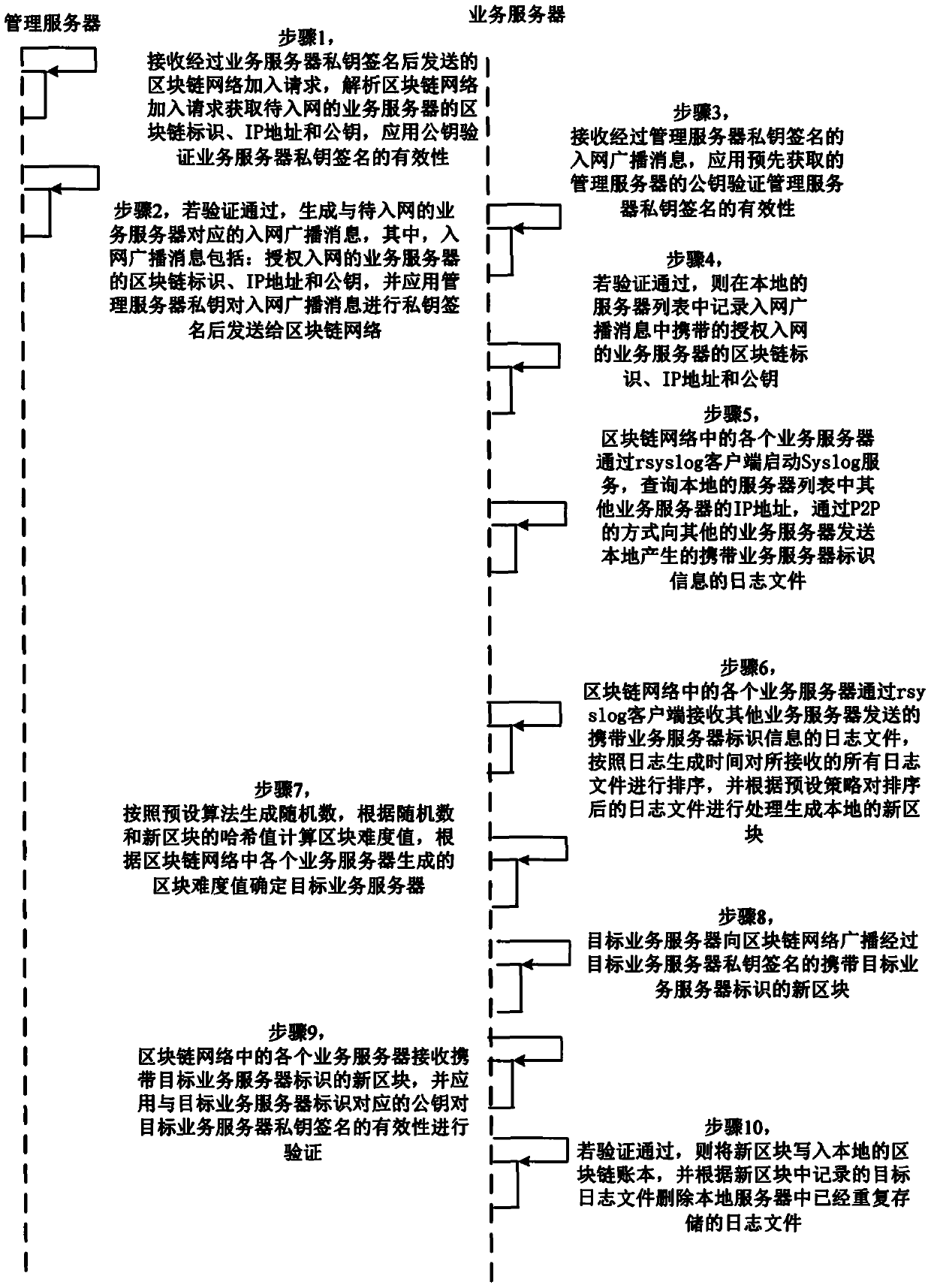
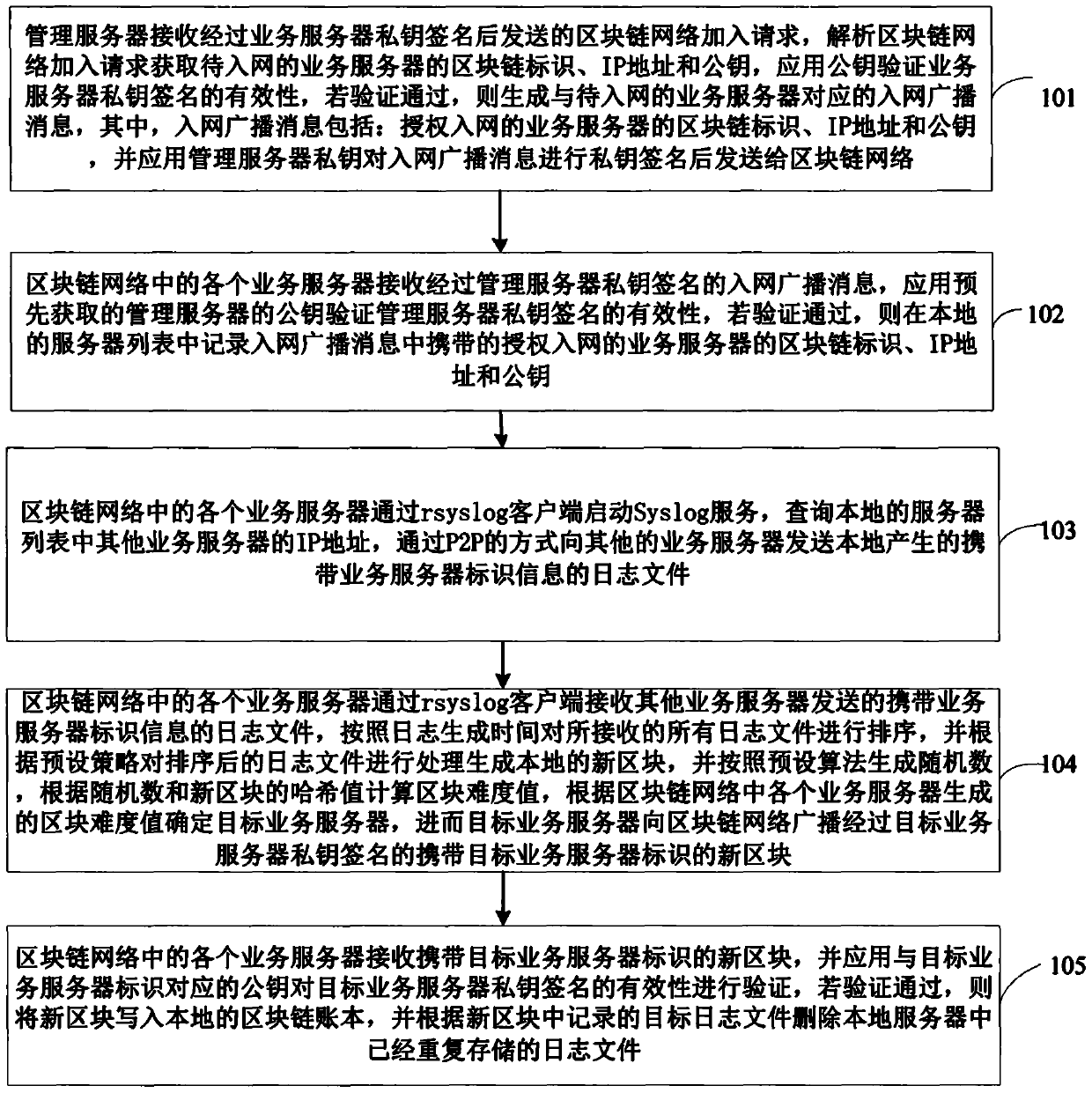
ActiveCN109902074AVerify validityProtection securityTransmissionFile system typesData centerOperability
The invention discloses a log storage method and system based on a data center. The method comprises the following steps that the management server receives a network access request of the service server; after the verification is legal, the service server is allowed to join the block chain network, receive a log file sent by a service server of the block chain network, sort all the received log files according to the log generation time, process the log files to generate a local new block, and broadcast a new block which is signed by a target service server private key and carries a target service server identifier to the block chain network by the related target service server; And each service server deletes log files repeatedly stored in the local server according to the target log files recorded in the new block. Therefore, the block chain network is formed by the servers in the data center, the log files are stored in a distributed mode, the safety of the log files is protected,a firewall mechanism of the data center is spanned, and operability is high.
Owner:江苏全链通信息科技有限公司
File protection method and apparatus, and terminal
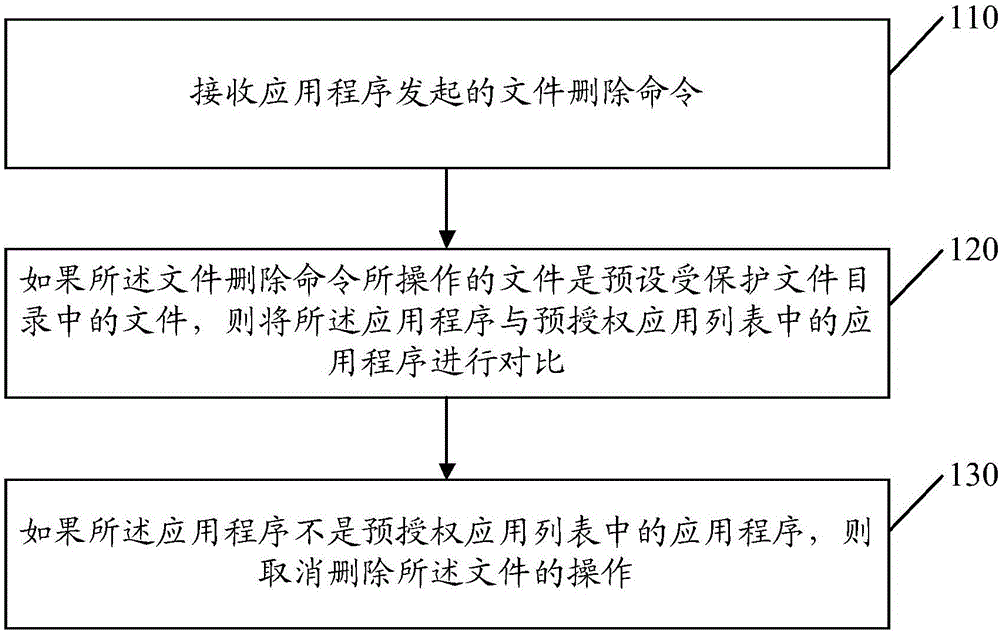
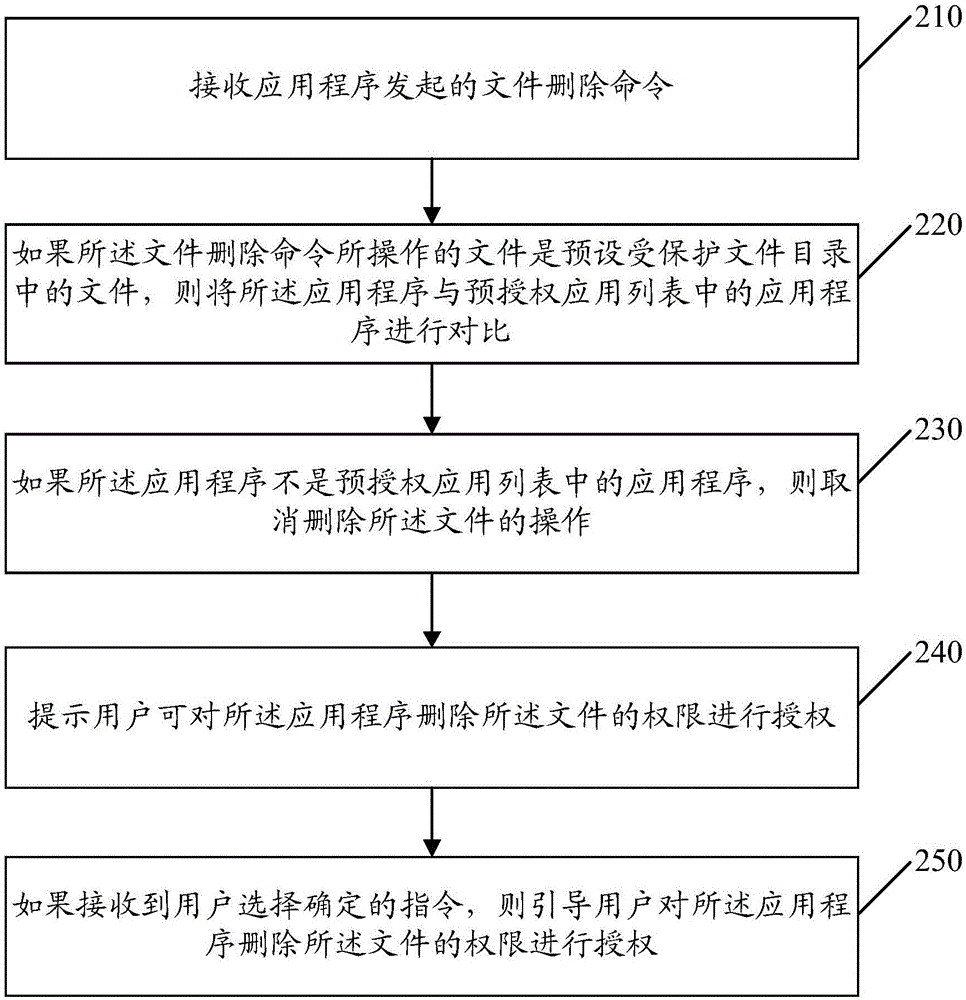
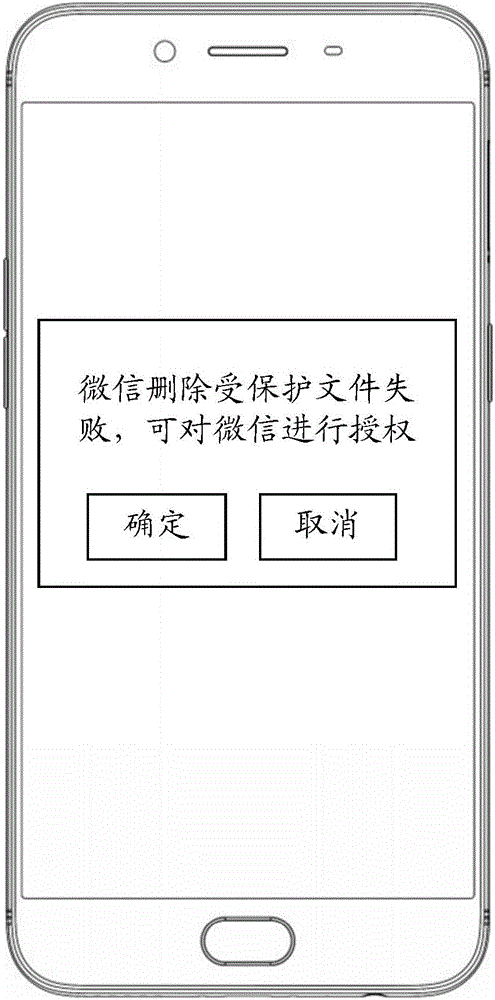
InactiveCN106709034ADelete is notAvoid lostDigital data protectionSpecial data processing applicationsComputer terminalApplication software
The present invention discloses a file protection method and apparatus, and a terminal. The method comprises: receiving a file deletion command initiated by an application; if the file operated by the file deletion command is a file in a preset protected file directory, carrying out comparison between the application and applications in a pre-authorized application list; and if the application is not an application in the pre-authorized application list, canceling the operation for deleting the file. According to the method, the apparatus and the terminal disclosed by the present invention, loss to users caused by that important files are deleted by unauthorized applications is avoided, and files can be protected from deleting by malicious applications.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com